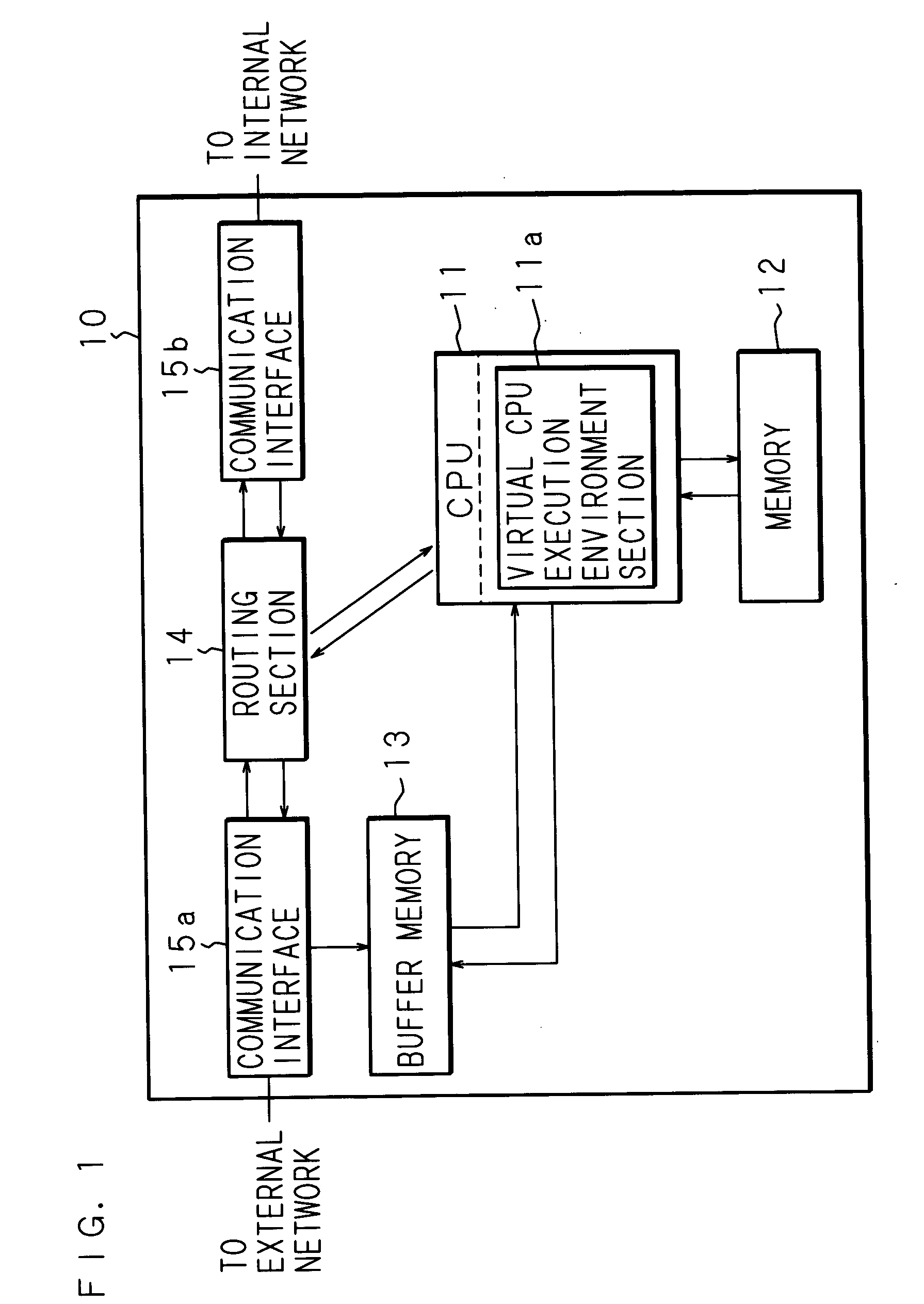
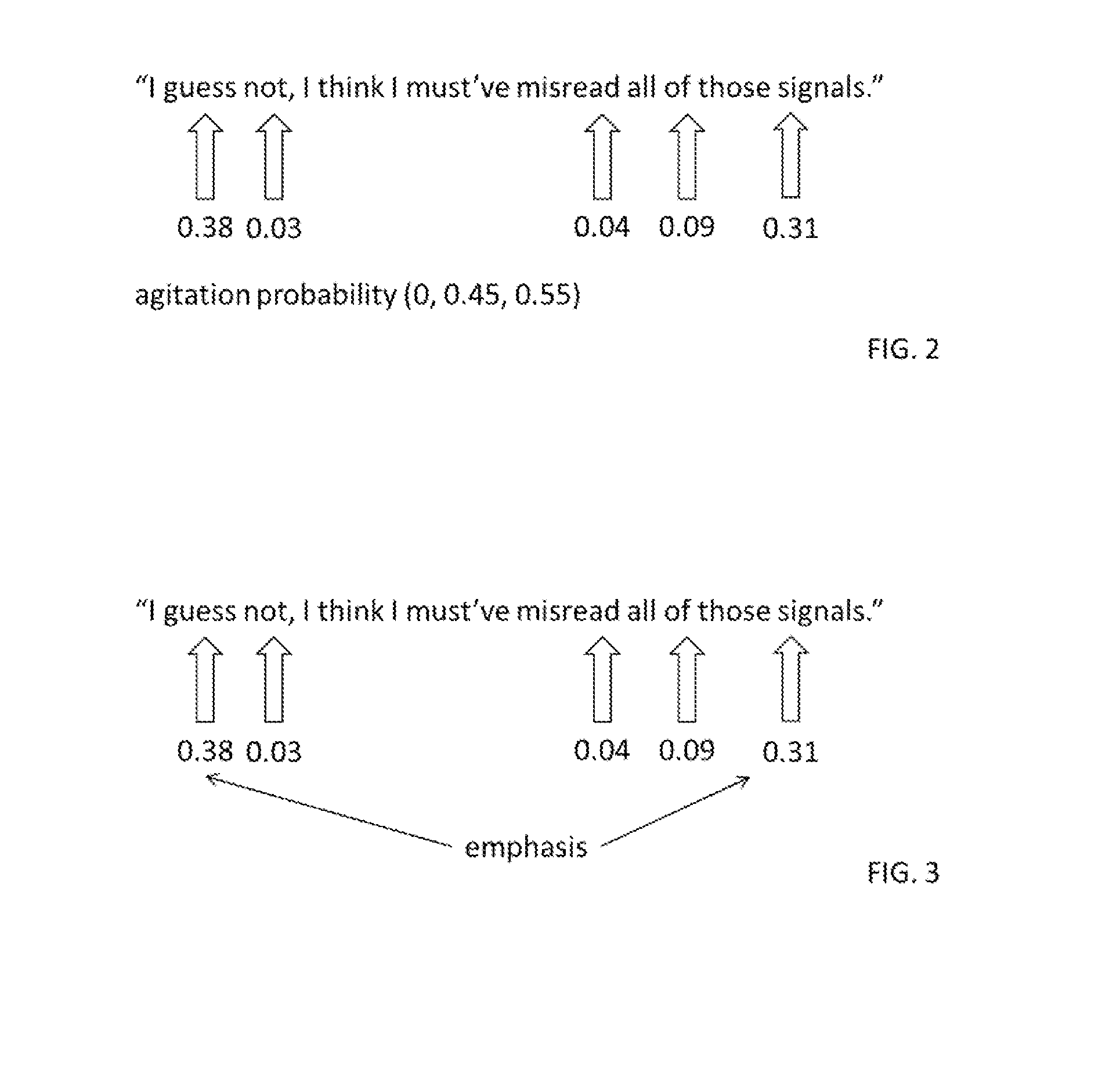
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
37 results about "Include directive" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Many programming languages and other computer files have a directive, often called include (as well as copy and import), that causes the contents of a second file to be inserted into the original file. These included files are called copybooks or header files. They are often used to define the physical layout of program data, pieces of procedural code and/or forward declarations while promoting encapsulation and the reuse of code.
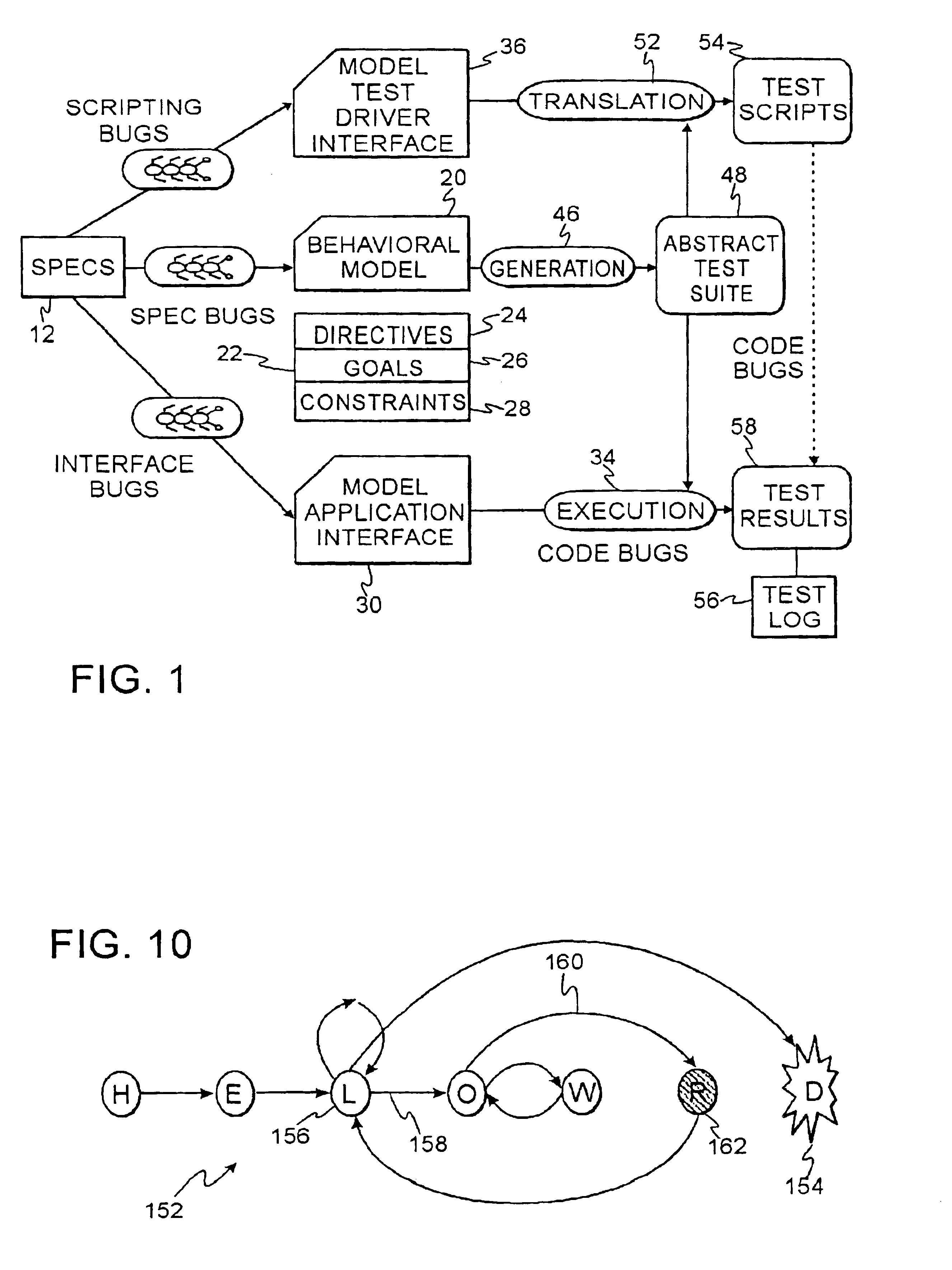
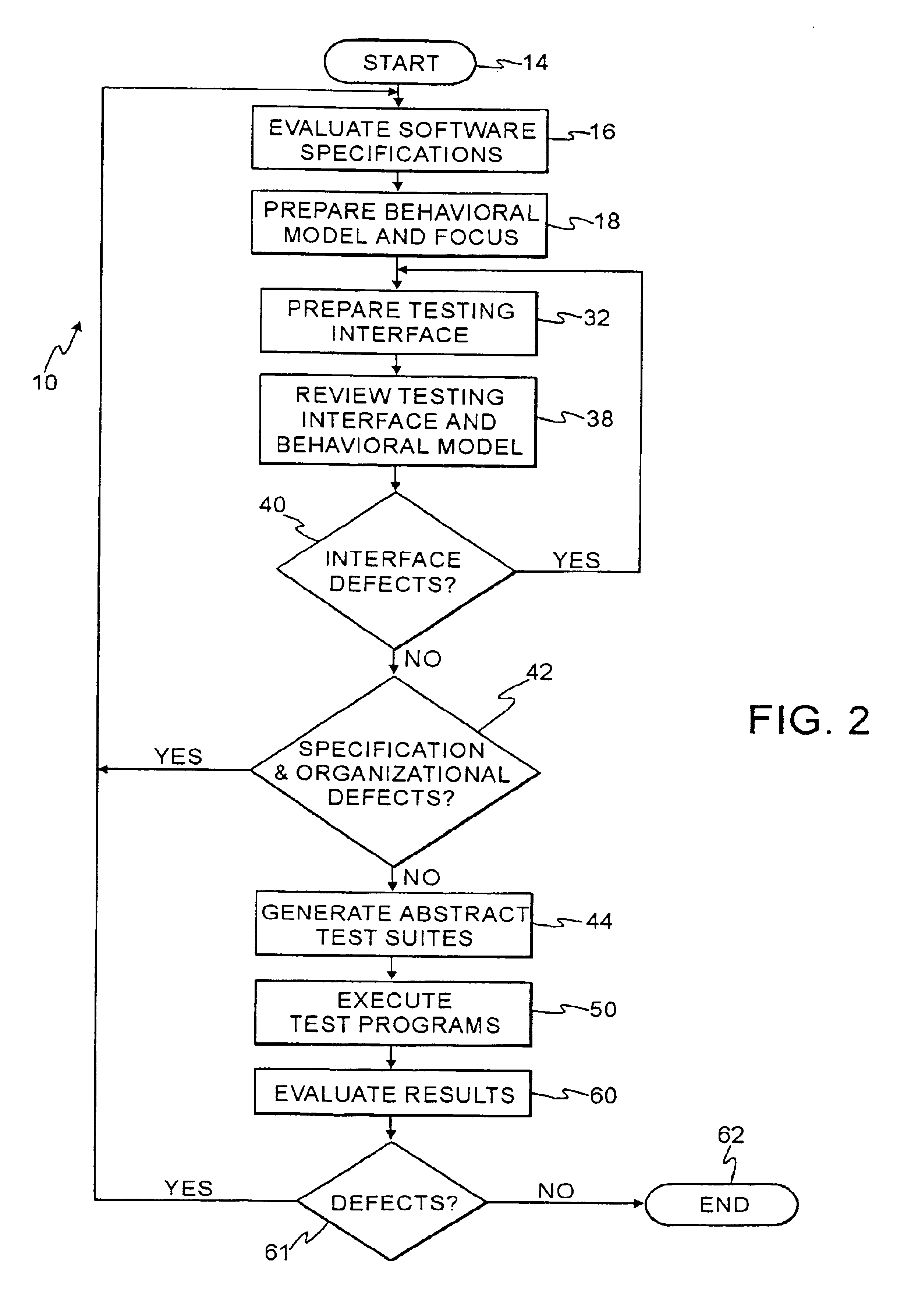
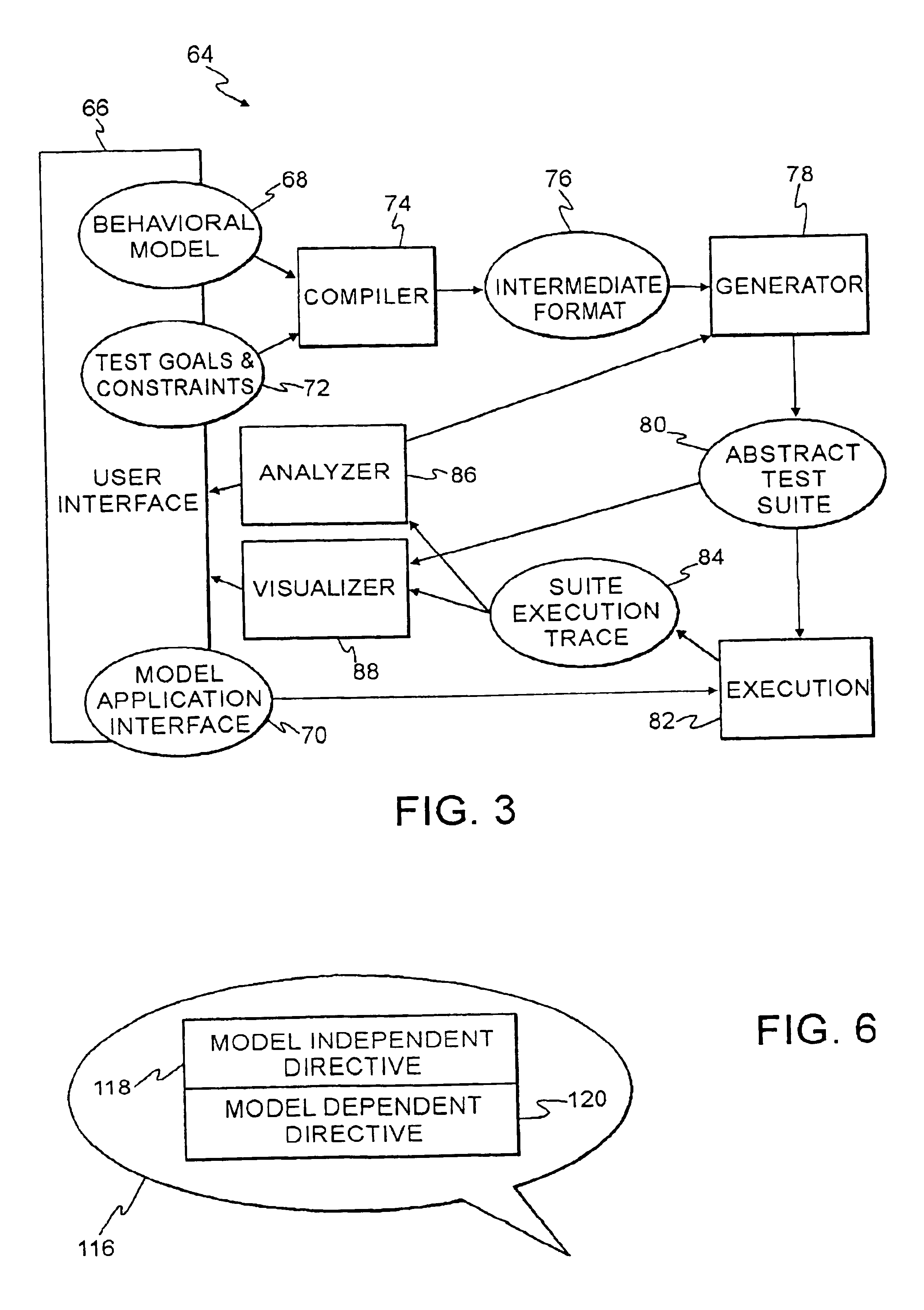
Technique using persistent foci for finite state machine based software test generation
InactiveUS6944848B2Reduce in quantitySoftware testing/debuggingSpecific program execution arrangementsTest suiteTheoretical computer science
A system for automatic generation of test programs employs test generation foci linked to a finite state machine behavioral model of a software application under test to produce abstract test suites that are executed by an execution engine. The foci include directive expressions that tag coverage variables of the behavioral model. The execution engine operates until the tagged coverage variables have assumed all their possible values. Both the behavioral models and the foci are archivable and can be retrieved and reused independently.
Owner:IBM CORP
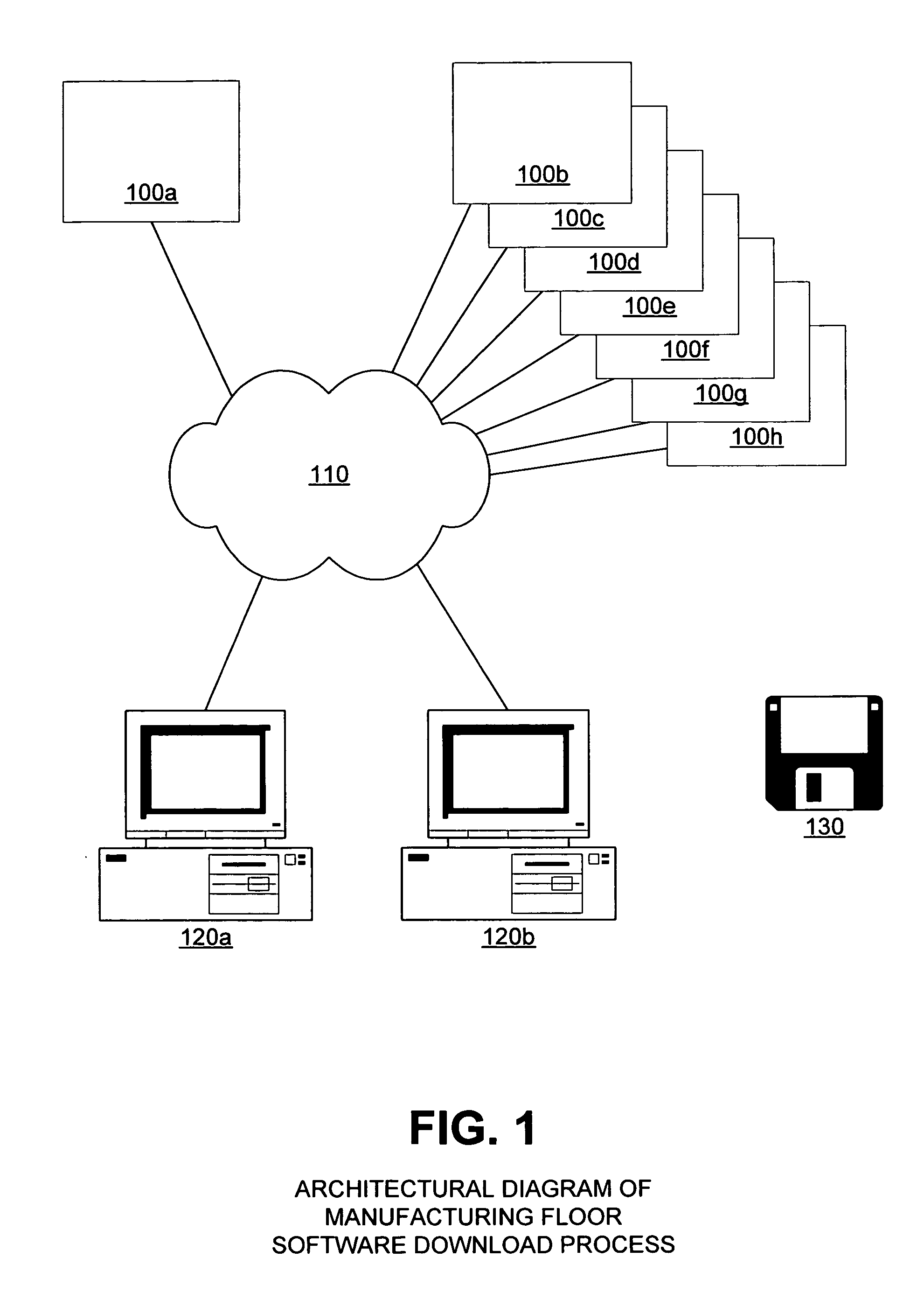
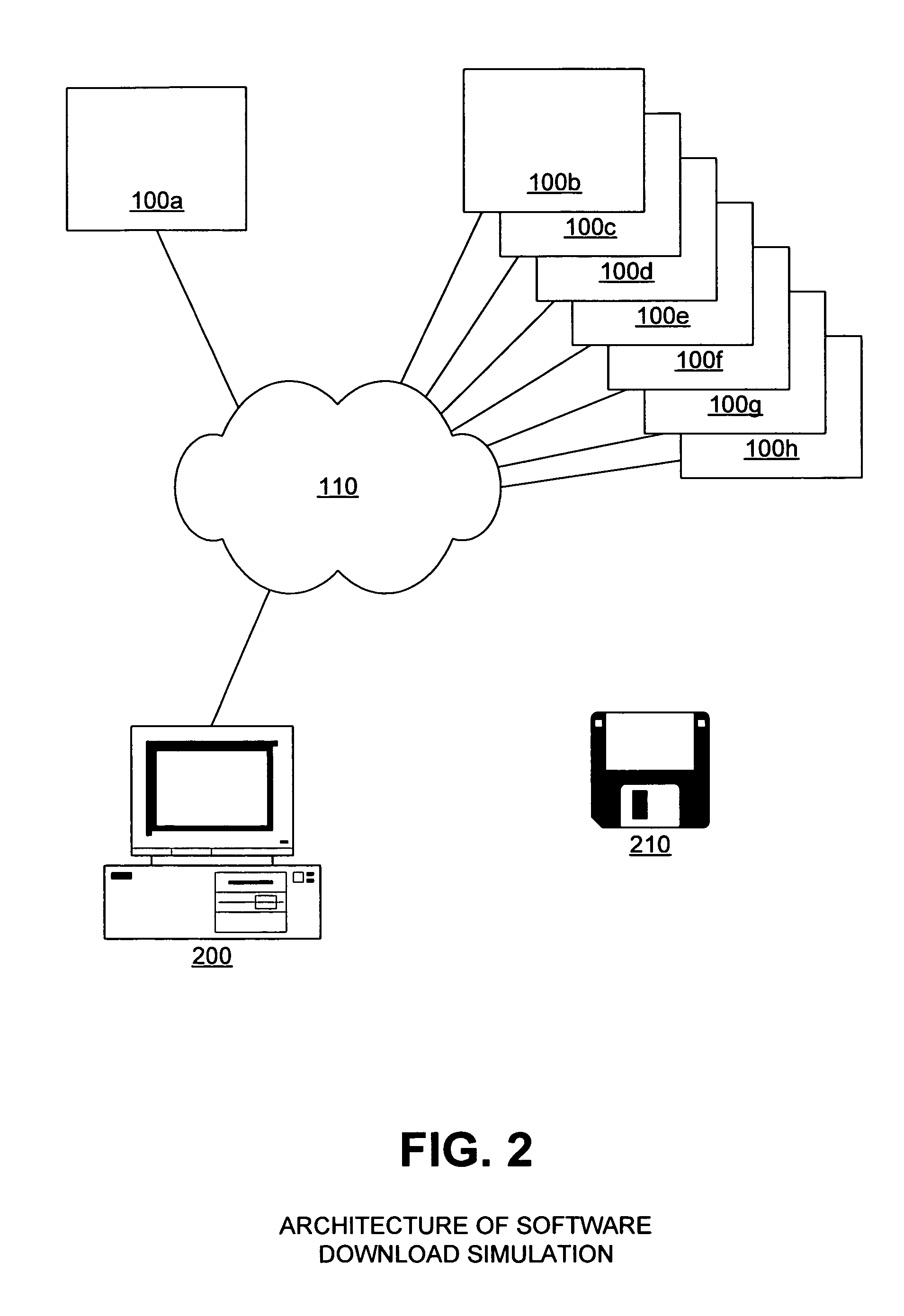
Interpretive simulation of software download process
InactiveUS7240336B1Avoid timeAvoid expensesProgram loading/initiatingSoftware simulation/interpretation/emulationSystems designPersonal computer
The present invention is a method and system designed to be used in a manufacturing environment to ensure the integrity of a manufacturing tool that downloads customer ordered software to personal computers. The present invention creates a computer environment in a lab setting that mimics the computer environment created in the manufacturing arena. The system and method then simulates the steps employed to download the software to a personal computer in a controlled environment to predetermine errors that may be encountered when the process is implemented in the manufacturing arena. This invention dynamically generates a file that contains instructions that when executed download and install customer ordered software to a target computer on the manufacturing floor. This invention then interprets the generated file in accordance with a set of evaluation rules such that the outcome of the execution of the file is determined. An analysis and report is then provided, so that the behavior of the download process can be evaluated for errors that may occur during the download process.
Owner:SCI SYST INC
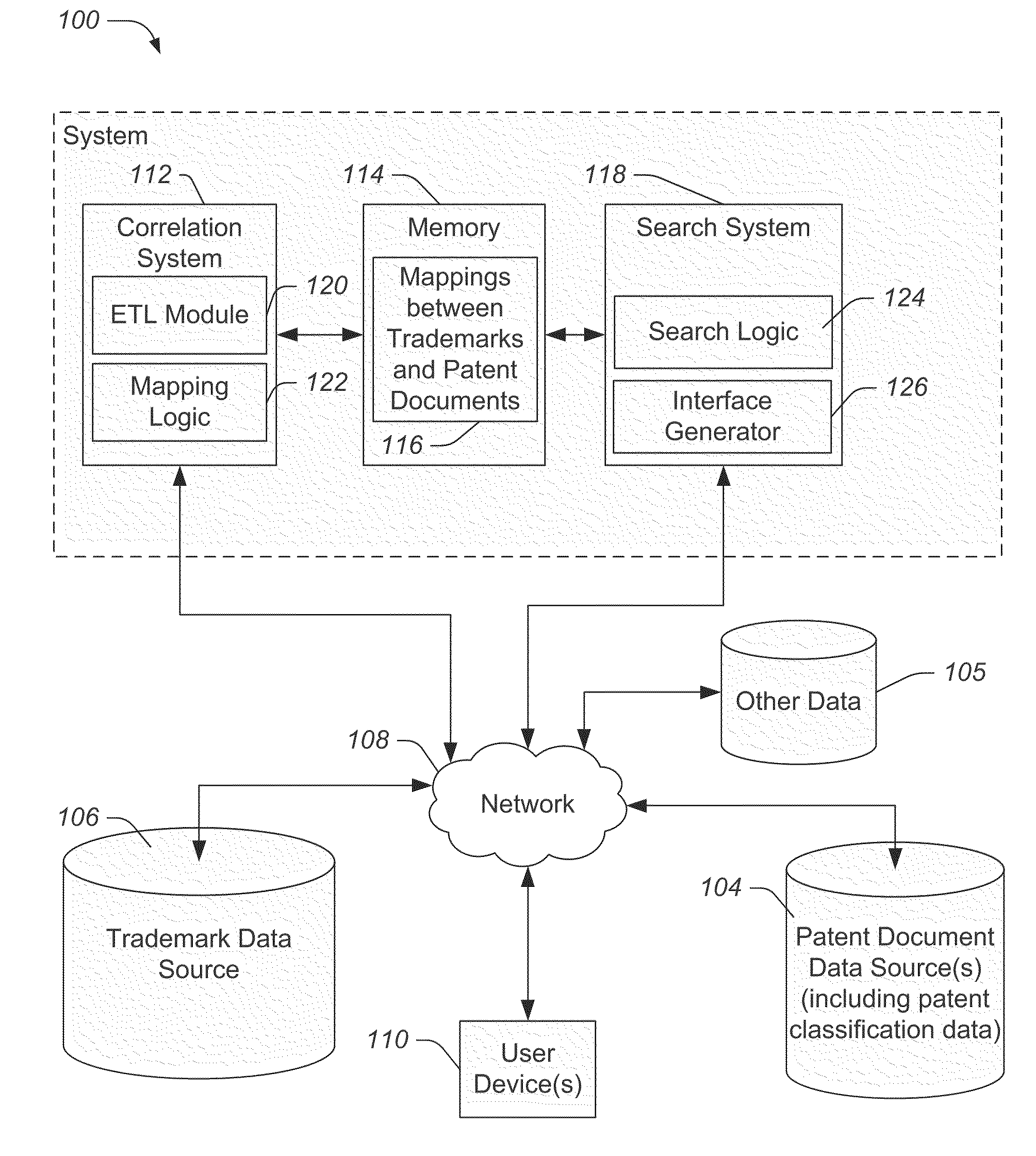
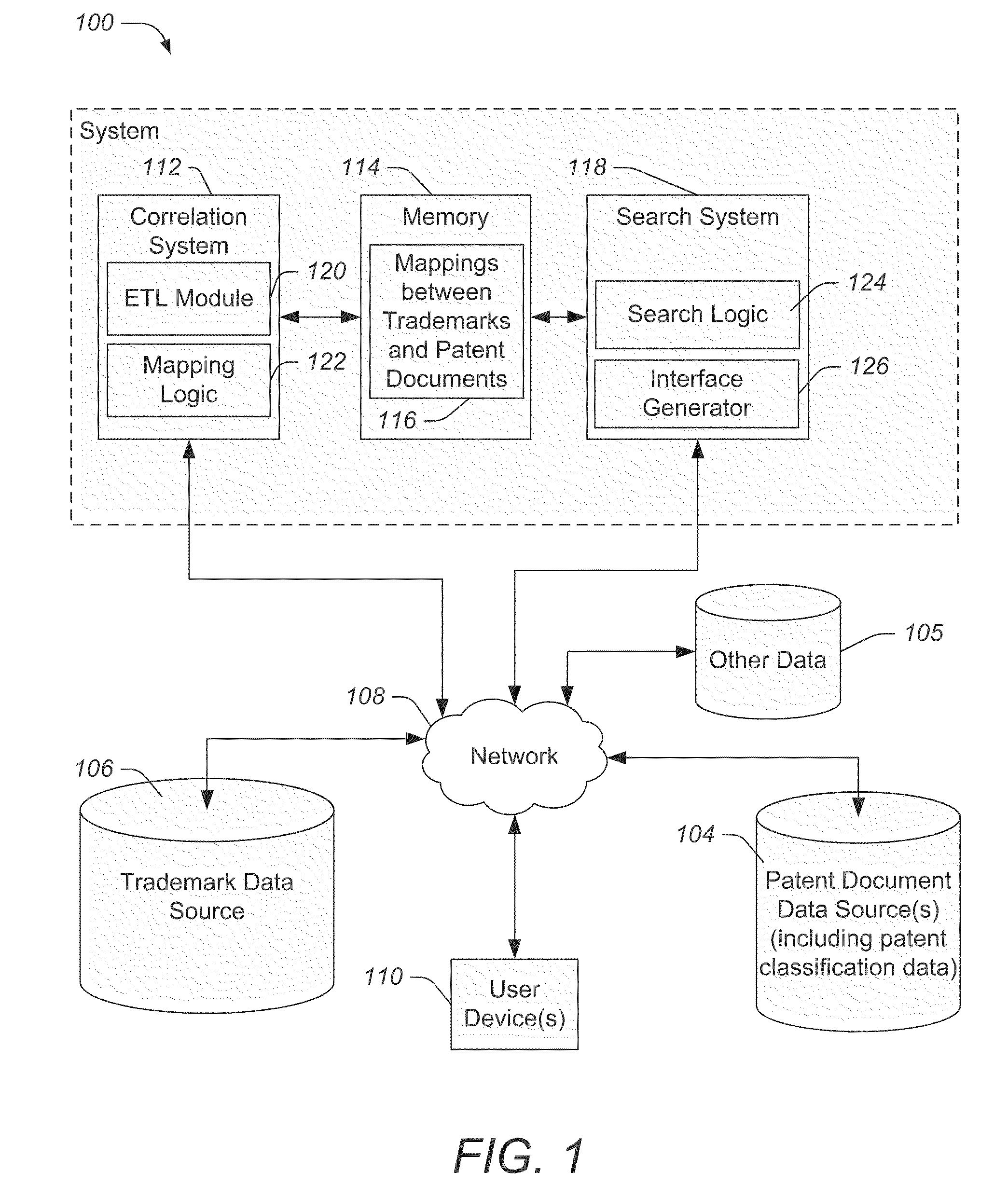
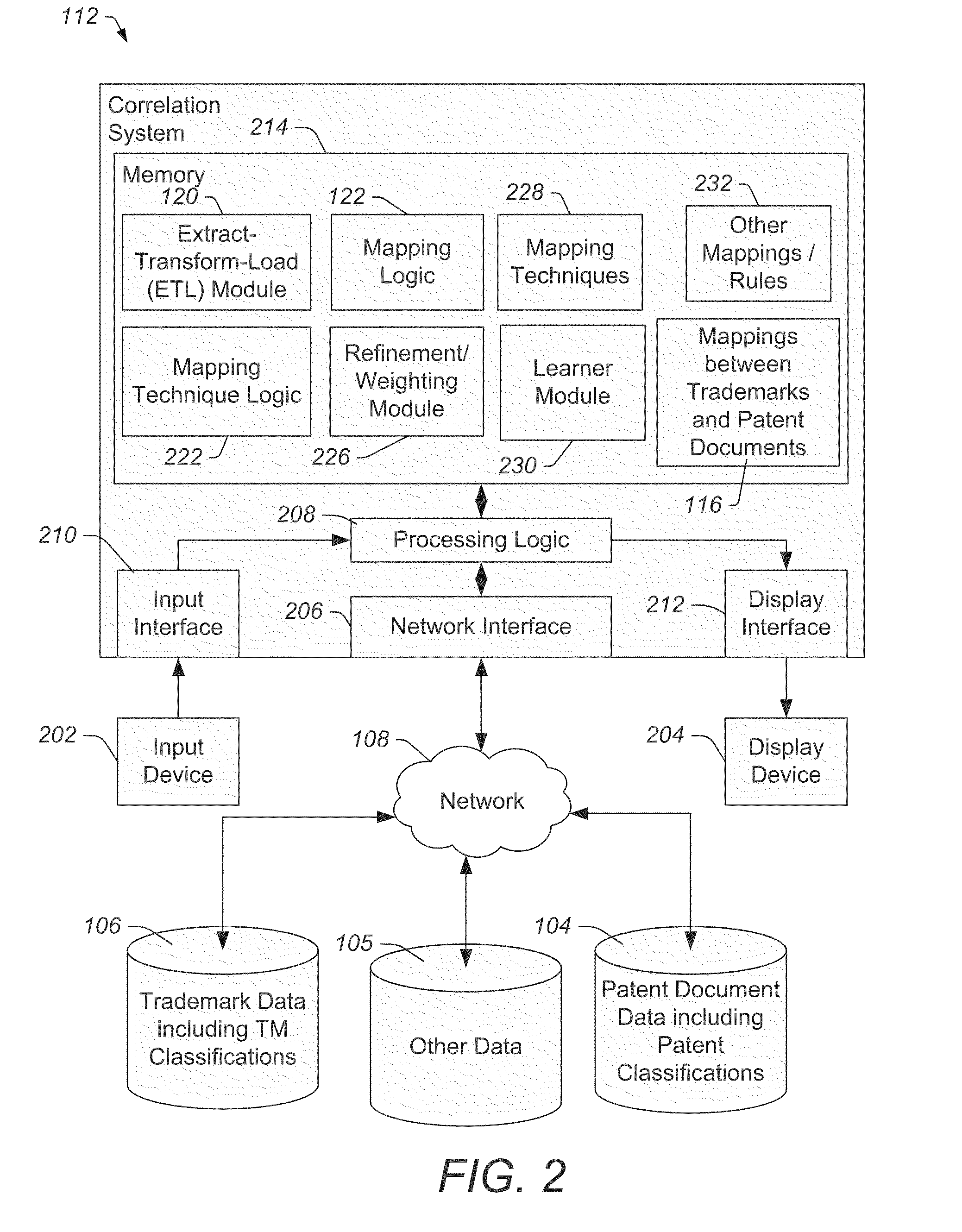
System and methods of relating trademarks and patent documents
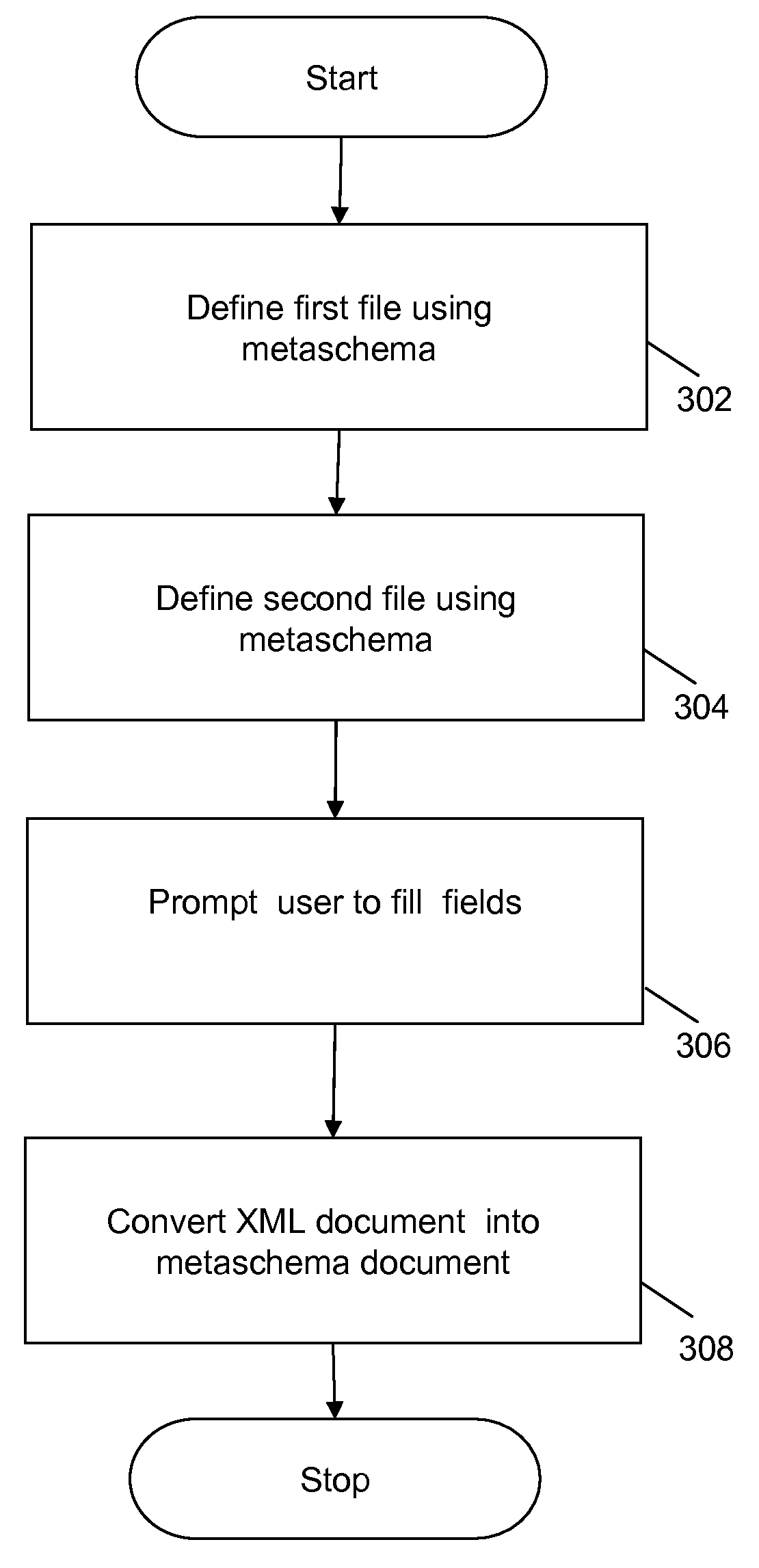
In an embodiment, a computer-readable medium embodies instructions that, when executed by at least one processor, cause a computing system to perform operations including automatically defining one or more associations between a trademark record and a patent document and storing the one or more associations as mappings between trademarks and patent documents.
Owner:INNOGRAPHY
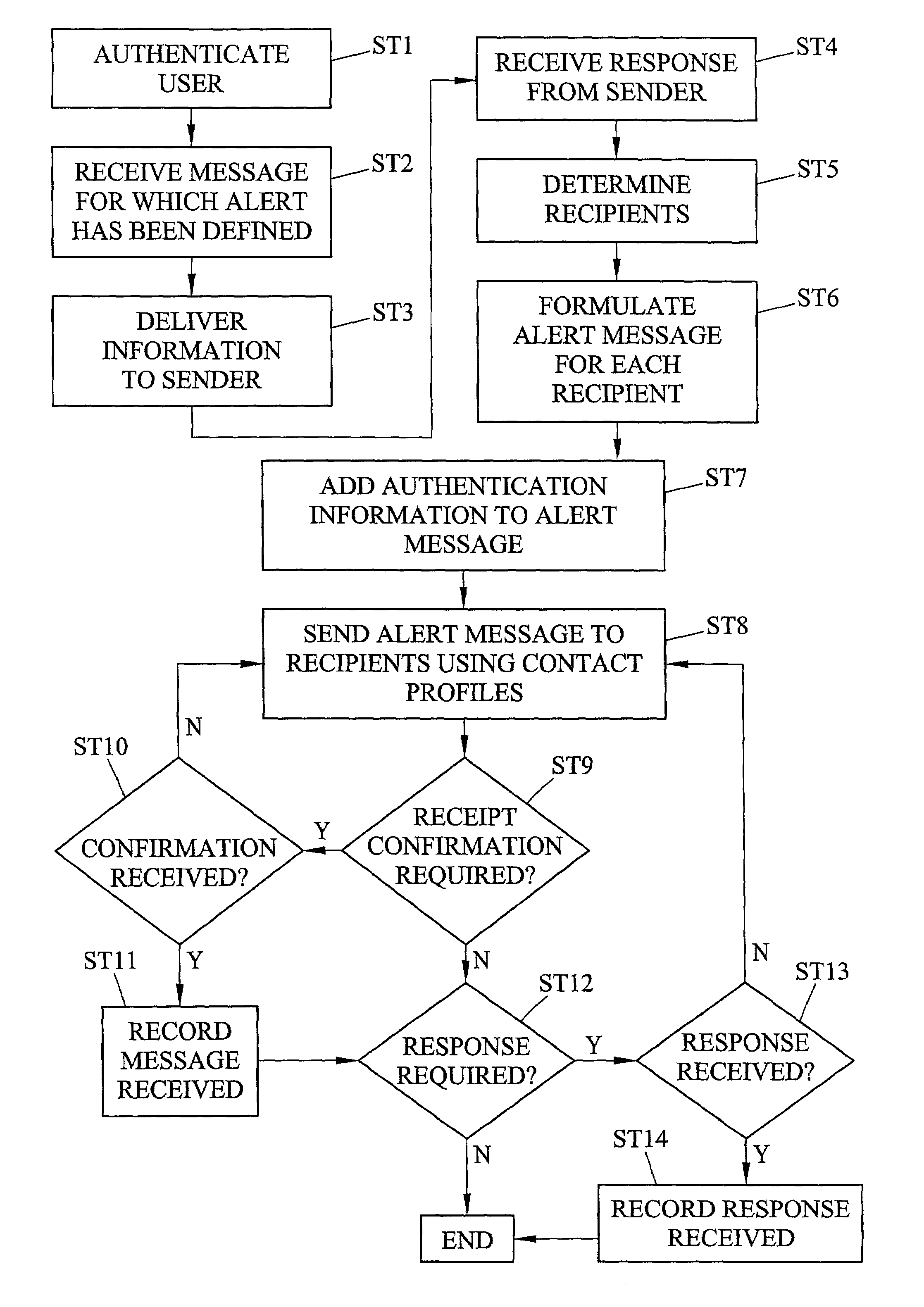
Methods and systems for and defining and distributing information alerts
InactiveUS7133869B2Avoid difficultySpecial service provision for substationDigital data processing detailsEvent triggerComputer science
Owner:TOPIC RADIO
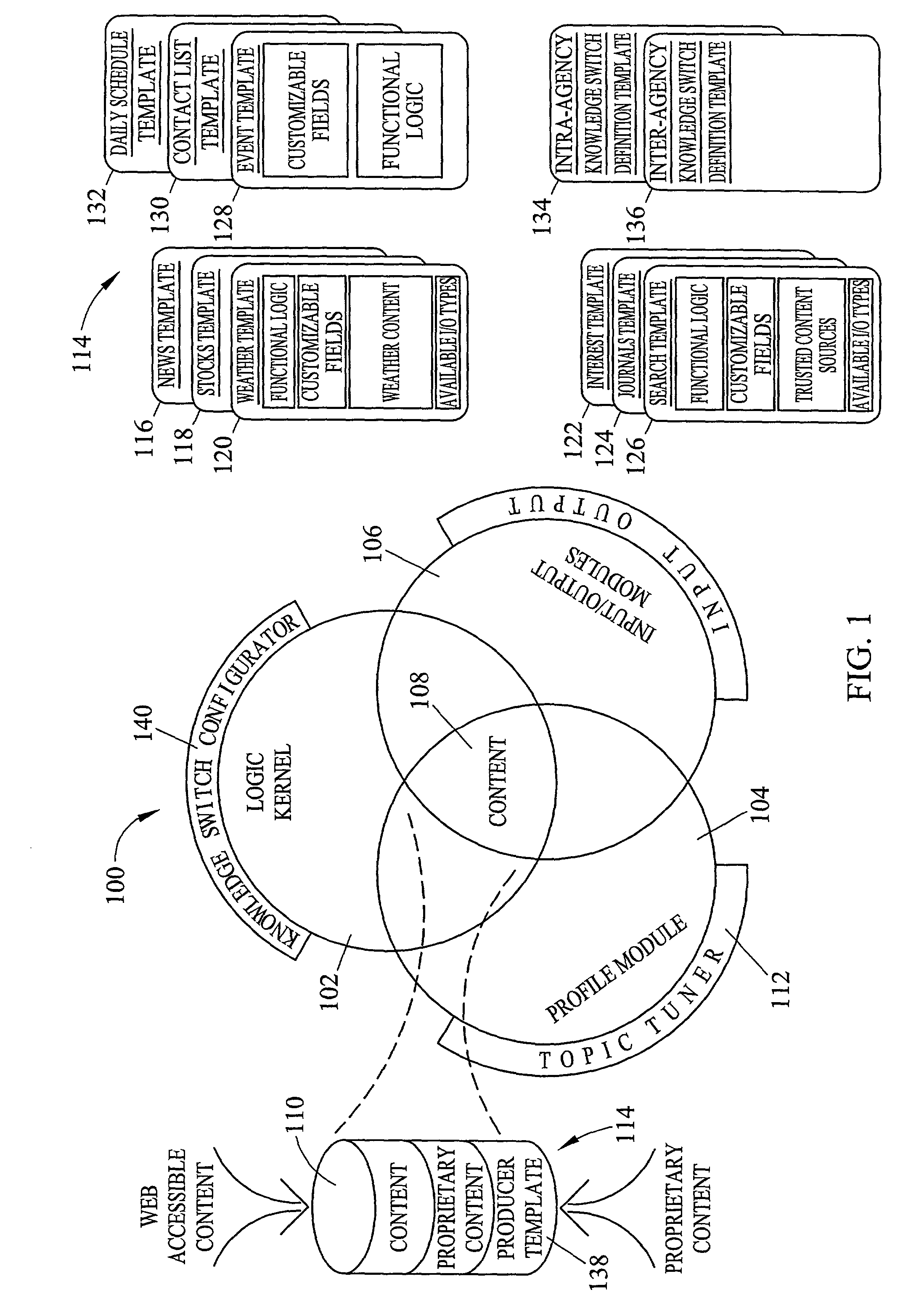
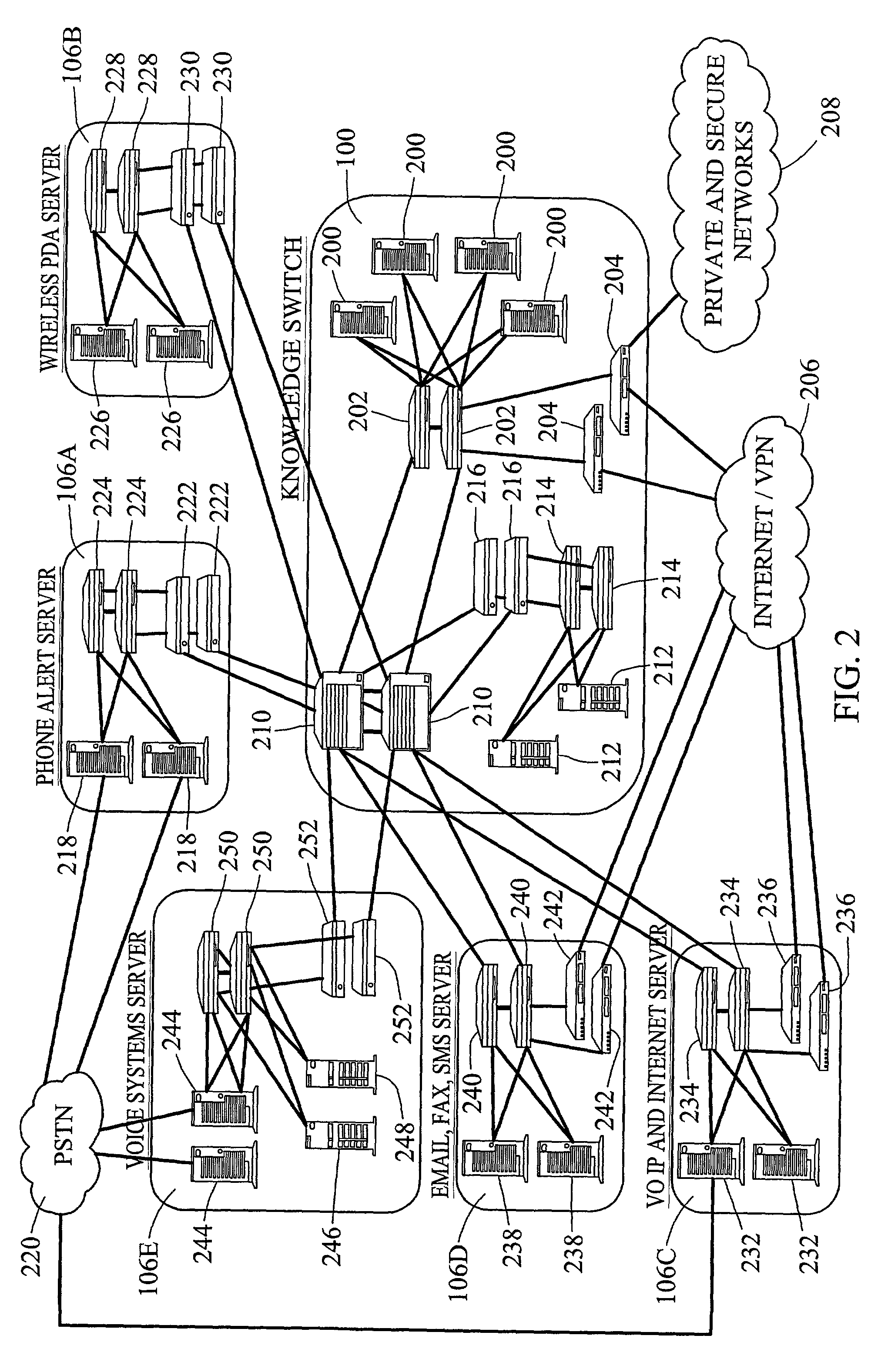
Automated context-sensitive updating on content in an audiovisual storage system
InactiveUS7890989B1Television system detailsElectronic editing digitised analogue information signalsHard disc driveContext data
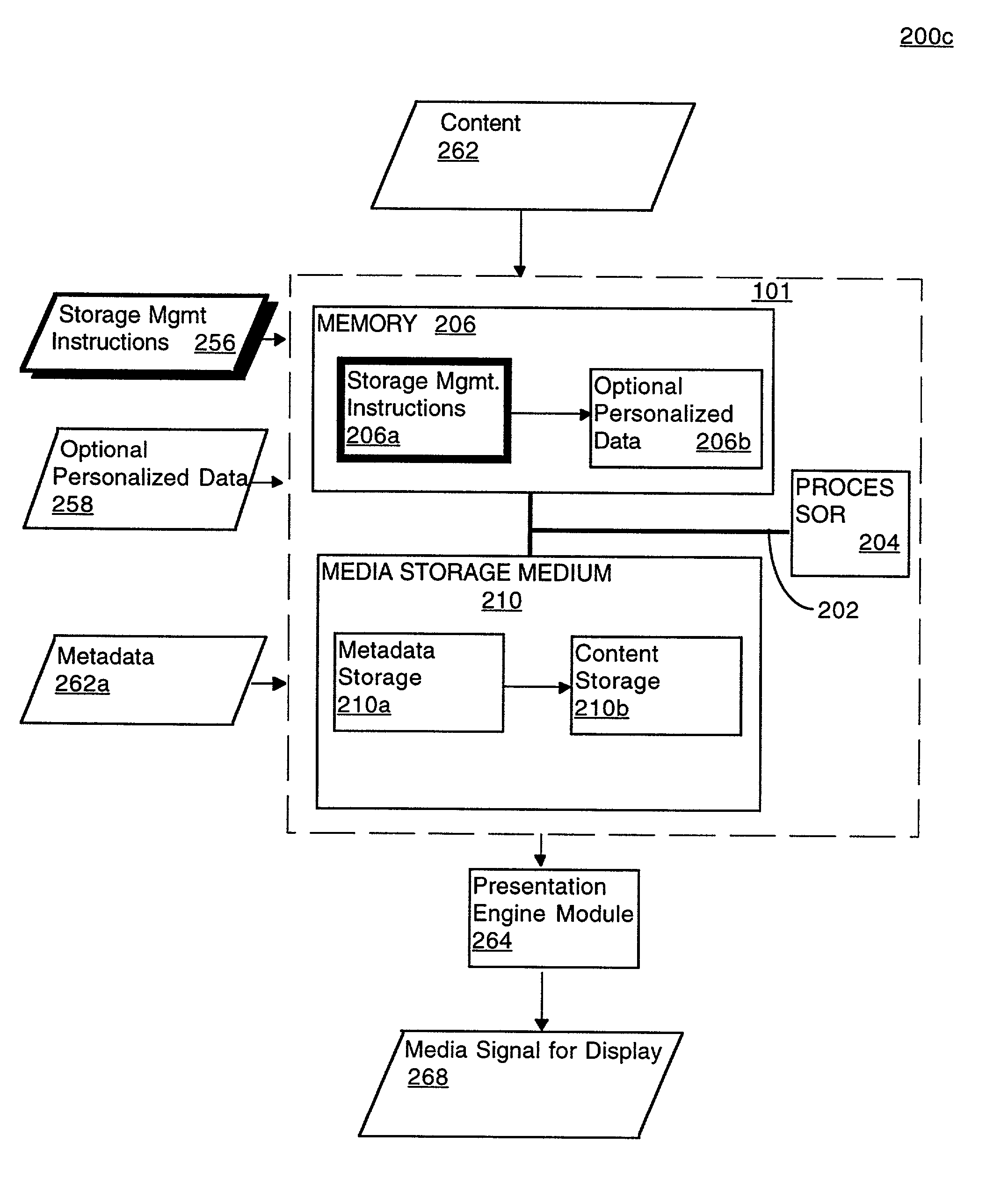
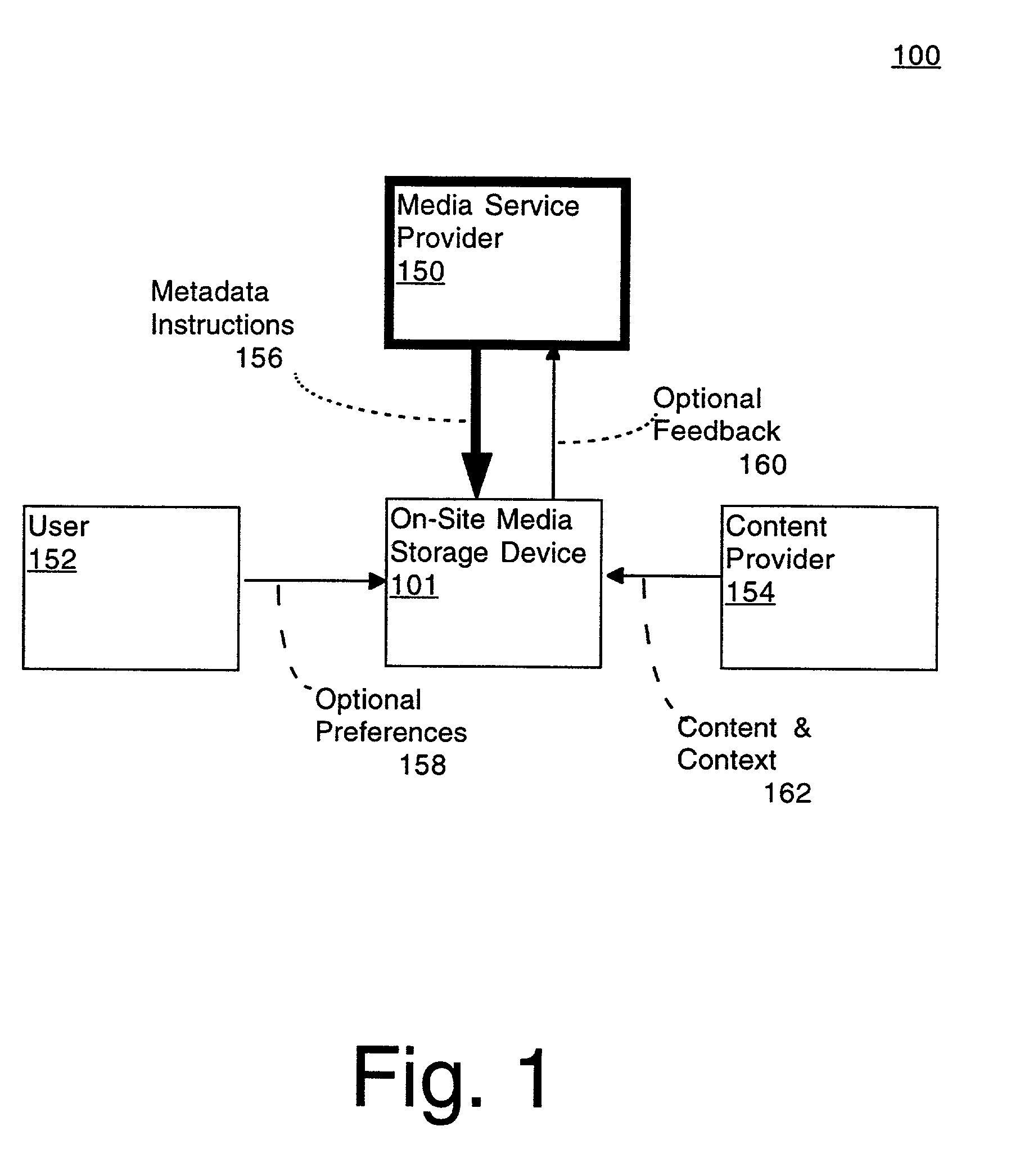
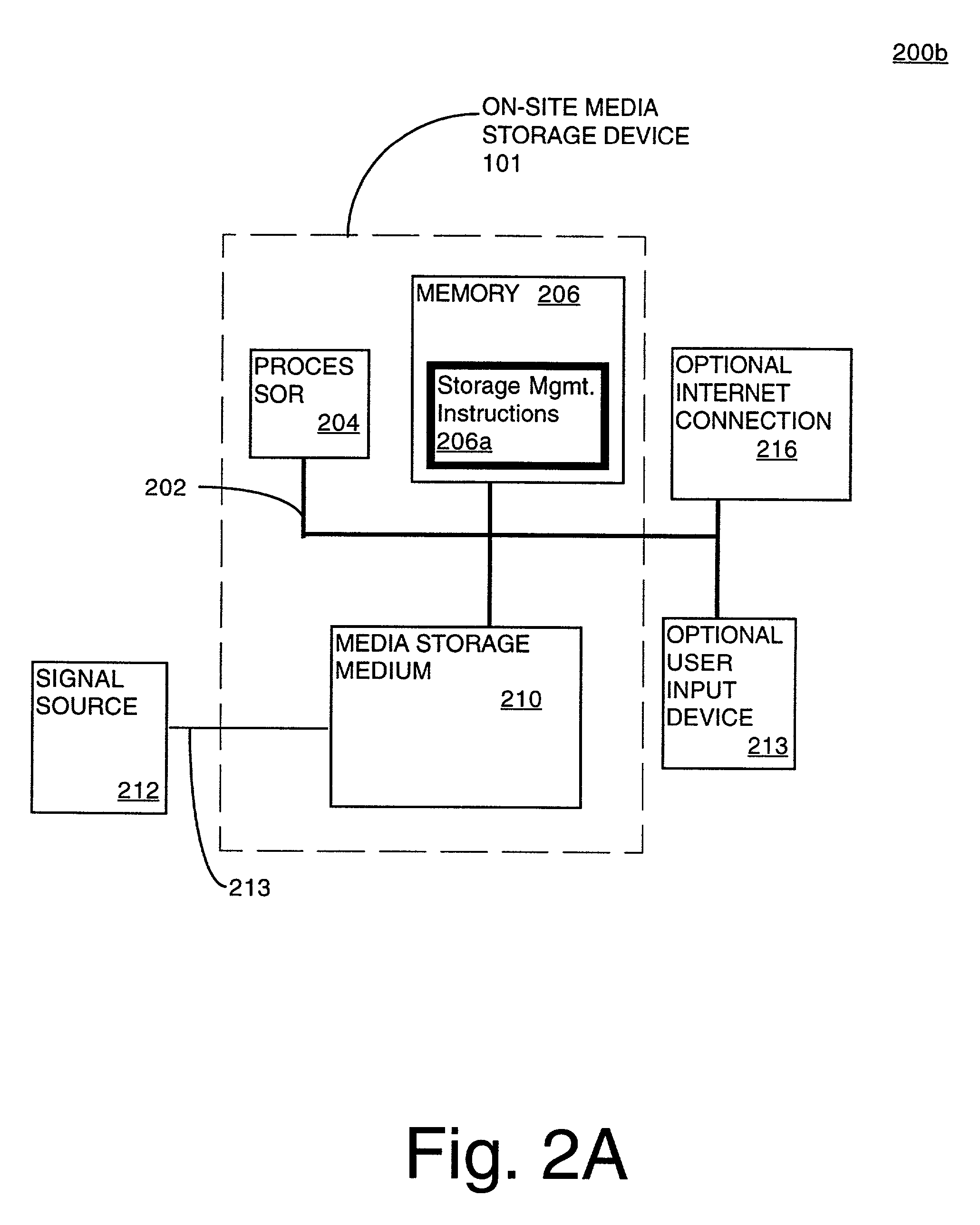
Automated context-sensitive updating of content in an audiovisual (AV) storage system is disclosed. A media storage device for storing a multimedia signal includes a storage medium, such as a dedicated hard drive, a processor, and memory. The storage medium is coupled to the processor and the memory. The memory contains instructions that, when implemented, enable a method of off-site management of data stored on the storage medium. The method includes a step of receiving a media signal with content data and context data at the media storage device. The method also includes a step of receiving storage management instructions from a storage management provider, remotely located from the media storage device. Lastly, the media signal is stored on the media storage device in accordance with the storage management instructions.
Owner:SONY CORP +1
Intelligent computer program debugger, and system and method for implementing the same
ActiveUS20090210862A1Error detection/correctionSpecific program execution arrangementsApplication softwareComputer software
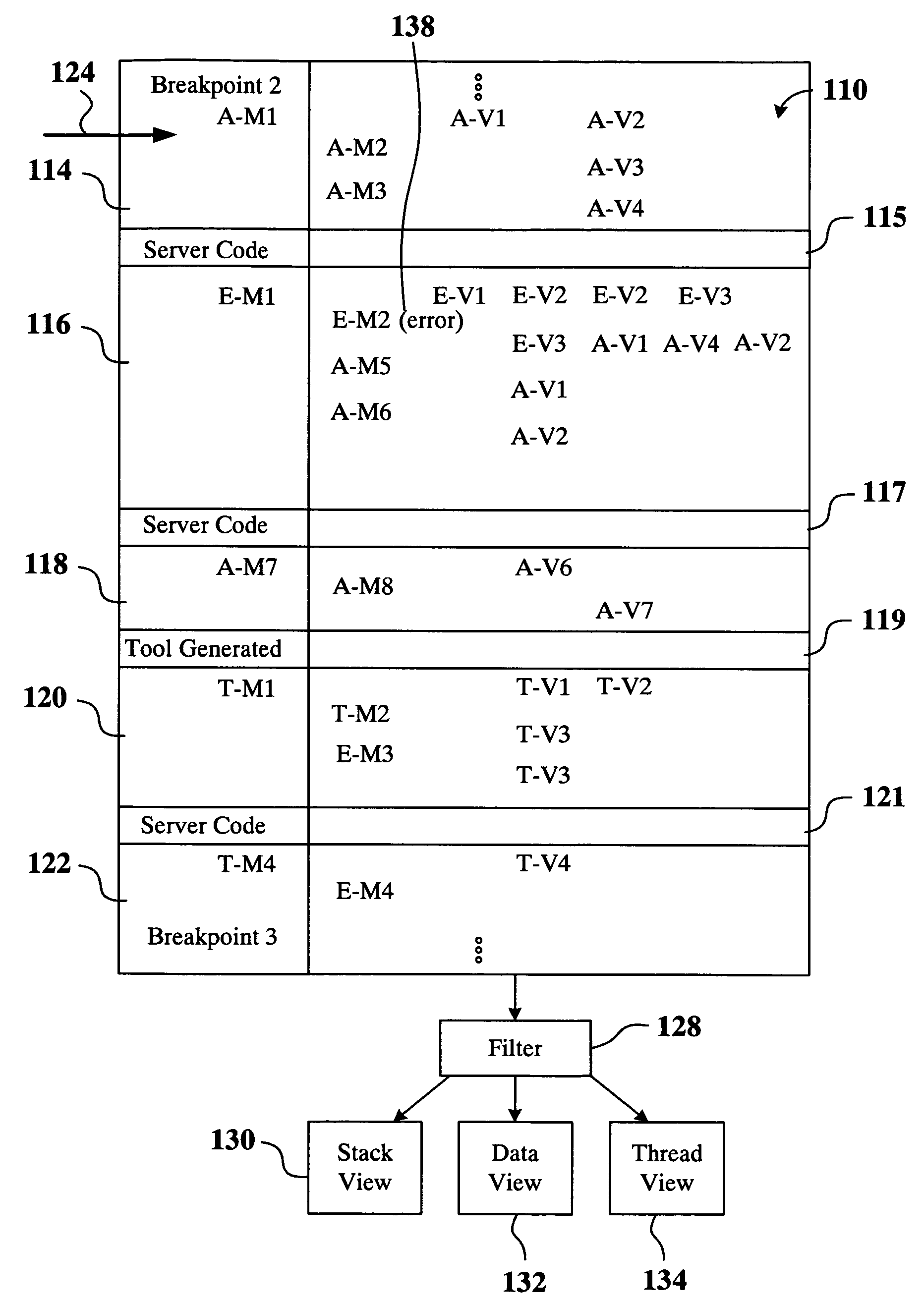
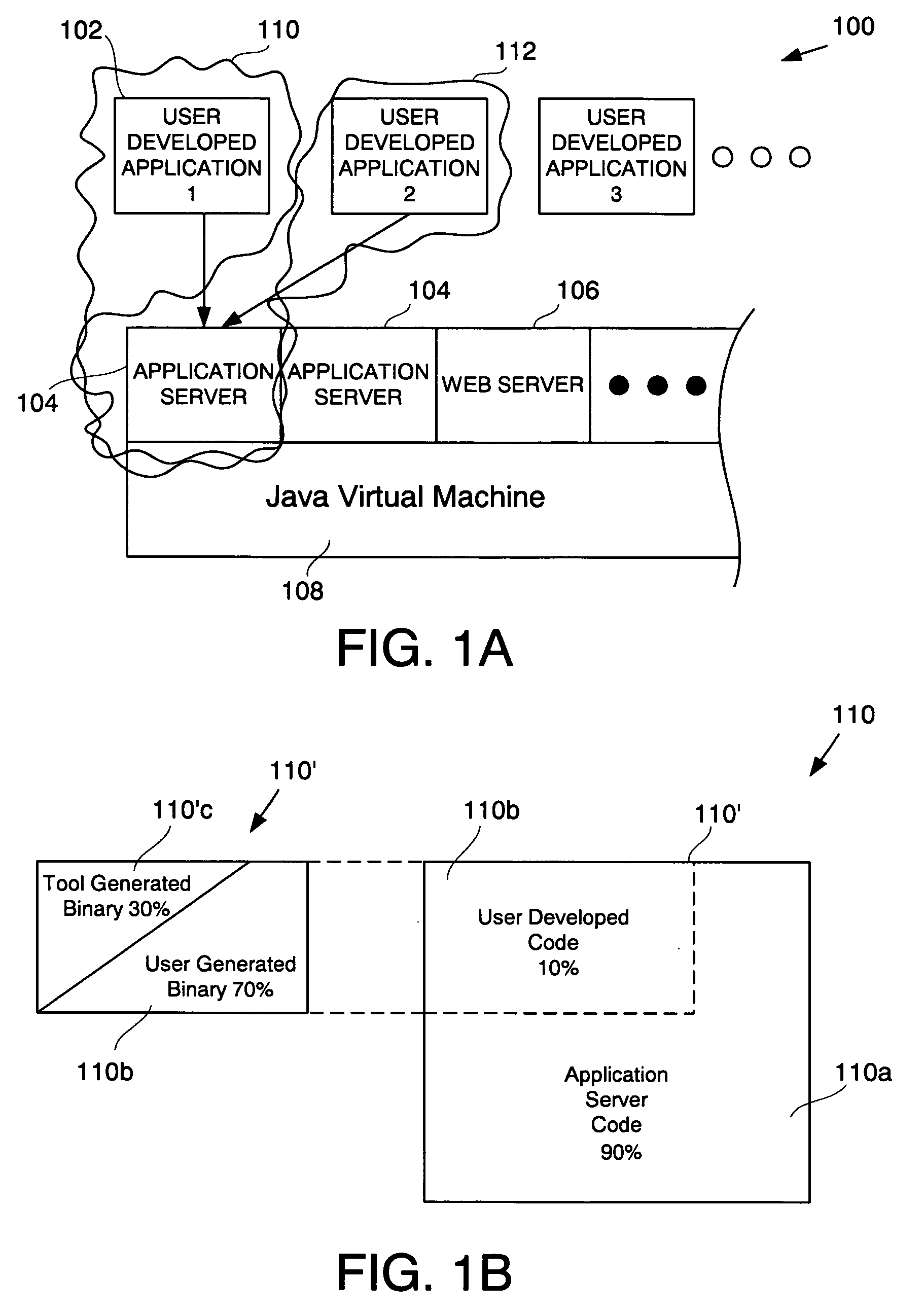
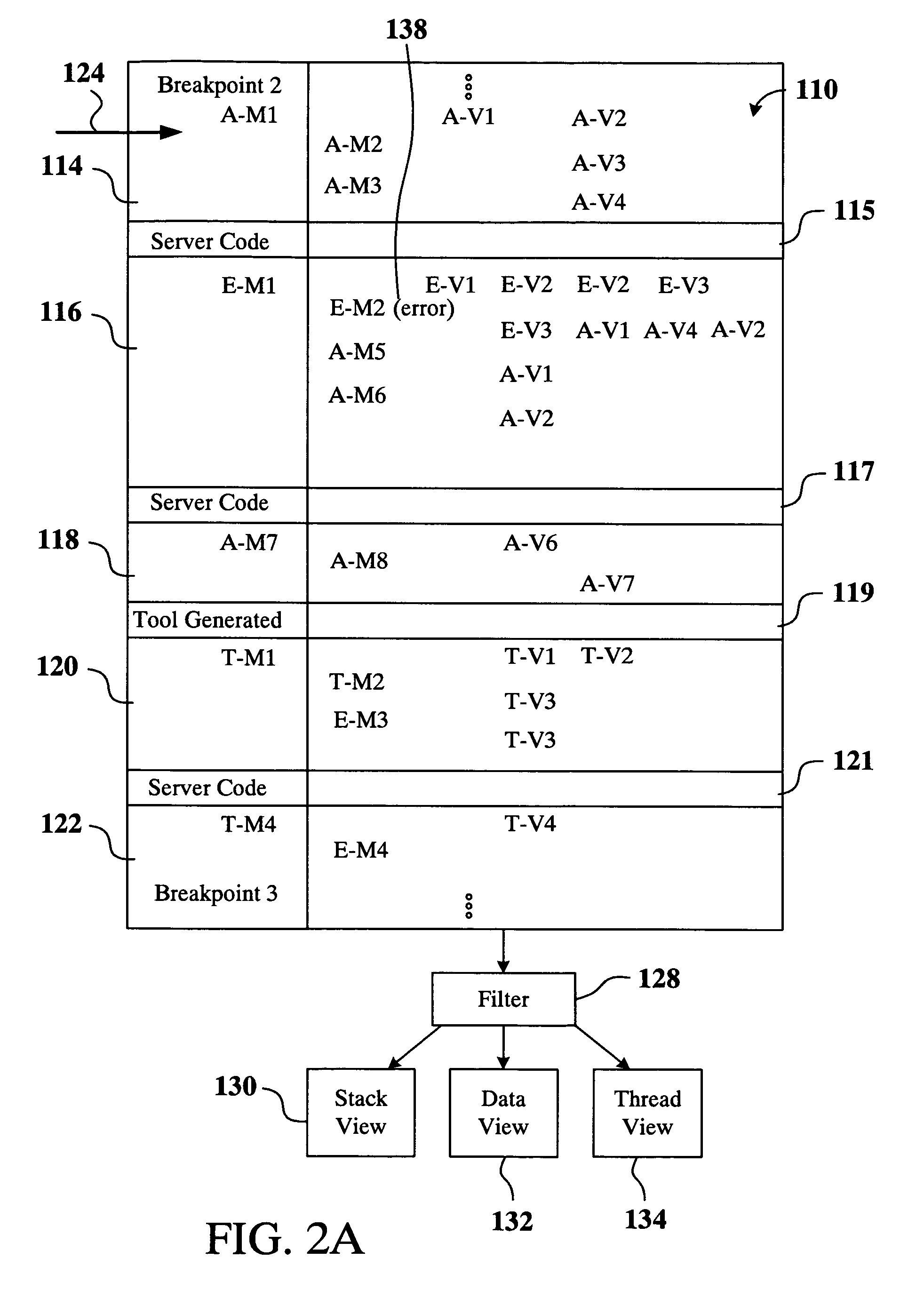
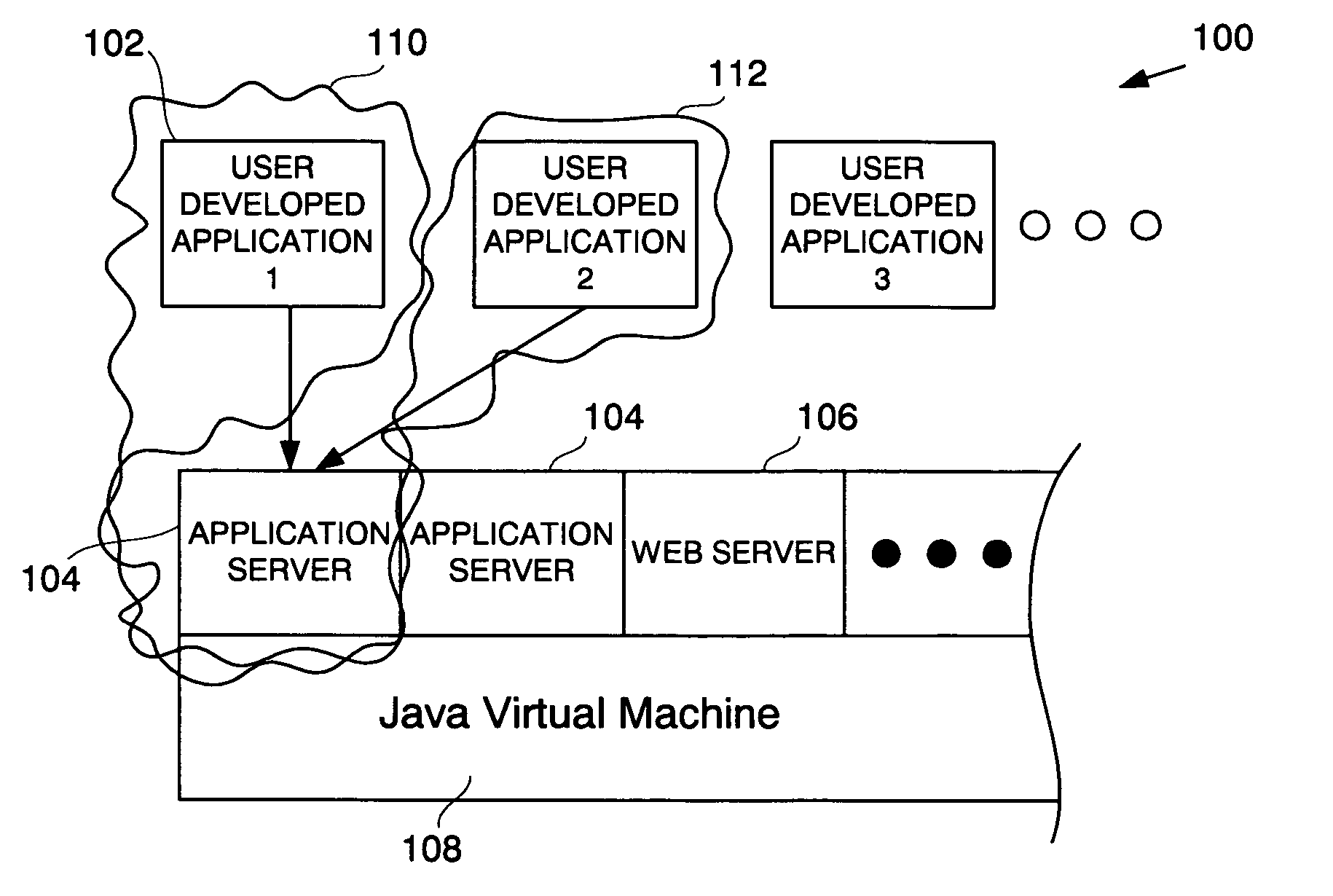
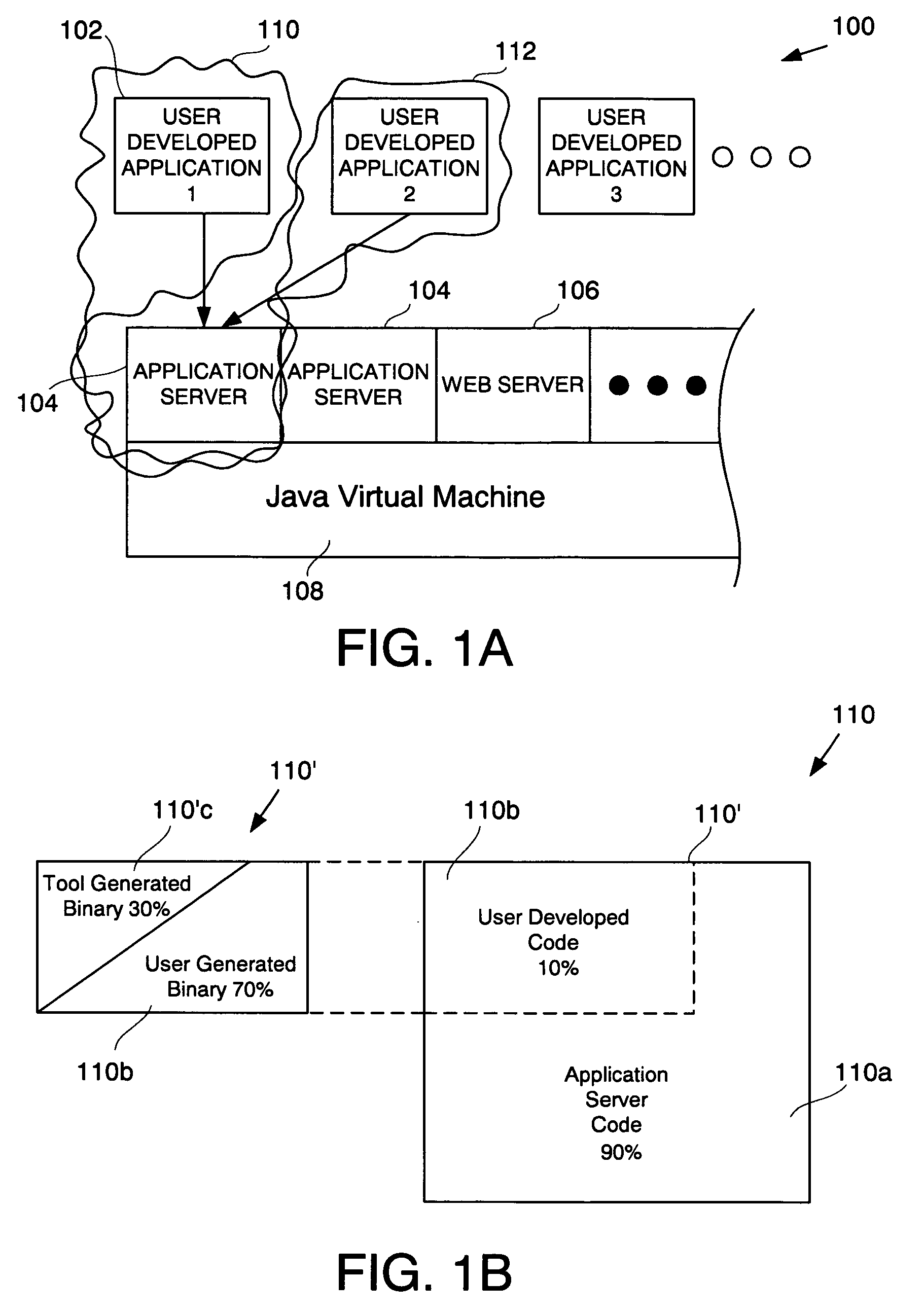
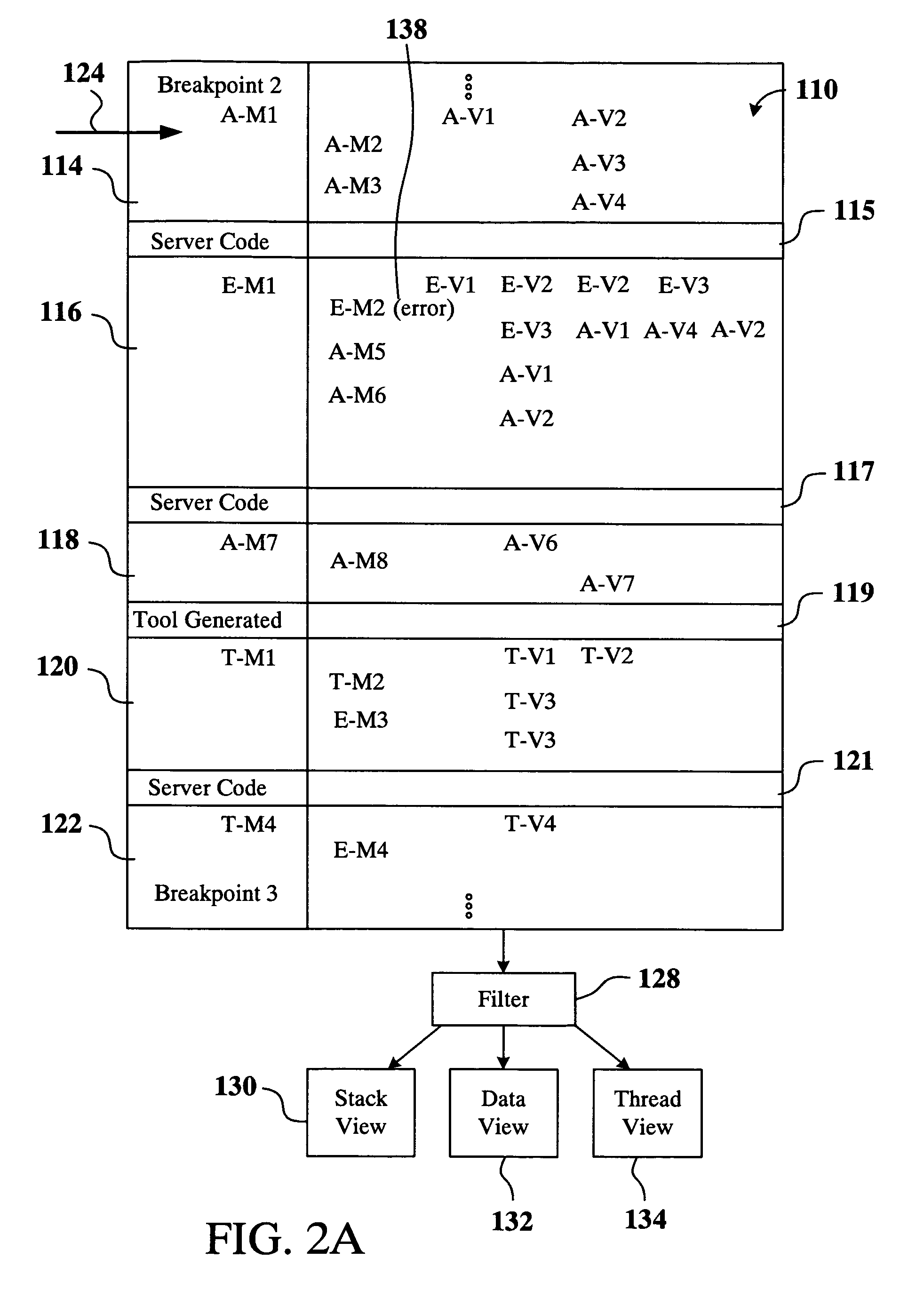
A method for displaying a user-defined artifact in a debugger view is provided. The user-defined artifact is defined in a software application that is developed by a computer software application developer. The software application is included in a packaged application that includes instructions, with each instruction being either a user-defined instruction or a non-user defined instruction. A breakpoint is defined at a desired instruction of the packaged application. The method includes initiating debugging of the packaged application and hitting the breakpoint defined at the desired instruction. Also included is identifying the user-defined artifact in the software application and obtaining data to populate the debugger view. Further included is filtering-in data associated with the user-defined artifact and displaying the debugger view showing the filtered-in data. The method also includes marking data not associated with the user-defined artifact and stepping through the user-defined instruction.
Owner:ORACLE INT CORP
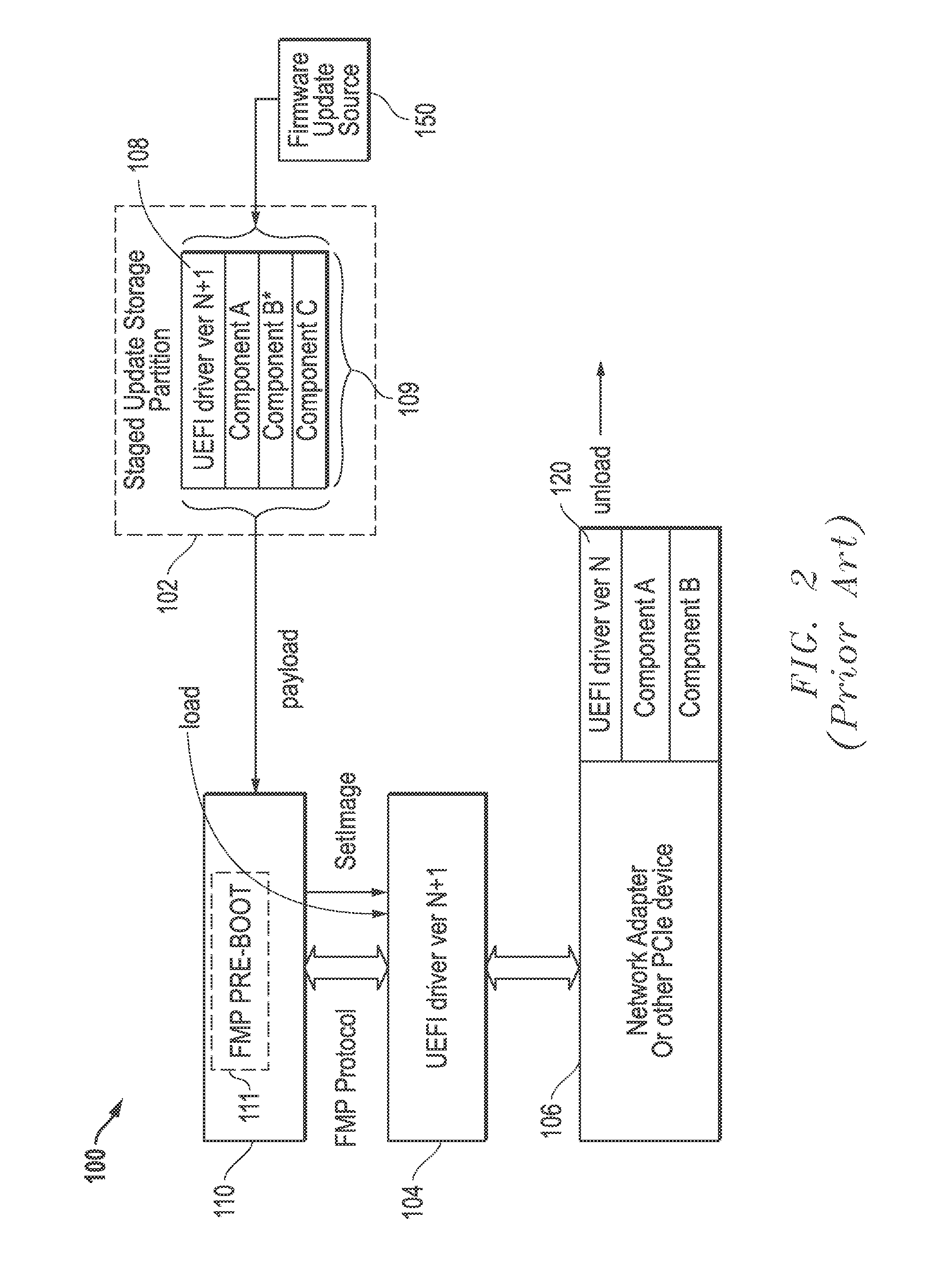
Systems And Methods Of Device Firmware Delivery For Pre-Boot Updates
ActiveUS20160202964A1Avoid the needMinimizing useError detection/correctionProgram loading/initiatingHandling systemInformation handling system
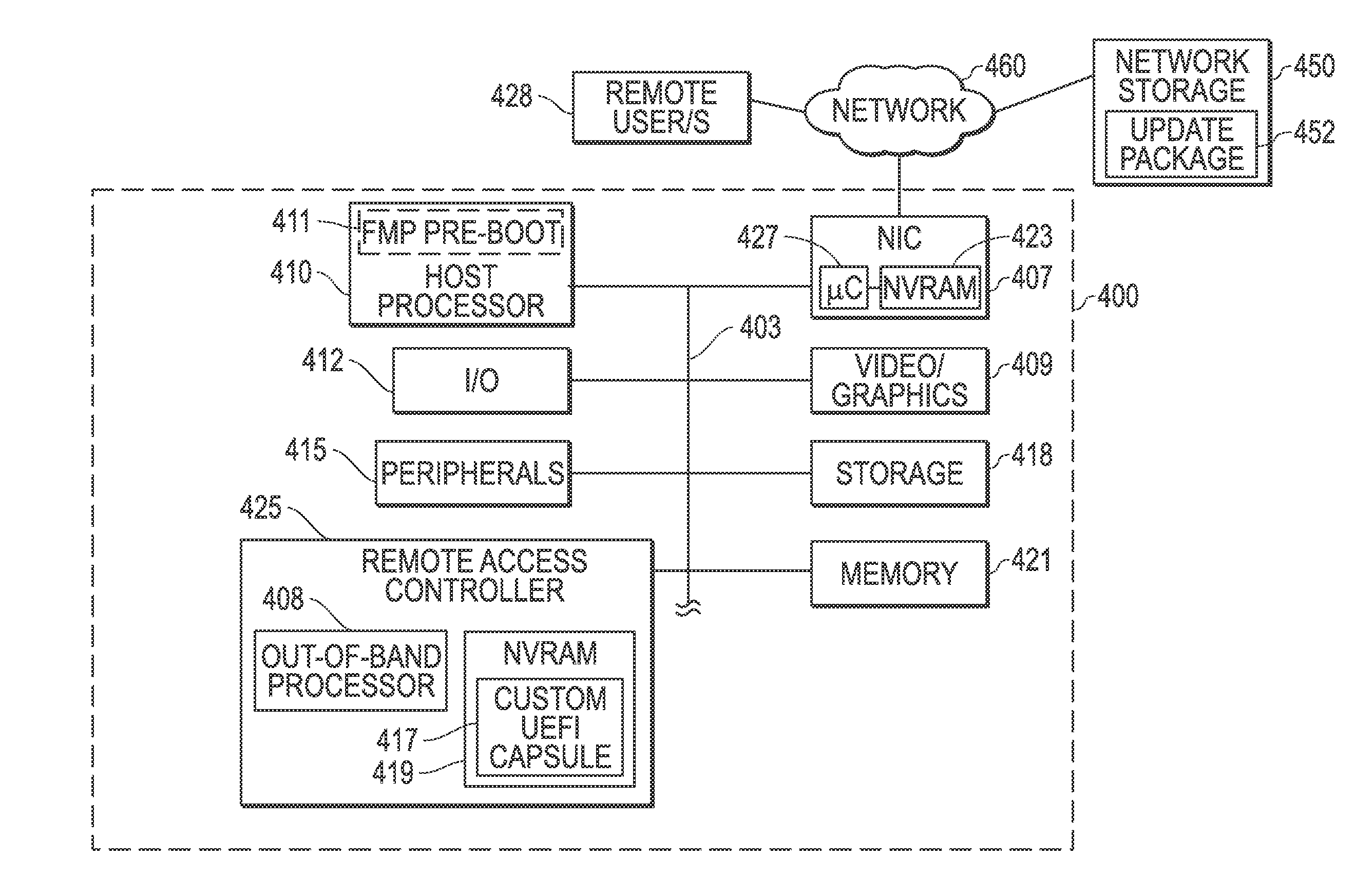
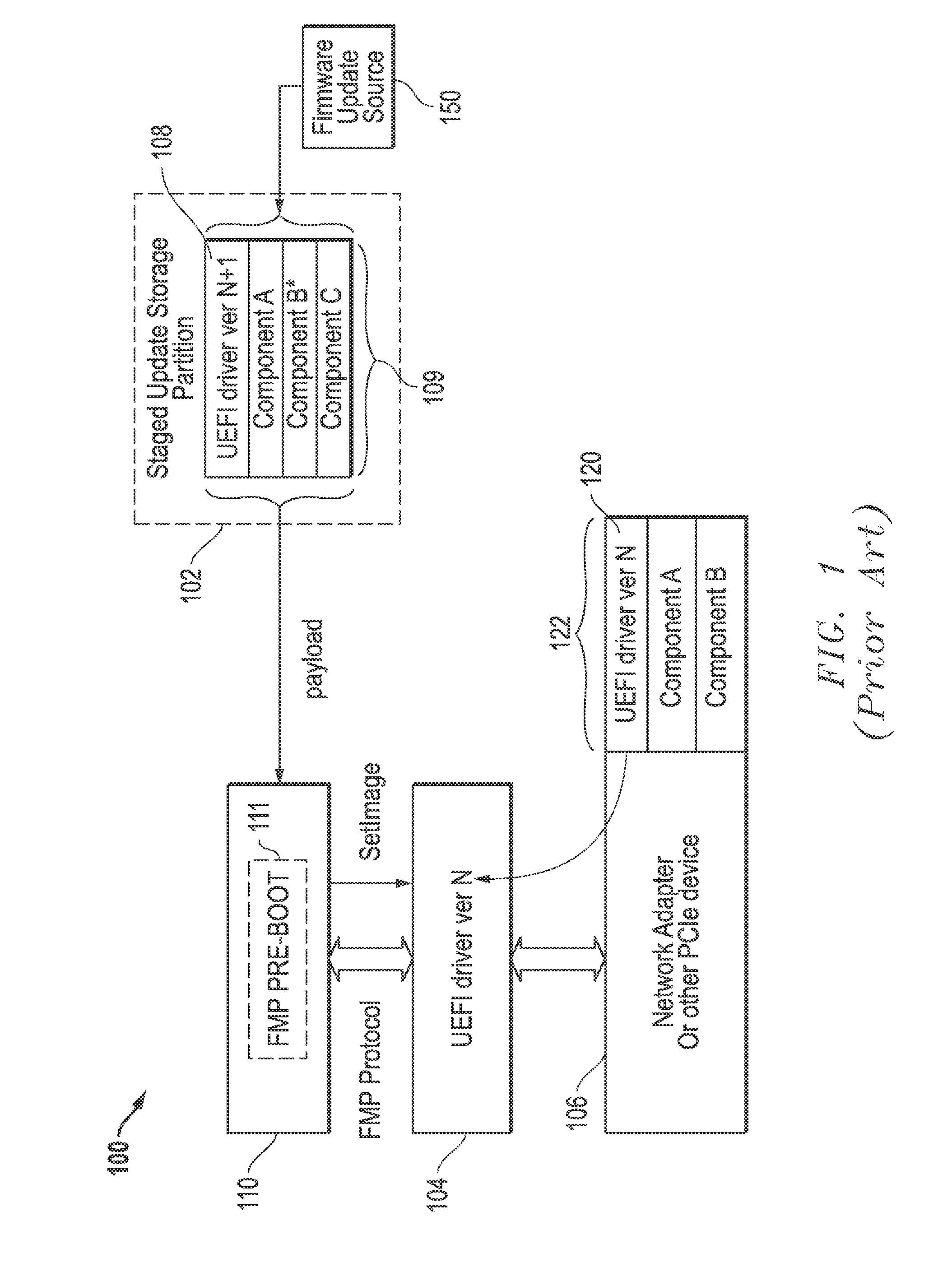
Systems and methods are provided that may be implemented to deliver firmware for pre-boot updates of targeted information handling system device / s using custom update capsules (e.g., such as custom UEFI capsules) and a separately-stored firmware update package that is remotely or locally stored. The custom update capsules may contain instruction payload information that may be used to determine location and desired components of the separately-stored firmware update package, and that also may be used to determine whether existing driver / s are to be retained in a firmware module in system memory or to be unloaded and replaced with a new (e.g., upgraded or downgraded) driver version in a firmware module in system memory as part of the firmware update.
Owner:DELL PROD LP
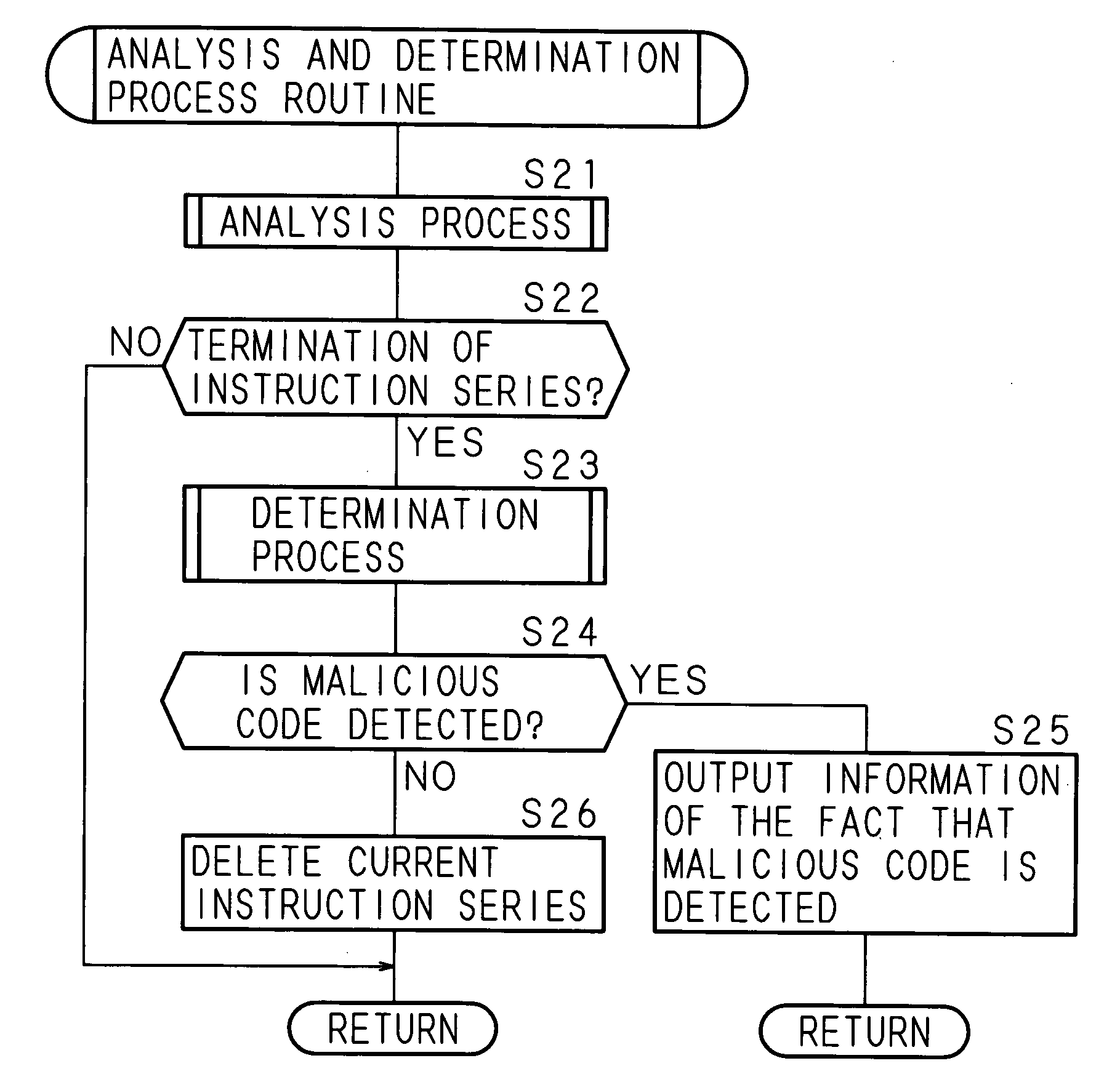
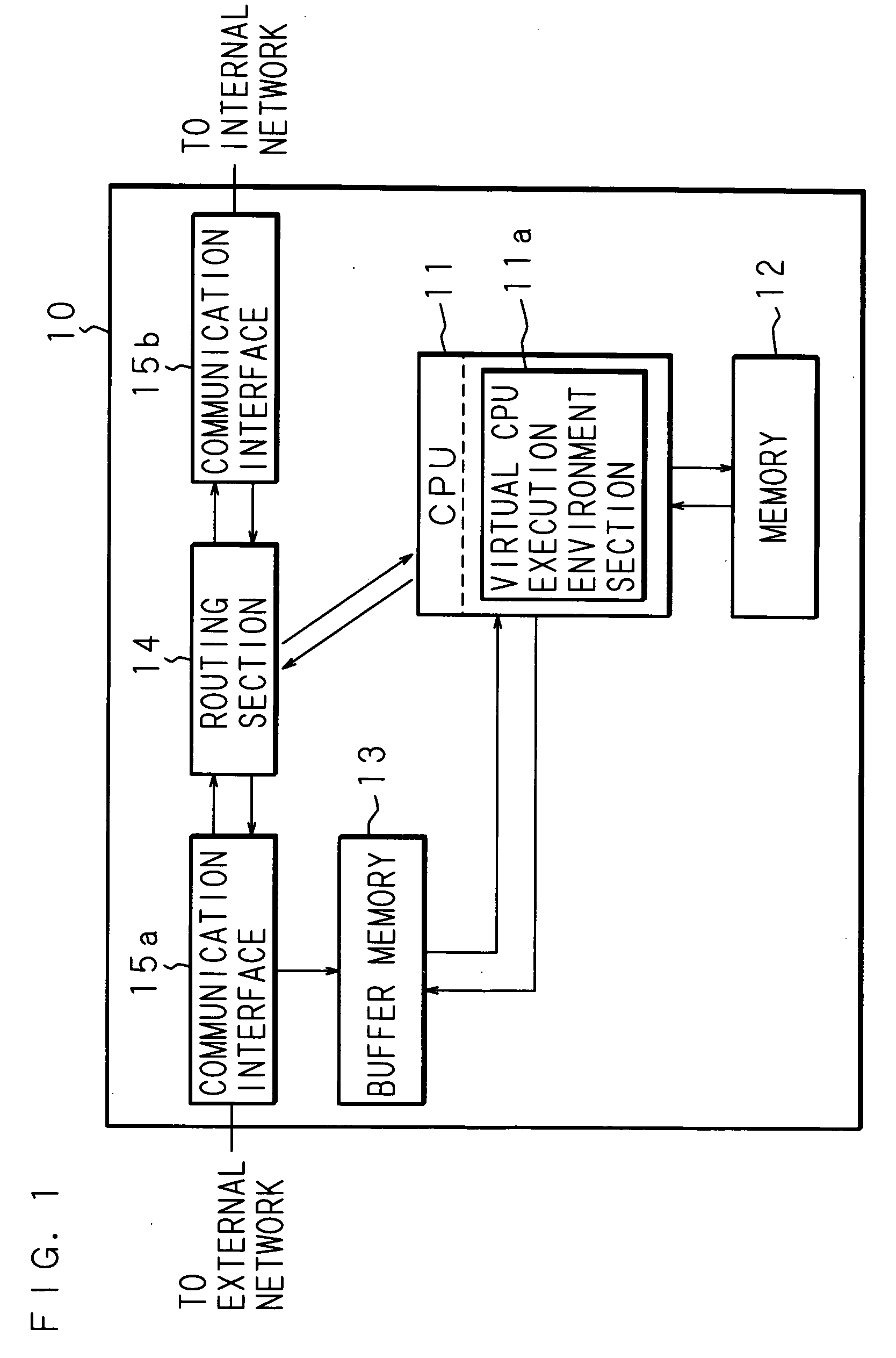
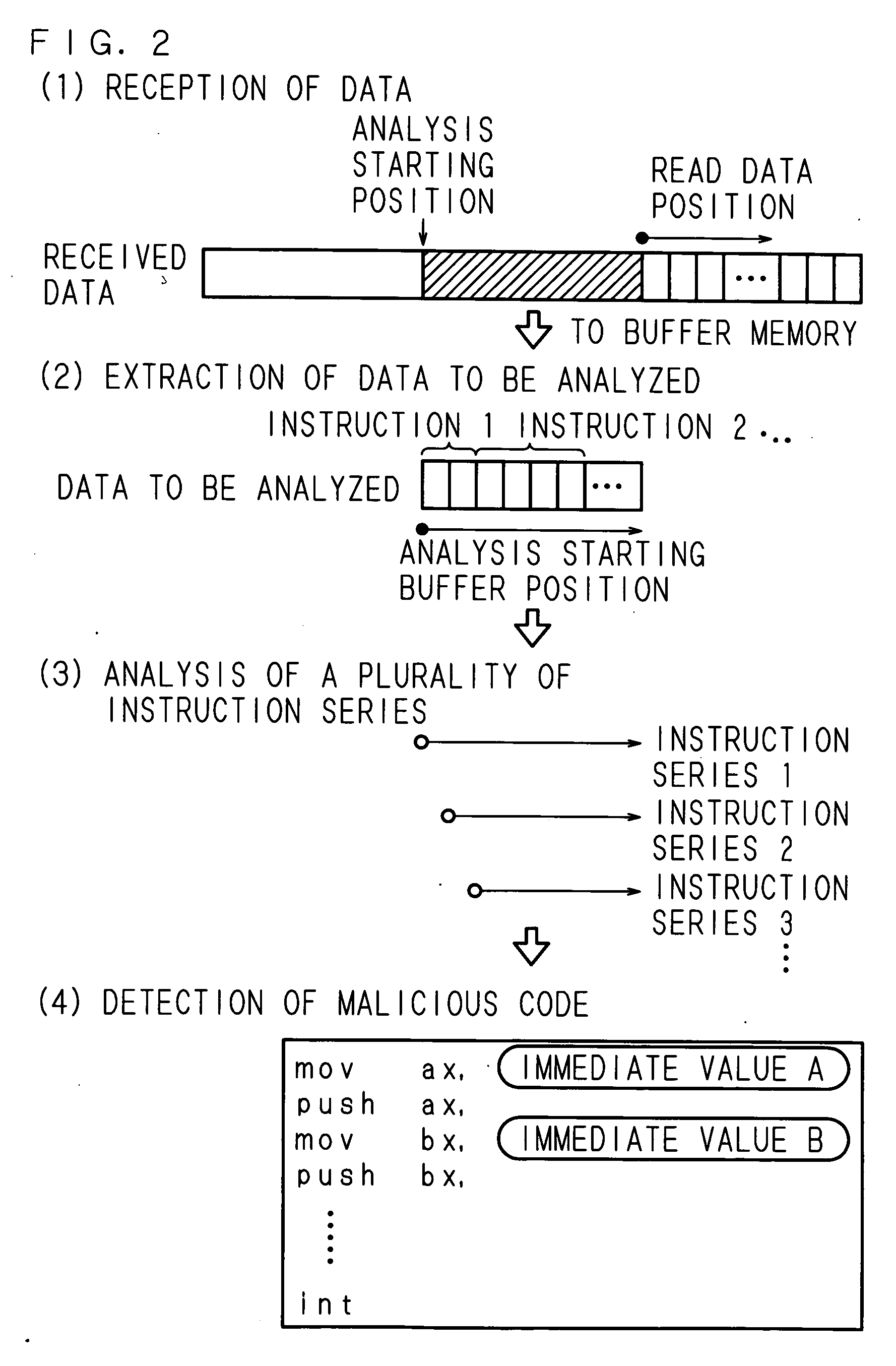
Malicious-process-determining method, data processing apparatus and recording medium
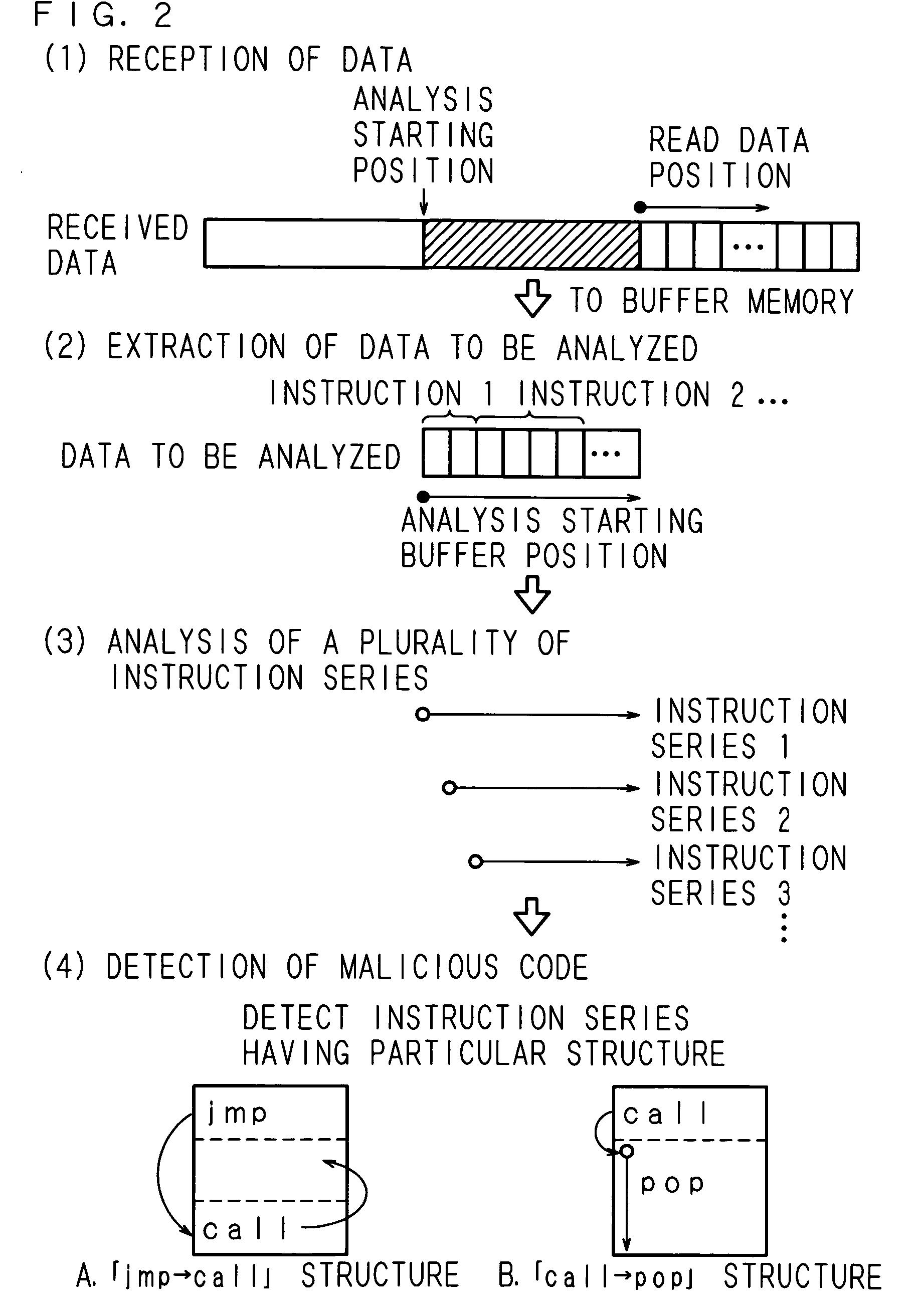
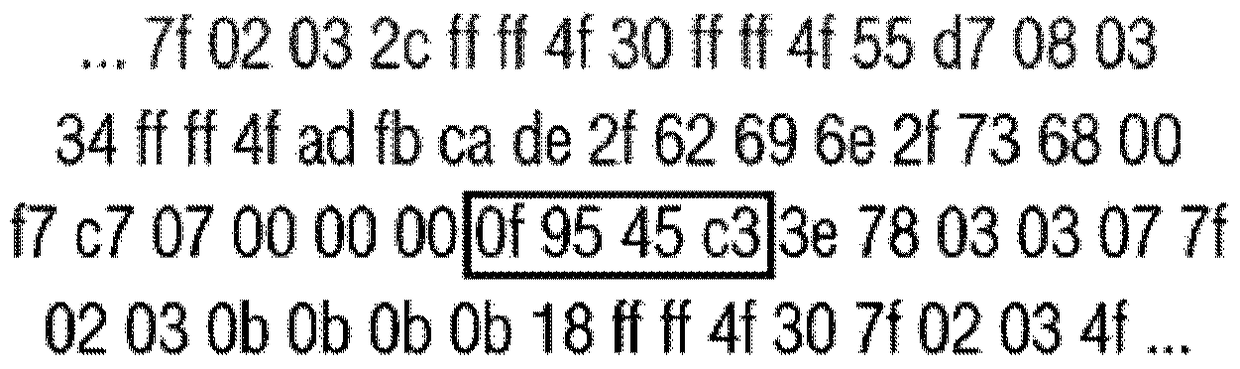
InactiveUS20050283838A1Reduce misjudgmentEasy to detectMemory loss protectionUser identity/authority verificationParallel computingByte
A malicious-process-determining method, a data processing apparatus, and a recording medium according to the present invention each consists of reading the data stored in a buffer memory by one byte, and for a plurality of instruction sequences each having a different read address, sequentially analyzing what kind of instruction code is contained therein. When the int instruction is contained in the analyzed instruction sequence, the number of times the immediate value is pushed to the stack is greater than 1, and the character code corresponding to “ / ” is contained in the virtual stack, a determination is made that a malicious code is contained in the relevant instruction sequence.
Owner:SECUREWARE INC
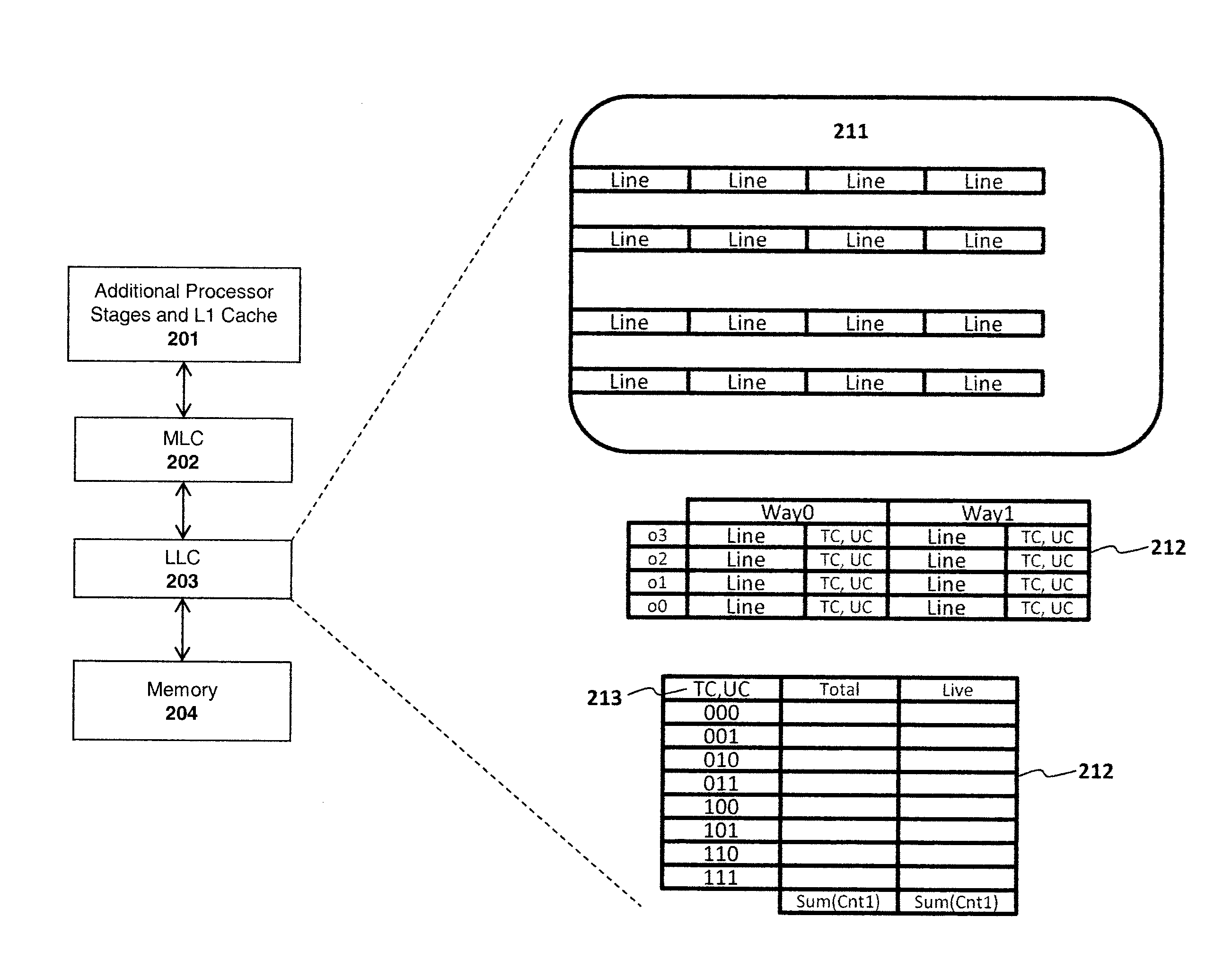
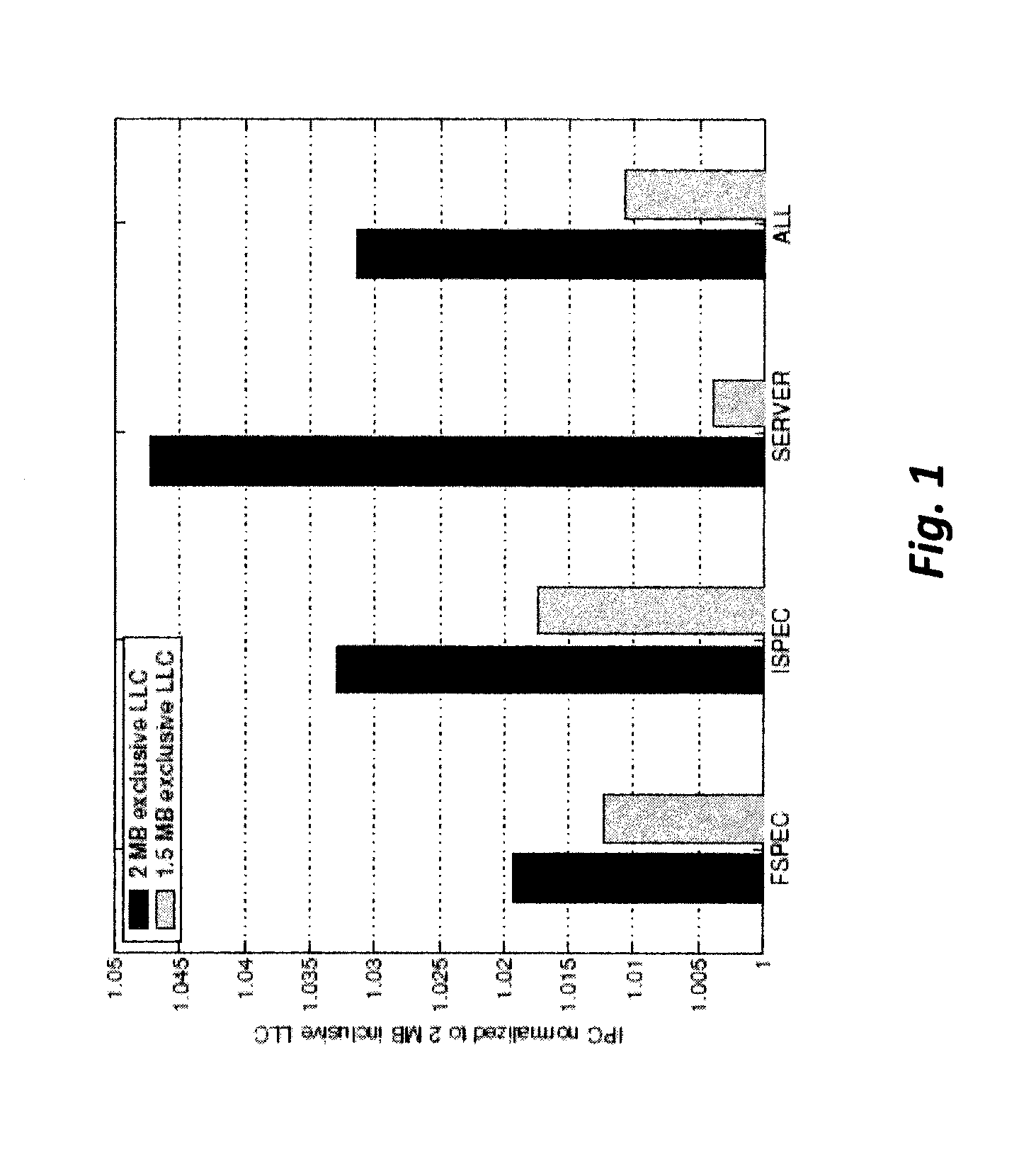
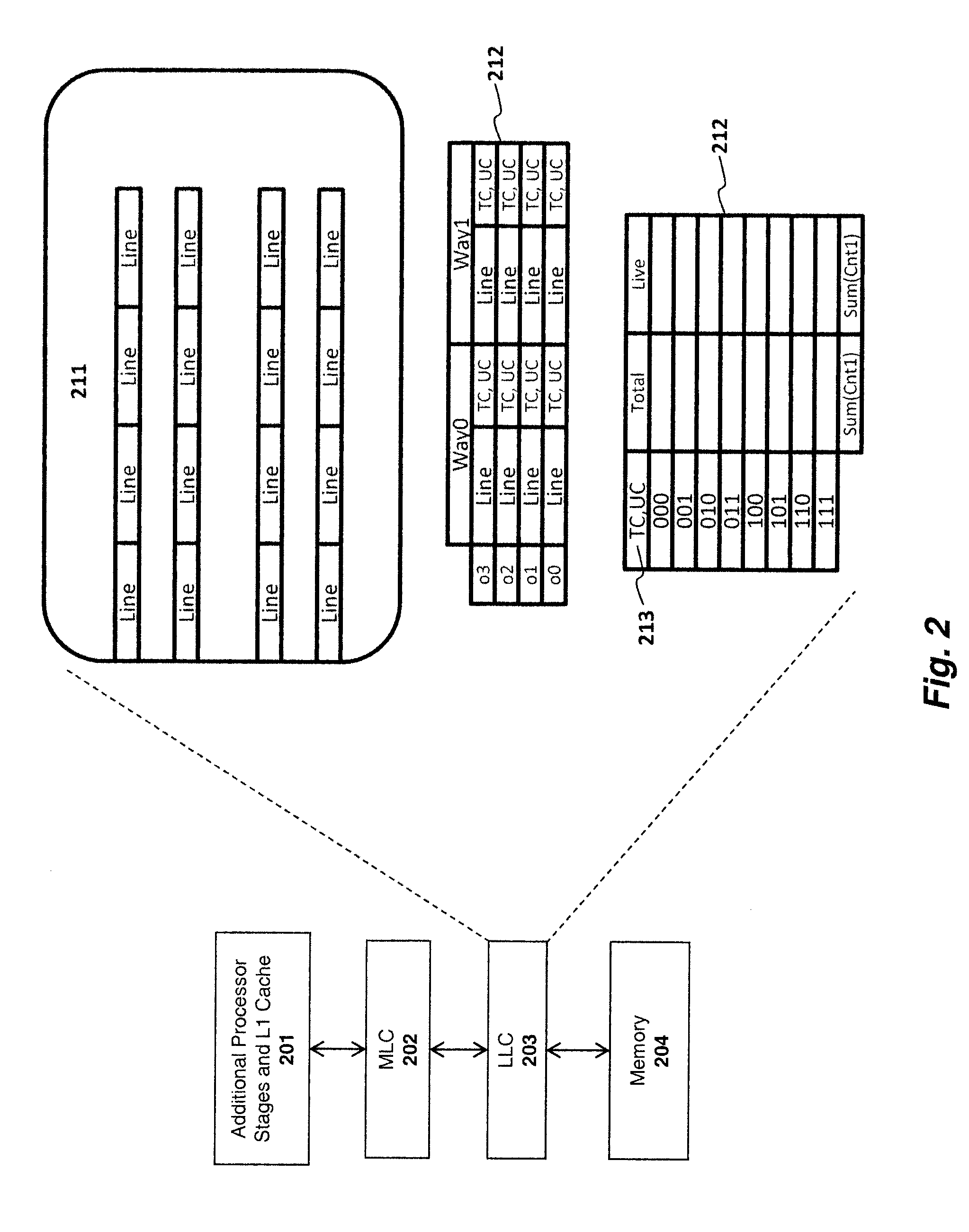
Bypass and insertion algorithms for exclusive last-level caches
An apparatus and method are described for implementing an exclusive lower level cache (LLC) policy within a computer processor. For example, one embodiment of a computer processor comprises: a mid-level cache circuit (MLC) for storing a first set of cache lines containing instructions and / or data; a lower level cache circuit (LLC) for storing a second set of cache lines of instructions and / or data; and an insertion circuit for implementing a policy for inserting or replacing cache lines within the LLC based on values of use recency and use frequency associated with the lines.
Owner:INTEL CORP
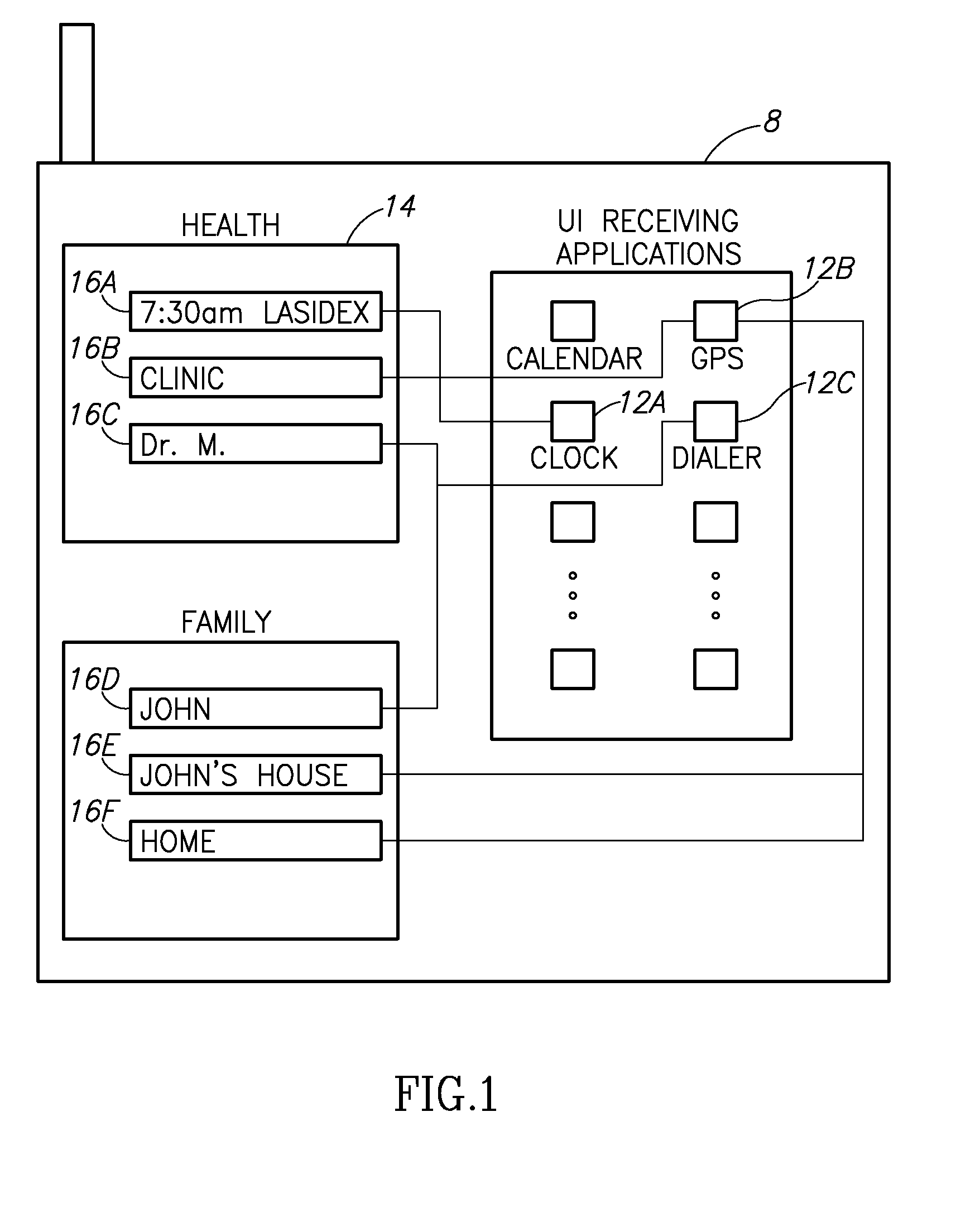
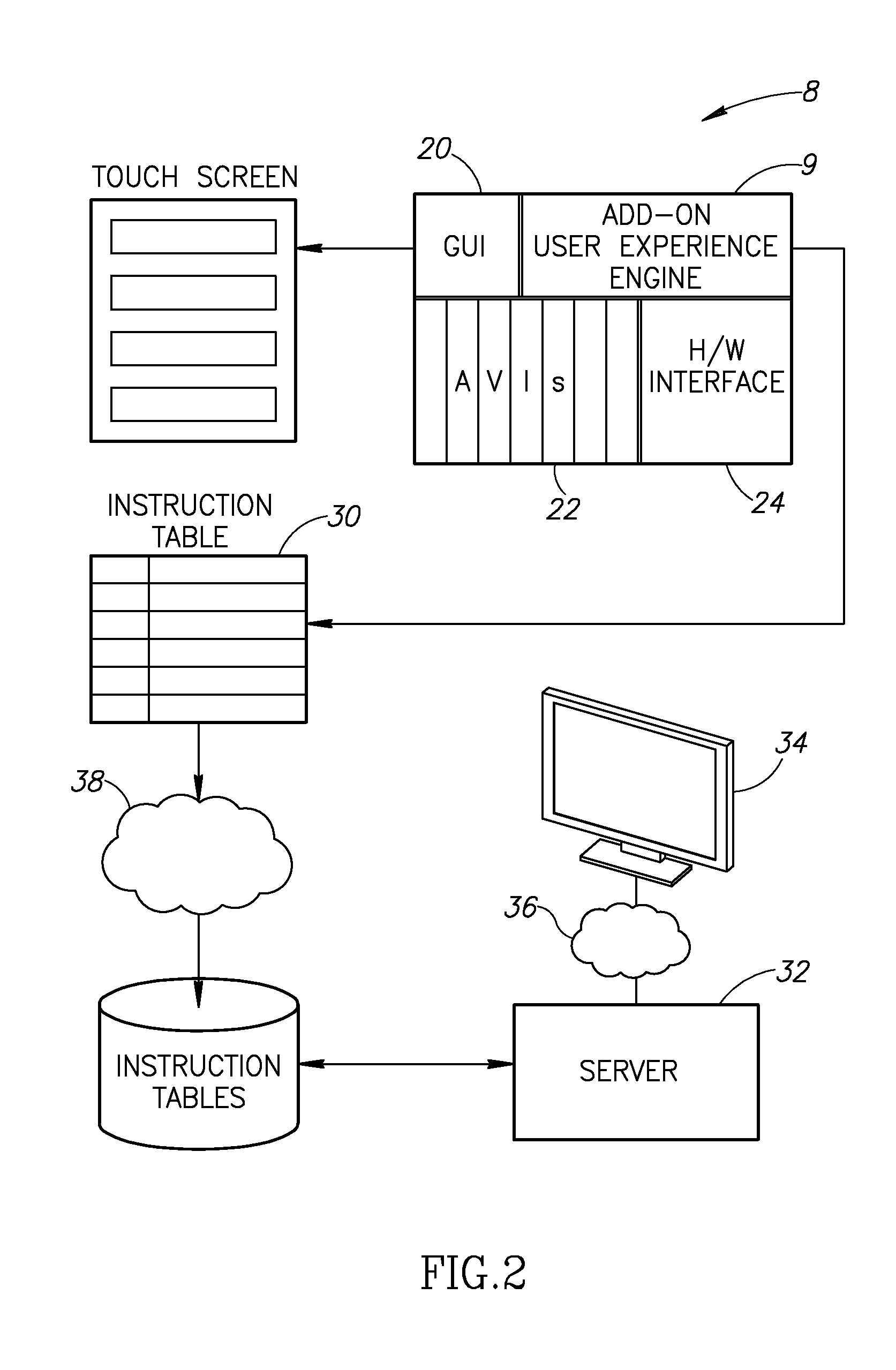
Method and system for customizing a user-interface of an end-user device
InactiveUS20110185313A1Substation equipmentExecution for user interfacesUser deviceApplication software
A mobile device includes a storage unit and an add-on user experience engine. The storage unit stores an instruction table which defines at least one contextual menu which is associated with multiple applications of the mobile device according to the context. The add-on user experience engine parses the instruction table and displays the at least one contextual menu with at least one button. Each button accesses one of the applications with parameters for the application as defined in the instruction table. A user experience menu definer includes an authorizer to provide an authorized individual with access to information about a mobile device of another person and a table defining unit which generates the instruction table from input of the authorized individual.
Owner:UIU
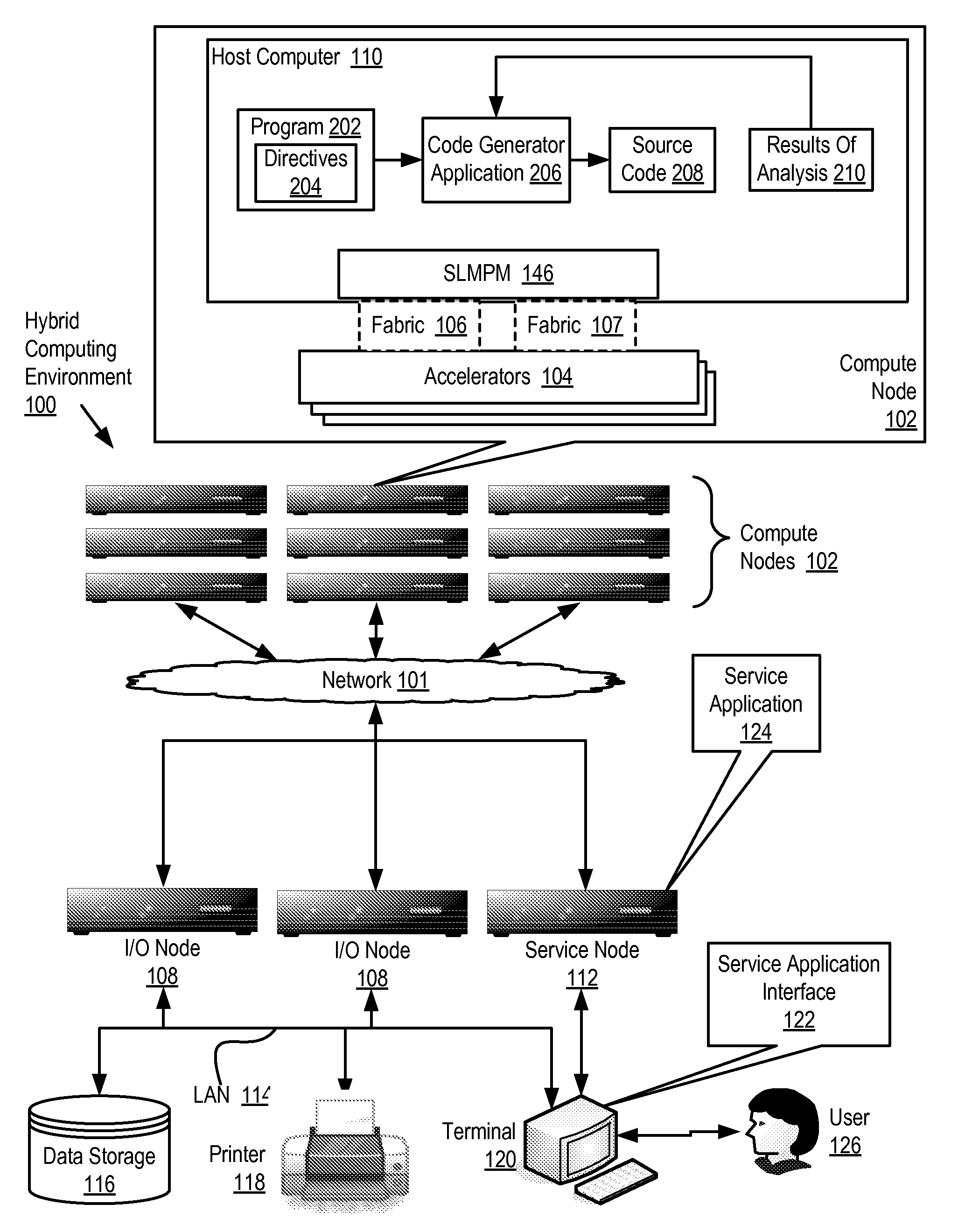
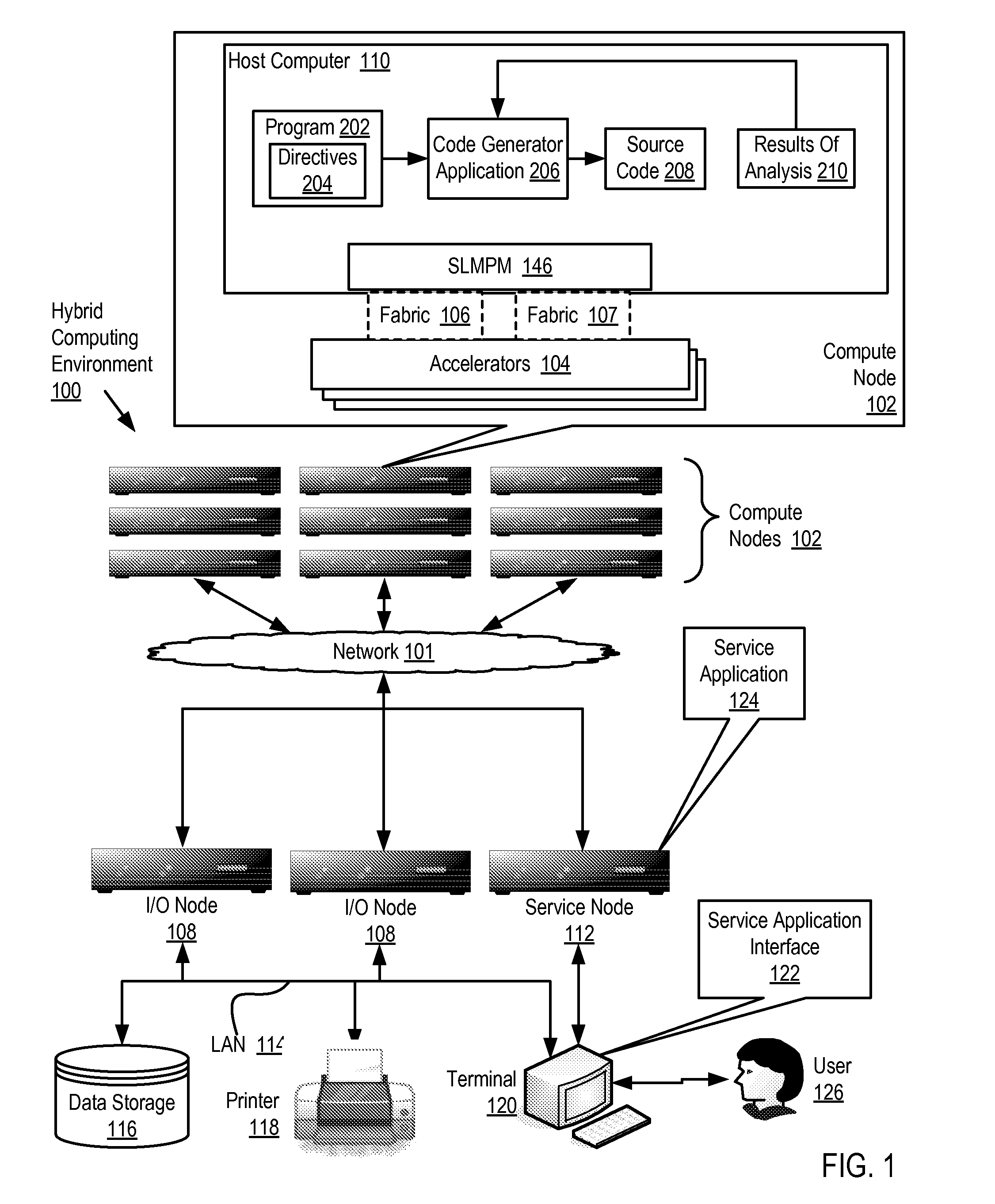
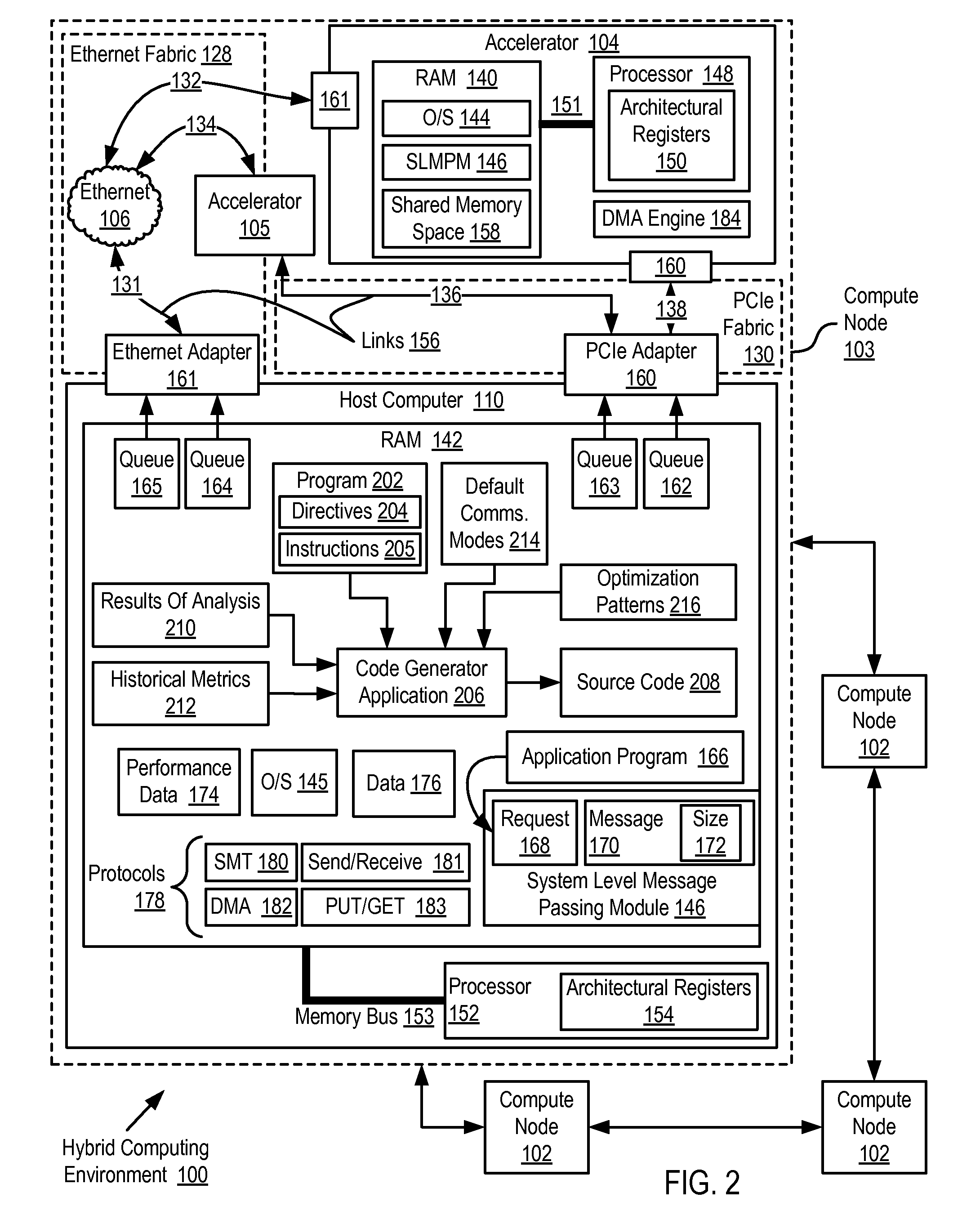
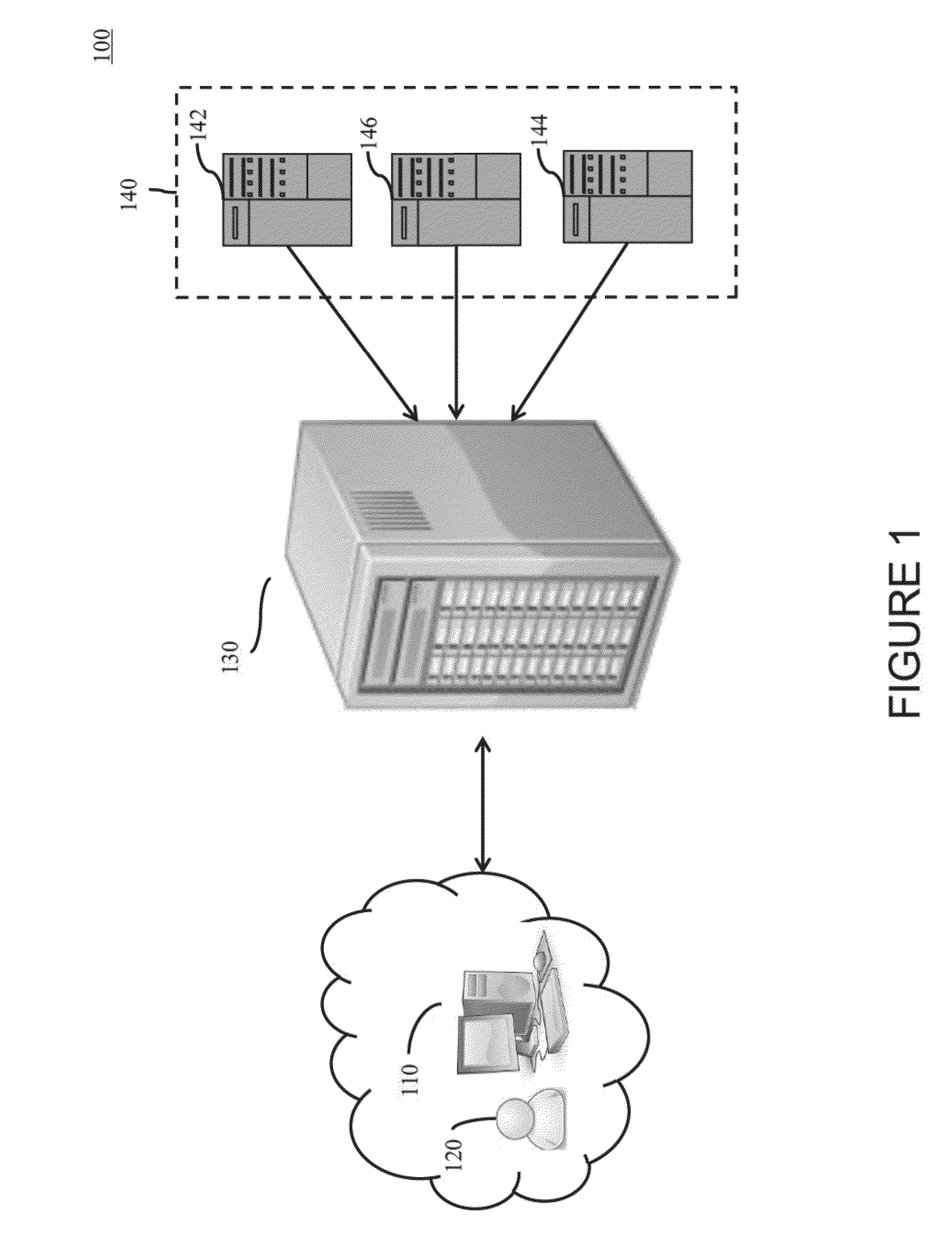
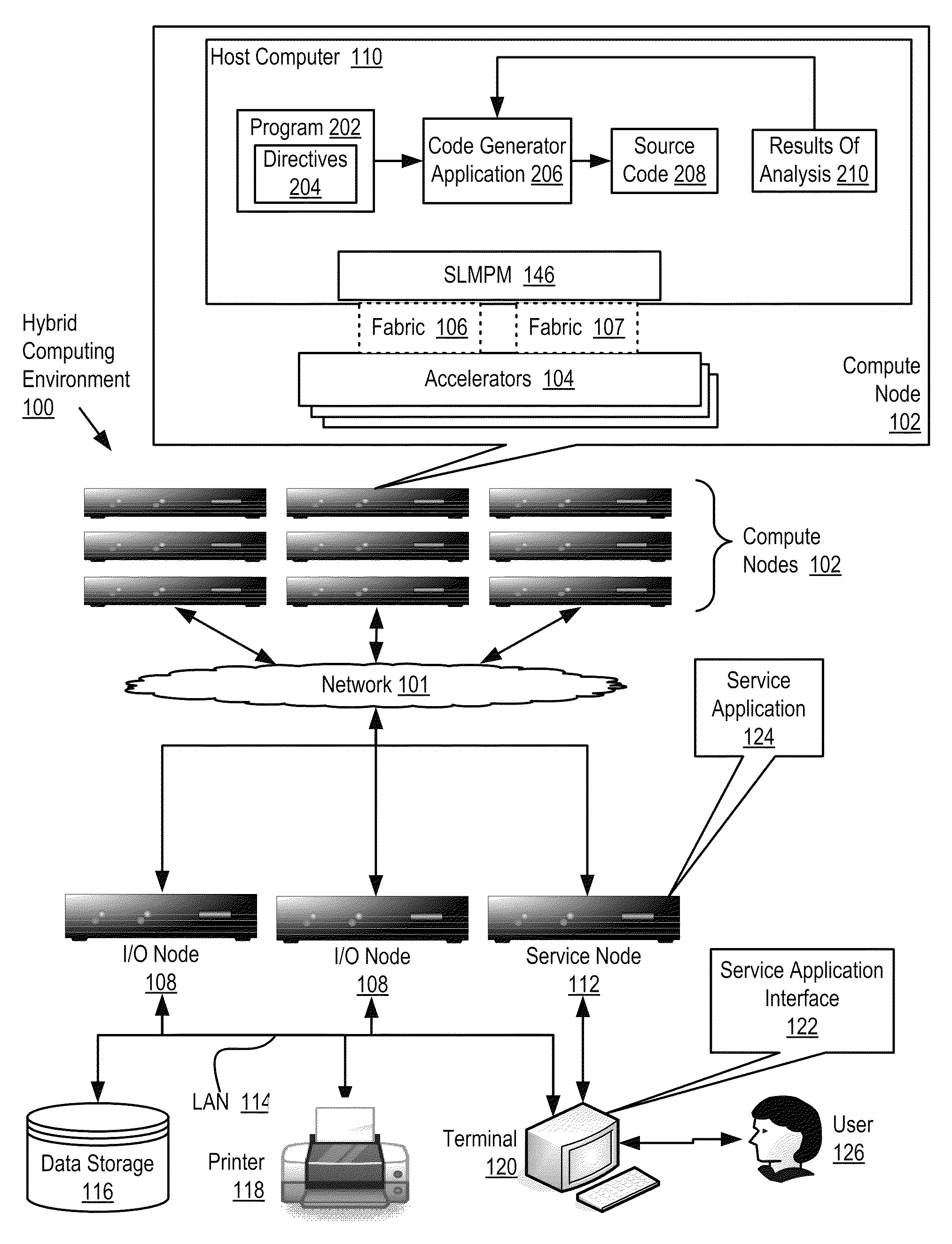
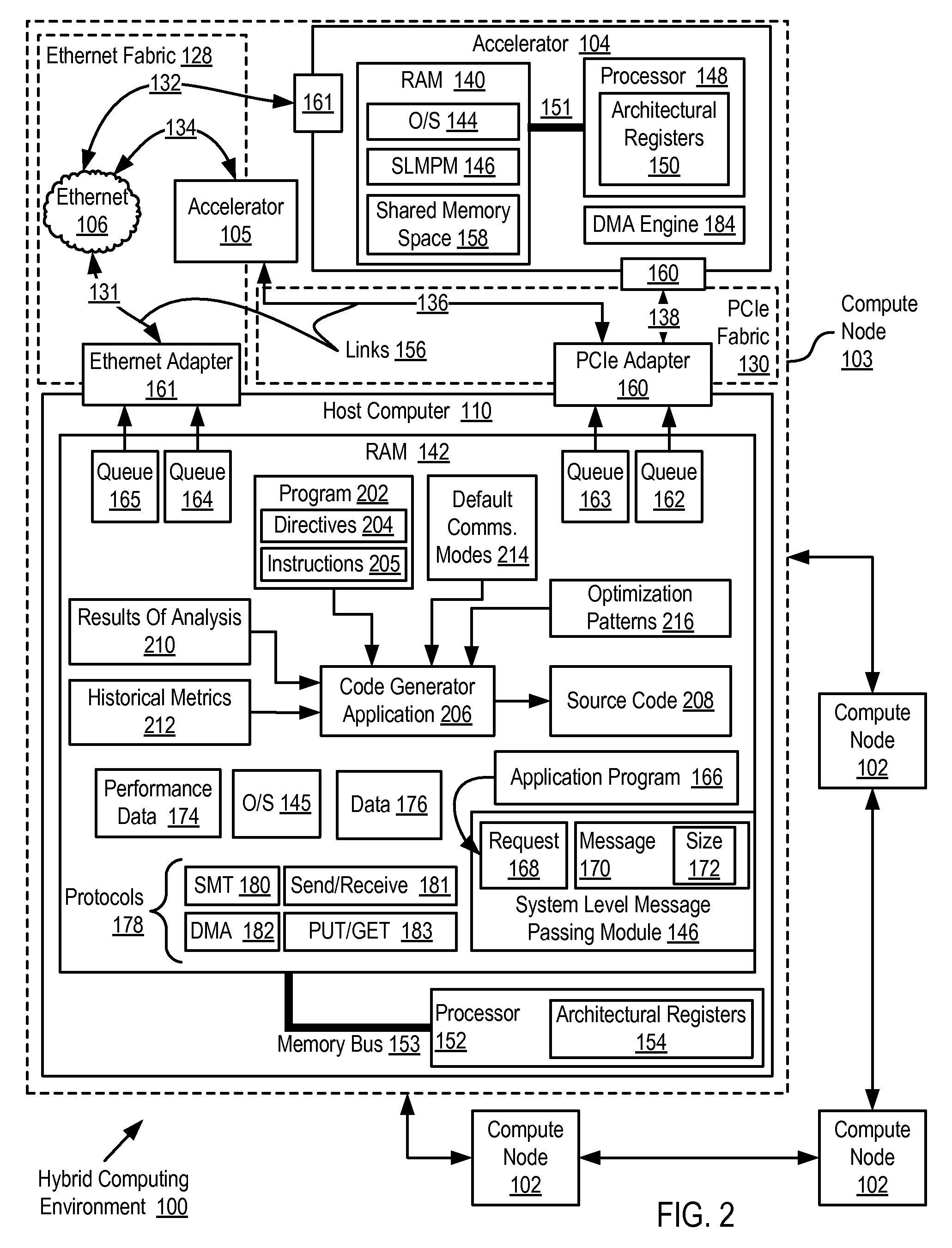
Software Development For A Hybrid Computing Environment
InactiveUS20100192123A1Specific program execution arrangementsMemory systemsAgile software developmentRemovable media
Software development for a hybrid computing environment that includes a host computer and an accelerator, the host computer and the accelerator adapted to one another for data communications by a system level message passing module and by two or more data communications fabrics of at least two different fabric types where software development includes creating, by a programmer, a computer program for execution in the hybrid computing environment, the computer program including directives for generation of computer program code that moves contents of memory among host computers and accelerators in the hybrid computing environment; generating, by a code generator application, source code in accordance with the directives; analyzing, by the code generator application, operation of the generated code for data movement and utilization of moved data; and regenerating, by the code generator application, the source code in accordance with the directives and further in accordance with results of the analysis.
Owner:IBM CORP
Method and system for creating management information base specifications
ActiveUS20070100871A1Digital data processing detailsDigital computer detailsInformation repositoryManagement information base
Owner:CISCO TECH INC
Intelligent computer program debugger, and system and method for implementing the same
ActiveUS7882492B2Error detection/correctionSpecific program execution arrangementsApplication softwareComputer software
A method for displaying a user-defined artifact in a debugger view is provided. The user-defined artifact is defined in a software application that is developed by a computer software application developer. The software application is included in a packaged application that includes instructions, with each instruction being either a user-defined instruction or a non-user defined instruction. A breakpoint is defined at a desired instruction of the packaged application. The method includes initiating debugging of the packaged application and hitting the breakpoint defined at the desired instruction. Also included is identifying the user-defined artifact in the software application and obtaining data to populate the debugger view. Further included is filtering-in data associated with the user-defined artifact and displaying the debugger view showing the filtered-in data. The method also includes marking data not associated with the user-defined artifact and stepping through the user-defined instruction.
Owner:ORACLE INT CORP
Malicious-process-determining method, data processing apparatus and recording medium
InactiveUS20060026685A1Sure easyIncrease probabilityMemory loss protectionError detection/correctionParallel computingByte
A malicious process method, a data processing apparatus and a recording medium according to the present invention reads data stored in a buffer memory in terms of bytes and sequentially analyzes what kind of instruction code is included in a plurality of instruction sequence having different read positions. It is determined that a malicious code is included in an instruction sequence when an int instruction is included in an analyzed instruction sequence, an instruction code has a particular emergence pattern and a character code corresponding to “ / ” is included in stored command data.
Owner:SECUREWARE INC
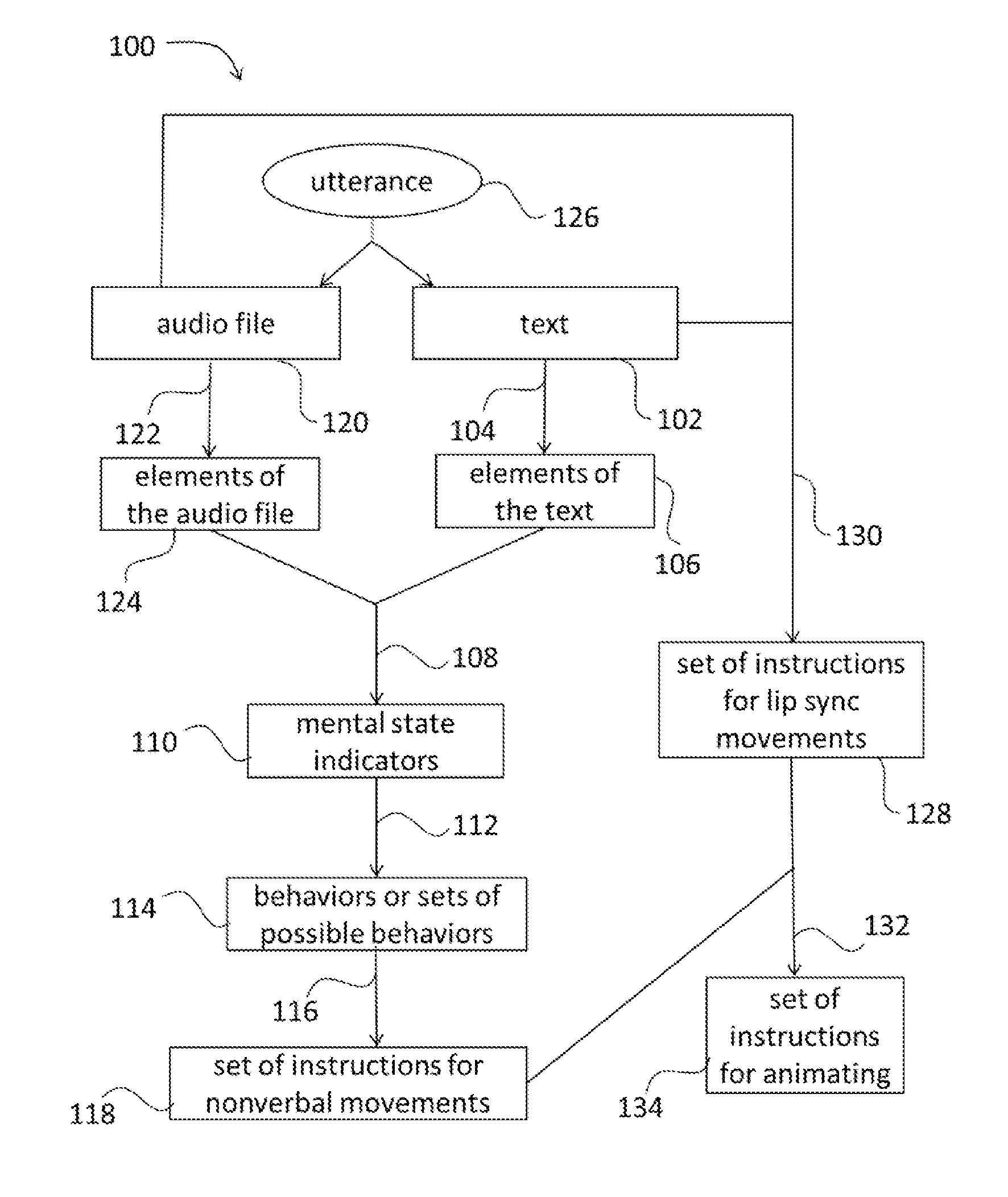
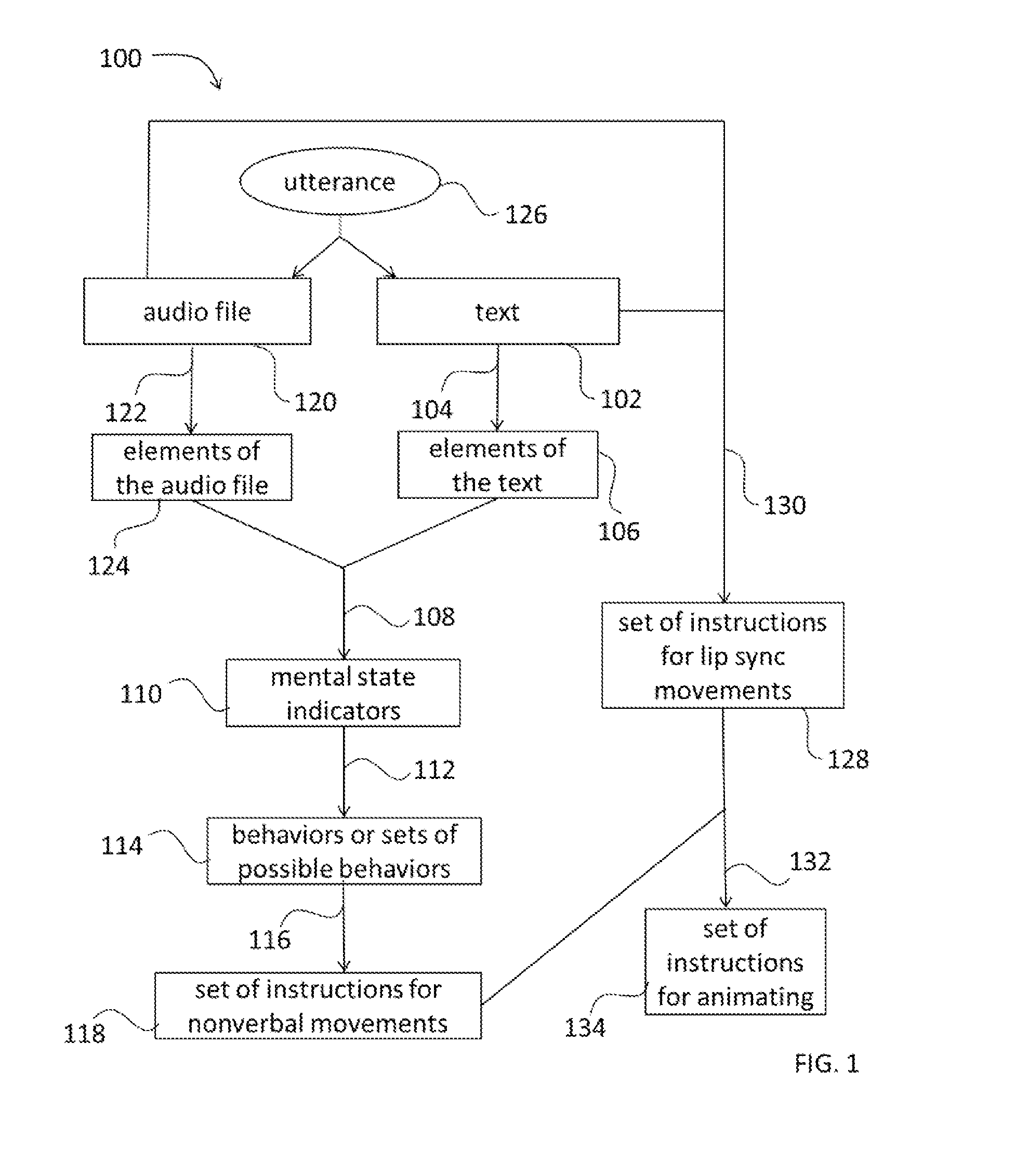
Generating instructions for nonverbal movements of a virtual character
Programs for creating a set of behaviors for lip sync movements and nonverbal communication may include analyzing a character's speaking behavior through the use of acoustic, syntactic, semantic, pragmatic, and rhetorical analyses of the utterance. For example, a non-transitory, tangible, computer-readable storage medium may contain a program of instructions that cause a computer system running the program of instructions to: receive a text specifying words to be spoken by a virtual character; extract metaphoric elements, discourse elements, or both from the text; generate one or more mental state indicators based on the metaphoric elements, the discourse elements, or both; map each of the one or more mental state indicators to a behavior that the virtual character should display with nonverbal movements that convey the mental state indicators; and generate a set of instructions for the nonverbal movements based on the behaviors.
Owner:UNIV OF SOUTHERN CALIFORNIA
Combined educational tool for imparting thematic knowledge and reinforcing related core principles
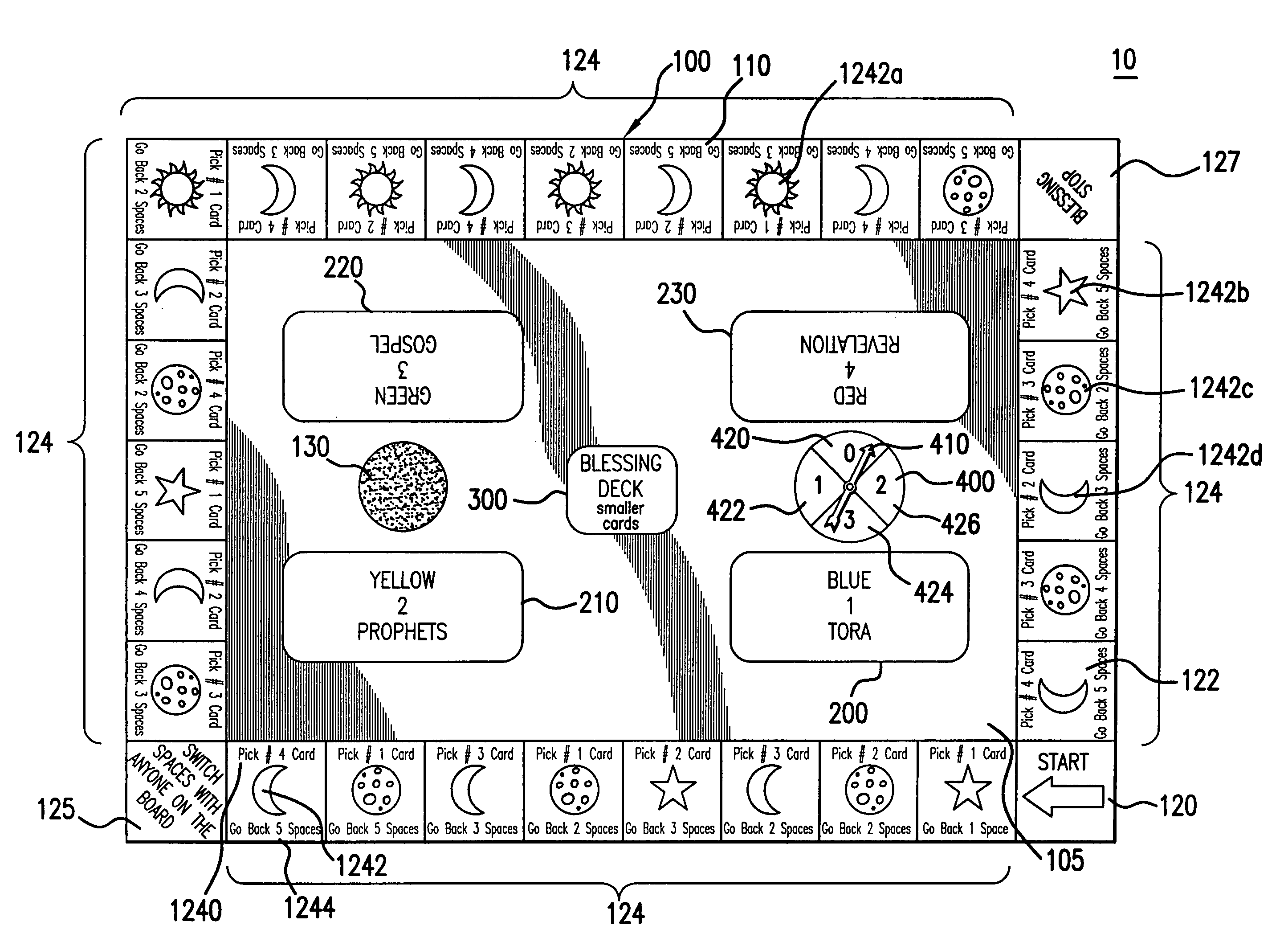
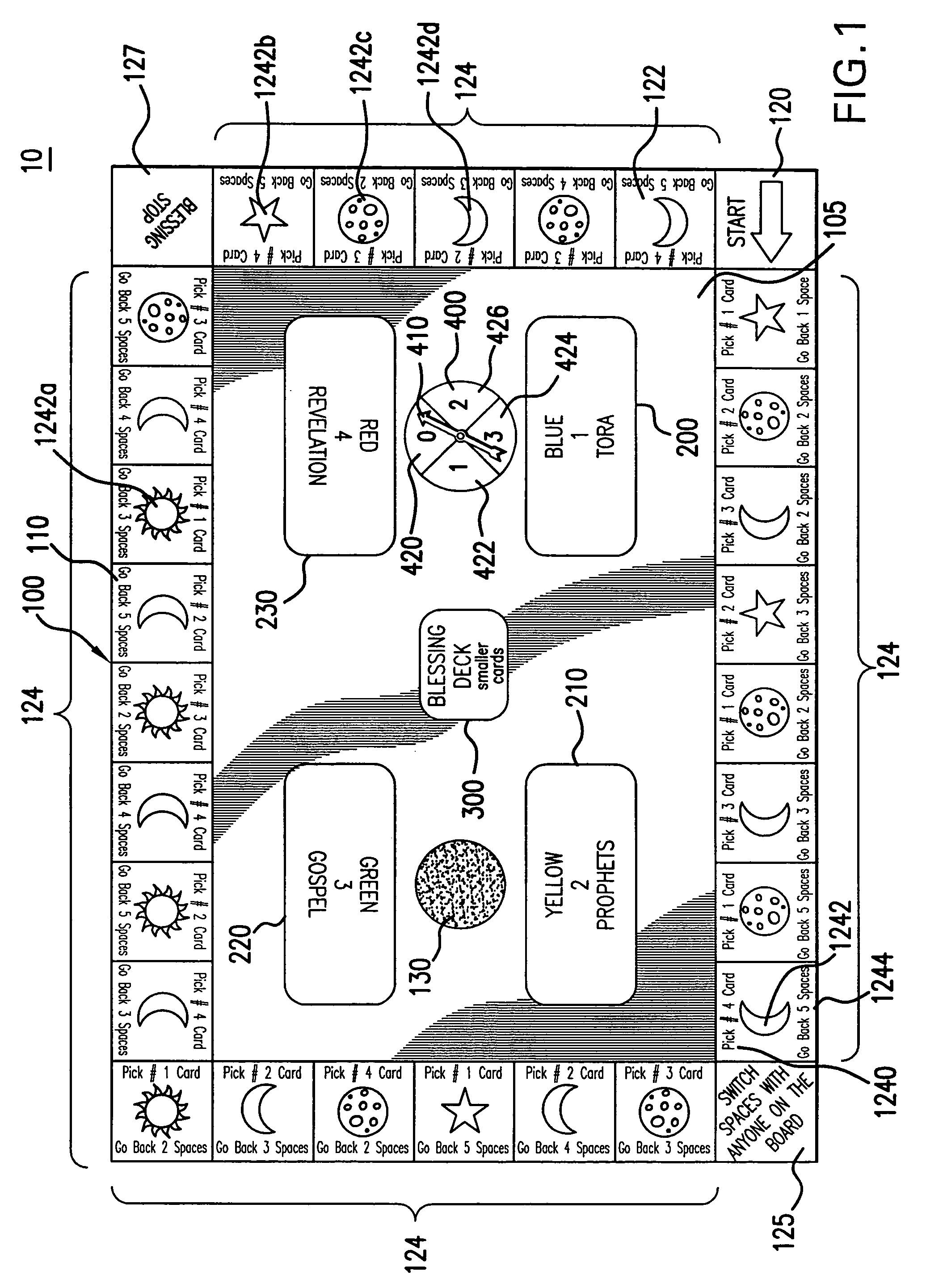
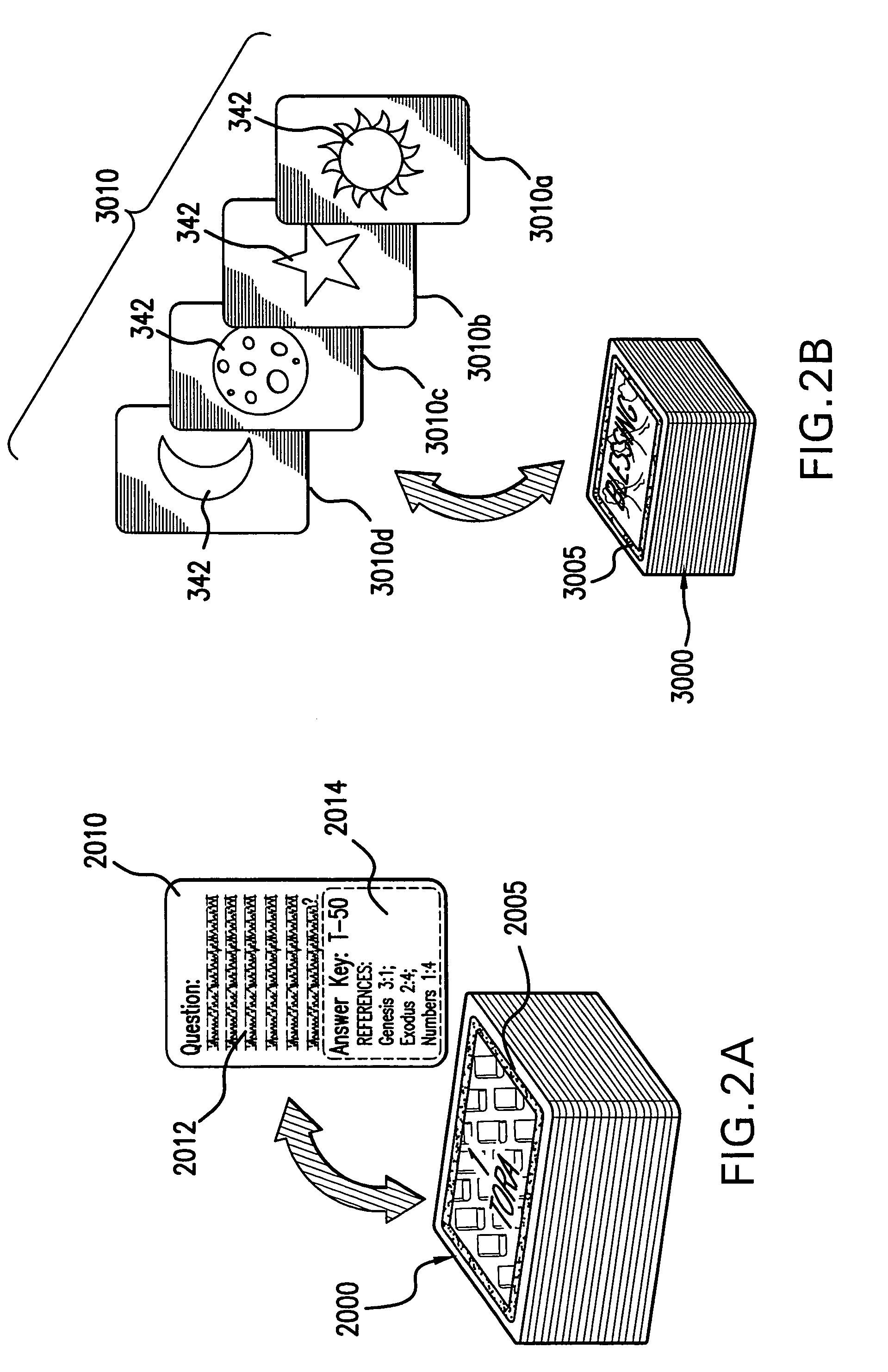
A combined instructional tool (10) is provided for imparting theological or other thematic knowledge to a plurality of participants while experientially reinforcing a core principle relating thereto. The tool (10) generally includes a game board (100), a plurality of categorized knowledge stores (200–230), at least one supplemental store (300), and a user-operable selector (400). The game board (100) defines a plurality of spaces (110) which progress between designated starting and end points, wherein at least a portion of the spaces (100) are formed with at least three types of indicia. The question stores (200–230) each include a plurality of predetermined thematic questions for selection and consideration by the participants, whereas the supplemental store (300) includes a plurality of redemptive tokens (3010). During use, participants take turns attempting to advance along the spaces (110), at each space complying with appropriate indicia which may include directives to select and answer a question from the question store. Upon failure to adequately answer the question, a participant is afforded an opportunity for redemption by selecting a potentially redemptive token from the supplemental store (300).
Owner:THOMAS DARRYL
Noise-enhanced clustering and competitive learning
InactiveUS20150161232A1Improve computing powerWeakening rangeMathematical modelsImage analysisData setComputerized system
Non-transitory, tangible, computer-readable storage media may contain a program of instructions that enhances the performance of a computing system running the program of instructions when segregating a set of data into subsets that each have at least one similar characteristic. The instructions may cause the computer system to perform operations comprising: receiving the set of data; applying an iterative clustering algorithm to the set of data that segregates the data into the subsets in iterative steps; during the iterative steps, injecting perturbations into the data that have an average magnitude that decreases during the iterative steps; and outputting information identifying the subsets.
Owner:UNIV OF SOUTHERN CALIFORNIA
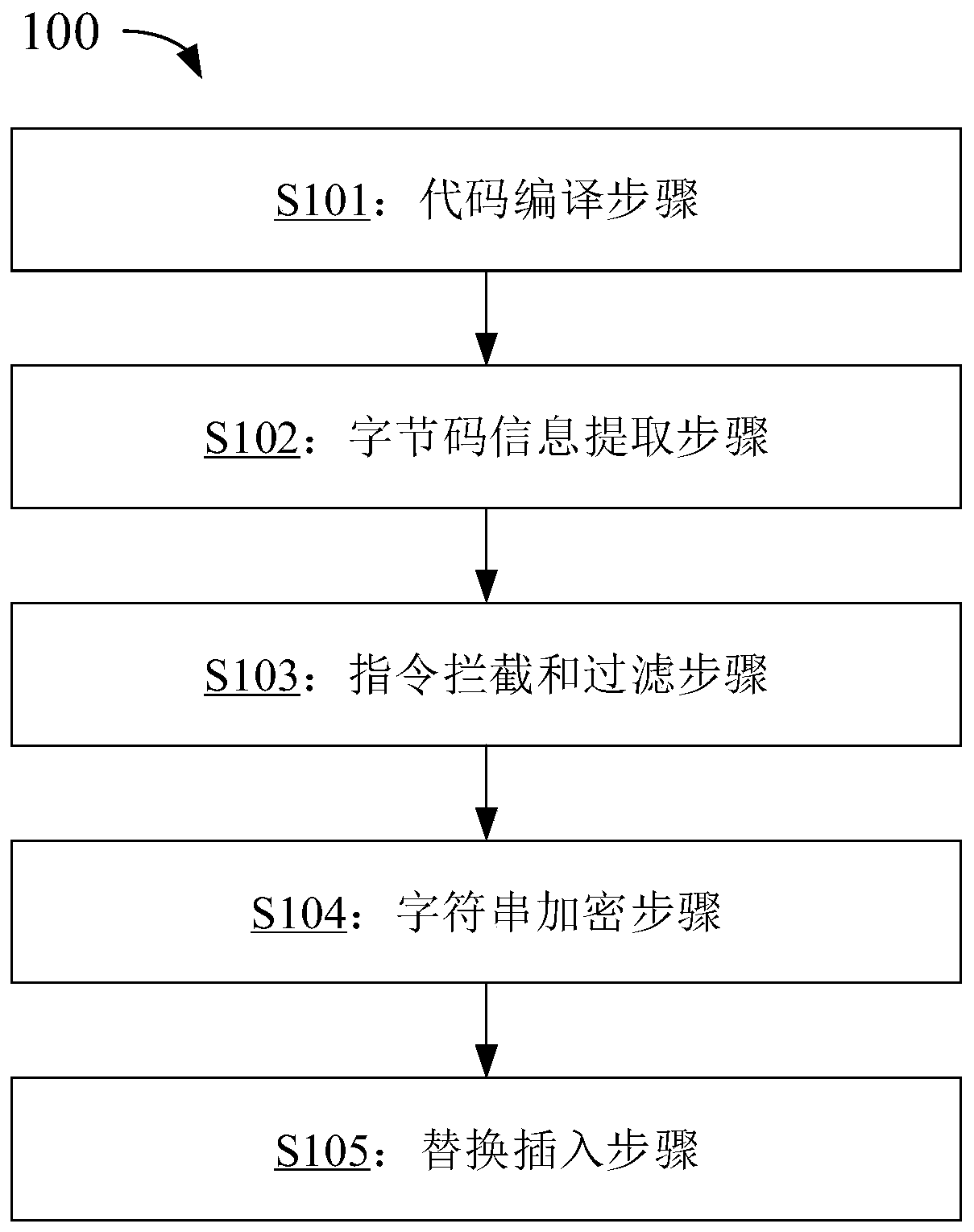
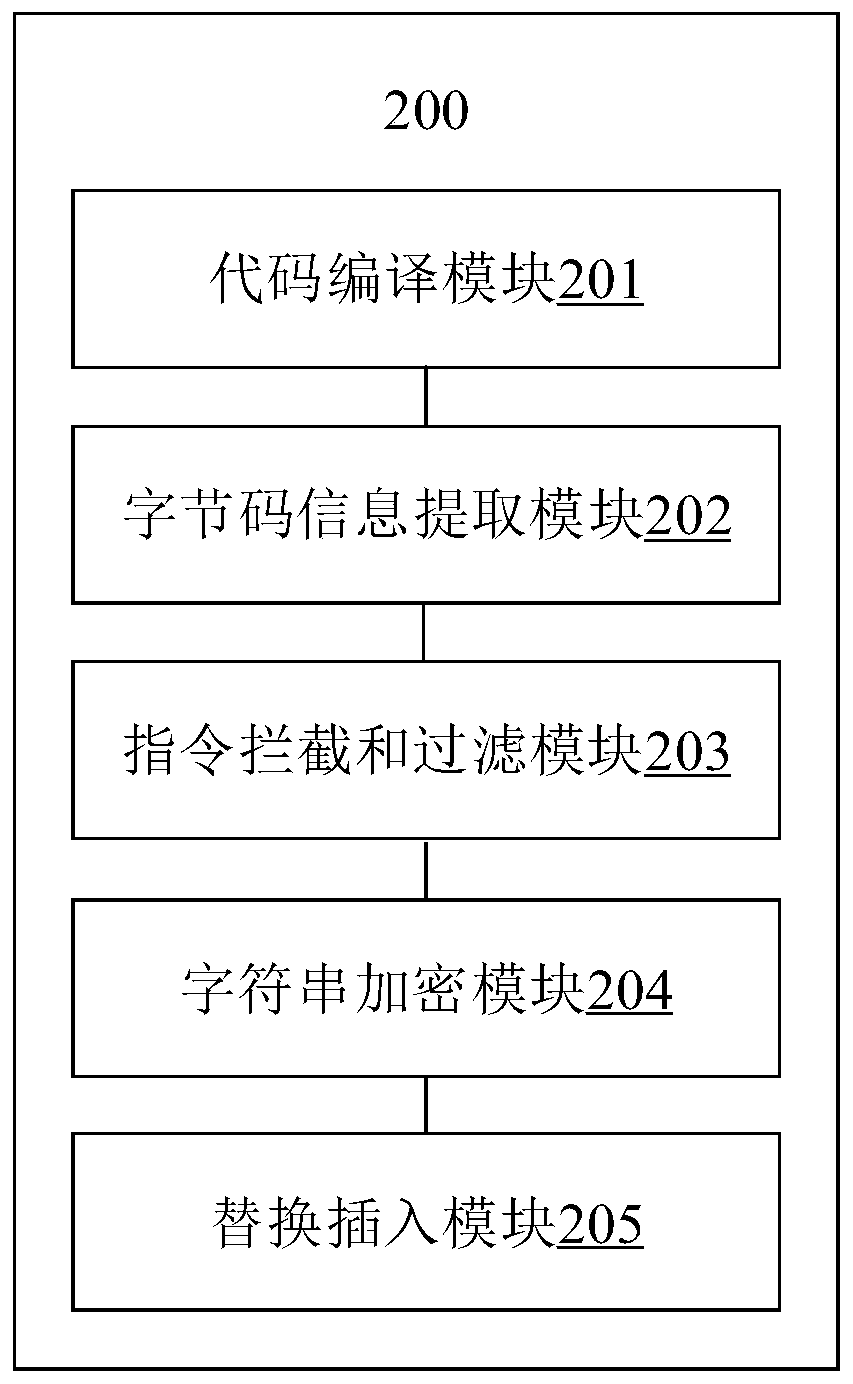
Code encryption method and device, electronic equipment and computer readable storage medium
InactiveCN110059455ASolve the security risks that are easy to bringSolve efficiency problemsProgram/content distribution protectionComputer hardwarePlaintext
The invention provides a code encryption method and device, electronic equipment and a computer readable storage medium. The code encryption method comprises the following steps: compiling a source code to generate an original intermediate file; extracting byte code information in the original intermediate file, with byte code information comprising one or more original instructions; interceptingone or more original instructions in the bytecode information, filtering the one or more original instructions according to instruction characteristics of a constant character string obtained in advance, and obtaining a plaintext constant character string corresponding to the original instruction containing the instruction characteristics in the one or more original instructions; performing encryption processing on the plaintext constant character string to obtain an encrypted constant character string; and replacing the plaintext constant character string with the encrypted constant characterstring, and inserting a decryption processing code corresponding to the encryption processing to obtain an encrypted intermediate file. According to the embodiment of the invention, the security level of the application program is improved, and the efficiency of searching encryption processing is improved.
Owner:MEGVII BEIJINGTECH CO LTD
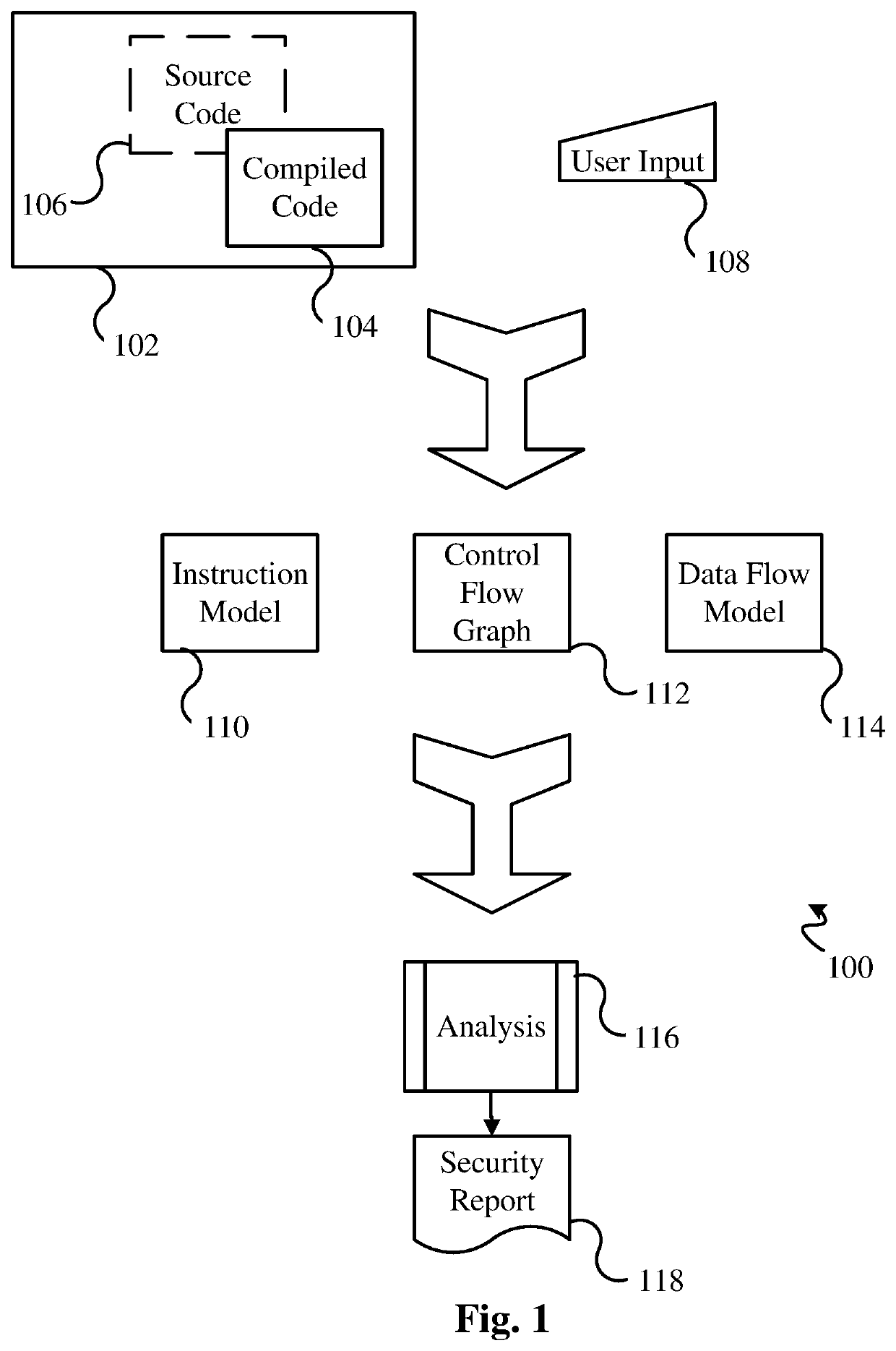
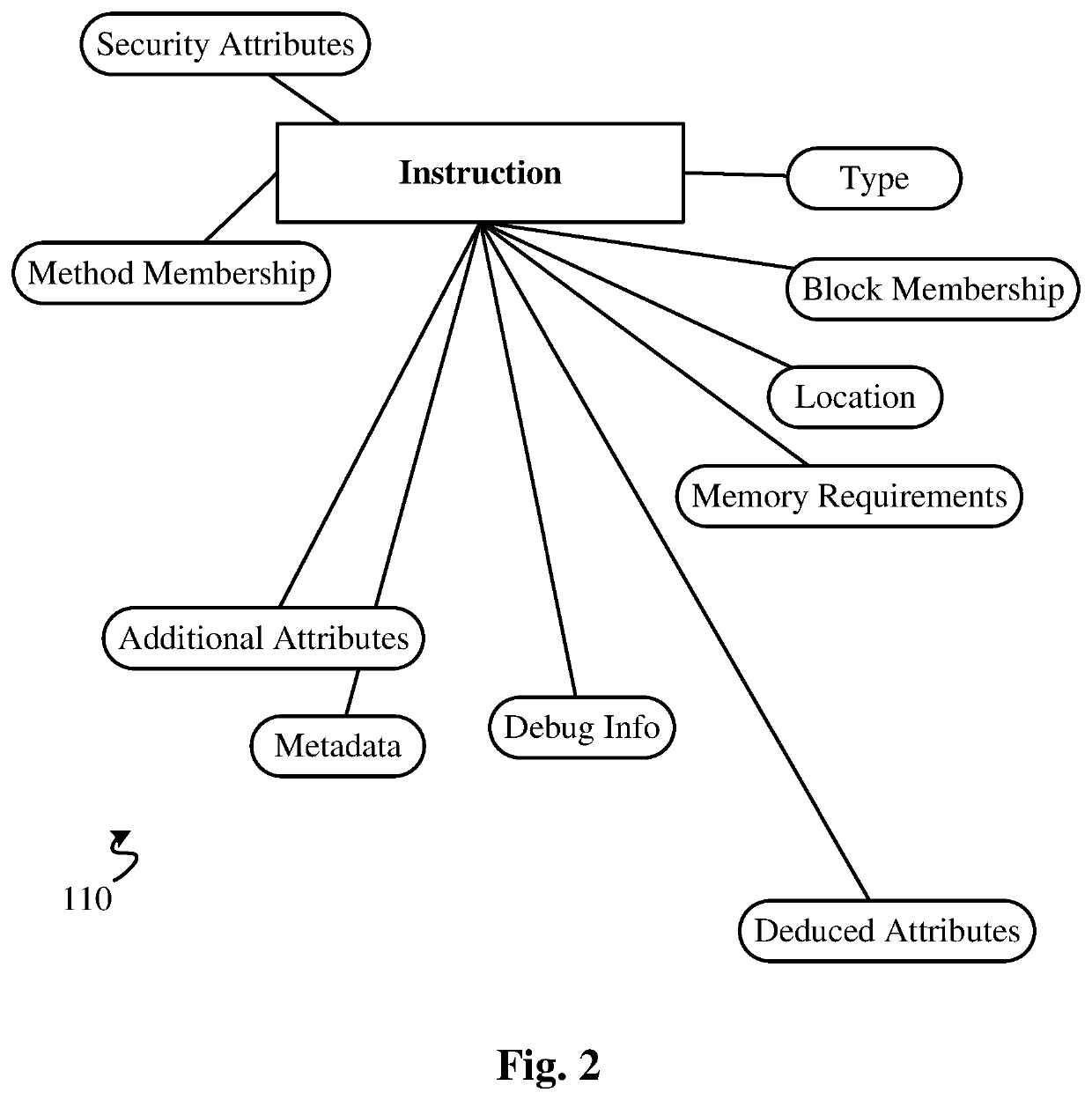
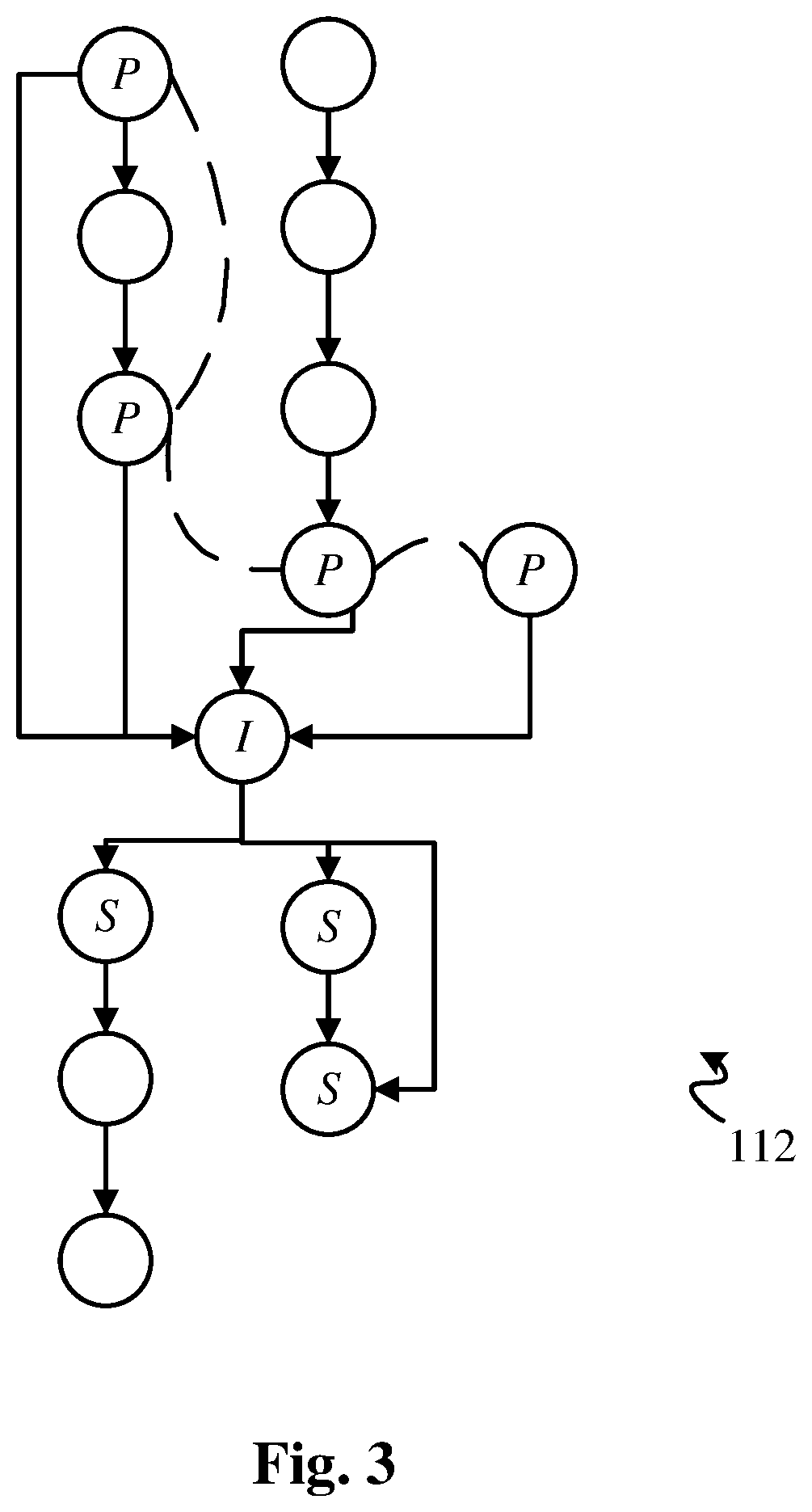
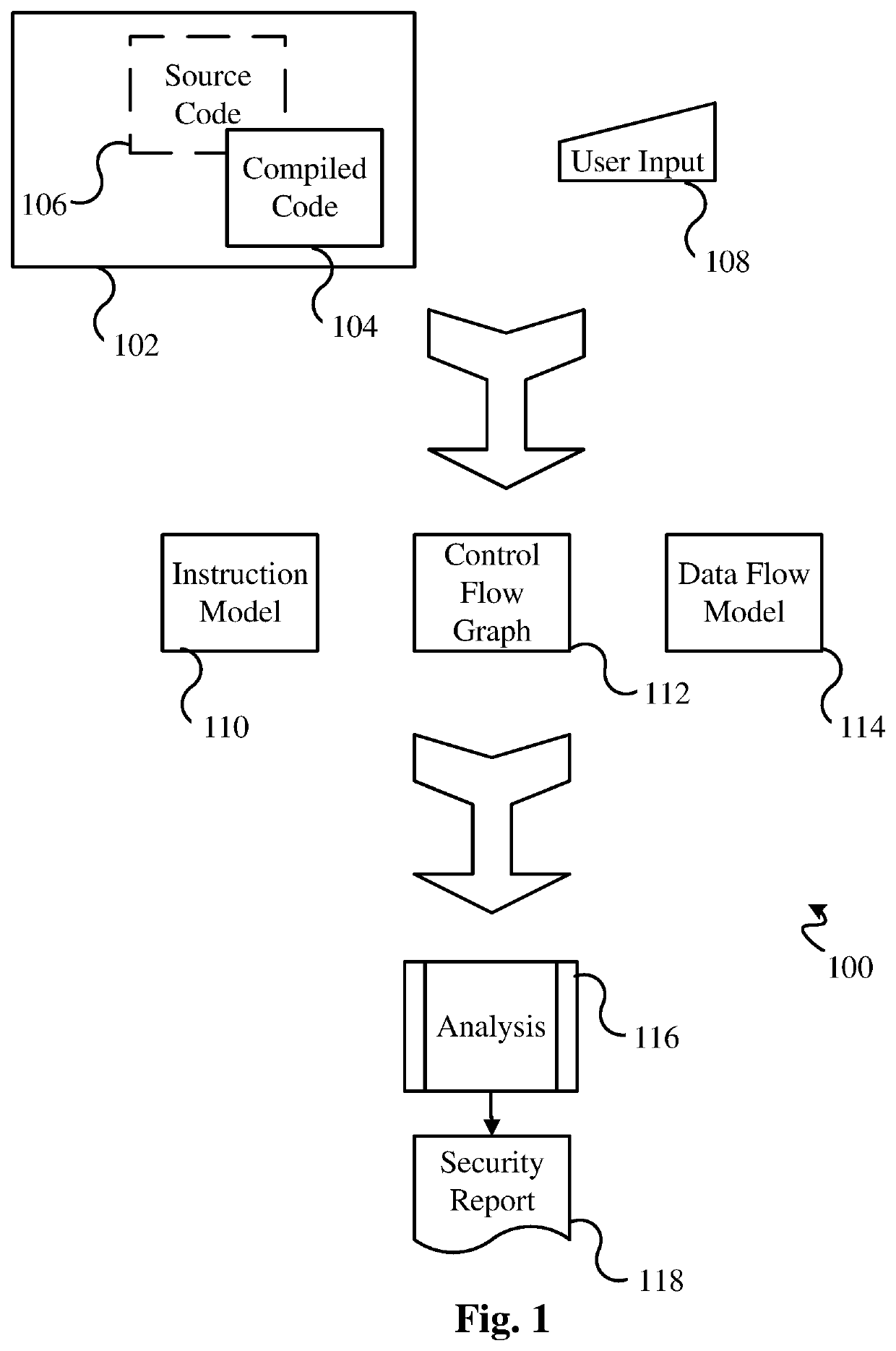
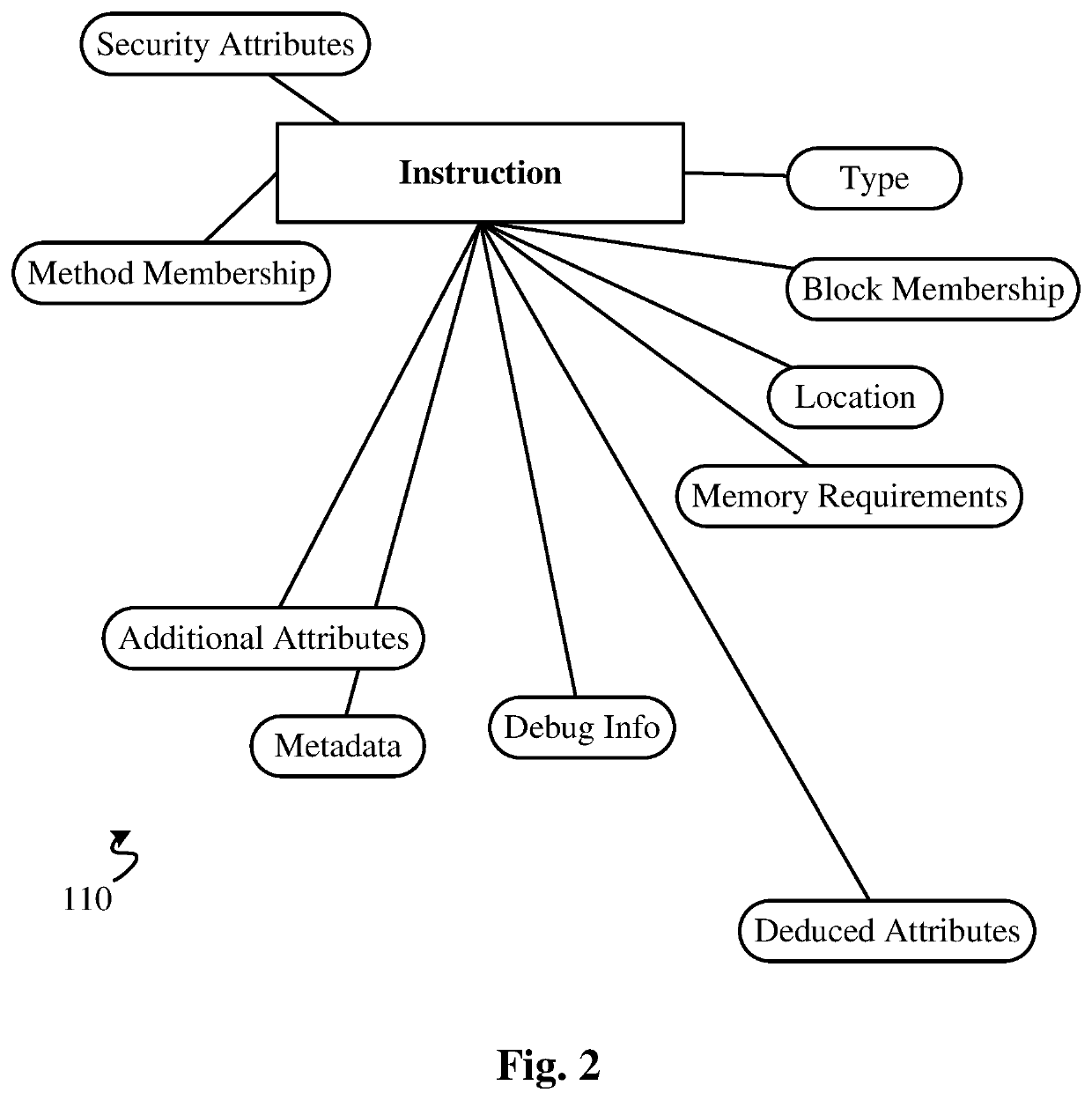
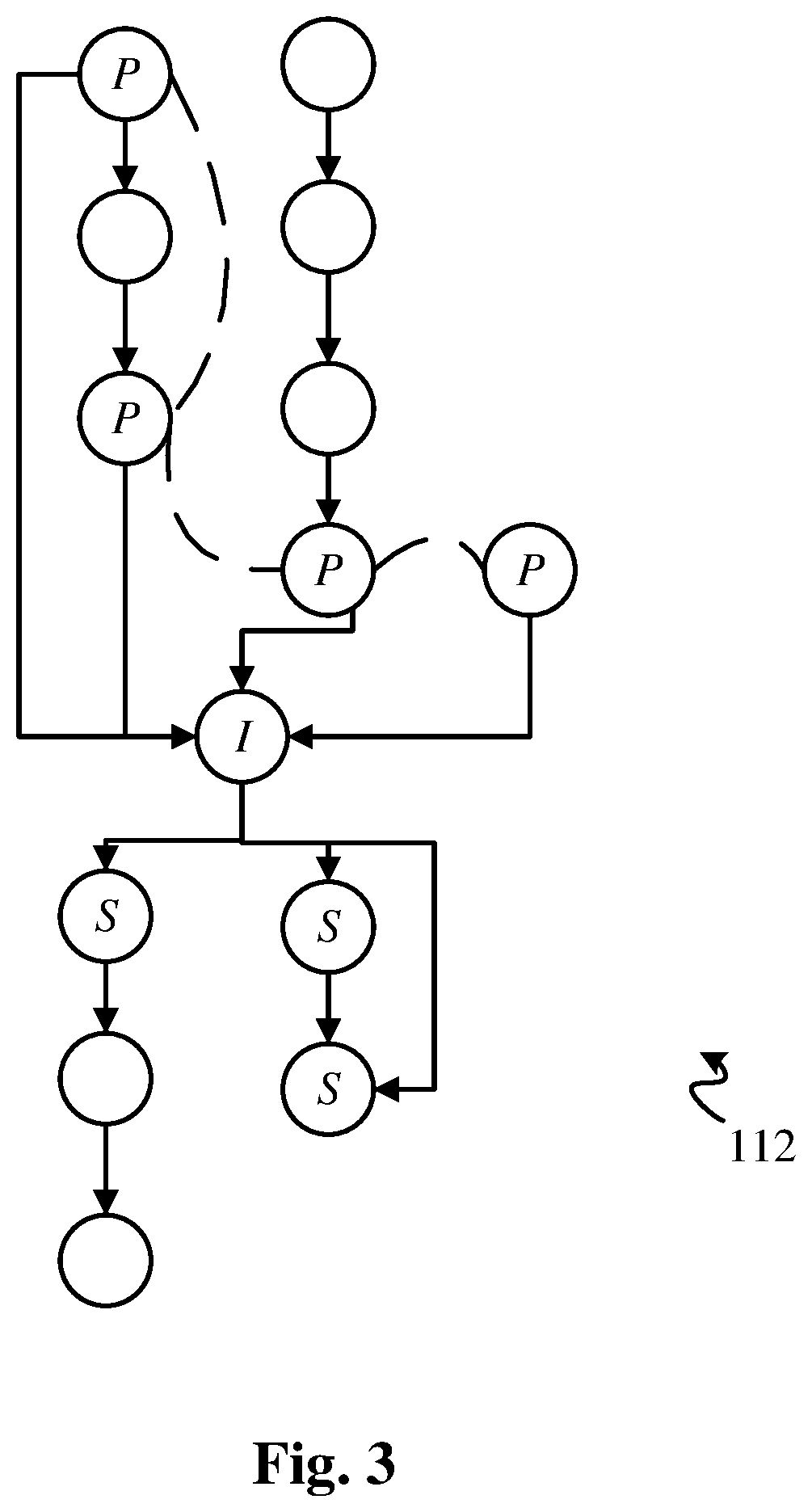
High performance software vulnerabilities detection system and methods
ActiveUS20200057856A1Improve accuracyReduce consumptionSoftware testing/debuggingPlatform integrity maintainancePathPingData stream
This invention teaches a system and methods of detecting software vulnerabilities in a computer program by analyzing the compiled code and optionally the source code of the computer program. The invention models compiled software to examine both control flow and data flow properties of the target program. A comprehensive instruction model is used for each instruction of the compiled code, and is complemented by a control flow graph that includes all potential control flow paths of the instruction. A data flow model is used to record the flow of unsafe data during the execution of the program. The system analyzes the data flow model and creates a security finding corresponding to each instruction that calls an unsafe function on unsafe data. The security findings are aggregated in a security report. To improve performance, the system further uses data flow merging, and caching of 1-to-many data flow maps for each basic block in the code.
Owner:SECURISEA INC
Bus communication emulation
InactiveUS20090089467A1Error detection/correctionInput/output processes for data processingOperational systemComputerized system
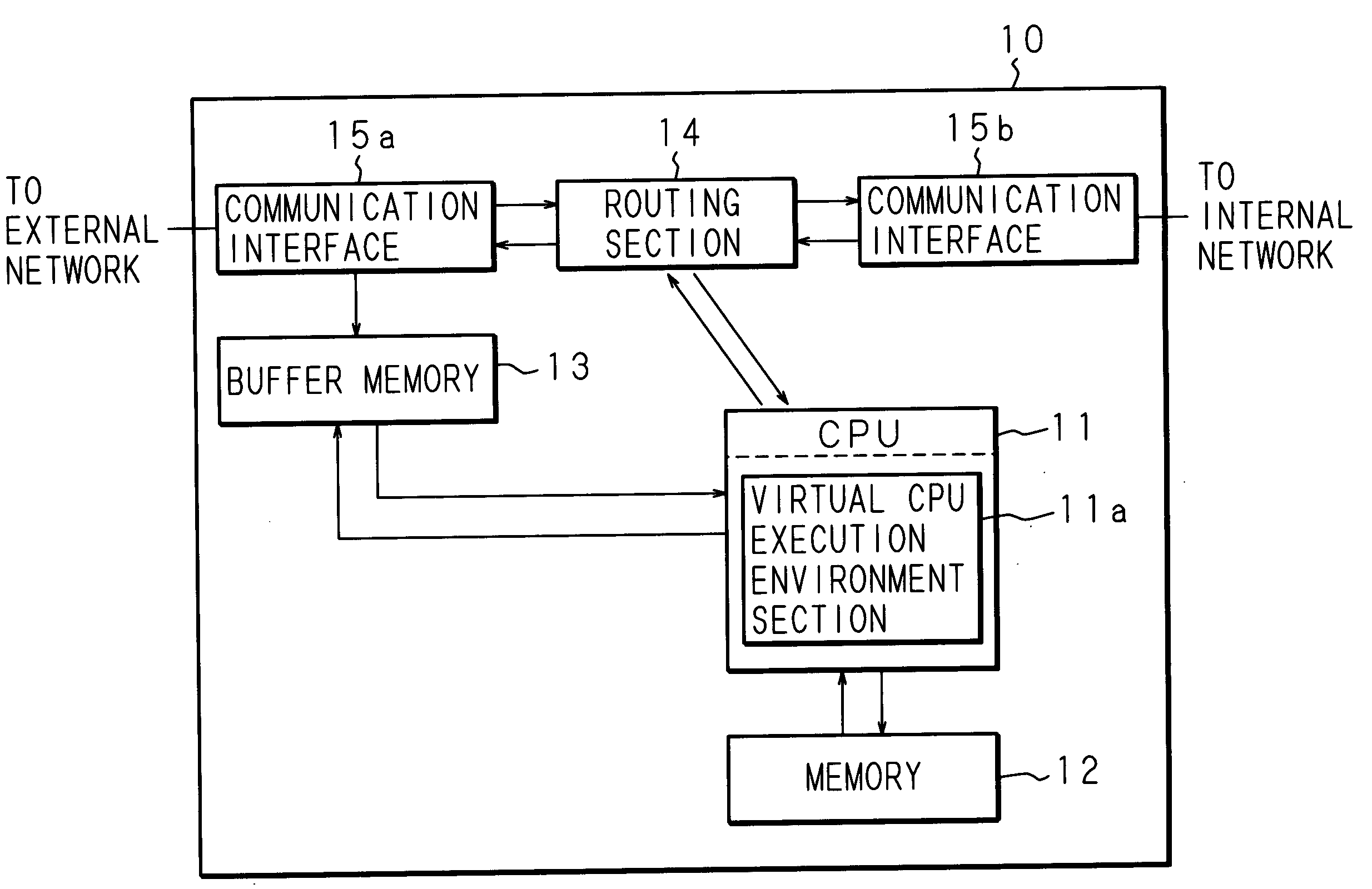
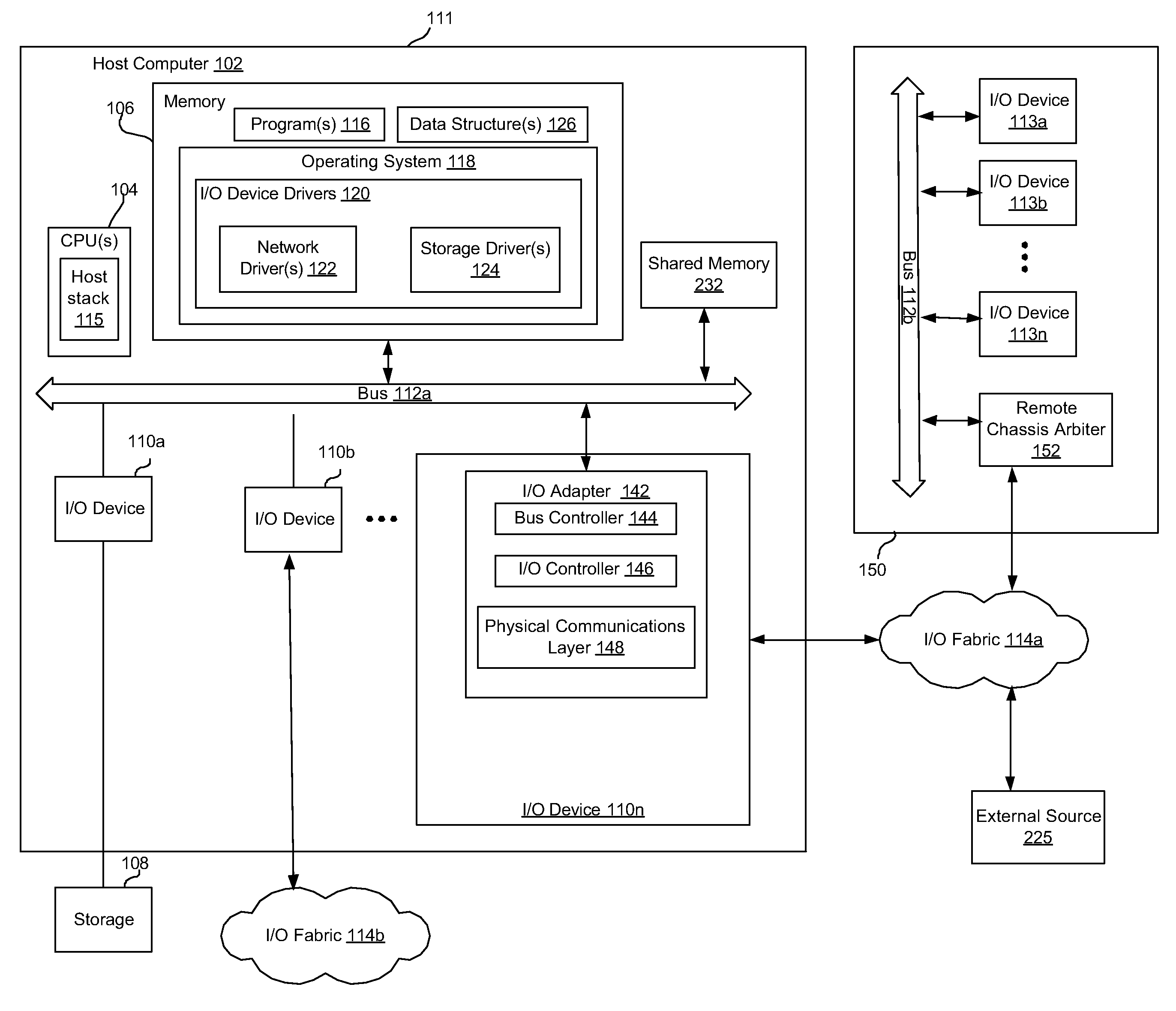
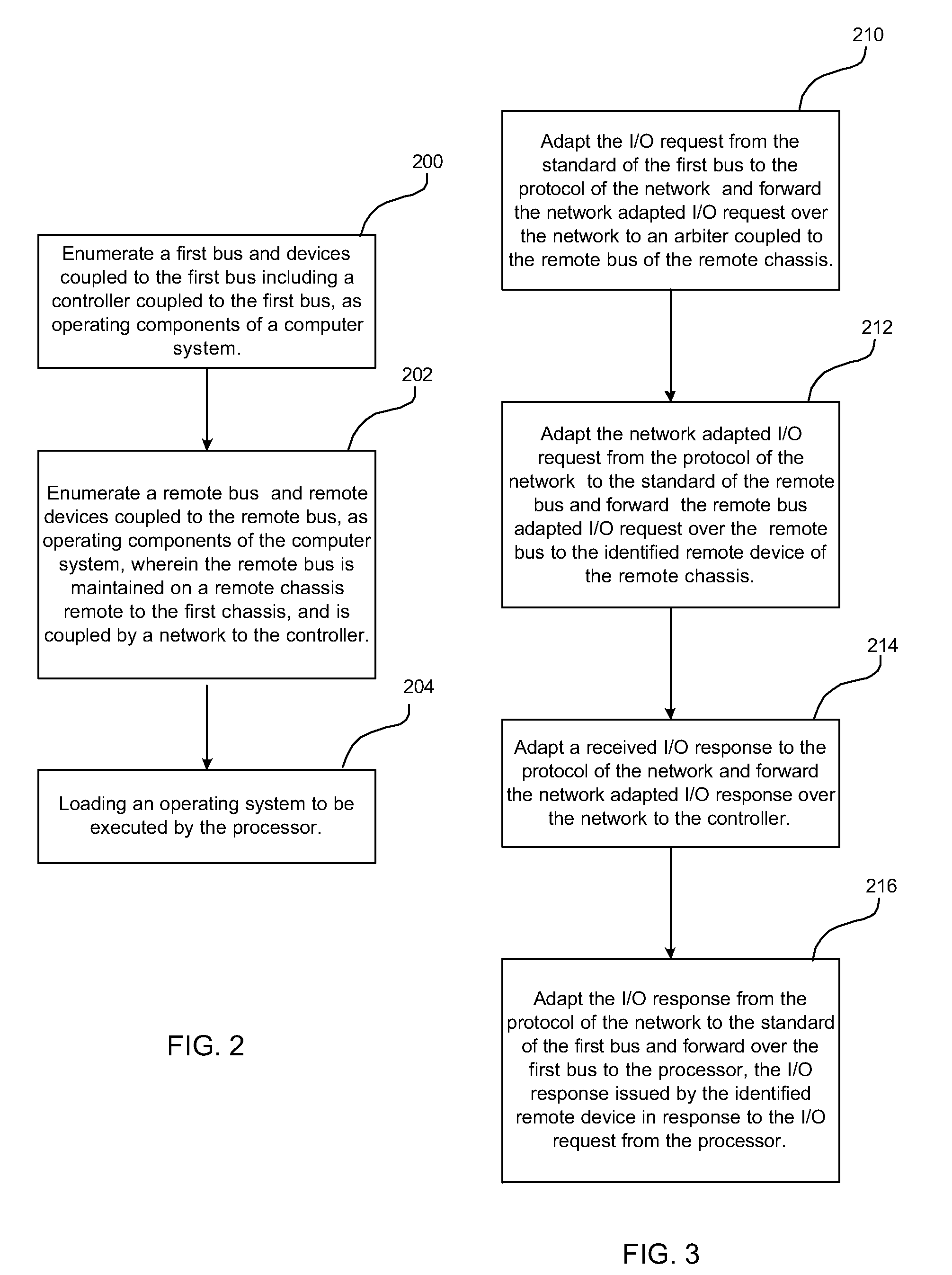
Provided are a method, system, and program for initializing a processor of a computer system, to enumerate a remote bus and remote devices coupled to the remote bus, as operating components of the computer system. In another embodiment, a controller stores a message containing a directive in a memory shared by a processor of a computer system and the controller which may be operated independently of the state of said processor and said operating system. The processor may read a message stored in the shared memory by the controller and process the message. In addition, the processor may store a message intended for the controller to provide, for example, status information to be forwarded to another computer system. Other embodiments are described and claimed.
Owner:INTEL CORP
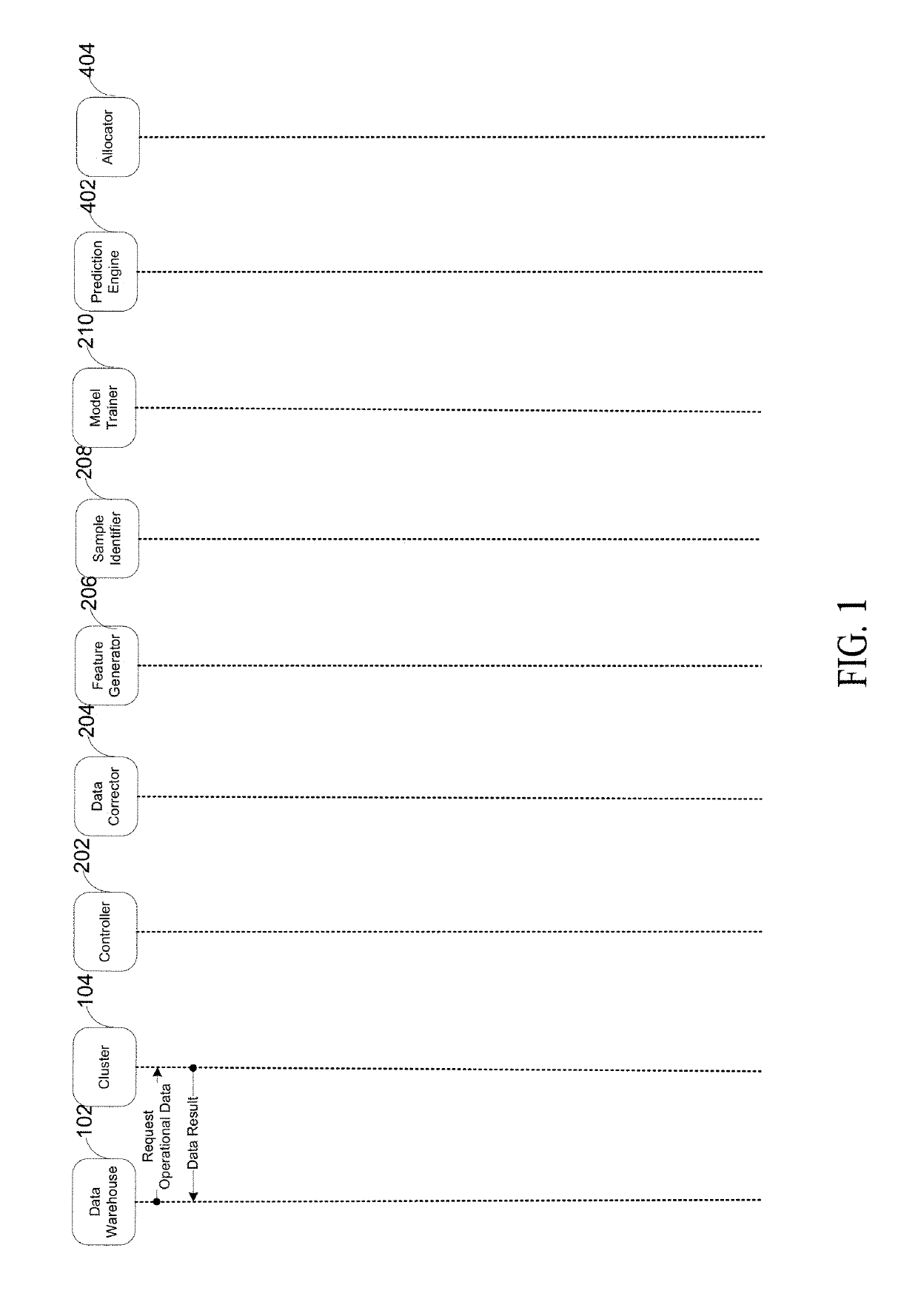
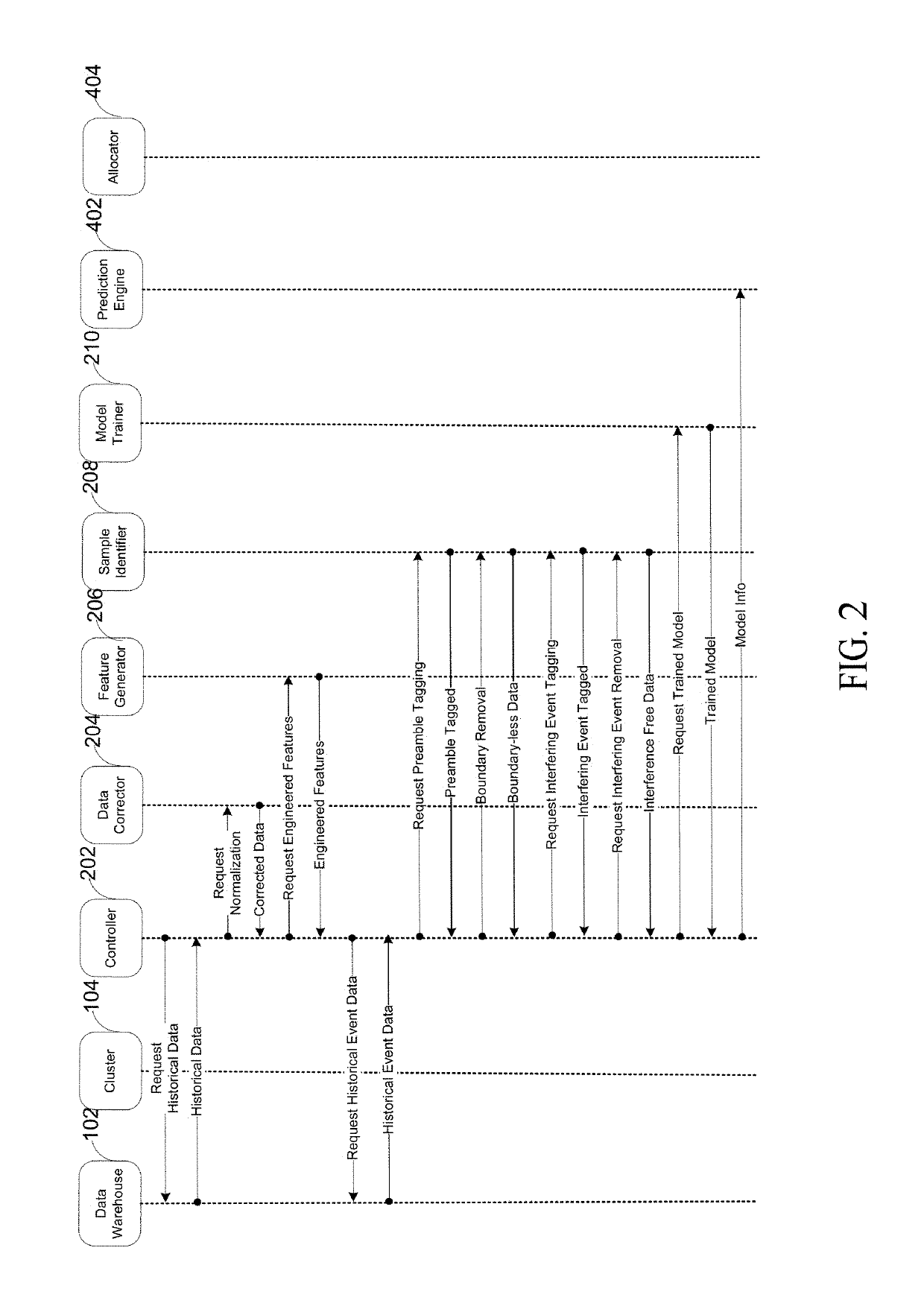
Robust event prediction
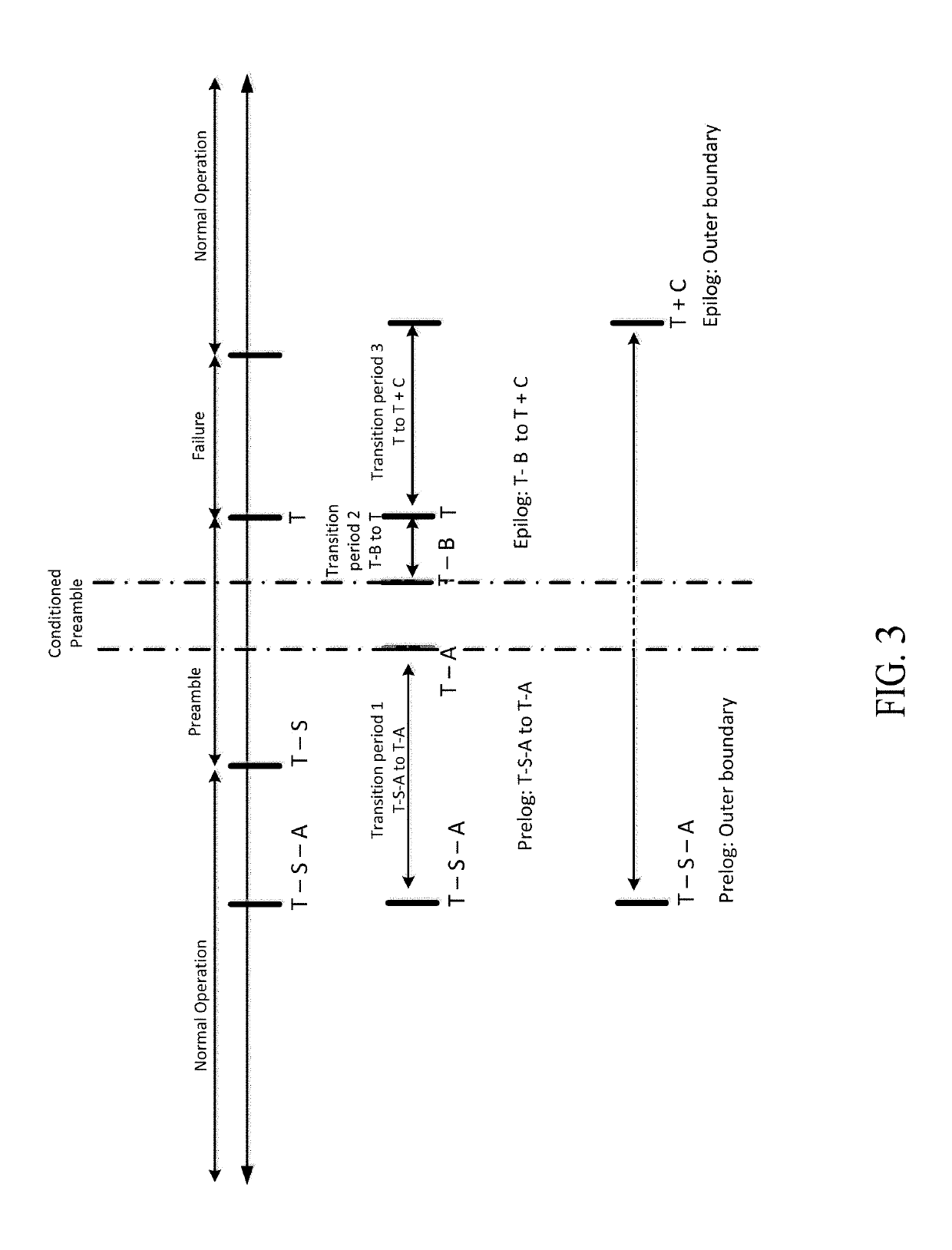
A system and method predicts events in a computer system. The system and method includes a controller that receives a crash profile. The controller generates granular information that identifies data indicative of a potential server cluster failure in an enterprise system without needing to identify an originating cause of the potential server cluster failure. The system and method trains a model by sampling portions of a profile that may include directives and data indicative of a normal operating state and a conditioned preamble operating state. The system and method provides a trained model to a prediction engine. The system and method modifies an allocation of computing resources in response to the prediction of the potential server cluster failure by the prediction engine monitoring one or more servers of a server cluster.
Owner:PROGRESSIVE CASUALTY INSURANCE
Securised microprocessor with jump verification
InactiveUS20070083795A1Avoid damageError detection/correctionPlatform integrity maintainanceProgram counterMicroprocessor
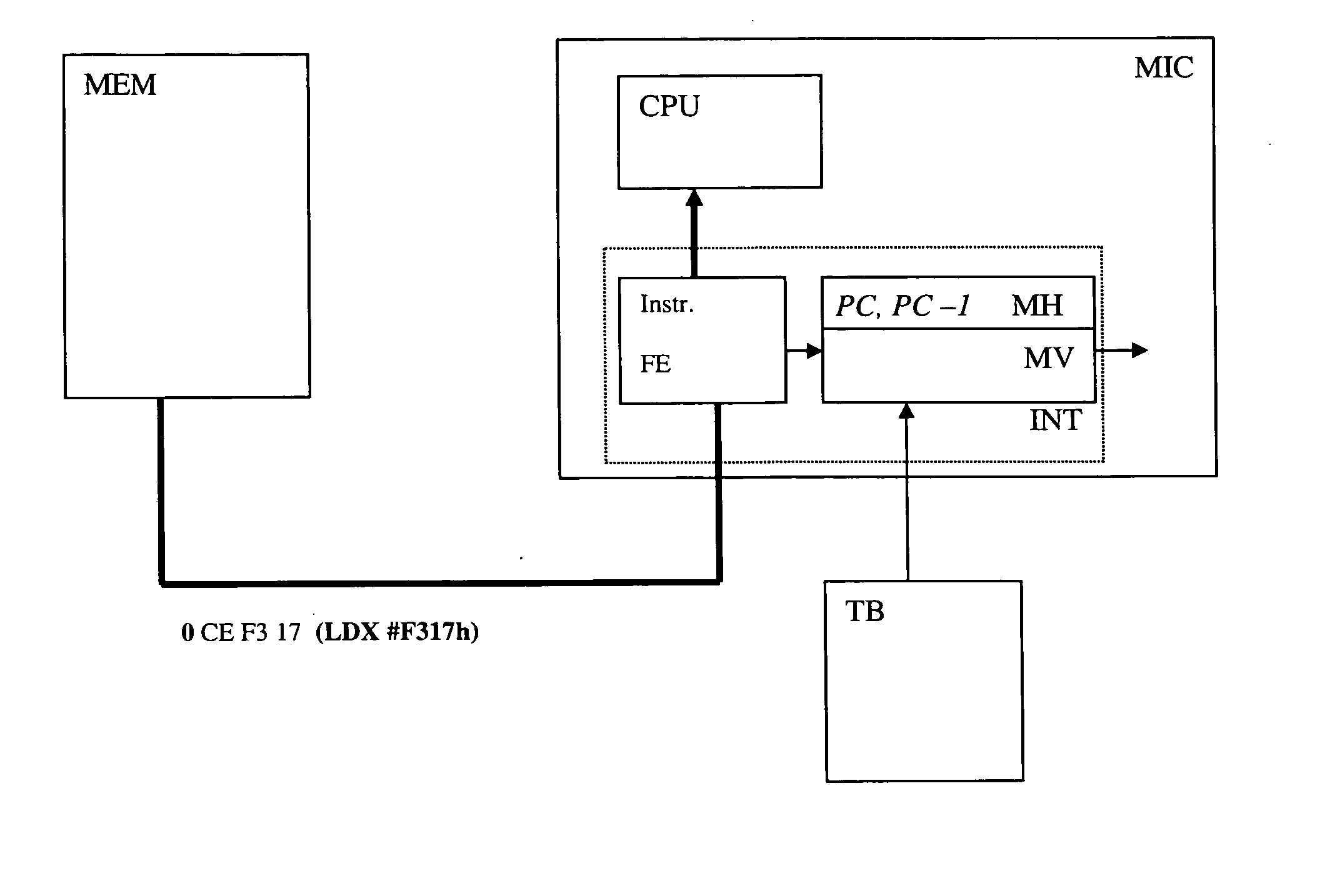
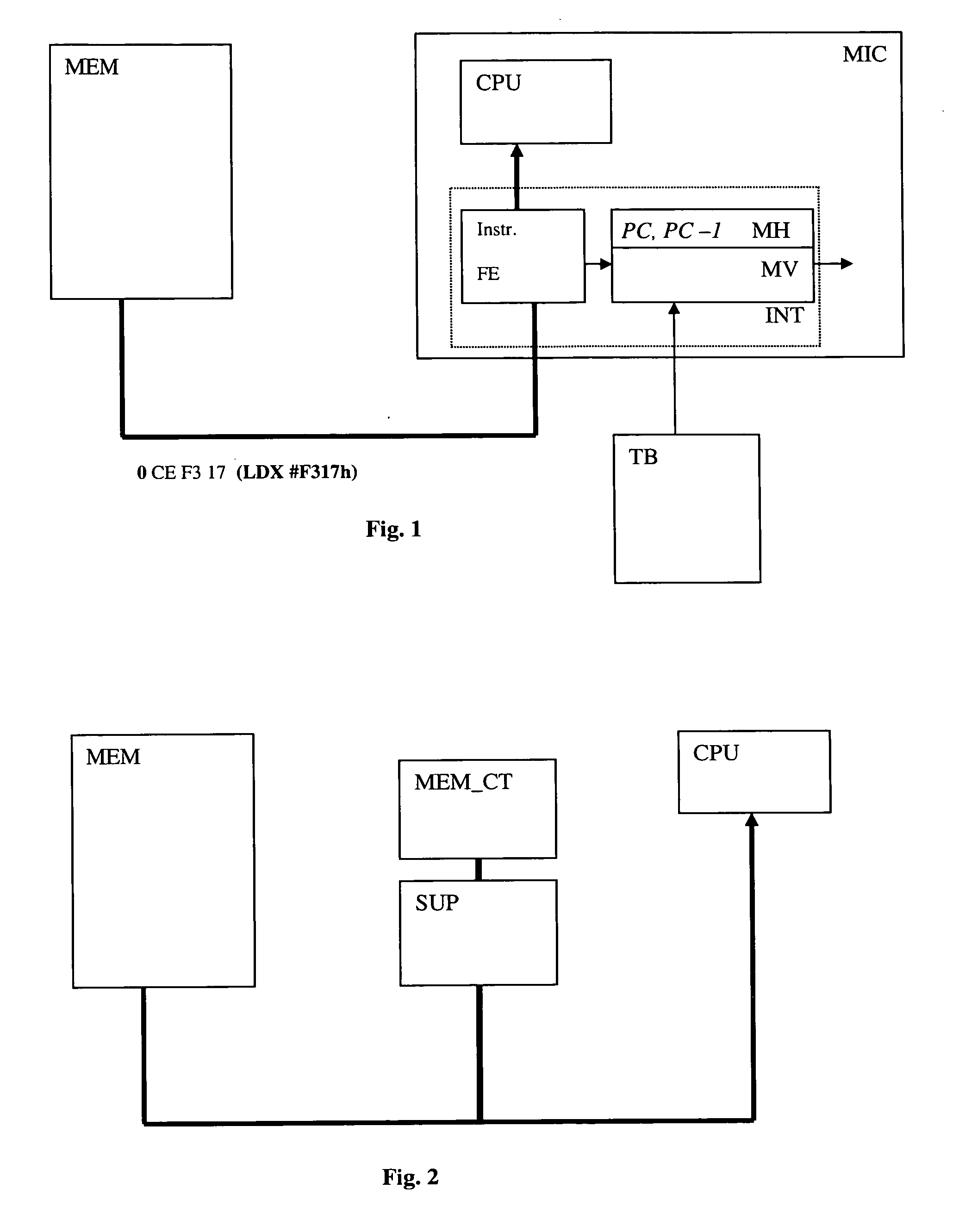
The aim of the present invention is to propose a method and a device in order to avoid damages that the desynchronisation of the program counter may cause. This aim is achieved by means of a secured microprocessor comprising a program counter and an interface with a program memory containing the instructions, this microprocessor being wherein it includes a historical memory of the program counter indicating the position of the program counter at the time of the execution of the previous instruction, and an instruction verification module, this module comprising reading means of an additional piece of verification information that defines for the instruction in progress, the supposed position of the previous program counter, this verification module comprising means to compare this verification information with that originating from the historical memory and means to generate an error if the verification indicates an incompatibility.
Owner:NAGRACARD
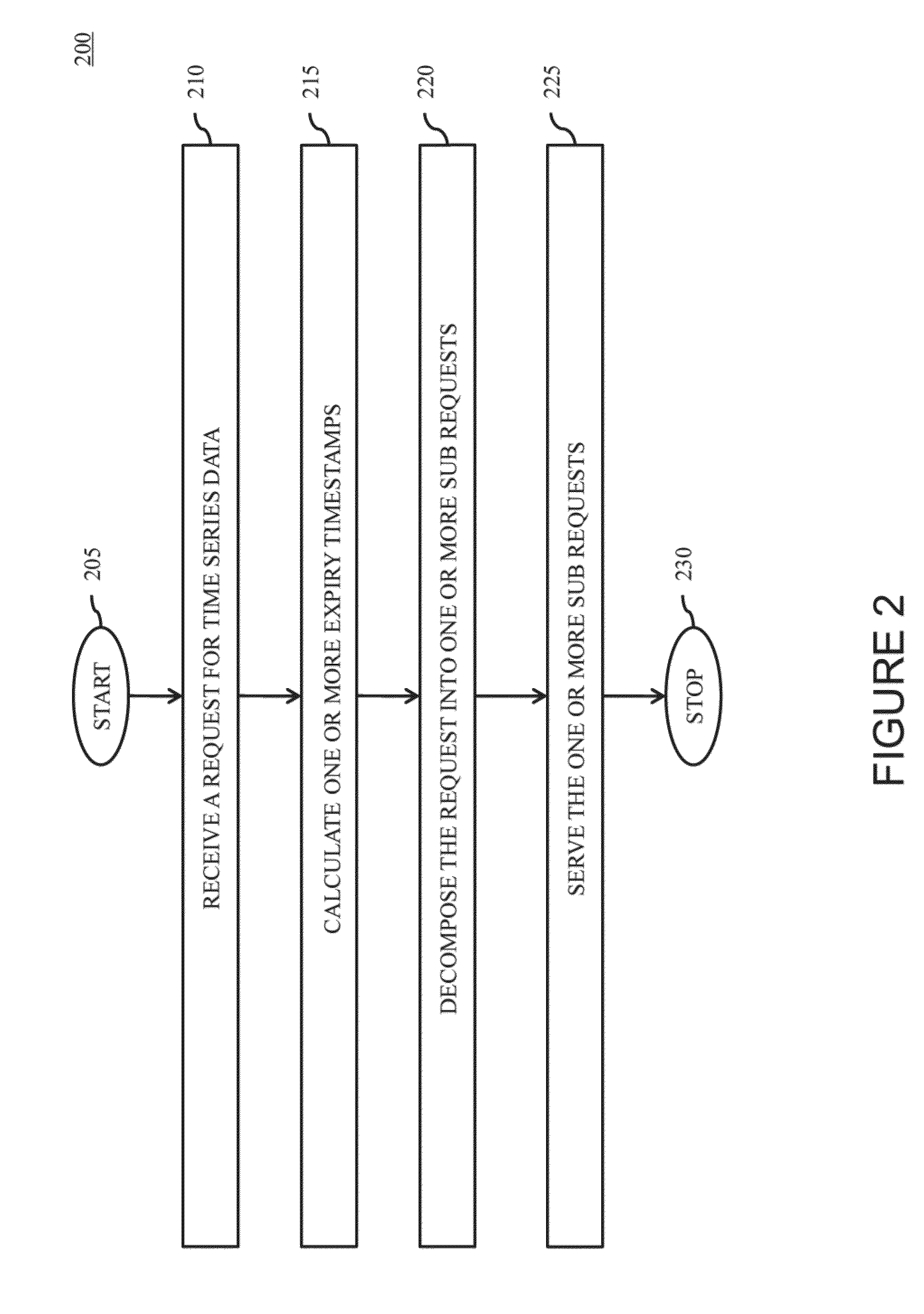
System and Method for Caching Time Series Data
InactiveUS20150242326A1Memory architecture accessing/allocationMemory adressing/allocation/relocationExpiration TimeTimestamp
The present invention provides a method and system for caching time series data. A computer system for caching time series data is disclosed. The computer system comprises one or more processors, at least one cache, and a computer readable storage medium. The computer readable storage medium contains instructions that, when executed by the one or more processors, causes the one or more processors to perform a set of steps comprising fetching the time series data from a time series data source, calculating one or more expiry timestamps, grouping the plurality of time series datum in to one or more time data chunks based on the one or more expiry timestamps, and storing a copy of the time series data and the one or more expiry timestamps in the at least one cache.
Owner:INMOBI
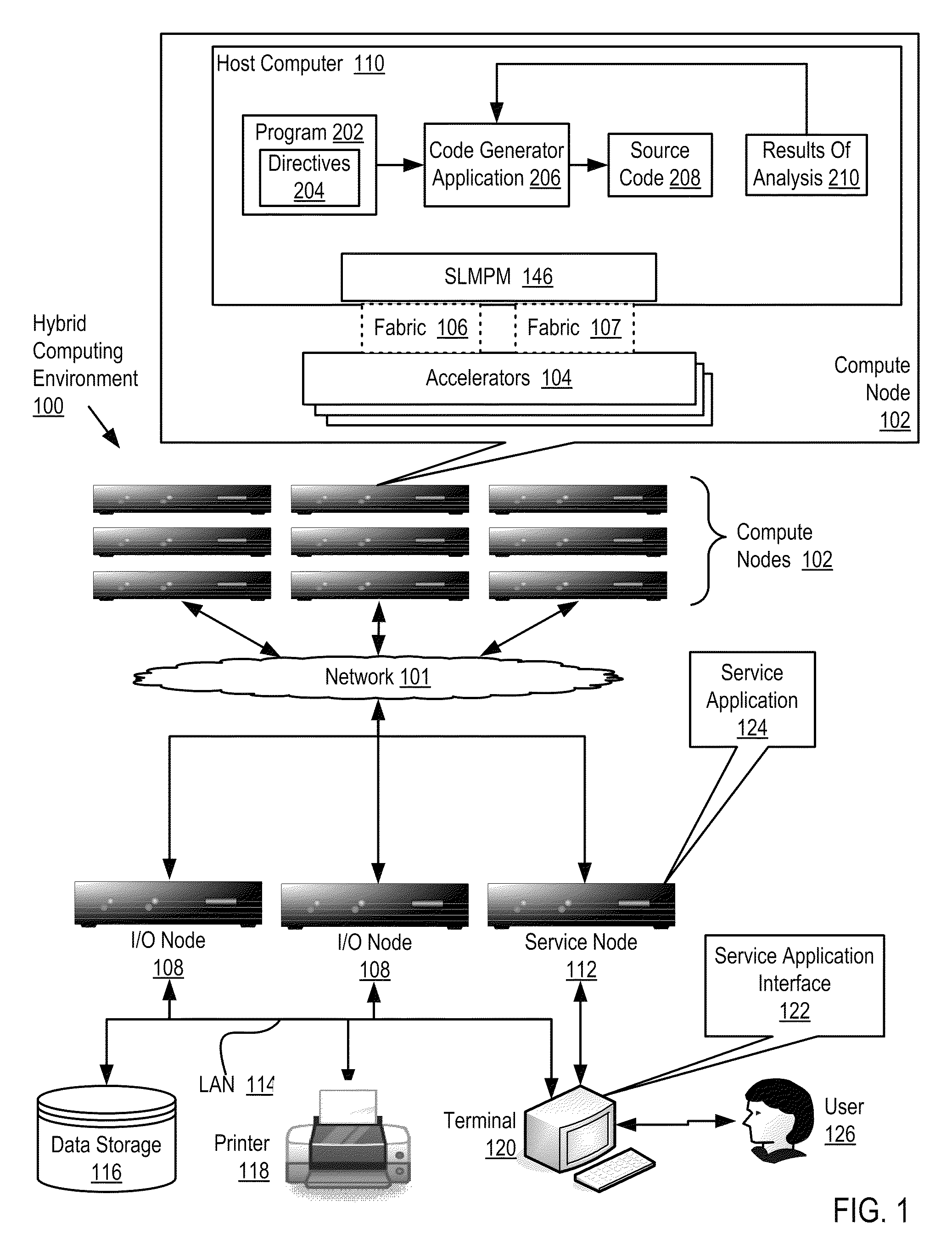
Software development for a hybrid computing environment
InactiveUS8843880B2Specific program execution arrangementsMemory systemsSoftware development processStructure of Management Information
Software development for a hybrid computing environment that includes a host computer and an accelerator, the host computer and the accelerator adapted to one another for data communications by a system level message passing module and by two or more data communications fabrics of at least two different fabric types where software development includes creating, by a programmer, a computer program for execution in the hybrid computing environment, the computer program including directives for generation of computer program code that moves contents of memory among host computers and accelerators in the hybrid computing environment; generating, by a code generator application, source code in accordance with the directives; analyzing, by the code generator application, operation of the generated code for data movement and utilization of moved data; and regenerating, by the code generator application, the source code in accordance with the directives and further in accordance with results of the analysis.
Owner:INT BUSINESS MASCH CORP
High performance software vulnerabilities detection system and methods
ActiveUS10599852B2Improve accuracyReduce consumptionSoftware testing/debuggingPlatform integrity maintainancePathPingData stream
This invention teaches a system and methods of detecting software vulnerabilities in a computer program by analyzing the compiled code and optionally the source code of the computer program. The invention models compiled software to examine both control flow and data flow properties of the target program. A comprehensive instruction model is used for each instruction of the compiled code, and is complemented by a control flow graph that includes all potential control flow paths of the instruction. A data flow model is used to record the flow of unsafe data during the execution of the program. The system analyzes the data flow model and creates a security finding corresponding to each instruction that calls an unsafe function on unsafe data. The security findings are aggregated in a security report. To improve performance, the system further uses data flow merging, and caching of 1-to-many data flow maps for each basic block in the code.
Owner:SECURISEA INC
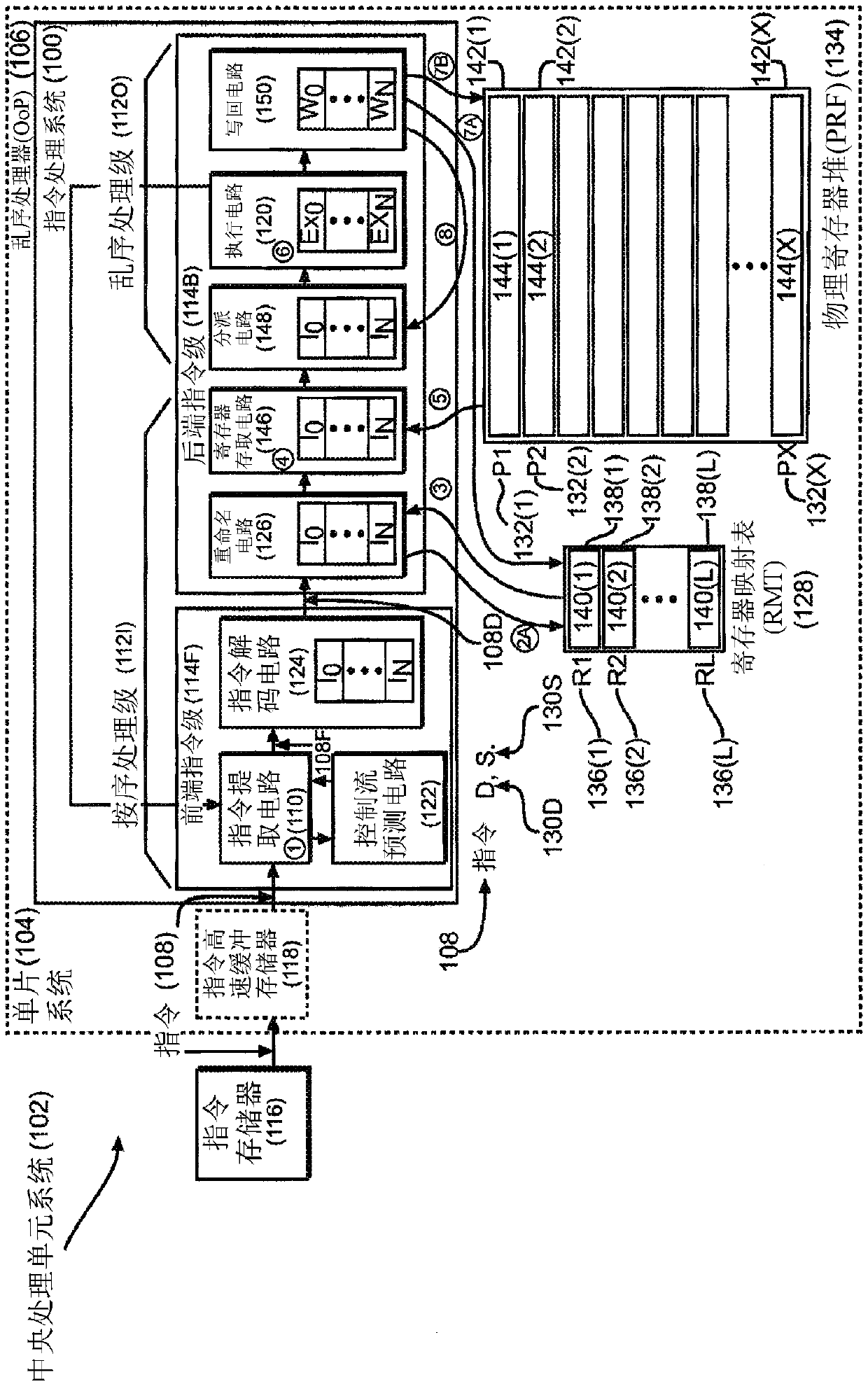
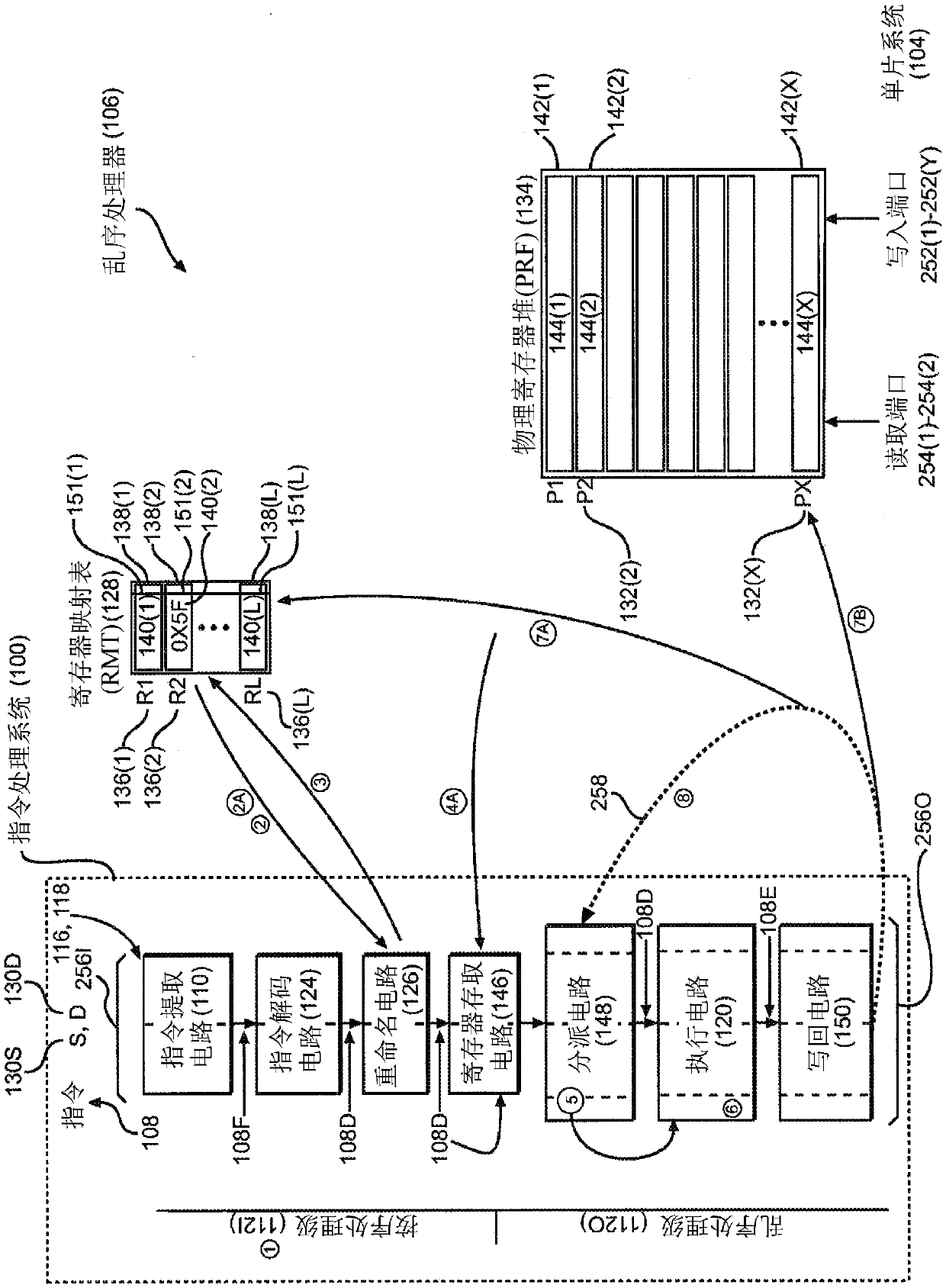
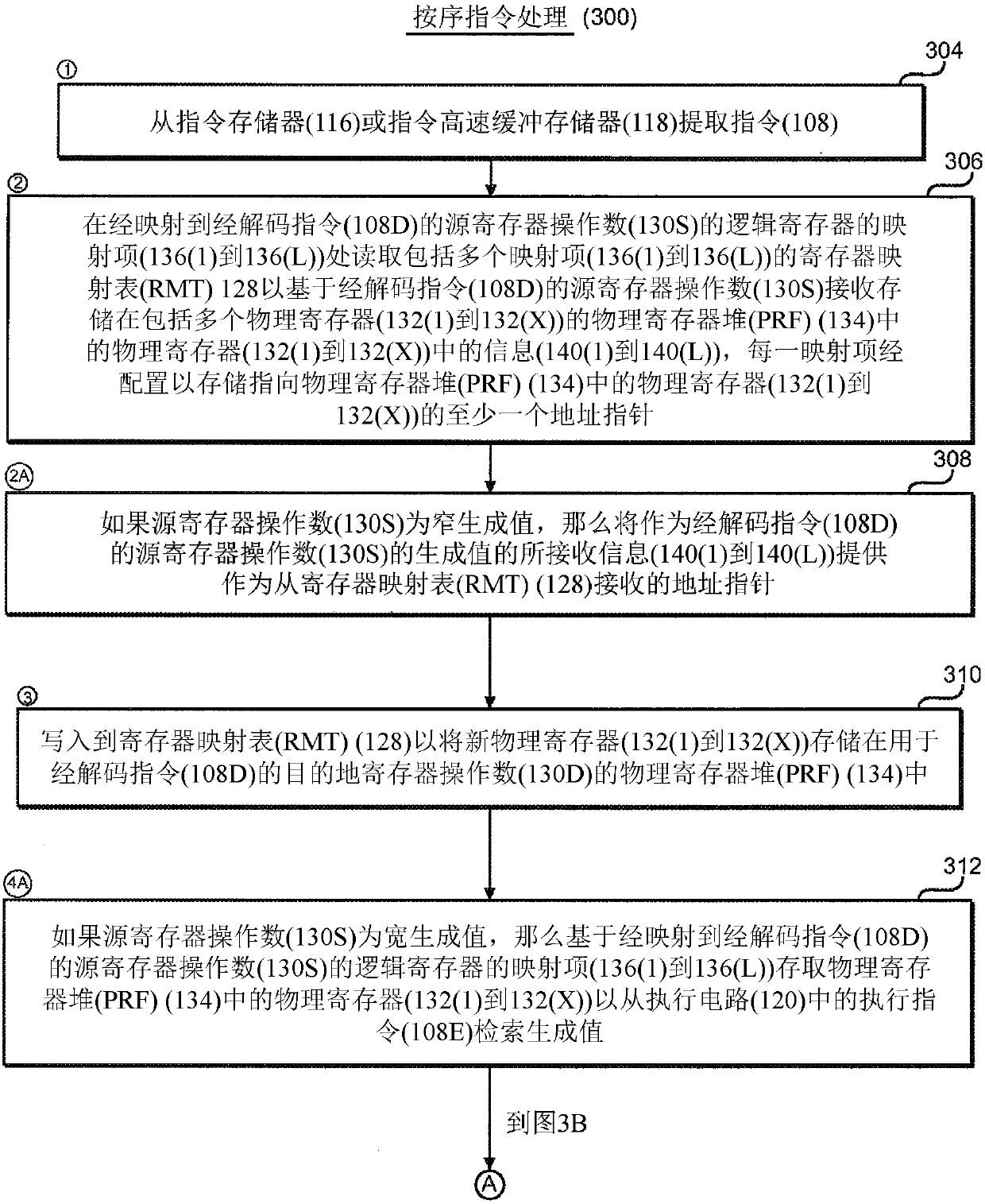
Storing narrow produced values for instruction operands directly in a register map in an out-of-order processor
InactiveCN107851028ARegister arrangementsConcurrent instruction executionData streamProcessor register
Storing narrow produced values for instruction operands directly in a register map in an out-of-order processor (OoP) is provided. An OoP is provided that includes an instruction processing system. The instruction processing system includes a number of instruction processing stages configured to pipeline the processing and execution of instructions according to a dataflow execution. The instruction processing system also includes a register map table (RMT) configured to store address pointers mapping logical registers to physical registers in a physical register file (PRF) for storing produceddata for use by consumer instructions without overwriting logical registers for later executed, out-of-order instructions. In certain aspects, the instruction processing system is configured to writeback (i.e., store) narrow values produced by executed instructions directly into the RMT, as opposed to writing the narrow produced values into the PRF in a write back stage.
Owner:QUALCOMM INC
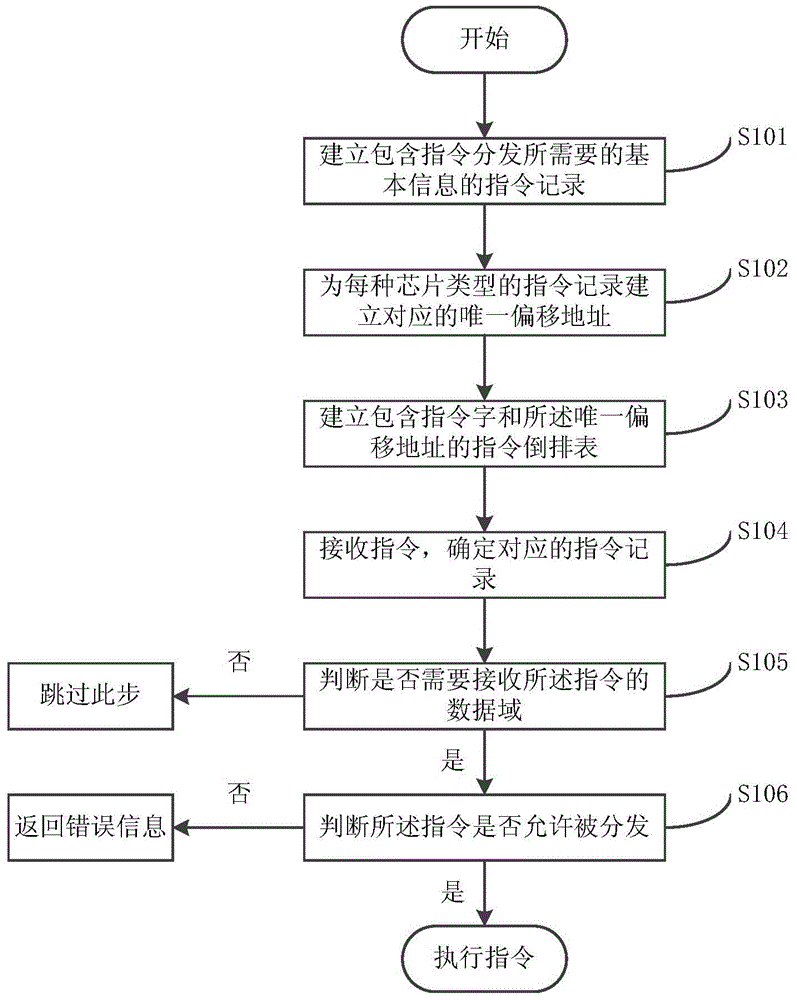
Inversion technology-based instruction distribution method and system for intelligent security chips
ActiveCN105608022AHigh speedImprove securityUnauthorized memory use protectionTerminal equipmentParallel computing
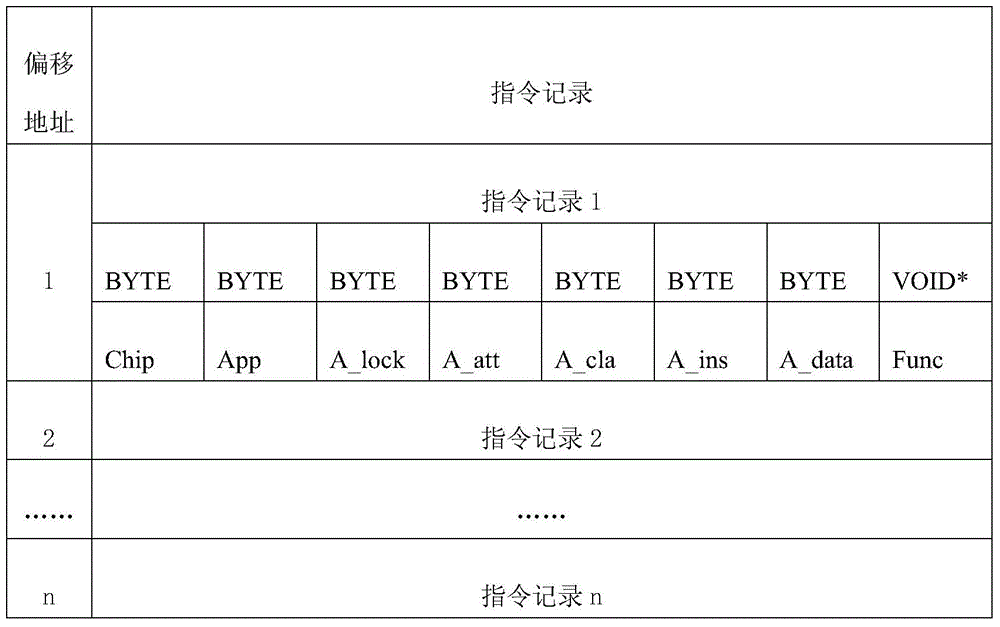
The invention discloses an inversion technology-based instruction distribution method and system for intelligent security chips. The method comprises the following steps: establishing instruction records which comprises the basic information required by instruction distribution; distributing a corresponding unique offset address for the instruction record of each chip type according to different chip types; establishing an instruction inversion table which comprises instruction words and the unique offset addresses, wherein each instruction word corresponds to a plurality of unique offset addresses and the number of the unique offset addresses is same as the number of the chip types; receiving an instruction from terminal equipment and determining a corresponding instruction record according to the instruction word and chip type of the instruction; judging whether a data domain of the instruction needs to be received according to an instruction data domain sign of the instruction and the corresponding instruction record; if the judging result is positive, receiving the data domain of the instruction; and of the judging result is negative, skipping the step.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD
Method and system for creating management information base specifications
ActiveUS7734588B2Digital data processing detailsDigital computer detailsInformation repositoryManagement information base
Owner:CISCO TECH INC
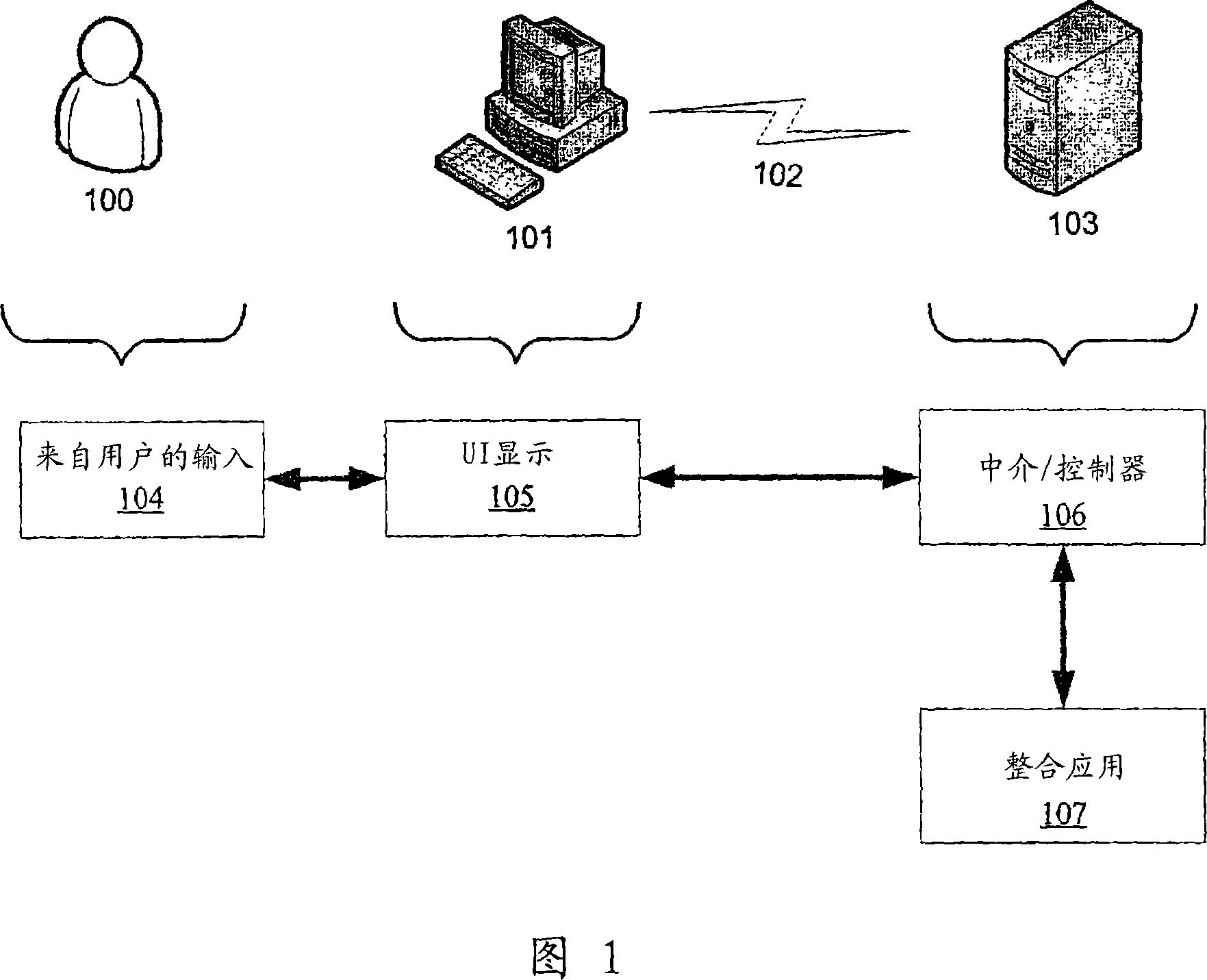
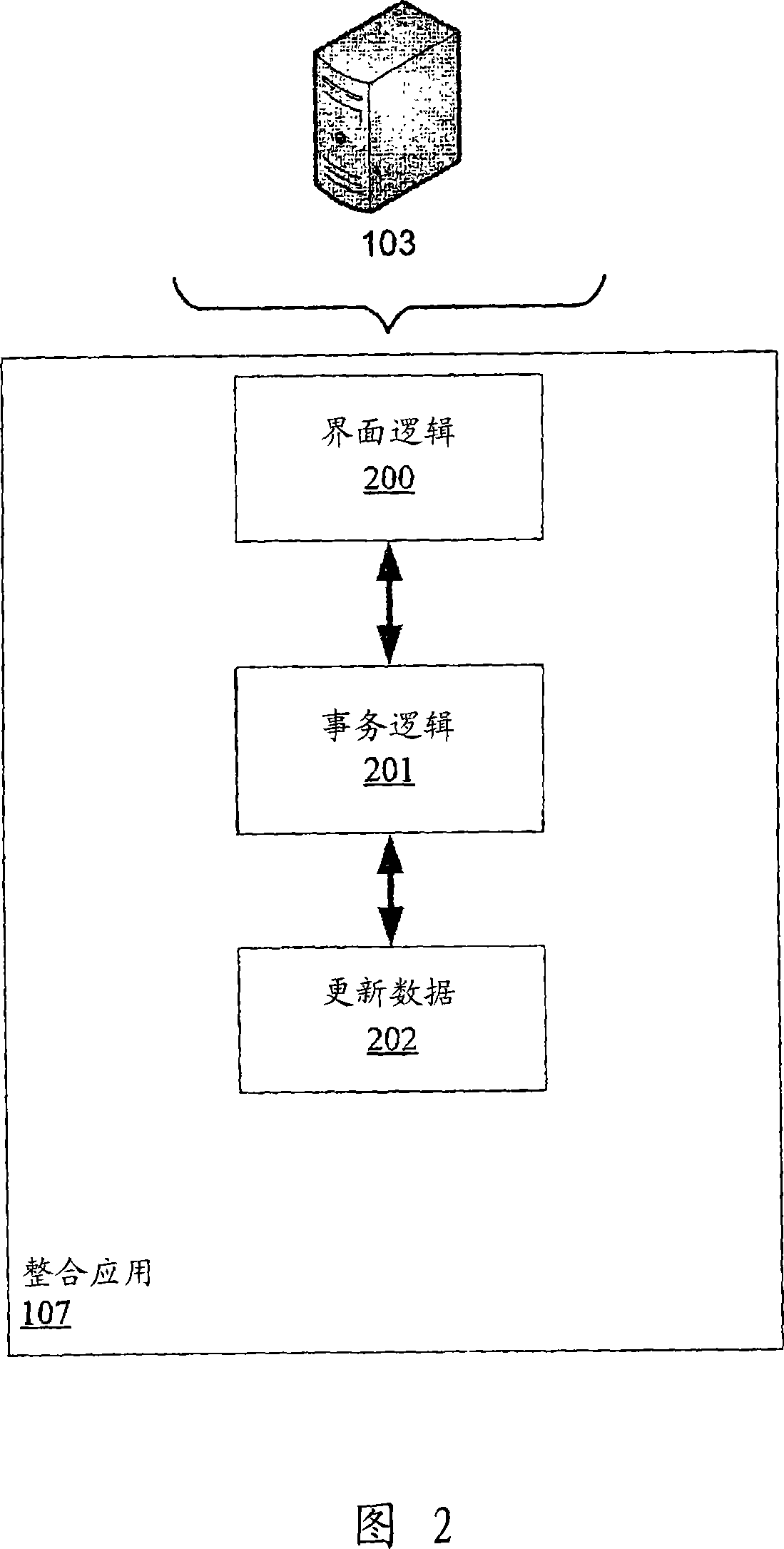
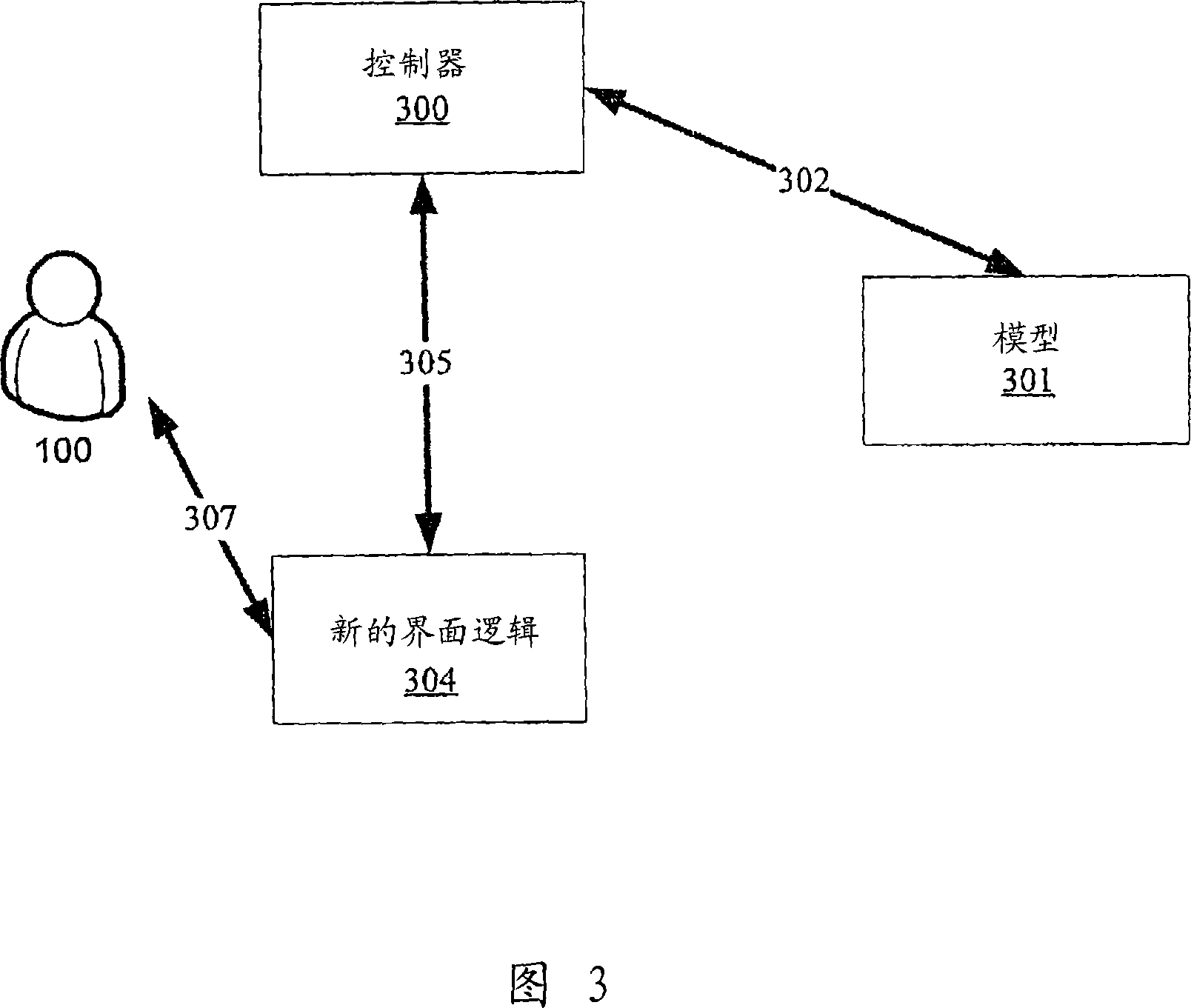
Mapping a new user interface onto an existing integrated interface
A method, system, computer readable medium containing instructions to execute a method for an intermediary, such as a controller, to interact between the interface of an older application and a newly programmed UI in order to take advantage of existing transactional logic while still allowing a user to interface with a new UI.
Owner:SAP AG
Return-Oriented Programming as an Obfuscation Technique
ActiveCN105095697BSoftware maintainance/managementConcurrent instruction executionCode snippetComputer software
The present invention discloses a method for obfuscating the functions of computer software. In one embodiment, the method includes determining a first set of instructions required to perform a target operation and a second set of instructions for at least one or more additional operations. The second set of instructions is adapted to contain instructions such that the functionality of the first set of instructions can be achieved by execution of the second set of instructions. Once the first set of instructions and the second set of instructions are determined and adjusted, a code base is created, the code segments in the code base corresponding to the code needed to implement the functionality of the first set of instructions. The instructions are then added to the second set of instructions such that, when executed, will cause the functionality of the first set of instructions to be implemented.
Owner:NXP BV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com