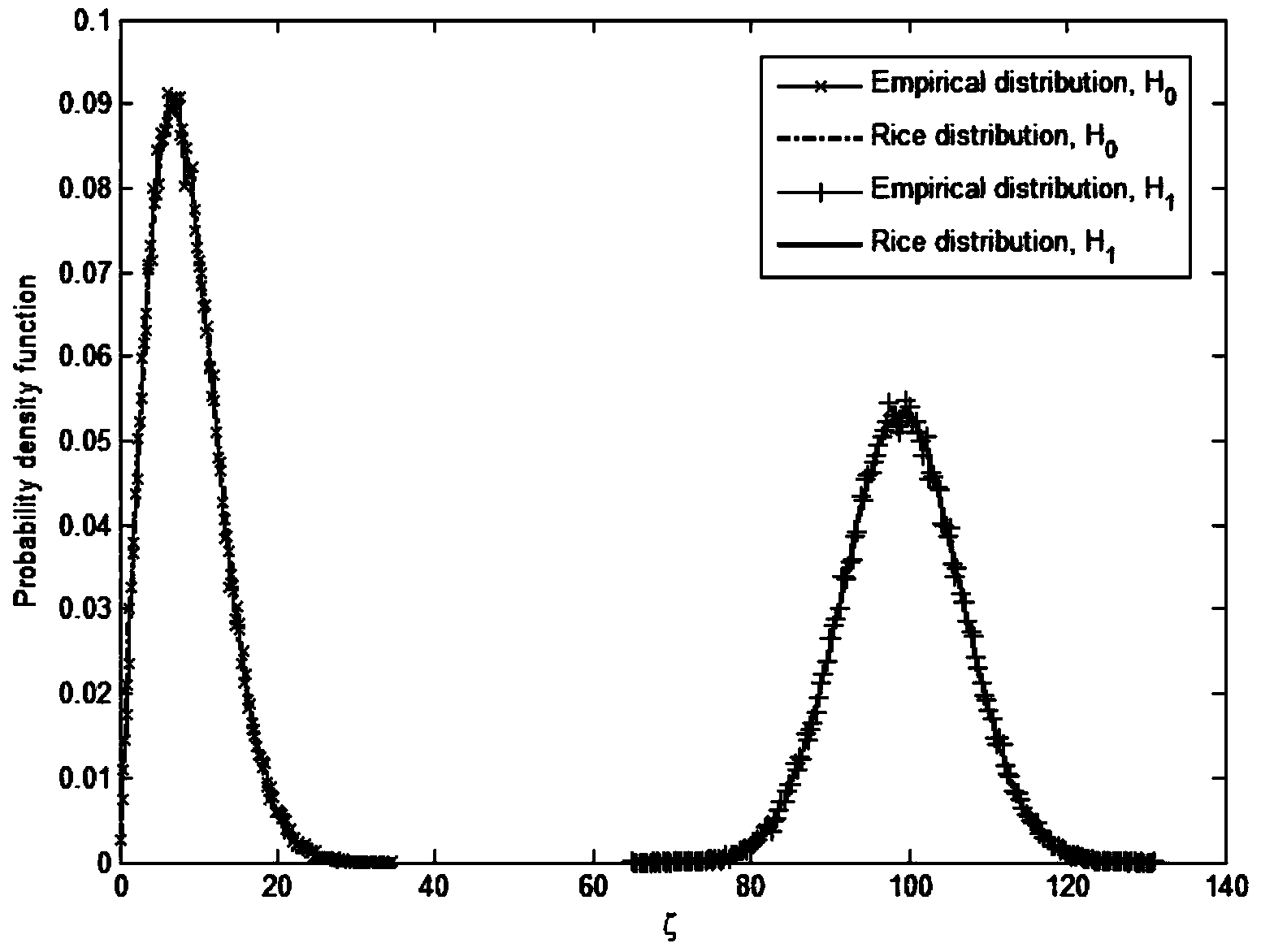
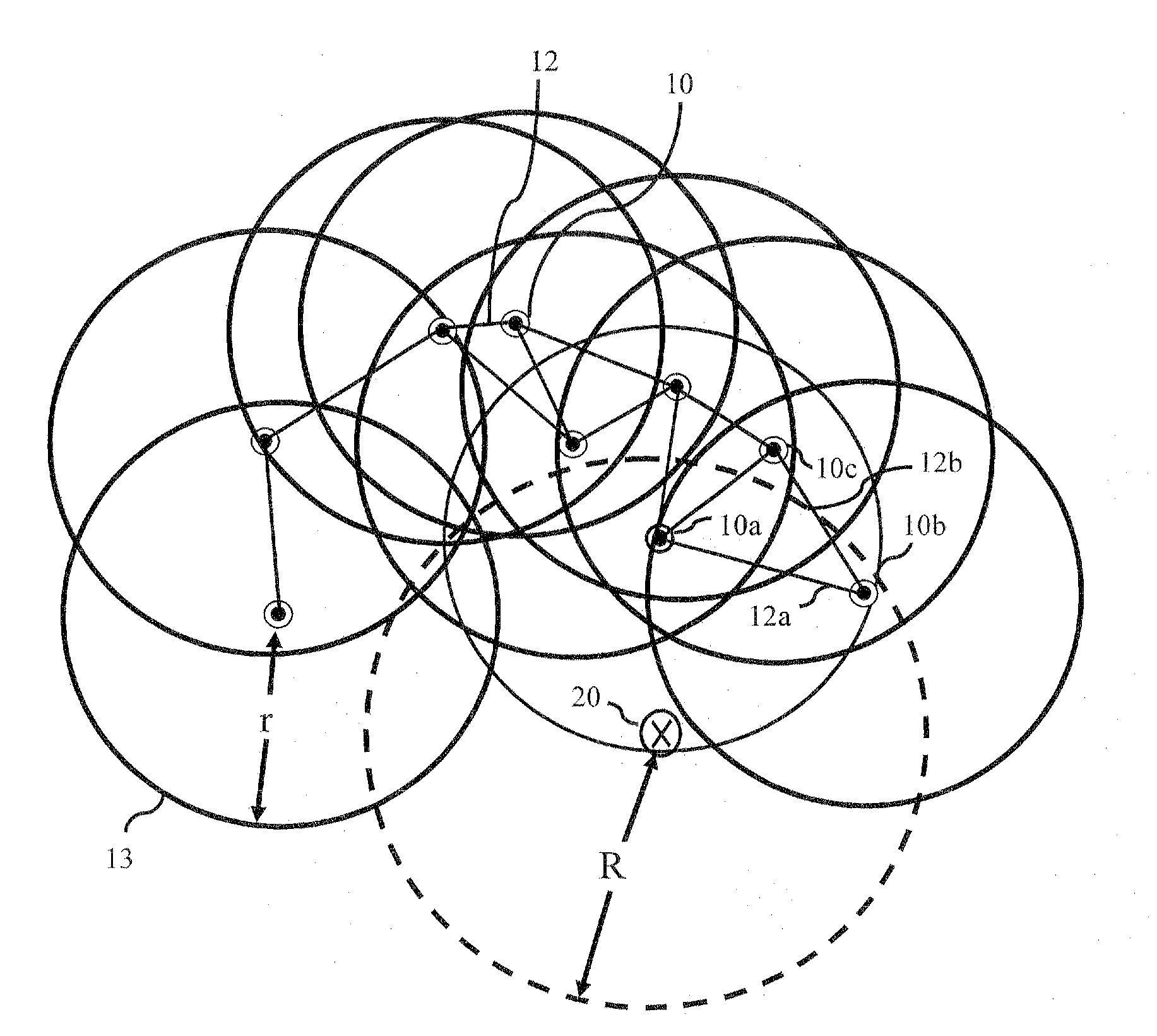
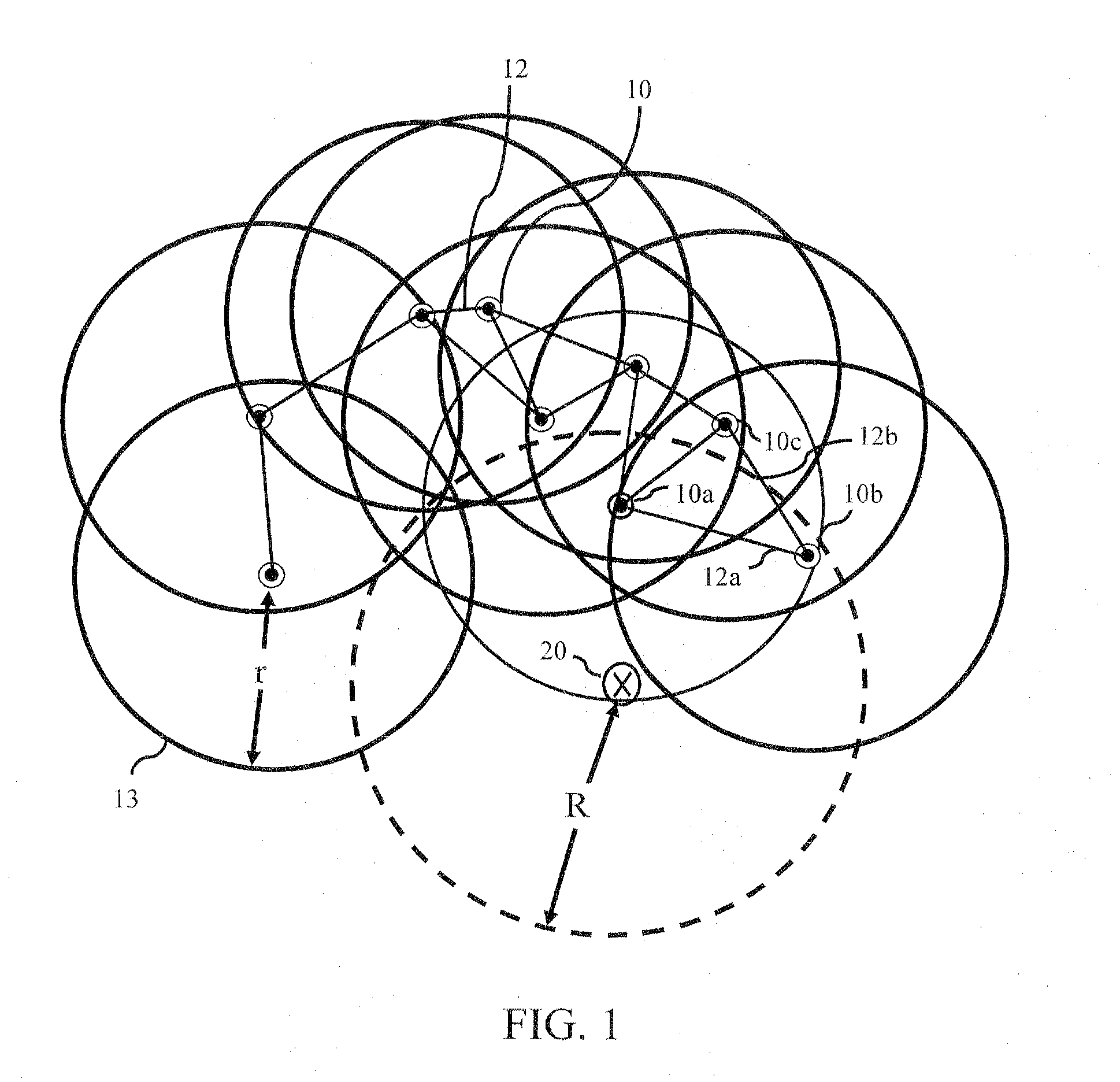
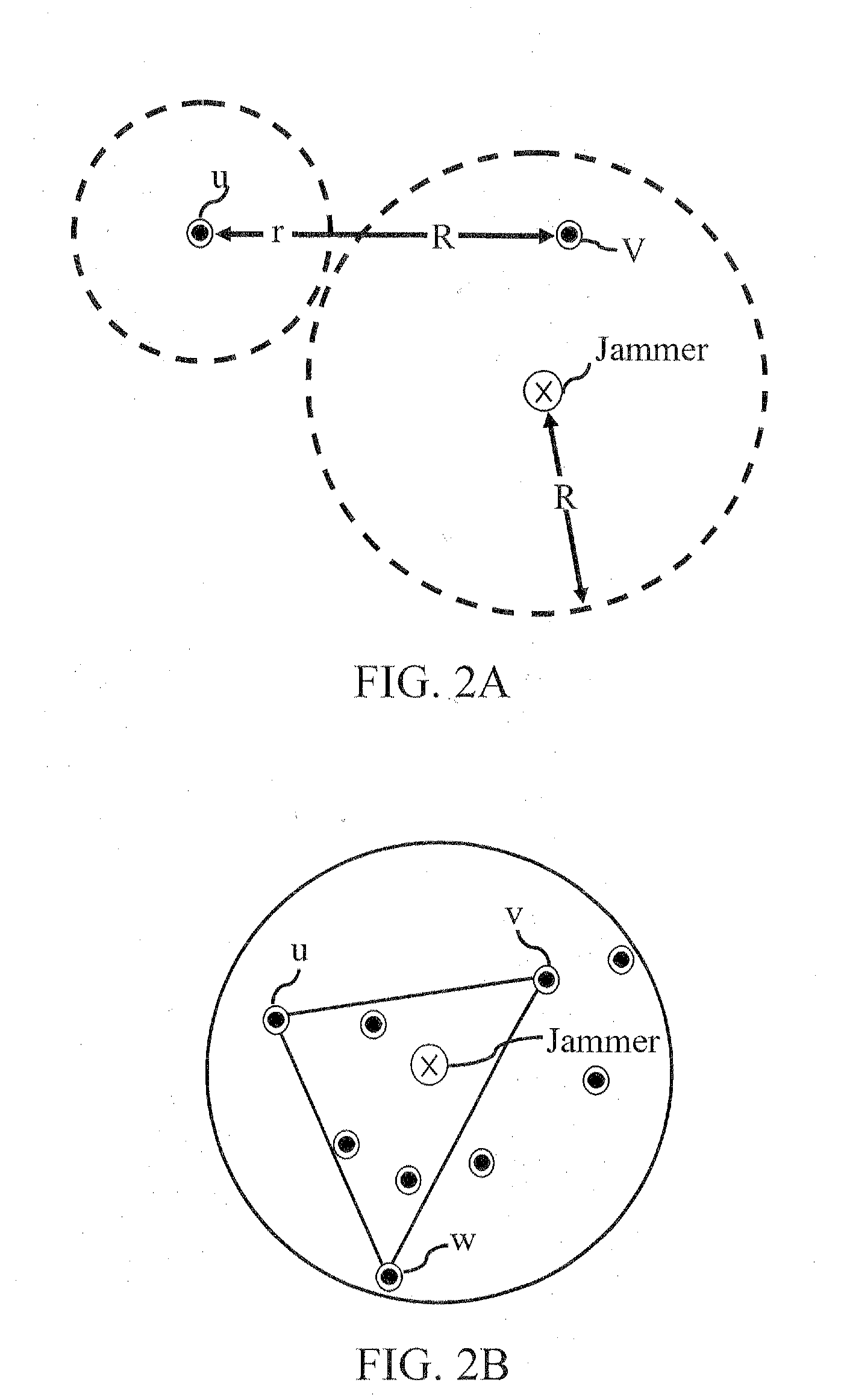
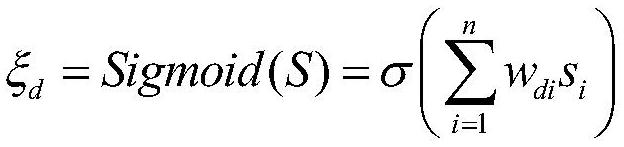Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
51 results about "Jamming attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
What is Jamming Attack. 1. A kind of Denial of Service attack, which prevents other nodes from using the channel to communicate by occupying the channel that they are communicating on Learn more in: Jamming Attacks and Countermeasures in Wireless Sensor Networks.
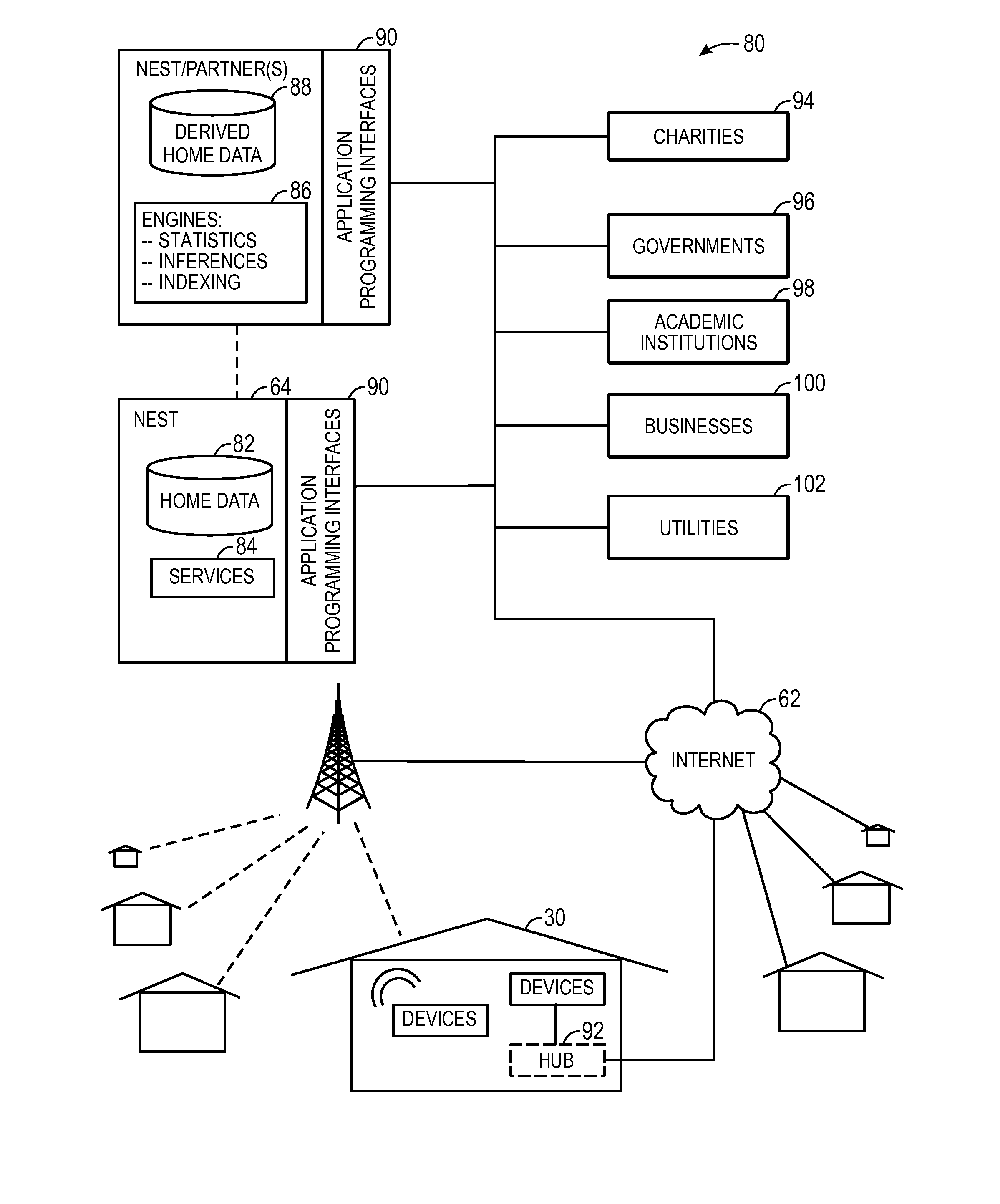
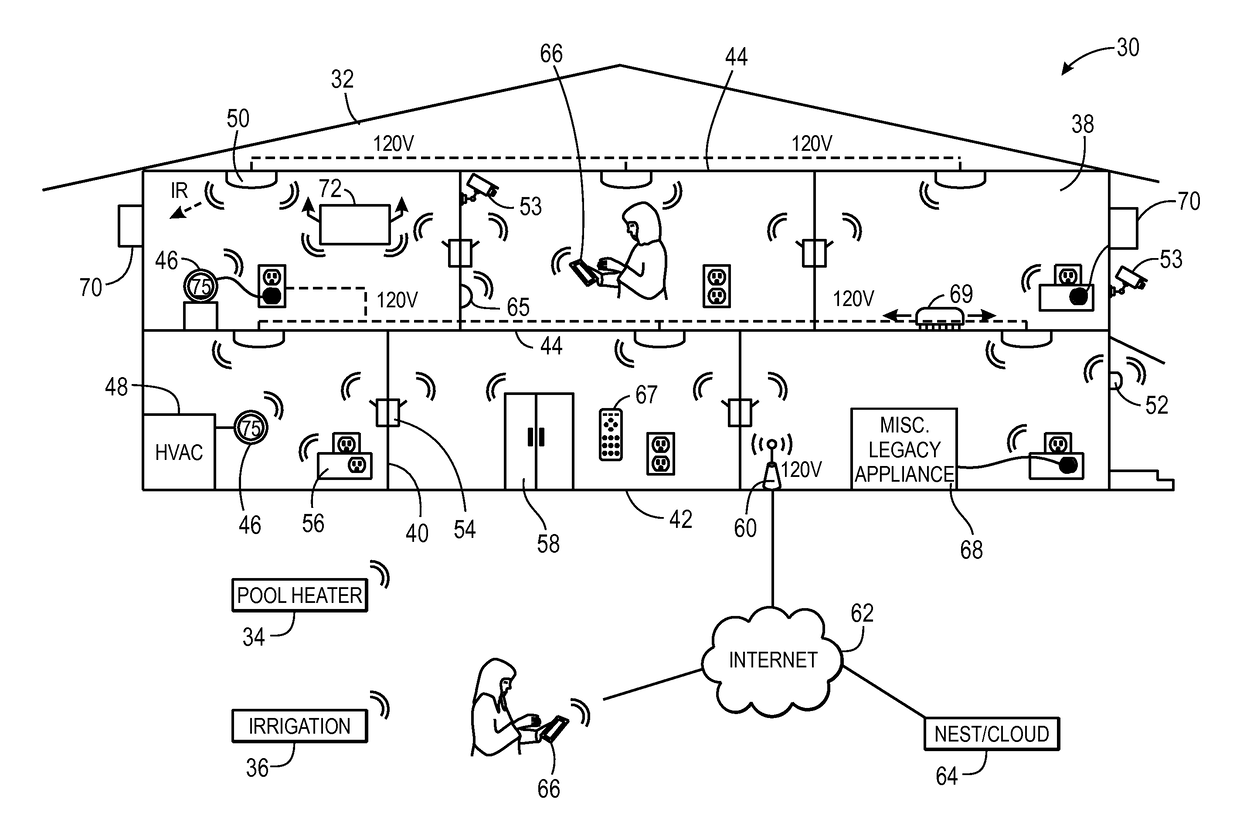
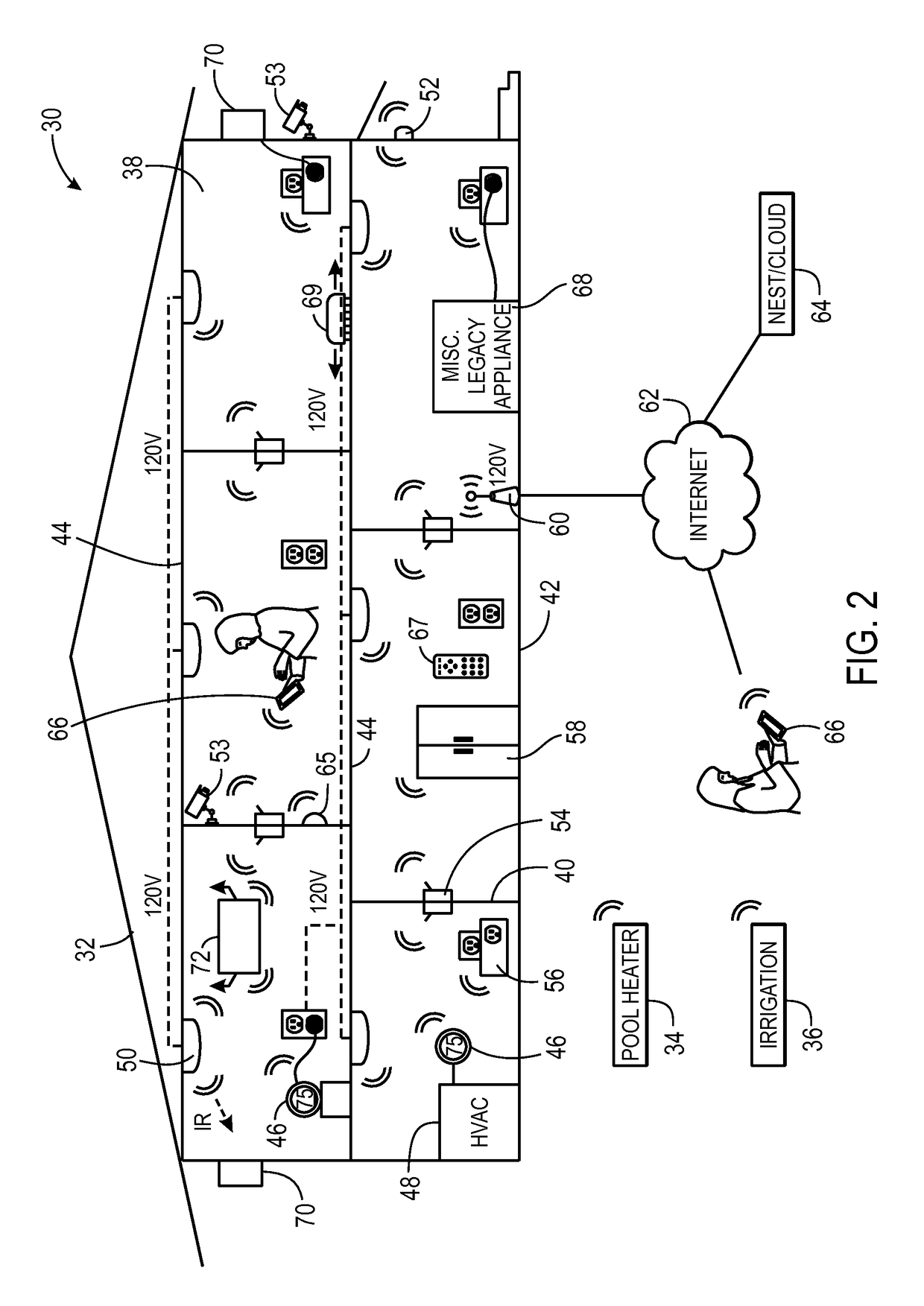
Systems and methods for detecting wireless communication jamming in a network
ActiveUS20160043827A1Error preventionFrequency-division multiplex detailsTelecommunicationsJamming attack
An electronic device may include a processor and a network interface that may include a first radio and a second radio. The processor may be configured to perform wireless communication jamming attack detection by occasionally performing clear channel verification utilizing the network interface to determine whether a threshold number of devices' channels are incapacitated in a wireless network within a threshold amount of time and / or by sending a heartbeat signal from the first radio and determining whether the second radio received the heartbeat signal.
Owner:GOOGLE LLC
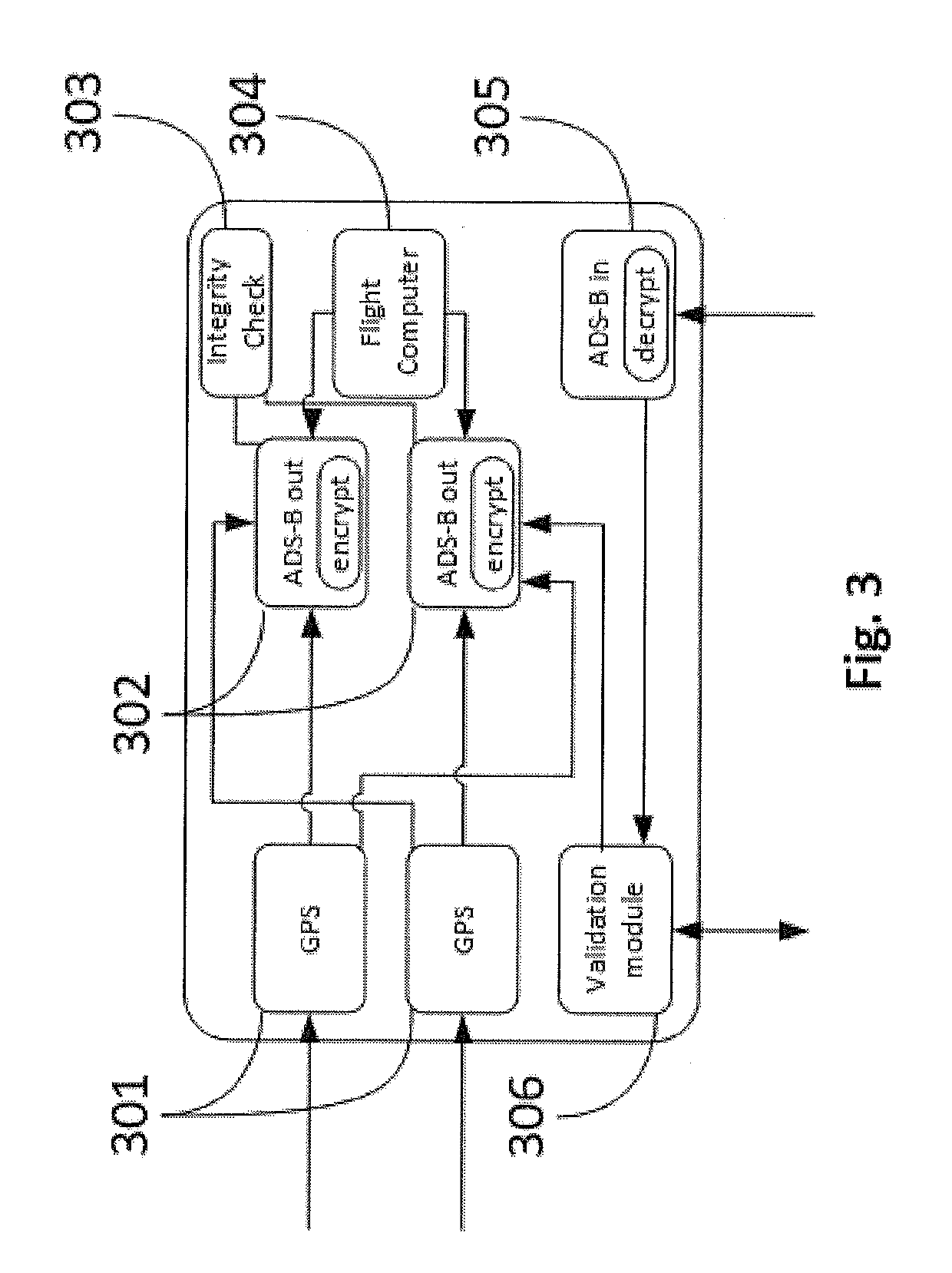
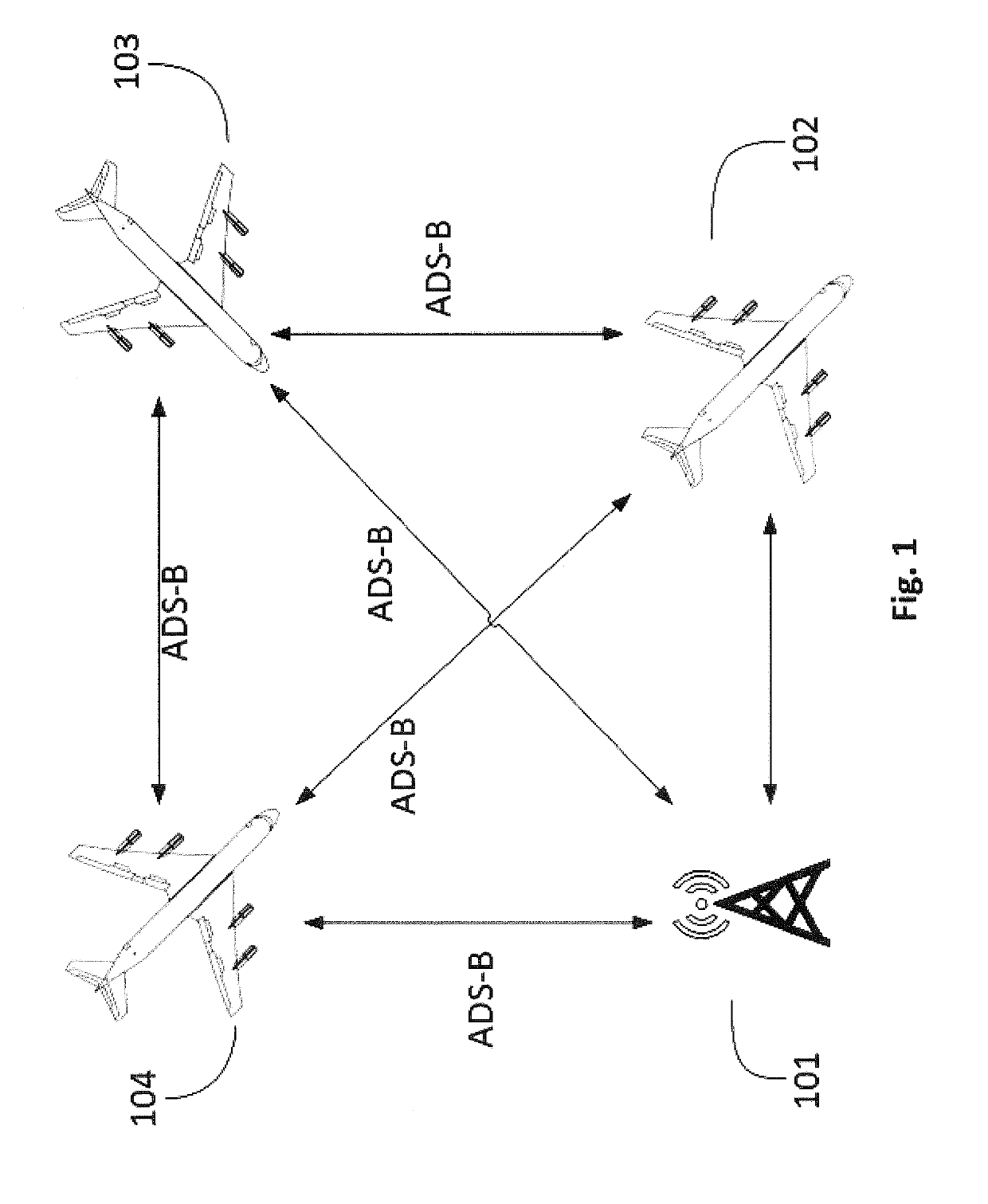
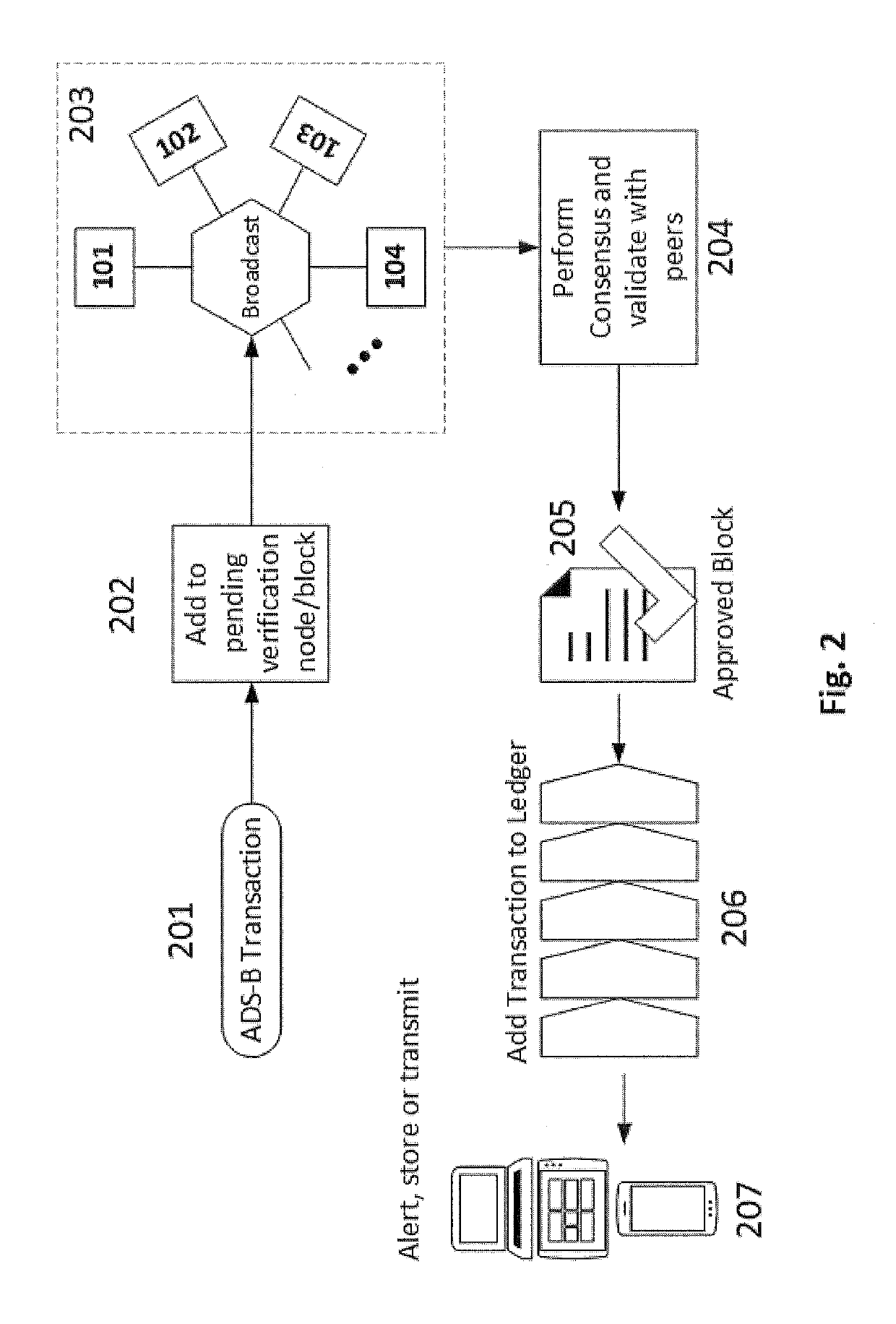
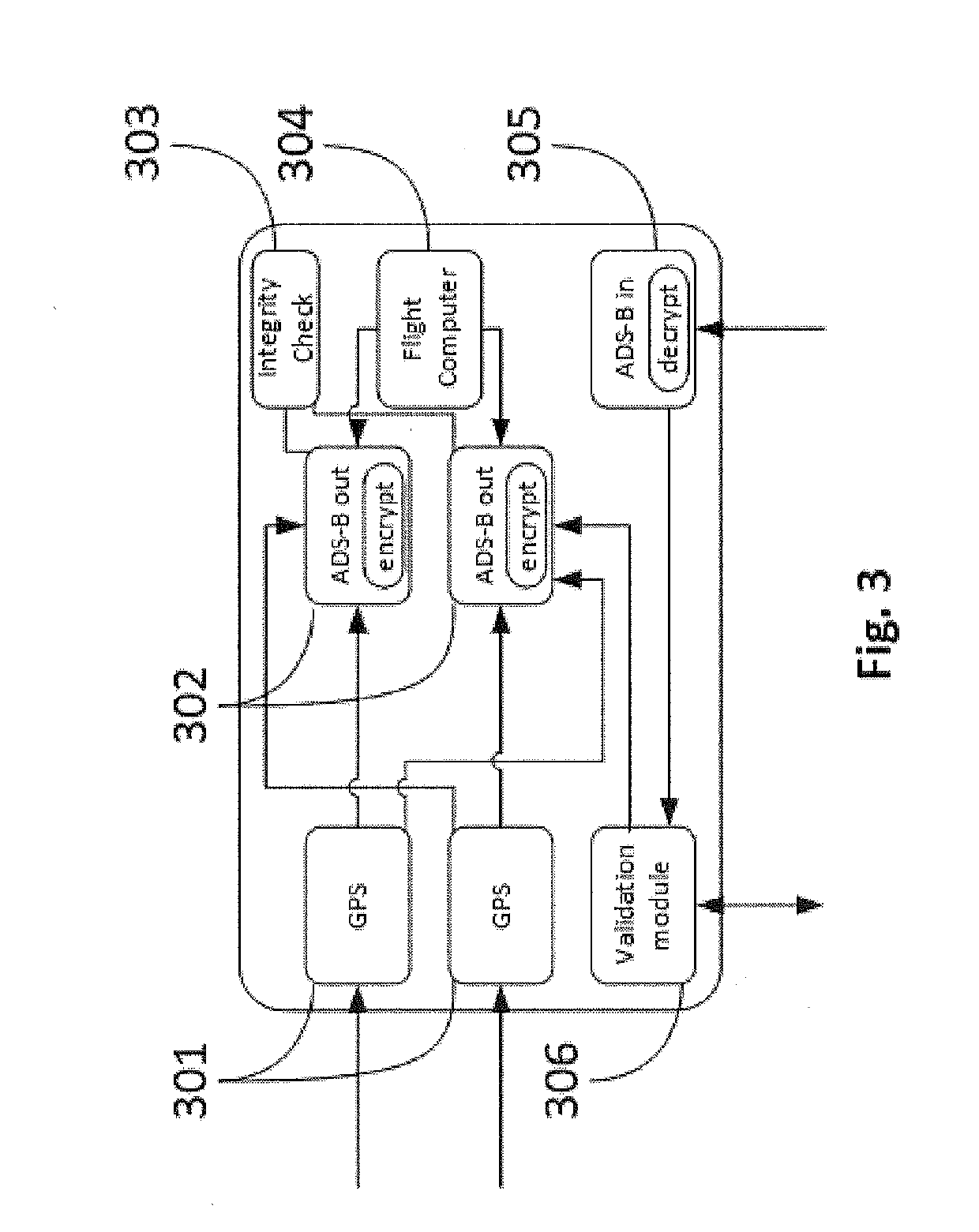
Method and network to implement decentralized validation and authentication mechanisms to prevent ads-b cyber-attacks
InactiveUS20190280871A1Improve securityOvercome disadvantagesEncryption apparatus with shift registers/memoriesUser identity/authority verificationCyber-attackEavesdropping
A method or network that addresses cybersecurity vulnerabilities in an ADS-B network by validating and authenticating ADS-B messages. Nodes of the network maintain a validated ledger of ADS-B transactions and use validated information from this ledger to improve security against common cybersecurity attacks including, but not limited to, denial of service attacks, jamming attacks, spoofing attacks, flooding attacks and eavesdropping.
Owner:ROBUST ANALYTICS INC
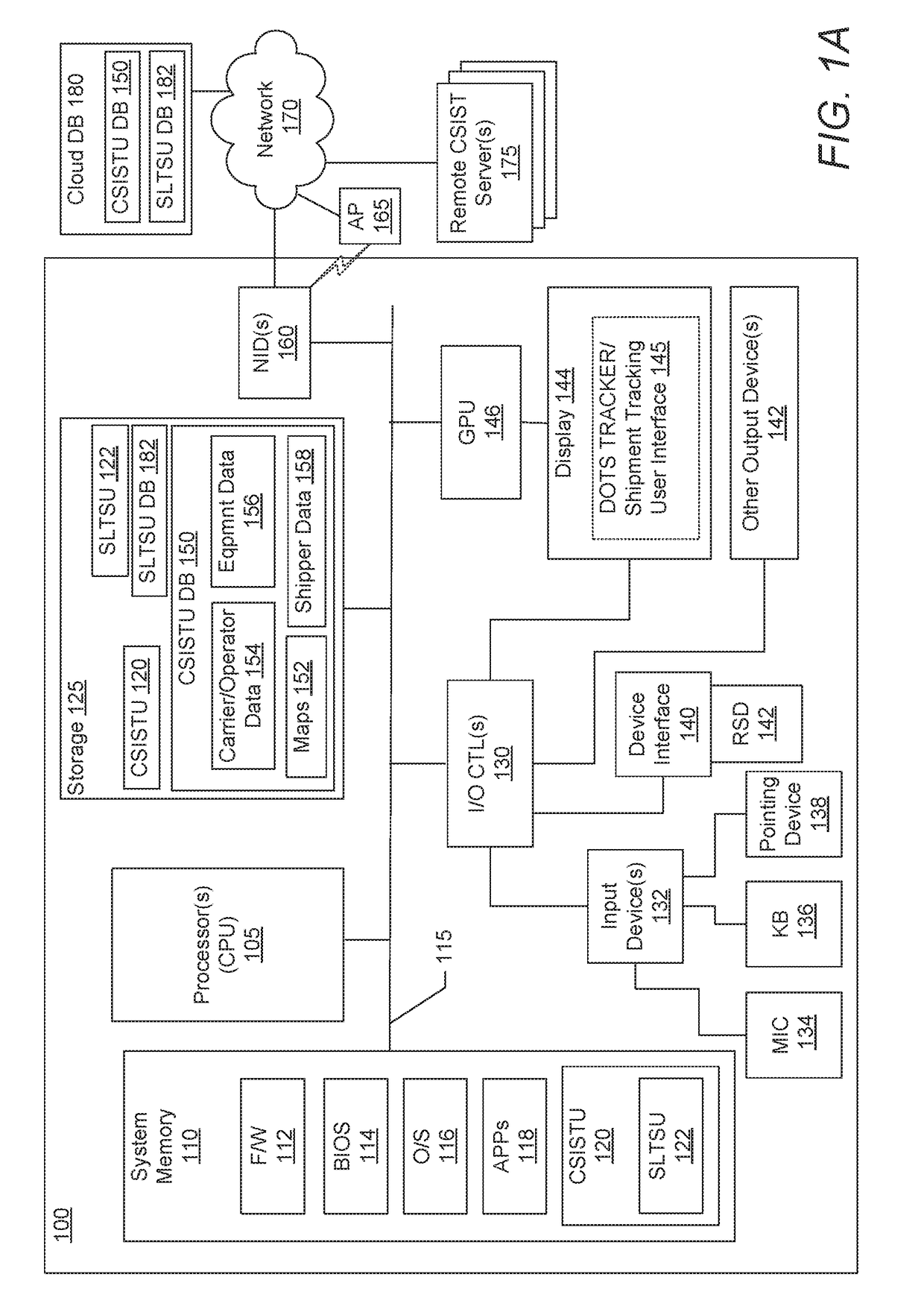
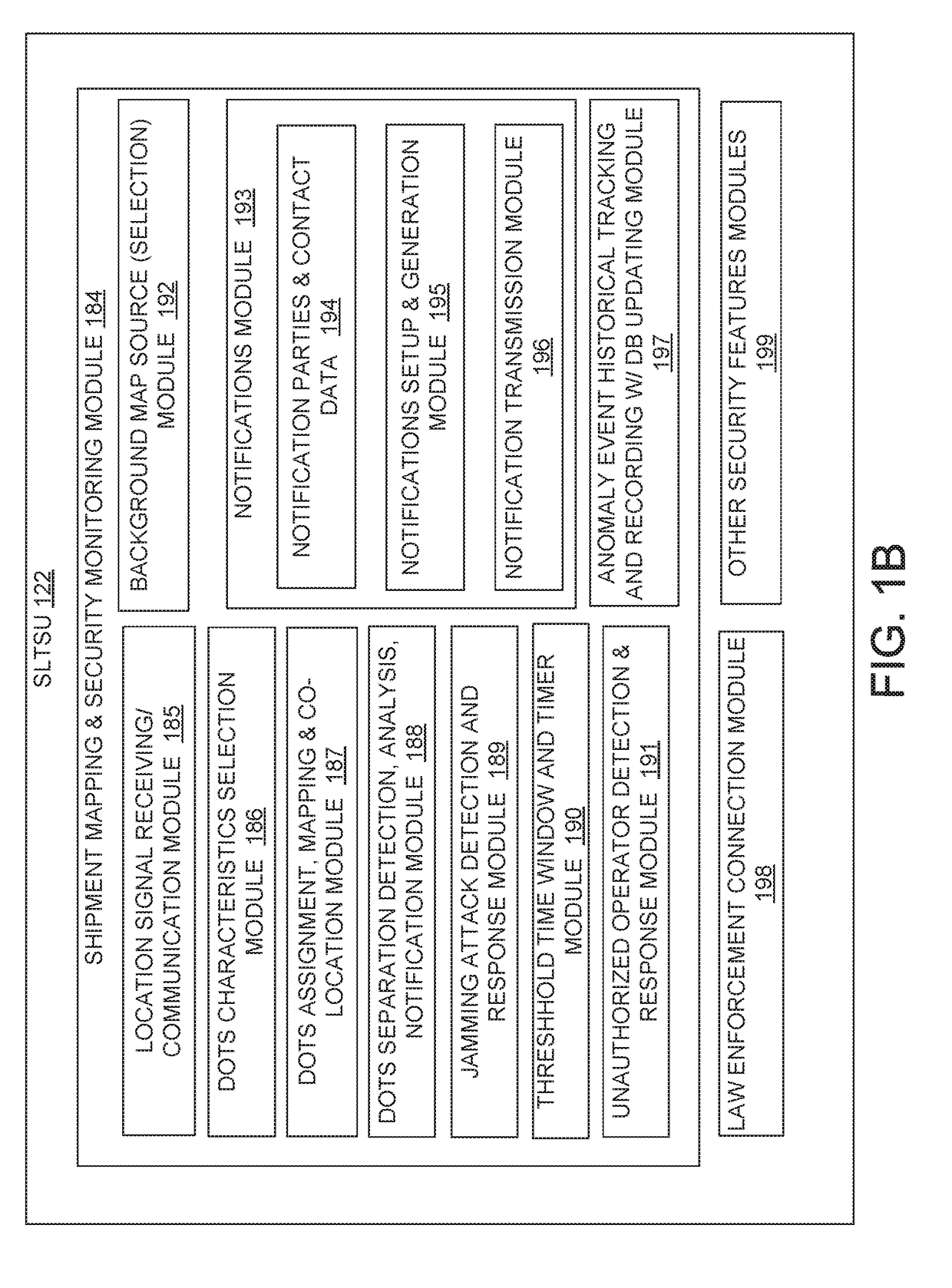
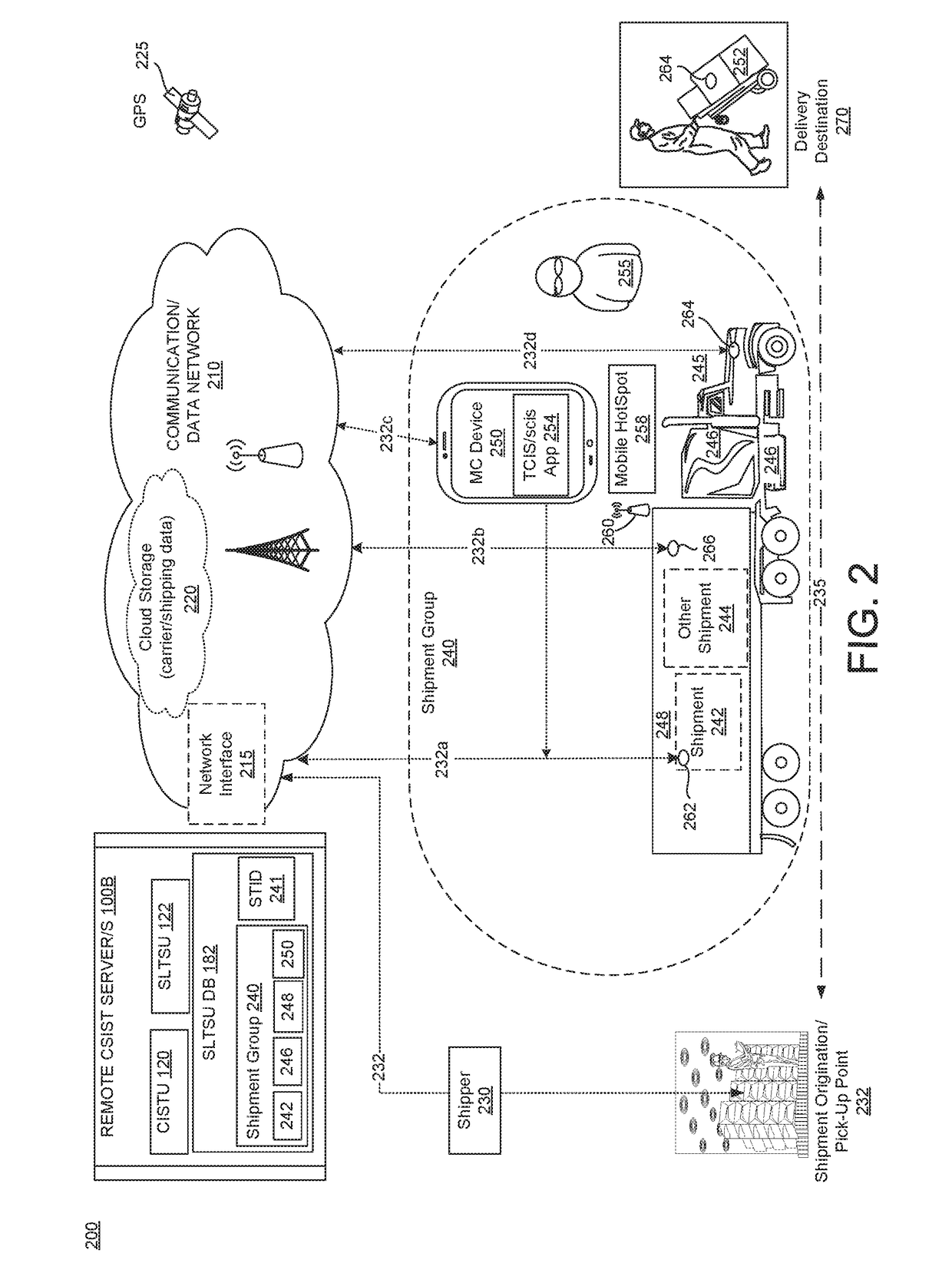
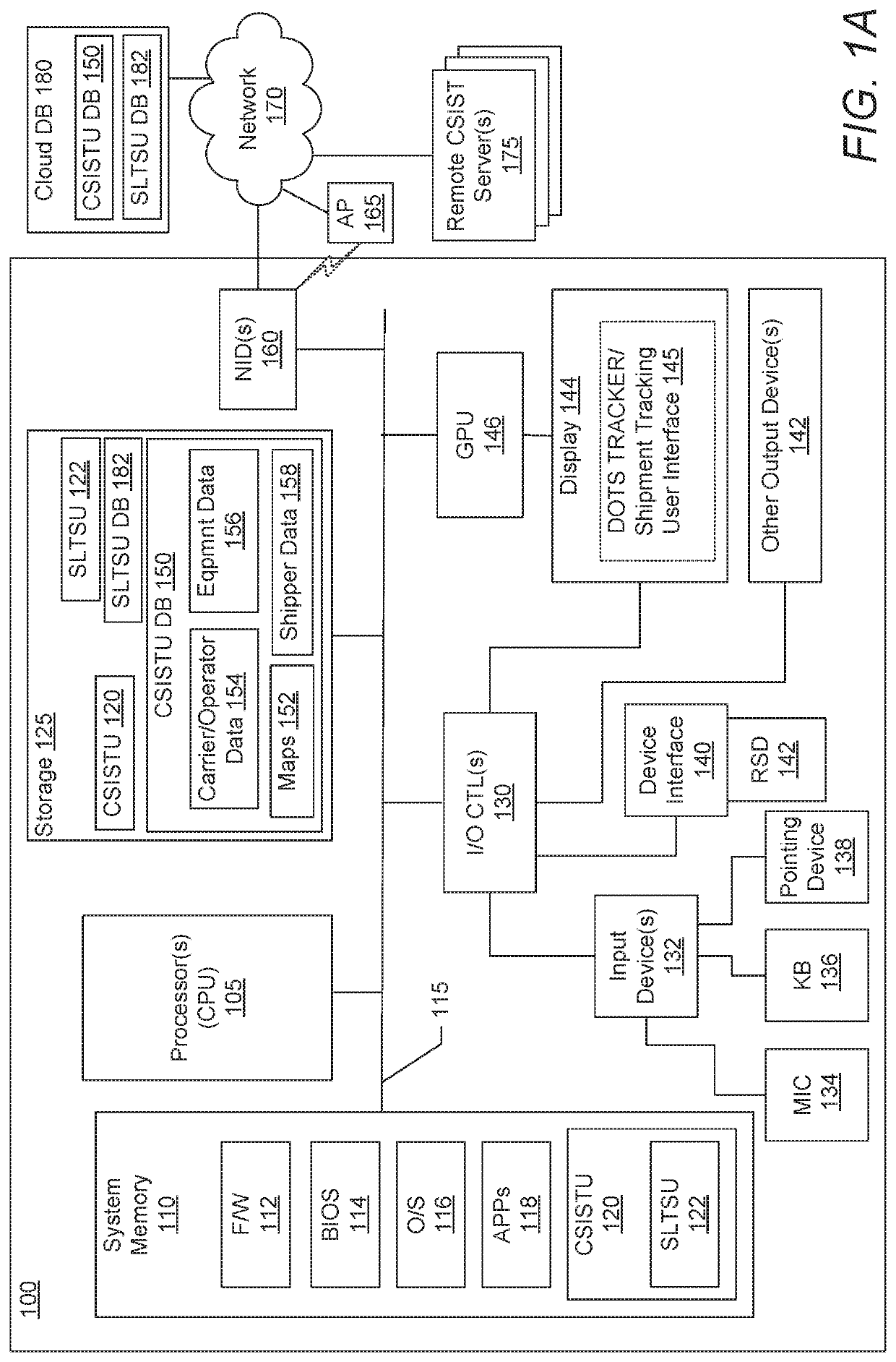
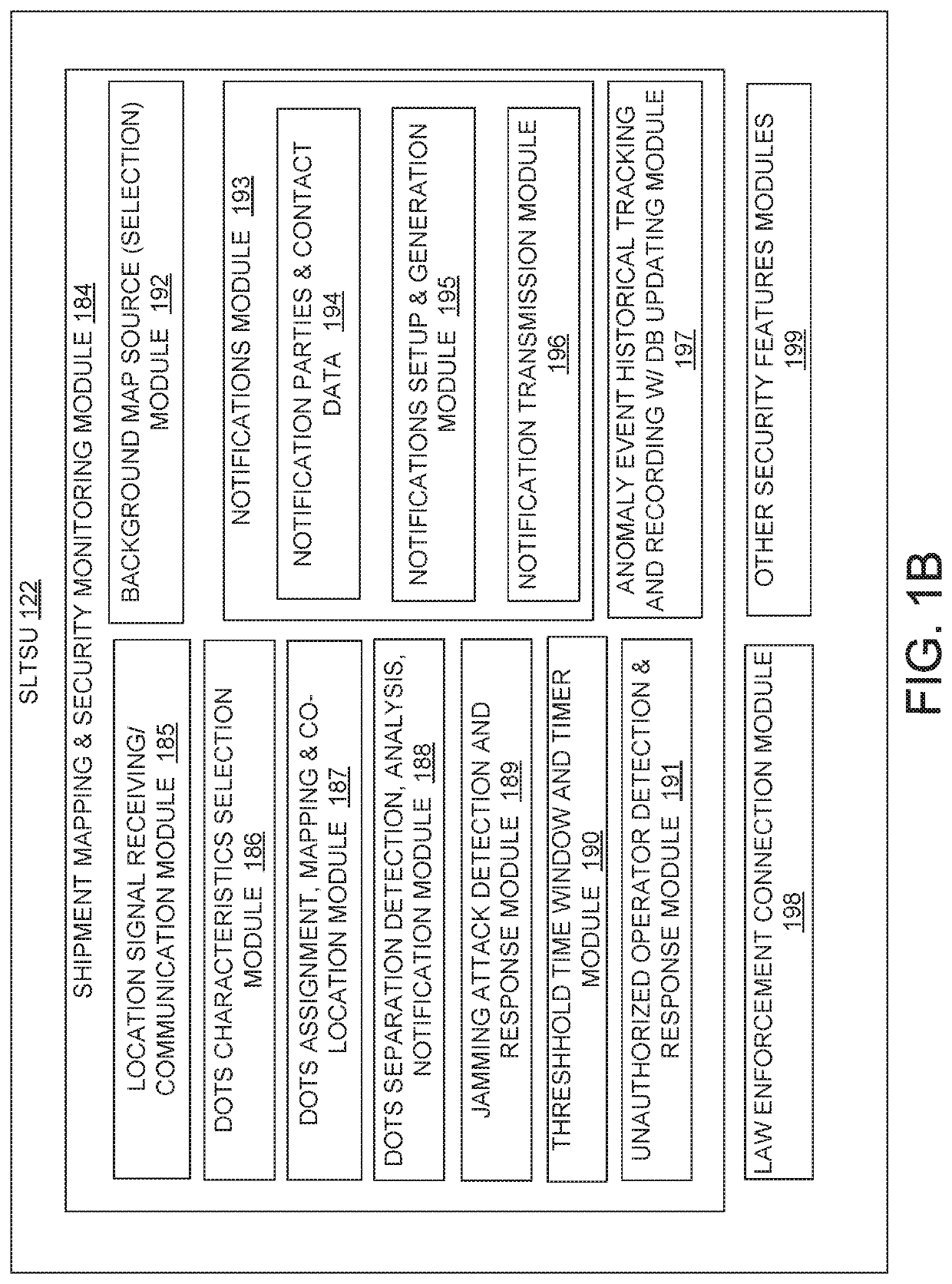
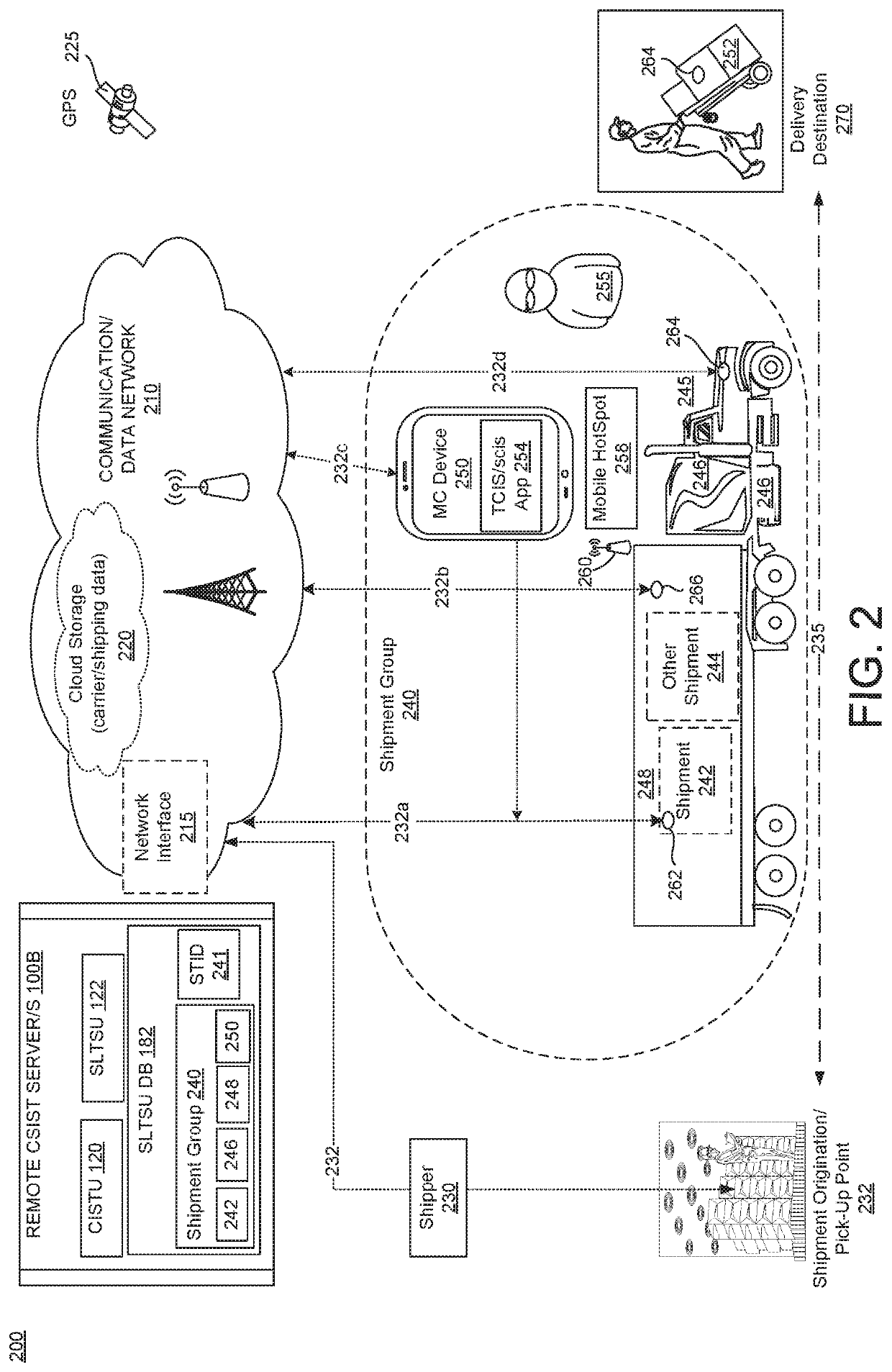
Tracking system and method for monitoring and ensuring security of shipments
ActiveUS20190066042A1Improve securityParticular environment based servicesBroadcast service distributionData processing systemGeographic site
A system electronically tracks each or multiple shipment-related entities as a group of co-located dots that are monitored to provide enhanced security of the shipment from attacks or unauthorized or illicit actions that can compromise the shipment's safety. A data processing system (DPS) receives a plurality of location tracking signals of multiple shipment-related entities, associates the location tracking signals as a shipment group that is assigned a unique shipment tracking identifier (STID), and presents the shipment group as a plurality of co-located dots on a shipment tracking user interface (STUI). The DPS monitors for any unscheduled deviations in at least one of an expected co-location / geo-location of the location tracking signals, identifies specific types of unscheduled deviations, and triggers a series of responsive actions to protect the shipment. The unscheduled deviations can include signal jamming attacks, incorrect pickup (or theft) of an operator-assigned shipment, and unexpected separation of the tracked entities.
Owner:OVERHAUL GRP INC
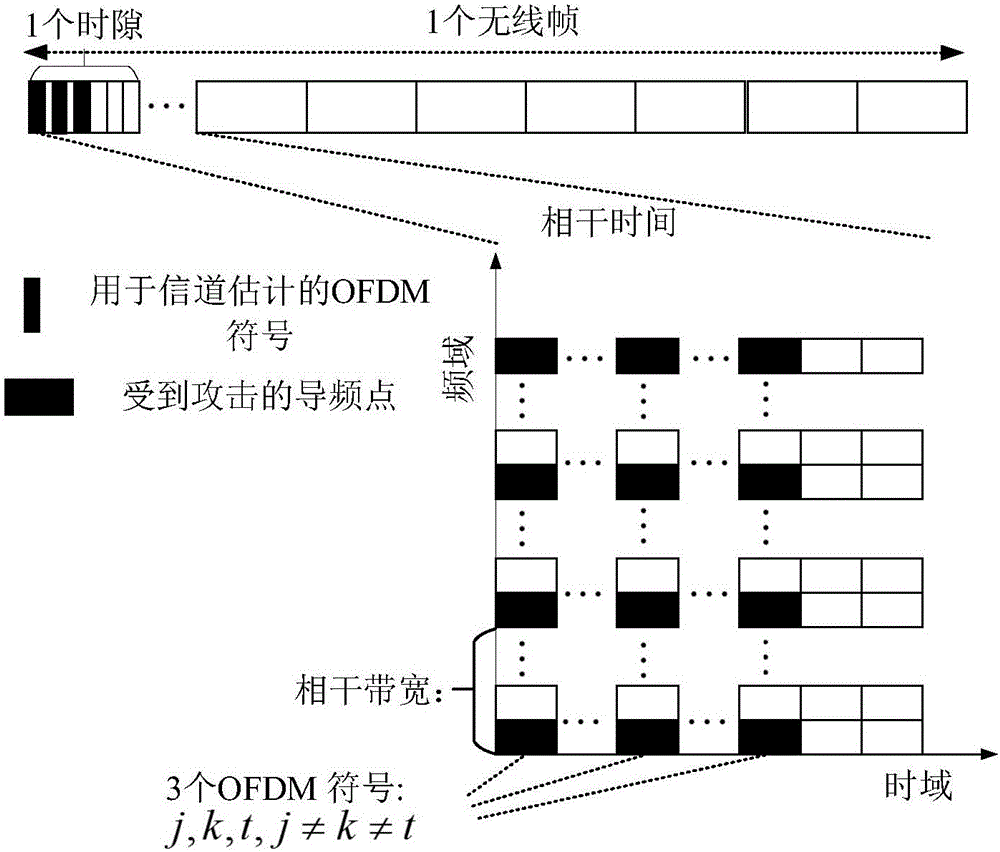
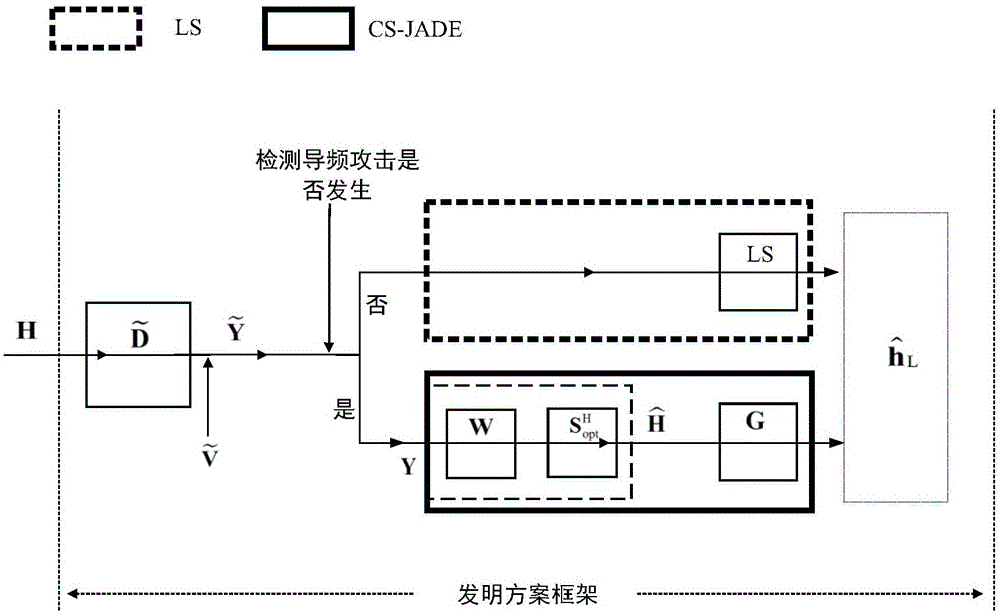
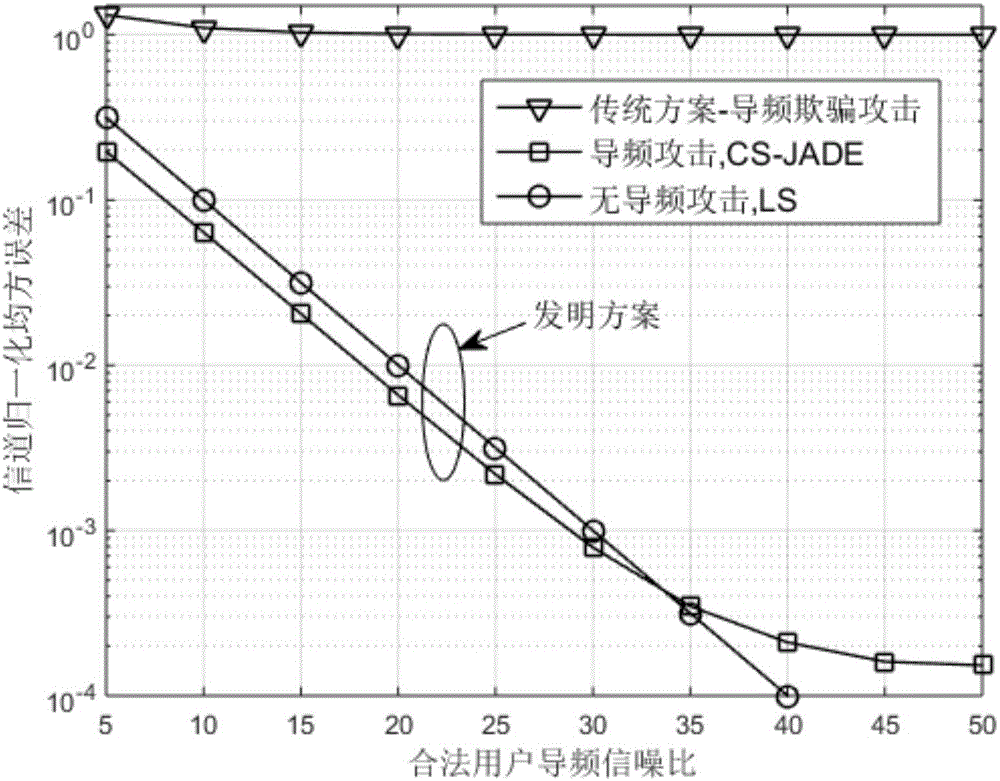
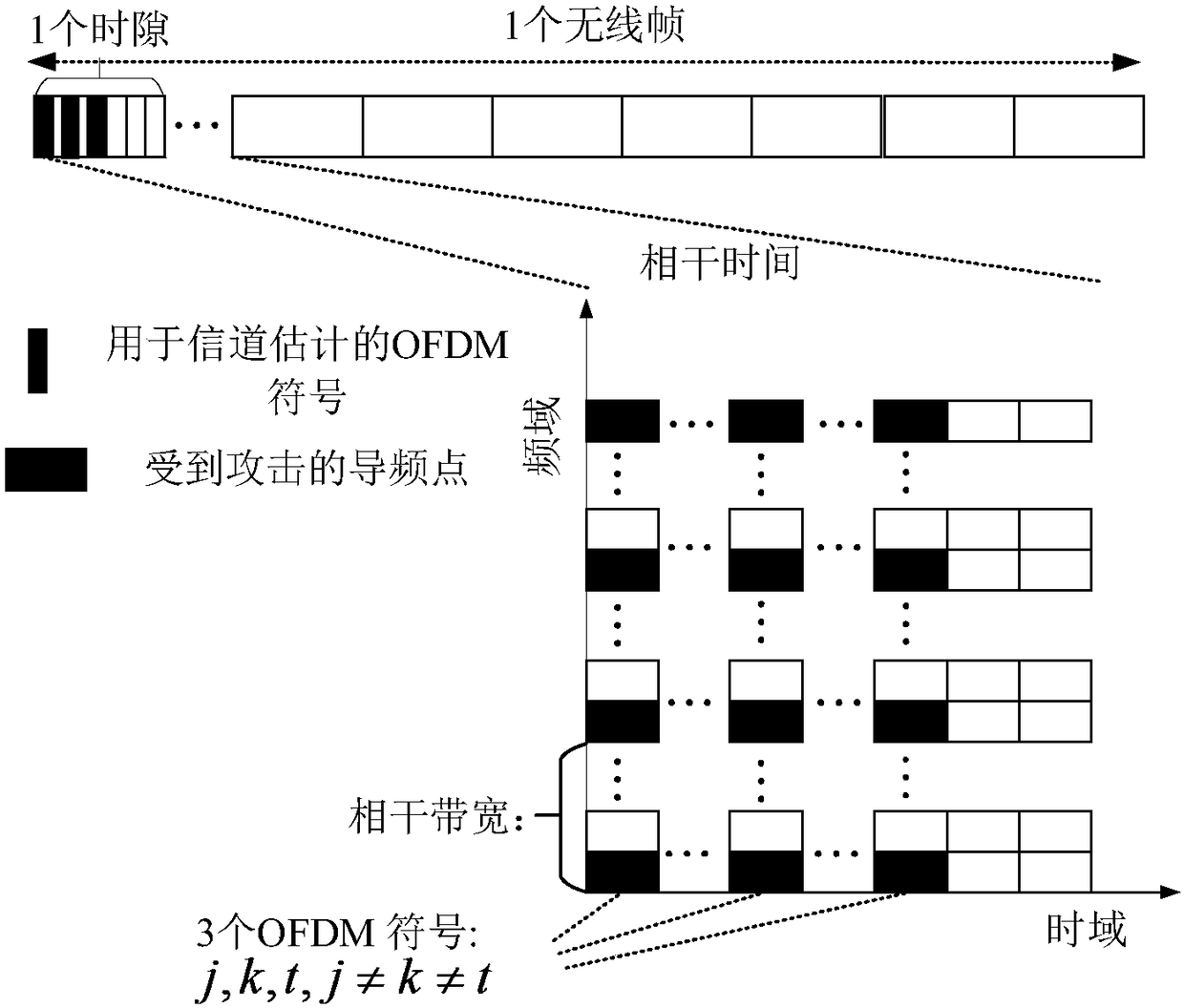
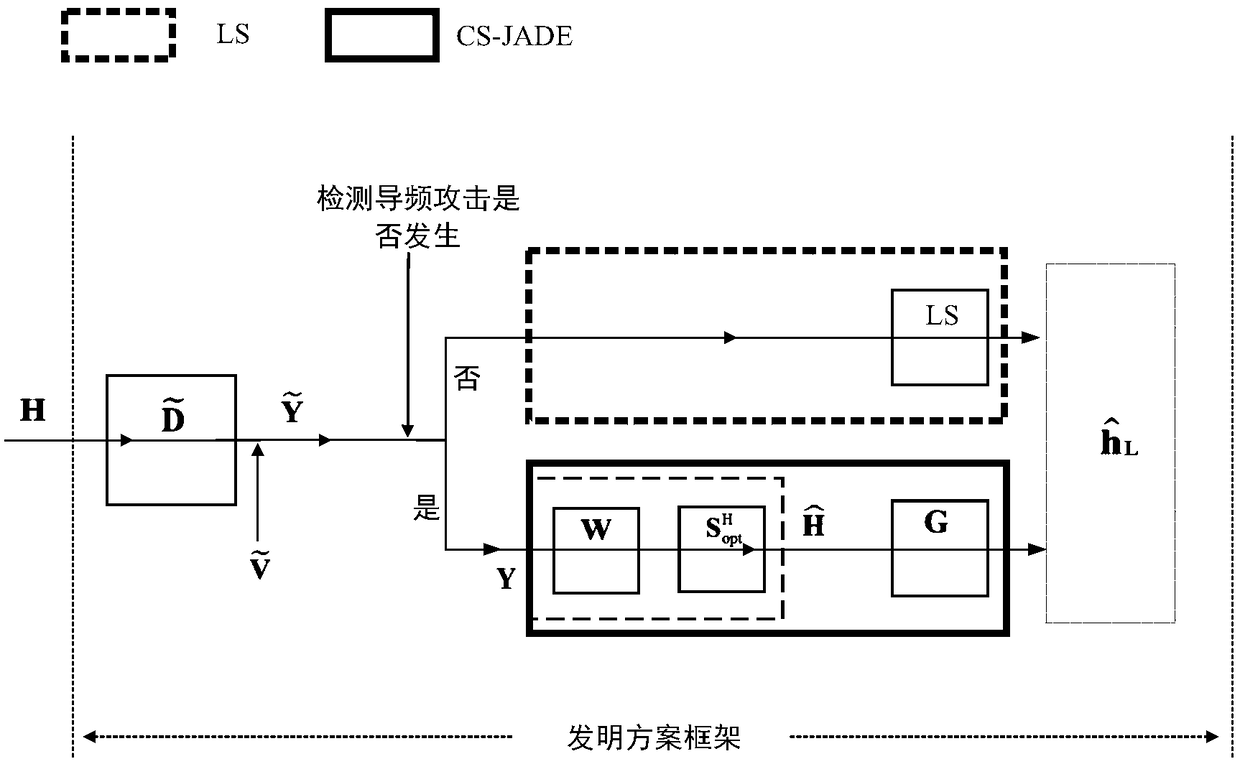
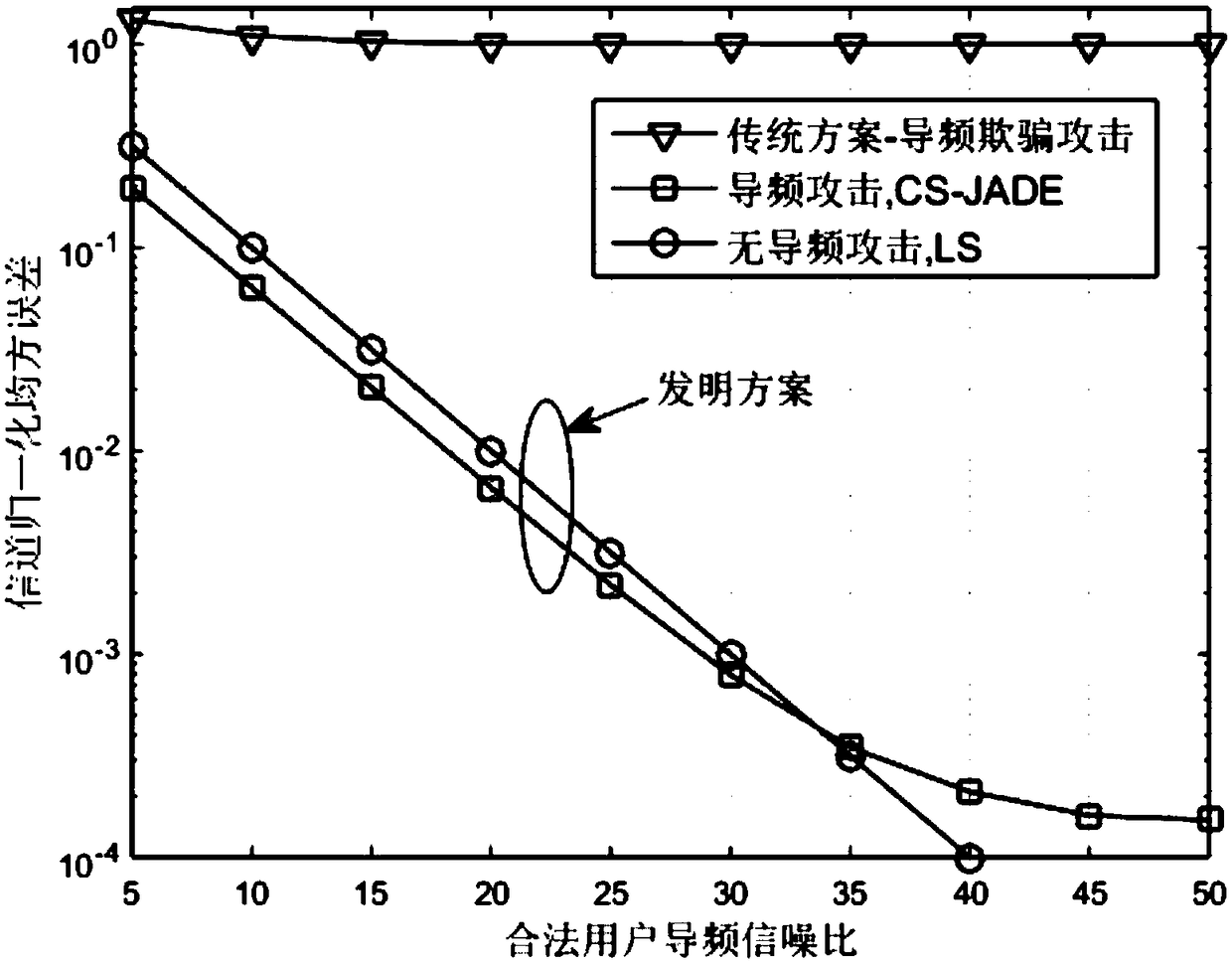
Method for channel estimation and identification against pilot spoofing attack based on independent component analysis in OFDM (Orthogonal Frequency Division Multiplexing) system
ActiveCN106161297AImprove estimation accuracySolve the problem of low estimation accuracyChannel estimationMulti-frequency code systemsIndependent component analysisJamming attack
The invention provides a method for channel estimation and identification against a pilot spoofing attack based on independent component analysis in an OFDM (Orthogonal Frequency Division Multiplexing) system. The method utilizes the characteristics of the random pilot to weaken the pilot spoofing attack to a pilot interference attack, and meanwhile, a legal channel between an uplink legal transmitter and a receiver under the pilot interference environment is estimated and identified according to the independent features of the channel. The method only need to spend time resources of three OFDM symbols and a certain number of frequency band resources and is immune to the pilot interference power of an active eavesdropper. The uplink legal transmitter disrupts the intentional pilot attack of the active eavesdropper through transmitting the uplink random pilot, and meanwhile, the receiver extracts legal channel information from a received contaminated signal through utilizing the mutual independence between the legal channel and an attack channel, so that the channel estimation accuracy of the legal channel is improved, and thus a problem of low channel estimation accuracy caused by the pilot spoofing attack is solved.
Owner:XI AN JIAOTONG UNIV
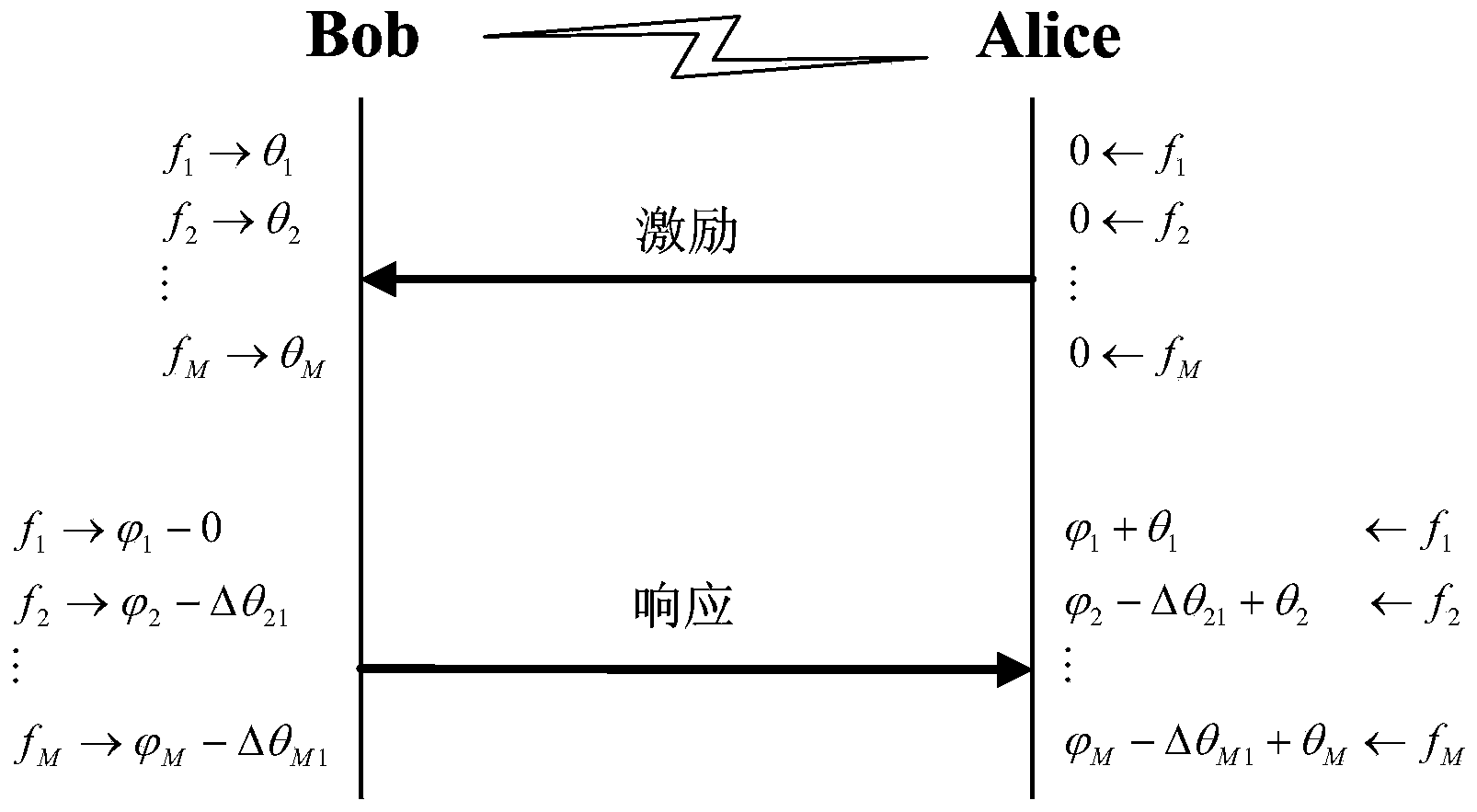
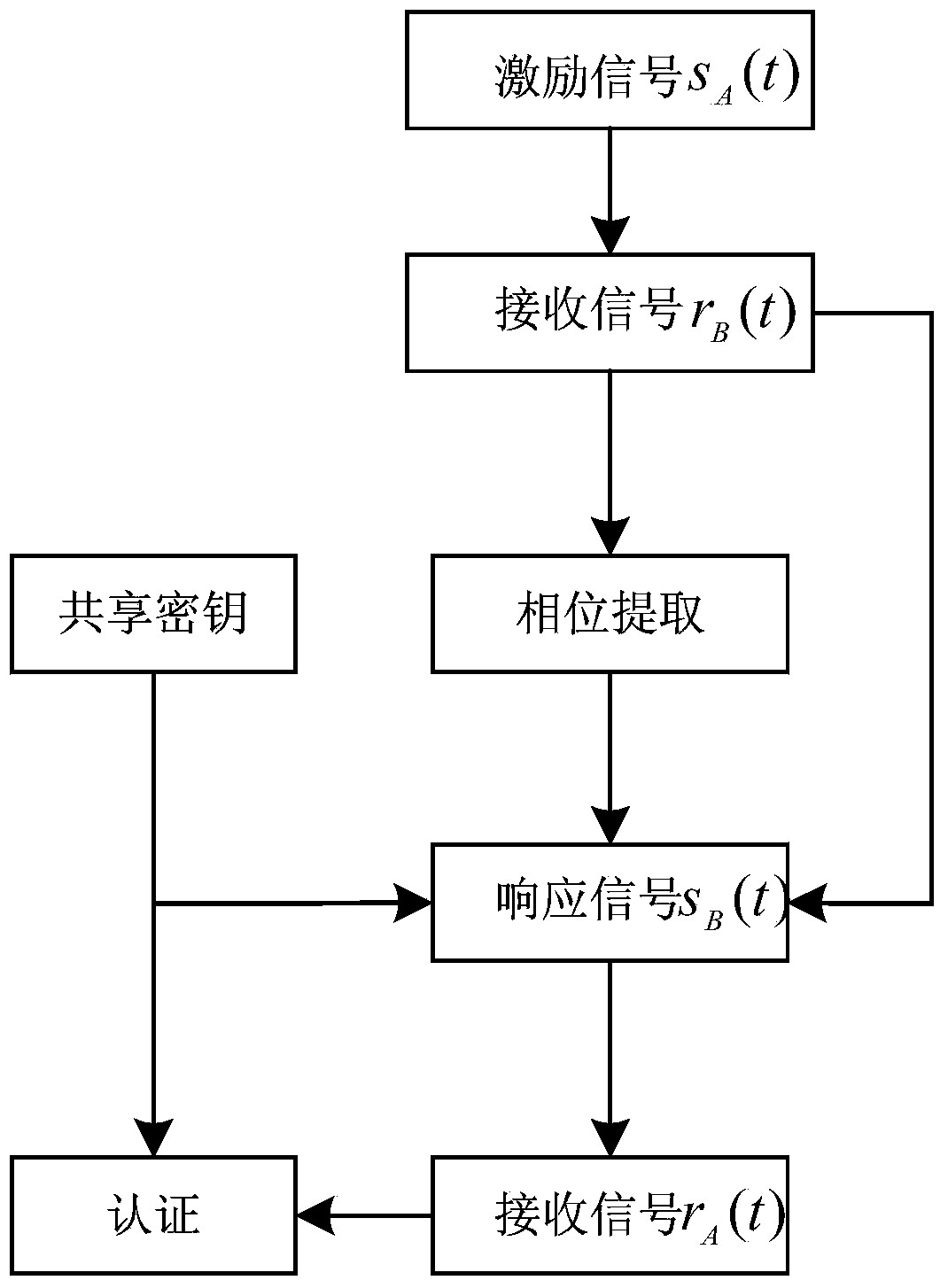
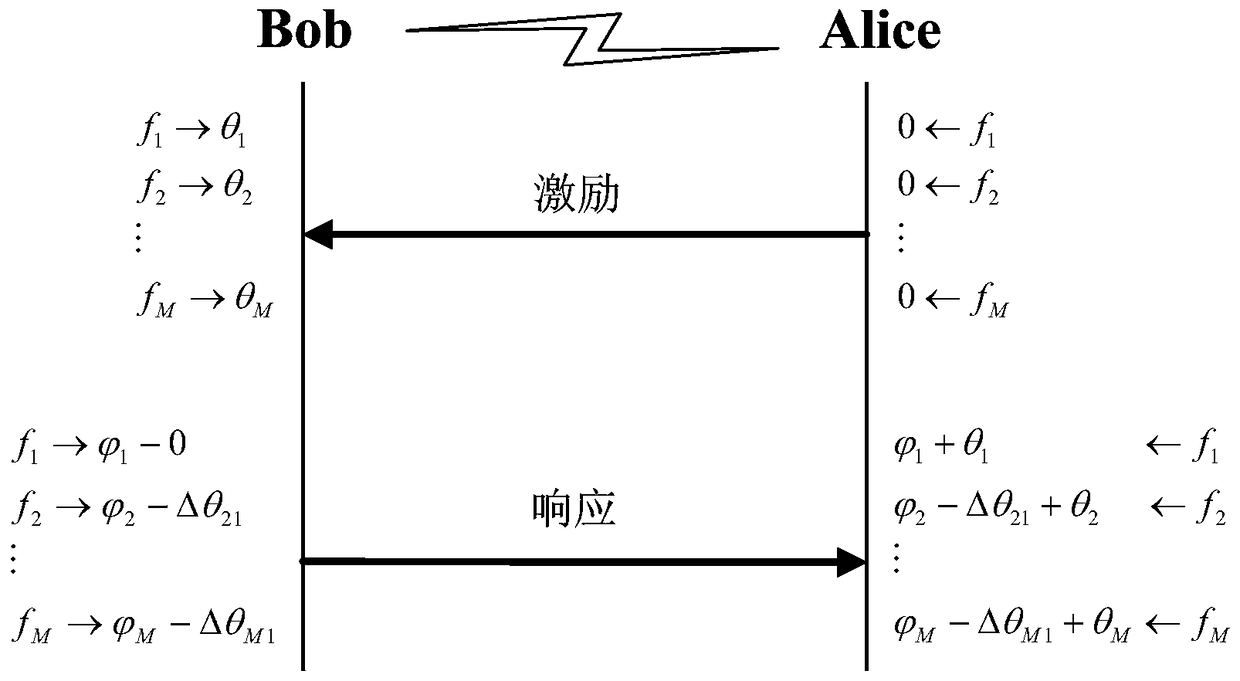
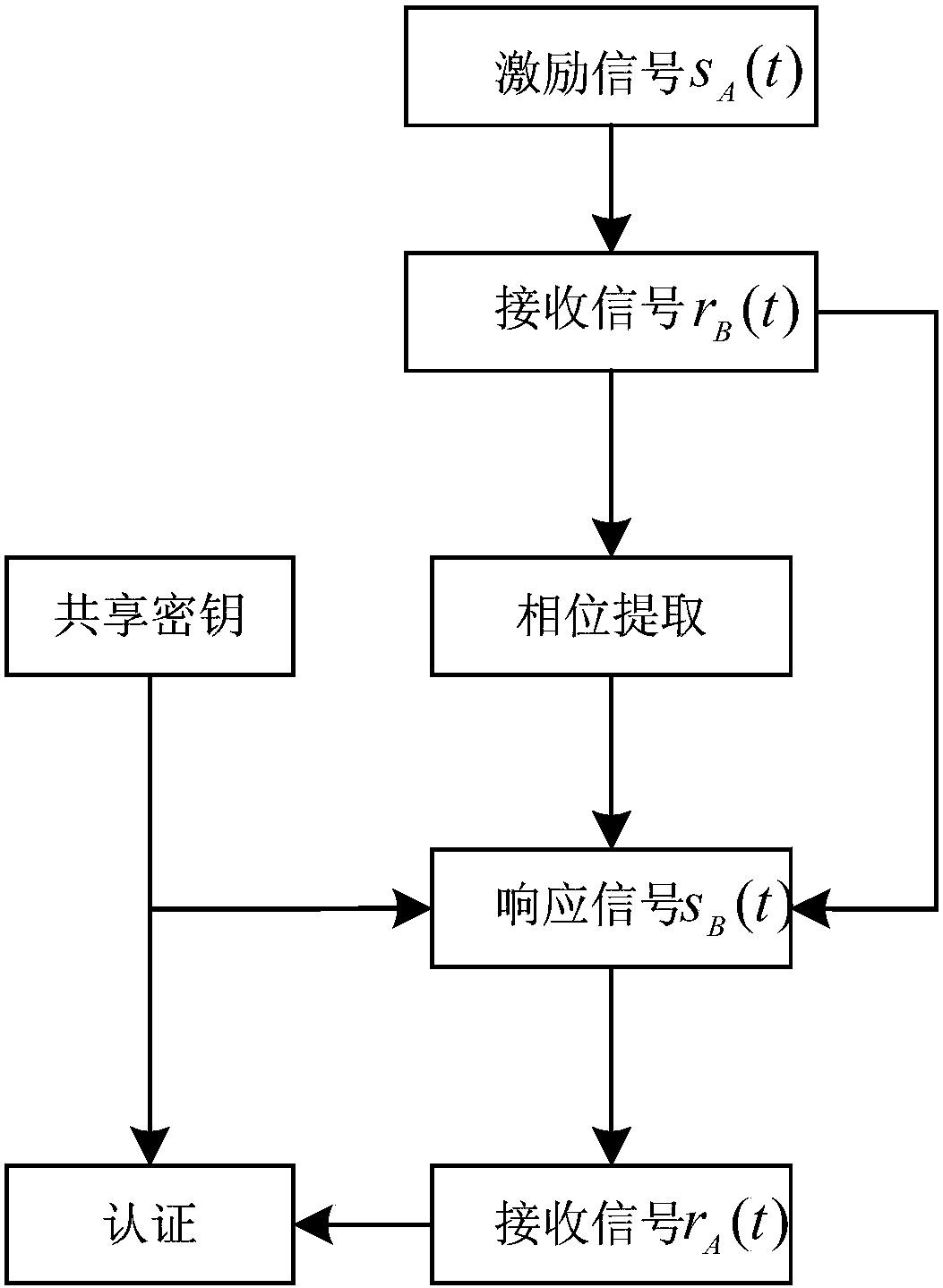
Physical layer authentication method based on multi-carrier transmission
ActiveCN104168562AGood authentication performanceImprove securityWireless network protocolsTransmission path multiple useComputer hardwarePhase response
The invention discloses a physical layer authentication method based on multi-carrier transmission. According to the method, based on the multi-carrier transmission, channels are regarded as a set of M fading sub-channels, and the reciprocity and randomness of phase responses of the sub-channels are used for performing on identity authentication on both parties of communication. The method includes the implementation steps that Alice transmits an excitation signal to Bob, the phase difference of the multi-carrier channels is measured after Bob receives the excitation signal, then Bob transmits a signal where a shared secrete key is packaged to Alice, and Alice authenticates whether the signal is from Bob or not according to the received signal and the shared secrete key. According to the authentication process of the method, the characteristics of the phase responses of the channels are used, and kinds of spoofing attacks such as the interference attack, the replay attach, impersonation attack are effectively resisted.
Owner:青岛联众芯云科技有限公司
Efficient protocols against sophisticated reactive jamming attacks
InactiveUS20120051239A1Avoid interferenceError preventionFrequency-division multiplex detailsWireless sensor networkingSensor node
Embodiments of the invention provide systems and methods for deactivating reactive jamming attacks and other sophisticated attacks in wireless sensor networks (WSNs). In one system, trigger nodes (nodes whose transmissions invoke jammer nodes) are identified and communications between the sensor nodes of the WSN are routed to avoid sending (e.g., transmitting) information from identified trigger nodes. For example, identified trigger nodes are routed as receivers only. One method of identification uses an advanced randomized error-tolerant non-adaptive group testing technique and a clique-independent set problem solution. Another method of identification uses a hexagon tiling coloring and sequential group testing scheme.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
Systems and methods for detecting wireless communication jamming in a network
An electronic device may include a processor and a network interface that may include a first radio and a second radio. The processor may be configured to perform wireless communication jamming attack detection by occasionally performing clear channel verification utilizing the network interface to determine whether a threshold number of devices' channels are incapacitated in a wireless network within a threshold amount of time and / or by sending a heartbeat signal from the first radio and determining whether the second radio received the heartbeat signal.
Owner:GOOGLE LLC
Method and network to implement decentralized validation and authentication mechanisms to prevent ads-b cyber-attacks
ActiveUS20190280870A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationCyber-attackEavesdropping
A method or network that addresses cybersecurity vulnerabilities in an ADS-B network by validating and authenticating ADS-B messages. Nodes of the network maintain a validated ledger of ADS-B transactions and use validated information from this ledger to improve security against common cybersecurity attacks including, but not limited to, denial of service attacks, jamming attacks, spoofing attacks, flooding attacks and eavesdropping.
Owner:ROBUST ANALYTICS INC
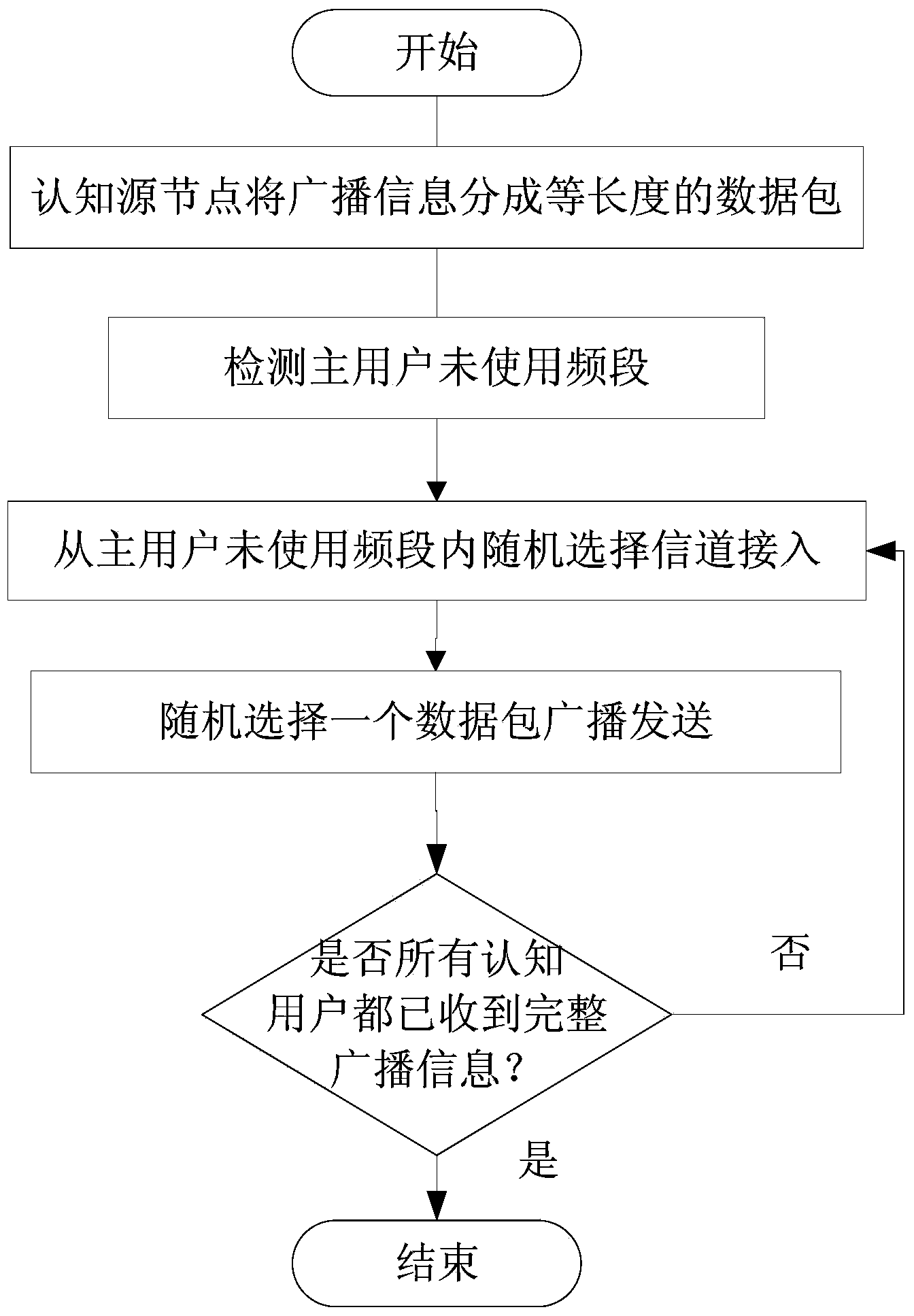
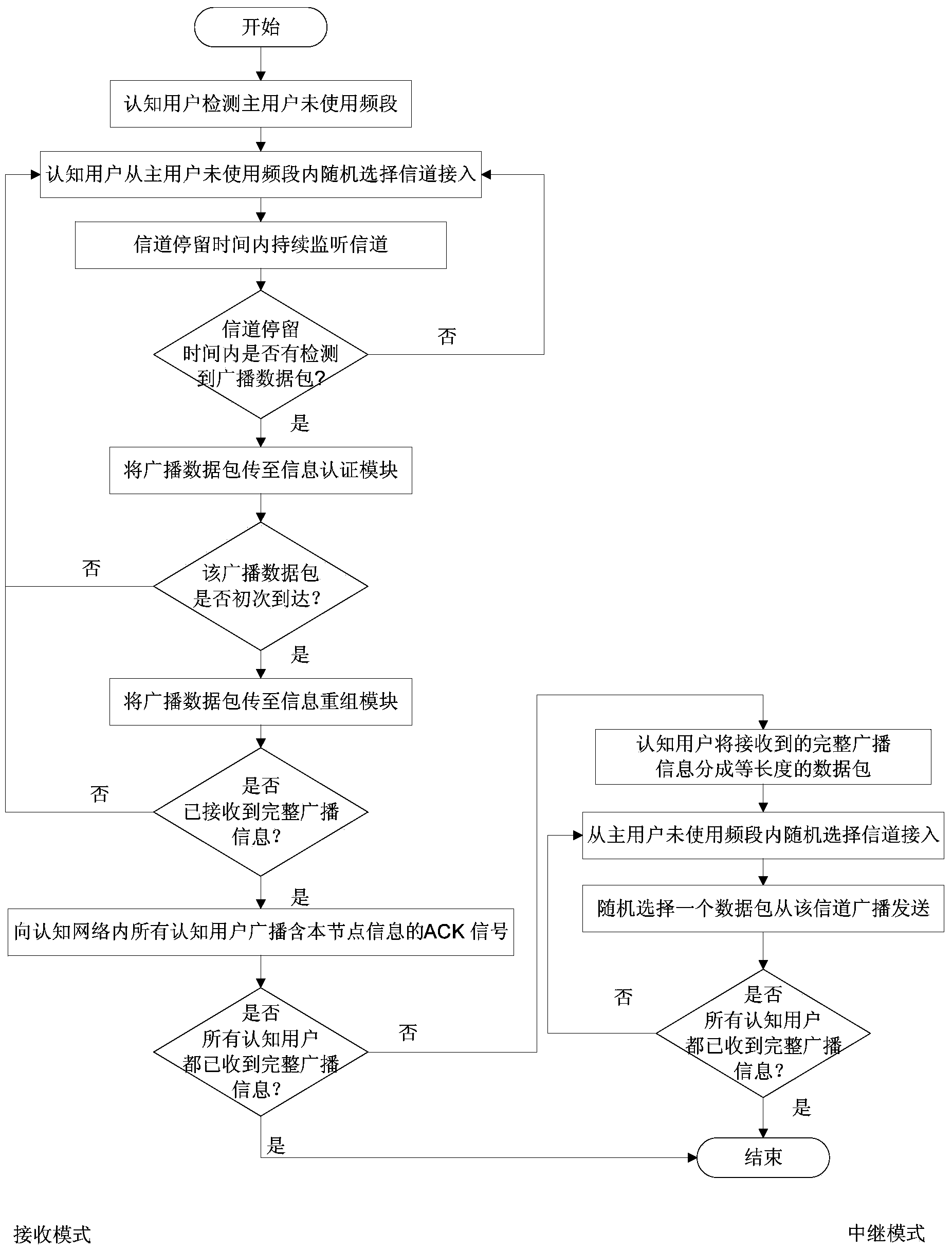
Cognitive radio network anti-hostile interference cooperative broadcasting method based on non-coordinated frequency hopping
InactiveCN103987018ADefense against hostile jamming attacksImprove communication efficiencyBroadcast service distributionCognitive userRadio networks
The invention provides a cognitive radio network anti-hostile interference cooperative broadcasting method based on non-coordinated frequency hopping, and relates to wireless network communication. The provided cognitive radio network anti-hostile interference cooperative broadcasting method based on non-coordinated frequency hopping is applied to a cognitive radio network on the premise of having no influence on expandability and communication efficiency of the network. The cognitive radio network anti-hostile interference cooperative broadcasting method based on non-coordinated frequency hopping is characterized in that firstly, a source node and a non-coordinated frequency hopping technology switched in a cognitive user random selection channel are adopted, so that the hostile interference of the radio network can be resisted, and meanwhile, the problems of poor expandability, low safety and the like caused by needing advance sharing of secret keys in a conventional frequency hopping technology are solved; and secondly, a cooperative broadcasting mechanism among cognitive users is introduced, namely, the cognitive users completing broadcast message receiving help the source node to transmit the broadcast message to other cognitive users in the network, and thus the communication efficiency of the cognitive radio network is improved.
Owner:XIAMEN UNIV
Efficient protocols against sophisticated reactive jamming attacks
InactiveUS8705407B2Avoid interferenceNetwork topologiesData switching by path configurationWireless sensor networkingSensor node
Embodiments of the invention provide systems and methods for deactivating reactive jamming attacks and other sophisticated attacks in wireless sensor networks (WSNs). In one system, trigger nodes (nodes whose transmissions invoke jammer nodes) are identified and communications between the sensor nodes of the WSN are routed to avoid sending (e.g., transmitting) information from identified trigger nodes. For example, identified trigger nodes are routed as receivers only. One method of identification uses an advanced randomized error-tolerant non-adaptive group testing technique and a clique-independent set problem solution. Another method of identification uses a hexagon tiling coloring and sequential group testing scheme.
Owner:UNIV OF FLORIDA RES FOUNDATION INC
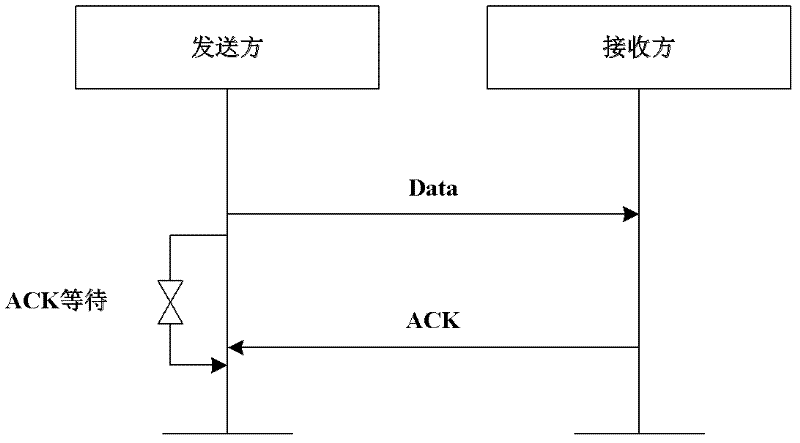
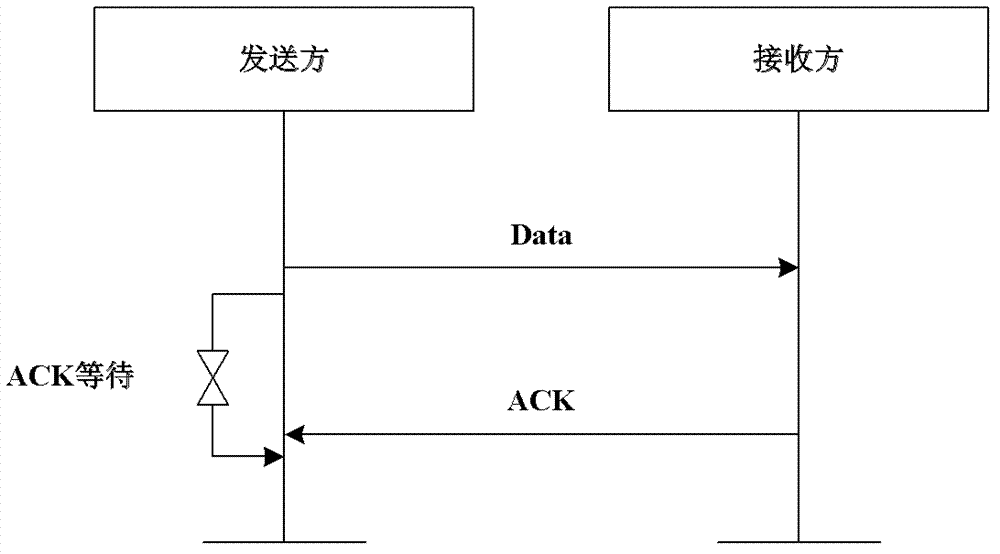
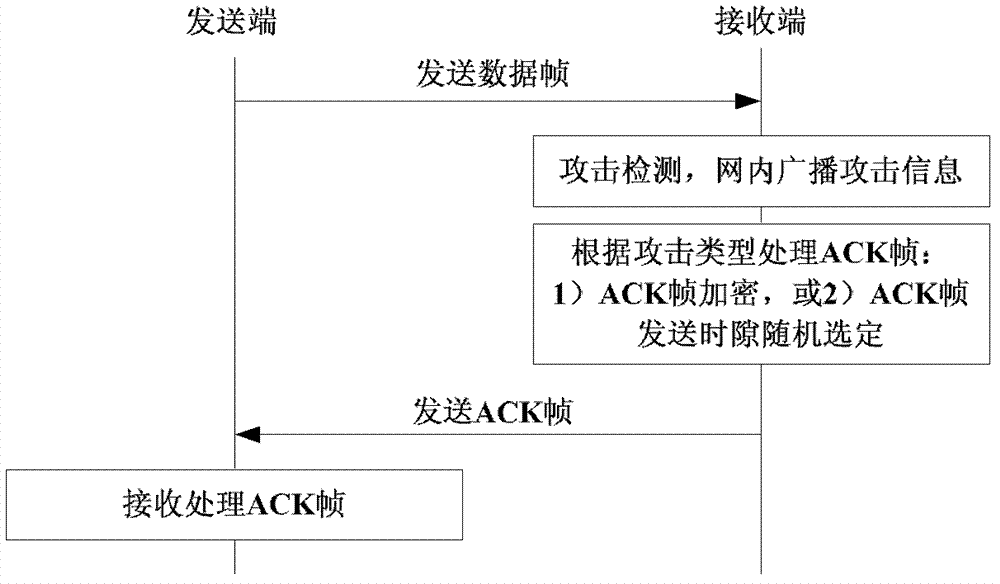
Detecting and protecting method for confirming frame attack of wireless sensor network
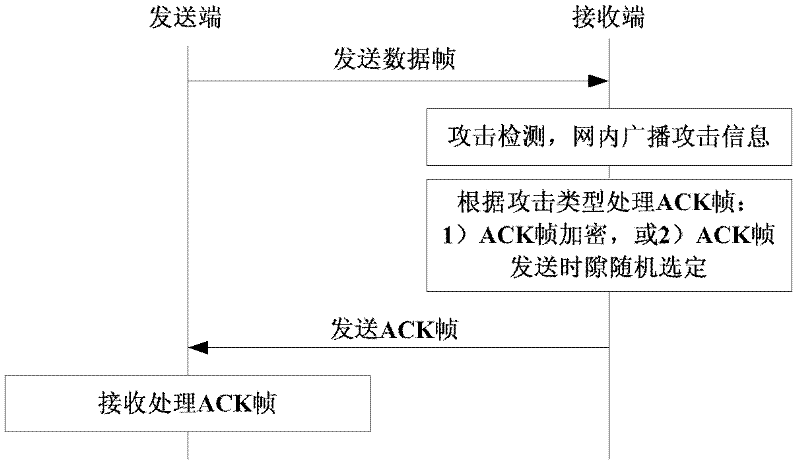
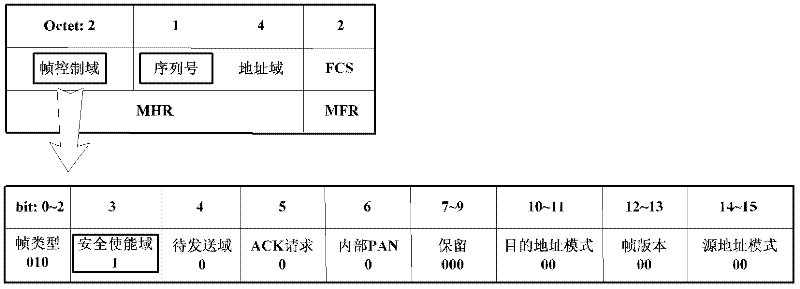
ActiveCN102404740AEnsure safetyGuaranteed reliabilityError prevention/detection by using return channelNetwork topologiesWireless sensor networkingJamming attack
The invention provides a detecting and protecting method for confirming frame attack of wireless sensor network, which is executed by the following steps of: detecting whether there is ACK frame interference attack by LQI (Link Quality Indicator) and times of re-transmitting data; resisting the ACK frame interference attack by randomly setting the ACK frame sending time slot; detecting whether there is ACK frame overwhelming attack by LQI information and the data receiving condition. The detecting and protecting method for confirming frame attack of wireless sensor network provides a method for detecting frame interference attack and frame overwhelming attack based on dynamic threshold value as well as provides self-defending measures by randomly selecting the sending time and hiding the sequences, which is simple and easy to implement.
Owner:CHINA ELECTRIC POWER RES INST +2
Processor transient attack defense method based on cache random invalidation
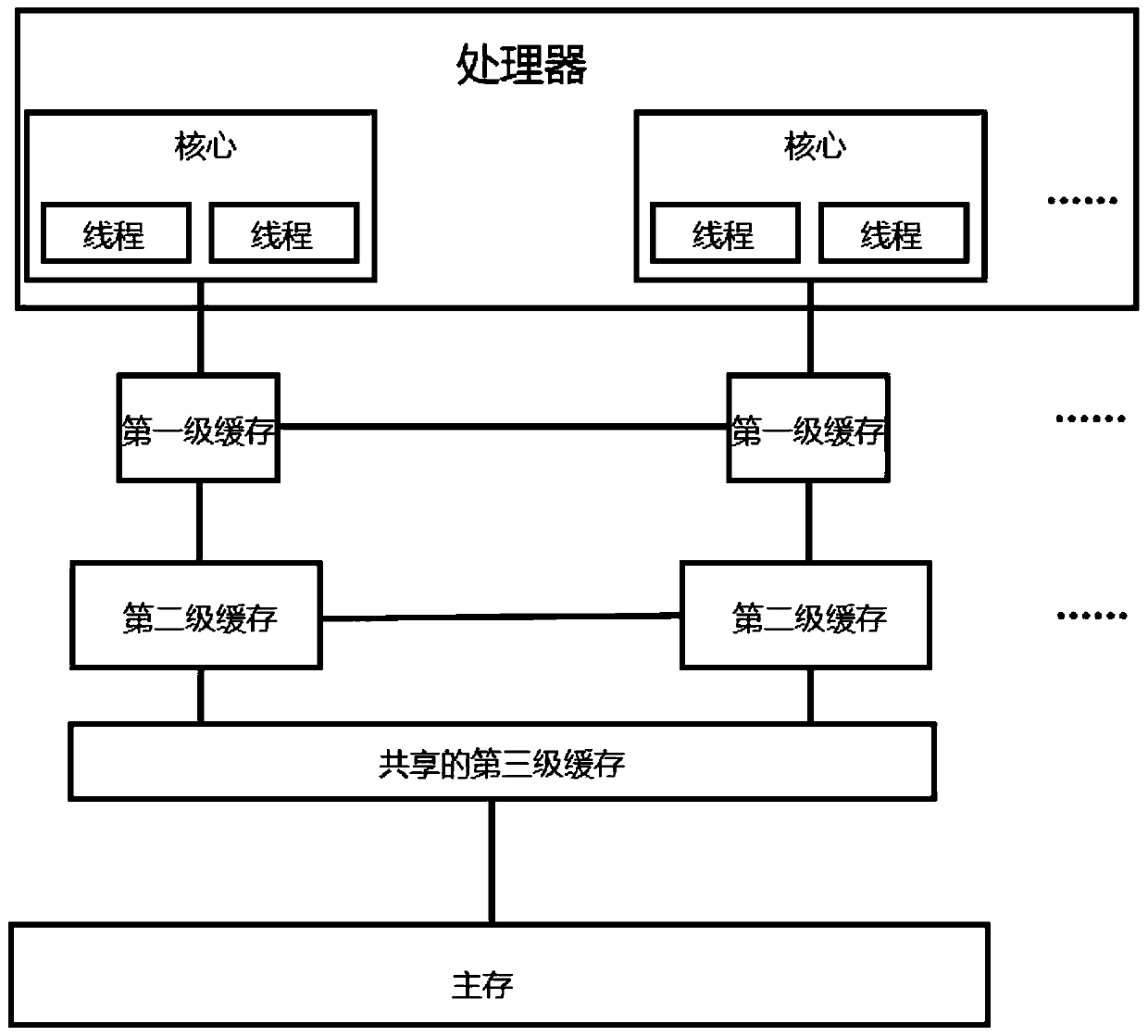
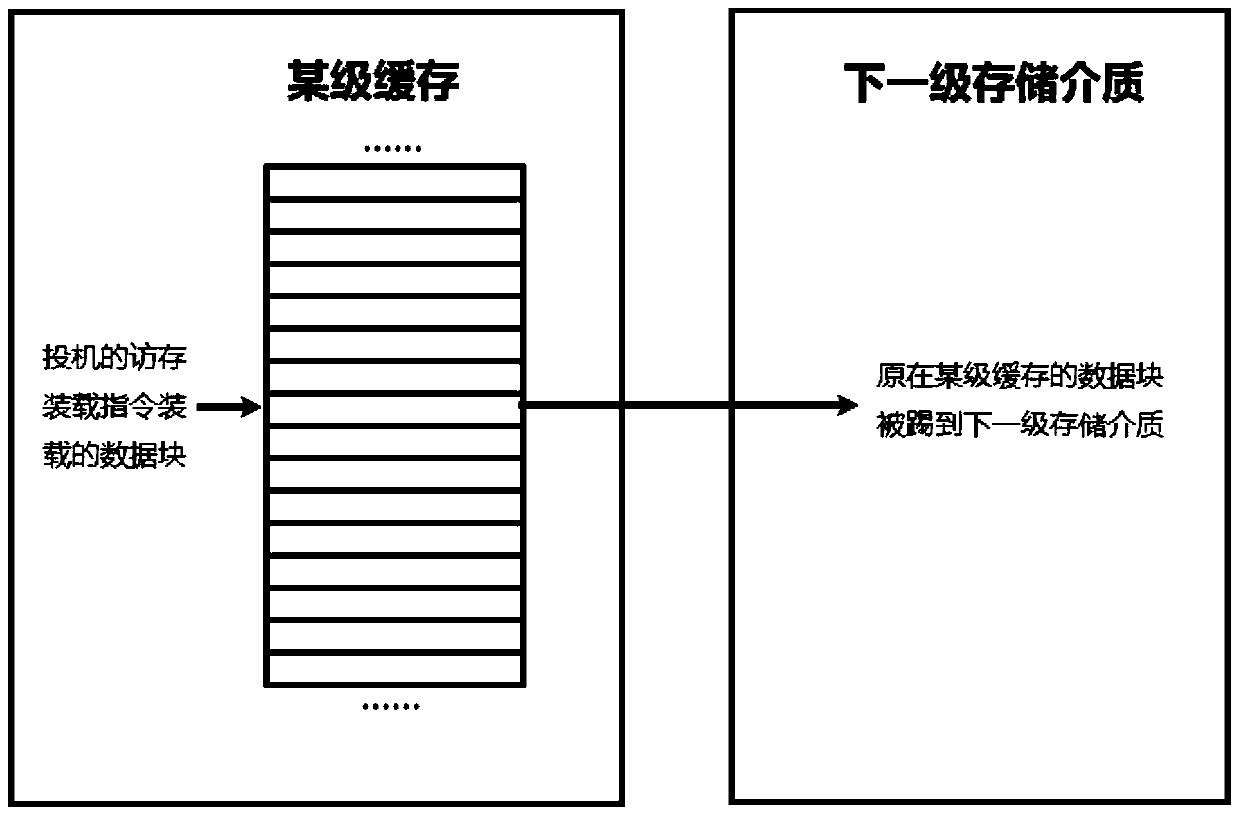
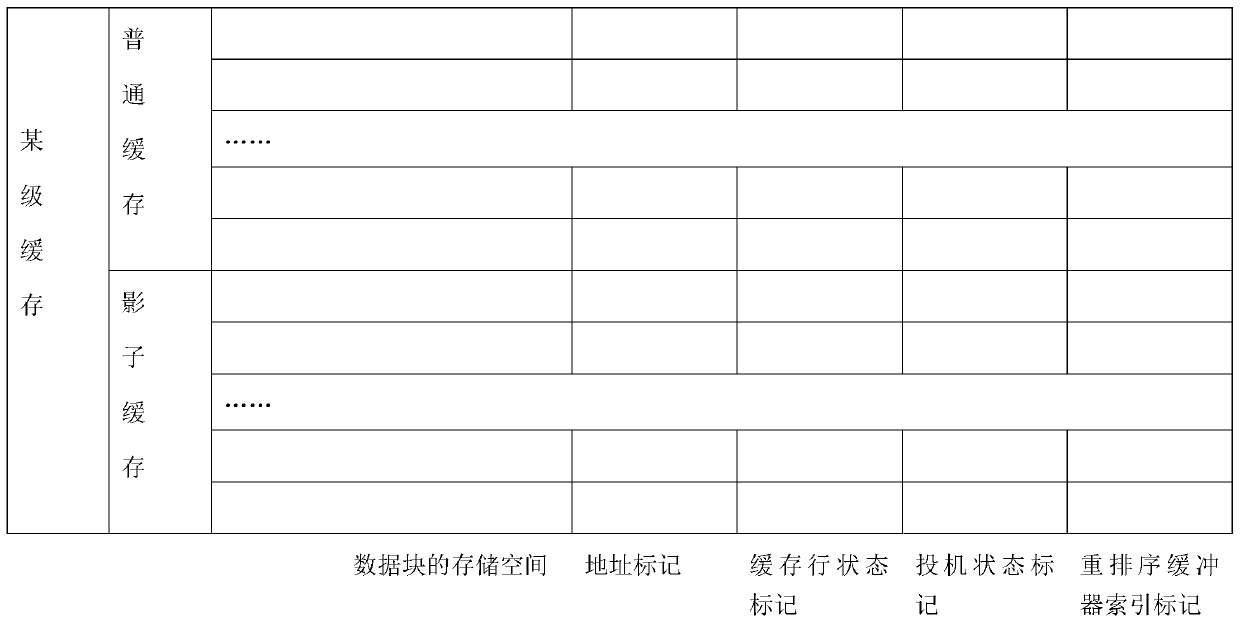
ActiveCN111259384APrevent detectionPlatform integrity maintainanceMemory systemsAttackParallel computing
The embodiment of the invention provides a cache management method. The method comprises the following steps: in response to a memory access request, loading a data block containing data required by aspeculated memory access loading instruction into a common cache, and executing the following operations when the cached data block of the common cache is kicked out of the common cache by the data block loaded by the speculated memory access loading instruction: loading the kicked-out data block into a shadow cache of the same-level cache; and randomly selecting an interference cache line from all cache lines of a common cache, writing a data block of the interference cache line into a next-level storage medium, and then invalidating the interference cache line. According to the invention, an attacker can be prevented from kicking a specific data block out of a certain level of cache by using a speculated memory access loading instruction, so that the access speed of the attacker is prevented from being changed; in addition, the interference cache line is randomly selected, and the data block of the interference cache line is set to be invalid, so that the access speed of the data block of the interference cache line is changed to interfere an attacker, and a secret value can be effectively prevented from being detected by a side channel attack.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
AMI network anti-interference attack routing algorithm for advanced measurement system of smart power grid
ActiveCN110932969AReduce failureReduce failure rateData switching networksPathPingInterference resistance
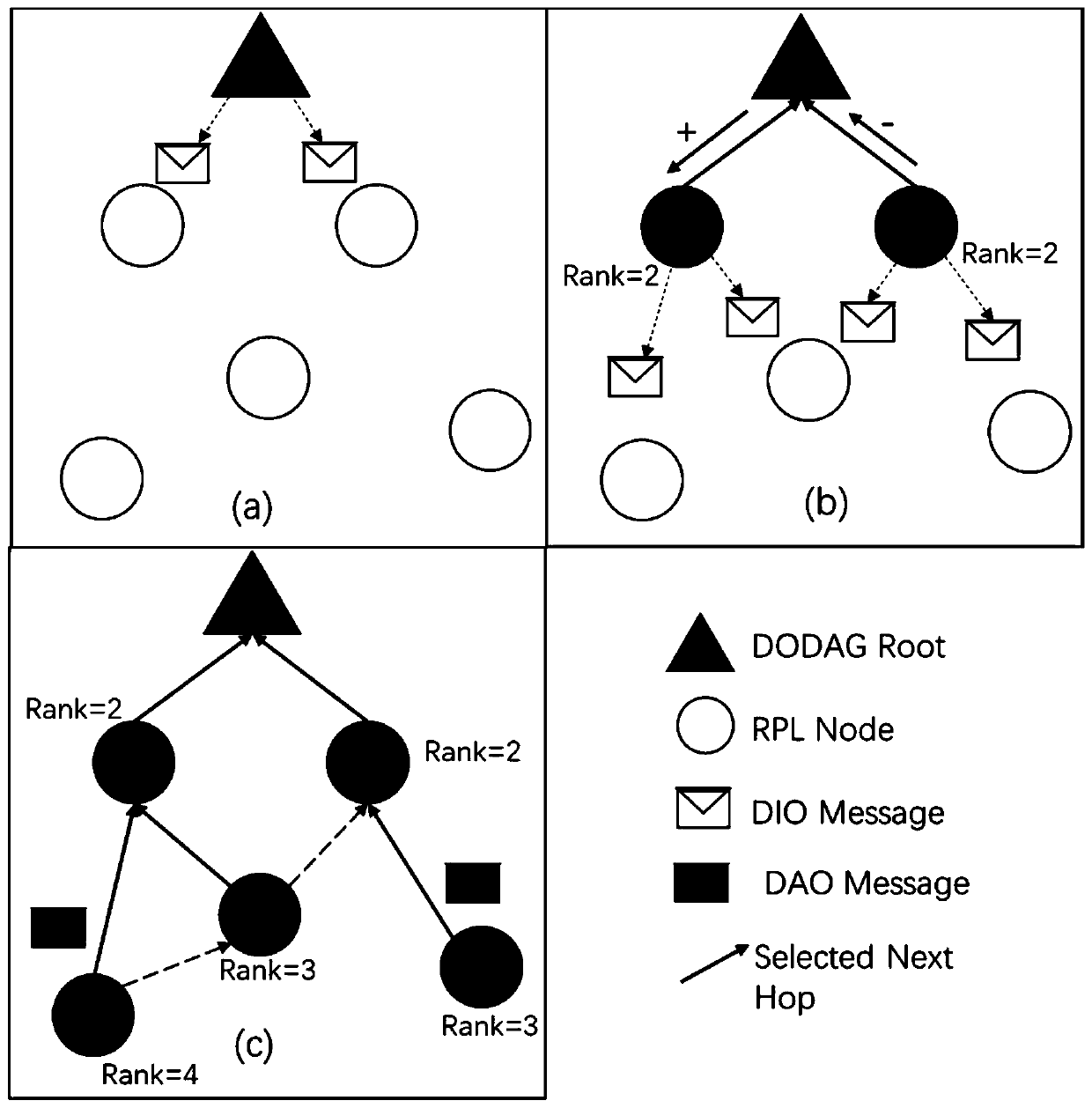
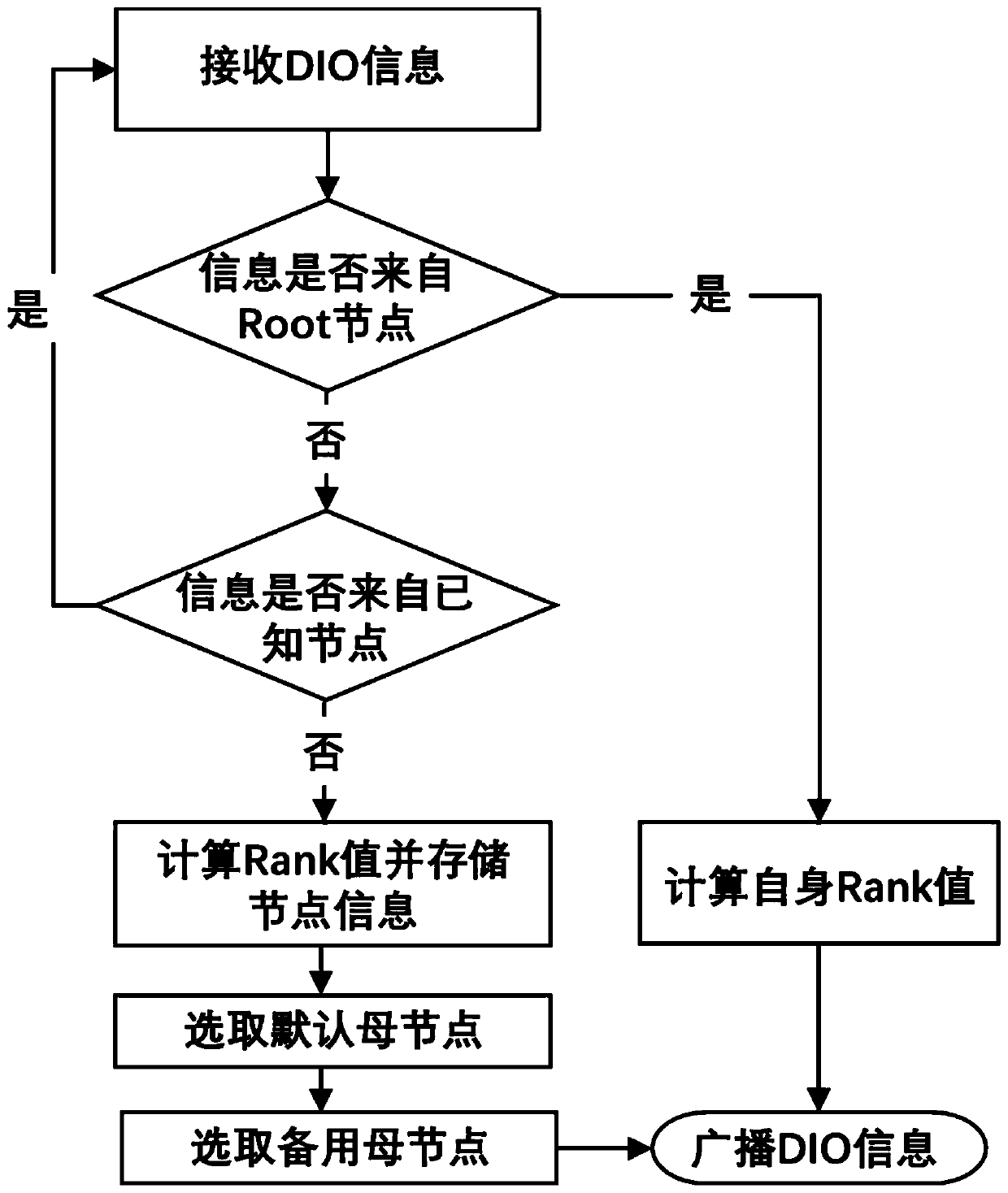
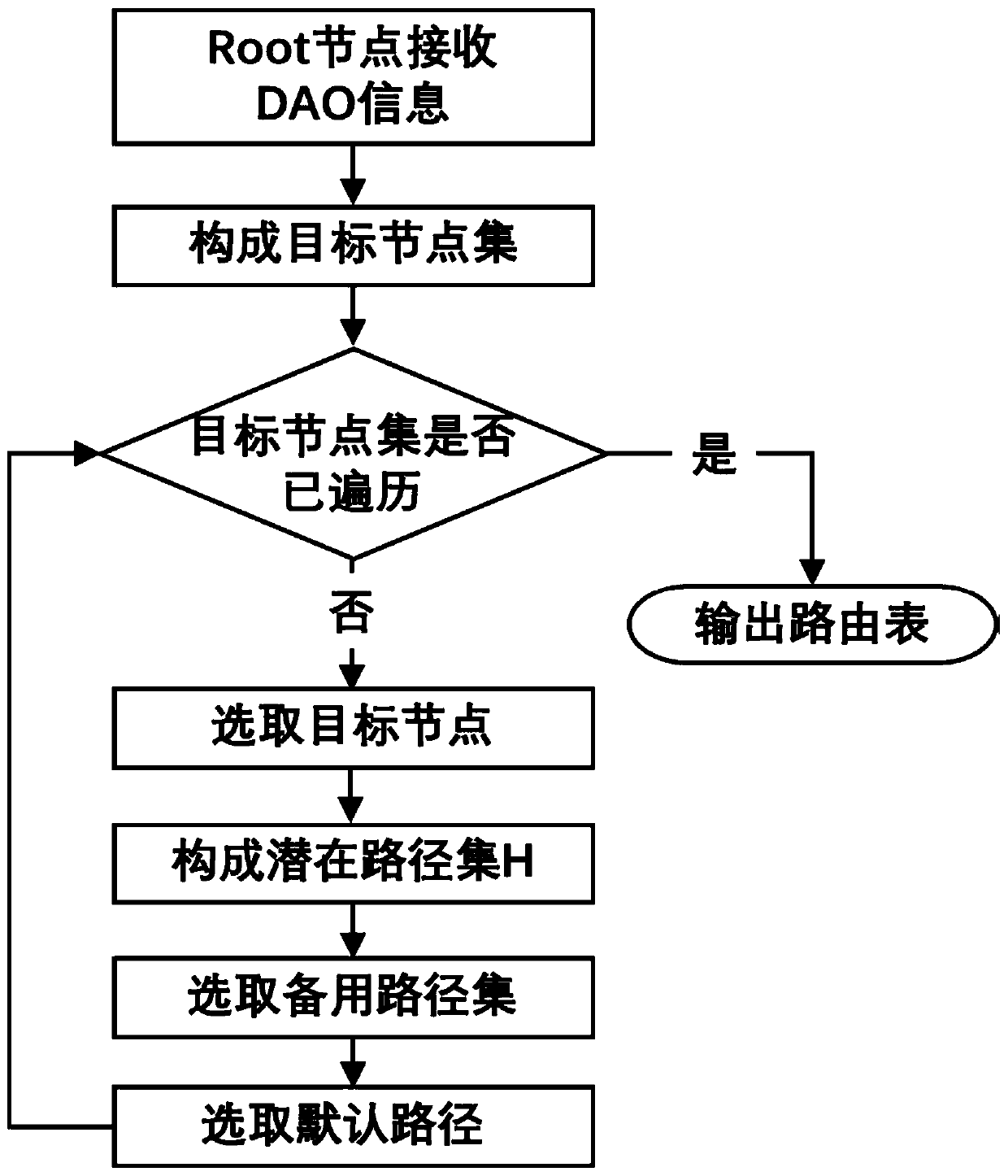
The invention discloses an AMI network anti-interference attack routing algorithm for an advanced measurement system of a smart power grid. The algorithm is an improvement of an RPL routing algorithm,a default RPL path with the optimal performance index can be optimally selected, multiple standby paths can be selected at the same time, and the probability that the standby paths and the default path fail at the same time under the condition that interference attacks exist can be minimum. According to the method, after a default mother node is selected, a penalty term is added to a Rank value of each potential mother node according to an availability history vector, and then a node with the Rank value still smaller than that of the node is selected as a standby mother node. And when the default mother node is unavailable due to Jamming attack, the node can be quickly switched to the standby mother node. When a downlink routing path is formed, DAO information of a node is sent to all mother nodes, so that Root nodes can collect downlink potential routing paths as much as possible, and then a default path and an alternative path reaching a certain downlink node are selected accordingto the provided path availability historical vector.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
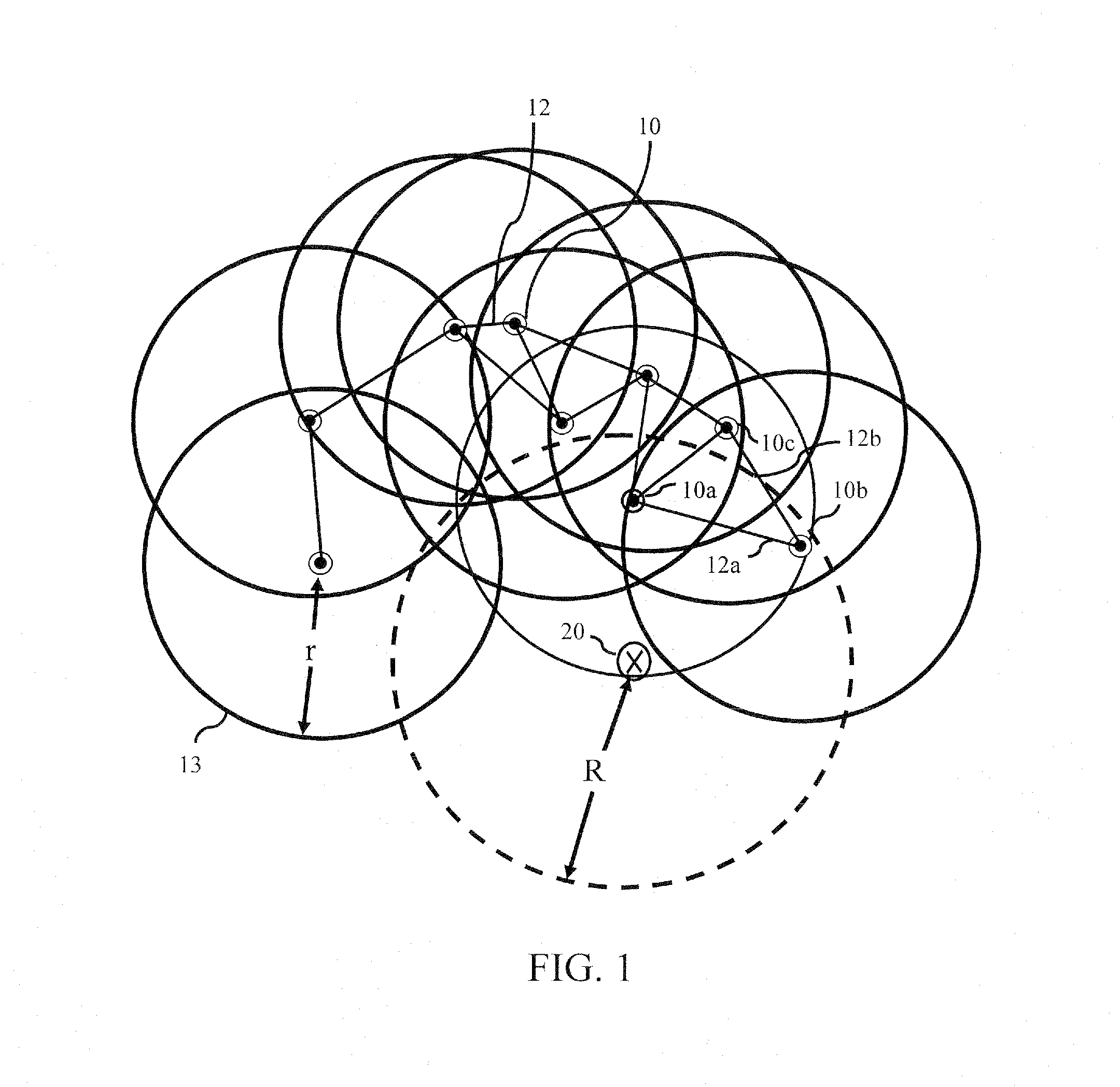
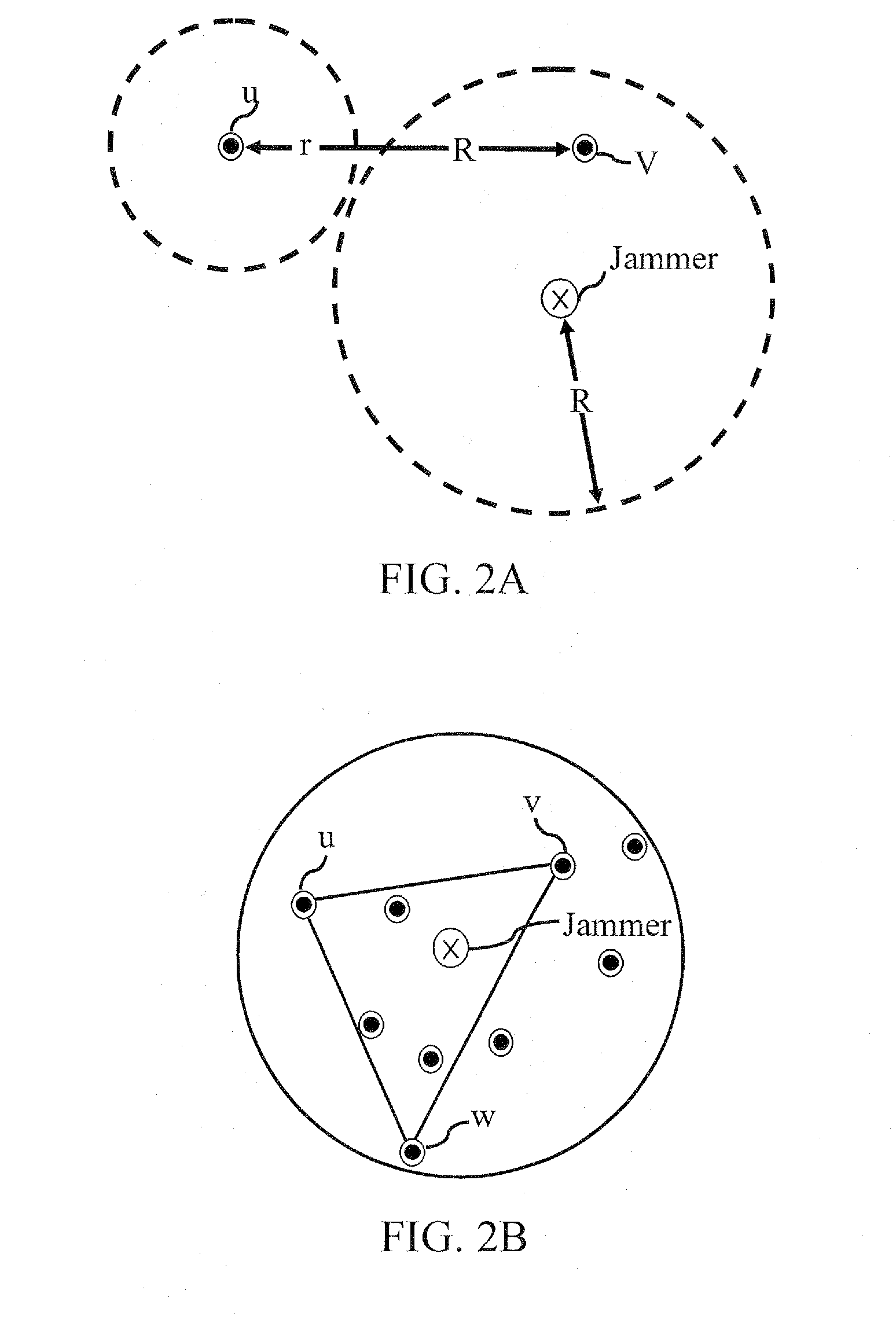
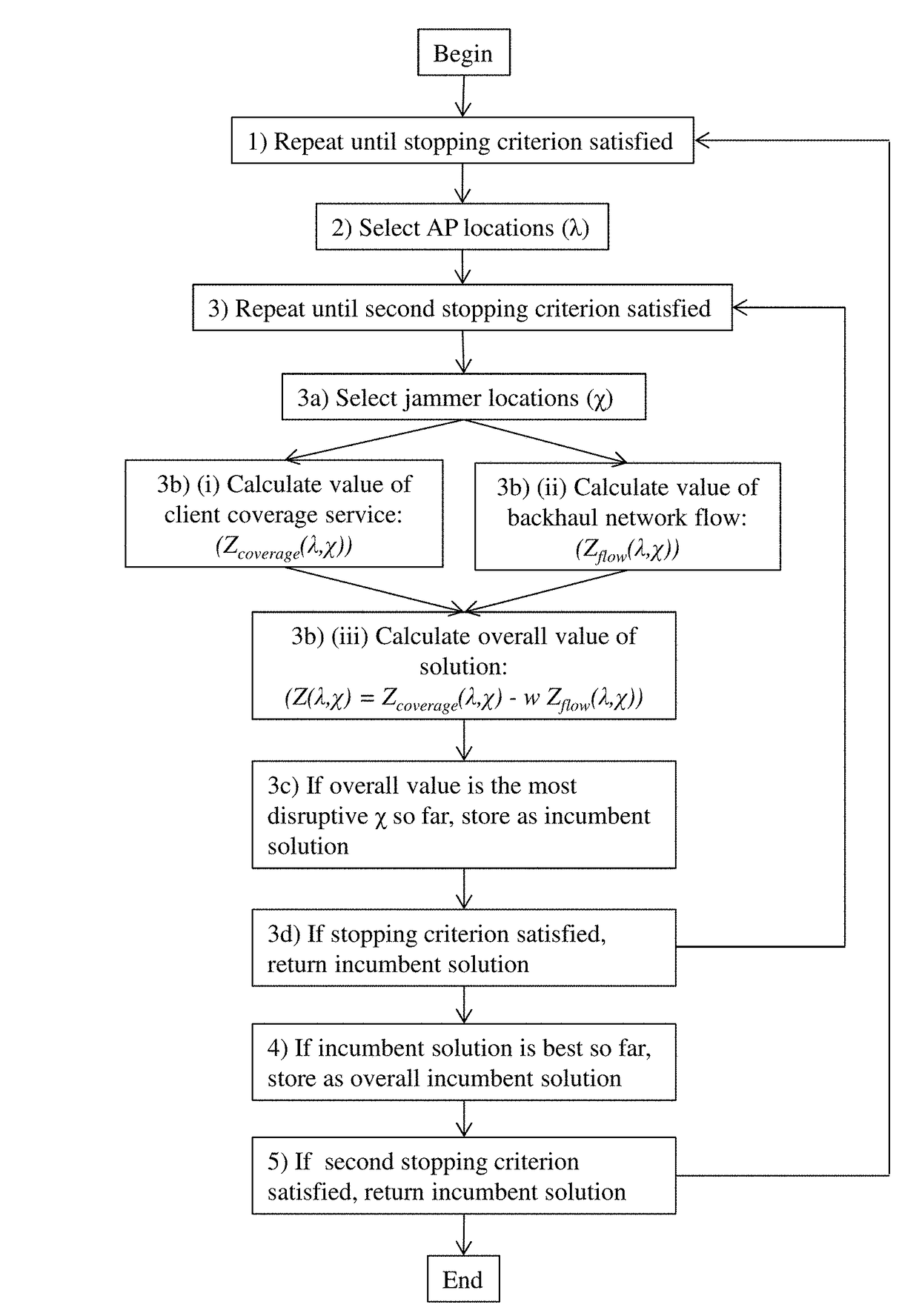
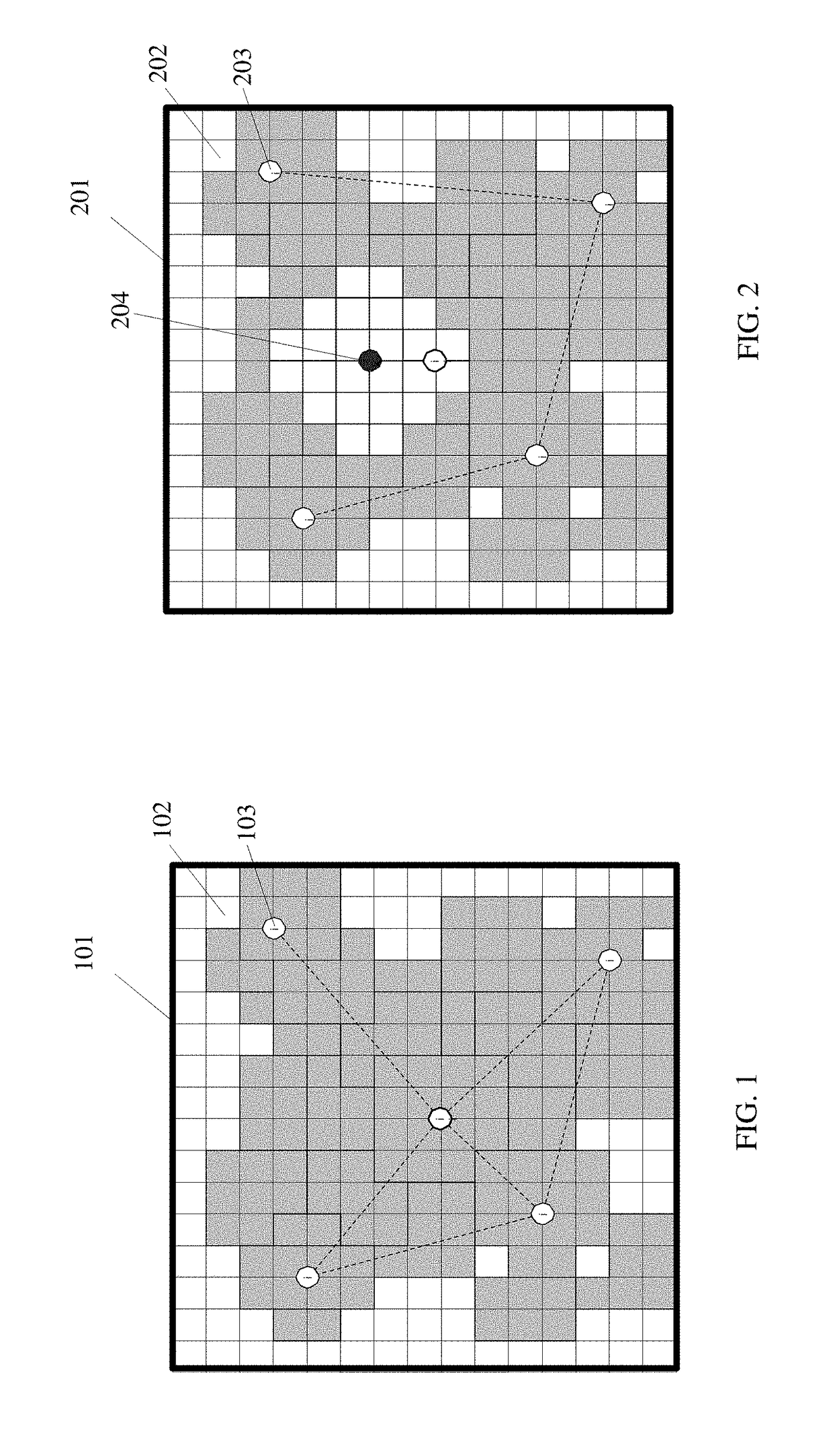
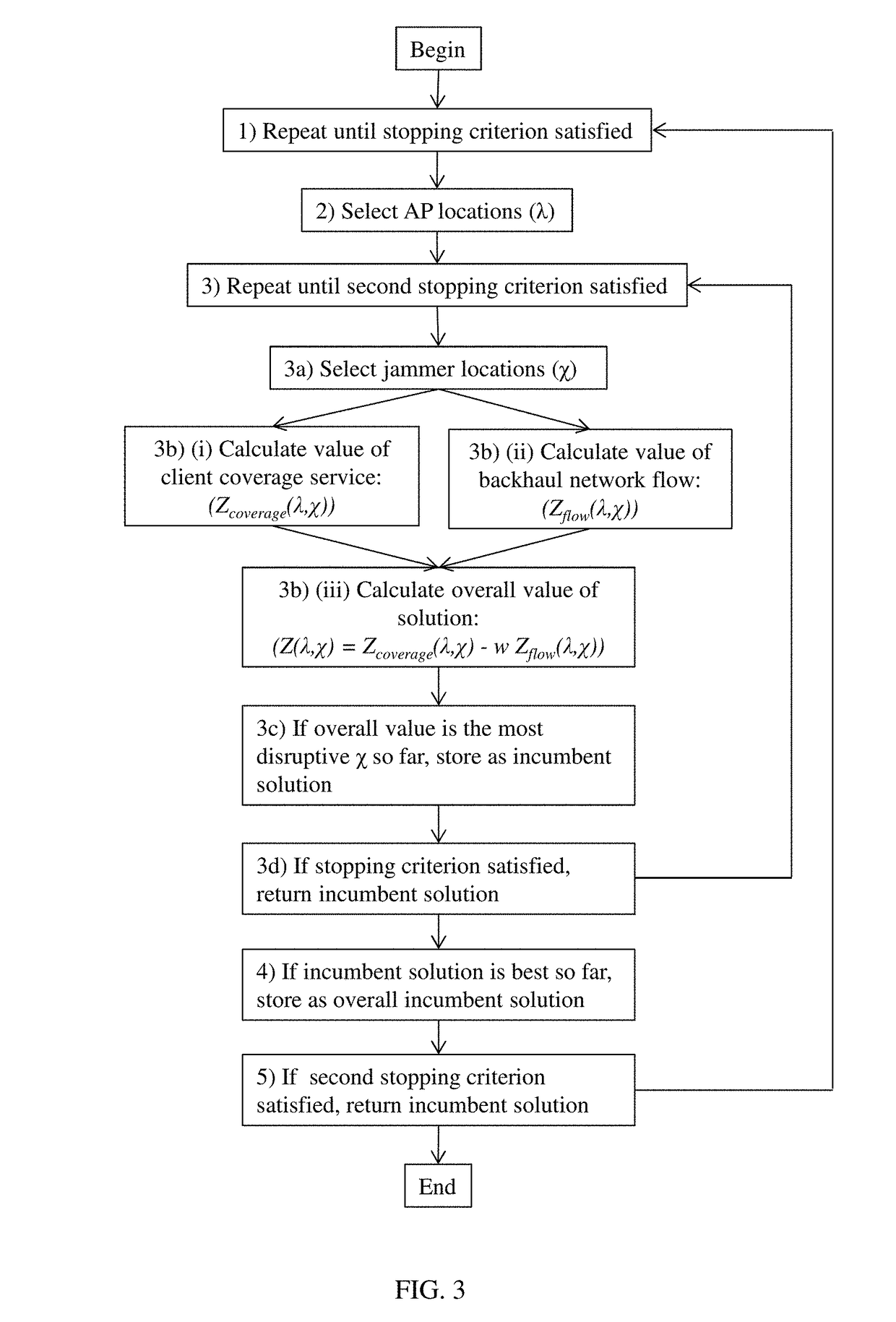
Method for interference-robust transmitter placement in wireless mesh networks
ActiveUS9788213B1Minimize impactMinimize disruptionNetwork topologiesCommunication jammingWireless mesh networkElectrical devices
The disclosure provides a computer-implemented system for establishing a wireless mesh network resistant to degradation induced by deliberate jamming or other electromagnetic interference emanating from point sources within an operating area. The computer-implemented system provides WMN AP locations that minimize disruptions to client coverage caused by jammers, subject to constraints on network service. The computer-implemented system considers jammers placed by an intelligent adversary and identifies the AP locations λ through quantification of an objective function of the general form Z(λ,χ)=Zcoverage(λ,χ)−w Zflow(λ,χ), where Zcoverage(λ,χ) reflects resulting coverage shortfall, Zflow(λ,χ) reflects traffic flow within the WMN, and w is a scalar reflecting the relative weight of the two terms. The final set of AP locations λ identifies the locations of APs to create a WMN that is the most robust to the worst possible jamming attack. Such an attack could represent the actions of a rational human opponent, or the worst-case positioning of unintentional interference sources such as civilian radios, other RF devices, or high-voltage electrical devices.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
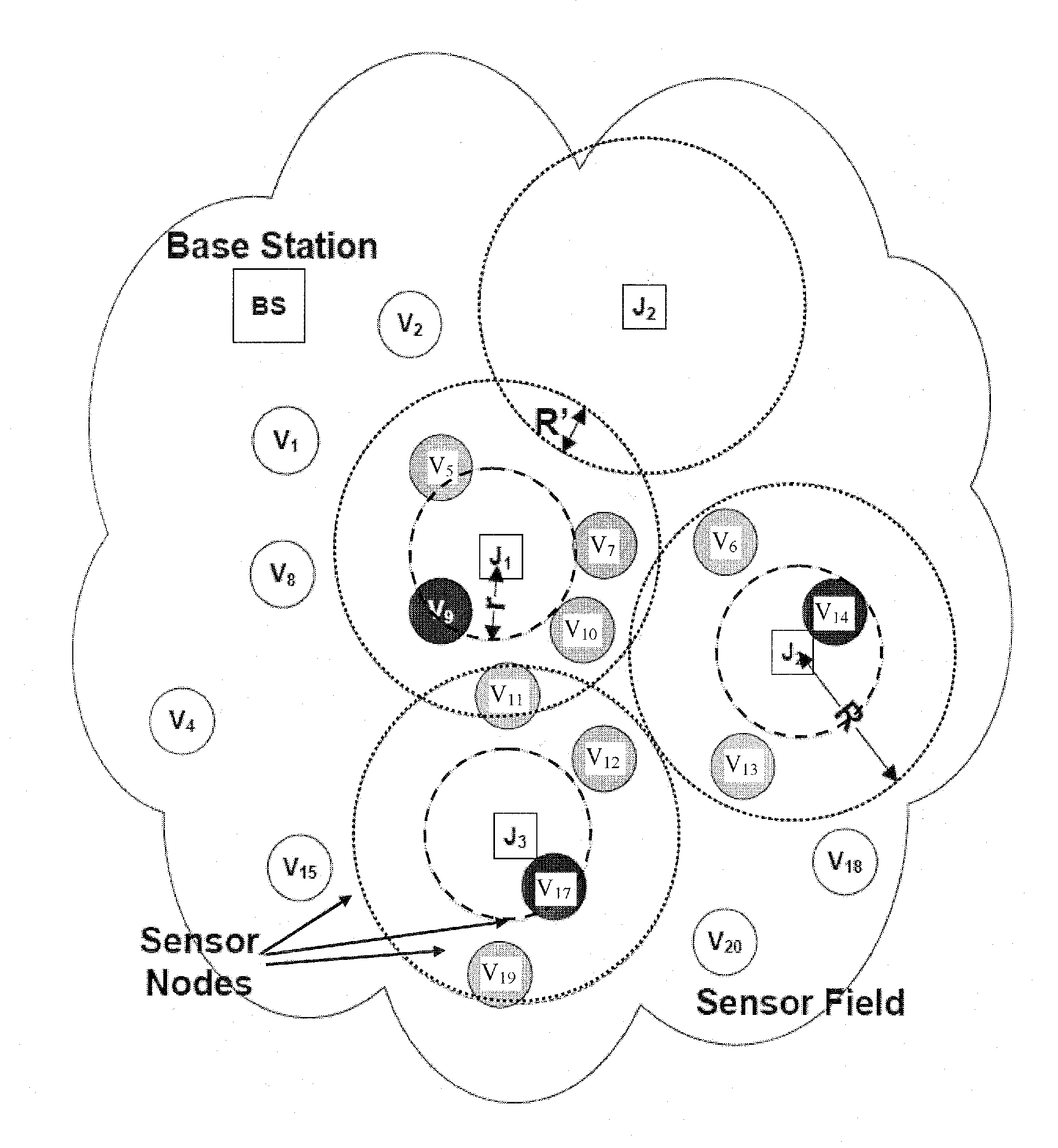
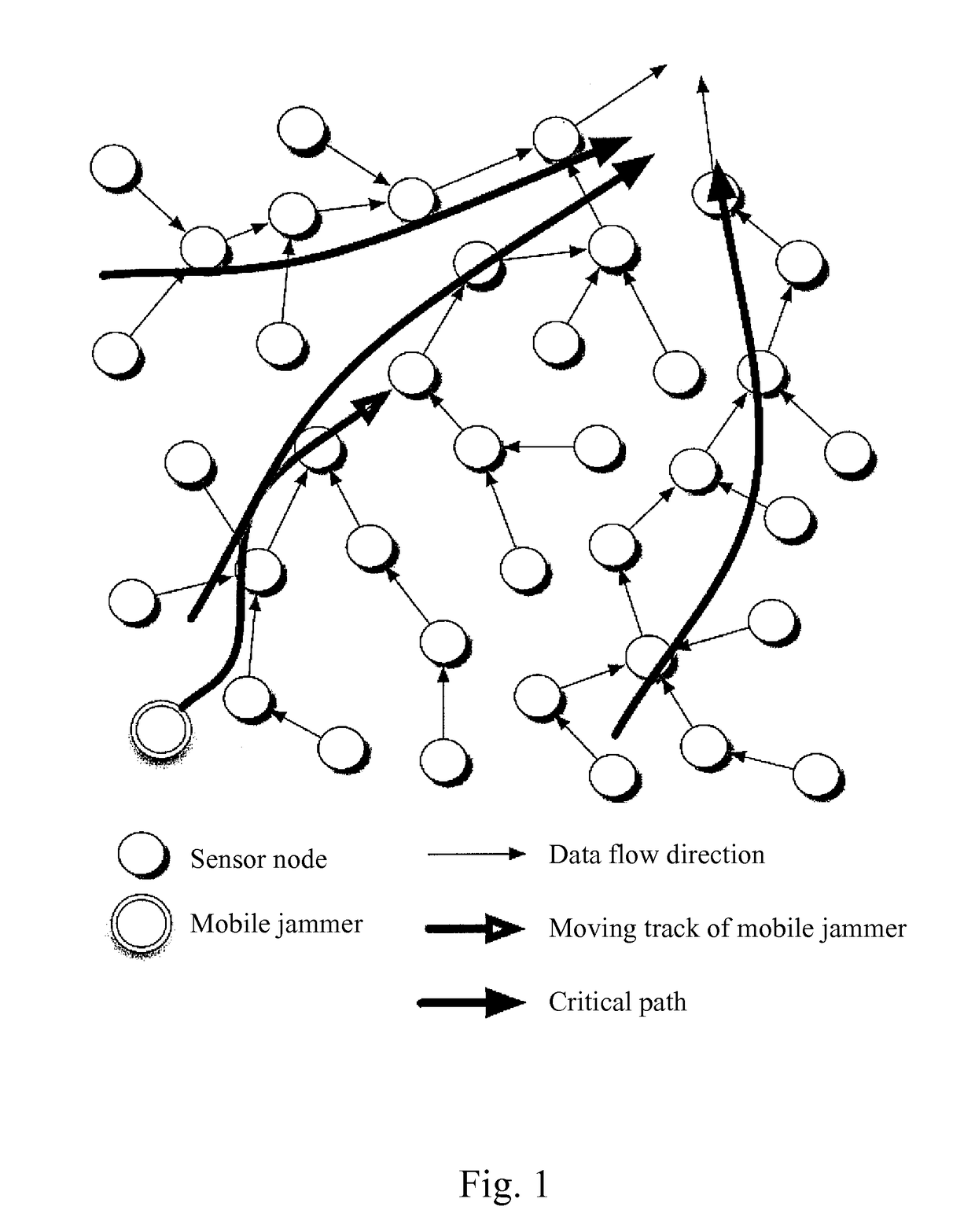
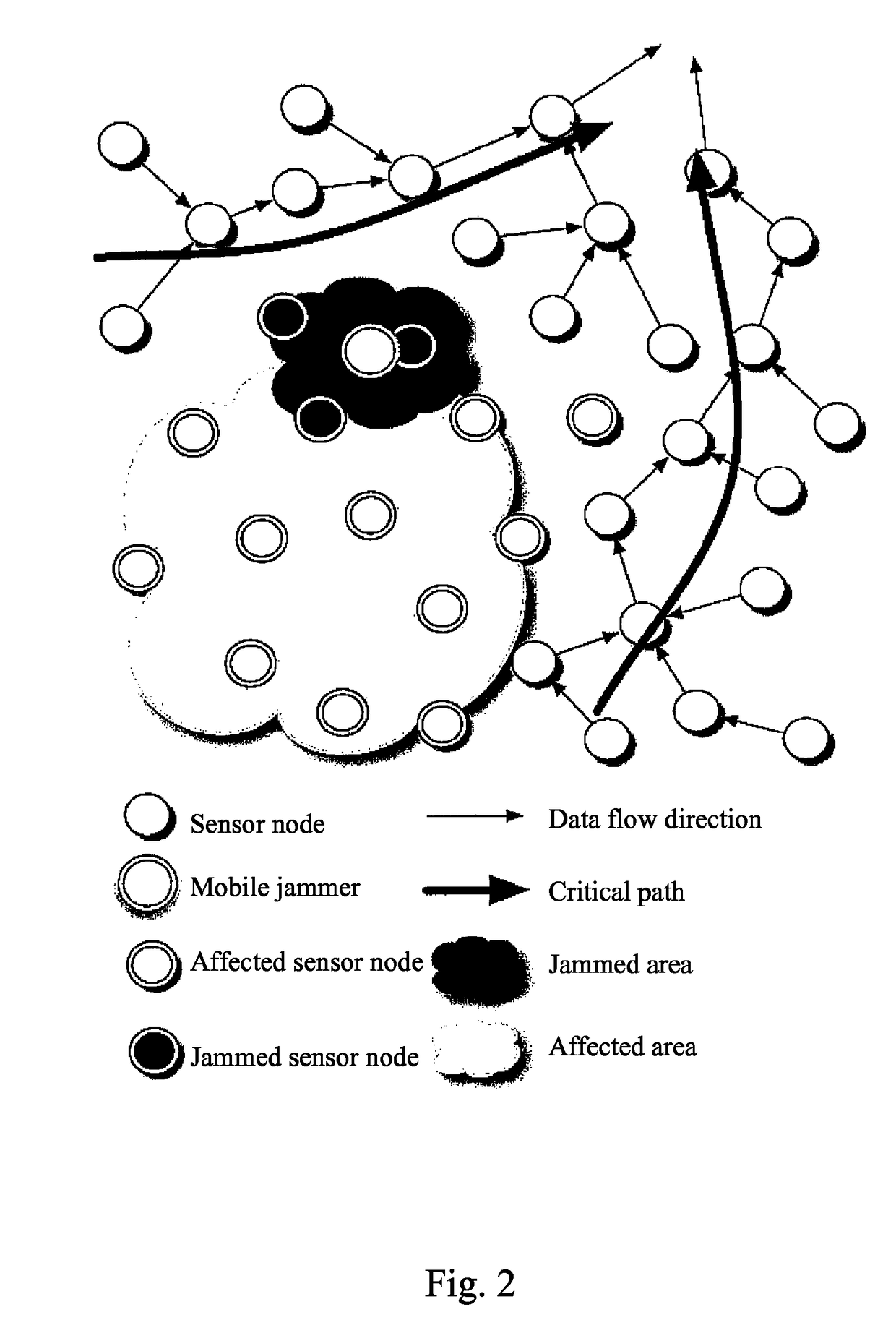
Mobile jamming attack method in wireless sensor network and method defending the same
ActiveUS7907888B2Error preventionFrequency-division multiplex detailsWireless mesh networkWireless sensor networking
The present invention relates to a mobile jamming attack method applied in a wireless sensor network (WSN) and method defending the same. The mobile jamming attack method is a power exhaustion denial-of-service attack, possesses mobility and self-learning capability and is unable to be defended with existing defending scheme due to its attack to the routing layer of the WSN; the mobile jamming defending method employs multi-topologies scheme to defend the mobile jamming attack so that the affected area is reduced, the base station can still receive reply packets under the attack, and the jammed area can be roughly located and the track of the mobile jammer can be traced.
Owner:NATIONAL TSING HUA UNIVERSITY
Interference identification method based on least square method and applicable to wireless sensor network
ActiveCN104660598AReduce consumptionThe method is simple and effectiveTransmissionSecurity arrangementWireless mesh networkEnergy expenditure
The invention discloses an interference attack identification method based on the least square method and applicable to a wireless sensor network. Due to the openness of the wireless media of the sensor network, communication of the sensor network is highly subject to any objective or subjective interference, and the performance of the network is impacted. Generally, the sensor network adopts measures such as frequency hopping according to the condition of a channel to avoid damage of interference. But the poor quality of the channel is not necessarily caused by interference, and also can be caused by own reasons of a node. Therefore, if the node can identify interference and non-interference, the node can perform correct processing choice more conveniently by self, and unnecessary energy consumption is avoided. The interference attack identification method is based on the least square method, and detects interference attack according to the characteristics of a sigmoid function, so that the detection rate is improved, and the power consumption is reduced.
Owner:UNIV OF SCI & TECH BEIJING
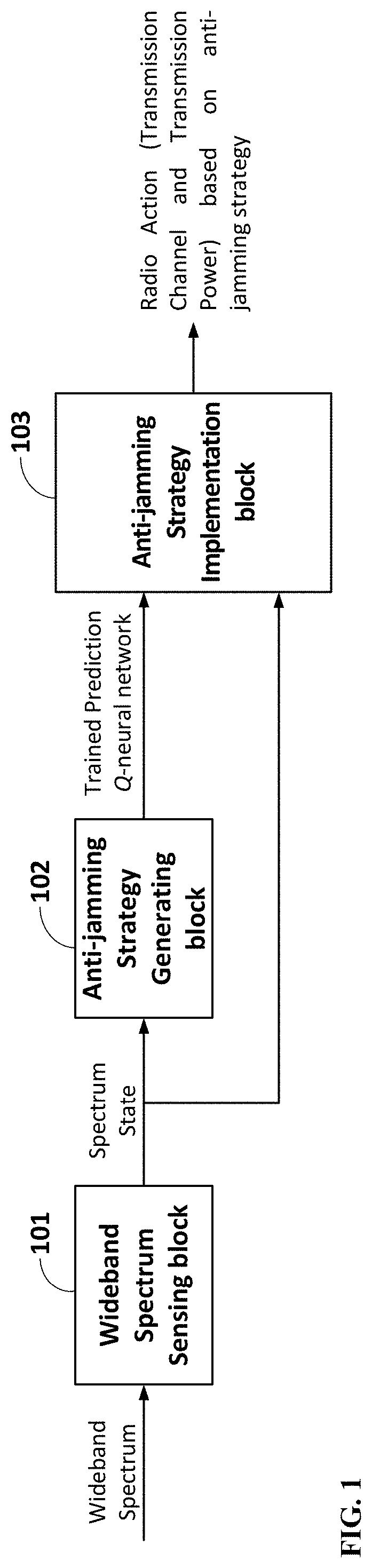
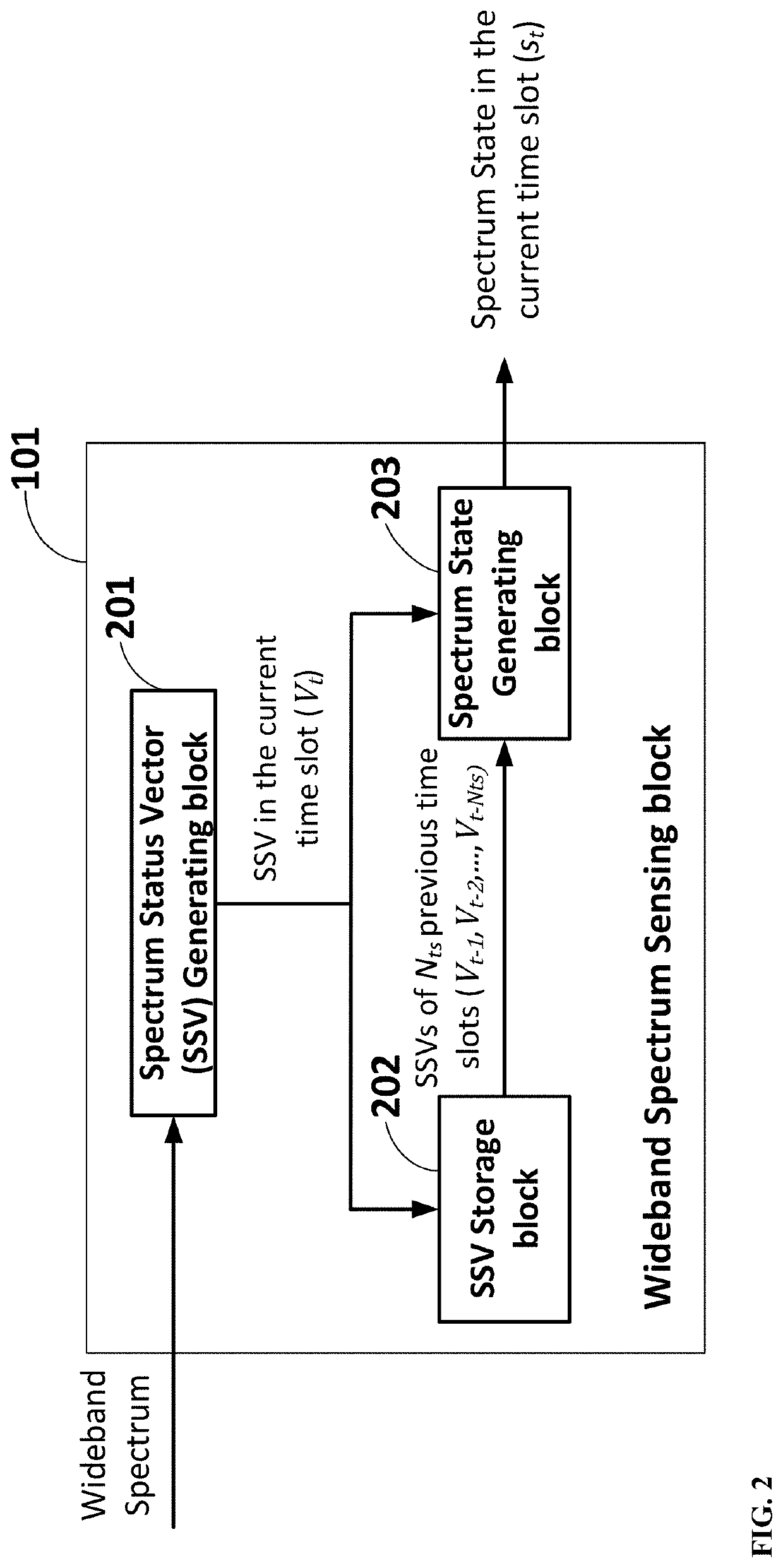
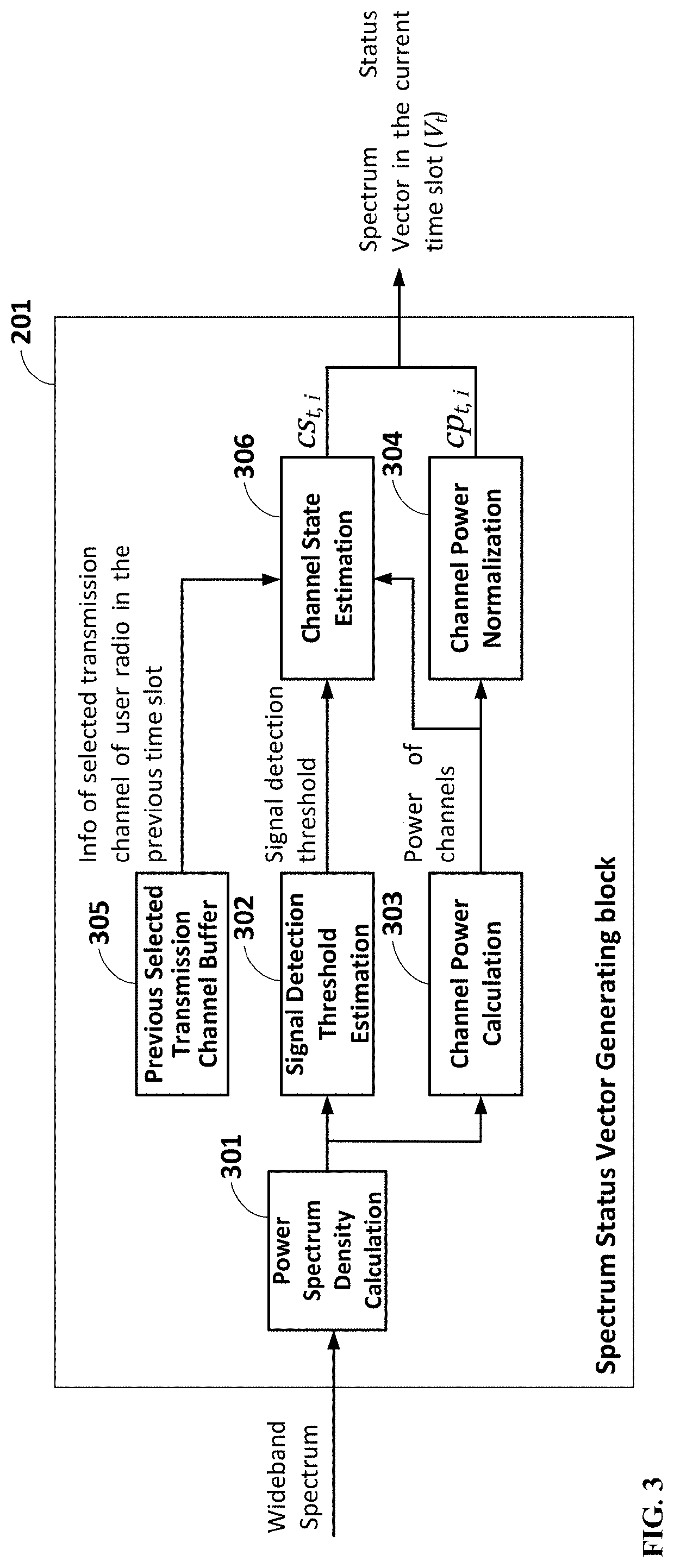
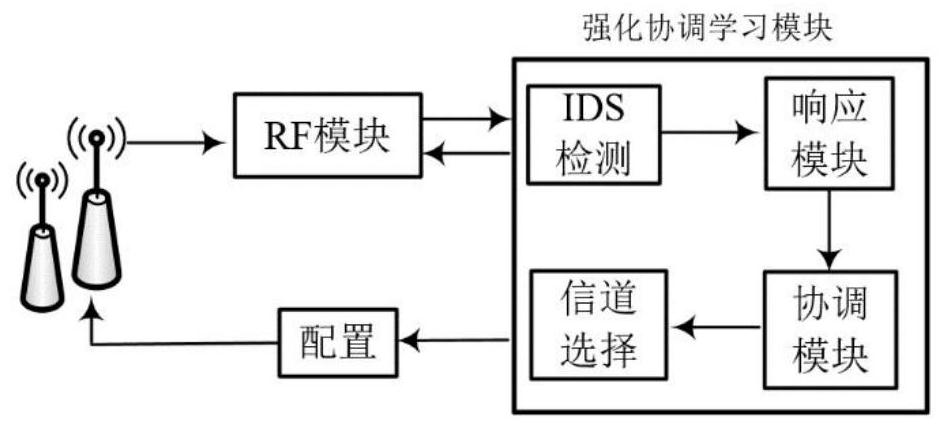
Method and apparatus for adaptive Anti-jamming communications based on deep double-q reinforcement learning
PendingUS20220209885A1Minimizes transmitted powerMaximize its transmission rateMathematical modelsArtificial lifeSuccessful transmissionAnti jamming
In order to avoid various jamming attacks from intelligent jammers in modern complex wireless environments, a system and method is presented for a user radio to generate and implement an adaptive anti-jamming communication strategy. The said adaptive anti-jamming communication strategy is obtained via the training process for a specific neural network using Deep Double-Q Reinforcement learning algorithm in the strategy generation phase. The objective of this process is to discover a strategy to select the optimal radio action including transmission channel and transmission power for the user radio, which is changed adaptively to different jamming patterns to maximize the successful transmission rate (“jamming-free”) while retaining the power consumption of user radio as low as possible. In the strategy implementation phase, the user radio chooses an appropriate radio action based on output of trained neural network after the training process; thus, achieves robust and efficient communications against diverse complex jamming scenarios.
Owner:VIETTEL GRP
WSNs source node position privacy protection method based on dynamic tree routing
ActiveCN111542059ARandomExtend your lifeNetwork topologiesSecurity arrangementComputer networkPrivacy protection
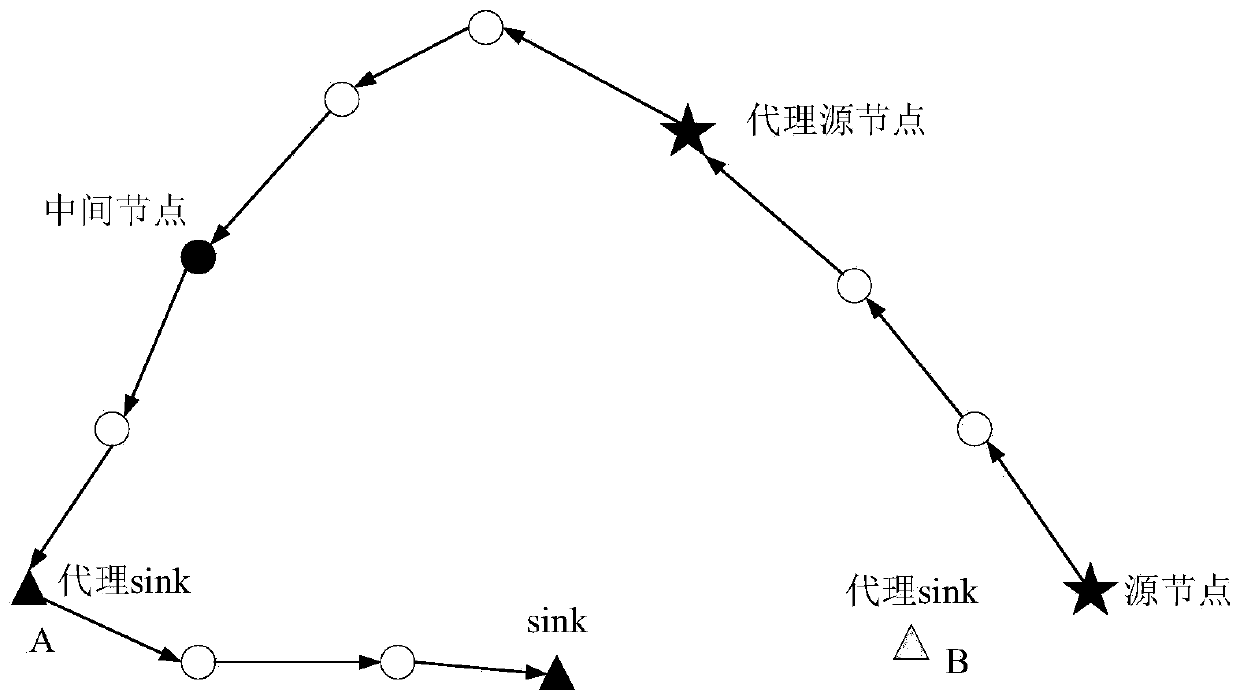
The invention discloses a WSNs source node position privacy protection method based on dynamic tree routing. The method is divided into four stages: a first stage: after a network is initialized, allnodes obtain hops from themselves to sink nodes; in the second stage, an intermediate node, an agent source node and an agent sink node are jointly determined by the randomly generated source node andthe sink node in the network; in the third stage, the network enters a data packet routing stage, and the data packet is routed to the sink node from the source node through the proxy source node, the intermediate node, the proxy sink node and the data packet in sequence; and meanwhile, the transmission of false data packets is doped in the routing process, so that the purpose of interfering thejudgment of attackers is achieved. According to the invention, the routing of the data packet from the source node to the sink node has randomness, and the false data packet is doped into the non-hotspot area, so that the service life of the network is prolonged and the relatively small time delay is ensured while the location privacy of the source node is protected.
Owner:HOHAI UNIV CHANGZHOU
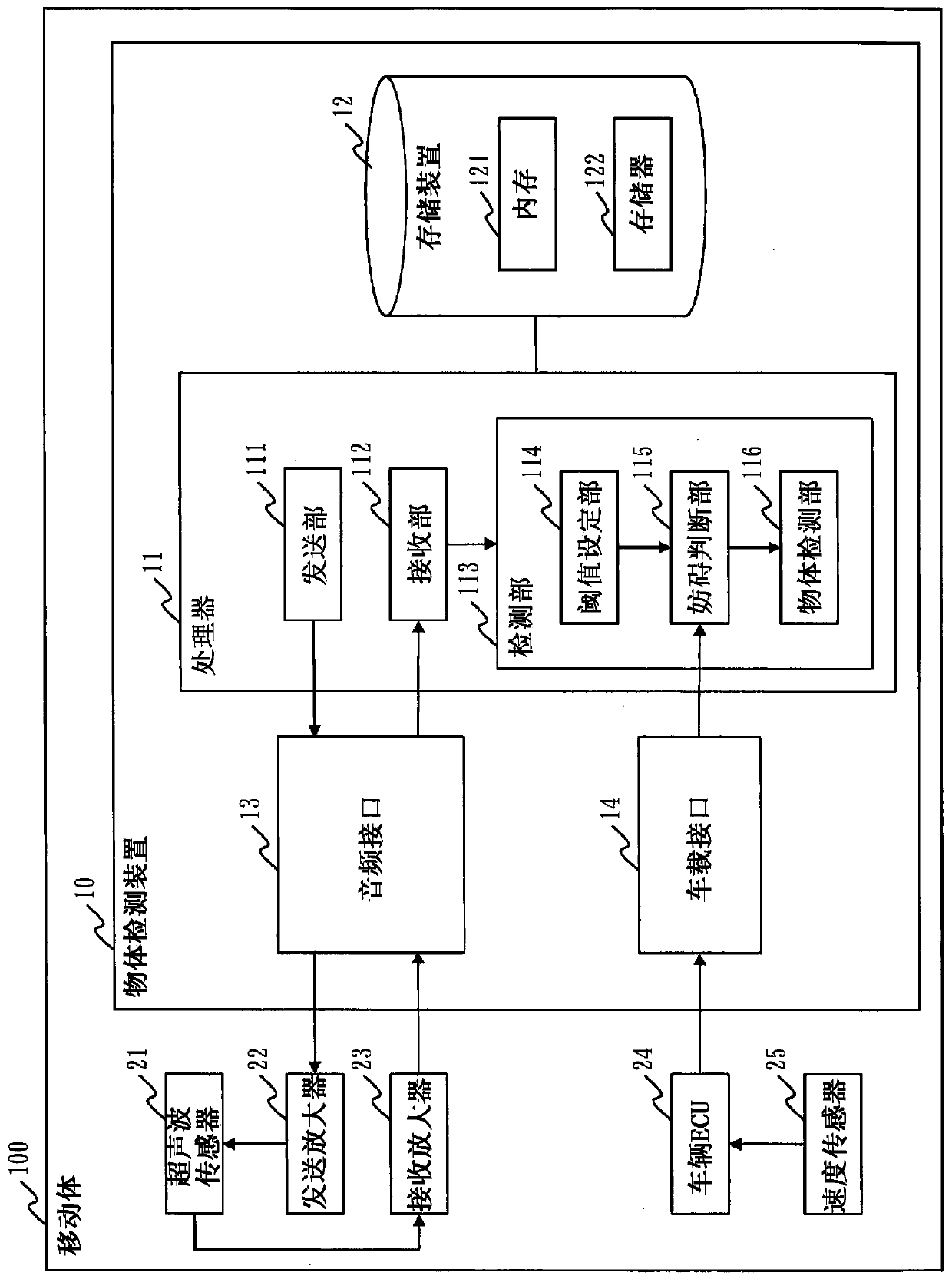
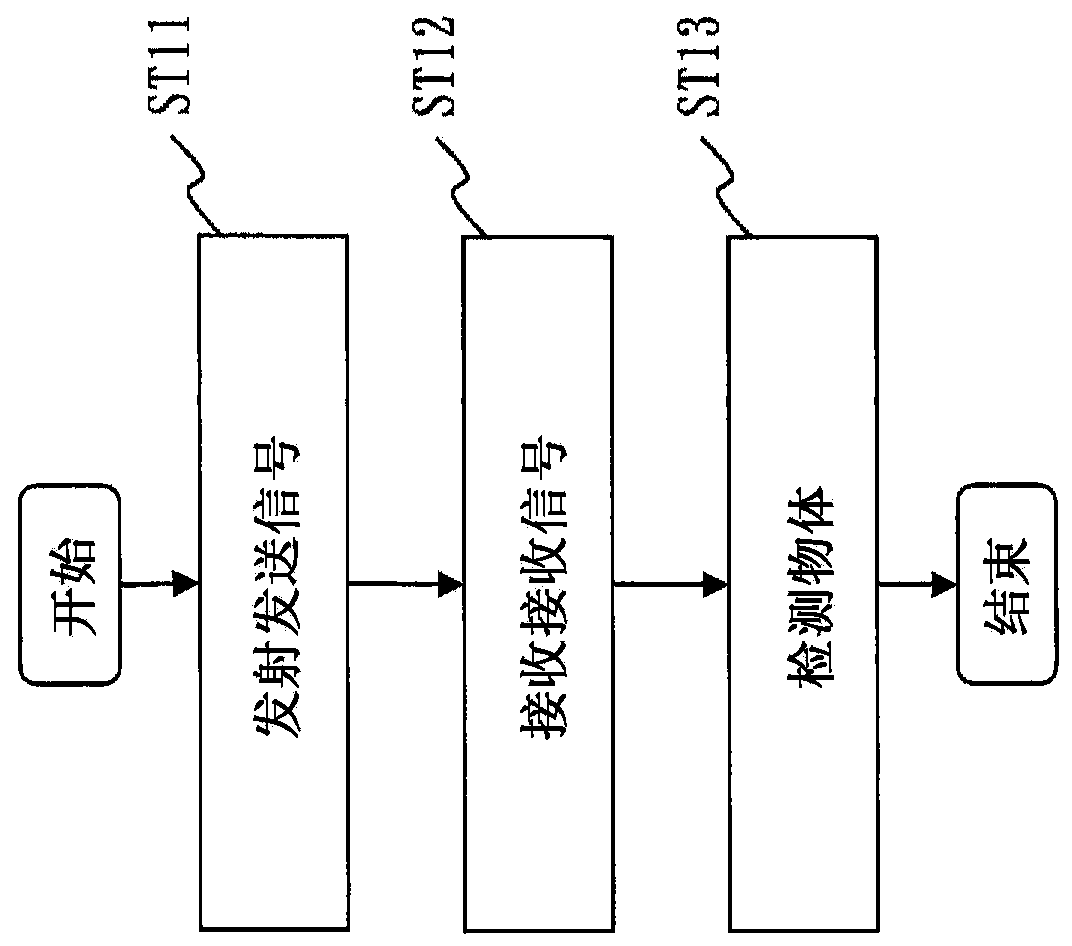
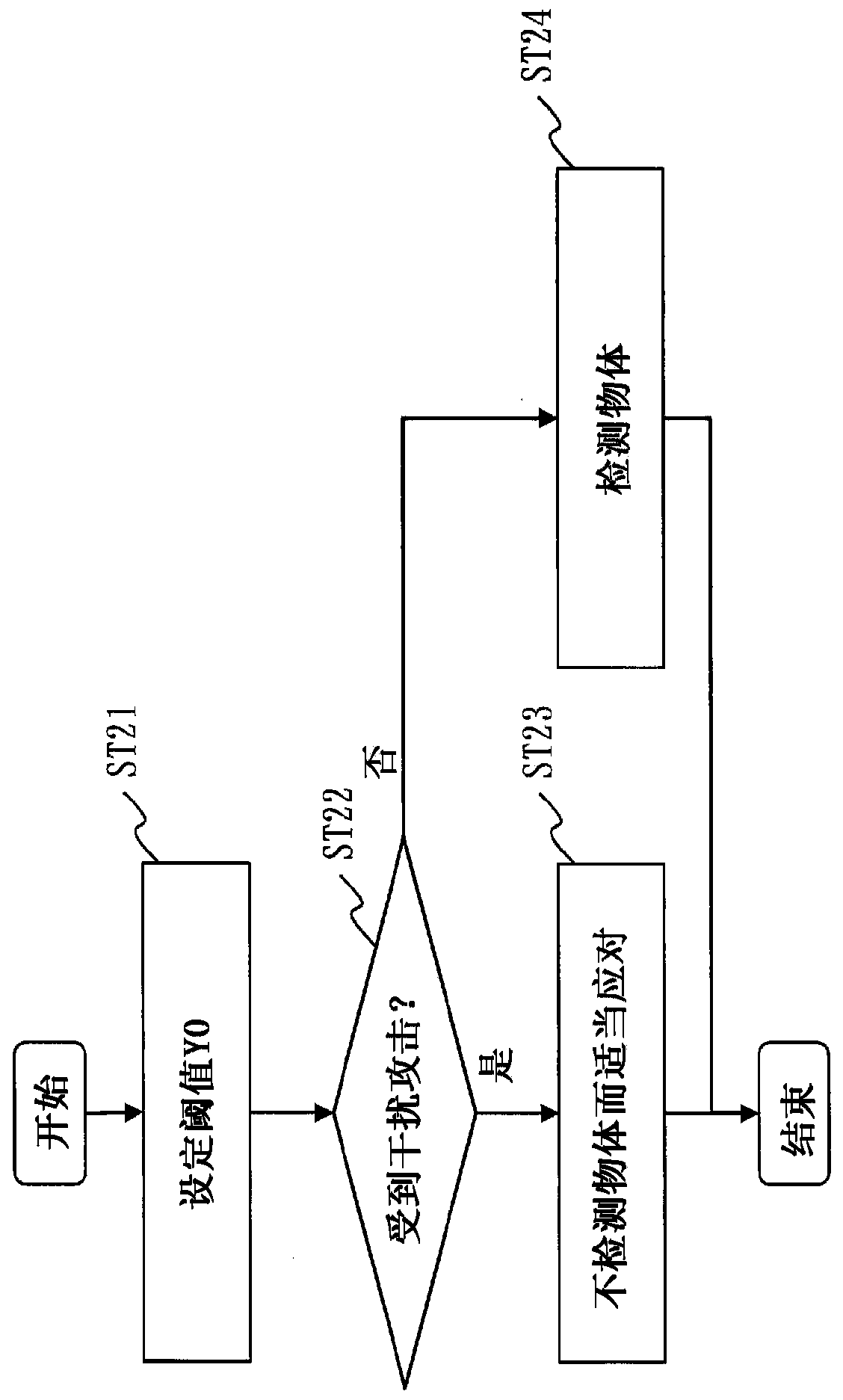
Object detection apparatus, object detection method, and object detection program
ActiveCN110678775APrevent false detectionImprove securityScene recognitionCommunication jammingReflected wavesEngineering
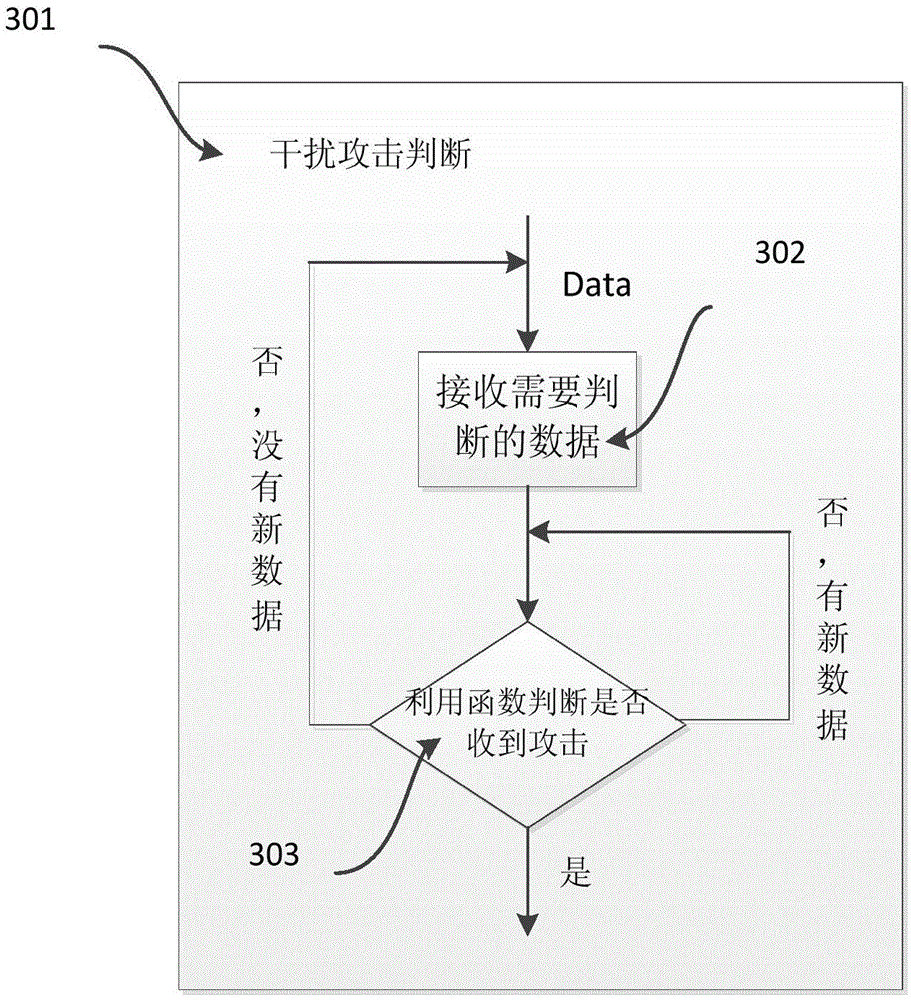
A reception unit (112) receives, by means of an ultrasonic sensor (21), a reception signal which includes a reflected wave obtained when an acoustic signal radiated from a moving body (100) is reflected on an object. A disturbance determination unit (115) determines, on the basis of the reception signal, whether or not a jamming attack is underway in which a jamming signal is transmitted from theoutside. An object detection unit (116) carries out detection of objects around the moving body on the basis of the reception signal when determination of an attack is not made, and does not carry outdetection of objects when determination of an attack is made.
Owner:MITSUBISHI ELECTRIC CORP
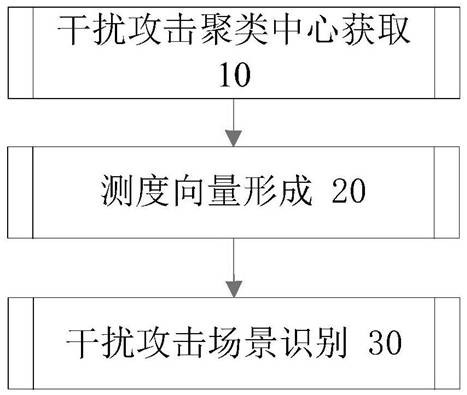
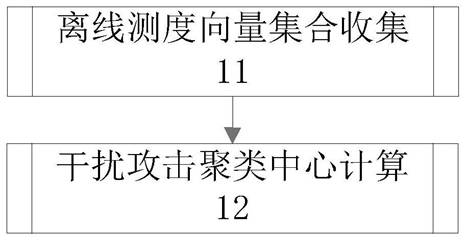
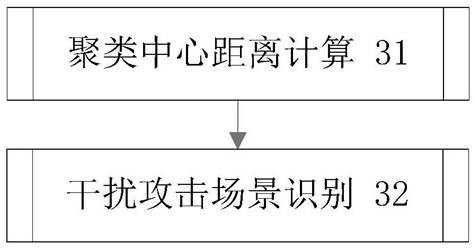
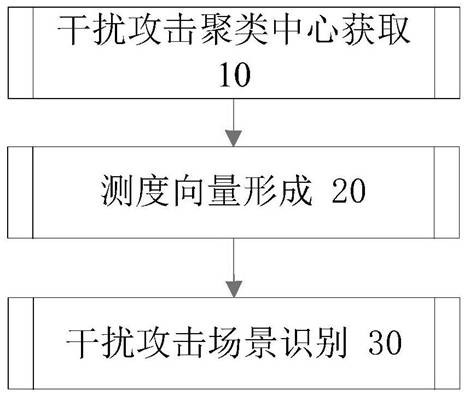
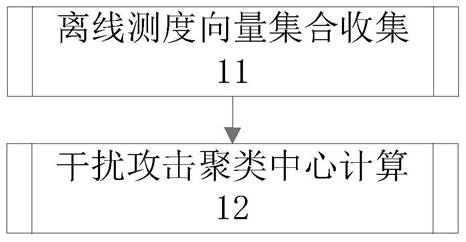
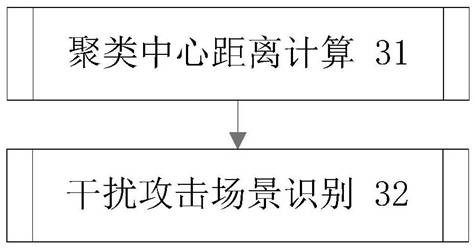
Scenario recognition method of wireless network interference attack based on distance measure
ActiveCN111711604BReduce overheadEasy to implementSecurity arrangementSecuring communicationEngineeringData mining
The invention discloses a wireless network interference attack scene recognition method based on distance measurement, which can accurately classify interference attack scenes. The wireless network interference attack scene identification method of the present invention comprises the following steps: (10) Acquisition of the interference attack clustering center: different attack scenes are set, and for each attack scene, the message interaction process data of the node and the neighbor node are collected , forming an offline measure vector set, and based on this set, calculate the interference attack clustering center of the attack scenario; (20) Online measure vector formation: collect the message interaction process data between the node and the neighbor node online, and form an online measure vector; (30) Jamming attack scene determination: Calculate the distance from the online measurement vector of this node to each jamming attack cluster center, and output the jamming attack scene corresponding to the jamming attack cluster center with the smallest distance as the recognition result.
Owner:NAT UNIV OF DEFENSE TECH
A physical layer authentication method based on multi-carrier transmission
ActiveCN104168562BImprove securityWireless network protocolsTransmission path multiple useComputer hardwarePhase response
The invention discloses a physical layer authentication method based on multi-carrier transmission. According to the method, based on the multi-carrier transmission, channels are regarded as a set of M fading sub-channels, and the reciprocity and randomness of phase responses of the sub-channels are used for performing on identity authentication on both parties of communication. The method includes the implementation steps that Alice transmits an excitation signal to Bob, the phase difference of the multi-carrier channels is measured after Bob receives the excitation signal, then Bob transmits a signal where a shared secrete key is packaged to Alice, and Alice authenticates whether the signal is from Bob or not according to the received signal and the shared secrete key. According to the authentication process of the method, the characteristics of the phase responses of the channels are used, and kinds of spoofing attacks such as the interference attack, the replay attach, impersonation attack are effectively resisted.
Owner:青岛联众芯云科技有限公司
Anti-pilot spoofing attack channel estimation and identification method based on independent component analysis in ofdm system
ActiveCN106161297BImprove estimation accuracySolve the problem of low estimation accuracyChannel estimationMulti-frequency code systemsIndependent component analysisJamming attack
The invention provides a method for channel estimation and identification against a pilot spoofing attack based on independent component analysis in an OFDM (Orthogonal Frequency Division Multiplexing) system. The method utilizes the characteristics of the random pilot to weaken the pilot spoofing attack to a pilot interference attack, and meanwhile, a legal channel between an uplink legal transmitter and a receiver under the pilot interference environment is estimated and identified according to the independent features of the channel. The method only need to spend time resources of three OFDM symbols and a certain number of frequency band resources and is immune to the pilot interference power of an active eavesdropper. The uplink legal transmitter disrupts the intentional pilot attack of the active eavesdropper through transmitting the uplink random pilot, and meanwhile, the receiver extracts legal channel information from a received contaminated signal through utilizing the mutual independence between the legal channel and an attack channel, so that the channel estimation accuracy of the legal channel is improved, and thus a problem of low channel estimation accuracy caused by the pilot spoofing attack is solved.
Owner:XI AN JIAOTONG UNIV
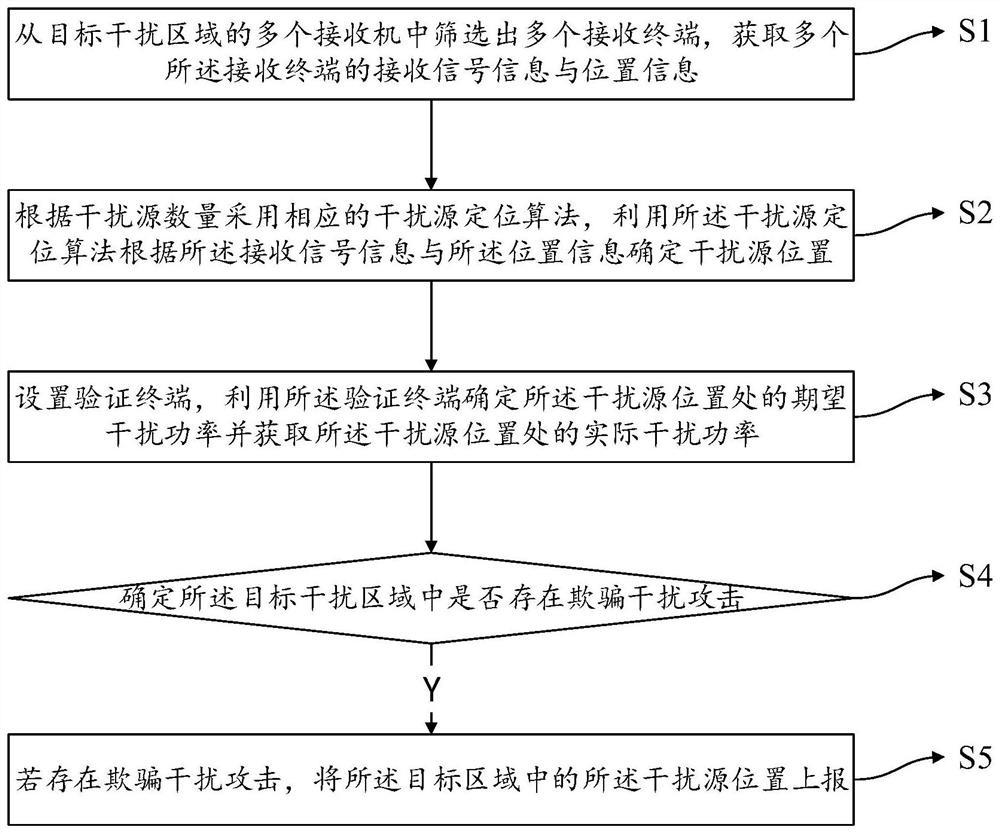
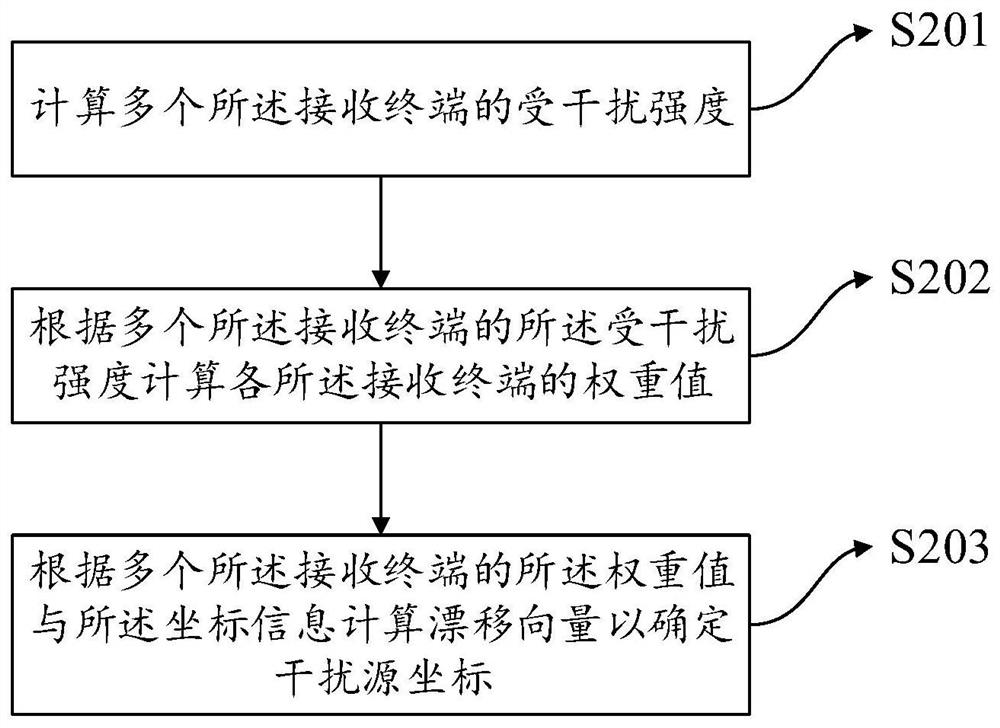
Deception interference source positioning method, electronic equipment and storage medium
The embodiment of the invention provides a deception interference source positioning method, electronic equipment and a storage medium, and the method comprises the steps: screening out a plurality of receiving terminals from a plurality of receivers in a target interference region, and obtaining the receiving signal information and position information of the plurality of receiving terminals; adopting a corresponding interference source positioning algorithm according to the number of interference sources, and employing the interference source positioning algorithm to determine the positions of the interference sources according to the received signal information and the position information; setting a verification terminal, determining an expected interference power at the position of the interference source by using the verification terminal, obtaining an estimated interference power at the position of the interference source, and comparing the expected interference power with the estimated interference power to determine whether a deception interference attack exists in the target interference area; and if the deception jamming attack exists, reporting the position of the interference source in the target area.
Owner:BEIJING UNIV OF POSTS & TELECOMM
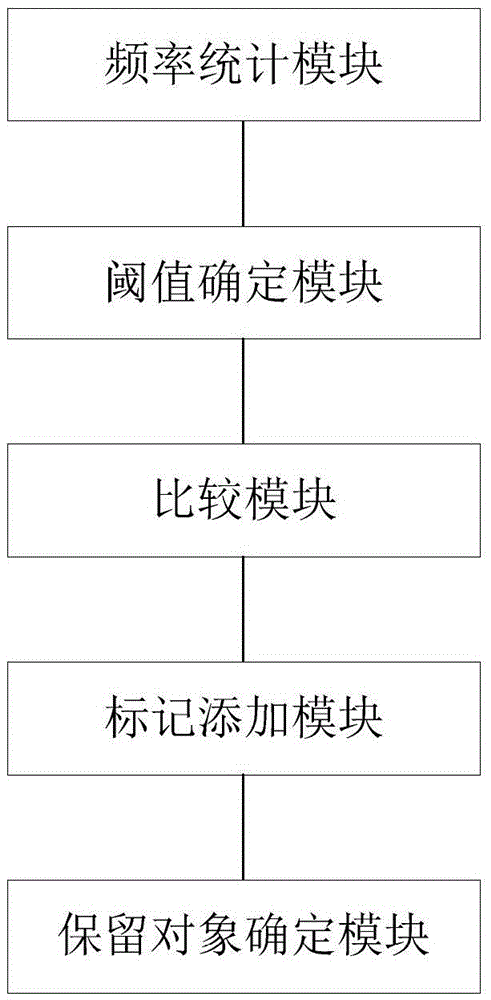
Determination method and apparatus for inference channel reservation object
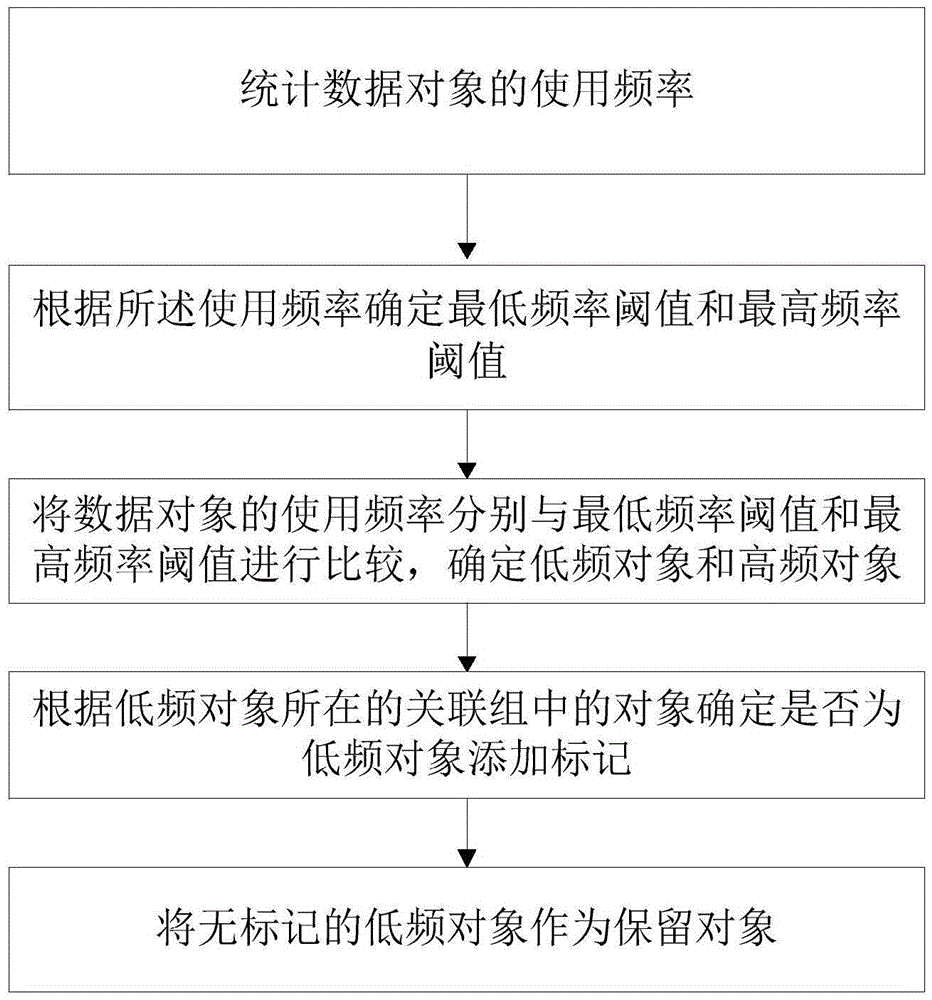
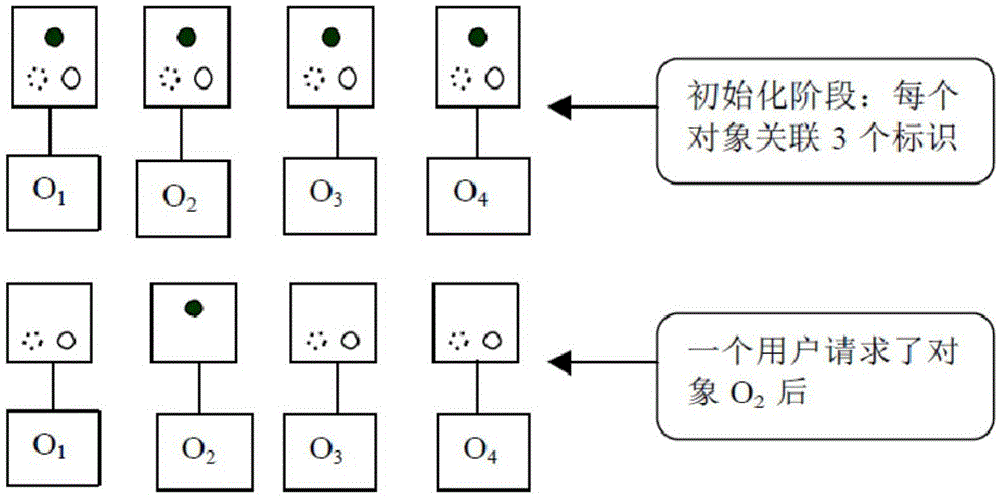
ActiveCN105574433AAvoid blocking attacksEasy accessDigital data protectionPattern recognitionJamming attack
The invention provides a determination method and apparatus for an inference channel reservation object. The method comprises the steps of making statistics on the operation frequency of a data object; according to the operation frequency, determining a lowest frequency threshold and a highest frequency threshold; comparing the operation frequency of the data object with the lowest frequency threshold and the highest frequency threshold separately to determine a low-frequency object and a high-frequency object; according to an object in a correlation group in which the low-frequency object is located, determining whether a mark is added to the low-frequency object or not; and taking the low-frequency object without the mark as a reservation object. The jamming attack of the data object can be effectively avoided. The normal access of other users to a database is ensured.
Owner:TIANJIN NANKAI UNIV GENERAL DATA TECH
Tracking system and method for monitoring and ensuring security of shipments
ActiveUS10832204B2Improve securityParticular environment based servicesBroadcast service distributionData processing systemLocation tracking
A system electronically tracks each or multiple shipment-related entities as a group of co-located dots that are monitored to provide enhanced security of the shipment from attacks or unauthorized or illicit actions that can compromise the shipment's safety. A data processing system (DPS) receives a plurality of location tracking signals of multiple shipment-related entities, associates the location tracking signals as a shipment group that is assigned a unique shipment tracking identifier (STID), and presents the shipment group as a plurality of co-located dots on a shipment tracking user interface (STUI). The DPS monitors for any unscheduled deviations in at least one of an expected co-location / geo-location of the location tracking signals, identifies specific types of unscheduled deviations, and triggers a series of responsive actions to protect the shipment. The unscheduled deviations can include signal jamming attacks, incorrect pickup (or theft) of an operator-assigned shipment, and unexpected separation of the tracked entities.
Owner:OVERHAUL GRP INC
Blocking attack prediction method and system for wireless energy transmission communication network
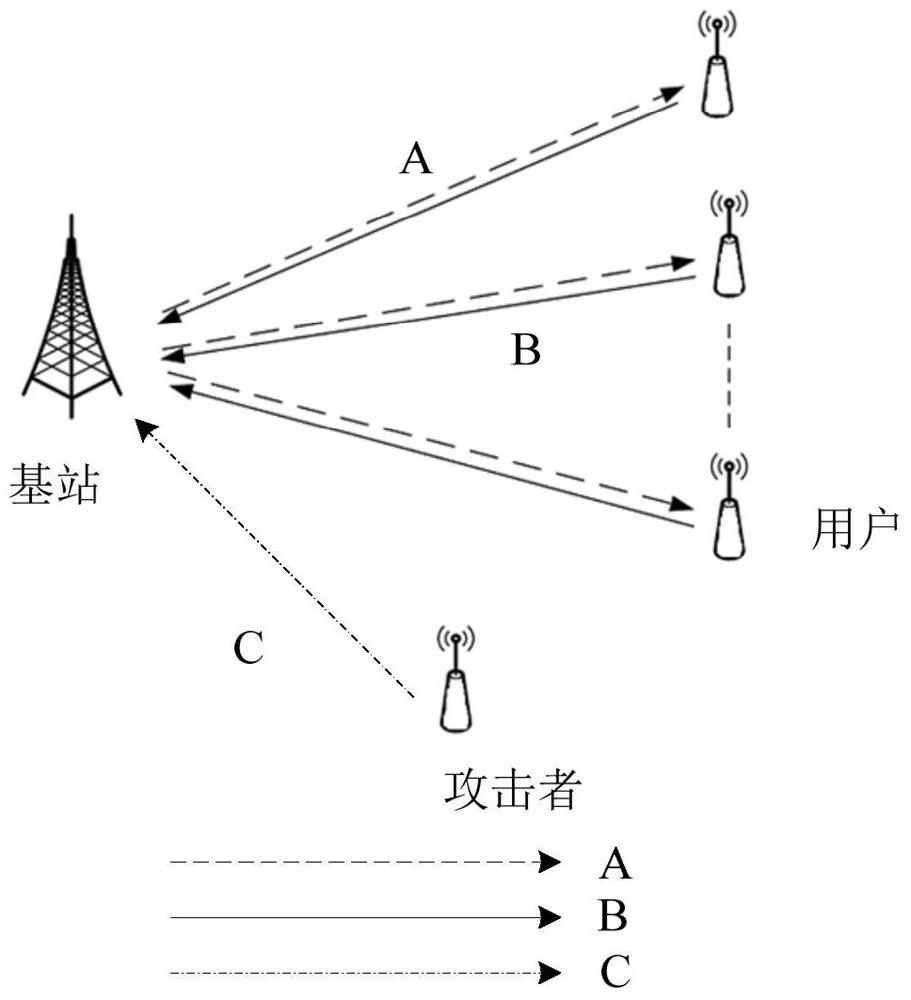
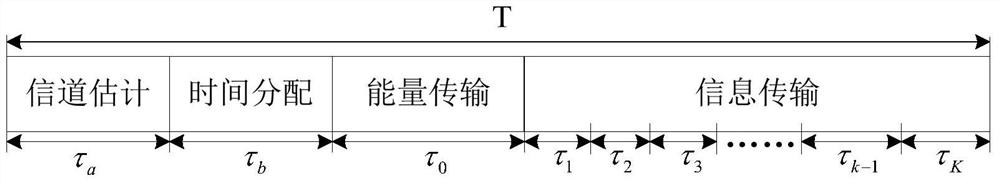
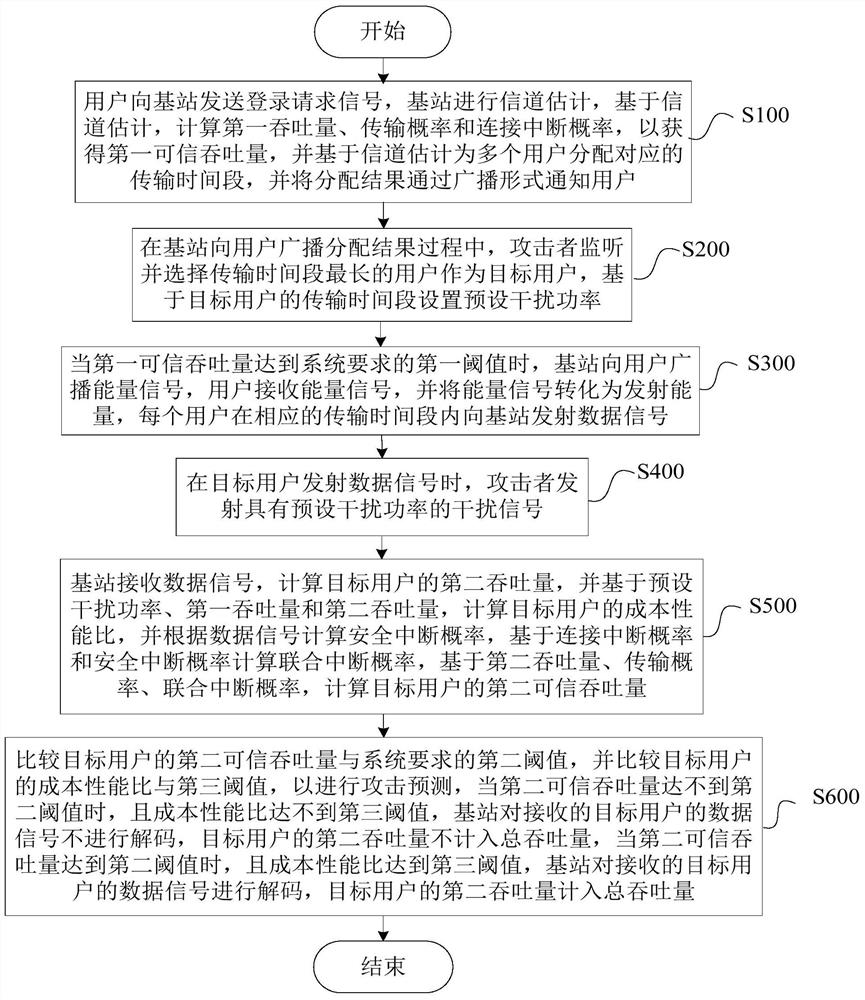
ActiveCN109275137BEnsure safetyGuaranteed reliabilityCommunication jammingTransmissionInterference (communication)Attack
This disclosure describes a method for predicting a jamming attack on a wireless energy transfer communication network, including the base station performing channel estimation, calculating the first credible throughput and assigning a transmission time period to each user. The assignment result is notified to the user through broadcasting, and the attacker listens As a result of the allocation, the user with the longest transmission time period is taken as the target user, and the preset interference power is set based on the transmission time period of the target user. When the first credible throughput reaches the first threshold, the base station transmits energy to the user, and the user receives energy And transmit a data signal to the base station, when the target user transmits the data signal, the attacker transmits an interference signal, the base station calculates the security outage probability, the second credible throughput and the cost-performance ratio based on the received data signal, and compares the second credible throughput of the target user Signal throughput and the second threshold required by the system, and compare the cost-performance ratio of the target user with the third threshold to predict the attack, and only decode the received signal if both thresholds are satisfied.
Owner:SHENZHEN UNIV
Invisible interference attack protection method and system for sensing edge cloud unloading link
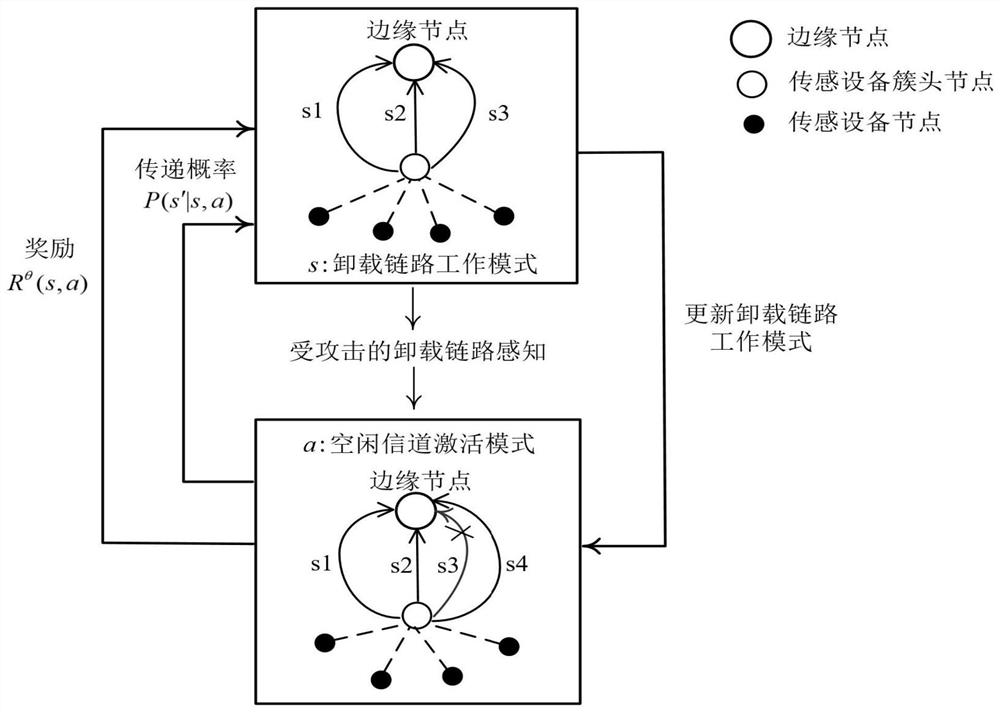
PendingCN114501457AImplement detectionAchieve defenseNetwork topologiesSecurity arrangementTelecommunicationsAttack
The invention discloses an invisible interference attack protection method and system for a sensing edge cloud unloading link, and aims to respond to behaviors of an invisible interference attacker by dynamically adjusting channel resources of sensing equipment in a sensing cluster so as to realize self-adaption to intrusion of the invisible interference attacker. Due to limited computing resources of a single sensing equipment node and distributed nonlinear interference attack characteristics of invisible attackers, detection and defense of the invisible interference attackers cannot be efficiently realized, and cooperative defense must be realized through collective interaction of the whole sensing equipment cluster and the invisible attackers. According to the method, the working mode of the unloading link is learned from past historical experience to optimize channel allocation to respond to the invisible interference attack, so that unloading link blockage caused by the invisible interference attack is eliminated more quickly, and the process is formalized as a reinforcement learning problem using a Markov decision process; and an optimal mode is automatically found, and an idle channel is activated to resist invisible interference attacks.
Owner:SHAOXING UNIVERSITY
Wireless network interference attack scene identification method based on distance measurement
ActiveCN111711604AReduce overheadEasy to implementTransmissionSecurity arrangementPattern recognitionComputer vision
The invention discloses a wireless network interference attack scene identification method based on distance measurement, which can accurately classify interference attack scenes. The wireless networkinterference attack scene identification method comprises the steps of (10) obtaining an interference attack clustering center: setting different attack scenes, collecting message interaction processdata of a current node and a neighbor node for each attack scene to form an offline measurement vector set, and calculating the interference attack clustering center of the attack scene based on theset; (20) forming an on-line measurement vector: collecting message interaction process data of the node and a neighbor node on line to form the on-line measurement vector; and (30) determining an interference attack scene: calculating the distance from the online measurement vector of the node to each interference attack clustering center, and outputting the interference attack scene corresponding to the interference attack clustering center with the minimum distance as an identification result.
Owner:NAT UNIV OF DEFENSE TECH
5g positioning truth detection and attack traceability method, system, equipment and application
ActiveCN112601173BHigh positioning accuracyGuaranteed to be authenticLocation information based serviceSecurity arrangementInterference (communication)Attack
The invention belongs to the technical field of user positioning security in mobile communication networks, and discloses a method, system, device and application for 5G positioning truth detection and attack traceability; relevant parameters are extracted from wireless signals sent by users, and the data fusion center utilizes clustering The method clusters the positioning data, excludes abnormal data, and realizes truth detection and credible positioning information calculation; uses the historical records of positioning parameters to extract relevant features, and completes the training of user attack detection model and base station traceability model. , respectively analyze the positioning parameters of the user to be detected and the parameters uploaded by the positioning base station, and effectively complete the attack detection of the target user and the attack traceability of the malicious base station. The invention can not only ensure the authenticity and reliability of user positioning, but also has extremely high positioning accuracy, and can effectively resist interference attacks on user wireless positioning signals and internal attacks on base stations responsible for positioning, ensuring the security of the positioning system, and has excellent robustness.
Owner:XIDIAN UNIV
Detecting and protecting method for confirming frame attack of wireless sensor network
ActiveCN102404740BEnsure safetyGuaranteed reliabilityError prevention/detection by using return channelNetwork topologiesWireless mesh networkWireless sensor networking
The invention provides a detecting and protecting method for confirming frame attack of wireless sensor network, which is executed by the following steps of: detecting whether there is ACK frame interference attack by LQI (Link Quality Indicator) and times of re-transmitting data; resisting the ACK frame interference attack by randomly setting the ACK frame sending time slot; detecting whether there is ACK frame overwhelming attack by LQI information and the data receiving condition. The detecting and protecting method for confirming frame attack of wireless sensor network provides a method for detecting frame interference attack and frame overwhelming attack based on dynamic threshold value as well as provides self-defending measures by randomly selecting the sending time and hiding the sequences, which is simple and easy to implement.
Owner:CHINA ELECTRIC POWER RES INST +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com