Interference identification method based on least square method and applicable to wireless sensor network
A least square method and wireless sensor technology, applied in the field of interference attack detection, can solve problems affecting network performance, affecting data transmission, and not mentioning the implementation method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
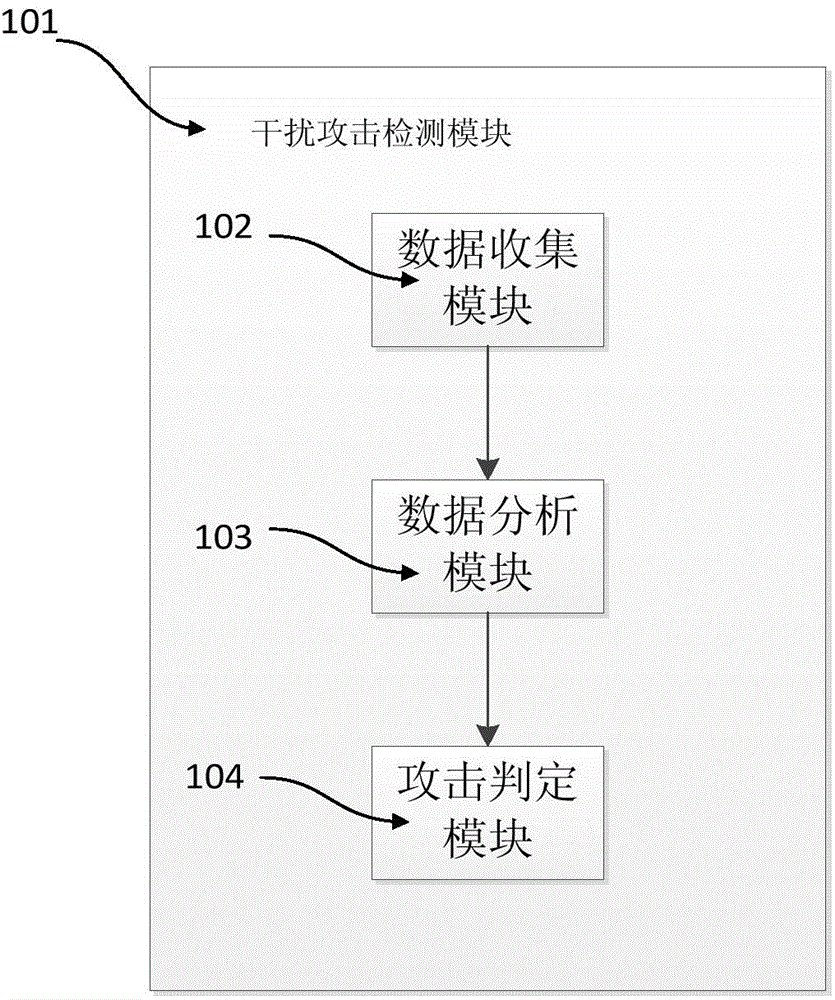
[0026] figure 1 Among them, 101 is an interference attack detection module, and 102 is a data collection module. After the data collection module completes the data collection, the data is handed over to the 103 data analysis module for analysis. After the data analysis is completed, the 104 attack determination module will carry out the final analysis of the interference attack. judge.
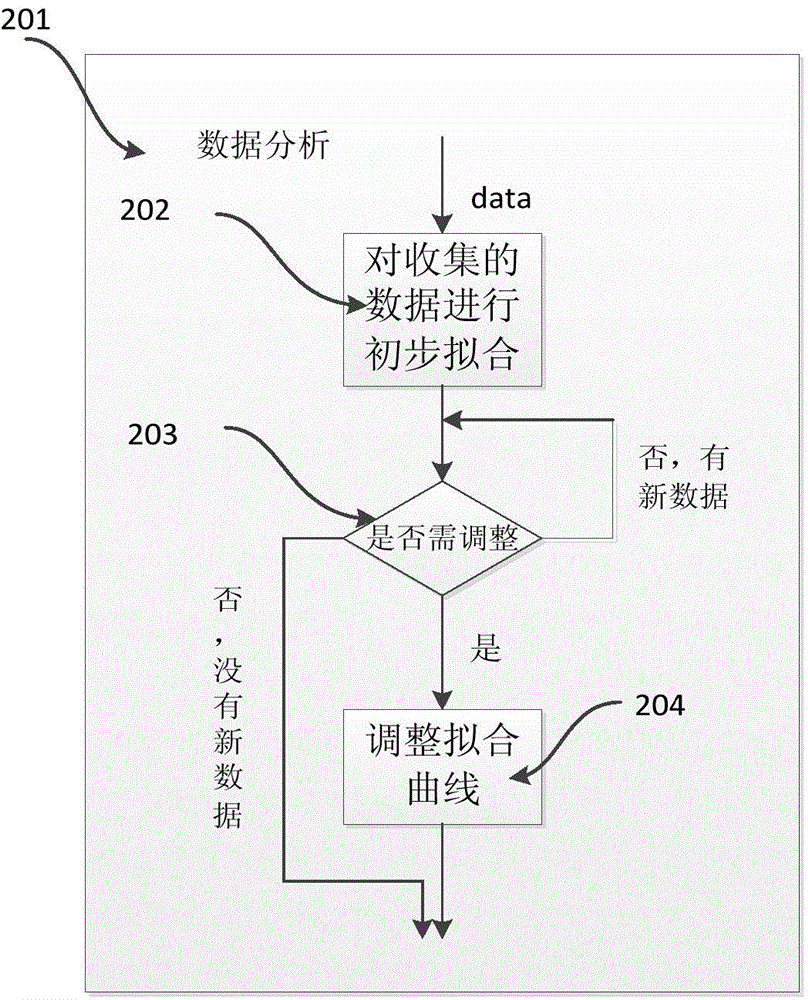
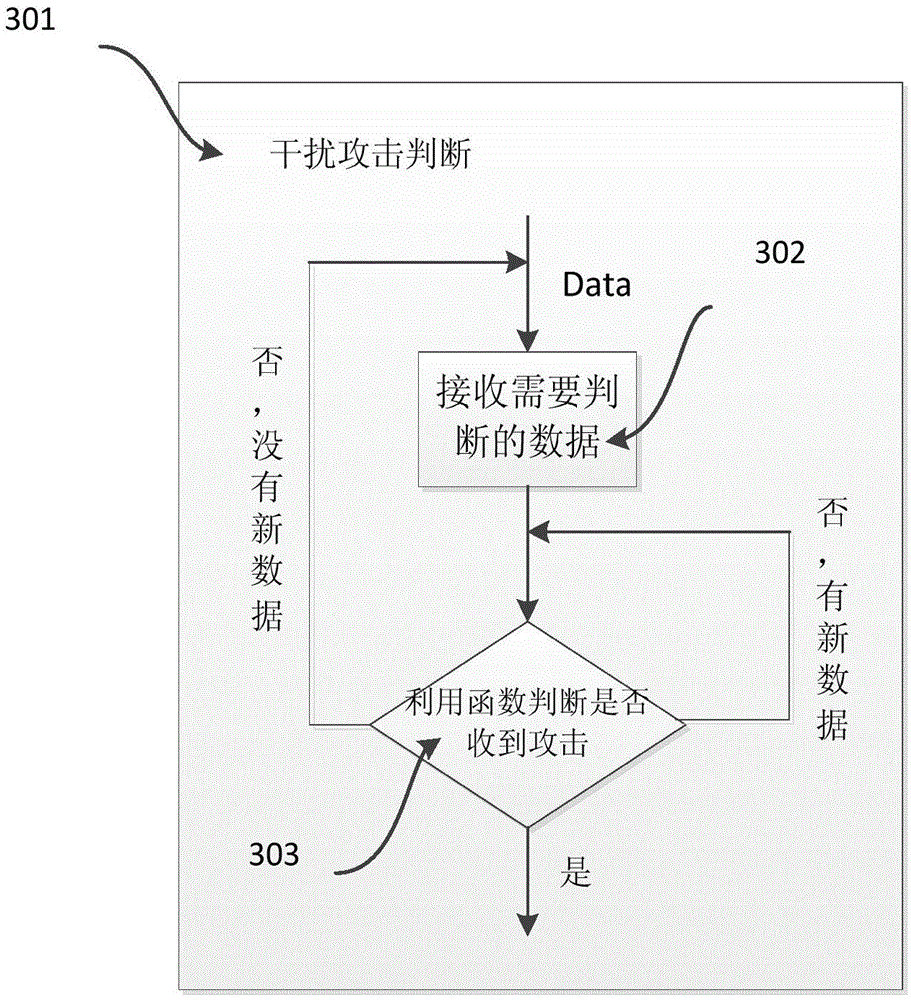
[0027] figure 2 201 is the data analysis module, and 202 is based on the sigmoid function Preliminary fitting is performed on the collected data, and subsequent received data is 203 to judge whether the function needs to be adjusted, and use the least square method to adjust the parameters of the fitted curve, that is, adjust the values of a and b. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com