Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
168results about How to "Effective security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
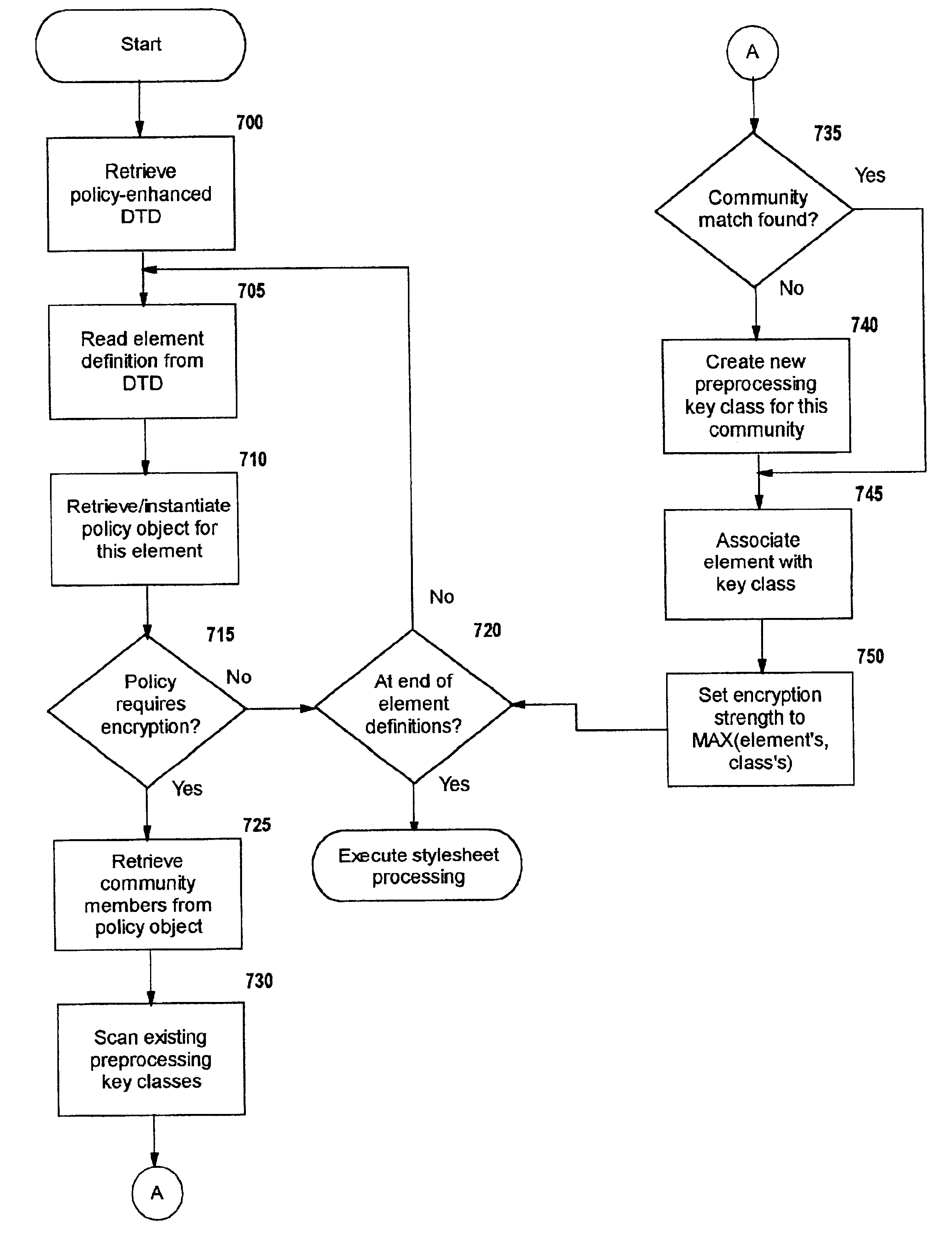
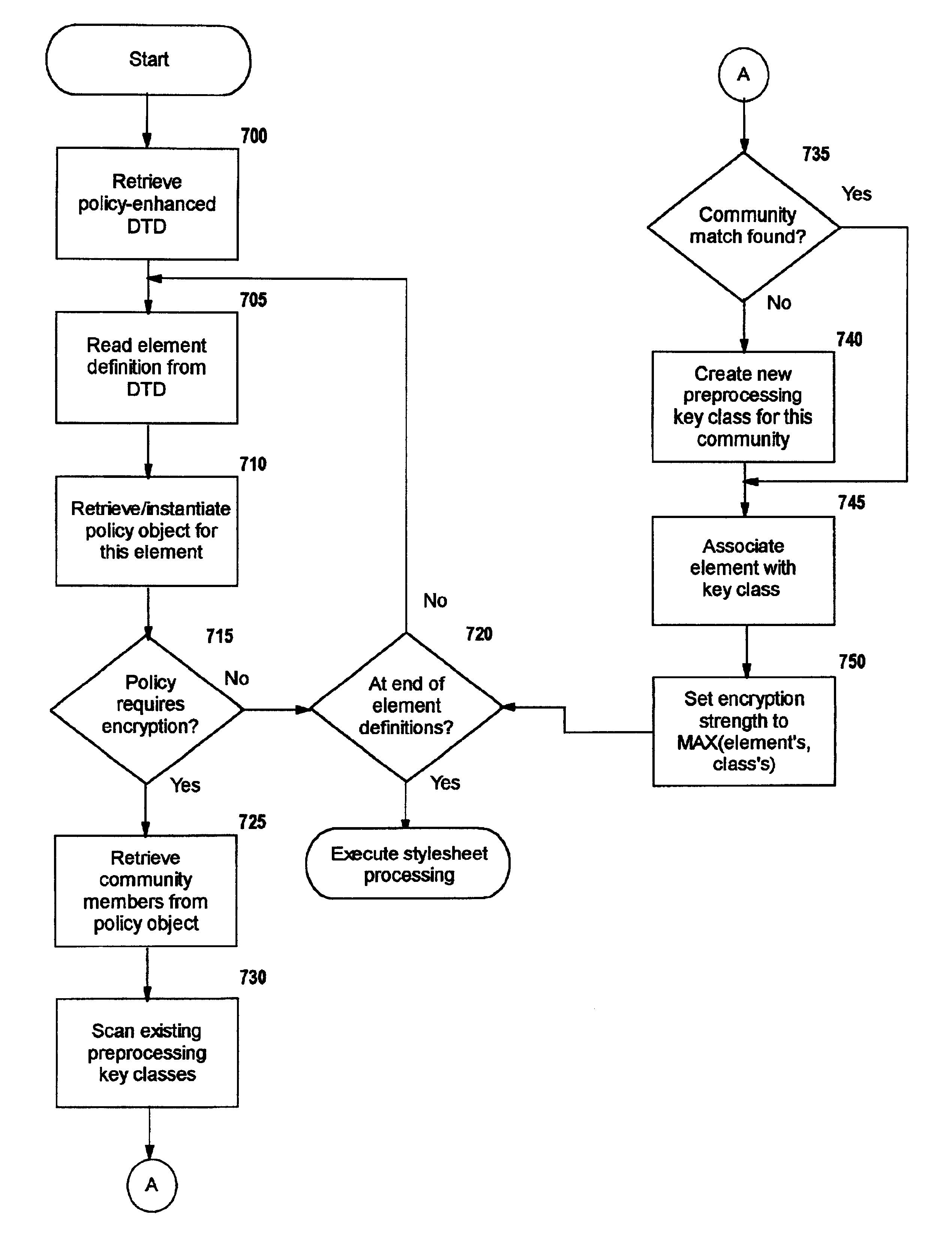
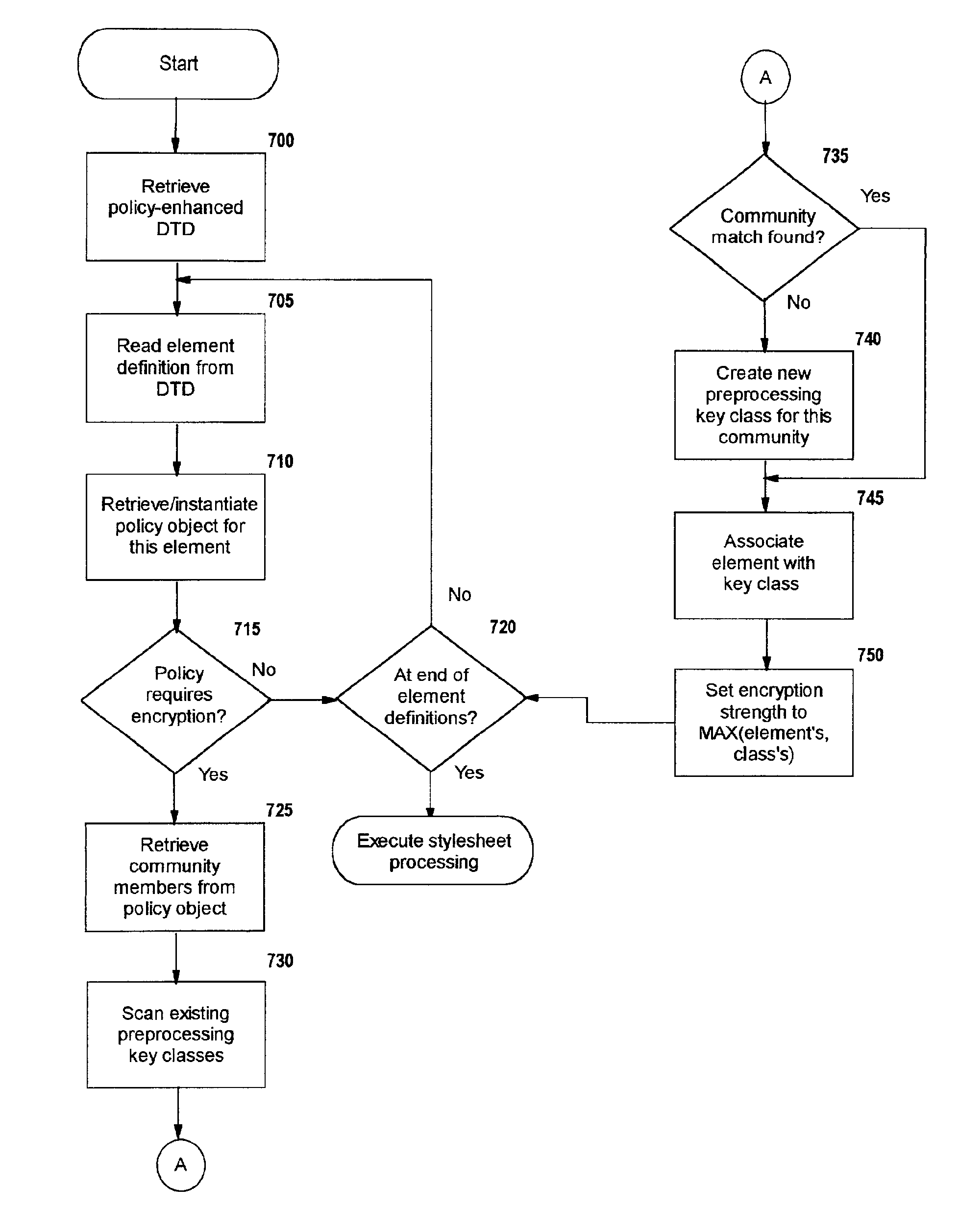
Selective data encryption using style sheet processing
InactiveUS6931532B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Selective data encryption using style sheet processing for decryption by a client proxy
InactiveUS6978367B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureDocument preparation
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Selective data encryption using style sheet processing for decryption by a key recovery agent
InactiveUS6941459B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationDocumentation procedureExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g. an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:PHONENICIA INNOVATIONS LLC SUBSIDIARY OF PENDRELL TECH
Selective data encryption using style sheet processing for decryption by a group clerk
InactiveUS6961849B1Security policy efficientlyEfficiently enforcedKey distribution for secure communicationUser identity/authority verificationEngineeringExtensible markup
A method, system, and computer program product for selectively encrypting one or more elements of a document using style sheet processing. Disclosed is a policy-driven augmented style sheet processor (e.g. an Extensible Stylesheet Language, or “XSL”, processor) that creates a selectively-encrypted document (e.g. an Extensible Markup Language, or “XML”, document) carrying key-distribution material, such that by using an augmented document processor (e.g., an augmented XML processing engine), an agent can recover only the information elements for which it is authorized. The Document Type Definition (DTD) or schema associated with a document is modified, such that the DTD or schema specifies a reference to stored security policy to be applied to document elements. Each document element may specify a different security policy, such that the different elements of a single document can be encrypted differently (and, some elements may remain unencrypted). The key distribution material enables a document to be encrypted for decryption by an audience that is unknown at the time of document creation, and enables access to the distinct elements of a single encrypted document to be controlled for multiple users and / or groups of users. In this manner, group collaboration is improved by giving more people easier access to information for which they are authorized, while protecting sensitive data from unauthorized agents. A key recovery technique is also defined, whereby the entire document can be decrypted by an authorized agent regardless of how the different elements were originally encrypted and the access protections which were applied to those elements.
Owner:IBM CORP
Method and device for extracting objects from the body
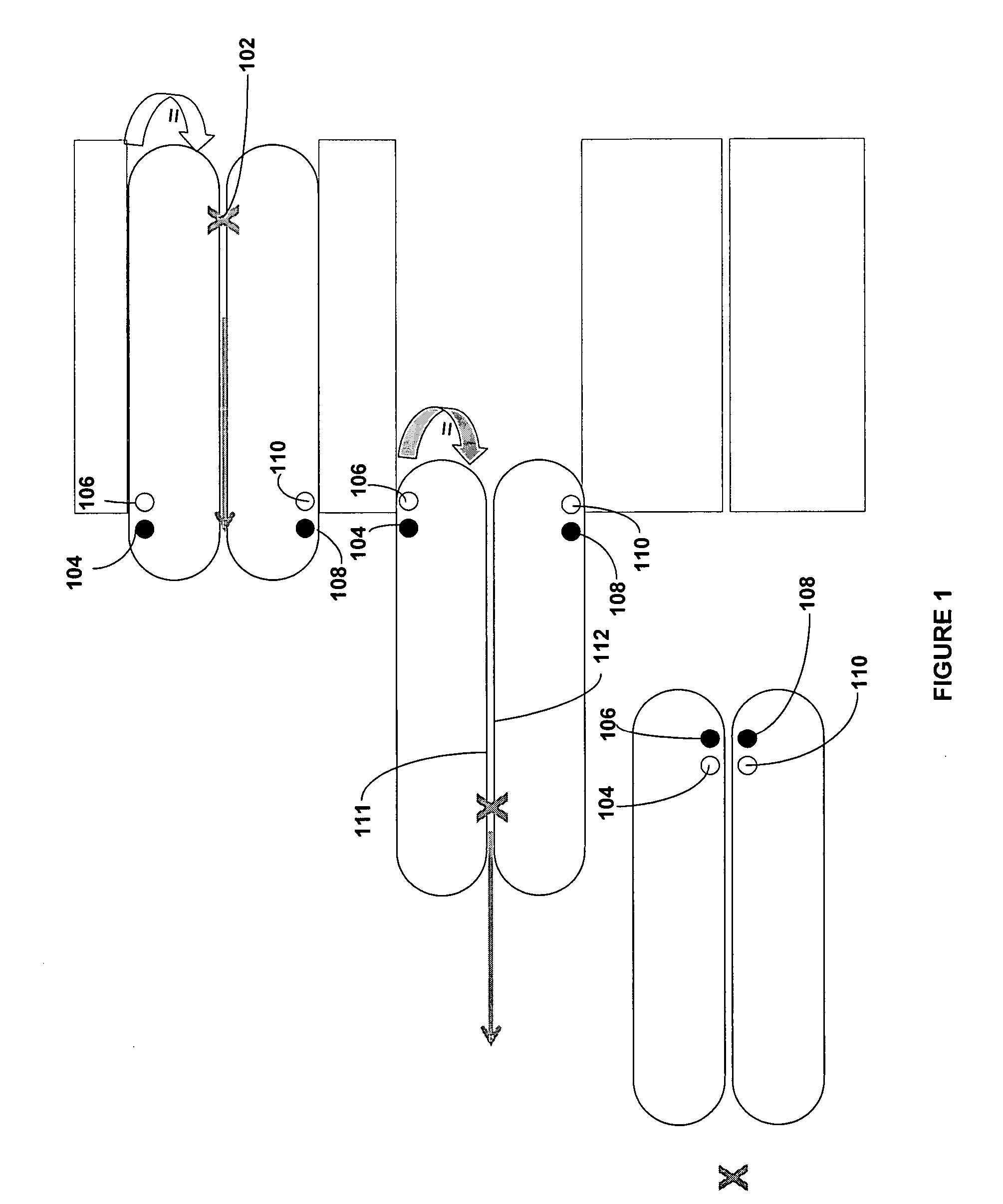
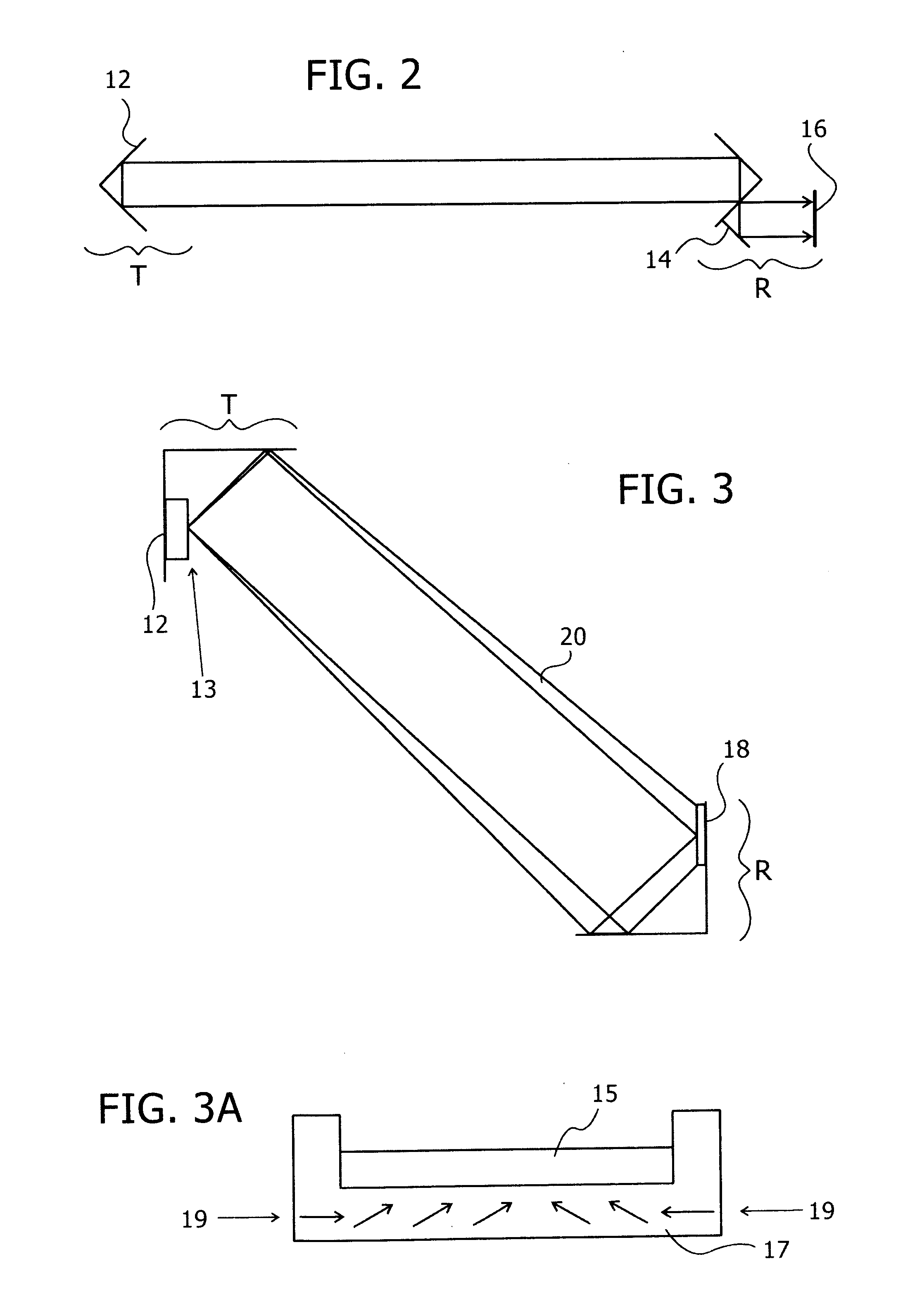
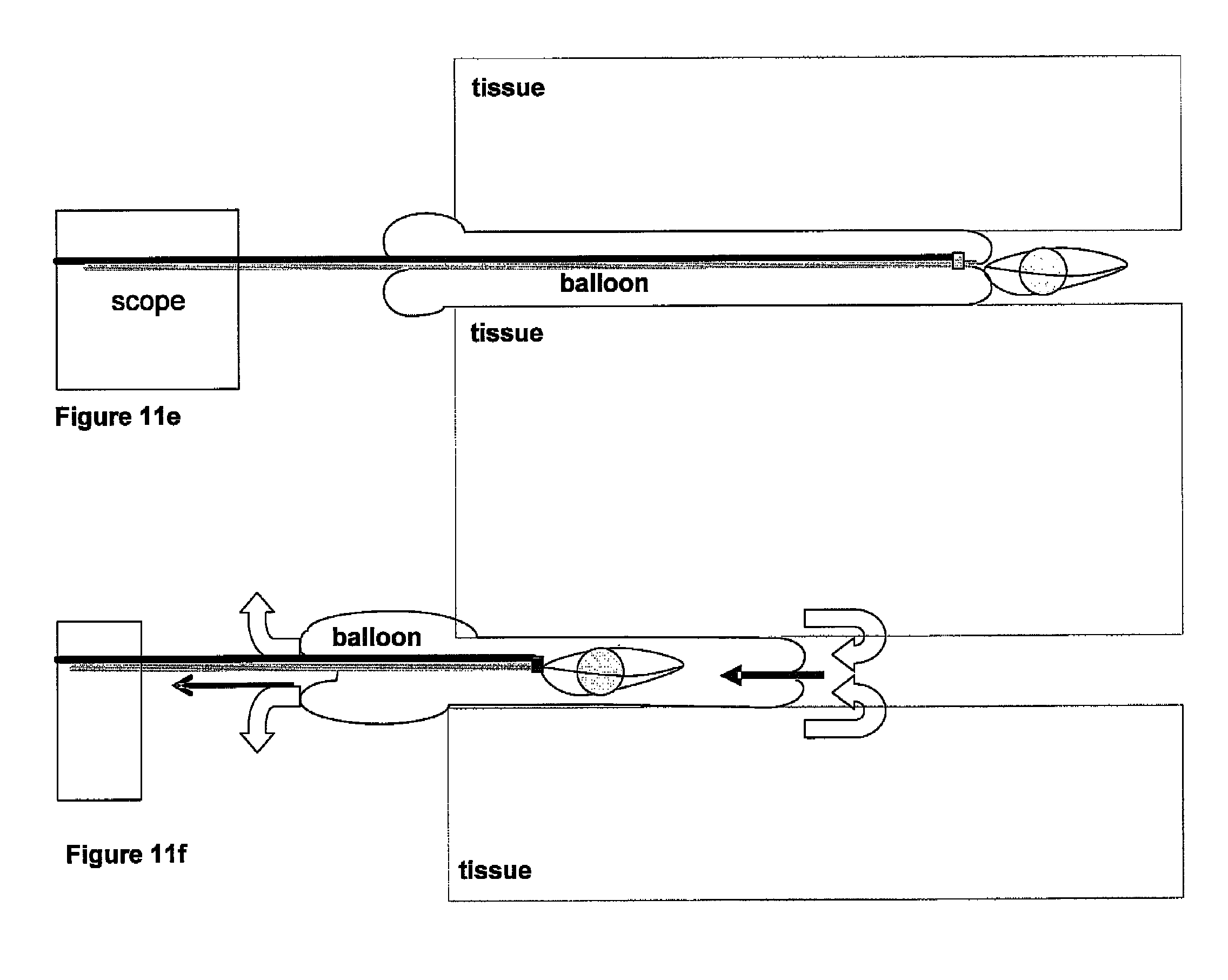
A device for extracting objects from the body, such as urinary stones, using a low pressure inflatable toroidal balloon that serves to engulf the object during extraction while dilating and protecting the passageway. The balloon loads onto an ureteroscope prior to insertion, rather than through the ureteroscope as do existing balloons. The toroidal balloon is a simple and unique device that may be applied external to the extracting telescope and does not interfere with existing methods for stone manipulation such as laser lithotripsy, irrigation and basket extraction in the case of urinary stone manipulation.
Owner:MASSICOTTE J MATHIEU +1
Wireless laser power transmitter
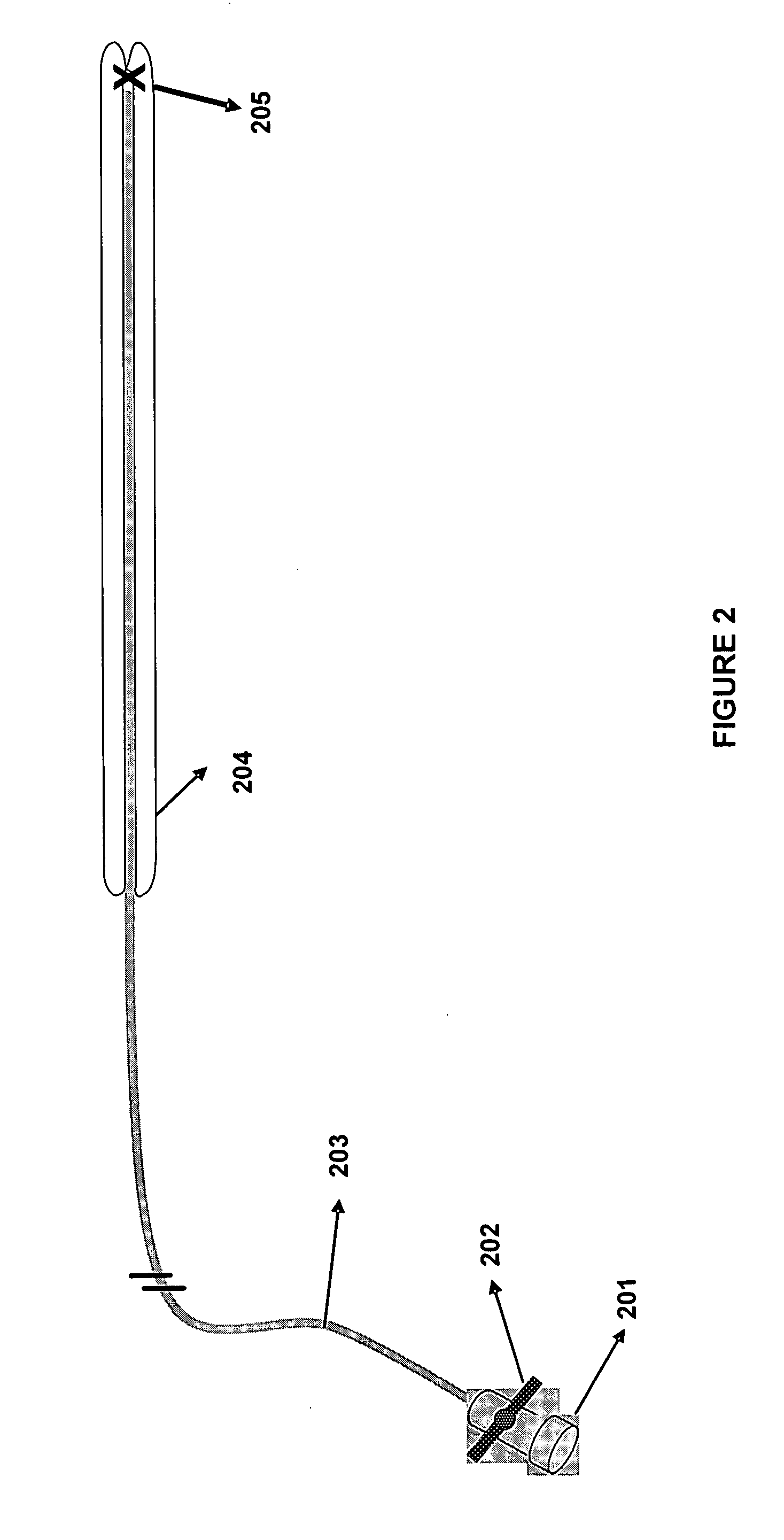
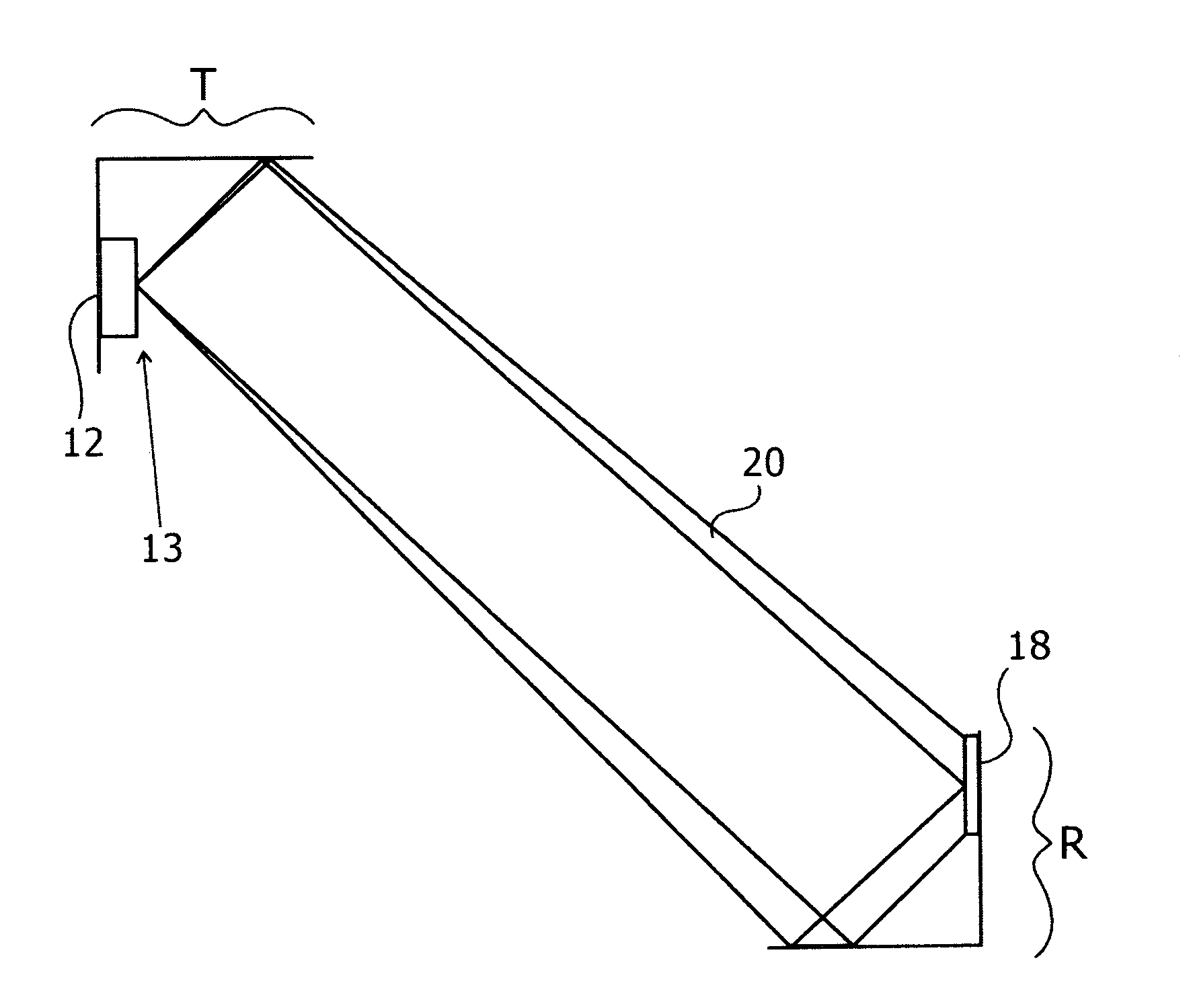
ActiveUS20100320362A1Efficient powerSufficient efficiencyLaser optical resonator constructionElectromagnetic wave systemOptical powerBeam transmission
An optical power beam transmission systems, with a directional light transmitter and receiver. The transmitter contains an amplifying laser medium, and this together with a retroreflector in the receiver, forms a laser resonator. When lasing sets in, the receiver can extract optical power through an output coupler and convert it to electrical power. The gain medium may be a disc having a thickness substantially smaller than its lateral dimensions. The laser resonator is operated as a stable resonator to ensure safe operation. This is achieved by use of an adaptive optical element, for reducing the diameter of the energy beam impinging on the gain medium, thereby increasing the overlap between the energy beam and the gain medium. As the transmitter-receiver distance is changed, such as by movement of the receiver, the adaptive optical element focal length changes to ensure that the cavity remains within its stability zone.
Owner:WI CHARGE
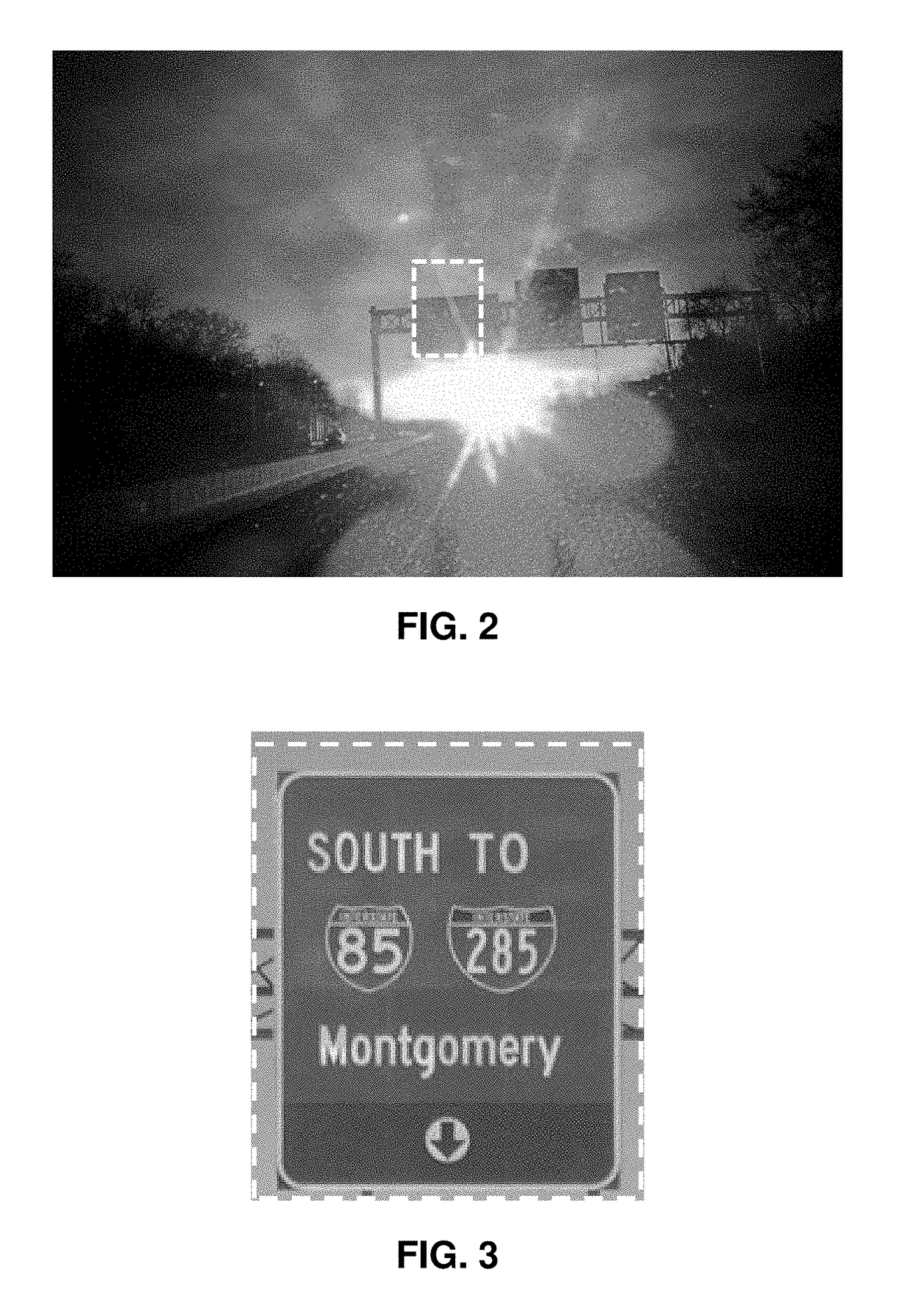
Real-time hdr video for vehicle control
ActiveUS20180048801A1Improve utilizationImprove securityTelevision system detailsColor signal processing circuitsVehicle controlLight level
The invention provides an autonomous vehicle with a video camera that merges images taken a different light levels by replacing saturated parts of an image with corresponding parts of a lower-light image to stream a video with a dynamic range that extends to include very low-light and very intensely lit parts of a scene. The high dynamic range (HDR) camera streams the HDR video to a HDR system in real time—as the vehicle operates. As pixel values are provided by the camera's image sensors, those values are streamed directly through a pipeline processing operation and on to the HDR system without any requirement to wait and collect entire images, or frames, before using the video information.
Owner:CONTRAST INC
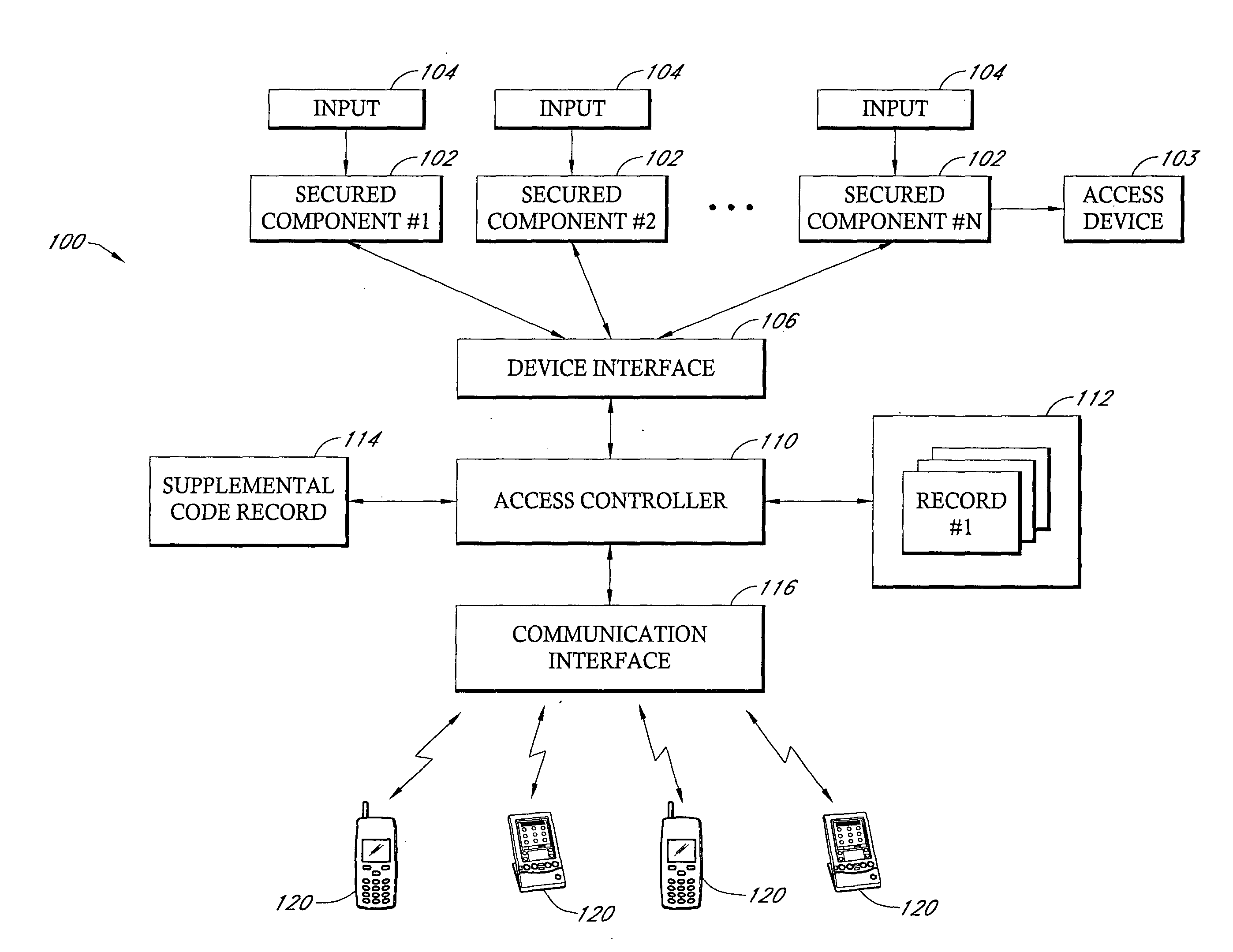
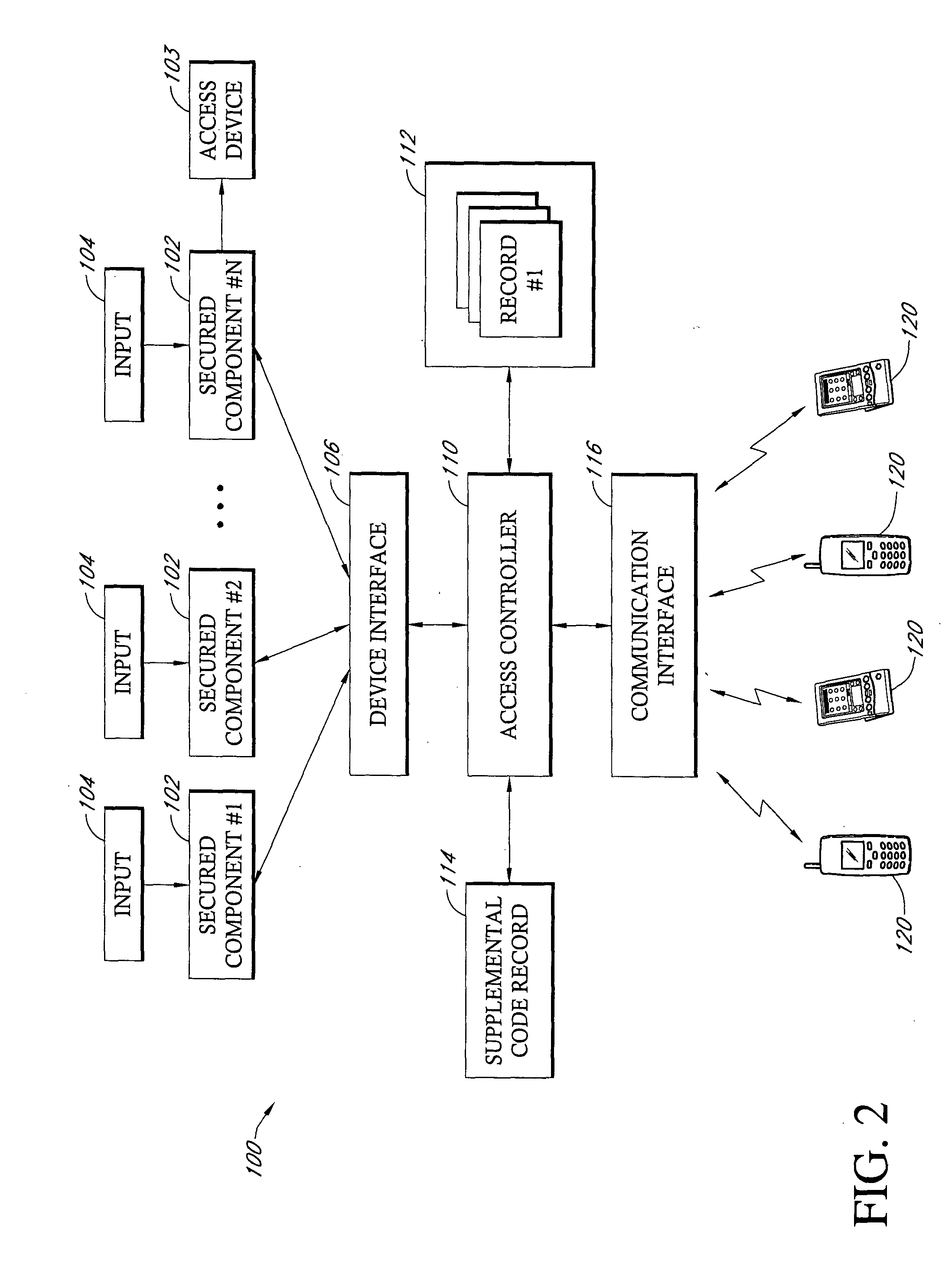
Method and system for alternative access using mobile electronic devices
InactiveUS20050048951A1Easy to implementLow costUnauthorised/fraudulent call preventionEavesdropping prevention circuitsCommunication interfacePager
An identity authentication system that controls access to devices information and areas only to authorized individuals. The system includes one or more processors that have a communication interface such that the processor can transmit signals to personal communication devices carried by individuals, such as cellular telephones, PDAs, pagers, and the like. The individual, to gain access to a particular secure component, area or information, is then prompted to provide PIN numbers or access codes via their personal communication device.
Owner:SAITO WILLIAM H
Multidimensional evaluation method for large-scale grounding grid
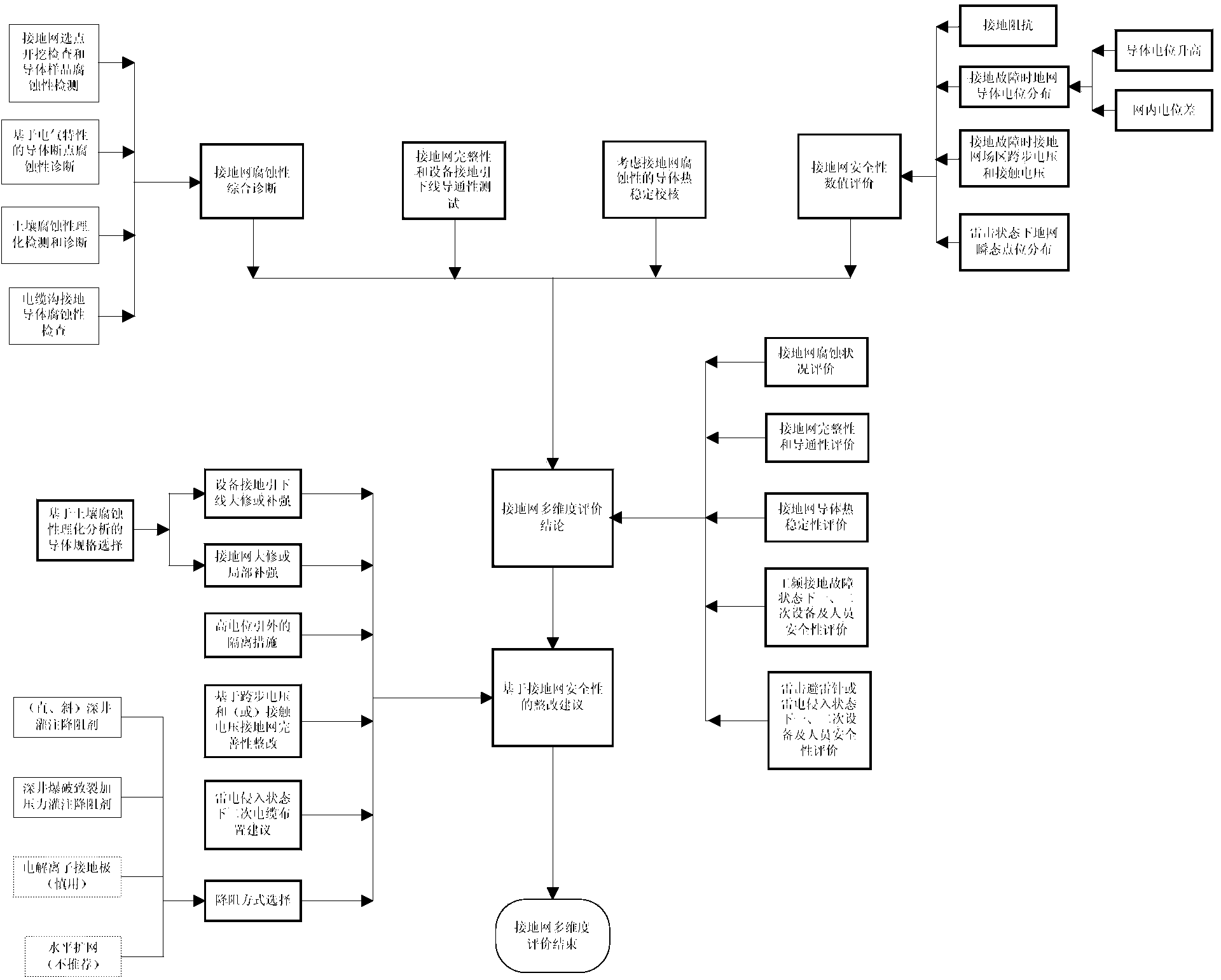
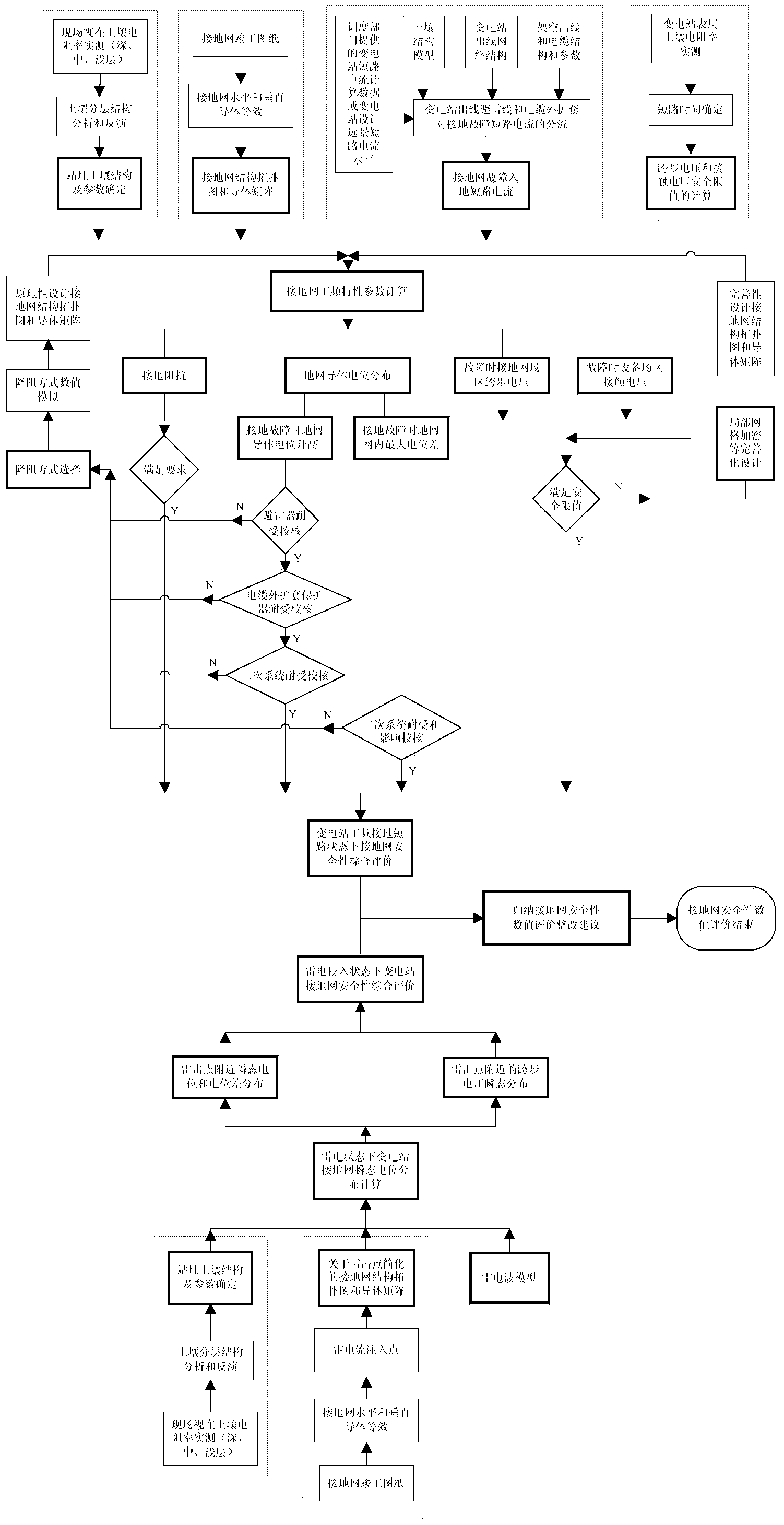
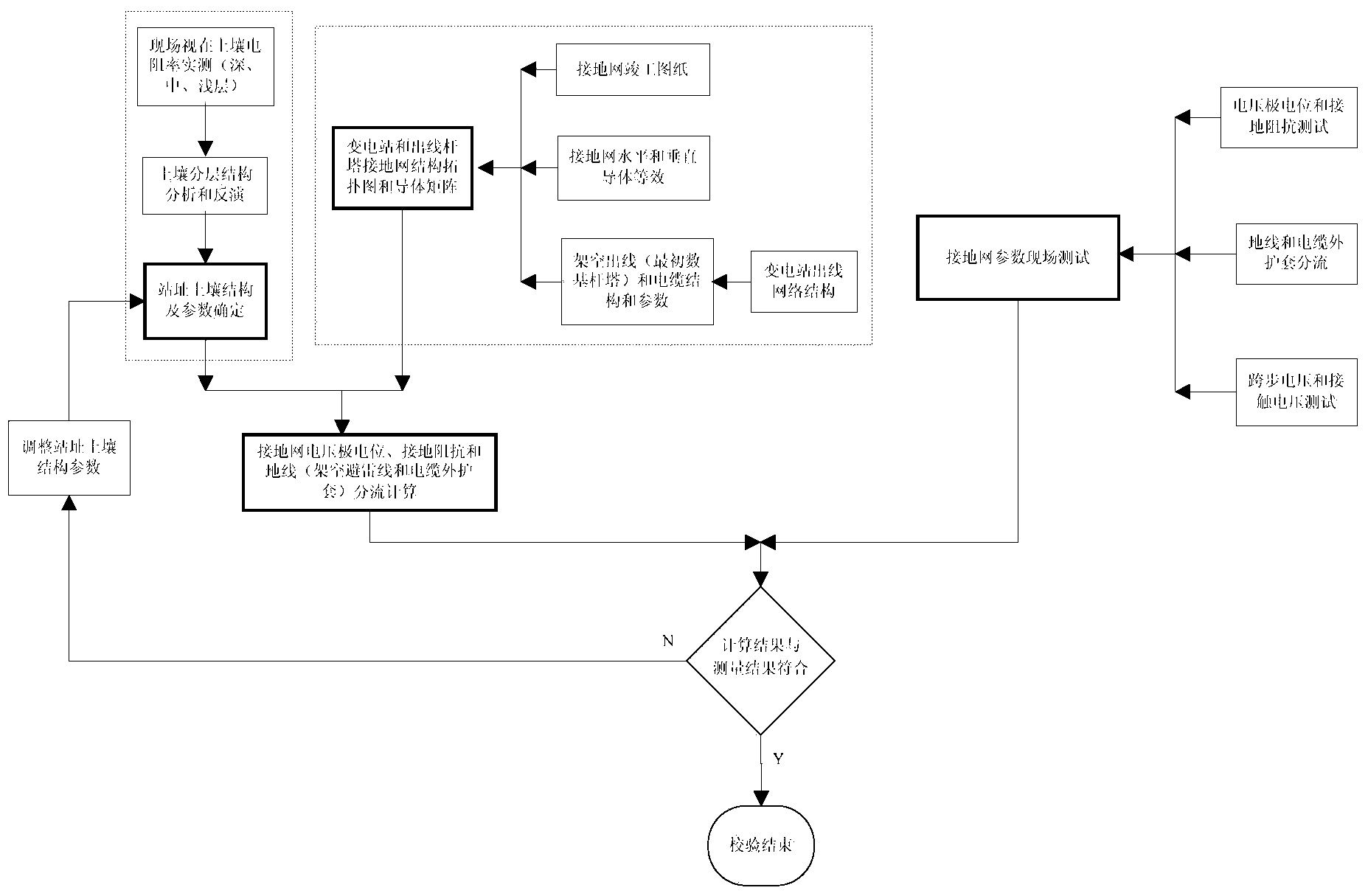
InactiveCN103616582AAccurate evaluationSolve evaluation problemsElectrical testingGrounding gridLightning strokes
A multidimensional evaluation method for a large-scale grounding grid includes the following steps of on-site testing, numerical calculation based on the electromagnetic field principle and multidimensional evaluation on the grounding grid. The foothold of the multidimensional evaluation method for the grounding grid is based on basic functions of the grounding grid, the basic functions are stream breaking and potential holding safety performance under power frequency grounding faults and lightning stroke faults, and the evaluation problems of characteristic parameters reflecting the safety performance of the grounding grid under the power frequency grounding faults and in the state of lightning stroke are mainly solved, wherein the characteristic parameters relate to grounding grid potential rising, potential difference in the grid, a step voltage, a contact voltage and the like. The multidimensional evaluation on the grounding grid is achieved from the aspects of the characteristic parameters of the grounding grid, integrity of the grounding grid, corrosion evaluation, thermal stability check and the like, safety of the grounding grid is expressed more scientifically, the evaluation on the state of the grounding grid is more accurate, and the safety problem and the defects of the grounding grid are rectified more effectively in a more pertinent mode.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID +1
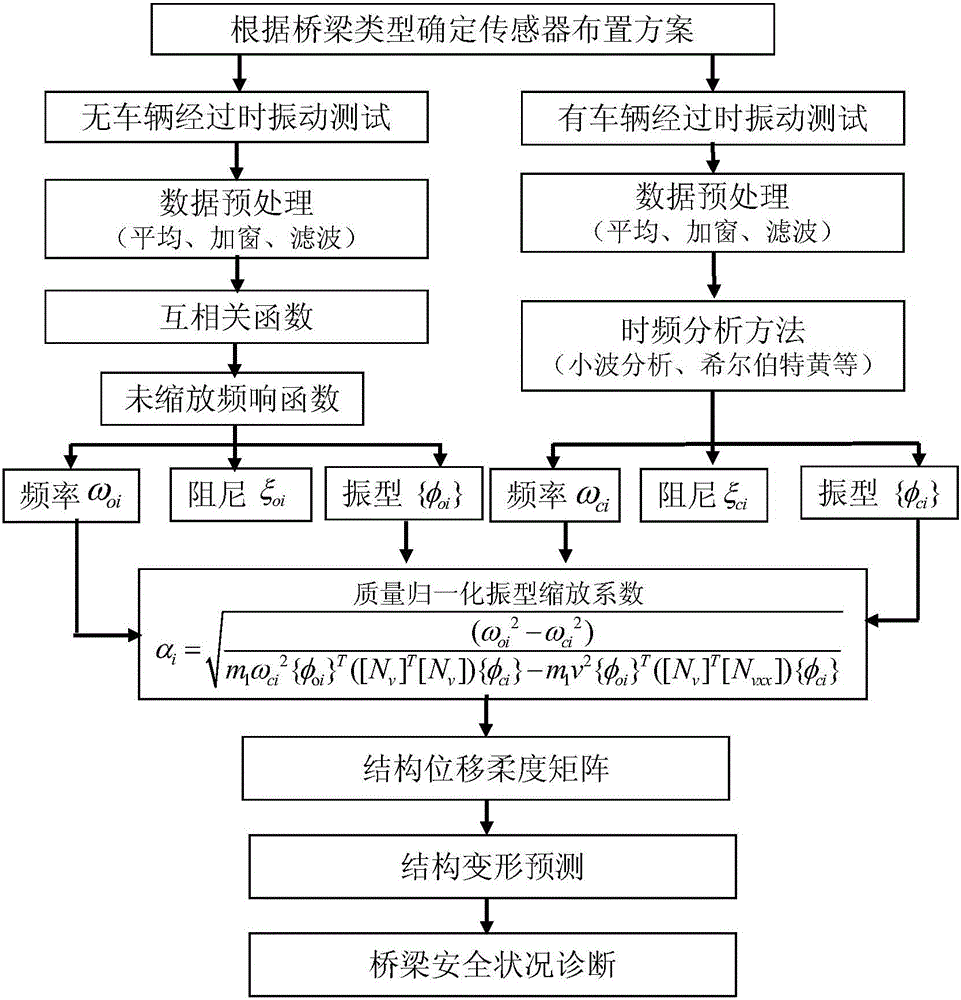
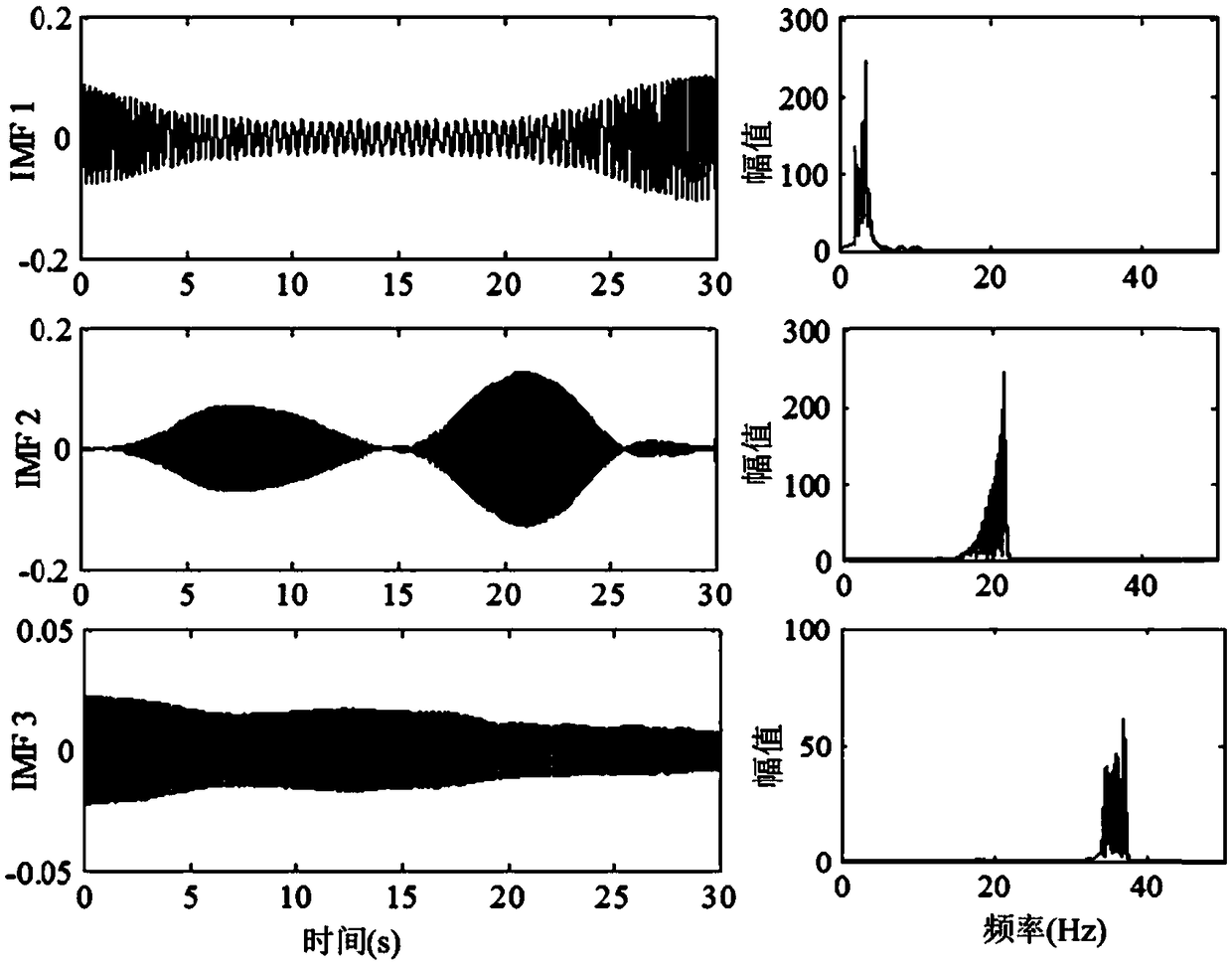
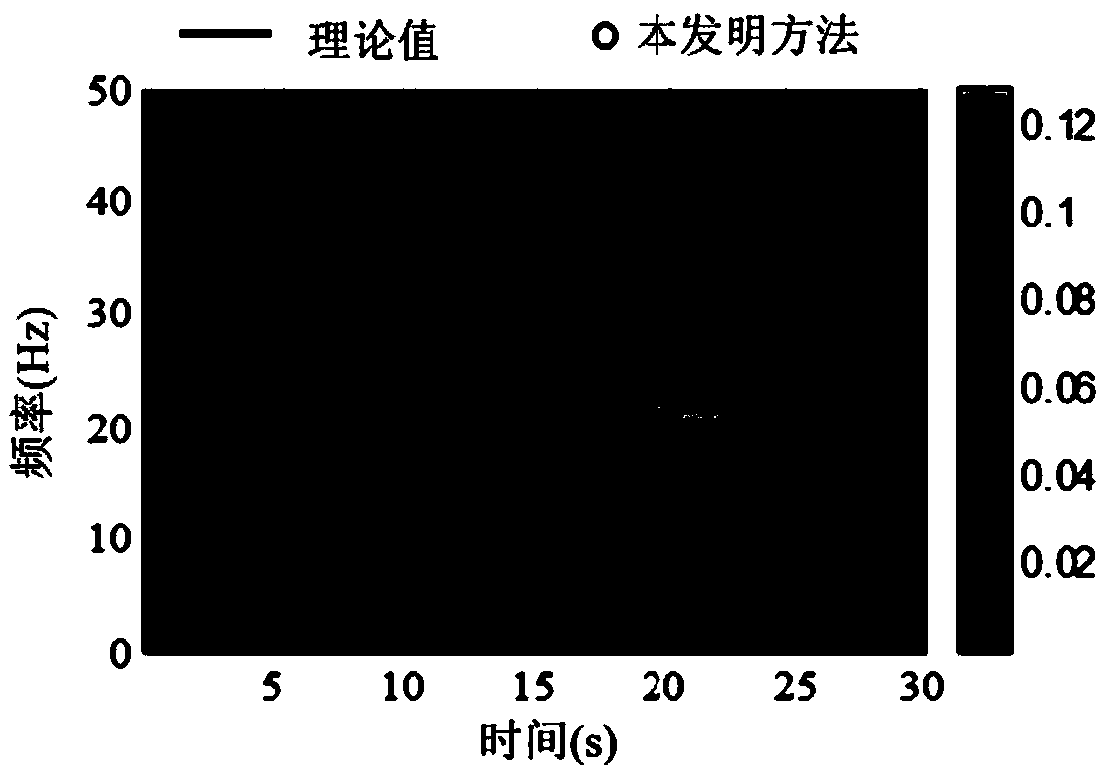
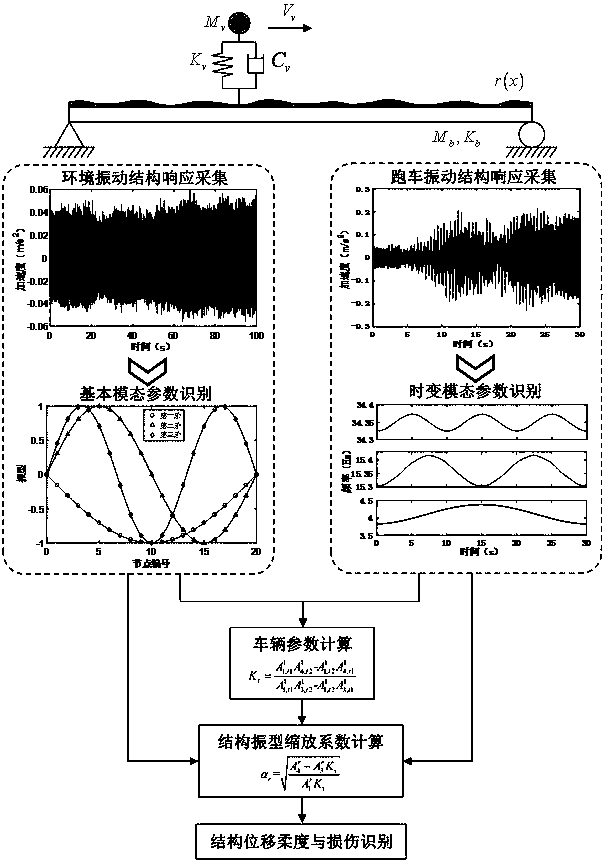
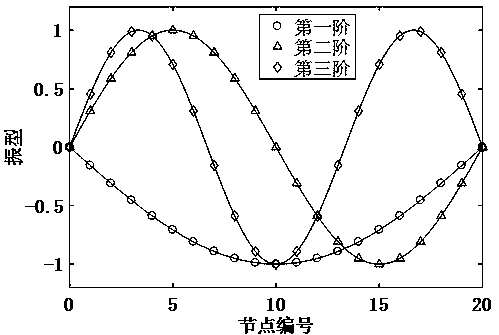
Bridge detection method and detection system based on vehicle-bridge coupling vibration analysis
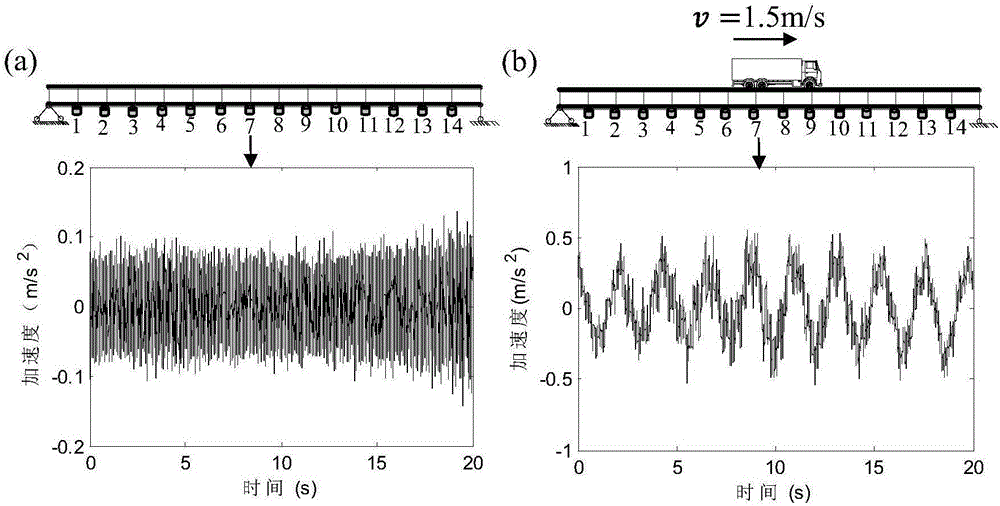
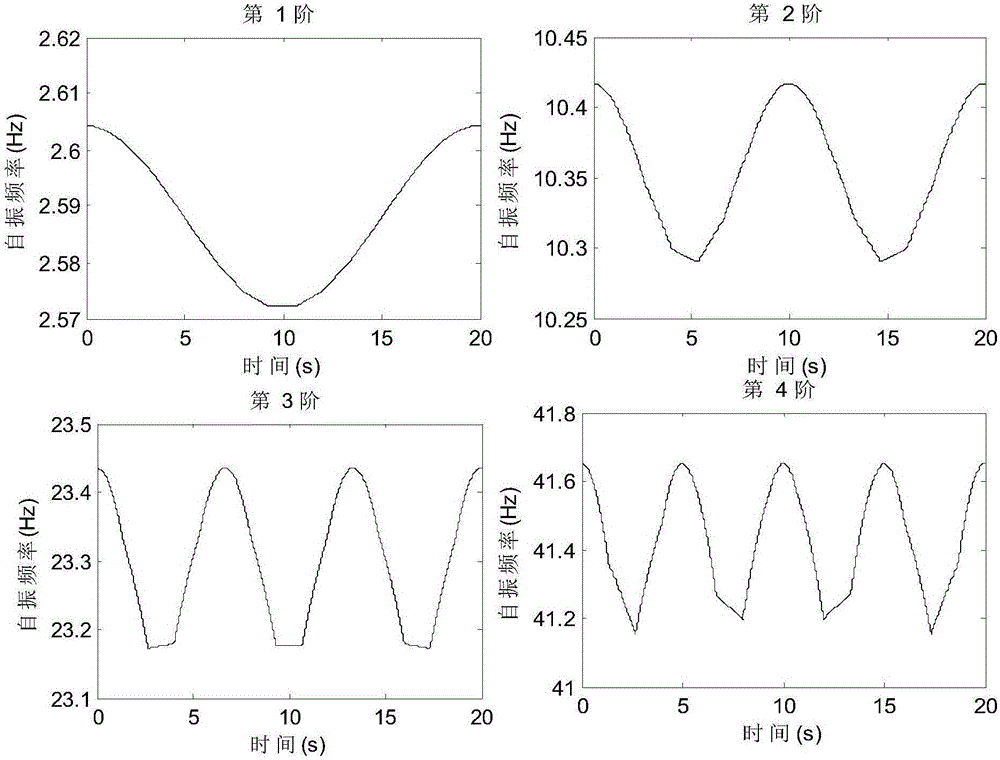
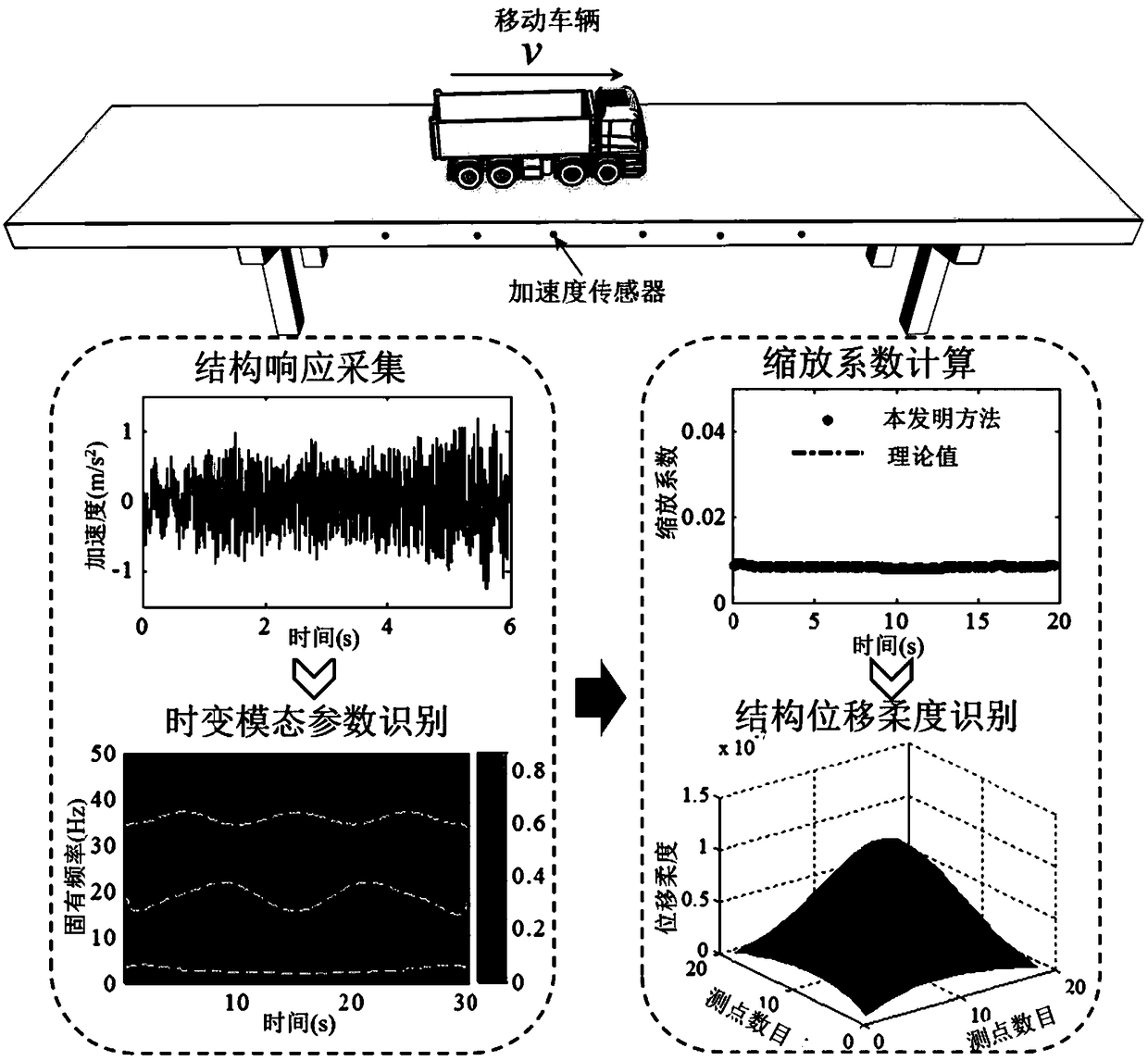
ActiveCN106197910AEffective securityEasy to operateElasticity measurementFrequency functionModel parameters
The invention discloses a bridge detection method and detection system based on vehicle-bridge coupling vibration analysis. The bridge detection method comprises the following steps: obtaining time-variant model parameters and time-invariant model parameters of having or not having vehicle passing through a group of sensors which are arranged on a bridge in the length direction; computing mass-normalized mode coefficients at moments of a bridge structure; resolving an average value of zoom coefficients at all moments; obtaining a mass-normalized mode of the structure; reconstructing a frequency-function matrix of the structure; conducting displacement flexibility identification. According to the invention, the bridge detection method addresses the inconvenience of on-site detection and poor precision of current flexibility detection devices, overcomes the inability of environment vibration to identify deep parameters of the structure and the high difficulty of impact vibration on-site detection. The detection method not only can obtain static deformation of the structure, and can obtain rigidity information of the structure, thus providing effective evaluation of the safety of the bridge structure.
Owner:SOUTHEAST UNIV
3D face live detection method, face authentication and recognition method and device
ActiveCN109086691AGuaranteed performanceImprove accuracyImage enhancementImage analysisPoint cloudMultiple frame
An embodiment of the specification relates to a three-dimensional face living detection method, a face authentication recognition method and a device thereof. The method comprises the following steps:acquiring a plurality of frames of depth images for a target detection object; performing alignment preprocessing on the multi-frame depth images to obtain the preprocessed point cloud data; normalizing the point cloud data to obtain a gray-scale depth image; a live detection being perform based on that gray-scale depth image and the live detection model.
Owner:ADVANCED NEW TECH CO LTD
Neural Networks for Discovering Latent Factors from Data
ActiveUS20190354806A1Effective trainingLow costCharacter and pattern recognitionChaos modelsMachine learningNeural network nn
Aspects of the disclosure relate to a method for discovering latent factors from data in a neural network environment. Aspects include adding, by a data noise unit of the neural network environment, noise to a set of input data; computing, by the encoder model and a set of stochastic non-linear units, a set of latent code based on the set of input data; obtaining, by decoding the latent code with a decoder model, a set of reconstructed data.
Owner:HITACHI LTD
Rapid bridge testing and estimation method based on change of time-varying dynamic characteristics of axle coupling system
ActiveCN109357822AAchieving Deformation PredictionEffective assessmentElasticity measurementMobile vehicleEstimation methods
The invention discloses a rapid bridge testing and estimation method based on change of time-varying dynamic characteristics of an axle coupling system. The rapid bridge testing and estimation methodcomprises the steps that vibration response of a structure under a moving vehicle is collected through a sensor arranged on a bridge, time-varying dynamic characteristic parameters of the axle coupling system are identified through a variational modal decomposition method and then substituted into a mapping relation among a vibration mode scaling factor, vehicle parameters and the time-varying dynamic characteristics, thus the vibration mode scaling factor and displacement flexibility matrix deep parameters of the structure can be calculated, accordingly, deformation of the structure at any static load is predicted, and structure damage identification based on a displacement flexibility matrix is conducted. The rapid bridge testing and estimation method has the advantage that the deep parameters of the structure are identified from only-output vibration response, and then structure performance is estimated, has the characteristics of low required test cost, short testing time and highidentification precision, and has wide prospects of being widely applied to safety estimation of multiple bridges on a national highway network.
Owner:SOUTHEAST UNIV
Flexible photovoltaic support
PendingCN104242800ARealize secondary useIncrease flexibilityPhotovoltaic supportsPhotovoltaic energy generationPhotovoltaic power generationElectrical and Electronics engineering
The invention provides a flexible photovoltaic support. The flexible photovoltaic support is used for fixing and supporting photovoltaic modules and comprises two or more supporting pieces and one or more flexible assemblies. The flexible assemblies are connected between the supporting pieces and made of flexible materials, and the photovoltaic modules are fixed to the flexible assemblies. The flexible photovoltaic support has the high adaptability, the use flexibility, the effective safety and the perfect land reutilization economy, is a revolutionary creation in the photovoltaic support field and will promote perfect development of photovoltaic power generation quickly.
Owner:ZHEJIANG GUOLI YINGHE ENERGY
Side slope anchoring structure with early warning energy consumption and damping control system and construction method
ActiveCN103850254AEffective supportEffective securityProtective foundationExcavationsMicrocomputerMicrocontroller
The invention discloses a side slope anchoring structure with an early warning energy consumption and damping control system and a construction method, belonging to the field of rock and soil anchorage disaster prevention and reduction. A framework 1 is anchored with an anchor rod 6 and a control anchor tube 16 through an anchorage device 14; a displacement sensor 11 on the framework 1 and an electro-hydraulic servo valve 25 of the control anchor tube 16 are connected with a single-chip microcomputer 9 through a communication line, thereby forming a damping control anchoring structure. The side slope anchoring structure is characterized in that an early warning program is installed in the single-chip microcomputer 9 and is connected with an alarm 13; a shock isolation layer 7 is formed between the framework 1 and an unstable soil body 30; the anchor rod 6 and the control anchor tube 16 are arranged at a certain interval, and pass through the framework 1; a power supply system 8 is connected with the single-chip microcomputer 9 through the communication line 10; the single-chip microcomputer 9 is connected with an amplifier 12, the displacement sensor 11 and the electro-hydraulic servo valve 25 respectively through the communication line 10.
Owner:LANZHOU UNIVERSITY OF TECHNOLOGY
Method and system for secure authentication using mobile electronic devices
InactiveUS20050071673A1Reduce problemEasy to implementDigital data processing detailsMultiple digital computer combinationsMobile electronicsPager
An identity authentication system that controls access to devices information and areas only to authorized individuals. The system includes one or more processors that have a communication interface such that the processor can transmit signals to personal communication devices carried by individuals, such as cellular telephones, PDAs, pagers, and the like. The individual, to gain access to a particular secure component, area or information, is then prompted to provide PIN numbers or access codes via their personal communication device.
Owner:SAITO WILLIAM H
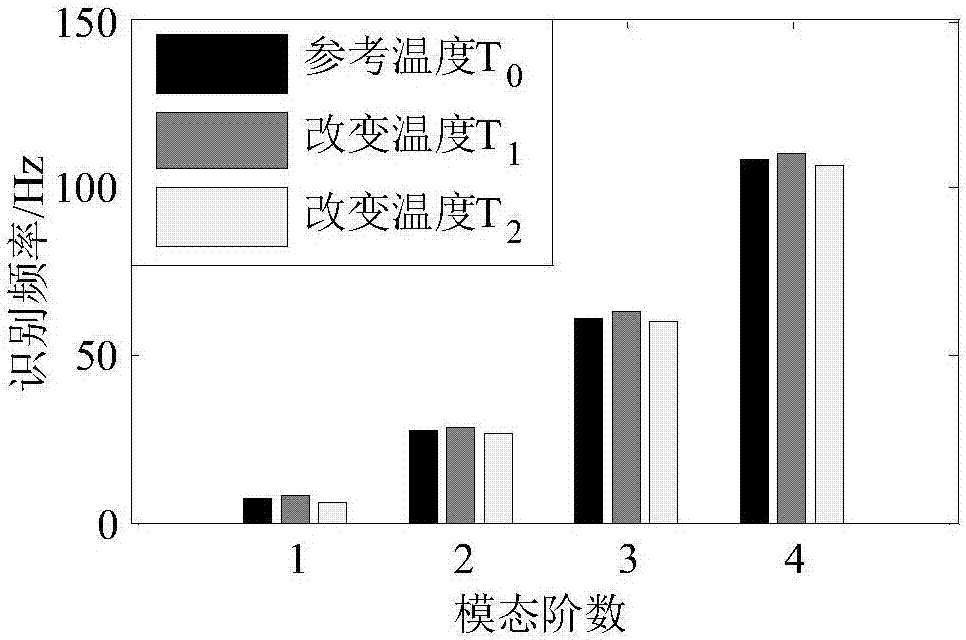
Bridge rapid test and evaluation method based on temperature change
ActiveCN107389285AEffective securityEffective maintenance managementElasticity measurementStructural dynamicsEngineering
The invention discloses a bridge rapid test and evaluation method based on temperature change. Structural dynamic response of the bridge structure under different temperature conditions is acquired through sensors arranged on the bridge; and the basic dynamic characteristic parameters of the bridge structure under different temperature conditions are identified by using a dynamic signal analysis method and substituted in the mapping relationship between the vibration mode scaling factor and the external temperature conditions and the dynamic parameters to obtain the vibration mode scaling factor of the bridge structure and the displacement flexibility matrix deep parameters under different temperature conditions so as to predict deformation of the structure under any static load and perform damage identification and long-term structural performance study. The disadvantages that the conventional impact vibration test requires an artificial excitation device and requires to close the traffic can be overcome, and the disadvantages that the present environmental vibration test method cannot effectively support bridge structure safety evaluation can also be overcome so that the method has the advantages of less test time without closing the traffic, high accuracy and high anti-noise capacity.
Owner:SOUTHEAST UNIV
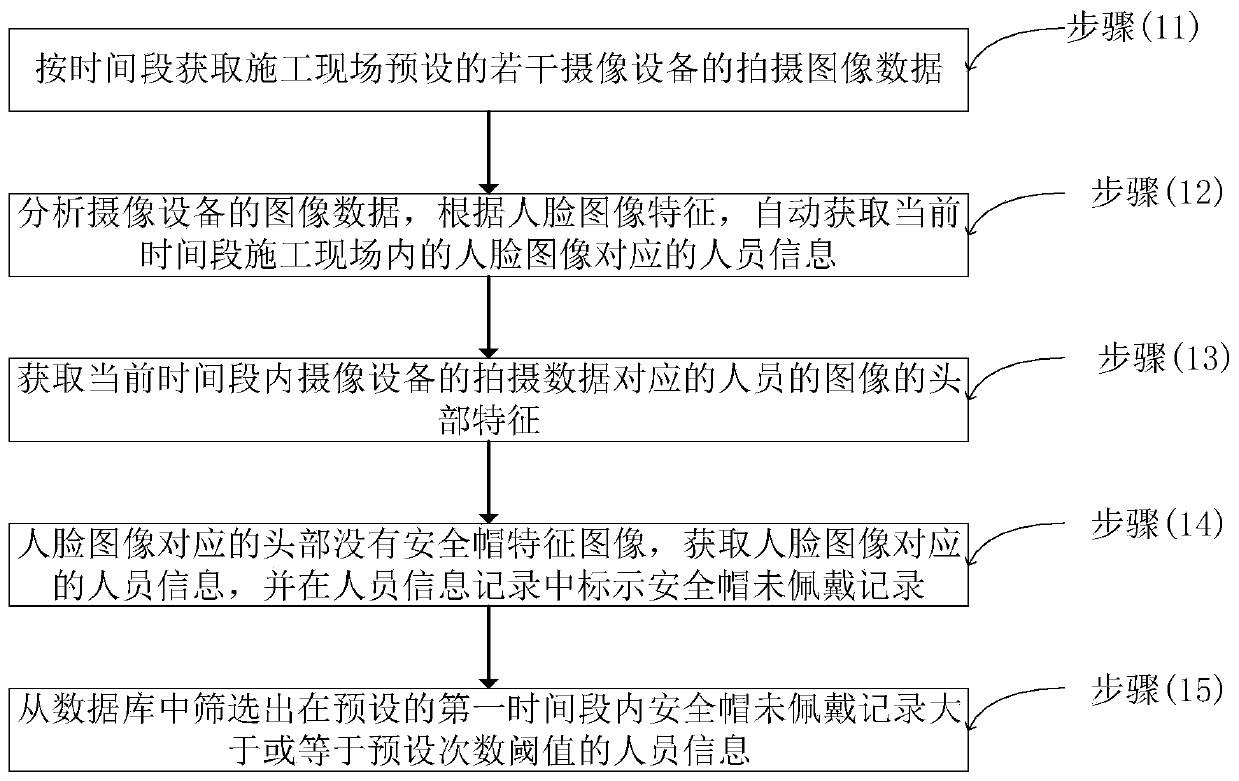
Power grid operator safety helmet wearing management control method and system
InactiveCN110309719AEffective securityEfficient managementData processing applicationsCharacter and pattern recognitionPower gridComputer science
The invention provides a power grid operator safety helmet wearing management control method and system. The power grid operator safety helmet wearing management control method includes the steps: obtaining image data of a construction site according to time periods; analyzing the image data of the camera equipment, and acquiring personnel information corresponding to the image in the constructionsite in the current time period according to the face image characteristics; obtaining head characteristics of the person image corresponding to the shooting data of the camera equipment in the current time period; if the head corresponding to the face image has no safety helmet feature image, obtaining personnel information corresponding to the face image, and marking a safety helmet unworn record in the personnel information record; and screening personnel information of which the safety helmet unworn records are greater than or equal to a preset time threshold in a preset first time periodfrom a database. According to the safety helmet wearing management method and system, the track graph is drawn based on the obtained safety helmet wearing conditions of the personnel, and the wearingconditions of the construction personnel are visually reflected, and the construction safety is guaranteed; meanwhile, an active alarm device is provided to facilitate the first-time alarm of constructors.
Owner:ANHUI JIYUAN SOFTWARE CO LTD +1
Method and device for extracting objects from the body
Owner:MASSICOTTE J MATHIEU +1
Wireless laser system for power transmission utilizing a gain medium between retroreflectors
ActiveUS8525097B2Efficient powerSufficient efficiencyLaser optical resonator constructionBeam/ray focussing/reflecting arrangementsElectric power transmissionTransport system
An optical power beam transmission systems, with a directional light transmitter and receiver. The transmitter contains an amplifying laser medium, and this together with a retroreflector in the receiver, forms a laser resonator. When lasing sets in, the receiver can extract optical power through an output coupler and convert it to electrical power. The gain medium may be a disc having a thickness substantially smaller than its lateral dimensions. The laser resonator is operated as a stable resonator to ensure safe operation. This is achieved by use of an adaptive optical element, for reducing the diameter of the energy beam impinging on the gain medium, thereby increasing the overlap between the energy beam and the gain medium. As the transmitter-receiver distance is changed, such as by movement of the receiver, the adaptive optical element focal length changes to ensure that the cavity remains within its stability zone.
Owner:WI CHARGE
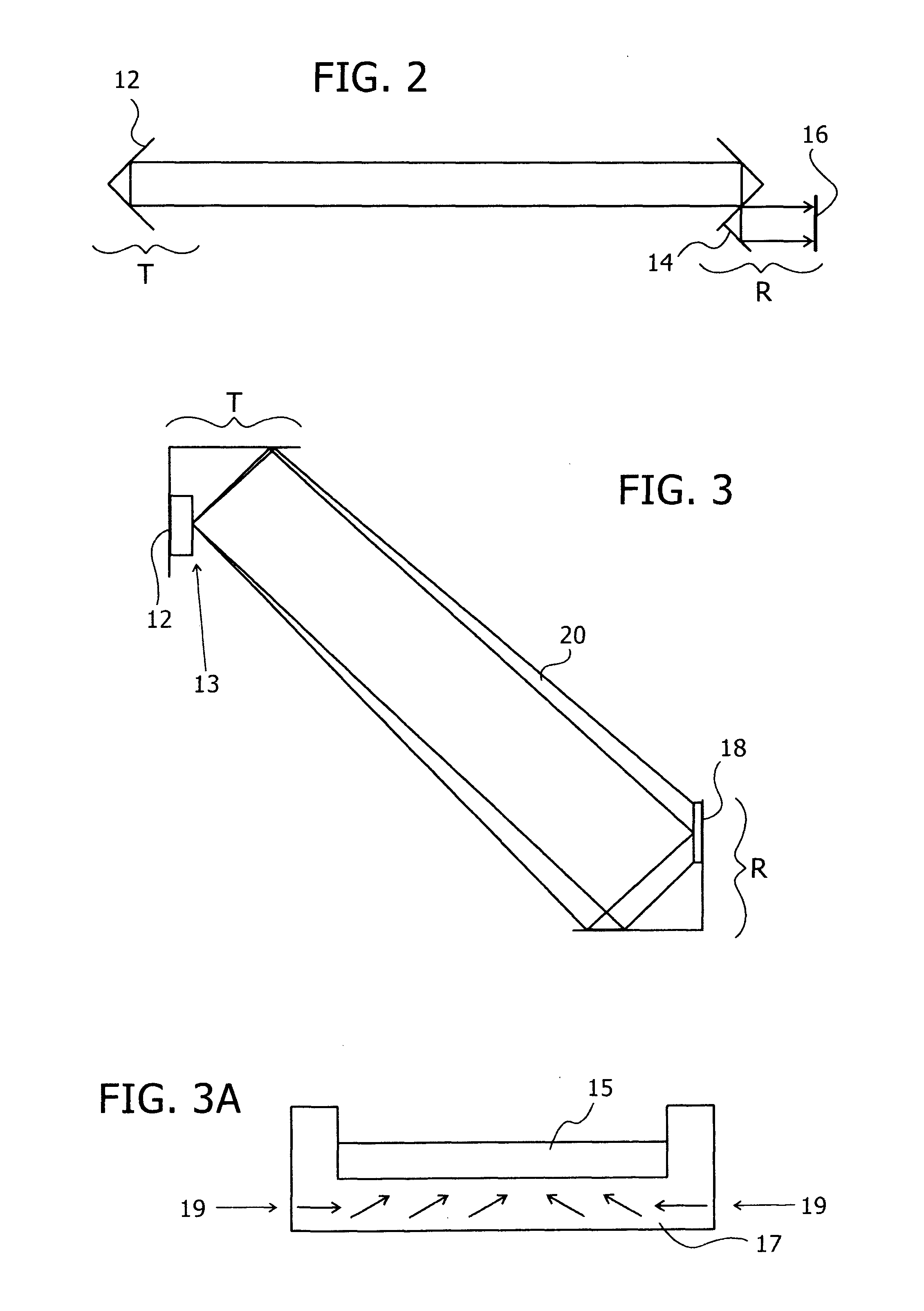
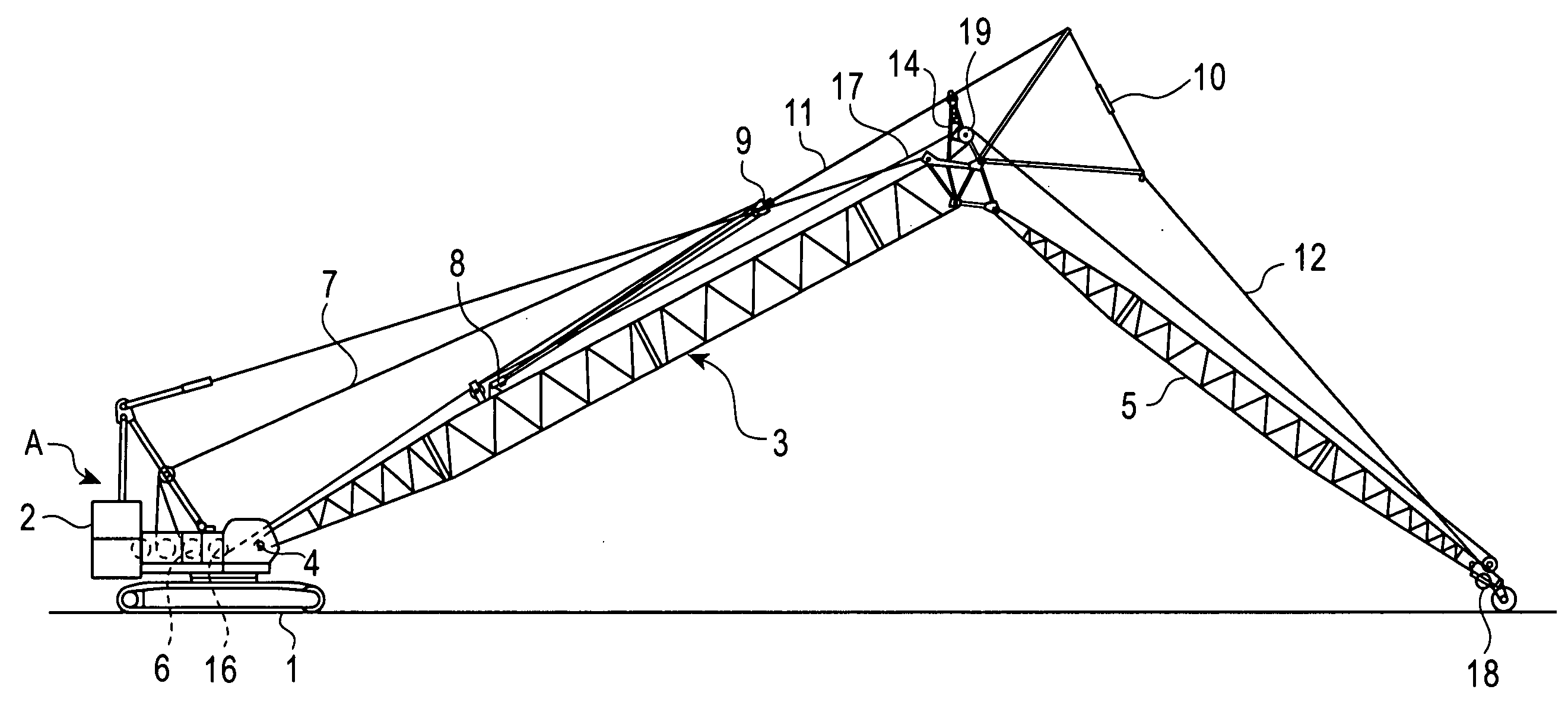
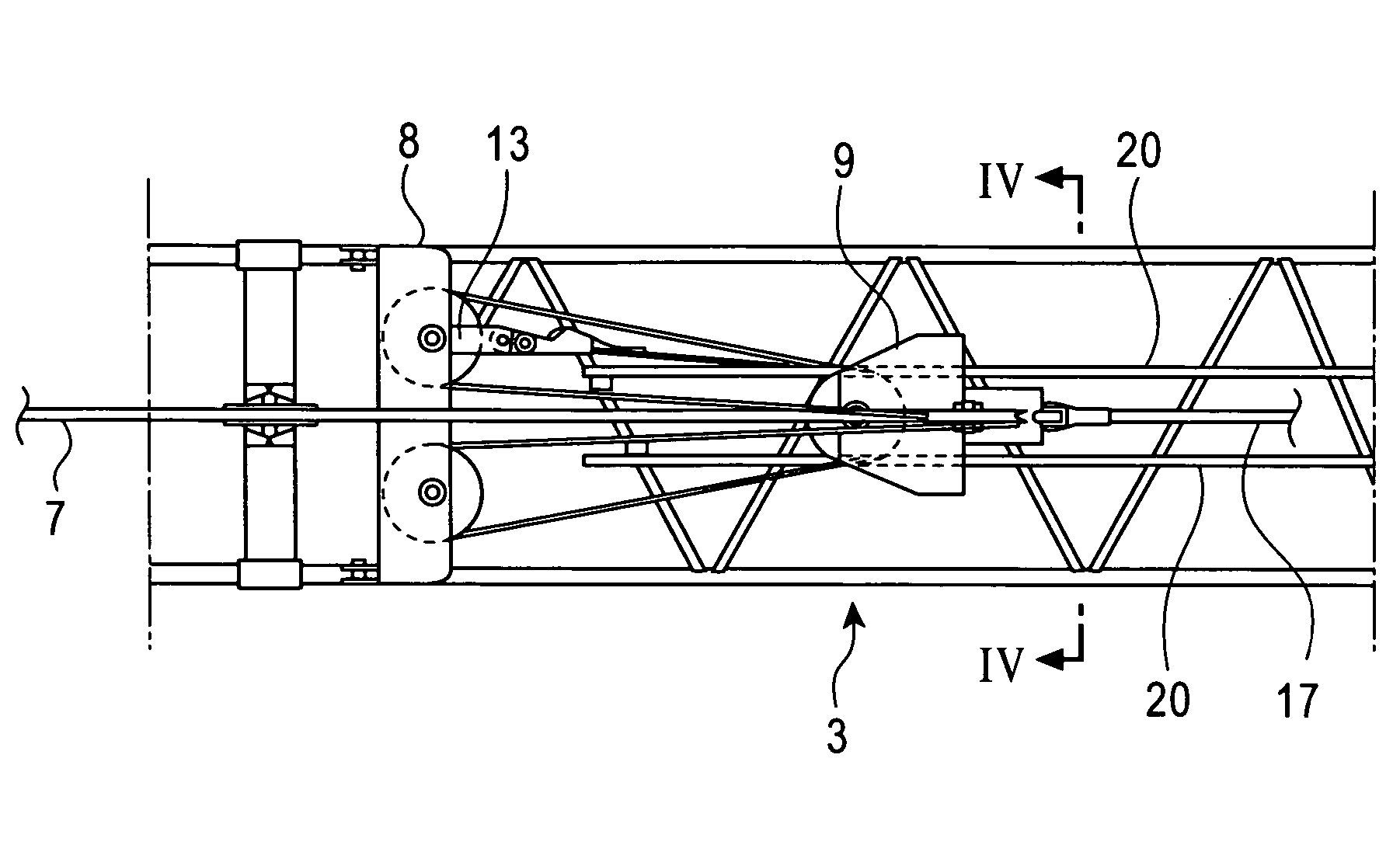
Traveling crane and assembling/disassembling method thereof
A traveling crane according to the present invention includes a hook hoisting guide sheave for guiding a hook hoisting rope from the top of a boom toward the end of a jib, and the hook hoisting guide sheave is arranged on the top of the boom in a state that the guide sheave can guide the hook hoisting rope along the upper surface of the boom by folding the rope toward an upper spreader placed at a position adjacent to a boom anchor during assembling / disassembling of the crane. Thereby, the upper spreader can be moved between the boom anchor and a far end of the boom without providing a guide sheave dedicated for moving the upper spreader. Pairs of support legs are downward provided on both sides and in front and in rear of the upper spreader and a roller is provided for each support leg, so that interference between the upper spreader during movement and obstacles on the boom upper surface can be prevented even in a horizontal movement system excellent in operating efficiency.
Owner:KOBELCO CONSTR MASCH CO LTD
Cyber security system and method
InactiveUS20190303583A1Risk minimizationIncrease awarenessPlatform integrity maintainanceResourcesReal-time webInternet privacy
An apparatus and method of using gamification and human behavioral analysis to quantify cyber security risks for a corporate or individual entity, in which the apparatus, or systems, can include a comprehensive real-time cyber security risk assessment, monitoring and remediation service, particularly through quantifying the qualitative aspects of individual user behavior and entity-level cyber security activities, and incentivizing and enabling effective cyber security outcomes through gamification. These capabilities will also enable the apparatus, or system, to deliver real-time cyber insurance to users on a risk-effective basis.
Owner:JOPHIEL PTY LTD
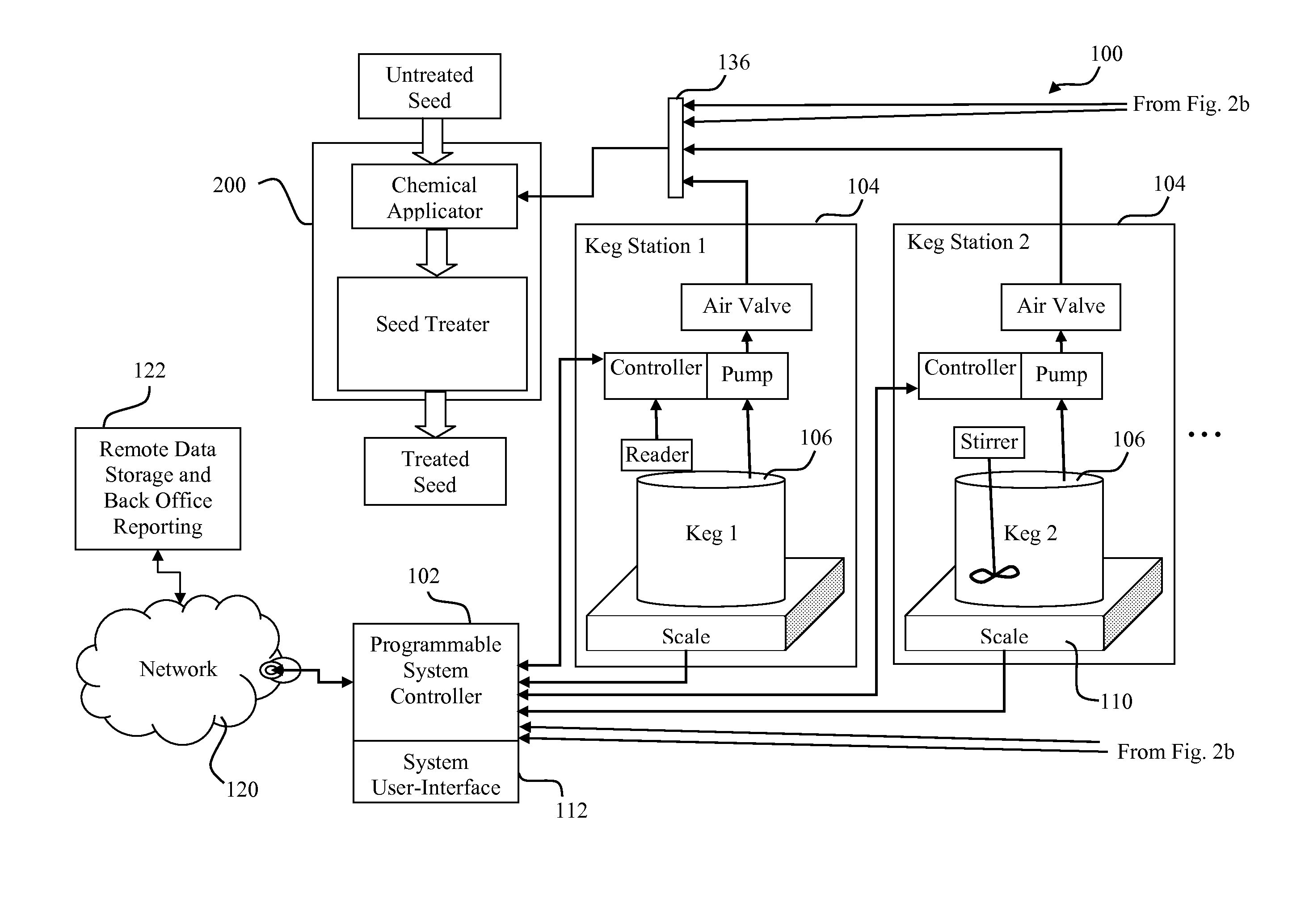
Seed treatment systems and methods
ActiveUS20120183675A1Provide controlChanging environmental conditionLiquid surface applicatorsDead plant preservationChemical treatmentThird party
An automated seed treatment system is adapted for on-site operation at a retail seed distributor. A sealed seed-treater vessel is configured to apply a plurality of chemical treatments to a batch of seed based on a recipe. A programmable system controller is electrically coupled to pump controllers of pump-stations. The controller is configured to receive a material transfer indication from each pump-stations and control the pump controllers in accord with the seed treatment recipe. The programmable system controller is configured to collect operational data representing at least consumption of chemical from the chemical container at each of the pump-stations based on the corresponding material transfer indication during seed treatment and to provide the operational data to a remotely hosted information system located remotely from the site of the retail seed distributor and accessible to at least one third party that is distinct from the retail seed distributor.
Owner:BAYER CROPSCI LP
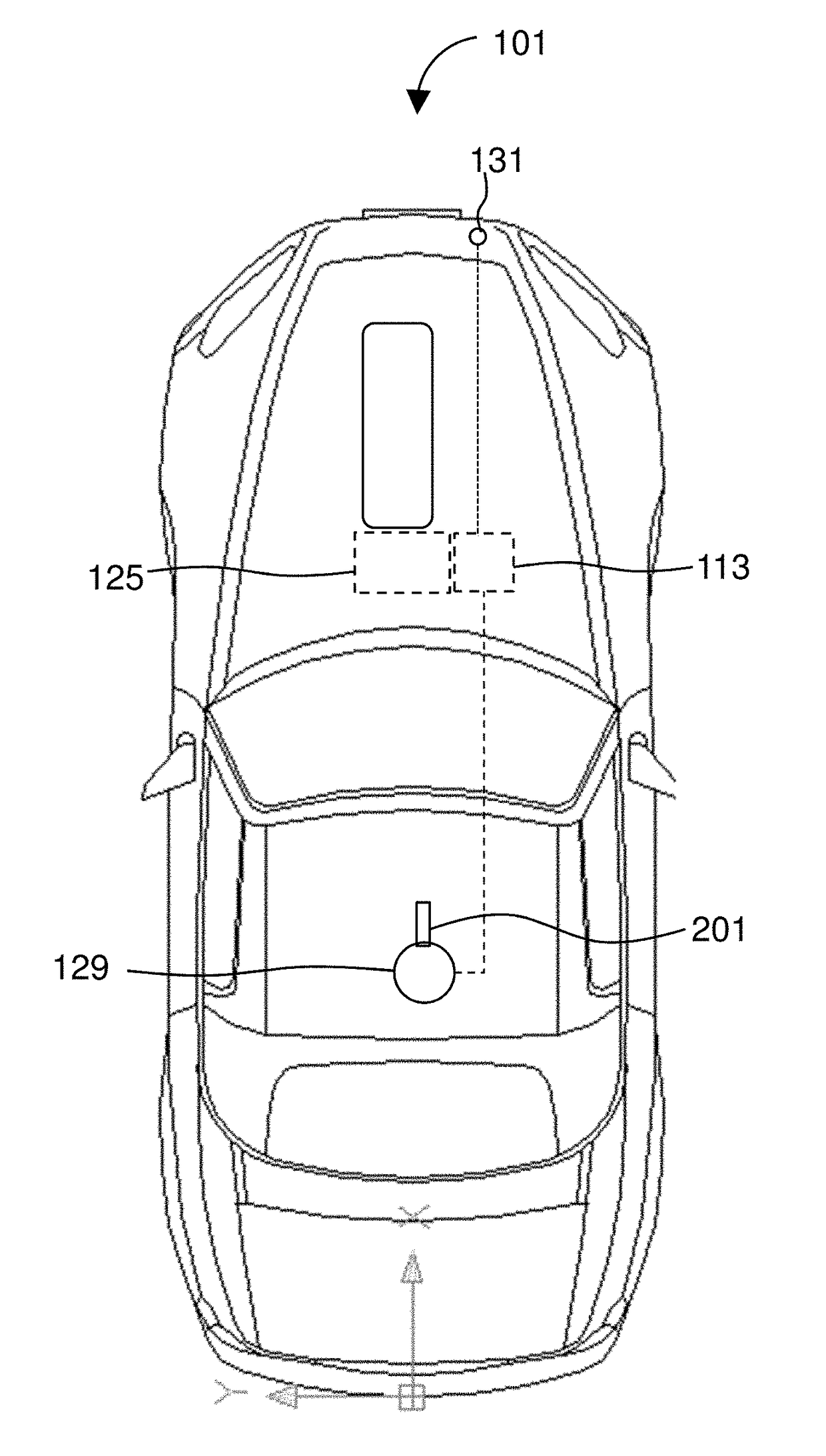
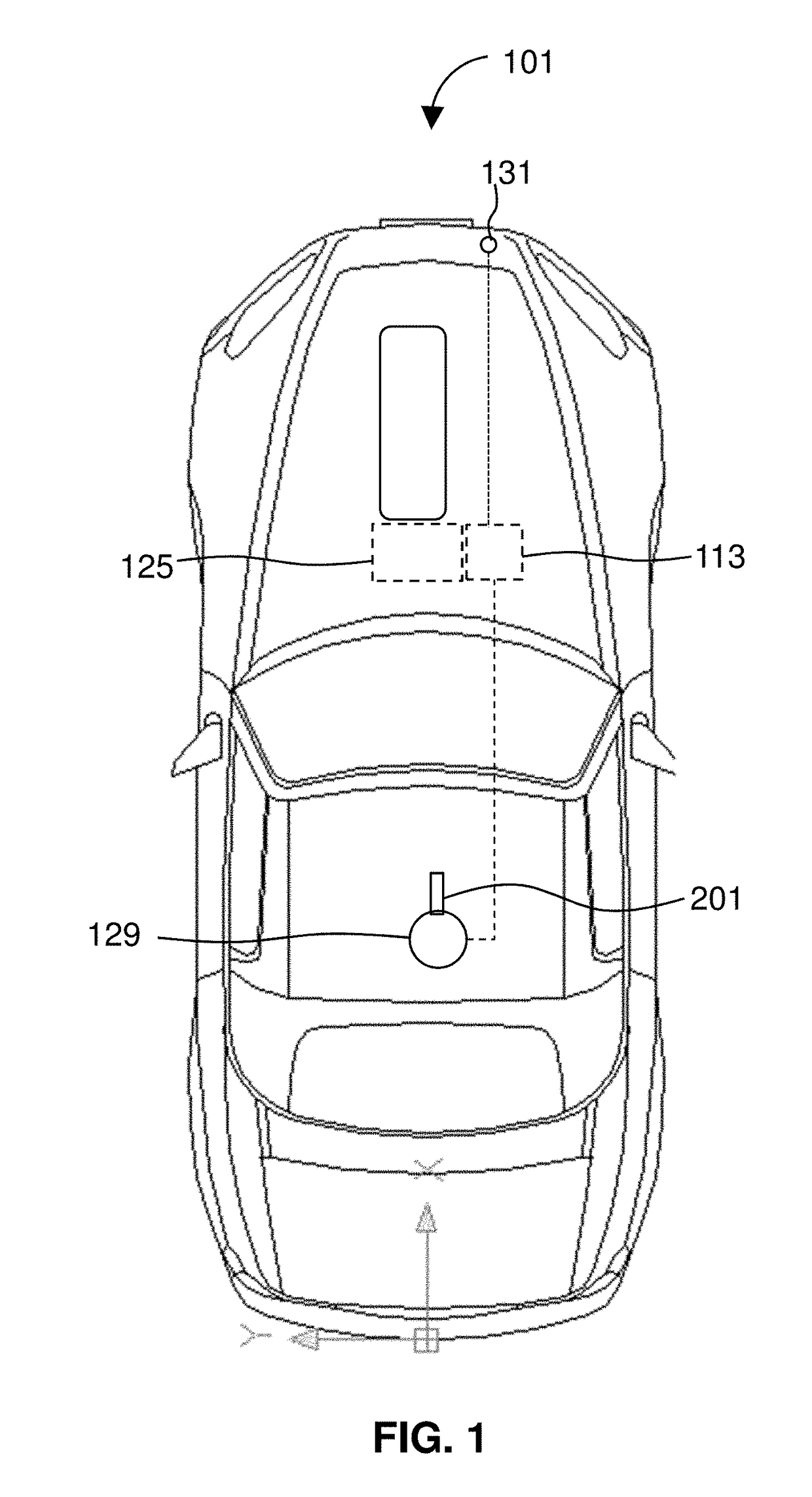
Safety Protection Apparatus for Personnel on Oil Drilling Derricks
InactiveUS20130199854A1Operational securityChanging the behavior of personnelSafety beltsDerricks/mastsOil drillingPetroleum
A safety apparatus for personnel on an oil drilling rig includes a cylindrical quick disconnect switch having a receptacle and a plunger. The receptacle has an open circuit pair of electrical wires. The plunger is configured to attach to a derrick man. The plunger and the receptacle are configured to mate when the plunger is inserted into the receptacle and to remain frictionally mated until pulled apart. The mating results in closing the circuit between the pair of electrical wires.
Owner:SAPHECO
Traveling crane and assembling/disassembling method thereof
A traveling crane according to the present invention includes a hook hoisting guide sheave for guiding a hook hoisting rope from the top of a boom toward the end of a jib, and the hook hoisting guide sheave is arranged on the top of the boom in a state that the guide sheave can guide the hook hoisting rope along the upper surface of the boom by folding the rope toward an upper spreader placed at a position adjacent to a boom anchor during assembling / disassembling of the crane. Thereby, the upper spreader can be moved between the boom anchor and a far end of the boom without providing a guide sheave dedicated for moving the upper spreader. Pairs of support legs are downward provided on both sides and in front and in rear of the upper spreader and a roller is provided for each support leg, so that interference between the upper spreader during movement and obstacles on the boom upper surface can be prevented even in a horizontal movement system excellent in operating efficiency.
Owner:KOBELCO CONSTR MASCH CO LTD
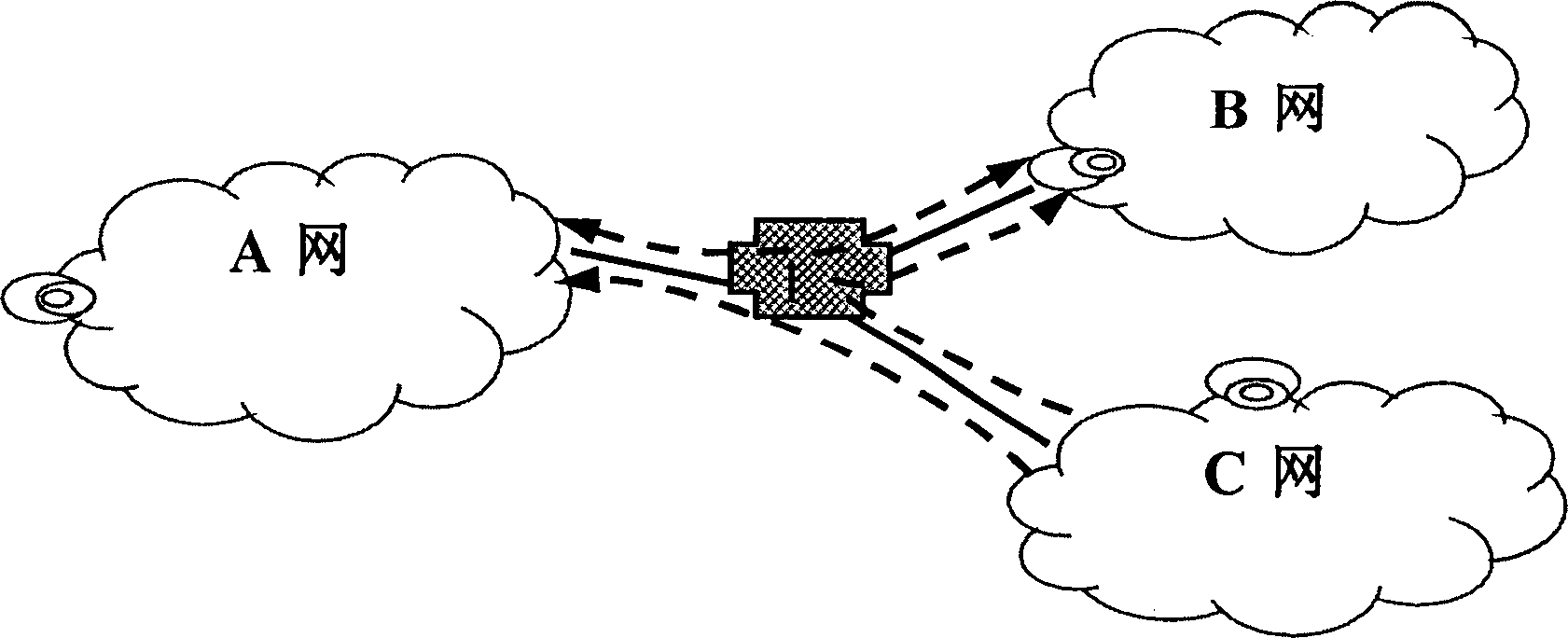
Isolation method and isolation switch apparatus between multiple different safety class networks
InactiveCN1791008AGuaranteed Logical IsolationSafe Safe ExchangeData switching networksElectronic switchNetworked system
The isolation method for different security level networks comprises: arranging a plurality of electric switches connected to buffer to make networks with different security physical isolate at any time; using two separated but centralized-control data paths to send and receive data; controlling the electric switches and connected buffer by intelligent logic control system to realize the safe isolation and data exchange. This invention has simple structure with low cost, and special fit to network construction for electric government affairs.
Owner:北邮英科(北京)信息技术研究所有限公司
Power safety system
InactiveUS20100231047A1Enhanced efficiencySize and cost be reduceSingle network parallel feeding arrangementsDc source parallel operationMOSFETReverse current
A power safety system includes a first MOS, a second MOS, a switch and a body controller. The first MOS is connected between a power input and a power output. The second MOSFET is connected between the power output and a charging output. The switch has an end connected to the body of the first MOS, and the opposite end switched between the source and the drain of the first MOS. A body controller controls the switch according to the voltage at the power input and the voltage at the power output, to connect the body of the first MOS to the source or the drain of the first MOS. By switching the switch, the first MOS will have a parasitic diode effective to prevent a reverse current from the power output to the power input.
Owner:RICHTEK TECH
Optical measurement method and quick testing system of human-caused impact load of bridge
ActiveCN108458847AShock vibration test implementationEnables structural performance assessmentVibration testingShock testingOptical measurementsEngineering
The invention discloses an optical measurement method and quick testing system of a human-caused impact load of a bridge. The method comprises: collecting an image; calculating vertical speed information in leaping of a pedestrian; calculating acceleration information of a pedestrian in vertical leaping; estimating a human-caused dynamic impact load; identifying structural parameters; and evaluating performances. According to the invention, the human-caused impact load testing method with non-contact measurement based on a high-speed camera is different from the traditional impact vibration testing based on an artificial excitation device. According to the testing method, the pedestrian load on a pedestrian overpass is used as an excitation source directly to realize impact vibration testing of the urban pedestrian bridge conveniently and quickly; and on the basis of the measured human-caused dynamic impact load, the deep structural parameter identification can be realized and the structural performance evaluation can be realized effectively and effectively.
Owner:SOUTHEAST UNIV
Vehicle and structure information simultaneous identification method based on axle coupling vibration
ActiveCN109858156AEffective securityAvoid the disadvantage of needing to predict vehicle parametersSustainable transportationSpecial data processing applicationsRoad networksSecure state
The invention discloses a vehicle and structure information simultaneous identification method based on axle coupling vibration. The method includes acquiring structural environment vibration responsedata and structural sports car vibration response data through sensors arranged on a bridge; respectively identifying a basic modal parameter and a time-varying modal parameter of the structure through a modal algorithm; substituting into a mapping parameter equation of a structural vibration mode scaling coefficient, a modal parameter and a vehicle parameter; calculating vehicle parameters by utilizing the time-varying modal parameters at different moments; further obtaining a structural vibration mode scaling coefficient; reconstructing deep-level parameters of a structure displacement flexibility matrix through the vibration mode scaling coefficient and furthermore, predicting the displacement of structure under any static load, and evaluating current safety state of structure. According to the method, the vehicle parameters and the structure parameters can be recognized only from the structure vibration response, and the method has the advantages of being convenient to test, shortin consumed time and high in precision and is suitable for safety evaluation of many bridges in a road network.
Owner:SOUTHEAST UNIV
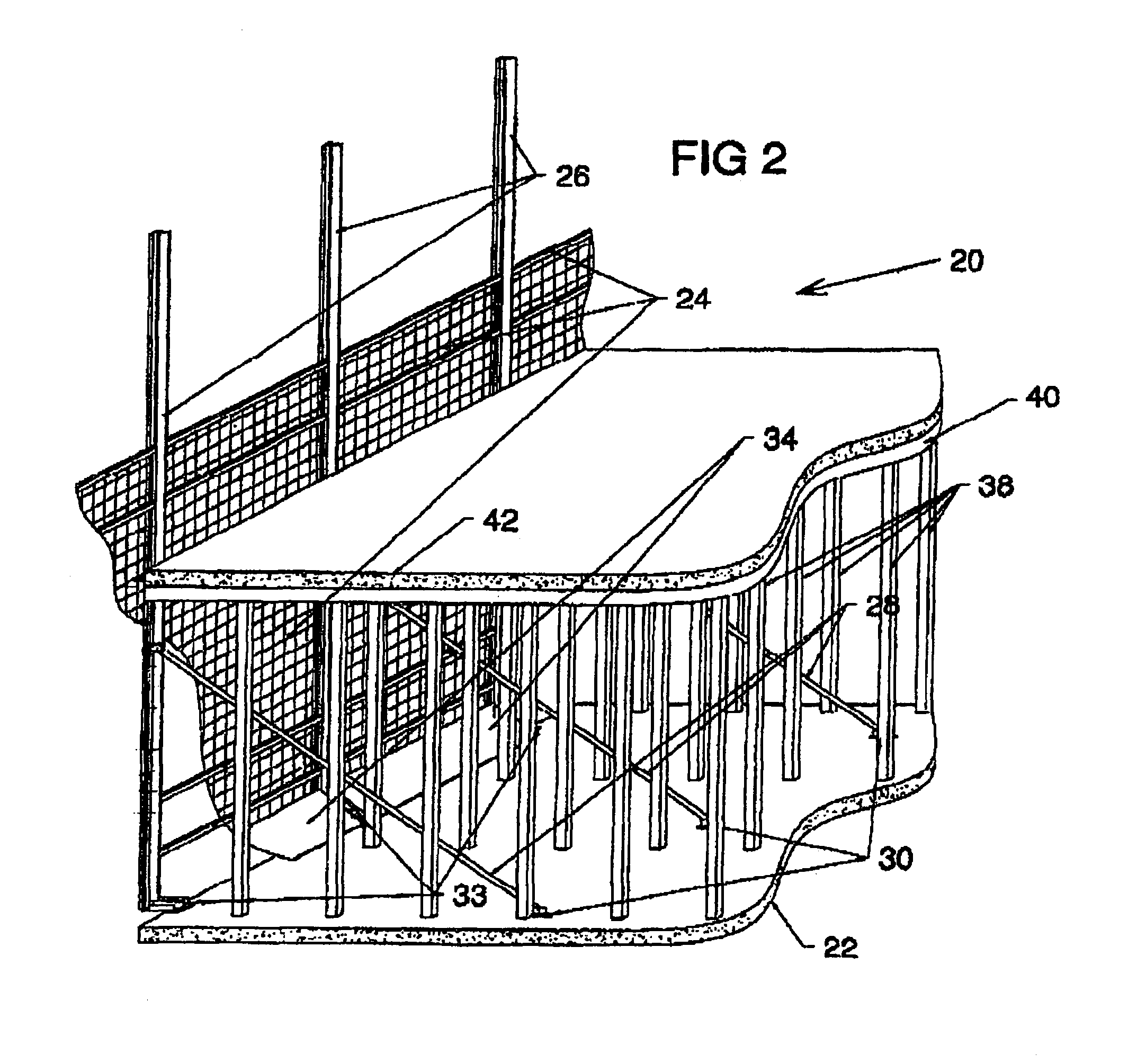
Safety barrier for multi-storey buildings
ActiveUS8511039B2Effective securityAvoid accidental movementBuilding roofsScaffold connectionsSystem elementFloor level
Owner:DOUGALL CAMERON BRUCE +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com