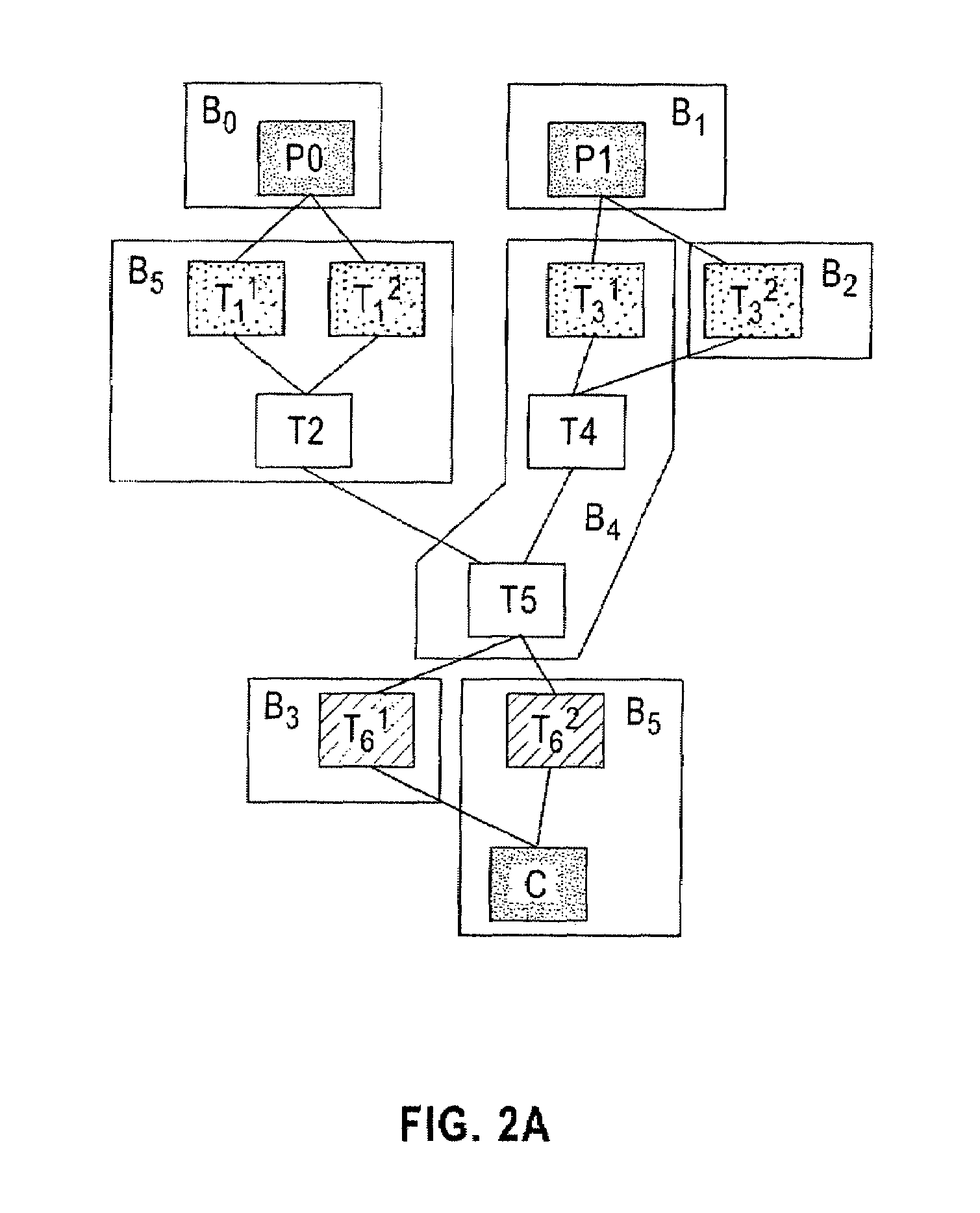
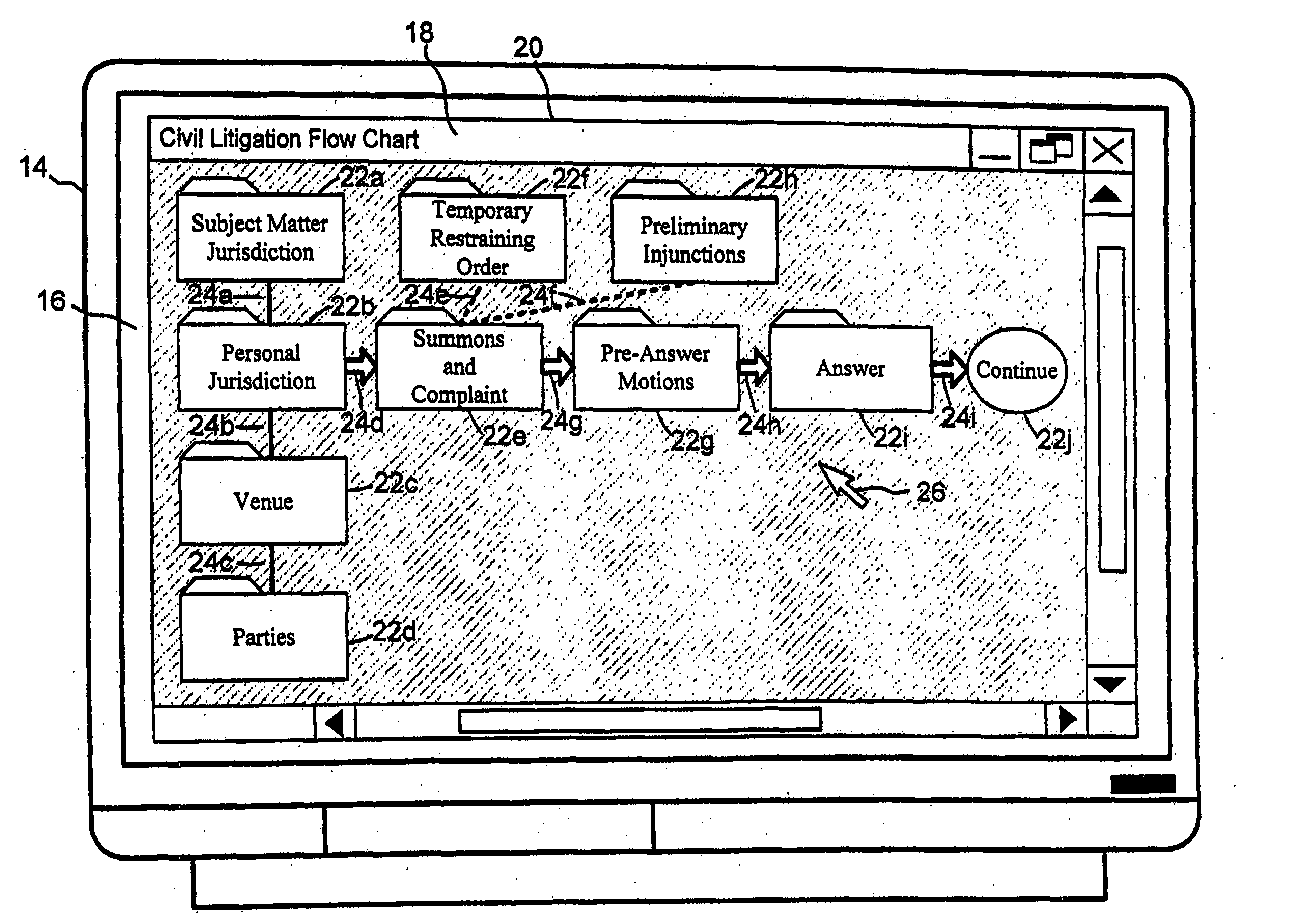
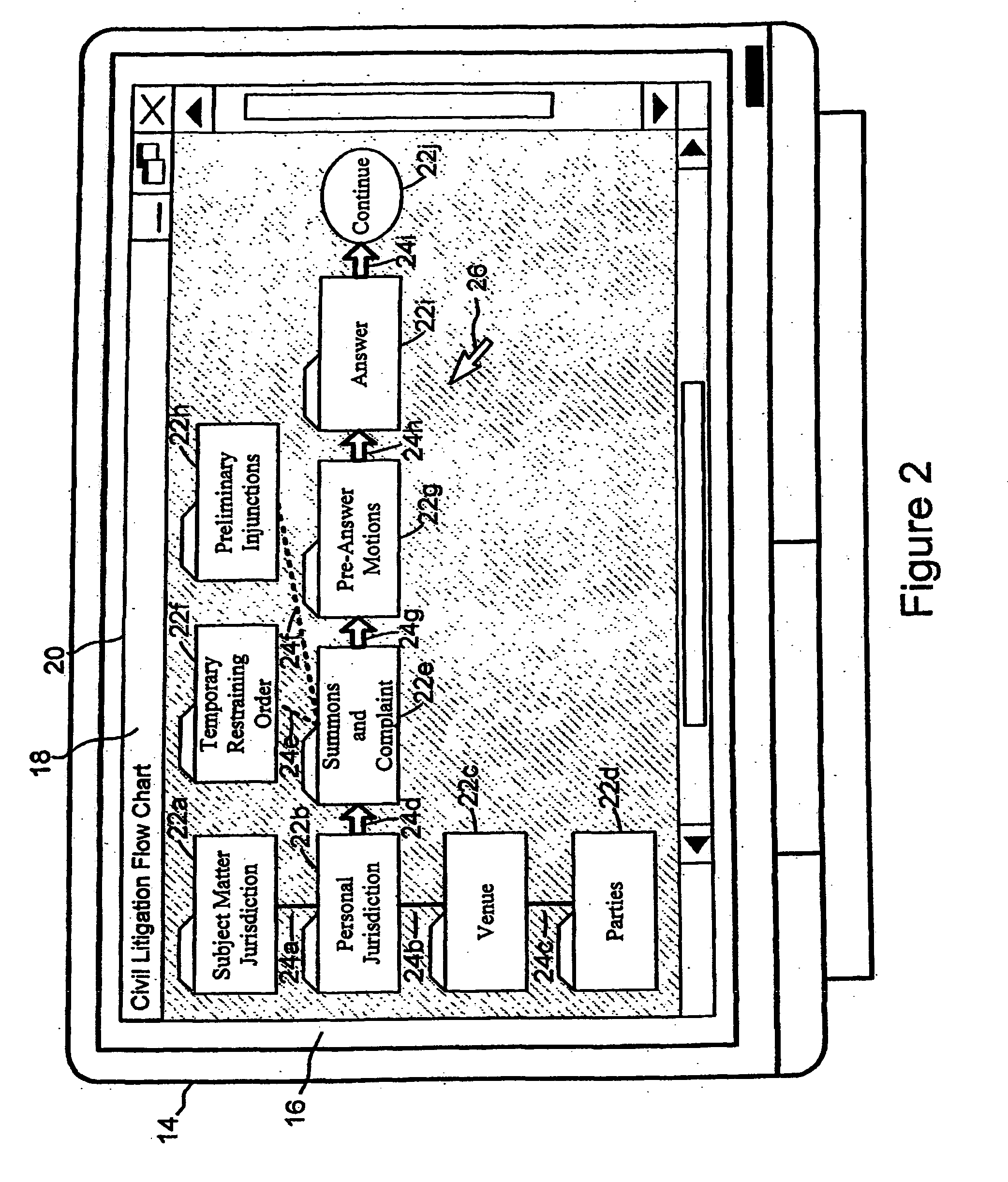
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
263 results about "Flow sheet" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Flow sheet. a patient care record that documents interventions through the use of check marks and brief notations. flow sheet. (in a patient record) a graphic summary of several changing factors, especially the patient's vital signs or weight and the treatments and medications given.
Method, system and computer program product for generating an electronic bill having optimized insurance claim items
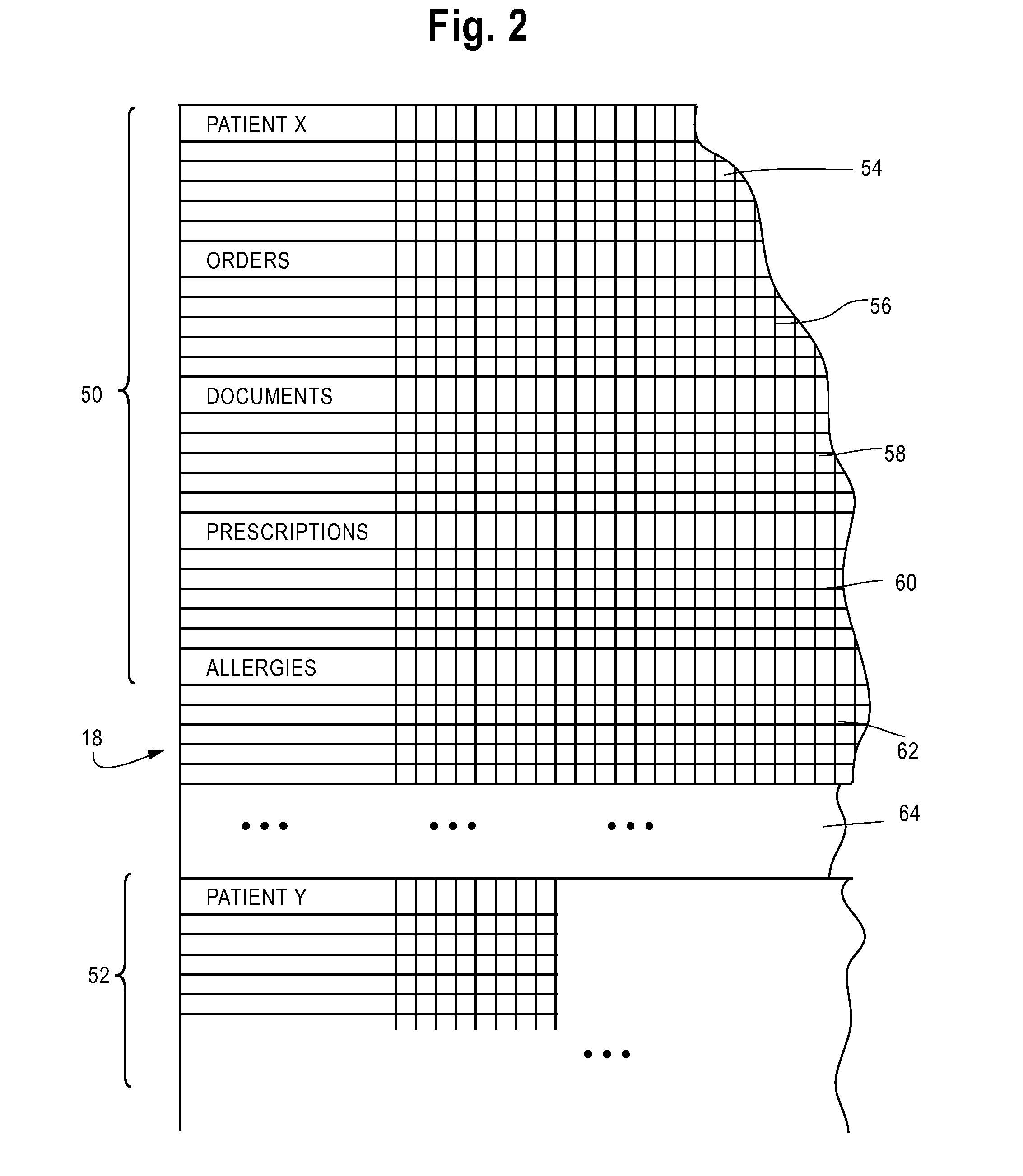
InactiveUS20070118410A1Accurate estimateFacilitate approvalFinanceDrug and medicationsDocumentation procedurePatient data
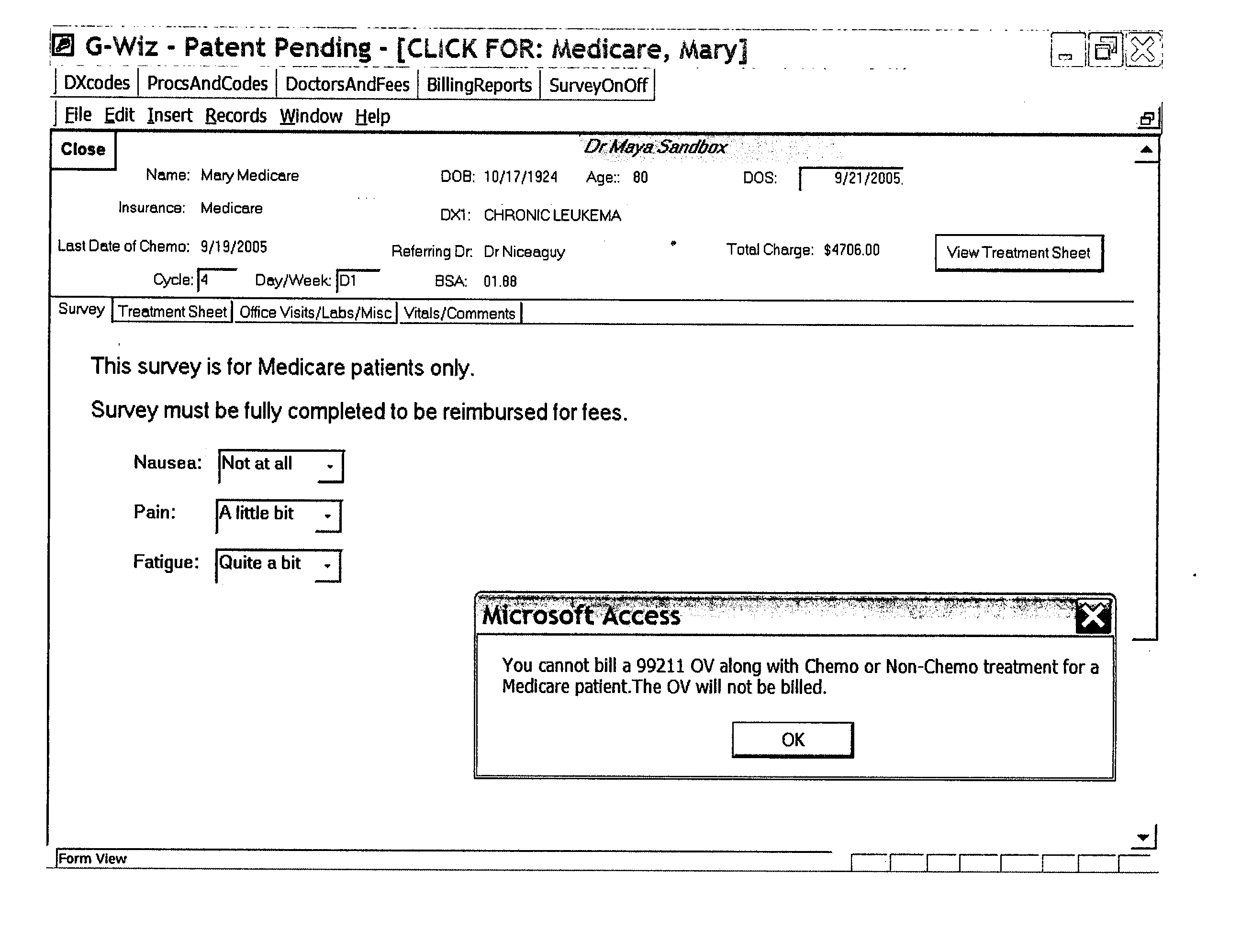
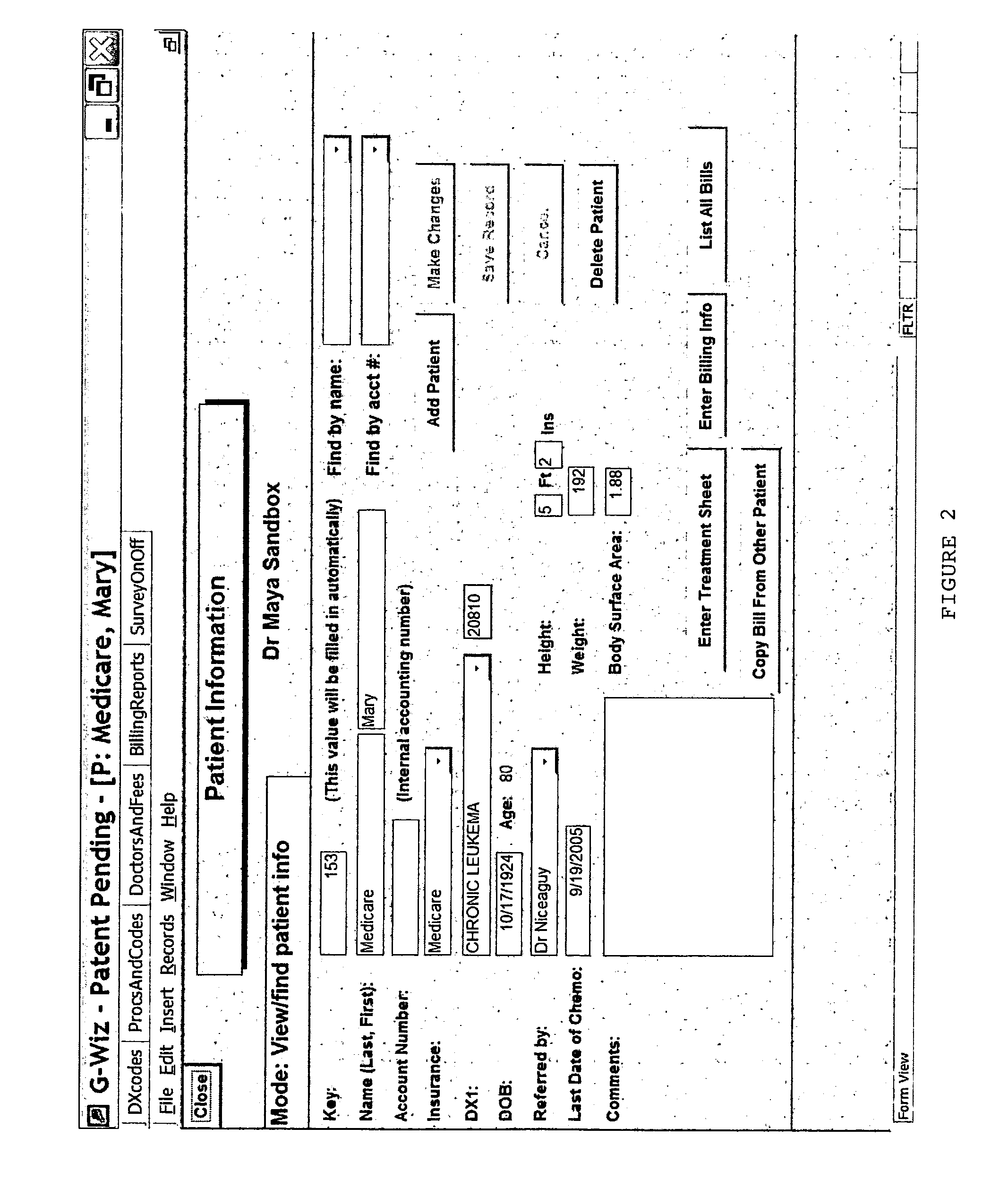
A method, system and computer program product for generating an electronic bill having optimized insurance claim items based on an insurance carrier of a patient are provided. The method includes receiving insurance carrier data which identifies a patient's insurance carrier and patient data which identifies a patient. The method also includes receiving treatment data which identifies a drug administered to the patient and a procedure performed on the patient on a date of service. The treatment data is processed to obtain nurse documentation, such as treatment and / or flow sheets. An electronic bill is automatically generated having optimized reimbursable insurance claim items including predetermined codes based on the treatment data and the insurance carrier data to facilitate approval of the bill by the insurance carrier.
Owner:NADAI ROBERT J
Electronic patient record documentation with push and pull of data to and from database
ActiveUS20130080190A1Good documentationSmooth transitionPatient personal data managementOffice automationMedical recordDisplay device
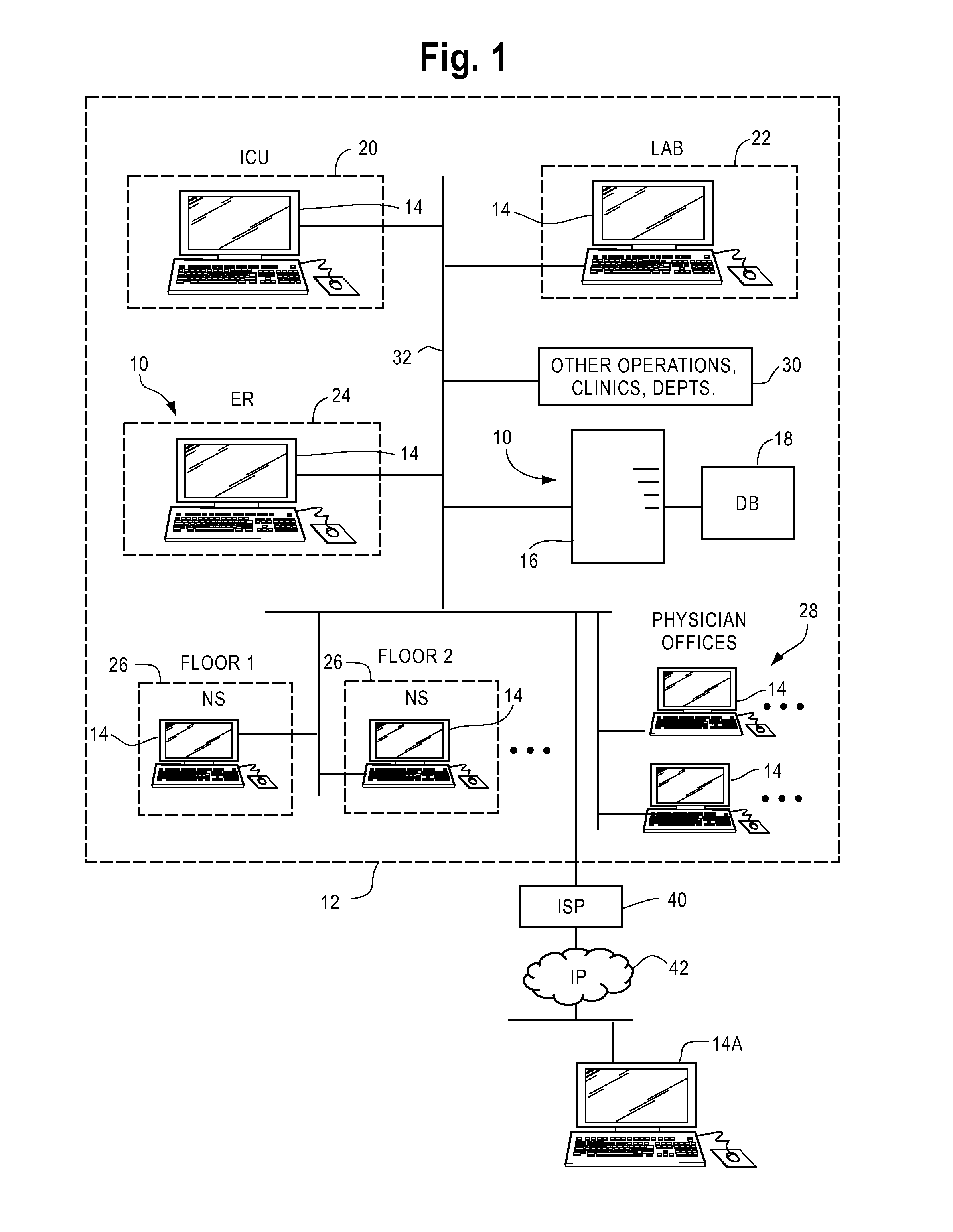
A medical records software apparatus and method is described that allows a clinician, e.g., nurse or doctor, to combine entry of new patient orders, prescriptions, flowsheet observations, etc. into the documentation process or workflow. A documentation user interface is provided that pulls patient data from a database into the display. The user can select on the user interface a category of a patient record, e.g., Significant Events or Orders, view or edit prior entries in the database in these categories, and add additional documentation for that category. The documentation is written or pushed to two areas of the database, one devoted to patient documentation and a second area corresponding to the selected category, e.g., Orders. The method and apparatus improves workflow efficiency and promotes a smooth transition from the thought process of the clinician to the ordering or prescription process, without the need for changing venues or screen displays.
Owner:ALLSCRIPTS SOFTWARE
Value predictable variable scoping for speculative automatic parallelization with transactional memory
ActiveUS20090235237A1Software engineeringSpecific program execution arrangementsCoding blockInner loop
Parallelize a computer program by scoping program variables at compile time and inserting code into the program. Identify as value predictable variables, variables that are: defined only once in a loop of the program; not defined in any inner loop of the loop; and used in the loop. Optionally also: identify a code block in the program that contains a variable assignment, and then traverse a path backwards from the block through a control flow graph of the program. Name in a set all blocks along the path until a loop header block. For each block in the set, determine program blocks that logically succeed the block and are not in the first set. Identify all paths between the block and the determined blocks as failure paths, and insert code into the failure paths. When executed at run time of the program, the inserted code fails the corresponding path.
Owner:ORACLE INT CORP
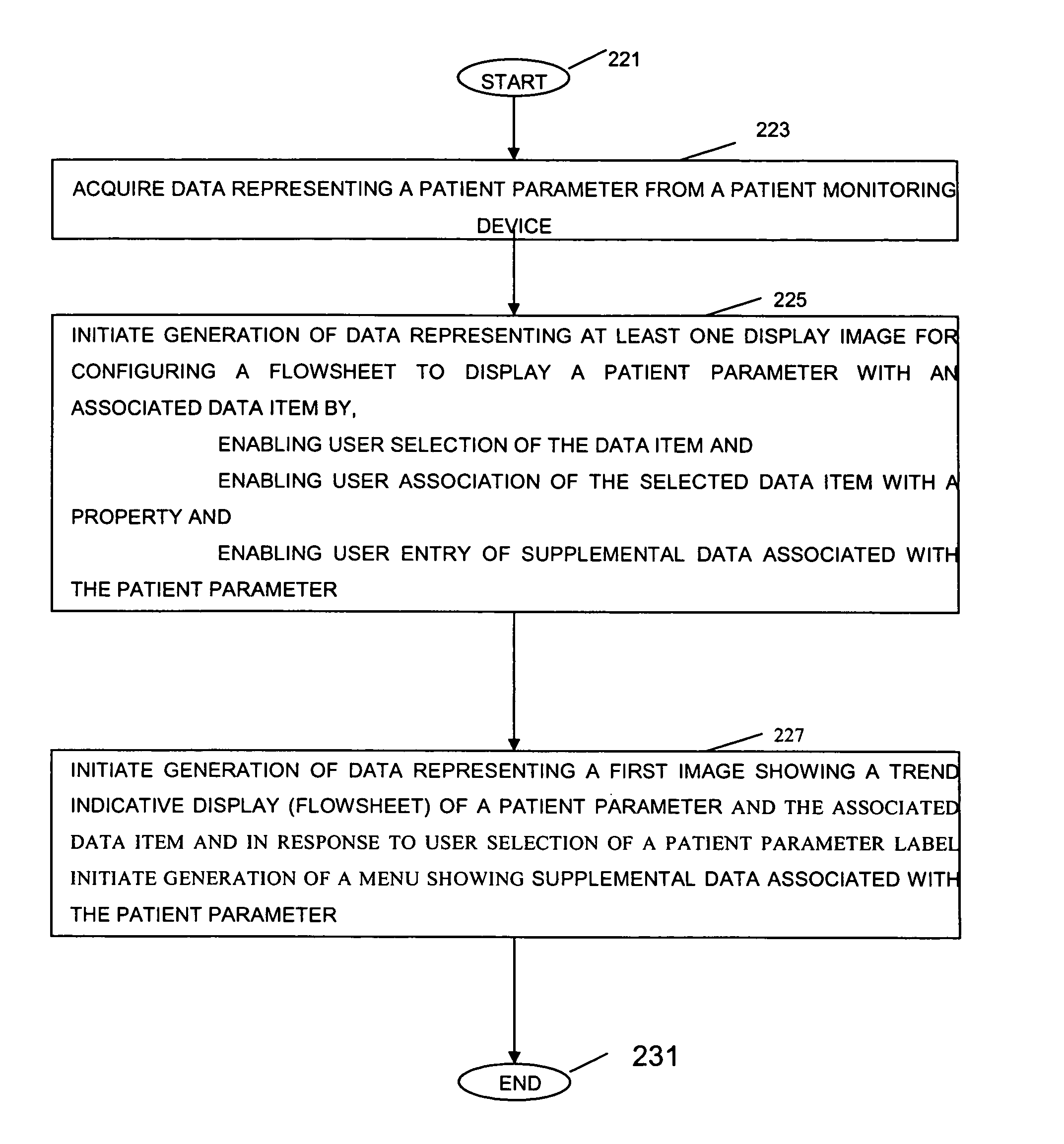
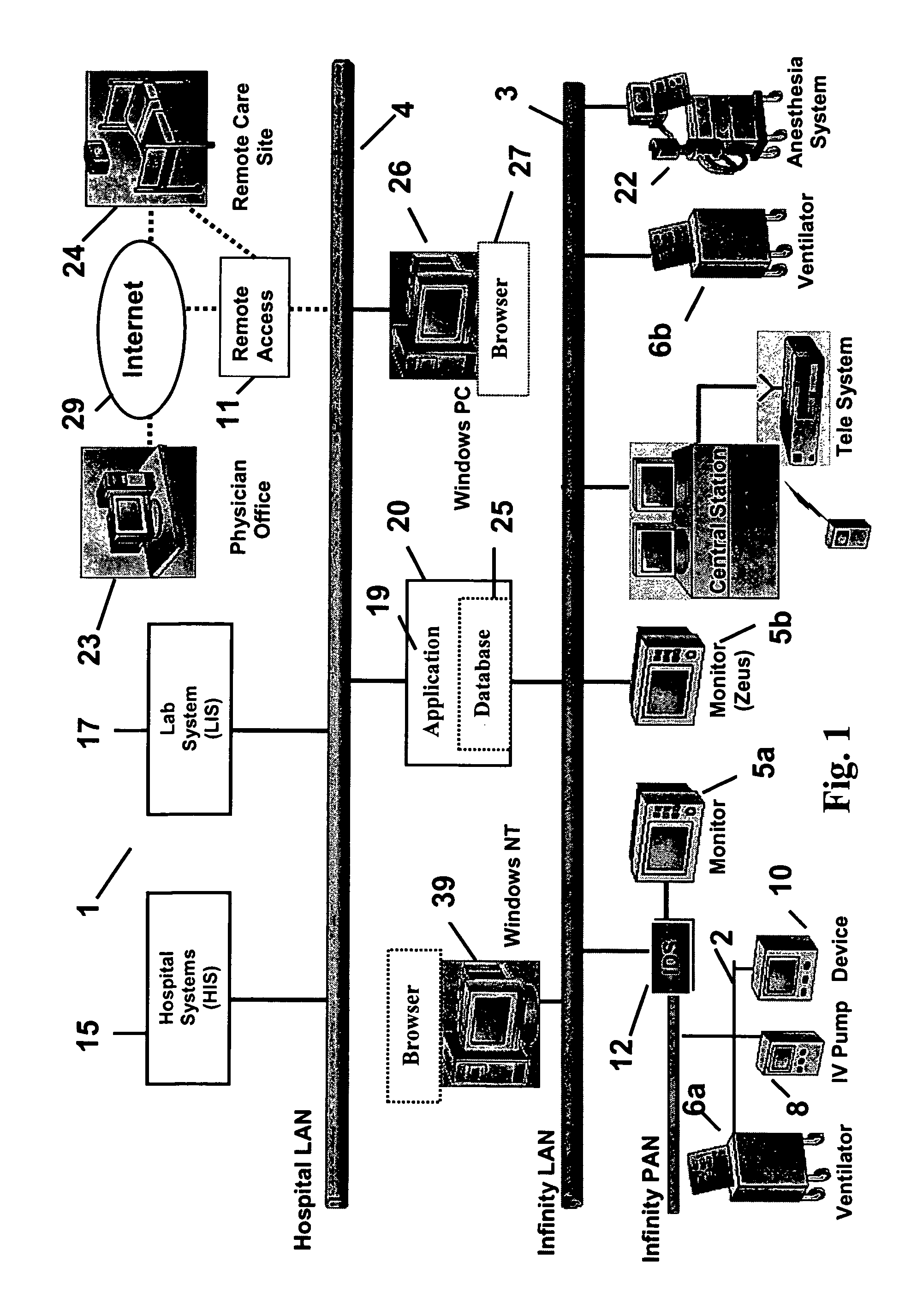
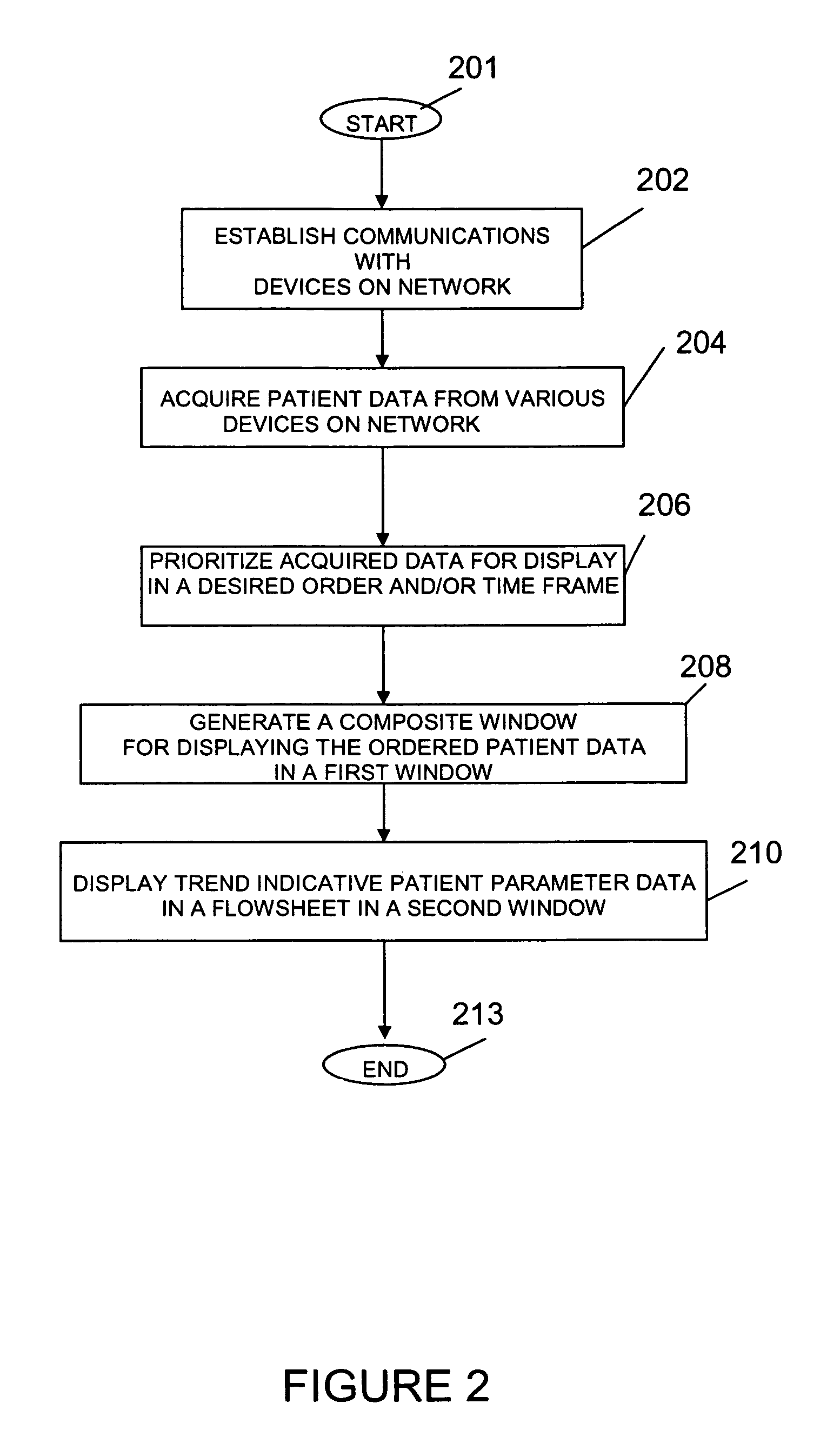
System and user interface for configuring and presenting a trend indicative display of patient medical parameters
ActiveUS7904822B2Increase flexibilityEnabling user configurabilityDrug and medicationsDiagnostic recording/measuringFluid infusionAcquisition time
A system provides an electronic patient parameter Flowsheet offering the flexible features of a paper chart by enabling user configurability of a Flowsheet trend indicative display to incorporate and locate desired patient parameters and associated data items and properties and to hide non-critical supplementary data. A system configures a user interface presenting patient medical parameter data in a trend indicative display indicating a time period comprising user selectable acquisition time intervals. An acquisition processor acquires, from a patient monitoring device, data representing a patient parameter. A processor initiates generation of data representing at least one display image for use in configuring a trend indicative display of a patient parameter and an associated data item by enabling user selection of the data item for trend indicative display and by enabling user association of the data item with a property indicating at least one of, (a) the data item represents volume data to be used in patient fluid infusion or output calculation, (b) the data item represents a rate for use in calculation of volume of patient fluid infusion or output and (c) the data item value is to be used in multiple acquisition time intervals of the trend indicative display.
Owner:DRAGERWERK AG
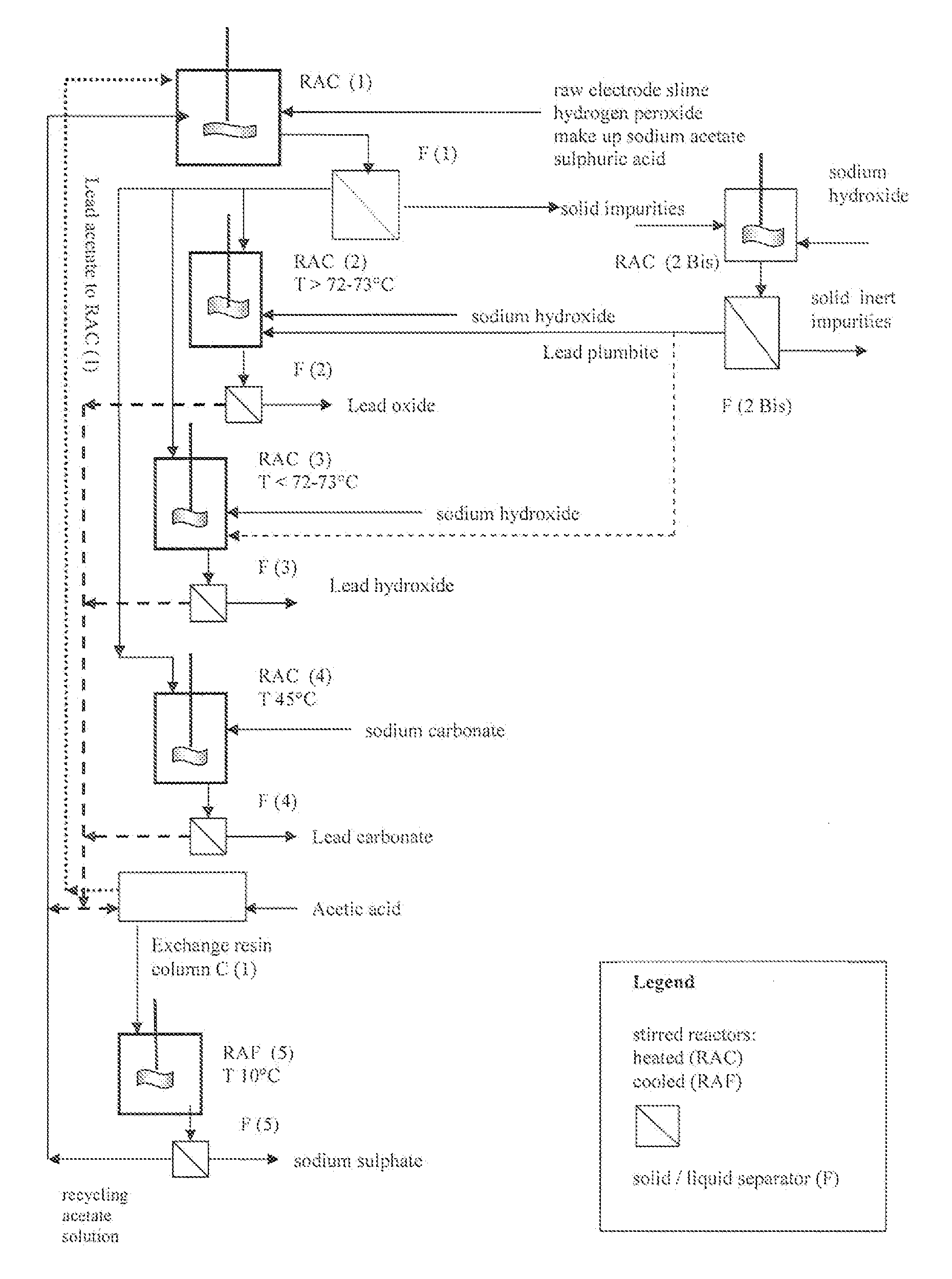
Reclaiming of lead in form of high purity lead compound from recovered electrode paste slime of dismissed lead batteries and/or of lead minerals
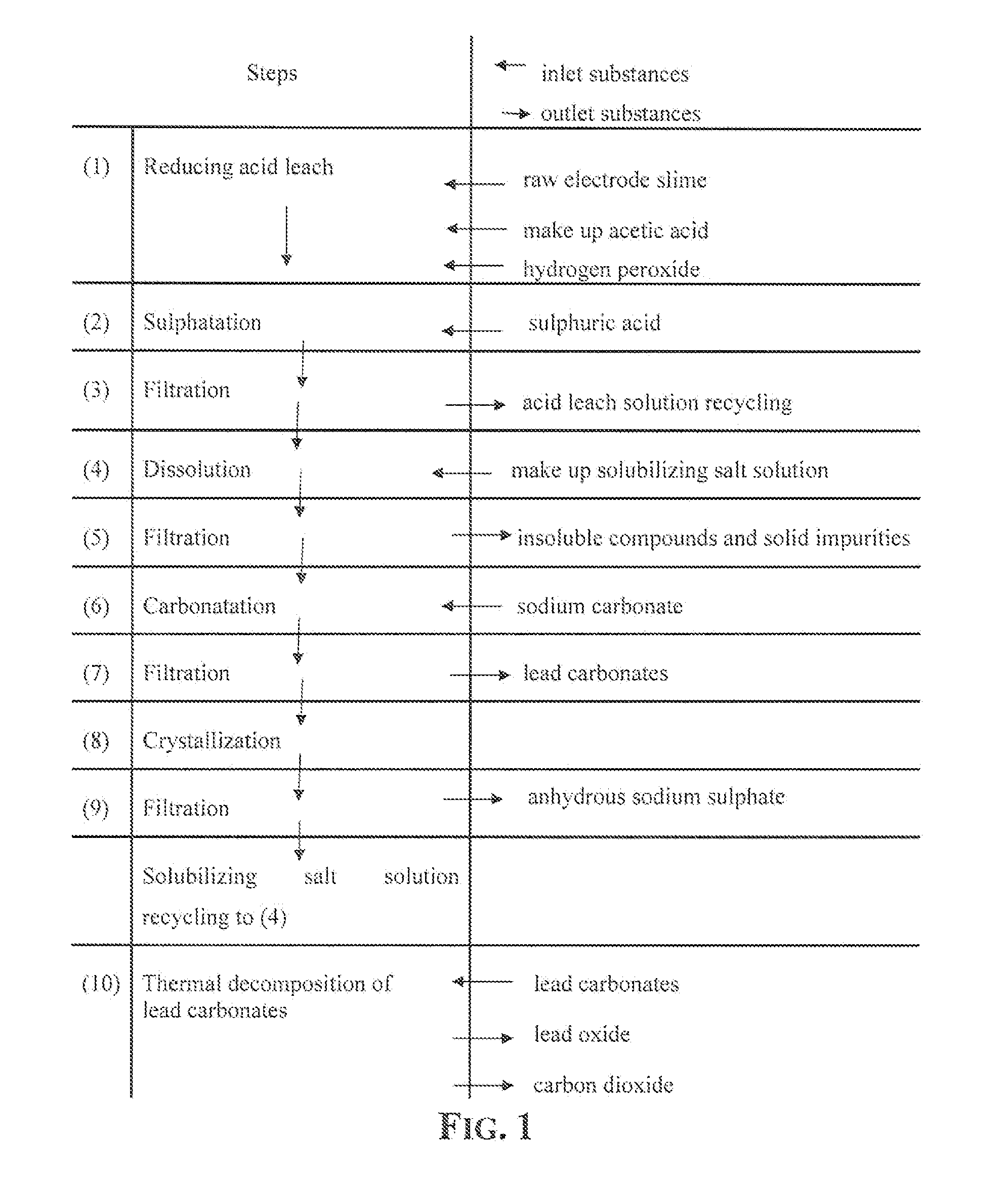
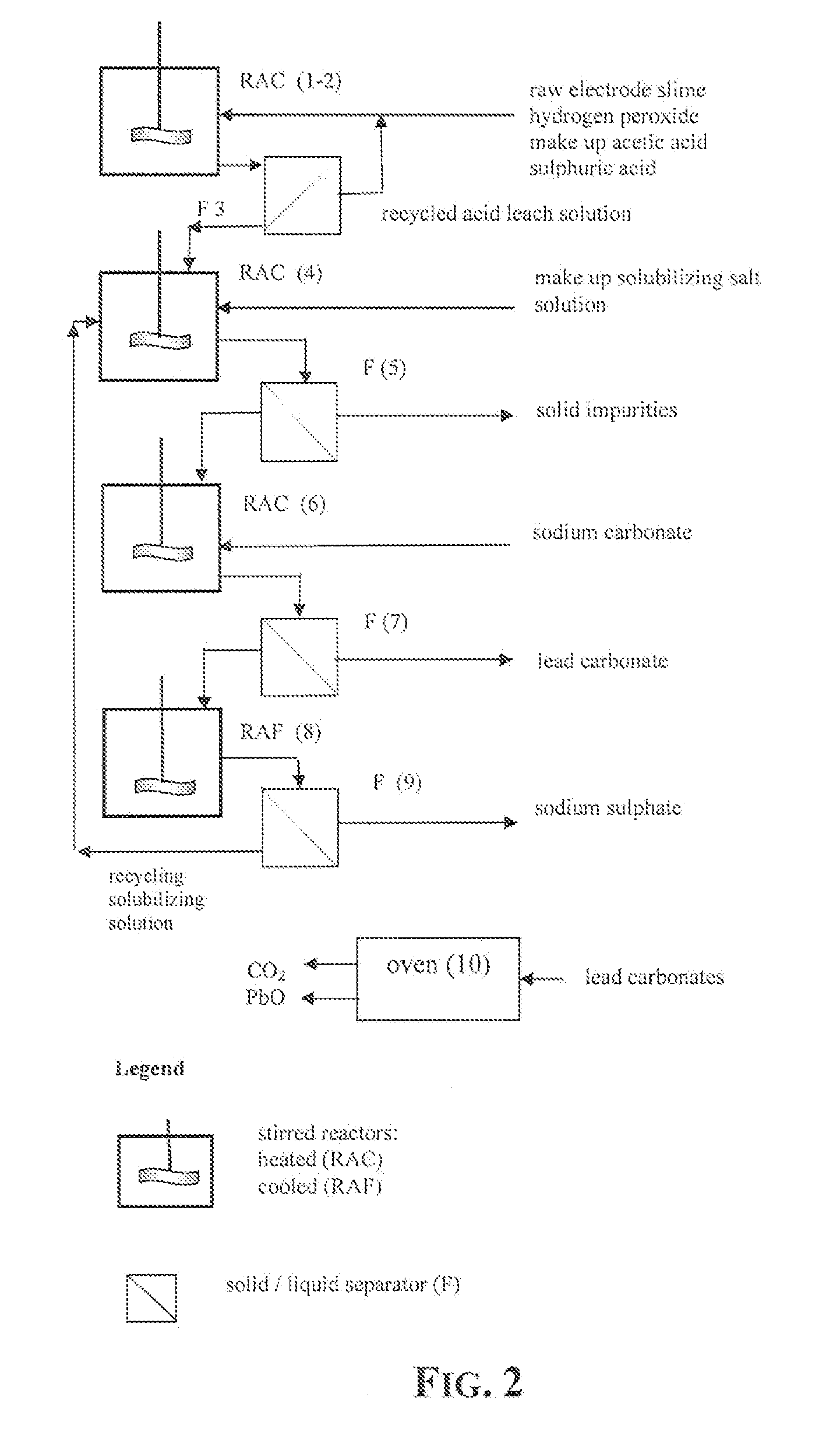
An outstandingly low environmental impact wet process recovers the lead content of an electrode slime and / or of lead minerals in the valuable form of high purity lead oxide or compound convertible to highly pure lead oxide by heat treatment in oven at relatively low temperature, perfectly suited for making active electrode pastes of new batteries or other uses. The process basically comprises the following treatments:a) suspending the impure lead containing material in an aqueous bath containing at least a lead oxide dissolving acid;b) reducing any insoluble lead dioxide to lead oxide by introducing in the suspension either hydrogen peroxide, a sulphite or sulphurous anhydride;c) converting all dissolved lead oxide to lead sulphate in the aqueous bath;d) obtaining a solution of lead sulphate obtained in an aqueous solution containing an acetate salt;e) precipitating and separating a purified lead compound in the form of either carbonate / oxycarbonate or of oxide / or hydroxide by adding to said acetate salt solution a carbonate salt or a hydroxide of the same cation of said acetate salt, respectively.Exemplary flow sheets according to several alternative embodiments and related processing plant diagrams are disclosed.
Owner:MILLBROOK LEAD RECYCLING TECH
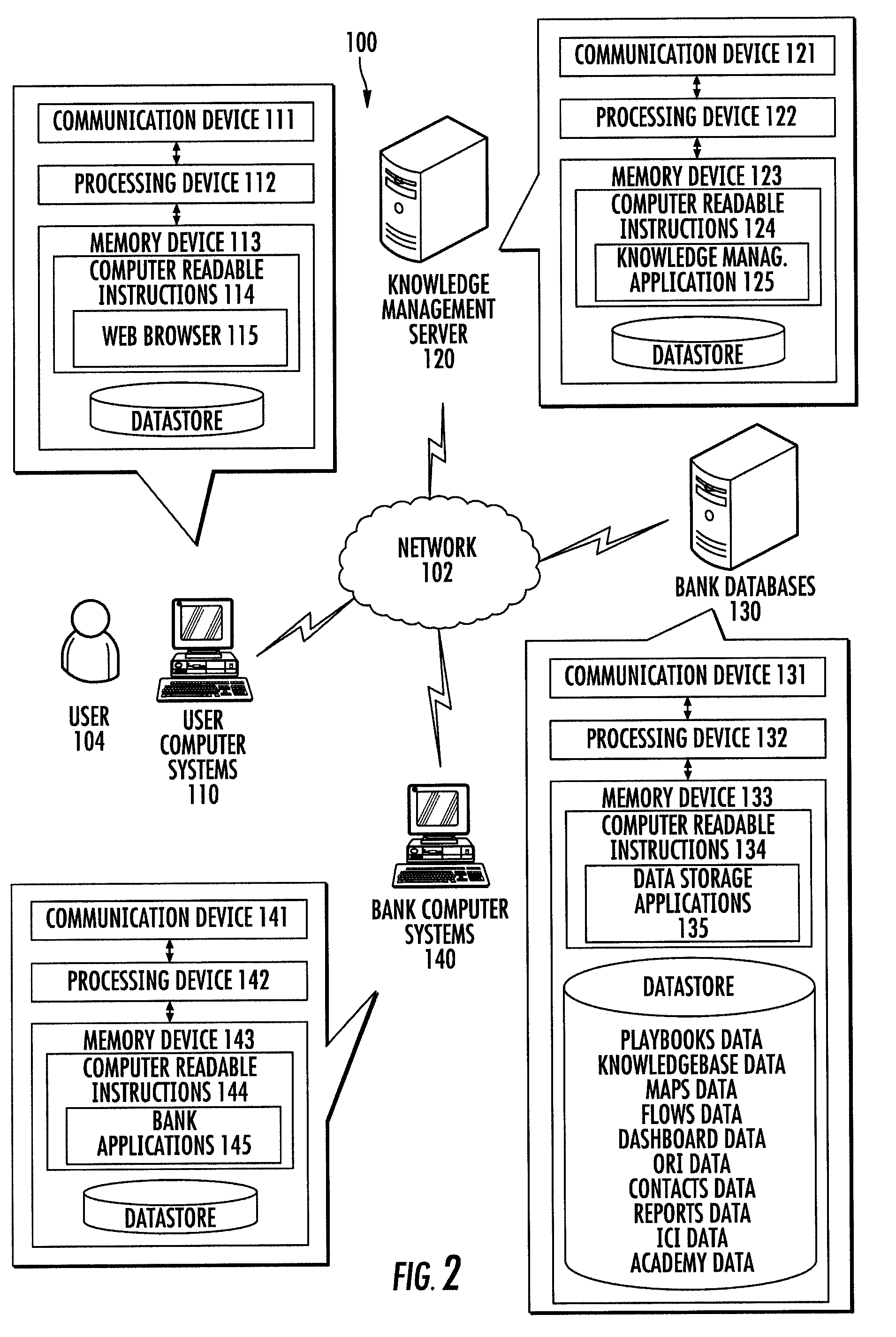
Knowledge management system
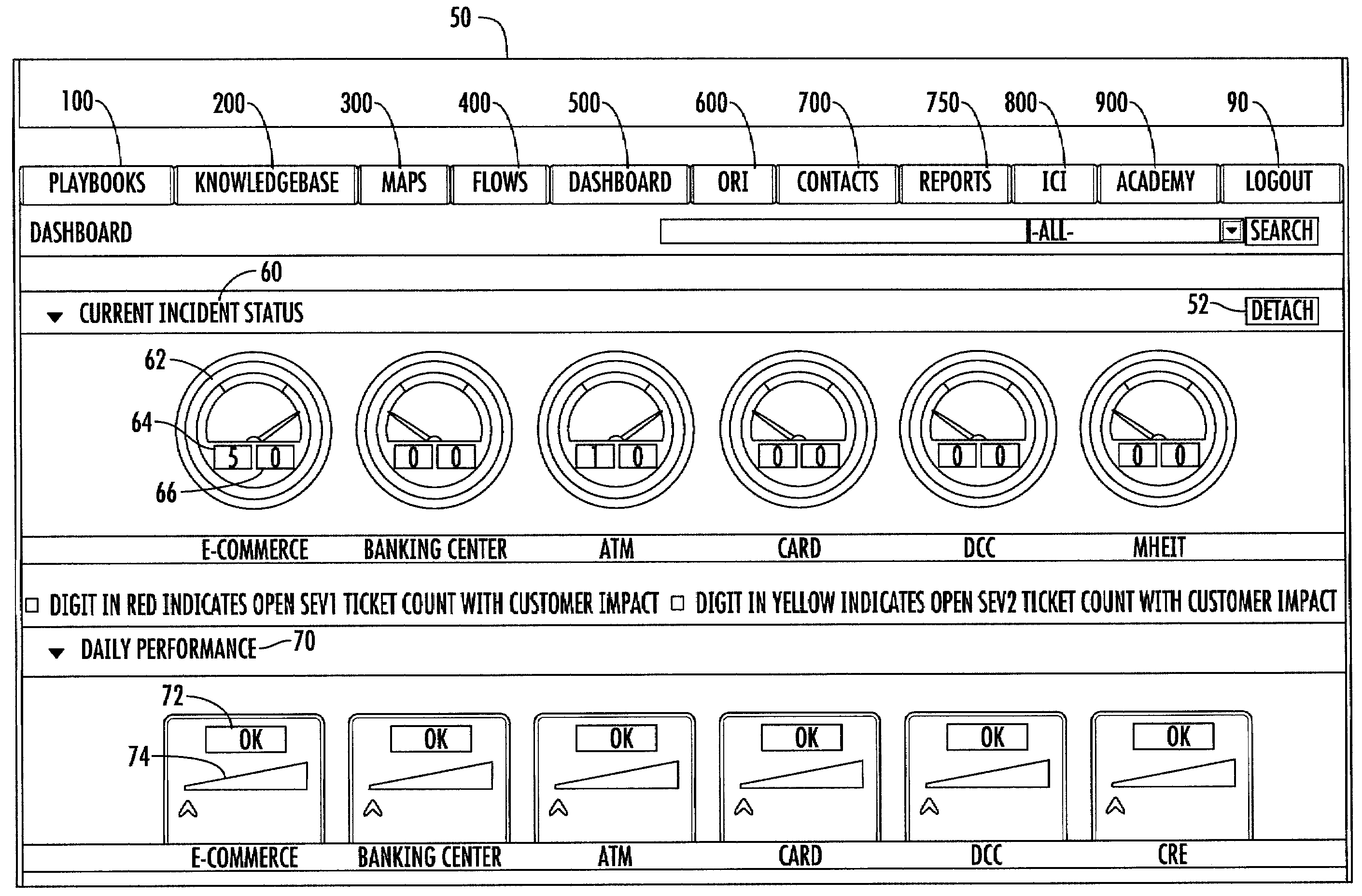
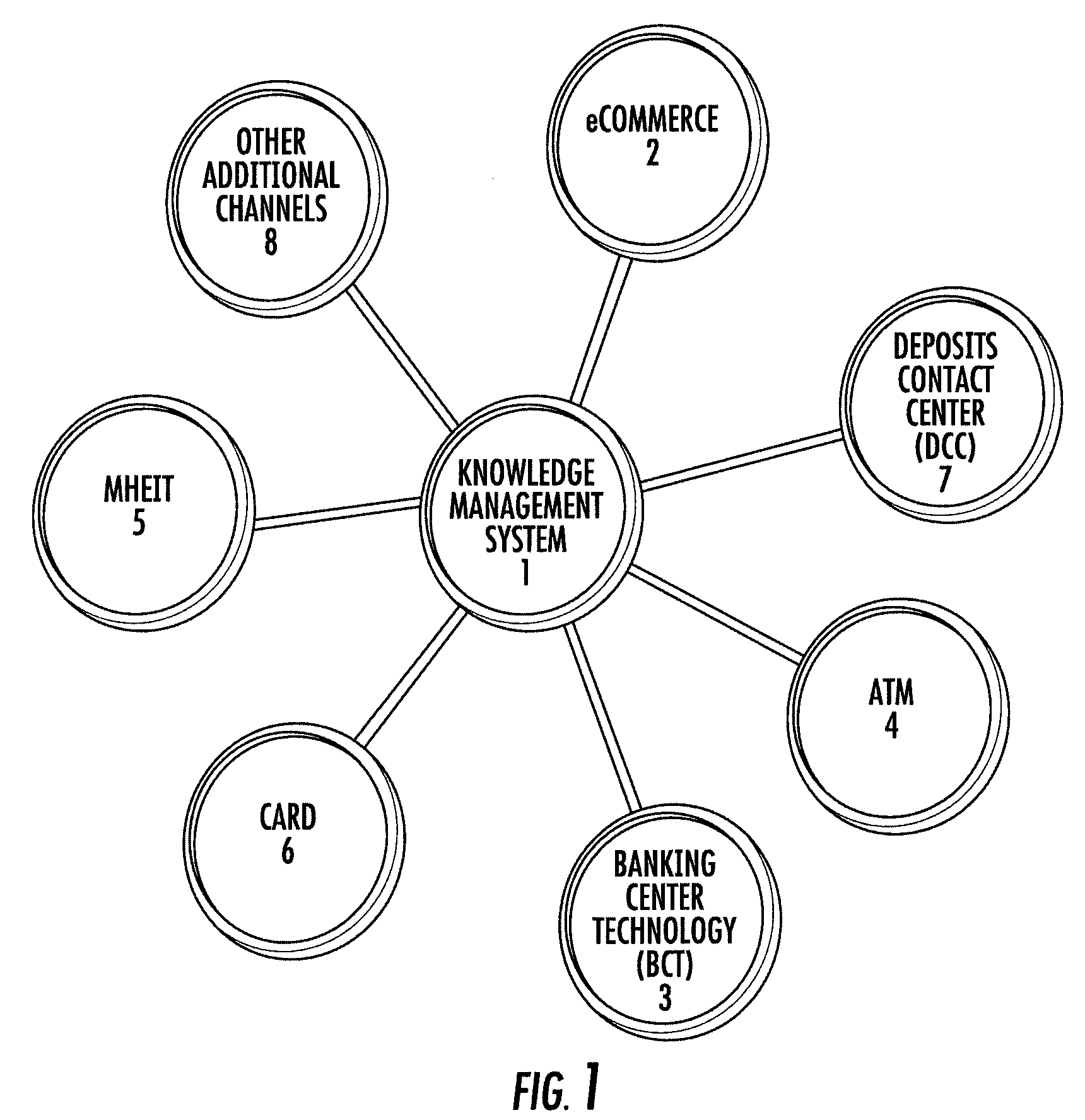
Embodiments of the present invention address the above needs and / or achieve other advantages by providing a method, system, computer program product, or a combination of the foregoing for creating a knowledge management system for production support that is standardized and centralized across the channels and sub-channels in an organization. The knowledge management system receives information relating to incidents from databases in the organization. The knowledge management system displays via a user interface at least the following information related to at least one incident, the current status of the incident, the recovery guidelines for effecting resolution of the incident, and scoring values associated with the incident. The knowledge management system also stores and displays historical information, contact information, incident reports, and outstanding incident tickets associated with the incident, as well as process maps or flowcharts for systems, applications, and customer views, and an academy for training associates.
Owner:BANK OF AMERICA CORP
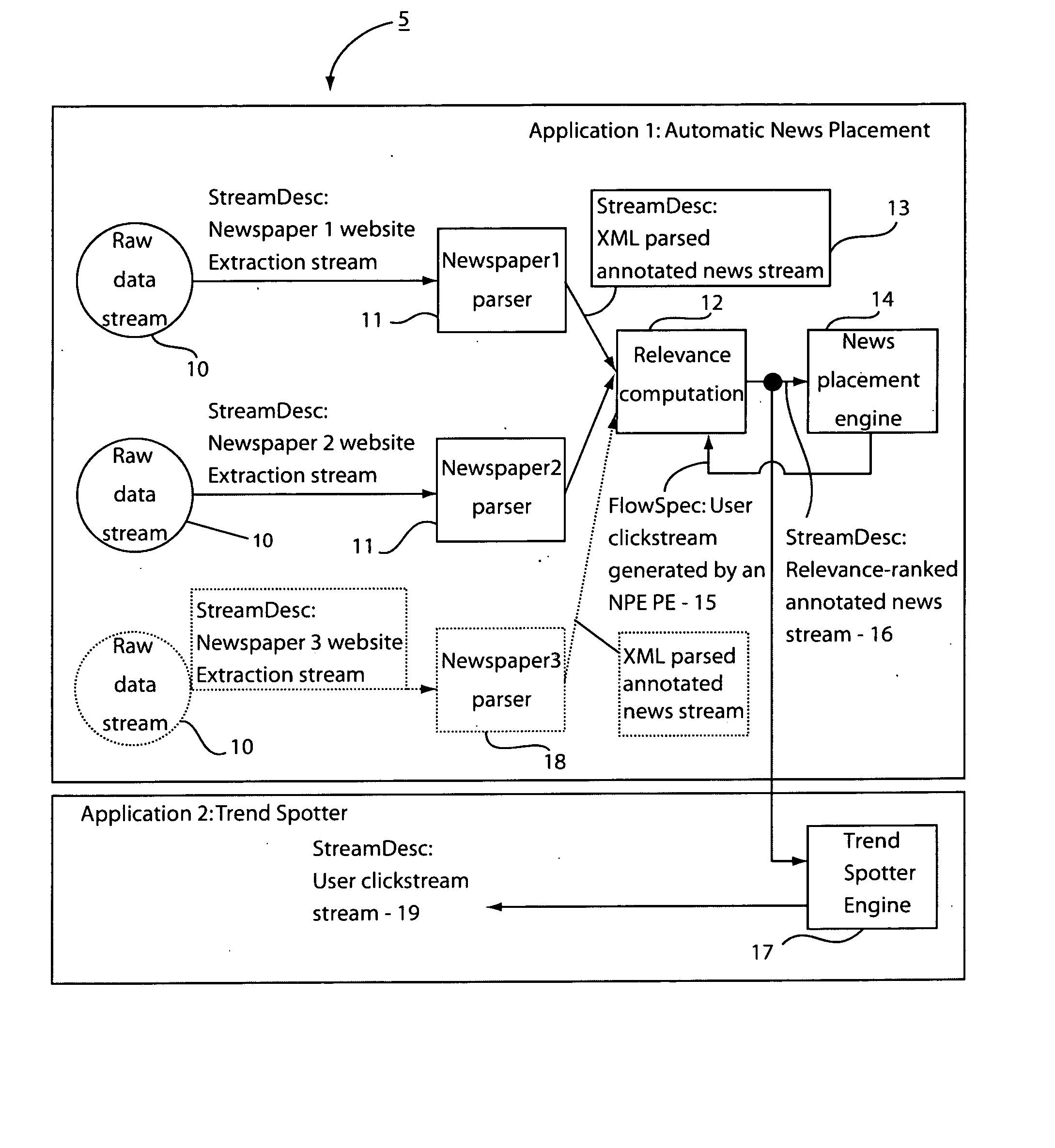
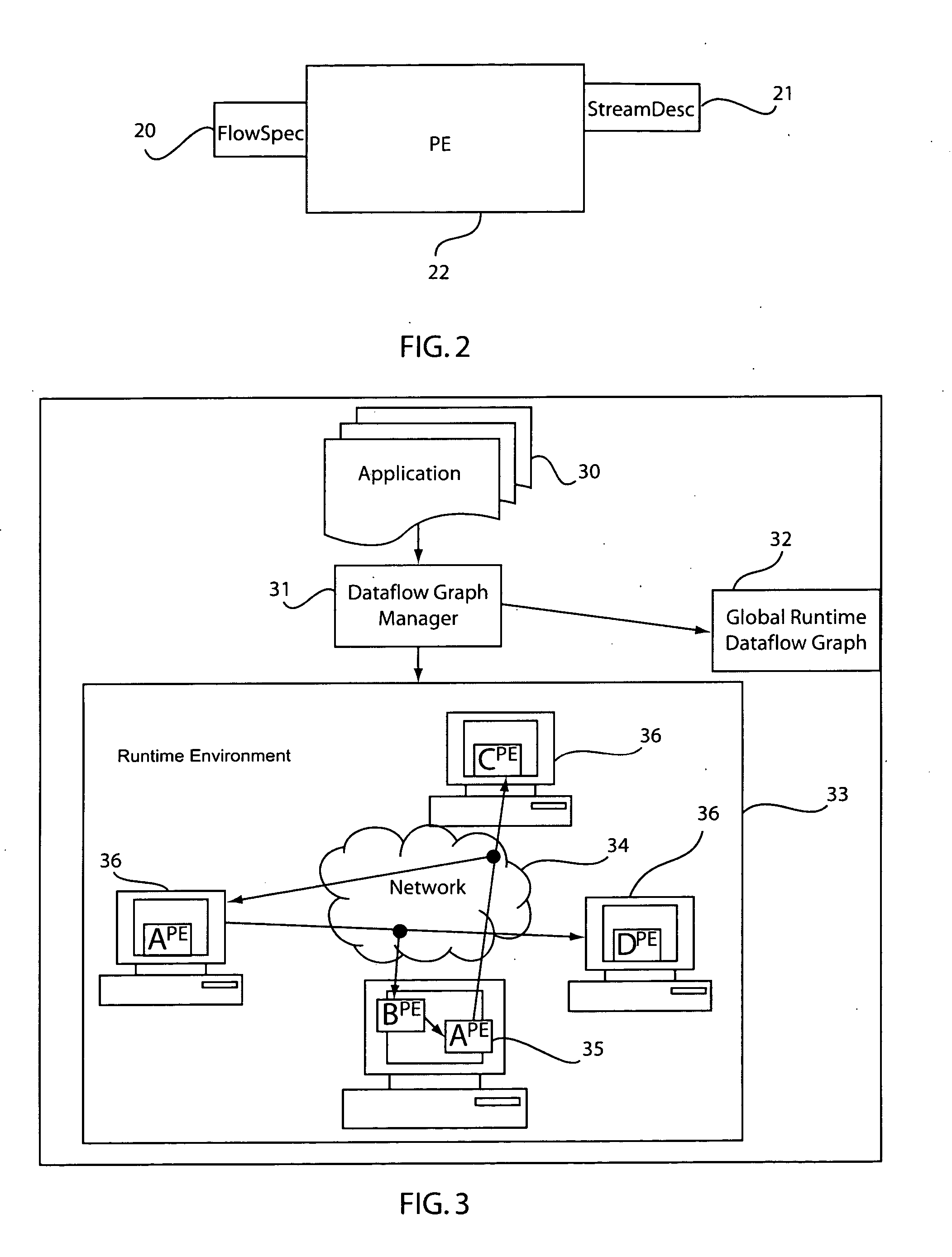
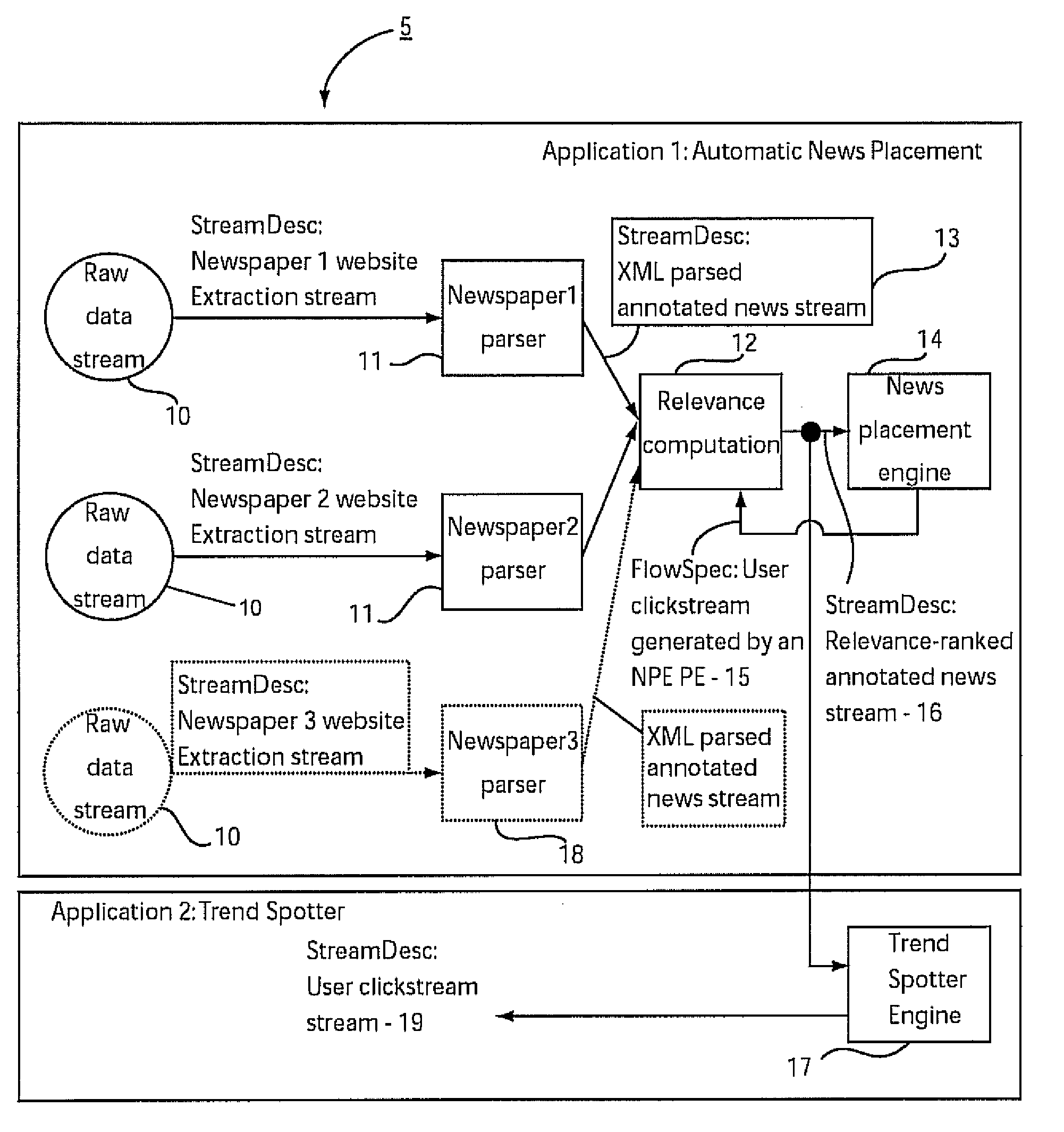
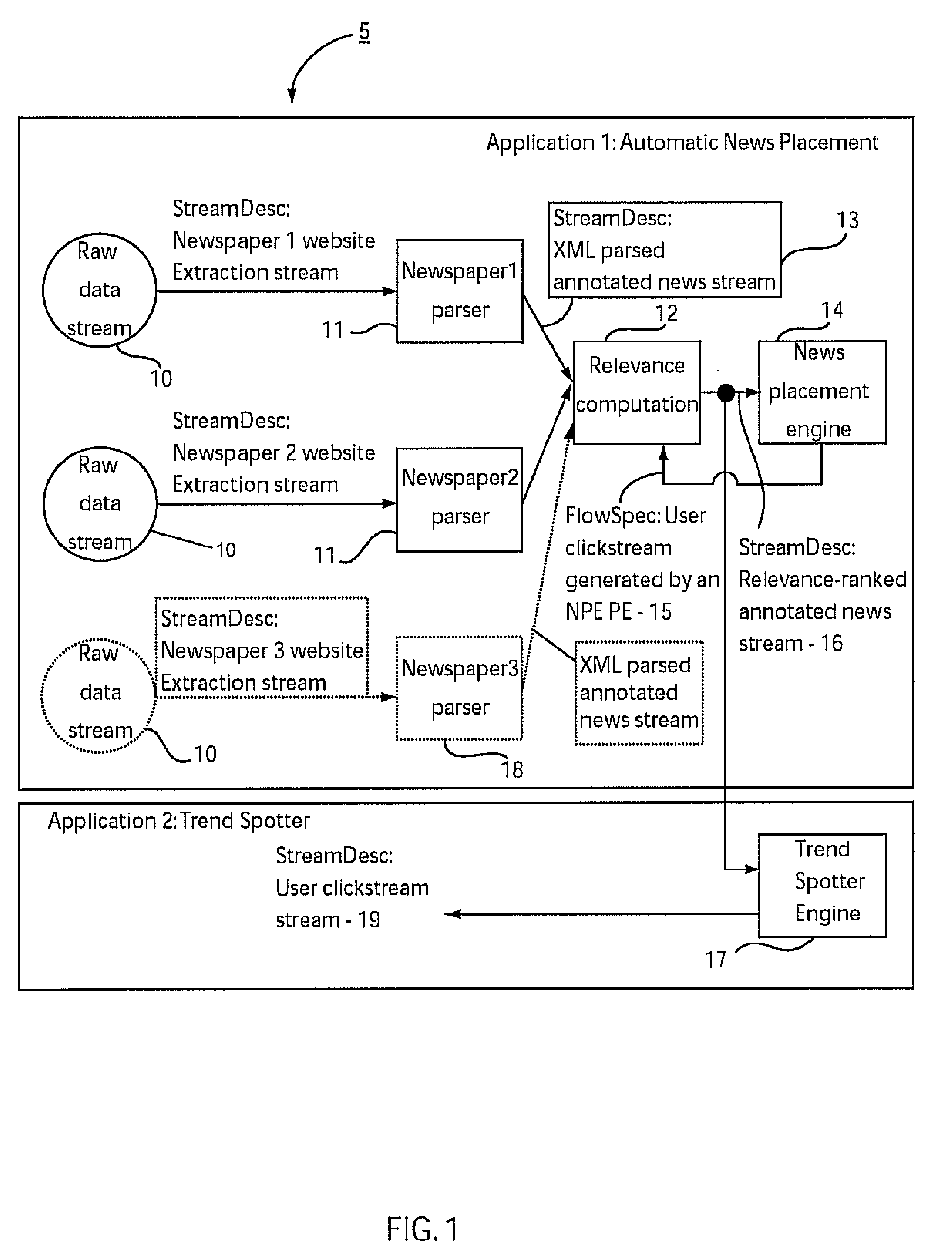
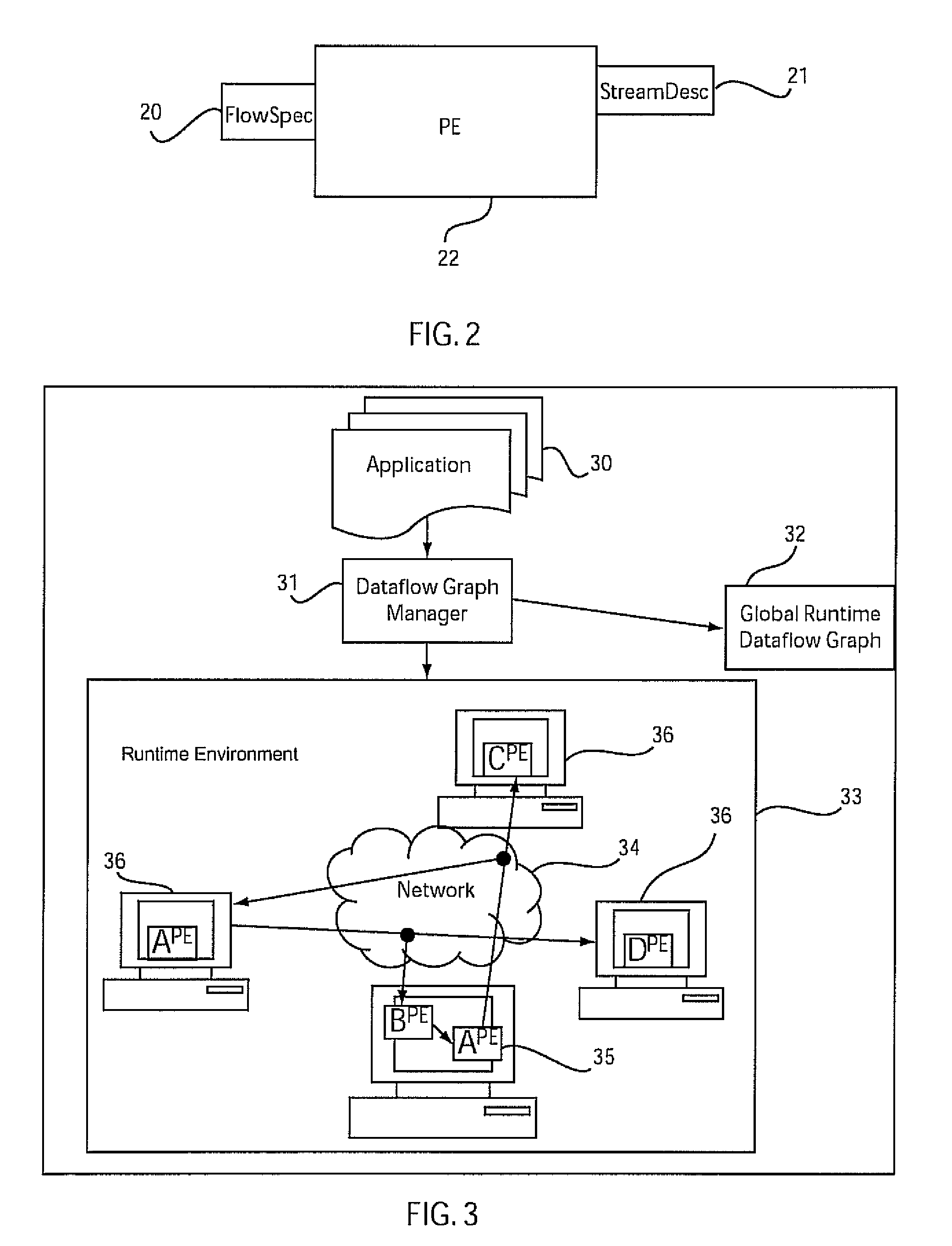
Method and system for dynamic application composition in streaming systems
InactiveUS20070261041A1Improved routing and flexibilityReduce the burden onProgram controlMemory systemsProcessing elementFlow sheet
A system and method for dynamically building applications for stream processing includes providing processing elements with a flow specification describing each input and a stream description describing each output such that the flow specification indicates a stream or streams which are to be received based on processing information and the stream descriptions indicate the processing information. Processing elements that can be reused are identified by determining equivalence between the processing elements. Processing elements that are new and are not reusable are instantiated in a flow graph. An application is dynamically composed, using the instantiated processing elements by routing available streams to the instantiated processing elements in accordance with the flow specifications.
Owner:IBM CORP
System, method and program product for detecting malicious software
InactiveUS20050091558A1Avoid damageError detection/correctionPlatform integrity maintainanceData streamSoftware system
System, method and program product for detecting malicious software within or attacking a computer system. In response to a system call, a hook routine is executed at a location of the system call to (a) determine a data flow or process requested by the call, (b) determine another data flow or process for data related to that of the call, (c) automatically generate a consolidated information flow diagram showing the data flow or process of the call and the other data flow or process. After steps (a-c), a routine is called to perform the data flow or process requested by the call. A user monitors the information flow diagram and compares the data flow or process of steps (a) and (b) with a data flow or process expected by said user. If there are differences, the user may investigate the matter or shut down the computer to prevent damage.
Owner:IBM CORP
Method for enhancing program analysis
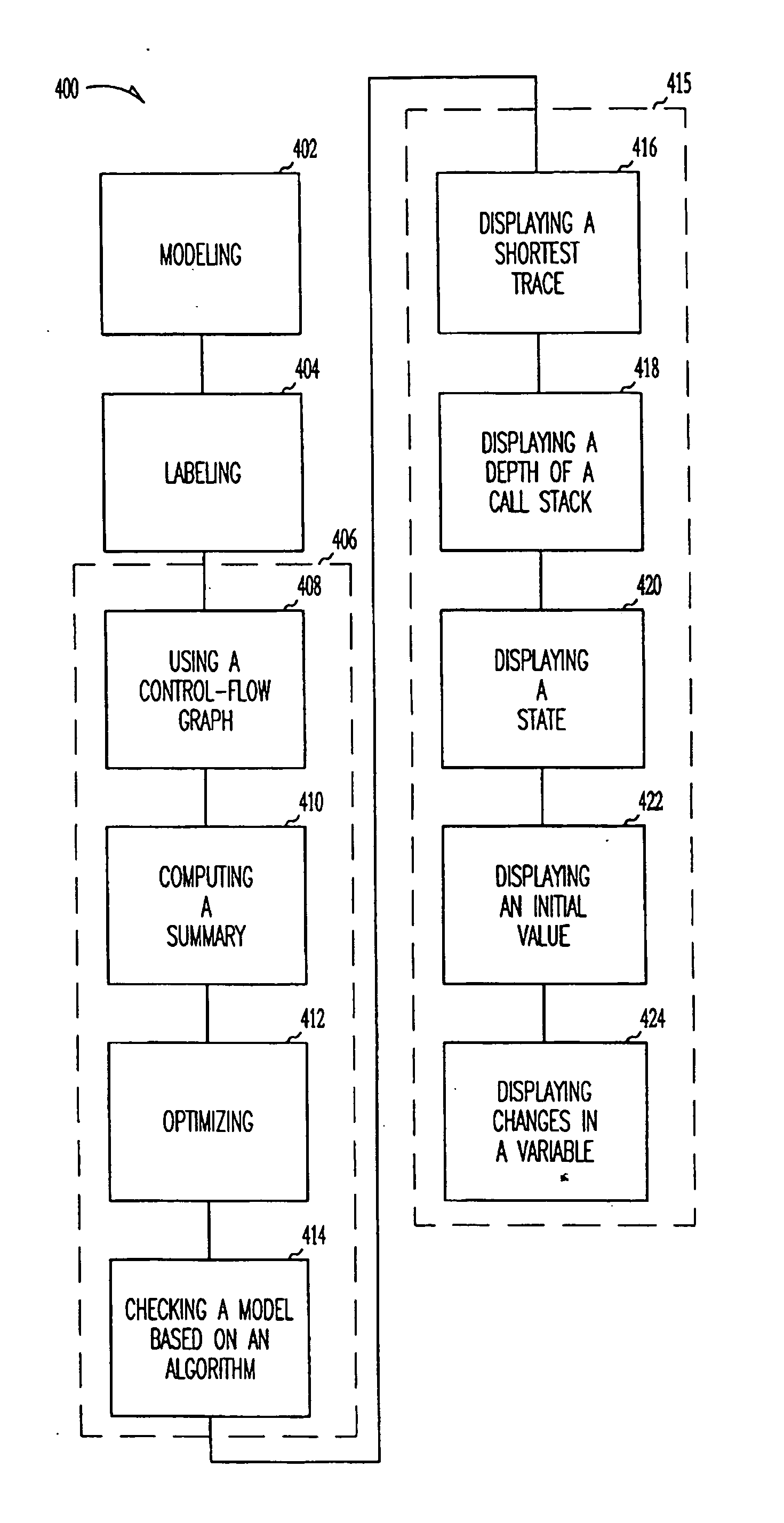
InactiveUS20050149904A1Easy to analyzeAvoid explosionSoftware testing/debuggingSpecific program execution arrangementsTheoretical computer scienceFlow sheet
Methods are discussed that enhance program analysis. One aspect of the invention includes a method for checking a model of a program. The method includes a control-flow graph having vertices from the model, applying a transfer function to each vertex to form a set of path edges, and analyzing the set of path edges of a vertex. The set of path edges includes valuations that are implicitly represented so as to inhibit an undesired explosion in the valuations that would hinder the act of analyzing.
Owner:MICROSOFT TECH LICENSING LLC
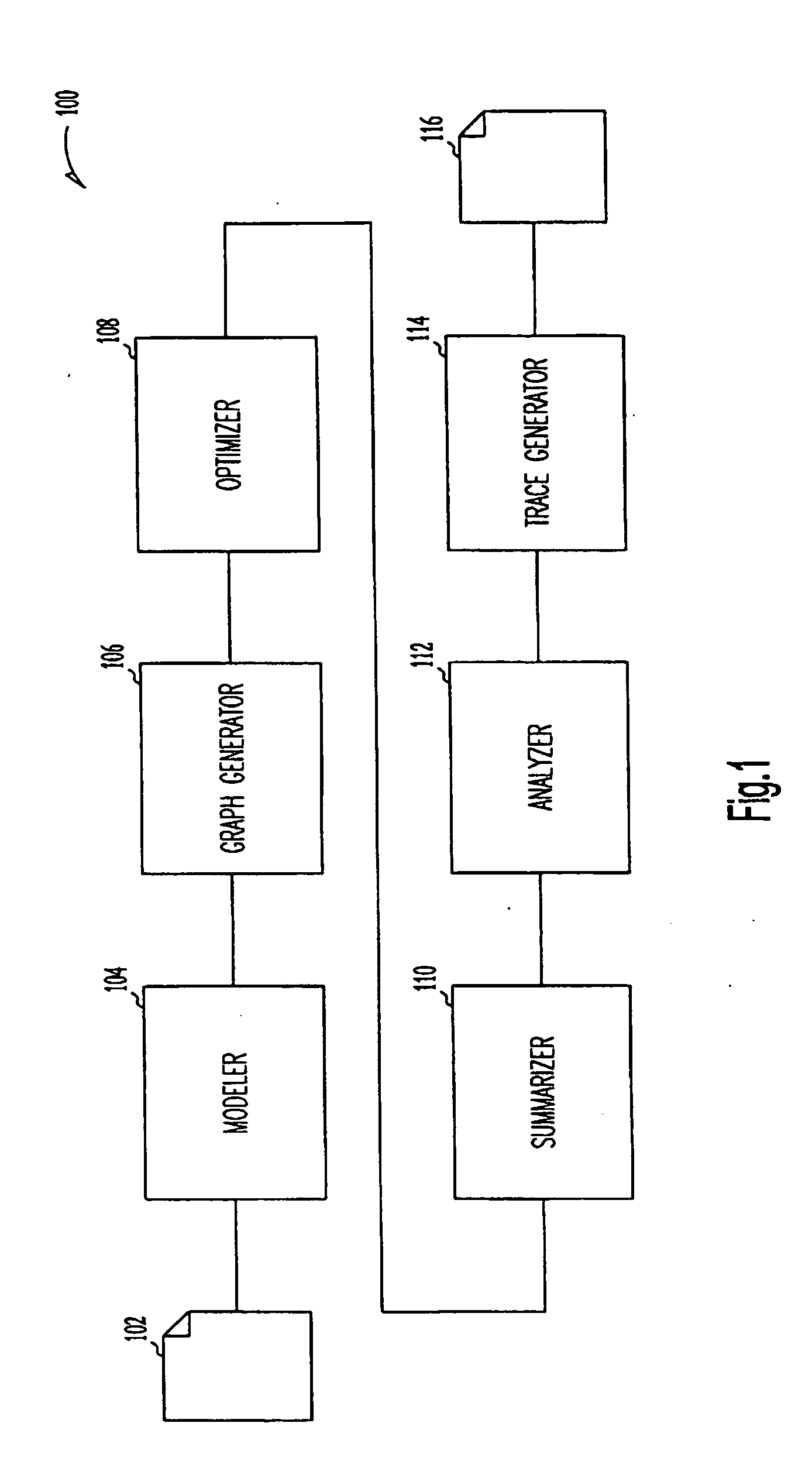
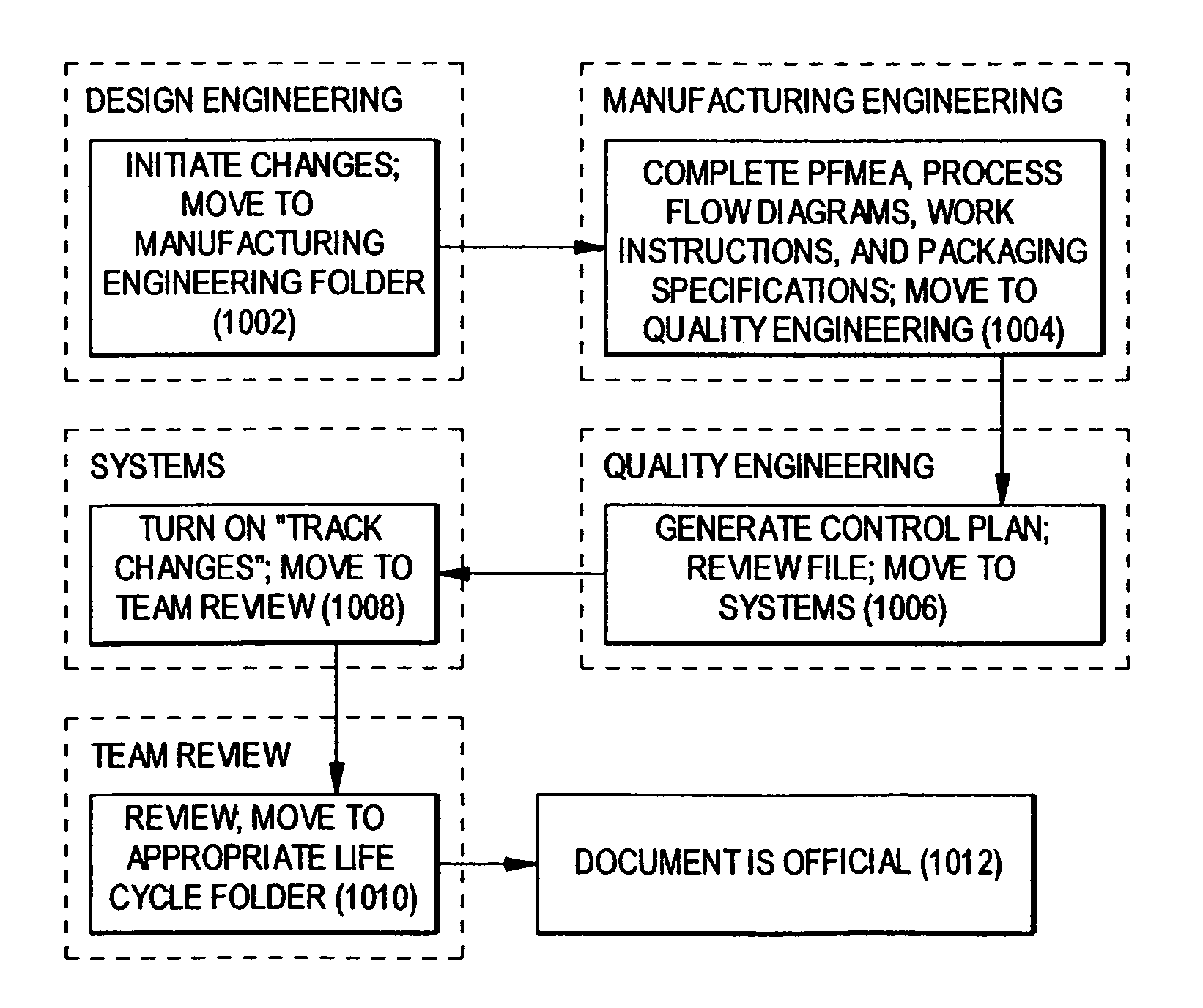
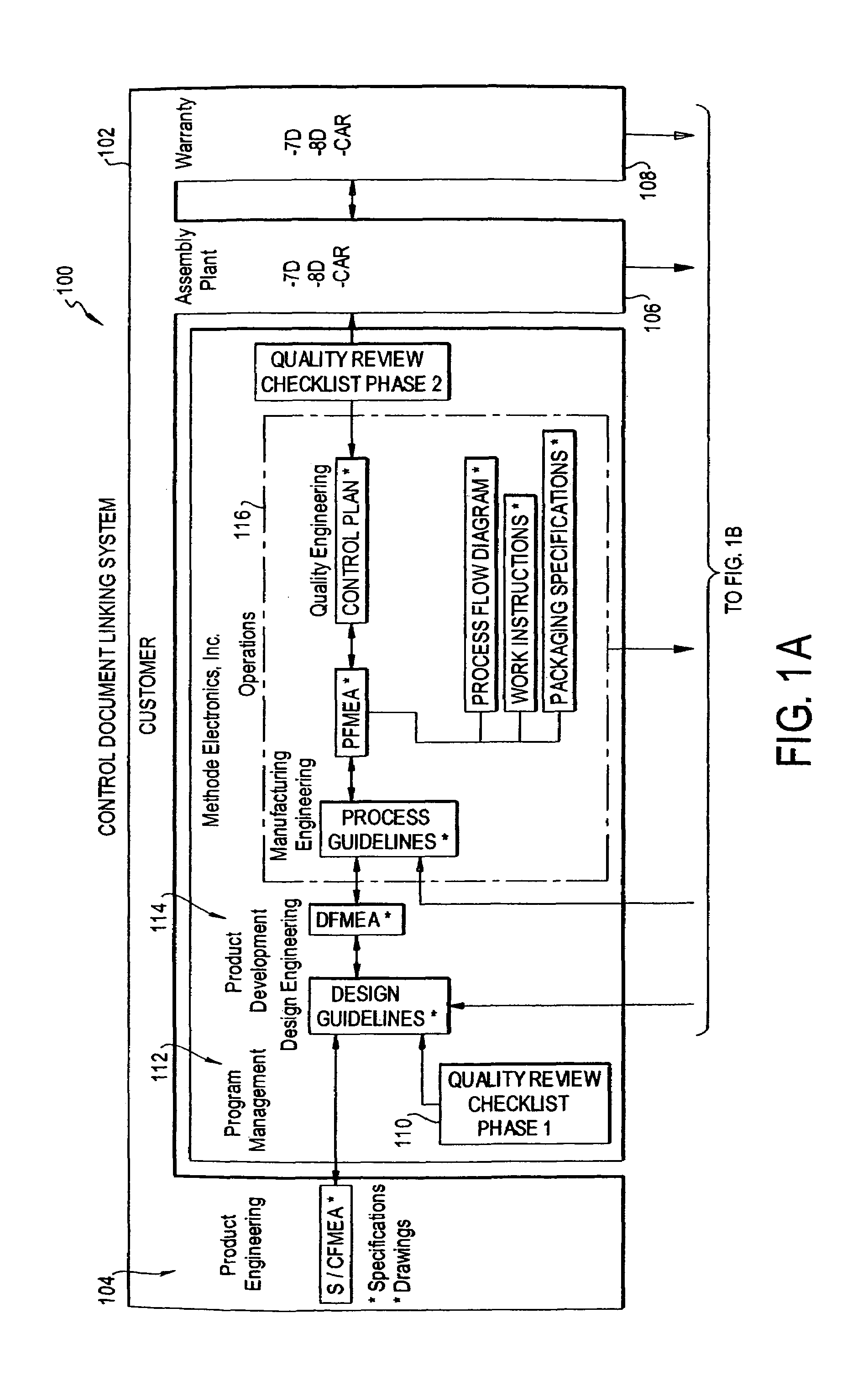
Design control document linking template
InactiveUS7096082B1Facilitate consistent entryWork lessFinanceAnimal feeding devicesOriginal dataElectronic form
A control document template streamlines the creation of control documents and facilitates consistent entry of data. A multi-page spreadsheet file incorporates the design and process failure mode effects analysis pages, the control plan, tools for forming the process flow diagram, the work instructions, and the packaging specifications. A macro sorts the failure mode effects analysis pages by risk priority number without overwriting the original data.
Owner:METHODE ELETRONICS INC
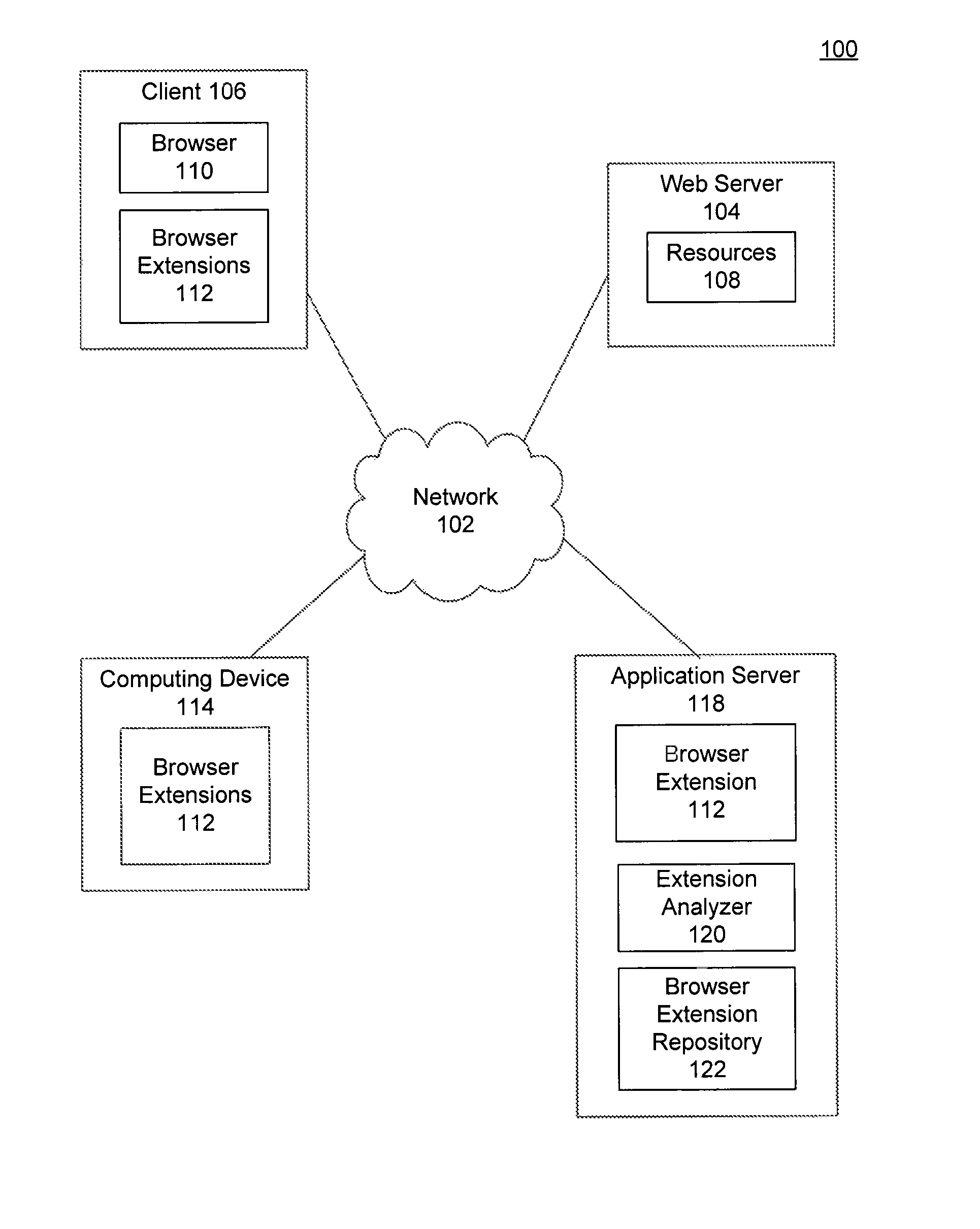
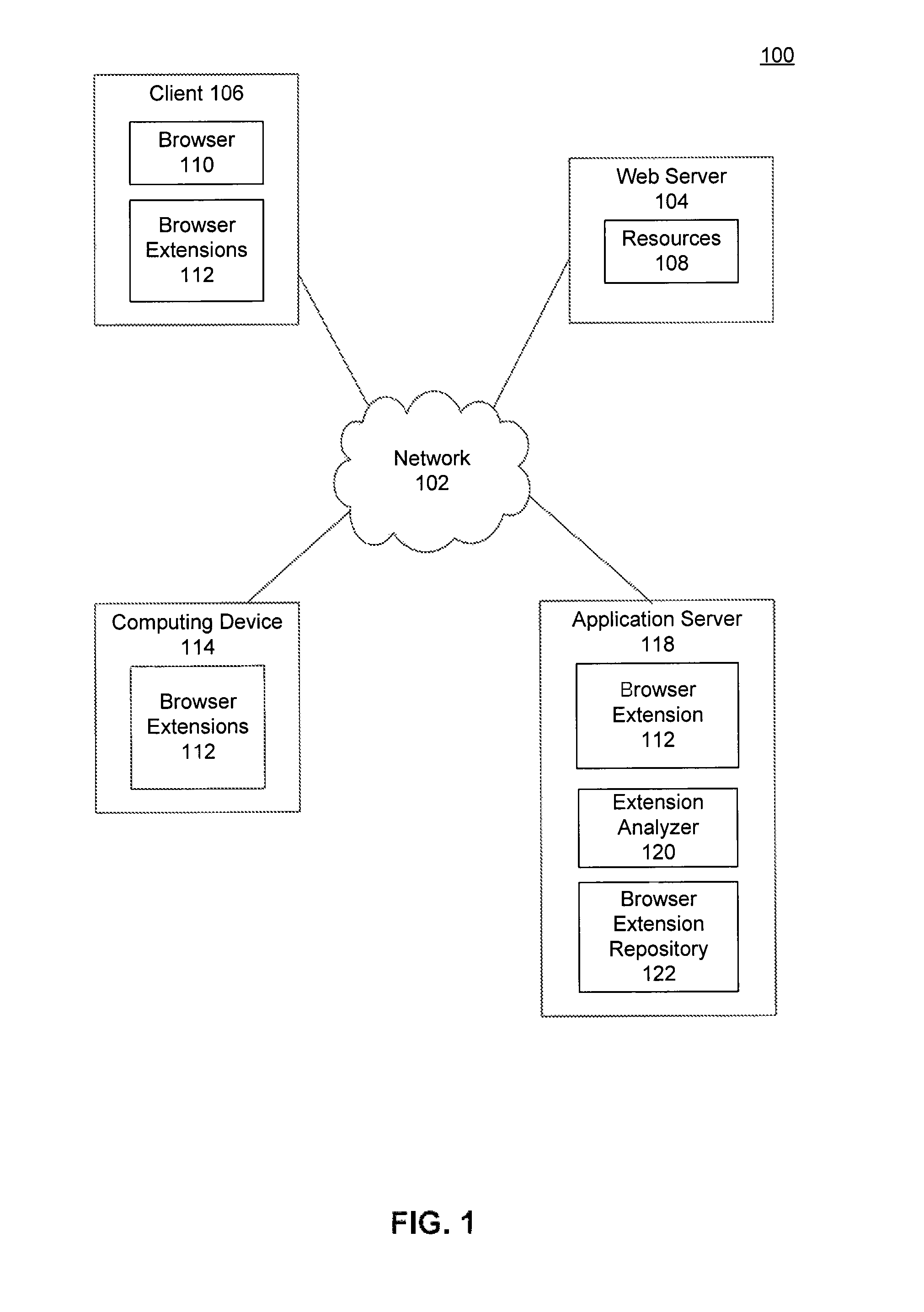
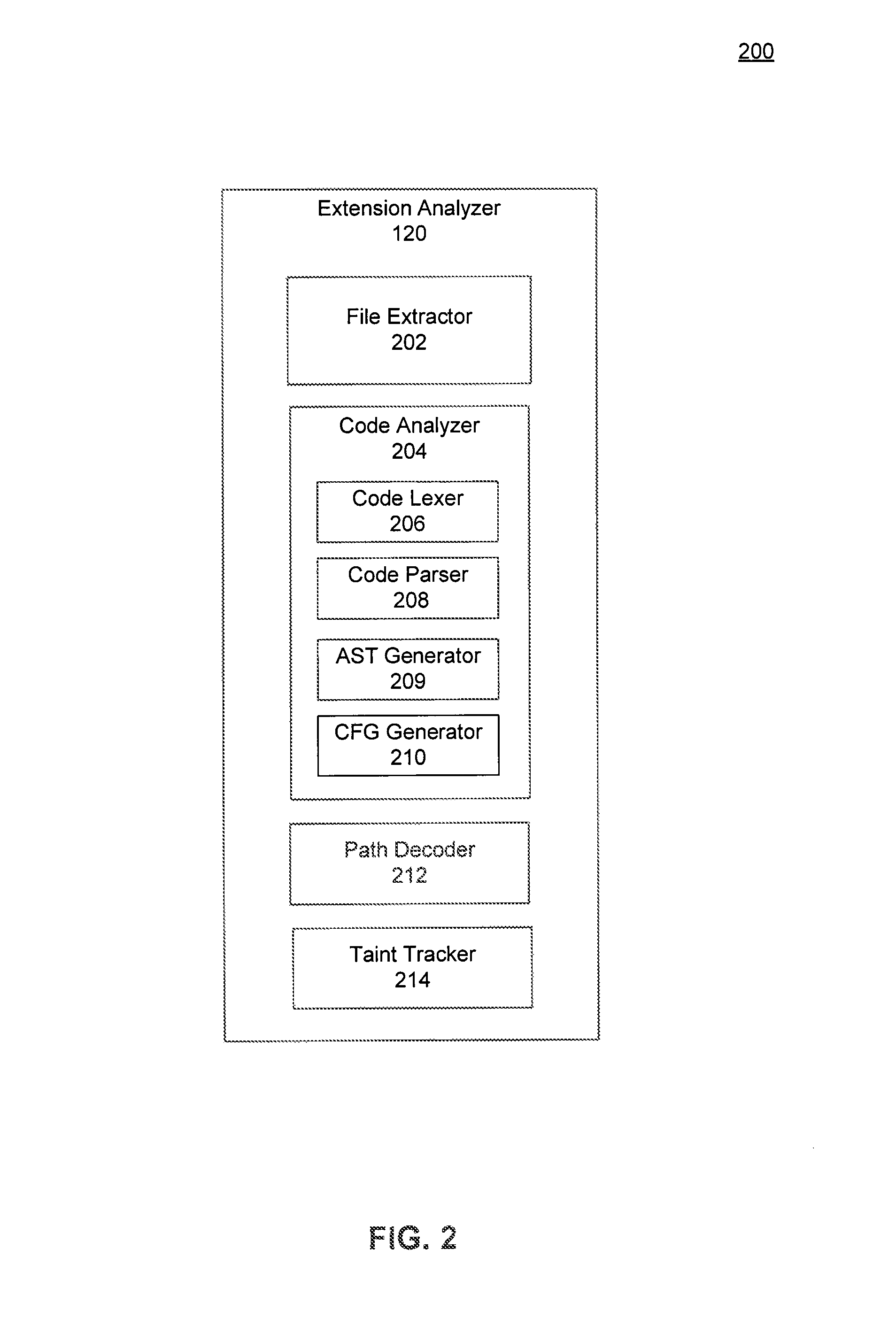
Browser extension control flow graph construction for determining sensitive paths
InactiveUS8286250B1Memory loss protectionError detection/correctionFlow sheetTheoretical computer science
A computer-implemented method, a system and a computer program product for determining whether a browser extension leaks information over a network, is provided. A control flow graph (CFG) is generated from a source code included in the browser extension. The CFG is particular to the programming language included in the source code. A sensitive path in the CFG is determined. The sensitive path begins at a sensitive source node and ends at a sensitive end node. A set of tainted variables in the CFG are identified, where each tainted variable stores sensitive or personal information. A subset of tainted variables is generated where each tainted variable in the subset is included in the sensitive path. When a tainted variable in the subset is included in the sensitive end node, the browser extension is determined to leak information over the network.
Owner:GOOGLE LLC
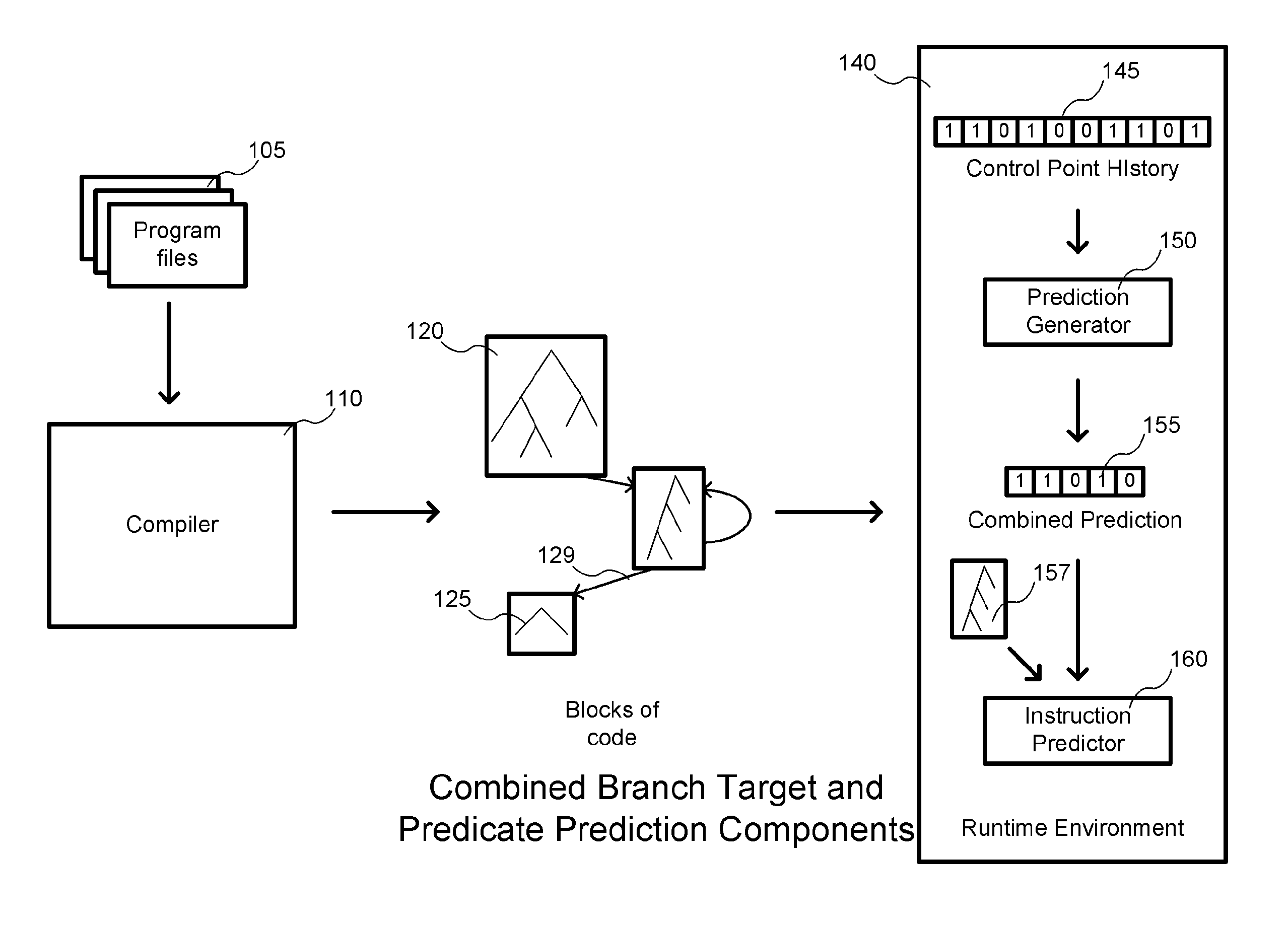
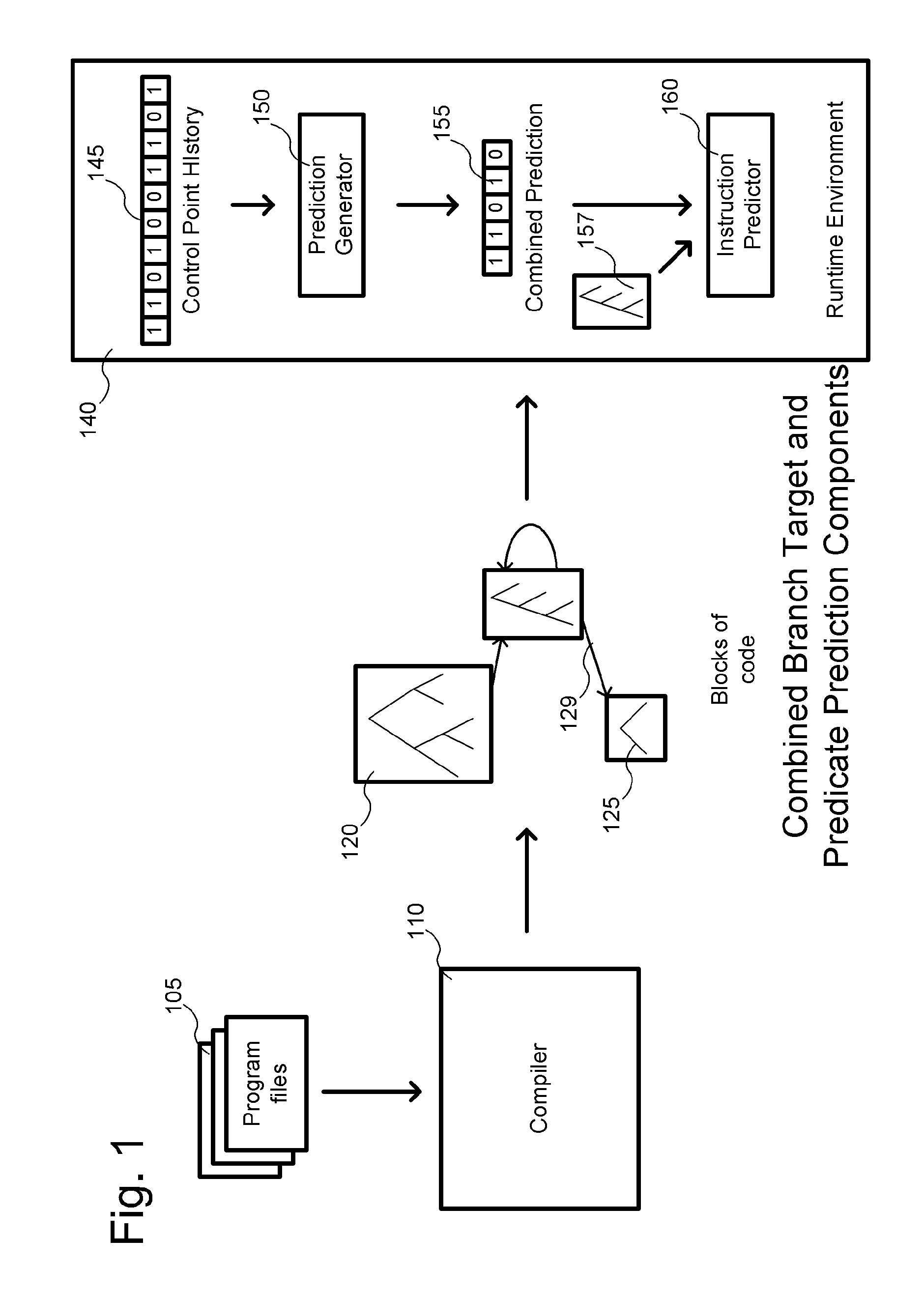
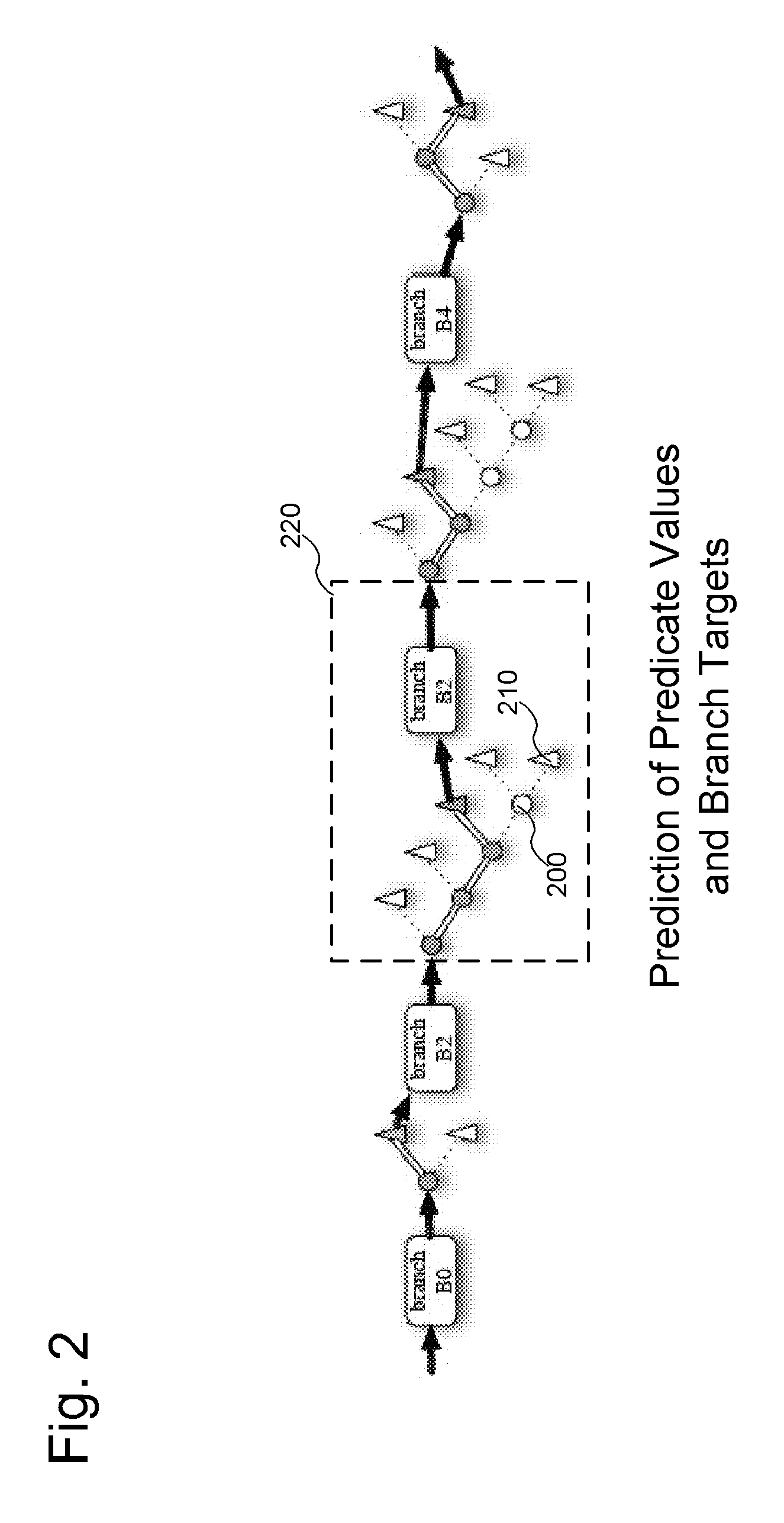
Combined branch target and predicate prediction for instruction blocks
Embodiments provide methods, apparatus, systems, and computer readable media associated with predicting predicates and branch targets during execution of programs using combined branch target and predicate predictions. The predictions may be made using one or more prediction control flow graphs which represent predicates in instruction blocks and branches between blocks in a program. The prediction control flow graphs may be structured as trees such that each node in the graphs is associated with a predicate instruction, and each leaf associated with a branch target which jumps to another block. During execution of a block, a prediction generator may take a control point history and generate a prediction. Following the path suggested by the prediction through the tree, both predicate values and branch targets may be predicted. Other embodiments may be described and claimed.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
Treatment of natural gas feeds
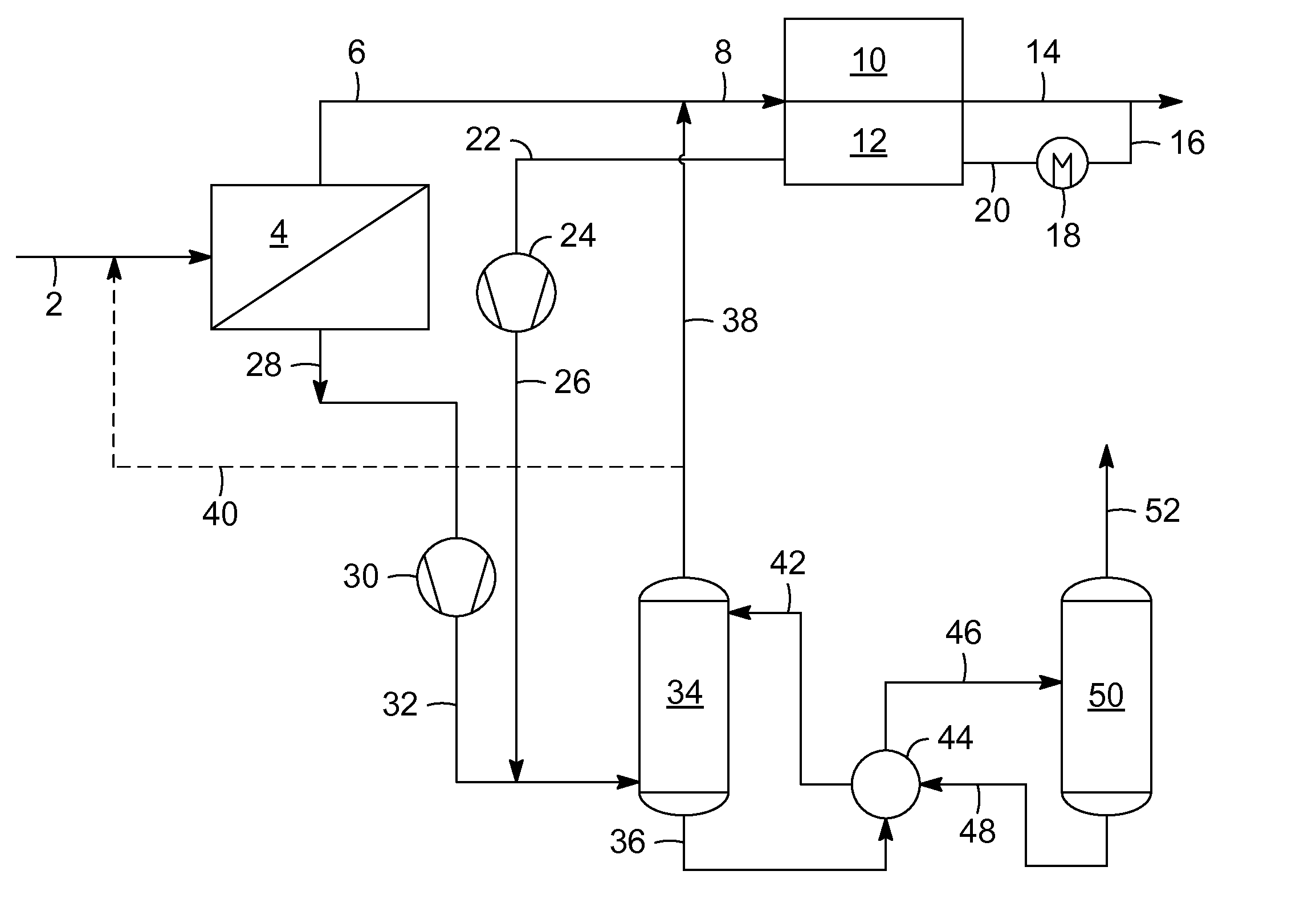
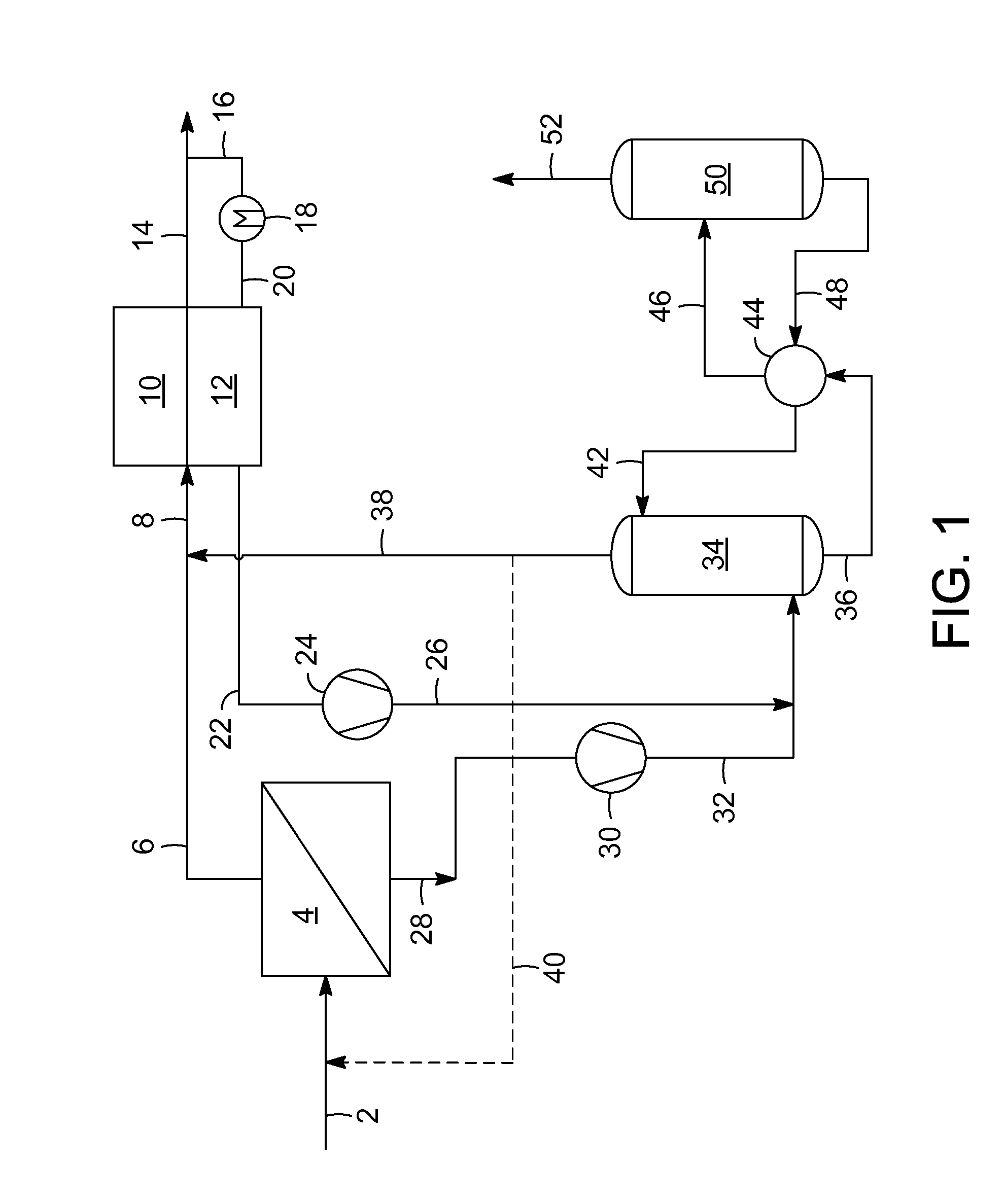
InactiveUS20110290111A1High carbon dioxide concentrationReduce concentrationMembranesGas treatmentHigh concentrationMolecular sieve
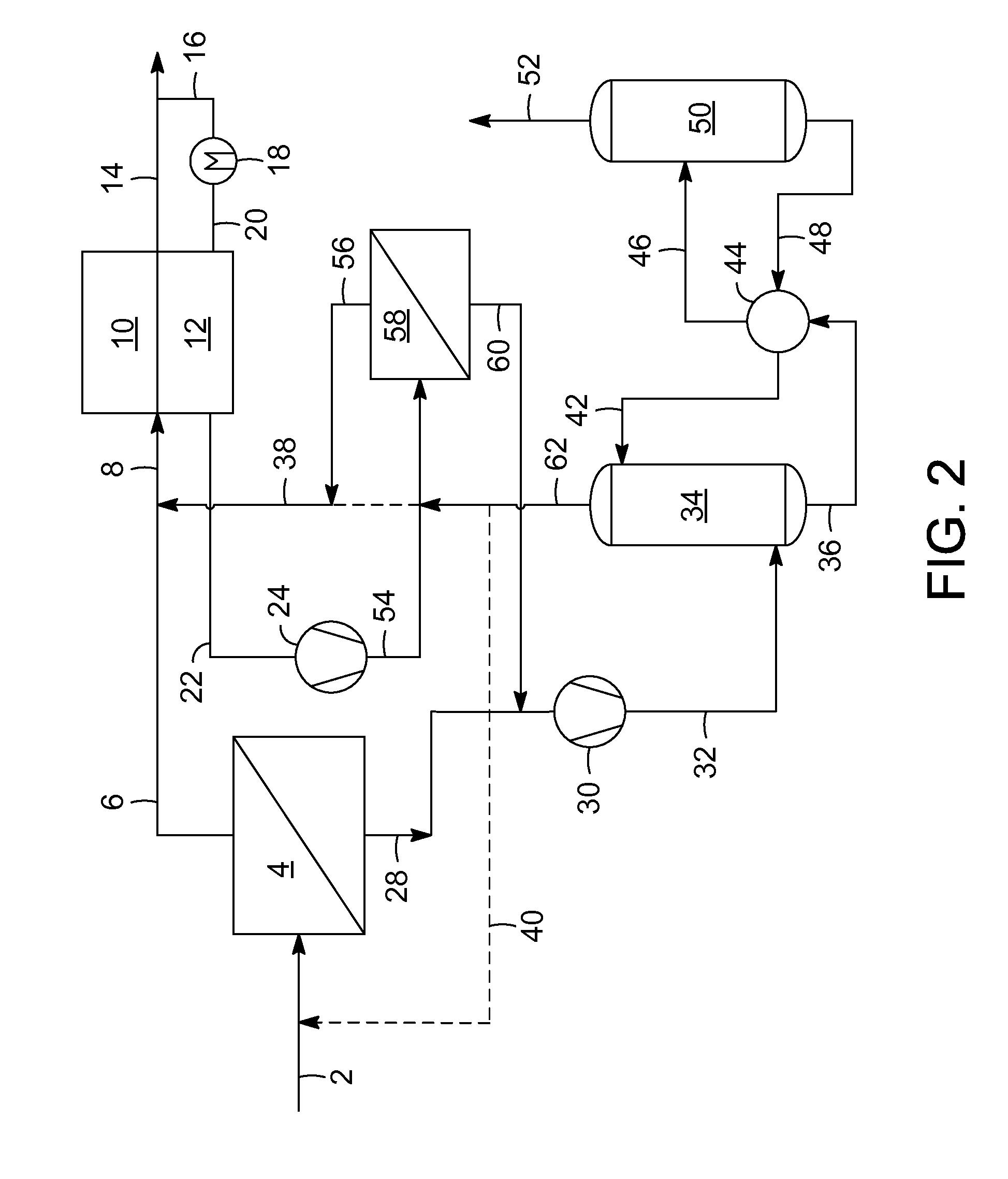
The present invention provides a process for treating a natural gas stream comprising sending a natural gas stream to at least one membrane unit to produce a permeate stream containing a higher concentration of carbon dioxide and a retentate stream containing a lower concentration of carbon dioxide. Then the retentate stream is sent to an adsorbent bed to remove carbon dioxide and other impurities to produce a natural gas product stream. The regeneration gas stream is sent through the molecular sieve adsorbent bed to desorb the carbon dioxide. In one process flow scheme, the regeneration stream is combined with the permeate stream from the membrane unit. Then the combined stream is sent to an absorbent column to remove carbon dioxide from the permeate stream to produce a second natural gas product stream. In the alternative flow scheme, a second membrane unit is used to improve efficiency.
Owner:UOP LLC
Method of tracing back the execution path in a debugger
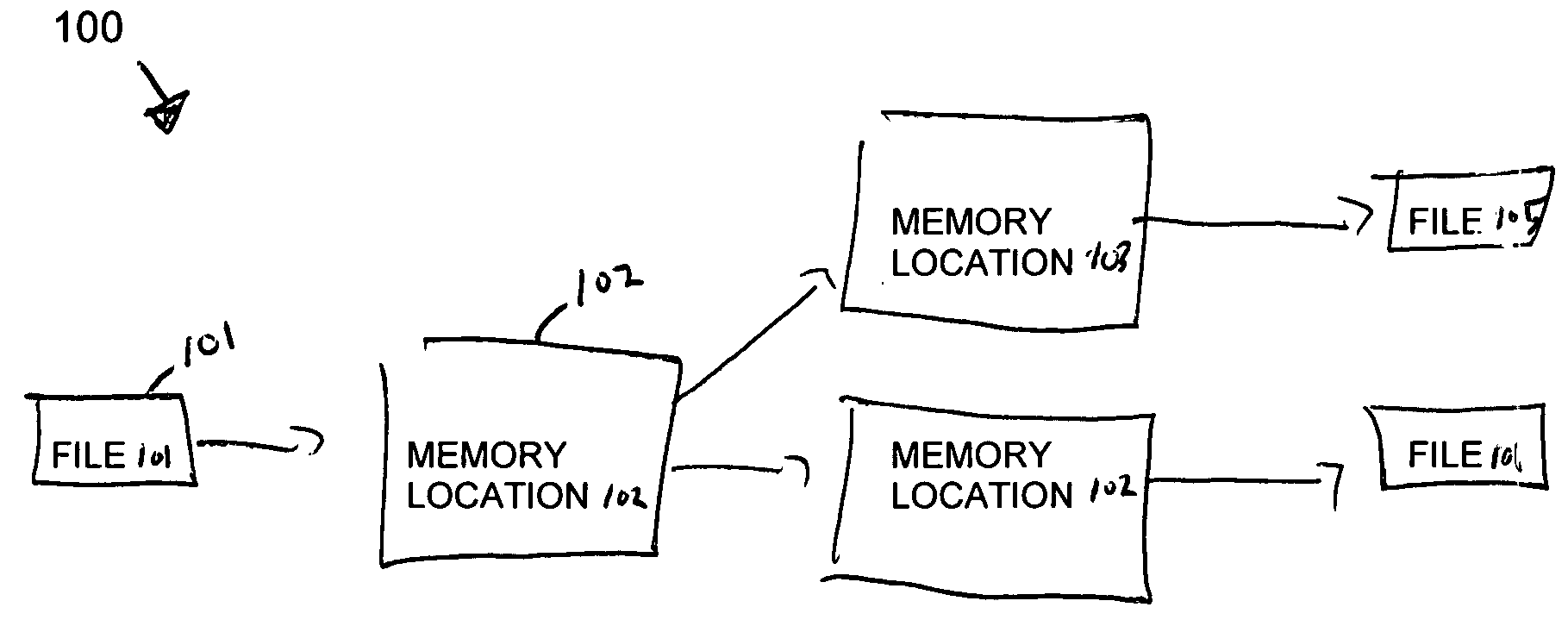
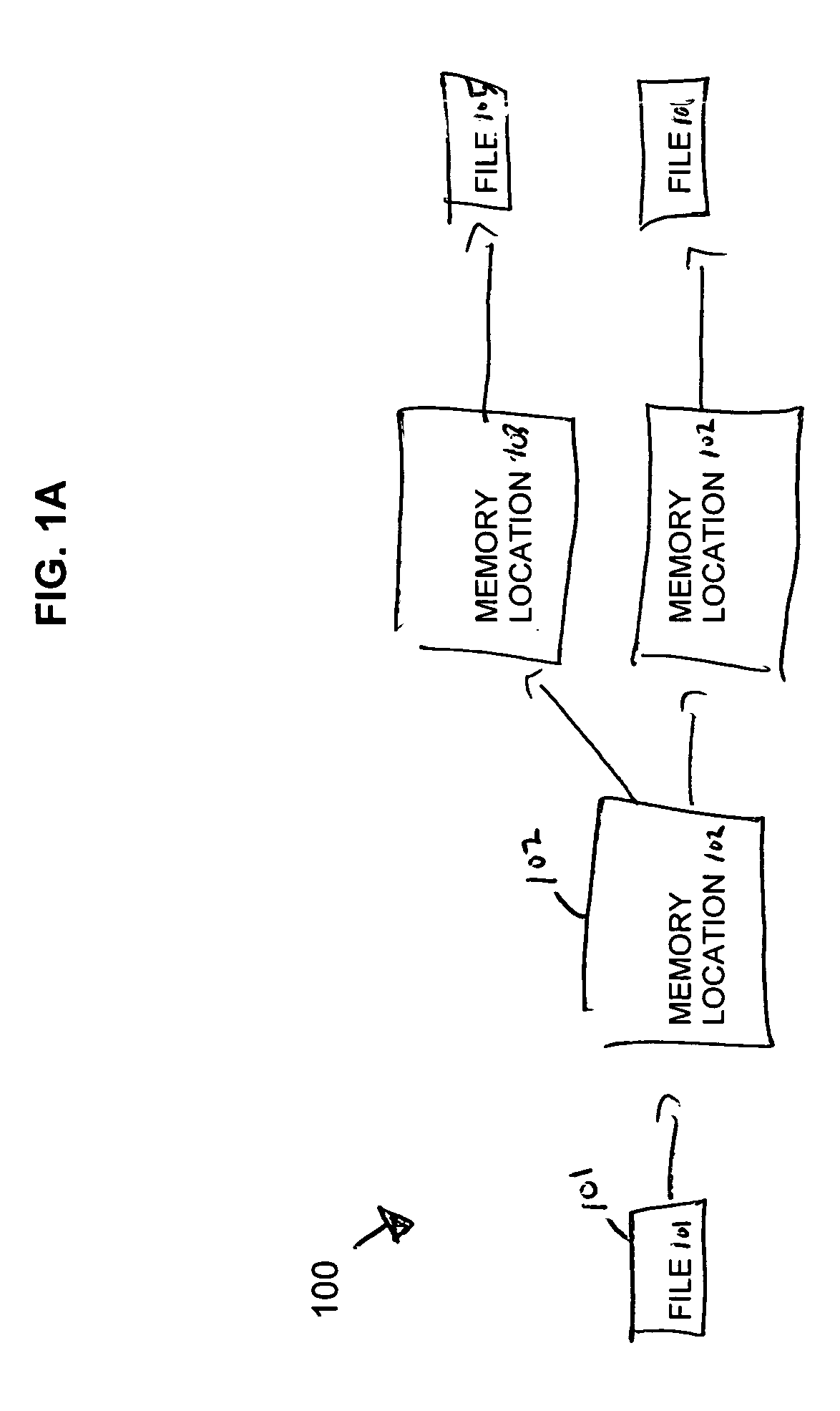
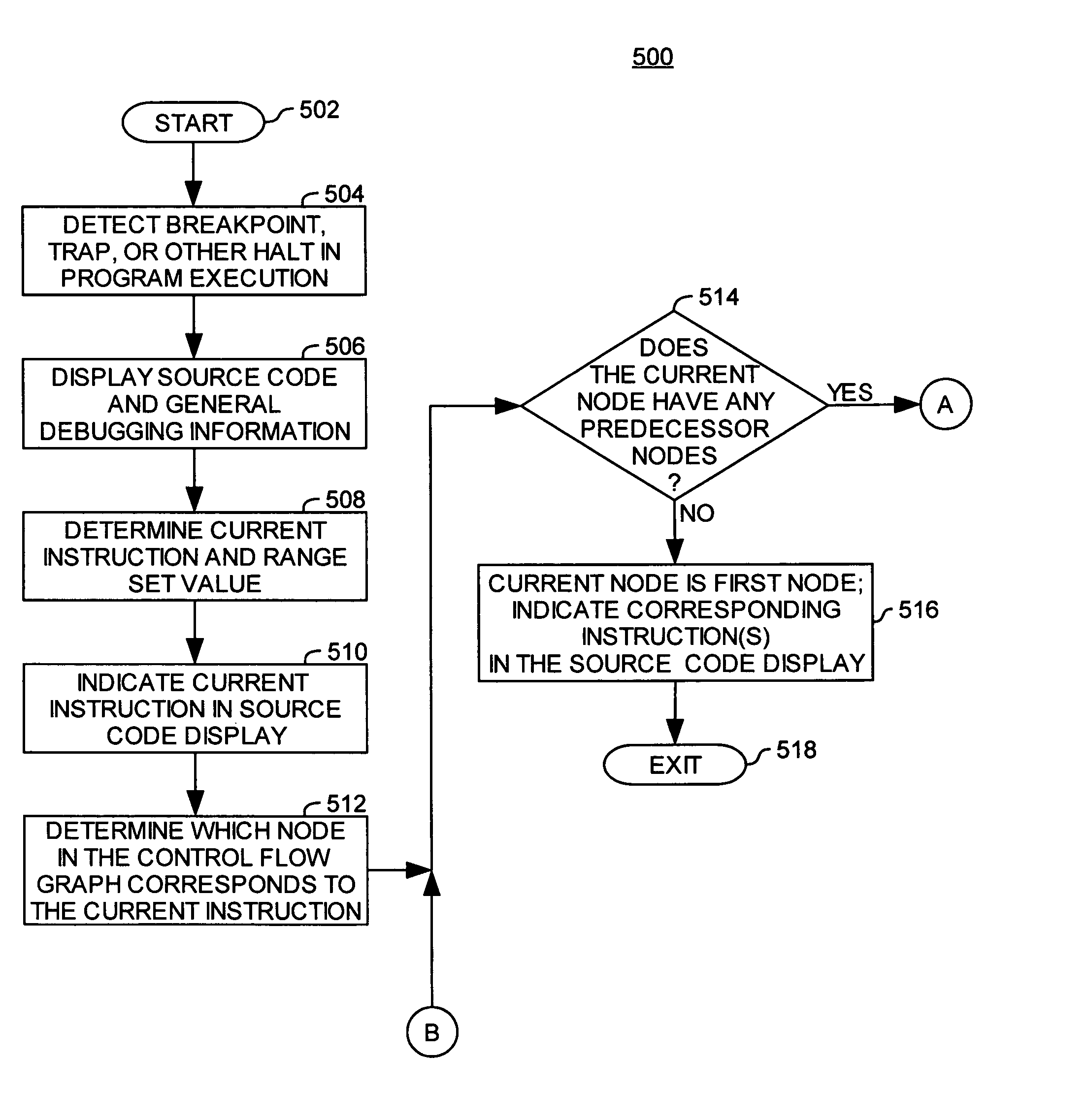
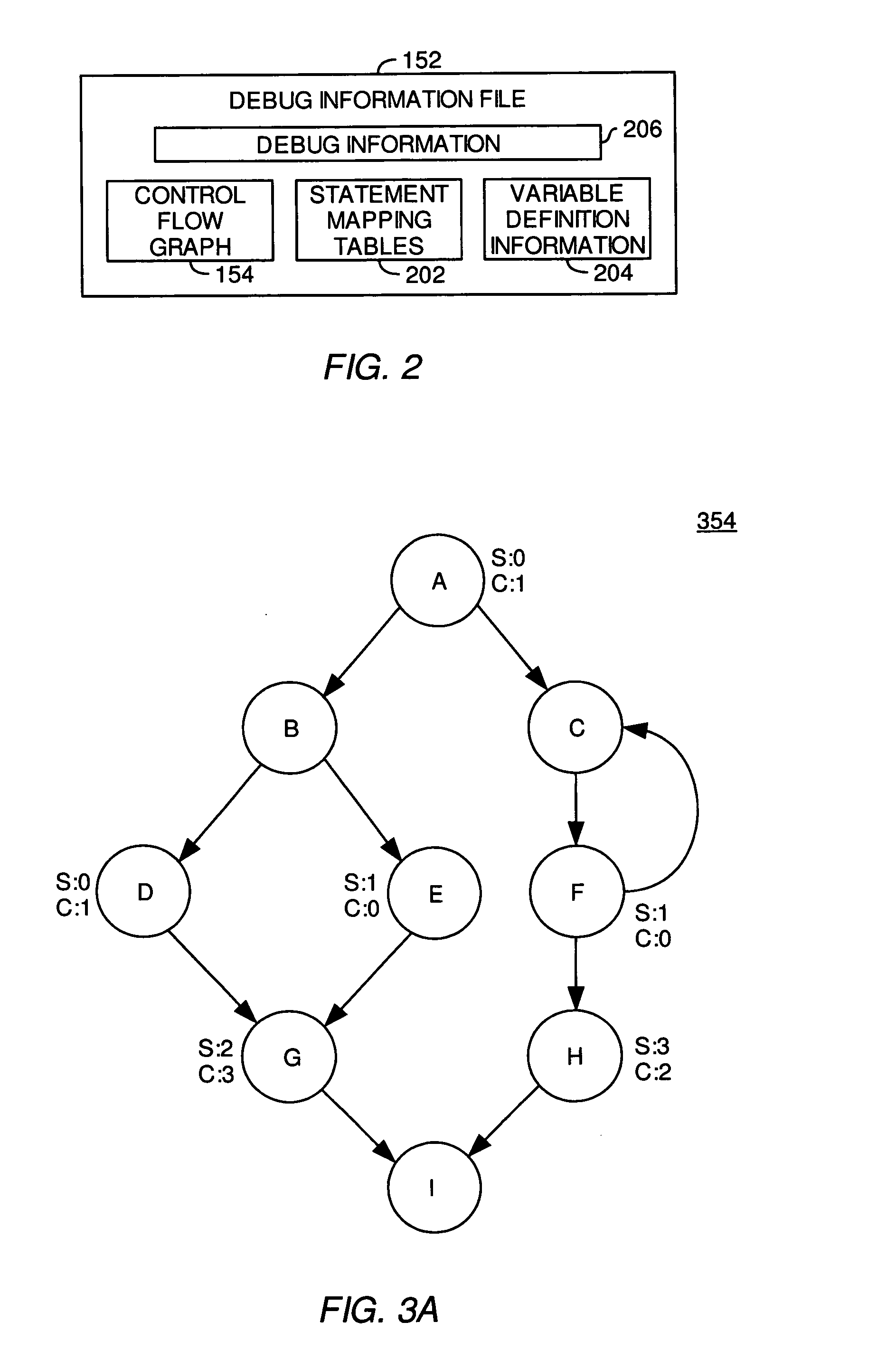
InactiveUS20070168992A1Error detection/correctionSpecific program execution arrangementsParallel computingFlow sheet
A method, computer-readable medium, and system for tracing the execution path of a program are provided. In one embodiment, a control flow graph is created for the program. For each node in the control flow graph, a determination is made of whether the node has two or more predecessor nodes. For each node determined to have two or more predecessor nodes, a set instruction is inserted into program code corresponding to the predecessor node which sets a corresponding value of a variable. The corresponding value of the variable indicates that one or more instructions in the predecessor node were executed during an execution of the program.
Owner:IBM CORP
Identity management system and method
InactiveUS20070233531A1Easy to manageTransmissionSpecial data processing applicationsFlow sheetKnowledge management
According to one embodiment, a method for implementing an identity management system for an organization includes developing a process flow diagram, the process flow diagram including one or more icons representing at least one process step for each of the events included in an event group and one or more icons representing at least one process step for each of the functional entities in an entity group, and implementing at least one of the process steps represented in the process flow diagram. The event group includes a status change for a system user, a request for an audit report, and an implementation of a new software application. The entity group includes a human resources department, an information technologies department, and a facilities department.
Owner:CA TECH INC
Methods, apparatus and programs for system development
InactiveUS20050137839A1Facilitates generating an accurate executable model of the systemAnalogue computers for electric apparatusRequirement analysisEvent flow graphPhysical entity
A method and apparatus for generating a model of a system, in which the system comprises a plurality of physical entities capable of performing interactions between each other. The method comprises receiving an interaction-based specification of the system defining interactions between the plurality of physical entities; dividing the interaction-based specification into a plurality of interaction sections; and generating a model defining each interaction section and its possible continuing interaction sections. An event flow diagram is generated from the model from which an executable model of the system can be automatically obtained.
Owner:KLOCWORK CORP
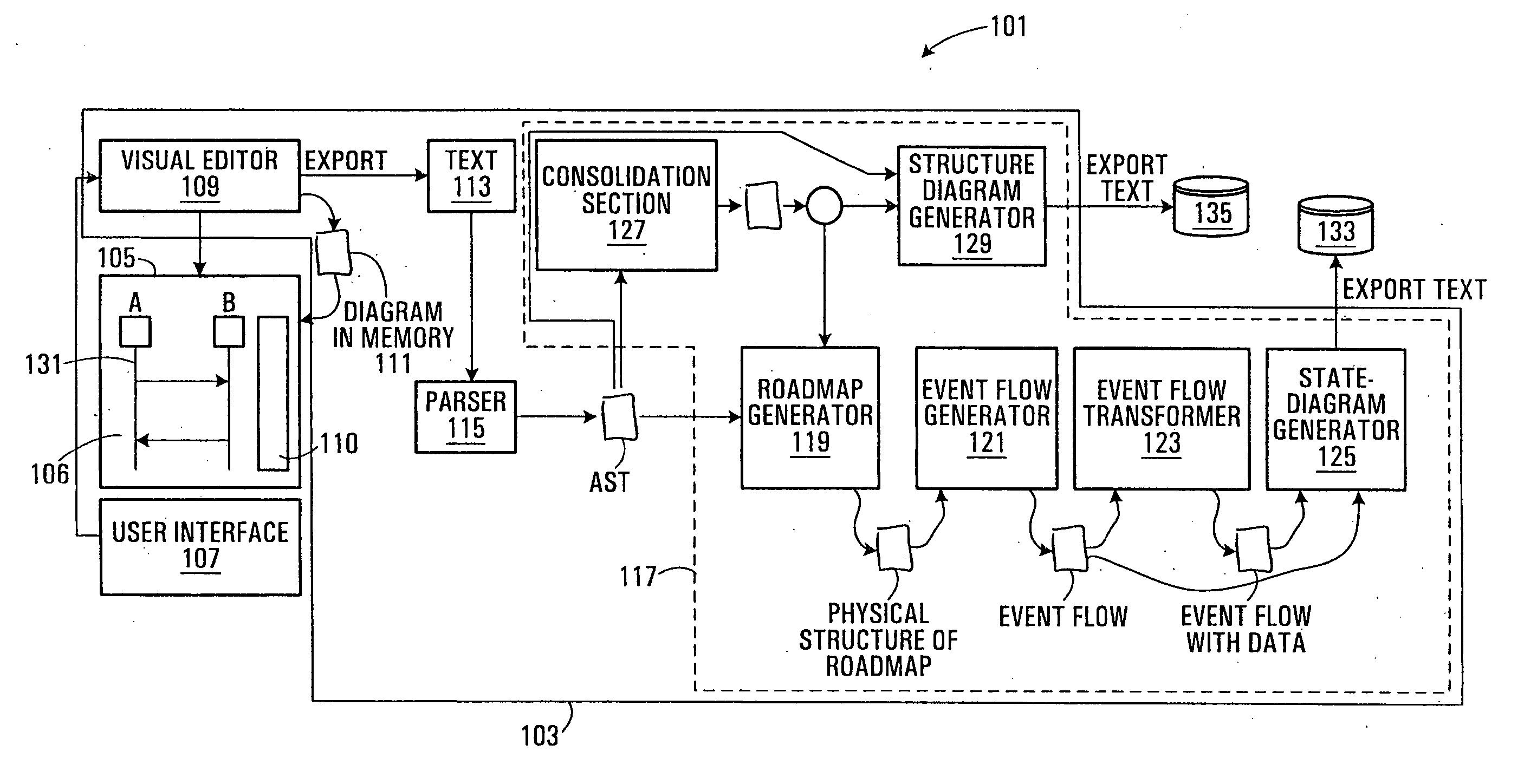
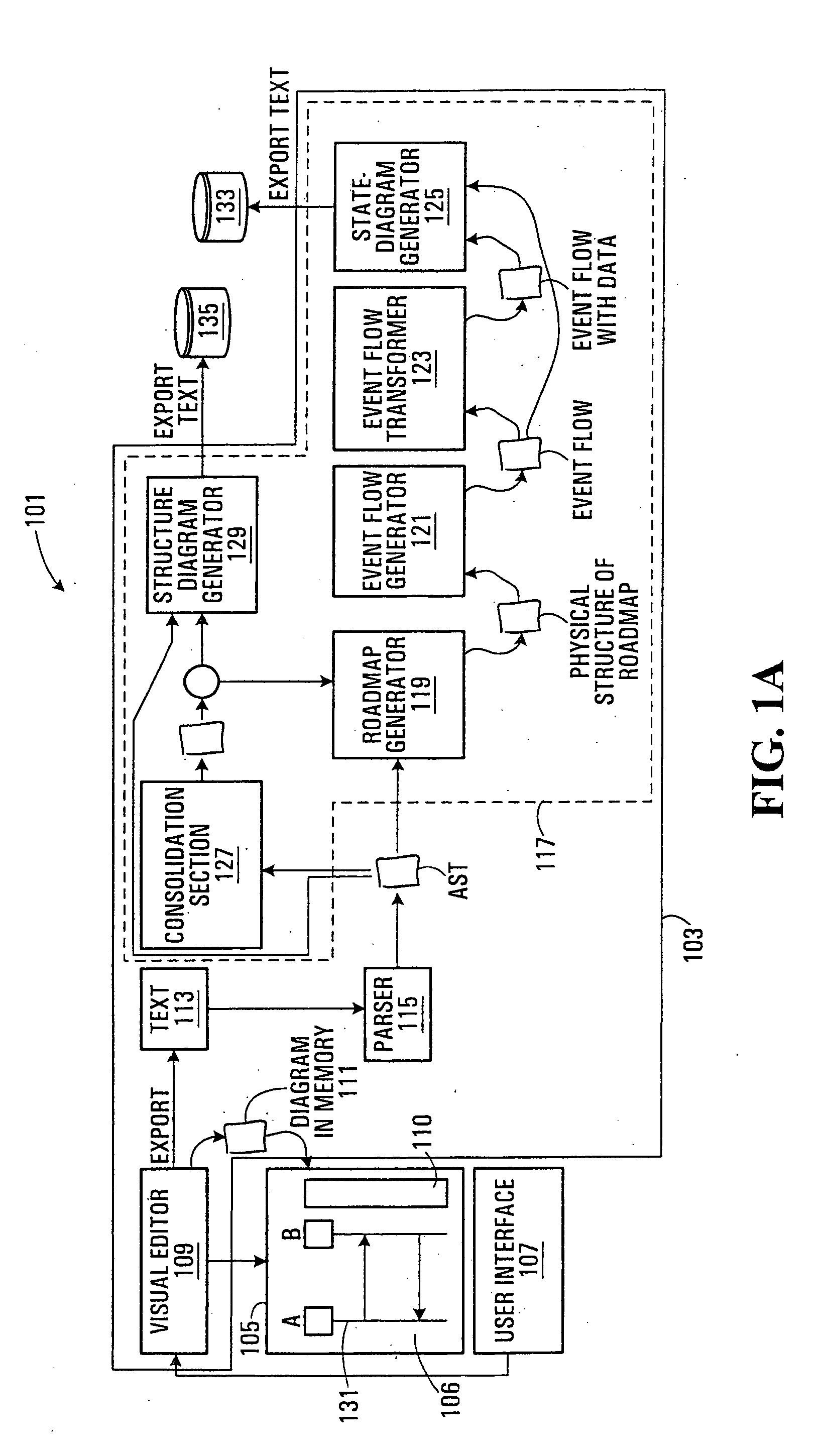
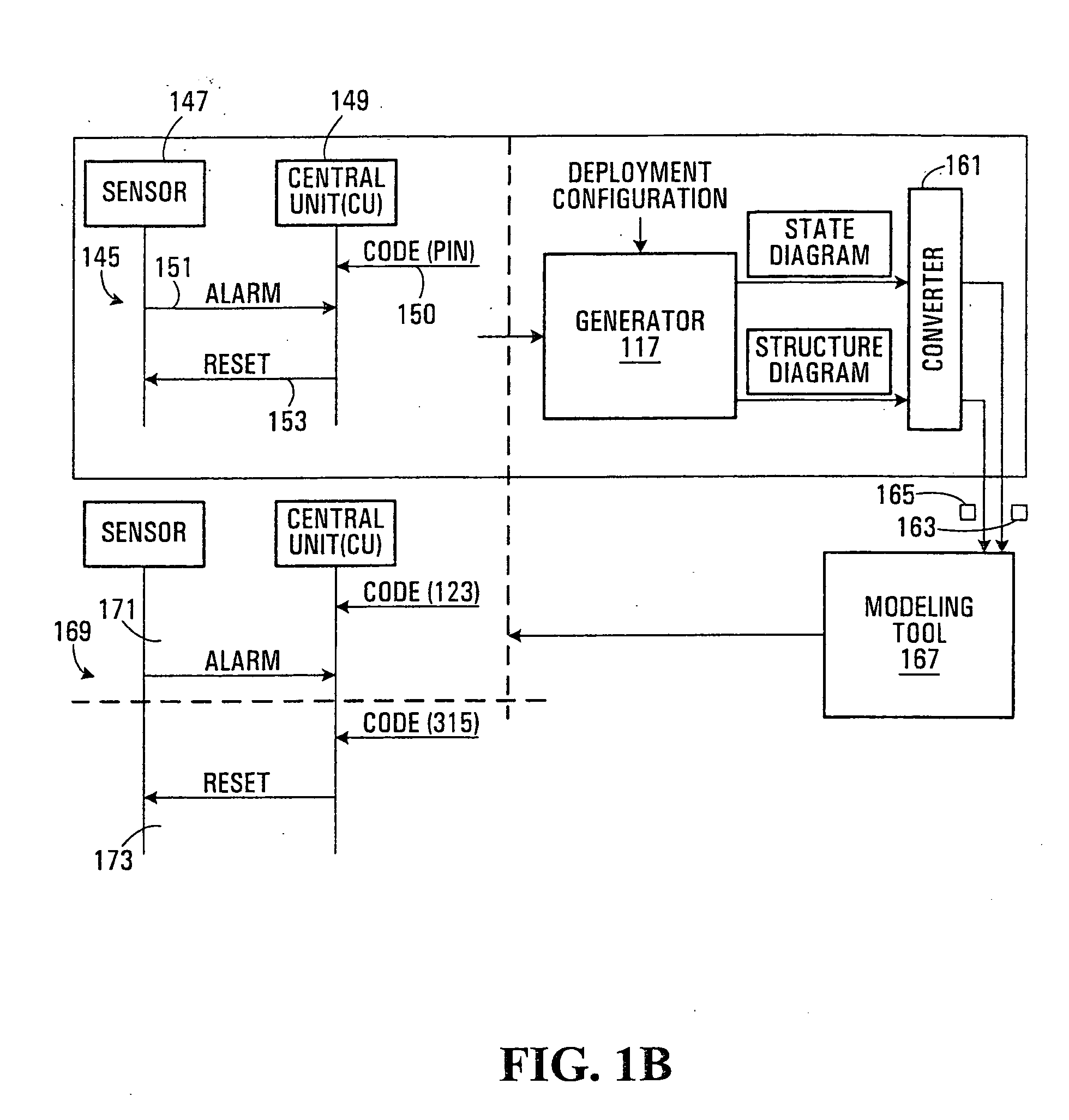
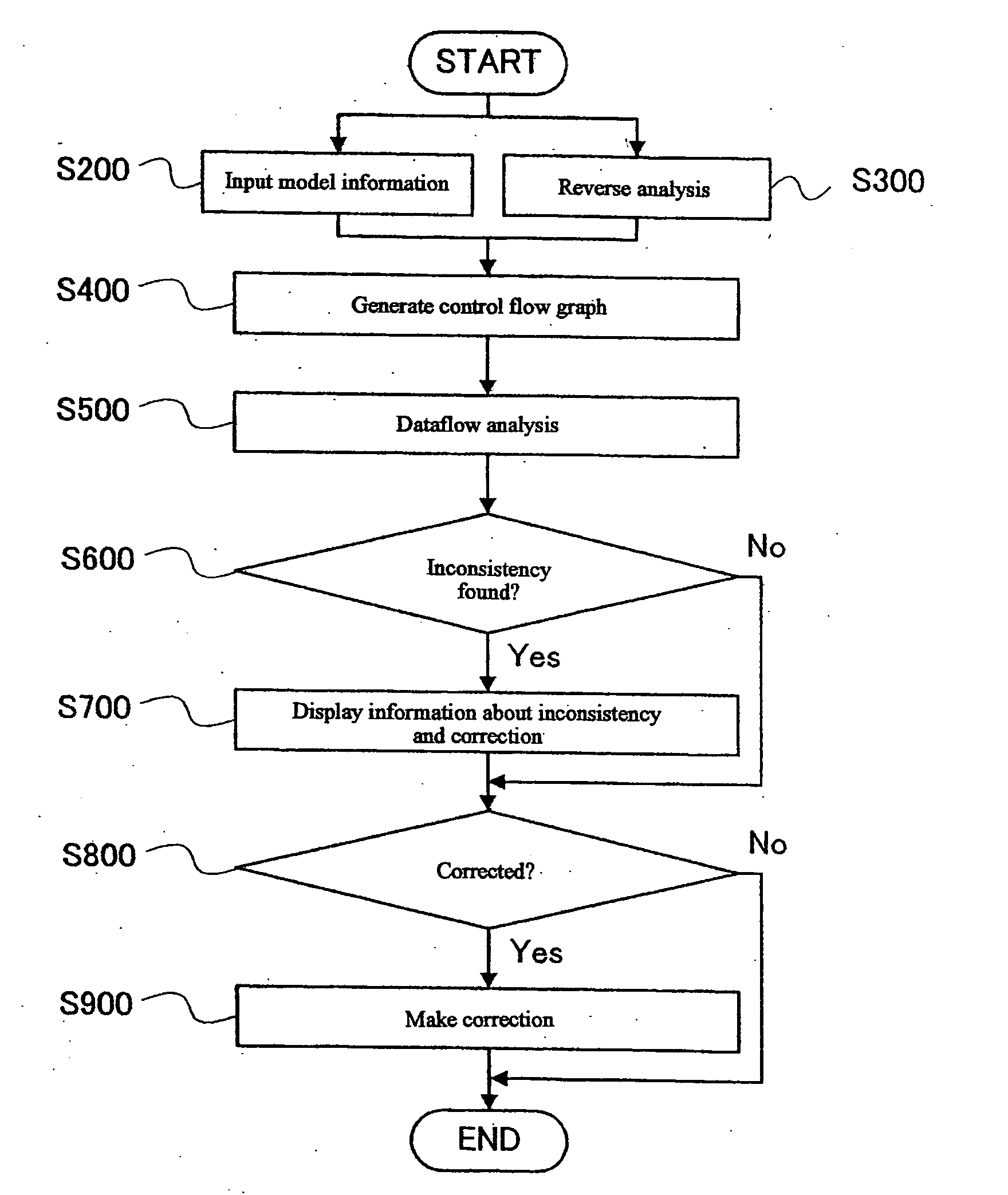
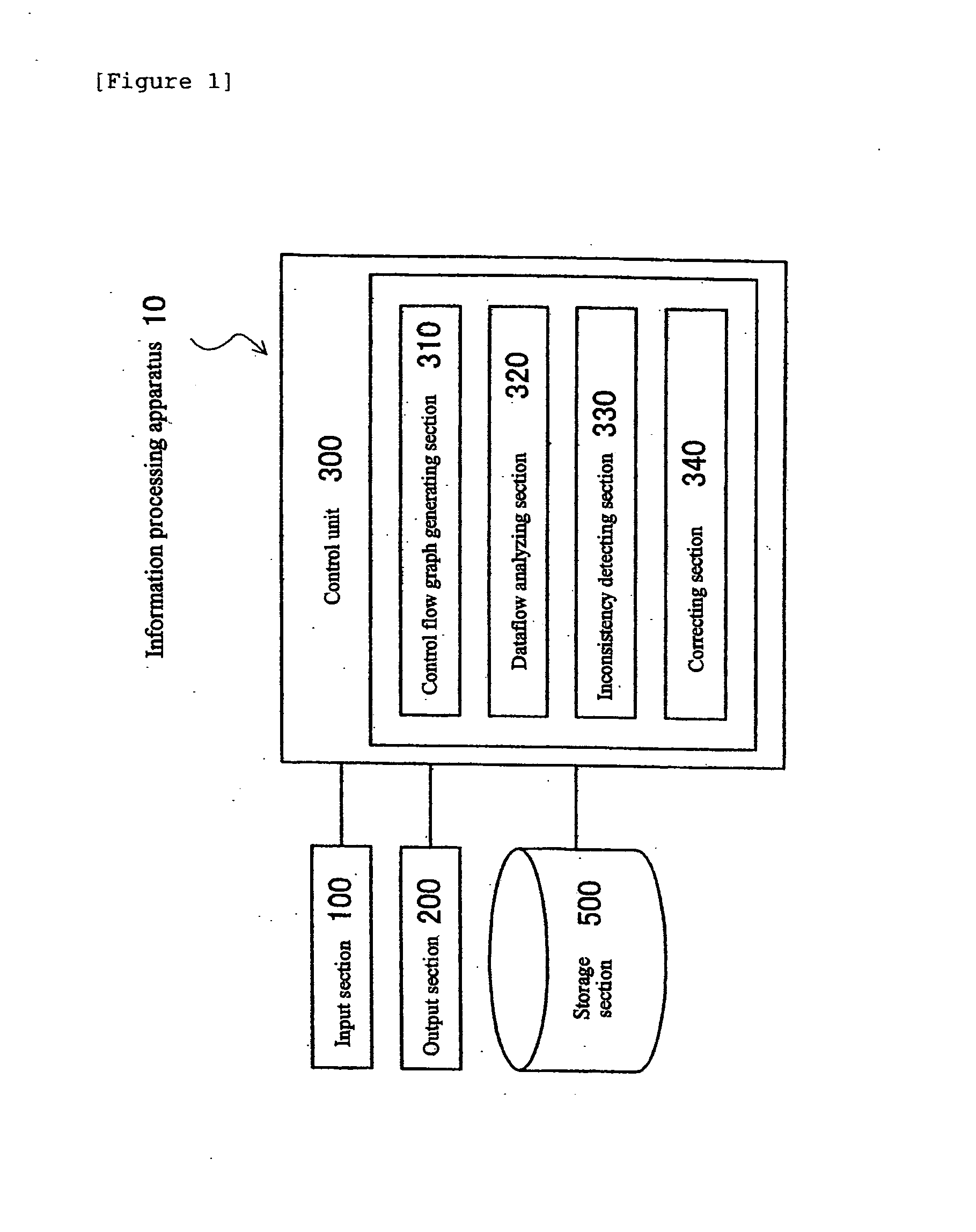
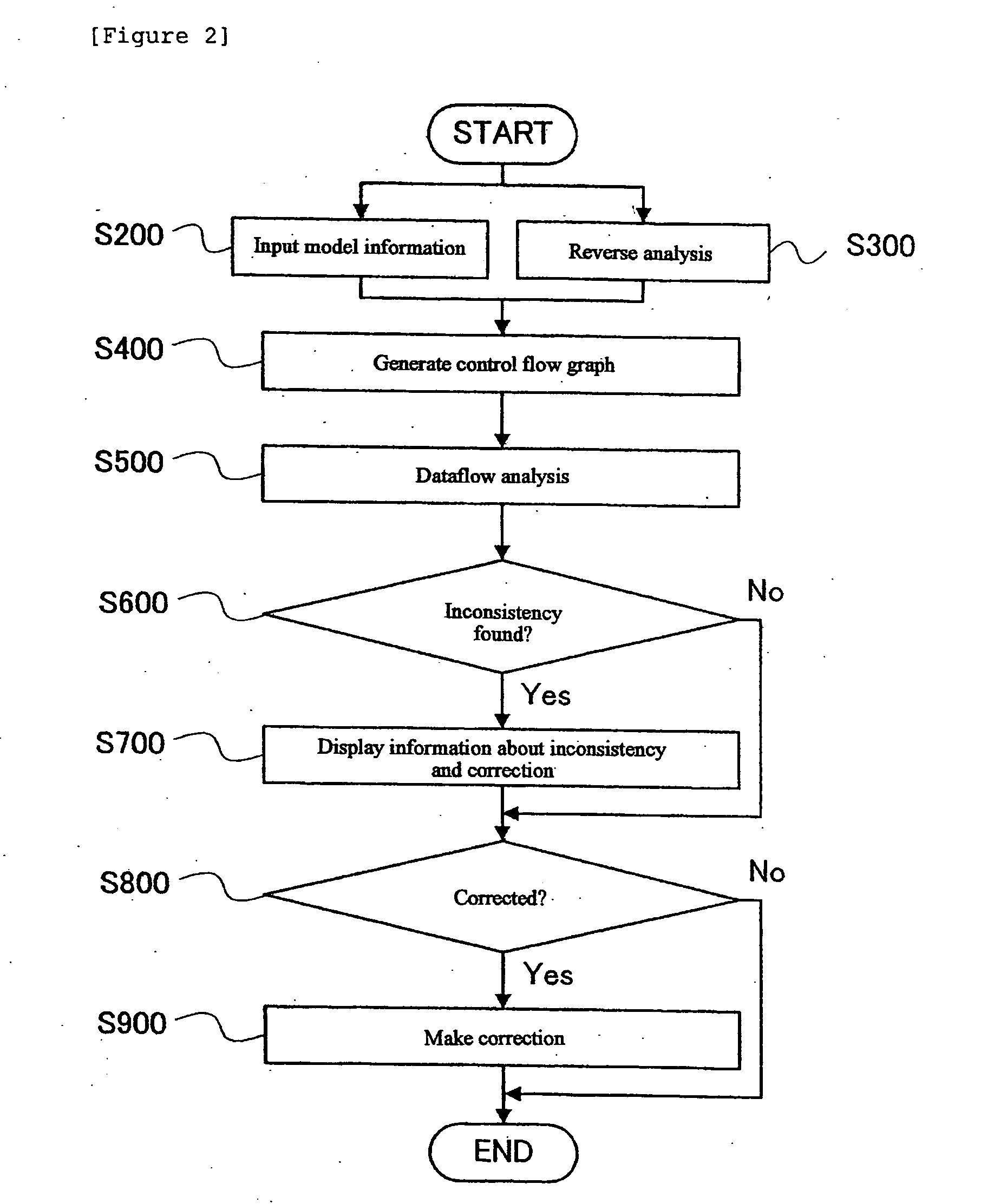
Application program development assisting method, program, and information processing apparatus
ActiveUS20090183141A1Frequency of occurrence of seriousReduce development costsError detection/correctionSpecific program execution arrangementsInformation processingData stream
A method, program, and information processing apparatus for detecting an inconsistency in an application program before the application program is implemented. The described is detecting a consistency or inconsistency in the design of screen transition of an application program, by generating a control flow graph for the application program, calculating from the control flow graph the solution of dataflow problem which occurs in the application program, detecting an inconsistency in the application program on the basis of the calculated solution, and displaying information concerning a detected inconsistency.
Owner:WRP IP MANAGEMENT LLC
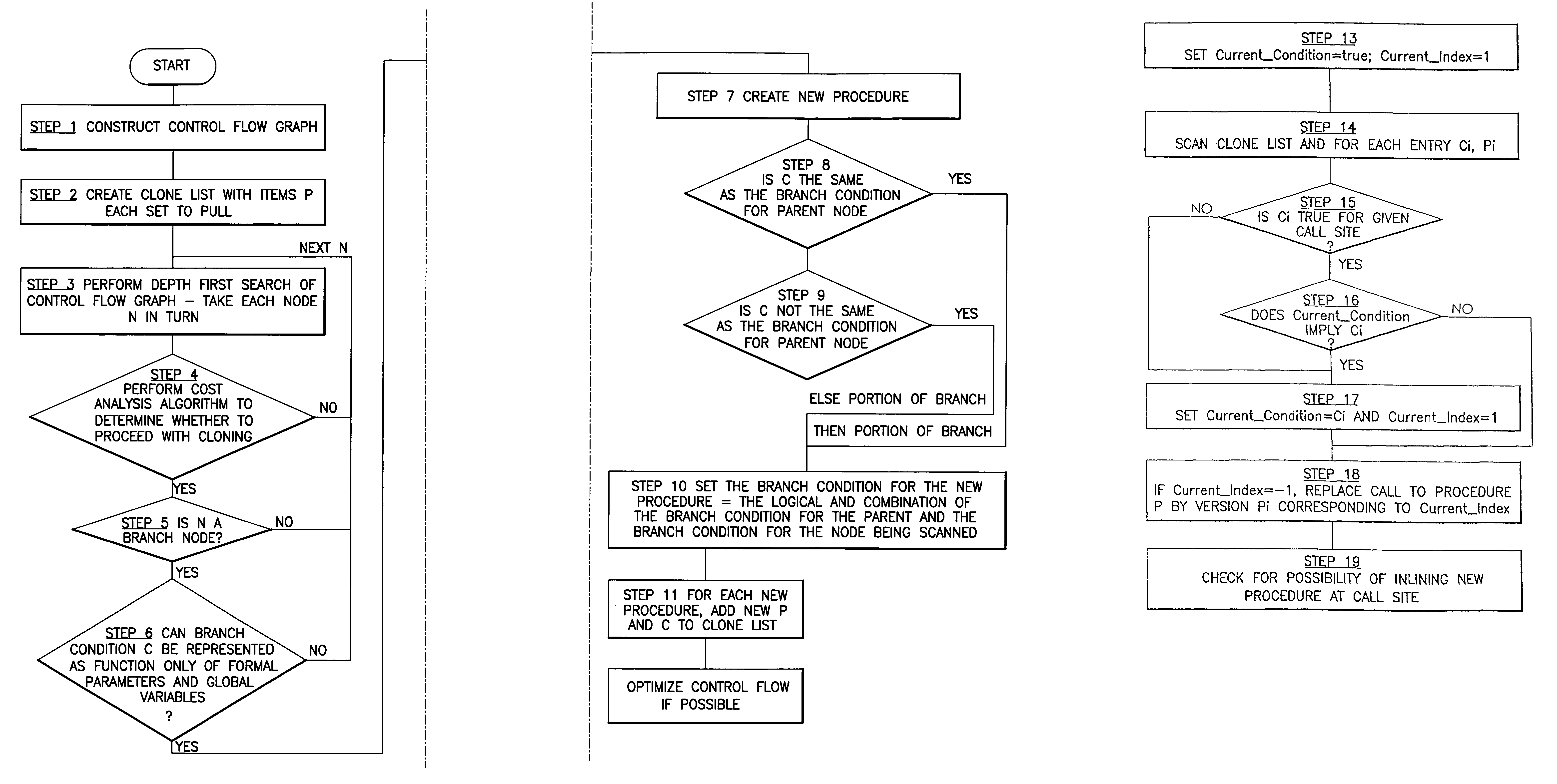
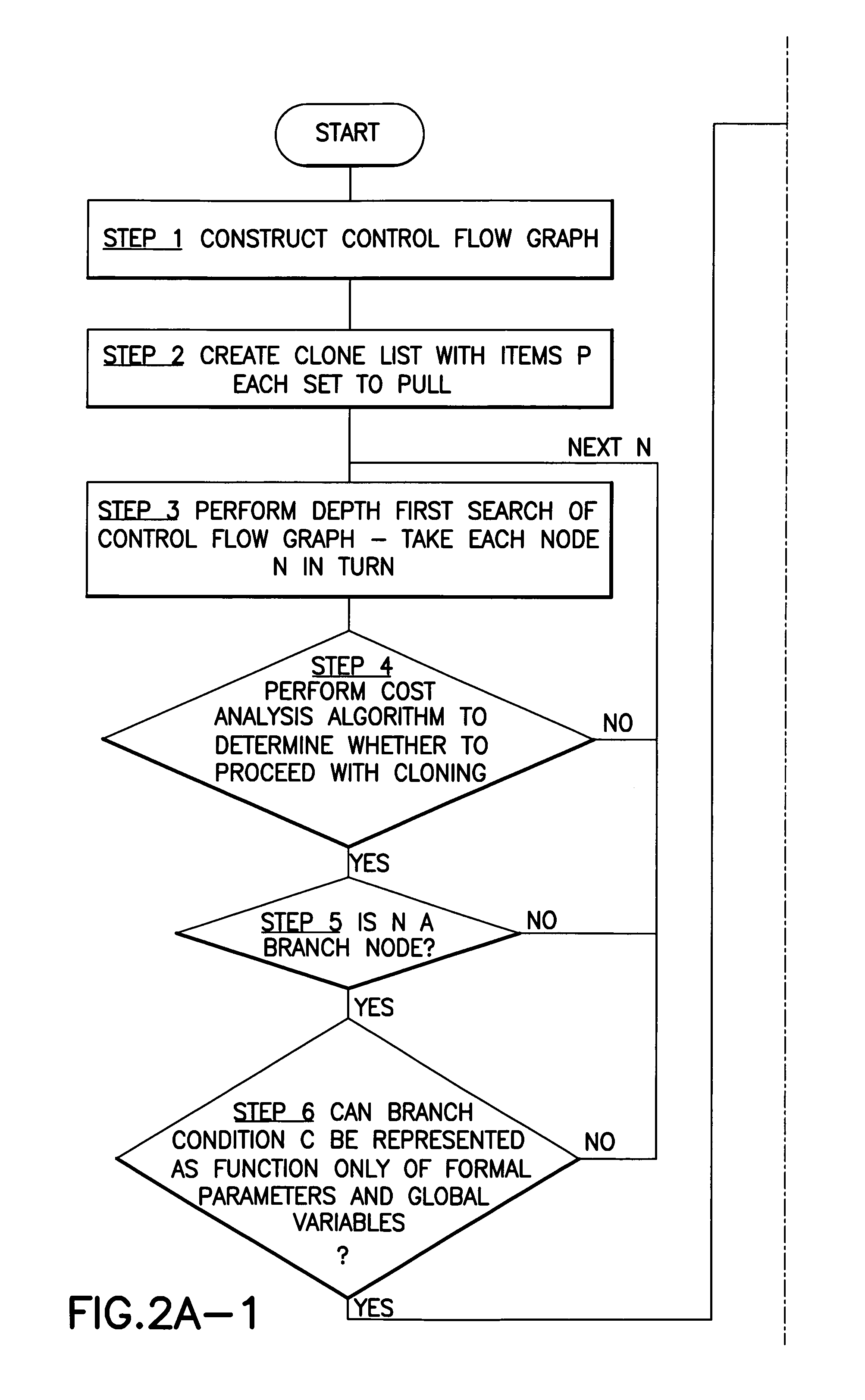
System, method and program product for optimising computer software by procedure cloning
InactiveUS7058561B1Facilitate further analysis and optimisationEasy to calculateProgram controlMemory systemsDead codeControl flow
A method, system and program product for optimizing software in which procedure clones are created based on the control flow information for the procedure body. In an example, a control flow graph for a called procedure is constructed and, for a branching node which can direct program flow to two or more code branches of the procedure, respective clones or new procedures are formed one for each code branch. A list containing pointers to the clones and the respective branch conditions for those clones is formed. Then, for each call site, the list is scanned to see if a particular call could be replaced by a call to a clone. Meanwhile, each clone is optimized and this may lead to removal of dead code or the replacement of a particular call statement by a constant.
Owner:IBM CORP
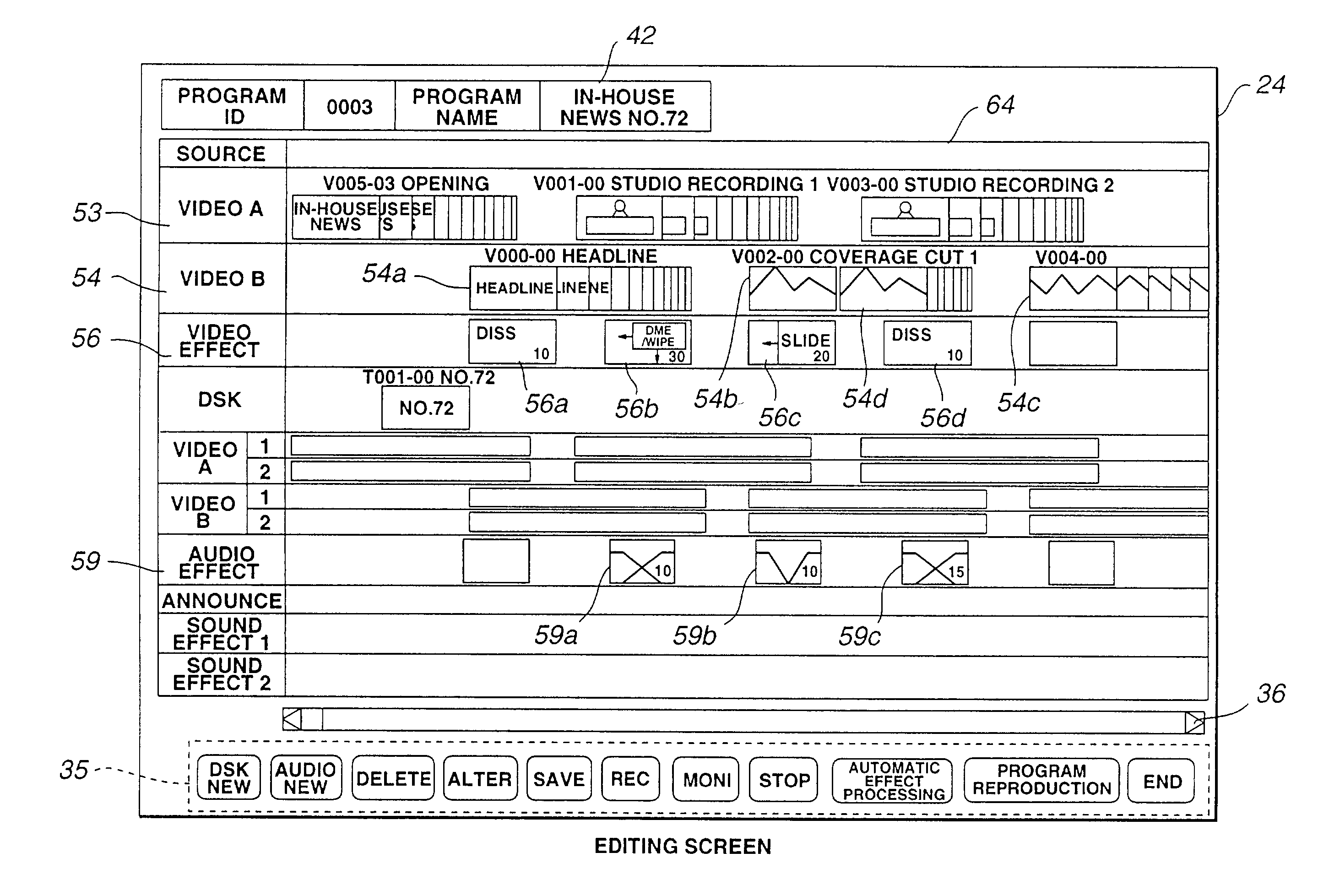
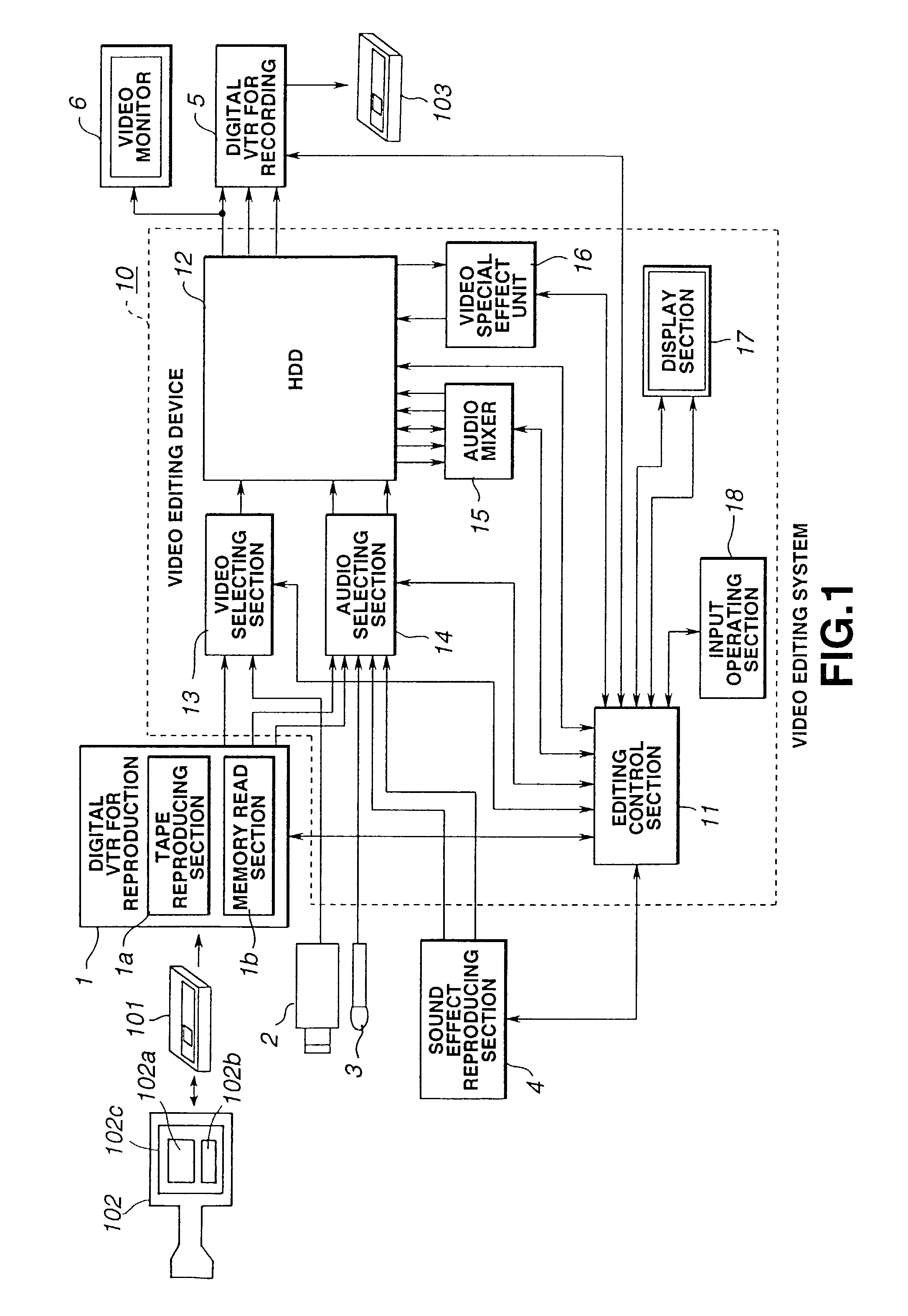
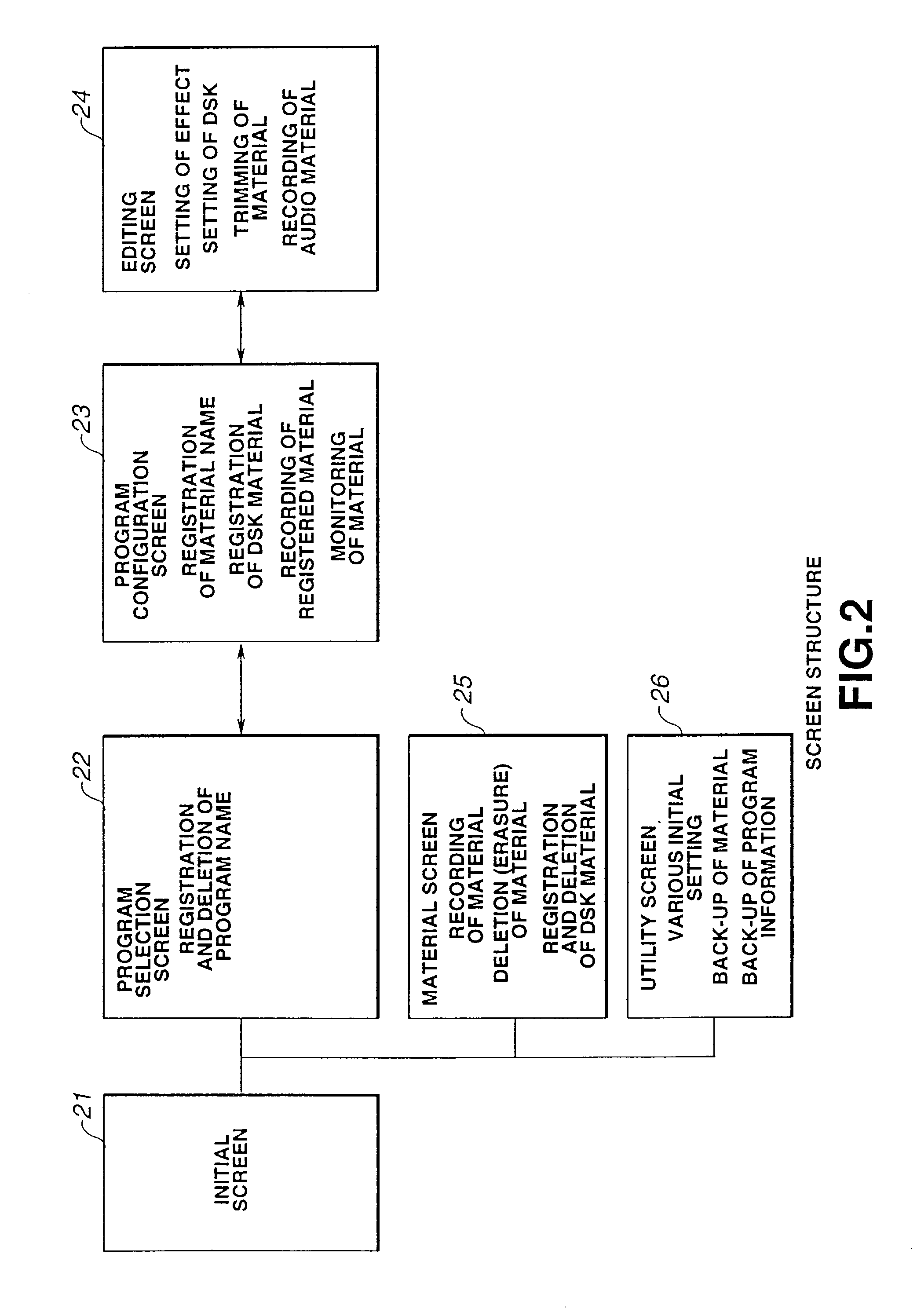
Editing device, editing system and editing method
Program configuration is carried out by using the screen of a display section 17 and an input operating section 18 of a video editing device 10, and data of this program configuration is recorded in a RAM 19. In accordance with the data of the program configuration, an editing control section 11 reads out a video material corresponding to material identification information of this program configuration from a digital VTR for reproduction 1 and records the video material onto a HDD 12. In accordance with the data of the program configuration, the editing control section 11 reproduces the video material of the corresponding material identification information from the HDD 12 and supplies the video material to a digital VTR for recording 5. Thus, the video editing device which automatically edits a program by inputting the video material having the material identification information after setting the program configuration is provided.
Owner:SONY CORP
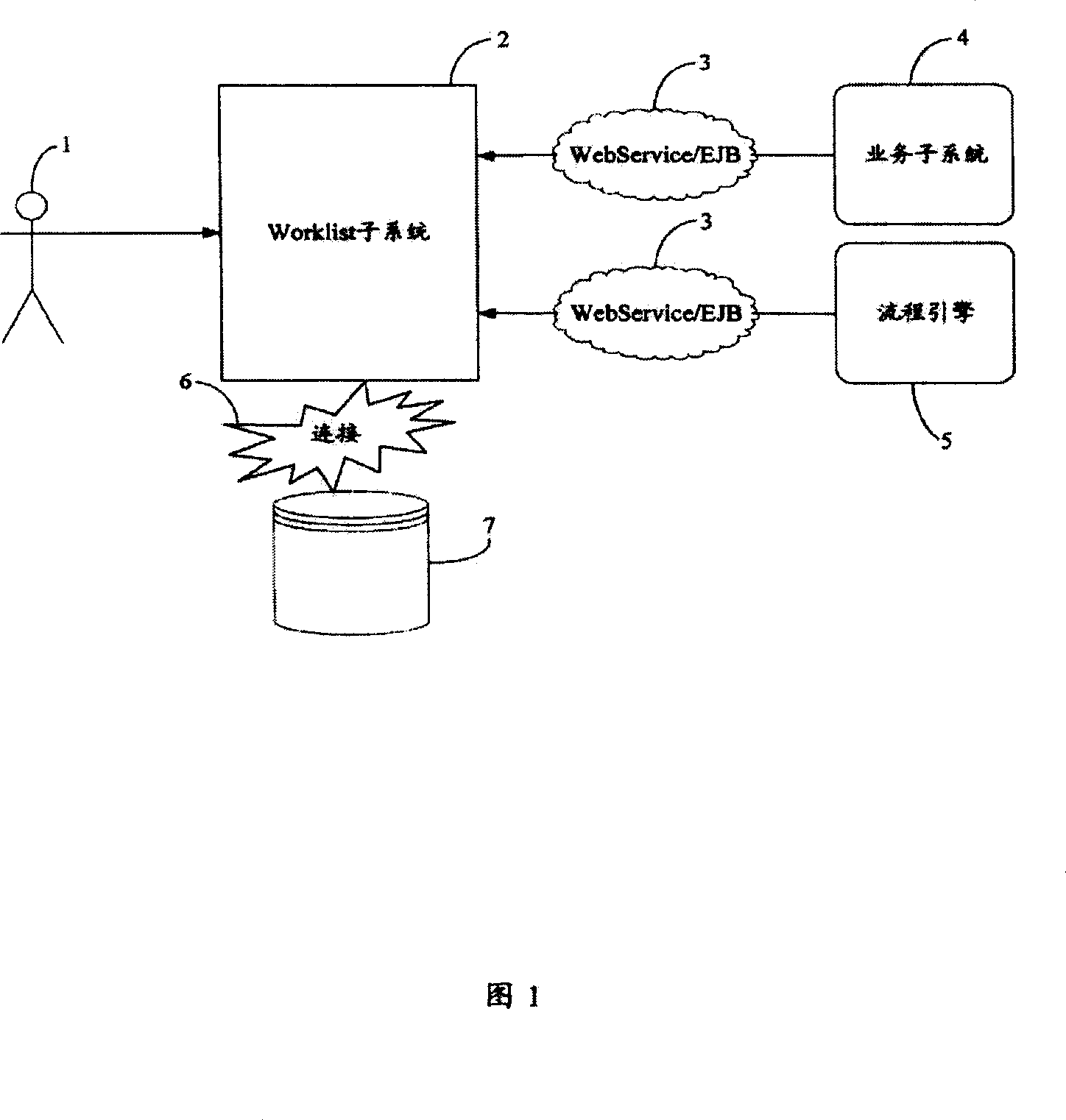
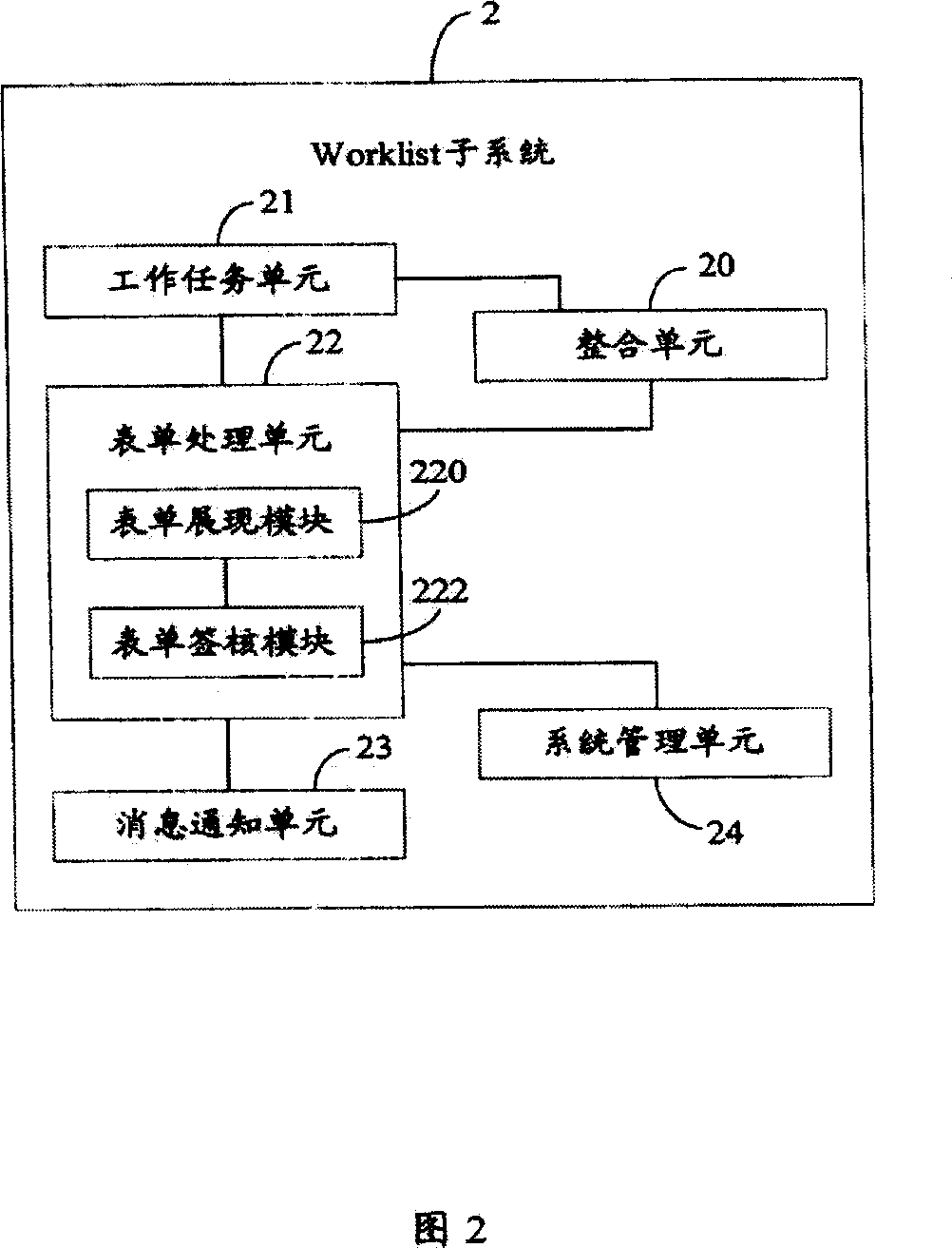
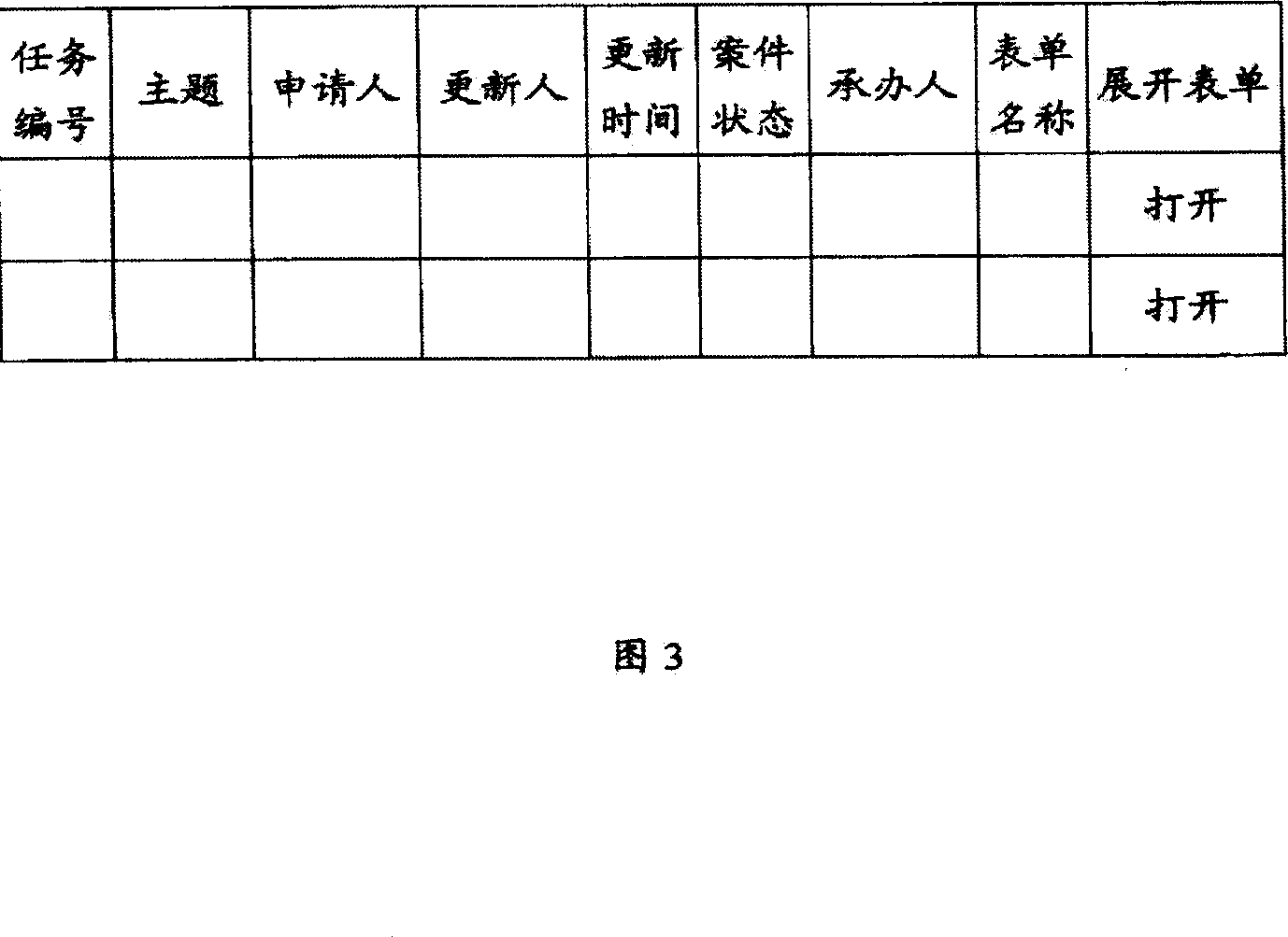
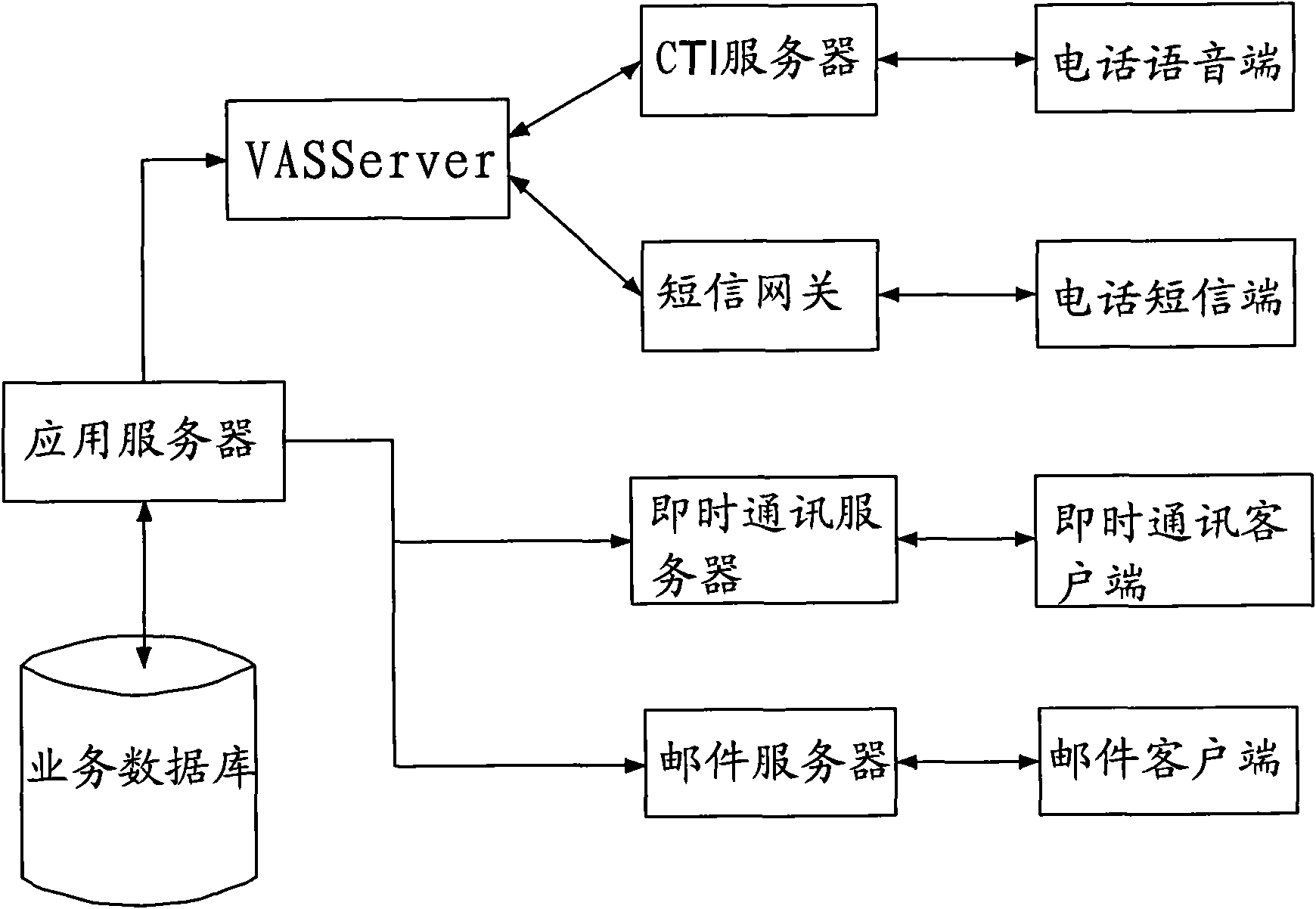
Flow process form processing system and method
InactiveCN101145217AEasy to expand other functionsOffice automationResourcesWeb servicePersonal details
The invention provides a flow-sheet processing method, which comprises the following procedures that: the flow engine and business subsystems in a computer with Web Service or EJB mode are integrated; the flow sheet processing requirement is received from a client; flow information corresponding to the sheet processing requirement is acquired from the flow engine according to the requirement of the client; related business information is acquired from the business subsystems according to the flow information; a pending work item is made according to the flow information, the business information and the personal data of the client; the pending work item is opened to display the flow sheet of the pending work item; and the flow sheet is processed. The invention also provides a flow-sheet processing system.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
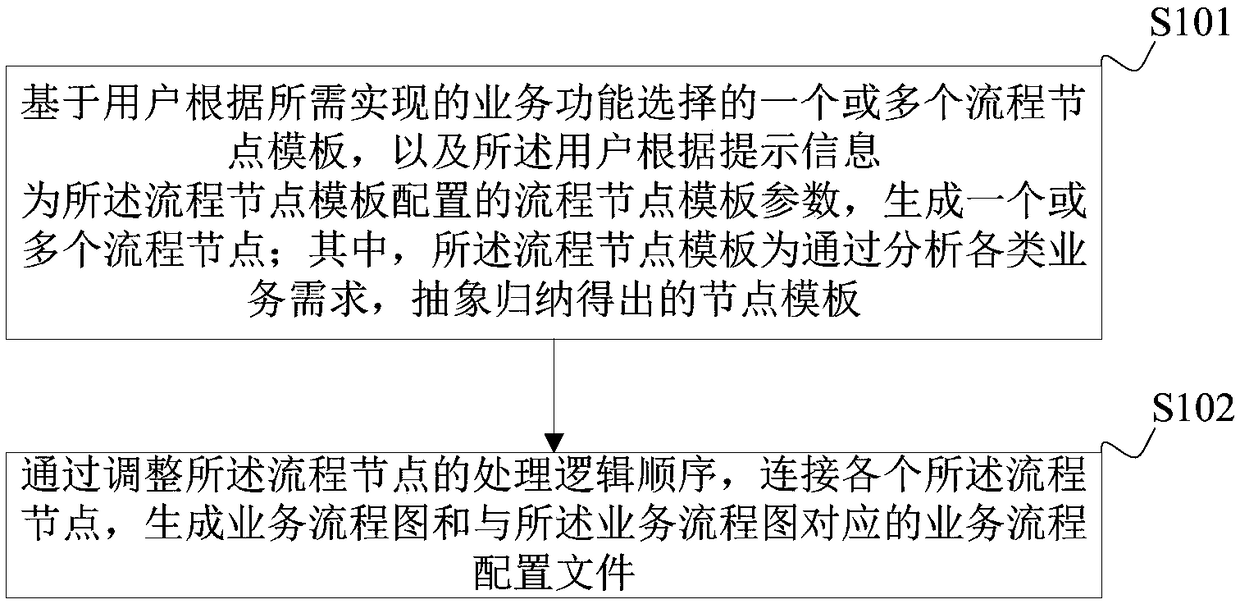
Financial self-service terminal service flow development method and device and terminal device
ActiveCN109324791AReduce development difficultyReduce maintenance difficultyVisual/graphical programmingService flowTerminal equipment
The embodiment of the invention is applicable to the technical field of software development, and discloses a financial self-service terminal service flow development method and device, a terminal device and a storage medium, wherein the method comprises the steps of: generating one or more process nodes based on one or more process node templates selected by a user according to a required servicefunction and the flow node template parameters configured by the user for the process node template according to a prompt information, wherein, the flow node template is a flow node template which isabstractly induced by analyzing various business requirements; by adjusting the processing logic order of the flow node, connecting each of the flow nodes to generate a business flow diagram and a business flow configuration file corresponding to the business flow diagram. Through the embodiment of the invention, the development and maintenance difficulty of the service software can be reduced, the development efficiency can be effectively improved, the technical threshold of the development and maintenance of the service software can be lowered, and the development cost can be saved.
Owner:SHENZHEN YIHUA COMP
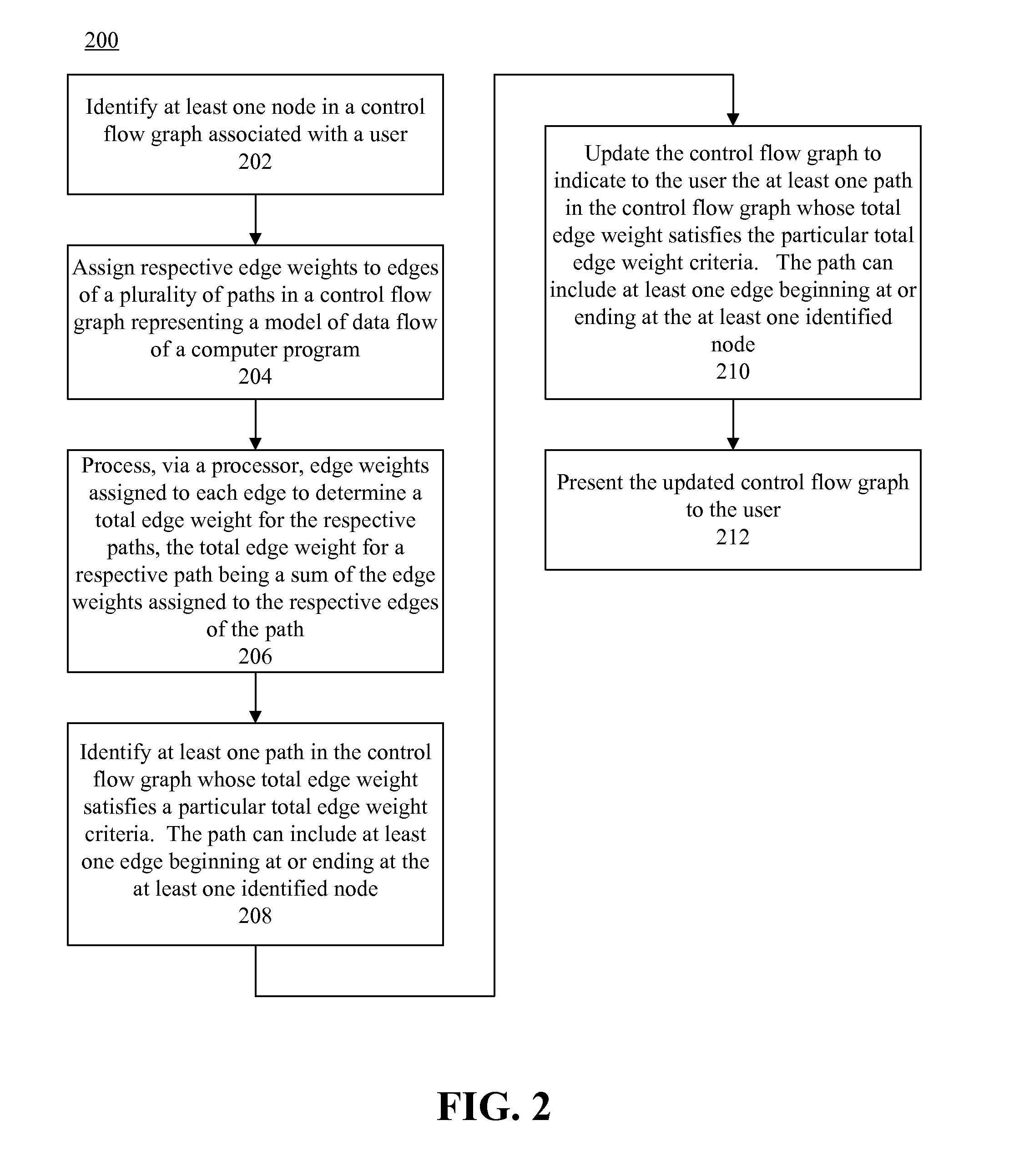
Customizing a security report using static analysis
ActiveUS20140090070A1Memory loss protectionError detection/correctionControl flowStatic timing analysis
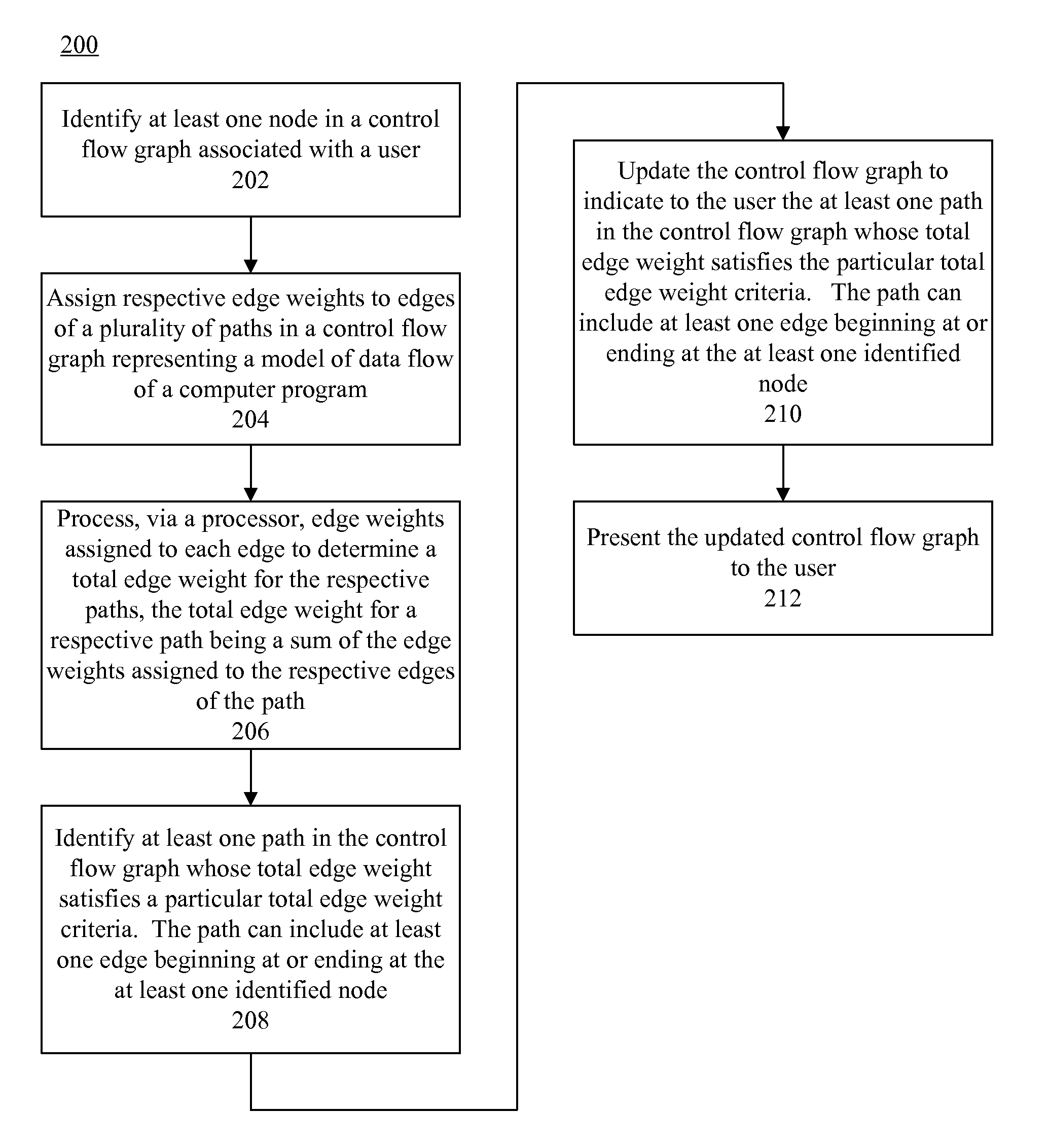
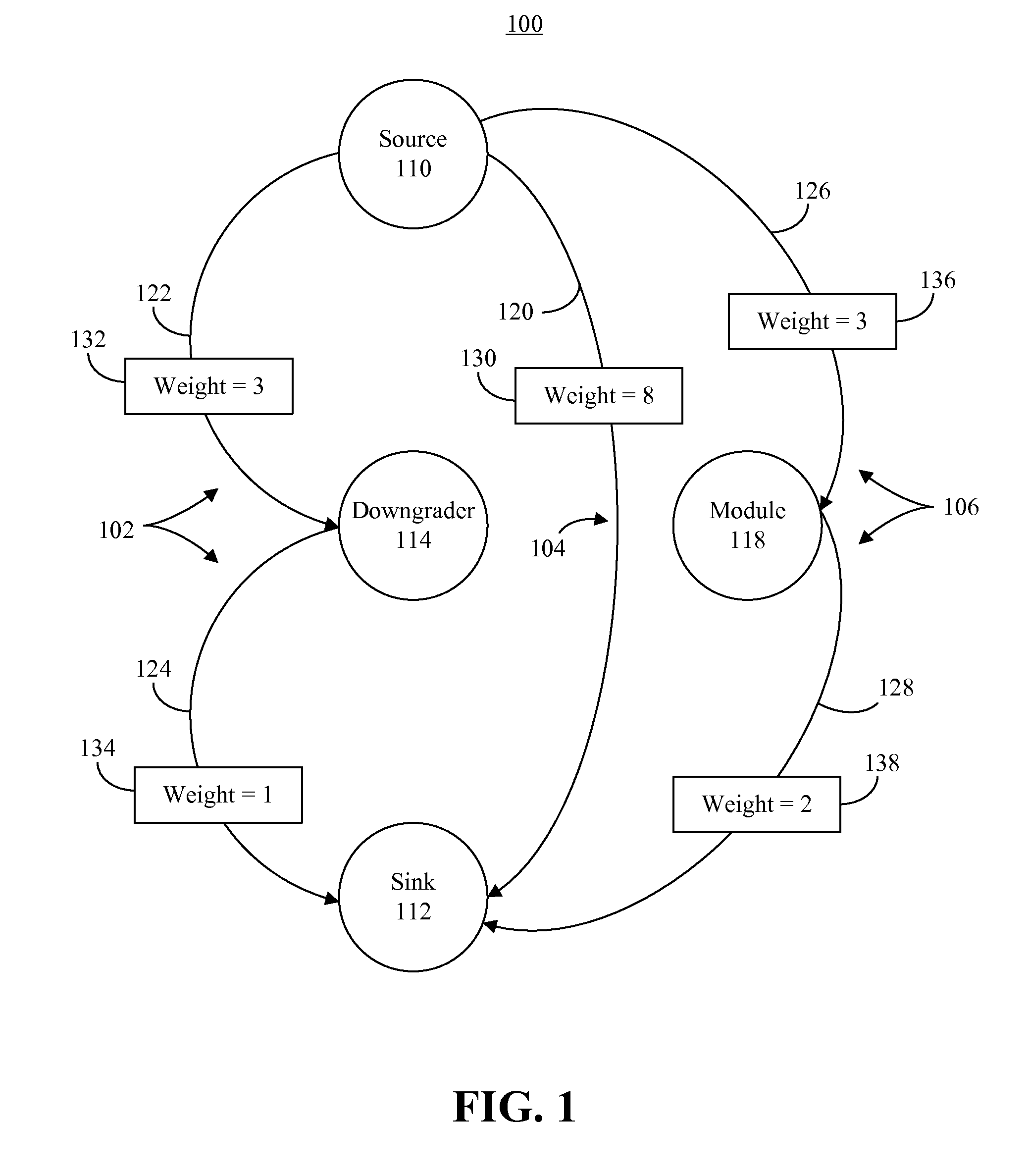
Respective edge weights are assigned to edges of a plurality of paths in a control flow graph representing a model of data flow of a computer program. Edge weights assigned to each edge are processed to determine a total edge weight for the respective paths, the total edge weight for a respective path being a sum of the edge weights assigned to the respective edges of the path. At least one path in the control flow graph whose total edge weight satisfies a particular total edge weight criteria can be identified, and the control flow graph can be updated to indicate to the user the at least one path in the control flow graph whose total edge weight satisfies the particular total edge weight criteria. The updated control flow graph can be presented to the user.
Owner:IBM CORP
Unmanned aerial vehicle-based control method of automatic storage system
InactiveCN106934579ARealize fully automated monitoringImprove work efficiencyLogisticsUncrewed vehicleFlow sheet
The invention discloses an unmanned aerial vehicle-based control method of an automatic storage system. The method comprises the following steps that: an unmanned aerial vehicle is utilized to complete the workflow of the entering of goods into warehouses; the unmanned aerial vehicle is utilized to complete of the workflow of the shifting of the goods between the warehouses; the unmanned aerial vehicle is utilized to complete of the workflow of goods inventory; the unmanned aerial vehicle is utilized to complete of the workflow of goods inspection; and the unmanned aerial vehicle is utilized to complete of the workflow of the outgoing of the goods from the warehouses. According to the unmanned aerial vehicle-based control method of the automatic storage system of the invention, the fully automatic monitoring of the entering of the goods into the warehouses, goods inventory, the shifting of the goods between the warehouses, goods inspection and the outgoing of the goods from the warehouses can be realized, the efficiency of the operation of the goods is improved, storage costs can be reduced, and the accurate and timely response of the distribution of the goods is realized.
Owner:JIANGSU PROVINCE HOSPITAL +1
Software vulnerabilities detection system and methods
ActiveUS20160300063A1Improve accuracyReduce consumptionSoftware testing/debuggingPlatform integrity maintainanceControl flowSystems analysis
Owner:SECURISEA INC
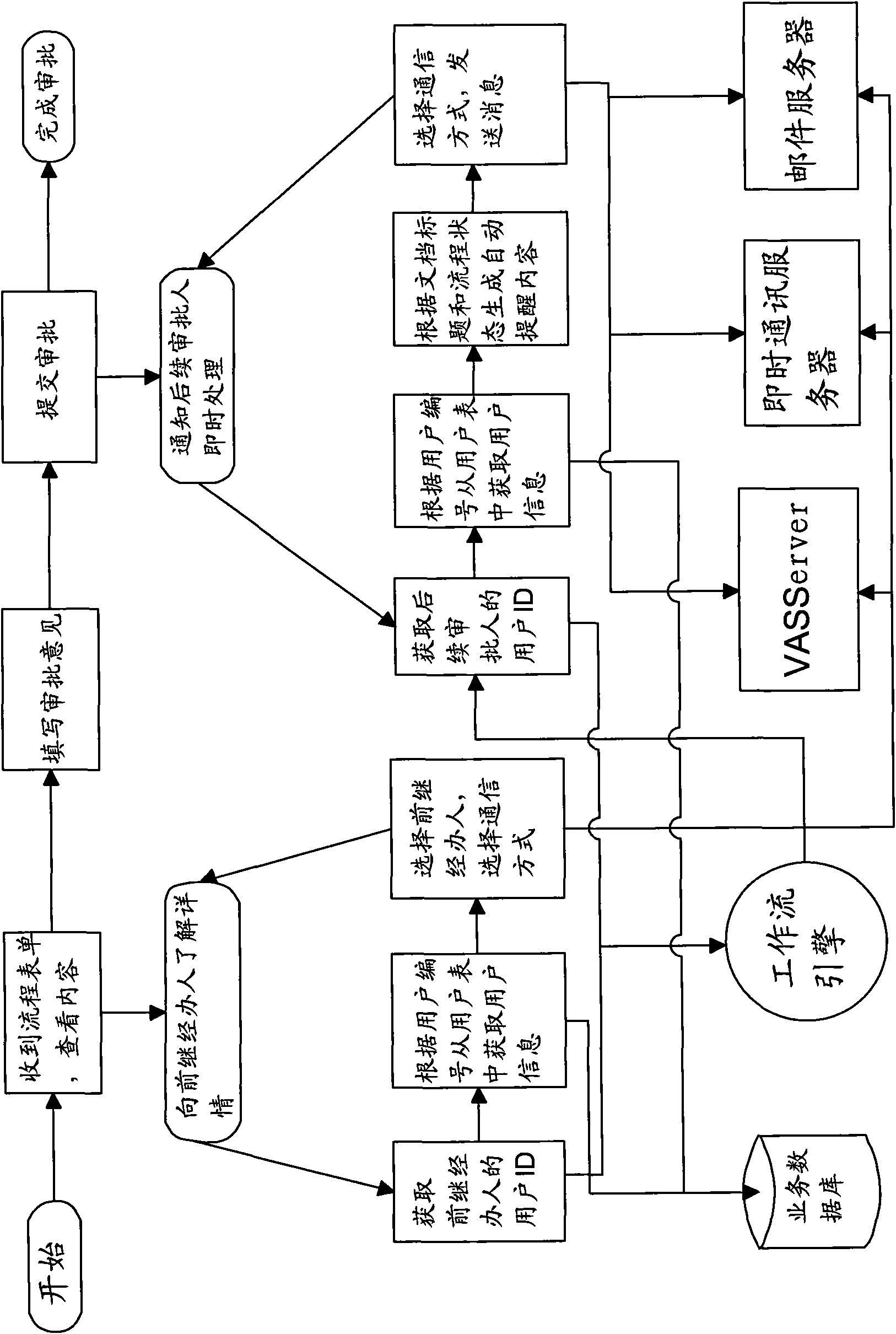
Method for approving workflow
ActiveCN101848238AImprove real-time performanceImprove process approval efficiencyResourcesData switching networksHandling systemFlow sheet
The invention relates to a method for approving the workflow, comprising the following steps: obtaining the communication information of the preceding handling personnel and the succeeding handling personnel by a service processing system after the preceding handling personnel receiving a flow sheet; selecting the preceding handling personnel and the succeeding handling personnel which need to carry out communication; selecting one communication mode from at least two communication modes; initiating the communication to the selected succeeding handling personnel and the selected succeeding handling personnel by the service processing system through a communication subsystem which corresponds to the selected communication mode with the selected communication mode. Adopting the method for approving the workflow, the succeeding handling personnel can communicate with the preceding handling personnel with one of the two or more communication modes flexibly and then approve the workflow so that the operation process and the operation step are simplified and the workflow approving efficiency is greatly improved.
Owner:杭州世导通讯有限公司
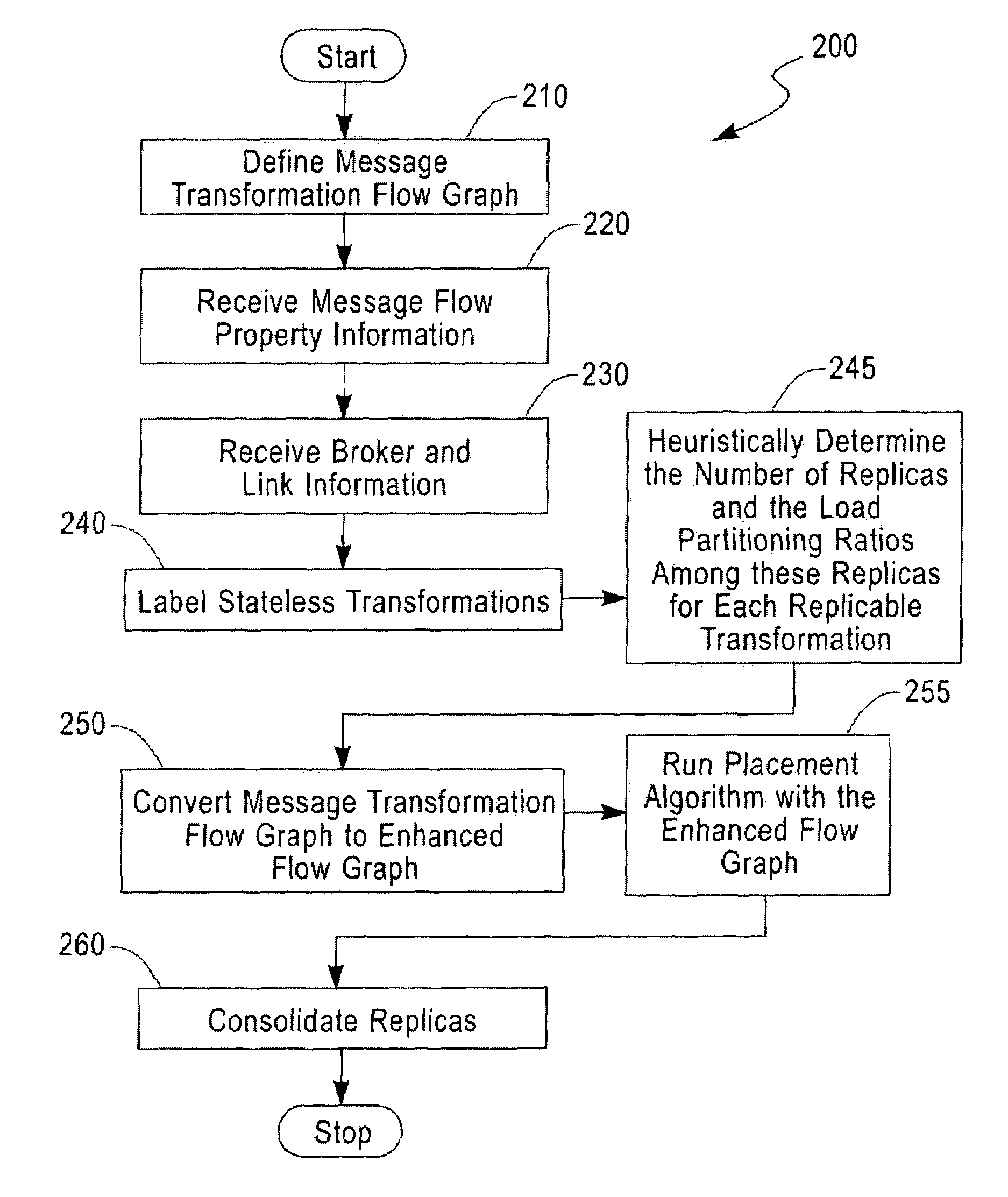
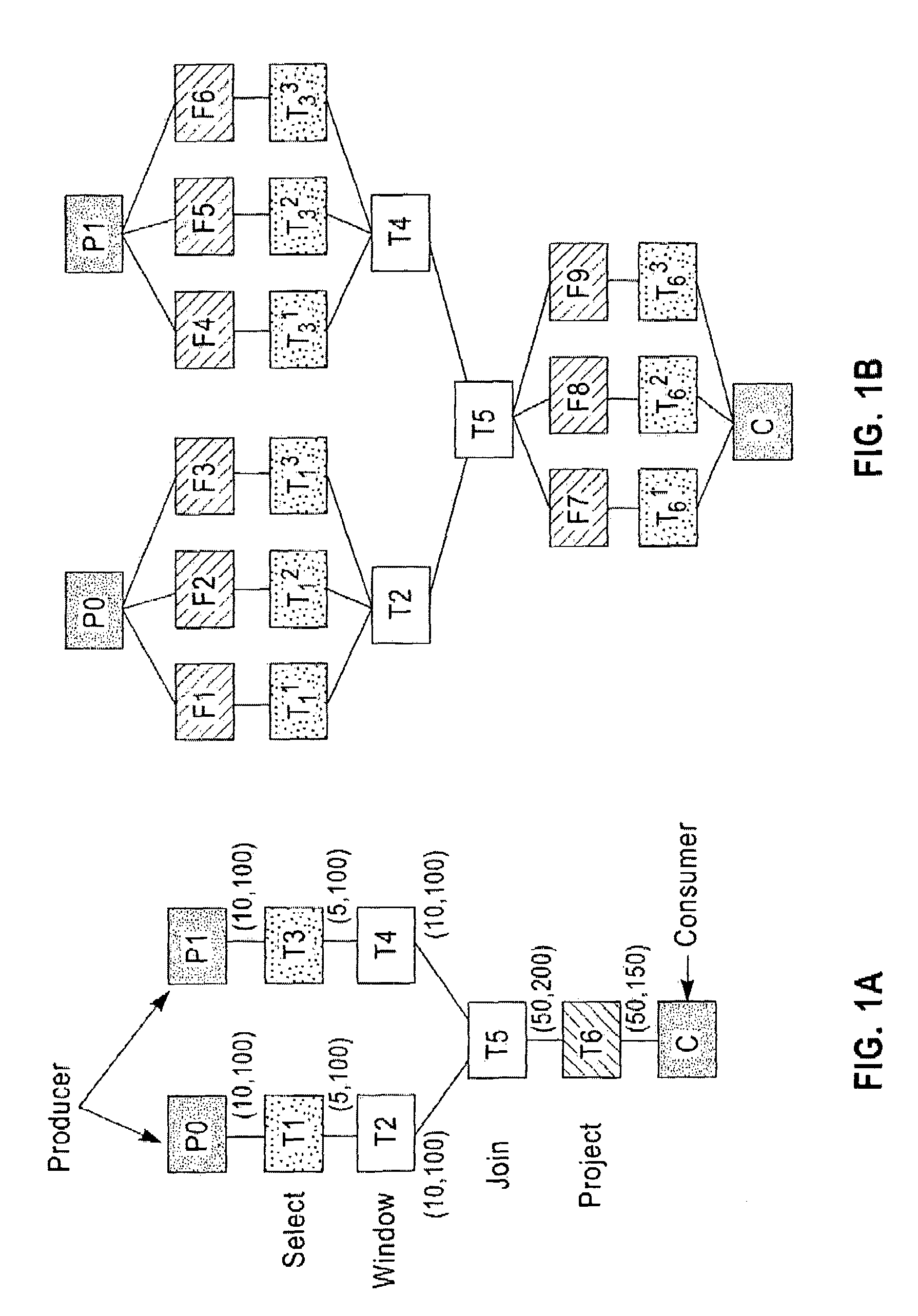
Systems, methods and computer program products for improving placement performance of message transforms by exploiting aggressive replication
ActiveUS7380005B1Flexible choiceImprove performanceDigital computer detailsMultiprogramming arrangementsMessage flowFlow sheet
Systems, methods and computer program products for improving overall end-to-end runtime latency of flow graphs of message transformations which are placed onto an overlay network of broker machines by aggressively replicating stateless transformations. Exemplary embodiments include a method including defining a message transformation graph, receiving information about measured and estimated properties of a message flow, receiving information about physical brokers and links in the overlay network onto which the message transformation graph is deployed, labeling each of a plurality of stateless transformations associated with the flow graph as replicable, heuristically determining a number of replicas and a corresponding load partitioning ratios among the number of replicas for each stateless transformation, converting the message transformation graph into an enhanced flow graph, running a placement algorithm with the enhanced flow graph and consolidating each of the plurality of virtual replicas that are assigned to a common message broker.
Owner:HULU
Electronic file system graphical user interface
InactiveUS20060069690A1Digital data information retrievalDigital data processing detailsGraphicsResearch software
A research software tool for use with an online external resource comprises a flowchart graphic user interface configured to be displayed on an electronic display. The flowchart graphic user interface includes a graphically indicated first defined area and a text string displayable therein. The flowchart graphic user interface further includes a graphically indicated second defined area and a text string displayable therein, at least one of the text strings being user selectable. The flowchart graphic user interface further includes relationship symbology displayable between the first and second defined areas and a user selectable link corresponding to one of the text strings. The user selectable link is an active link that is configured to interface with the online external resource, and that includes a search criterion related to at least one of the text strings, for use with the online external resource.
Owner:ON A CHART
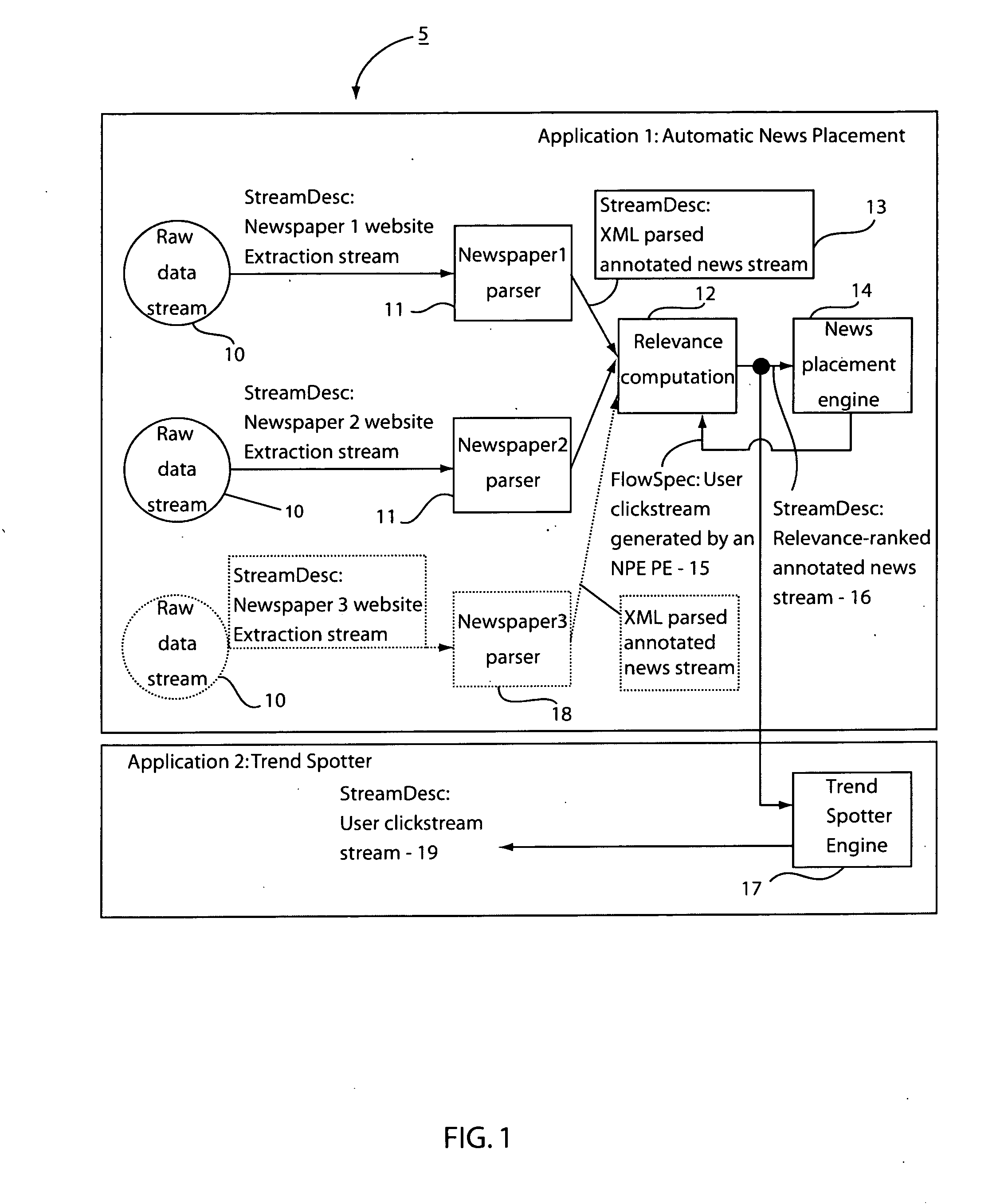
Method and system for dynamic application composition in streaming systems
ActiveUS20080235685A1Improved routing and flexibilityReduce the burden onMultiprogramming arrangementsMultiple digital computer combinationsProcessing elementFlow sheet
A system and method for dynamically building applications for stream processing includes providing processing elements with a flow specification describing each input and a stream description describing each output such that the flow specification indicates a stream or streams which are to be received based on processing information and the stream descriptions indicate the processing information. Processing elements that can be reused are identified by determining equivalence between the processing elements. Processing elements that are new and are not reusable are instantiated in a flow graph. An application is dynamically composed, using the instantiated processing elements by routing available streams to the instantiated processing elements in accordance with the flow specifications.
Owner:INT BUSINESS MASCH CORP
Method and a device for abstracting instruction sequences with tail merging
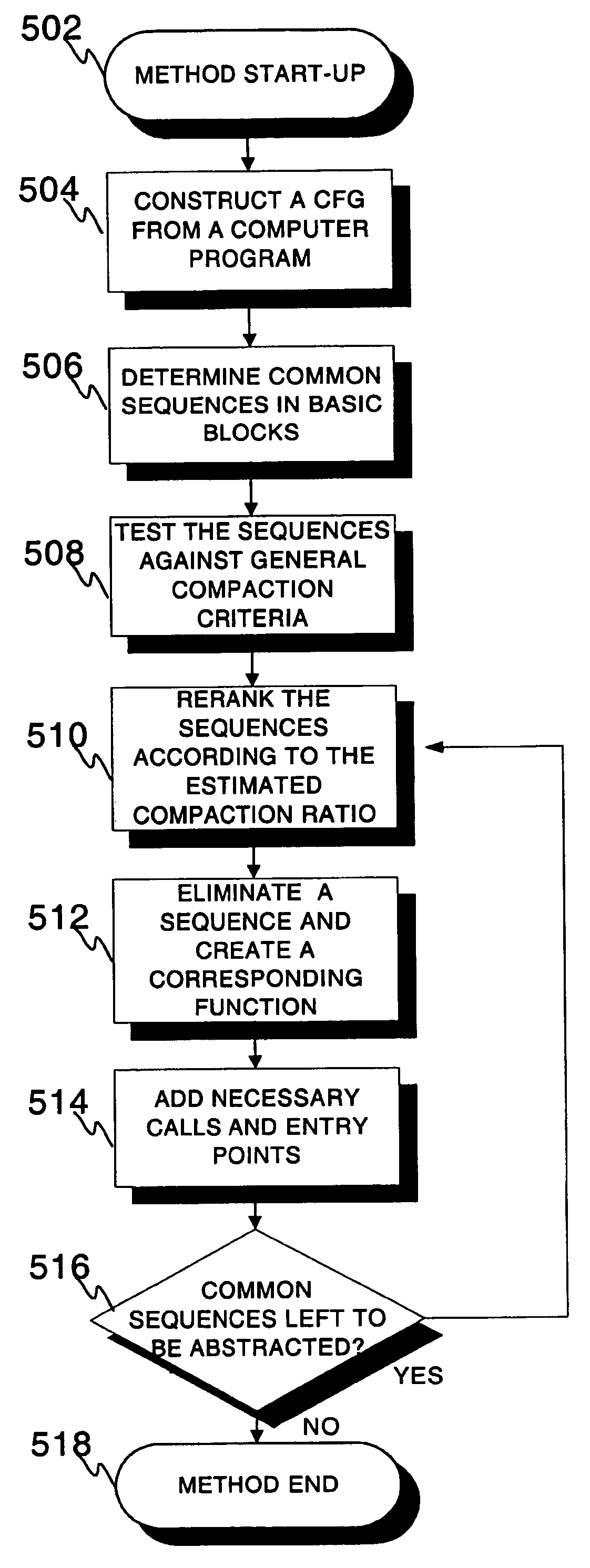
InactiveUS20050060697A1Small program sizeLess memory spaceSoftware engineeringProgram controlTailFlow sheet
A method and a device for abstracting instruction sequences in a computer program. First, a control flow graph of the program is generated and analysed in order to detect multiple occurrences of a same instruction sequence (504, 506). Then, a function including the longest sequence common to at least two instruction sequences from a plurality of sequences having a common instruction sequence of equal or shorter length compared to the longest sequence is created (512). Finally, the original occurrences of the instruction sequences in the plurality of sequences with a reference to a proper position in the newly created function are deleted and a reference to a proper position in the created function inserted instead (514).
Owner:NOKIA CORP
Method, system and product for identifying and executing locked read regions and locked write regions in programming languages that offer synchronization without explicit means to distinguish between such regions
InactiveUS20050198626A1Efficient executionProgram synchronisationConcurrent instruction executionTheoretical computer scienceProgram code
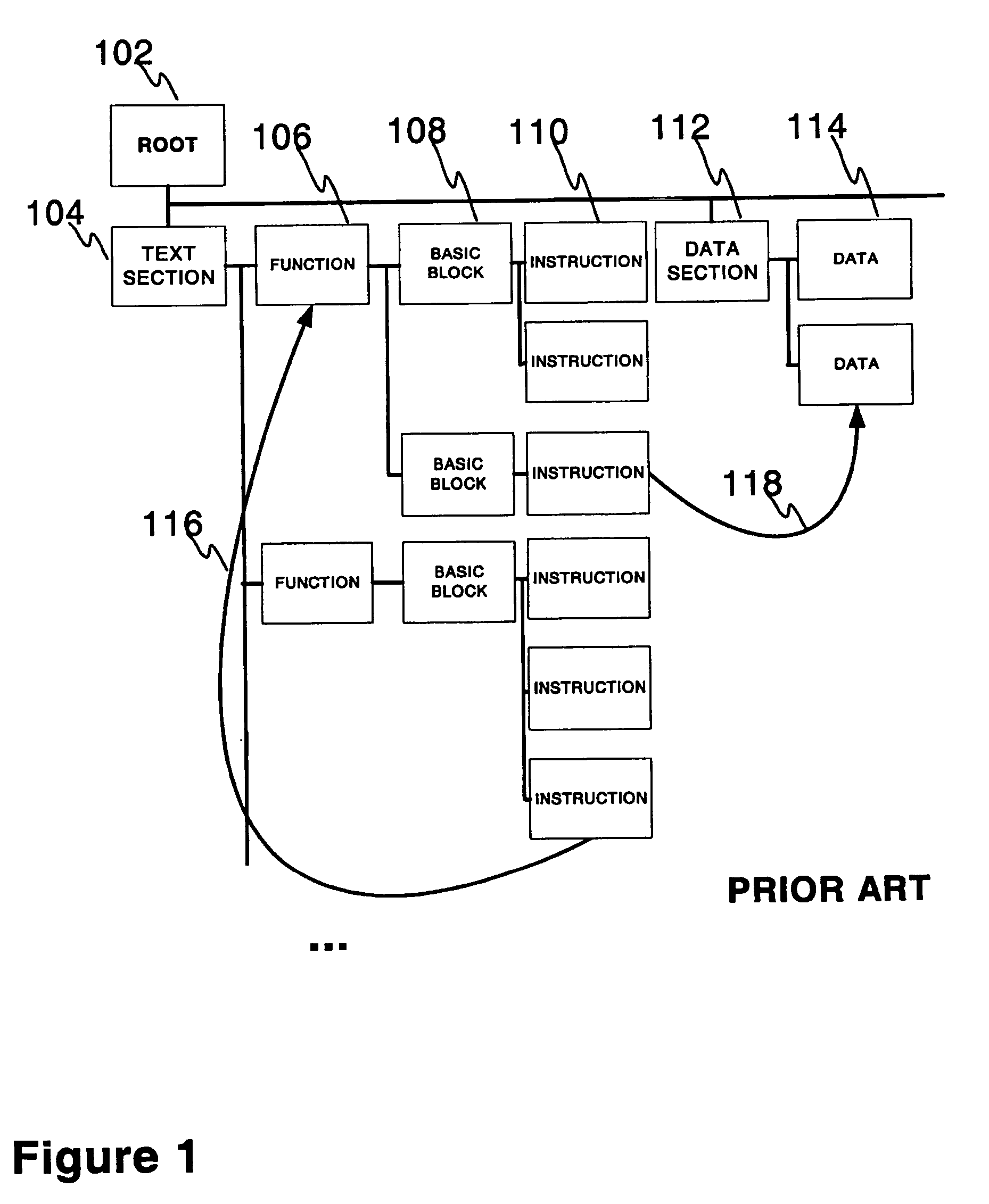
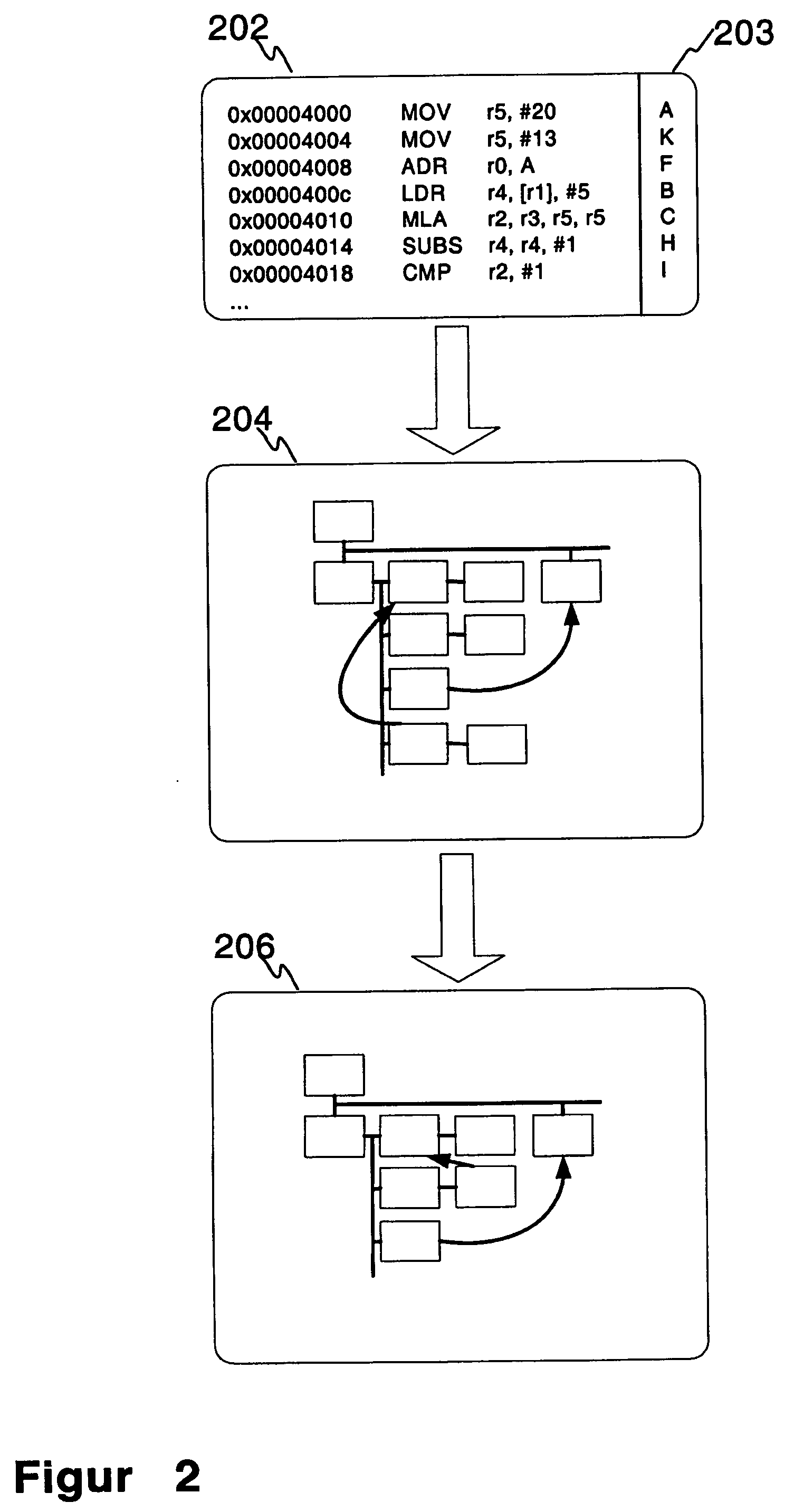
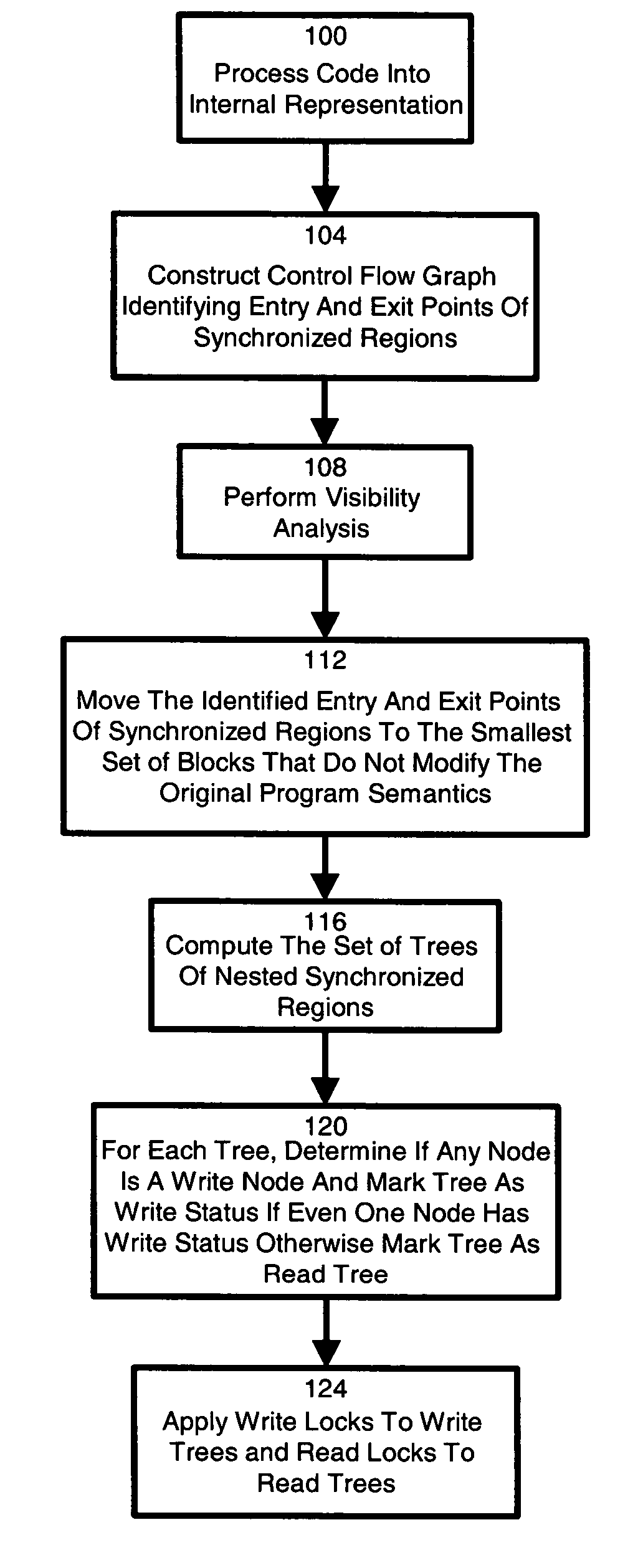
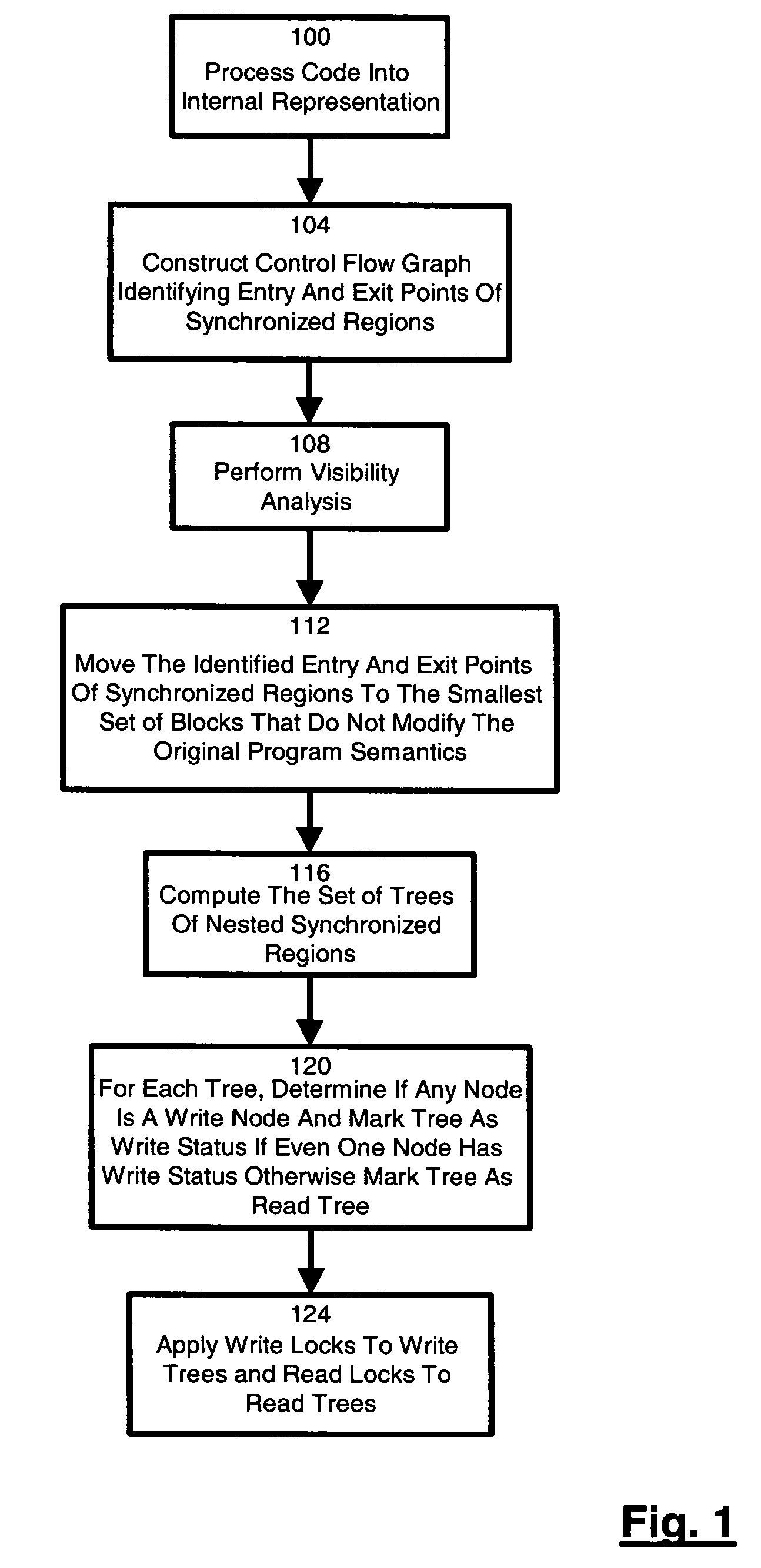
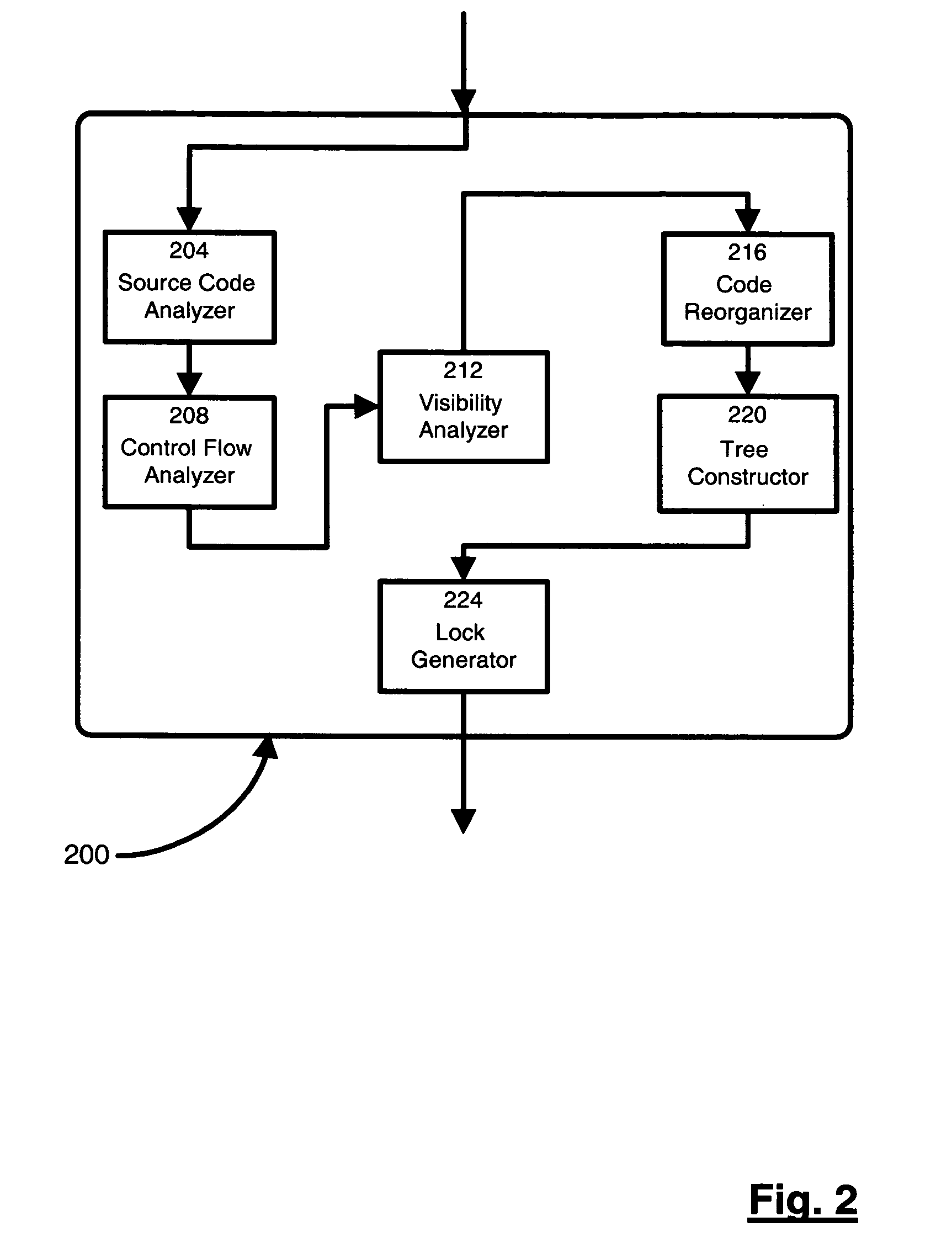
A technique for identifying and executing synchronized read regions and synchronized write regions is provided. The technique processes program code with a software tool to convert the code to an internal representation for the software tool and constructs a control flow graph of code blocks which also identifies the entry and exit points for each region of code subject to a lock. For each code block in the control flow graph, visibility analysis is performed. Each determined entry and exit point is moved to enclose the smallest set of code blocks subject to a lock which can be achieved without altering code semantics. A set of trees is created to represent the manner in which the synchronized regions are nested. If the tree contains at least one block previously identified, then the tree is marked a write. Otherwise, the tree is marked a read tree. A write lock is then created for the region in each tree identified as a write tree and a read lock is created for the regions in each tree identified as a read tree.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com