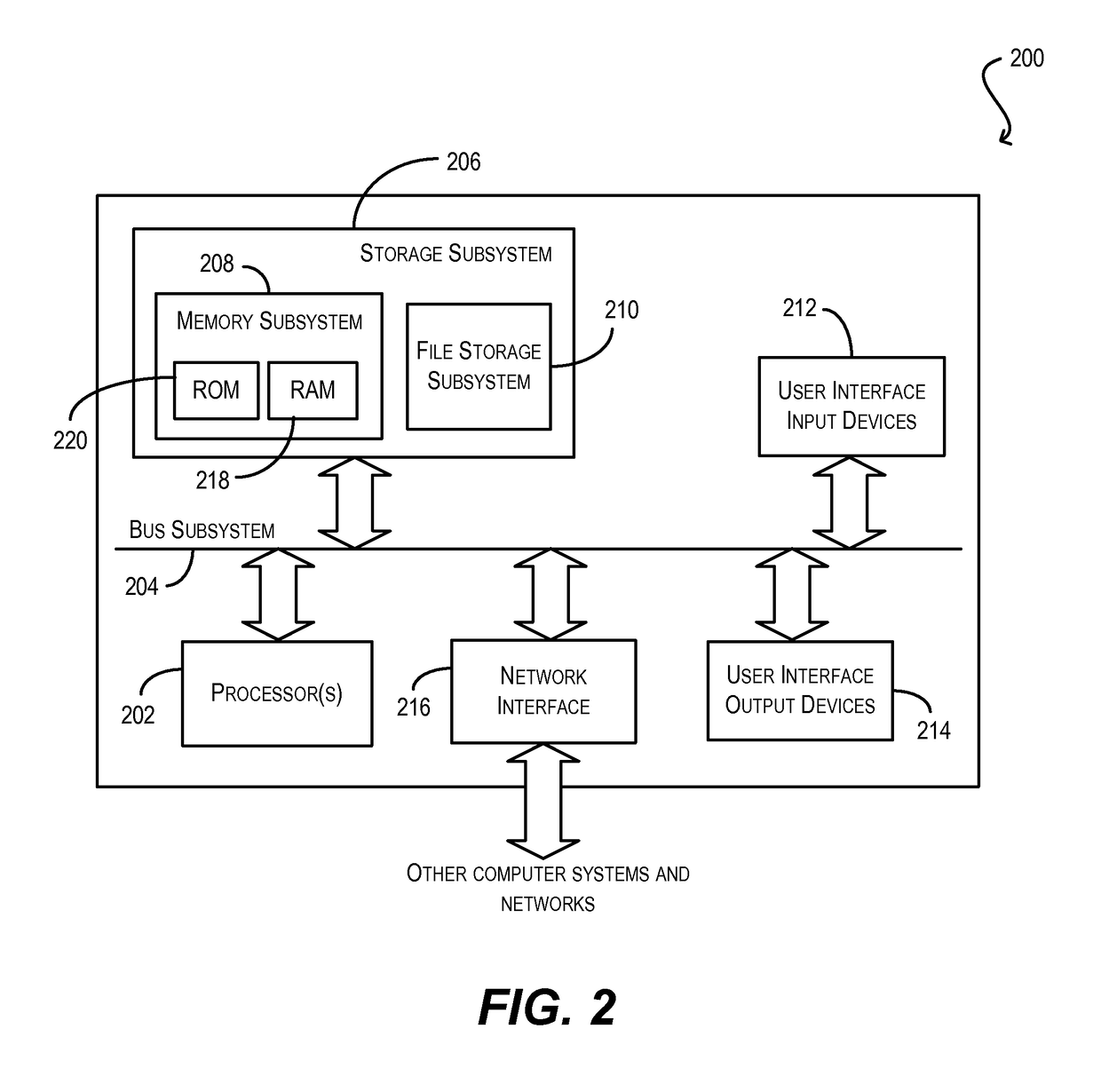
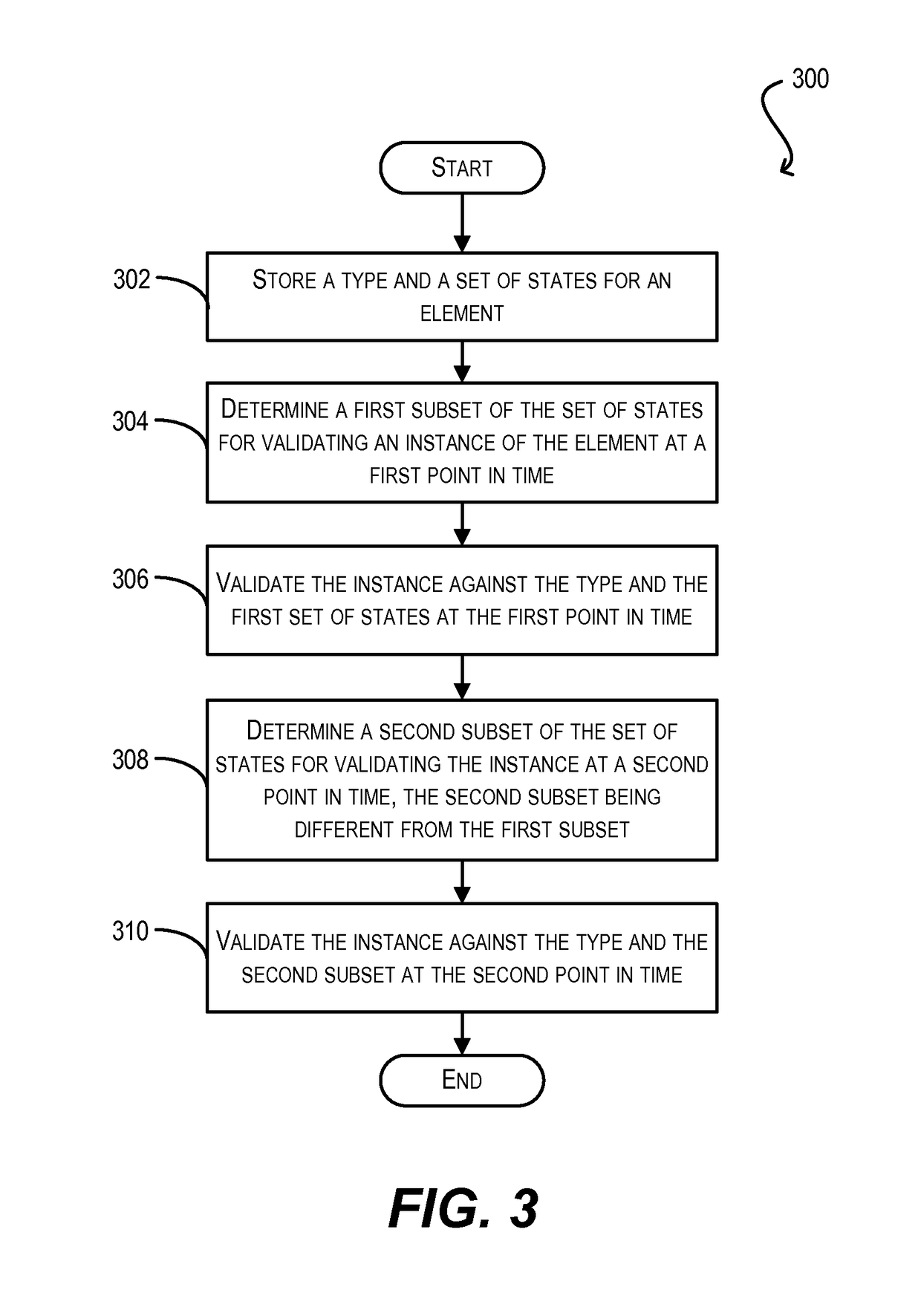
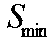Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
109 results about "Program model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
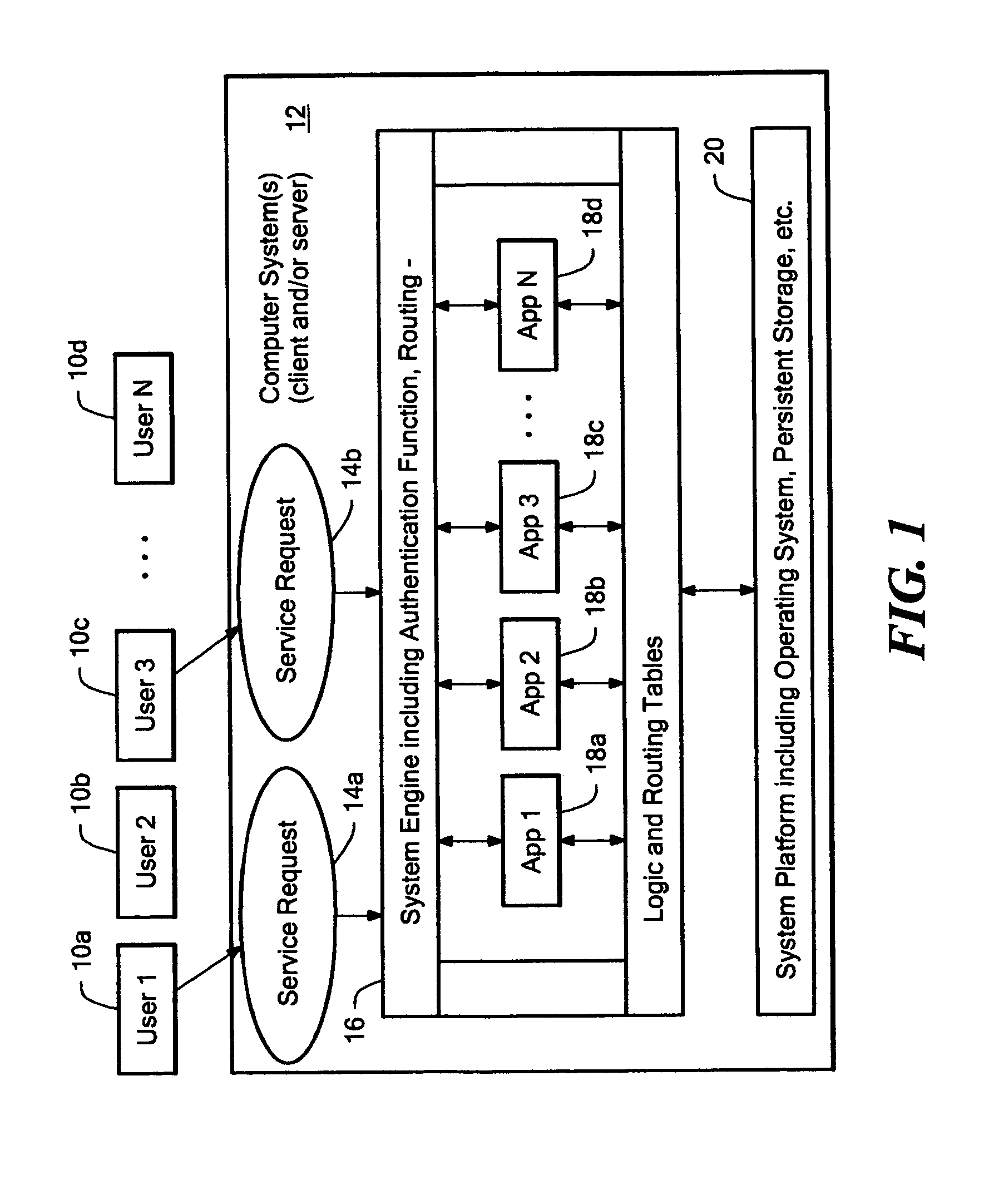
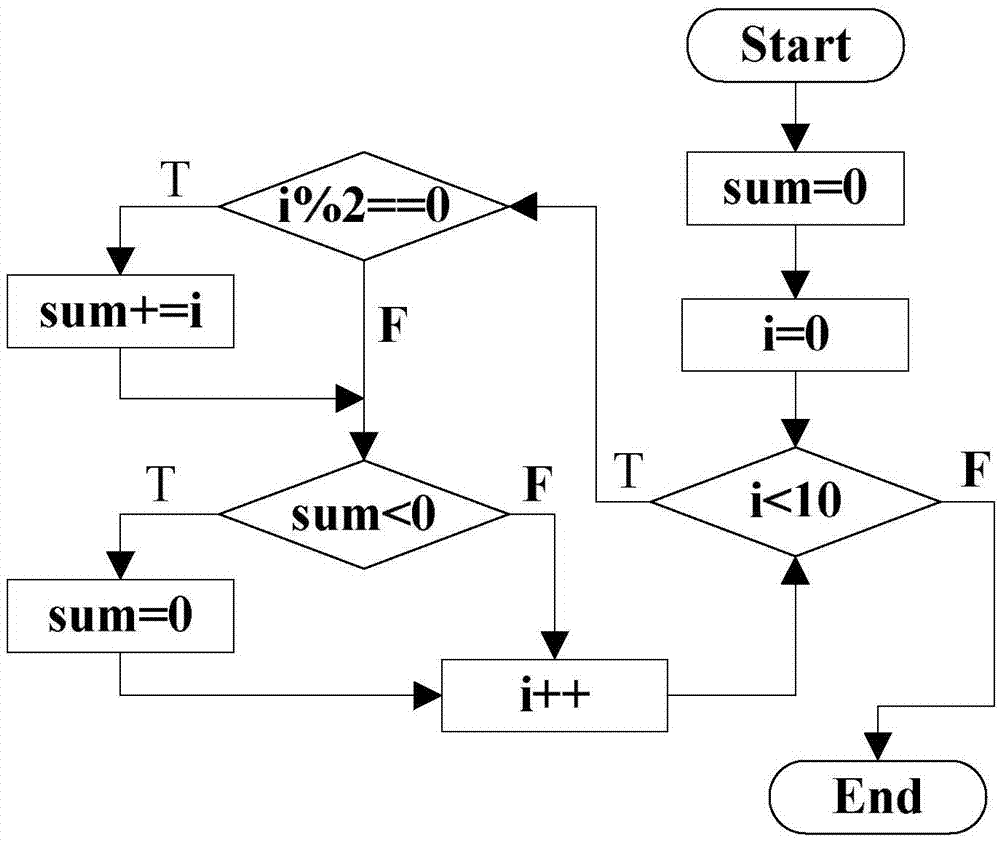
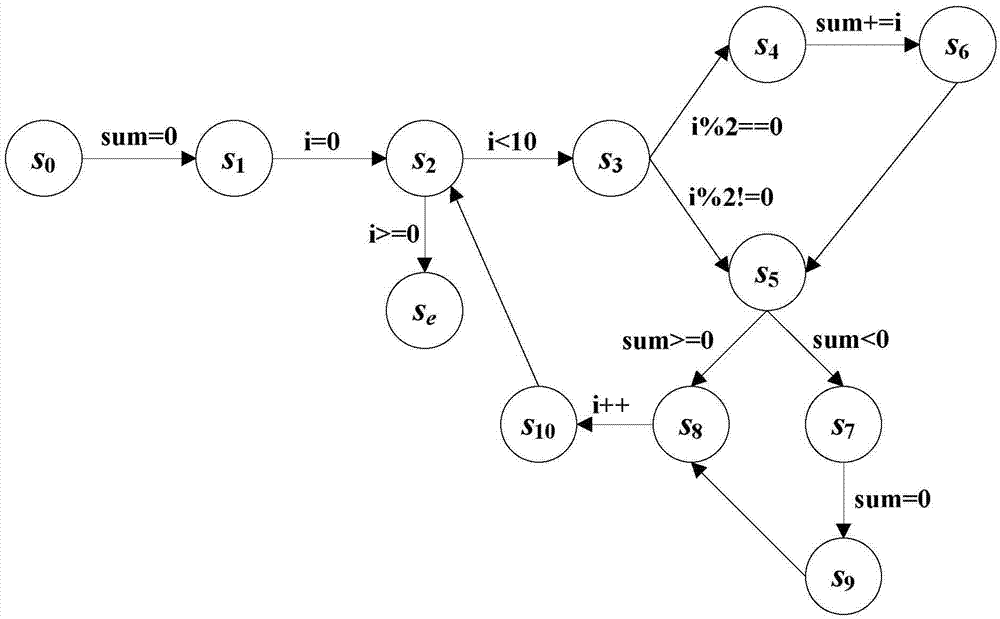
A model program is a set of rules written in a programming language, such as C#, that enables the expression of both interaction-oriented and state-oriented modeling styles. In this documentation, the terms model program and rule program are synonymous. In Spec Explorer, the modeling effort involves writing a model program class...
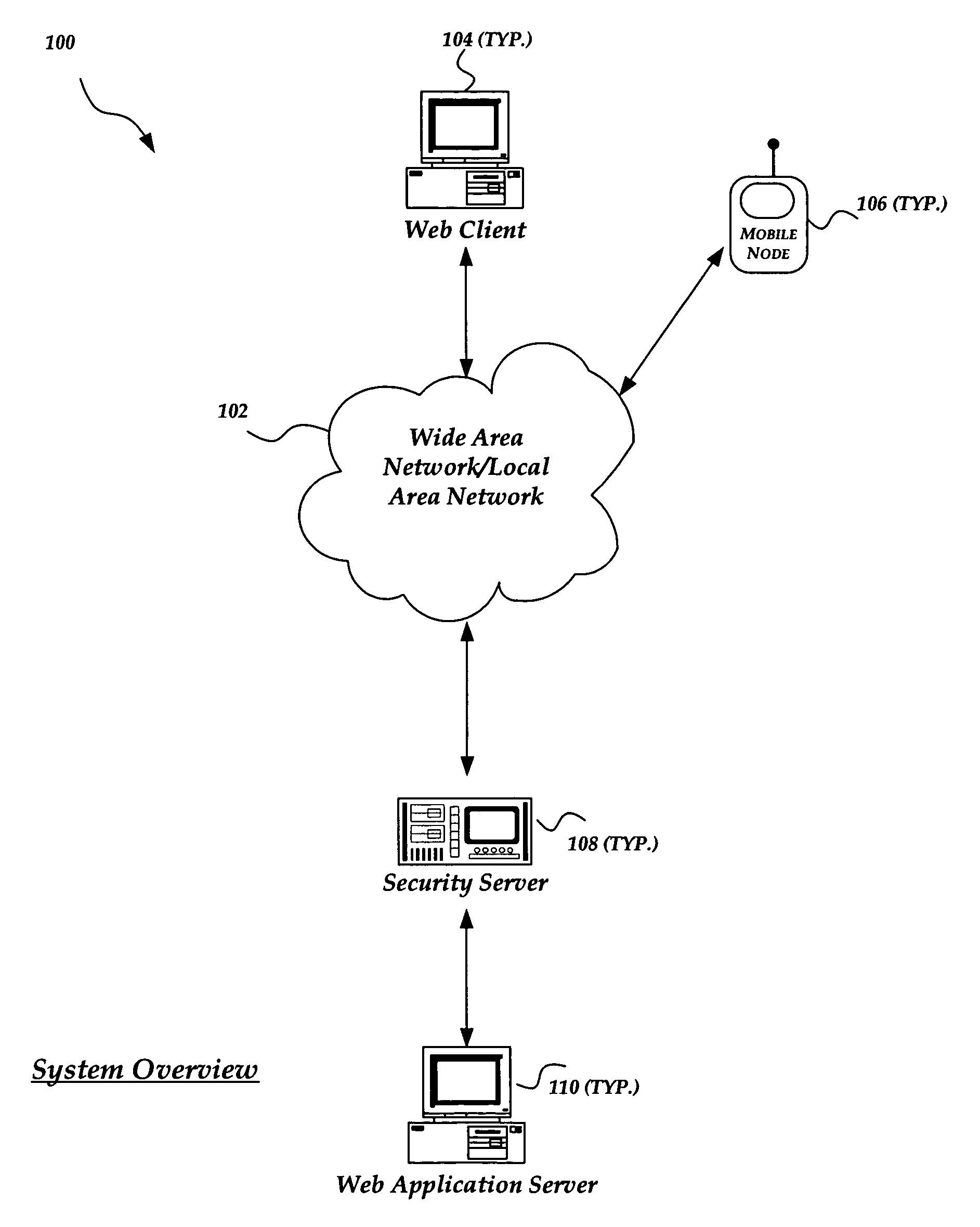
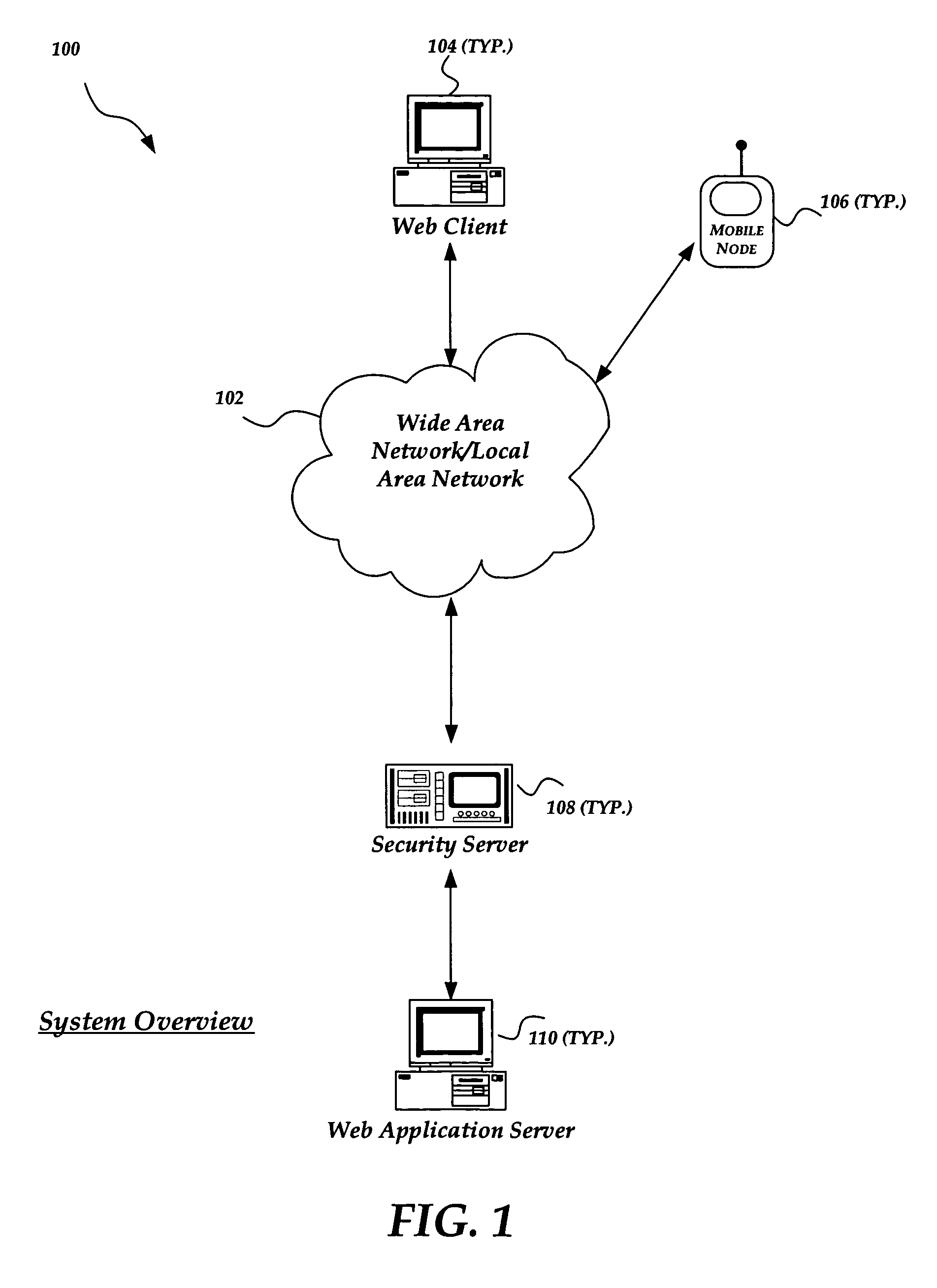
Security for WAP servers
ActiveUS7472413B1Digital data processing detailsMultiple digital computer combinationsApplication serverWeb application
A method and system for improving the security and control of internet / network web application processes, such as web applications. The invention enables validation of requests from web clients before the request reaches a web application server. Incoming web client requests are compared to an application model that may include an allowed navigation path within an underlying web application. Requests inconsistent with the application model are blocked before reaching the application server. The invention may also verify that application state data sent to application servers has not been inappropriately modified. Furthermore, the invention enables application models to be automatically generated by employing, for example, a web crawler to probe target applications. Once a preliminary application model is generated it can be operated in a training mode. An administrator may tune the application model by adding a request that was incorrectly marked as non-compliant to the application model.
Owner:F5 NETWORKS INC
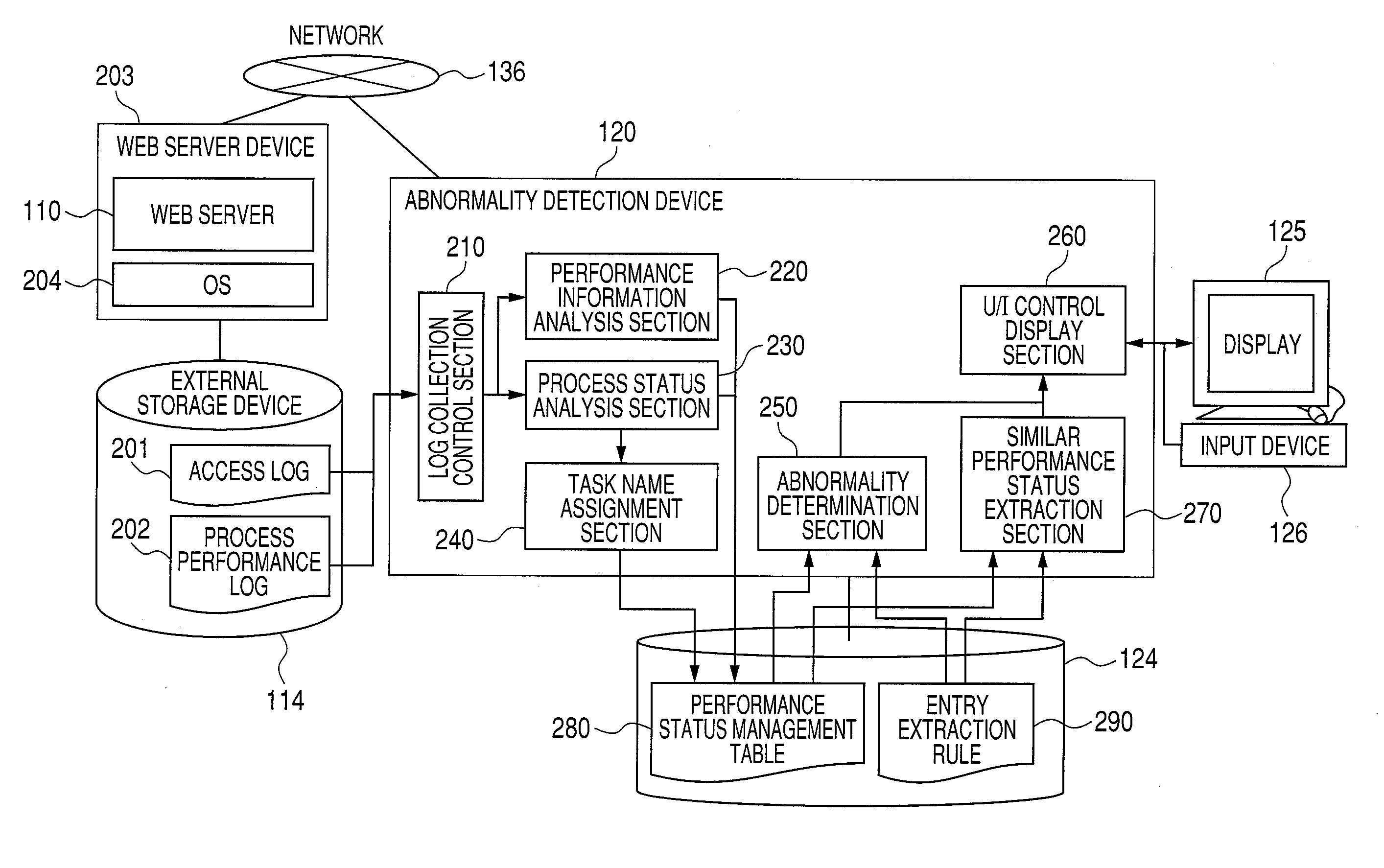
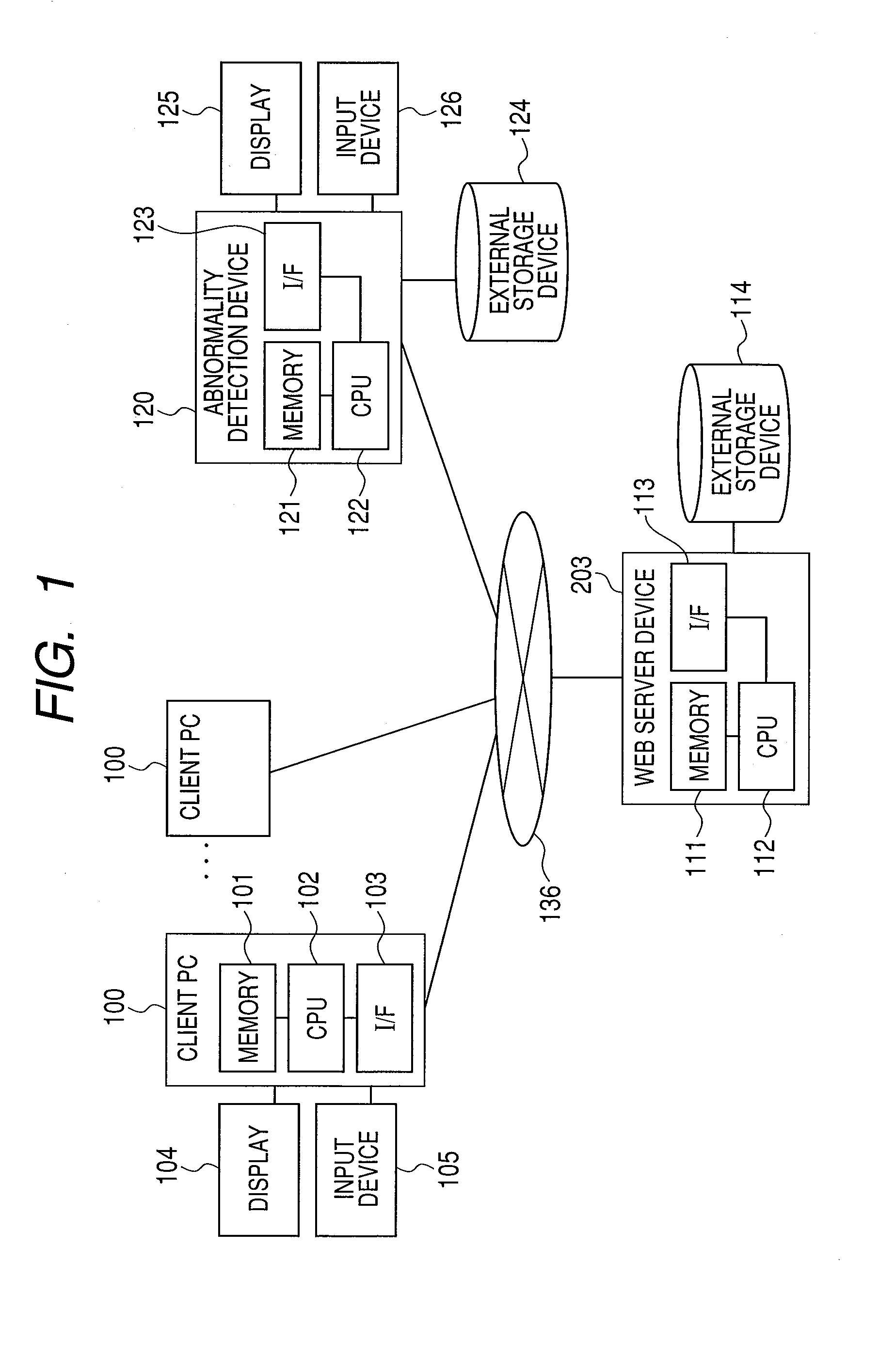
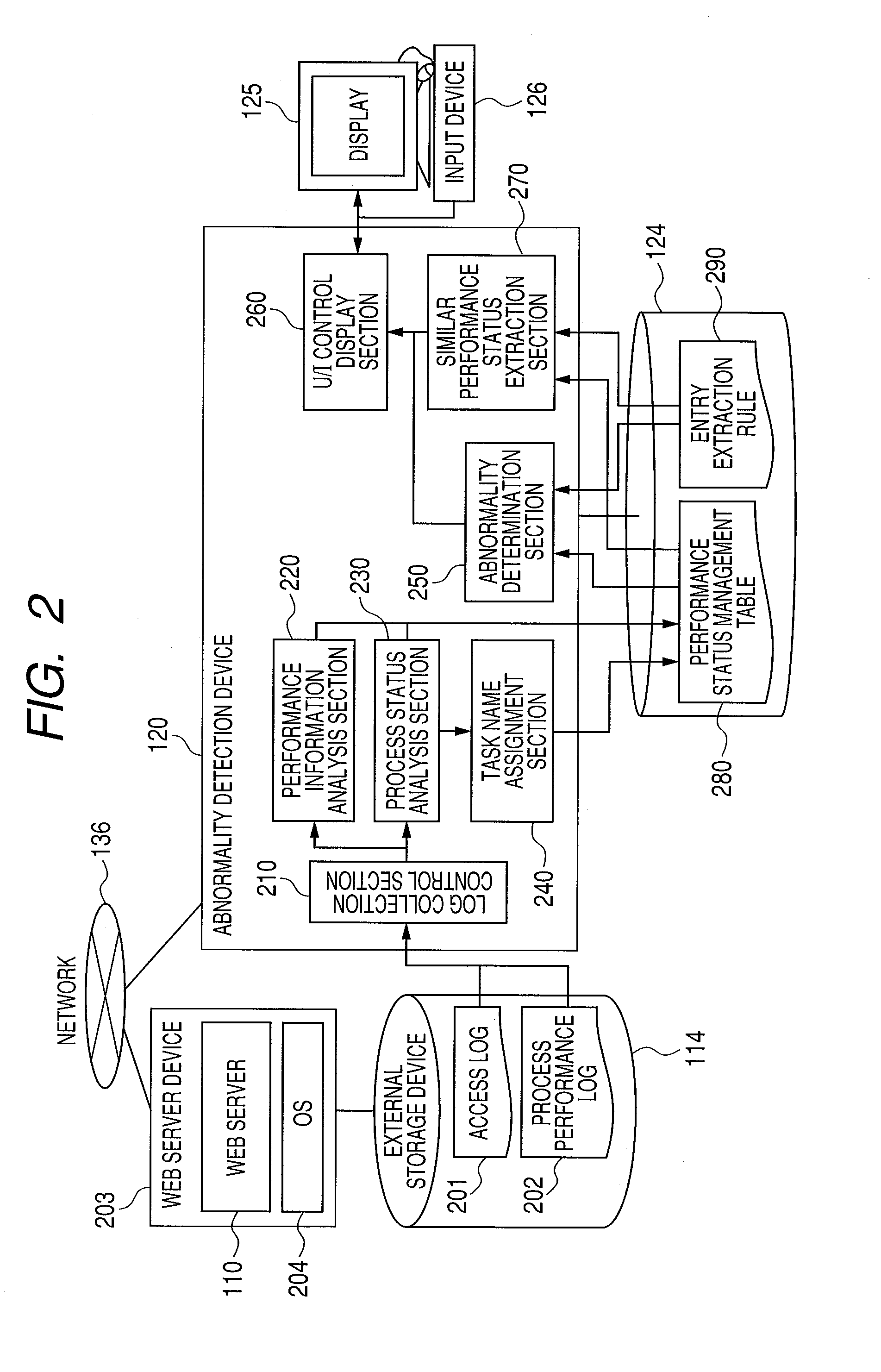
Abnormality detection method, device and program
InactiveUS20110029817A1Improve accuracyLess timeNon-redundant fault processingInformation analysisAnomaly detection
Model data is generated from performance information sorted by day of the week, time period, and process status by a performance information analysis section and a process status analysis section. An abnormality determination section detects abnormality using appropriate model data. What the graph of an expected status is like, how much the graph of the current status that has been determined abnormal differs from the graph of the expected status, and how much the current status is like the expected status are displayed allowing a system manager to observe detailed information about abnormality determination.
Owner:HITACHI LTD
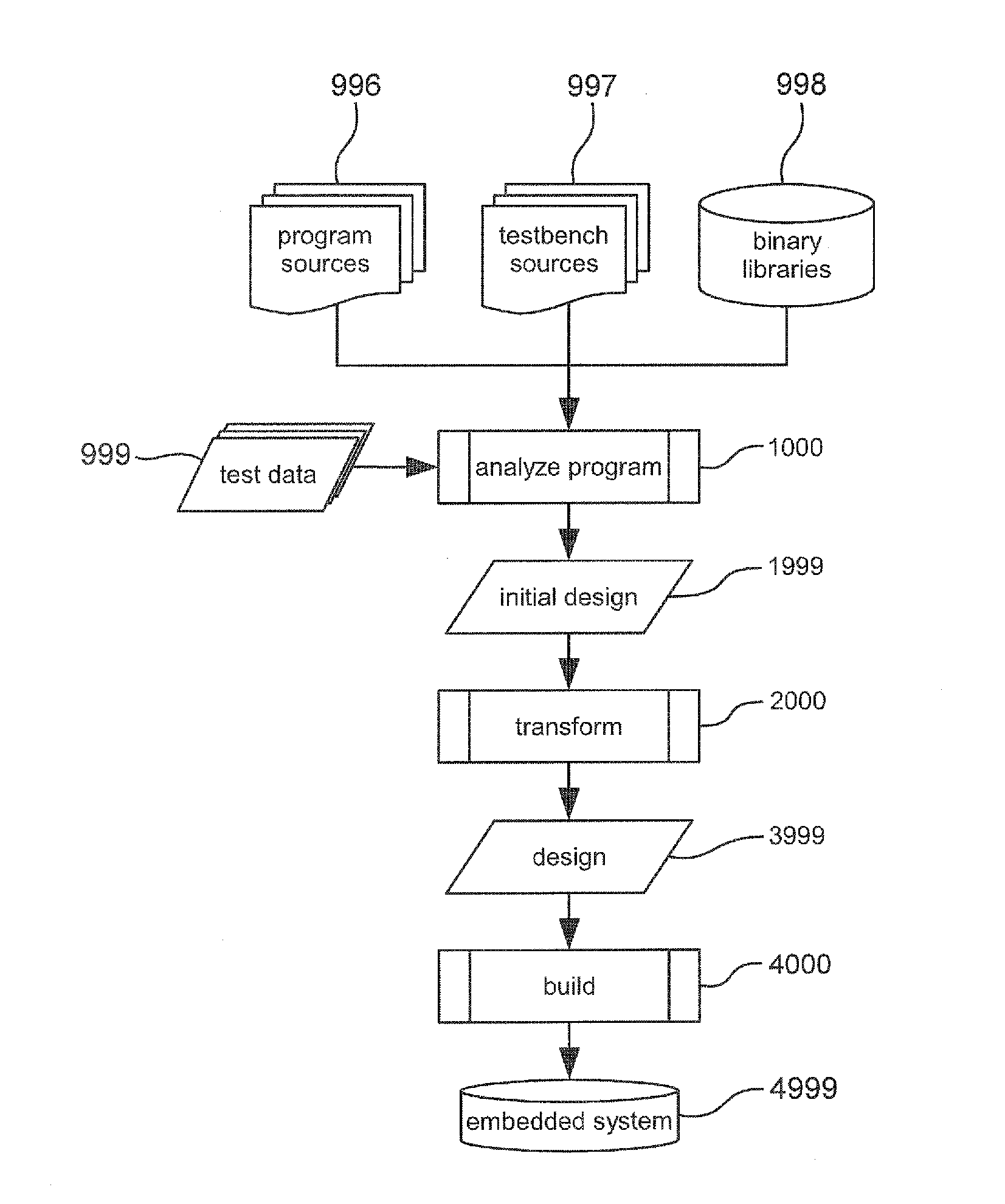
Embedded system performance
InactiveUS20130080993A1Good choiceLow costModel driven codeSpecific program execution arrangementsParallel computingSystem usage
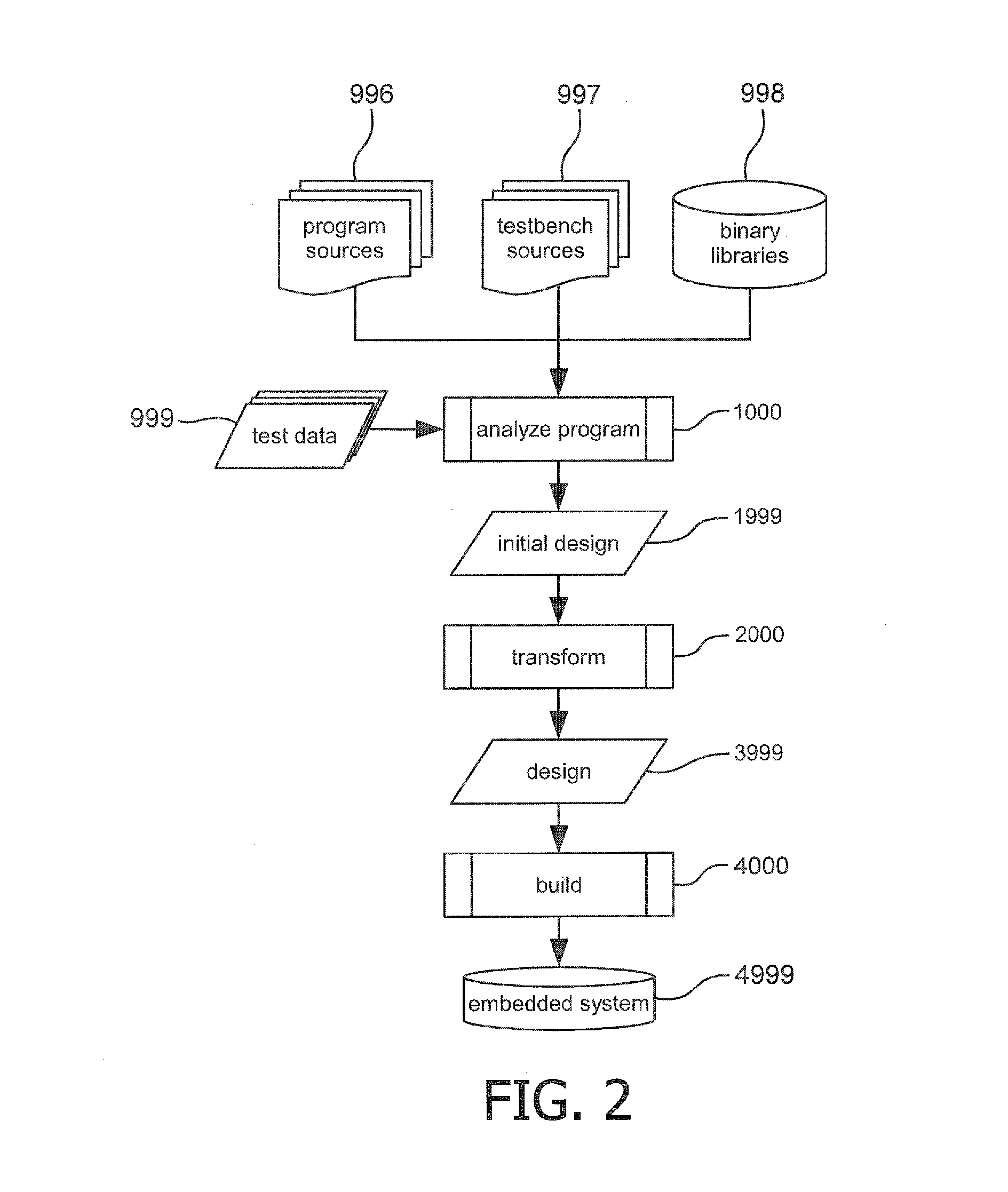
A method of generating an embedded system (4999) from an original computer program (996) which embedded system (4999) provides a parallellized hardware (4598) and software (4599) implementation of the original computer program (996), which parallellized implementation (4598, 4599) satisfies one or more criteria regarding hardware constraints of the embedded system (4999). The system provides partitioning of functionality from the original computer program (996) using structural and behavioral program models and detects streaming and memory dependencies to improve the partitioning, relying on added indications of source lines and variables in said original computer program to relate partitions and dependencies in the program model with locations in the original program source code.
Owner:VECTOR FABRICS BV
Methods for enhancing program analysis
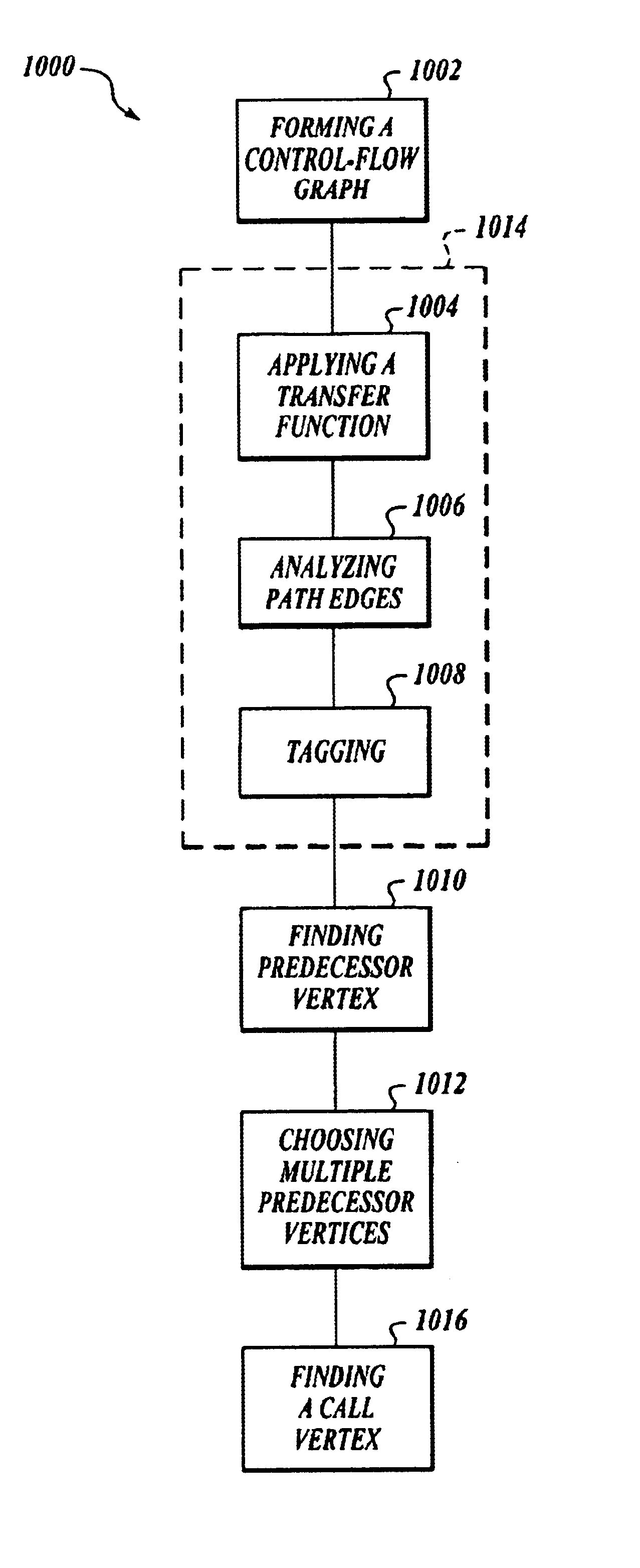
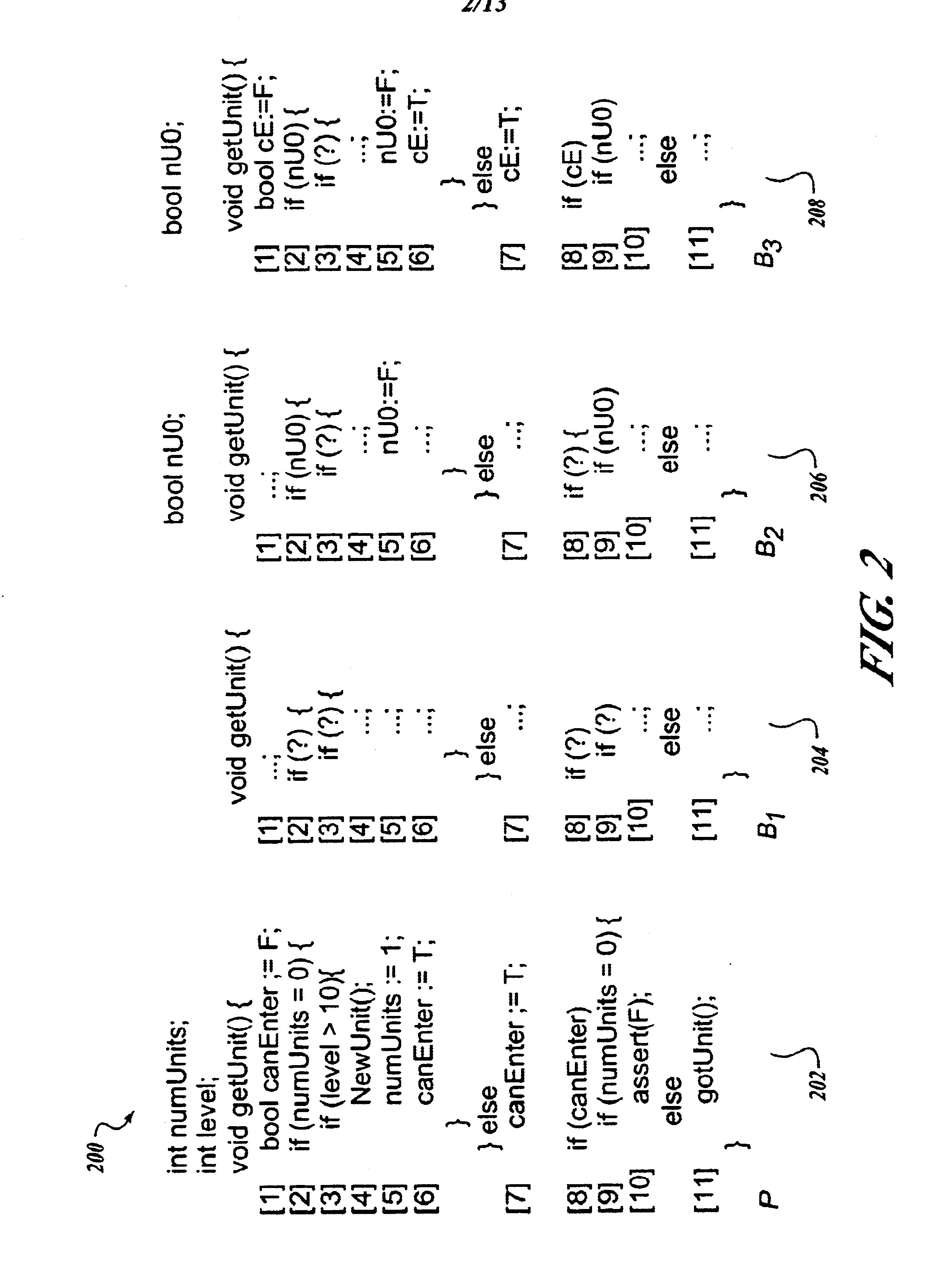
InactiveUS6904590B2Enhance program analysisInhibit computational explosionSoftware testing/debuggingSpecific program execution arrangementsTheoretical computer scienceProgram analysis
Methods are discussed that enhance program analysis. One aspect of the invention includes a method for checking a model of a program. The method includes a control-flow graph having vertices from the model, applying a transfer function to each vertex to form a set of path edges, and analyzing the set of path edges of a vertex. The set of path edges includes valuations that are implicitly represented so as to inhibit an undesired explosion in the valuations that would hinder the act of analyzing.
Owner:MICROSOFT TECH LICENSING LLC
Intersection signal control and speed guidance system in cooperative vehicle infrastructure environment
ActiveCN110085037ARealize green wave traffic travelReduce delaysControlling traffic signalsTransmission systemsGuidance systemInformation transmission
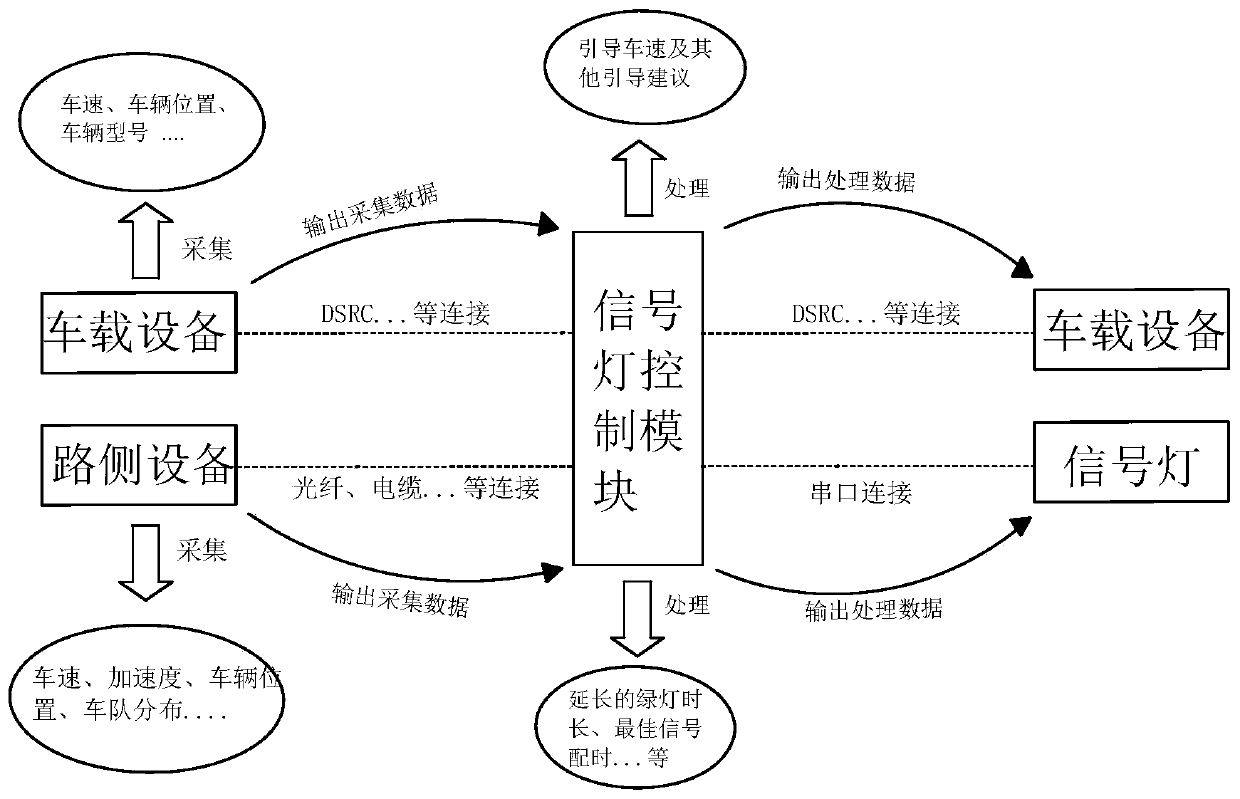
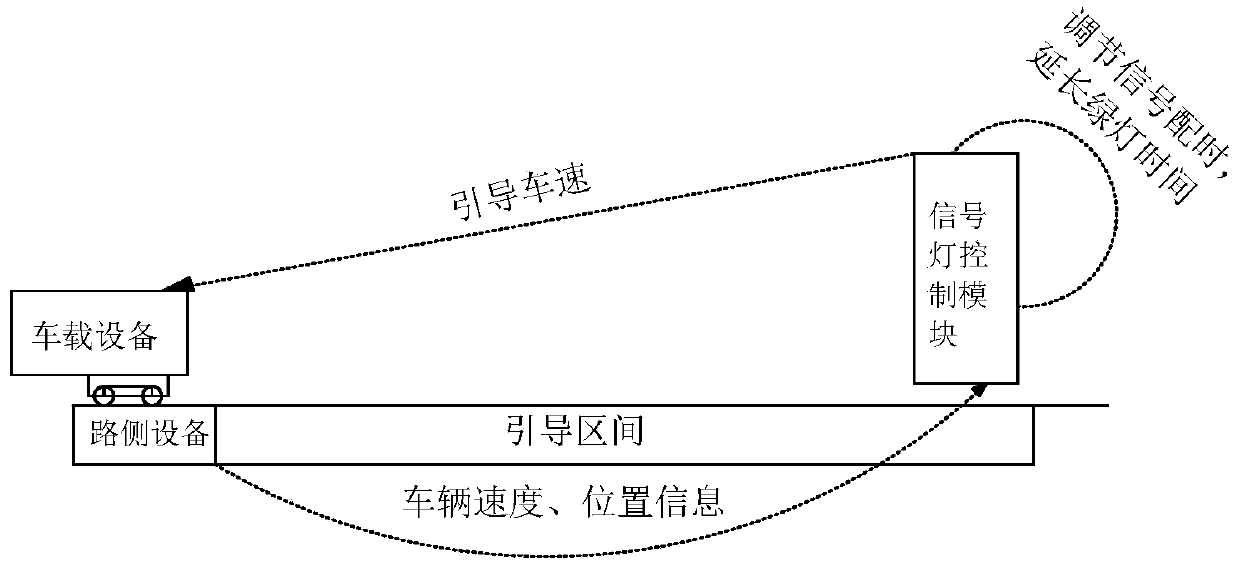
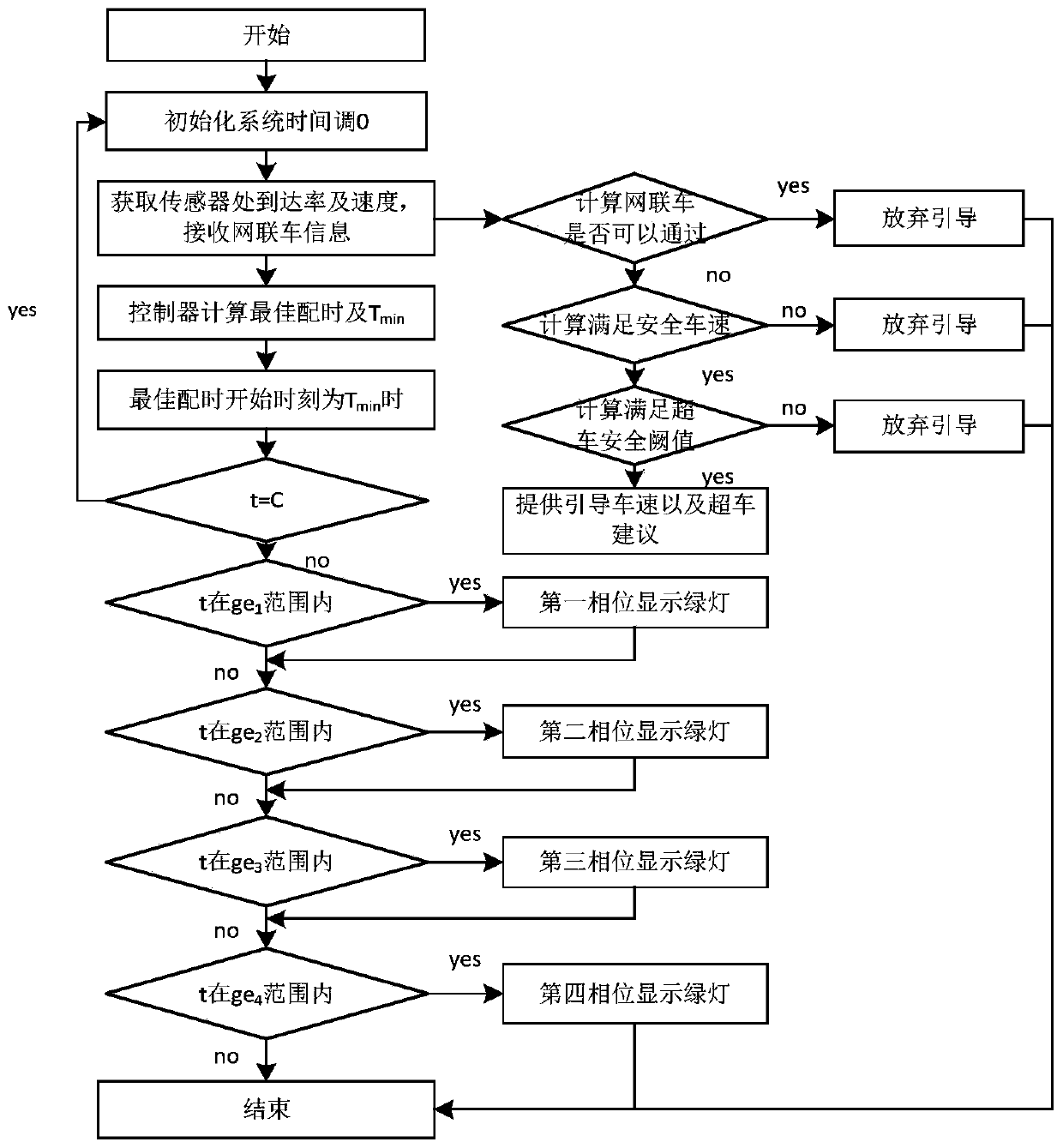
The invention discloses an intersection signal control and speed guidance system in a cooperative vehicle infrastructure environment. The system comprises on-board units, a road side unit and a signallight control module, wherein an on-board information transmission module in each on-board unit acquires vehicle information and transmits the vehicle information to the signal light control module,and the information fed back by the signal light control module is sent to an information acquisition module; a road side information acquisition module in the road side unit acquires road side information and stores the road side information into an intersection basic information storage module, the intersection basic information storage module pre-stores intersection information and historical data, and a wireless communication module wirelessly transmits the road side information, the intersection information and the historical data to the signal light control module; and in the signal light control module, optimal timing scheme information and travel advice information are obtained through calculation by use of a program model in the signal light control module based on the vehicle information, the road side information, the intersection information and the historical data, and the travel advice information is fed back to the on-board units.
Owner:HEFEI UNIV OF TECH
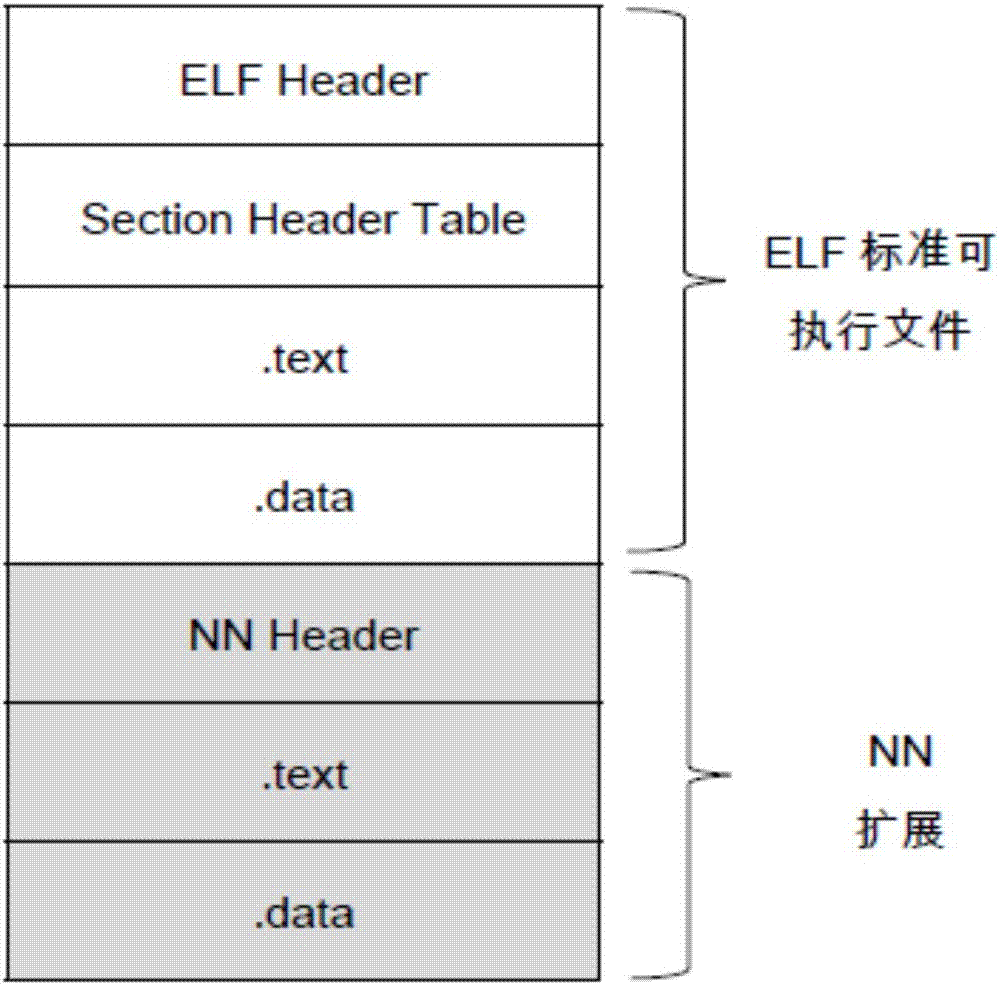
Programming model oriented to neural network heterogeneous computing platform
ActiveCN107239315AGood computing powerImprove scalabilityLink editingVersion controlNerve networkNetwork model
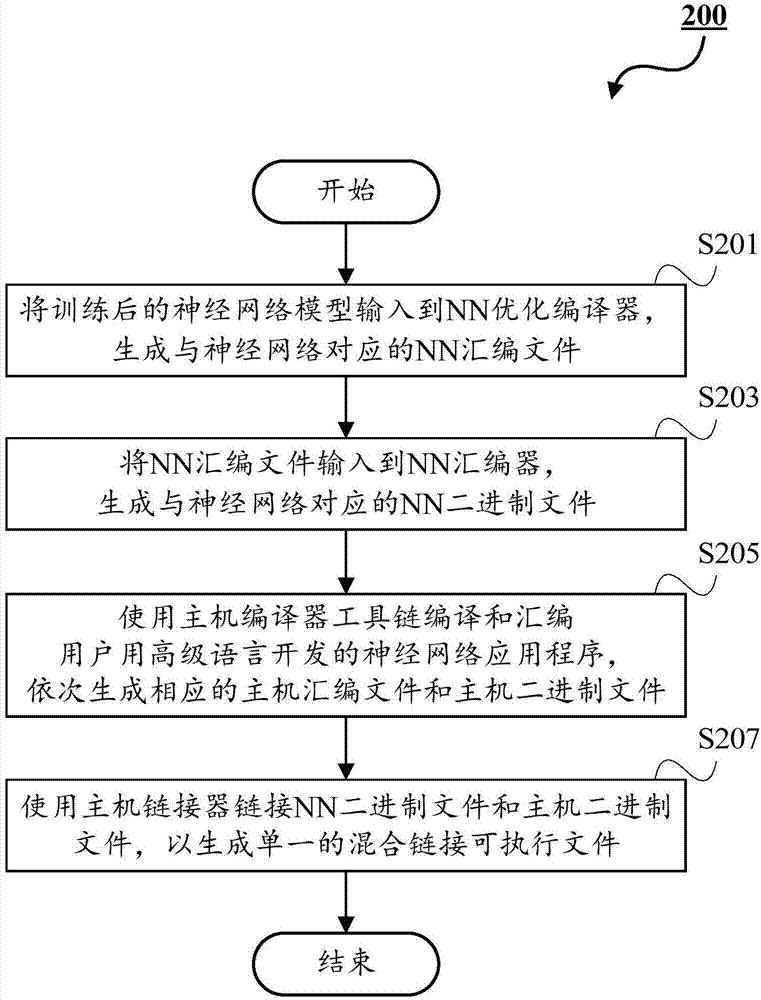
The invention provides a programming model oriented to a neural network heterogeneous computing platform. Specifically, the invention provides a compiling method and system of a heterogeneous computing platform and a program running support method and system thereof. A trained neural network model is input to a neural network (NN) optimization complier to generate a NN assembling file corresponding to the NN. The NN assembling file is input to a NN assembler to generate a NN binary file corresponding to the neural network; a host complier tool chain is used for compiling and assembling a neural network application program developed by a user by using the high-level language, and orderly generates a corresponding host assembling file and a host binary file. The host linker is used for linking the NN binary file and the host binary file to generate a single mixed link executable file. The technical scheme provided by the invention has the features of being good in calculation performance, strong in expandability, strong in compatibility and high in flexibility.
Owner:XILINX INC
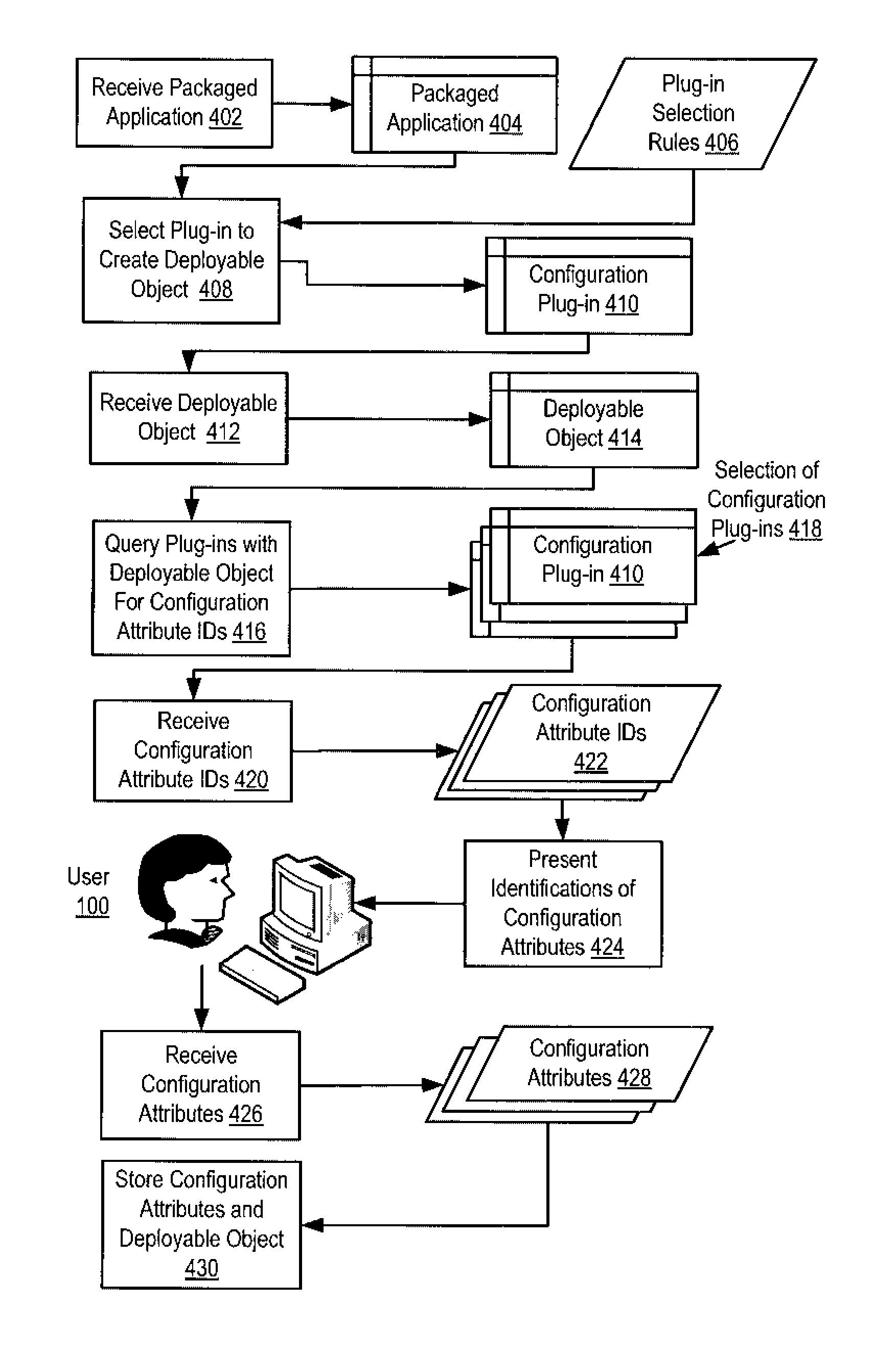
Programming model generic application deployment
Methods, systems, and computer program products are provided for deploying an application. Embodiments include receiving a packaged application for deployment and an instruction to perform a deployment management operation; selecting in dependence upon plug-in selection rules one of a plurality of configuration plug-ins for creating a deployable object from the packaged application; receiving from the selected configuration plug-in a deployable object; querying one or more of the plurality of configuration plug-ins with the deployable object for identifications of configuration attributes needed to perform the deployment management operation; receiving from each of the queried configuration plug-ins identifications of configuration attributes needed to deploy the deployable object; presenting the identifications of configuration attributes needed to deploy the deployable object to a user; receiving from the user the configuration attributes needed to deploy the deployable object; and storing the deployable object and the configuration attributes.
Owner:IBM CORP
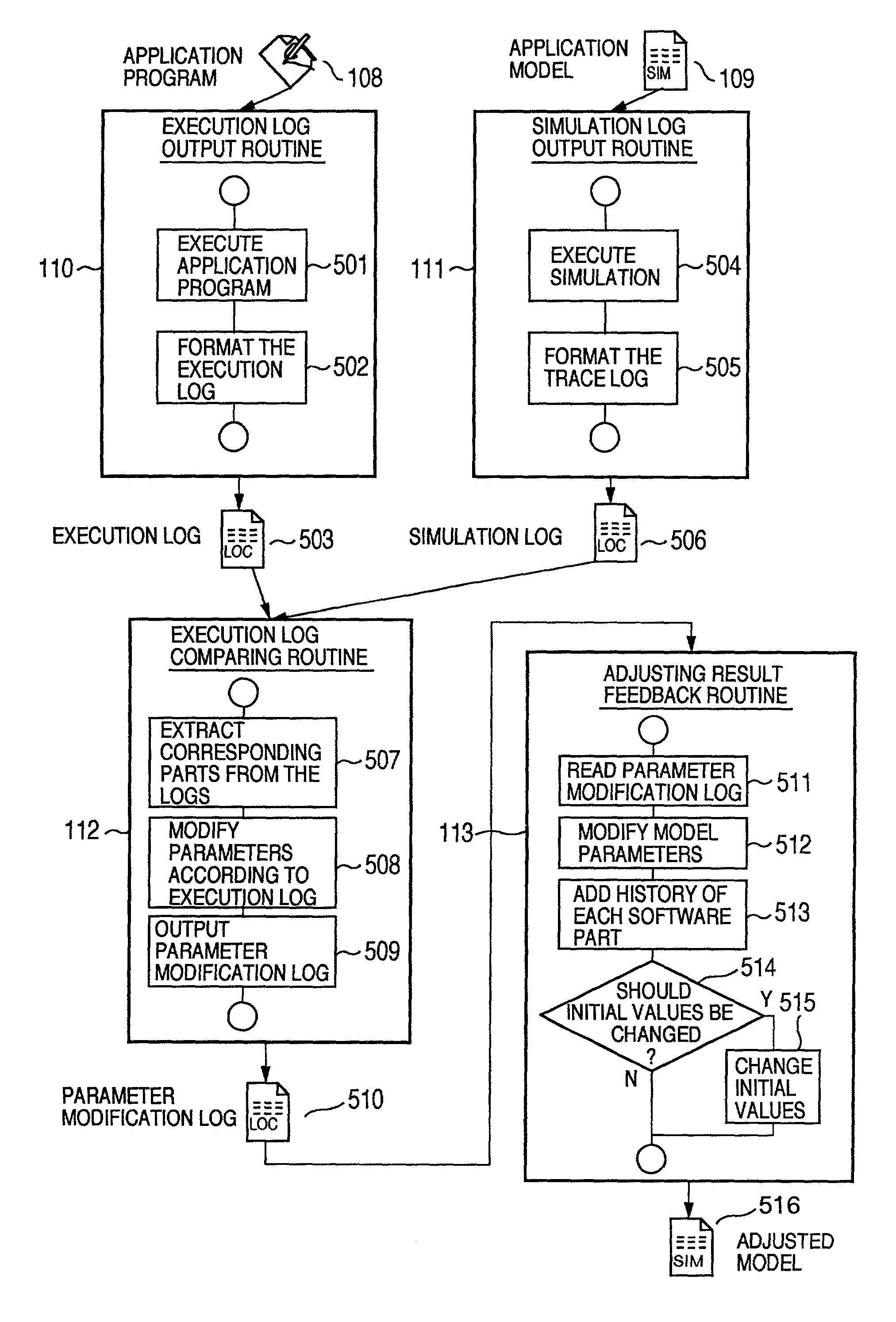
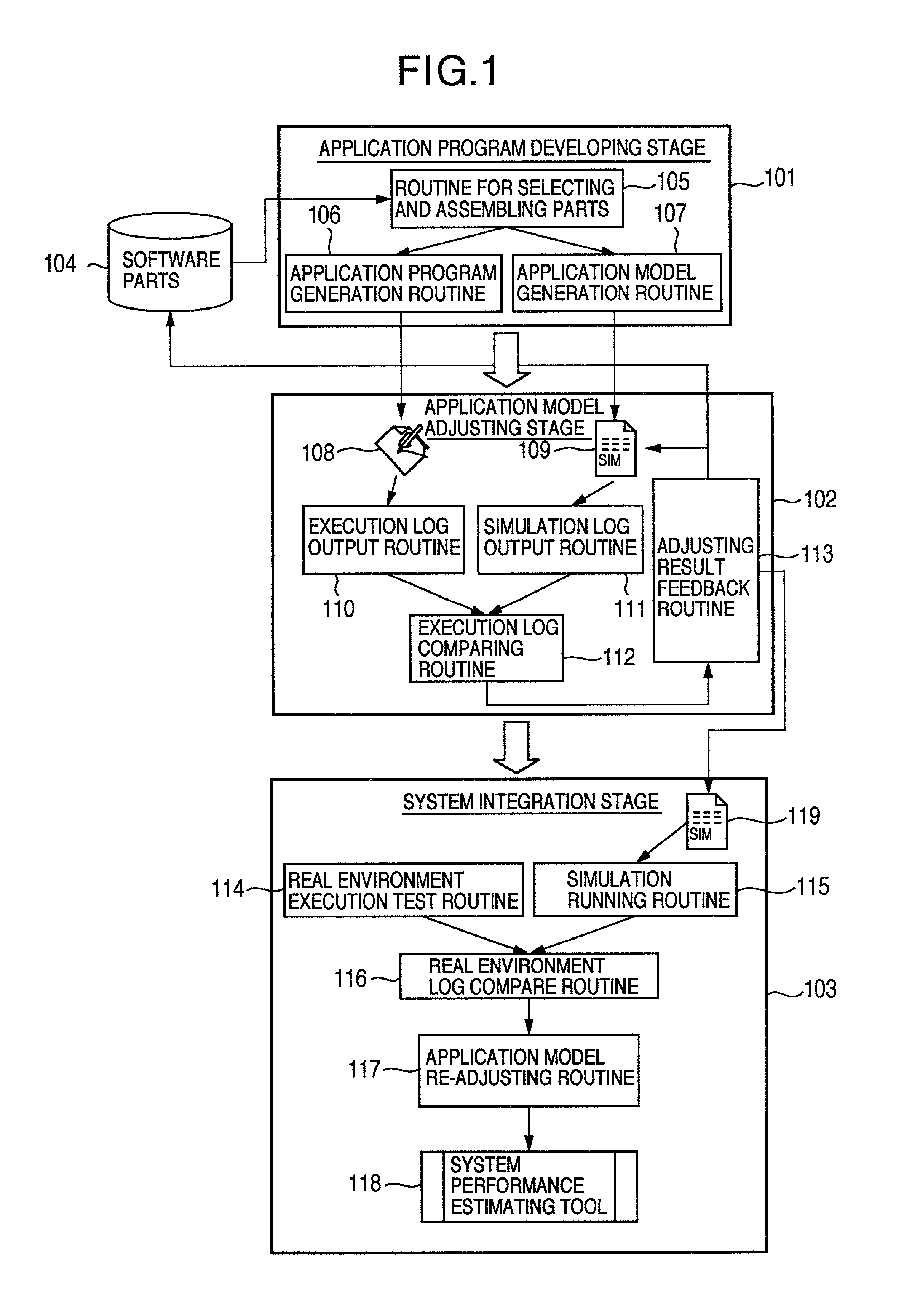
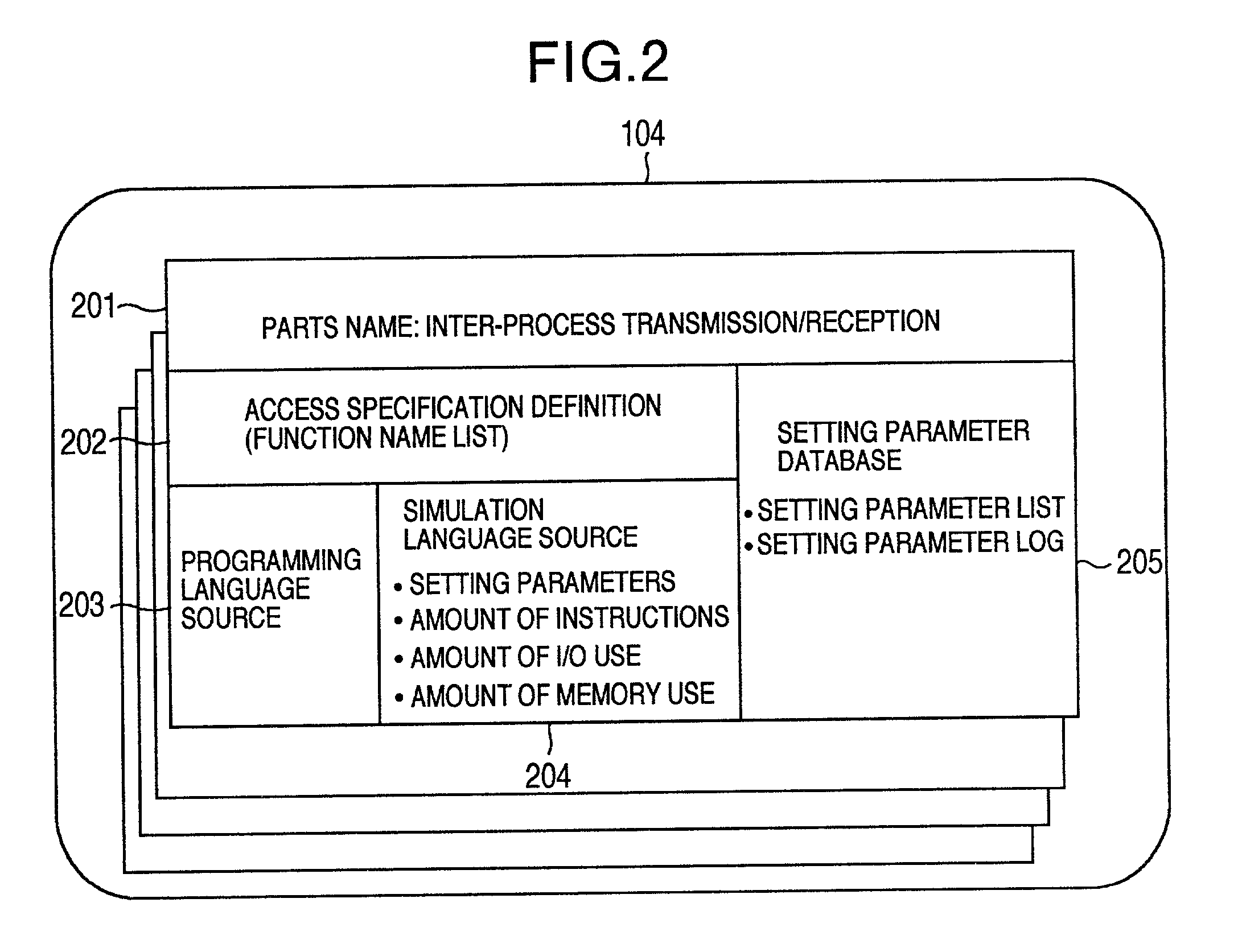
Method for creating a performance model of an application program adjusted with an execution result of the application program
InactiveUS6996811B2Reduced measurement timeFunctional testingSoftware testing/debuggingApplication softwareProgram model
There are previously involved: a program source-into which a log output instruction for adjusting an application model is embedded; a simulation source for performance simulation corresponding to the program source; and initial parameter values for adjusting the application model. Software parts capable of storing a history of parameter values after adjustment are combined to create an application program and the application model. Logs obtained by executing the application program and the application model are compared, and the parameters of the application model are automatically adjusted in conformance with actual measurement results of the application program. The adjusting result is fed back to the application model, and added to the history of original software parts, in which the parameter initial values are changed at need.
Owner:HITACHI LTD
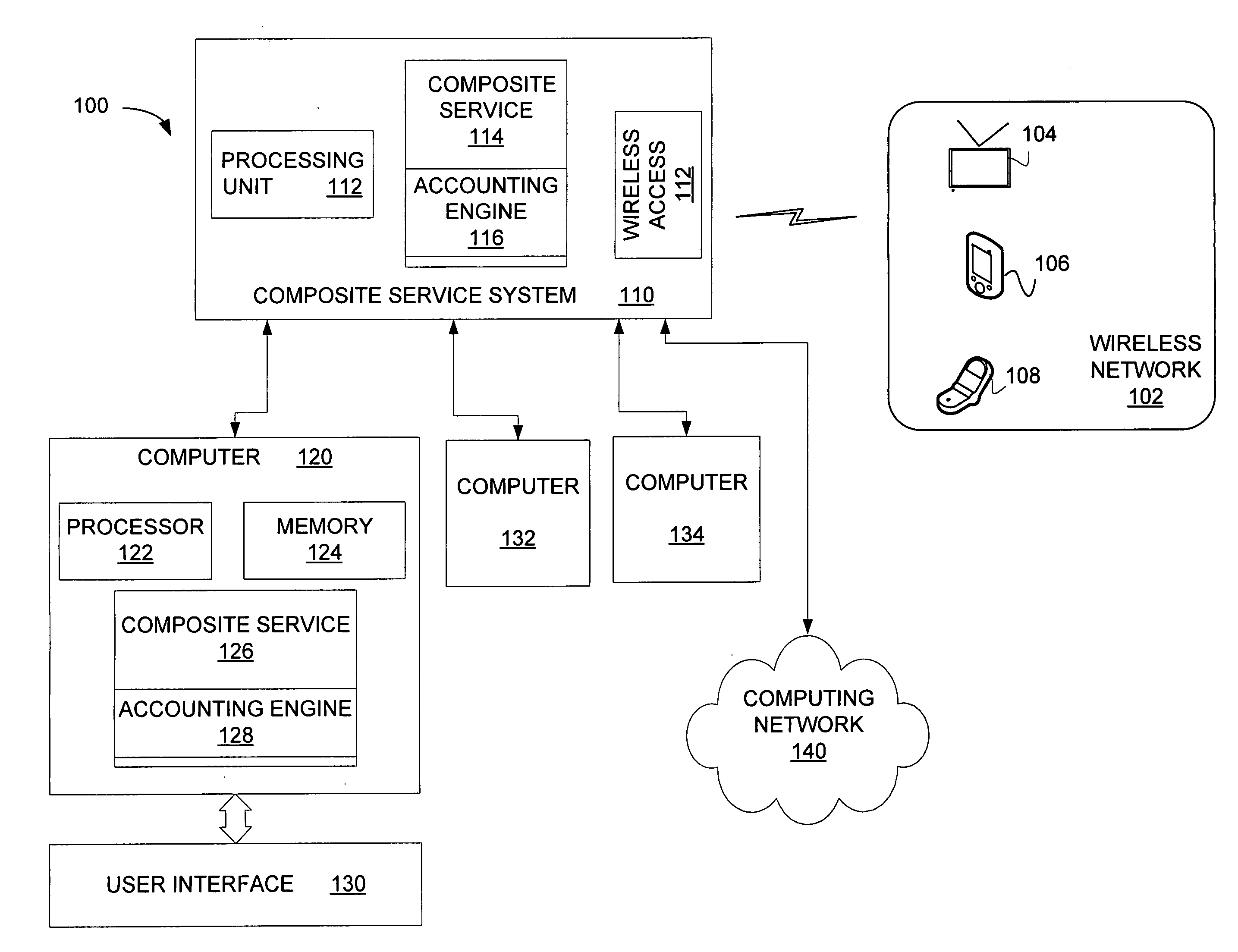
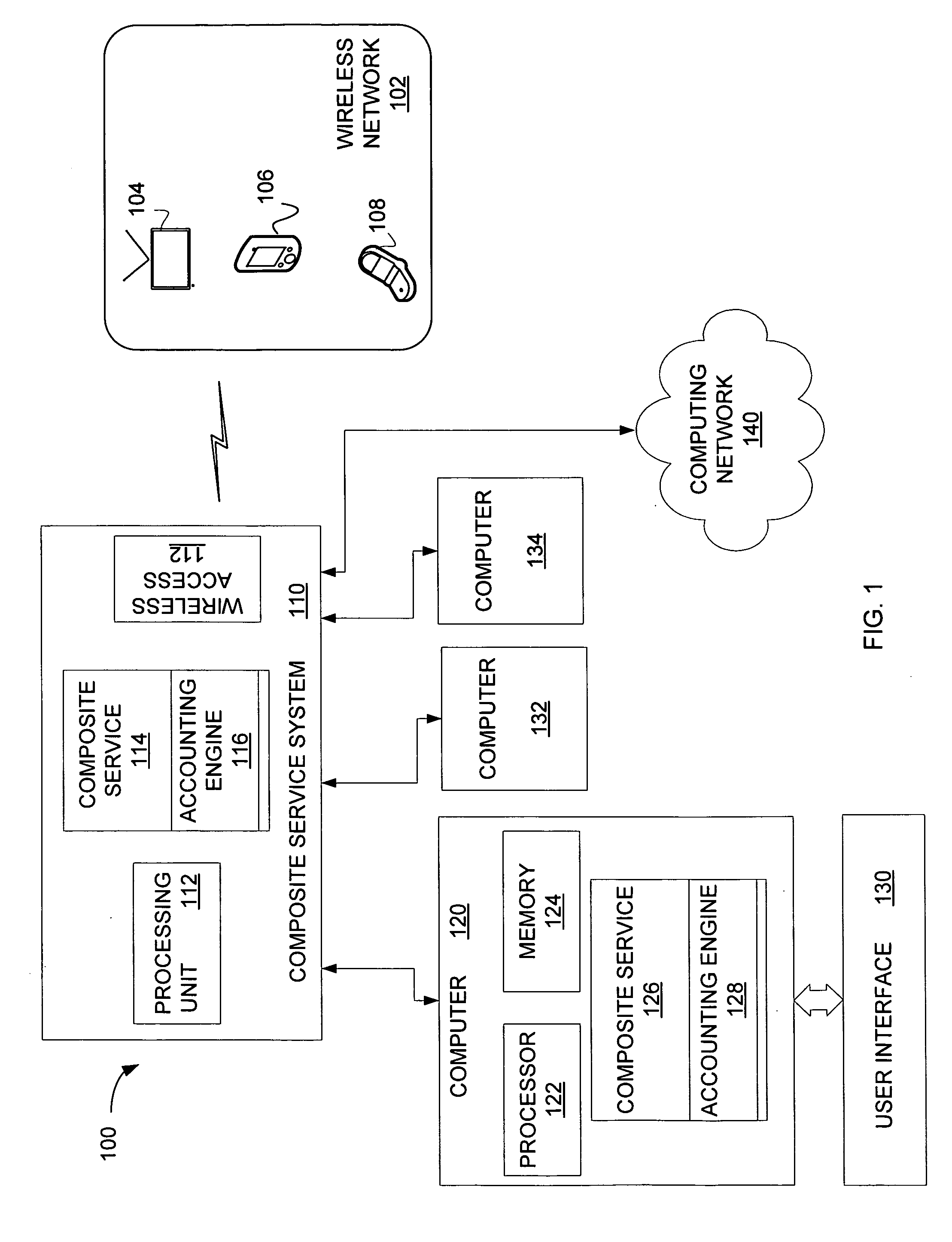
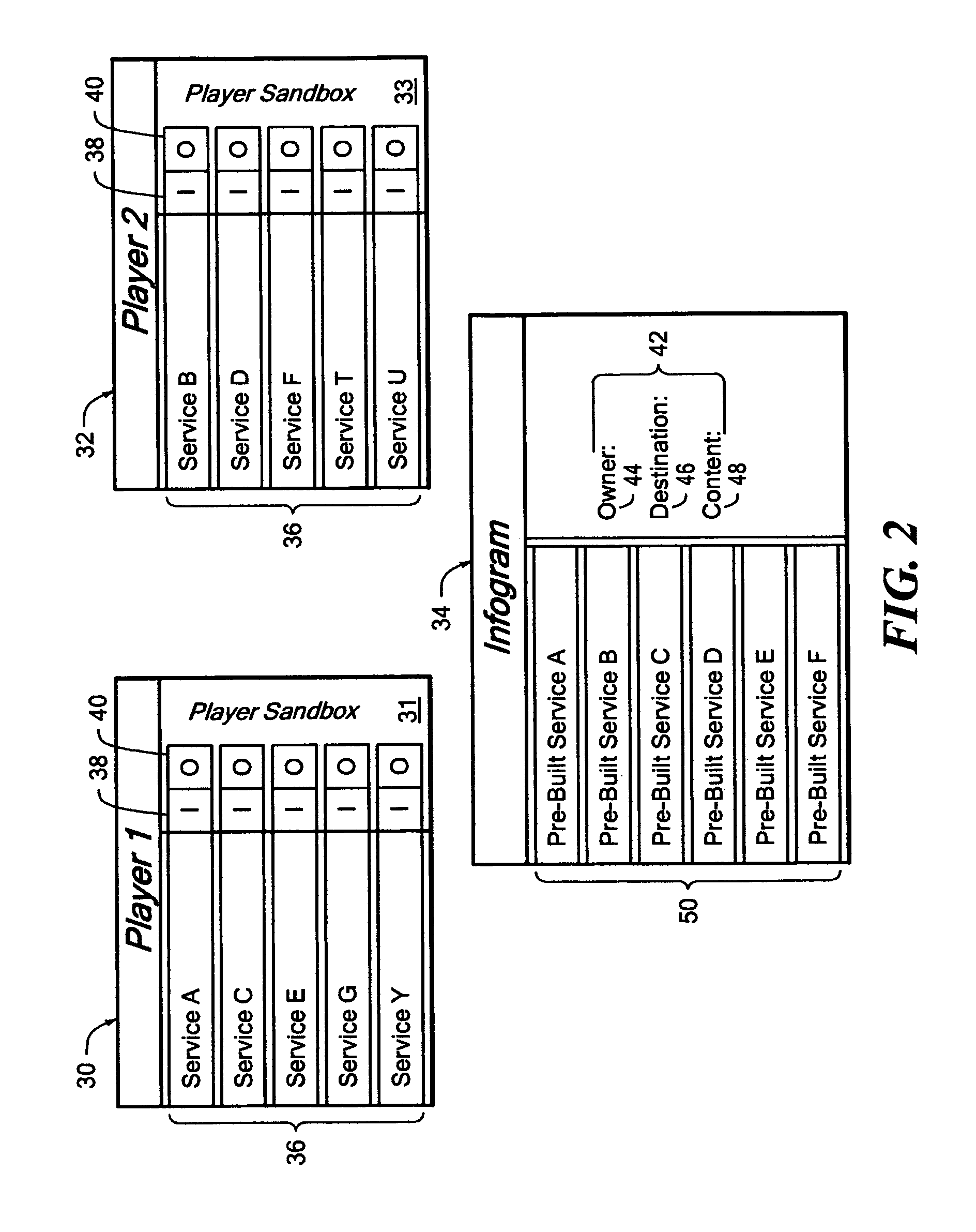
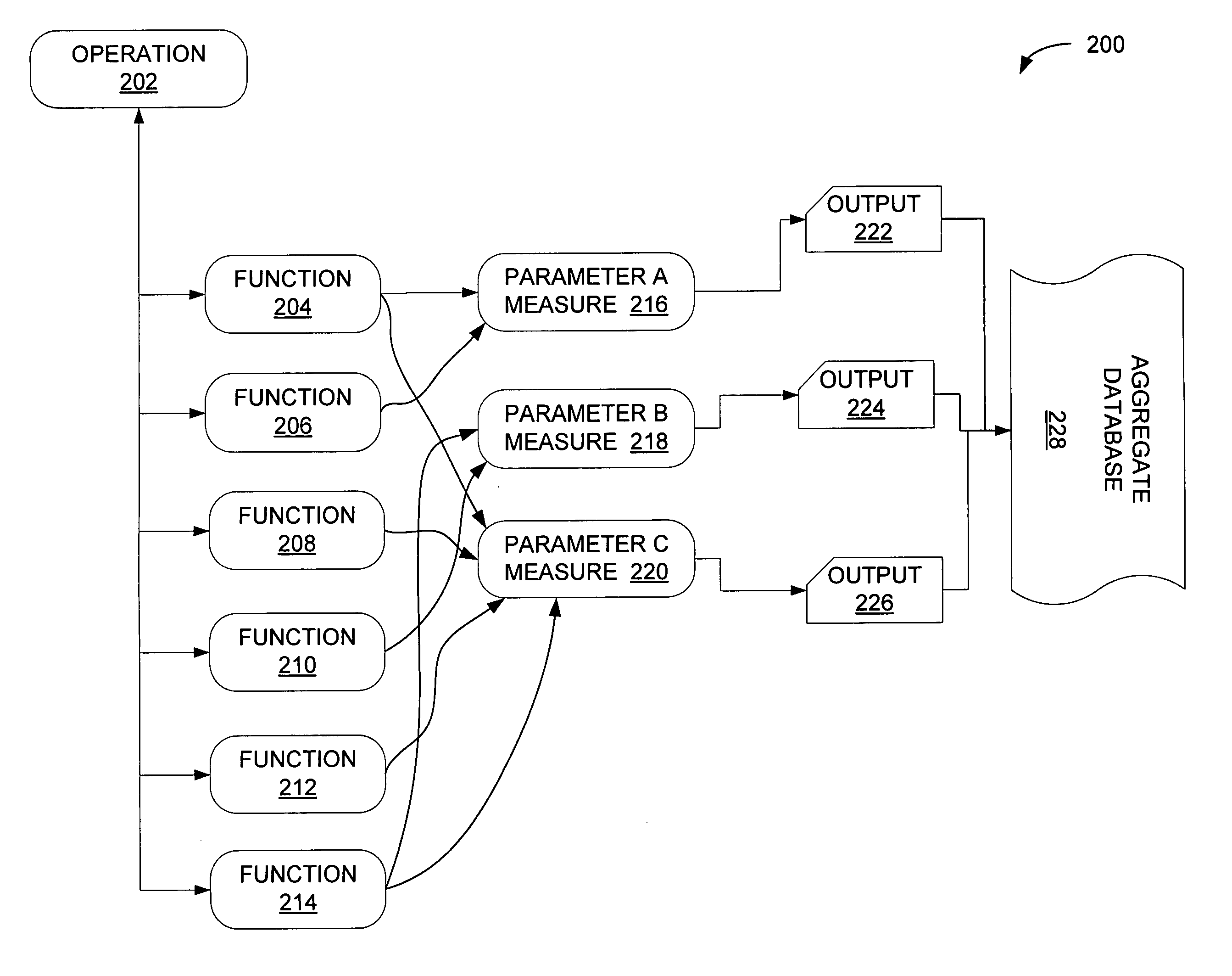
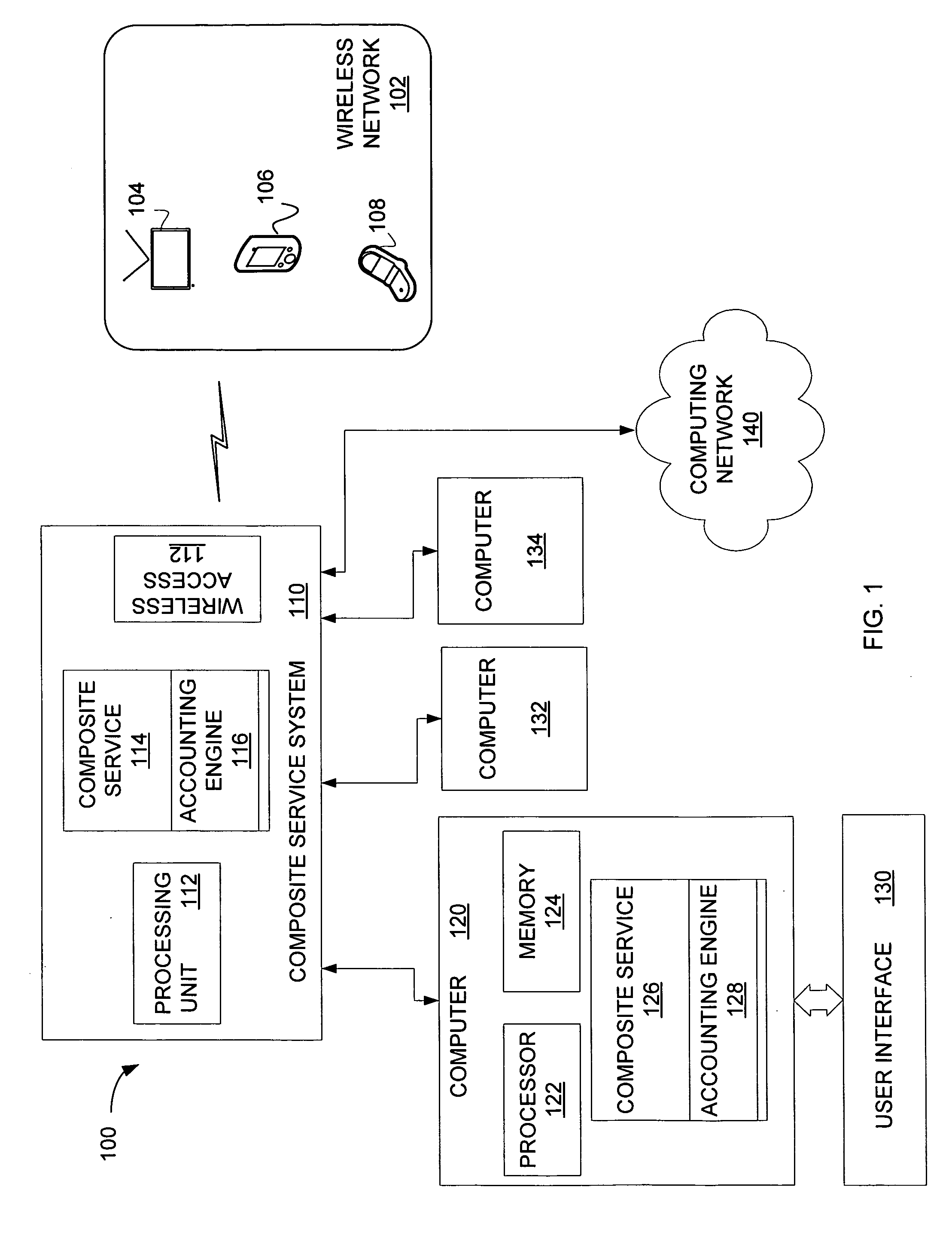
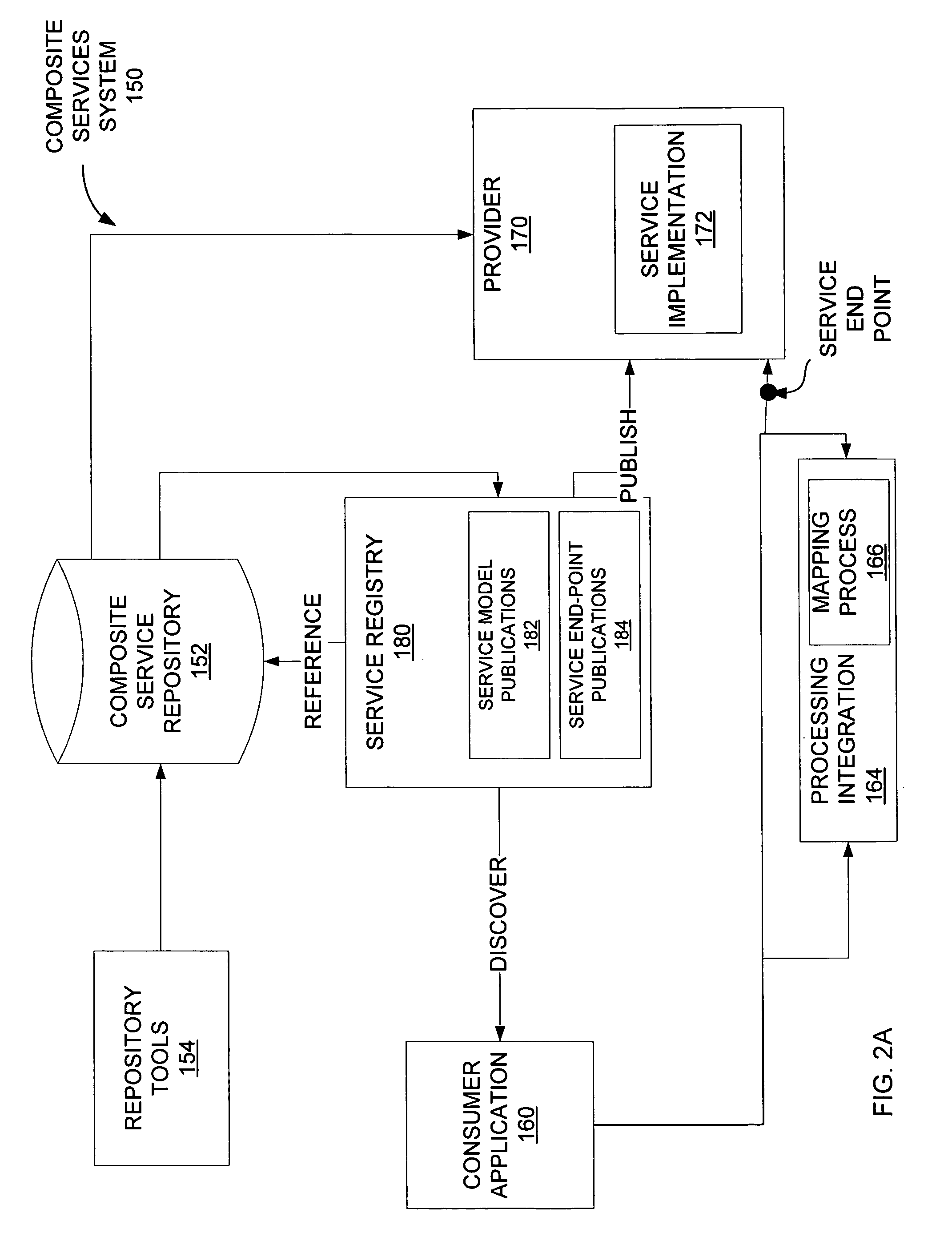
Service accounting method and apparatus for composite service
A system for an accounting infrastructure, including monitoring and reporting, for individual services within a composite service. An accounting engine integrates with the composite service to monitor components and parameters of at least one service in the composite service, to provide reporting on the measurements and statistics associated therewith over time. The accounting engine aggregates data for components and services. One example provides the accounting infrastructure as an object-oriented program model, instantiating statistics as objects. The reporting distinguishes each statistic allowing analysis and optimization of processes and services.
Owner:SAP AG
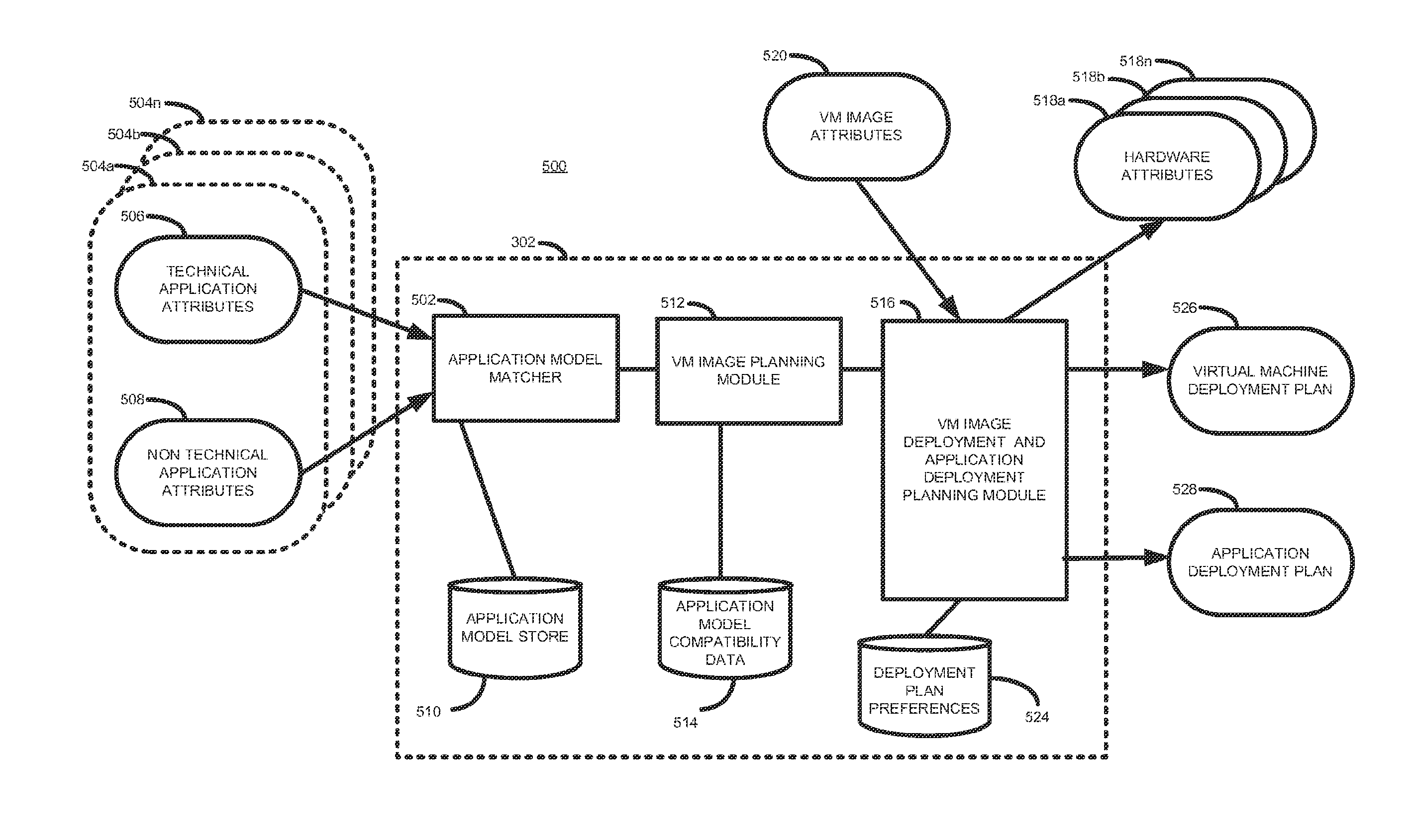
Methods and systems for planning application deployment
ActiveUS20130097597A1Simplify illustrationProgram loading/initiatingMemory systemsAcquired characteristicComputerized system
According to one example, there is provided a method of deploying applications in a computer system. The method comprises obtaining, for each of a plurality of computer applications, a set of application characteristics, assigning, based on the obtained characteristics, each of the plurality of applications to one of a set of predetermined application models, and determining, based in part on the obtained characteristics and in part on application model compatibility data, a set of hardware characteristics, a virtual server distribution plan, and an application distribution plan.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method for user producing mobile phone electronic book, picture album, game by website
InactiveCN101174205AEasy to manufactureImprove versatilitySpecial data processing applicationsSpecific program execution arrangementsWeb sitePassword
The invention relates to a method which can make users to use websites to manufacture an e-book, an album and a game. The invention is characterized in that JAVA language development software is adopted and is operated on the website, the invention comprises the following steps: a program model is the manufactured, a user name and a password input into a user logging page is validated with the logon message of a user in a database, and then the choice is judged, the page is jumped to the corresponding cell phone application manufacture page; the user commits the self made cell phone application content to a server, according to the difference of the manufacture content chosen by the user, the manufacture method can be divided into three types: the server establishes a file folder, and three types, uploading pictures and texts are copied in the file folder according to the manufacture requirements; the server sets according to the choice of the user, the content is packed into a cell phone applicator program file according to the packing of a JAR file; the generated cell phone applicator program file is stored to the database; a corresponding downloading page is generated for the user to visit, download or send to the cell phone. The invention has the advantages that the operation is convenient.
Owner:SHANGHAI LUXINGSHA INFORMATION TECH
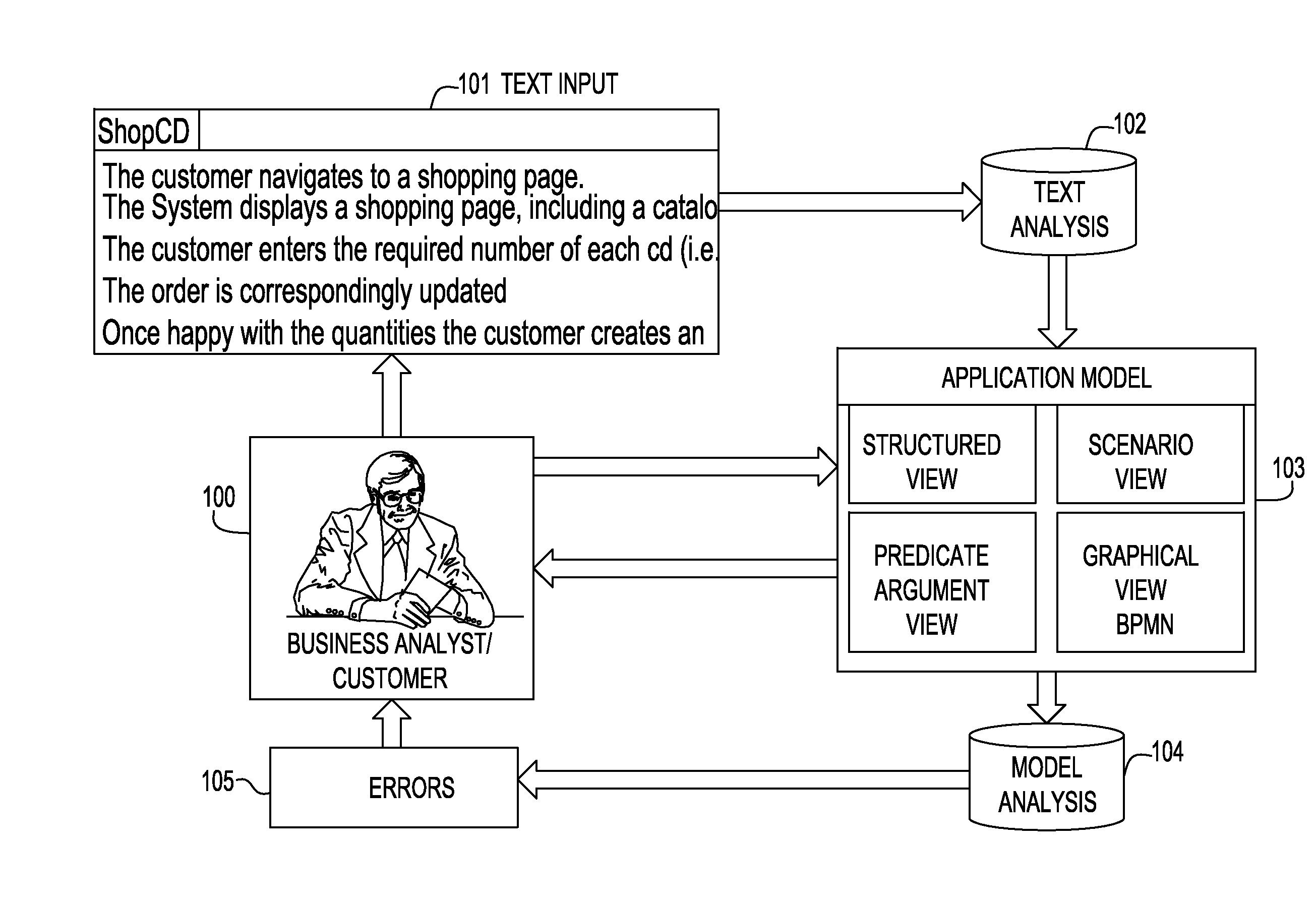
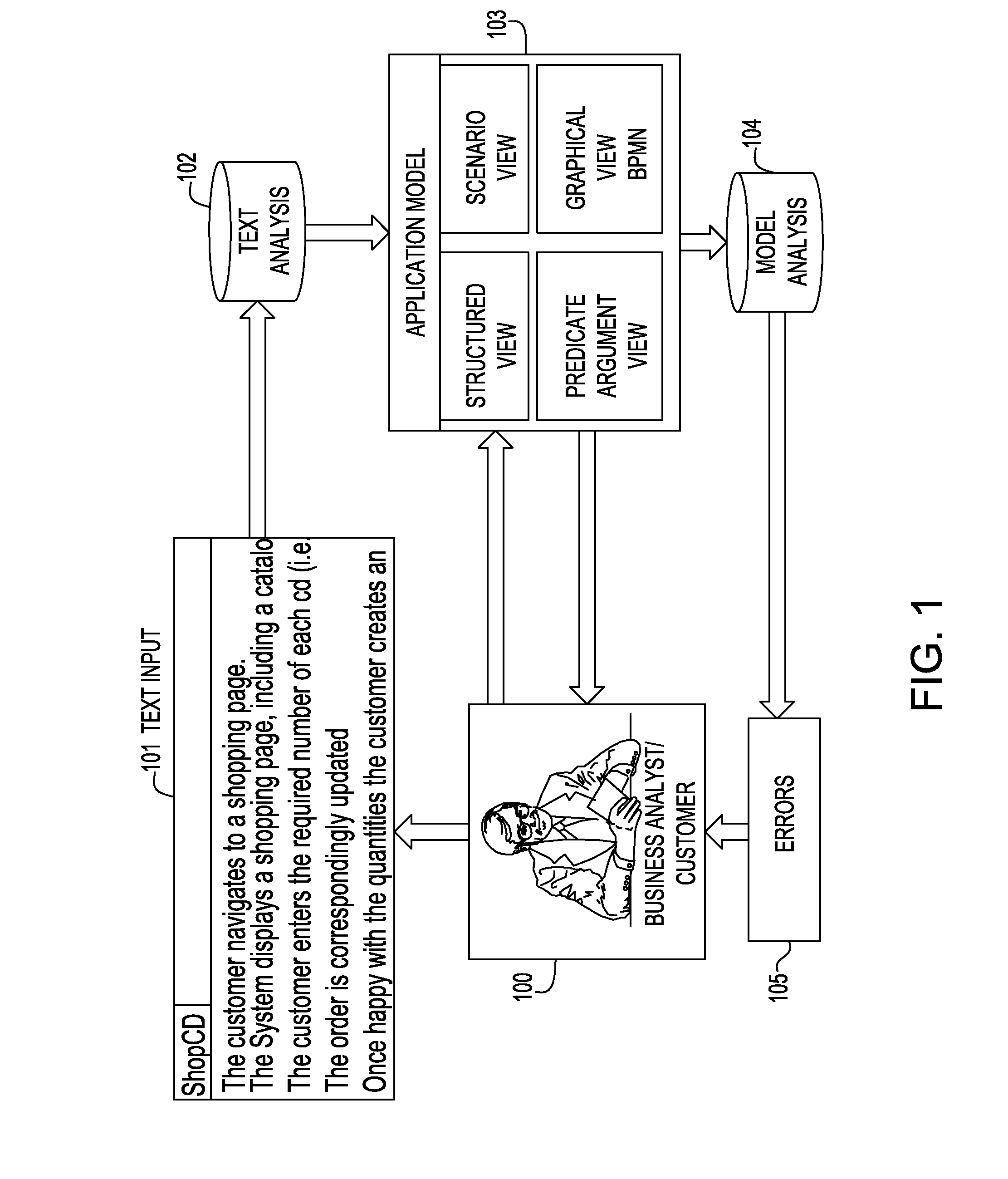
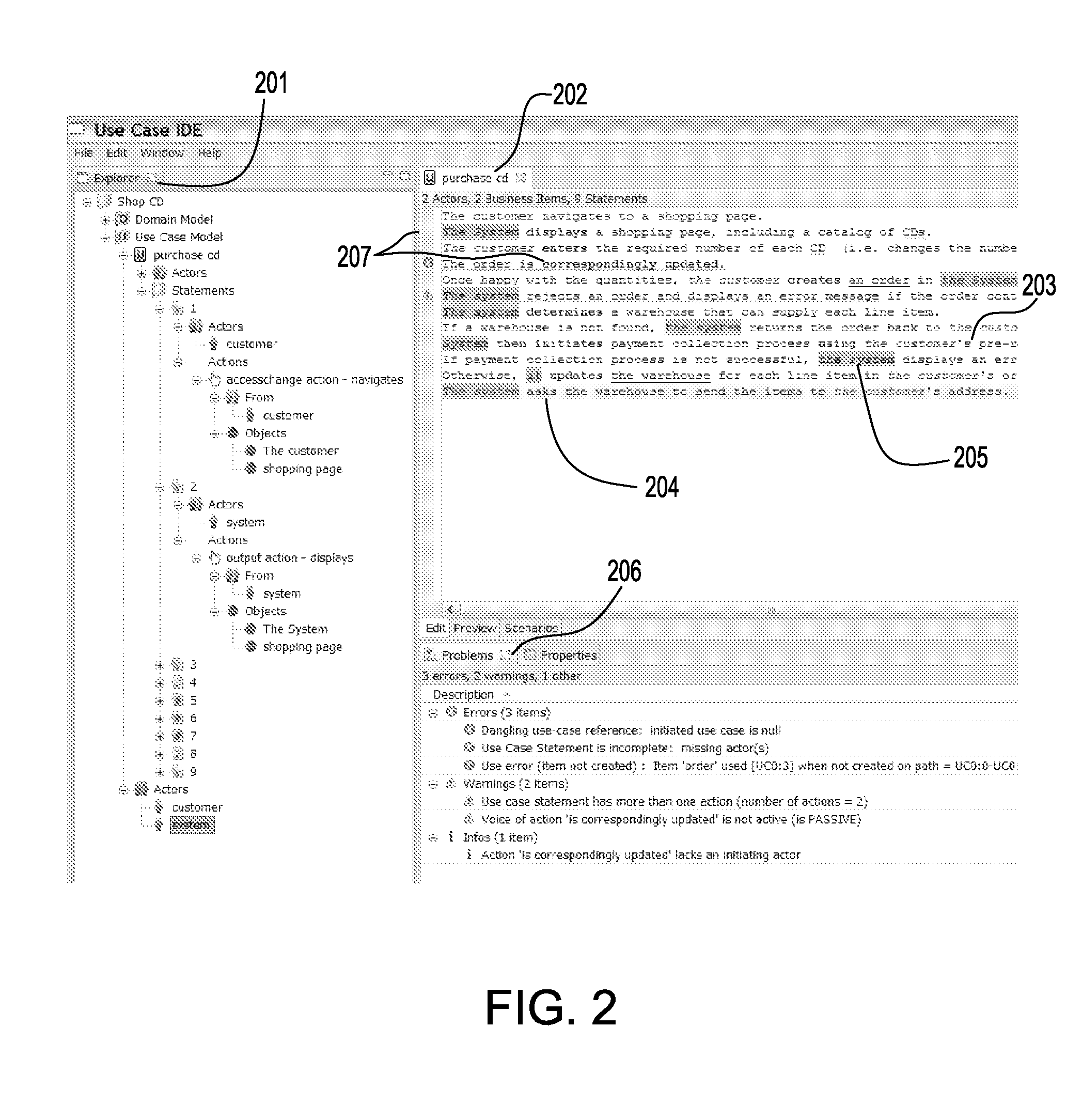
Mining a use case model by analyzing its description in plain language and analyzing textural use case models to identify modeling errors
InactiveUS20100325491A1Reverse engineeringNatural language data processingSoftware engineeringApplication software
A system and method for identifying modeling errors in textual use case description analyze an input text describing a use case and create an application model representing the use case, the application model containing information obtained from analyzing the input text describing the use case. The application model may be automatically analyzed using automatic process and one or more errors in the use case and / or reports about the use case may be generated. In one aspect, processing components may be integrated into a user development environment to allow developing use cases and improving them incrementally and / or iteratively as information is identified about the use cases.
Owner:IBM CORP
User-driven, service oriented software application model
A user-driven, service-oriented application model, in which conformant applications implement and process instances of two program object types. Components in conformant applications consist of objects having built-in behaviors that are common across different applications. Each application object is either an instance of a predefined active object type, or an instance of a predefined reactive object type. Active objects are associated with individual users of their application, are allowed to activate services, and encapsulate all their inputs and outputs within a bounded space. Reactive objects are instantiated or processed by services, and, in one embodiment, each one is owned by an individual active object at any given point in time. During operation of the disclosed system, services activated by active objects route reactive objects to active objects. An active object assumes ownership of a received reactive object upon receipt. All components may be designed to operate in a pre-defined run-time execution space. Additionally, all applications may interact with their associated users using a pre-defined service invocation model.
Owner:CERYLION
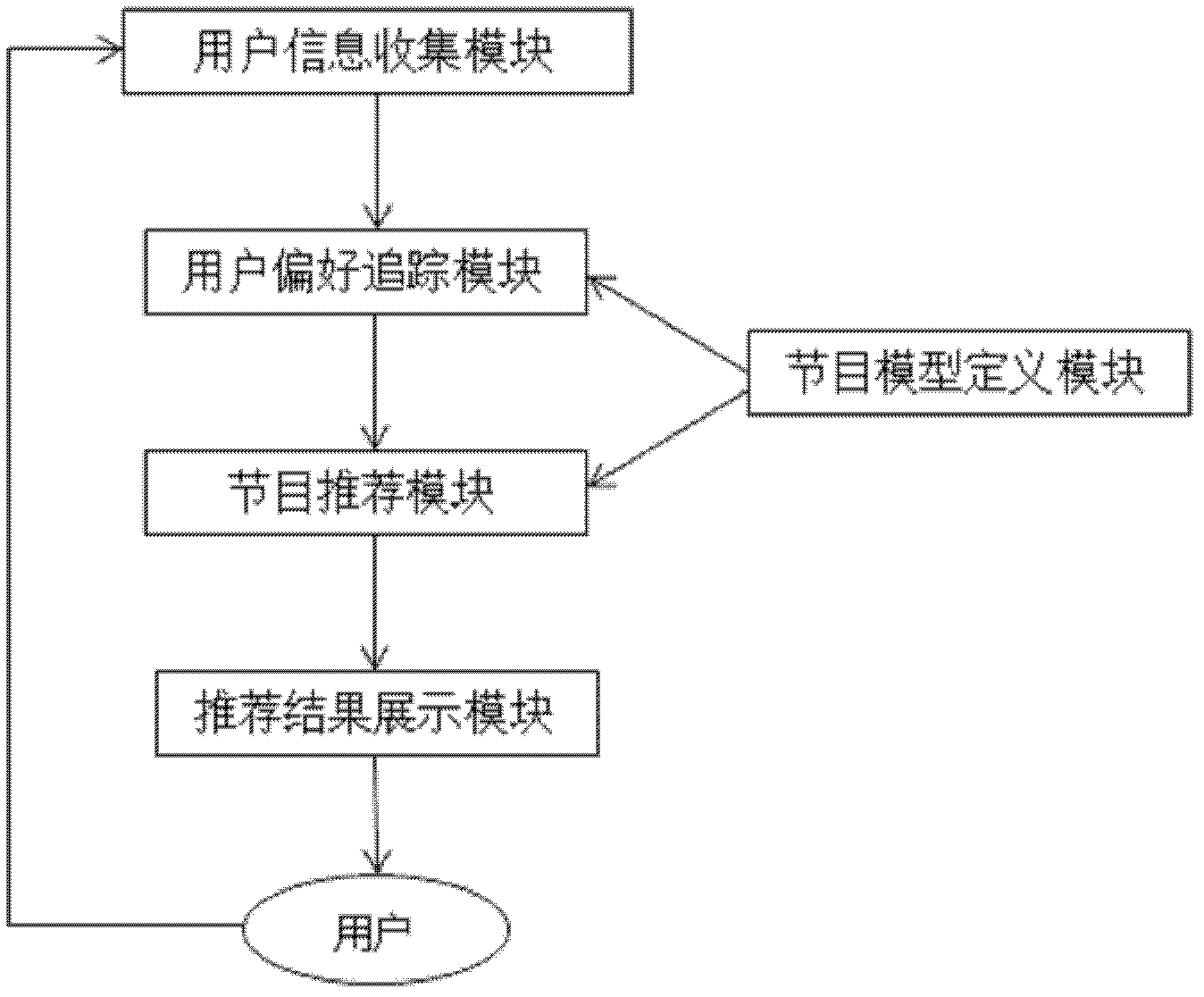
Real time streaming-oriented television program recommendation system
InactiveCN102630052AStrong personalizationAddress issues with explicit feedbackSelective content distributionPersonalizationAnimation
The invention discloses a real time streaming-oriented television program recommendation system. The real time streaming-oriented television program recommendation system comprises a user information collecting module, a program model definition module, a user preference tracking module, a program recommendation module and a recommendation result display module, wherein the user information collecting module is used for automatically and transparently collecting user watching information when users watch television programs; the program model definition module is used for extracting program related information from internet and establishing a program model by adopting an information extraction technology; the user preference tracking module is for generating a user preference model by using the user watching information collected by the user information collecting module and the program model established by the program model definition module; the program recommendation module is used for generating recommendation results by using extended Jaccard similarity according to the current user preference; and the recommendation result display module is used for adding art designing and animation effects to the recommendation results on the basis of text recommendation results generated by the program recommendation module. The real time streaming-oriented television program recommended system has the advantages of having stronger individuation, keeping in step with the preference of the user to change, solving the problem that the traditional system asks for the clear feedback of users, adding time maintenance for programs and carrying out pertinence recommendation.
Owner:SHANGHAI JIAO TONG UNIV
Microgrid energy storage power station program control method based on economical evaluation
ActiveCN105260797AReduce charge and discharge timesReduce depthEnergy industryForecastingSystem capacityMicrogrid
The invention relates to a microgrid energy storage power station program control method based on economical evaluation, comprising predicting the microgrid load data of N days, wind power output power and photovoltaic output power, and characterized by calculating the energy storage system capacity meeting load requirements based on obtained data; utilizing an improved empirical mode decomposition algorithm to decompose the energy storage system capacity to obtain n IMF components, wherein k is respectively 1-n, the sum of 1-(k-1) IMF components is used as a cell capacity, and the sum of k-n IMF components is used as a super capacitor capacity; substituting the power and capacity of a cell and a capacitor into a microgrid energy storage power station program model, determining whether meeting constrained conditions, and calculating a corresponding objective function value; and utilizing a genetic algorithm to search optimization for the model, obtaining a k value meeting the constrained conditions and minimizing an objective function, and determining the optimal capacity configuration and annual mean least cost of an energy storage system.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING) +2
Service accounting method and apparatus for composite service
A system for an accounting infrastructure, including monitoring and reporting, for individual services within a composite service. An accounting engine integrates with the composite service to monitor components and parameters of at least one service in the composite service, to provide reporting on the measurements and statistics associated therewith over time. The accounting engine aggregates data for components and services. One example provides the accounting infrastructure as an object-oriented program model, instantiating statistics as objects. The reporting distinguishes each statistic allowing analysis and optimization of processes and services.
Owner:SAP AG
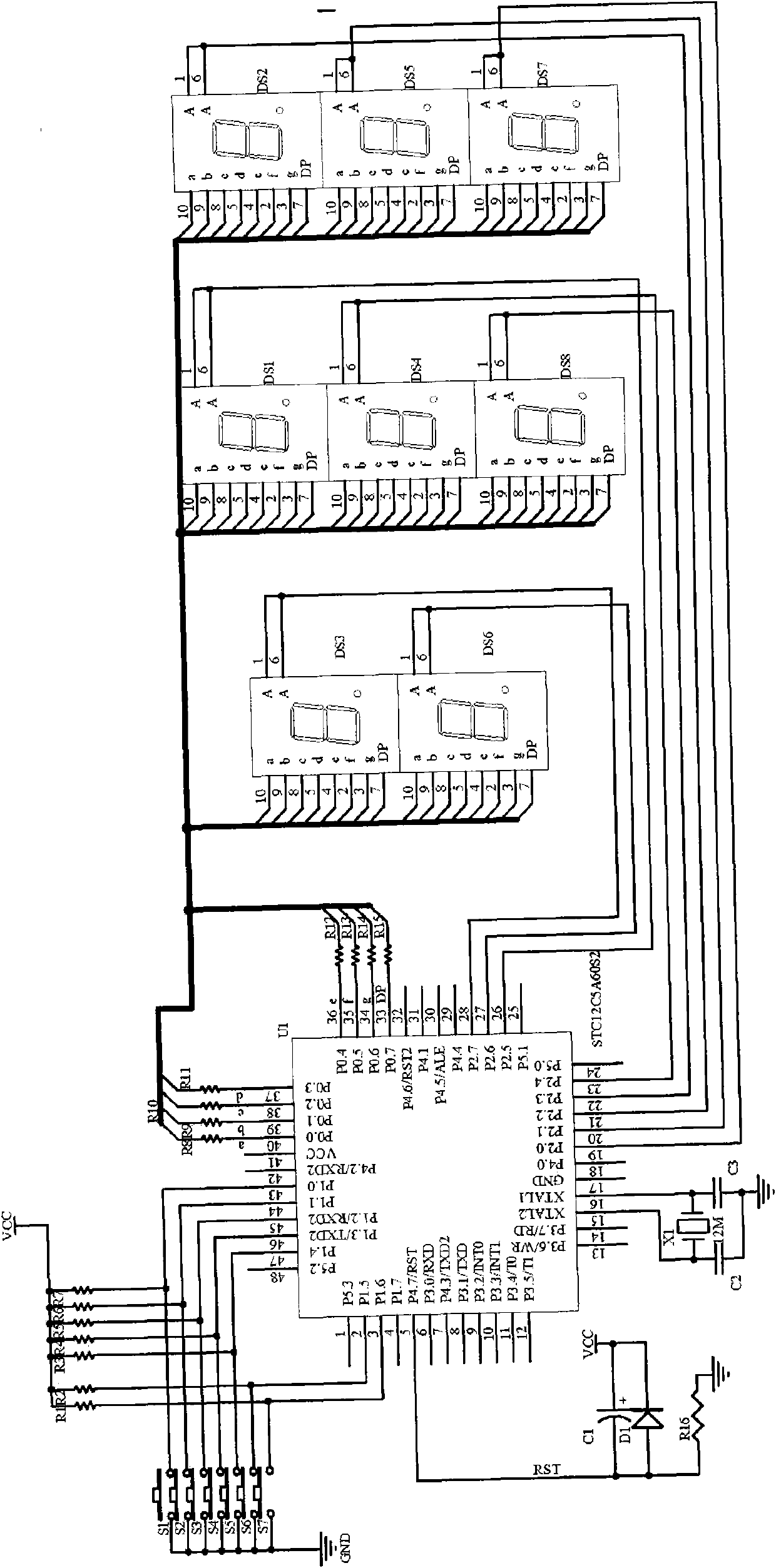
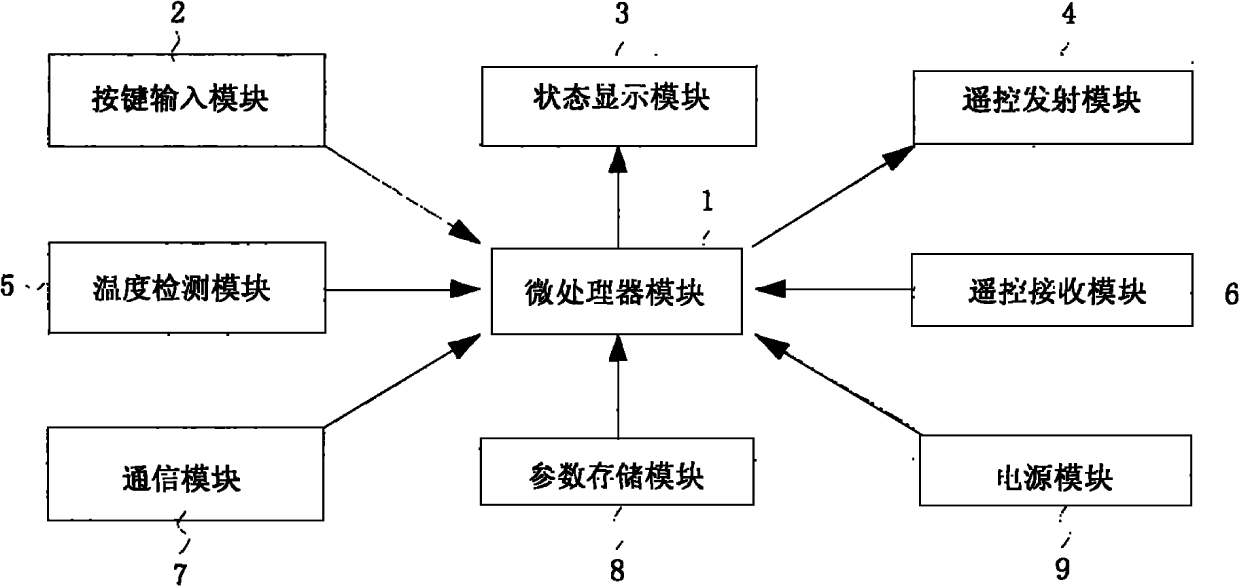
Energy-saving remote controller of air conditioner
InactiveCN101865514AGood effectChange judgment is accurateSpace heating and ventilation safety systemsLighting and heating apparatusStart stopControl signal
The invention discloses an energy-saving remote controller of an air conditioner. The energy-saving remote controller of the air conditioner comprises a microprocessor module; the microprocessor module is connected with a keystroke input module, a state display module, a remote-control transmission module, a power module and a temperature detection module; the temperature detection module comprises an ambient temperature sensor used for detecting indoor temperature and an air opening temperature sensor used for detecting the temperature of the air outlet of the air conditioner; a mode conversion program model is preinstalled in the microprocessor module; the mode conversion program model calculates and analyzes the temperature data input by the temperature detection module to respectively obtain the working time the air conditioner under the refrigeration mode and the air supply mode; and the microprocessor module transmits a control signal for converting the working mode of the air condition to an air-conditioning switch through the remote-control transmission module. The energy-saving remote controller of the invention finds the optimal compressor start-stop time meeting the environment and temperature requirements, thus achieving the purpose of saving energy.
Owner:朱永强 +1
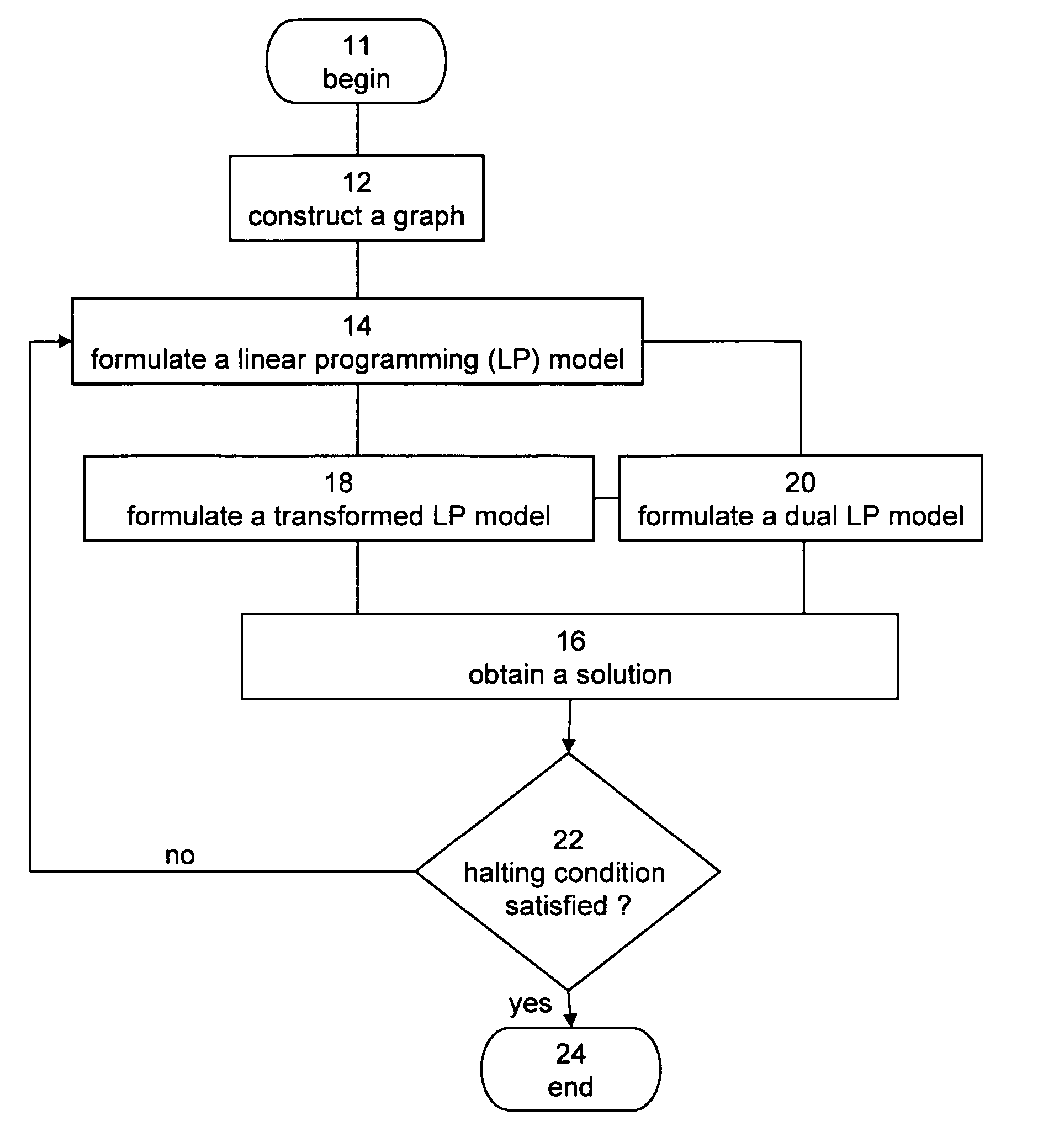
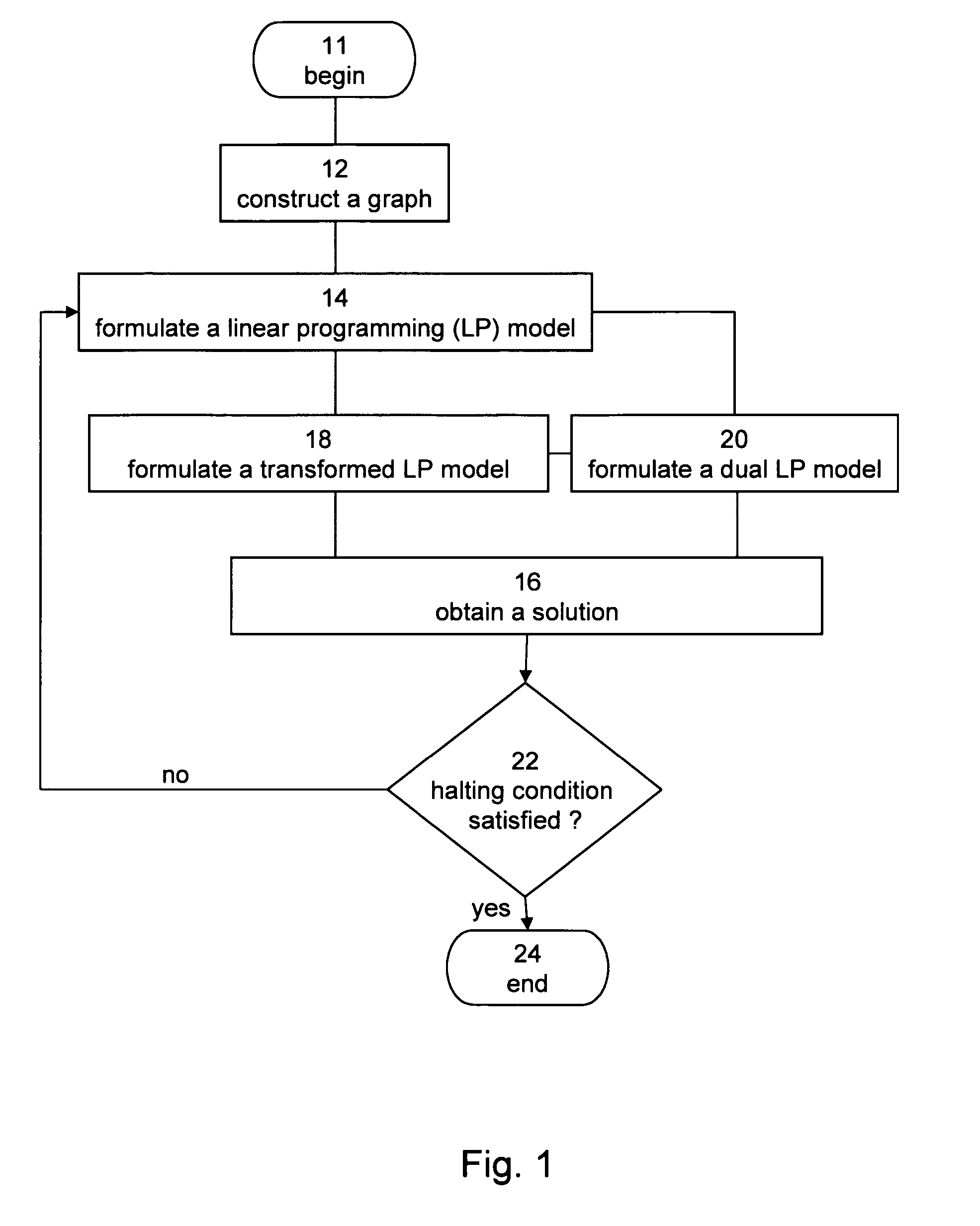
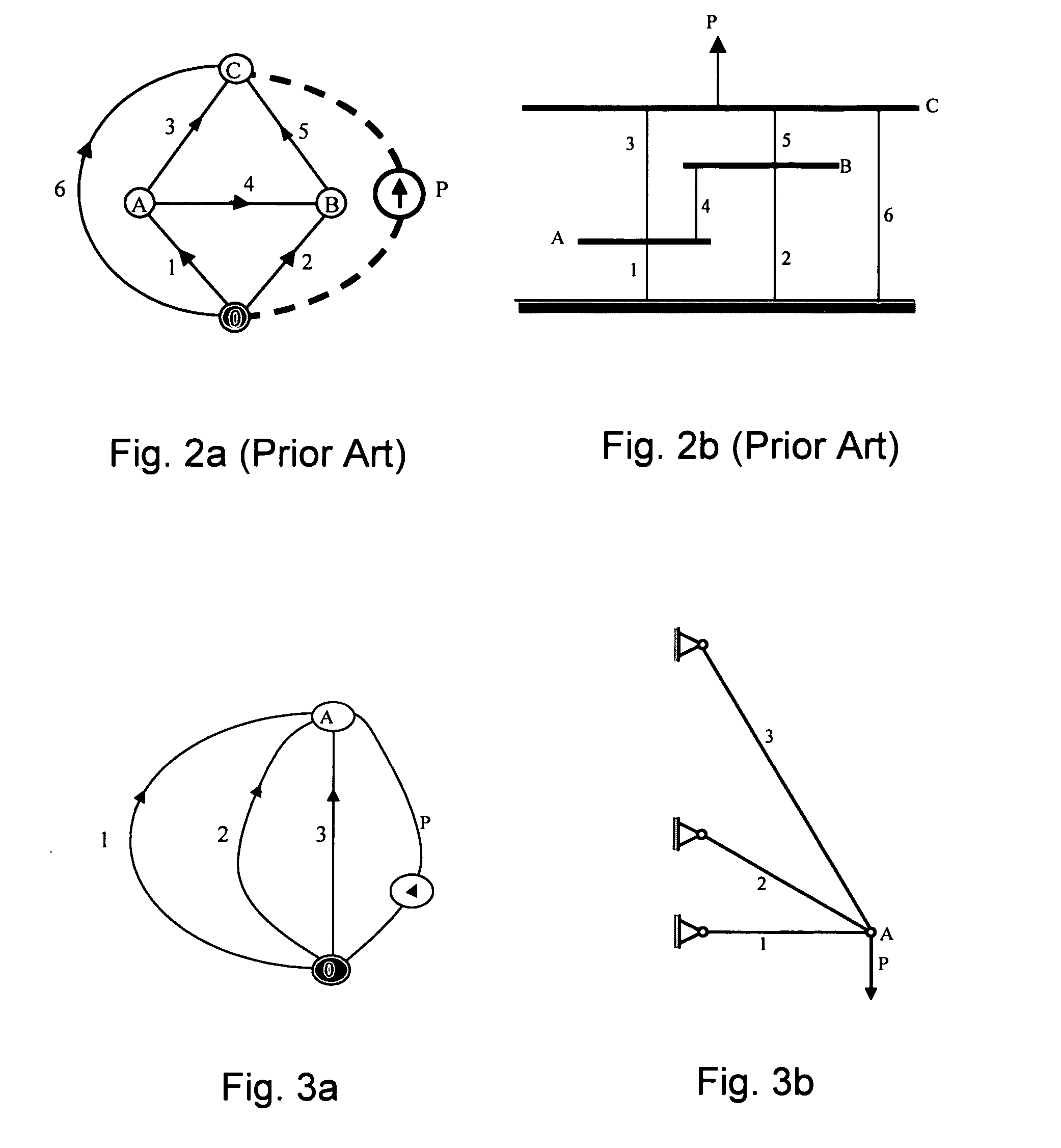
Method and Apparatus for Optimizing Multidimensional Systems
InactiveUS20070244675A1Easy to solveForecastingComputation using non-denominational number representationLinear programming algorithmGraphics
Method for optimizing a flow network is disclosed. The method comprises: constructing a multidimensional graph representation which is characterized by a plurality of vertices and a plurality of edges, whereby at least one edge of the plurality of edges is associated with a vector quantity over the flow network. The method further comprises formulating a linear programming model over the multidimensional graph representation, and using a linear programming algorithm for obtaining a substantially optimal solution to the linear program model.
Owner:RAMOT AT TEL AVIV UNIV LTD
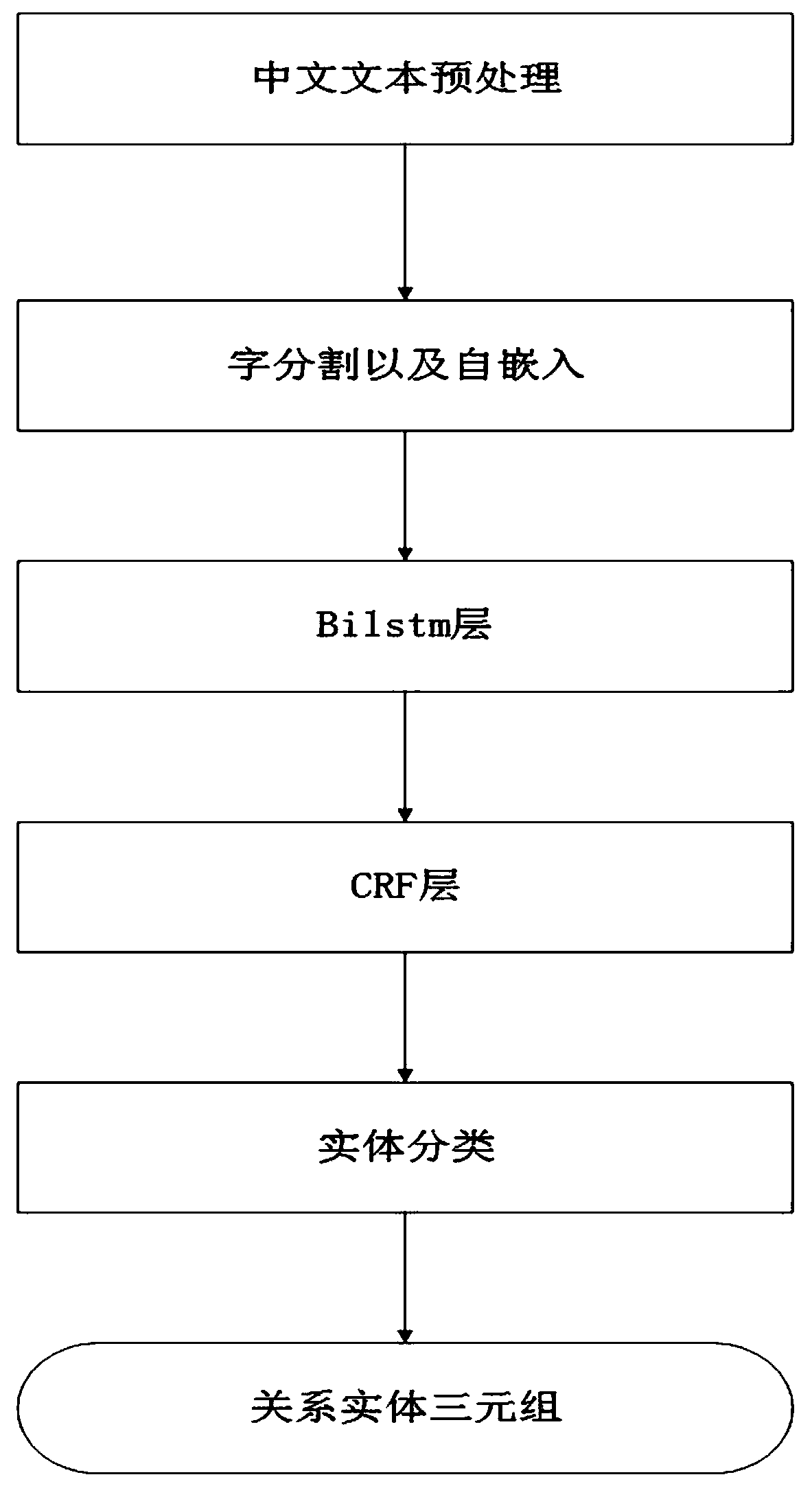
Method of entity relation extraction based on neural network
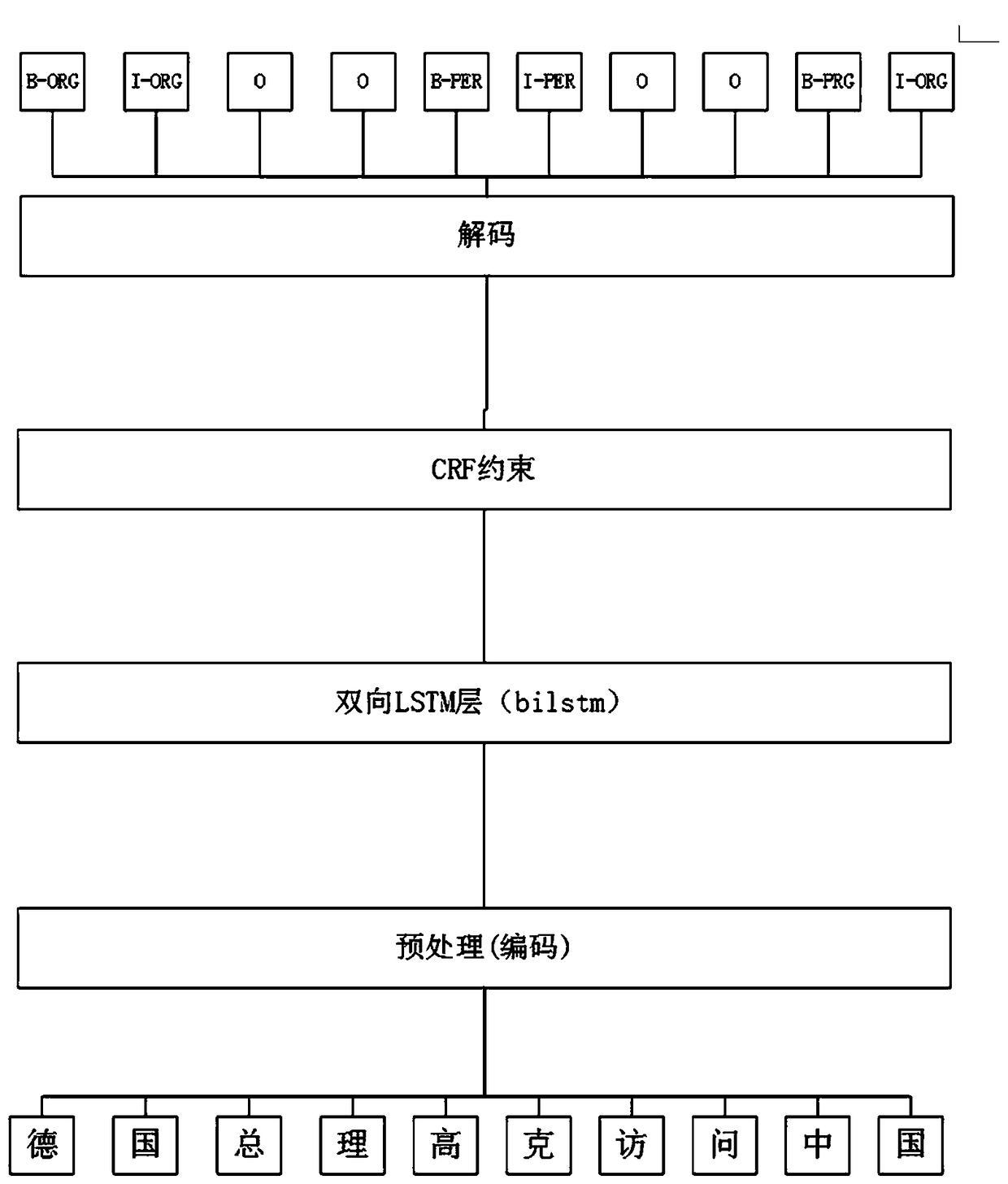
ActiveCN109063159AAchieve the effect of separationImprove developmentSpecial data processing applicationsAlgorithmNetwork model
The invention discloses an entity relation extraction method based on a neural network, using the algorithm of machine learning and neural network model, Input a Chinese sentence into the program model, the model will give a special label to the entity words or statements, that is, the entity in the text can be extracted, and then through a classification algorithm for the extracted entity to do relationship classification, entity relationship classification is completed. Specifically, assign an ID to each word that appears in the Chinese text, Then the IDs corresponding to these sentences aretransformed into input vectors of the neural network model, and the results obtained through bilstm and CRF layer are mapped to corresponding entity tags to complete entity extraction. Finally, the entities in the text are classified by machine learning classification algorithm, and finally such a triple form of an entity of the entities-relationsientities is obtained. . This method only needs training text and input statements to complete the extraction of relational entities, which is a flexible and convenient method.
Owner:GUILIN UNIV OF ELECTRONIC TECH
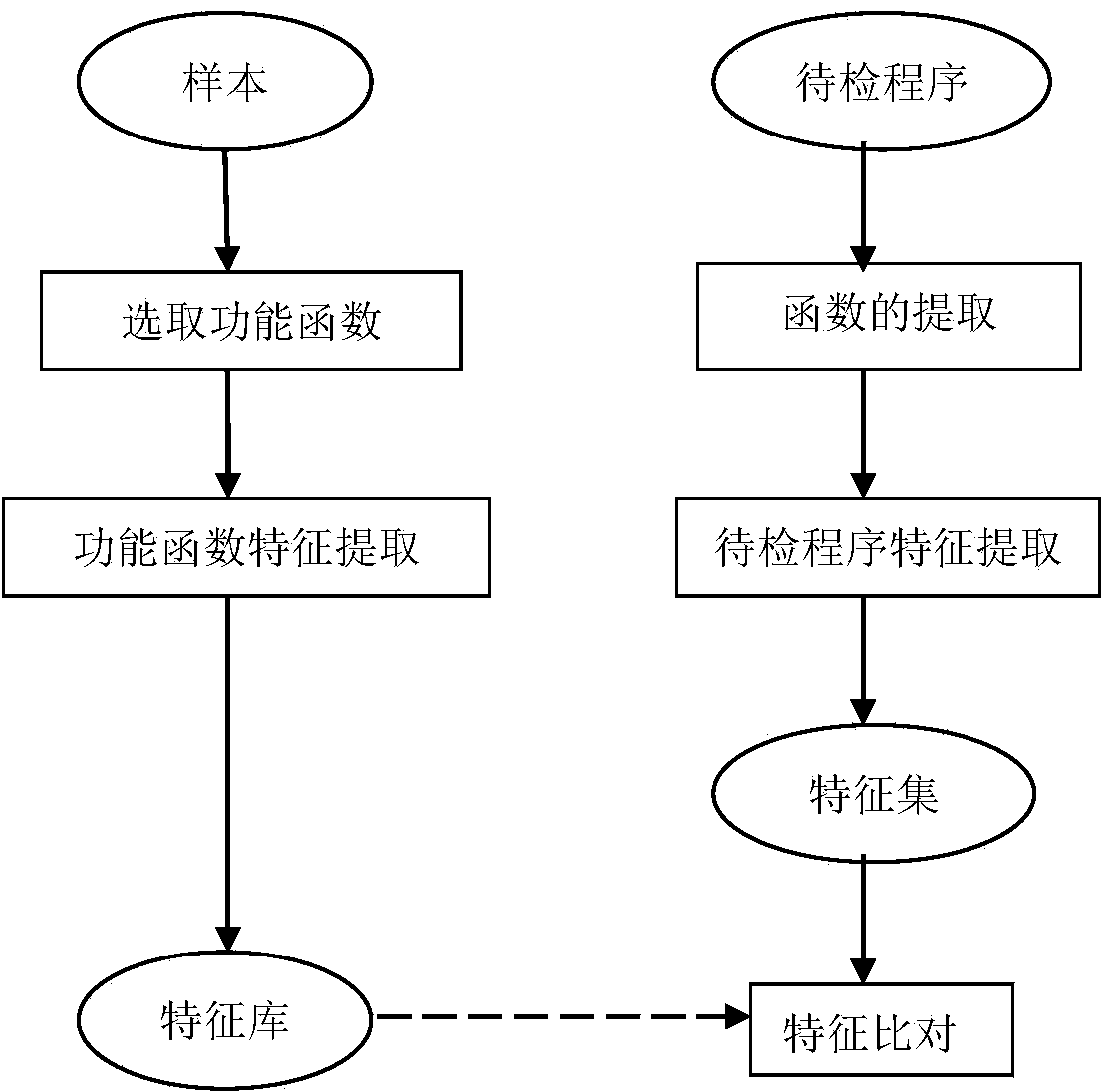
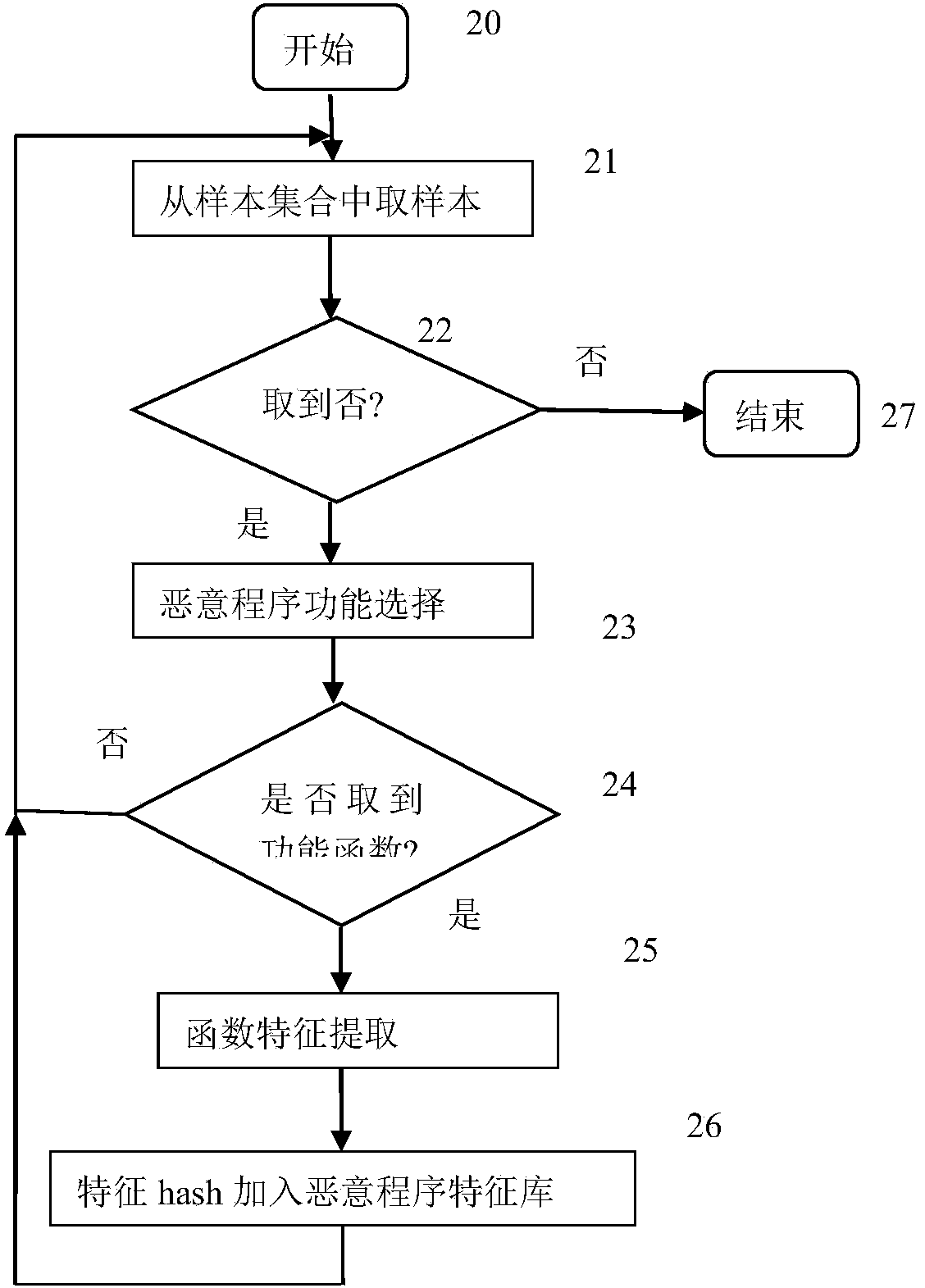
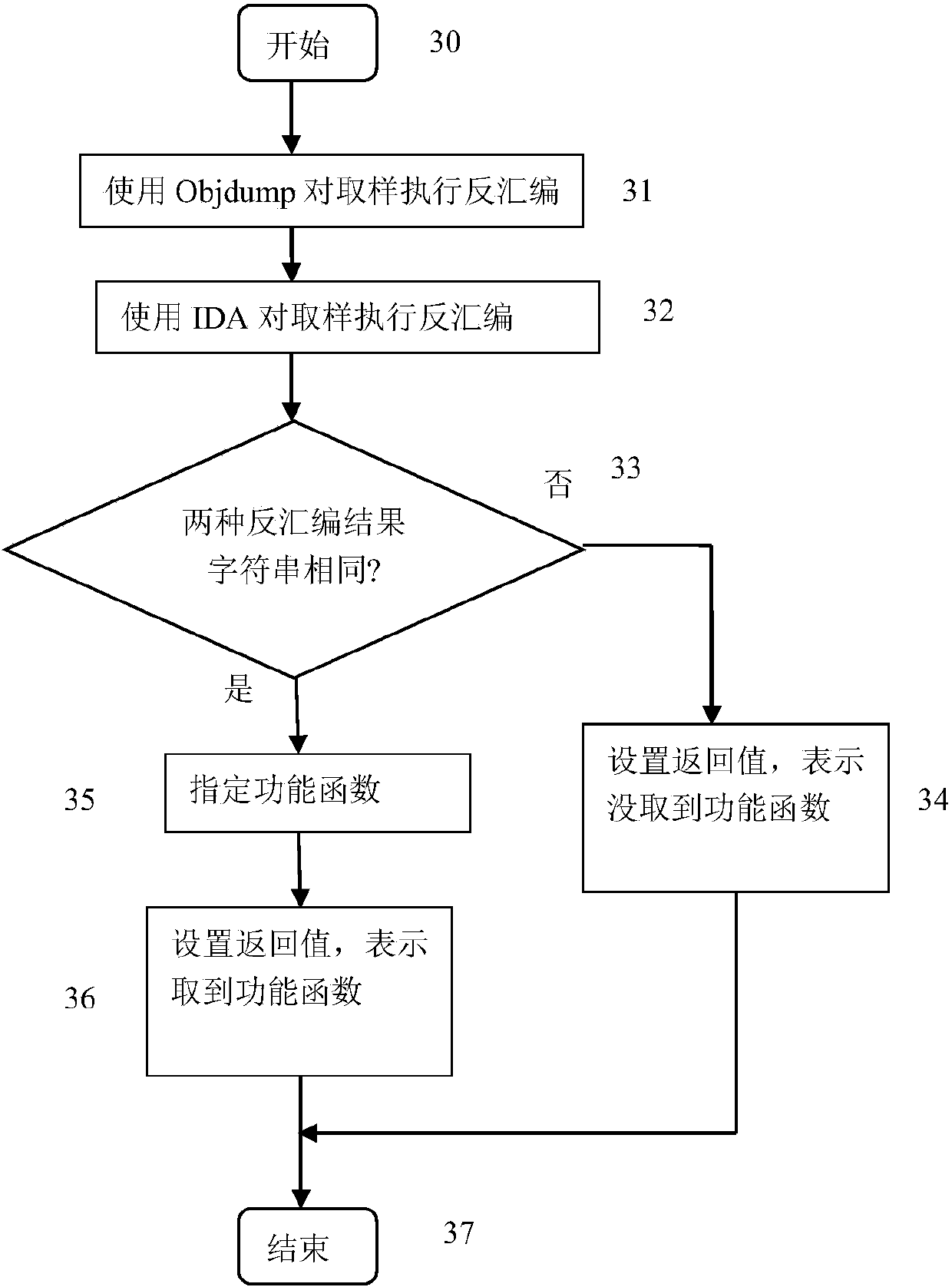
Malicious program detection method based on function characteristics
The invention provides a malicious program detection method based on function characteristics. The malicious program detection method includes the steps of (1) selection of performance functions of malicious programs, namely selecting malicious program samples, carrying out disassembling and manual analysis and specifying functions closely related to malicious behaviors as the performance functions, (2) extraction of function characteristics, namely processing function body codes of the functions closely related to malicious behaviors, removing interference instructions, identifying conditional judgment statements and loop statements, and converting all the statements into equivalent expression forms as the function characteristics, (3) establishment of malicious program characteristic library, namely establishing a malicious program characteristic library as a malicious program model by using the function characteristics of the performance functions of all the malicious program samples and by using of a malicious program sample library; and (4) detection of malicious programs, namely analyzing a function characteristic set of all functions of a program to be detected by using the malicious program characteristic library, and determining whether the function characteristic set is consistent with a characteristic model in the malicious program characteristic library or not to identify whether the program to be detected is the malicious program or not.
Owner:NANJING UNIV
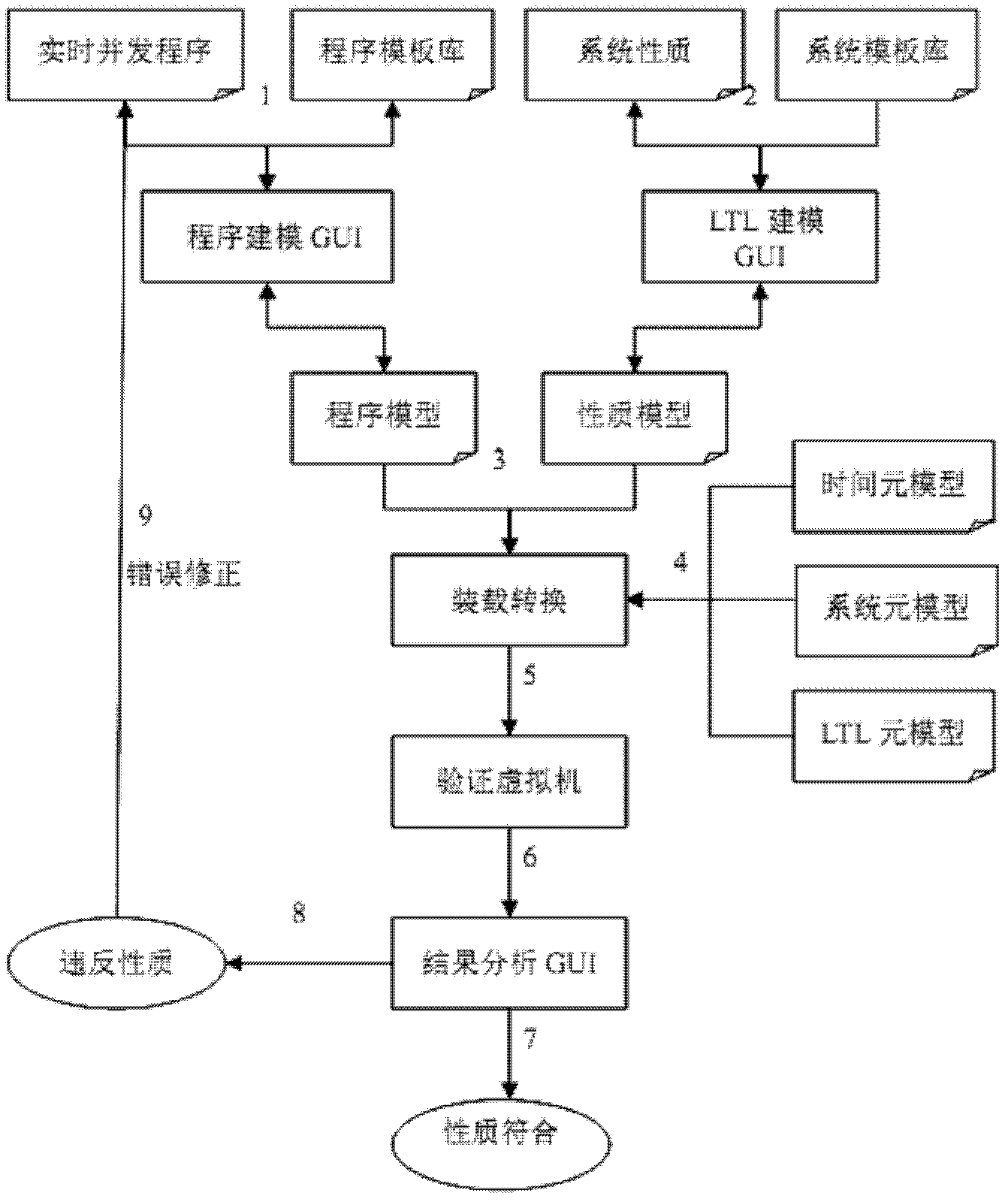
Concurrent real-time program verification ptimized processing system and method based on rewrite logic
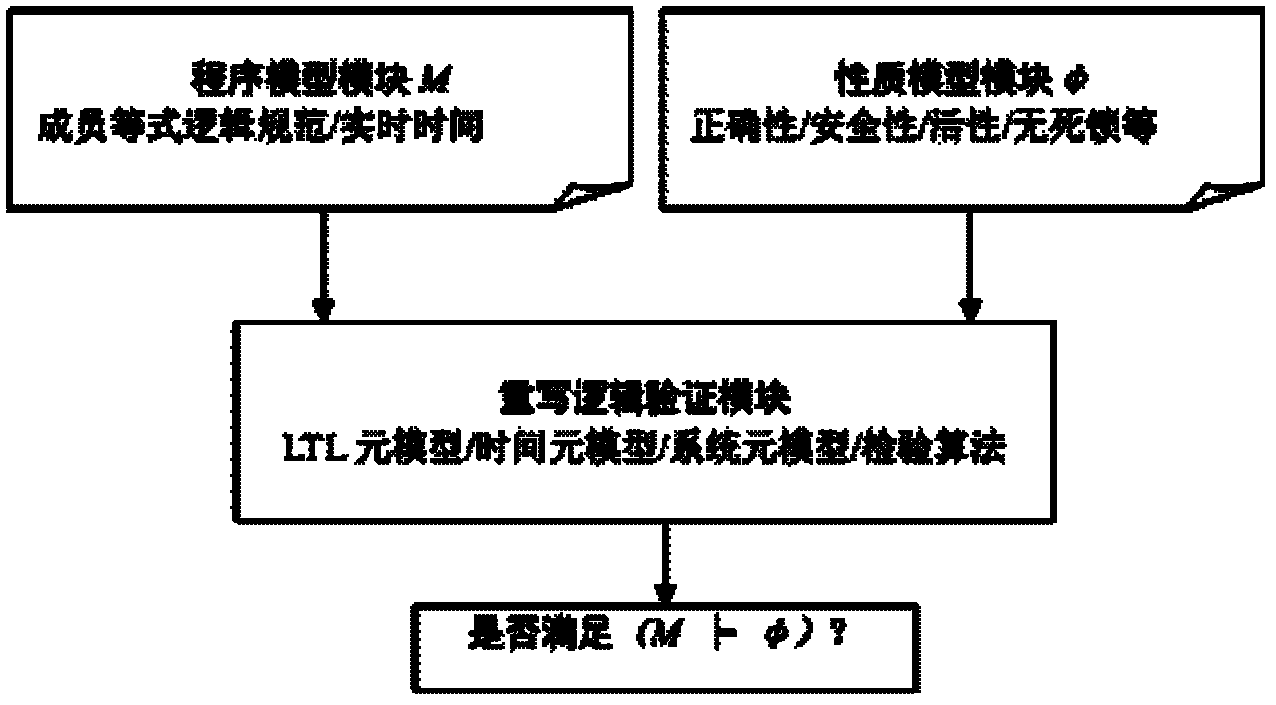
InactiveCN102231133ASystem status loweredImprove verification efficiencySoftware testing/debuggingProgram validationComputer module
The invention provides a concurrent real-time program verification optimized processing system and method based on rewrite logic and belongs to the technical field of computer application. The system comprises a program model module, a property model module and a rewrite logic verification module. The method comprises the following steps: verifying a concurrent real-time program by virtue of rewrite logic; carrying out status space optimization on the property to be verified and model of the system by virtue of an algebraic model; adopting a time meta model to process real-time related property; and using equivalent state compression and algebraic simulation optimization so as to improve the program verification efficiency.
Owner:上海钰祺网络科技有限公司
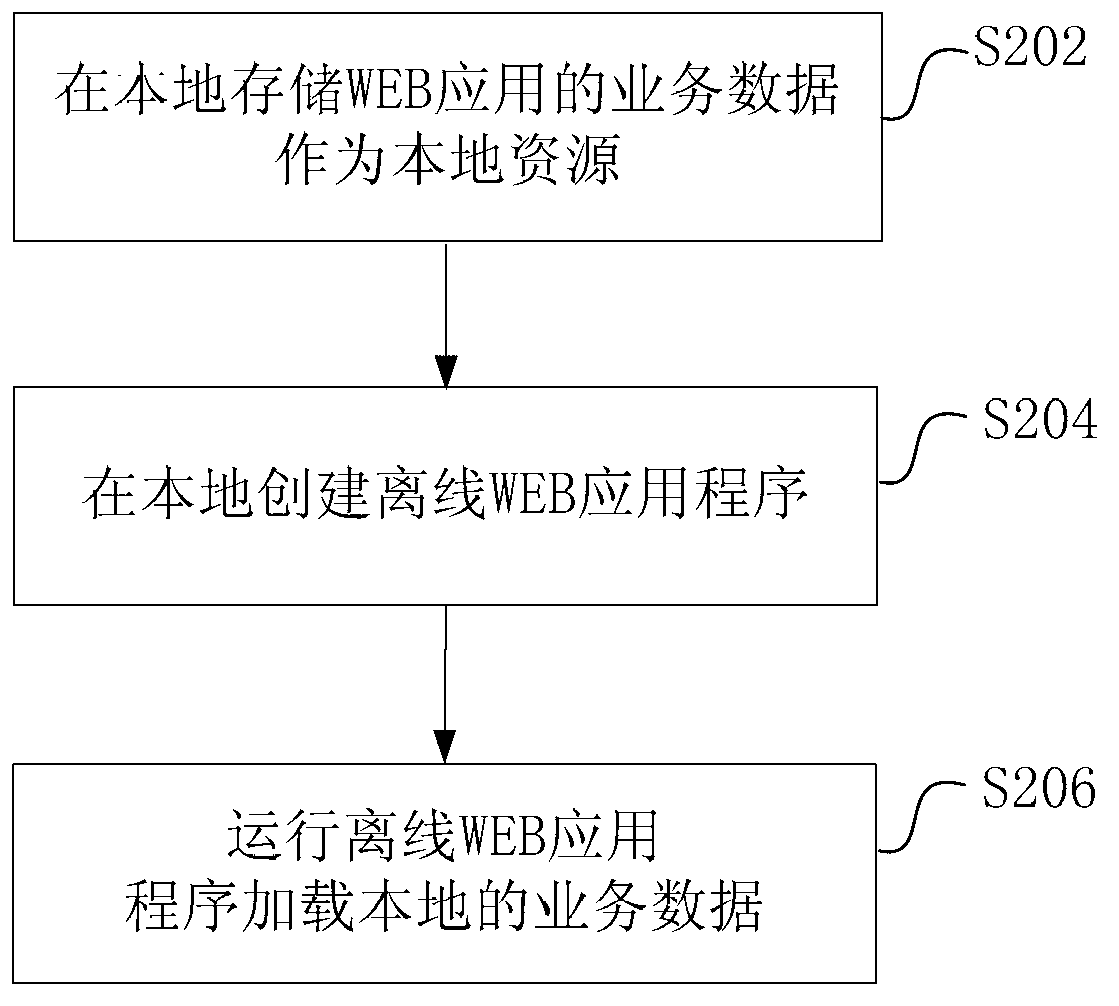
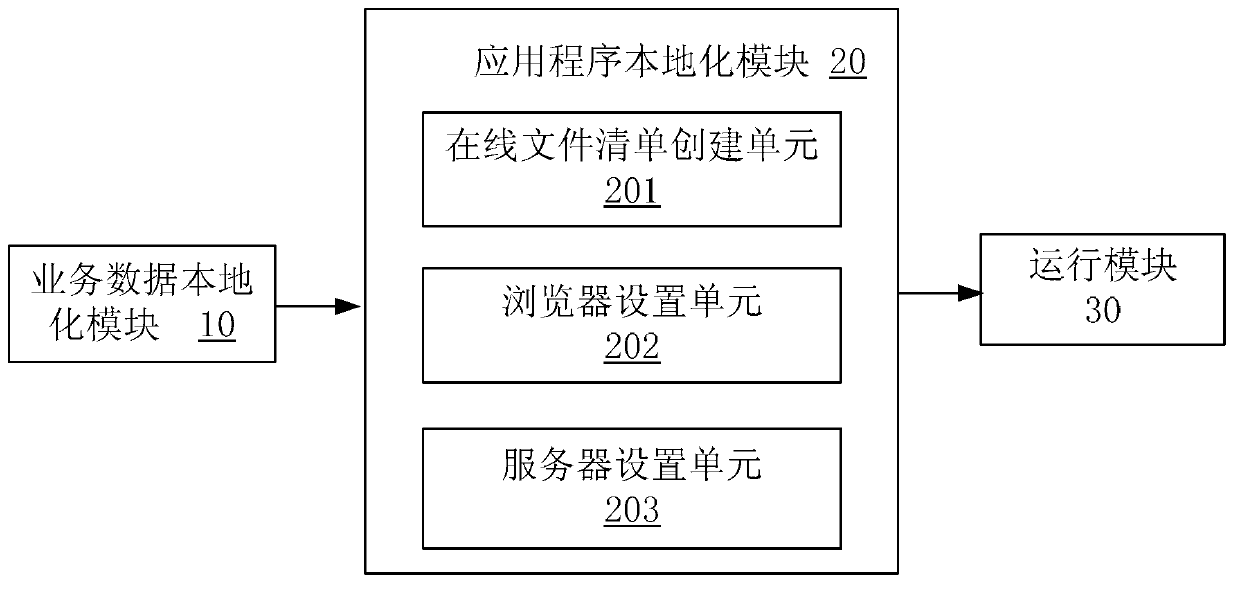
Application localization method and device based on web-based operating system (WEBOS)
InactiveCN103108035ARun offline operations directlyProgram loading/initiatingTransmissionWeb applicationBusiness data
The invention discloses an application localization method and a device based on web-based operating system (WEBOS) and belongs to the WEB technical field. The method includes the following steps: storing business data applied by WEB locally as local resources; establishing a local off-line WEB application program; and loading the local resources during running of the off-line WEB application program. According to the application localization method and the device based on the WEBOS, the business data of the WEB application program are stored by a local database introduced by standard hypertext markup language (HTML) 5 and an inventory file off-line technology is adopted, and therefore the localized WEB application program can directly run to perform offline operation.
Owner:NUBIA TECHNOLOGY CO LTD
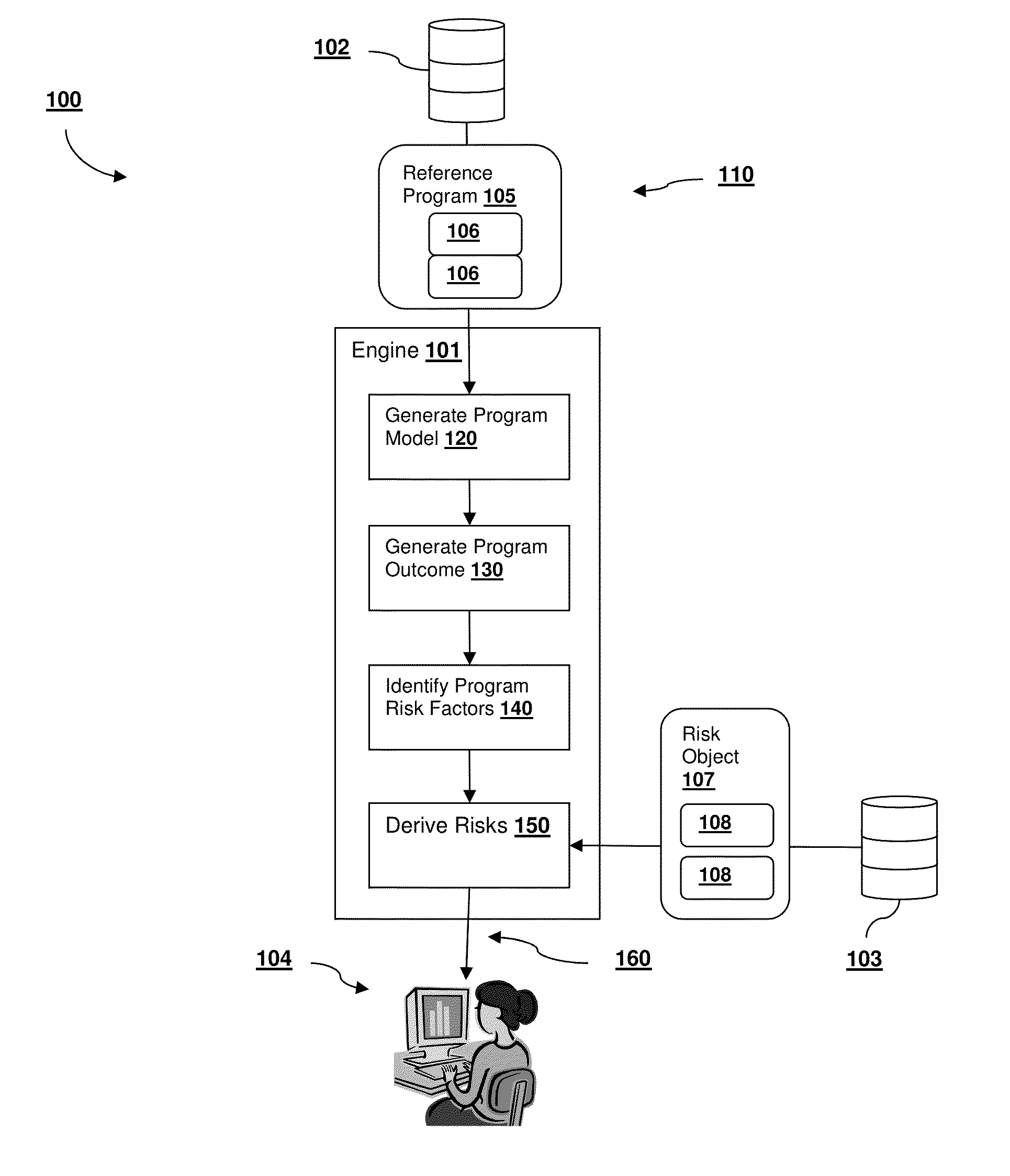
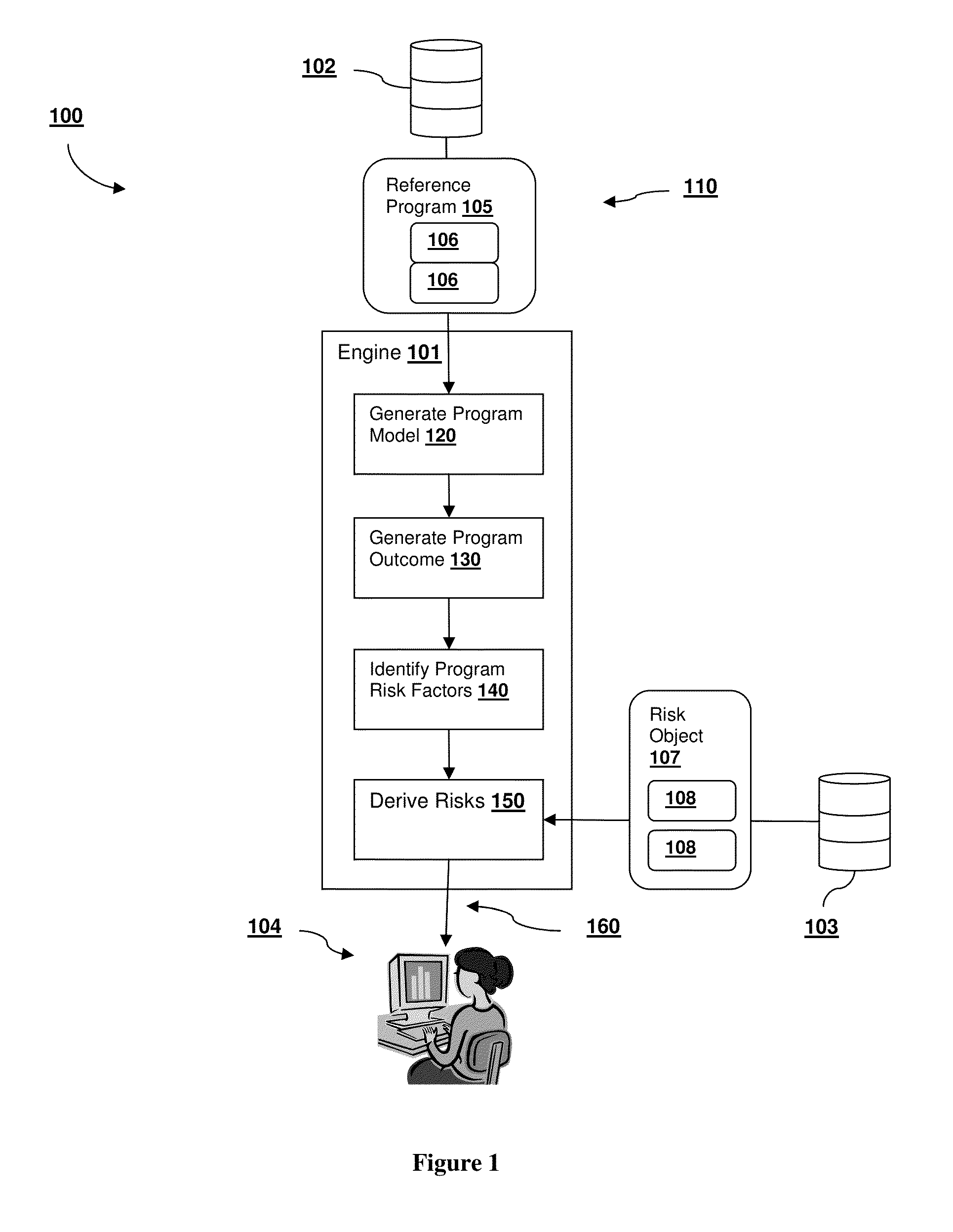
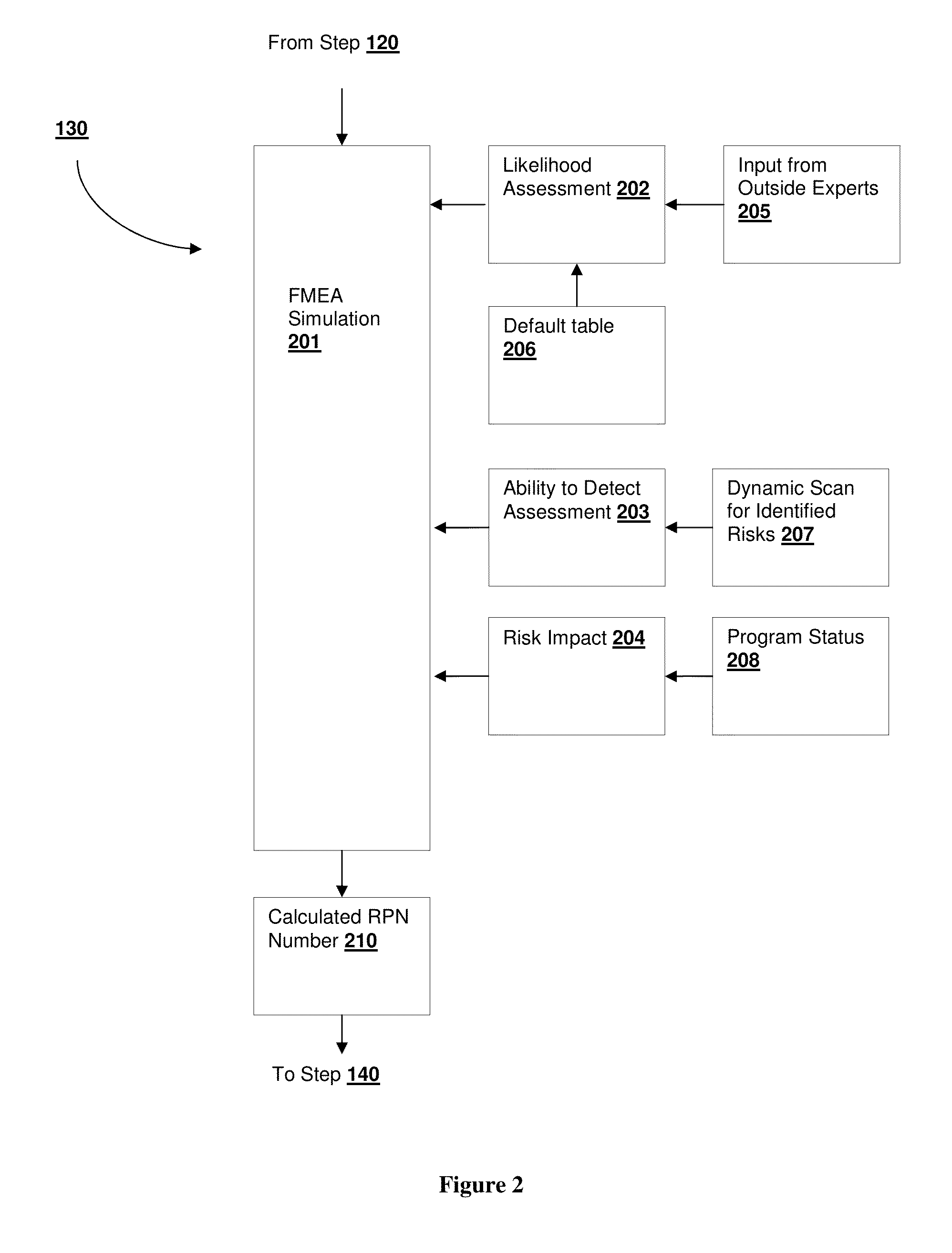
Identifying, Assessing, And Tracking Black Swan Risks For An Engineering And Construction Program
A risk analysis system having a risk analysis engine that can identify a set of risks for a program based on a constructed program model. The program model can be based on known, historical programs using current program attribute information. The risks can be identified by executing one or more simulations using the program model. The outcome of the simulation can be used to identify individual drivers of risk, which can in turn be used to identify one or more previously undetected and unanticipated black swan-level risks facing the program.
Owner:FLUOR TECH CORP
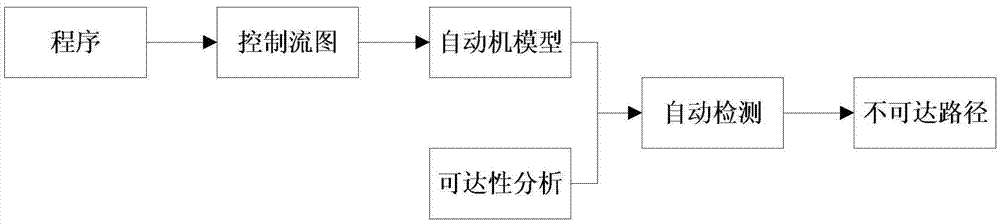
Automatic detection method for program unaccessible paths
InactiveCN105446881ASimple principleSimple processSoftware testing/debuggingReachabilityAccessibility
The present invention discloses an automatic detection method for program unaccessible paths. The method comprises the steps of: converting a to-be-detected computer program into a control flow diagram; and converting the control flow diagram into a program model, performing accessibility analysis to obtain unaccessible states, automatically detecting the unaccessible states to obtain an unaccessible state set, and then obtaining an unaccessible path set according to the unaccessible state set. The automatic detection method for the program unaccessible paths is based on a state searching technology being simple in theory, and effectively lowers the technology application and promotion difficult when being compared with the prior art usually based on complex mathematical technology; the detection method for the program unaccessible paths is complete and has high automatization degree; the problem of accessibility detection of the control flow diagram is solved; problems of difficulties and low efficiency of a static analysis technology in processing of complex programs are solved; and the problem that the static analysis technology has difficult in expressing compound data in processing a multi-branch procedure is solved.
Owner:FUJIAN UNIV OF TECH
Method and apparatus for improving the accuracy of linear program based models
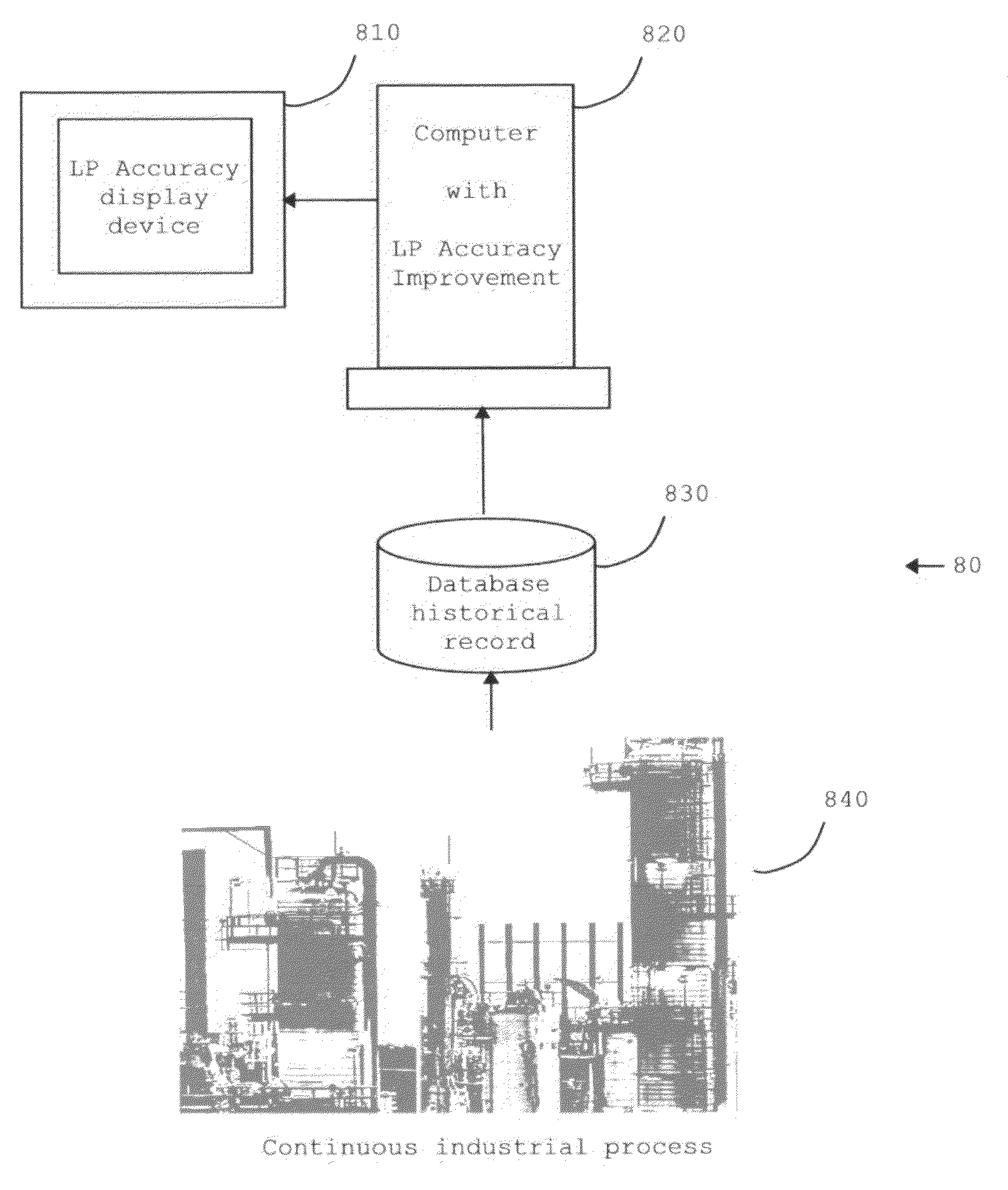
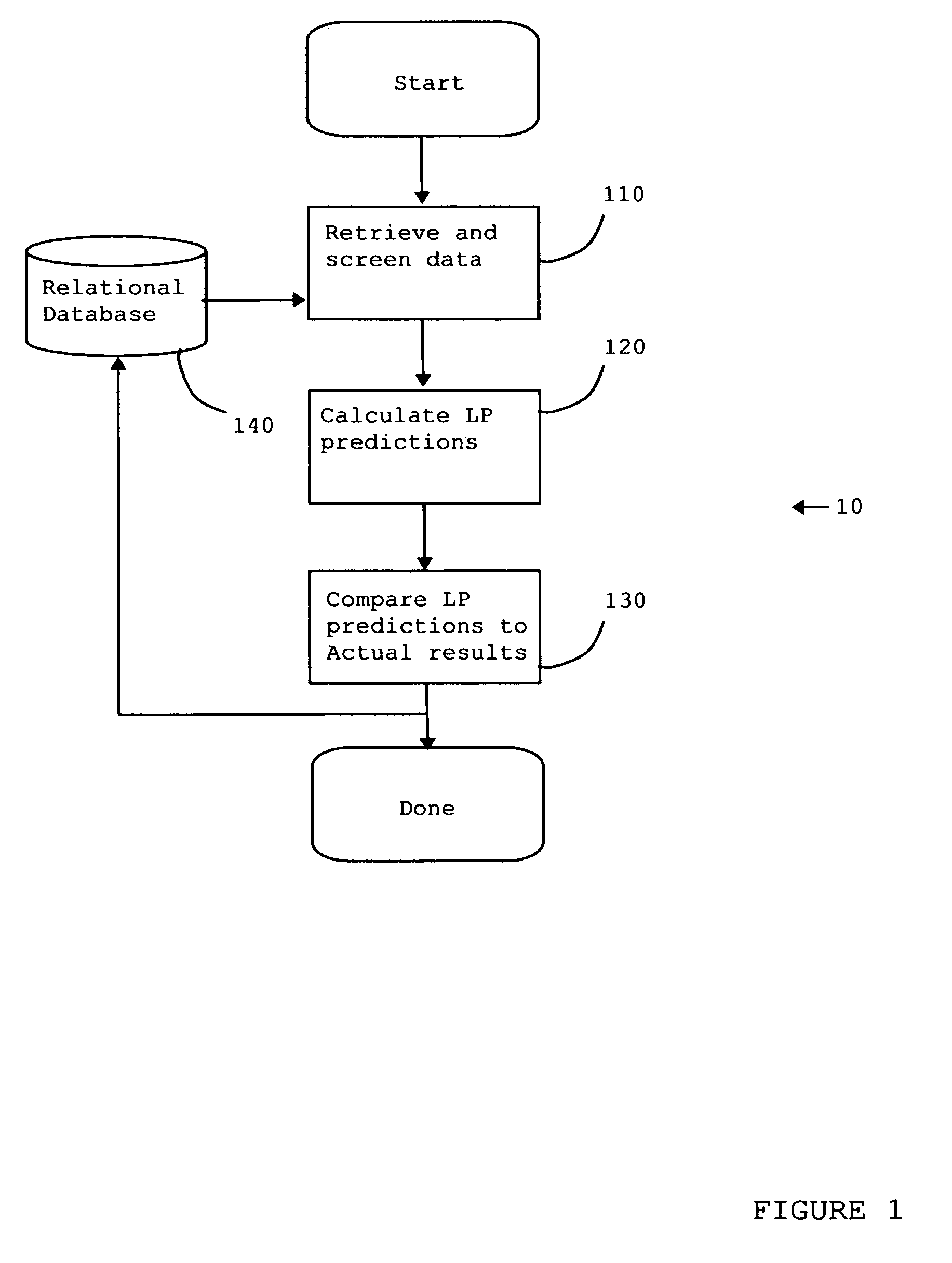
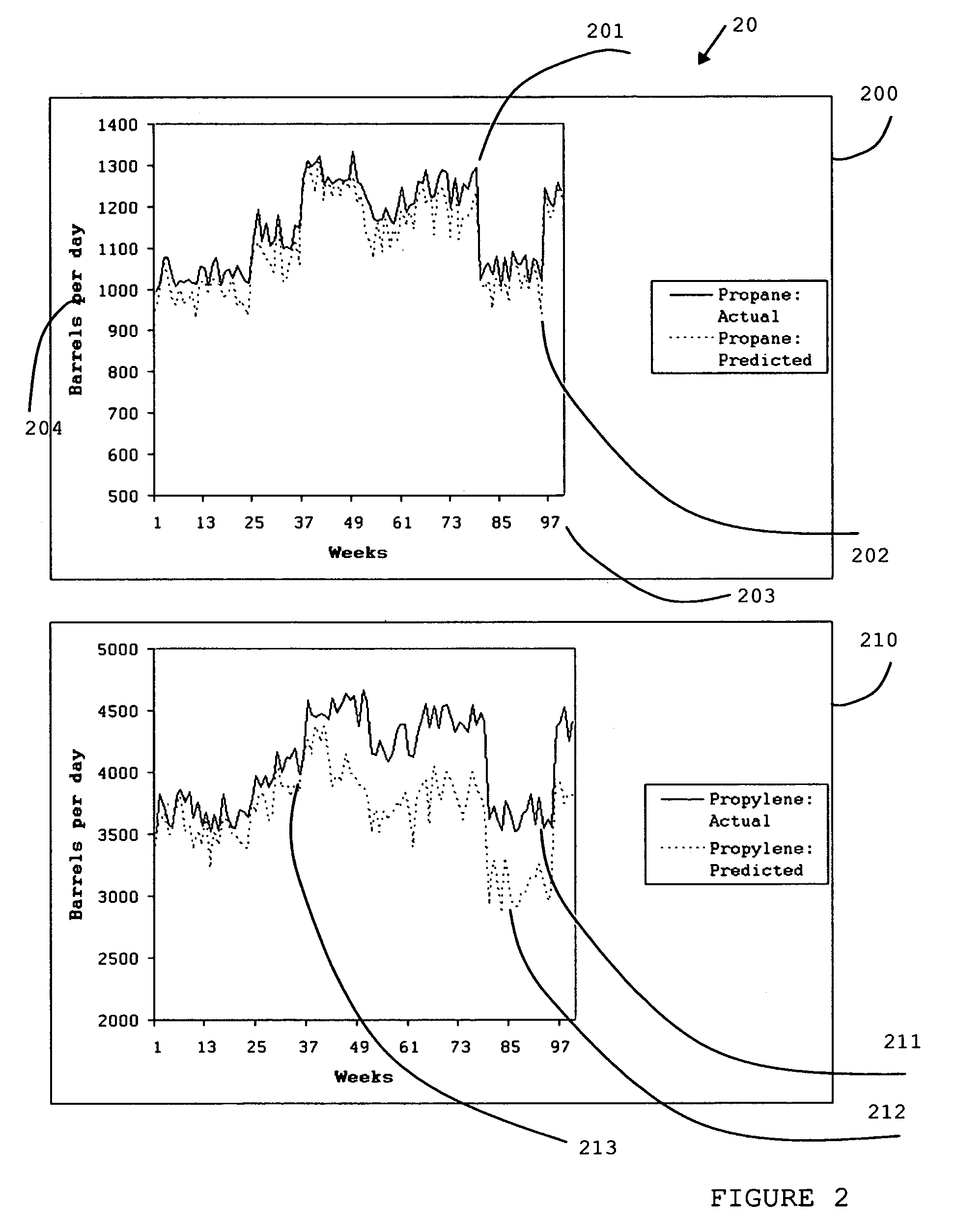
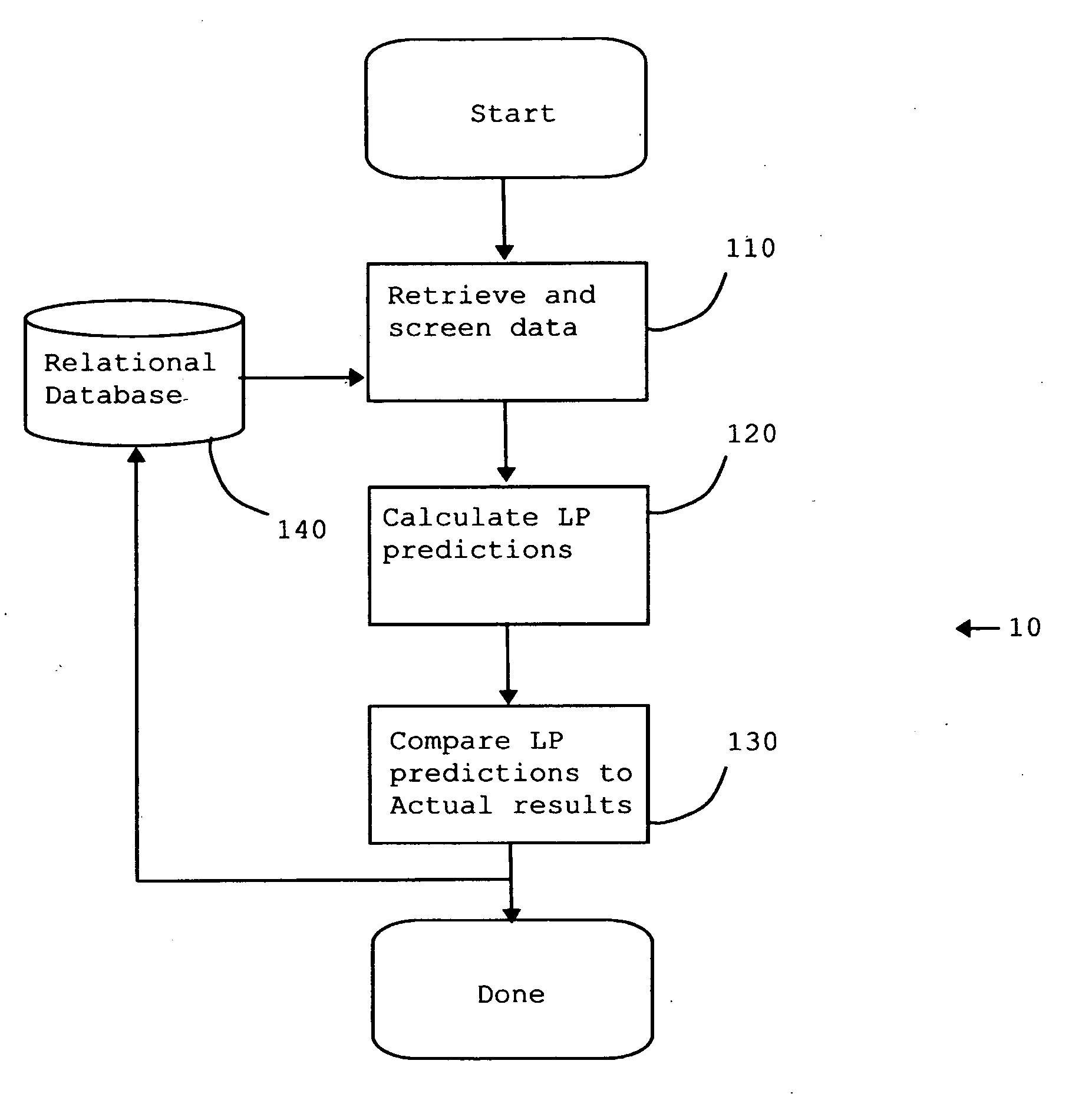
ActiveUS20070106399A1Improve modeling accuracyReduces total prediction errorSimulator controlAdaptive controlGraphicsQuality assessment
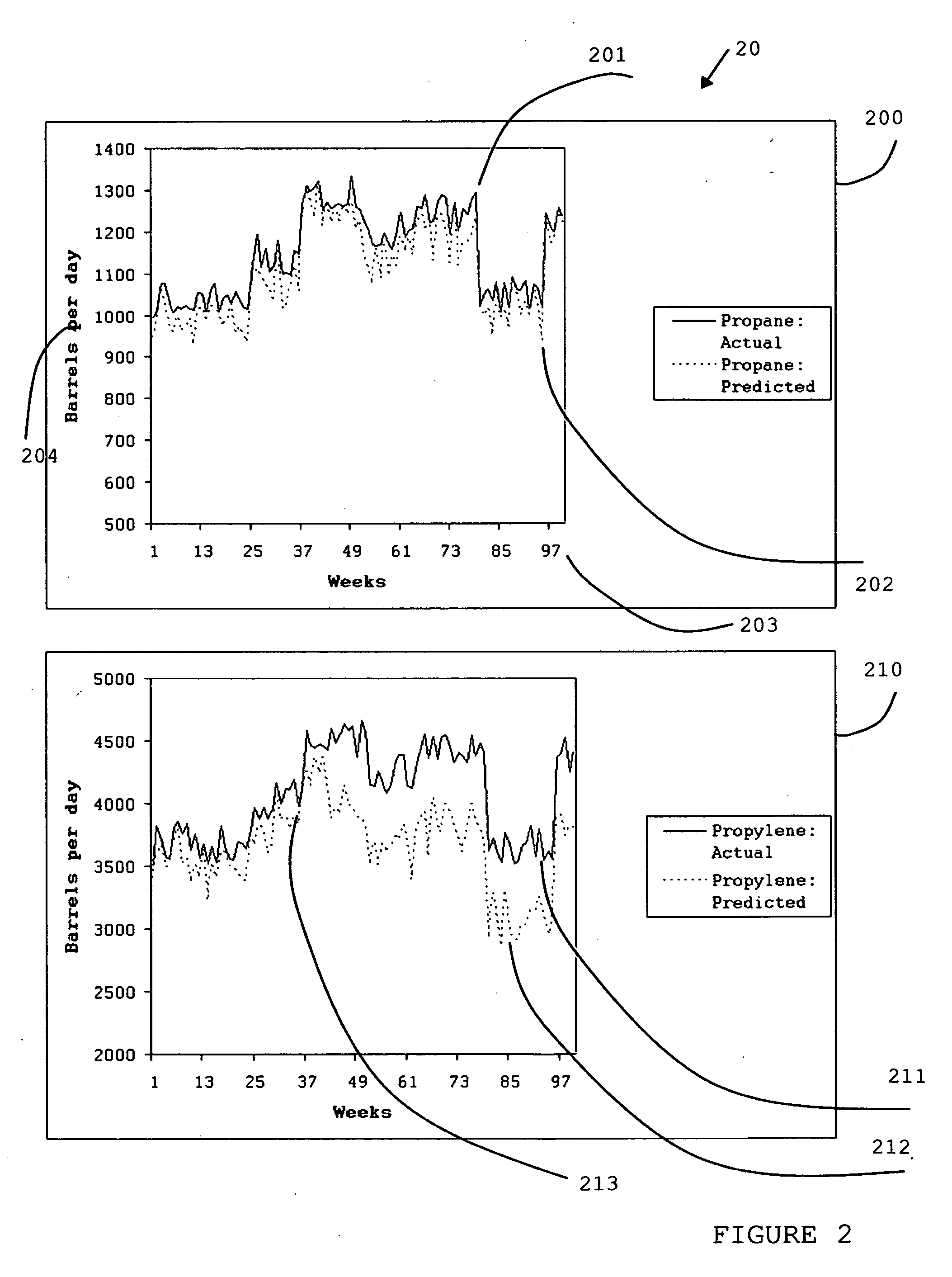
A method and apparatus are disclosed for evaluating the performance of a Linear Program model of an operation. The significant properties of the current invention include the use of a historical record or operating data as a means to improve the evaluation of the Linear Program model quality. The historical record of operating data also allows a more reliable means for calculating corrected Linear Program model coefficients. Related applications are disclosed for viewing graphically both the uncorrected and the corrected Linear Program model's performance. Statistical methods are disclosed as further aids in understanding both the uncorrected and corrected Linear Program model's performance.
Owner:MATSON TODD
Methods For Simultaneous Process and Utility Systems Synthesis in Partially and Fully Decentralized Environments
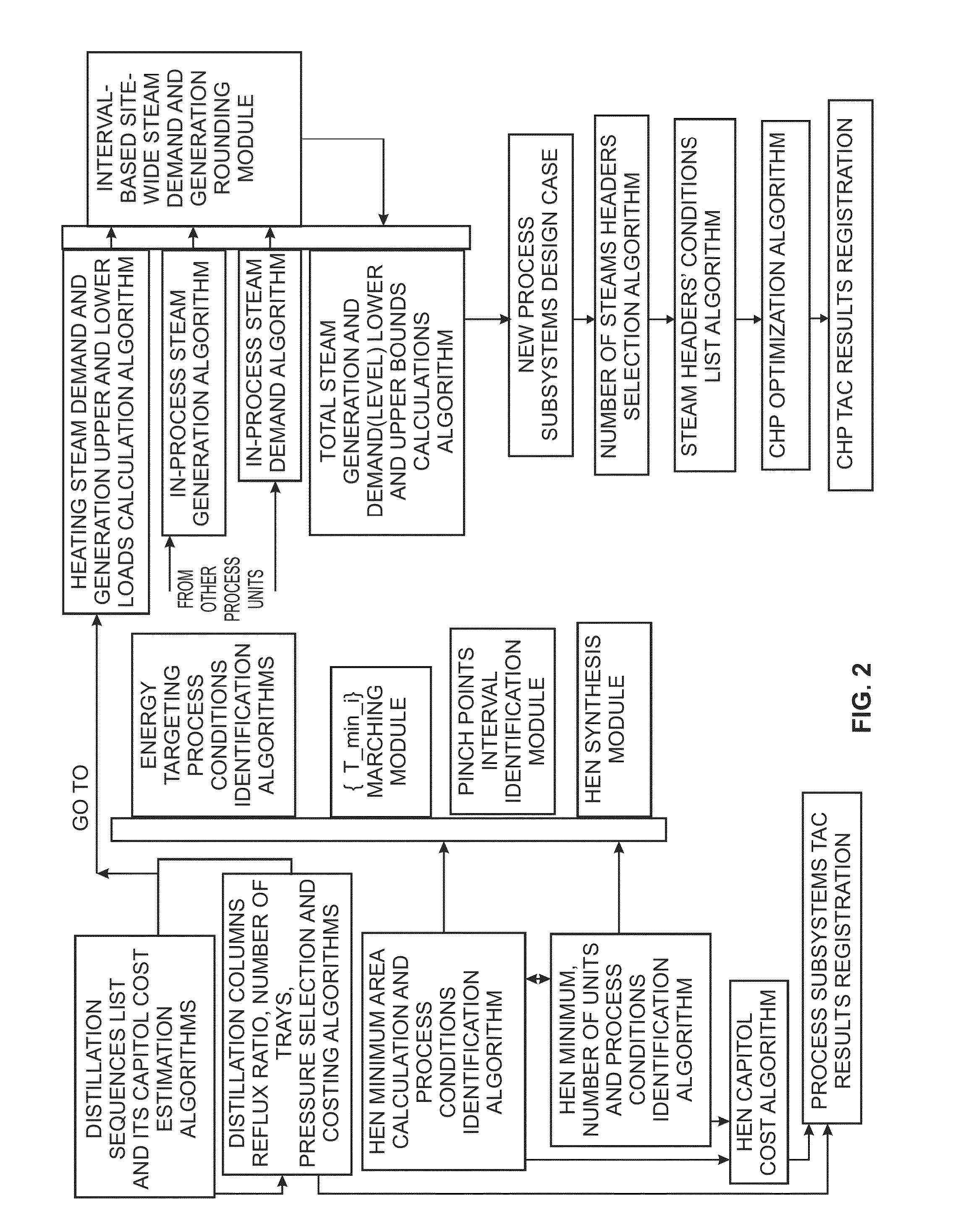
Methods of providing a combined synthesis of cost-effective heat and power (CHP) utility systems and the key process systems are provided. An exemplary method includes process steps for identifying the best key subsystem design and operating conditions for both the process and the utility systems. The method can include the step of determining an optimal allocation of steam and power between both process and utility systems for one or more industrial process facilities in both partially and totally decentralized environments. This can include defining rigorously bounded decision variables as model input data, processing the model input data by a combined heat and power utility and process subsystem mathematical program model, and determining a plurality of at least substantially optimal process and utility subsystem conditions.
Owner:SAUDI ARABIAN OIL CO
GPU-accelerated fluid-structure coupling simulation method through immersion boundary and lattice Boltzmann methods
InactiveCN104866695AImprove computing efficiencyThe interaction realization process is simple and straightforwardSpecial data processing applicationsBody shapeMeasurement point
The invention provides a GPU-accelerated fluid-structure coupling simulation method through immersion boundary and lattice Boltzmann methods. The GPU-accelerated fluid-structure coupling simulation method comprises the following steps: 1, establishing a structure body to be detected and an internal fluid immersion boundary body shape in professional pre-processing software, and dividing a boundary lattice for program read; reading boundary body shape data through a program, and setting a boundary condition of a point required to be measured and a program model parameter; calculating the boundary acting force applied to a fluid by using a finite element method according to a structure of the boundary at the current time and a reference structure; diffusing the boundary acting force to surrounding fluids through the Dirac function; solving a Navier-Stokes equation carrying an external force term by using the lattice Boltzmann method; interpolating the fluid speed into the boundary through the Dirac function to obtain a boundary movement speed to further update the boundary position; repeatedly performing the steps 3-6 till the updated boundary position reaches an calculated ending point. According to the GPU-accelerated fluid-structure coupling simulation method, structure bodies in any shapes can be processed, an underlying fluid lattice does not require to be reconstructed in the calculation process, and the calculation efficiency is high.
Owner:WUHAN UNIV
Type system for building extensible business applications
ActiveUS8473506B2High degreeDigital data processing detailsSemi-structured data queryingExtensibilityExtensible markup
Owner:ORACLE INT CORP
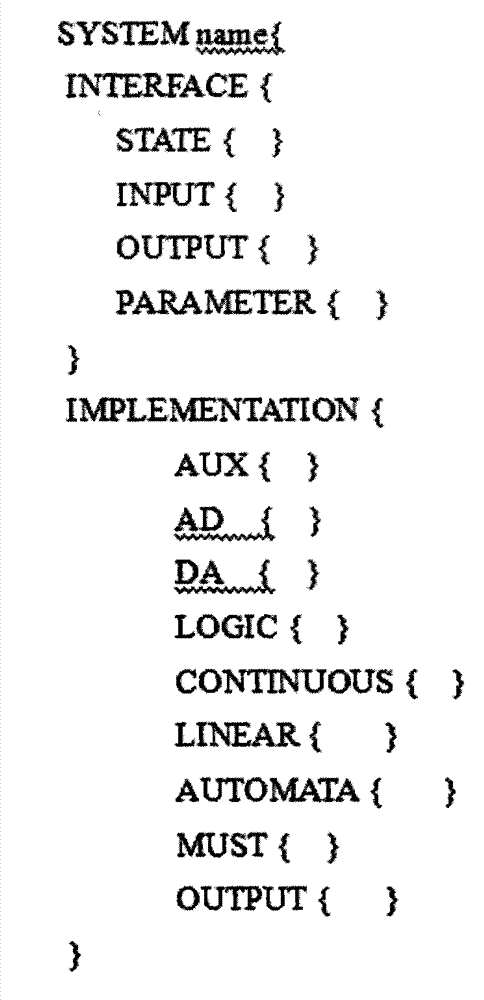
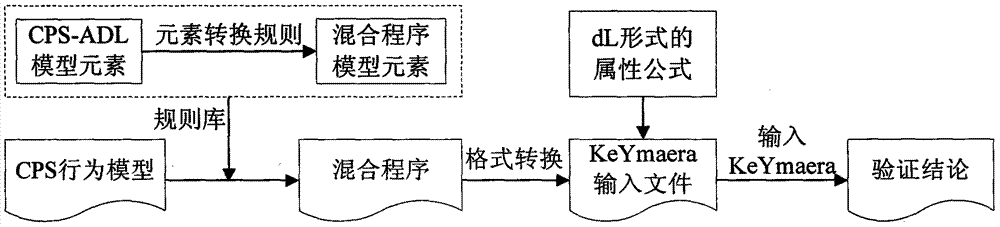
CPS (cyber physical system) modeling and verifying method based on conversion from CPS-ADL (architecture description language) model into hybrid program
InactiveCN103699743AImplement the rules for conversionSpecial data processing applicationsArchitecture description languageValidation methods
The invention discloses a CPS (cyber physical system) modeling and verifying method based on conversion from a CPS-ADL (architecture description language) model into a hybrid program. The method is mainly used for modeling a CPS and verifying attributes. The method is characterized in that a CPS is modeled on a CPS-ADL platform by the aid of an E-HYSDEL (expanded-hybrid system description language); a formalized definition HPM (hybrid program model) of an HP (hybrid program) model is given, and conversion rules among the CPS-ADL model elements and HP model elements are established when model conversion consistency is met; model description codes of a specific CPS are automatically converted into the hybrid program based on the conversion rules; input files of a KeYmaera are generated by the aid of the hybrid program and a dynamic differential logic description system attribute formula according to an input format of the KeYmaera of a theorem prover; the input files are opened in the KeYmaera to perform reasoning and verifying. The method and the mechanism based on conversion from the CPS-ADL model into the HP are elaborated, and the rules of conversion from the CPS-ADL model elements into the HP model elements are realized.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com