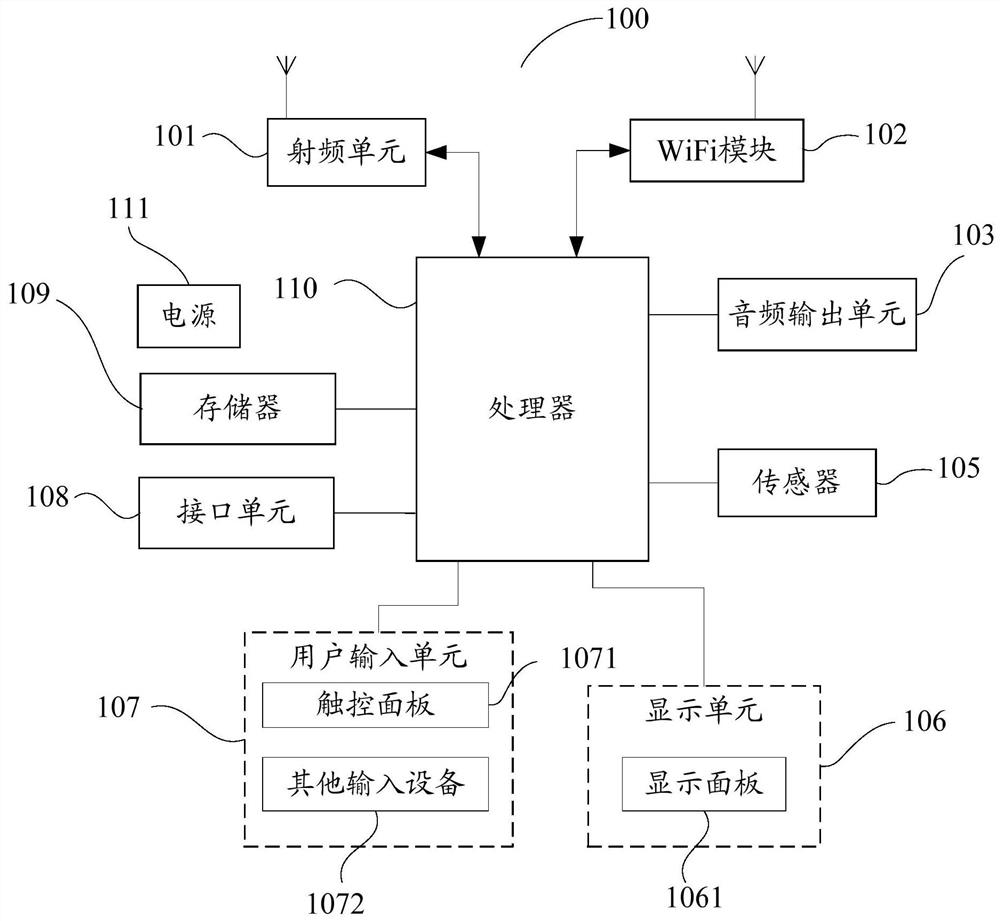
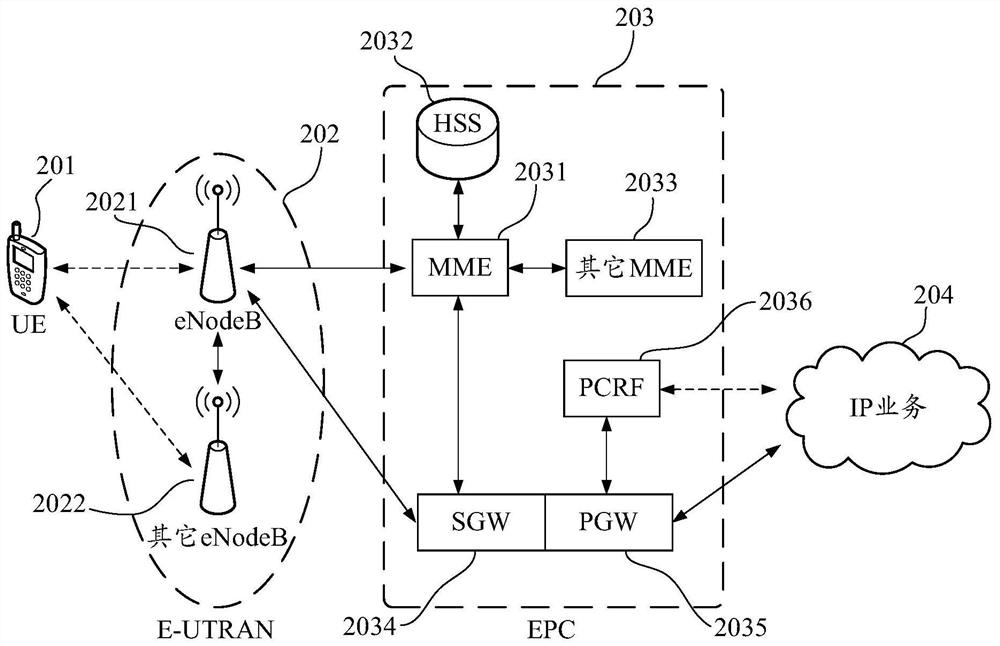
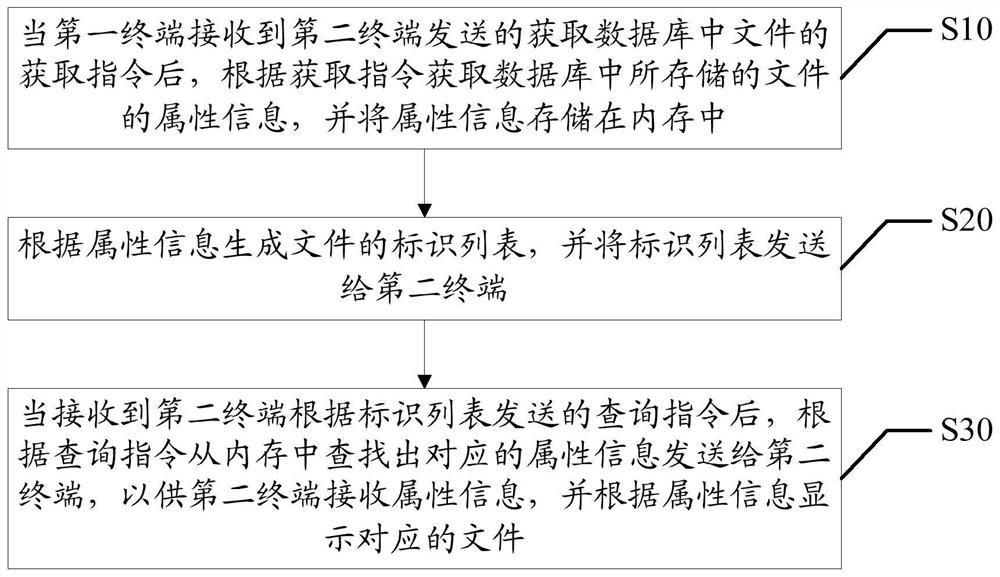
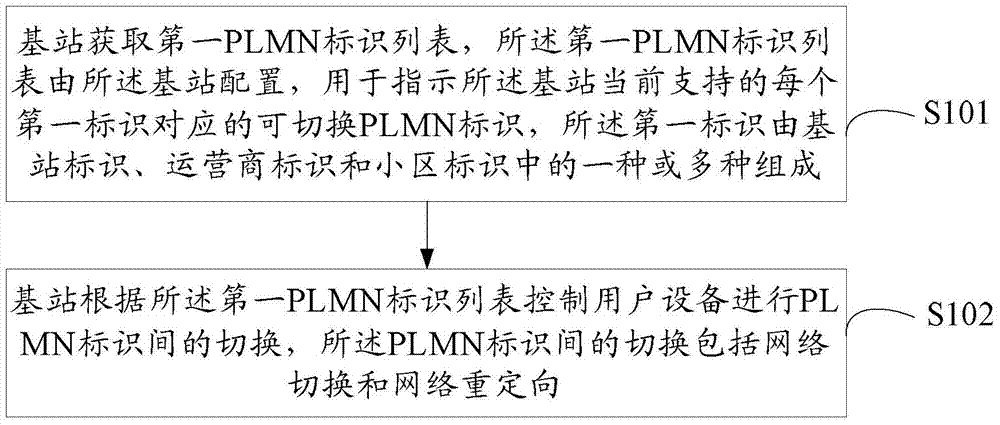
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33 results about "Identity column" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
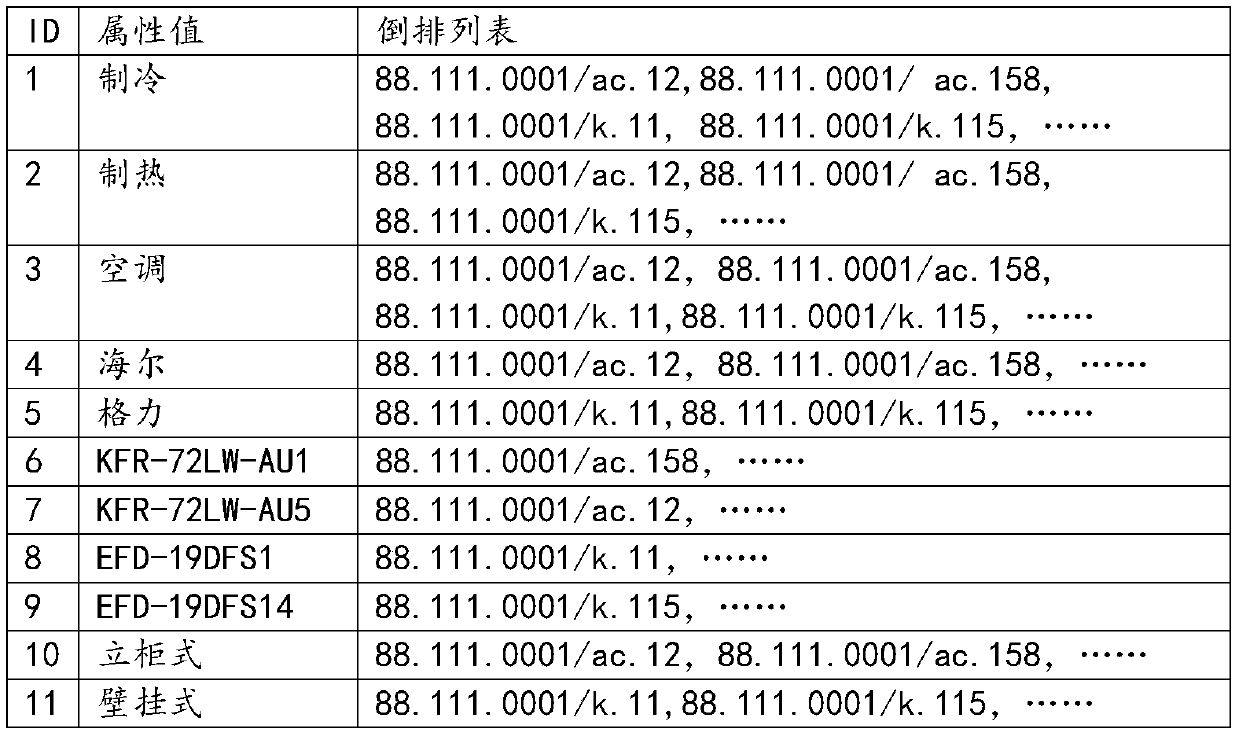
An identity column is a column (also known as a field) in a database table that is made up of values generated by the database. This is much like an AutoNumber field in Microsoft Access or a sequence in Oracle. Because the concept is so important in database science, many RDBMS systems implement some type of generated key, although each has its own terminology.
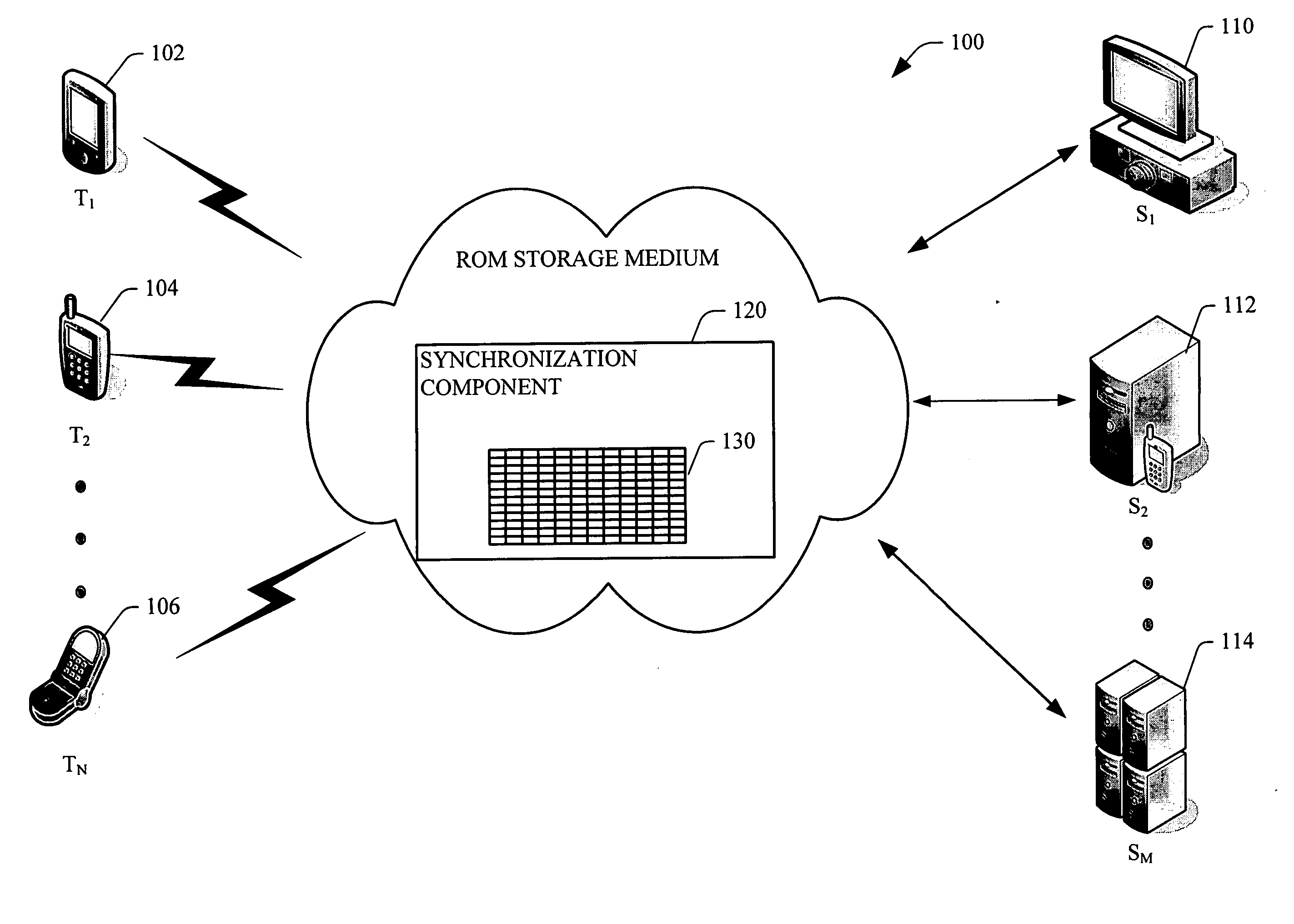
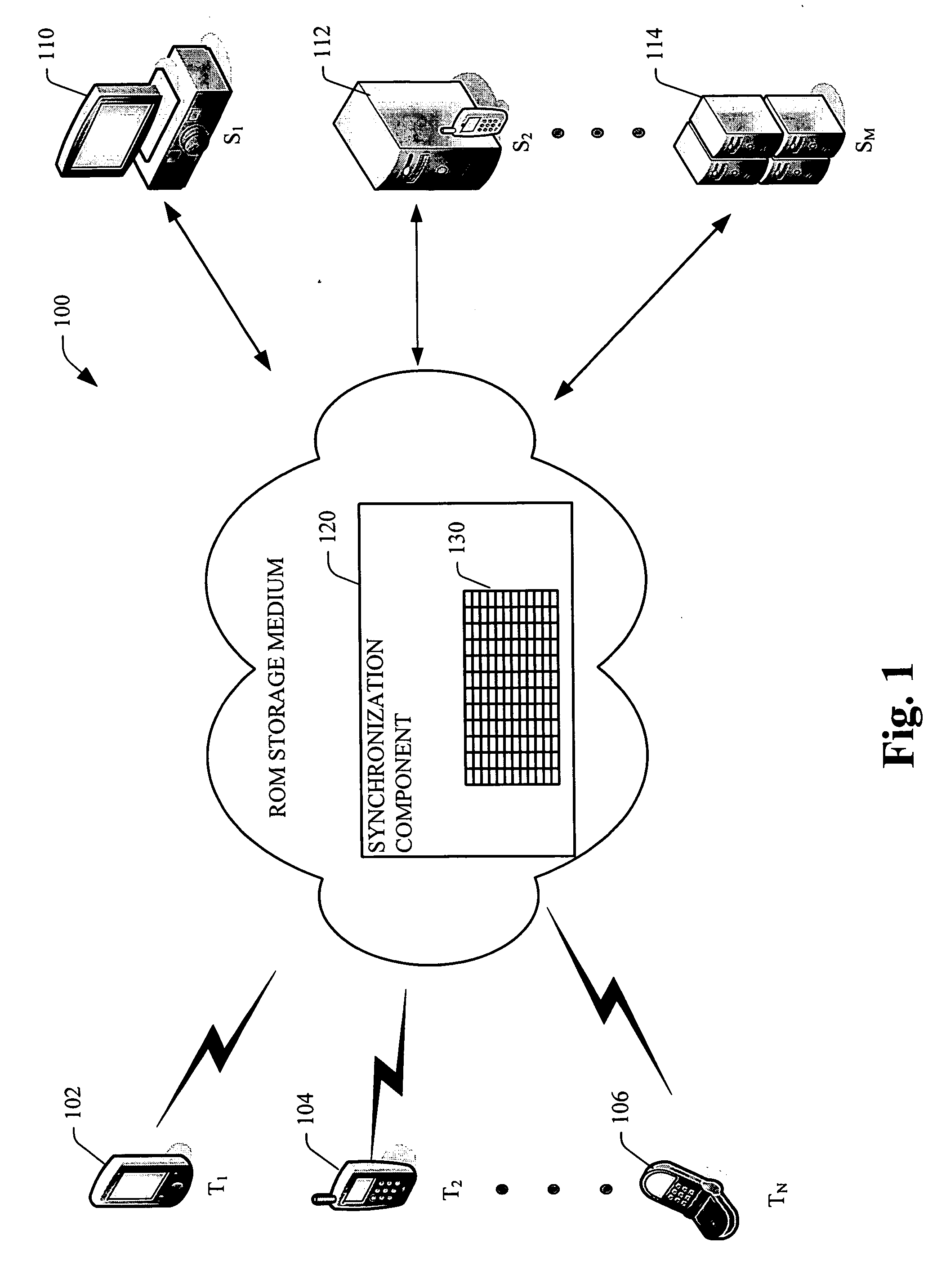
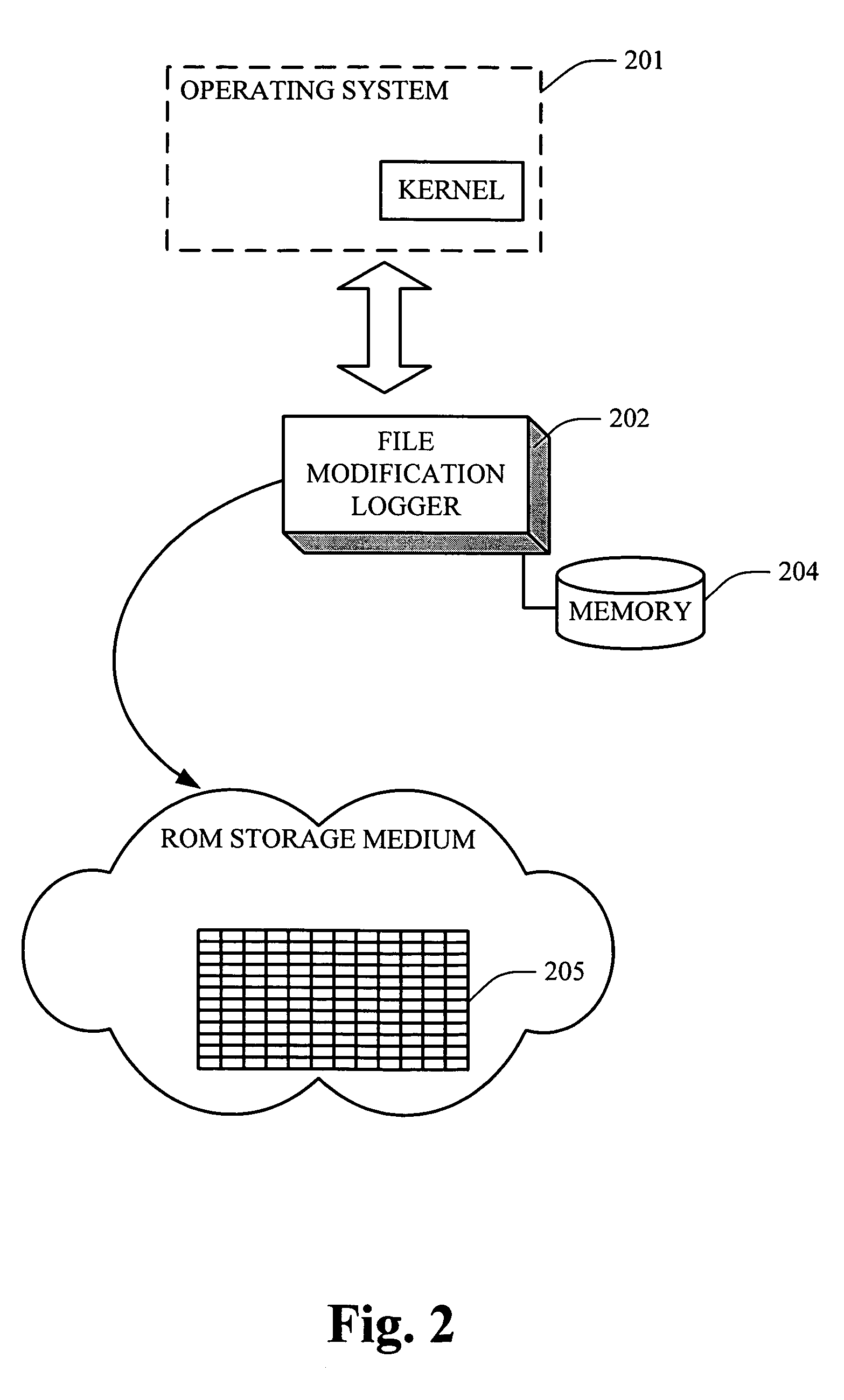
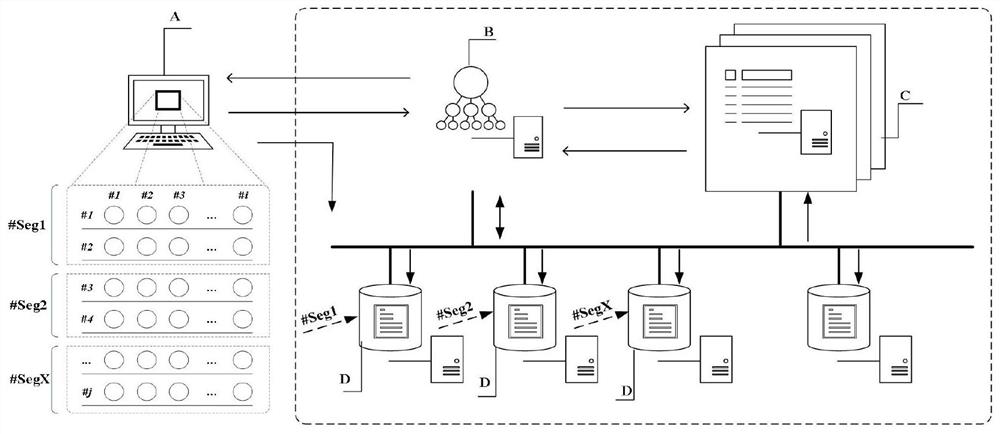
Persistent storage file change tracking
ActiveUS20060277223A1Digital data information retrievalData processing applicationsFile systemMobile device
Systems and methodologies that facilitate synchronization of a mobile device with a source, via employing a file change tracking database table created in non-volatile memory to designate files for synchronization. The subject invention includes a file modification logger that detects and track changes to files across multiple file systems. The file change tracking database table has a plurality of columns such as: a unique identification column that identifies a file, a file name, previous time the file was changed, and previous time the file was synchronized with a particular machine. A list of files that have changed between a current time and an earlier time can be designated for synchronization, by evaluating when was the file last changed and / or synchronized with a source device (e.g., a desktop, lap top and the like.)
Owner:MICROSOFT TECH LICENSING LLC
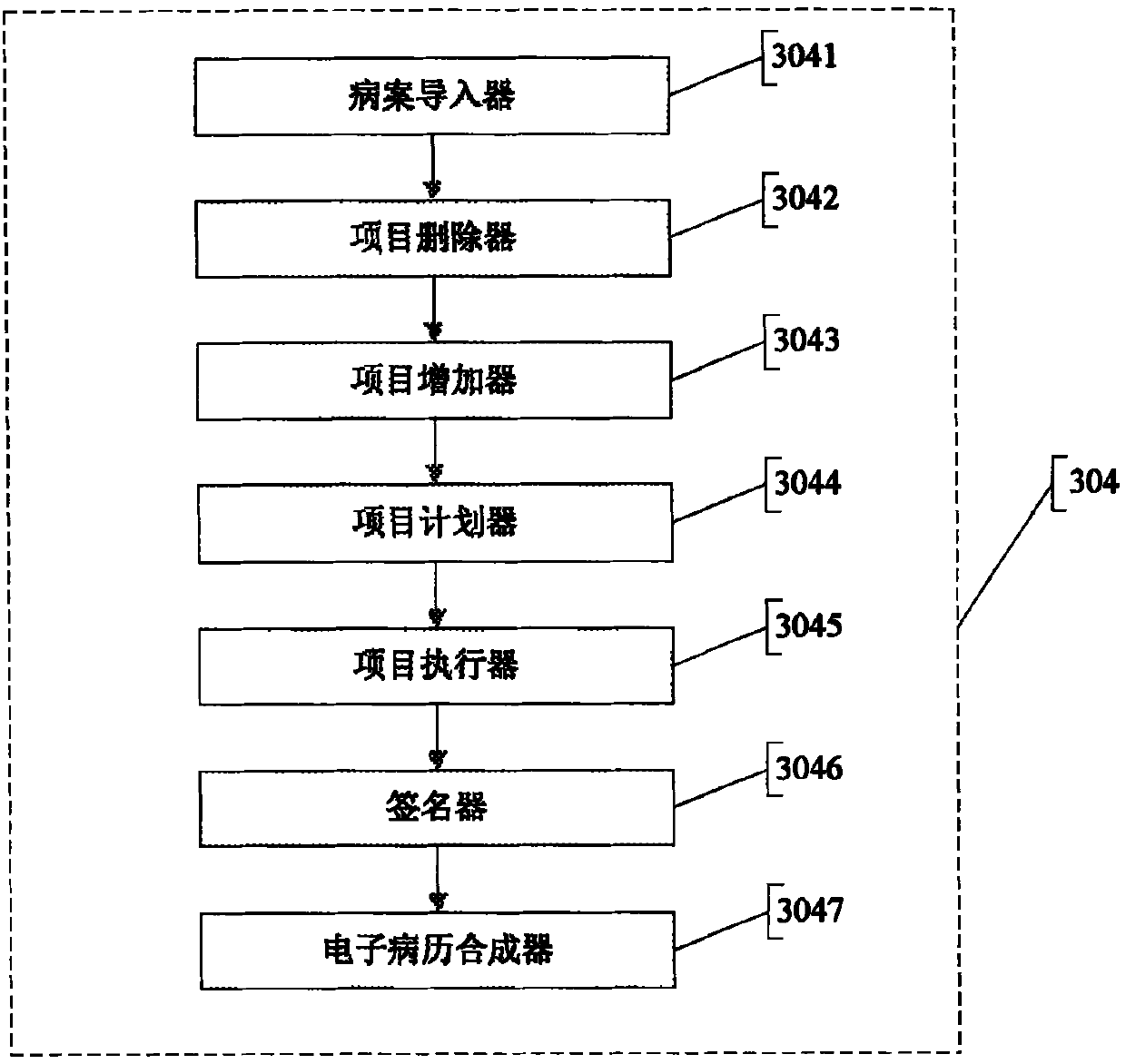
Electronic medical record and method and system for controlling medical process on the basis of same
InactiveCN101908093AImprove accuracyGuarantee authenticitySpecial data processing applicationsMedical recordDisease
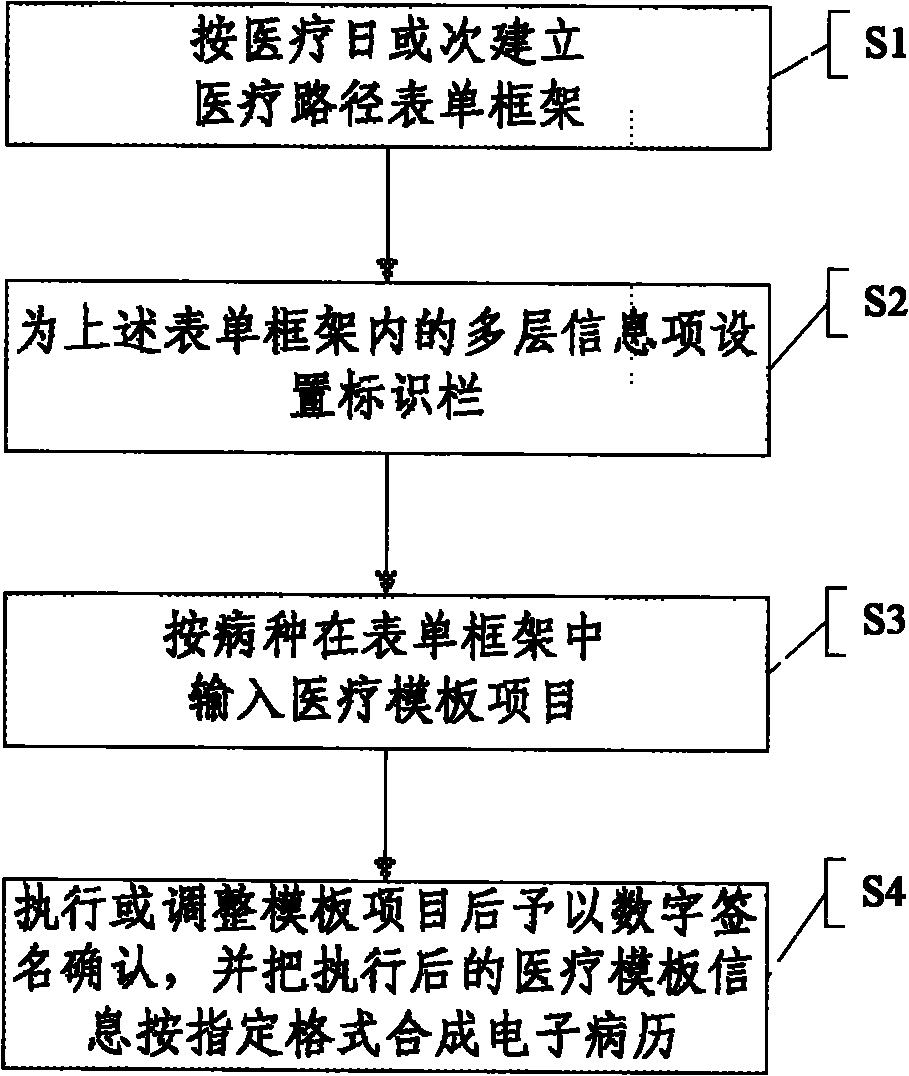
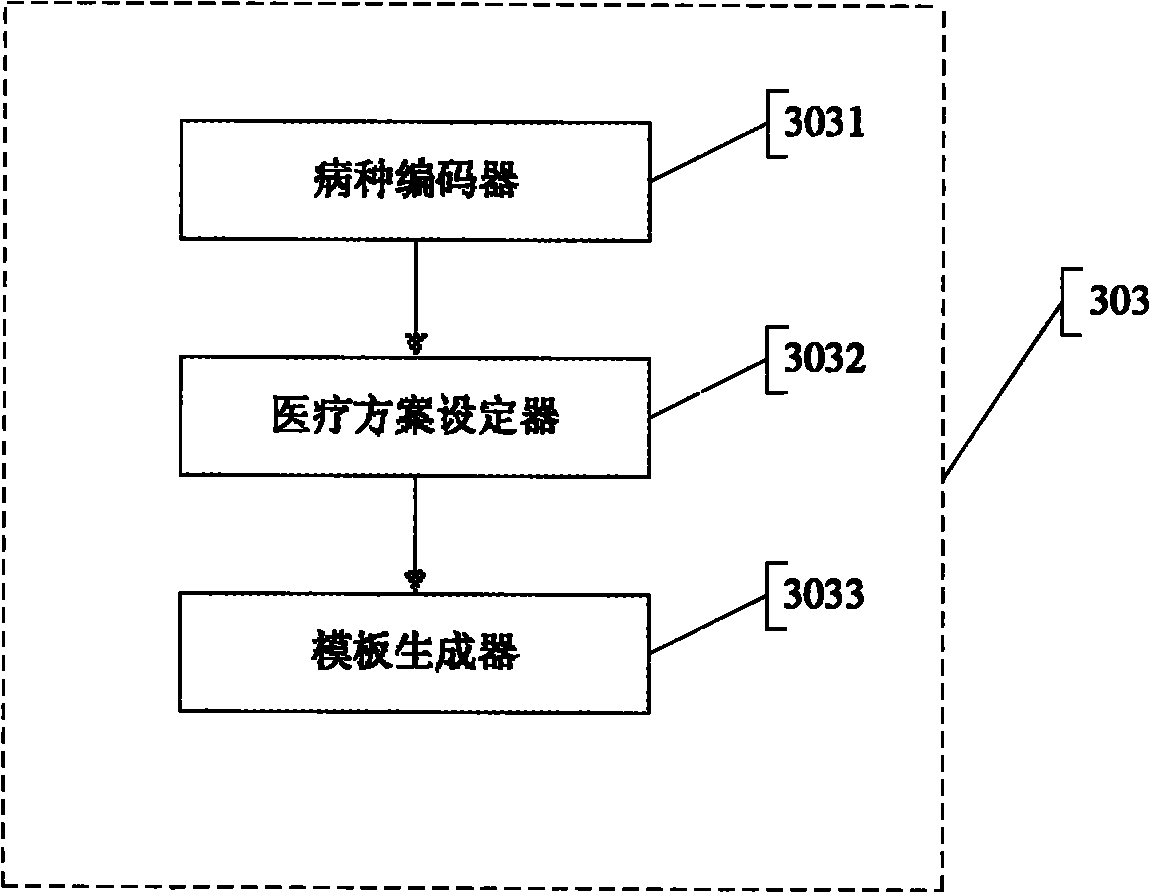
The invention discloses an electronic medical record and a method and a system for controlling the medical process on the basis of the same. The method for controlling the medical process comprises the following steps of: establishing a medical path form frame according to medical dates or times; setting identity columns for multi-layer information items inside the medical path form frame; inputting medical template items into the medical path form frame according to disease kinds; executing or regulating the medical template items, and then carrying out digital signature confirmation; and combining executed medical template information into the electronic medical record according to a specified format. The invention provides the method for controlling the medical process of a disease by adopting a standard clinical path for doctors, thereby ensuring the medical quality; and in addition, the invention records and manages the information of the medical process, thereby generating the electronic medical record.
Owner:田小平
Method, device and system used for configuring and generating application software report forms
InactiveCN102184099AReduce developmentSave human resourcesSpecific program execution arrangementsOperational costsSoftware engineering
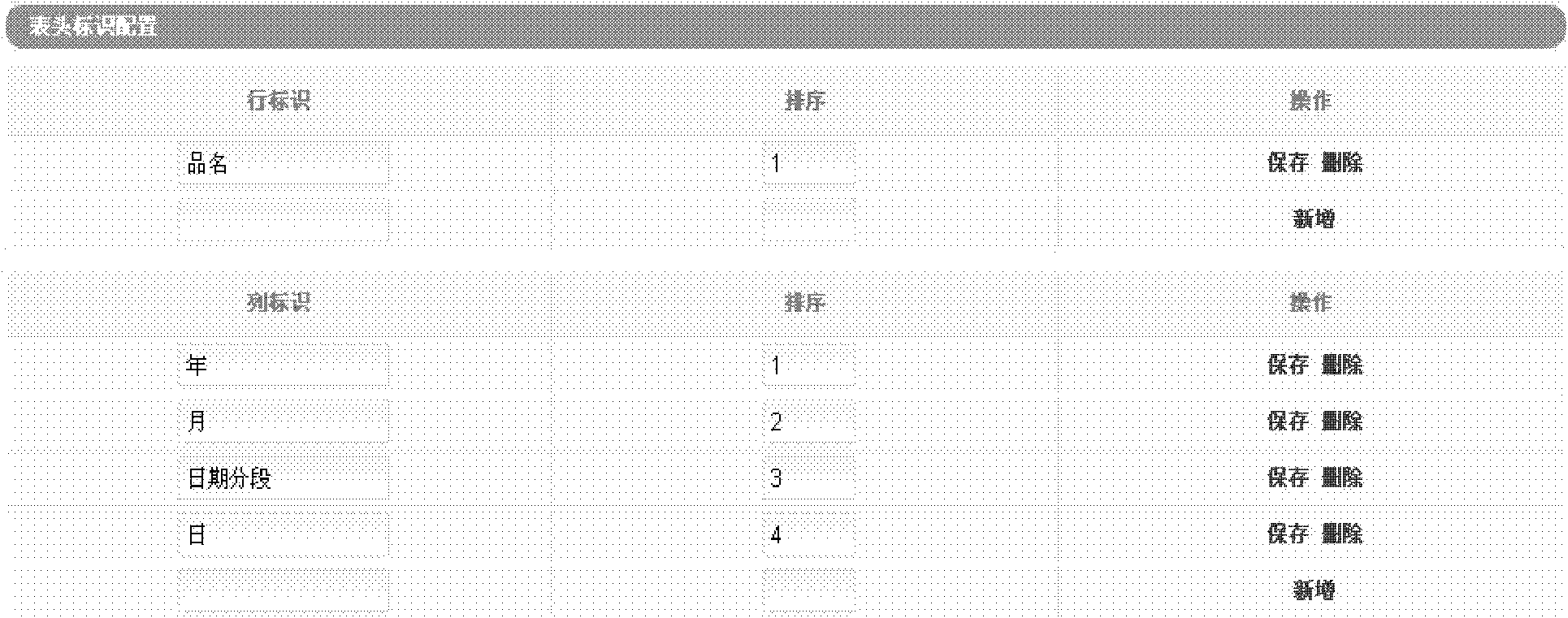
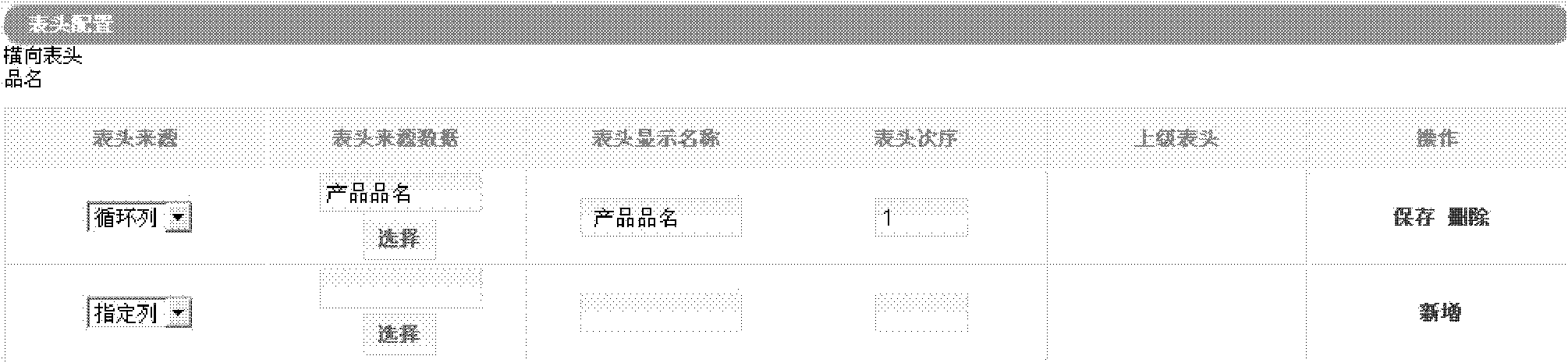
The embodiment of the invention provides a method, a device and a system used for configuring and generating application software report forms, belonging to the field of data processing. The embodiment of the method configuring the application software report form comprises the steps of configuring row identifier, column identifier, the sequencing corresponding to the row identifier, and the sequencing corresponding to the column identifier; configuring a transverse head of form according to the sequencing corresponding to the row identifier on the basis of the row identifier; configuring a longitudinal head of form according to the sequencing corresponding to the column identifier on the basis of the column identifier; configuring a data cell, and enabling each data cell to be relevant to the transverse head of form and the longitudinal head of form. The embodiment of the method reduces operating costs.
Owner:北京高森明晨信息科技有限公司
Event data processing method and device based on knowledge graph, equipment and medium
ActiveCN113590737APrecise positioningFast indexing capabilityNatural language data processingText database indexingTarget arrayTheoretical computer science
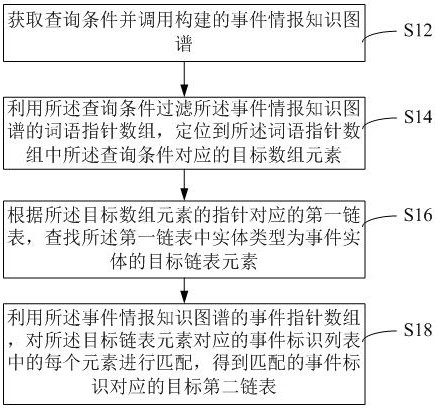
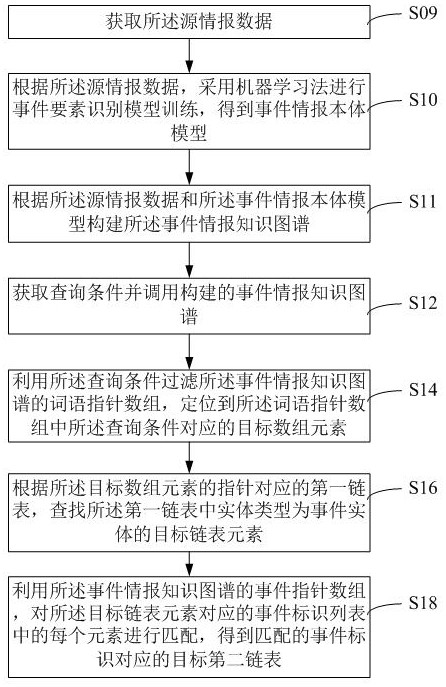
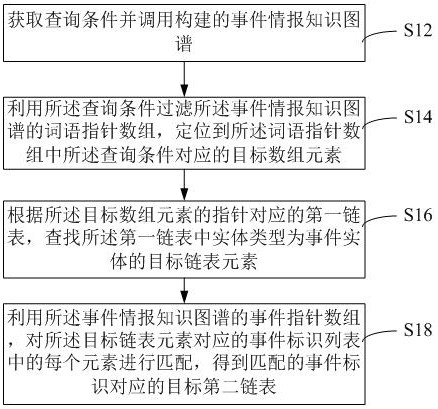
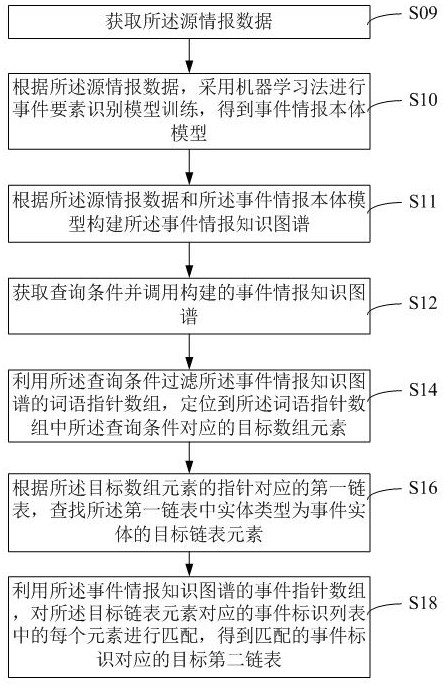
The invention relates to an event data processing method and device based on a knowledge graph, equipment and a medium. The method comprises the steps of obtaining a query condition; filtering a word pointer array of the called event intelligence knowledge graph by utilizing the query condition, and positioning a target array element corresponding to the query condition in the word pointer array; and matching each element in the event identifier list corresponding to the target linked list element by utilizing an event pointer array of the event information knowledge graph to obtain a target second linked list corresponding to the matched event identifier so as to indicate element information of the target event information corresponding to the to-be-retrieved event in the event information knowledge graph. The event information knowledge graph comprises an event entity, a time entity, a place entity, a figure entity, an origin entity, a passing entity and a result entity, and the relation types of the graph comprise a time description relation, a place description relation, a participation description relation and a development description relation. And analysis processing of event information data can be reliably completed.
Owner:NAT UNIV OF DEFENSE TECH
Secure communication system for improving a software defined network
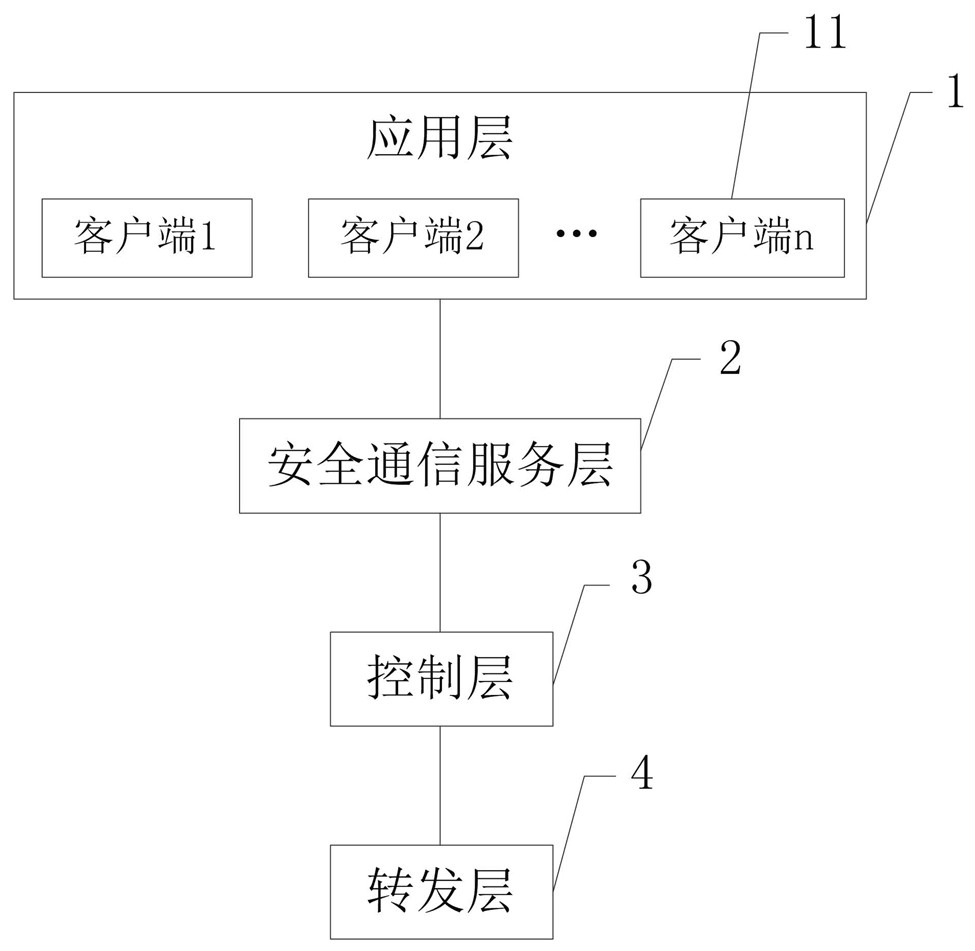
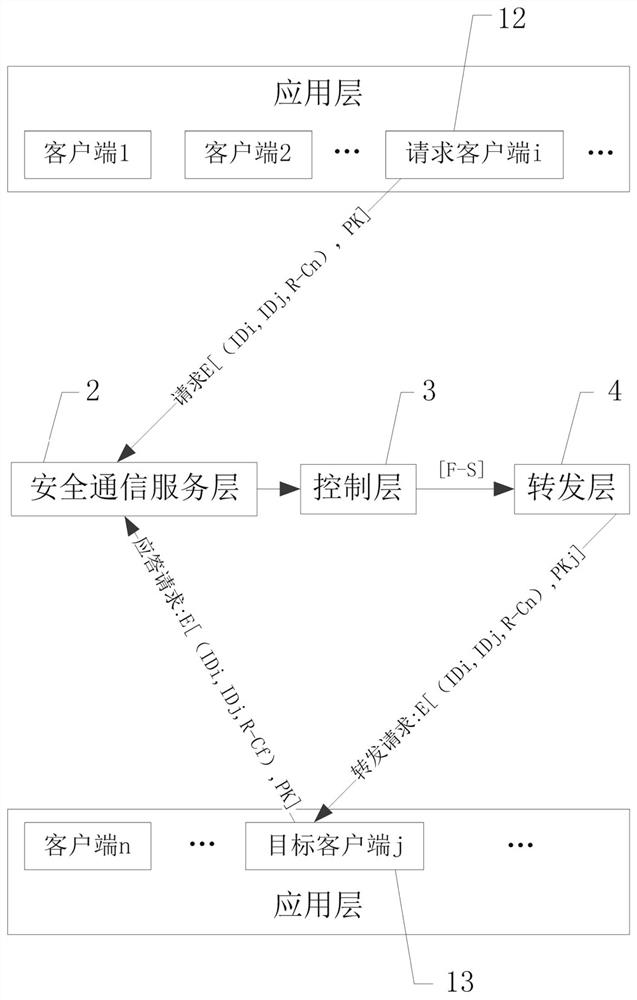
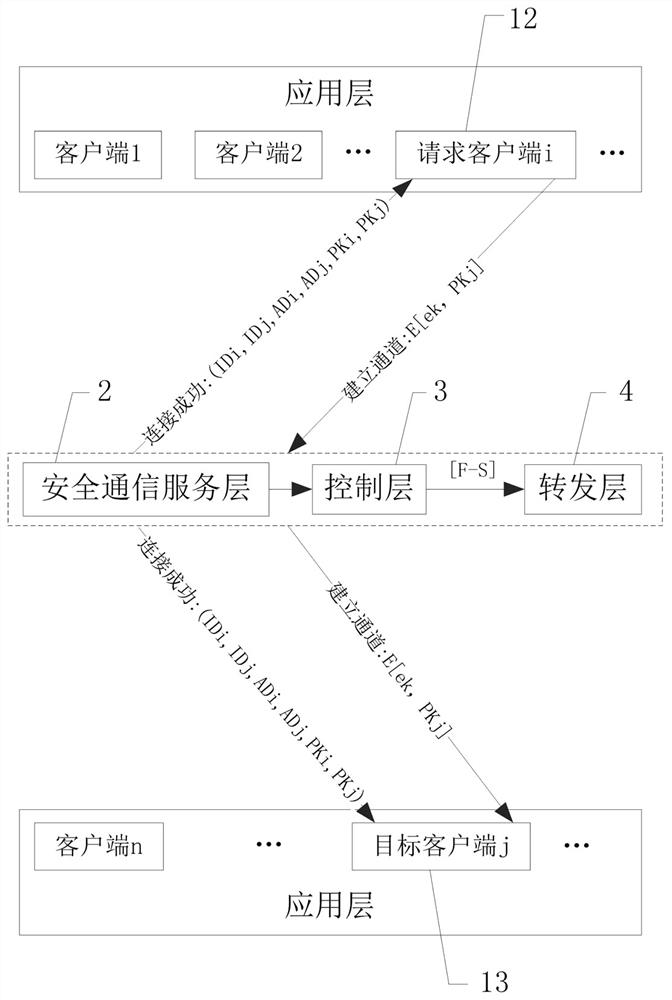
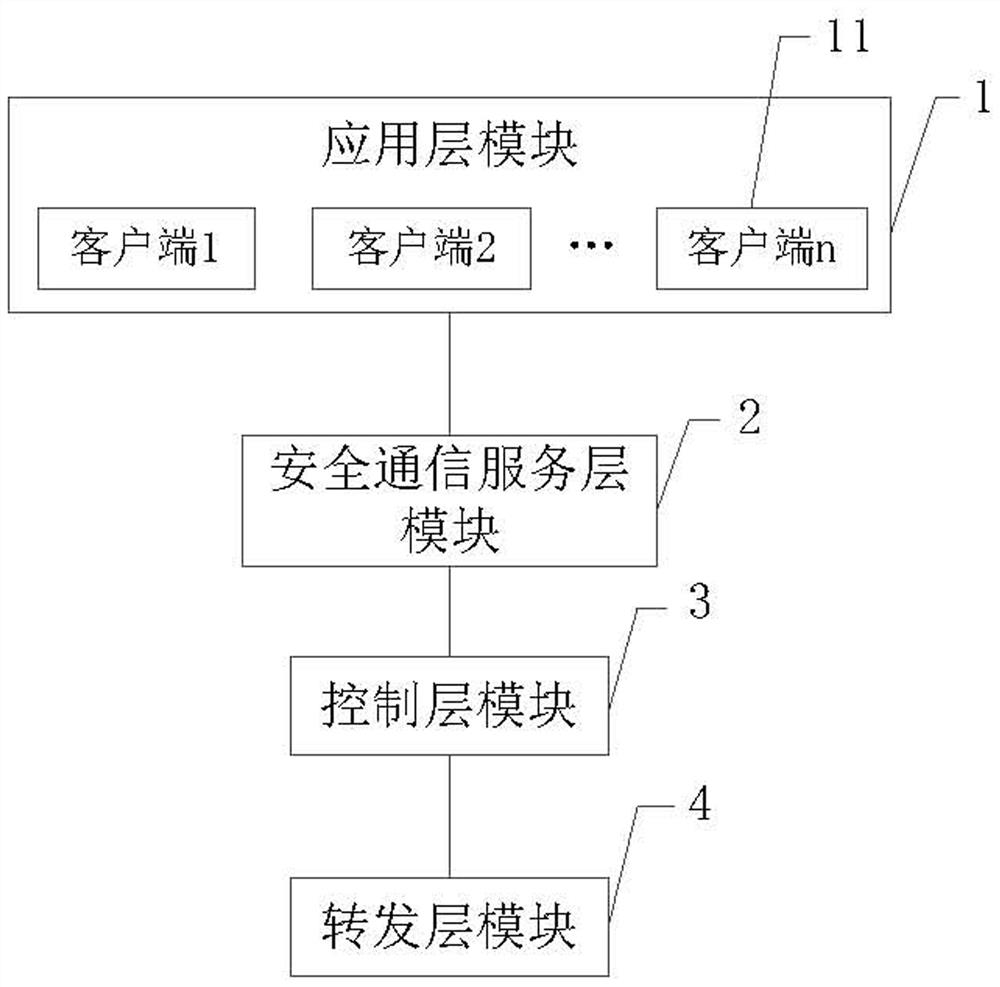
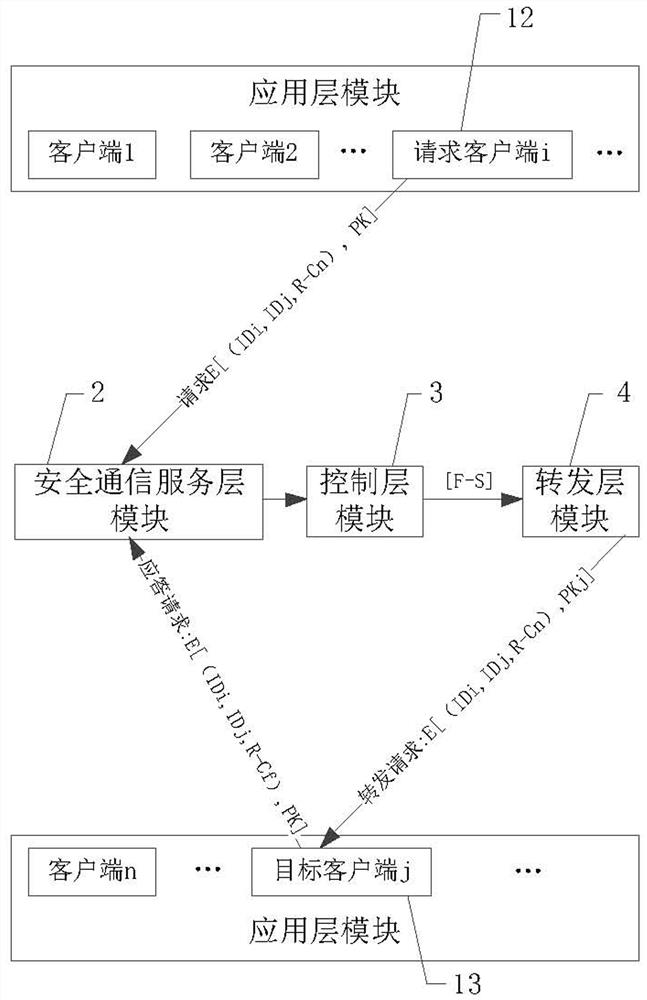
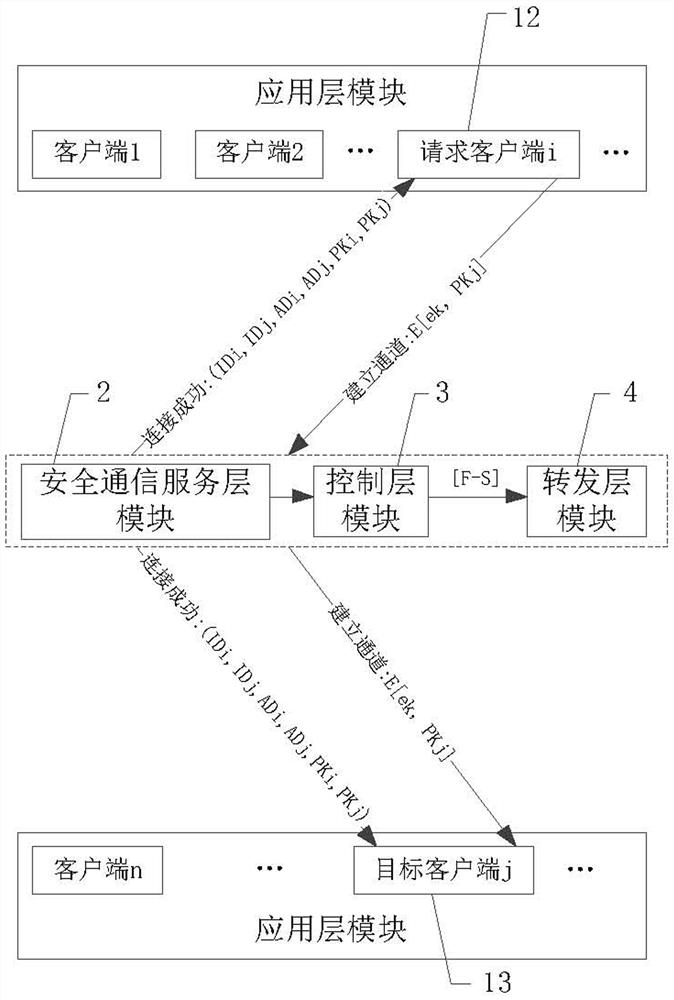
ActiveCN111934888APrivacy protectionReliable communicationUser identity/authority verificationEngineeringNetwork address
The invention discloses a secure communication system for improving a software defined network. The secure communication system comprises an application layer, a secure communication service layer, acontrol layer and a forwarding layer, wherein the application layer comprises a plurality of clients, and the clients are used as request clients or target clients; and the security communication service layer is provided with a security database, and the security database stores a client identity identifier list, a security communication service layer public and private key pair, a plurality of client public keys and a plurality of client network addresses. The problem that privacy is prone to leakage due to the fact that information and data of an existing software-defined network are spreadon the network in a plaintext mode can be solved. The external malicious invasion is easily caused by programmability of a software-defined network, and the like.
Owner:南京可信区块链与算法经济研究院有限公司
User authentication method and device, server and storage medium
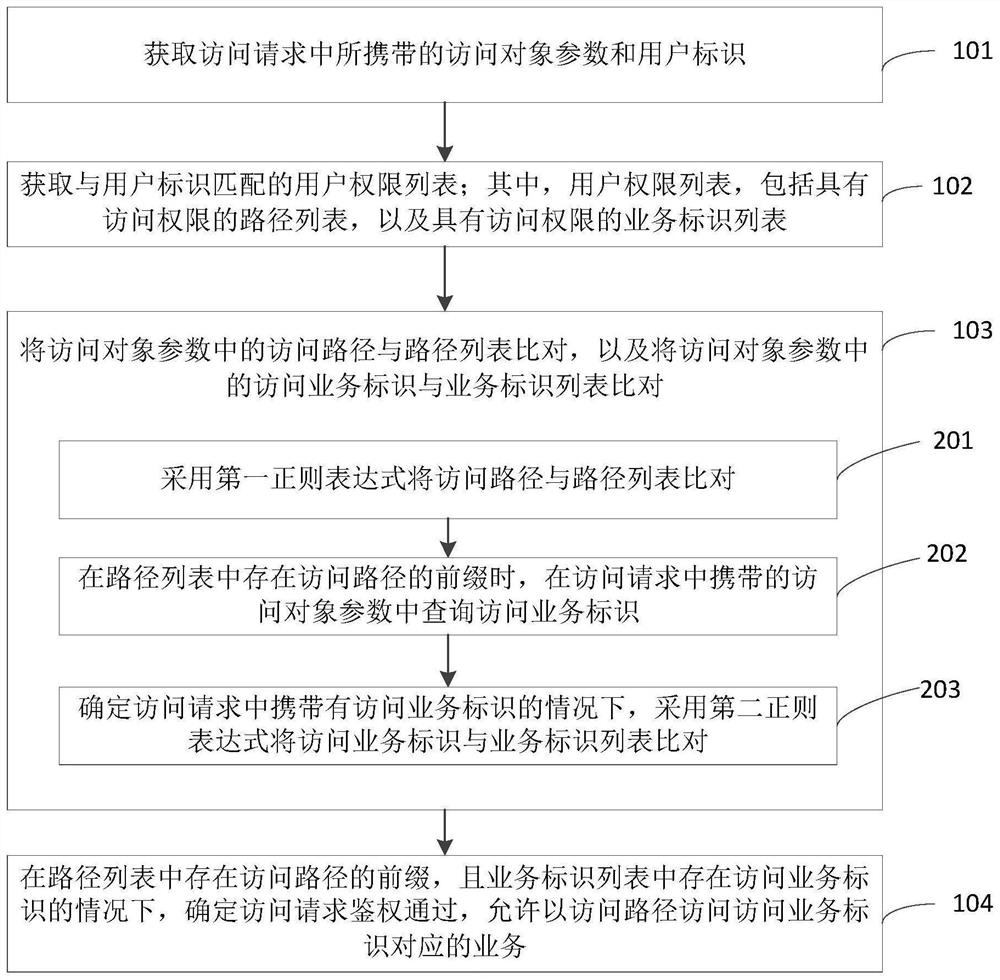
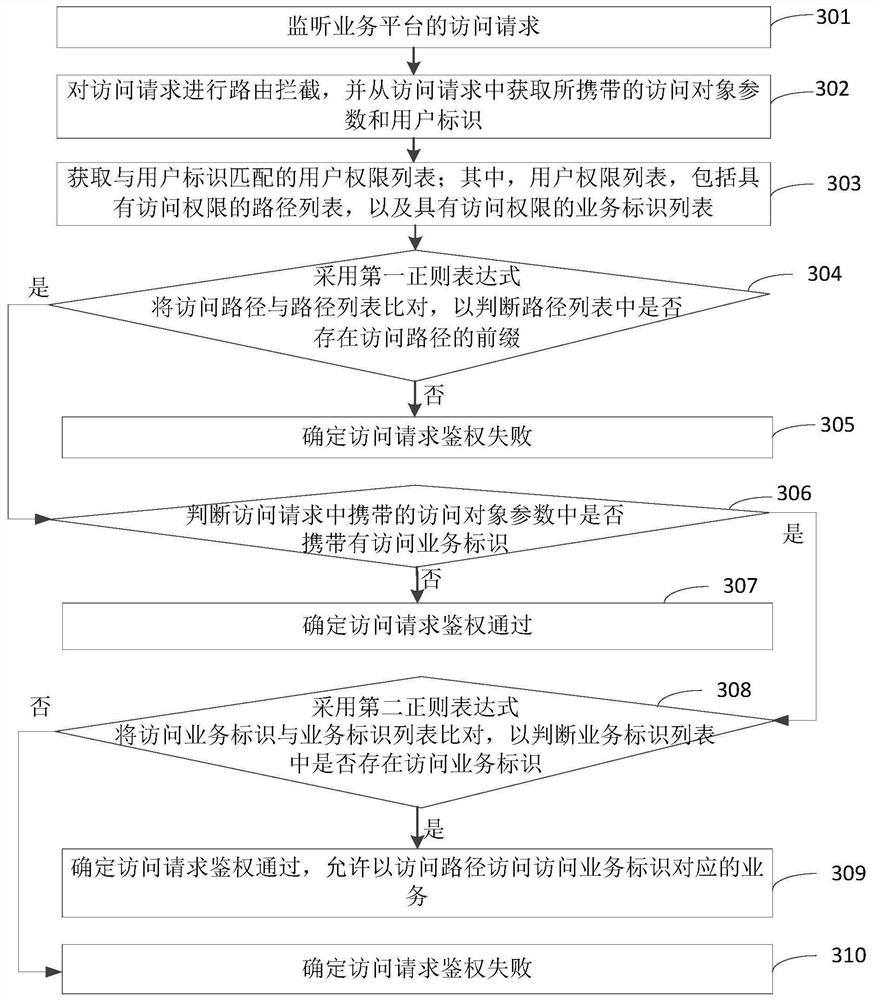
PendingCN112507298ARealize authenticationImprove authentication speedDigital data authenticationOther databases queryingPathPingUser Privilege
The invention relates to a user authentication method and device, a server and a storage medium, and relates to the technical field of computers, and the method comprises the steps of obtaining an access object parameter and a user identification carried in an access request; obtaining a user permission list matched with the user identifier, wherein the user permission list comprises a path list with access permission and a service identifier list with access permission; comparing an access path in the access object parameter with a path list, and comparing an access service identifier in theaccess object parameter with a service identifier list; and under the condition that the prefix of the access path exists in the path list and the access service identifier exists in the service identifier list, determining that the access request passes the authentication, and allowing the access path to access the service corresponding to the access service identifier. The authentication of theaccess request of the user is realized, the authentication speed is improved, and the workload of authority maintenance is reduced.
Owner:BEIJING DAJIA INTERNET INFORMATION TECH CO LTD
Load balancing method, device and system
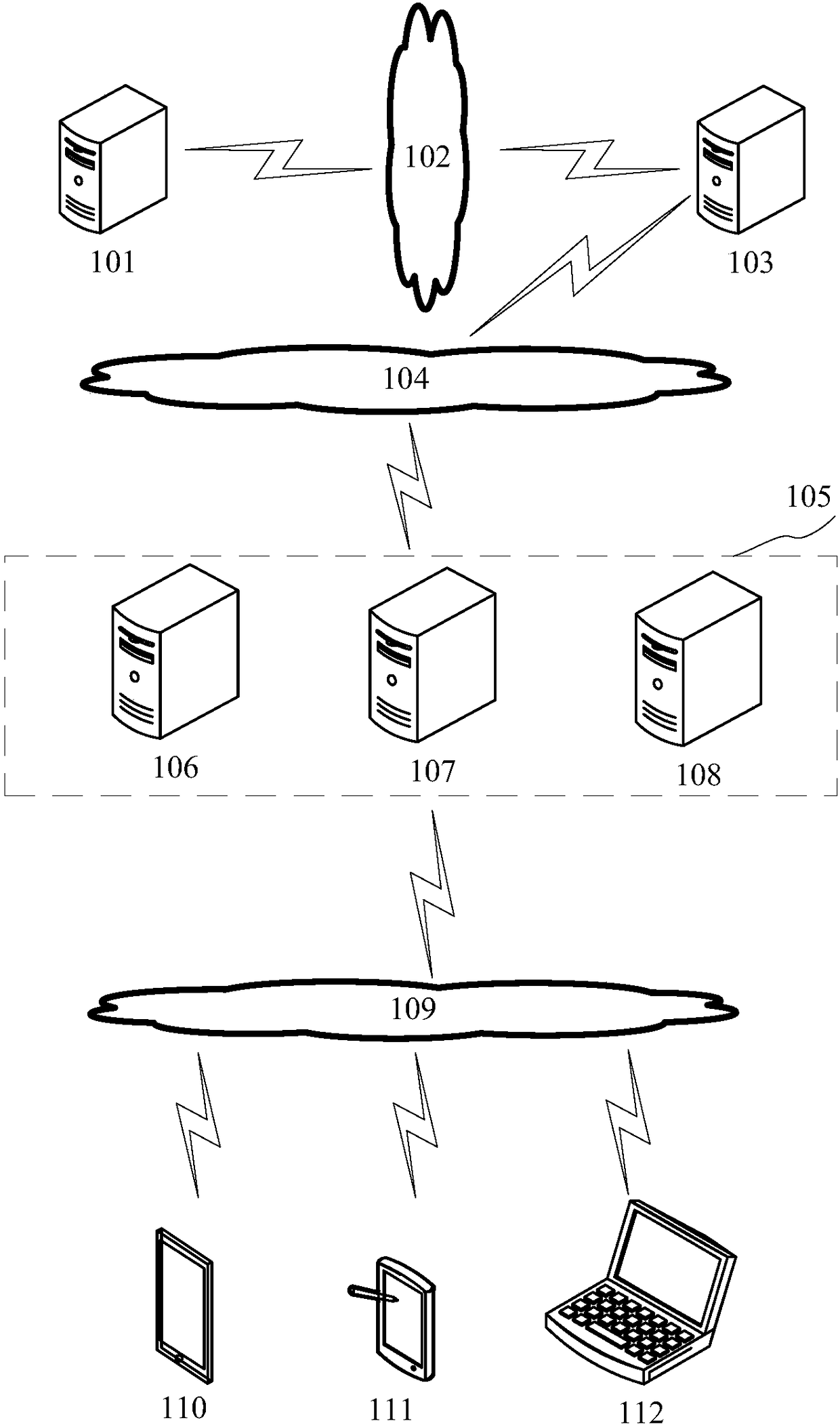
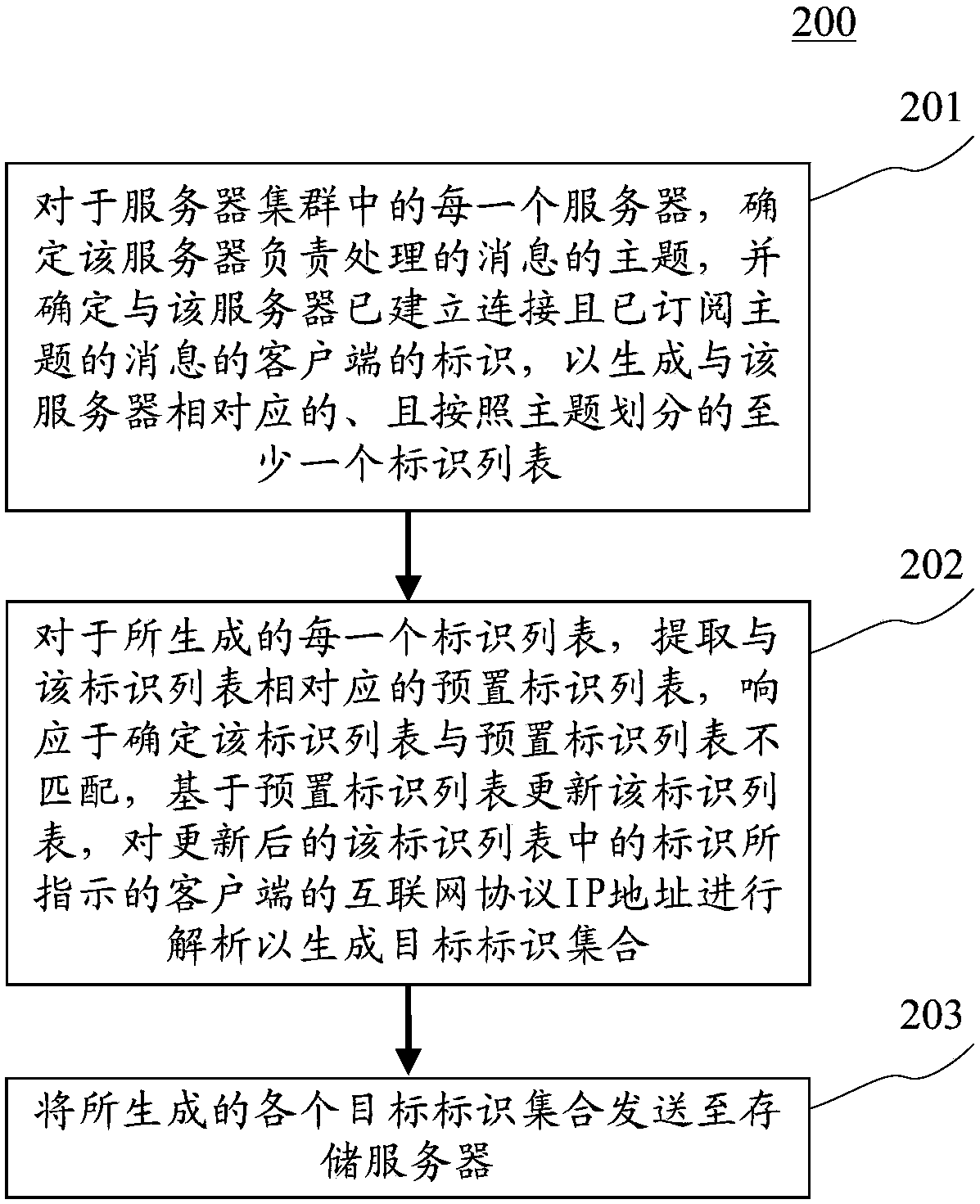
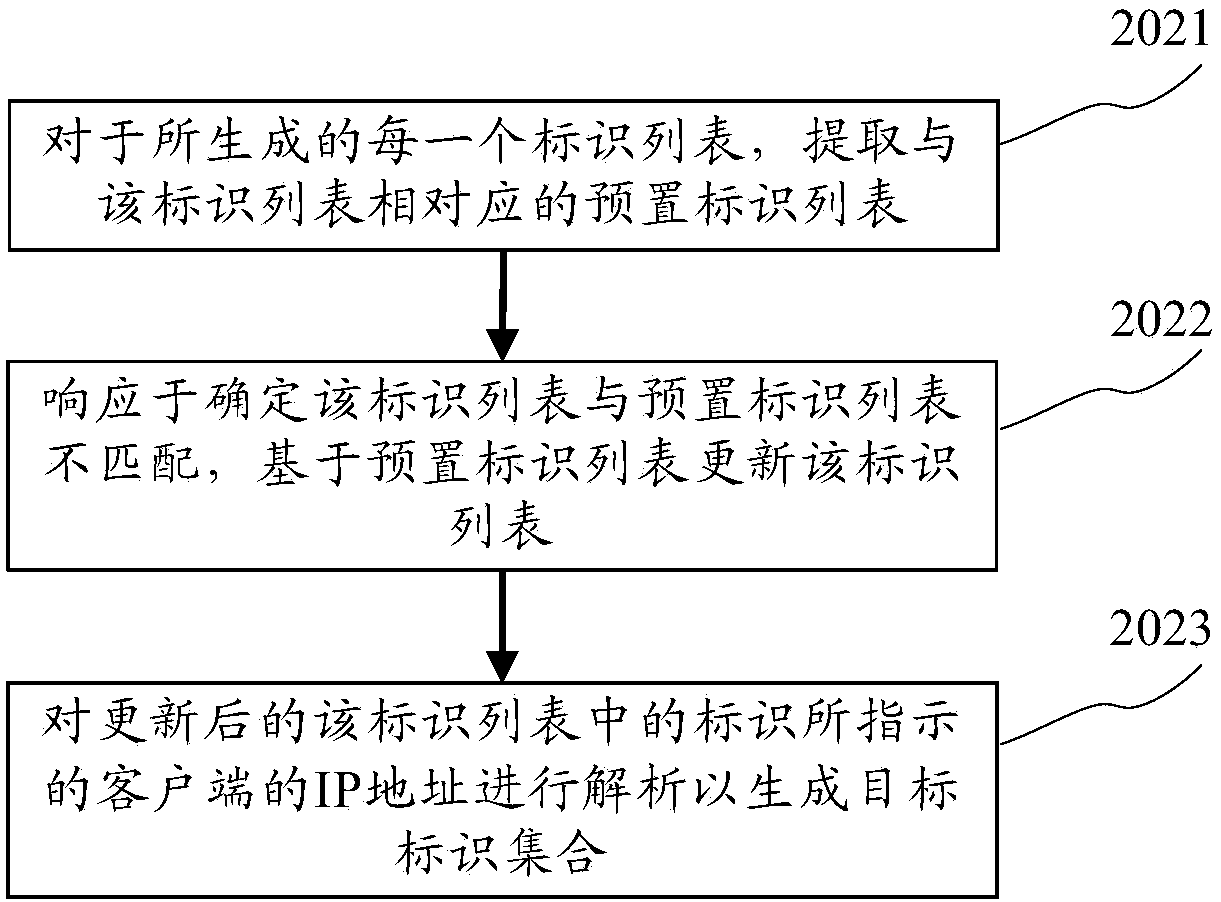
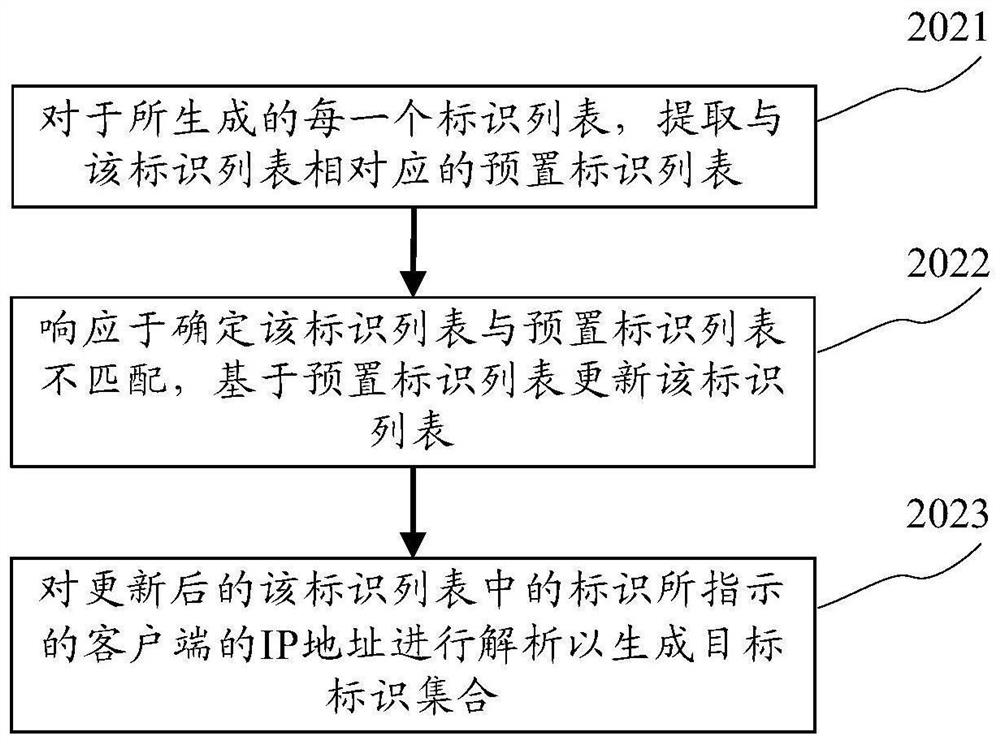
ActiveCN108696549AReduce the number of connectionsImprove the efficiency of connection establishmentTransmissionIp addressClient-side
The application discloses a load balancing method, device and system. A specific embodiment of the load balancing method comprises the following steps: for each server in a server cluster, a subject of the messages processed by the server is confirmed, and an identifier of a client which establishes a connection with the server and makes subscription to the messages of the subject is confirmed, soas to generate at least one identifier list that is corresponding to the server and is divided according to the subject; for each generated identifier list, a preset identifier list corresponding tothe identifier list is extracted, and the identifier list is updated based on the preset identifier list in response to that the identifier list does not match the preset identifier list; the IP address of the clients indicated by the identifier in the updated identifier list is parsed to generate a target identifier set; and each generated target identifier set is sent to the storage server. Theembodiment of the load balancing method improves the efficiency of establishing the connection and improves the stability of the connection.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Data uniqueness identification method in database
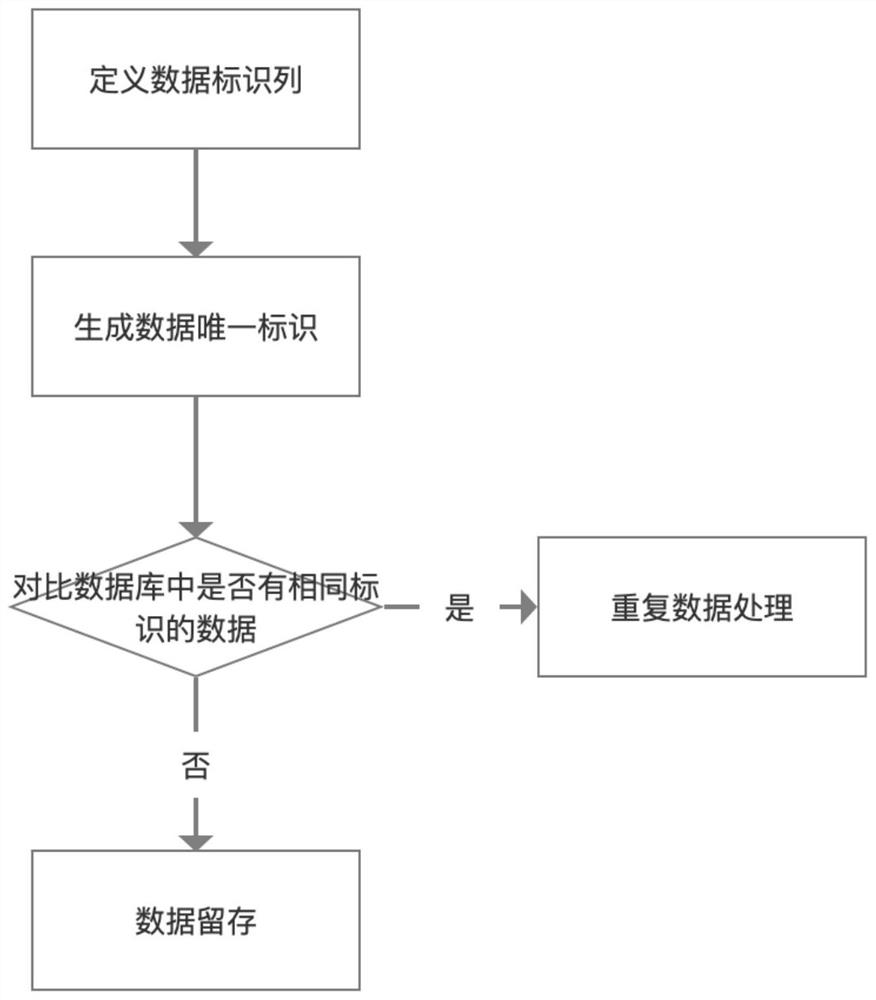
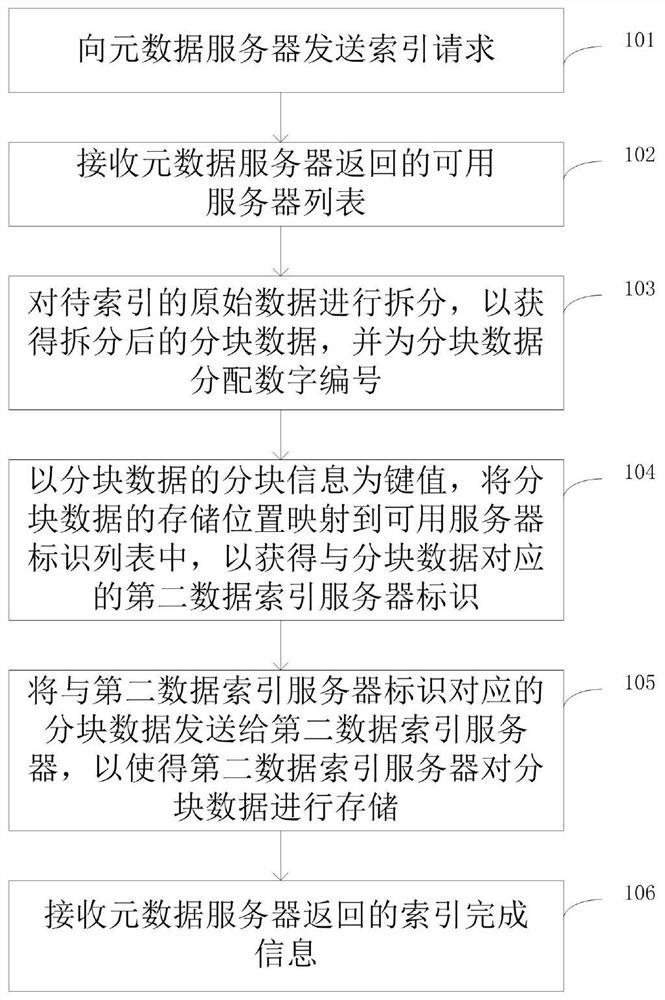
PendingCN113760907ASave resourcesSolve the technical problem of not being able to effectively identify the uniqueness of the recorded data contentSpecial data processing applicationsDatabase indexingOriginal dataData content
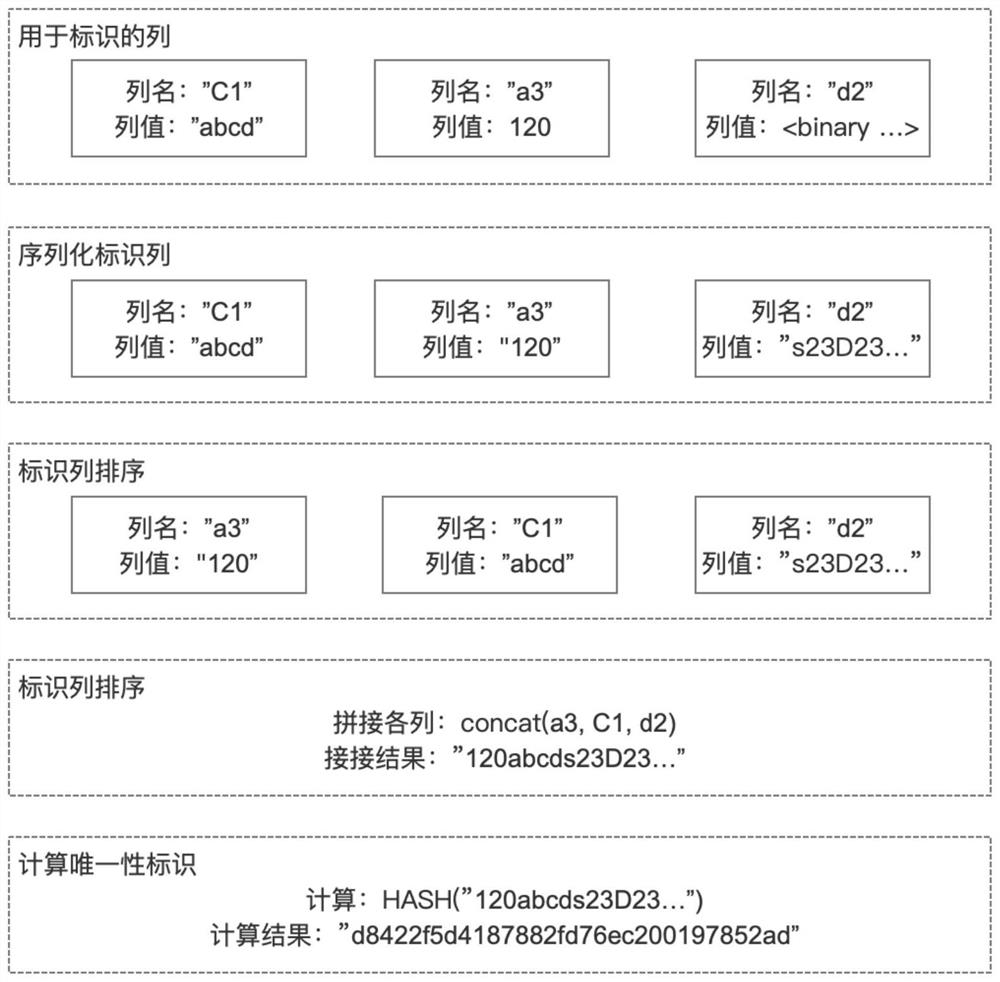
The invention discloses a data uniqueness identification method in a database. The method comprises the following steps: defining a data identification column, namely selecting original data fields, defining a data identification field, selecting a related column of which uniqueness needs to be judged, and adding a new data identification column; generating data unique identification, namely generating the data unique identification for the selected column, and storing a generation result in the newly added identification column for later use; judging data uniqueness, namely comparing a generated uniqueness identification column with a uniqueness identification column of existing data in a database, wherein it is considered that same data exists if same uniqueness identification exists, and it is considered that the same data does not exist if the same uniqueness identification does not exist; when the same data exists, performing related processing on the repeated data according to business scene requirements; and when the same data does not exist, storing new data into the database and adding data initial version identification. According to the invention, the technical problems that only the uniqueness of data records can be kept, and the uniqueness of recorded data content cannot be effectively identified are solved.
Owner:紫金诚征信有限公司
Cross-application login method and device, equipment and medium
PendingCN112287318AEnsure safetyLogin implementationCharacter and pattern recognitionDigital data authenticationComputer hardwareApplication procedure
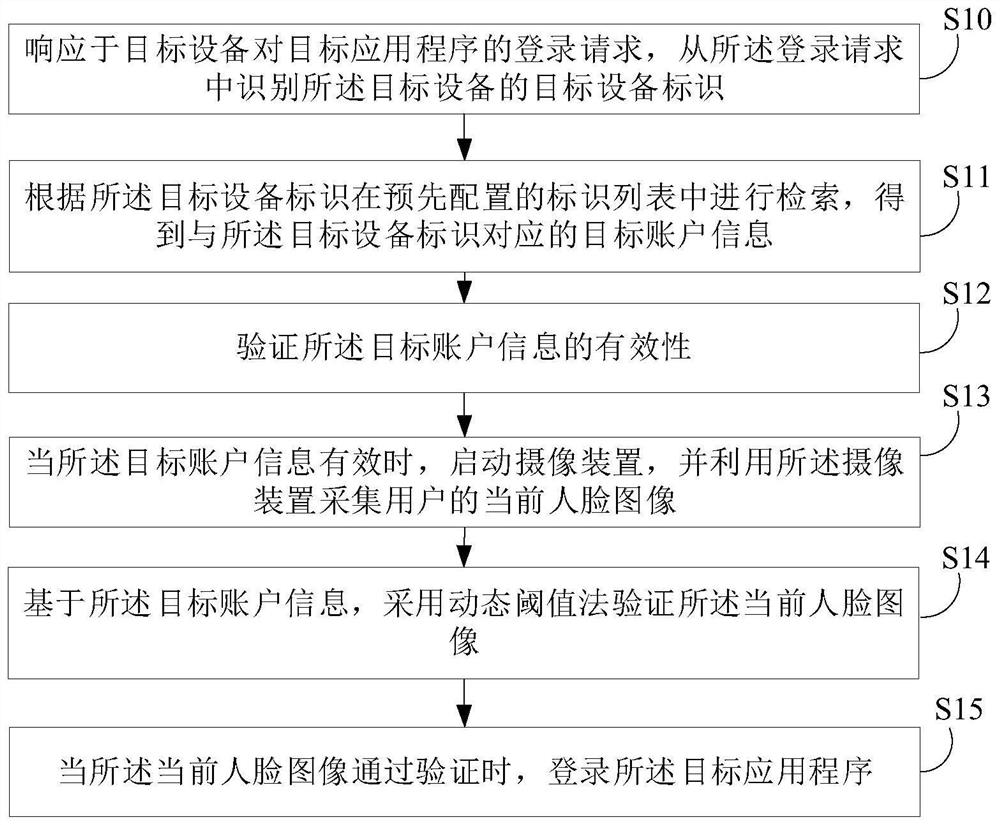
The invention relates to the field of artificial intelligence, and provides a cross-application login method and apparatus, a device and a medium, which can perform retrieval in an identifier list according to a target device identifier to obtain target account information corresponding to the target device identifier, so as to ensure that the target account information corresponding to the targetdevice identifier can be stored in the same group or the same organization. The equipment identifiers of one piece of equipment on different application programs are consistent, verifying the validity of the target account information, acquiring the current face image of the user by utilizing the camera device when the equipment identifiers are valid, verifying the current face image by adoptinga dynamic threshold method based on the target account information, and logging in the target application program when the equipment identifiers pass the verification; therefore, the related information of face authentication can be called through the unified equipment identifier to implement face login, the login security is ensured, cross-application login among different applications in the same organization is realized, and the login efficiency is improved. In addition, the invention also relates to a blockchain technology, and the identification list can be stored in the blockchain node.
Owner:PING AN TECH (SHENZHEN) CO LTD
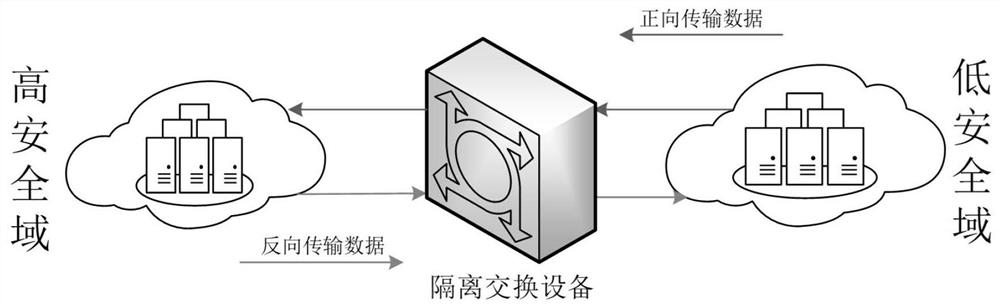
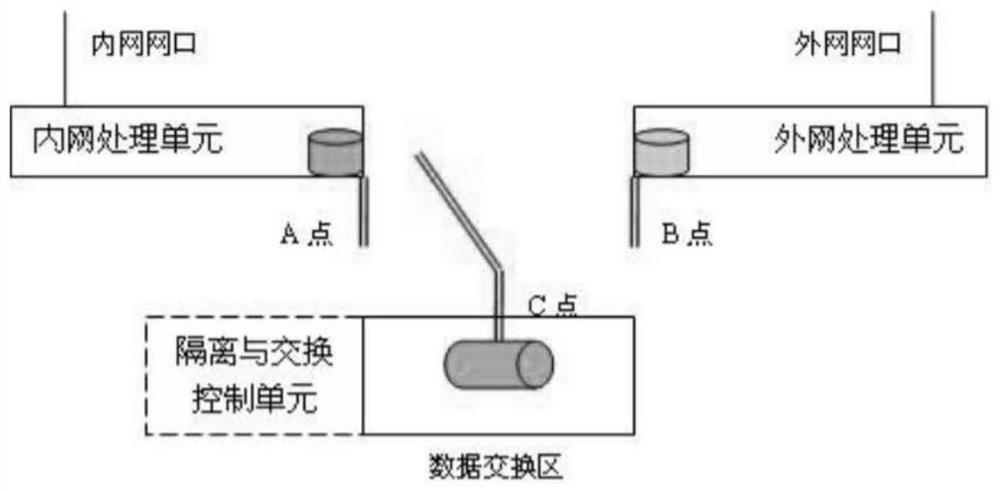
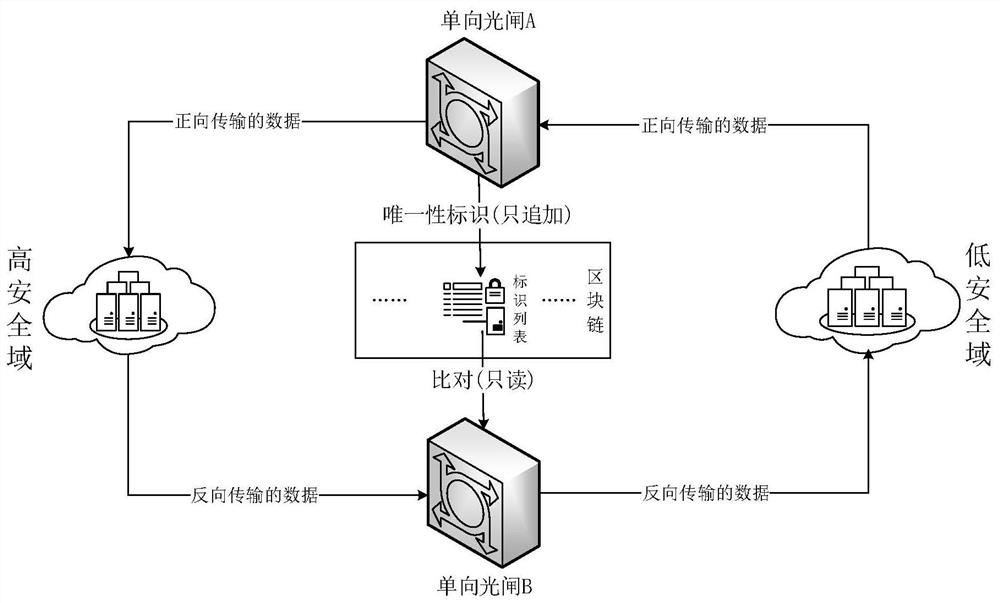
Data cross-security domain reverse transmission method
PendingCN113378205ASimplify the security review processReduce consumptionDigital data protectionData packOriginal data
The invention discloses a data across security domain reverse transmission method, which comprises the following specific steps: S1, acquiring an original data unit in a data packet which needs to be transmitted forwards, performing identity identification operation on the original data unit to obtain a unique identifier, and storing the unique identifier in an identifier list; s2, when a data packet needs to be reversely transmitted, firstly obtaining a to-be-checked data unit in the data packet which needs to be reversely transmitted; performing identity identification operation on the to-be-checked data unit to obtain a unique identification; reading the identifier list, comparing the obtained unique identifier with the unique identifier in the identifier list, and if the obtained unique identifier is in comparison with the unique identifier in the identifier list, releasing the data packet; otherwise, forbidding the release of the data packet. According to the invention, the data security examination step of the intranet processing unit can be simplified, and the cross-security domain communication efficiency is improved.
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY +1
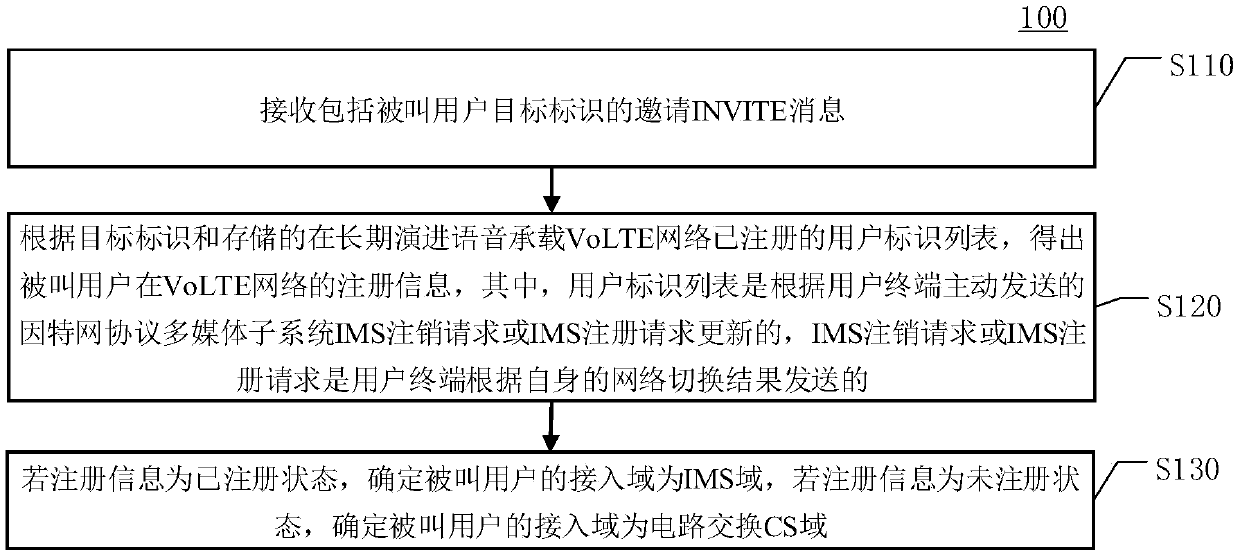
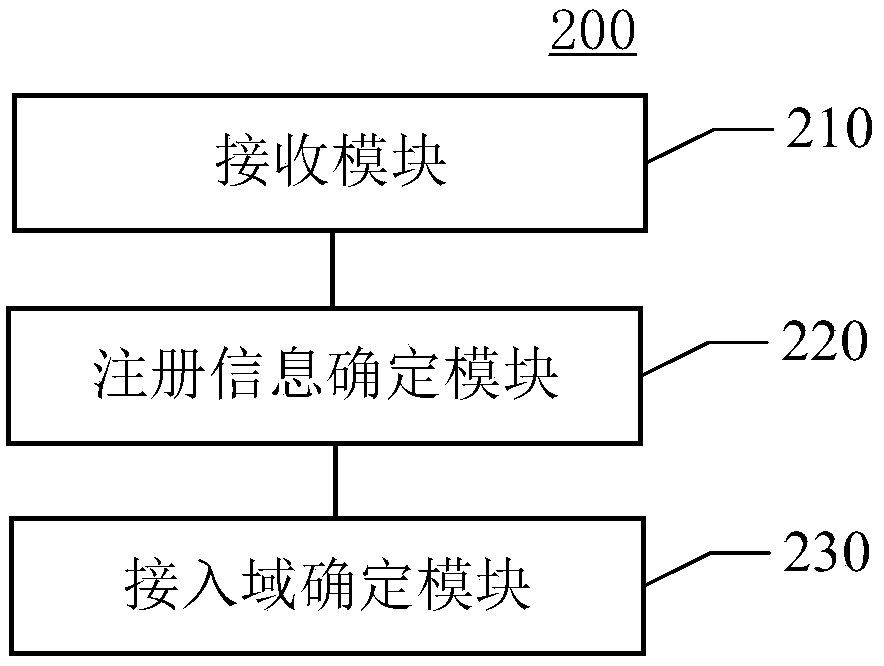
Determination method of access domain and auxiliary method for determining access domain
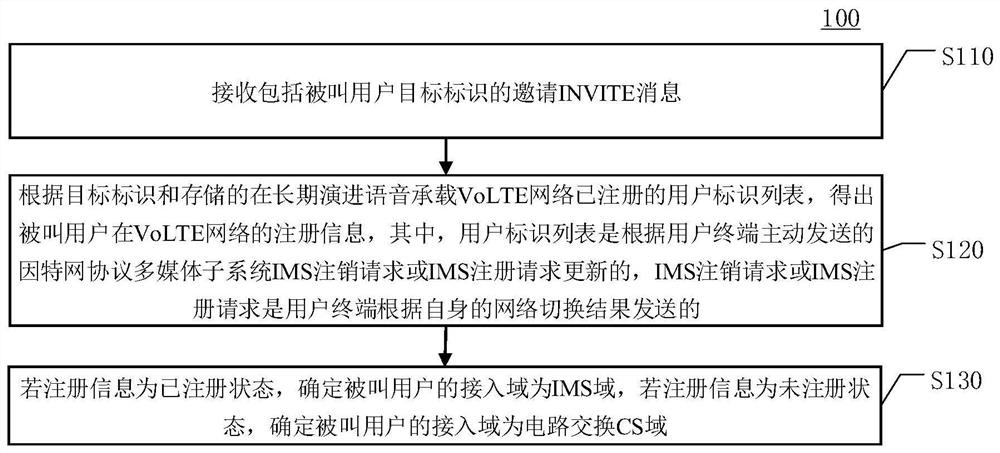
The invention discloses a method for determining an access domain and an auxiliary method for determining the access domain. The method for determining the access domain comprises the following steps:receiving an INVITE message comprising a called user target identifier; obtaining registration information of the called user in the VoLTE network according to the target identifier and a stored useridentifier list registered in the VoLTE network; if the registration information is in a registered state, determining that the access domain of the called user is an internet protocol multimedia subsystem IMS domain; and if the registration information is in an unregistered state, determining that the access domain of the called user is a circuit switching (CS) domain. The user identification list is updated according to an IMS logout request or an IMS registration request actively sent by the user terminal, and the IMS logout request or the IMS registration request is sent by the user terminal according to a network switching result of the user terminal. According to the access domain determination method and the auxiliary method for determining the access domain provided by the embodiment of the invention, the access domain can be rapidly determined.
Owner:CHINA MOBILE GROUP ANHUI +1
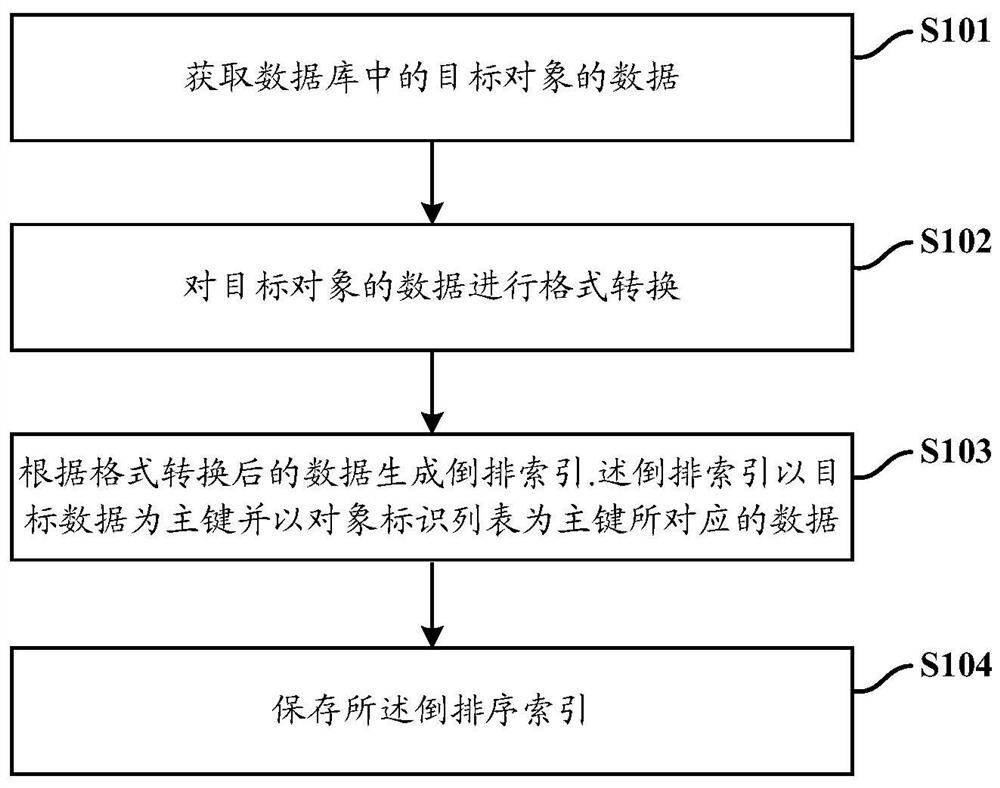
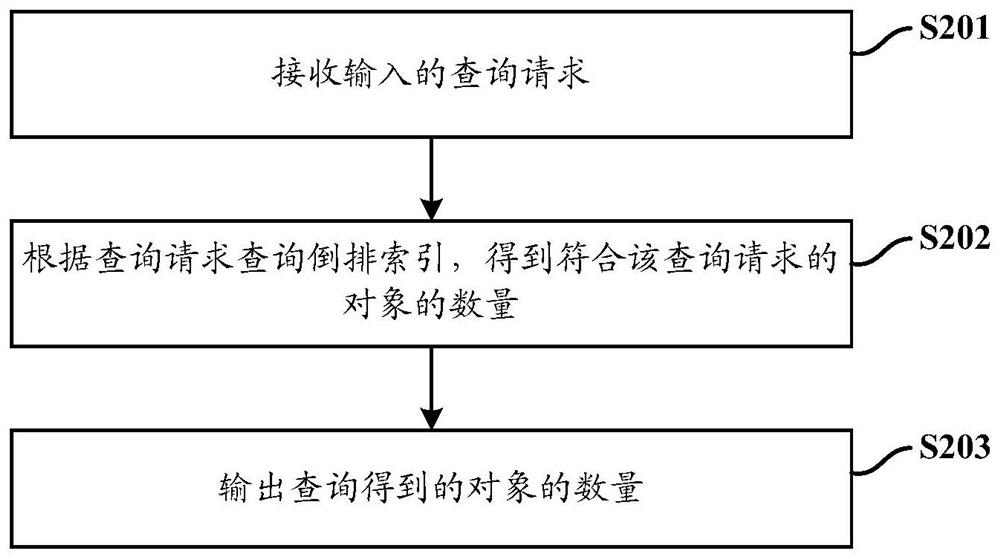
Information processing method and system
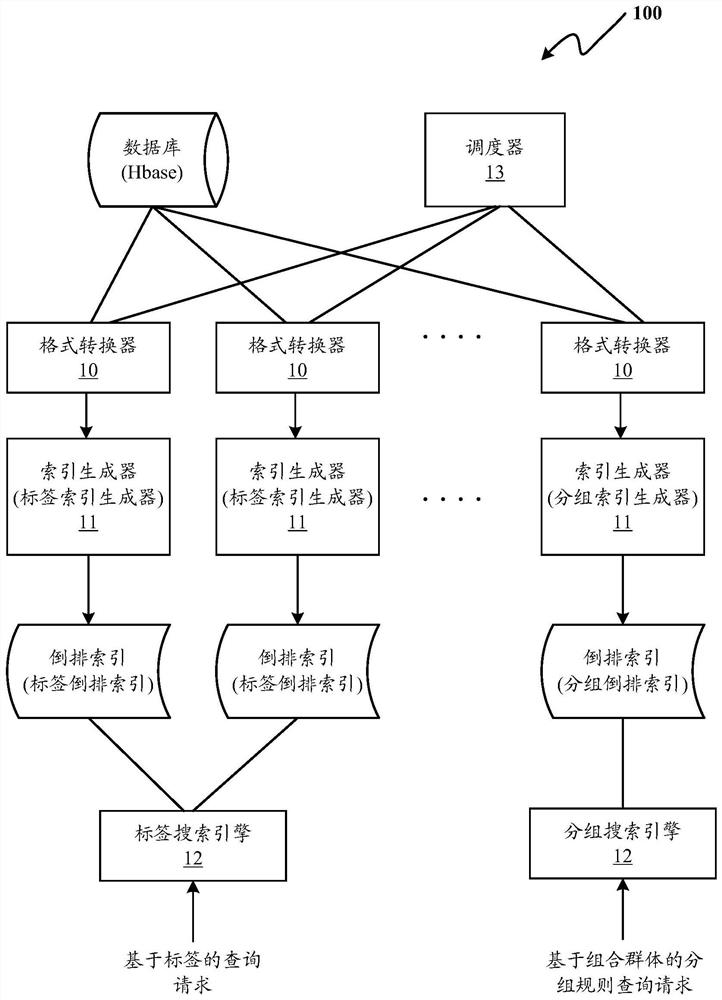
ActiveCN112559514AConvenient and Efficient StatisticsConvenient and Efficient QueryEnergy efficient computingSpecial data processing applicationsInformation processingEngineering
The invention discloses an information processing method and system. The method comprises the steps of performing format conversion on data of a target object in a database, and generating an invertedindex according to the data after format conversion, wherein the converted data format is a data format supported by an index generator for generating an inverted index, and the inverted index takesthe target data as a main key and takes an object identifier list as data corresponding to the main key; and in response to a query request received by the search engine, querying the inverted index according to the query request to obtain the number of objects conforming to the query request.
Owner:SHANGHAI BILIBILI TECH CO LTD
Database query optimization method and device
InactiveCN104765731BImprove execution efficiencyReduce running timeSpecial data processing applicationsProgramming languageQuery optimization
Owner:INT BUSINESS MASCH CORP
A secure communication system for improved software-defined networking
ActiveCN111934888BPrivacy protectionReliable communicationUser identity/authority verificationEngineeringNetwork address
The invention discloses a secure communication system for improving a software defined network. The secure communication system comprises an application layer, a secure communication service layer, acontrol layer and a forwarding layer, wherein the application layer comprises a plurality of clients, and the clients are used as request clients or target clients; and the security communication service layer is provided with a security database, and the security database stores a client identity identifier list, a security communication service layer public and private key pair, a plurality of client public keys and a plurality of client network addresses. The problem that privacy is prone to leakage due to the fact that information and data of an existing software-defined network are spreadon the network in a plaintext mode can be solved. The external malicious invasion is easily caused by programmability of a software-defined network, and the like.
Owner:南京可信区块链与算法经济研究院有限公司
Distributed massive data processing method and device
ActiveCN108256076BImprove storage efficiencyImprove retrieval efficiencyDatabase distribution/replicationFile access structuresOriginal dataIndexing Service
Owner:GUANGZHOU UNIVERSITY +1
Metadata-based translation of natural language queries into database queries
PendingUS20220083546A1Improve performanceImprove responsivenessDatabase management systemsSpecial data processing applicationsTable (database)Data citation
A system may include: a database table, a grammar containing metadata-referencing non-terminals, and metadata mapping the metadata-referencing non-terminals into alternative terms for the table and a column therein. The system may also include a server device configured to: (i) receive a natural language query, the grammar, and the metadata, wherein the natural language query contains a first alternative term for the table and a second alternative term for the column; (ii) parse, using the grammar, the natural language query into a series of terminals and non-terminals including a first metadata-referencing non-terminal that the metadata maps to the first alternative term and a second metadata-referencing non-terminal that the metadata maps to the second alternative term; (iii) identify, based on the first metadata-referencing non-terminal, the table; (iv) identify, based on the second metadata-referencing non-terminal, the column; and (v) generate, based on the table and the column as identified, a database language query.
Owner:SERVICENOW INC
A method and device for implementing data update and snapshot in olap database
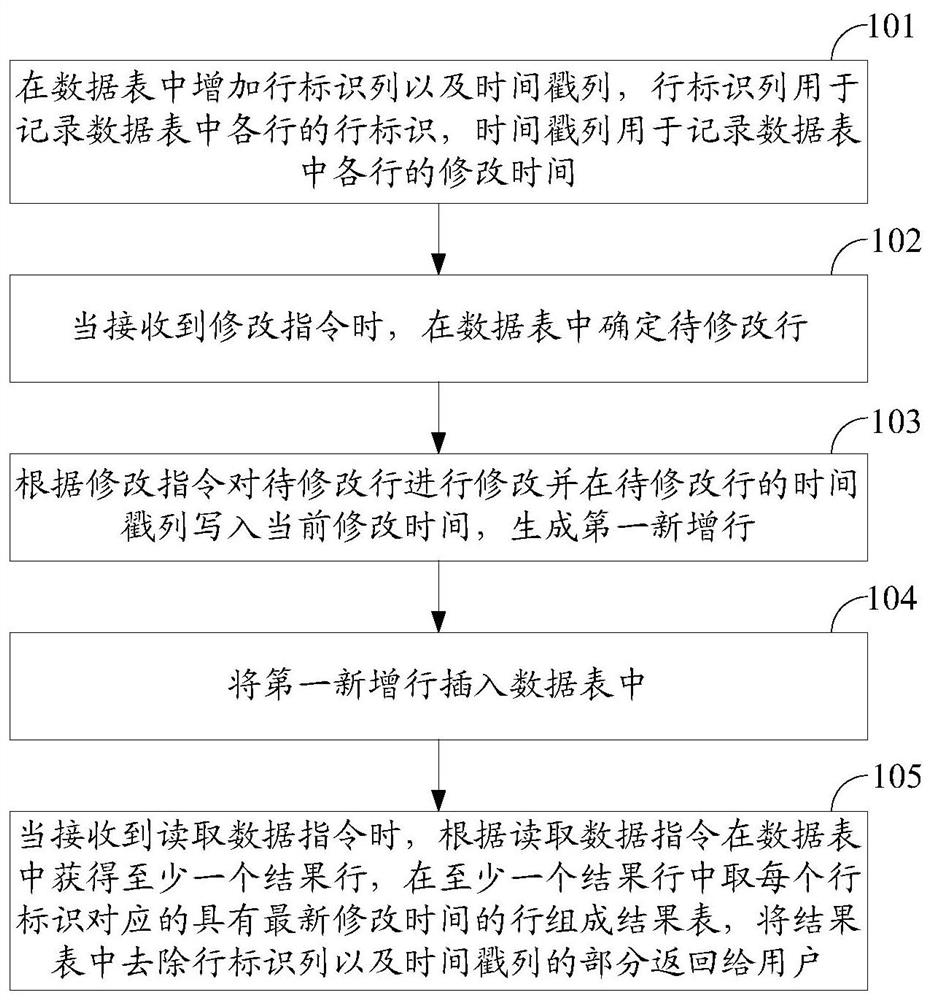
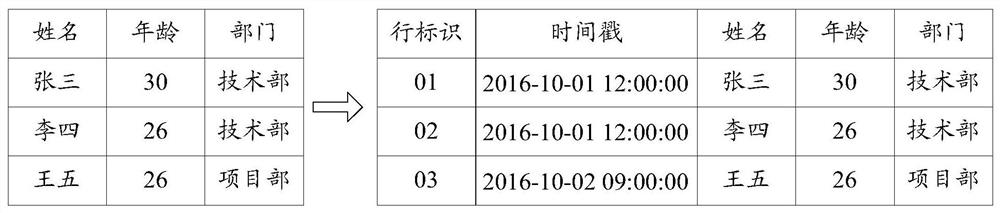
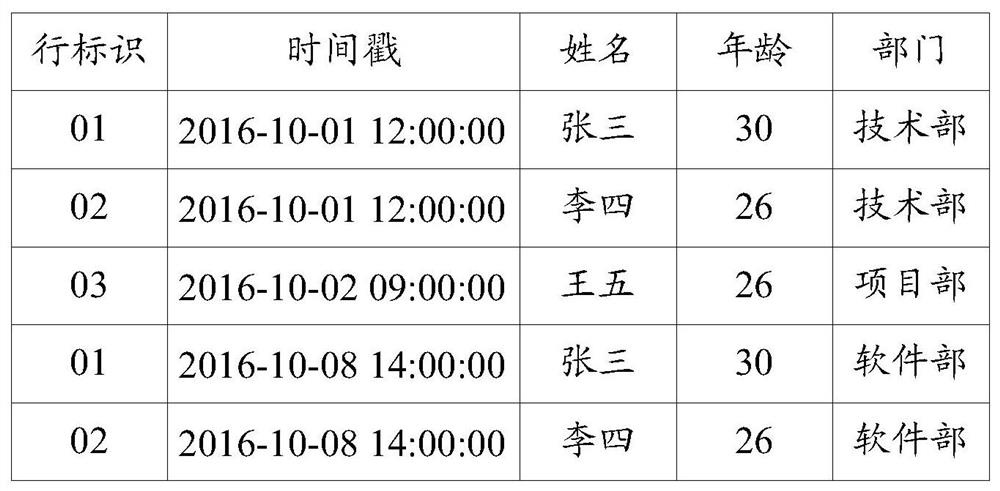
ActiveCN108073595BImplement the function of reading snapshotsMeet the needs of implementing data updatesMulti-dimensional databasesSpecial data processing applicationsDatasheetAlgorithm
The invention discloses a method and a device of realizing data updating at an OLAP (Online Analytical Processing) database. The method includes: adding a row identifier column and a time stamp columnin a data table, wherein the row identifier column is used for recording a row identifier of each row in the data table, and the time stamp column is used for recording modification time of each rowin the data table; determining a to-be-modified row in the data table when a modification instruction is received; modifying the to-be-modified row according to the modification instruction, and writing current modification time into the time stamp column of the to-be-modified row to generate a first newly-added row; inserting the first newly-added row into the data table; when a data reading instruction is received, obtaining at least one result row in the data table according to the data reading instruction, acquiring a row, which corresponds to each row identifier and has most recent modification time, in the at least one result row to form a result table, and returning, to a user, parts in the result table after removing the row identifier column and the time stamp column. The invention also discloses a method and a device of realizing a data snapshot at the OLAP database.
Owner:BEIJING GRIDSUM TECH CO LTD
File query method, system and computer-readable storage medium
ActiveCN108021631BImprove the efficiency of displaying first terminal filesFile metadata searchingSpecial data processing applicationsEngineeringTerm memory
The invention discloses a file query method, system, and computer-readable storage medium. The method includes the steps of: after the first terminal receives an acquisition instruction for acquiring files in the database sent by the second terminal, acquire all files in the database according to the acquisition instruction. Store the attribute information of the file, and store the attribute information in the memory; generate the identification list of the file according to the attribute information, and send the identification list to the second terminal; after receiving the query instruction sent by the second terminal according to the identification list, Find out the corresponding attribute information from the memory according to the query instruction and send it to the second terminal, so that the second terminal can receive the attribute information and display the corresponding file according to the attribute information. The present invention realizes that when the second terminal needs to display the files stored in the first terminal, it does not need to inquire the database of the first terminal every time a file is displayed, and improves the efficiency of the second terminal in displaying the files of the first terminal.
Owner:NUBIA TECHNOLOGY CO LTD
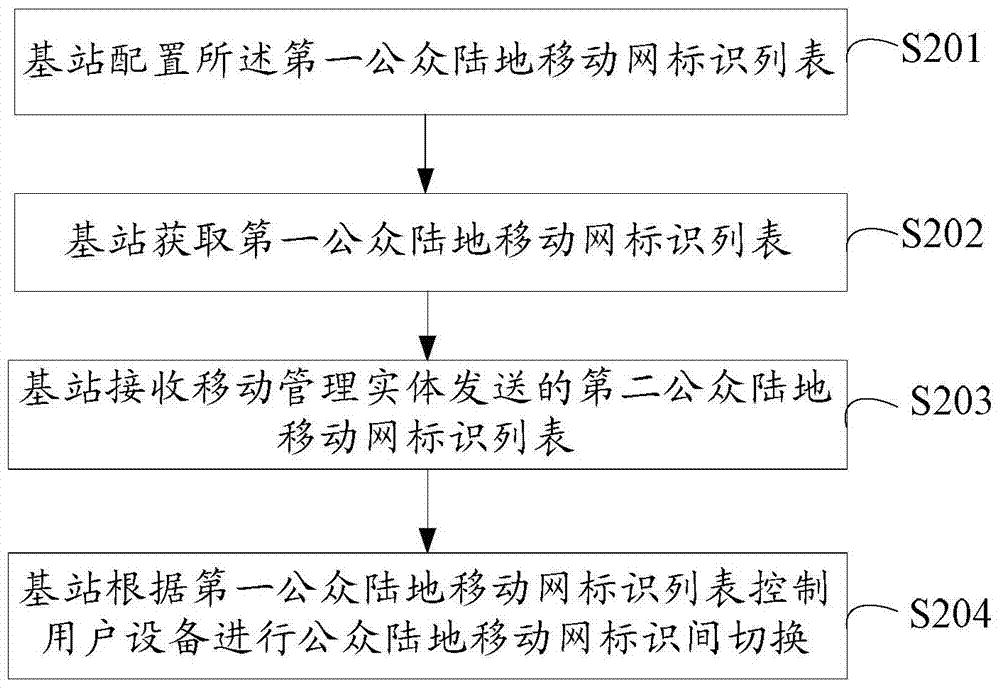
Handover method, base station and communication network between public land mobile network identities
Owner:HUAWEI TECH CO LTD
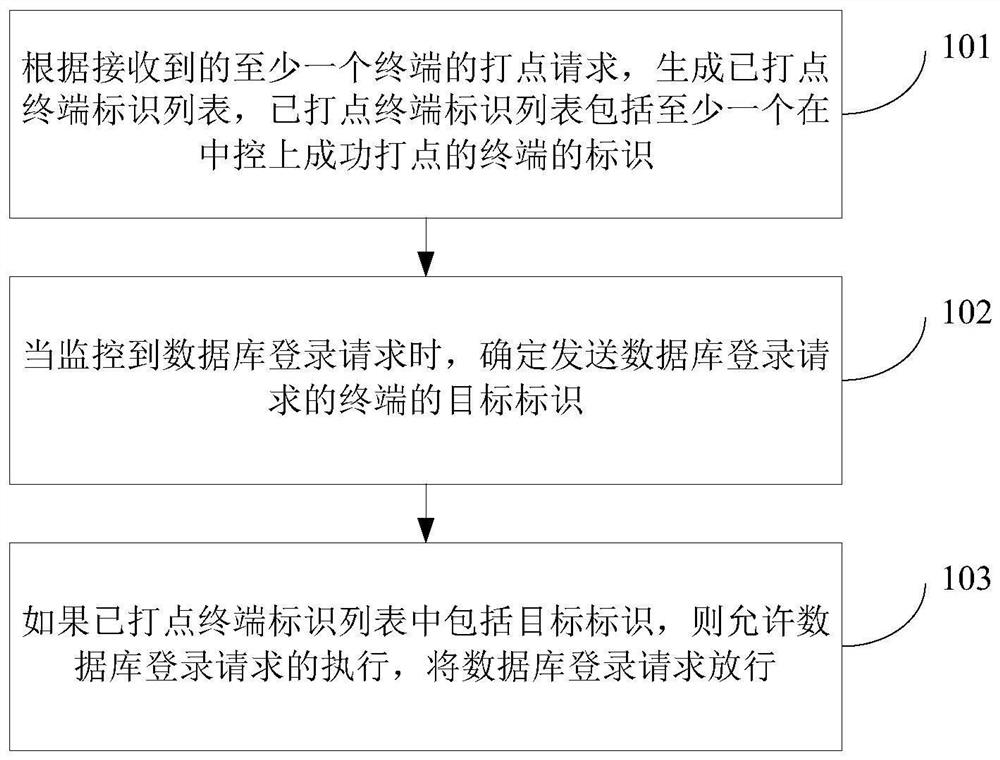
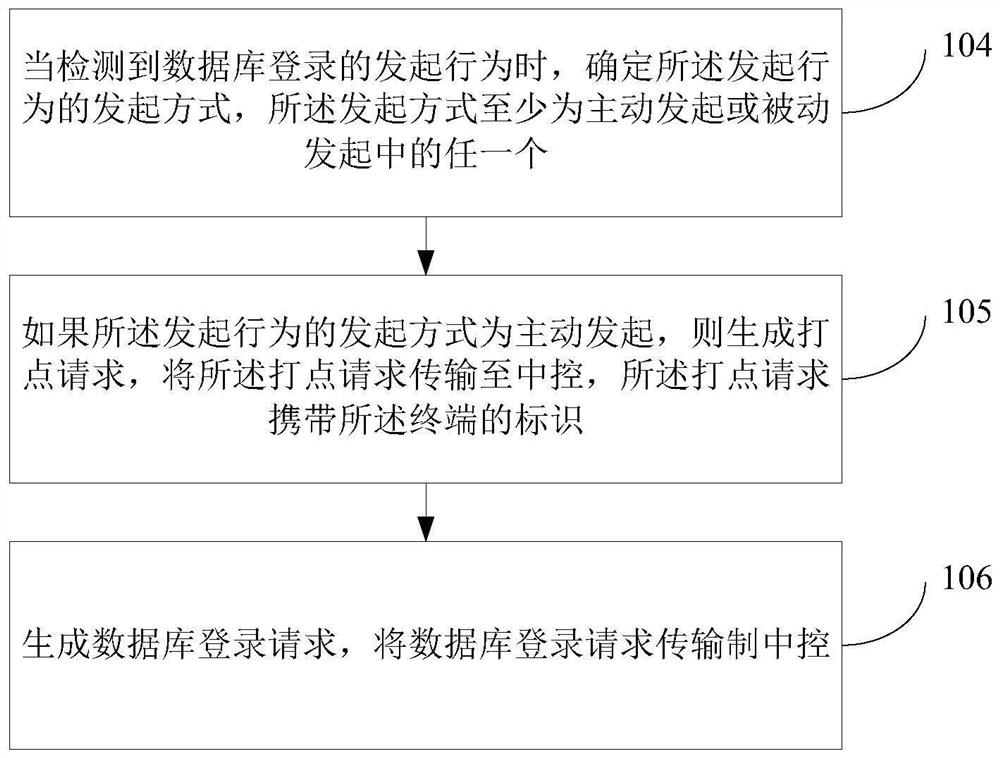
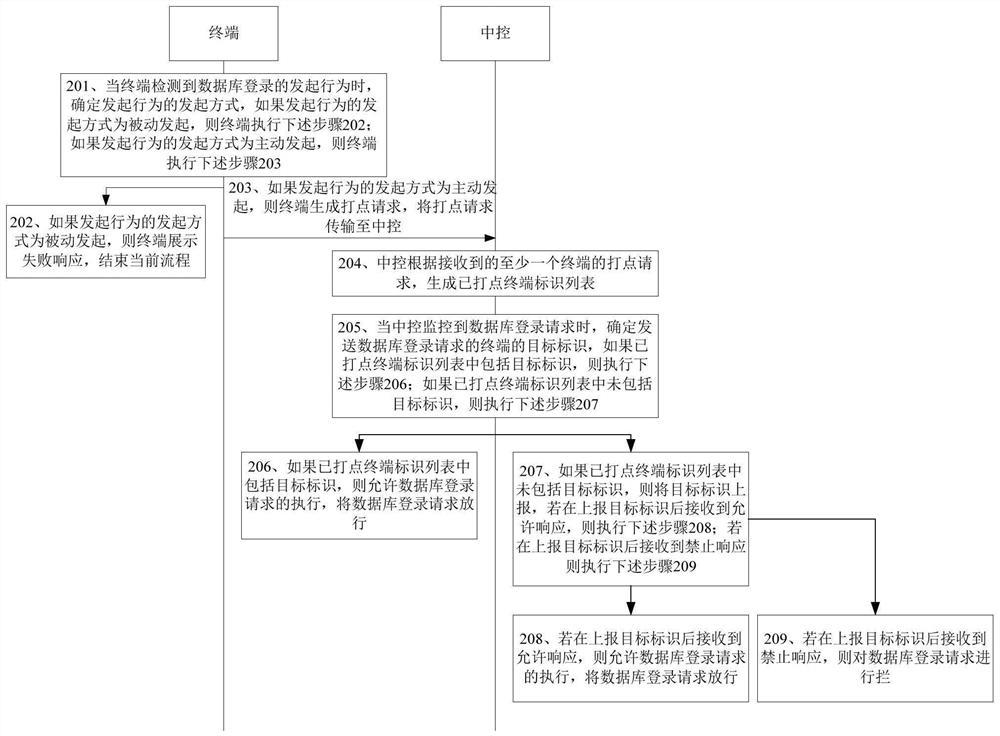
Database service login method, apparatus and device, and readable storage medium
ActiveCN112395585ARealize identificationAvoid Malicious LoginsDigital data protectionDigital data authenticationPasswordInformation networks
The invention discloses a database service login method, apparatus and device, and a readable storage medium, relates to the field of information network security, and aims to control a login requestfor a database through a dotted terminal identifier list, realize identification of a terminal in an identity verification mode, avoid malicious login possibly caused when a password is embezzled, andthe protection capability of database service login is improved, and the security is relatively good. The method comprises the steps of forming a dotted terminal identification list according to a received dotting request of at least one terminal, and the dotted terminal identification list comprises an identification of at least one terminal which is successfully dotted on the central controller; when a database login request is monitored, determining a target identifier of a terminal sending the database login request; and if the dotted terminal identifier list comprises the target identifier, allowing execution of the database login request, and releasing the database login request.
Owner:QI AN XIN SECURITY TECH ZHUHAI CO LTD +1
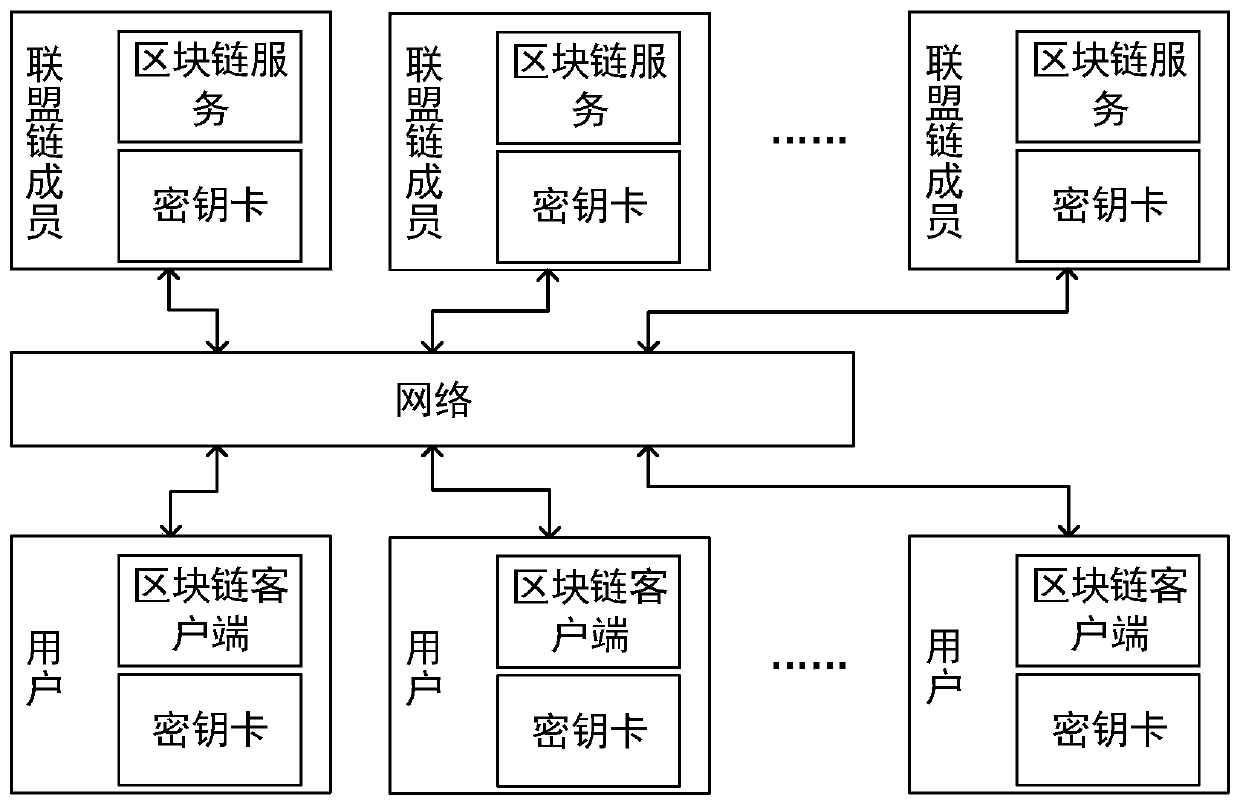
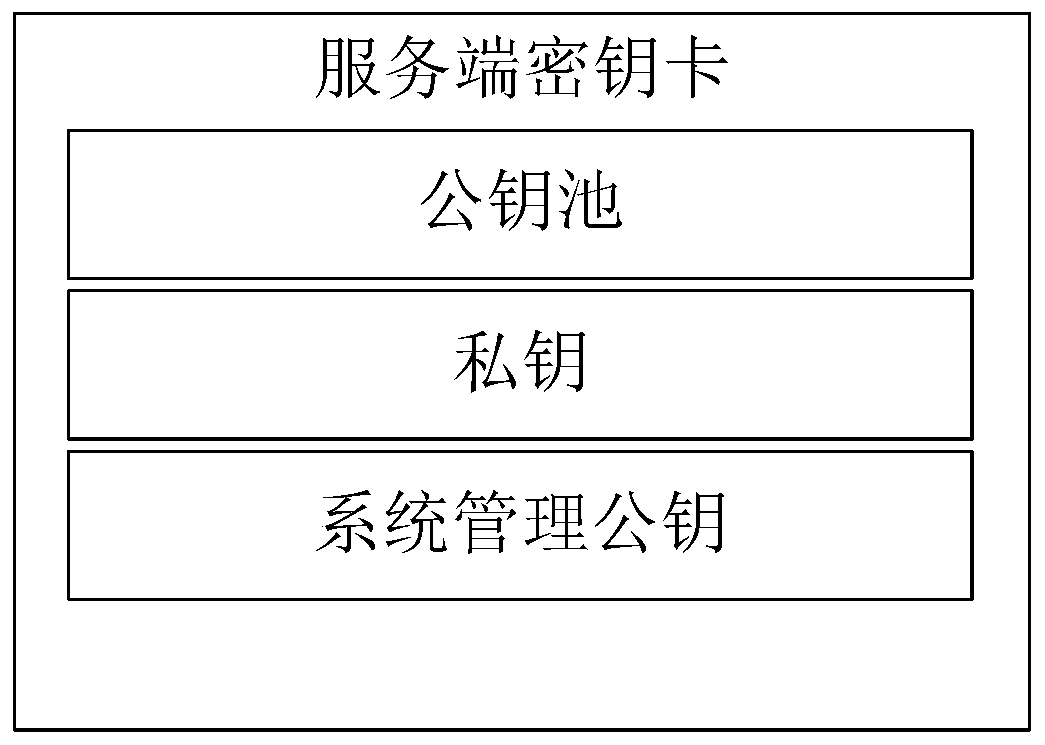
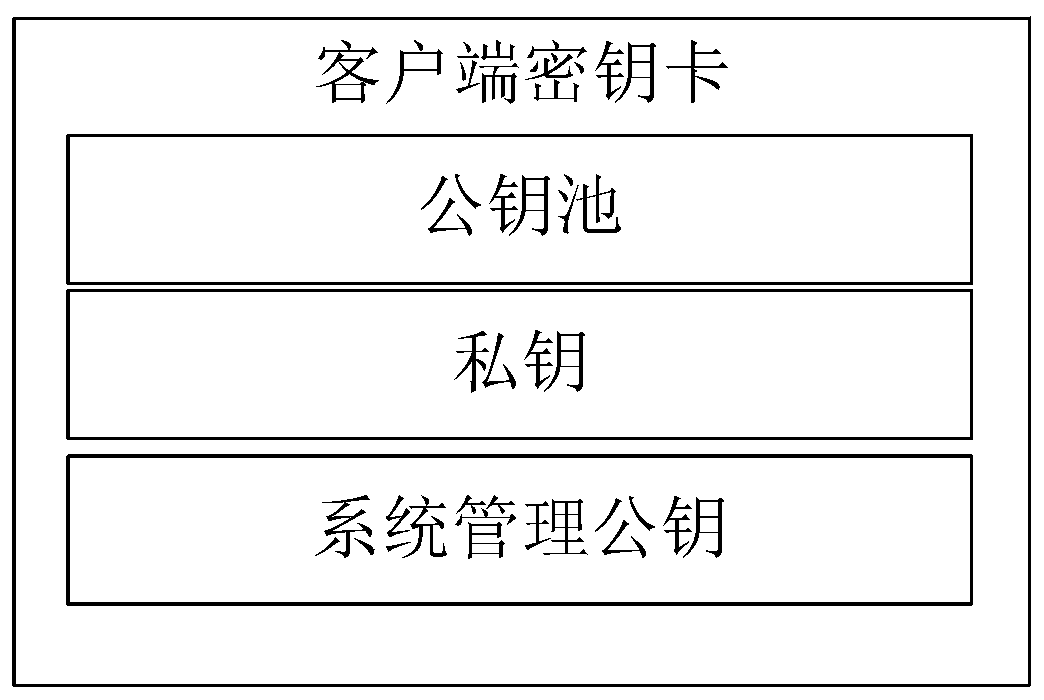
Anti-quantum computing private key backup, loss reporting and recovery method and system based on alliance chain and identity cryptography
ActiveCN110929872APrevent leakageProtection securityQuantum computersDigital data protectionKey (cryptography)Internet privacy
The invention relates to an anti-quantum computing private key backup, loss reporting and recovery method and system based on an alliance chain and identity cryptography. The method is implemented among alliance chain members communicating with each other. The alliance chain members comprise client members and server members, each party is configured with a key fob; all the key cards store respective private keys and public key pools related to all alliance chain members; public key units in one-to-one correspondence with the alliance chain members are stored in the public key pool; the publickey unit comprises a user name corresponding to an alliance chain member, a current identity identifier, a public key random number, a backup identity identifier list and an invalid identity identifier column; and obtaining a corresponding public key unit in the public key pool according to the user name of the alliance chain member, and obtaining a public key of the alliance chain member according to a public key random number in the public key unit. By adopting the method, the protection of a private key can be improved.
Owner:RUBAN QUANTUM TECH CO LTD +1
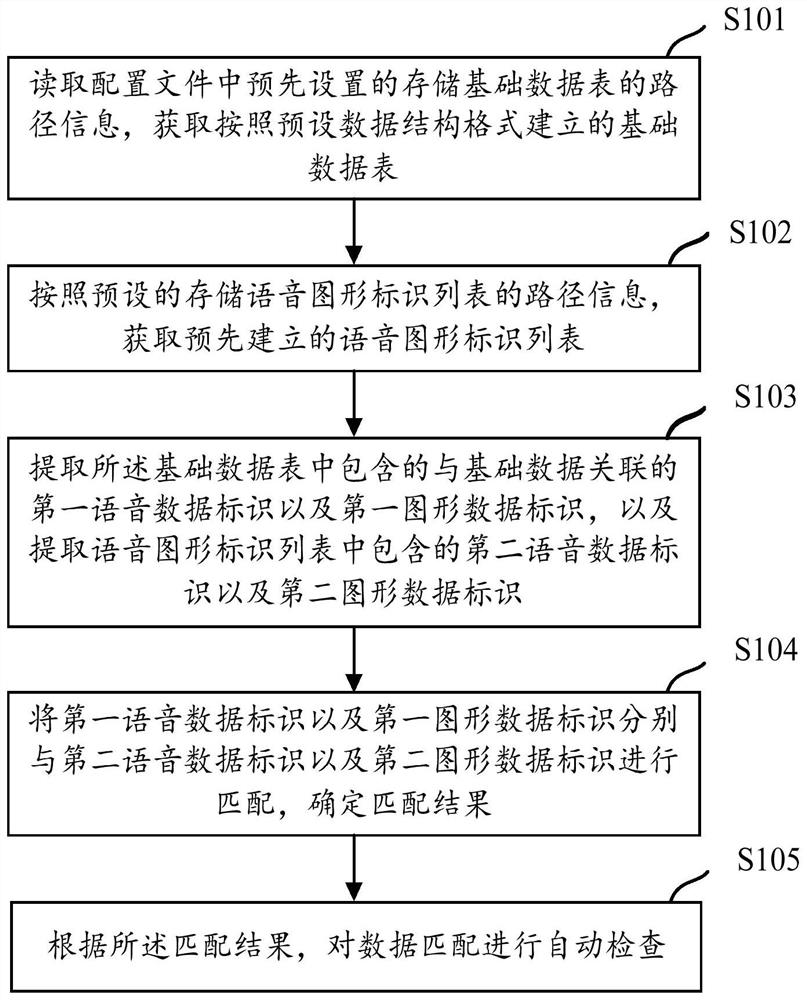
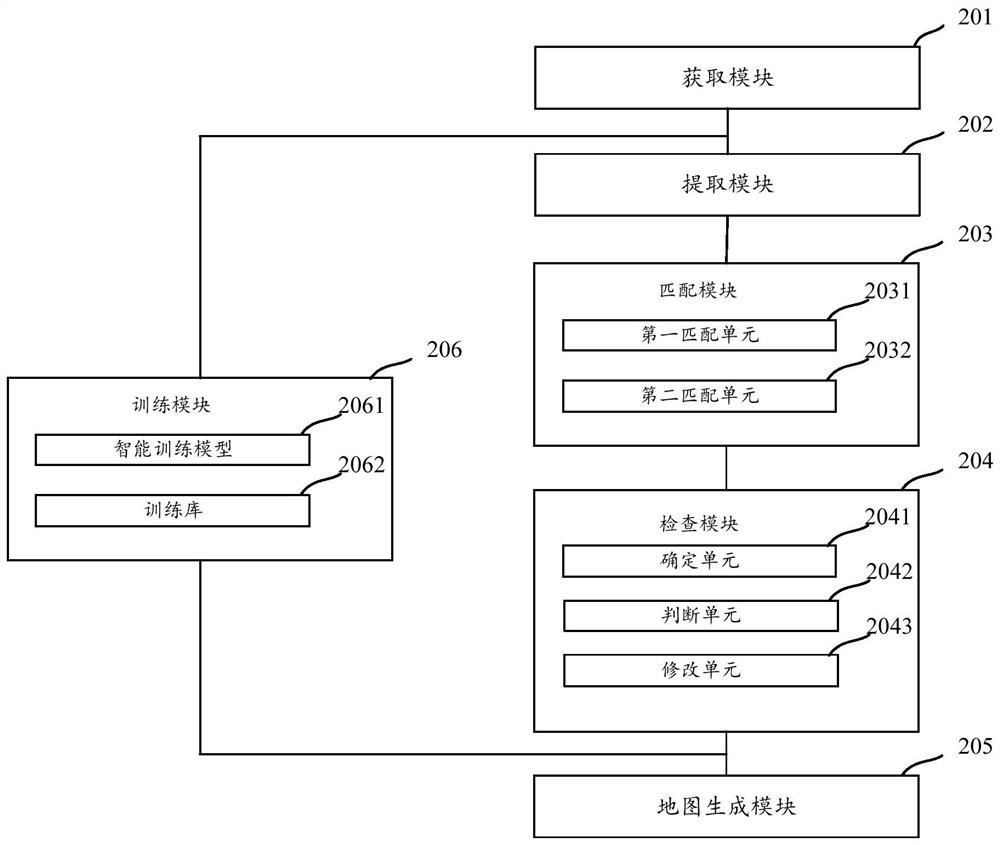
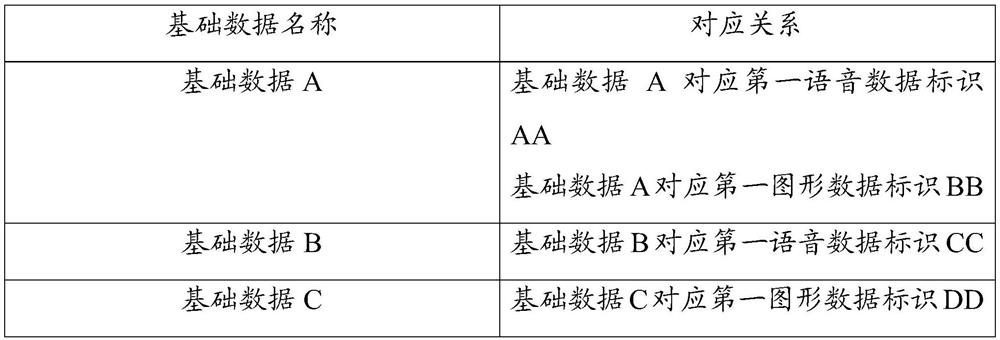
An automatic inspection method and device for data matching
ActiveCN107766367BImprove the efficiency of automated inspectionsImprove accuracyMultimedia data queryingGeographical information databasesData matchingGraphics
The present application discloses a method and device for automatically checking data matching. The method includes: reading the path information of the preset stored basic data table and the path information of the stored voice graphic identification list, and obtaining the basic data table and the voice graphic identification respectively. list, extract the first voice data identifier and the first graphic data identifier associated with the basic data contained in the basic data table, and the second voice data identifier and the second graphic data identifier contained in the voice graphic identifier list, and convert the first The voice data identifier and the first graphic data identifier are matched with the second voice data identifier and the second graphic data identifier respectively, and data matching is automatically checked according to the matching result. Through the above method, the efficiency of automatic checking of data matching can be effectively improved, and the accuracy rate of automatic checking of data matching can also be improved.
Owner:NAVINFO
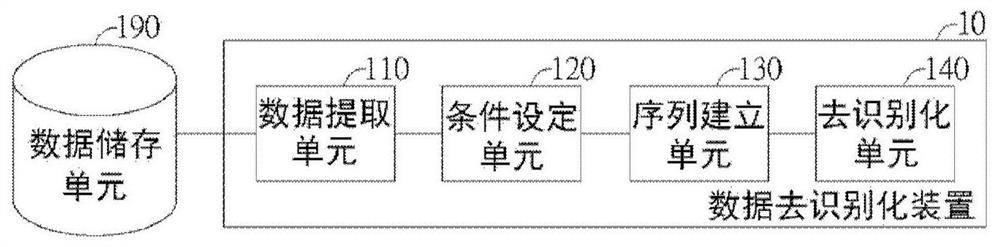
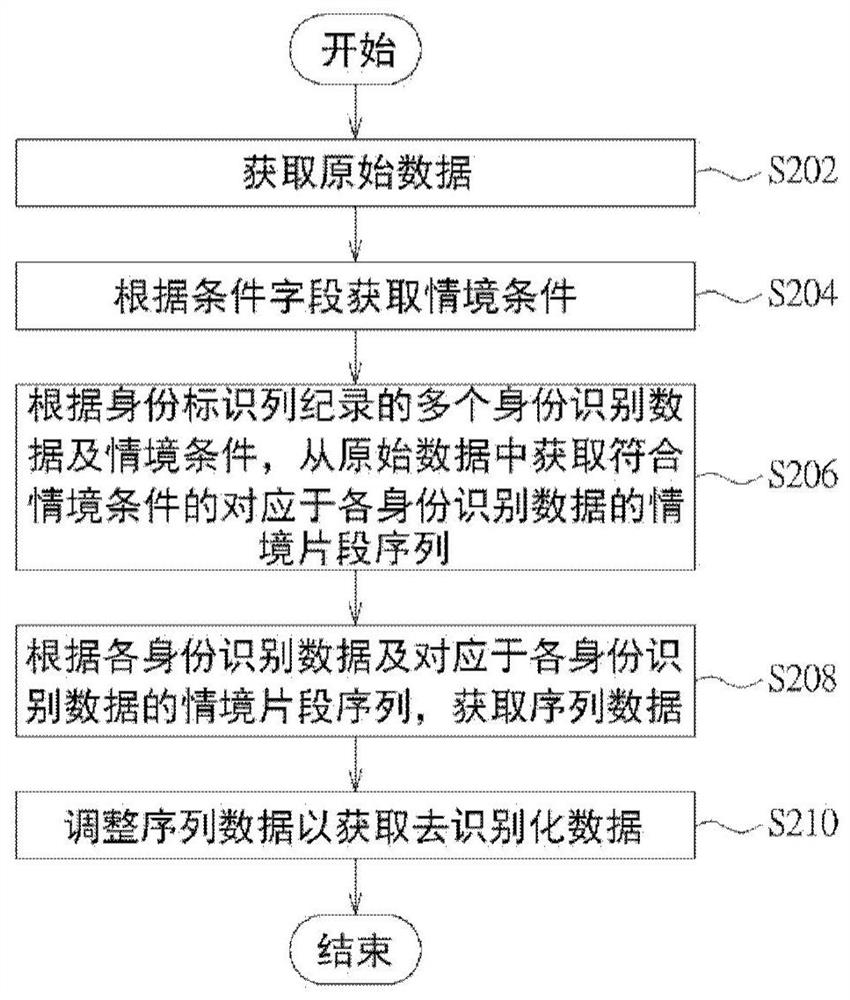
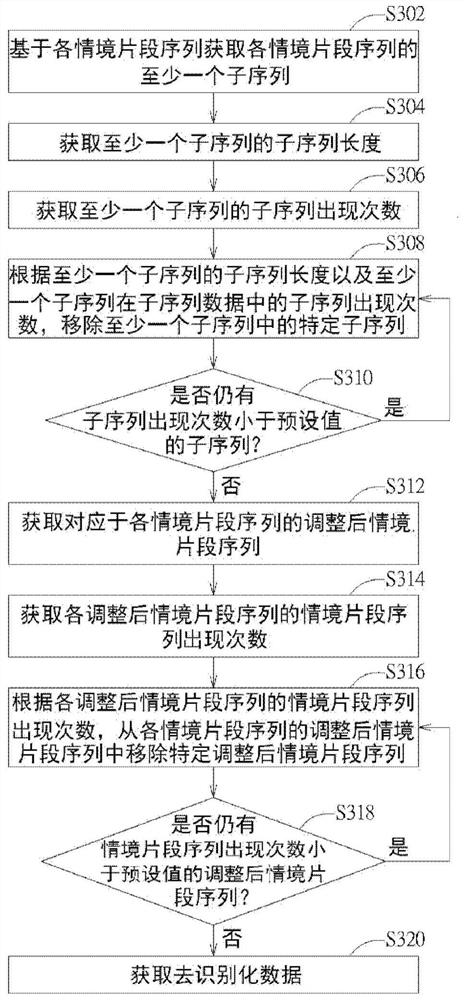
Data de-identification method, device and computer-readable storage medium
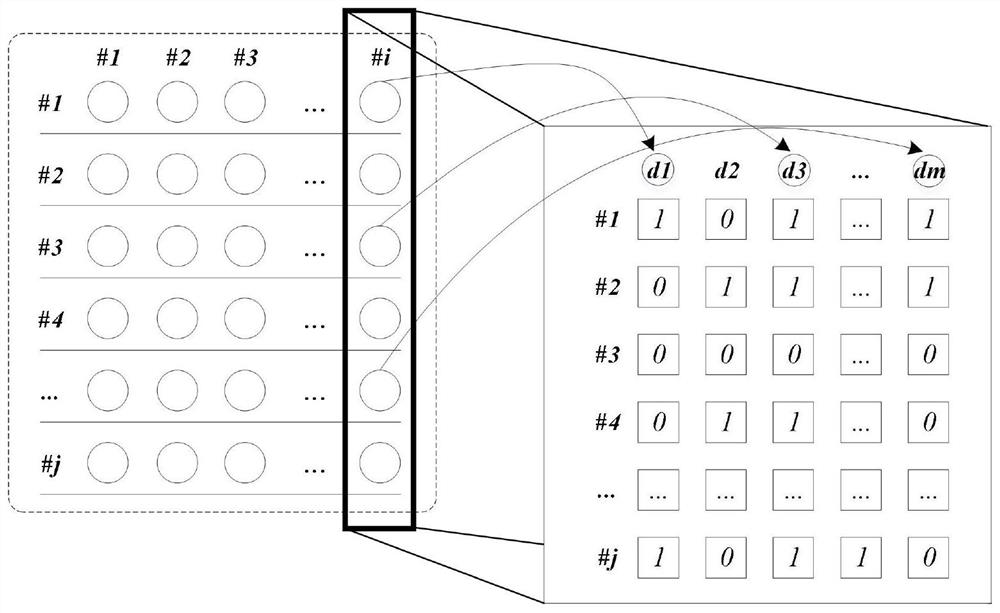
The invention provides a data de-identification method, a data de-identification device and a non-volatile computer-readable storage medium for executing the data de-identification method. The data de-identification method includes: obtaining original data, wherein the original data includes an identity column, a condition field, and a record field, obtaining situational conditions according to the condition field, and obtaining multiple identification data and situational conditions according to the identity column records, from Acquiring context segment sequences corresponding to each identification data that meet the context conditions from the original data, obtaining sequence data according to the identification data and the context segment sequences corresponding to the identification data, and adjusting the sequence data to obtain de-identified data.
Owner:IND TECH RES INST
Retrieval method and system for reverse analysis of product database identifier
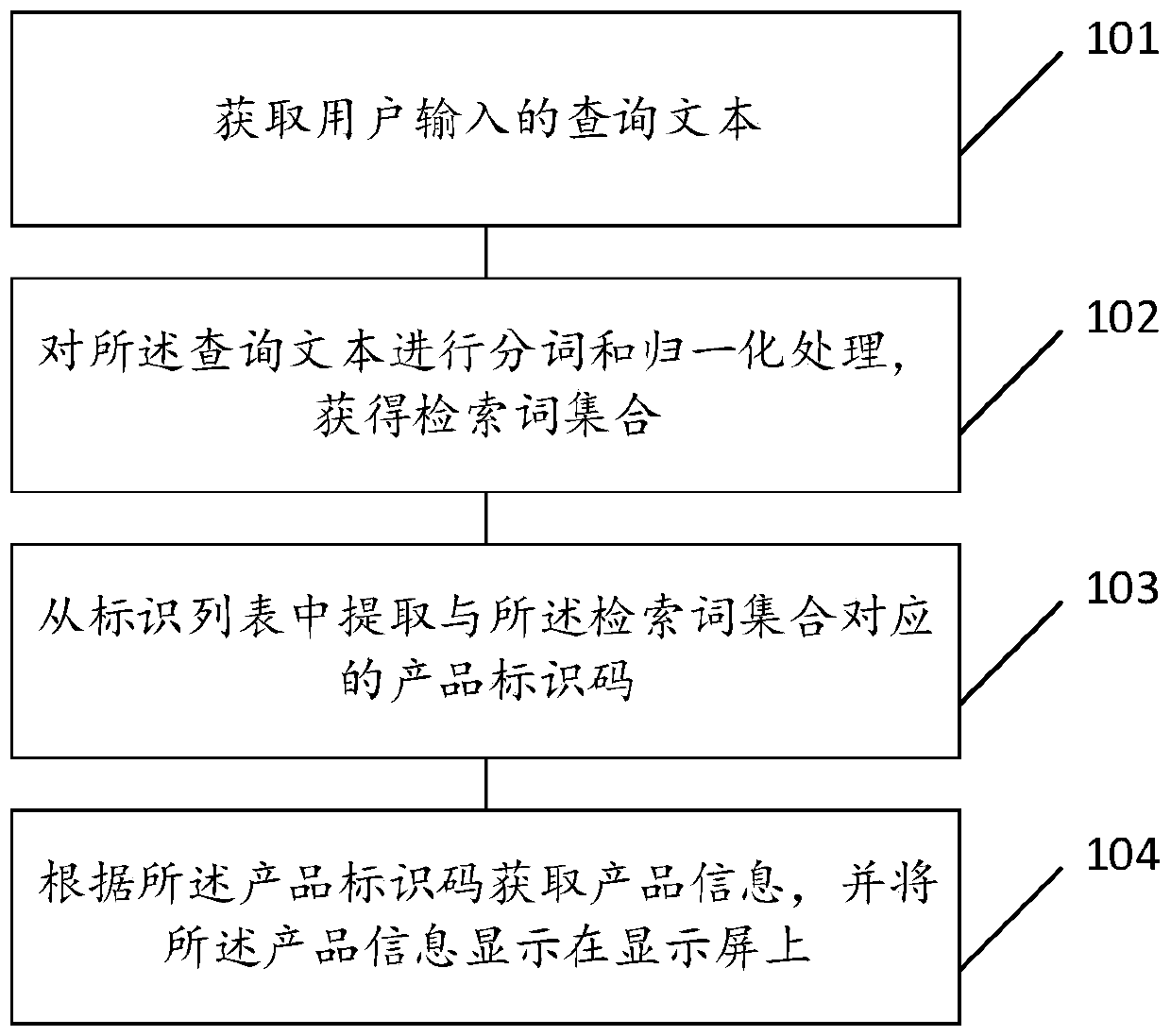
ActiveCN111400339AImprove experienceImprove retrieval efficiencyDigital data information retrievalNatural language data processingReverse analysisData mining
The invention discloses a retrieval method and system for reverse analysis of a product database identifier. The method comprises the following steps: firstly, obtaining a query text input by a user;performing word segmentation and normalization processing on the query text to obtain a retrieval word set; extracting a product identification code corresponding to the retrieval word set from an identification list; obtaining product information according to the product identification code, and displaying the product information on a display screen; according to the technical scheme, the productinformation is acquired on the premise of not depending on the identification information input by the user, so that the acquisition efficiency of the product information is improved.
Owner:GUANGZHOU UNIVERSITY
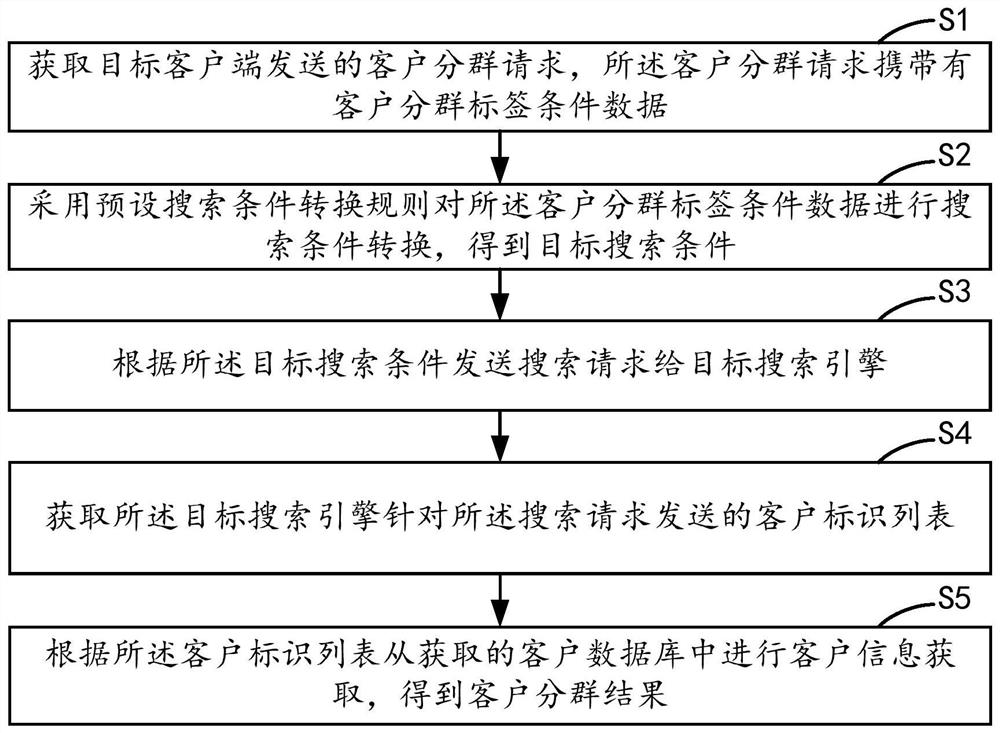
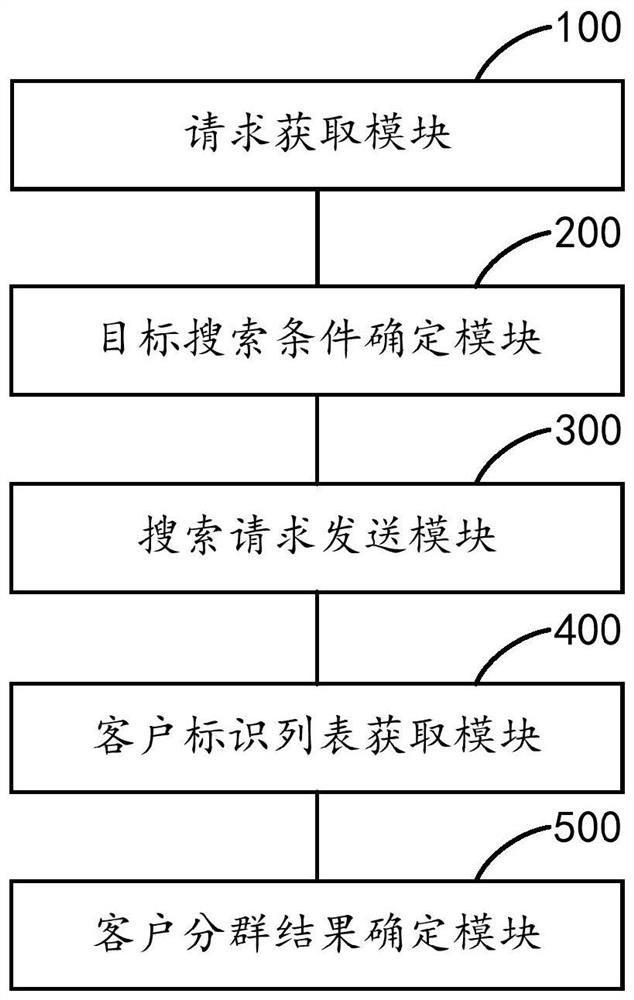
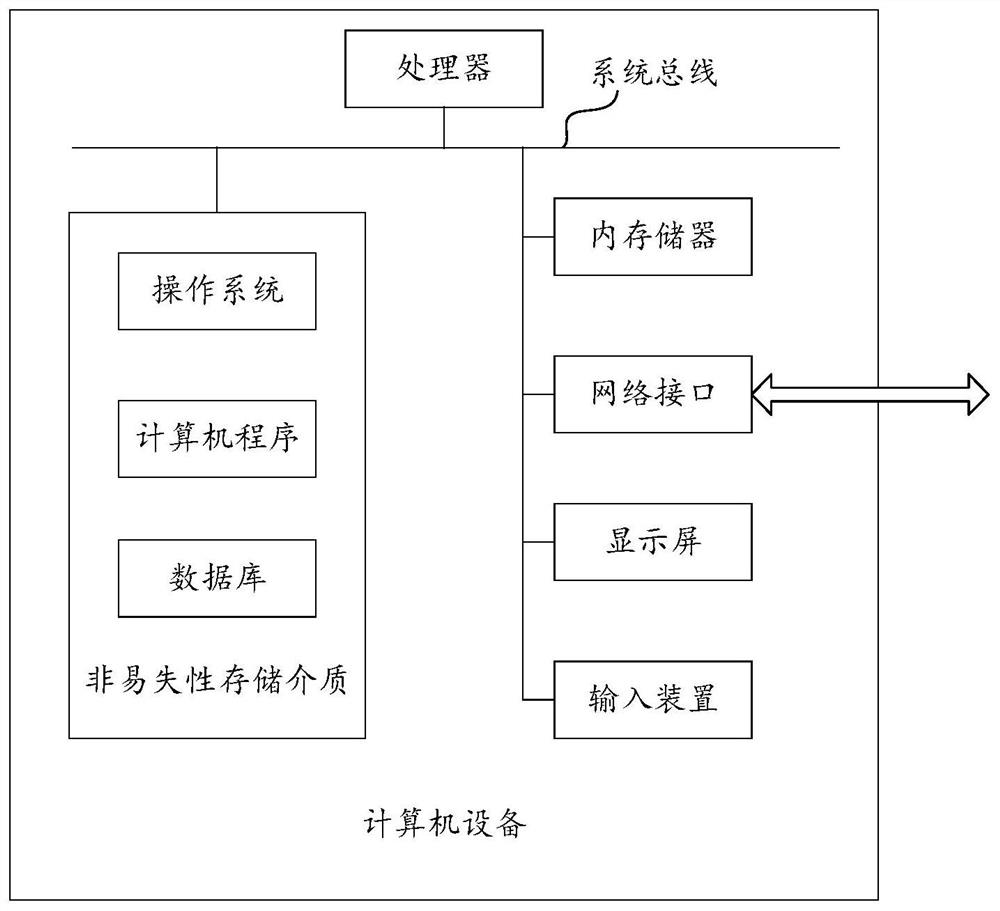
Customer grouping method and device, equipment and storage medium
PendingCN114003813AMeet group needsImprove accuracyWeb data indexingSpecial data processing applicationsPersonalizationEngineering
The invention relates to the technical field of artificial intelligence, and discloses a customer grouping method, device and equipment and a storage medium, and the method comprises the steps of obtaining a customer grouping request sent by a target client, and the customer grouping request carries customer grouping label condition data; performing search condition conversion on the customer grouping label condition data by adopting a preset search condition conversion rule to obtain a target search condition; sending a search request to a target search engine according to the target search condition; obtaining a client identifier list sent by the target search engine for the search request; and obtaining customer information from the obtained customer database according to the customer identifier list to obtain a customer grouping result. Real-time customer grouping according to the customer grouping label condition data is realized, the customer grouping accuracy is improved, and personalized customer grouping requirements can be met.
Owner:PINGAN INT SMART CITY TECH CO LTD
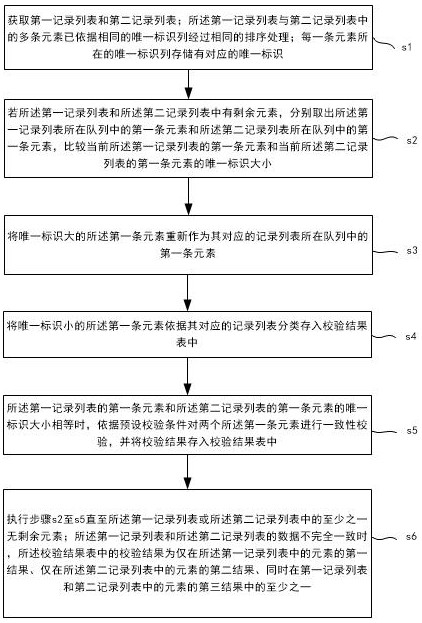
Data consistency checking method, device, electronic device and readable storage medium
ActiveCN113495928BMeet the needs of verifying data consistencyDatabase distribution/replicationSpecial data processing applicationsTable (database)Source Data Verification
The invention provides a data consistency verification method, device, electronic equipment and readable storage medium, and relates to the field of computer technology. After the same sorting process, take out the first elements of the two record lists and compare their unique identifier sizes until there are no remaining elements in either list, and put the first element with the largest unique identifier back into the original queue. The first element with the smallest unique identifier is classified into the verification result table to realize data consistency verification for each element in the two record lists. The verification result table includes: only the elements in the first record list The first result of the , the second result of only elements in the second record list. The problem of difficult data verification in the prior art when the data in the target database and the source database are not exactly the same is solved.
Owner:云账户技术(天津)有限公司
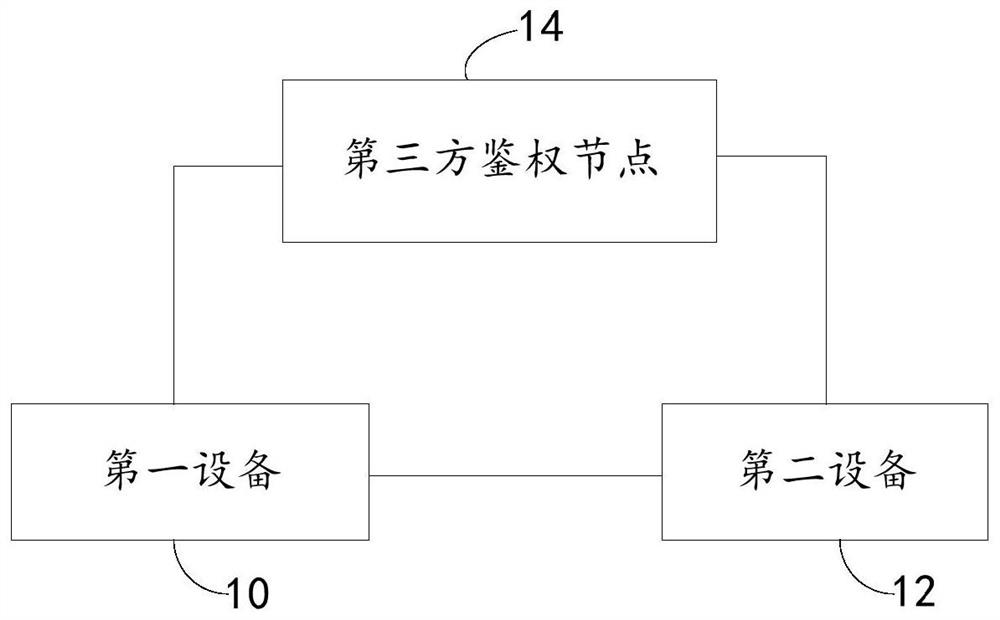
Joint modeling method, system and device and device with storage function
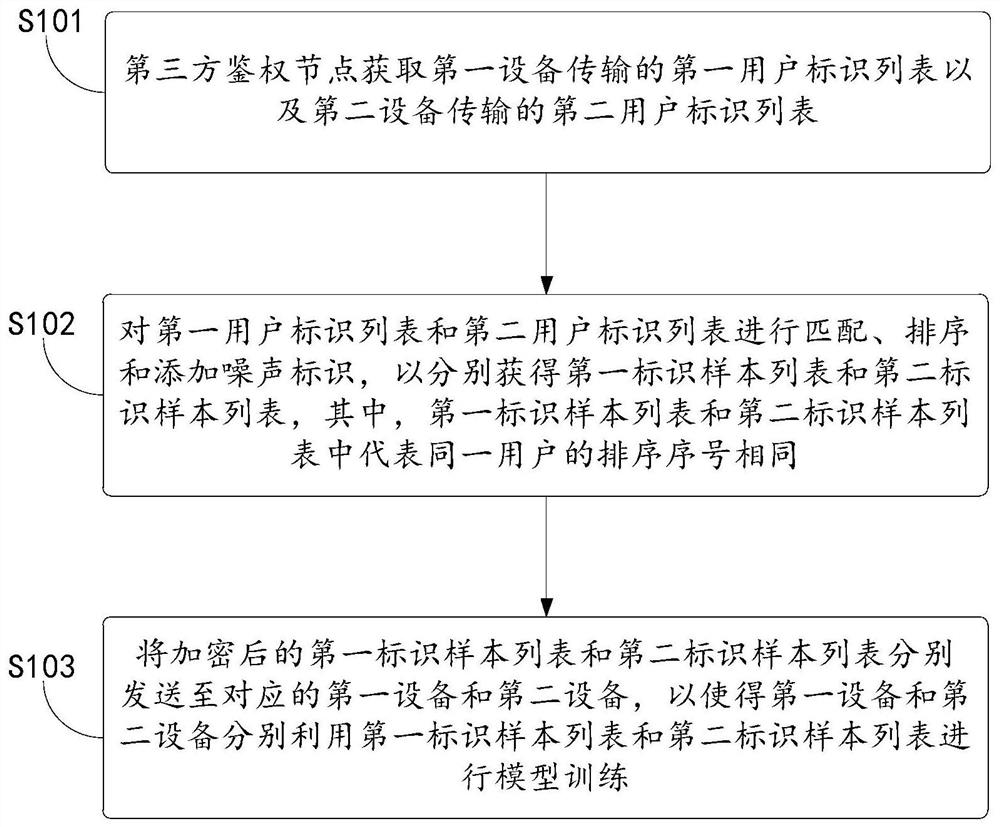
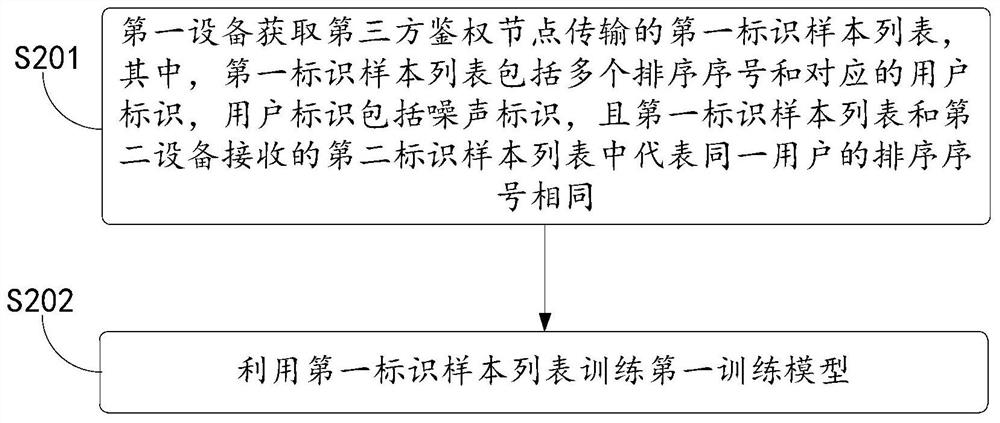
The invention discloses a joint modeling method, system and device and a device with a storage function. The joint modeling method applied to a third-party authentication node comprises the steps that a first user identification list transmitted by first equipment and a second user identification list transmitted by second equipment are acquired; the first user identification list and the second user identification list are matched, sorted and added with noise identifications to obtain a first identification sample list and a second identification sample list respectively, and sorting serial numbers representing the same user in the first identification sample list and the second identification sample list are the same; and the encrypted first identification sample list and second identification sample list are sent to corresponding first equipment and second equipment, so that the first equipment and the second equipment perform model training by utilizing the corresponding identification sample lists respectively. By means of the mode, the technical problem of matching attacks during joint modeling can be solved.
Owner:IFLYTEK CO LTD
Load balancing method, device and system
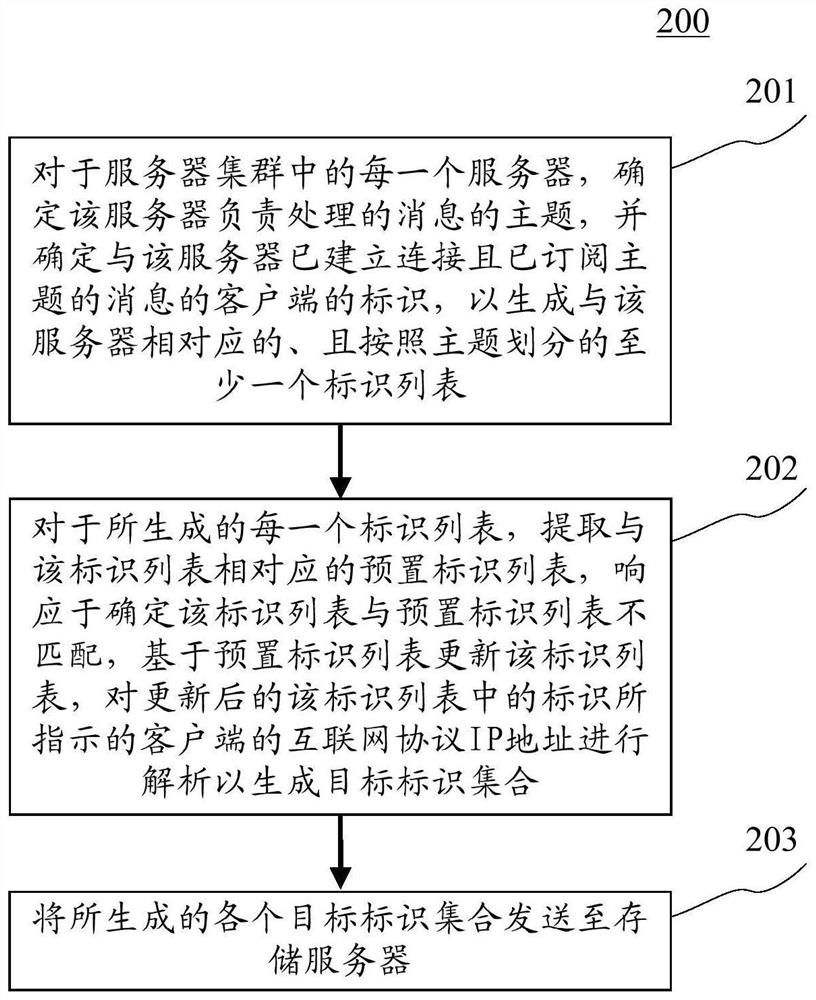
ActiveCN108696549BReduce the number of connectionsImprove the efficiency of connection establishmentTransmissionIp addressIdentity column
The application discloses a load balancing method, device and system. A specific implementation of the method includes: for each server in the server cluster, determine the topic of the message that the server is responsible for processing, and determine the identification of the client that has established a connection with the server and subscribed to the message of the topic, so as to generate At least one identification list corresponding to the server and divided according to the topic; for each generated identification list, extracting a preset identification list corresponding to the identification list, and in response to determining that the identification list is consistent with the preset identification list No match, update the identification list based on the preset identification list; analyze the IP address of the client indicated by the identification in the updated identification list to generate a target identification set; send each generated target identification set to the storage server. This embodiment improves the efficiency of establishing a connection and improves the stability of the connection.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
Determination method of access domain and auxiliary method for determining access domain
The invention discloses a method for determining an access domain and an auxiliary method for determining the access domain. The method for determining the access domain includes: receiving an invitation INVITE message including the target identifier of the called user; according to the target identifier and the stored user identifier list registered in the long-term evolution voice bearer VoLTE network, obtain the called user in the VoLTE network Registration information; if the registration information is a registered state, it is determined that the called user's access domain is an Internet Protocol Multimedia Subsystem IMS domain; if the registration information is an unregistered state, it is determined that the called user's access domain is a circuit switched CS domain; Wherein, the user identification list is updated according to the IMS deregistration request or IMS registration request actively sent by the user terminal, and the IMS deregistration request or IMS registration request is sent by the user terminal according to the result of its own network switching. According to the method for determining the access domain and the auxiliary method for determining the access domain provided in the embodiments of the present invention, the determination of the access domain can be quickly realized.
Owner:CHINA MOBILE GROUP ANHUI +1
Event data processing method, device, equipment and medium based on knowledge graph
ActiveCN113590737BPrecise positioningFast indexing capabilityNatural language data processingText database indexingEvent dataKnowledge graph
The present application relates to a knowledge graph-based event data processing method, device, device, and medium. The method includes: obtaining query conditions; using the query conditions to filter and call the word pointer array of the event intelligence knowledge graph, and locate the word pointer array corresponding to the query condition Target array element; using the event pointer array of the event intelligence knowledge map, match each element in the event identification list corresponding to the target linked list element, and obtain the target second linked list corresponding to the matched event identification, to indicate that the event to be retrieved is in the event The element information of the corresponding target event intelligence in the intelligence knowledge graph. The event intelligence knowledge graph includes event entities, time entities, location entities, person entities, cause entities, process entities, and result entities. The relationship types of the graph include time description relationships, location description relationships, participation description relationships, and development description relationships. It can reliably complete the analysis and processing of event intelligence data.
Owner:NAT UNIV OF DEFENSE TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com