Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
58results about How to "Efficiently authenticating" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
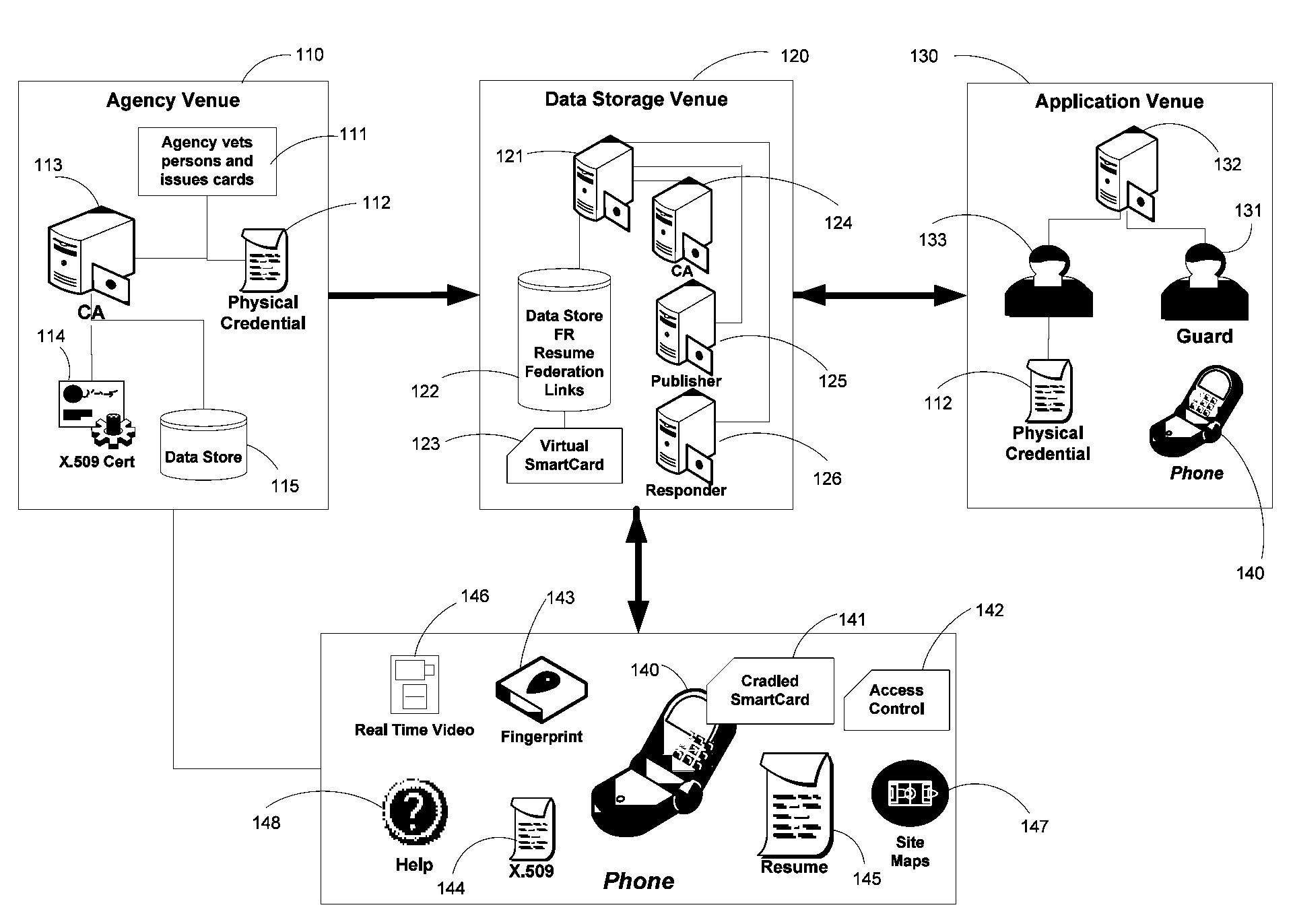
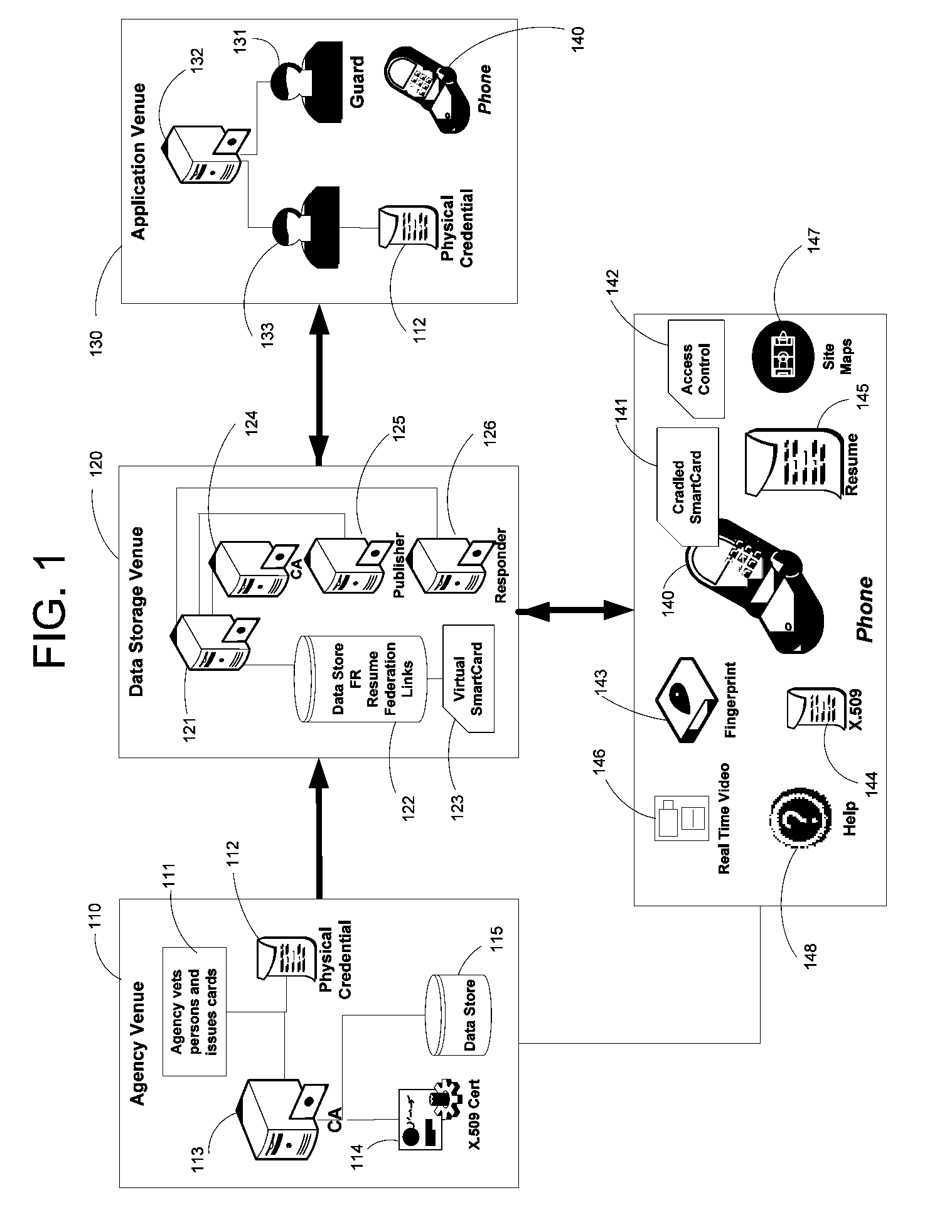
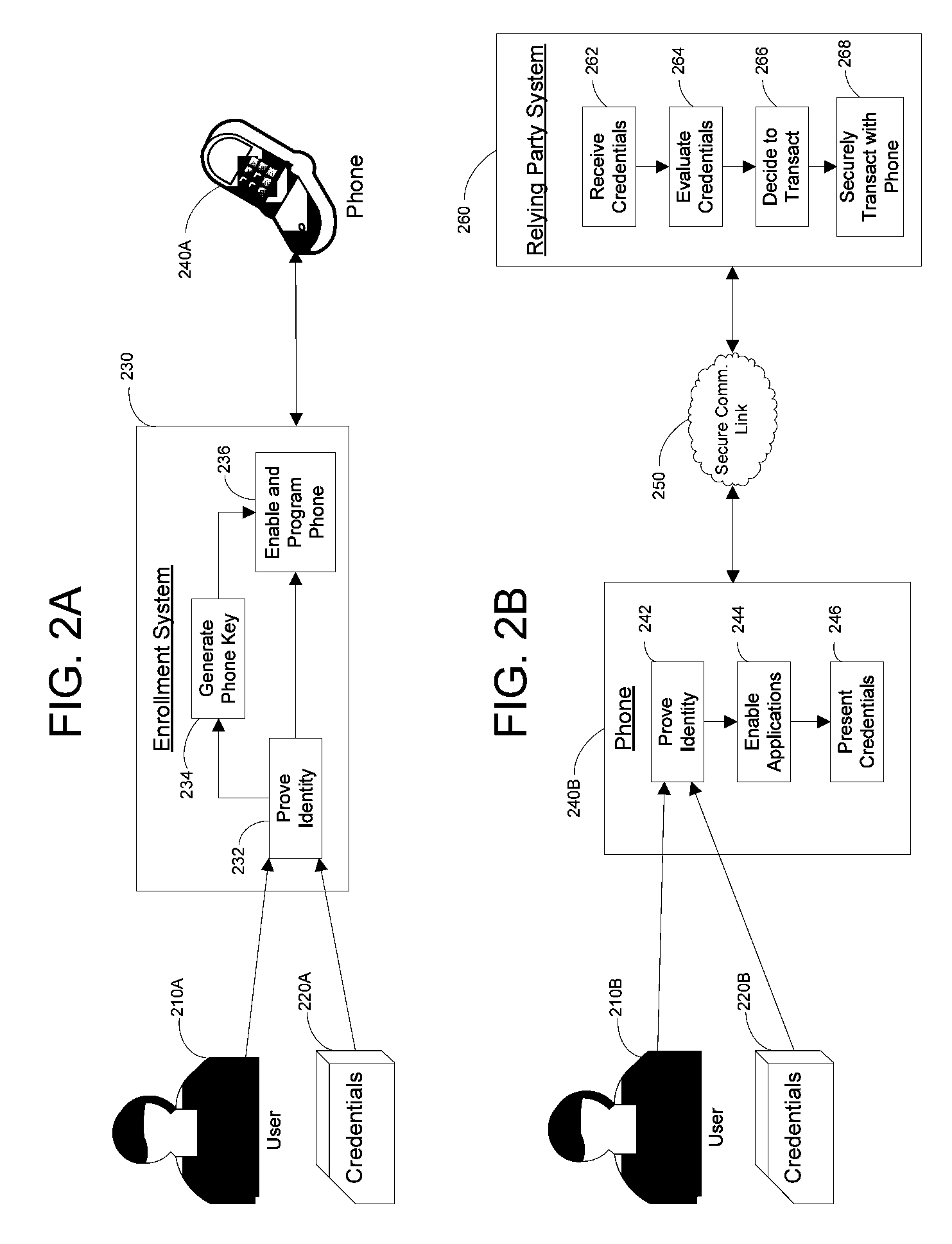
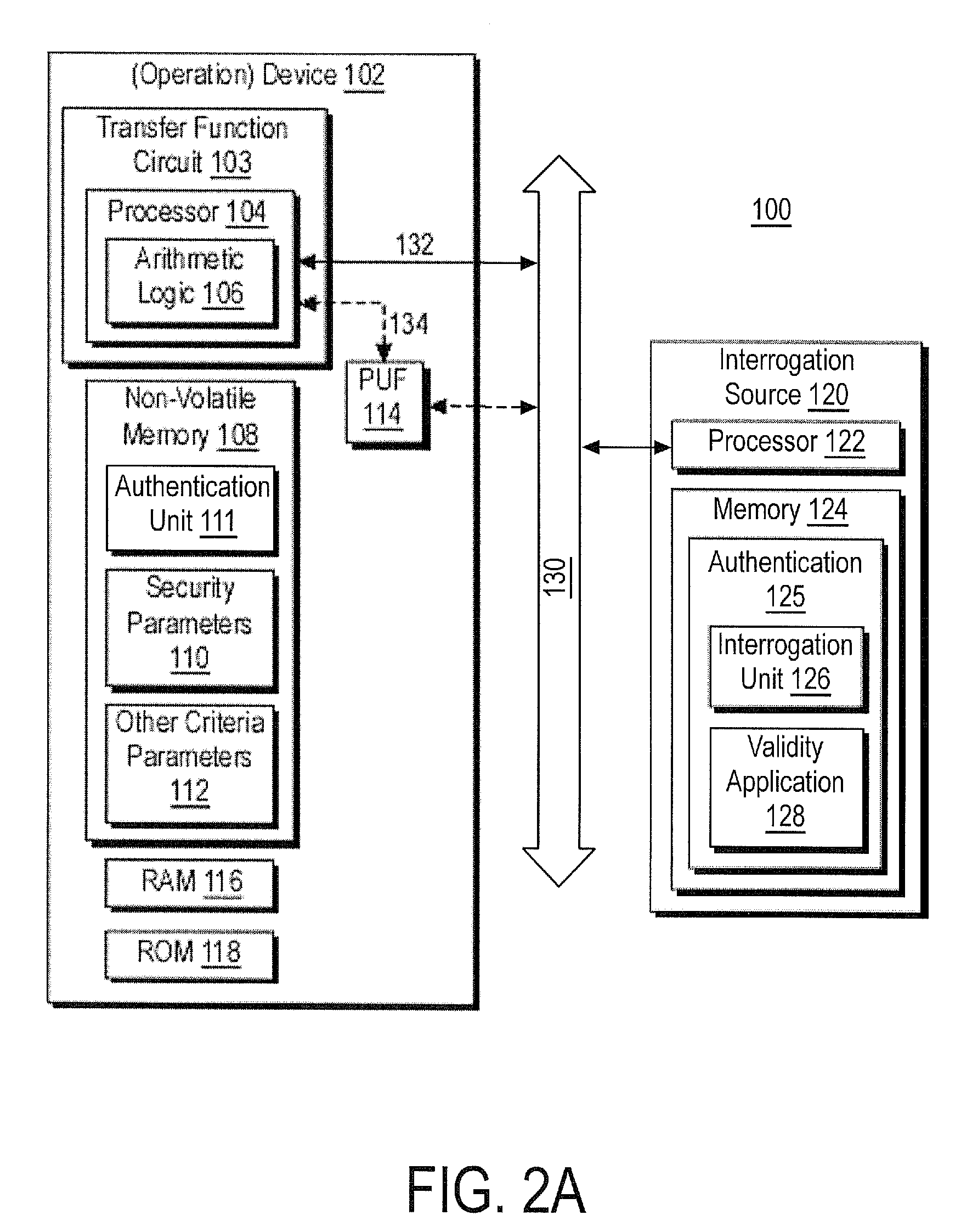
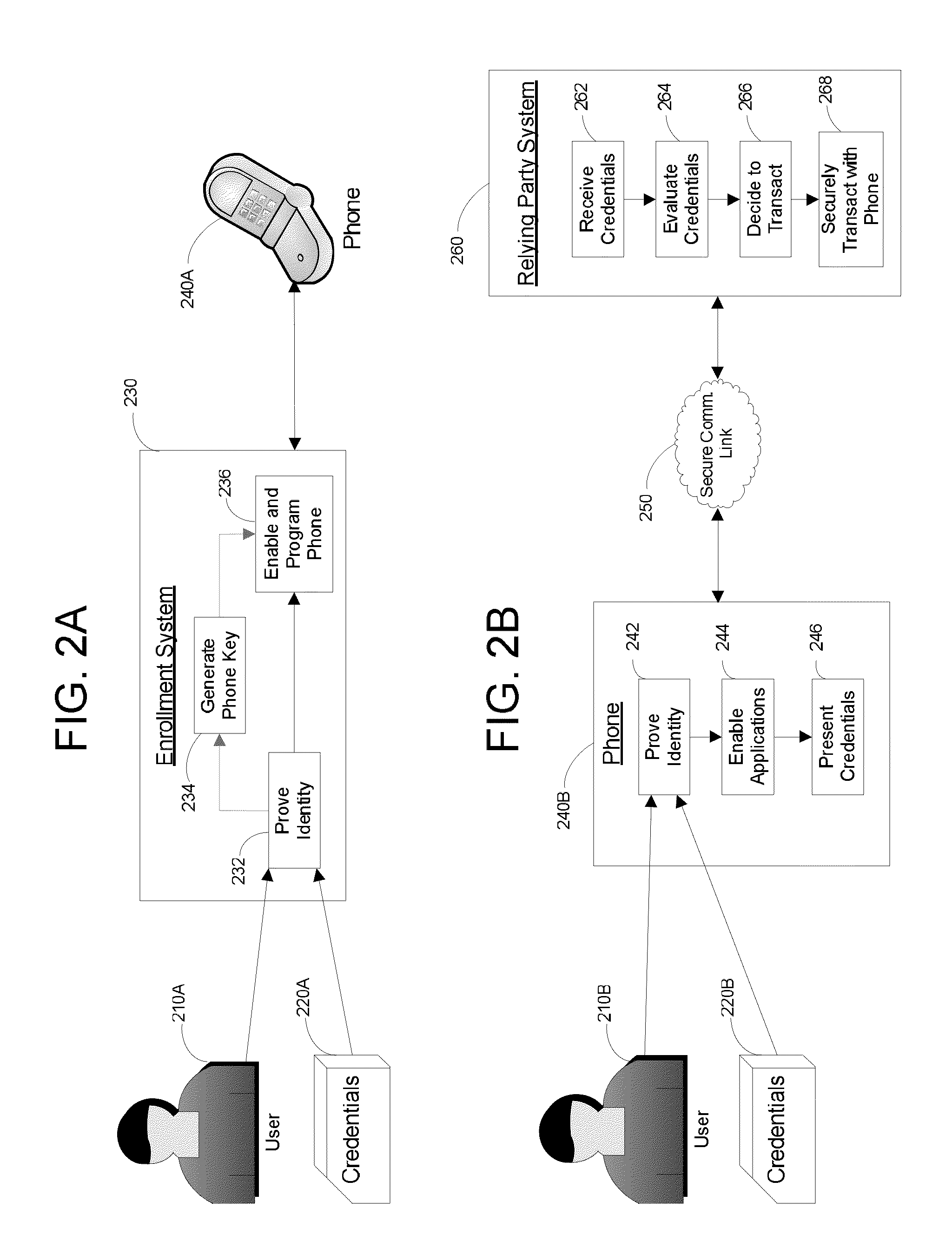
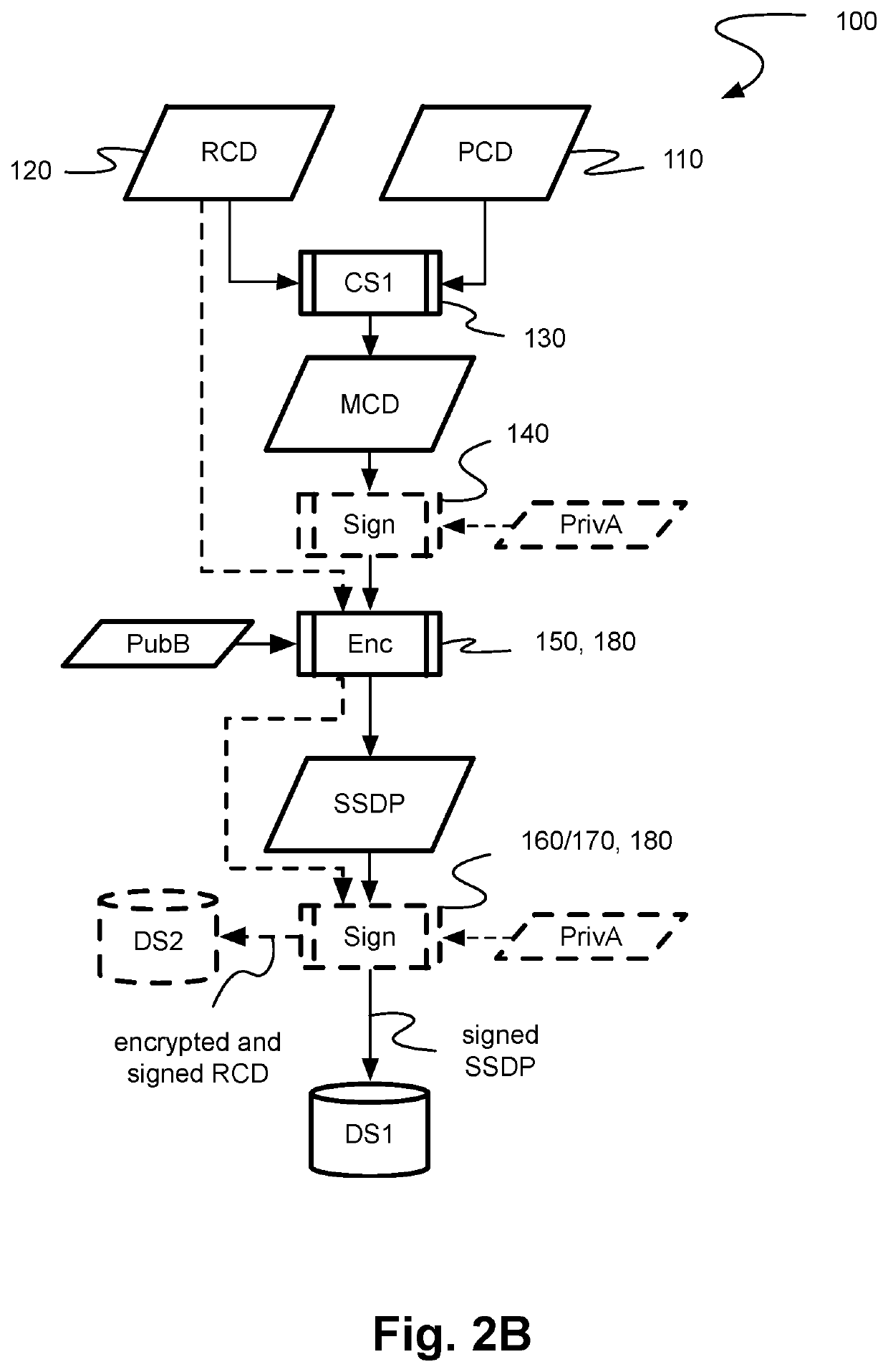
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20090132813A1Save bandwidthSaving response timeDigital data processing detailsUser identity/authority verificationElectronic systemsFinancial transaction
Apparatus and methods perform transactions in a secure environment between an individual and another party, such as a merchant, in various embodiments. The individual possesses a mobile electronic device, such as a smartphone, that can encrypt data according to a public key infrastructure. The individual authenticates the individual's identity to the device, thereby unlocking credentials that may be used in a secure transaction. The individual causes the device to communicate the credentials, in a secure fashion, to an electronic system of a relying party, in order to obtain the relying party's authorization to enter the transaction. The relying party system determines whether to grant the authorization, and communicates the grant and the outcome of the transaction to the device using encryption according to the public key infrastructure.
Owner:SURIDX
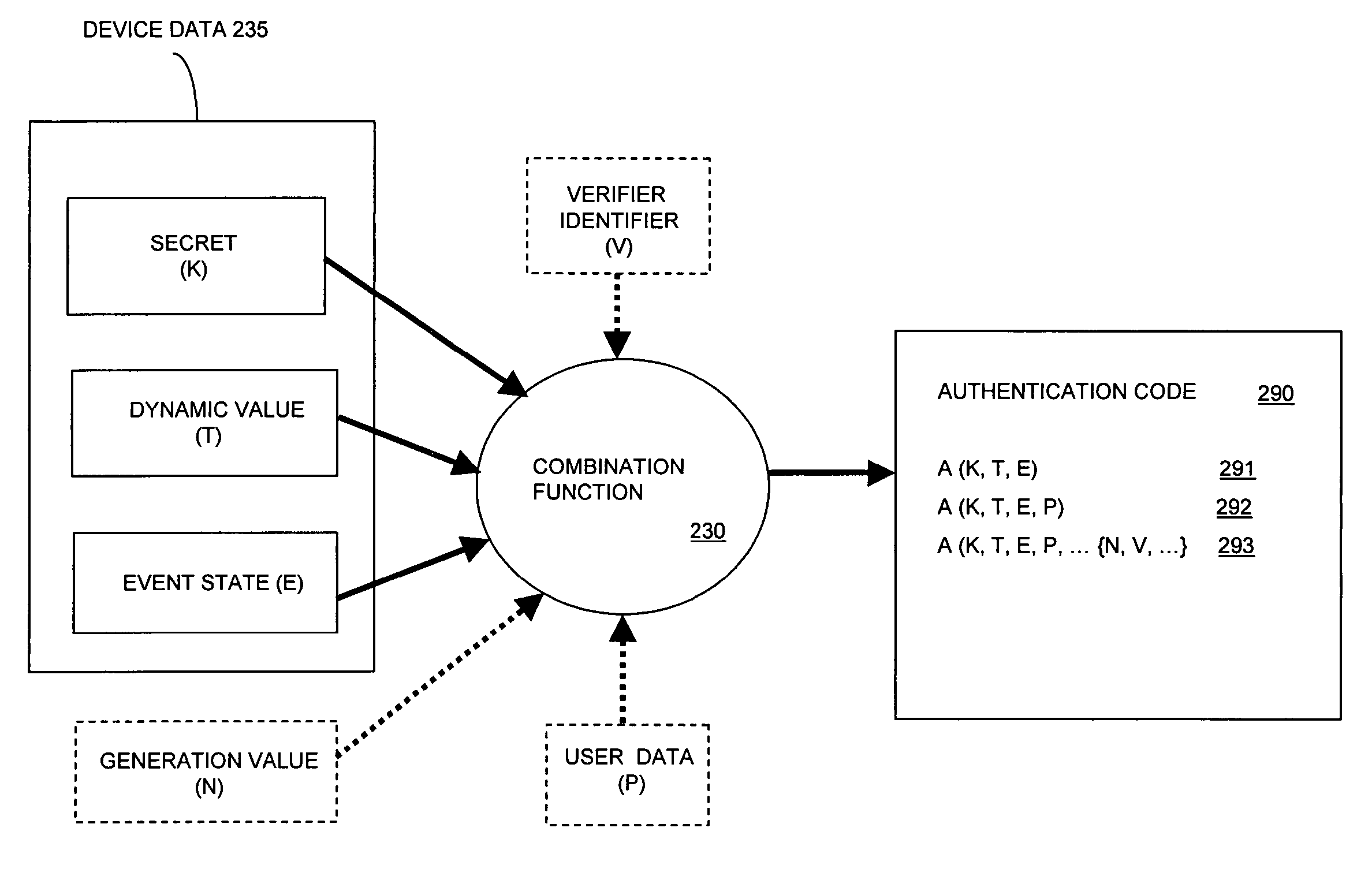
Identity authentication system and method
ActiveUS7502933B2Efficient verificationEfficiently authenticatingDigital data processing detailsUser identity/authority verificationInternet privacyEngineering
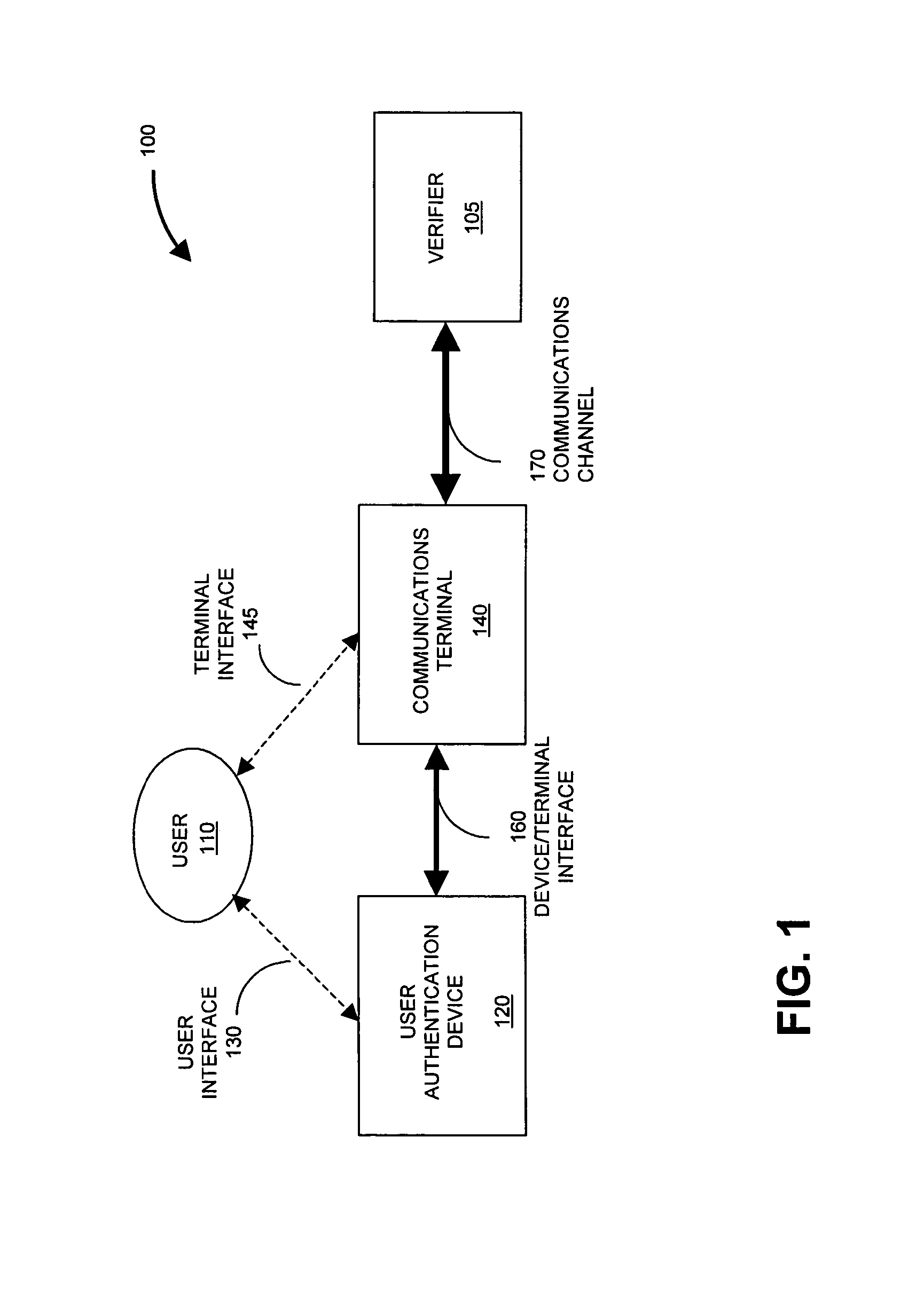
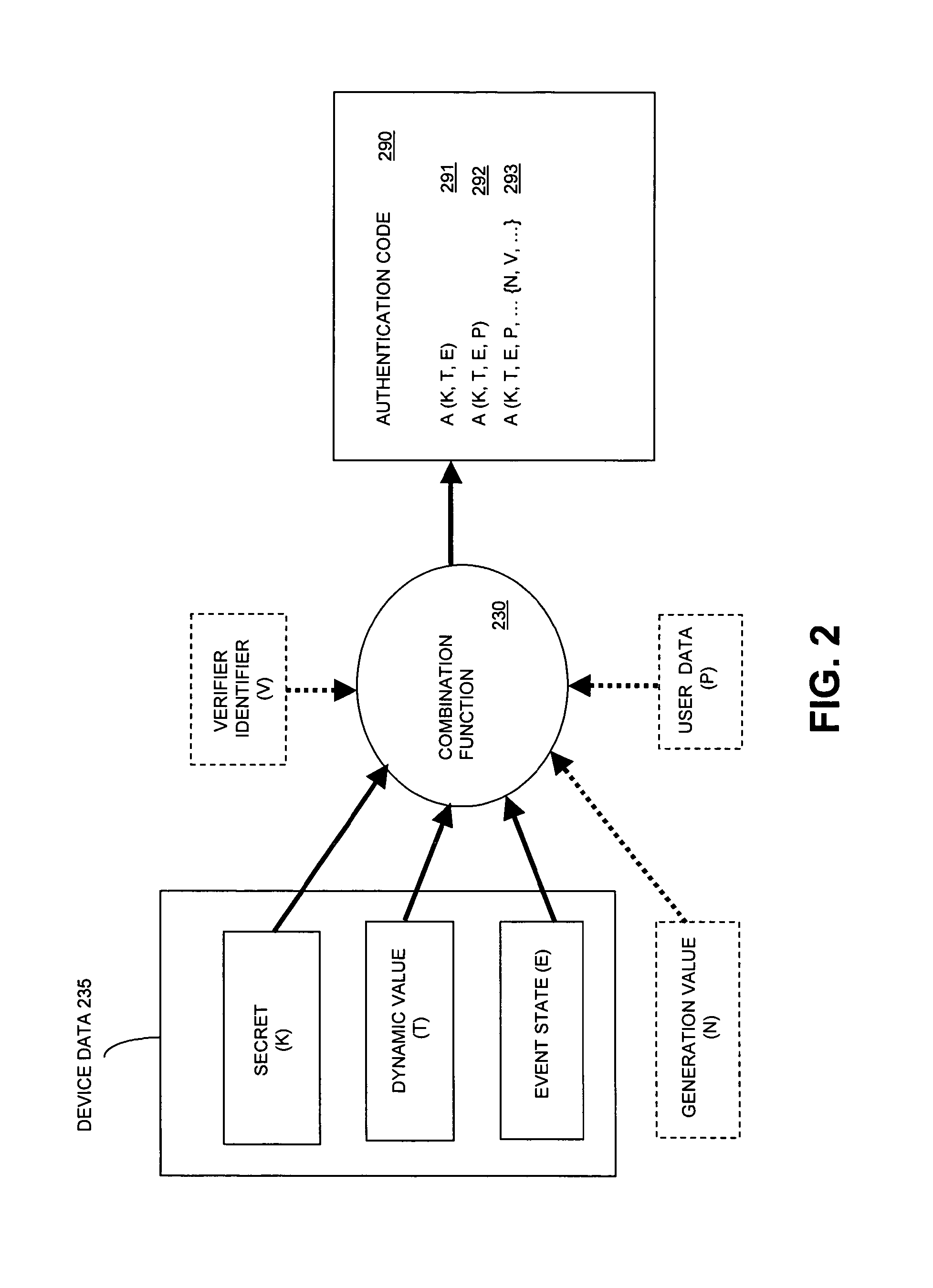
A method and system for generating an authentication code that depends at least in part on a dynamic value that changes over time, an event state associated with the occurrence of an event, and a secret associated with an authentication device. By generating the authentication code responsive to an event state, an identity authentication code can be used to verify identity and to communicate event state information, and to do so in a secure manner.
Owner:EMC IP HLDG CO LLC
Method and System for Electronically Securing an Electronic Biometric Device Using Physically Unclonable Functions
InactiveUS20110002461A1Consume minimalCost of producingKey distribution for secure communicationElectric signal transmission systemsPhysical unclonable functionSecurity validation
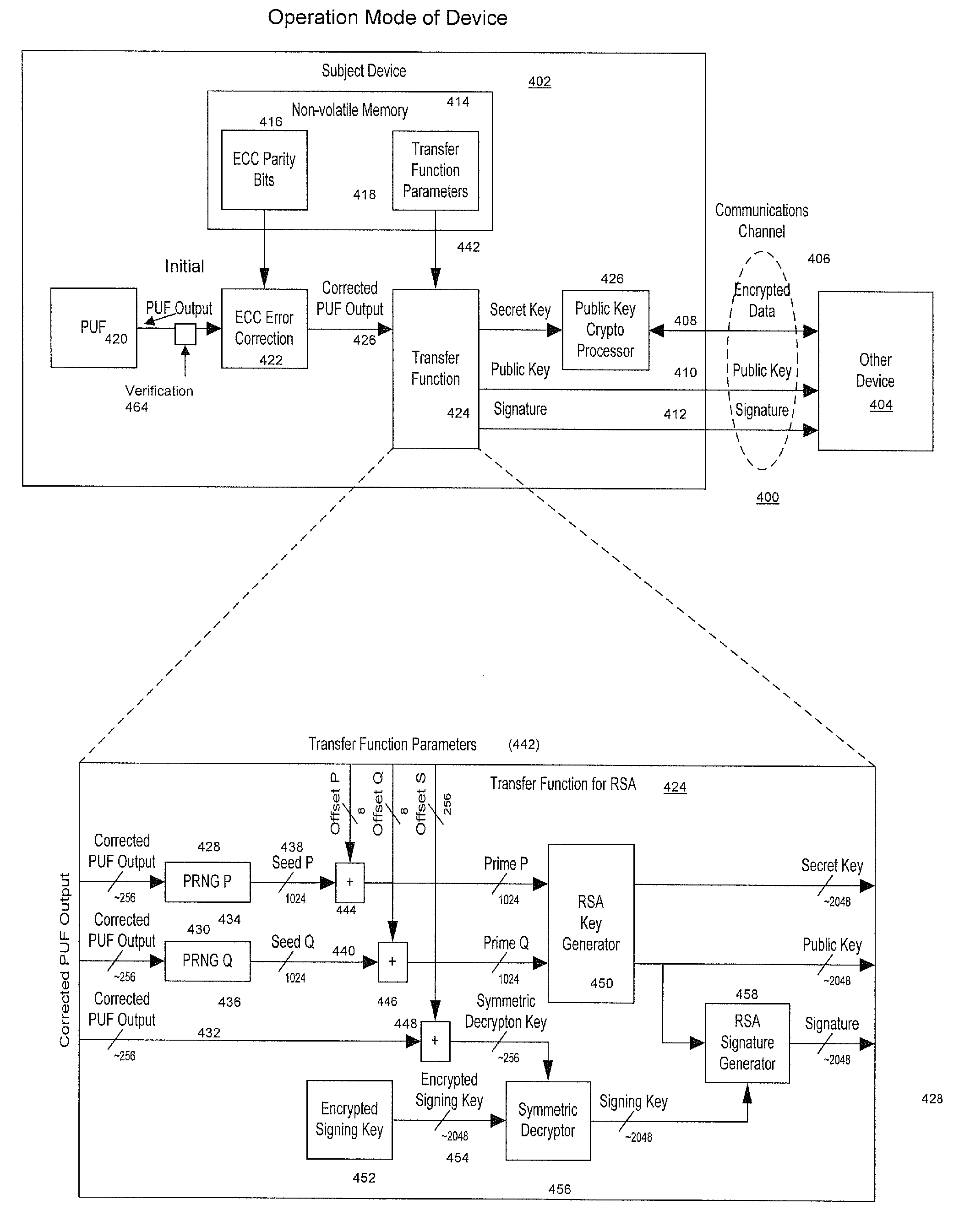
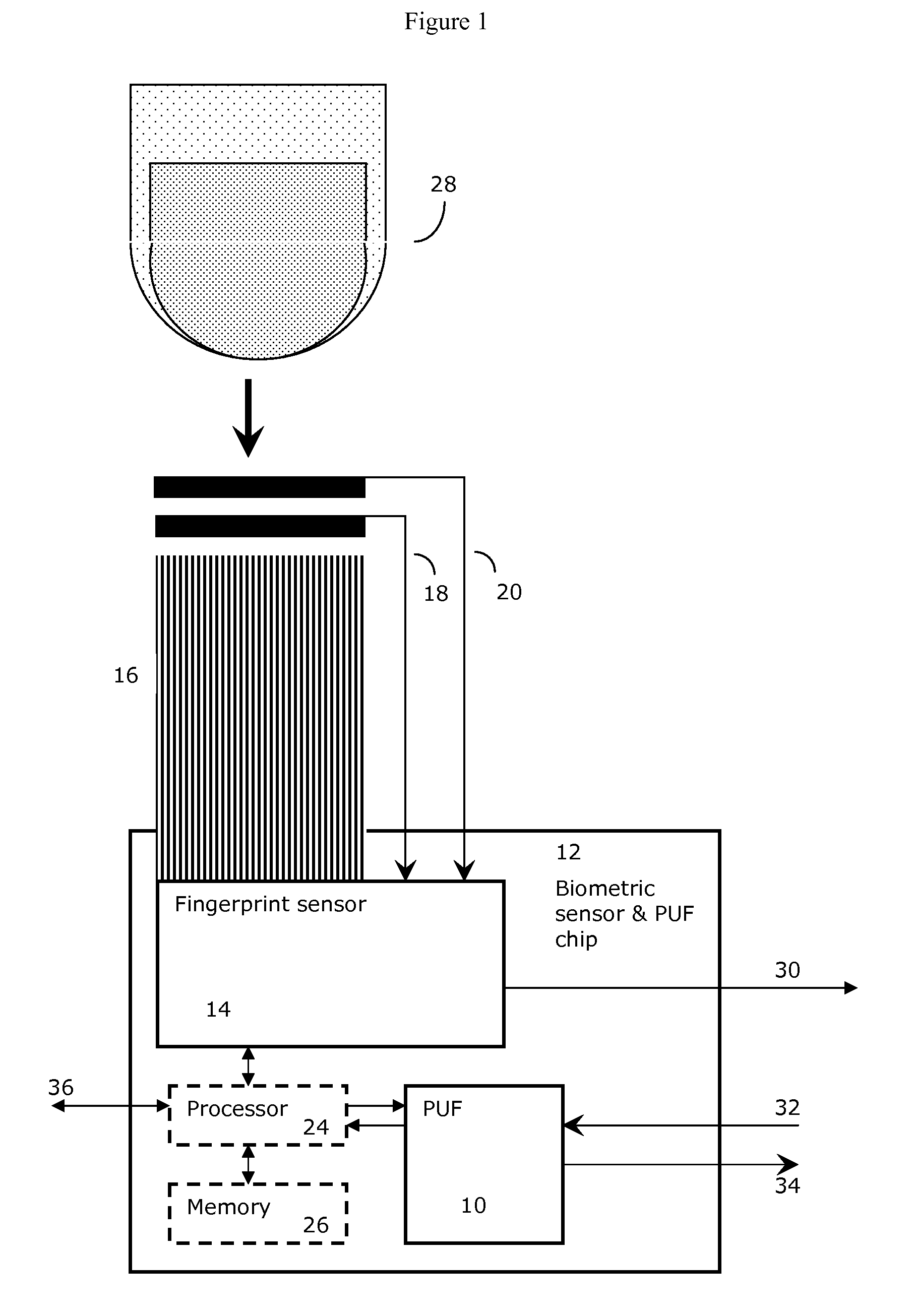
A system for securing an integrated circuit chip used for biometric sensors, or other electronic devices, by utilizing a physically unclonable function (PUF) circuit. These PUF functions are in turn used to generate security words and keys, such as an RSA public or private key. Such a system can be used to protect biometric security sensors and IC chips, such as fingerprint sensors and sensor driver chips, from attack or spoofing. The system may also be used in an efficient method to produce unique device set-up or power-up authentication security keys. These keys can be generated on a low frequency basis, and then frequently reused for later security verification purposes. In operation, the stored keys can be used to efficiently authenticate the device without the need to frequently run burdensome security key generation processes each time, while maintaining good device security.
Owner:SYNAPTICS INC
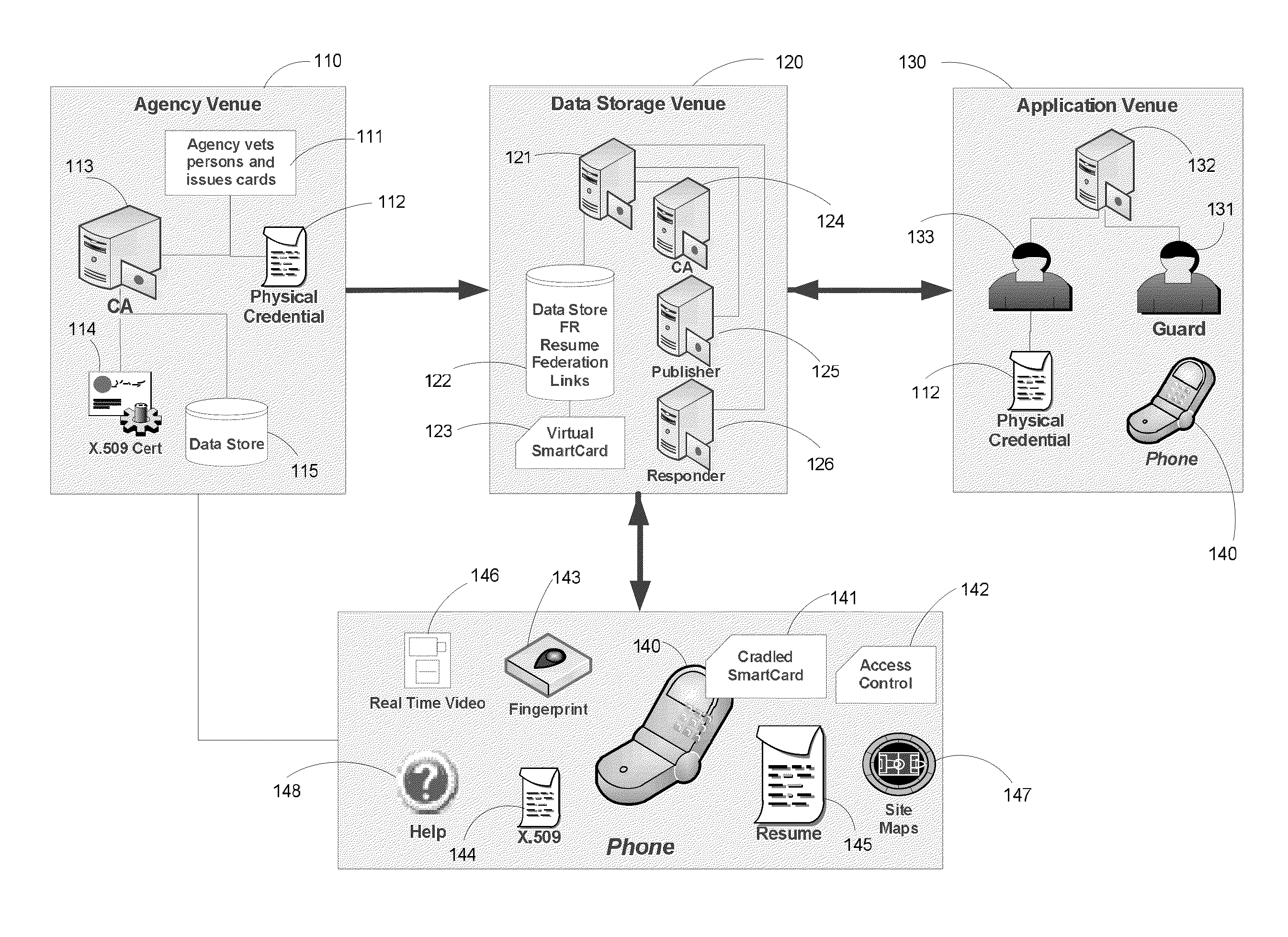
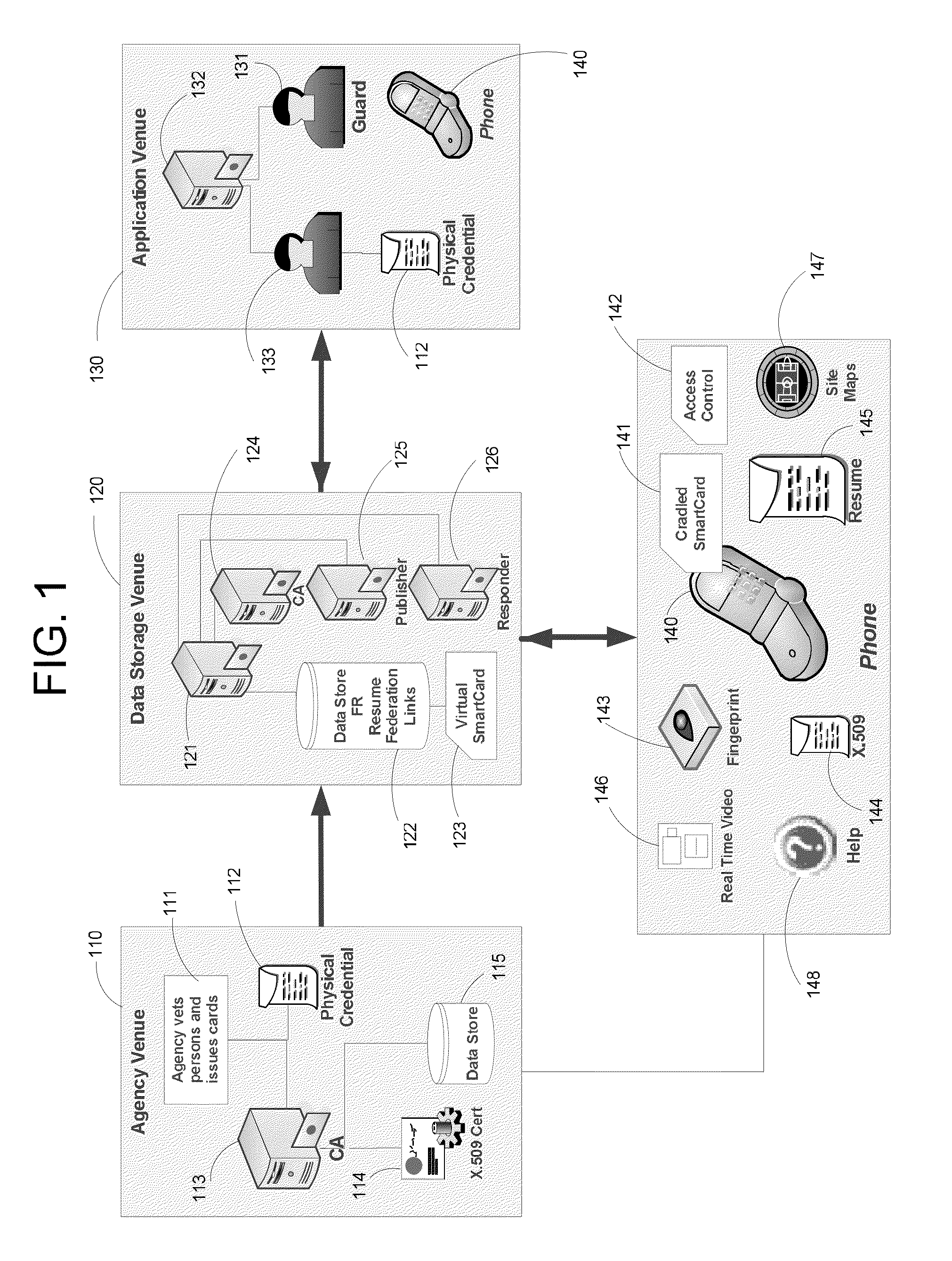
Apparatus and Methods for Providing Scalable, Dynamic, Individualized Credential Services Using Mobile Telephones
InactiveUS20130061055A1Reduce computing power requirementsIncrease the number ofDigital data processing detailsUser identity/authority verificationCredit cardHardware security module
A virtual smartcard and methods for creating the same are provided. A virtual smartcard is a set of computer-implemented processes, associated with an individual, which simulate the behavior of a physical smartcard or other authentication token containing a hardware security module. In one embodiment, a computer receives credential data derived from the physical credential and authentication data pertinent to the individual such as a biometric imprint, and creates a virtual smartcard by storing the credential data in association with the authentication data in a network storage. The credential data may later be used for identification and encryption purposes upon the individual providing the authentication data to the network storage, even if the physical credential itself has been lost. Thus, the virtual smartcard provides a network-based method for backing up a passport, driver's license, credit card, public transportation card, or other such identification card or device.
Owner:INFERSPECT
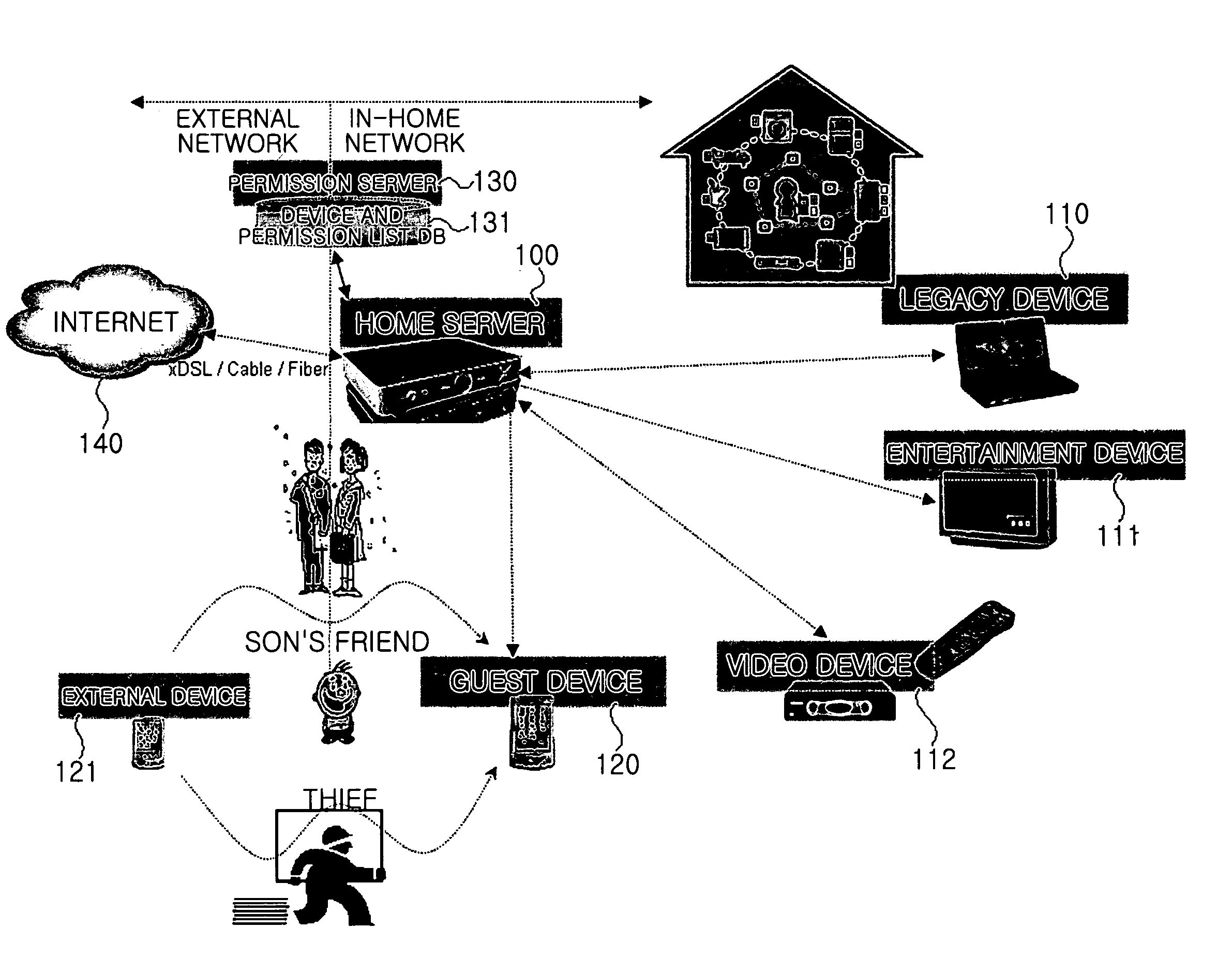
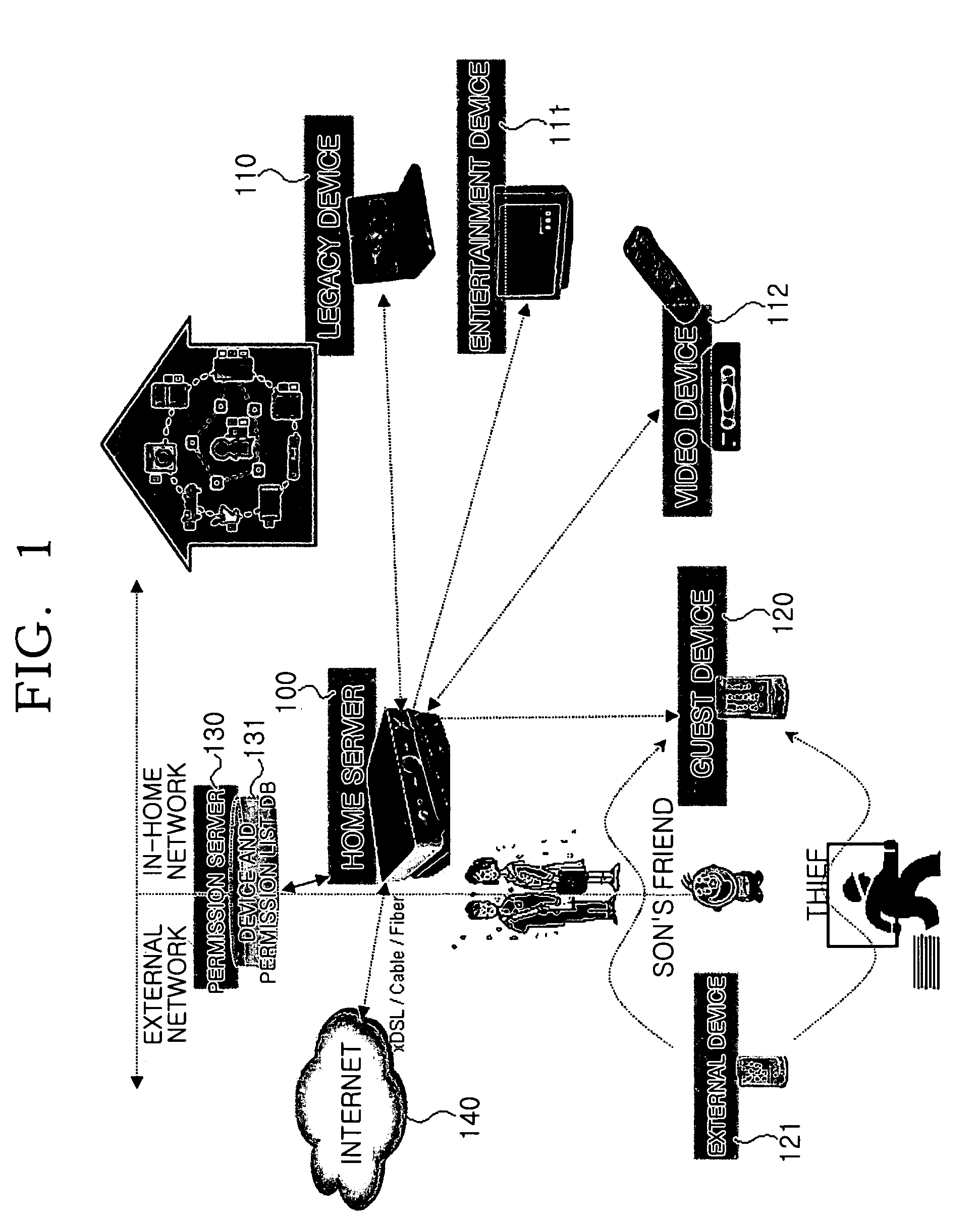
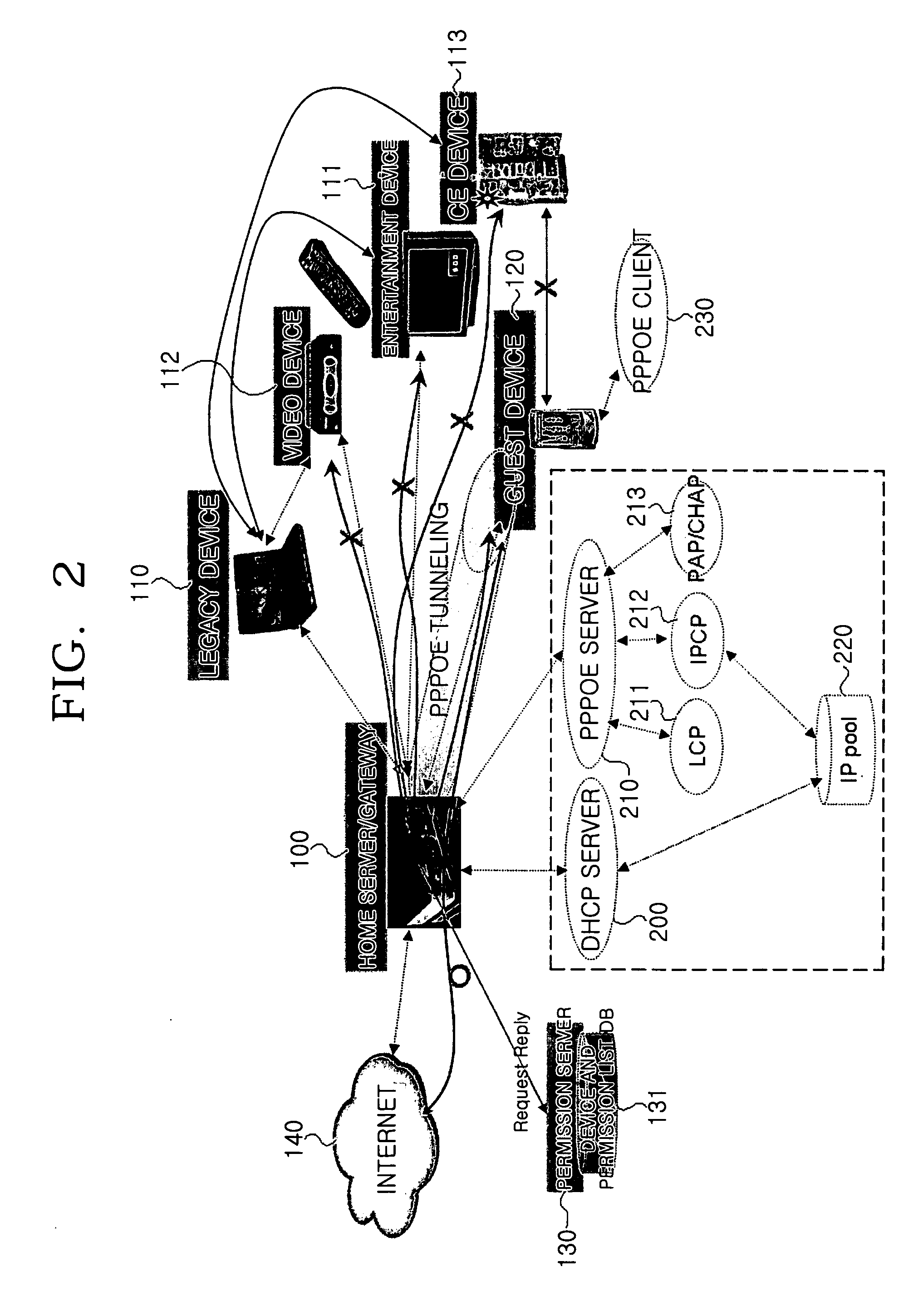
System for and method of authenticating device and user in home network
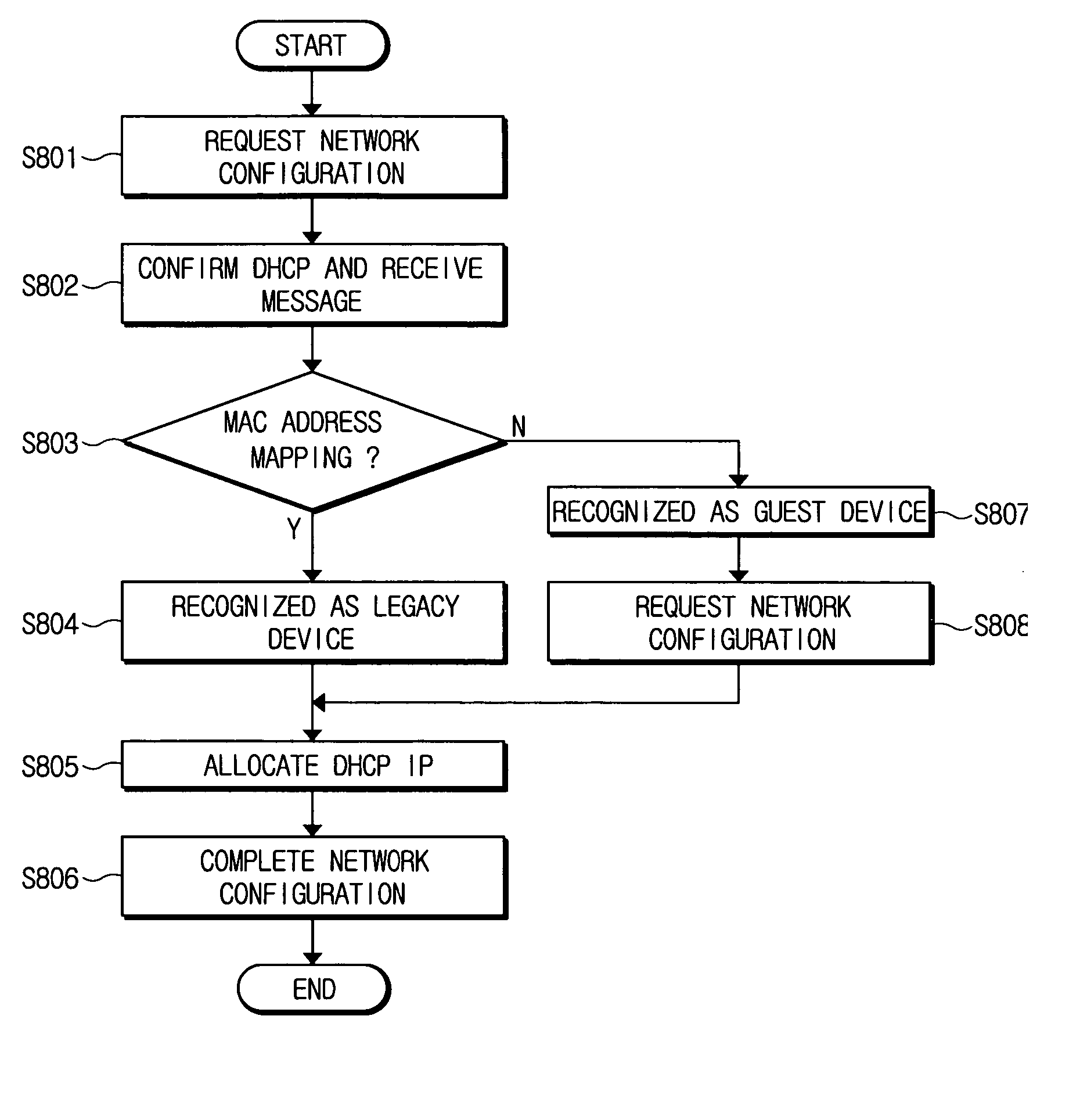
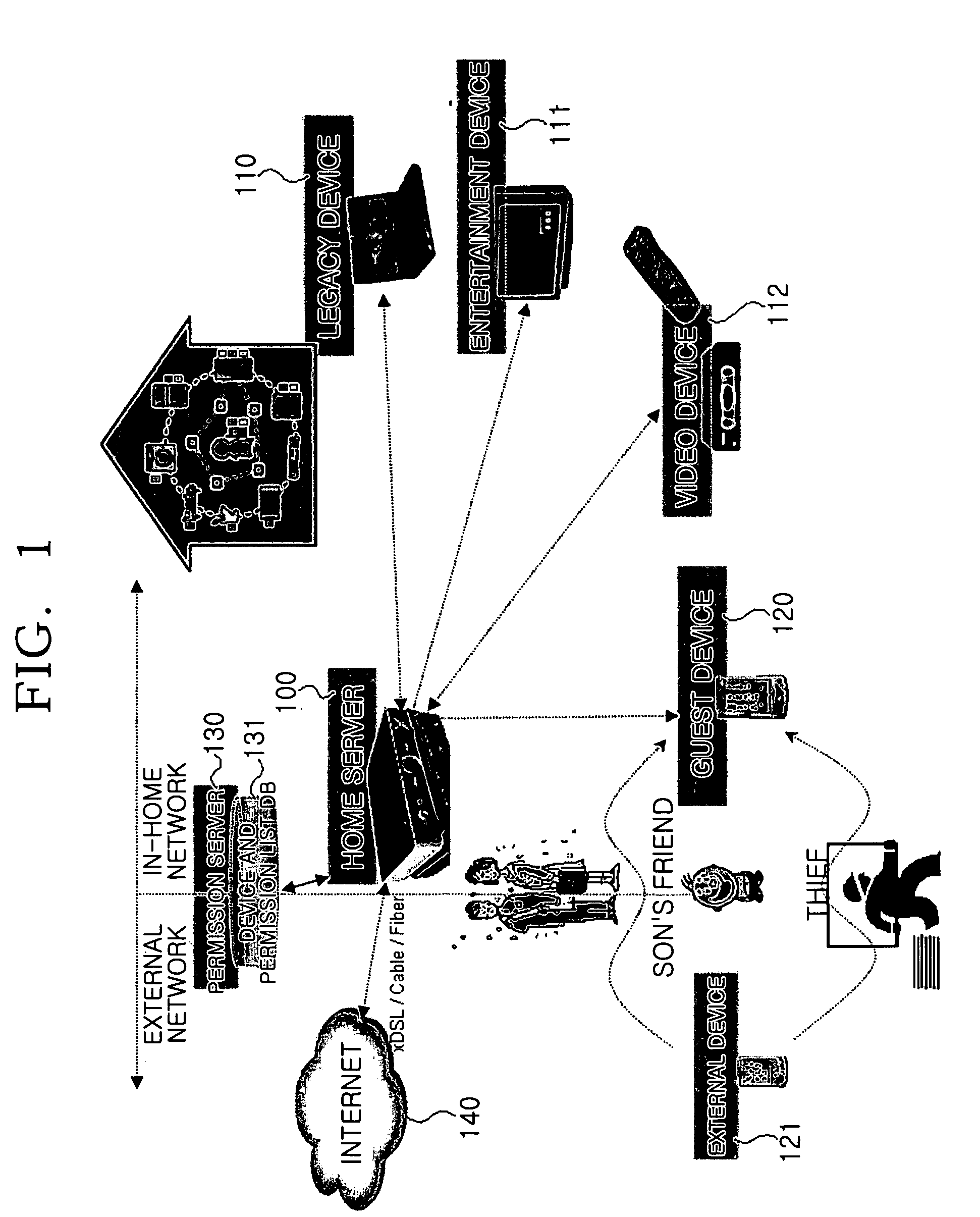
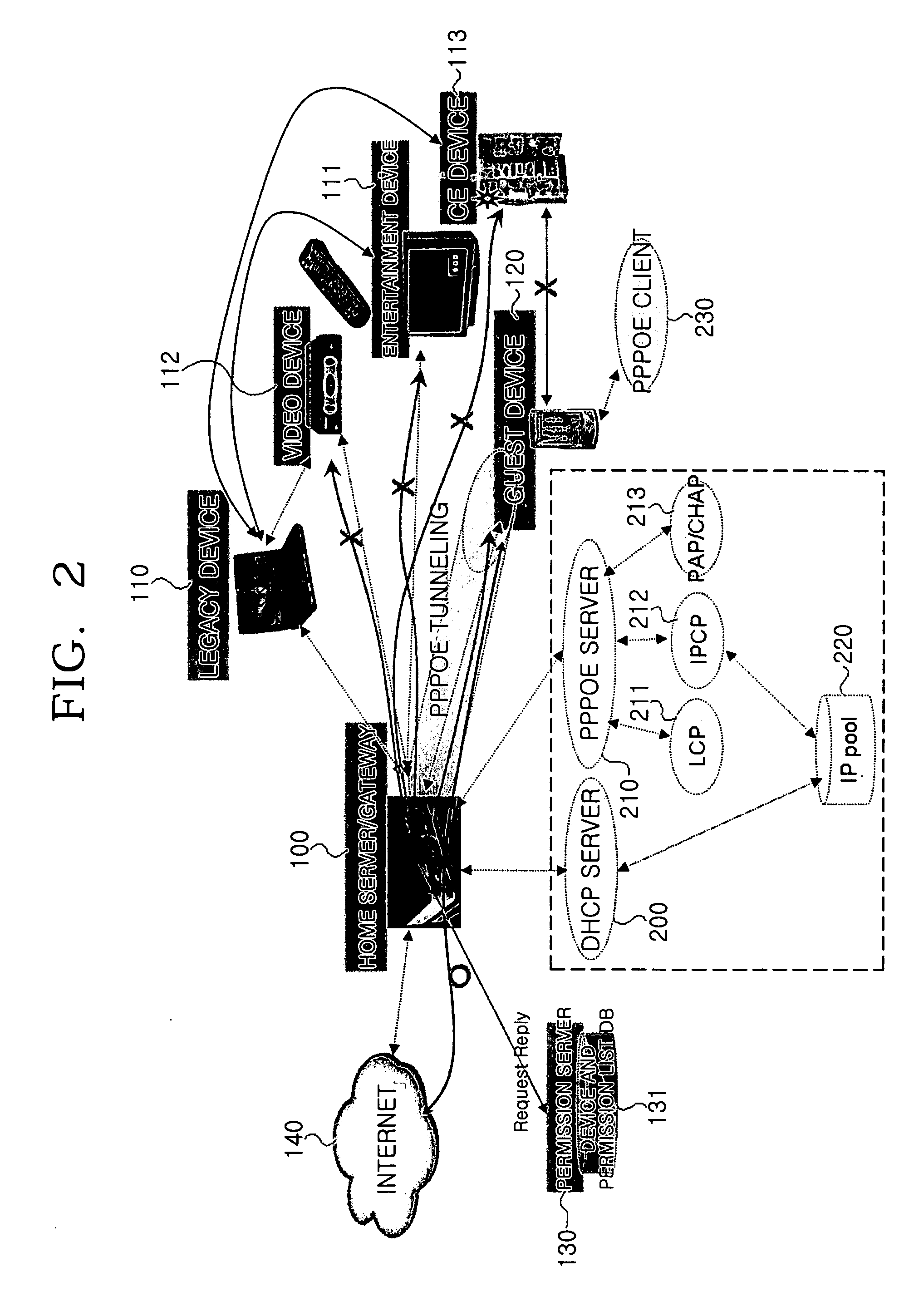
ActiveUS20060137005A1Efficient supplyEfficiently authenticatingDigital data processing detailsUser identity/authority verificationComputer scienceFamily network
A system for authenticating a device and a user in a home network. The home network manages one or more devices through a home server. The system includes a service device for providing service contents according to the control of a control device. The system includes a home server for containing authentication information for the respective devices. The home server performs a network configuration for the respective devices according to the authentication information. A permission server is connected with the home server. The permission server contains service permission information according to the characteristics of the respective control devices. The control device performs a network authentication through the home server, and is provided with service contents from the service device according to whether the permission server allows the requested service contents. The system can perform an authentication procedure and a network configuration for the control devices.
Owner:SAMSUNG ELECTRONICS CO LTD
Mobile Device With Secure Element
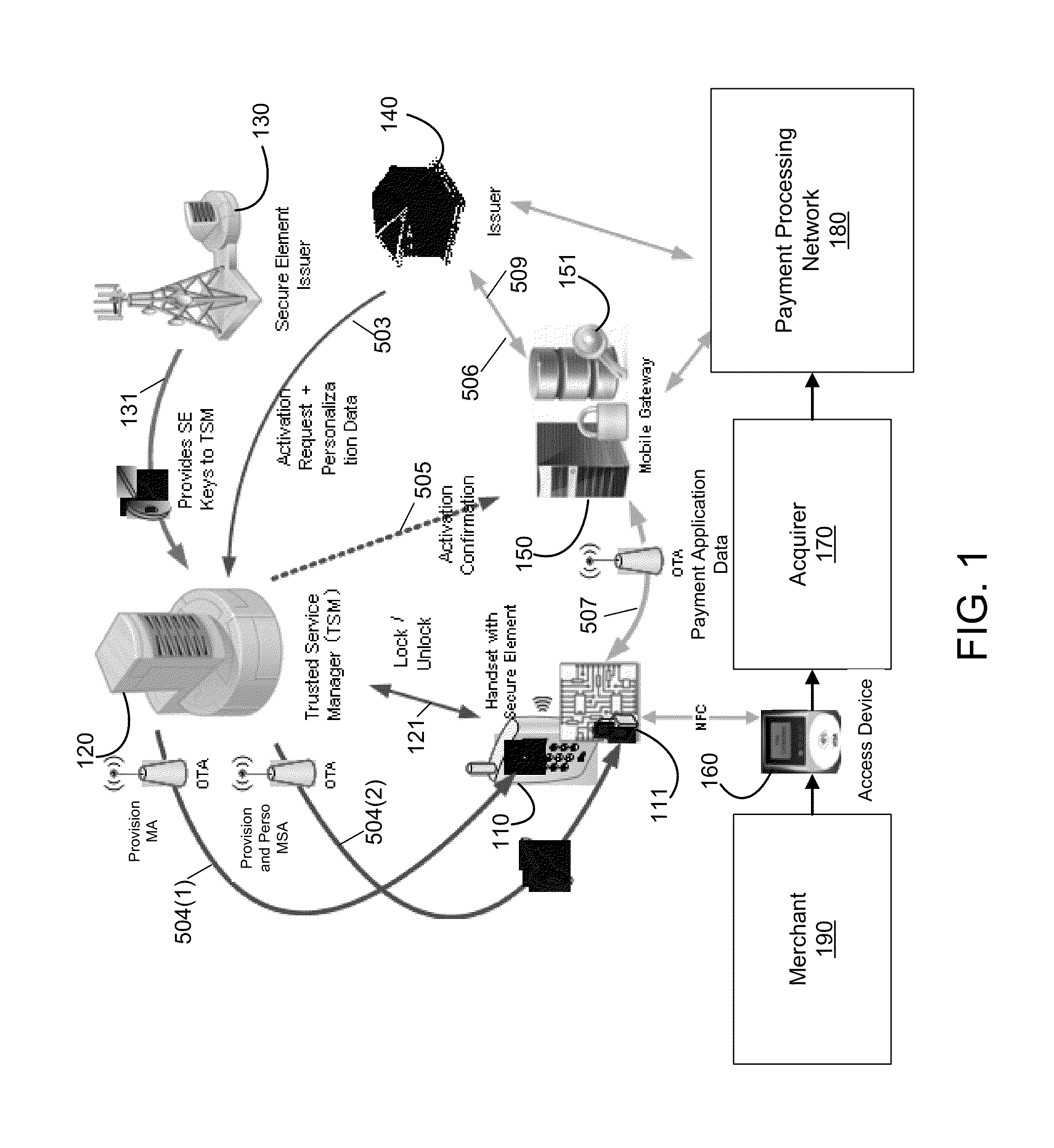
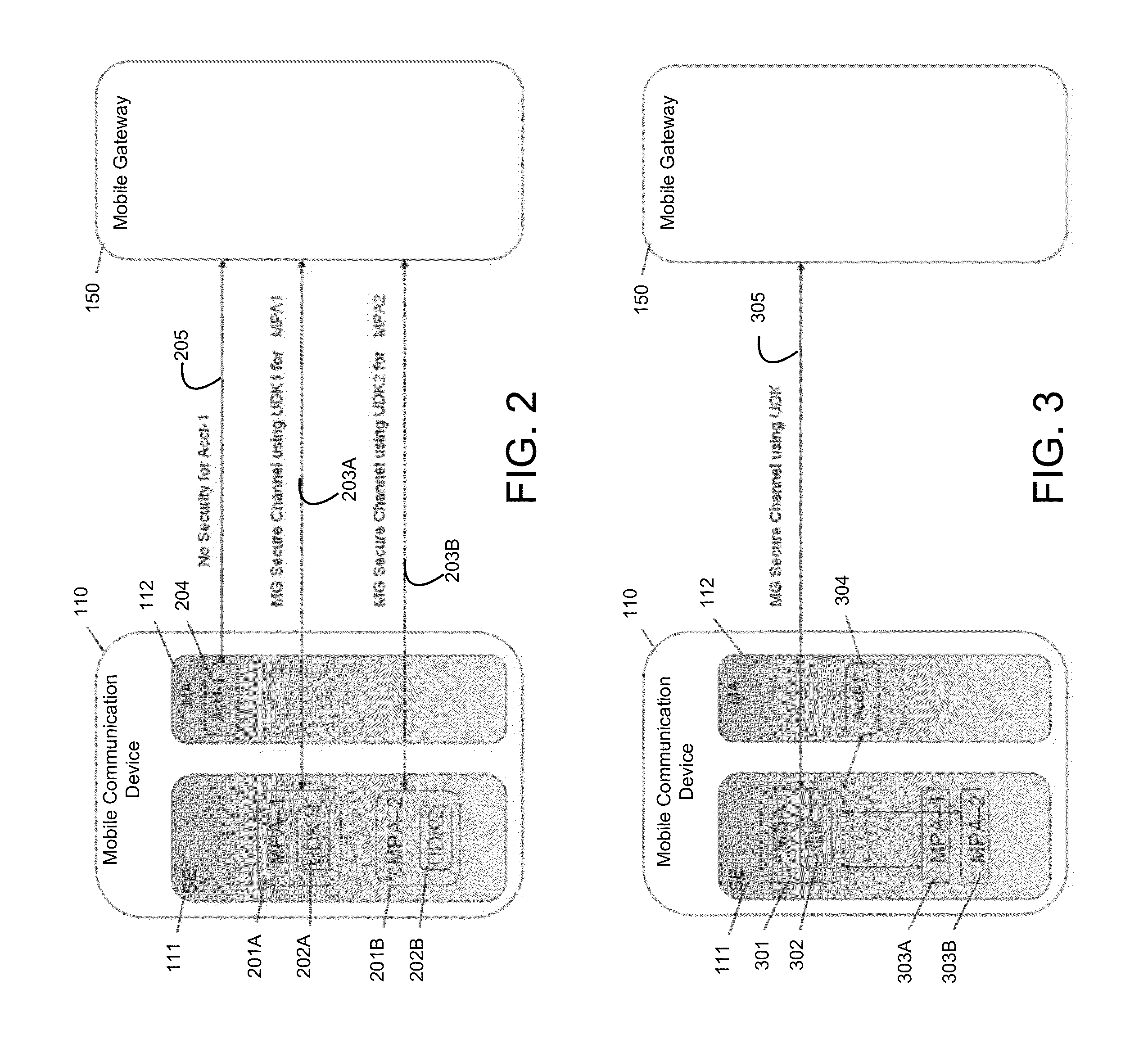
InactiveUS20130024383A1Improve information securityEfficiently authenticatingSecurity arrangementSecuring communicationUpgradeMobile payment
Embodiments of the present invention are directed to methods, systems, and apparatuses for securely communicating issuer updates, upgrades, and allowing configuration of payment-related applications on a mobile communication device using a mobile security application. One embodiment is directed to a method of using a mobile communication device comprising a mobile security application, a key associated with the mobile security application, a first mobile payment application in communication with the mobile security application and a second mobile payment application in communication with the mobile security application. The method includes communicating, by the first mobile payment application in the mobile communication device with a mobile gateway, in a first communication, wherein the first communication is encrypted using the key and communicating, by the second mobile payment application in the mobile communication device with a mobile gateway, in a second communication, wherein the second communication is encrypted using the key.
Owner:VISA INT SERVICE ASSOC
Pressure activated fingerprint input apparatus
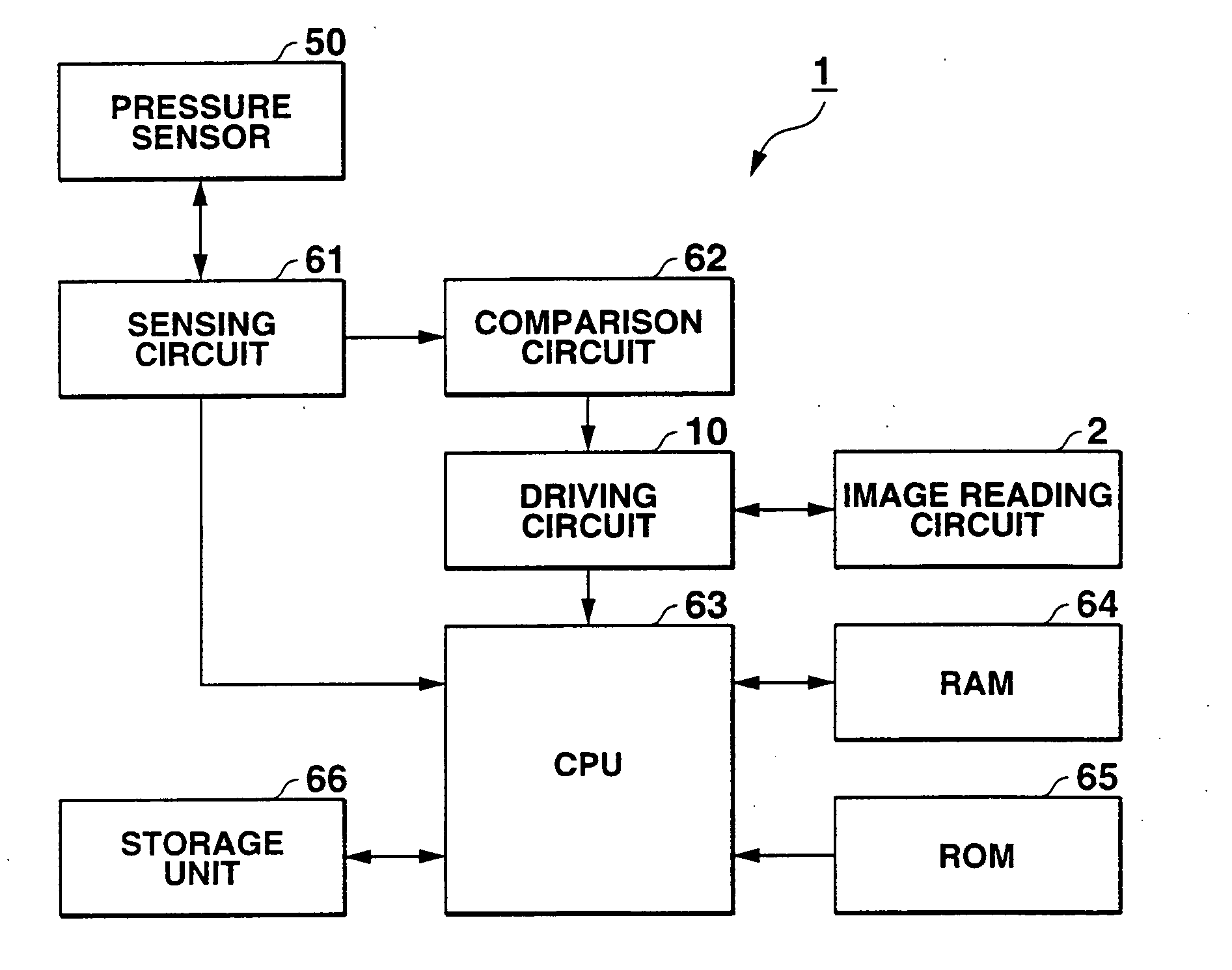
InactiveUS20050213799A1Simply and reliably readingClear readingPrint image acquisitionComputer scienceFingerprint
An image input apparatus includes an image reading assembly positioned below a placement surface on which an object to be examined is placed, and a sensing circuit for sensing that the object is placed on the placement surface, in accordance with a pressure applied to the placement surface.
Owner:CASIO COMPUTER CO LTD
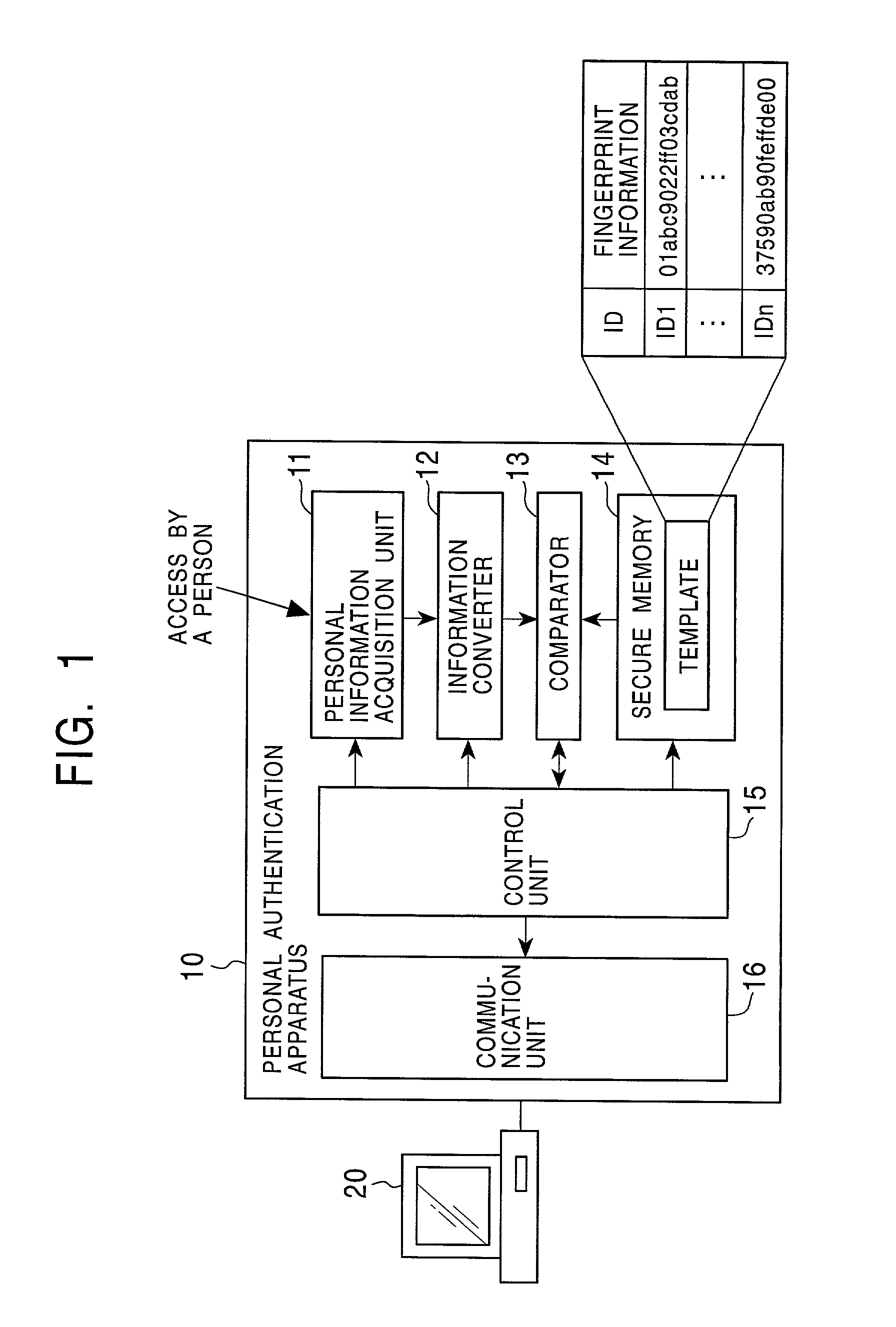
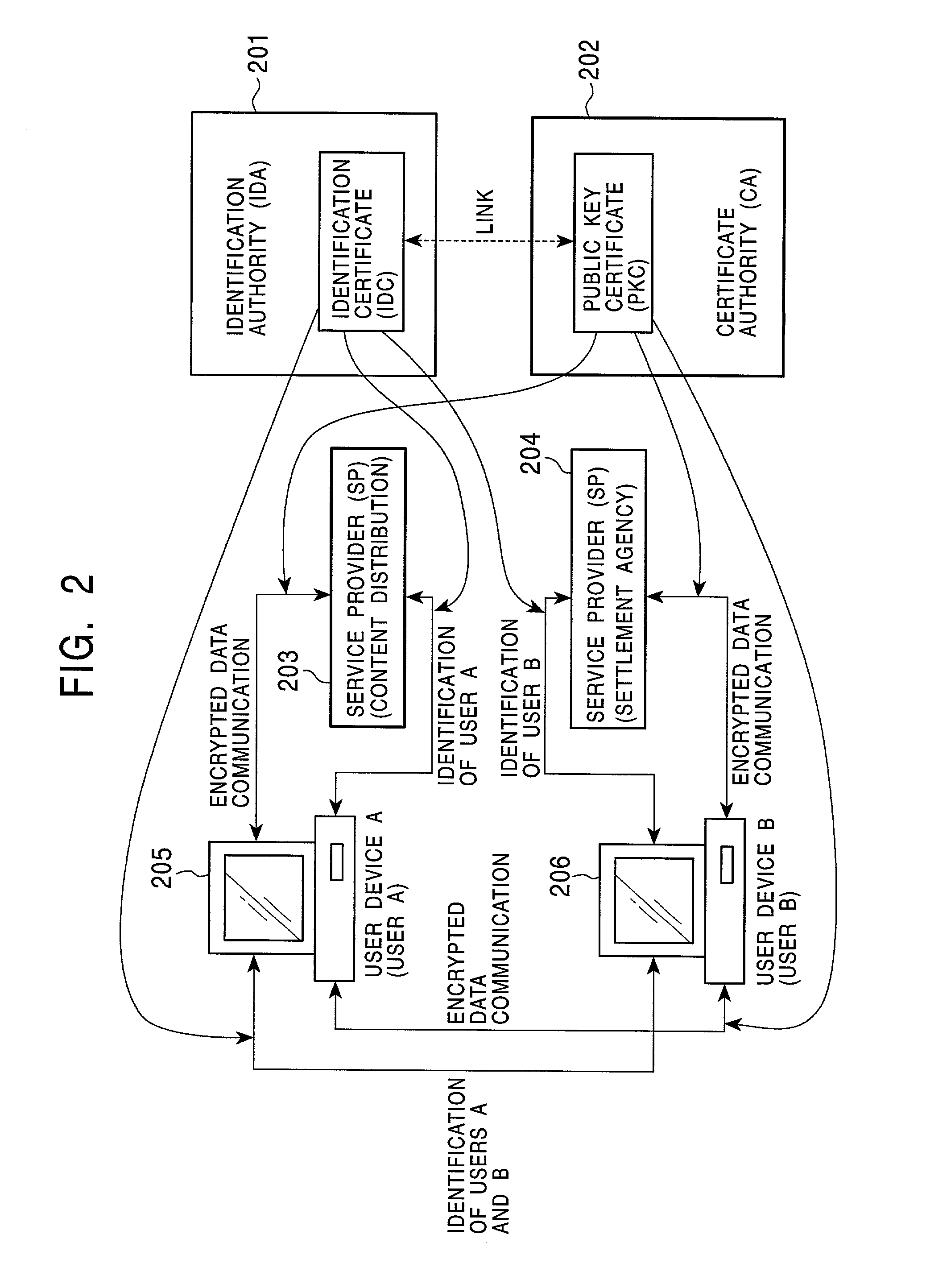
Information processing apparatus, information processing method, and program providing medium
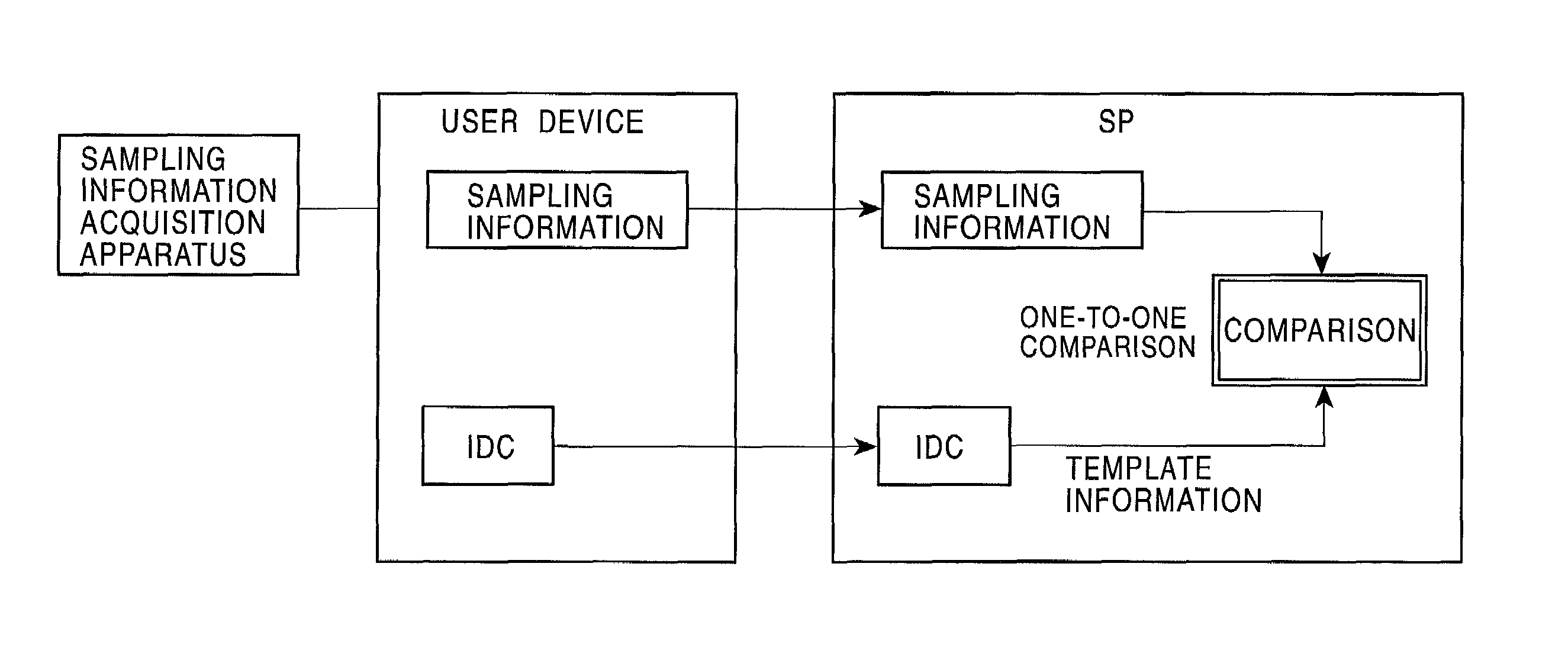
InactiveUS7103778B2Improve reliabilitySafe storageUser identity/authority verificationDigital data authenticationInformation processingComputer hardware
Disclosed are an information processing apparatus and an information processing method which execute person authentication and allows various services such as receiving of contents to be received, provided that the authentication is successfully passed. In the information processing apparatus for executing, by a connection to an external server providing various services such as contents transmission, a process such as receiving of contents, person authentication is executed by comparing a template acquired from a person identification certificate storing a template which is person identification data of a user using the information processing apparatus with sampling information input by the user, and a connection to the external server is executed provided that the authentication is successfully passed. In addition, the person identification certificate and the public key certificate are stored in a memory together with link information in which the person identification certificate and the public key certificate applied during a process of establishing a connection to the server are related to each other.
Owner:SONY CORP
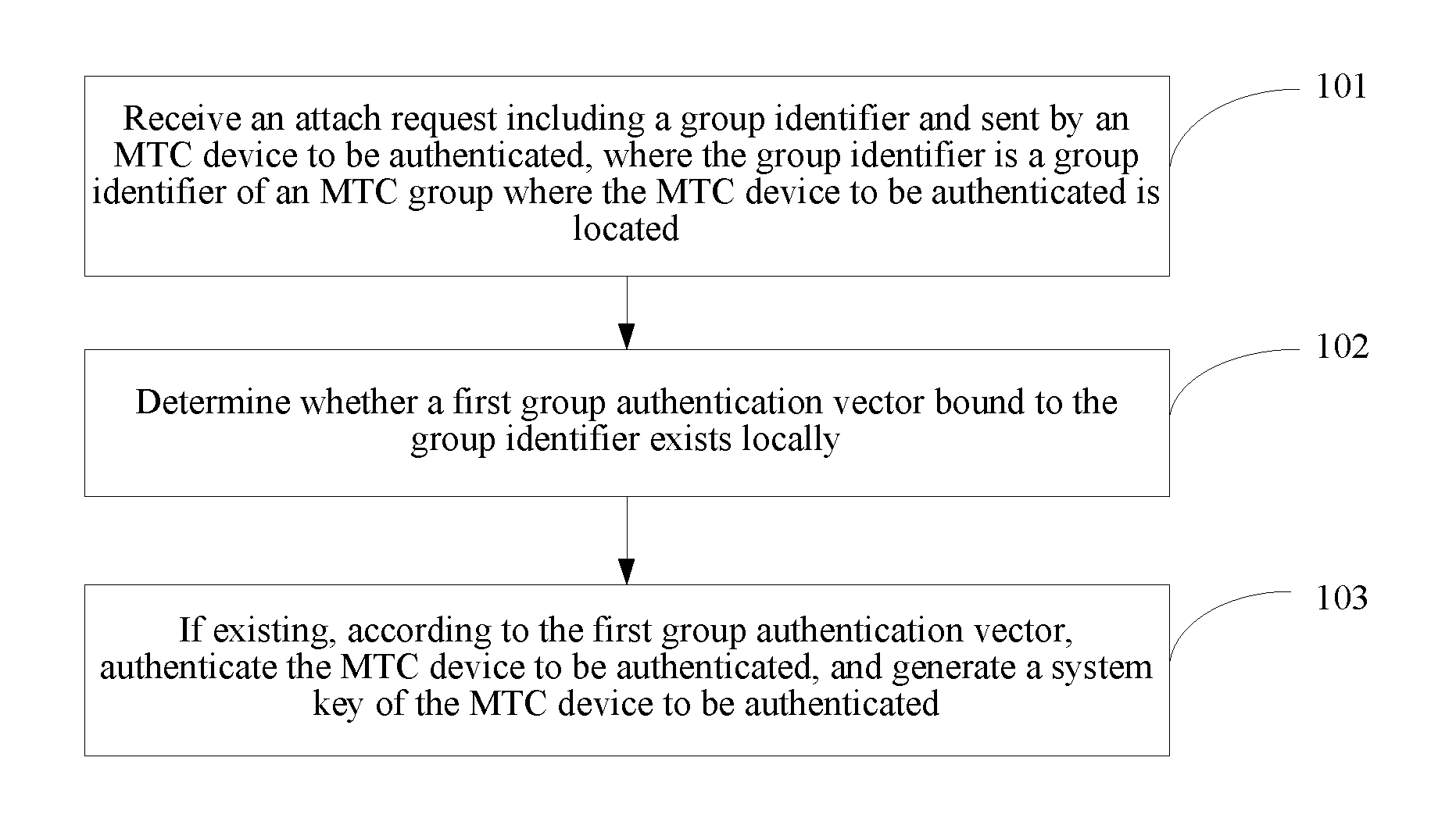
Method and apparatus for authenticating communication device
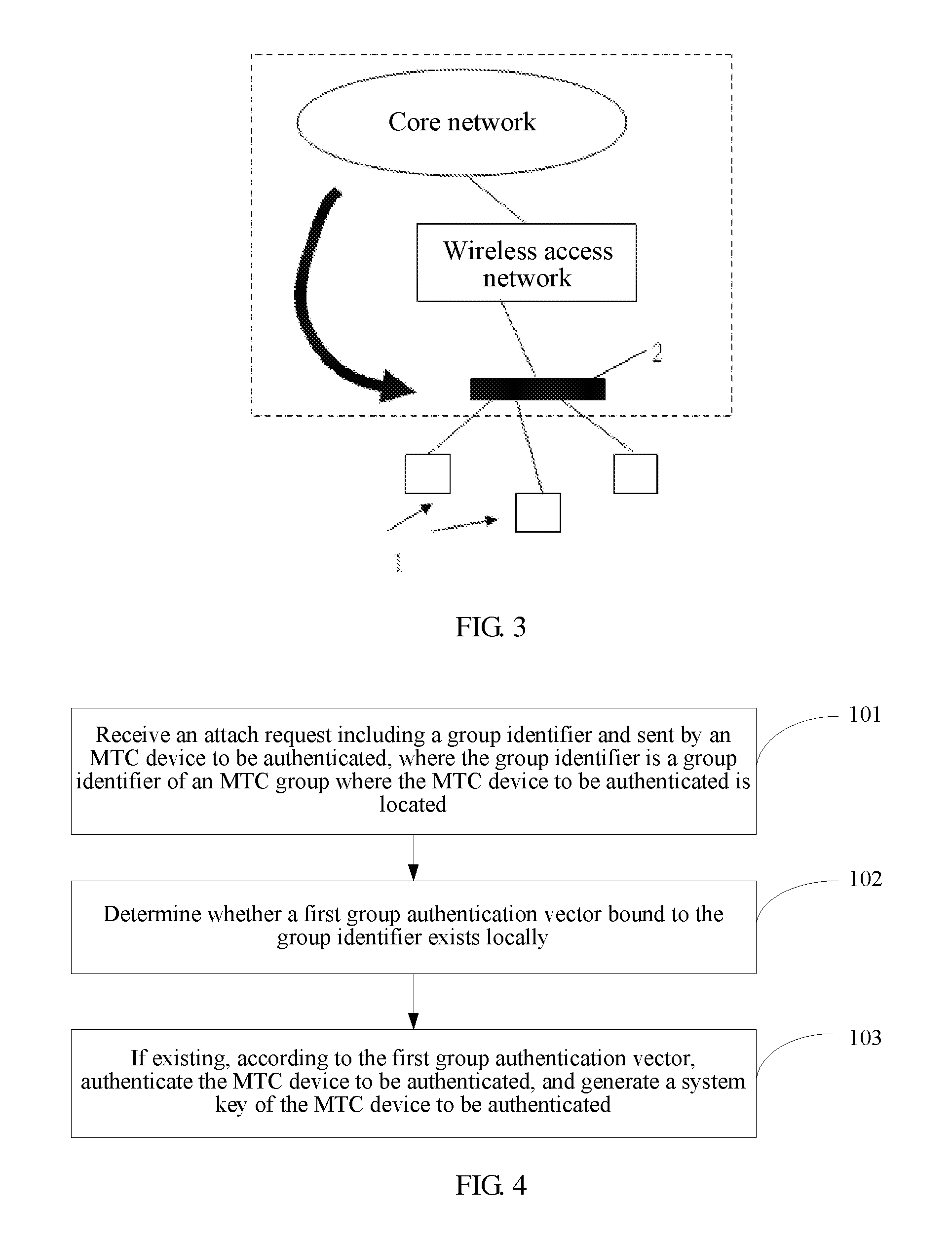
ActiveUS20130035067A1Efficiently authenticatingUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunication deviceAuthentication
Embodiments of the present invention disclose a method and an apparatus for authenticating a communication device, where the method includes: receiving an attach request including a group identifier and sent by an MTC device to be authenticated, where the group identifier is a group identifier of an MTC group where the MTC device to be authenticated is located; determining whether a first group authentication vector bound to the group identifier exists locally, where the first group authentication vector is an authentication vector used for authenticating MTC devices in the MTC group; and if existing, according to the first group authentication vector, authenticating the MTC device to be authenticated, and generating a system key of the MTC device to be authenticated. The technical solutions provided in the present invention can be applied to the technical field of authenticating the MTC device.
Owner:HUAWEI TECH CO LTD
Self-enrollment and authentication method
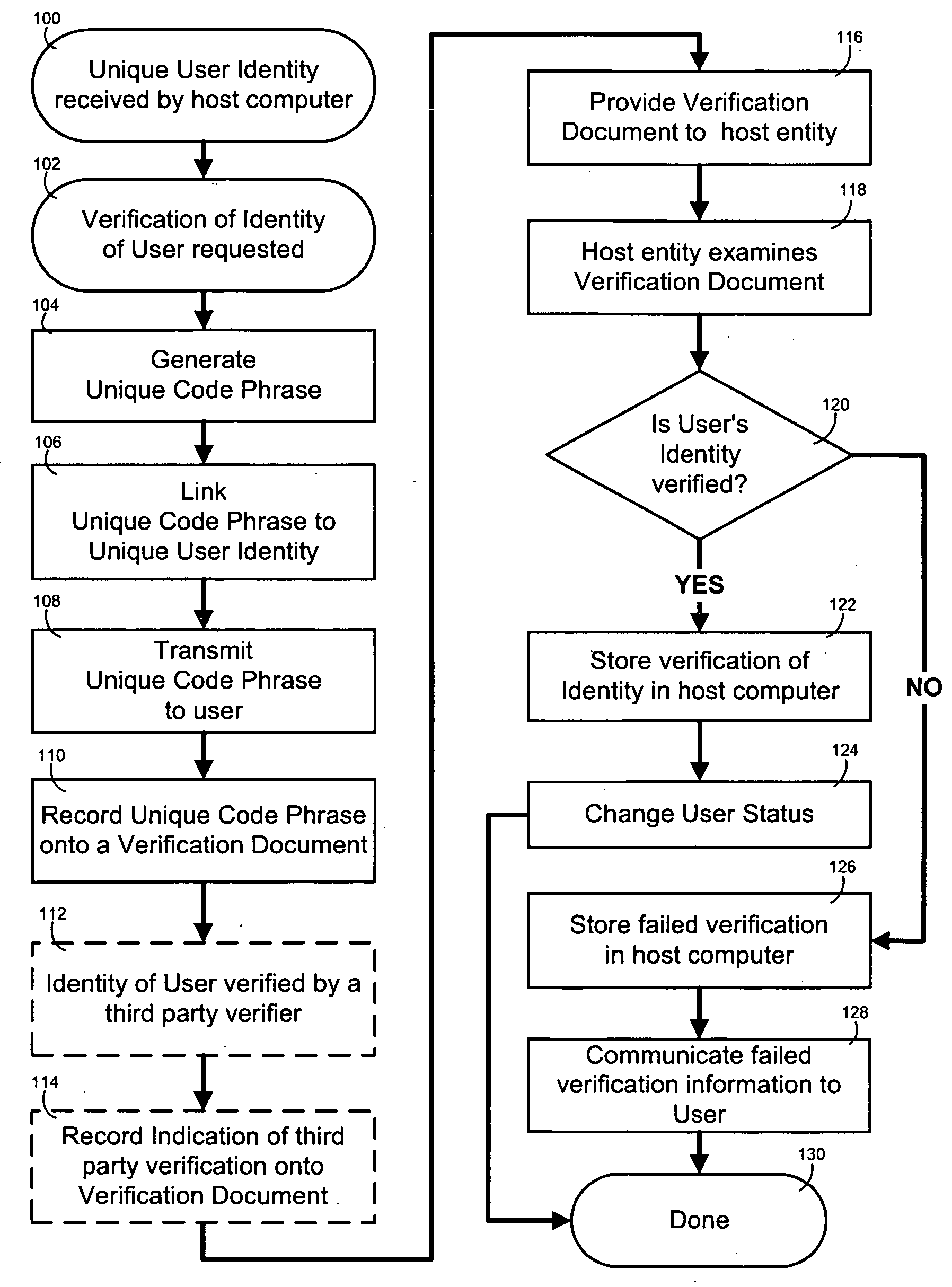
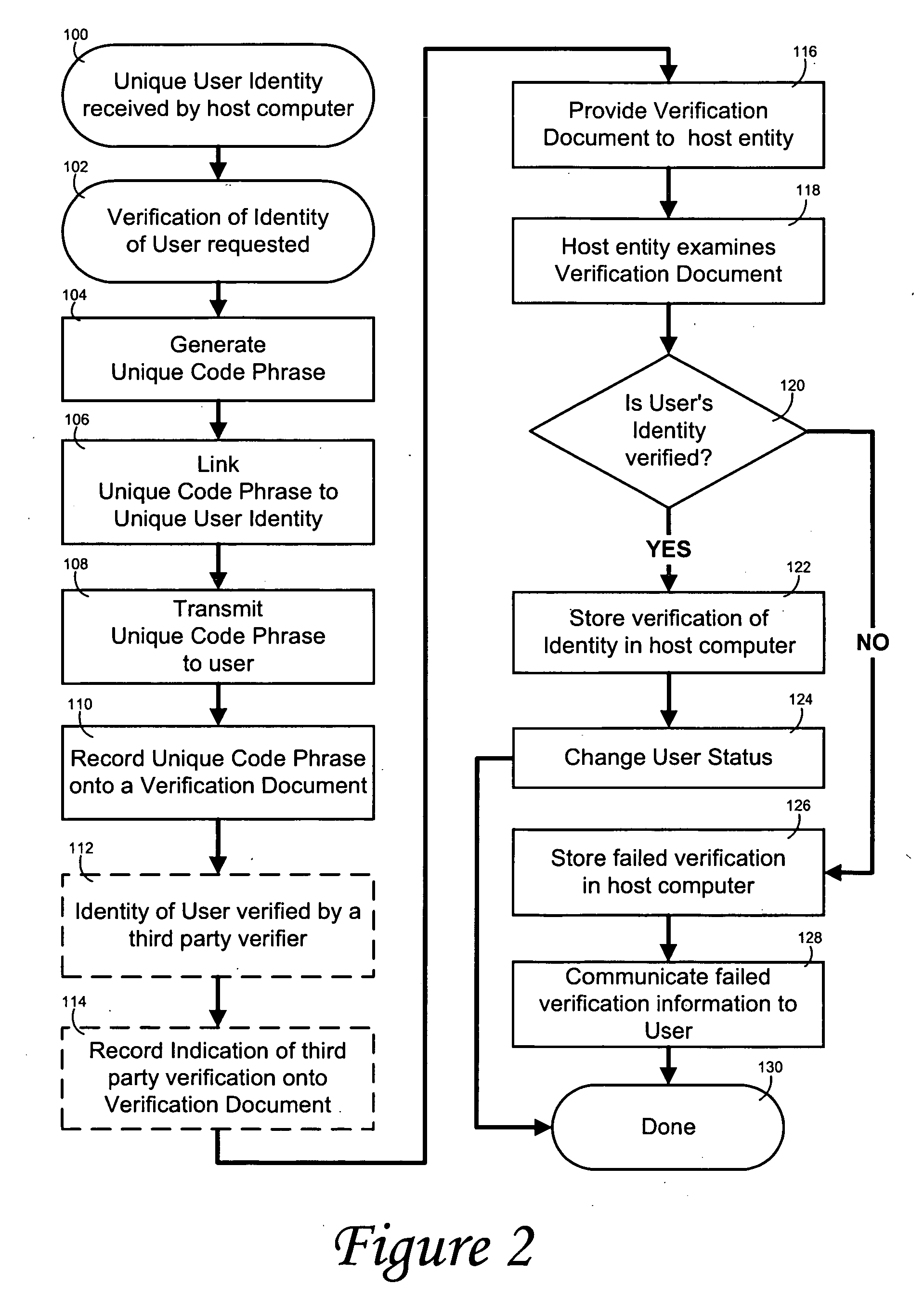
InactiveUS20050076213A1Low costEasy and inexpensive and accurateUser identity/authority verificationMarketingEngineeringWorld Wide Web
A self-enrollment and authentication method provides that, when a user logs onto a host computer and requests that the user's physical identity be verified, a Unique User Identity (UUI) is created to identify the user on the host computer, and a Unique Code Phrase (UCP) is created which is linked with the user's UUI. The UCP is recorded on a document which the user executes before a notary public averring that the user is an identified person. If upon review of the executed document, it is determined that the user's identity has been verified, a Verified Physical Identity (VPI) is established and stored on the host computer and the user's status is upgraded to entitled the user access to reserved privileges on the host computer.
Owner:CONLOW JAMES
Instrumentation for alarming a software product
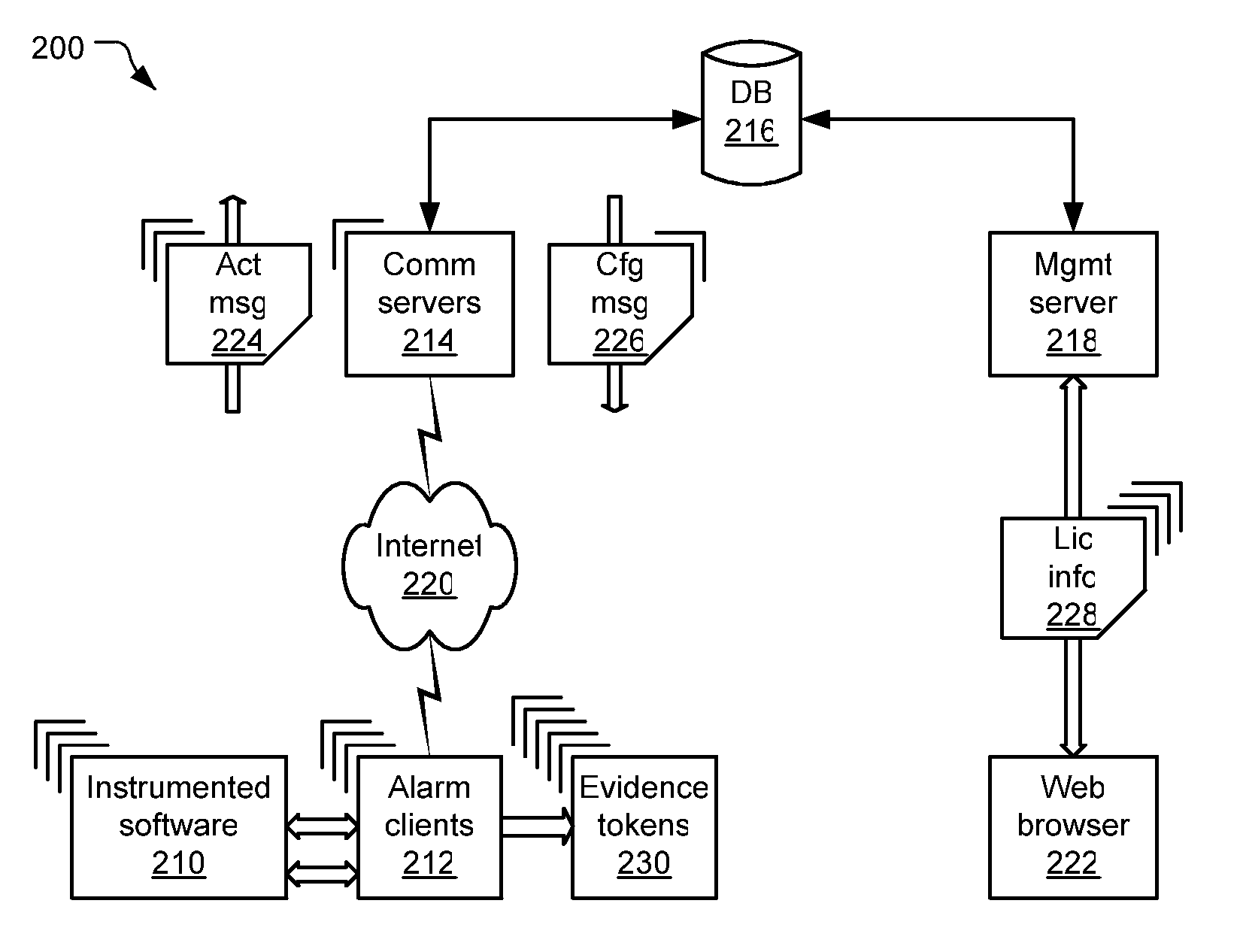
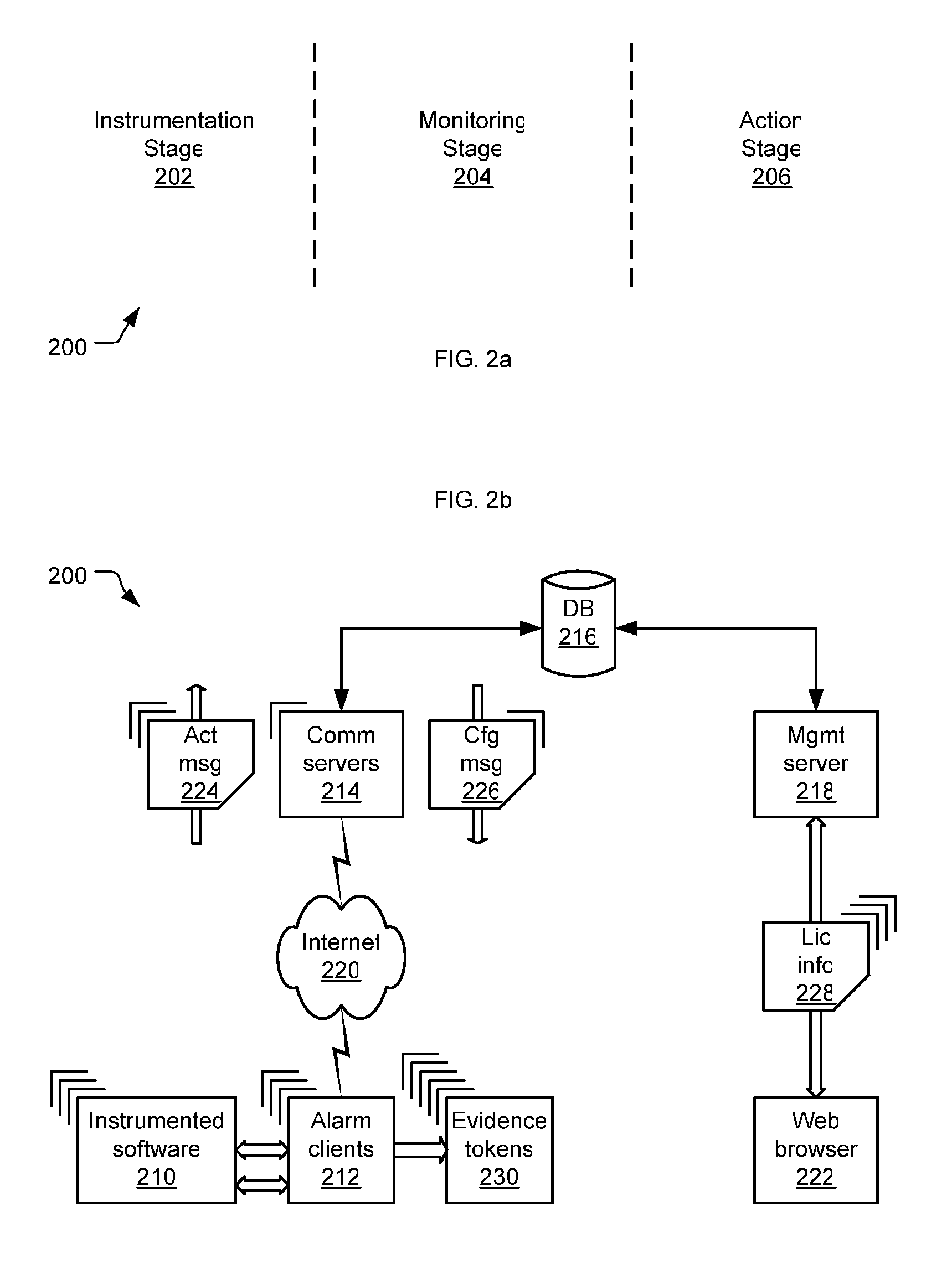
InactiveUS20060174346A1Efficiently authenticatingDigital data processing detailsAnalogue secracy/subscription systemsLicenseInstrumentation
An instrumentation for alarming a software product (210) that is subject to a license (108). An alarm client (212) is incorporated with the software product to collect usage information about the software product while it runs on a computer. This usage information permits determining whether the software product is being used in accord with the license. The alarm client further communicates an activity message (224) including the usage information to a remote server (214) via a communications network (220).
Owner:BEYONDTRUST SOFTWARE INC
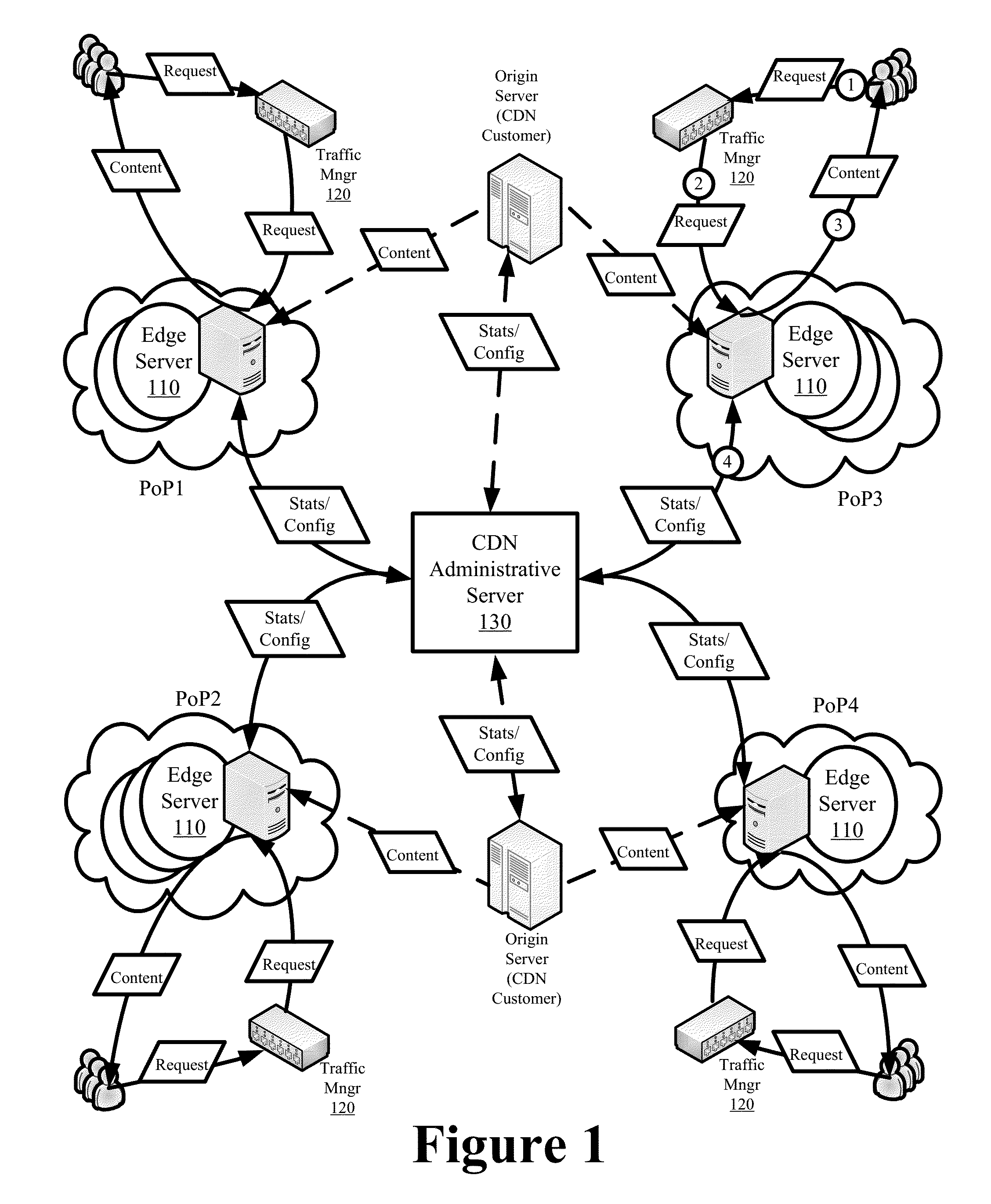
Providing localized content delivery with remote token authentication
ActiveUS20150249651A1Improve content delivery performanceHighly optimized and localized content deliveryDigital data processing detailsUser identity/authority verificationInternet privacyEngineering
Some embodiments set forth systems and methods enabling a first network to use the resources of various second networks in order to localize delivery of the first network content from the various second networks in a secure manner. Some embodiments provide a token-based authentication scheme to ensure that any configured content access restrictions are effectuated at the first network and any of the second networks providing localized content delivery for the first network. The scheme involves a two phase user authentication, wherein the user is separately authenticated at the first network and the redirected to second network using either the same or different set of access restrictions. The first network exchanges a first encryption key with content providers for encrypting / decrypting the first access restriction and a second encryption key with a second network for encrypting / decrypting the second access restriction.
Owner:EDGIO INC
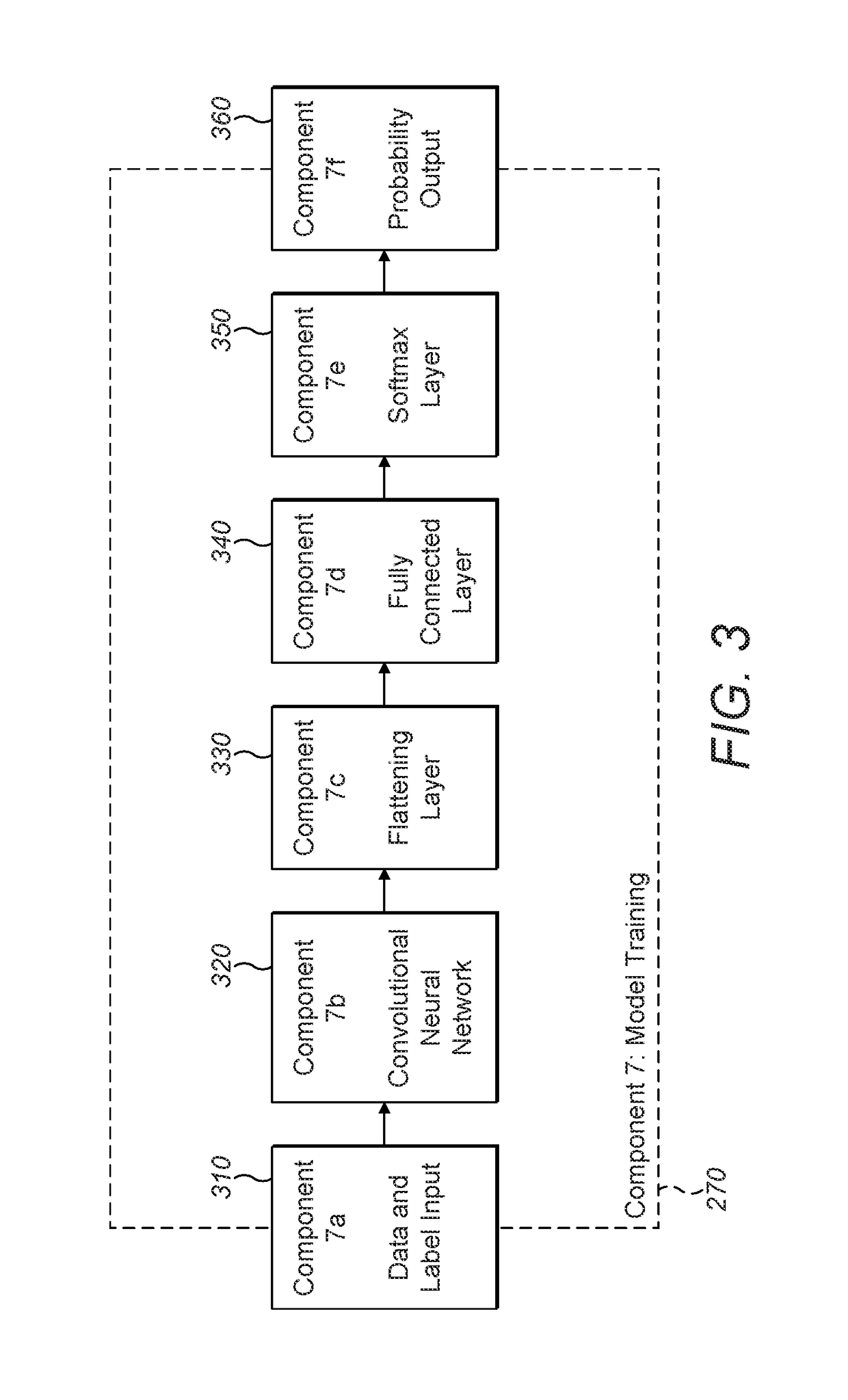
Deep Learning for Behavior-Based, Invisible Multi-Factor Authentication
InactiveUS20190044942A1Efficiently authenticatingOvercome obstaclesOther decoding techniquesDigital data authenticationUser deviceInternet privacy
Biometric behavior-based authentication may be enhanced by using convolutional deep neural networks to learn subject-specific features for each subject. The advantage is two-fold. First the need for a domain expert is eliminated, and the search space can be algorithmically explored. Second, the features that allow each subject to be differentiated from other subjects may be used. This allows the algorithm to learn the aspects of each subject that make them unique, rather than taking a set of fixed aspects and learning how those aspects are differentiated across subjects. The combined result is a far more effective authentication in terms of reduction of errors. Behavior-based, invisible multi-factor authentication (BIMFA) mays also automate the responses to authentication second and third factor requests (something you have and something you are). BIMFA leverages continuous, invisible behavioral biometrics on user devices to gain a continuous estimate of the authorization state of the user across multiple devices without requiring any explicit user interaction or input for authentication. As a result, BIMFA can demonstrate that a device is under the control of the authorized user without requiring any direct user interaction.
Owner:TWOSENSE INC
Method for authentication
InactiveUS20070067631A1Simple calculationFew transmissionUser identity/authority verificationHash functionValidation methods
A method for authentication between at least two nodes within a network, preferably a wireless sensor network, is disclosed. The sending node computes a t-bit long hash value by using a hash function h. A transmission of possibly few additional data over the network is designed in such a way that from the sending node to the receiving node only t-k bits of the hash value are transferred as truncated hash value, whereby k is a fix but arbitrary natural number between 1 and t-1. The transmitted hash value is compared to a computed hash value at the receiving node.
Owner:NEC CORP
Authentication method using biometric information and electronic device therefor
InactiveUS20160173492A1Prevent illegal useEffectively and accurately authenticatedDigital data processing detailsCharacter and pattern recognitionAuthenticationElectronic equipment
An authentication method using biometric information and an electronic device. An authentication method using biometric information in an electronic device includes: receiving biometric information from an external electronic device. An authentication is performed for the received biometric information by comparing the received biometric information with biometric information stored in the electronic device. An authentication result us transmitted to the external electronic device such that the external electronic device performs a predesignated operation.
Owner:SAMSUNG ELECTRONICS CO LTD
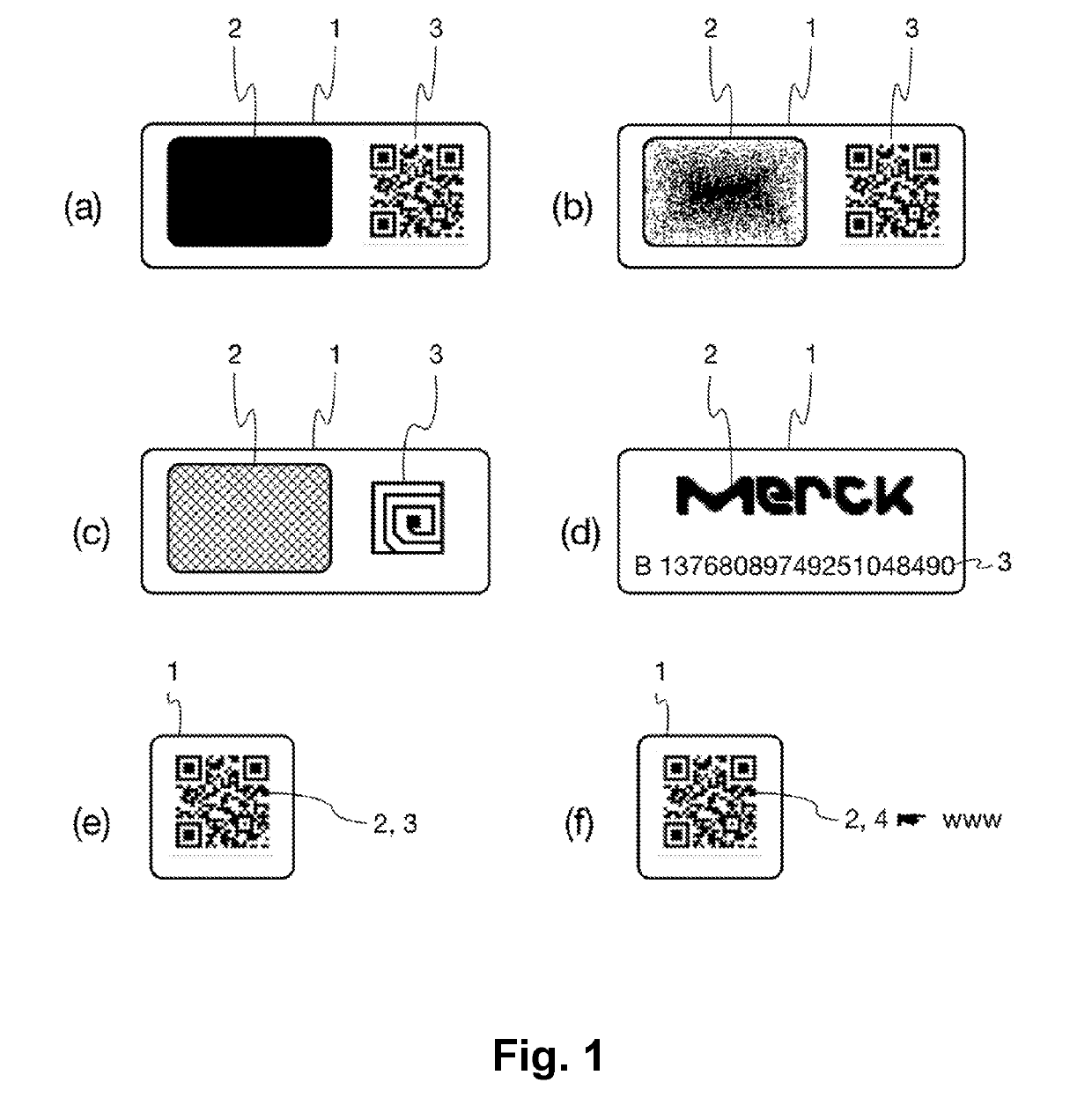
Composite security marking and methods and apparatuses for providing and reading same
ActiveUS20190334730A1Increase achievable security levelEffective protectionUser identity/authority verificationCharacter and pattern recognitionCryptographic hash functionPassword hashing
In one embodiment, the invention is directed to a method of reading a marking, comprising a stimulation step, wherein a physical challenge according to a predetermined challenge-response authentication scheme corresponding to the PUF is created and applied to a PUF; a detection step, wherein a response generated by the PUF in accordance with the challenge-response authentication scheme in reaction to the challenge is detected and a digital signal representing the response is generated; a processing step, wherein the digital signal is processed in order to generate a hash value of the response by application of a predetermined cryptographic hash function to the digital signal; and an output step, wherein data representing the generated hash value as a first reading result is output.
Owner:MERCK PATENT GMBH
Homogeneous Atomic Pattern for Double, Add, and Subtract Operations for Digital Authentication Using Elliptic Curve Cryptography
ActiveUS20160087802A1Efficiently authenticatingReduced side-channel detectabilityUser identity/authority verificationUnauthorized memory use protectionCountermeasureElliptic curve cryptography
A method of performing finite field addition and doubling operations in an elliptic curve cryptography (ECC) authentication scheme as a countermeasure to side-channel attack. The addition and doubling operations are executed using atomic patterns that involve the same sequence and number of operation types, so that the noise consumption and electromagnetic emanation profile of circuitry performing the operations is identical regardless of operation. A subtraction operation using such an atomic pattern is also disclosed.
Owner:TEXAS INSTR INC
Methods and systems for preparing and performing an object authentication
ActiveUS10554405B1Way of increaseEfficiently authenticatingKey distribution for secure communicationPublic key for secure communicationAlgorithmTheoretical computer science
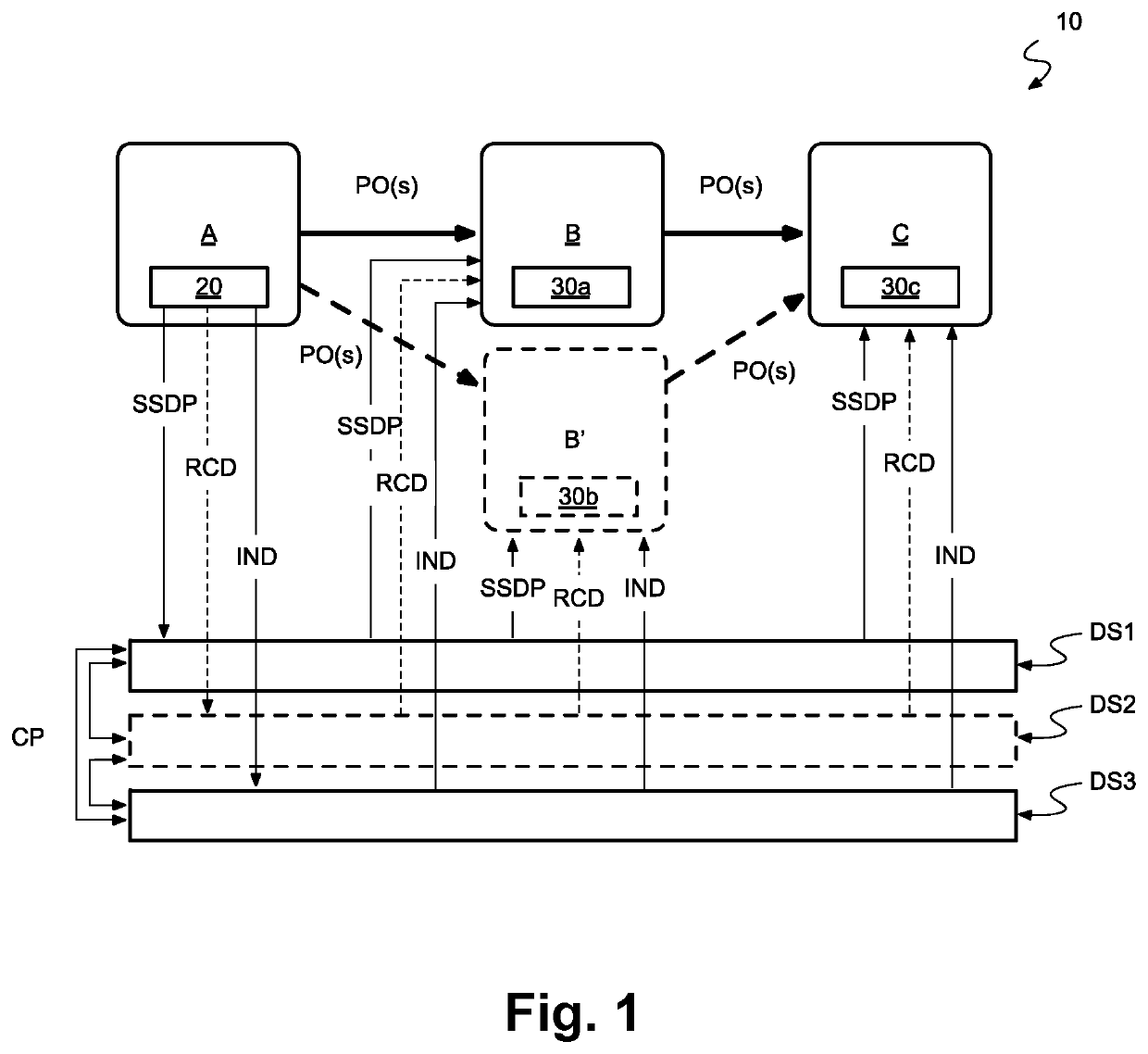
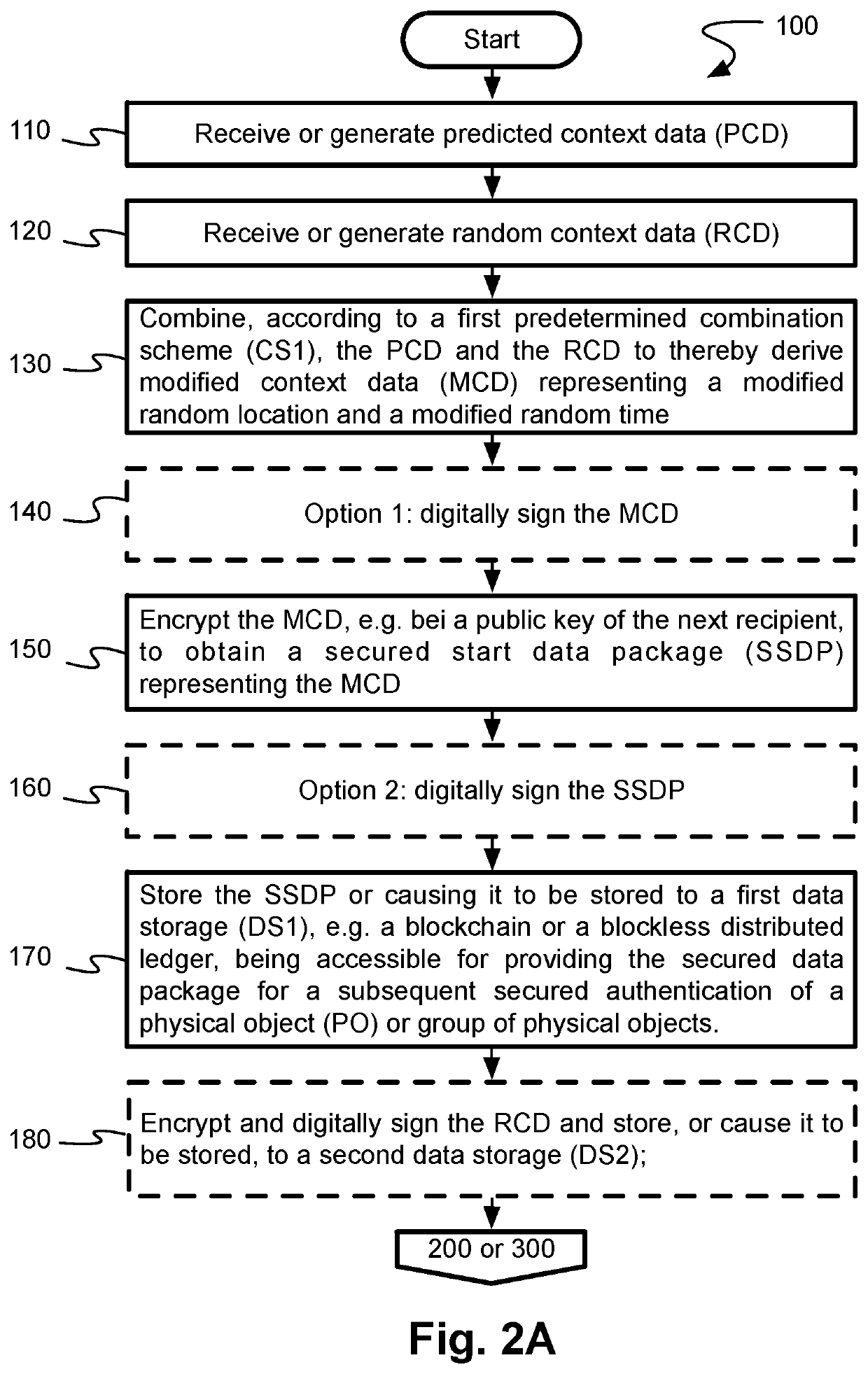
The present invention relates to the field of tracing and anti-counterfeit protection of physical objects, and particularly to preparing and performing a secure authentication of such objects. Specifically, the invention is directed to a method and a system for preparing a subsequent secured authentication of a physical object or group of physical objects by a recipient thereof, to a method and system for authenticating a physical object or group of physical objects, to a method and system of securely providing a time-variant combination scheme for authenticating a physical object or group of physical objects according to the above methods, and to related computer programs corresponding to said methods. The invention is based on the concept of increasing the security level by increasing the information entropy of the data on which the anti-counterfeit protection is based by means of random data communicated to authenticating entities in an algorithmically hidden way.
Owner:MERCK PATENT GMBH
System for and method of authenticating device and user in home network
ActiveUS8495729B2Efficiently authenticatingEfficient supplyDigital data processing detailsUser identity/authority verificationFamily networkControl equipment
A system for authenticating a device and a user in a home network. The home network manages one or more devices through a home server. The system includes a service device for providing service contents according to the control of a control device. The system includes a home server for containing authentication information for the respective devices. The home server performs a network configuration for the respective devices according to the authentication information. A permission server is connected with the home server. The permission server contains service permission information according to the characteristics of the respective control devices. The control device performs a network authentication through the home server, and is provided with service contents from the service device according to whether the permission server allows the requested service contents. The system can perform an authentication procedure and a network configuration for the control devices.
Owner:SAMSUNG ELECTRONICS CO LTD
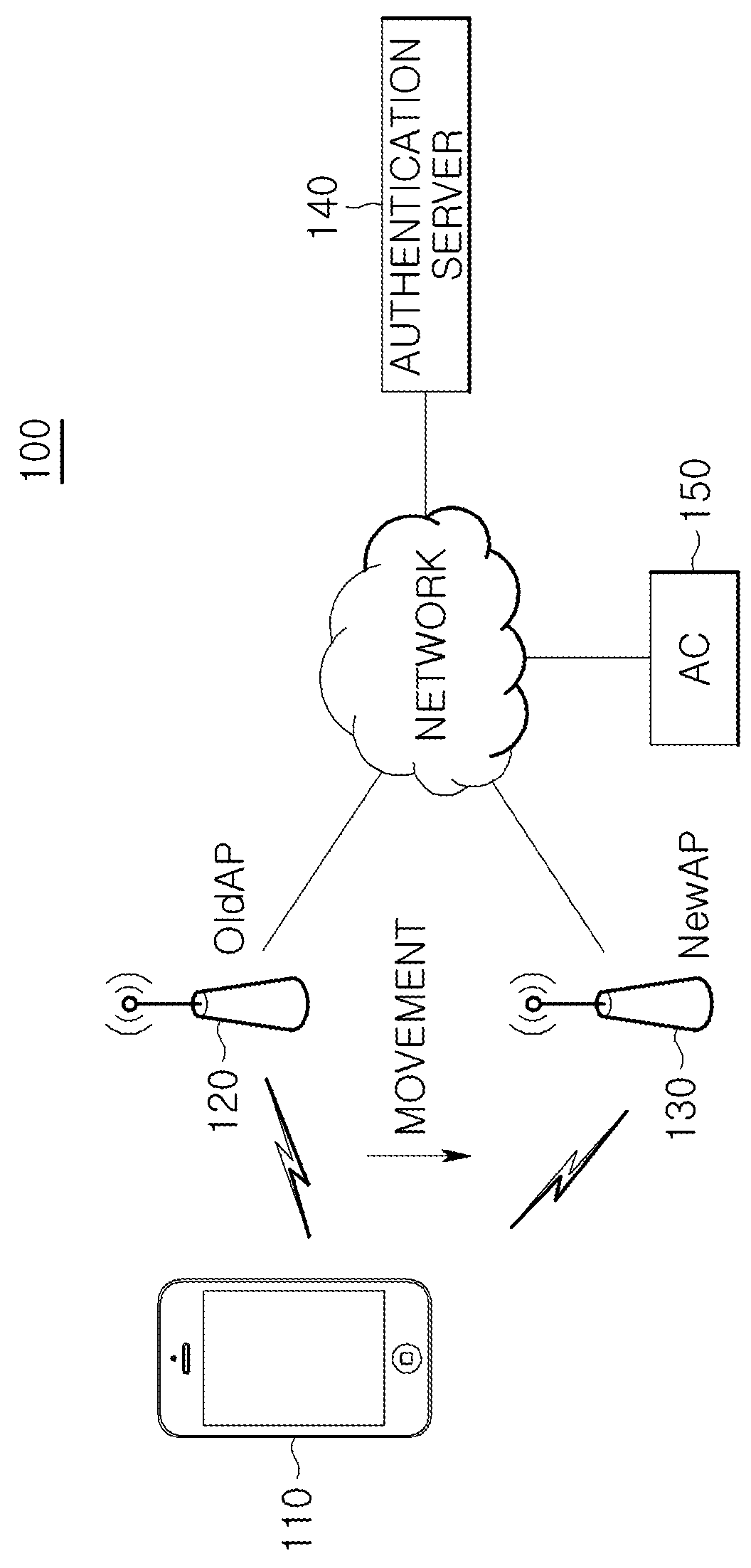
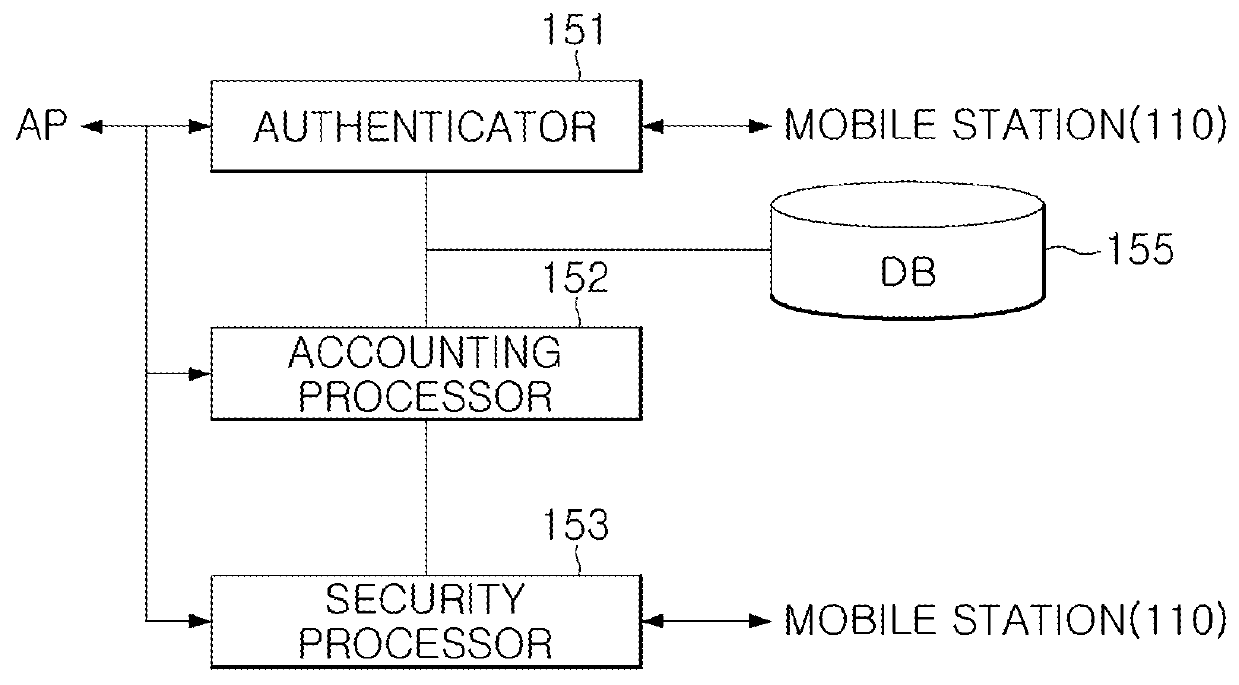
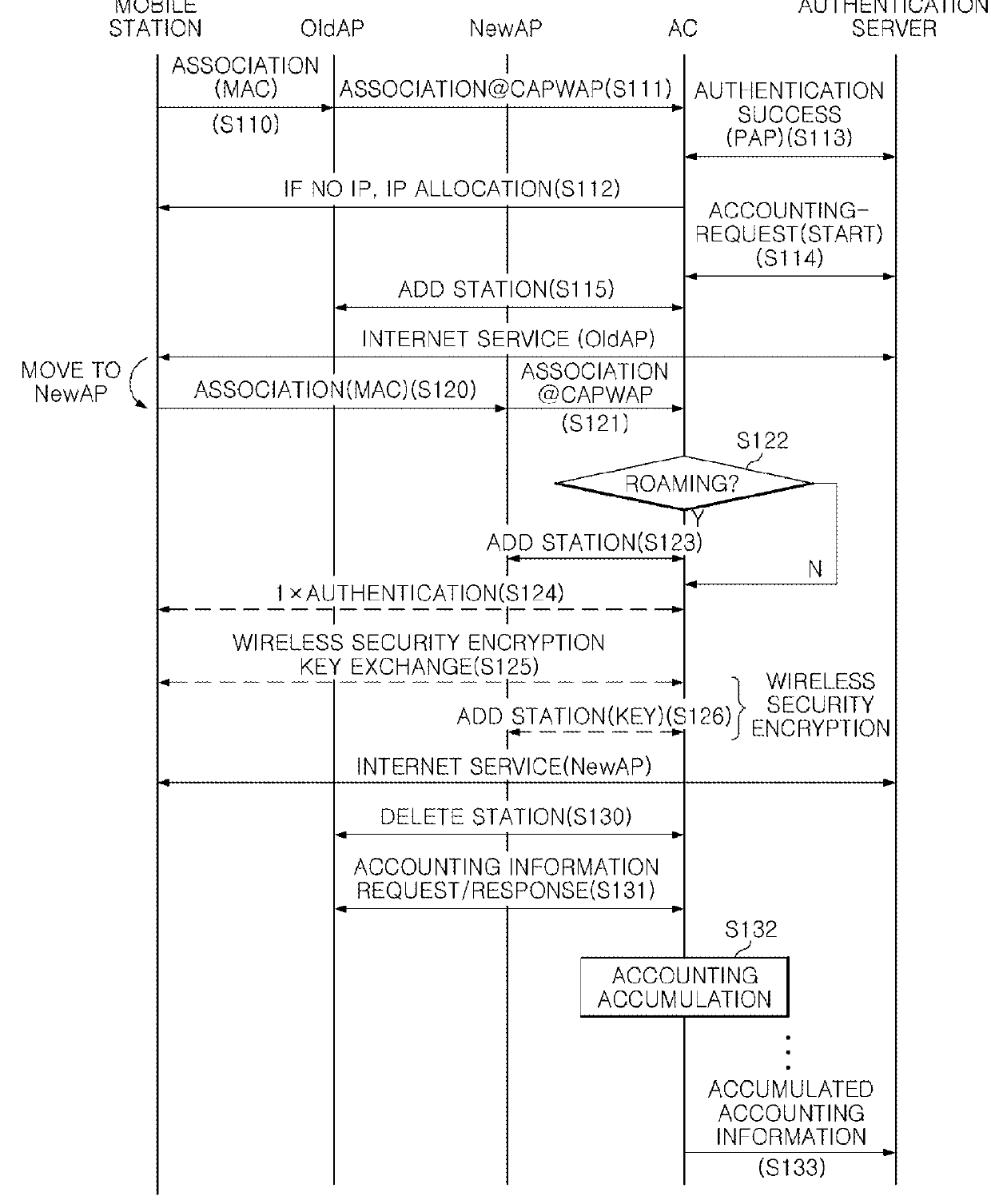
Method and device for accounting in WIFI roaming based on ac and ap interworking
ActiveUS20140341185A1Reduce loadEfficiently authenticatingMetering/charging/biilling arrangementsAccounting/billing servicesSession managementComputer terminal
A WiFi roaming method and device which perform an authentication and accounting process once for multiple APs, thereby reducing the load of an authentication server (RADIUS) in a WiFi roaming method, which separates a terminal session management function and a traffic control function by a access controller and a access point interworked with a tunneling method according to a CAPWAP (Control and Provisioning of Wireless Access Points) protocol.
Owner:KT CORP
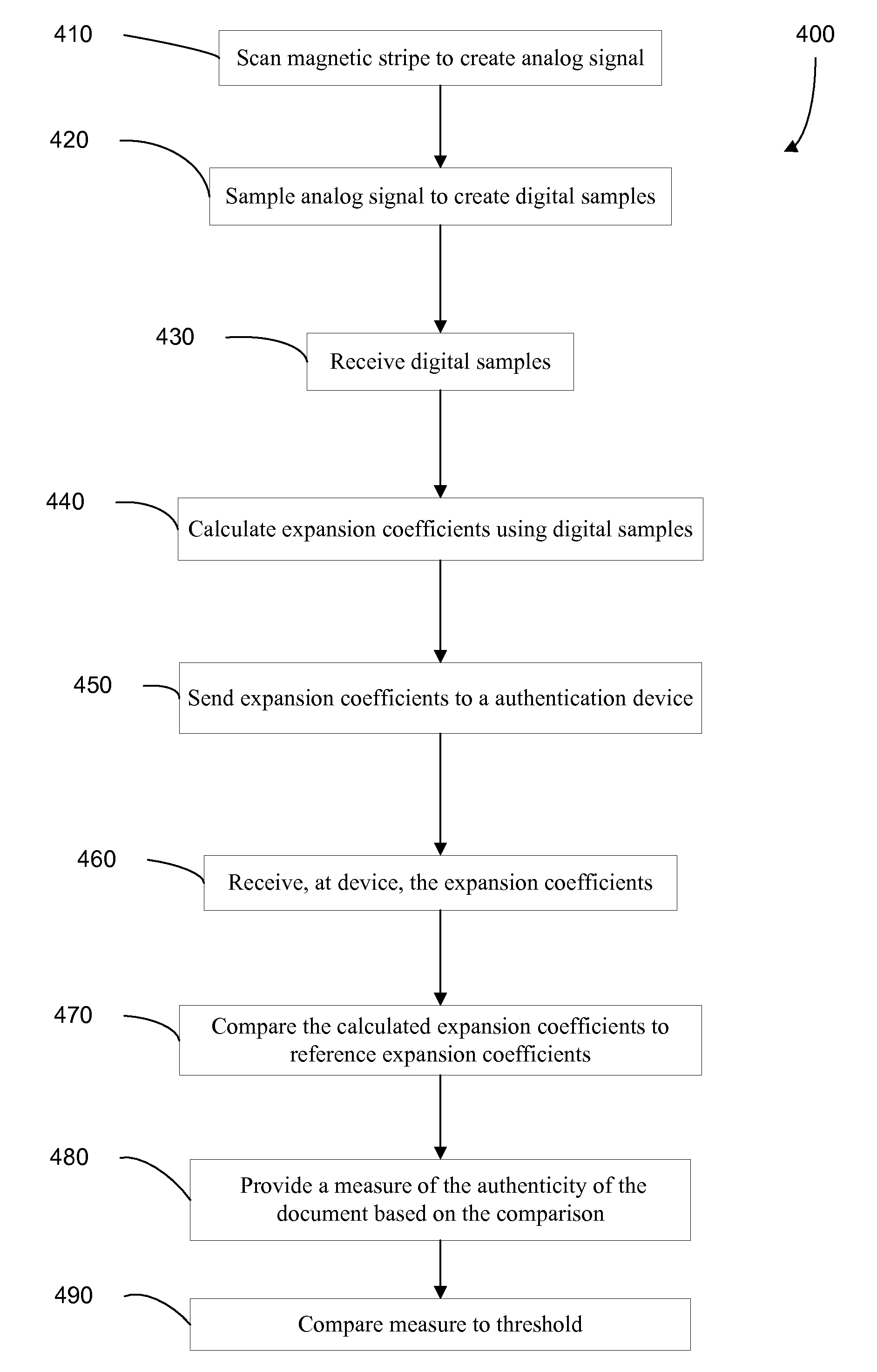
Authenticating a document with a magnetic stripe
ActiveUS20100127065A1Efficiently authenticatingSensing record carriersSpecial data processing applicationsCredit cardDocumentation
Methods, systems, and apparatus for efficiently authenticating a document (e.g. a credit card) having a magnetic stripe are provided. The magnetic field at different points of the magnetic stripe are measured, e.g., by a checkout scanner to create a magnetic signature. Digital samples of the measurements may be transformed into coefficients of continuous basis functions, e.g., a Fourier transform. These coefficients are then compared to reference values (e.g. corresponding coefficients) to produce a measure of the authenticity of the document. The number of coefficients used can advantageously be smaller than the number of digital samples without compromising accuracy, thus using less bandwidth between a scanner and an authentication entity.
Owner:VISA INT SERVICE ASSOC
Cryptographic techniques for a communications network
InactiveUS20080032669A1Efficiently authenticatingKey distribution for secure communicationUnauthorised/fraudulent call preventionHome environmentComputer science
Techniques are described for enabling authentication and / or key agreement between communications network stations and service networks. The techniques described include the negotiation and use of a cryptographic primitive shared between a service network and a home environment of a station. The techniques described also feature a key usage indicator, such as a sequence number, maintained by the service network and a station. Comparison of the key usage indicators can, for example, permit efficient authentication of the service network.
Owner:VERIZON LAB
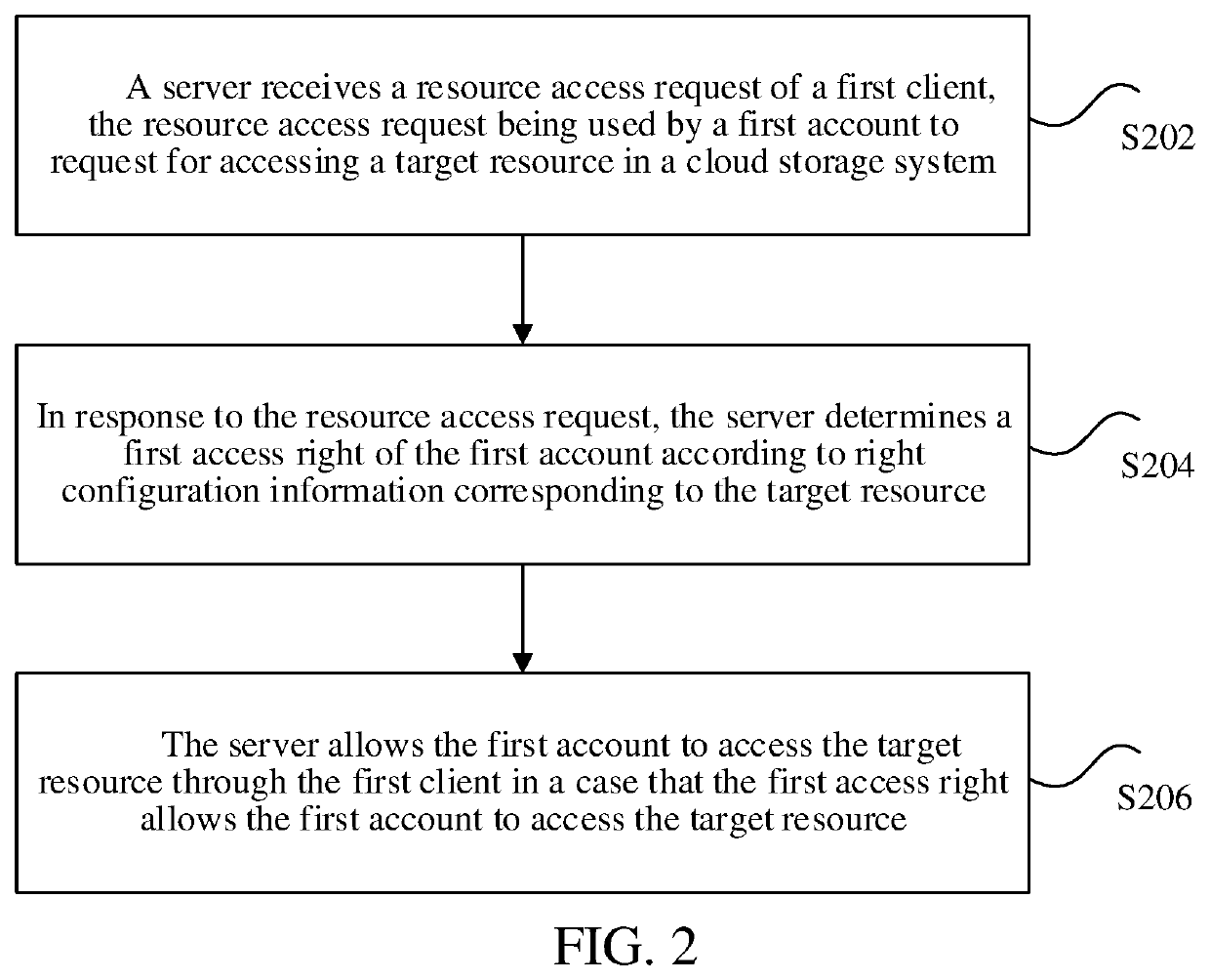
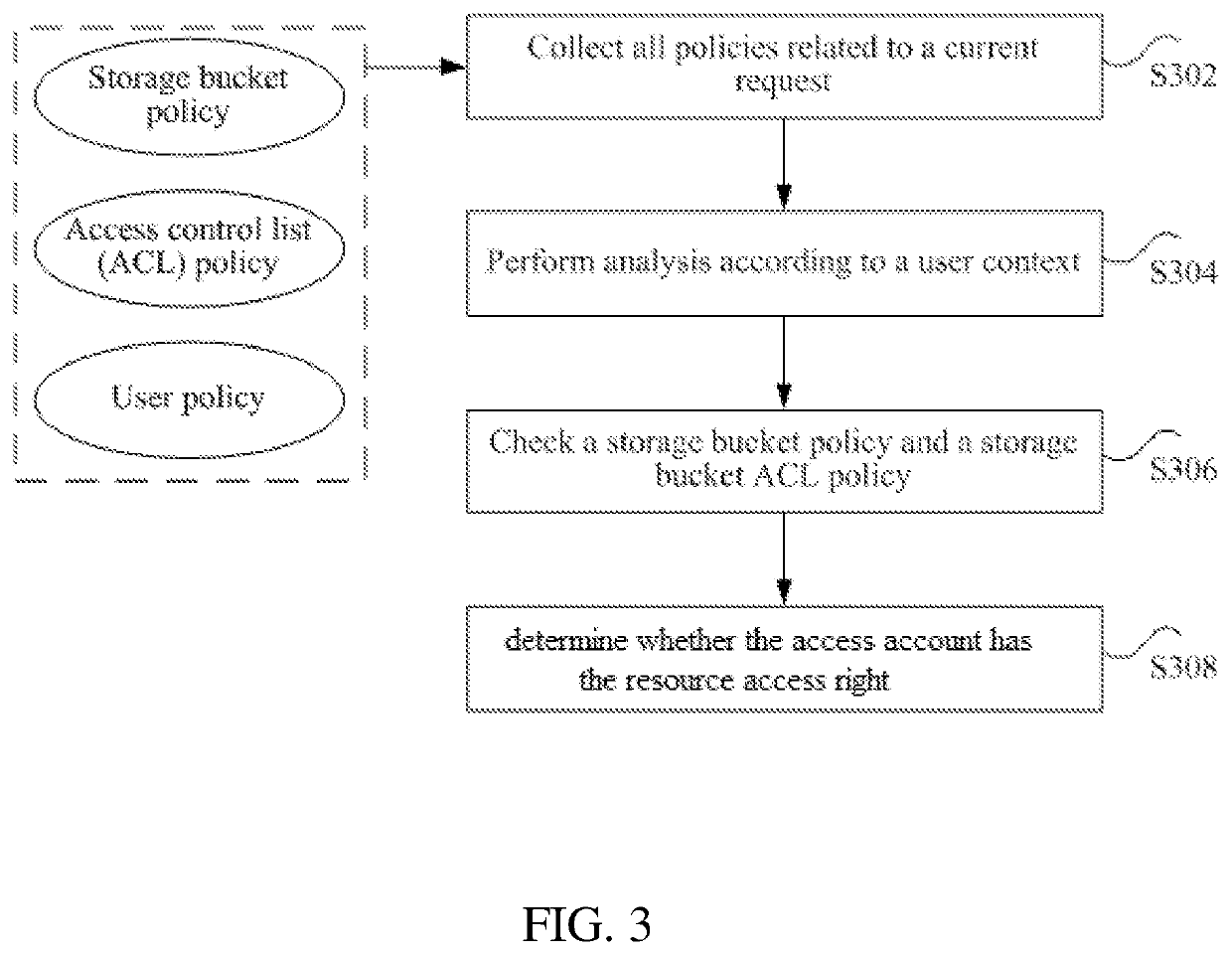
Account authentication method for cloud storage, and server
ActiveUS20200028838A1Efficiently authenticatingLow efficiencyData switching networksSecurity arrangementCloud storage systemDatabase
A method of authenticating an account is provided. A resource access request requesting for accessing, by a first account, a target resource in a cloud storage system is received by a server from a first client, the first account logging in to the first client. In response to the resource access request, a first access right of the first account is determined by the server based on right configuration information corresponding to the target resource, the right configuration information indicating an association relationship between an account and an access right of the account to the target resource. The first account is allowed by the server to access the target resource through the first client based on the first access right indicating that the first account is allowed to access the target resource.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Pressure activated fingerprint input apparatus
InactiveUS7760921B2Simply and reliably readingClear readingPrint image acquisitionComputer scienceFingerprint
Owner:CASIO COMPUTER CO LTD
Information processing apparatus, information processing method, program, and recording medium
ActiveUS20140205087A1Efficiently authenticatingPublic key for secure communicationSecret communicationInformation processingRecording media
Provided is an information processing apparatus including a message generating unit that generates messages of N times (where N≧2) based on a multi-order multivariate polynomial set F=(f1, . . . , fm) defined on a ring K and a vector s that is an element of a set Kn, and calculates a first hash value based on the messages of N times, a message providing unit that provides a verifier with the first hash value, an interim information generating unit that generates third information of N times using first information randomly selected by the verifier and second information of N times, and generates a second hash value based on the third information of N times, an interim information providing unit that provides the verifier with the second hash value, and a response providing unit that provides the verifier with response information of N times.
Owner:SONY CORP
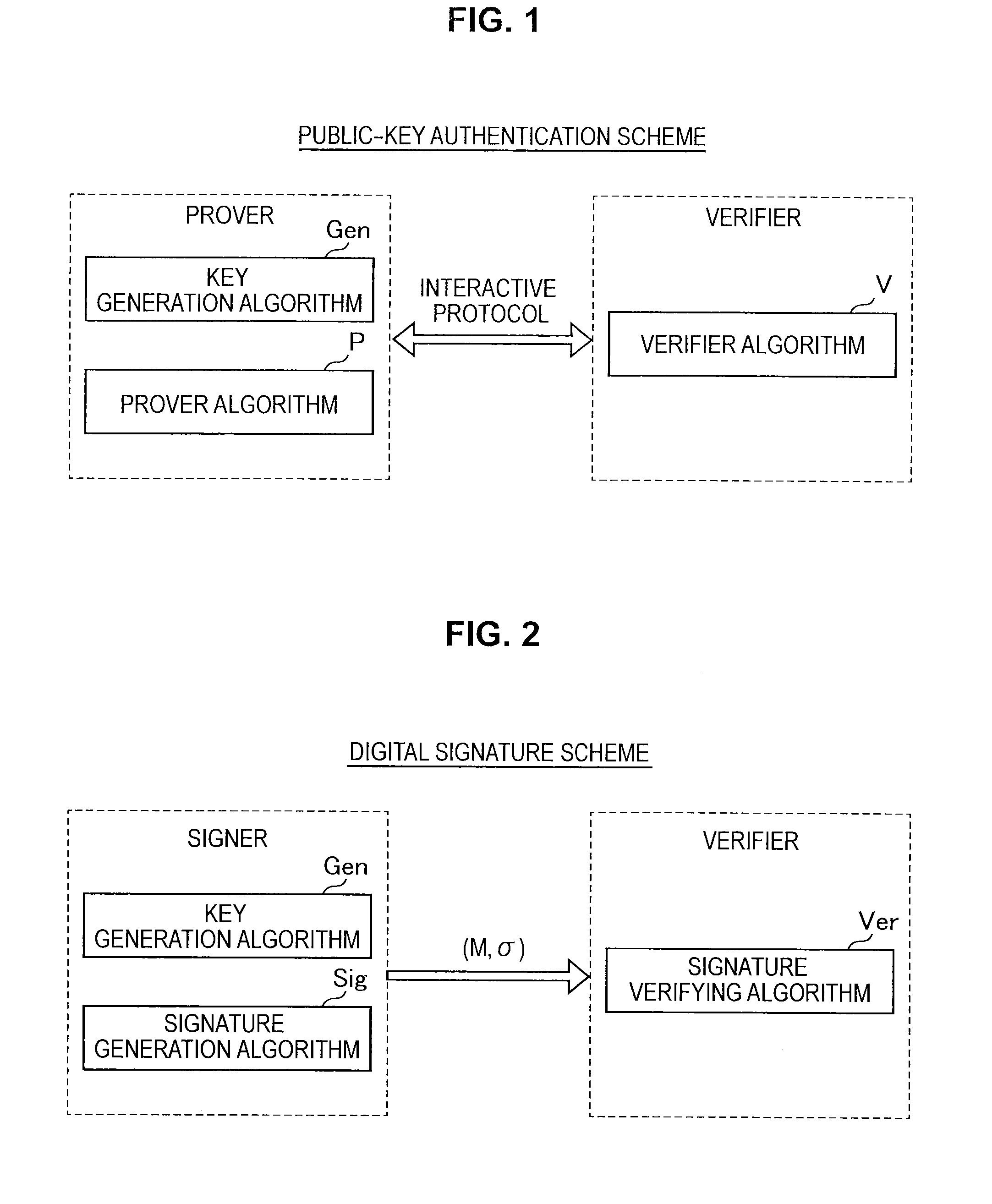
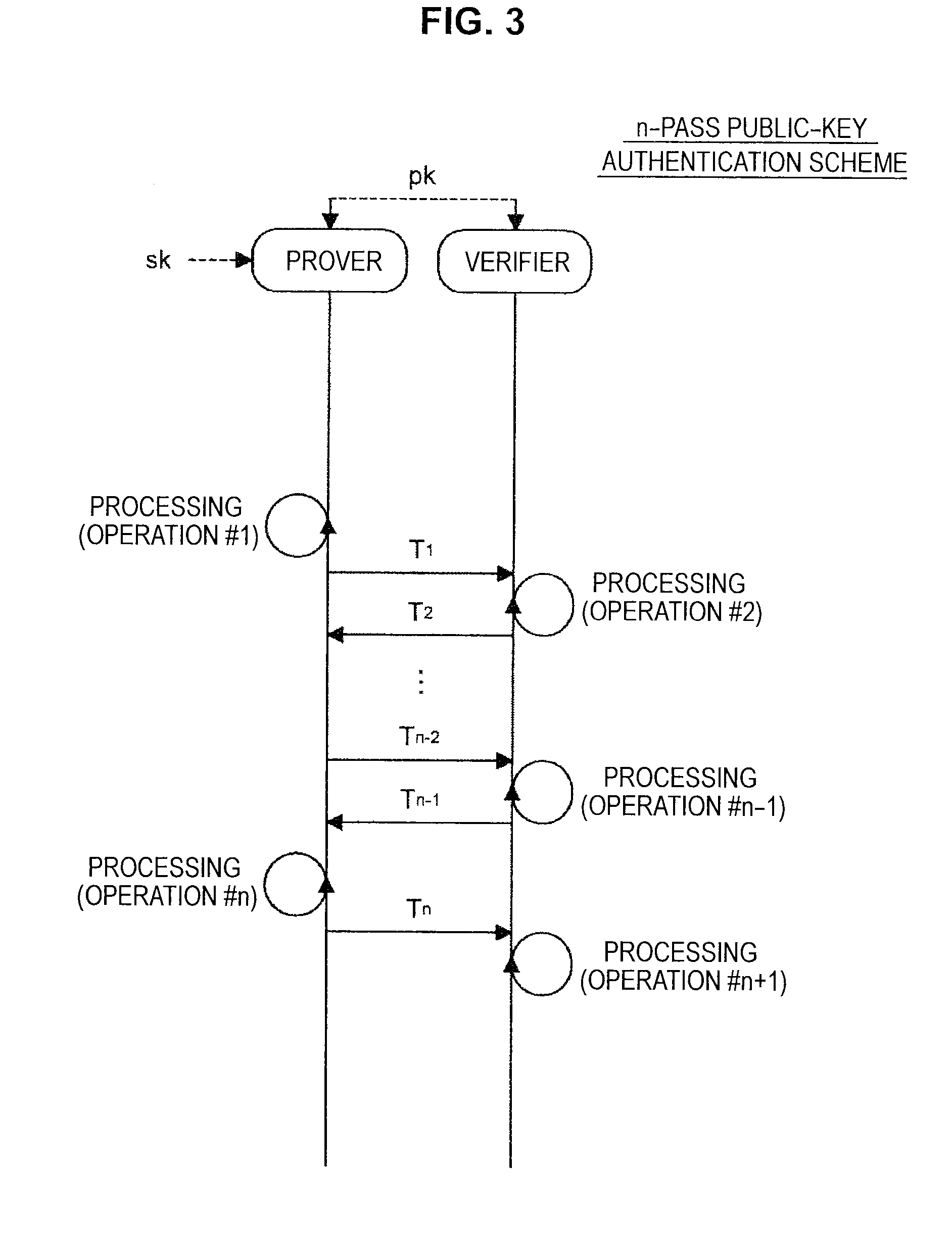
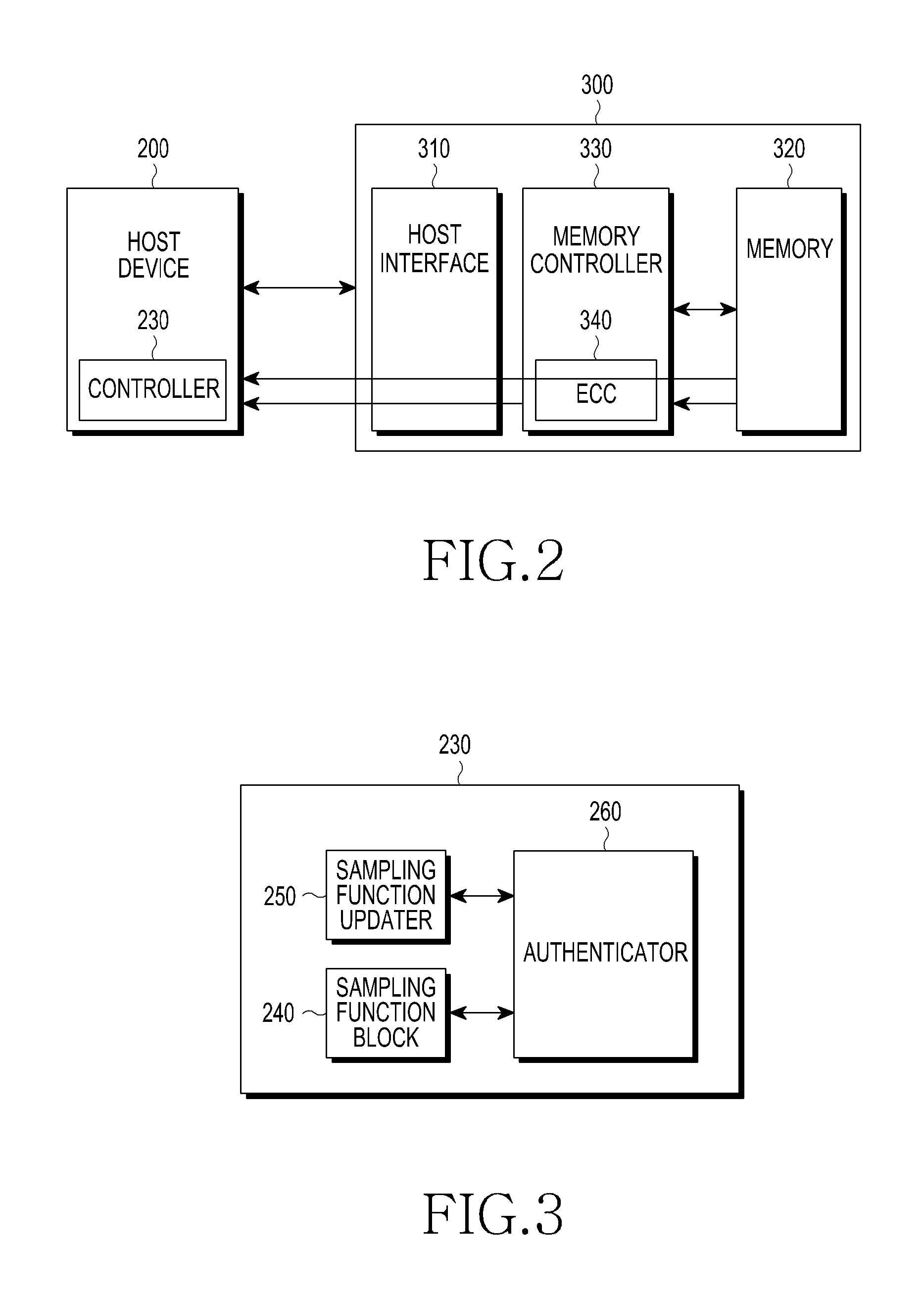
Method for authenticating a storage device, machine-readable storage medium, and host device
ActiveUS20130061287A1Verifies suitability of a deviceEffective massDigital data processing detailsRecord information storageAuthenticationHost machine
A method for authentication, by a host device, of a storage device having a plurality of unit storage areas comprises acquiring information on the distribution of locations of defect referenceive areas to be used for uniquely identifying the storage device, sampling the unit storage areas of the storage device, identifying the distribution of locations of physically defective areas among the sampled areas, determining the similarity between the acquired distribution of locations and the identified distribution of location, and authenticating the storage device according to the result of the determination.
Owner:SAMSUNG ELECTRONICS CO LTD
Composite security marking and methods and apparatuses for providing and reading same
ActiveUS11296897B2Effective protectionEfficiently recognizingUser identity/authority verificationCharacter and pattern recognitionDigital signal processingCryptographic hash function
In one embodiment, the invention is directed to a method of reading a marking, comprising a stimulation step, wherein a physical challenge according to a predetermined challenge-response authentication scheme corresponding to the PUF is created and applied to a PUF; a detection step, wherein a response generated by the PUF in accordance with the challenge-response authentication scheme in reaction to the challenge is detected and a digital signal representing the response is generated; a processing step, wherein the digital signal is processed in order to generate a hash value of the response by application of a predetermined cryptographic hash function to the digital signal; and an output step, wherein data representing the generated hash value as a first reading result is output.
Owner:MERCK PATENT GMBH
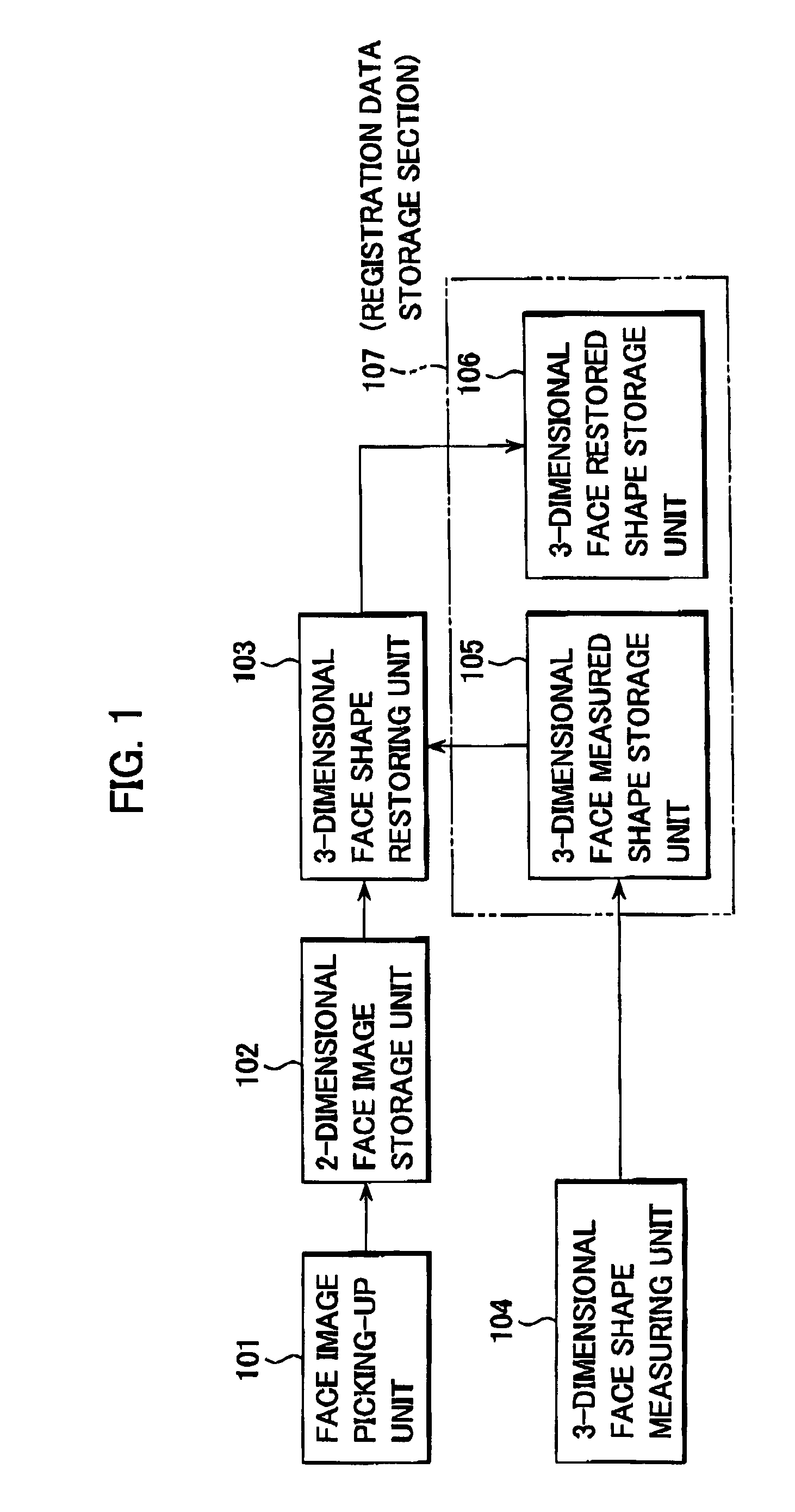
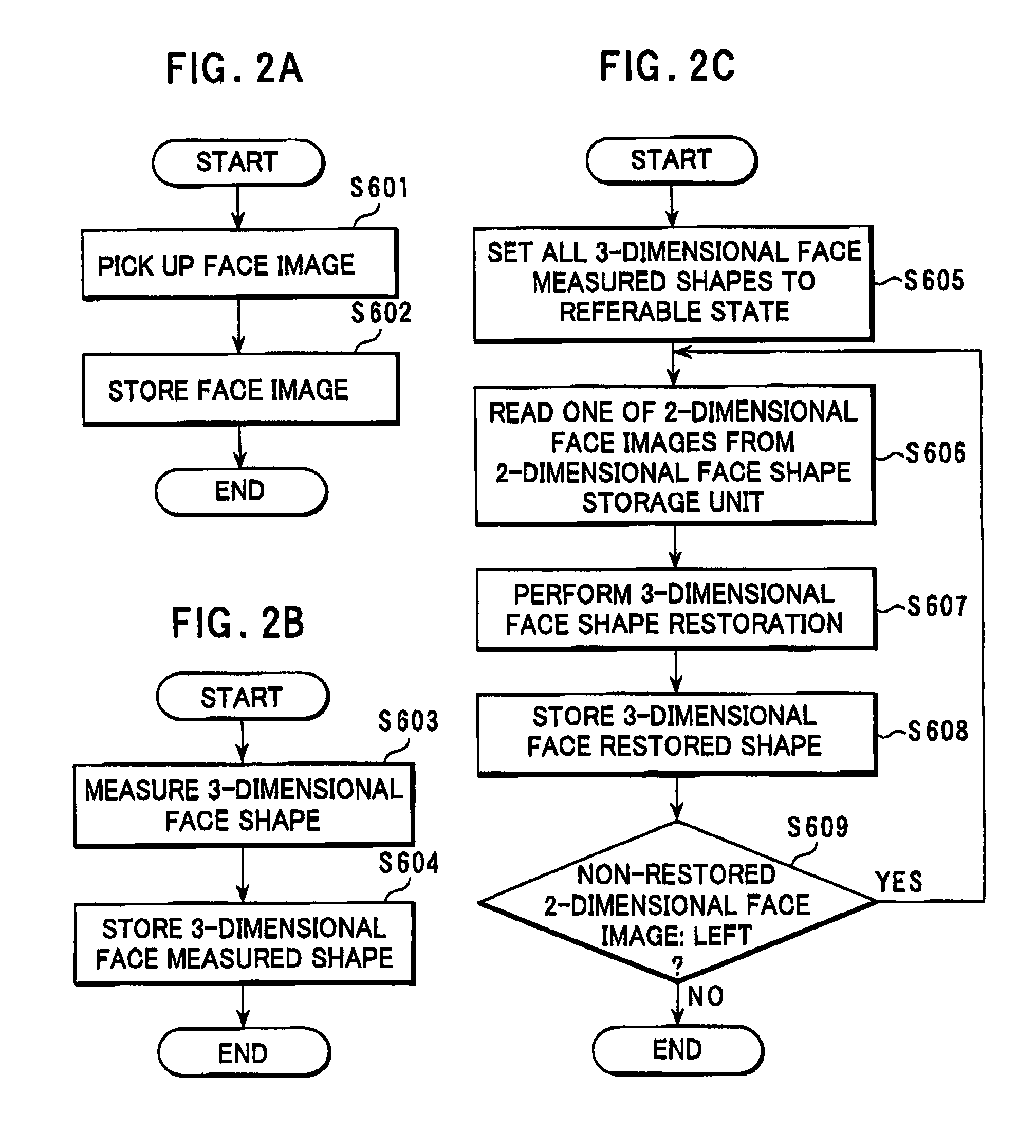
Restoring and collating system and method for 3-dimensional face data
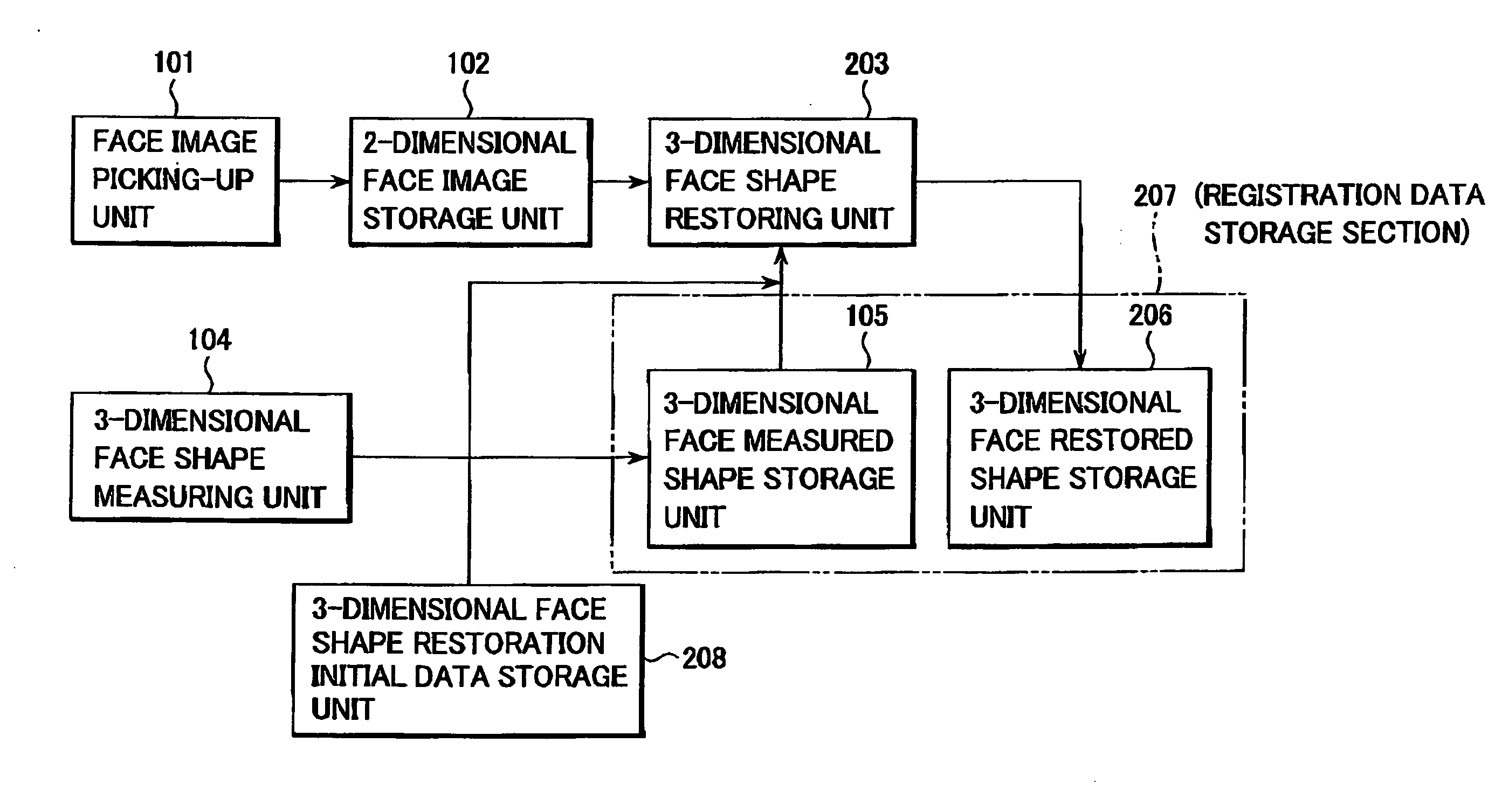
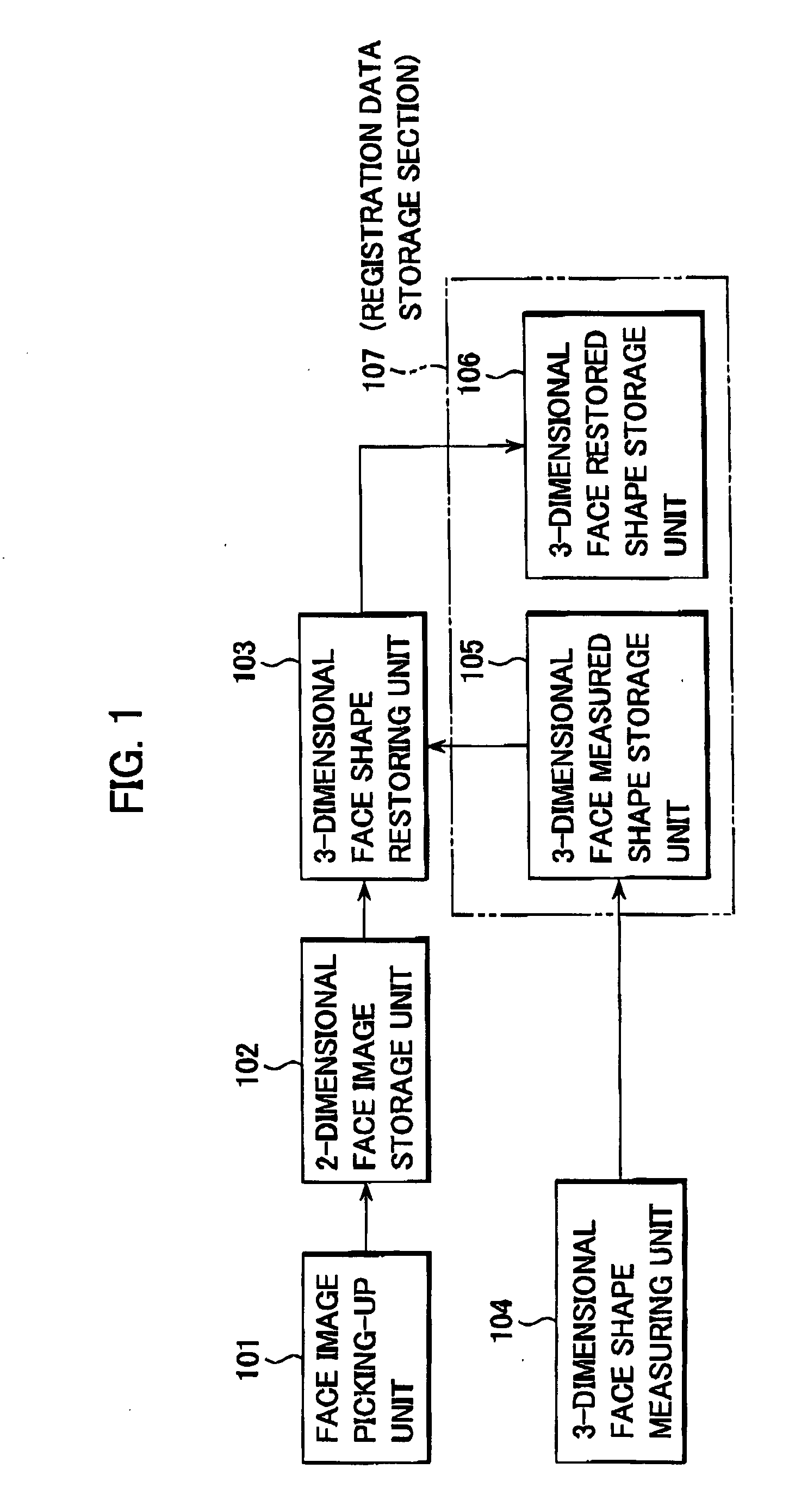
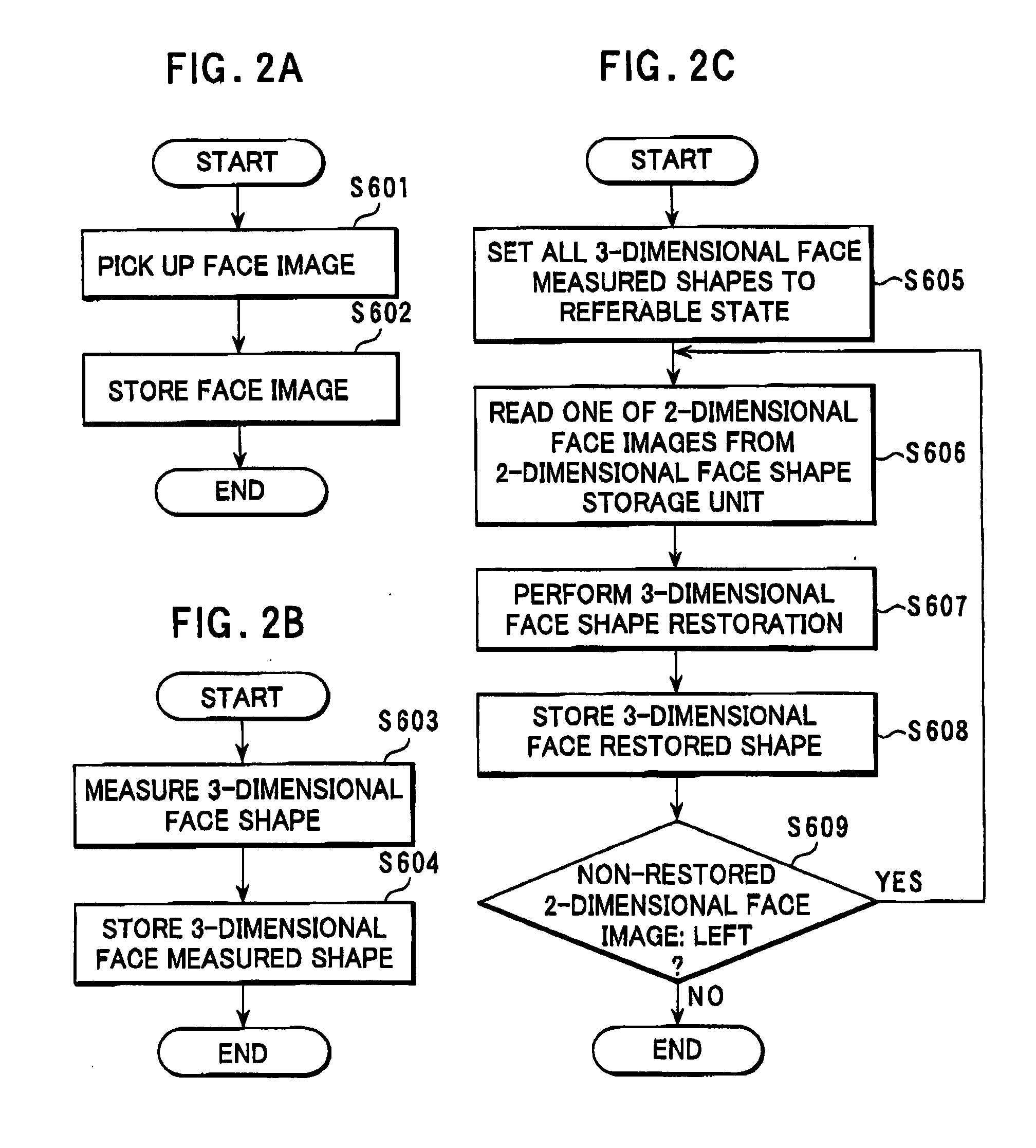
InactiveUS20070229499A1High accuracyShort time3D modellingThree-dimensional object recognitionImage storageStorage cell
A 3-dimensional face data restoring and collating system includes a 2-dimension face image storage unit configured to store a plurality of 2-dimensional face images of persons, and a 3-dimensional face restored shape storage unit. A 3-dimensional face shape restoring unit restores a 3-dimensional face shape data from one of the plurality of 2-dimensional face images for a target one of the persons based on a 3-dimensional reference face shape data, and stores the 3-dimensional restored face shape data in the 3-dimensional face restored shape storage unit.
Owner:NEC CORP
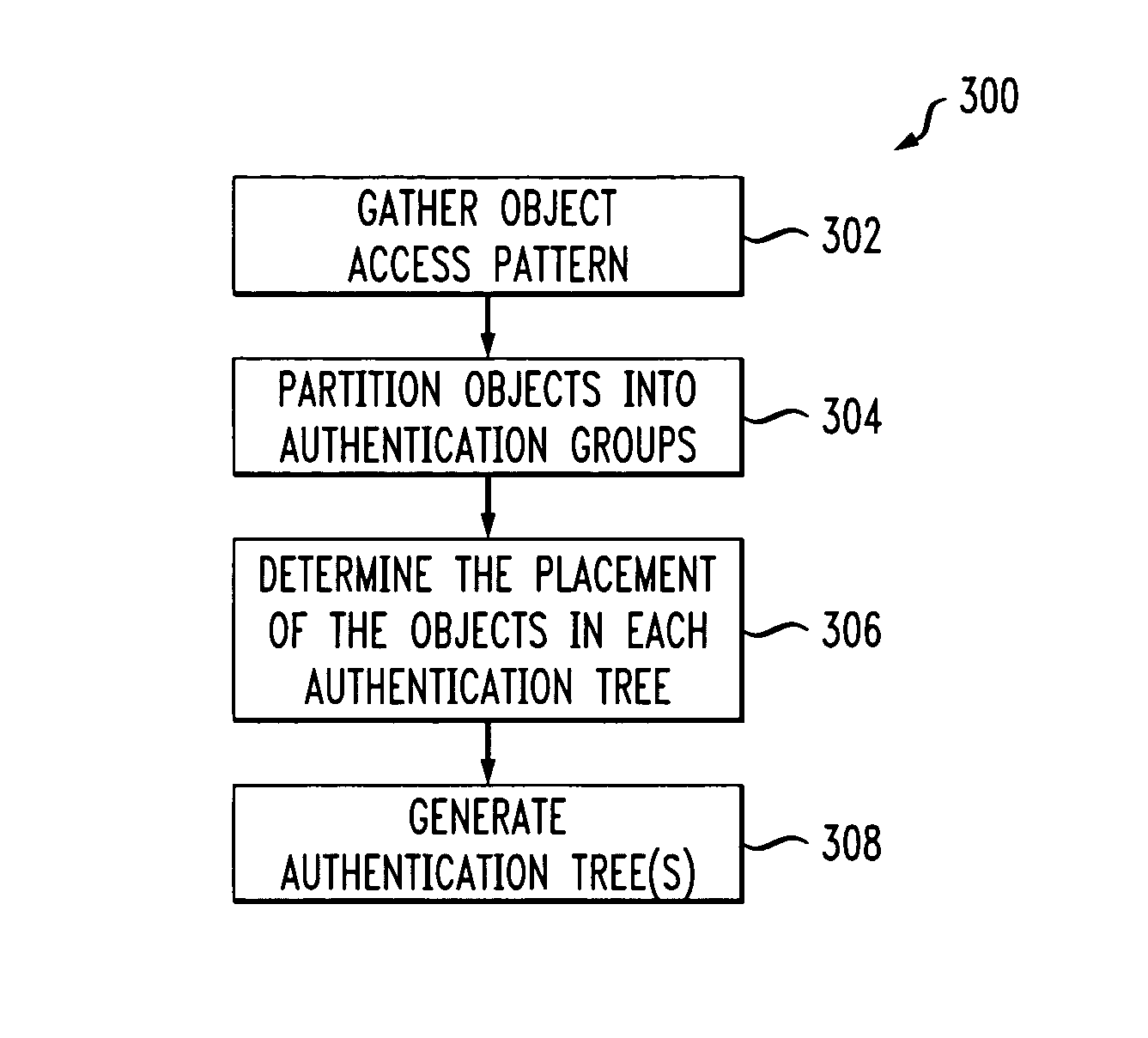
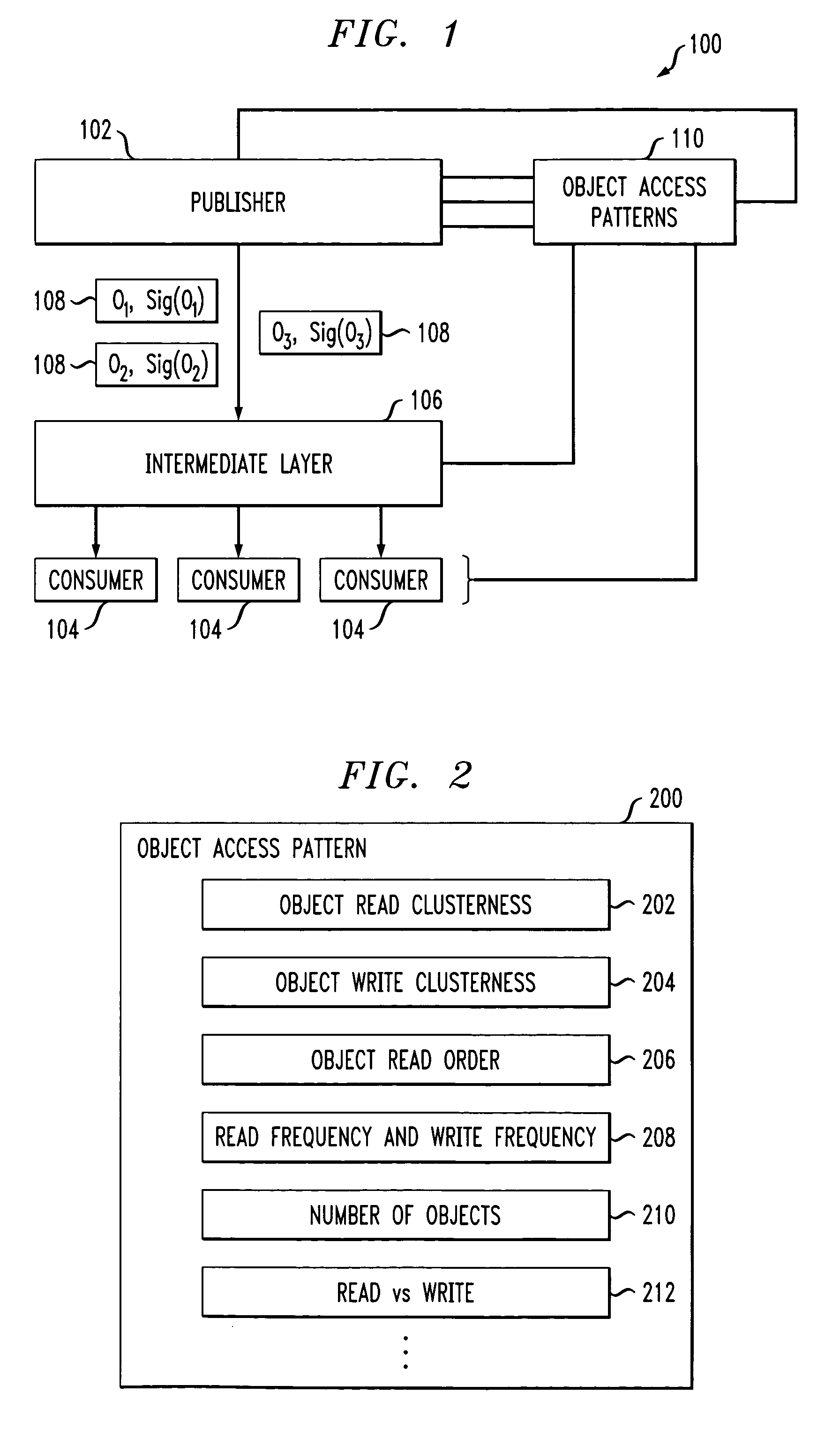
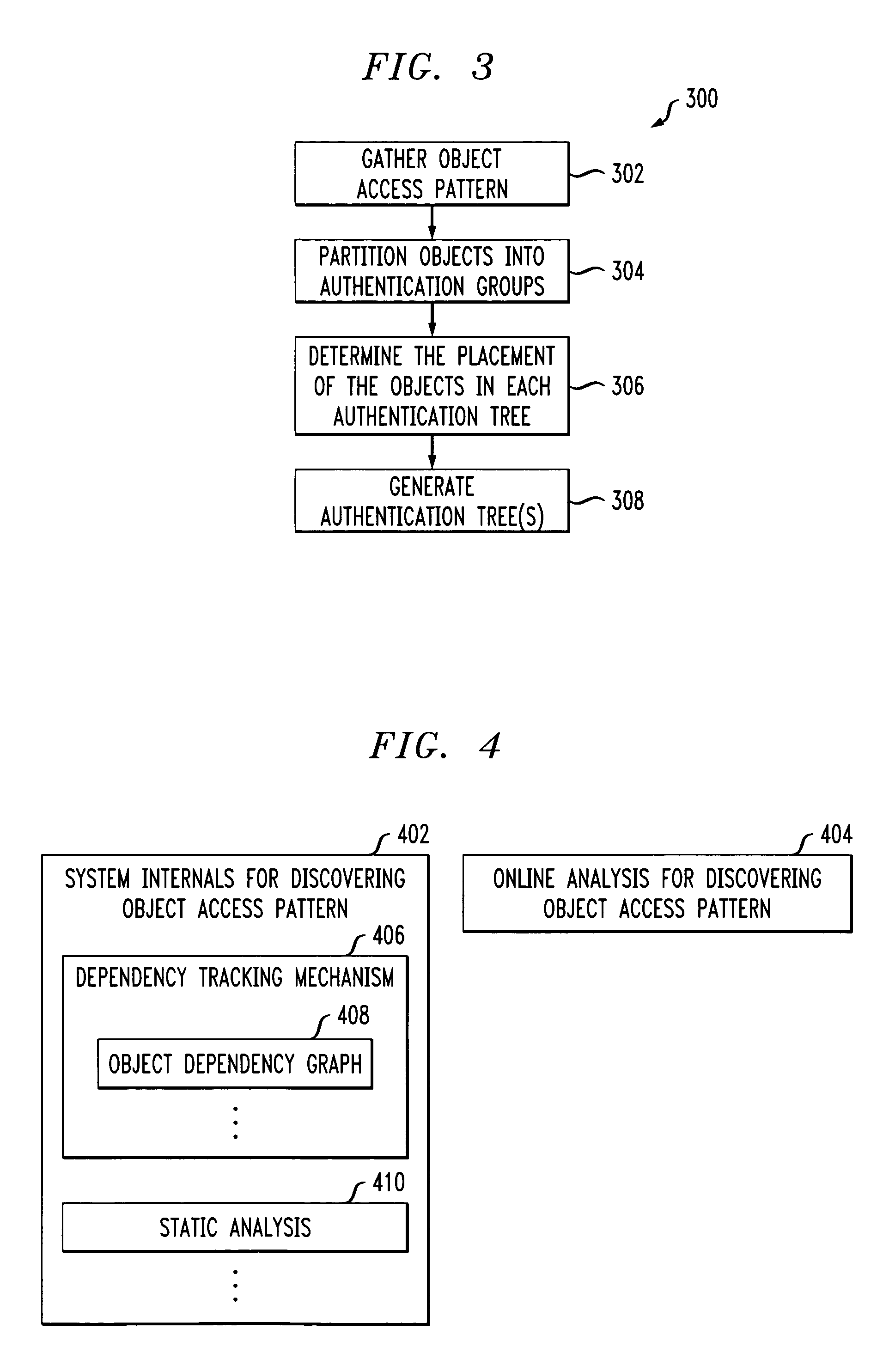
Methods for efficiently authenticating multiple objects based on access patterns
InactiveUS7406597B2Efficiently authenticatingReduce overheadMultiple digital computer combinationsProgram controlObject basedTheoretical computer science
Techniques for efficiently authenticating multiple objects and clustering objects based on access patterns are provided. For example, in an illustrative aspect of the invention, a technique for generating and / or reading authentication information, wherein the authentication information provides evidence that a plurality of objects were one of generated and sent by an entity, comprises using one or more object access patterns indicative of whether at least two of the plurality of objects are accessed within a similar time period to group objects together to reduce an overhead for at least one of generating and reading the authentication information.
Owner:INT BUSINESS MASCH CORP
Restoring and collating system and method for 3-dimensional face data
InactiveUS8035640B2Efficiently authenticatingExcellent 3-dimensional face registeringDigital data authenticationThree-dimensional object recognitionComputer graphics (images)Face shape
A 3-dimensional face data restoring and collating system includes a 2-dimension face image storage unit configured to store a plurality of 2-dimensional face images of persons, and a 3-dimensional face restored shape storage unit. A 3-dimensional face shape restoring unit restores a 3-dimensional face shape data from one of the plurality of 2-dimensional face images for a target one of the persons based on a 3-dimensional reference face shape data, and stores the 3-dimensional restored face shape data in the 3-dimensional face restored shape storage unit.
Owner:NEC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com