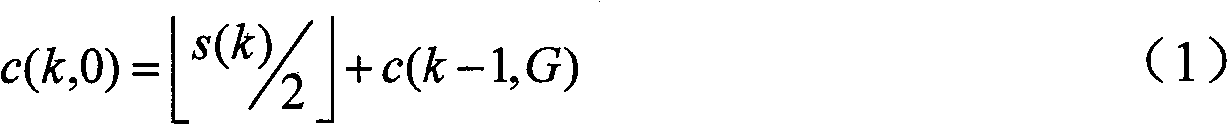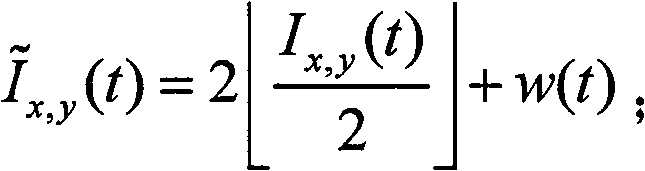Document authentication method based on interweaving watermark and biological characteristic
A biometric, authentication method technology, applied in the usage of multiple keys/algorithms, electrical components, digital transmission systems, etc., to achieve the effect of preventing repudiation, accurate and complete
Inactive Publication Date: 2010-08-11
BEIJING JIAOTONG UNIV
View PDF0 Cites 0 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
In general, the positioning accuracy of such methods is limited by the size of the packet or block and the length of the authentication code
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
Embodiment Construction
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More PUM
 Login to View More
Login to View More Abstract
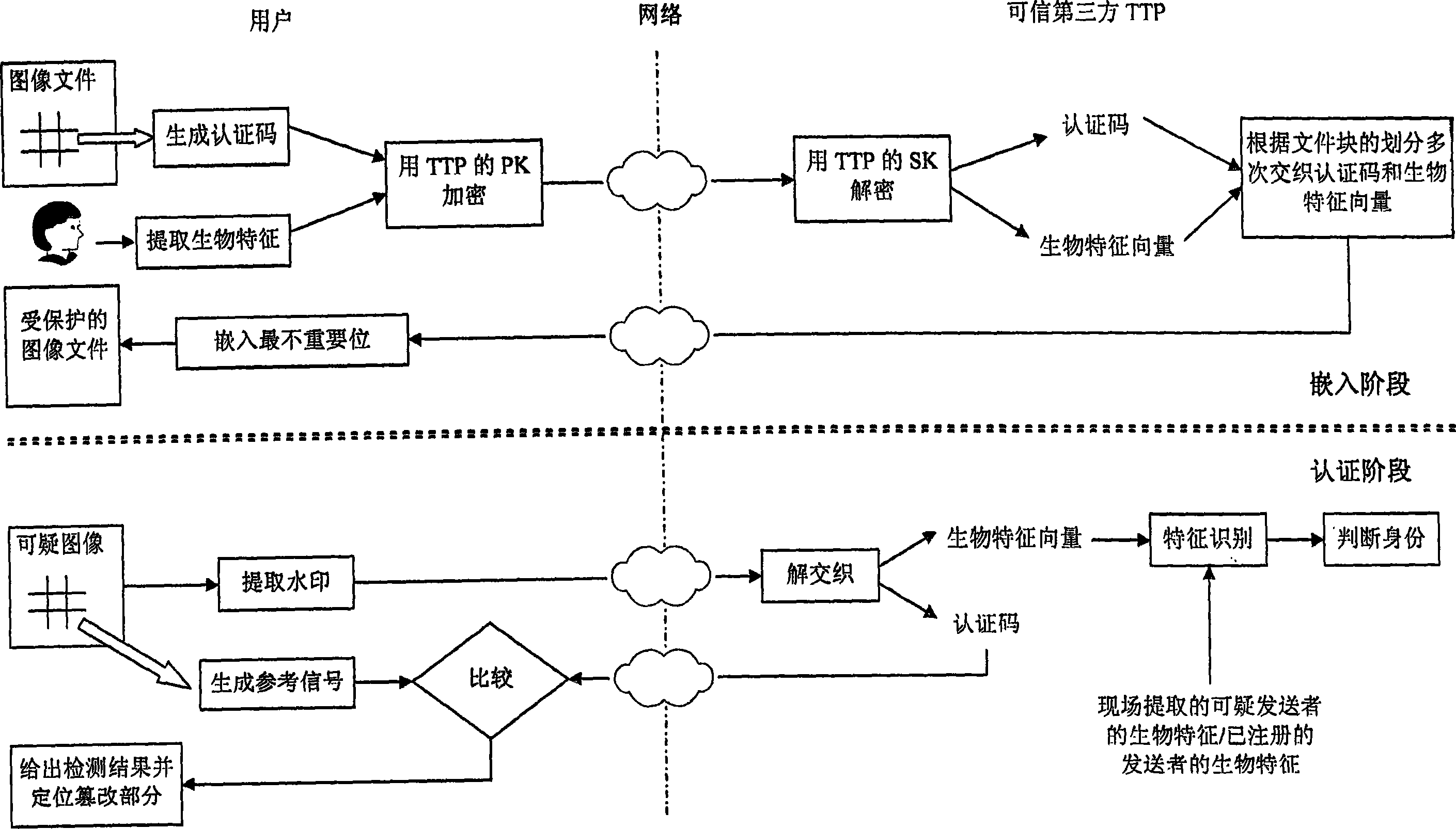
The present invention relates to a document integrity authentication method based on an interleaving watermark and a biological feature, a chaos model is adopted to generate an authentication code, and the biological information of a deliverer is generated to a biological feature code streaming after being extracted through the feature. The authentication code and the biological feature code streaming are returned to the deliverer after a plurality of interleaving treatments under the control of a third party, and then the deliverer inserts the interleaving information in the document. When being authenticated, on the one hand, the extracted authentication code and a generated reference sequence are compared, the integrity of the document content is determined, and a tampered area is positioned; on the other hand, the extracted biological feature is identified, the identity of the deliverer is determined, and a disavowal behavior is prevented. The present invention can authenticate the integrality of the document, and can detect and position a tampered location. The different requirements of users to the precision are supported, and the positioning precision is adjustable and controllable. An authentication result is given by error, and the tampered location can be directly and visually reflected. The identity of the deliver can be determined, and the disavowal behavior is prevented.
Description
technical field The invention relates to a digital file integrity detection and authentication method, in particular to a file authentication method based on interlaced watermarks and biometric features, and belongs to the field of integrity authentication. Background technique With the development of computer and network technology, the trend of mutual promotion and interdependence between global economic integration and information networking is becoming more and more obvious. The expansion of the degree of network interconnection, the openness of the network and the sharing of resources have made information security, especially content security, increasingly prominent. The security of information content refers to the protection of information confidentiality, integrity, authenticity, availability, etc., to prevent attackers from taking advantage of system security loopholes to eavesdrop, impersonate, fraud, embezzle and other behaviors that harm the interests of legitim...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More Patent Type & Authority Patents(China)
IPC IPC(8): H04L29/06H04L9/00H04L9/14
Inventor 倪蓉蓉王艳霞阮秋琦
Owner BEIJING JIAOTONG UNIV
Who we serve
- R&D Engineer
- R&D Manager
- IP Professional
Why Patsnap Eureka
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com