Blocking attack prediction method and system for wireless energy transmission communication network
A technology of wireless energy transmission and communication network, which is applied in the field of jamming attack prediction of wireless energy transmission communication network, and can solve the problem that there is no method for accurately predicting the attacker's attack behavior
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] Hereinafter, preferred embodiments of the present disclosure will be described in detail with reference to the drawings. In the following description, the same reference numerals are given to the same components, and repeated descriptions are omitted. In addition, the drawings are only schematic diagrams, and the ratio of dimensions between components, the shape of components, and the like may be different from the actual ones.
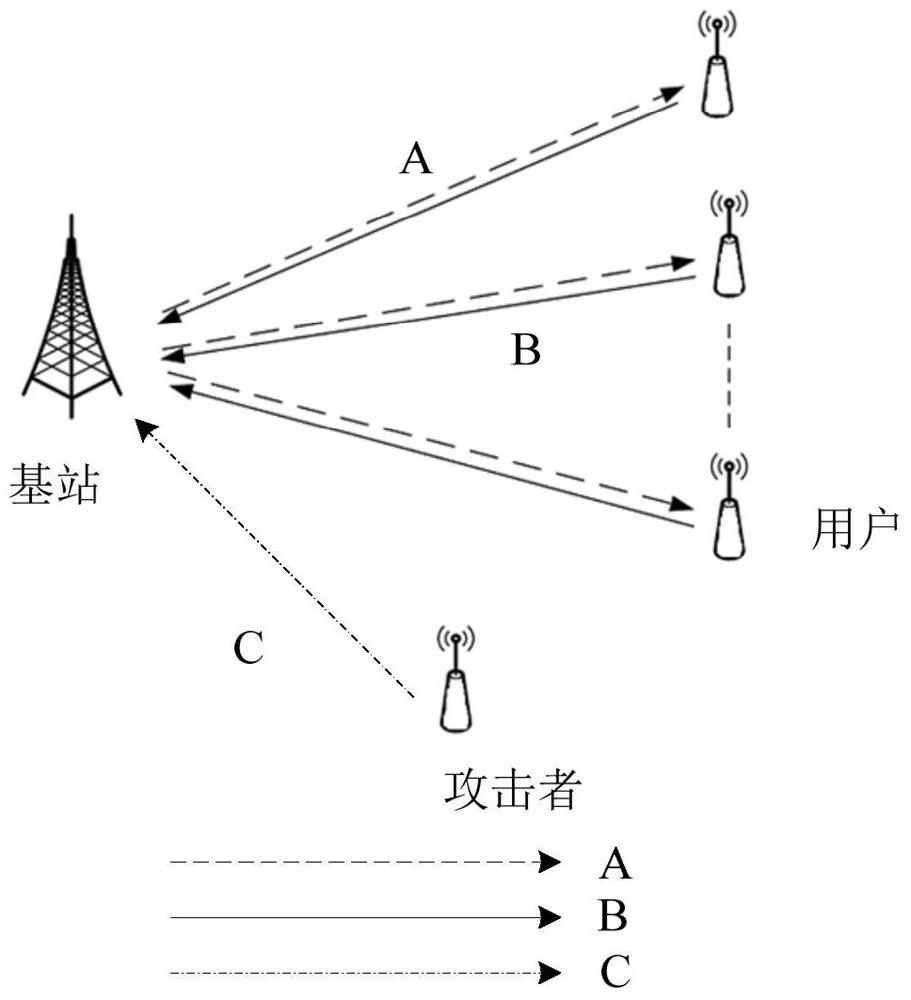
[0028] figure 1 is a schematic diagram showing a communication network model of a wireless energy transfer communication network involved in an example of the present disclosure. In some examples, such as figure 1 As shown, the base station can have one. Users can include at least one. The base station and each user are equipped with an antenna. In addition, the base station and all users work in the same frequency band. Attackers can include at least one.
[0029] In some examples, figure 1 In the signal model shown, a base station (su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com