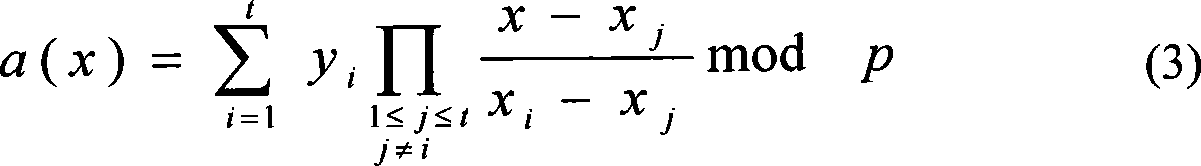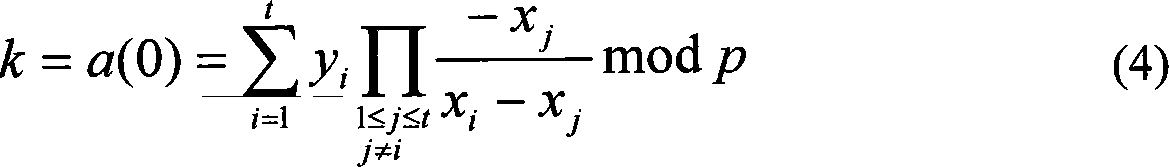Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
77 results about "Labelling algorithm" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
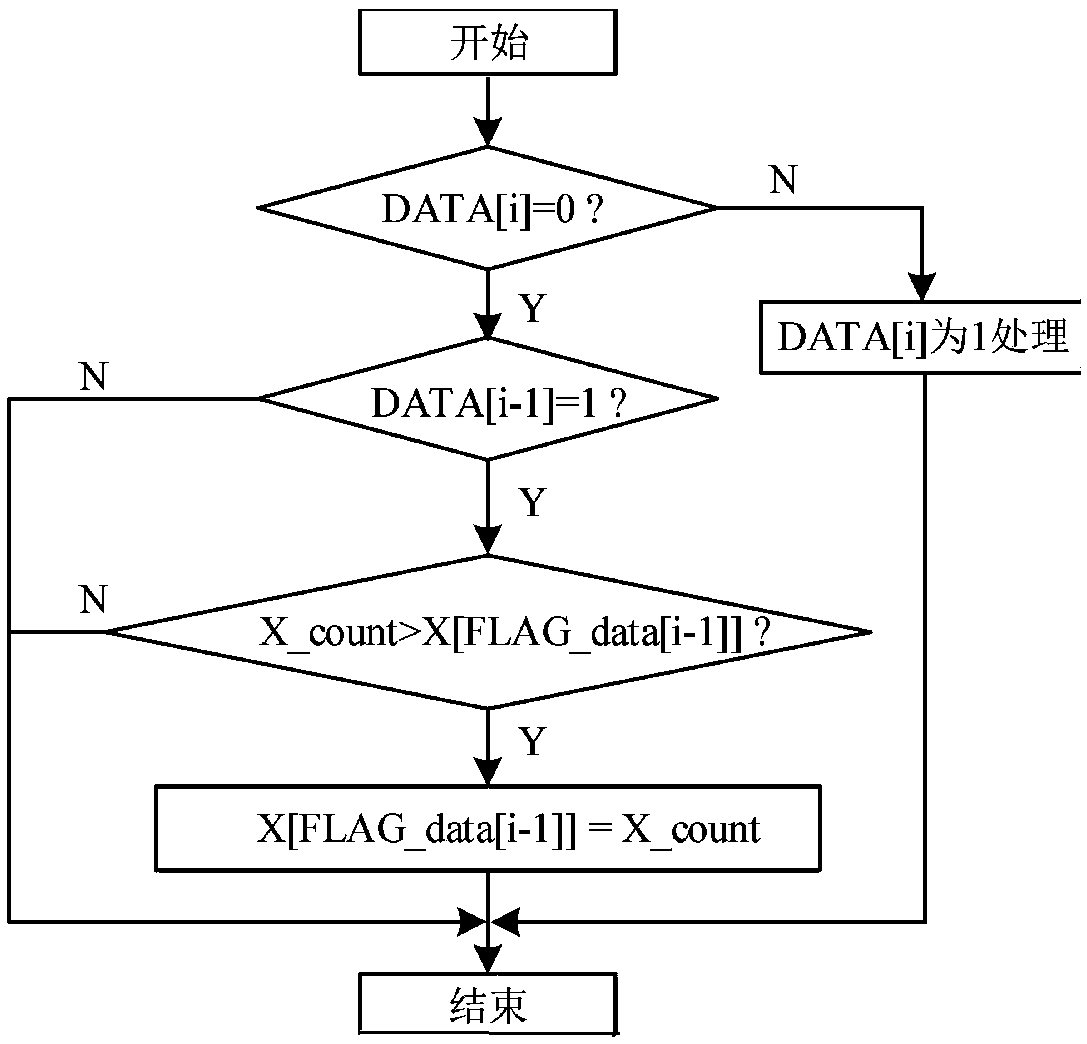
More on the Labeling Algorithm As stated in class, the Labeling Algorithm is an algorithm which will find a collection of flows in a given network which produces the largest possible value being sent from the source to the sink.
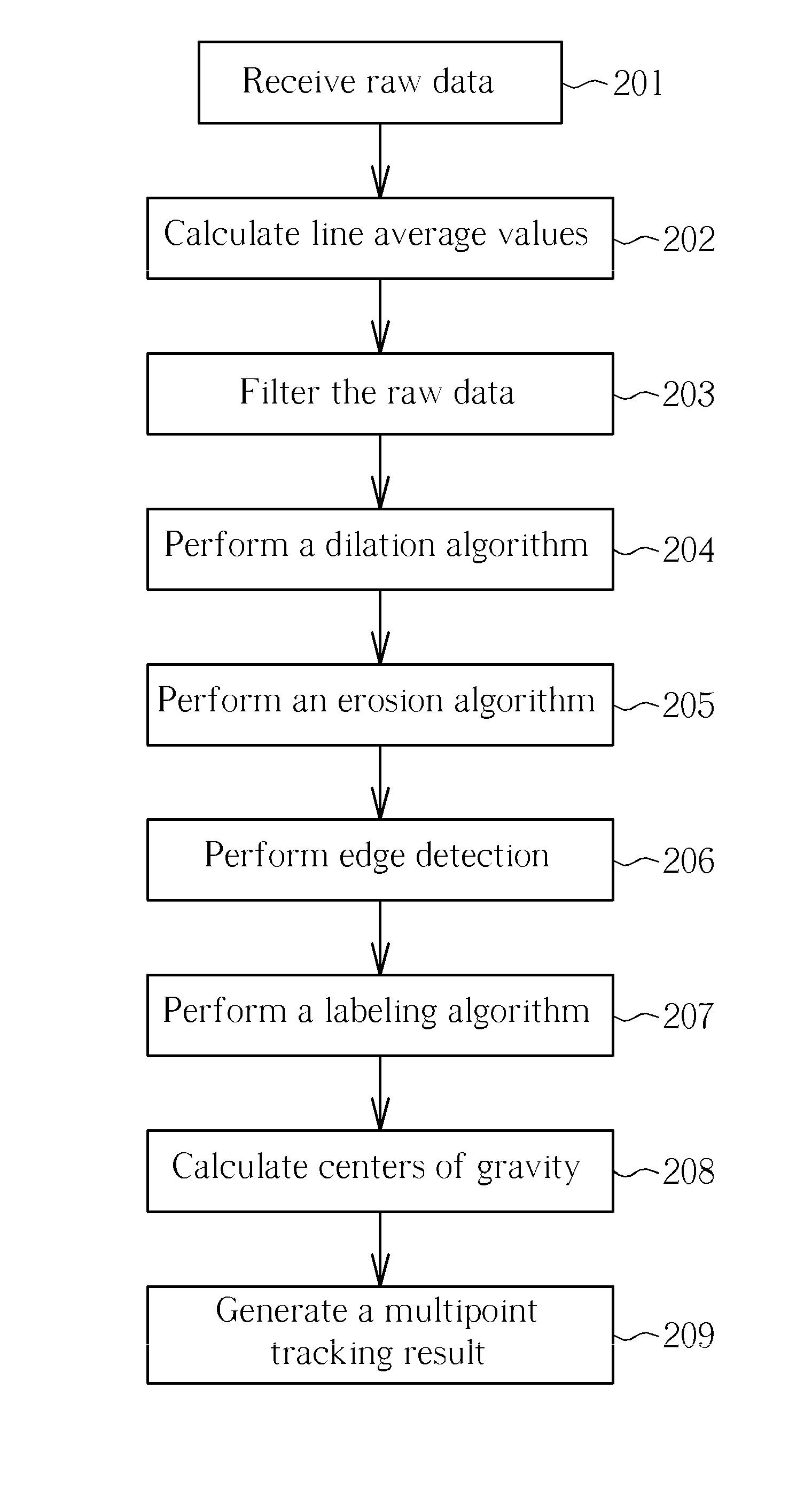
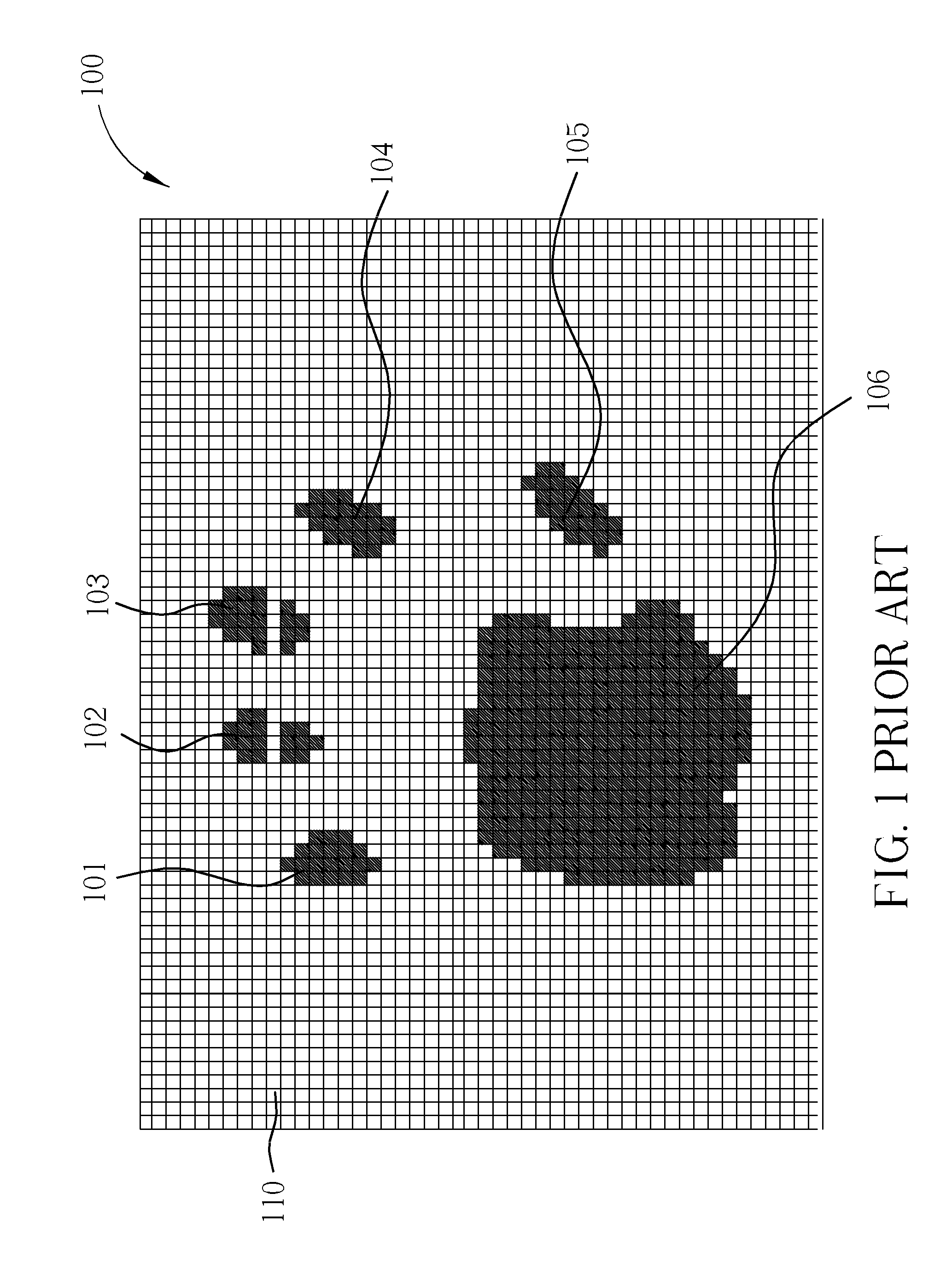
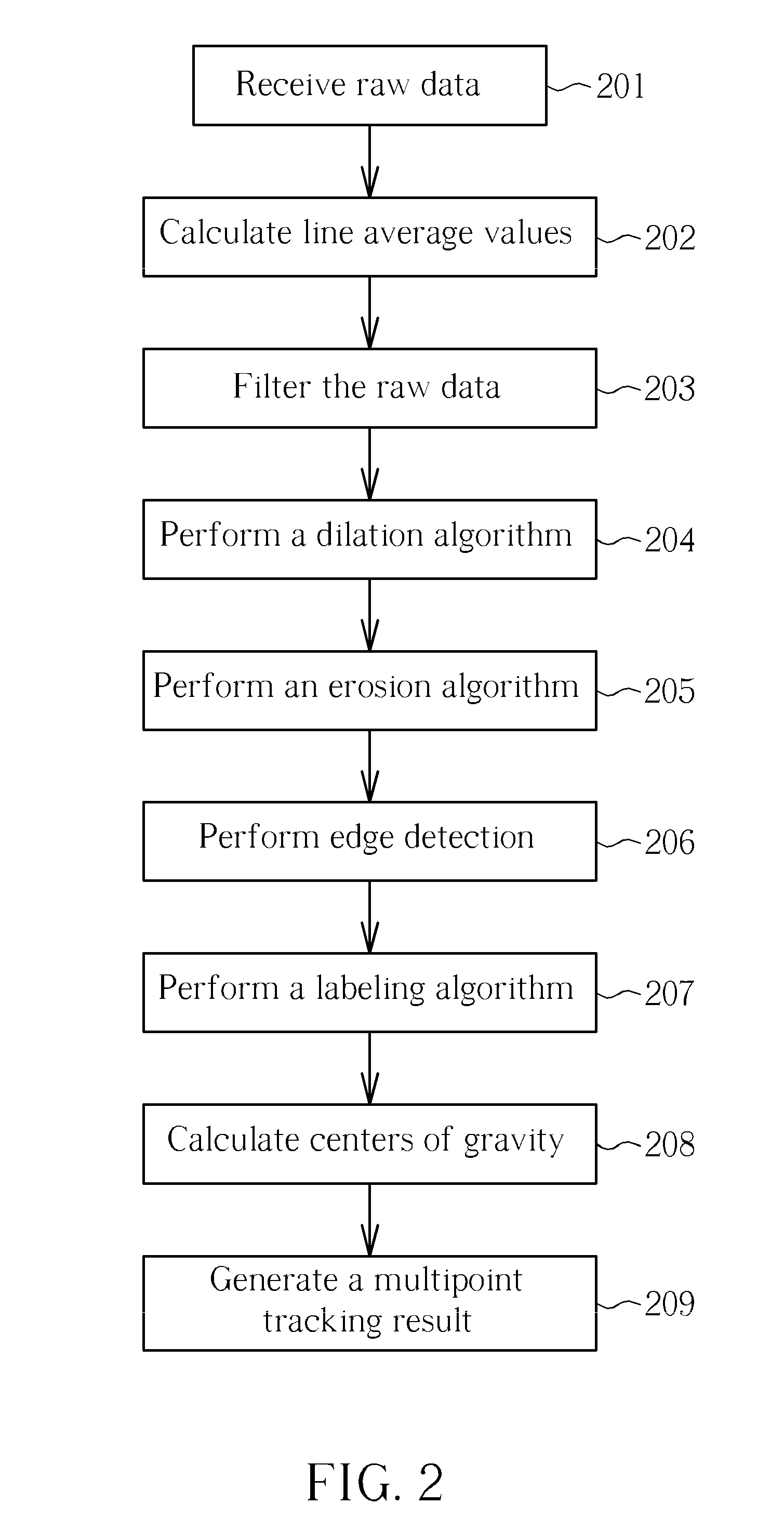
Multipoint tracking method and related device
Owner:OPTRONIC SCI LLC
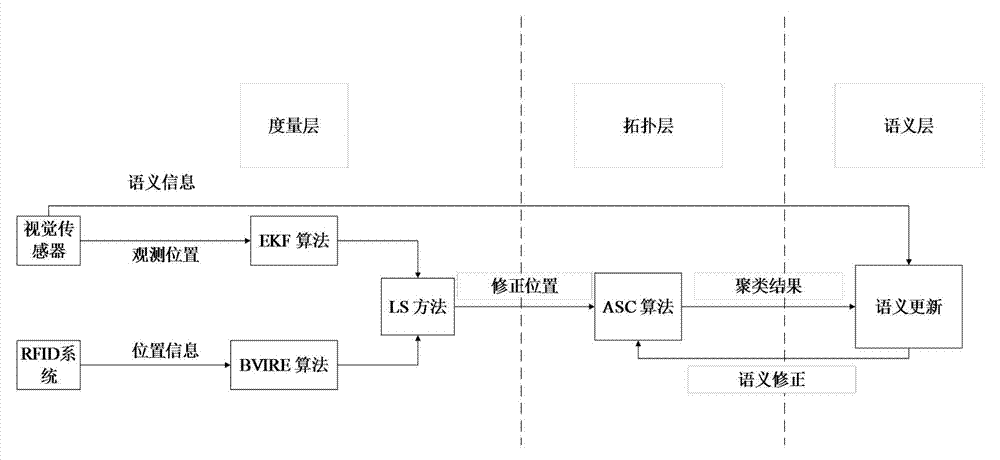
Robot distributed type representation intelligent semantic map establishment method
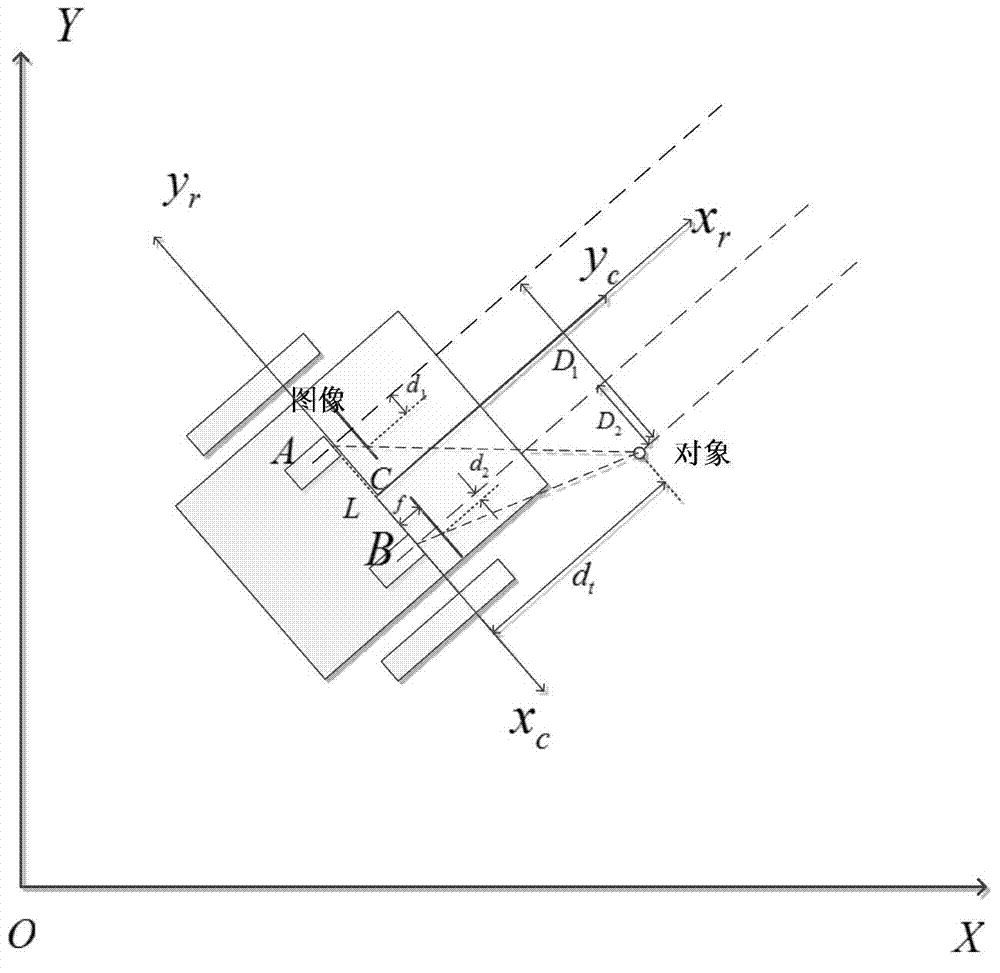
InactiveCN104330090AAddress limitationsHigh precisionInstruments for road network navigationVehicle position/course/altitude controlVisual positioningVisual perception
The invention discloses a robot distributed type representation intelligent semantic map establishment method which comprises the steps of firstly, traversing an indoor environment by a robot, and respectively positioning the robot and an artificial landmark with a quick identification code by a visual positioning method based on an extended kalman filtering algorithm and a radio frequency identification system based on a boundary virtual label algorithm, and constructing a measuring layer; then optimizing coordinates of a sampling point by a least square method, classifying positioning results by an adaptive spectral clustering method, and constructing a topological layer; and finally, updating the semantic property of a map according to QR code semantic information quickly identified by a camera, and constructing a semantic layer. When a state of an object in the indoor environment is detected, due to the adoption of the artificial landmark with a QR code, the efficiency of semantic map establishing is greatly improved, and the establishing difficulty is reduced; meanwhile, with the adoption of a method combining the QR code and an RFID technology, the precision of robot positioning and the map establishing reliability are improved.
Owner:BEIJING UNIV OF CHEM TECH
Wireless radio frequency positioning method based on virtual reference label algorithm
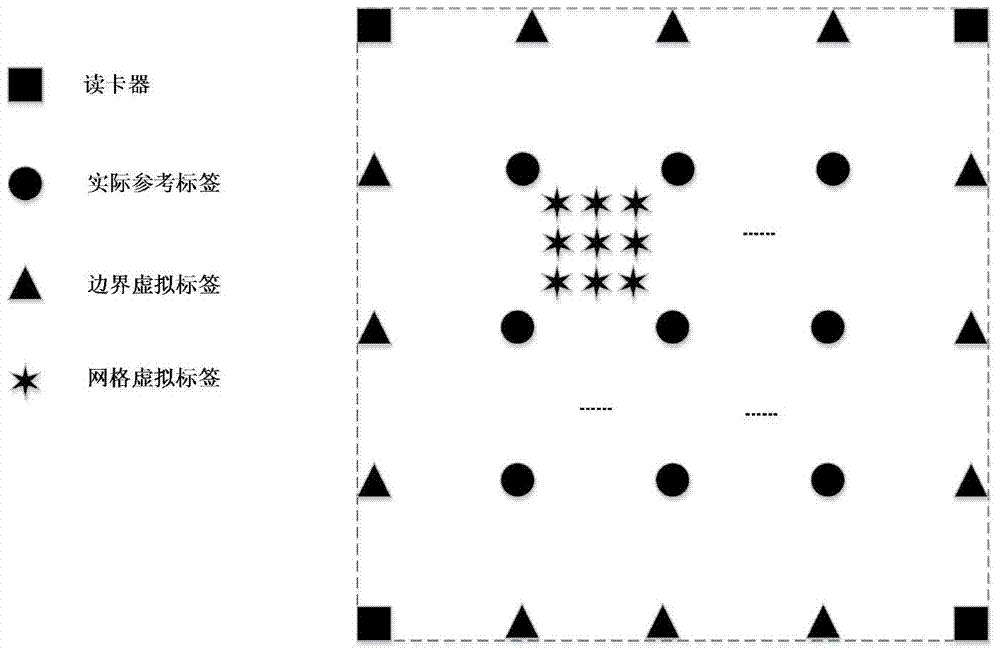
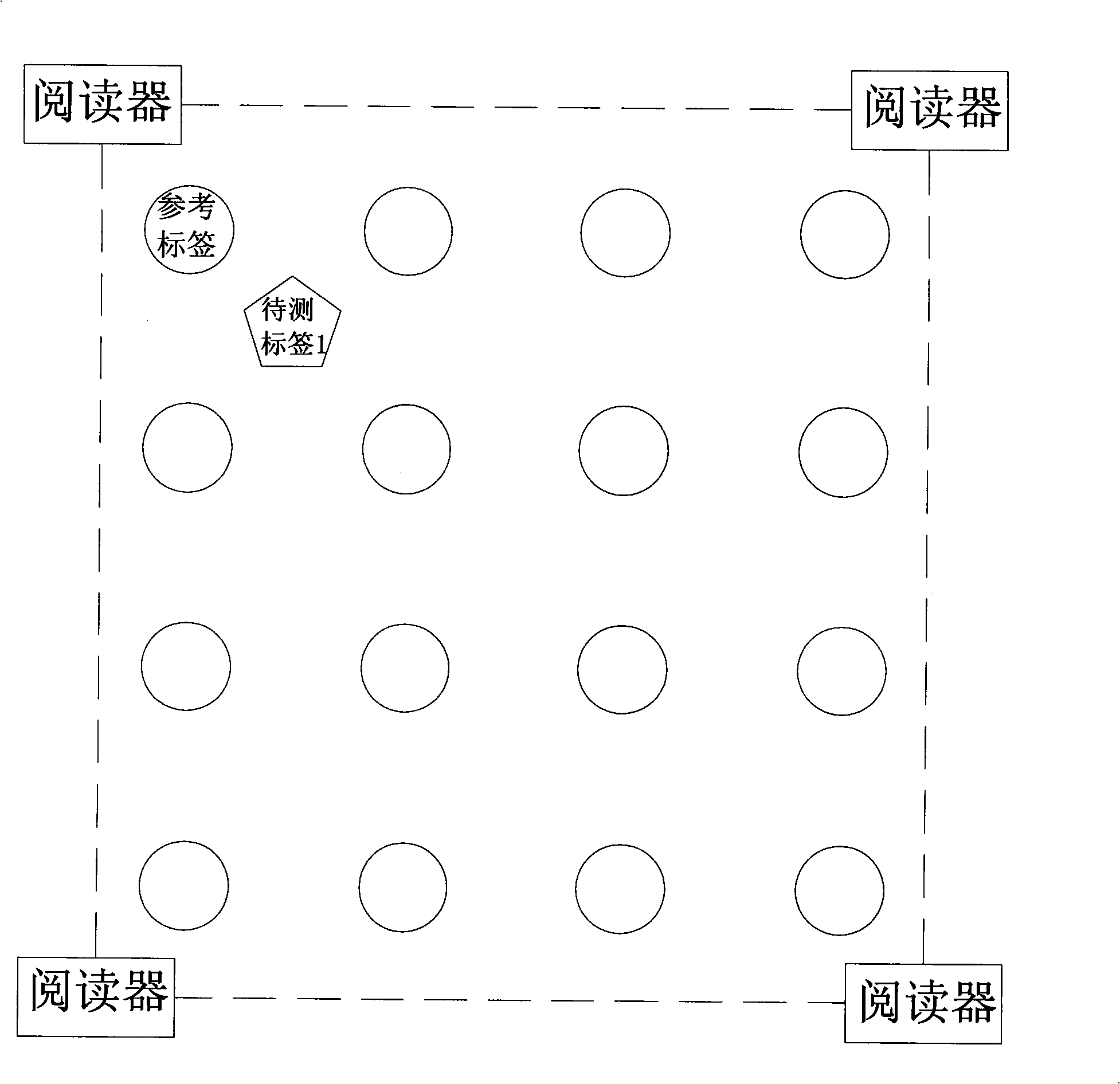
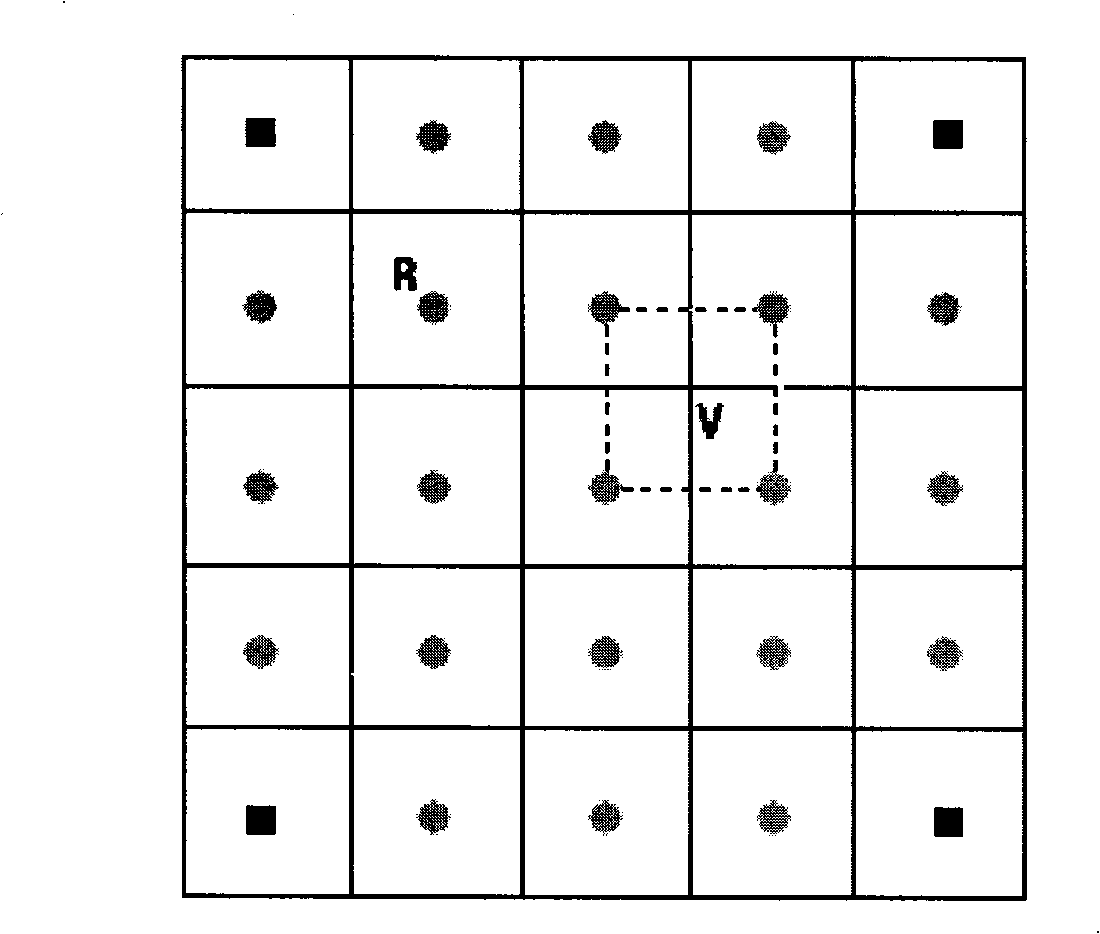
InactiveCN101349746AGood precisionAdapting to dynamicsPosition fixationSensing record carriersLabelling algorithmRadio frequency signal
A wireless radio frequency positioning method based on virtual reference label algorism comprises the steps of: arranging reader at the boundary of an object region, distributing the reference labels as a rectangular grid type in the indoor object region; arranging an object with a radio frequency label in the object region, using each reader to reach the radio frequency signal intensity of each reference label and object label to be transmitted to a host computer to be processed to attain the coordinates of the object. The invention is characterized in that the host computer builds a virtual reference label in calculation, uses the virtual reference label as substrate to induce the concept of similar map; the host computer preliminarily finds the positioning region of the object on the similar map corresponding to each reader; the similar maps are intersected to reduce the positioning region of the object; the residual weighting algorism between the possible positions and the position information of the virtual reference label are used to attain the position coordinate of the object. The method has the advantages of low power consumption and high positioning accuracy.
Owner:黄以华
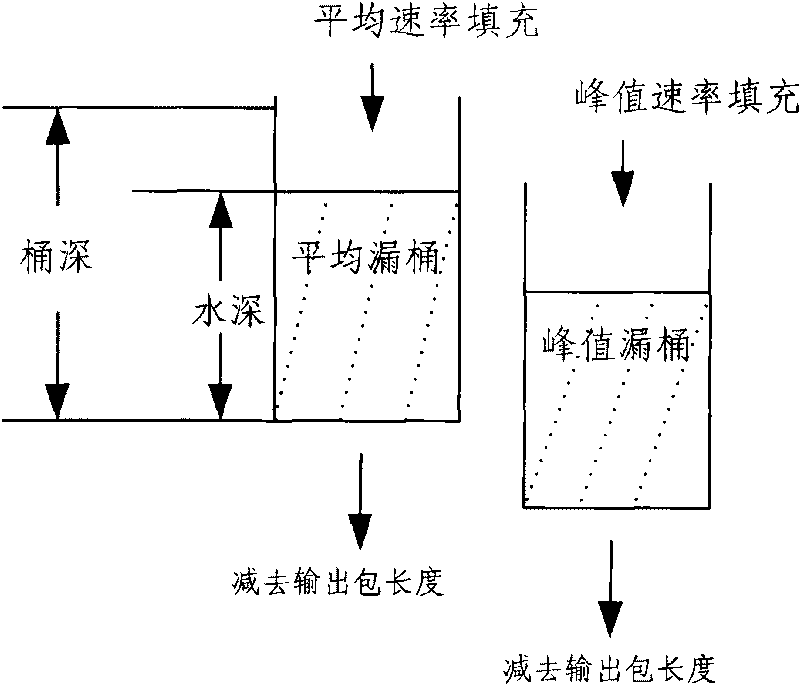
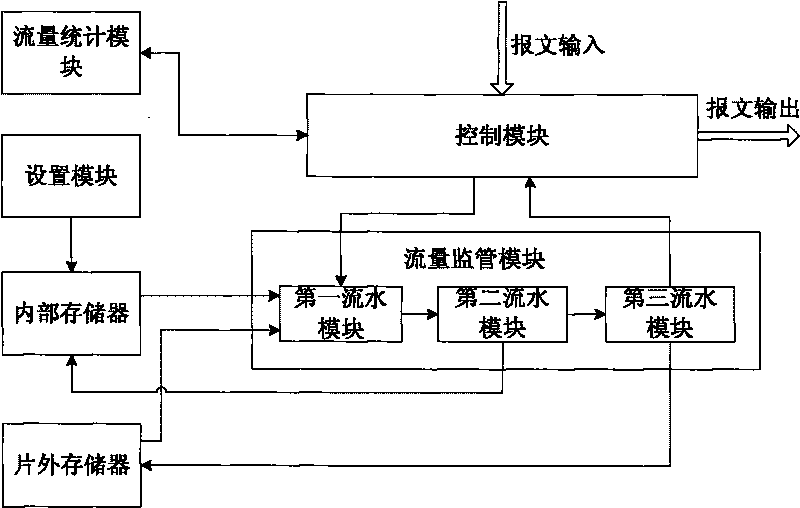
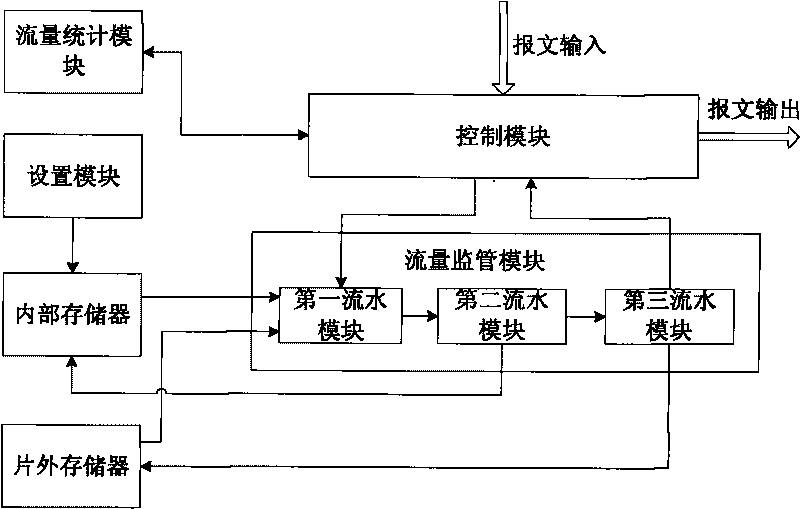
Method and device for supervising traffic based on token bucket
InactiveCN101741603AImprove compatibilityBreak through the bottleneck of processing powerData switching networksTraffic capacityLabelling algorithm
The invention discloses a method and a device for supervising traffic based on a token bucket. The device comprises a setting module, a memory, a control module and a traffic supervising module. The corresponding method comprises the following steps that: 1) setting different leaky bucket algorithm rules, and establishing a mapping relationship table between stream IDs and the leaky bucket algorithm rules; and 2) acquiring a message to be supervised; searching for the corresponding leaky bucket algorithm rule and a leaky bucket parameter by using a stream ID as an index; accordingly determining the number of available tokens in the current average leaky bucket and the peak leaky bucket; comparing the length of the message with the number of the available tokens in the current average leaky bucket and the peak leaky bucket respectively; coloring the message by adopting a corresponding leaky bucket algorithm rule and according to the comparison result; updating and storing the leaky bucket parameter serving as a standby parameter for processing the next stage of message with the same stream ID; and then discarding or forwarding the message according to the coloring result. The method and the device simultaneously support a single-rate marker algorithm and a double-rate marker algorithm, have excellent compatibility, break through the bottle neck of processing capacity and have high processing rate.
Owner:ZTE CORP
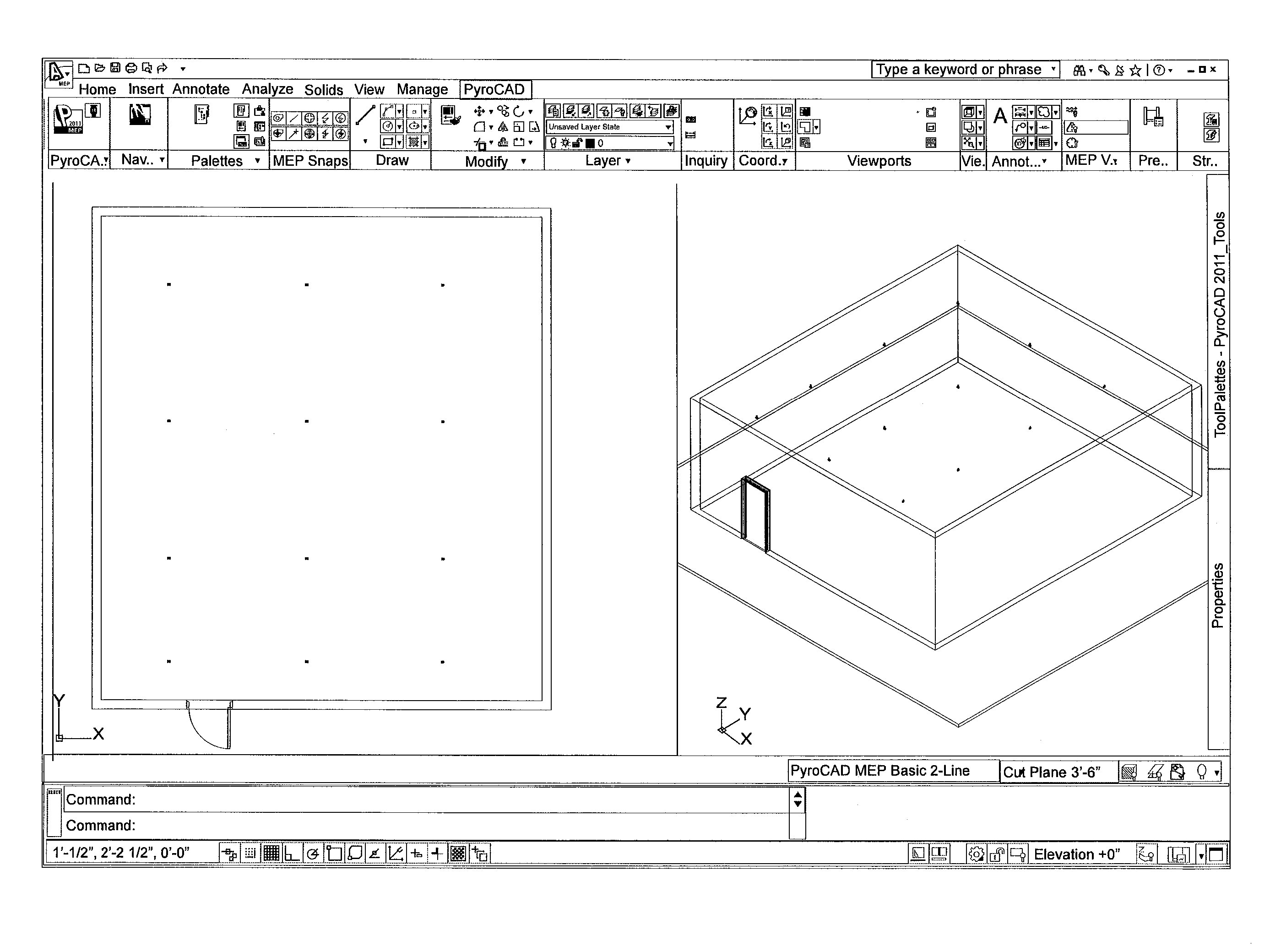
Computer-implemented system and method for designing a fire protection system
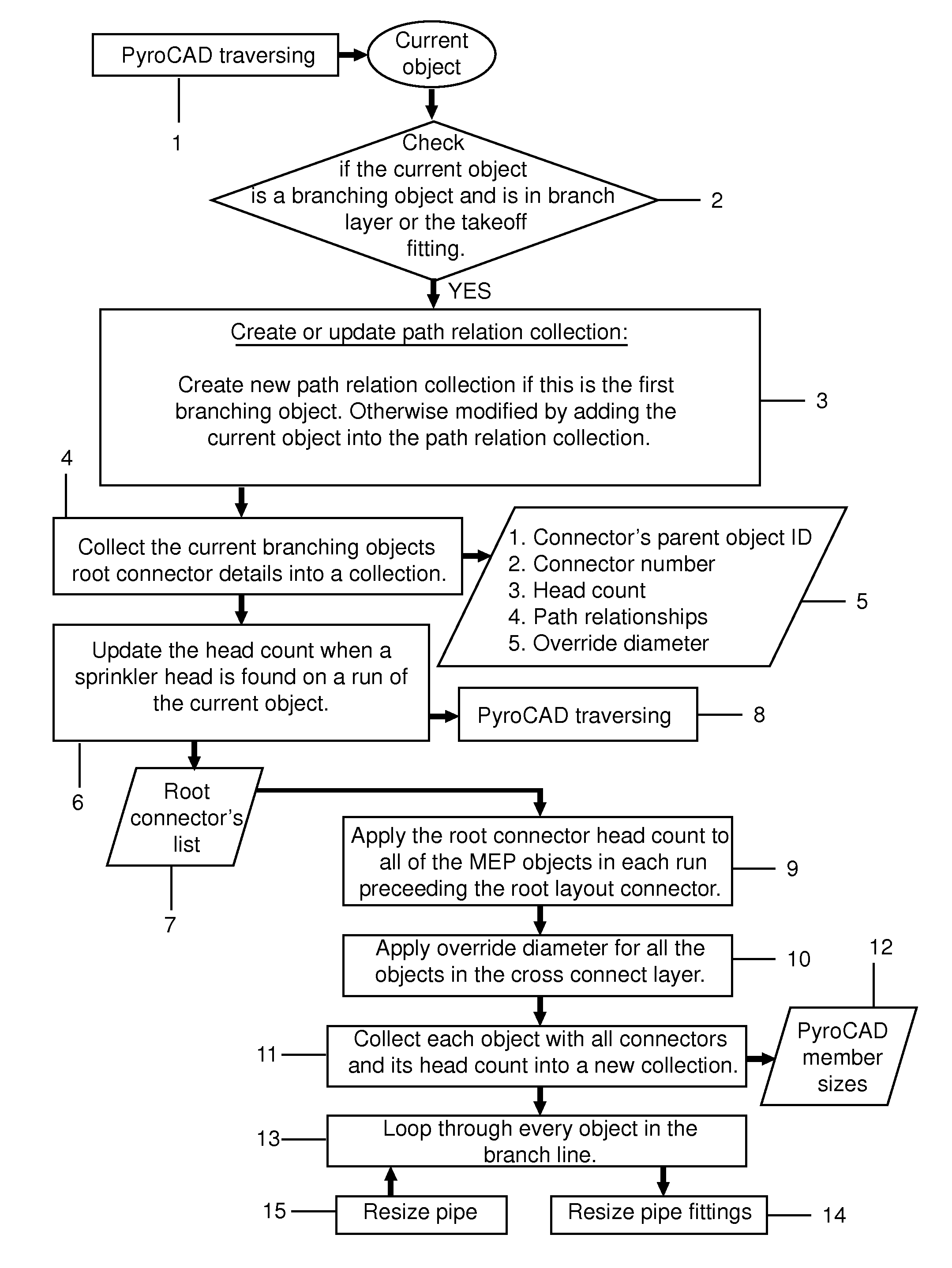
ActiveUS8874413B2Geometric CADComputation using non-denominational number representationError checkingData validation
A computer-implemented system for designing a fire protection and / or piping system comprising a personal computer for loading programs into dynamic memory and storing data on a static memory device, means for providing user input, and program files comprising a process algorithm, traversing algorithm, and tagging algorithm. The process algorithm performs data validation, error checking and error resolution, saves data to a start point inserted by a user, pulls layer details into programming variables, applies processing logic to the system, and comprises a main pipes algorithm and a branch resizing algorithm. The traversing algorithm travels the system and presents objects to the process, main pipes and branch resizing algorithms in a logical order. The tagging algorithm attaches to each pipe in the system a tag with property set data pulled into and displayed in the tag. A method of using the foregoing system to design a fire protection and / or piping system.
Owner:RAEL AUTOMATIC SPRINKLER COMPANY
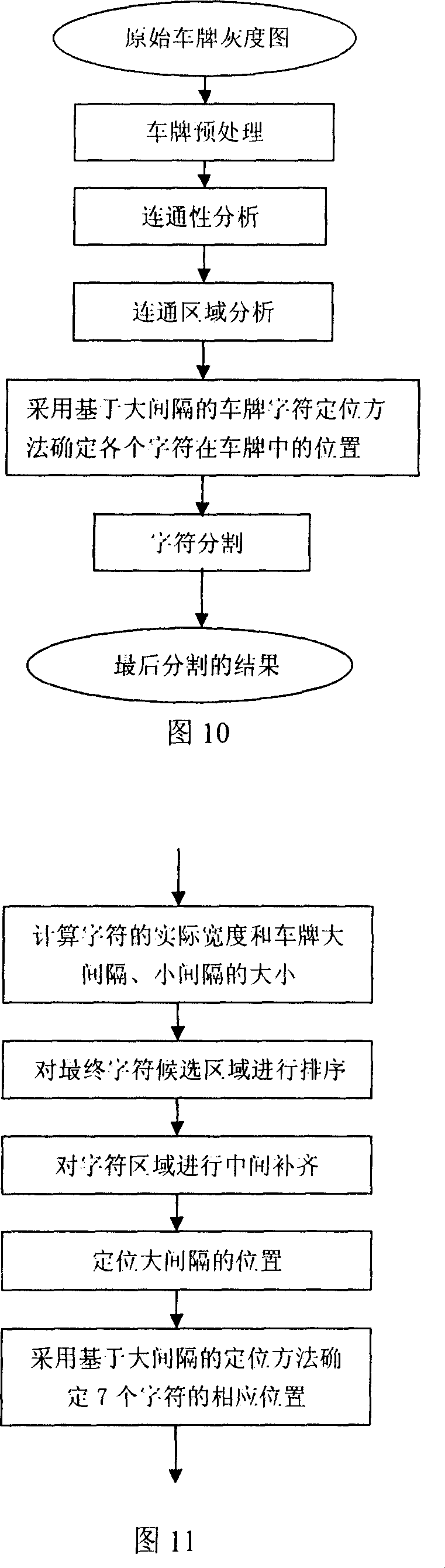
License plate character segmentation method based on fast area labeling algorithm and license plate large-spacing locating method
InactiveCN101154271AEnhanced meanEnhanced standard deviationCharacter and pattern recognitionPattern recognitionImaging processing
A license plate character partitioning method based on a quick region labeling algorithm and a license plate master space location method belongs to the image processing technical field and relates to a license plate automatic recognition technique. Firstly the license plate region is converted through grey level histogram and grey level stretching conversion to realize reinforcement of the character region on the license plate; secondly a two-valued threshold value is calculated and the license plate grey level image is converted into a two-valued image; thirdly a connectivity analysis of the license plate two-valued image is carried out according to the quick region labeling algorithm and an alternate region of characters is obtain through a region growing method; fourthly a master space location is fixed from the license plate two-valued image; fifthly the final character region is obtained through mending and making up for the character region based on the feature of the license plate master space location; finally the characters are partitioned from the license plate grey level image. The license plate character partitioning method based on the quick region labeling algorithm and the license plate master space location method provided by the invention can effectively improve performances such as systematic versatility and location accuracy.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA ZHONGSHAN INST
Computer-implemented system and method for designing a fire protection system
A computer-implemented system for designing a fire protection and / or piping system comprising a personal computer for loading programs into dynamic memory and storing data on a static memory device, means for providing user input, and program files comprising a process algorithm, traversing algorithm, and tagging algorithm. The process algorithm performs data validation, error checking and error resolution, saves data to a start point inserted by a user, pulls layer details into programming variables, applies processing logic to the system, and comprises a main pipes algorithm and a branch resizing algorithm. The traversing algorithm travels the system and presents objects to the process, main pipes and branch resizing algorithms in a logical order. The tagging algorithm attaches to each pipe in the system a tag with property set data pulled into and displayed in the tag. A method of using the foregoing system to design a fire protection and / or piping system.
Owner:RAEL AUTOMATIC SPRINKLER COMPANY
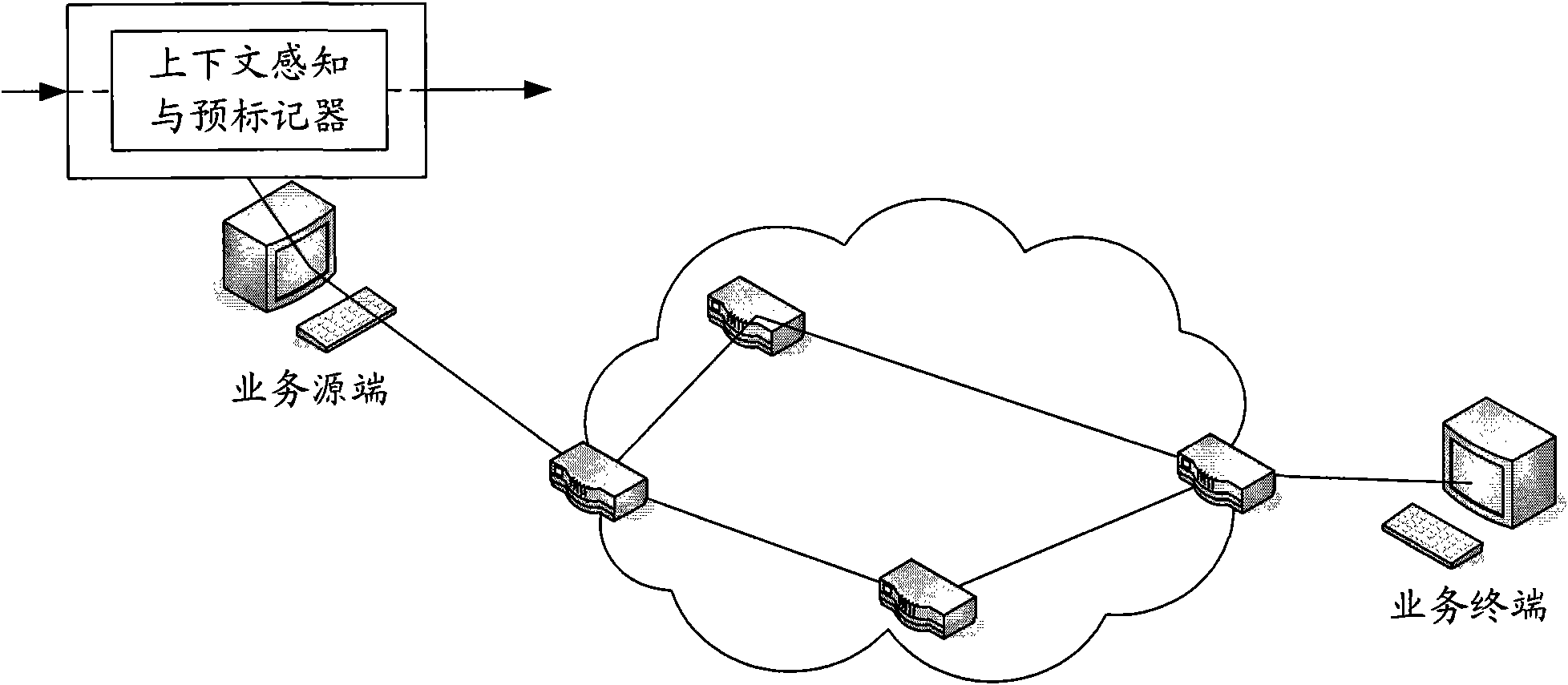
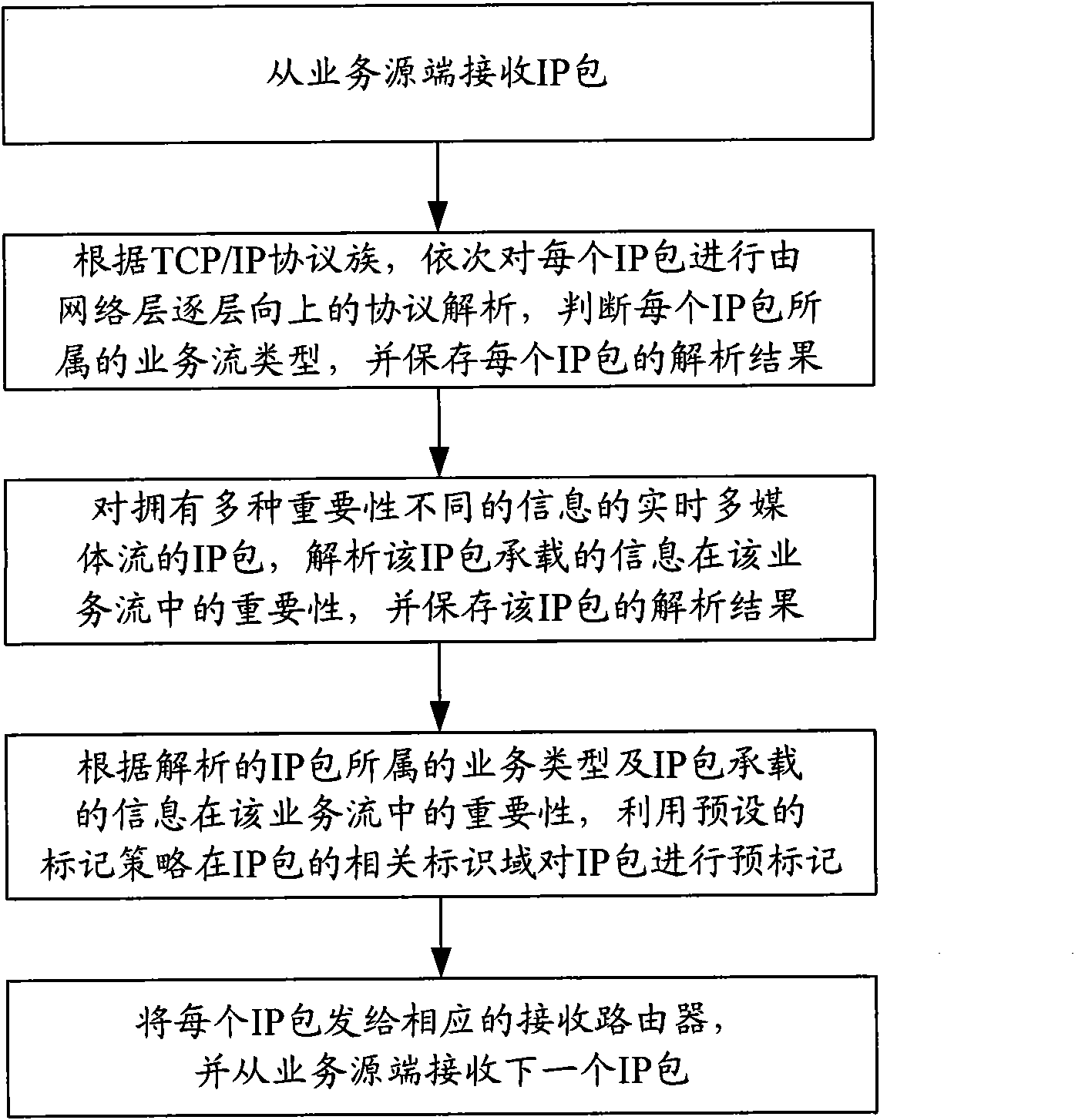
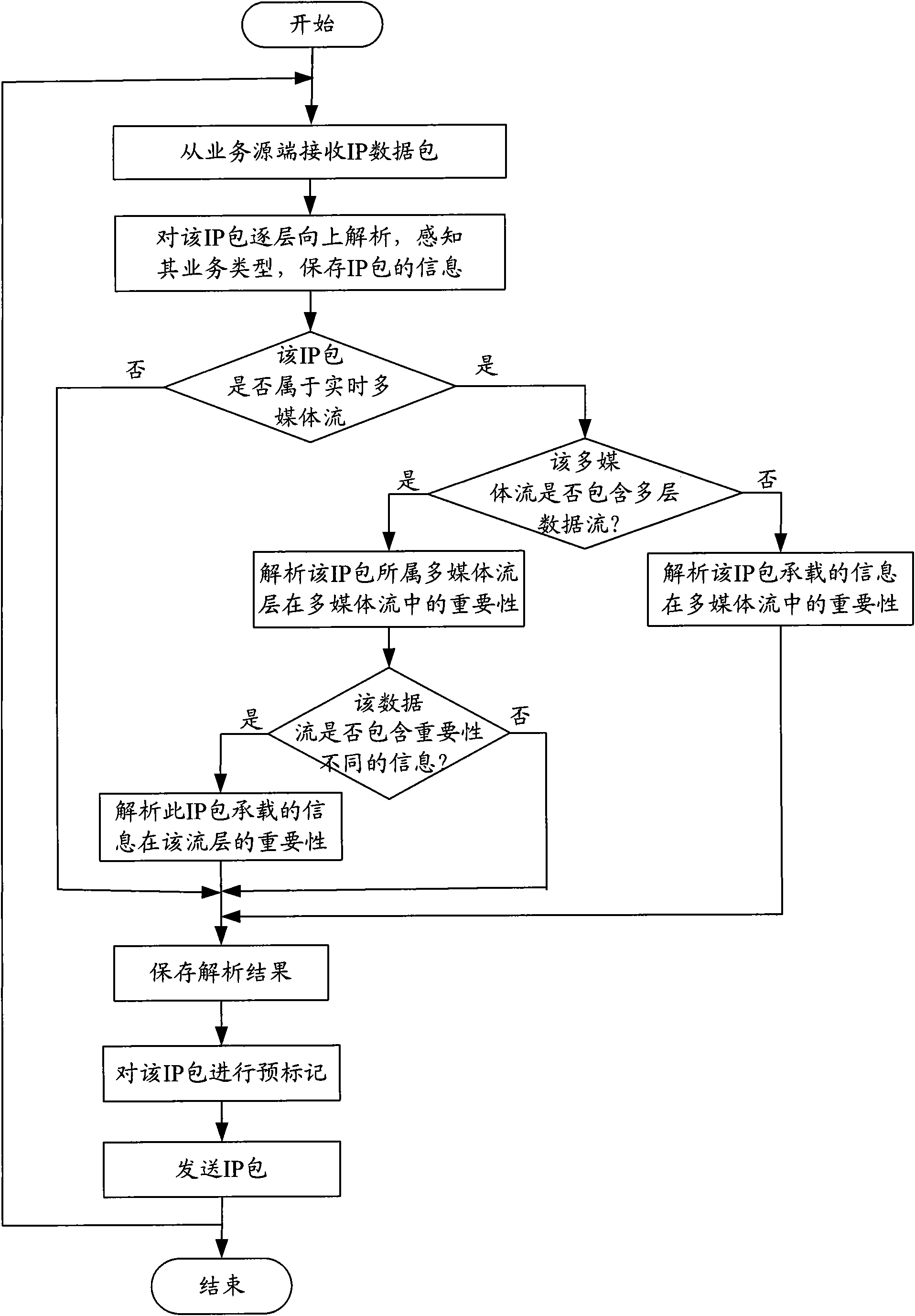
Real-time context perceiving and classification marking method of internet business flow
InactiveCN101610257AWatch itSmooth viewingData switching networksLabelling algorithmInternet business
The invention provides a real-time context perceiving and classification marking method of internet business flow, comprising the following steps: analyzing IP data packet received from a business resource terminal; perceiving business types thereof; dynamically perceiving importance of the each IP data packet in business stream for real-time multimedia stream; if the real-time multimedia stream is coded by the means of classification, not only perceiving importance level of the stream layer at which the IP packet is positioned, but also perceiving importance level of the IP packet in the stream layer; and according to an analyzing result and a preset IP packet marking strategy, previously marking correlative mark field of the IP packet. The method can be taken as foundation of marking algorithm for a traditional internet router or an autonomy network inlet edge router based on diffserv, to divide the IP packet with different importance into different QoS levels, minimize lose of high priority IP packet when the network blocks, heighten probability for successfully transmitting the IP packet for bearing important information, and provide effective QoS guarantee for a user.
Owner:BEIJING UNIV OF POSTS & TELECOMM
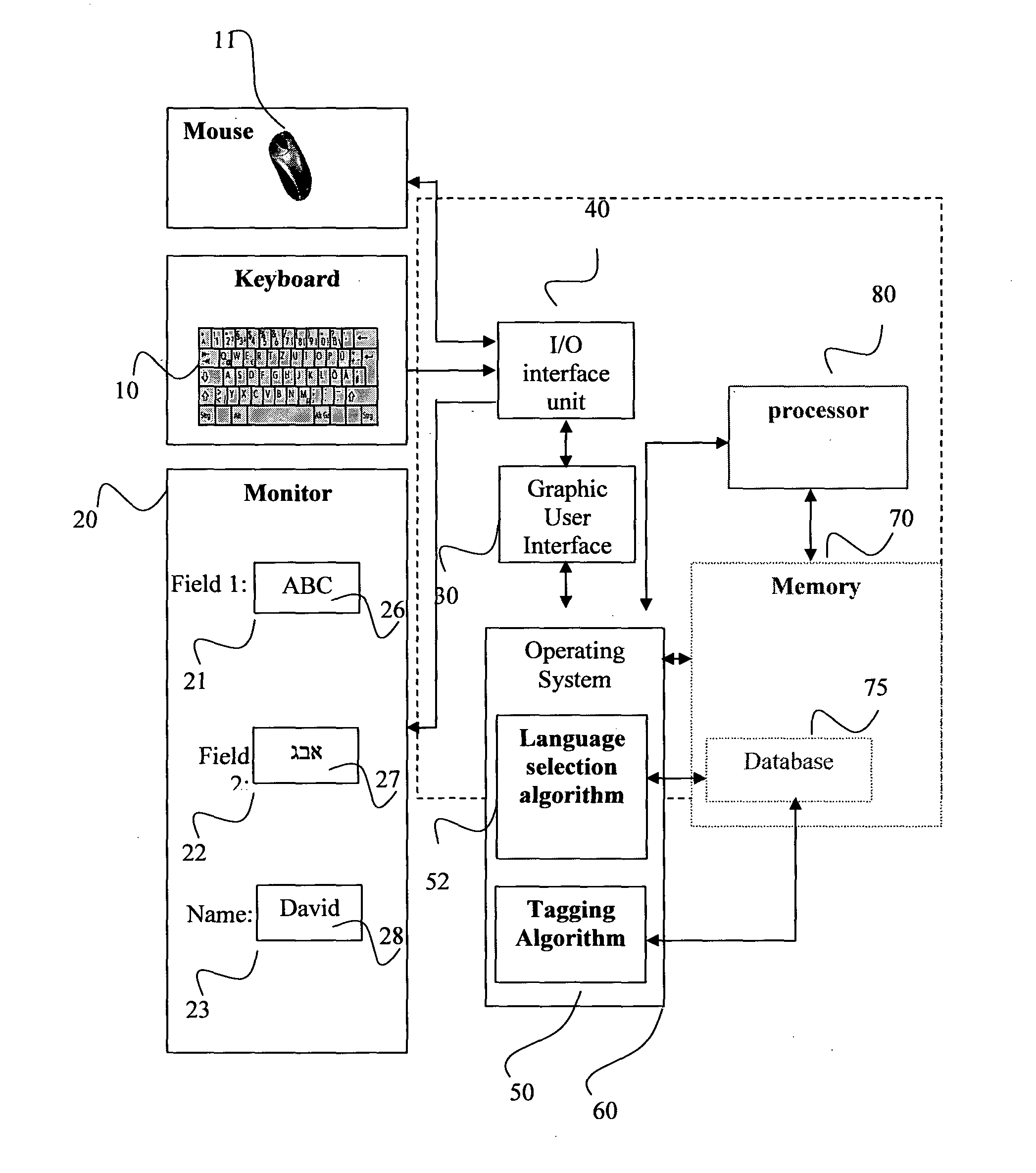
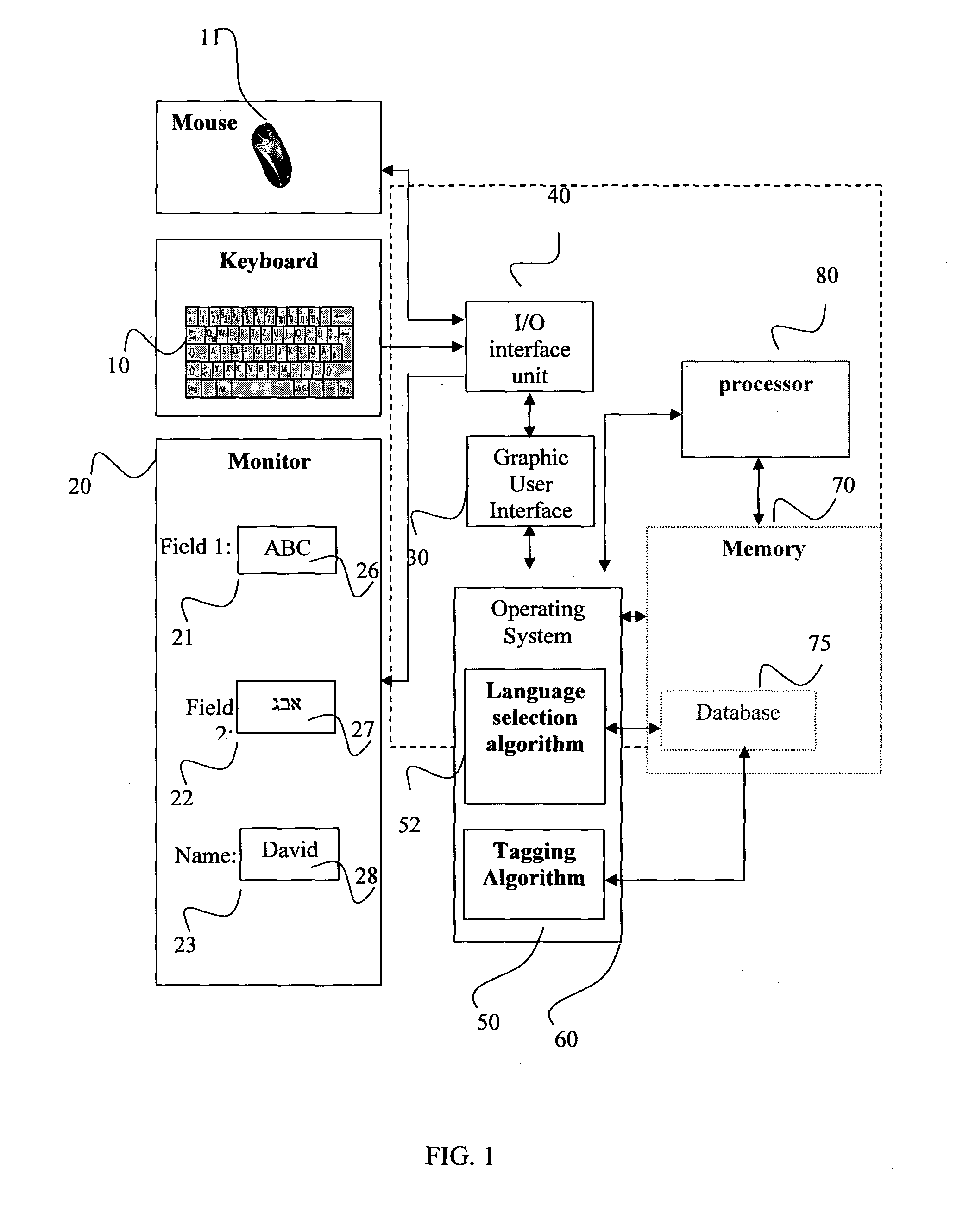
Content sensitive system and method for automatic input language selection
InactiveUS20120226490A1Natural language data processingSpecial data processing applicationsNatural language processingComputer users
The present invention discloses a computer system for providing an automatic selection of input language according to a content of the input text typed by a computer user. The system comprises a plurality of text input fields to receiving text characters by the input means; each the text input field is uniquely identified by Application / Document / Field triplet; a tagging algorithm for tagging each the input field with the default input language based on the data in the database related to the input field; and a language selection algorithm for automatic selection of typing language in the input field to the default input language of the input field. The default input language of each the input field is predetermined by the tagging algorithm according to the language properties of each the input field.
Owner:MASHIAH ELIYAHU
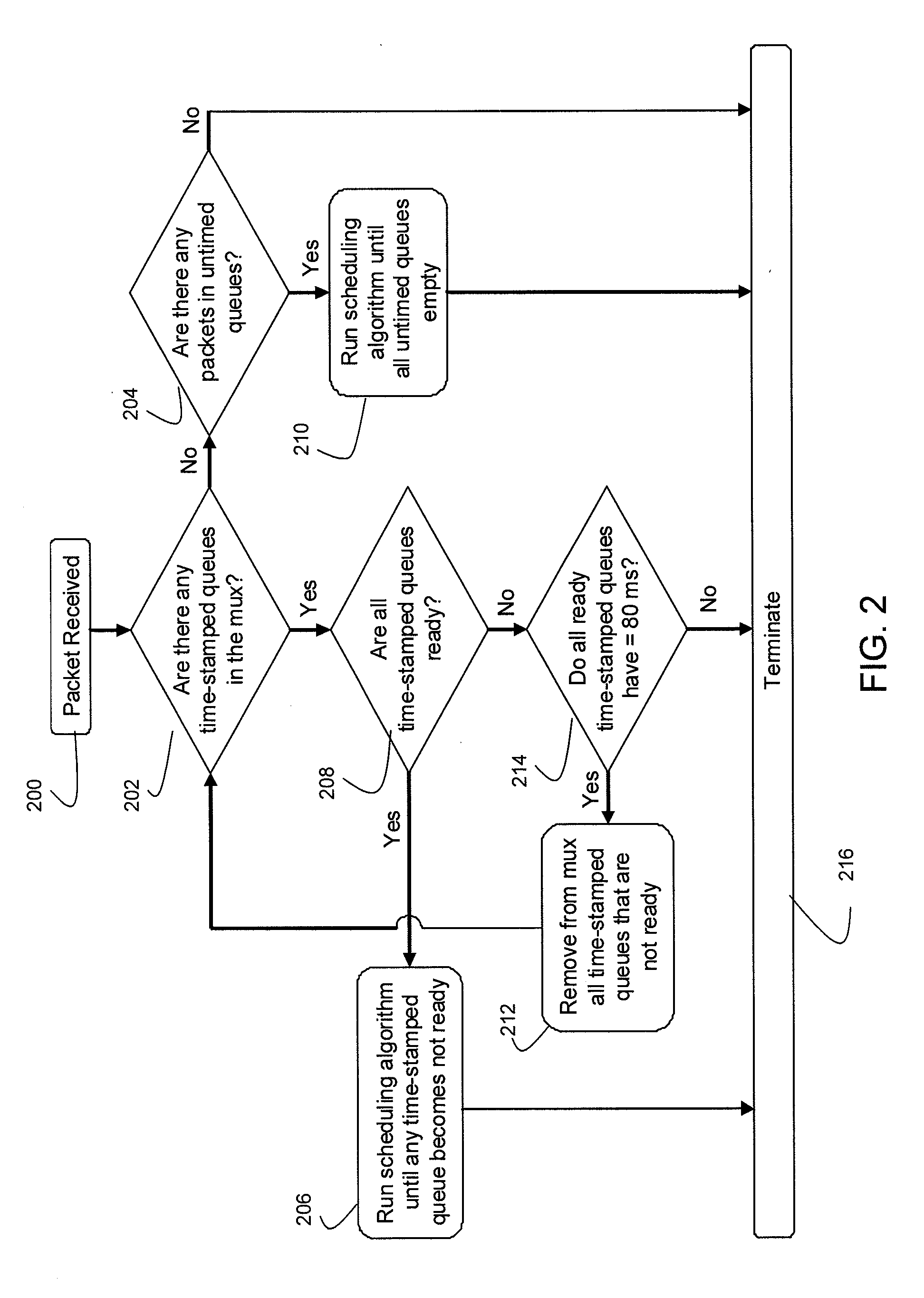
Systems and methods for mutiplexing MPEG services for IP networks
InactiveUS20100150182A1Time-division multiplexSelective content distributionTraffic capacityMultiplexer
A multiplexer handling different types of traffic in different queue types, including in one embodiment time-stamped content such as in the form of MPEG service data, untimed content such as in the form of other variable bit rate data, and periodic tables, such as in the form of MPEG program specific information, allocates a tag to each packet, which is used to schedule packets for transmission. A tagging algorithm tags each packet in the queue, and a packet scheduling algorithm uses the tag to determine which packet is next to be transmitted, and a control algorithm determines when the scheduling algorithm will be executed. The algorithms cooperate to allow the multiplexer to handle traffic without requiring an internal clock to be synchronized with the input streams, nor stuffing of packets to pad out the contents of the variable bit rate traffic.
Owner:ERICSSON TELEVISION
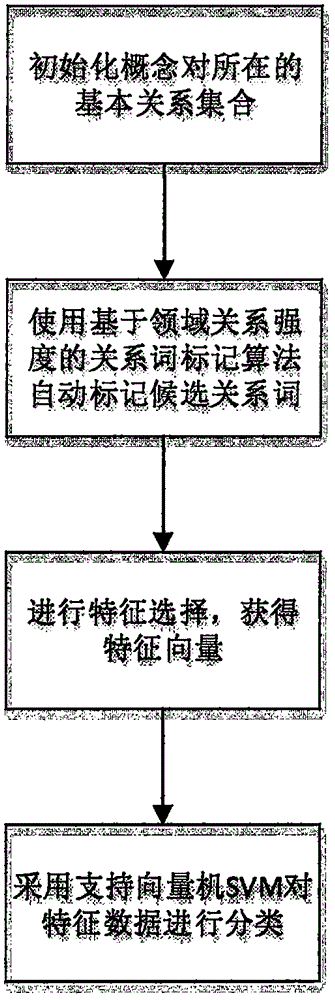
Method for extracting non-taxonomy relations between entities for Chinese patents
InactiveCN105678327AMeet the needs of practical applicationsSolve the problem that the instance structure is correct but the semantics are wrongCharacter and pattern recognitionNatural language data processingFeature vectorSupport vector machine
The invention relates to a method for extracting non-taxonomy relations between entities for Chinese patents. The method comprises following steps: S1): initializing basic relation sets of concept pairs; S2): automatically marking candidate relational words by use of a relational word marking algorithm based on domain relation intensity; S3): performing characteristic selection to obtain characteristic vectors; S4): performing classification to the characteristic data obtained in S3) by use of a support vector machine SVM. According to the invention, the extraction of non-taxonomy relations between entities for Chinese patents is defined as extraction of relations between entities which suit a SAO structure; a method of syntactic analysis characteristics and relational word dictionary characteristics in combination with traditional characteristics is brought forward, and a support vector machine is used for relation extraction so that the problem of right relation example structures with semantic errors in SAO structure relation extraction task is solved; the method is prior to traditional relation extraction method and can better satisfy practical application needs.
Owner:BEIJING INFORMATION SCI & TECH UNIV +1
Secondary encryption-based data validation and data recovery algorithm in cloud storage
The invention provides a secondary encryption-based data validation and data recovery algorithm in cloud storage. The algorithm comprises the steps of firstly carrying out first encryption after data segmentation, generating a hash value of a file by adopting an asymmetric encryption technology, utilizing the hash value of an original file as a secret key for secondary encryption of a random ciphertext data block and then utilizing the hash value as the secret key of a next ciphertext data block; and integrating data integrity and possession validation into a decryption operation of data access and then defining a data recovery label algorithm to generate a recovery label of the data for recovering original data. By adopting a secondary encryption technology, the overhead of computation and the complexity of validation are reduced by integrating data validation into a decryption process, and the data integrity and possession are validated in each access, so that the loss due to the fact that a user is misguided by wrong data is avoided. The memory space occupied by the recovery label is small and the recovery is simple and accurate.
Owner:SICHUAN YONGLIAN INFORMATION TECH CO LTD
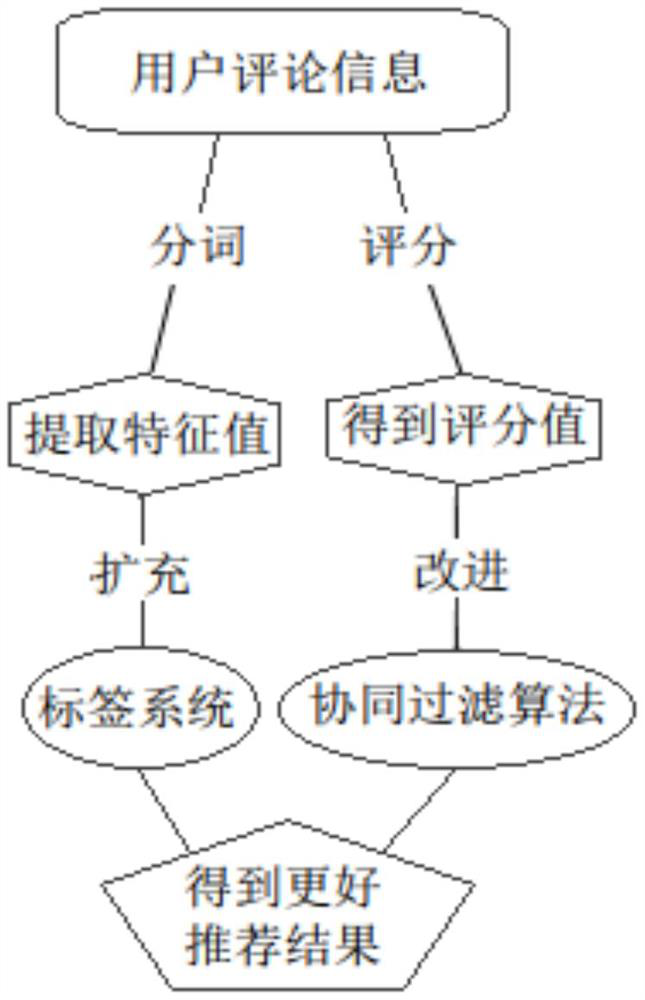
Label system accurate recommendation method based on user comment analysis
PendingCN112991017AImprove performanceImprove accuracySemantic analysisBuying/selling/leasing transactionsLabelling algorithmChinese word
The invention provides a label system accurate recommendation method based on user comment analysis. The interest model is constructed according to the user-commodity-label ternary relation, the accurate recommendation method more suitable for the label system is obtained, and in view of the problems that label information data of users in the label system generally has data sparseness and the user similarity calculated by using sparse data is low in accuracy, user comment data is creatively introduced, text analysis on user comment information is carried out, Chinese word segmentation and keyword extraction on the comment information are carried out, the extracted keywords are taken as pseudo tags, user labels are extracted, the label information data is expanded, the problem of label information data sparseness is solved, meanwhile, based on the fact that user comment information contains user preferences, value assignment calculation is conducted on emotion words in the comment information, the score value of a user for a commodity is obtained from user comments, the obtained score value information is used for further improving a label algorithm, and the accuracy of a recommendation result is improved.
Owner:刘秀萍
Method for delineation of tissue lesions
The present invention relates to a method for estimating a measure of a penumbra size of a penumbra in biological tissue wherein first and second images obtained respectively by perfusion weighted imaging (PWI) and diffusion weighted imaging (DWI) are analyzed, and wherein the analysis of the first image includes application of a level set method, and the analysis of the second image includes application of a grayscale morphological operation. In a further embodiment of the invention, a connected component labeling algorithm maybe applied on any one of the first and second image. The invention further relates to a system, a computer program product and use of a corresponding method.
Owner:AARHUS UNIV +1
Method for testing categorical data set
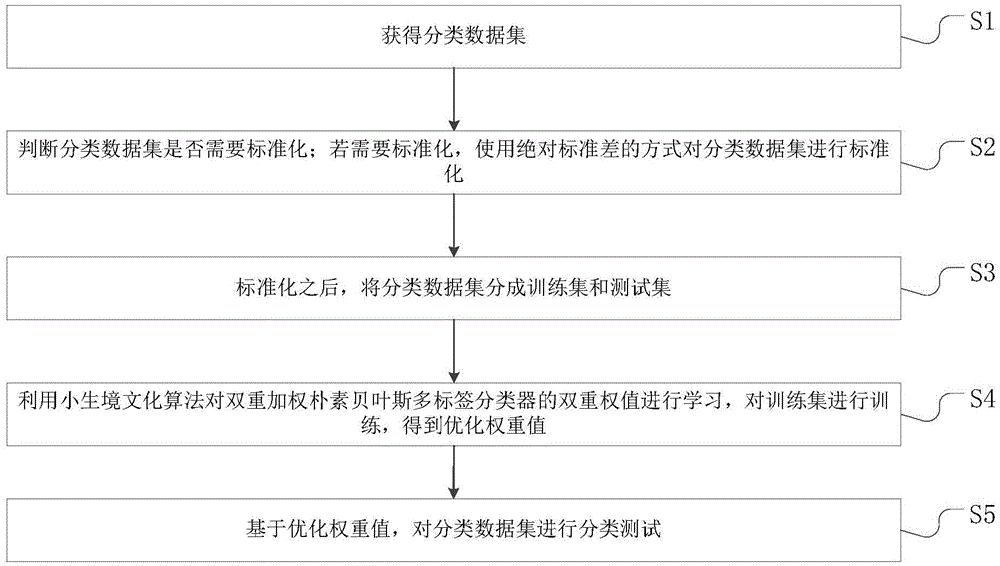
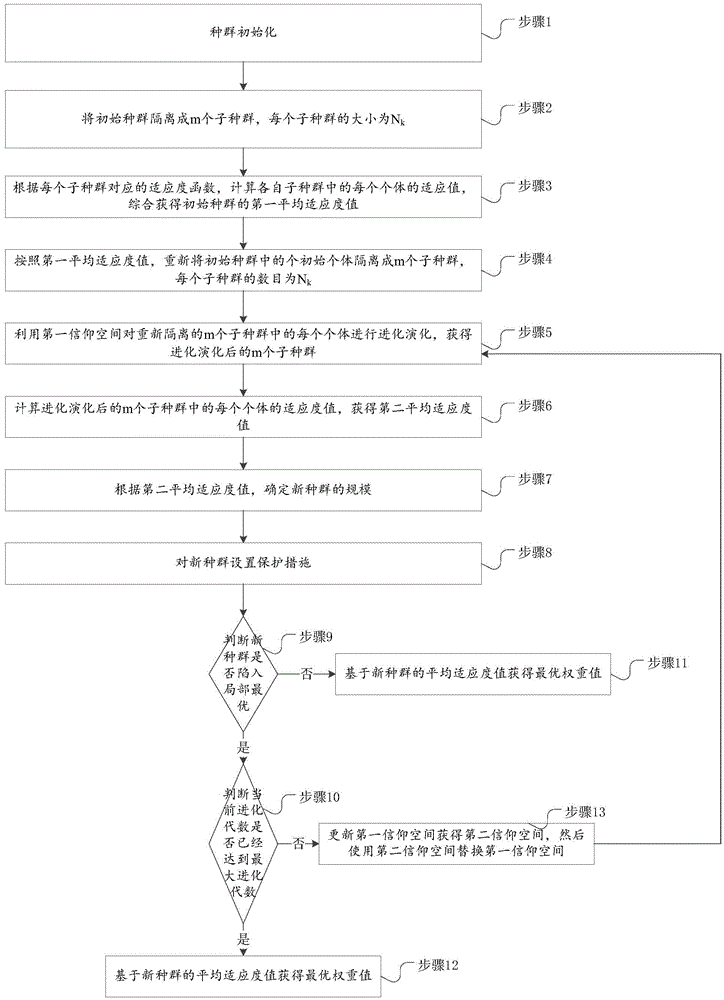
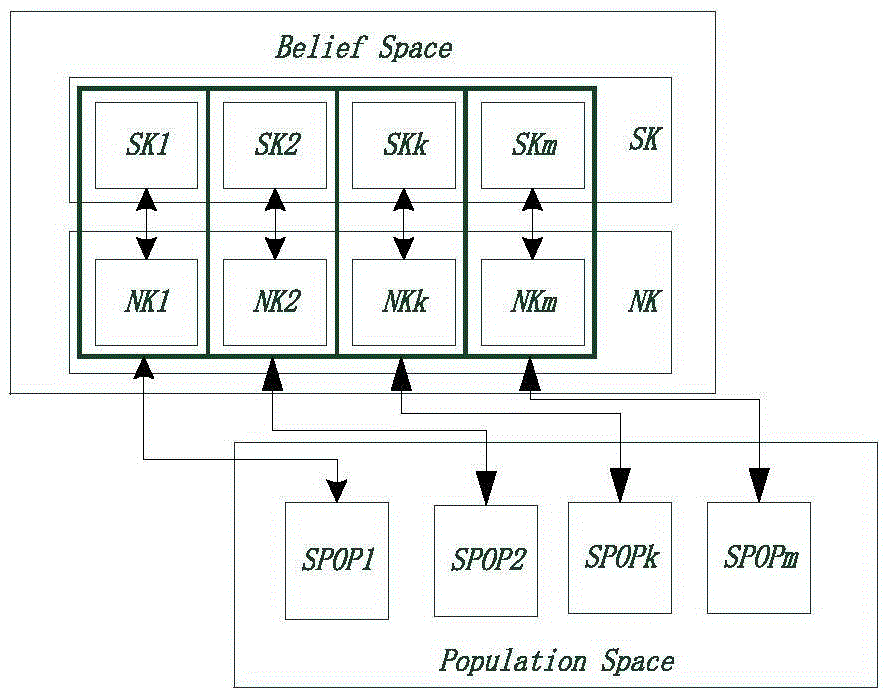
InactiveCN105095494AAccelerated trainingImprove accuracySpecial data processing applicationsData setMulti-label classification
The invention discloses a method for testing a categorical data set. The method includes the steps that after the categorical data set is obtained, if the categorical data set needs to be processed in a standardization mode, the categorical data set is standardized in an absolute standard deviation mode; the categorical data set is divided into a training set and a test set, an ecological niche cultural algorithm is used for learning to obtain dual weight values of a dual weighted naive Bayes multi-label classifier, and then the training set is trained to obtain optimized weight values; the optimized weight values are substituted into the test set for prediction. A data training process is added on the basis of a traditional naive Bayes multi-label algorithm, and then the categorical data set is predicted. As traditional data classification is improved through a particle swarm optimization algorithm, the improved algorithm can improve the classification accuracy.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
Relational database water mark embed and extraction method based on (t,n) threshold
InactiveCN101105832AChange instabilityImprove robustnessImage data processing detailsProgram/content distribution protectionRadix pointRelational database
The invention discloses a watermark embedding method of relational database based on (t, n) threshold, which sets the following parameters according to relational database: A watermark picture, a big prime number p in Lagrange interpolation polynomial, a user key in marker algorithm, t and n values in (t, n) threshold, and a data changing range len. The data changing range len is the tth after the radix point; the system makes value treatment on the watermark picture to obtain the value expression form bigint; the system completes the embedding of watermark via (t, n) threshold algorithm and Lagrange interpolation polynomial. The invention also provides the extracting method of the watermark. Therefore, the invention has the advantages of good robustness, stable watermark pictures, high calculation efficiency, and high practice.
Owner:ZHEJIANG UNIV OF TECH
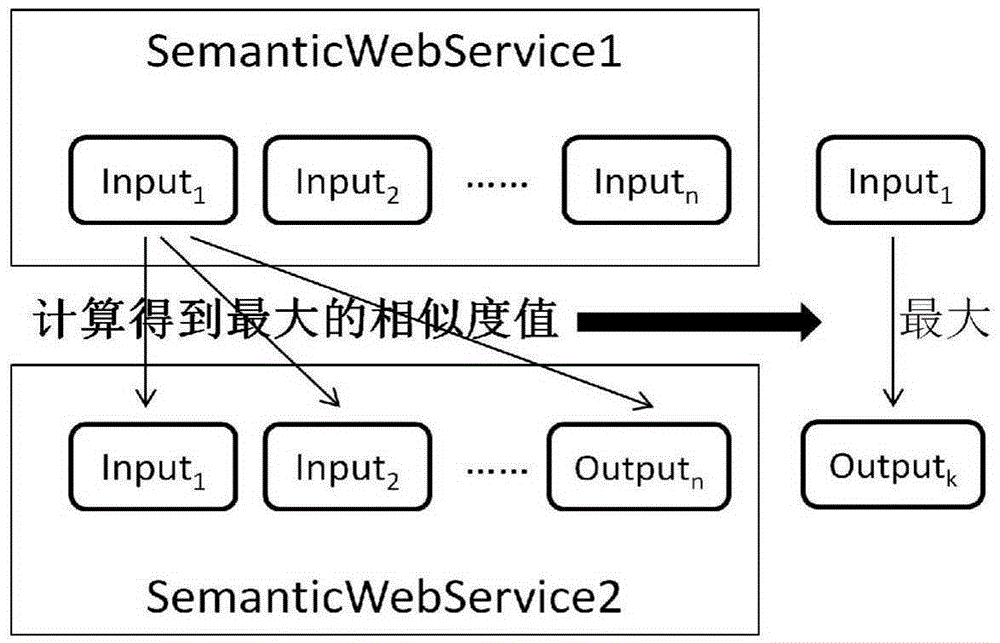
Similarity based semantic Web service clustering labeling method
ActiveCN105404619AImprove accuracyImprove performanceSpecial data processing applicationsSemantic web servicesLabelling algorithm
The invention discloses a similarity based semantic Web service clustering labeling method. The method is characterized by comprising two parts of realizing semantic Web service similarity calculation and realizing a semantic Web service clustering labeling algorithm. During the semantic Web service similarity calculation, in combination with results of input / output (I / O) parameter mixed similarity calculation and service description keyword similarity calculation, a calculation result of semantic Web service similarity is comprehensively obtained, and the difference and similarity between service functions are reflected; and I / O parameters can directly describe functions of corresponding service modules and serve as measurement standards for calculating the semantic Web service similarity from a functional perspective. According to the method, the accuracy of similarity calculation can be improved and the performance of a service discovery system is further improved.
Owner:SOUTH CHINA UNIV OF TECH
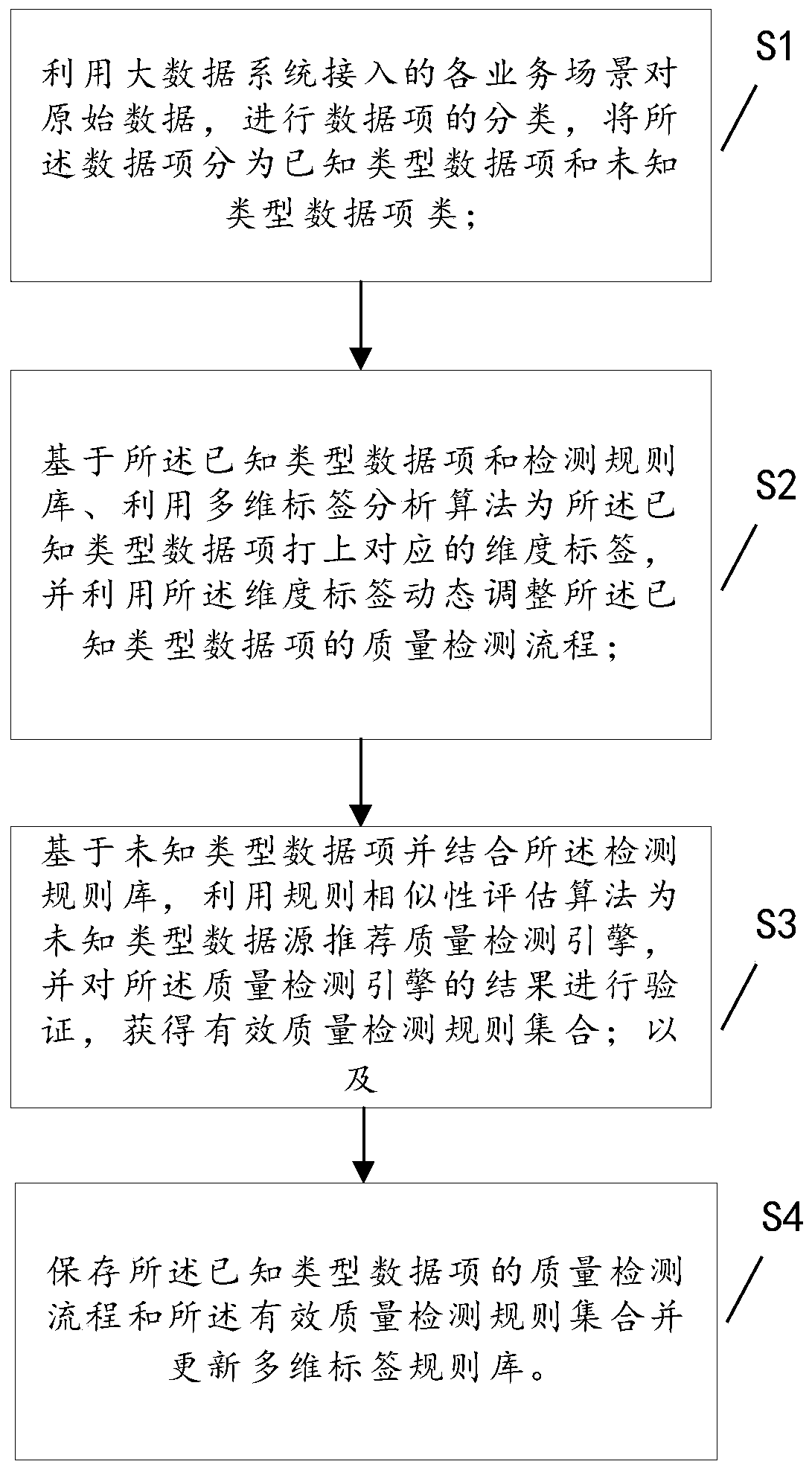
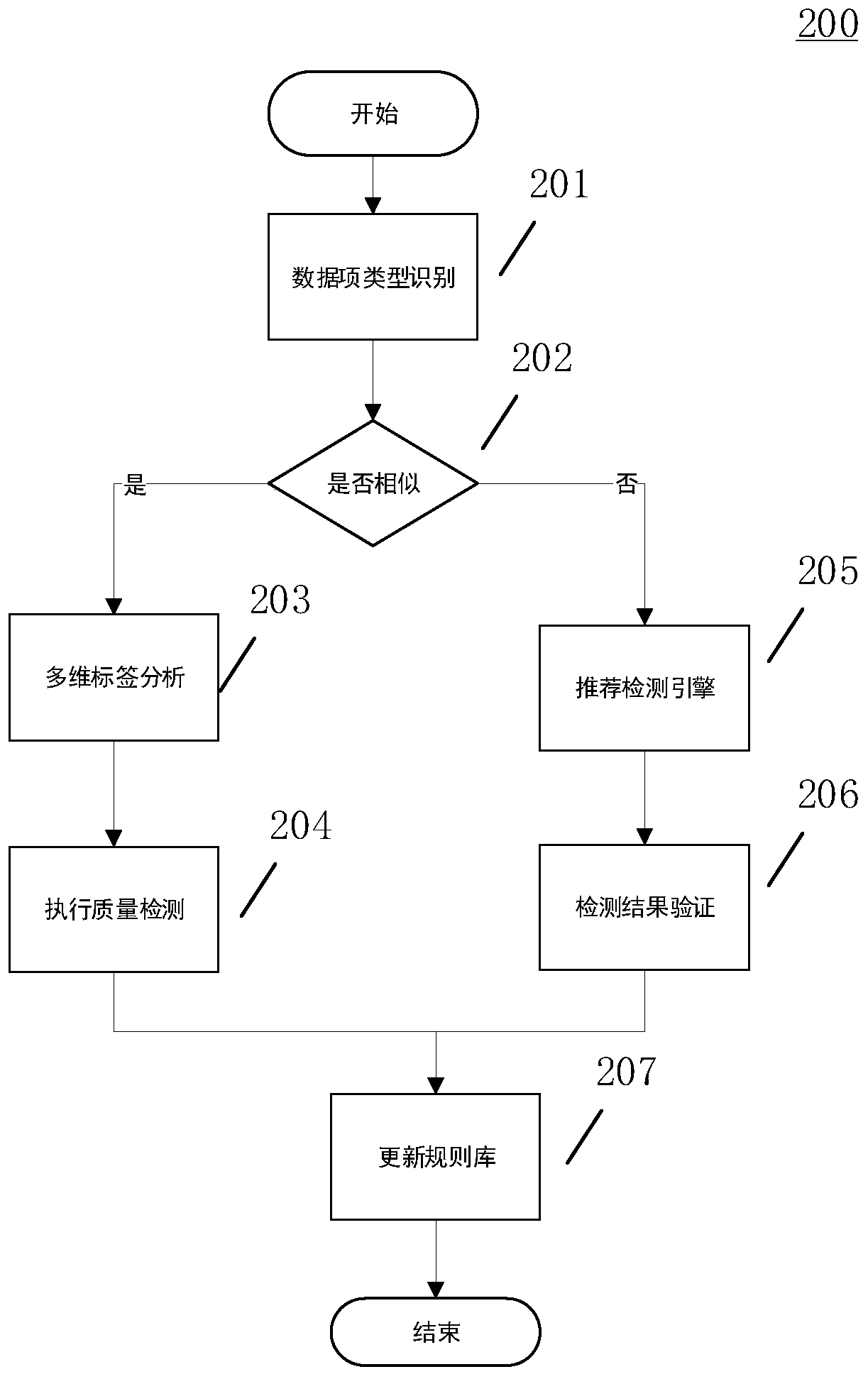
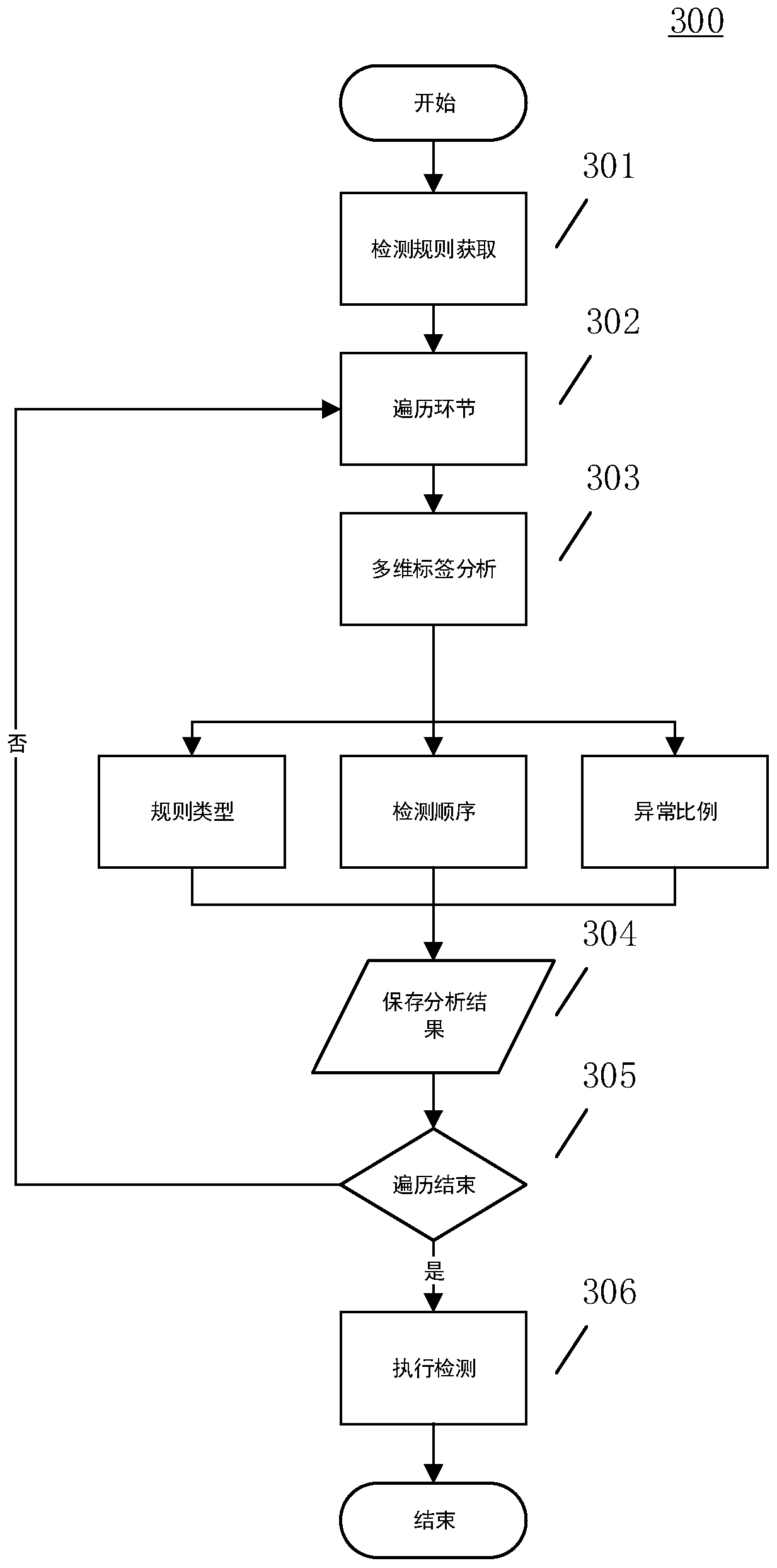
Data quality detection method and system based on multi-dimensional label
ActiveCN111563074AAvoid affecting storage operationsImprove timelinessMulti-dimensional databasesSpecial data processing applicationsLabelling algorithmData source
The invention discloses a data quality detection method and system based on a multi-dimensional label. Based on the known type data items and the detection rule base, a multi-dimensional label analysis algorithm is used for marking corresponding dimension labels on the known type data items, and the dimension labels are used for dynamically adjusting the quality detection process of the known typedata items; a quality detection engine is recommended for the unknown type data source by using a rule similarity evaluation algorithm based on the unknown type data item and in combination with a detection rule base, and a result of the quality detection engine is verified to obtain an effective quality detection rule set; and the quality detection process and the effective quality detection rule set of the known type of data items are stored, and the multi-dimensional label rule base is updated. According to the scheme, through a multi-dimensional label algorithm and a rule similarity evaluation algorithm, the problems of poor accuracy, weak timeliness and the like caused by a fixed detection rule template are solved, rapid and accurate detection of data quality is realized, a detectionresult is fed back in time, and the quality of a data source is improved.
Owner:XIAMEN MEIYA PICO INFORMATION
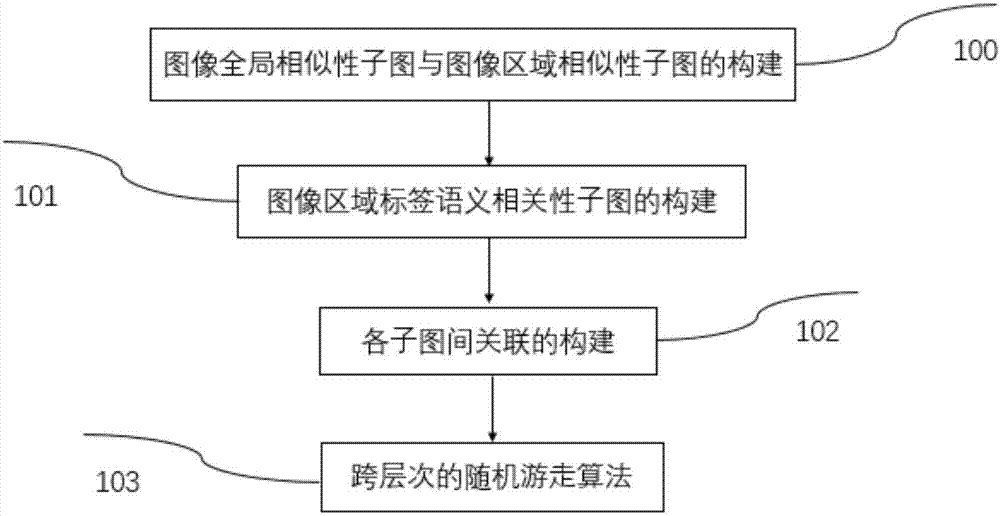
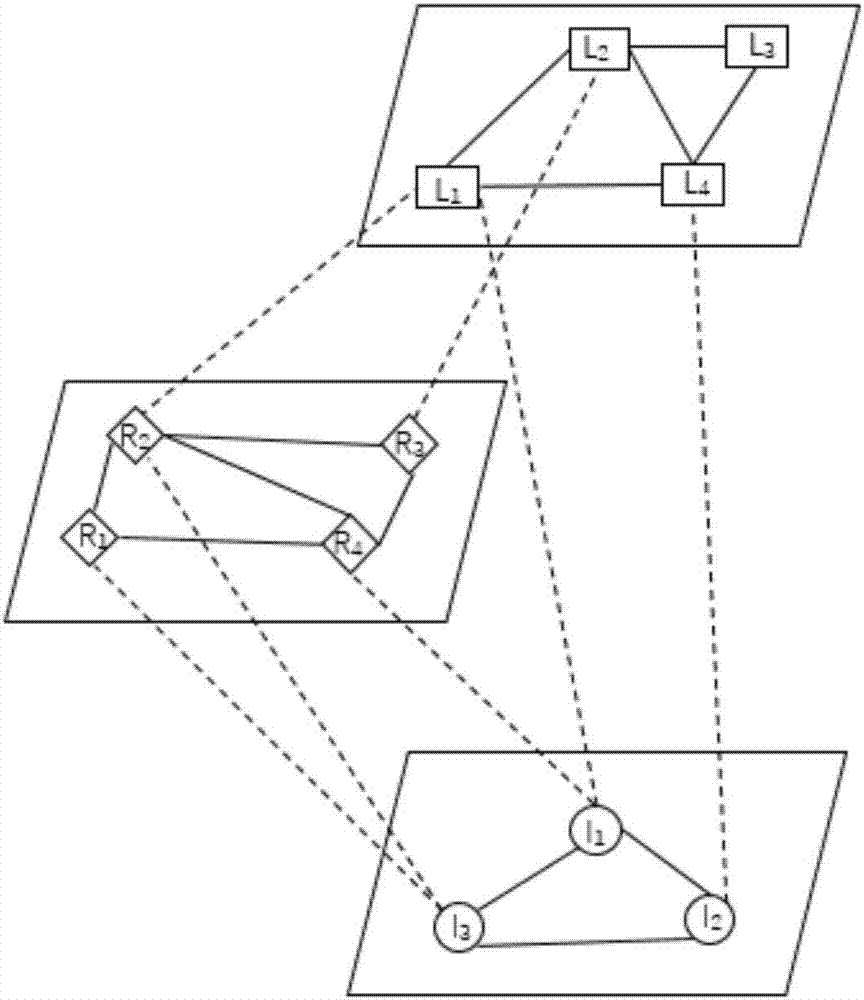
Image area labeling method based on visual semantic relation graph
The invention discloses an image labeling algorithm based on a visual sense and semantics and the algorithm can be used to realize automatic labeling of an image area. An image area labeling algorithmbased on a visual semantic relation graph comprises two portions: construction of the visual semantic relation graph and image labeling based on the visual semantic relation graph. In the visual semantic relation graph construction, a global similarity and an area similarity among images, semantic association of image area labels and association among levels are considered. On the constructed visual semantic relation graph, semi-supervised learning is performed, an association degree between an unlabeled image area and the image area labels is acquired and label prediction is performed on theunlabeled image area.
Owner:EAST CHINA UNIV OF SCI & TECH
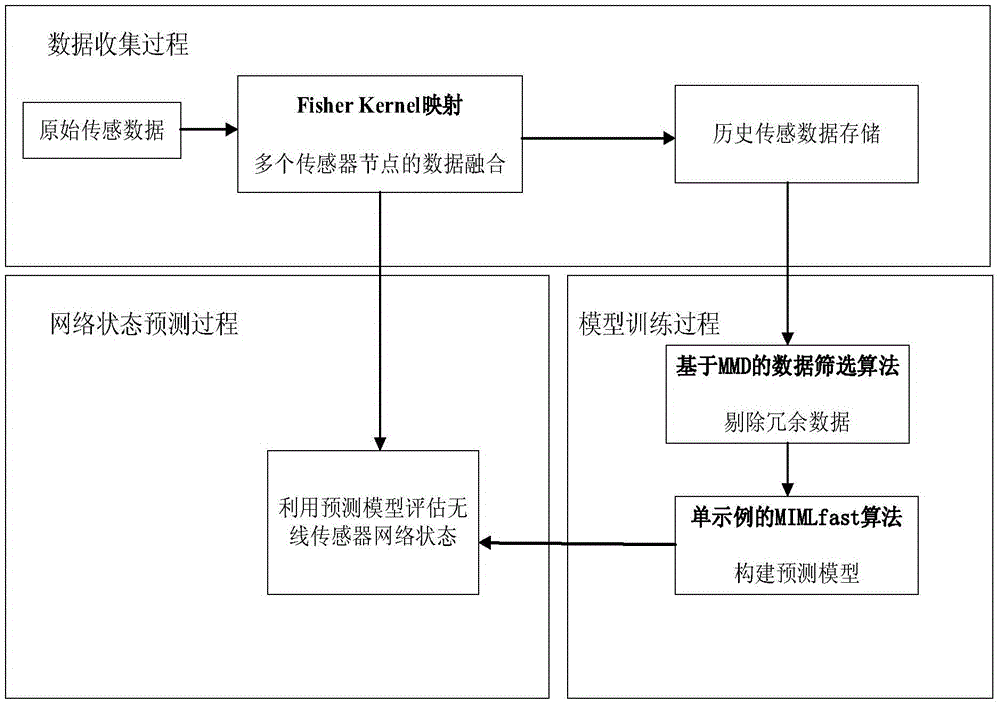
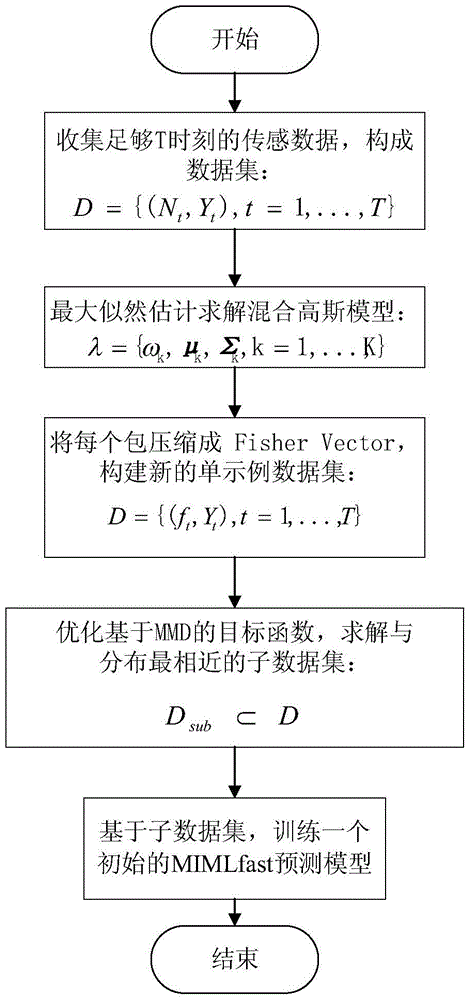
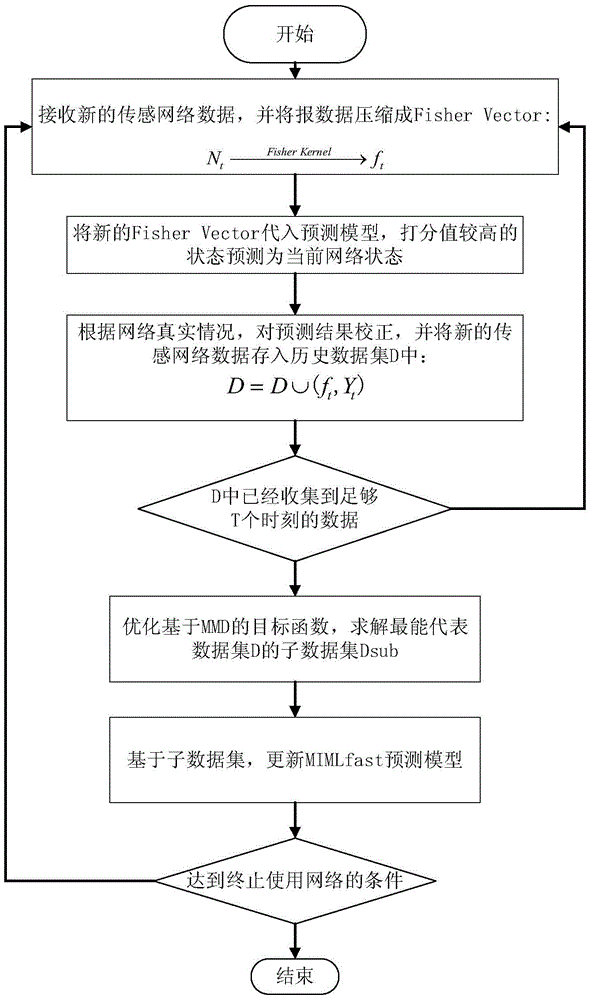
Multi-instance multi-label learning based area monitoring method used in wireless sensor network
ActiveCN105656692ASolving Data Fusion ProblemsNo need to increase node performanceNetwork topologiesRelational databasesData compressionWireless mesh network
The invention discloses a multi-instance multi-label learning based area monitoring method used in a wireless sensor network. Fisher Kernel is utilized to compress multiple sensor node data at the same moment; after compression, the whole wireless sensor network corresponds to a single sample data rather than multiple sample data at a certain moment; an MMD is utilized to compress historical packet data, and most representative packet data is picked out to form a data subset. Training of the compressed data and assessment on a monitoring region state are completed by utilizing a rapid multi-instance multi-label algorithm. Rapid network state prediction can be achieved by establishing a sensor network state prediction model on sensing datasets subjected to two-layer compression.
Owner:NANJING UNIV OF POSTS & TELECOMM
Safe development method for application middleware of mobile internet intelligent terminal
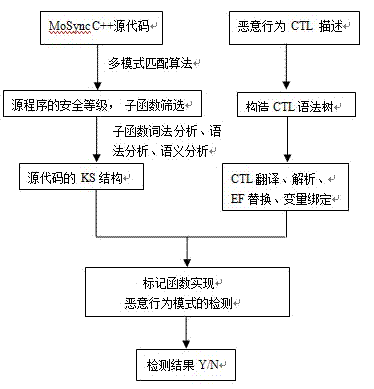
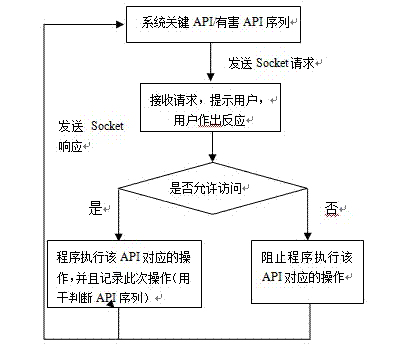
ActiveCN102902538AProtection securityDigital data protectionSpecific program execution arrangementsPattern matchingApplication programming interface
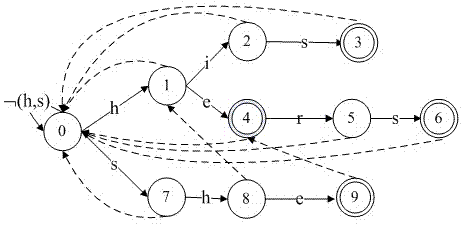
The invention provides a safe development method for application middleware of a mobile internet intelligent terminal. The safe development method includes: A, modeling: A1, determining the safety level of a program through a multi-pattern matching algorithm and screening out a subfunction containing sensitive application program interfaces (API), A2, analyzing the subfunction, and A3, constructing a system migration picture of the subfunction to complete modeling of the system; B, specification: using standard language complementary transistor logic (CTL) to describe malicious actions of a program to construct a syntax tree of a CTL formula, and performing translation, analyzing, EF replacing and variable binding on the CTL formula; and C, verification: using a non-recursive marker algorithm to achieve model verification. The safe development method for the application middleware of the mobile internet intelligent terminal remedies shortcomings of traditional Android systems in authority endowment and can effectively protect safety of user private data, actual active defense is achieved, and all access to the private data needs to be chosen by users.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
Labeling algorithm for biomedical image based on invisible dirichlet model
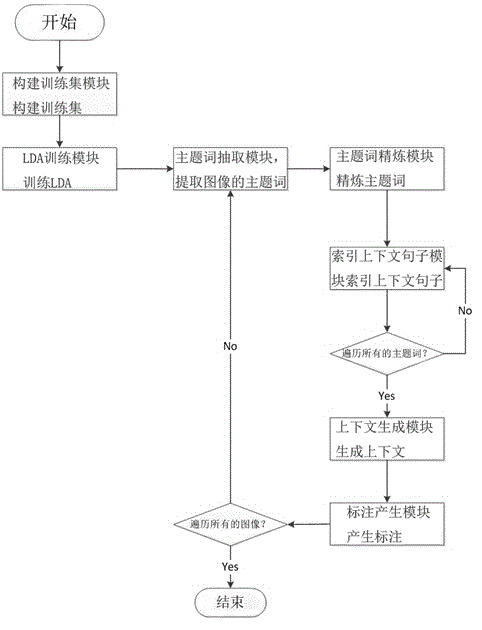
InactiveCN104021222AImprove accuracyIn line with text retrieval habitsMetadata still image retrievalSpecial data processing applicationsData setLabelling algorithm
The invention provides a labeling algorithm for a biomedical image based on LDA (Lejeune Dirichlet Allocation), mainly aiming at that the biomedical image is labeled, each image has a corresponding text file in a biomedical image language database and the particularity is combined. The LDA is used for extracting a subject term from captions of the image; then a context is extracted from the corresponding text file of the image according to the captions; and finally, the LDA is used for modeling the context; an obtained subject term is used as a final label of the biomedical image. The labeling algorithm has the beneficial effects that the biomedical image is labeled and the captions and the text file which are related to the image in a data set are sufficiently utilized to dig label words of the image; the accuracy is high and the plurality of label words can be generated at one time. After the biomedical image is accurately labeled, the related image is searched by using keyword index; the labeling algorithm is convenient and rapid and meets a text retrieval habit of people.
Owner:SHENZHEN INSTITUTE OF INFORMATION TECHNOLOGY +1
A fast connected domain marking algorithm for binary image streams
InactiveCN109146908AThe maximum number of statisticsImplement Connected Domain LabelingImage enhancementImage analysisLabelling algorithmHorizontal and vertical
The invention discloses a fast connected region marking algorithm for binary image streams, which can quickly identify the connected region according to the continuous image streams formed by a lineararray image sensor, and proposes a fast connected region marking algorithm for binary image which is suitable for FPGA parallel implementation. The algorithm scans the image line by line from left toright and from top to bottom, tags the target pixels, calculates the number of connected regions, and computes the maximum number of horizontal and vertical target pixels of each connected region. Only two adjacent lines of data are needed to make the tagging judgment, and only one scan is needed for the image. The algorithm can not only mark the connected region of binary continuous image stream, but also mark the connected region of static binary image.
Owner:ANHUI NORMAL UNIV
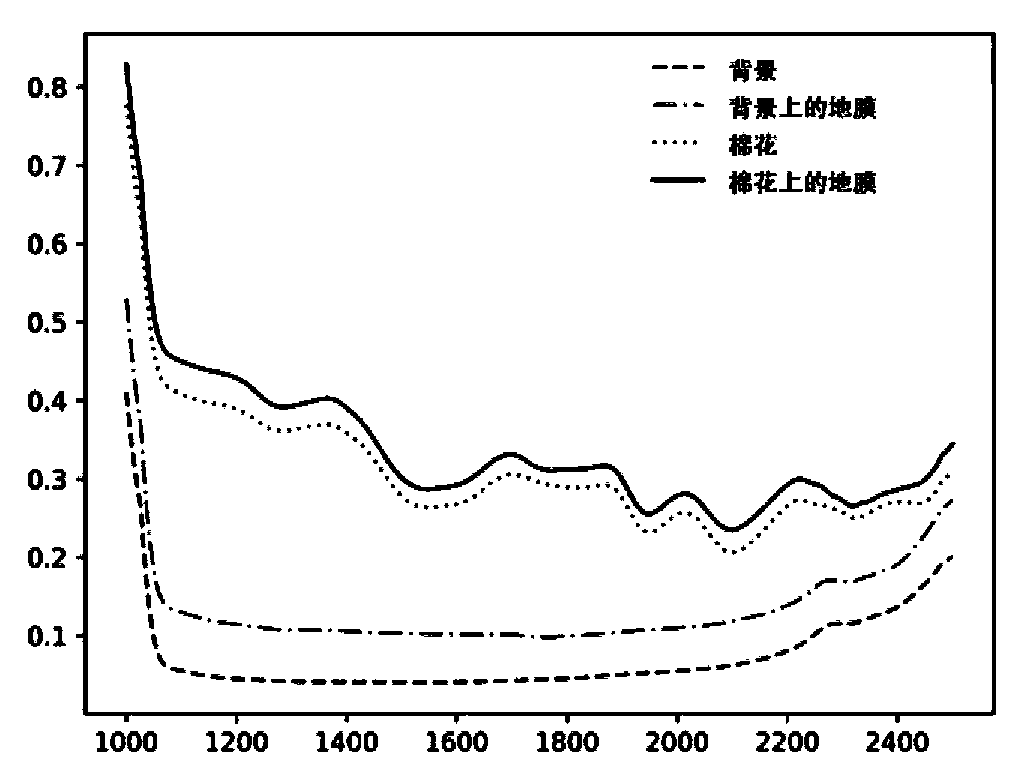
Seed cotton mulching film hyperspectral visual label algorithm for deep learning
The invention discloses a seed cotton mulching film hyperspectral visual label algorithm for deep learning, and belongs to the technical field of hyperspectral imaging and deep learning. The method comprises the following steps: analyzing a characteristic spectrum section of a spectrum by utilizing an adjacent alternative algorithm, performing dimensionality reduction on image data by combining adichotomy, generating a hyperspectral pseudo-color image of the seed cotton mulching film, marking the pseudo-color image in a frame selection marking form, and correspondingly generating an image label of a high-dimensional spectrum through two-dimensional image marking. The hyperspectral technology is applied to the field of seed cotton mulching film recognition, for residual transparent mulching films which cannot be recognized by a color camera and a black-white camera, hyperspectral images of the seed cotton mulching films at 1000-2500 nm are collected through a hyperspectral imager, andthen the residual films with different spectral characteristics from seed cotton are recognized and classified.
Owner:NANJING FORESTRY UNIV
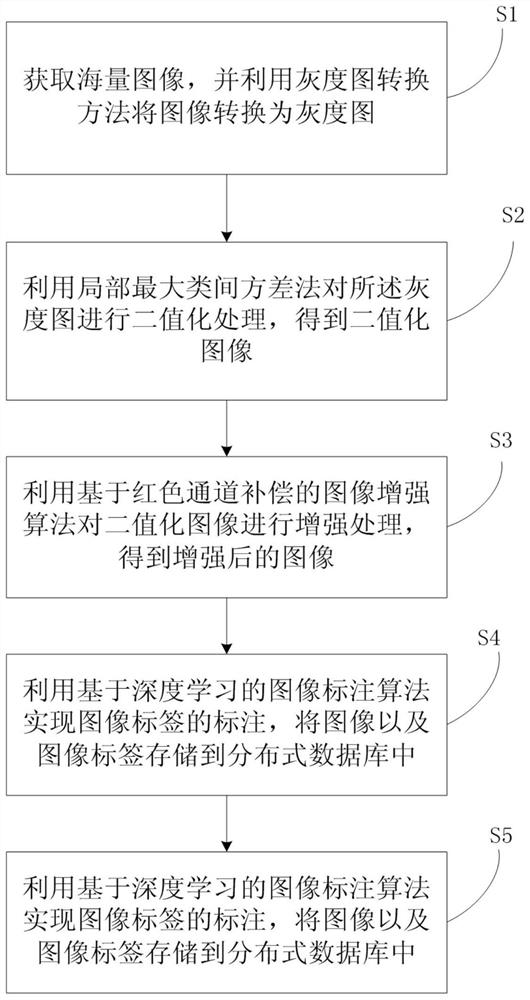
Image analysis method and system based on big data
InactiveCN112308802AEfficient Image Analysis and RetrievalImage enhancementImage analysisImaging analysisLabelling algorithm
The invention relates to the technical field of image analysis, and discloses an image analysis method based on big data. The method comprises the following steps: obtaining massive images, and converting the images into grey-scale maps by using a grey-scale map conversion method; performing binarization processing on the gray-scale maps by using a local maximum between-cluster variance method toobtain binarized images; performing enhancement processing on the binarized images by using an image enhancement algorithm based on red channel compensation to obtain enhanced images; utilizing an image labeling algorithm based on deep learning to label image labels, and storing the images and the image labels into a distributed database; and caching the images and the image labels in the distributed database into the system by utilizing a path-based caching algorithm, thereby realizing more efficient image analysis and retrieval. The invention also provides an image analysis system based on big data. According to the invention, image analysis based on big data is realized.
Owner:汪秀英
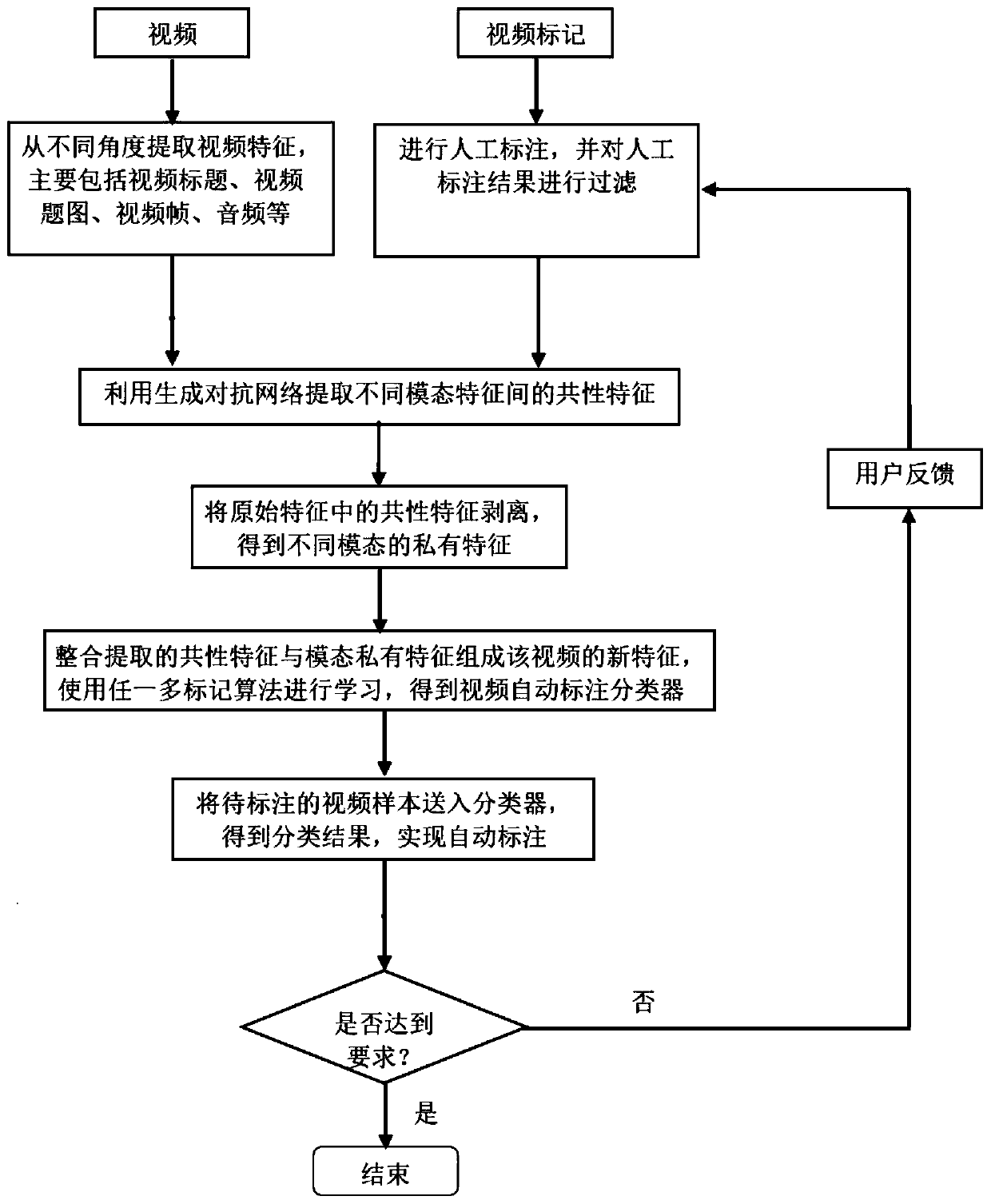
Automatic video annotation method based on multi-modal private features
ActiveCN110377790AShorten the timeLow costVideo data clustering/classificationCharacter and pattern recognitionManual annotationLabelling algorithm
The invention discloses an automatic video annotation method based on multi-modal private features, and the method comprises the steps: carrying out the preprocessing and manual annotation of a videofile, and filtering a manual annotation result; utilizing a generative adversarial network to extract common features among different modal features; stripping common features in the original featuresto obtain private features of different modes; integrating the extracted common features and modal private features to form new features of the video, and learning by using a multi-marking algorithmto obtain an automatic video marking classifier; sending the to-be-labeled video sample into a classifier to obtain a classification result, and realizing automatic labeling; and performing sampling inspection on the labeling result. By adopting the method, the classification model for automatic video annotation can be trained, the video features are integrated again by utilizing the private features of different modes of unknown annotated videos, the annotation task is automatically completed, and the manual annotation time and cost can be remarkably reduced.
Owner:SOUTHEAST UNIV
Lung cancer frontier trend prediction method based on multi-label classification
ActiveCN111651605AImprove classification effectFill vacancyNeural architecturesSpecial data processing applicationsData setMulti-label classification
The invention discloses a lung cancer frontier trend prediction method based on multi-label classification, and the method comprises the steps: collecting serial numbers, titles, abstracts and publishing dates of papers in the field of lung cancer research, and forming a data set; formulating a category set corresponding to themes of papers in the lung cancer research field; labeling the collectedabstract text according to the category set; preprocessing the text in the data set; dividing the data set into a training set and a verification set according to the publishing date of the paper; inputting the training sample into a Bert-based multi-label classification network, setting a loss function loss, performing back propagation on a loss value, updating a weight parameter, and continuously iterating the training network until the loss value does not drop any more; and classifying the data of the verification set by using the trained classification network to obtain a classification result. According to the method, the problem that the traditional multi-label algorithm neglects the label correlation is improved; meanwhile, the artificial intelligence technology is combined with medical treatment, and a new thought for trend prediction in the medical field is provided.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
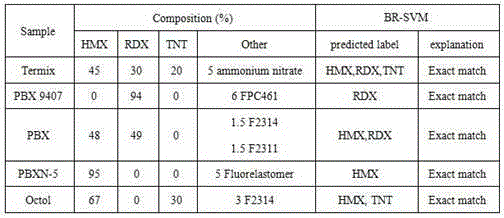
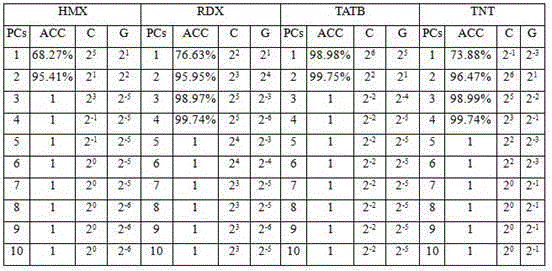
New method for quantitatively recognizing mixed explosive components by combining infrared spectroscopy and chemometrics
InactiveCN105300918AImprove robustnessImprove stabilityMaterial analysis by optical meansNear-infrared spectroscopySupport vector machine
The invention discloses a new multi-label algorithm analysis method combining infrared spectroscopy and chemometrics. Four components of (octogen (HMX), hexogen(RDX), triamino trinitrobenzene (TATB) and trinitrotoluene (TNT)) in plastic bonded explosives (PBX) can be fast and quantitatively recognized at the same time, and measurable samples comprise single-component, double-component and three-component PBX. The method includes the following main steps that PBX samples in different concentrations are prepared, wherein 118 training sets exist, 28 independent testing sets exist, four kinds of explosives in the training sets are recognized through a support vector machine to be subjected to modeling and optimization, an optimal model is applied to the training sets and five true samples, and whether unknown mixed explosives contain HMX, RDX, TATB and TNT or not can be directly predicted. Compared with a traditional experimental method, no pre-separation needs to be performed on PBX, only the sample infrared spectrum needs to be measured, operation is easy, analysis speed is high, and accuracy is high.
Owner:SICHUAN UNIV
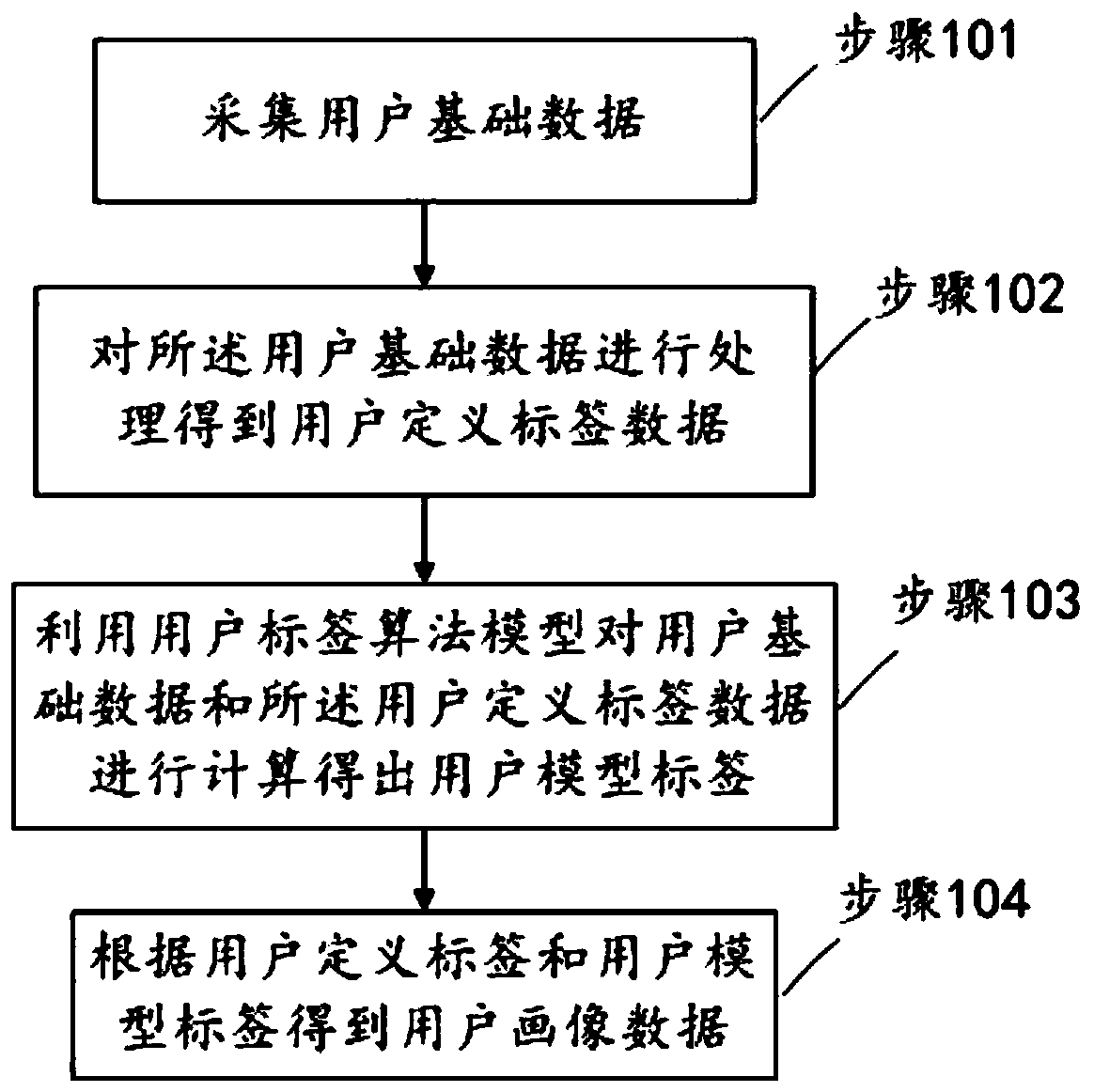
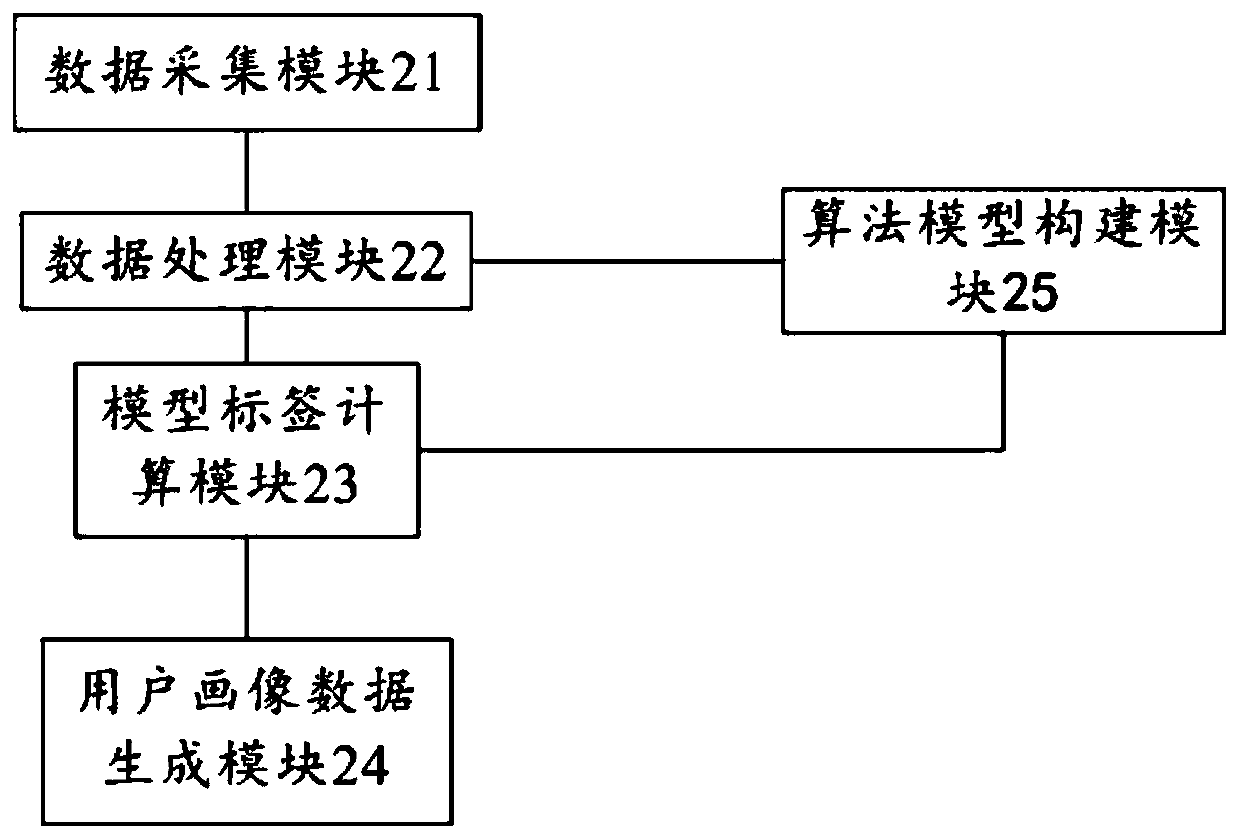
E-commerce user portrait data generation method and apparatus, and computing device
PendingCN111553729AAccurate recommendationAccurate Ad RecommendationsBuying/selling/leasing transactionsMarket data gatheringLabelling algorithmEngineering
The invention relates to an e-commerce user portrait data generation method and apparatus, and a computing device, wherein the method comprises the steps of collecting user basic data; processing theuser basic data to generate user-defined label data; calculating the user basic data and the user-defined label data by using a user label algorithm model to obtain a user model label; and generatinguser portrait data according to the user-defined label and the user model label. According to the embodiment of the invention, the user tag comprises the basic definition tag, and the user model tag is expanded, and the user tag type is expanded, so that more complete and accurate user portrait data can be generated, and more accurate user commodity recommendation, advertisement recommendation andchannel selection can be made for an e-commerce platform.
Owner:广州探途网络技术有限公司
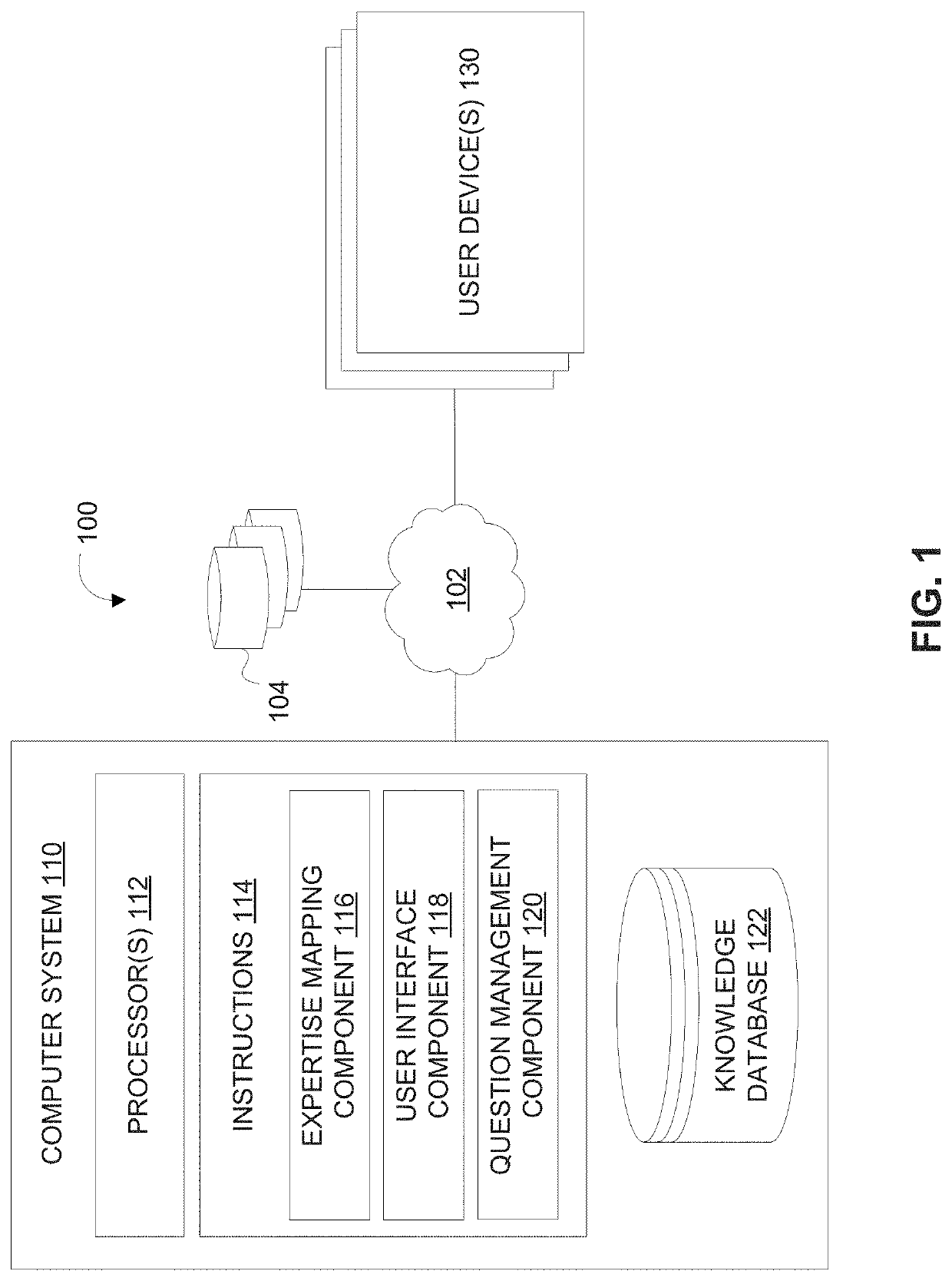
Advanced text tagging using key phrase extraction and key phrase generation
ActiveUS10878174B1Effectively and efficiently resolveQuick fixWeb data indexingSemantic analysisRelevant informationSkills management
The systems and methods described herein describe a comprehensive knowledge and / or skills management technology tool to address these and other issues with an advanced text tagging algorithm to extract the relevant topics from a text segment. The tagging algorithm includes a key phrase extraction technique and a key phrase generation technique. The key phrase extraction includes identifying phrases from the original text that represents its most relevant information. The key phrase generation technique includes generating additional phrases that do not necessarily appear in the text, but which describe its subject.
Owner:STARMIND AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com