System, method and program product for detecting malicious software
a technology of malicious software and detection method, applied in the field of computer systems, can solve problems such as the inability to detect malicious software, the inability to disable a computer or conduct a denial of service attack on another computer, and the harmful nature of computer programs, so as to prevent damage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
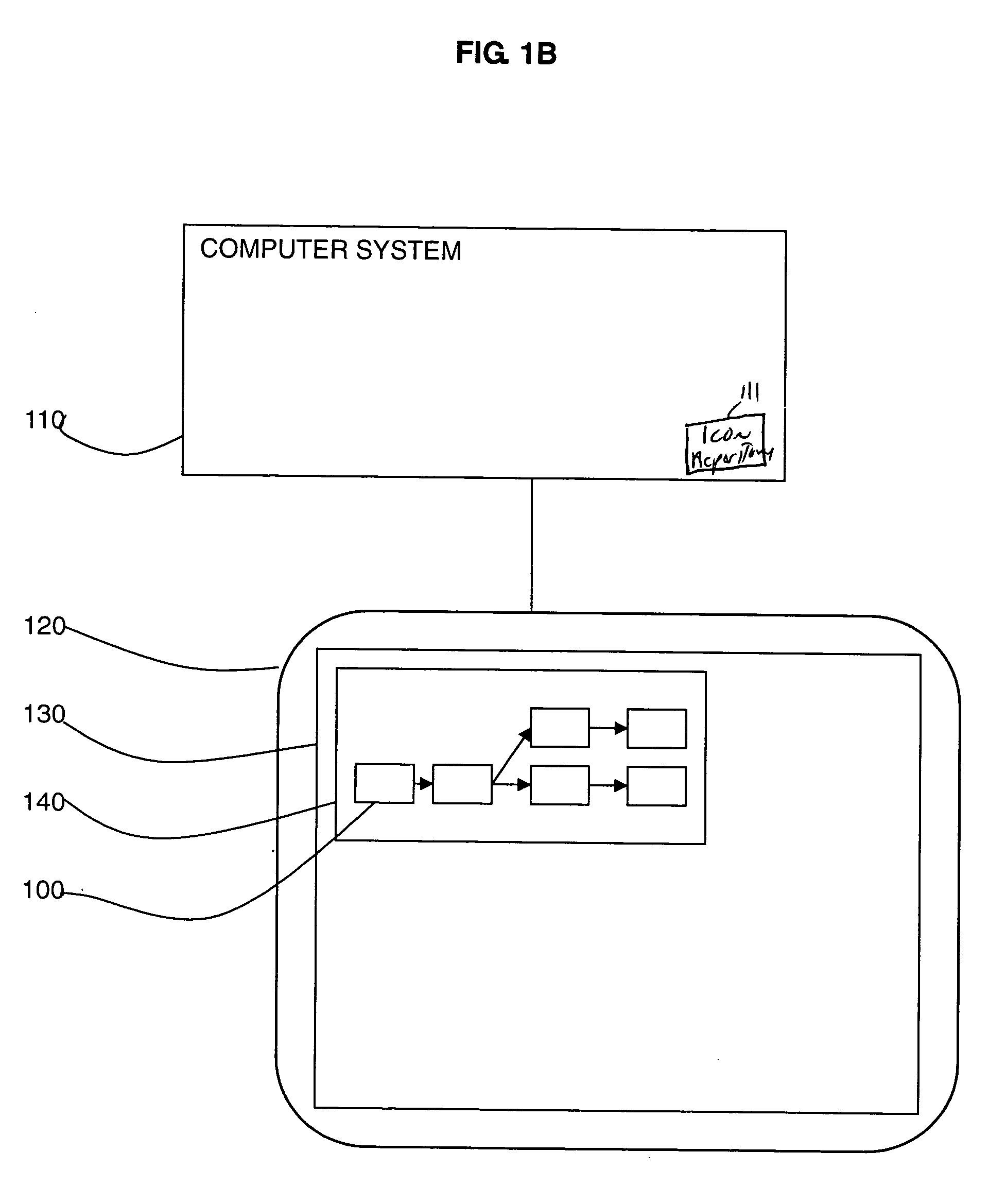
[0024] The present invention provides a system, method and program product for monitoring and displaying the activity of a computer system in real time as an information flow diagram. This permits an operator to determine if the activity appears consistent with the bona fide work requested of the computer system. The information flow diagrams show the physical and virtual location of information entities at all stages of their processing and the operations, such as the copying, encryption and transmission of information. The information flow diagrams are generated in real time as the information is being processed and moved about the computer.
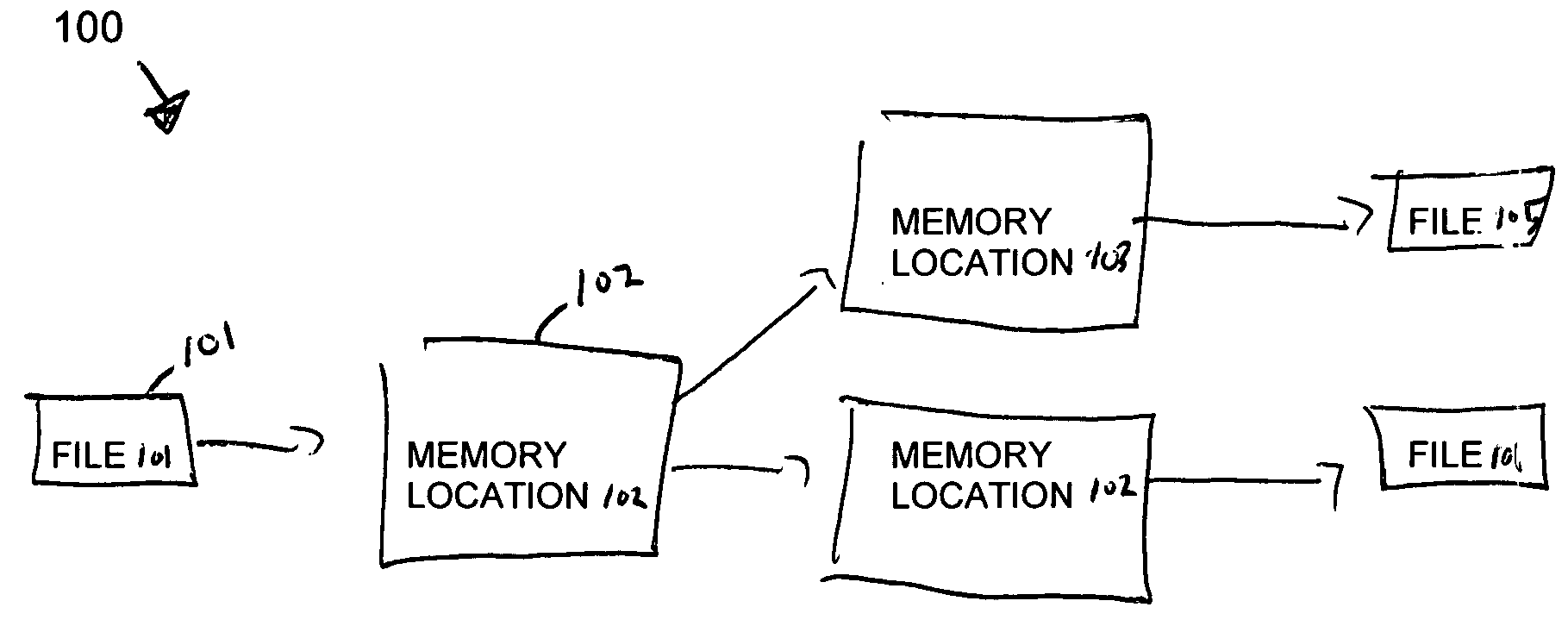
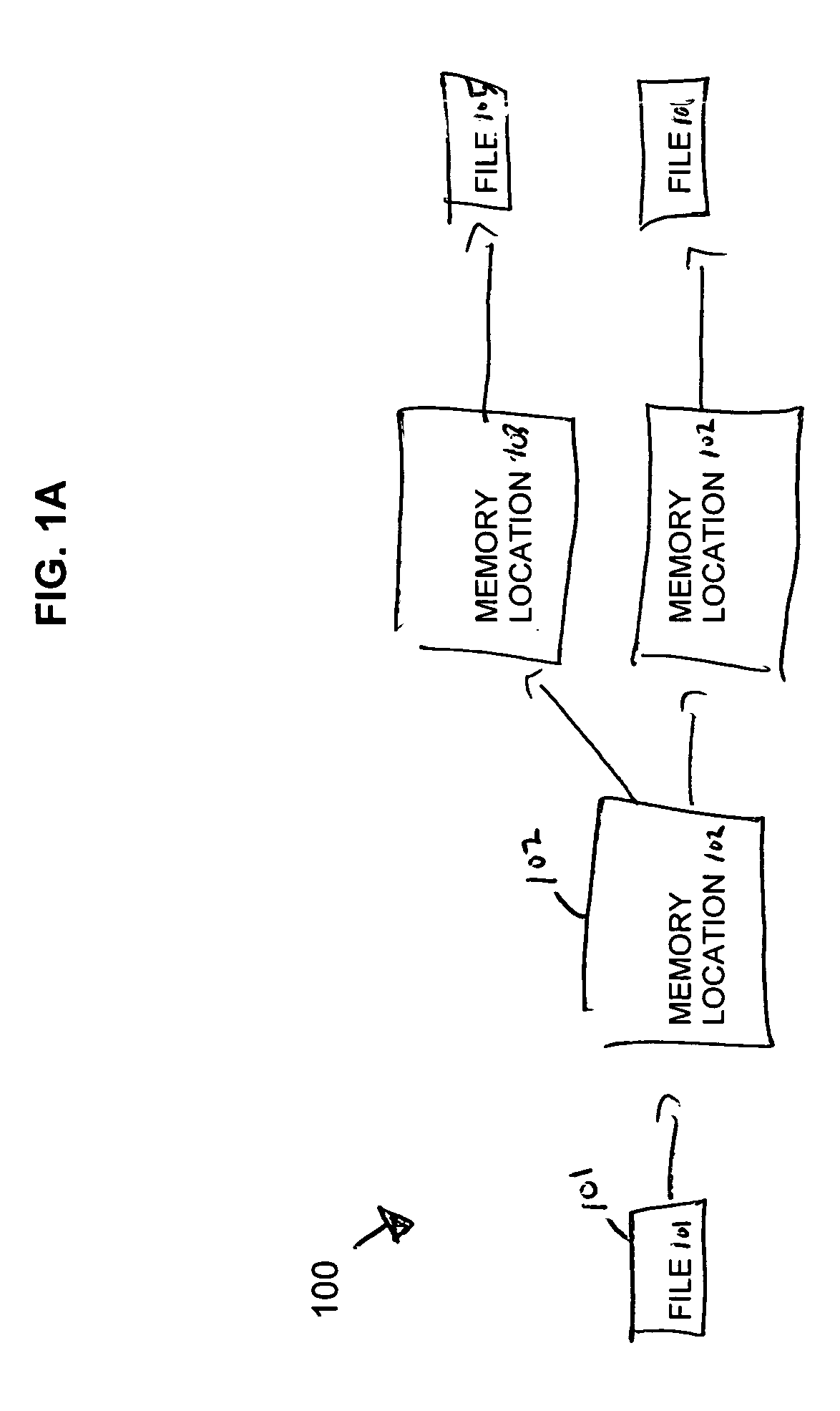
[0025]FIG. 1A shows an information flow diagram 100 for copying a file and renaming the copied file. A file 101 is saved at a first memory location 102. The file 101 is then copied from the first memory location 102 to a second memory location 103. At this time, the same file 101 concurrently resides at both the first and second memory locatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com