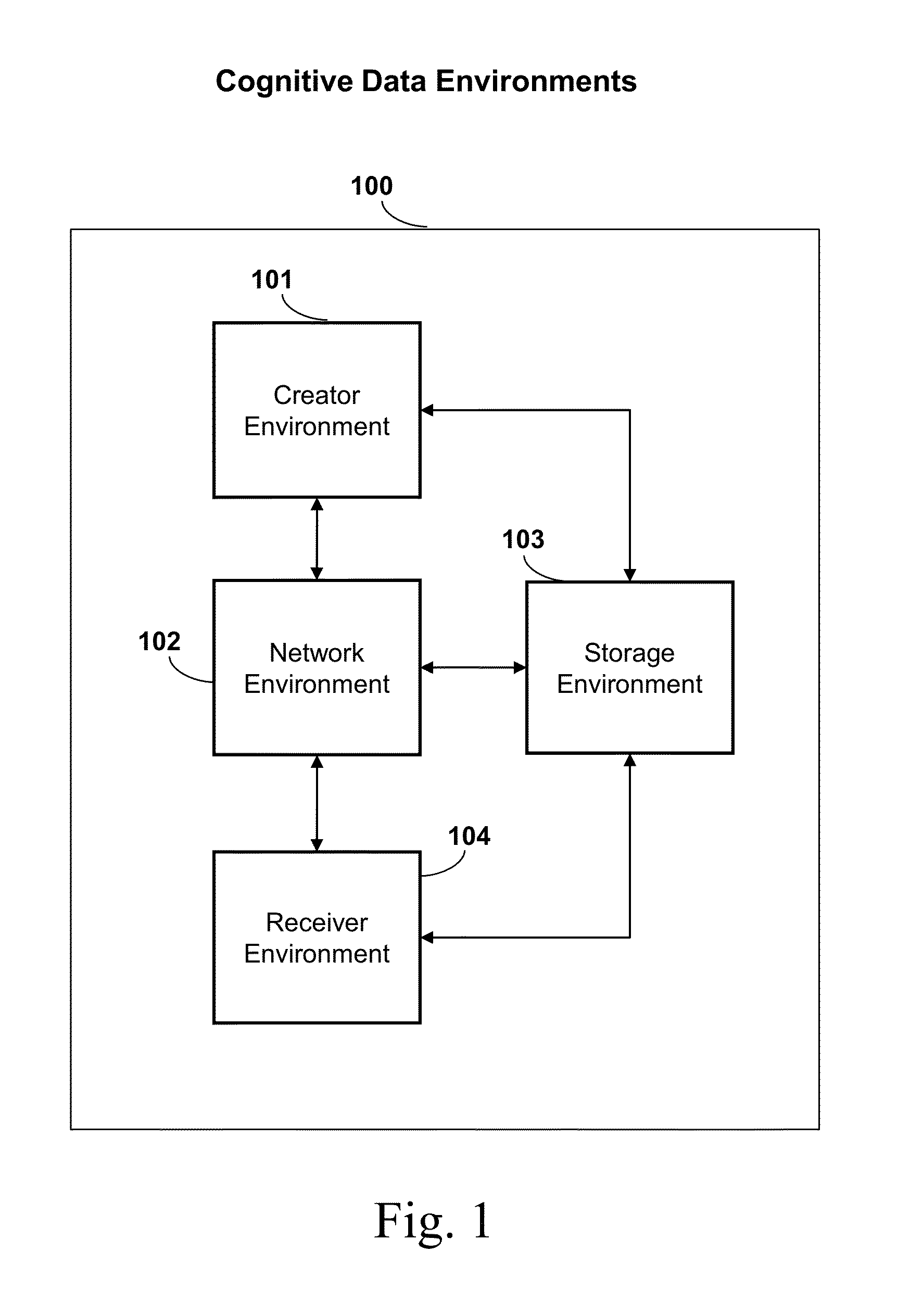
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
186 results about "Keyfile" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
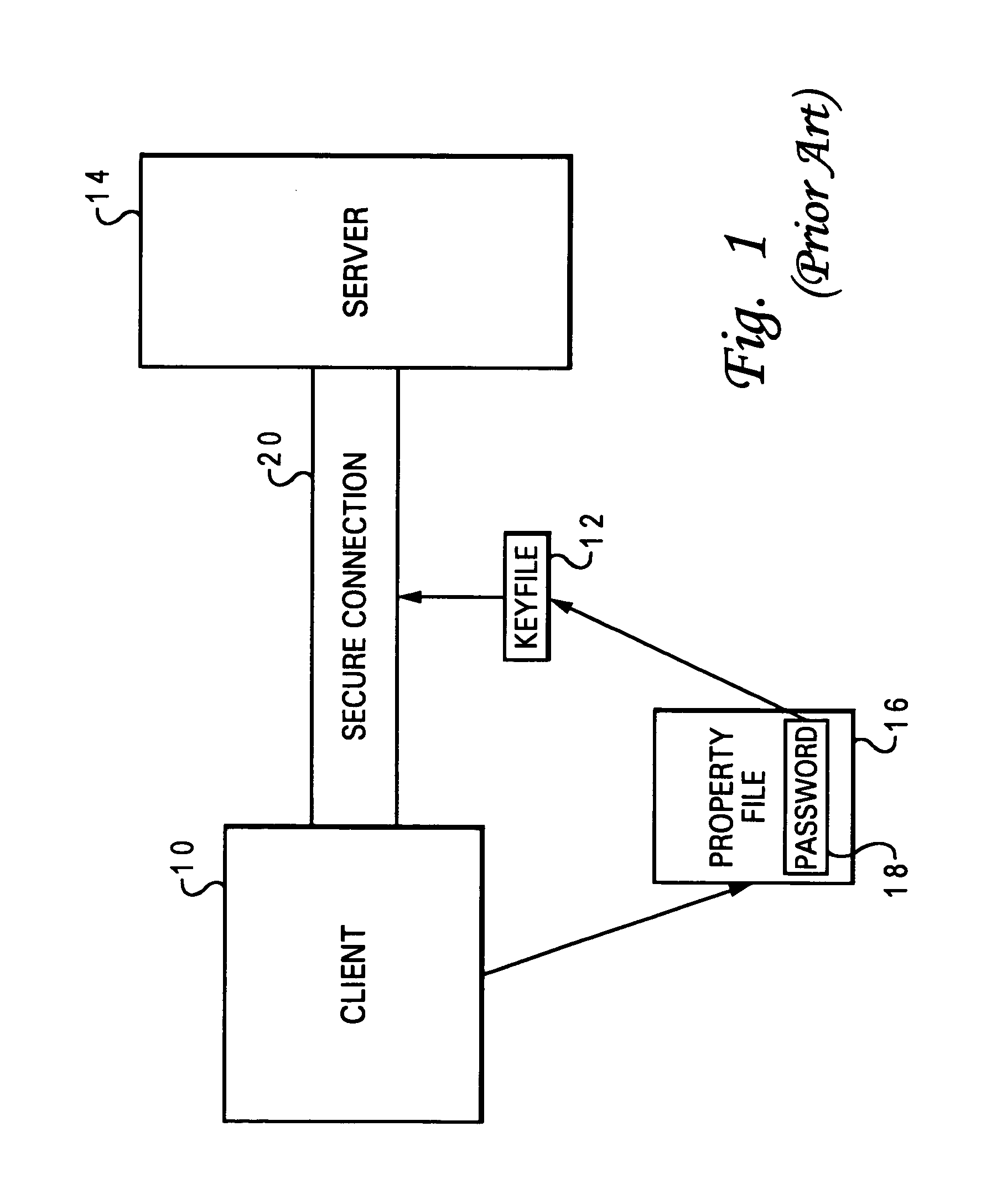
A keyfile (or key-file) is a file on a computer which contains encryption or license keys. A common use is web server software running secure socket layer (SSL) protocols. Server-specific keys issued by trusted authorities are merged into the keyfile along with the trusted root certificates. By this method keys can be updated without recompiling software or rebooting the server.
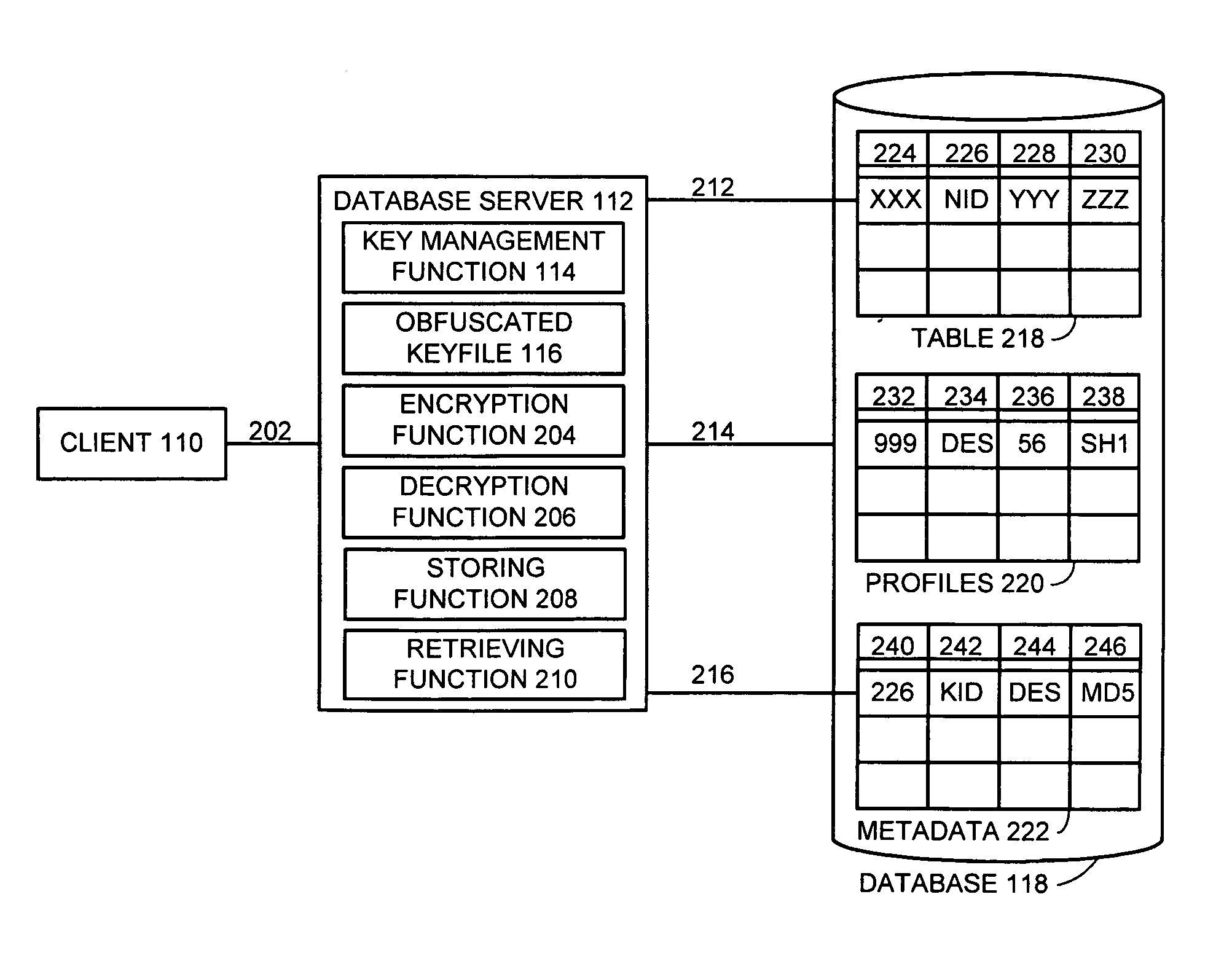
Method and apparatus for automatic database encryption
InactiveUS7111005B1Data processing applicationsMultiple keys/algorithms usageEncrypted functionDatabase encryption
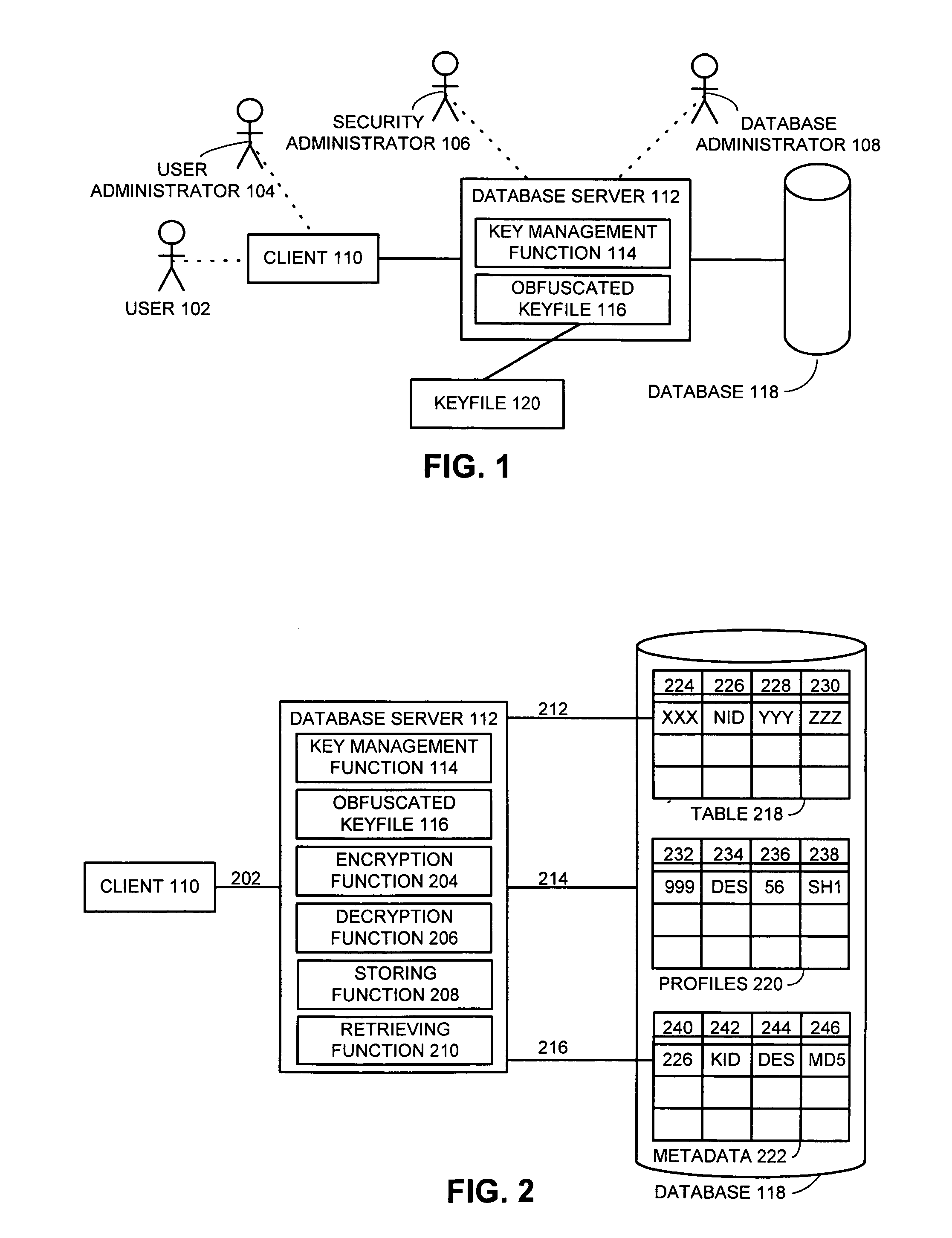
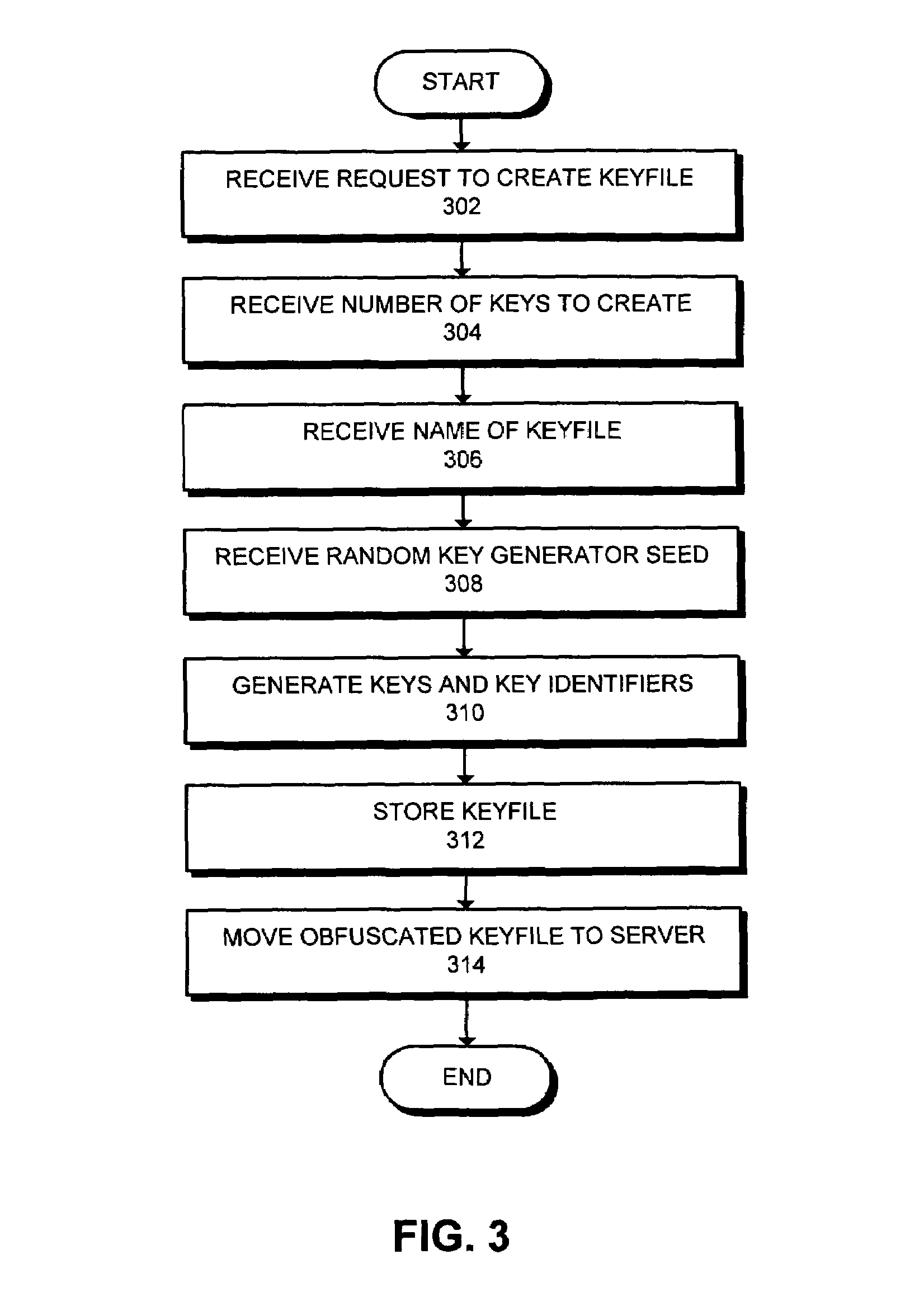
One embodiment of the present invention provides a system for managing encryption within a database system that is managed by a database administrator, and wherein a user administrator not otherwise associated with the database system, manages users of the database system. This system performs encryption automatically and transparently to a user of the database system. The system operates by receiving a request to store data in a column of the database system. If a user has designated the column as an encrypted column, the system automatically encrypts the data using an encryption function. This encryption function uses a key stored in a keyfile managed by the security administrator. After encrypting the data, the system stores the data in the database system using a storage function of the database system.
Owner:ORACLE INT CORP
Distributed cryptographic management for computer systems
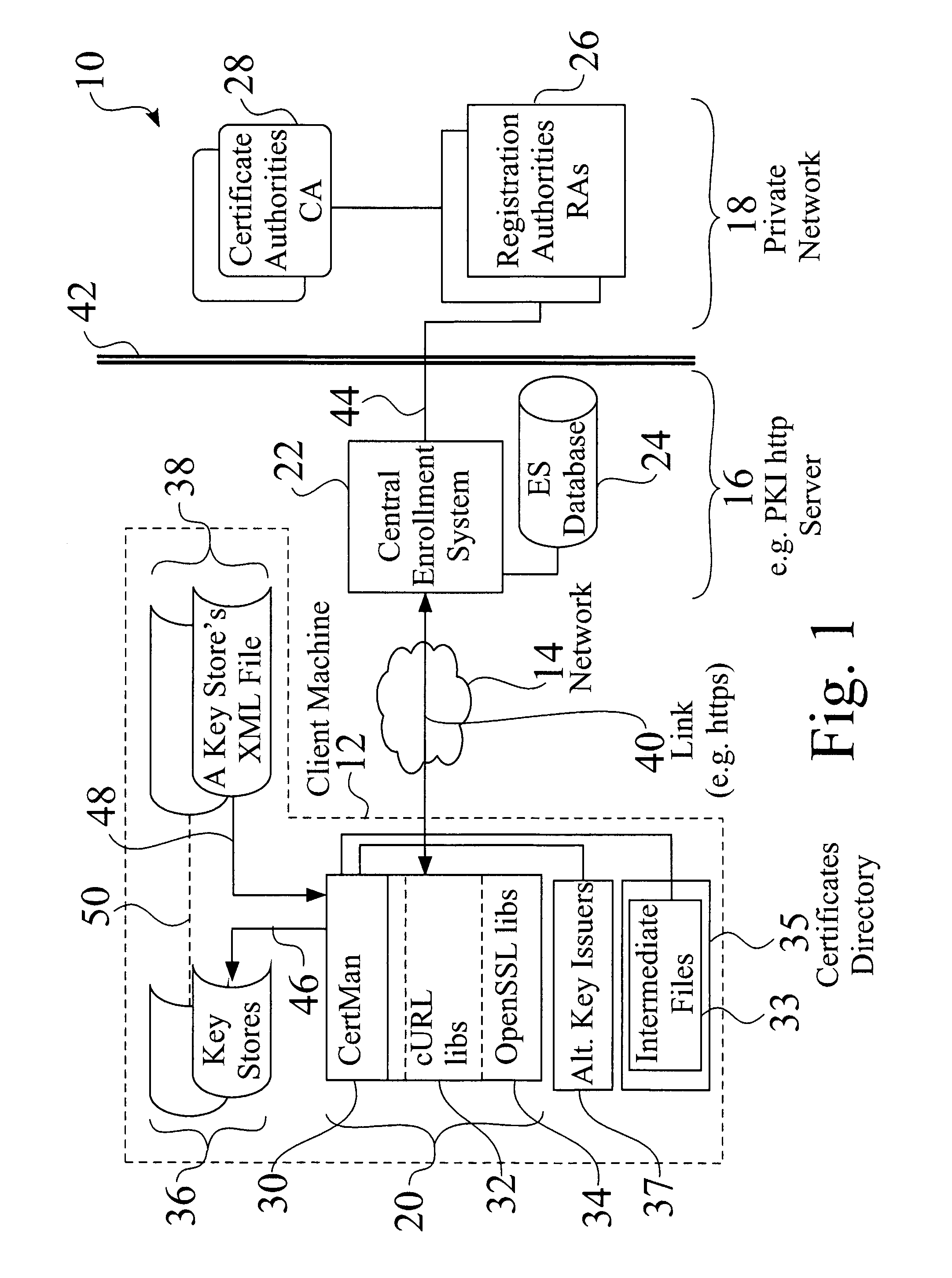
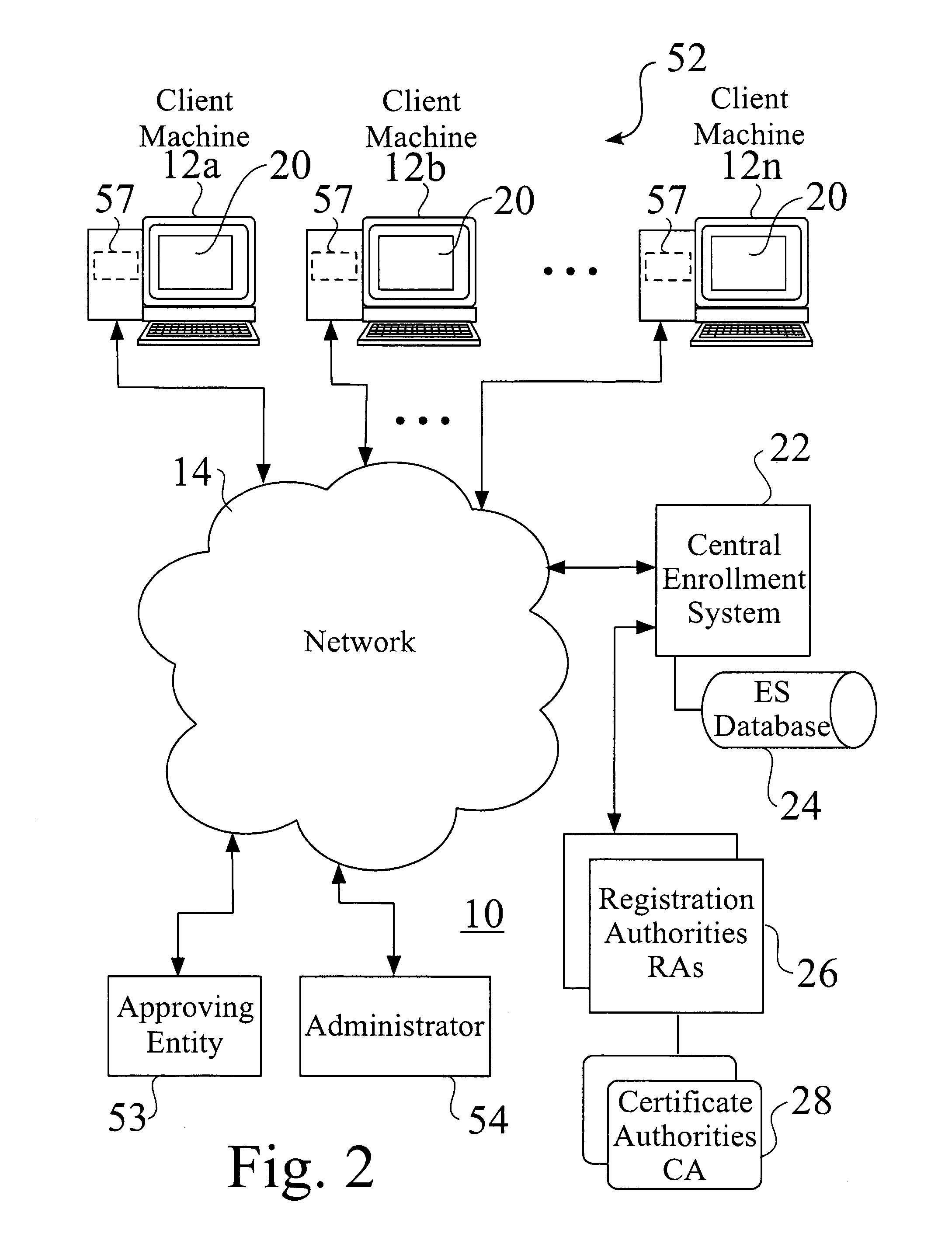
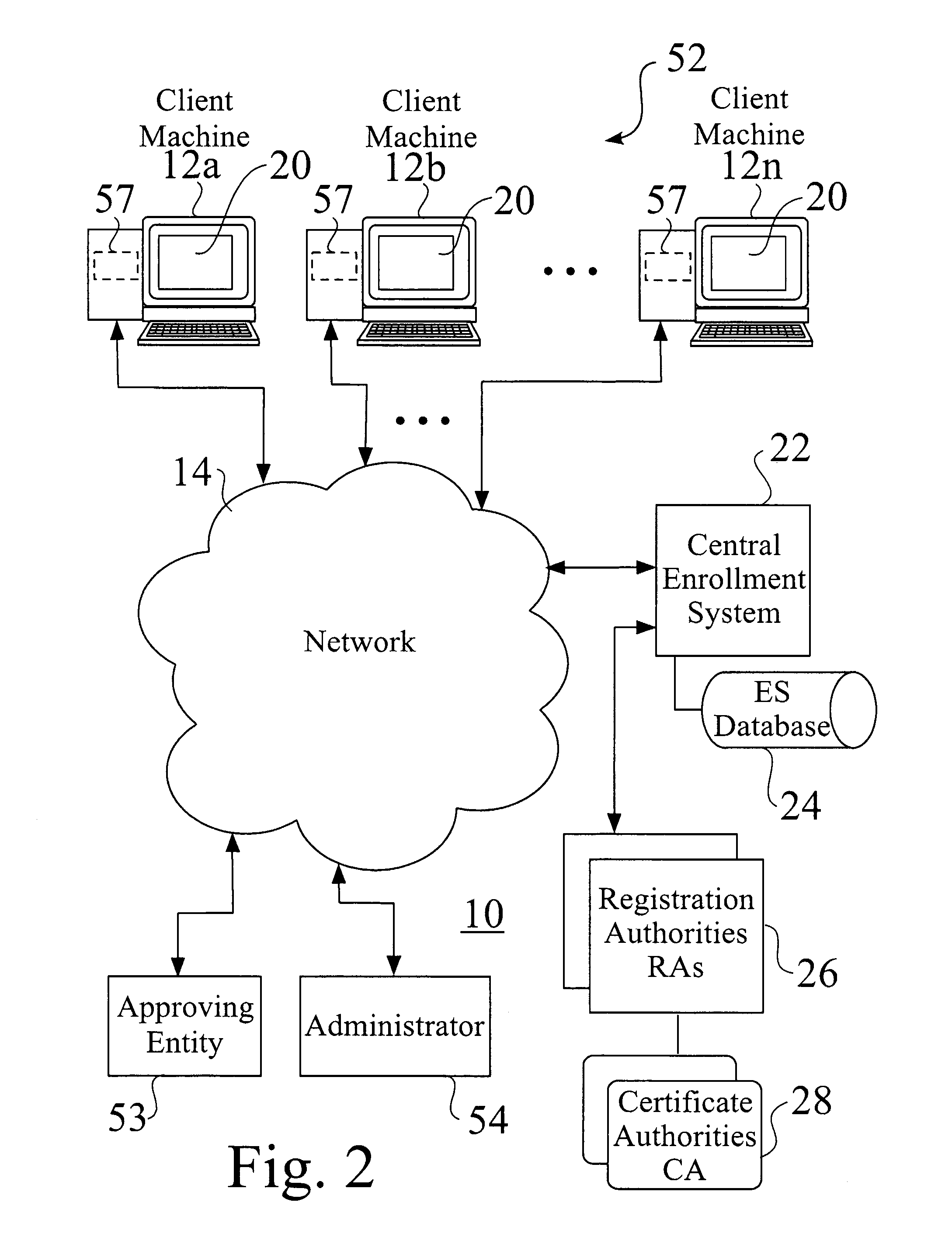
ActiveUS20060236096A1Key distribution for secure communicationUser identity/authority verificationSupporting systemComputerized system
An administrator installs a key management agent on a previously approved client machine. The agent is started on the client machine, which posts requests for keys to a central key management service. The central key management service logs requests posted to it by clients, and checks for existing pre-approval records. If none are found, a message is typically sent to an approver for the requesting client machine. When a request is verified as approved, the request is flagged for further processing. The supported systems continuously or periodically look for records flagged for processing, use requests to generate keys and other appropriate elements for the requesting client machine, and post keys and other elements to the key management database. The key management agent polls the central key management service periodically until finding the expected key file, which it downloads and installs into a protected file location on the client machine. The key management agent periodically sends status messages to the central key management service, which tracks expected behavior of the client machine and / or key management agent.
Owner:WELLS FARGO BANK NA
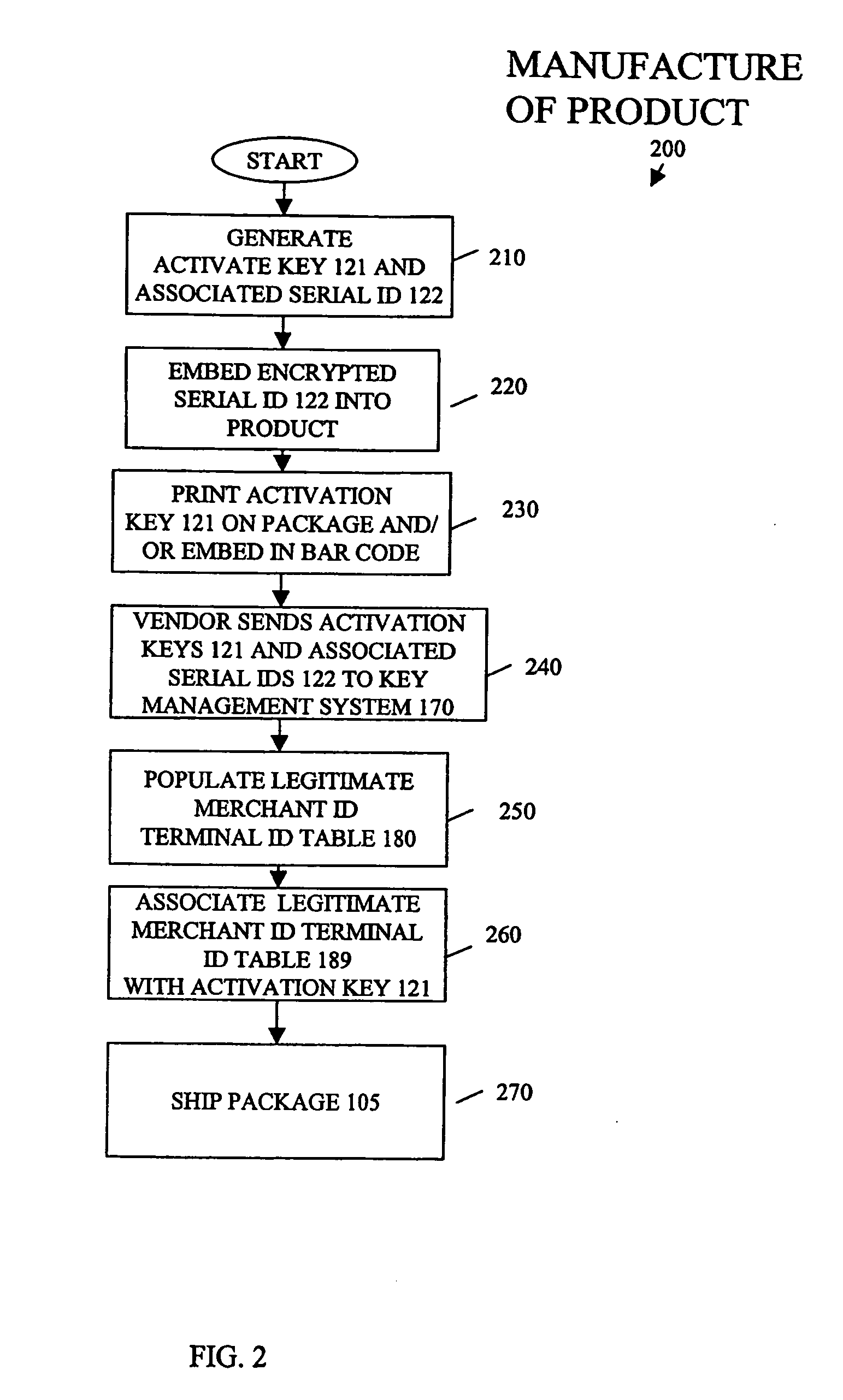
Point of sale product authorization
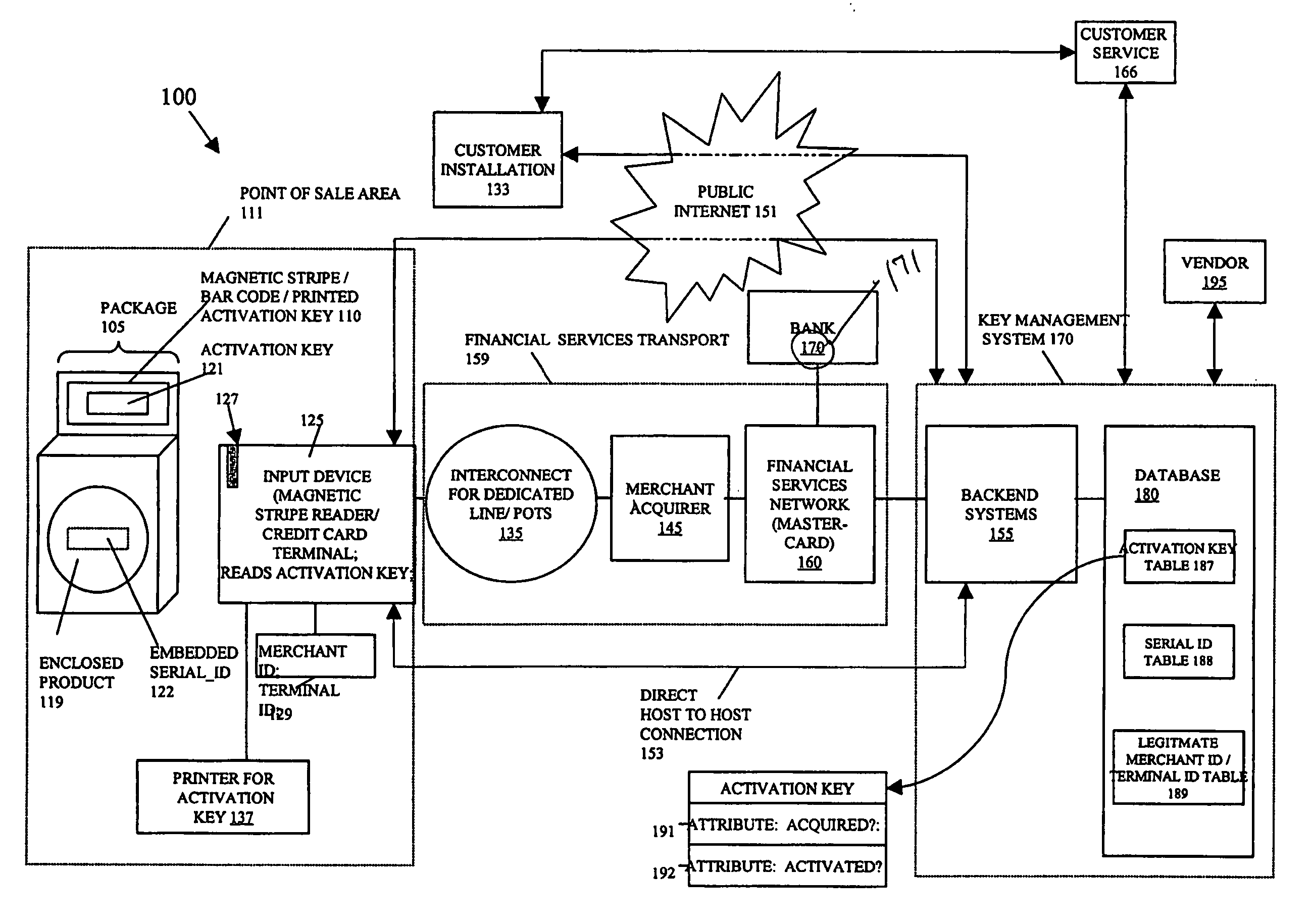
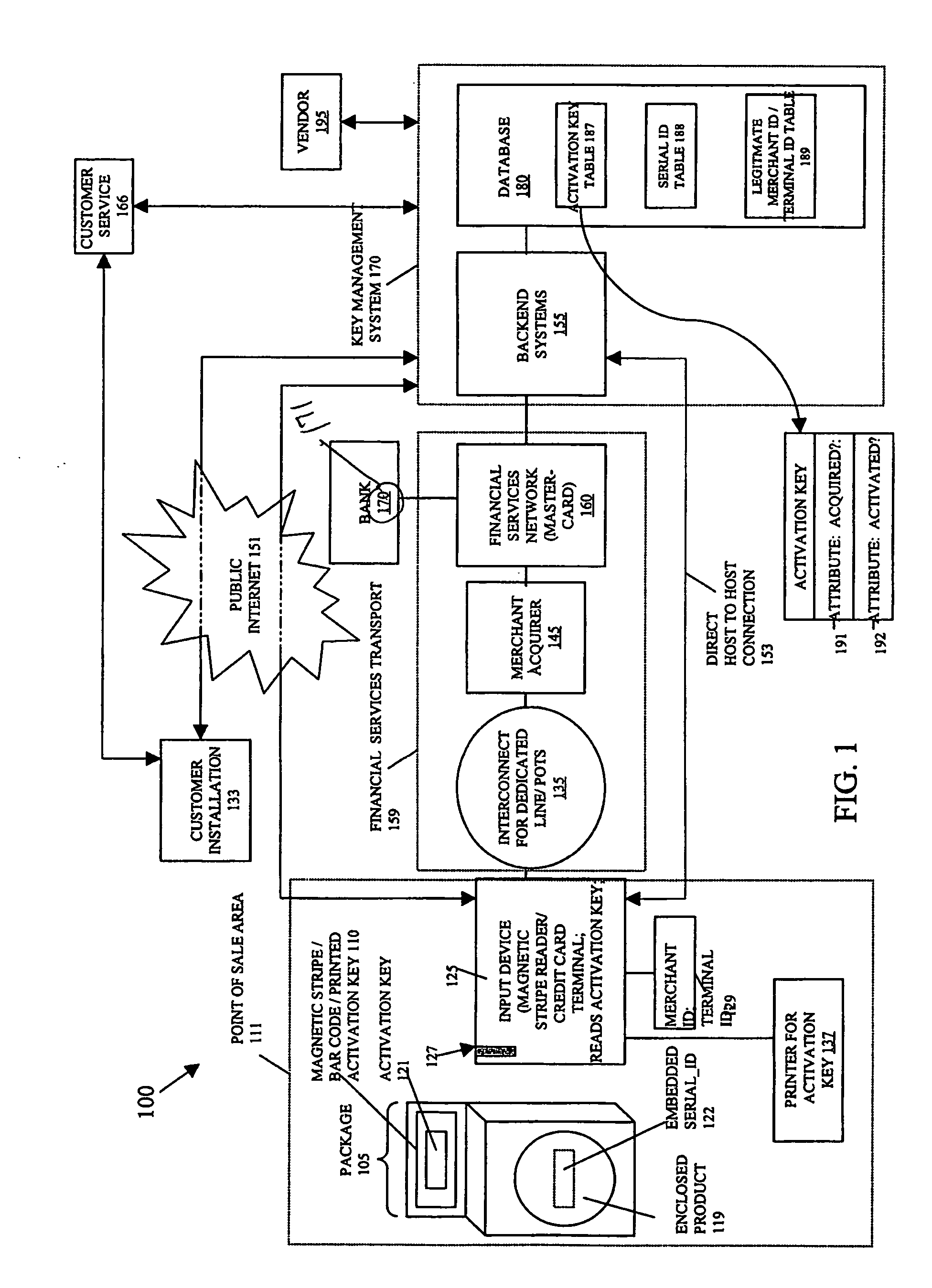
InactiveUS20070043682A1Payment architectureBuying/selling/leasing transactionsProduct baseAuthorization
A method for authorizing a sale of a product, comprising: sending a first key from a point of sale device to a key management system; determining if the first key is found in the key management system; determining whether the first key is associated with a valid merchant identifier and terminal identifier; and authorizing a sale at a point of sale of the product if the first key is found in the key management system and if the first key is associated with a valid merchant identifier and terminal identifier, wherein a purchaser receives a copy of a second key associated with the first key at time of purchase. The system has a Key Management System (KMS) with databases. The system also has a first key file and associated second key(s) file in said databases. The system also has an input device at a retail-outlet terminal that inputs an identifier during a sale at the point of sale, wherein the KMS compares the identifier with the first key file and key attributes to determine if the first key is found and if its associated attributes are favorable. The KMS permits or denies the sale of the product based on these attributes. The KMS subsequently permits or denies the installation of the product on target devices based on vendor rules and product attributes.
Owner:IDT CORPORATION
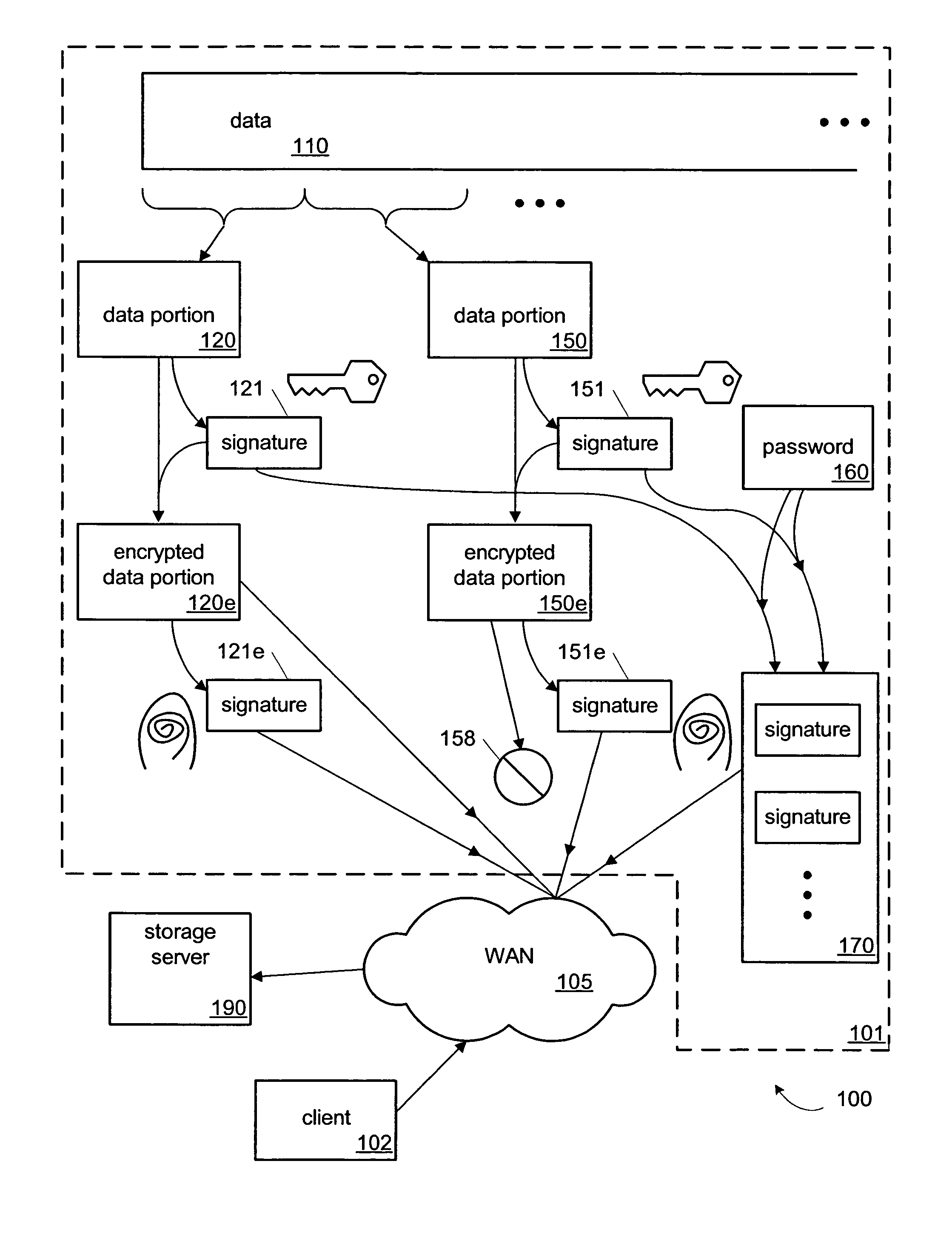
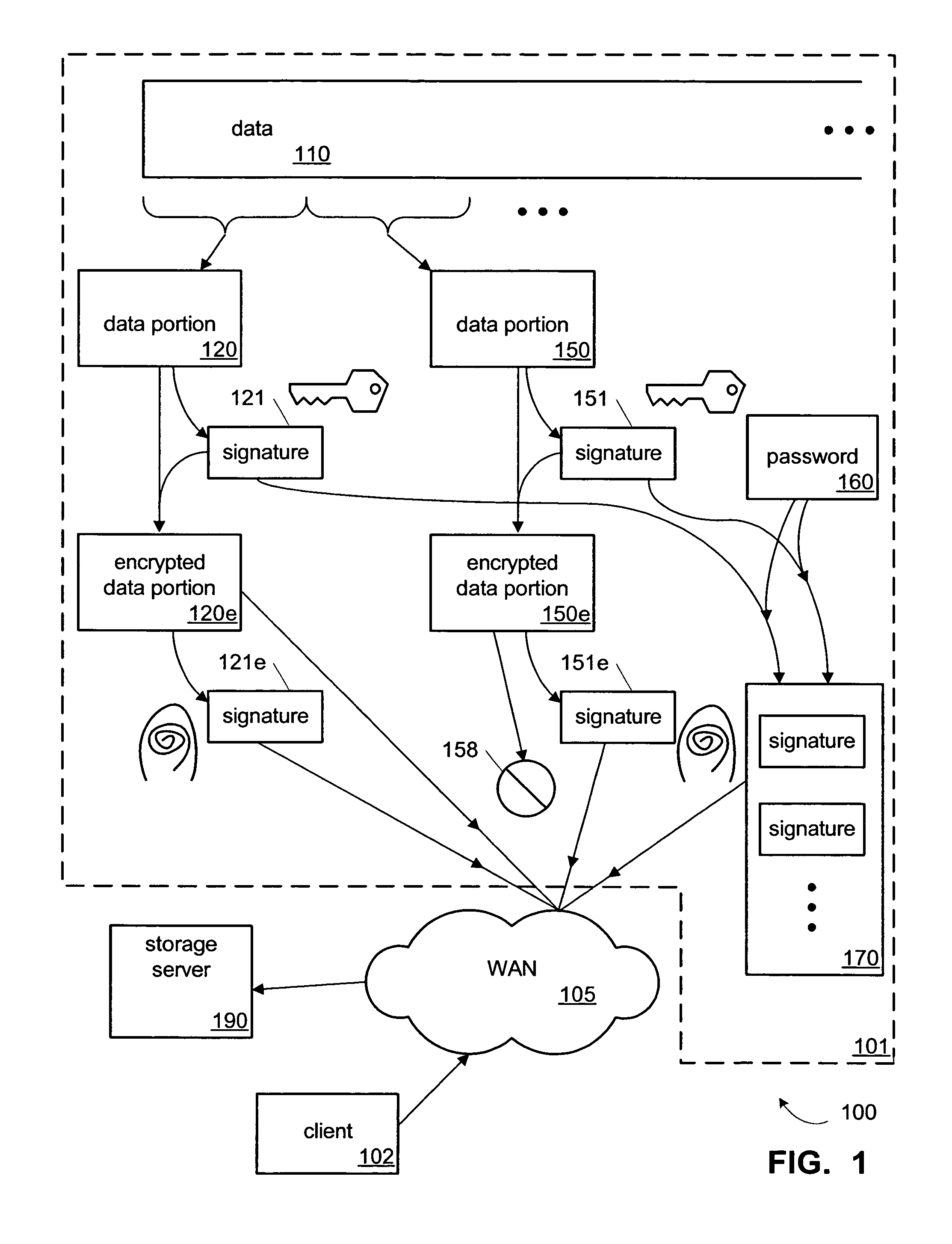
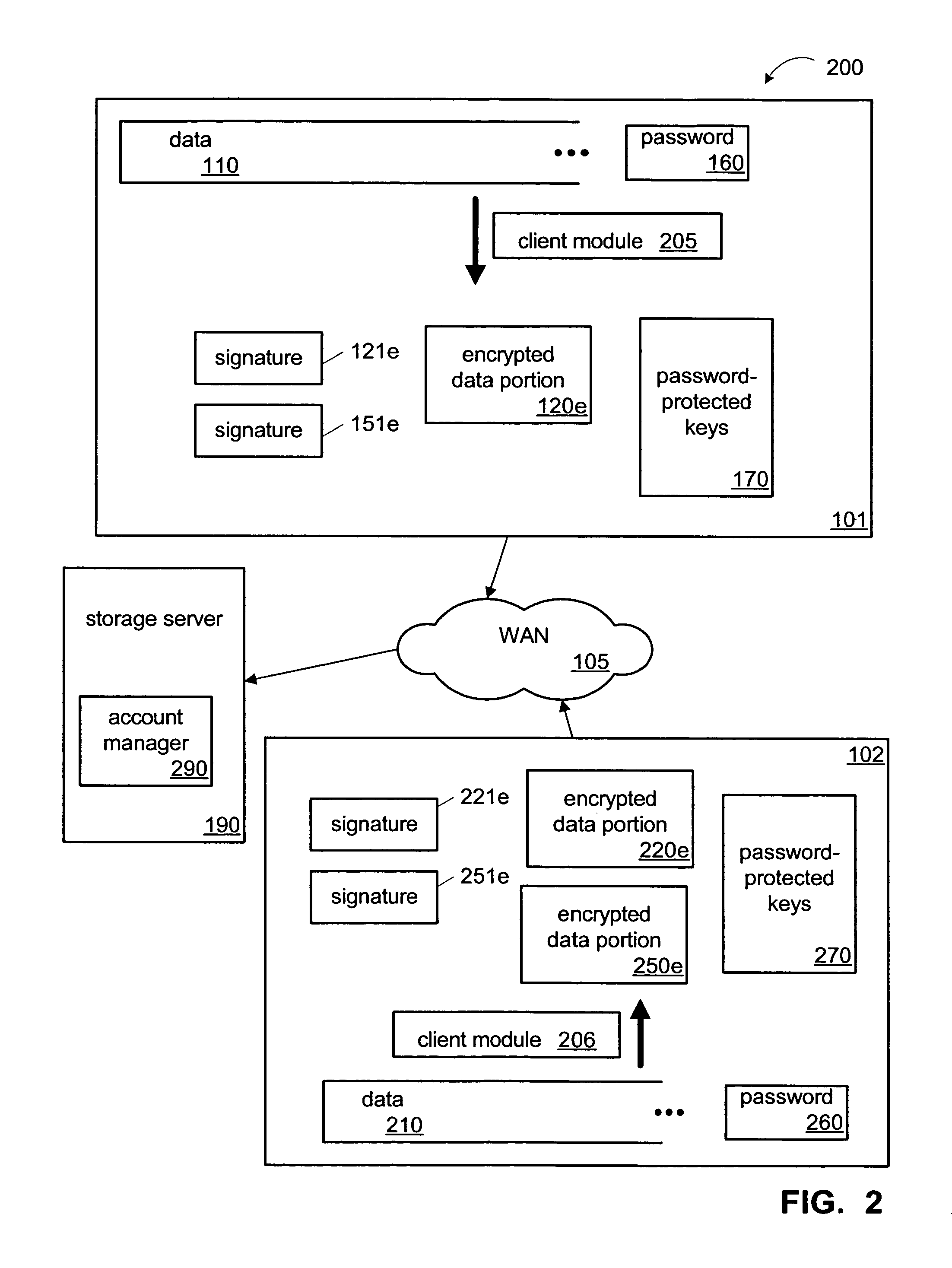
Backup service and appliance with single-instance storage of encrypted data
ActiveUS8041641B1Prevent unauthorized accessAccess is deniedError detection/correctionDigital data processing detailsPasswordClient-side
One implementation of a method for providing backup storage services for encrypted data includes receiving signatures of convergently encrypted portions of data from client computers, determining whether the encrypted portions are already present on a backup storage, and obtaining only the needed portions. Users unassociated with a particular user account are denied access to information backed up in that account. The backup storage also stores password protected key files holding signatures of the unencrypted portions of data. One implementation of a system includes a memory, a single-instance storage circuit, a user account management circuit, and a signature index. The memory holds a user-account database and backup copies of convergently encrypted portions of data. The single-instance storage circuit uses the signature index to prevent duplicative backup copies. The user account management circuit responds to download requests after authenticating the user information associated with the requested data.
Owner:SYMANTEC OPERATING CORP
System, method and device for dynamically encrypting data based on key library
ActiveCN112929172AImprove securityReduce operation and maintenance costsKey distribution for secure communicationMultiple keys/algorithms usageApplication serverEngineering
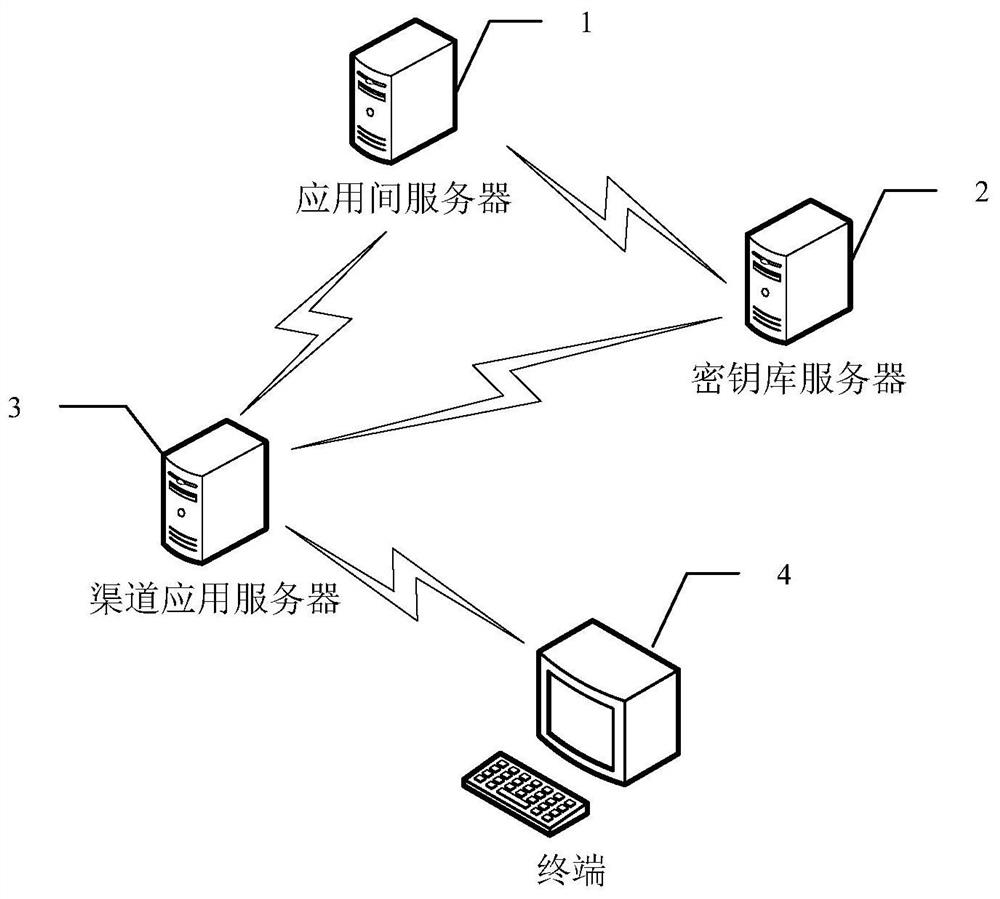
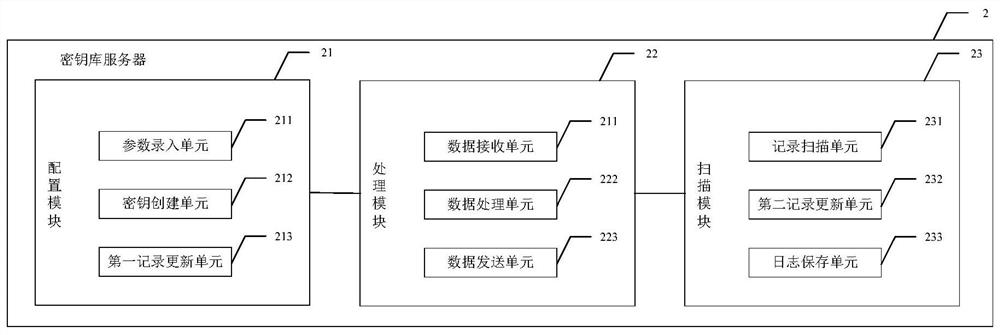
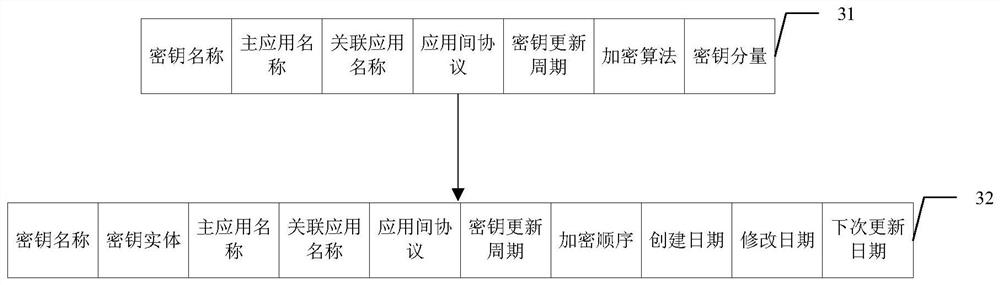
The invention discloses a system, method and device for dynamically encrypting data based on a key library, which can be used in the field of information security, and the system comprises an inter-application server, a key library server, a plurality of channel application servers and terminals interacting with respective channel application servers, wherein the key library server is used for configuring a data encryption rule for data interacting among different channel application servers and data interacting in the same channel application server, and generating a corresponding encryption program and a key file according to the data encryption rule; the inter-application server is used for downloading a corresponding encryption program and the key file from the key library server according to a data processing request of each channel application server, and encrypting or decrypting application data; and the channel application servers are used for downloading the corresponding encryption program and the key file from the key library server according to the data processing request of the terminal, and encrypting or decrypting the application data. According to the invention, the system safety can be improved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Multiple secure socket layer keyfiles for client login support
InactiveUS7139918B2Digital data processing detailsUnauthorized memory use protectionGraphicsGraphical user interface
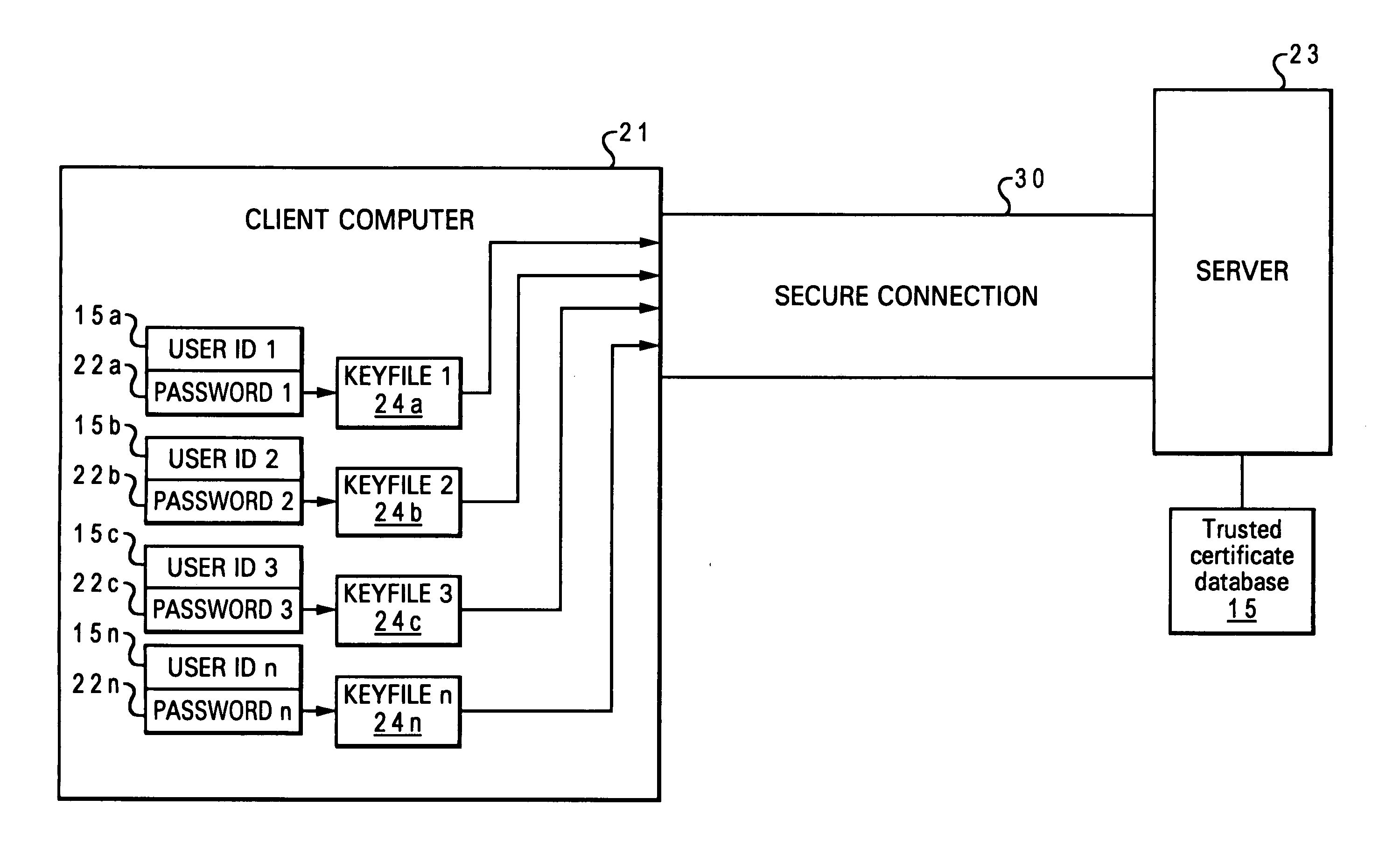
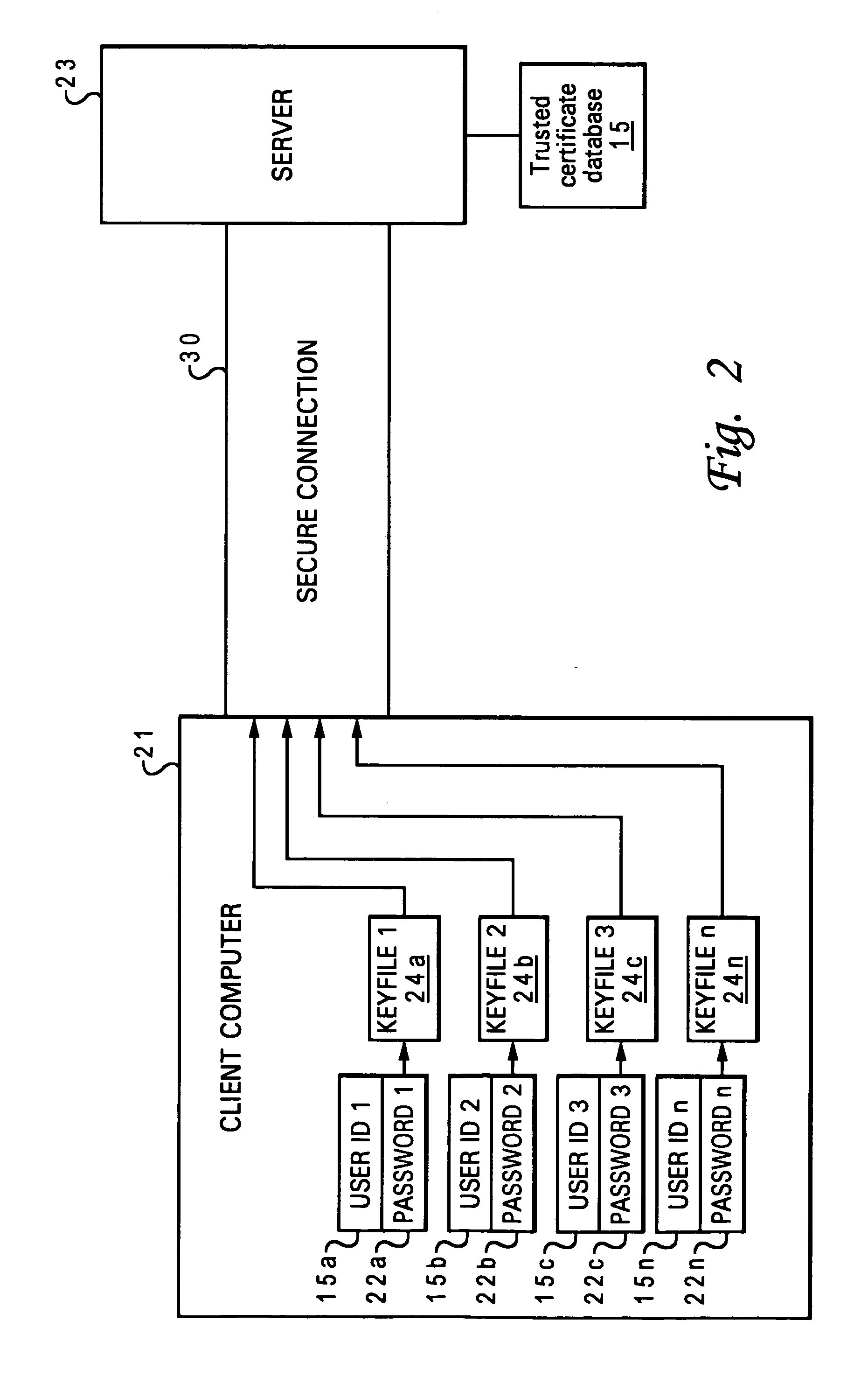
A method and system to allow multiple users of a client computer to establish a secure connection for each of the multiple users between the client computer and a server computer. Each user is allowed to unlock a keyfile unique to that user. The unique keyfile is able to authenticate the user's identity to the server computer. Access to the users unique keyfile is accomplished by the user inputting into the client computer a unique user password for the user's unique keyfile. A Graphical User Interface (GUI) is provided to allow the user to input the unique user password for that user's unique keyfile. Upon input of the password, the selected keyfile is opened to enable a user authentication process to authenticate the user's identity to the server computer, thus creating an authenticated secure connection between the server computer and the client computer for the specific user.
Owner:IBM CORP
Block chain key hierarchical management method
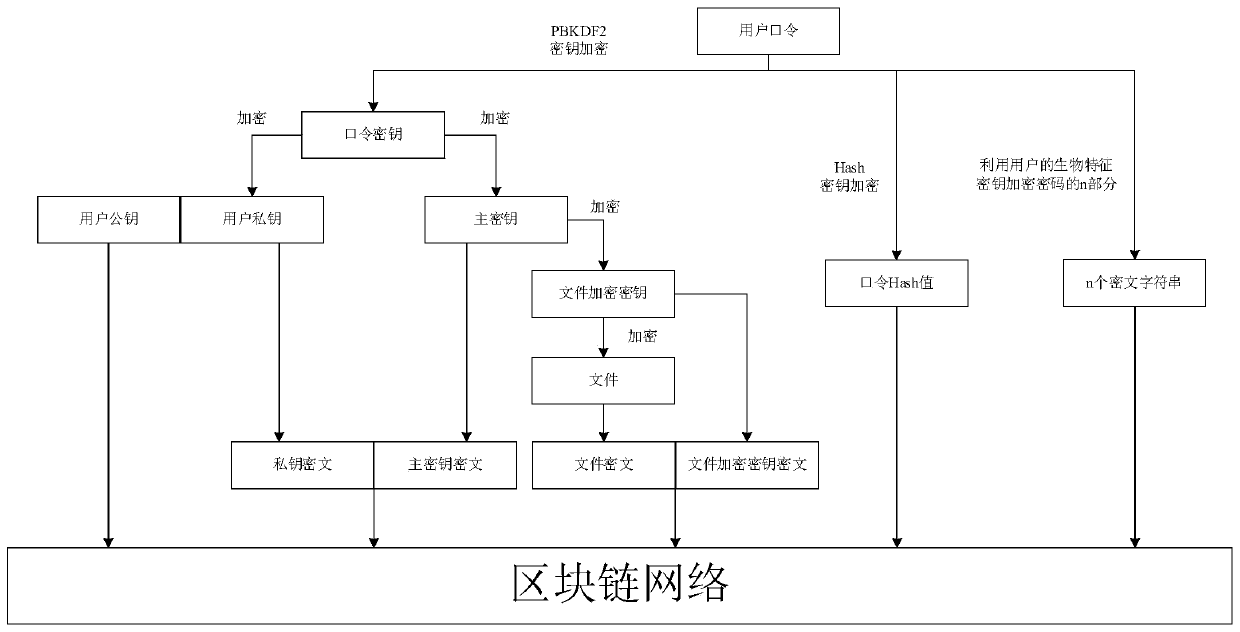
ActiveCN110300112AImprove management efficiencyEnsure safetyKey distribution for secure communicationPublic key for secure communicationCiphertextPassword
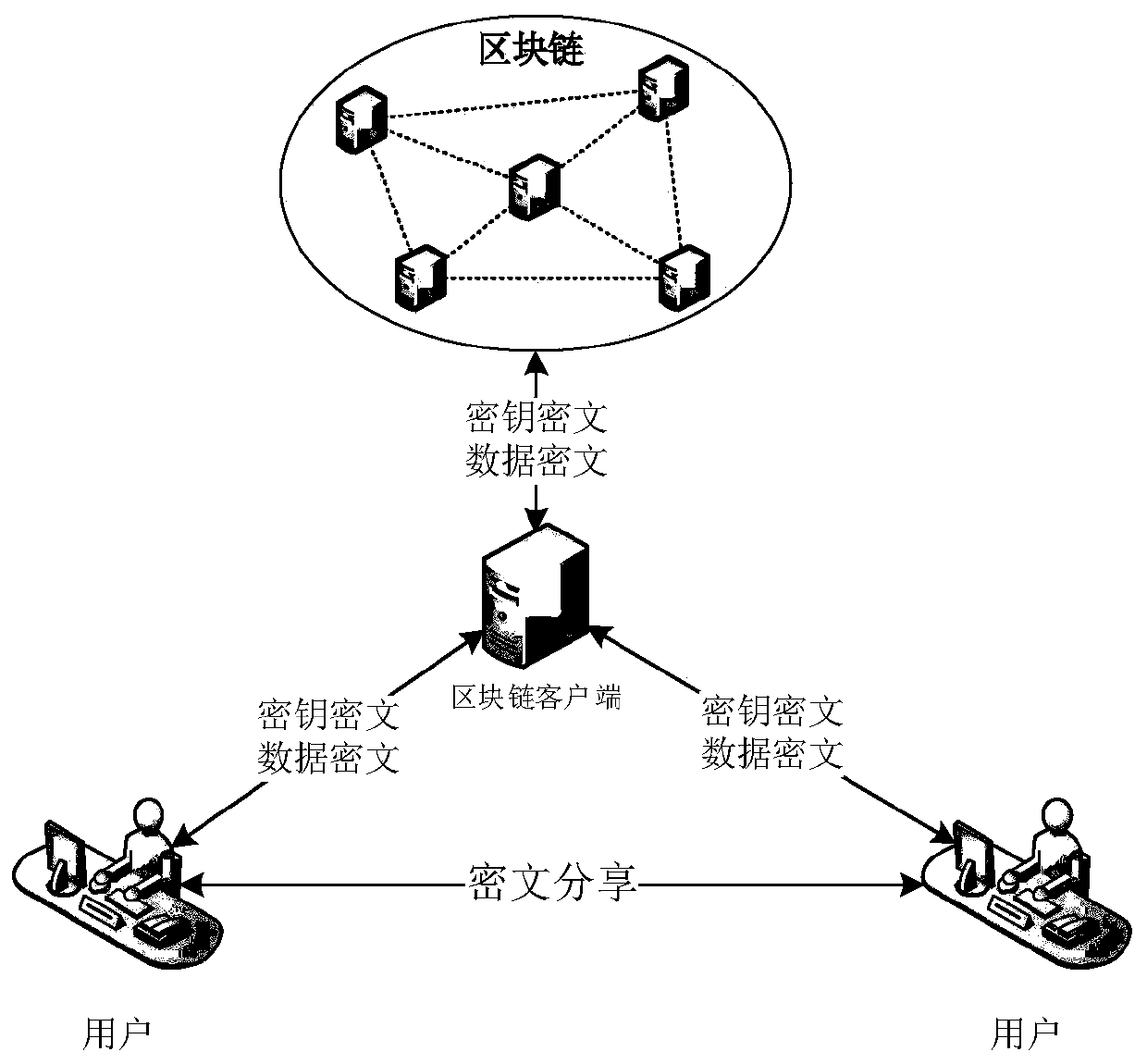
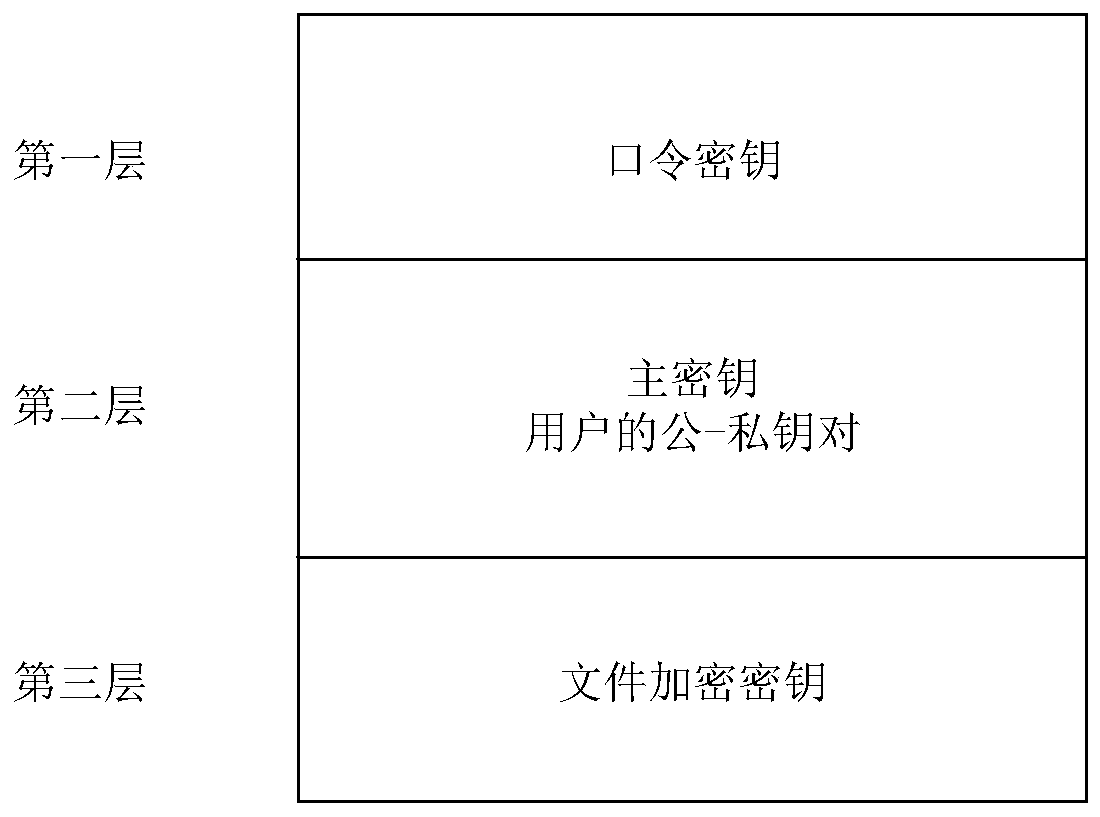
The invention discloses a block chain key hierarchical management method, and relates to the technical field of data encryption management methods. The method comprises the following steps: initializing a user password, a login certificate, a password secret key, a main secret key and a main secret key ciphertext in a block chain system; generating a user private key, a user public key, a key fileand a user private key ciphertext; performing hierarchical management on the file encryption key, the file, the file ciphertext, the file encryption key ciphertext and the uploaded file; sharing corresponding files, and completing block chain key hierarchical management. According to the method, the key management efficiency can be improved, and the security of all keys is ensured. Meanwhile, anattacker cannot tamper the secret key, and the probability that the secret key is illegally stolen is low. In the transmission and storage process, even if the secret key is embezzled by an attacker,the attacker cannot obtain valuable information.
Owner:峰杰技术有限公司
Anti-virus method based on security chip
ActiveUS20090144582A1Operational securityOvercome defectsMemory loss protectionUnauthorized memory use protectionAnti virusOperational system
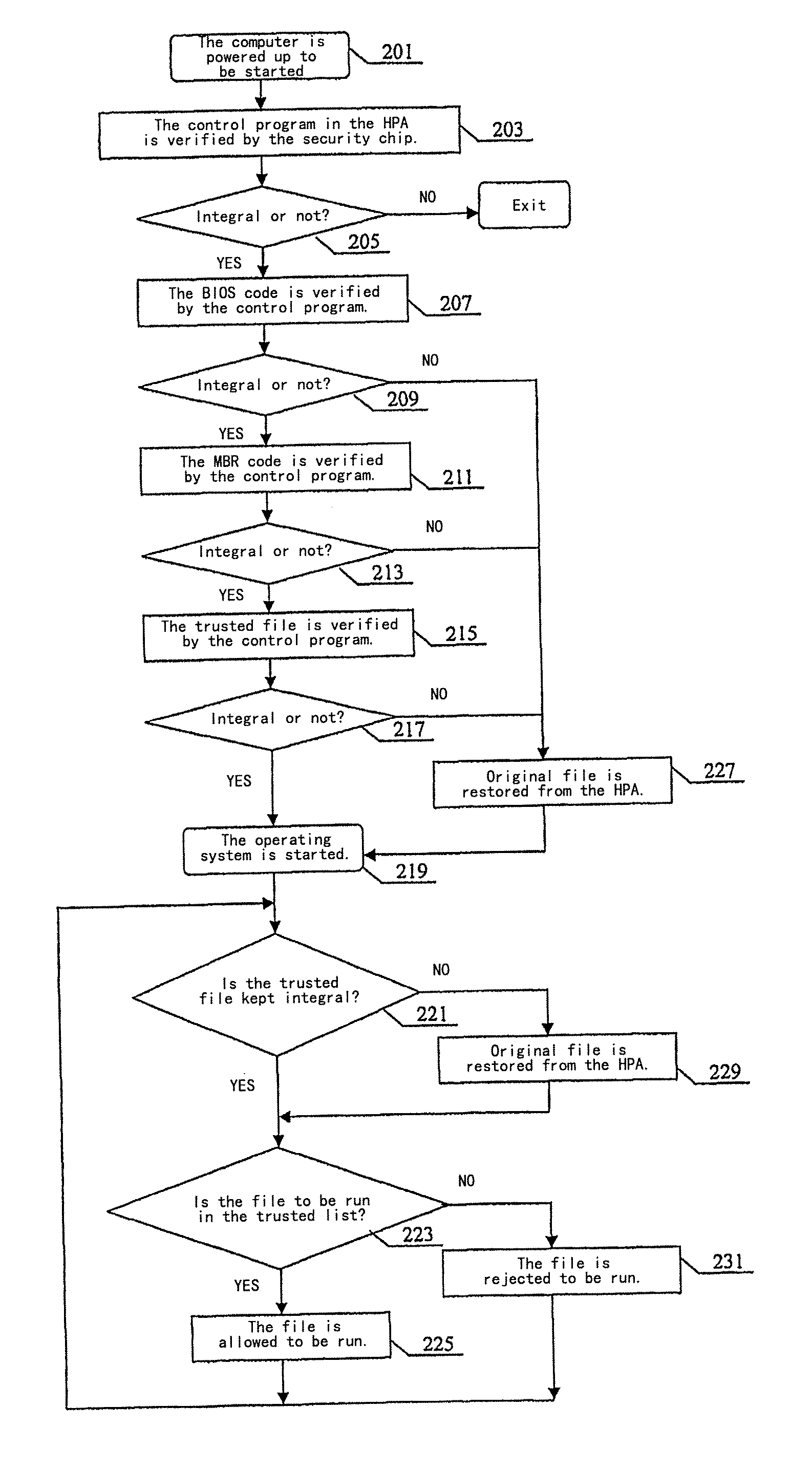
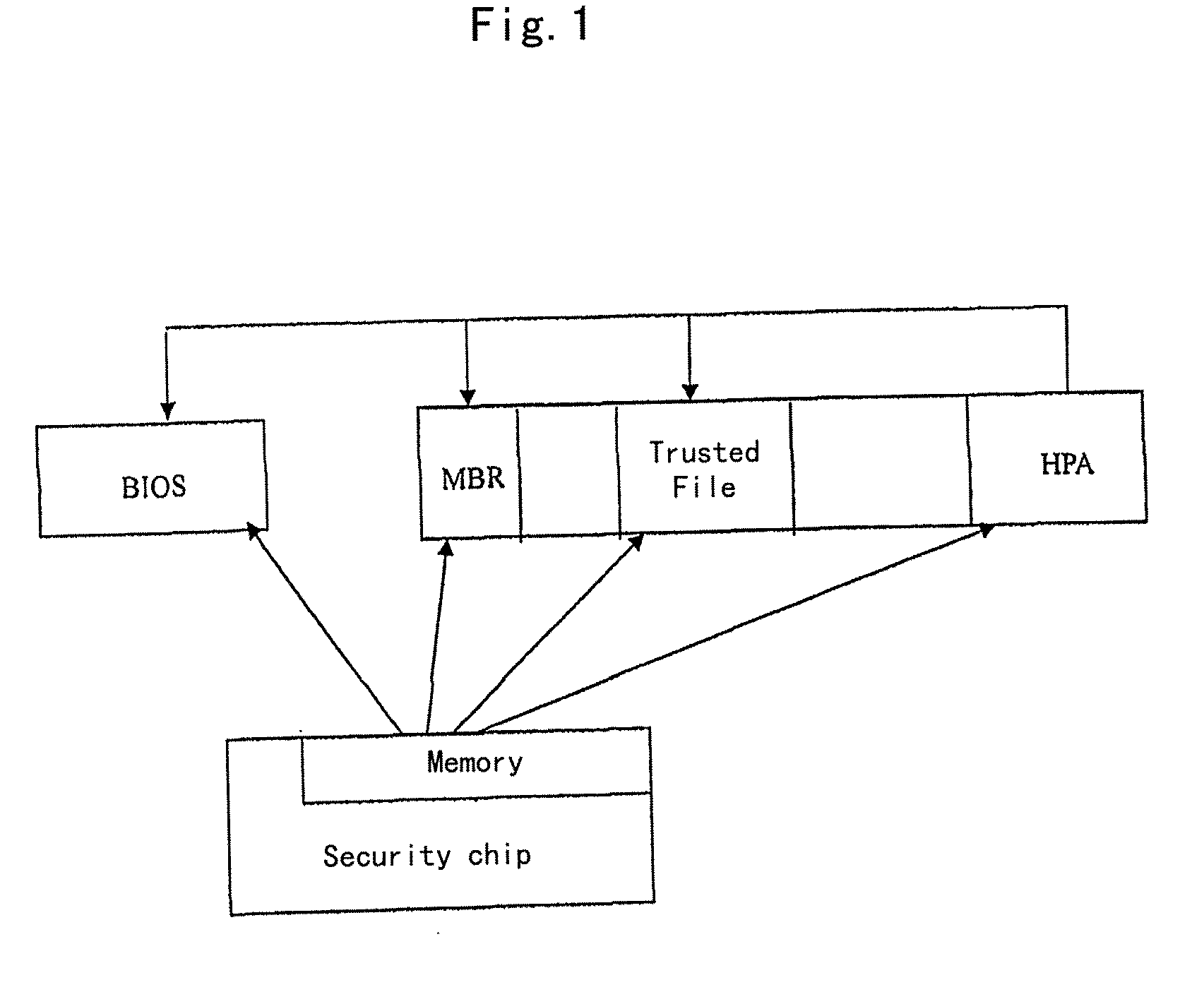
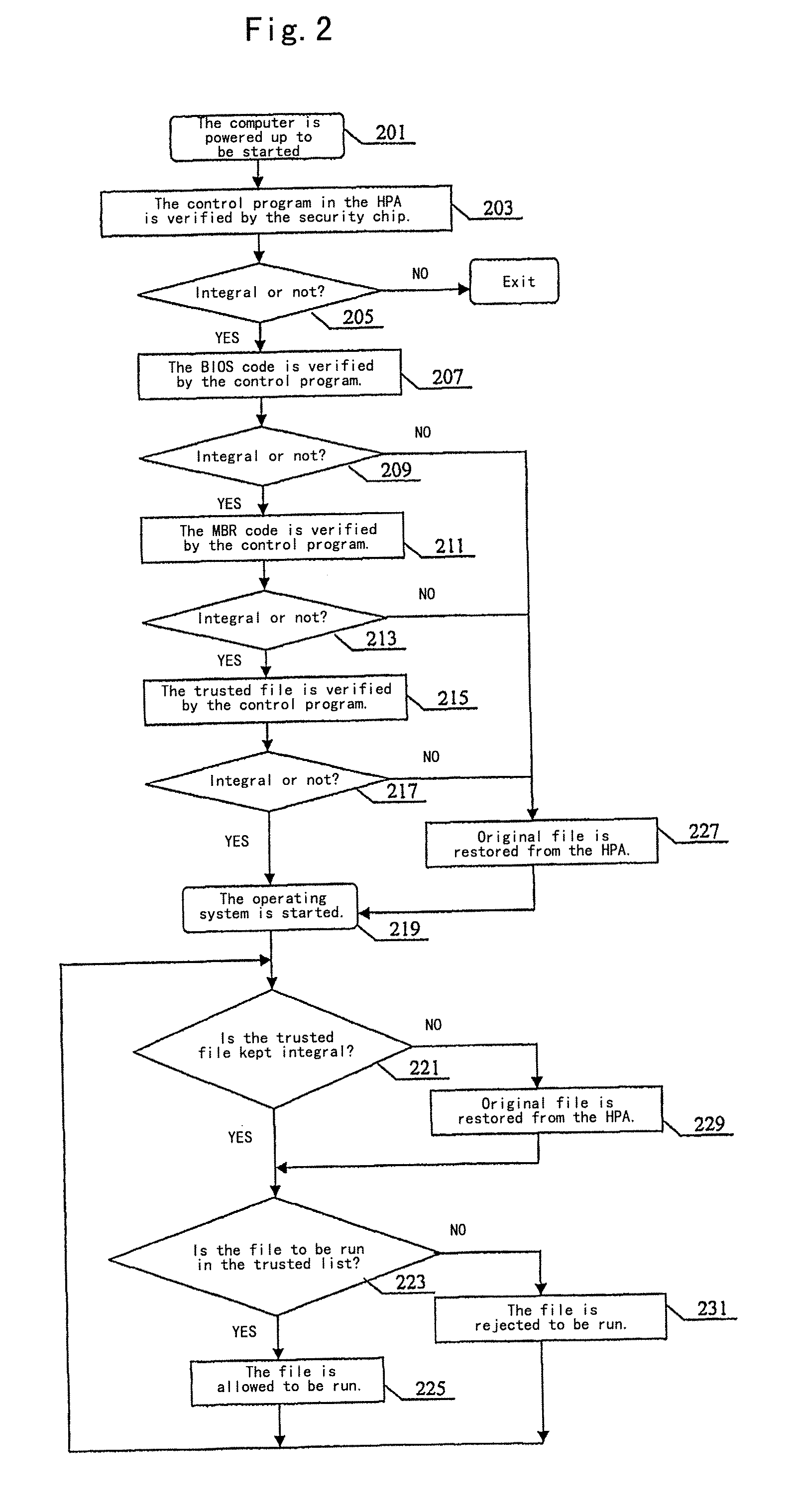
An anti-virus method based on a security chip according to the present invention is provided. The method comprises the following steps: a hash value obtained by a hashing operation for a computer key file and a system control program are stored in a memory of the security chip, and a backup file of the computer key file is stored in a backup storage area. When power up, the integrity of the system control program is verified by using the hash value of the system control program stored in the memory of the security chip. If the system control program is integral, a control is executed by the system control program, and the system control program verifies the integrity of the computer key file using the hash value of the computer key file stored in the memory of the security chip. If all the computer key files are integral, the operating system is started; on the contrary, if any of the computer key file is not integral, it will be restored using the backup file of the computer key file stored in the backup storage area.
Owner:LENOVO (BEIJING) CO LTD
File system atomic lock
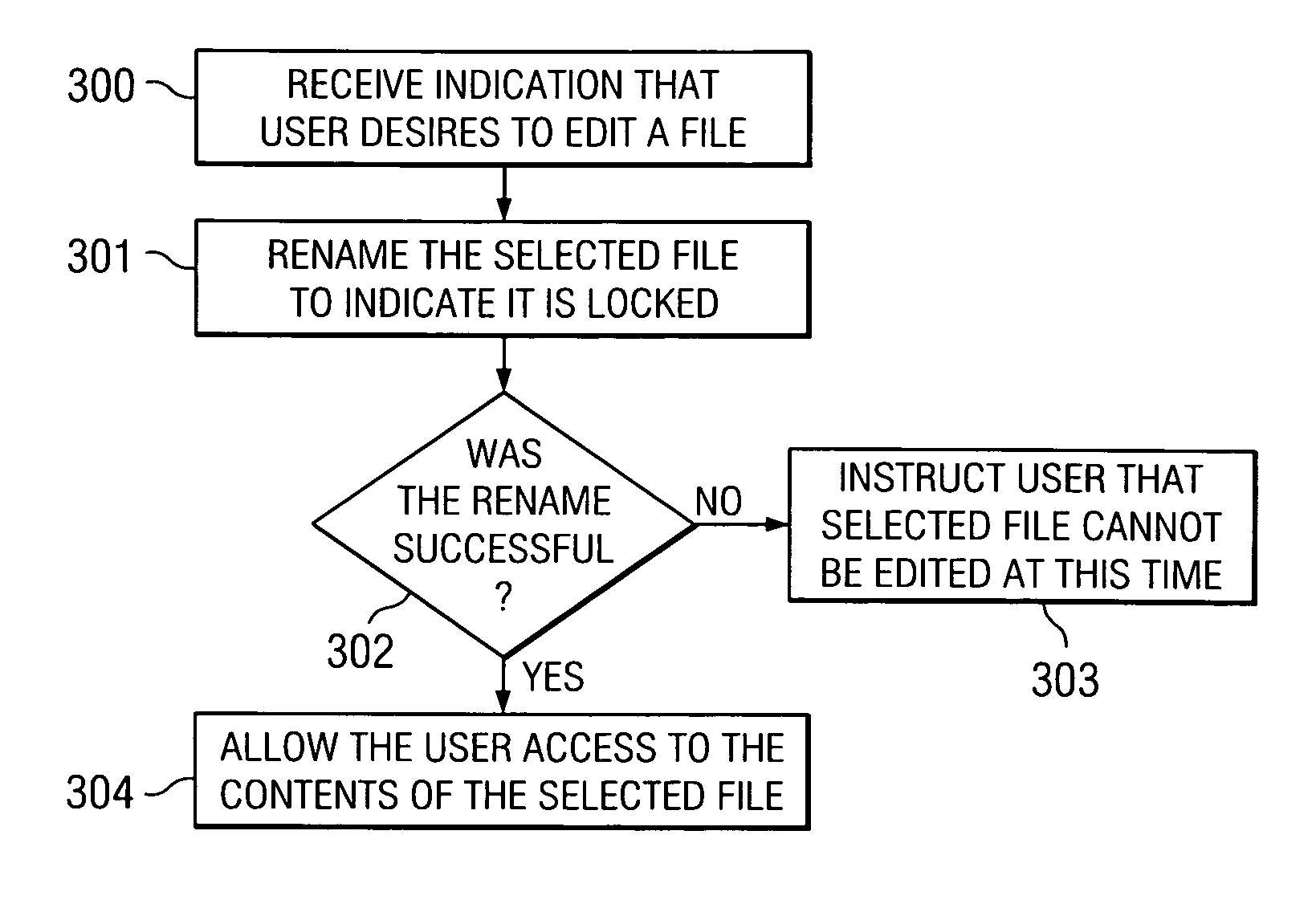
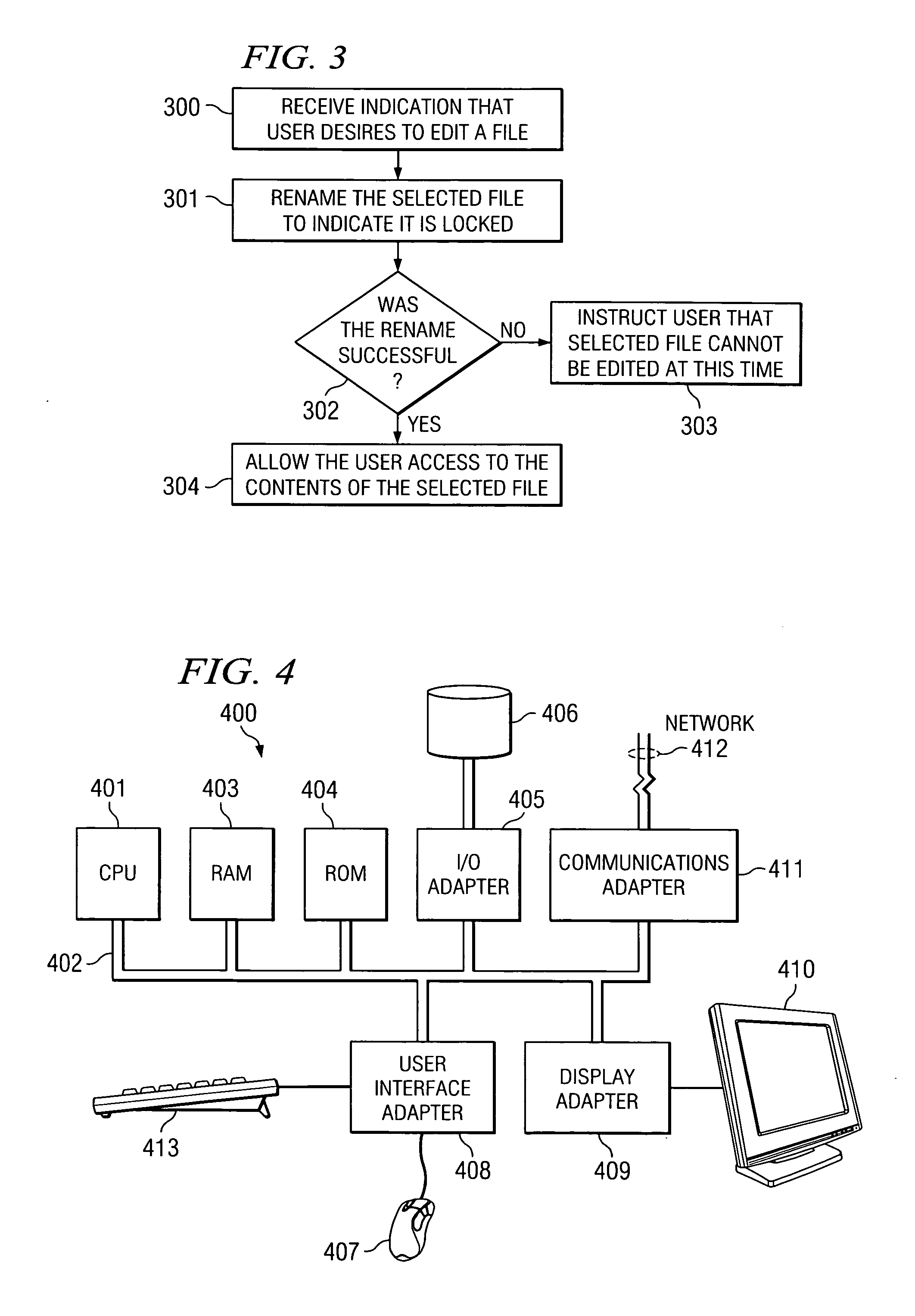
ActiveUS7650336B1Leverage functionDigital data processing detailsSpecial data processing applicationsLocking mechanismFile system
A locking mechanism for an electronic file creates a key file for each electronic file stored on a file system. The key file is created when the electronic file is loaded or first created on the system. As a user requests to edit the electronic file, the file system is requested to rename the key file with a lock. If the file system returns an error in response to the request to rename, the user is informed that the electronic file is locked or inaccessible. If the system successfully renames the key file, the user is allowed access to the electronic file.
Owner:ADOBE SYST INC
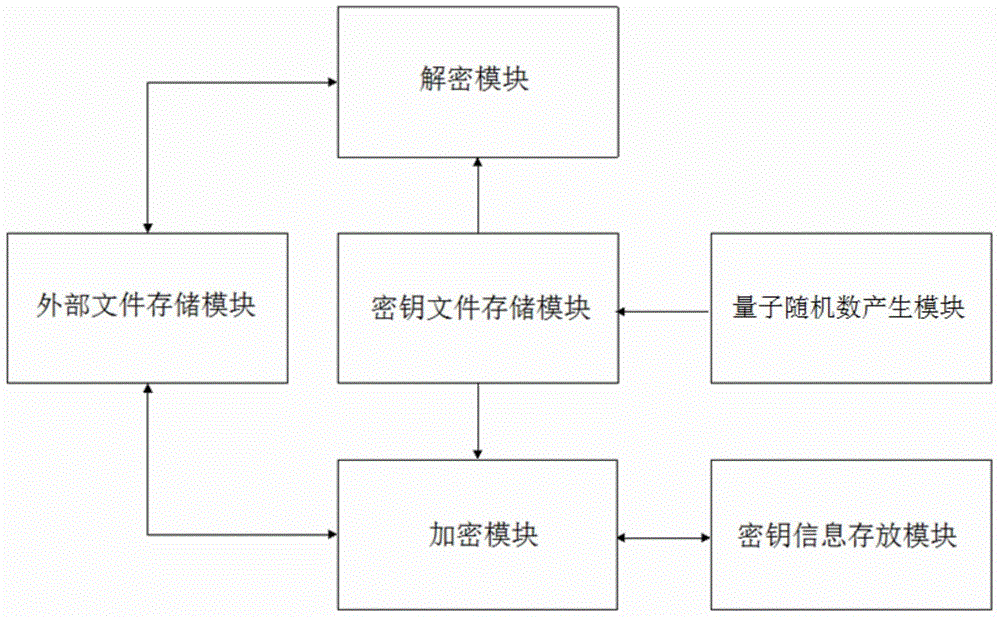
Mobile terminal secrecy system and method based on quantum true random number
ActiveCN104918243AKey distribution for secure communicationSecurity arrangementComputer hardwareEncryption
The invention discloses a mobile terminal secrecy system and method based on a quantum true random number. The system comprises a quantum random number generating module, a key file storage module, an encryption module, a decryption module, a key information storage module and an external file storage module, wherein the quantum random number generating module is connected with the key file storage module and used for transmitting random number key information, the key file storage module is respectively connected with the encryption module and the decryption module and used for transmitting encrypted key information and decrypted key information; the decryption module is connected with the external file storage module and used for transmitting a to-be-decrypted file and a decrypted file; the encryption module is connected with the external file storage module and used for transmitting the to-be-encrypted file and the encrypted file; the encryption module is connected with the key information storage module and used for transmitting key use condition information. The feasibility of guaranteeing the absolute security of the data through the daily application of one-time padding is provided, and the encryption of the data can be easily realized.
Owner:SHANGHAI JIAODA INTELLECTUAL PORPERTY MANAGEMENT CO LTD
Autonomous Field Reprogramming
InactiveUS20080101613A1Key distribution for secure communicationPublic key for secure communicationProgrammable logic deviceKeyfile
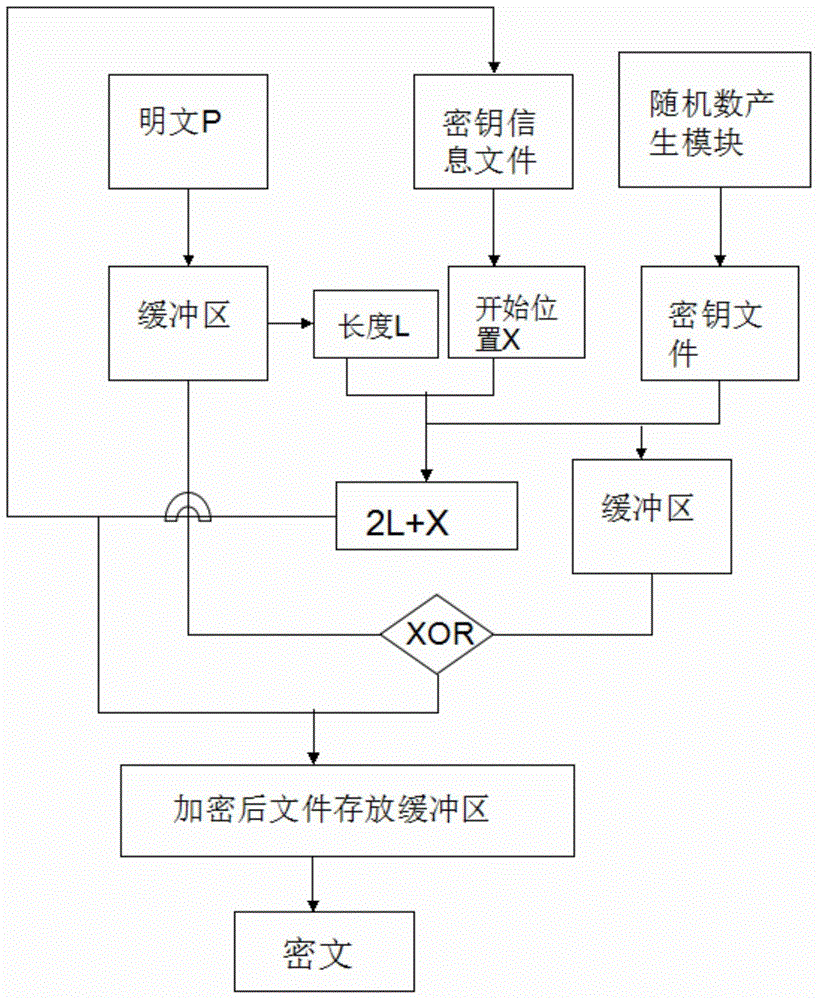
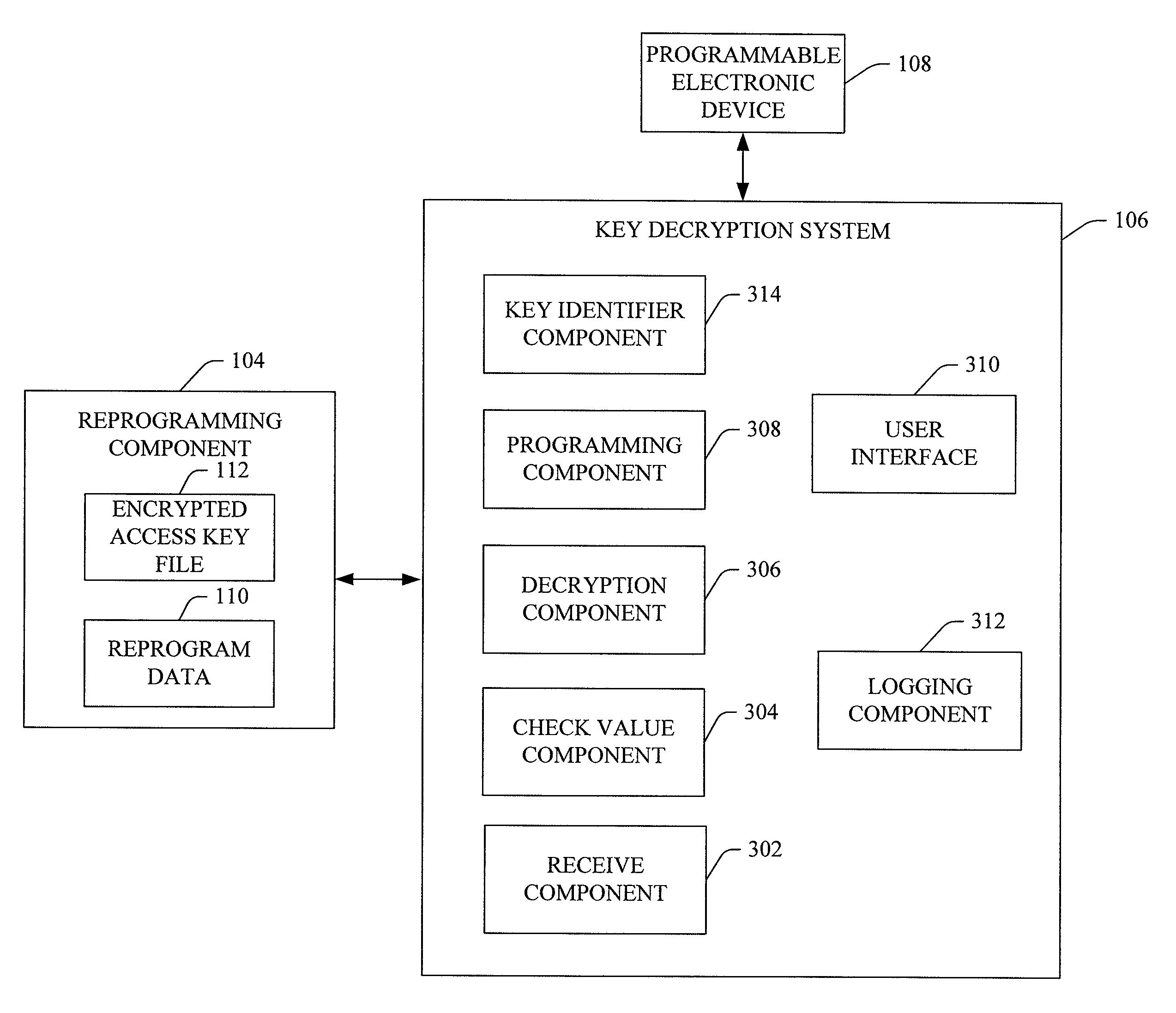
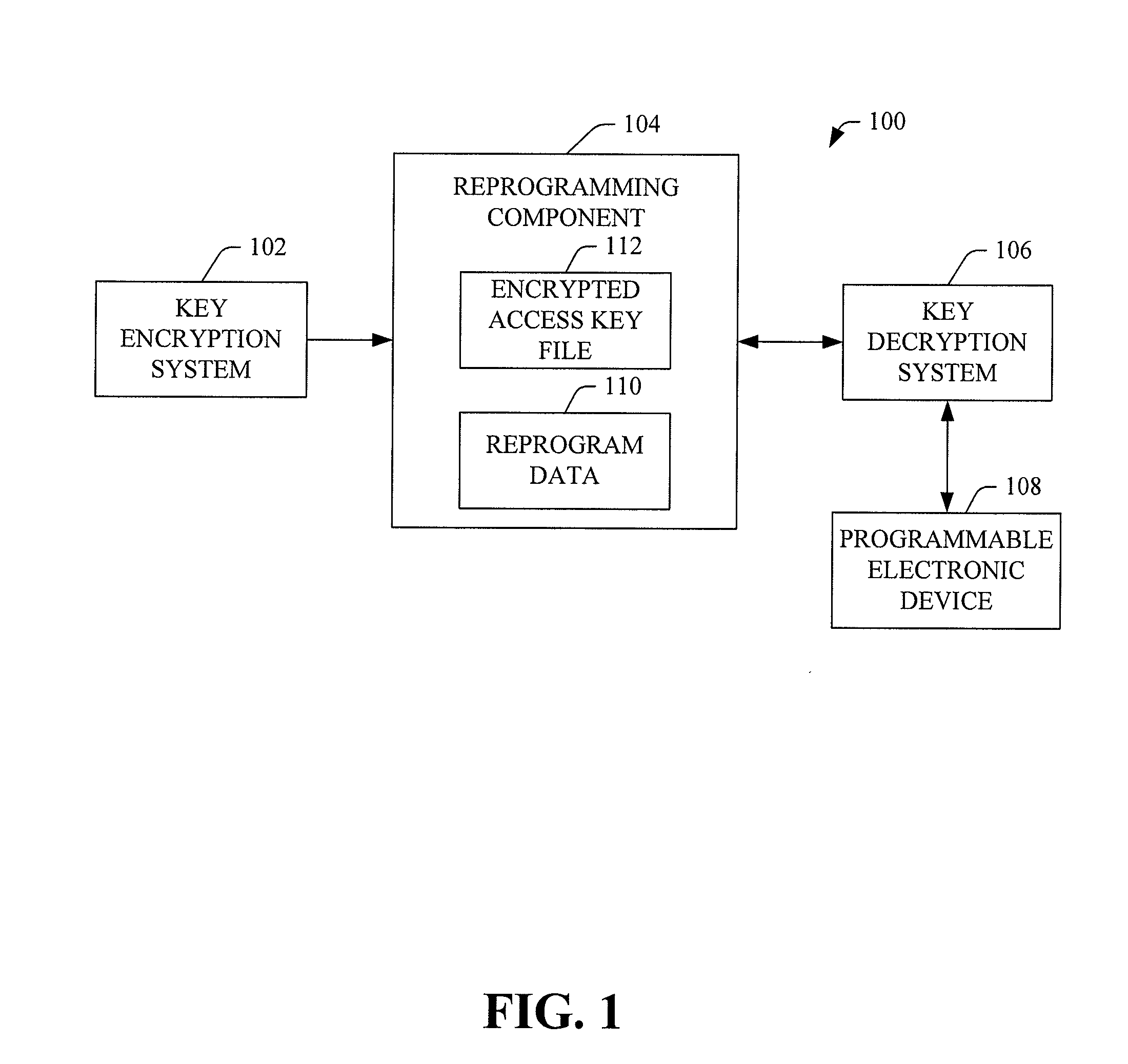
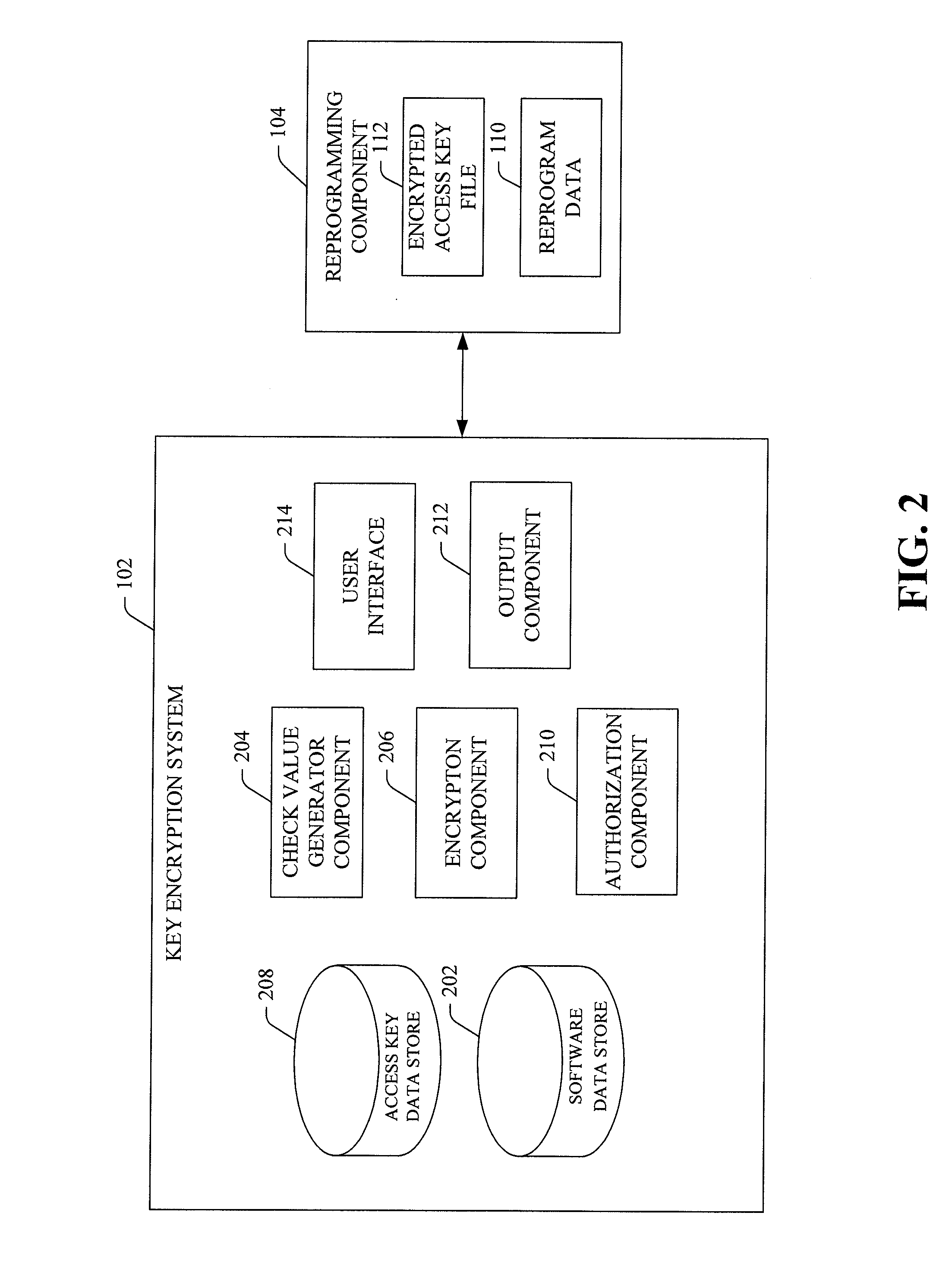
The reprogramming system provides for field reprogramming of programmable devices. In particular, a key encryption system generates reprogramming components used to install reprogram data on programmable devices located in the field. The reprogramming component includes an encrypted access key file necessary to unlock the programmable device and reprogram software files and data installed on the programmable device. The encrypted access key file is encrypted as a function of a check value derived from the reprogram data, ensuring that permission to reprogram the programmable device is tied to the specific data being installed. A key decryption system that receives a reprogramming component generates the check value from the program data, decrypts the key access file, unlocks the programmable device, and installs the software files and / or program data.
Owner:DELPHI TECH INC
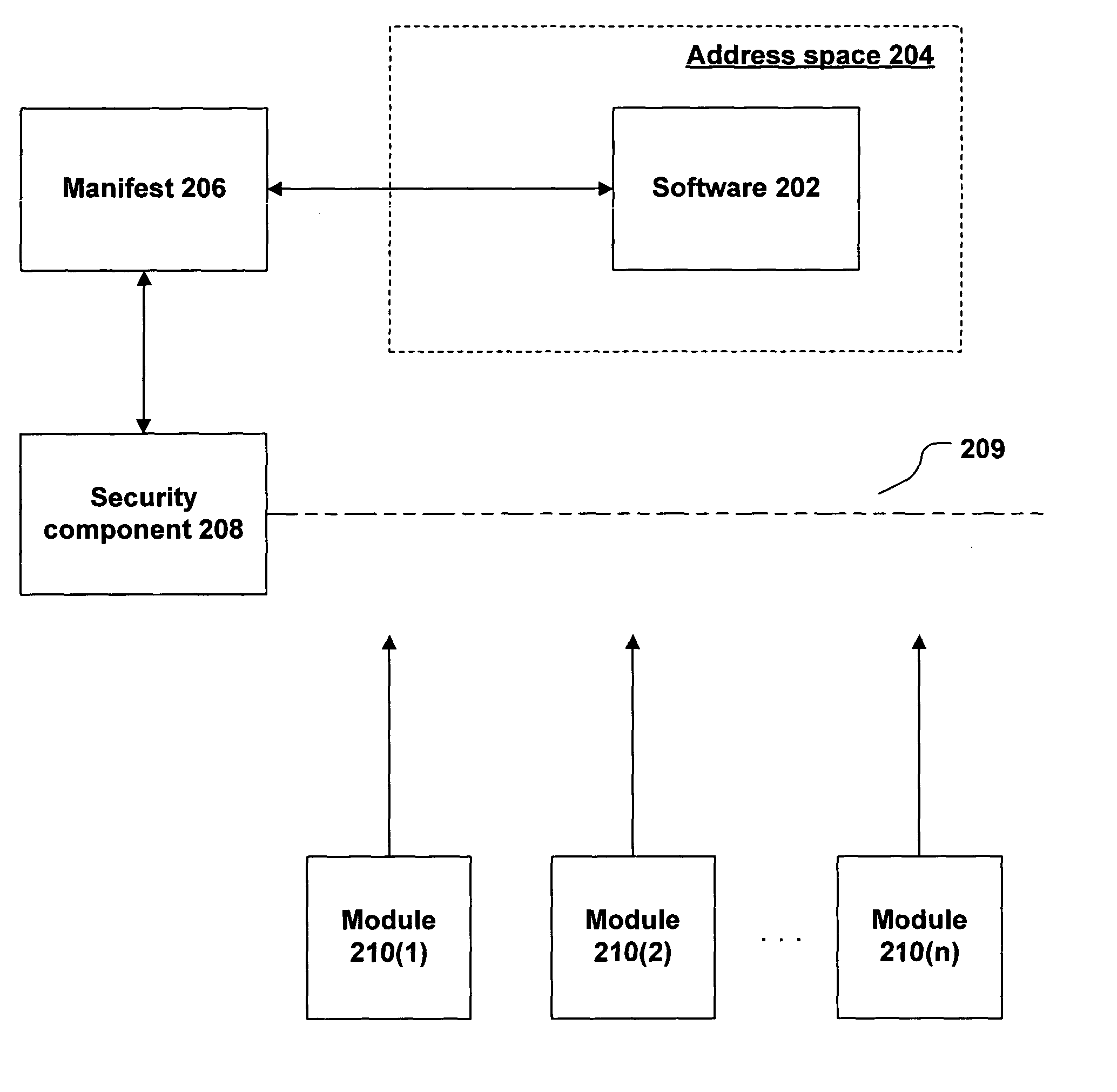
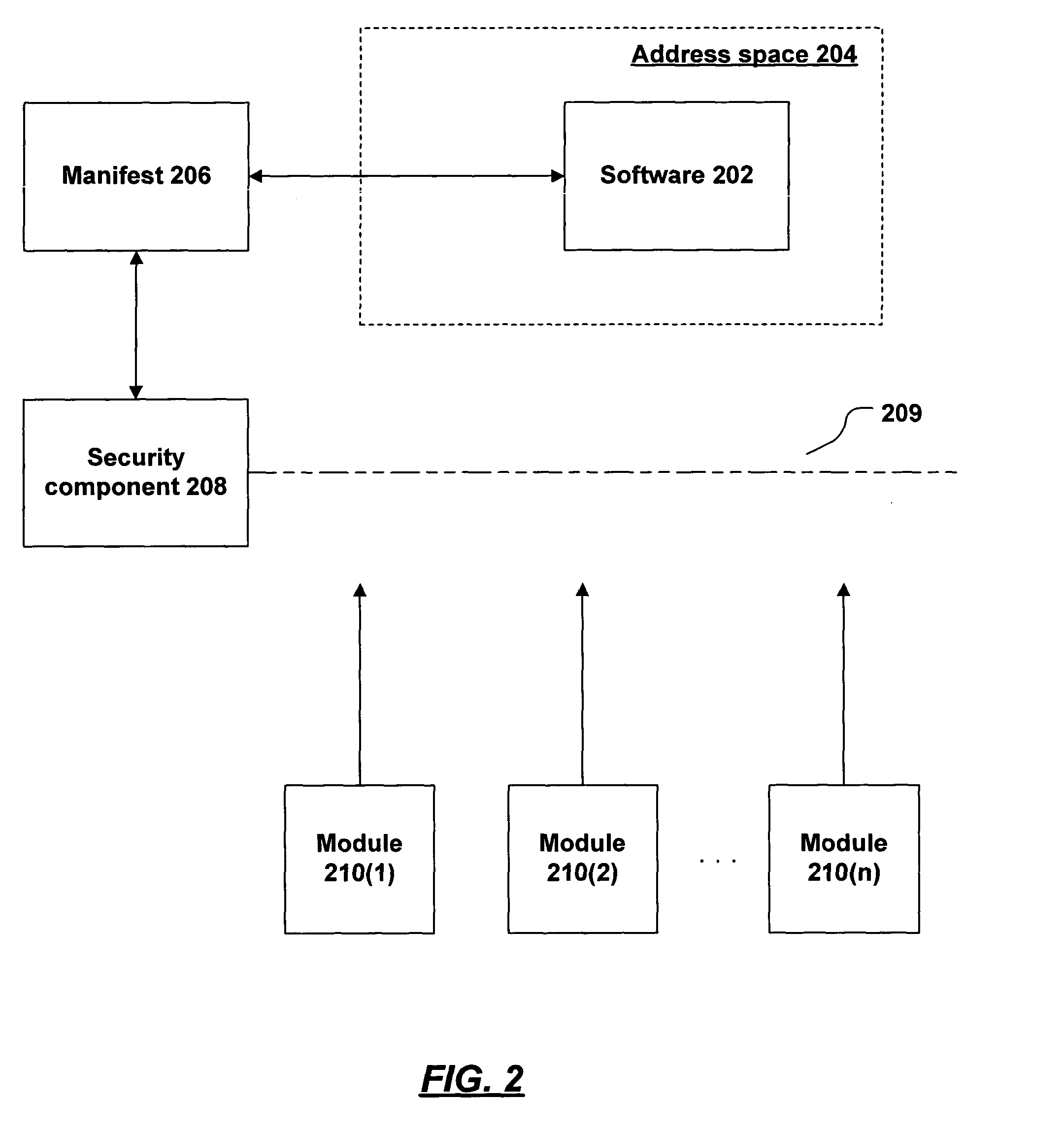
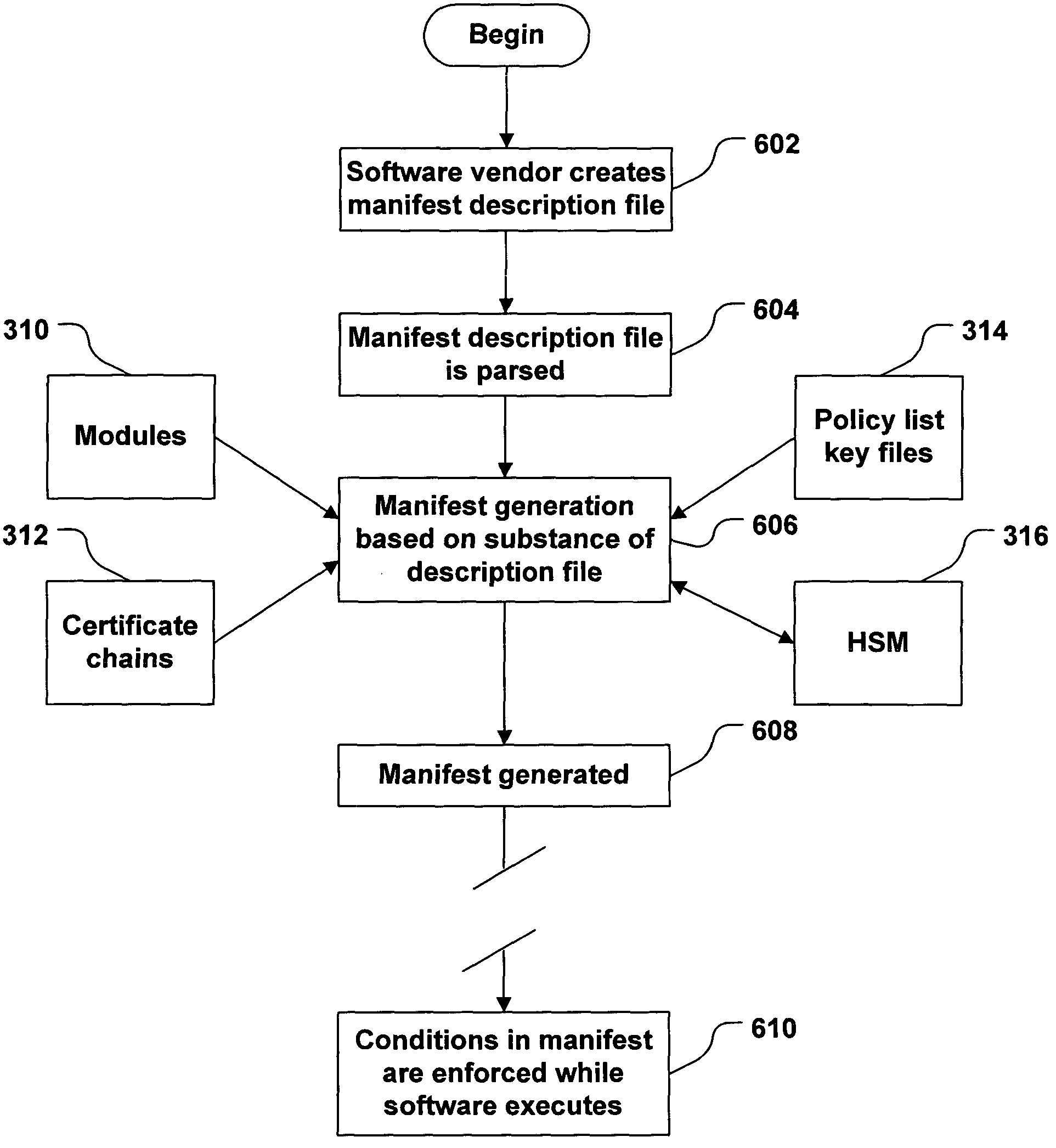
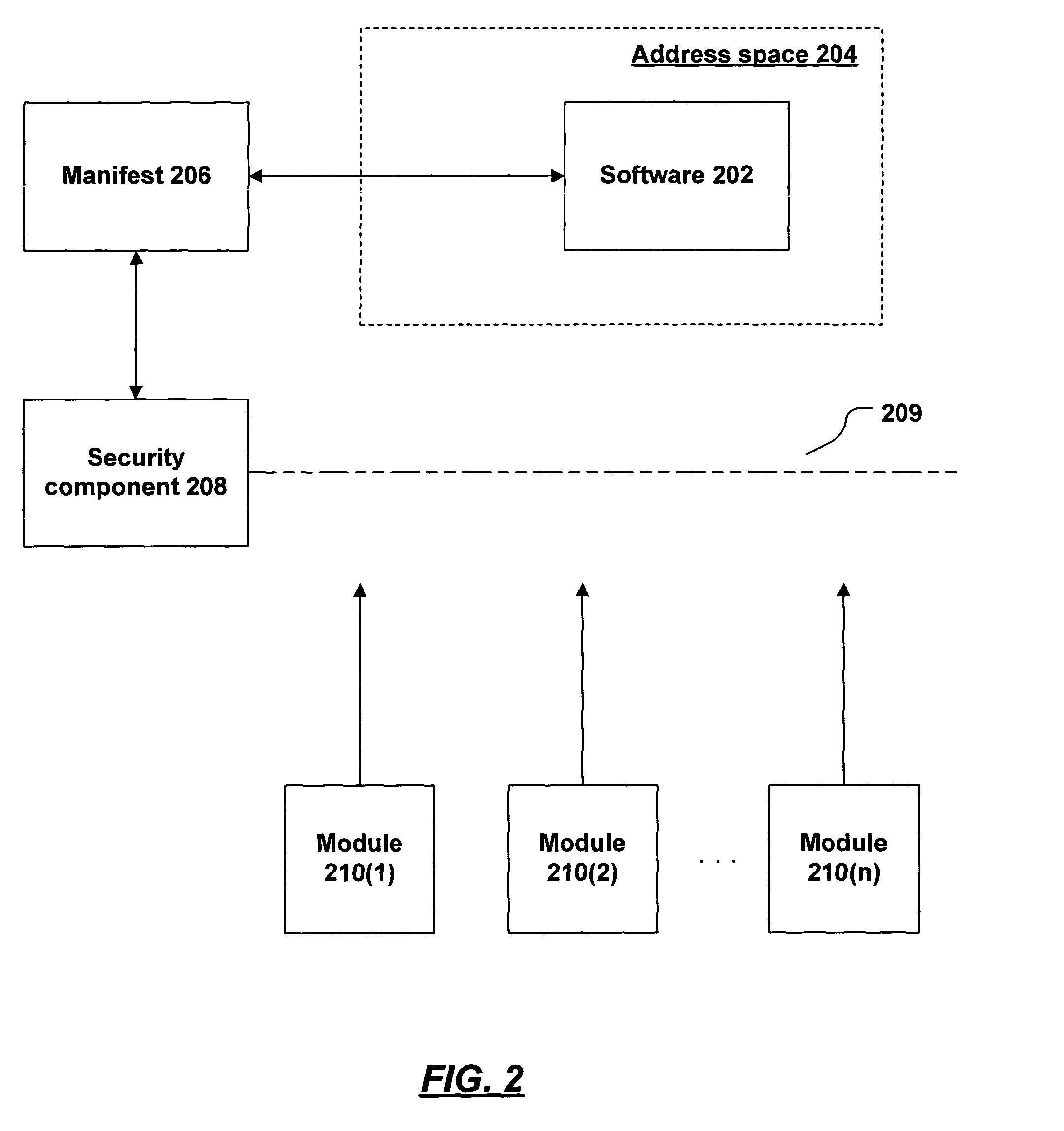
System and method for manifest generation
InactiveUS20050055315A1Simplify manifest descriptionDigital data processing detailsAnalogue secracy/subscription systemsSpecification languageSecurity policy
The execution of software may be controlled by a security policy expressed in a manifest. The software vendor or distributor specifies requirements for the use of software (e.g., which modules may be loaded into the software's address space, which module-signing keys are trustworthy, etc.), using a manifest specification language. A generation tool reads the specification and creates a manifest based on the specification. The tool may handle such details as retrieving keys from key files, computing software hashes, and the like. The manifest is distributed with the software and used by the environment in which the software executes to enforce the security policy.
Owner:MICROSOFT TECH LICENSING LLC
System, method, and apparatus for data, data structure, or encryption key cognition incorporating autonomous security protection
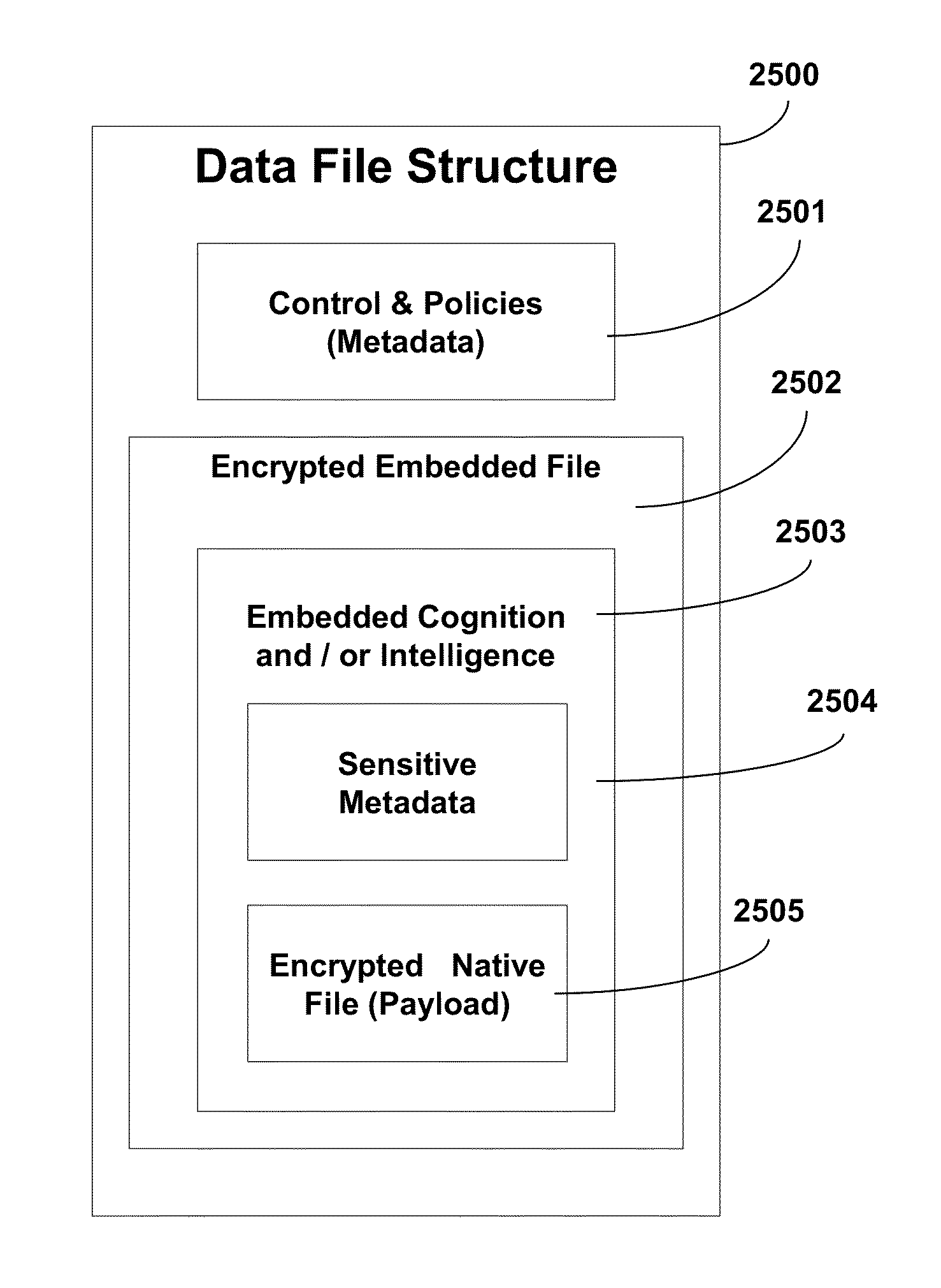
InactiveUS20140201526A1Reduce errorsReduce incidenceSubstation remote connection/disconnectionDigital data protectionCognitionData file
A system, method, and apparatus for securing a date file or a cognitive encryption key data file stored in a storage medium or memory device. The date file or encryption key file having stored instructions for an embedded autonomous executable program which is executed each time there is an attempt to access, control, or manipulate the encryption key file includes querying a user of the date file or encryption key file, the user environment of the date file or encryption key file, or both, for information required for analyzing a computational environment in relation to required security parameters for the cognitive date file or encryption key file. The information in relation to the security parameters is received and analyzed. The computational environment of the user is determined and analyzed in relation to the required security parameters. Access to and / or use of the date file or encryption key file is either permitted or denied based on the analysis of the user and computational environment. Autonomous embedded data cognition enables data, cryptographic data, authentication codes, etc. to perform real-time environmental configuration control, self-manage, self-obfuscate, perform analyses, determine its current situation, and evaluate behavior to respond accordingly. Data-to-data reasoning and analyses can be performed.
Owner:BURGESS SHELIA JEAN
System and method for manifest generation
InactiveUS7814551B2Digital data processing detailsAnalogue secracy/subscription systemsSpecification languageDistributor
The execution of software may be controlled by a security policy expressed in a manifest. The software vendor or distributor specifies requirements for the use of software (e.g., which modules may be loaded into the software's address space, which module-signing keys are trustworthy, etc.), using a manifest specification language. A generation tool reads the specification and creates a manifest based on the specification. The tool may handle such details as retrieving keys from key files, computing software hashes, and the like. The manifest is distributed with the software and used by the environment in which the software executes to enforce the security policy.
Owner:MICROSOFT TECH LICENSING LLC
Data File Decryption Method, Decryption Device and Data Broadcasting System
ActiveUS20120137122A1Rapid positioningImprove experienceSynchronising transmission/receiving encryption devicesMultiple keys/algorithms usageService experienceData file
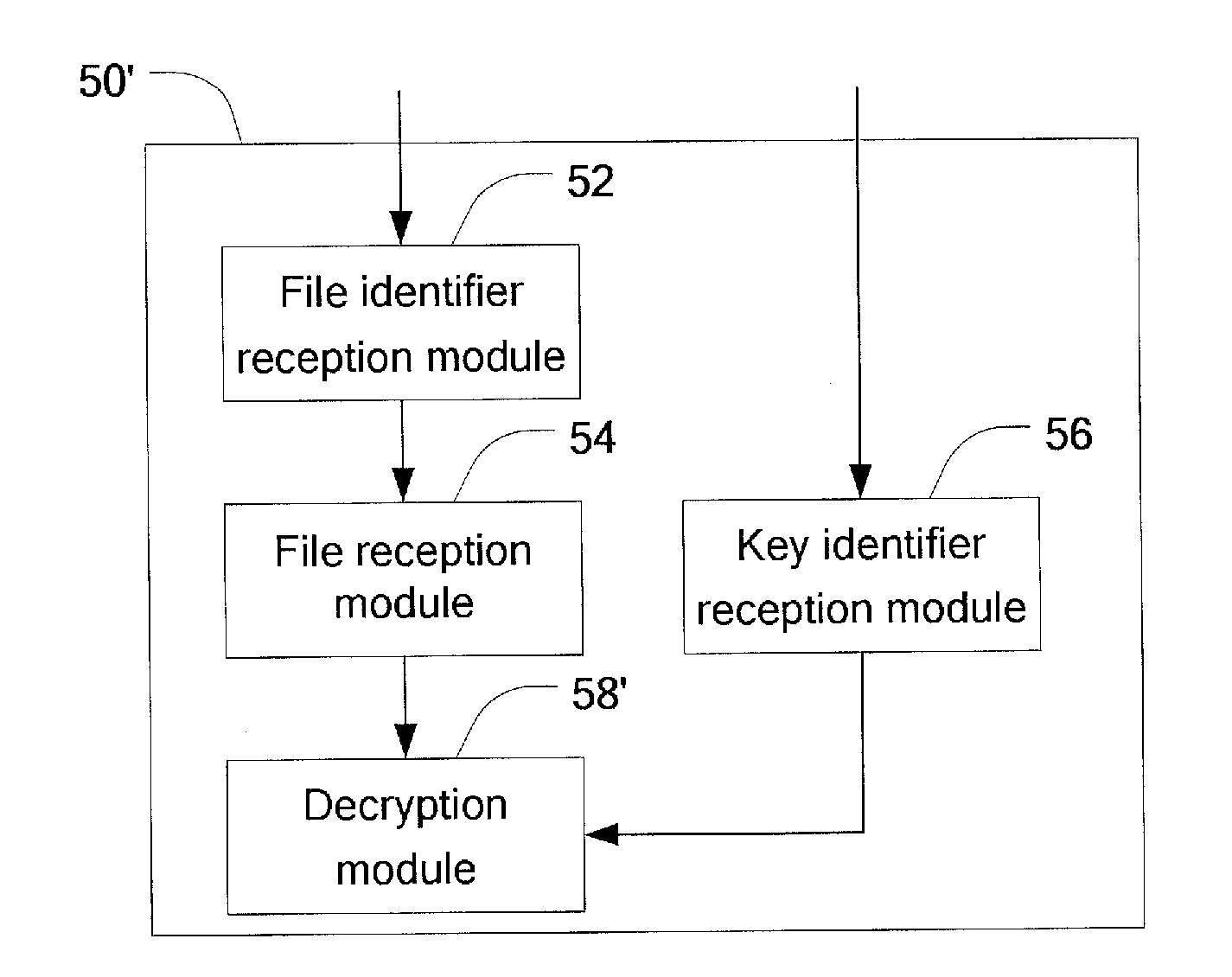
A data file decryption method, a decryption device and a data broadcasting system are disclosed, which are applied to a data broadcasting service. Among them, the data file decryption method includes the steps of: receiving the file delivery information which includes a data file identification and a key file identification corresponding to the data file; receiving the corresponding data file and key file according to the data file identification and the key file identification; and decrypting the data file according to the key file. According to the data file decryption method, decryption device and the data broadcasting system of the present invention, by setting the data file identification and the corresponding key file identification in the file delivery information and receiving the corresponding file according to the data file identification and the key file identification, the resource dissipation due to a large quantity of useless information received at a terminal is avoided, and the file to be received can be quickly located by the terminal, so that the time delay due to the decryption of a data file is avoided, and the service experience for users is improved.
Owner:CHINA MOBILE COMM GRP CO LTD
Secure key signature method based on block chain technology
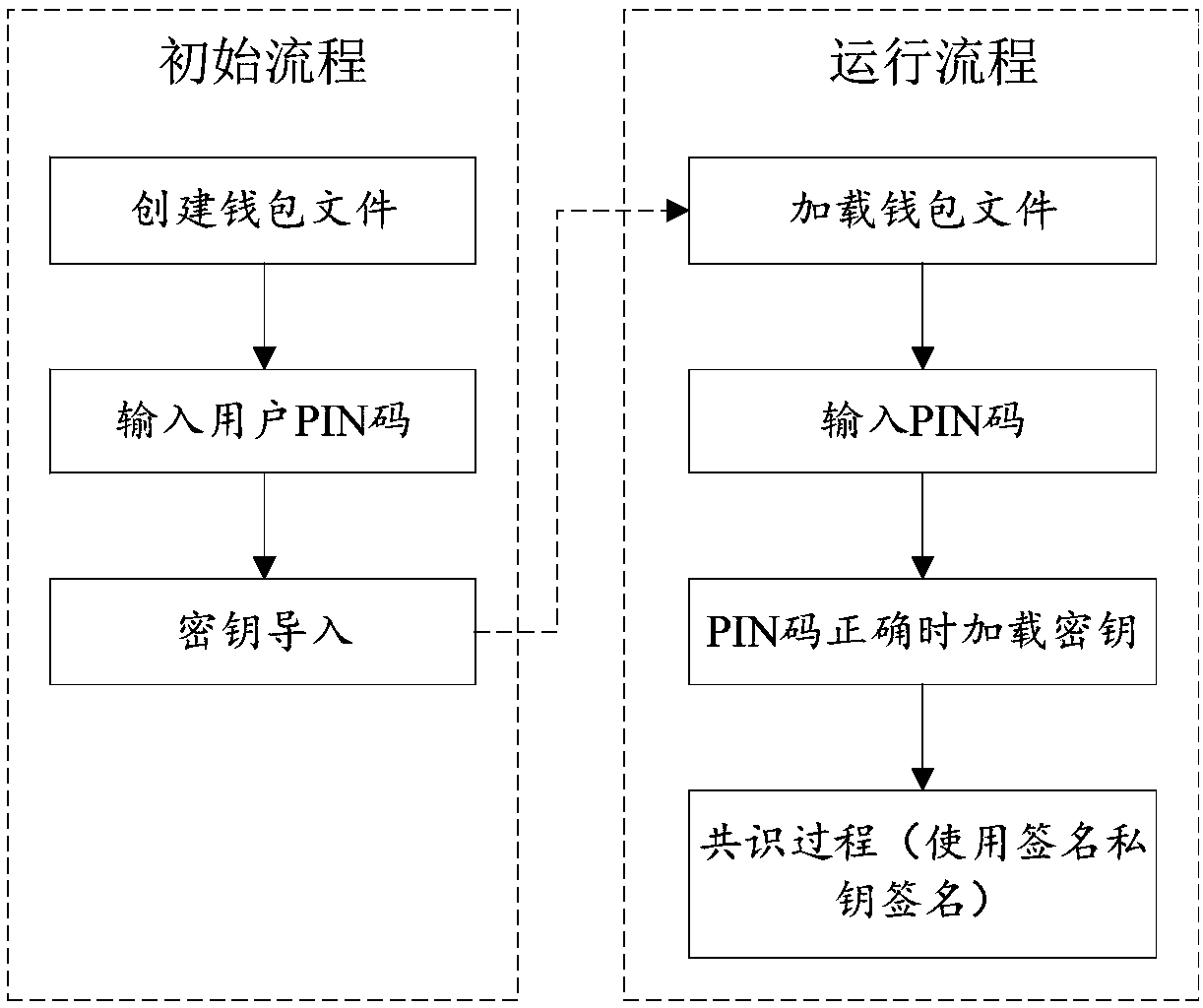
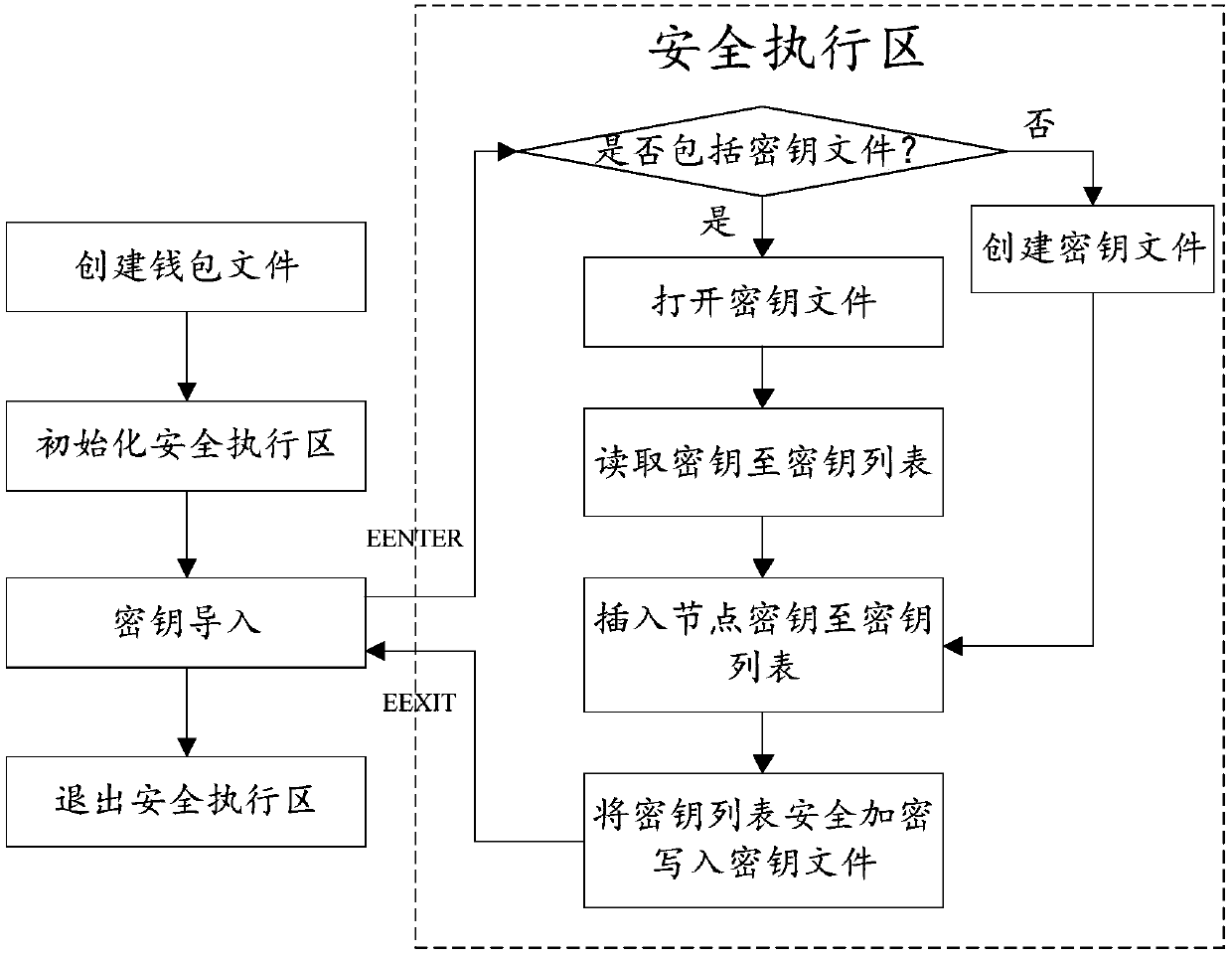
ActiveCN108055133AProtection securityImprove securityUser identity/authority verificationPlatform integrity maintainanceChain systemKeyfile
The invention discloses a secure key signature method based on the block chain technology, and relates to the technical field of block chains. The method comprises the following steps: dynamically creating and initializing a security execution area, calling a security area entry instruction through a key loading function to enter the security execution area, loading a node key in a key file to thesecurity execution area, in a consensus process with other nodes in a block chain system, calling the security area entry instruction through a signature function to enter the security execution area, wherein the parameters of the signature function comprises a private key identifier and data to be signed, determining a signature private key corresponding to the private key identifier in the security execution area, signing the data to be signed by using the signature private key, and returning a signature result. According to the method, the security execution area of the CPU is fully used,the key of the node is stored in the security execution area, and the signature process is also executed in the security execution area, so that the security of the key is protected.
Owner:江苏安凰领御科技有限公司
Digital film secret key distributing method, device and system based on management website
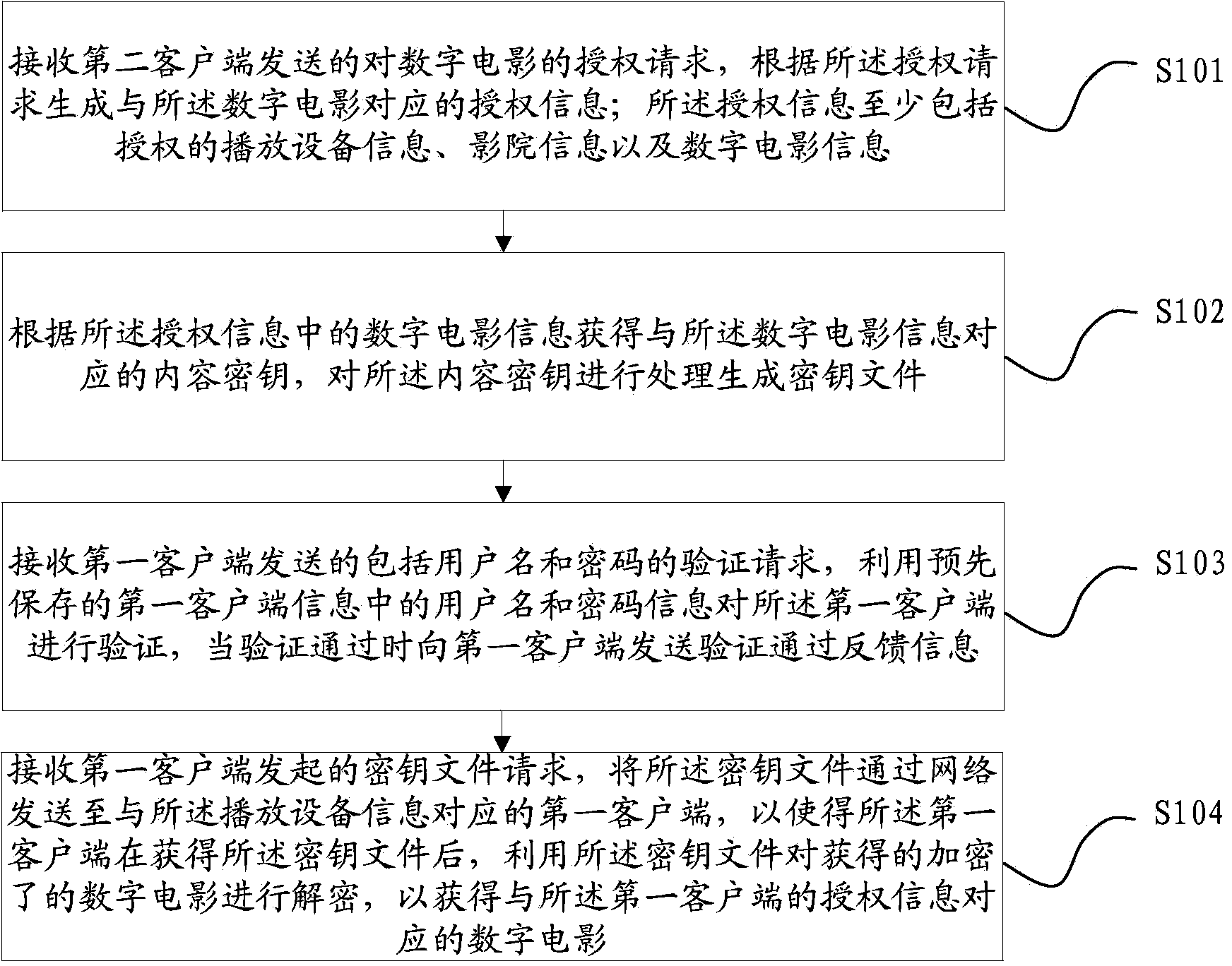
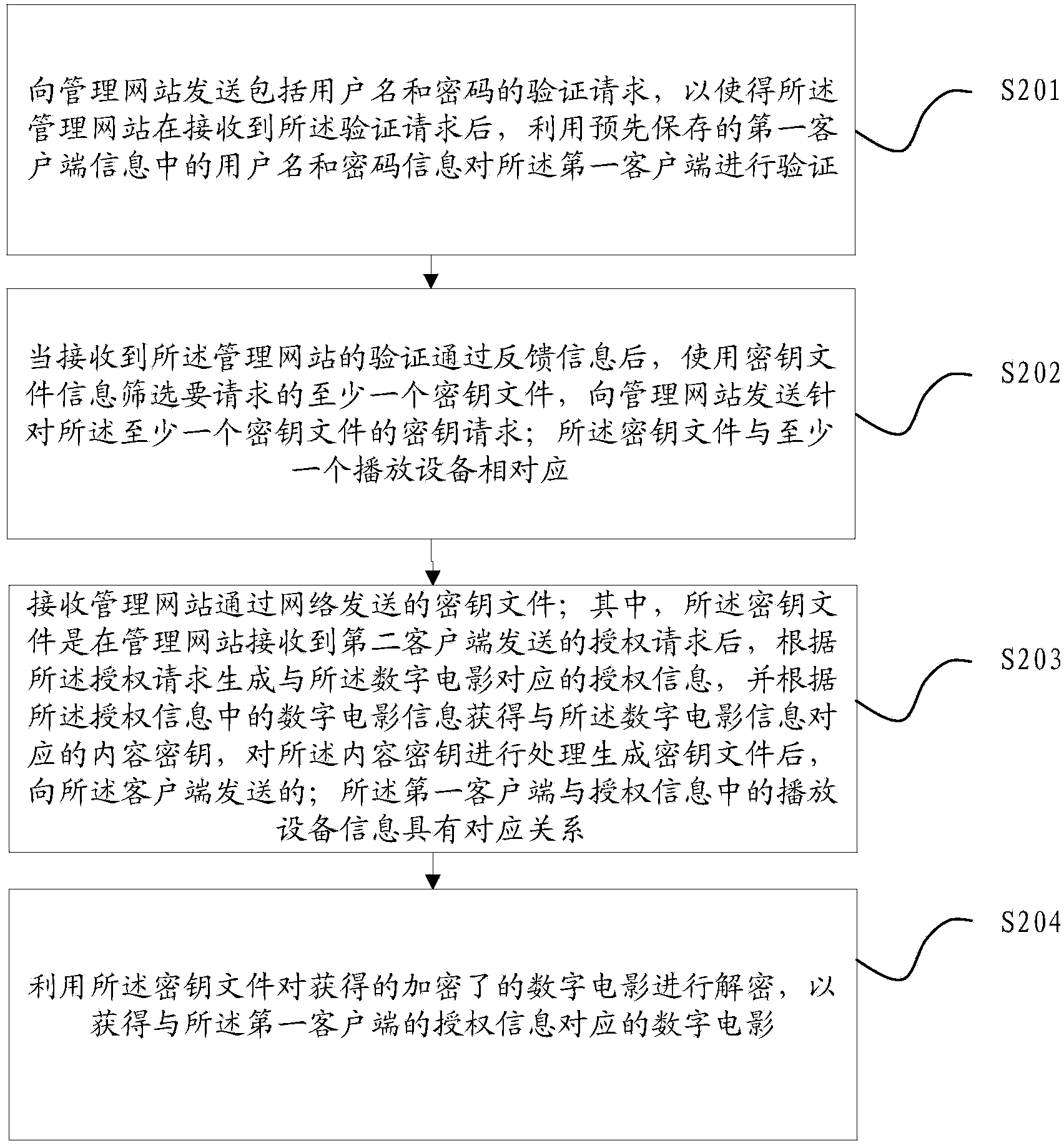
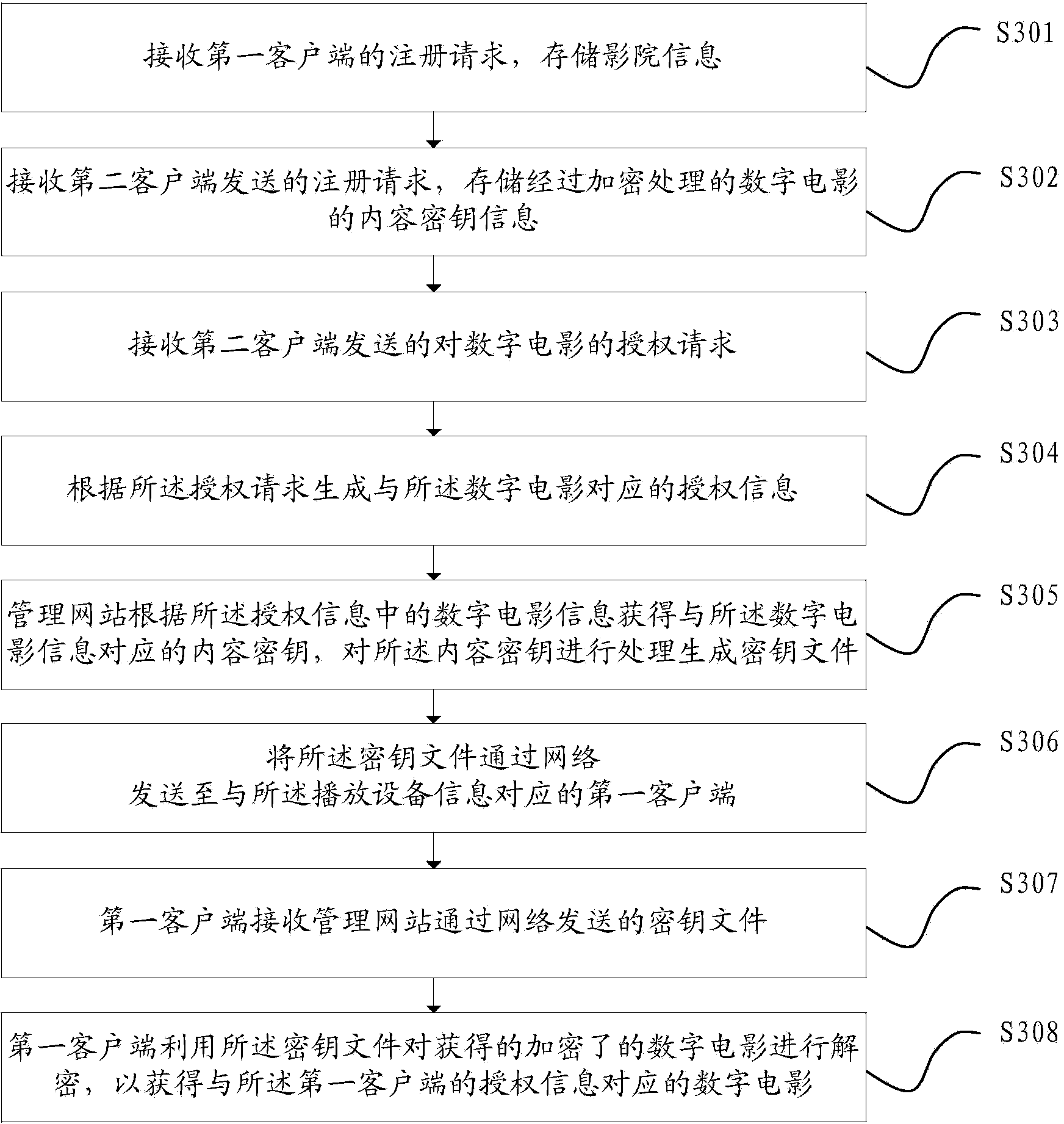
ActiveCN103873233AImprove the efficiency of key distributionEnsure safetyKey distribution for secure communicationClient-sideAuthorization
The invention relates to the data processing field, in particular to a digital film secret key distributing method, device and system based on a management website. The method includes the steps that the authorization request for a digital film sent by a second client is received, and authorization information corresponding the digital film is generated according to the authorization request; the authorization information at least comprises authorized information of a playing device, theater information and digital film information; according to the digital film information in the authorization information, content secret keys corresponding to the digital film information are acquired, and the content secret keys are processed to generate secret key files; the secret key files are sent to a first client corresponding to the information of the playing device through a network so that after the first client acquires the secret key files, the acquired encrypted digital film can be decrypted through the secret key files and the digital film corresponding to the authorization information of the first client can be acquired. With the method, device and system, safety of digital films in the propagation process is effectively improved, and safety of the copyright of digital films is protected.
Owner:中央宣传部电影数字节目管理中心
Encryption and decryption method for protecting safety of cloud storage data
InactiveCN103078959AConvenience guaranteedData SecurityUser identity/authority verificationComputer hardwareWeb service
The invention provides an encryption and decryption method for protecting safety of cloud storage data. A user stores an uploaded primary file in a cloud storage after encrypting the uploaded primary file by a certain encryption algorithm, and a key file is generated when the user uploads the file and is stored at a user side, and the key file is used for deciphering a downloaded ciphertext, and thus, even an administrator on the cloud storage also cannot be look up file contents optionally so as to ensure the privacy of the file of the user. On the premise that web service convenience is ensured, key-based encryption is performed on the file uploaded to the cloud storage, and therefore, a cloud storage service capable of enabling file uploading and downloading to be safer and protecting the safety of the data is realized, and problems existing in the cloud storage at present are shielded.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
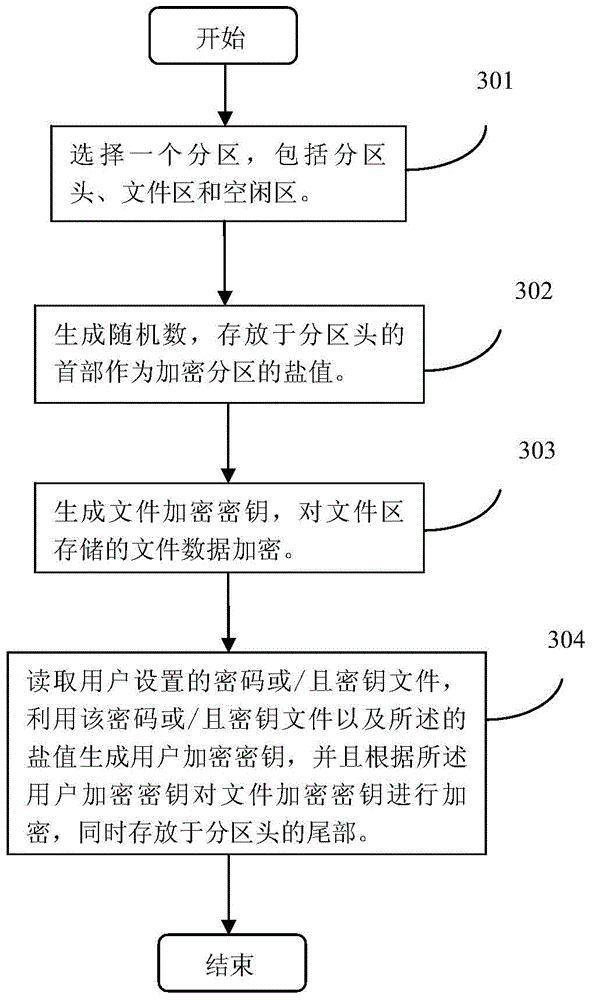
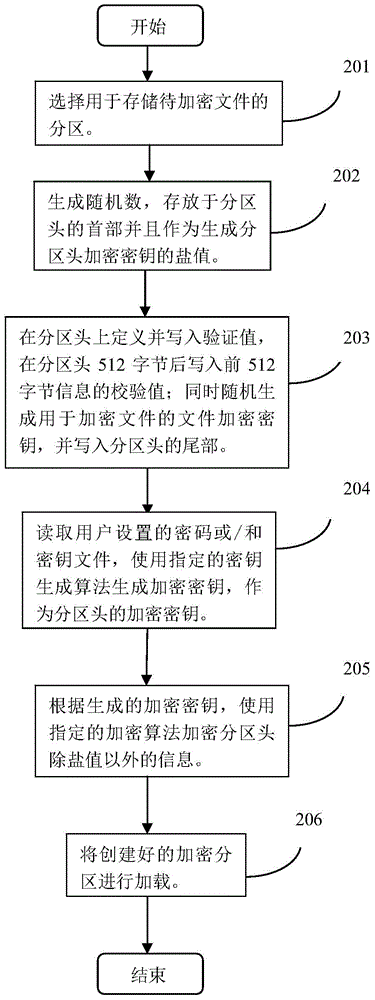
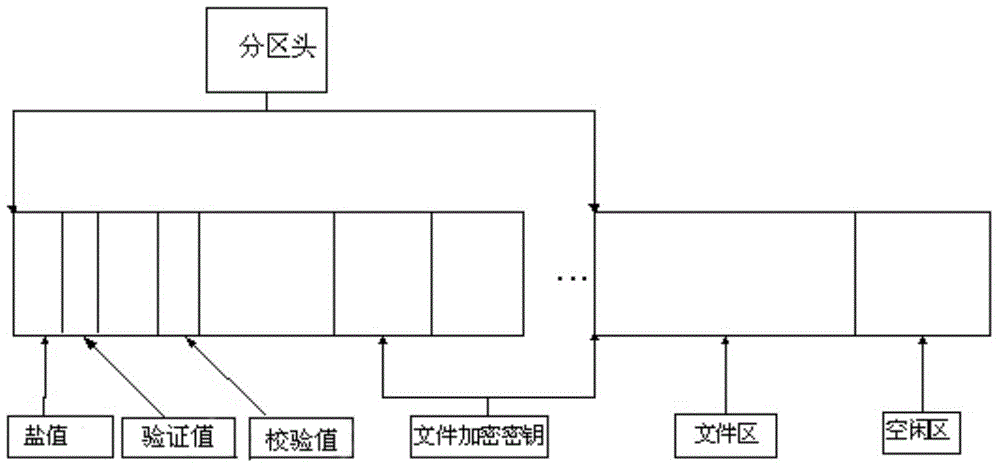
File encryption and decryption method and device on the basis of partitions
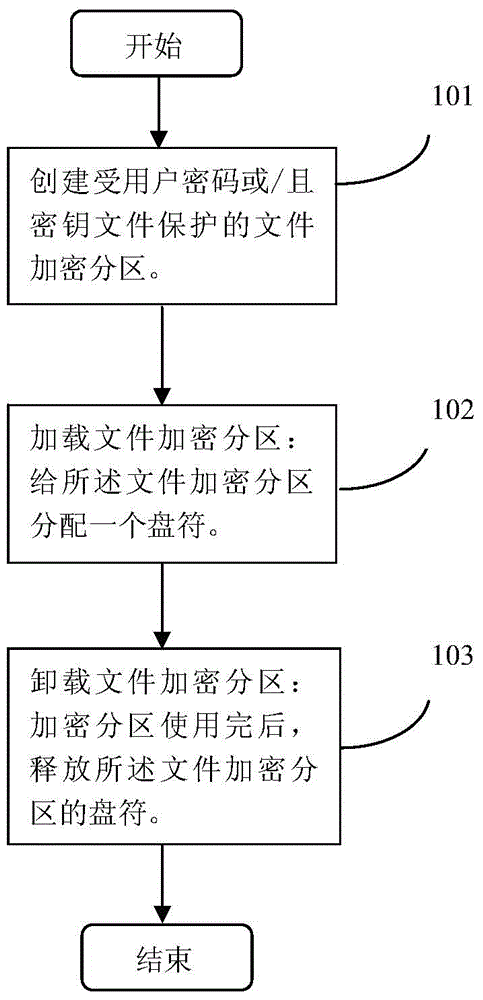
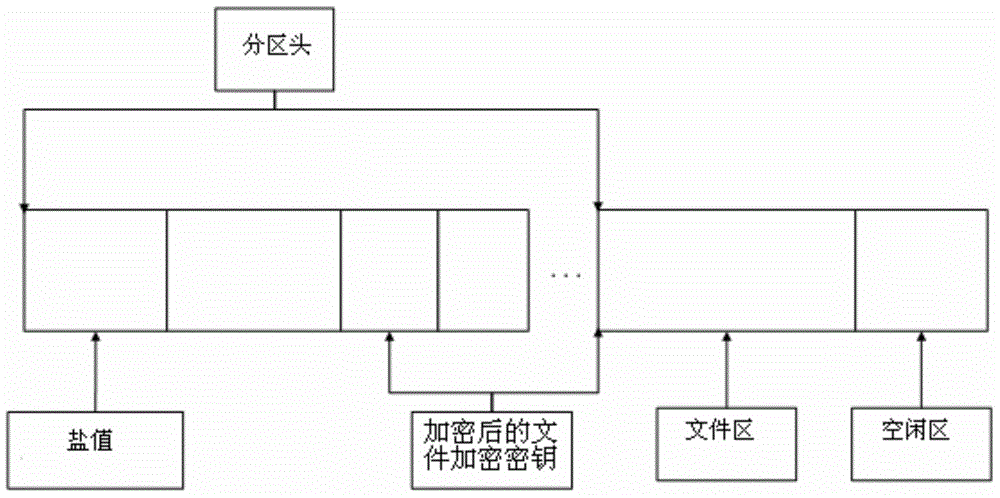
InactiveCN103914666AIncreased complexityEnsure safetyInternal/peripheral component protectionComputer hardwarePassword
The invention discloses a file encryption method and device on the basis of partitions. The method includes that file encryption partitions which are protected by user password and / or key file are established; firstly, one of partitions is selected, which comprises a partition head, a file area and an idle area; then a random number is generated and stored as a salt figure in a first part of the partition head, and a file encryption key is generated to encrypt file data of the file area; the password and / or the key file set by a user are / is read, a user encryption key is generated by the password and / or the key file and the salt figure, and the file encryption key is encrypted according to the generated user encryption key to be stored on a tail portion of the partition head; a file encryption partition is loaded, which includes that a drive is distributed to the file encryption partition; after the use of the encryption partition is finished, the file encryption partition is unloaded, which includes that the drive of the file encryption partition is released. Thereby, by means of the method and the device, strength and encryption strength of the file password can be improved.
Owner:ASIA EURO BOLOD INFORMATION SECURITY TECHHUNAN
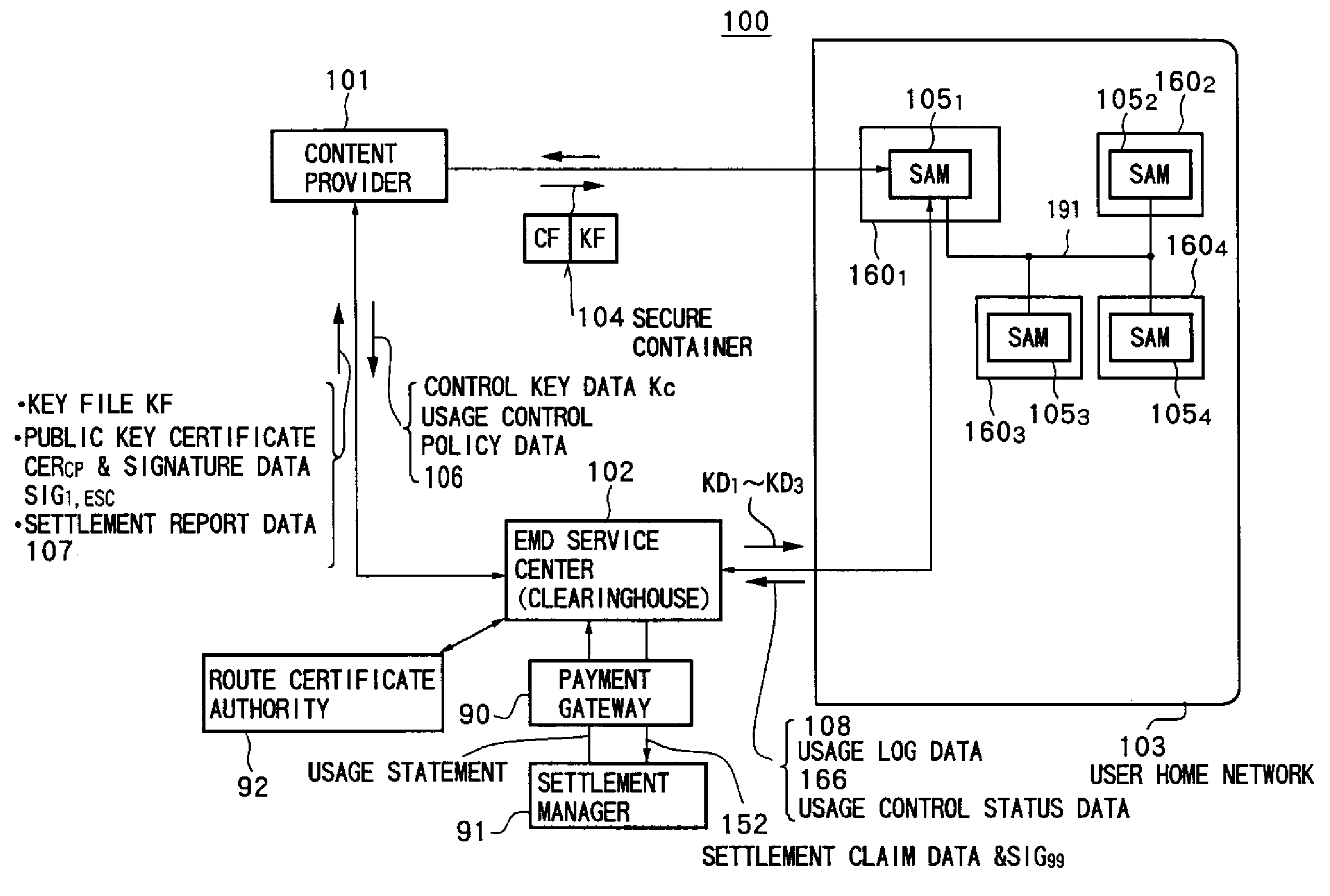
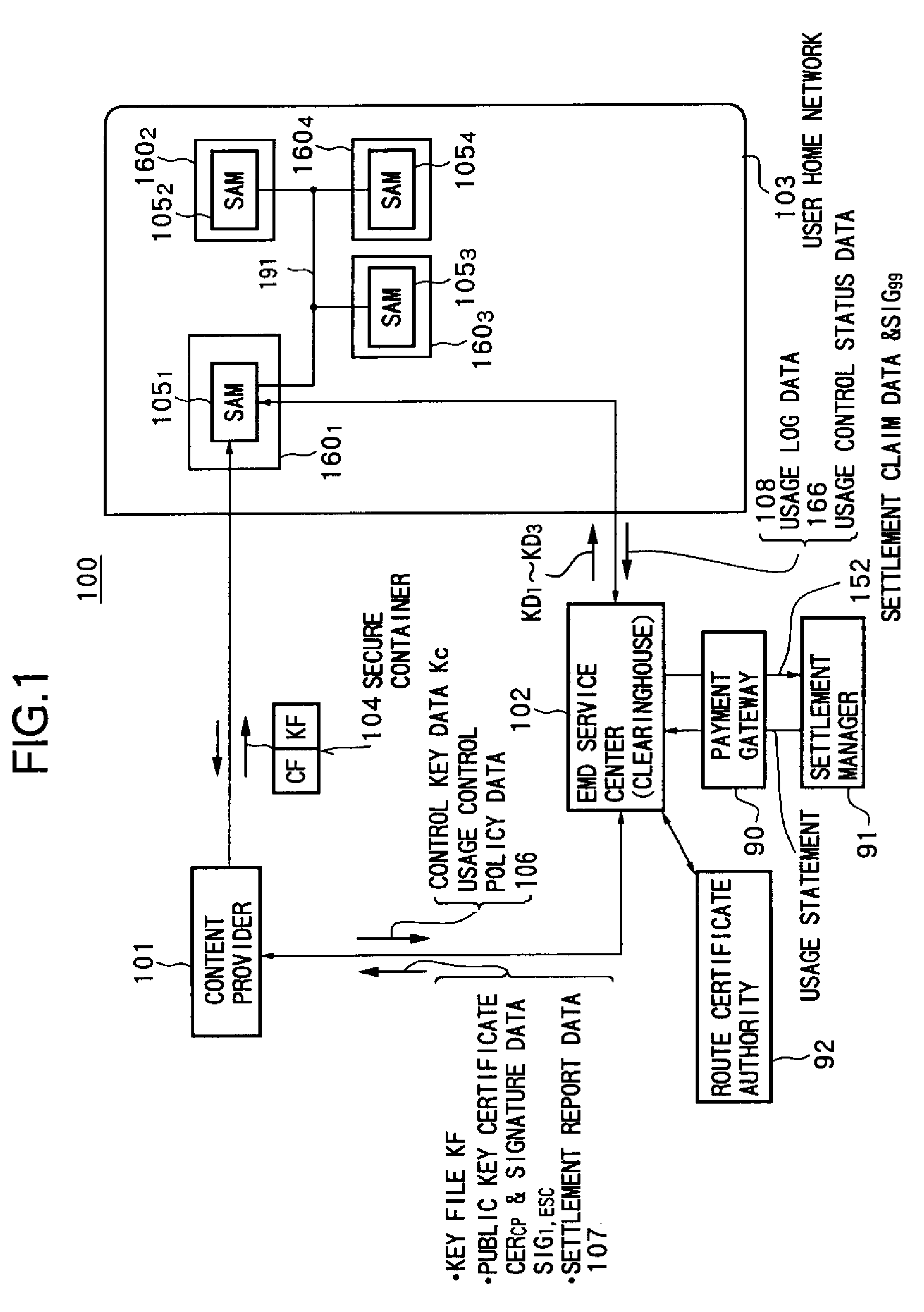
Data processing system andmethod therefor
InactiveUS20100281056A1Sufficient protectionReduce loadDigital data processing detailsSound producing devicesData processing systemData storing
A data providing system for distributing content data from a data providing apparatus to a data processing apparatus and managing said data providing apparatus and said processing apparatus by a management apparatus. In the system, the management apparatus is configured to provide a key file in which is stored content key data and usage control policy data indicating a content of rights, including permission conditions of the content data. At least a part of said key file is encrypted. The data providing apparatus is configured to provide the content data encrypted by using the content key data stored in the key file. The data processing apparatus is configured to decrypt the key file to obtain the content key data from the key file and determine handling of the content data based on the usage control policy data stored in the key file.
Owner:SONY CORP
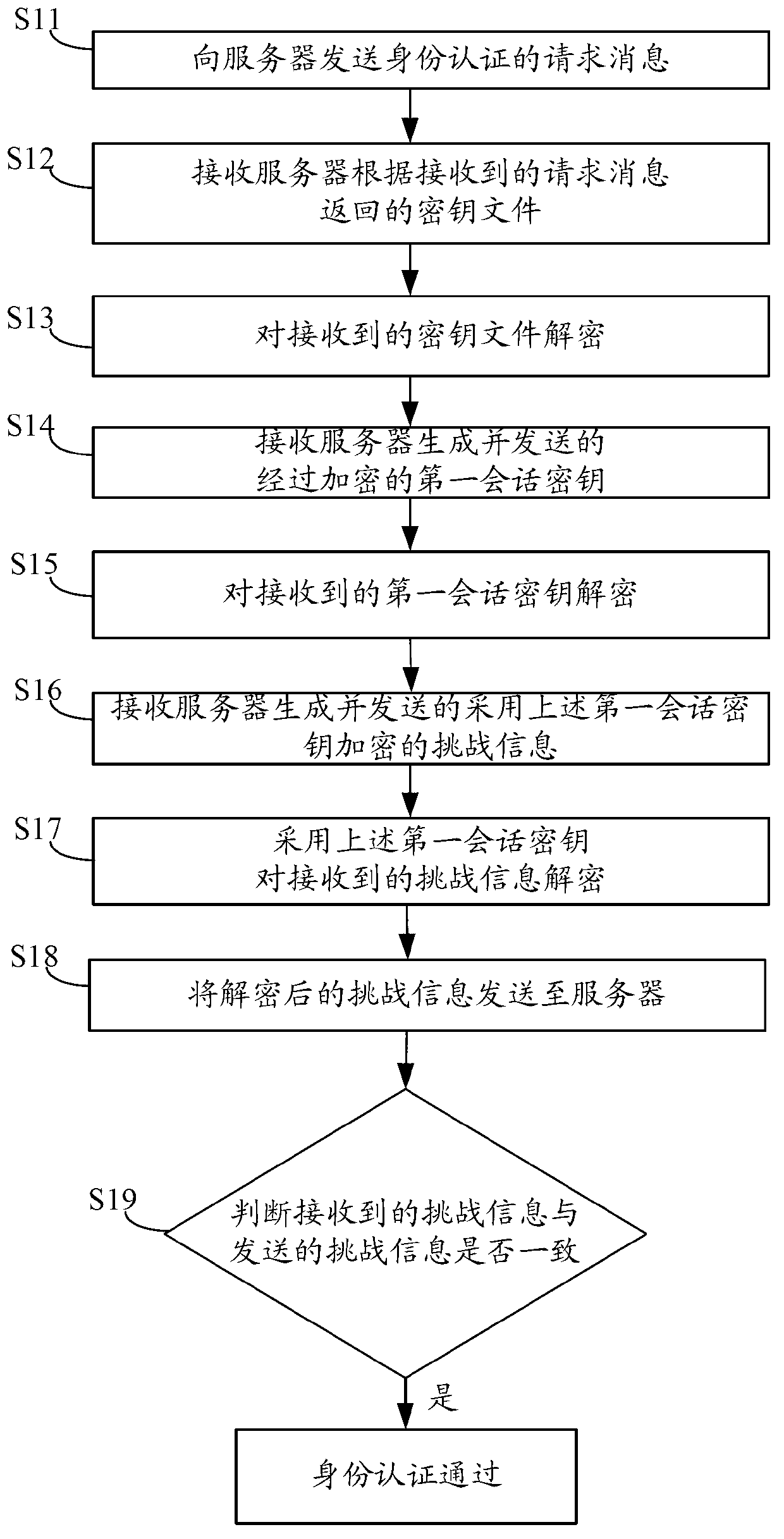
Identity authentication method and system and data transmission method and device based on same
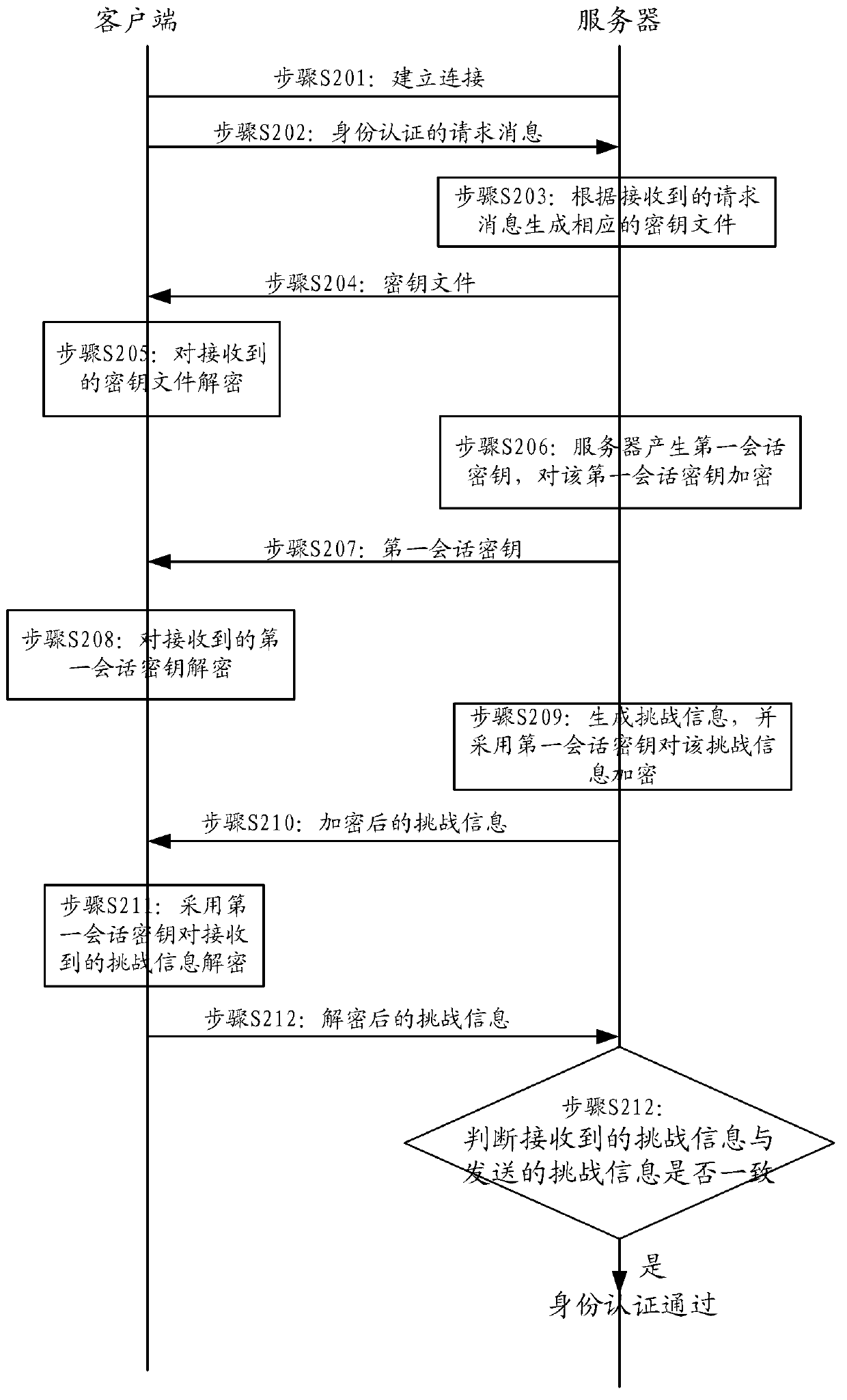
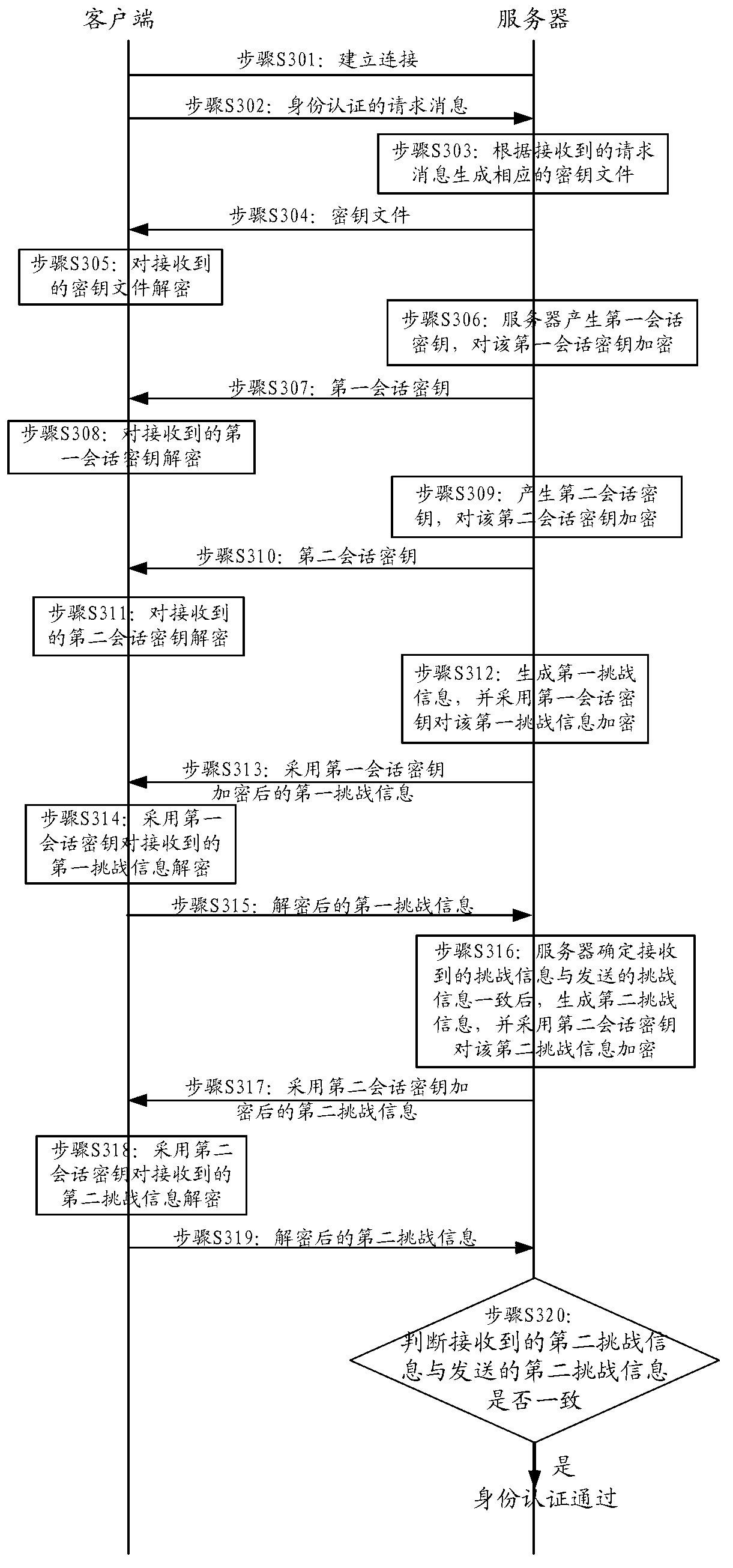
ActiveCN103281193AEnsure safetyAuthentication method securityUser identity/authority verificationClient-sideData transmission
The invention provides an identity authentication method and system and a data transmission method and device based on the identity authentication method and system. The identity authentication method comprises the steps: sending a request message of identity authentication to a server, receiving a secret key file returned by the server according to the request message, decoding the secret key file, receiving a first session secret key sent by the server, decoding the first session secret key, receiving a challenge message which is generated and sent by the server and encrypted through the first session secret key, and decoding the challenge message through the first session secret key. Compared with a simple identity authentication method in the prior art, the identity authentication method is safer, and accordingly safety of communication between a client and the server is ensured.
Owner:中科芯云微电子科技有限公司
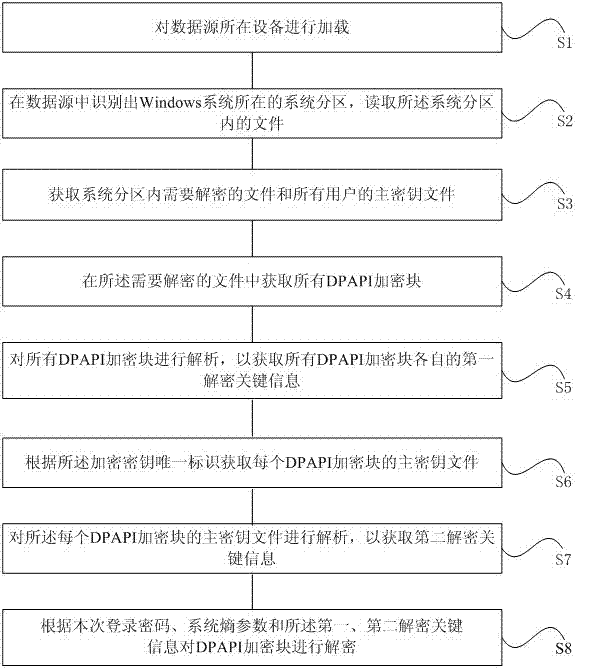
Deciphering method and system of data protection application programming interface (DPAPI) enciphered data
ActiveCN103116730AImplement offline decryptionMeet the read-only requirementEncryption apparatus with shift registers/memoriesDigital data protectionComputer hardwareOperational system
The invention provides a deciphering method and system of data protection application programming interface (DPAPI) enciphered data. The method comprises the following steps: loading a device, wherein a data source is in the device, identifying a system partition from the data source and reading files in the system partition, wherein the Windows system is in the system partition, acquiring files which need to be deciphered and master key files of all users, acquiring all DPAPI enciphered blocks from the files which need to be deciphered, analyzing all the DPAPI enciphered blocks to acquire the first deciphering key information which comprises encipherment secret key unique identification, acquiring the master key files of each DPAPI enciphered block according to the encipherment secret key unique identification, analyzing the master key files to acquire the second deciphering key information which comprises a second annoyance value and a second secret key derive function iteration based on commands, and deciphering the DPAPI enciphered blocks according to a login password, system entropy parameters, the first deciphering key information and the second deciphering key information. The method and the system can achieve read only operation of the data source and meet the need of cross-platform without restriction of operating system.
Owner:XIAMEN MEIYA PICO INFORMATION
Access control method and device of file encrypting system on the basis of partitions
InactiveCN103914662AEasy to operateLow costUser identity/authority verificationDigital data protectionPasswordUser input
The invention discloses an access control method and device of a file encrypting system on the basis of partitions. The method includes that a password and / or a key file input by a user are / is read to determine whether an encrypting partition exists or not; if the encrypting partition does not exist, the user sets the password and / or the key file which are / is read so as to establish the encrypting partition which is protected by the user password and / or key file, and then the password and / or the key file input by the user are / is read to determine whether the encrypting partition exists or not; if the encrypting partition exists, a decryption key is generated by a possible algorithm according to the password and / or the key file input by the user, and a verification value and a checking value are obtained through the decryption key by the possible algorithm; whether the verification value and the checking value obtained after decryption are consistent to set verification value and checking value or not is determined respectively; if the verification value and the checking value obtained after decryption are consistent to the set verification value and checking value, identity verification passes to obtain file data; otherwise, the password and / or the key file are / or incorrect. Thereby, by means of the access control method and device of the file encrypting system on the basis of the partitions, identity verification grade of the file encrypting system can be improved.
Owner:ASIA EURO BOLOD INFORMATION SECURITY TECHHUNAN
Distributed cryptographic management for computer systems
ActiveUS8291224B2Key distribution for secure communicationUser identity/authority verificationSupporting systemComputerized system
Owner:WELLS FARGO BANK NA
Systems, methods and devices for ai-driven automatic test generation
ActiveUS20190042400A1Natural language data processingSoftware testing/debuggingTest scriptMaster key
A test script is generated in an automated fashion based on a master key file (and optionally, additionally based on user logs) in order to test a software application. The master key file may include one or more scripts of every (or nearly every) possible interaction (e.g., request, presentation, executed action, and so on) a user may have with the software application under test. Often times, the master key file captures each and every request that could be made from a client device to the software application under test executing at a server.
Owner:APPVANCE
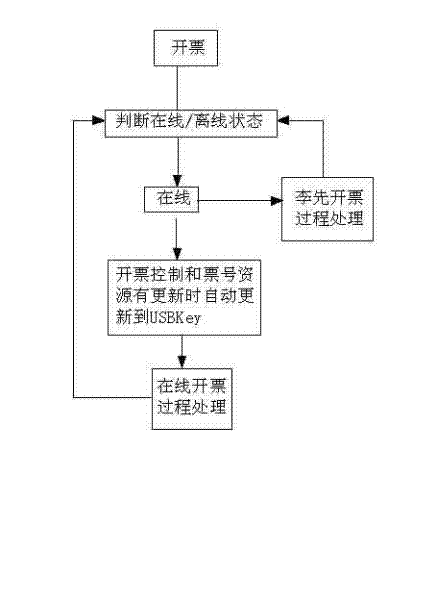
Online/offline invoicing automatic switching method based on password key
InactiveCN102419852AEnsure loose couplingGuaranteed scalabilityUser identity/authority verificationBilling/invoicingComputer hardwareAutomatic control
The invention provides an online / offline invoicing automatic switching method based on a password key. Based on a software and hardware combined mode as well as Web service and information safety technique, the method can guarantee that tax payers can still normally invoice by using network invoice client software and achieve digital anti-counterfeiting, reliable storage and safe transmission of invoicing data when a tax bureau terminal network invoice management and control system cannot be used. The method adopts an intelligent password key as a shared storage medium of an invoicing control file, an invoice number resource file and a key file under an online / offline invoicing state, and automatically controls smooth switching between online invoicing and offline invoicing through the network invoice client software installed on a password key host computer. Invoicing interfaces of the client software under online and offline states are completely identical and are completely public for the tax payers.
Owner:INSPUR QILU SOFTWARE IND
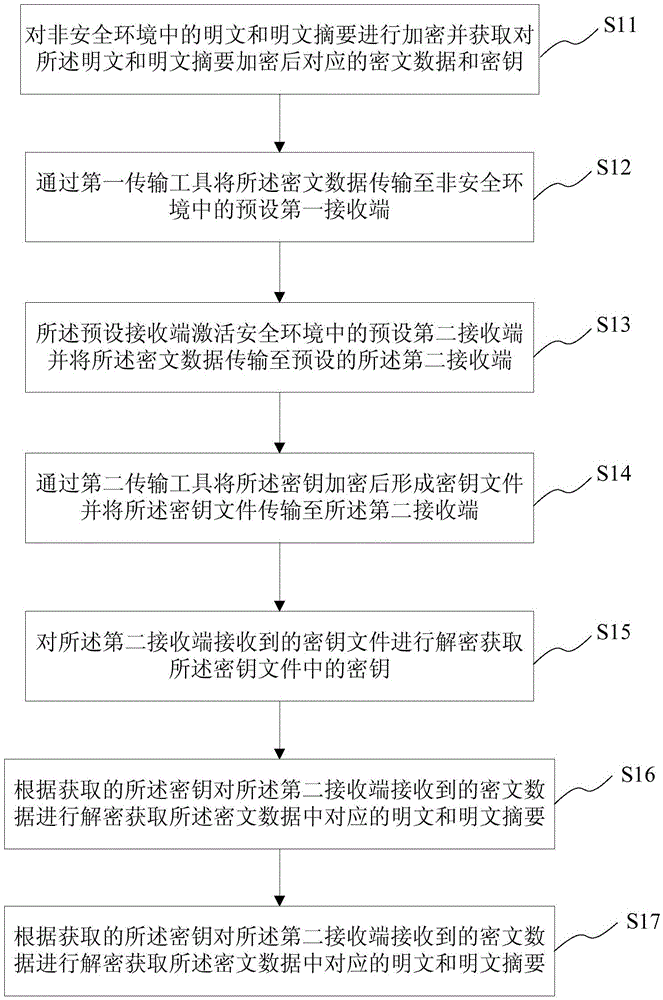
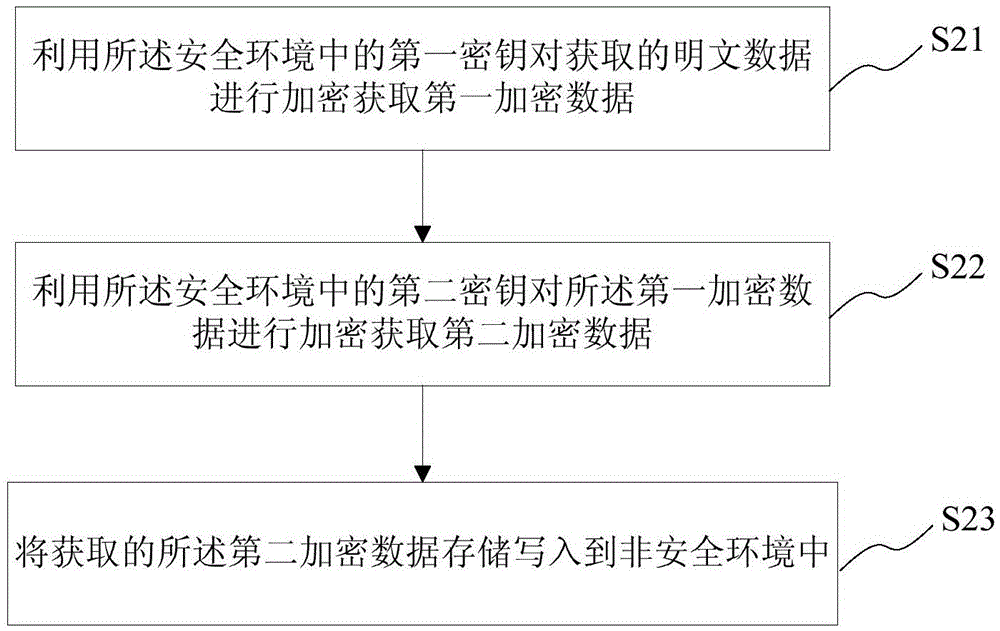
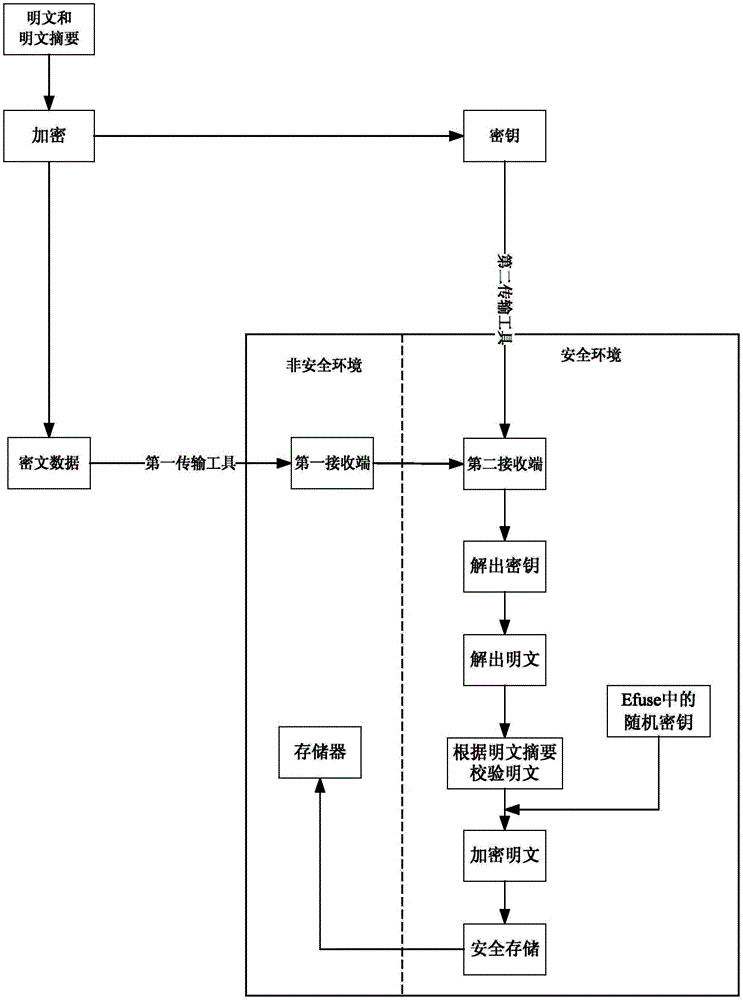
Data transmission and storage method and system
InactiveCN106709360AIncrease the difficulty of crackingImprove transmission securityDigital data protectionPlaintextComputer hardware
The invention provides a data transmission and storage method and system. The data transmission method comprises the steps that plaintext and plaintext abstracts in an unsecured environment are encrypted, and corresponding encrypted data and secret keys are obtained; the encrypted data is transmitted to a preset first receiving end in the unsecured environment through a first transmission tool; the preset first receiving end activates a preset second receiving end in a secure environment, and the encrypted data is transmitted to the preset second receiving end; after the secrete keys are encrypted through a second transmission tool, a secret key file is formed and transmitted to the second receiving end; the secrete key file received by the second receiving end is decrypted to obtain the secrete keys in the secret key file; the encrypted data received by the second receiving end is decrypted according to the obtained secret keys to obtain the corresponding plaintext and plaintext abstracts, and the integrity of the plaintext is verified according to the plaintext abstracts. According to the data transmission and storage method and system, the secret keys and the encrypted data are subjected to time-share transmission through different transmission channels, the transmission security is improved, and the plaintext cracking difficulty is increased.
Owner:FUZHOU ROCKCHIP SEMICON
System and method for optimization of antivirus processing of disk files
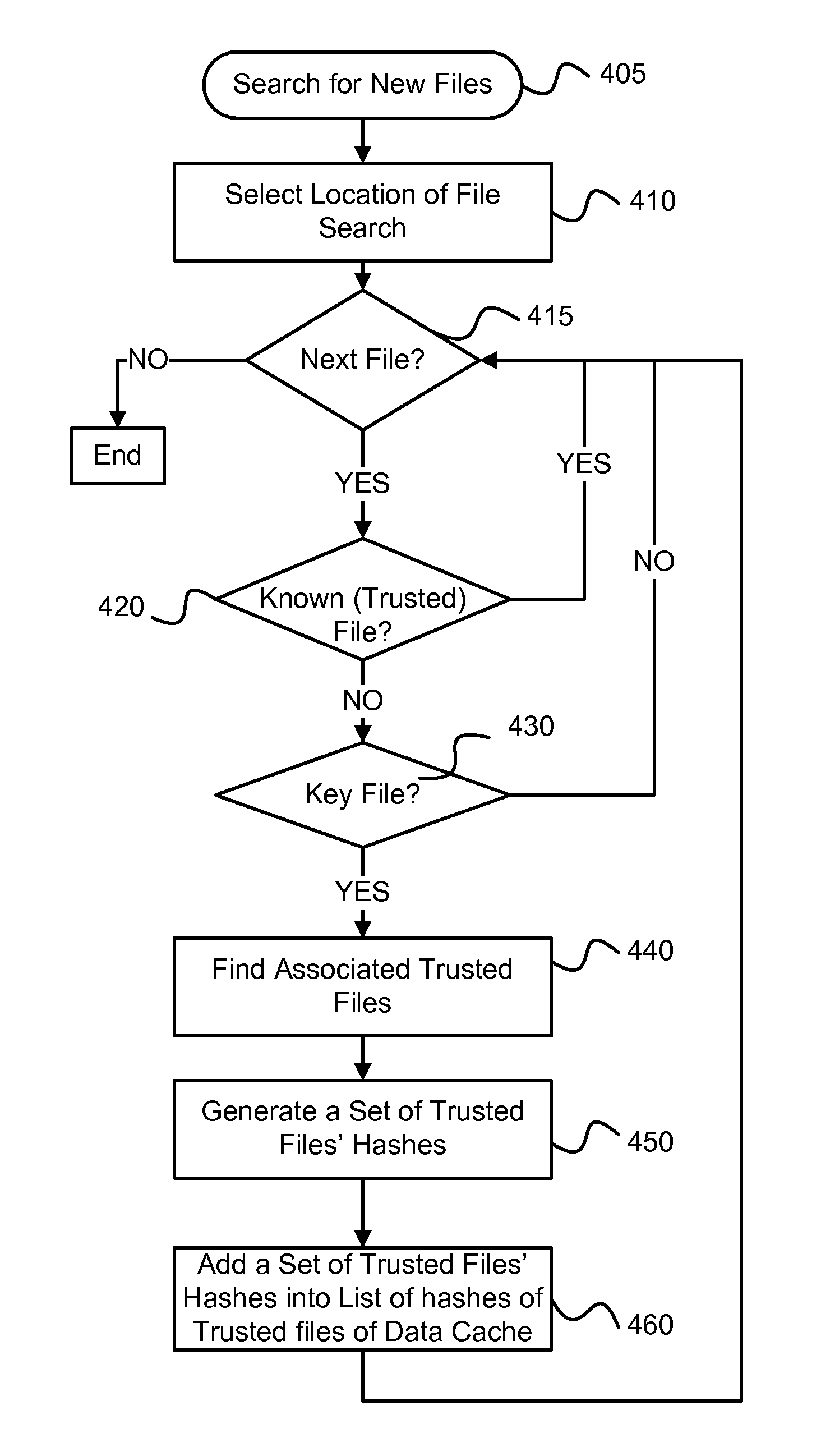
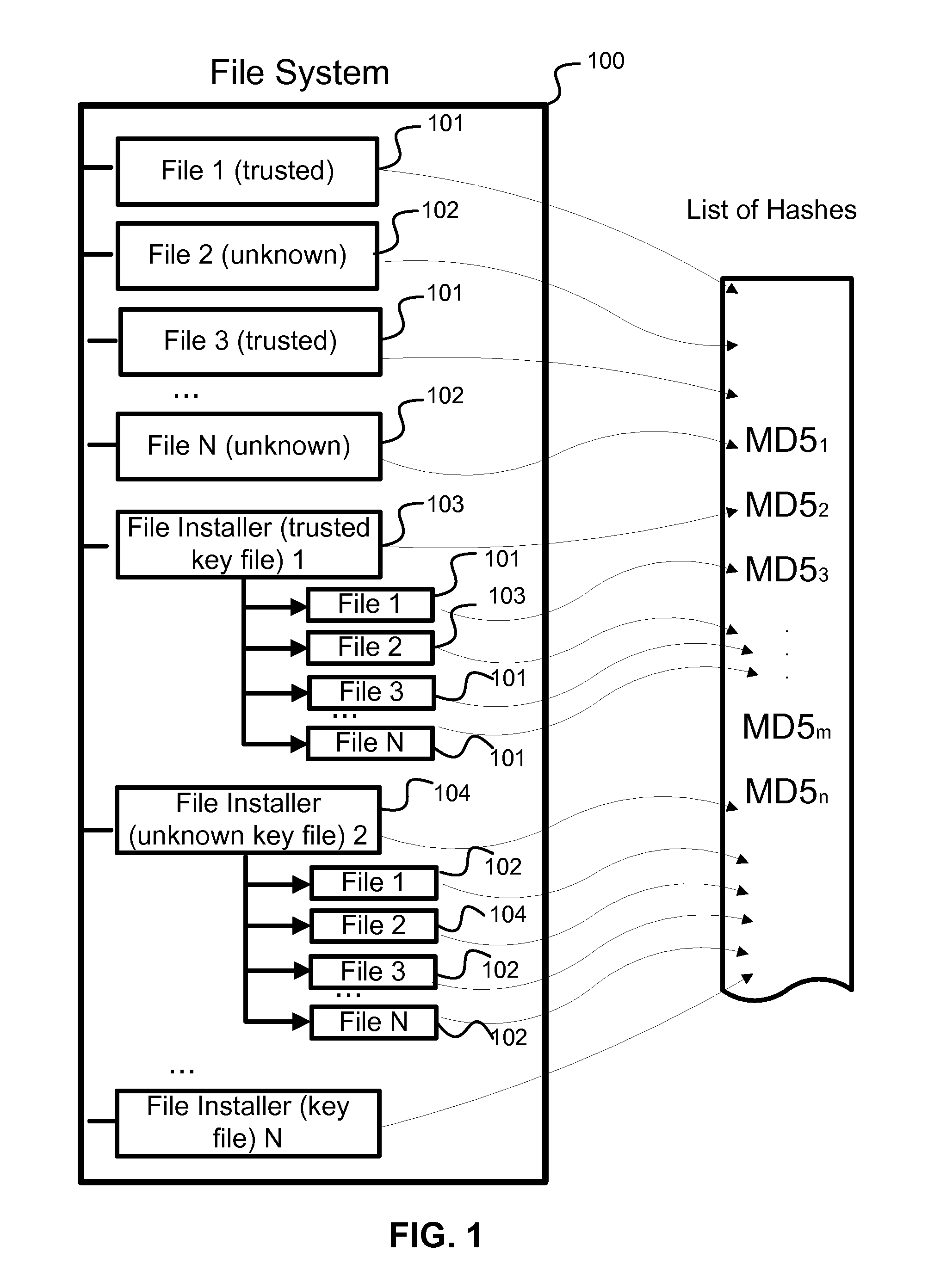
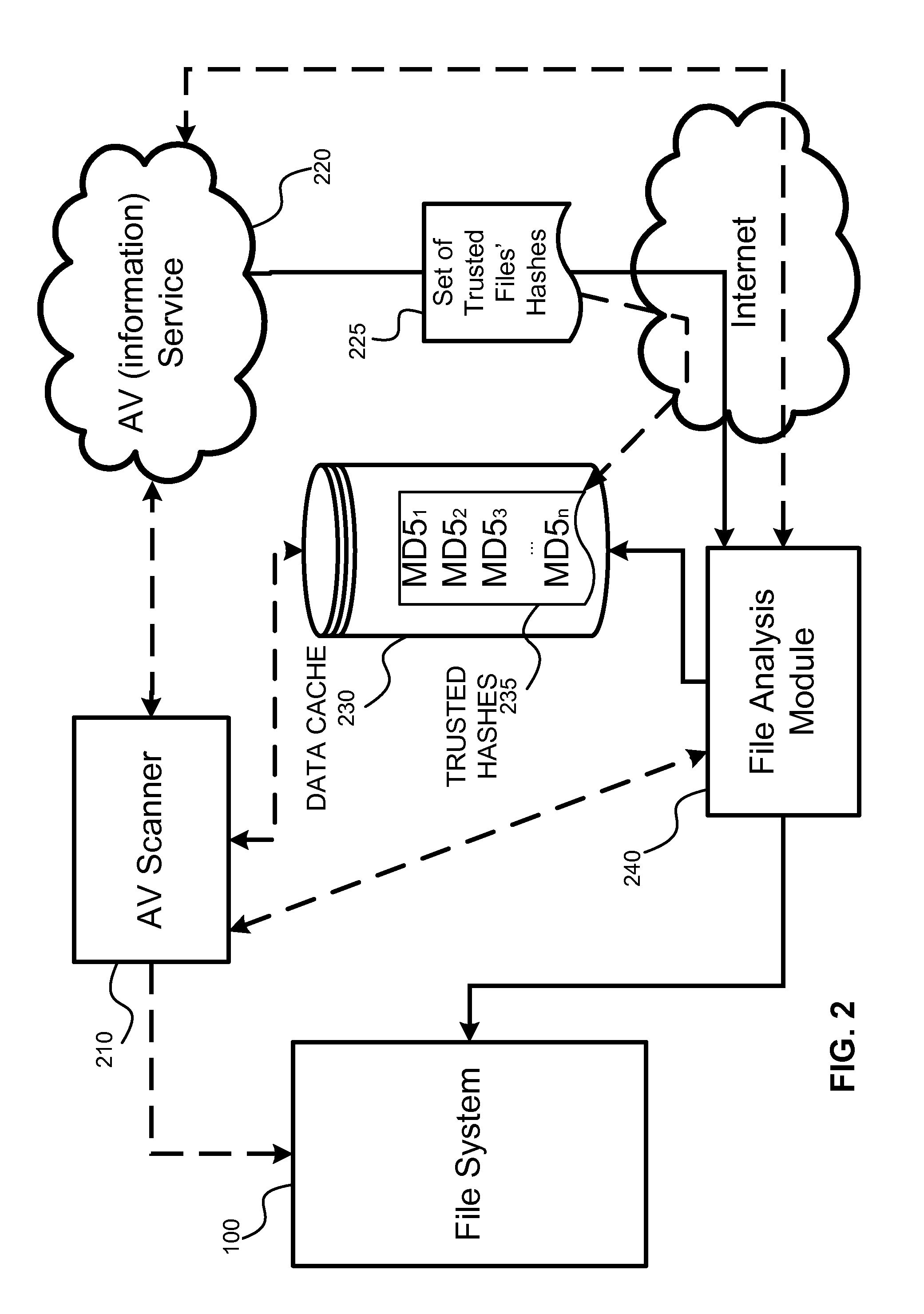
ActiveUS20130227692A1Reduce AV/security file check scanning timeReduce scan timeMemory loss protectionError detection/correctionOperating systemKeyfile
A system and method for optimization of AV processing of disk files. The system includes an AV scanner, a data cache module, an AV service and file analysis module. The optimization allows for reduction of time needed for the AV processing. Trusted files associated with a trusted key file are found. The trusted files that have been found are cached and excluded from further AV processing and the AV processing time is reduced.
Owner:AO KASPERSKY LAB
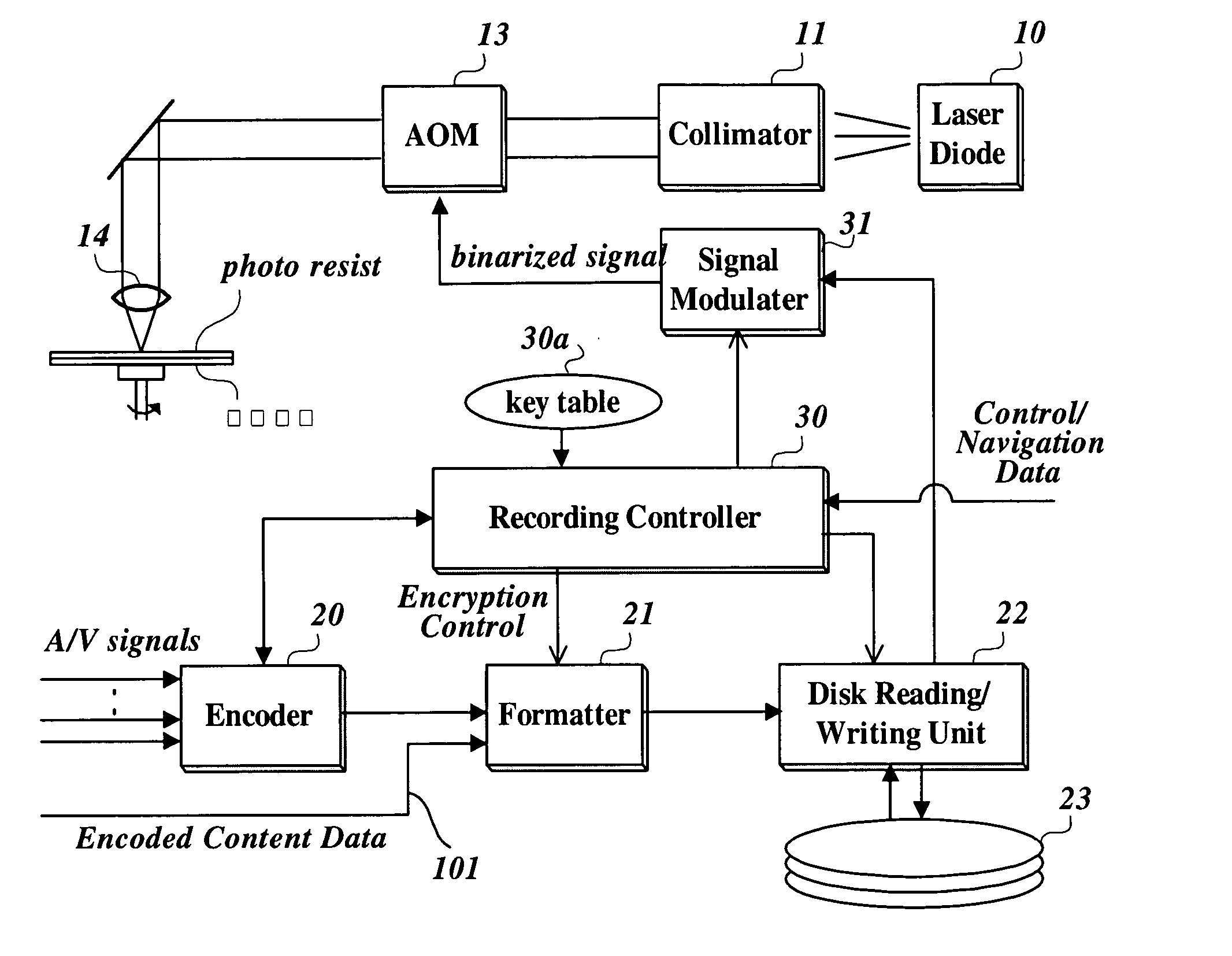
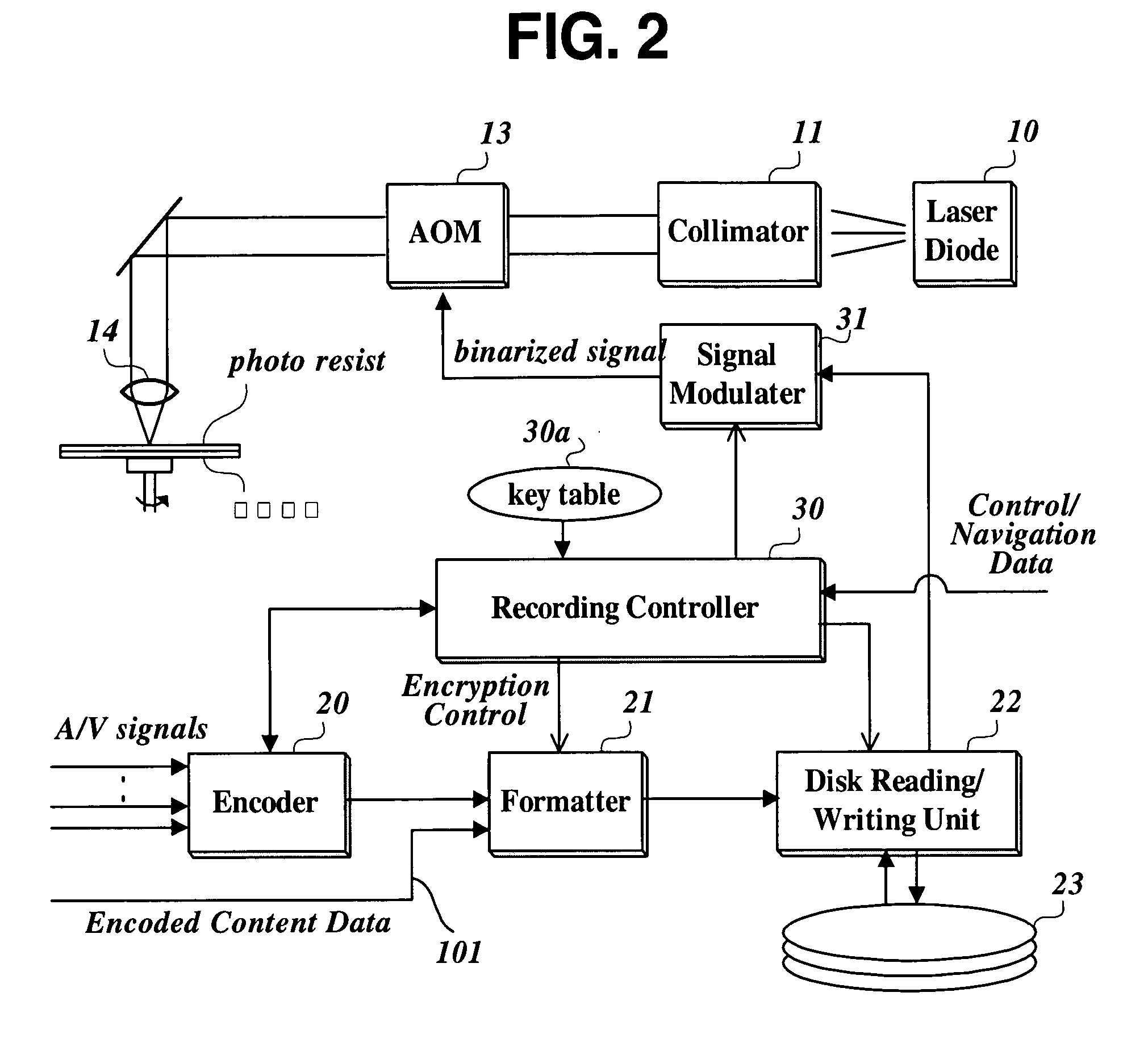
Method and apparatus for writing and using keys for encrypting/decrypting a content and a recording medium storing keys written by the method
Content encryption information on content data recorded on a recording medium. A plurality of encryption keys used for encrypting a plurality of data clips containing content data is stored in a key file and index information for associating each of the plurality of encryption keys with a data segment encrypted with the encryption key is placed in the key file or in another management information file (e.g., clip information file). As a consequence, it is allowed to decrypt encrypted content data with different encryption keys by applying each of the plurality of encryption keys to each associated data segment.
Owner:LG ELECTRONICS INC
Dynamic encryption and decryption method based on stream ciphers
InactiveCN103095449AEasy to implementImprove securitySecuring communicationPlaintextComputer hardware
The invention discloses a dynamic encryption and decryption method based on stream ciphers. The method comprises the following steps: encryption coefficient is selected according to the length of a plaintext file; corresponding encryption rules and corresponding deciphering rules are set for different binary digits of a key file; a reference file is selected, the key file is read, a binary digit of the key file is selected, the binary digit of the plaintext file is processed in a read-write mode according to the encryption rules corresponding to the binary digit and combining the encryption coefficient and the reference file, and then a ciphertext file is generated; the key file is read, the binary digit of the ciphertext file is processed in a read-write mode according to the deciphering rules corresponding to the binary digit selected in the encryption process, combining the encryption coefficient and the reference file, and then the restored plaintext file is obtained. The dynamic encryption and decryption method based on stream ciphers is simple in implementation, high in safety and flexibility, and capable of being widely used in the field of computer communications.
Owner:JILIN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com