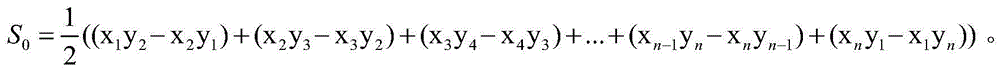Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
160results about How to "Avoid registration" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
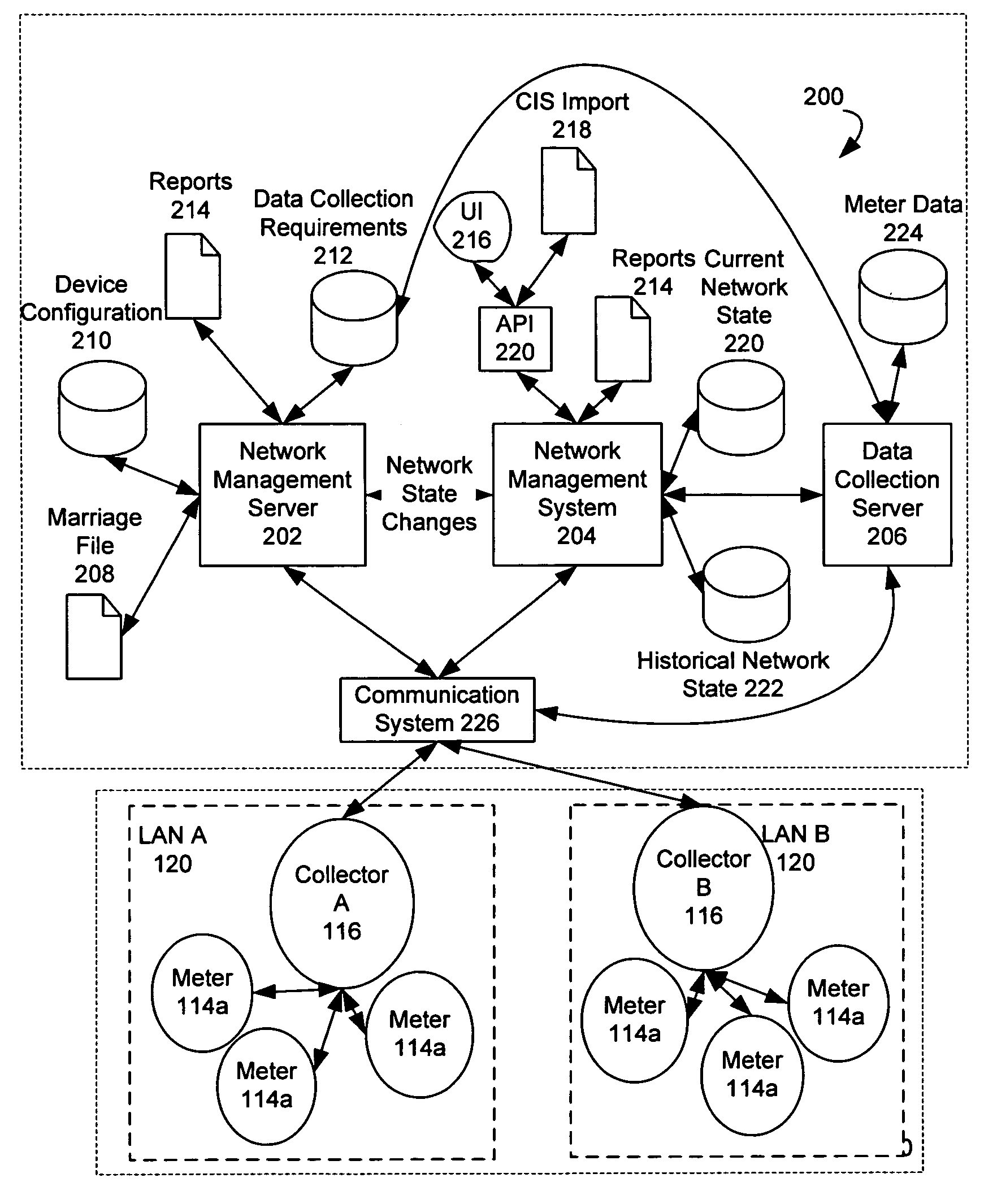
System and method for creating multiple operating territories within a meter reading system
InactiveUS7170425B2Close proximityAvoid registrationElectric signal transmission systemsMobile data collection deviceTime of useComputer science
Owner:ELSTER ELECTRICTY LLC
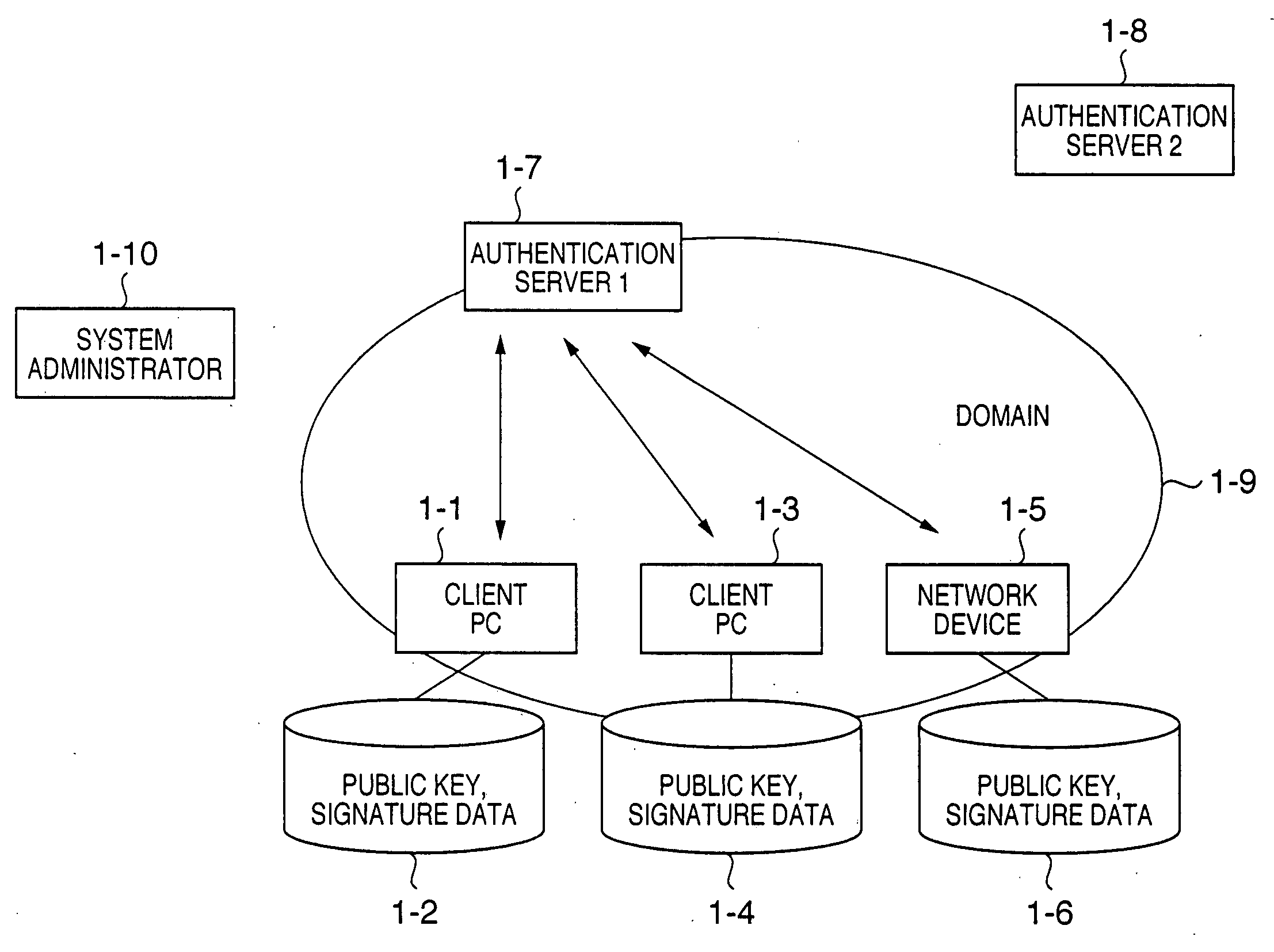
Assurance system and assurance method
InactiveUS20050055552A1Ensure reliabilityAvoid registrationKey distribution for secure communicationPublic key for secure communicationMultiplexingAuthentication server
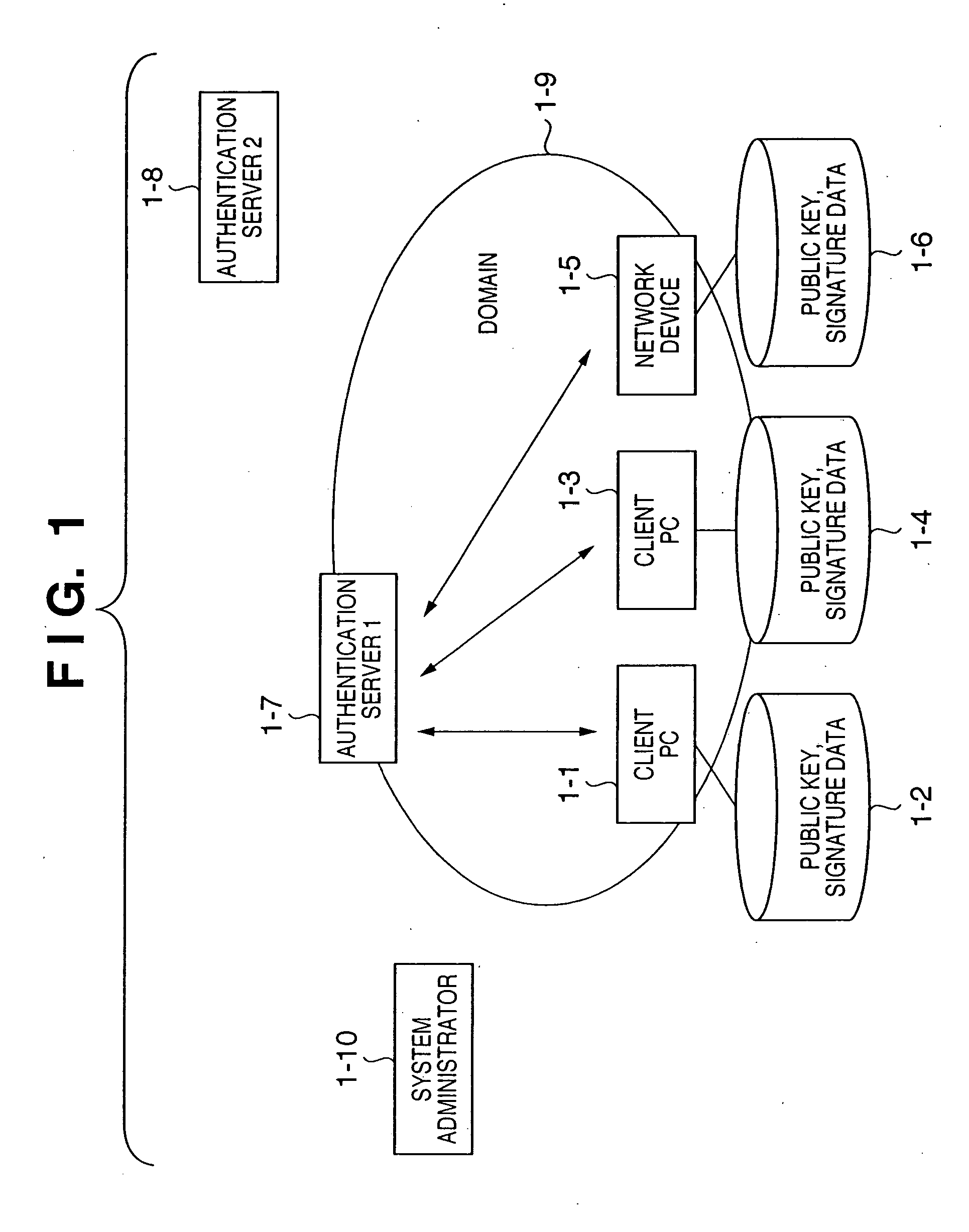
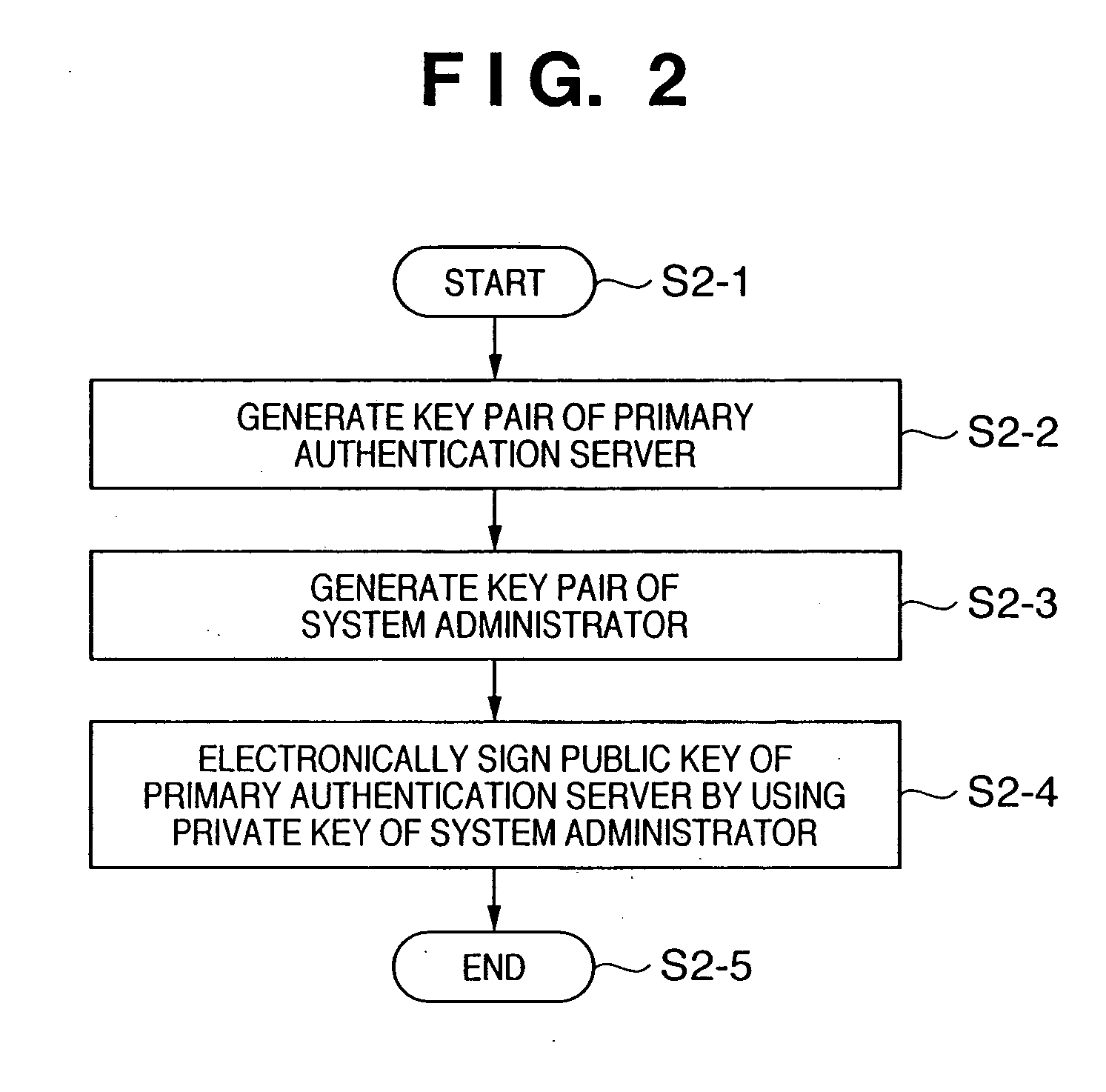
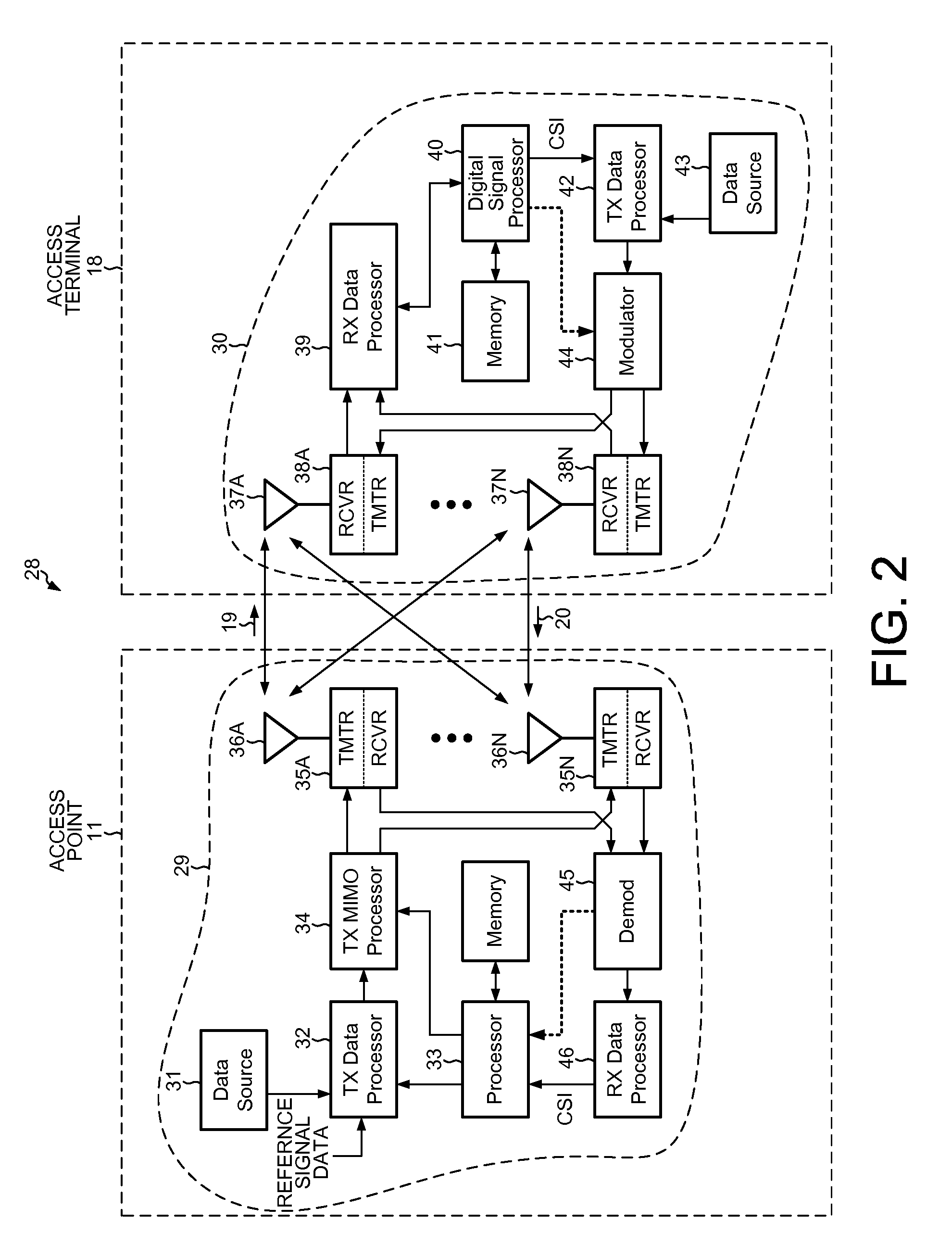
In a client PC or device, the reliability of multiplexed authentication servers is assured. In an assurance system including a client PC (1-1, 1-3), an authentication server 1 (1-7), and a device (1-5) connected to a network, a multiplexed system is built by arranging an authentication server 2 (1-8) in order to back up the authentication server 1 (1-7), public key cryptography is used for encrypted communication between the client PC, the authentication servers 1 and 2, and the device, and the public keys of the authentication servers 1 and 2 are electronically signed by using the private key of one system administrator (1-10) by public key cryptography.
Owner:CANON KK
Staff access control method based on face recognition and staff access control device based on face recognition
InactiveCN106846577AAchieve autonomous controlReduce investmentIndividual entry/exit registersTelecommunicationsUser input
The invention discloses a staff access control method based on face recognition and a staff access control device based on face recognition. The staff access control method comprises the following steps of: receiving log-on messages input by a user, storing and verifying the log-on messages; after the log-on message verification is successful, receiving and storing the messages of staff intending to come in and go out input by the user and the credibility of the staff intending to come in and go out set by the user; receiving the field facial images of field access staff, and comparing the field facial images with the log-on messages and the messages of staff intending to come in and go out to determine the credibility of the field access staff; carrying out first control measures on the field access staff determined as the staff with the first credibility; carrying out second control measures on the field access staff determined as the staff with the secondary credibility; and carrying out third control measures on the field access staff determined as the staff with the third credibility. The staff access control method is capable of realizing the classifying access control on staff coming in and going out according to the difference of credibility.
Owner:TAIKANG LIFE INSURANCE CO LTD
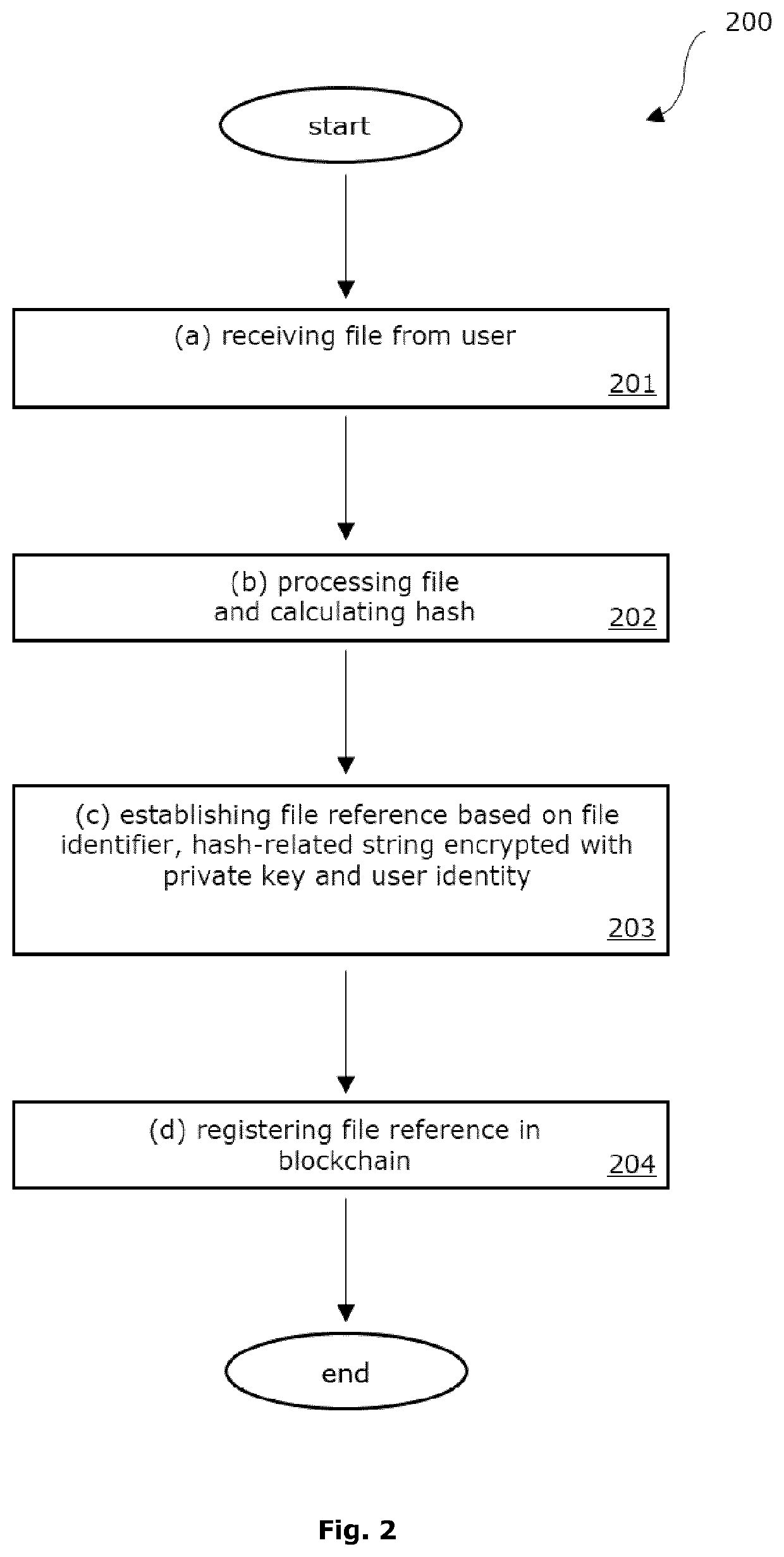
Improved Blockchain-Based Method for Registration and Verification of a File
ActiveUS20200099534A1Avoid registrationImprove securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationCryptographic hash functionSoftware engineering
Owner:ITEXT GRP
Distributed Blockchain-Based Method for Maintaining the Validity of a File
ActiveUS20190347444A1Avoid registrationDecentralized approachKey distribution for secure communicationEncryption apparatus with shift registers/memoriesBlockchain
The present invention relates to a computer-implemented method for maintaining the validity of a file by two users, that are a receiver and a validating instance, said method comprising the sequential realization of the following set of steps for each of said plurality of users: (a) providing said file to the user; (b) searching a publisher-related file signature in a blockchain, said publisher-related file signature belonging to said file; (c) confirming a validity of said publisher-related file signature; (d) determining an identification string belonging to said file based on said file and / or optionally based on said publisher-related file signature; (e) establishing a renewed file signature based on at least both said identification string belonging to said file and a private key belonging to the user; (f) registering said renewed file signature in said blockchain.
Owner:ITEXT GRP
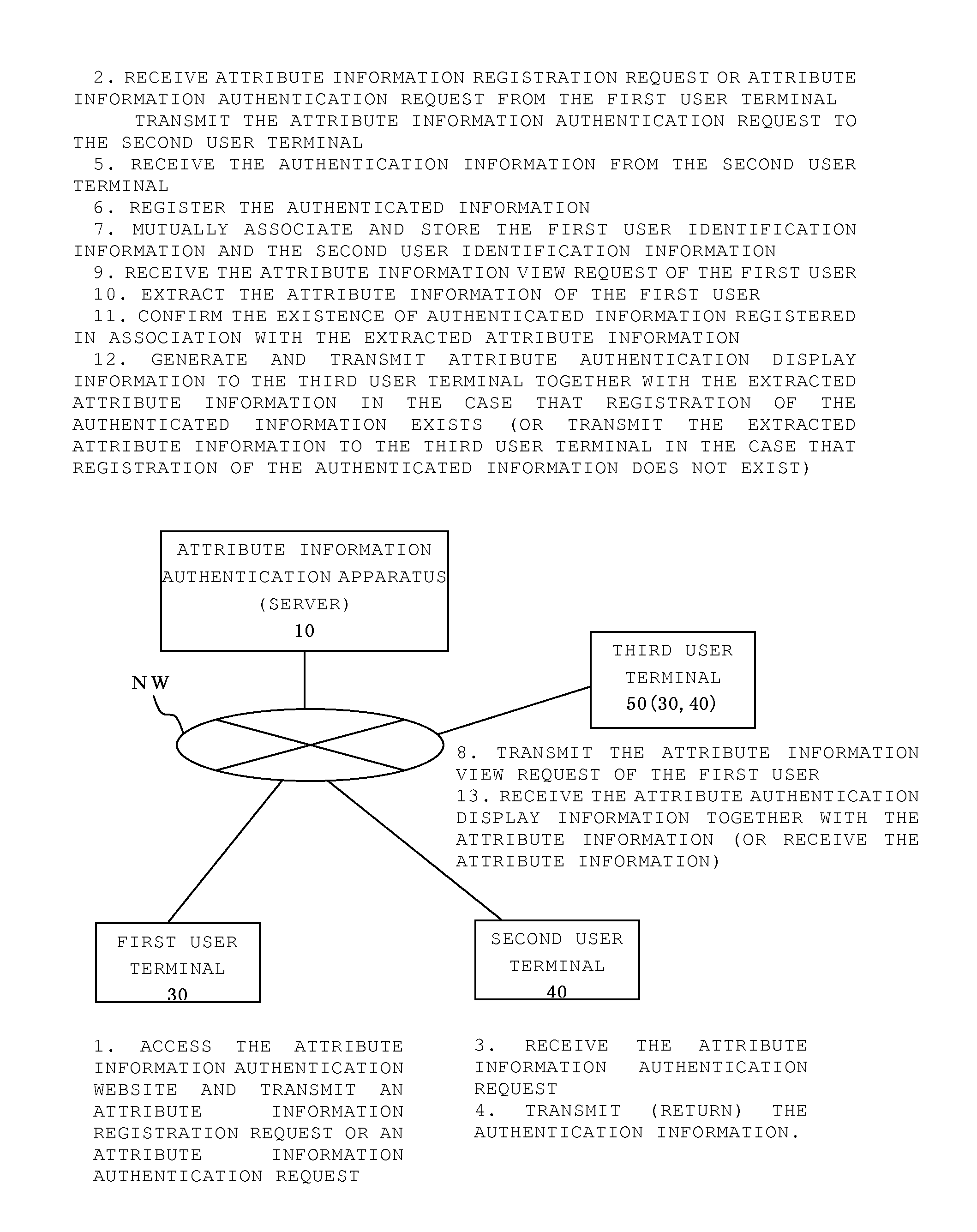
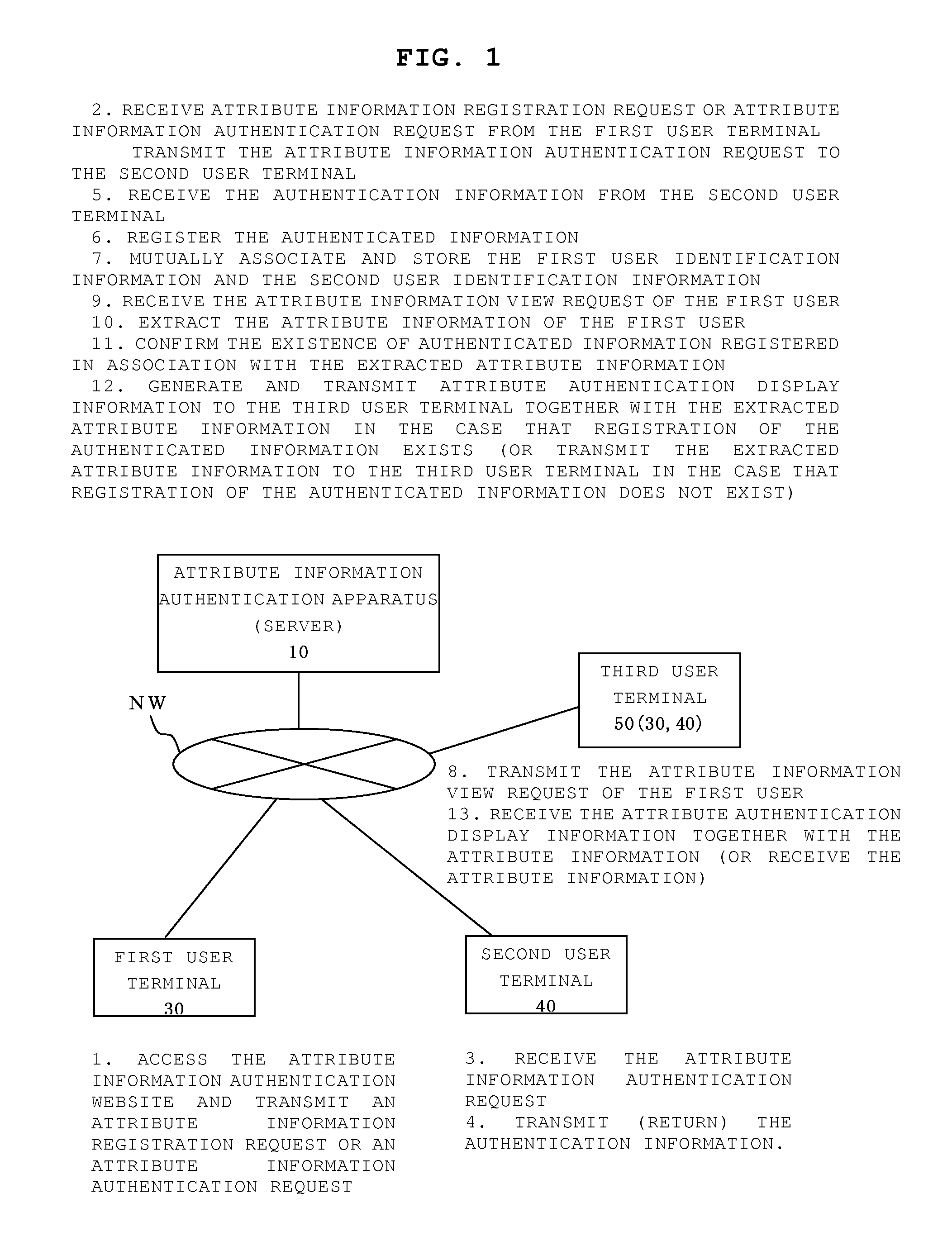
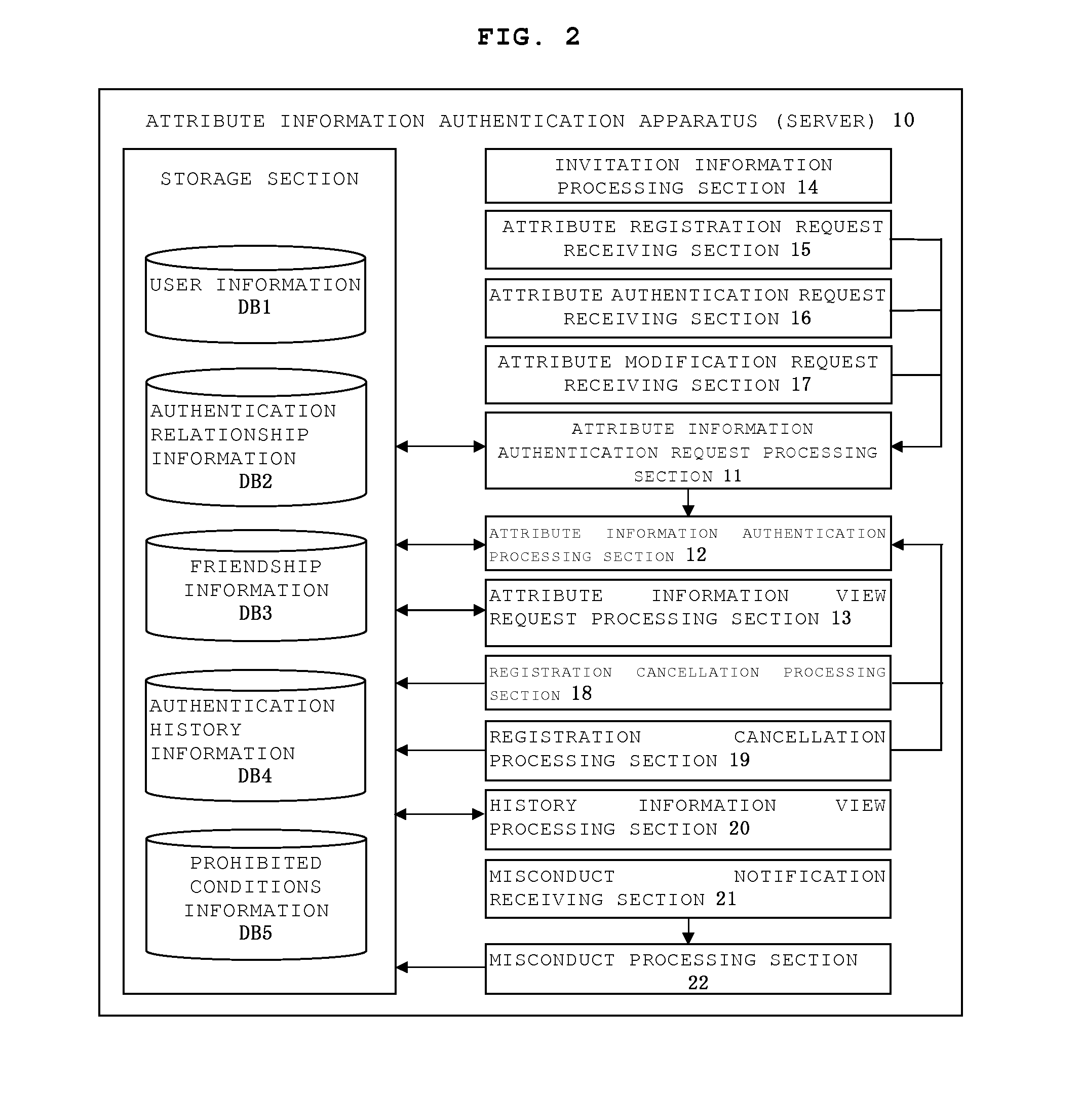
Attribute information authentication apparatus, attribute information authentication method, and storage medium for storing computer program
InactiveUS20100281520A1Encourage registrationAmicable relationshipDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyAuthentication information
A present server transmits to a second user terminal attribute information authentication request information for requesting authentication of attribute information registered by a first user when a predetermined request is received from a first user terminal. Also, the server registers authenticated information in association with the attribute information of the first user when the authentication information, which indicates that the attribute information registered by the first user has been authenticated, has been received. When a request is made to view the attribute information of the first user, the existence of the authenticated information is determined, and if the authenticated information is registered, attribute authentication display information is generated and transmitted so as to be visually and identifiably displayed on the user terminal to indicate that authenticated information exists.
Owner:MEKIKI CREATES CO LTD
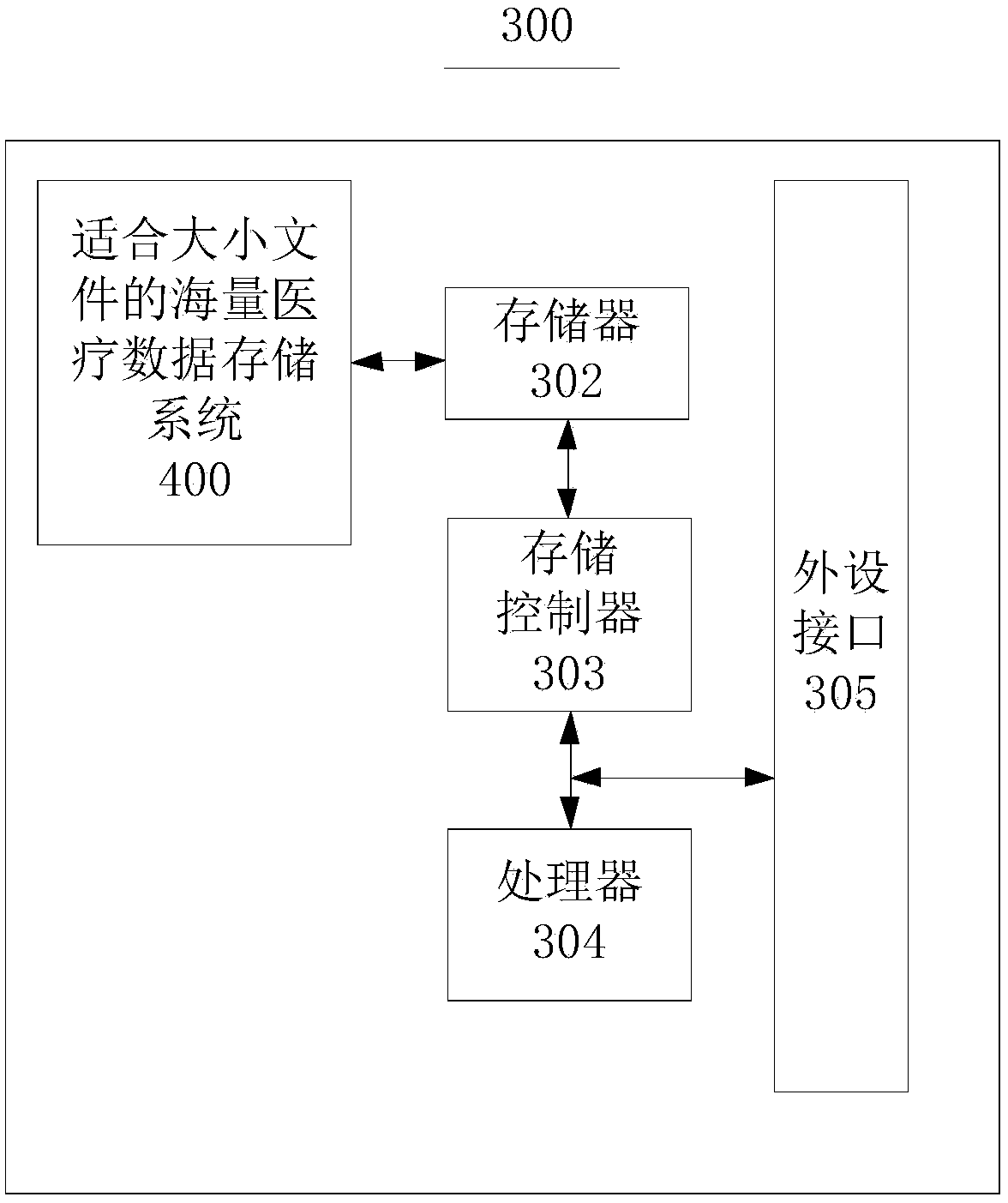
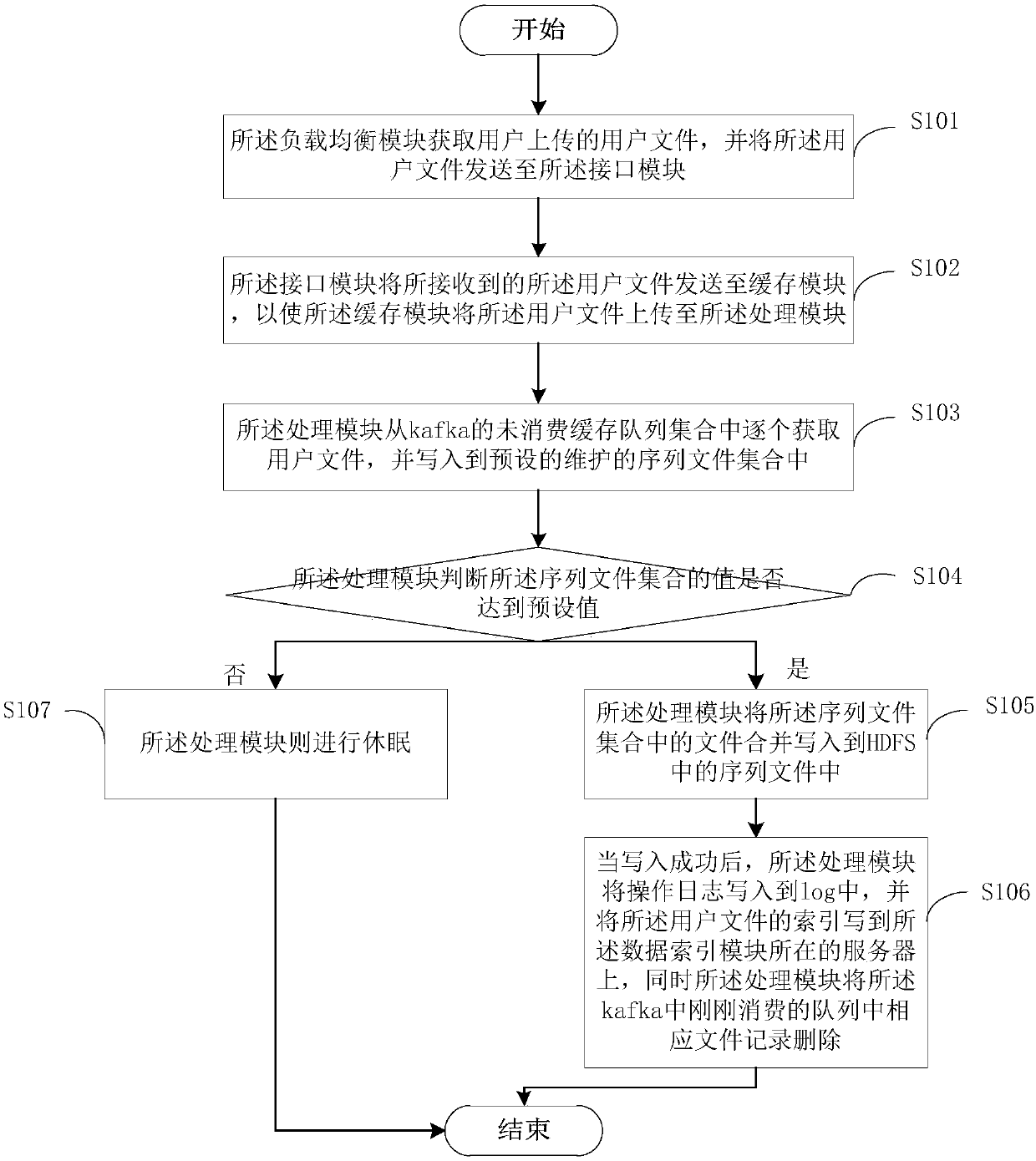
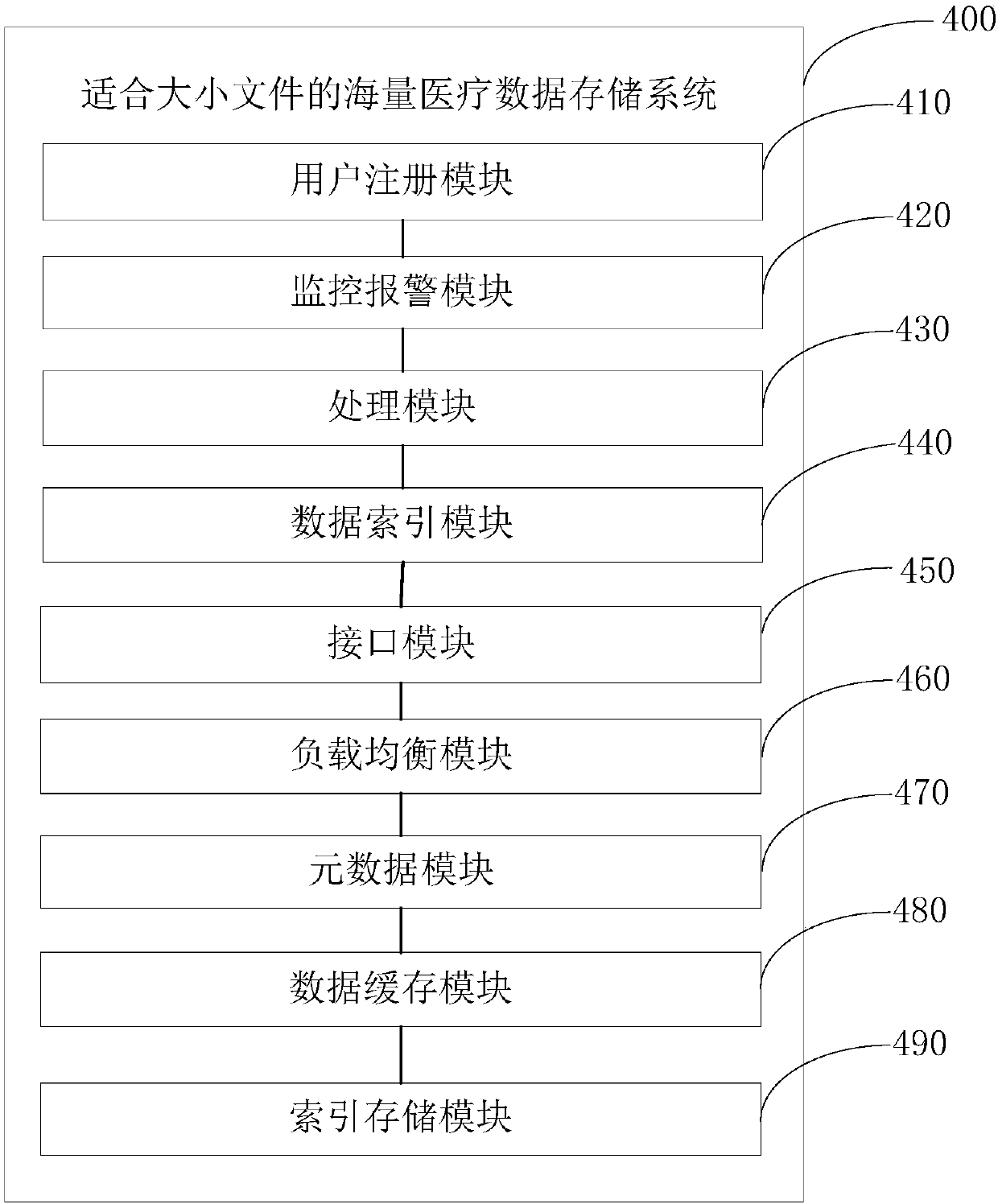
Mass medical data storage system and data storage method suitable for files of different sizes
ActiveCN108053863AAvoid visitingAvoid registrationPatient healthcareFile access structuresRelational databaseInstability
An embodiment of the invention provides a mass medical data storage system and a data storage method suitable for files of different sizes and belongs to the technical field of data storage. Aiming atapplication scenes with coexistence of mass large files and small files in the medical field, the system solves a problem that a traditional relational database is not suitable for unstructured data,a problem that redis is not suitable for mass data storage, a problem of system instability when only hbase is adopted for storage and problems of inadaptability to large files and inconvenient fileretrieval when hdfs is adopted merely for solving a problem of small file storage.
Owner:THE FIRST AFFILIATED HOSPITAL OF THIRD MILITARY MEDICAL UNIVERSITY OF PLA
Dishonest registration preventive apparatus in personal authentication system
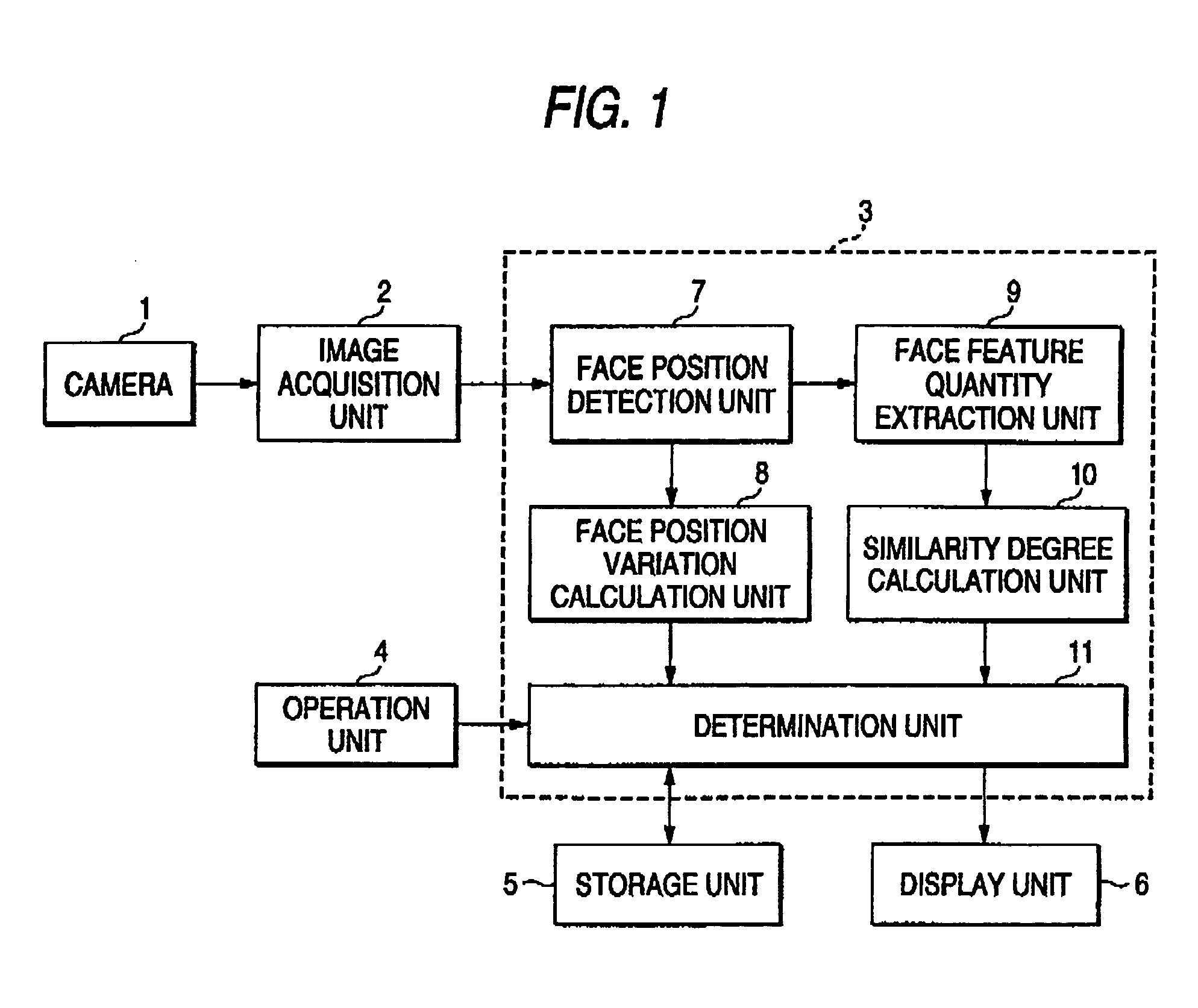
ActiveUS7336807B2Preventing dishonest registrationAvoid registrationImage analysisCharacter and pattern recognitionAuthentication systemComputer vision
Owner:ORMON CORP
Reference signal management in mobile systems
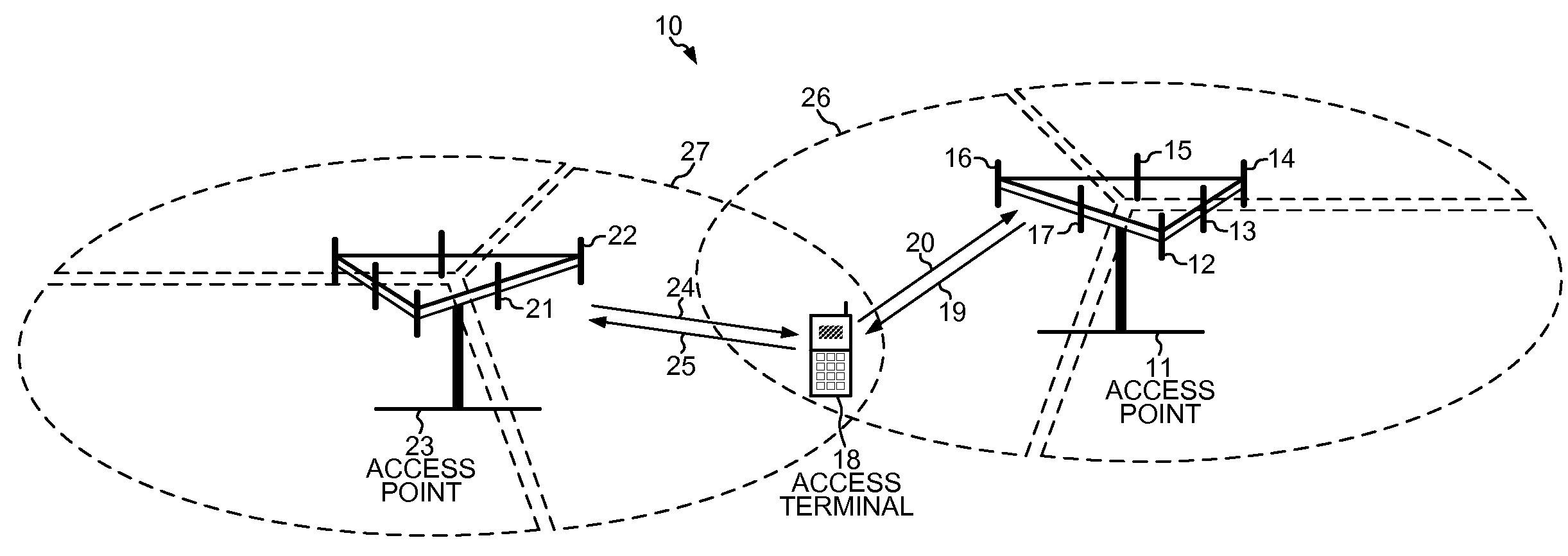
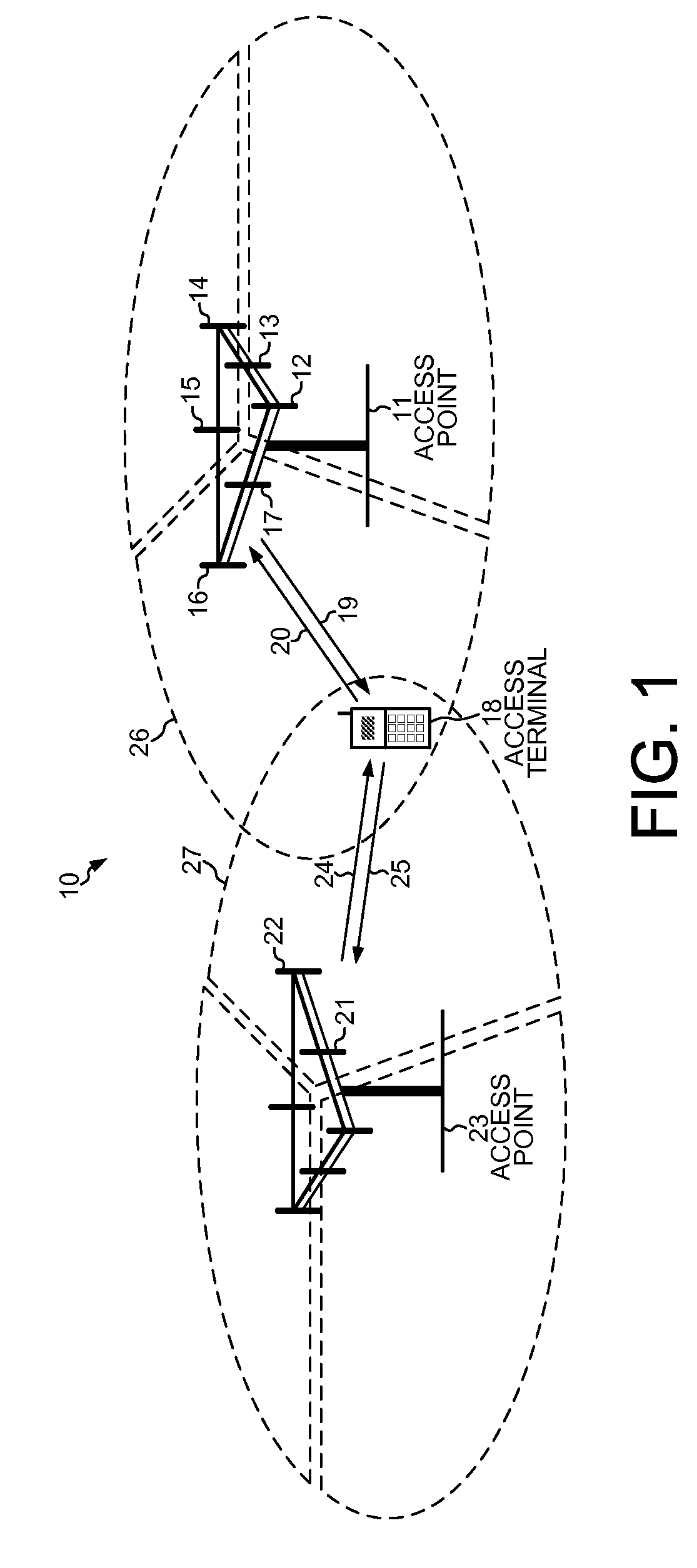
InactiveUS20090247156A1Easy to useAvoid accessPower managementAssess restrictionComputer networkEngineering
A reference signal management (RSM) program executing on a mobile device detects multiple reference signals, allocates those reference signals into groups, and performs reference signal management functions using information conveyed in the reference signals. The RSM program detects both broadband and narrowband reference signals and maintains updated groups of reference signals that are transmitted from access points with independent configurations or different radio technologies. Battery power of the mobile device is efficiently used to manage reference signals in heterogeneous network environments by preventing unnecessary handoffs, overhead downloads, access probes and new registrations. Reference signals are managed from both synchronous and asynchronous sectors and in idle mode as well as in connected state mode. The RSM program performs functions such as managing handoffs between access points, managing an idle mode of the mobile device, managing an active group of the detected reference signals, and collecting overhead parameters for the mobile device.
Owner:QUALCOMM INC
Visual servo control method of multi-task surgical robot
ActiveCN109998687AAvoid installationAvoid calibrationPhysical therapies and activitiesMechanical/radiation/invasive therapiesSurgical robotRobot control
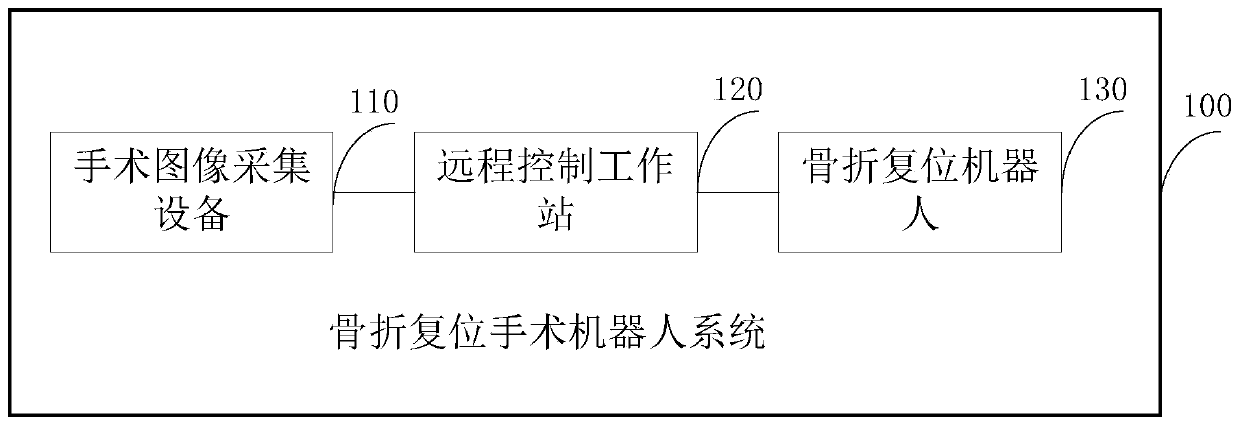
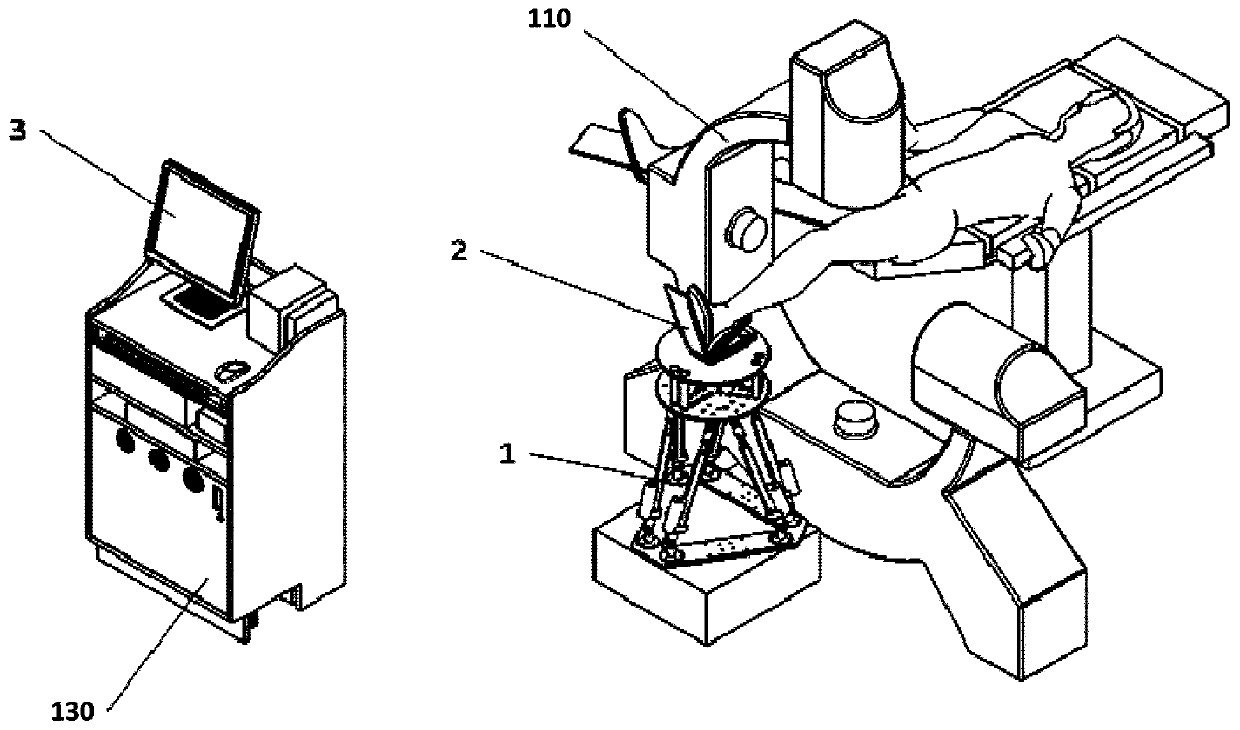
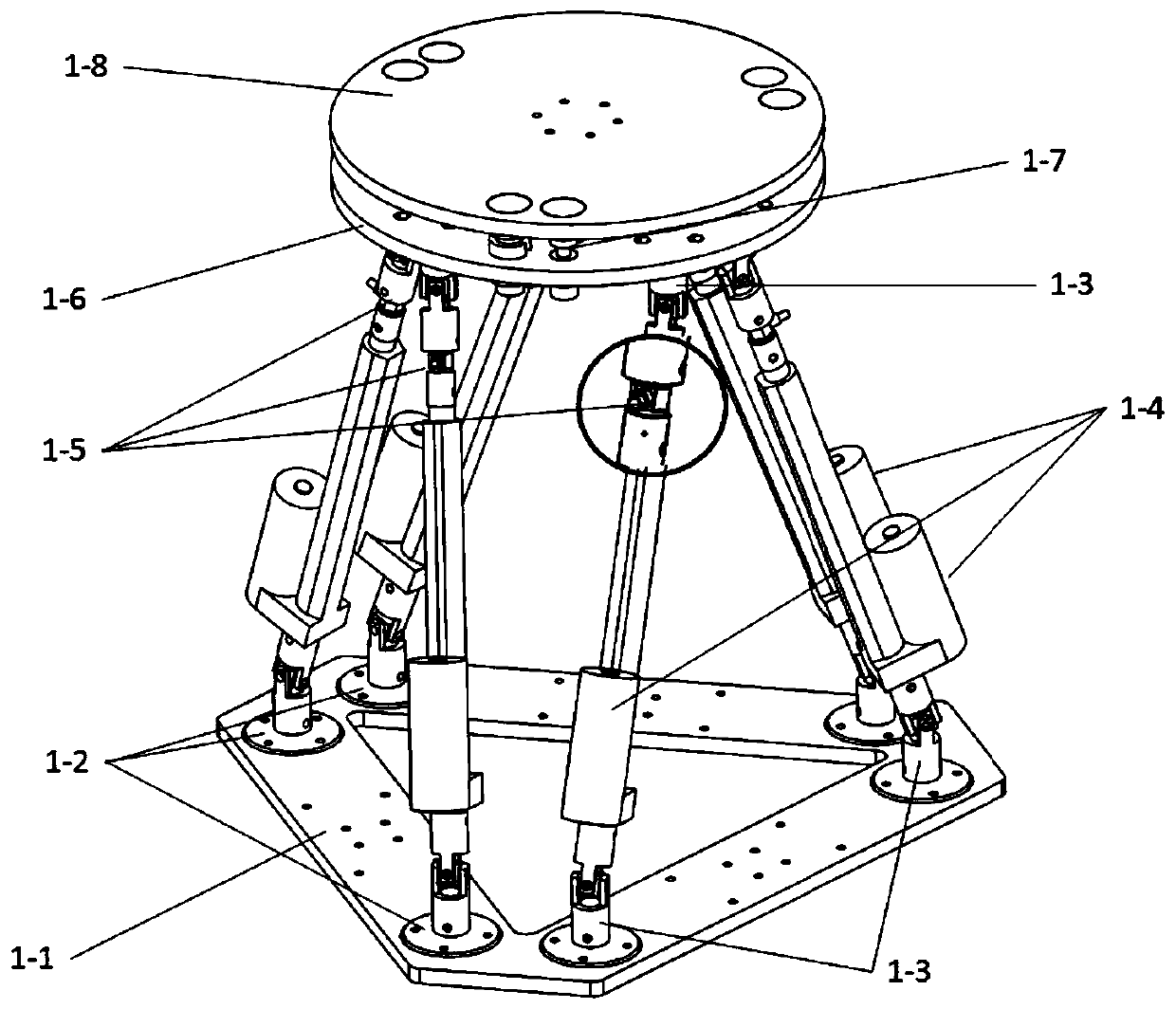
The invention provides a visual servo control method of a multi-task surgical robot, and belongs to the technical field of surgical robots. The method comprises the steps of adopting the relative coordinate relation of the front end of the surgical robot and a surgery part as a control basis, extracting a control characteristic from an image acquired by image acquisition equipment, updating relative coordinate information in real time, according to the relative coordinate information, planning a surgery motion path, controlling the motion of a motion mechanism, achieving target surgery operation, and by replacing types of the control characteristic and the front end of the surgical robot, achieving a multi-task function. According to the visual servo control method of the multi-task surgical robot, the installation of additional markers and a calibration process are avoided, moreover, when a work mode based on visual servo is compared with a traditional work mode of the surgical robot,namely, 'planning before surgery and execution during surgery', higher surgery precision can be obtained.
Owner:TSINGHUA UNIV
Distributed Blockchain-Based Method for the Collective Signing of a File by Several Parties
ActiveUS20190354724A1Decentralized approachAvoid registrationEncryption apparatus with shift registers/memoriesUser identity/authority verificationEngineeringDocumentation
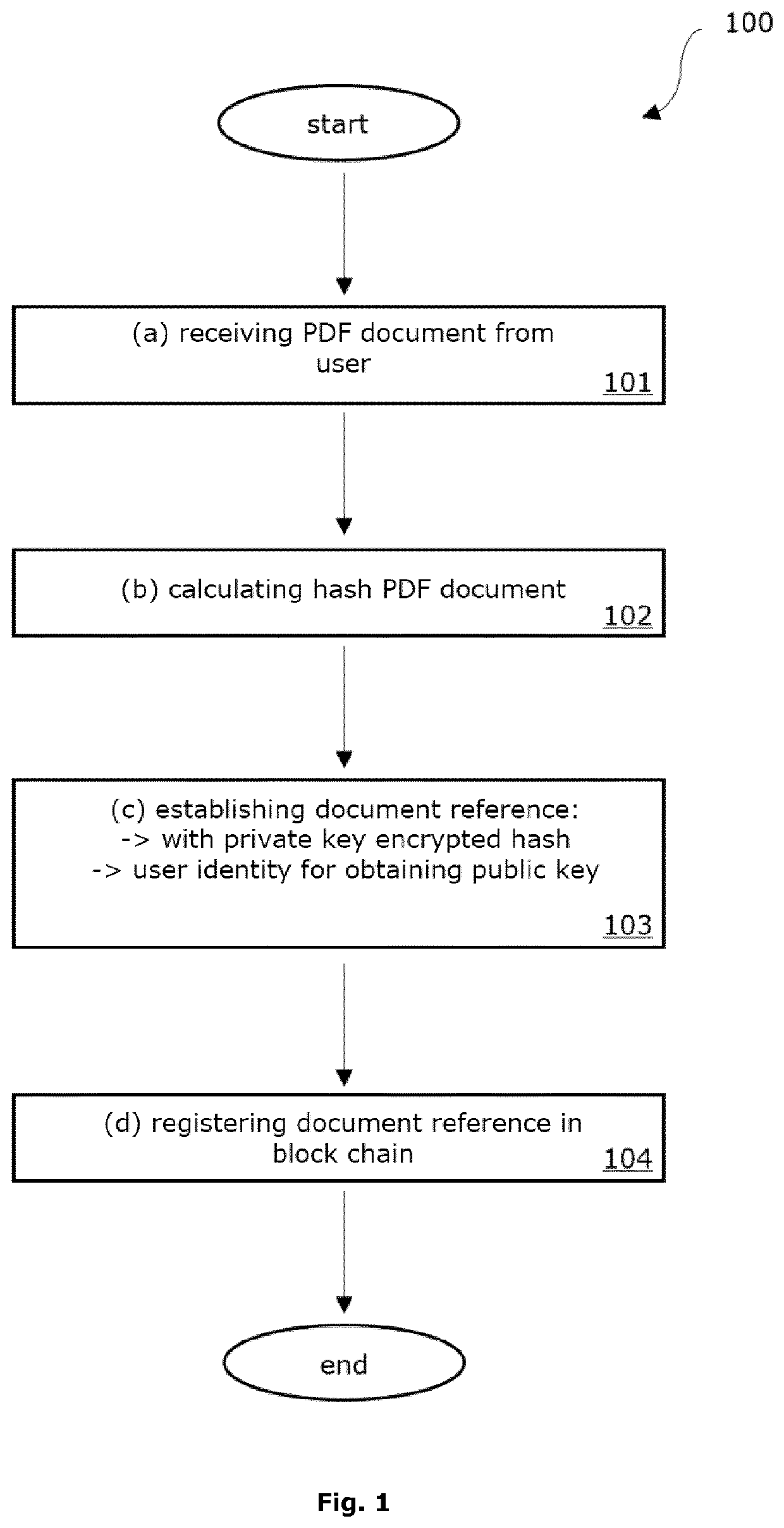
The present invention relates to a computer-implemented method for the collective signing of a file, preferably a PDF-based document, by a plurality of users, said method comprising the sequential realization of the following set of steps for each of said plurality of users: (a) providing the user with said file, and optionally with one or more existing identification strings belonging to said file; (b) determining an identification string belonging to said file based on at least said file and optionally based on said one or more existing identification strings; (c) establishing a document signature based on at least both said identification string belonging to said PDF-based document and a private key belonging to the user; (d) registering said document signature in a blockchain.
Owner:ITEXT GRP
Signal repeater and switching device, method of detecting connecting relation between signal repeater and switching device and communication system
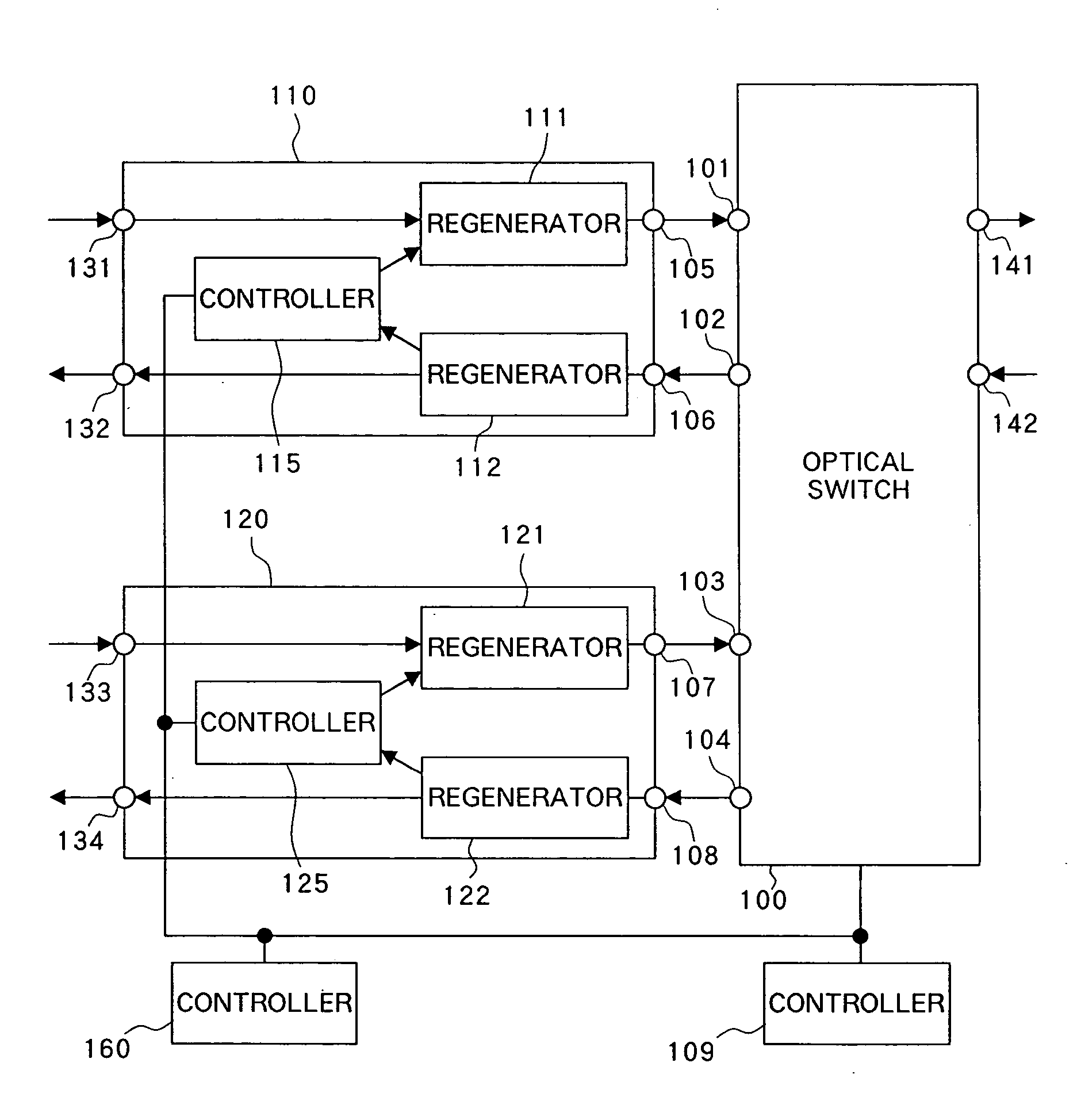
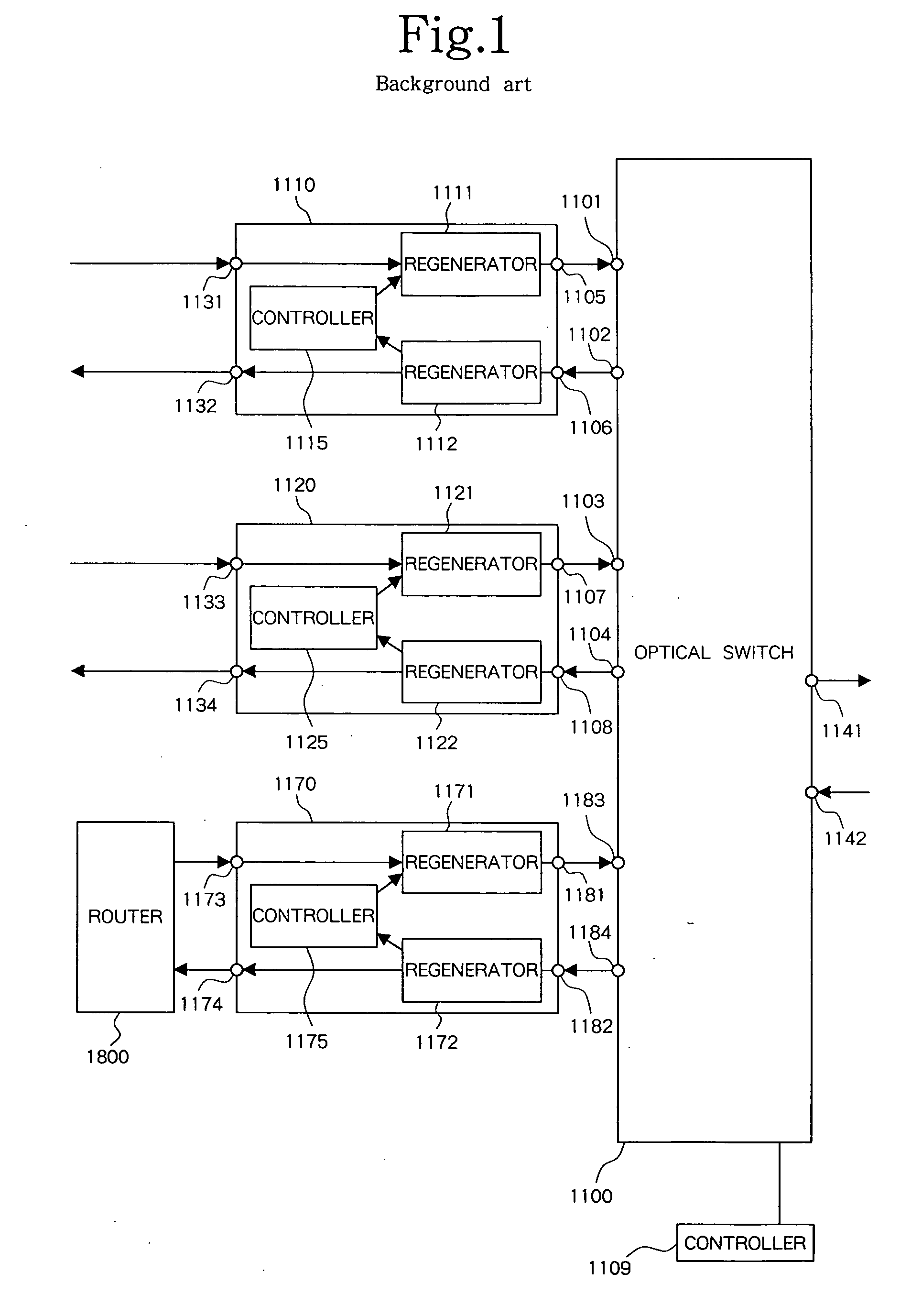
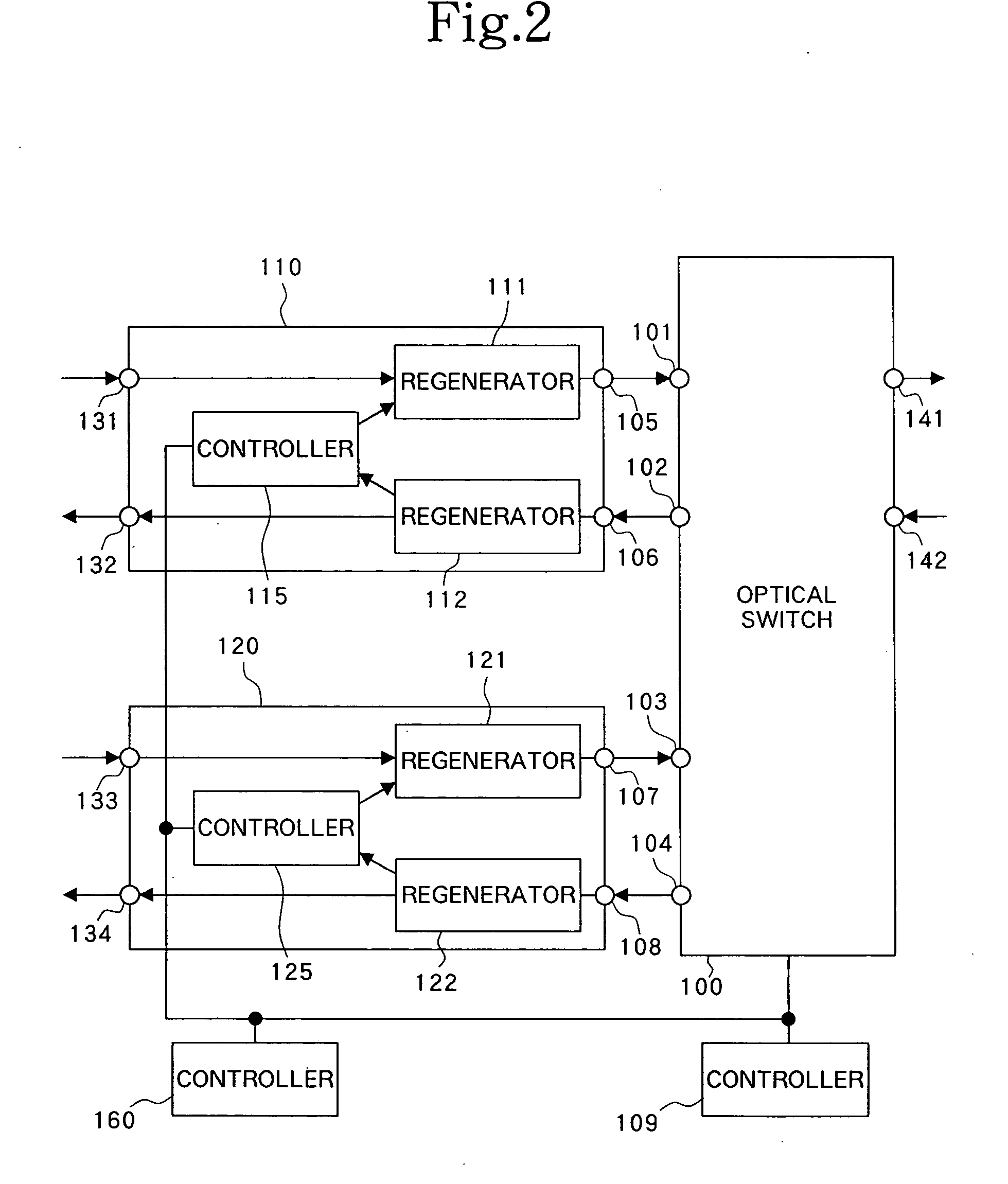
InactiveUS20050002386A1Avoid registrationConfirming normalityMultiplex system selection arrangementsError preventionCommunications systemOptical switch
The present invention is intended to find a connecting state of a bidirectional signal repeater with an optical switch to prevent an erroneous registration of the topology. The present invention also has an object to confirm the normality of a link between the optical switch and bidirectional signal repeater even when no main signal is flowing by directing a signal from the bidirectional signal repeater to the optical switch. An identifier is added to the signal. One bidirectional port pair of the optical switch is set into a loop back configuration, without setting the remaining bidirectional port pairs into the loop back configuration. A controller checks whether or not a signal received by a regenerator is the same as a signal transmitted from a different regenerator. The normality of the link between the bidirectional signal repeater and optical switch is confirmed to evaluate the quality of a signal which returns from the bidirectional port pair which is in the loop back state.
Owner:NEC CORP
Authentication system and authentication method for container services in hybrid cloud computing environment
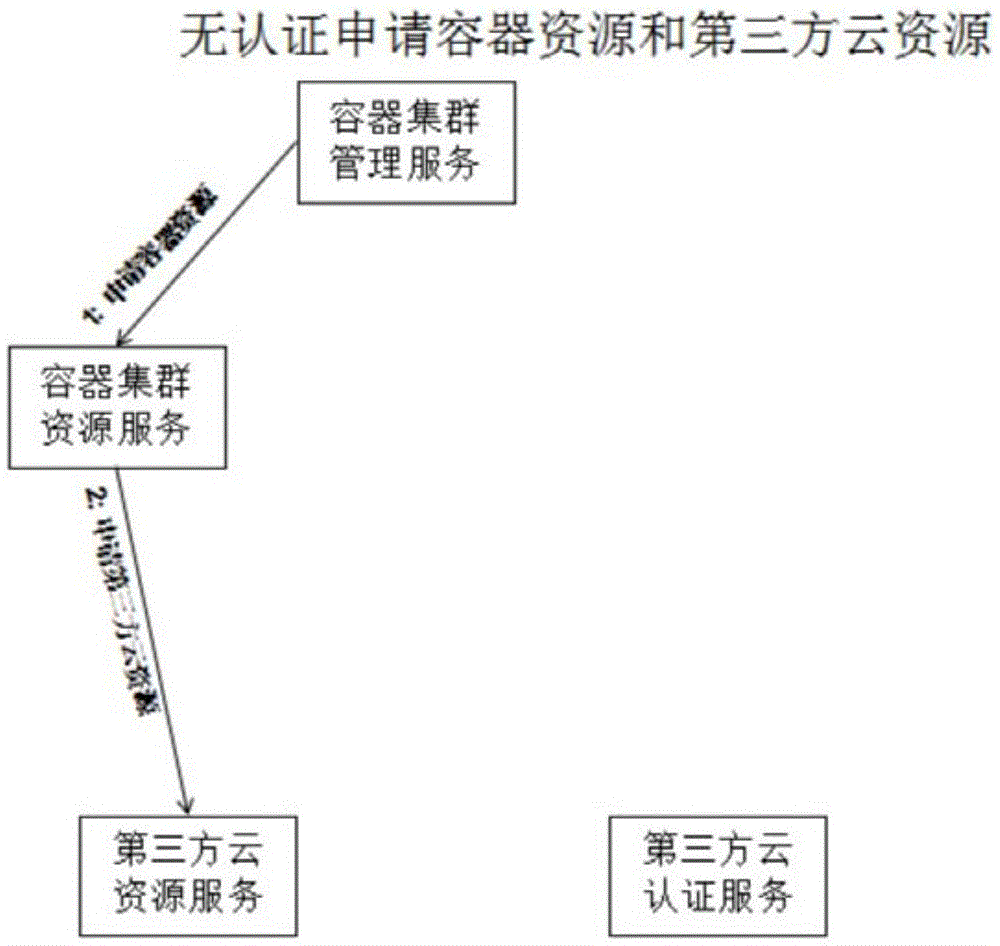
ActiveCN105554004AEnsure safetyAvoid registrationUser identity/authority verificationThird partyAuthentication system
The invention discloses an authentication system and an authentication method for container services in a hybrid cloud computing environment, which relate to the field of a container cluster in a cloud computing environment. The method comprises the following steps of: judging whether an information of a user, which is going to access to a third party cloud computing system, belongs to a user container registration information, if not, prompting the user to register; if so, after verifying and finding a key information with mapping relation with the container registration information of the user, applying to the third party cloud computing system for a session token by a container authentication module; and generating a container session token with the mapping relation with the session token, storing the mapping of the session token and the container session token, and completing authentication. With the system and the method provided by the invention, a request for additionally proposing authentication to the third party cloud computing system is avoided, meanwhile, convenience is provided for users to use a hybrid cloud system.
Owner:BEIJING QING YUAN TECH CO LTD
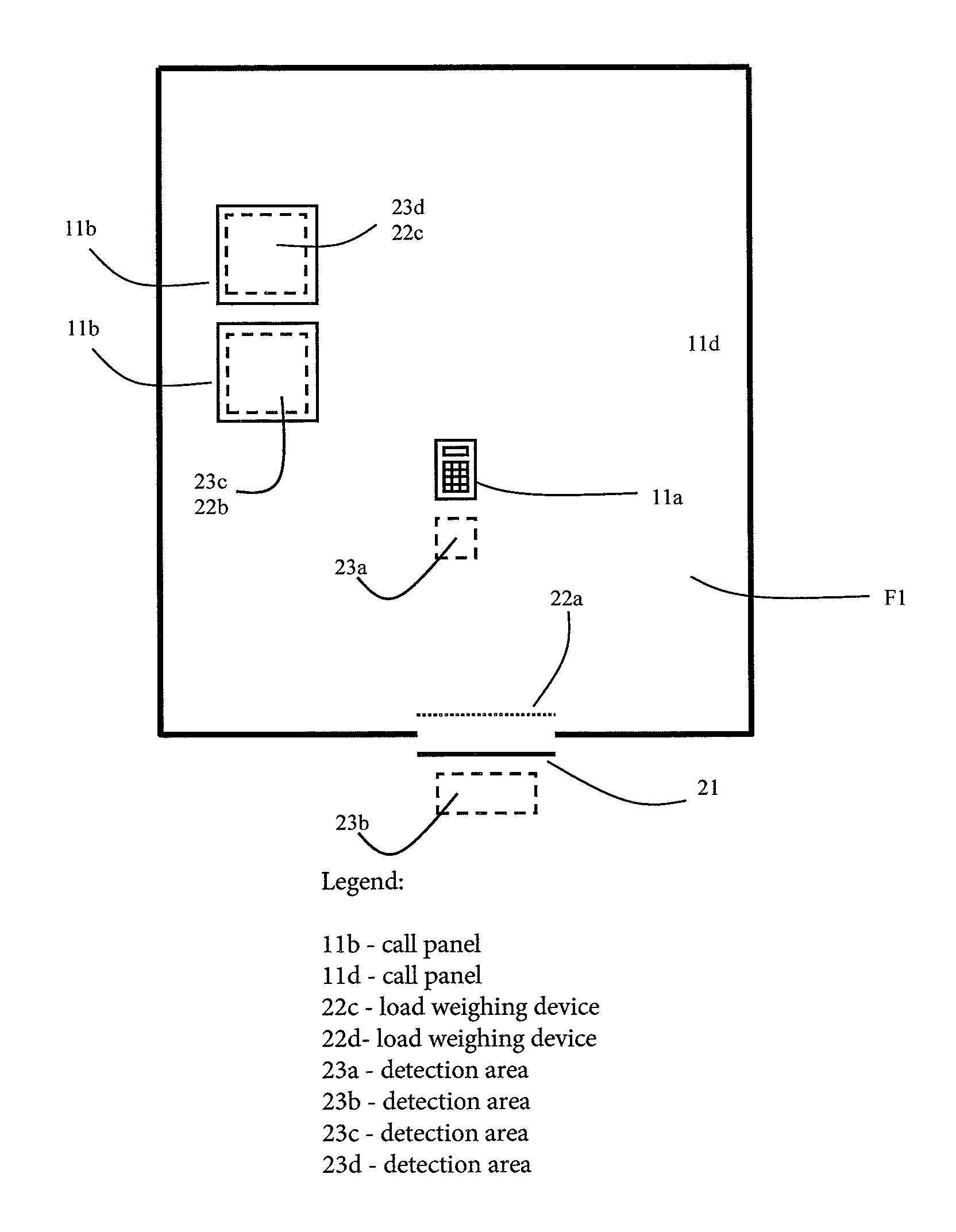
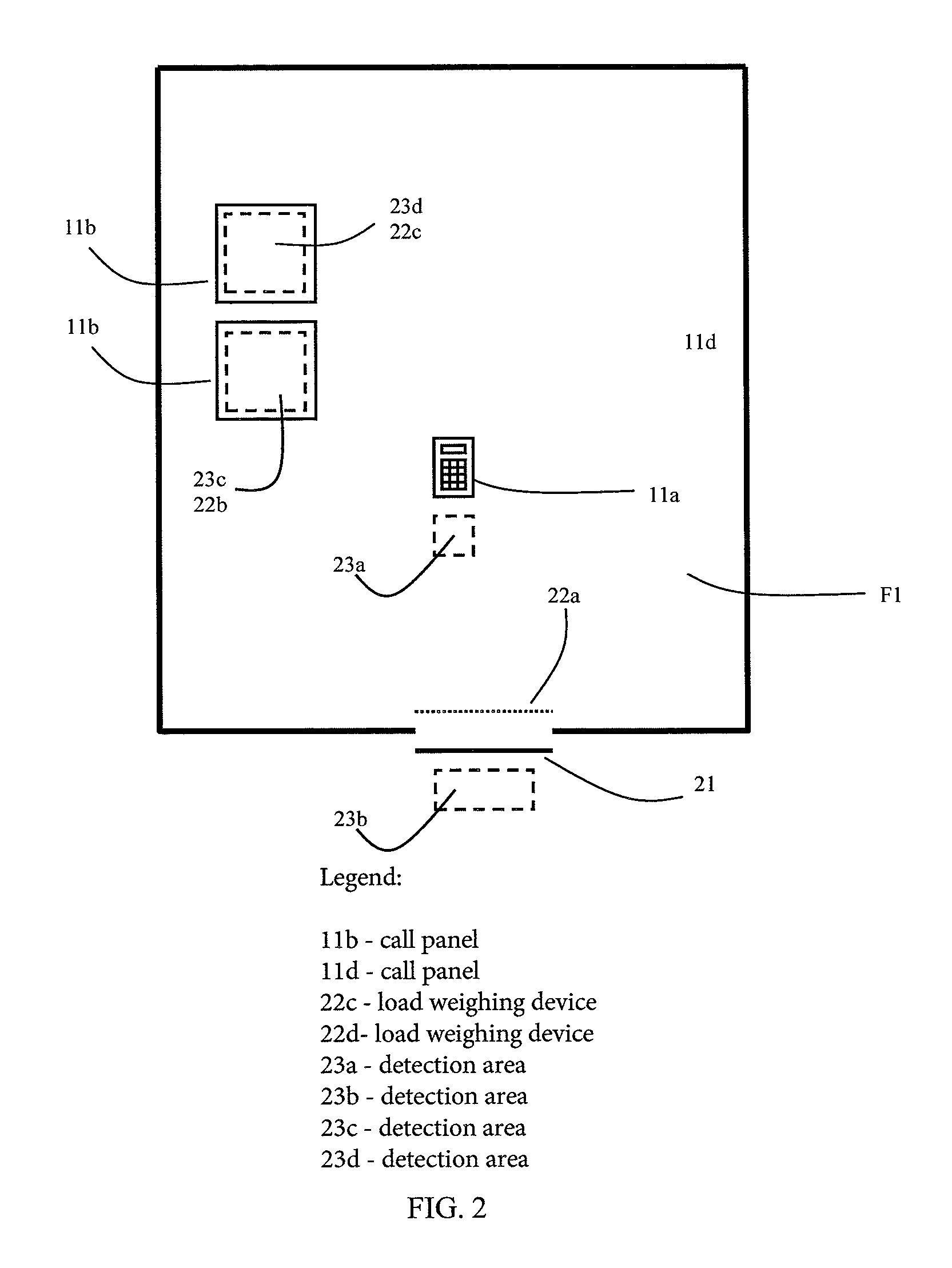
Conveying system having a detection area
A conveying system and a method for registering service requests in a conveying system, including at least one transport device, is provided. A detection area bounded on a floor surface is in connection with the transport device, in which detection area the identification data contained in the personal identifiers of passengers is read. The service profiles of passengers who have arrived in the detection area and / or who have left the detection area are determined on the basis of the identification data, and a service request according to the service profiles is registered for transporting and / or admitting passengers in the detection area to the location indicated by the service request.
Owner:KONE CORP
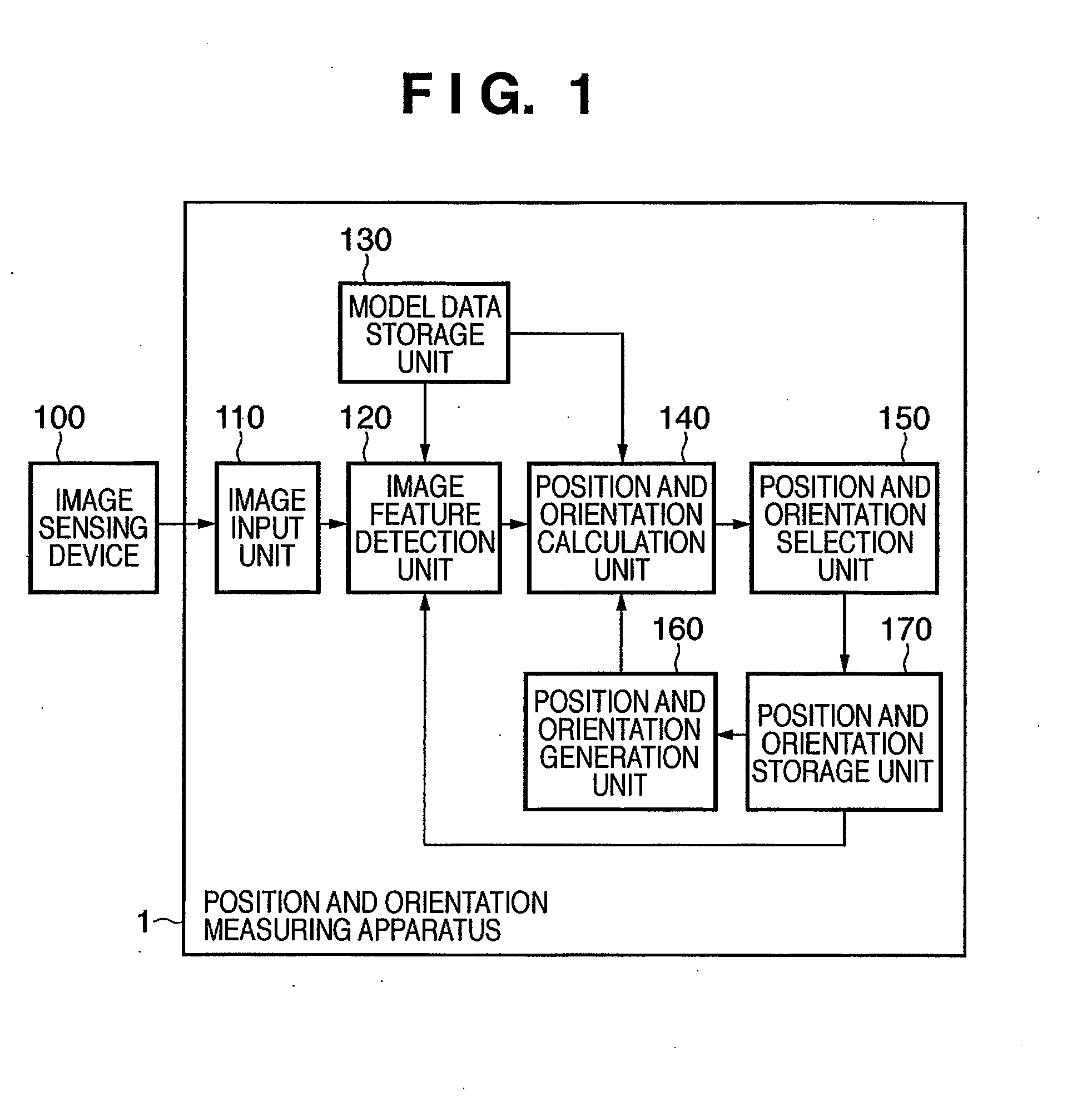
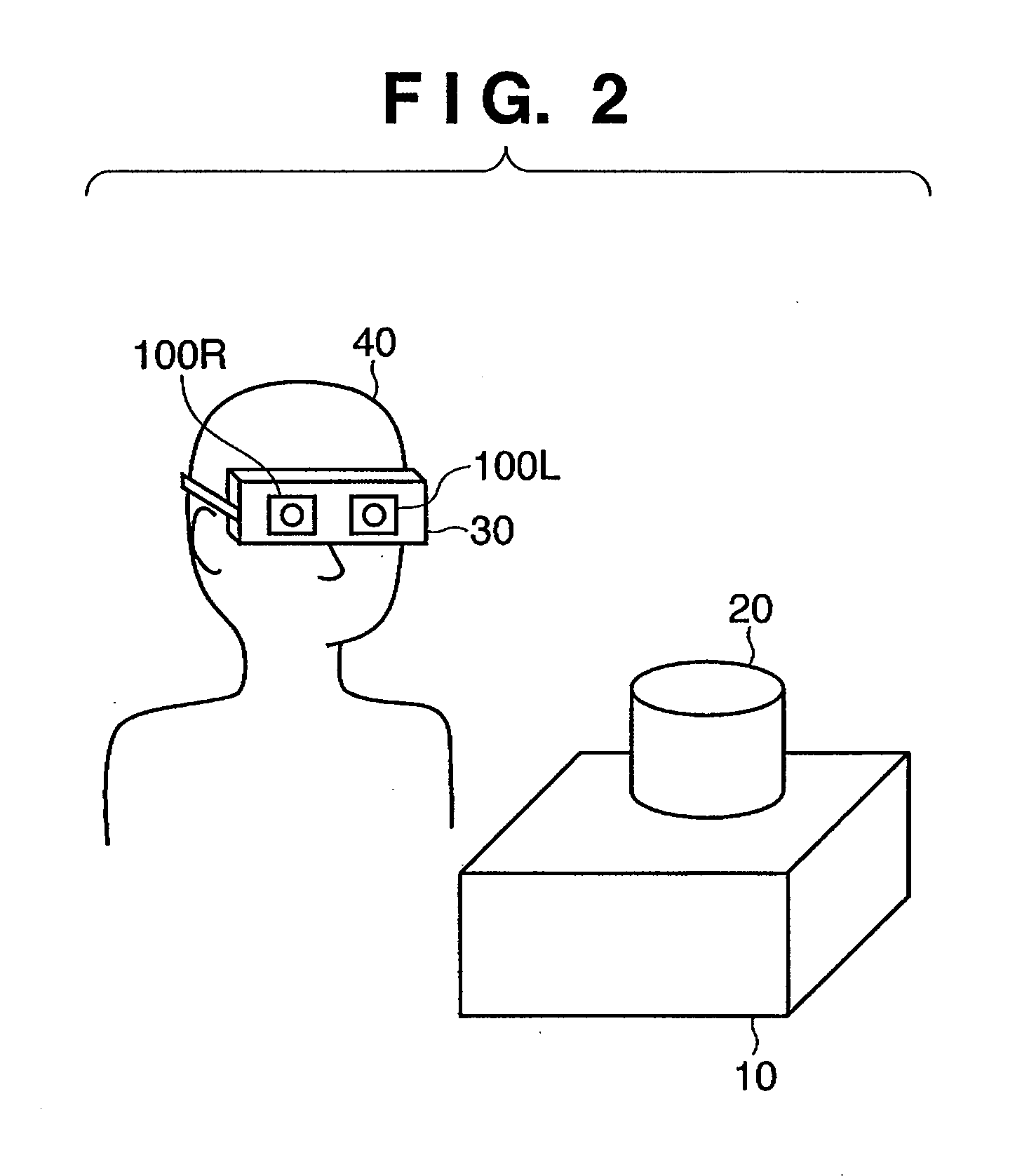
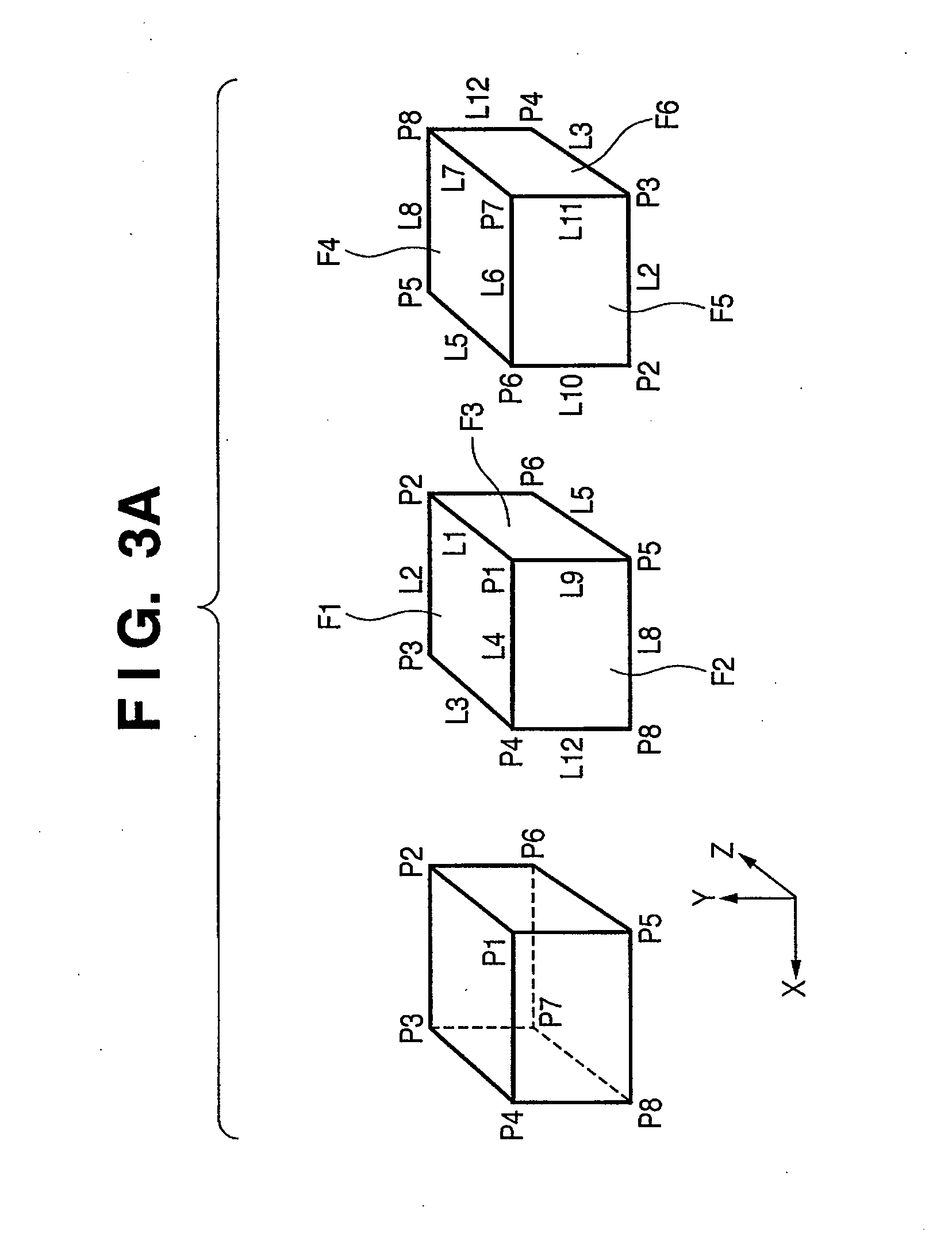
Information processing apparatus and method
InactiveUS20080172201A1Easily accurately calculatingAvoid registrationImage analysisPhotogrammetry/videogrammetryInformation processingDirection information
Owner:CANON KK
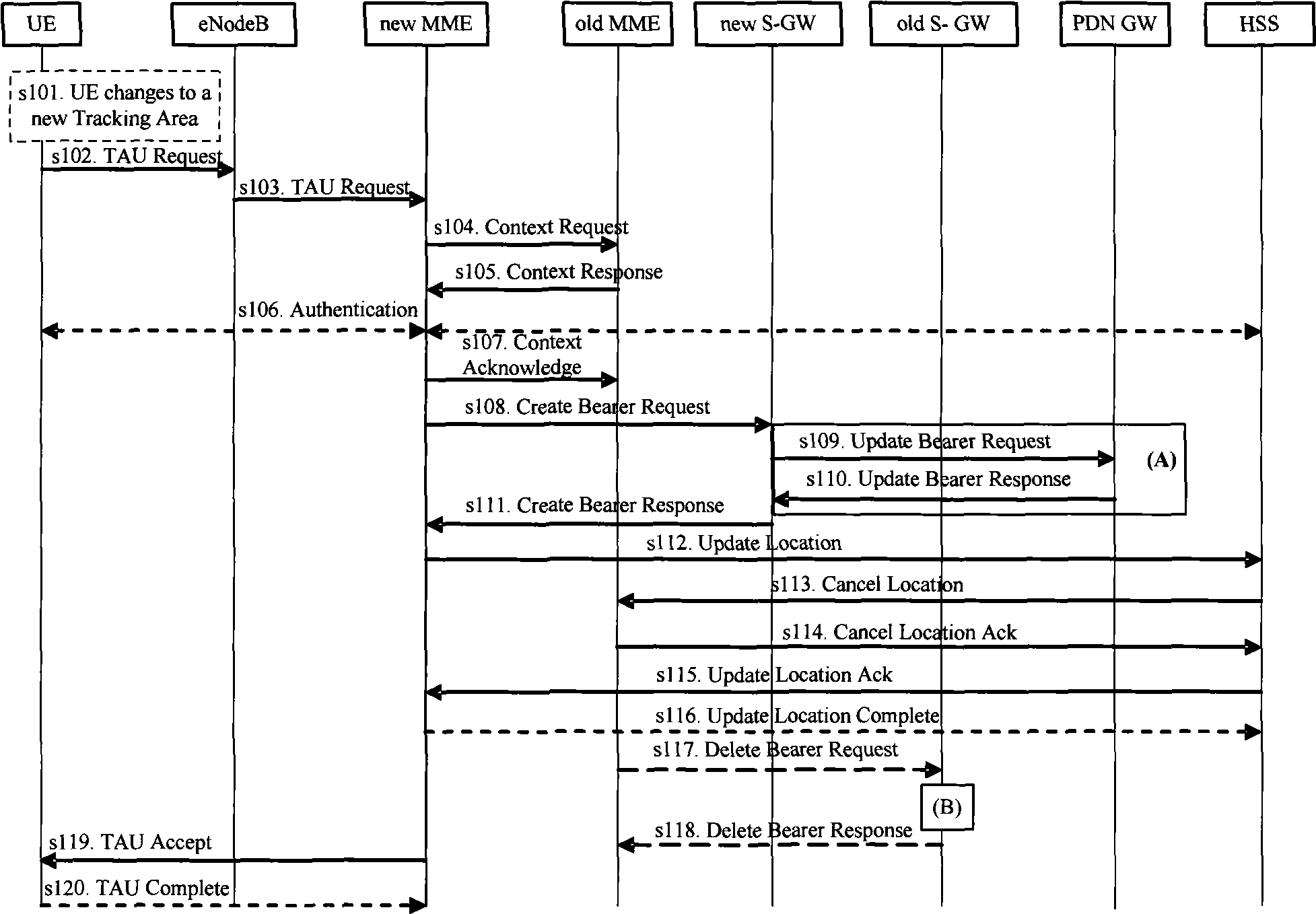
Registration zone updating method and apparatus
InactiveCN101489209AReduce consumptionCommunication service quality impactNetwork data managementQuality of serviceComputer science
The present invention discloses a method for updating registration area, wherein the method comprises the following steps: when a user terminal UE enters a new registration area or a plurality of registration areas exist for selection, determining whether the updating condition of registration area is satisfied; and when the updating condition is satisfied, initiating the updating to a new registration area or another registration area by the UE. The invention also discloses a device which is used for updating the registration area. The embodiment of the invention sets different updating conditions of registration area for the UE in the registration area, so that only the UE satisfying the updating condition initiates the registration area updating. The registering process of simultaneously initiating of large number of UEs to the new registration area is effectively prevented. Not only is the load of system signaling reduced, but also the consumption of wireless interface resource and network resource can be reduced. The possibility of affecting the service quality of subscriber communication service is reduced and the system performance is increased.
Owner:HUAWEI TECH CO LTD
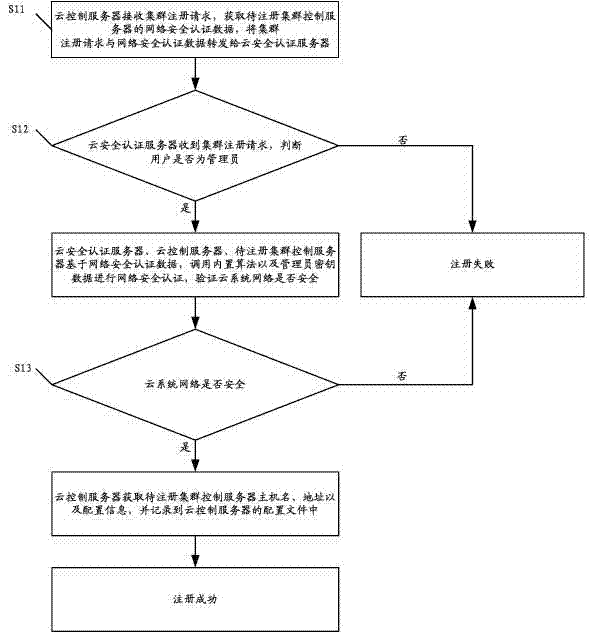
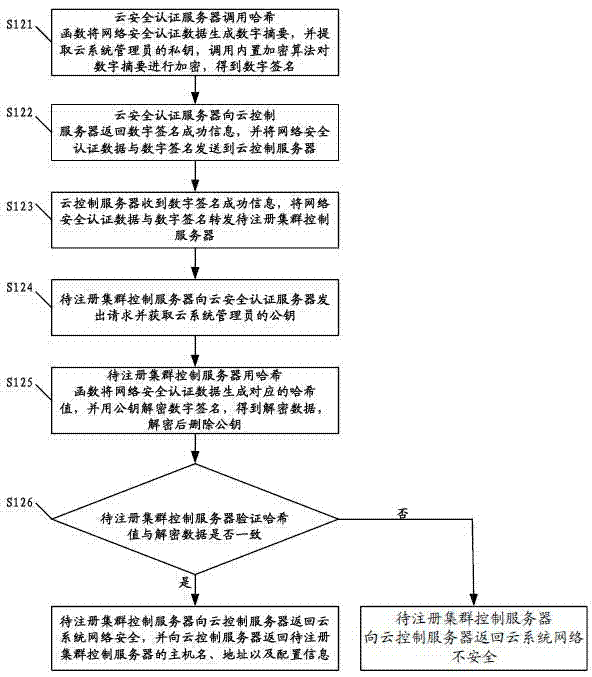
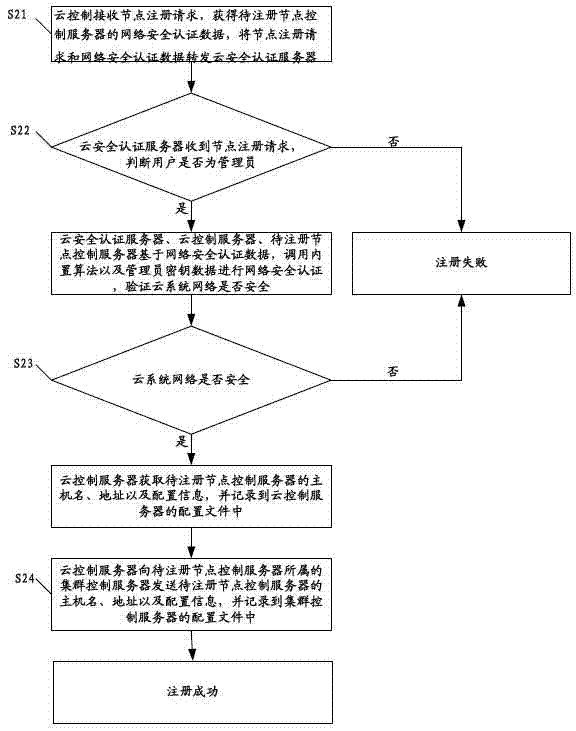
Method and cloud system for registering cluster control server and node control server
ActiveCN102833256AAvoid the authentication processThe authentication server prevents theTransmissionAuthentication serverSecurity authentication
The invention discloses a method for registering a cluster control server. The method comprises the following steps that a cloud control server receives a cluster registration request, obtains network security authentication data and forwards the cluster registration request and the network security authentication data to a cloud security authentication server; the cloud security authentication server determines whether a user is an administrator, if yes, the cloud security authentication server, the cloud control server and a cluster control server to be registered carry out network security authentication, and whether the cloud system network is safe is verified; if the cloud system network is safe, the cloud control server obtains the host name, the address and the configuration information of the cluster control server to be registered, the host name, the address and the configuration information are recorded into configuration files, and finally the registration is successful; and if else, the registration is failed. The invention also discloses a method and a cloud system for registering a node control server. The embodiment of the invention can increased the security of the registration process for registering the cluster control server and the node control server.
Owner:GCI SCI & TECH
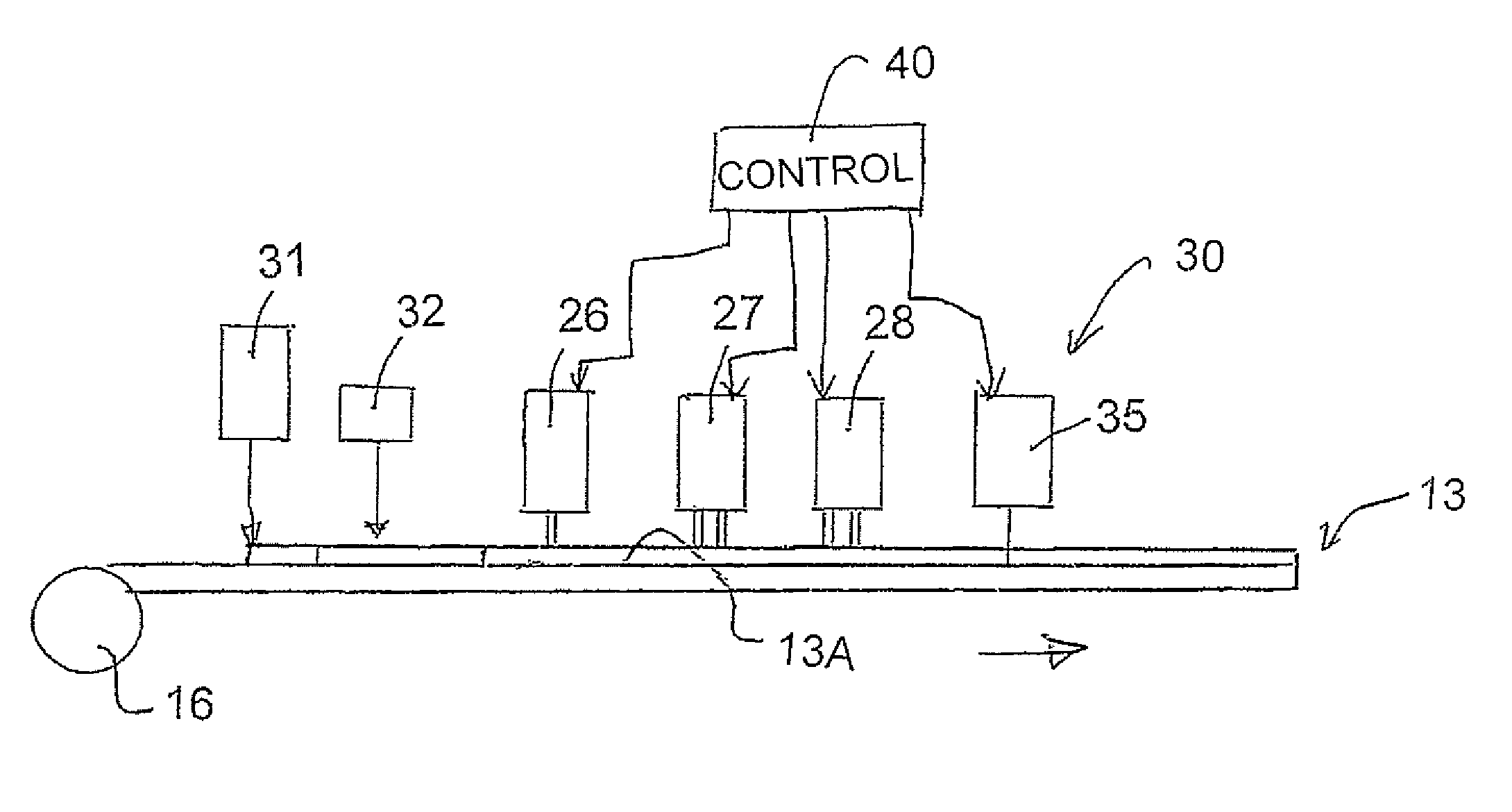
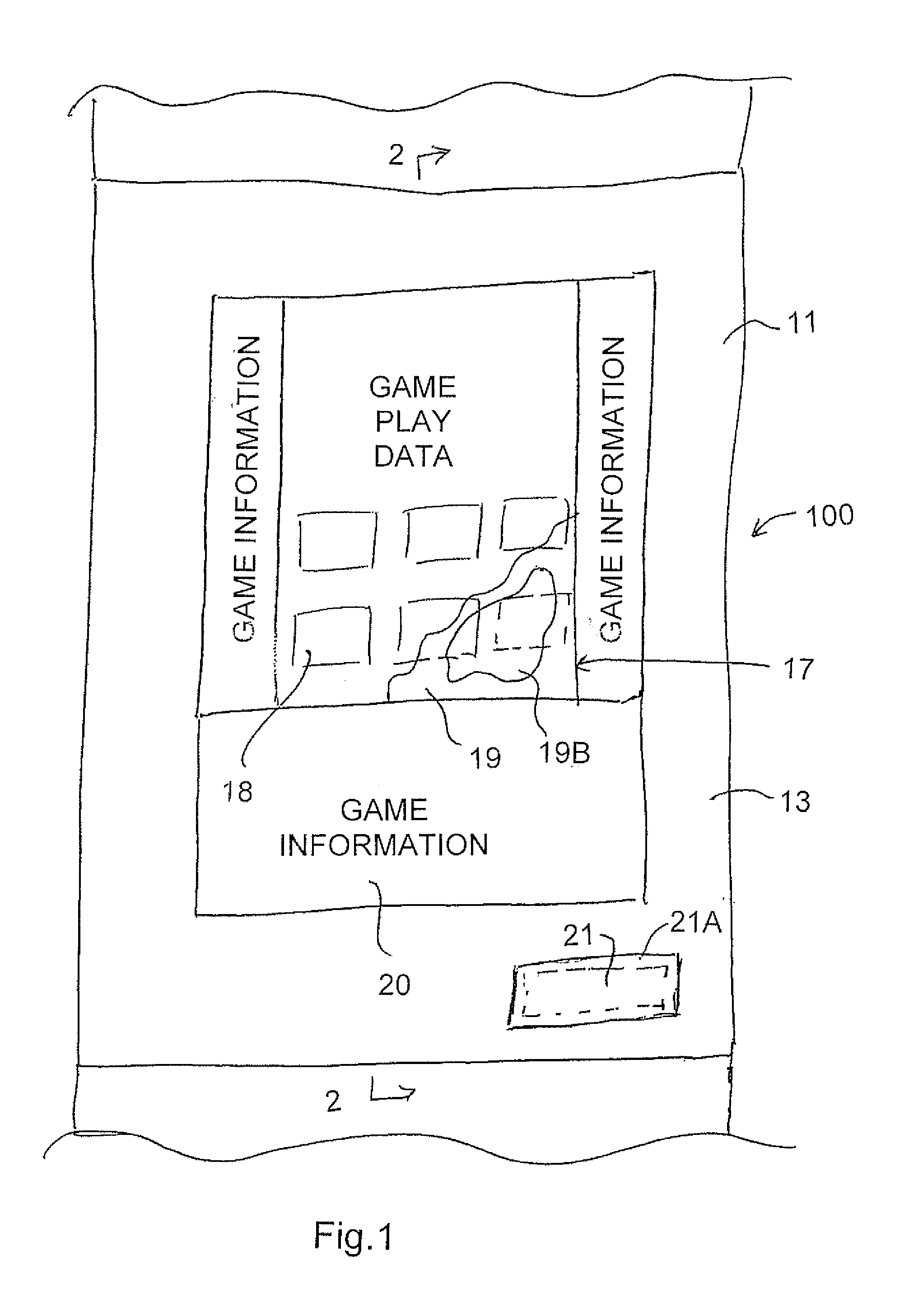
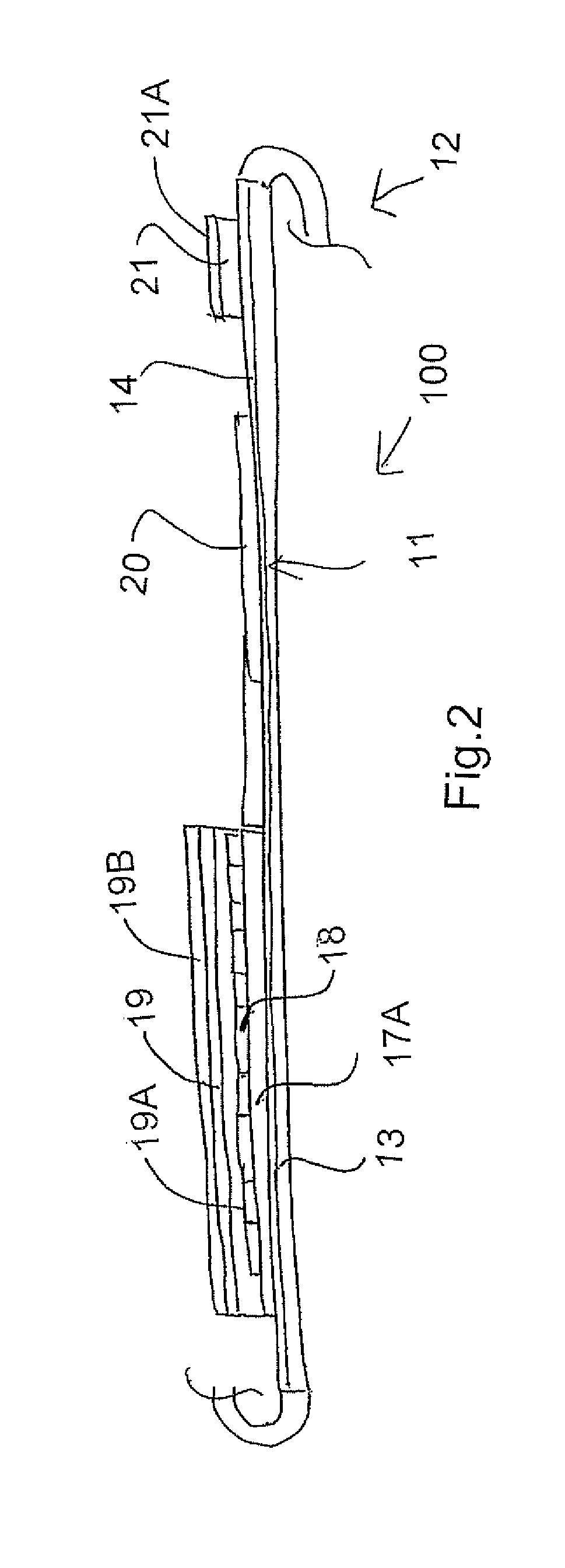
Printing of Game Tickets
In a row of lottery tickets each ticket has variable image printing game data printed onto a base layer on a substrate and a series of covering layers including at least one sealing layer and at least one scratch-off layer. Simultaneously game information is printed as a multi-color digital image for each ticket using a variable image printing system. The game information graphics can indicate different values for different ones of the tickets. The tickets in the row can be of different series for sale to different retailers. The printing system automatically correlates the game data and game information to ensure no registration errors thus allowing much improved variability and allowing the game to take into account both game data and game information in determining a winning ticket.
Owner:POLLARD BANKNOTE PARTNERSHIP
Intelligent device, registration management method thereof and cloud server
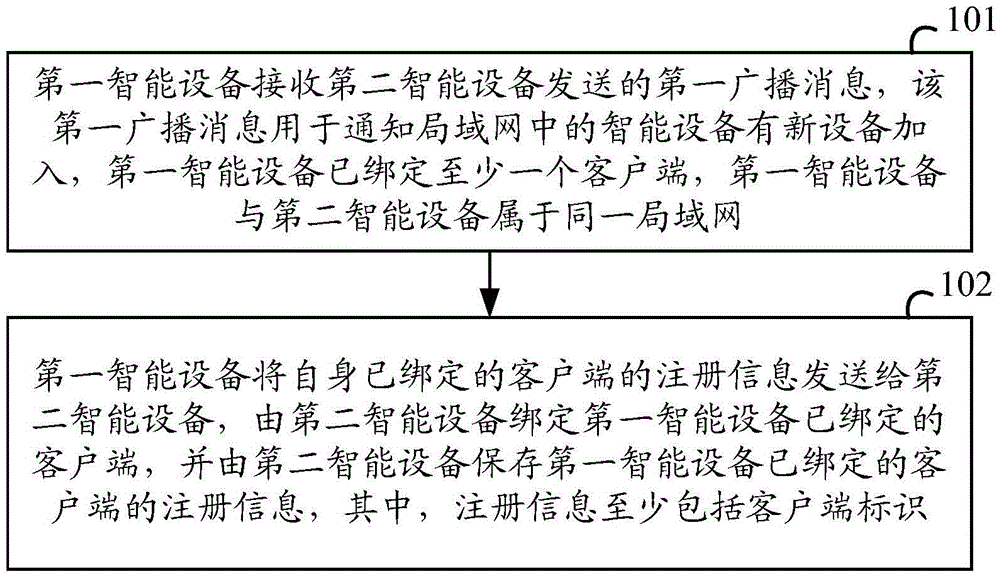
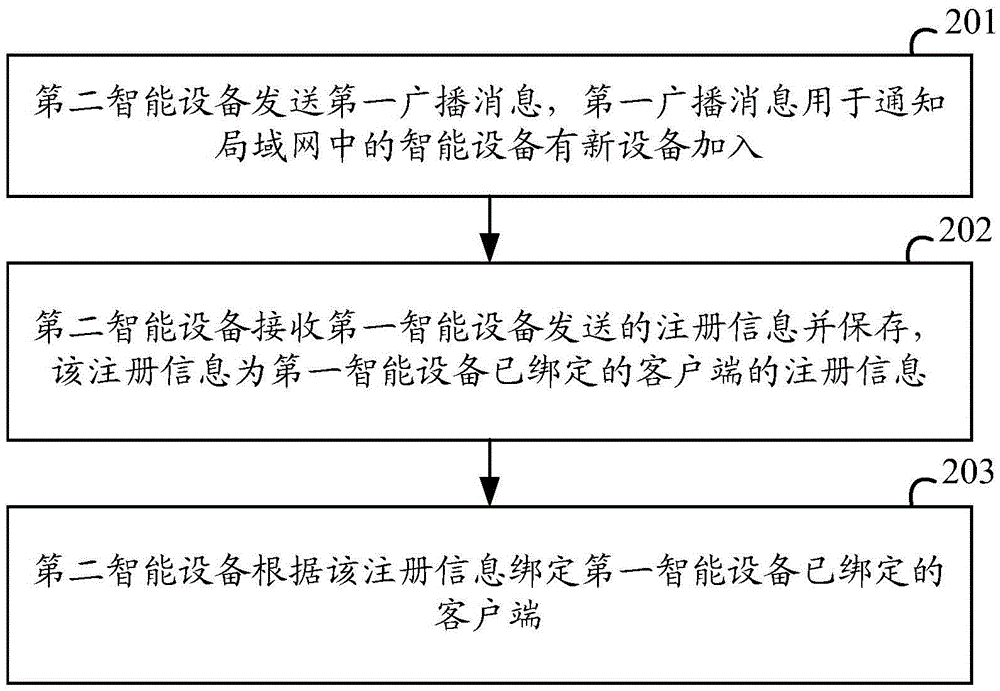
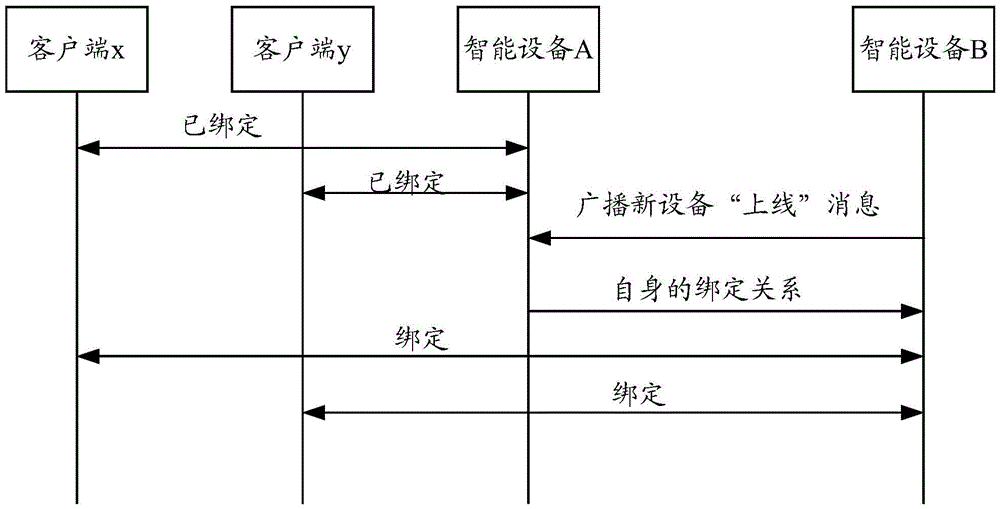
InactiveCN105487390ASimplify the registration processAvoid registrationComputer controlTotal factory controlNew deviceLocal area network
The invention discloses an intelligent device, a registration management method thereof and a cloud server. The method is used to simplify the registration process of multiple intelligent devices which belong to the same local area network (LAN). The method comprises that the first intelligent device receives a first broadcast message sent by the second intelligent device, the first broadcast message is used to notify the intelligent devices in the LAN of addition of the new device, the first intelligent device is bound to at least one client, and both the first intelligent device and the second intelligent device belong to the same LAN; and the first intelligent device sends registration information of the bound client to the second intelligent device, the second intelligent device is bound to the client to which the first intelligent device is bound, and stores the registration information of the bound client, and the registration information comprises identification of the client at least.
Owner:QINGDAO HISENSE MOBILE COMM TECH CO LTD
Converter and a method for controlling a converter
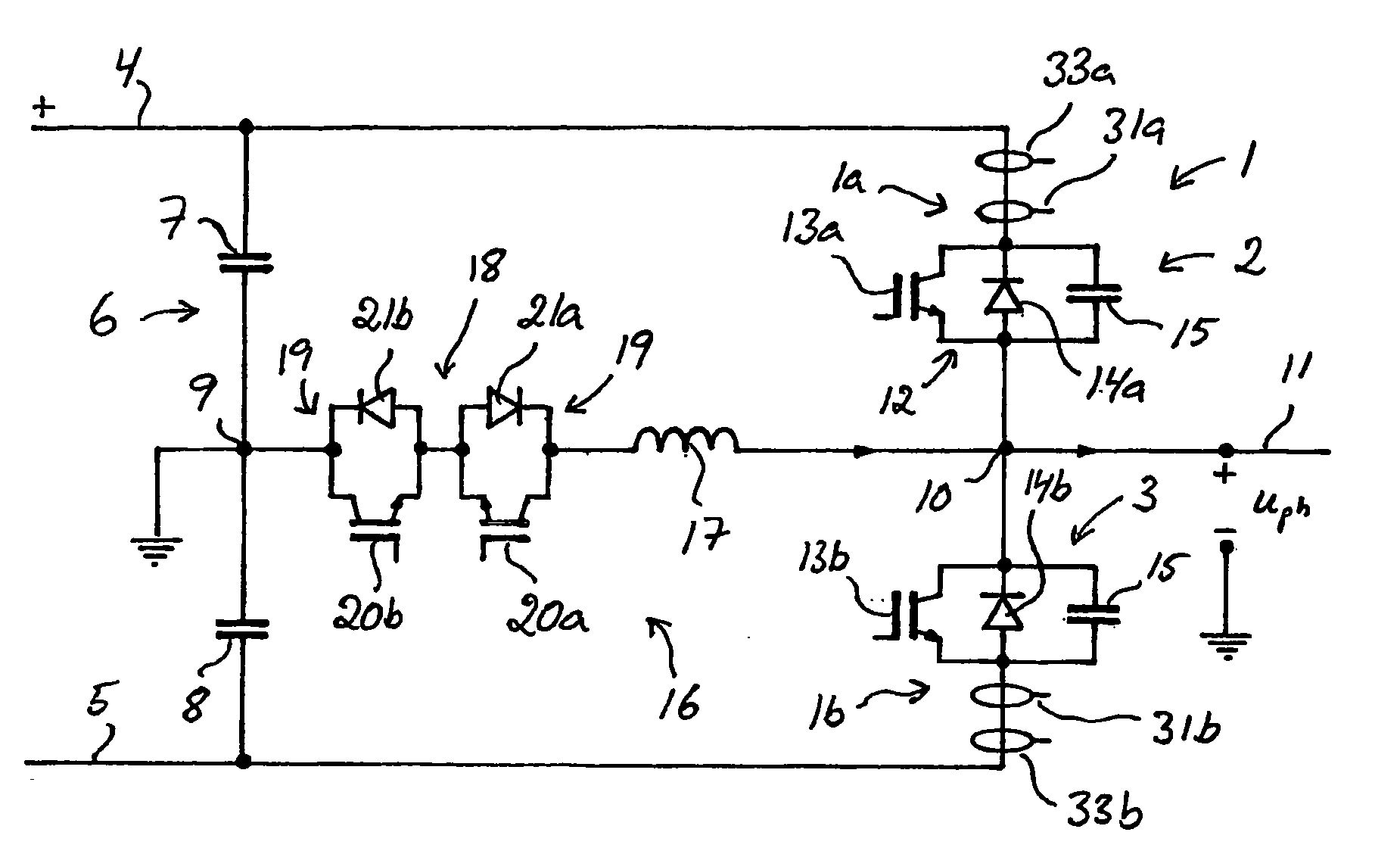
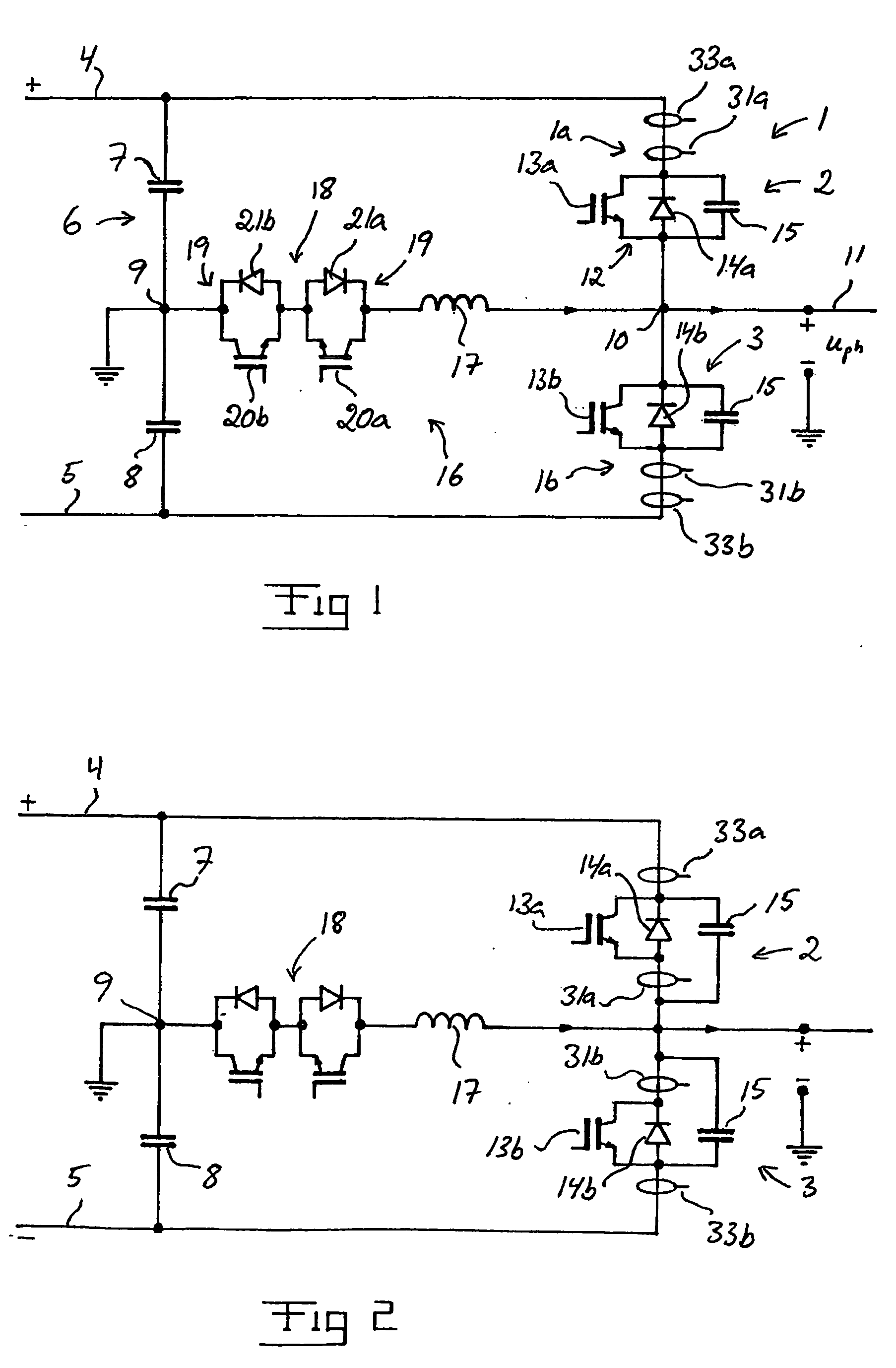
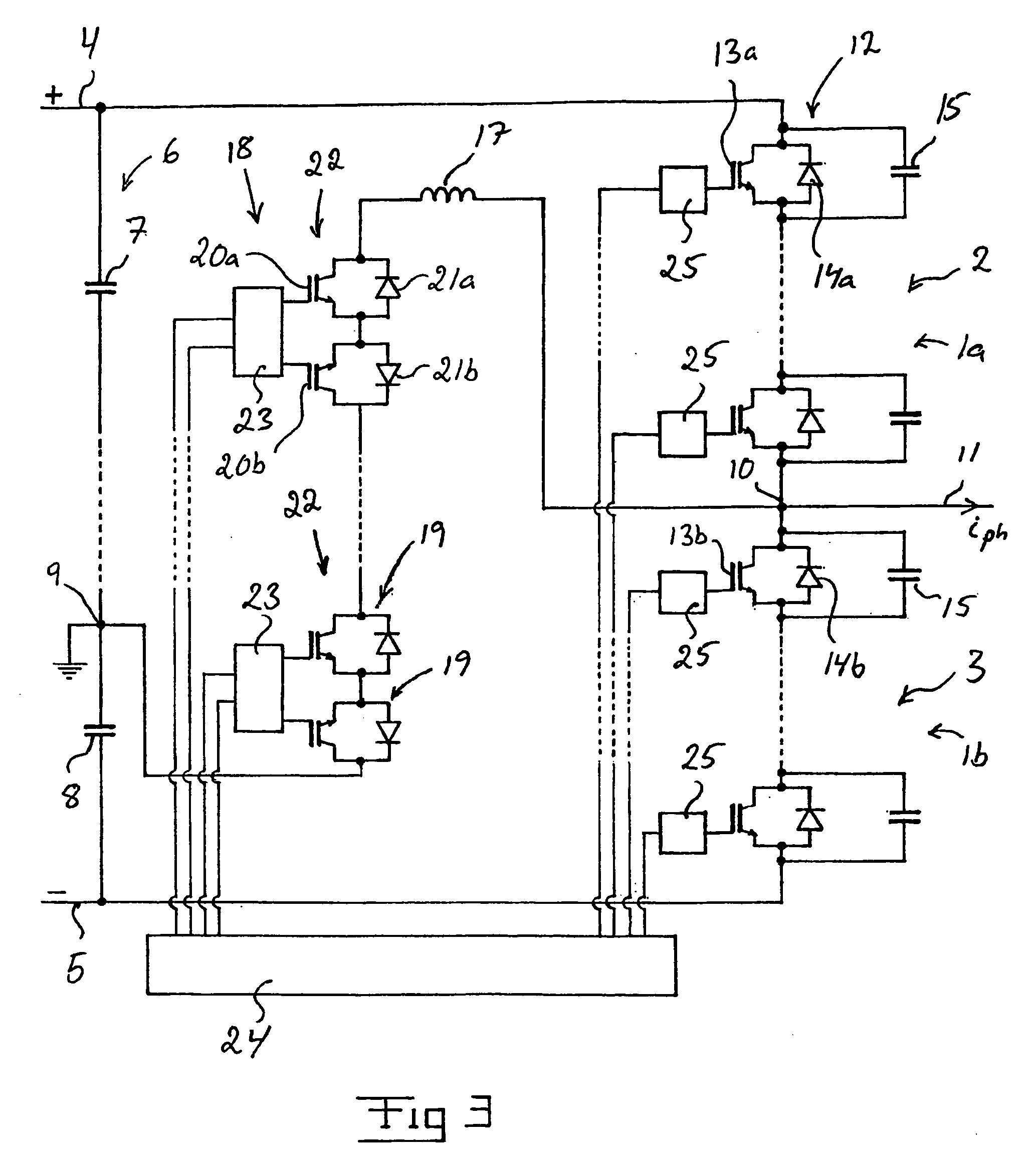
InactiveUS6995994B2Efficient and rapid detectionAvoid componentsEmergency protective circuit arrangementsDc-ac conversion without reversalEngineeringLimit value
The invention relates to a converter provided with a resonant circuit (16), which converter comprises a device (31) for measuring the derivative (dI / dt) of the current through the current valves 82, 3) and a detection device (32) co-operating with said measuring device (31) for detecting a short-circuit in the converter, the detection device (32) being adapted to detect a short-circuit current when the current derivative (dI / dt) measured by the measuring device (31) is equal to or exceeds a stipulated current derivative limit value (dI / dtlim) during a length of time exceeding a stipulated time limit value (tlim). The invention also relates to a method for controlling such a converter.
Owner:ABB (SCHWEIZ) AG
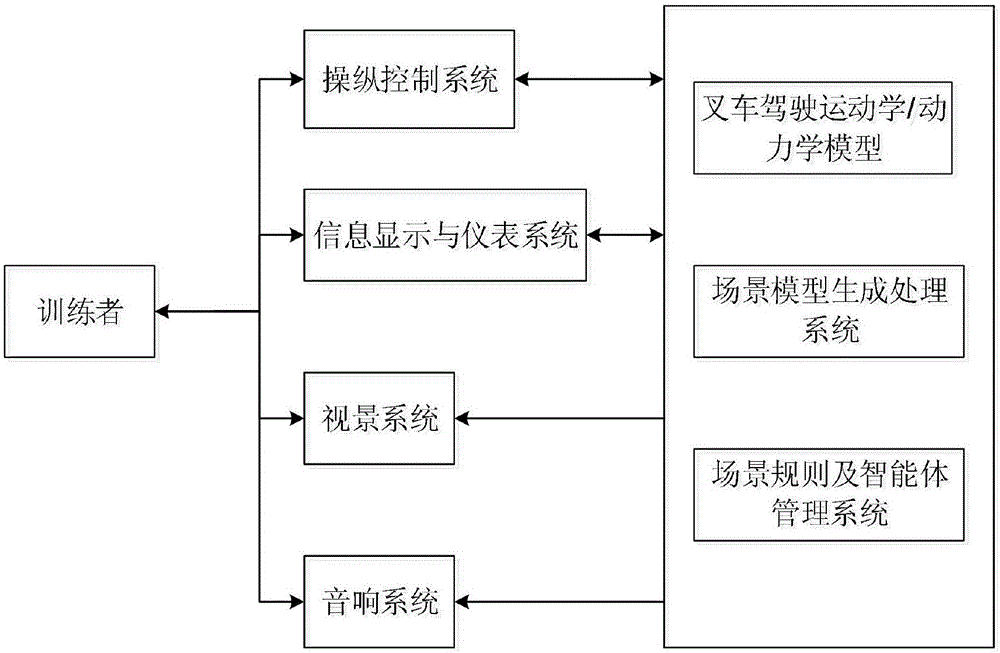
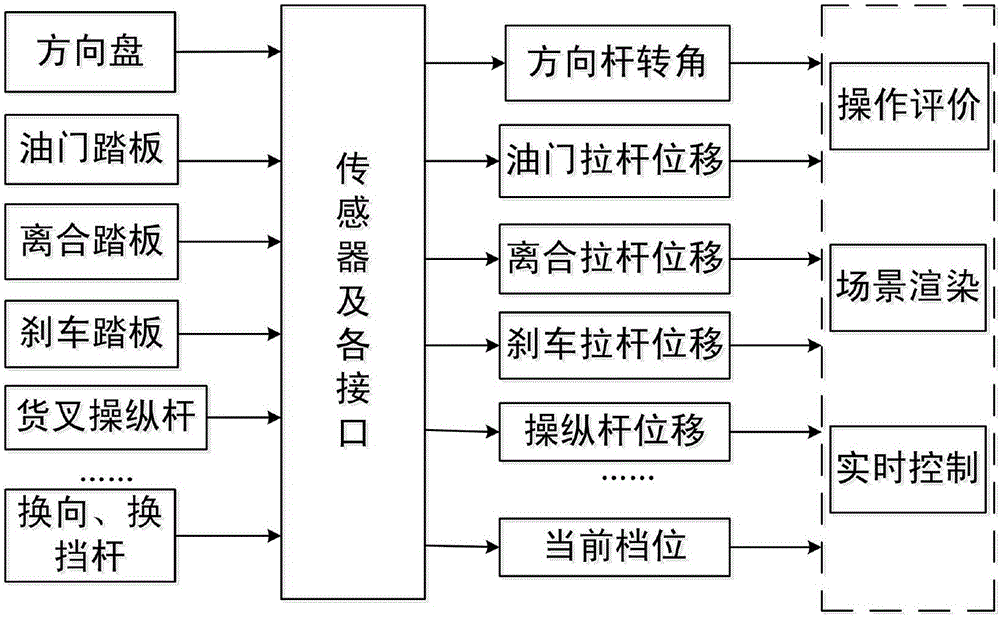
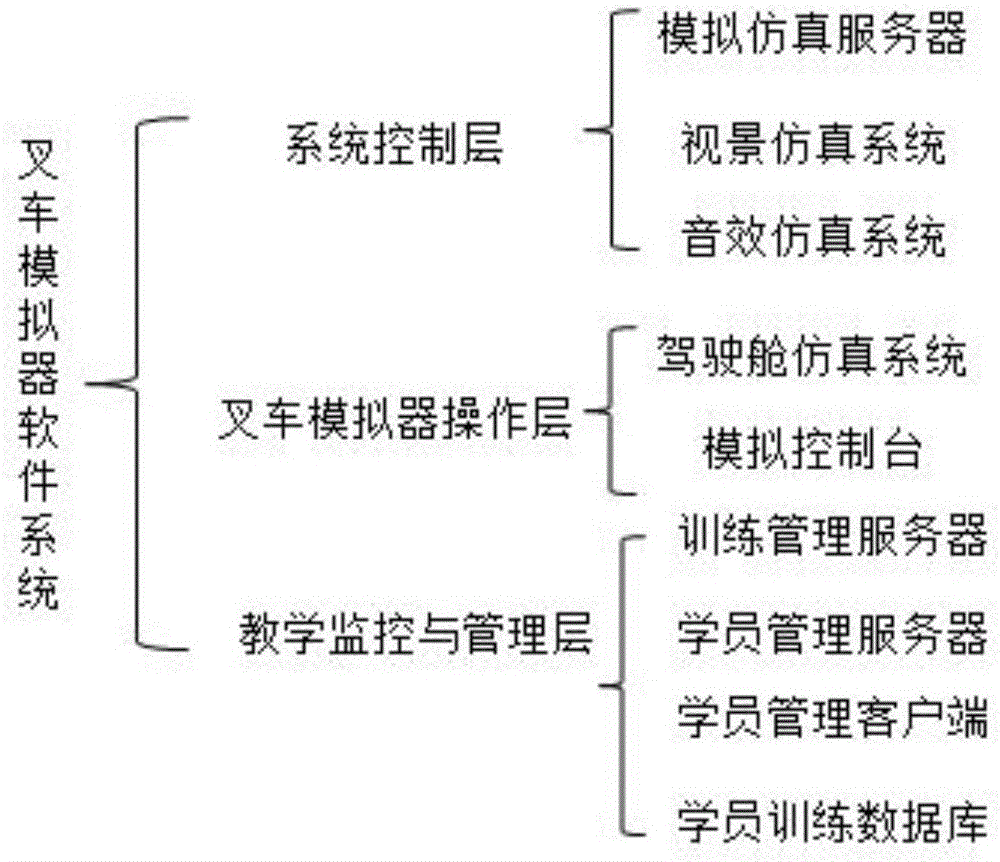
Forklift operation training simulator
InactiveCN106652642ARapid responseAvoid registrationCosmonautic condition simulationsSimulatorsTraining periodSoftware system
The invention relates to a forklift operation training simulator. A main structure of the forklift operation training simulator comprises hardware equipment and a software system. The hardware equipment comprise a simulation cab, an steering control system, an instrument system, a multimedia computer, an audio system, an instructor control panel and the like. The software system comprises an operation platform and is used for real-time working environment animation generation of the computer, dynamic forklift driving simulation, sound simulation, operation evaluation, data management, network control and the like. The forklift operation training simulator has the advantages that a whole training period of a student can be shortened greatly, the student is enabled to finish training tasks in a short time, sudden incidents which rarely happen during practical training can be simulated conveniently, accurate-judging ability, good psychological quality and the ability of handling emergency circumstances correctly of the student can be cultivated, and training quality is improved.
Owner:武汉科码软件有限公司
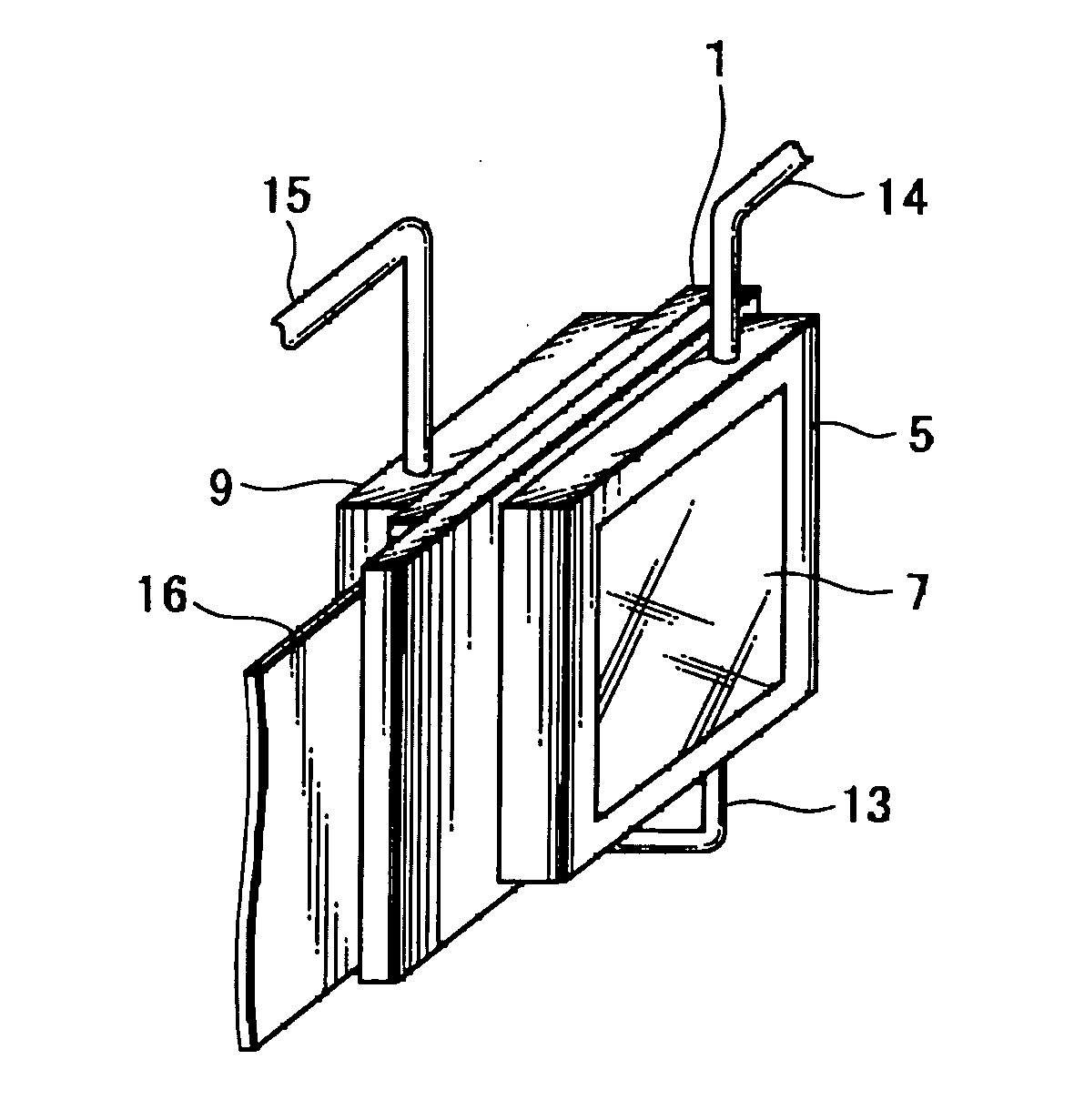
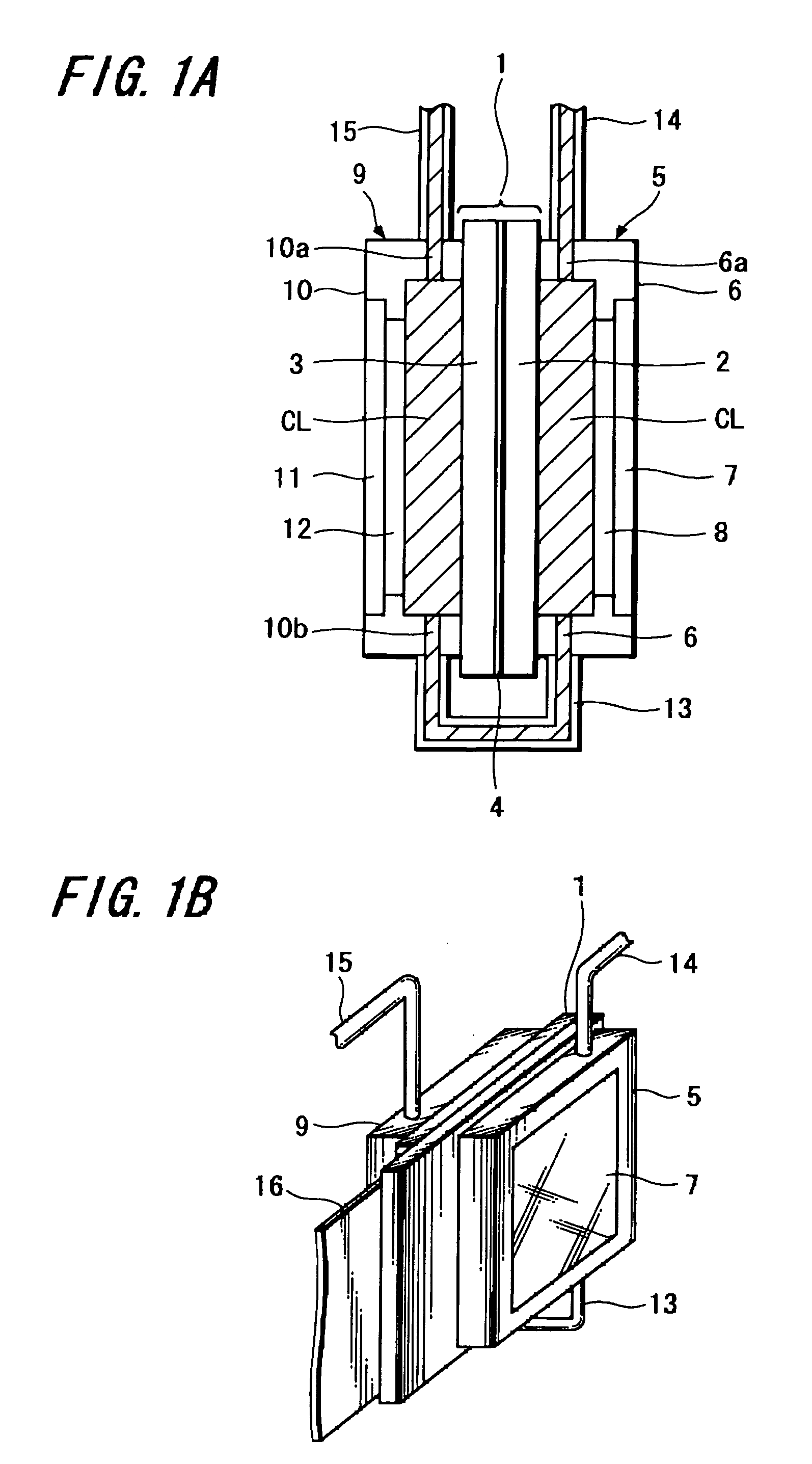
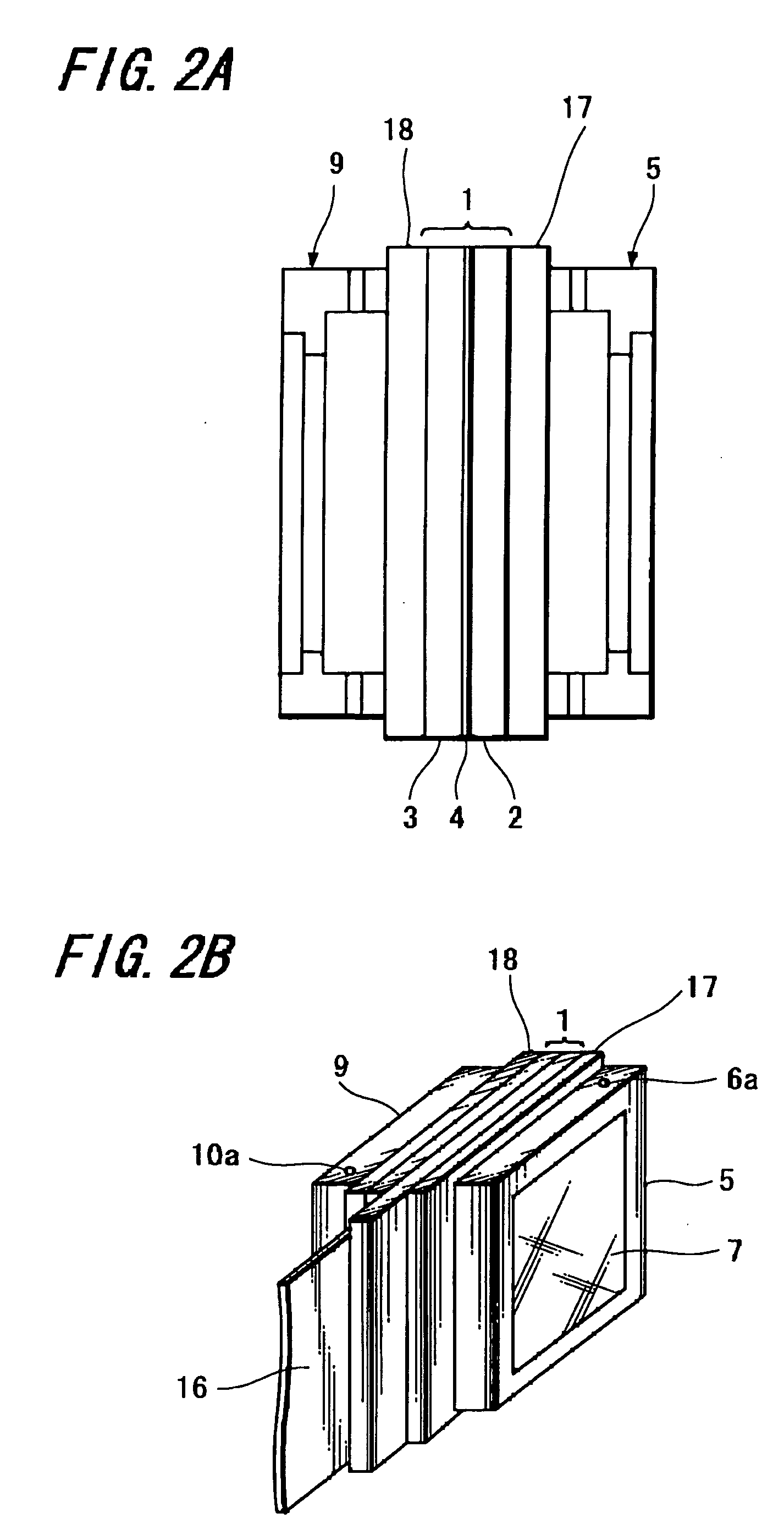
Liquid-cooled liquid crystal panel and method of manufacturing the same as well as liquid crystal projector
InactiveUS20050270495A1Avoid loadReduce loadTelevision system detailsProjectorsEngineeringLCD projector
A liquid crystal panel is provided in which rise in temperature of the liquid crystal panel is sufficiently restrained by cooling the liquid crystal panel by means of cooling liquid and exudation of the cooling liquid toward a liquid crystal material is prevented. Cover members 5 and 9 are attached to a liquid crystal panel 1 where the cover members form cavities on the light entering side and on the light emitting side of the liquid crystal panel 1, respectively, cover the liquid crystal panel 1 such that a sealed portion 4 of the liquid crystal material is not in contact with the cavities, and transmit light entering the liquid crystal panel 1 and light emitted from liquid crystal panel 1; and the cavities are filled with cooling liquid CL.
Owner:SONY CORP
Information processor and multi-hit control method
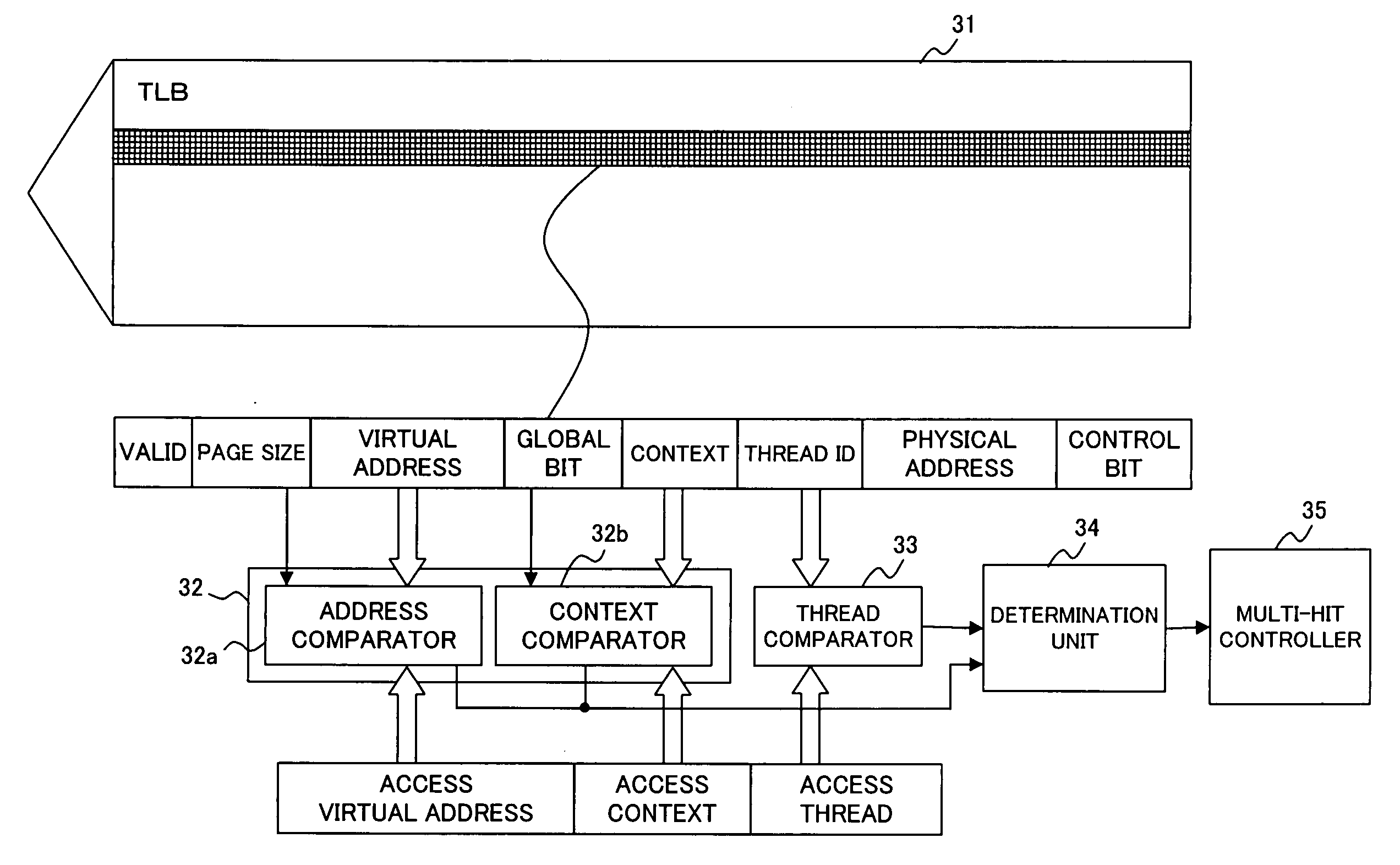
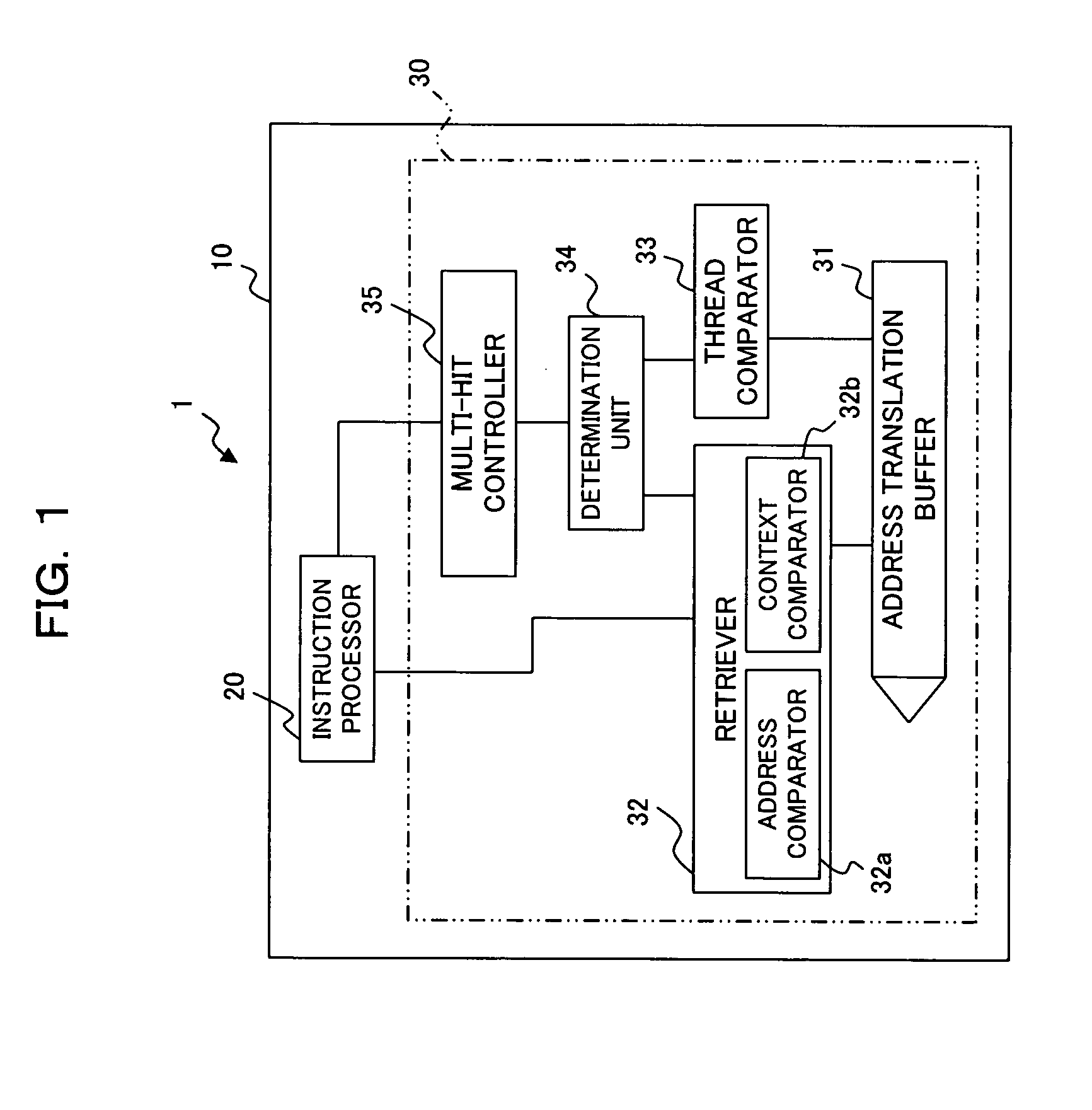
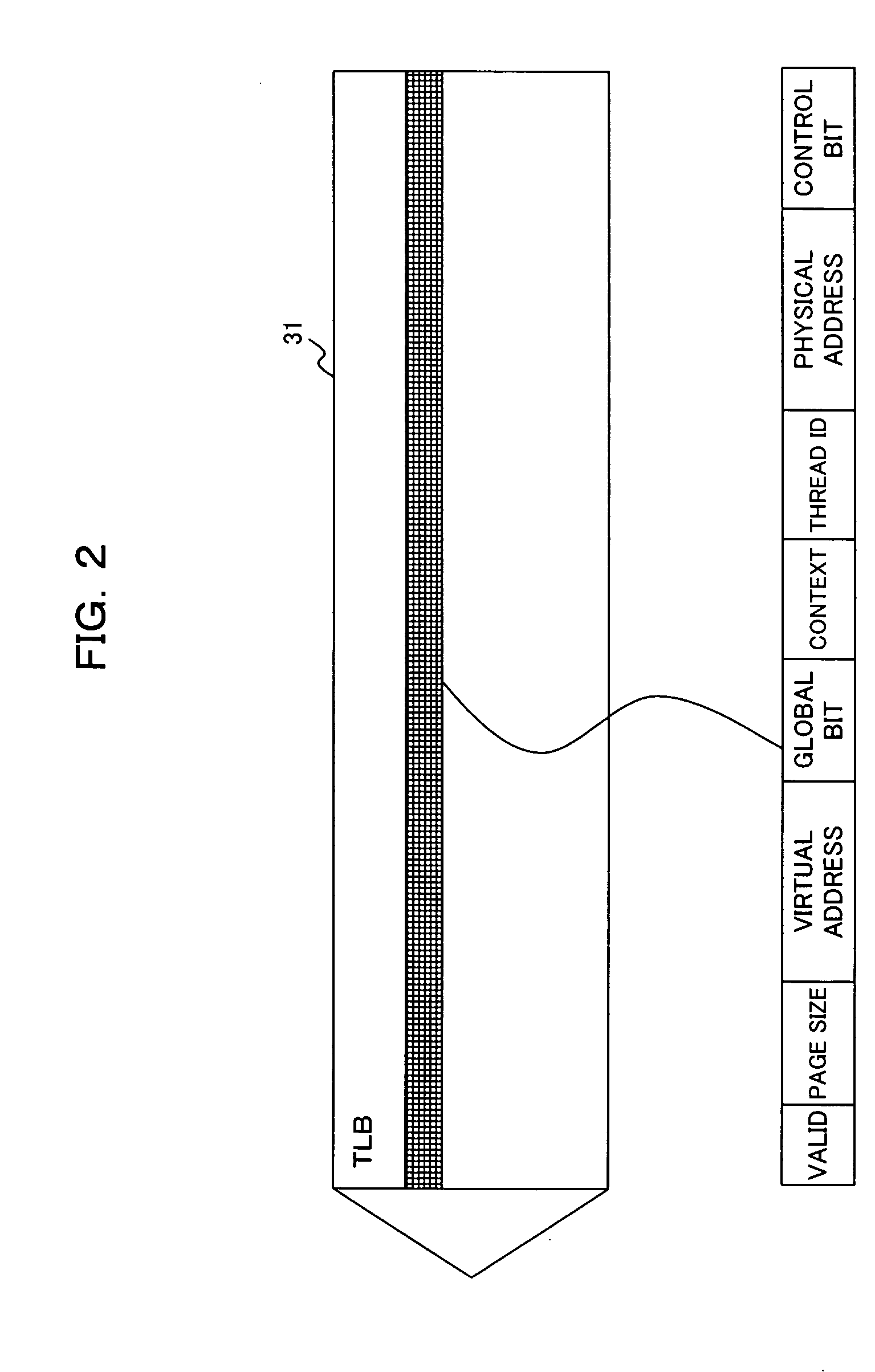
InactiveUS20060026382A1Ensure safetyAvoid registrationMemory adressing/allocation/relocationMicro-instruction address formationInformation processorOperating system
The present invention comprises, for enabling sharing an address translation buffer (TLB=Translation Lookaside Buffer) between plural threads without generating undesirable multi-hits in an information processor which operates in multi-thread mode, an address translation buffer for storing address translation pairs and thread information, a retriever for retrieving an address translation pair of a virtual addresses identical to said virtual address from the address translation buffer for translating the virtual address into a physical address, a determination unit for determining, when plural addresses translation pairs are retrieved by the retriever, whether or not two or more of said thread information are identical among plural thread information corresponding to plural address translation pairs, and a multi-hit controller for suppressing output of multi-hits and directing execution of address translation if the thread information are determined to be different according to the determination unit.
Owner:FUJITSU LTD
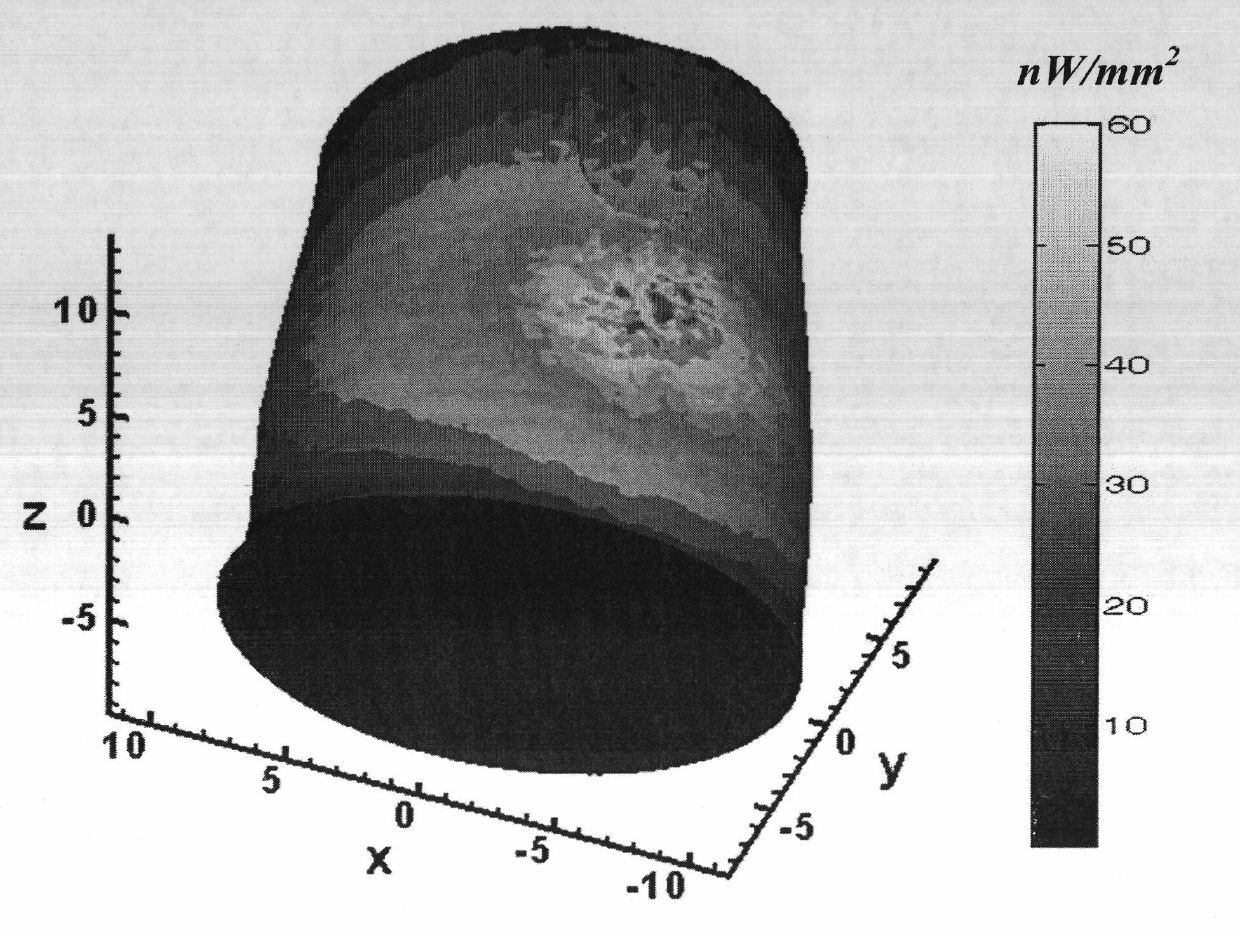
Optical bioluminescence tomography method
InactiveCN101947103AHigh sensitivityLow costDiagnostic recording/measuringSensorsIn vivoMR - Magnetic resonance
The invention discloses an optical bioluminescence tomography method and solves the problem that the three-dimensional reconstruction can be realized by integrating structure imaging technology, such as computer tomography or magnetic resonance imaging. In the method, the three-dimensional profile of the surface of an organism is obtained by a white light signal image and is used for the inversion of the bioluminescence source in vivo by combining quantitive reconstruction of the energy distribution of the surface of the organism so as to implement a low-cost optical bioluminescence tomography process. The method comprises the following specific steps of: acquiring data and preprocessing; reconstructing the three-dimensional profile of the surface of the organism; reconstructing the energy distribution of the surface of the organism; performing quantitive calibration on the surface energy; and inverting the source in vivo and performing three-dimensional display. The optical bioluminescence tomography method has the characteristics of high sensitivity and low cost, saves complex, time and power-consuming segmentation and rectification links and can be used in the field of bioluminescence tomography.
Owner:XIDIAN UNIV
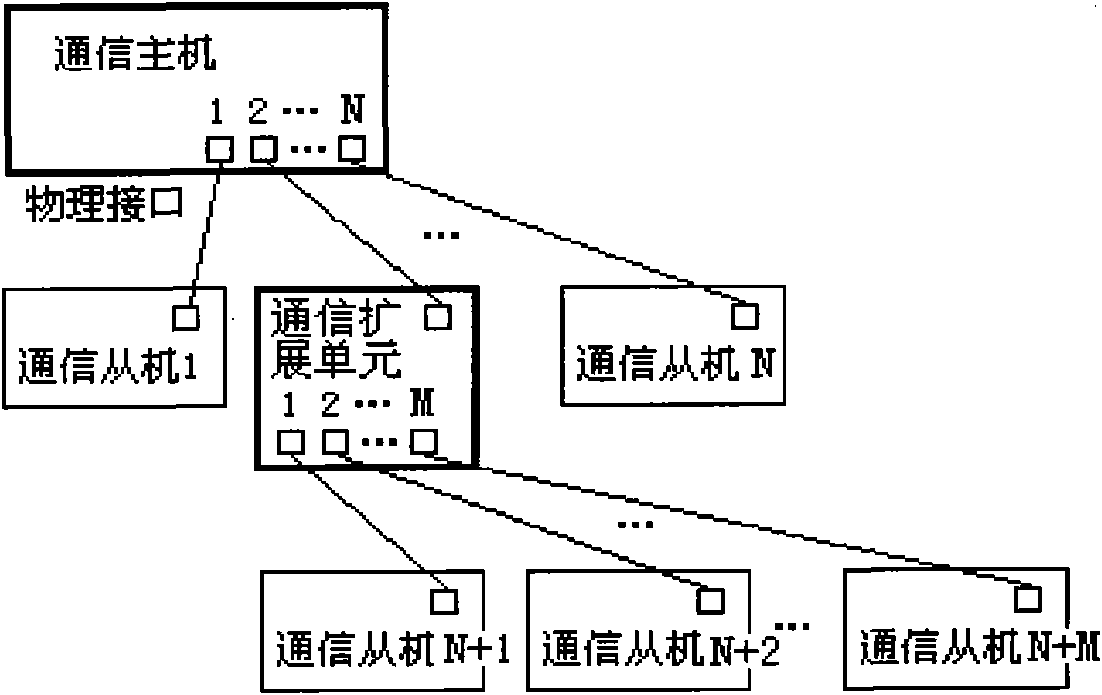
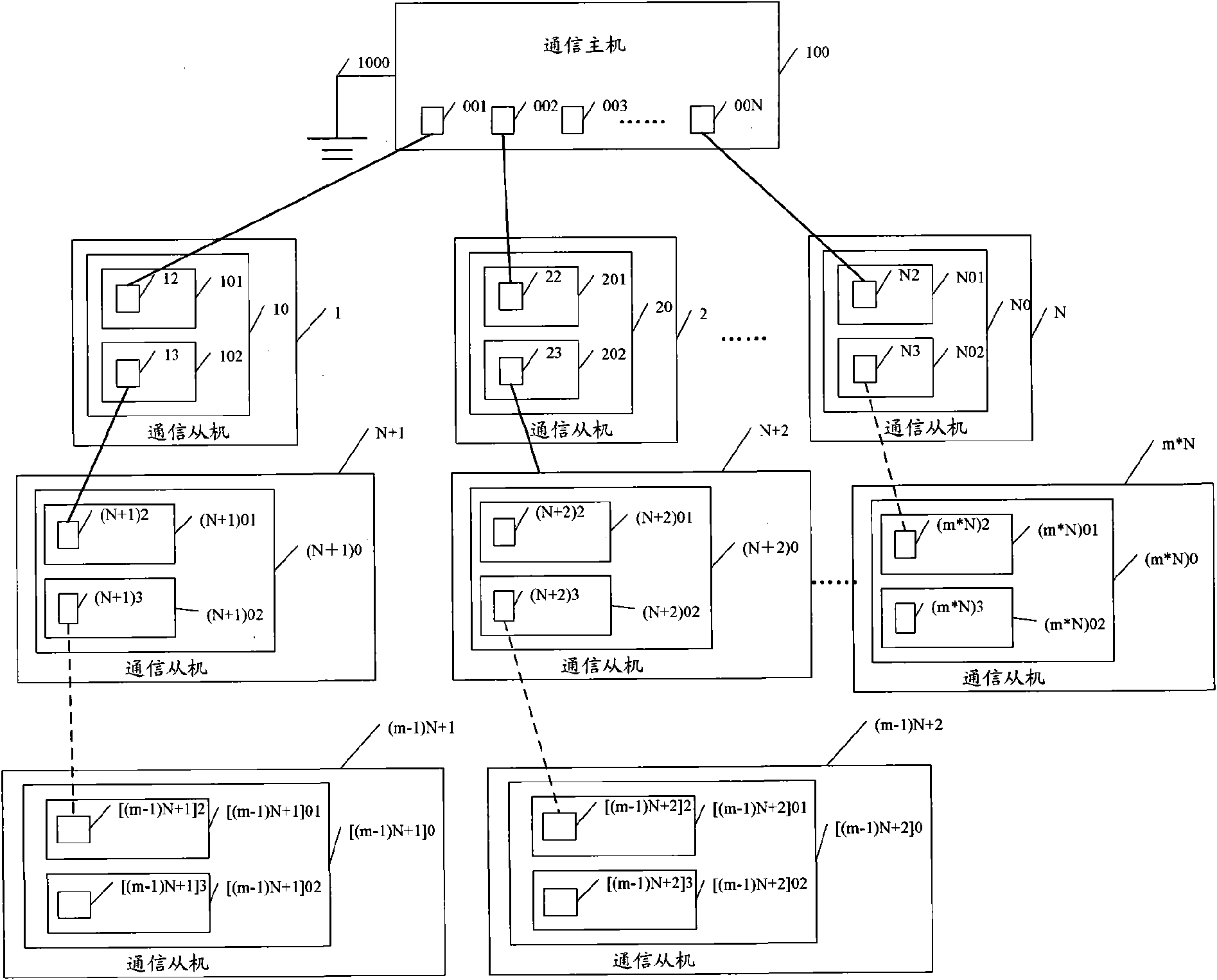
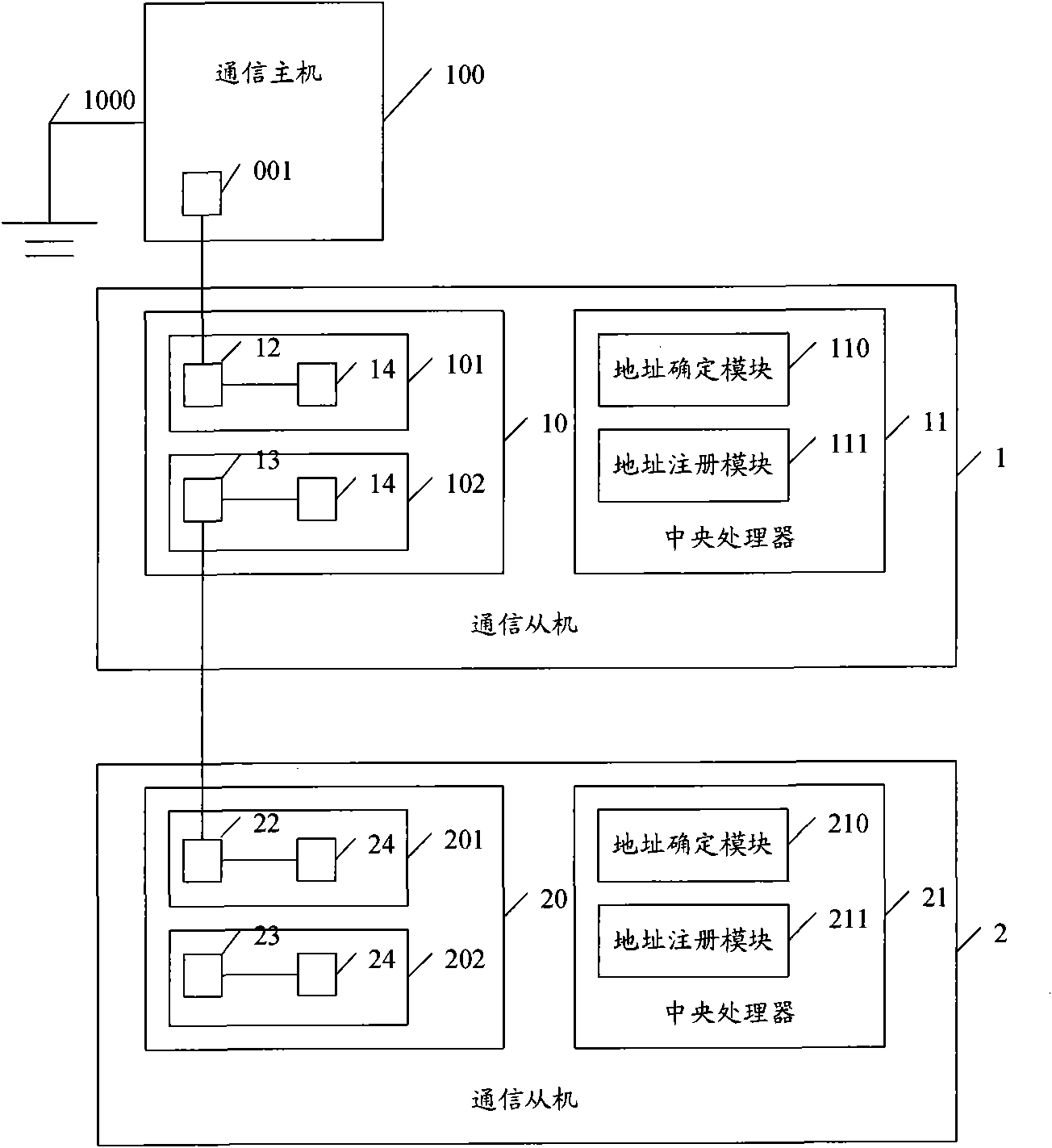
Communication slave, bus cascading method and system
The embodiment of the invention discloses a communication slave, a bus cascading method and a bus cascading system. When the cascading hierarchy has two levels, the bus cascading system comprises a communication host, a first communication slave connected with the communication host, and a second communication slave connected with the first communication slave. The method comprises that: the first communication slave receives a level signal of the communication host, which is opposite to the level defaulted by the first communication slave self; and the first communication slave changes self defaulted level state according to the received level signal, and changes self defaulted logical address. By adopting the embodiment of the invention to carry out logical address register on the communication host, the communication host does not need to increase a communication port to connect the communication slave, and the communication slave can determine self logical address so as to realize logical address register and identification.
Owner:HUAWEI TECH CO LTD
Improved mobile phone identity verification method and system
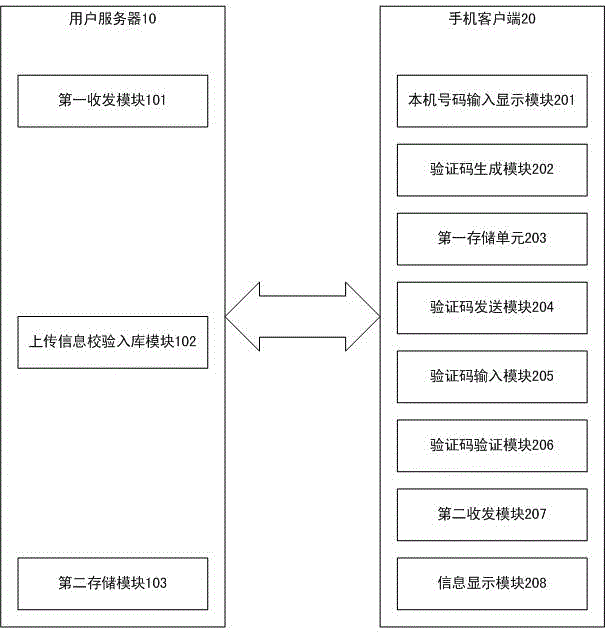
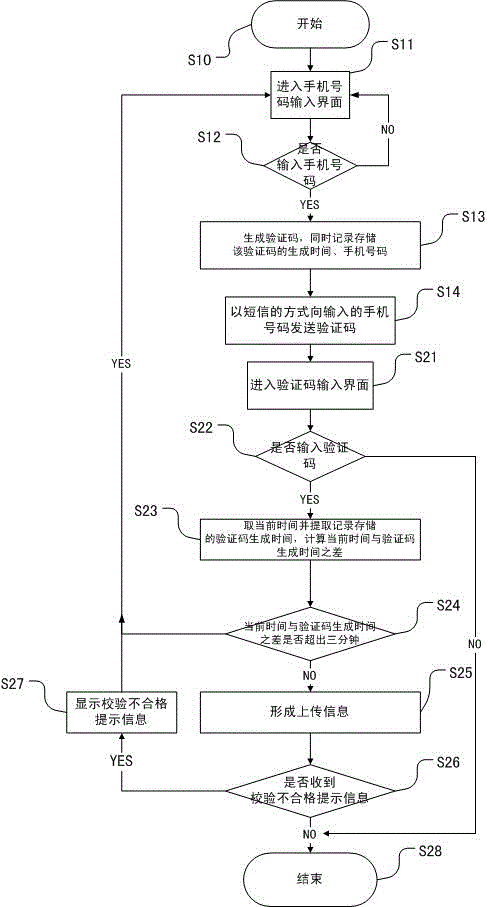
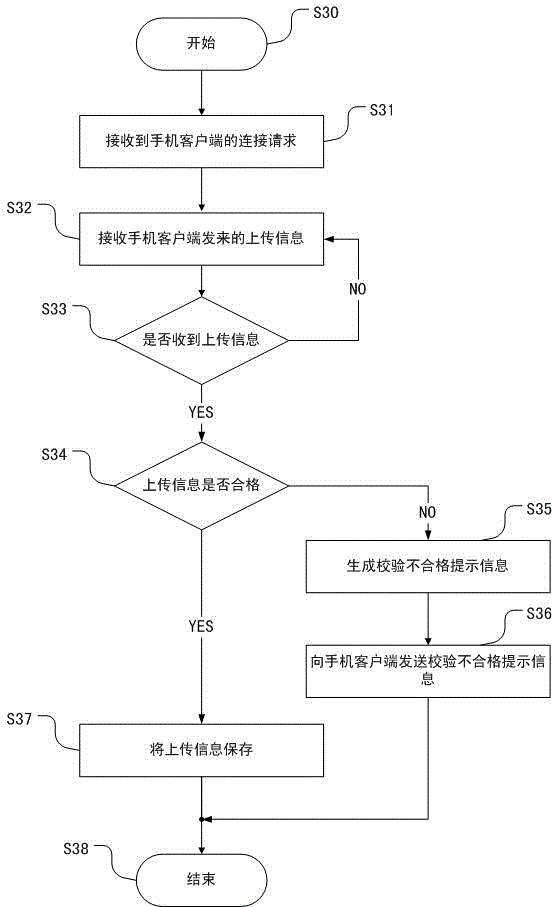
InactiveCN103607400AEliminate the hassle of networkingImprove experienceTransmissionSecurity arrangementComputer hardwareValidation methods
The invention discloses an improved mobile phone identity verification method and system. The mobile phone identity verification method is characterized by including the steps that a verification code is generated by a mobile phone client side and sent to the mobile phone client side in the form of a short massage, the verification code is input and verified after the mobile phone client side receives the verification code short massage, and upload information is generated and uploaded to a user server after the input verification code passes verification. The mobile phone identity verification system comprises the user server and a verification unit system located on the mobile phone client side, wherein the verification unit system comprises a local mobile phone number input and display module, a verification code generation module, a first storage unit, a verification code transmission module, a verification code input module, a verification code verification module, a second transmitting-receiving module and an information display module, and the user server comprises a first transmitting-receiving module, an upload information check and storage module and a second storage module. Compared with the prior art, the improved mobile phone identity verification method and system improve user experience and reduce hardware investment for service providers.
Owner:SHENZHEN ZHANGZHONG INFORMATION TECH
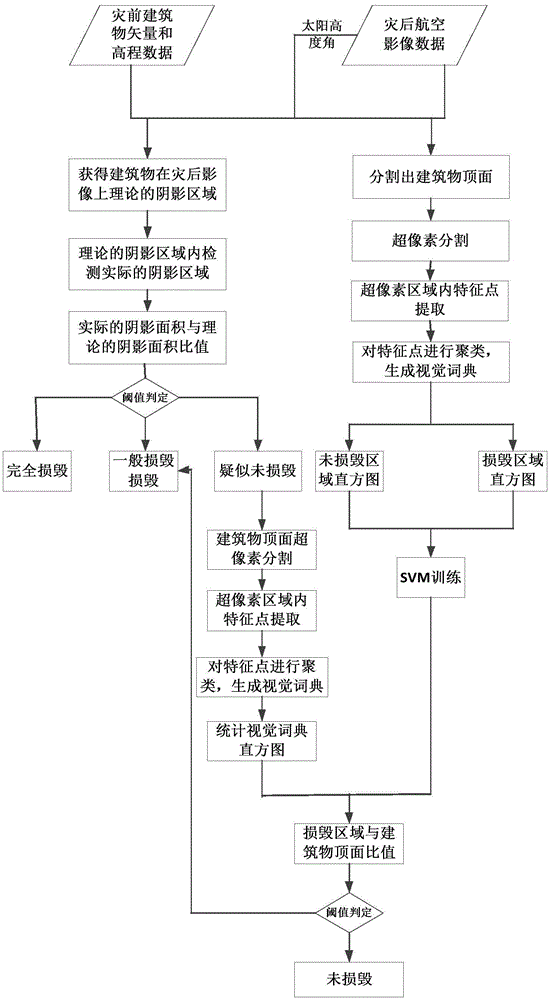
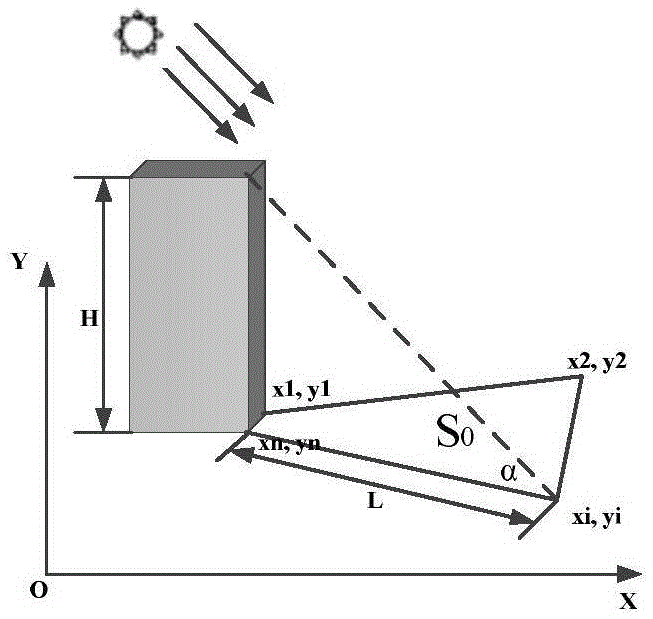
Aviation image building damage detection method based on shadow and texture characteristics
ActiveCN105631892AAchieve the effect of damageHigh precisionImage enhancementImage analysisAviationThree level
The invention discloses an aviation image building damage detection method based on shadow and texture characteristics, and the method comprises the steps: estimating a theoretical shadow area of a building in an image through the vector data and altitude data of the building before damages and a solar altitude angle; carrying out the detection of an actual shadow in the theoretical shadow area through employing constrained color invariance; obtaining the actual shadow area of the building; obtaining the damage level of the building according to the proportional relation of the actual shadow area and the theoretical shadow area, and dividing the damage level into three levels: complete damage, general damage, and suspected intactness; detecting the top surface of the intact building through employing a vision bag-of-word model, and further judging whether the building is damaged or not. The method integrates the shadow information (height) and top surface information (texture) of the building for detection, avoids registering difficulties in conventional data fusion, and improves the detection accuracy of the damage of the building.
Owner:WUHAN UNIV
Routing procedure for a communication system
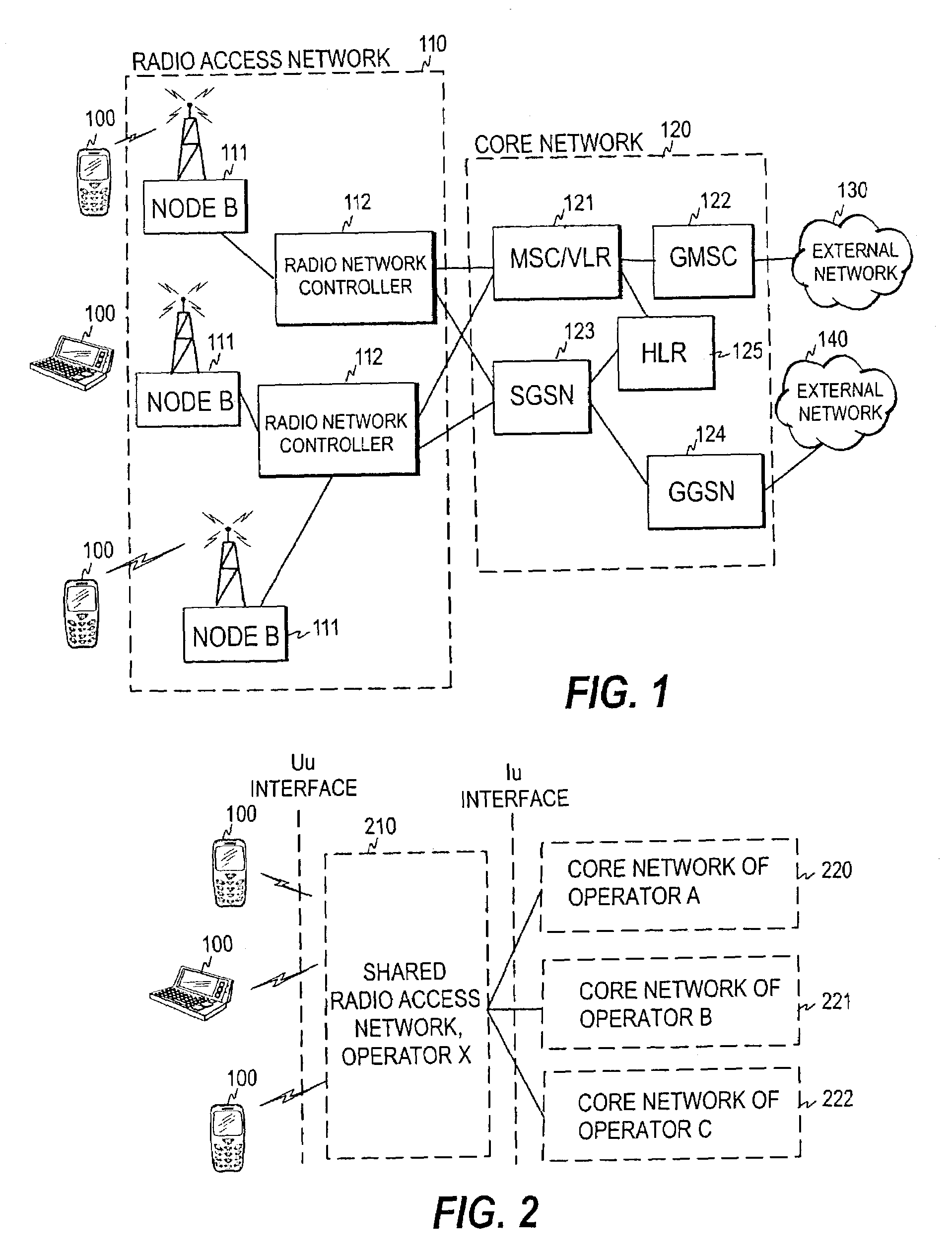
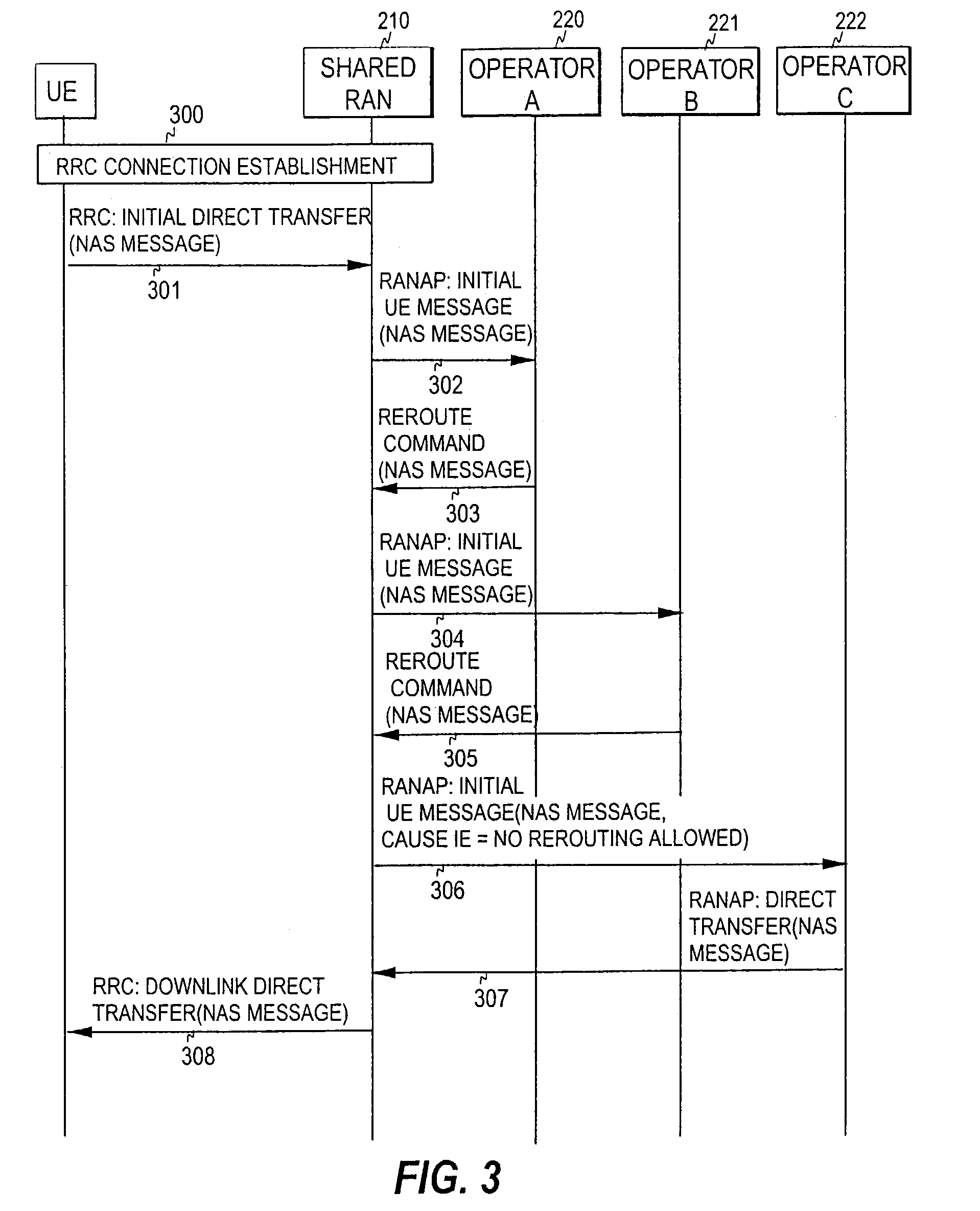
InactiveUS7415274B2Avoid registrationAssess restrictionConnection managementCore networkControl manner
A mechanism for performing routing in a communication system including a radio access network and a plurality of core networks connected to the radio access network. In order to accomplish a mechanism whereby the routing of a registration request to a serving core network, and also the rejection of a registration request, can be carried out in a controlled manner, a core network is first selected for a registration request received. The registration request is then forwarded to the selected core network and, in response to at least one predetermined criterion being fulfilled, the selected core network is notified that the registration request is to be served by that core network, i.e. that the registration request cannot be rerouted to another core network.
Owner:NOKIA CORP
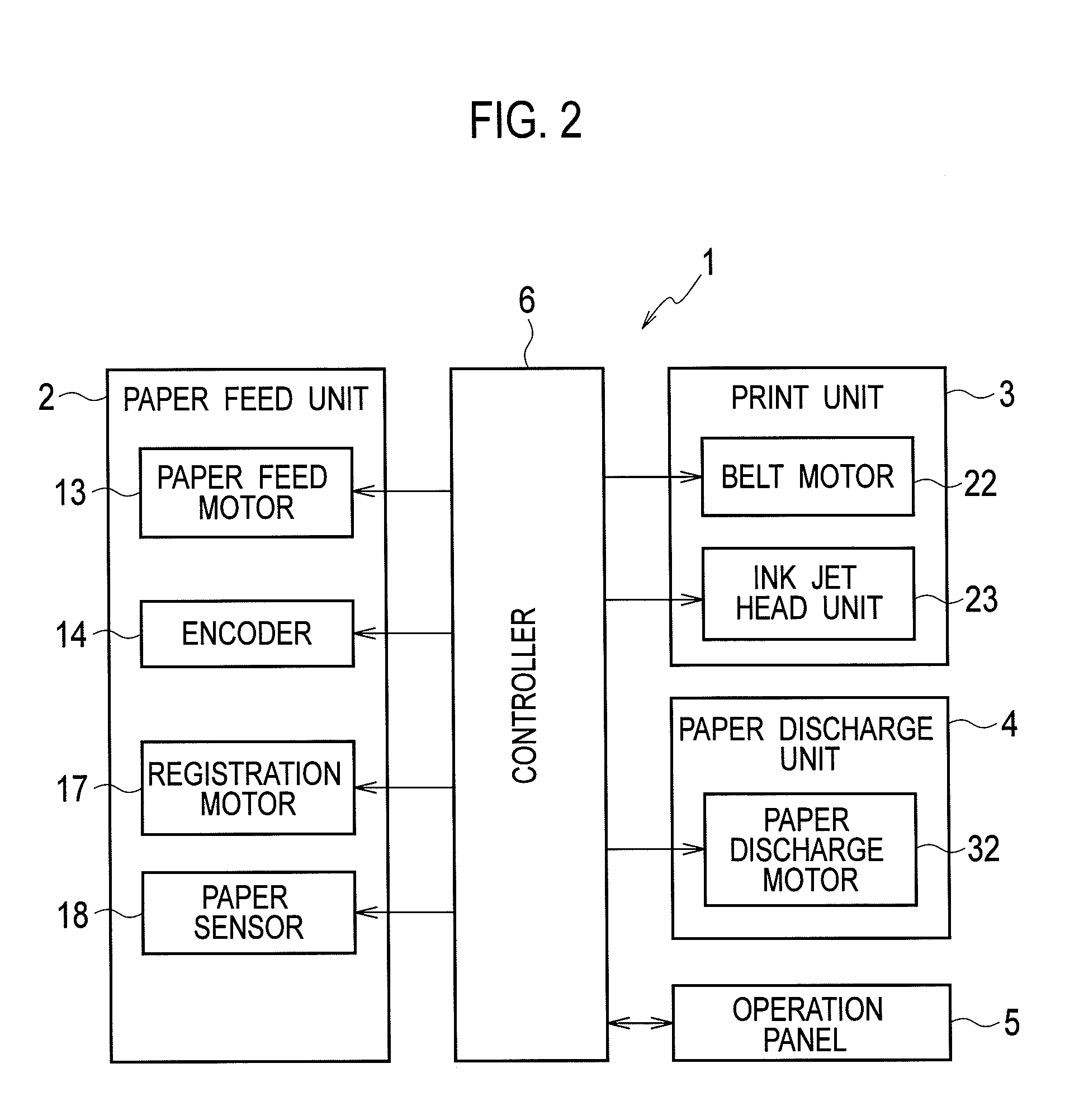
Paper feeder and printer
ActiveUS20140232055A1Avoid registrationReduce conveying speedRegistering devicesFunction indicatorsComputer printingPulp and paper industry
Upon continuous feeding of a plurality of sheets and upon detection of a leading end of a sheet by a detection unit before an elapse of a first time after a start of a paper feed roller, a controller performs control such that a paper conveyance speed of the paper feed roller is set lower than a paper conveyance speed of a registration roller, and the paper feed roller is stopped after conveying the sheet having the leading end detected for a specified conveyance distance before a next timing of starting the registration roller.
Owner:RISO KAGAKU CORP
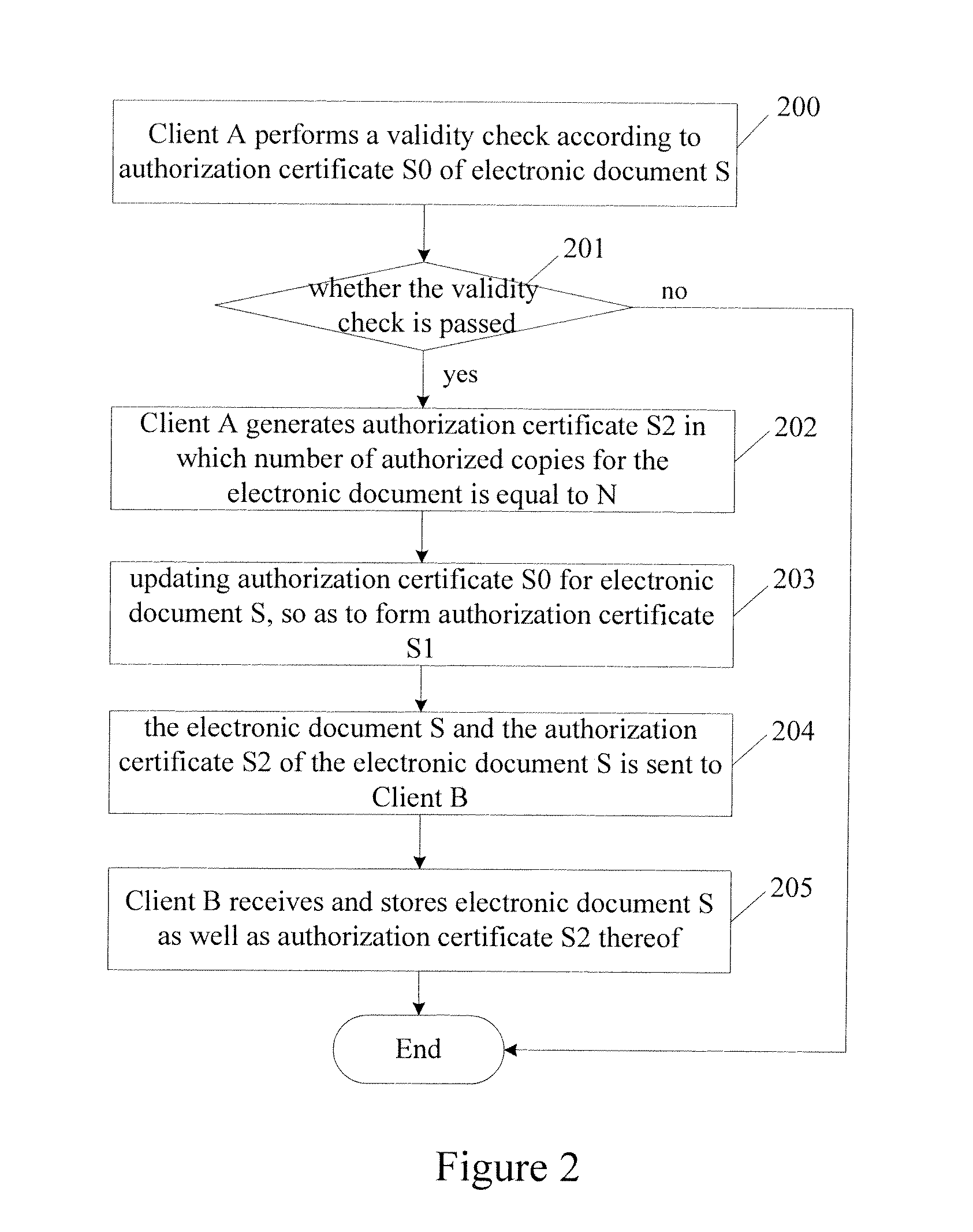
Method and device for distributing electronic documents
InactiveUS20100146640A1Reduce in quantityProcess safetyDigital data processing detailsUnstructured textual data retrievalElectronic documentDocumentation
Embodiments provide a method and device for distributing an electronic document. The electronic document possesses first authorized copies information used to record a first number of authorized copies for the electronic document a local user may distribute. Every time the electronic document is distributed to a user, second authorized copies information is sent to the user, which second authorized copies information is used to record a second number of authorized copies for the electronic document the user may distribute, and the second number of authorized copies is less than or equal to the first number of authorized copies currently recorded in the first authorized copies information.
Owner:SURSEN
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com