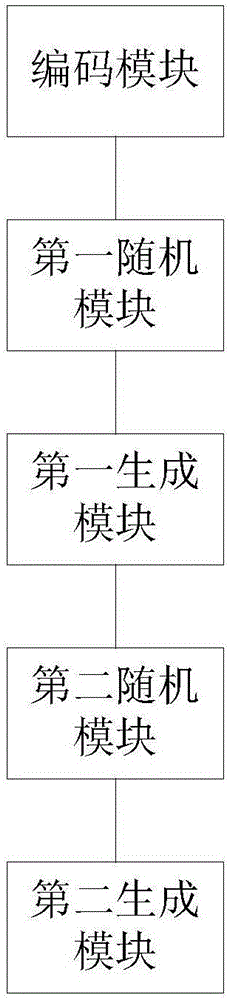
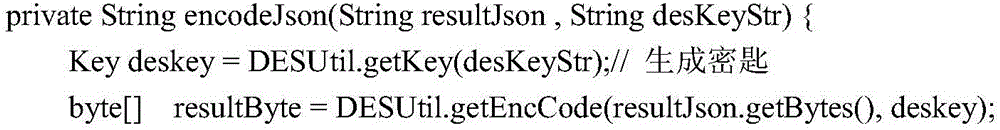Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
156 results about "Base64" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, Base64 is a group of binary-to-text encoding schemes that represent binary data in an ASCII string format by translating it into a radix-64 representation. The term Base64 originates from a specific MIME content transfer encoding. Each Base64 digit represents exactly 6 bits of data. Three 8-bit bytes (i.e., a total of 24 bits) can therefore be represented by four 6-bit Base64 digits.
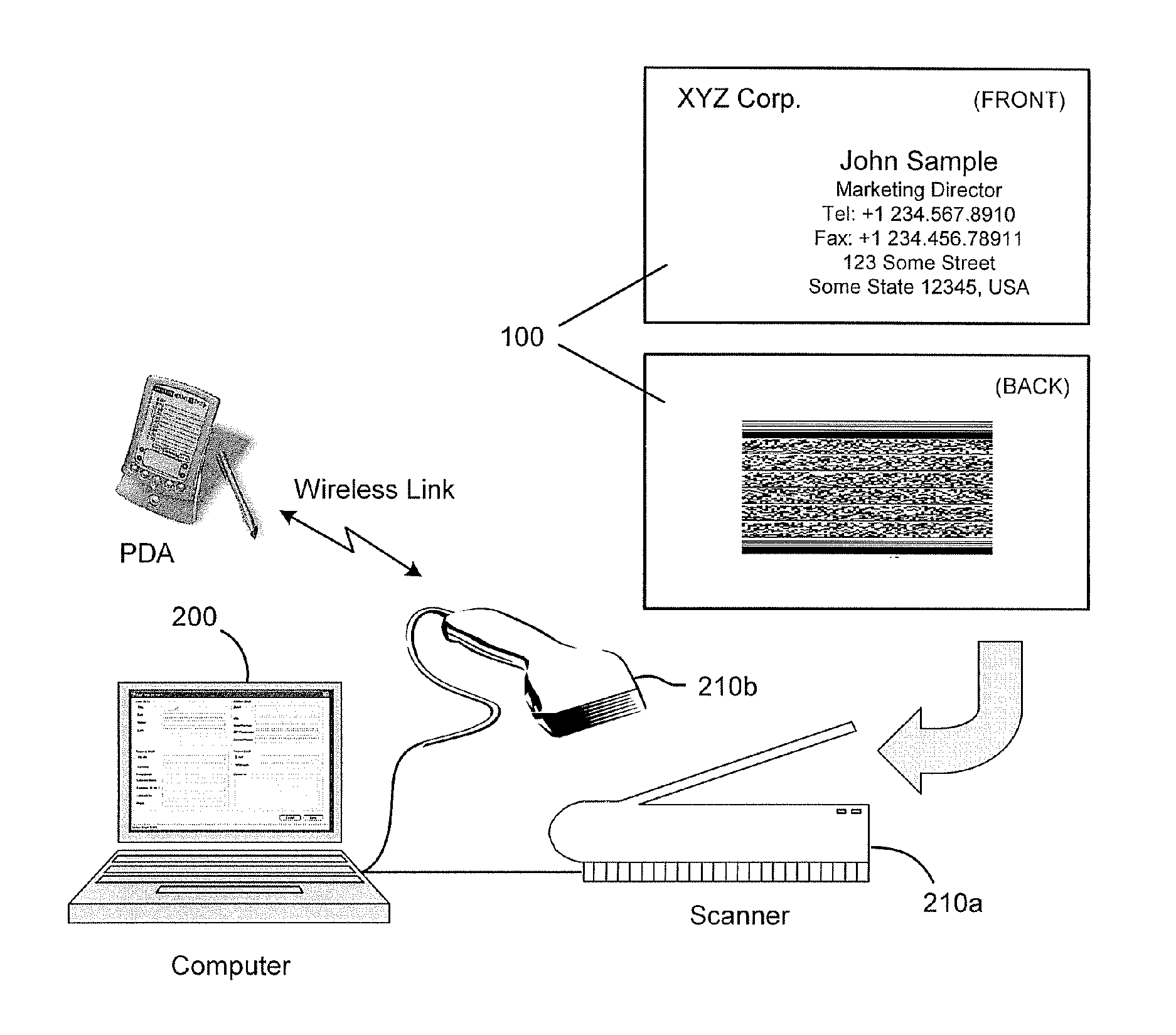
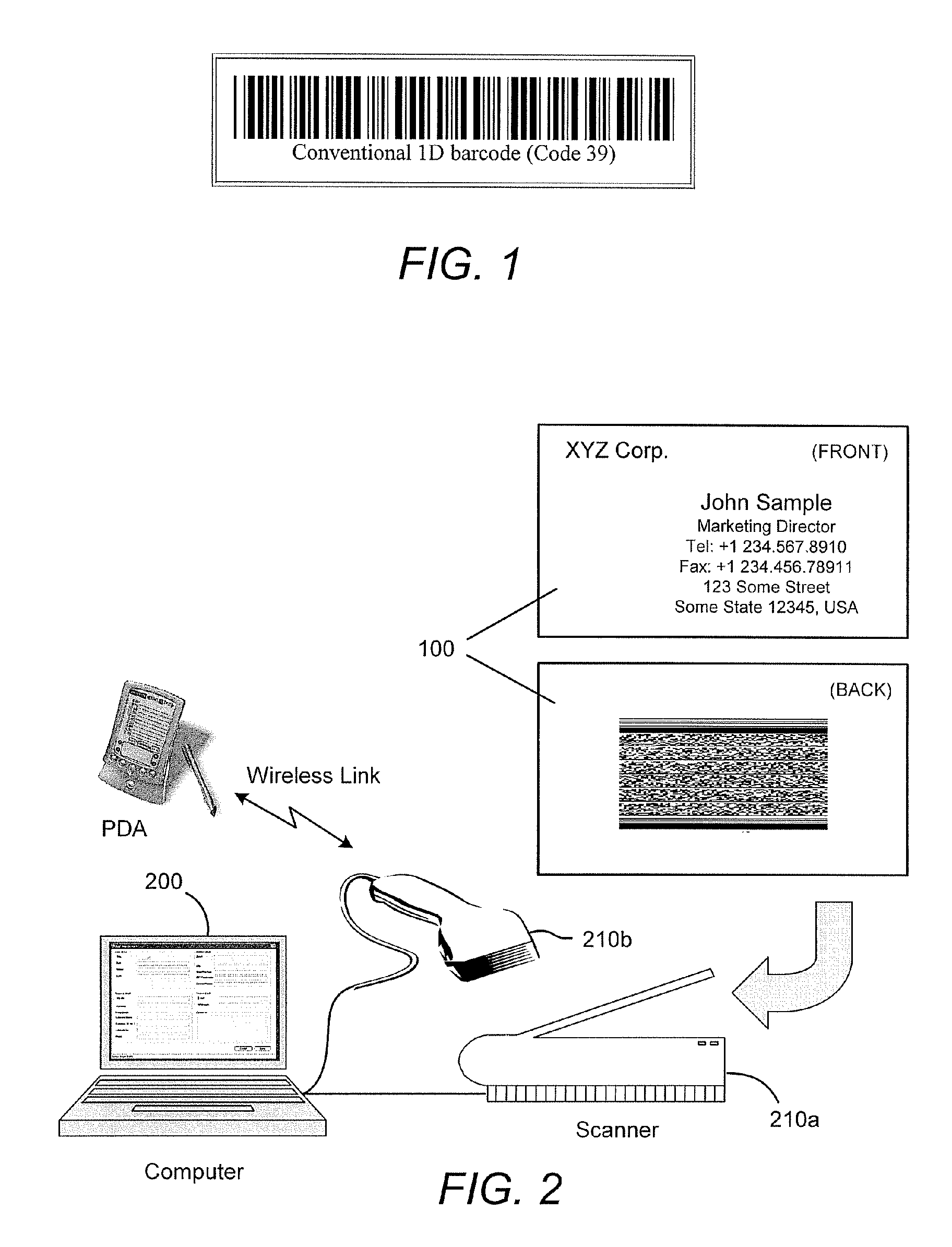
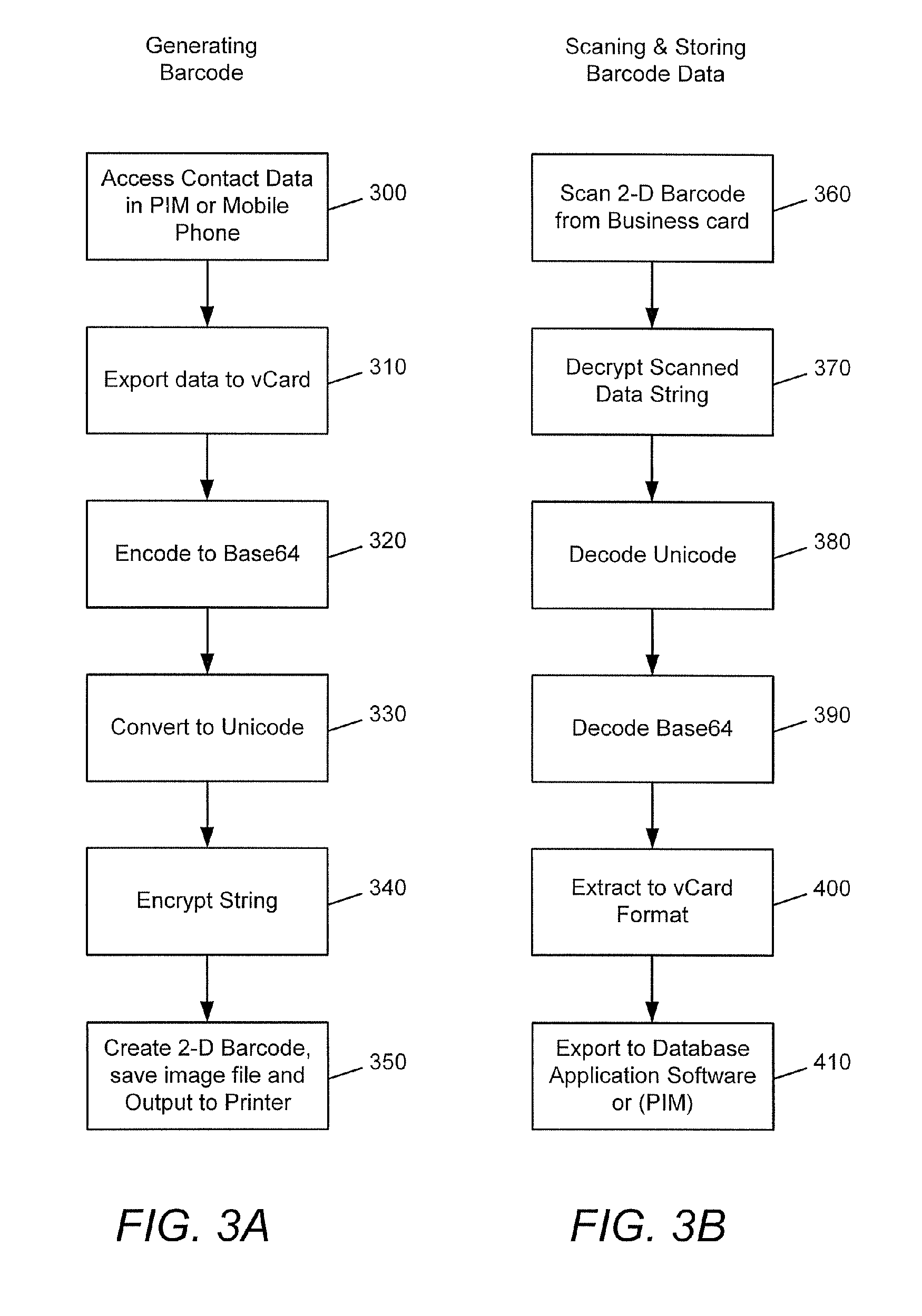
Method and system for using barcoded contact information for compatible use with various software
InactiveUS20070102521A1Easily imprintedCharacter and pattern recognitionOffice automationCustomer relationship managementNon western
The present invention discloses a method and system for generating, analyzing and decoding a two-dimensional barcodes representing, for example, the contents of a business card or contact information in stored in a PDA or mobile phone. In an embodiment of the invention, a process is provided for generating a two-dimensional barcode from the contact information stored in a software database such as a Personal Information Manager (PIM), Customer Relationship Manager (CRM), PDA or mobile phone contact list. The contact data is exported from the database or handheld device into a standardized format such as vCard that is broadly used for exchanging contact information. The vCard data strings are encoded into Base64 and converted into the Unicode universal character set that provide wide ranging compatibility for various language scripts including many non-western character scripts. The data strings are encrypted and from which a unique two-dimensional barcode is generated that can be imprinted on business cards or on other printed material. In another embodiment of the invention, business cards and other printed material having a two-dimensional barcode generated by the invention can be quickly scanned such that the barcoded contact information is analyzed and converted for compatible use with numerous types of software such as personal information managers (PIM), Customer Relationship Managers (CRM), or electronic device contact lists without the need for supplementary user intervention.
Owner:PETERSSON URBAN
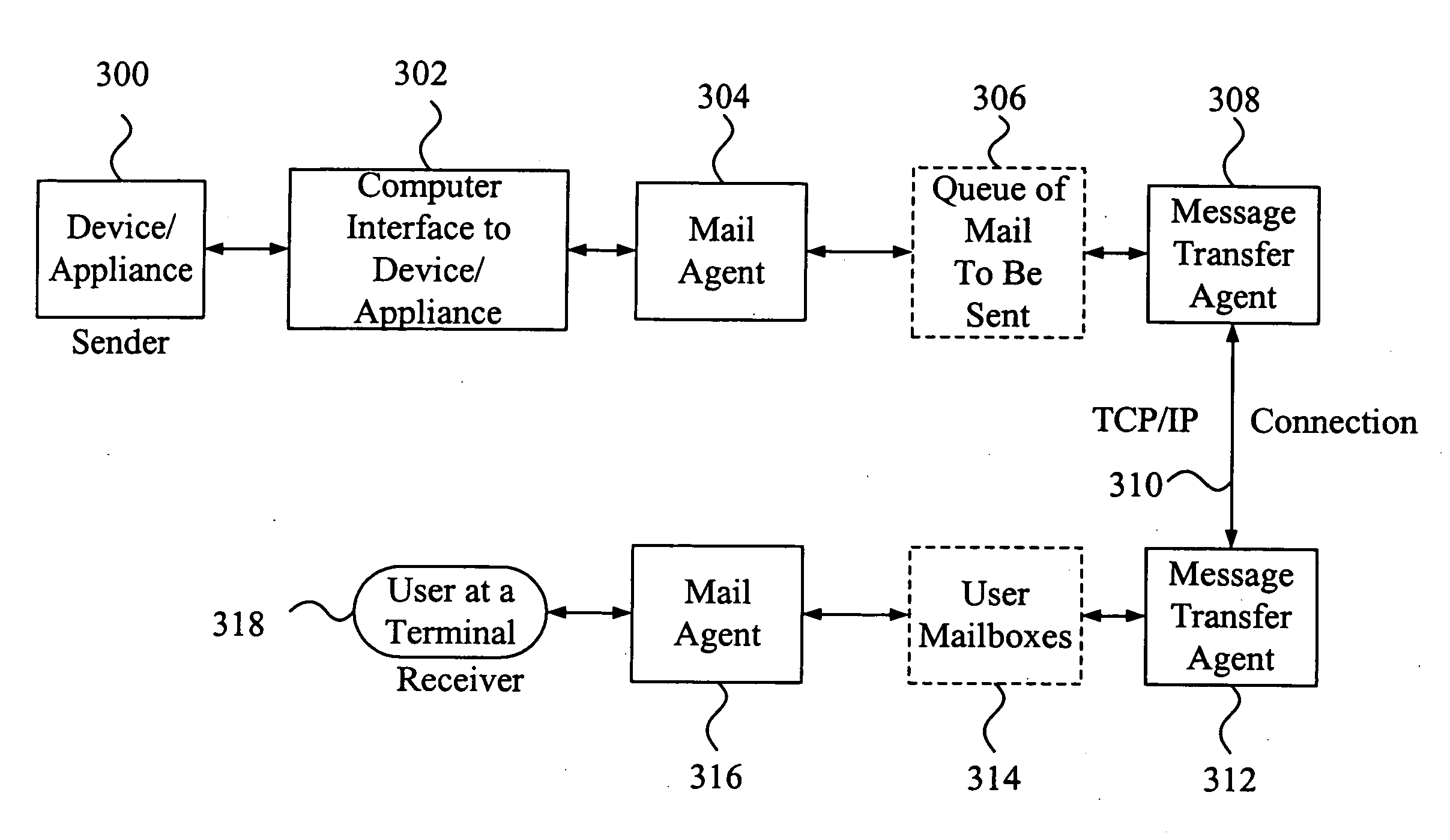
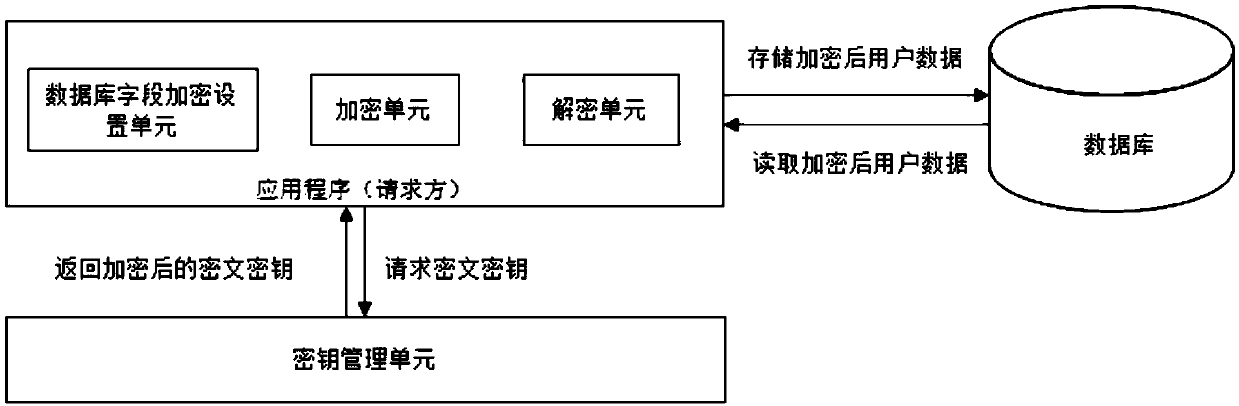
Method and system of remote monitoring and support of devices, using POP3 and decryption using virtual function
ActiveUS6925571B1Quickly and easily changeEasy to doMemory loss protectionUser identity/authority verificationProcess moduleComputer module
A method involves retrieving from an email message, information concerning at least one remotely monitored device. The method involves obtaining a line of the email message containing the information, decoding the line obtained from the email message if it has been encoded, and decrypting the decoded line. The decrypting involves using an abstract decrypter class configured to perform a virtual function and using any one of a plurality of derived decrypter classes each of which is configured as a derived class of the abstract decrypter class. The abstract decrypter class and the any one of the derived decrypter classes are collectively configured to decrypt the decoded email message, using the any one of the derived decrypter classes with the abstract decrypter class without having to modify the abstract decrypter class. An exemplary system for remotely monitoring devices uses the SMTP email protocol to send status, configuration, or other information concerning at least one of the devices in a MIME attachment of an email message. A POP3 processing module in the receiver of the email has a class structure. An interface class accesses an email server and obtain the email message including the MIME attachment. An extractor class extracts the MIME attachment from the email message, and a decoder class performs Base64 decoding of the attachment. An abstract decrypter class and each of plural derived decrypter classes configured as a derived class thereof, permit flexibility in adopting new decryption processes without having to modify the abstract decrypter class.
Owner:RICOH KK
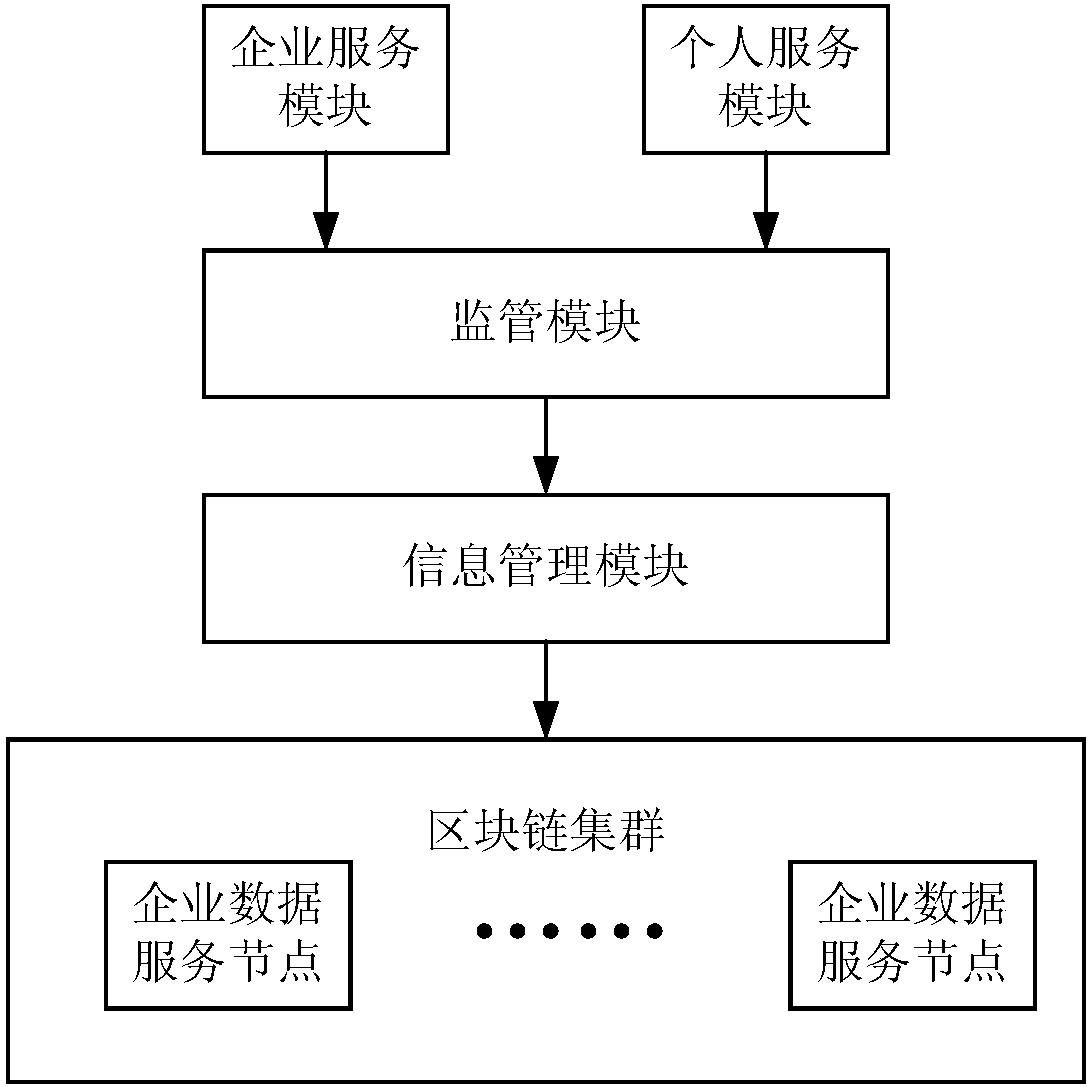
Personal credit information sharing system and method based on block chain
InactiveCN108234478ATrusted Shared ServiceExpress Sharing ServiceUser identity/authority verificationEnterprise servicesE-commerce
The invention discloses a personal credit information sharing system and method based on a block chain. The personal credit information sharing system based on the block chain comprises a block chaincluster, an enterprise service module, a personal service module, an information management module and a supervision module. The system is characterized in that the information management module is used for carrying out user information management comprising real-name authentication according to identity card information of a personal user and generation of a unique identity ID of the personal user through a hash algorithm and BASE64 code, creating assets on the block chain cluster, managing the assets on the block chain cluster and carrying out real-name authentication on the personal user; the enterprise service module is used for carrying out authentication on an enterprise user and distributing a login credential to an authenticated enterprise while providing relevant operation of thepersonal information for the enterprise user according to the authority provided by the supervision module, wherein the login credential comprises a private key and a digital certificate. The system and the method can be widely applied to the fields of banks, credit, games, electronic commerce and the like.
Owner:重庆小犀智能科技有限公司
Device identification for management and policy in the cloud
ActiveUS20200077265A1Digital data authenticationPlatform integrity maintainanceUser deviceSoftware engineering
Systems and methods for device identification for management and policy in the cloud, using a combination of several hardware parameters and user's identification to generate a unique identifier for a user device and associated user. IOCTL and Assembly can be used to get the different hardware parameters. All the hardware parameters can then run through a process to generate a fixed size hardware fingerprint. A base64 encoding can be performed to convert it into a string, for consumption of database. The resultant identifier is unique and it is never stored on machine. The application can simply generate it whenever needed. The resultant identifier can used by a service provider to uniquely identify the device even when the device is moving hands or locations. The resultant identifier is never stored, so moving data from one device to another will not result in the same identifier for two devices.
Owner:ZSCALER INC
Design method of separate-storage type key-value storage system
InactiveCN103559027AImprove read performanceEasy to modifySpecific program execution arrangementsSystems designComputer architecture
The invention discloses a design method of a separate-storage type key-value storage system and relates to the technical field of storage system and program design. The method comprises constructing writing and reading functions of value in files and storing the value in a separate file according to a writing sequence; combining the offset of the value in the file and the length of the value into a 64-bit information field and base64-encoding the information field; writing key and the base64-encoded information field as a key-value pair in to an existing key-value storage system; reading the value in a memory mapping mode. The design method of the separate-storage type key-value storage system improves the prior art a little and can greatly improve the reading performance of the key-value storage system when a reading sequence is close to the writing sequence.
Owner:BEIHANG UNIV
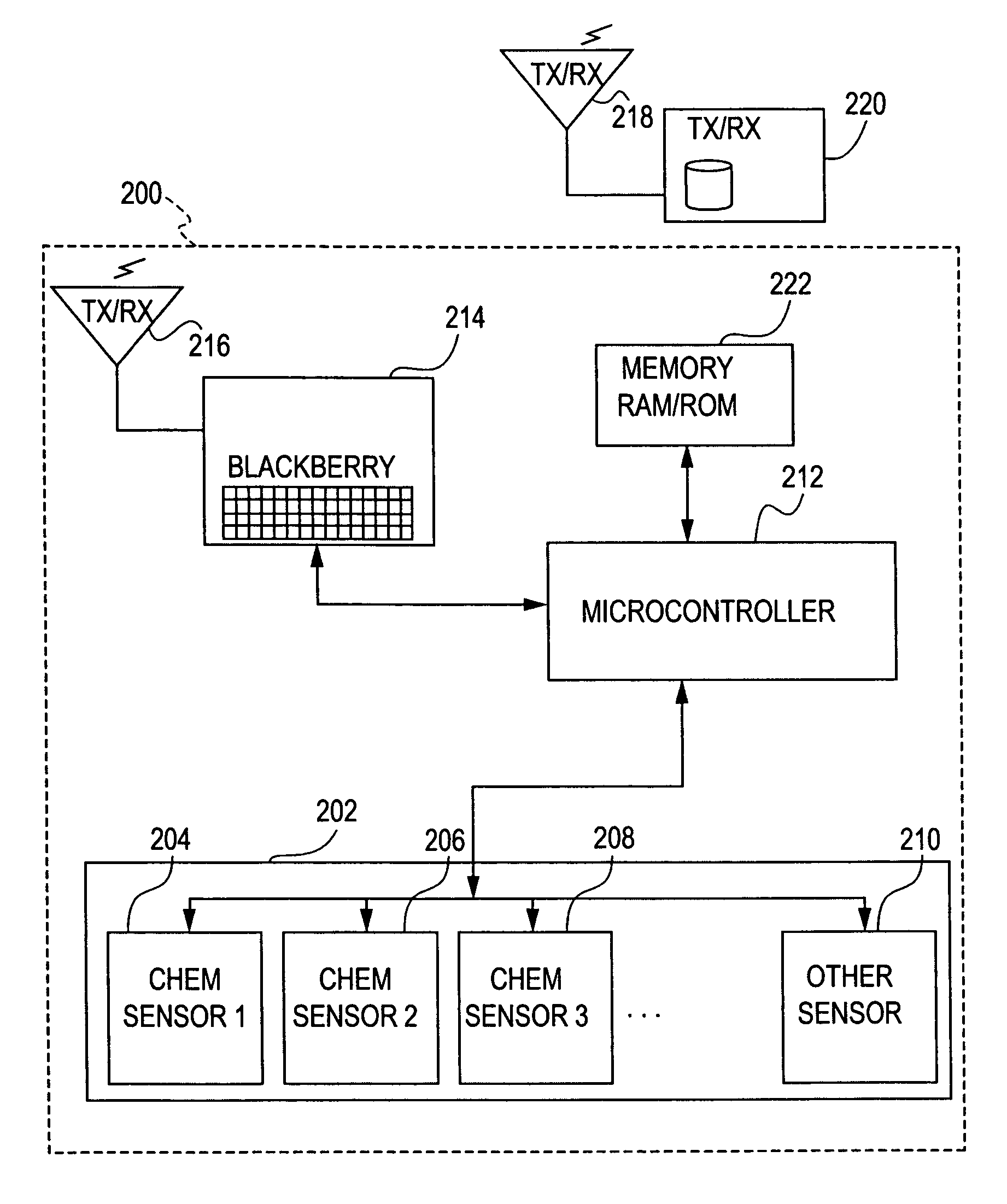
System and method for monitoring environmental conditions
ActiveUS7916015B1Securely makingMinimize false alertsAlarmsElectric signalling detailsMonitoring systemBase64
A monitoring system and method for detecting environmental conditions is provided, the monitoring system including a sensing unit including a plurality of sensors for obtaining data related to environmental conditions, a controller interfaced with the sensing unit for receiving and encoding the data related to environmental conditions into a predetermined format using a base64 encoding scheme, and a communication device for receiving the data in the predetermined format from the controller, forming an e-mail message (which can be further encoded) including instructions on how to decode the email message and transmitting the e-mail message including the data in the predetermined format to at least one predetermined recipient.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
Method and system of remote monitoring and support of devices, using POP3 and decryption using virtual function
InactiveUS20050251692A1Quickly and easily changeEasy to changeUser identity/authority verificationUnauthorized memory use protectionProcess moduleBase64
A method involves retrieving from an email message, information concerning at least one remotely monitored device. The method involves obtaining a line of the email message containing the information, decoding the line obtained from the email message if it has been encoded, and decrypting the decoded line. The decrypting involves using an abstract decrypter class configured to perform a virtual function and using any one of a plurality of derived decrypter classes each of which is configured as a derived class of the abstract decrypter class. The abstract decrypter class and the any one of the derived decrypter classes are collectively configured to decrypt the decoded email message, using the any one of the derived decrypter classes with the abstract decrypter class without having to modify the abstract decrypter class. An exemplary system for remotely monitoring devices uses the SMTP email protocol to send status, configuration, or other information concerning at least one of the devices in a MIME attachment of an email message. A POP3 processing module in the receiver of the email has a class structure. An interface class accesses an email server and obtain the email message including the MIME attachment. An extractor class extracts the MIME attachment from the email message, and a decoder class performs Base64 decoding of the attachment. An abstract decrypter class and each of plural derived decrypter classes configured as a derived class thereof, permit flexibility in adopting new decryption processes without having to modify the abstract decrypter class.
Owner:RICOH KK
Method and system of remote monitoring and support of devices, using POP3 and decryption using virtual function
InactiveUS7181619B2Quickly and easily changeEasy to changeUser identity/authority verificationUnauthorized memory use protectionProcess moduleComputer module
A method involves retrieving from an email message, information concerning at least one remotely monitored device. The method involves obtaining a line of the email message containing the information, decoding the line obtained from the email message if it has been encoded, and decrypting the decoded line. The decrypting involves using an abstract decrypter class configured to perform a virtual function and using any one of a plurality of derived decrypter classes each of which is configured as a derived class of the abstract decrypter class. The abstract decrypter class and the any one of the derived decrypter classes are collectively configured to decrypt the decoded email message, using the any one of the derived decrypter classes with the abstract decrypter class without having to modify the abstract decrypter class. An exemplary system for remotely monitoring devices uses the SMTP email protocol to send status, configuration, or other information concerning at least one of the devices in a MIME attachment of an email message. A POP3 processing module in the receiver of the email has a class structure. An interface class accesses an email server and obtain the email message including the MIME attachment. An extractor class extracts the MIME attachment from the email message, and a decoder class performs Base64 decoding of the attachment. An abstract decrypter class and each of plural derived decrypter classes configured as a derived class thereof, permit flexibility in adopting new decryption processes without having to modify the abstract decrypter class.
Owner:RICOH KK
Chinese text classification method based on Base64 coding
InactiveCN102081667AEasy to follow upOvercome troubleSpecial data processing applicationsPretreatment methodCharacteristic space
The invention discloses a Chinese text preprocessing method based on Base64 coding, comprising the following steps of: (1) preprocessing Chinese text by using the Base64 coding and converting the text to character string text; (2) segmenting words of the converted character string text and extracting text feature items by using 4-gram; (3) screening the text feature items by utilizing IG (Information Gain) to generate a feature space; (4) counting word frequency of the text feature items, wherein the word frequency is used for expressing weight of the feature items and the Chinese text is expressed as an eigenvector; and (5) training an SVM (Support Vector Machine) classifier by utilizing an LIBLINEAR toolbox to obtain an SVM classification model and classifying the Chinese text to judge the category of the text. According to the Chinese text preprocessing method based on the Base64 coding, the Base64 coding is used for cording the Chinese text and the 4-gram is used for extracting the text feature items; therefore, the problems that the Chinese text classification is time-consuming and not high in accuracy rate of Chinese word segmentation during the Chinese text classification are solved; in the mean time, the IG is used for feature selection and the word frequency is used for expressing text feature, therefore, the accuracy rate and efficiency of the Chinese text classification can be effectively enhanced.
Owner:ZHEJIANG UNIV
Web technology-based webpage screen capture method
ActiveCN107885848AAvoid dependenceSave storage spaceWebsite content managementSpecial data processing applicationsThird partyWeb browser
The invention discloses a Web technology-based webpage screen capture method. The method comprises the following steps of calling a program interface of a web page browser to obtain HTML elements of ato-be-captured webpage; calling the program interface of the browser to analyze attributes of the HTML elements, and storing the analyzed attributes as an ordered HTML element attribute list; callingthe program interface of the browser to create a canvas of an HTML; calling the program interface of the browser to cyclically scan the HTML element attribute list, and drawing HTML attribute contents in the HTML element attribute list on the canvas; calling a program interface of the canvas to convert codes of the drawn canvas into base64 character strings, and performing storage; and guiding auser to download the canvas by adding a button to the page. The method has the characteristics of no dependency on other tools and solving of the technical problem of dependency of webpage screen capture on a third-party tool.
Owner:杭州美创科技有限公司
Internet e-commerce platform user privacy data encryption and decryption method
ActiveCN109583217AAvoid problemsAvoid gettingEncryption apparatus with shift registers/memoriesDigital data protectionPlaintextCiphertext
The invention discloses an Internet e-commerce platform user privacy data encryption method, which comprises the following steps of: encrypting and storing a ciphertext key, and generating a vector ivaccording to input original user data; Acquiring an encrypted and stored ciphertext key; Decrypting the ciphertext key into a plaintext ciphertext key; Encrypting the original user data byte stream by using an AES256 / CFB8 / NOPADDING algorithm through a plaintext ciphertext key and a vector iv to obtain a first encrypted character string; Carrying out Base64 coding on the first encrypted characterstring to obtain a second encrypted character string; connecting E-, iv and the second encrypted character string in sequence to obtain a third encrypted character string, and storing the third encrypted character string as encrypted data in a database. The user privacy data is encrypted, the user privacy data information of the database system is prevented from being leaked, and the processing efficiency is improved.
Owner:SHENZHEN YIXUNTIANKONG INTERNET TECH CO LTD
Method for hiding URL (Uniform Resource Locator) in content delivery network
InactiveCN102801810AImprove securityImprove data transfer efficiencyTransmissionBase64Uniform resource locator
The invention provides a method for hiding a URL (Uniform Resource Locator) in content delivery network. The method comprises the following steps that: a user player carries out Base64 encryption on a video file path in a request URL in advance and requests available CDN (Content Delivery Network) nodes to a CDN scheduling server by the encrypted request URL; the CDN scheduling server carries out Base64 decryption on the request URL and then selects an available CDN node according to a scheduling strategy; the CND scheduling server returns an available CDN node address to the user player; the user player carries out Base64 encryption on the video file path in the request URL after receiving the available CDN node address, and the encrypted request URL sends a video data request to the available CDN node; and the available CND node receives the encrypted video data request, then carries out Base64 decryption on the encrypted video data request and sends the requested video data to the user player. The method disclosed by the invention has the advantage of improving the safety of CDN service.
Owner:LETV CLOUD COMPUTING CO LTD
Machine-processable global knowledge representation system and method using an extensible markup language consisting of natural language-independent BASE64-encoded words
A global knowledge representation system and method using an extensible, language-independent markup language made up of KODAXIL encoded words, includes crafting a universal representation of knowledge in any natural language composed of words and symbols as a string of KODAXIL words which are an extensible set of BASE64 encodings of common and reserved vocabulary by assigning to each word and each symbol a KODAXIL word composed of an artificial handle derived in part using BASE64 encoding to encode within each KODAXIL word information about each word and symbol including lexical class of the word, other semantic information, and expression structure including implicit and explicit context markup; and stringing the KODAXIL words together to provide the universal representation of knowledge.
Owner:LEVY GERARD JEAN CHARLES
Data communication coding and decoding method
InactiveCN105740215ANatural language data processingSpecial data processing applicationsDecoding methodsOriginal data
The invention discloses a data communication coding and decoding method. The method comprises following steps of step 1, making a mapping table, thus enabling binary byte data to be mapped to visible text characters, wherein the text characters are a set of ASCII characters; step 2, obtaining binary data of data needing to communicate; and converting binary data of any one byte into corresponding Base64 coding text characters. According to the method, the binary data is coded in a fixed length mode; therefore, the length of the original data is easy to obtain through base64 coding; and analysis is very convenient, therefore, it is very beneficial for the calculation of a computer processor.
Owner:BEIJING ZHANGKUO MOBILE MEDIA TECH
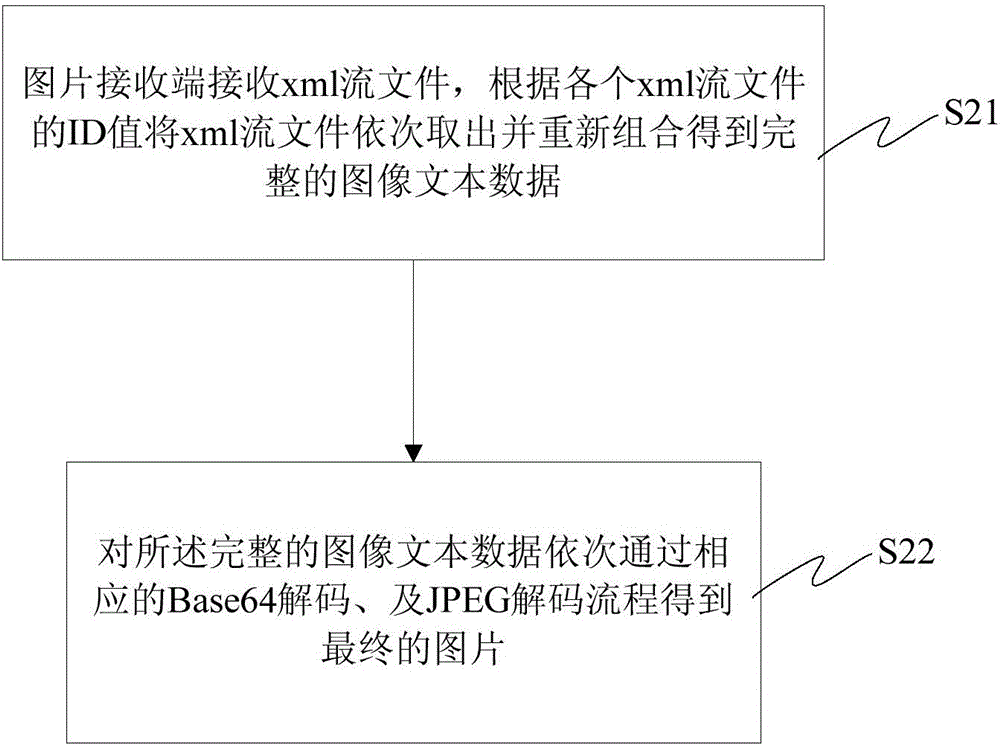
Transmission method and presentation method of progressive picture based on XMPP
The invention provides a transmission method and presentation method of a progressive picture based on the XMPP. The transmission method comprises steps: 1) obtaining binary data of a picture file by a picture transmitting end according to a format of a to-be-transmitted picture, and recoding the obtained binary data according to a JPEG progressive encoding mode; 2) recoding the binary data of the JPEG picture after compression through a Base64 method, and converting the binary data into text data; and 3) ordering segmenting the text data after going through Base64 recoding to form a text flow, defining a sending sequence of the text flow through an ID value, and then converting the text data into an ordered xml flow file. In cross-terminal collaborative interaction equipment based on the XMPP, the cross-terminal collaborative interaction is achieved, split-screen presentation and cross-terminal operation of businesses are supported, and then a lot of picture files can be rapidly transmitted in different equipment terminals.
Owner:SHANGHAI BROADBAND TECH
Information encryption and decryption method
InactiveCN103580851AOvercoming encryptionOvercome the problem that decryption cannot communicate with each otherEncryption apparatus with shift registers/memoriesPlaintextExclusive or
The invention discloses an information encryption and decryption method. A replacement / permutation network method is adopted to fix cleartext packet length as 128b, and the key expansion process and the encryption process are carried out. The method is achieved through shifting and the exclusive OR operation achieved by the combinatorial logic. The achieving method replaces the complex multiplication, the encryption speed is increased, parallel running water is adopted to process a plurality of data blocks at the same time, and the throughput capacity is improved. Base64 is adopted by the calculated binary data to conduct secondary encryption on ciphertext and secrete key encryption, messages between different platforms are communicated through the base64 message mode, the platforms conduct analysis on results obtained after the base64 encryption, the problem of the difference between the message analysis results of the different platforms is solved, and the cross-platform data encryption and decryption are achieved.
Owner:FUJIAN ZHONGGENG SHITONG INFORMATION TECH CO LTD
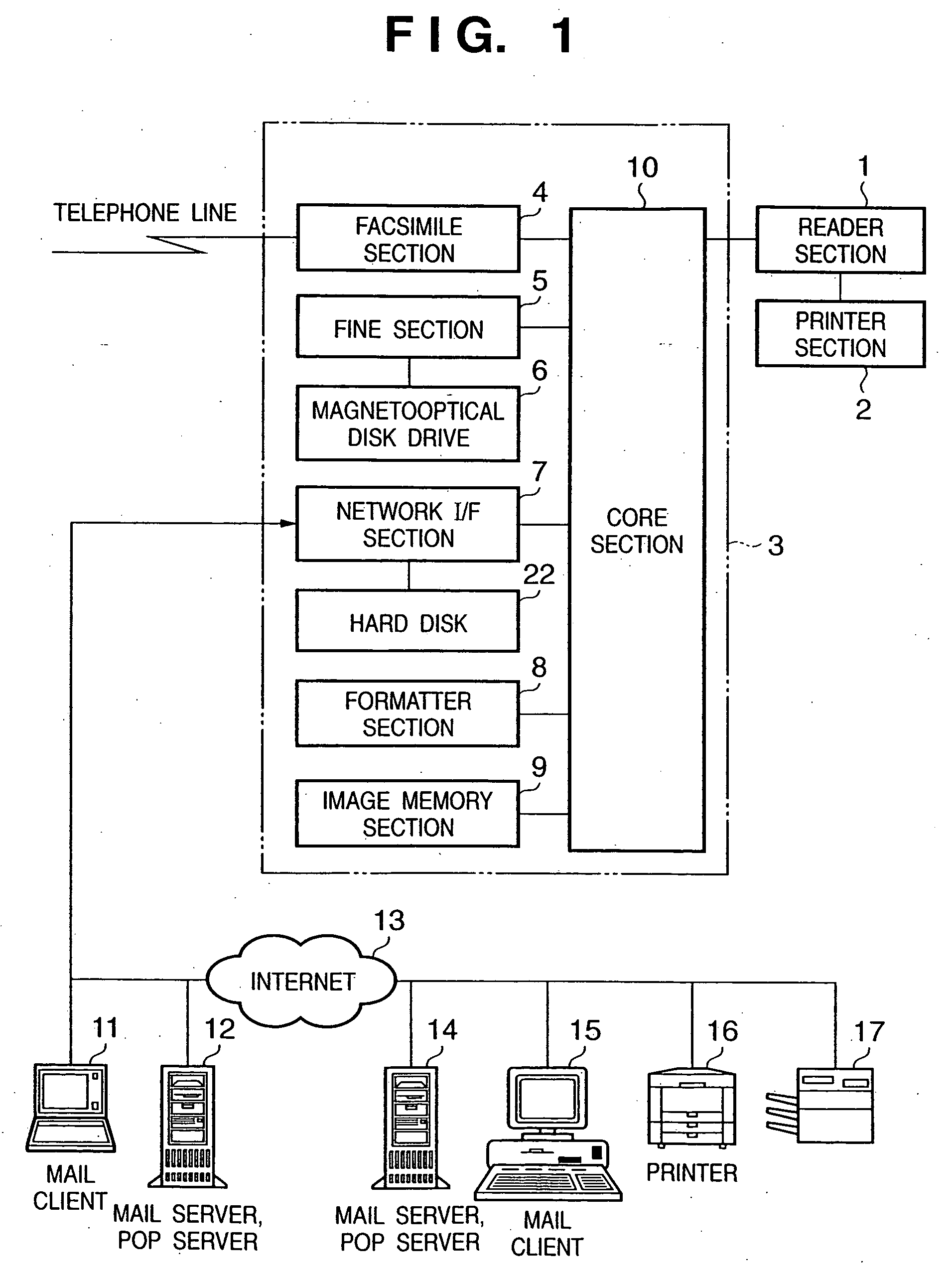
Communication apparatus, control method, and storage medium that can identify communication errors
InactiveUS6952721B2Inhibit transferAvoid storageTelephonic communicationMultiple digital computer combinationsTagged Image File FormatBase64
A communication apparatus capable of notifying a receiver of a reception mail error or transmission mail error by printing or the like and preventing incorrect data or error notification mail from being transferred or stored without notifying the user of the error, and a control method and storage medium therefor. To accomplish this, when analysis of electronic mail data reveals a MIME analysis error, BASE64 decoding error, TIFF analysis error, or image decoding error, i.e., when data which cannot be handled by the communication apparatus is contained, a global variable FORWARD is set to “1”. Also, when the received electronic mail is an error notification mail, the variable FORWARD is set to “1”. When the variable FORWARD is set to “1”, transfer and BOX storage of the received mail are inhibited, and the mail is printed by a printer section (2). When the variable FORWARD is not set to “1”, the received mail is transferred to the designated transfer destination or stored by BOX storage.
Owner:CANON KK
Method for realizing web encrypted access and information encryption storage based on gateway device
ActiveCN106713360ASafe and efficient data transmissionGuaranteed processing logicTransmissionProtocol processingOriginal data
The invention relates to a method for realizing web encrypted access and information encrypted storage based on a gateway device. The method comprises the following steps: processing data transmission between a user and a device by use of an openssl secure socket layer protocol; separating the data processing from the data transmission business, creating a local socket service specially for processing the network data and generating response data; creating a remote socket service specially for the encrypted data interaction with a network client; performing plaintext interaction between the remote socket and the local socket; encrypting a user secret key, the permission and other sensitive information needing to be stored in the device by use of an AES+base64 encoded encryption way, and saving the ciphertext information in the device storage system. By use of the method disclosed by the invention, the web access of the gateway device can be automatically redirected to the access to a secure socket character, the security and the high efficiency of the data transmission and the original data processing logic and the user information security are guaranteed, and the method has extensive application range.
Owner:SHANGHAI GONGJIN COMM TECH
MD5-based two-way encryption data protection method
InactiveCN105812146AEnsure safetyEncryption apparatus with shift registers/memoriesUser identity/authority verificationPlaintextCiphertext
The invention relates to an MD5-based two-way encryption data protection method, comprising: a key processing process, an encryption process and a decryption process, wherein the key processing process includes: subjecting a key to MD5 and BASE64 transcoding; intercepting the key; processing with a pseudorandom algorithm and converting a character string into a key box; the encryption process includes: converting a plaintext character string into ASCII code, circulating the ASCII code, and carrying out pseudorandom arrangement through an algorithm; adding ASCII code value of a check character string generated by intercepting in the key processing process; performing circulating bitwise XOR to convert the value into a character string; subjecting the generated character string to BASE64 transcoding to obtain a cyphertext character string; the decryption process includes: subjecting the cyphertext character string to BASE64 decoding, and carrying out ASCII coding; performing circulating bitwise XOR operation; matching a check portion with a check sequence, failing the check in case of inconformity; subjecting the cyphertext ASCII code string and the key box to circulating bitwise XOR operation to convert the obtained ASCII code string into a character string, and reversely executing as a random process to finally obtain a plaintext character string.
Owner:王云鹏
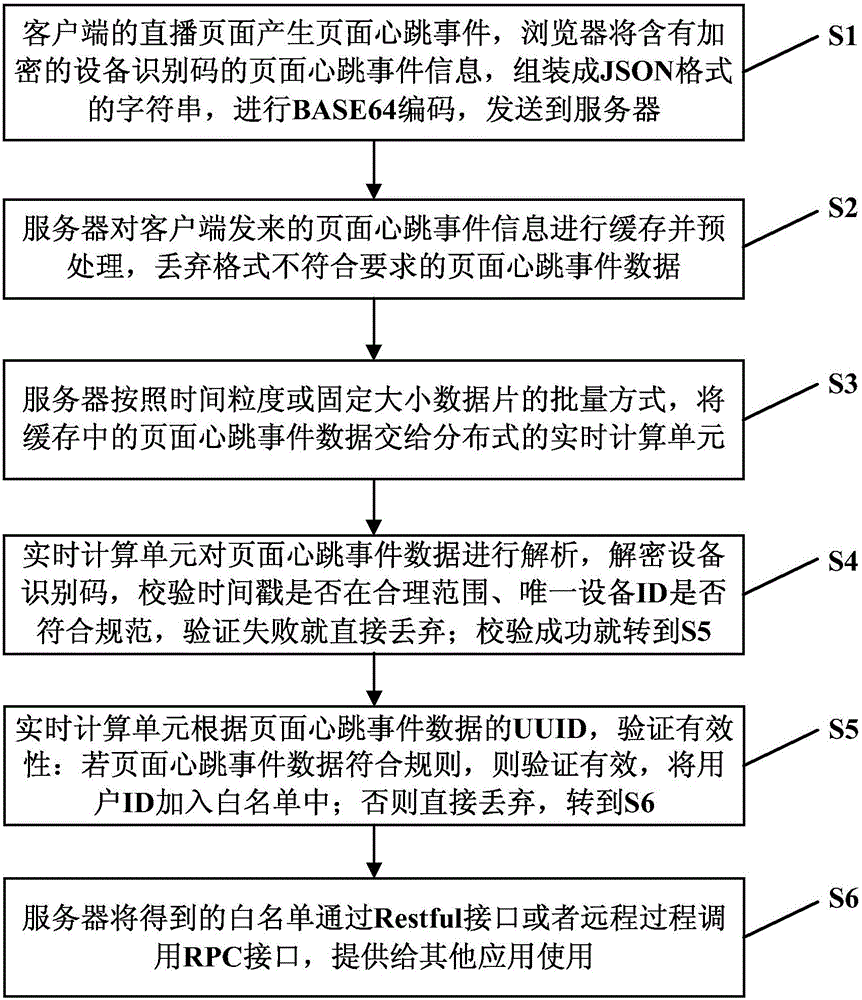
System and method for generating white list based on page heartbeat event of a live broadcast website
The invention discloses a system and a method for generating a white list based on a page heartbeat event of a live broadcast website, and relates to the field of live broadcast. The method comprises the following steps of: generating a page heartbeat event in a live broadcast page of a client, assembling page heartbeat event data into a character string in a JSON format by a browser, performing BASE64 coding and sending the coded character string to a server; caching and pre-processing the page heartbeat event data and submitting the page heartbeat event data in a cache to a real-time computing unit; analyzing the page heartbeat event data by the real-time computing unit, decoding a device identification code, checking whether a time stamp is in a reasonable range and whether the unique device ID is in accordance with a standard, and discarding if the verification is failed; and adding the user ID into the white list if the verification is successful and the page heartbeat event data are verified to be effective. The system and the method for generating the white list based on the page heartbeat event of the live broadcast website can restrain inactive users and cheating users from participating in the interactive activity of an anchor so as to ensure the interactive activity to be carried out effectively.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
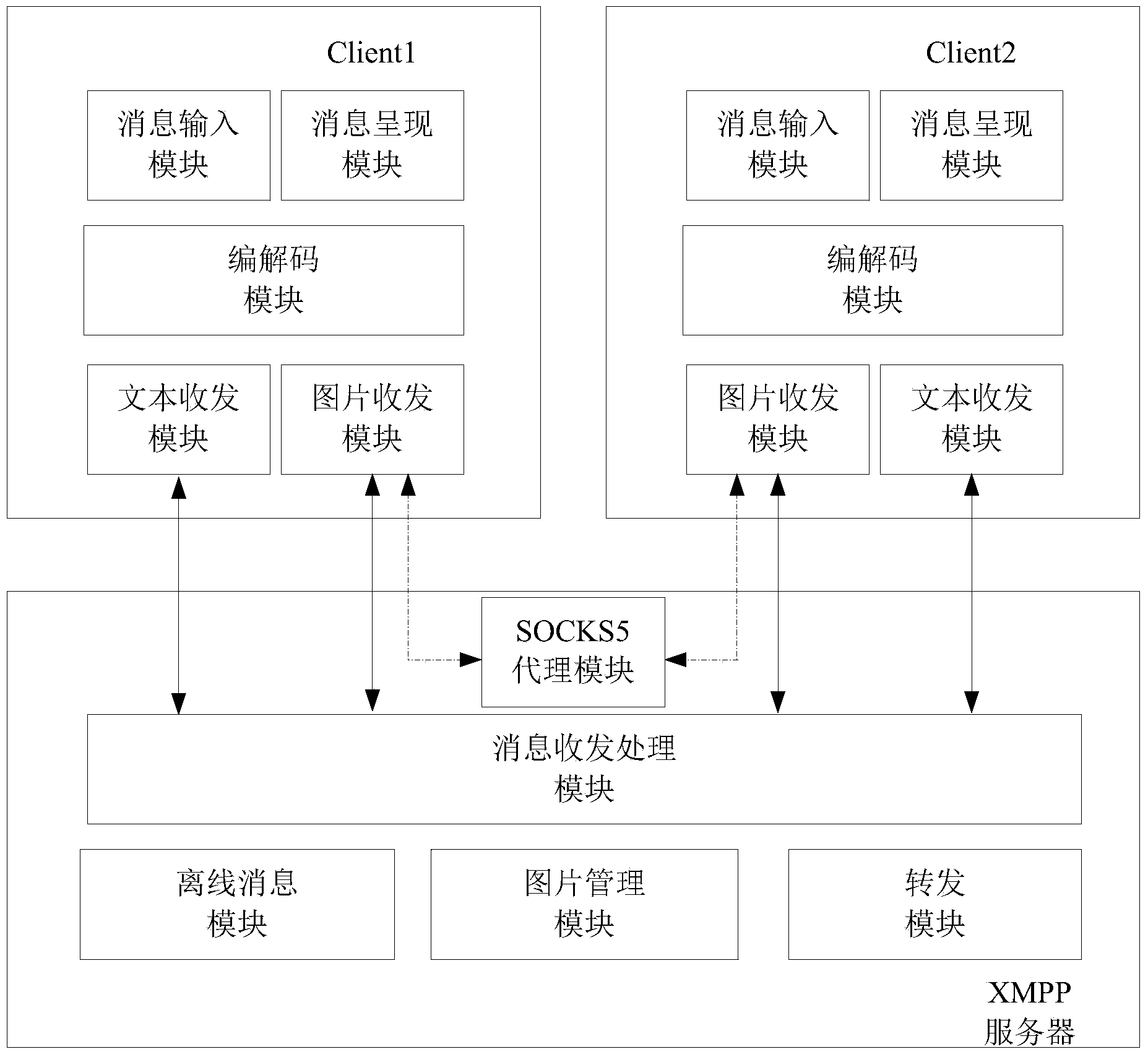
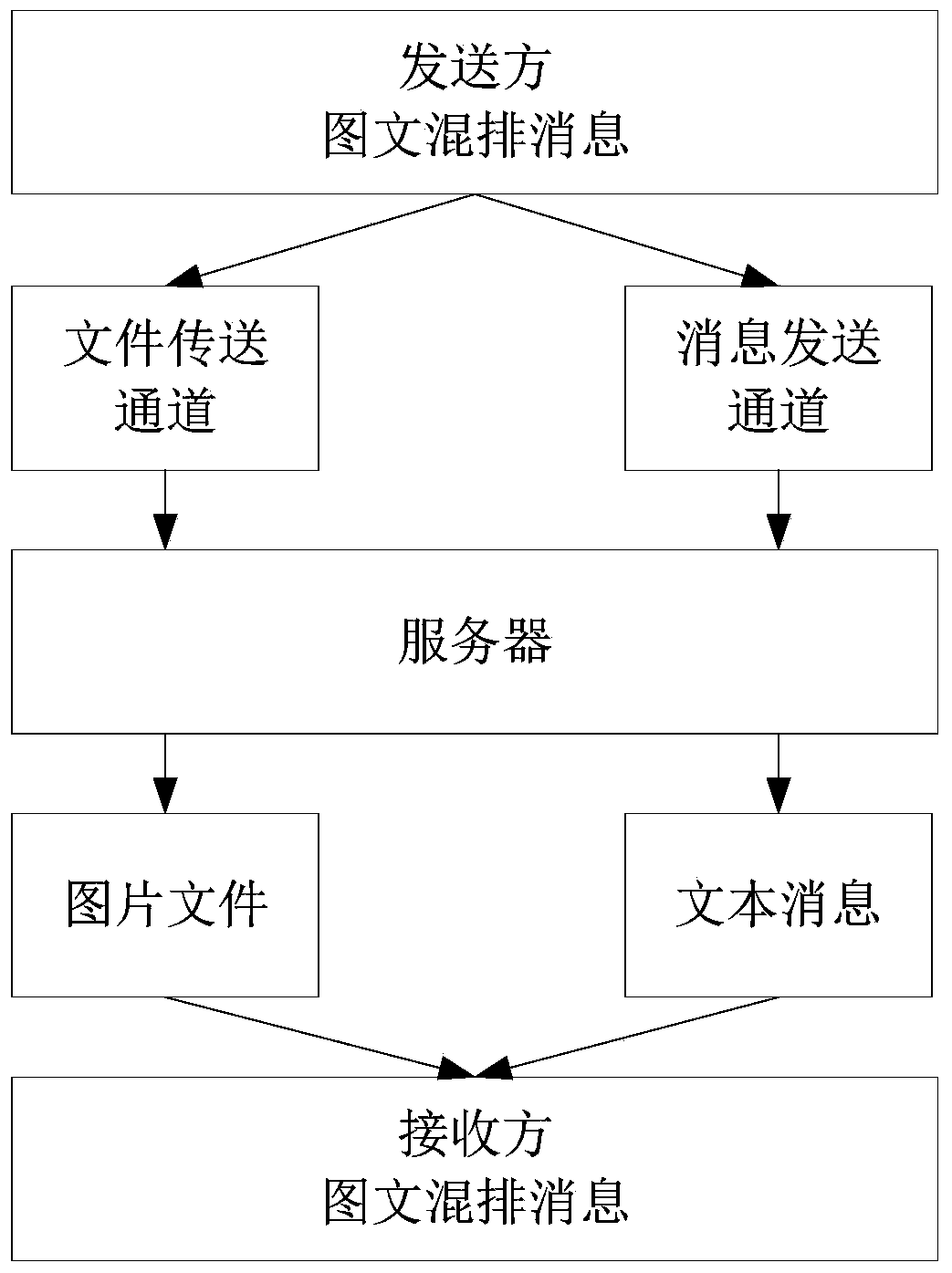
Rich text format realization system and method based on expanded XMPP (xml based messaging and presence protocol)
ActiveCN103532828AImprove good performanceImprove interoperabilityData switching networksBase64Protocol for Carrying Authentication for Network Access
The invention provides a rich text format realization system and a rich text format realization method based on an expanded XMPP (xml based messaging and presence protocol). The system comprises a client and a server end, wherein the client comprises an encoding and decoding module, a text receiving and sending module and an image receiving and sending module, the encoding and decoding module is used for encoding and decoding instant messages, the text receiving and sending module is used for sending and receiving the text messages, the picture receiving and sending module is used for sending and receiving image information, the server end comprises a message receiving and sending processing module, an off-line message module and an image management module, the message receiving and sending processing module is used for receiving and transferring instant messages from the client, the off-line message module is used for temporarily storing the text messages, and the picture management module is used for storing and managing the picture information. The system and the method provided by the invention have the advantages that expansibility and intercommunity are good, the separated picture and text sending is realized, the message passage blockage caused by over size pictures is prevented, the base64 coding is adopted for sending the pictures in the instant messages, and the efficiency is relatively higher.
Owner:STATE GRID CORP OF CHINA +3
Internet of scenes data processing method and system
ActiveCN109769123AEasy to operateImprove experienceTransmissionSelective content distributionUser needsThe Internet
The invention provides an Internet of scenes data processing method and system. When a user needs to use the Internet terminal to watch a live video located in the Internet of scenes, the user can watch the live video; a user can control the Internet terminal to scan the two-dimensional code; the method comprises the following steps: obtaining terminal information of a plurality of Internet of scenes terminals in an Internet of scenes from a protocol conversion server, determining a target Internet of scenes terminal according to the terminal information; and then the live video stream issuedby the target Internet of scenes terminal is acquired through the protocol conversion server, the Internet of scenes server and the target Internet of scenes terminal, and then the live video stream can be played by the Internet terminal, so that a user can watch the live video in the Internet of scenes on the Internet terminal. Secondly, the first login information is encrypted and compressed through a Base64 algorithm to obtain second login information, so that the second login information is sent to the protocol conversion server, and therefore, the security of the login information can beimproved, and the network load can be reduced.
Owner:VISIONVERA INFORMATION TECH CO LTD
Communication apparatus, control method, and storage medium that can identify communication errors
InactiveUS20050235040A1Inhibit transferAvoid storageTelephonic communicationMultiple digital computer combinationsComputer printingBase64
A communication apparatus capable of notifying a receiver of a reception mail error or transmission mail error by printing or the like and preventing incorrect data or error notification mail from being transferred or stored without notifying the user of the error, and a control method and storage medium therefor. To accomplish this, when analysis of electronic mail data reveals a MIME analysis error, BASE64 decoding error, TIFF analysis error, or image decoding error, i.e., when data which cannot be handled by the communication apparatus is contained, a global variable FORWARD is set to “1”. Also, when the received electronic mail is an error notification mail, the variable FORWARD is set to “1”. When the variable FORWARD is set to “1”, transfer and BOX storage of the received mail are inhibited, and the mail is printed by a printer section (2). When the variable FORWARD is not set to “1”, the received mail is transferred to the designated transfer destination or stored by BOX storage.
Owner:CANON KK
High-efficiency and safe network communication method
InactiveCN106789004AFix security issuesSolve the problem of transmitting large amounts of informationKey distribution for secure communicationTimestampInformation transmission
The invention relates to the field of security of information transmission between a server side and a client side, and in particular relates to a high-efficiency and safe network communication method. The high-efficiency and safe network communication method comprises the following steps: after a user successfully logs in, a series of certificates having the survival time can be generated at first; then, a client side encrypts a content, a certificate and a current timestamp to be transmitted at first; an encrypted ciphertext is compressed; finally, URL security Base64 coding of the compressed ciphertext is carried out; the ciphertext is sent to a server side; after the server side receives the ciphertext, URL security Base64 decoding is carried out at first; then, decompression and decryption are carried out; after being obtained, the certificate is checked; after the certificate is checked successfully, whether a request exists or not can be judged according to the timestamp; if the request does not exist, a changed timestamp is recorded on a server; and thus, repetitive submission of the request is prevented. By means of the high-efficiency and safe network communication method disclosed by the invention, the security problem of information sent by users and the transmission problem of a large amount of information can be solved; and thus, the high-efficiency and safe network communication method can be used for transmitting information between the server side and the client side.
Owner:G CLOUD TECH
An encoding and decoding method and system based on a blockchain smart contract
ActiveCN109933404ASupport codec operationExamples cannot be limitedSoftware simulation/interpretation/emulationSpecial data processing applicationsDecoding methodsBase64
The invention discloses a BASE64 coding and decoding method and a BASE64 coding and decoding system based on a block chain smart contract. In the embodiment of the specification, On one hand, a BASE64coding instruction and a BASE64 decoding instruction are defined and added into an instruction set of a block chain virtual machine; Meanwhile, BASE64 encoding logic corresponding to the BASE64 encoding instruction and BASE64 decoding logic corresponding to the BASE64 decoding instruction are deployed in the blockchain virtual machine. And on the other hand, a defined BASE64 coding instruction and a defined BASE64 decoding instruction need to be added into an instruction set of the intelligent contract compiler, so that the business intelligent contract compiled by the intelligent contract compiler contains the BASE64 coding instruction and / or the BASE64 decoding instruction. Therefore, if the business intelligent contract is deployed in the block chain network, the user can simultaneously assign and call the business intelligent contract to execute the business initiation transaction when constructing the business initiation transaction.
Owner:ADVANCED NEW TECH CO LTD
Centralized management method of distributed storage ceph cluster network
The invention discloses a centralized management method of a distributed storage ceph cluster network. A server end analyzes a received created cluster task, and obtains a network segment providing service for a cluster. The server end determines the IP address of the client which needs to be connected according to the task of creating the cluster and sends the instruction to the designated routeof the client port. After receiving the instruction, the client calls the local command according to the preset routing instruction to generate the unique uuid of the cluster, and sends the uuid to the server through the http protocol. The server receives the uuid of the client and stores it in the database for standby. The client end generates the key files needed for adding mon, adding osd and managing, reads the three key files in the form of string and encrypts them with base64, and sends the encrypted key files to the server end. The server receives three key files respectively, and directly stores them in the database for standby, and the cluster network creation is completed. The invention has the advantages of safety, there in not need to log on the server for operation, and controllability is enhanced.
Owner:陕西中光电信高科技有限公司
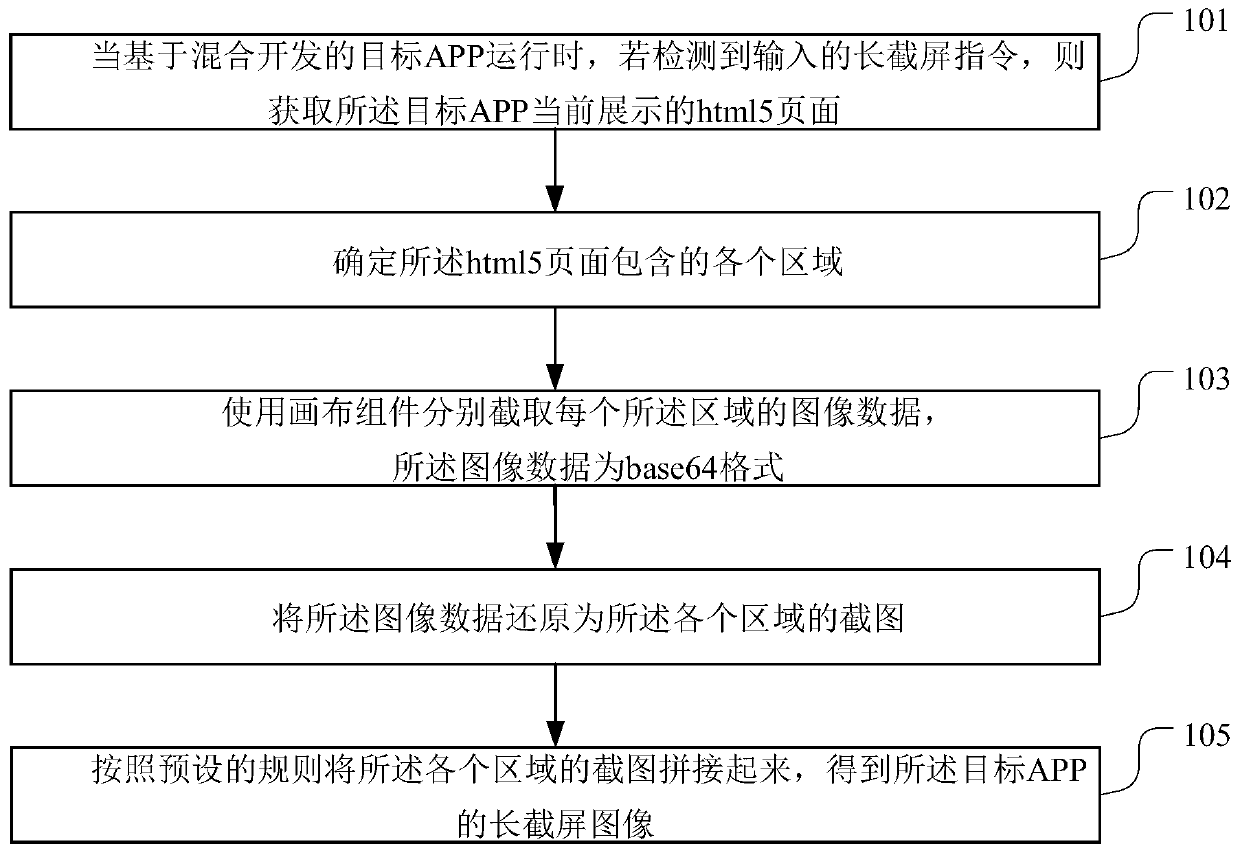
Long screen capture method and device, storage medium and terminal device
ActiveCN110032314AGeometric image transformationInput/output processes for data processingHTML5Computer graphics (images)
The invention relates to the technical field of computers, and provides a long screen capture method and device, a storage medium and a terminal device. The method is applied to a target APP developedin a hybrid mode, and comprises the steps of when the target APP runs, if an inputted long screen capture instruction is detected, obtaining an html5 page currently displayed by the target APP, and determining all areas contained in the html5 page; respectively intercepting the image data of each area by using a canvas component, wherein the image data is in a Base64 format; restoring the image data into a screenshot of each area; and splicing the screenshots of the regions according to a preset rule to obtain a long screenshot image of the target APP. During the above process, by intercepting the image data of each area of the html5 page by using a canvas assembly, and then restoring and splicing the image data, the long screenshot image is obtained.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
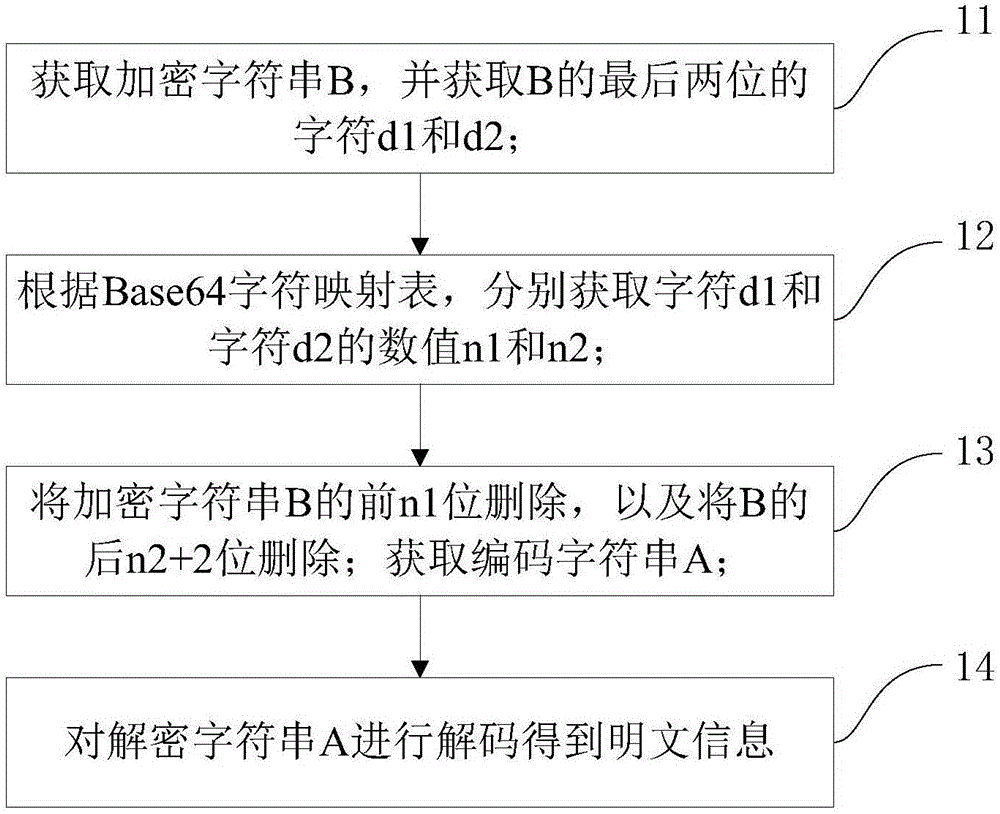
Encryption-decryption method based on Base64 and device thereof
The invention discloses an encryption-decryption method based on Base64 and a device thereof. The method comprises the steps of obtaining to-be-encrypted plaintext information; carrying out Base 64 encoding on the plaintext information to generate an encoded character string; randomly generating a first numerical value m1 between 3 and 63; obtaining a first character corresponding to the first numerical value from a Base64 character mapping table; randomly obtaining m1 characters from the Base64 character mapping table, and forming a first character string; and adding the first character string to the front of the coded character string, and adding the first character to the rear of the coded character string to generate a final encrypted character string. The encryption-decryption method based on the Base64 and the device thereof disclosed by the invention have the advantage that the encryption is further carried out on the plaintext information based on a Base64 encoding technology and other decryption algorithms cannot be used for decoding, so the security is relatively high.
Owner:GUANGDONG YOUMAI INFORMATION COMM TECH
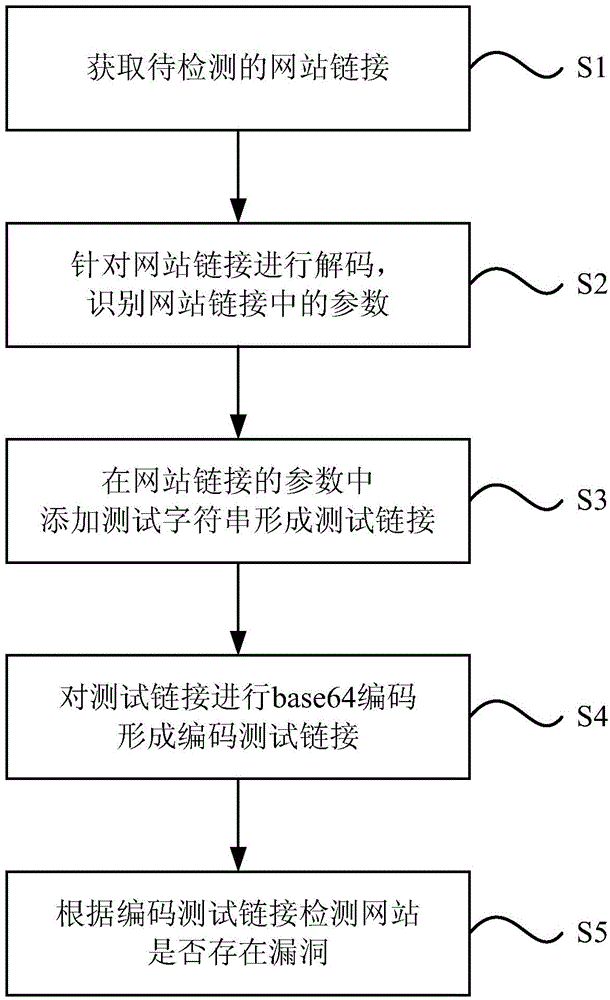
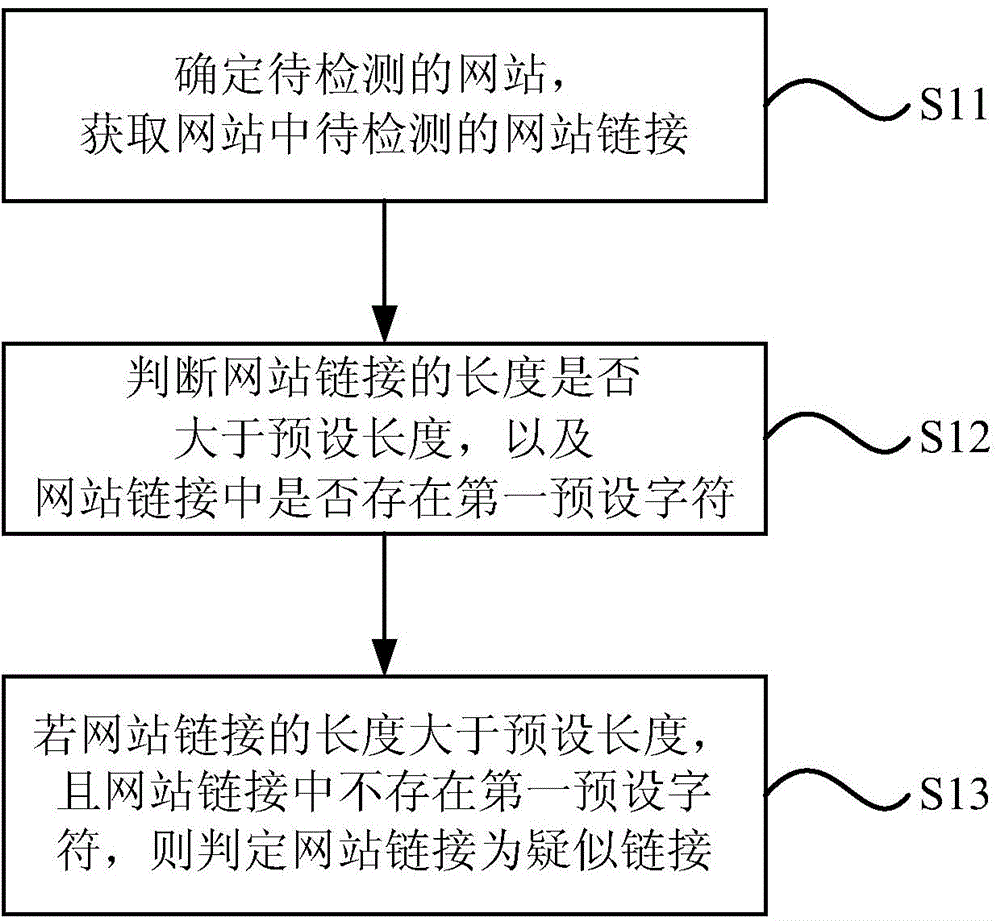
Method and system for detecting website vulnerability
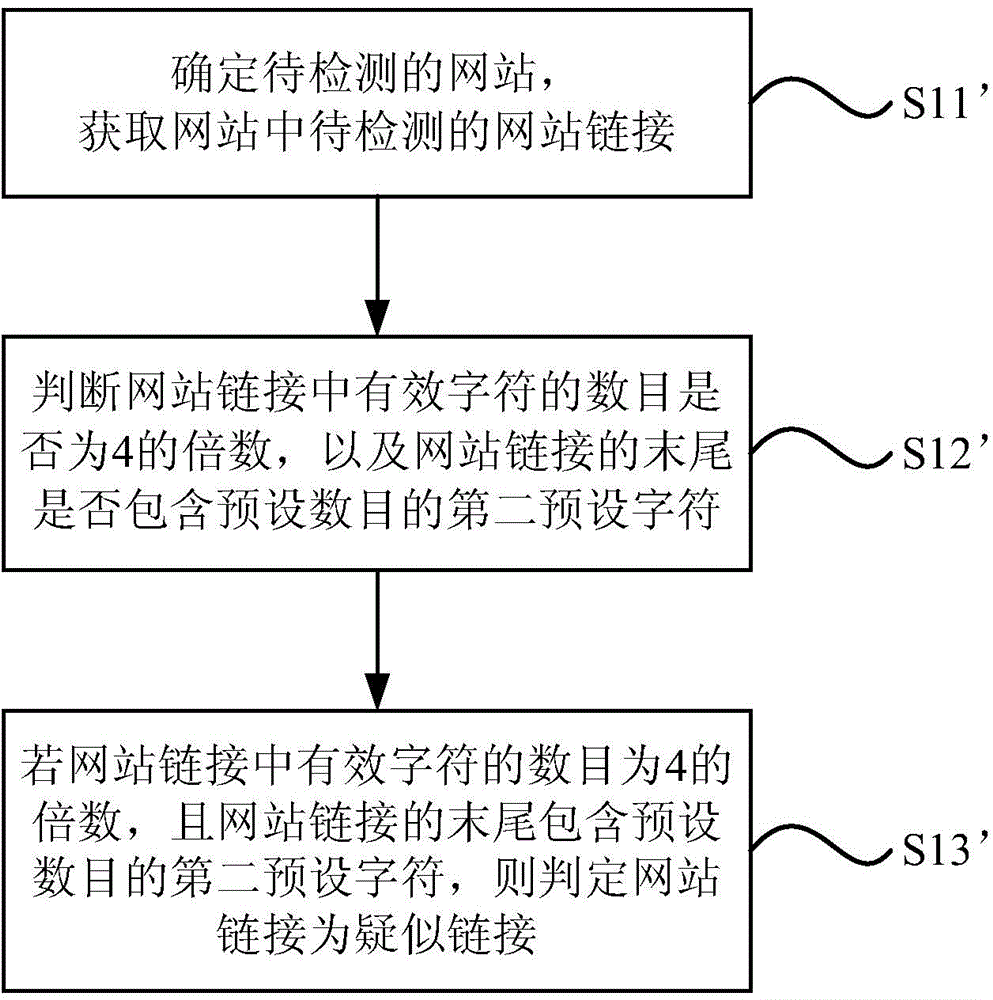
InactiveCN104537307AImprove securityAccurate queryPlatform integrity maintainanceSpecial data processing applicationsBase64Web site
The invention relates to a method and system for detecting website vulnerability. The method includes the steps of obtaining a to-be-detected website link, wherein the website link is in a Base64 coded format; carrying out decoding for the website link to recognize parameters in the website link; adding a testing character string into the parameters of the website link to form a testing link; carrying out Base64 coding on the testing link to form a coded testing link; and detecting whether a website has the vulnerability or not according to the coded testing link. By means of the technical scheme of the method and system, the vulnerability in the Base64 link can be accurately detected, and the network information interaction safety degree can be improved.
Owner:BEIJING QIANXIN TECH
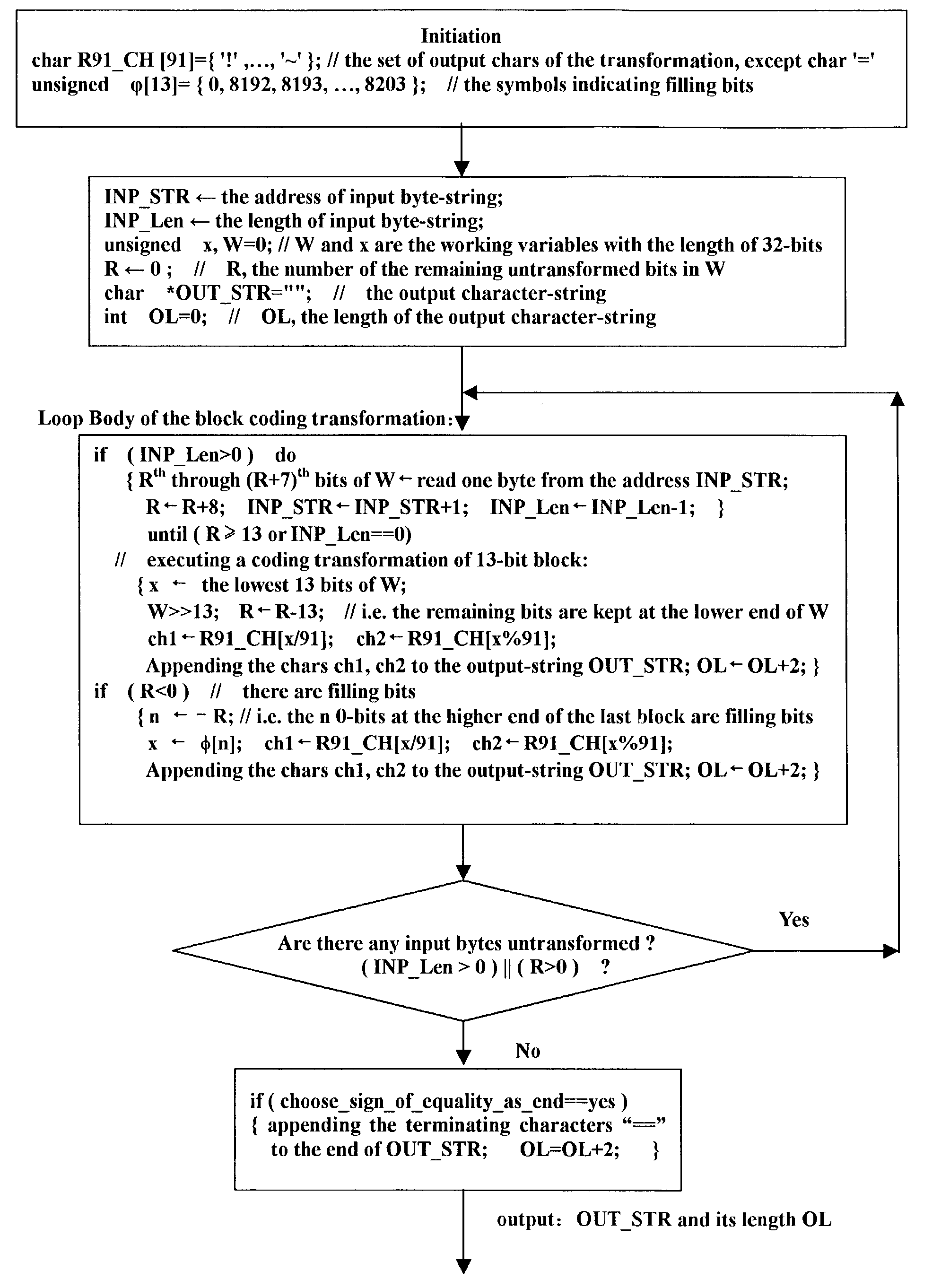
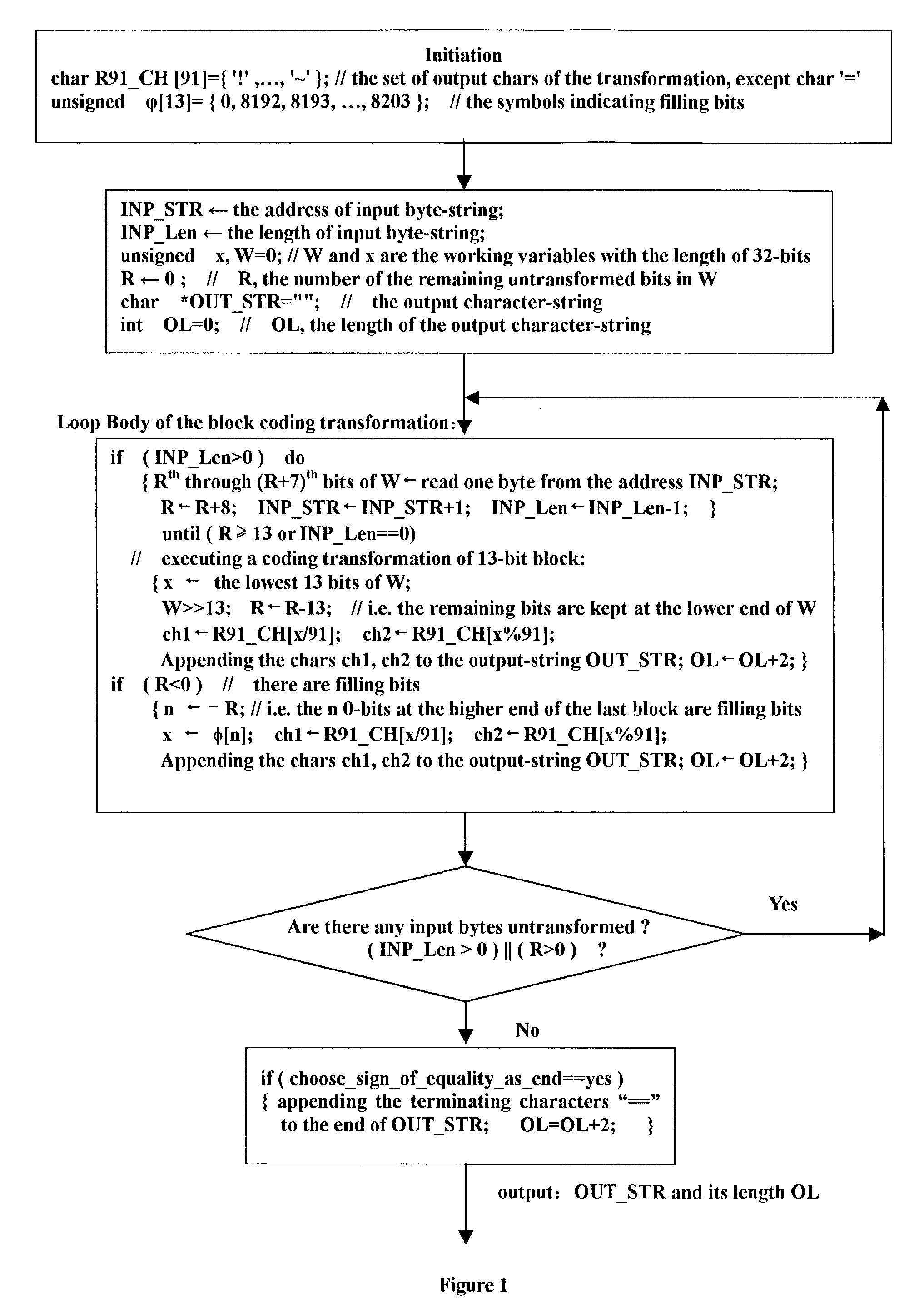
Digital data transforming method
InactiveUS20030152220A1Improve coding efficiencyShorten the timeCode conversionNatural language data processingDigital dataBase64
The present invention discloses a digital data transforming method. The method solves the problems of low encoding efficiency and increasing the network load when prepared to transmit enciphered e-mails or any 8-bit data sequence. The key technology is designing a "base-91 encoding" general bit strings to printable ASCII characters which is also referred to base91 encoding or Radix-91 encoding. Combined with Internet standard SMTP, MIME, S / MIME etc., the present invention can reduce 7.7 % of transmitted data or storage demand in place of Base64 encoding; and reduce 58.97 % of transmitted data or storage demand in place of QP encoding which processes the byte data with the high bit being 1. The present invention is applied in enciphering the Internet e-mails and transmitting or storing the compressed data.
Owner:SOUTHWEST JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com