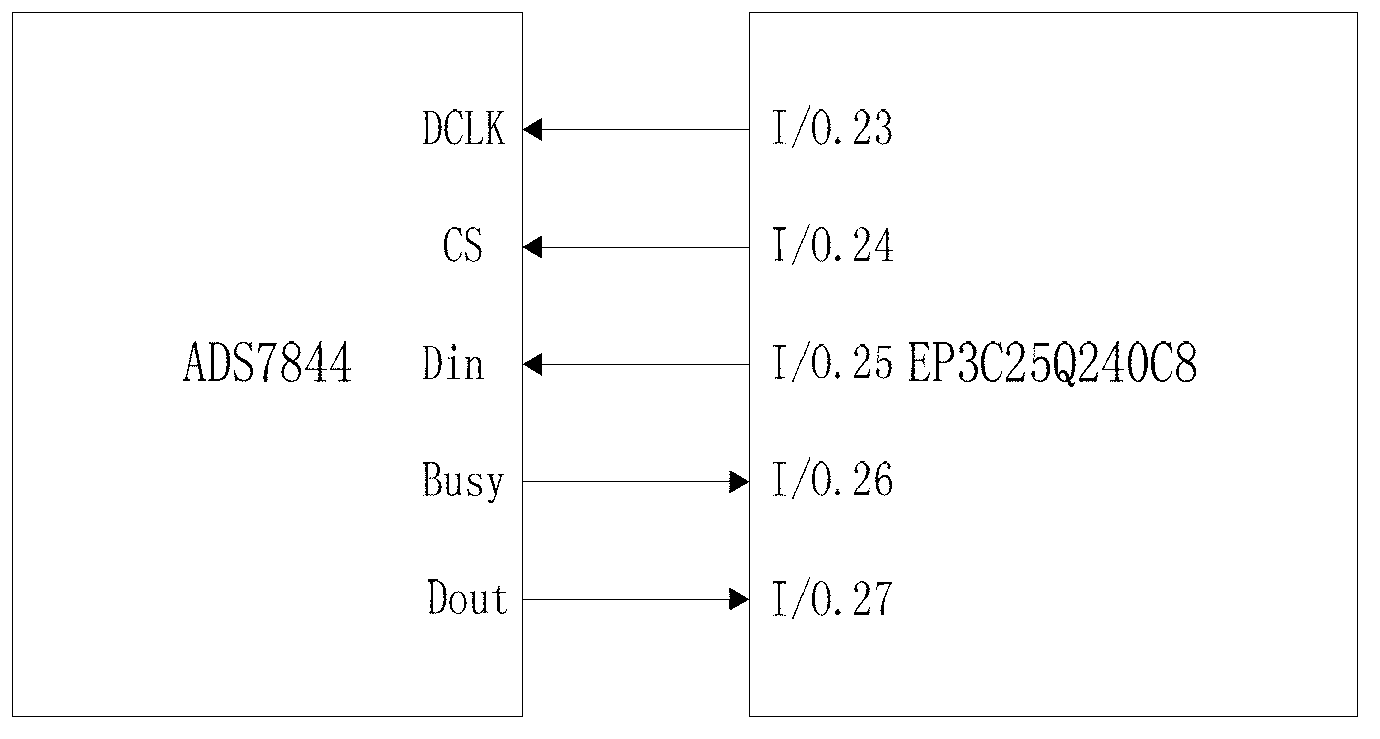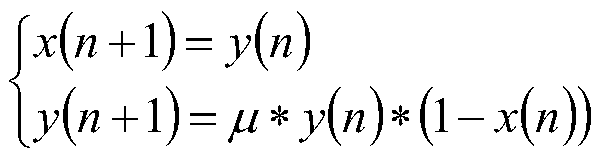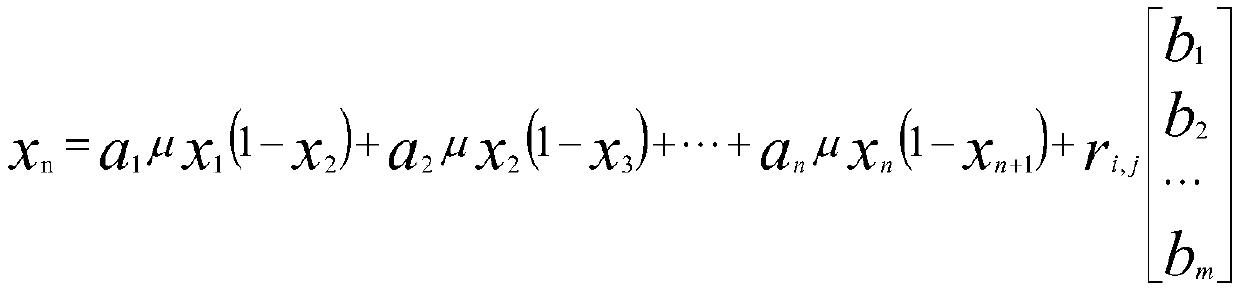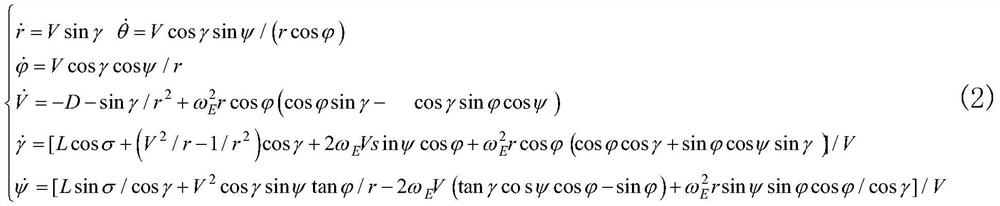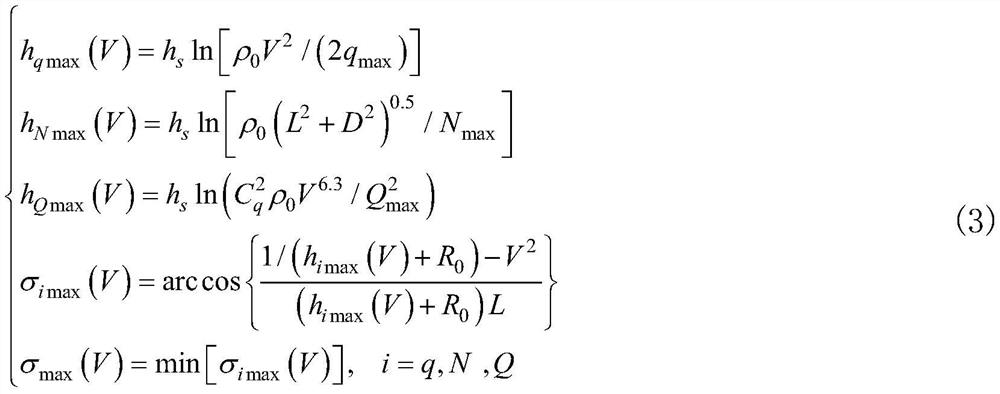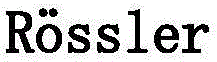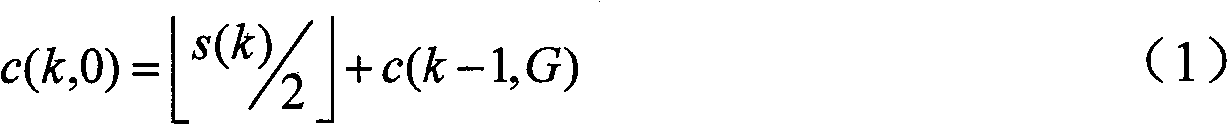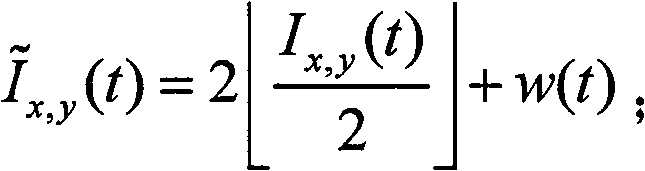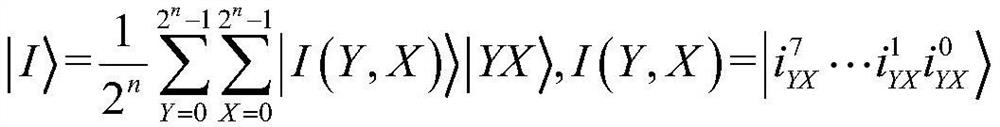Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30 results about "Chaos model" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computing, the chaos model is a structure of software development. Its creator, who used the pseudonym L.B.S. Raccoon, noted that project management models such as the spiral model and waterfall model, while good at managing schedules and staff, didn't provide methods to fix bugs or solve other technical problems. At the same time, programming methodologies, while effective at fixing bugs and solving technical problems, do not help in managing deadlines or responding to customer requests. The structure attempts to bridge this gap. Chaos theory was used as a tool to help understand these issues.
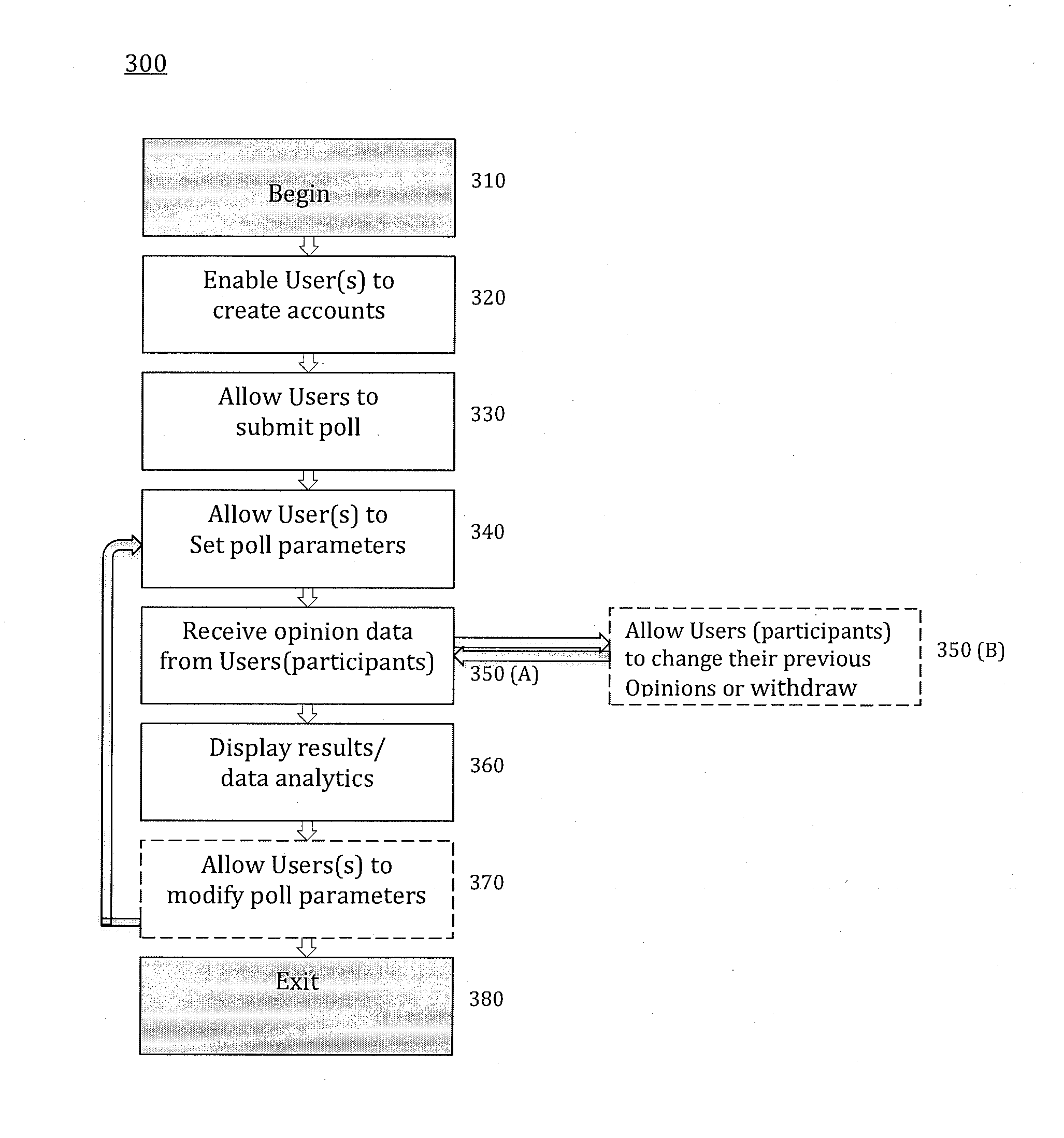
System of poll initiation and data collection through a global computer/communication network and methods thereof
A computer-implemented method of public opinion poll initiation and public opinion data collection for using non-deterministic mathematical models (e.g. chaos model), independent of third parties involvement (e.g., campaign managers, marketers, pollsters, etc.) is provided. In exemplary embodiments, the method may comprise receiving a post and an instruction for public opinion poll from a first user; initiating the public opinion poll and displaying it to a second user(s) / the public, receiving an initial answer to the public opinion poll from the second user(s); generating results of the public opinion poll based on the initial answer; receiving an alternative answer(s) from the second user(s) if wished by the second users, updating the results of the public opinion poll based on the alternative answer(s); and displaying a real-time feed of the public opinion poll results, the real-time feed updated when public opinion poll answers are entered or changed by a user.
Owner:GOLD ZARA A +1
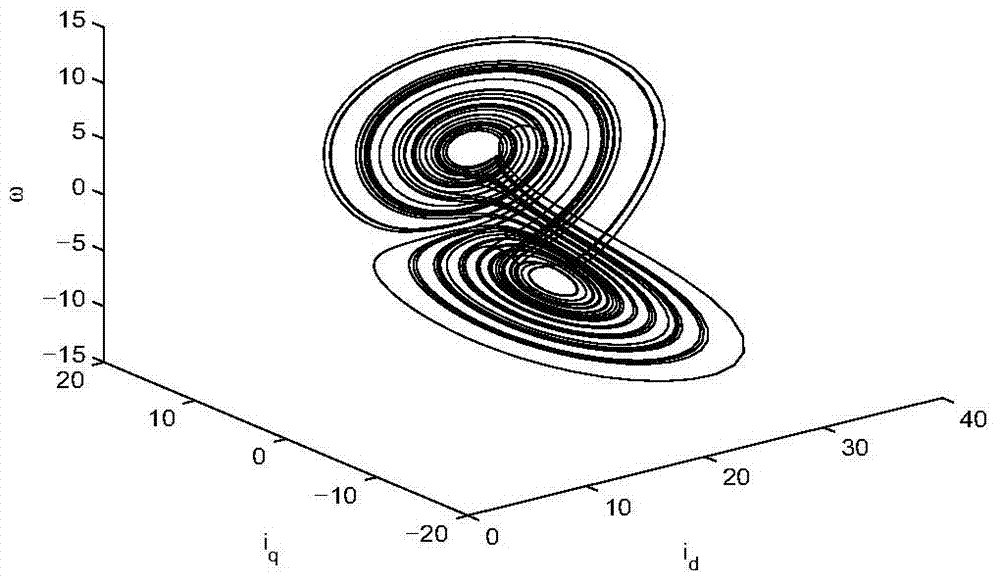
Permanent magnet synchronous motor chaos control method based on nonlinear expanded state observer
ActiveCN104201941AImprove efficiencyHigh control precisionElectronic commutation motor controlObserver controlState observerPermanent magnet synchronous motor
The invention discloses a permanent magnet synchronous motor chaos control method based on a nonlinear expanded state observer. The permanent magnet synchronous motor chaos control method comprises the steps of: building a chaos model of a permanent magnet synchronous motor system, and initializing a system state and related control parameters; through coordinate transformation, converting the chaos model of the permanent magnet synchronous motor system to be Brunovsky standard form that is more suitable for designing the nonlinear expanded state observer; designing the nonlinear expanded state observer for estimating the unpredictable system state and parameter perturbation; designing a self-adaptive sliding mode variable structure controller, improving problem about buffeting in sliding mode control, and ensuring that the chaos state of the system is rapidly and stably converged to zero according to the system state and parameter perturbation estimated by the nonlinear expanded state observer.
Owner:ZHEJIANG UNIV OF TECH
On-chip network mapping method based on ant-colony chaos genetic algorithm
InactiveCN102508935AImprove search capabilitiesGood practical valueGenetic modelsSpecial data processing applicationsLocal optimumMutation probability
Disclosed is an on-chip network mapping method based on the ant-colony chaos genetic algorithm. The standard ant-colony algorithm is basically used and the genetic algorithm is introduced in the on-chip network mapping method, parameters about each ant are coded by real numbers, codes of the ants are utilized as chromosome in the genetic algorithm, and algorithm parameters of coded ants are adjusted by the genetic algorithm in each iteration. During running of the algorithm, recycled results of each iteration of the algorithm are monitored, if the fact that the algorithm is trapped in a local optimum solution is monitored, mutation probability of the genetic algorithm is increased by a method of introducing a chaos model, and further, the parameters of the ant-colony algorithm are changed by means of the genetic algorithm. By the aid of the on-chip network mapping method, capability of the anti-colony chaos genetic algorithm for searching the solution space can be improved effectively, and trapping in the local optimum solution is avoided. In addition, the on-chip network mapping method has excellent practical values and wide application prospect for solution of massive on-chip network mapping.
Owner:NANJING UNIV
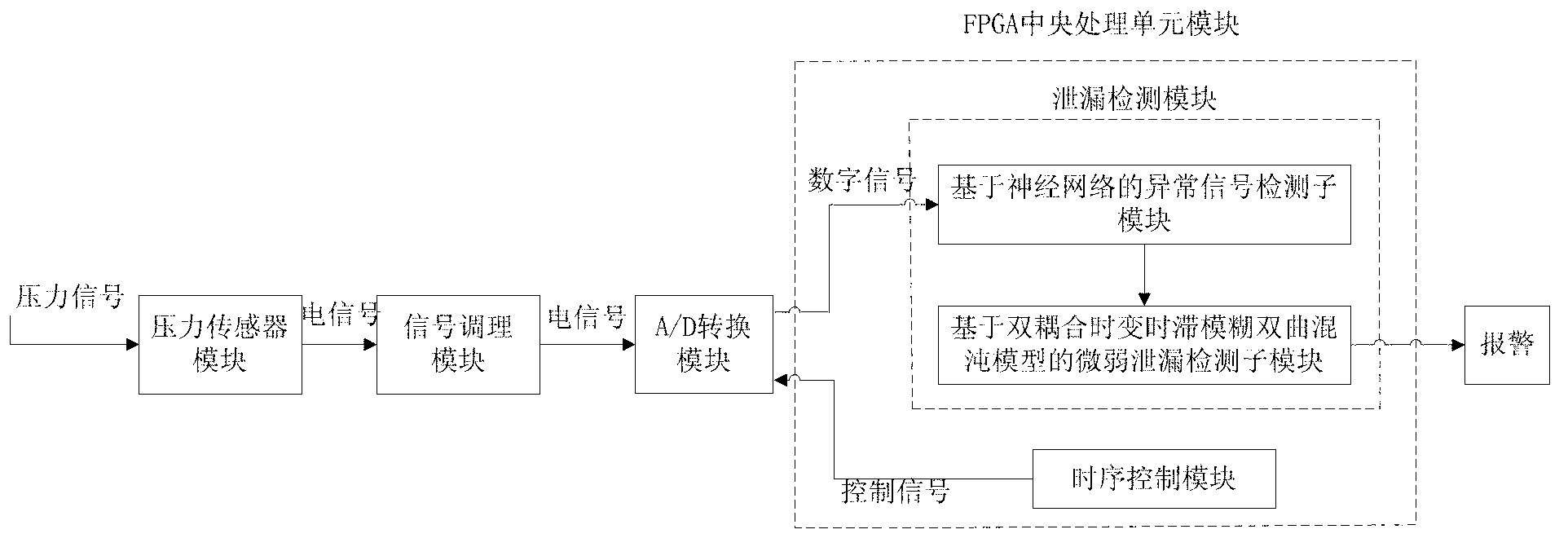
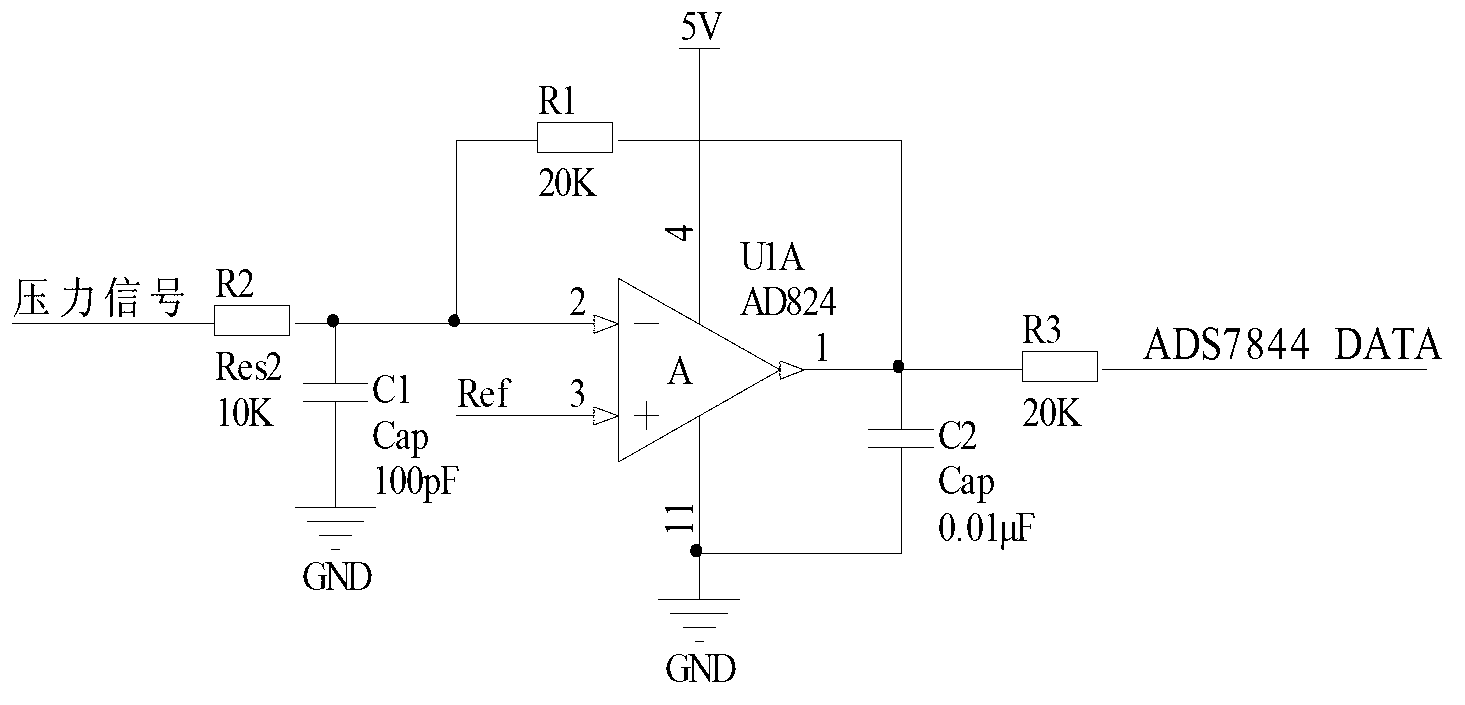
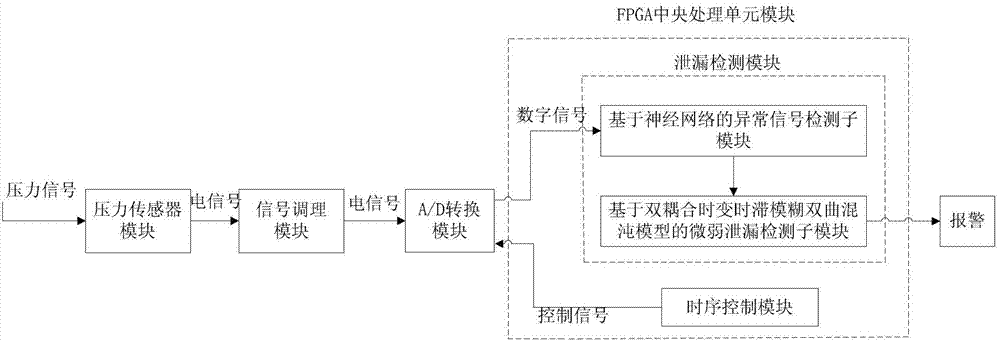
Pipeline weak leakage detecting device and detecting method based on fuzzy hyperbolic chaos model
ActiveCN103322416AEasy to detectEasy to identifyPipeline systemsPattern recognitionSignal-to-noise ratio (imaging)
The invention discloses a pipeline weak leakage detecting device and a detecting method based on a fuzzy hyperbolic chaos model and belongs to the technical field of pipeline detection. Two-stage detection is used, the first-stage detection is abnormal signal detection based on a neural network to mark abnormal signals, and the second-stage detection detects the abnormal signals marked by the first-state detection. By the two-stage detection, the first-stage primary detection is fast, the second-stage detection detects the abnormal signals marked by the first-state detection, and leakage detection capability is increased. The two-stage detection can be implemented on a FPGA (field programmable gate array) hardware platform, and overall system response speed is increased. By the double coupling time-varying delay fuzzy hyperbolic chaos model of the second-stage detection, initial value sensitivity and noise immunity of the chaos system is utilized to increase identification capability of weak leakage signals submerged in noise so as to highlight chaos phenomenon, system requirements for signal to noise ratio is lowered, and weak leakage detection is achieved.
Owner:NORTHEASTERN UNIV
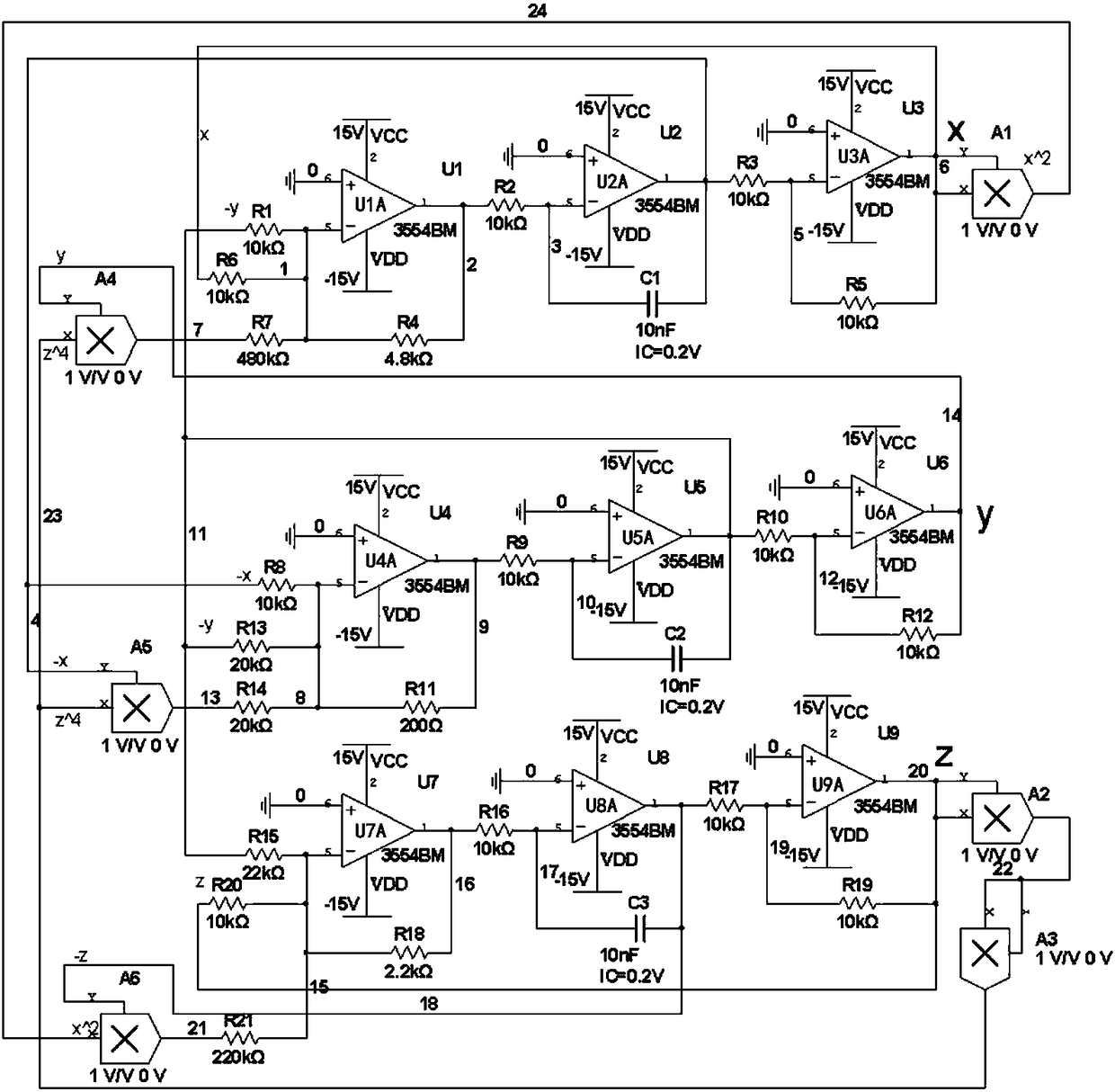
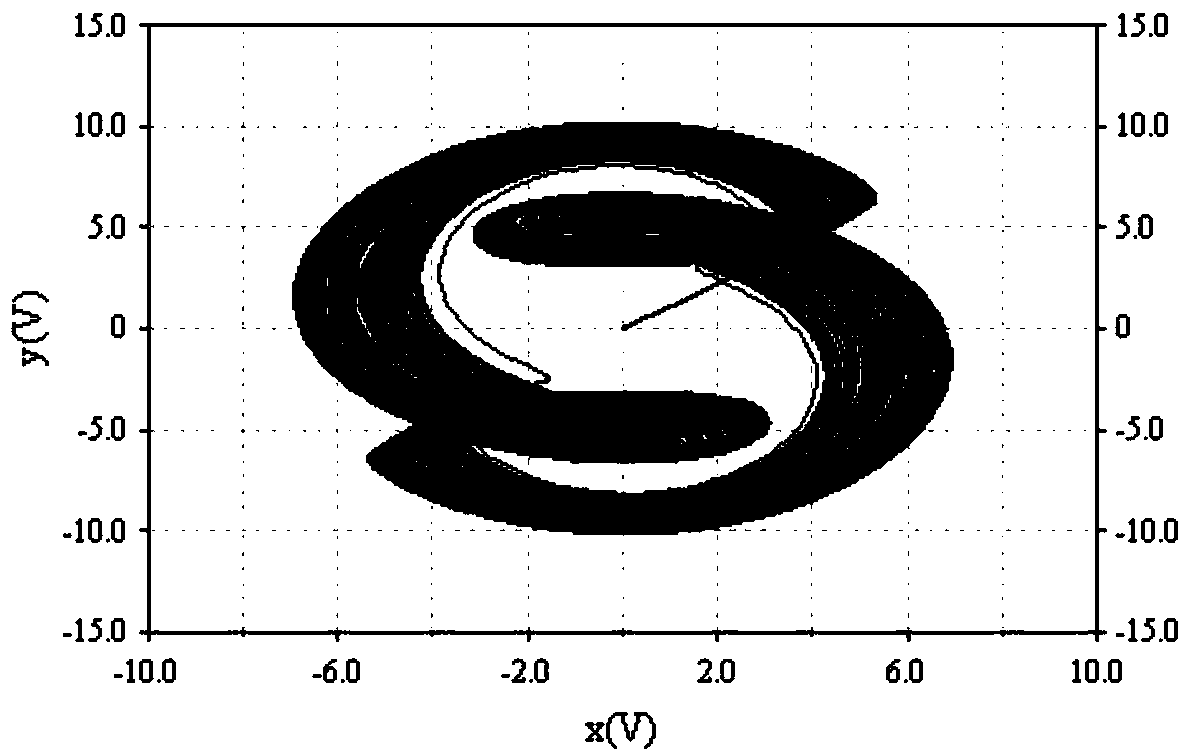
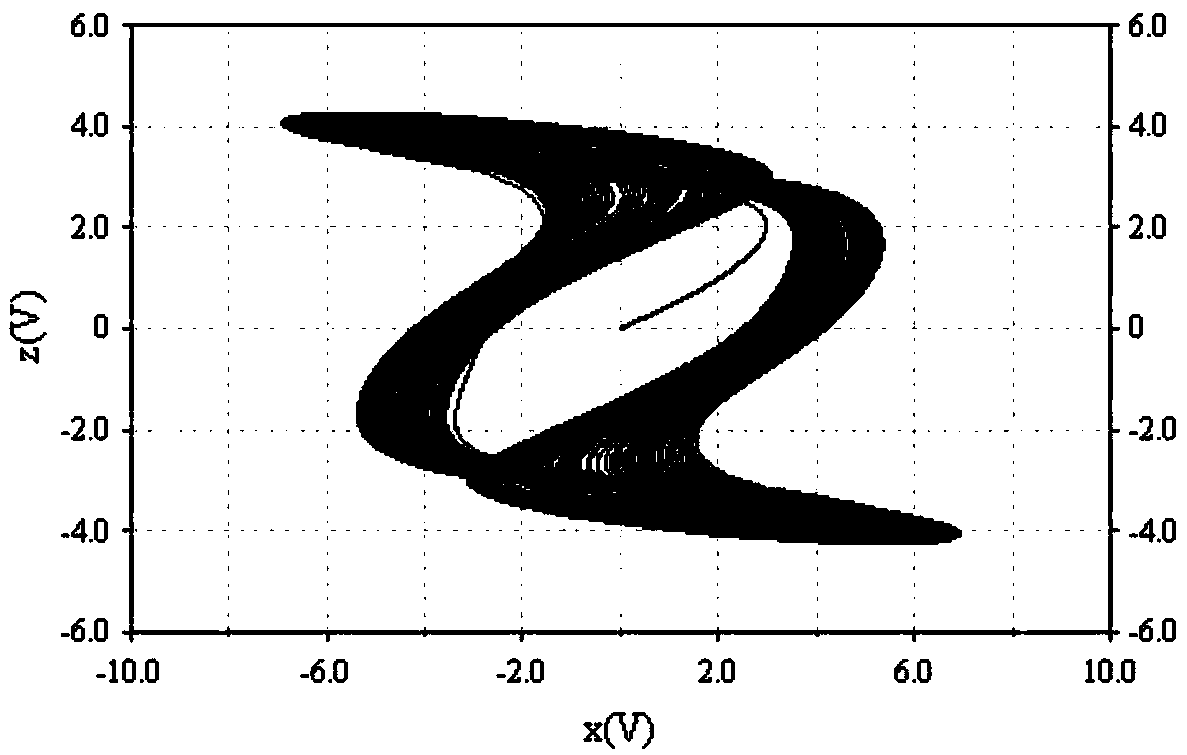
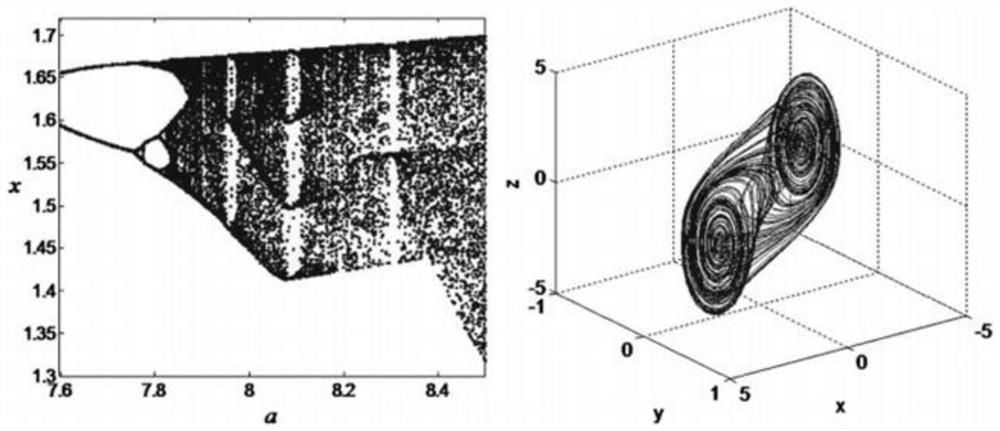
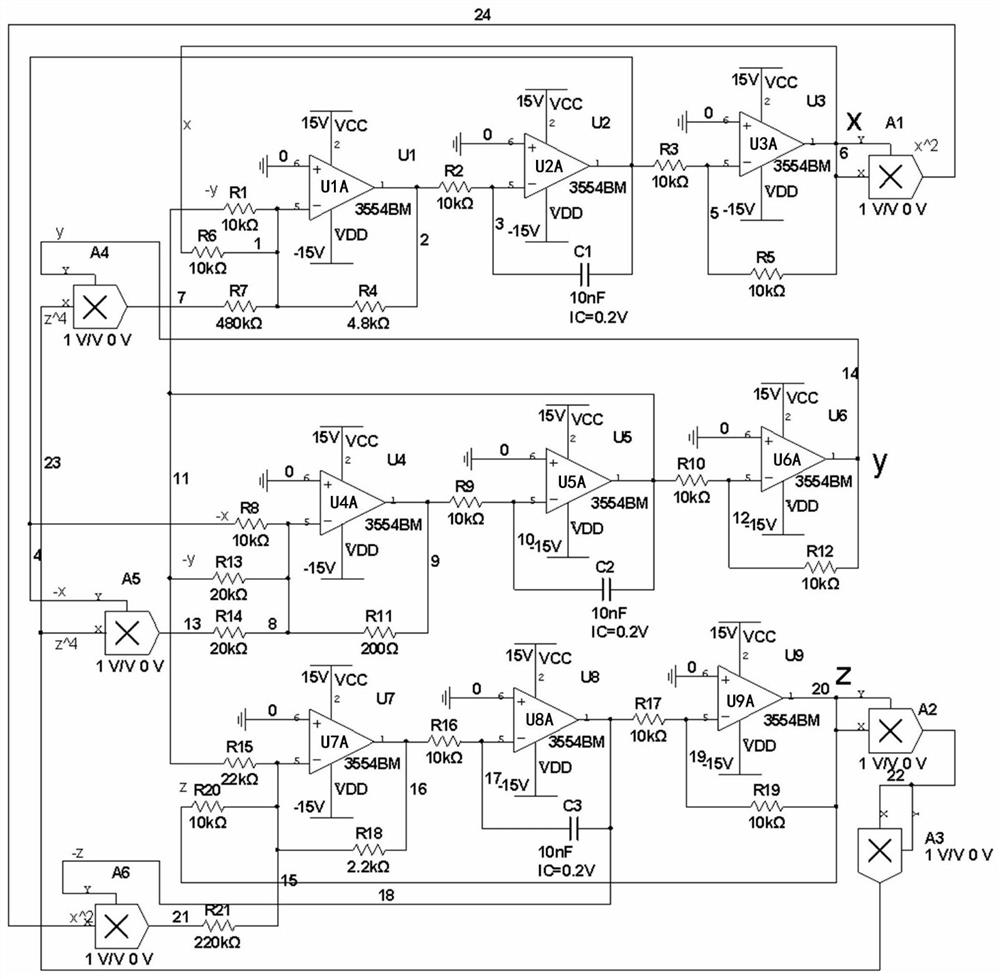
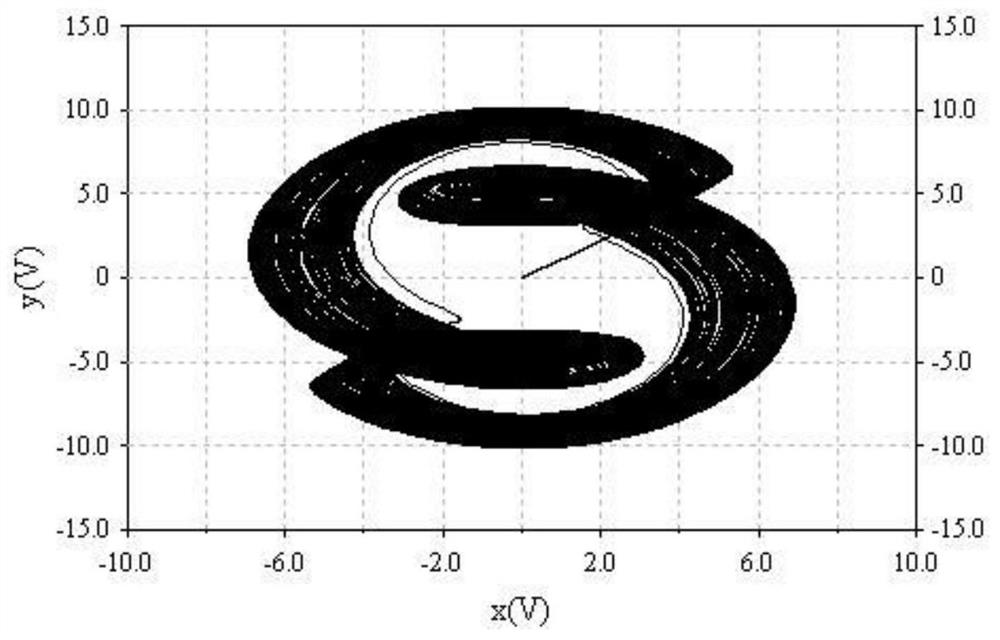
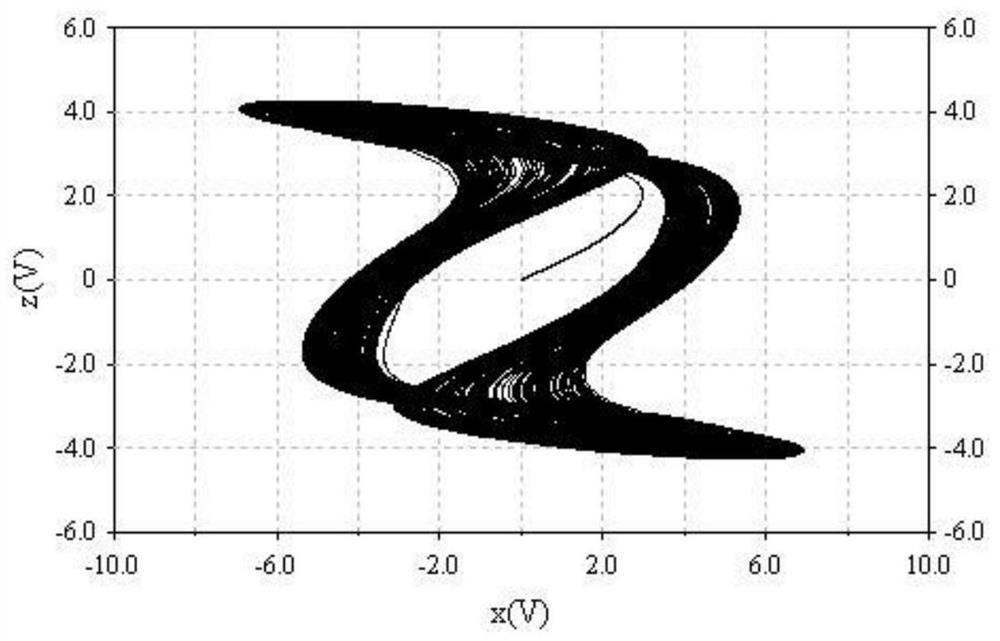
High-order novel three-dimensional chaos model and circuit thereof
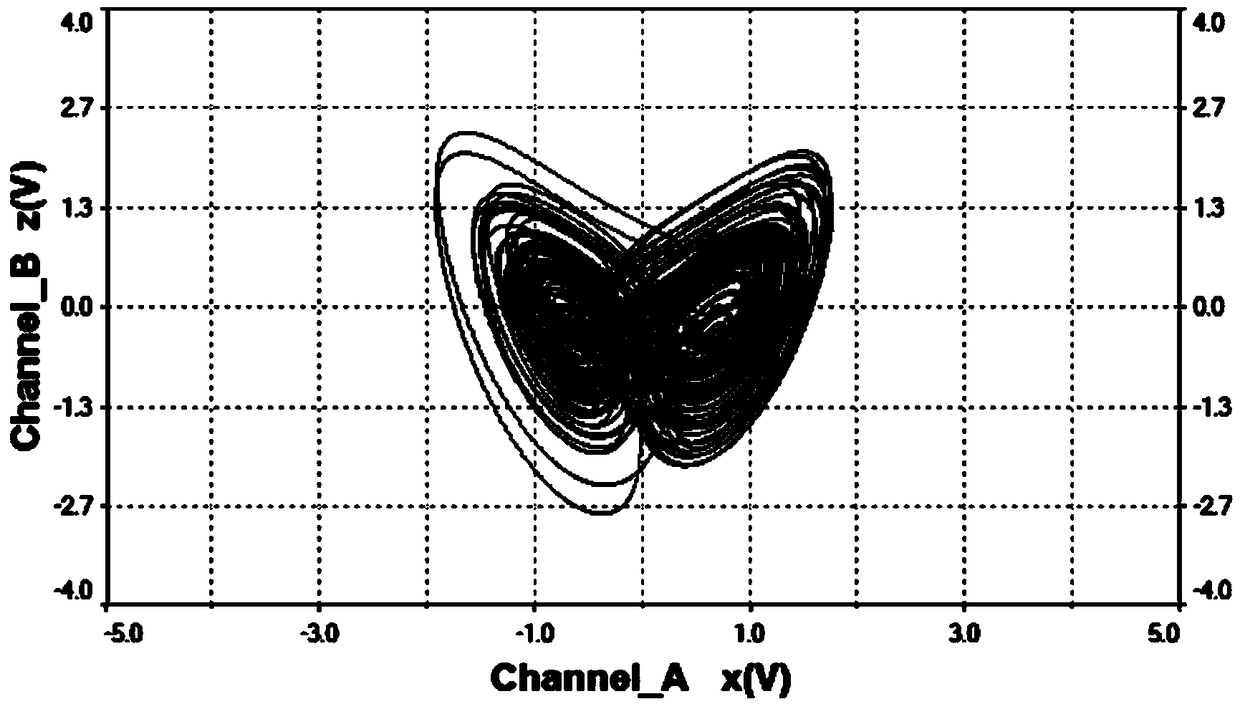
ActiveCN108075732AOvercoming the drawbacks of encryption that is easy to be decipheredRich Dynamic BehaviorSecuring communication by chaotic signalsOscillations generatorsCapacitanceElectrical resistance and conductance
The invention belongs to the technical field of chaos systems, and discloses a high-order novel three-dimensional chaos model and a circuit thereof. The circuit of the high-order novel three-dimensional chaos model comprises three channel circuits. The circuit of the high-order novel three-dimensional chaos model consists of thirty-nine elements, including nine 3554BM operational amplifiers, six multiplying units, three capacitors and twenty-one resistors. The high-order novel three-dimensional chaos circuit disclosed by the invention has a plurality of balance points and a high-order non-linear term, is more complex and abundant in dynamic behaviors, and can be applied to non-linear circuit course experiments. Moreover, the defect that encrypted information of an existing Chaos system isliable to decryption can be overcome, and a basis is laid for the application of a Chaos system.
Owner:XIDIAN UNIV
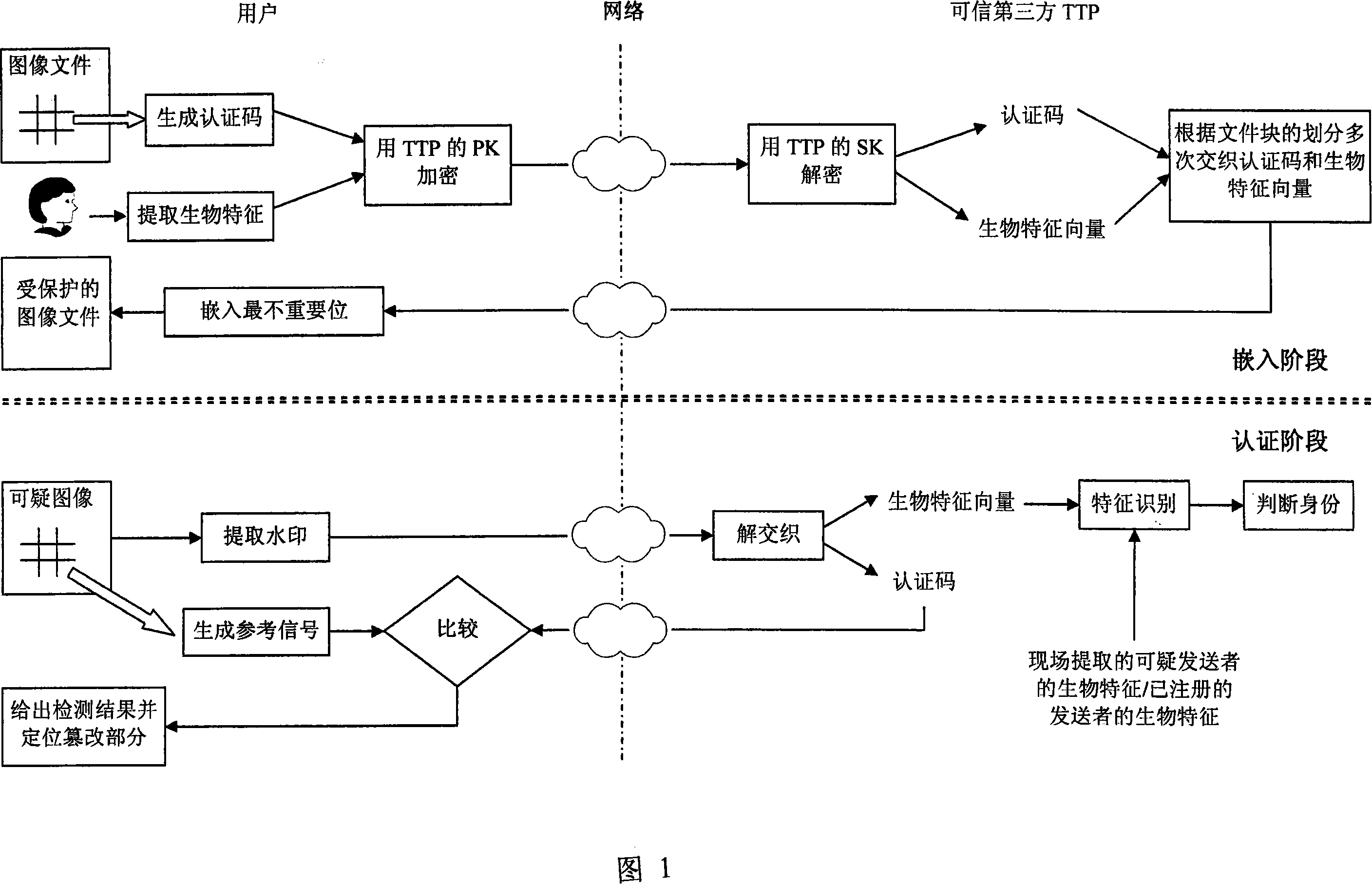
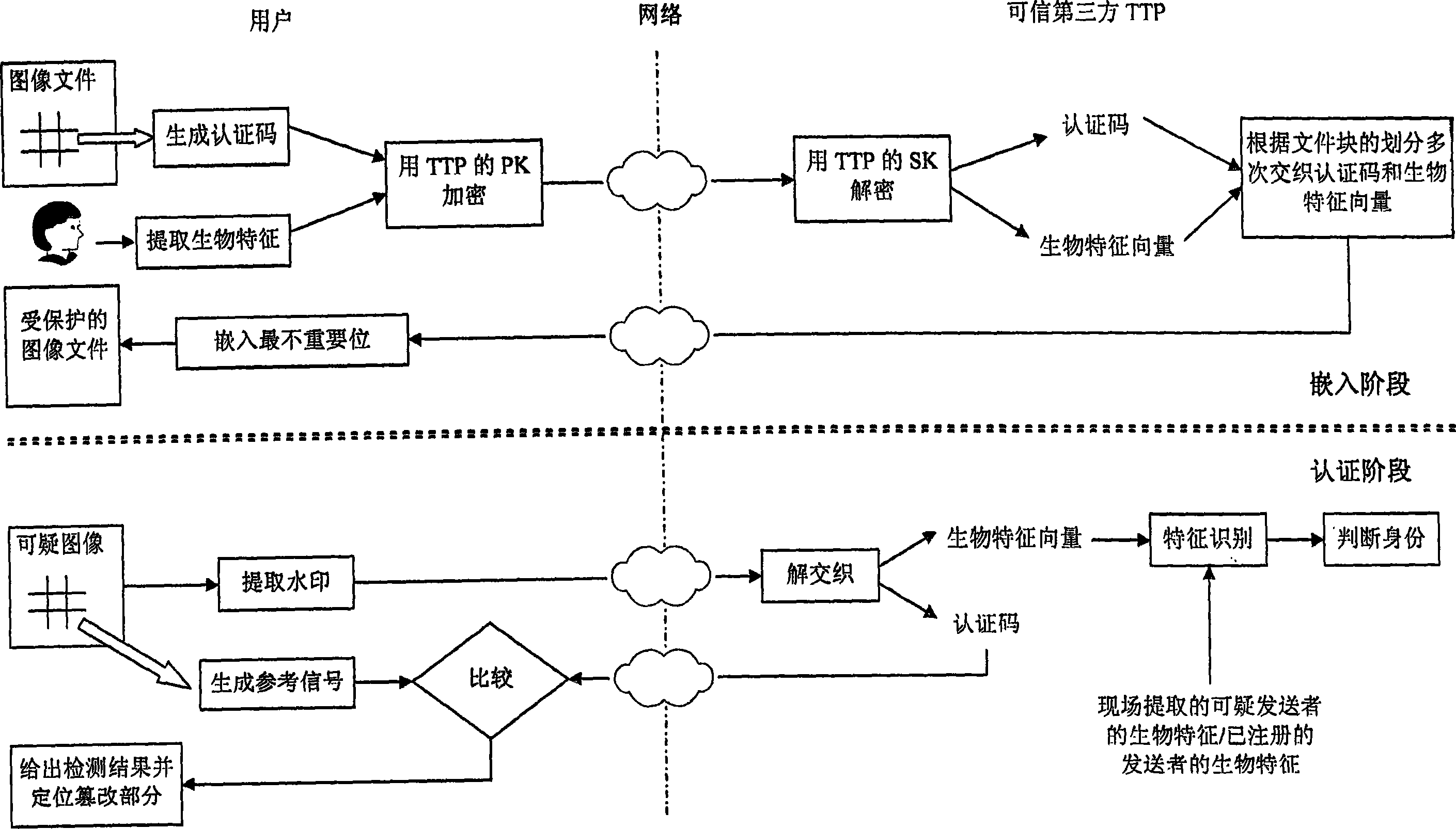
Document authentication method based on interweaving watermark and biological characteristic
InactiveCN101141466AVerify integrityPrevent repudiationMultiple keys/algorithms usageThird partyComputer science
The present invention relates to a document integrity authentication method based on an interleaving watermark and a biological feature, a chaos model is adopted to generate an authentication code, and the biological information of a deliverer is generated to a biological feature code streaming after being extracted through the feature. The authentication code and the biological feature code streaming are returned to the deliverer after a plurality of interleaving treatments under the control of a third party, and then the deliverer inserts the interleaving information in the document. When being authenticated, on the one hand, the extracted authentication code and a generated reference sequence are compared, the integrity of the document content is determined, and a tampered area is positioned; on the other hand, the extracted biological feature is identified, the identity of the deliverer is determined, and a disavowal behavior is prevented. The present invention can authenticate the integrality of the document, and can detect and position a tampered location. The different requirements of users to the precision are supported, and the positioning precision is adjustable and controllable. An authentication result is given by error, and the tampered location can be directly and visually reflected. The identity of the deliver can be determined, and the disavowal behavior is prevented.
Owner:BEIJING JIAOTONG UNIV
GAN game confrontation encryption system (method) based on chaotic model
ActiveCN110324147AImprove securityKey distribution for secure communicationMultiple keys/algorithms usageGenerative adversarial networkAdversarial network
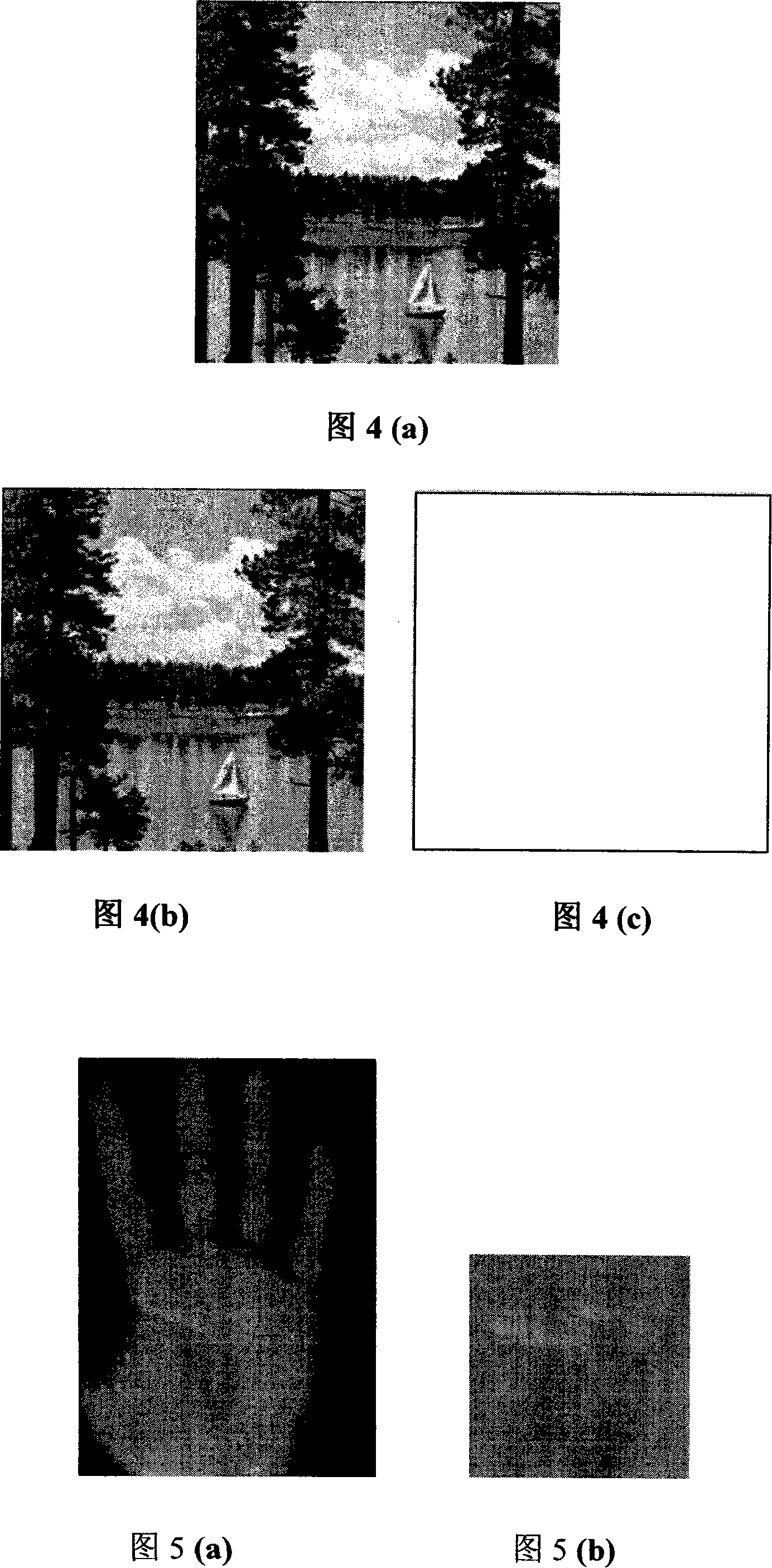
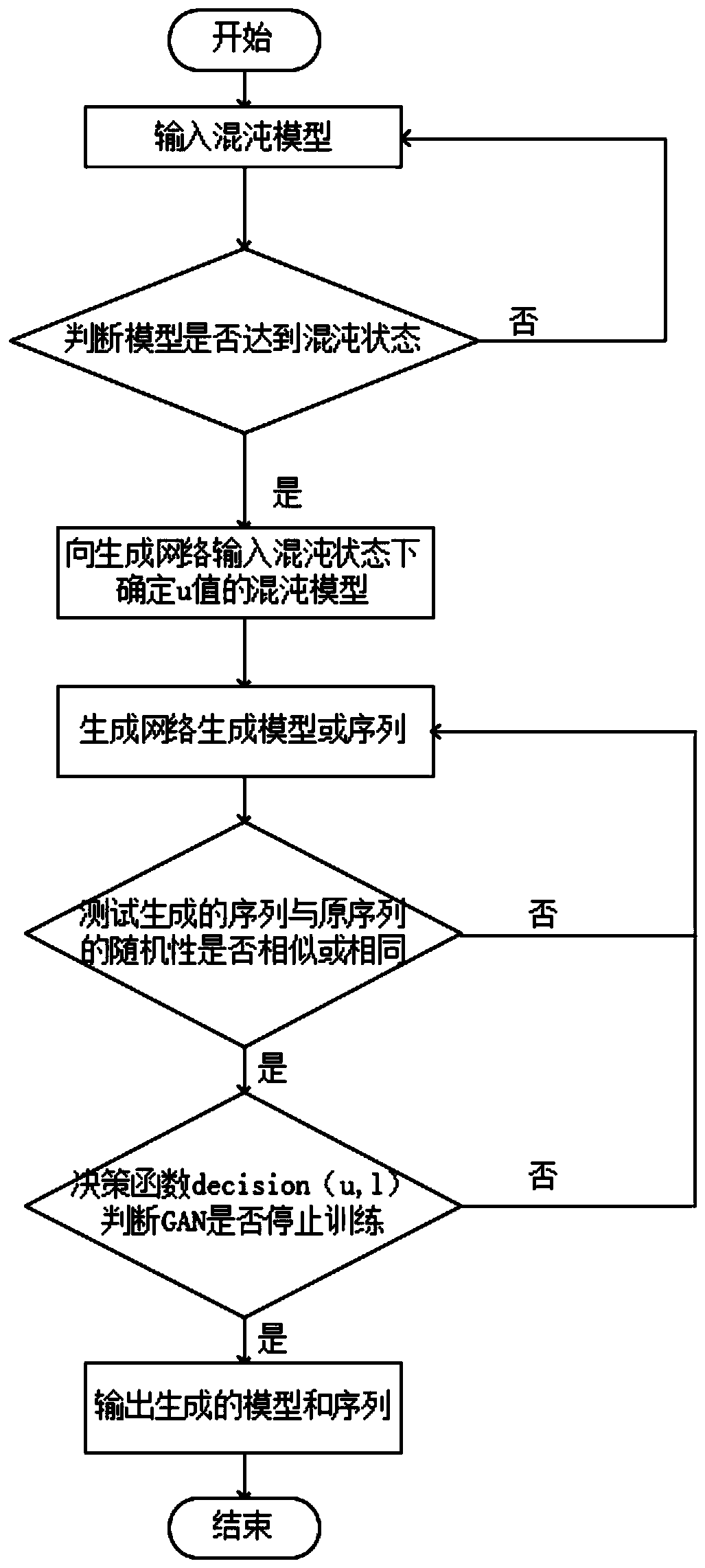
The invention discloses a GAN game confrontation encryption system (method) based on a chaotic model, relates to a chaotic encryption method and a confrontation neural network in machine learning, andgenerates a dynamic encryption algorithm and an encryption key based on the thought of the game theory. The invention aims to solve the problem that encrypted data is easy to attack in the existing encryption technology. According to the technical scheme, the system comprises the following steps: 1, analyzing the characteristics of an insect mouth logistic chaotic model; 2, inputting a determined[mu]m value, and generating a chaotic model under the mu value and a one-time pad security key by utilizing generative adversarial network adversarial; 3, testing random number generation: testing whether the randomness of the generated sequence is the same as or similar to that of the original sequence or not; 4, setting different loss convergence values, and synthesizing the different loss convergence values and [mu]m into a decision (mu, l) as decision parameters of the discriminator; and 5, inputting different [mu]m values in an interval where [mu]m is located when the model is in chaos,and generating a chaos model corresponding to the [mu]m values by utilizing the generation model; and judging when to stop according to the decision parameter, wherein the model obtained when to stopis the GAN encryption algorithm based on chaos. The invention is applied to the field of communication.
Owner:HEILONGJIANG UNIV
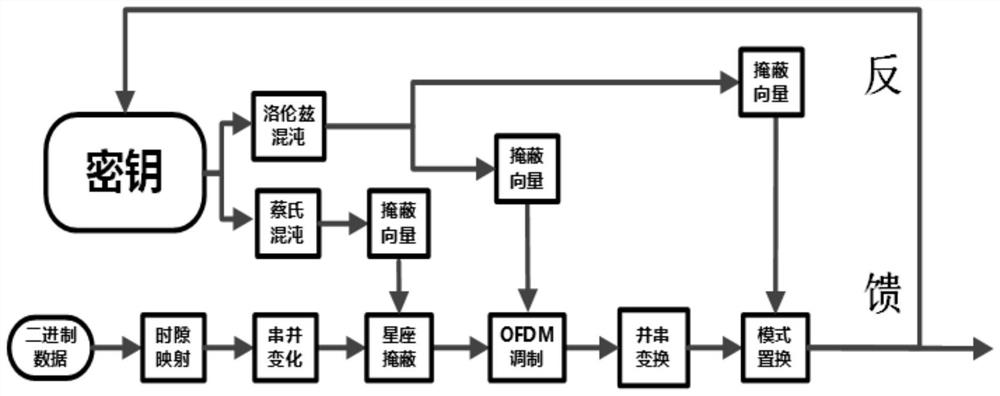
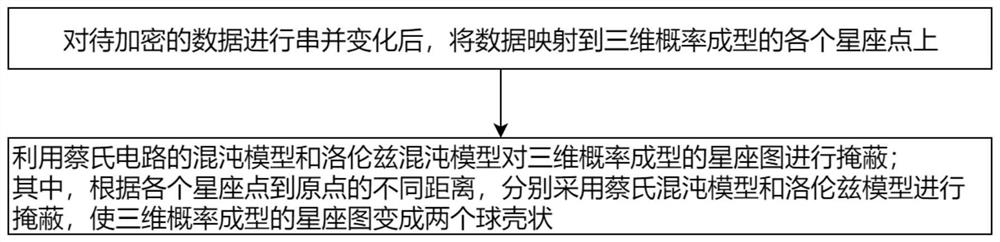
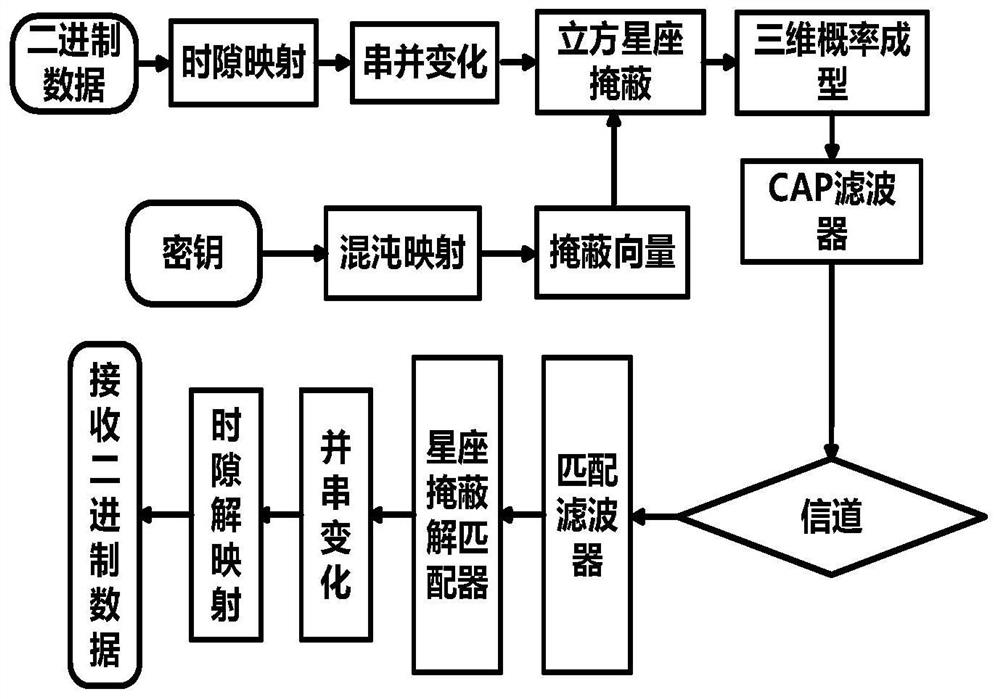
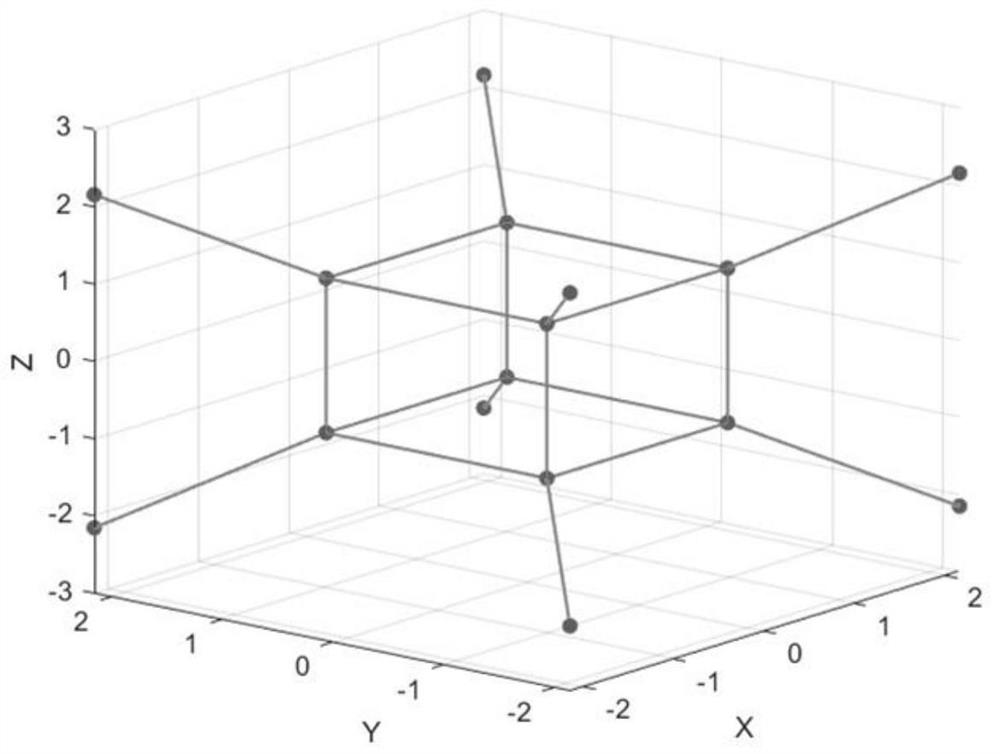
Security-level-controllable carrier, constellation and mode multi-chaos masking light transmission method
ActiveCN112054888ASecret level controllableLarge key spaceFree-space transmissionSecuring communication by chaotic signalsAlgorithmTheoretical computer science
The invention provides a security-level-controllable carrier, constellation and mode multi-chaos masking light transmission method, which comprises the following steps of: performing serial-parallel change on data, and mapping the data to each constellation point; masking the three-dimensional constellation diagram by using a Chua's chaotic model, so that the three-dimensional constellation pointsare converted into a sphere; then, the Lorentz model being used for masking the subcarrier and the orthogonal mode, meanwhile, parameters of the Lorentz model and the Chua's circuit model being modulated, and therefore security level controllability of chaotic encryption being achieved. At the receiving end, an original Chua's circuit and an original Lorentz model secret key are used for decrypting the chaotic constellation diagram. The signals decrpted by the receiving end are compared with the transmitting end, thus to calculate the system error ratio, thereby judging the system performance. By the control over the parameters a chaos model, encryption of one dimension or multiple dimensions can be conducted, thus security classification can be achieved. According to different conditions, high-security transmission is realized at the lowest encryption cost.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
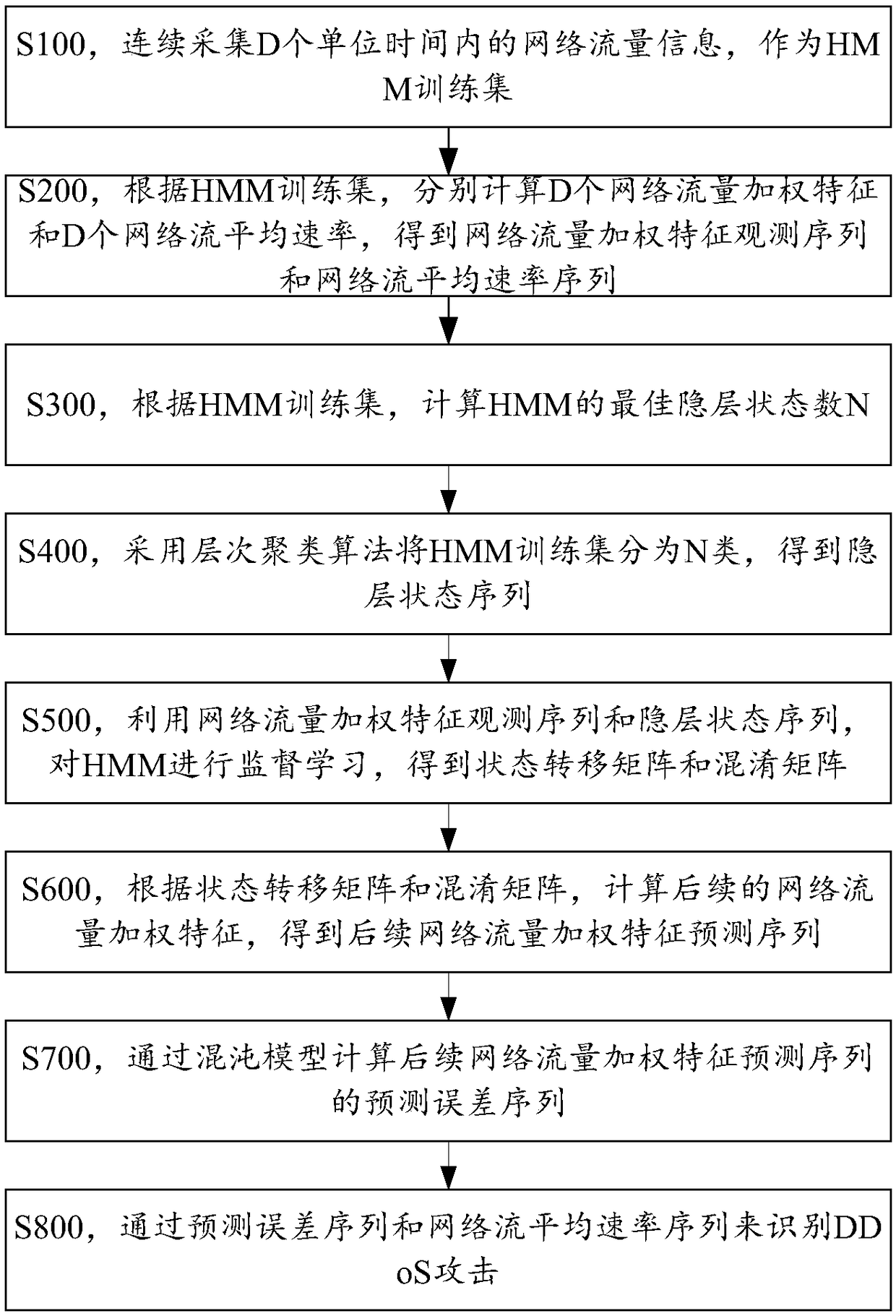
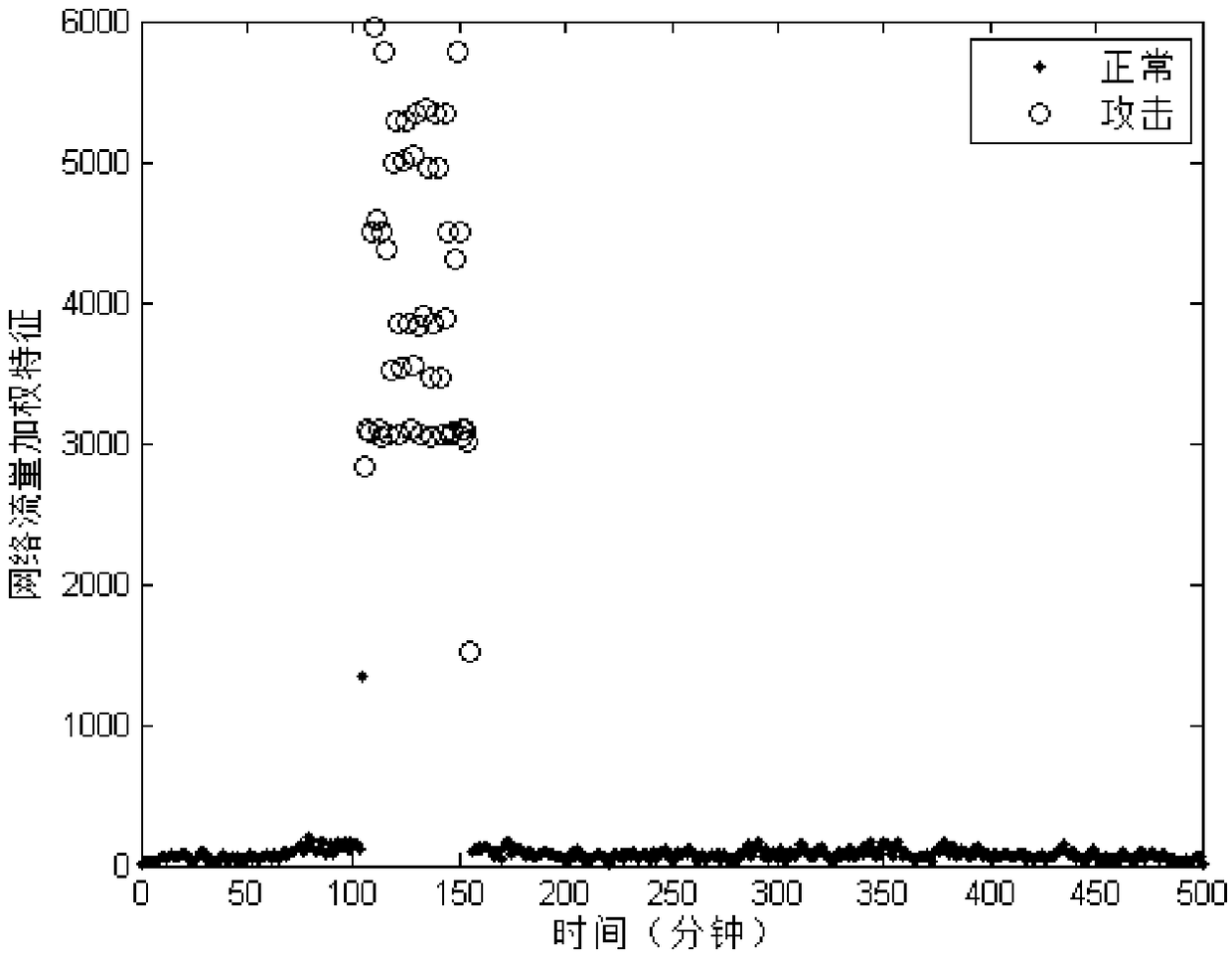
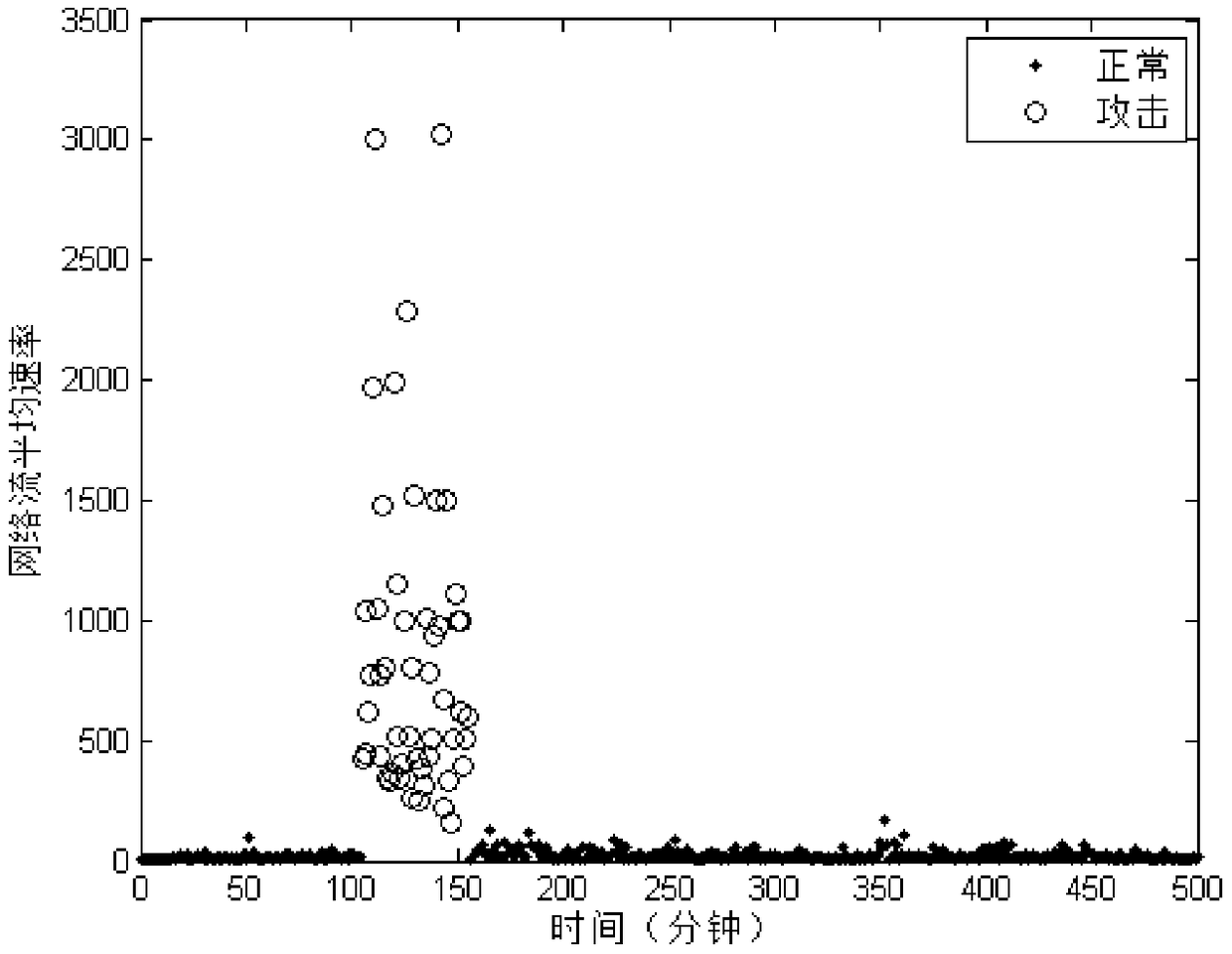
DDoS attack detection method based on HMM and chaos model
ActiveCN108900556AReduce attack misjudgment rateOvercome limitationsCharacter and pattern recognitionChaos modelsHierarchical cluster algorithmTransfer matrix
An embodiment of the invention discloses a DDoS attack detection method based on HMM and chaos model. The method comprises the following steps: acquiring network traffic information as an HMM trainingset; calculating to obtain a network traffic weighting feature observation sequence and a network flow average speed sequence; calculating the optimal number N of implicit strata states according tothe HMM training set; classifying the HMM training set into N types by a hierarchical clustering algorithm to obtain an implicit strata state sequence; performing supervised learning of HMM by use ofthe network traffic weighting feature observation sequence and the implicit strata state sequence, to obtain a state transfer matrix and a confusion matrix; calculating follow-up network traffic weighting features according to the state transfer matrix and the confusion matrix, to obtain a follow-up network traffic weighting feature prediction sequence; calculating a prediction error sequence of the follow-up network traffic weighting feature prediction sequence according to a chaos model; identifying DDoS attack according to the prediction error sequence and the network flow average speed sequence.
Owner:维森派沃(无锡)科技有限公司 +1
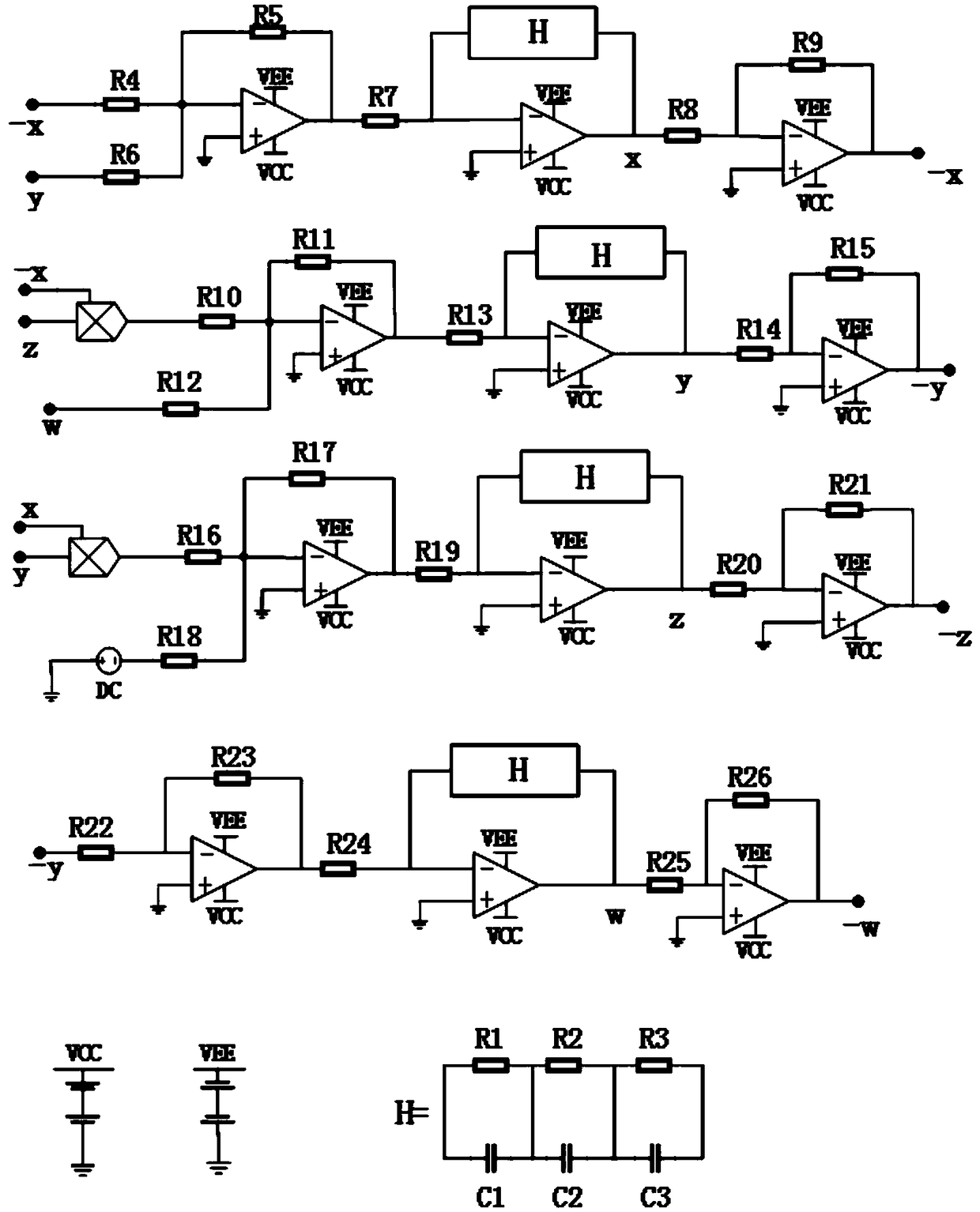
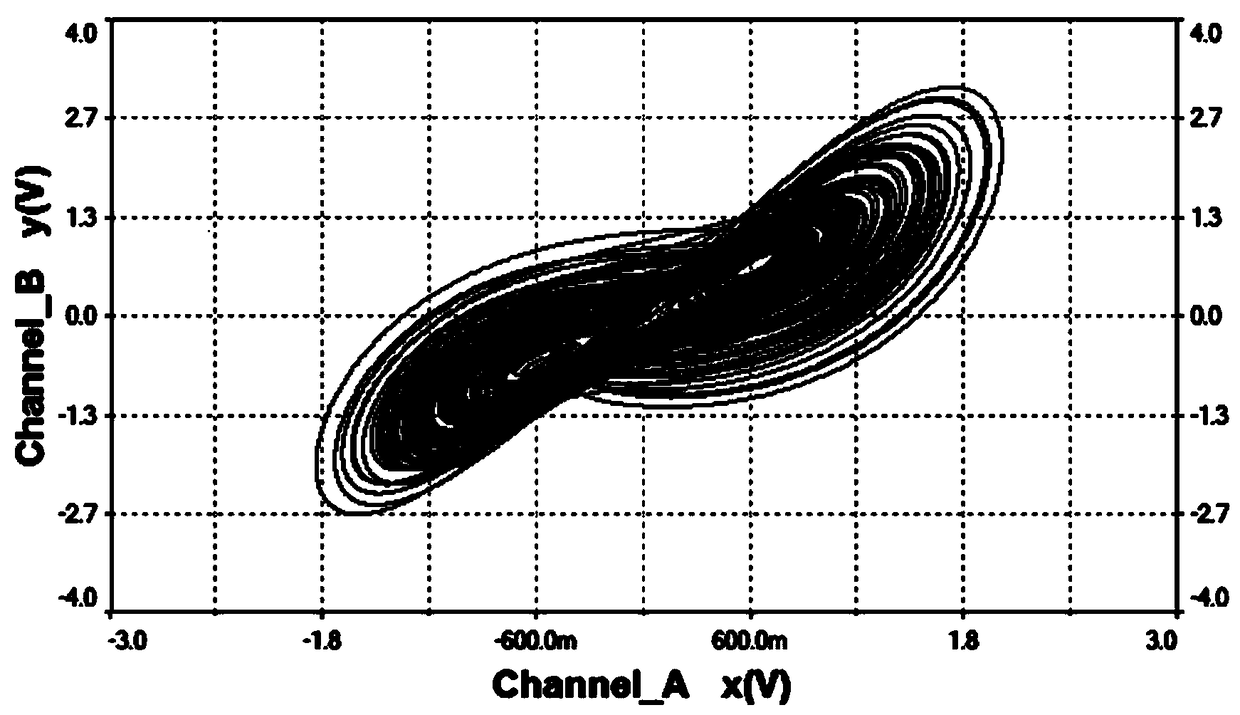
Four-dimensional fractional-order chaos model and circuit
InactiveCN109302277ASimple structureOvercoming the drawbacks of encryption that is easy to be decipheredSecuring communication by chaotic signalsMultiplexerEngineering
The invention discloses a four-dimensional fractional-order chaos model and a circuit. The circuit of the four-dimensional fractional-order chaos model comprises four channel circuits; an output signal -x of a first channel is connected with a signal input end of the first channel and the signal input end of a second channel; a previous output signal of the first channel x is connected with the signal input end of a third channel; an output signal -y of a second channel is connected with the signal input end of a fourth channel, the previous output signal y of the second channel is connected with the signal input end of the first channel, and a multiplier A2; the previous output signal z of the third channel is connected with a multiplexer A1; and the previous output signal w of the fourthchannel is connected with the signal input end of the second channel. The fractional-order chaos model provided by the invention has higher complexity in comparison with the integer-order chaos model, and can produce more complex dynamics behavior; the fractional-order chaos model can be used for fractional-order chaos system circuit design and experiment, and can overcome the disadvantage that the existing chaos system information encryption can be easily decoded due to low complexity, thereby providing evidence for the application of the chaos system.
Owner:XIANGTAN UNIV
Underwater acoustic communication balanced decoding method based on recursive chaotic code
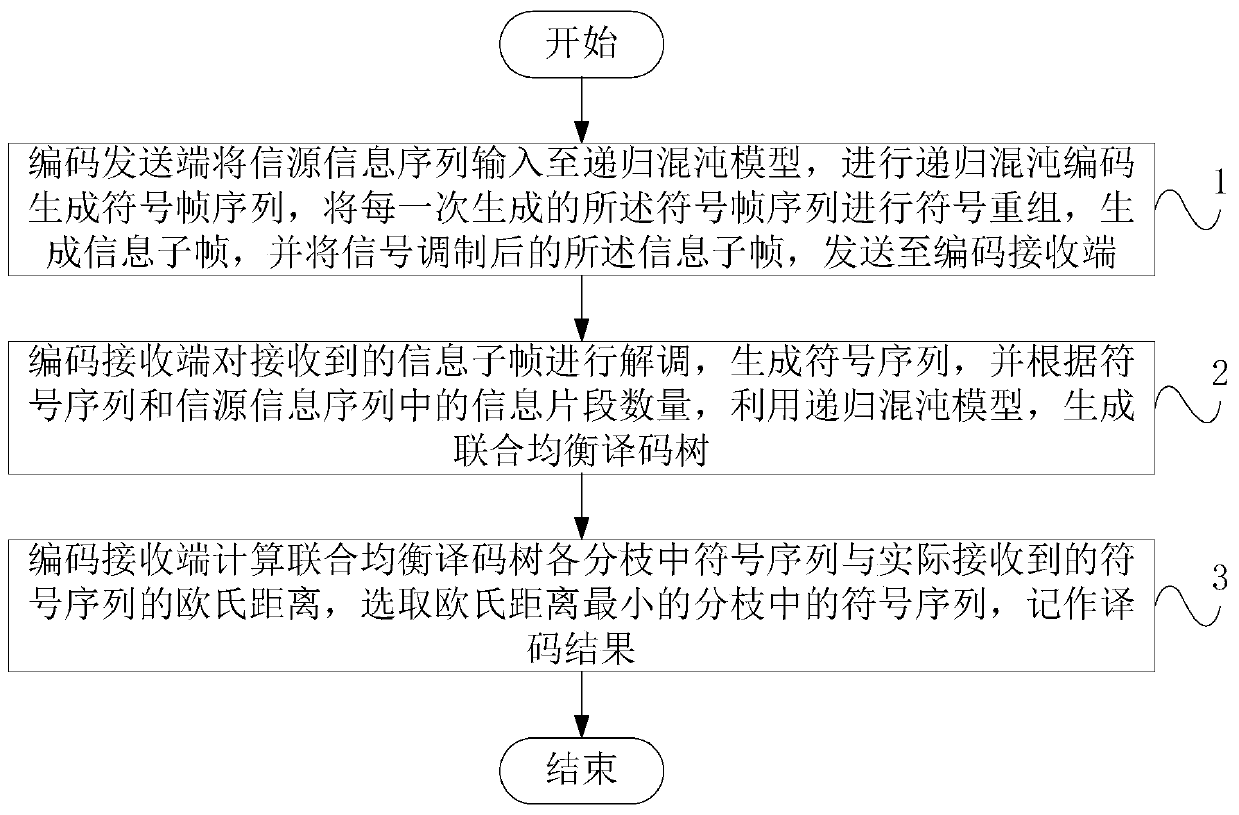
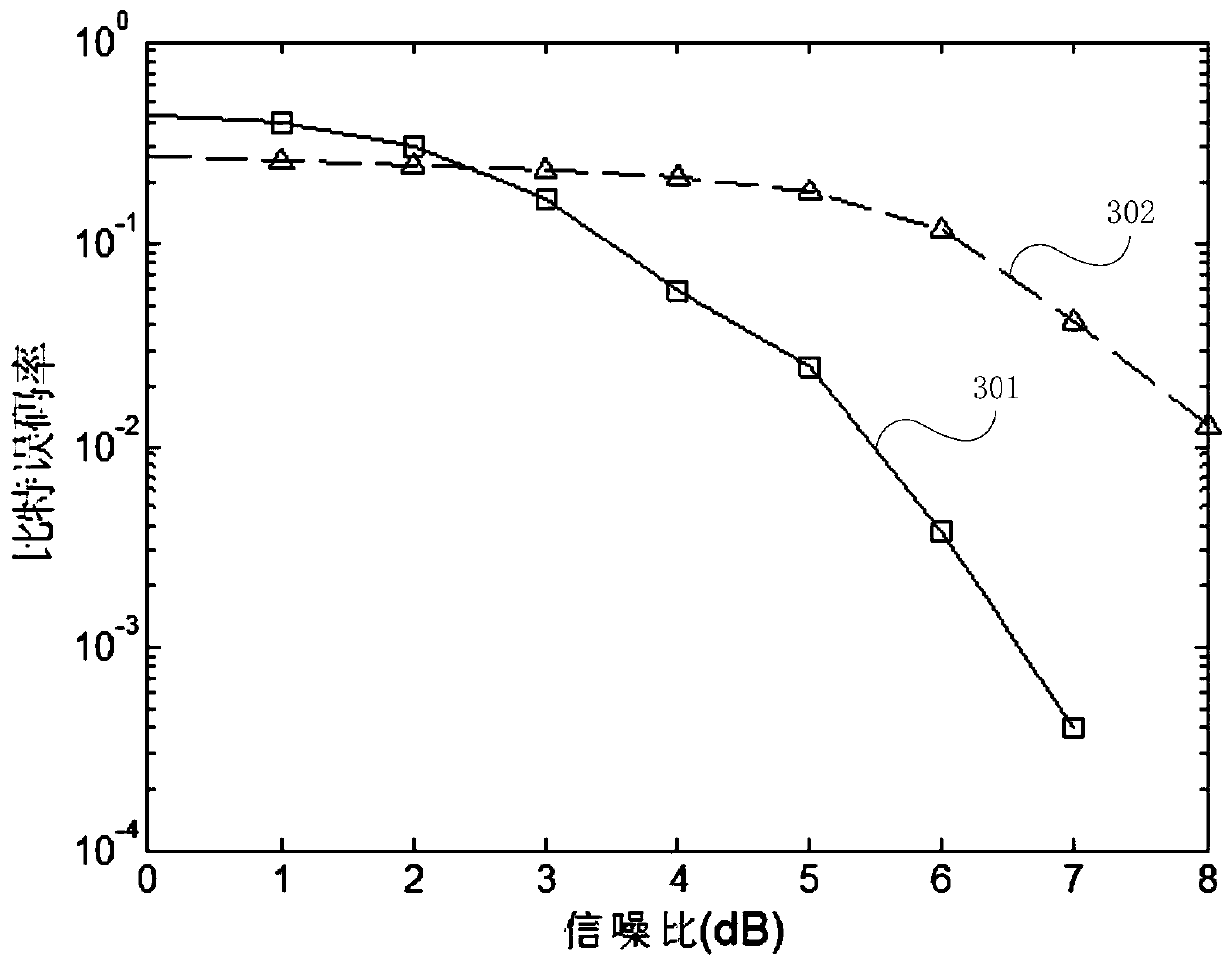
ActiveCN110166386AApparent Bit Error Rate ThresholdLower SNR ThresholdTransmitter/receiver shaping networksForward error control useFrame sequenceEqualization
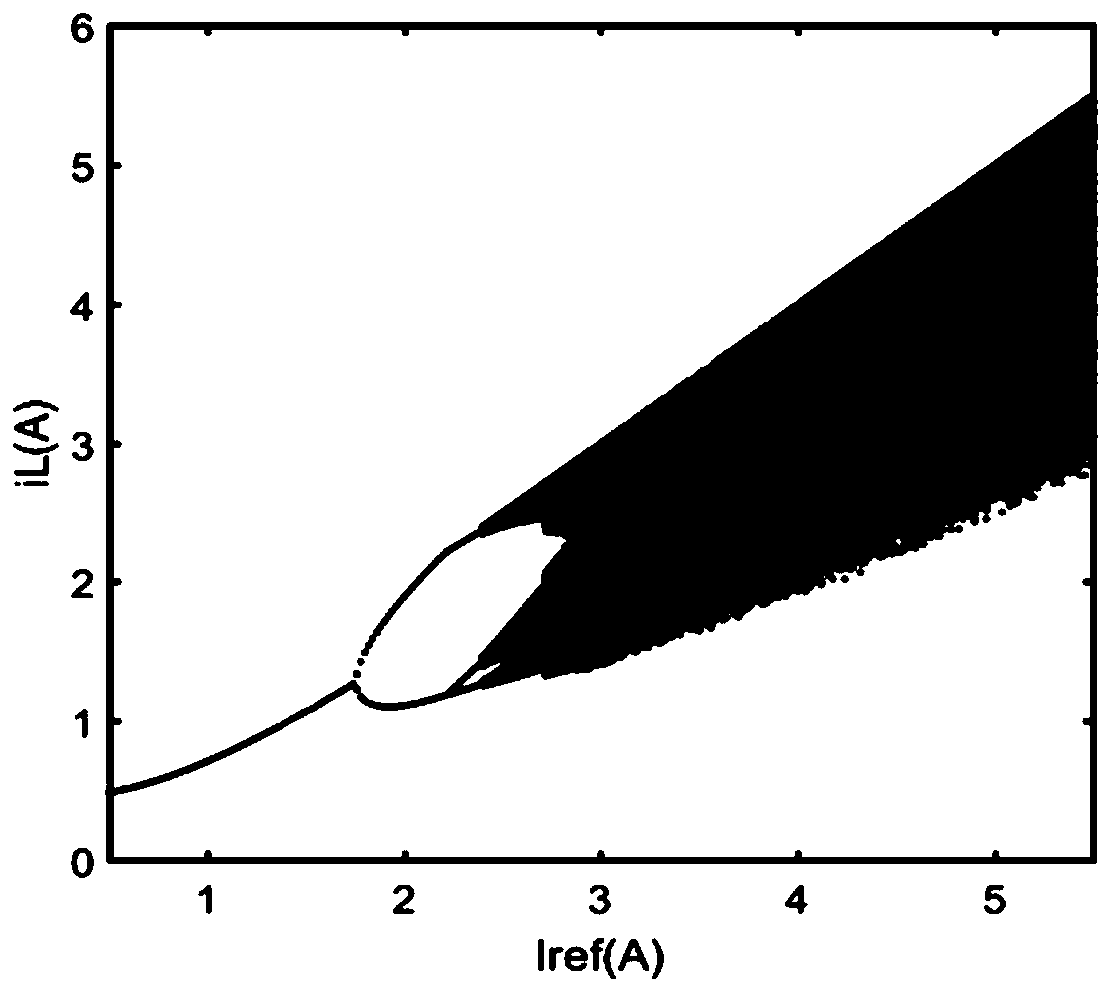
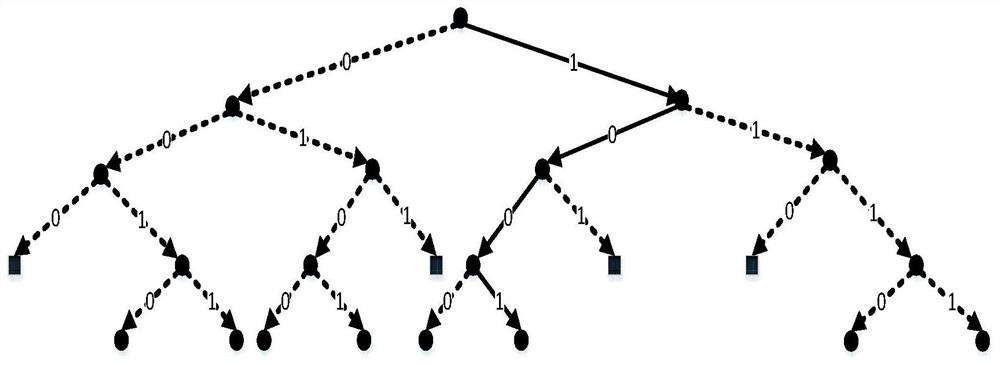
The invention discloses an underwater acoustic communication balanced decoding method based on a recursive chaotic code, and the method comprises: step 1, inputting an information source information sequence into a recursive chaos model by a coding sending end, carrying out the recursive chaotic coding, generating a symbol frame sequence, generating an information sub-frame, and sending the information sub-frame after signal modulation to a coding receiving end; step 2, the coding receiving end demodulating the received information subframes to generate a symbol sequence, and generating a joint equalization decoding tree according to the number of information fragments in the symbol sequence and the number of information fragments in the information source information sequence; and step 3,the coding receiving end calculating the Euclidean distance between the symbol sequence in each branch and the symbol sequence which is actually received, selecting the branch with the minimum Euclidean distance, and marking the branch as a decoding result. Through the technical scheme provided by the invention, the bit error rate performance of the underwater acoustic communication system is improved, the influence of strong inter-code crosstalk of the underwater acoustic channel and the complexity of a joint equalization decoding algorithm are reduced, and the transmission reliability of the underwater acoustic channel is improved.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
Ocean wave height prediction method and system, computer equipment, storage medium, and terminal
PendingCN113722980AImprove accuracyLow costDesign optimisation/simulationNeural architecturesSea wavesEngineering
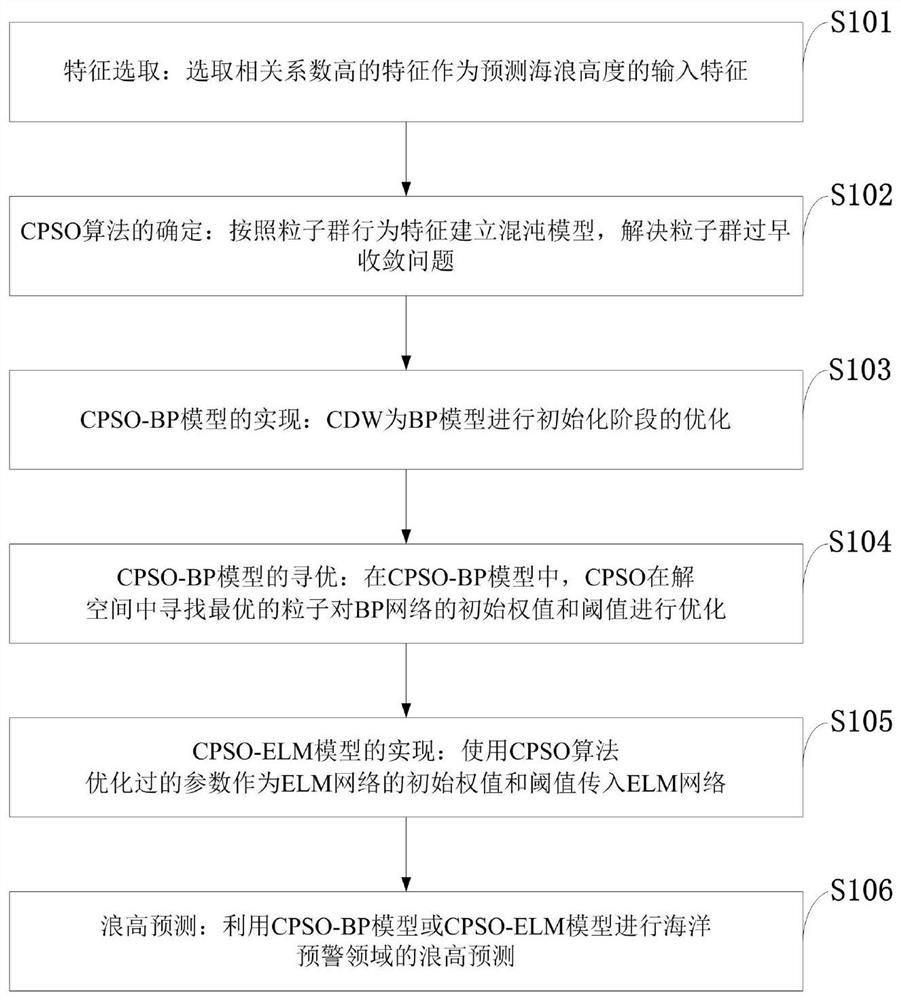
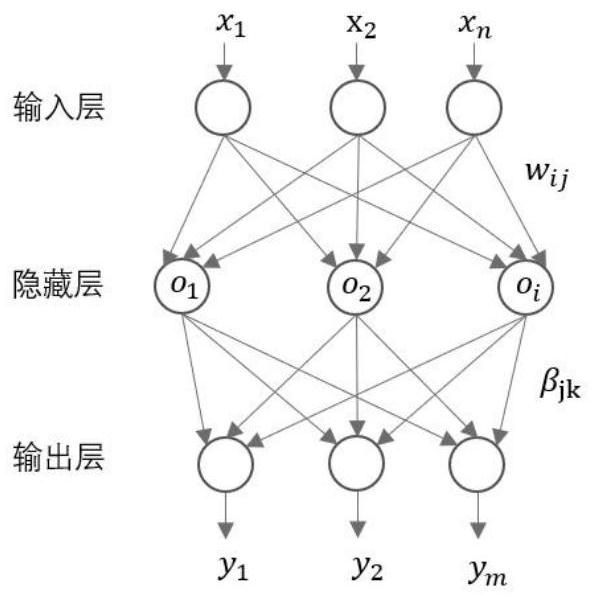
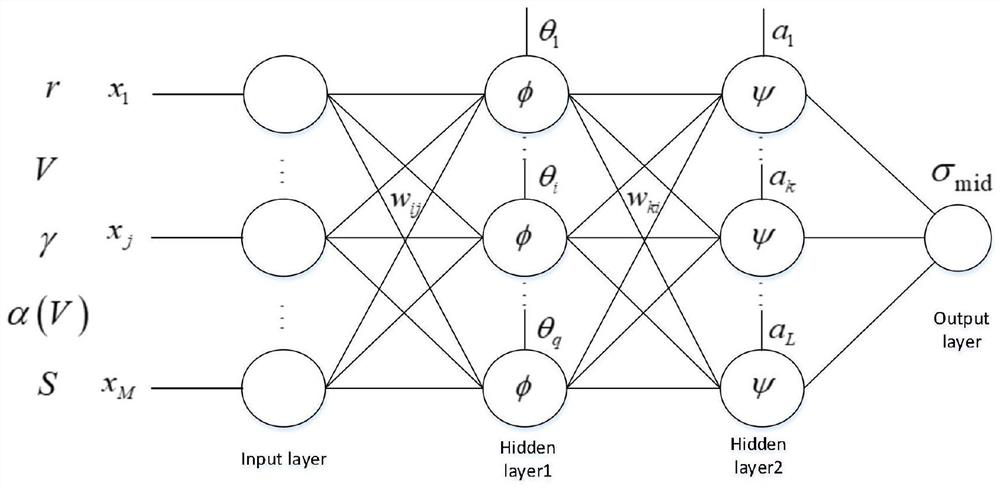
The invention belongs to the technical field of ocean wave height prediction, and discloses an ocean wave height prediction method and system, computer equipment, a storage medium, and a terminal. The method comprises the following steps: selecting a feature with a high correlation coefficient as an input feature for predicting an ocean wave height; establishing a chaos model according to particle swarm behavior characteristics to solve the problem of premature convergence of particle swarms, wherein the CDW performs optimization in an initialization stage for a BP model, and in a CPSO-BP model, a chaotic particle swarm optimization (CPSO) algorithm searches optimal particles in a solution space to optimize initial weights and threshold values of a BP network; using parameters optimized by the CPSO algorithm as initial weights and threshold values of an ELM network to be transmitted to an ELM network; carrying out wave height prediction in the ocean early warning field by using a CPSO-BP model or a CPSO-ELM model. The deep learning method is used for wave height prediction, and the method has the advantages of high accuracy, low cost and high operation speed.
Owner:OCEAN UNIV OF CHINA
Aircraft intelligent trajectory planning method based on chaotic model and DNN
ActiveCN114442673AOvercome limitationsIncrease chaosSustainable transportationPosition/course control in three dimensionsFlight heightFlight vehicle
The invention discloses an aircraft intelligent trajectory planning method based on a chaos model and a DNN, and belongs to the technical field of aircraft trajectory planning. The method comprises the following steps: obtaining a network mapping relation between a flight state quantity and a flight control quantity; converting the process constraint into flight height and heeling angle constraint; generating a final chaotic signal in the guidance instruction; calculating a heeling angle section median meeting task constraints and a heeling angle required in real time; the size of the heeling angle after chaos processing is obtained; determining a heeling angle direction by adopting a sight angle error corridor; and restraining the amplitude of the heeling angle and the amplitude of the heeling rate. According to the method, the model limitation during the traditional flight path design is overcome, and the unpredictability of the guide instruction and the flight path is increased; and the influence of uncertainty on task reachability is limited. Therefore, the chaos of the flight path is increased on the premise of ensuring the feasibility of the predetermined task, the process constraint is met in the guidance instruction calculation, and the method has a certain engineering practical value.
Owner:哈尔滨逐宇航天科技有限责任公司
HEVC video encryption method by adopting dynamic integer chaos
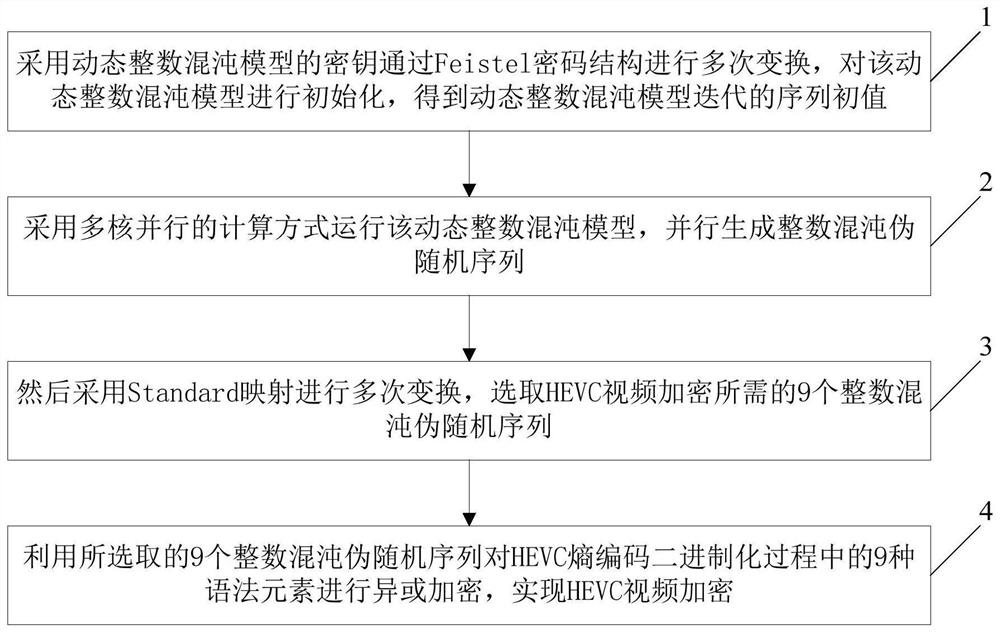
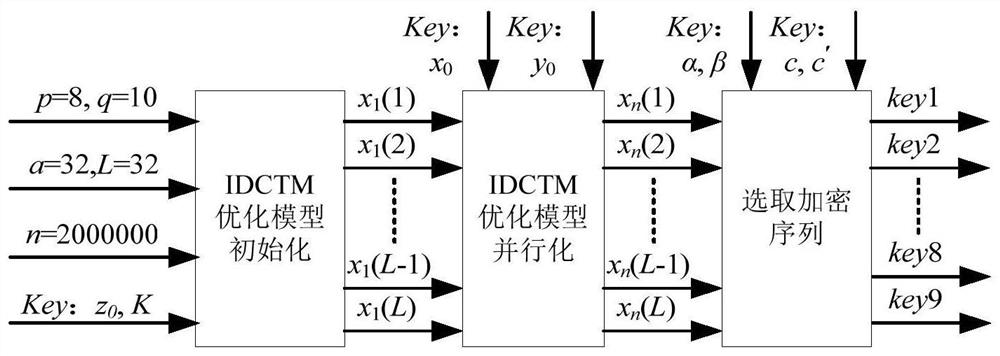
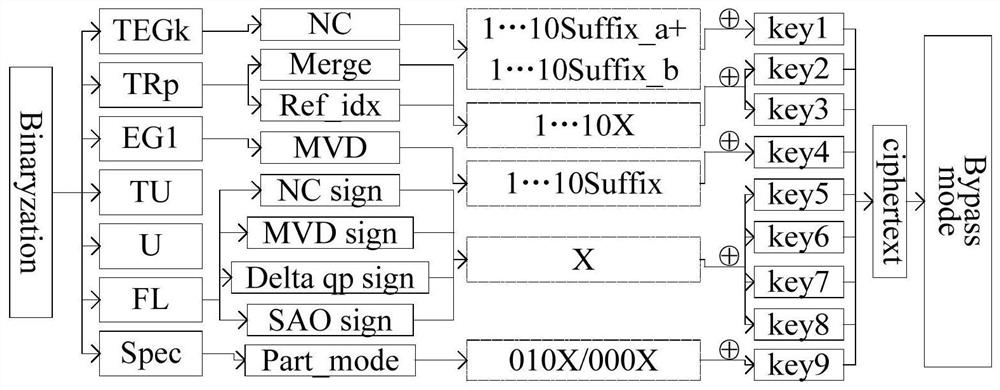
PendingCN111698077AGuaranteed encryption securityImprove efficiencyEncryption apparatus with shift registers/memoriesSecuring communication by chaotic signalsPasswordTheoretical computer science
The invention discloses an HEVC video encryption method by adopting dynamic integer chaos, which comprises the following steps: firstly, carrying out multiple times of transformation by adopting a keyof a dynamic integer chaos model through a Feistel password structure, and initializing the dynamic integer chaos model to obtain an iterative sequence initial value of the dynamic integer chaos model; adopting a multi-core parallel computing mode to run the chaotic model, and generating an integer chaotic pseudo-random sequence in parallel; secondly, performing transformation for multiple timesby adopting Standard mapping, and selecting 9 integer chaotic pseudo-random sequences required by HEVC video encryption; and carrying out XOR encryption on nine syntax elements in the HEVC entropy coding binarization process by utilizing the nine selected integer chaotic pseudo-random sequences to realize HEVC video encryption. According to the method, the high efficiency of video encryption can be improved on the basis of ensuring the security of video encryption, and the method is suitable for the fields of video conferences with strict requirements on real-time performance and the like.
Owner:BEIJING INSTITUTE OF PETROCHEMICAL TECHNOLOGY
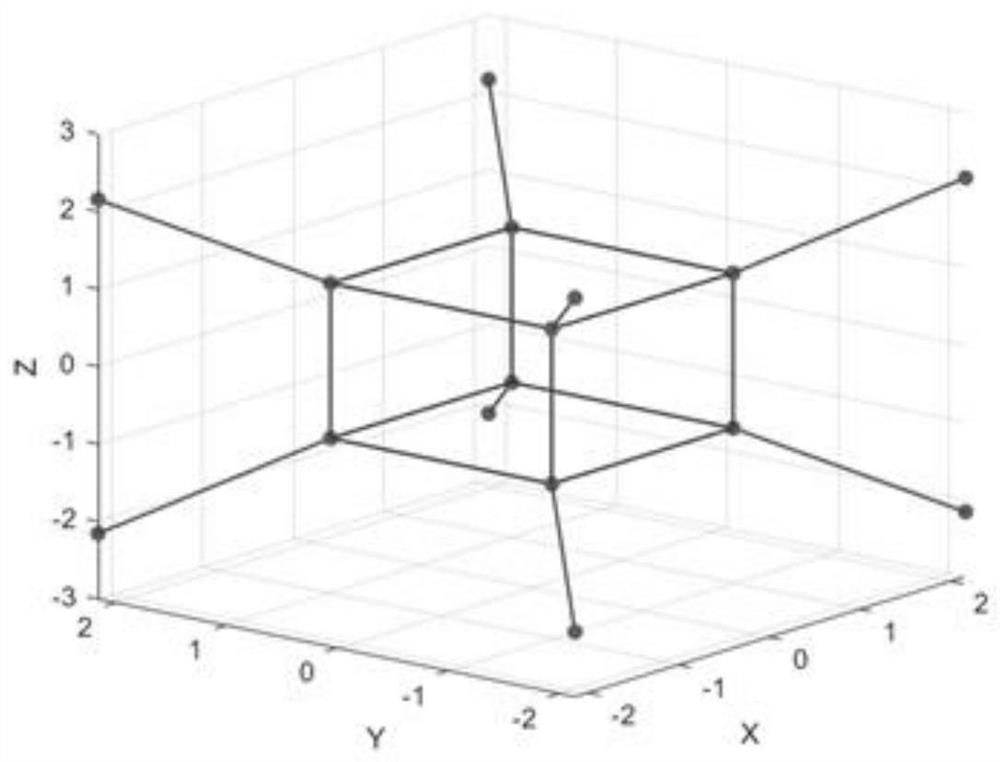
Space encryption method based on three-dimensional CAP constellation
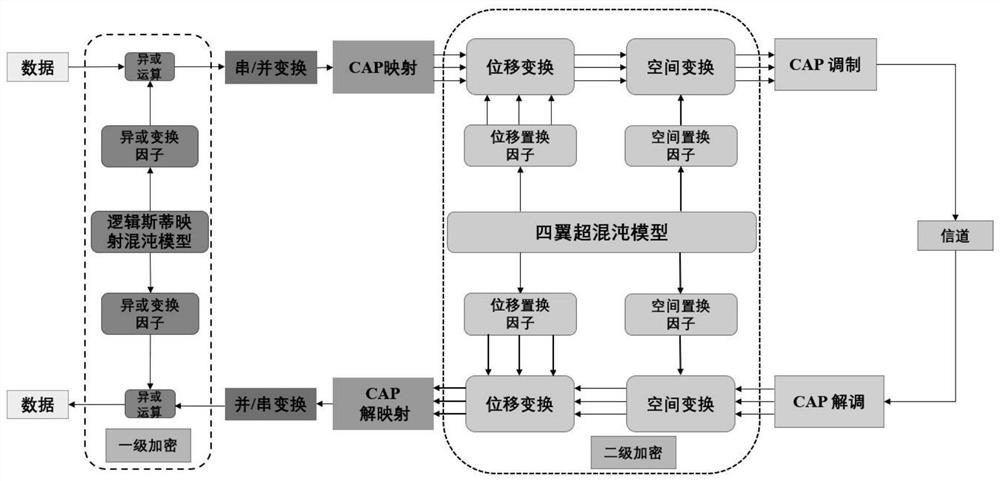
ActiveCN113965312AImprove securityIncreased encryption flexibilityMultiple keys/algorithms usageSecuring communication by chaotic signalsCommunications securityAlgorithm
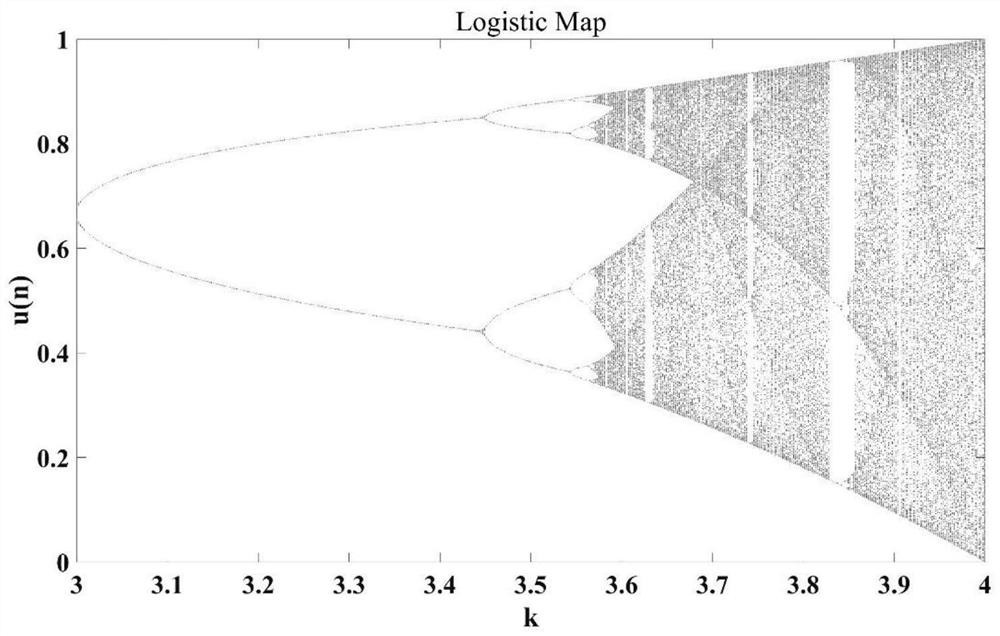
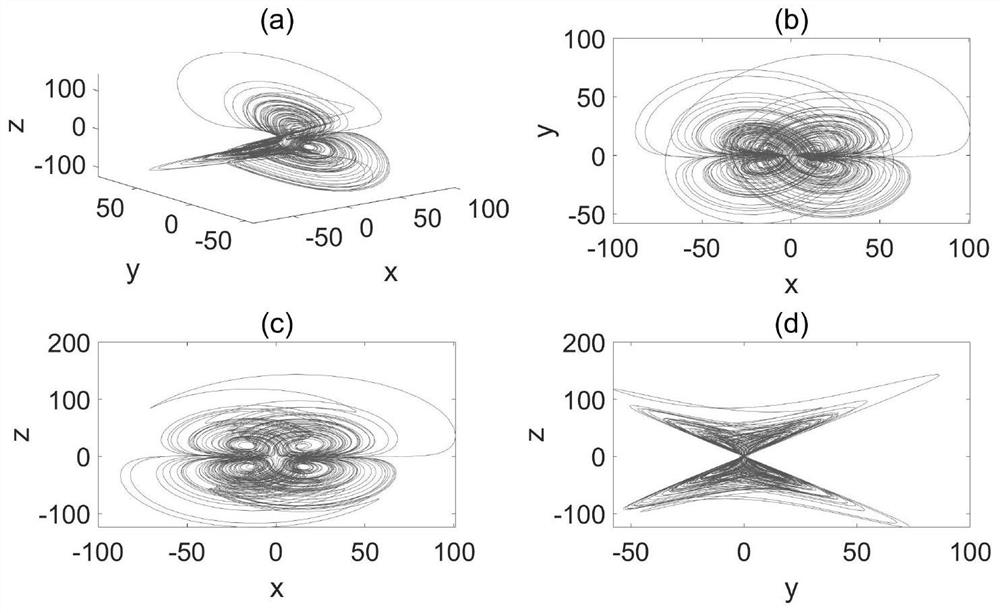
The invention belongs to the technical field of communication, and particularly relates to a space encryption method based on a three-dimensional CAP constellation. The space encryption method comprises the following steps: taking a Logistic Map model as a first chaos model, and generating a first-level masking factor for performing exclusive-or operation on pseudo-random input data; taking the super-four-wing chaotic model as a second chaotic model and used for generating a second-level masking factor and a third-level masking factor which are used for carrying out displacement transformation and spatial transformation on the three-dimensional CAP constellation respectively; and applying the three-level masking factor to encryption modulation of the three-dimensional CAP constellation. According to the method, two chaos models are combined, exclusive-or operation is firstly carried out on pseudo-random input data, then displacement transformation and spatial transformation of a three-dimensional constellation are realized, and the effect of communication security can be effectively improved; according to the spatial encryption method based on the three-dimensional CAP constellation, the encryption flexibility is improved, and meanwhile, due to the fact that the Euclidean distance is larger than that of a two-dimensional constellation, higher encryption performance is achieved, and meanwhile better bit error rate performance is achieved.
Owner:常州京信新一代信息技术研究院有限公司
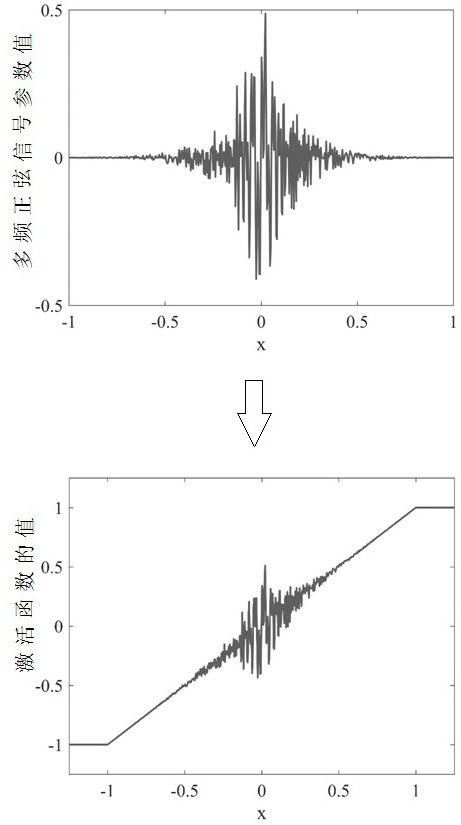
Optical access encryption method based on multi-frequency sine chaos neural network
InactiveCN112804047AIncreased complexityImprove securityMultiplex system selection arrangementsSecuring communication by chaotic signalsMultiple encryptionBrute force
The invention relates to an optical access encryption method based on a multi-frequency sine chaos neural network. Through the multi-frequency sine chaos neural network, a key library with a great space is generated, and multiple encryption processing is performed on original data, so compared with a traditional encryption mode, the complexity of a chaos model is further enhanced; while the information sending cost is reduced, the information transmission security is greatly enhanced, and an eavesdropper can be effectively prevented from brute force cracking through big operation. According to the invention, in a one-time one-password encryption mode, the security and flexibility of communication transmission can be greatly enhanced.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Power system chaos model monitoring method based on Lyapunov exponent
InactiveCN105488587AHas chaotic propertiesEnsure safe and economical operationForecastingElectric power systemPredictive methods
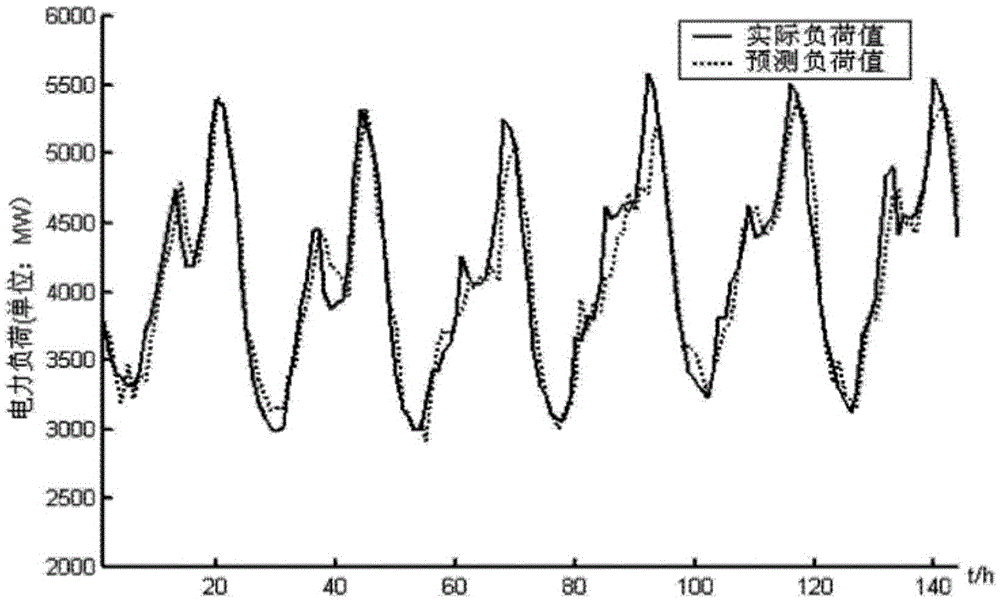
The invention provides a power system chaos model monitoring method based on a Lyapunov exponent. The method is a prediction method which carries out modeling on the basis of a maximum Lyapunov exponent [Lambda]1. The model favorably keeps the statistical property of a power hour load phase space attractor, is high in prediction accuracy, has a satisfactory prediction effect, and can effectively monitor the change rule of the power hour load so as to guarantee the safe and economic operation of the power system.
Owner:GUANGDONG UNIV OF TECH
Nerve electrical stimulation system and nerve electrical stimulation control method based on Rossler chaos model
ActiveCN106377840AEasy to optimizeRich electrical stimulation effectImplantable neurostimulatorsArtificial respirationElectricityData acquisition
Owner:YULIN NORMAL UNIVERSITY
Traffic flow prediction parallel method based on chaos and reinforcement learning
PendingCN114463994AEasy to adjustFast learningRoad vehicles traffic controlNeural learning methodsData setEngineering
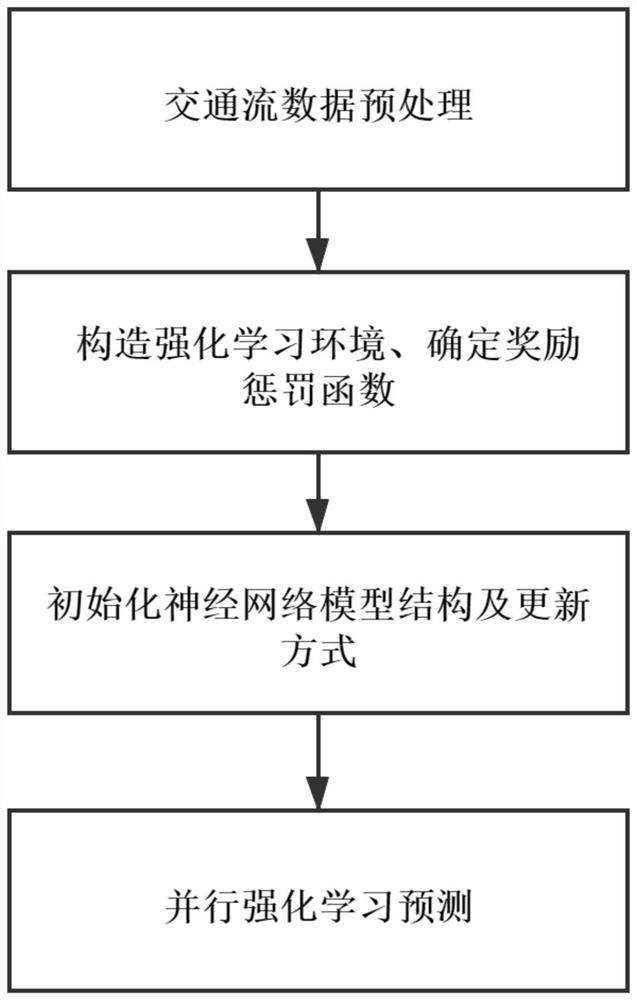
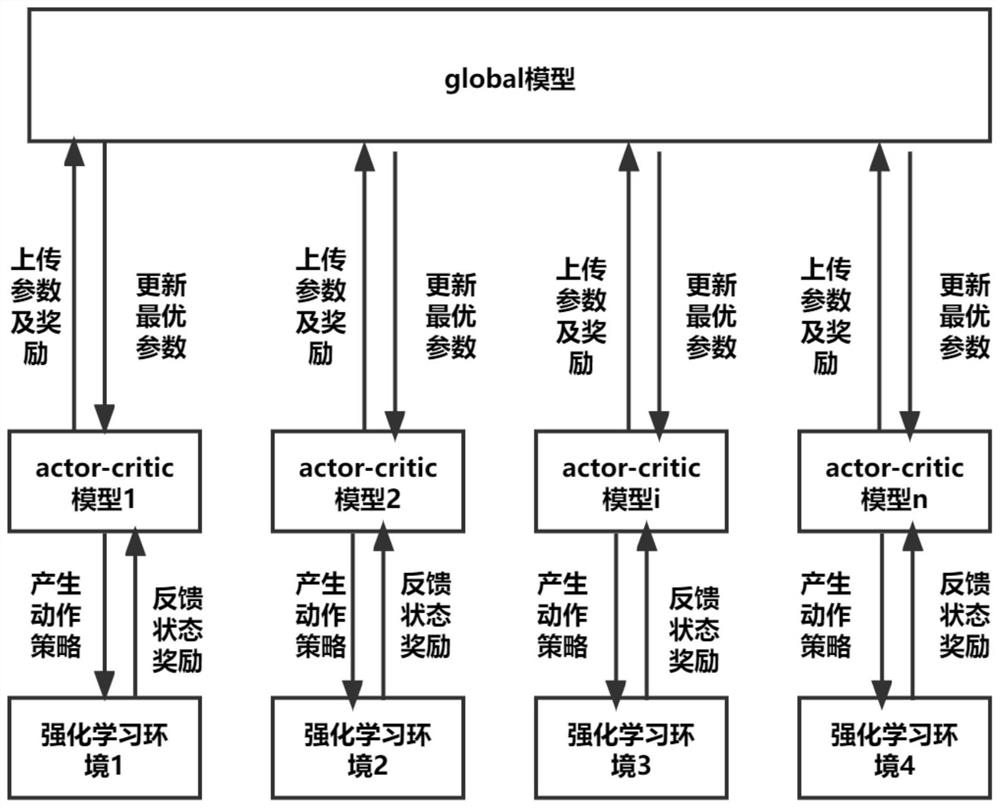
The invention provides a traffic flow prediction parallel method based on chaos and reinforcement learning. Comprising the following steps: 1, carrying out preprocessing and chaotic analysis on data, generating a comparison chaotic time sequence through a chaotic model, and carrying out reconstruction, standardization and data set division; 2, performing reinforcement learning training and comparison environment construction by using the preprocessed data; 3, constructing an act-critic neural network model to learn an intelligent agent strategy and judge a behavior value; and 4, generating a plurality of training models by the slave process under the parallel framework to interact with the environment, realizing parallel updating through dispersion comparison and reward with the central neural network model of the host process, and finally performing prediction verification by the host process. According to the method, the traffic flow is predicted by adopting reinforcement learning and a chaotic time sequence, and compared with a traditional statistical prediction method, the method has higher interpretability and online adjustment learning ability; parallel reinforcement learning can learn and adjust more quickly, and an optimal prediction result is generated.
Owner:HARBIN UNIV OF SCI & TECH
A new high-order three-dimensional chaos model and its circuit
ActiveCN108075732BOvercoming the drawbacks of encryption that is easy to be decipheredRich Dynamic BehaviorSecuring communication by chaotic signalsOscillations generatorsCapacitanceAlgorithm
The invention belongs to the technical field of chaotic systems, and discloses a new high-order three-dimensional chaos model and its circuit. The circuit of the high-order new three-dimensional chaos model includes three channel circuits; the circuit of the high-order new three-dimensional chaos model consists of 39 Components, including nine 3554BM operational amplifiers, six multipliers, three capacitors and 21 resistors. The high-order new three-dimensional chaotic circuit of the present invention has multiple equilibrium points and high-order nonlinear terms, and its dynamic behavior is more complex and rich. It can not only be applied to nonlinear circuit course experiments, but also overcome the information encryption of existing chaotic systems The disadvantage of being easily deciphered provides a basis for the application of chaotic systems.
Owner:XIDIAN UNIV
Pipeline weak leakage detecting device and detecting method based on fuzzy hyperbolic chaos model
ActiveCN103322416BEasy to detectEasy to identifyPipeline systemsPattern recognitionSystem requirements
The invention discloses a pipeline weak leakage detecting device and a detecting method based on a fuzzy hyperbolic chaos model and belongs to the technical field of pipeline detection. Two-stage detection is used, the first-stage detection is abnormal signal detection based on a neural network to mark abnormal signals, and the second-stage detection detects the abnormal signals marked by the first-state detection. By the two-stage detection, the first-stage primary detection is fast, the second-stage detection detects the abnormal signals marked by the first-state detection, and leakage detection capability is increased. The two-stage detection can be implemented on a FPGA (field programmable gate array) hardware platform, and overall system response speed is increased. By the double coupling time-varying delay fuzzy hyperbolic chaos model of the second-stage detection, initial value sensitivity and noise immunity of the chaos system is utilized to increase identification capability of weak leakage signals submerged in noise so as to highlight chaos phenomenon, system requirements for signal to noise ratio is lowered, and weak leakage detection is achieved.
Owner:NORTHEASTERN UNIV LIAONING
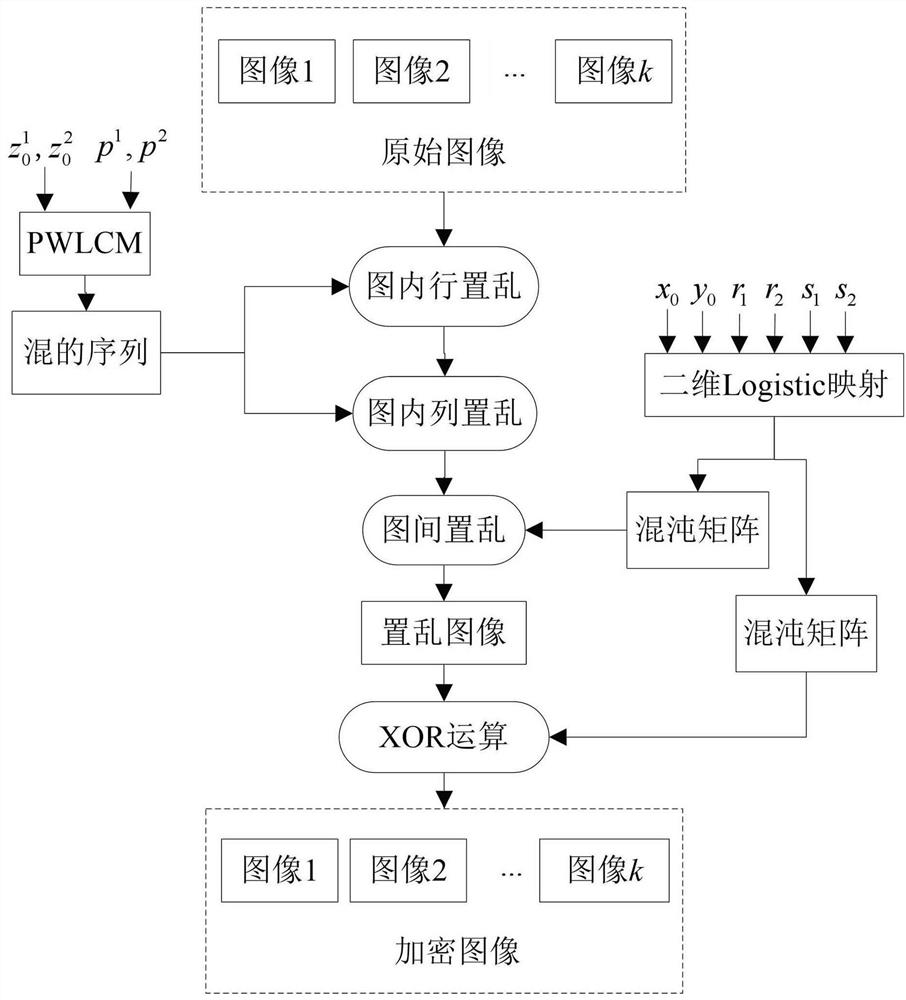
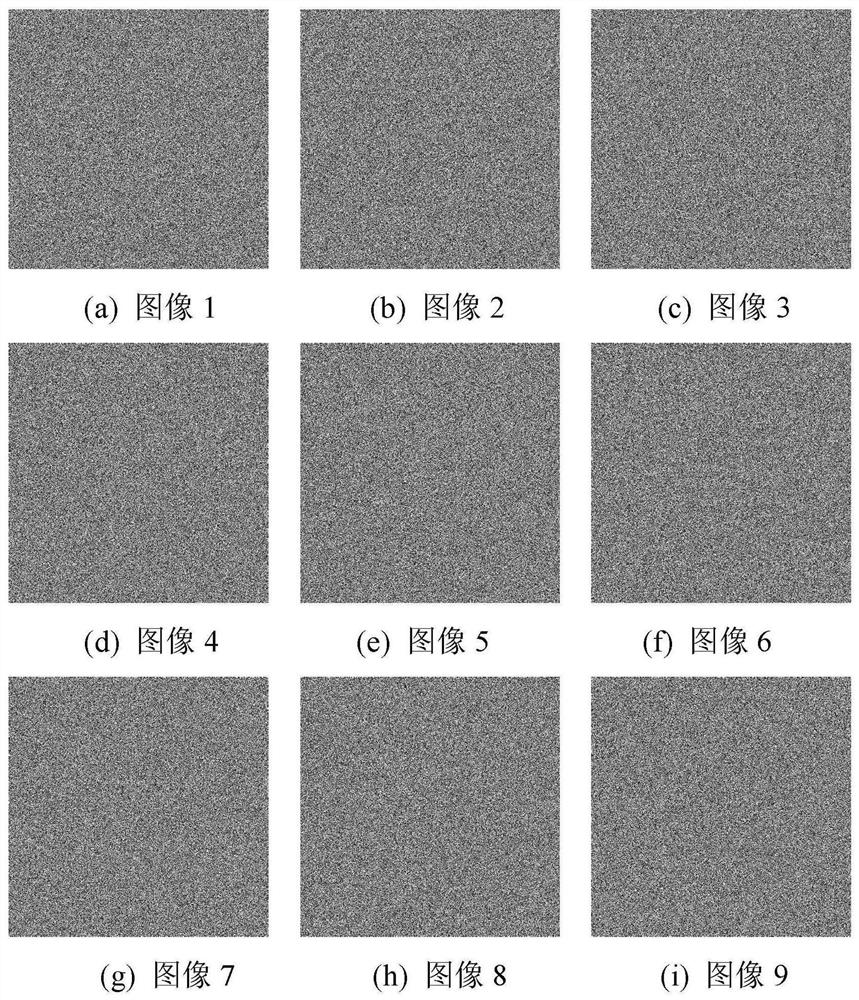
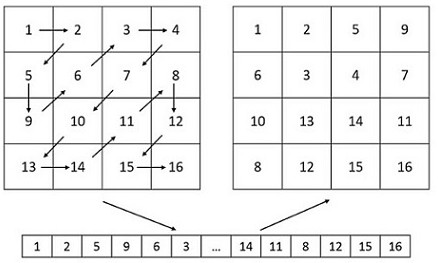
Multi-image encryption method based on 3D scrambling model and chaos
ActiveCN109150492BImprove securityProtection securityKey distribution for secure communicationSecuring communication by chaotic signalsKey spaceMulti-image
The invention discloses a multi-image encryption method based on a three-dimensional scrambling model and chaos, which belongs to the field of information encryption. At present, network batch image transmission and storage become more and more frequent, in order to protect the security of multiple interactive image content, the present invention proposes a multi-image encryption method based on three-dimensional scrambling model and chaos. Inspired by the Rubik's Cube game, based on the definition of row scrambling, column scrambling and inter-graph scrambling, a three-dimensional image scrambling model is established. First, using the 3D scrambling model to k Pixel scrambling of the original image; then, using chaos, XOR (exclusive OR, XOR) operation is performed on the scrambling result to generate k An encrypted image. Experiments show that the algorithm can encrypt multiple interactive images at the same time, and the algorithm has good encryption effect, large key space, strong key sensitivity, high security and high efficiency.
Owner:CHINA UNIV OF MINING & TECH
Image encryption method based on 3D scrambling model and chaos
ActiveCN109241755BImprove securityProtection securityDigital data protectionKey spaceTheoretical computer science
An image encryption method based on a three-dimensional scrambling model and chaos belongs to the field of information encryption. At present, with the rapid development of multimedia communication technology, how to protect the security of image content has aroused the common concern of industry and academia. The invention proposes an image encryption method based on three-dimensional scrambling model and chaos. Inspired by the Rubik's Cube game, on the basis of defining row scrambling, column scrambling and plane scrambling, a three-dimensional image scrambling model is established. First, the pixels of the original image are scrambled using the three-dimensional scrambling model; then, using chaos, an exclusive OR (XOR) operation is performed on the scrambling result to generate an encrypted image. Experiments show that the algorithm has good encryption effect, large key space, strong key sensitivity, high security and high efficiency.
Owner:CHINA UNIV OF MINING & TECH
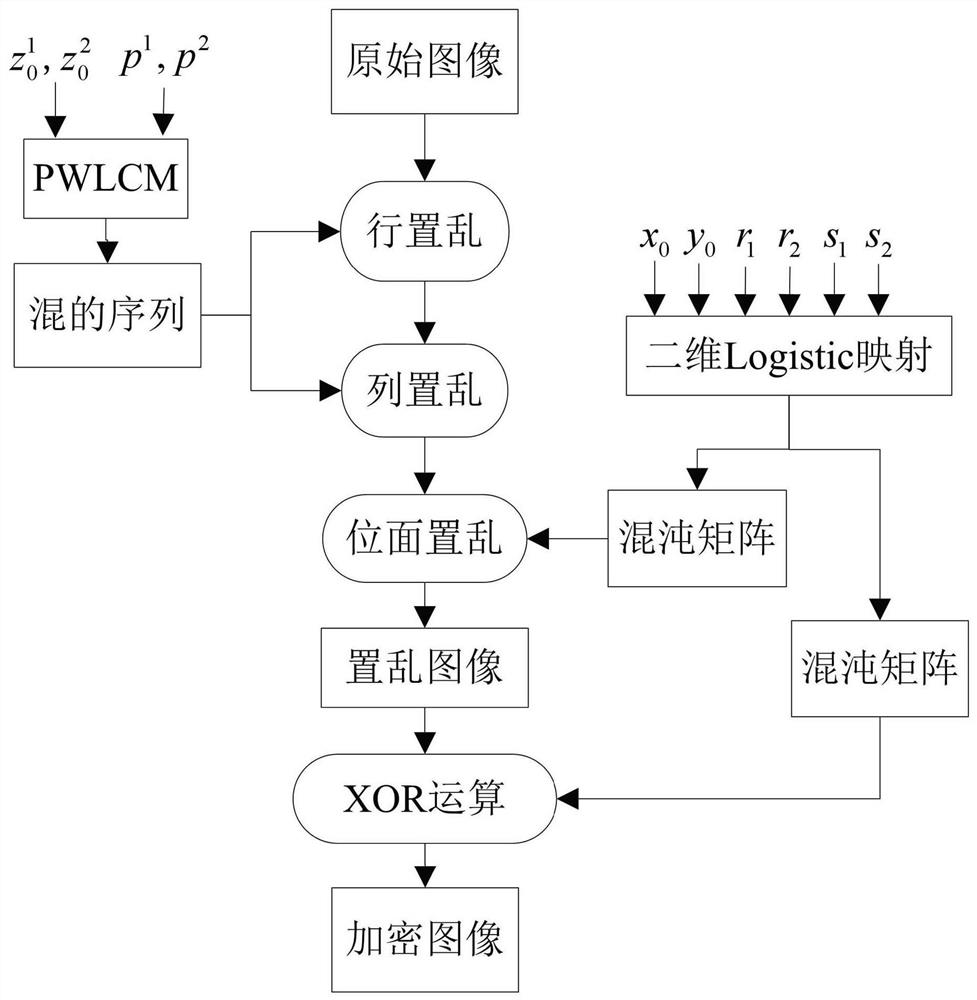
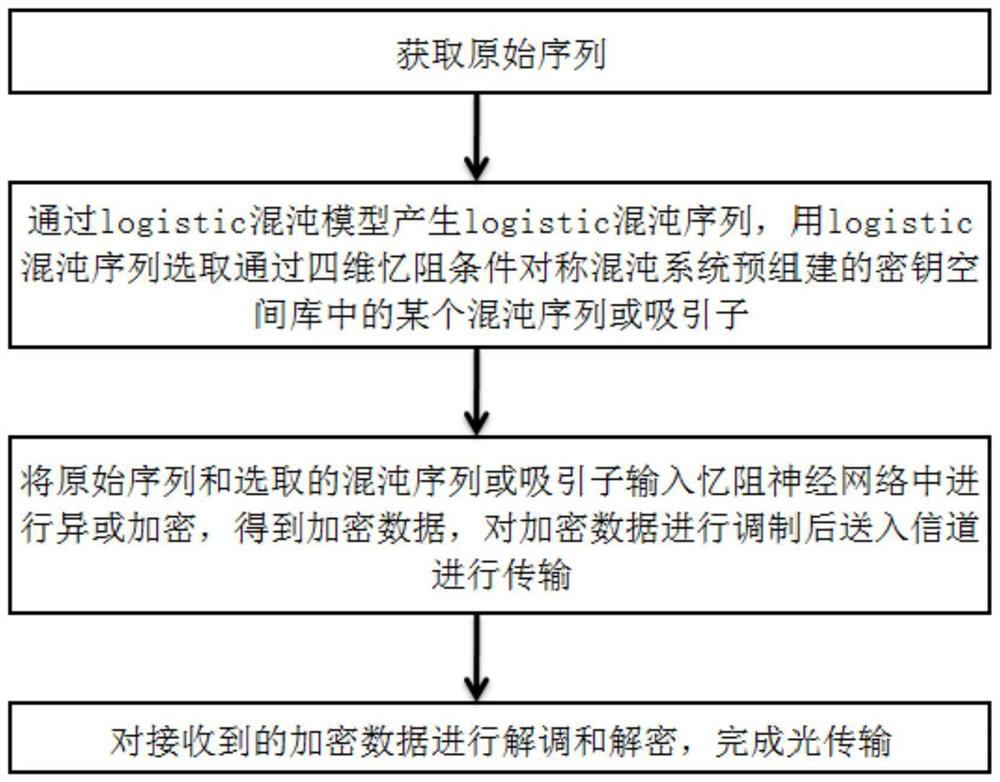
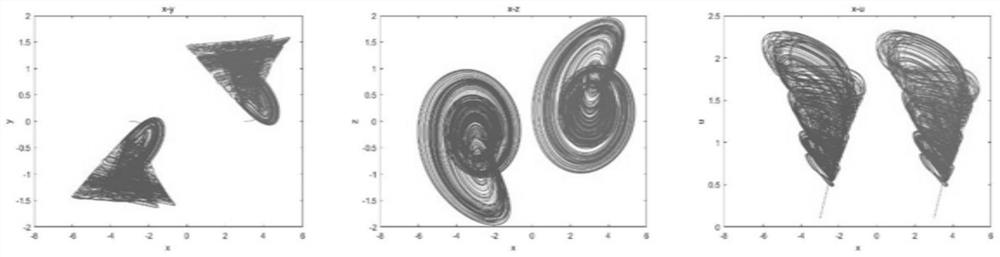
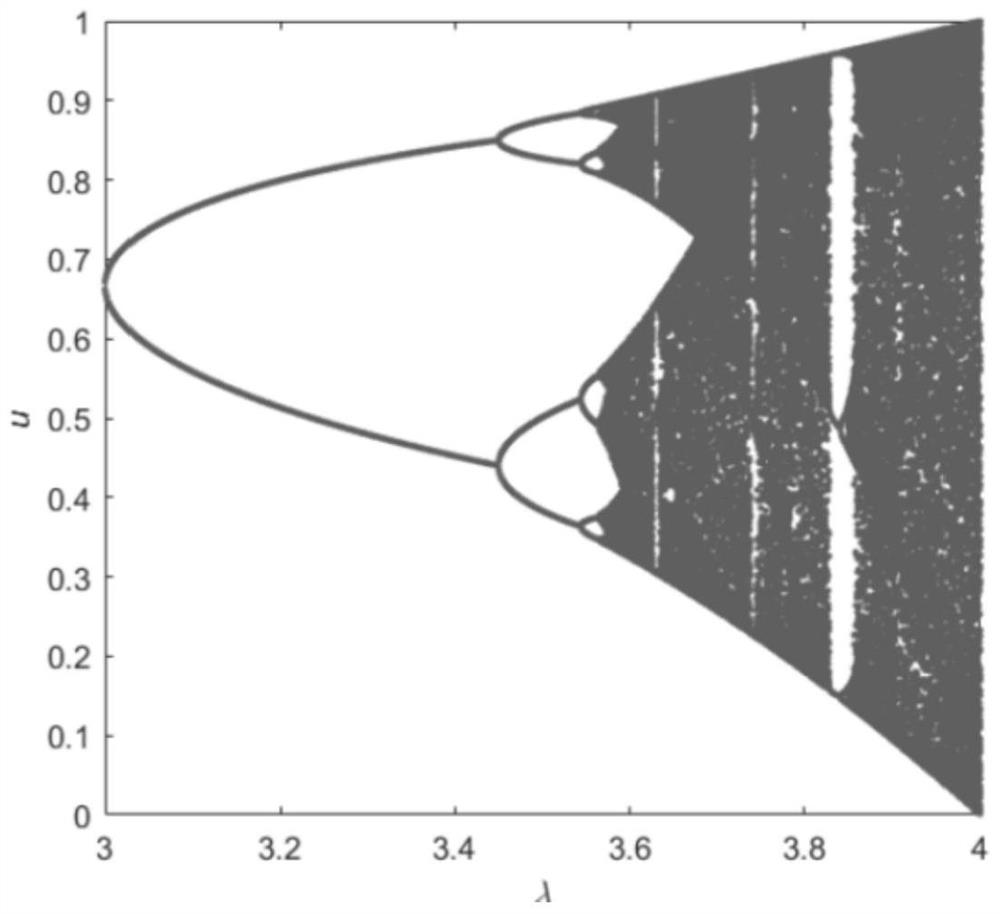
Encrypted light transmission method and system based on four-dimensional memristor condition symmetric chaotic system and memristor neural network
PendingCN114666033AXOR function structure is simpleImprove anti-interference abilityElectromagnetic transmission optical aspectsSecuring communication by chaotic signalsKey spaceAlgorithm
The invention discloses an encrypted optical transmission method and system based on a four-dimensional memristor condition symmetric chaotic system and a memristor neural network, and belongs to the technical field of optical transmission. The method comprises the following steps: generating a logistic chaos sequence through a logistic chaos model, and selecting a certain chaos sequence or attractor in a key space library pre-established through a four-dimensional memristor condition symmetric chaos system by using the logistic chaos sequence; inputting the original sequence and the selected chaotic sequence or attractor into a memristor neural network for XOR encryption to obtain encrypted data, modulating the encrypted data, and transmitting the modulated encrypted data into a channel for transmission; the received encrypted data are demodulated and decrypted, and optical transmission is completed; multi-layer encryption of data is realized, the security performance of optical transmission is improved, and the defect that the transmission security is less considered in the prior art is overcome; the overall complexity is further reduced, and the method is very suitable for an OFDM-PON scene.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Document authentication method based on interweaving watermark and biological characteristic
InactiveCN101141466BVerify integrityIdentifyMultiple keys/algorithms usageThird partyComputer science
The present invention relates to a document integrity authentication method based on an interleaving watermark and a biological feature, a chaos model is adopted to generate an authentication code, and the biological information of a deliverer is generated to a biological feature code streaming after being extracted through the feature. The authentication code and the biological feature code streaming are returned to the deliverer after a plurality of interleaving treatments under the control of a third party, and then the deliverer inserts the interleaving information in the document. When being authenticated, on the one hand, the extracted authentication code and a generated reference sequence are compared, the integrity of the document content is determined, and a tampered area is positioned; on the other hand, the extracted biological feature is identified, the identity of the deliverer is determined, and a disavowal behavior is prevented. The present invention can authenticate the integrality of the document, and can detect and position a tampered location. The different requirements of users to the precision are supported, and the positioning precision is adjustable and controllable. An authentication result is given by error, and the tampered location can be directly and visually reflected. The identity of the deliver can be determined, and the disavowal behavior is prevented.
Owner:BEIJING JIAOTONG UNIV
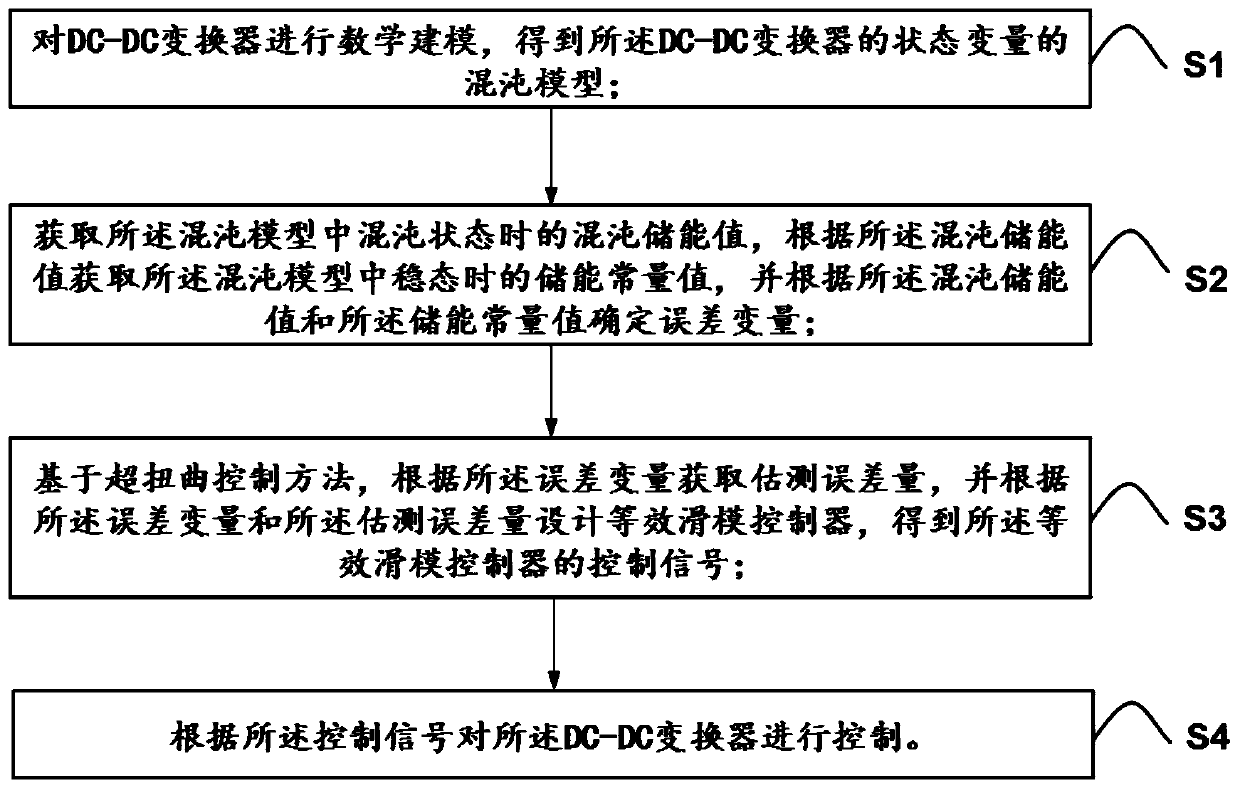
Chaos control method, system and medium of dc-dc converter based on supertwist control
ActiveCN109742941BImprove performance indicatorsGuaranteed convergence speedDc-dc conversionElectric variable regulationStored energyControl signal
The present invention relates to a DC-DC converter chaos control method, system and medium based on super-twisting control. The method includes mathematical modeling of the DC-DC converter to obtain the chaos model of the state variable of the DC-DC converter Obtain the chaotic energy storage value in the chaotic state in the chaotic model, obtain the energy storage constant value in the steady state in the chaotic model according to the chaotic energy storage value, and according to the chaotic energy storage value and the storage The error variable can be determined by a constant value; based on the super twist control method, an estimated error amount is obtained according to the error variable, and an equivalent sliding mode controller is designed according to the error variable and the estimated error amount to obtain the equivalent A control signal of a sliding mode controller; the DC-DC converter is controlled according to the control signal. The present invention can effectively control the DC-DC converter in the chaotic state to orbit in the 1-period state, effectively eliminate the chaotic phenomenon, have faster dynamic response, stronger robustness, and lower voltage ripple.
Owner:WUHAN INSTITUTE OF TECHNOLOGY
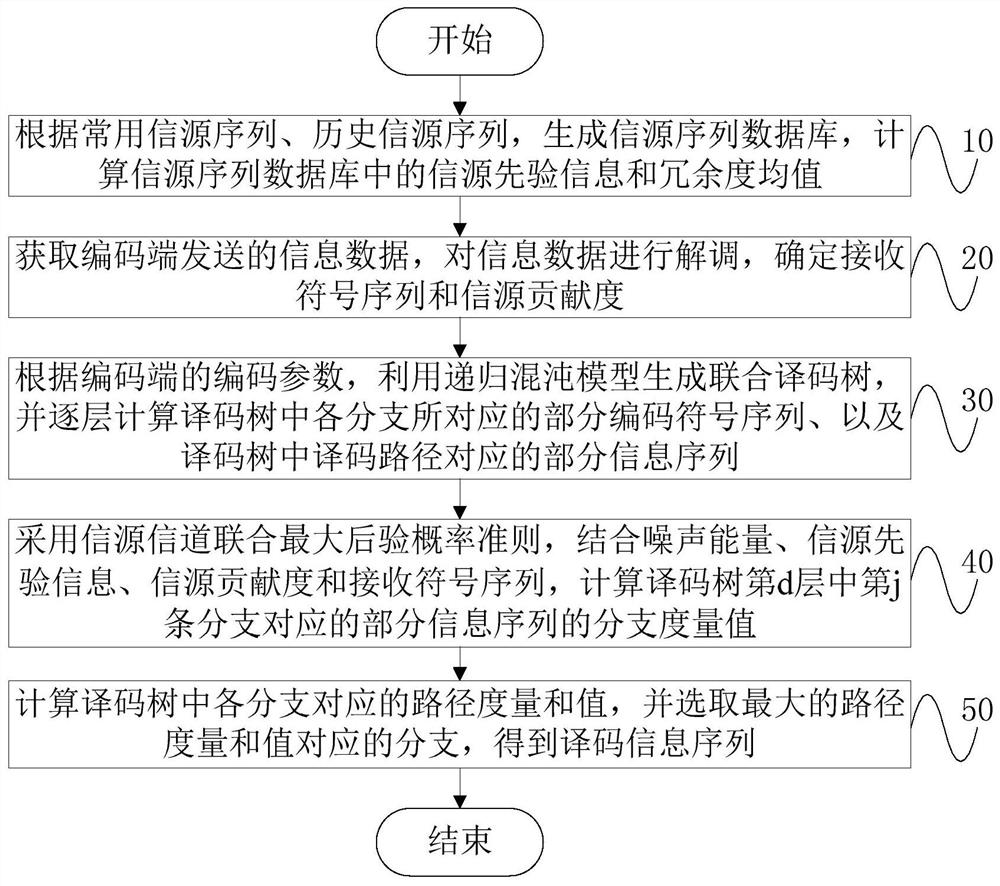
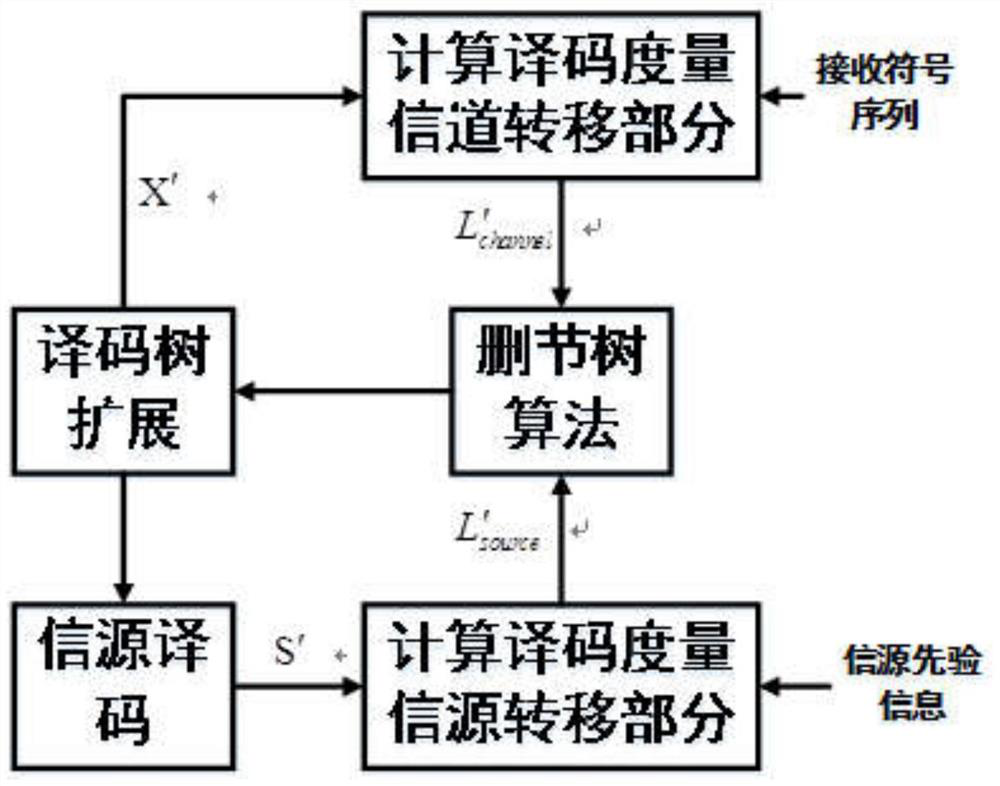
A combined source-channel decoding method for underwater acoustic communication
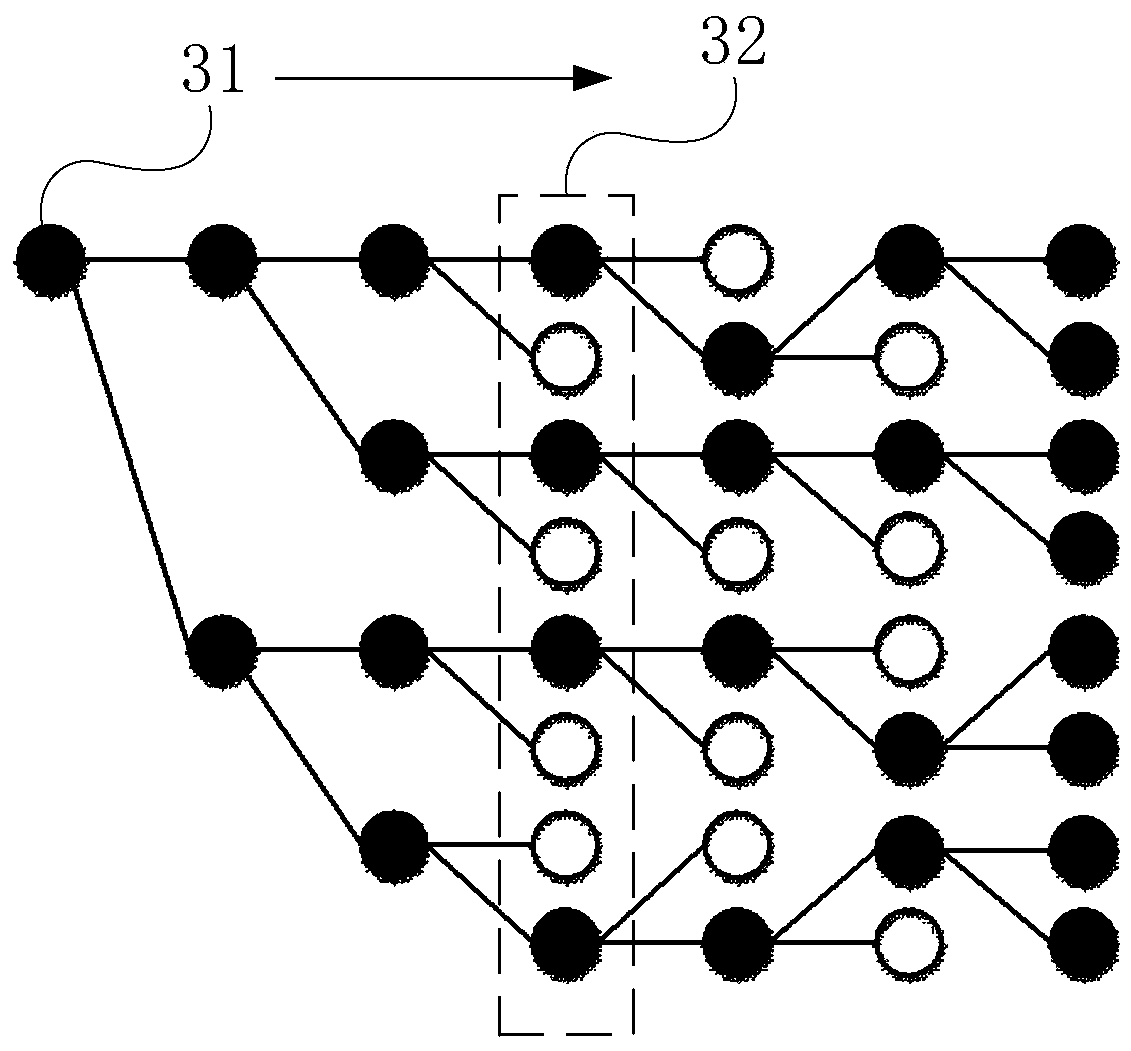
ActiveCN111262590BImprove decoding performanceHigh complexityCode conversionDecoding methodsSignal source
The invention discloses an underwater acoustic communication information source channel joint decoding method, which comprises the following steps: acquiring information data sent by an encoding end,demodulating the information data, and determining a receiving symbol sequence and an information source contribution degree, the information source contribution degree being a ratio of redundancy ofa sending information source sequence to a redundancy mean value; generating a joint decoding tree by utilizing a recursive chaos model according to the encoding parameters of the encoding end, and calculating a part of encoding symbol sequences corresponding to each branch in the decoding tree and a part of information sequences corresponding to decoding paths in the decoding tree layer by layer;calculating a branch metric value of eac information sequence of the decoding tree by adopting an information source channel joint maximum posteriori probability criterion and combining noise energy,information source prior information, the information source contribution degree and the receiving symbol sequence; and calculating a path metric sum value corresponding to each branch in the decoding tree, and selecting the branch corresponding to the maximum path metric sum value to obtain a decoding information sequence. According to the method, the correlation between signal source symbols isfully utilized, channel decoding is corrected, and the decoding performance of underwater acoustic communication is improved.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI
A Chaos Encryption Method and System Based on 3D Probabilistic Forming
ActiveCN111245596BSuitable for transmissionReduce transmit powerFibre transmissionSecuring communication by chaotic signalsKey spaceCarrier signal
The invention discloses a chaotic encryption method based on three-dimensional probability shaping. The Lenz chaos model masks the constellation diagram formed by the three-dimensional probability; among them, according to the different distances from each constellation point to the origin, the Chua's chaotic model and the Lorentz model are used for masking, so that the three-dimensional probability forming constellation diagram becomes two spherical. The invention can greatly reduce the transmission power of the whole system after the spherical three-dimensional probability shaping, and the new carrier wave after the probability shaping will have a Gaussian energy distribution, which is more suitable for the transmission of optical signals in the optical fiber channel; using Chua's circuit model and Compared with the traditional masking method, the Lorentz model for chaotic mapping has a good encryption effect, and provides a larger key space and greater flexibility.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Image Encryption Method Based on Stereo Composite Scrambling Model and Chaos
ActiveCN111031193BImprove encryptionImprove securitySecuring communication by chaotic signalsPictoral communicationAlgorithmTheoretical computer science
The invention relates to an image encryption method based on a three-dimensional composite scrambling model and chaos, which belongs to the field of information encryption. The current network transmission security problem is becoming more and more serious. In order to protect the network interactive image content, the present invention proposes an image encryption method based on a three-dimensional composite scrambling model and chaos. Combining technologies such as bit-plane decomposition, piecewise linear chaotic mapping and two-dimensional Zigzag transformation, a three-dimensional compound scrambling model is established on the basis of defining block internal scrambling and block scrambling. The model is used to scramble the pixels of the original image, and then the Chenchao system and XOR operation are used to diffuse the scrambled image to obtain an encrypted image. Experiments show that the algorithm has good encryption effect, high security and high efficiency.
Owner:CHINA UNIV OF MINING & TECH
Image encryption method based on quantum Baker mapping and sine chaos model
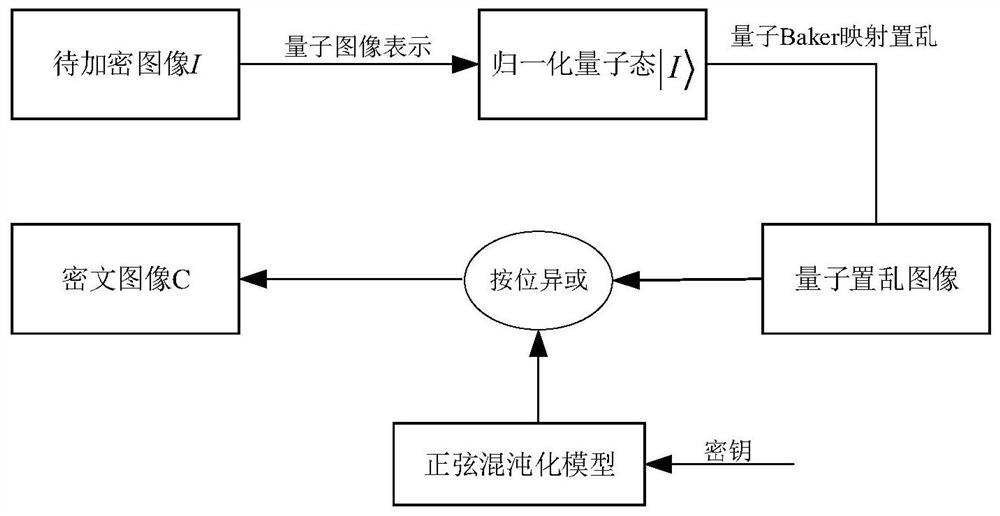
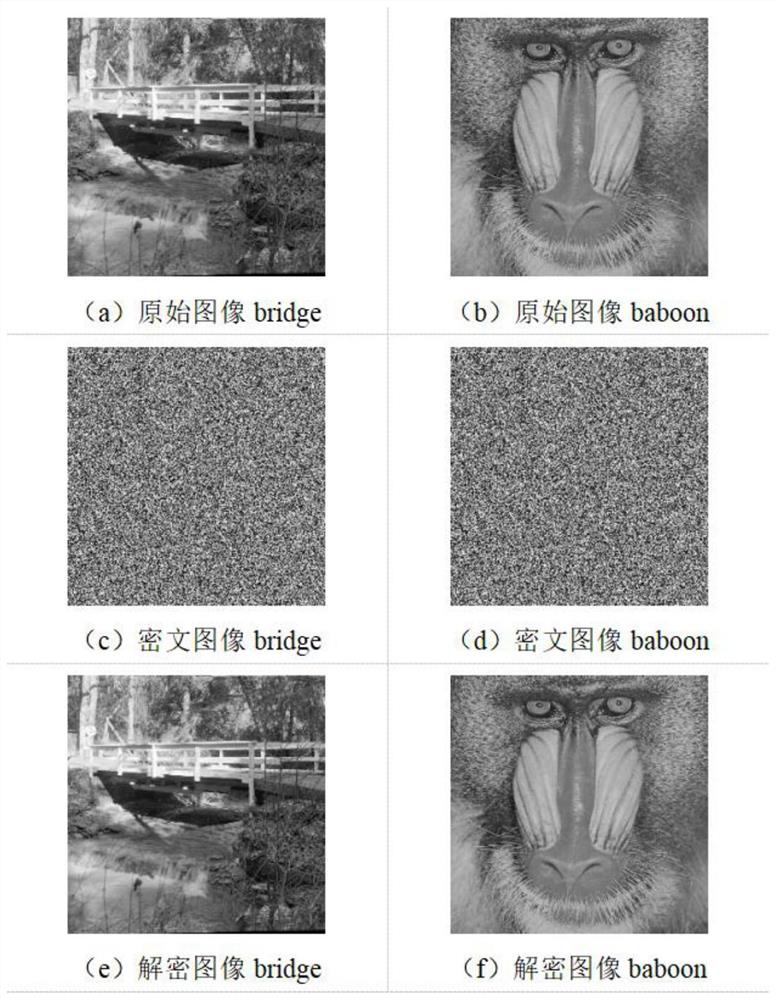
ActiveCN114157774AExpand the key spaceGuaranteed storage securityQuantum computersKey distribution for secure communicationKey spaceInformation processing
The invention relates to an image encryption method based on quantum Baker mapping and a sine chaos model, and belongs to the technical field of quantum calculation and image information processing. The method comprises the following steps: S1, performing quantum image representation on a to-be-encrypted image; s2, carrying out the scrambling of the pixel values of the quantum representation image through the adoption of quantum Baker transform (QBT), and carrying out the scrambling of the pixel values of the quantum representation image; s3, generating a chaos sequence by adopting a sine chaos model; and S4, performing bitwise exclusive or on the chaotic sequence and the scrambled image to obtain a final encrypted image. Compared with the prior art, the method has the advantages that pixel position scrambling of quantum Baker mapping and XOR operation of a sine chaos model are achieved, the key space of an encryption system can be remarkably improved, safe storage and transmission of images are guaranteed, and compared with traditional image encryption, the algorithm complexity is reduced, and the encryption performance is improved.
Owner:SOUTHWEST UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com