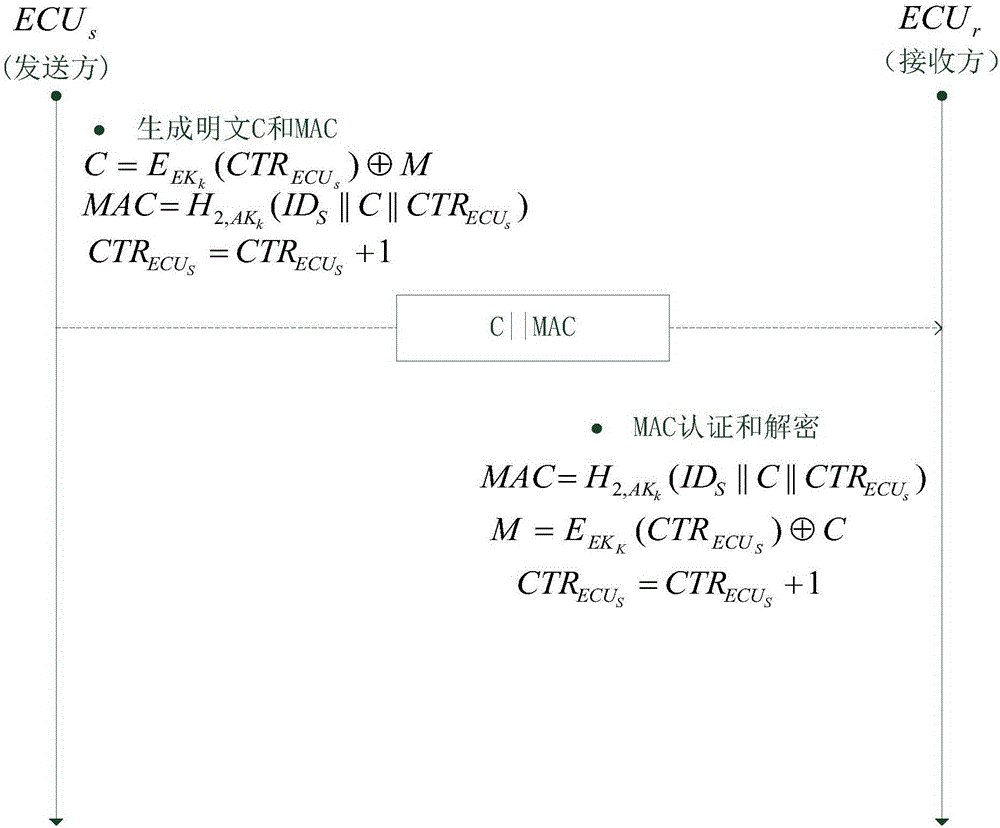Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
135 results about "Relay attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
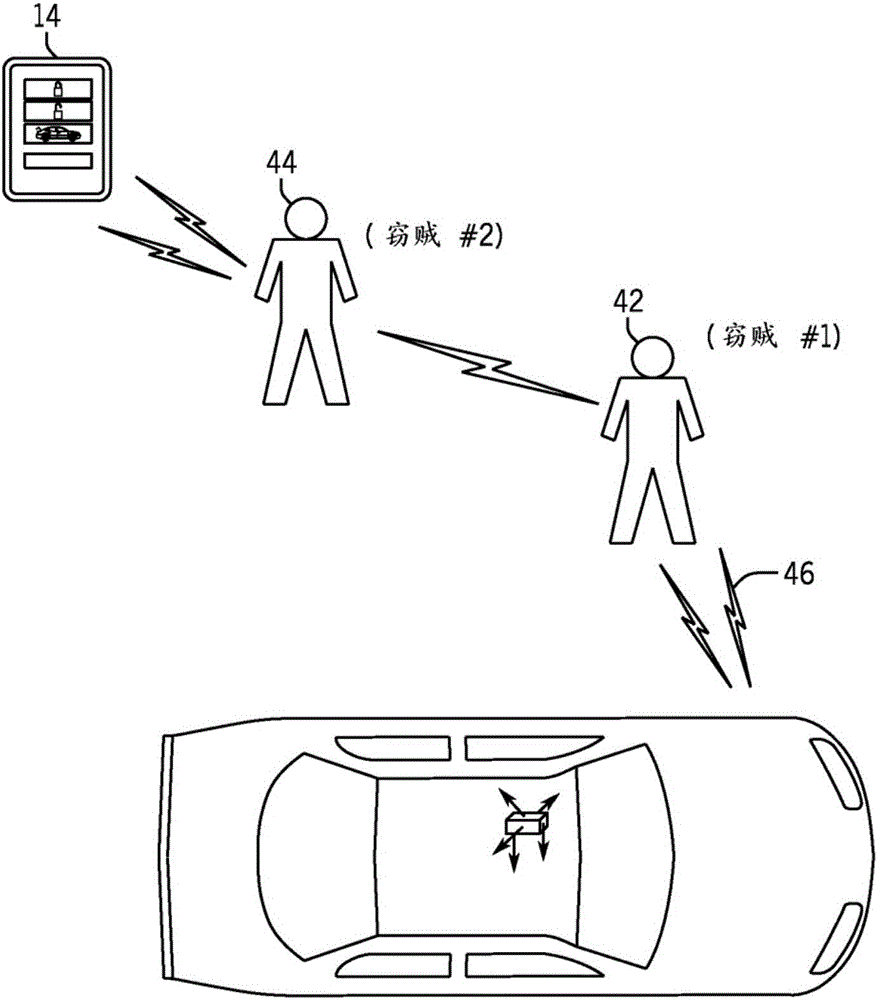
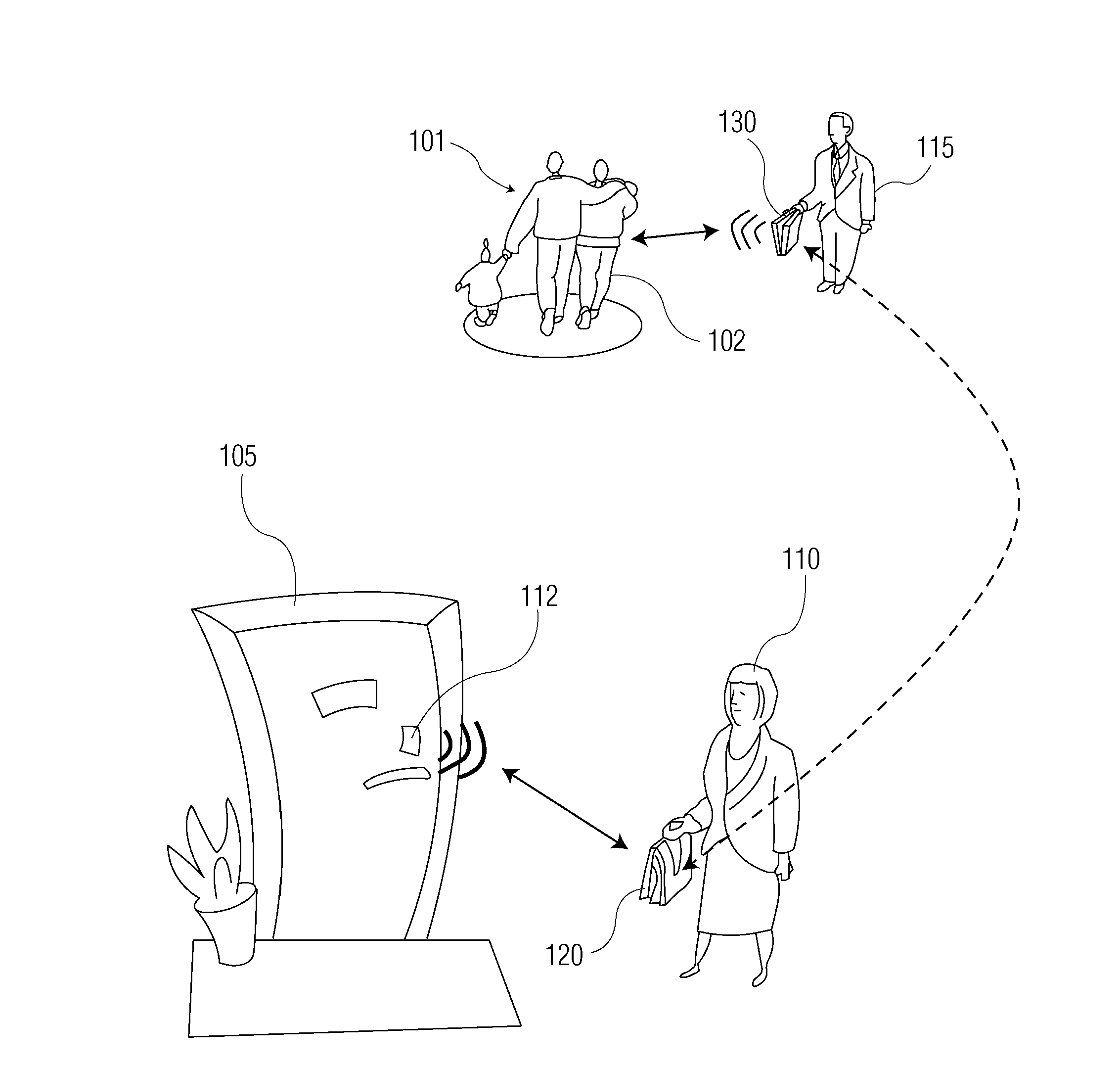
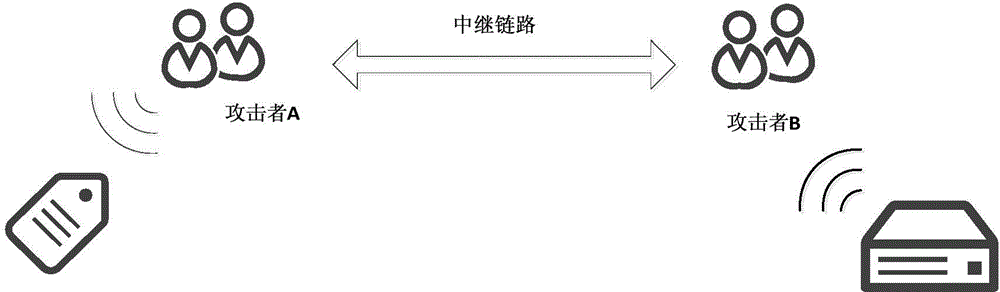
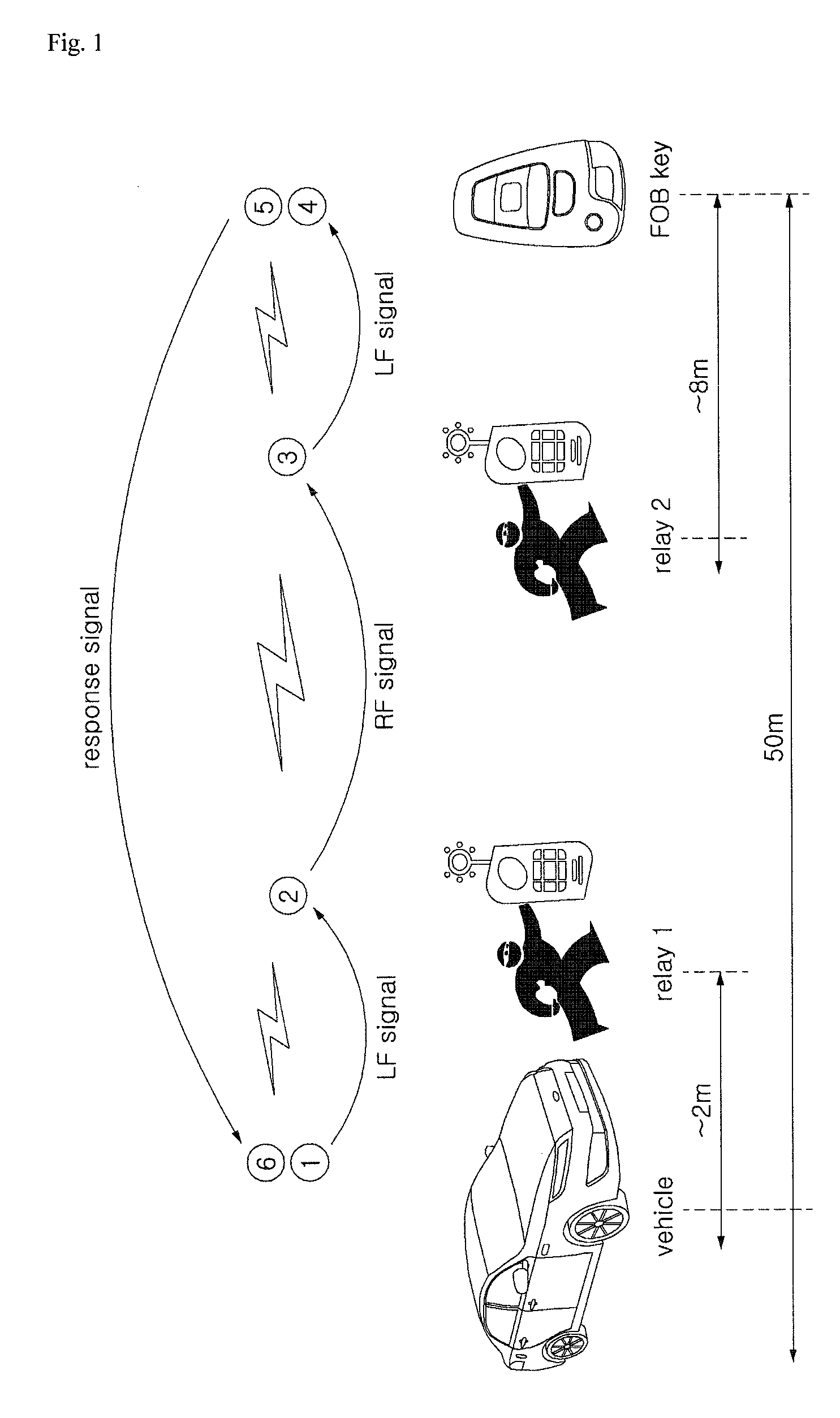
A relay attack in computer security is a type of hacking technique related to man-in-the-middle and replay attacks. In a classic man-in-the-middle attack, an attacker intercepts and manipulates communications between two parties initiated by one of the parties. In a classic relay attack, communication with both parties is initiated by the attacker who then merely relays messages between the two parties without manipulating them or even necessarily reading them.
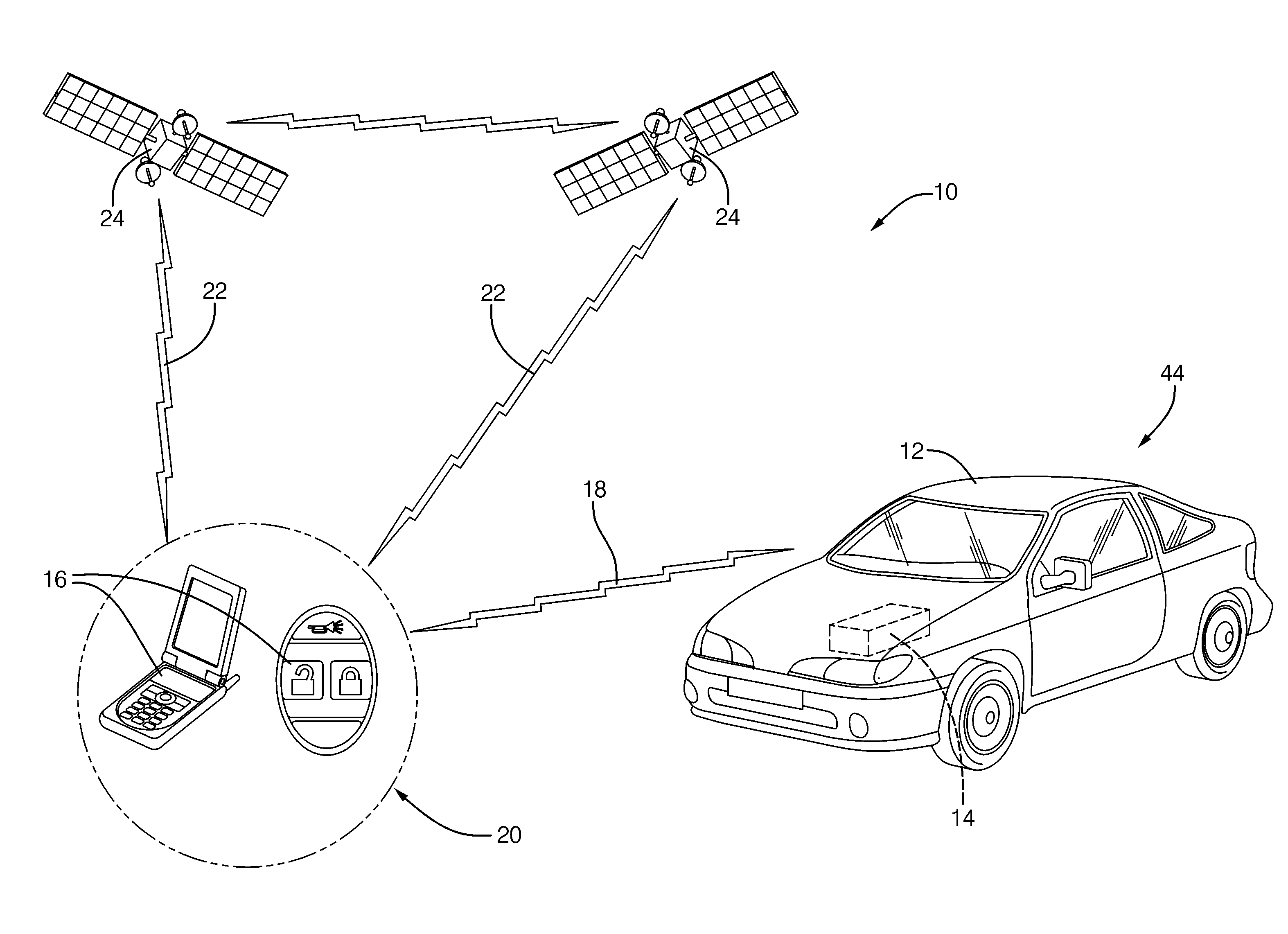
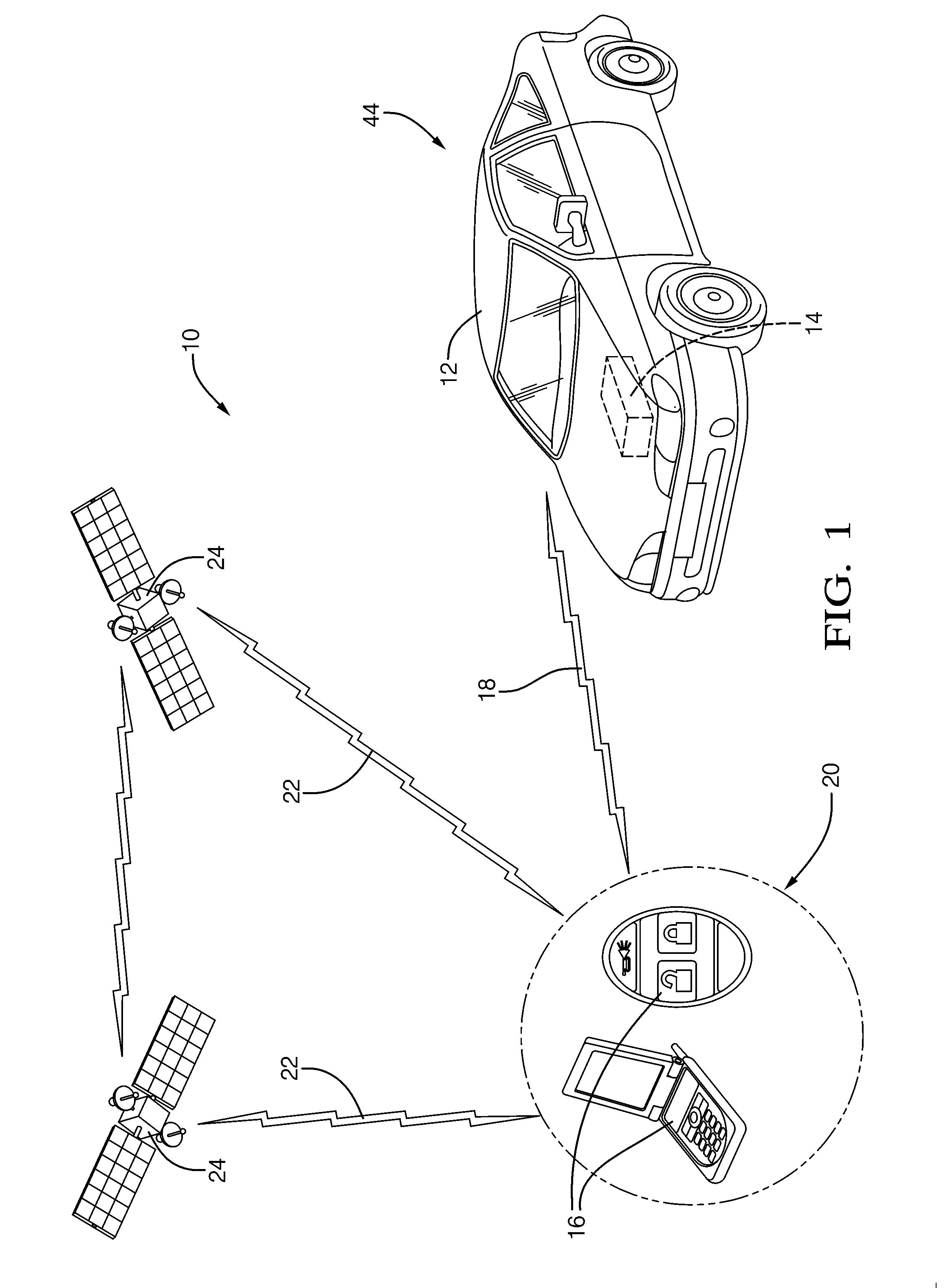
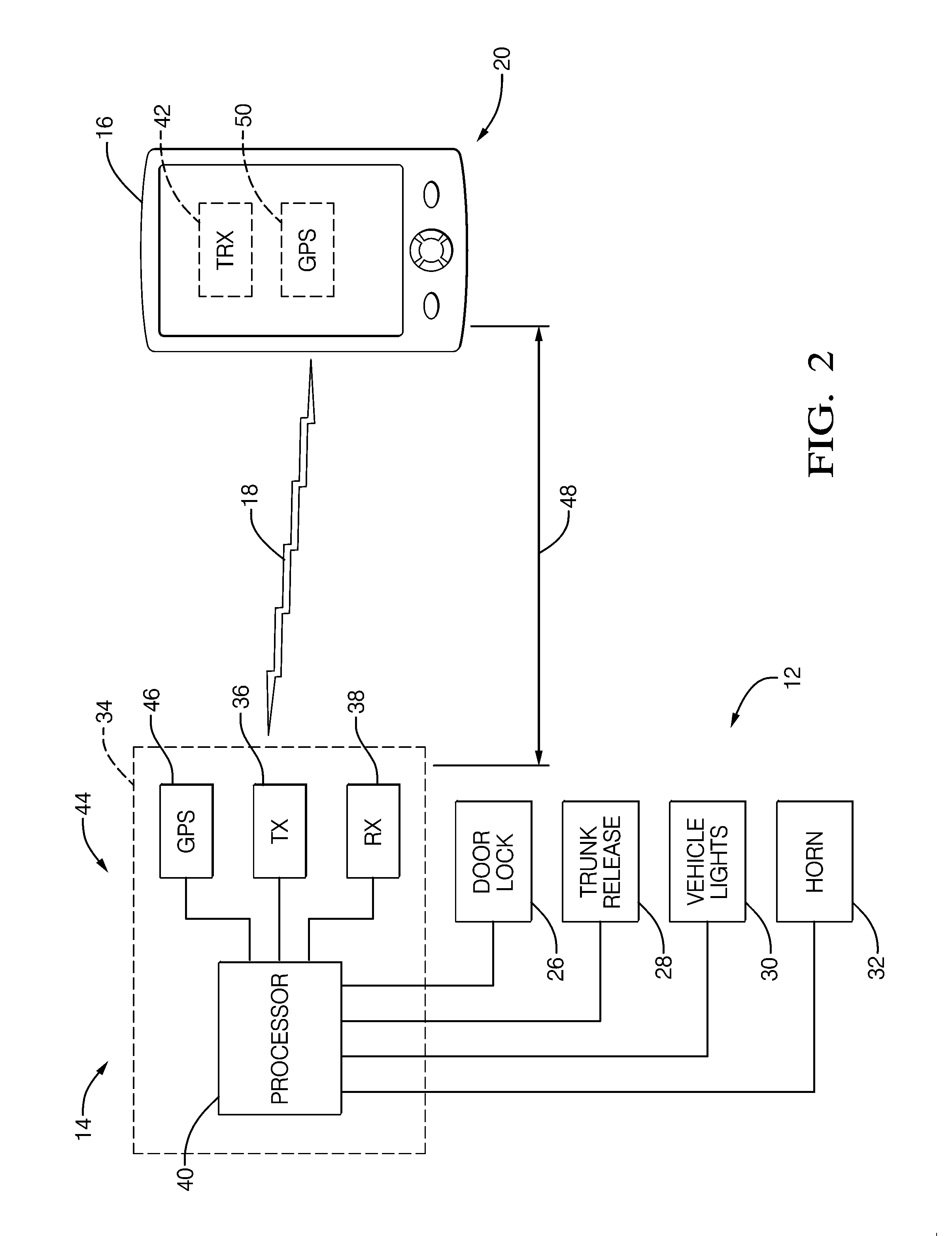
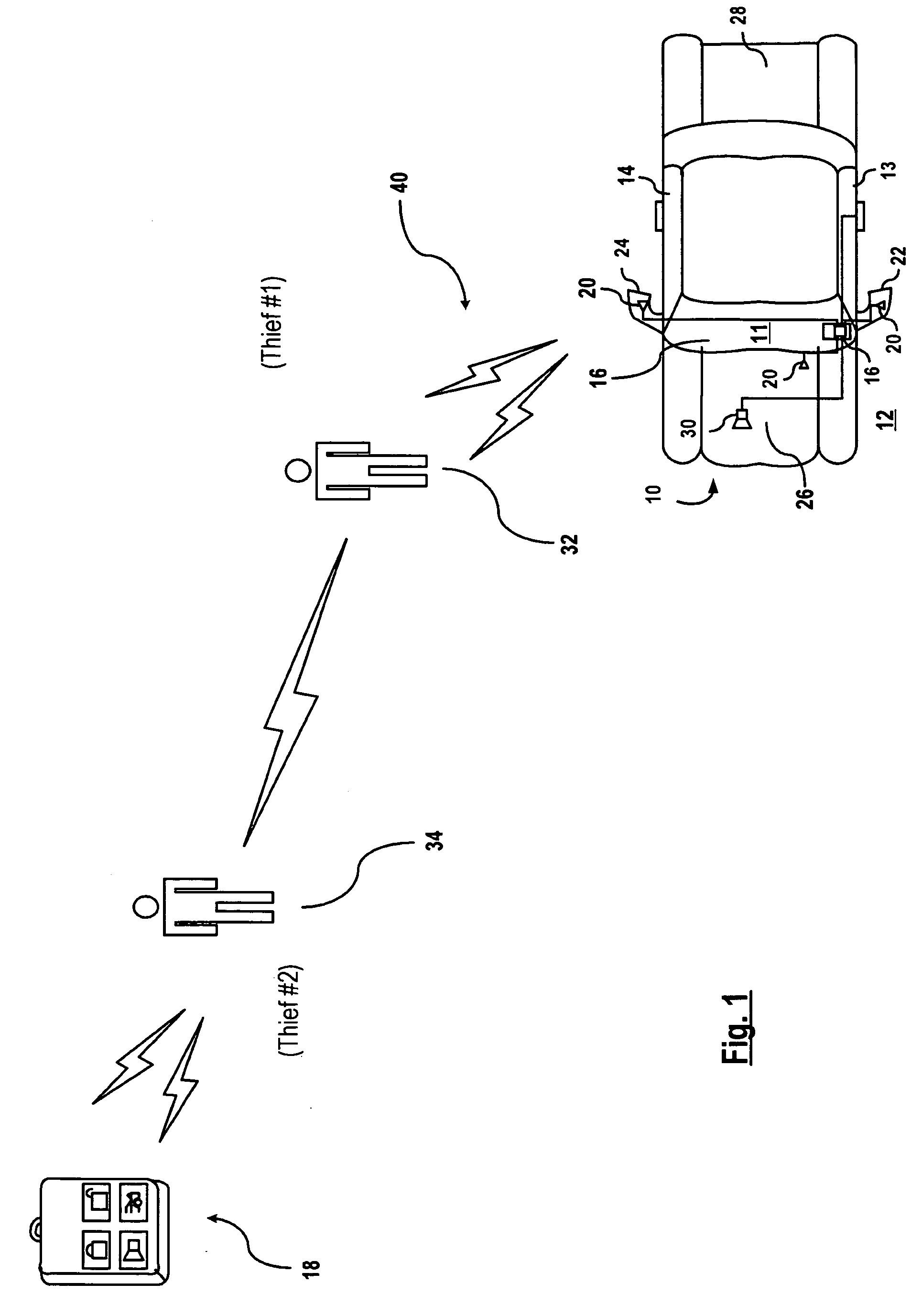
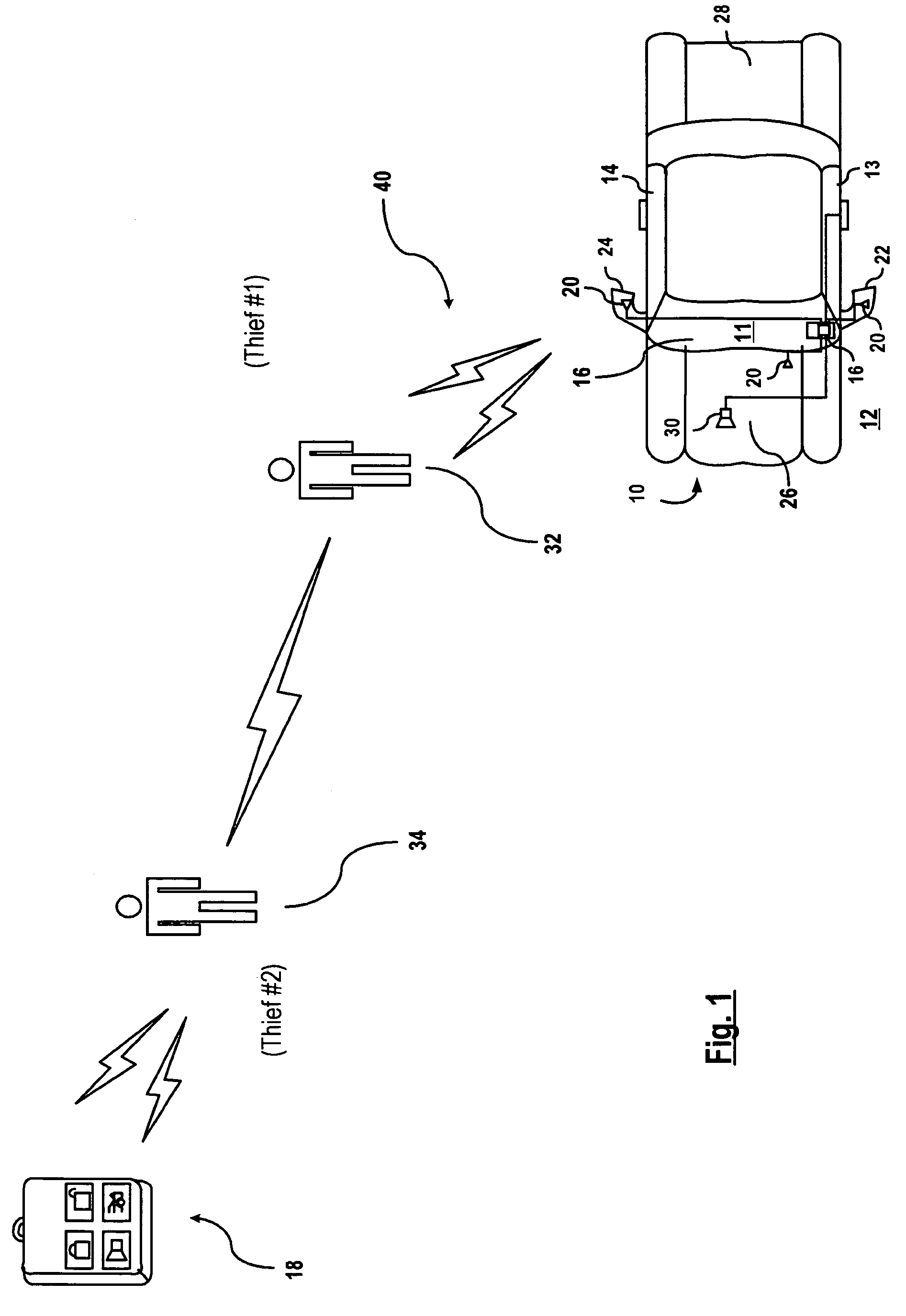
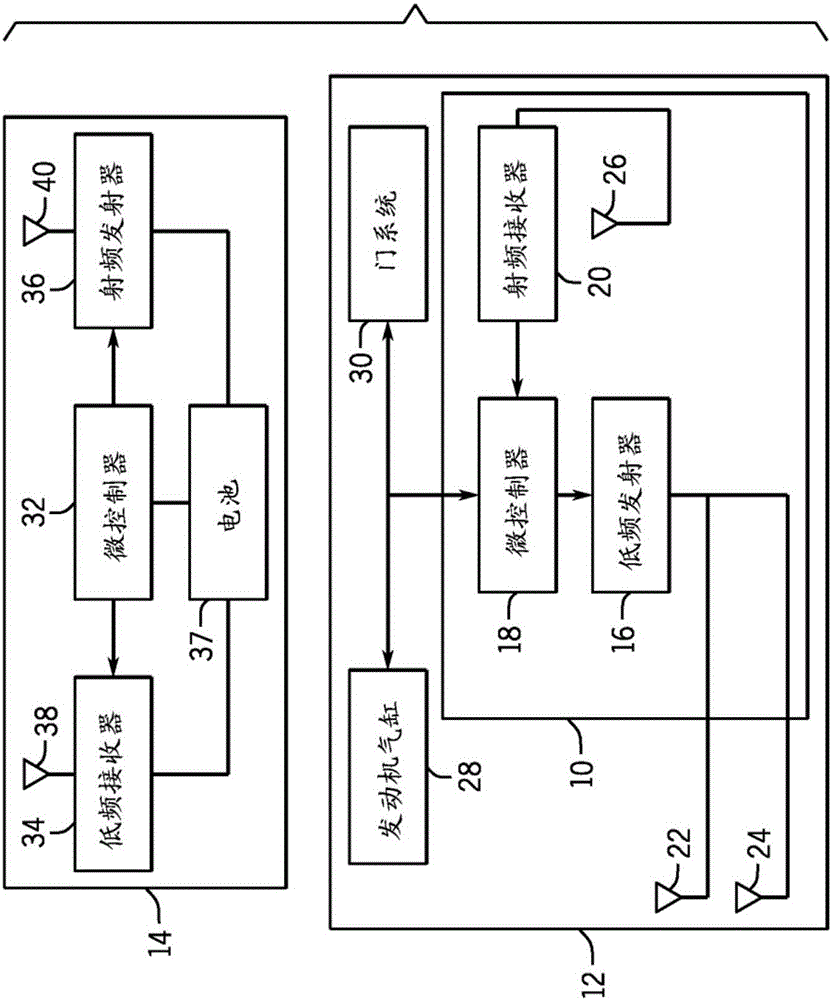
Vehicle security system and method of operation based on a nomadic device location
A vehicle security system for a vehicle equipped with a passive keyless entry / passive start (PEPS) security system including a nomadic device configured to determine a present location of the nomadic device (e.g. key fob, smart phone), and a controller configured to control a security-status based on the present location. The controller determines the security status based on the proximity of the nomadic device in order to thwart theft of the vehicle using a relay attack.
Owner:DELPHI TECH INC
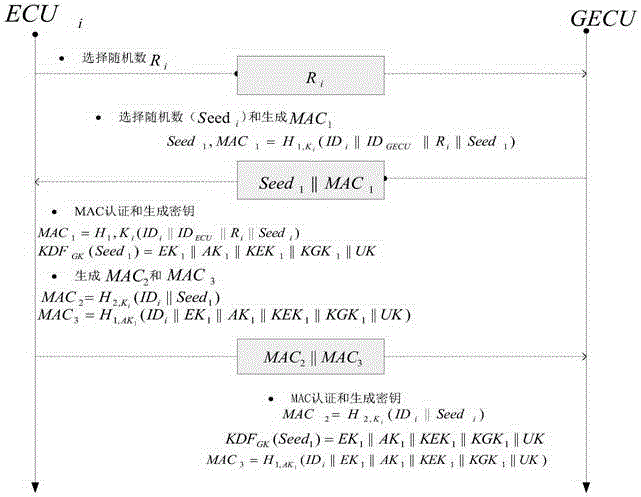
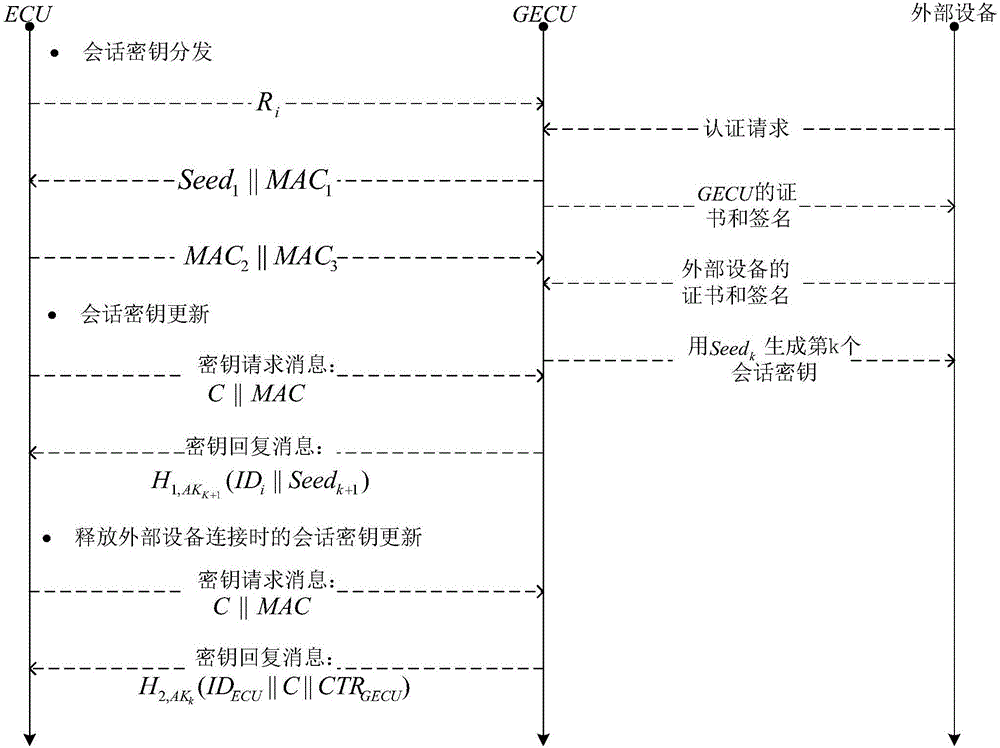
Method for safety communication of ECUs (Electronic Control Unit) in CAN (controller area network) bus
ActiveCN106790053AReduce computing costImprove efficiencyKey distribution for secure communicationEncryption apparatus with shift registers/memoriesArea networkKey generation
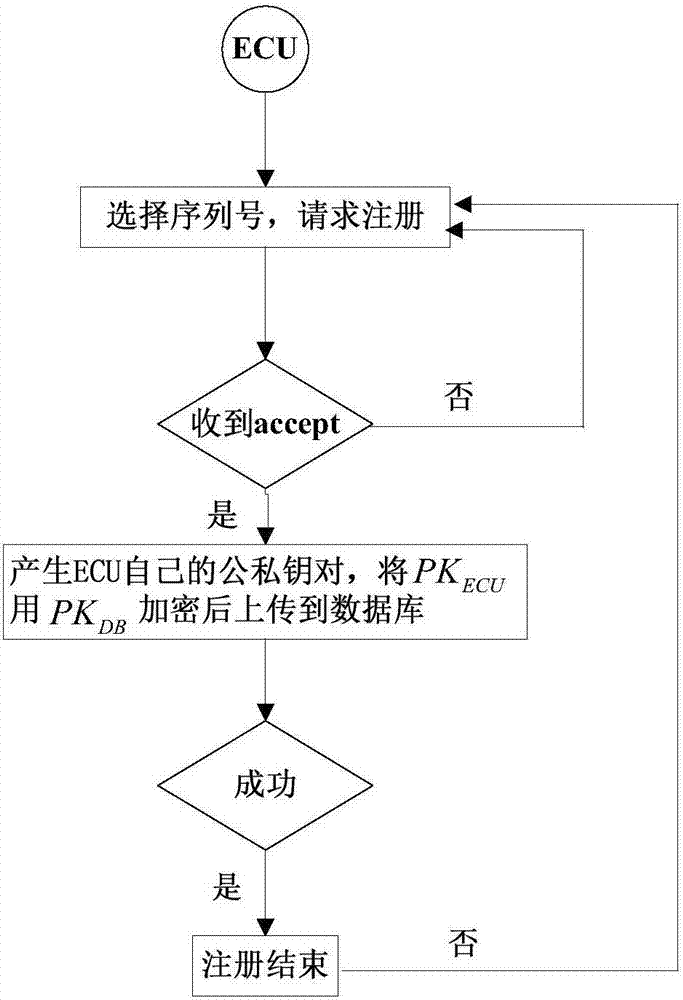
The invention discloses a method for safety communication of ECUs (Electronic Control Unit) in a CAN (controller area network) bus, which comprises the steps that: 1, a system model is established; 2, an GECU (Gateway Electronic Control Unit) loads a session key into a safety storage of the GECU; 3, the GECU carries out session key distribution on each ECU in the CAN bus; 4, a receiver ECUr carries out authentication on an encrypted data frame sent by a sender ECUs; 5, the GECU updates an encryption key and an authentication key which are used for communication, wherein update is mainly divided into two stages of in-vehicle ECU key update and key update when a connection of external equipment is released; and 6, when a vehicle is connected with the external equipment, designing an additional authentication and key distribution method so as to ensure legality of the accessed external equipment. According to the method disclosed by the invention, calculation cost can be obviously reduced, and a load of the CAN bus is reduced; and optimization is carried out for a key distribution protocol in the in-vehicle CAN bus, a key update problem generated when the external equipment is connected and released is considered, a counter is used for generating a random number to change a parameter for key generation, and a relay attack is effectively prevented.
Owner:JIANGSU UNIV
Method and apparatus for an anti-theft system against radio relay attack in passive keyless entry/start systems
An apparatus and method is provided for identifying unauthorized access to a vehicle having a keyless-passive entry system. An interrogation signal is broadcast from a vehicle based transmission device. The interrogation signal includes a first pulse transmitted at a first amplitude and a second pulse transmitted at a second amplitude where the second amplitude is greater than the first amplitude by at least a predetermined difference threshold. The interrogation signal is received by a portable communication device. A determination is made whether the second amplitude of the second pulse is greater than the first amplitude of the first pulse by a predetermined difference threshold. A determination is made that the interrogation signal is an authorized interrogation signal in response to the determination that the interrogation signal includes the first pulse transmitted at the first amplitude following by the second pulse transmitted at the second amplitude where the second amplitude is greater than the first amplitude by at least a predetermined difference threshold.
Owner:LEAR CORP
Radio Identification With an Additional Close-Range Check
ActiveUS20080157929A1Improve securityElectric signal transmission systemsImage analysisBiological activationData transmission
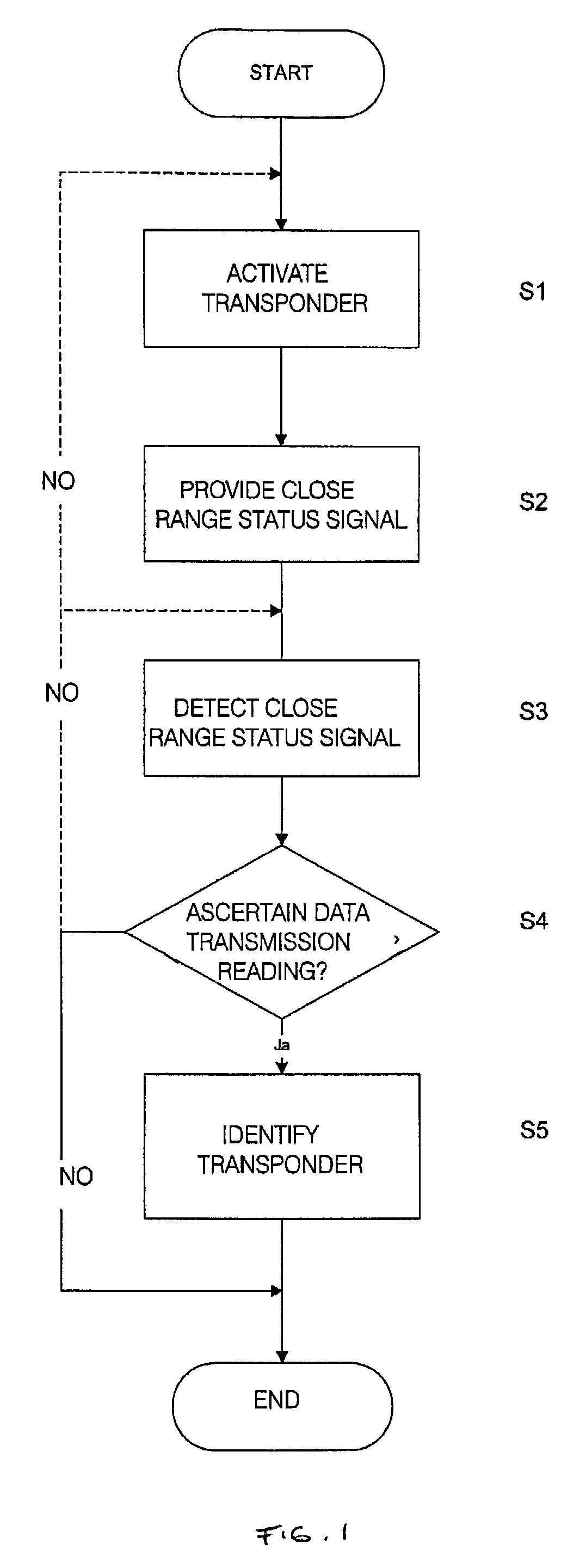
The invention relates to a method and a system for radio identification with an additional close-range check, which prevent misuse of a radio identification system and increase the security of radio identification. In particular, so-called relay attacks are to be largely prevented in passive entry systems. The method according to the invention firstly provides for activation of a transponder (S1) for reading of its data. After this step, an additional close-range status signal is provided (S2) which indicates the close range of a reader. Once the close-range status signal has been detected by a transponder (S3), data transmission for reading of the data stored in the transponder by the reader is possibly enabled in reaction to the detection of the close-range status signal (S4) and the data can be read by the reader for identification of the transponder (S5). The system according to the invention for radio identification with an additional close-range check consists of a reader for reading the data stored in a transponder and of an evaluation unit which is connected to the reader for identifying the transponder on the basis of the read data.
Owner:NXP BV
Method and apparatus for an anti-theft system against radio relay attack in passive keyless entry/start systems
Owner:LEAR CORP
Method for preventing relay-attack on smart key system
ActiveUS20150074805A1Prevent theftMemory loss protectionError detection/correctionVisibilityEngineering
The present invention relates to a method for preventing a relay-attack on a smart key system, and in particular, provides an advantage of preventing a vehicle and equipment stored inside the vehicle from being stolen by using predetermined information transmitted and received when the SMK UNIT of the vehicle and a FOB Key wirelessly communicate with each other and enabling a holder of the FOB Key to make the relay-attack once the holder secures visibility from the vehicle.
Owner:SEOYON ELECTRONICS CO LTD
System for preventing relay attack for vehicle entry
InactiveUS20140067161A1Digital data processing detailsAnti-theft devicesOperational systemEmbedded system
A system for preventing a relay attack on a vehicle is provided. The system includes a base unit positioned in the vehicle and operably connected to at least one vehicle system. The base unit is configured to obtain position information of the base unit. The system further includes a portable operating unit configured to obtain and transmit position information of the portable operating unit to the base unit. The base unit determines the position of the portable operating unit relative to the base unit and selectively controls operation of the at least one vehicle system based on the determination of the position of the portable operating system relative to the base unit.
Owner:GM GLOBAL TECH OPERATIONS LLC
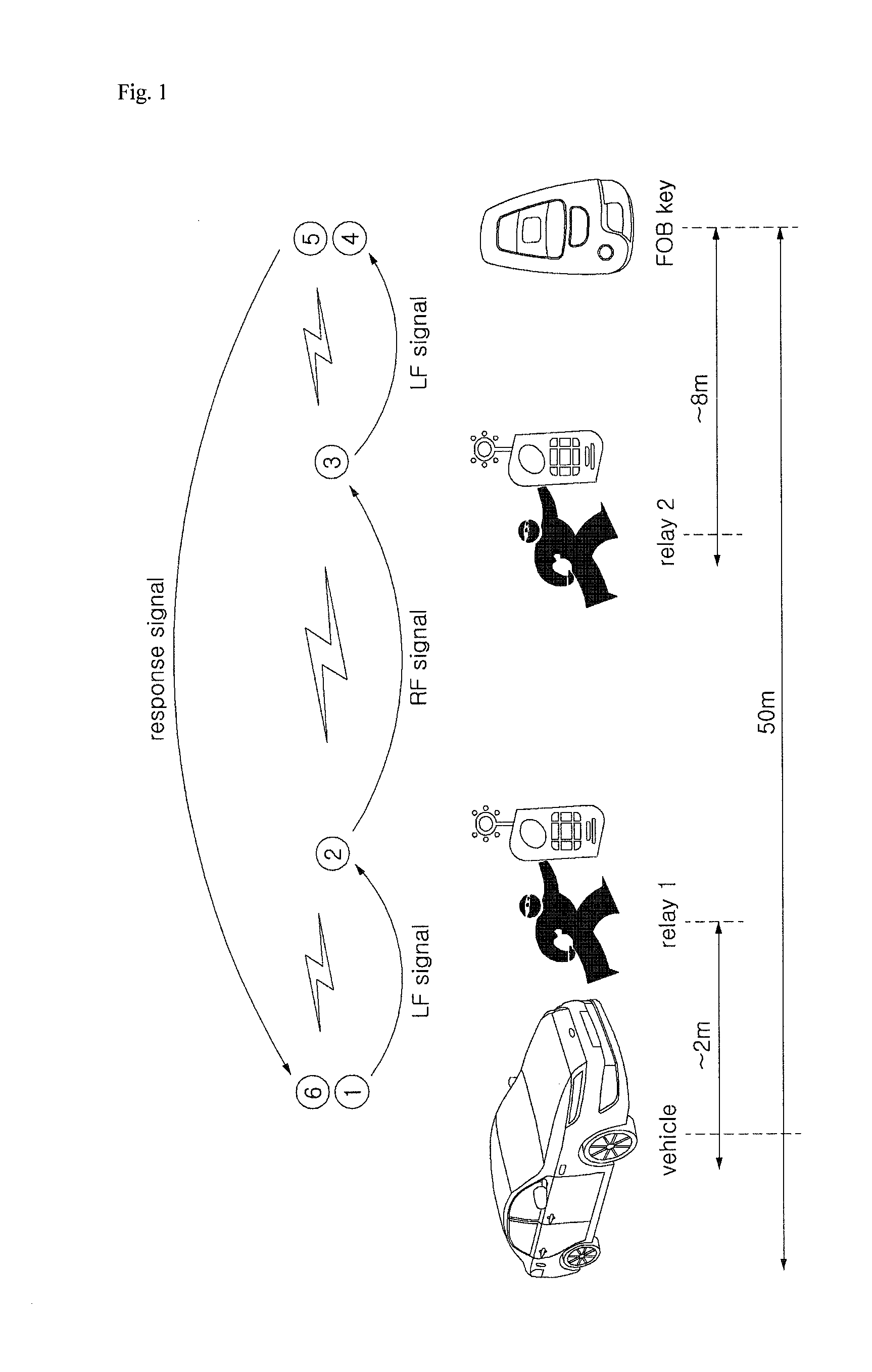
Solutions for Relay Attacks on Passive Keyless ENTRY and GO
InactiveUS20140240090A1Communication is limitedElectric signal transmission systemsRegistering/indicating working of vehiclesTransceiverOperation mode
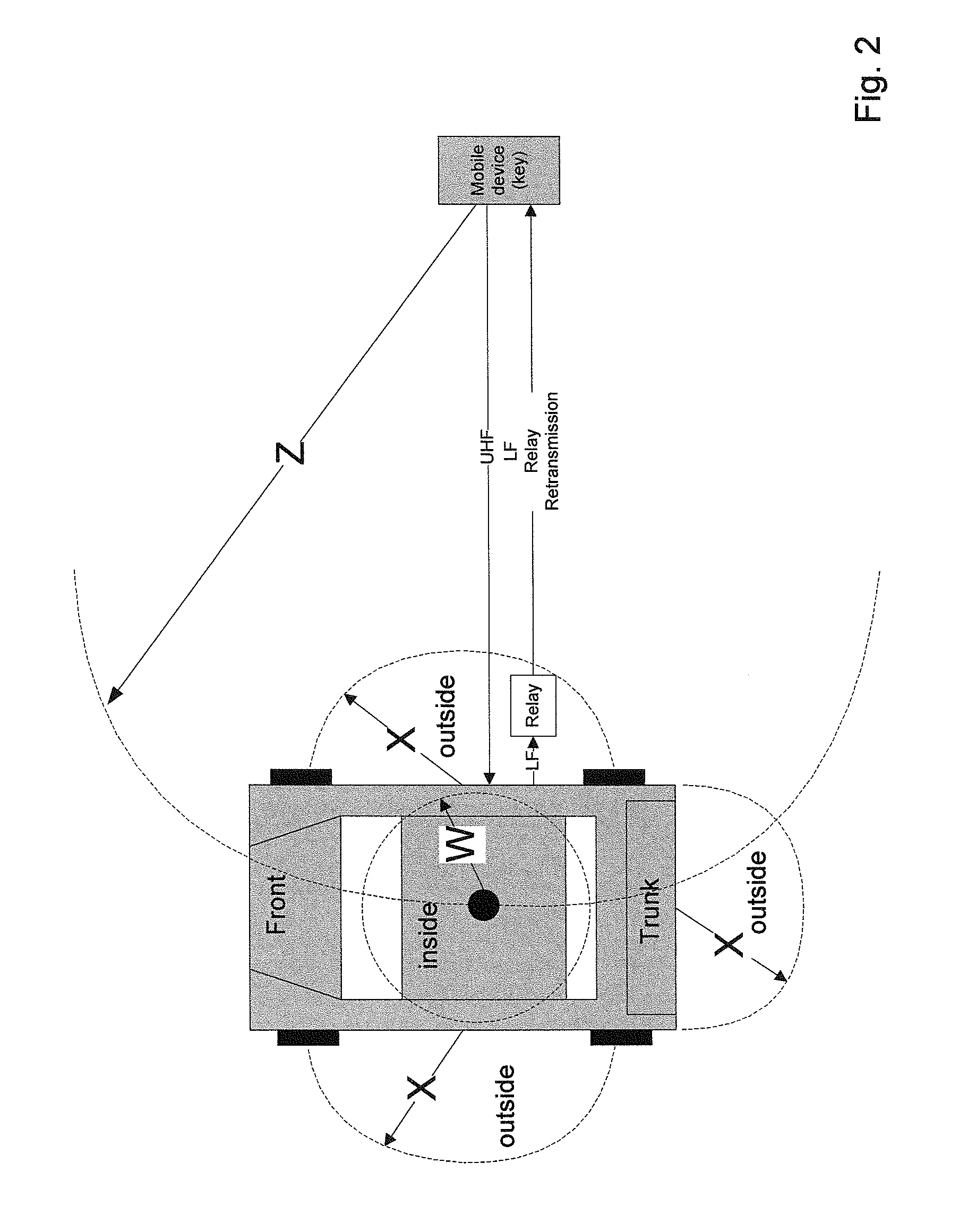
A passive entry system, in particular for a motor vehicle, comprising: a mobile device to be carried by a user, said mobile device comprising a low-frequency transceiver for short range communication, an ultra-high-frequency transceiver for long range communication and information concerning access, such as an access code, which is transmittable by said transceivers; and a locking device which is to be unlocked by the mobile device, said locking device comprising a low-frequency transceiver for short-range communication and an ultra-high frequency transceiver for long range communication to receive said information concerning access, such the access code. The transceivers of the mobile device communicates with the transceiver of the locking device and exchange information concerning access, such as said access code, to the locking system via the respective transceivers, wherein the communication range of the ultra-high-frequency transceiver of the mobile device is limited to a short range in a normal operating mode of the mobile device.
Owner:FAB VEHICLE SECURITY SOLUTIONS SRO
Vehicle-inside one-time-one-password communication method based on ECU identity concealment
ActiveCN107104791APrevent tamperingPrevent replay attacksKey distribution for secure communicationInformation securityEmbedded system
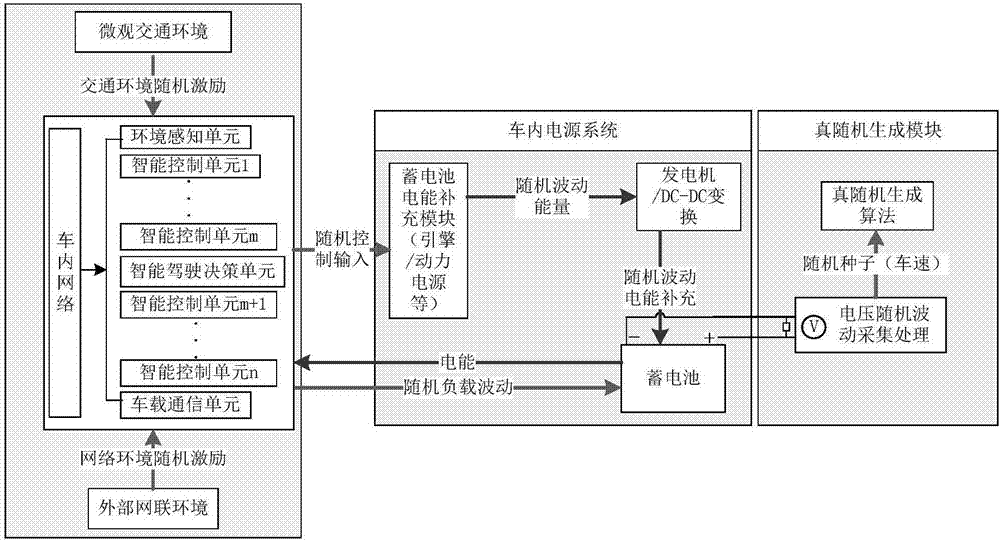
The invention discloses a vehicle-inside one-time-one-password communication method based on ECU identity concealment. The method comprises the following steps: 1) creating a system model; 2) prior to the one-time-one-ciphering by ECU, registering information in the gateway database; 3) using the operation behaviors to the vehicle by the intelligent ECU as the media to generate a coupling effect between vehicle mounted power supply systems so that the vehicle mounted power supply voltage change possess the Markov characteristics and that a true random number is generated to serve as the session key; 4) updating in a fixed time the session key between the ECUs in need of communication so as to prevent replay attacks; and 5) according to the obtained session key, using the attributes of the ECU in the database, creating one-time-one-ciphering data communications based on the ECU ciphered text attributes to ensure the secure communications of ECU inside the vehicle. According to the invention, through the utilization of the stochastic behavior of the power supply voltage inside the vehicle to generate a session key, it is possible to effectively avoid the problem with the tampering and the forgery of information. Through the combination of the vehicle speed unit with the steering wheel, the 500ms cycle dynamic state generates the vehicle speed and serves as the session key for the ECU in order to prevent relay attacks.
Owner:东台城东科技创业园管理有限公司
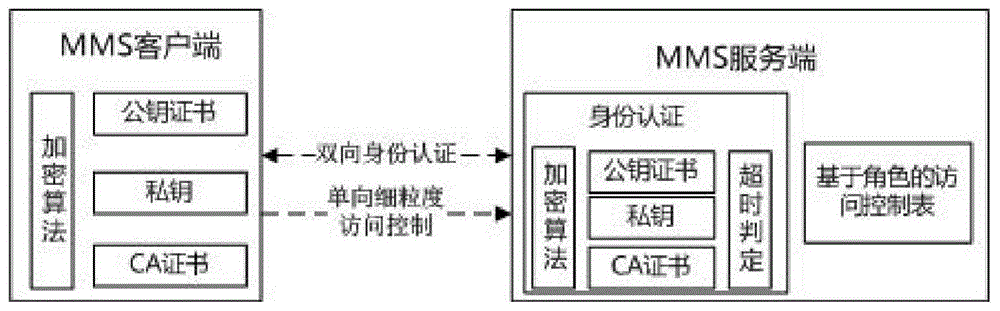
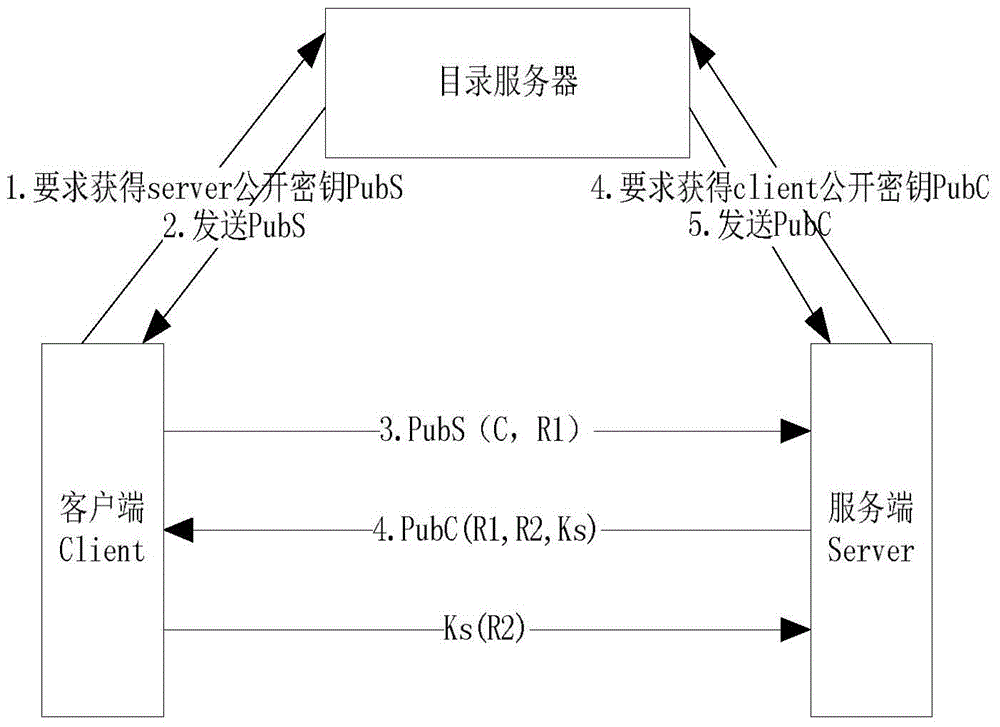
Safety exchange method for MMS specification application layer
InactiveCN104702599AEnsure safetyEnhanced authenticationUser identity/authority verificationSmart substationProtocol Application
The invention discloses a safety exchange method for an MMS specification application layer. When an intelligent substation device uses MMS message communication, the MMS application layer safety reinforcing exchange method enables both MMS protocol communication sides to perform identity authentication at the application through carrying out safety improvement on the MMS application layer and controls the access authority of an MMS client through using role-based access based on the authentication. The safety exchange method for the MMS specification application layer includes steps that 1) starting an MMS association authorization function, and extending authorization data structure; 2) through extending the authorization data structure, using a public encryption algorithm to carry out identity authorization on the association process of the MMS application layer, and at the same time, performing relay attack protection; 3) using a role-based access control technology to construct the access control relationship between the MMS client and MMS service, after passing the association authentication, allowing an MMS server to use a configured access control relation table to carry out fine-grained access control on the MMS client, if the MMS client meets the demand, allowing the MMS client to access the corresponding service, otherwise, refusing to provide service.
Owner:CHINA SOUTHERN POWER GRID COMPANY
Vehicle control system to prevent relay attack
A passive entry system for an automotive vehicle that is configured to prevent relay attacks by analyzing magnet vectors and angles created by a plurality of antennas mounted on the vehicle is disclosed. A vehicle including a control unit configured to broadcast a wake-up signal to prompt a fob to power-up if the fob is in a low-power consumption mode and to transmit signals through a plurality of antennas coupled to the vehicle is provided, along with a fob configured to recognize the wake-up signal and to generate a response signal for the control unit in response to recognize the wake-up signal. The fob includes a controller that is programmed to receive signals transmitted from each of the plurality of antennas coupled to the vehicle, retrieve constant values from stored a memory, and calculate a magnetic integrity defining the relative position of each of the plurality of antennas. The controller allows access to the vehicle if magnetic integrity is found, and denies access to the vehicle if magnetic integrity is not found.
Owner:HUF NORTH AMERICA AUTOMOTIVE PARTS MFG +1
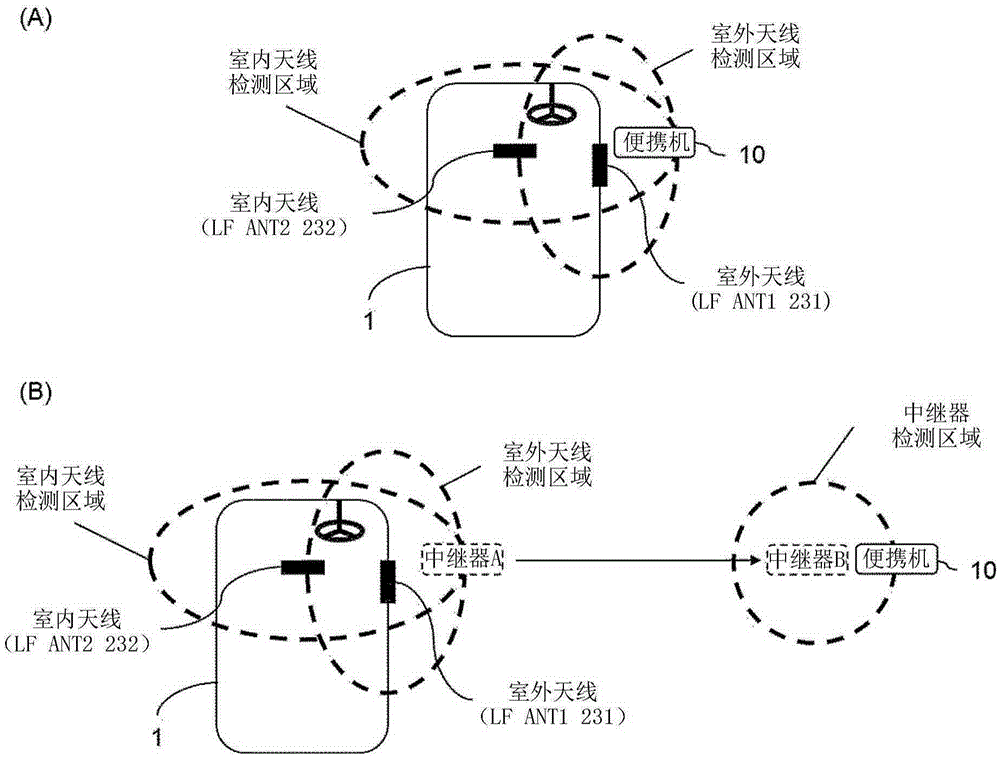
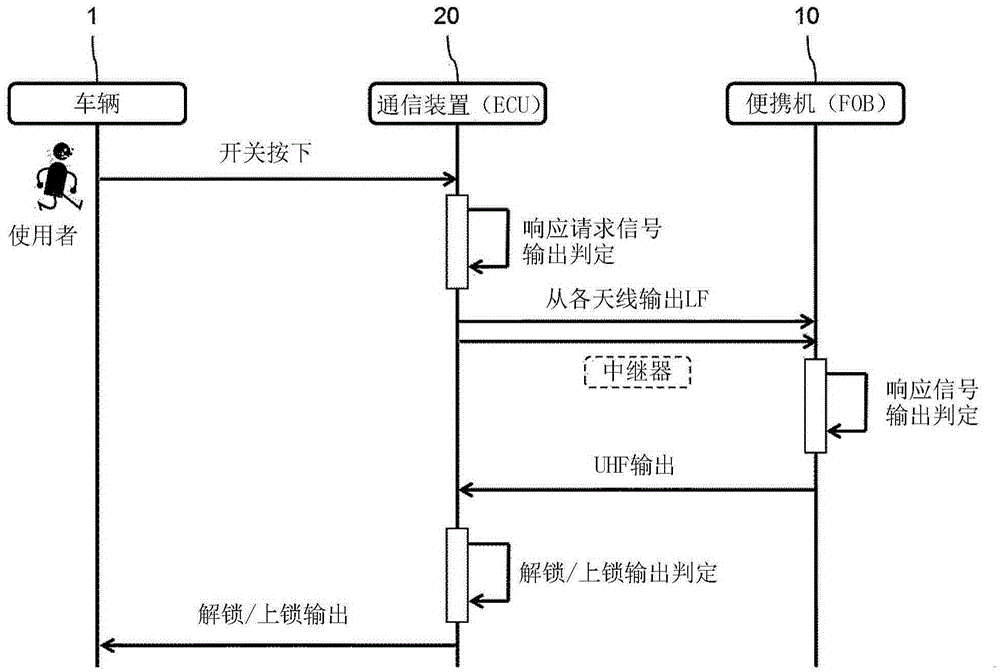
Portable device, communication device, and communication system
ActiveCN105553496AImprove prevention capabilitiesIndividual entry/exit registersTransmissionCommunications systemEngineering
The invention provides a portable device, a communication device, and a communication system with high prevention and capable of determining whether relay attack is performed. The communication system (100) includes: a vehicle (1)-mounted communication device (20) and a portable device (10). The communication device (20) includes: a vehicle transmission unit (22) which transmits a plurality of first signals to the portable device, and a vehicle reception unit (21) which receives a second signal transmitted from the portable device. The portable device (10) includes: a portable device reception unit (11) which receives the first signals, a portable device controller (15) which detects signal intensities of the received first signals, and which compares the signal intensities of the first signals, and a portable device transmission unit (12) which transmits the second signal according to control of the portable device controller. The portable device controller (15) sets an output value of the second signal to a predetermined value when a difference between the compared signal intensities of the first signals is equal to or less than a threshold.
Owner:OMRON AUTOMOTIVE ELECTRONICS CO LTD
Passive keyless entry system for preventing relay attacks
ActiveUS20190114857A1Prevent relay attackEfficiently signaledAnti-theft devicesIndividual entry/exit registersIn vehicleAuthorization
A passive keyless entry (PKE) system is disclosed. The PKE includes an in-vehicle apparatus. The in-vehicle apparatus includes a control unit that is configured to measure magnetic field and compute at least one angle between two projections of the magnetic field. When the measured angle is lower than a threshold value, an authorization signal is prevented.
Owner:NXP BV
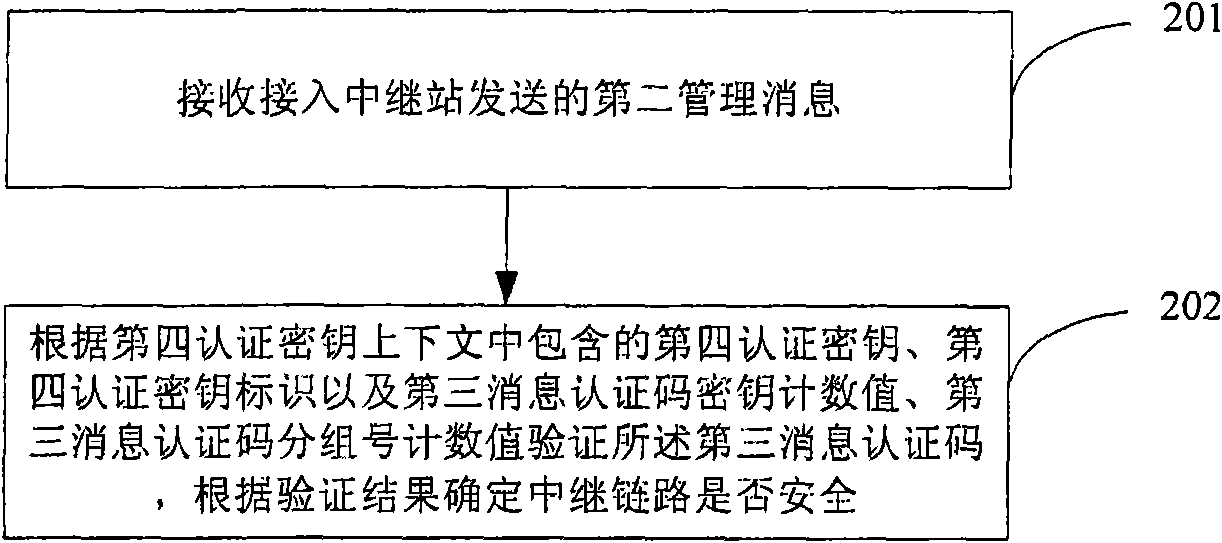
Link security certification method, device and system in wireless relay network
ActiveCN101815293APrevent replay attacksEncryption apparatus with shift registers/memoriesSecurity arrangementComputer hardwareMulti hop relay
The invention discloses a link security certification method, a device and a system in a wireless relay network. The method comprises the following steps that: a multi-hop relay base station or an access relay station receives a first management message sent by a mobile station; the first management message carries a first message authentication code, and a first message authentication code key counting value and a first message authentication code grouping number counting value which are contained in the context of a first authentication key stored by the mobile station per se; the first message authentication code is verified according to a second authentication key, a second authentication key mark, the first message authentication code key counting value and the first message authentication code grouping number counting value, wherein the second authentication key and the second authentication key mark are contained in the context of a second authentication key; and whether the access link between the mobile station and the access relay station is secure or not is determined according to the verification results. When the technical scheme of the invention is adopted, the relay attack in the wireless relay network can be effectively prevented.
Owner:HUAWEI TECH CO LTD
System and method of non-contact IC card for defending relay attack
ActiveCN103679058AEnsure safetyLow costInternal/peripheral component protectionCard readerInformation security
The invention discloses a system and method of a non-contact IC card for defending a relay attack, and relates to the field of information security. The system comprises the non-contact IC card and a card reader. The card reader sends three-time magnetic field intensity information to the non-contact IC card and records sending time, the non-contact IC card detects actual magnetic field intensity of the card reader for three times, and the actual magnetic field intensity is compared with the received corresponding magnetic field intensity to judge whether the non-contact IC card is under attack or not; meanwhile, the card reader calculates the received time difference of the non-contact IC card returning to a normal instruction, the time difference is compared with a corresponding magnetic field intensity change time difference to judge whether the non-contact IC card is under the attack or not, and when the non-contact IC card is under the attack, the non-contact IC card sends out an abnormal instruction, and the card reader stops communicating and sends out an alerting signal. According to the system and method, the non-contact IC card can be effectively prevented from being subjected to the relay attack, safety of the non-contact IC card is guaranteed, and the system is wide in application range, low in cost and convenient to use.
Owner:湖北警官学院
Defense against relay attack in passive keyless entry systems
A system includes a first unit associated with an object and a second unit. The first unit includes a first transceiver coupled with first processing circuitry. The second unit includes a second transceiver coupled with second processing circuitry. Methodology includes establishing a bidirectional wireless communication link between the first and second units. Following establishment of the communication link, the first and second units exchange messages. The first processing circuitry measures a first received signal strength indicator (RSSI) value for each of the messages received at the first unit and sends the first RSSI value in a subsequent message to the second unit. The second processing circuitry measures a second RSSI value for each of the messages received at the second unit and sends the second RSSI value in another subsequent message to the first unit. A relay attack is determined in response to the first and second RSSI values.
Owner:NXP BV
Secure seamless access control
ActiveUS20190182672A1Improve security featuresAnti-theft devicesConnection managementNon detectionMedia access control
A method of secure access through a wireless connection is provided. The method includes detecting availability of an access control wirelessly by a mobile device. A predicted intent is determined of a user of the mobile device to have the access control open a lock. The method determines whether a relay attack is detected. Based on detection of the relay attack, a prompt to confirm an intent of the user of the mobile device to have the access control open a lock is determined. Based on non-detection of the relay attack, a lock actuator is activated through the access control to open the lock responsive to a credential based on affirmatively confirming the intent or the predicted intent.
Owner:CARRIER CORP
System for preventing relay attack for vehicle entry
A system for preventing a relay attack on a vehicle is provided. The system includes a base unit positioned in the vehicle and operably connected to at least one vehicle system. The base unit is configured to obtain position information of the base unit. The system further includes a portable operating unit configured to obtain and transmit position information of the portable operating unit to the base unit. The base unit determines the position of the portable operating unit relative to the base unit and selectively controls operation of the at least one vehicle system based on the determination of the position of the portable operating system relative to the base unit.
Owner:GM GLOBAL TECH OPERATIONS LLC
Vehicle entry system, vehicle key, and vehicle sharing method
InactiveCN109462626AAchieve sharingRealize remote controlAnti-theft devicesTransmissionRemote controlThird generation
The invention provides a vehicle entry system, a vehicle key, and a vehicle sharing method. The vehicle entry system comprises a vehicle owner key module, a cloud service module, a satellite positioning module, and a vehicle control module, wherein the cloud service module is in communication with the vehicle owner key module through the Internet of Things, and configured to, after receiving an entry application of a vehicle, apply for and obtain a virtual key of the vehicle from the vehicle owner key module, obtain the position information of the vehicle through the satellite positioning module, and feed back the virtual key and the position information of the vehicle; and the vehicle control module unlocks and / or starts the vehicle when verifying that the virtual key is legal. Based on the vehicle entry system, the vehicle key, and the vehicle sharing method provided by the invention, the user does not no longer rely on the intelligent terminal and 2G, 3G, and 4G networks, vehicle key sharing, vehicle sharing, and remote control of the vehicle are realized through communication technologies such as IOT and V2C, and anti-relay attack of the vehicle is realized by GPS positioning or base station positioning, and the like.
Owner:HELLA SHANGHAI ELECTRONICS
Smart key and method of controlling the same
ActiveUS20170193717A1Prevent hackingAnti-theft devicesIndividual entry/exit registersCommunication unitEngineering
A smart key for a vehicle includes: a communication unit including a low frequency (LF) antenna which receives an LF signal; and a control unit determining a strength and a direction vector of the LF signal. The control unit estimates a first location of the smart key based on the strength of the LF signal, estimates a second location of the smart key based on the direction vector of the LF signal, and determines a presence of a relay attack by analyzing the first location and the second location and comparing the first location with the second location.
Owner:HYUNDAI MOTOR CO LTD
Protection against relay attacks in a white-box implementation
ActiveUS20180351743A1User identity/authority verificationComputer security arrangementsComputer hardwareTime segment
A method is provided for performing a cryptographic operation in a white-box implementation on a mobile device. The cryptographic operation is performed in the mobile device for a response to a challenge from a mobile device reader. The mobile device reader includes a time-out period within which the cryptographic operation must be completed by the mobile device. In accordance with an embodiment, a first time period to complete the cryptographic operation on the mobile device is determined. A predetermined number of dummy computations are added to the cryptographic operation to increase the first time period to a second time period. The second time period is only slightly less than the time-out period by a predetermined safety value to make it less likely a relay attack with be successful.
Owner:NXP BV
Method and system for preventing a physical layer relay attack
ActiveUS20180374290A1Avoid attackReduce chanceAnti-theft devicesElectric motor startersTransceiverPhysical layer
There is provided a method and a system for authorizing a user device (102) to send a request to a vehicle (104) in order to prevent a physical layer relay attack. The system comprises a vehicle comprising an acoustic transducer (106) and an RF transceiver (108) and a user device comprising an acoustic transducer and an RF transceiver. The method relates to a signaling scheme using a combination of acoustic and RF signals for preventing a successful physical layer relay attack.
Owner:VOLVO CAR CORP
Proximity assurance for short-range communication channels
ActiveCN103095346ANear-field transmissionMemory record carrier reading problemsEngineeringNear field communication
A proximity check ensures that a card is physically close to the reader device in order to inhibit relay attacks. The proximity check makes relay attacks more difficult because an additional channel must be intercepted and / or spoofed or relayed. This solution can be used for any kind of short-range communication, including near field communications (NFC).
Owner:NXP BV
Defensive system of relay attack of near-field mobile payment and realization method thereof
InactiveCN104821945AGet temperatureGet data informationNear-field transmissionCo-operative working arrangementsData informationSmart card
The invention discloses a defensive system of a relay attack of near-field mobile payment and a realization method thereof. The system comprises an intelligent card temperature tag and an intelligent card reader. The intelligent card temperature tag consists of an RFID electronic tag, a temperature sensor, and a wireless communication module; and the intelligent card reader includes an RFID reader, a temperature sensor and a wireless communication module. According to the system, the wireless communication modules use RFID and near-field-communication (NFC) channels to carry out data information transmission; the intelligent card temperature tag can monitor the environment temperature in real time; and the intelligent card reader can carry out communication with the intelligent card temperature tag and obtain information of the temperature and data and the like of the temperature tag. The information interaction flow of the intelligent card reader and the intelligent card tag is carried out by four steps: an initialization module step, a temperature measurement module step, a message interaction module step, and a verification module step.
Owner:NANJING UNIV OF POSTS & TELECOMM
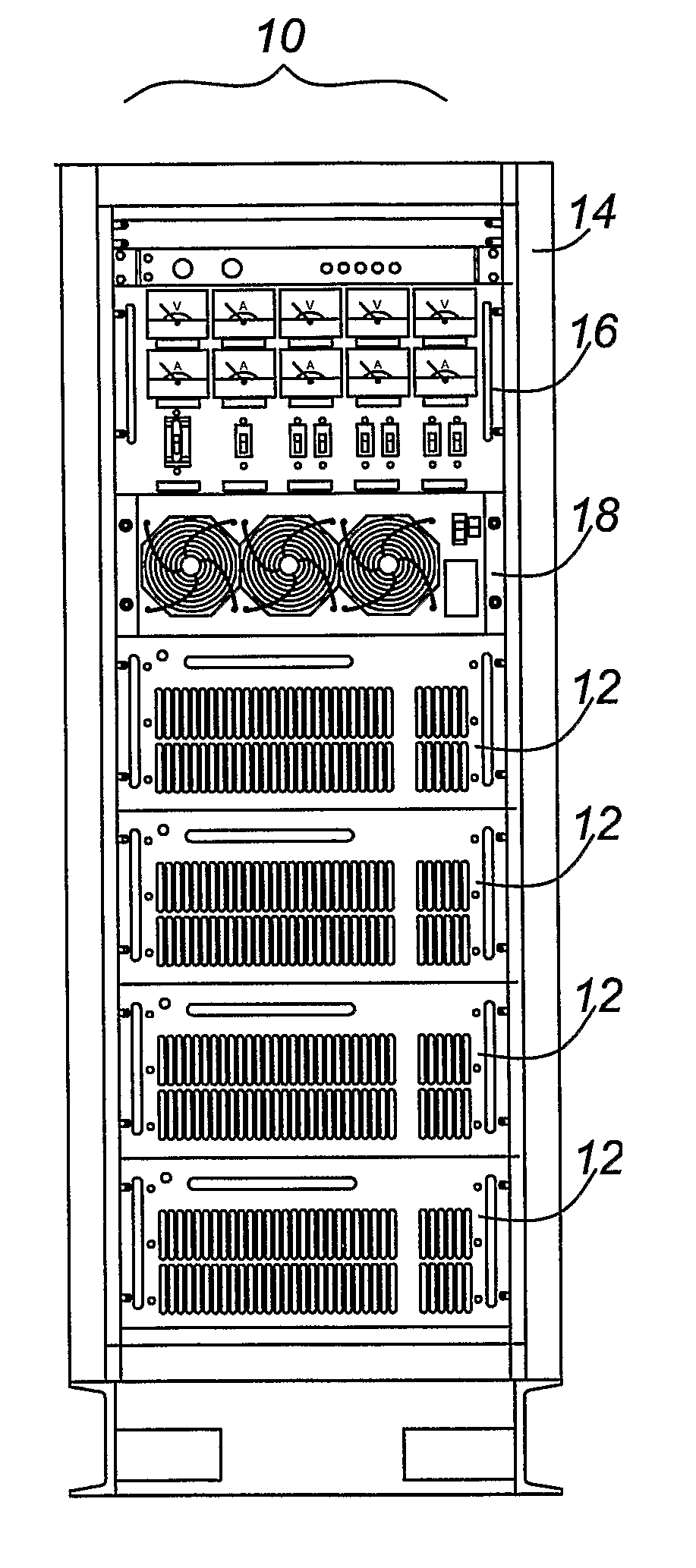
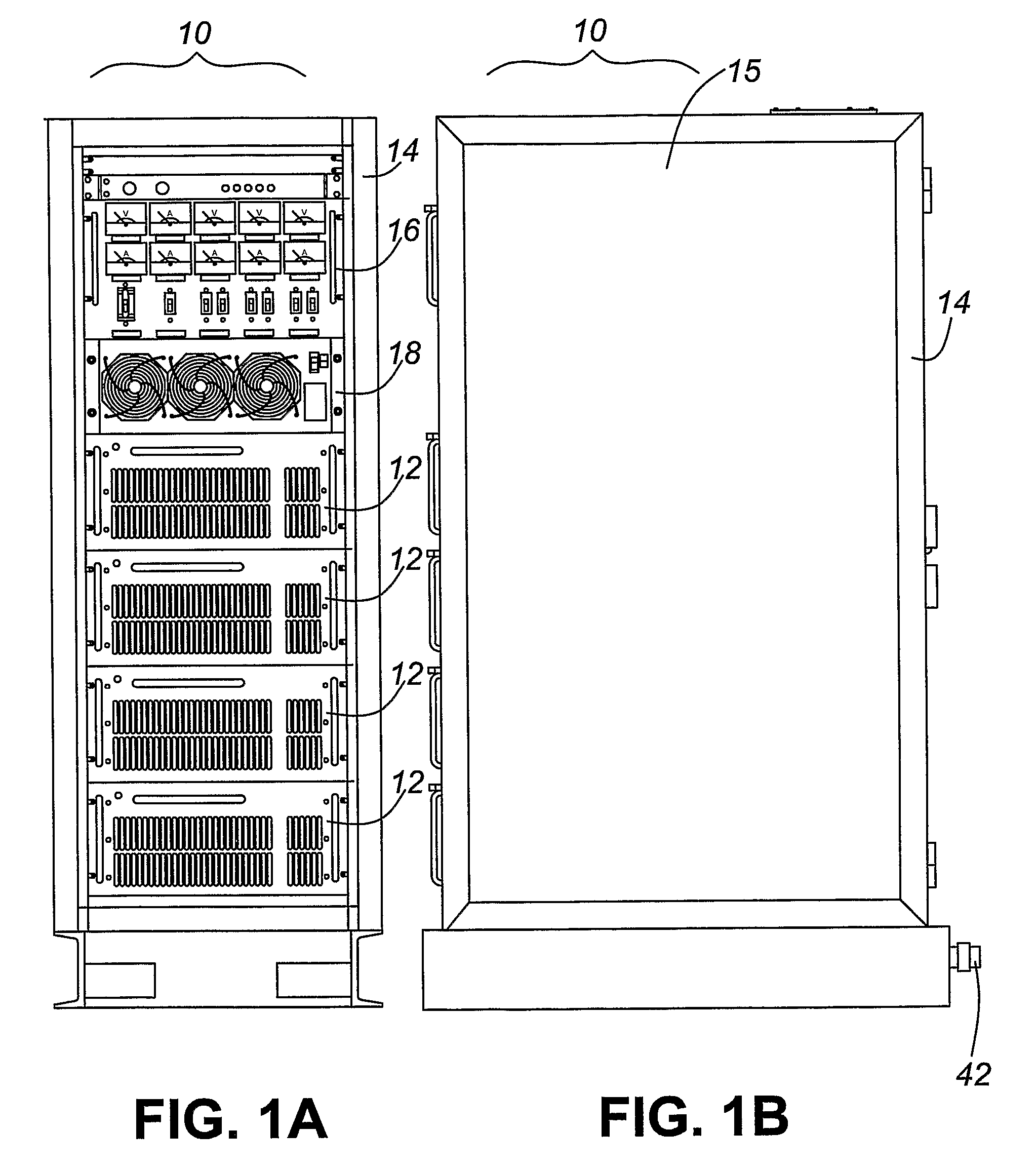
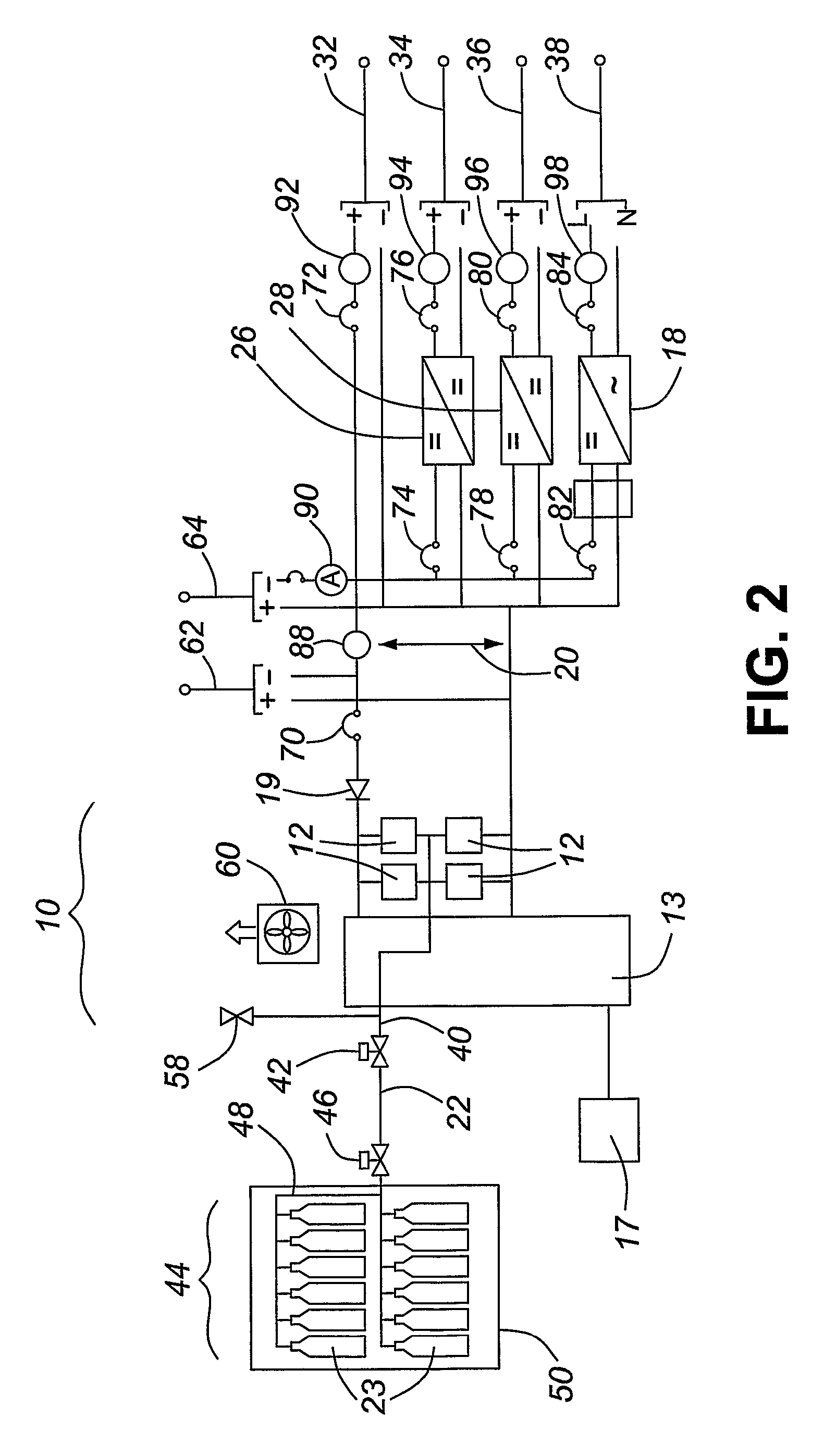
Fuel cell power generation system
InactiveUS8216732B2Relieve pressureDc network circuit arrangementsBatteries circuit arrangementsElectricityPower flow
An electric power generator is particularly suitable for providing back-up power to sites with multiple power requirements. This generator comprises a rack having multiple module bays; at least one power conversion module is mounted in one of the bays and is electrically coupled to a fuel cell stack also mounted in the rack or located remote from the rack. The power conversion module converts the voltage level and / or current type of some of the electricity produced by the stack such that the generator can simultaneously output electricity at multiple voltage levels and / or current types. The rack can be a standardized nineteen relay rack, making the generator relatively compact and compatible with sites configured accept such racks.
Owner:BRITISH COLUMBIA HYDRO & POWER AUTHORITY
Method for preventing relay-attack on smart key system
The present invention relates to a method for preventing a relay-attack on a smart key system, and in particular, provides an advantage of preventing a vehicle and equipment stored inside the vehicle from being stolen by using predetermined information transmitted and received when the SMK UNIT of the vehicle and a FOB Key wirelessly communicate with each other and enabling a holder of the FOB Key to make the relay-attack once the holder secures visibility from the vehicle.
Owner:SEOYON ELECTRONICS CO LTD
Device Proximity Detection
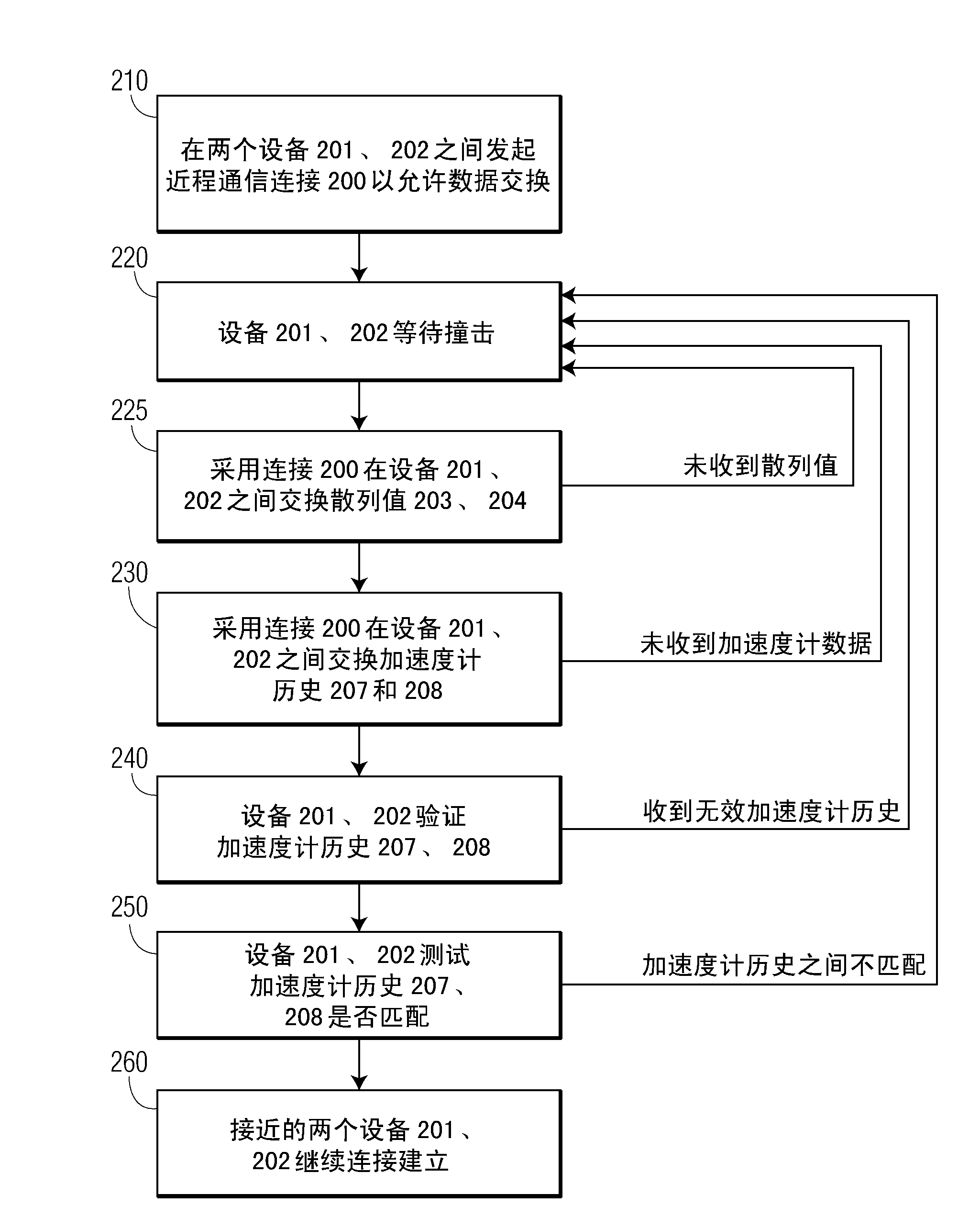
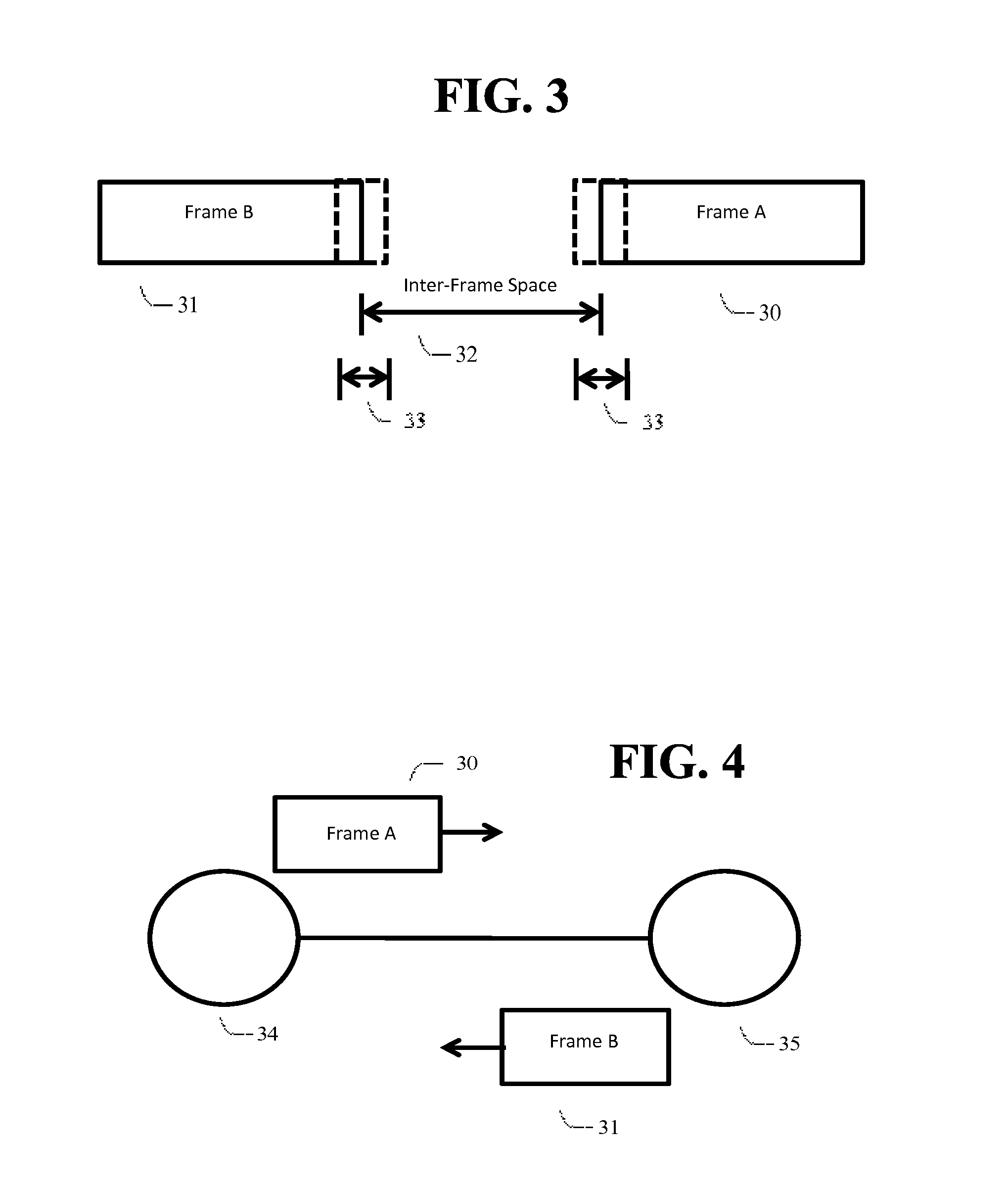
InactiveUS20150280843A1Prevent and mitigate relay attackSynchronisation arrangementReceivers monitoringInter frame spaceCommunication device
A method for detecting proximity of two communicating devices is disclosed. Proximity may be determined by measuring deviation from standardized signal timing specifications. An embodiment uses inter-frame space parameters specified by the Bluetooth Low Energy protocol to do proximity detection, and presents a solution that may prevent or mitigate relay attacks. The method offers the advantage that the use of an existent frame timing protocol eliminates the need for specific hardware or firmware modifications.
Owner:GOOGLE LLC
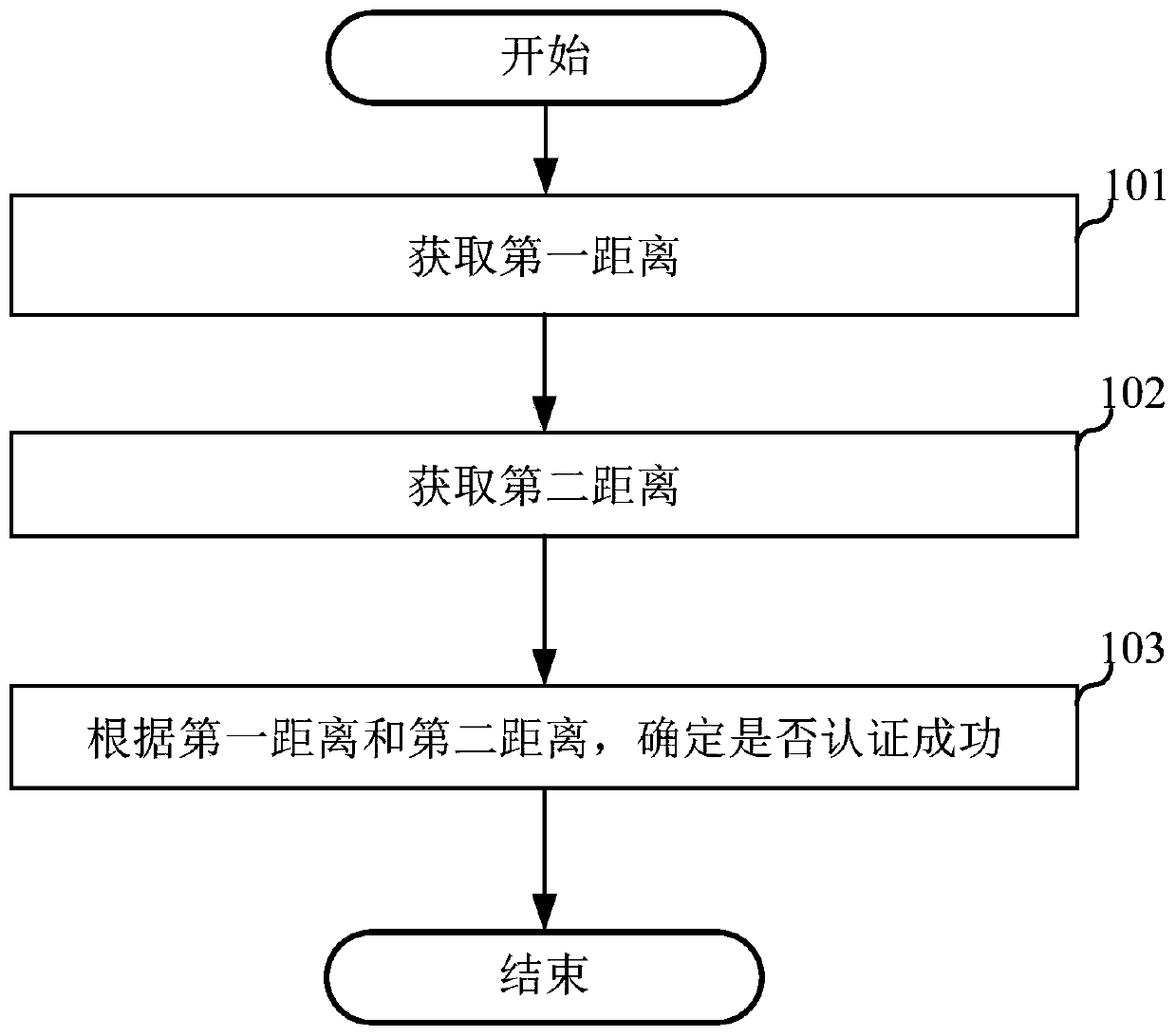
Authentication method and equipment, electronic equipment and storage medium
InactiveCN110223425AThe certification result is accurateAuthentication results are safeIndividual entry/exit registersSecurity arrangementComputer engineeringElectronic equipment
The embodiments of the invention relate to the field of authentication, and disclose an authentication method and equipment, electronic equipment and a storage medium. In the authentication method andequipment, the electronic equipment and the storage medium, the authentication method includes the steps that a first distance is acquired, and the first distance is a distance between first equipment and equipment which directly transmits a first authentication request to the first equipment, wherein the first authentication request is originally generated and sent by second equipment; a seconddistance is acquired, and the second distance is a distance between the second equipment and equipment which directly transmits a second authentication request to the second equipment, wherein the second authentication request is originally generated and sent by the first equipment; and according to the first distance and the second distance, whether the authentication is successful or not is determined. Bidirectional positioning is carried out through the first equipment and the second equipment, the first distance is compared with the second distance, according to the comparison result, whether the authentication is successful or not is determined, the security of the first equipment is ensured, and the relay attack is effectively prevented.
Owner:上海银基信息安全技术股份有限公司
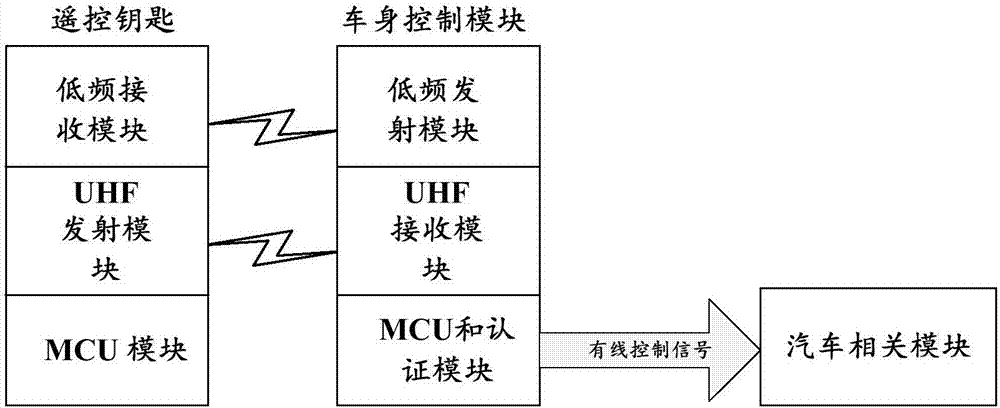
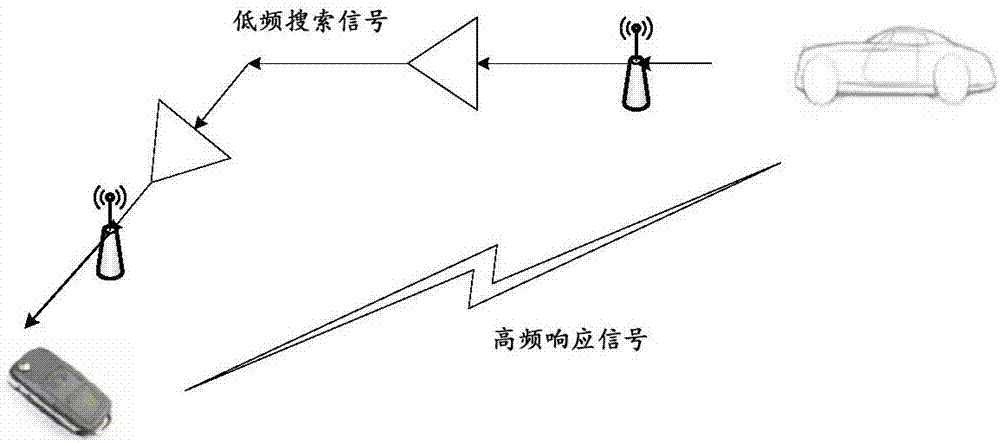
Identity authentication method and device
ActiveCN107968766AImprove signal-to-noise ratioAvoiding Relay Attack ProblemsTransmissionSecurity arrangementComputer hardwareSignal-to-noise ratio (imaging)
Embodiments of the invention provide an identity authentication method and device. The method comprises the steps of determining signal intensity of a received response signal sent by a second authentication object and a signal to noise ratio corresponding to the signal intensity, wherein the response signal is used for responding to a search signal sent by a first authentication object; and authenticating the identity of the second authentication object according to the signal intensity of the response signal and the signal to noise ratio and standard signal intensity as well as standard signal to noise ratio. If the signal intensity of a response signal received by the first authentication object (such as a car) is greater than the standard signal intensity, but the signal to noise ratiothereof is less than the standard signal to noise ratio, the first authentication object receives relay attack, then authentication of the second authentication object by the first authentication object fails, so as to prevent relay attack in identity authentication.
Owner:CHINA MOBILE COMM LTD RES INST +1
Relay method for service data and relay node system
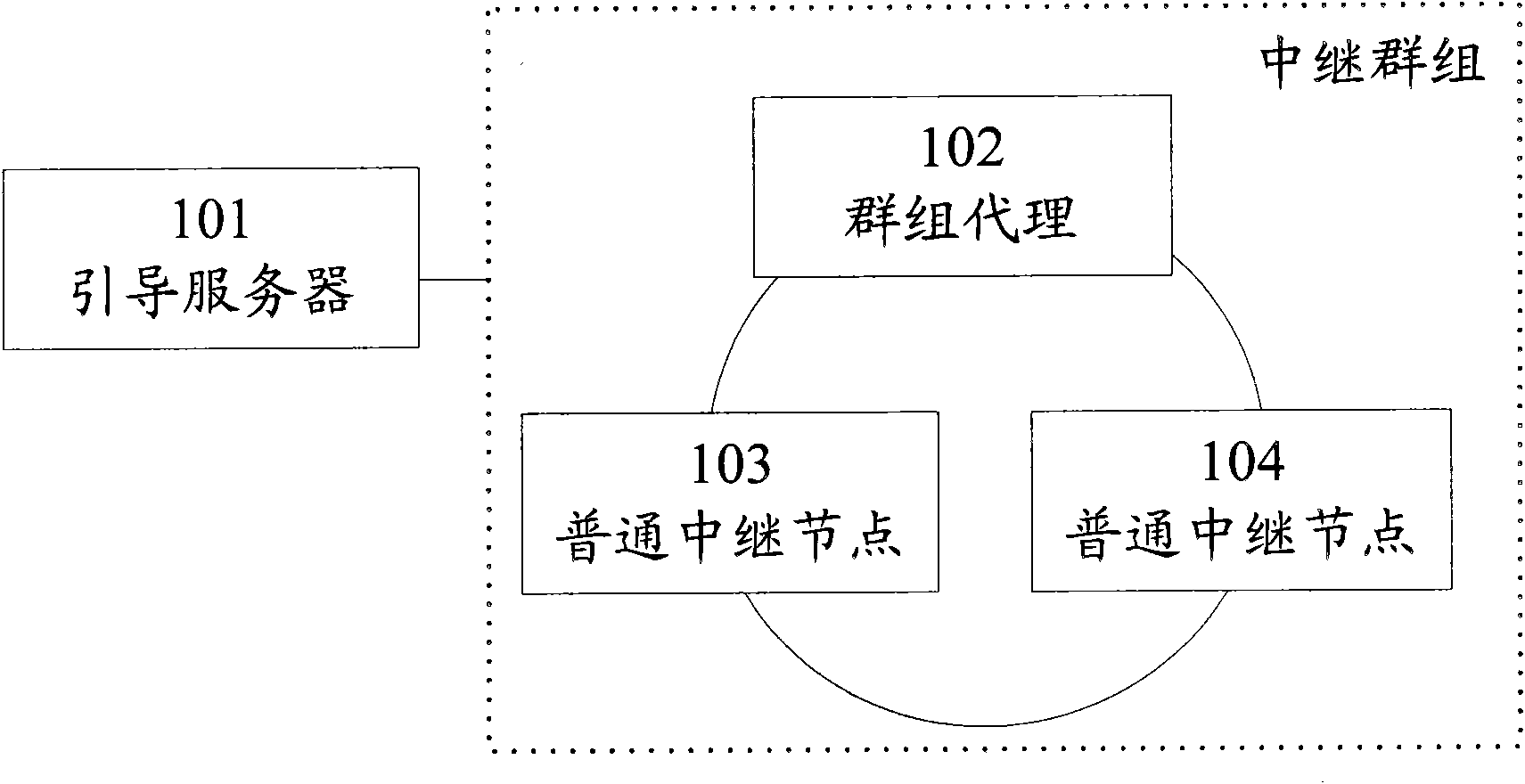
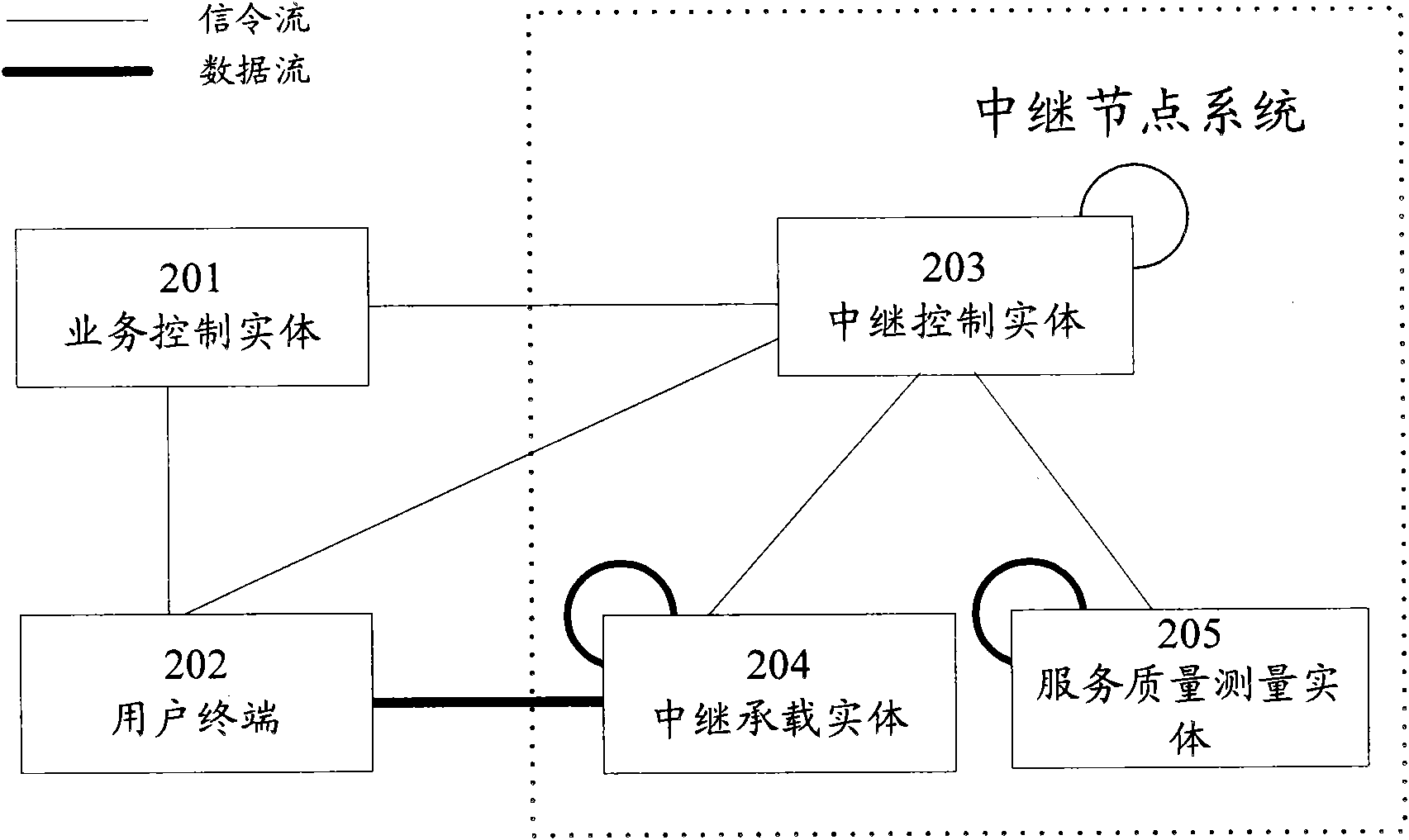
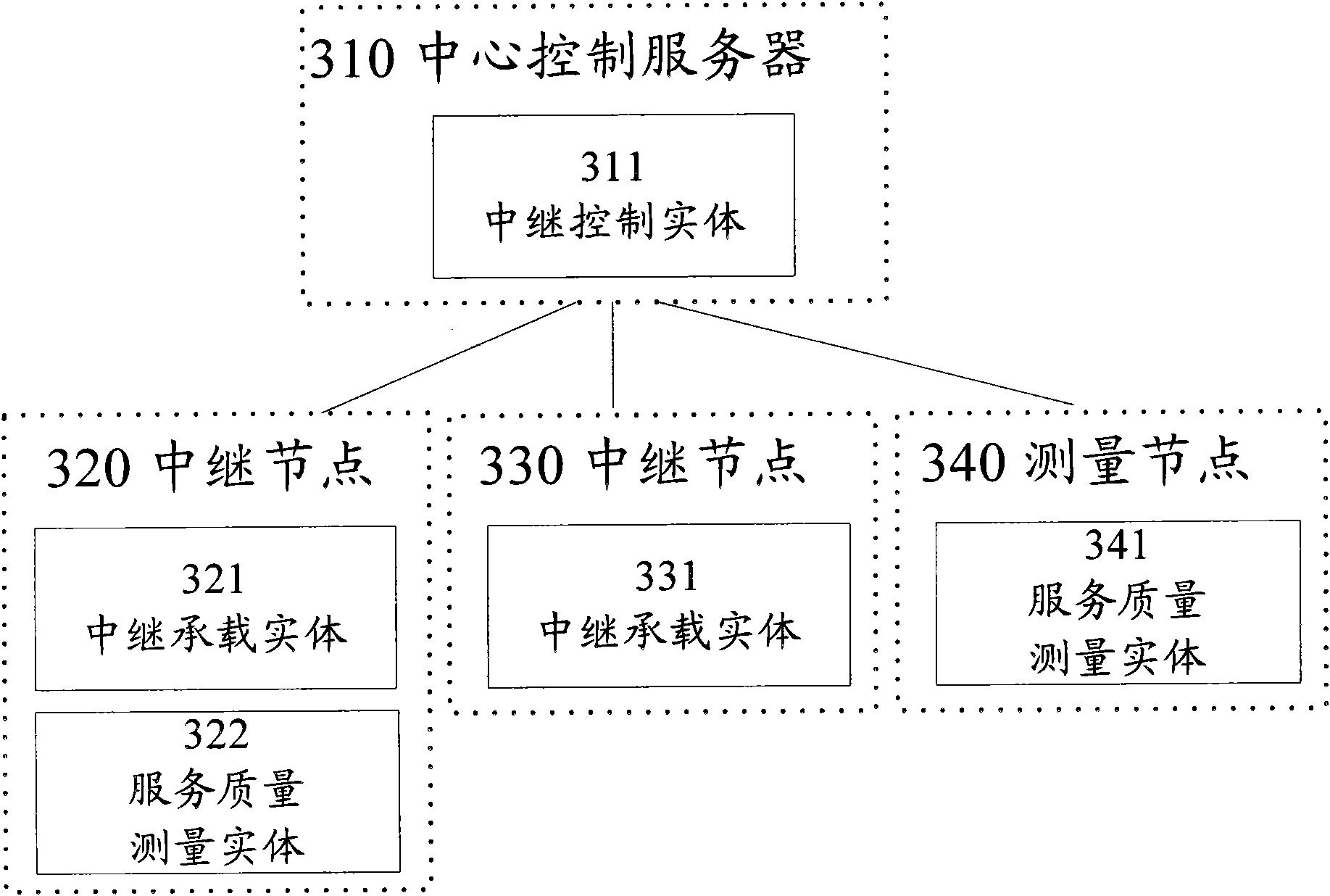
InactiveCN102316086AFlexible configurationReduce the difficulty of implementationRadio transmissionData switching networksQuality of serviceDistributed computing
The invention discloses a relay method for service data and a relay node system. The relay node system comprises a relay control entity, a relay bearing entity and a quality of service measurement entity, wherein the relay control entity is used for receiving a relay request, selecting the relay bearing entity for a relay task requested by the relay request, requesting the relay bearing entity to execute the relay task and acquiring quality of service measurement information from the quality of service measurement entity; the relay bearing entity is used for executing the relay task and relaying the service data related to the relay task; and the quality of service measurement entity is used for executing a quality of service measurement task and reporting the obtained quality of service measurement information to the relay control entity. By the method and the system, each function entity of a relay node can be flexibly configured.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com