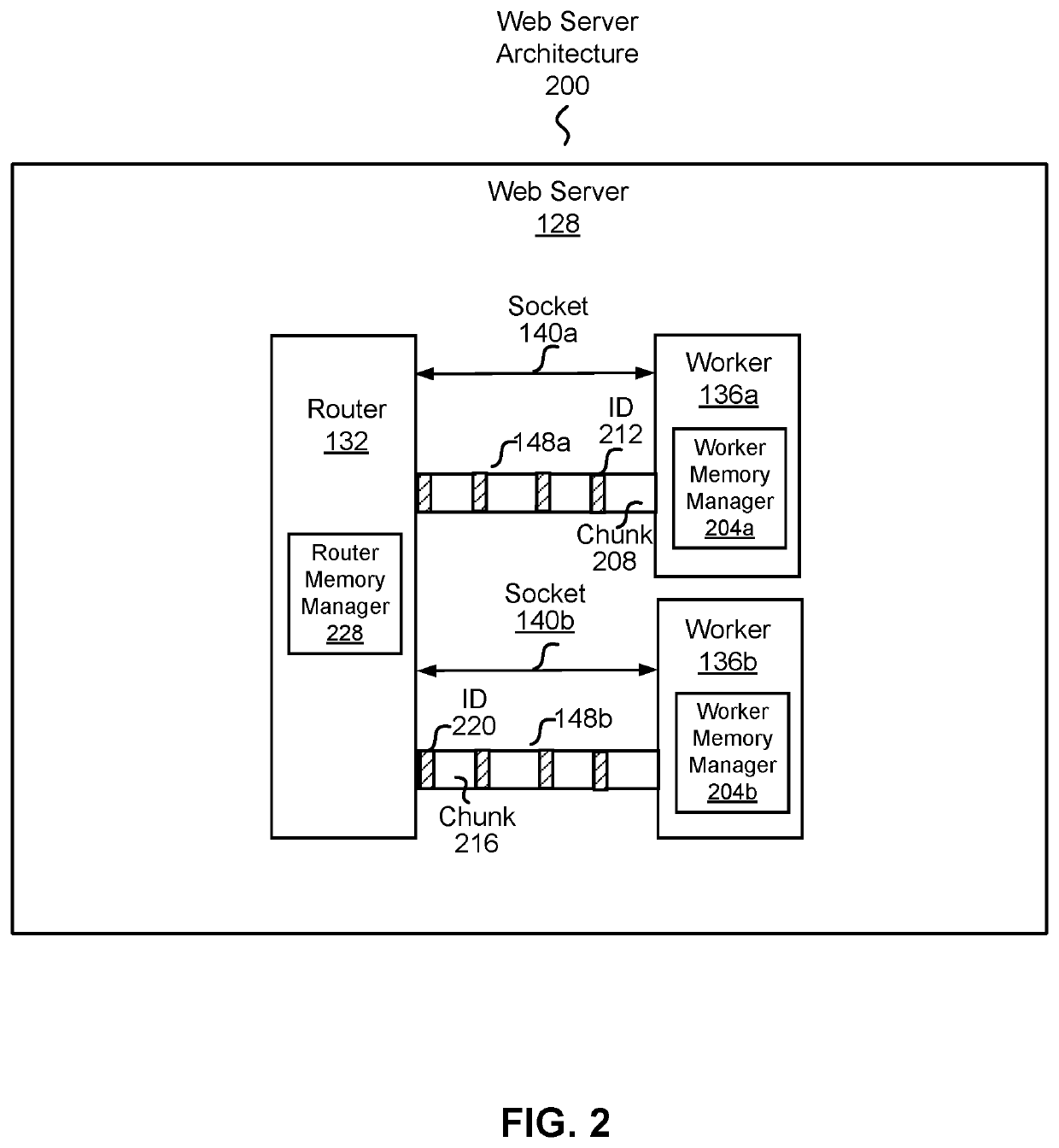
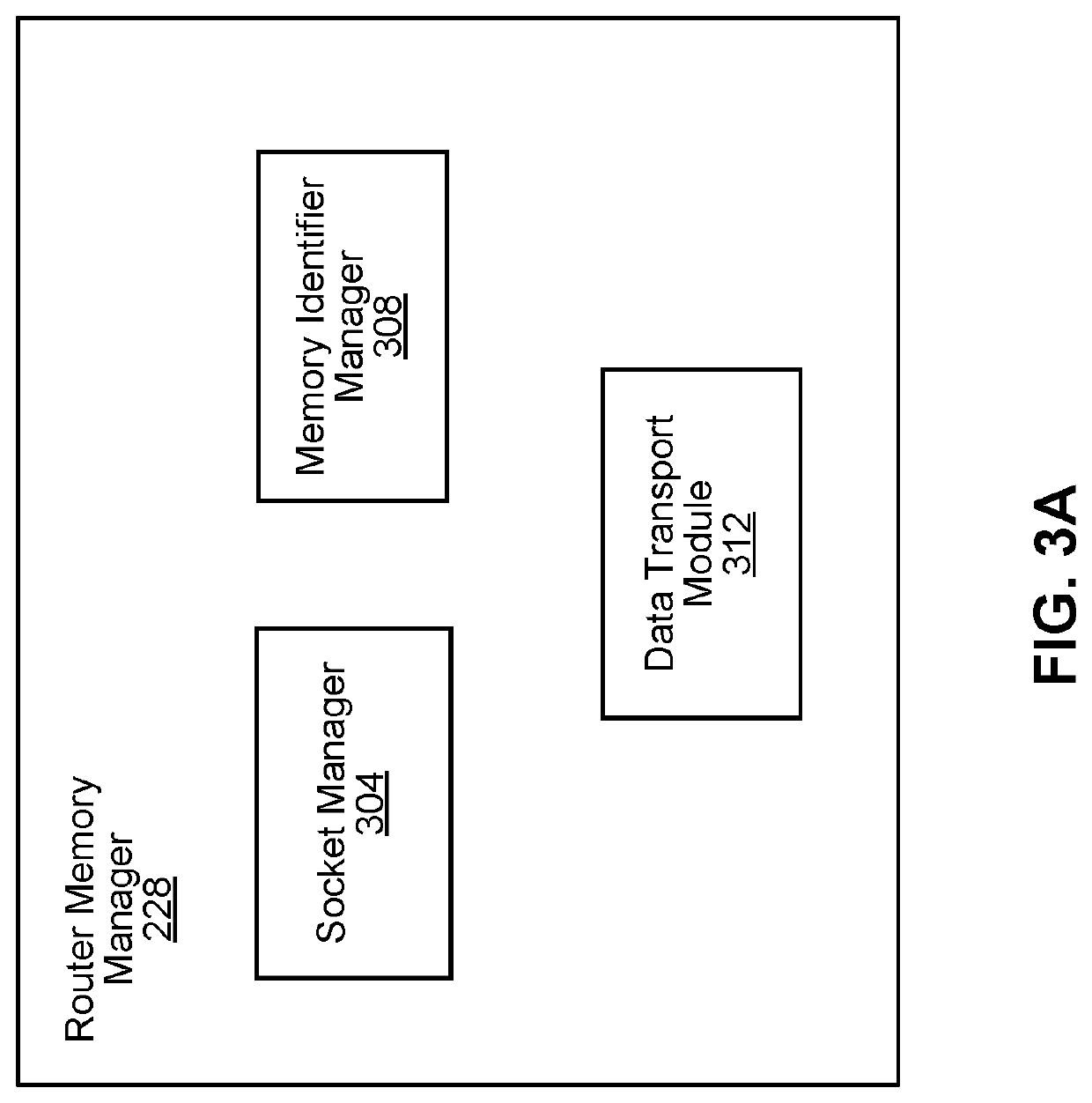
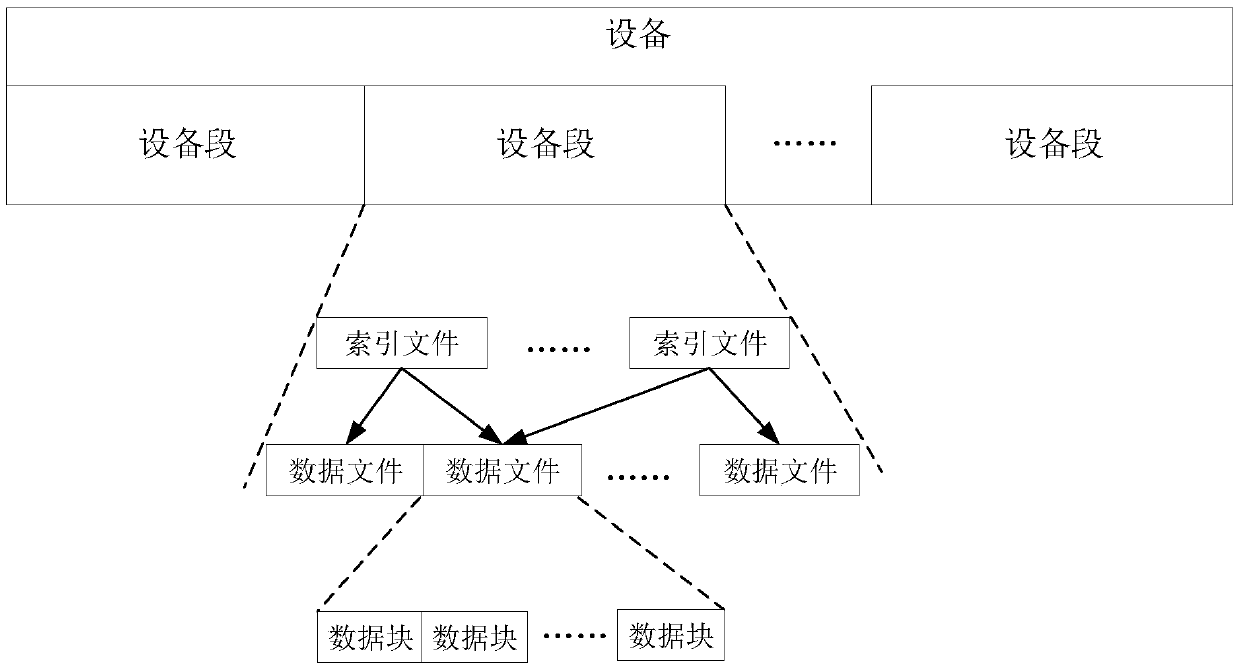
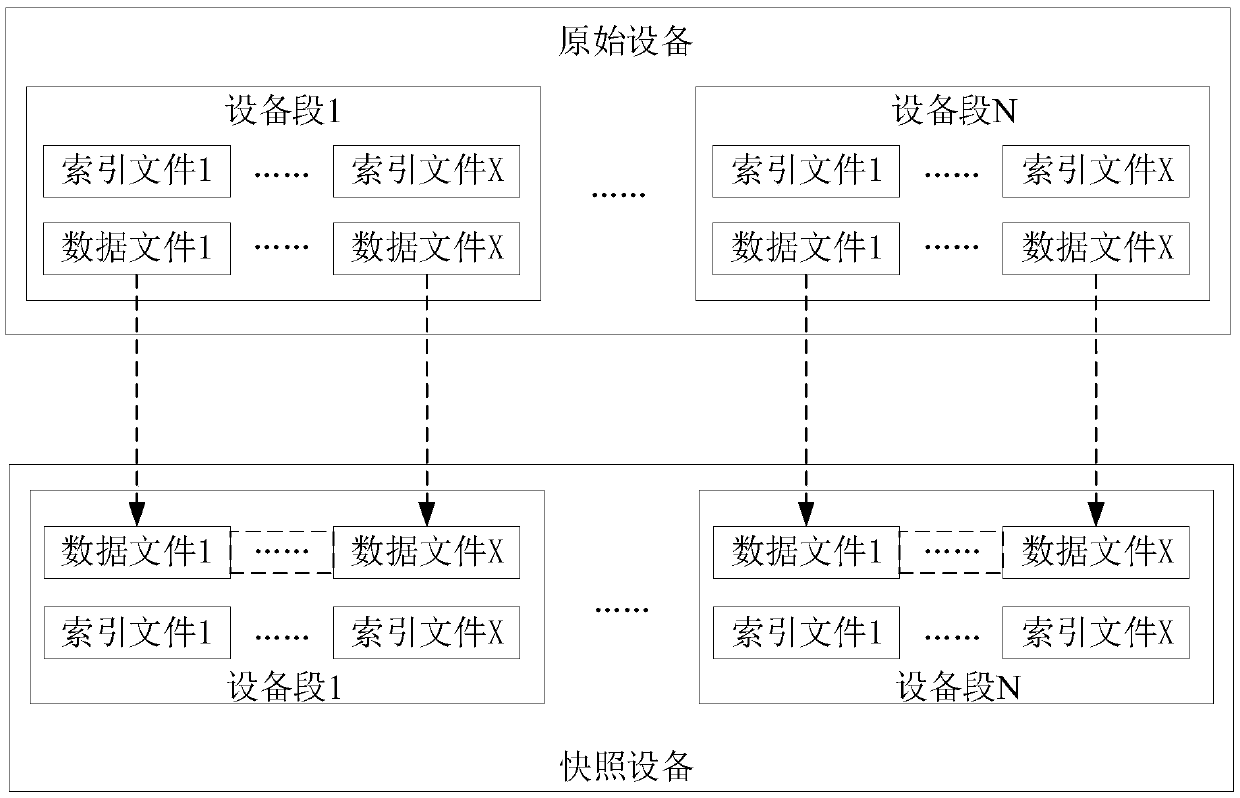
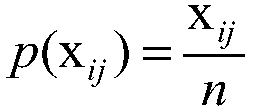Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
58 results about "Data citation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Data citation is the provision of accurate, consistent and standardised referencing for datasets just as bibliographic citations are provided for other published sources like research articles or monographs. Typically the well established Digital Object Identifier (DOI) approach is used with DOIs taking users to a website that contains the metadata on the dataset and the dataset itself.
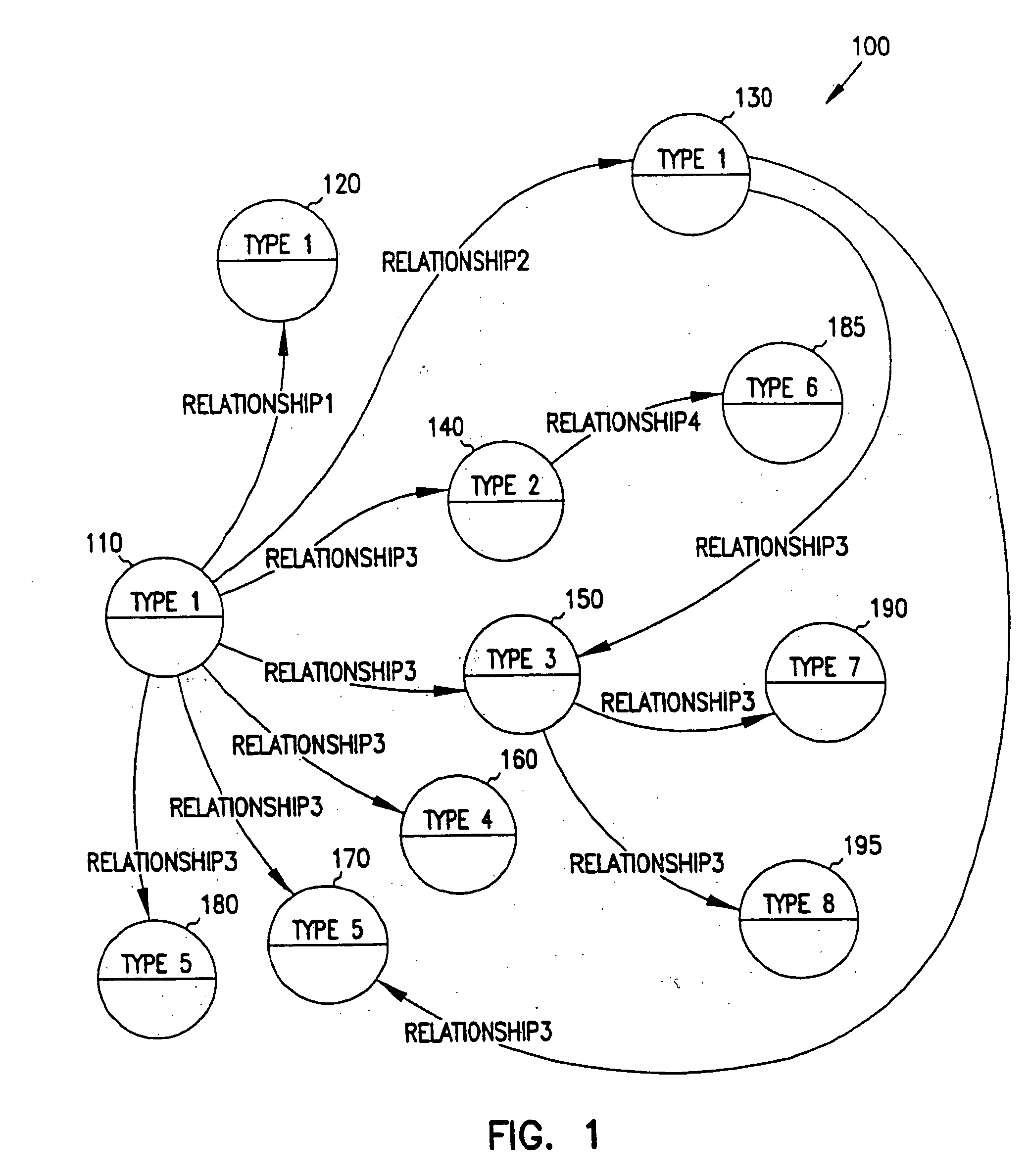
Navigation of view relationships in database system
InactiveUS6609122B1Maintaining correctness and consistency of dataData inconsistencyData processing applicationsDigital data processing detailsOriginal dataApplication software
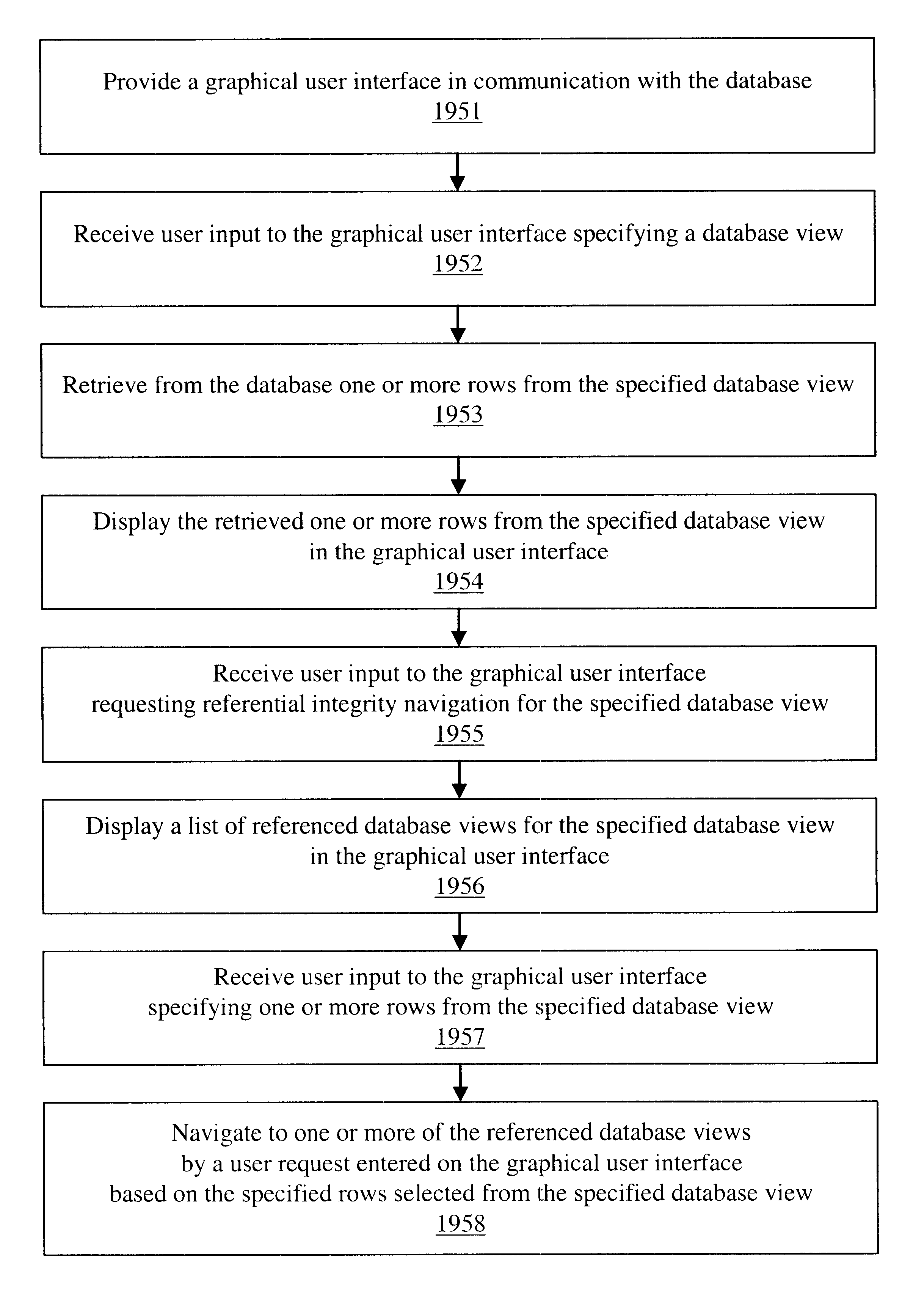
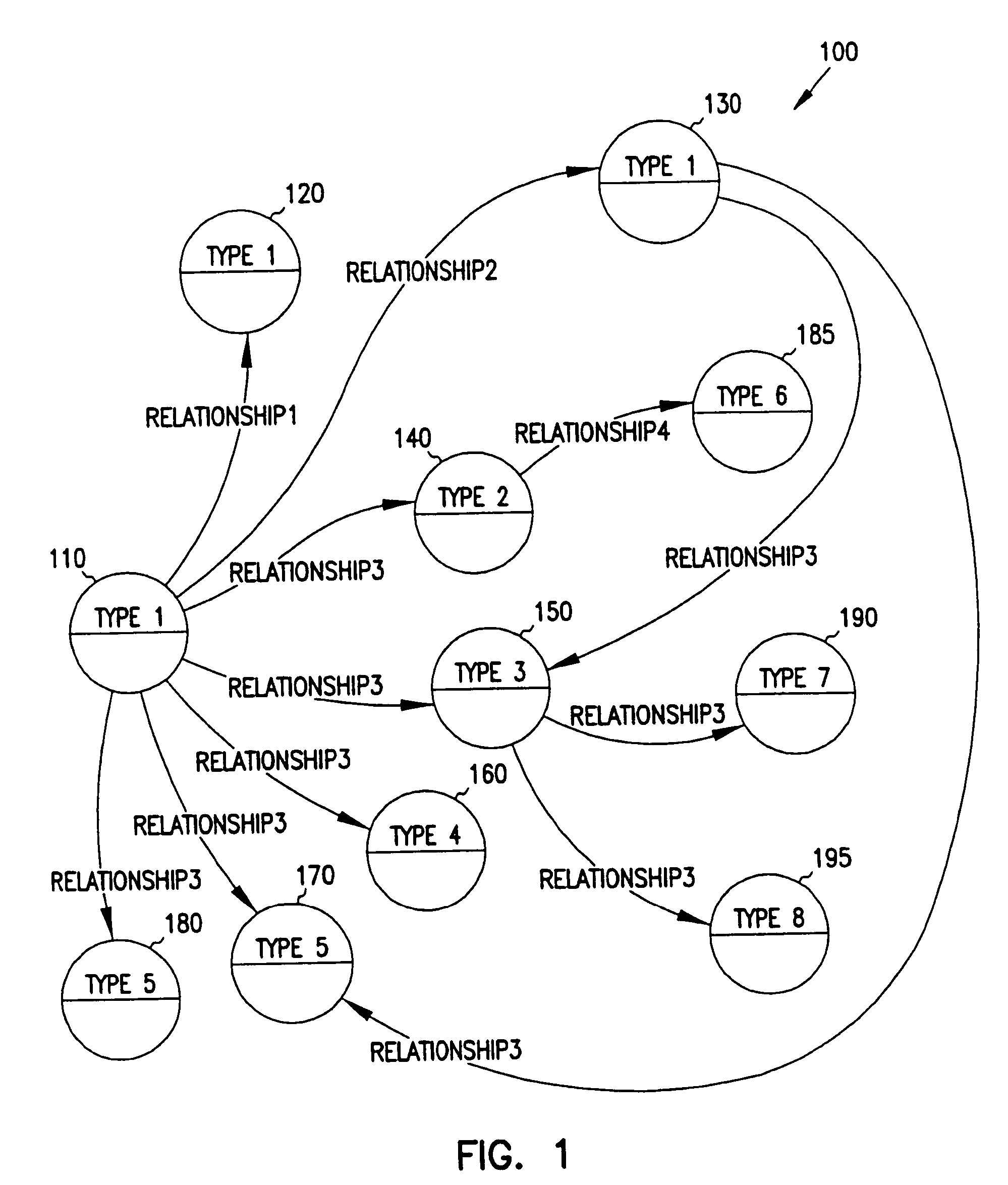
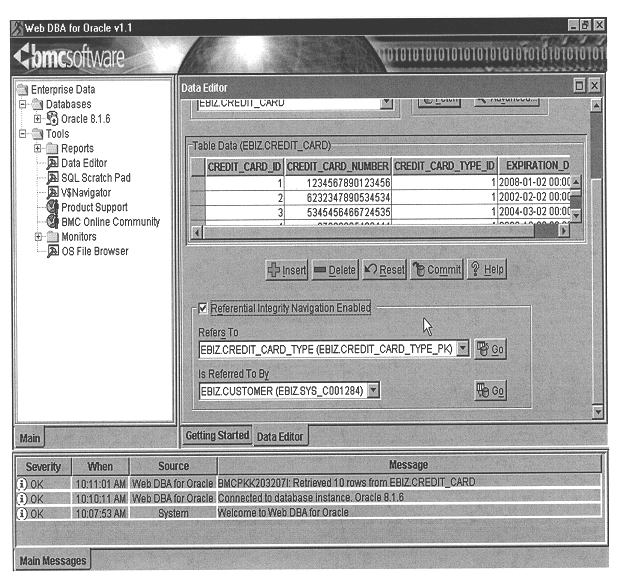
The invention is an improved system and method for browsing and editing data residing in database tables. The method of the present invention includes the steps of providing a graphical user interface in communication with a database, receiving user input to the graphical user interface, retrieving data from the database, displaying the retrieved data in the graphical user interface, and navigating to one or more referenced database tables or views by user request entered on the graphical user interface. The purpose of referential integrity is to prevent database users or applications from entering inconsistent data into a database. The goal of referential integrity navigation is to allow the user, having retrieved one or more rows of data, to navigate easily to the data in other tables that either refers to or is referred to by that data. These relationships are defined by referential integrity constraints, and the data thus retrieved by navigation is then available for all the operations possible on the original data, including data editing and further relational navigation. By storing a catalog of the relationships known to exist between Oracle's V$ views, the same form of navigation can be provided between these data sources.
Owner:BMC SOFTWARE
Tiered and content based database searching
InactiveUS6928452B2Simple interfaceEfficient and accurate search resultData processing applicationsWeb data indexingRelevant informationData citation
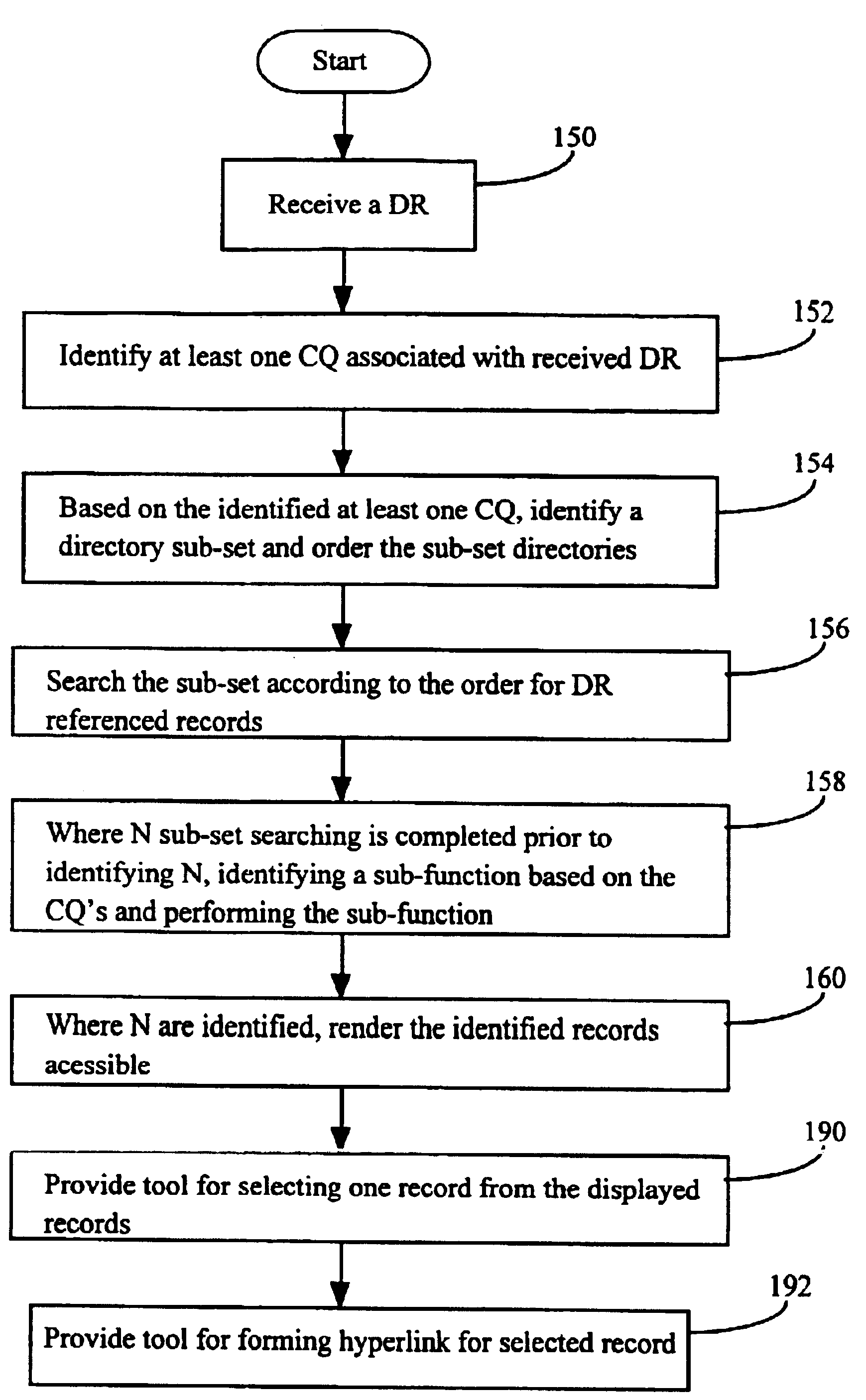
A method and apparatus for facilitating efficient database searching for records referenced by a data reference, the method including examining a data reference and related information to identify markup language codes or tags associated with the data reference and, based the markup language codes or tags, selecting a sub-set of databases to be searched for data referenced records and rendering identified records accessible.
Owner:HYPERPHRASE TECH
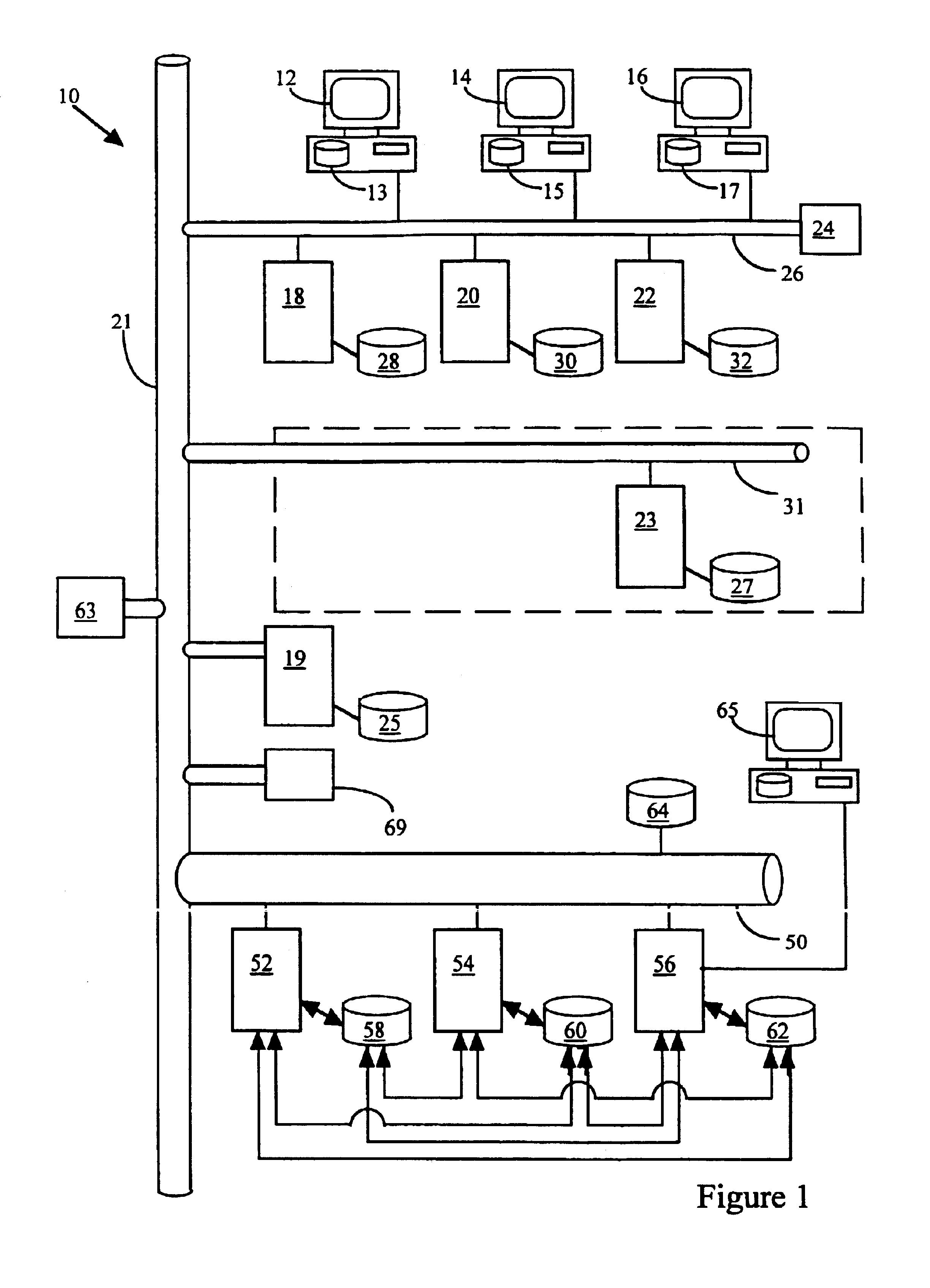
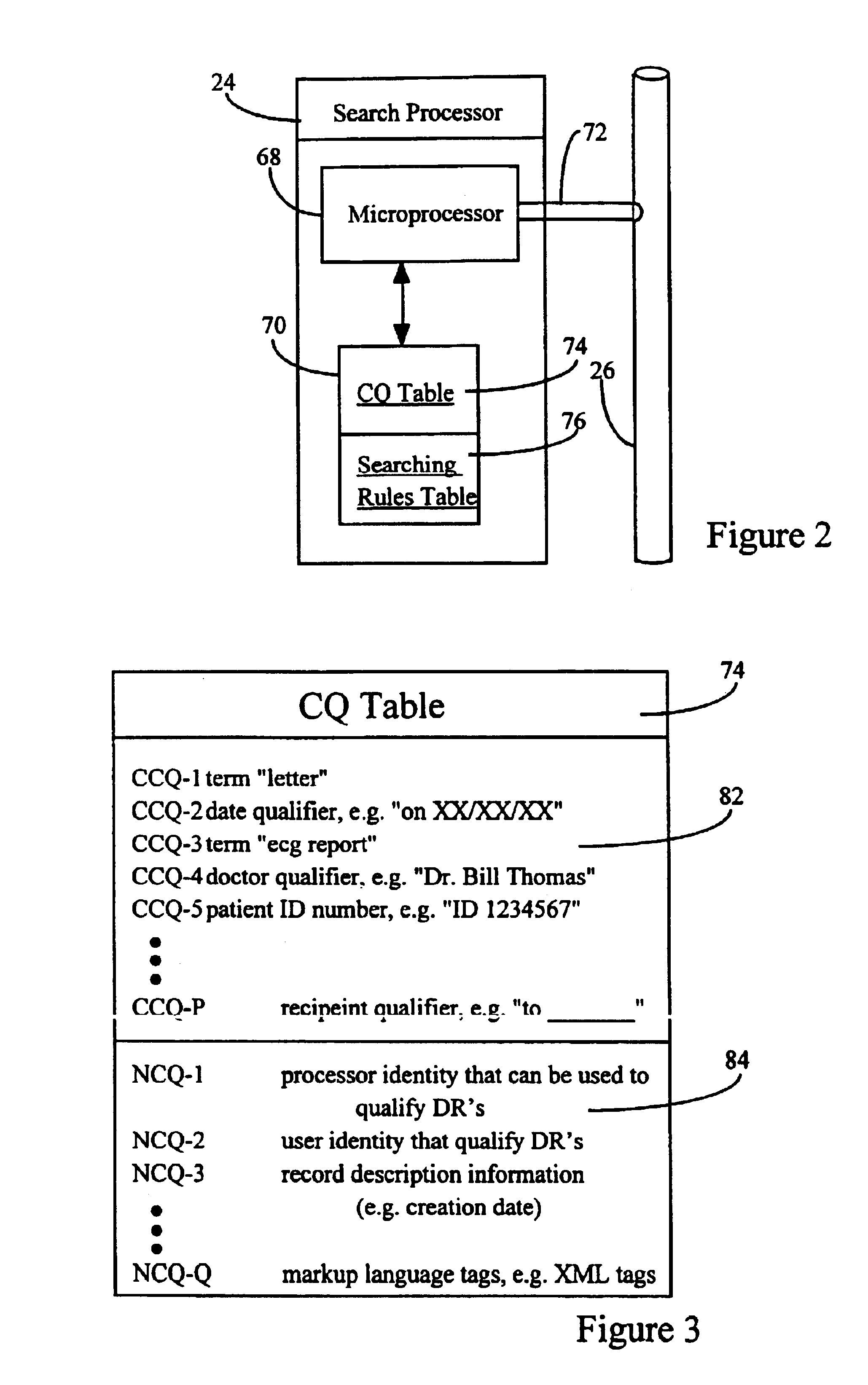
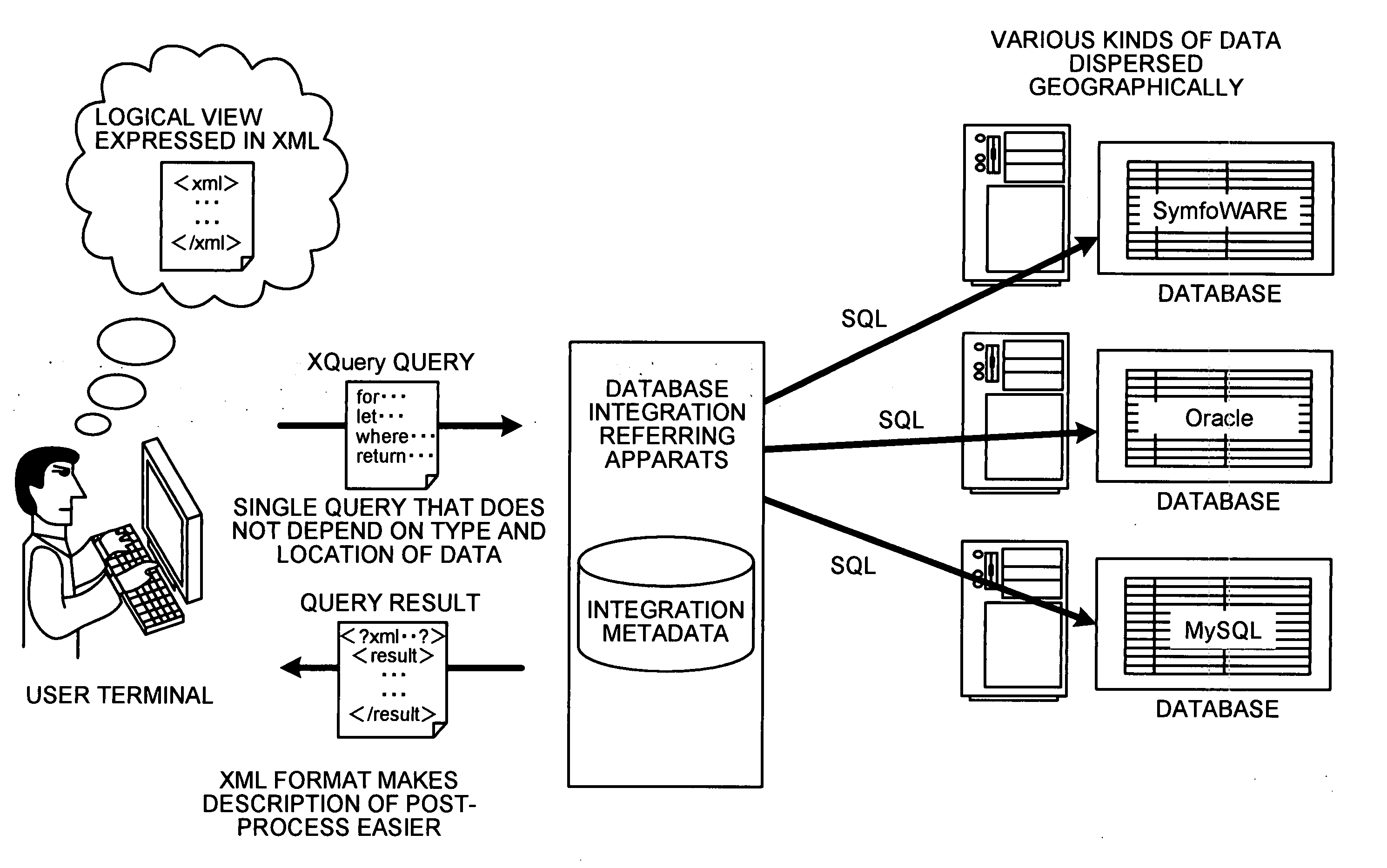
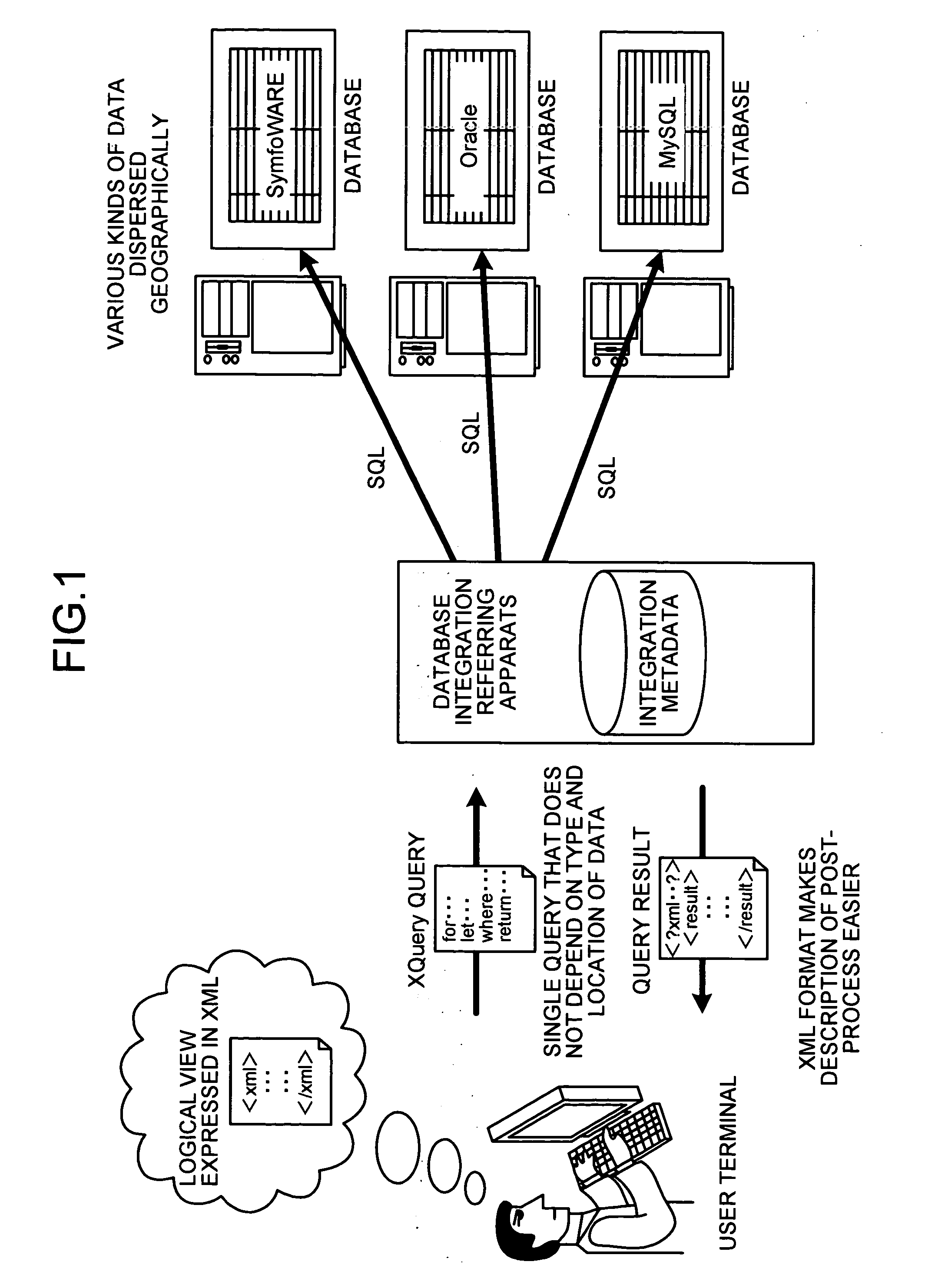
Method and apparatus for referring to database integration, and computer product
InactiveUS20050160076A1Solve problemsDatabase management systemsSpecial data processing applicationsReference databaseCitation database
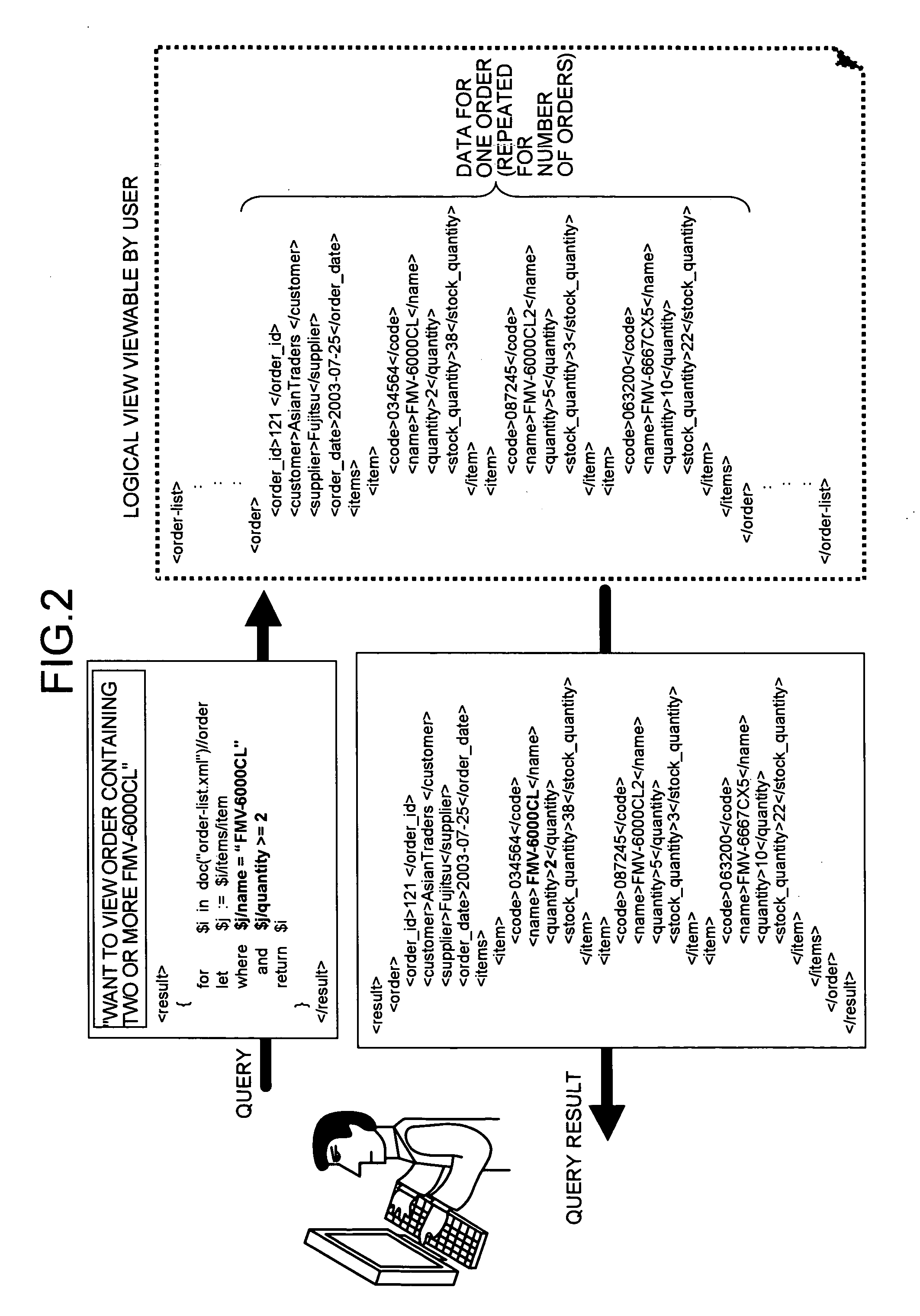
When referring to database integration, integration metadata is stored. The integration metadata defines a format of a tagged document used for outputting a result of a query for data reference to a plurality of databases, a relation between each element in the tagged document and each element in each database, and a relation between the elements in each database. When a query is received in a format of the tagged document, the integration metadata is referred to and queries are made to various databases to acquire data. Finally a result of the queries is generated in the format of the tagged document.
Owner:FUJITSU LTD
Electronic camera and image processing method
ActiveUS20040135906A1Television system detailsGeometric image transformationImaging processingImage plane
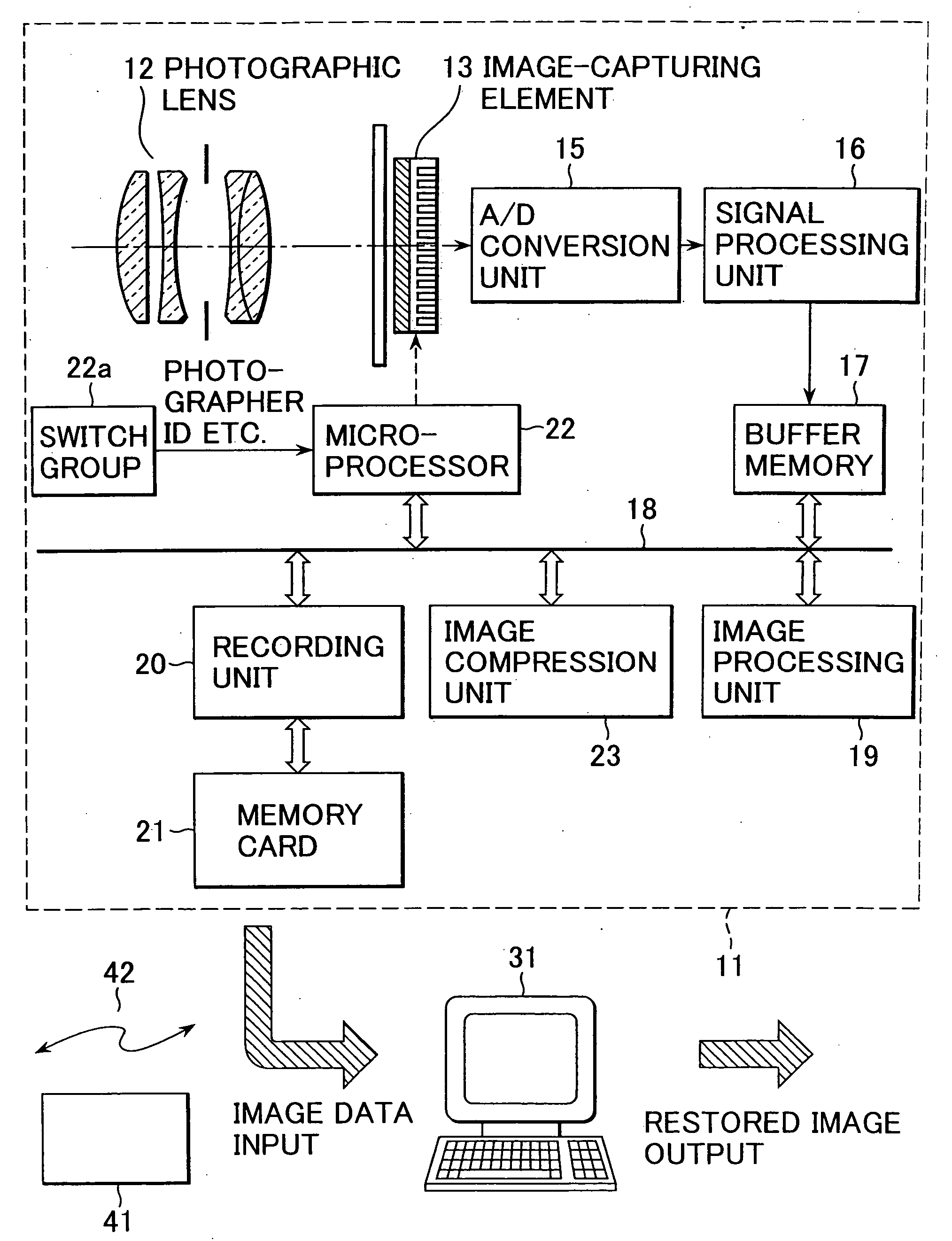
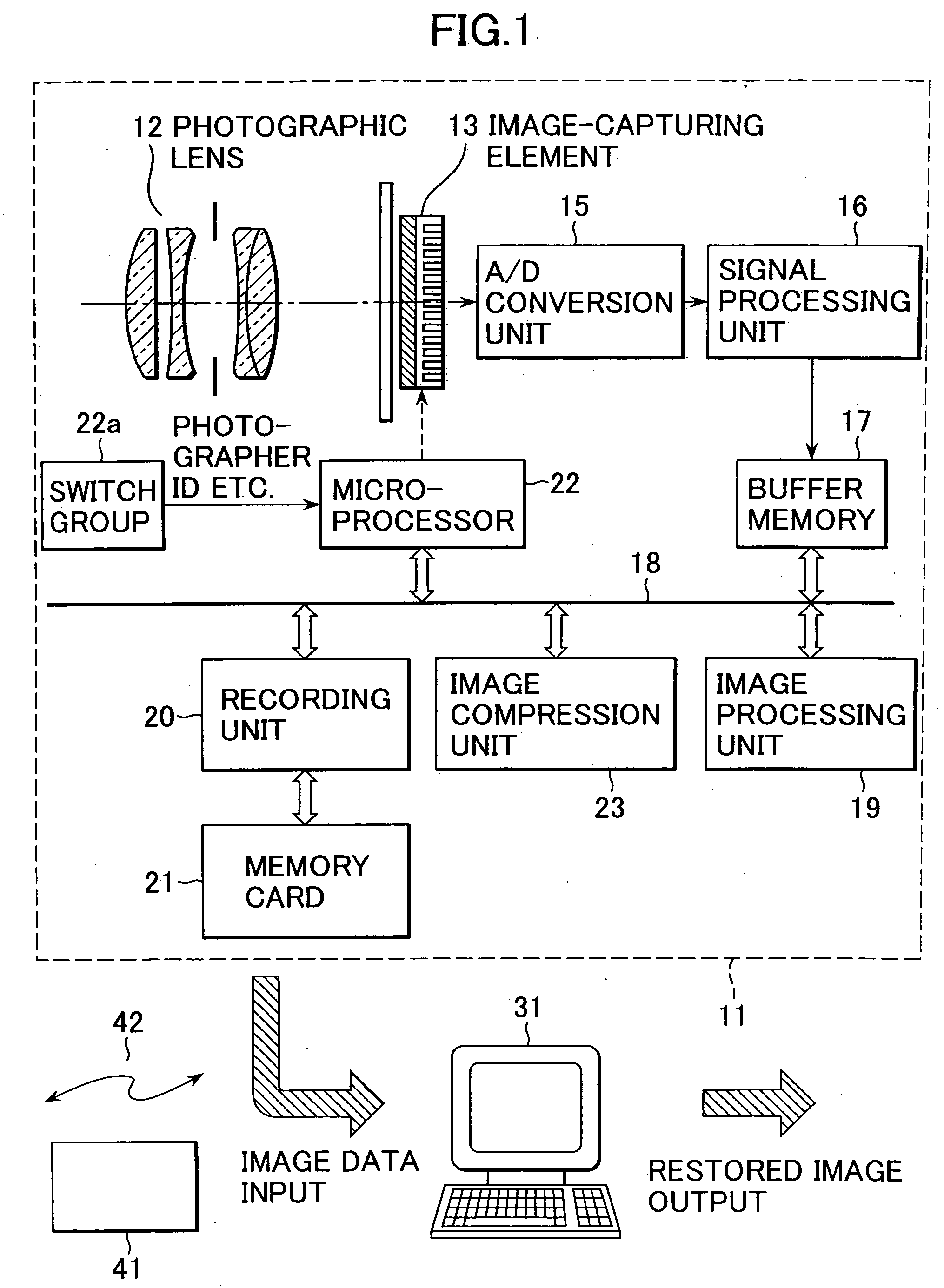
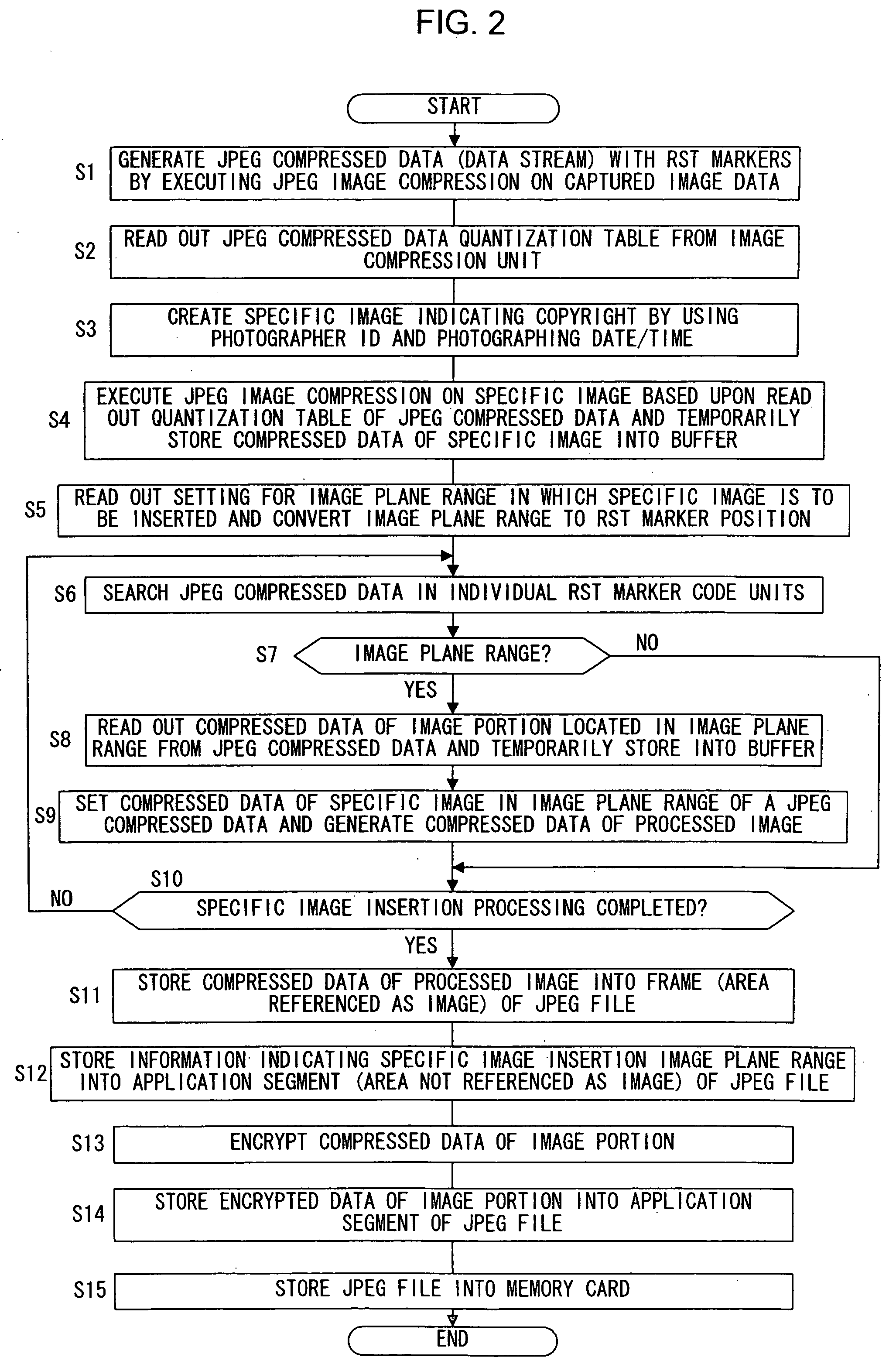
An electronic camera that creates an image file by processing image data obtained through an image-capturing operation, includes: an image-capturing unit that generates the image data by capturing a subject image; a data extraction unit that sets an image plane range corresponding to an image portion of the image data and extracts data of the image portion in the image plane range; a data insertion unit that writes data of a predetermined specific image over the image plane range of the image data and generates data of a processed image; and a file creation unit that creates an image file by storing the data of the processed image into an image data area of the image file, which is referenced as image data and storing the data of the image portion into a non-image data area of the image file which is not referenced as image data.
Owner:NIKON CORP
Aggregate structure identification and its application to program analysis
InactiveUS6279149B1Digital data processing detailsReverse engineeringArray data structureSimple component
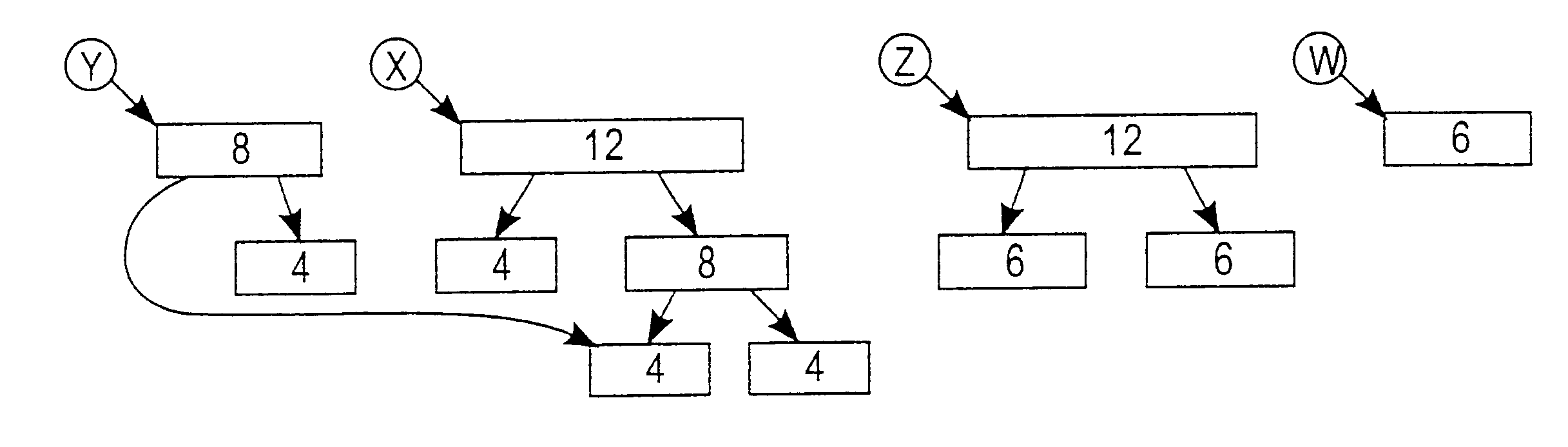
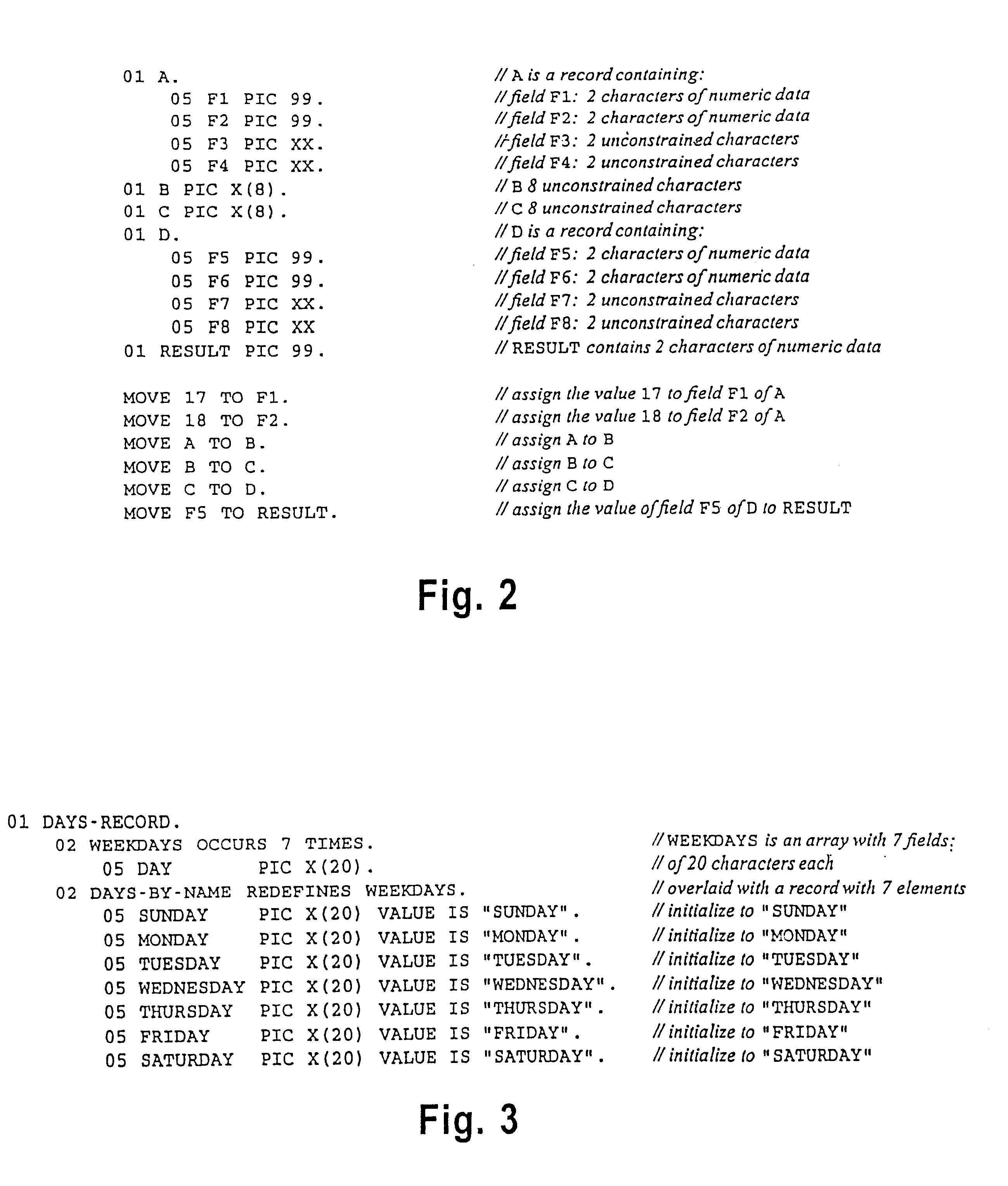
An efficient program analysis method is provided for lazily decomposing aggregates (such as records and arrays) into simpler components based on the access patterns specific to a given program. This process allows us both to identify implicit aggregate structure not evident from declarative information in the program, and to simplify the representation of declared aggregates when references are made only to a subset of their components. The method can be exploited to yield: (i) a fast type analysis method applicable to program maintenance applications (such as date usage inference for the Year 2000 problem); and (ii) an efficient method for atomization of aggregates. More specifically, aggregate atomization decomposes all of the data that can be manipulated by the program into a set of disjoint atoms such that each data reference can be modeled as one or more references to atoms without loss of semantic information. Aggregate atomization can be used to adapt program analyses and representations designed for scalar data to aggregate data. In particular, atomization can be used to build more precise versions of program representations such as SSA form or PDGs. Such representations can in turn yield more accurate results for problems such as program slicing. Our techniques are especially useful in weakly-typed languages such as Cobol (where a variable need not be declared as an aggregate to store an aggregate value) and in languages where references to statically-defined sub-ranges of data such as arrays or strings are allowed.
Owner:IBM CORP
Data referencing within a database graph
InactiveUS20050151738A1Drawing from basic elementsData processing applicationsDatum referenceTheoretical computer science
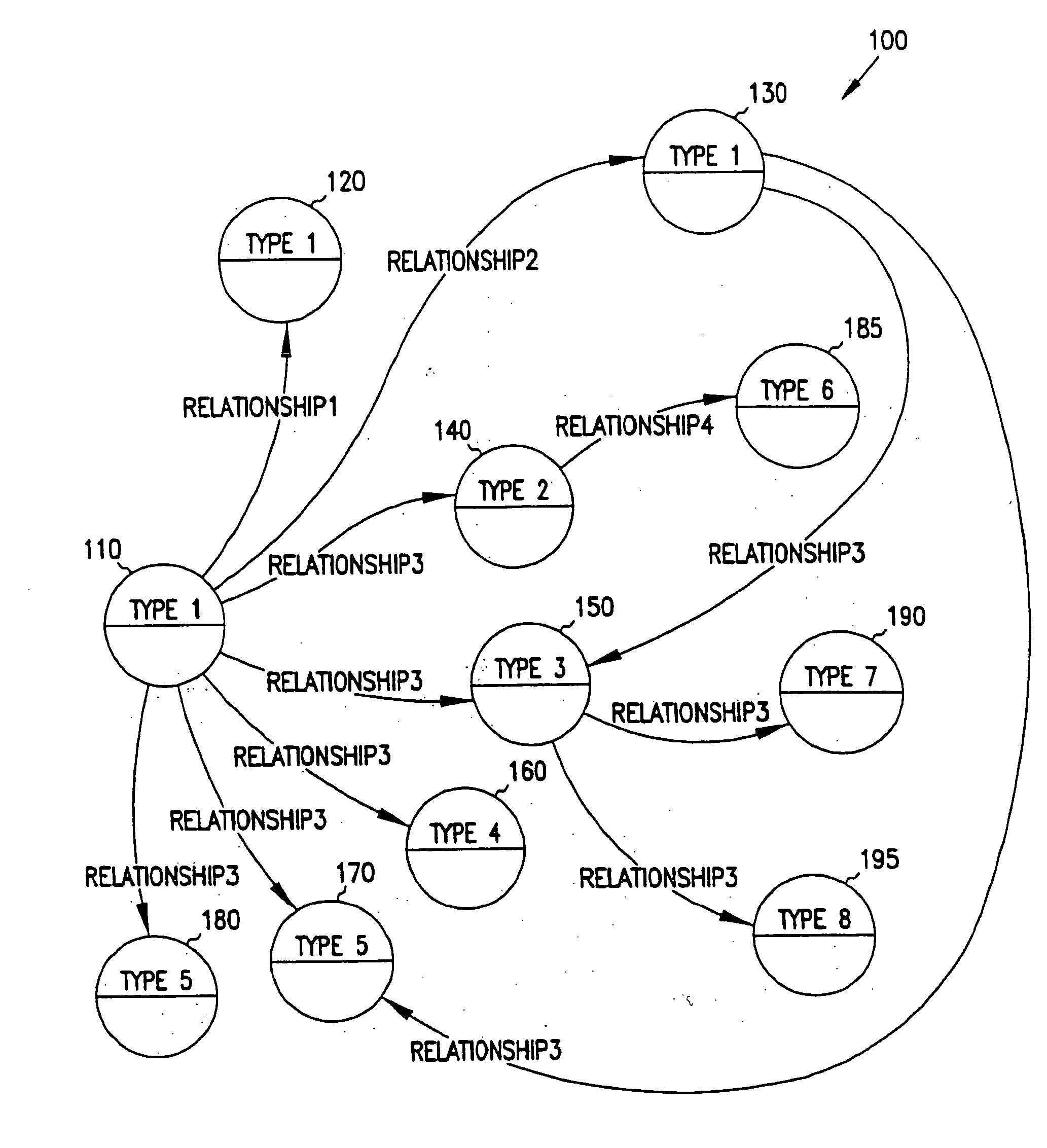
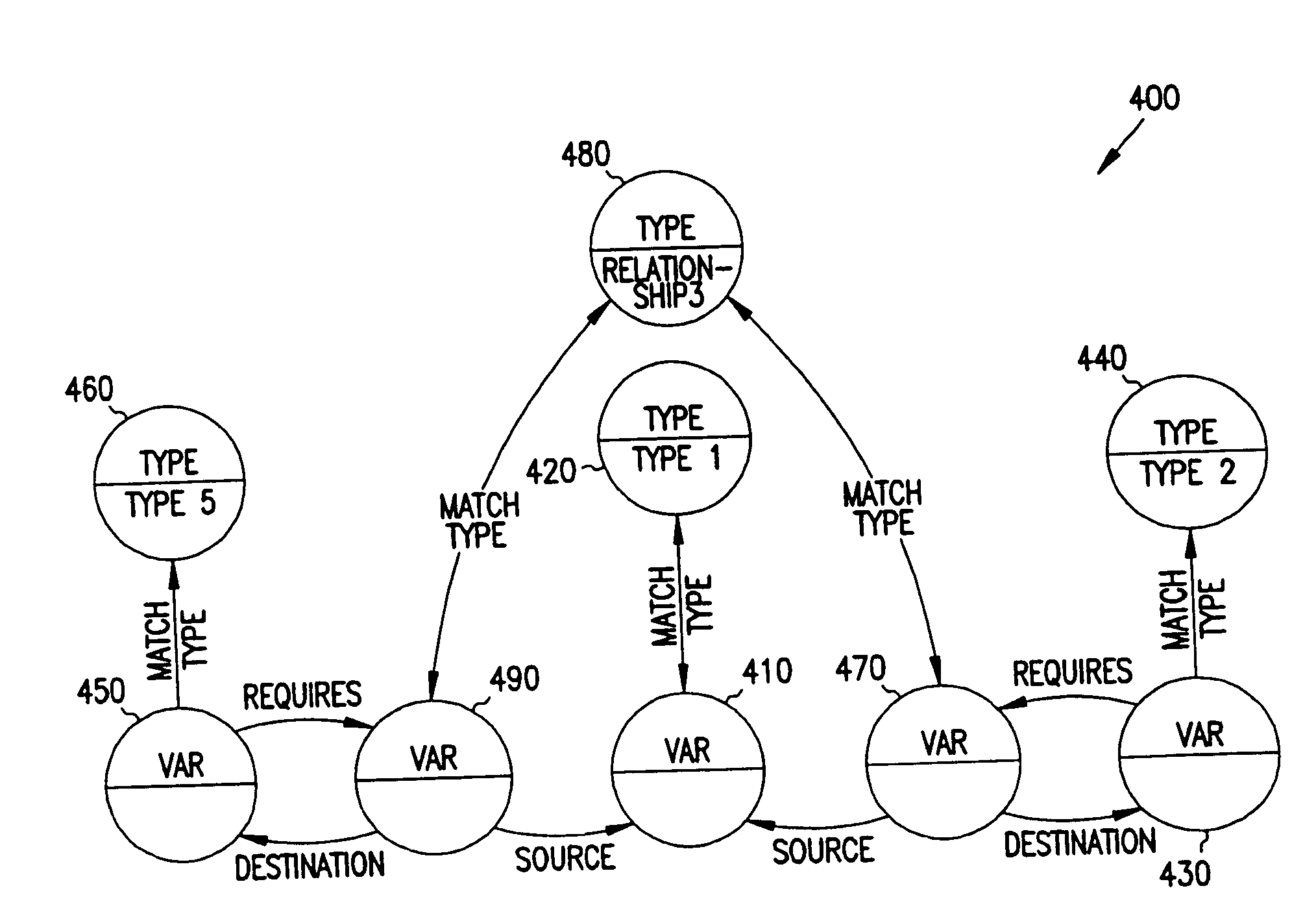
The present invention is directed to providing a higher degree of association between nodes and links in a graph by creating data structures (spiders) that provide views into graphs that transcend the relatively static association of a conventional graph. A spider's variables bind to any number of nodes and links in the graph, enabling all of the bound nodes and links by addressing the spider. By adding constraints on the extent or degree of binding in a spider to a graph, a subset of the graph is identified. The spider can then used to address the subset of the graph as constrained by the spider. A spider can bind to a link in order to identify a parent / child structural subset of the graph. More specifically a spider is a collection of variables that create a template or pattern and bind to the nodes and links in the graph. A spider traverses a graph by binding its variables to various nodes and links in the graph.
Owner:MICROSOFT TECH LICENSING LLC
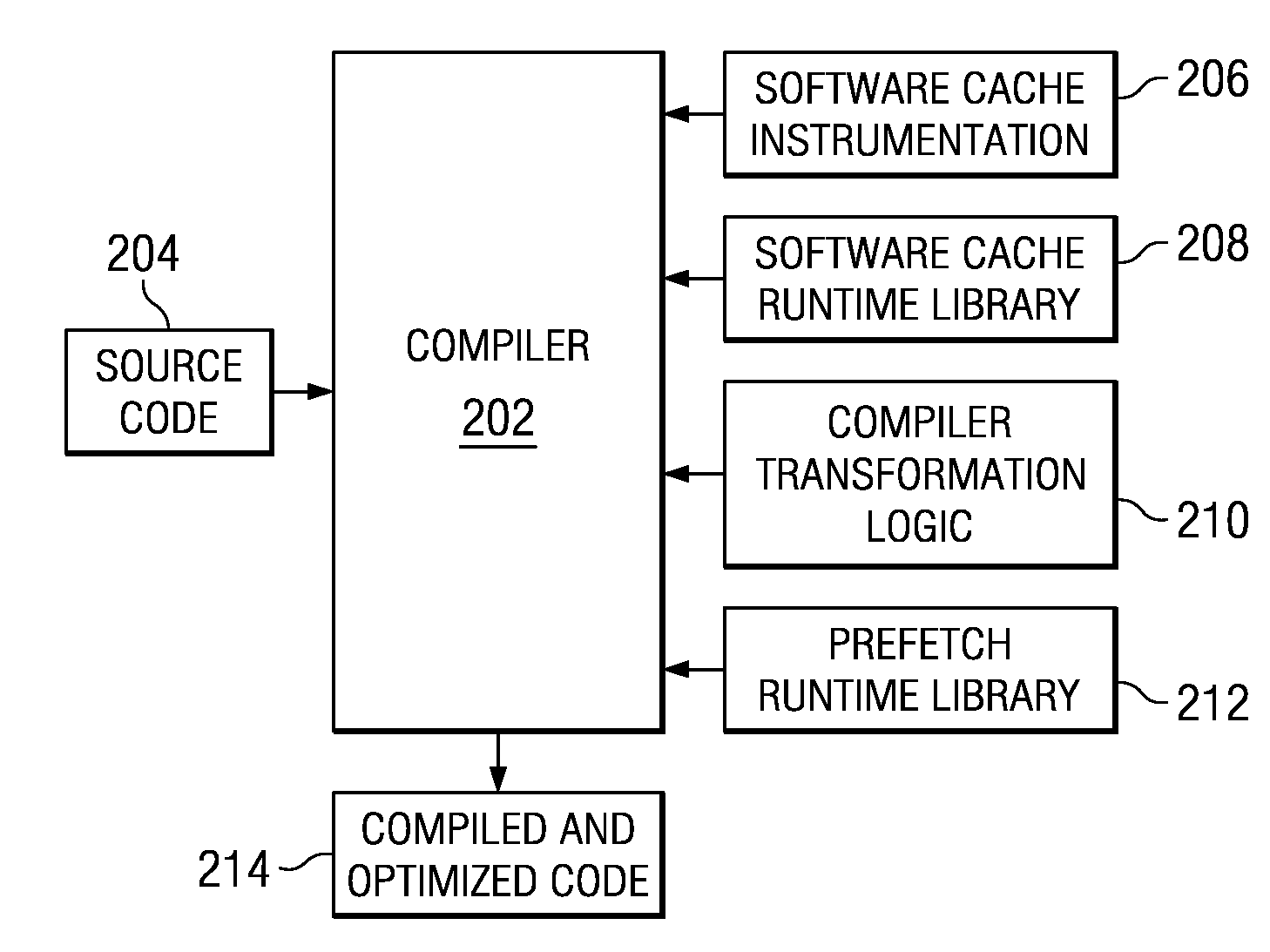
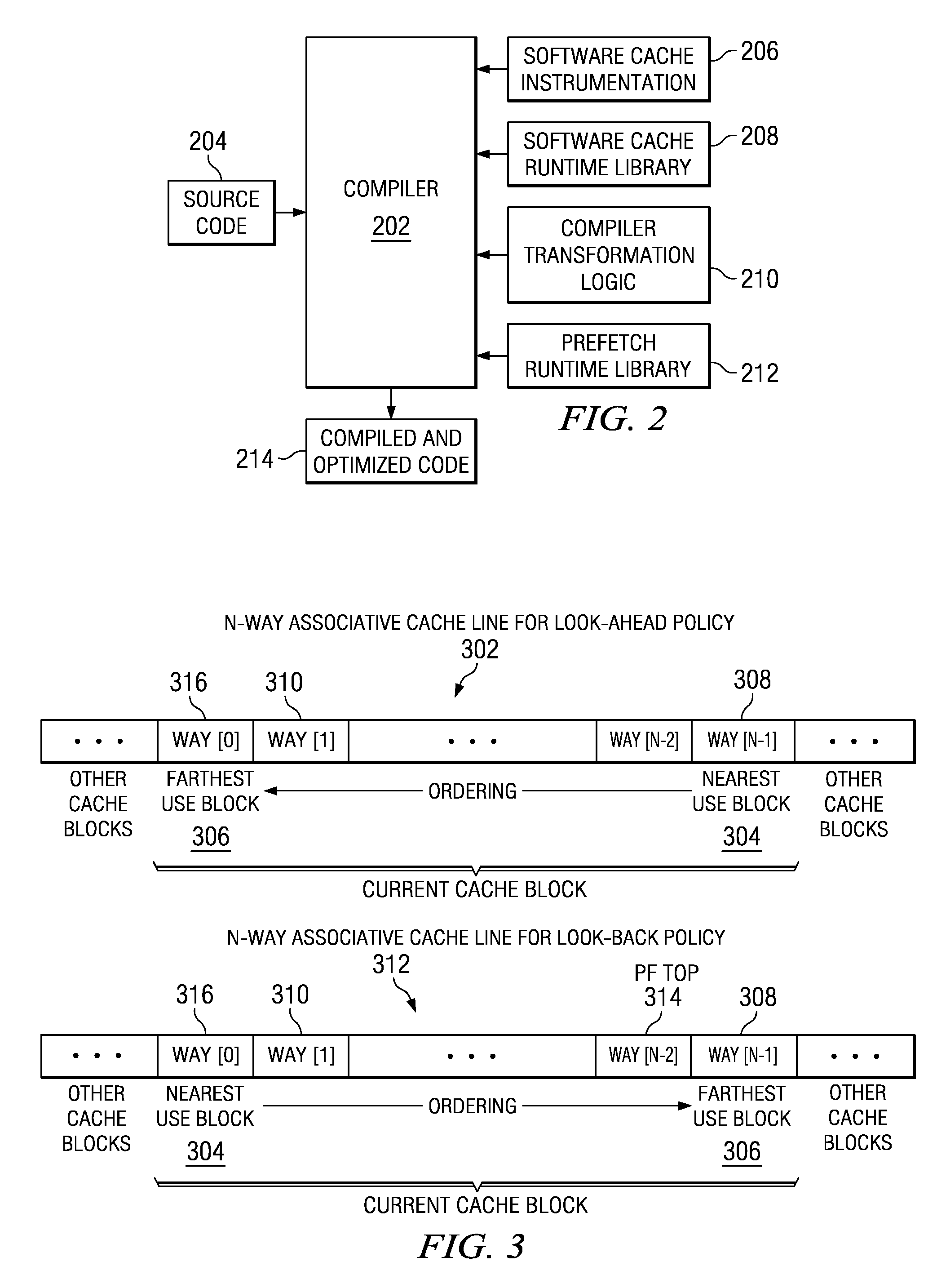
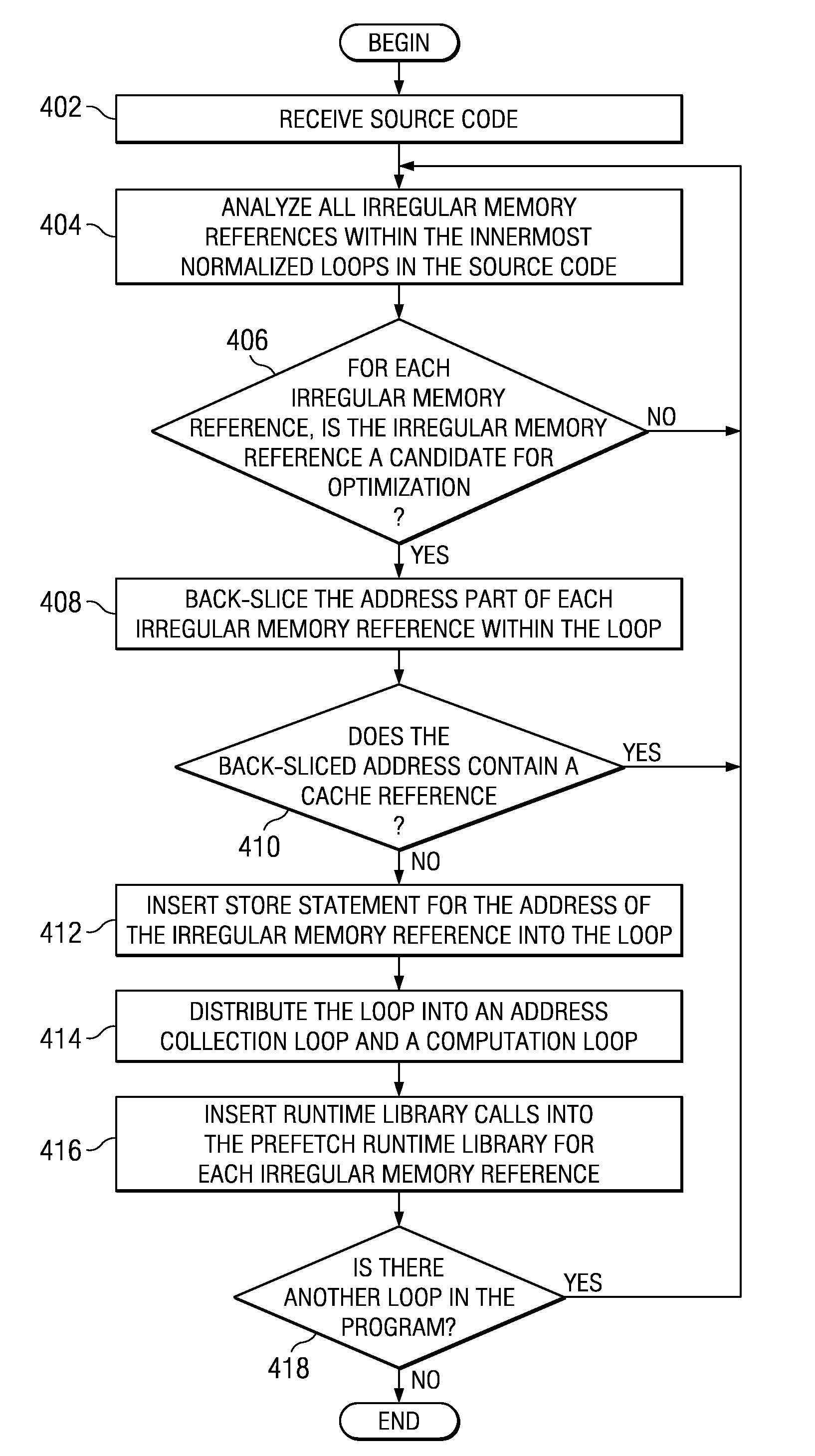
Prefetching Irregular Data References for Software Controlled Caches
Prefetching irregular memory references into a software controlled cache is provided. A compiler analyzes source code to identify at least one of a plurality of loops that contain an irregular memory reference. The compiler determines if the irregular memory reference within the at least one loop is a candidate for optimization. Responsive to an indication that the irregular memory reference may be optimized, the compiler determines if the irregular memory reference is valid for prefetching. Responsive to an indication that the irregular memory reference is valid for prefetching, a store statement for an address of the irregular memory reference is inserted into the at least one loop. A runtime library call is inserted into a prefetch runtime library for the irregular memory reference. Data associated with the irregular memory reference is prefetched into the software controlled cache when the runtime library call is invoked.
Owner:IBM CORP
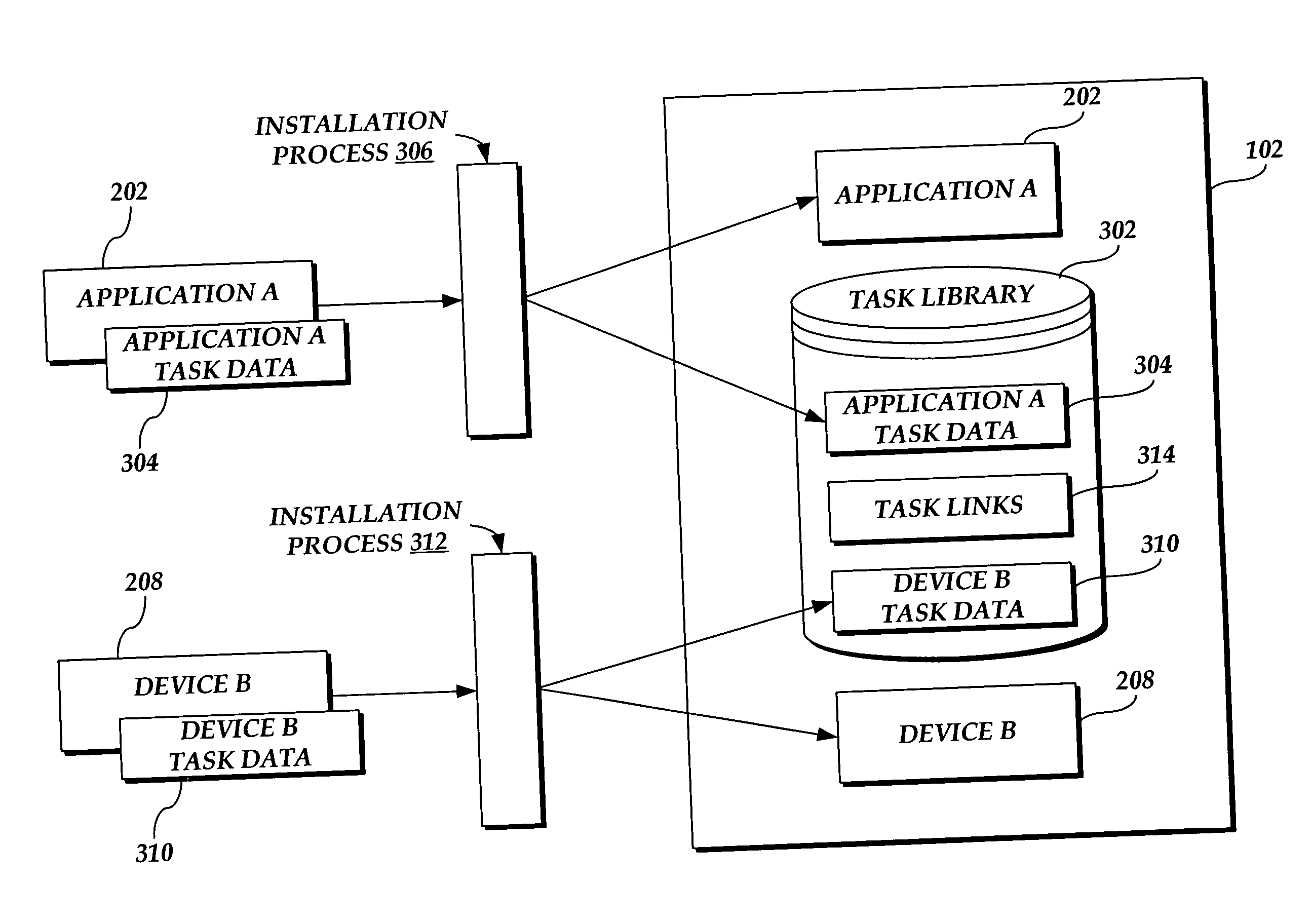
Task library of task data for a plurality of components on a computer system
A task library comprising task data for a plurality of components installed on a computer system is provided. The task library includes task data for a plurality of components installed on a computer system. The task links, that reference task data elements, are generated and stored with the task library. The task links are generated according to predetermined schemas associated with the task library. Task data elements may be configured such that the installed component corresponding to the task data may be manipulated / configured from within the context of the task library. The components installed on the computer may be hardware or software components. Installed components may include modules that are “installed” on the computer though they are located remote to the computer.
Owner:MICROSOFT TECH LICENSING LLC
Data referencing within a database graph
The present invention is directed to providing a higher degree of association between nodes and links in a graph by creating data structures (spiders) that provide views into graphs that transcend the relatively static association of a conventional graph. A spider's variables bind to any number of nodes and links in the graph, enabling all of the bound nodes and links by addressing the spider. By adding constraints on the extent or degree of binding in a spider to a graph, a subset of the graph is identified. The spider can then used to address the subset of the graph as constrained by the spider. A spider can bind to a link in order to identify a parent / child structural subset of the graph. More specifically a spider is a collection of variables that create a template or pattern and bind to the nodes and links in the graph. A spider traverses a graph by binding its variables to various nodes and links in the graph.
Owner:MICROSOFT TECH LICENSING LLC
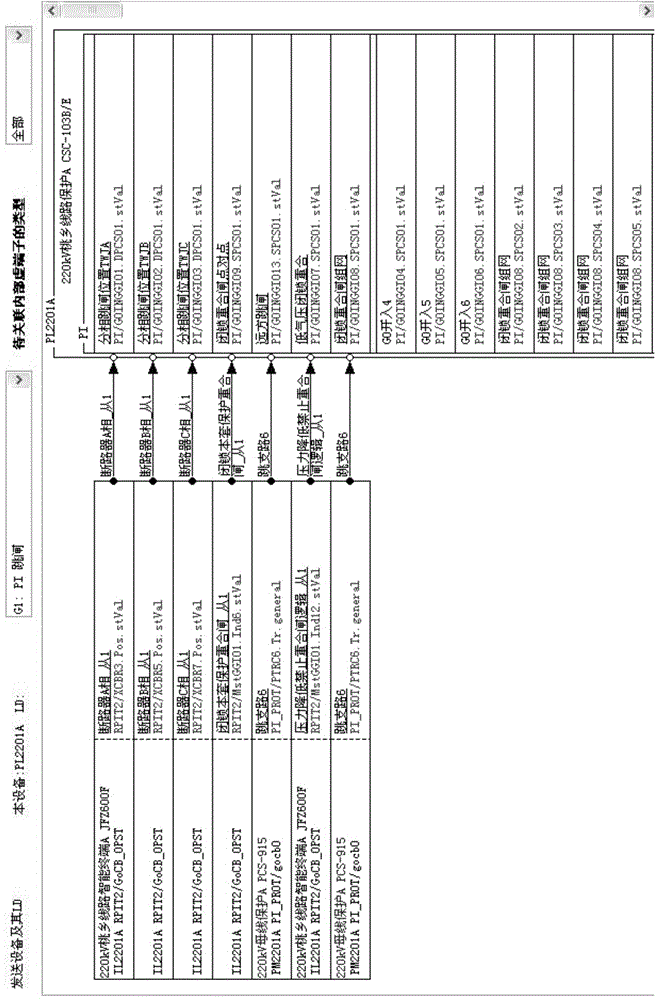
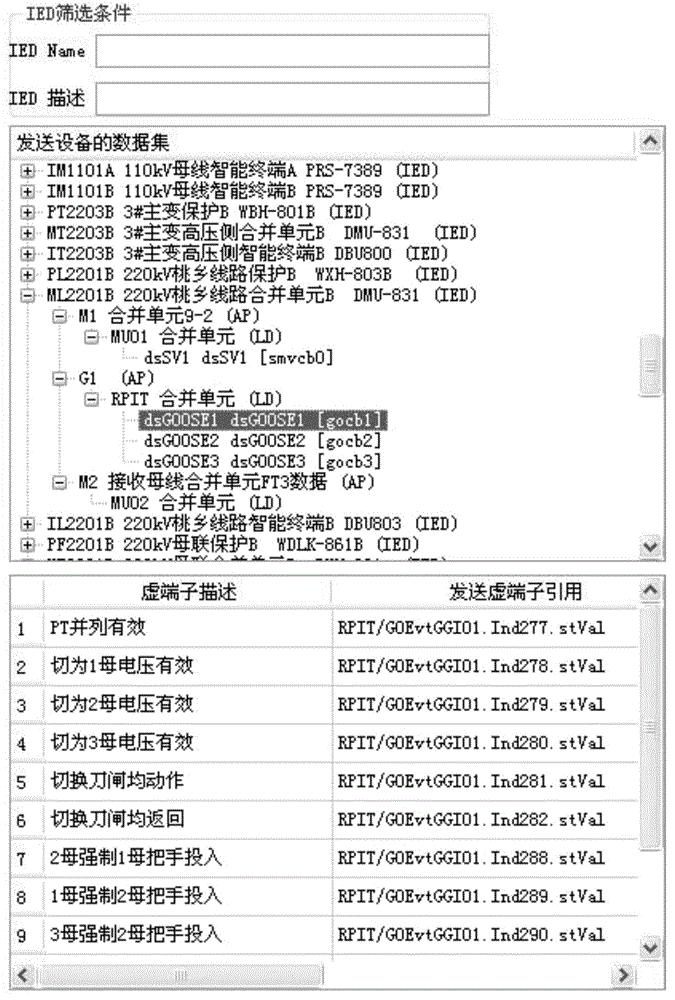
Imaging generation method for input virtual terminal of intelligent substation SCD (System Configuration Description)
InactiveCN103984806AAvoid searchingImprove efficiencySpecial data processing applicationsInformation technology support systemVirtual terminalSmart substation
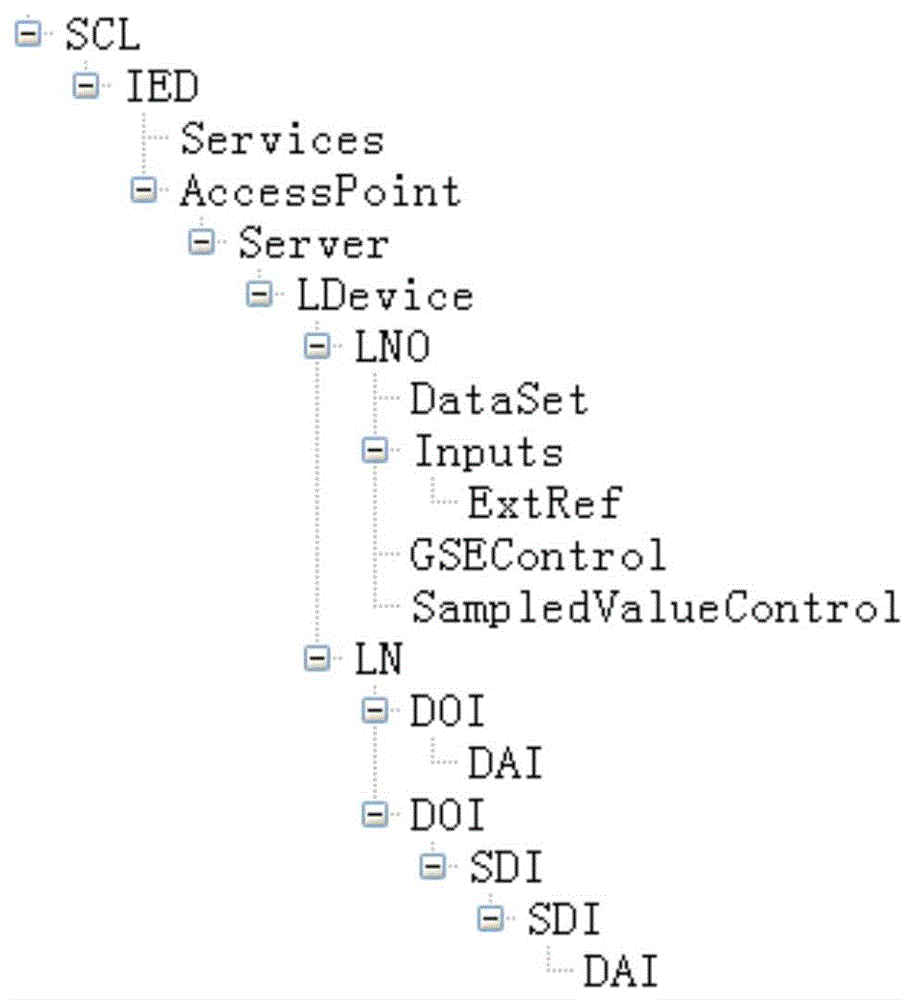
The invention provides an imaging generation method for an input virtual terminal of an intelligent substation SCD (System Configuration Description). The imaging generation method comprises the following steps: firstly, automatically searching an inner virtual terminal of a certain IED (Intelligent Electronic Device); utilizing an imaging technology to display a related virtual terminal, the input virtual terminal and sending source information thereof, and an inner virtual terminal to be related on an interface in a partition and column graphing manner; applying imaging dragging and dropping to appointing the corresponding input virtual terminal to the inner virtual terminal; submitting in two phases to officially form the input virtual terminal. The imaging generation method has the beneficial effects that (1) all the inner virtual terminals of the local IED are automatically searched and displayed; (2) all the inner virtual terminals of equipment are displayed in upper and lower regions in a partitioning manner; (3) the sending source information of each input virtual terminal and description thereof and data citing are given in columns and displayed; (4) all sending virtual terminals sent by the certain IED can be found rapidly and accurately to be used as standby input virtual terminals of the local IED; (5) the input virtual terminal is generated or updated through dragging and dropping operation and two times of submitting; the operation process is direct and convenient.
Owner:SOUTHWEST JIAOTONG UNIV +2
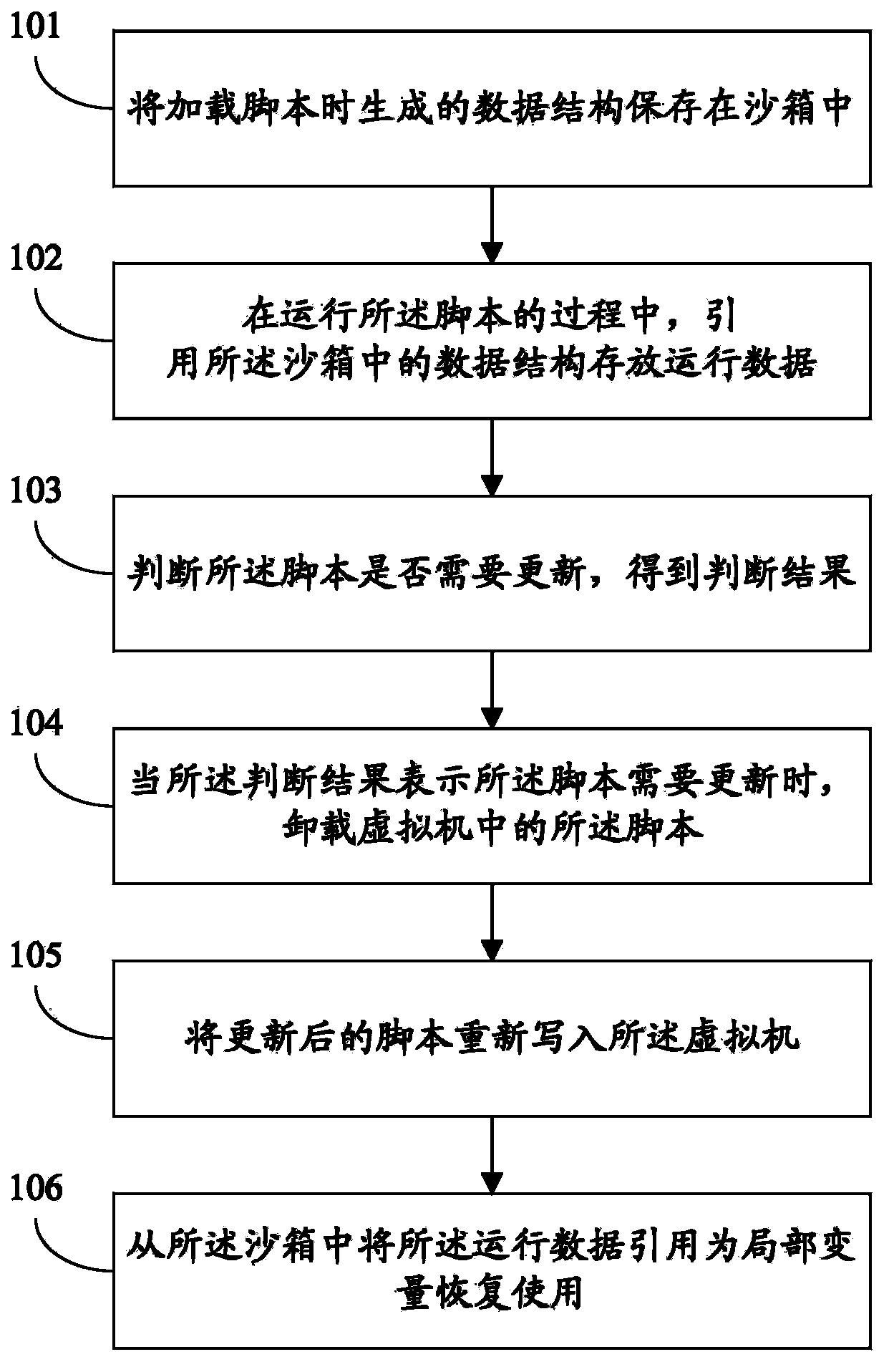
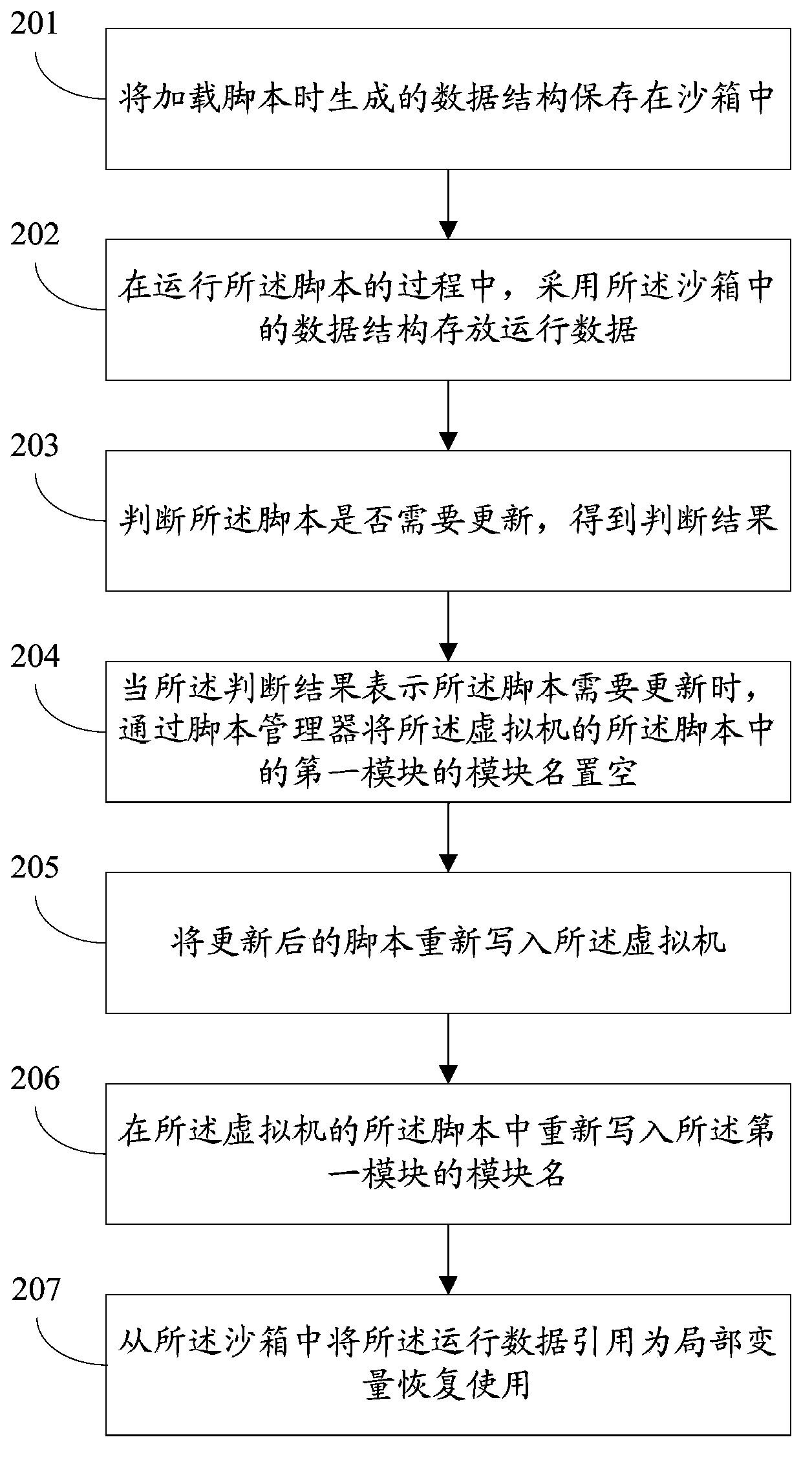
Sandbox based script updating method and system
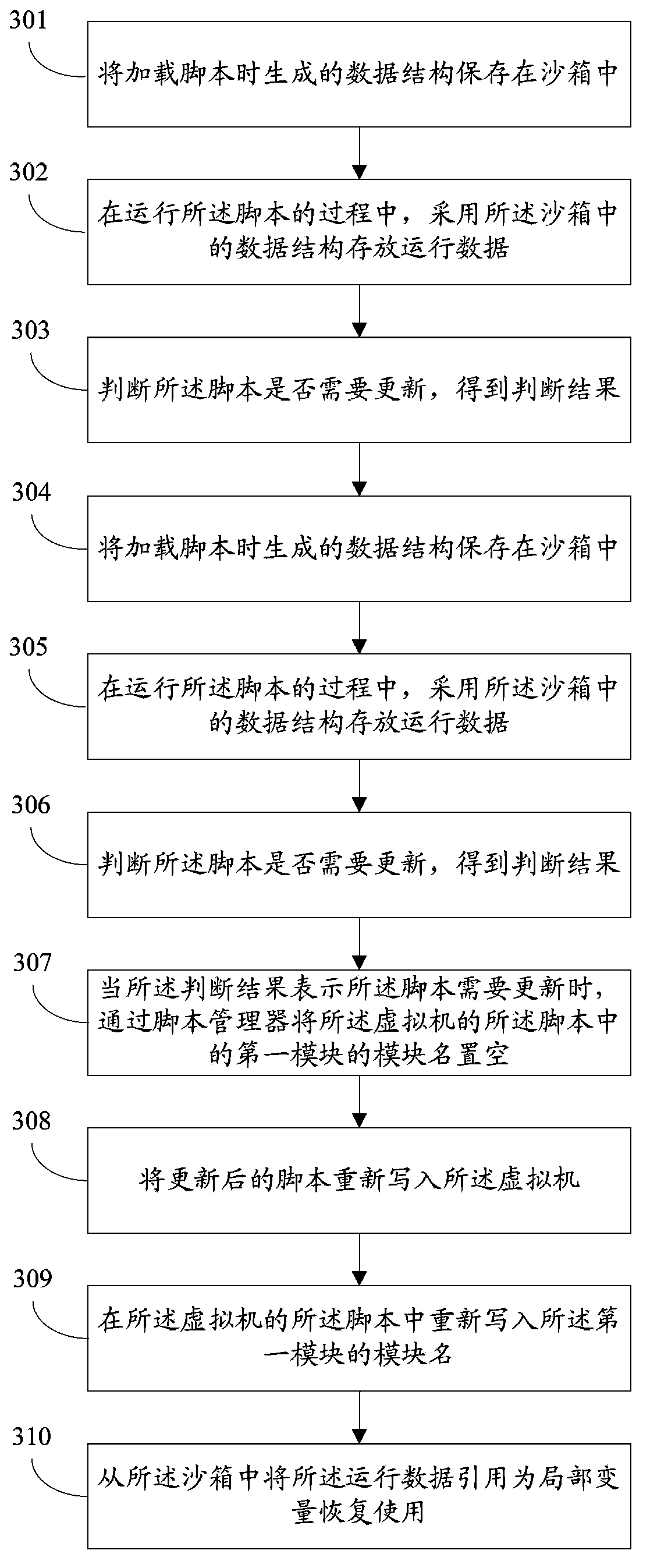
InactiveCN104111843AImplement updateReduce replacement costsProgram loading/initiatingSoftware simulation/interpretation/emulationLocal variableSoftware engineering
The invention discloses a sandbox based script updating method and system. The sandbox based script updating method includes steps of storing data structures generated during script loading into a sandbox; storing running data by citing the data structures in the sandbox during running of scripts; judging whether the scripts need to be updated or not to obtain judgment results; when the judgment results indicate that the scripts need to be updated, unloading the scripts in a virtual machine; rewriting the updated scripts into the virtual machine; citing the running data from the sandbox as local variables for returning to serve. By the sandbox based script updating method and system, program running is not interrupted while the programs can be updated, updating cost of the programs is reduced, and user experience is improved.
Owner:SUZHOU METIS INFORMATION TECH
Referential integrity navigation in a database system
InactiveUS6502092B1Data processing applicationsDigital data information retrievalOriginal dataApplication software
The invention is an improved system and method for browsing and editing data residing in database tables. The method of the present invention includes the steps of providing a graphical user interface in communication with a database, receiving user input to the graphical user interface, retrieving data from the database, displaying the retrieved data in the graphical user interface, and navigating to one or more referenced database tables or views by user request entered on the graphical user interface. The purpose of referential integrity is to prevent database users or applications from entering inconsistent data into a database. The goal of referential integrity navigation is to allow the user, having retrieved one or more rows of data, to navigate easily to the data in other tables that either refers to or is referred to by that data. These relationships are defined by referential integrity constraints, and the data thus retrieved by navigation is then available for all the operations possible on the original data, including data editing and further relational navigation. By storing a catalog of the relationships known to exist between Oracle's V$ views, the same form of navigation can be provided between these data sources.
Owner:BMC SOFTWARE
Prefetching irregular data references for software controlled caches
InactiveUS8239841B2Software engineeringSpecific program execution arrangementsDatum referenceParallel computing
Prefetching irregular memory references into a software controlled cache is provided. A compiler analyzes source code to identify at least one of a plurality of loops that contain an irregular memory reference. The compiler determines if the irregular memory reference within the at least one loop is a candidate for optimization. Responsive to an indication that the irregular memory reference may be optimized, the compiler determines if the irregular memory reference is valid for prefetching. Responsive to an indication that the irregular memory reference is valid for prefetching, a store statement for an address of the irregular memory reference is inserted into the at least one loop. A runtime library call is inserted into a prefetch runtime library for the irregular memory reference. Data associated with the irregular memory reference is prefetched into the software controlled cache when the runtime library call is invoked.
Owner:INT BUSINESS MASCH CORP
System modeling method and system based on model system engineering and super network theory
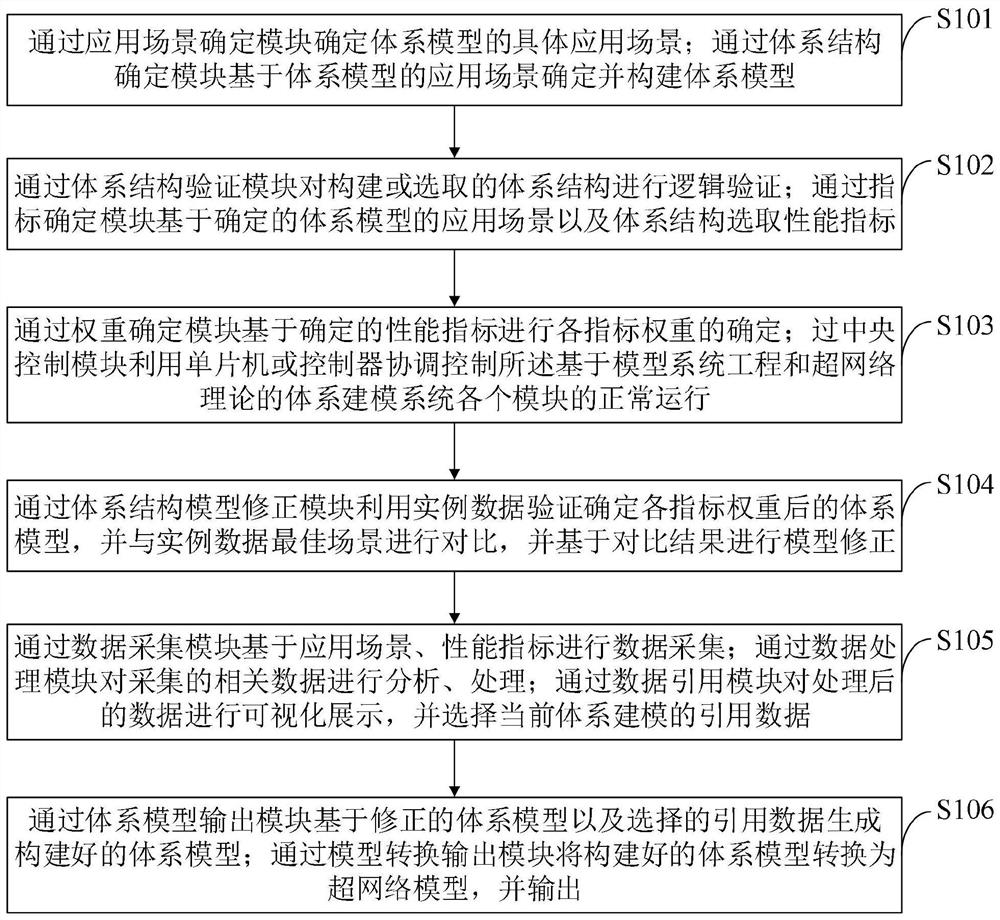
ActiveCN112560213AImprove design efficiencyEffective assistanceGeometric CADCharacter and pattern recognitionTheoretical computer scienceData acquisition
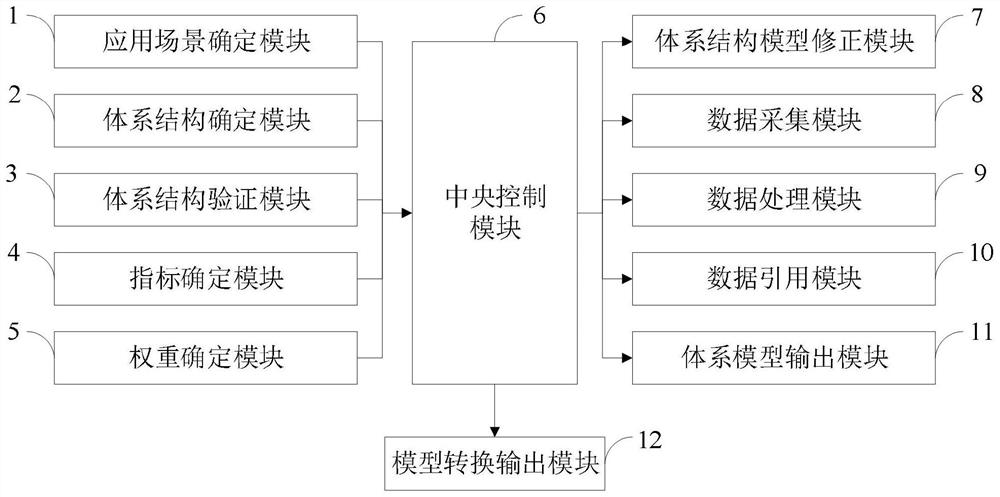
The invention belongs to the technical field of system modeling, and discloses a system modeling method and system based on model system engineering and a super network theory. The system modeling system based on the model system engineering and the super network theory comprises an application scene determination module, a system structure determination module, a system structure verification module, an index determination module, a weight determination module, a central control module, a system structure model correction module, a data acquisition module, a data processing module, a data reference module, a system model output module and a model conversion output module. According to the invention, the constructed system model group is converted into the super-network model, the system model mapping relationship among the visual angles is analyzed, the generated system super-network model group is combined, and finally the multi-layer super-network model of the system structure is generated, so that the indexes of the system structure can be quantitatively analyzed by using a mathematical tool; and through combing from top to bottom and integrating from bottom to top, the integrity and effectiveness of the combed data can be ensured.
Owner:NAT UNIV OF DEFENSE TECH
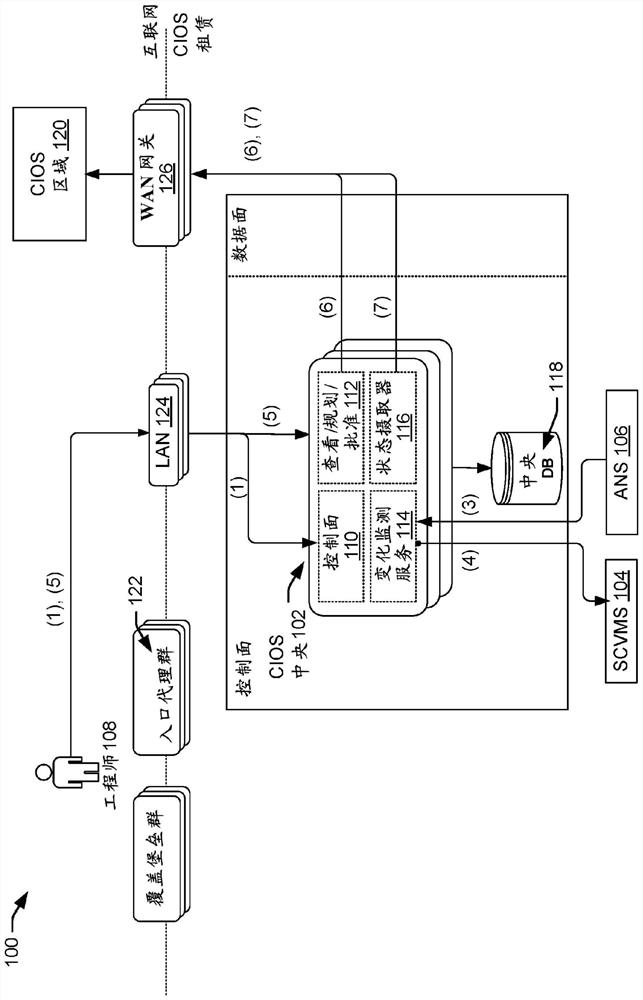
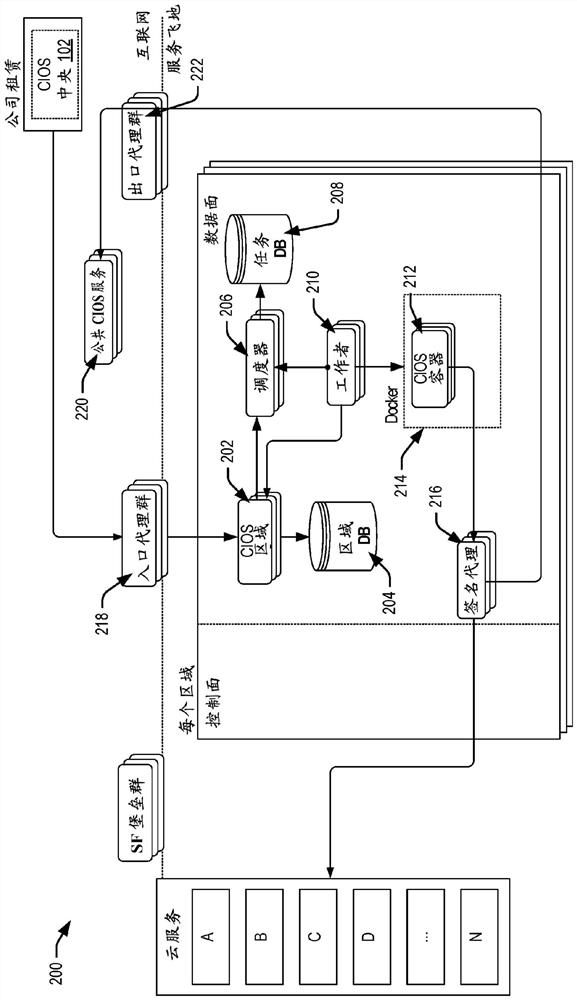
Techniques for resolving application updates
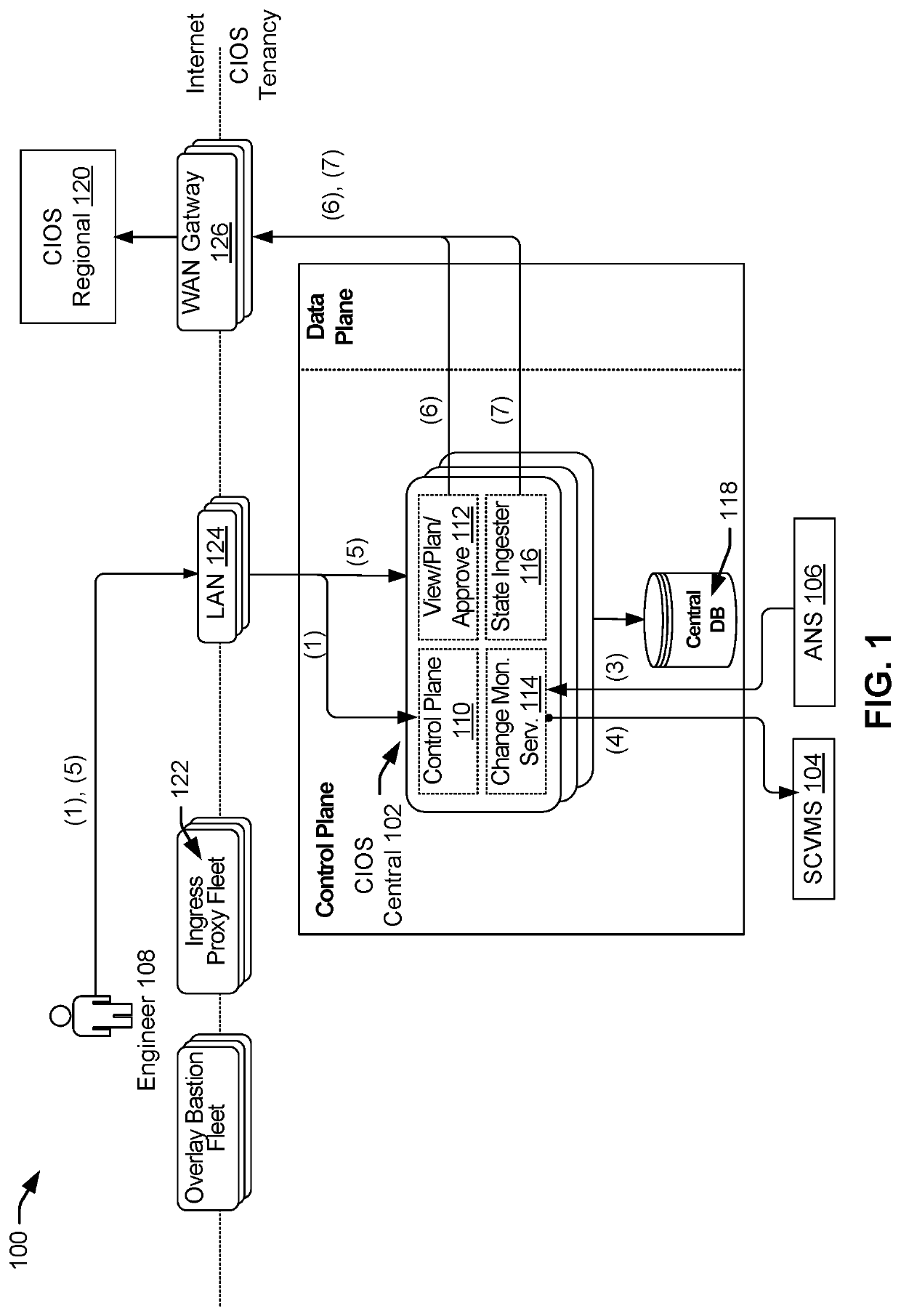
Techniques are disclosed for implementing, by a computer infrastructure orchestration service (CIOS) changes to a first service. The CIOS may manage a declarative infrastructure provisioner to deploy infrastructure resources and artifacts based at least in part on declarative instructions. CIOS may detect a first modification to a first service (e.g., a sidecar application). CIOS may identify that configuration data of a second service references (e.g., via a git submodule) the first service. In response to identifying a second modification to the second service, CIOS may present, via a graphical interface, changes comprising the first modification to the first service. User input may be received indicating acceptance or rejection of the changes of the first modification. CIOS may then implement the changes to the first service according to the user input. For example, CIOS may ensure that the first service, as modified, is deployed alongside the second service in subsequent deployments.
Owner:ORACLE INT CORP
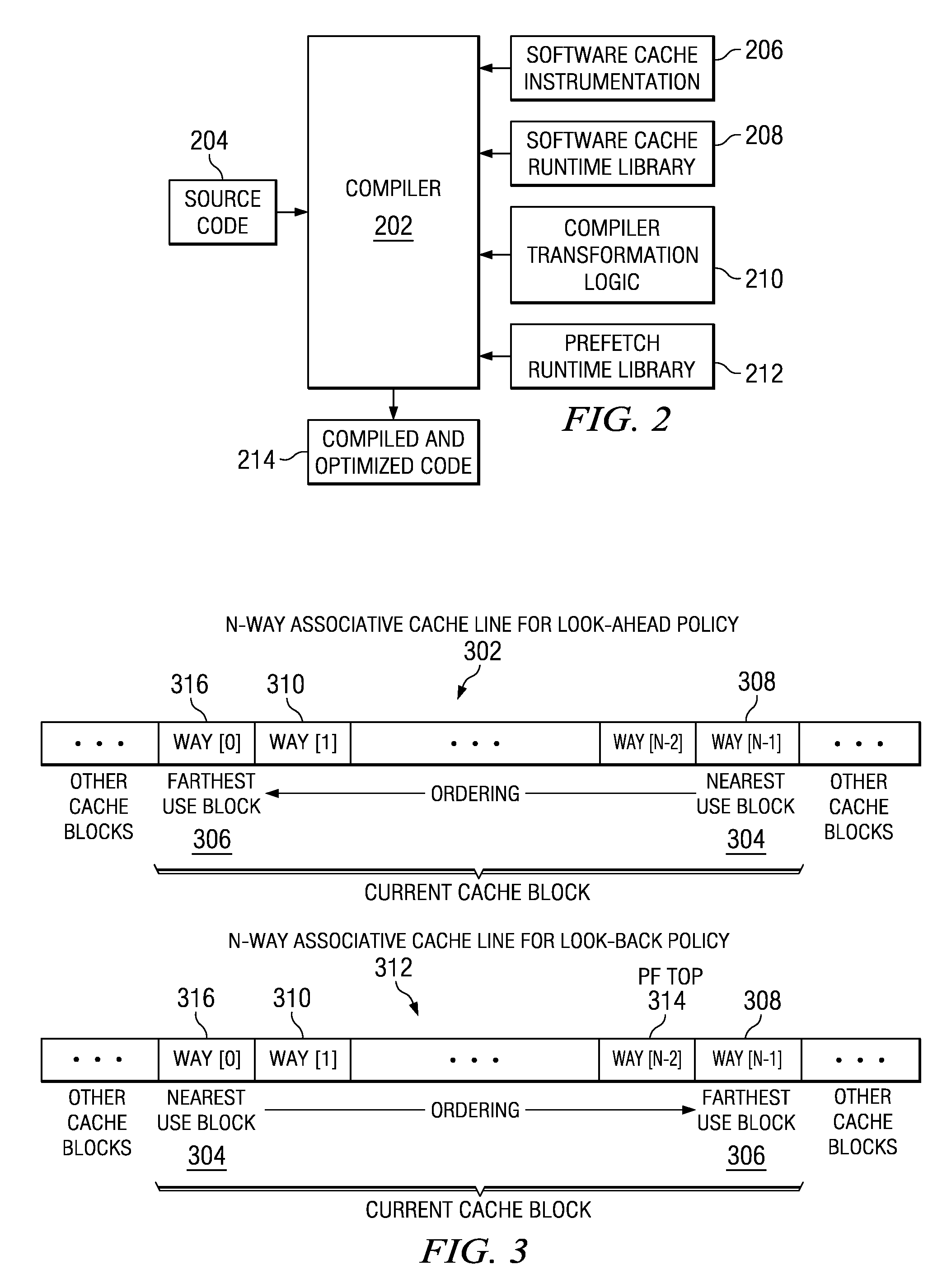
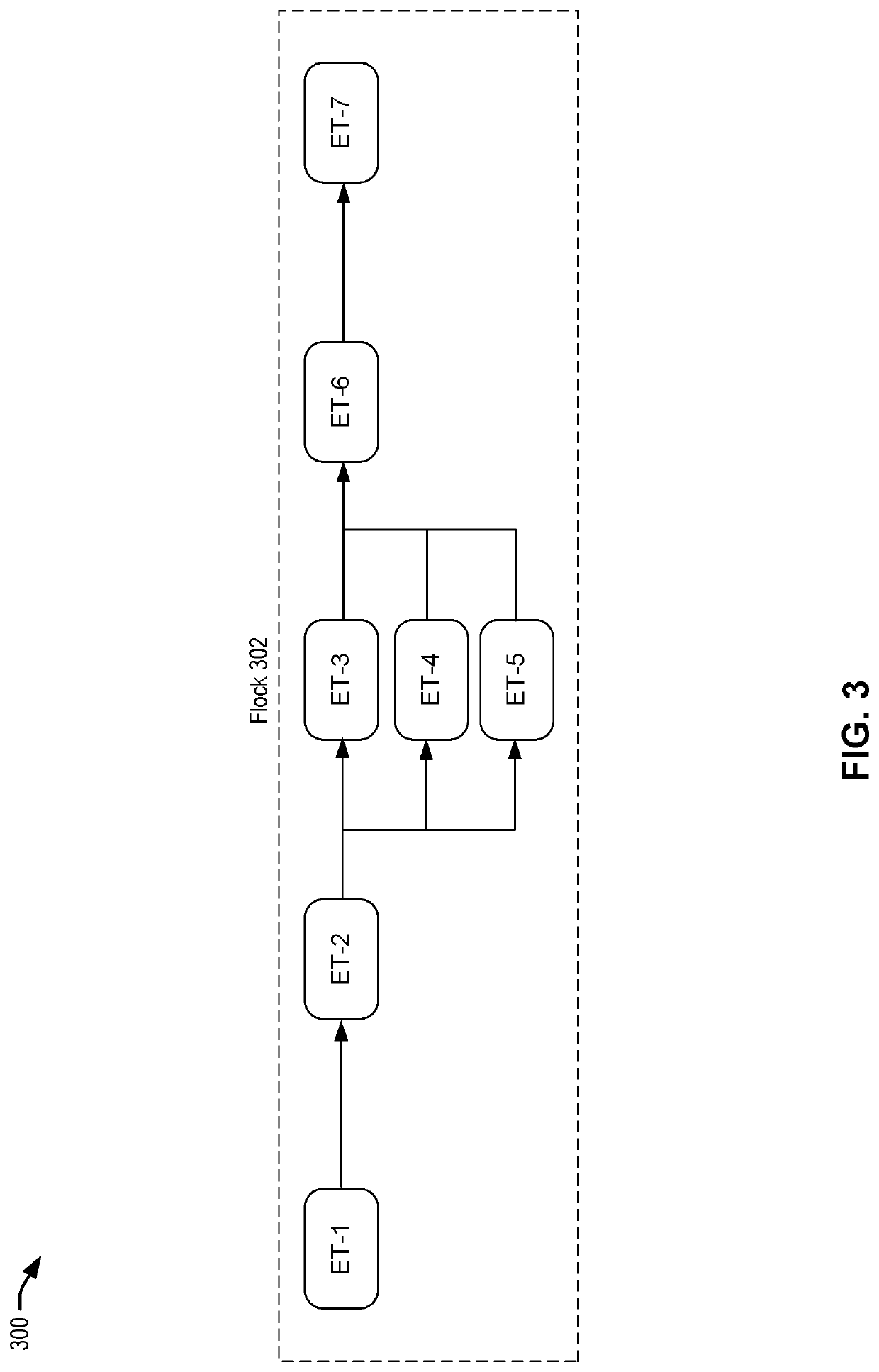
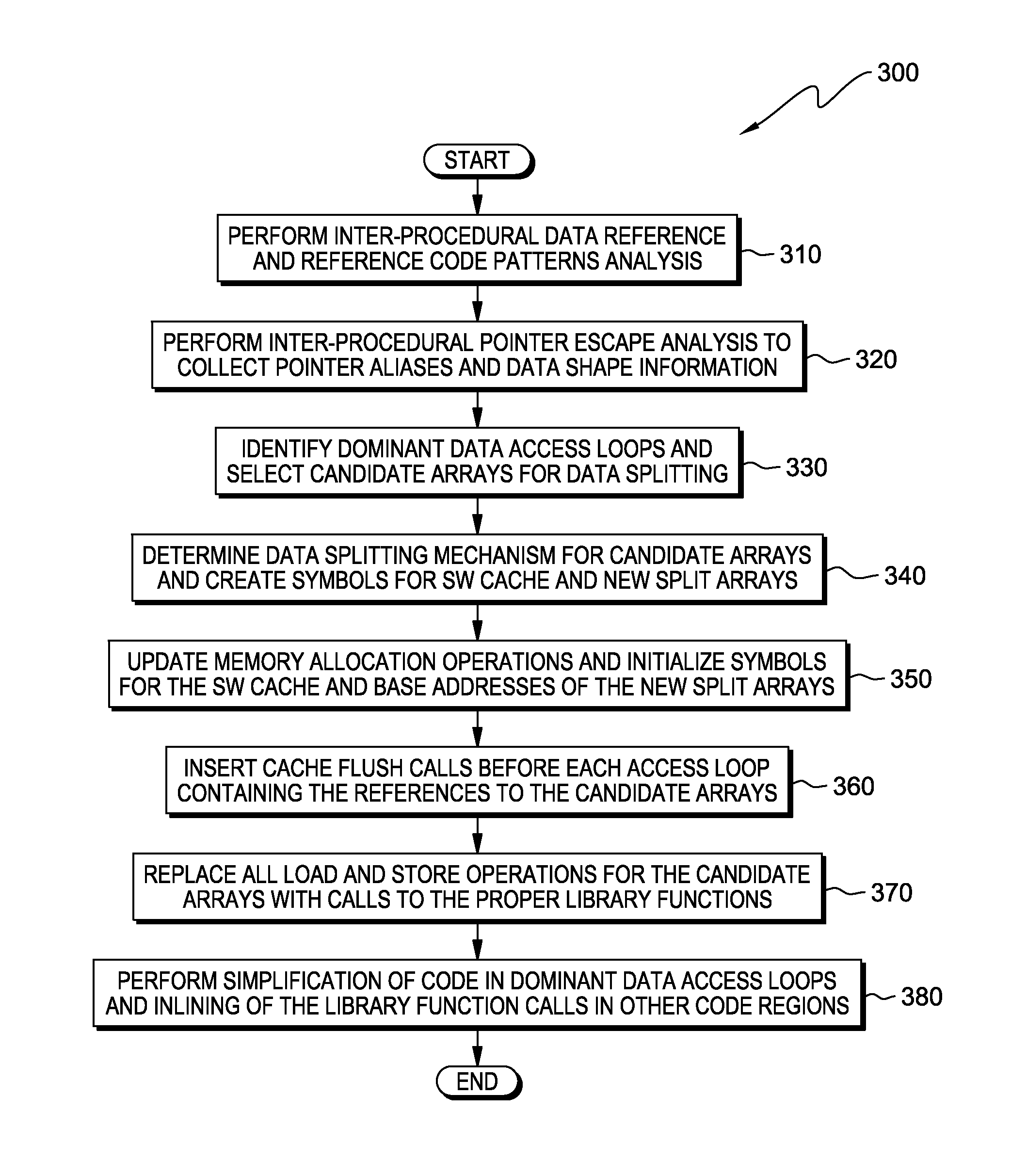
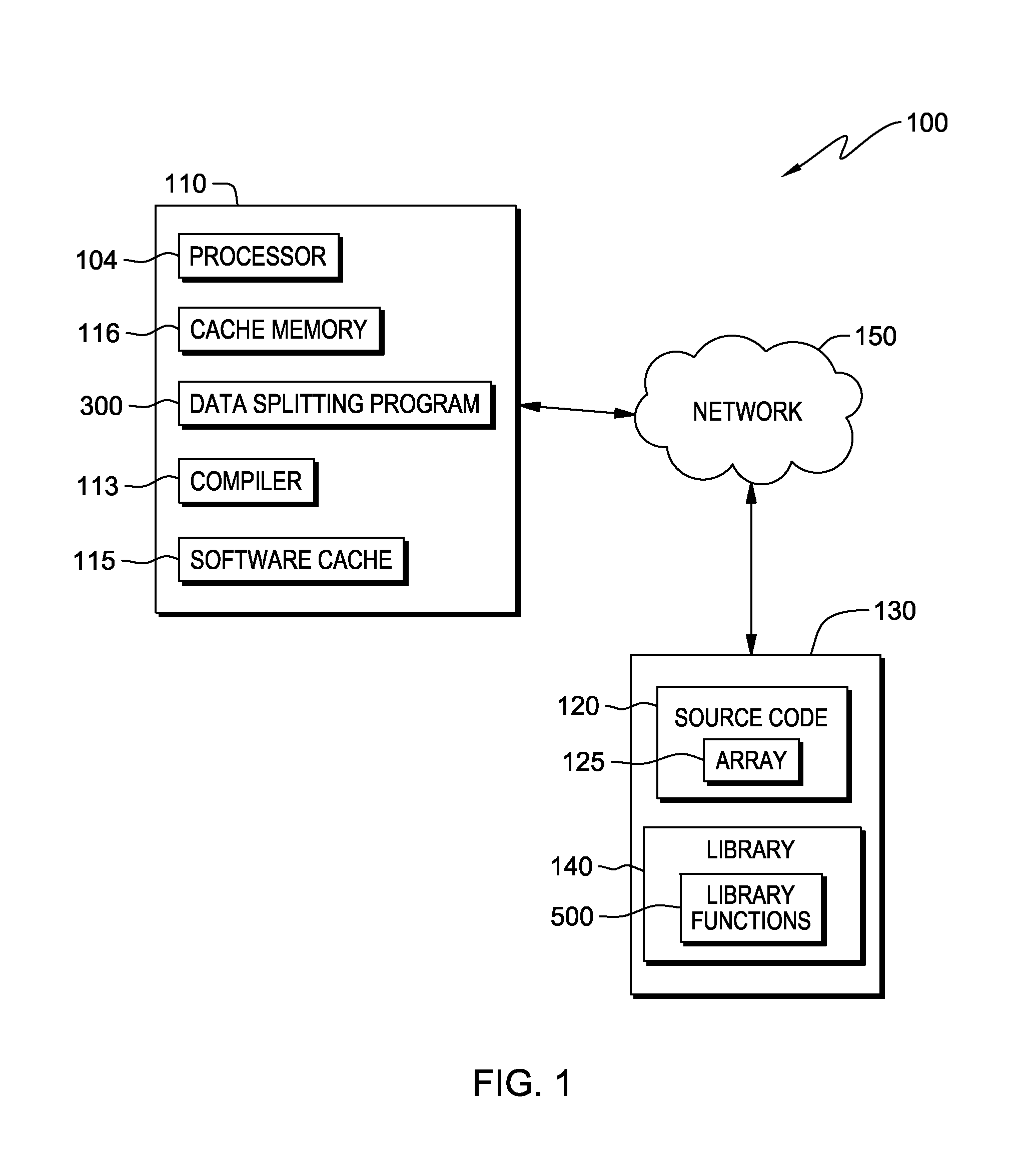
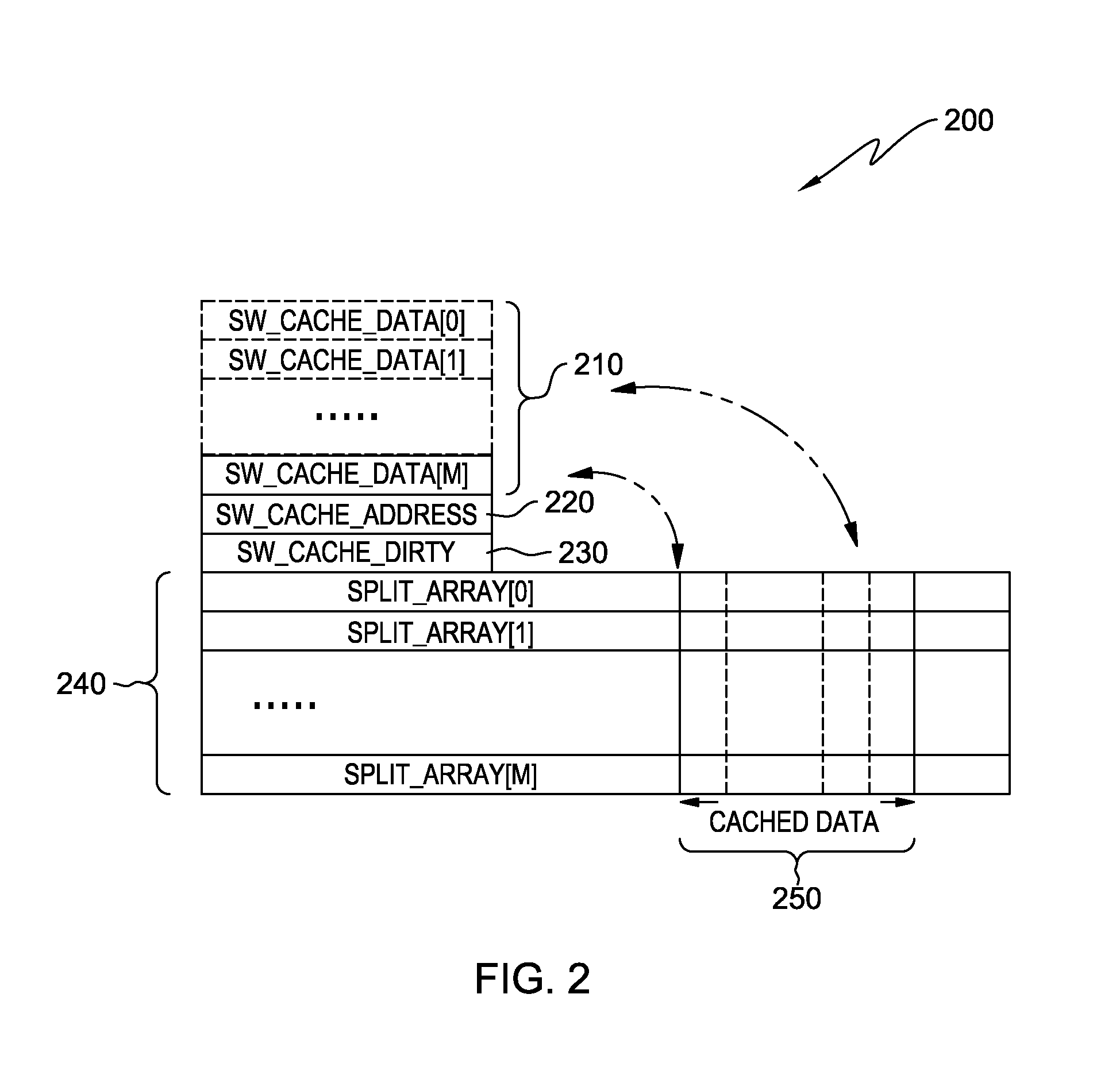
Optimizing memory bandwidth consumption using data splitting with software caching
InactiveUS9104577B2Memory architecture accessing/allocationMemory adressing/allocation/relocationCircular referenceDatum reference
A computer processor collects information for a dominant data access loop and reference code patterns based on data reference pattern analysis, and for pointer aliasing and data shape based on pointer escape analysis. The computer processor selects a candidate array for data splitting wherein the candidate array is referenced by a dominant data access loop. The computer processor determines a data splitting mode by which to split the data of the candidate array, based on the reference code patterns, the pointer aliasing, and the data shape information, and splits the data into two or more split arrays. The computer processor creates a software cache that includes a portion of the data of the two or more split arrays in a transposed format, and maintains the portion of the transposed data within the software cache and consults the software cache during an access of the split arrays.
Owner:GLOBALFOUNDRIES INC
Query and result rebinding
InactiveUS20120072439A1Easy to changeDatabase management systemsDigital data processing detailsDatabaseData source
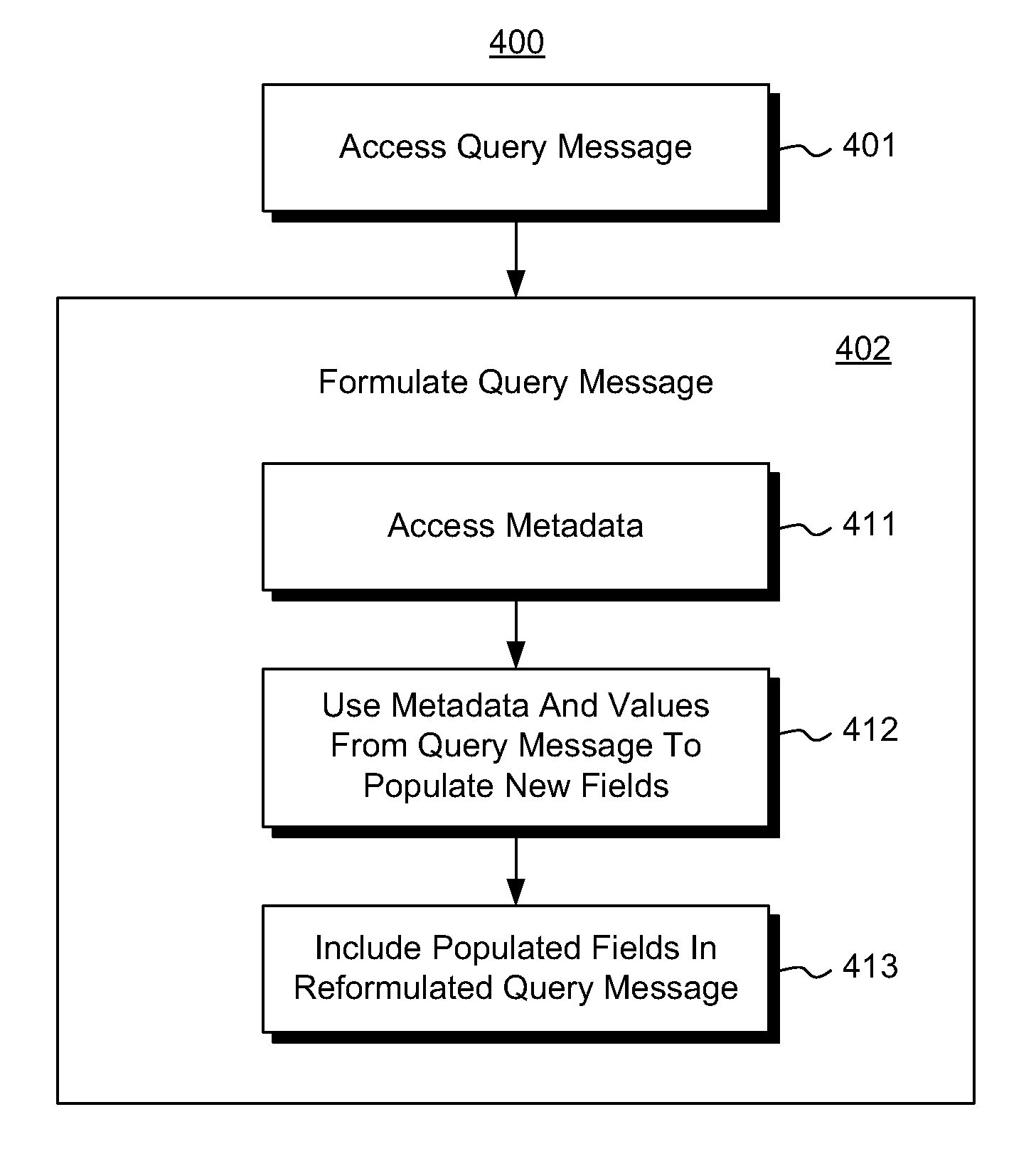
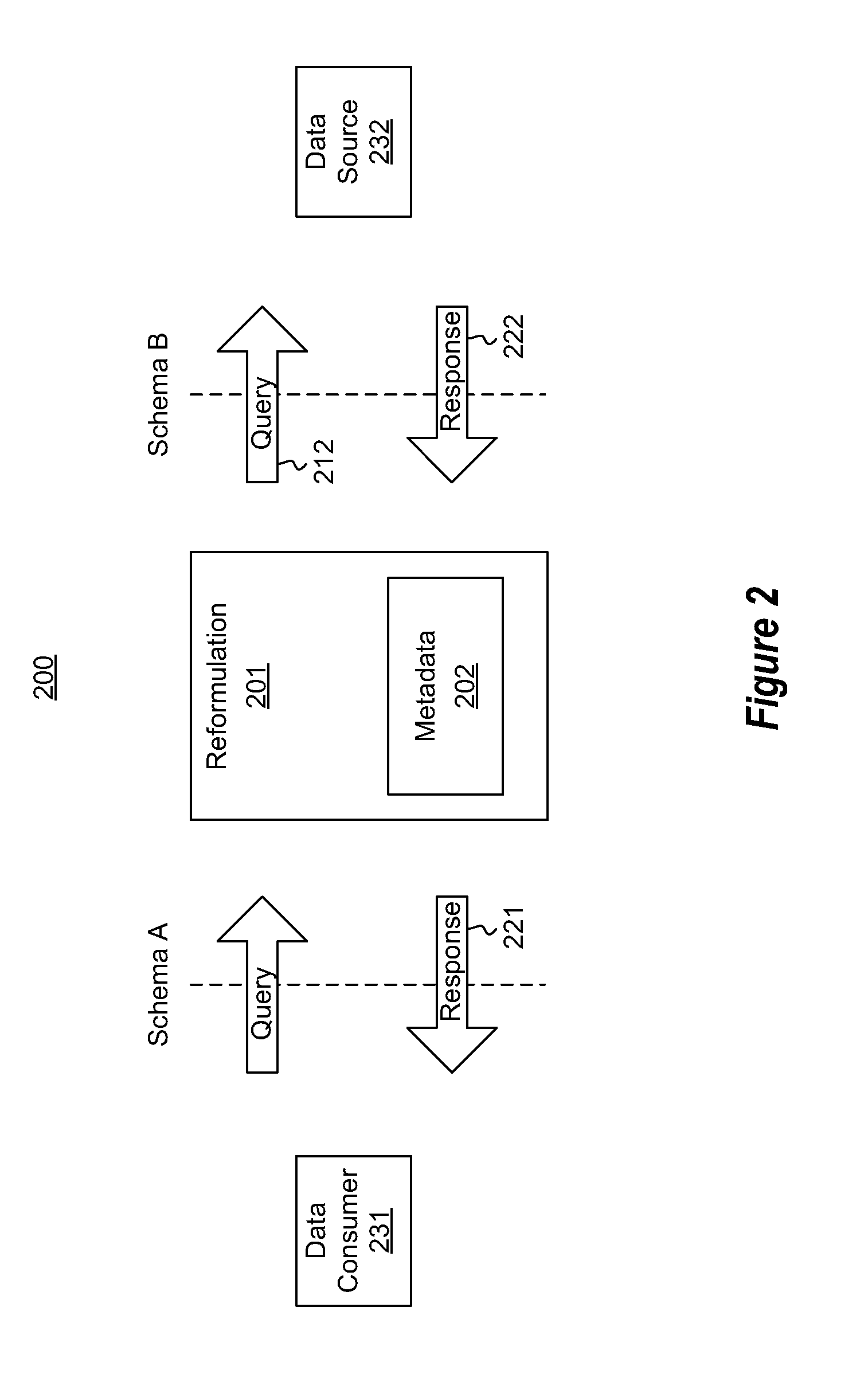
The metadata-based intermediation between two data sources. A computing system accesses a query message (e.g., a query or a query response). The query message is structured to be compatible with the first data source. The computing system uses metadata either directly, or indirectly through the execution of code referenced by the metadata to convert the query message into a semantically equivalent query message that is compatible with the second data source. If the query message were a query, then a query response may be acquired and the metadata may perhaps be used again to convert the query response into a form that is compatible with the first data source. In one embodiment, the conversion using the metadata is performed with the assistance of a framework, making changes to the conversion process as simple as perhaps just editing the metadata itself.
Owner:MICROSOFT TECH LICENSING LLC
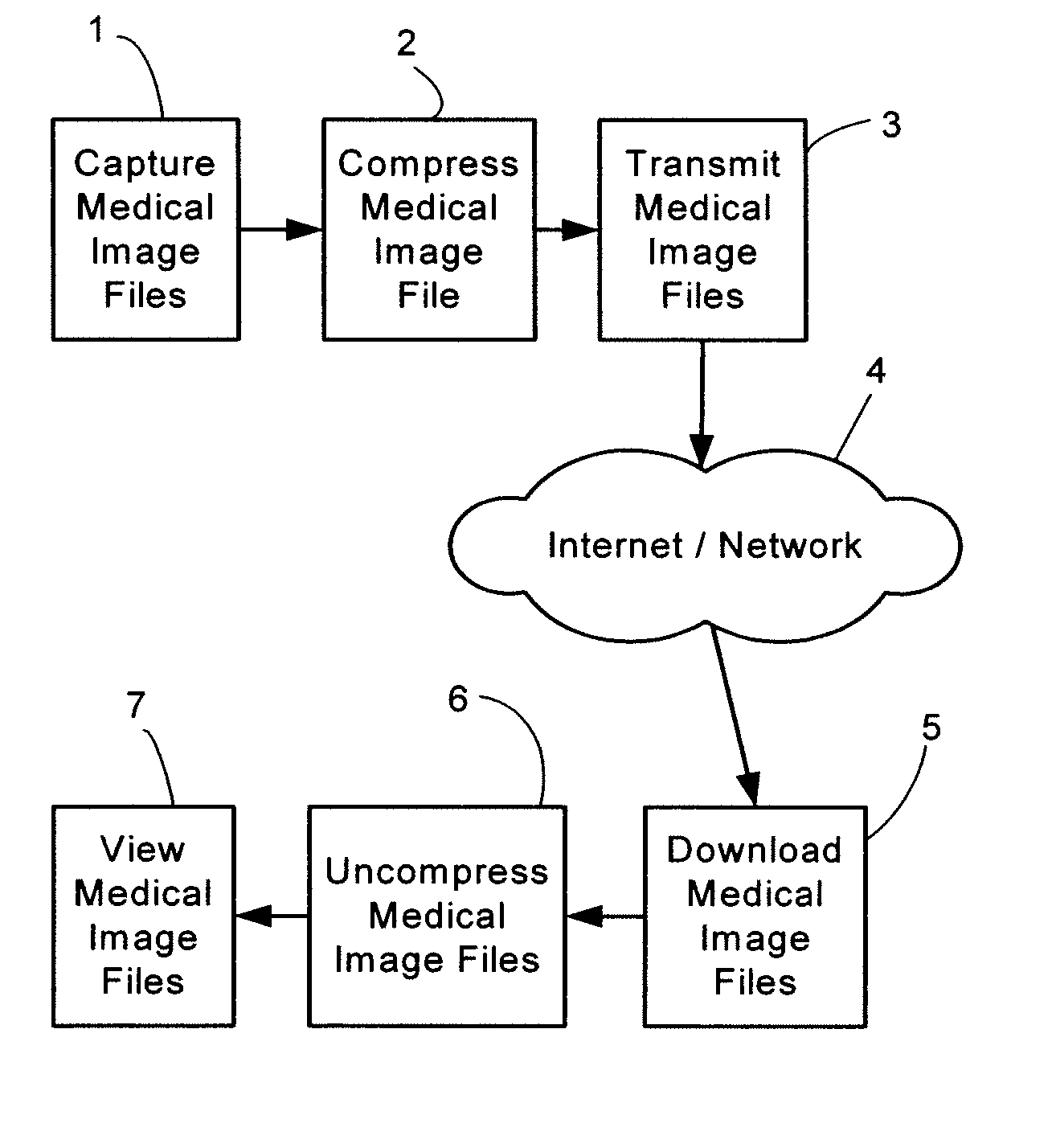
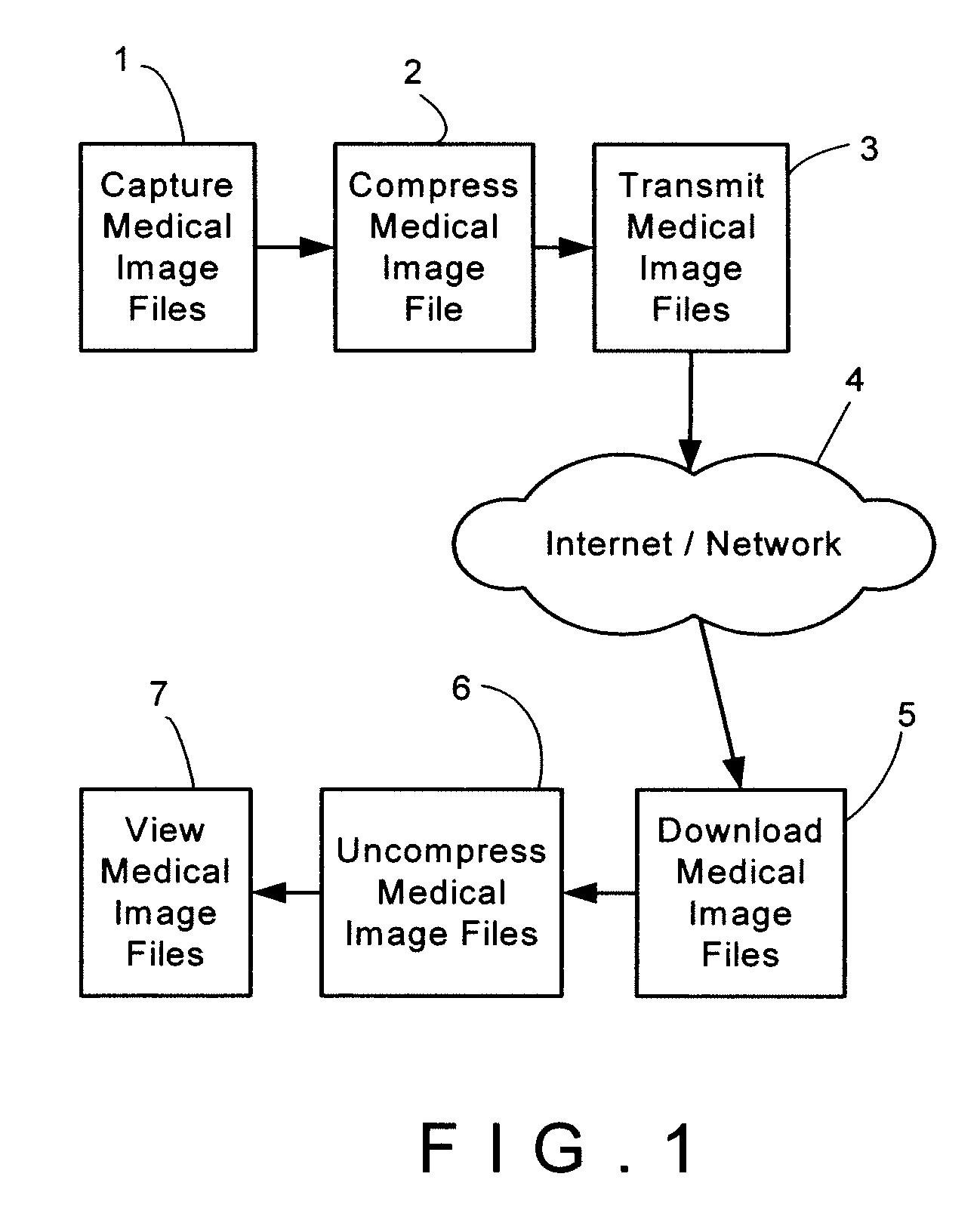
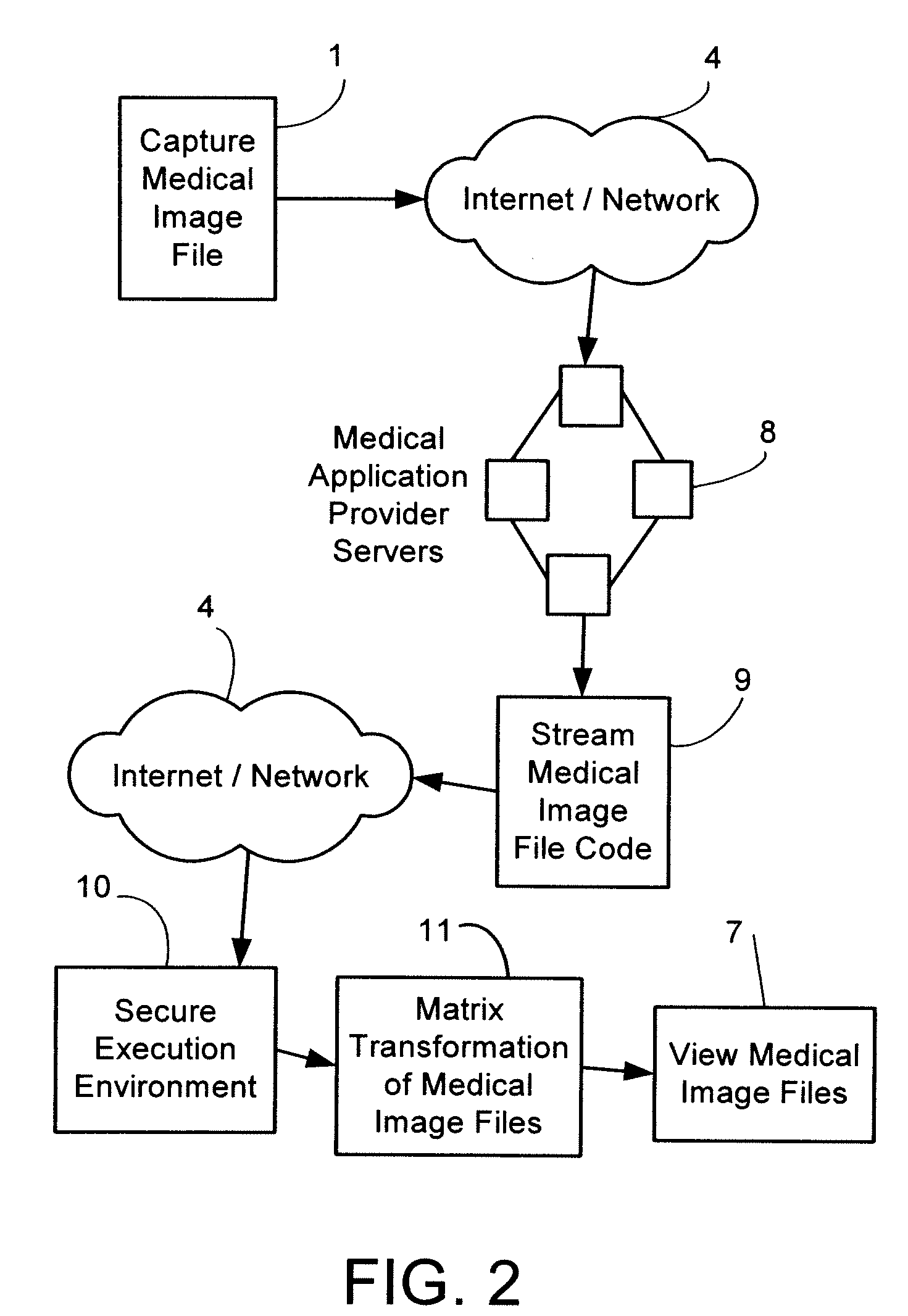
Remote Virtual Medical Diagnostic Imaging Viewer
InactiveUS20070130459A1Efficient methodLow costData processing applications2D-image generationOperational systemRelevant information
A medical image and data application service provider system provides a way of remotely viewing and manipulating medical images and data for diagnostic and visualization purposes by users unconstrained by geography. Medical images and data are stored on one or more servers running application service provider software along with meta-data such as access control information, origin of information and references to related data. A set of medical data consisting related information is sent as an encrypted stream to a viewing station running client software in a secure execution environment that is logically independent of the viewing station's operating system.
Owner:TAILSTREAM TECH +1
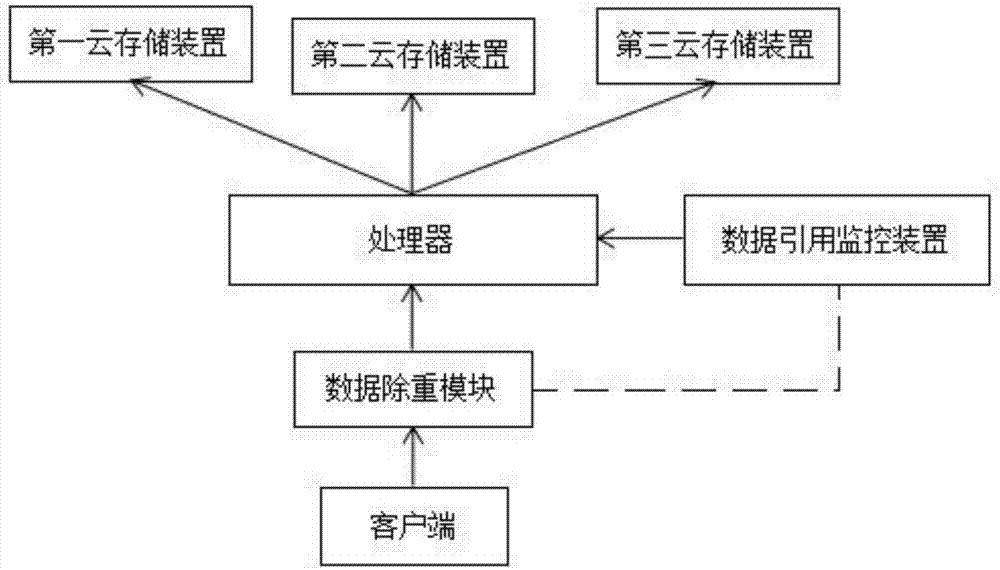
Data scattered storage system based on cloud storage
ActiveCN107977168AReduce operation stepsImprove storage efficiencyInput/output to record carriersTransmissionData informationData citation
The invention discloses a data scattered storage system based on cloud storage and relates to the field of data storage technology. The system comprises a client, a data repetition removal module, a processor, a data citation monitoring device, a first cloud storage device, a second cloud storage device and a third cloud storage device, wherein the data repetition removal module receives data information uploaded by the client and performs repetition removal on the data information through repeated data deletion, and the processor performs data arrangement on the data information obtained after repetition removal and stores the data information to the first cloud storage device, the second cloud storage device and the third cloud storage device respectively. According to the system, data is processed to obtain the data information after repetition removal, and a data citation rate is obtained; properties of the data information are judged through the data citation rate, a data distribution strategy based on duplication is adopted to store the data information, and therefore operation steps needed by the processor are reduced; and a data arrangement strategy based on an erasure codeis adopted, and therefore high storage efficiency can be obtained.
Owner:安徽长泰科技有限公司
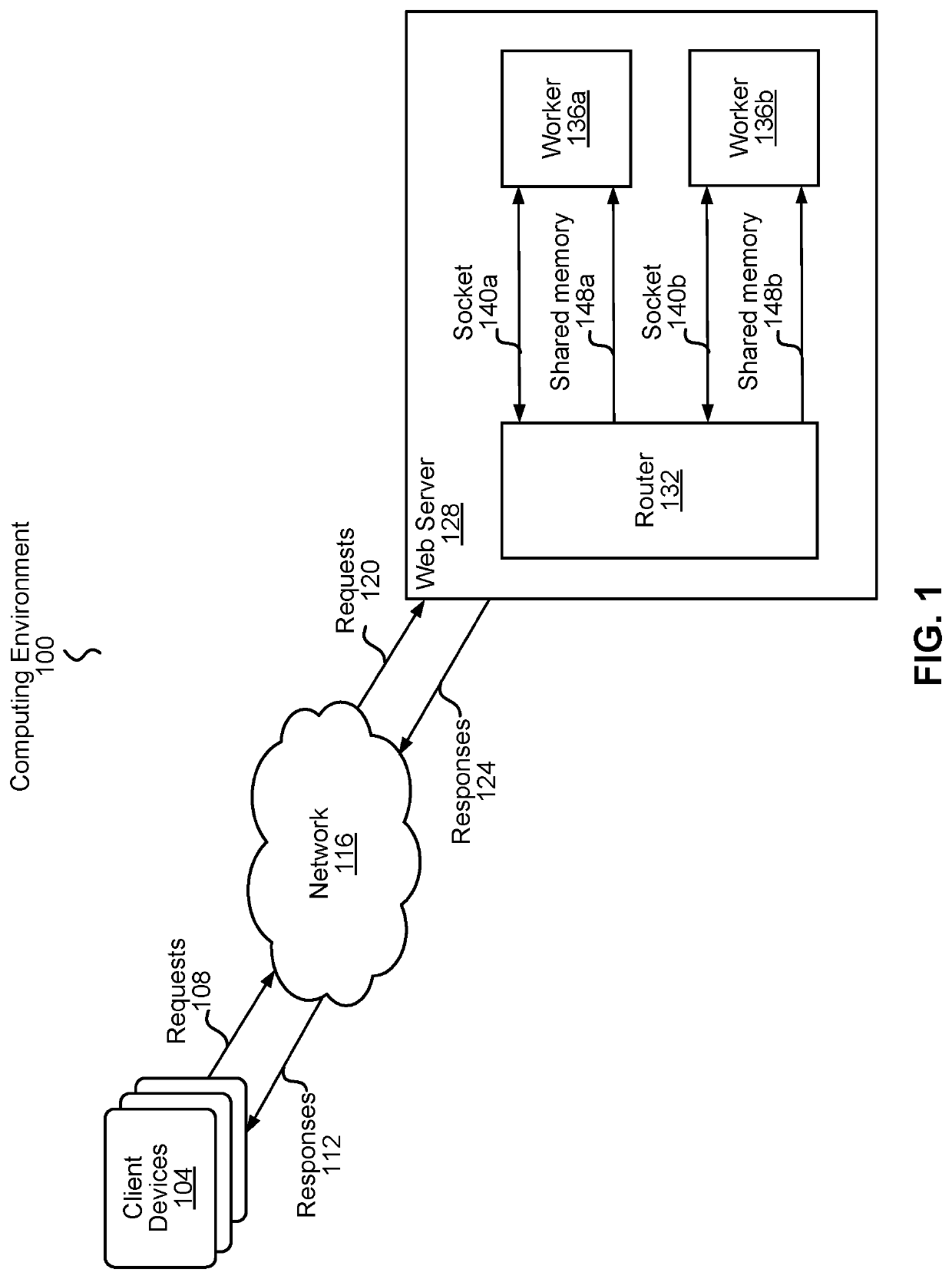
Pipelined request processing using shared memory
ActiveUS11042424B1Prevent race conditionAvoid adjustmentResource allocationInterprogram communicationComputer networkComputer architecture
Pipelined request processing using shared memory includes writing, by a first process, data associated with a request and an identifier referencing the data to a shared memory segment. The first process transmits, to a second process, the identifier referencing the data. The second process compares the transmitted identifier to the identifier in the shared memory segment. Responsive to the transmitted identifier matching the identifier in the shared memory segment, the second process updates the identifier in the shared memory segment to indicate that the data has been retrieved by the second process. The comparison and update is performed using an atomic compare-and-swap operation. Using the identifiers prevents race conditions between the different processes in trying to access the data. The second process processes the data to generate a response and transmits the response to the first process.
Owner:F5 NETWORKS INC
Junk data recovery processing method and device, and electronic equipment
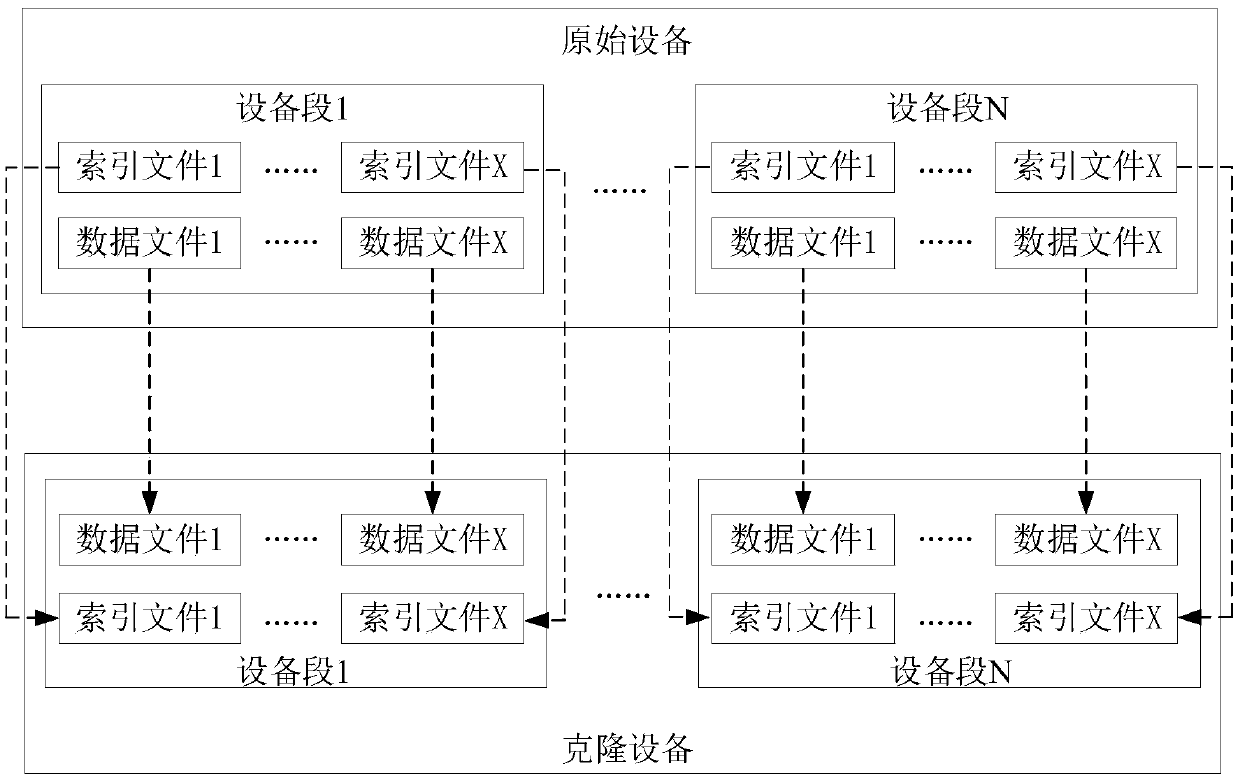
ActiveCN110851398AAccurately determineFile access structuresFile/folder operationsSoftware engineeringData citation
Embodiments of the invention provide a junk data recovery processing method and a device, and electronic equipment. The method comprises the steps of obtaining at least one first data file in a sharedstate in a device segment; obtaining a first index file corresponding to the first data file and a second index file corresponding to at least one second data file having a sharing relationship withthe first data file; and determining a junk data block in the first data file according to the first index file and the second index file, and executing first junk recovery processing. According to the junk data recovery processing method, junk recovery in a data sharing state can be realized, and in the process of determining the junk data block, the direct and indirect data reference relationship of the shared data block is fully considered, so that the junk data block is accurately determined, and the junk recovery processing is further executed.
Owner:ALIBABA GRP HLDG LTD
Decentralized control system operation logic display method and device, equipment and storage medium
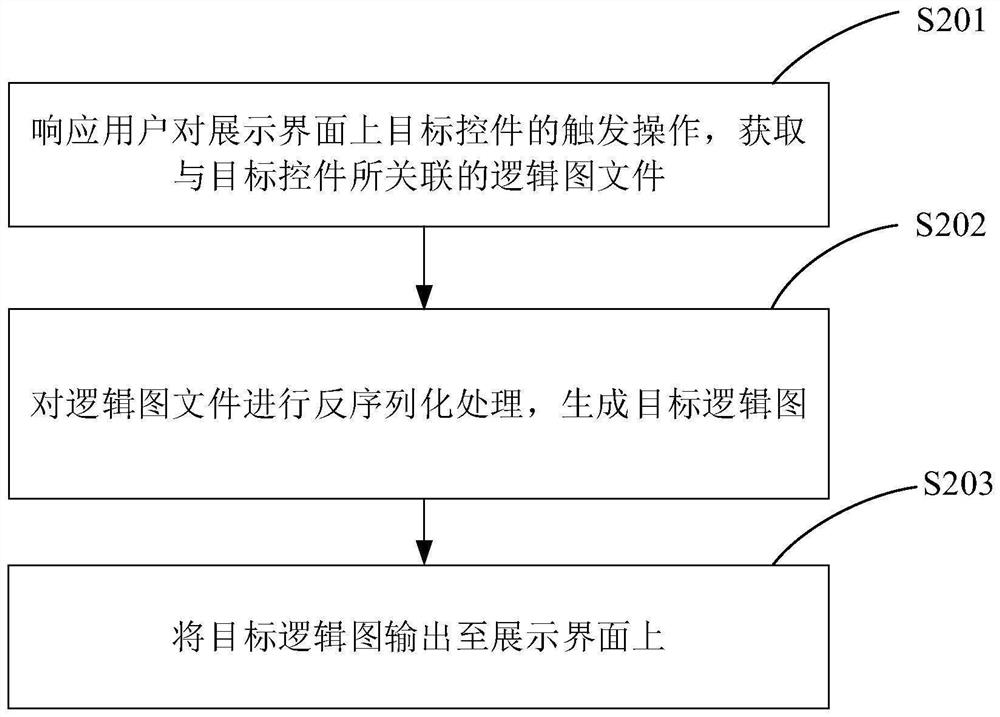
PendingCN114545828AEasy to viewImprove securityProgramme controlComputer controlBlocked ConnectionLogisim
The invention provides a decentralized control system operation logic display method and device, equipment and a storage medium, and relates to the technical field of industrial control. The method comprises the steps of obtaining a logic diagram file associated with a target control in response to a trigger operation of a user on the target control on a display interface; deserializing the logic diagram file to generate a target logic diagram; and outputting the target logic diagram to a display interface. According to the scheme, a display interface for visually displaying the function block diagram is provided, so that a user can conveniently check data reference, function block connection logic and function block connection logic in all (or part) function block diagrams which are pre-configured according to each device in the distributed control system from the target logic diagram; and information such as real-time data reference and real-time values of the function blocks can be checked, so that field industrial control personnel can be assisted to accurately judge the current running state of the distributed control system, and the effect of improving the running safety of the distributed control system is achieved.
Owner:ZHEJIANG SUPCON TECH
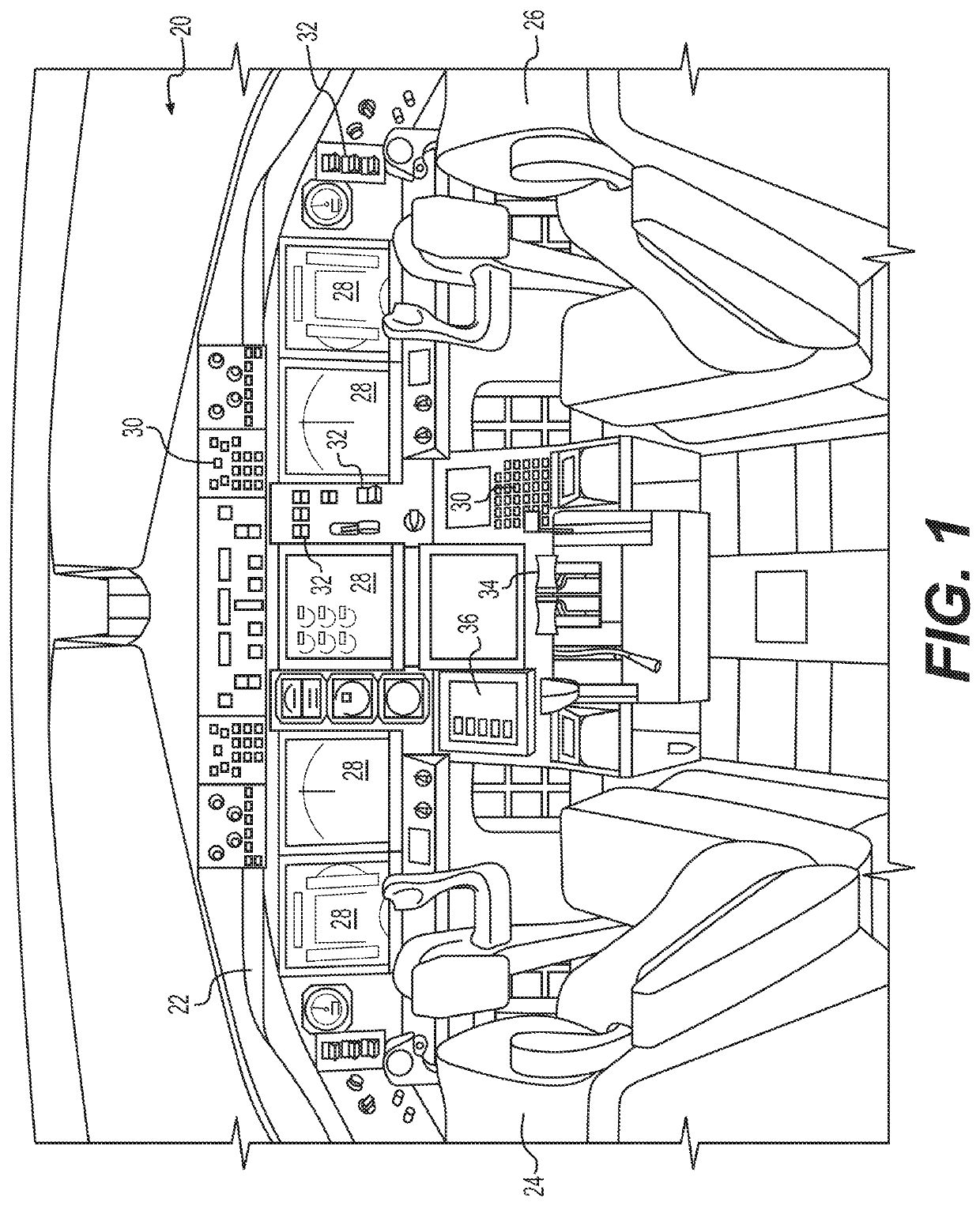
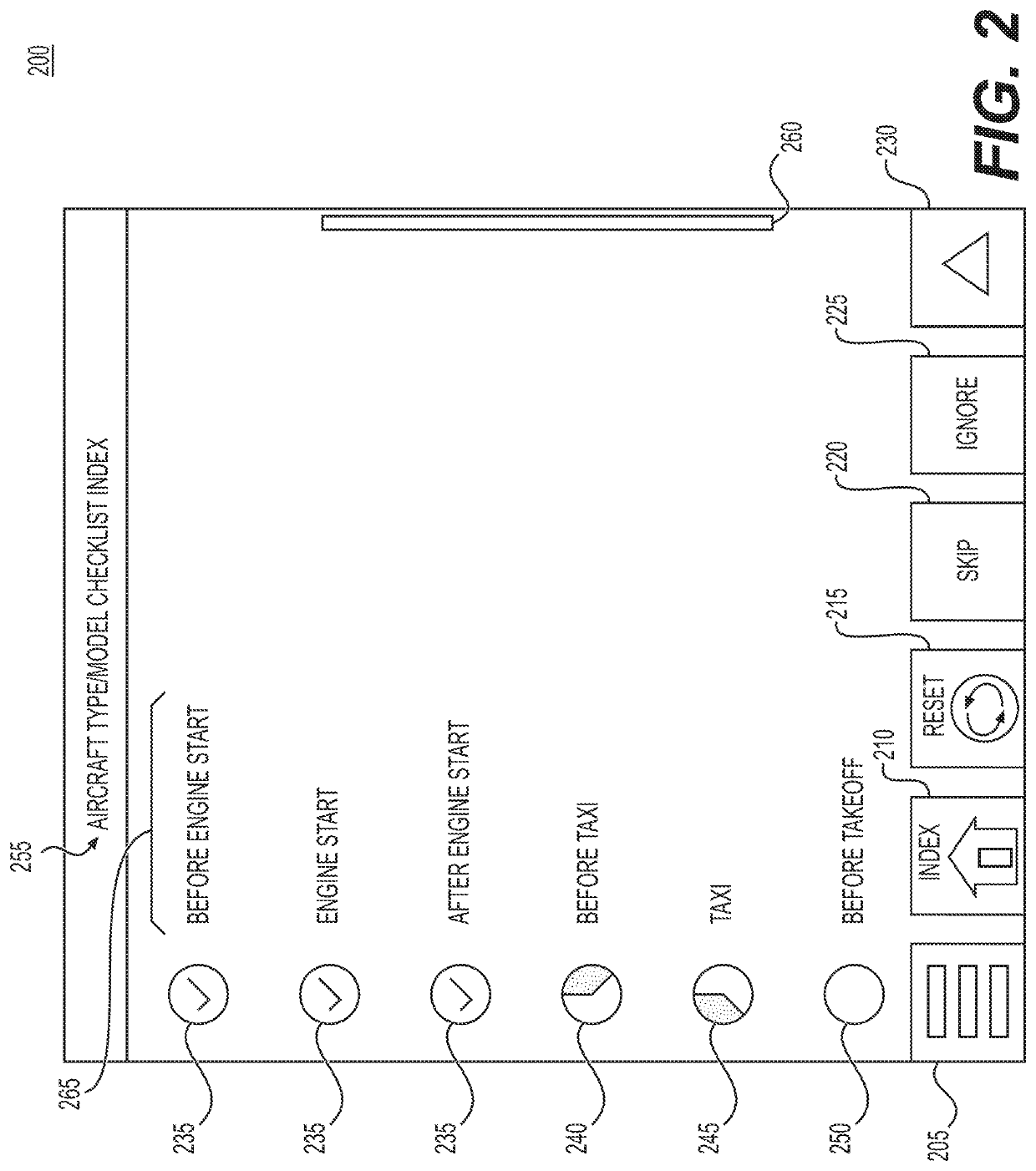
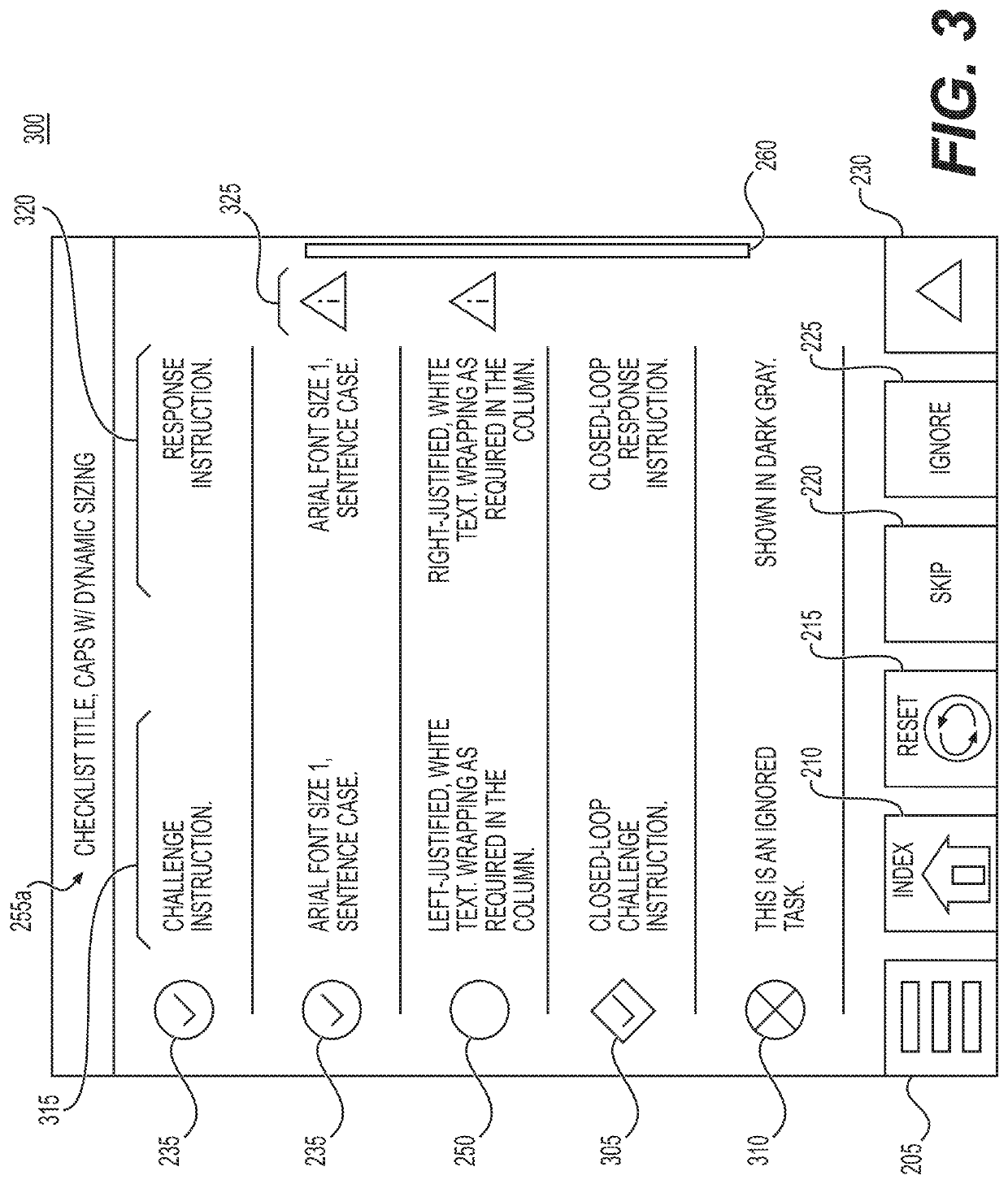
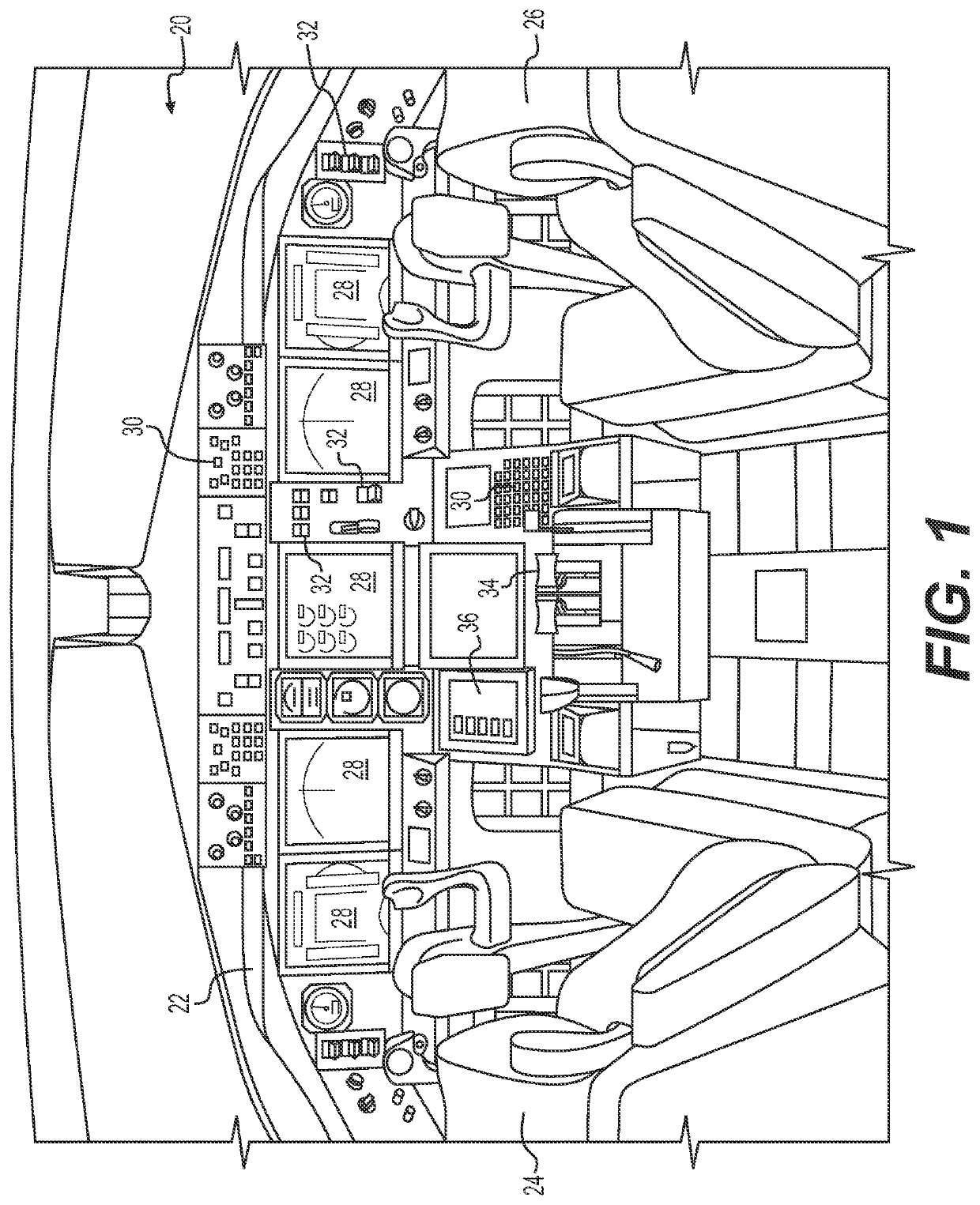
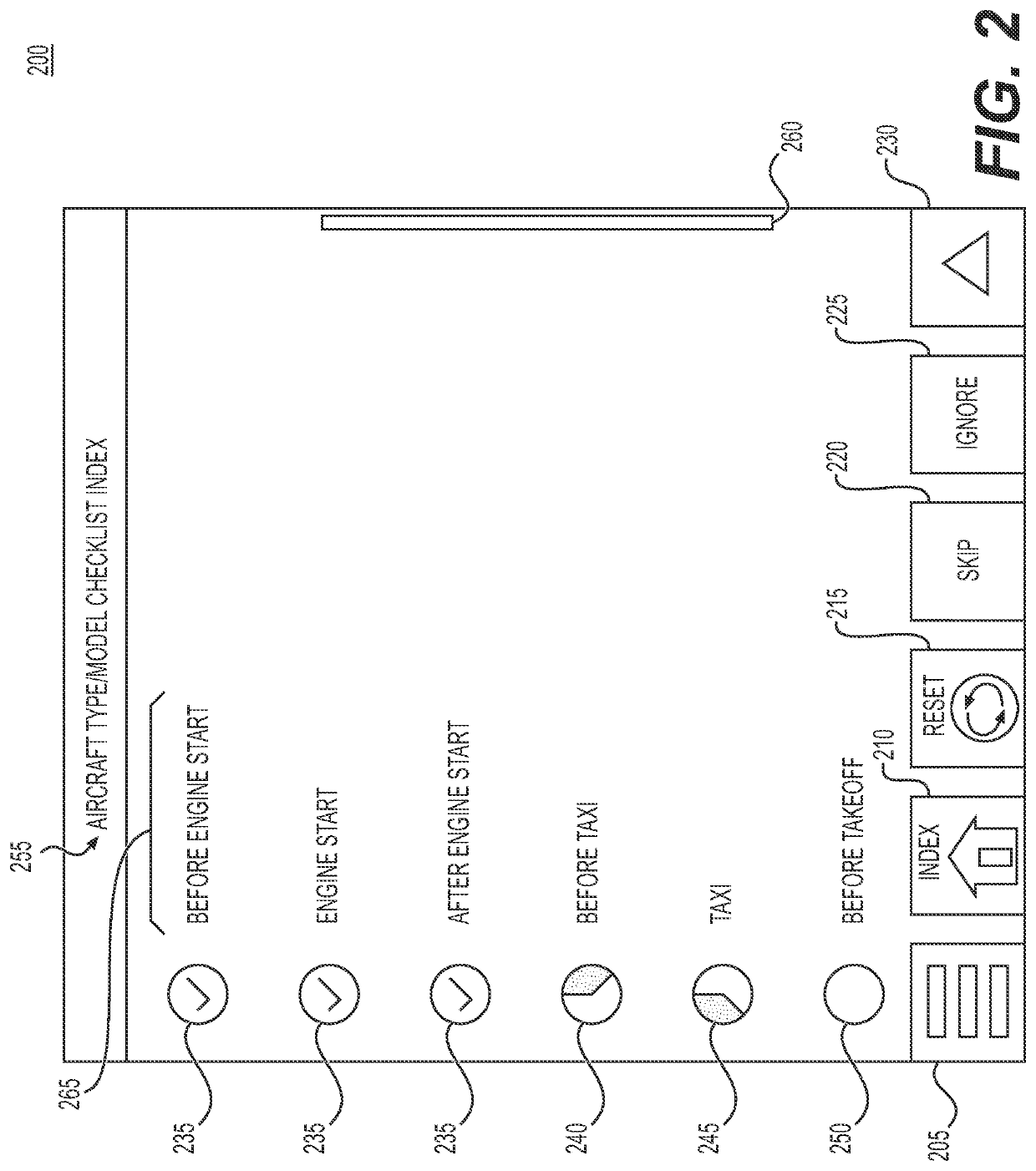
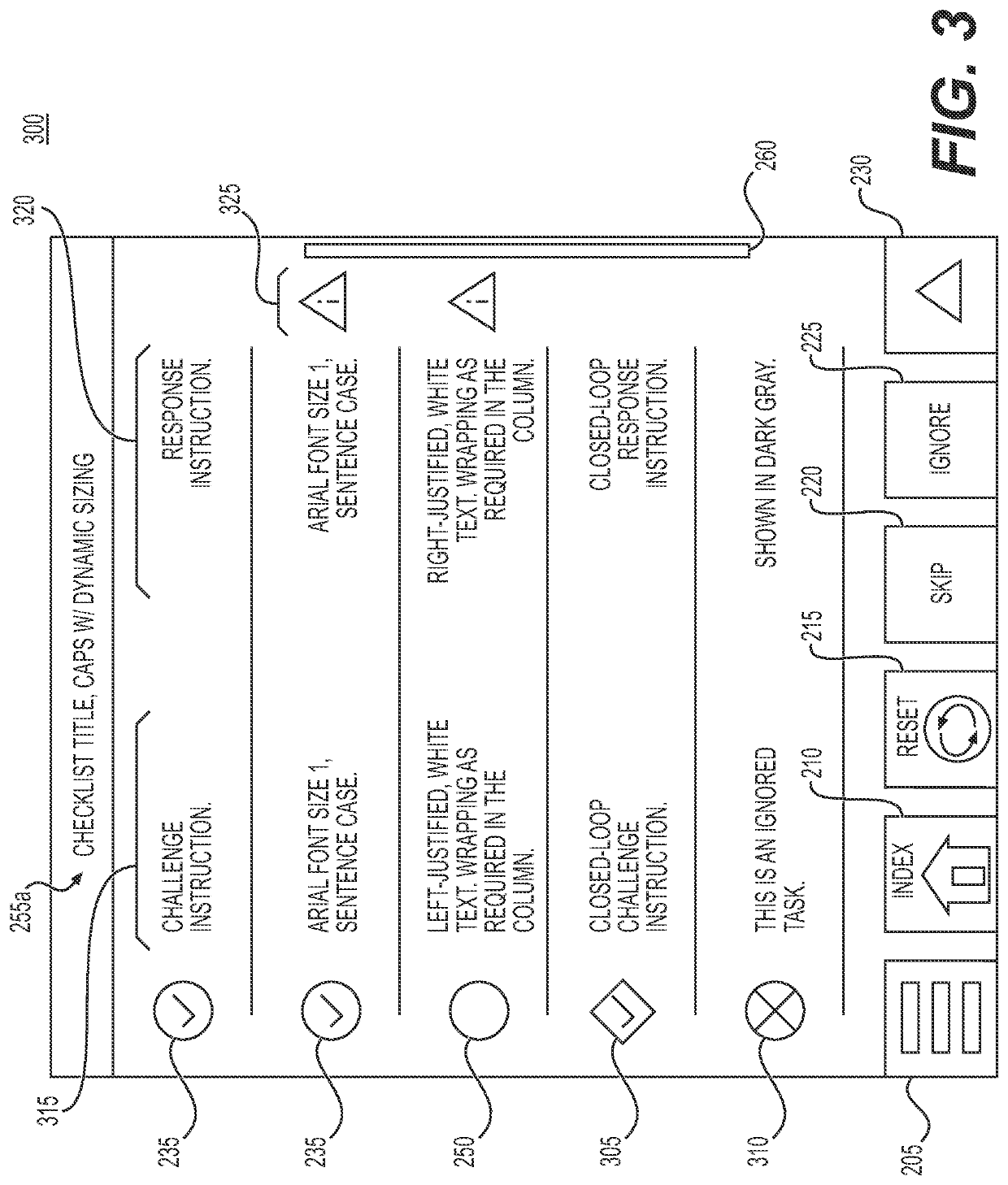
Methods and systems for electronic checklist data references
Disclosed are methods, systems, and non-transitory computer-readable medium for electronic checklist data references. For instance, the method may include: displaying, in a GUI, a checklist GUI corresponding to a checklist of an electronic checklist system; determining whether the checklist includes one or more dynamic data references and / or one or more static data references; in response to determining the checklist includes the one or more dynamic data references, performing a dynamic data reference process to display specific data in the checklist GUI for the one more dynamic data references; and in response to determining the checklist includes the one or more static data references, displaying one or more static data fields in the checklist GUI for the one or more static data references to initiate performing a static data reference process for the one or more static data fields.
Owner:HONEYWELL INT INC
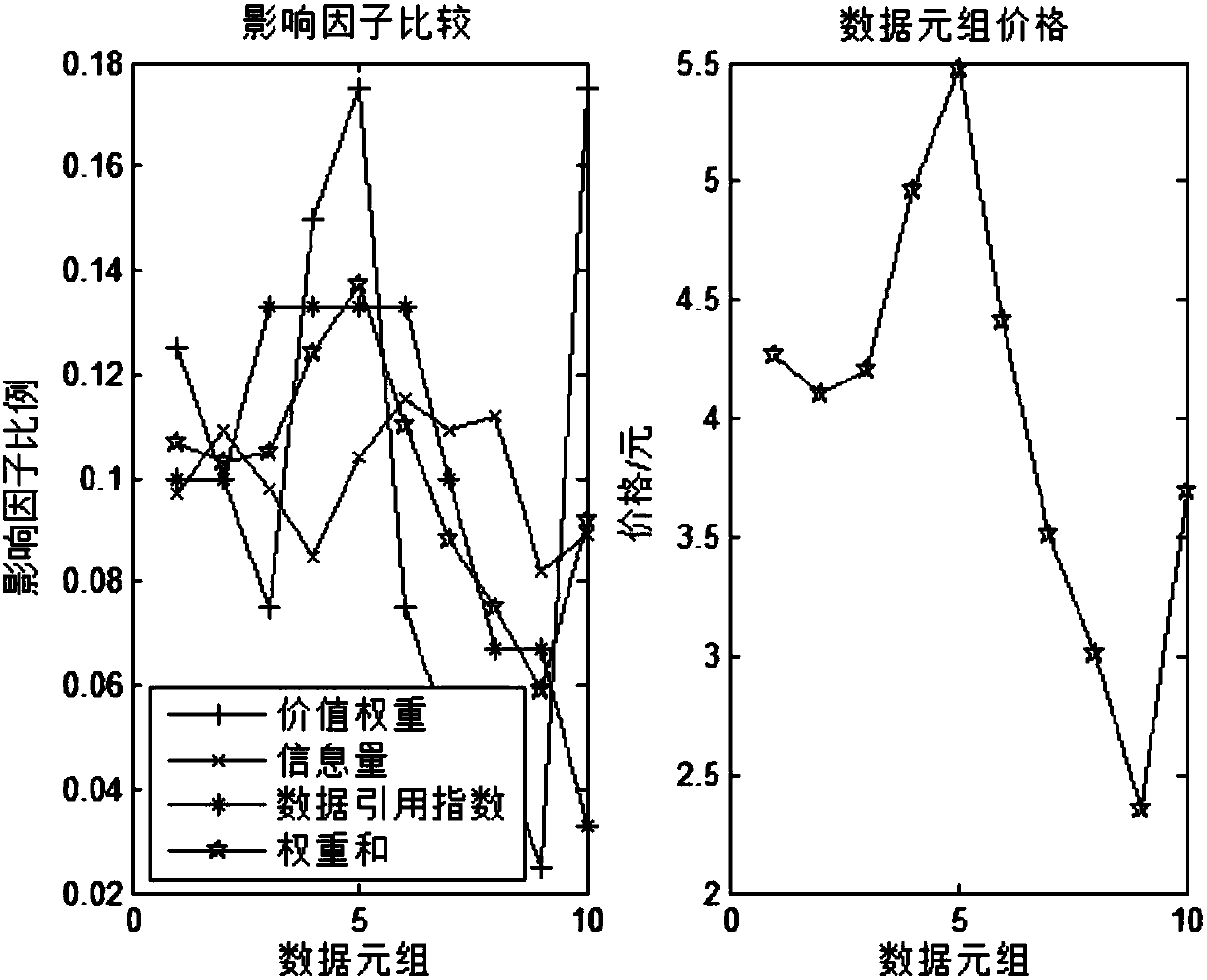
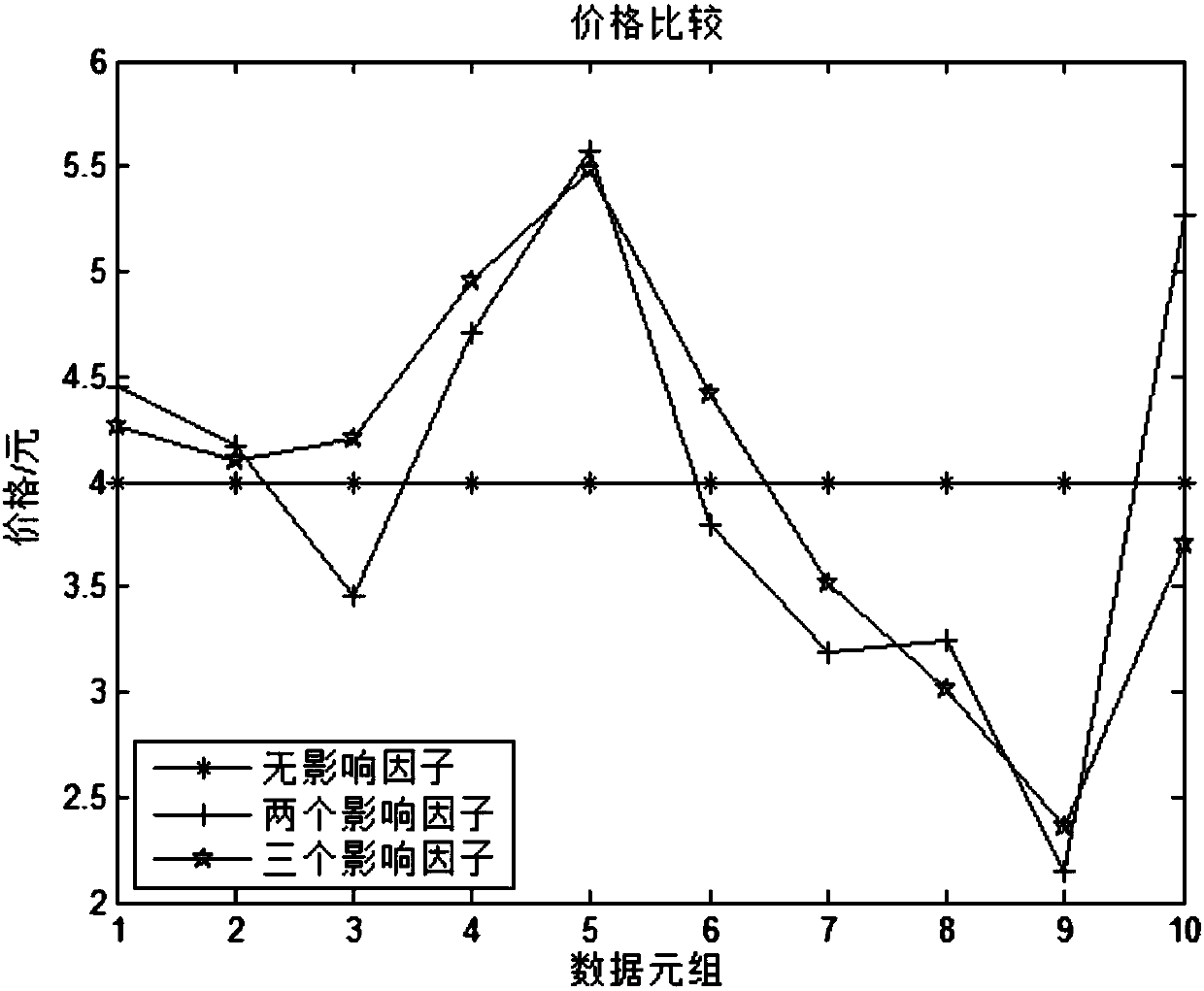
Tuple granularity-based individual big data pricing method
The invention discloses a personal big data pricing method based on tuple granularity. First, investigate the data attributes that affect the value of data, and then analyze the influence of factors such as information entropy, value weight, data reference index, and data cost on the value of data tuples, and derive a value calculation method for data tuples, which can be based on Parameters are dynamically adjusted. With the increase of data scale, reduction of data cost and improvement of data quality, all parties in data transactions will get more benefits. Finally, a concrete example is used to verify the correctness and validity of the pricing method.
Owner:成都大征创智科技有限公司
Method and apparatus for adding supplemental information to PATRICIA tries
InactiveUS7693850B2Digital data information retrievalSpecial data processing applicationsDatum referenceInode
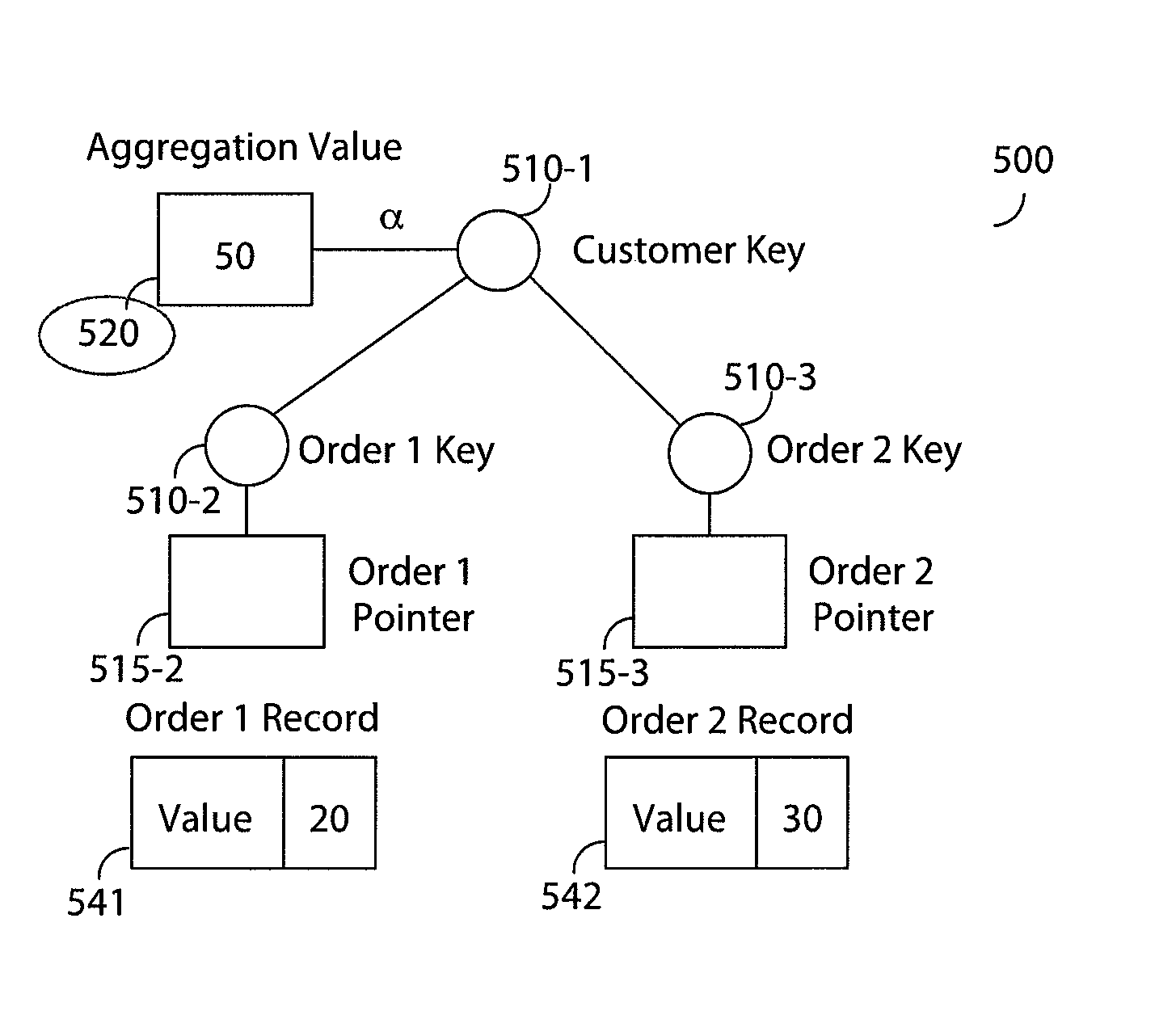
Method and apparatus for adding annotations to an index are disclosed. Annotation is defined as any supplemental information that may be stored in an index node in addition to the usual key and data references. Adding annotations to the index opens numerous applicative possibilities, including but not limited to, storing and retrieving aggregation, statistical, and security information pertaining to the indexed data and to the index itself.
Owner:RIGHTORDER
Burying point data access control method and device, computer equipment and storage medium
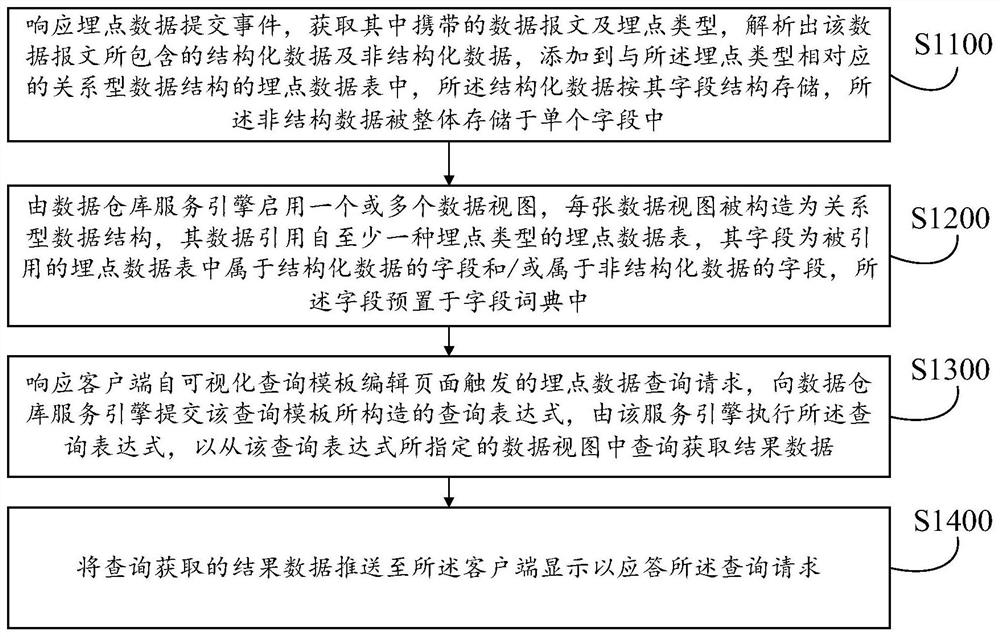
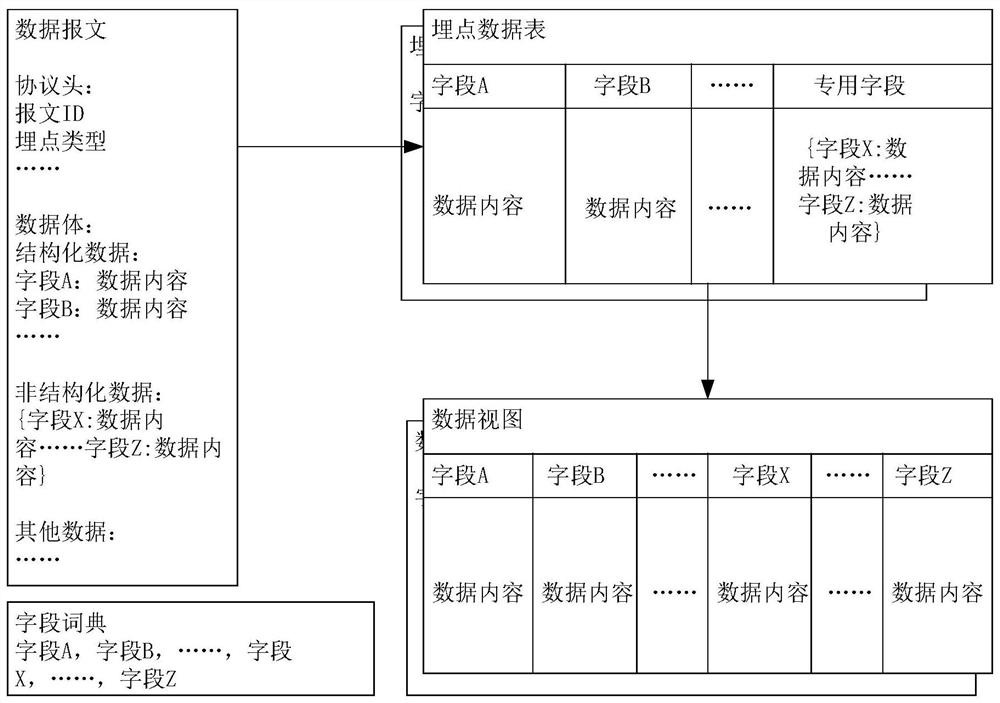
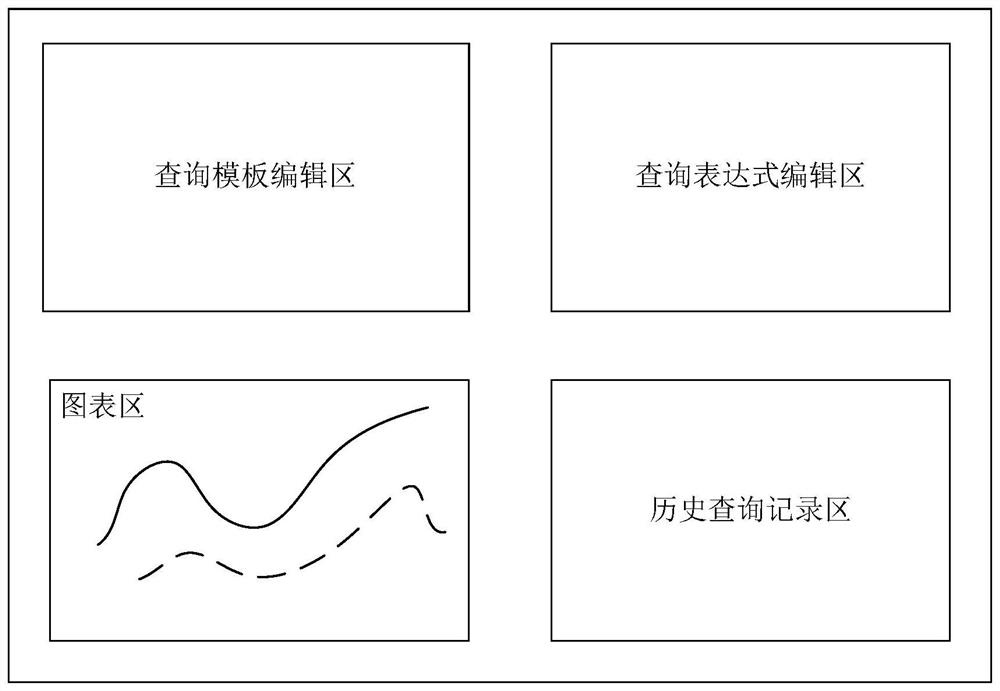
ActiveCN113420099ATo achieve a high degree of coordination and unityHighly unified result data formatRelational databasesMulti-dimensional databasesData citationPoint data
The invention discloses a burying point data access control method and device, computer equipment and a storage medium, and relates to the field of internet live broadcast. The method comprises the following steps: responding to a burying point data submission event, analyzing structured data and unstructured data, and adding the structured data and the unstructured data into a burying point data table of a relational data structure; enabling a data warehouse service engine to start a data view, constructing the data view into a relational data structure, wherein data of the data view is referenced from a buried point data table, fields of the data view are fields belonging to structured data and / or fields belonging to unstructured data in the buried point data table, and the fields are preset in a field dictionary; querying the expression from a data warehouse service engine, and querying from a data view specified by the query expression to obtain result data; and pushing the result data to the client for display. According to the method, unified and standardized processing can be performed on the multi-source burying point data, and the collection and access efficiency of the burying point data of the Internet live broadcast application program product can be improved.
Owner:广州方硅信息技术有限公司
Updating code in distributed version control system
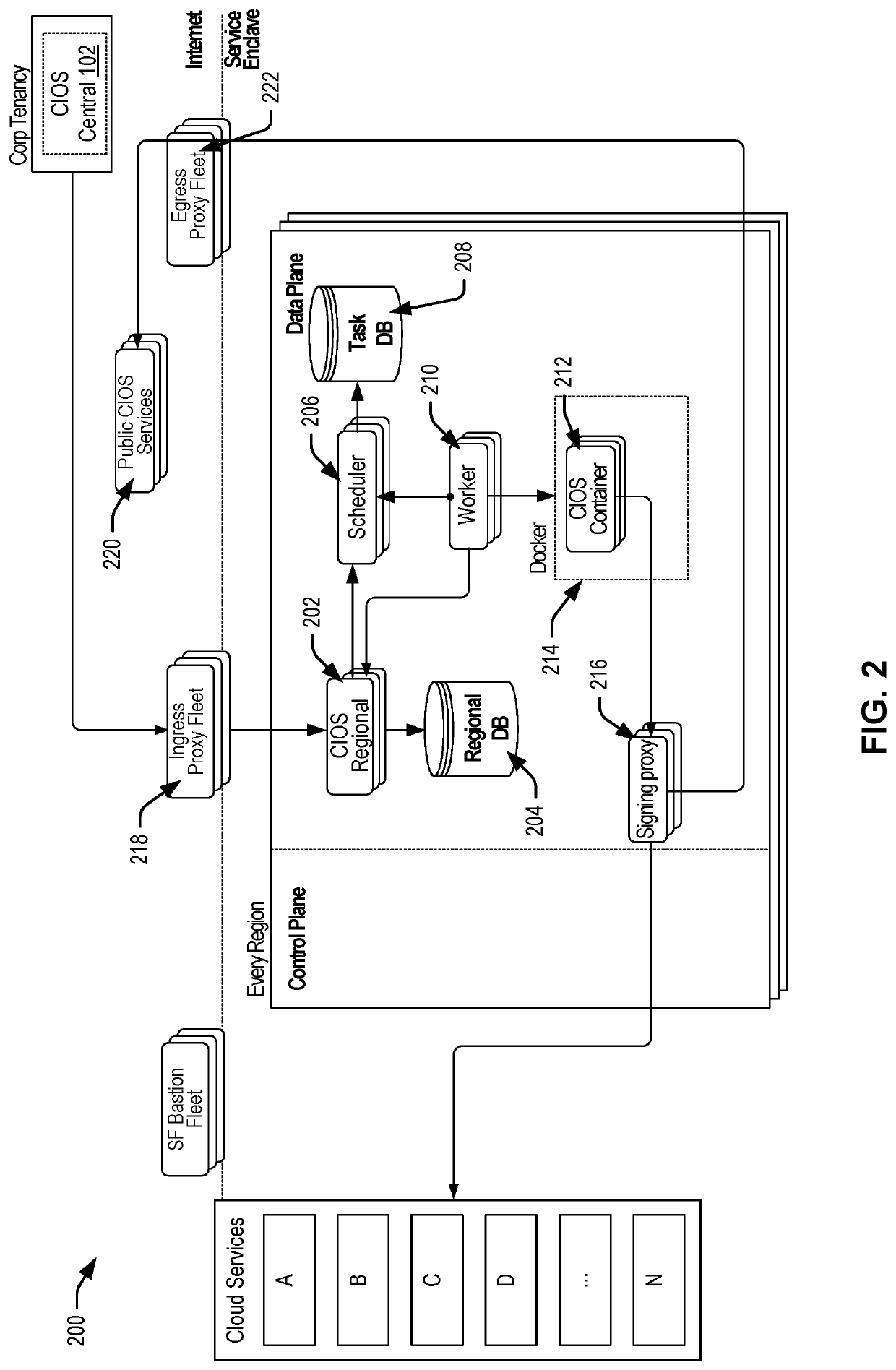
Techniques for implementing a change to a first service by a computer infrastructure deployment service (CIOS) are disclosed. The CIOS may manage declarative infrastructure providers to deploy infrastructure resources and workpieces based at least in part on declarative instructions. The CIOS may detect a first modification to a first service (e.g., a sidecar application). The CIOS may identify that configuration data of the second service references the first service (e.g., via a git sub-module). In response to identifying the second modification to the second service, the CIOS may present a change via the graphical interface, the change including the first modification to the first service. A user input may be received indicating acceptance or rejection of the change to the first modification. The CIOS may then effect a change to the first service in accordance with the user input. For example, the CIOS may ensure that the modified first service is deployed alongside the second service in a subsequent deployment.
Owner:ORACLE INT CORP
Off-line programming method of plug-in machine program
PendingCN111897519AOut-of-line programming implementationSoftware designProduction lineBill of materials
The invention relates to an off-line programming method for a plug-in machine program, which comprises the following programming steps: 1, quoting BOM (Bill of Materials) data in combination with an ERP system, and obtaining inserted specific points, element codes, used material models and an insertion process by using a formula link; 2, combining the point location information obtained in the BOMwith the inserted point location coordinates extracted from the original coordinates; and step 3, linking and combining coordinates by using a reference function, performing data reference accordingto a program format of the plug-in machine, and finally importing the manufactured program into the plug-in machine online. By means of the program off-line programming method, manual operation and manual guarantee in the whole process of original on-line program manufacturing are changed into existing program manufacturing through associated data linkage, off-line advanced programming is achieved, and off-line advanced programming is transmitted to a production line for use through system management and control. After the circuit board is replaced, the plug-in machine does not need to be shutdown, and a new plug-in program can be operated after the plug-in machine receives a program compiled in advance, so that plug-and-play replacement is realized.
Owner:东莞新技电子有限公司
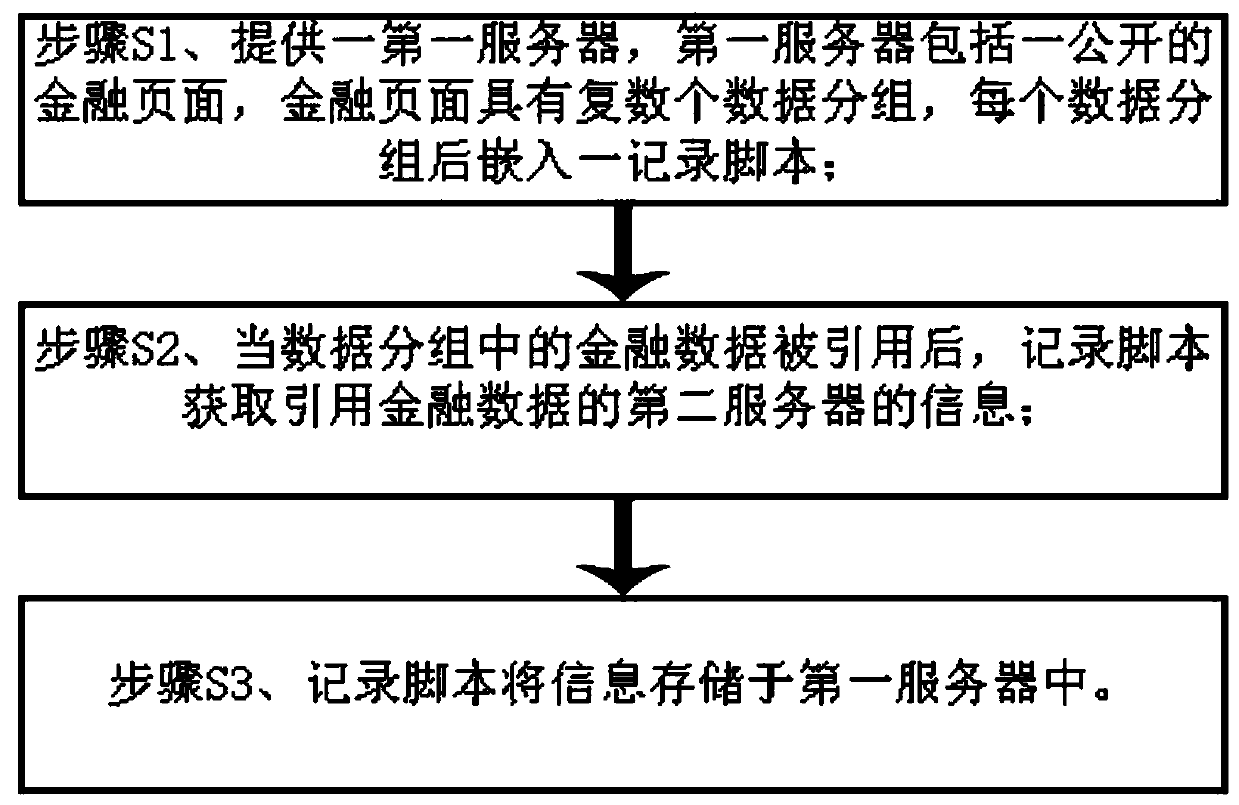
Data reference recording method
PendingCN109948025ATo achieve the purpose of positioningWeb data indexingSoftware designDatum referenceData citation
The invention discloses a data reference recording method, which comprises the following steps that: S1, providing a first server, the first server comprises a public financial page, the financial page is provided with a plurality of data packets, and embedding a recording script into each data packet; S2, after the financial data in the data group are quoted, recording a script to obtain information of a second server quoting the financial data; and S3, enabling the recording script to store the information in a first server. The method comprises the following steps: after grouping a plurality of data of a financial page in a first server, embedding a recording script; after the financial data in any data group is quoted, the recording script is started, the information of the second server quoting the data is obtained, the information is stored in the first server, and the server illegally obtaining the data is effectively positioned.
Owner:SHANGHAI GOOAO ELECTRONIC TECHNOLOGY CORP
Methods and systems for electronic checklist data references
ActiveUS20220269381A1Aircraft componentsData processing applicationsSoftware engineeringData citation
Disclosed are methods, systems, and non-transitory computer-readable medium for electronic checklist data references. For instance, the method may include: displaying, in a GUI, a checklist GUI corresponding to a checklist of an electronic checklist system; determining whether the checklist includes one or more dynamic data references and / or one or more static data references; in response to determining the checklist includes the one or more dynamic data references, performing a dynamic data reference process to display specific data in the checklist GUI for the one more dynamic data references; and in response to determining the checklist includes the one or more static data references, displaying one or more static data fields in the checklist GUI for the one or more static data references to initiate performing a static data reference process for the one or more static data fields.
Owner:HONEYWELL INT INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com