Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
35 results about "Content based networking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Named data networking (NDN) (related to content-centric networking (CCN), content-based networking, data-oriented networking or information-centric networking (ICN)) is a proposed Future Internet architecture inspired by years of empirical research into network usage and a growing awareness of unsolved problems in contemporary internet architectures ...
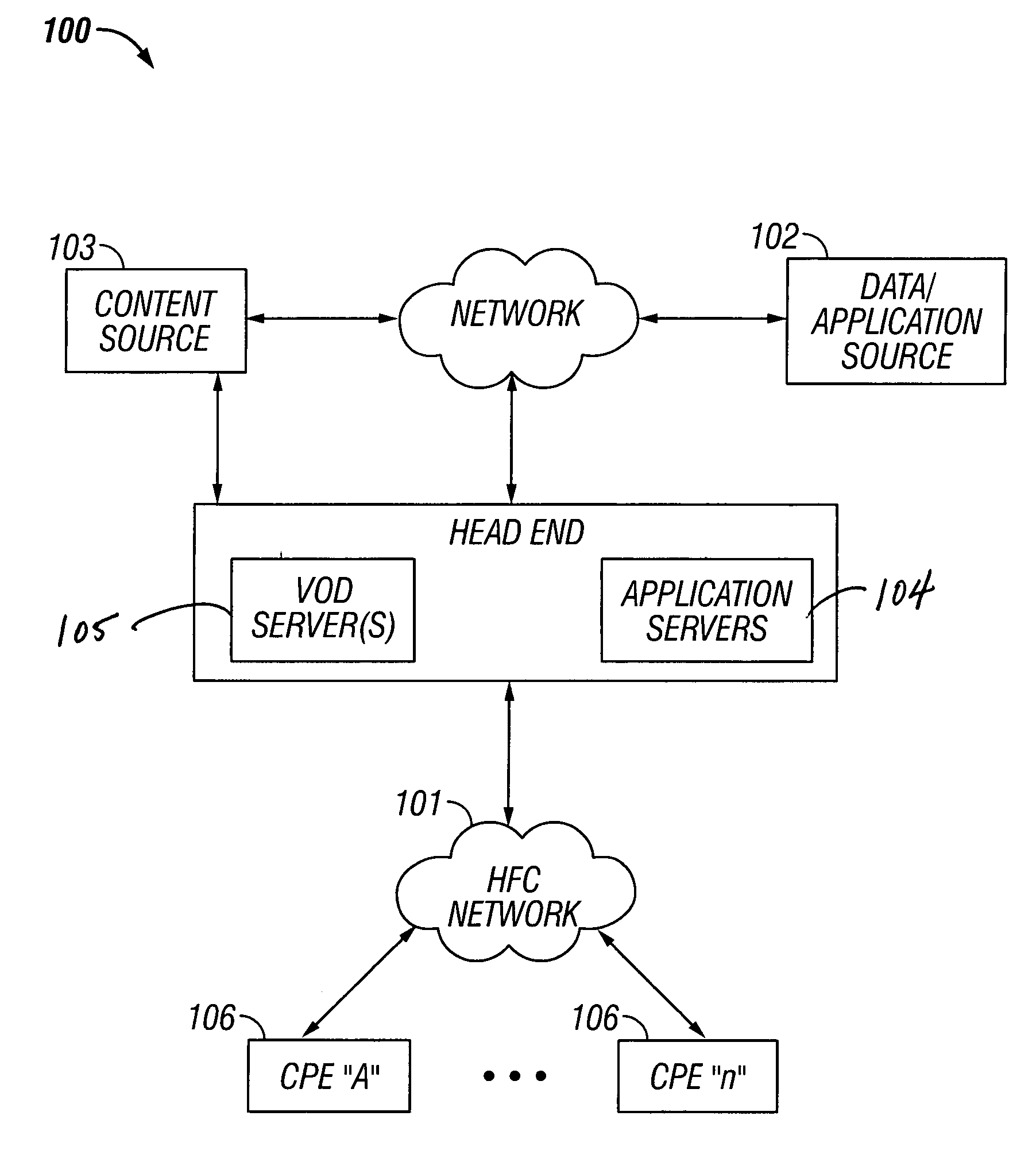
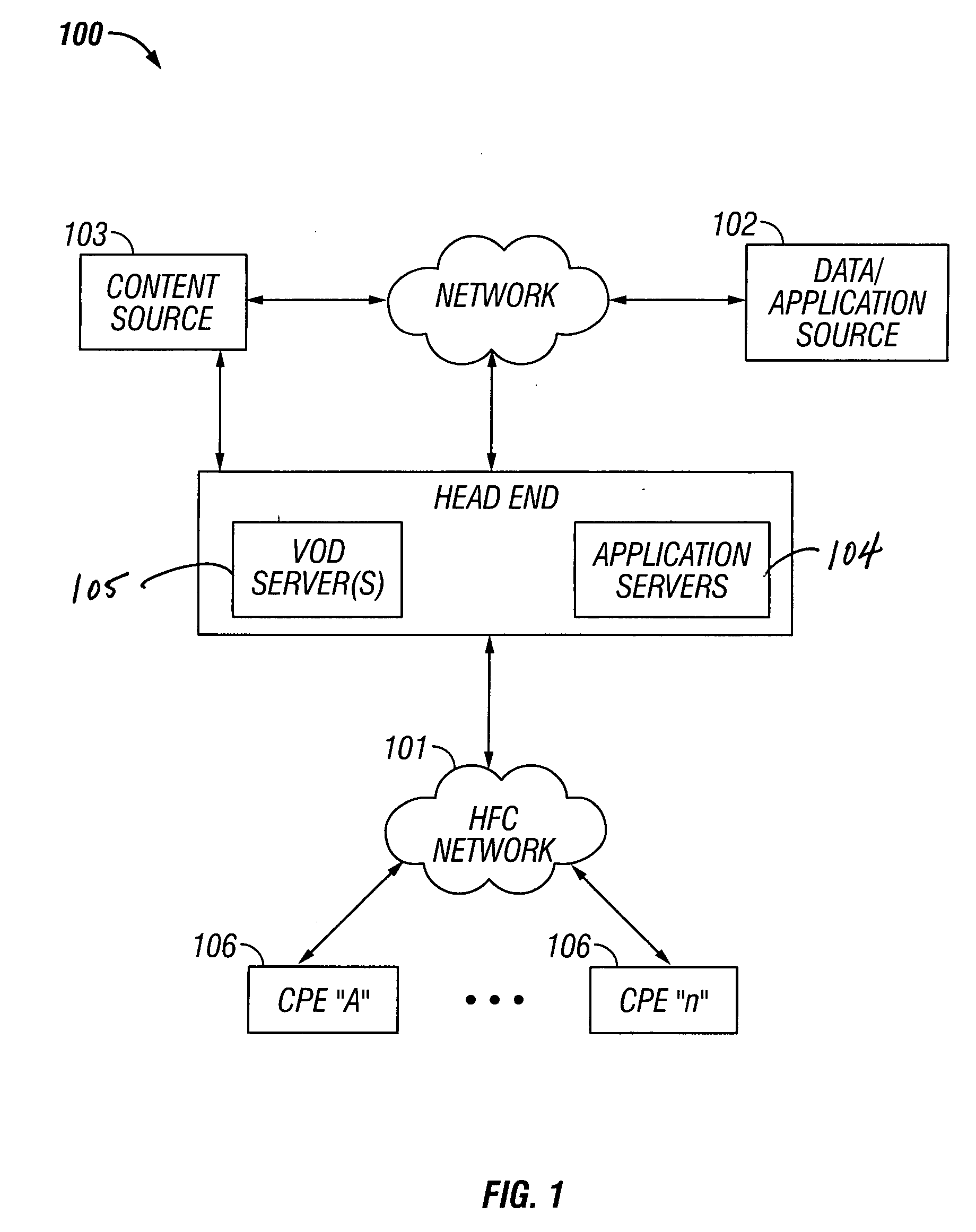
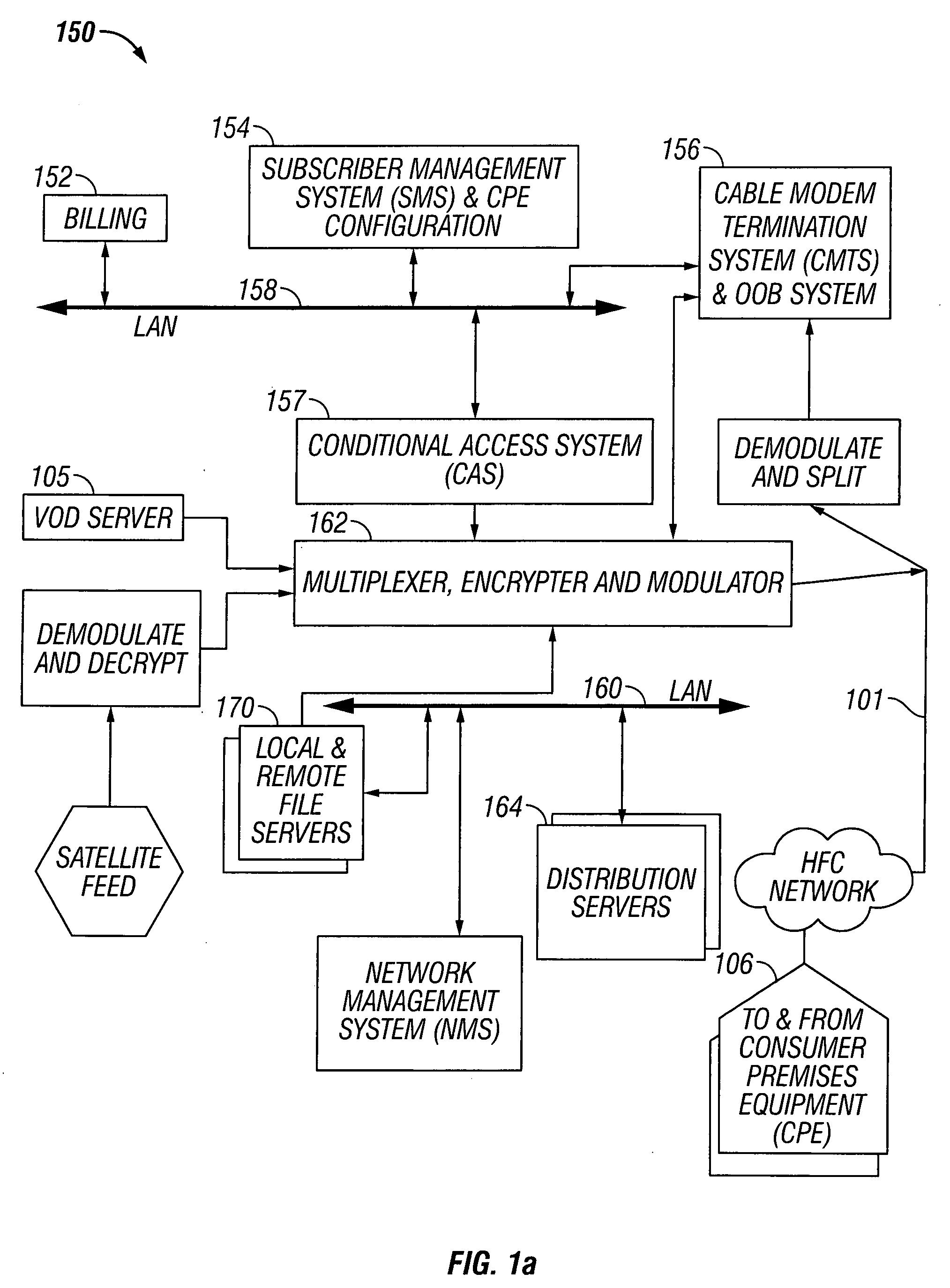
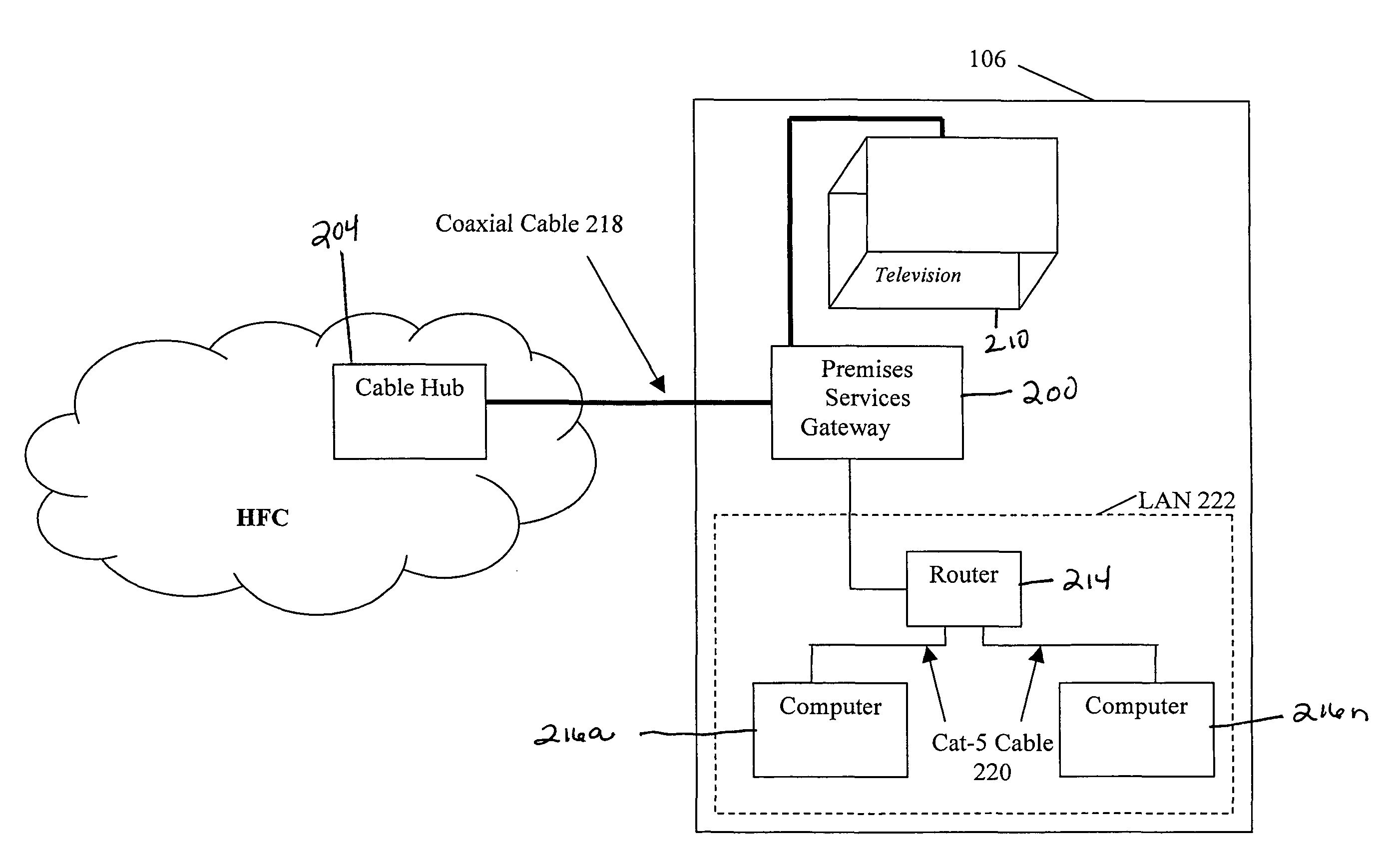
Premises gateway apparatus and methods for use in a content-based network
ActiveUS20080313691A1Satisfies needColor television signals processingNetwork topologiesDigital videoComputer network
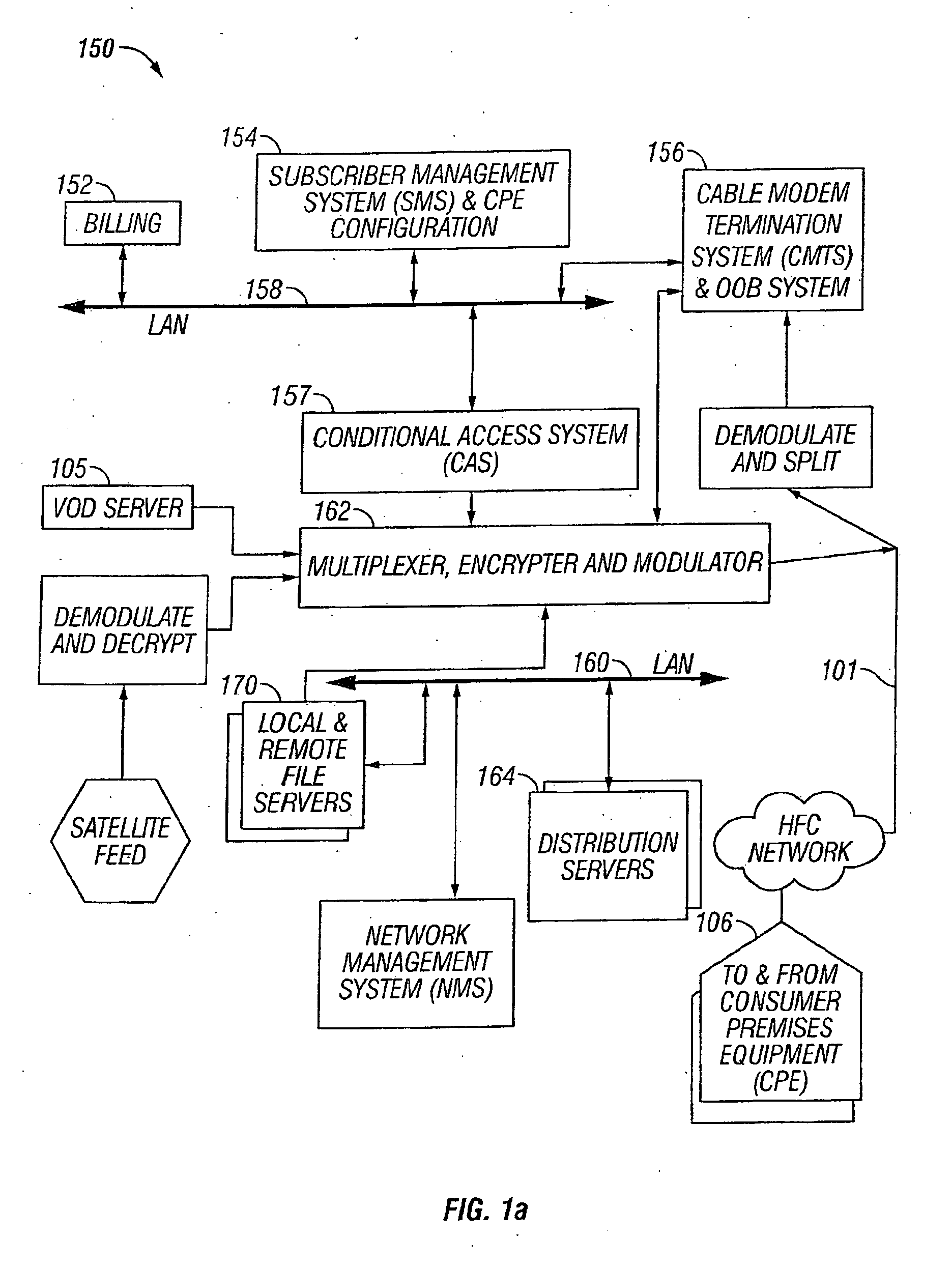
Apparatus and methods for premises gateway functions that integrate or unify functions typically distributed across multiple devices within a content-based network. In one embodiment, the out-of-band (OOB) signaling functionality normally provided in each of a set-top-box (STB) and digital video recorder (DVR) are unified into a common OOB (e.g., DOCSIS) capable premises gateway device, thereby obviating OOB tuners and related components from each device. In another variant, the premises gateway is adapted for all-IP operation, such as for use with IP-based computers and IP set-top boxes, etc. Fully unified variants are also disclosed, wherein the DVR and / or STB functions are physically integrated within the premises gateway.
Owner:TIME WARNER CABLE ENTERPRISES LLC
Premises gateway apparatus and methods for use in a content-based network
Apparatus and methods for premises gateway functions that integrate or unify functions typically distributed across multiple devices within a content-based network. In one embodiment, the out-of-band (OOB) signaling functionality normally provided in each of a set-top-box (STB) and digital video recorder (DVR) are unified into a common OOB (e.g., DOCSIS) capable premises gateway device, thereby obviating OOB tuners and related components from each device. In another variant, the premises gateway is adapted for all-IP operation, such as for use with IP-based computers and IP set-top boxes, etc. Fully unified variants are also disclosed, wherein the DVR and / or STB functions are physically integrated within the premises gateway.
Owner:TIME WARNER CABLE ENTERPRISES LLC
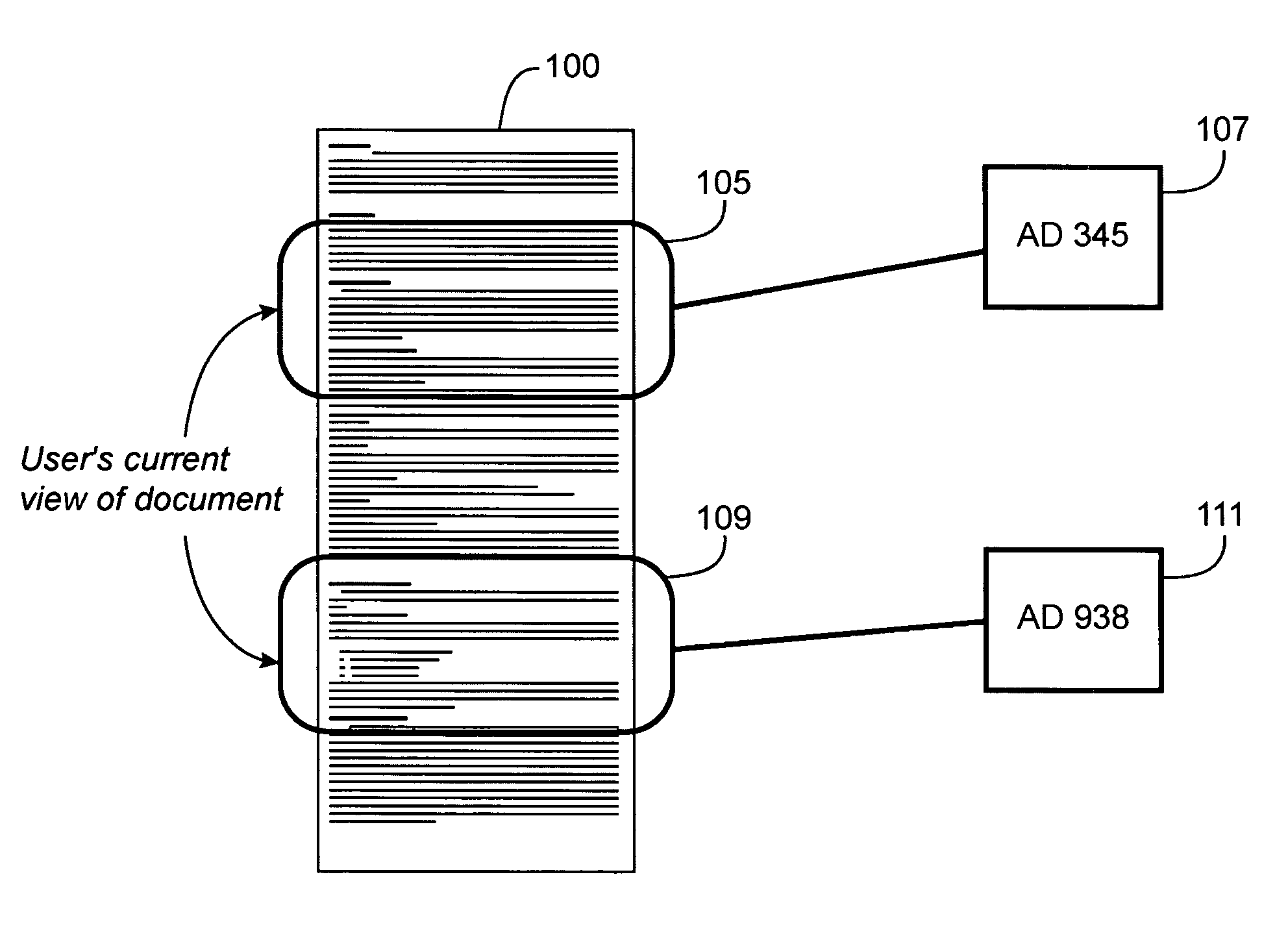
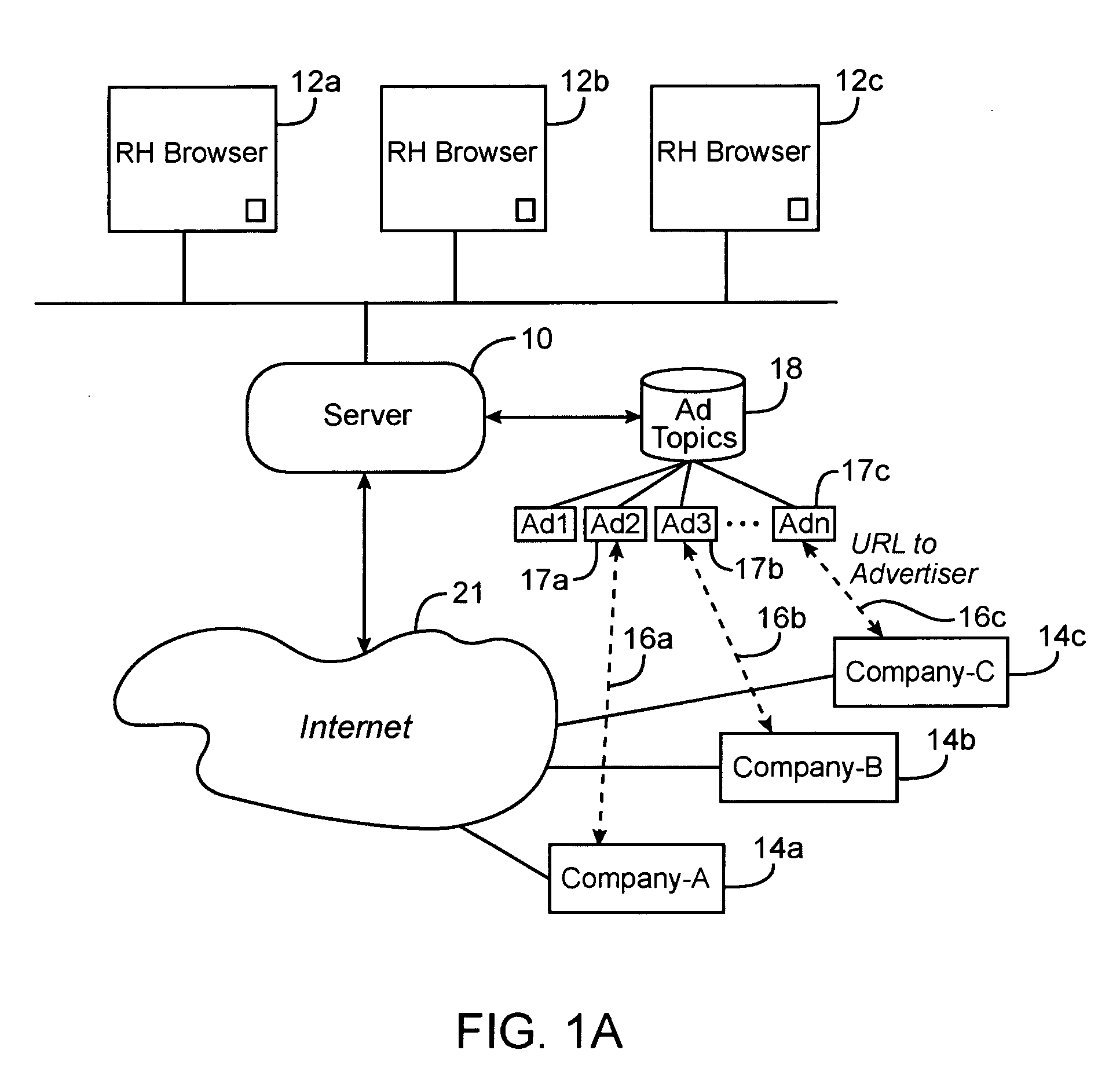
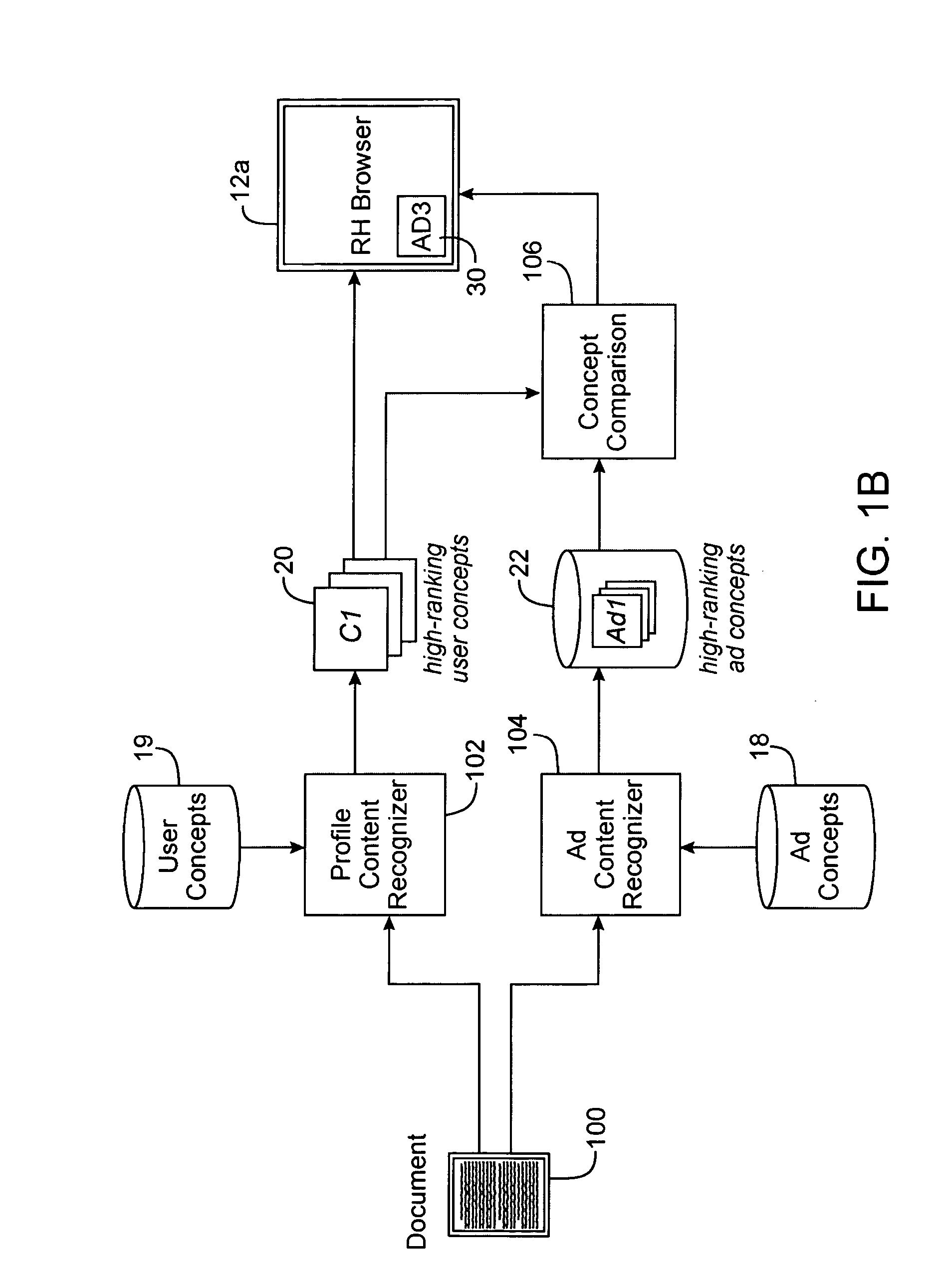
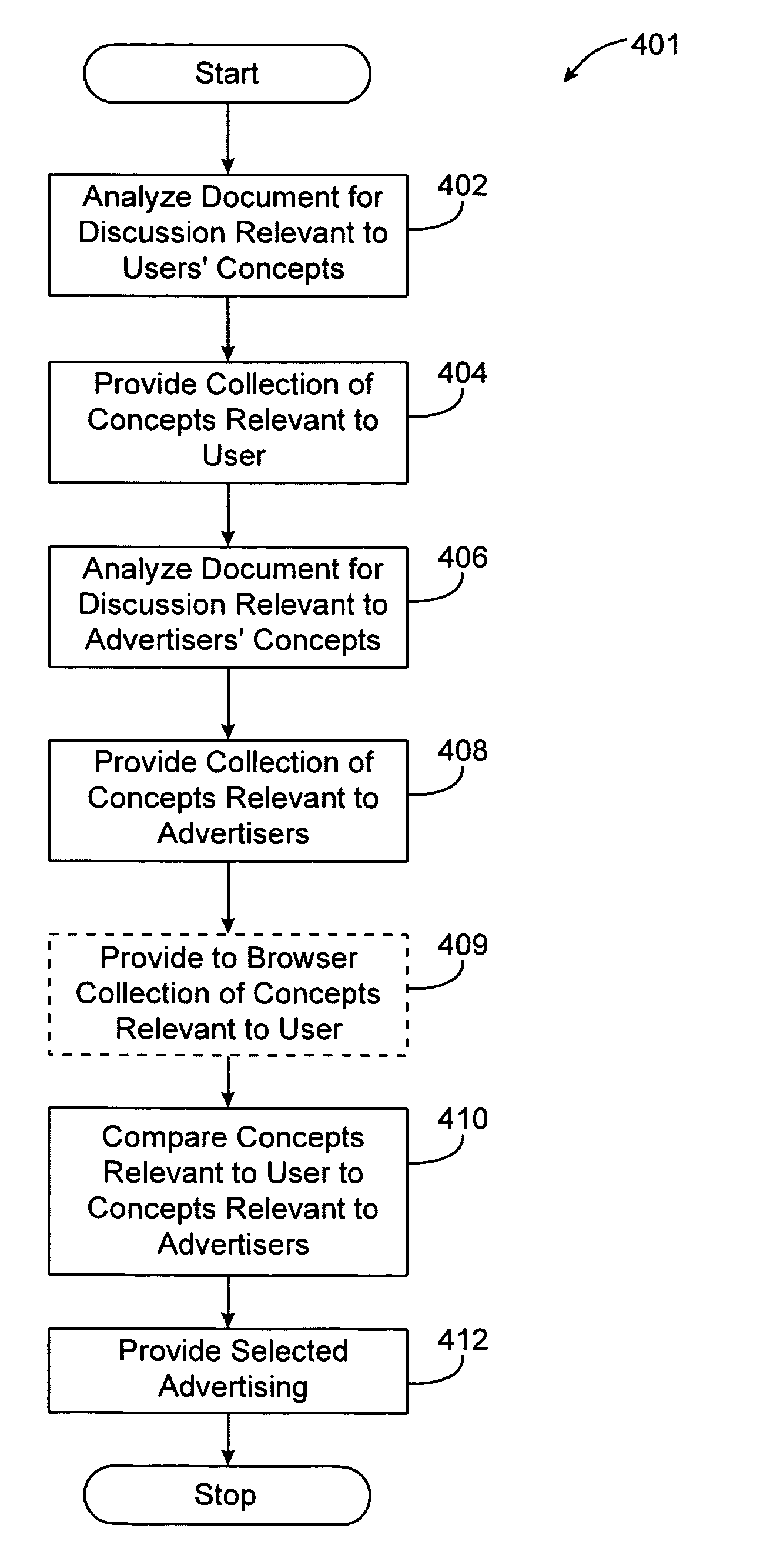
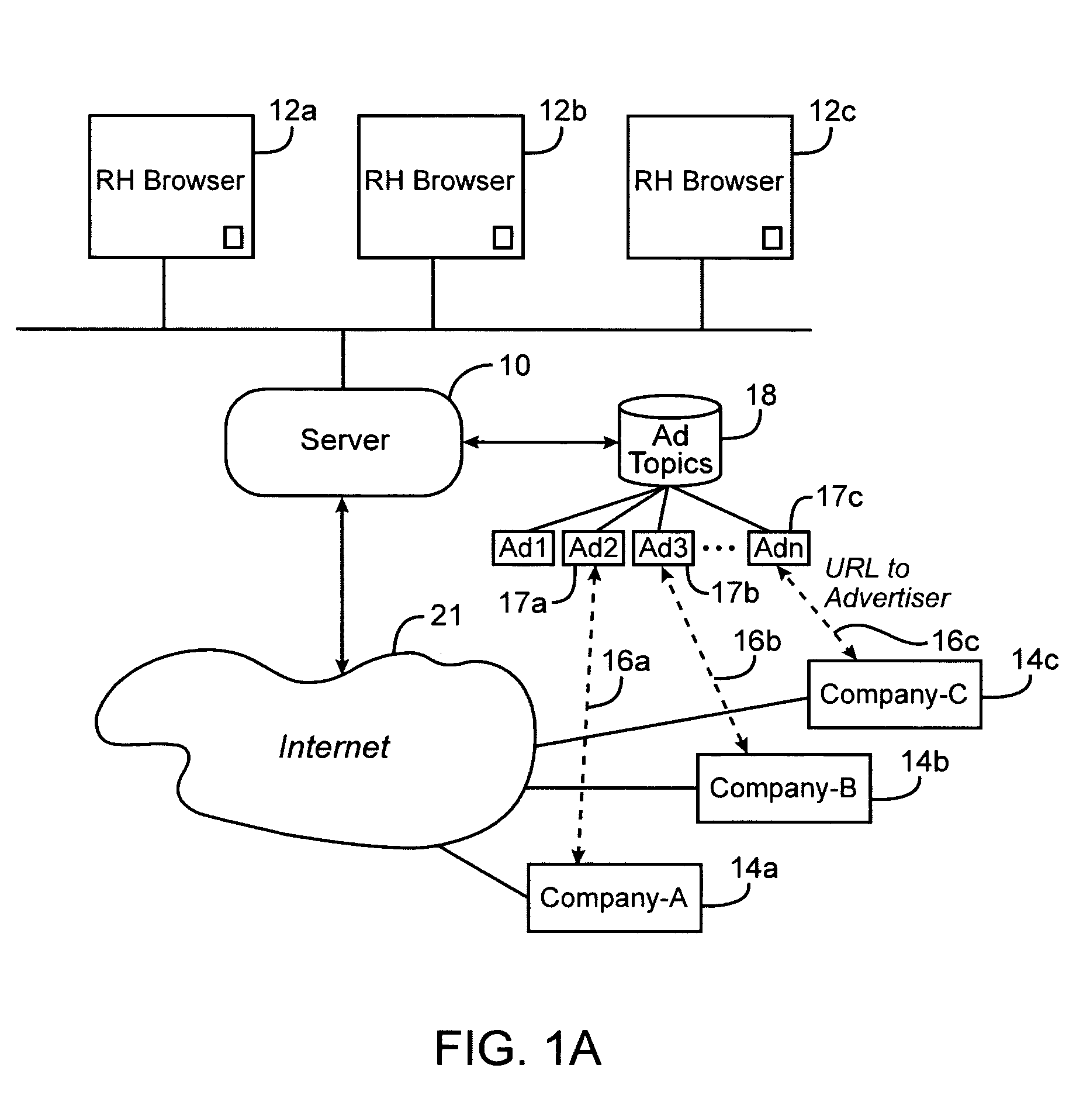
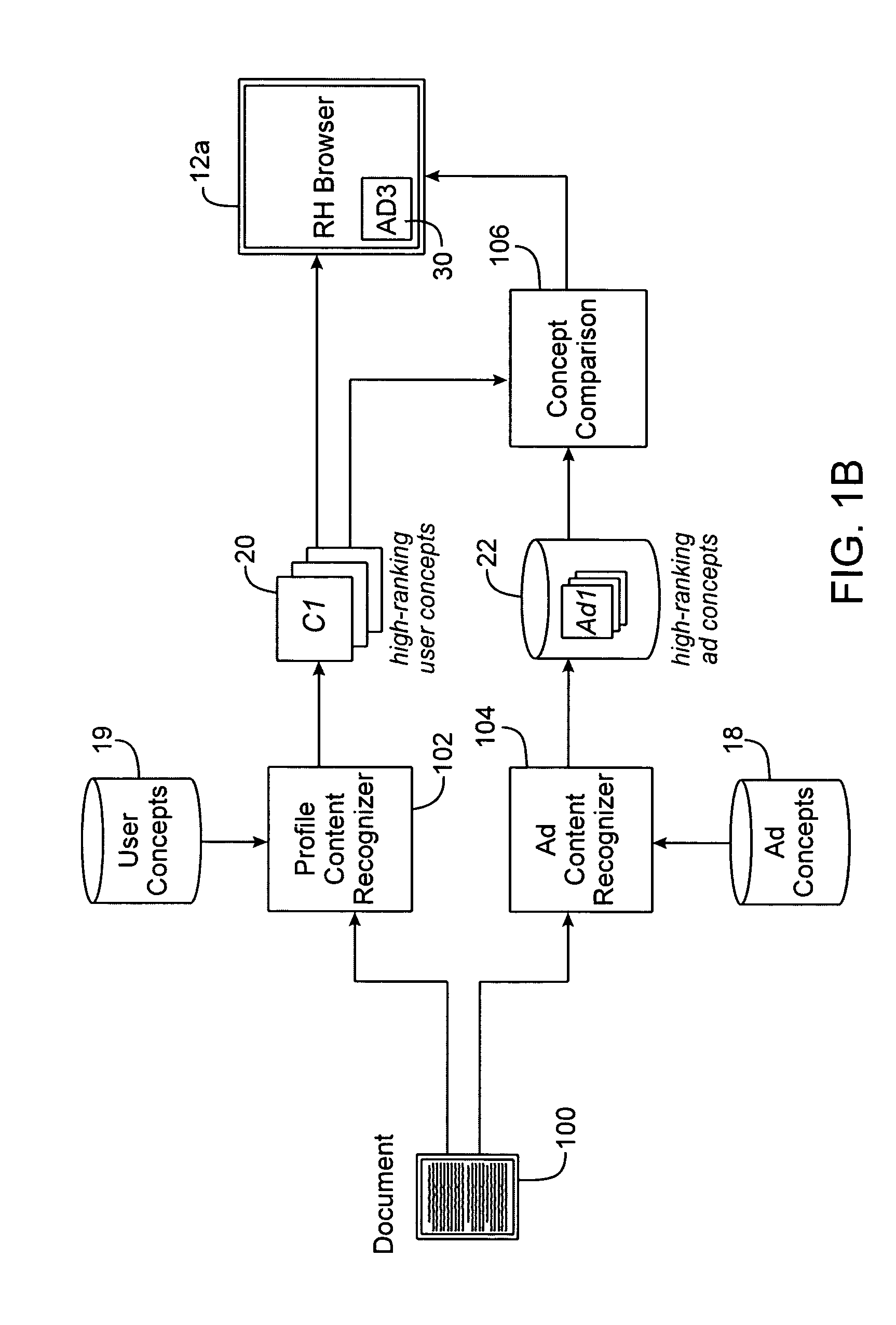
Method, system and computer code for content based web advertising
InactiveUS20060122884A1Specific targetingTargeted optimizationAdvertisementsOnline advertisingDocumentation
An internet target marketing system, method, and computer program for distributing online advertising to viewers based upon the viewers' interests is provided. The system, method, and computer program may involve identifying one or more document-related concepts derived from analysis of content of a web document capable of being displayed to the user, identifying one or more advertisement-related concepts relevant to an advertising, comparing the one or more document-related concepts to the one or more advertising-related concepts to determine a relevance, and selecting the advertising based on the relevance.
Owner:RICOH KK
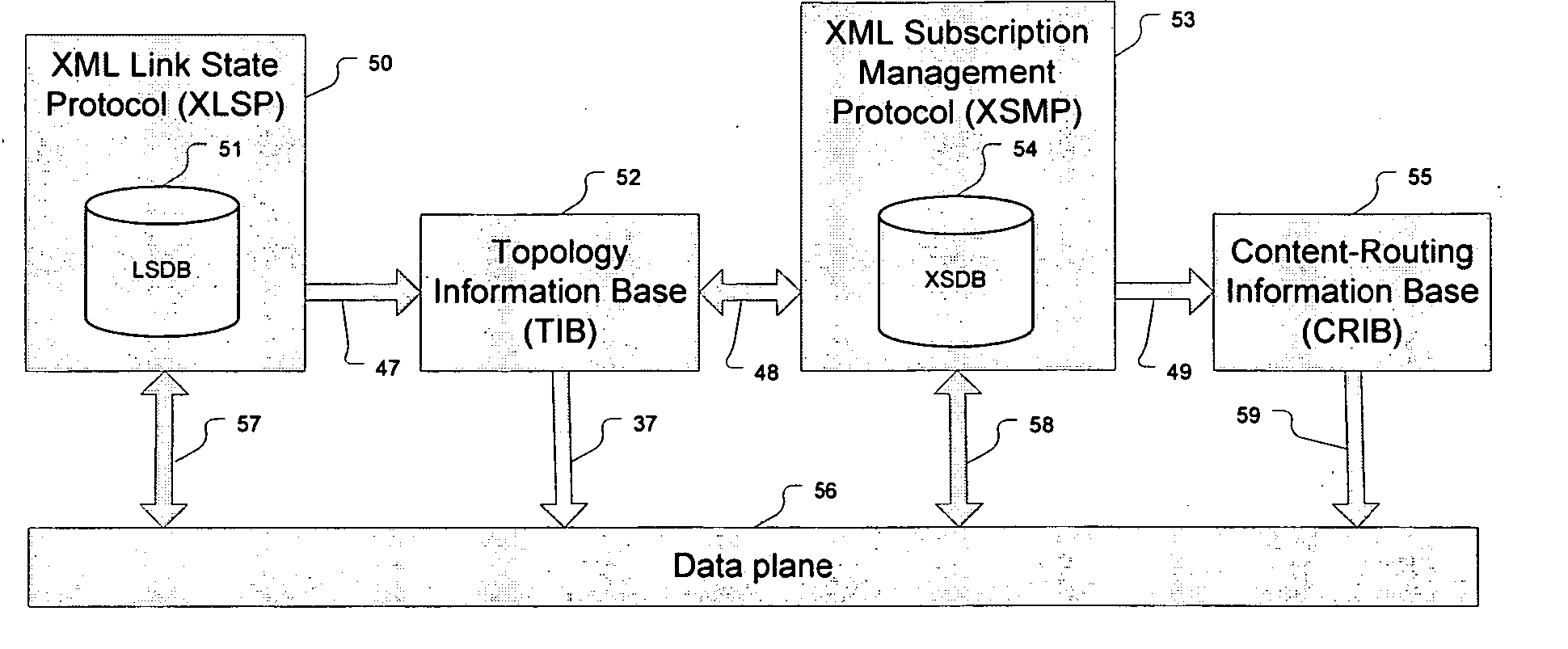
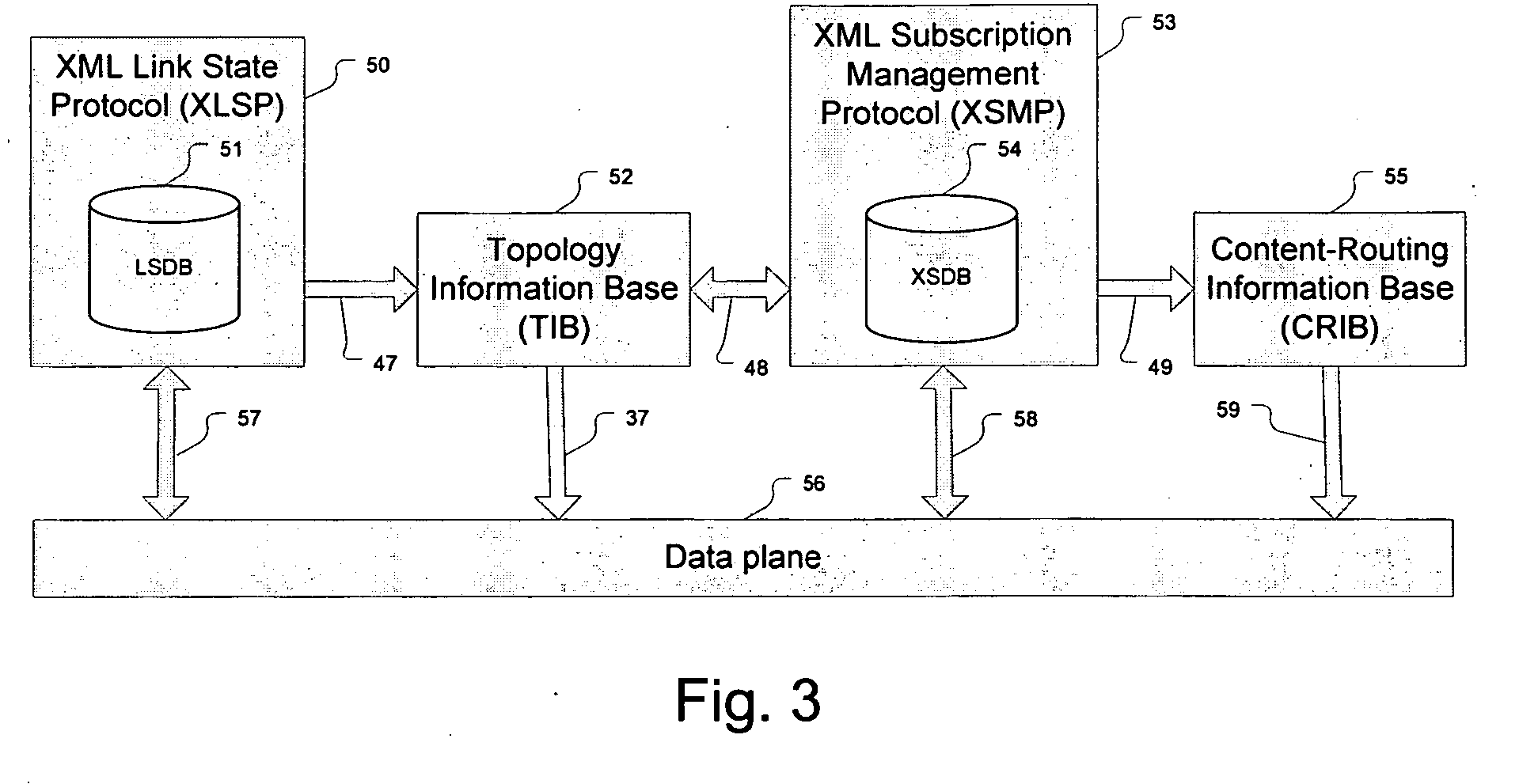
Implicit routing in content based networks
ActiveUS20050152286A1Improve robustnessAvoid formingData switching by path configurationContent based networkingXML
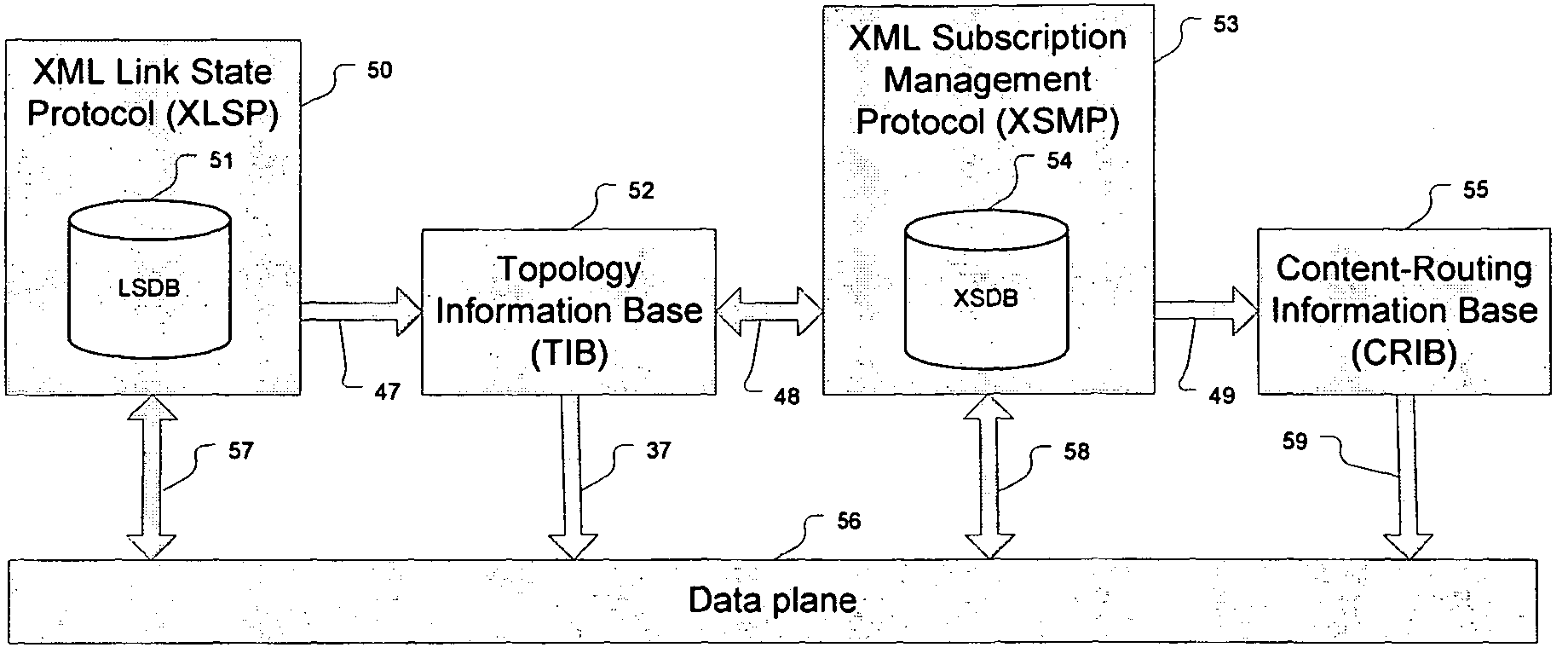
In a method of managing a content-based network, which is typically XML-based, and optionally may be overlaid on an underlying network having a plurality of network elements interconnected by links, a link state protocol maintains each network element's topological view of the overlay network from the underlying network. A subscription management protocol ensures dissemination of published content within the content-based network independently of the link state protocol.
Owner:SOLACE CORP
Method, system and computer code for content based web advertising
InactiveUS7124093B1Targeted optimizationImprove protectionAdvertisementsCash registersDocumentation procedurePage view
Owner:RICOH KK
Special audio event layered and generalized identification method based on SVM (Support Vector Machine) and GMM (Gaussian Mixture Model)
InactiveCN102799899AReduce distractionsEasy extractionCharacter and pattern recognitionSvm classifierData mining
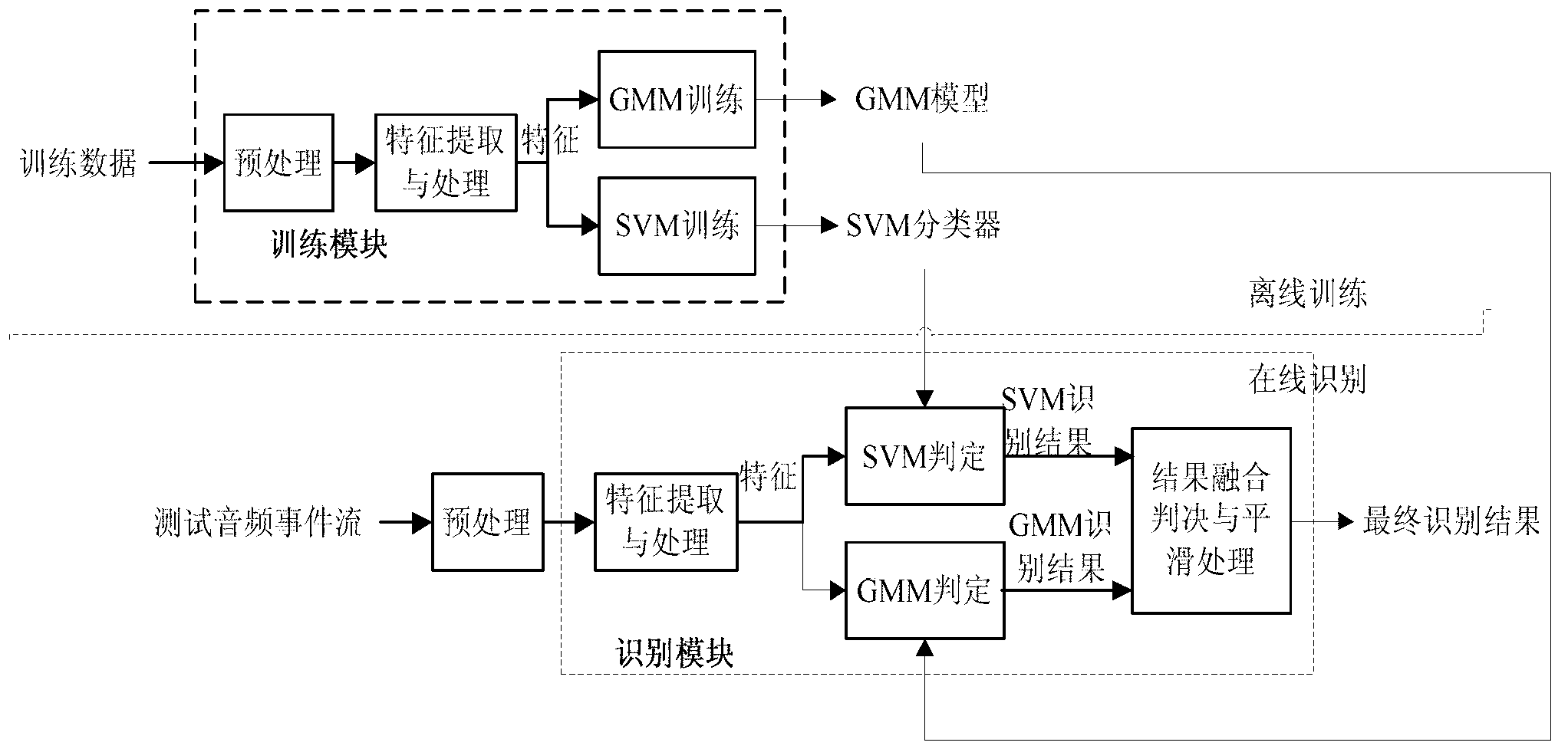
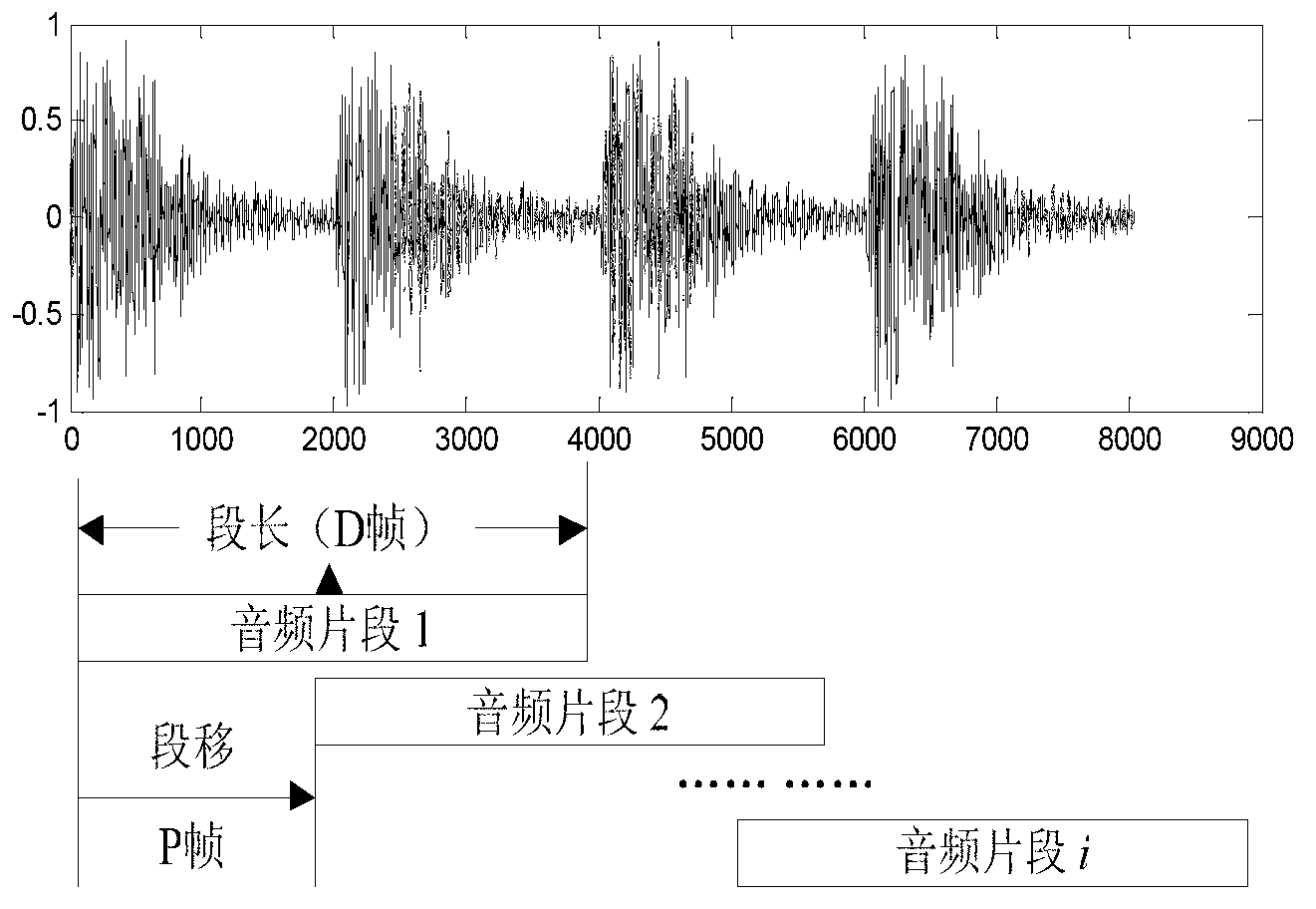
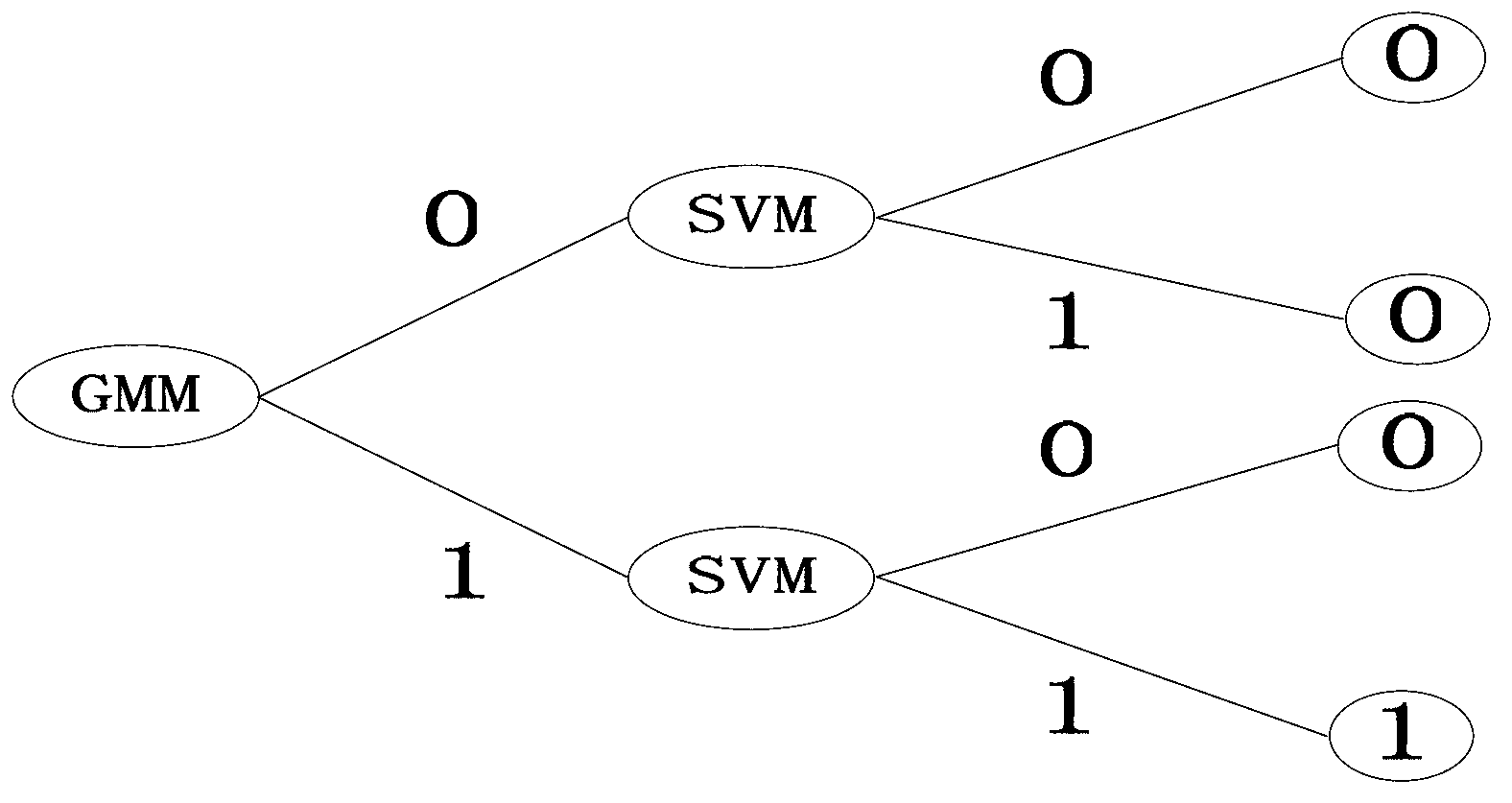
The invention relates to a special audio event layered and generalized identification method based on a combination of an SVM (Support Vector Machine) and a GMM (Gaussian Mixture Model), and belongs to the technical field of a computer and audio event identification. The special audio event layered and generalized identification method comprises the following steps of: firstly, obtaining an audio characteristic vector file of a training sample; secondly, respectively carrying out model training on a great quantity of audio characteristic vector files (of the training samples) with various types by using a GMM method and an SVM method, so as to obtain the GMM model with generalization capability and an SVM classifier, and complete offline training; and finally, carrying out layered identification on the audio characteristic vector files to be identified by using the GMM model and the SVM classifier. With the adoption of the method provided by the invention, the problems that the conventional special audio event identification is low in identification efficiency on a continuous audio stream, very short in continuing time, high in audio event false dismissal probability can be solved. The method can be applied to searching a special audio and monitoring a network audio based on contents.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Aggregate signing of data in content centric networking
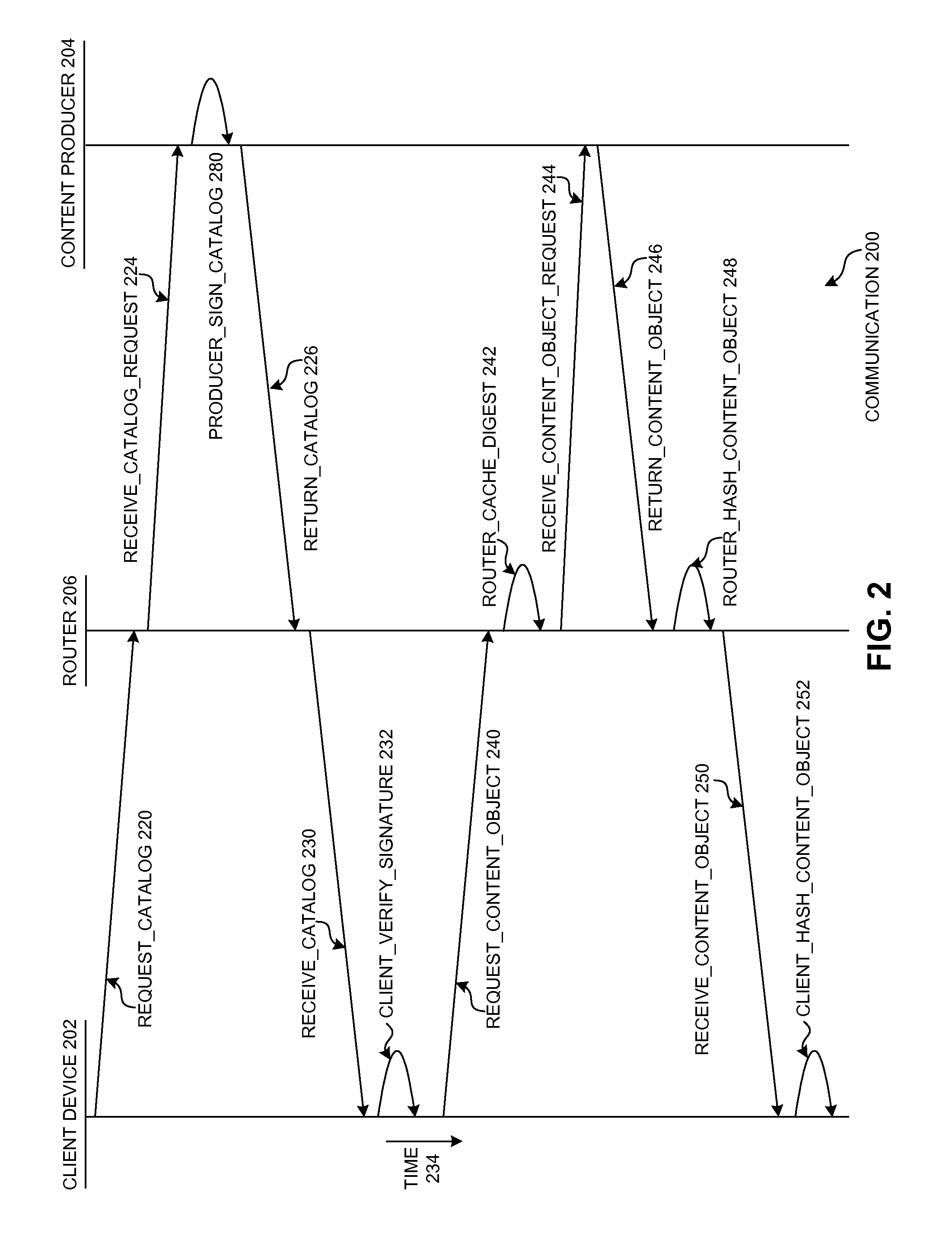
ActiveUS20150280918A1Facilitates routers in verifying content objectsData processing applicationsPublic key for secure communicationIndication of interestDigital signature
One embodiment provides a system that facilitates routers in verifying content objects in a cost-effective manner by aggregating content objects into a secure content catalog. During operation, a client computing device receives a secure content catalog, which indicates a set of content objects and their corresponding digests. The catalog is digitally signed with the private key of a producer of the catalog. The client computing device constructs an interest for a content object, where the interest indicates a name for the content object and the corresponding digest for the content object, which is based on the secure content catalog. The name for the request content object is a hierarchically structured variable length identifier (HSVLI) which comprises name components ordered from a most general level to a most specific level.
Owner:CISCO TECH INC
Content-based and time-evolving social network analysis
ActiveUS20110055379A1Easy to deriveReduced dimensional representationDigital computer detailsCharacter and pattern recognitionContent based networkingTime evolution
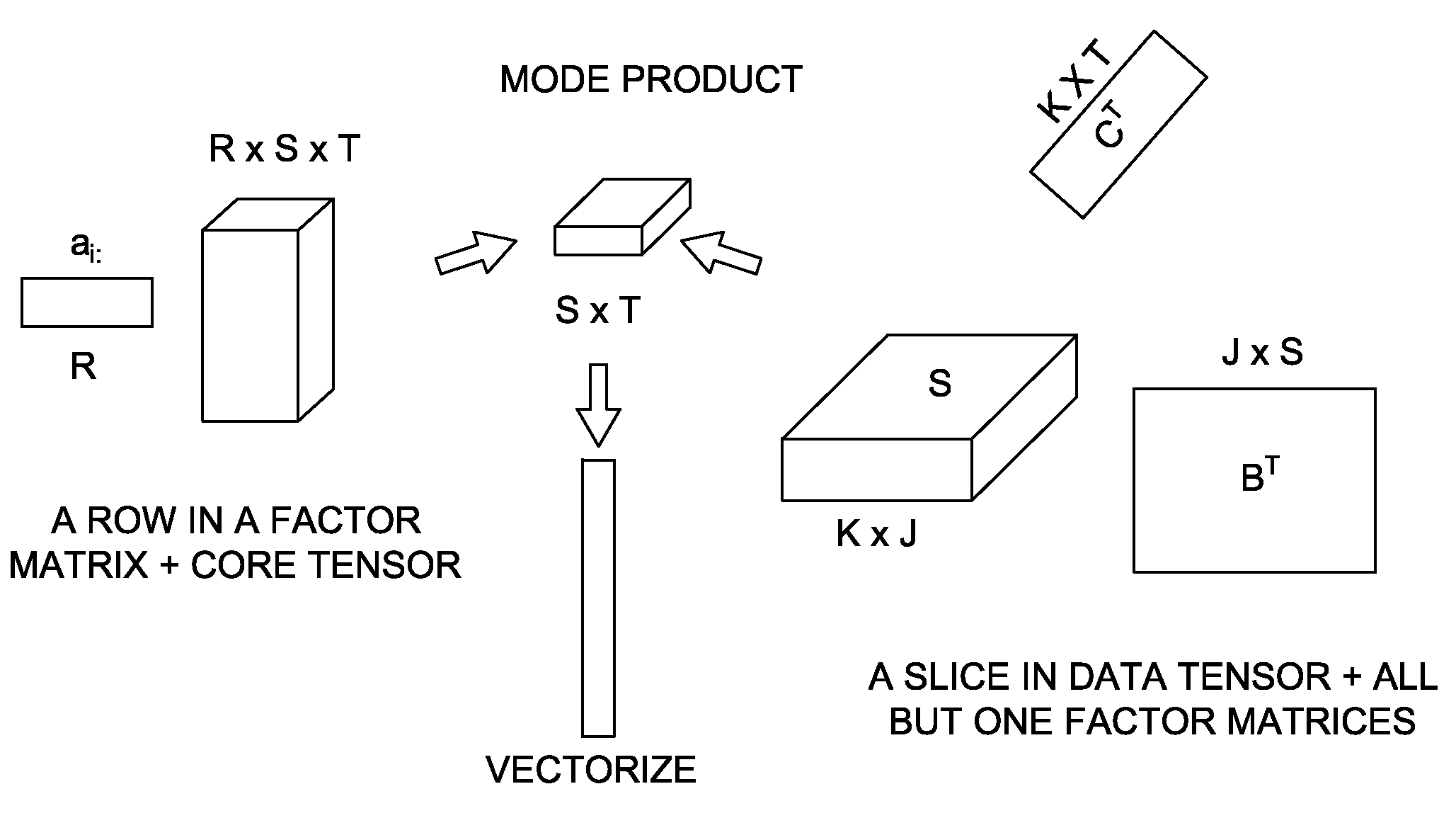
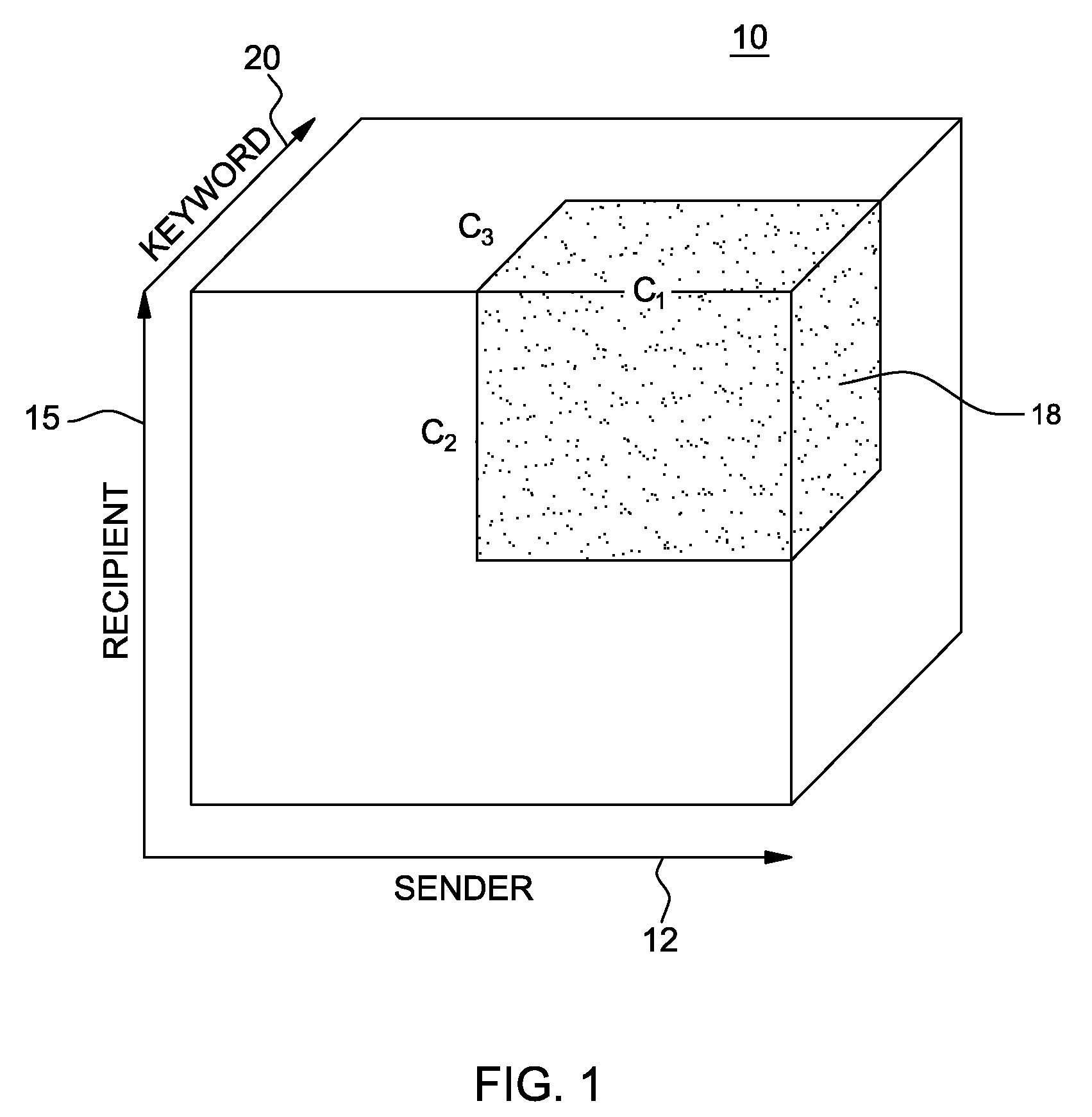
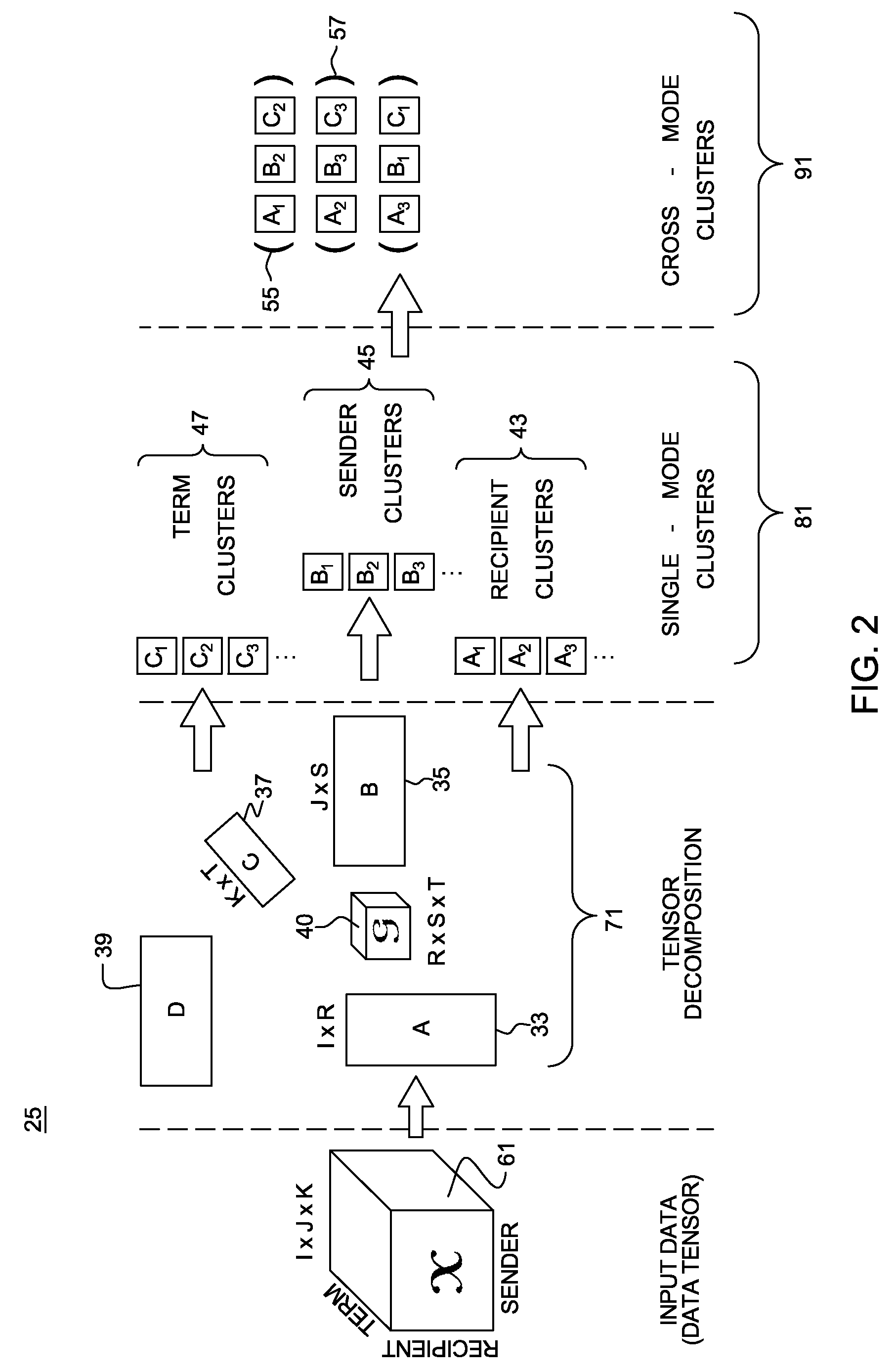
System and method for modeling a content-based network. The method includes finding single mode clusters from among network (sender and recipient) and content dimensions represented as a tensor data structure. The method allows for derivation of useful cross-mode clusters (interpretable patterns) that reveal key relationships among user communities and keyword concepts for presentation to users in a meaningful and intuitive way. Additionally, the derivation of useful cross-mode clusters is facilitated by constructing a reduced low-dimensional representation of the content-based network. Moreover, the invention may be enhanced for modeling and analyzing the time evolution of social communication networks and the content related to such networks. To this end, a set of non-overlapping or possibly overlapping time-based windows is constructed and the analysis performed at each successive time interval.
Owner:IBM CORP
Methods and apparatus for targeted secondary content insertion
ActiveUS20150058883A1Improve efficiencyBroadcast-related systemsElectrical cable transmission adaptationDecision makerContent based networking
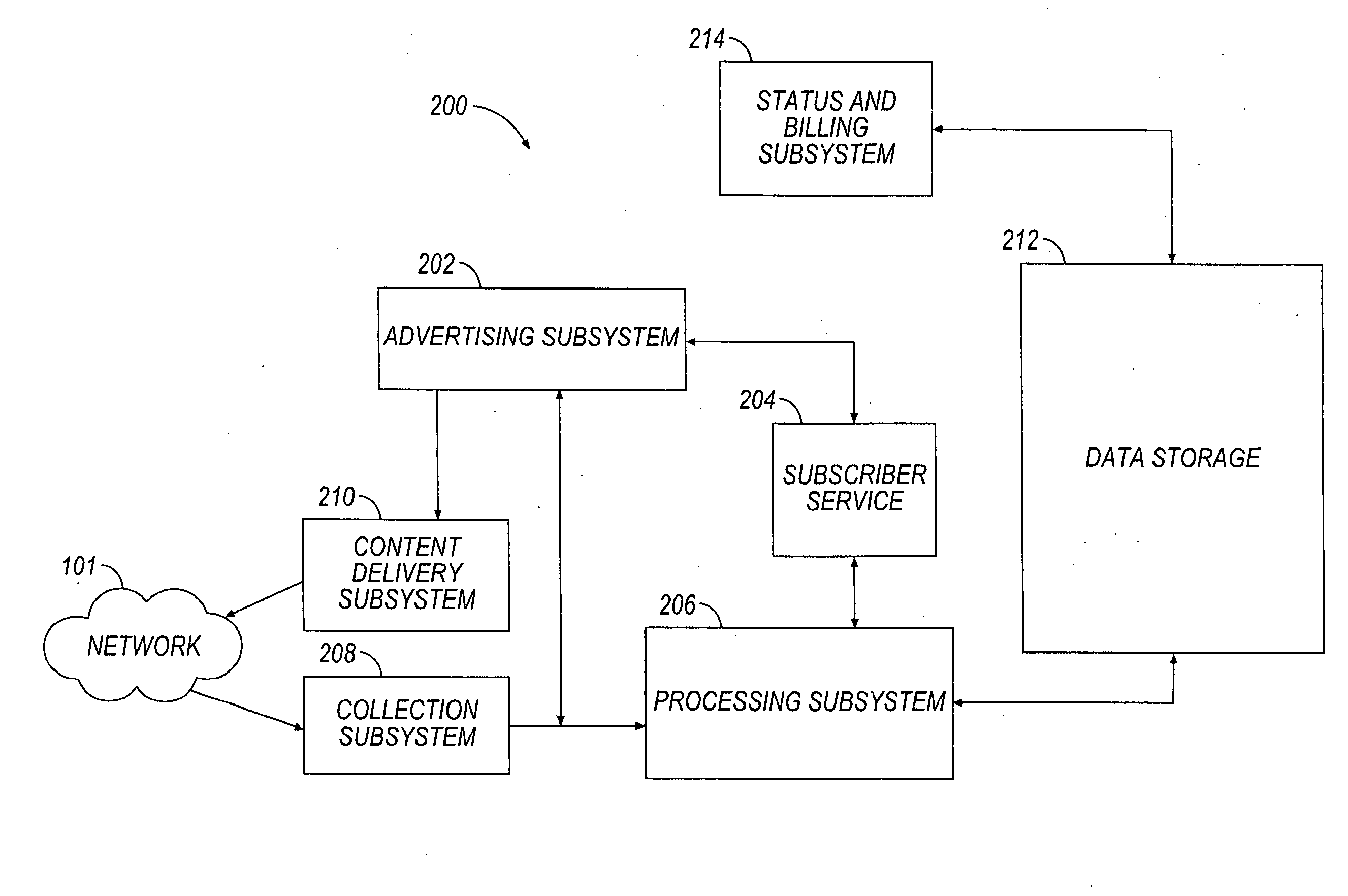
Methods and apparatus for identification and insertion of content targeted to a particular audience within a content-based network, such as a cable television or satellite network. In one embodiment of the invention, audience qualities are identified and distributed to an advertisement decision maker, which uses the information to fulfill advertisement placement opportunities. Qualifiers about an existing or projected audience are classified utilizing an algorithm for qualifier weight and variance in order to determine the proximity any given qualifier may be to a target audience for an advertisement. Subscriber privacy and anonymity is also optionally maintained via e.g., hashing or encrypting data relating to the CPE and / or subscriber, thus ensuring that audience data is not traceable to a specific user account. Business methods are also disclosed.
Owner:TIME WARNER CABLE ENTERPRISES LLC
Implicit routing in content based networks
ActiveUS7801857B2Improve robustnessImprove scalabilityDigital data processing detailsData switching by path configurationContent based networkingDissemination
In a method of managing a content-based network, which is typically XML-based, and optionally may be overlaid on an underlying network having a plurality of network elements interconnected by links, a link state protocol maintains each network element's topological view of the overlay network from the underlying network. A subscription management protocol ensures dissemination of published content within the content-based network independently of the link state protocol.
Owner:SOLACE CORP
Network communication encryption method based on contents
The invention provides a network communication encryption method based on contents. Symmetrical encryption algorithms are respectively arranged at a sending end and a receiving end, and then steps are listed as follows: 1) the sending end confirms an encryption algorithm factor according to the contents in the current data to be sent, then the minimum number of bytes N needed by a secret key of the current encryption algorithm and a corresponding algorithm is selected according to the encryption algorithm factor, and then the current encryption secret key is obtained via calculation; 2) the sending end uses the current encryption algorithm and the current encryption secret key to encrypt the current data to be sent to obtain the current encryption data so that the current communication cipher is generated and sent; and 3) the receiving end receives the current communication cipher to obtain the corresponding decryption algorithm factor and data to be decrypted, and corresponding decryption is performed so that the current communication plaintext is generated. The adopted encryption algorithm number and the adopted secret key are selected according to the contents of the data to be sent via calculation without transmission of extra secret key information so that the method is simple and rapid and high in security.
Owner:XIAMEN YAXON NETWORKS CO LTD
Facilitating smart advertising on curated content-based networking websites in an on-demand services environment
In accordance with embodiments, there are provided mechanisms and methods for facilitating smart advertising on curated content-based networking websites in an on-demand services environment in a multi-tenant environment according to one embodiment. In one embodiment and by way of example, a method includes receiving a request for advertisement on a website, where the request may be received from an advertising organization. The method may further include estimating one or more factors relating to the advertisement, computing, based on the estimation, expected revenue relating to the advertisement, and placing the advertisement on the website based on the expected revenue.
Owner:SALESFORCE COM INC
Caching method and device for content centric networking (CCN)
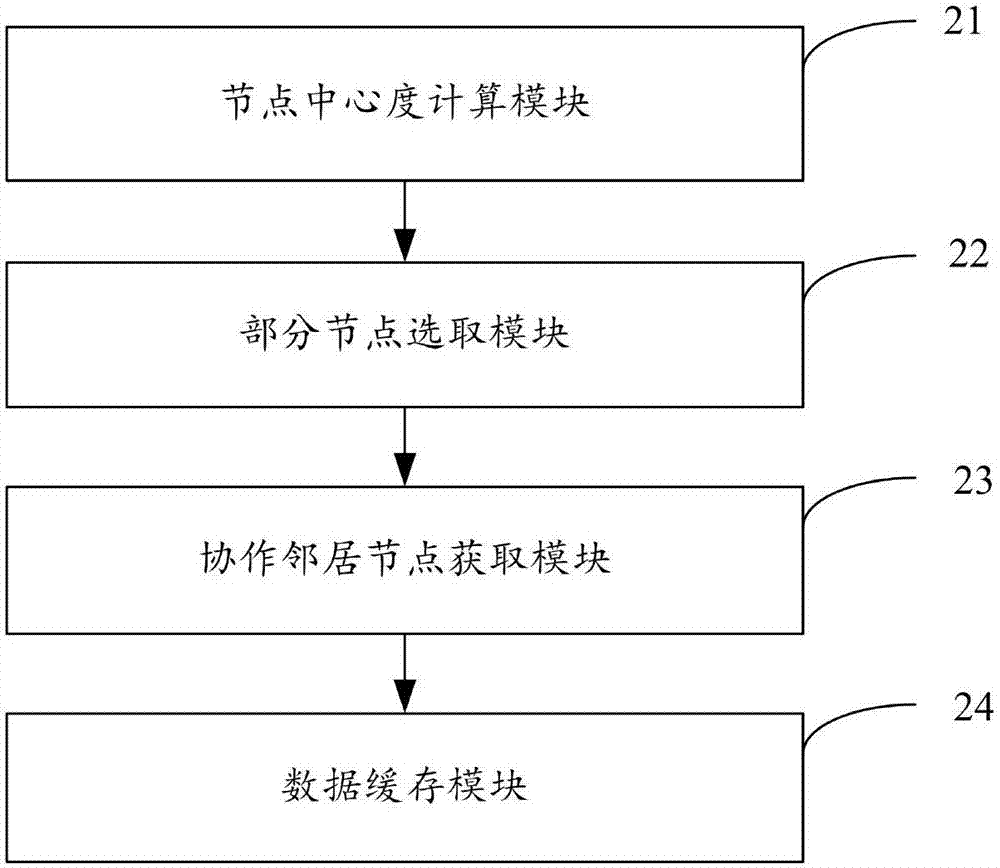
ActiveCN106982248AReduce redundancyReduce overheadTransmissionContent based networkingDistributed computing
The invention is applicable to the technical field of computers, and provides a caching method and device for content centric networking (CCN). The method comprises the following steps: according to a preset node centricity calculation formula, generating the node centricity of each node in the CCN; according to the centricities of all the nodes, selecting a part of the nodes; calculating the number of collaborative neighbor nodes corresponding to each node in the part of the nodes, and acquiring the collaborative neighbor nodes corresponding to each node in the part of the nodes according to the number of the collaborative neighbor nodes; and when one of the collaborative neighbor nodes receives data to be cached, determining a caching node corresponding to the data among the collaborative neighbor nodes, and caching the data in the caching node. The method and device provided by the invention has the advantages that the redundancy of cached contents in the CCN is effectively reduced, the variety of the cached contents is improved, and expenses for collaborative communication among the nodes in the CCN are effectively reduced.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
Content centric networking edge node potential enhanced routing method
The invention relates to a content centric networking edge node potential enhanced routing method and belongs to the field of the Internet. For the problem that the routing efficiency is low due to the fact that a content centric networking cannot sense cache content, the ENPER (Edge Node Potential-enhanced Routing) based on potential is provided. A potential model of nodes is established and through enhancement of the potential of edge nodes, interest packets are attracted to nearby cache nodes for response, so the forwarding time of the interest packets is reduced and a cache hit rate is improved. According to the ENPER, statistics and prediction are carried out on the popularity of content through the edge nodes, and through combination of a size of the networking, potential notification ranges of the content with different popularity are distinguished, thereby reducing the network overhead. According to the method, the load and cache notification overhead of an issuer server are effectively reduced, and compared with Best-routing, the ENPER has the advantage that the average request time delay of the content is reduced by 43%.
Owner:CHONGQING UNIV
Content-based and time-evolving social network analysis
ActiveUS8204988B2Easy to deriveReduced dimensional representationDigital computer detailsCharacter and pattern recognitionTime evolutionContent based networking
System and method for modeling a content-based network. The method includes finding single mode clusters from among network (sender and recipient) and content dimensions represented as a tensor data structure. The method allows for derivation of useful cross-mode clusters (interpretable patterns) that reveal key relationships among user communities and keyword concepts for presentation to users in a meaningful and intuitive way. Additionally, the derivation of useful cross-mode clusters is facilitated by constructing a reduced low-dimensional representation of the content-based network. Moreover, the invention may be enhanced for modeling and analyzing the time evolution of social communication networks and the content related to such networks. To this end, a set of non-overlapping or possibly overlapping time-based windows is constructed and the analysis performed at each successive time interval.
Owner:IBM CORP
Network management module for a vehicle communication network
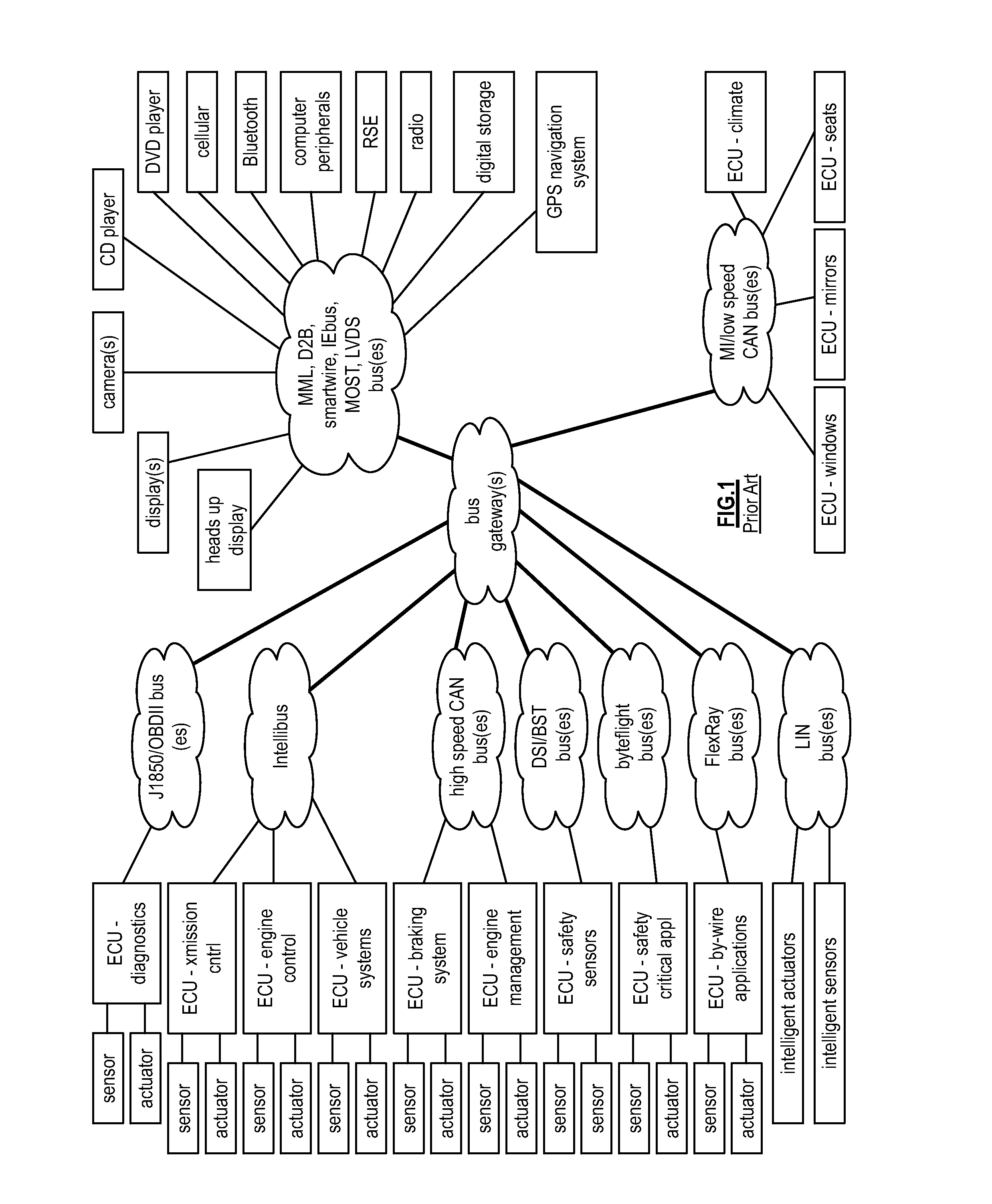
ActiveUS20120106549A1Registering/indicating working of vehiclesDigital data processing detailsNetwork managementContent based networking
A network management module includes a network interface module, memory, and a processing module. The network interface module is operable for coupling the network management module to a vehicle communication network. The processing module is operable to manage a global vehicle network communication protocol that includes instituting a content-based network packet processing protocol and managing the vehicle communication network to support the network packet processing protocol. The content-based network packet processing protocol includes determining content type of a packet, determining a processing requirement of the packet, and prioritizing execution of the processing requirement based on the content type.
Owner:AVAGO TECH INT SALES PTE LTD
Multi-parameter cache pollution attack detection method in content centric networking
The invention relates to content centric networking, in particular to a multi-parameter cache pollution attack detection method in the content centric networking. The multi-parameter cache pollution attack detection method in the content centric networking comprises the following steps: performing attack detection periodically and circularly, and calculating a sampling value of the attack impact degree in the current cycle; defining the variable quantity of the sampling value of the current attack impact degree to the last cycle as the variable quantity of the attack impact degree; setting a threshold according to the standard deviation of the variable quantity of the attack impact degree in a number of cycles; and determining that the attack occurs if the variable quantity of the attack impact degree exceeds the threshold. Compared with the traditional cache pollution attack detection method, the multi-parameter cache pollution attack detection method in the content centric networkingcan cope with more complex network environment, and can detect the cache pollution attack behavior in time and accurately, therefore, the multi-parameter cache pollution attack detection method in the content centric networking helps to improve the overall security performance of the content centric networking.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Access network flow scheduling system and method based on content
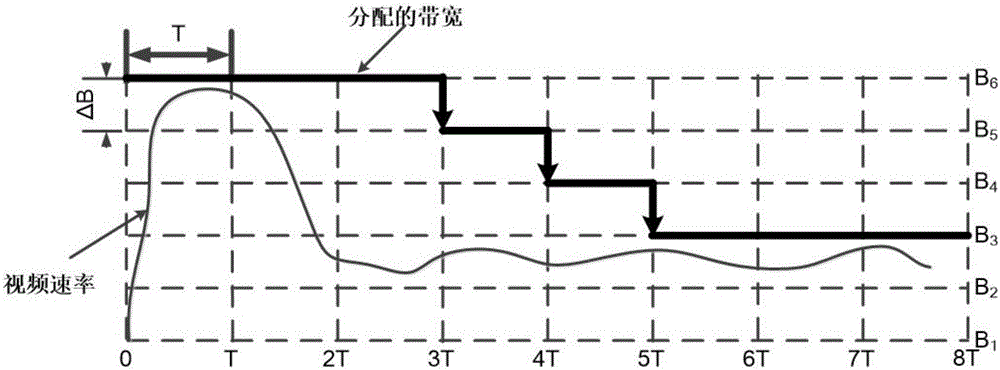
ActiveCN105704058AImprove user experienceGuaranteed transmission qualityData switching networksLow delayContent based networking
The invention discloses an access network flow scheduling system and method based on content.A software-defined networking (SDN) technology is utilized for opening an access network interface, and the problem that due to the fact that the data transmission needs of multiple types of applications cannot be met through a best mode in a traditional network, user experience is poor through a programmable mode.According to the access network flow scheduling system and method based on content, network flow is divided into three classes, namely, interactive network flow, video flow and other background flow according to the preference of a user to different applications and the transmission needs of the applications, different kinds of network flow are distinguished through application layer information in network data packages, low-delay transmission is provided for the interactive network flow, and a minimum bandwidth is provided for the video network flow to guarantee that the aim of improving the overall network experience of the user in the network is achieved.
Owner:NANJING UNIV
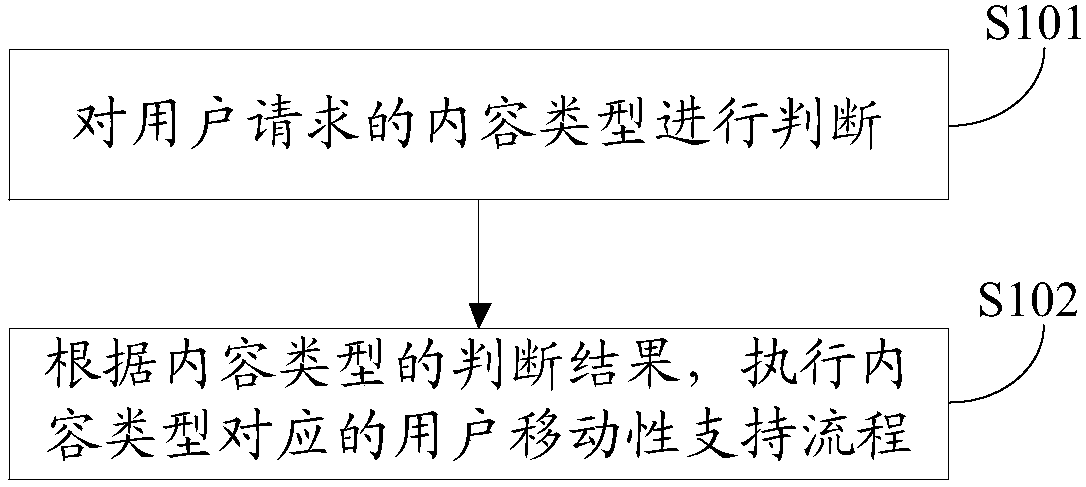
User mobility supporting method distinguishing content in content centric networking (CCN)
ActiveCN107733948AIncrease flexibilityImprove reliabilityTransmissionNon real timeProtocol for Carrying Authentication for Network Access
The invention provides a user mobility supporting method distinguishing content in a content centric networking (CCN). The method comprises the steps of determining a type of content requested by a user; and according to a determining result of the content type, executing a user mobility supporting process corresponding to the content type. According to the method, an original access router cachesa data message sent to an original position of the user, so as to prevent data message loss caused by user mobility switch; content that is not obtained in the user mobility switch is cached proactively, so that mobility switch delay caused by user mobility switch is shortened effectively; independent user mobility supporting processes are combined according to the content type, so that the usermobility supporting method is more flexible and reliable; the adverse effect of user mobility switch on a non-real time service is lowered; and the method extends multiple protocols and applications supporting traditional internet and can be widely used.
Owner:CHINA ACADEMY OF ELECTRONICS & INFORMATION TECH OF CETC
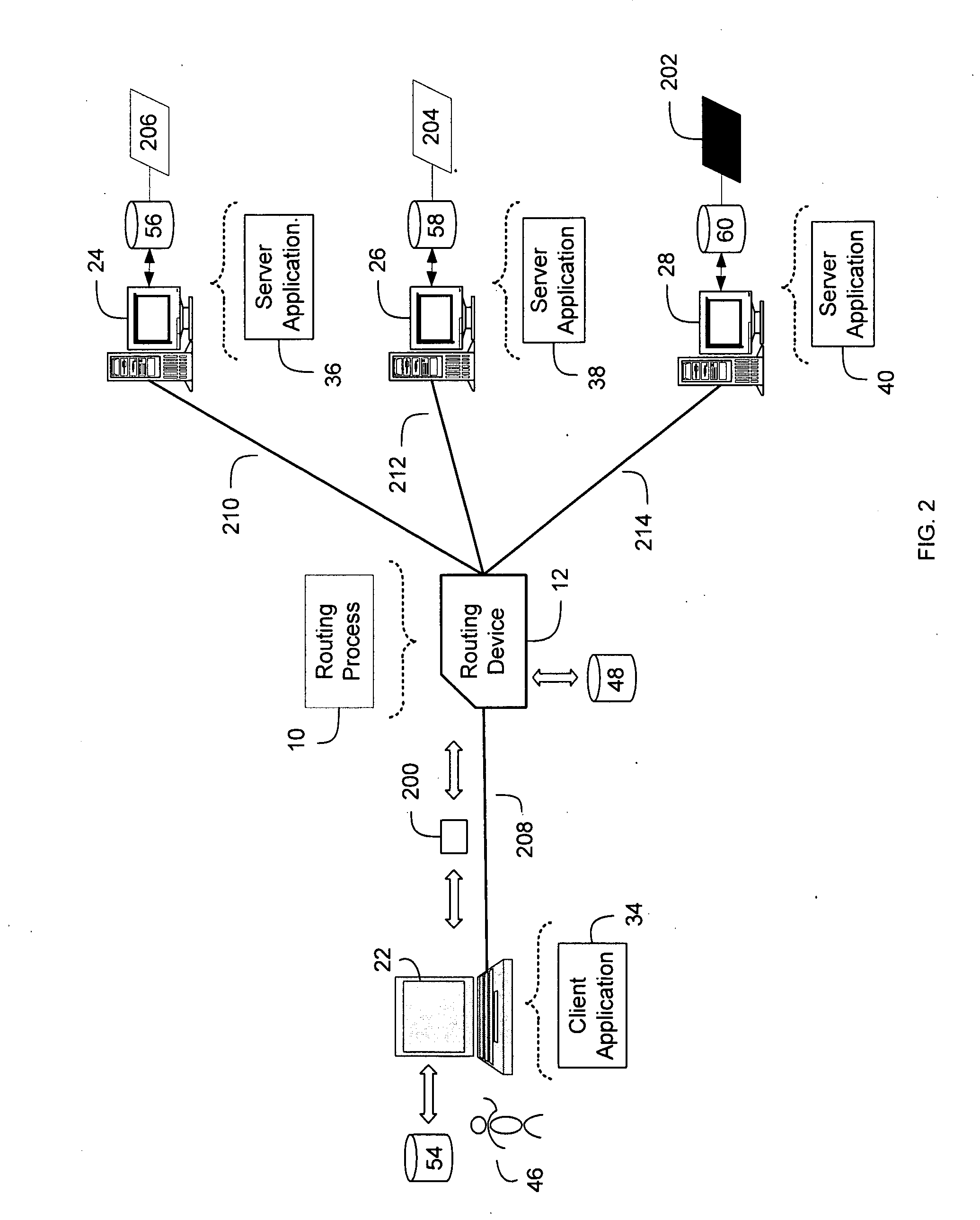
Method and system for content-based routing of network traffic
A method, computer program product, and system for routing computer network traffic include associating, on a routing device, a unique identifier with at least one application server running an application. Network traffic that includes the unique identifier and an intended network address may be received. In response to receiving the network traffic at least one of the application servers associated with the unique identifier may be identified. The network traffic may be forwarded to at least one of the application servers associated with the unique identifier.
Owner:IBM CORP
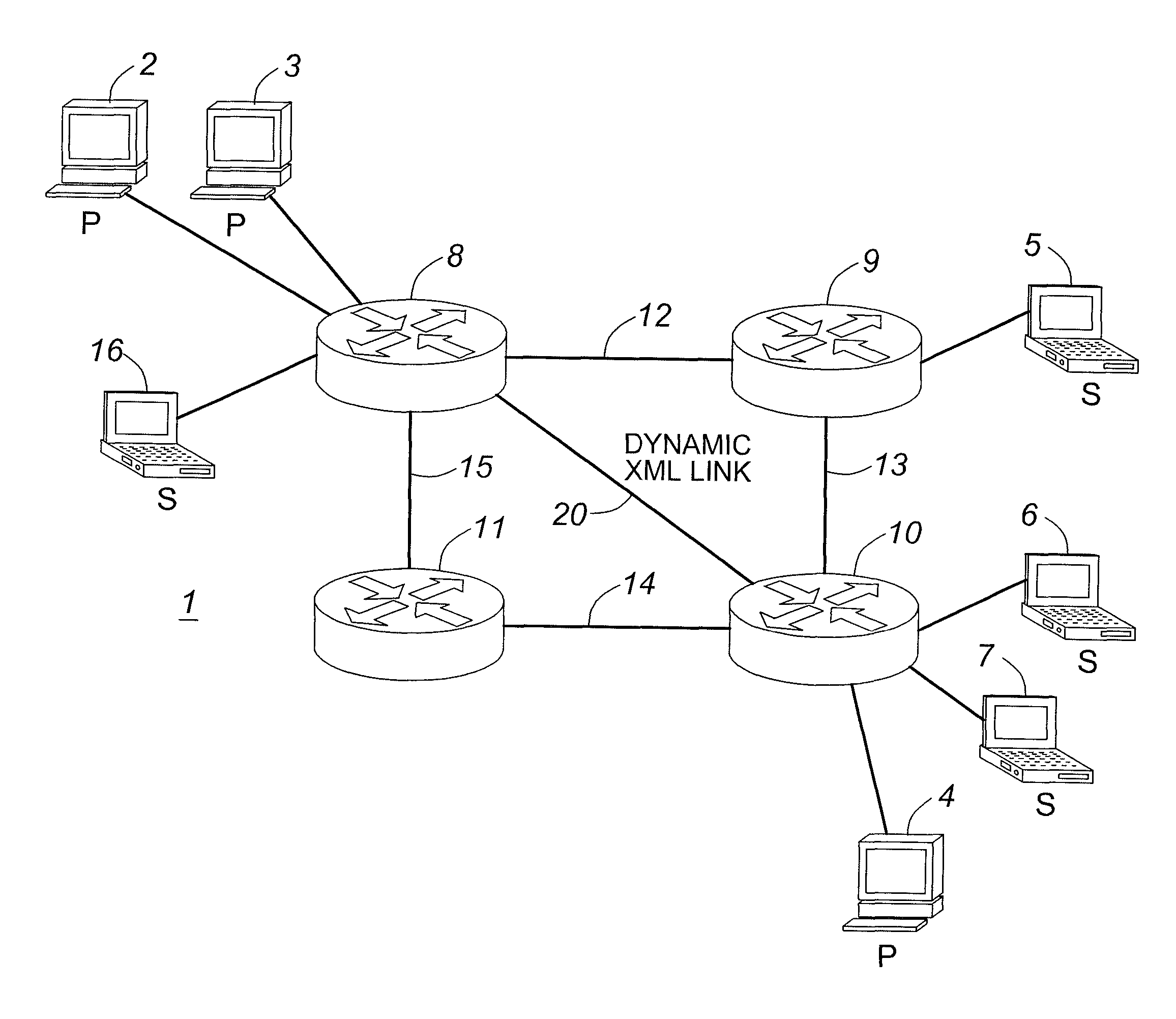
Dynamic links in content-based networks
ActiveUS7895299B2Reduce in quantityReduce delaysError preventionTransmission systemsComputer networkContent based networking
In a method of managing a content-based network including a plurality of content routers, such as XML routers, dynamic links are established between the content routers which are not direct neighbors.
Owner:SOLACE CORP
Aggregate signing of data in content centric networking
ActiveUS9363086B2Facilitates routers in verifying content objectsData processing applicationsPublic key for secure communicationIndication of interestInternet privacy
One embodiment provides a system that facilitates routers in verifying content objects in a cost-effective manner by aggregating content objects into a secure content catalog. During operation, a client computing device receives a secure content catalog, which indicates a set of content objects and their corresponding digests. The catalog is digitally signed with the private key of a producer of the catalog. The client computing device constructs an interest for a content object, where the interest indicates a name for the content object and the corresponding digest for the content object, which is based on the secure content catalog. The name for the request content object is a hierarchically structured variable length identifier (HSVLI) which comprises name components ordered from a most general level to a most specific level.
Owner:CISCO TECH INC
Methods and apparatus for targeted secondary content insertion
ActiveUS10051304B2Improve efficiencyBroadcast-related systemsSelective content distributionContent based networkingAnonymity
Methods and apparatus for identification and insertion of content targeted to a particular audience within a content-based network, such as a cable television or satellite network. In one embodiment of the invention, audience qualities are identified and distributed to an advertisement decision maker, which uses the information to fulfill advertisement placement opportunities. Qualifiers about an existing or projected audience are classified utilizing an algorithm for qualifier weight and variance in order to determine the proximity any given qualifier may be to a target audience for an advertisement. Subscriber privacy and anonymity is also optionally maintained via e.g., hashing or encrypting data relating to the CPE and / or subscriber, thus ensuring that audience data is not traceable to a specific user account. Business methods are also disclosed.
Owner:TIME WARNER CABLE ENTERPRISES LLC
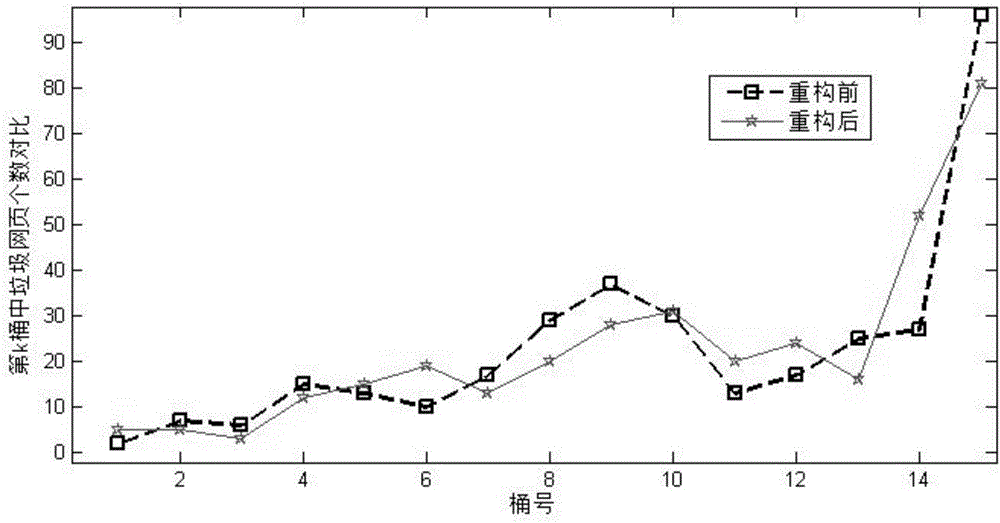
Network link topology reconstruction method based on content
InactiveCN105930365AOvercome the possibility of ignoring the presence of spam linksEasy to detectWeb data indexingSpecial data processing applicationsFeature vectorNetwork link
A network link topology reconstruction method based on content includes: eliminating redundancy and uncorrelated feature attributes from a content feature aspect and a link feature aspect, and combining a new feature vector; calculating the similarity between two connected web pages, and determining the correlation between the two connected web pages; eliminating spamming links according to the correlation of the web pages so as to obtain a weight calculation formula, wherein the similarity between the two pages connected by a link with a high weight is high in topology; and regenerating a network link topology according to the weight of the link. Based on the Trust Rank algorithm and web page analysis, the spamming links can be recognized through a similarity distance between the web pages and the number of the spamming links, the network link topology can be reconstructed from the content aspect, and then it can be effectively overcome that the web page detection method based on links ignores the possibility of the spamming links, and the efficiency of detecting and recognizing spamming web pages can be improved.
Owner:TIANJIN UNIV
Content-based network system and method of controlling transmission of content therein
ActiveUS20130170442A1Improve efficiencyReduce wasteNetwork traffic/resource managementWireless commuication servicesComputer networkContent based networking
Disclosed herein are a content-based network system and a method of controlling the transmission of content therein. The content-based network system includes a plurality of user terminals, a plurality of access points, a plurality of content origin servers, and a transmission control device. The plurality of access points is wirelessly connected to the plurality of user terminals. The plurality of content origin servers provides content to the access points. The transmission control device determines the priority of transmission of the content based on the characteristics of the content and allocates channels and sets interfaces based on the determined priority of transmission of the content.
Owner:INST FOR BASIC SCI
Fair caching algorithm and device for content centric networking
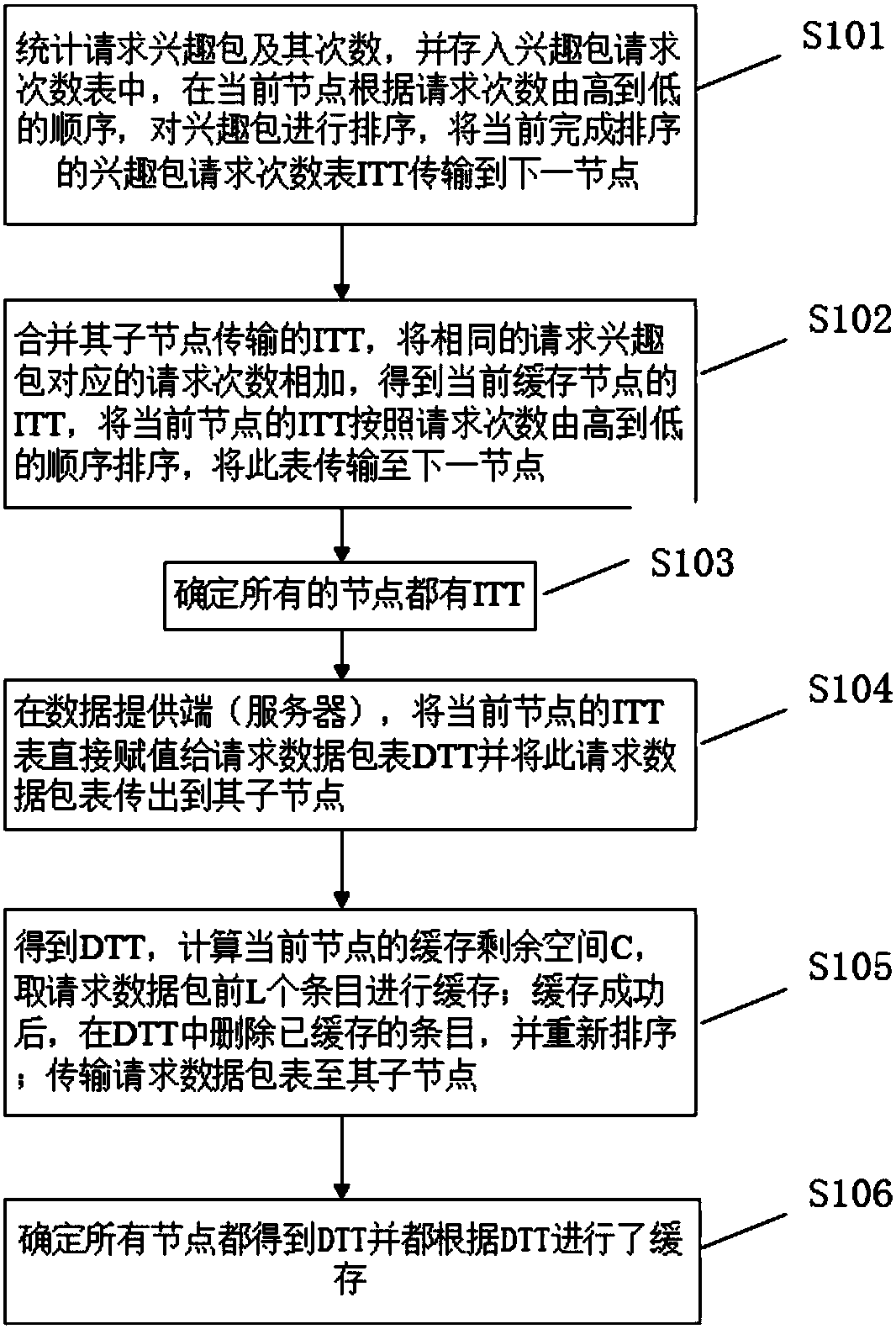
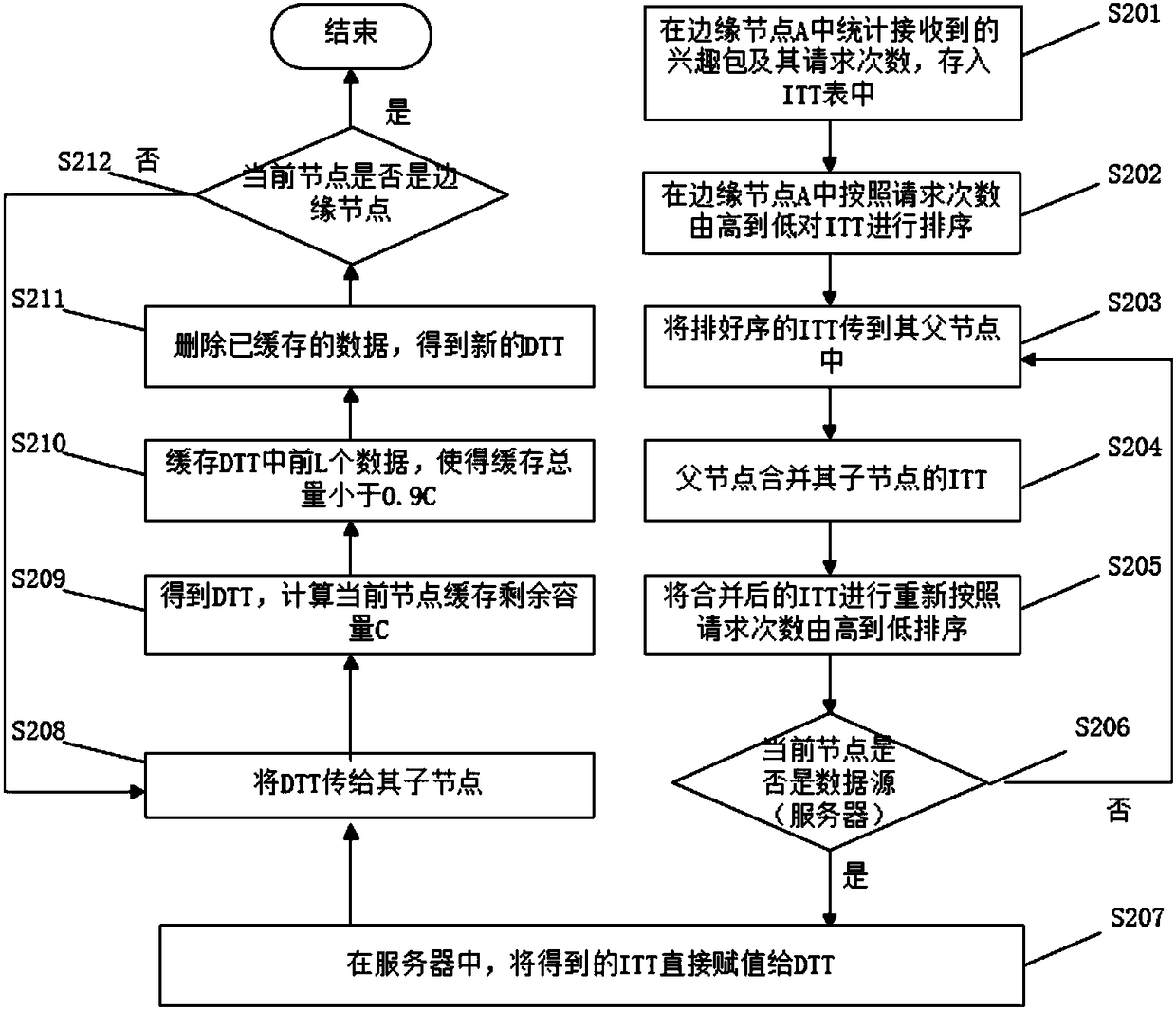
The invention discloses a fair caching algorithm and device for content centric networking. The fair caching algorithm for content centric networking comprises: in a process of requesting for interestpackets, the requested interest packets and the times thereof are counted; furthermore, the interest packets are sorted according to the decreasing order of the requesting times; then, the interest packets are stored in an ITT (Interest Times Table), and transmitted to a next node; in a process of sending data, the ITT of the current node is directly assigned to a DTT (Data Times Table) at a dataprovider (a server); furthermore, the DTT is transmitted to other sub-nodes; in a non-data provision node, the DTT is obtained; the caching residual space C of the current node is calculated; previous L entries are cached; furthermore, the fact that the total data size of the L entries is less than or equal to 0.9C can be ensured; after caching is successful, cached entries are deleted from the DTT; sorting is carried out again; and the DTT is transmitted to other sub-nodes. By means of the fair caching algorithm and device for content centric networking disclosed by the invention, the content popularity is defined according to the requesting times; the caching threshold is set; therefore, the data redundancy of the content centric networking is reduced; the hit rate is increased; the hitrate variance is reduced; and thus, the caching fairness is realized.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Non-hybrid ant colony routing method in content centric networking
ActiveCN107888502AReduce request latencyImprove performanceData switching networksNetwork overheadContent based networking
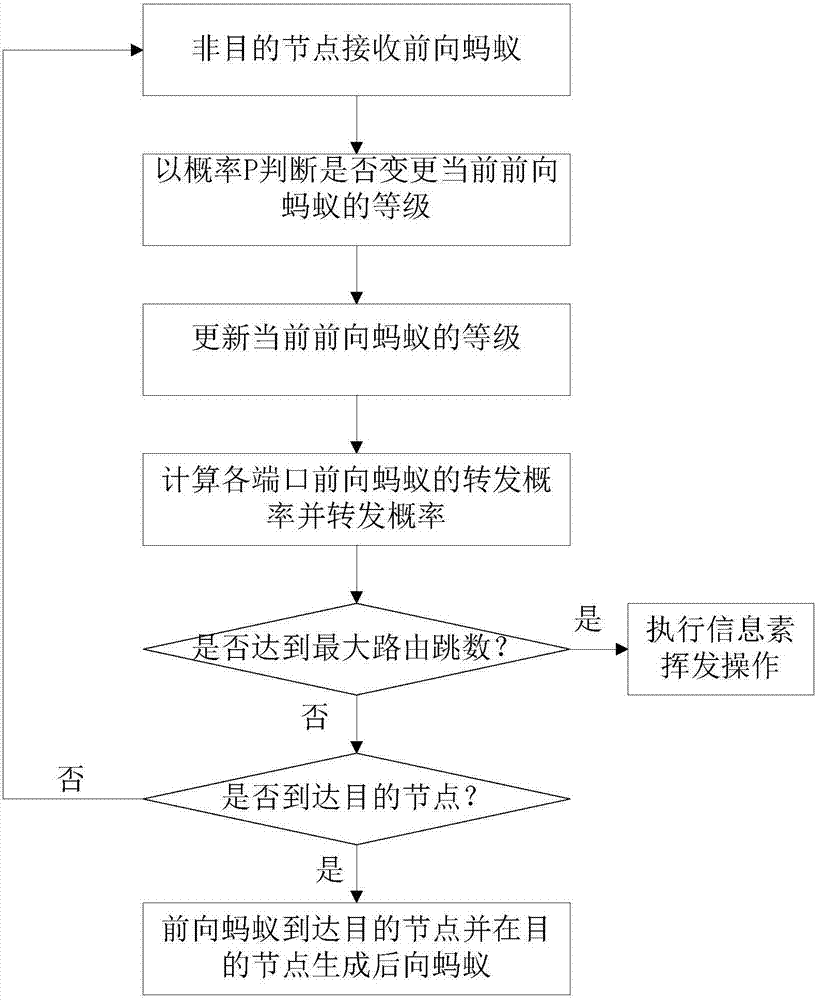
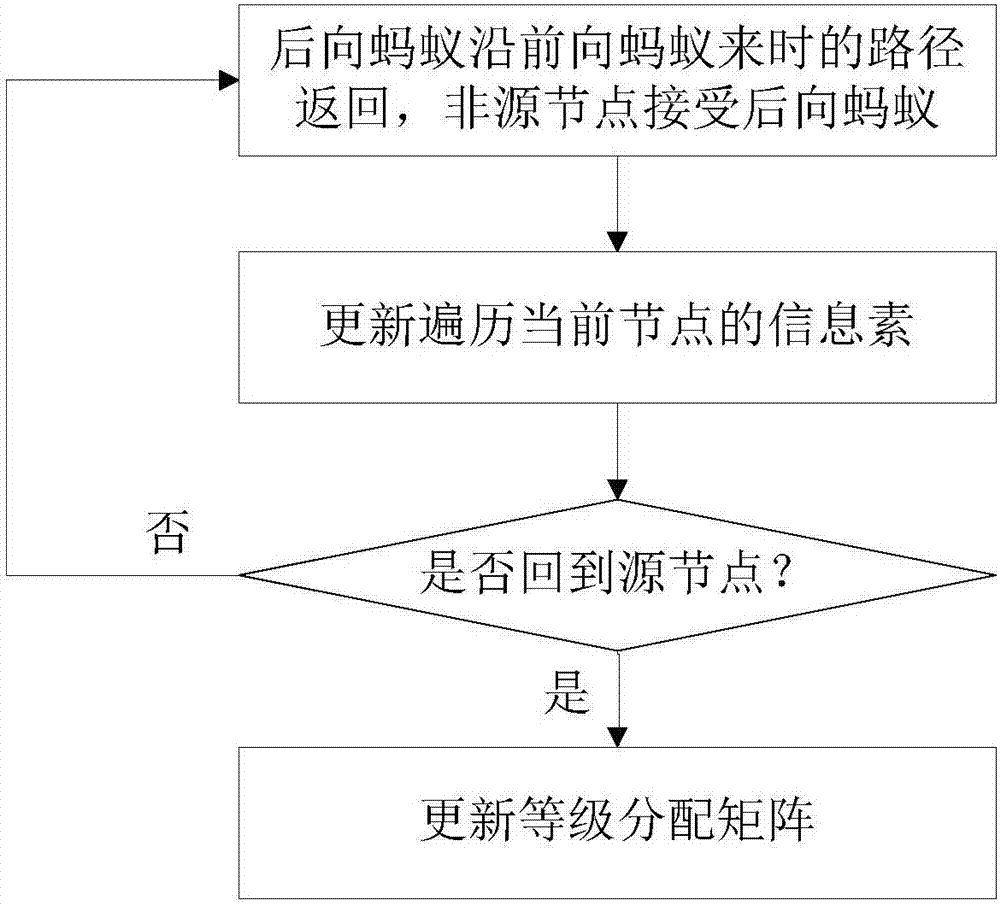
The invention relates to the technical field of communication, and particularly relates to a non-hybrid ant colony routing method in content centric networking. The method comprises the steps of building pheromone tables, wherein each node stores a pheromone table, when a previous ant arrives at a certain node, a port related to a current ant has a corresponding pheromone value, and a port not related to the current ant has no pheromone value; forwarding the previous ant from a source node to an intermediate node, and forwarding the previous ant to other intermediate node by the intermediate node till highest routing hops are achieved or a destination node is found; if the highest routing hops are achieved, executing a pheromone volatile operation; and if the previous ant rinds the destination node, generating a next ant by the destination node, and allowing the next ant to return from the destination node along the forwarding path of the previous ant to the source node and update pheromones of the node passed by. The method keeps the network overhead cost low and prevents premature and stagnation effectively.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
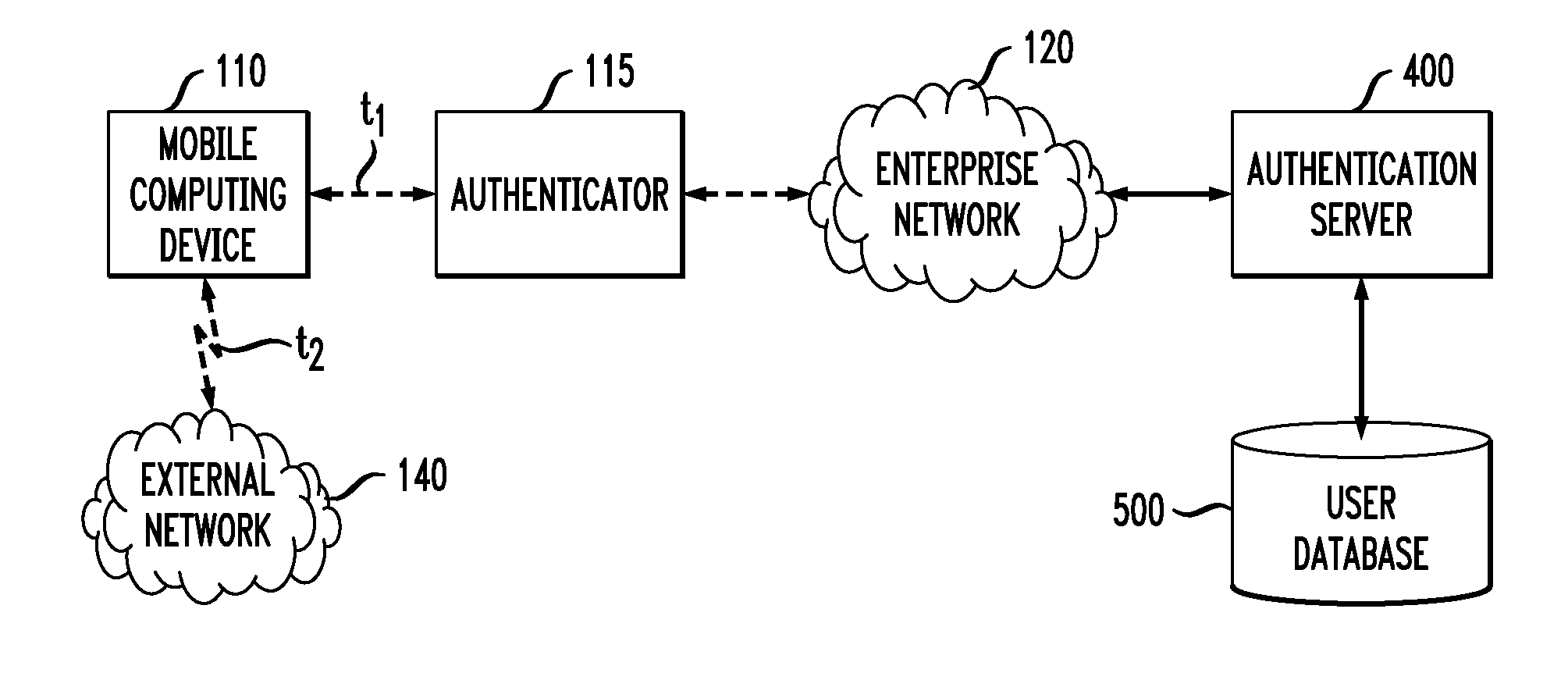
Method and Apparatus for Content Based Authentication for Network Access
InactiveUS20090031399A1Digital data processing detailsComputer security arrangementsContent based networkingEnterprise networking
A method and apparatus are provided for authenticating the contents of a device requesting access to a first network, such as an enterprise network. If a device has connected to at least one other network then the content of the device is evaluated prior to obtaining access. The scope of the content evaluation may be based, for example, on properties of the other network or on one or more defined content authentication rules. If a device attempts to access a network, the content of the device is evaluated and the device may be restricted to accessing only one or more restoration services if the content fails to satisfy one or more predefined criteria, such as a content item that is out of date or a determination that the device connected to one or more external networks. The restoration service(s) can update a content item that is out of date, reinstall one or more programs or return configuration settings to default values.
Owner:AVAYA INC
Systems and methods for content-based indexing of videos at web-scale
Techniques for content-based indexing of videos at web-scale are described. As one example, a computer-implemented method includes receiving a video file, splitting the video file into video frames and audio for the video frames, determining audial features for the audio, clustering each of a plurality of subsets of the audial features into a respective audio centroid for a shared set of bases, determining a first adjacency matrix of distances between the respective audio centroids, determining visual features for the video frames, clustering each of a plurality of subsets of the visual features into a respective video centroid, and determining a second adjacency matrix of distances between the respective video centroids.
Owner:AMAZON TECH INC
Constructing linear representation of a content based network
ActiveUS20100306641A1Website content managementSpecial data processing applicationsLink weightAlgorithm
Described herein are systems and methods for constructing linear representations of content based networks. The methods comprise receiving a sub-network of a content based network comprising a plurality of fragments connected by one or more links, calculating fragment weight for at least some of the plurality of fragments, calculating link weight for at least one of the one or more links, creating a hierarchical structure from the sub-network, based on at least some of the calculated fragment weights and at least some of the calculated link weights, and converting the hierarchical structure to a linear representation. The linear representation may be augmented by additional overview information such as table of contents and index, which may be automatically generated.
Owner:SAP AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com