Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
59 results about "Host type" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
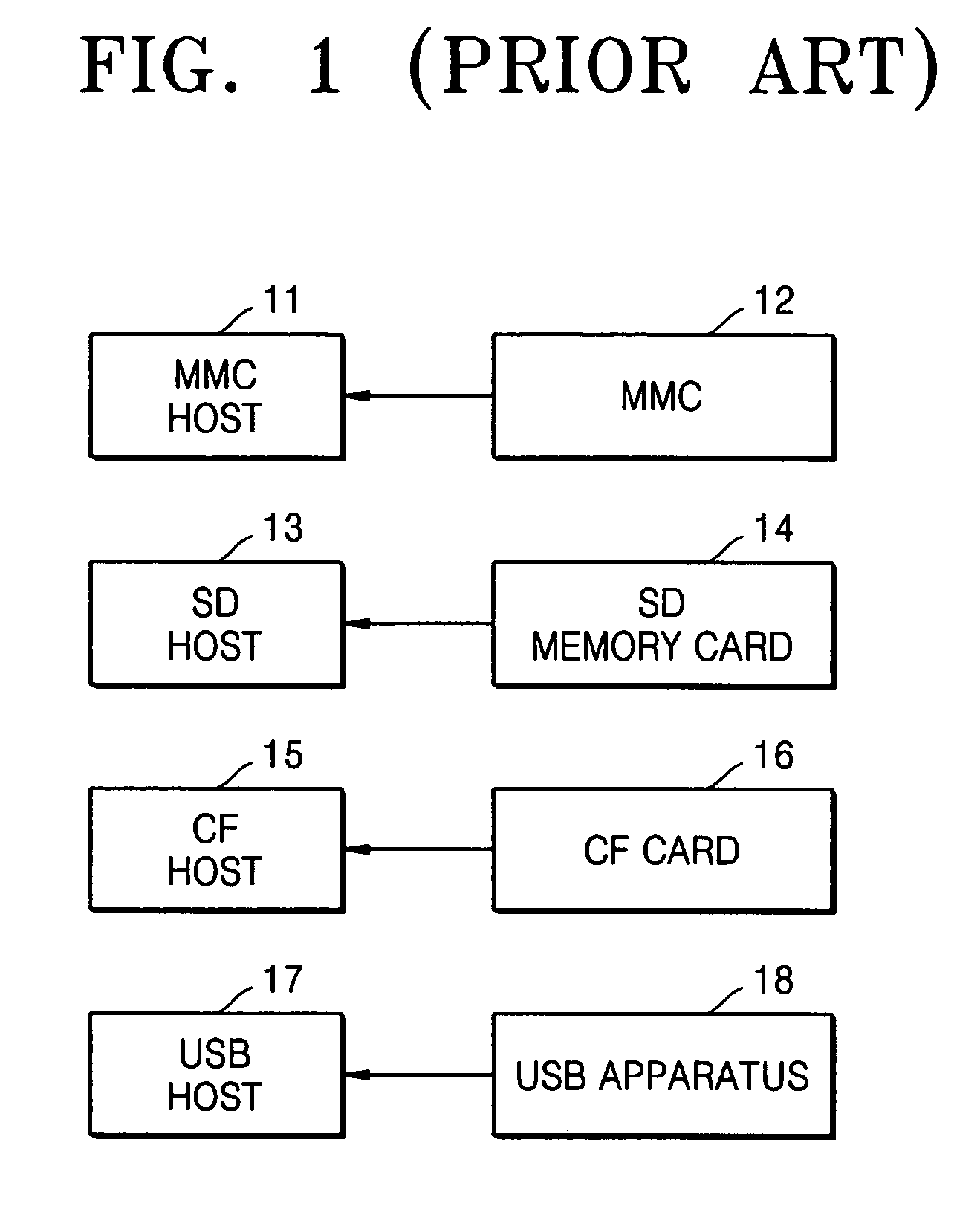
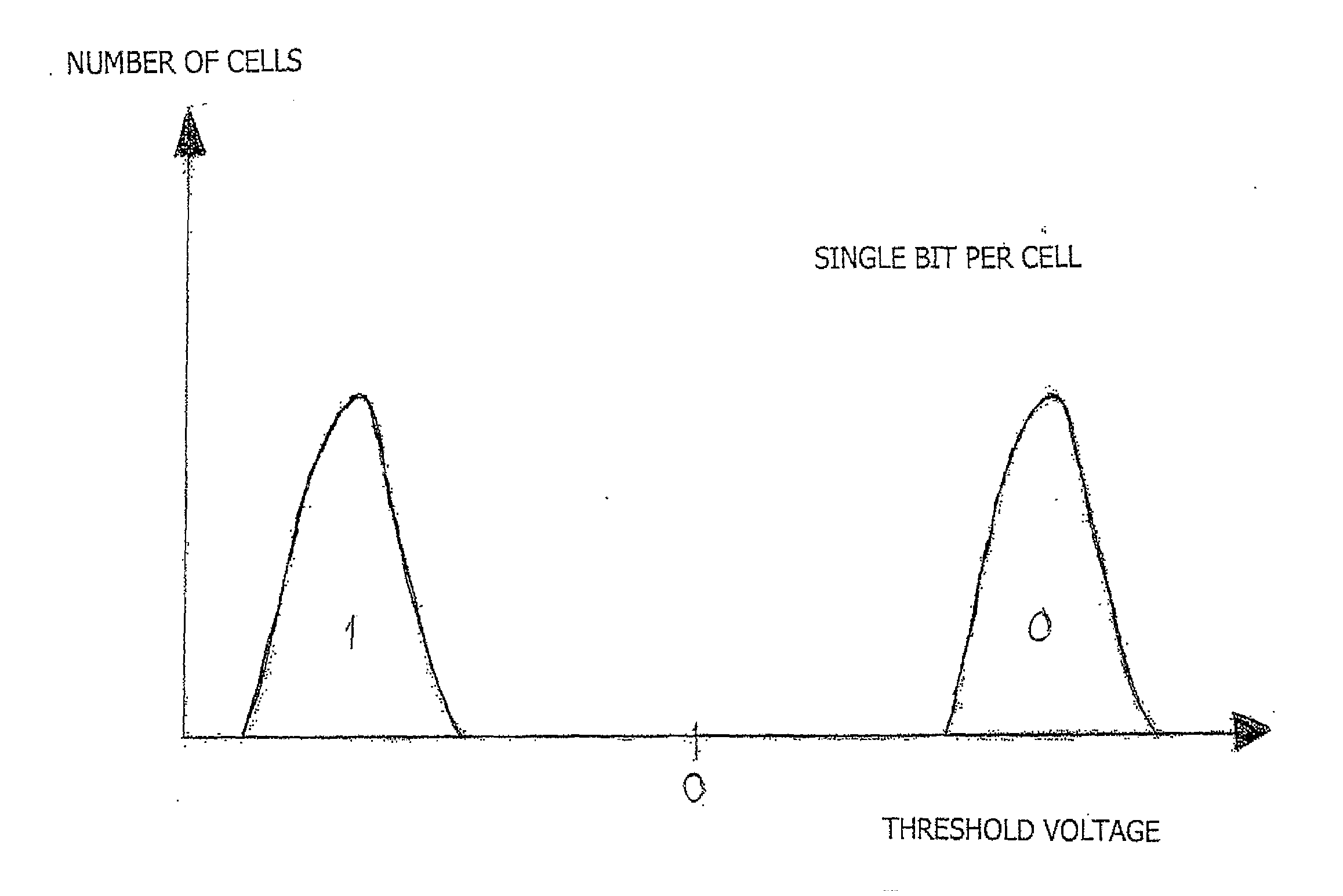
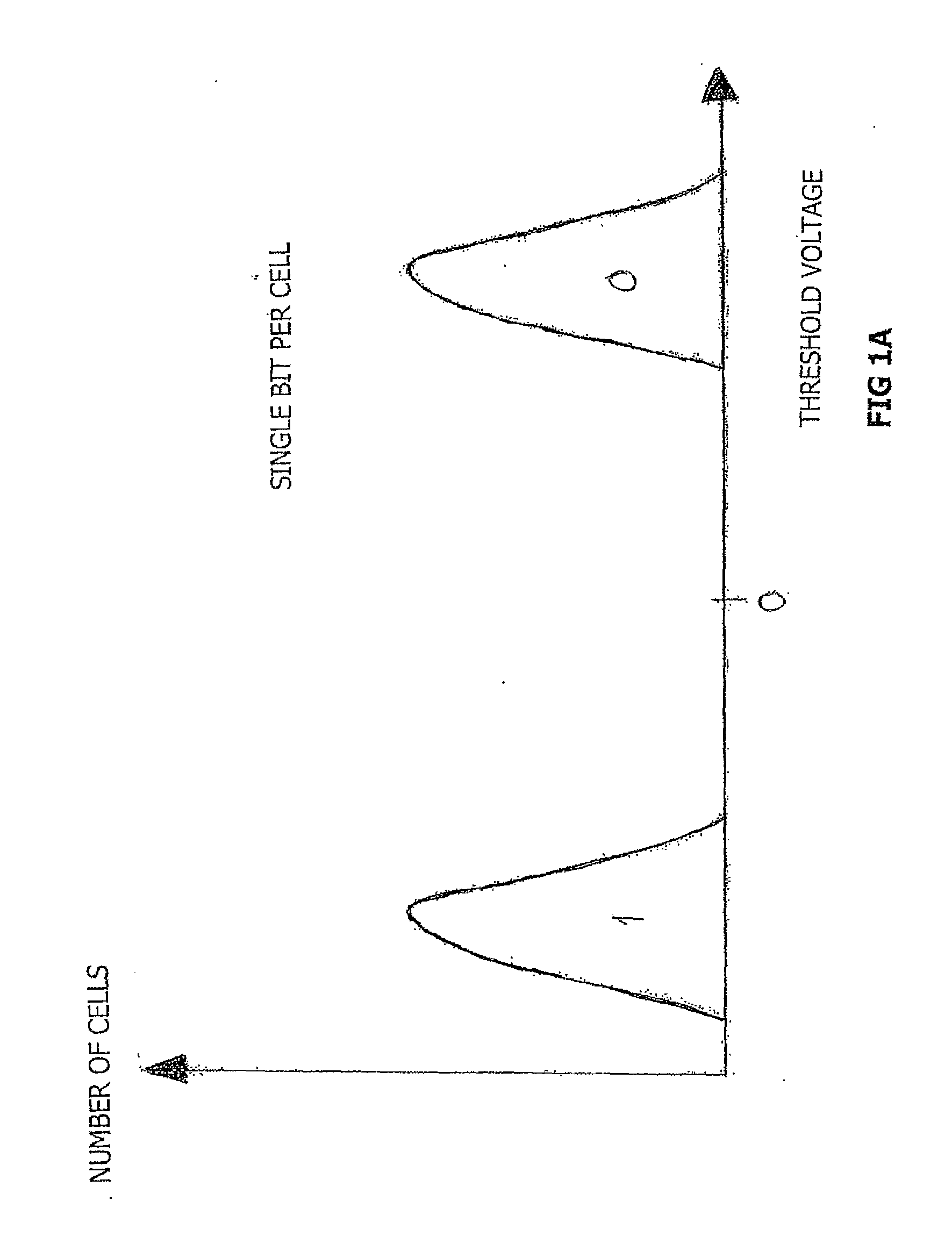
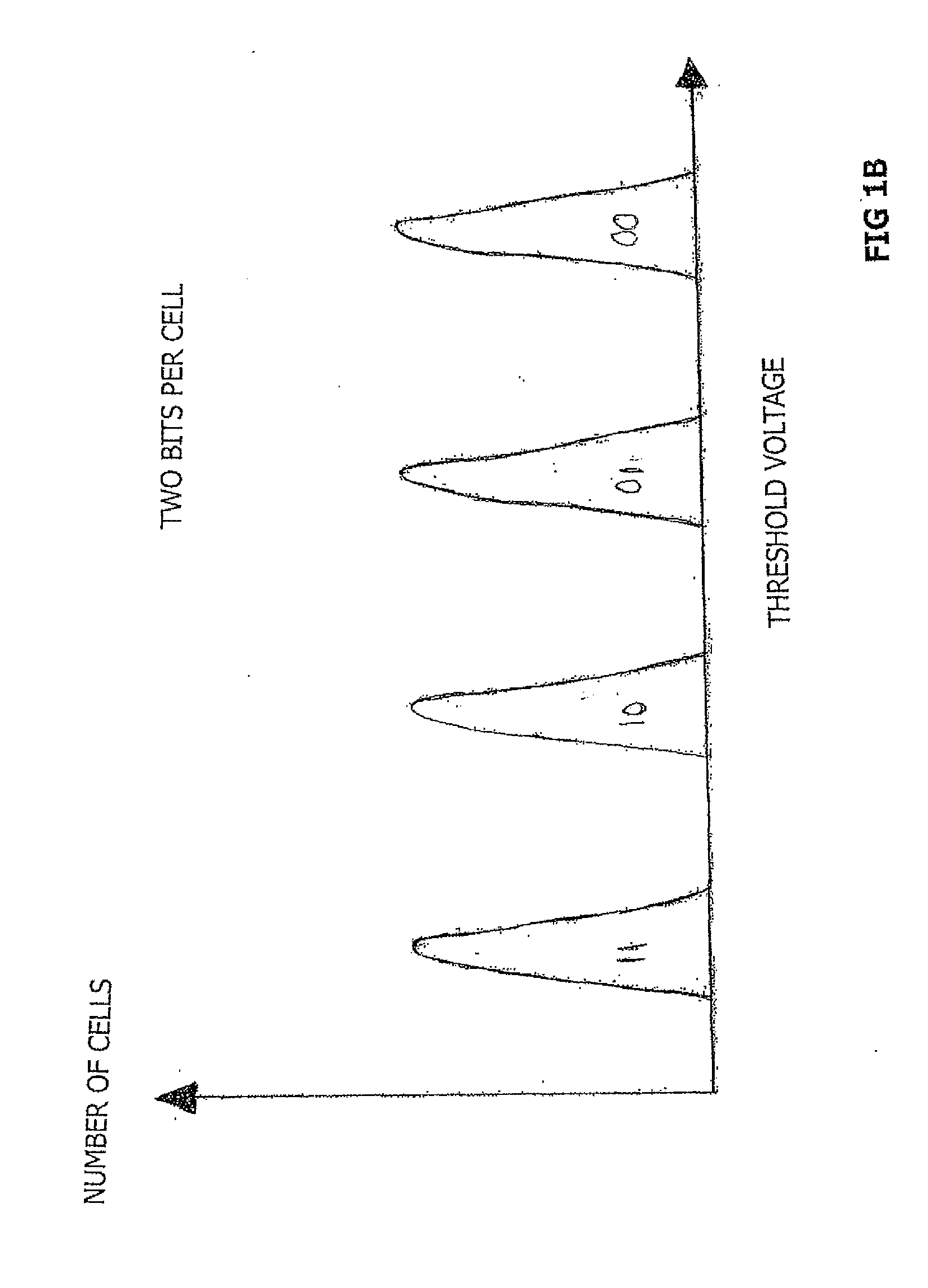
Host Type (A): This host type is a basic host type and most commonly used. It simply points a hostname to an IP address. This change has a TTL (Time To Live) of 60 seconds. This means it will take 60 seconds to be live.
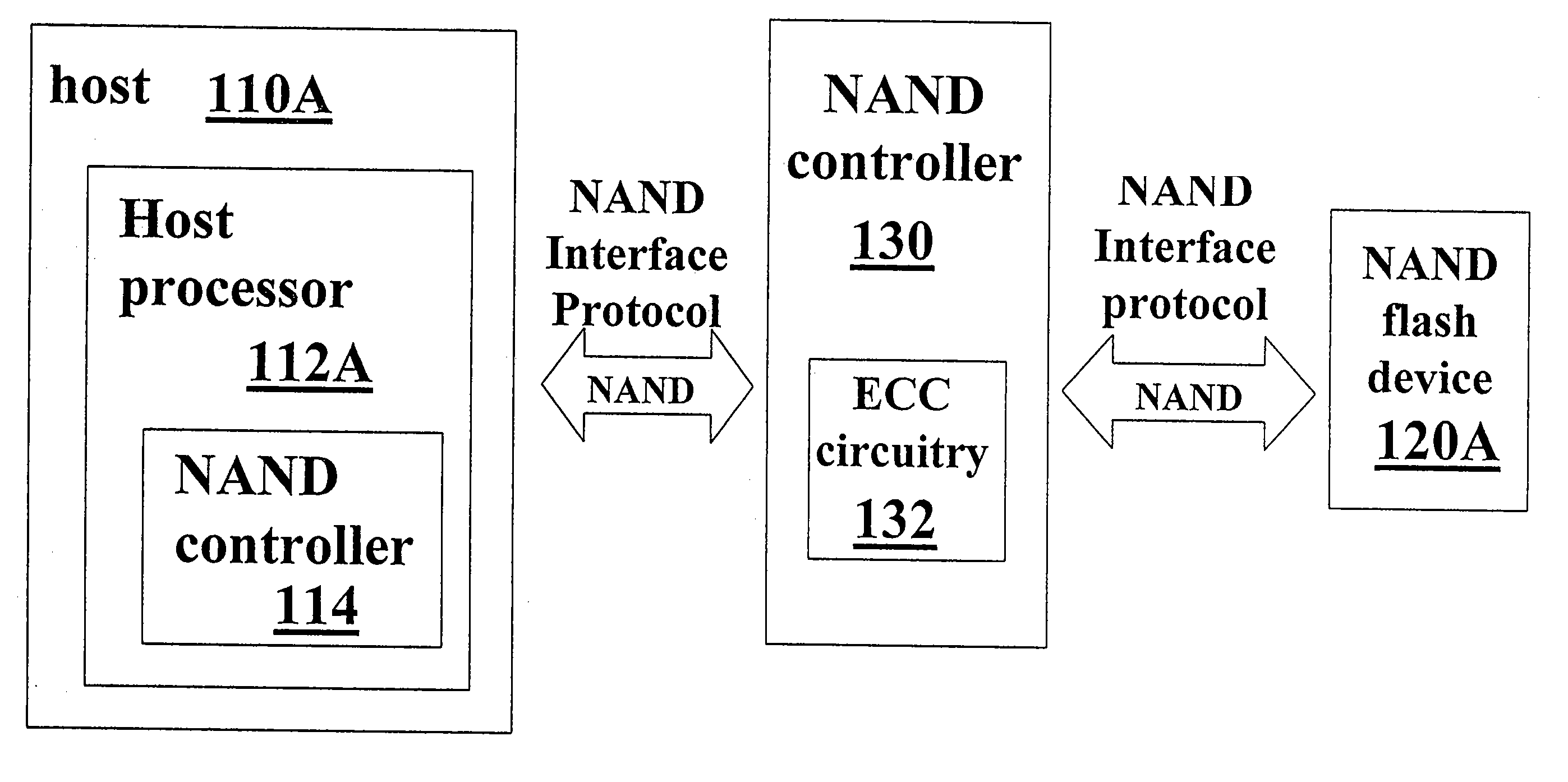
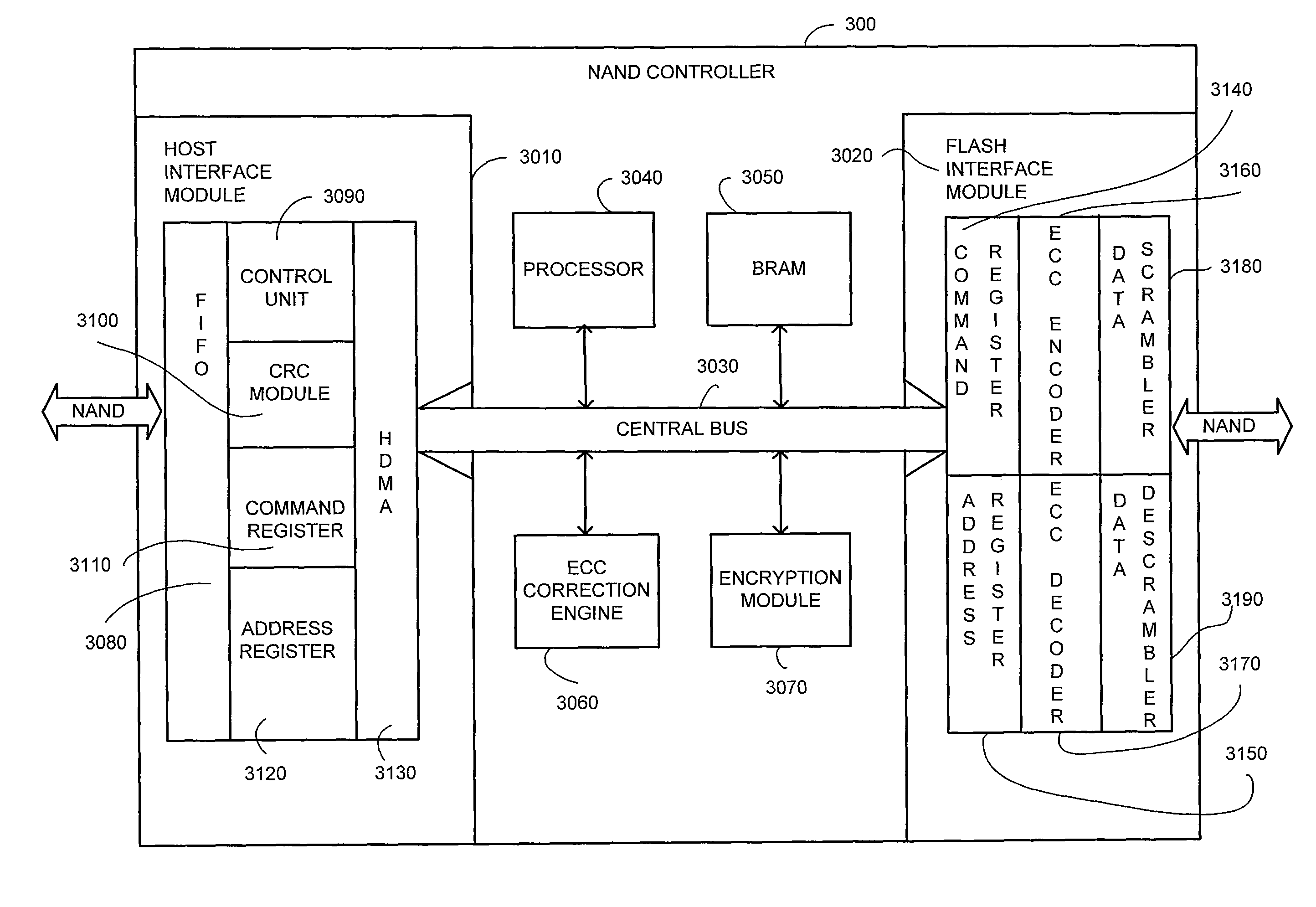
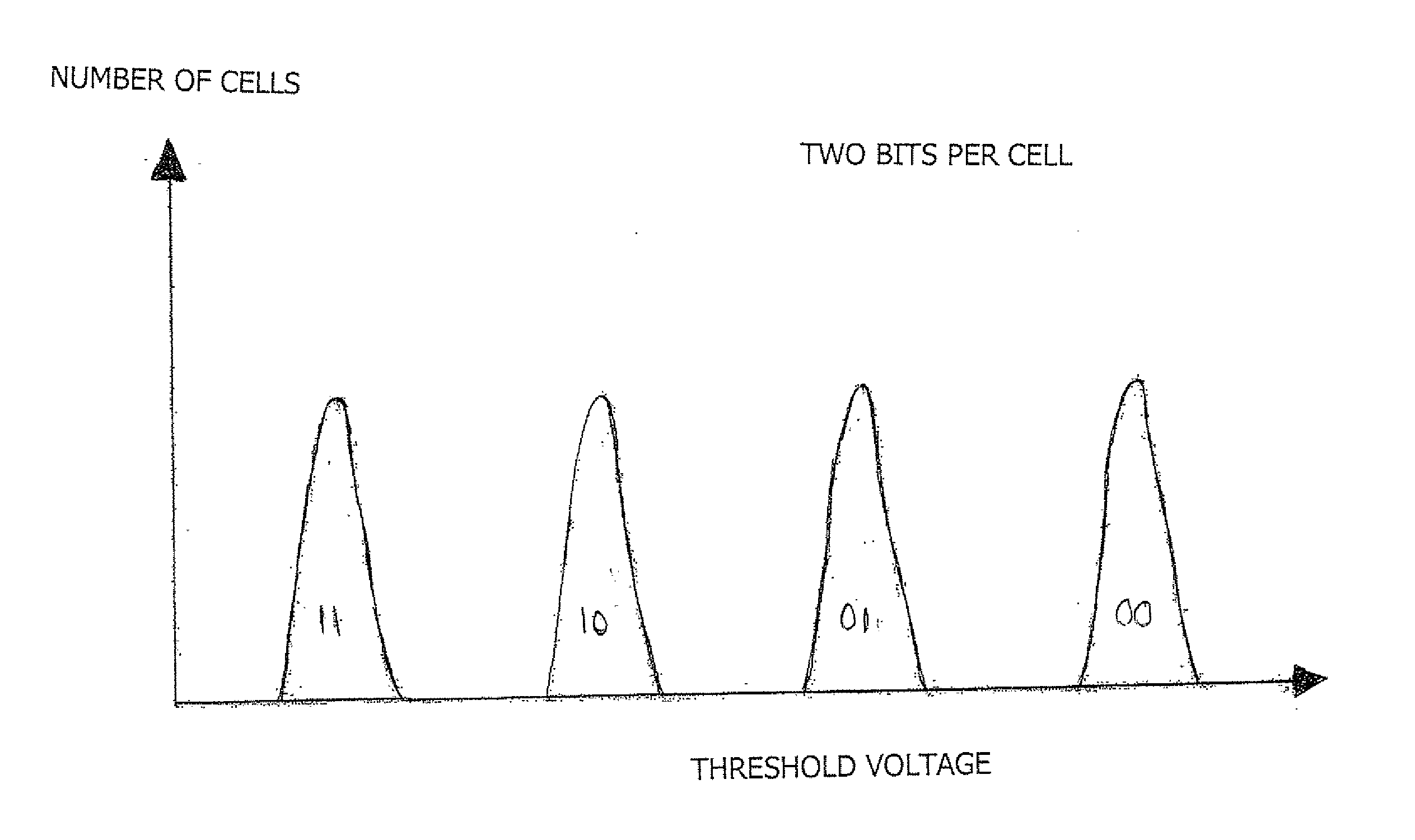
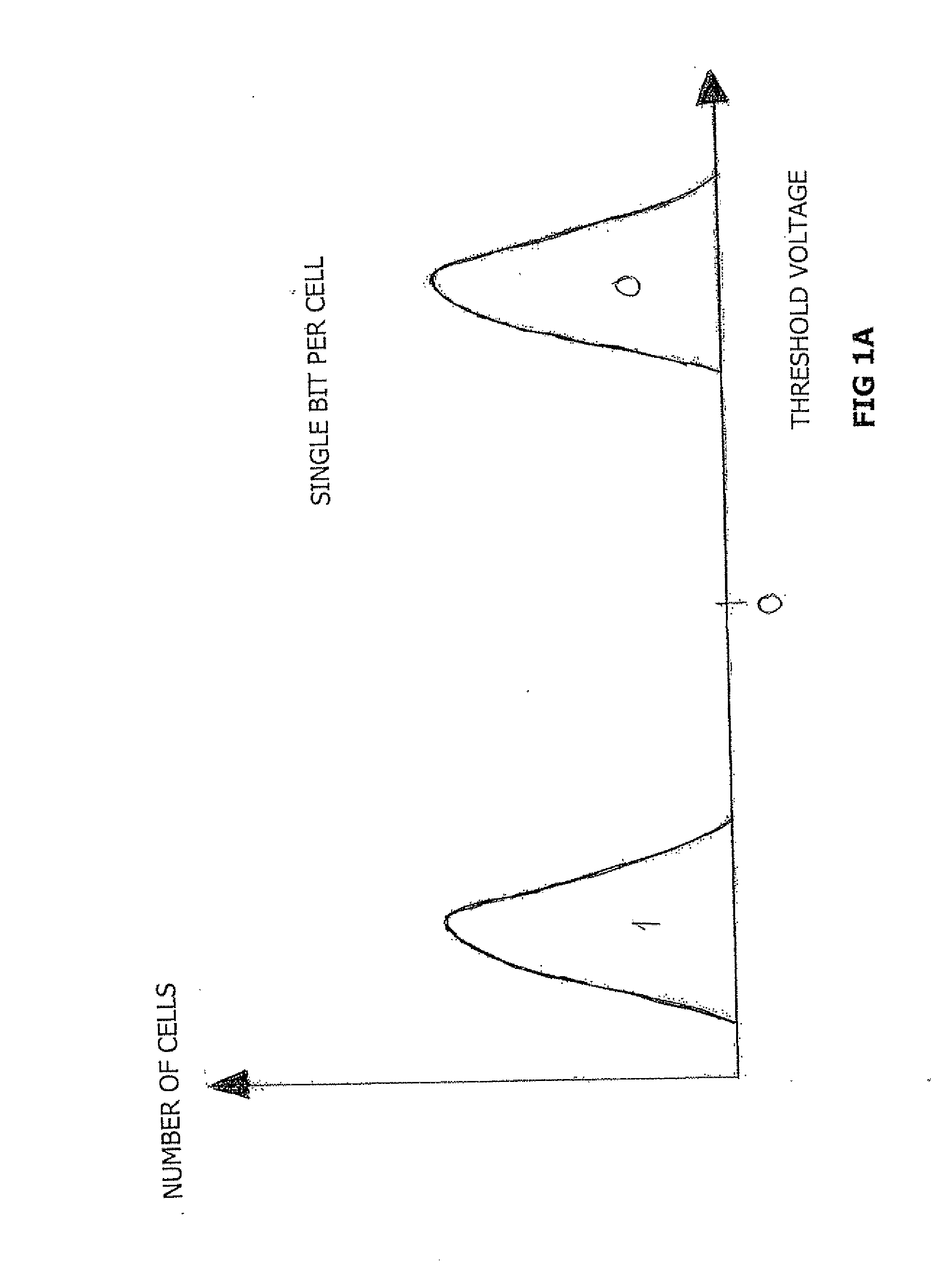
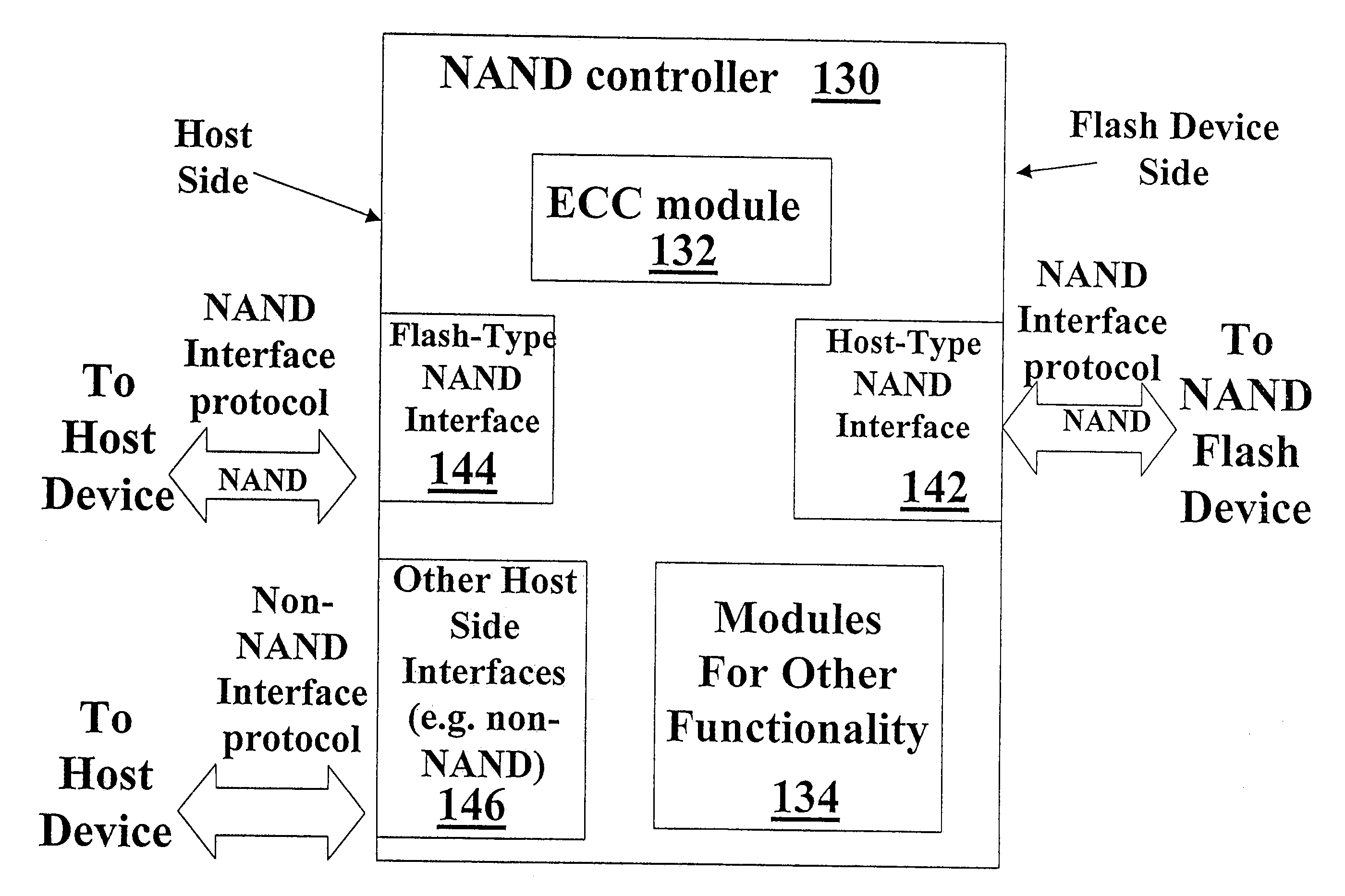
NAND Flash Memory Controller Exporting a NAND Interface
ActiveUS20100023800A1Satisfies needMemory architecture accessing/allocationData representation error detection/correctionHost typeHost machine
A NAND controller for interfacing between a host device and a flash memory device (e.g., a NAND flash memory device) fabricated on a flash die is disclosed. In some embodiments, the presently disclosed NAND controller includes electronic circuitry fabricated on a controller die, the controller die being distinct from the flash die, a first interface (e.g. a host-type interface, for example, a NAND interface) for interfacing between the electronic circuitry and the flash memory device, and a second interface (e.g. a flash-type interface) for interfacing between the controller and the host device, wherein the second interface is a NAND interface. According to some embodiments, the first interface is an inter-die interface. According to some embodiments, the first interface is a NAND interface. Systems including the presently disclosed NAND controller are also disclosed. Methods for assembling the aforementioned systems, and for reading and writing data using NAND controllers are also disclosed.
Owner:INNOVATIVE MEMORY SYST INC
NAND flash memory controller exporting and NAND interface
A NAND controller for interfacing between a host device and a flash memory device (e.g. a NAND flash memory device) fabricated on a flash die is disclosed. In some embodiments, the presently disclosed NAND controller includes electronic circuitry fabricated on a controller die, the controller die being distinct from the flash die, a first interface (e.g. a host-type interface, for example, a NAND interface) for interfacing between the electronic circuitry and the flash memory device, and a second interface (e.g. a flash-type interface) for interfacing between the controller and the host device, wherein the second interface is a NAND interface. According to some embodiments, the first interface is an inter-die interface. According to some embodiments, the first interface is a NAND interface. Systems including the presently disclosed NAND controller are also disclosed. Methods for assembling the aforementioned systems, and for reading and writing data using NAND controllers are also disclosed.
Owner:INNOVATIVE MEMORY SYST INC
NAND flash memory controller exporting a NAND interface
Owner:INNOVATIVE MEMORY SYST INC
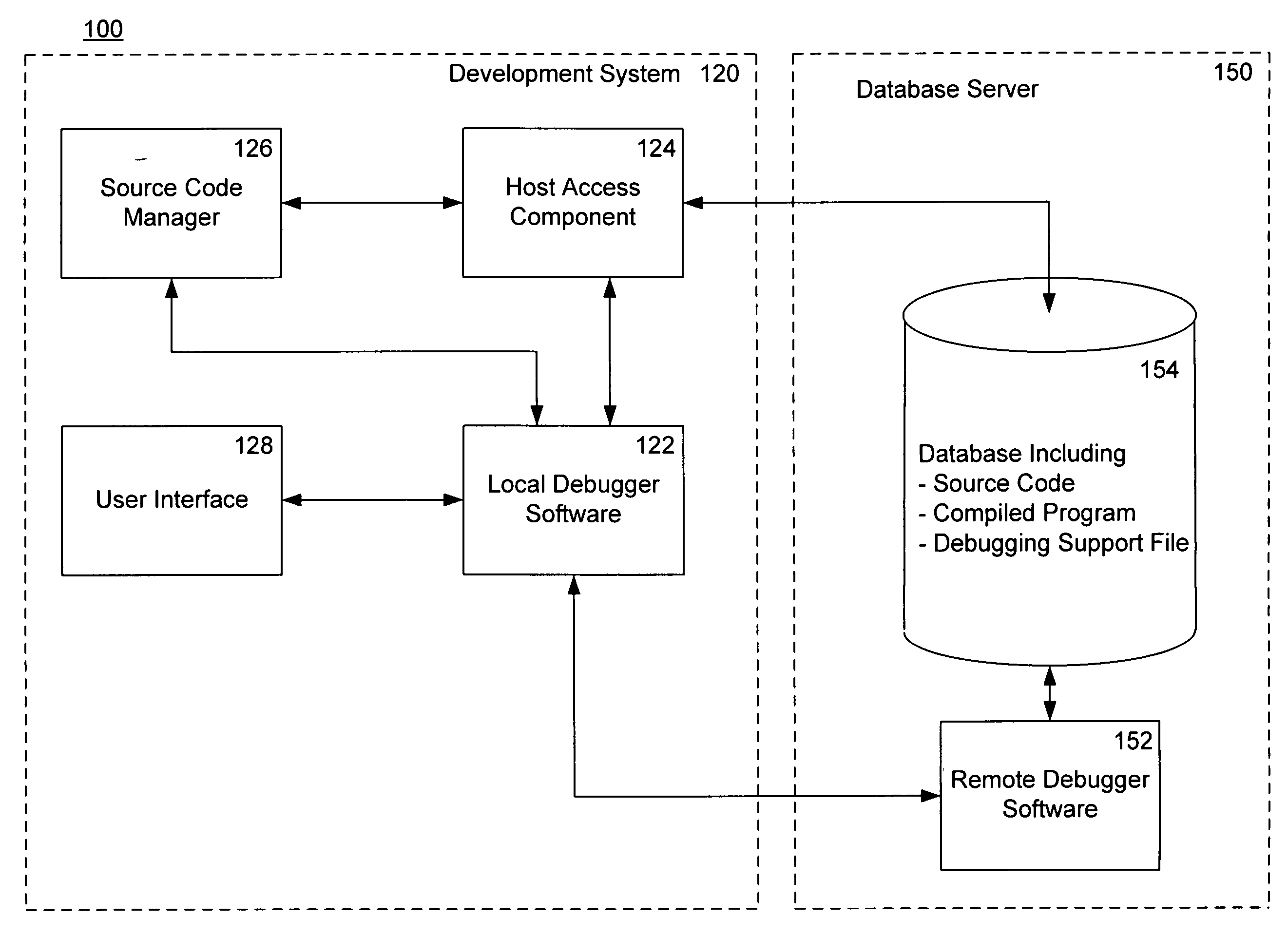
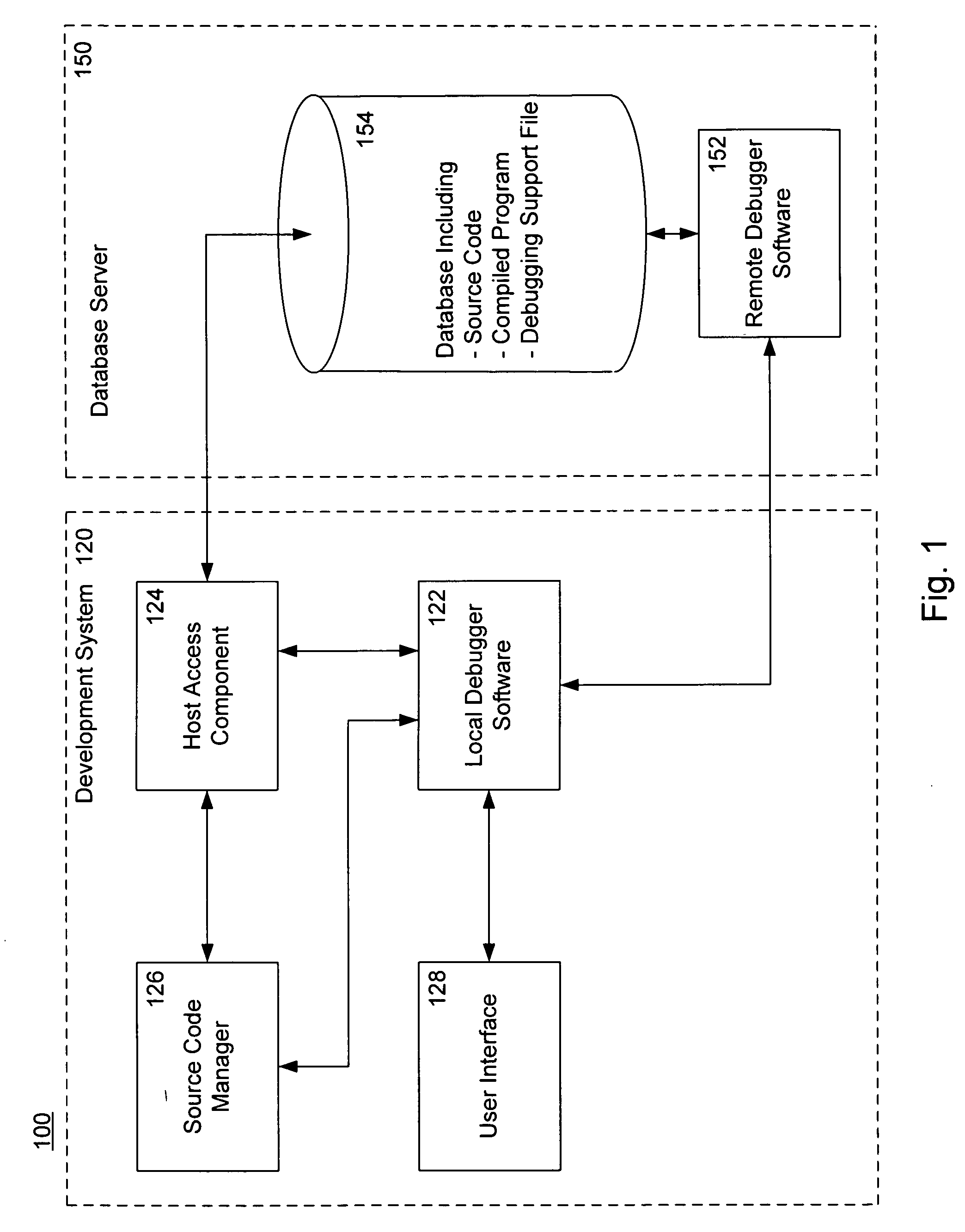
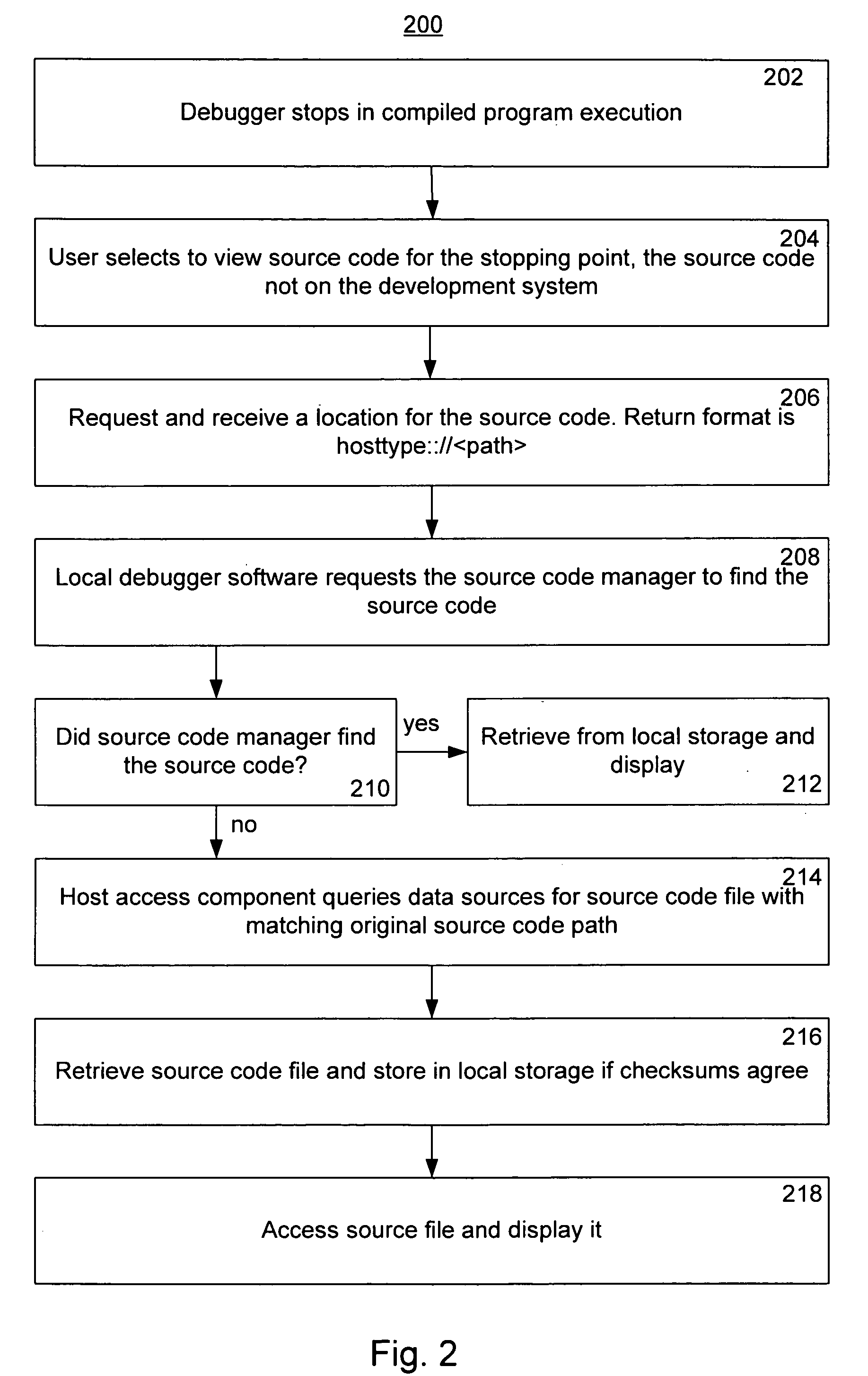
Locating source code when stopping in a debugger
InactiveUS20070006155A1Error detection/correctionSpecific program execution arrangementsParallel computingChecksum
A method for automatically retrieving source code during software debugging sessions using a development system includes stopping in an object with compiled code where the compiled code is associated with corresponding source code via a debugging support file. The compiled code can be run on different hosts. During a debugging session, a local debugger portion of the software in the development system requests a unique resource locator for the source code. A remote software debugger portion on a host responds by providing a hosttype, which specifies the host specific search algorithm, and the original path for the source code. A development system host access component requests a file with matching name and original path from the host. An original source file checksum is compared with a retrieved checksum. Upon a match, the retrieved source code is stored in the development system and accessed for user display.
Owner:MICROSOFT TECH LICENSING LLC
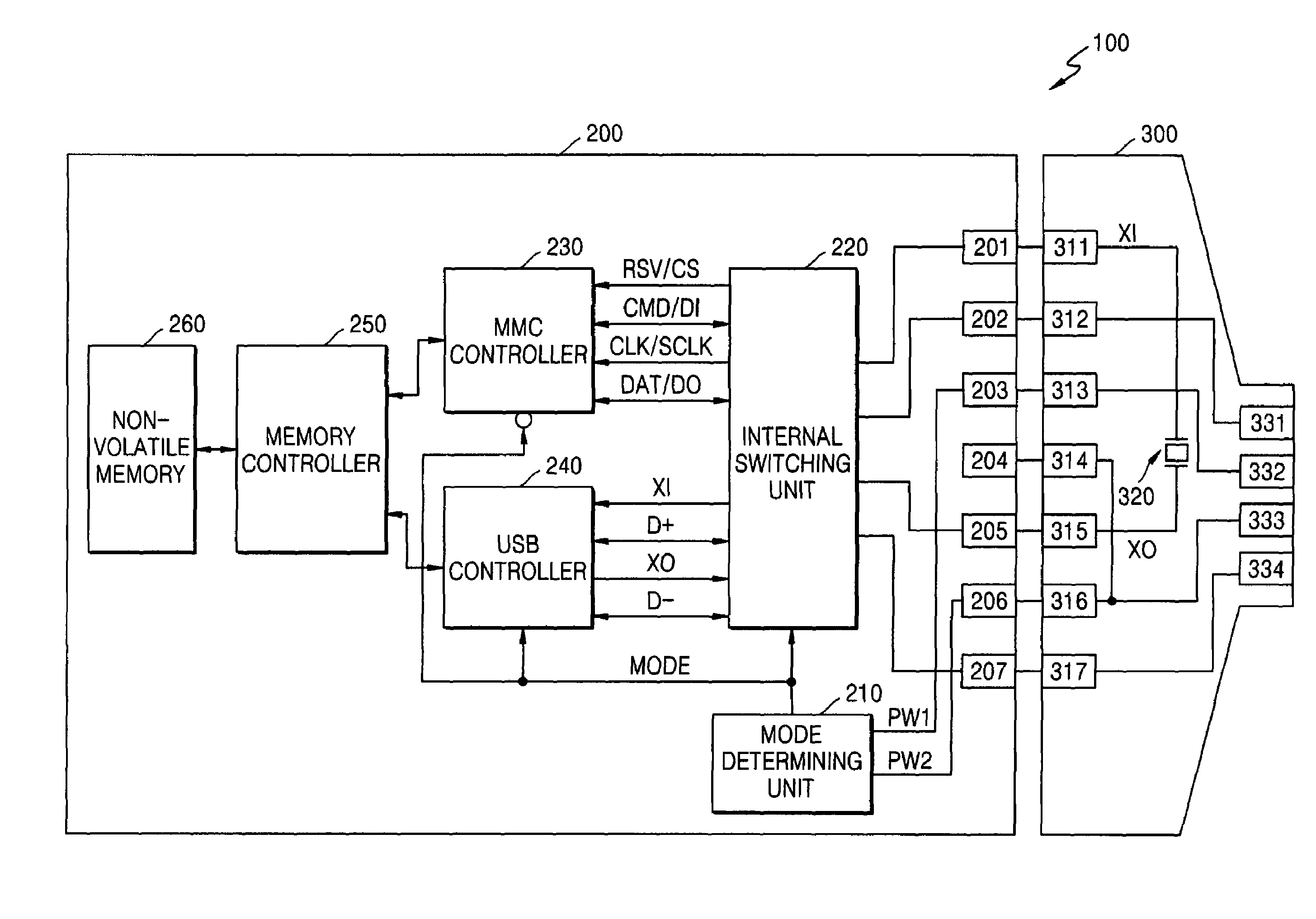
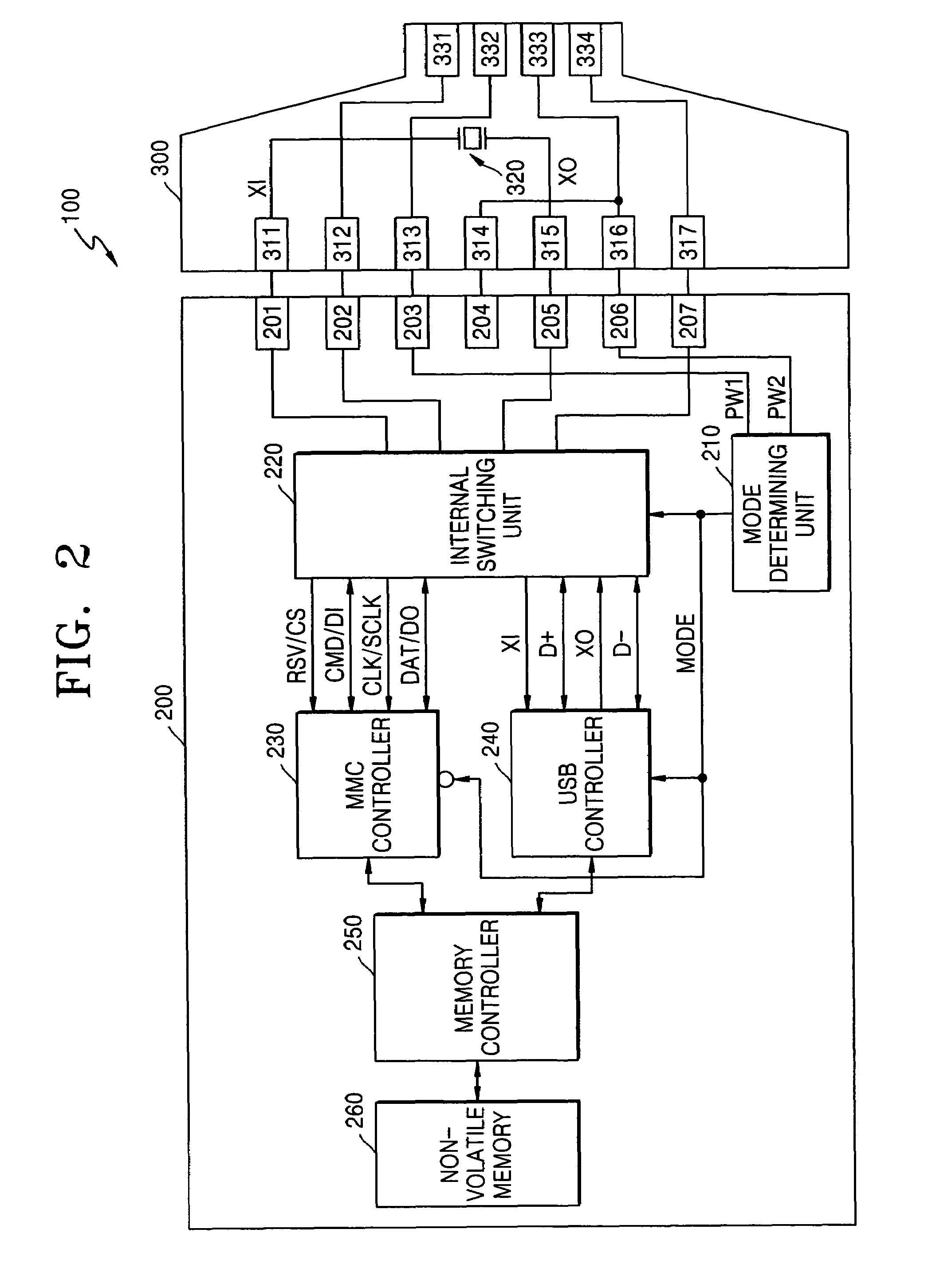
Multimedia/secure digital cards and adapters for interfacing using voltage levels to determine host types and methods of operating
InactiveUS7237049B2Program control using wired connectionsCo-operative working arrangementsEngineeringVoltage
A Multimedia (MMC) / Secure Digital (SD) form-factor compliant card apparatus can include a mode determining circuit connected to first and second pins of the card apparatus and configured to determine a type of host connected to the first and second pins based on comparing voltages at the first and second pins to an internal voltage level. Related adaptors and methods are also disclosed.
Owner:SAMSUNG ELECTRONICS CO LTD
NAND flash memory controller exporting a logical sector-based interface
InactiveUS20080046641A1Small sizeRead-only memoriesMemory systemsData processing systemFlash memory controller
A controller of a flash memory device exchanges data pages with the memory device via a host-type NAND interface and exchanges data sectors with a host via a flash-type NAND interface. The data sectors are different in size than the data pages. A data storage system includes the controller and the memory device. Another data storage system includes a memory whose physical pages have a common size and circuitry for exporting a flash-type NAND interface for exchanging data sectors, that differ in size from the physical pages, with a host. A data processing system includes the data storage system and the host.
Owner:SANDISK IL
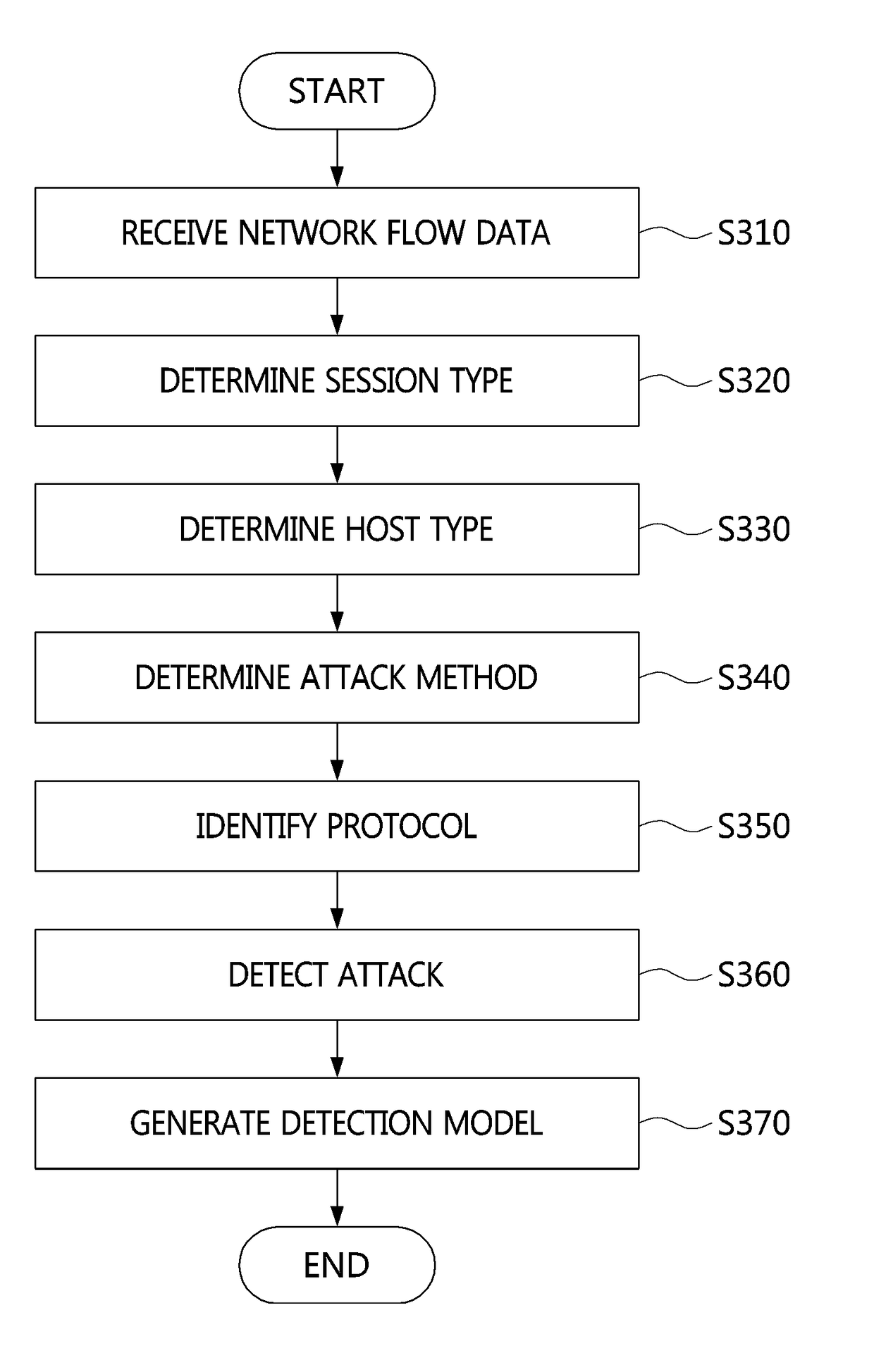
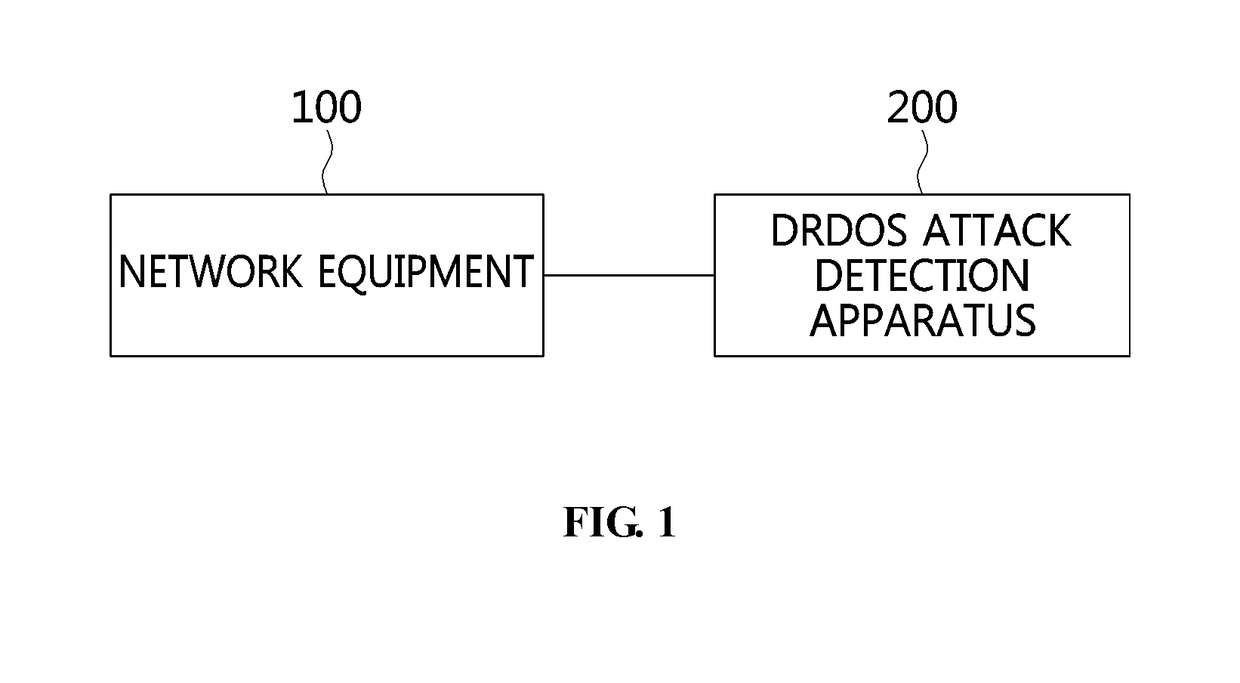
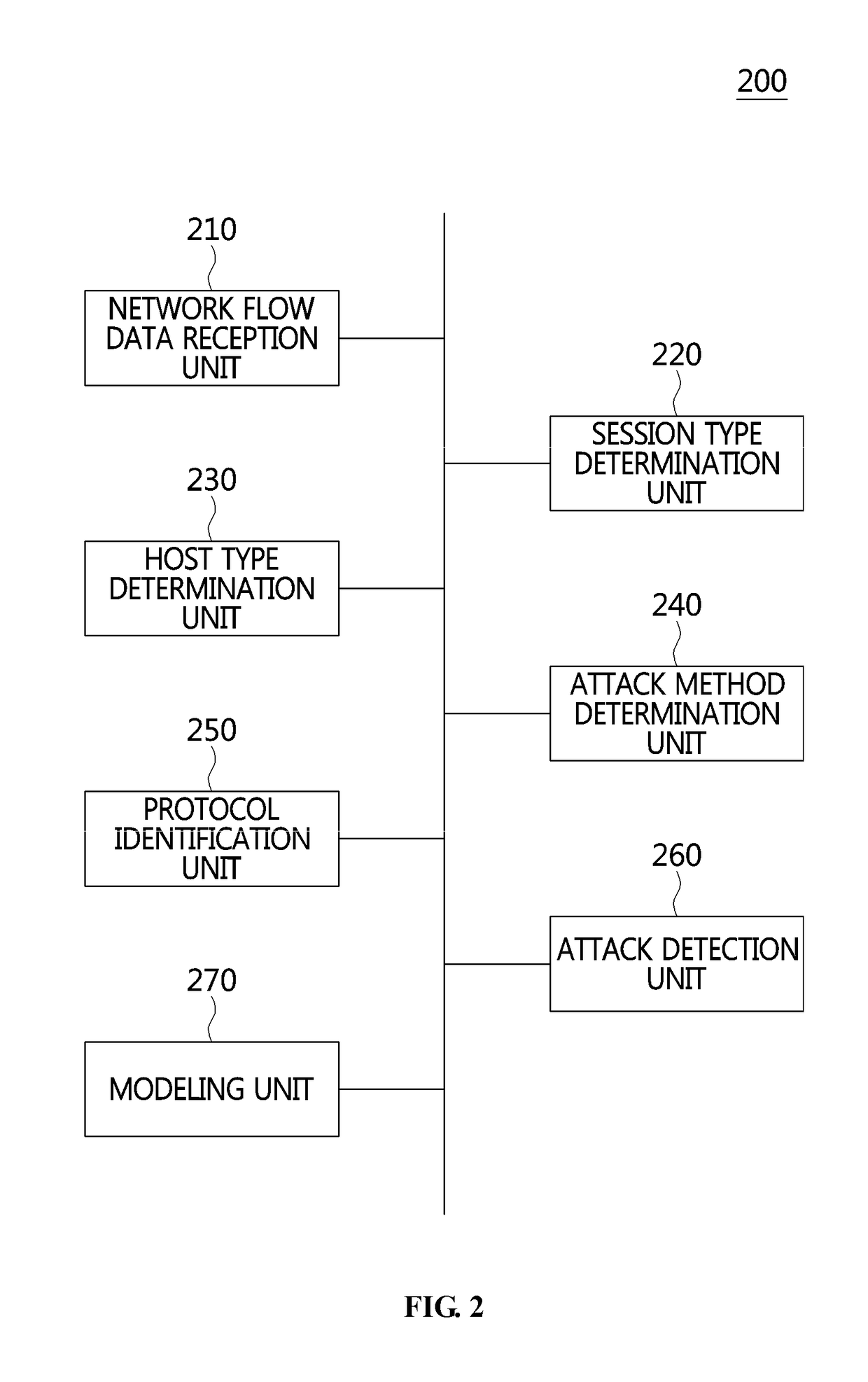
Apparatus and method for detecting distributed reflection denial of service attack
Disclosed herein are an apparatus and method for detecting a Distributed Reflection Denial of Service (DRDoS) attack. The DRDoS attack detection apparatus includes a network flow data reception unit for receiving network flow data from network equipment, a session type determination unit for determining a session type of the received network flow data, a host type determination unit for determining a type of host corresponding to the network flow data based on the session type, an attack method determination unit for determining an attack method corresponding to the network flow data, a protocol identification unit for identifying a protocol of the network flow data, and an attack detection unit for detecting a DRDoS attack based on the session type, the host type, the attack method, and the protocol.
Owner:ELECTRONICS & TELECOMM RES INST
Controller, System, and Method for Mapping Logical Sector Addresses to Physical Addresses
InactiveUS20130191580A1Small sizeMemory architecture accessing/allocationMemory systemsData processing systemPhysical address
A controller of a flash memory device exchanges data pages with the memory device via a host-type NAND interface and exchanges data sectors with a host via a flash-type NAND interface. The data sectors are different in size than the data pages. A data storage system includes the controller and the memory device. Another data storage system includes a memory whose physical pages have a common size and circuitry for exporting a flash-type NAND interface for exchanging data sectors, that differ in size from the physical pages, with a host. A data processing system includes the data storage system and the host.
Owner:LASSER MENAHEM
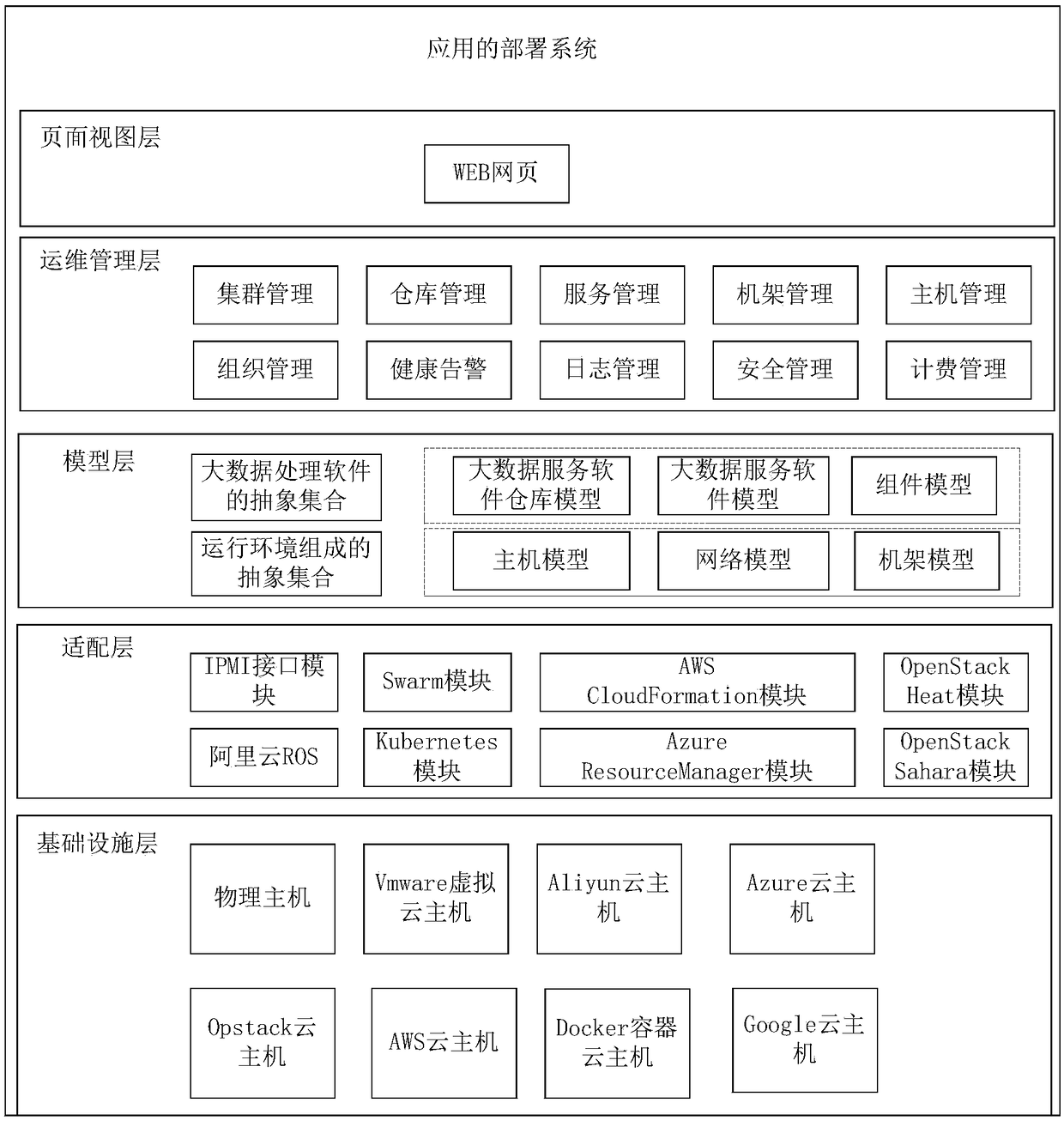
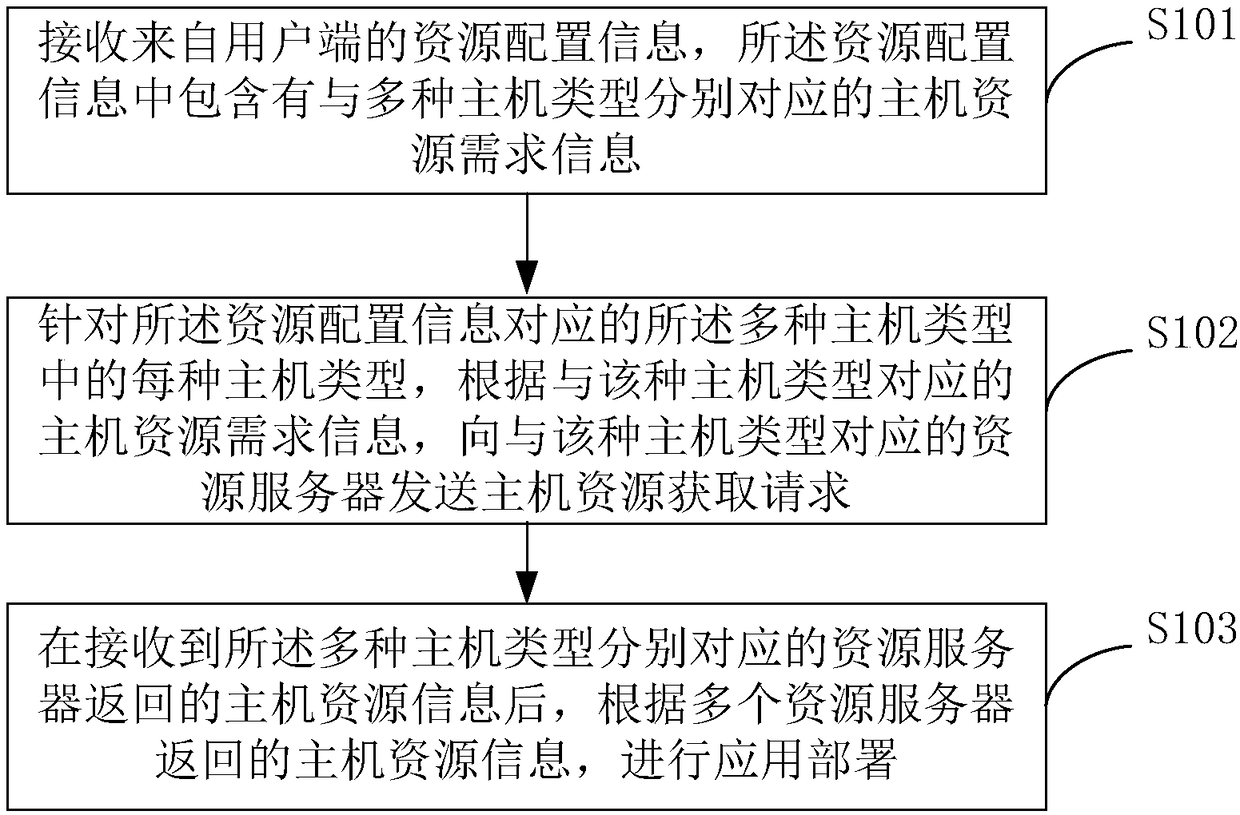
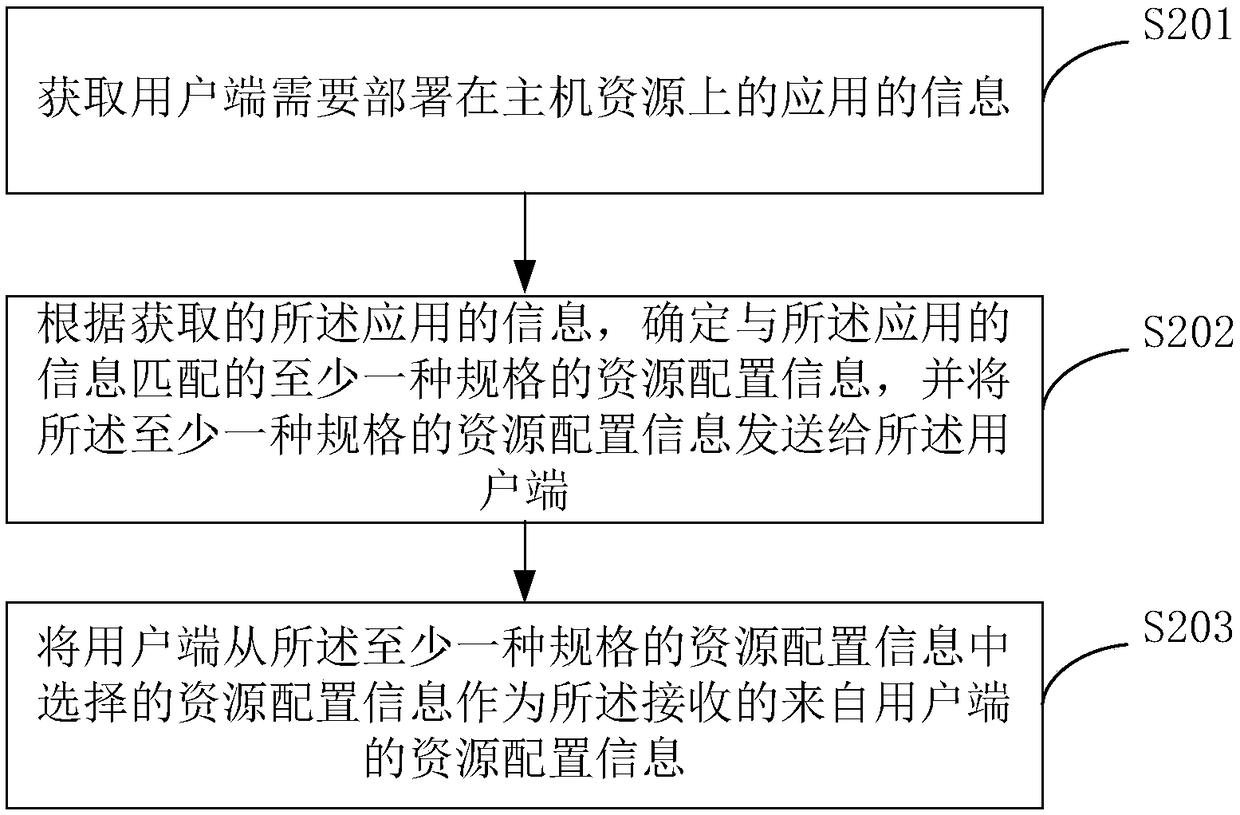
Application deployment method and device
ActiveCN108255497AReduce workloadReduce the number of interactionsSoftware deploymentResource informationWorkload
The invention relates to the technical field of application deployment, in particular to an application deployment method and device. The method includes the steps of receiving resource allocation information from a client; aiming at each host type in multiple host types corresponding to the resource allocation information, according to host resource requirement information corresponding to the host type, sending a host resource obtaining request to a resource server corresponding to the host type; after receiving host resource information returned by the resource servers corresponding to themultiple host types respectively, according to the host resource information returned by the multiple resource servers, conducting application deployment. Host resources corresponding to the host types can be obtained from the resource servers corresponding to the multiple different host types through one-time interaction with the client, applications are deployed in the obtained multiple types ofhost resources, the number of times of interaction between the client and the different resource servers is reduced, the workload of the client is reduced, and the deployment efficiency of the applications is improved.
Owner:NEW H3C BIG DATA TECH CO LTD
USB device and method for recognizing USB mode of the same
InactiveUS20090327530A1Digital data processing detailsInput/output processes for data processingCommunication interfaceMass storage
A universal serial bus (USB) device and a method of recognizing a USB mode whereby the USB device automatically recognizes a mass-storage or PictBridge mode according to a type of a connected host such that the USB device configures a communication interface suitable for the recognized host. The USB device includes: a controller to control a USB communication with the host; and an interface unit to automatically determine a mode of the USB communication, from among a plurality of modes, according to a type of the connected host, and to provide a communication interface in the determined mode corresponding to the host. Although the host connected to the USB device does not support several configuration descriptors, a timer of a mass-storage module switches a current mode to the USB mode suitable for a corresponding host, such that the USB device universally supports the USB multi-mode irrespective of host types.
Owner:SAMSUNG ELECTRONICS CO LTD
Risk identification method and device for industrial control system
ActiveCN107332859ARisk effectiveEffective risk identificationTransmissionMessage typeNetwork communication
Embodiments of the invention disclose a risk identification method and device for an industrial control system. The method comprises the following steps of capturing a protocol message which is sent in a network communication process of a monitored industrial control system; extracting feature values of the protocol message; comparing the feature values of the protocol message with features in a protocol message feature library and determining a message type of the protocol message; determining a message communication sequence of the protocol message; comparing the message communication sequence with message communication sequences in a protocol message communication sequence library, and determining a protocol version corresponding to the protocol message; determining a host type corresponding to the protocol message according to the message type of the protocol message; and determining the risk of the industrial control system according to the host type and the protocol version. The host type and the protocol version which are corresponding to the protocol message can be determined according to the protocol message, so that the risk of the industrial control system is determined according to the host type and the protocol version, and thus a purpose of carrying out effective risk identification on the industrial control system is realized.
Owner:浙江国利网安科技有限公司
Automatic stereo display
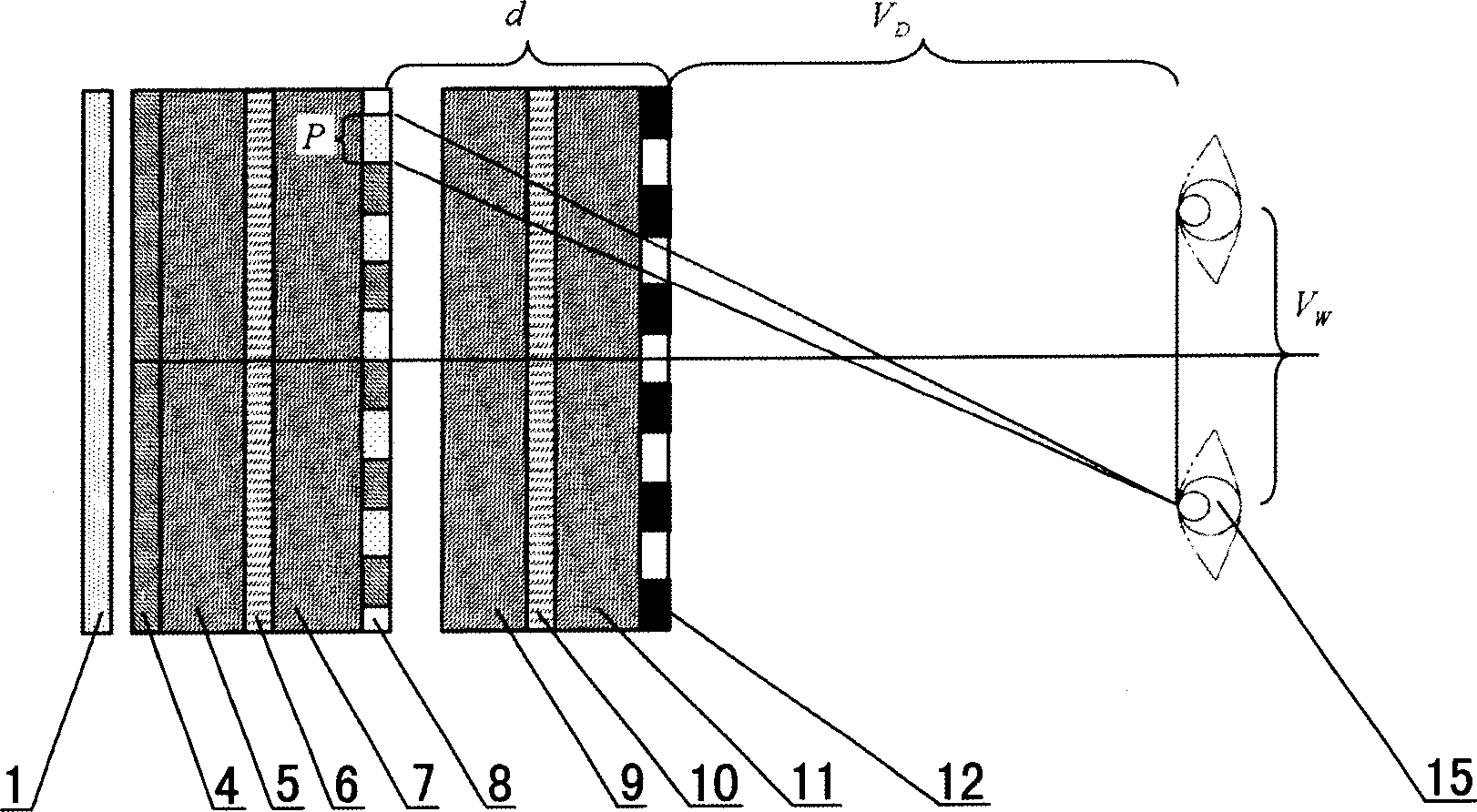
InactiveCN1804681ALittle loss of brightnessIncrease molecular contentStatic indicating devicesElectroluminescent light sourcesParallaxLiquid-crystal display
The invention relates to an automatic stereoscopic display which comprises an image display. It is characterized in that it arranges a custom-host type LCD on the front of the image display.
Owner:SHANTOU GOWORLD DISPLAY +1
NAND Flash Memory Controller Exporting a NAND Interface
ActiveUS20100049909A1Error detection/correctionSemiconductor/solid-state device detailsHost typeElectronic circuit
A NAND controller for interfacing between a host device and a flash memory device (e.g. a NAND flash memory device) fabricated on a flash die is disclosed. In some embodiments, the presently disclosed NAND controller includes electronic circuitry fabricated on a controller die, the controller die being distinct from the flash die, a first interface (e.g. a host-type interface, for example, a NAND interface) for interfacing between the electronic circuitry and the flash memory device, and a second interface (e.g. a flash-type interface) for interfacing between the controller and the host device, wherein the second interface is a NAND interface. According to some embodiments, the first interface is an inter-die interface. According to some embodiments, the first interface is a NAND interface. Systems including the presently disclosed NAND controller are also disclosed. Methods for assembling the aforementioned systems, and for reading and writing data using NAND controllers are also disclosed.
Owner:INNOVATIVE MEMORY SYST INC
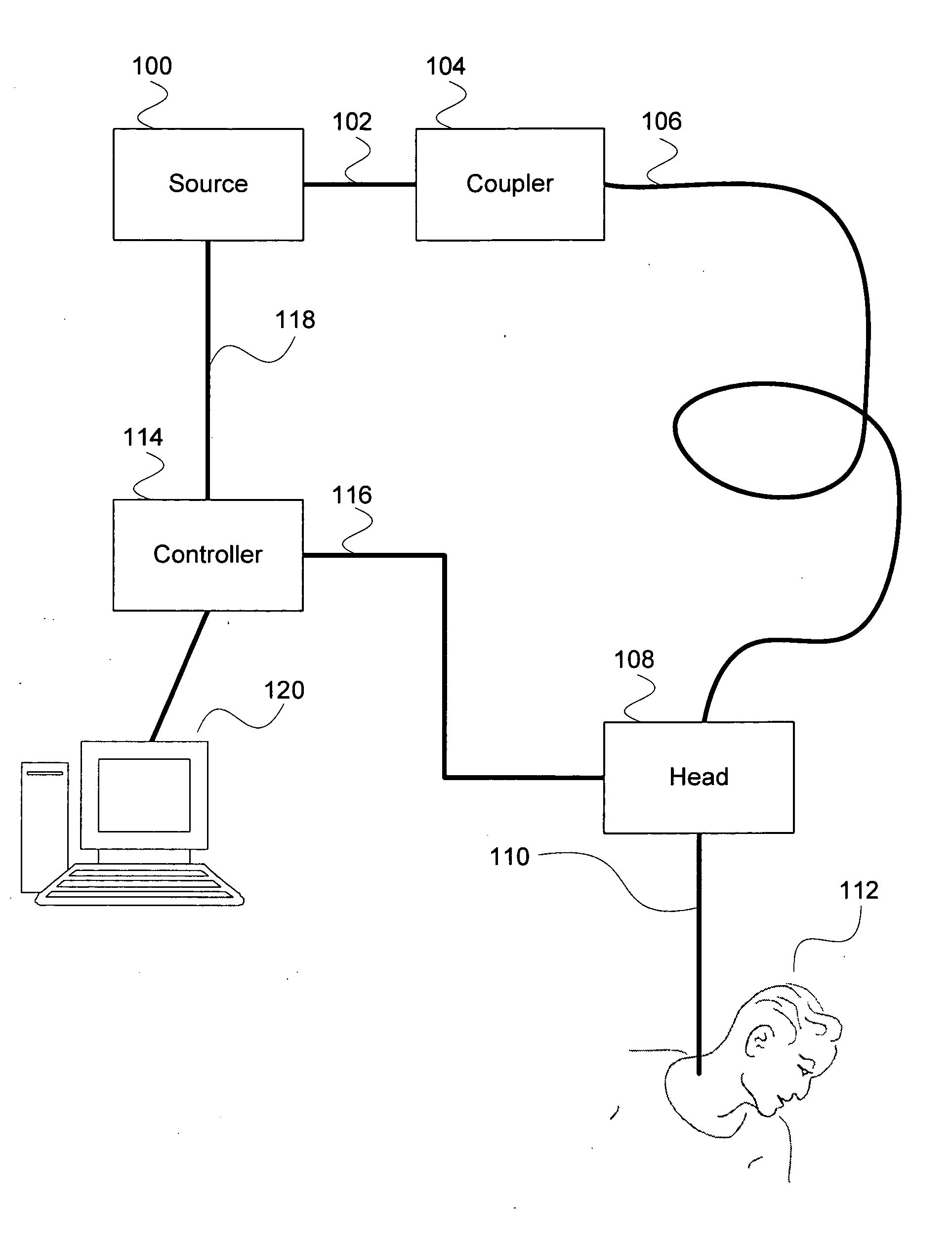
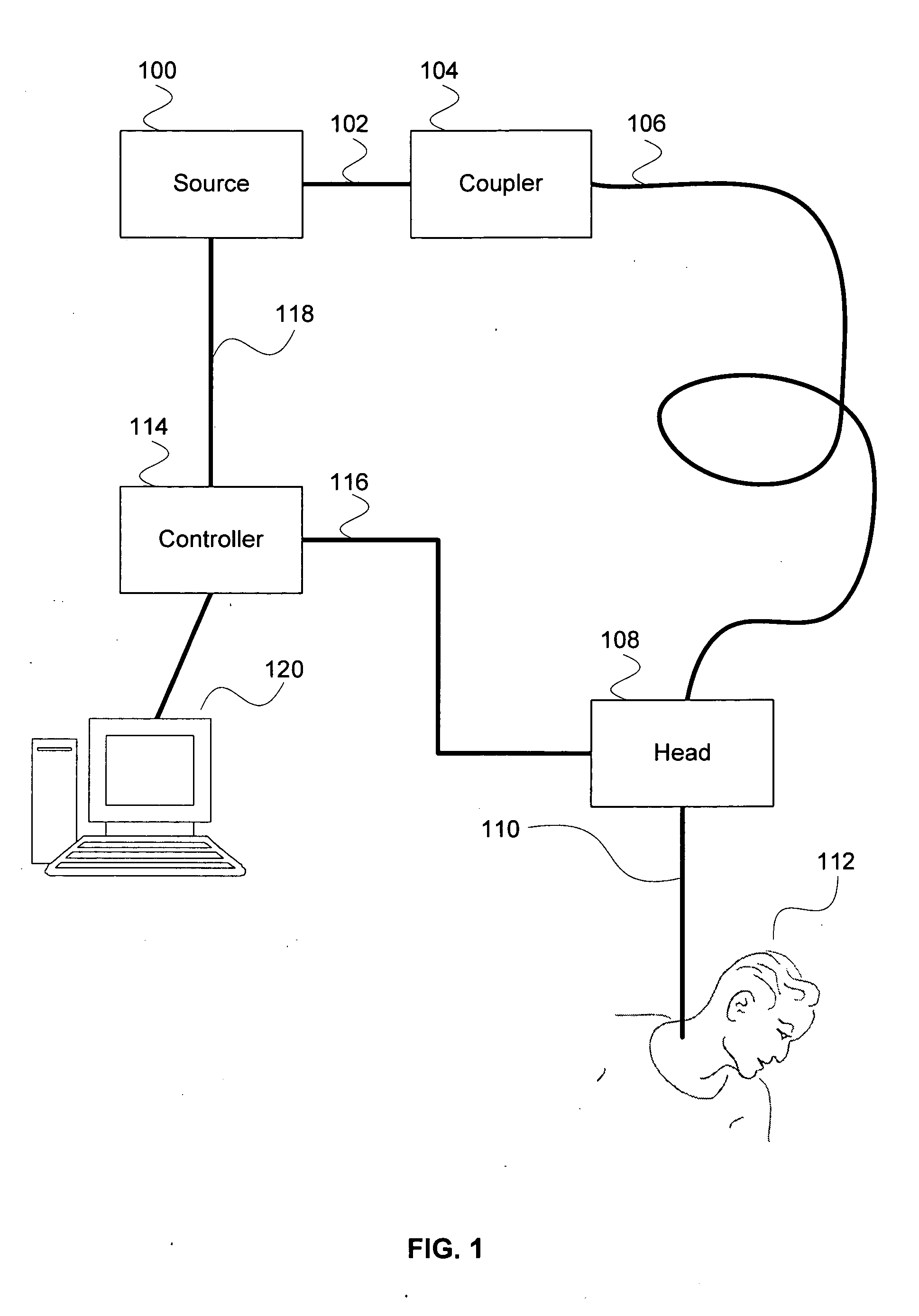
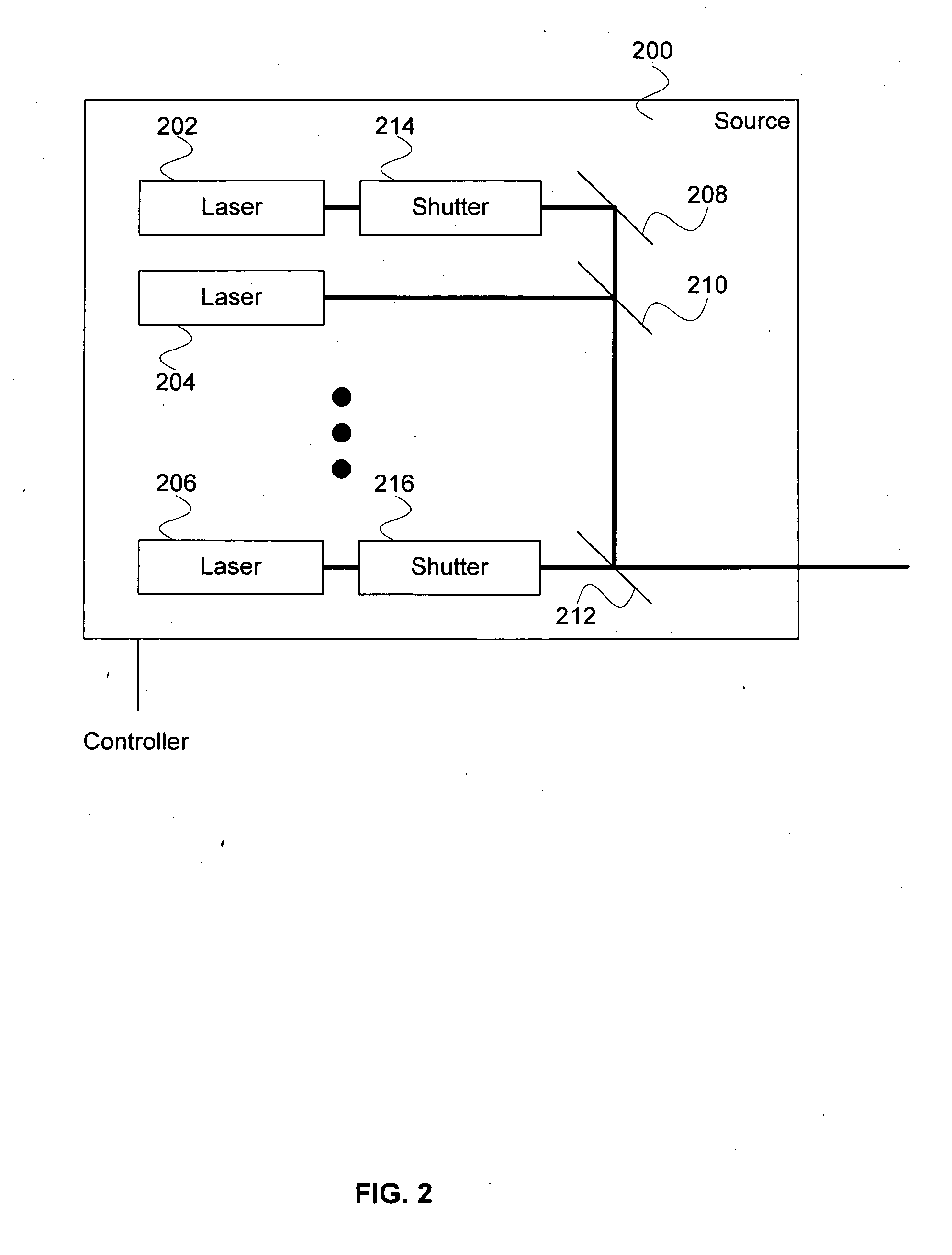
Cancer treatment using selective photo-apoptosis
A system for cancer treatment comprises a processor and a memory. The processor is configured to receive a target type and a host type and determine one or more illumination source characteristics such that: an illumination of the target type employing the one or more illumination source characteristics induces apoptosis in the target type without initiating thermolysis or ablation of the target type; and an illumination of the host type employing the one or more illumination source characteristics does not substantially induce apoptosis, thermolysis, or ablation in the host type. The memory is coupled to the processor and configured to provide the processor with instructions.
Owner:PHOTOMETICS
Optical element
ActiveCN104854492AFacilitate transmissionImprove featuresPolarising elementsLight protection screensDichroic dyeFlexible display
An optical element and a use of the optical element are provided. The exemplary optical element can be useful in realizing a smart blind having excellent transmission and blocking characteristics in front and lateral surfaces thereof without using a retardation film by employing a polarizing layer whose polarization characteristics are patterned using a guest / host-type dye layer including a polymerizable liquid crystal compound and a dichroic dye. Such an optical element may be applied to various light modulating devices such as smart blinds, smart windows, window protective films, flexible display elements, active retarders for displaying a 3D image, or viewing angle adjustment films.
Owner:LG CHEM LTD
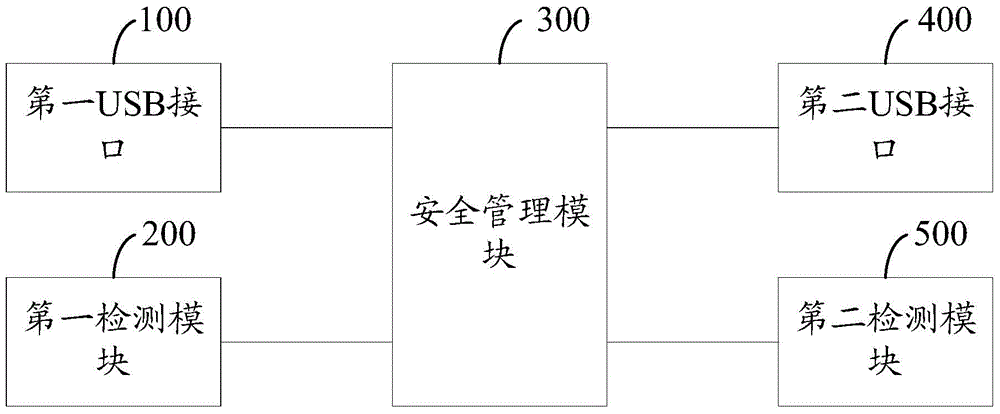
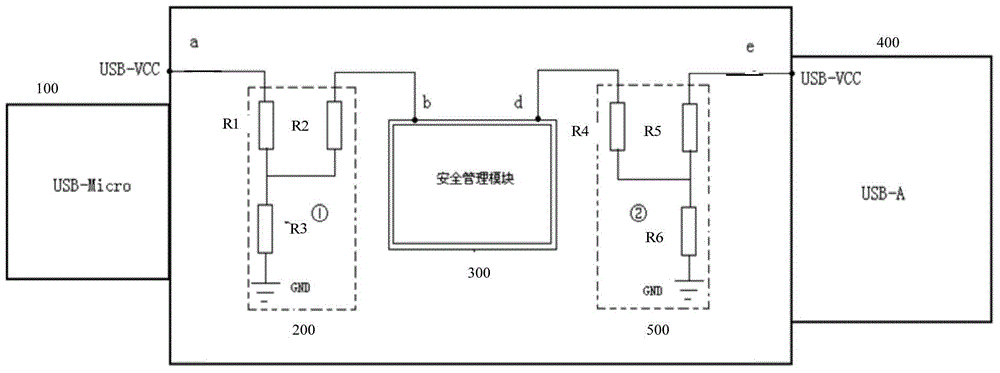
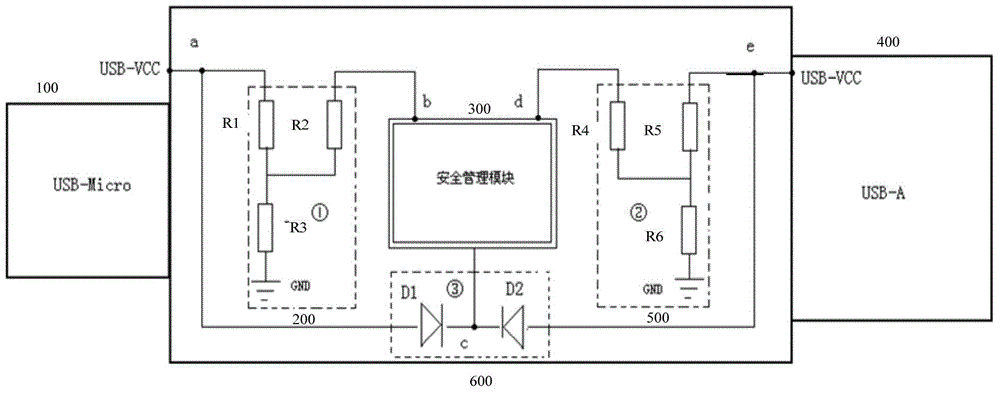
Single-kernel security authentication device with multiple USB (universal serial bus) interfaces
InactiveCN104573468ARealize communicationSolve the real problemDigital data authenticationComputer moduleSecurity authentication
The invention provides a single-kernel security authentication device with multiple USB (universal serial bus) interfaces. The security authentication device comprises at least two types of USB interfaces, namely a first USB interface and a second USB interface and further comprises a first detection module, a second detection module and a security management module. The first detection module is used for detecting a first voltage signal of the first USB interface; the second detection module is used for detecting a second voltage signal of the second USB interface; the security management module is used for enumerating the security authentication device as a host type corresponding to the second USB interface when the second voltage signal is judged to be effective; when both the first voltage signal and the second voltage signal are judged to be effective, a USB bus is hung up. When both the USB interfaces are judged to be connected into hosts, the USB bus is hung up, and a USB bus command is prevented from being interfered. Normal communication when the USB interfaces are available can be realized, and protective measures when the multiple hosts are connected in are available.
Owner:CENTURY LONGMAI TECH
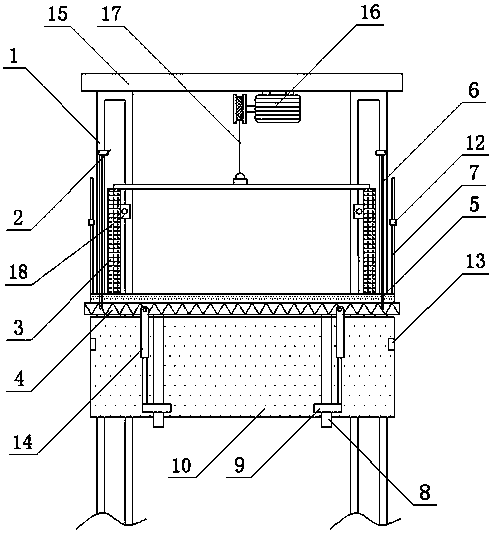
Movable hoisted-type automatic lifting platform for shear wall well structure construction
ActiveCN107724661AWith automatic lifting functionImprove lifting efficiencyBuilding support scaffoldsEngineeringHost type
Provided is a movable hosted-type automatic lifting platform for shear wall well structure construction. The platform includes a lifting supporting rack (1) and is characterized in that sliding rails(2) are vertically arranged at the outer sides of the left and right branches of the lifting supporting rack (1) respectively, and internally provided with bearing sliding bases (3), the outer side ofthe lower portion of each bearing sliding base (3) is horizontally and fixedly provided with a platform framework (4), a lifting platform (5) is fixed to the upper surfaces of the platform frameworks(4), the two sides of the lifting platform (5) are fixedly provided with side surface guard railings (7) respectively, the outer side of each platform framework (4) is vertically and fixedly providedwith a sliding rod (8), and the sliding rods (8) are provided with lifting guard rails (10) through sliding bases (9). The movable hosted-type automatic lifting platform is reasonable in structure, capable of achieving automatic lifting, high in lifting efficiency and great in protection captivity, and under the situation that the safety is ensured, the guard rails can be automatically opened, access of staff and materials is very convenient, and the safety performance and construction efficiency are both improved.
Owner:民族建设集团有限公司
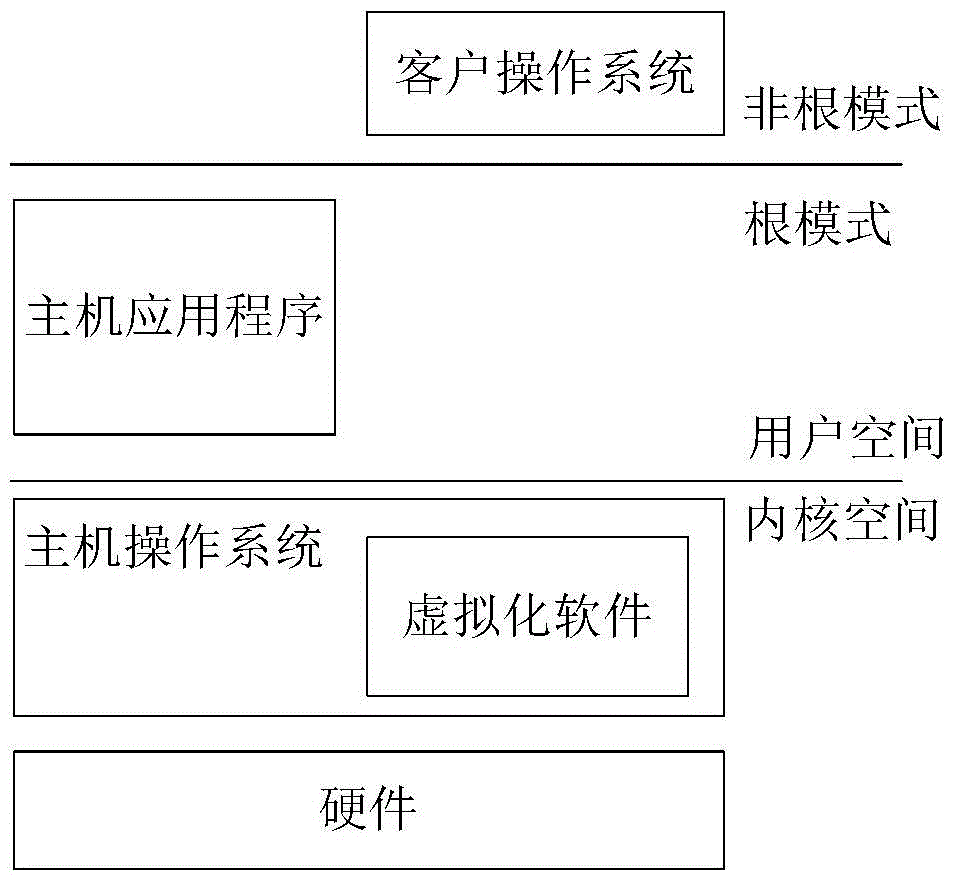
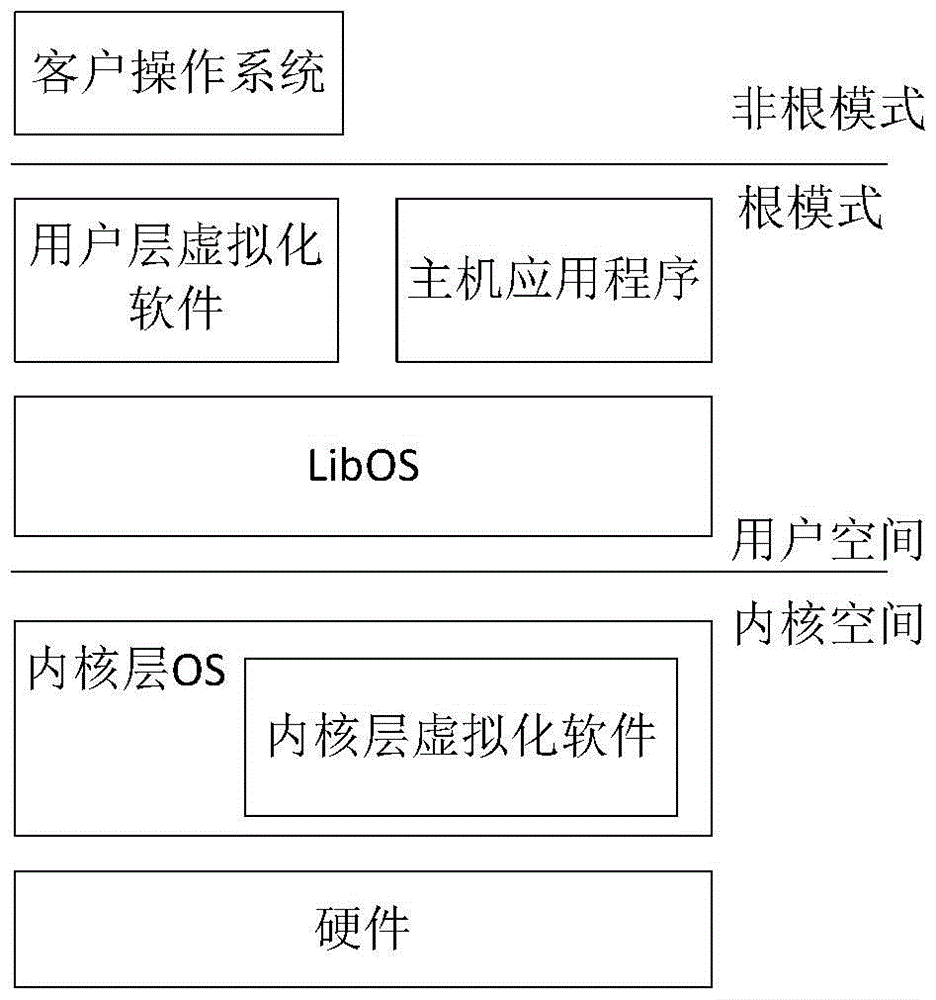
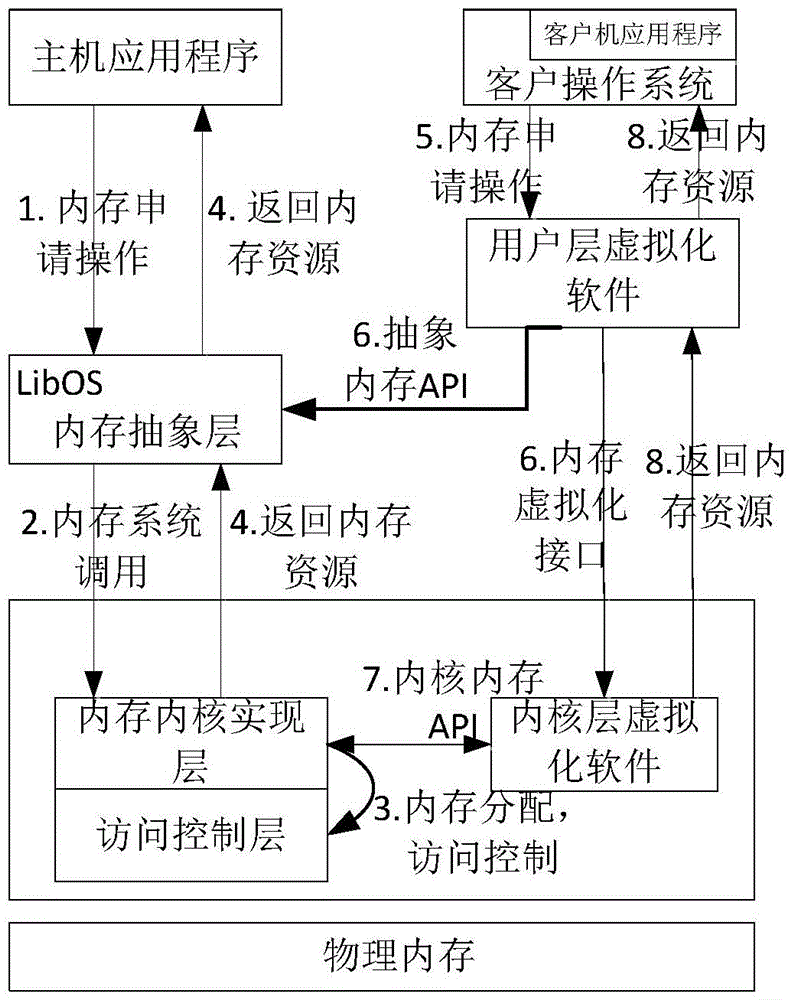
Method for reducing trusted computing base of host virtual software
The invention discloses a method for reducing trusted computing base of host type virtual software, wherein specific to privilege code of a host operation system (host OS), the functions of the host OS are provided for upper layer applications to use in a user space through adoption of a ''base'' form, wherein the upper layer applications comprise virtual software and other application programs; specific to privilege code of the virtual software, the privilege code of the virtual software is degraded and separated; privilege code ''minor OS'' operated in a kernel space is set and is used for finishing necessary communication with hardware resources; OS ''libOS'' of a non-privilege level user space is set and is used for finishing user layer realization of the OS function; virtual software ''hypervisor'' operated in the user space is set; and a privilege part ''minor hypervisor'' which is operated in the kernel space and is used for processing a virtual software request is set.
Owner:HUAZHONG UNIV OF SCI & TECH
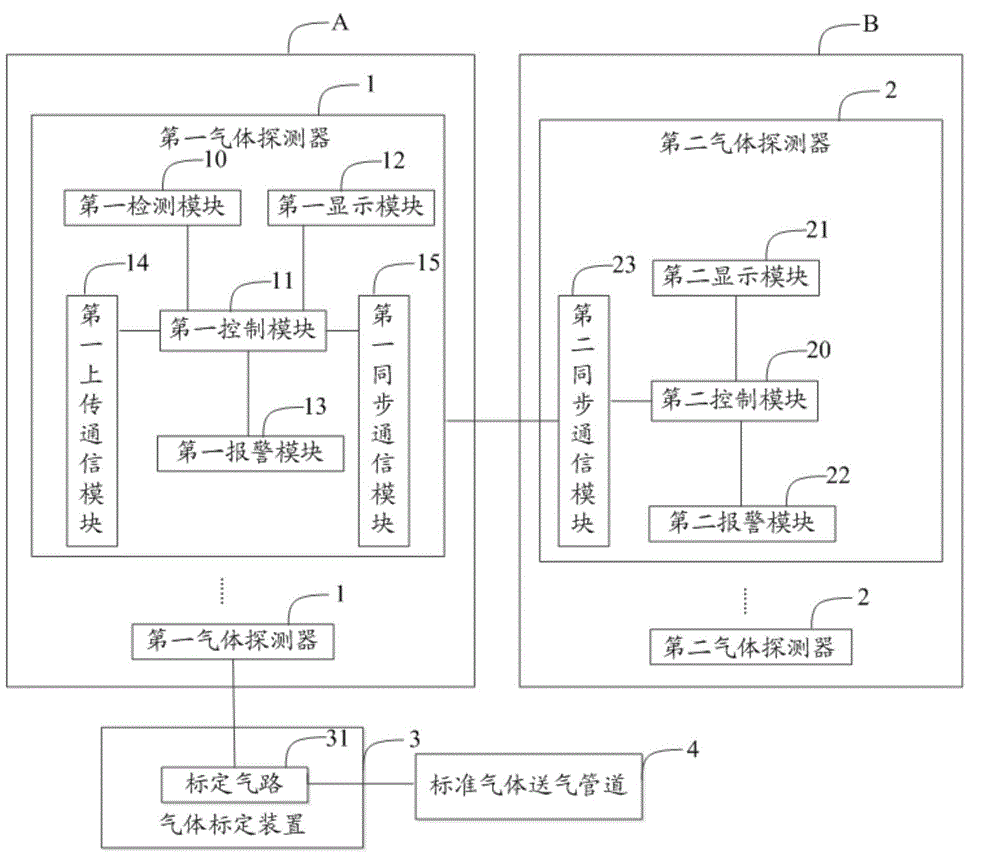
Multi-host type gas detector system
InactiveCN104881962AImprove convenienceImprove securityAnalysing gaseous mixturesAlarmsGas detectorGaseous detectors
The invention discloses a multi-host type gas detector system. The multi-host type gas detector system comprises a plurality of first gas detectors and a plurality of second gas detectors, wherein the plurality of first gas detectors are arranged in a danger release source area, each first gas detector comprises a first detection module, a first control module, a first display module, a first alarm module, a first uploading communication module, and a first synchronous communication module, the plurality of second gas detectors are arranged in an area which danger may relate to, and each second gas detector comprises a second control module, a second display module, a second alarm module, and a second synchronous communication module. When the gas concentration value acquired by the first detection module is higher than the gas concentration threshold set in the first control module, the first control emits an alarm signal to the first alarm module, and the second synchronous communication module can communicate with the first synchronous communication module in order to receive the gas concentration value and the alarm signal detected by the first detection module.
Owner:HARBIN EAST ALARM EQUIP DEV
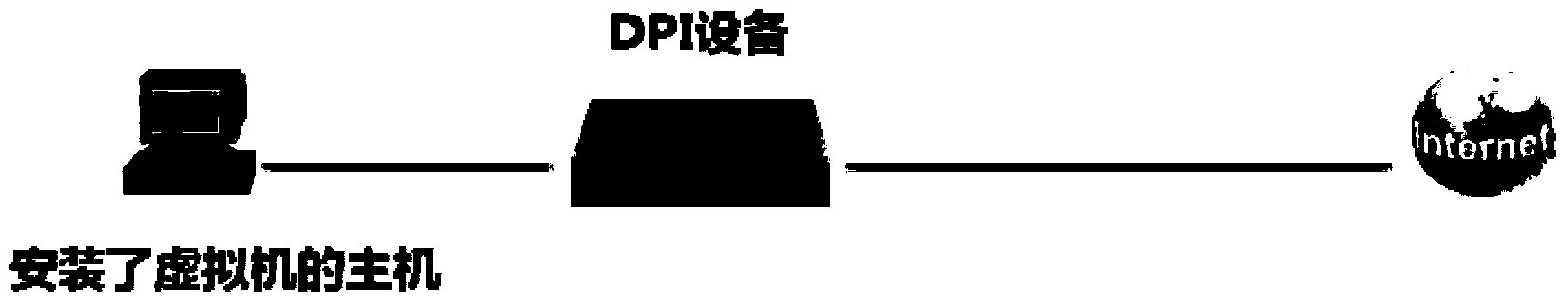
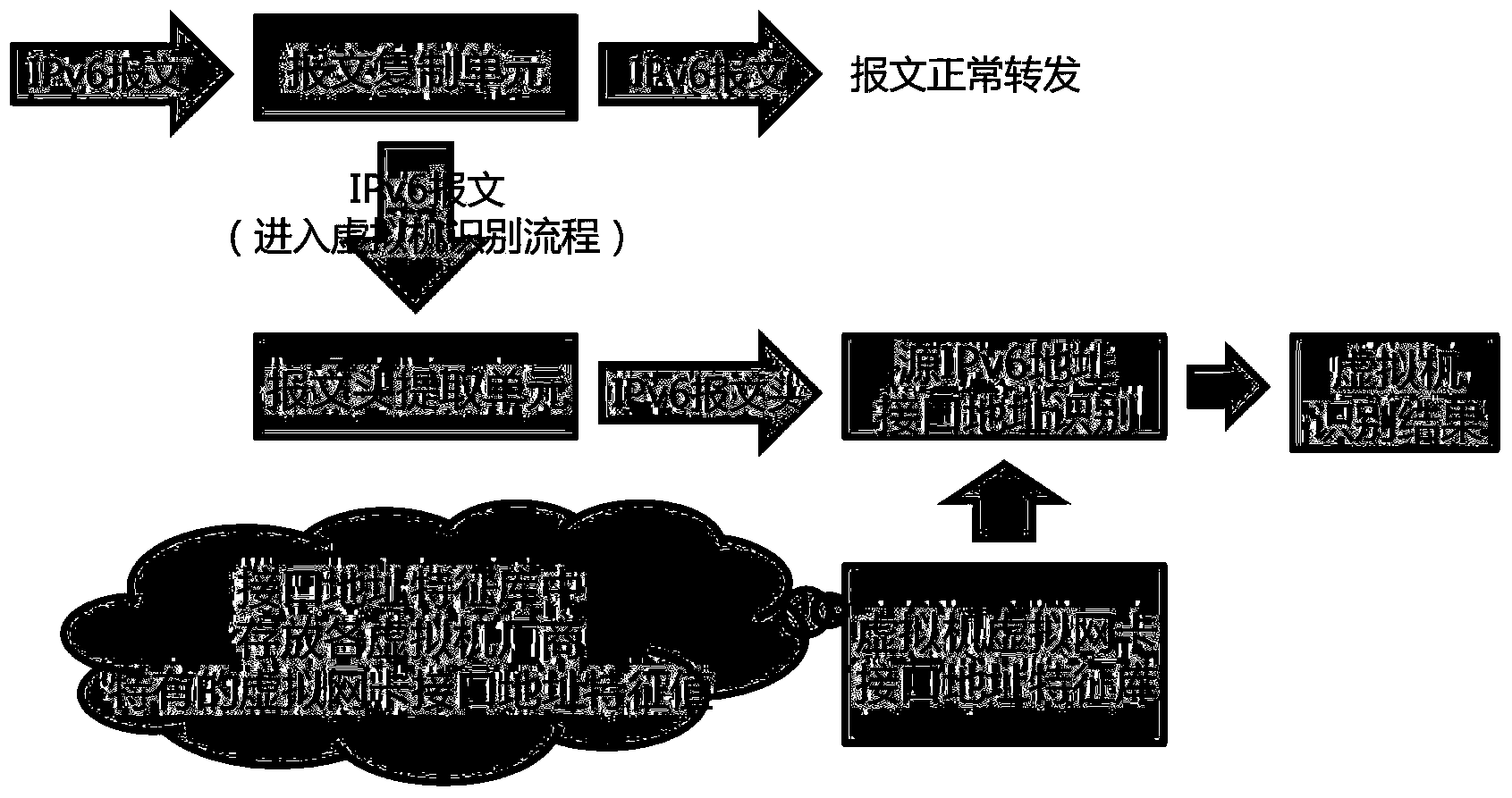
Method for identifying virtual host in IPv6 network and DPI equipment
InactiveCN104348671AData switching networksSoftware simulation/interpretation/emulationVirtual hostingManufacturer code
The disclosure relates to a method for identifying a virtual host in an IPv6 network and DPI equipment. The method comprises a step of receiving, copying and forwarding an IPv6 message, a step of extracting the message head of the copied IPv6 message, a step of extracting and sending the interface address of a source IPv6 address of the IPv6 message from the message head, a step of matching a manufacturer code part in the interface address with a characteristic value in a virtual machine virtual network card interface address characteristic value library, and a step of determining that the IPv6 message is sent by the virtual host if the manufacturer code part in the interface address is same with any characteristic value in the interface address characteristic value library, otherwise, determining that the IPv6 message is sent by a physical host. According to the method and the DPI equipment, in the condition of not installing a virtual machine detection program, the type of the host which sends the message can be identified.
Owner:CHINA TELECOM CORP LTD
Hosting type task scheduling and decomposing method
InactiveCN106201687ASolve the problem of interface periodic task collectionGuaranteed reliabilityProgram initiation/switchingData acquisitionComputer science
The invention discloses a hosting type task scheduling and decomposing method and belongs to the technical field of task scheduling. The hosting type task scheduling and decomposing method comprises the steps of task management, task state viewing, viewing of task result details, task parameter configuration, task scheduling and decomposing, task result checking and alarm reporting and specifically comprises visual interface management, adoption of a scalable execution interface and execution result checking. Configurable interface methods are provided for various task execution types through the centralized task hosting type operation method, dynamic task execution call is finished with a reflection mechanism, and the method is applicable to scheduling scenes of all O-domain data acquisition task types.
Owner:INSPUR QILU SOFTWARE IND
Modular fresh air system and dust-free construction method thereof
ActiveCN107606736AGuaranteed cleanlinessIncrease flexibilityDucting arrangementsMechanical apparatusFresh airEngineering
The invention provides a modular fresh air system. Adopted modules include the draught fan module (1), the heat exchange module (2), the filter module (3), the air valve module (4), the air duct module (5), the air port module (6) and the connection module (7). The modules are connected through buckles and rubber pads. The specifications of the modules are designed by means of modularization. Thedesign and assembly construction of the fresh air system can be completed by selecting the modules according to the engineering requirements. Compared with a host type fresh air system, the modular fresh air system has better flexibility in matching of space and performance.
Owner:北京华标环能科技有限公司
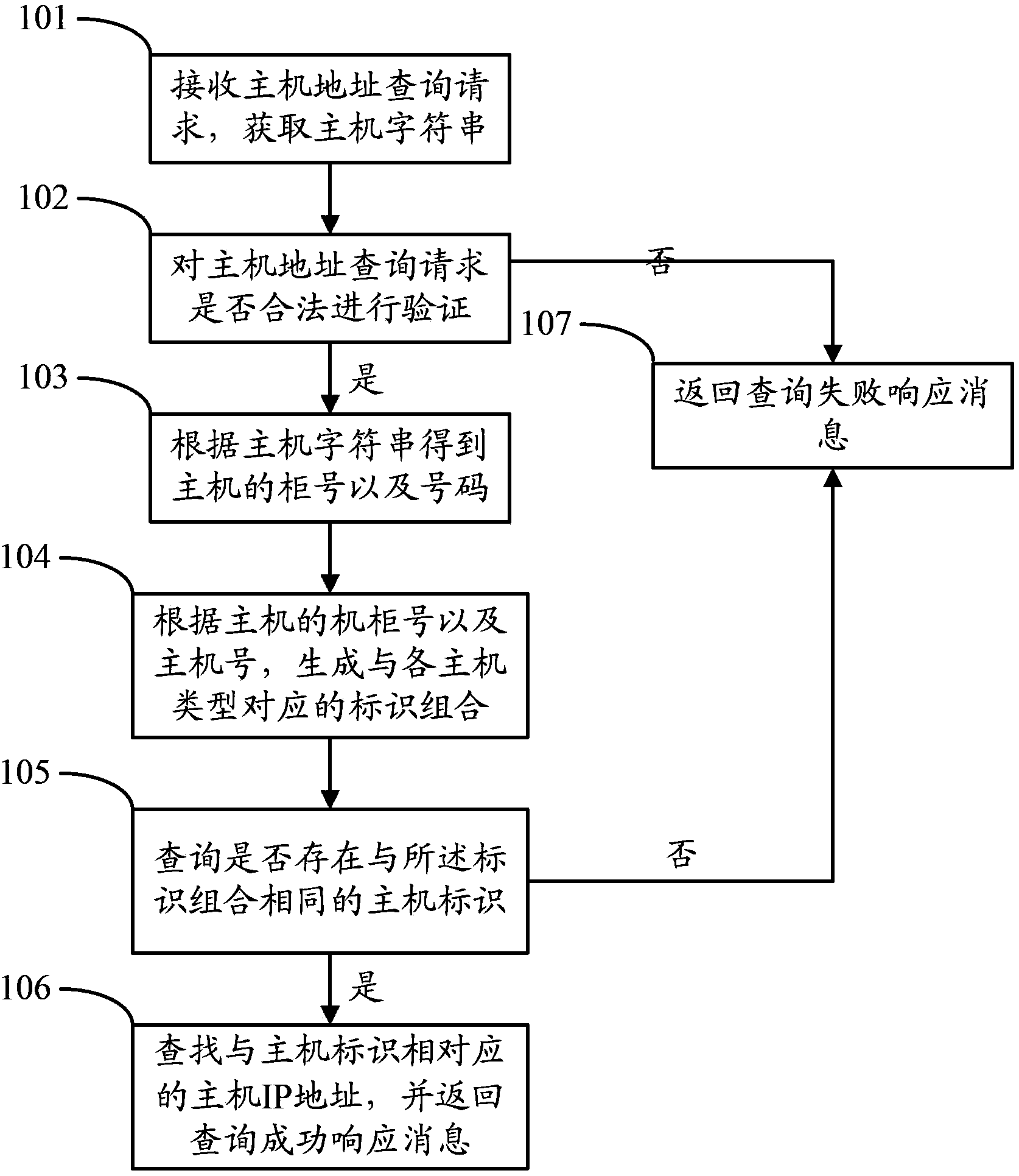
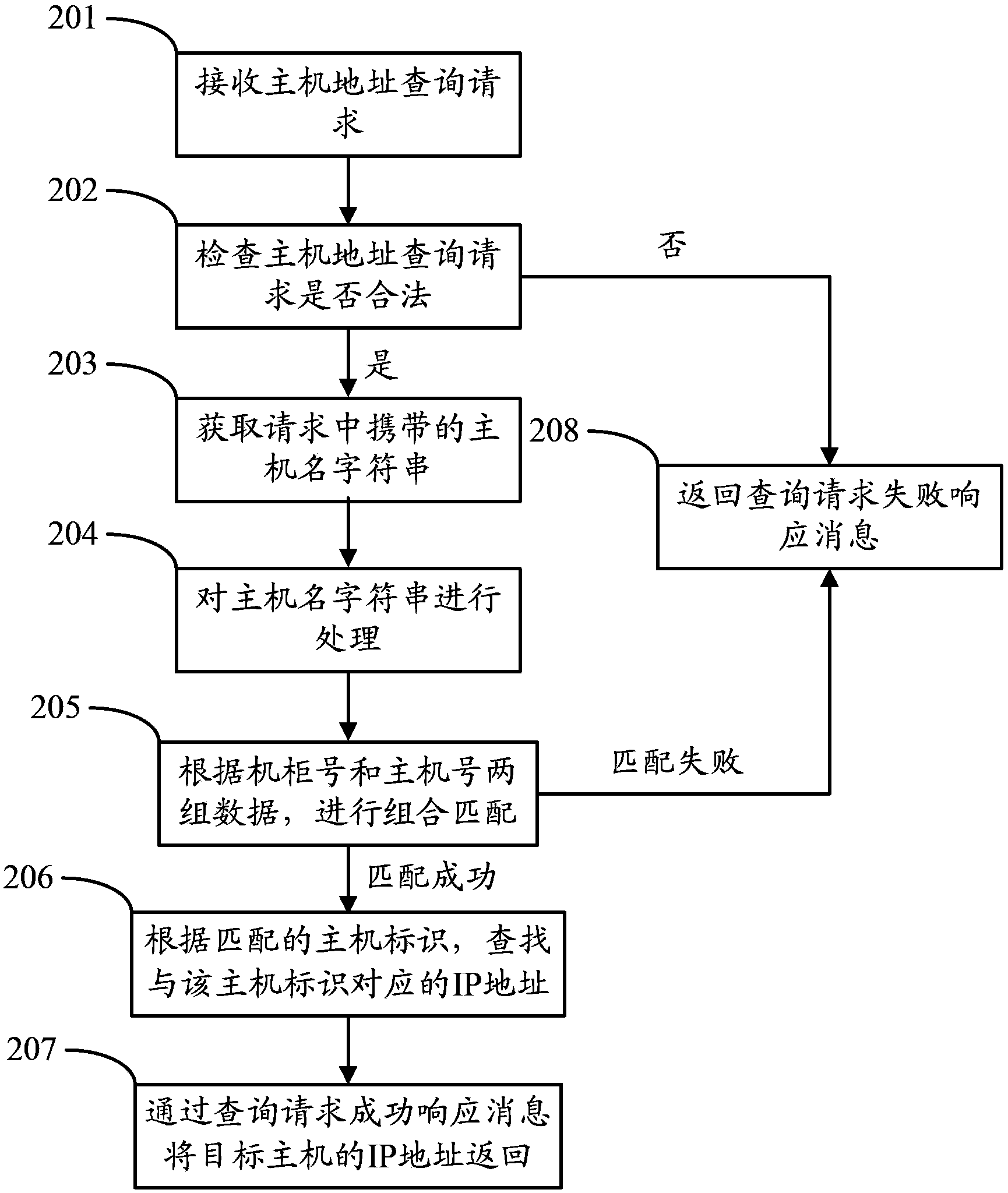
Method and equipment of searching address of cloud computing cluster host
The invention discloses a method of searching an address of a cloud computing cluster host. The method comprises the following steps that: through analyzing a host address search request, a cabinet number of a host and a host number are extracted from a host character string, the cabinet number of the host, the host number and a known host type form all kinds of identifier combinations, and searching is performed hereby, so that an IP (Internet Protocol) address of the host is quickly and accurately searched according to the cabinet number of the host and the host number under the condition that the host type information is unclear or incomplete. The invention also discloses equipment of searching the address of the cloud computing cluster host.
Owner:CHINA MOBILE COMM GRP CO LTD
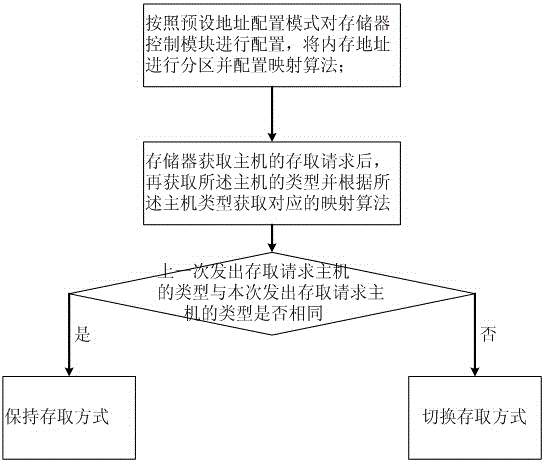
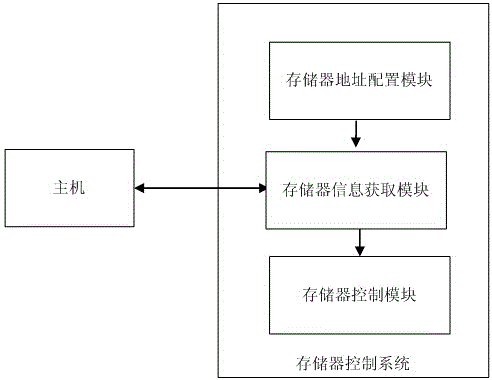
Memorizer address mapping method and memorizer address mapping system
ActiveCN104407985AImprove access efficiencyMemory adressing/allocation/relocationPersonalizationMemory address
A memorizer address mapping method comprises the steps of configuring a memorizer control module according to a preset address configuration mode, partitioning a memory address and configuring mapping algorithms; configuring different address sub-partitions for different types of mainframes in the preset address configuration mode; enabling a memorizer to obtain access requests of the mainframes; obtaining the types of the mainframes and obtaining the mapping algorithms corresponding to the types of the mainframes; obtaining the types of the mainframes sending out the access requests the last time; control the memorizer to switch an access mode by means of the mapping algorithms if the types of the mainframes sending out the access requests this time are different. By means of the memorizer address mapping method, a memorizer address mapping control function is added for the memorizer, the whole memory area is divided into a plurality of sub-partitions, different characteristics of address intervals fixedly accessed by different mainframes are utilized to conduct personalized address mapping configuration on different memory sub-intervals, and the accessing efficiency of the different mainframes can be improved. In addition, the invention further provides a memorizer address mapping system.
Owner:TECHTOTOP MICROELECTRONICS
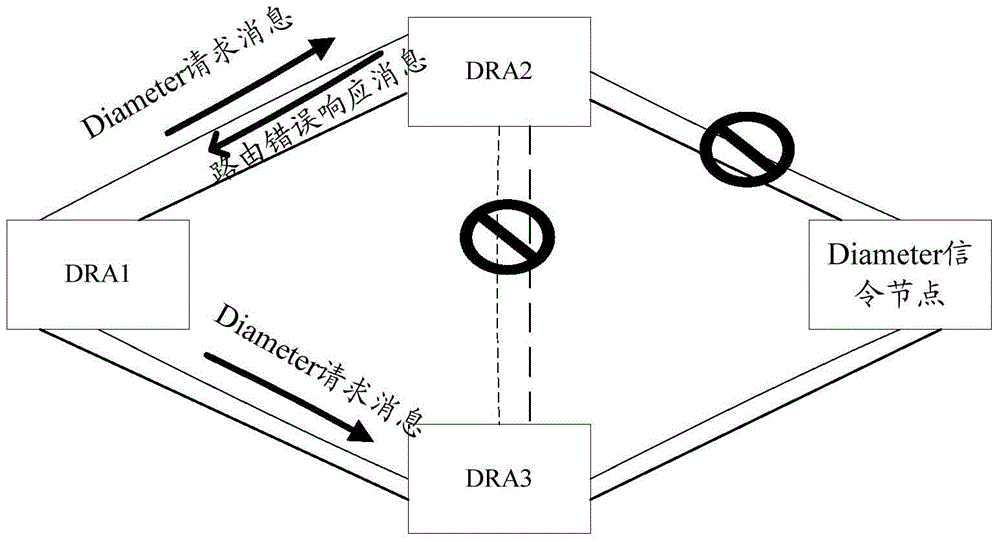
Routing reselection determination method and apparatus thereof
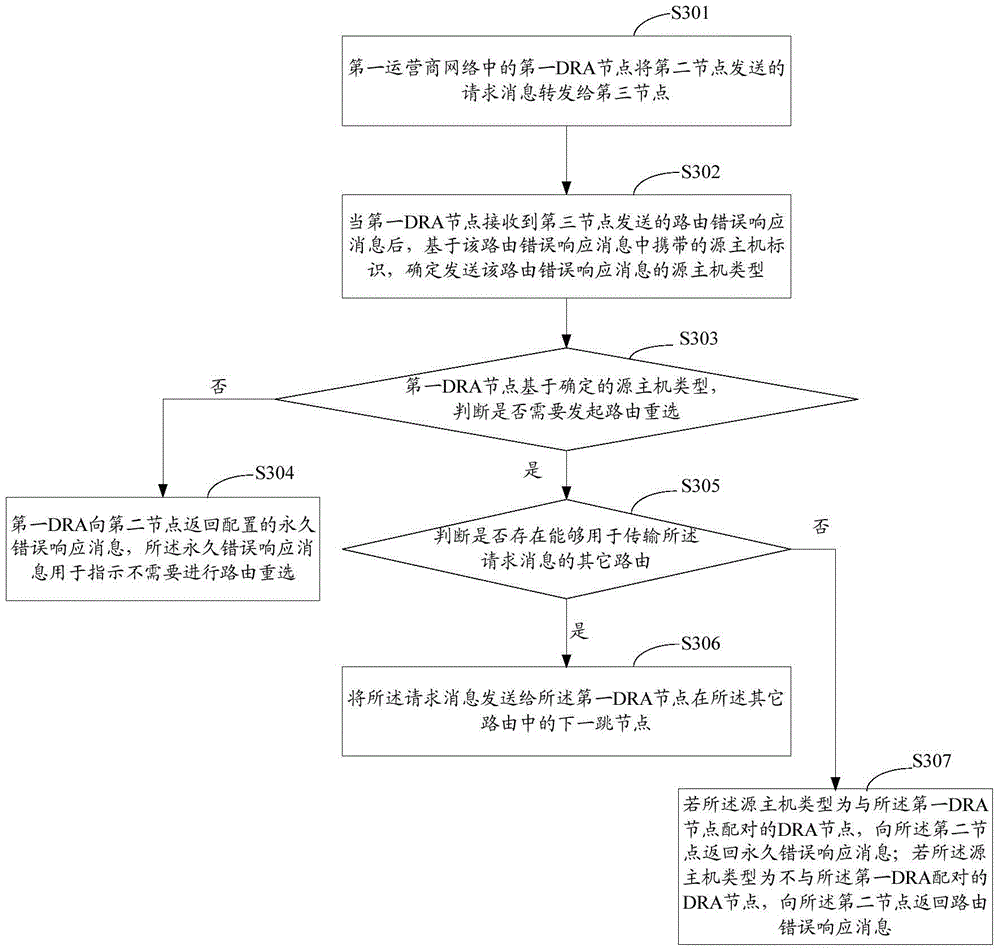
ActiveCN105991429AReduce loadReduce the number of invalid reselectionsData switching networksProtocol for Carrying Authentication for Network AccessComputer science
The method relates to the communication technology field and especially relates to a routing reselection determination method based on a diameter protocol and an apparatus thereof. The method comprises the following steps of forwarding a request message sent by a second node to a third node by a first DRA node; after a routing error response message is received, based on a source host identification carried by the message, determining a source host type which sends the routing error response message; based on the source host type, determining whether routing reselection needs to be initiated; after the routing reselection is determined not to be initiated, returning a permanent error response message to the second node; after the routing reselection is determined to be initiated, determining whether there are other routings used for transmitting the request message, if there is no other routings and if the source host type is a DRA node which forms a pair with the first DRA node, returning the permanent error response message to the second node, and if the source host type is a DRA node which does not form a pair with the first DRA node, returning the routing error response message to the second node.
Owner:CHINA MOBILE COMM GRP CO LTD
Apparatus, system, and method for validating logical volume configuration
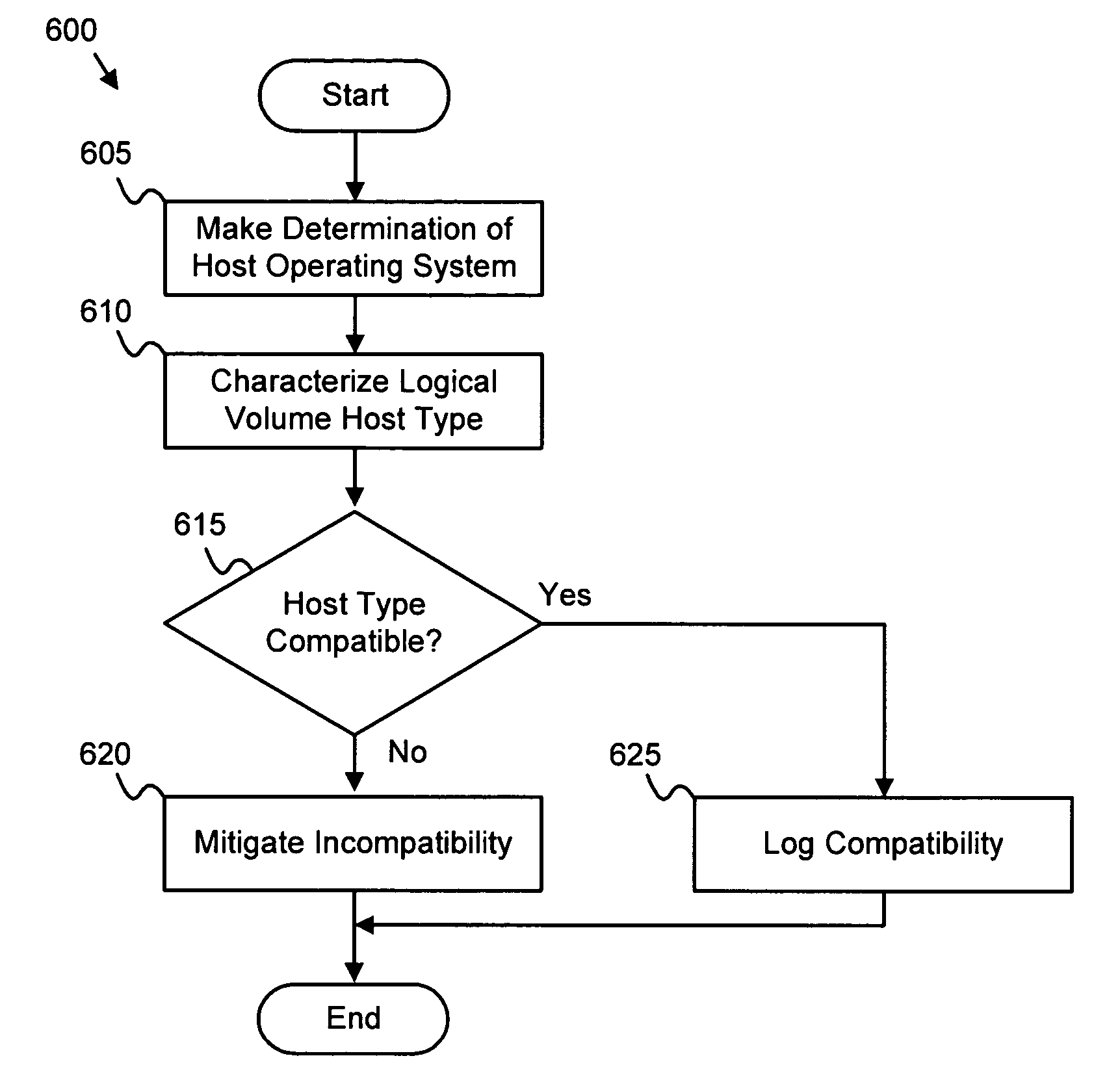
InactiveUS7493462B2Reduce misconfigurationMemory systemsInput/output processes for data processingOperational systemSystem configuration
An apparatus, system, and method are disclosed for validating logical volume configuration. A determination module makes a determination of a type of a host operating system of a host computer requesting access to a logical volume. A characterization module characterizes the host type of the logical volume. A compatibility module determines if the logical volume is configured for the host operating system. A mitigation module mitigates the mis-configuration if the logical volume is not configured for the host operating system.
Owner:IBM CORP
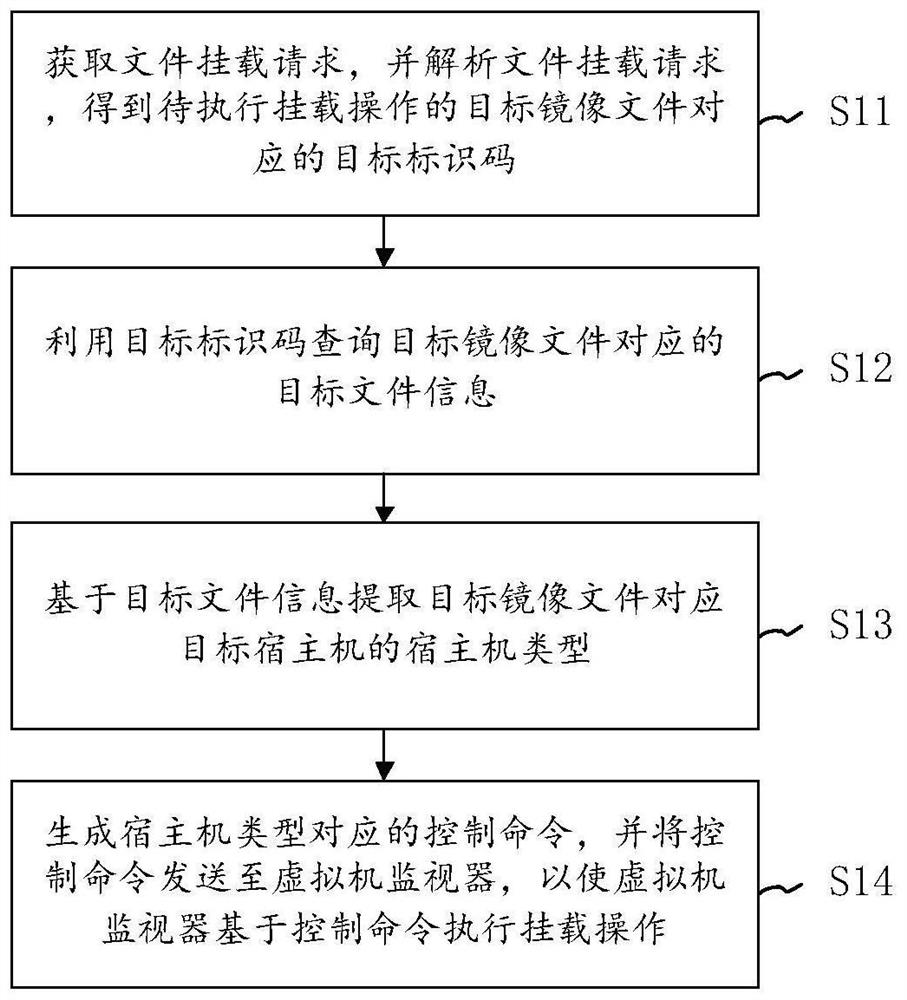
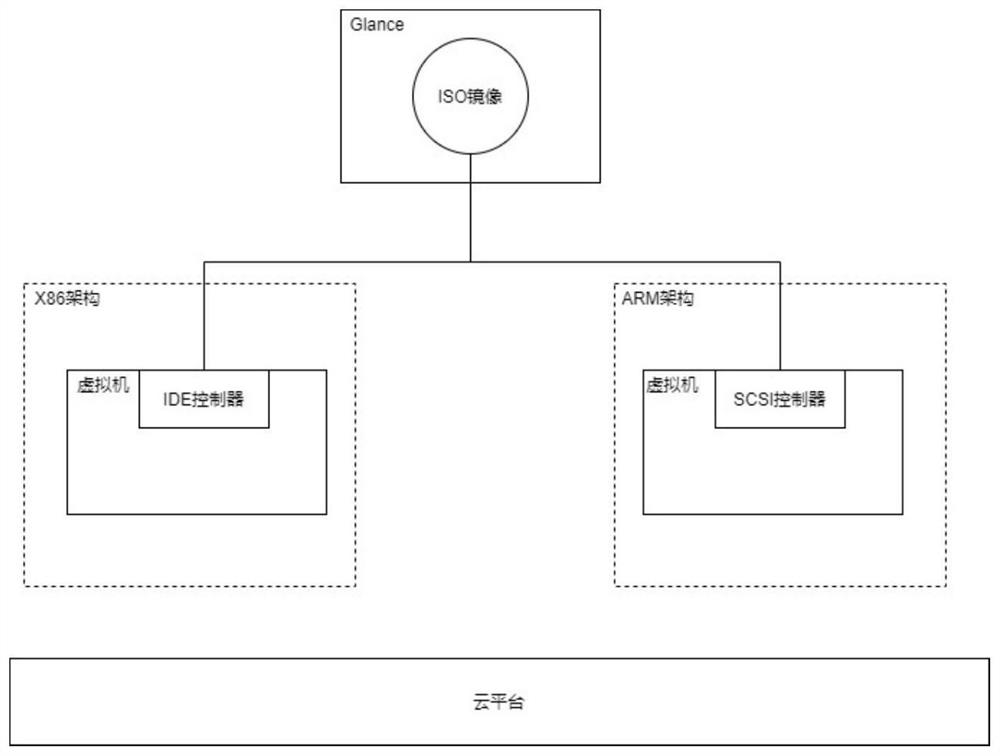
Mirror image file mounting method and device, electronic equipment and storage medium
The invention discloses a mounting method and device of a mirror image file, electronic equipment and a storage medium. The method comprises the following steps: acquiring a file mounting request, and analyzing the file mounting request to obtain a target identification code corresponding to a target mirror image file to be subjected to mounting operation; querying target file information corresponding to the target mirror image file by using the target identification code; extracting a host machine type of a target host machine corresponding to the target mirror image file based on the target file information; and generating a control command corresponding to the host machine type, and sending the control command to a virtual machine monitor, so that the virtual machine monitor executes mounting operation based on the control command. According to the method provided by the invention, different control commands can be generated according to the host machine type of the host machine corresponding to the target mirror image file, so that the target of mounting the ISO mirror image under various different types of host machines is realized, and the problem that mirror image mounting cannot be realized under a hybrid architecture in the prior art is solved.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
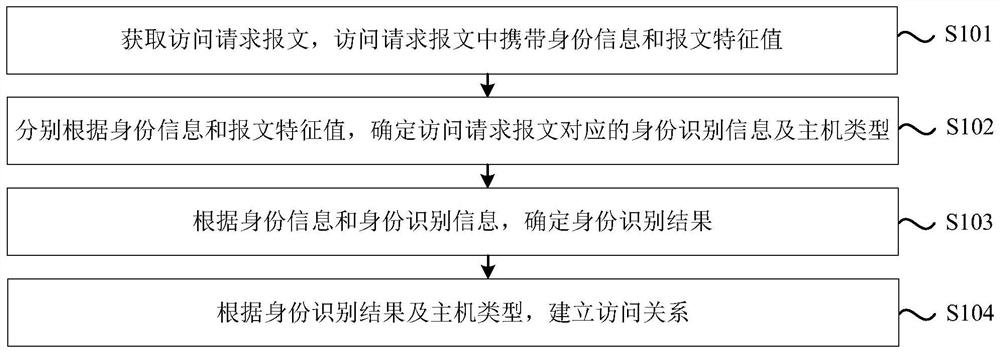
Method and device for establishing access relationship, electronic equipment and storage medium
PendingCN114866258ACanonical Access ControlLegal access controlEncryption apparatus with shift registers/memoriesUser identity/authority verificationInternet privacyIdentity recognition
The invention discloses an access relationship establishment method and device, electronic equipment and a storage medium. The method comprises the following steps: acquiring an access request message, wherein the access request message carries identity information and a message feature value; determining identity identification information and a host type corresponding to the access request message according to the identity information and the message feature value; determining an identity recognition result according to the identity information and the identity recognition information; and establishing an access relationship according to the identity recognition result and the host type. According to the technical scheme, the identity information and the message feature value in the access request message are confirmed, and whether the access relation is established or not is determined based on the identity recognition information and the host type, so that operations such as identity counterfeiting, malicious permission utilization and unauthorized access can be effectively avoided, and normative, legal, effective and safe access control is realized.
Owner:海恒数字科技(青岛)有限公司 +2
Hostless packet speech communication device and its communication method
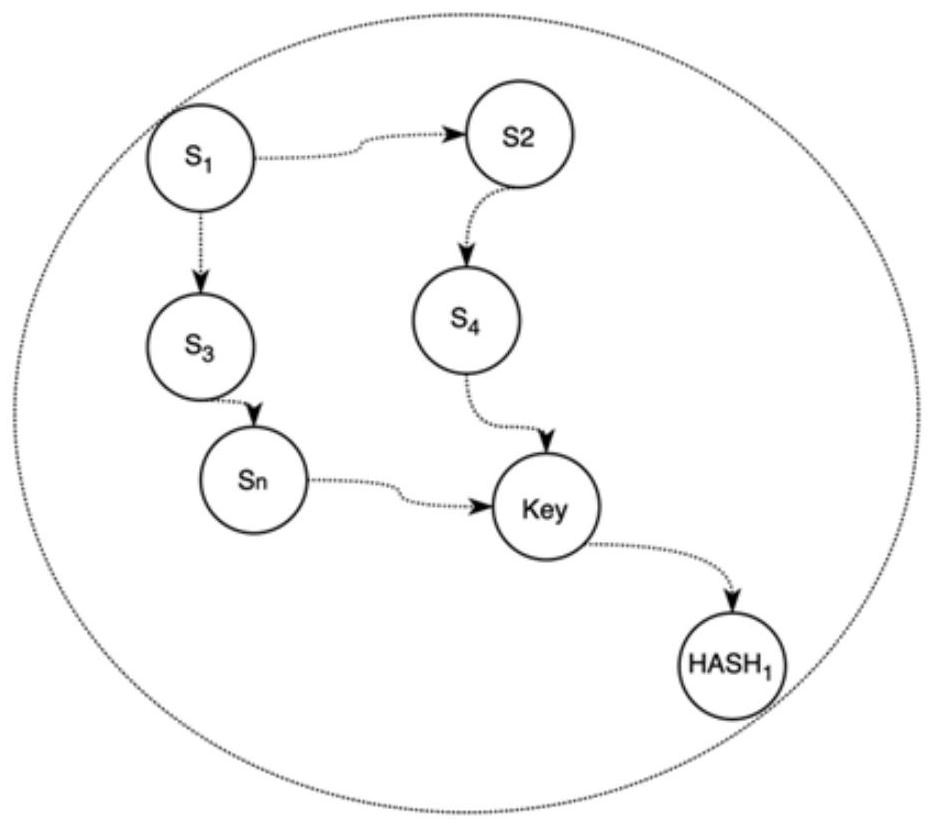
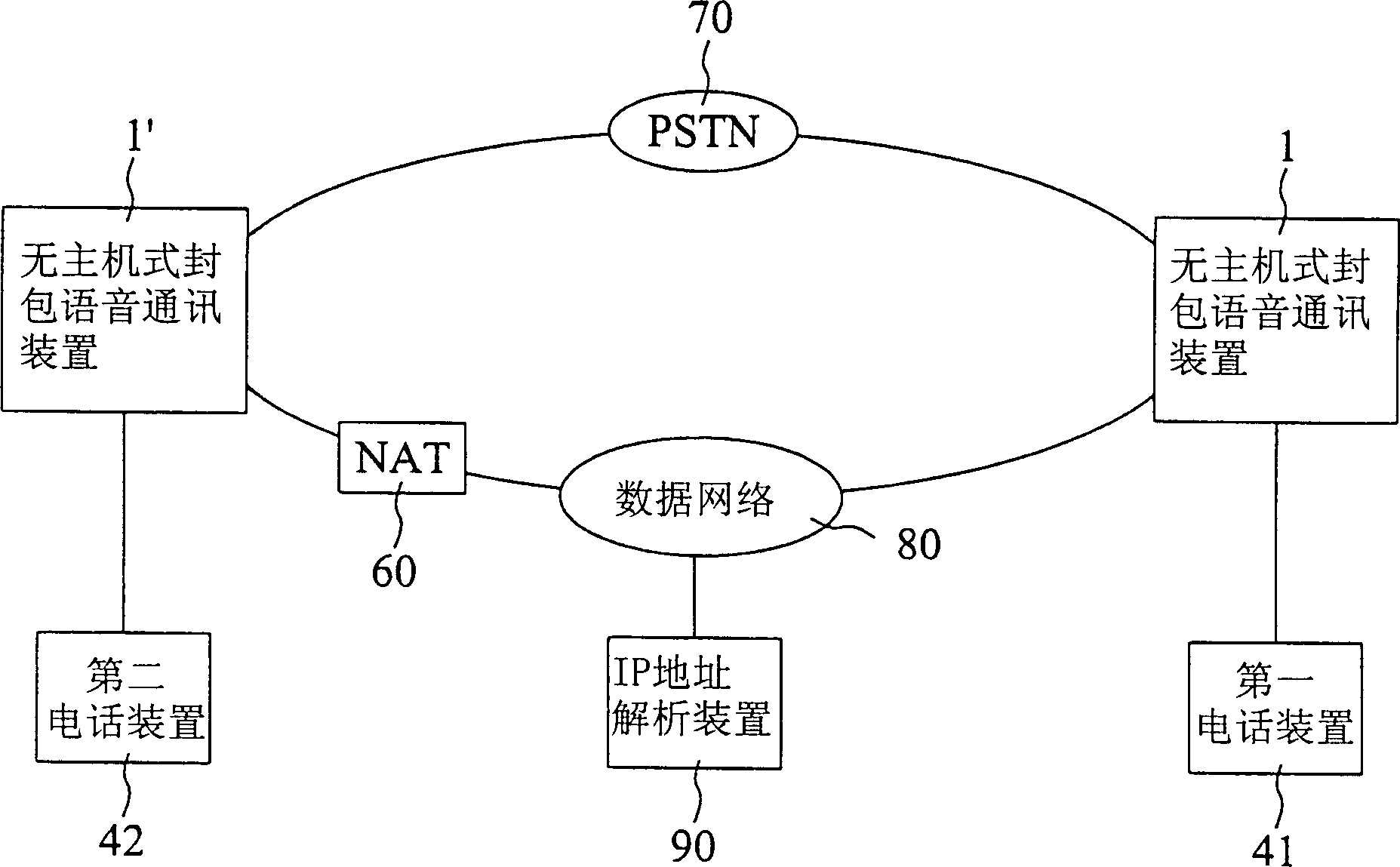
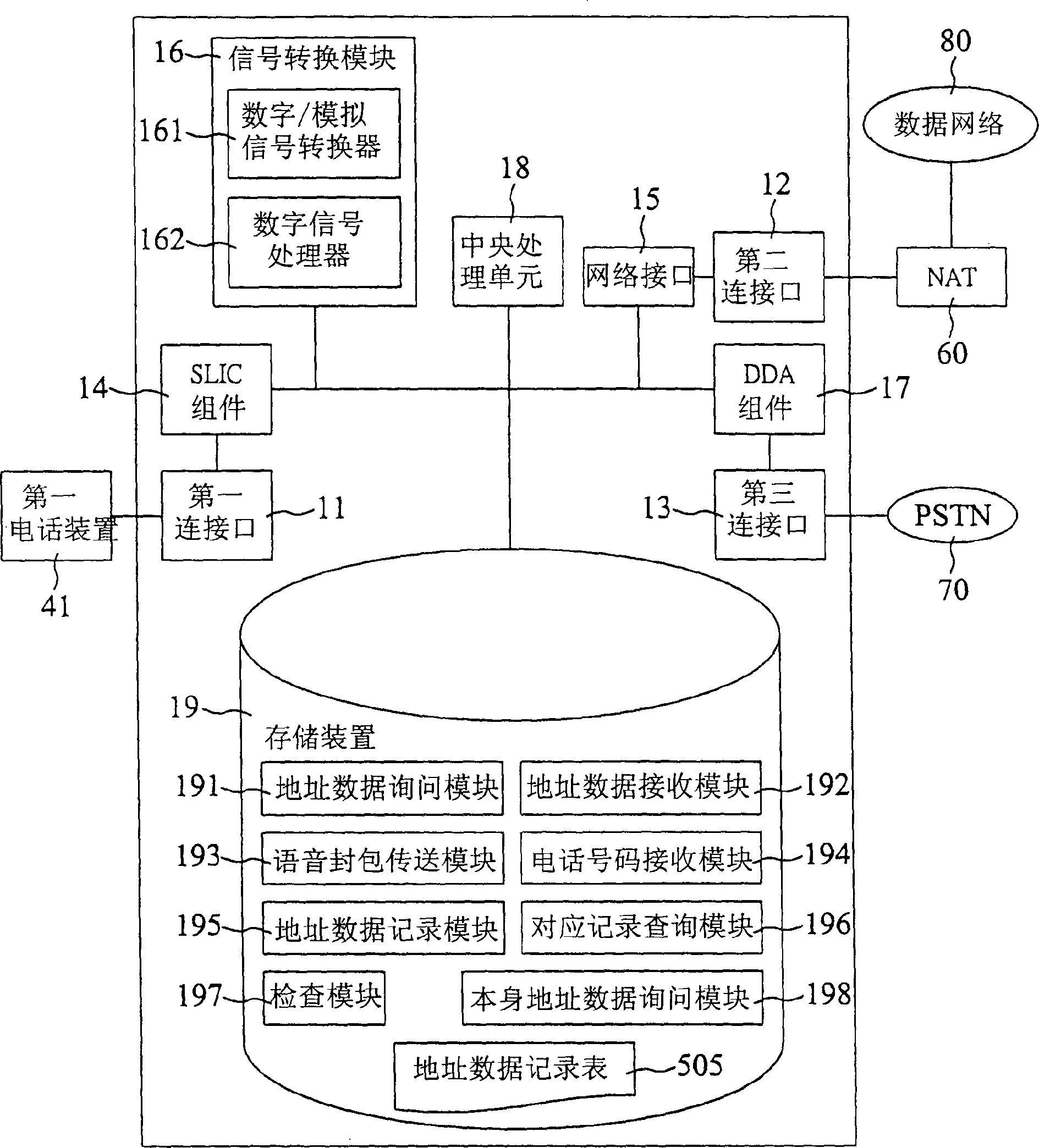
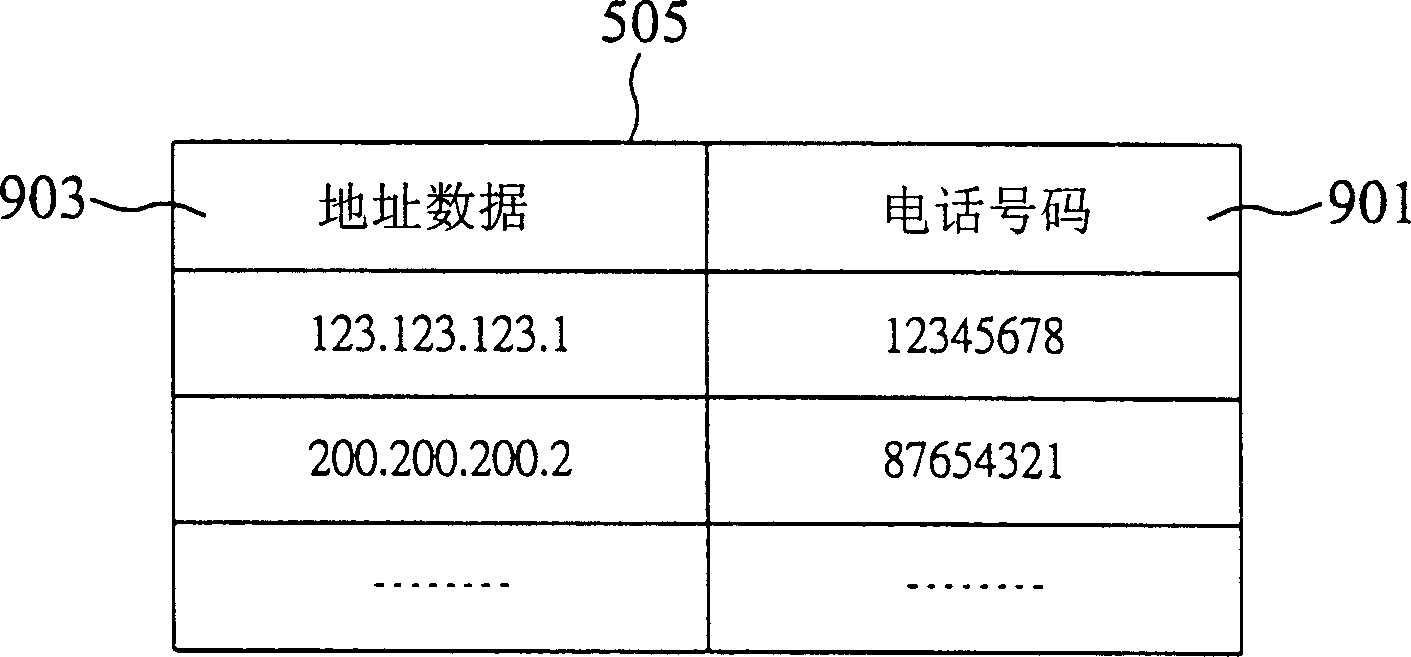
InactiveCN1395411AImprove convenienceWill not be affectedTelephonic communicationComputer scienceSpeech sound
The invention discloses the non-host type method for communication the packed voice. The method incldues the address data inquiring steps, the the addres data receivin steps and the packed voice transferring steps. The address data inquiring steps transfers the address data inquiring information to the non-host type communication device of the packed voice by using the dialing tone. The address data receiving steps receives the address data sent by the non-host type communication device of the packed voice transferred through the dialing tone. Based on the address data, the packed voice transferring steps transfers at least one packed voice to the non-host type communication device for the packed voice. The invention also discloses the non-host type communication device of the packed voice used for realizing the invented method.
Owner:VODTEL COMM
Virtual asset transfer hosting method and device, electronic equipment and storage medium
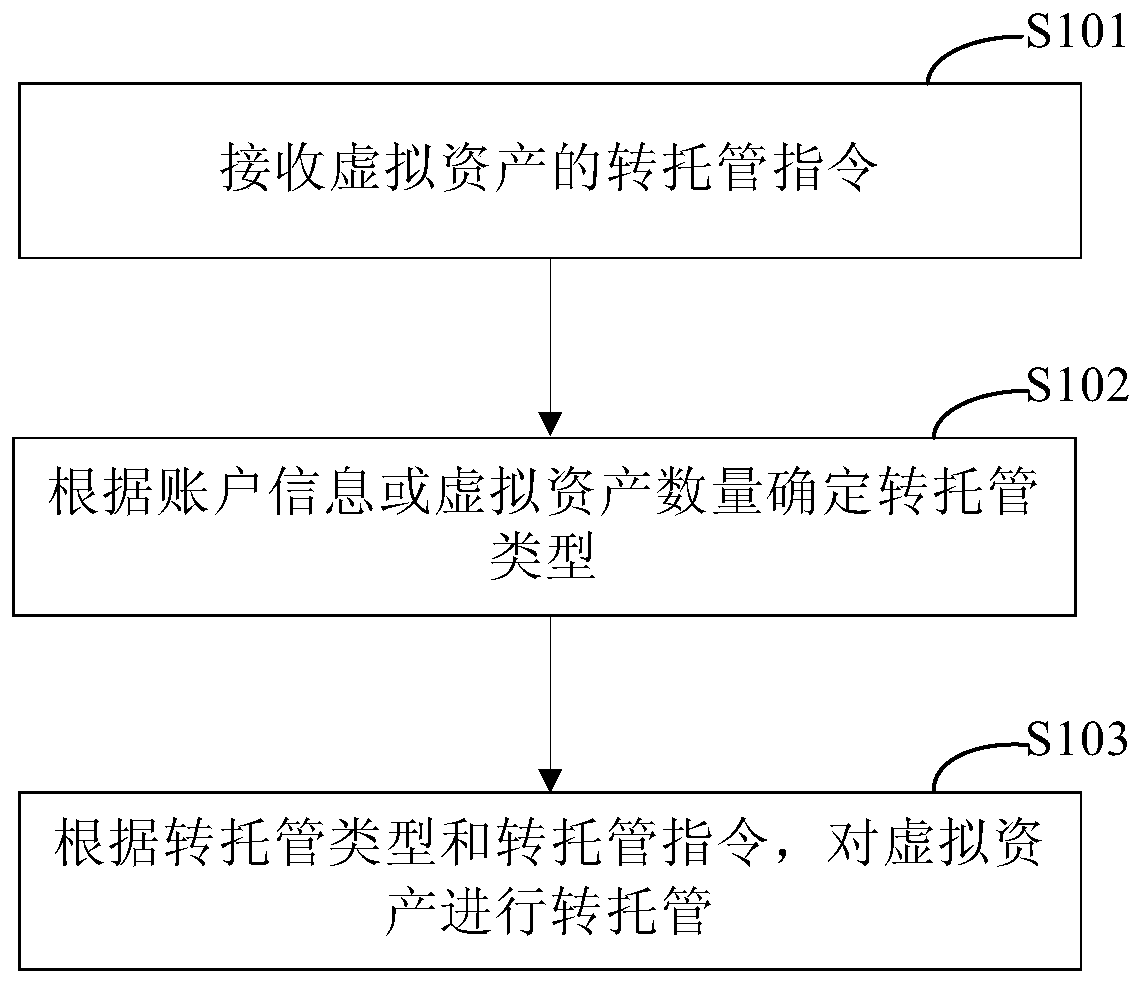
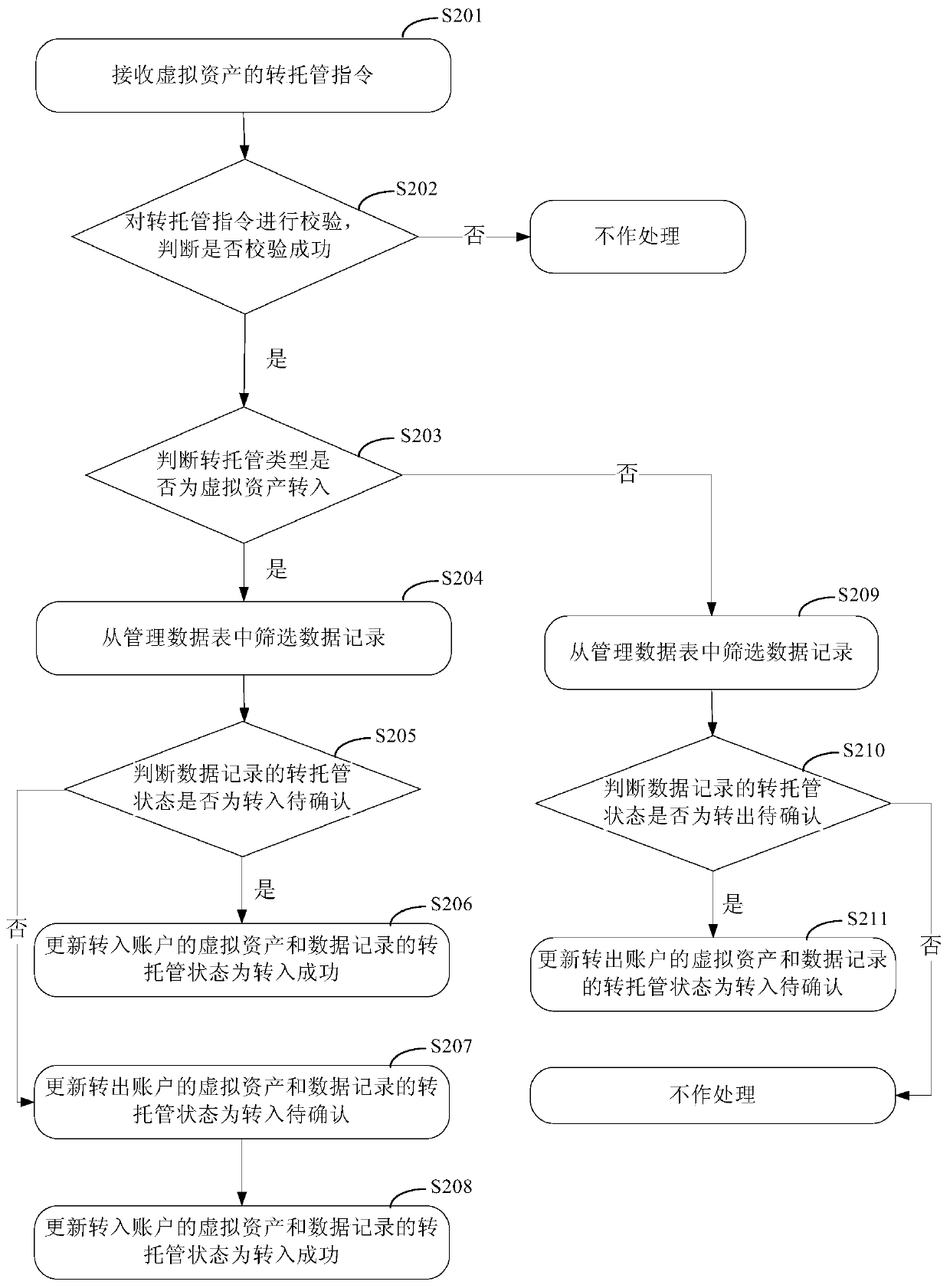
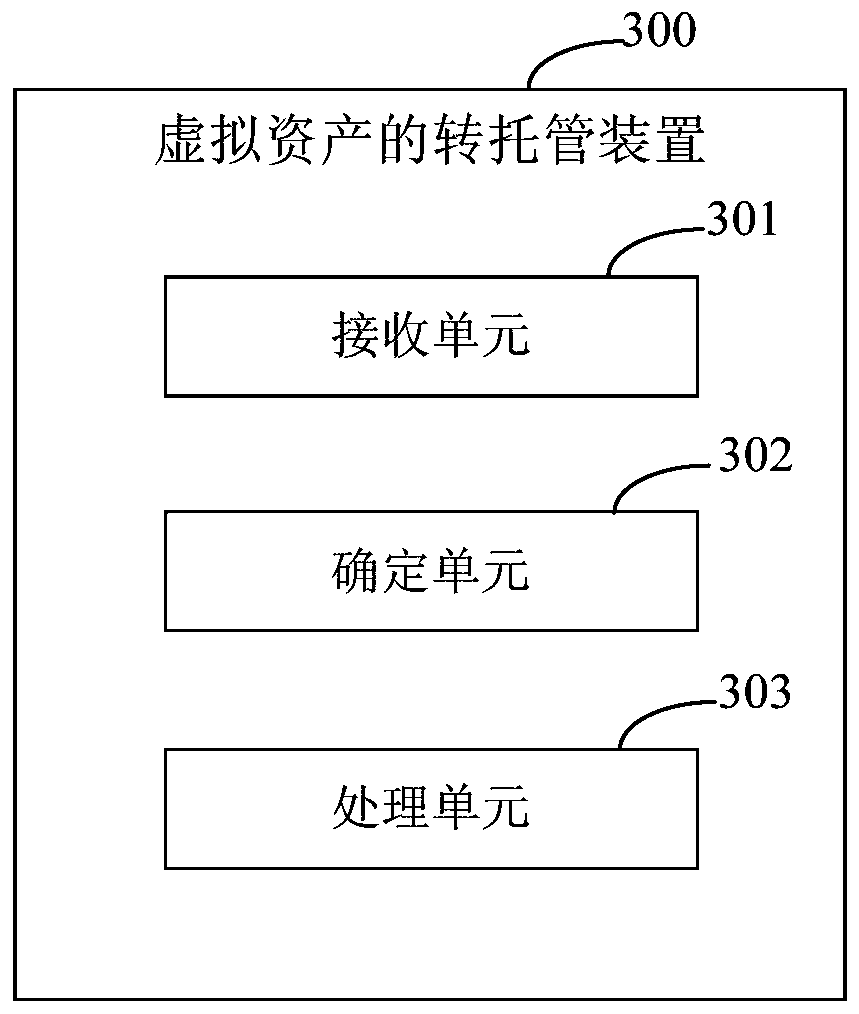
PendingCN111210349AImprove efficiencyReduce Settlement RiskFinanceSoftware engineeringOperating system
The invention discloses a virtual asset transfer hosting method and device, electronic equipment and a storage medium, and relates to the technical field of computers. One specific embodiment of the method comprises the following steps: receiving a trans-hosting instruction of virtual assets, wherein the trans-hosting instruction comprises trans-hosting account information, the quantity of the trans-hosted virtual assets and identifiers of the virtual assets; determining a transfer trusteeship type according to the account information or the number of the virtual assets, wherein the transfer trusteeship type comprises virtual asset transfer-in and virtual asset transfer-out; According to the trans-hosting type and the trans-hosting instruction, performing trans-hosting on the virtual assets. According to the embodiment, the problems that a traditional escrow mode needs to consume a large amount of labor and time, the cost is high, and the efficiency is low can be solved.
Owner:CHINA CONSTRUCTION BANK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com