Method for channel estimation and identification against pilot spoofing attack based on independent component analysis in OFDM (Orthogonal Frequency Division Multiplexing) system
An independent component analysis and channel estimation technology, which is applied in the field of anti-pilot spoofing attack channel estimation and identification based on independent component analysis, can solve the problem that it is difficult for legal transceivers to obtain accurate channel state information of legal links
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be further described in detail below in conjunction with specific embodiments, which are explanations of the present invention rather than limitations.
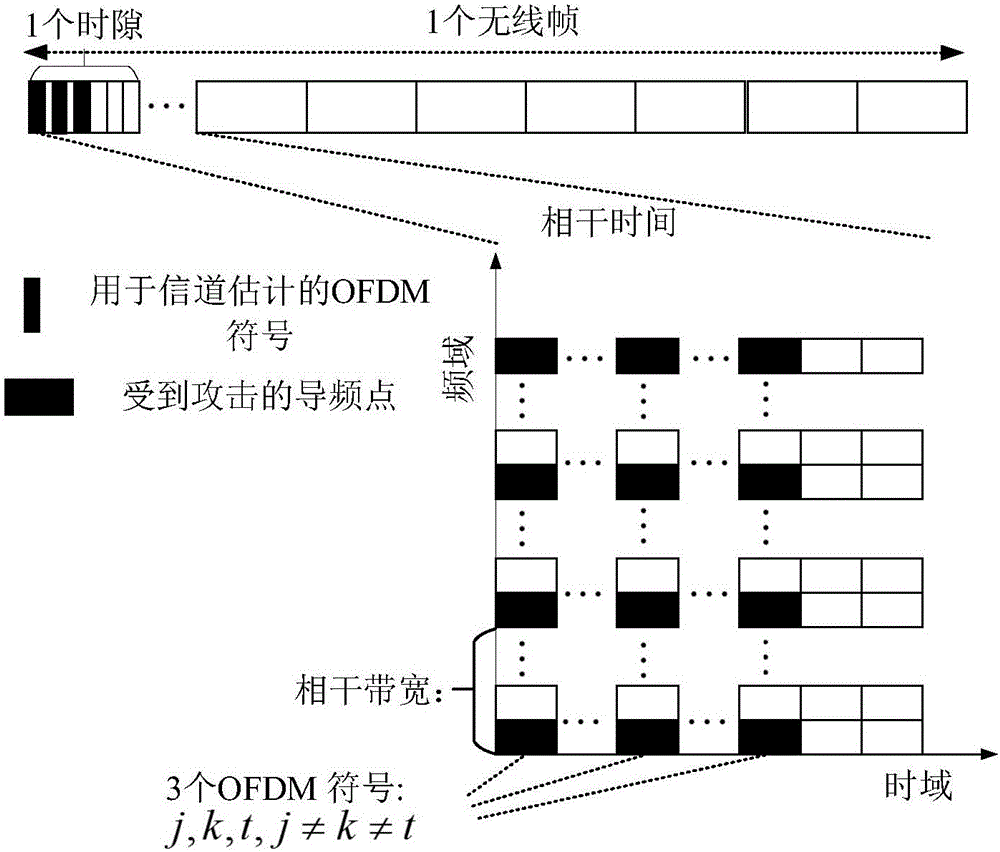
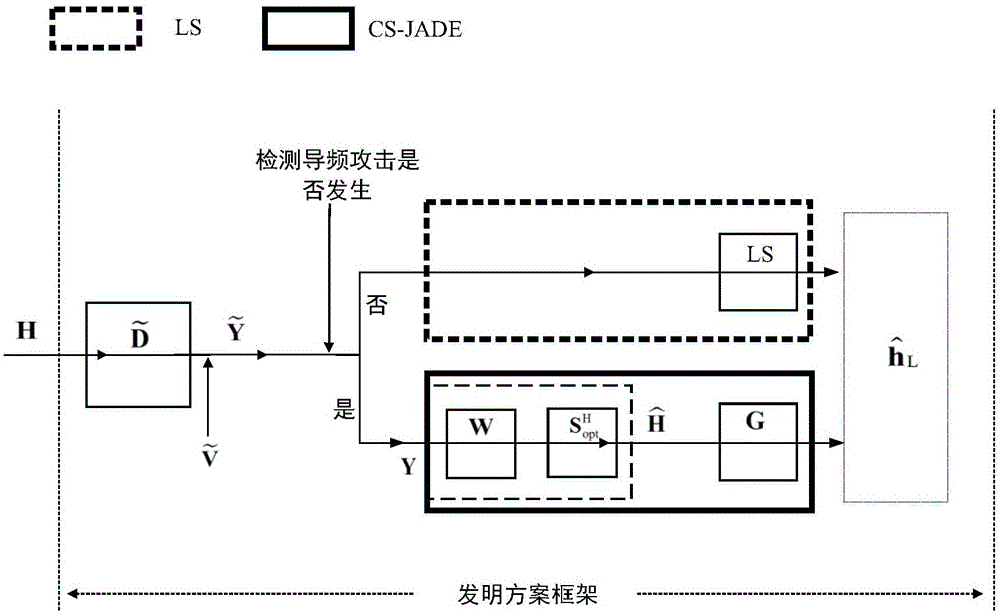
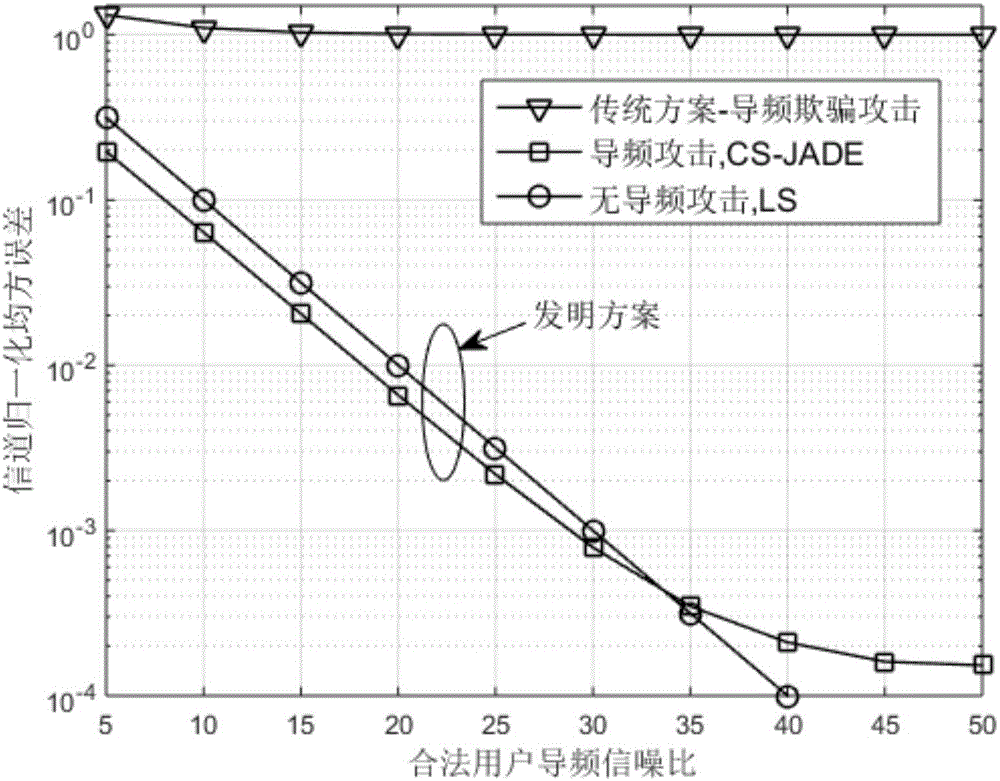
[0041] In the method of the present invention, when the system model is set up, a pair of legal transceivers and an active eavesdropper are considered, and two uplink communication links are respectively 1. uplink transmitter→receiver, defined as legal channel 2. Active eavesdropper → receiver is defined as the attack channel. The receiver has N T The root antenna, the uplink transmitter and the active eavesdropper are all single antennas, such as figure 1 As shown, each antenna of each uplink simultaneously occupies N subcarriers in each OFDM symbol. The channel coefficients on each subcarrier obey the independent and identical distribution with a mean value of 0 and a variance of 1, and the noise on each subcarrier obeys an independent and identically distributed Gaussian white noise with...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com