Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35 results about "Luser" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Internet slang prior to the popularization of the Internet in the late 1990s, defined a luser (sometimes expanded to local user; also luzer or luzzer) as a painfully annoying, stupid, or irritating computer user. The word is a blend of "loser" and "user". Among hackers, the word luser takes on a broad meaning, referring to any normal user (in other words, not a "guru"), with the implication the person is also a loser. The term is partially interchangeable with the hacker term lamer.
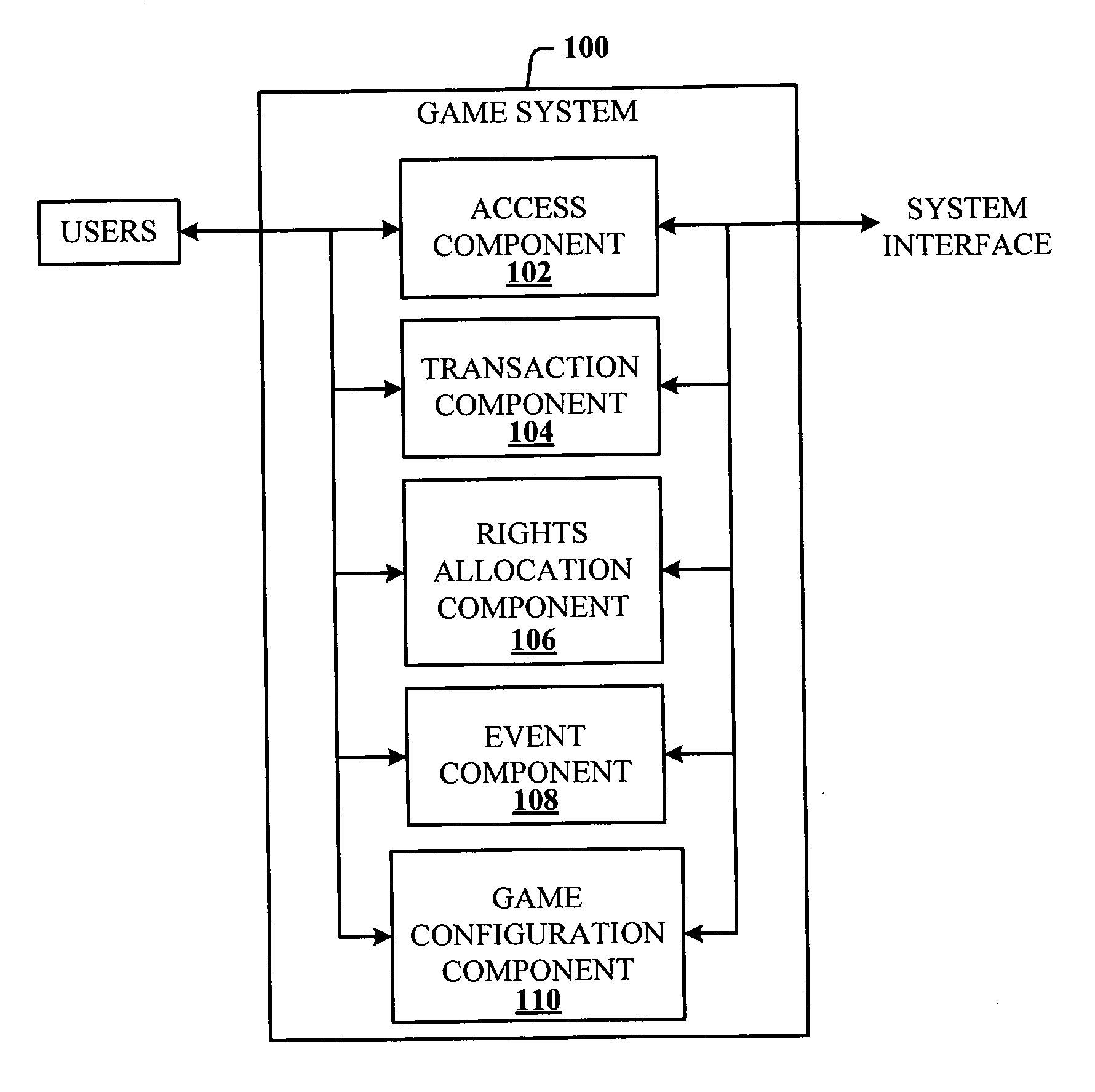
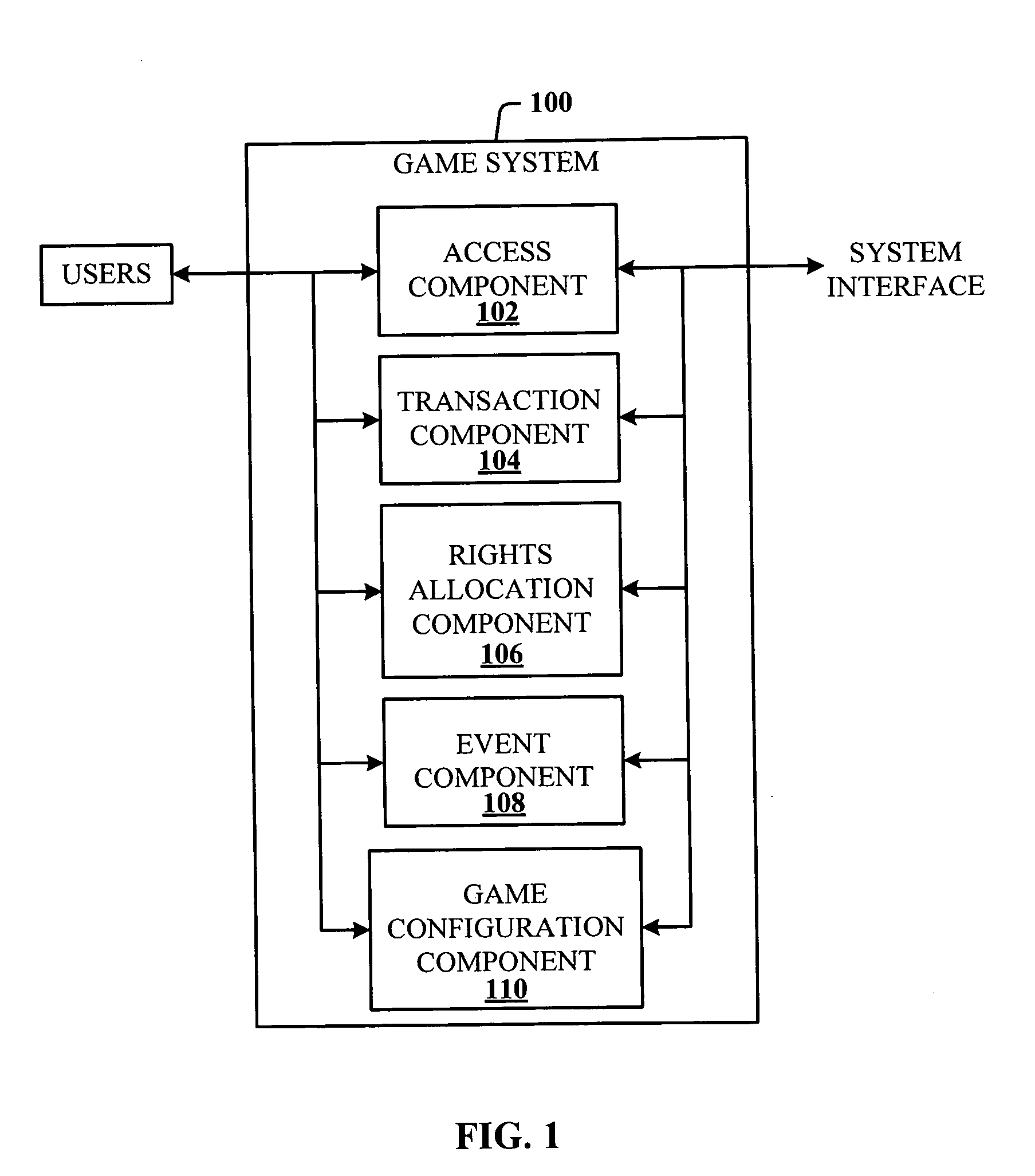
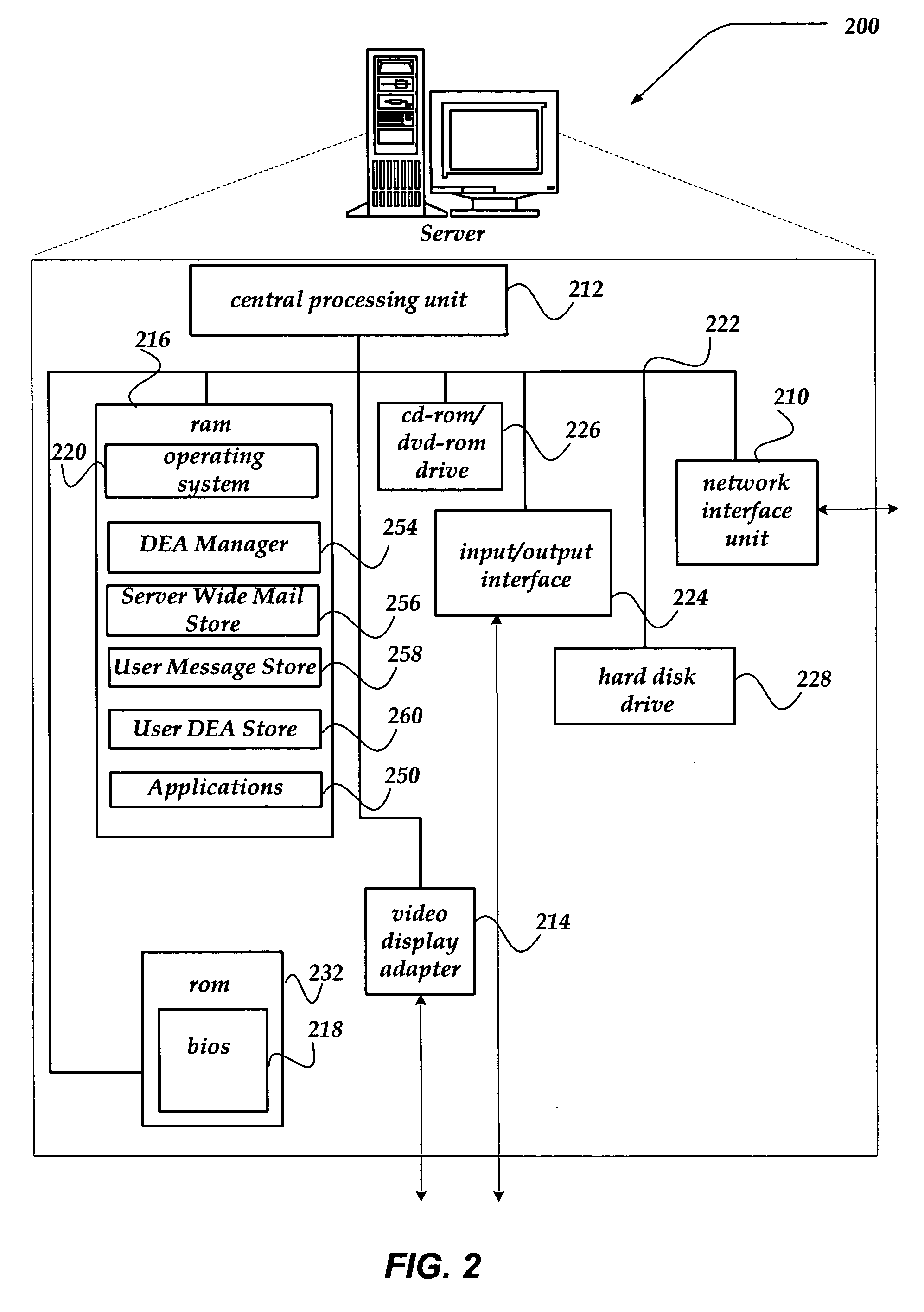
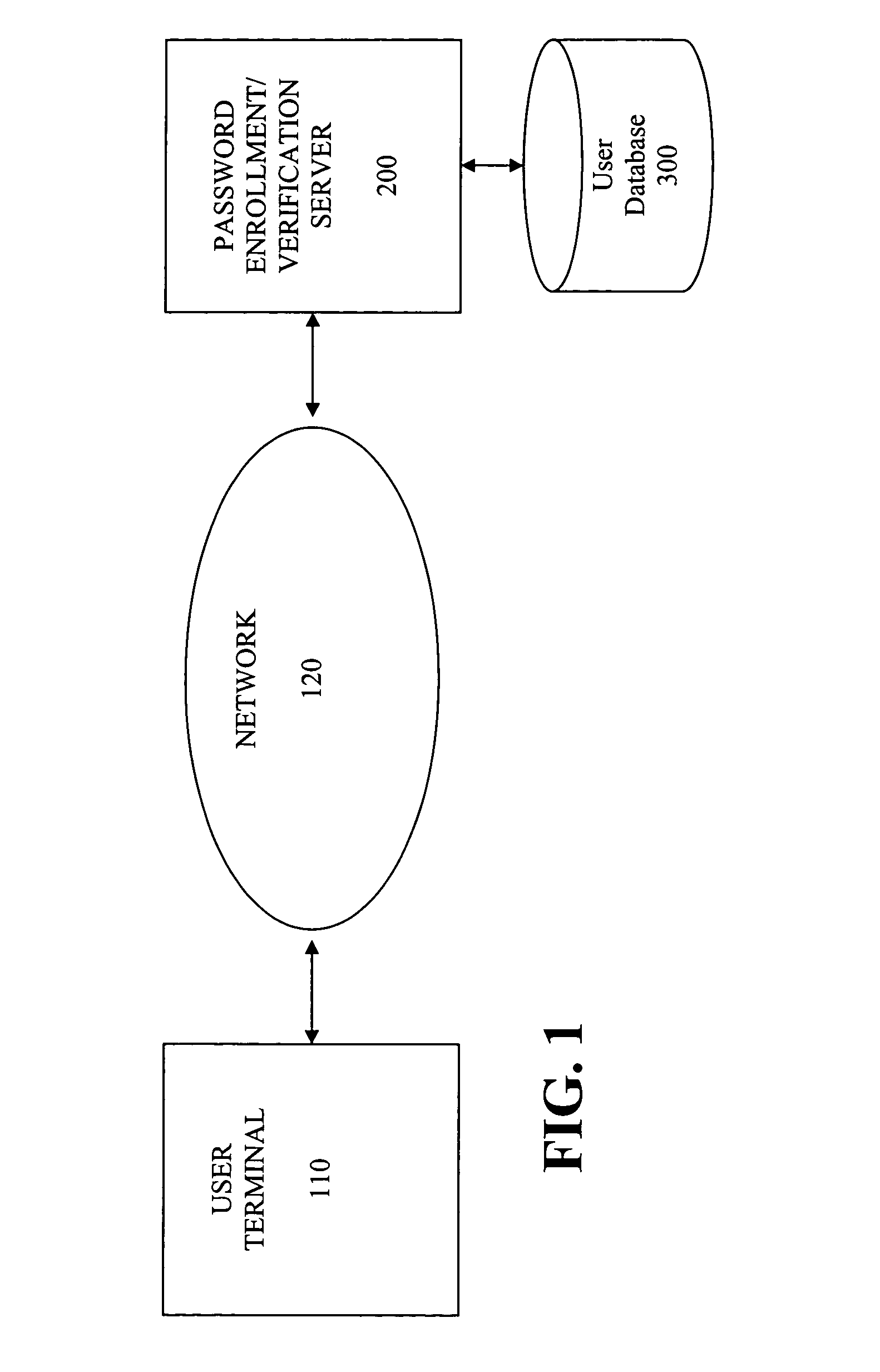
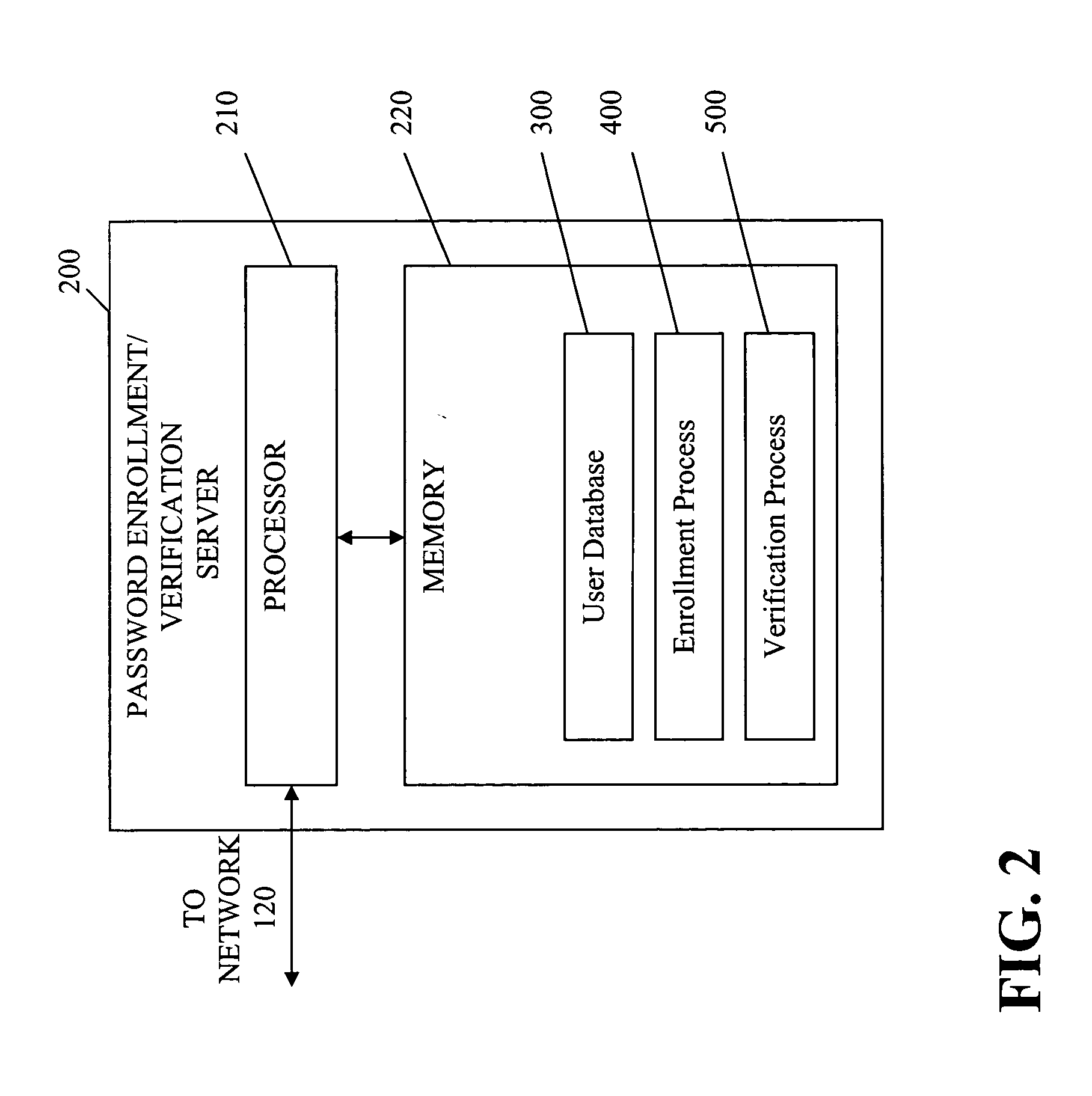
System and method for authentication of network users
InactiveUS7234156B2Reducing cost and unnecessary useChanceDigital data processing detailsUser identity/authority verificationBatch processingInformation design
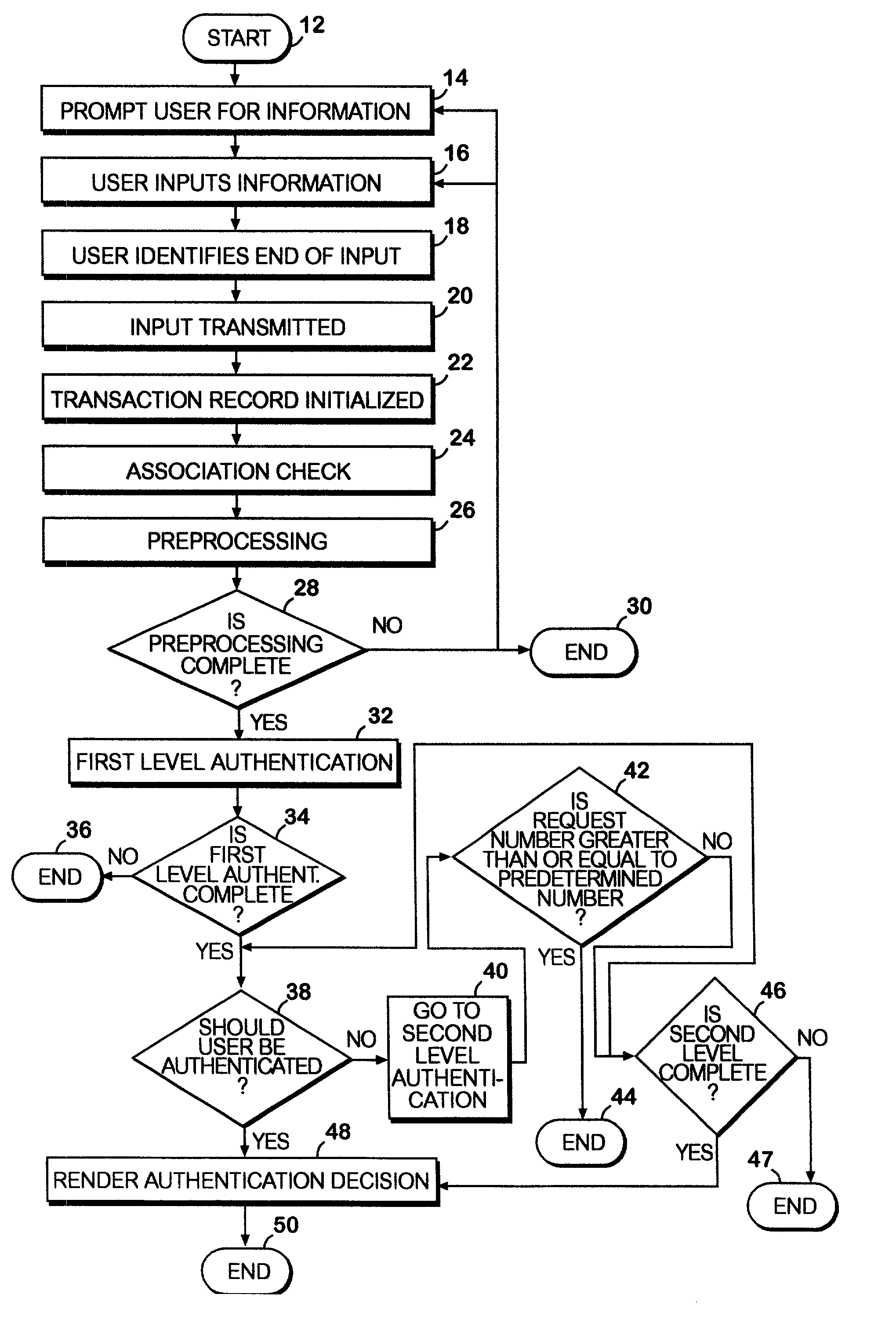
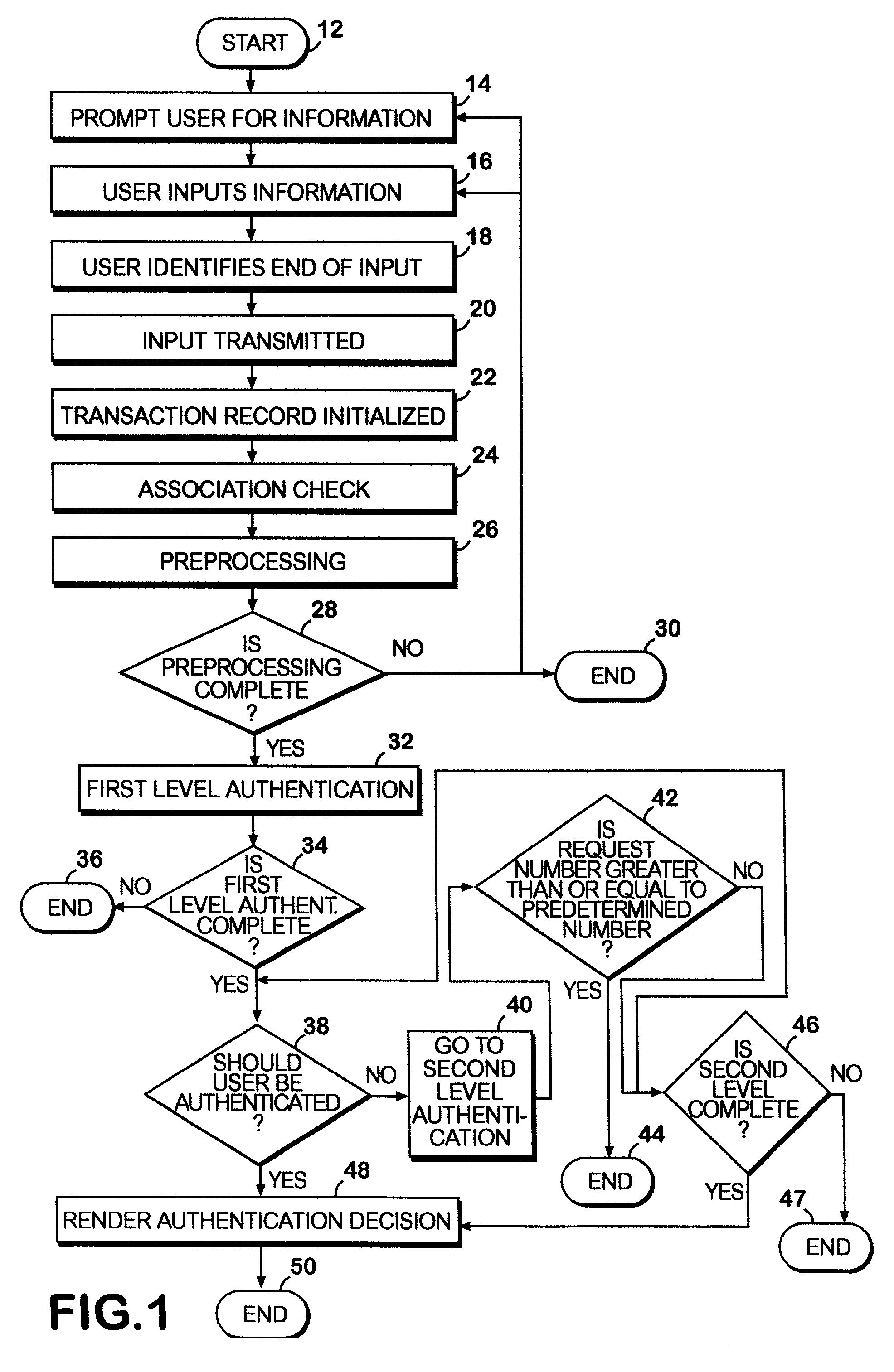
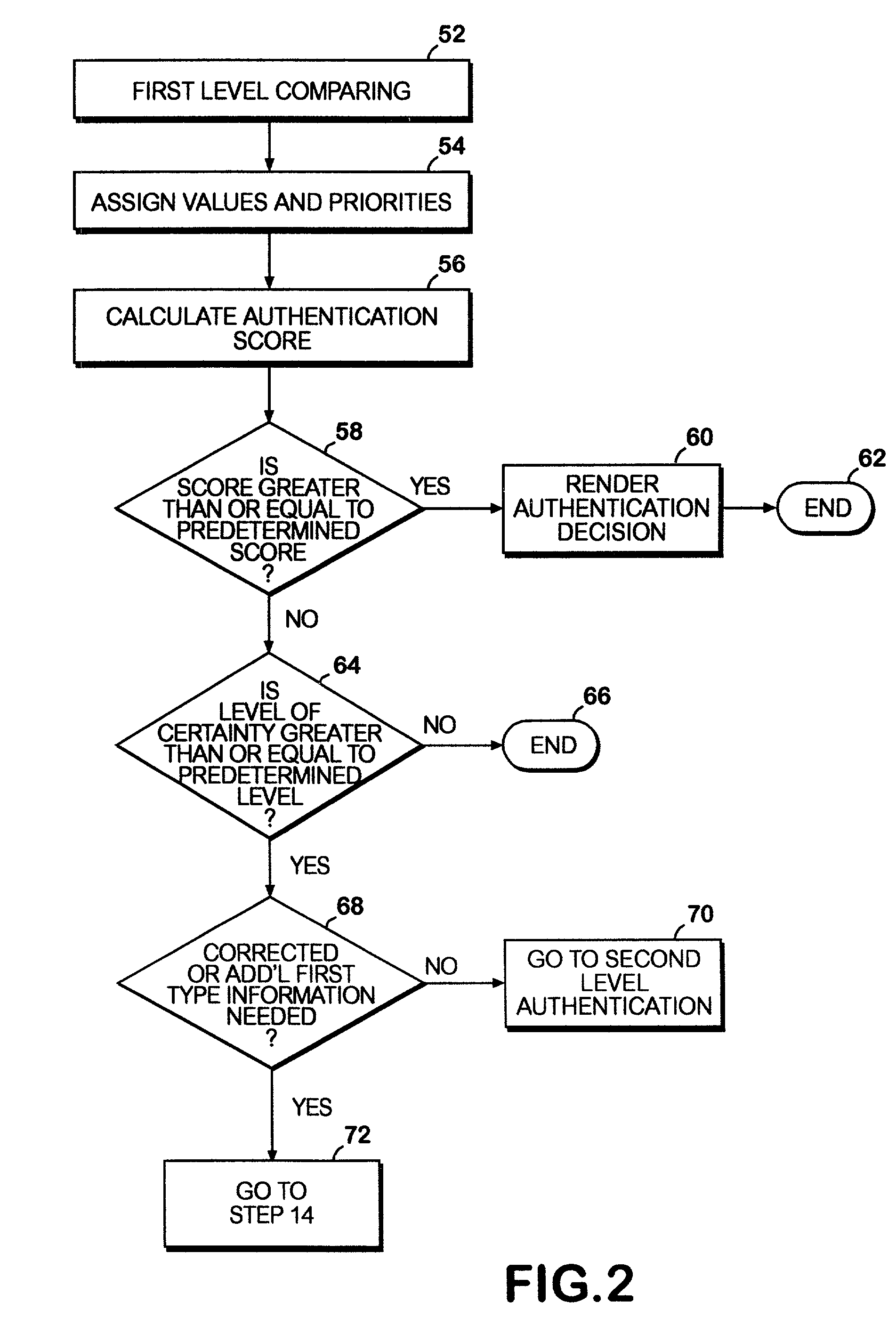
A network authentication system provides verification of the identity or other attributes of a network user to conduct a transaction, access data or avail themselves of other resources. The user is presented with a hierarchy of queries based on wallet-type (basic identification) and non-wallet type (more private) information designed to ensure the identity of the user and prevent fraud, false negatives and other undesirable results. A preprocessing stage may be employed to ensure correct formatting of the input information and clean up routine mistakes (such as missing digits, typos, etc.) that might otherwise halt the transaction. Queries can be presented in interactive, batch processed or other format. The authenticator can be configured to require differing levels of input or award differing levels of authentication according to security criteria.
Owner:EQUIFAX INC
System and method for the classification of electronic communication
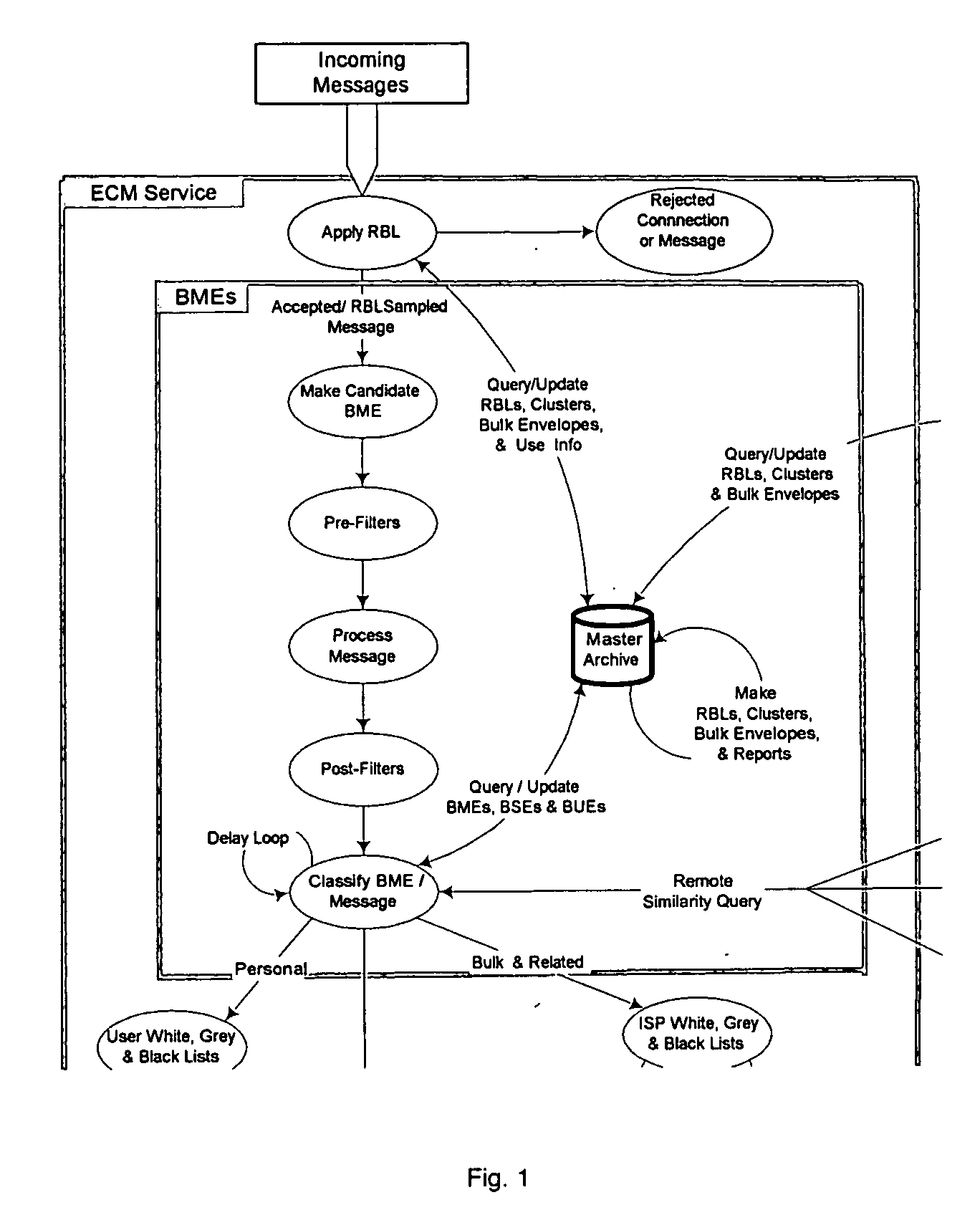
InactiveUS20060168006A1Multiple digital computer combinationsData switching networksElectronic communicationSpamming
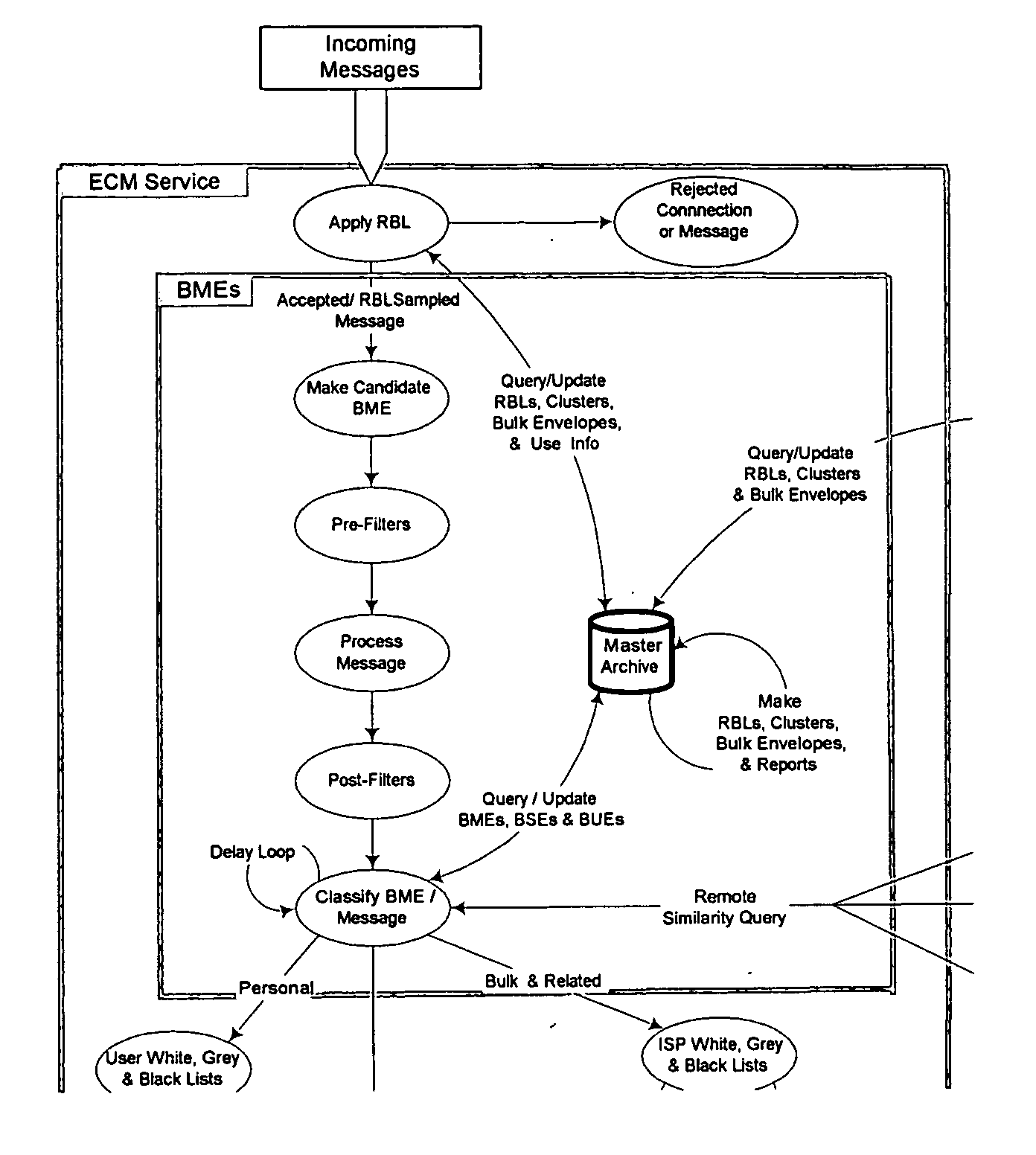
From an electronic message, we extract any destinations in selectable links, and we reduce the message to a “canonical” (standard) form that we define. It minimizes the possible variability that a spammer can introduce, to produce unique copies of a message. We then make multiple hashes. These can be compared with those from messages received by different users to objectively find bulk messages. From these, we build hash tables of bulk messages and make a list of destinations from the most frequent messages. The destinations can be used in a Real time Blacklist (RBL) against links in bodies of messages. Similarly, the hash tables can be used to identify other messages as bulk or spam. Our method can be used by a message provider or group of users (where the group can do so in a p2p fashion) independently of whether any other provider or group does so. Each user can maintain a “gray list” of bulk mail senders that she subscribes to, to distinguish between wanted bulk mail and unwanted bulk mail (spam). The gray list can be used instead of a whitelist, and is far easier for the user to maintain.
Owner:METASWARM INC
Changed file identification, software conflict resolution and unwanted file removal
InactiveUS20050155031A1Memory loss protectionUnauthorized memory use protectionData miningProcess information
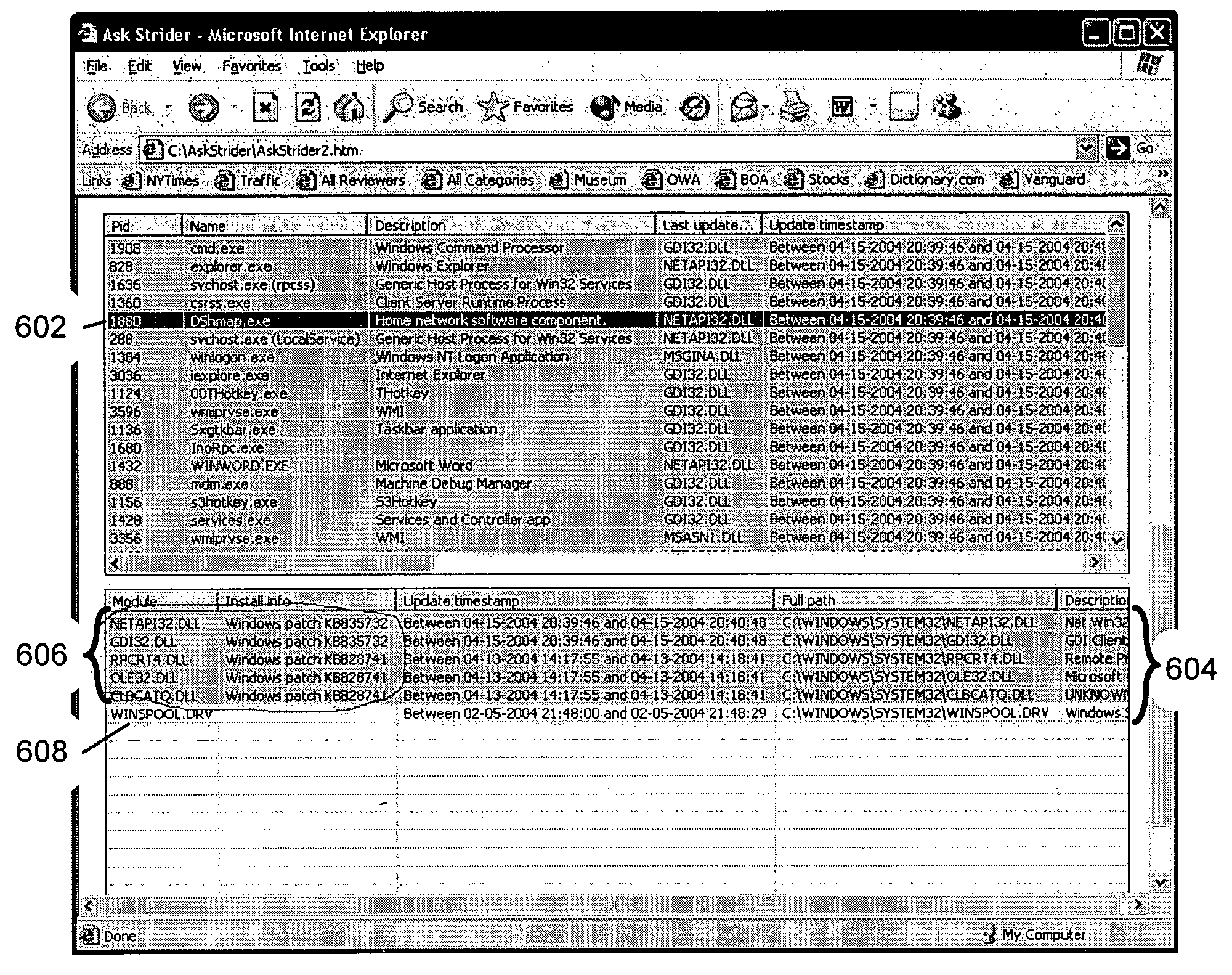
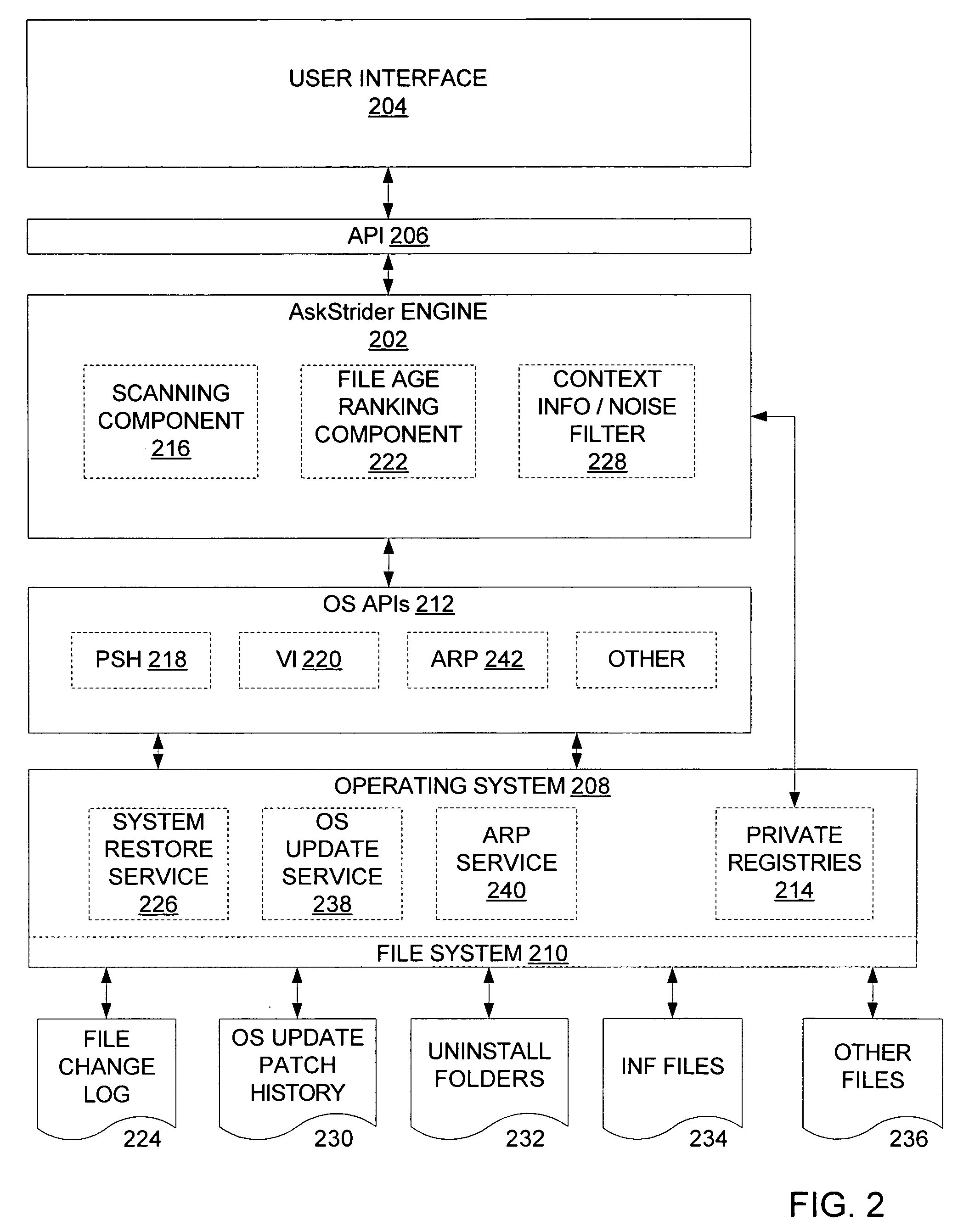
As computer programs grow more complex, extensible, and connected, it becomes increasingly difficult for users to understand what has changed on their machines and what impact those changes have. An embodiment of the invention is described via a software tool, called AskStrider, that answers those questions by correlating volatile process information with persistent-state context information and change history. AskStrider scans a system for active components, matches them against a change log to identify recently updated and hence more interesting state, and searches for context information to help users understand the changes. Several real-world cases are provided to demonstrate the effectiveness of using AskStrider to quickly identify the presence of unwanted software, to determine if a software patch is potentially breaking an application, and to detect lingering components left over from an unclean uninstallation.
Owner:MICROSOFT TECH LICENSING LLC
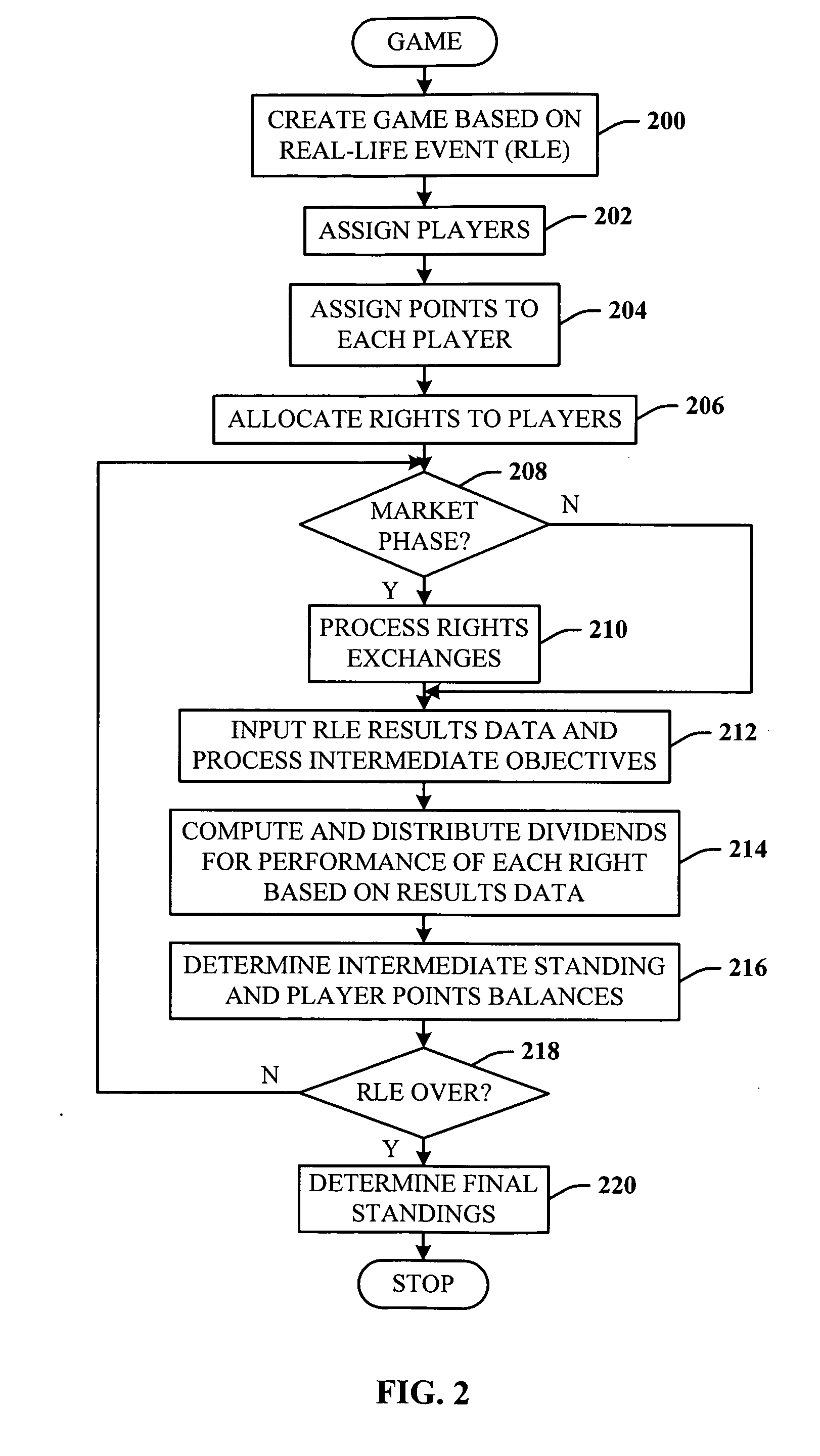
Strategy gaming format with outcomes determined by external events and auction- and market-based transactions by the players
InactiveUS20060100006A1Apparatus for meter-controlled dispensingVideo gamesFinancial transactionLife events
Owner:ONROO ENTERTAINMENT
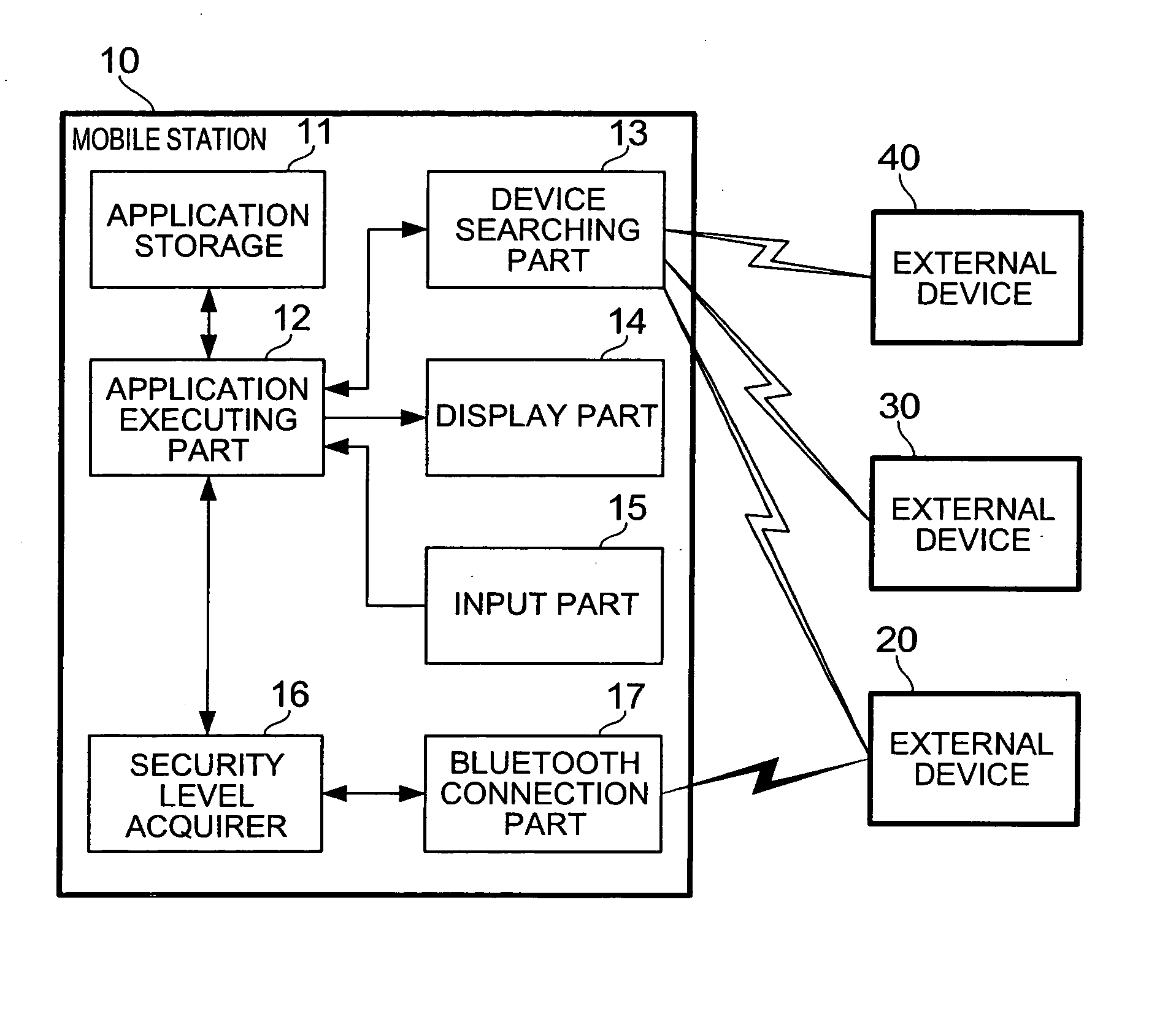
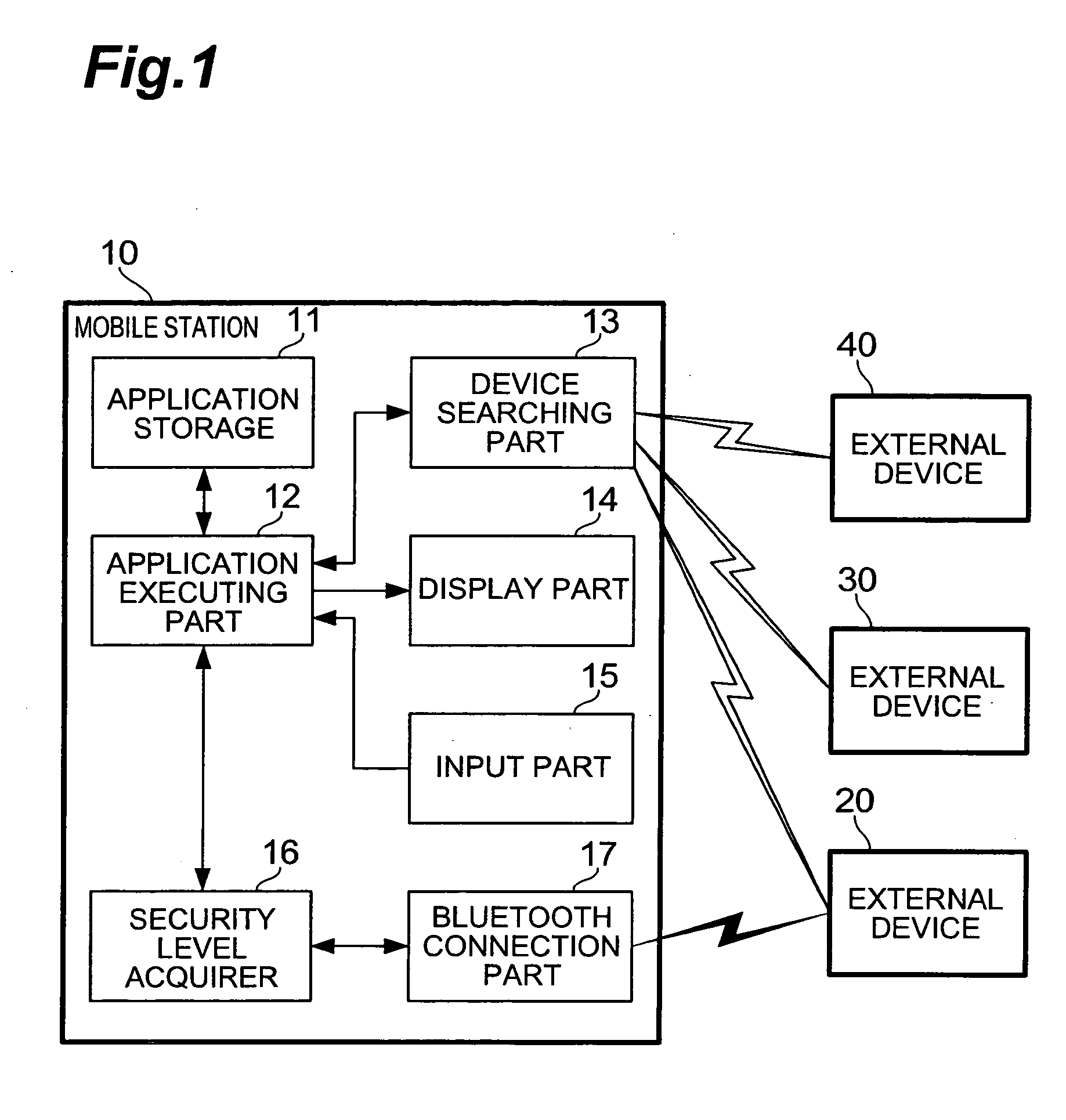
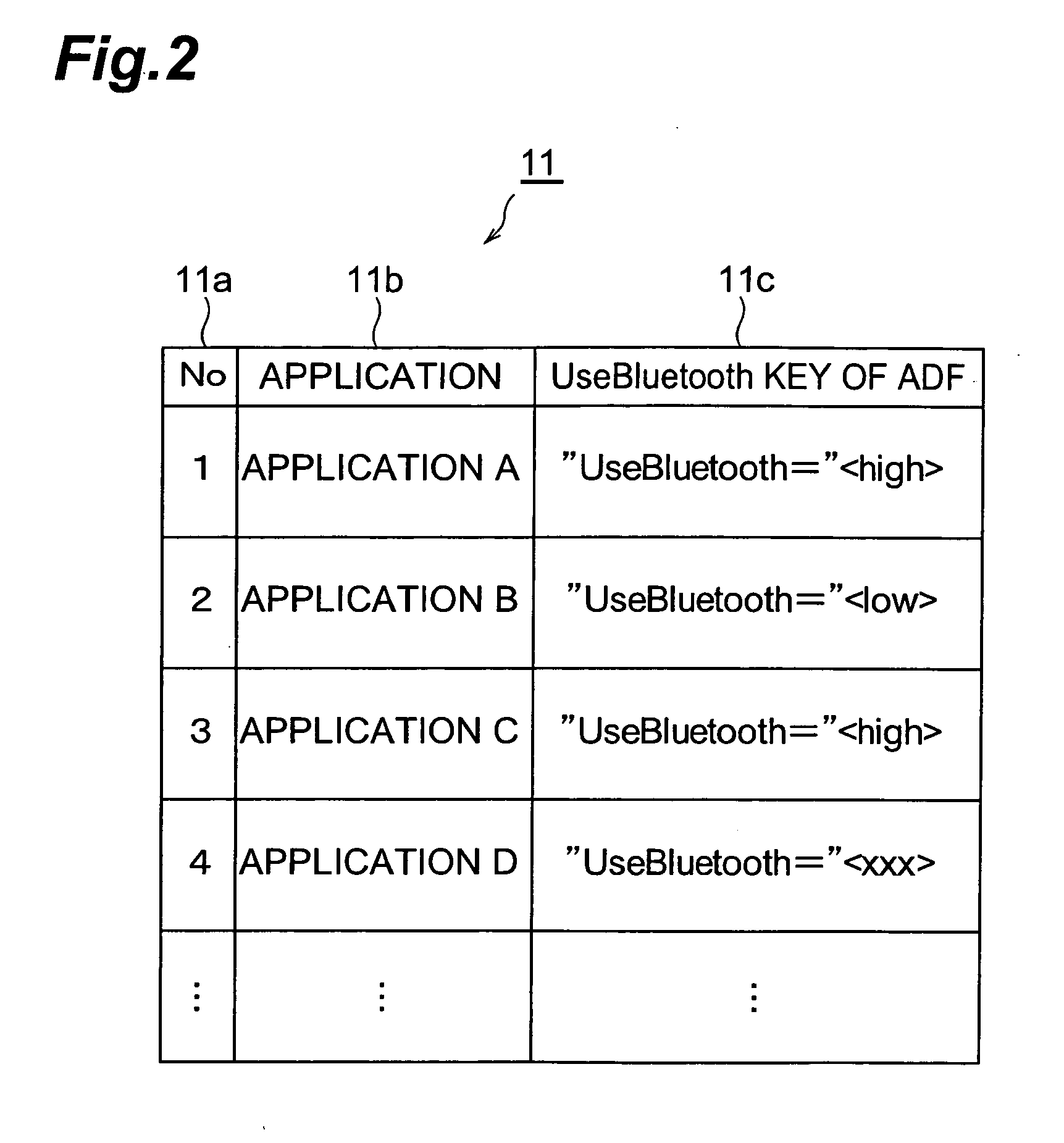
Mobile station and communication control method
InactiveUS20050257052A1Maintain securityFast communicationDigital data processing detailsUser identity/authority verificationMobile stationCommunication control
When an application is activated, a mobile station 10 detects external devices 20, 30, 40 as candidates for a BLUETOOTH connection out of external devices existing in the surrounding area, and presents a list of the devices to a user. When the user selects from the list an external device 20 with which a connection is to be attempted to make, a link is established by a connection procedure according to a security level described in an ADF of the application. Namely, when “high” is described as the security level, an authentication process and an encryption process requiring input of a PIN are executed prior to the establishment of the link. On the other hand, when “low” is described as the security level, a link is established without executing these processes.
Owner:NTT DOCOMO INC
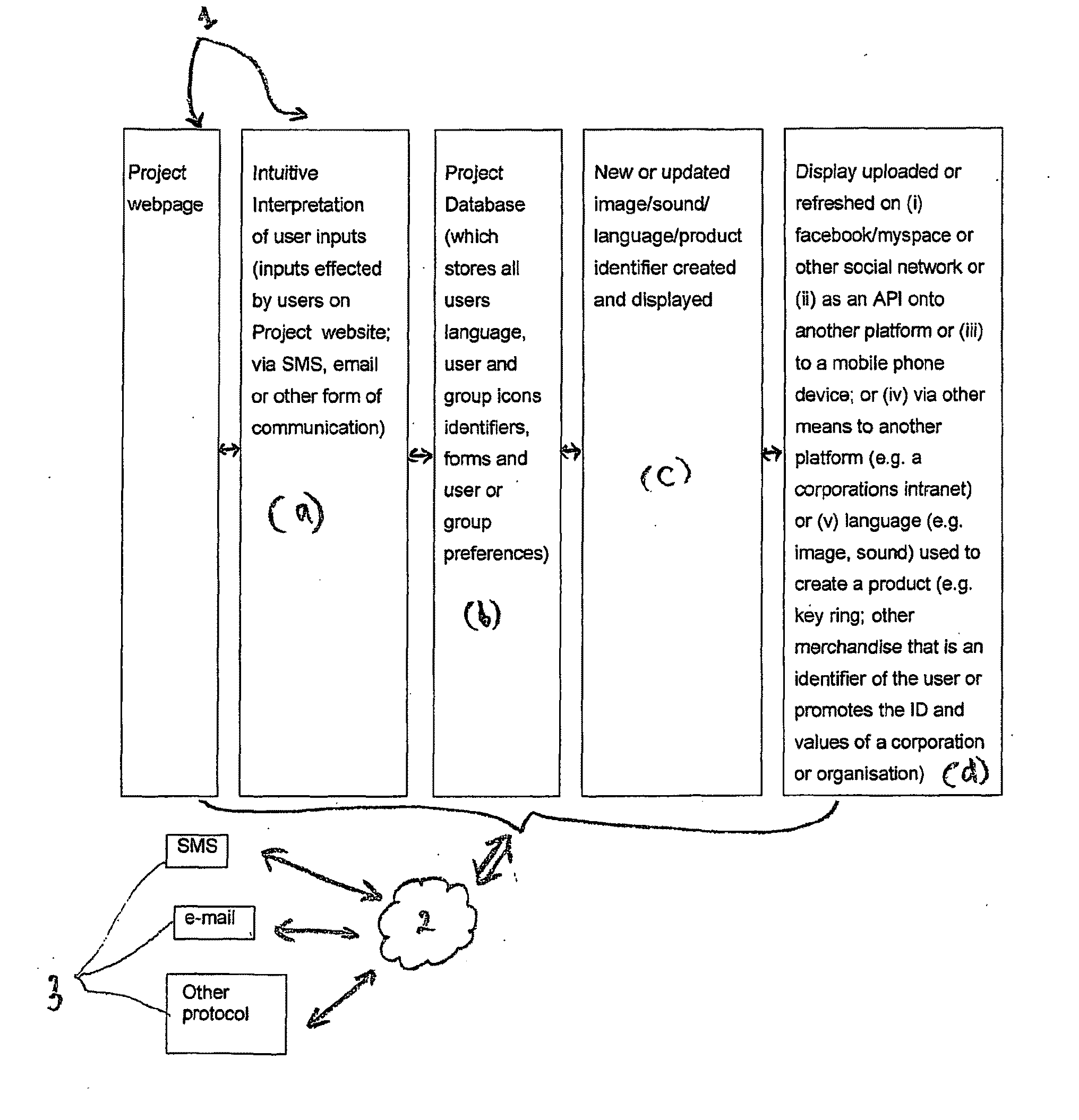
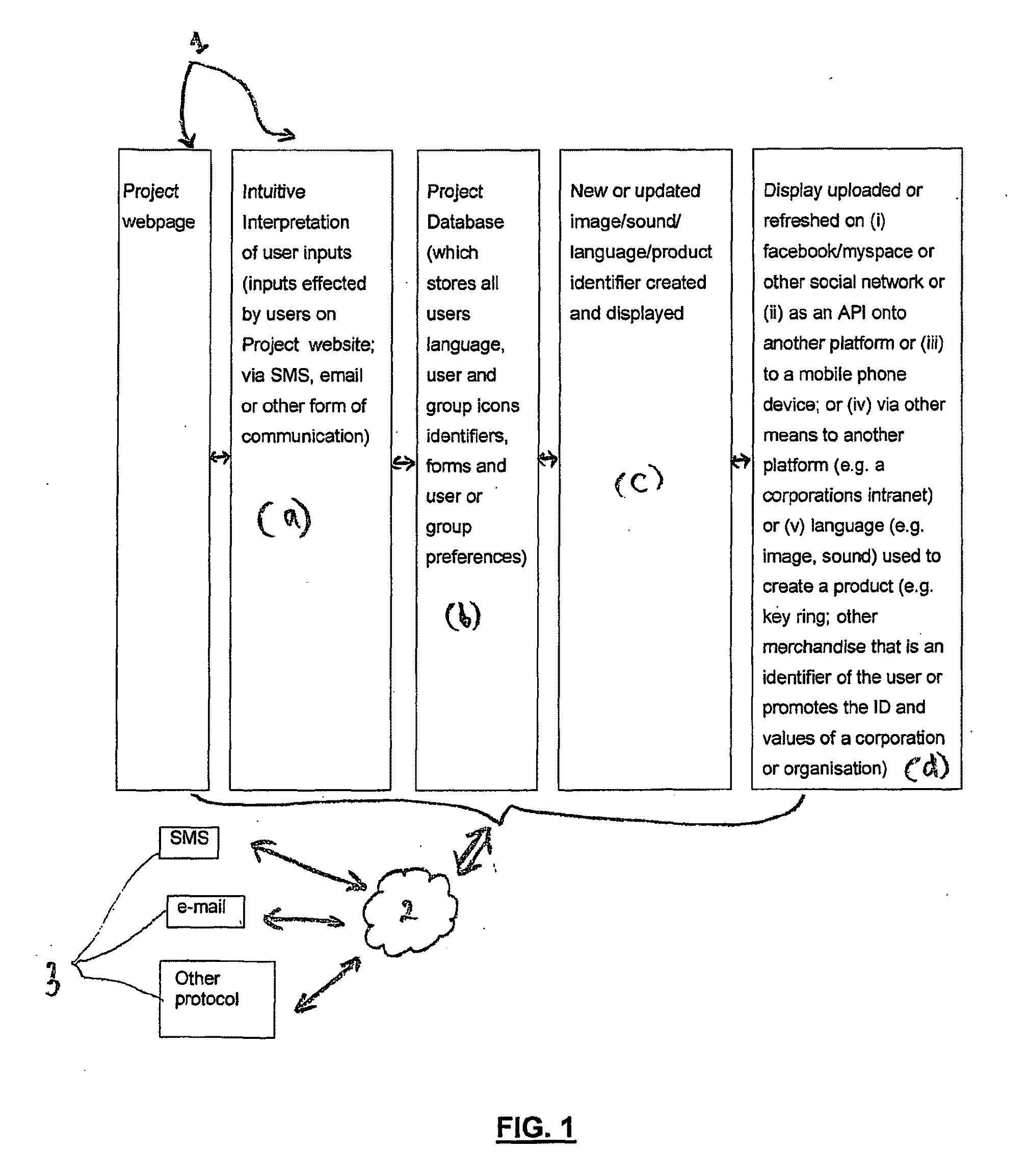
Communication method, system and products
InactiveUS20100153453A1Simple methodImprove abilitiesDigital data information retrievalDigital data processing detailsPersonalizationAs element
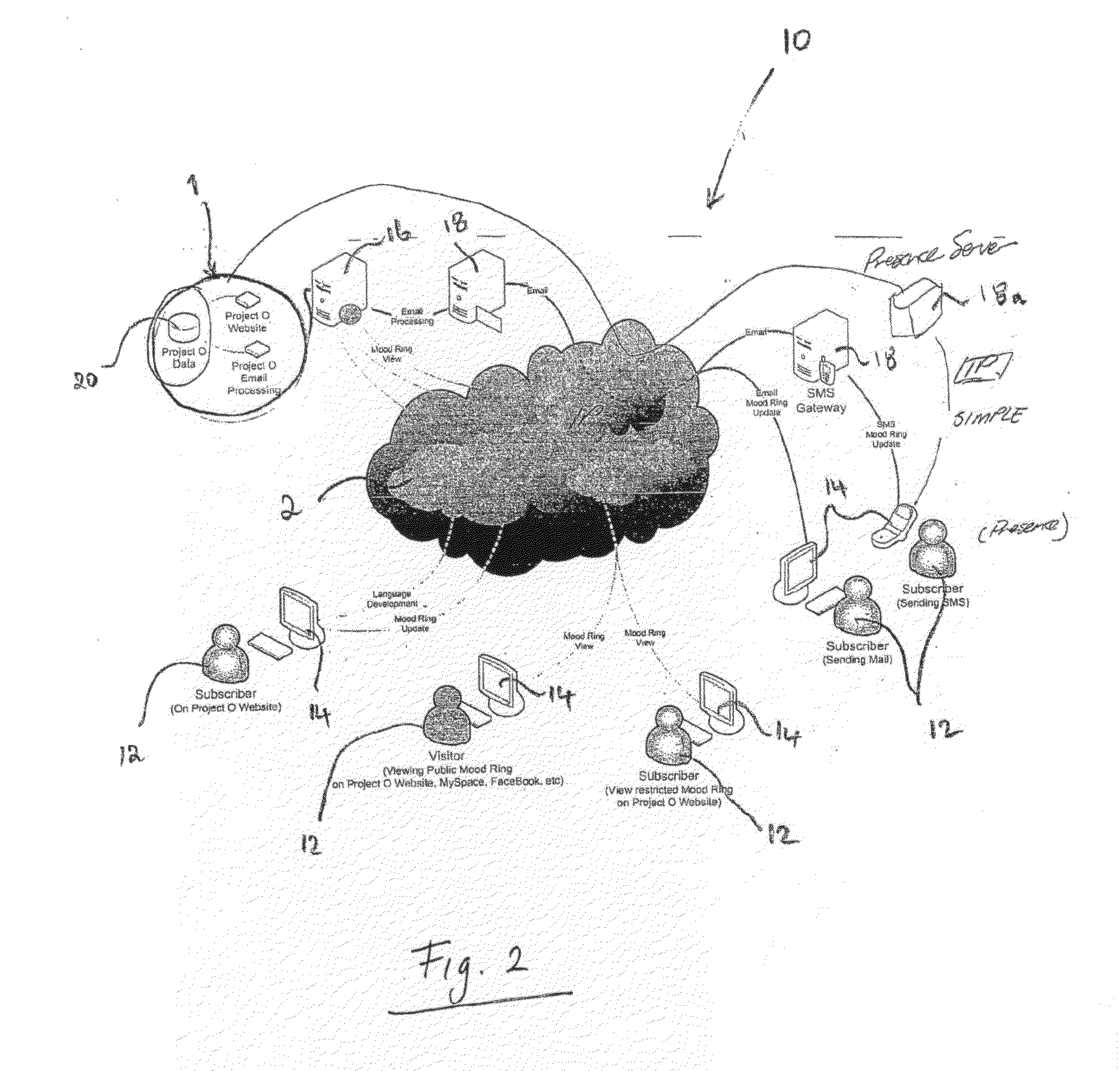
The present invention provides a communication method and / or system (10) that enables the creation of personalised identifiers (40) and / or language that can be used to convey information, messages, instructions, and / or attributes for the purpose of enhancing and / or integrating communications. In a preferred form the personalised identifiers (40) and / or language can act as elements that may be used as a means of expression that is driven by users (12), groups of users (12), or entities, in order to convey personal attributes or identity. In a further preferred form the personalised identifiers (40) may act as visual representations of identity in order to, for example, facilitate convenient and readily accessible means of cross-referencing indexed information. The present invention may also provide refined search facilities that feature graphical functions that enable enhanced visualisation of search results, and / or visualisation display applications.
Owner:KAREN KNOWLES ENTERPRISES PTY LTD
Event data translation system
InactiveUS20070220063A1Data processing applicationsDigital data information retrievalData translationElectronic mail
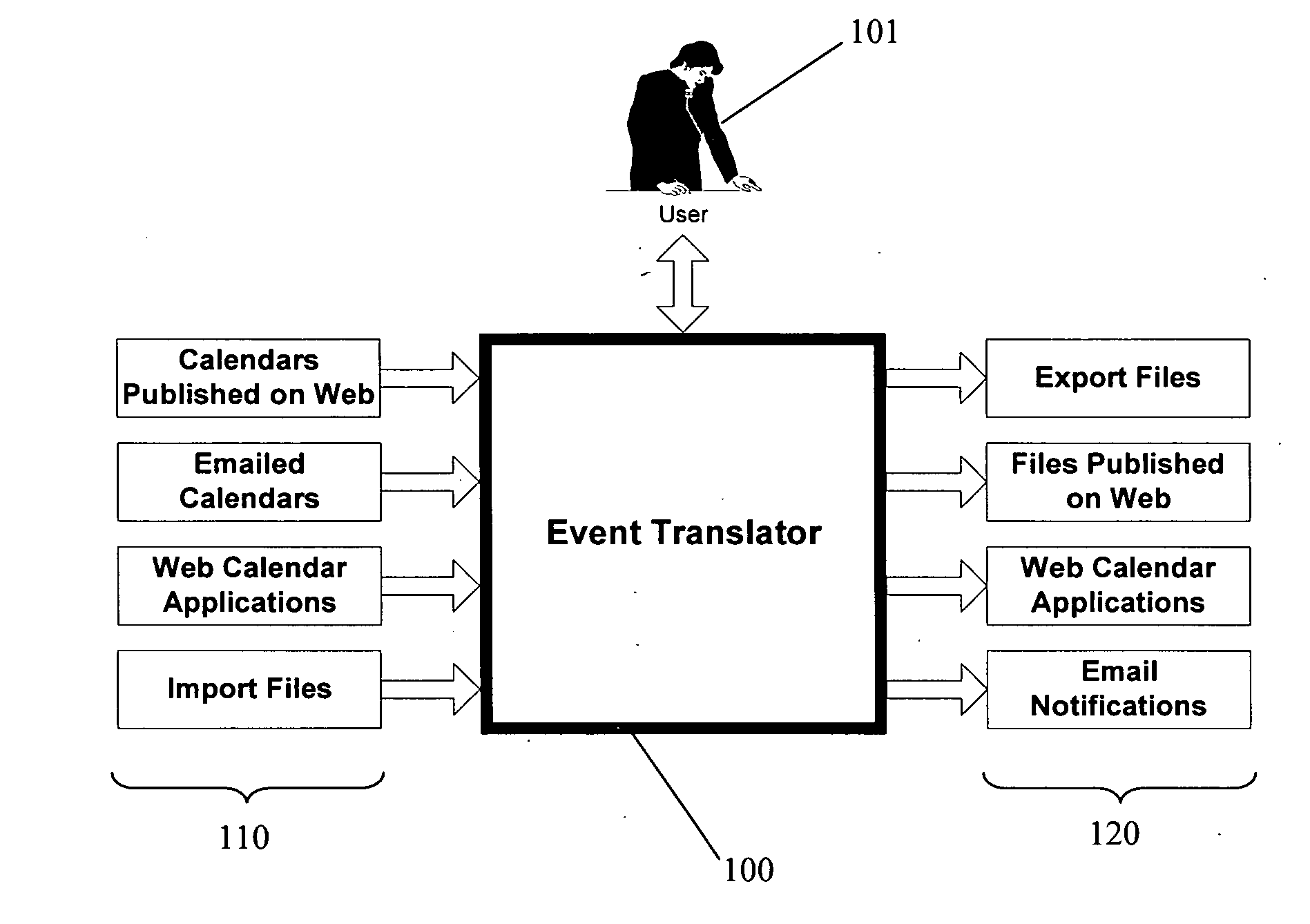
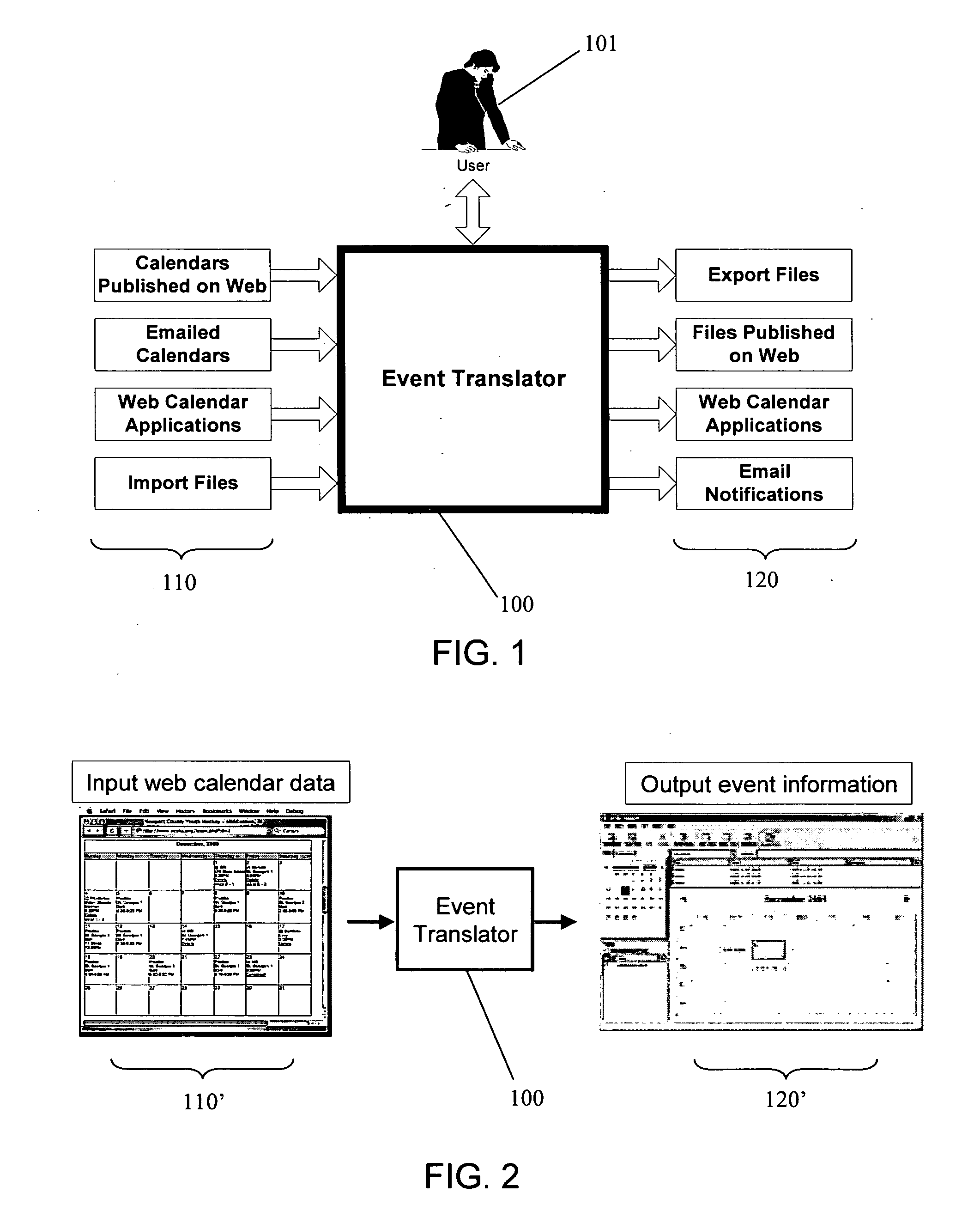
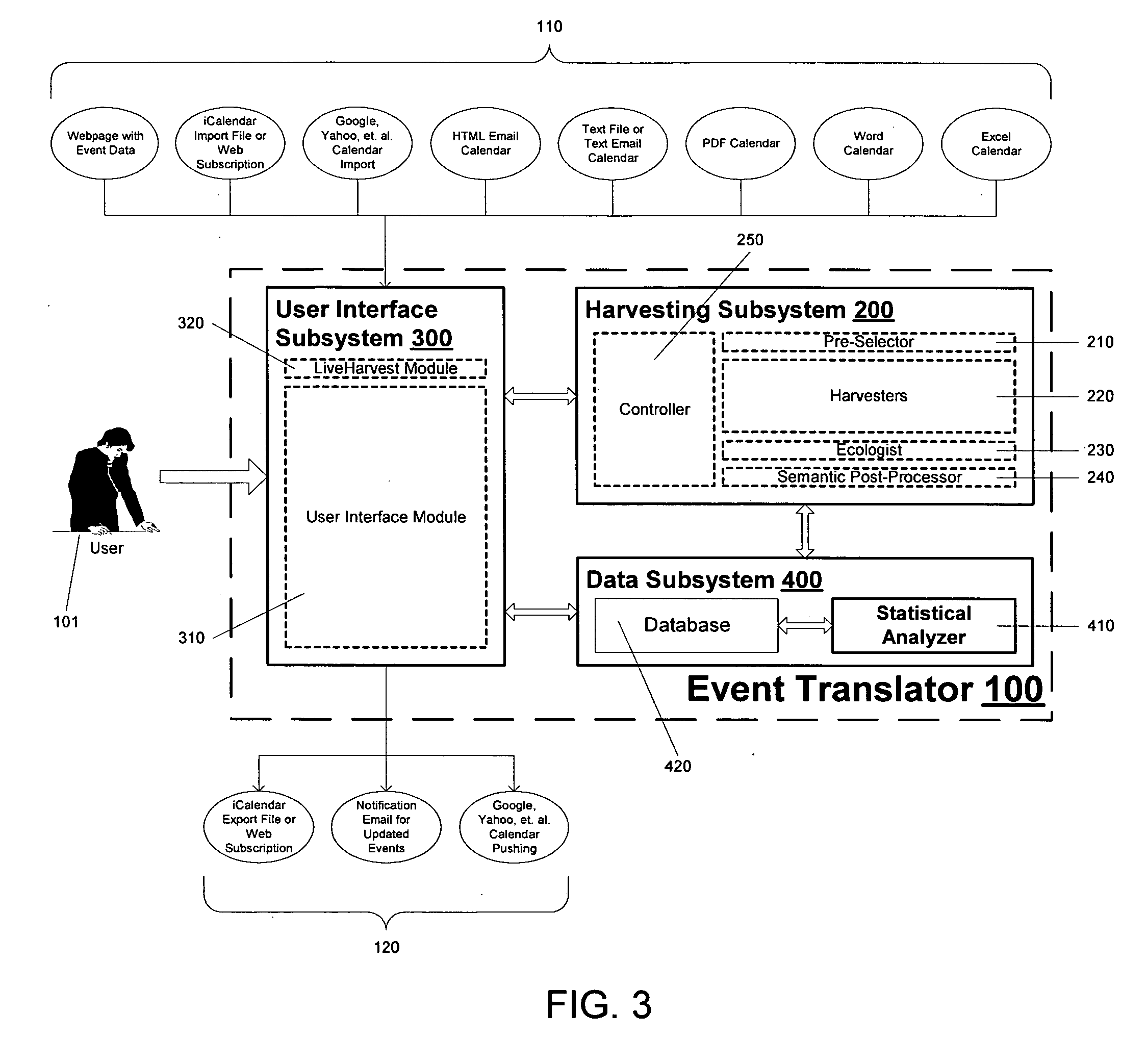
An event translator system may perform at least three tasks: (1) extract or “harvest” date, time, description, and other information from digital files generated for human reading, such as web calendars or other event lists, emailed calendars, and imported files; (2) present the extracted event data to a user for modification, management, and monitoring; and (3) export the events to PIM software, web pages and / or application programming interfaces as appropriate file formats. The event translation system may be incorporated into a web site that is accessed by the user who enters a desired web address for event translation or otherwise transmits the digital files for translation. Alternatively, the system may be incorporated into a webpage as a browser plug-in that provides a user-selectable option to extract event information from a visited webpage. Other implementations are possible, including incorporation into desktop software, enterprise software on a server, and plug-ins for e-mail or other applications, among others.
Owner:HUNTE VADIM +1
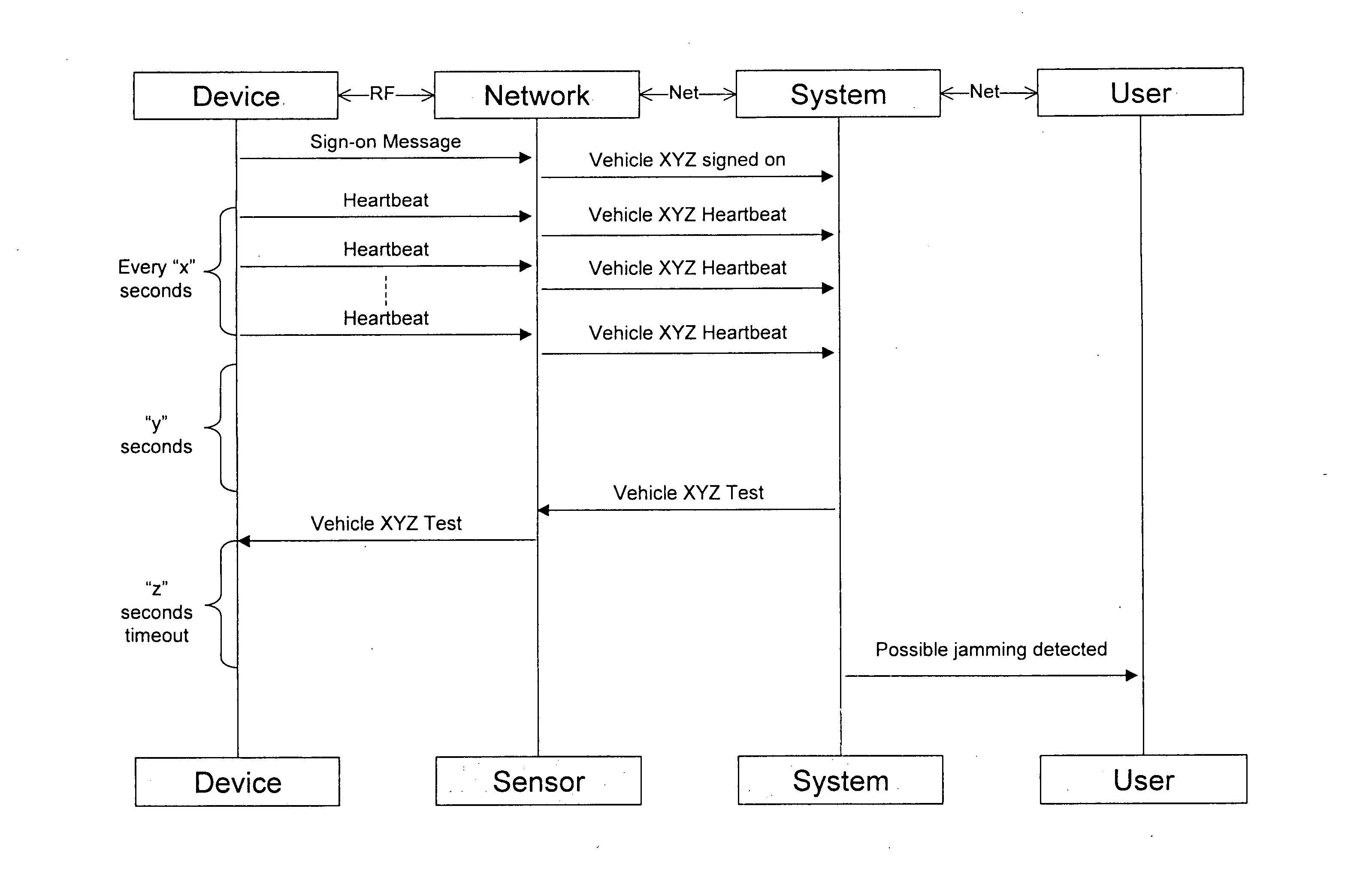
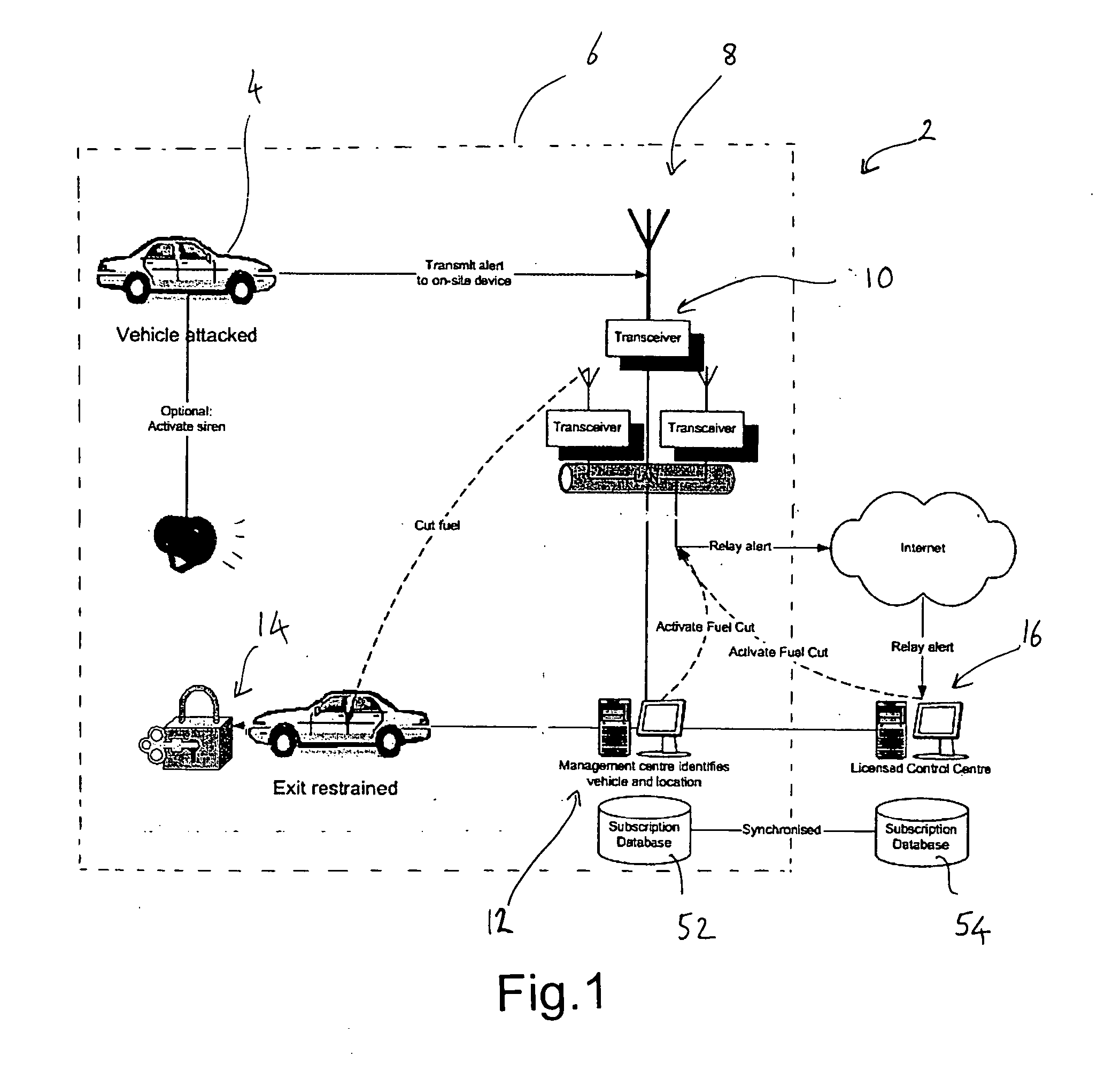
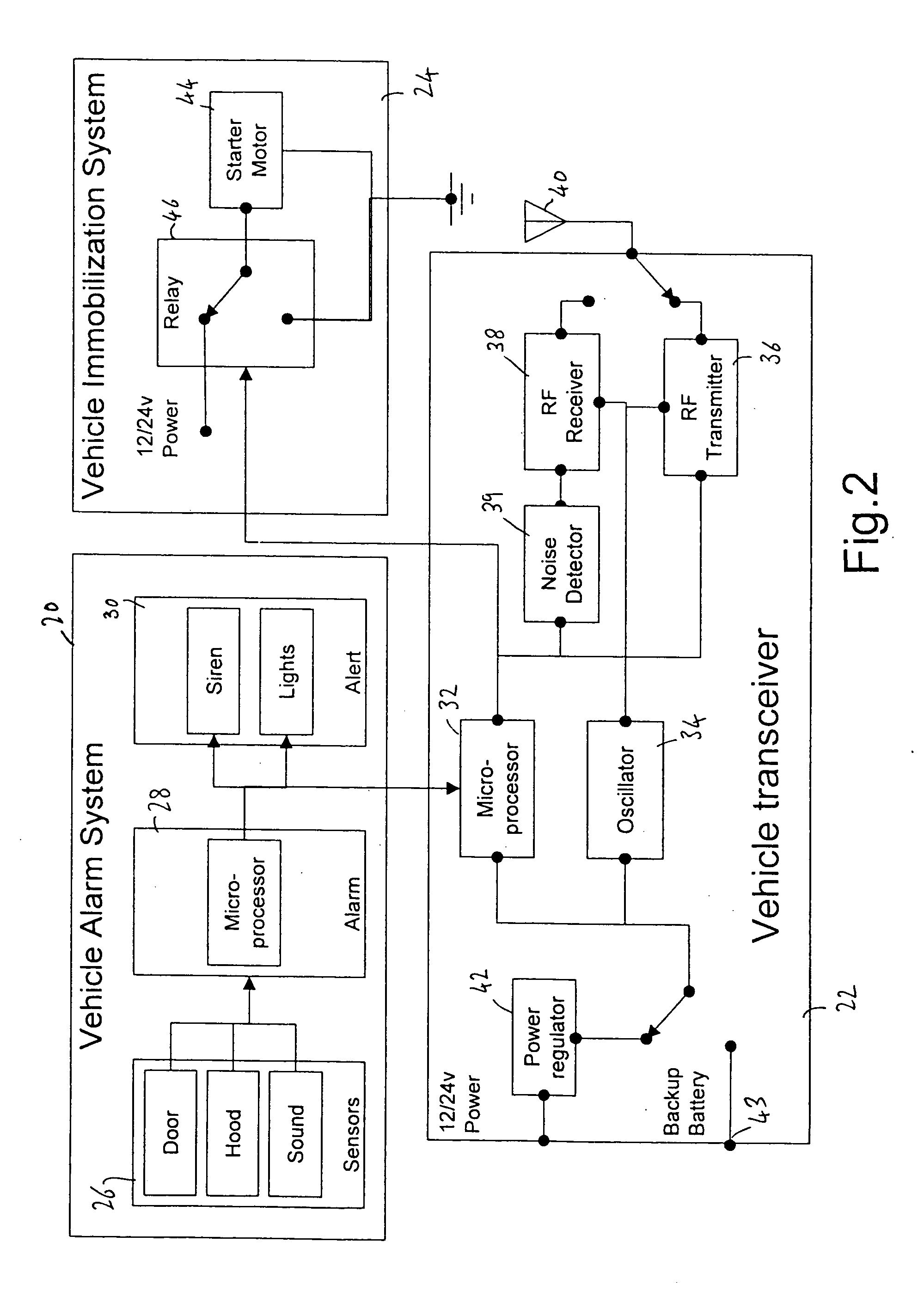
Vehicle security system
A vehicle security system for use in a predefined area such as a car park includes an array of sensors (9) for receiving a vehicle alarm signal transmitted by radio frequency from a system-subscribing vehicle fitted with a transceiver (22) in the event of attempted vehicle tampering or removal. A control centre (12) receives alarm signals and communicates them to a user as an alarm message. Detection of radio frequency signal jamming or attempted jamming is achieved in one embodiment with noise detectors (39, 139) actively detecting jamming noise or alternatively an arrangement of transmitters and receivers using test transmissions therebetween, whereby transmission failure indicates jamming.
Owner:THE LOCATION
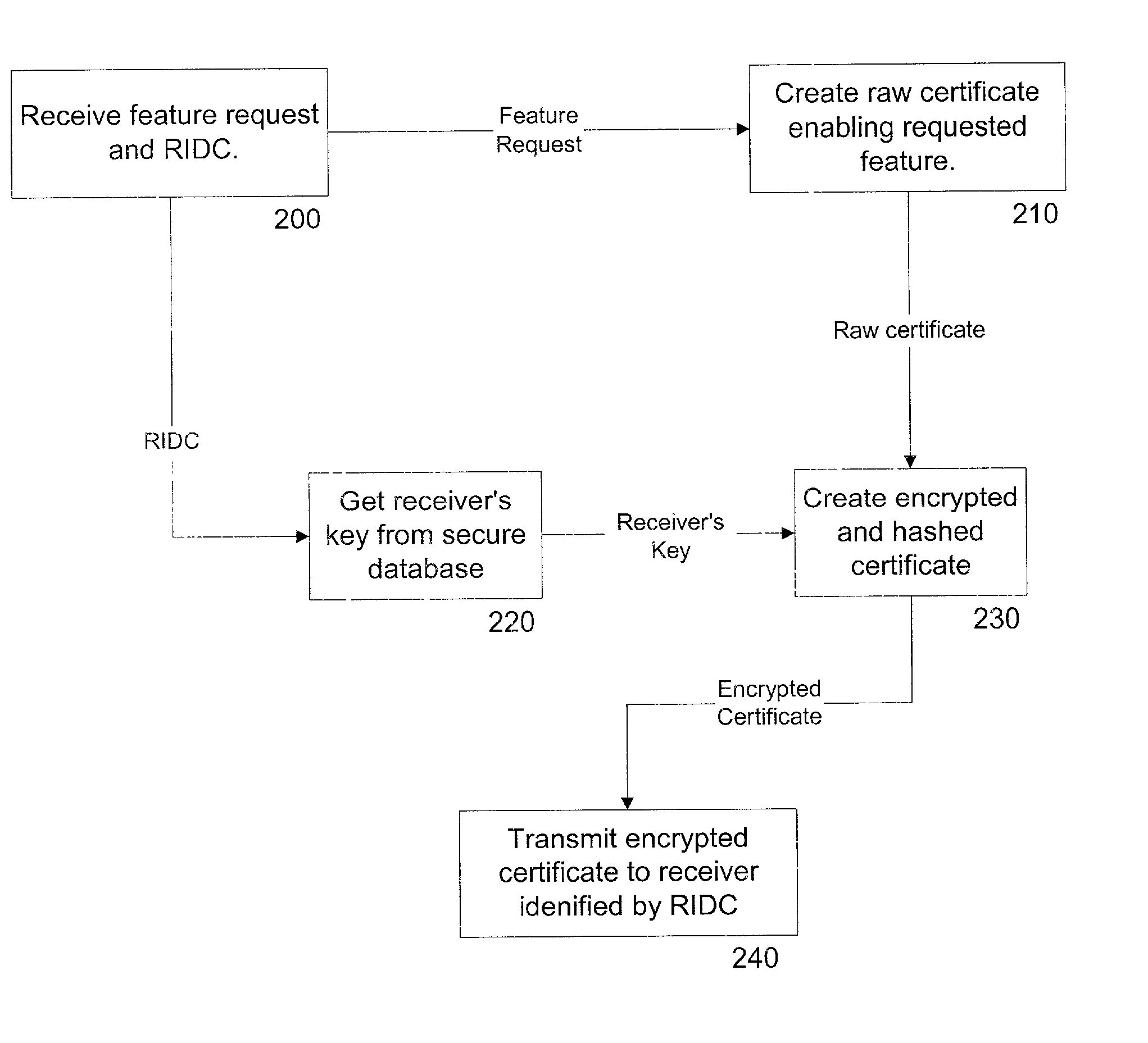
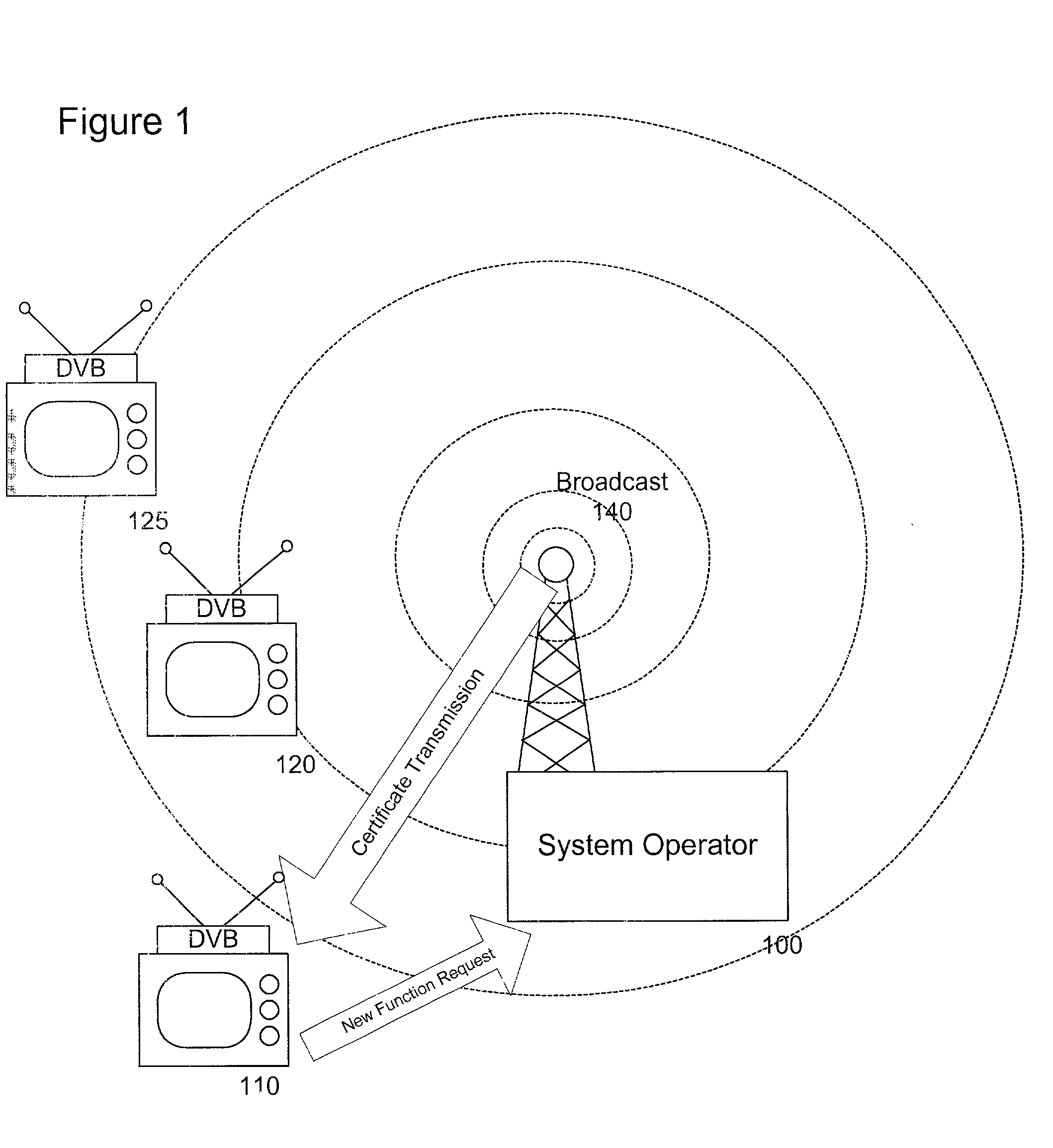
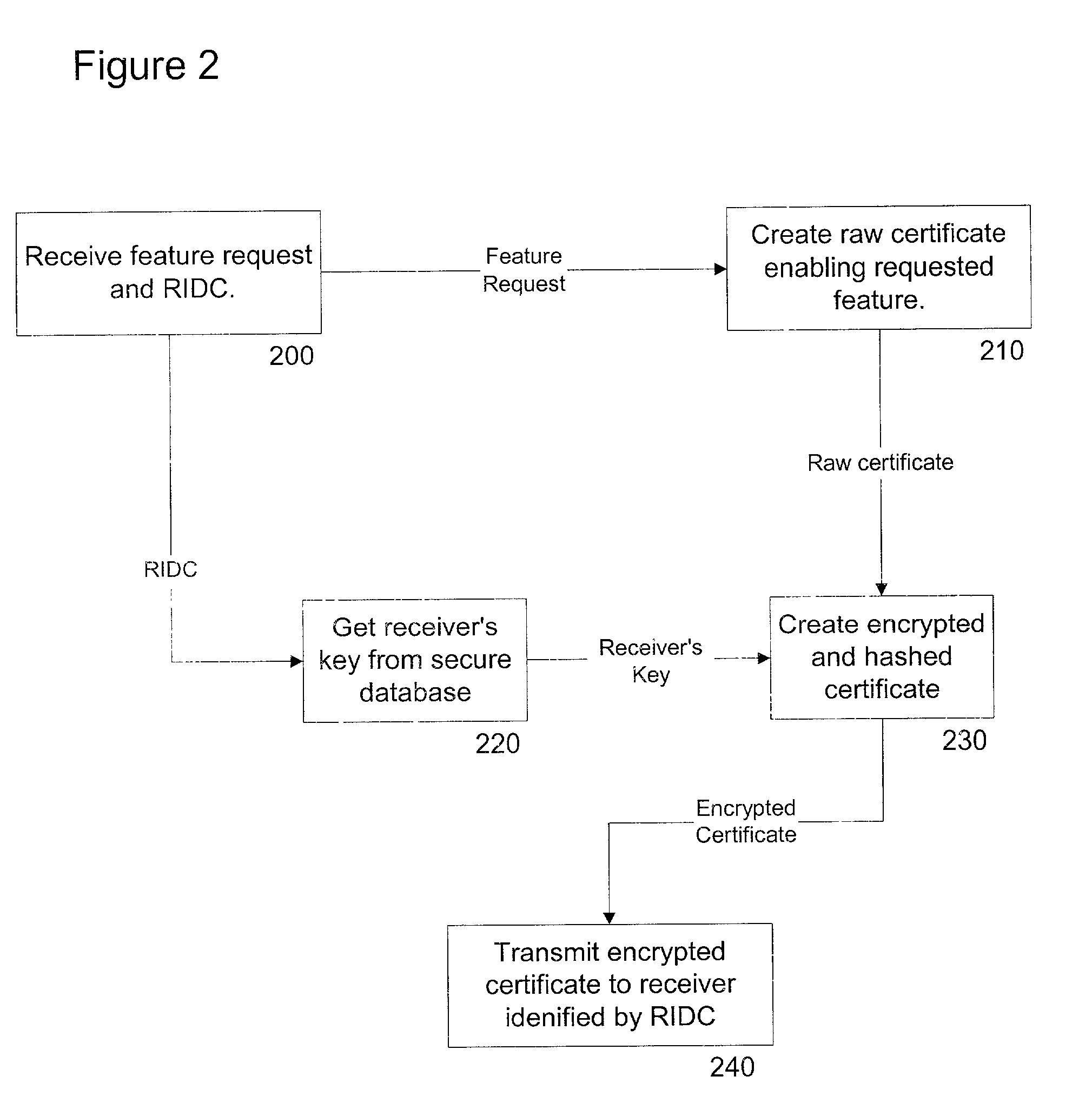
System and method for activating individualized software modules in a digital broadcast environment
ActiveUS20050005286A1Easy maintenanceEasy to manageAnalogue secracy/subscription systemsSecret communicationPersonalizationDigital broadcasting
A system and method is disclosed for enabling individualized software functions in a device. In accordance with one embodiment of the present invention software is distributed as omnibus installations containing various software modules that are initially turned off. The user gains access to the turned off modules by requesting a certificate from a system provider. The system provider creates and transmits a certificate containing the information required to enable the desired module. The device can then use the certificate to access the desired software.
Owner:WSOU INVESTMENTS LLC
Alarm system comprising an alarm mobile terminal and an alarm server
InactiveUS20060145841A1Alarms using portable personal devicesElectric signal transmission systemsComputer networkService provision
Using a mobile terminal (2) while moving, a user has a voice conversation with a security terminal (1) provided by a security service provider. This conversation creates a situation in which it is possible to immediately send an alarm if an emergency occurs, thus repelling assaulters or abductors lurking near the user. The mobile terminal (2) is provided with GPS or the like, and position information of the mobile terminal (2) is sent to the security terminal (1). <??>The security service provider takes advertisements from advertisers selling goods or services, and prepares conversation scenarios that are the content of the conversations for automatic response based on those advertisements. The security terminal (1) firstly provides the user with a voice conversation partner proxy service based on the conversation scenarios and secondly detects emergencies by detecting emergency messages from the mobile terminal (2) or detecting the interruption of the conversation. After that, the security service provider can restrict the danger to the user to a minimum by undertaking emergency measures such as dispatching someone to the location where the mobile terminal (2) is located.
Owner:ALCATEL LUCENT SAS
Systems and methods for advanced communications and control
InactiveUS20060190543A1Add featureImprove functionalityMultiple digital computer combinationsData switching networksTime controlMessage passing
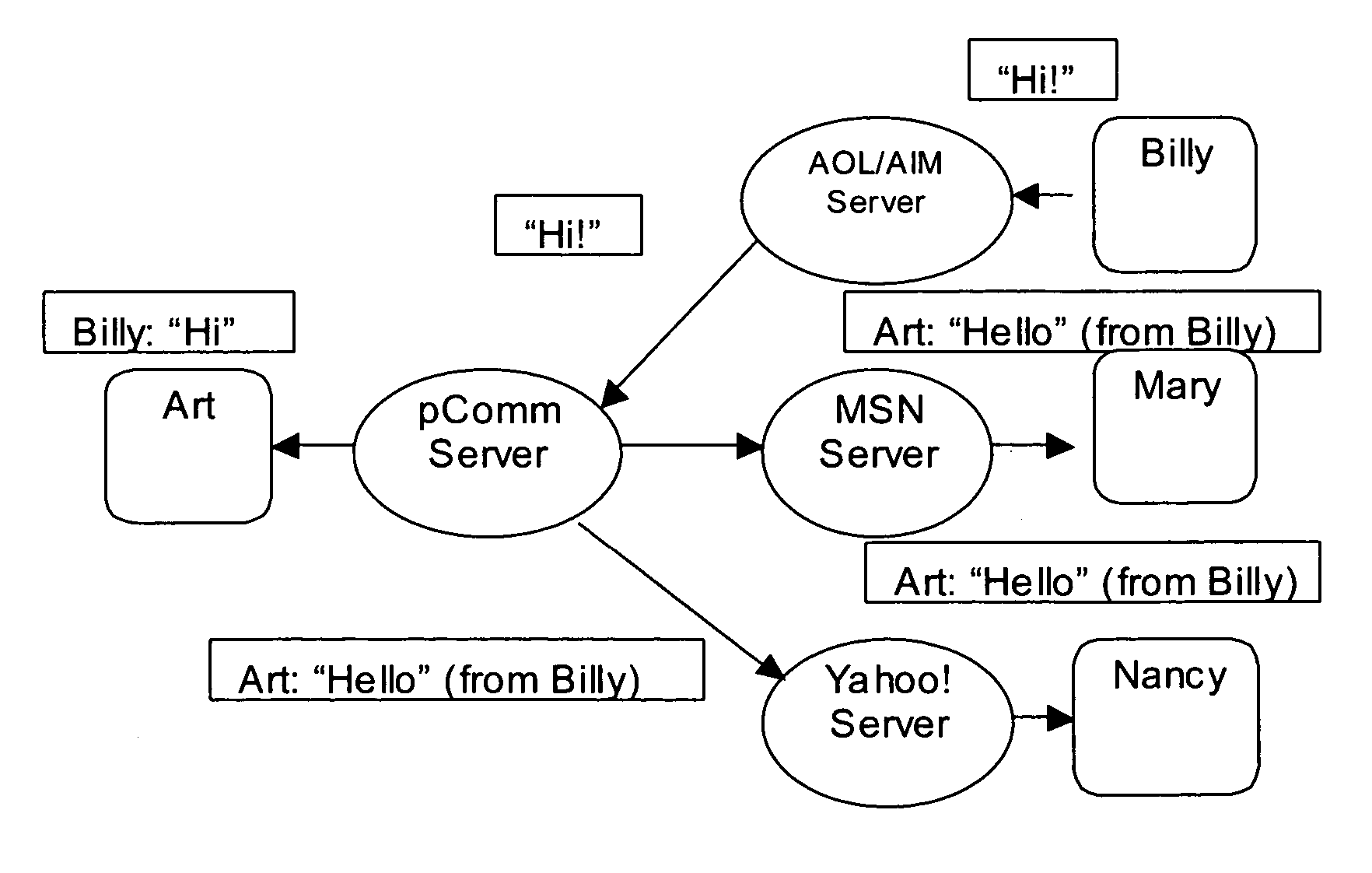
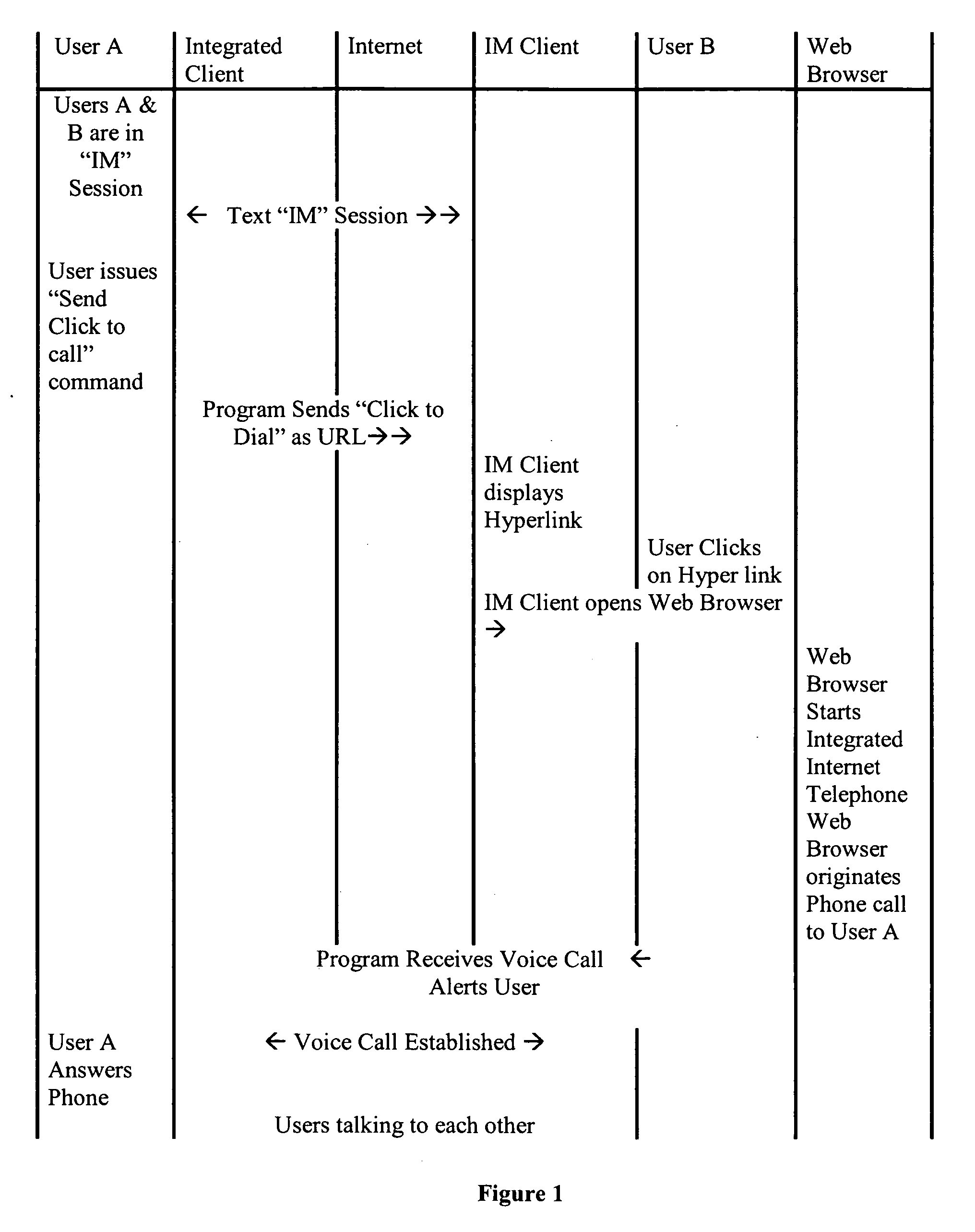
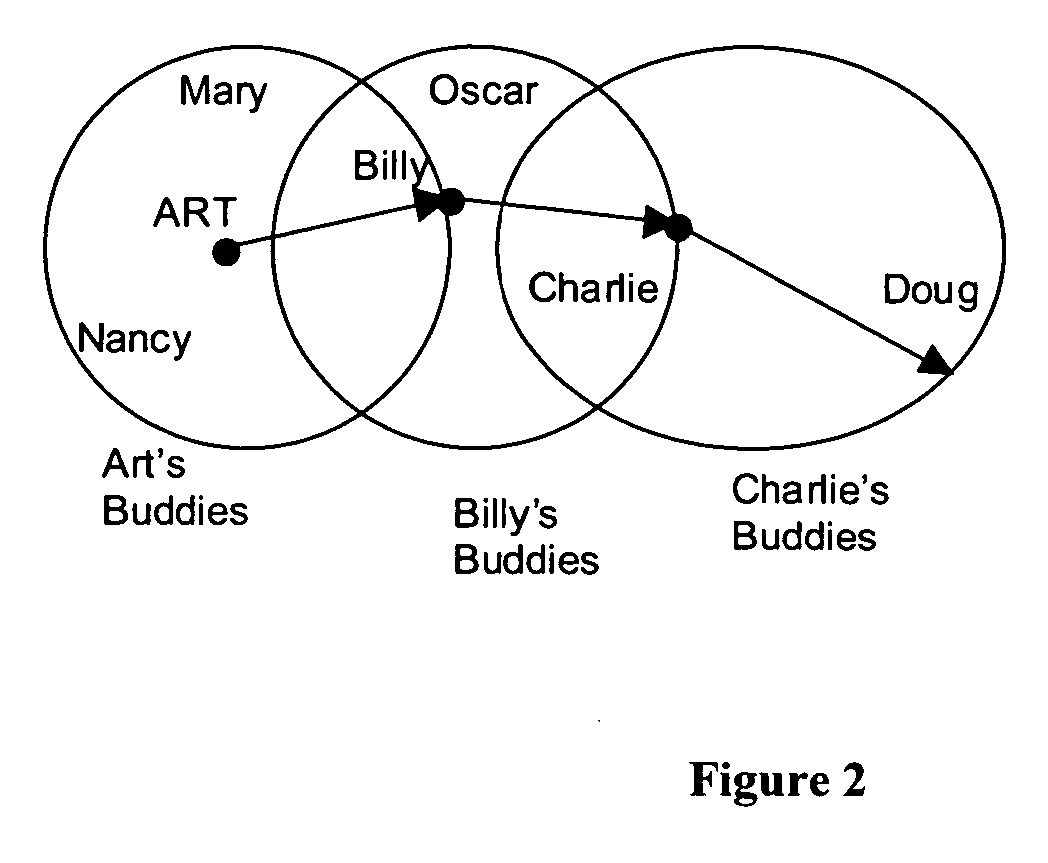
Methods and systems for telecommunications operations and controls include (1) an enhanced text message process or methodology that allows a remote user who does not have, already installed, a specialized voice telephony program to nevertheless place and participate in a voice call, (2) call admission control using a “degrees of separation” metric, (3) real time controlled sharing of contact (buddy) lists, (4) multi-service instance messaging conferences, and (5) “meta buddies” or buddy lists that can be automatically imported and made part of a user's own buddy list.
Owner:PULVER COM
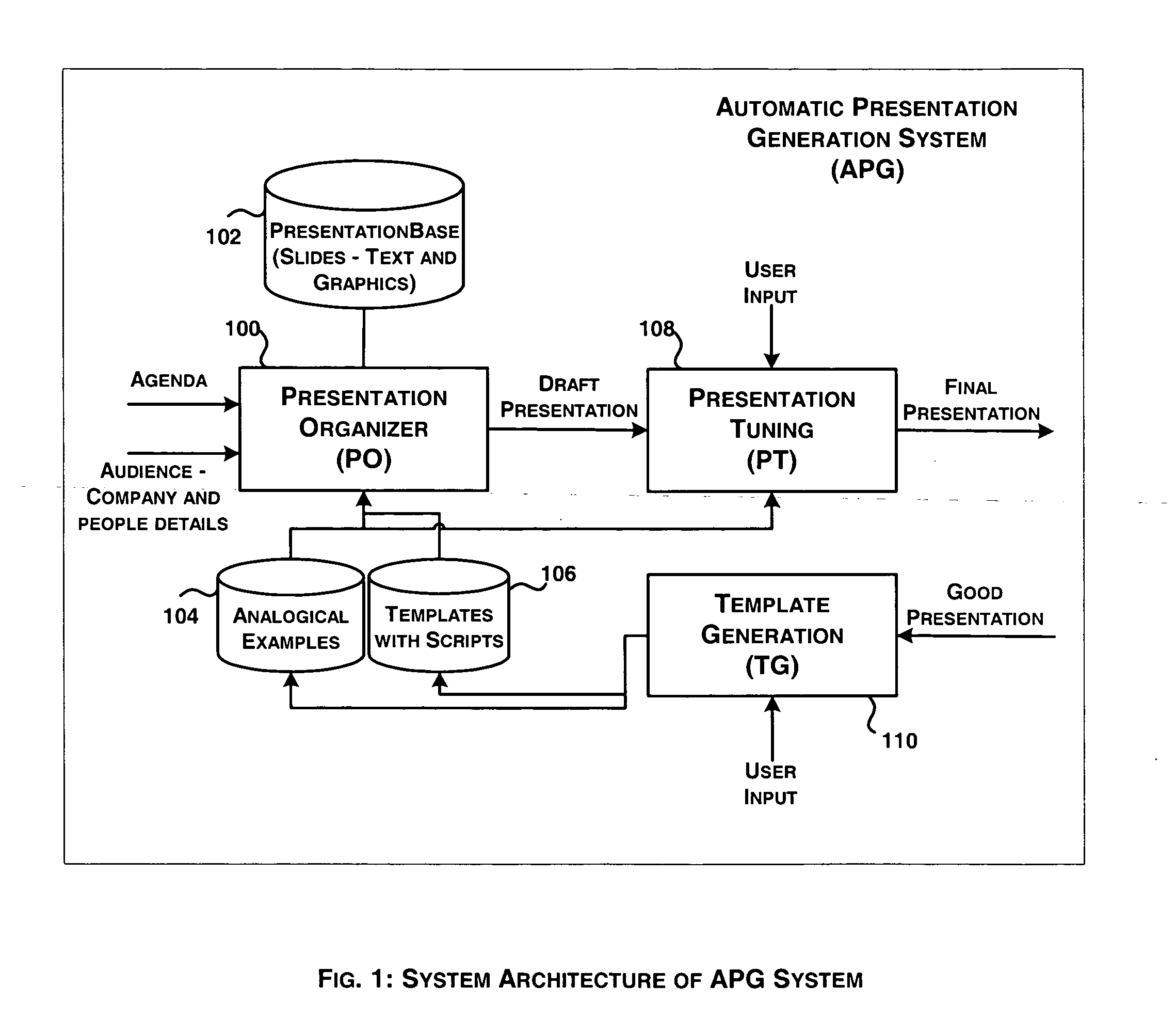
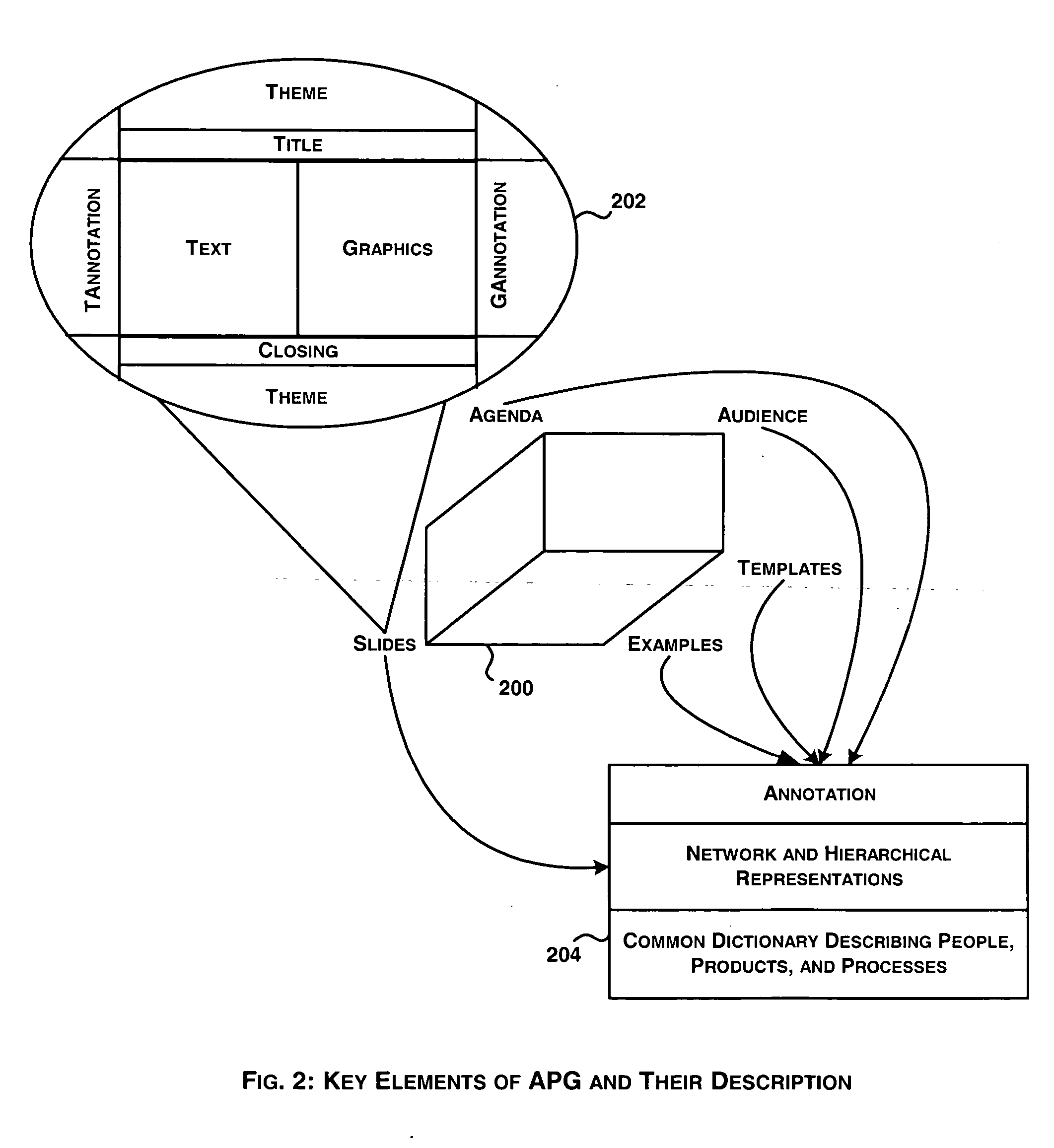
System and method for automatic generation of presentations based on agenda
InactiveUS20050223314A1Improve efficiencyNatural language data processingSpecial data processing applicationsFinal versionComputer science
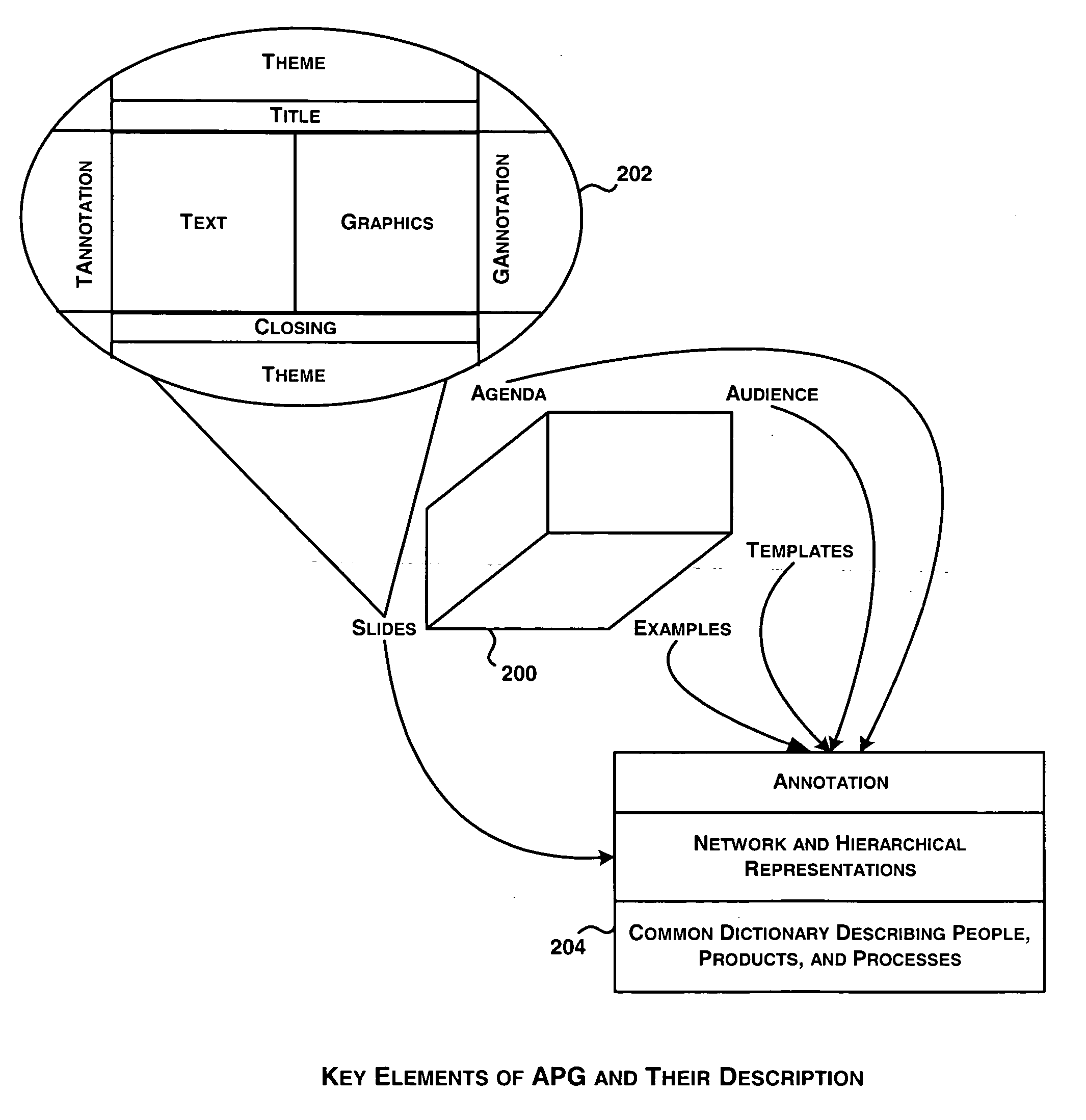
In enterprises, presentations are designed and made to visiting clients on a routine basis and it is expected that such presentations are required to be effective as much of business depends on right kind of information in right depth and volume made to right audience. The typically followed manual process depends on the capabilities of a person to create “right” presentation targeted for the right audience. It is required to obtain as much information as possible from such persons and use it to generate presentations as much automatically as possible. The automatic generation of presentation is based on (a) agenda; (b) audience profile; (c) analogical examples; and (d) templates. The system generates draft version of presentations and lets users to interactively tune the draft presentations to generate final version of the presentations. The analogical examples are identified manually and are made part of the system while the templates are automatically generated based on “best” presentations that are provided as input to the system.
Owner:SATYAM COMP SERVICES
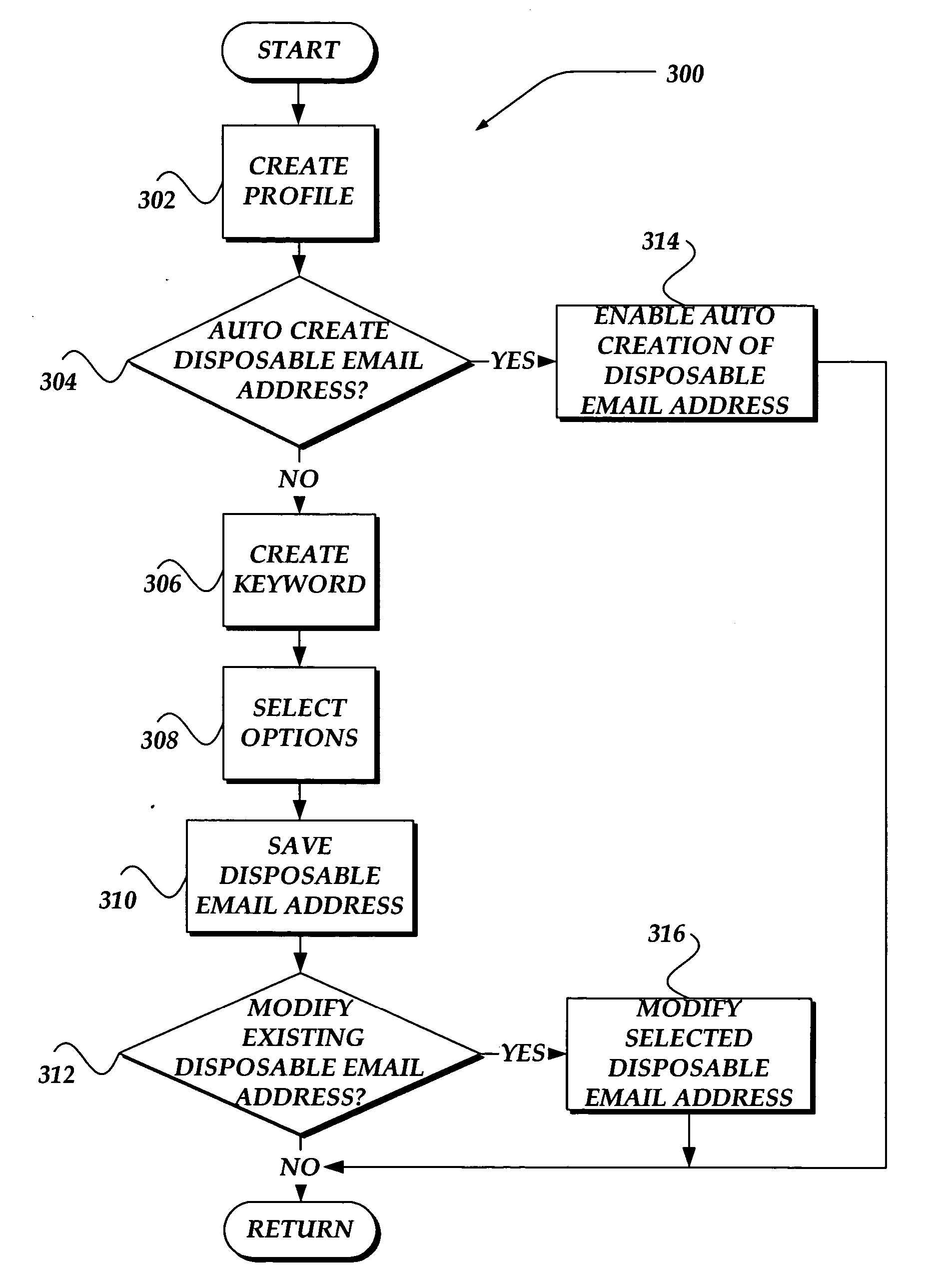
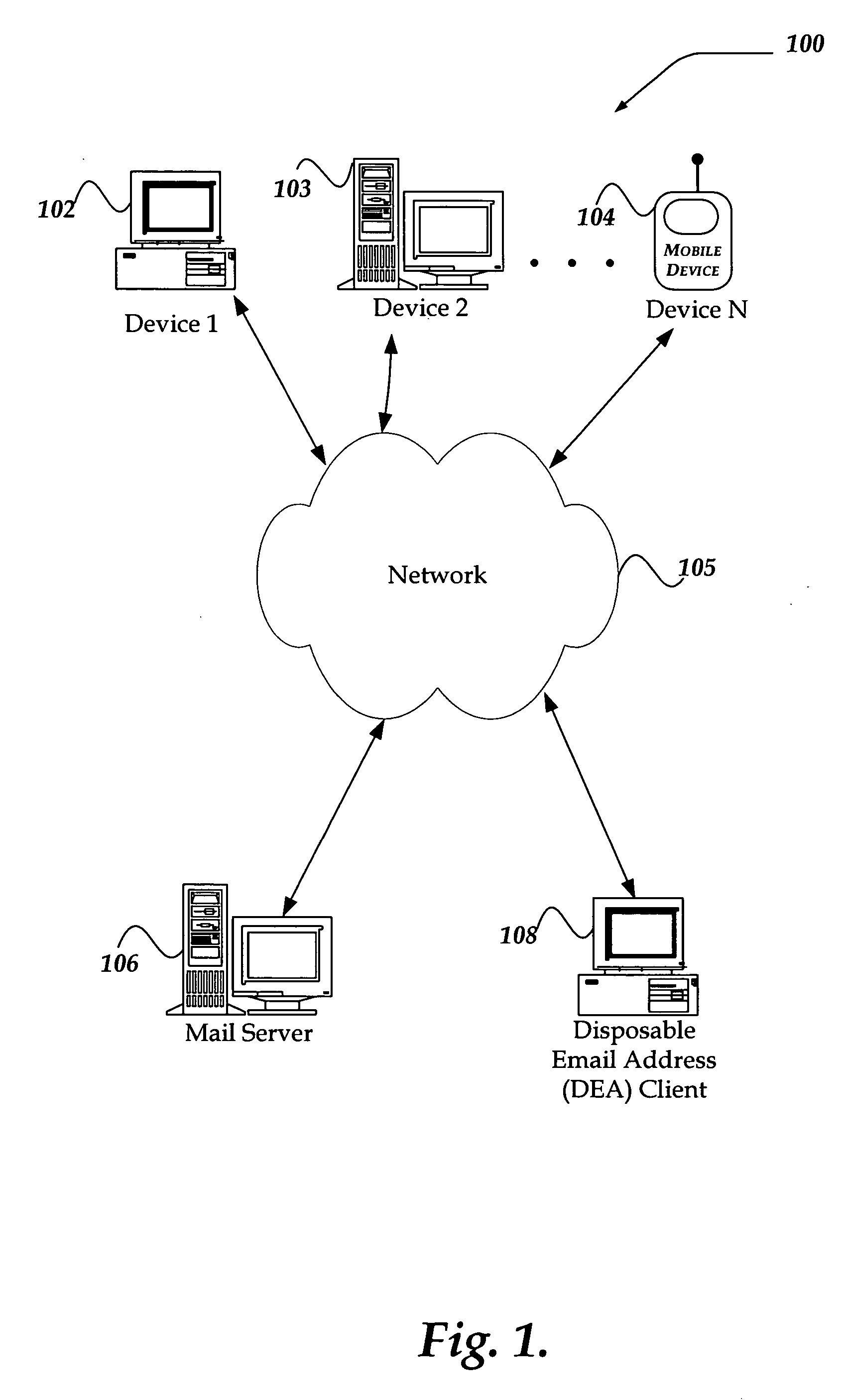
Method and system for providing a disposable email address
InactiveUS20060041621A1Multiple digital computer combinationsTransmissionDisposable email addressEmail spam
A method, apparatus, and system are directed towards providing a Disposable Email Address (DEA) that may be employed, in part, to manage email spam. The DEA may be generated based, in part, on an end-user profile, a keyword, and a domain address. The DEA may be distinguishable from a non-DEA by a selection of at least one preserved character, such as a dash. Moreover, the DEA may be discarded at some time later, without affecting an end-user's ‘permanent’ email address.
Owner:OATH INC
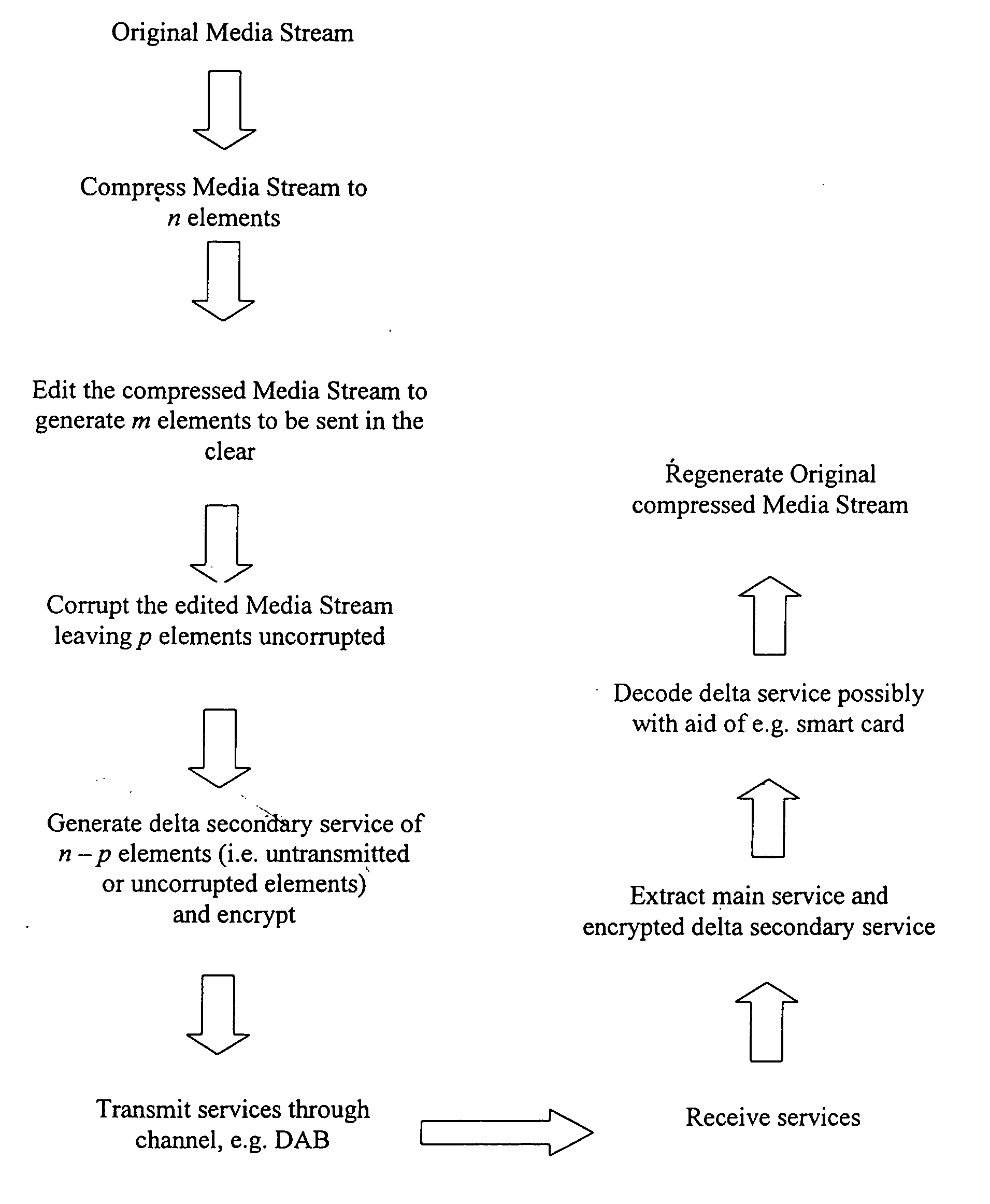
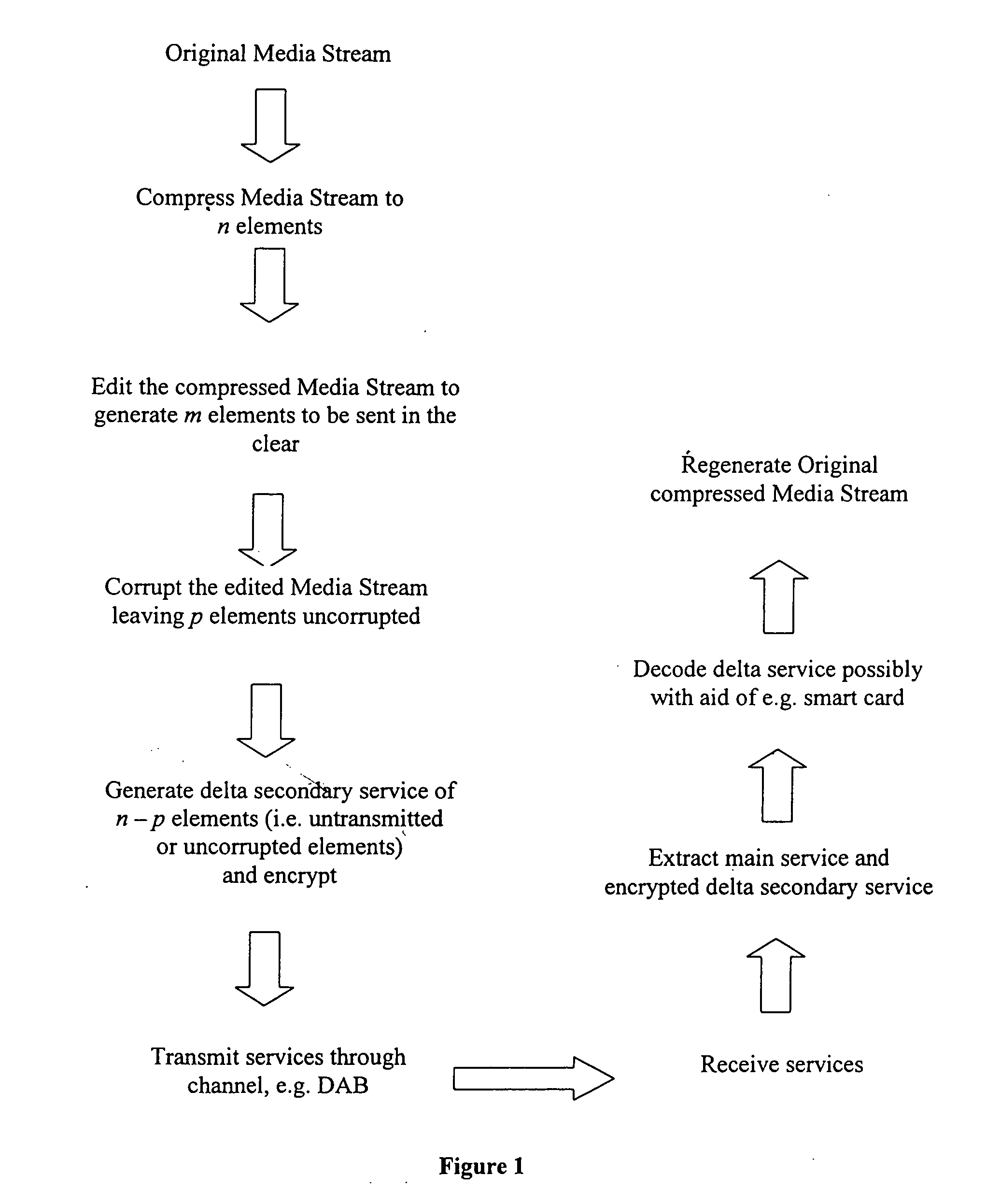
Digital transactions for the delivery of media files
InactiveUS20050278380A1Convenient to listenerDigital data processing detailsBroadcast transmission systemsDigital radioBroadcasting
An incomplete / partly corrupted media file is delivered ‘in the clear’; in addition, a delta file is delivered to users meeting access control criteria which, when combined with the incomplete / partly corrupted parts allows a complete and uncorrupted version of the media file to be re-constructed. The method allows, in one implementation, a secure music purchase system to operate over digital radio: for example, the start of a song when played over the radio is usually deliberately talked over and the end cut short to prevent listeners being able to record a complete copy. With the present system, this practice can continue, but listeners can also purchase the missing or corrupted sections to enable them to possess a complete and uncorrupted version for playback.
Owner:HILLSIDE LICENSING LLC +1
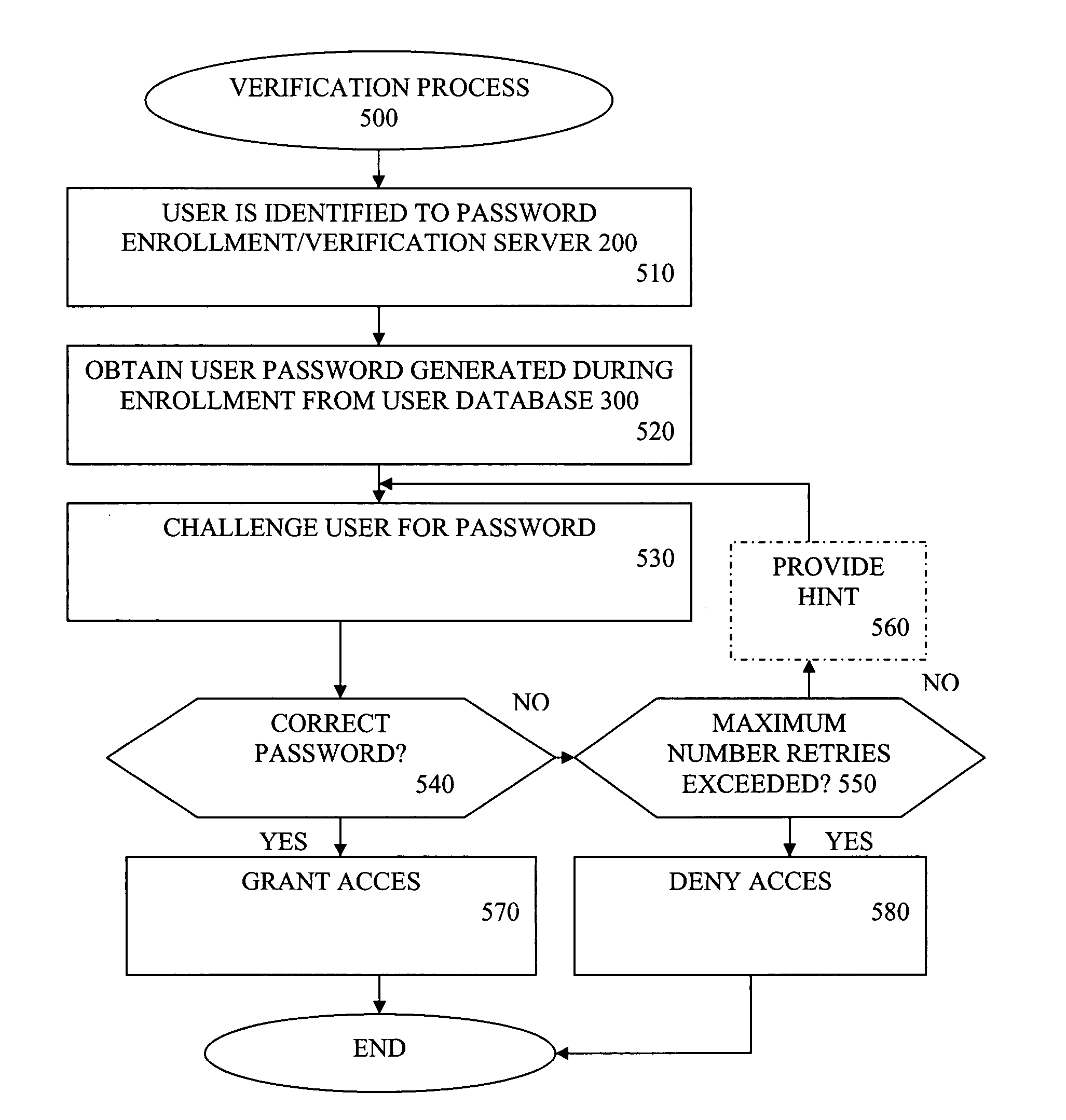
Method and apparatus for extracting authentication information from a user
ActiveUS20050114679A1Enhance memoryImprove recallDigital data authenticationSecret communicationPersonal detailsQuestions and answers
A method and apparatus are provided for extracting information from a user's memory that will be easily recalled during future authentication yet is hard for an attacker to guess. The information might be a little-known fact of personal relevance to the user or the personal details surrounding a public event. The user is guided to appropriate topics and forms an indirect hint that is useful to the user yet not to an attacker. Information extraction techniques verify that the information is not easily attacked and to estimate how many bits of assurance the question and answer provide. The information extracted may be, e.g., Boolean (Yes / No), multiple choice, numeric, textual, or a combination of the foregoing. The enrollment process may schedule the sending of one or more reminder messages to the user containing the question (but not the answer) to reinforce the memory of the user.
Owner:AVAYA INC
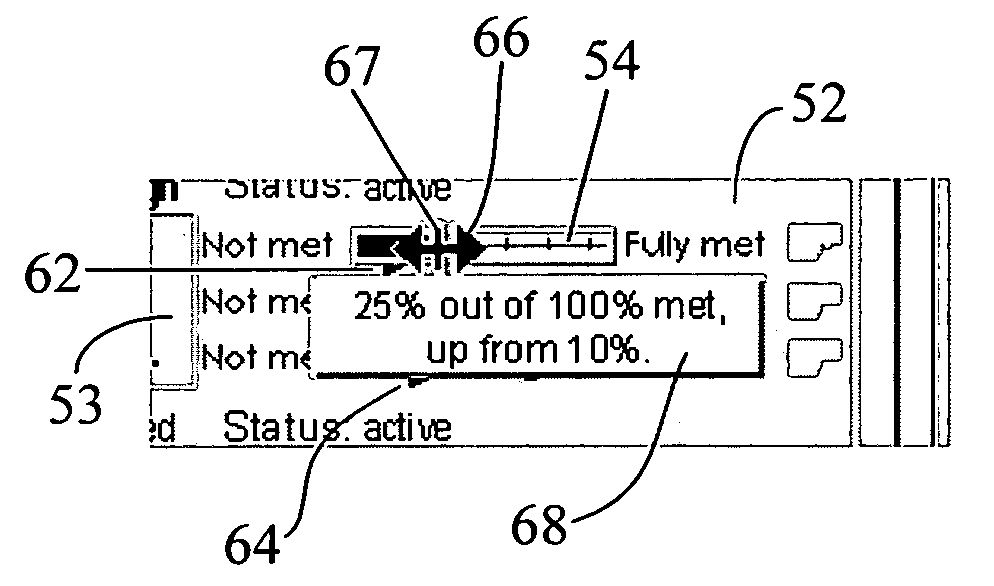
Scoring mechanism with visual communication of more than one reading
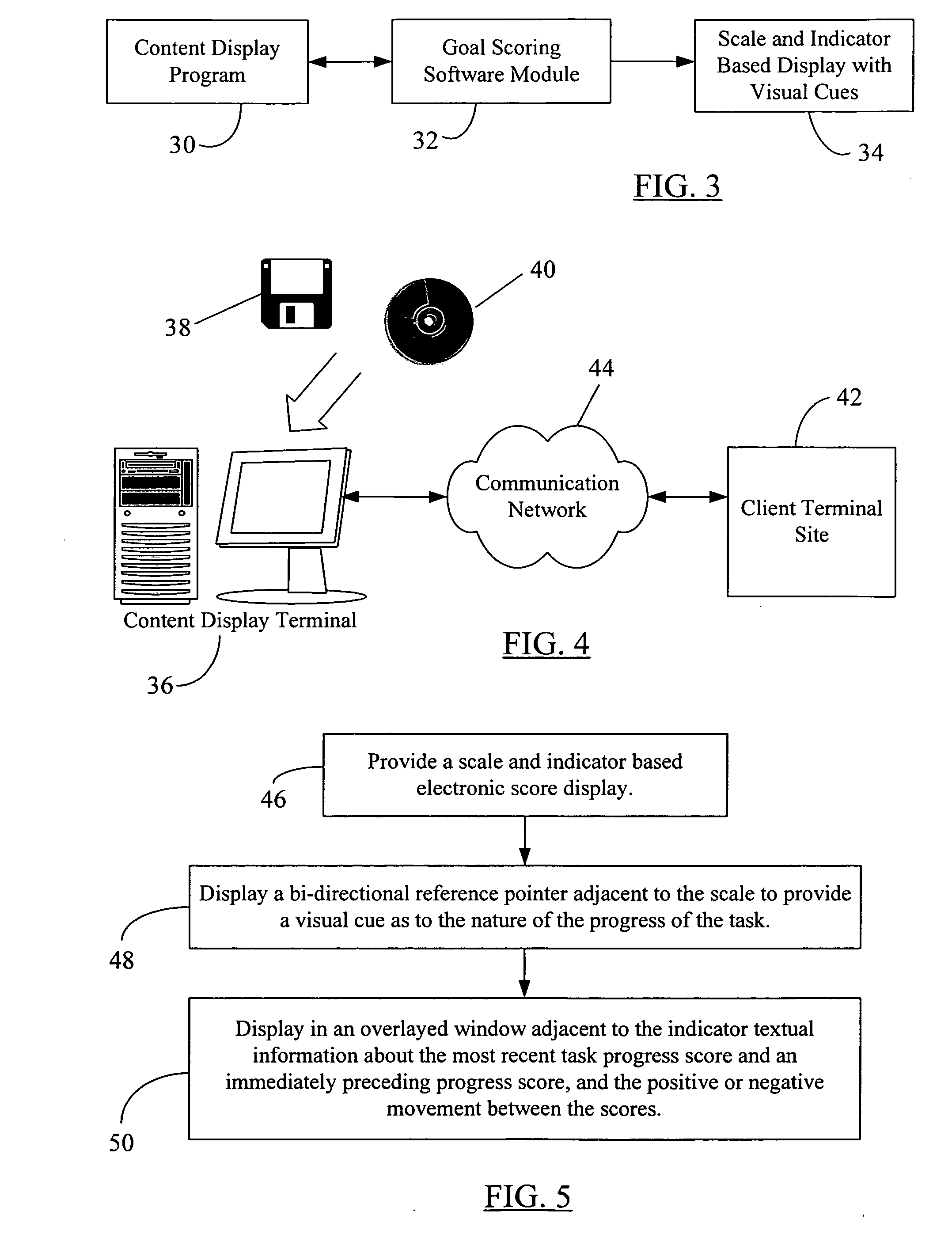
InactiveUS20070186187A1Special data processing applicationsInput/output processes for data processingTask completionDividing attention
An electronic progress scoring mechanism or indicator visually informs the user of how much of a task is complete and what is the nature or direction of the progress of task completion (positive or negative). A goal scoring software provides a scale and indicator based display for a task whose progress is to be monitored. The indicator can slide over the scale to indicate the most recent status of the task. A bi-directional reference pointer is displayed adjacent to the scale to provide a visual cue as to whether the most recent status indicates an upward (e.g. “better”) or downward (e.g. “worse”) progress from the immediately preceding status. An overlayed display window may also be provided adjacent to the sliding indicator to textually display the two most recent scores of progress and the relationship between them (i.e., whether there is a positive or negative movement from an earlier score to the most recent score). The task status indicator display can provide significantly more information on the progress of a task in an intuitive, but non-intrusive (non-distracting) manner. Because of the rules governing abstracts, this abstract should not be used to construe the claims.
Owner:MCKESSON INFORMATION SOLUTIONS
Printing device and medium type setting method
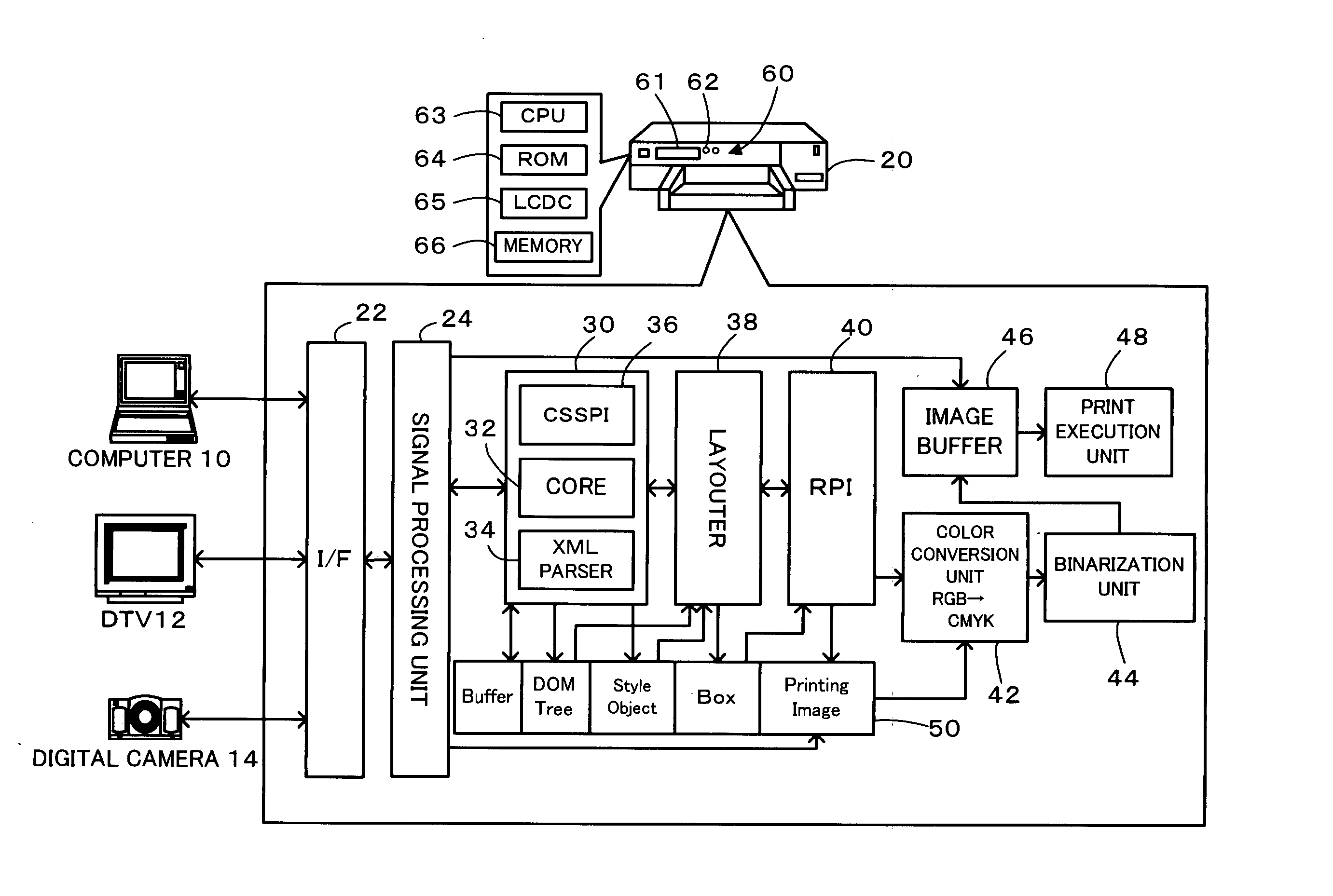
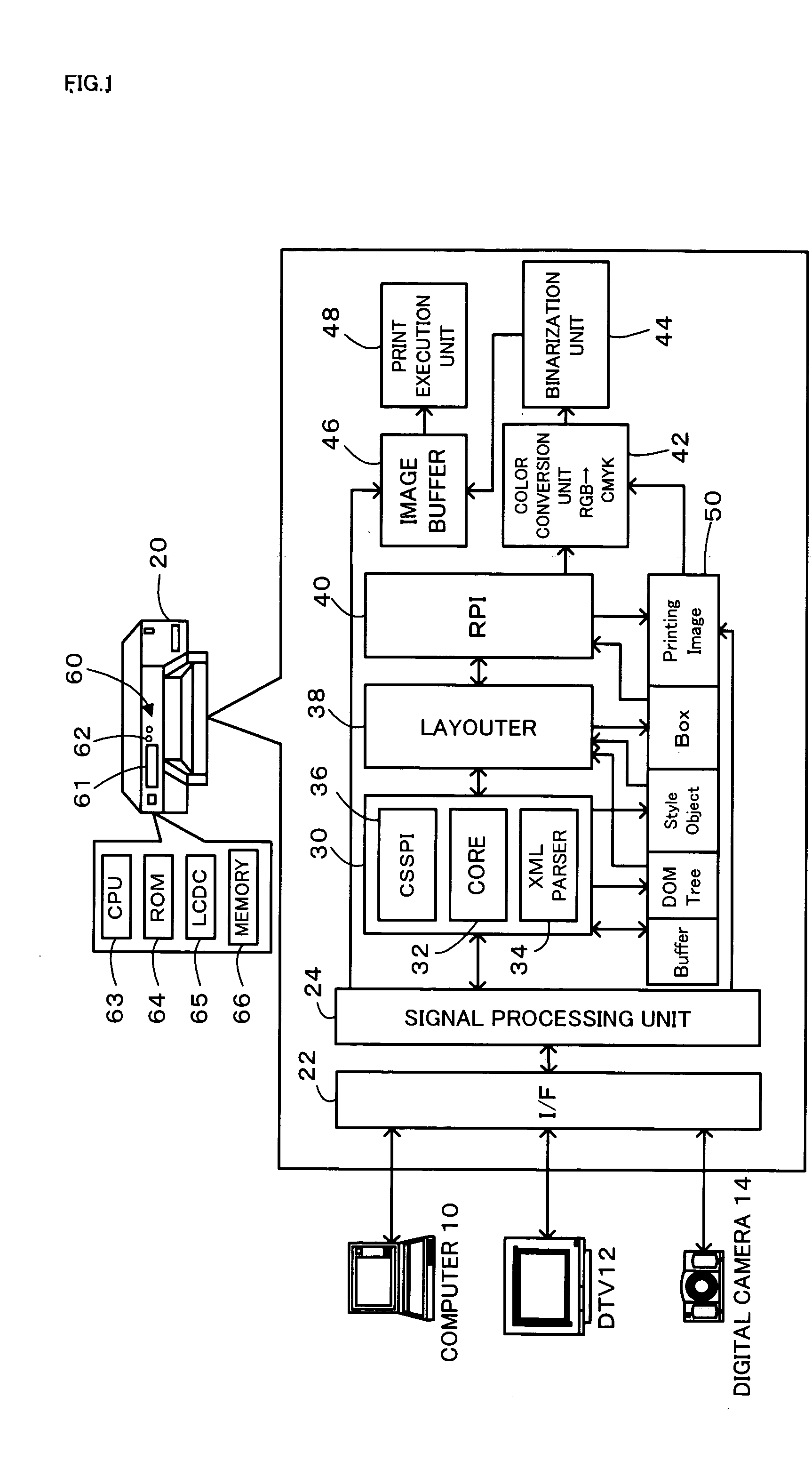
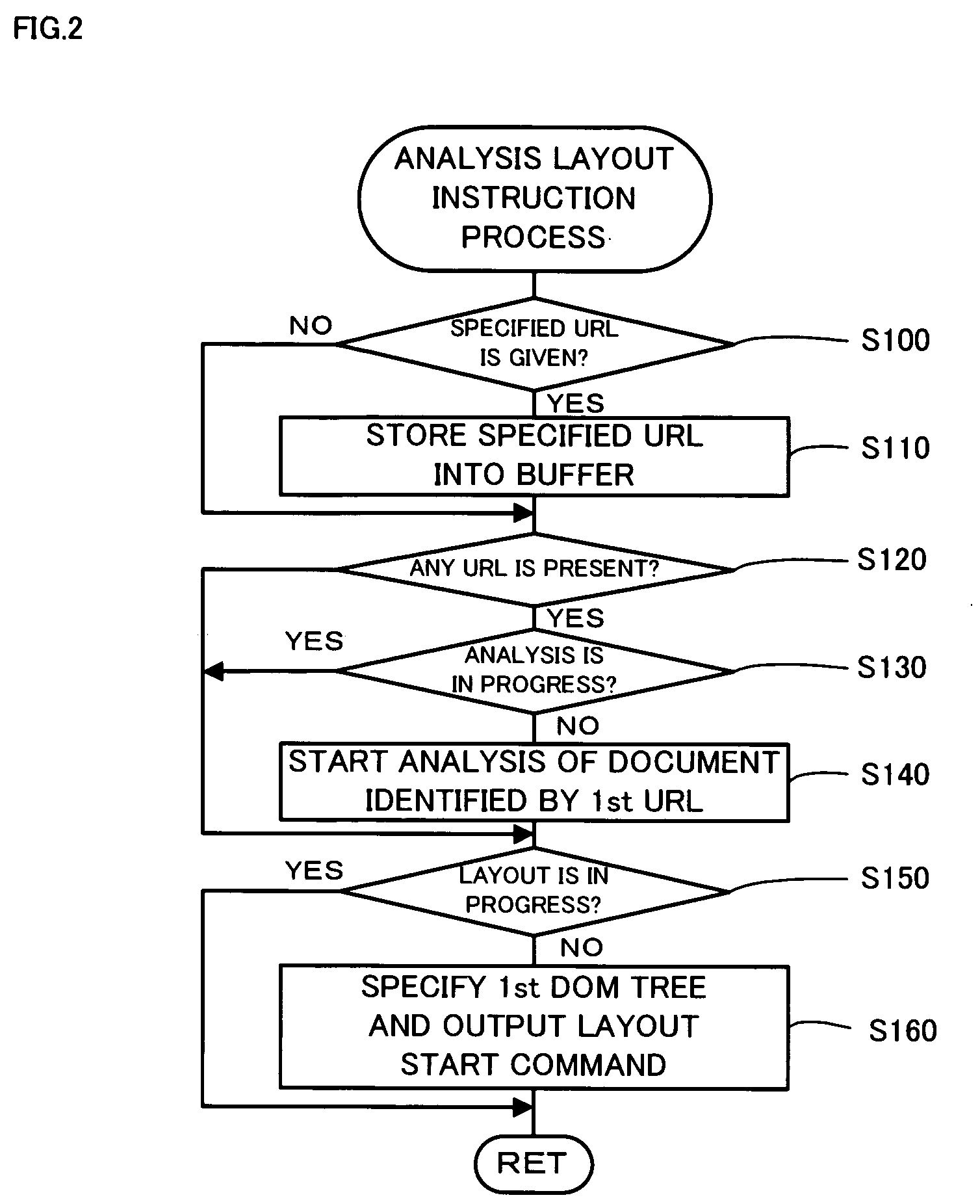
InactiveUS20050213154A1Digital computer detailsVisual presentation using printersComputer printingComputer science
The processing flow of the invention calculates a total image area S or a sum of areas of images among elements laid out on a 1st page (step S306), and computes an image area ratio ρ of the total image area S to a total paper area A of the currently set paper size (step S308). The calculated image area ratio ρ of greater than a preset reference value ρref leads to selection of ‘Photo Paper’ as the paper type (step S312). The calculated image area ratio ρ of not greater than the preset reference value ρref, on the other hand, leads to selection of ‘Plain Paper’ as the paper type (step S314). The processing flow subsequently determines whether the selected paper type is inconsistent with the paper type currently set in a printer (step S316). In the case of inconsistency of the paper type, the processing flow outputs a display of the type and the size of printing paper to be set in the printer (step S318) and waits for entry of the user's confirmation (step S320).
Owner:SEIKO EPSON CORP
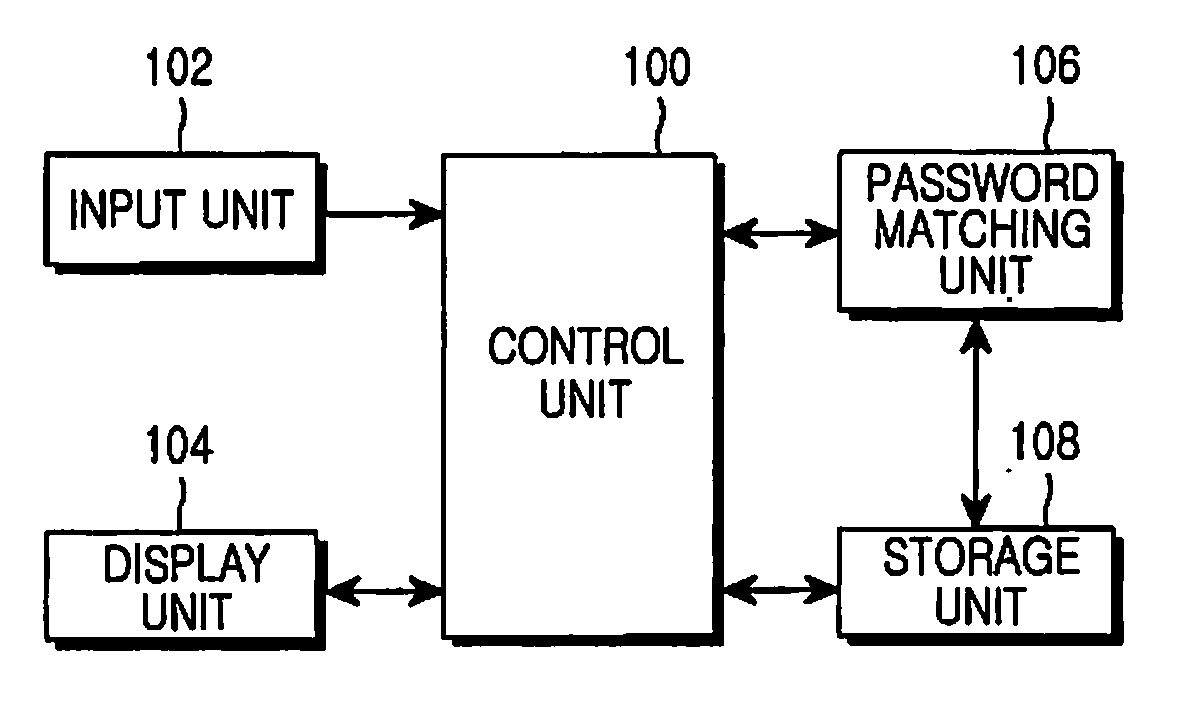
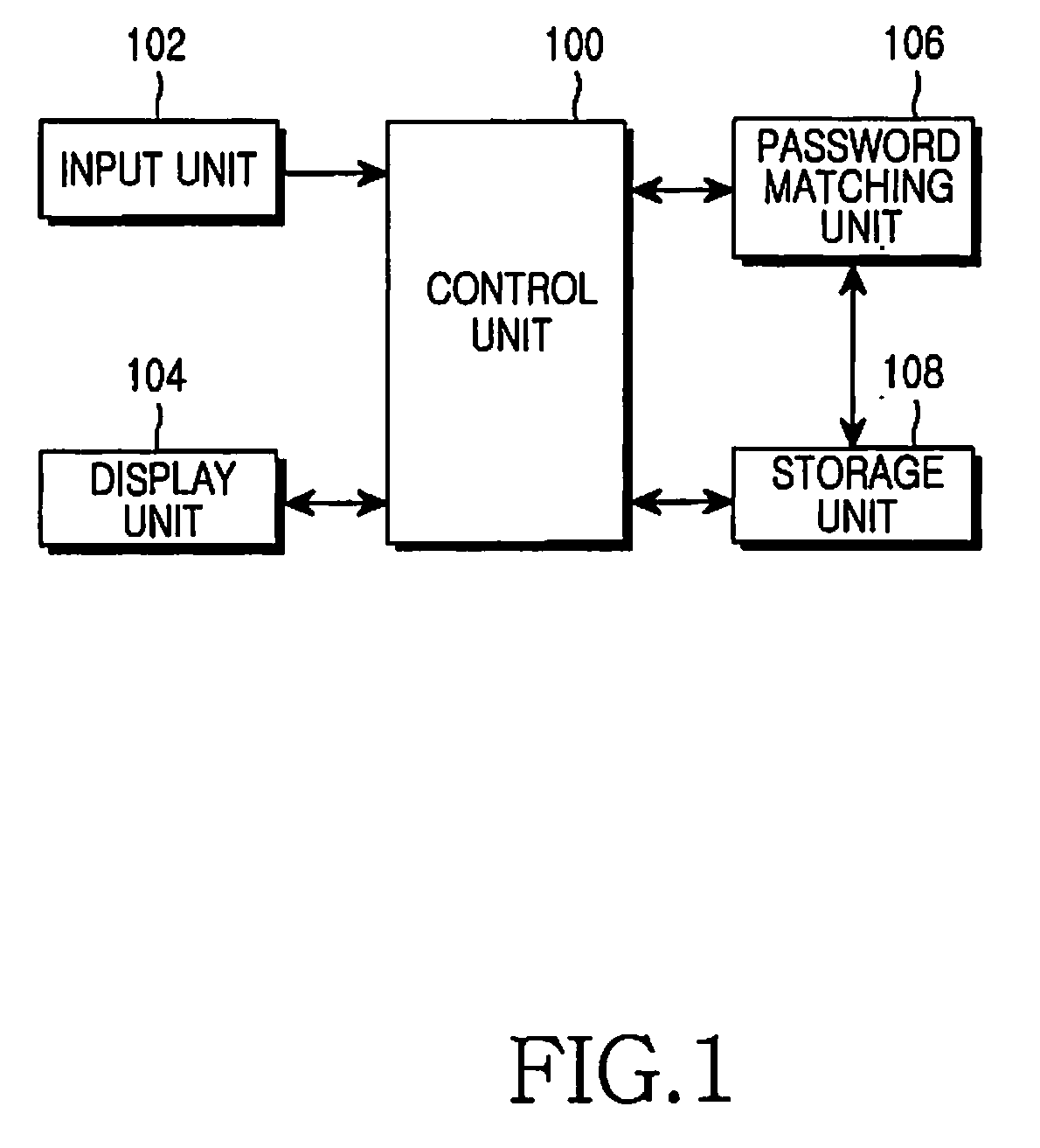
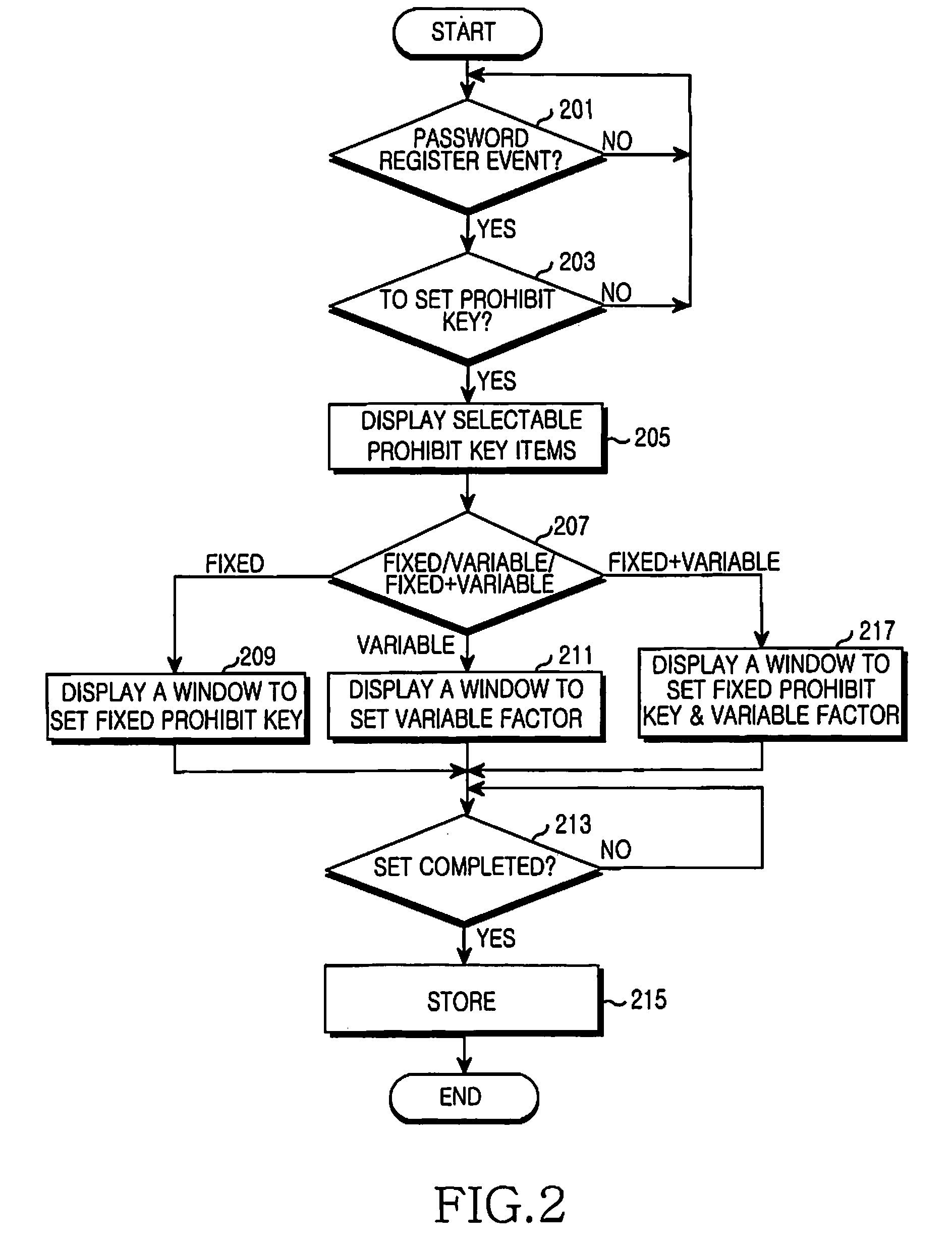
Method and apparatus for preventing illegal access using prohibit key in electronic device
InactiveUS20080077985A1Prevent unauthorized accessAvoid contactDigital data processing detailsUser identity/authority verificationPasswordLuser
A method and an apparatus for preventing illegal access by using a prohibit key in an electronic device, is provided. The method includes determining a variable prohibit key which is dynamically varied according to a predetermined variable factor, if a password is input to access a system, determining the existence of the determined variable prohibit key in the input password, and rejecting an access of a user to the system, if the variable prohibit key exists in the input password.
Owner:SAMSUNG ELECTRONICS CO LTD
Key information management device, key information management method, and non-transitory computer-readable recording medium
ActiveUS20190122470A1Avoid registrationReduce registrationService provisioningKey distribution for secure communicationInformation processingService use
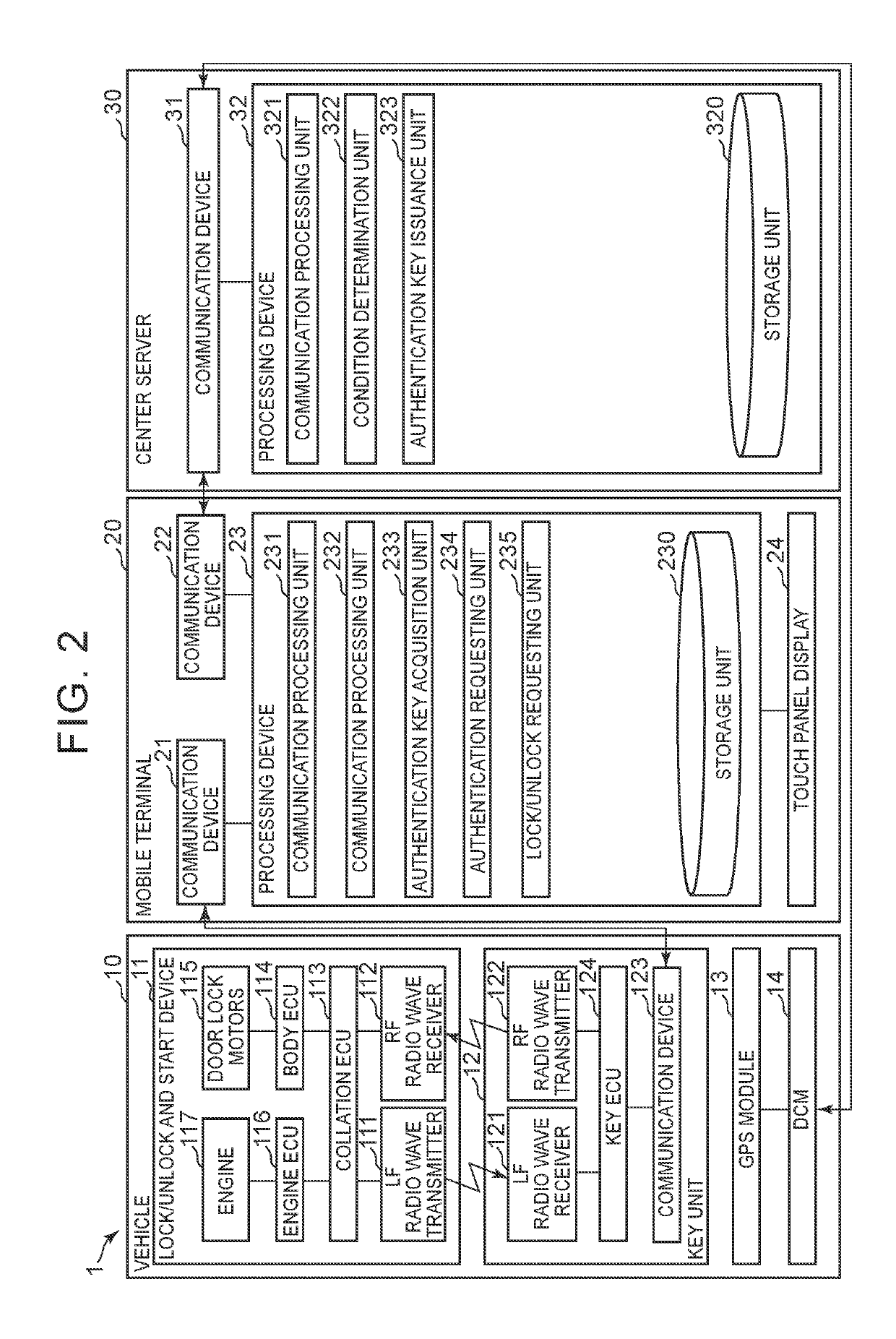
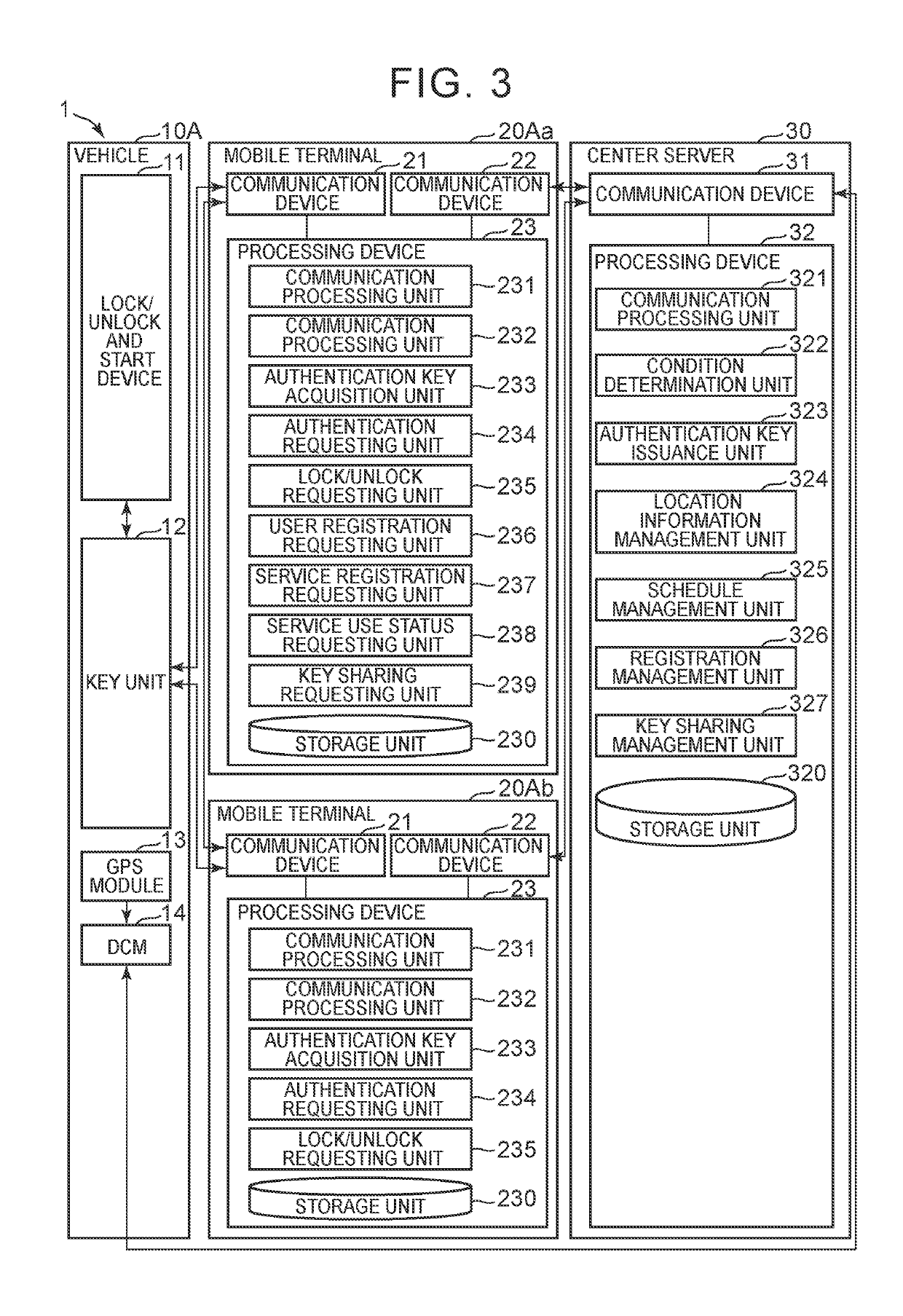
A key information management device includes an information processing device. The information processing device is configured to deliver key information to a mobile terminal as the mobile terminal transmits a predetermined transmission signal toward a vehicle. The key information is information for unlocking the vehicle, starting the vehicle, or unlocking and starting the vehicle. The information processing device is configured to register permission for a user of the vehicle to use a predetermined service using the vehicle. The permission is permission to cause the information processing device to deliver the key information to a mobile terminal of a third party concerned with the predetermined service, other than the user of the vehicle, as an external device concerned with the predetermined service transmits a predetermined request signal.
Owner:TOYOTA JIDOSHA KK
System and method of annotating utterances based on tags assigned by unmanaged crowds
ActiveUS20170068651A1Increase in sizeReduce cognitive loadSemantic analysisSpecial data processing applicationsNamed-entity recognitionCrowds
A system and method of tagging utterances with Named Entity Recognition (“NER”) labels using unmanaged crowds is provided. The system may generate various annotation jobs in which a user, among a crowd, is asked to tag which parts of an utterance, if any, relate to various entities associated with a domain. For a given domain that is associated with a number of entities that exceeds a threshold N value, multiple batches of jobs (each batch having jobs that have a limited number of entities for tagging) may be used to tag a given utterance from that domain. This reduces the cognitive load imposed on a user, and prevents the user from having to tag more than N entities. As such, a domain with a large number of entities may be tagged efficiently by crowd participants without overloading each crowd participant with too many entities to tag.
Owner:VOICEBOX TECH INC
Method and a user interaction system for controlling a lighting system, a portable electronic device and a computer program product
ActiveUS9041731B2Less functionalEasy to controlInput/output for user-computer interactionElectrical apparatusInteraction systemsComputer graphics (images)
The invention provides a user interaction system (100) and a method of controlling a lighting system. The user interaction system (100) comprises a display (106), a means for receiving a location indication (102), a location identification means (104) and an overlay image creator (108). The display (106) displays a subarea image and an overlay image. The subarea image is an image of a specific subarea of the environment. The location identification means (104) detects which specific location in the environment is indicated by the location indication. The overlay image creator (108) generates the overlay image. The overlay image comprises information related to a lighting effect which is obtainable by the lighting system at the specific location. The obtainable effect is an effect of at least two controllable light sources of the lighting system. The information which is related to the obtainable lighting effect is based on a lighting system model (110) which represents effects that are obtainable in the environment by controllable light sources of the lighting system.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
System and method for automatic page turning for book imaging
ActiveUS9266376B1Low costImprove reliabilityTelevision system detailsColor television detailsDigital imagingComputer graphics (images)
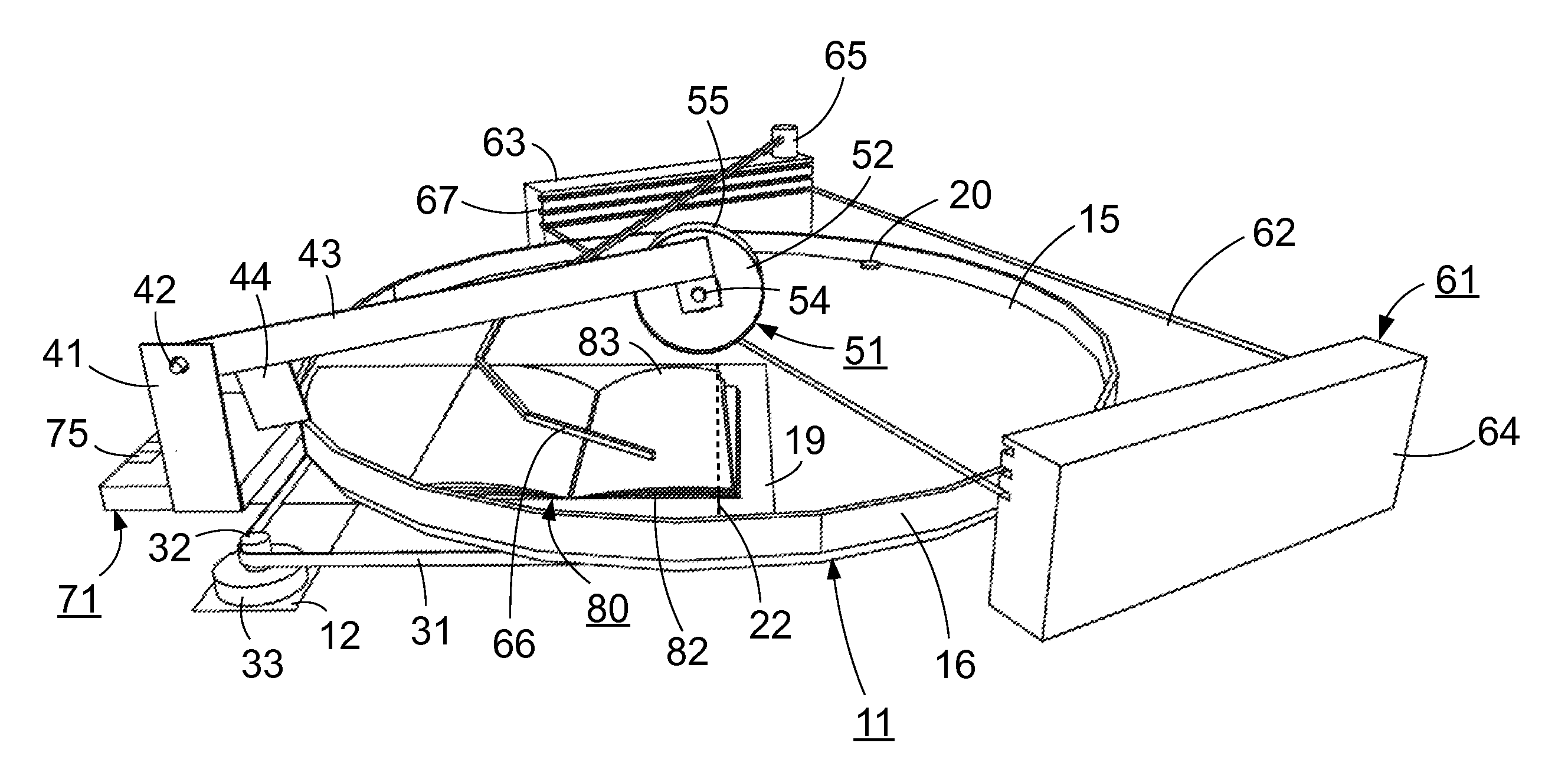
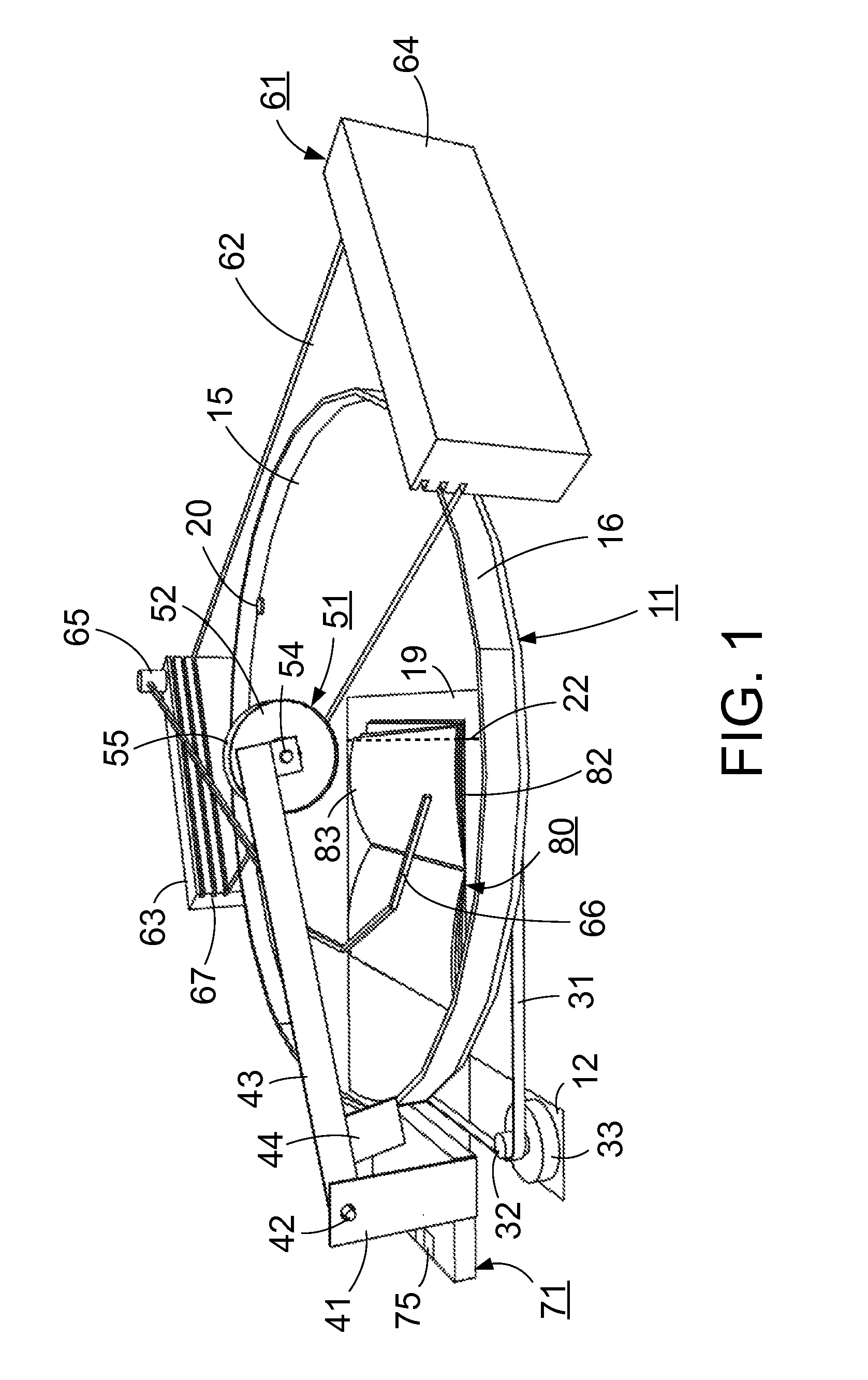
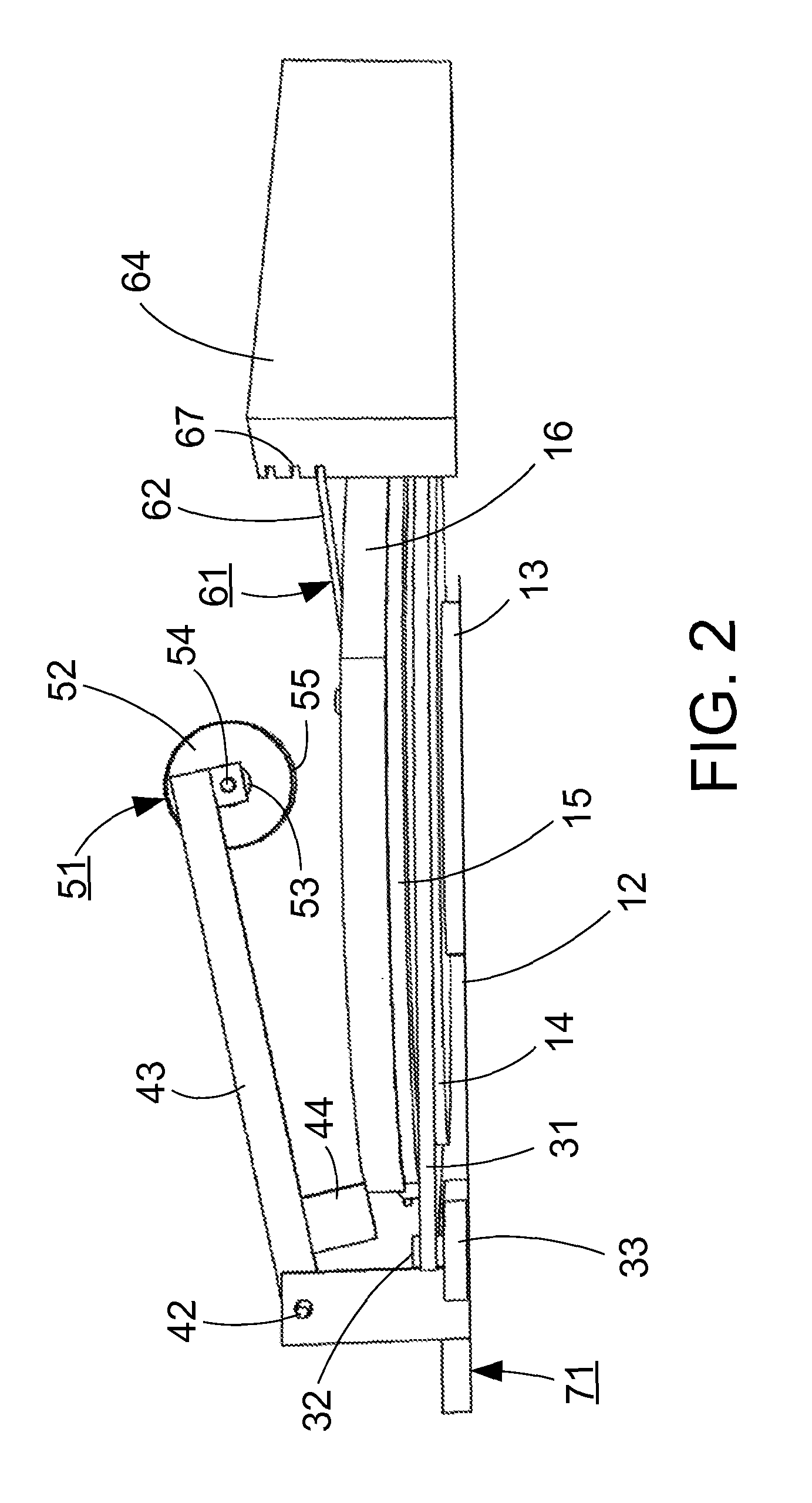
A system and method for automatically turning the pages of an open book (80) without user intervention for the purposes of digital imaging or viewing. One embodiment of the system includes a rotating platform (15) for mounting the open book (80), a page lifter (51), a transparent stationary hood (62), and a camera (201). As the platform (15) rotates, the page lifter (51) is dropped onto the uppermost page on the leading side of the book (80). The uppermost page is held fast and lifted up by the page lifter (51). The platform (15) continues to rotate, peeling the uppermost page free from the page lifter (51) and eventually trapping the book completely under the hood (62) which holds the book (80) open and keeps the uppermost pages visible. The platform (15) rotation is paused momentarily to allow for image capture by a camera (201) viewing the open book (80) through the hood (62). Other embodiments are described and shown.
Owner:MAH KENNETH JACK
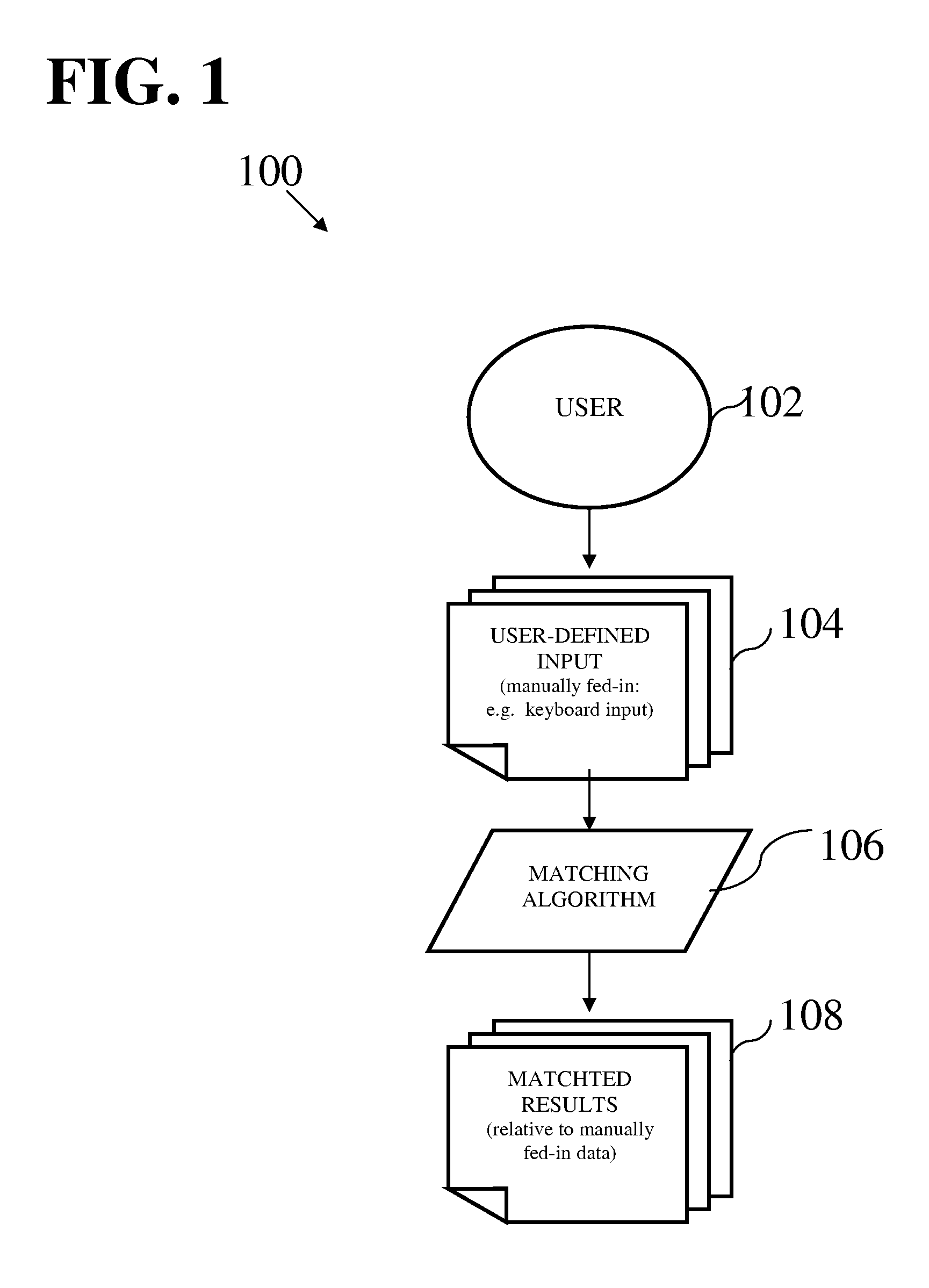
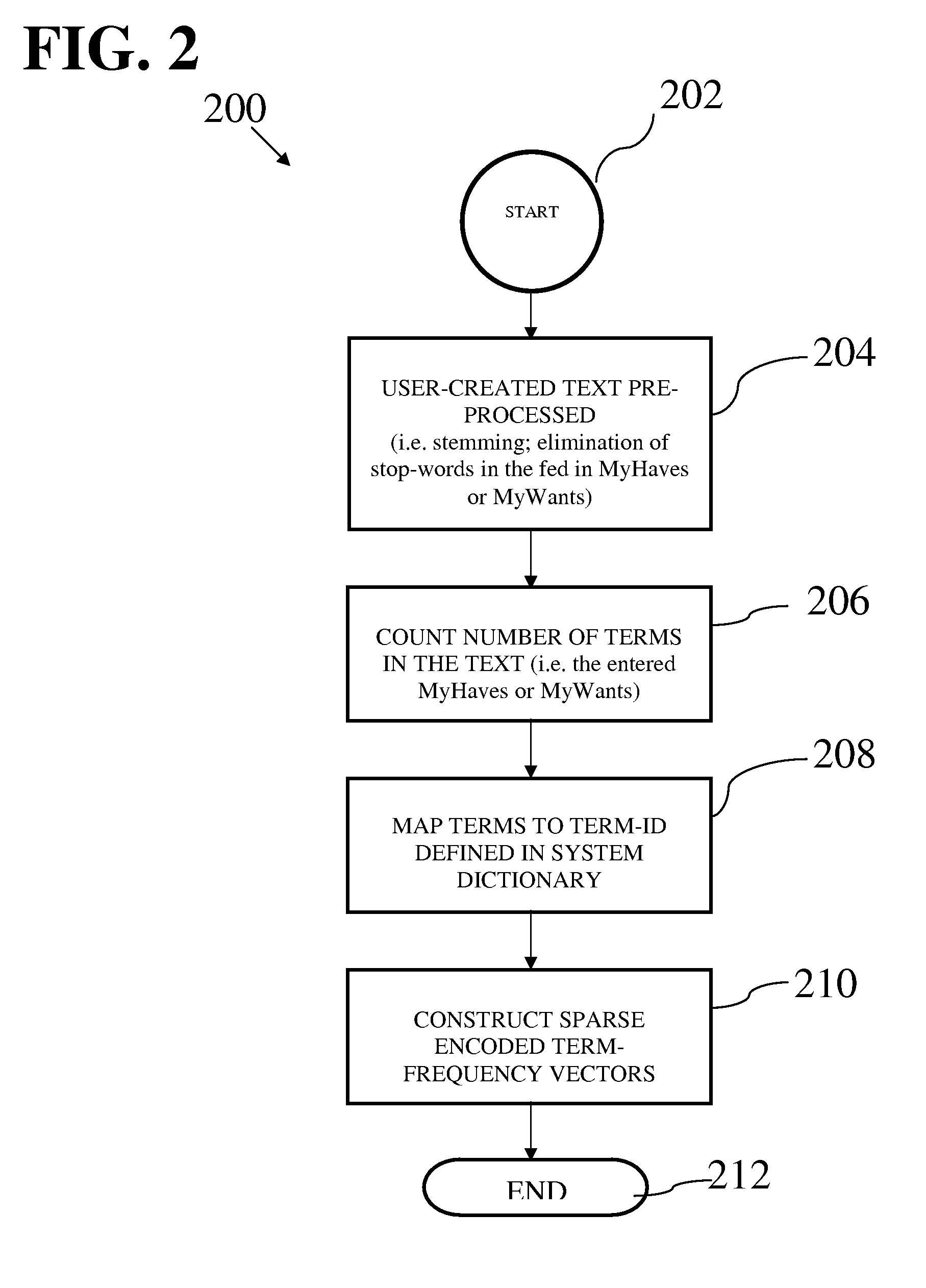
Method and system for matching user-generated text content
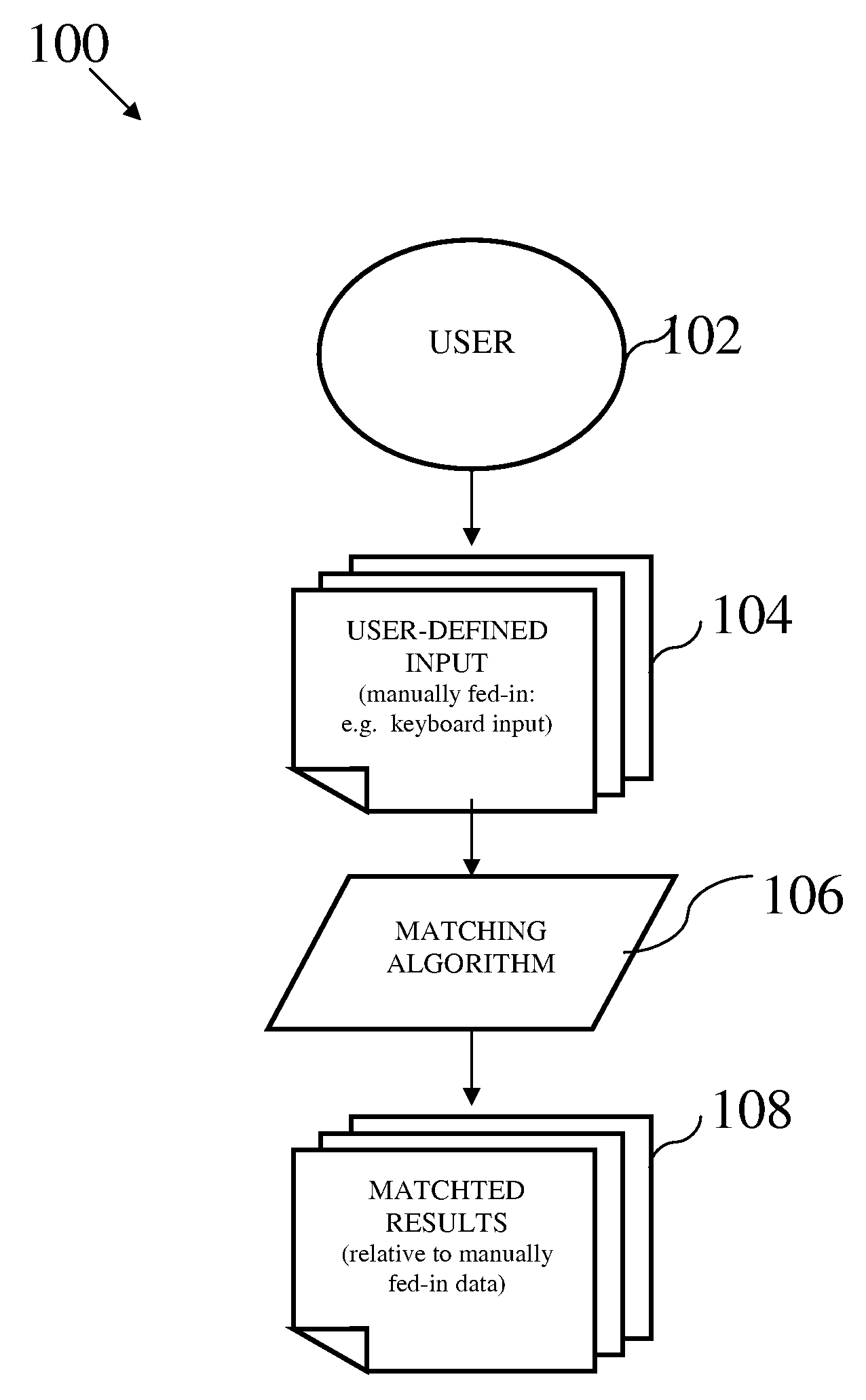
According to a computer implemented method and system for matching user-generated text content, users “freely” specify content by means of fed-in texts which are matched automatically, according to rules in the embodiment. An embodiment of the invention allows customers to specify what items or services to request or offer by adding, to the “MyHaves” or “MyWants” selection criteria, using typed-in descriptions. Traditionally, for the purpose of matching supplies and demands, the specification of an individual's “wants” and “haves” is done by selecting options that are predefined by, or hard-coded into, the system's “drop-down menu”—rather than allowing customers to freely define what they want or have. This method under consideration, however, provides an efficacious solution: customers are free to request an item or service by entering standard descriptive texts describing what s / he wants in a customizable manner very akin to the flexibility associated with verbal speech, with the assurance that these human-entered texts will be matched automatically. Similarly, a customer is free to offer an item or service in the aforementioned (text-descriptive) way. The entered texts are in the form of a specific human language (e.g. English, Chinese, etcetera) using the desired input device, such as a computer keyboard. The system algorithm of an implementation then “crawls” through the network of user generated texts (user-defined texts) to find matches between what people are offering and what others are requesting, while watching out for typographical errors (in the text content) made by customers. That is to say, the algorithm in the embodiment scours the texts in the “MyWants” section of requesters and sees if there are corresponding matches found in the “MyHaves” section of offerers, while paying attention to certain system rules.Although the invention essentially lies in the ability to match raw user-generated texts—that fall out of system-provided categories—to achieve any desired purpose of an embodiment, the invention has applicability in sundry areas where utility may be derived. In an embodiment of the invention, for example, when a match is found, the system automatically triggers an email that is sent to the offerer, notifying him / her that a fellow customer wants what the offerer-customer has to offer. If the offerer-customer agrees to deliver the item or service to the requester, the implementation proceeds to require the requester customer to confirm receipt once the item is received. The utility here is the expeditious re-allocation of resources whose descriptions fall outside the predefined categories of the system and, consequently, may only be accurately provided by the persons wanting or offering the resources (items or services).
Owner:TECHTAIN
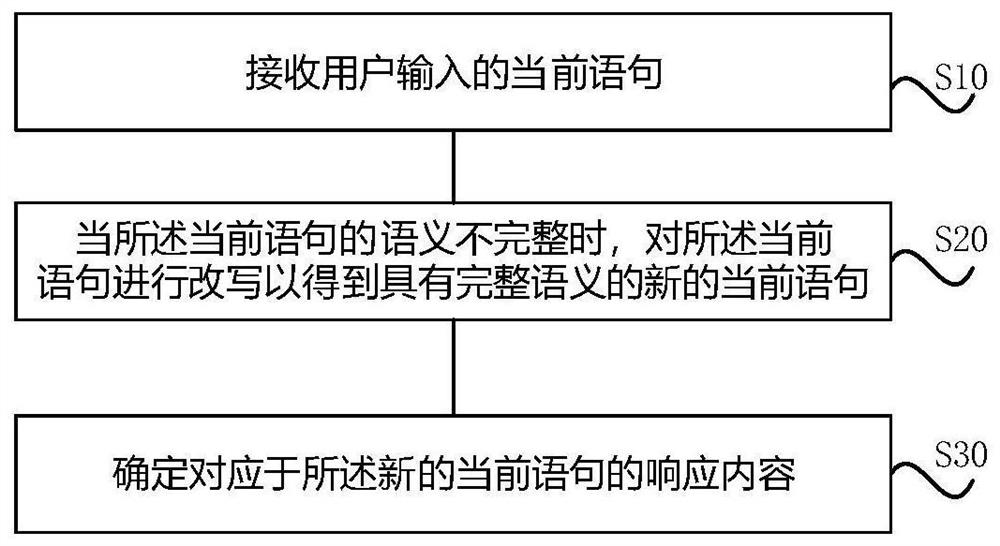
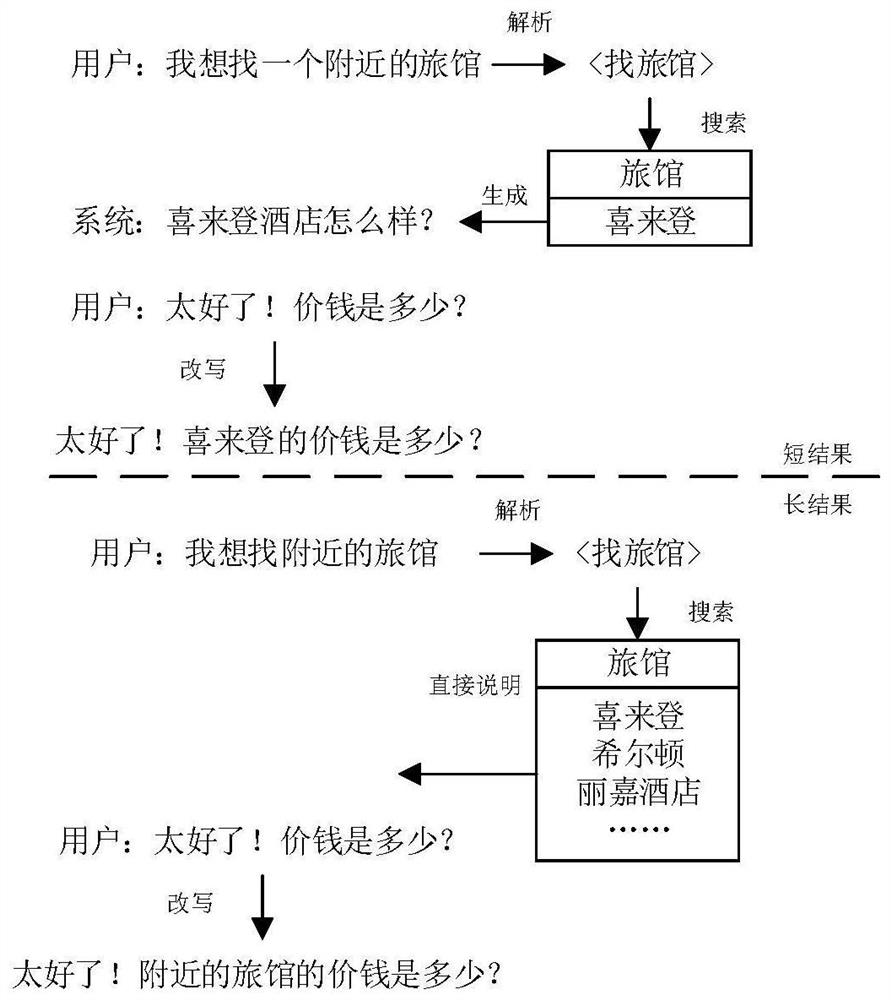
Man-machine conversation method, electronic equipment and storage medium
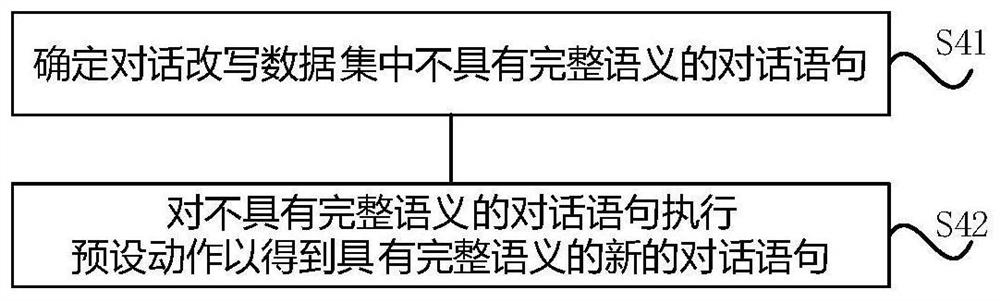
PendingCN113064985AAvoid parsing errorsAvoid accuracySemantic analysisText database queryingUser inputTheoretical computer science
The invention discloses a man-machine conversation method. The method comprises the following steps: receiving a current statement input by a user; when the semantics of the current statement is incomplete, rewriting the current statement to obtain a new current statement with complete semantics; and determining response content corresponding to the new current statement. The embodiment of the invention has the beneficial effects that the corresponding response content is not urgently determined when the received current statement does not have the complete semantics, but the response content is determined based on the new current statement after the current statement is rewritten to obtain the new current statement with the complete semantics. The defects that errors exist and the accuracy is low when the current statement is directly analyzed under the condition of incomplete semantics are overcome.
Owner:AISPEECH CO LTD
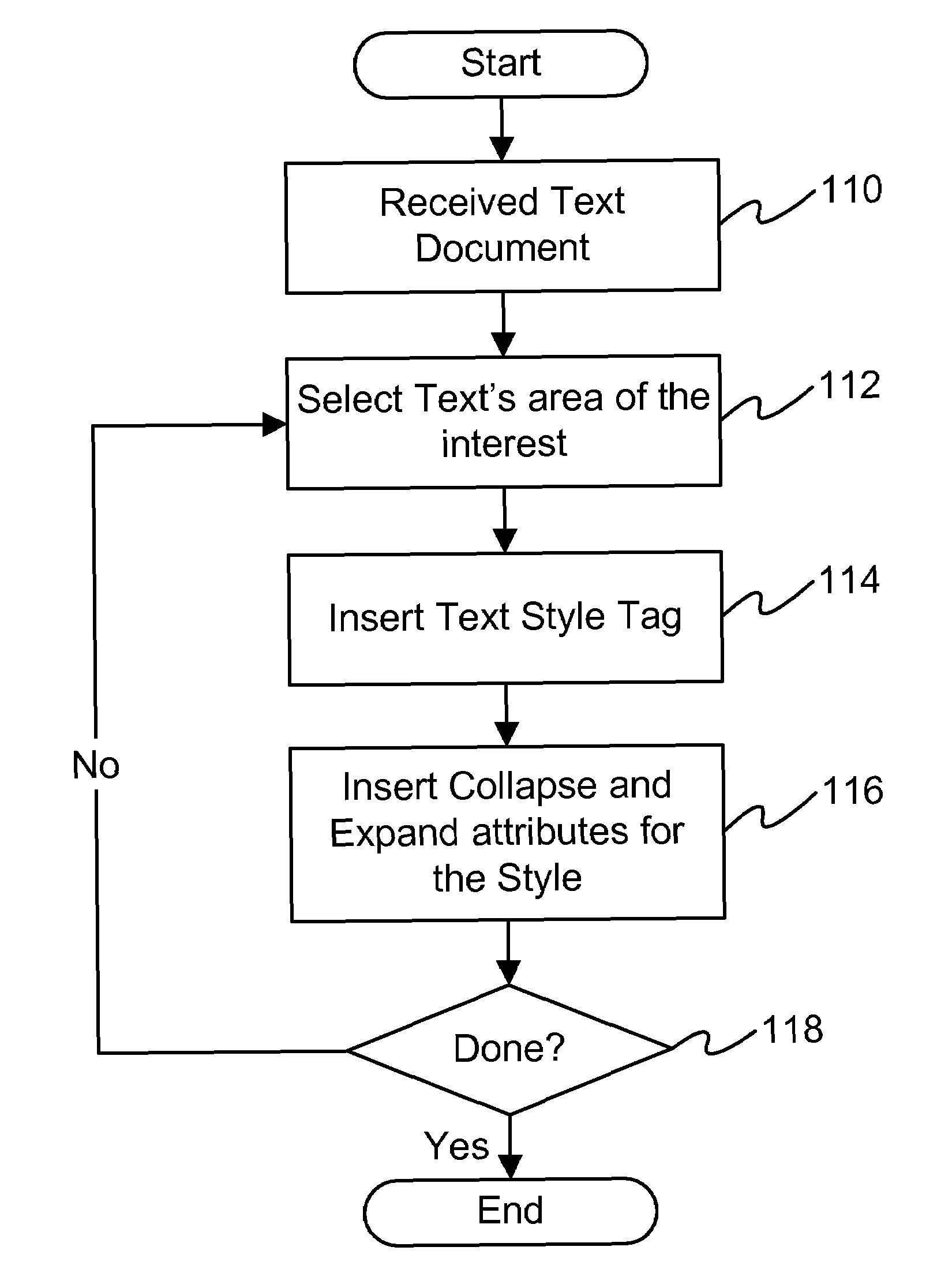
System and method for customizing collapse feature for editors
InactiveUS7506266B1Natural language data processingSpecial data processing applicationsDocumentationDatabase
Document editors have the ability to collapse or expand some part of a file content they are viewing (as an example). However, the few editors that already provide such a feature only provide it for a particular file type or using reserved language words. However, this system (as an example) makes the Collapse / Expand feature available to any file, while it accords strictly to the piece of text the user is writing. Thus, the Collapse / Expand feature might be bound and transferable with any paragraph of the file. A user is able to choose the delimiters of such a collapse action according to its own style and the document type.
Owner:IBM CORP
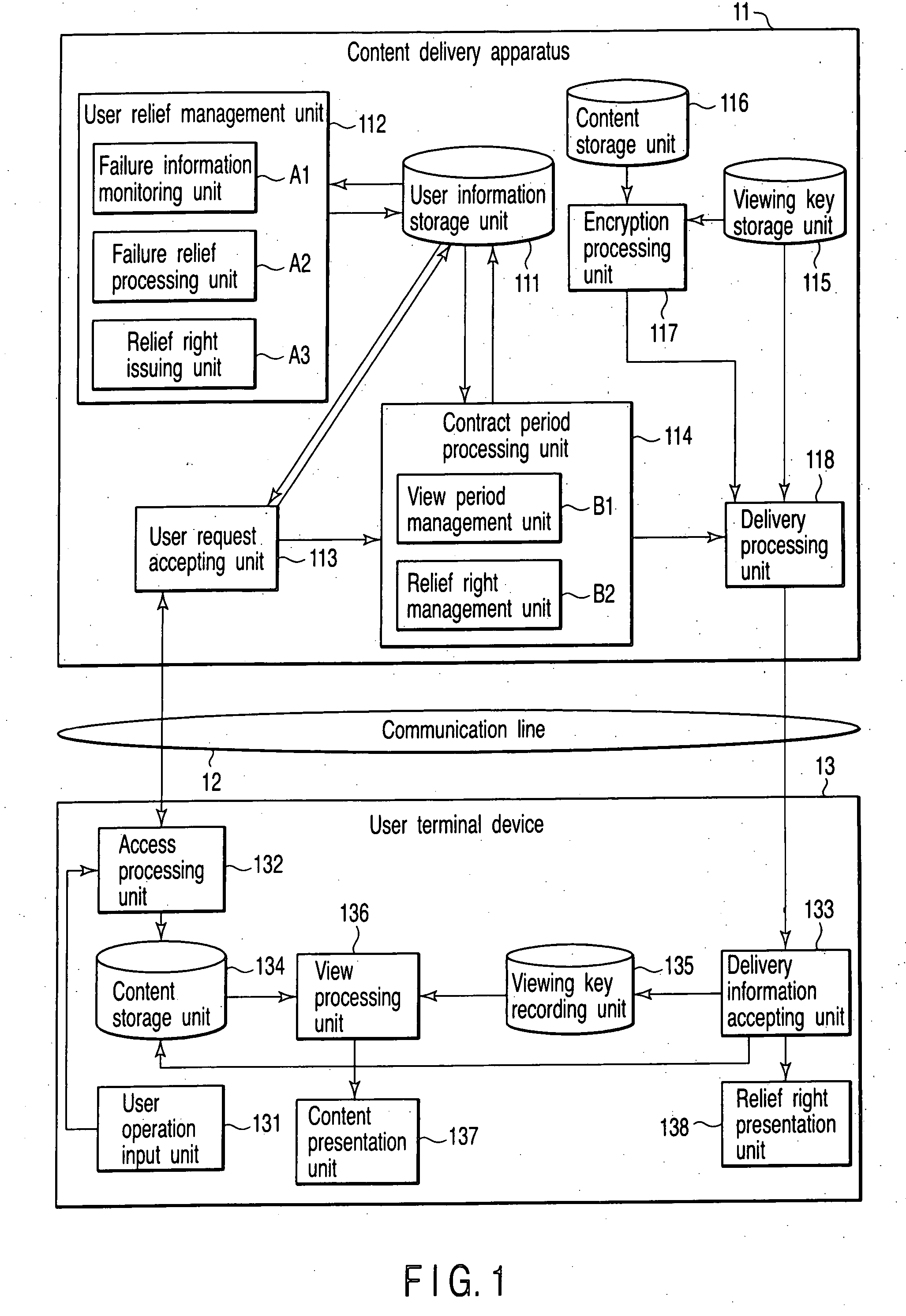
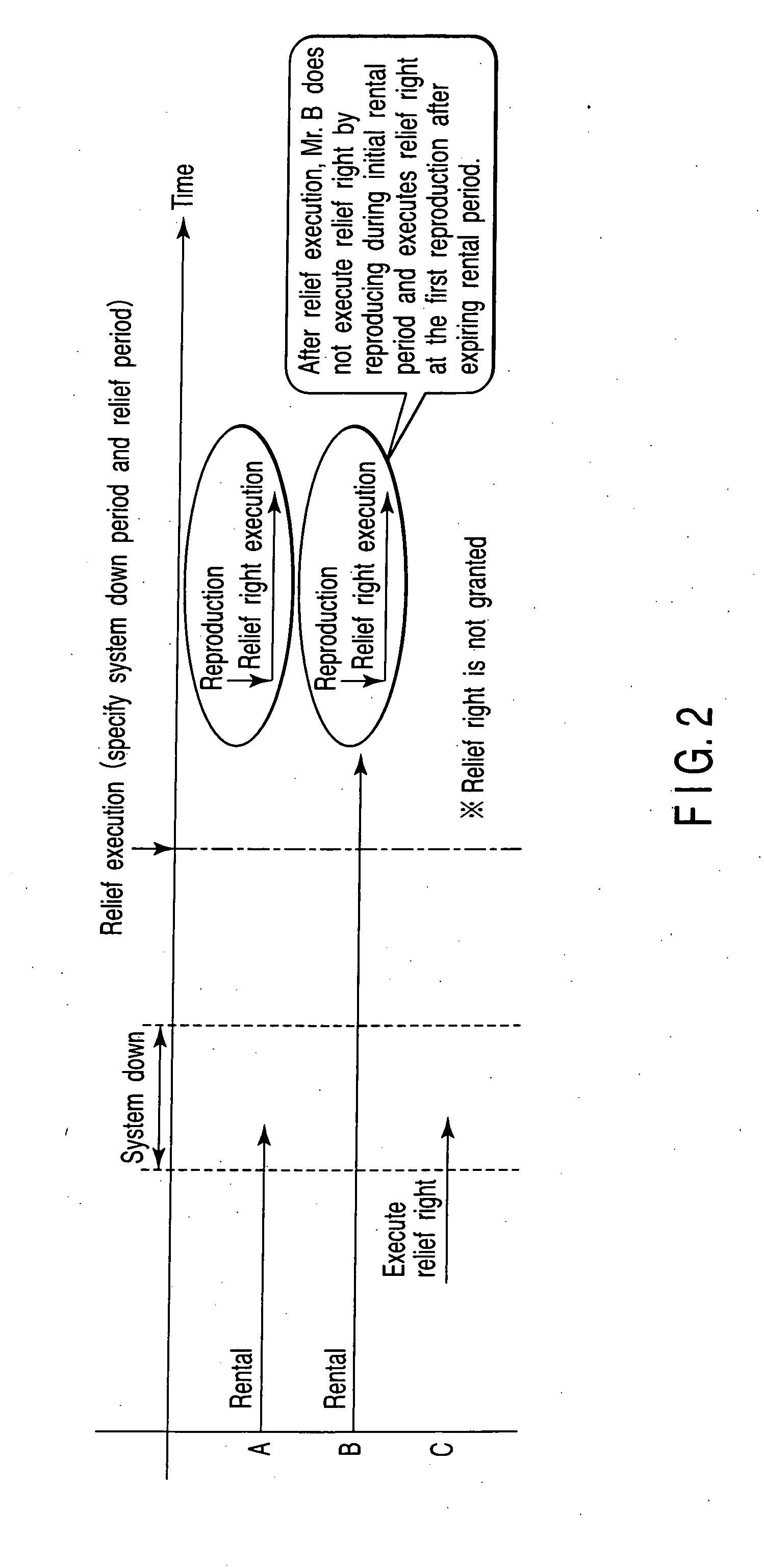
Content delivery apparatus, user terminal device, relief management method and computer program
InactiveUS20080052239A1DissatisfactionSecure beliefAnalogue secracy/subscription systemsPayment architectureManagement unitTerminal equipment
A content delivery apparatus, when a content delivery request is outputted from a user terminal device, encrypts the requested content with an encryption key, adds a view period to it to deliver it to a request source and delivers a viewing key in response to a view request from the user terminal device within the view period. A user relief management unit monitors failure information notifying, grasps a delivery disabled period from the failure information, specifies a delivery destination user for a content of which the view period is overlapped with the delivery disabled period and issues a relief right with a relief period specified thereto to the specified user. A contract period processing unit manages the relief right and permits viewing within the relief period set by the relief right when a view right based on the relief right is output from the user terminal device.
Owner:KK TOSHIBA
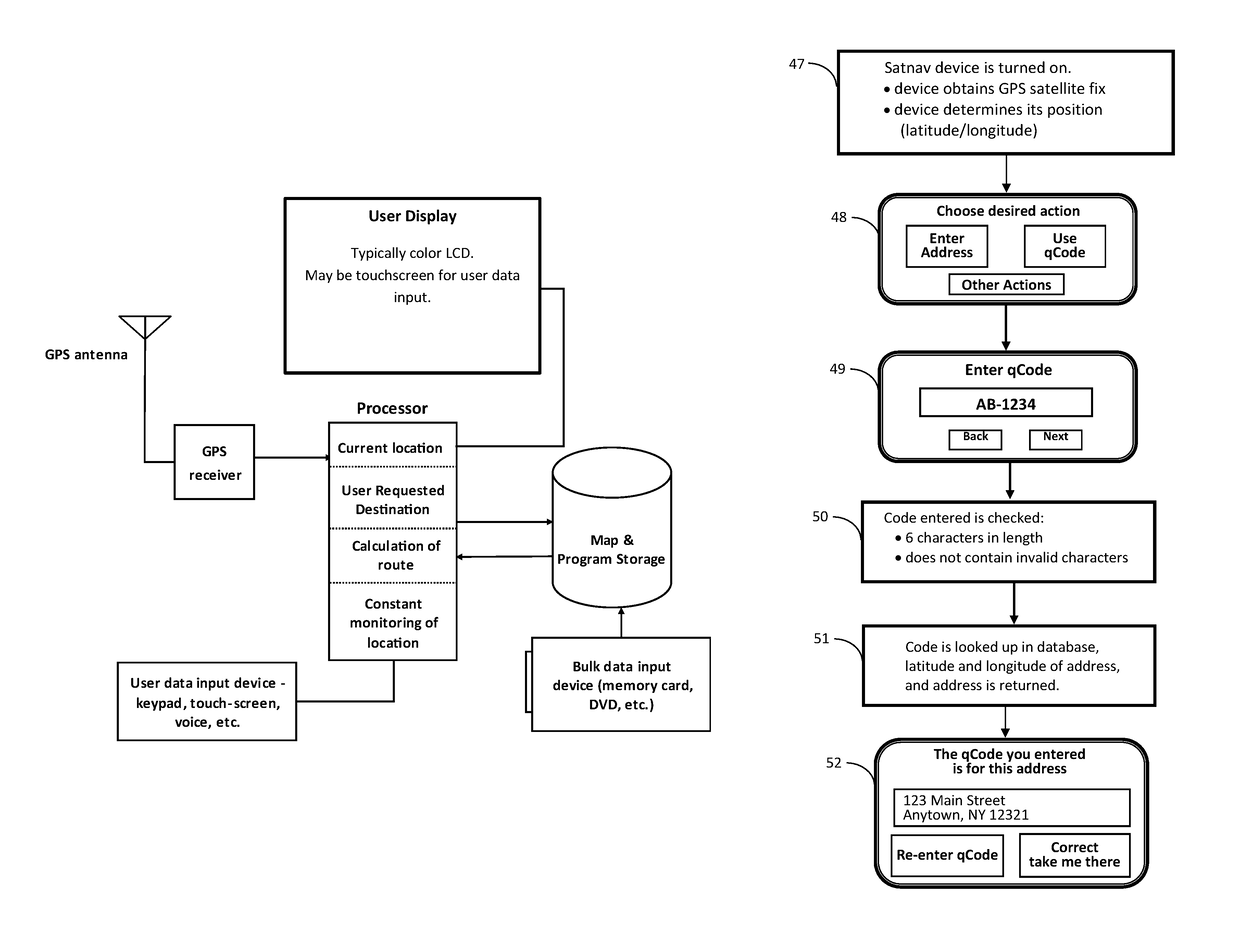
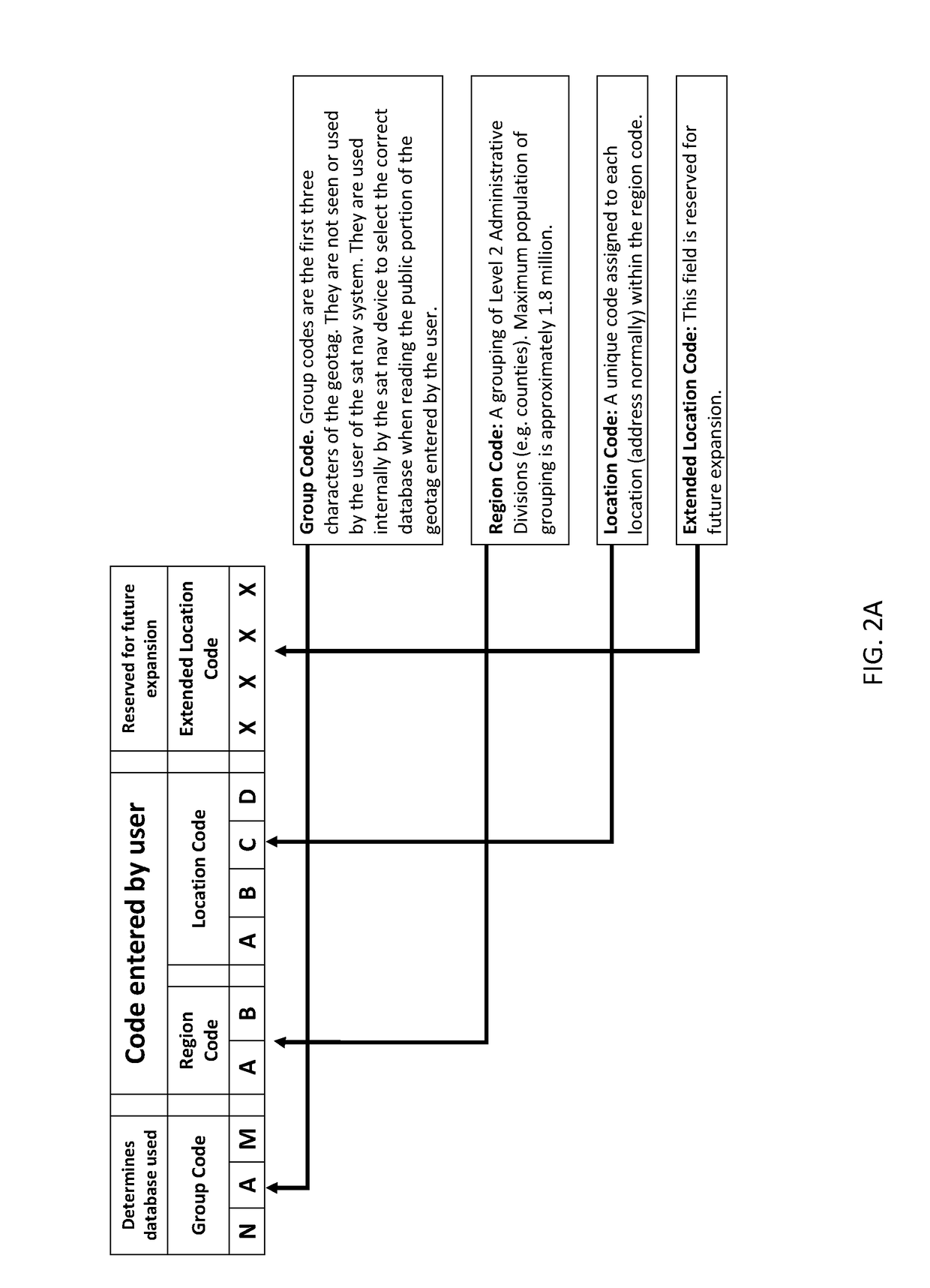
Coding system for satellite navigation system
ActiveUS9952052B2Instruments for road network navigationGeographical information databasesParking areaYankee
The present invention provides a method, the QCODE method, of geotagging all postal addresses and other points of interest that one might want to navigate to and which allows the user to identify these addresses and other points of interest with a code consisting of 6 alphanumeric characters or less. A point of interest may or may not have a street address, for example, “the main entrance to the Jefferson Building at the USPTO complex in Alexandria Virginia” or “the entrance to the VIP parking area at Yankee Stadium”. The disclosure teaches embodiments that are naturally upgraded to integrate changing spatial information due to addition of countries, better data, political changes, and other similar changes in geographical data. A single geocoding engine is capable of handling the various address formats in use in different countries and jurisdictions.
Owner:HALE MERTON G
Dynamic POIs recommendation method based on TS24
ActiveCN112784162AHigh precisionImprove recallData processing applicationsDigital data information retrievalPersonalizationTime information
The invention discloses a dynamic POIs (Point of Interest) recommendation method based on TS24, and belongs to the technical field of computer application. The method comprises the following steps: 1, building a dynamic POIs recommendation architecture based on 24 time periods; 2, converting the sign-in frequency of a user into a preference value of the user for the sign-in POIs of the user by using a TF-IDF technology, and constructing a sample set theta cur in a current time period; 3, establishing a SemiDAE geographical influence model on the Tau cur; 4, according to the similarity of the sign-in behaviors of the users in the similar time periods, establishing a T-SemiDAEPOIs recommendation model with the time influence on the Tau cur; and 5, according to the two steps of pre-training and parameter fine tuning, training the T-SemiDAEPOIs recommendation model on the Tau cur. According to the method, the dynamic POIs recommendation model based on the deep learning technology is built in a novel and more reasonable mode, geographical and time information of the location social network is mined and fused, and experimental results show that the applied technology can remarkably improve the precision and recall rate of personalized POIs recommendation.
Owner:DONGBEI UNIVERSITY OF FINANCE AND ECONOMICS
Terminal attack defense method and device, terminal and cloud server
The invention discloses a terminal attack defense method and device, a terminal and a cloud server. Before CA and TA communicate, scene feature information, such as screen click information, corresponding to a current CA operation is verified by a safety execution environment, such as TEE, so that whether the current CA operation is a real operation of a user or an attack behavior of a hacker is determined, and if the current CA operation is the attack behavior of the hacker, the screen click information does not exist. If the risk of hacker attack exists, communication between the CA and theTA is not established, so that the CA cannot run normally, and heuristics initiated by the hacker for discovering system vulnerabilities are blocked.
Owner:HUAWEI TECH CO LTD
Content delivery apparatus, user terminal device, relief management method and computer program
InactiveUS20080052240A1DissatisfactionSecure beliefAnalogue secracy/subscription systemsPayment architectureManagement unitTerminal equipment
A content delivery apparatus, when a content delivery request is outputted from a user terminal device, encrypts the requested content with an encryption key, adds a view period to it to deliver it to a request source and delivers a viewing key in response to a view request from the user terminal device within the view period. A user relief management unit monitors failure information notifying, grasps a delivery disabled period from the failure information, specifies a delivery destination user for a content of which the view period is overlapped with the delivery disabled period and issues a relief right with a relief period specified thereto to the specified user. A contract period processing unit manages the relief right and permits viewing within the relief period set by the relief right when a view right based on the relief right is output from the user terminal device.
Owner:KK TOSHIBA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com