Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
61results about How to "Prevent access" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
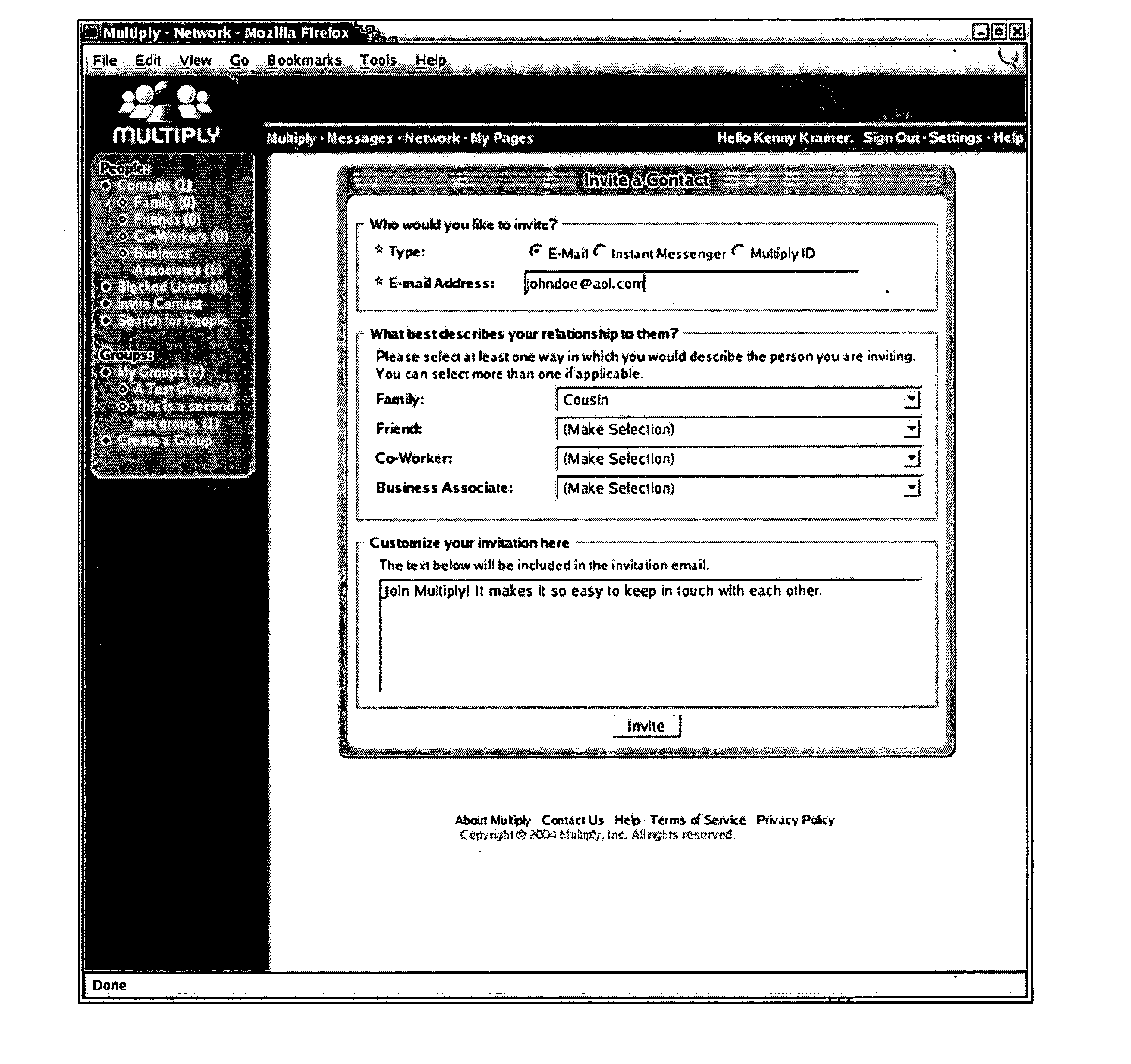
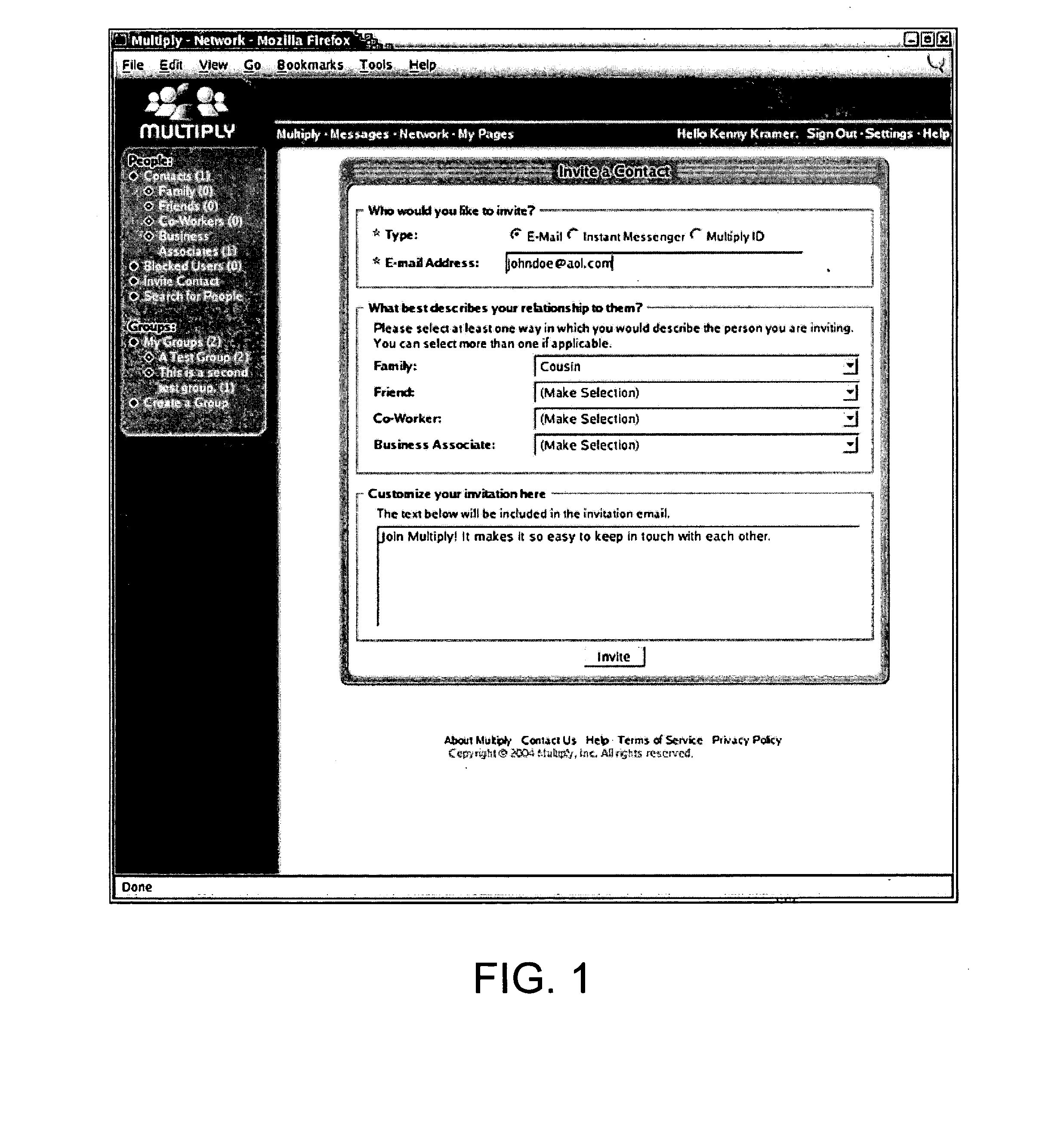
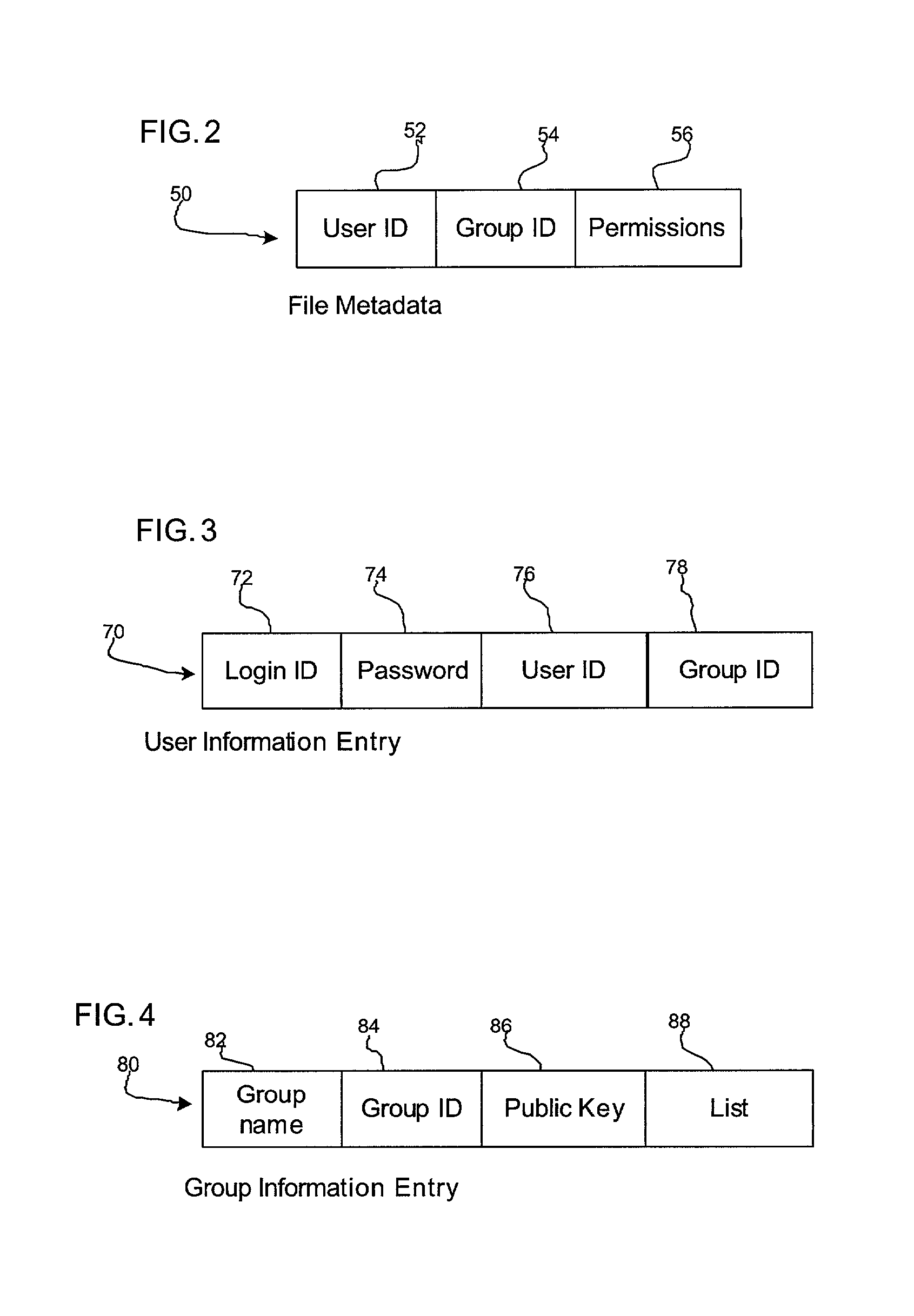
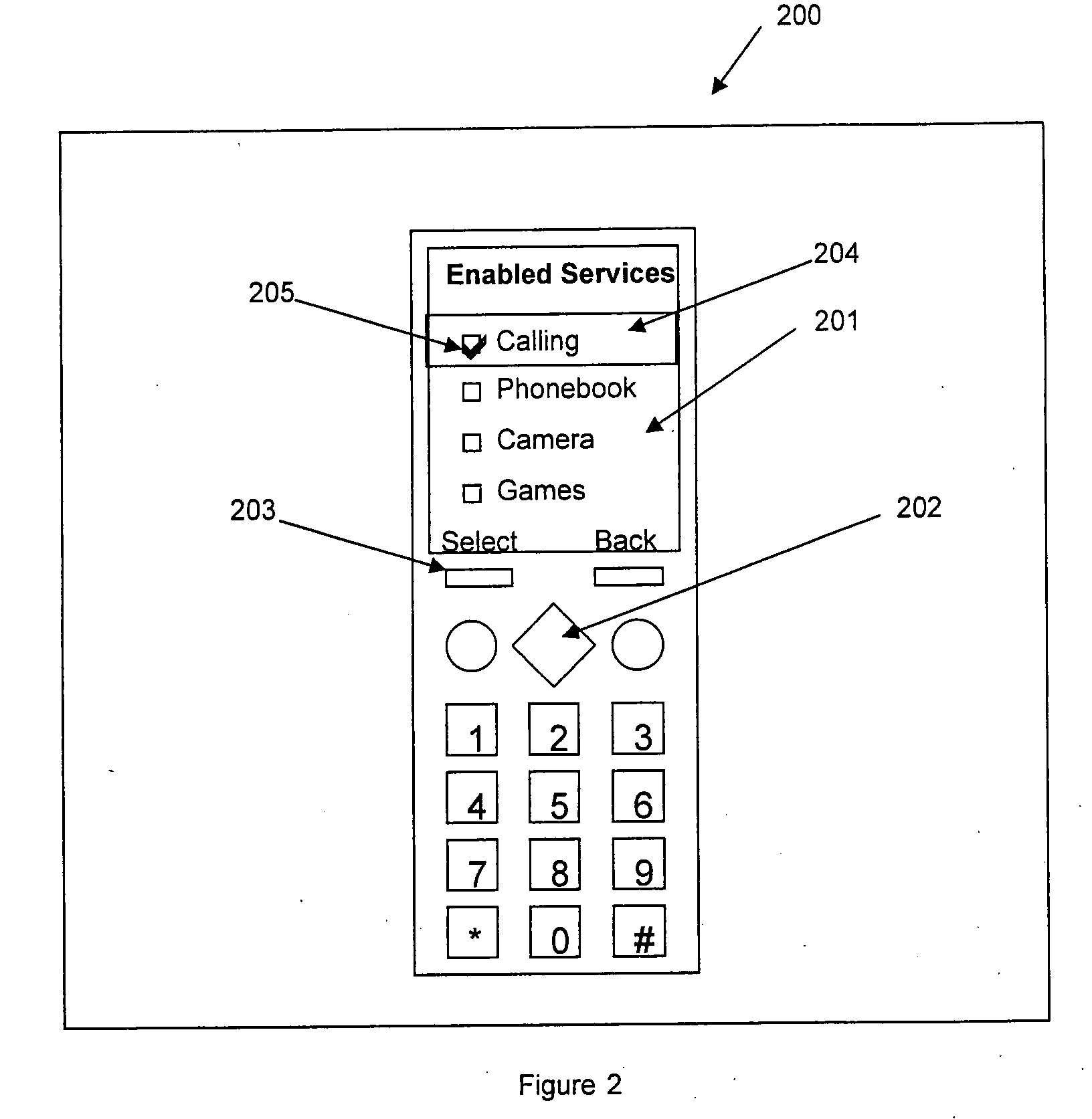
Method and system for controlling access to user information in a social networking environment
InactiveUS20050198031A1Prevent accessInformation formatServices signallingSocial internet of thingsUser information
Owner:MULTIPLY
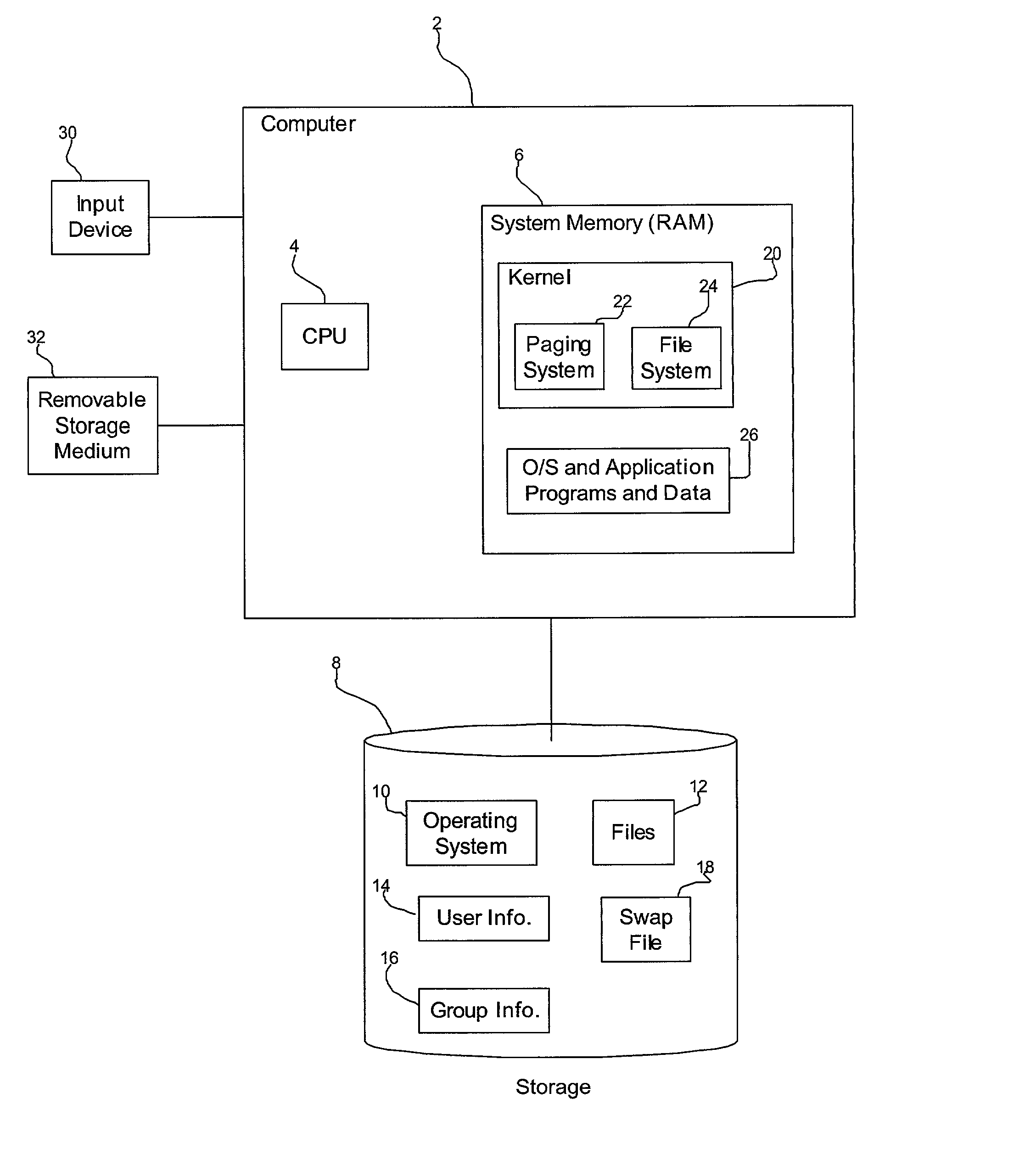
Method, system, and program for encrypting files in a computer system
ActiveUS20020166053A1Prevent accessDigital data processing detailsUser identity/authority verificationEncryptionVolatile memory
Provided is a method, system, and program for encrypting files in a computer in communication with a volatile memory and non-volatile storage device. An encryption code is generated to encrypt a file and a decryption code is generated to decrypt one file encrypted with the encryption code. The decryption code is loaded into the volatile memory, wherein the decryption code is erased from the volatile memory when the computer reboots. Files written to the non-volatile storage device are encrypted using the encryption code and the decryption code in the non-volatile memory is used to decrypt files encrypted with the encryption code to transfer from the non-volatile storage device to the volatile memory.
Owner:ORACLE INT CORP
System and Method for Third Party Creation of Applications for Mobile Appliances
ActiveUS20110276805A1Prevent accessAvoid accessUnauthorized memory use protectionHardware monitoringThird partyApplication software
The creation of an application for any mobile appliance, for example Apple's iPhone, requires several elements to be present at compile time. In the Apple example of an enterprise application where an entity wishes to develop applications internally for its staff, two of these elements are the source code and a digital certificate. These must be combined in the compiler so that the application may be properly authorized to run in the appliance. Where the owner of the source code and the owner of the digital certificate are not the same, serious concerns arise because each element must be secured. An intermediating system and method are described that allows each party to cooperate securely through a third party escrow service to produce the complied application whilst leaving no unwanted residue of the independent parts.
Owner:BLACKBERRY LTD
Theft deterrent system
Apparatus for dispensing products is disclosed. Certain embodiments of the apparatus include a housing adapted to store a plurality of products, at least one product dispensing mechanism within the housing, at least one theft deterrent mechanism for securing products within the housing, a power source within the housing, an electric motor within the housing for activating the product dispensing mechanism, and an operable control button mounted on the exterior of the housing and electronically connected to the power source and the motor so that activation of the button operates the motor. The apparatus may include a time delay to prevent multiple dispensing within a particular time period. The apparatus may include a sound producing mechanism to alert others of the dispensing of a product.
Owner:ROCK TENN SHARED SERVICES
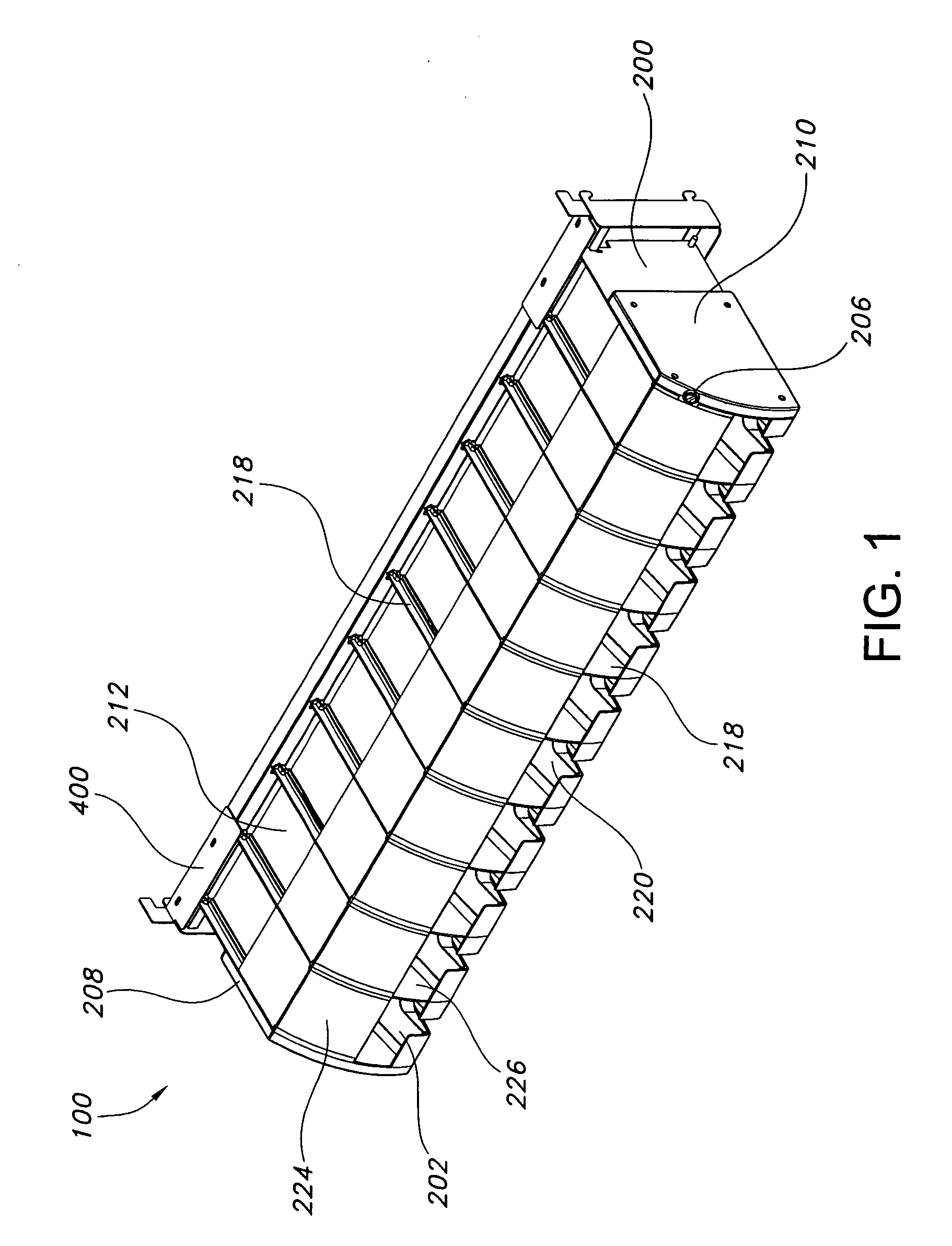
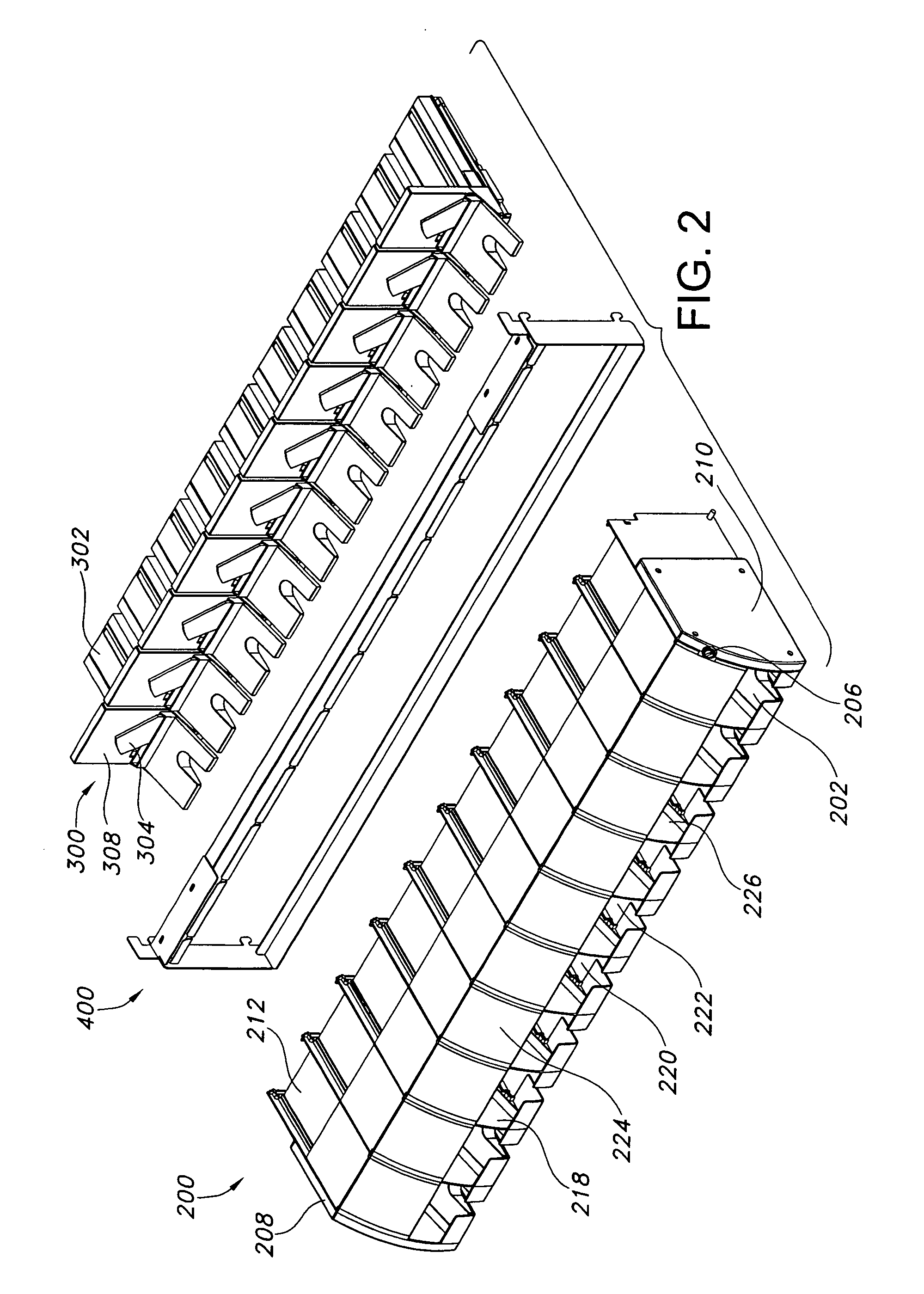
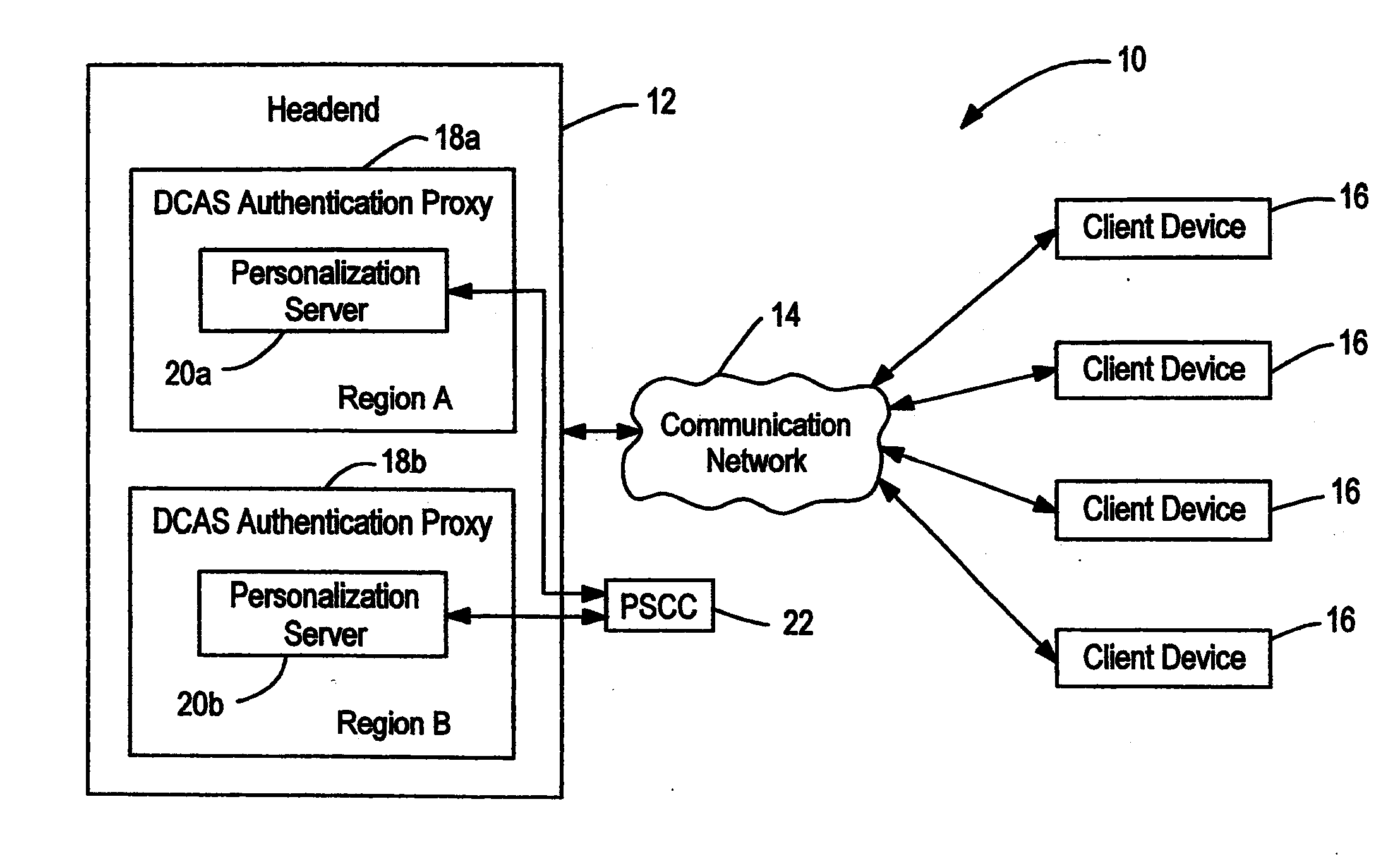
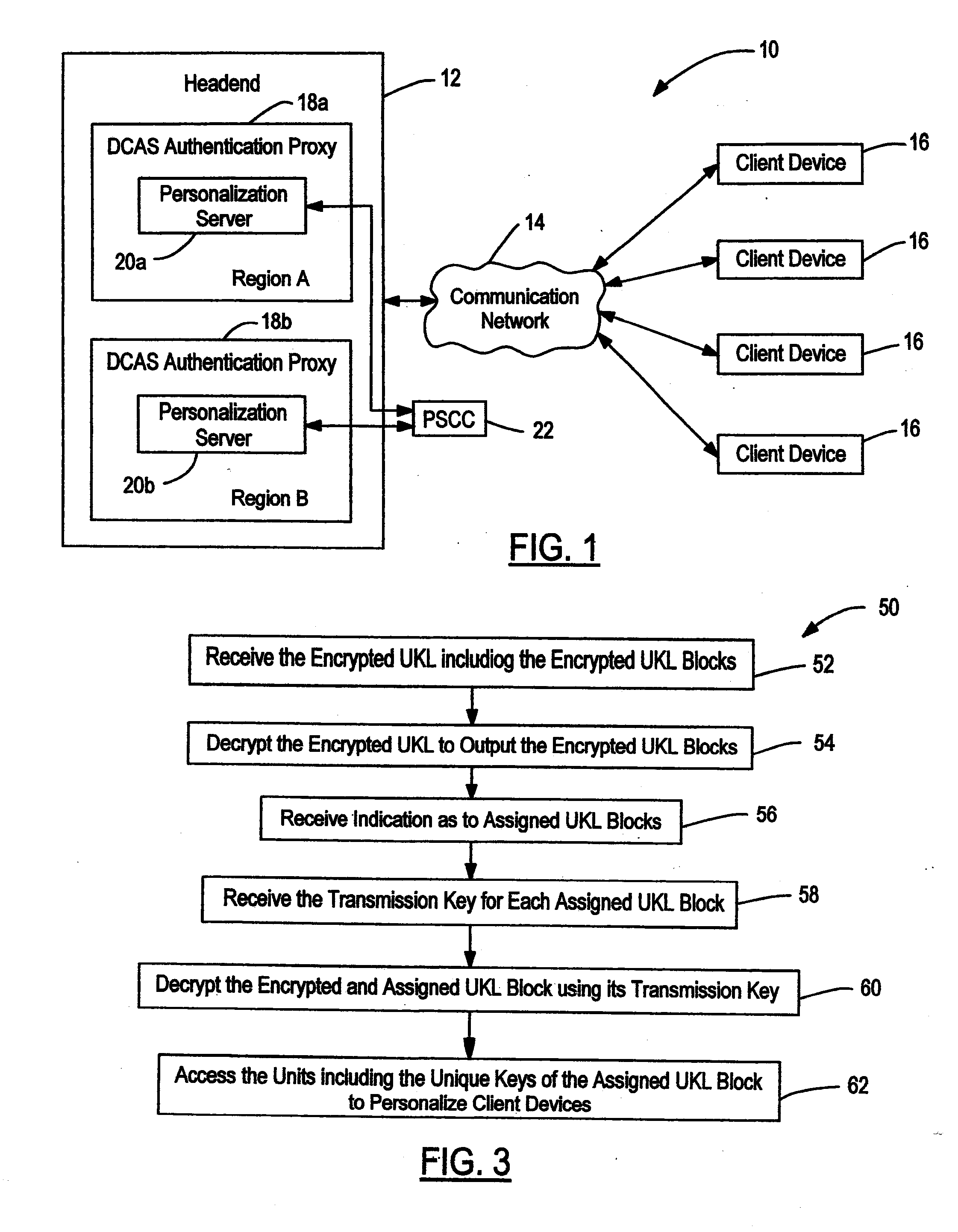
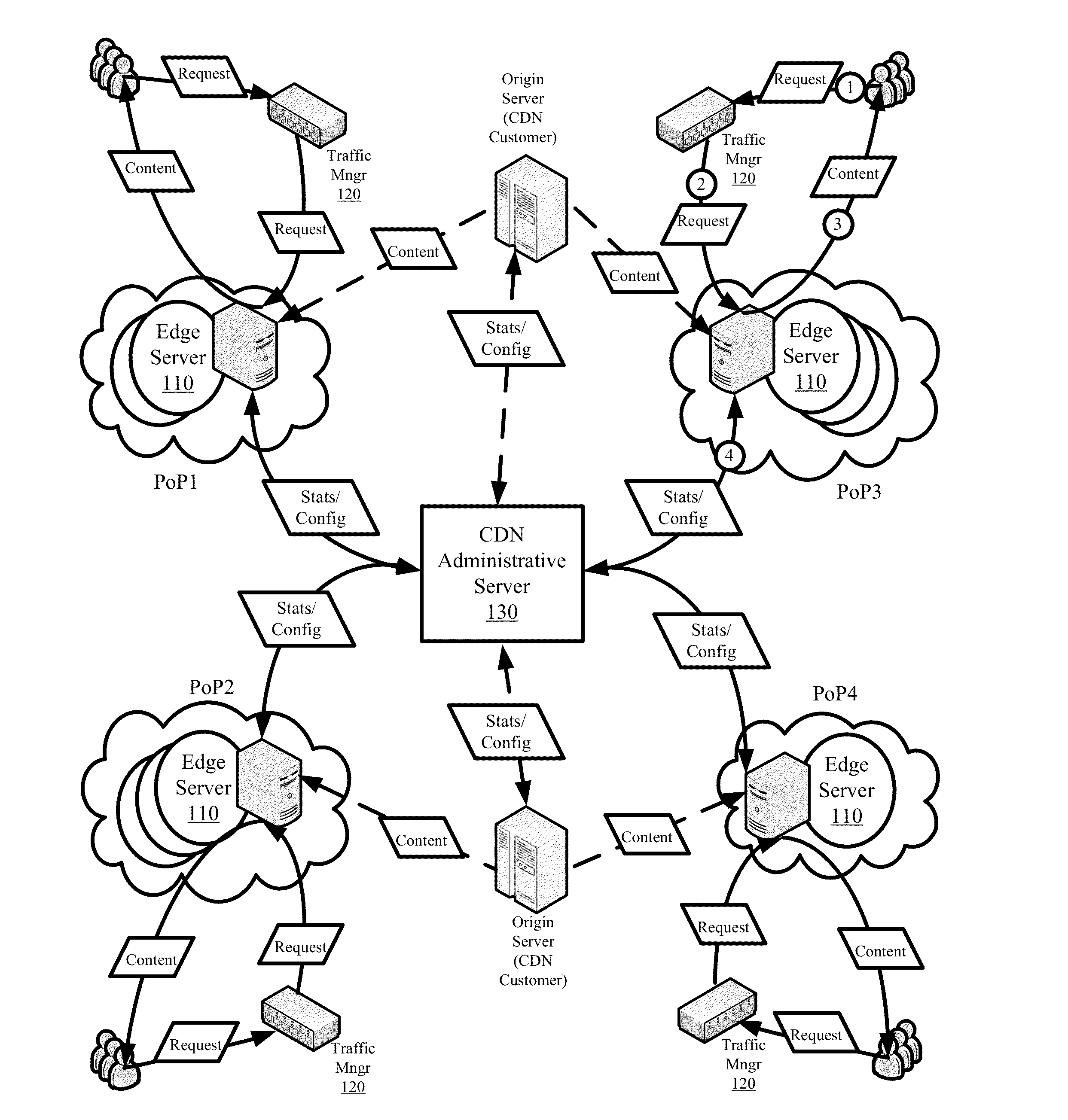
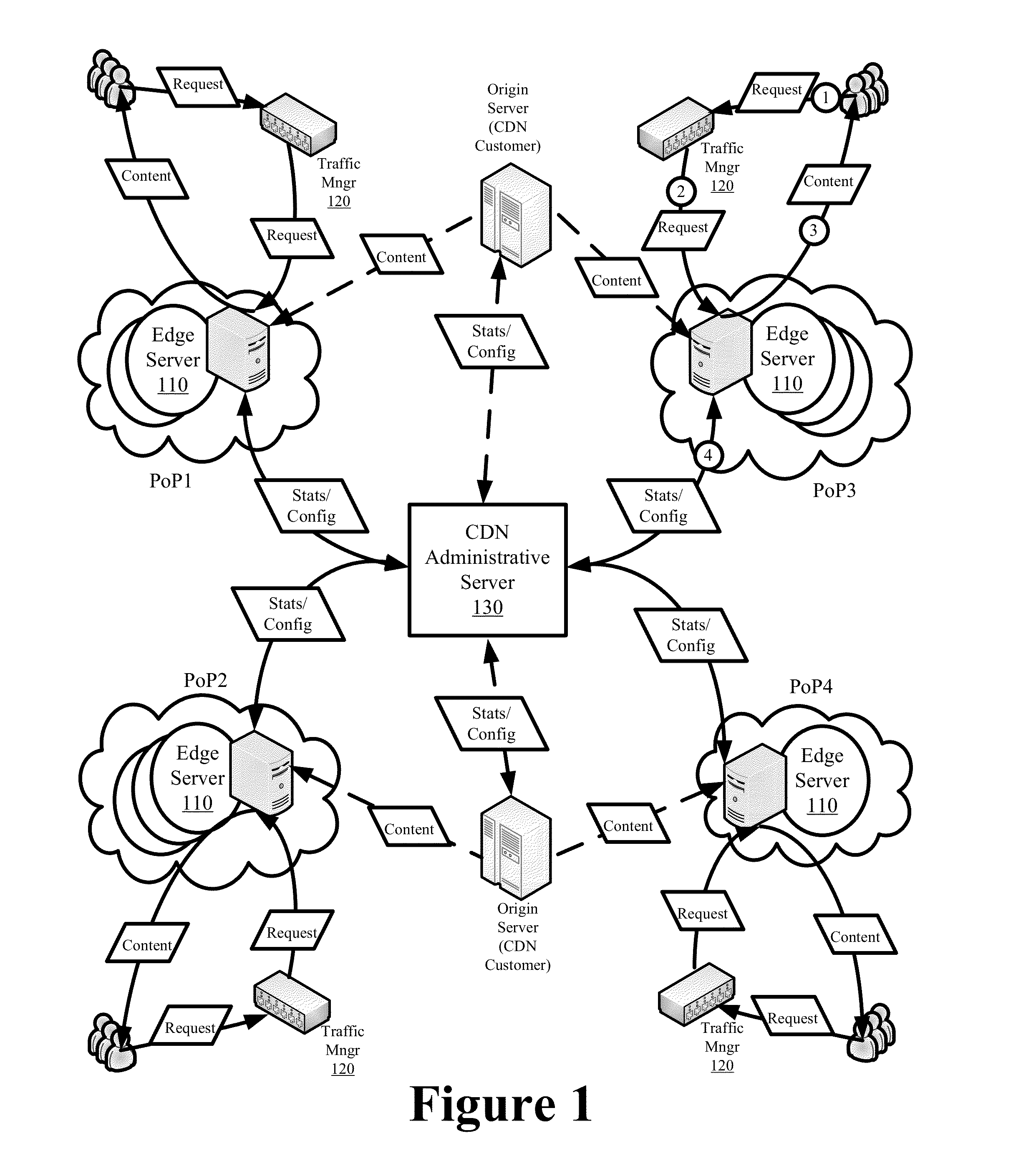
Content Delivery Network Having Downloadable Conditional Access System with Personalization Servers for Personalizing Client Devices
ActiveUS20100142712A1Prevent accessKey distribution for secure communicationMultiple keys/algorithms usageClient-sidePersonalization service
A content delivery network and method employing a Downloadable Conditional Access System (“DCAS”) includes first and second personalization servers. A unit key list having unique keys is segmented into different blocks. Each block is encrypted with a separate transmission key corresponding to that block such that first and second blocks are respectively encrypted with first and second transmission keys. The encrypted blocks are communicated to the personalization servers. The first transmission key is communicated to the first personalization server without being communicated to another personalization server such that the first server can decrypt the first block using the first transmission key to access the keys of the first block. The second transmission key is communicated to the second personalization server without being communicated to another personalization server such that the second server can decrypt the second block using the second transmission key to access the keys of the second block.
Owner:COMBINED CONDITIONAL ACCESS DEV & SUPPORT
System and method for limiting access to features in a mobile telecommunications device
InactiveUS20080254767A1Prevent accessAvoid accessUnauthorised/fraudulent call preventionEavesdropping prevention circuitsElectronic communicationTelecommunications service
A mobile telecommunications device with a processor, memory in electronic communication with the processor, and instructions stored in the memory, the instructions being executable to implement a method for childproof operation wherein the user's access is limited to a subset of applications and services while the device is in childproof mode. A preferred embodiment includes providing a default set of applications and services to enable while in childproof mode and allowing the user to individually specify the applications and services to enable while in childproof mode.
Owner:SHARP LAB OF AMERICA
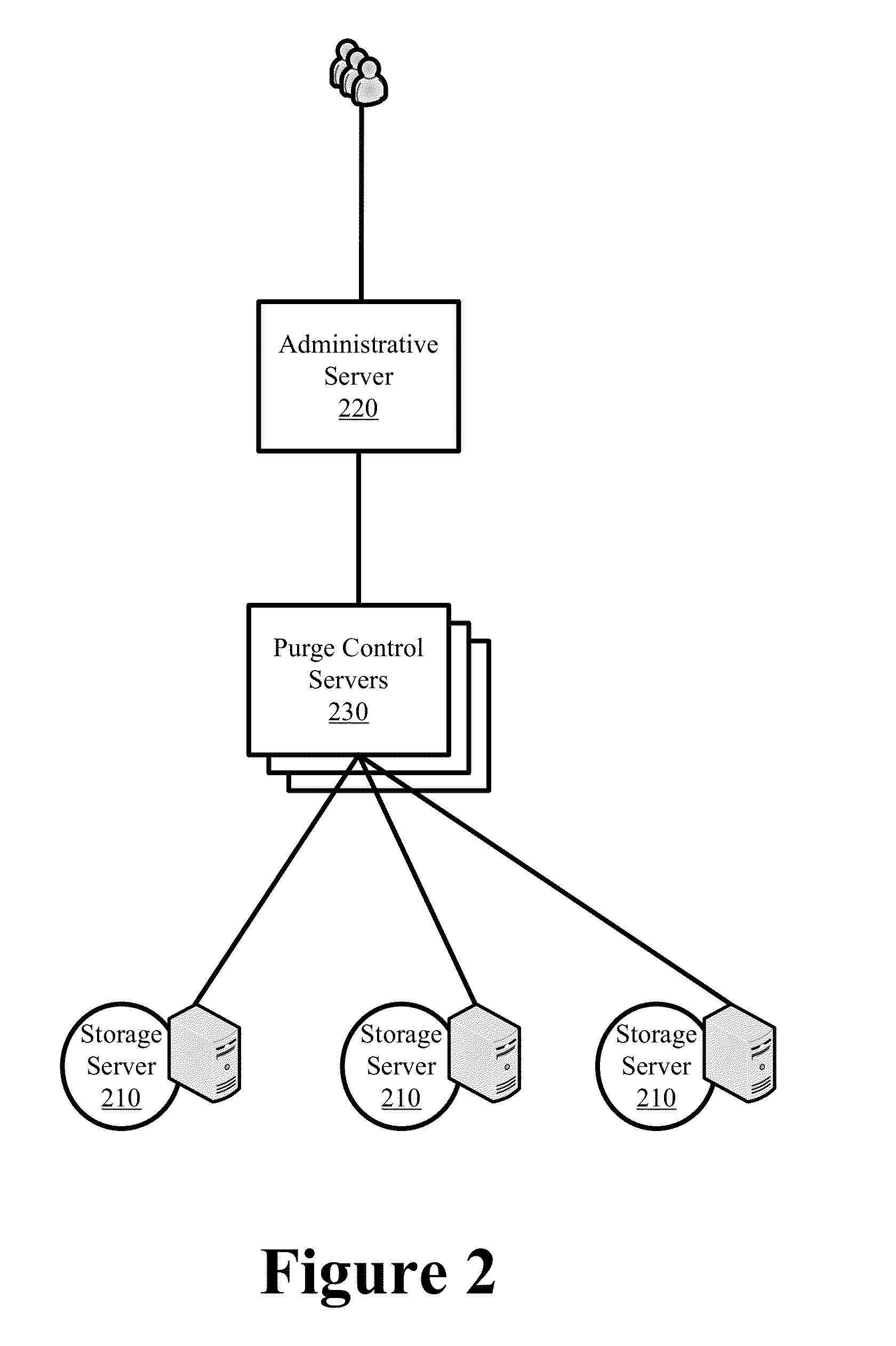
Instantaneous non-blocking content purging in a distributed platform
ActiveUS20150088964A1Prevent accessInhibitory contentTransmissionMemory systemsCache missWorld Wide Web
Some embodiments provide instantaneous and non-blocking content purging across storage servers of a distributed platform. When a server receives a purge operation, it extracts an identifier from the purge operation. The server then generates a content purge pattern from the identifier and injects the pattern to its configuration. Instantaneous purging is then realized as the server averts access to any cached content identified by the pattern. The purging also occurs in a non-blocking fashion as the physical purge of the content occurs in-line with the server's cache miss operation. The content purge pattern causes the server to respond to a subsequently received content request with a cache miss, whereby the server retrieves the requested content from an origin source, serves the retrieved content to the requesting user, and replaces a previously cached copy of the content that is to be purged with the newly retrieved copy.
Owner:EDGIO INC
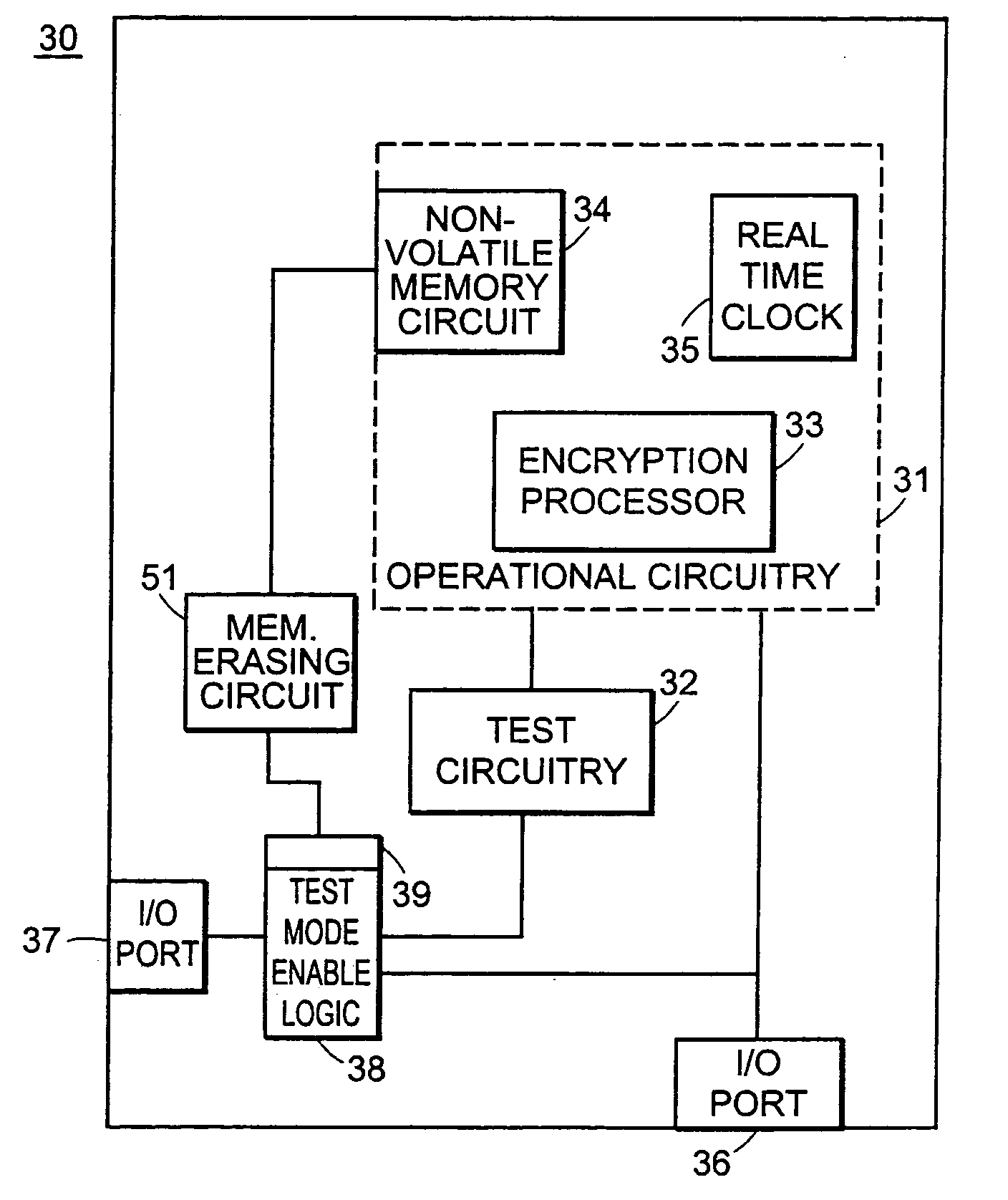
Inter integrated circuit bus router for preventing communication to an unauthorized port
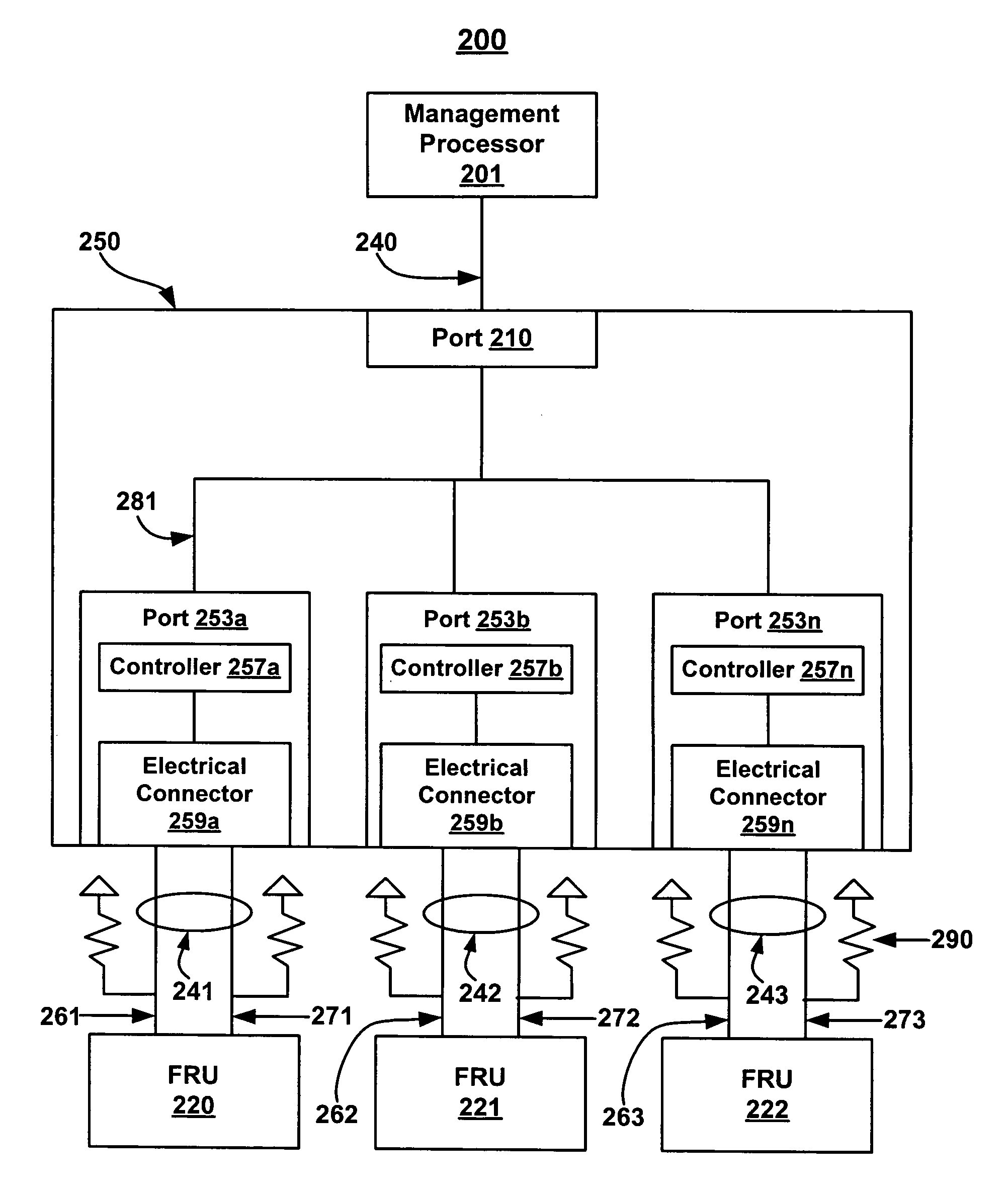
InactiveUS7010639B2Prevent accessPrevent unauthorized accessVolume/mass flow measurementAnalogue secracy/subscription systemsEmbedded systemIntegrated circuit
An inter-integrated circuit port comprising an electrical connector for communicatively coupling to an I2C bus and a controller coupled to the electrical connector. The controller controls data communication flow through the electrical connector, including preventing the electrical connector from unauthorized access to the data.
Owner:HEWLETT PACKARD DEV CO LP
Child-resistant container
InactiveUS20050115862A1Prevent accessSmall article dispensingPharmaceutical containersEngineeringElectrical and Electronics engineering
A child-resistant container for holding at least one item includes a housing having upper and lower walls and a first tray pivotally mounted to the housing on a pivot axis. The first tray is pivotable between a retracted position in which the first tray is positioned in the housing and an exposed position in which the first tray extends from the housing. A second tray is pivotally mounted to the housing for movement between a retracted position in which the second tray is positioned in the housing and an exposed position in which the second tray extends from the housing. The first and second trays are adapted for holding the at least item. A common locking mechanism engages the first and second trays to releasably lock the first and second trays in the retracted position.
Owner:WEST PHARM SERVICES INC
Container assembly
ActiveUS20090178946A1Prevent accessResist damageWing fastenersOther accessoriesEngineeringMechanical engineering
A container assembly for the storage and transport of goods, the assembly including a first portion having an interior with a substantially flat interior bottom surface. The assembly further includes a second portion pivotally connected to the first portion. The first portion has an outer surface that includes a first stacking pattern and the second portion has an outer surface that includes a second stacking pattern which is different from the first stacking pattern and configured to engage the first stacking pattern enabling the container assembly to be bi-directionally stacked on another of the container assemblies.
Owner:CASE-MATE +1
Locking mechanism override and disable for personal computer ROM access protection
InactiveUS7003676B1Not allowPrevent accessVolume/mass flow measurementUser identity/authority verificationPersonal computerMemory address
A method and system for overriding access locks on secure assets in a computer system. The system includes a processor and a device coupled to the processor. The device includes one or more sub-devices, one or more access locks, and an access lock override register that stores one or more access lock override bits, including a lock override bit. The one or more access locks are configured to prevent access to the one or more sub-devices when the one or more access locks are engaged. Access to the one or more sub-devices is not allowed when the lock override bit is set. The method includes requesting a memory transaction for one or more memory addresses and determining a lock status for the one or more memory addresses. The method also includes returning the lock status for the one or more memory addresses. The method may determine if the lock status for the one or more memory address can be changed. The method may change the lock status of the one or more memory addresses to allow the memory transaction.
Owner:GLOBALFOUNDRIES INC
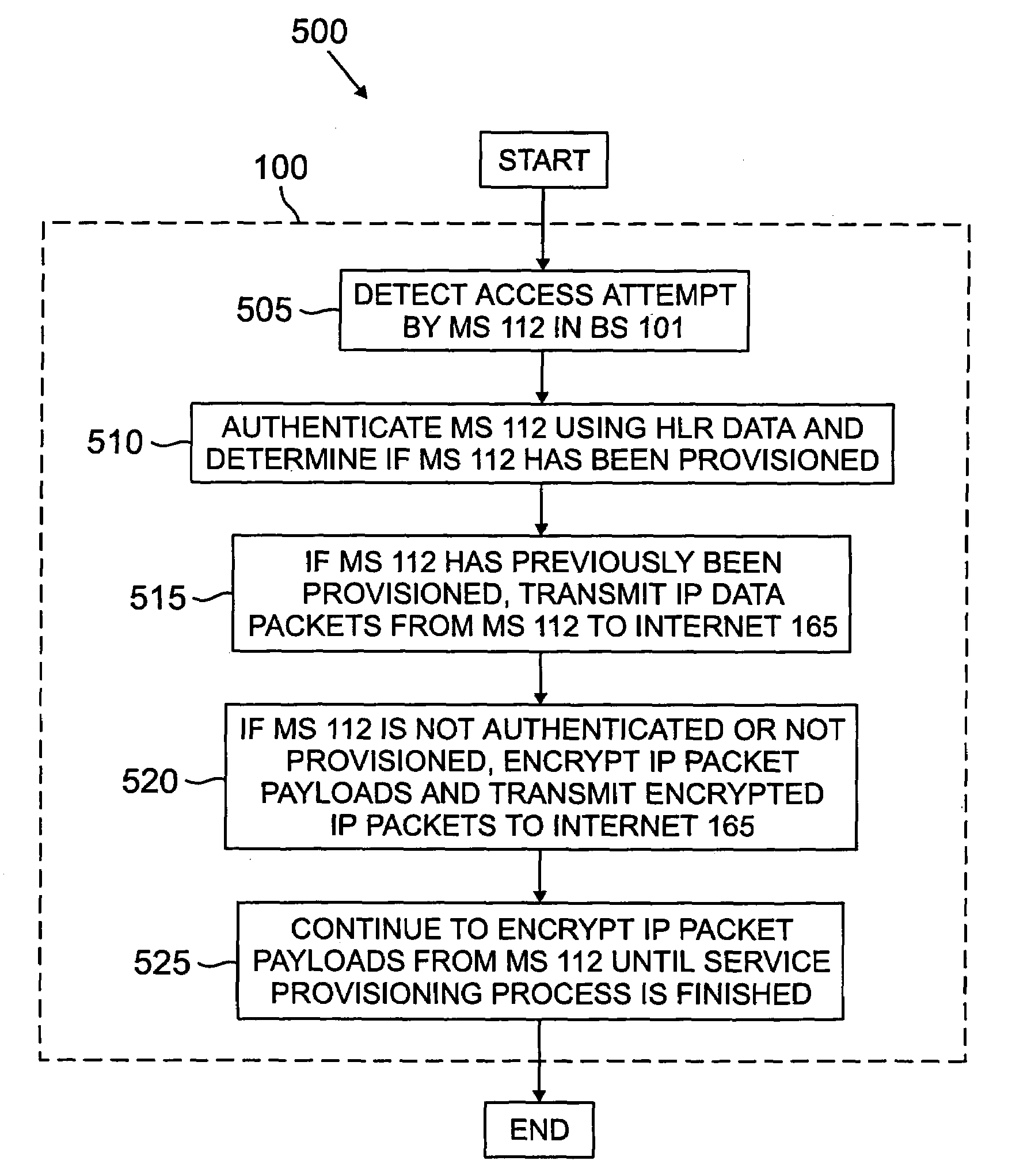
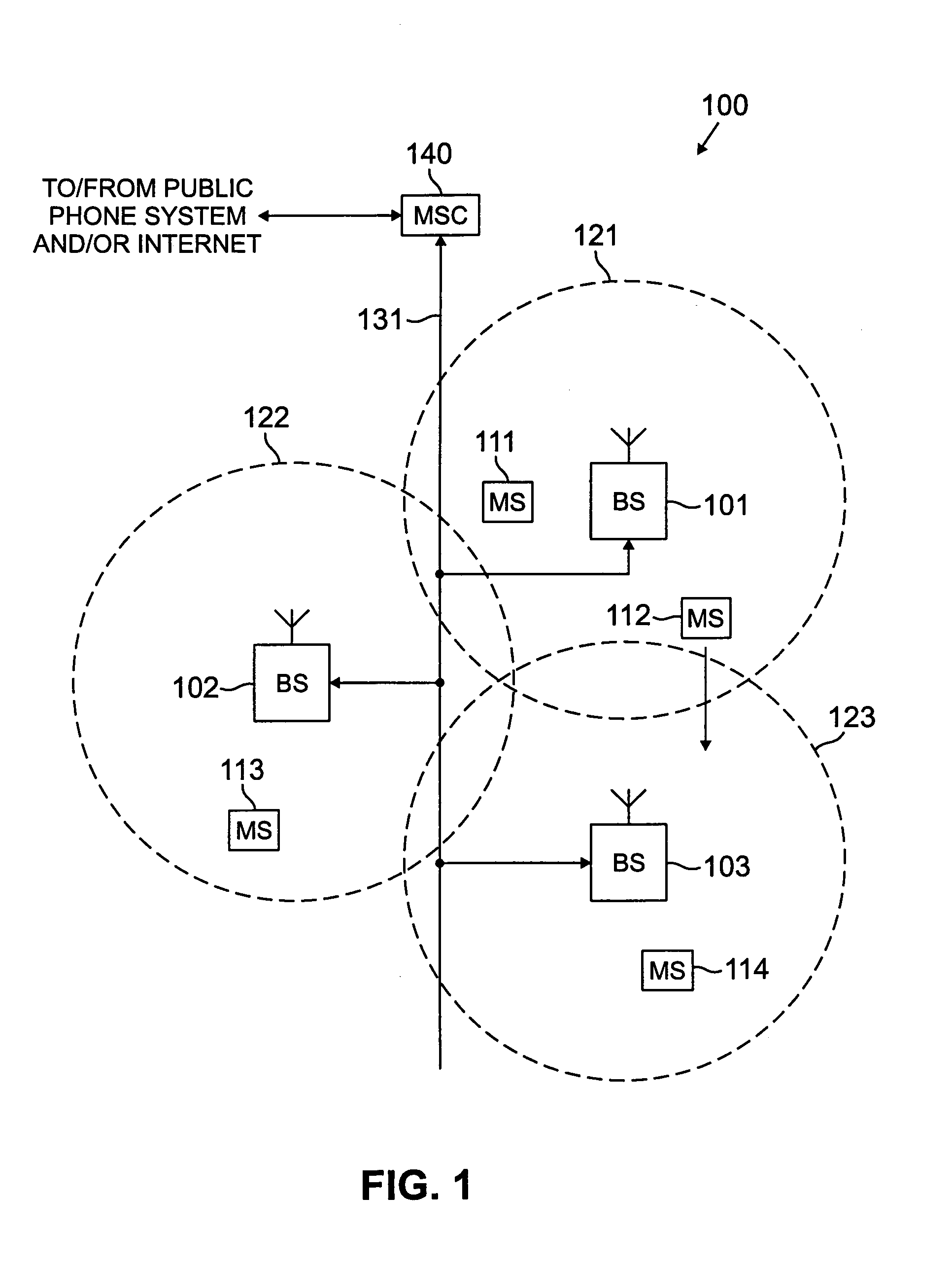
System and method for secure provisioning of a mobile station from a provisioning server using encryption
InactiveUS7024557B1Prevent accessSynchronising transmission/receiving encryption devicesUser identity/authority verificationPacket payloadData processing
There is disclosed a security device for use in a wireless network comprising a plurality of base stations that communicate with a plurality of mobile stations. The security device prevents unprovisioned mobile stations from accessing an Internet protocol (IP) data network through the wireless network. The security device comprises a first controller for receiving from the unprovisioned mobile station an IP data packet comprising an IP packet header and an IP packet payload and encrypting at least a portion of the IP payload. The security device also comprises a second controller for determining that the unprovisioned mobile station is, in fact, unprovisioned. In one embodiment, the first controller comprises a data processor that executes an encryption program stored in a memory associated with the data processor.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for providing global media content delivery
InactiveUS7721103B2Prevent unauthorized accessPrevent accessUser identity/authority verificationAnalogue secracy/subscription systemsClient-sidePoint of presence
One embodiment of the present invention enables global delivery of “on-demand” high fidelity media content to client computers via a network, such as, the Internet or a wide area network (WAN) while restricting unauthorized users from directly retrieving media content from its sources. The present embodiment includes a global media content delivery network that may include multiple “points of presence” which may be located throughout the world. Each point of presence may store a portion or the entirety of a media content library that may be provided to client devices. Each one of the points of presence may provide media content to client devices in their respective vicinity of the world. Once a client receives media, it is stored using hidden directories to prevent easy redistribution with other devices. An access key procedure and rate control restrictor may also be implemented to monitor and restrict suspicious media requests.
Owner:MUSIC PUBLIC BROADCASTING
Identifying risks in conflicting duties
InactiveUS20060074739A1Prevent accessEfficiently determineFinanceMultiprogramming arrangementsKnowledge managementBusiness function
An audit system includes a set of business processes that describe the operations of an enterprise. The audit system has a registry of incompatible business functions created from a library of business processes. Each pair of incompatible business functions is associated with one or more risks. Each risk can include a category, a risk probability, and / or a risk impact. An audit manager compares the business function incompatibilities of the registry with the set of business functions assigned to the employee, and a report generator creates a report identifying the risk introduced by the match. The audit manager creates an audit task in response to a match. An impacted financial statement manager displays a financial statement, a set of financial accounts, a set of business functions and the set of risks associated with the set of financial accounts.
Owner:ORACLE INT CORP
System and method for preventing disk cloning in set-top boxes
InactiveUS20070050294A1Prevent accessAvoid accessTelevision system detailsData processing applicationsHard disc driveHigh definition
Owner:ENCENTRUS SYST
Memory access protection apparatus and methods
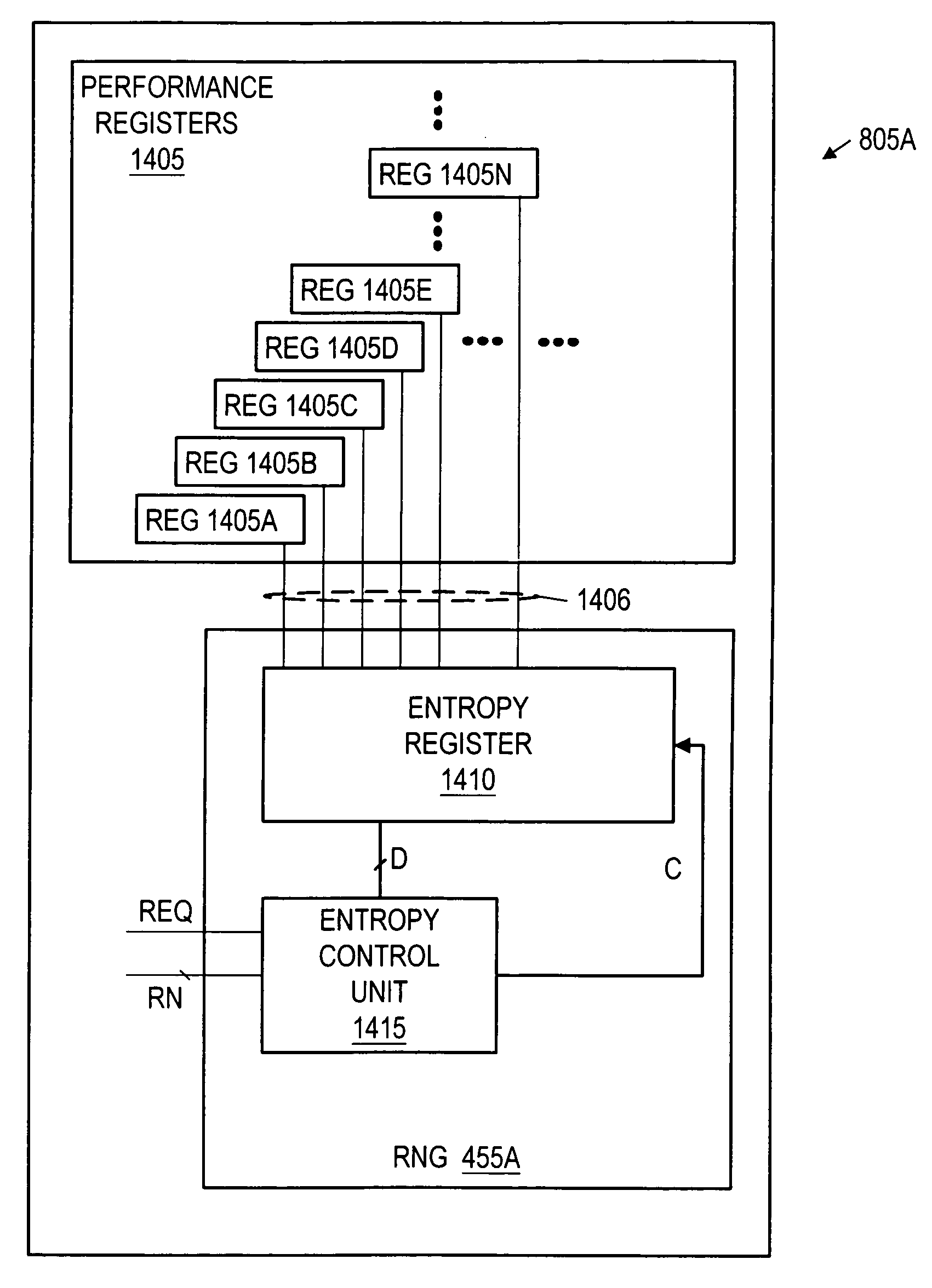
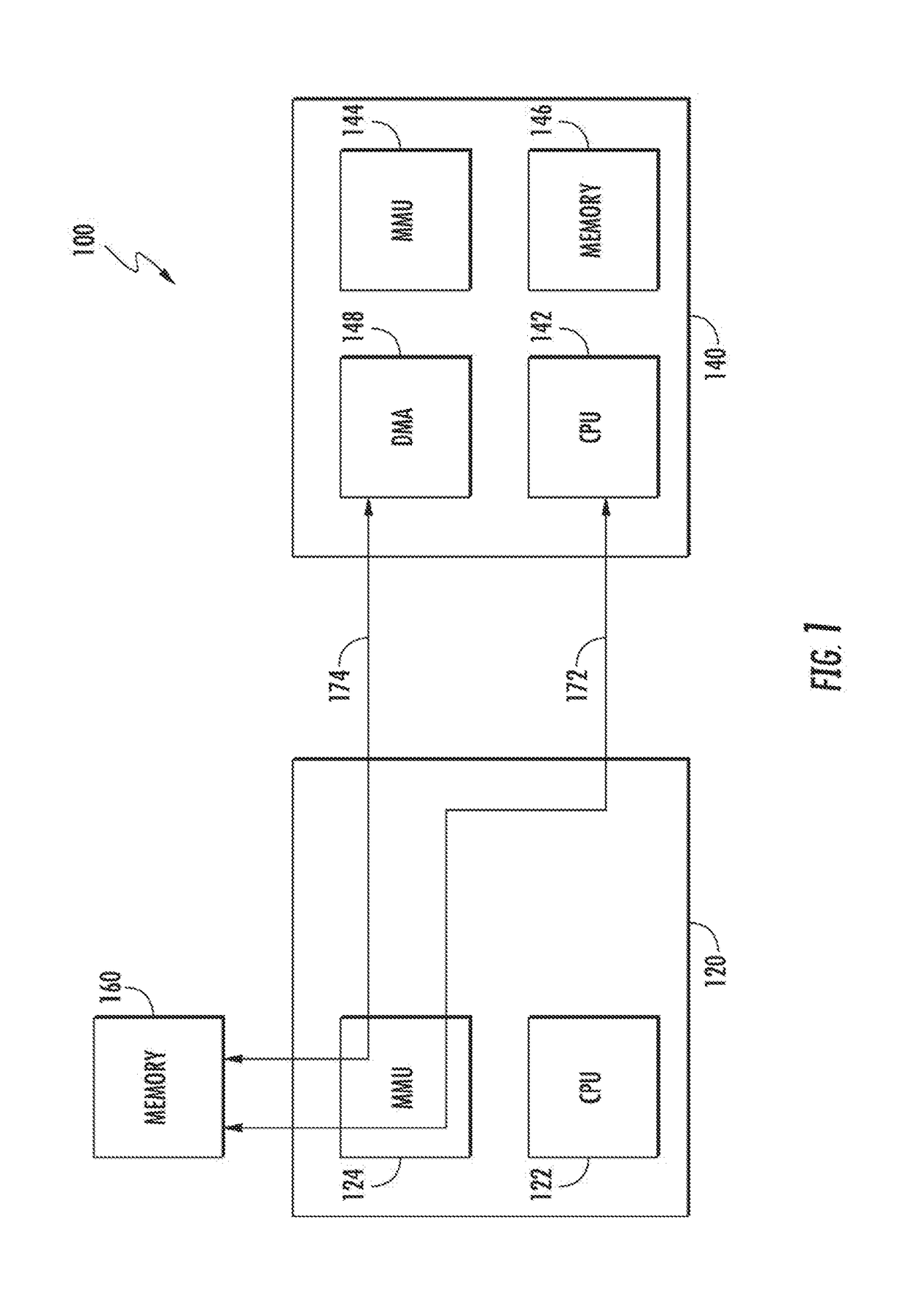
ActiveUS20170286323A1Prevent accessMemory architecture accessing/allocationUnauthorized memory use protectionAddress spaceProcessor register
Methods and apparatus for providing access to a shared memory resource. In one embodiment, a first processor generates a first window register associated with the shared memory resource; and transmits the first window register from the first processor to a second processor, the first window register defining a first extent of address space within the shared memory resource that is directly accessible by the second processor without requiring a performance of arbitration operations by the first processor.
Owner:APPLE INC
Cryptographic Secure Program Overlays
ActiveUS20080301468A1Prevent accessVolume/mass flow measurementAnalogue secracy/subscription systemsLarge applicationsApplication software
Owner:IBM CORP
Autonomic removal of a user from a client and network
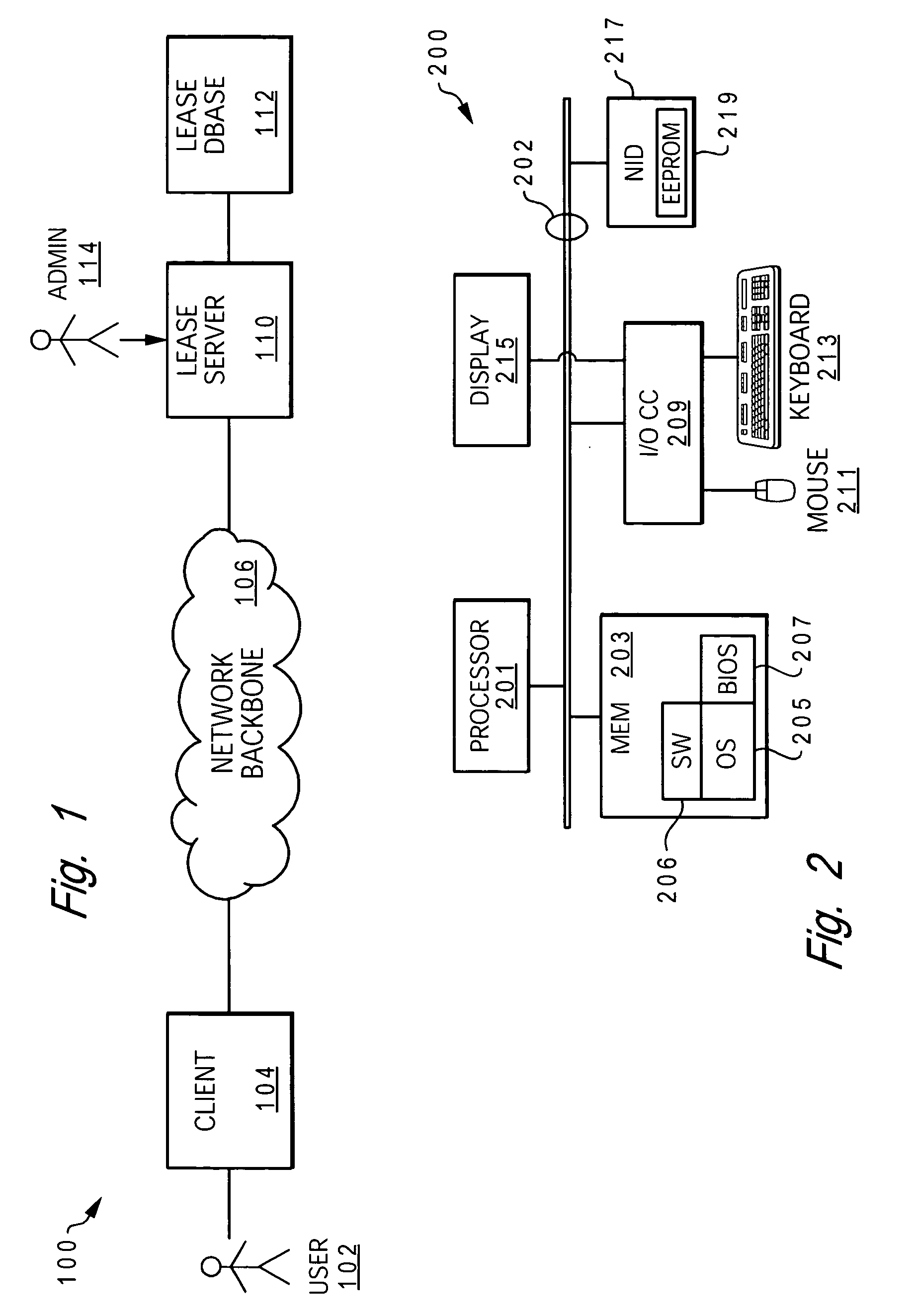
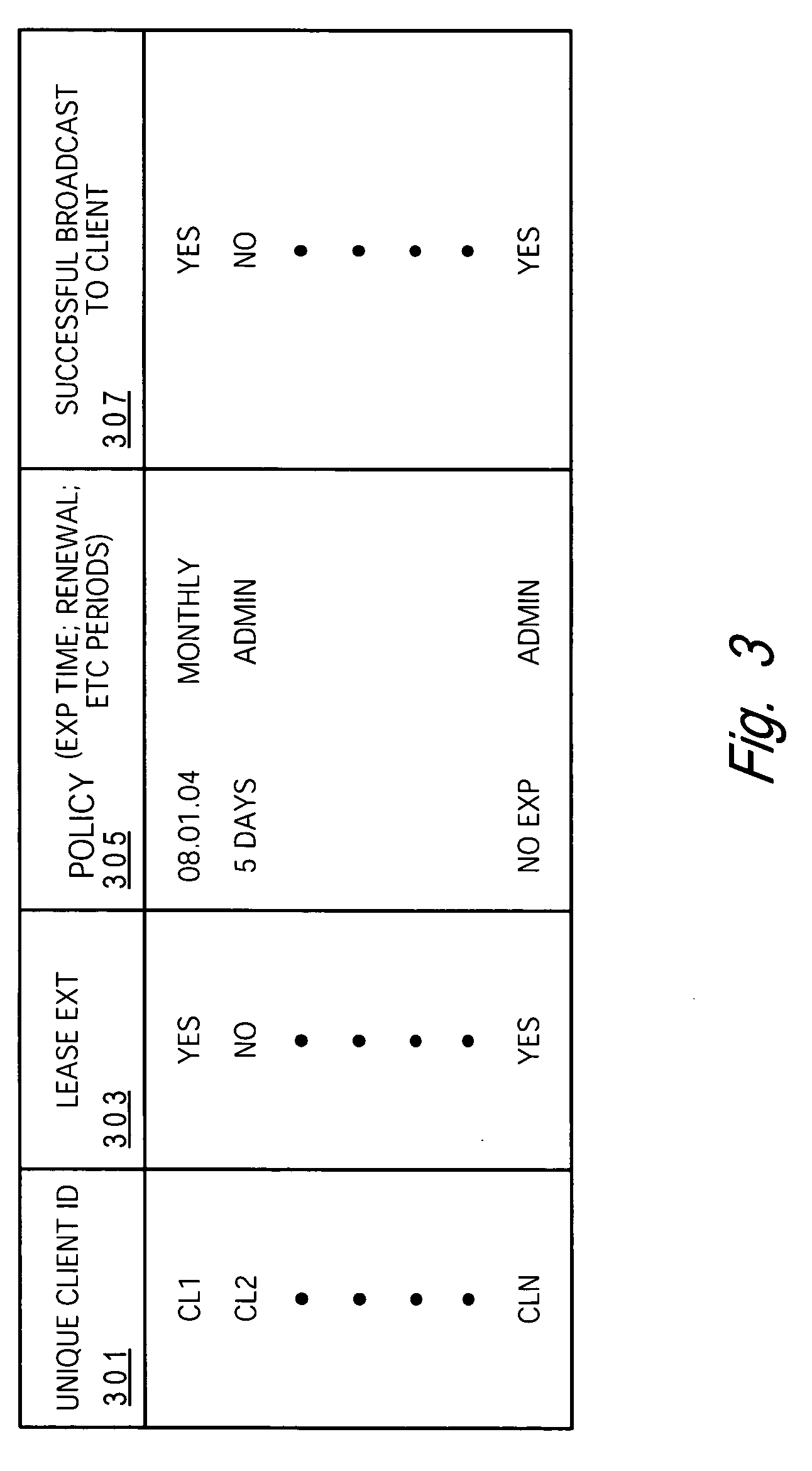
InactiveUS20060085648A1Prevent accessComputer security arrangementsSecuring communicationClient-sideClient system
A method that restricts a user's access to critical data on a client and network by requiring renewal of a client's lease for accessing the network by an administrative utility of the network during each login by a user to the client. A user / client logon policy is created for each user and / or each client and stored at the lease server. The lease server executes a utility that utilizes the policies to control whether a user is allowed to access a particular client on the network. User access to the client and ultimately the network is only provided when the lease term is renewed for the client (and user). When a lease term is not renewed / extended, the user is blocked from accessing the client system.
Owner:LENOVO (SINGAPORE) PTE LTD
Secure ephemeral decryptability
Owner:ORACLE INT CORP
Resource sequester mechanism
InactiveUS7043581B1Prevent accessInternal/peripheral component protectionSecret communicationEmbedded systemTimer
A method and system for controlling access to selected resources in a computer system. The system includes a processor and a device coupled to the processor. The device includes one or more sub-devices and one or more access locks. The access locks are configured to prevent access to the sub-devices when the access locks are engaged. The device may include a bridge. The sub-devices may include a duration timer, mailbox RAM, locks for a storage device, overrides for the locks for the storage device, a TCO counter, a monotonic counter, scratchpad RAM, and / or a random number generator. The method includes unlocking security hardware and accessing a first device. The method also includes locking the security hardware and calling an SMM exit routine.
Owner:GLOBALFOUNDRIES INC
Device for melting and remolding crayons
InactiveUS20050008729A1Prevent accessEnhance safe operationConfectioneryNon-propelling pencilsHeating elementGate control
A device suitable for use by children which recycles broken crayons and other materials by melting and molding. A stationary melting pot securely retains the charge material during heating. A housing substantially surrounds the melting pot and an associated mold chamber to isolate young operators from all heated surfaces. The melting pot is charged from outside of the housing by use of a filling port. A remotely operated gate controls the flow from the melting pot to a mold. A door provides access to the mold when open and prevents access to the mold chamber when closed. A warning light glows when a heating element for the melting chamber is energized. Various safety switches interrupt power to the heating element if certain conditions are not met.
Owner:FERNANDEZ MARK S +1
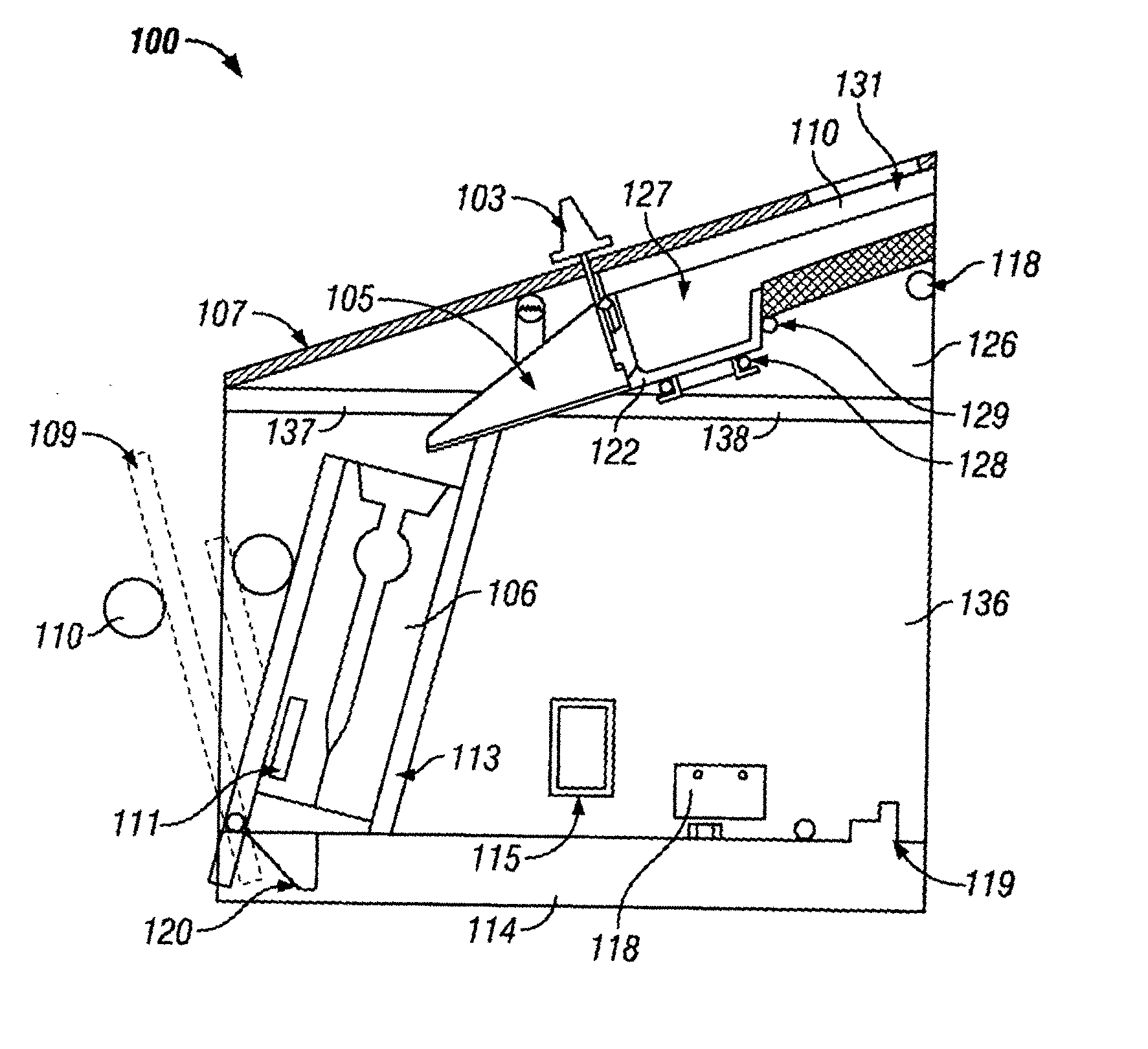
Safety window shade assembly
InactiveUS20120031569A1Prevent accessExtensible doors/windowsShutters/ movable grillesEngineeringMechanical engineering
A dual shade apparatus comprises a first shade, which may be a Roman or natural woven shade, and a second shade, which may be a cellular shade, coupled to each other in a back-to-back arrangement with one or more dual channeled couplers. Any lift cords employed in the apparatus are concealed in between the pair of shades so as to prevent any direct contact. No portion of any employed cords is exposed or accessible for direct or inadvertent contact, thereby enhancing safety in operating the apparatus. The coupler has a double-C configuration to receive corresponding retaining mechanisms of the front and rear shades. A head rail houses a lifting mechanism. Each lifting cord extends from the lifting mechanism, in between the two shades, and down to a bottom rail. The dual shades are drawn down or retracted in unison by pulling or pushing up the bottom rail.
Owner:MARIAK INDS
Network interface device, apparatus, and methods
ActiveUS20070160195A1Prevent accessPrevent unauthorized accessInterconnection arrangementsElectrically conductive connectionsMechanical engineeringInsulation-displacement connector
A line module includes a plurality of pivoting insulation displacement connector holders, an insulation displacement connector (IDC) positionable in at least one holder when the holder is in a connected position, and a gel-less jack in electrical communication with at least one IDC.
Owner:CORNING OPTICAL COMM LLC
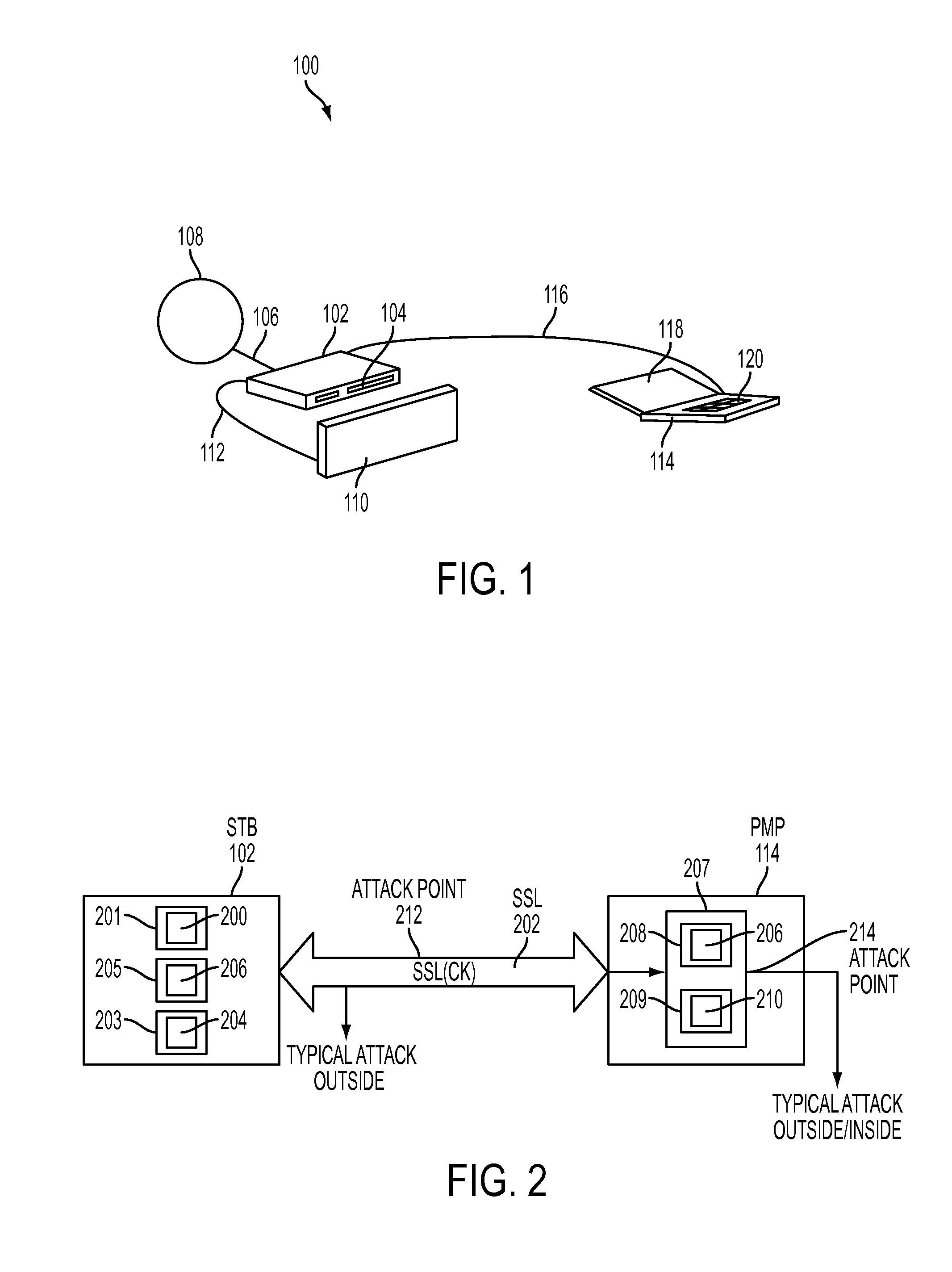
System and method for securely transfering content from set-top box to personal media player
InactiveUS20110145562A1Prevent accessKey distribution for secure communicationDigital data processing detailsSet top boxSession key
A media player is provided for receiving session data from a security socket layer. The session data includes encrypted content data, a content key and digital rights data, wherein the content key and the digital rights data have been encrypted with a SSL session key. The said media player includes a first processor portion and a second processor portion. The first processor portion is arranged to receive the session data, has a second key. The first processor portion and can generate the SSL session key and can decrypt the session data with the SSL session key. The first processor portion can further re-encrypt the decrypted content key with the second key and can output the re-encrypted content key and digital rights data. The second processor portion is arranged to receive the re-encrypted content key and digital rights data. The first processor portion can further decrypt the content, and is externally inaccessible.
Owner:GOOGLE TECH HLDG LLC
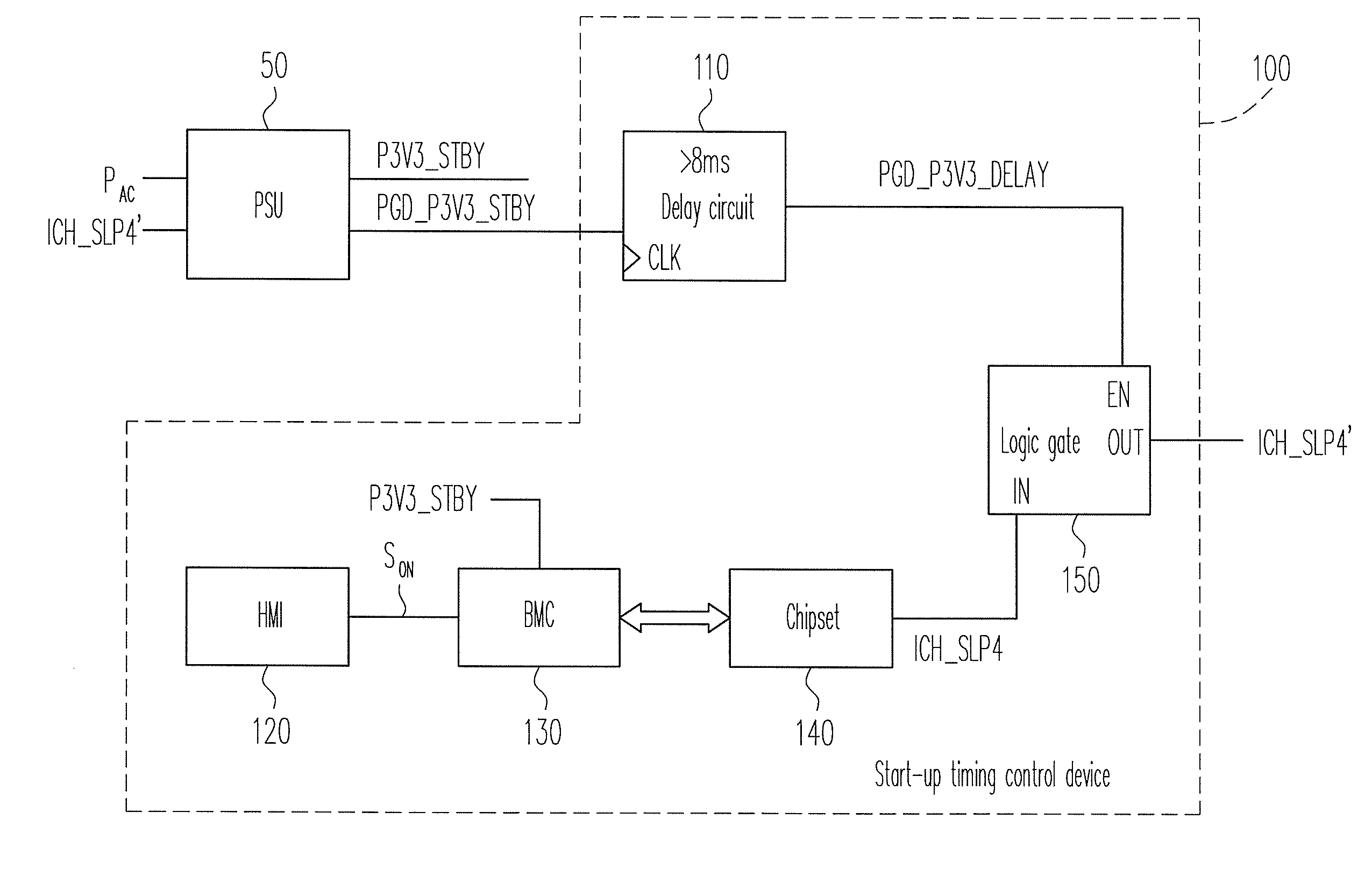
Computer start-up timing control device and method thereof
InactiveUS20100095138A1Prevent accessData resettingPower supply for data processingStart up timeInit
A computer start-up timing control device and a method thereof are provided for generating a power supply signal to enable a power supply unit (PSU) to provide power. The device includes a chipset, a delay circuit, and a logic gate. The delay circuit delays a standby power ready signal of the computer to generate a standby power delay signal. The chipset generates a power supply signal. The standby power delay signal enables the logic gate to transmit the power supply signal to the PSU via the logic gate. The PSU provides a power to make the computer enter a start-up procedure. The standby power delay signal delays the time for the chipset to send a power supply signal, so that a baseboard management controller (BMC) has enough time to complete initialization. Therefore, the chipset is prevented from accessing the BMC and obtaining erroneous information before the BMC finishes initialization.
Owner:INVENTEC CORP
Method and device for data communication in a network
ActiveUS20160066208A1Prevent accessBlocking in networkError preventionTransmission systemsMechanism basedDistributed computing
The invention relates to a communication device and a method of sending data over a communication network. The communication device includes a controller for accessing the network using contention type access mechanism based on computation of back-off values, and includes a plurality of traffic queues for serving data traffic at different priorities. The controller includes a plurality of back-off engines, each associated with one traffic queue and configured to compute a back-off value in accordance with the priority of the associated traffic queue. One or more back-off engine may be adjusted to prevent the back-off value of such back-off engine to reach zero. When an access to the network is obtained for the device. a traffic queue may be selected based on its associated back-off value, and data may be transmitted from the selected traffic queue.
Owner:CANON KK
Data processing device and data processing method
ActiveUS20070204171A1Enhanced securityPrevent accessDigital data processing detailsUnauthorized memory use protectionData processingComputer hardware
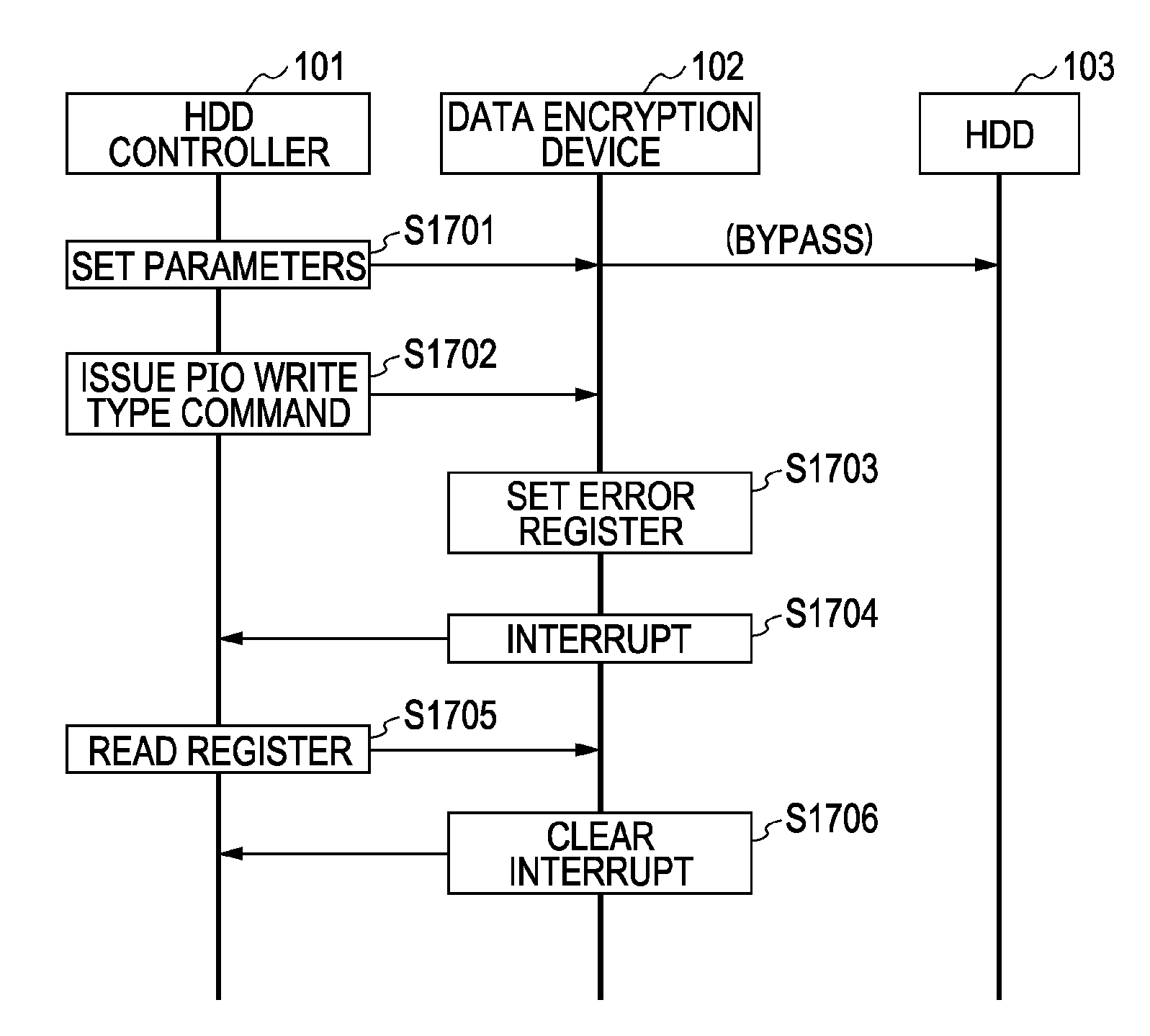
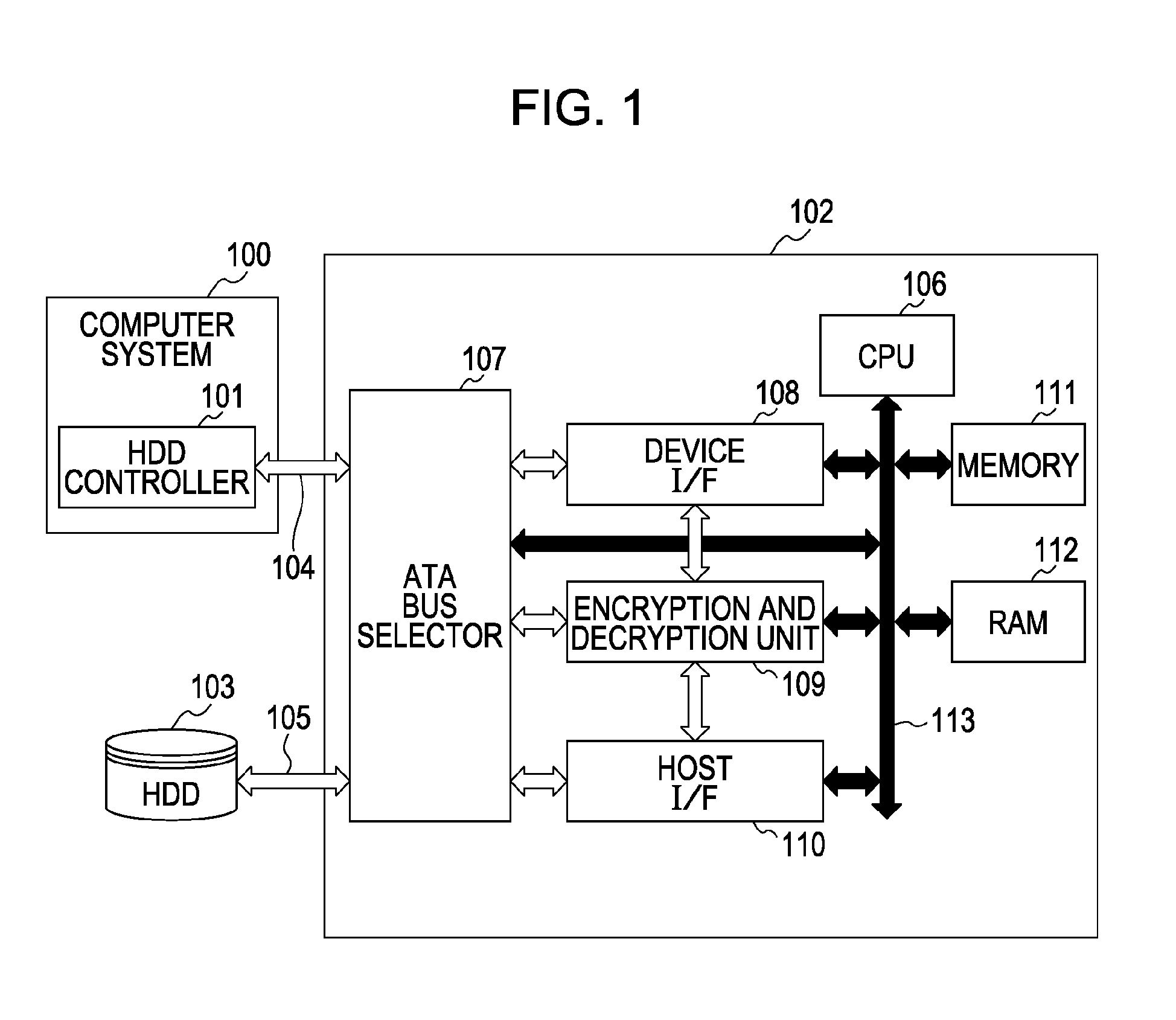
A data encryption device is connected between an HDD and an HDD controller that controls the HDD. The data encryption device encrypts data that is stored from the HDD controller to the HDD, and decrypts data that is read from the HDD. A CPU of the data encryption device receives a command issued from the HDD controller to the HDD, and determines whether the command is executable at the HDD. When it is determined that the command is executable, the command is issued to the HDD. On the other hand, when it is determined that the command is unexecutable, the CPU prohibits issuance of the command to the HDD. Furthermore, when a command issued to the HDD is a specific command, the CPU bypasses data transferred between the HDD controller and the HDD without encryption or decryption.
Owner:CANON KK
Method and apparatus for selecting an encryption integrated circuit operating mode
InactiveUS7009419B2Prevent accessAvoid accessDigital circuit testingDigital storageIntegrated circuitElectricity
A method and circuit for preventing external access to secure data of an integrated circuit while supporting DFT is disclosed. In accordance with the method the integrated circuit is automatically placed into the test mode at integrated circuit power-up from a power-down state. At power up, secure data is other than present within a secure data-path of the integrated circuit. Access is provided to the secure data path via a second data path coupled with the first secure data-path. Via the access path, data other than secure data is provided to the integrated circuit, the data for performing test functions of the integrated circuit operating in the test mode. Once data other than secure data is provided to first secure data path, the test mode is terminated and access via other than the secure ports is disabled. The test mode is only re-entered by powering down the integrated circuit and re-initialising it.
Owner:TAIWAN SEMICON MFG CO LTD
Covering apparatuses for prevention of bed bug intrusion and methods of use thereof
A bed covering apparatus that prevents bed bugs from intrusion to an enclosed sleeping area, wherein the bed covering apparatus has a net for exclusion of insects, and also contains at least one slippery section to which bed bugs cannot adhere, thereby causing the bed bugs to fall from the netted sleeping area before they have an opportunity to enter the sleeping enclosure.
Owner:PARK JEE SUN +2
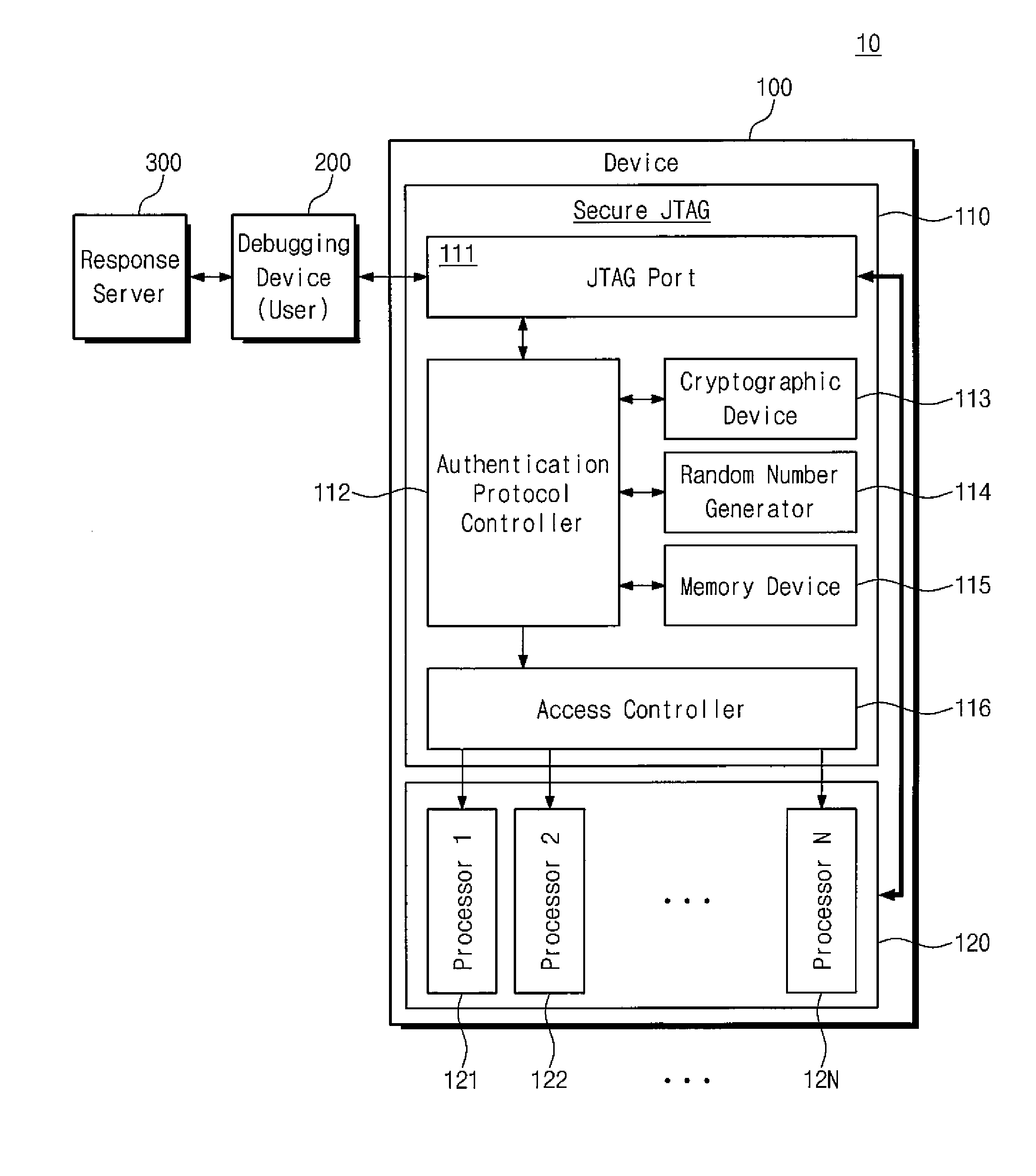
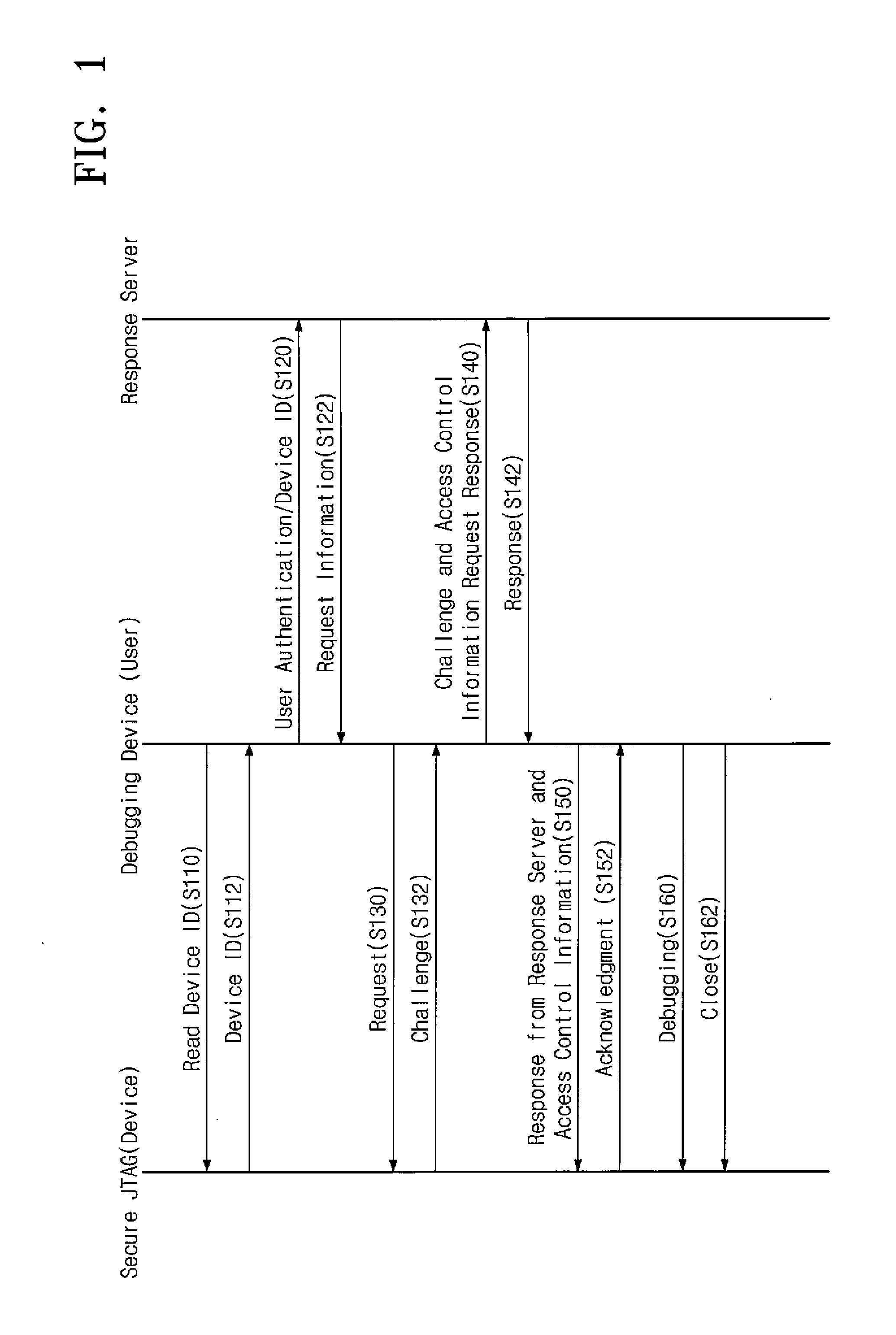
Device having secure jtag and debugging method for the same
ActiveUS20150242606A1Prevent accessAvoid accessDigital data processing detailsElectrical testingChallenge responseComputer hardware
A method of debugging a device which includes a plurality of processors is provided. The method includes verifying a request to initiate authentication that is provided to the device to a user; performing a challenge-response authentication operation between the user and the device in response to the request to initiate authentication being a request from a non-malicious user; activating or deactivating an access to a Joint Test Action Group (JTAG) port of each of the processors, based on access control information from the user; and permitting a debugging operation via an access that is activated.
Owner:SAMSUNG ELECTRONICS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com