Database service login method, apparatus and device, and readable storage medium
A login method and database technology, applied in the fields of devices, equipment, readable storage media, and database service login methods, can solve problems such as low protection capability and poor security, and achieve improved protection capability, good security, and avoiding malicious login Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0065]An exemplary embodiment of the present invention will be described in more detail below with reference to the accompanying drawings. While the exemplary embodiments of the present invention are shown in the drawings, it is understood that the present invention can be implemented in various forms and is not limited thereto. Instead, these embodiments are provided to be more thoroughly understood, and the range of the scope of the invention can be communicated to those skilled in the art.
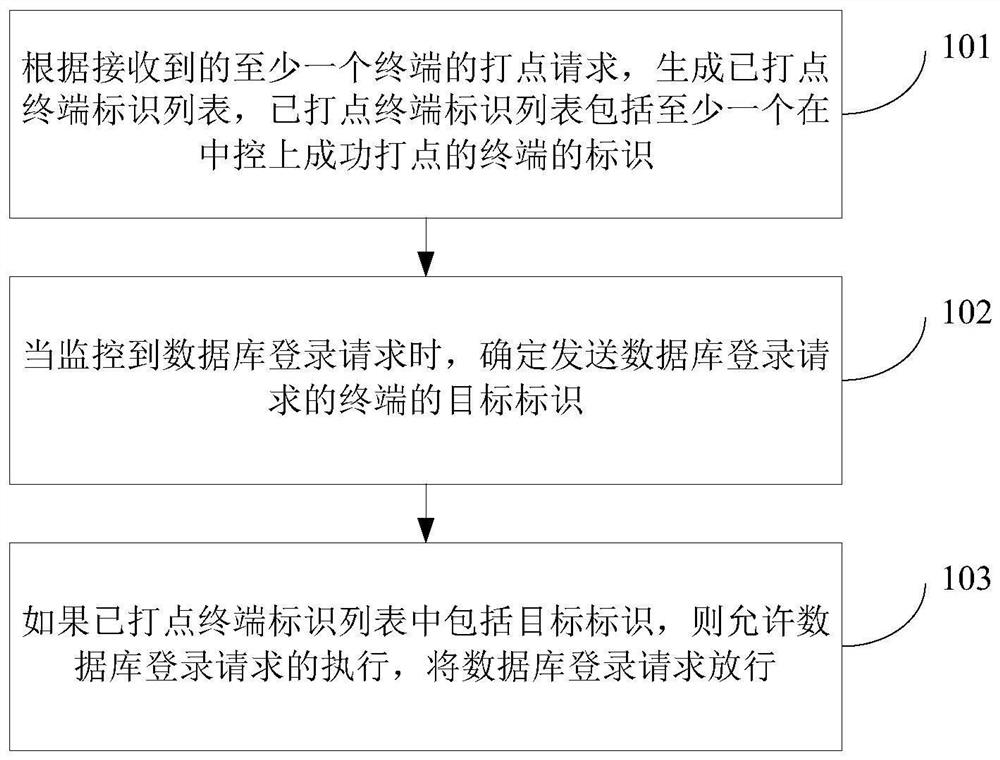
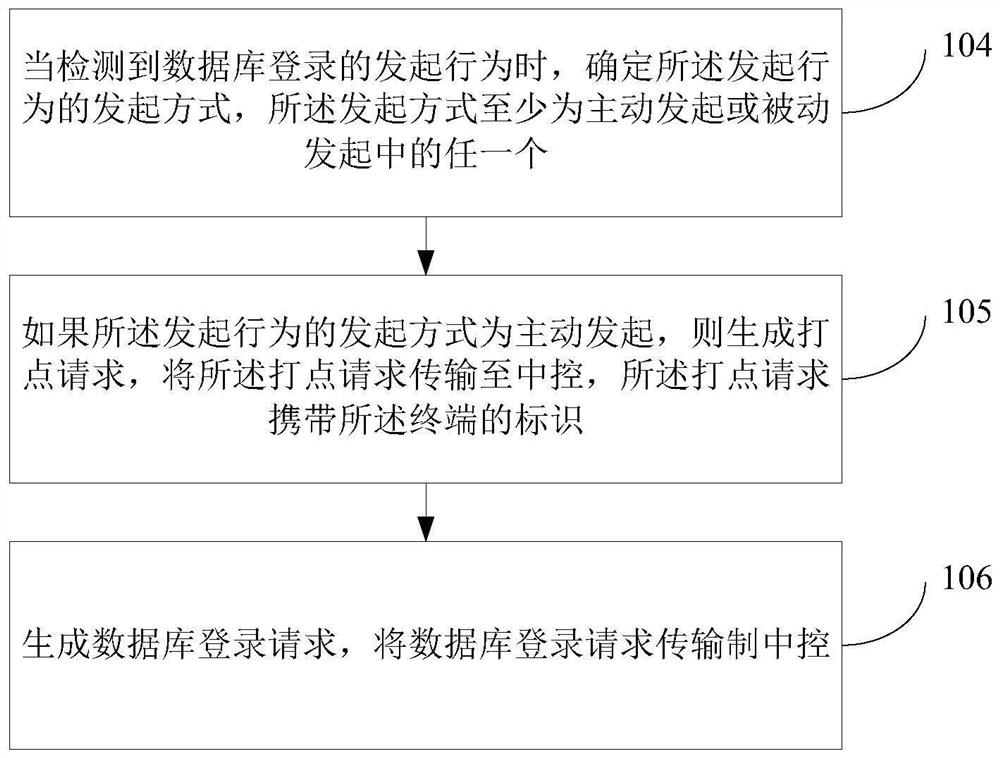
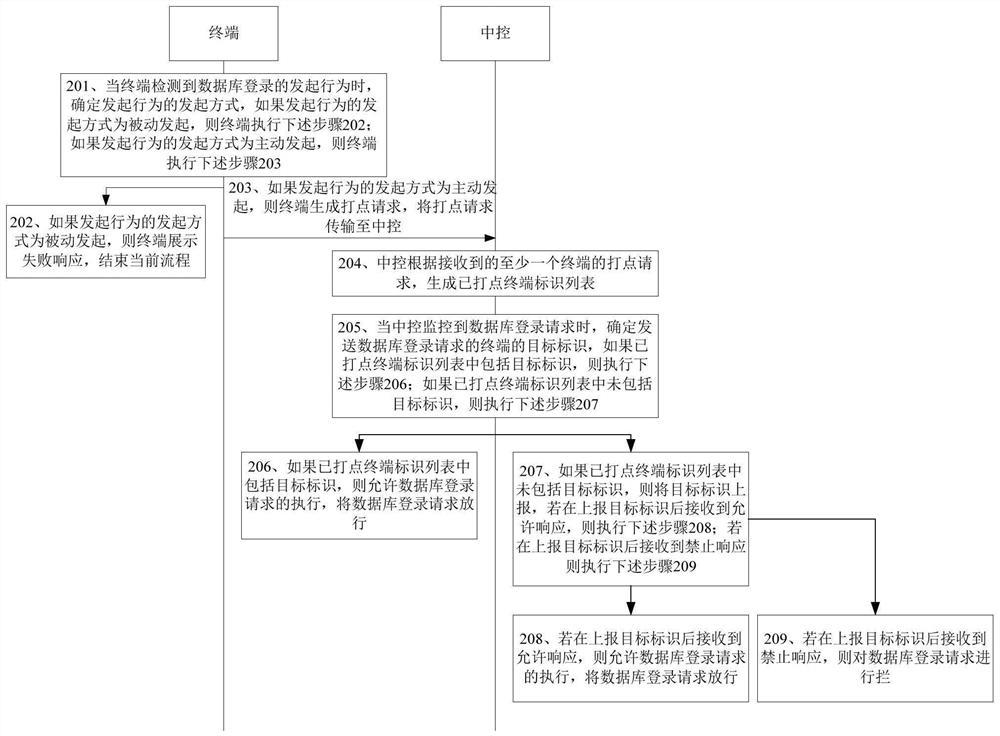
[0066]The embodiment of the present invention provides a database service login method, such asFigure 1A As shown, the method is applied to central control, including:
[0067]101. Based on the point request of the received at least one terminal, generates a list of todped terminal identity, the list terminal identity list includes at least one logo of the terminal that is successfully todged on the central control.
[0068]102. When monitoring the database login request, determine the target identity...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com