Identity authentication method and device
An identity authentication and authentication module technology, applied in the field of identity authentication, can solve the problems of ineffective resistance to relay attacks, high cost, and inability to resist attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0085] see Figure 5 , the figure shows a method of identity authentication, which is suitable for the first authentication object, and the specific steps are as follows:
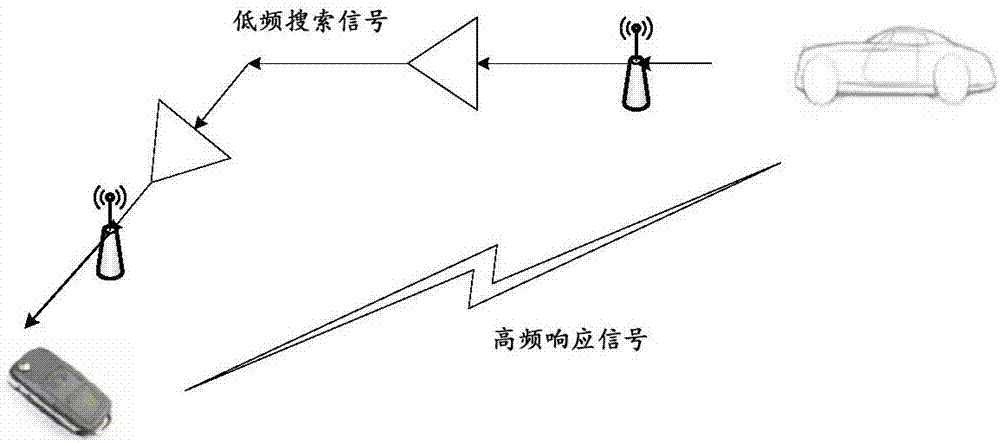
[0086] Step 501. Determine the signal strength of the received response signal sent by the second authentication object and the signal-to-noise ratio corresponding to the signal strength, and the response signal is used to respond to the search signal sent by the first authentication object;
[0087] The above-mentioned response signal may be a UHF response signal. Of course, it should be noted that the frequency of the response signal is not limited in this embodiment.
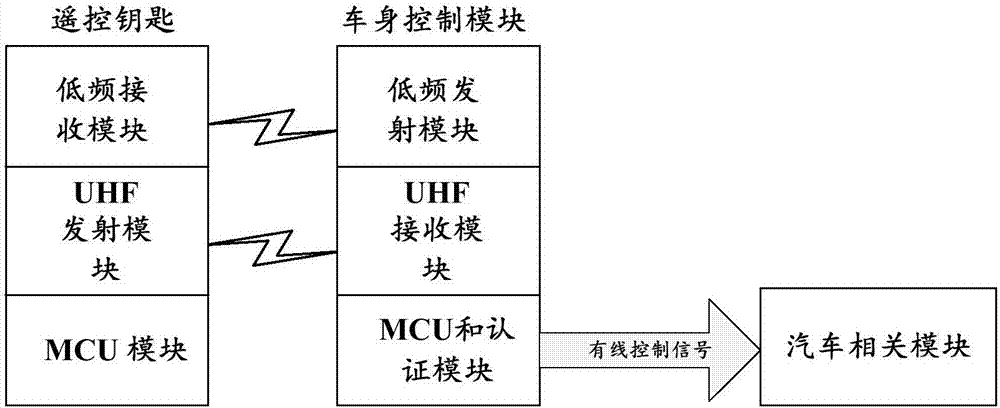
[0088] The above-mentioned first authentication object can be a car, and the corresponding second authentication object can be a remote control key (or called a remote control car key). Of course, it can be understood that the above-mentioned first authentication object and second authentication object can also be other products.
[0089]...
Embodiment 2
[0102] see Figure 6 , the figure shows a method of identity authentication, which is applicable to the second authentication object, and the specific steps are as follows:
[0103] Step 601. Receive a search signal sent by the first authentication object;
[0104] The above-mentioned first authentication object can be a car, and the corresponding second authentication object can be a remote control key (or called a remote control car key). Of course, it can be understood that the above-mentioned first authentication object and second authentication object can also be other products.
[0105] Step 602: Send a response signal for responding to the search signal to the first authentication object, so that the first authentication object performs a search on the first authentication object according to the signal strength and signal-to-noise ratio of the response signal and the standard signal strength and standard signal-to-noise ratio. 2. The authentication object performs ide...
Embodiment 3
[0114] In this embodiment, taking the first authentication object as a car and the second authentication object as a remote control key as an example, the applicable scenario is the keyless entry of a car.
[0115] see Figure 7 , the car shown in the figure (taking an ordinary car as an example, assuming that the length is 4m and the width is 1.7m) is equipped with an antenna A with signal receiving and sending functions 1 and antenna A 2 , it should be noted that the above-mentioned antenna A is not limited in this embodiment 1 and antenna A 2 specific installation location. Example: Antenna A 1 and antenna A 2 Used to send LF search signal (or called low frequency search signal) and UHF test signal (or called UHF test signal), and receive UHF response signal (or called UHF response signal) and respond according to the received UHF The strength of the signal determines the distance between the remote key and the car.
[0116] Assume that the original remote control ke...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com