Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
39results about How to "Securely making" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
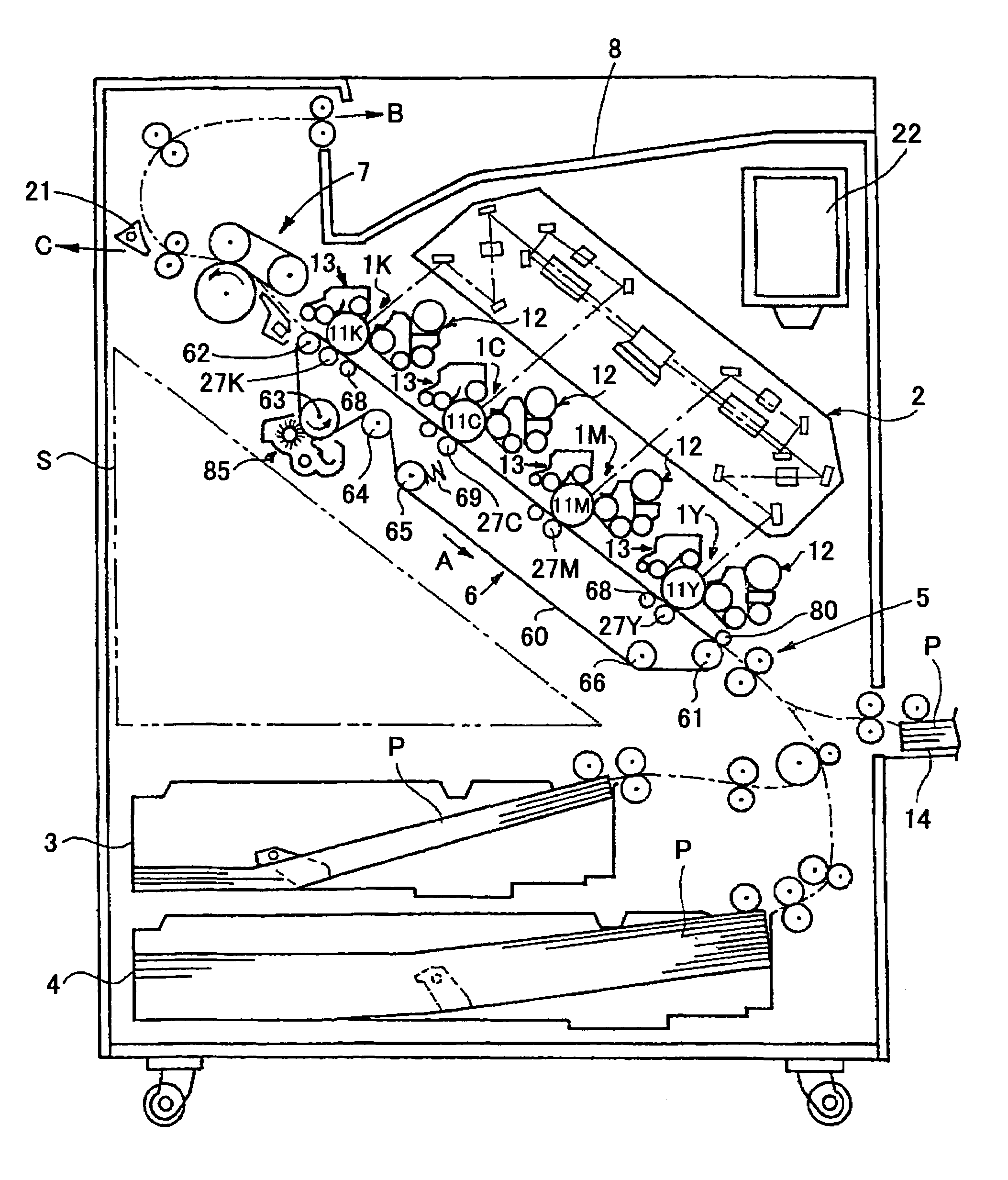
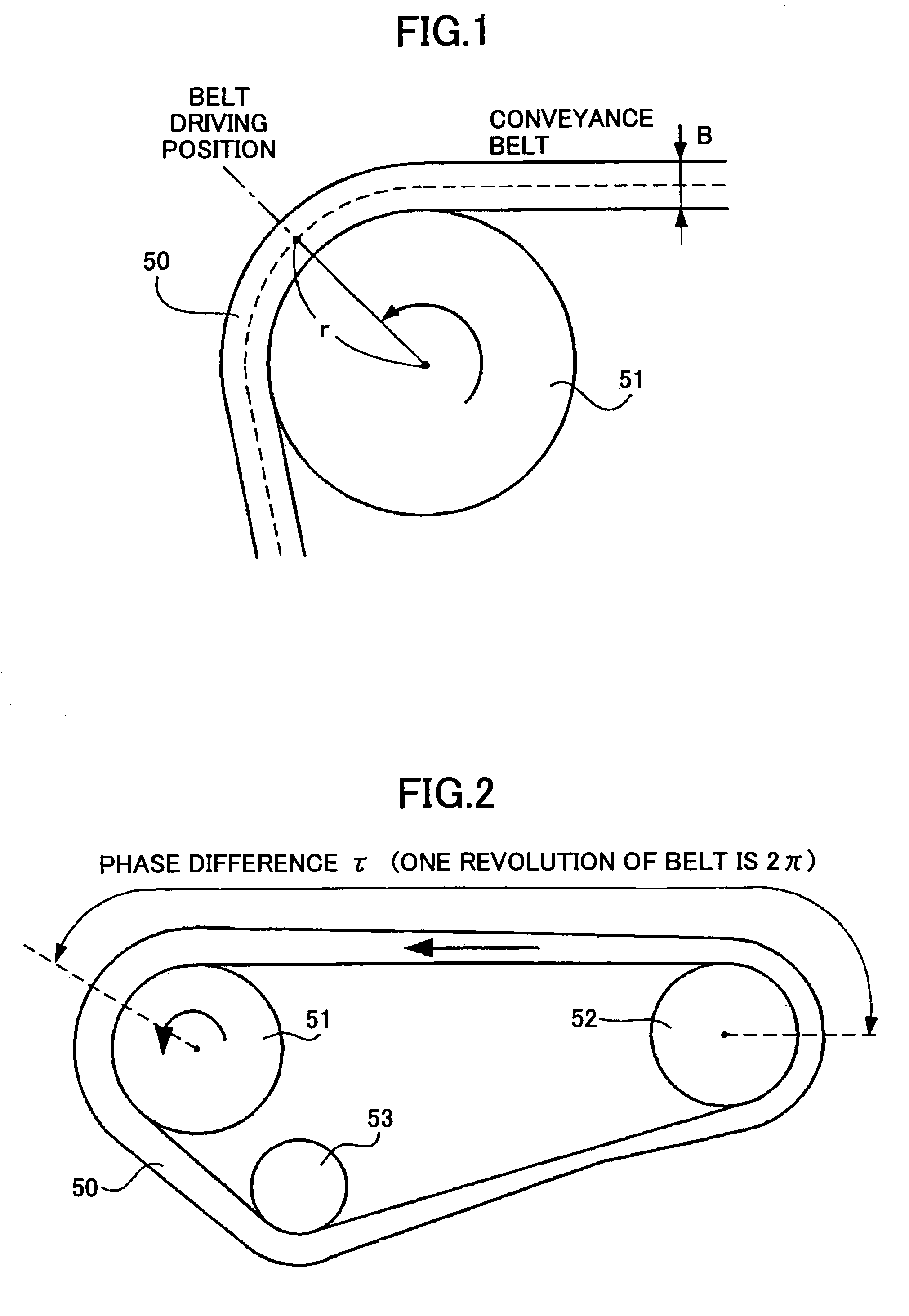
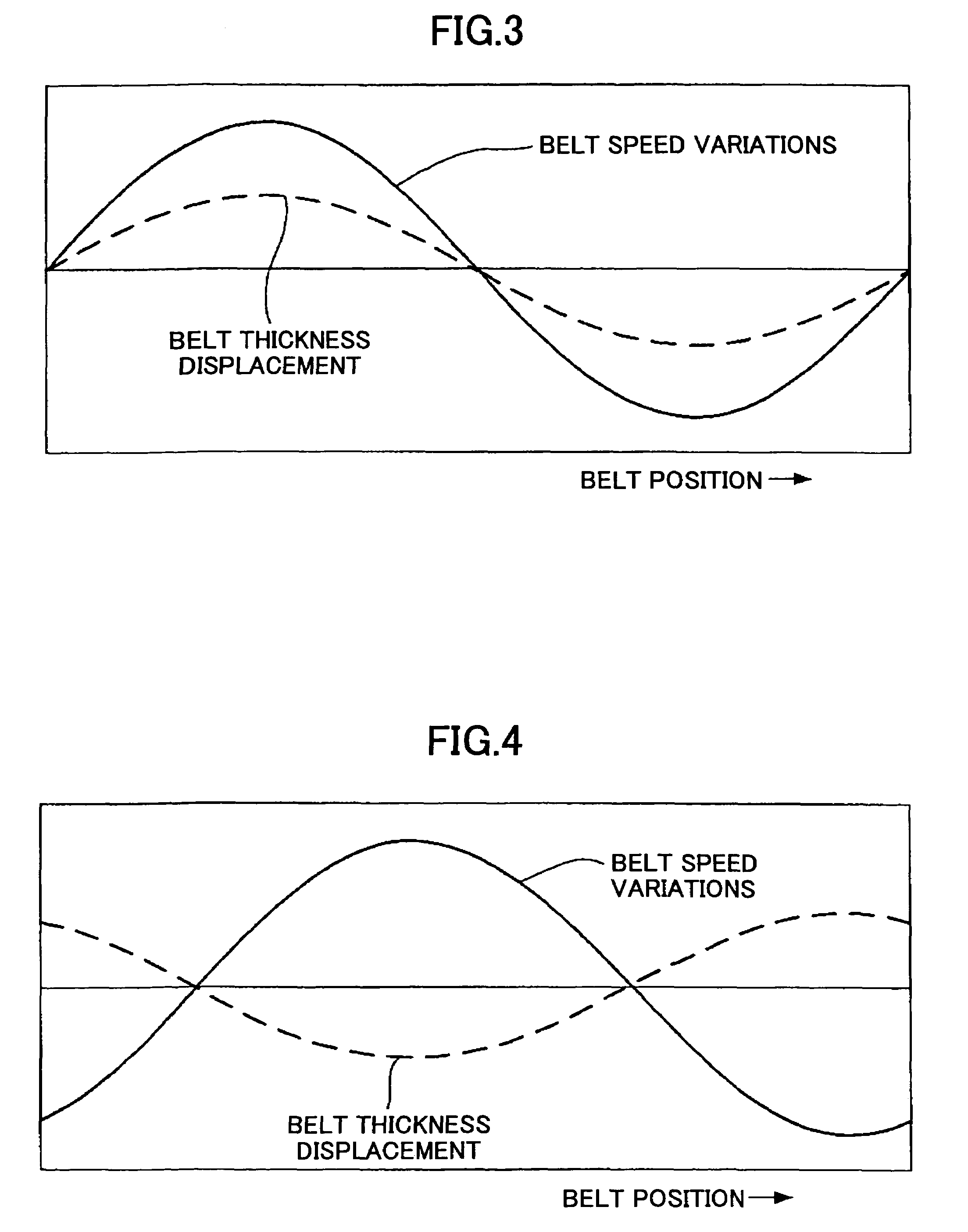
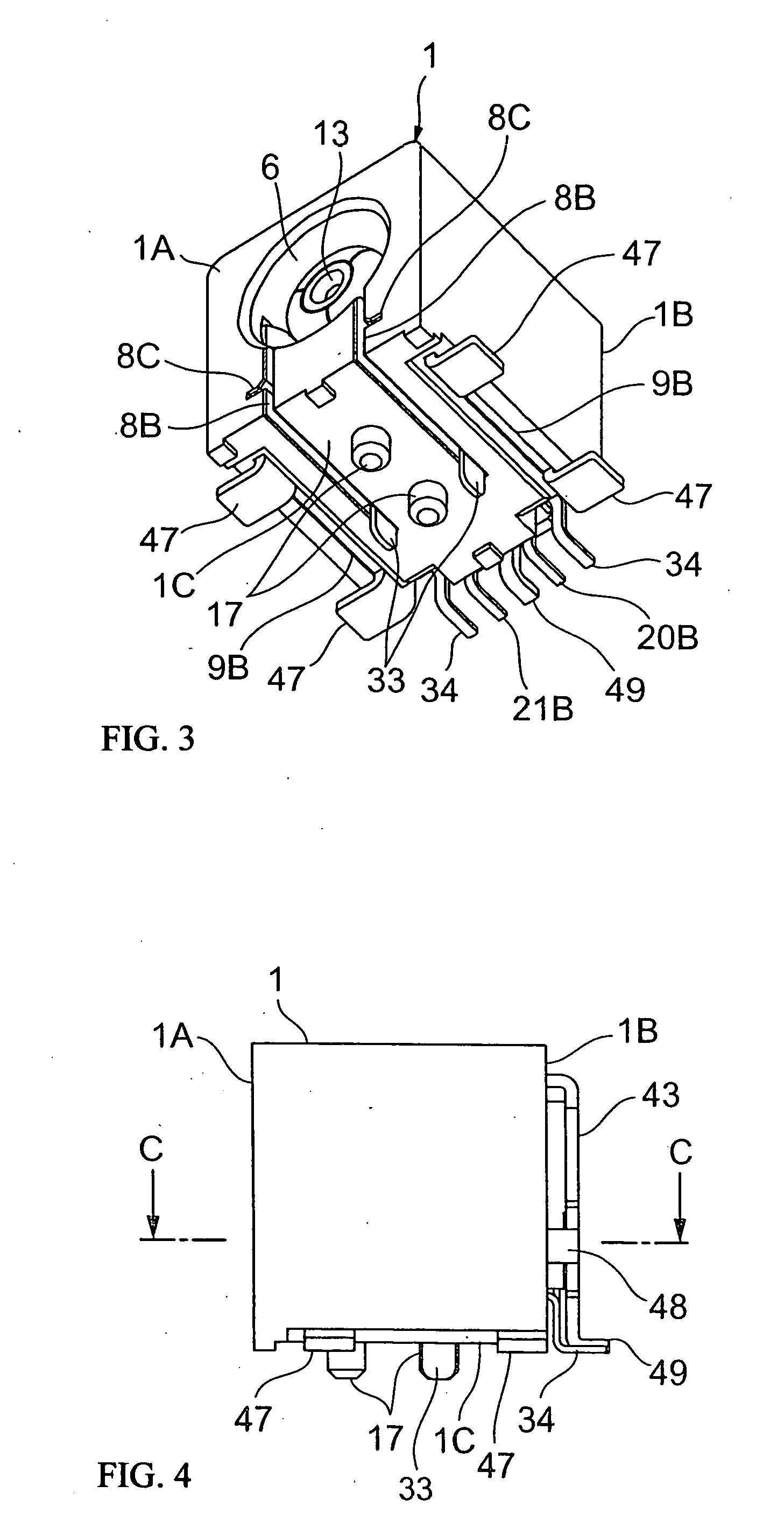
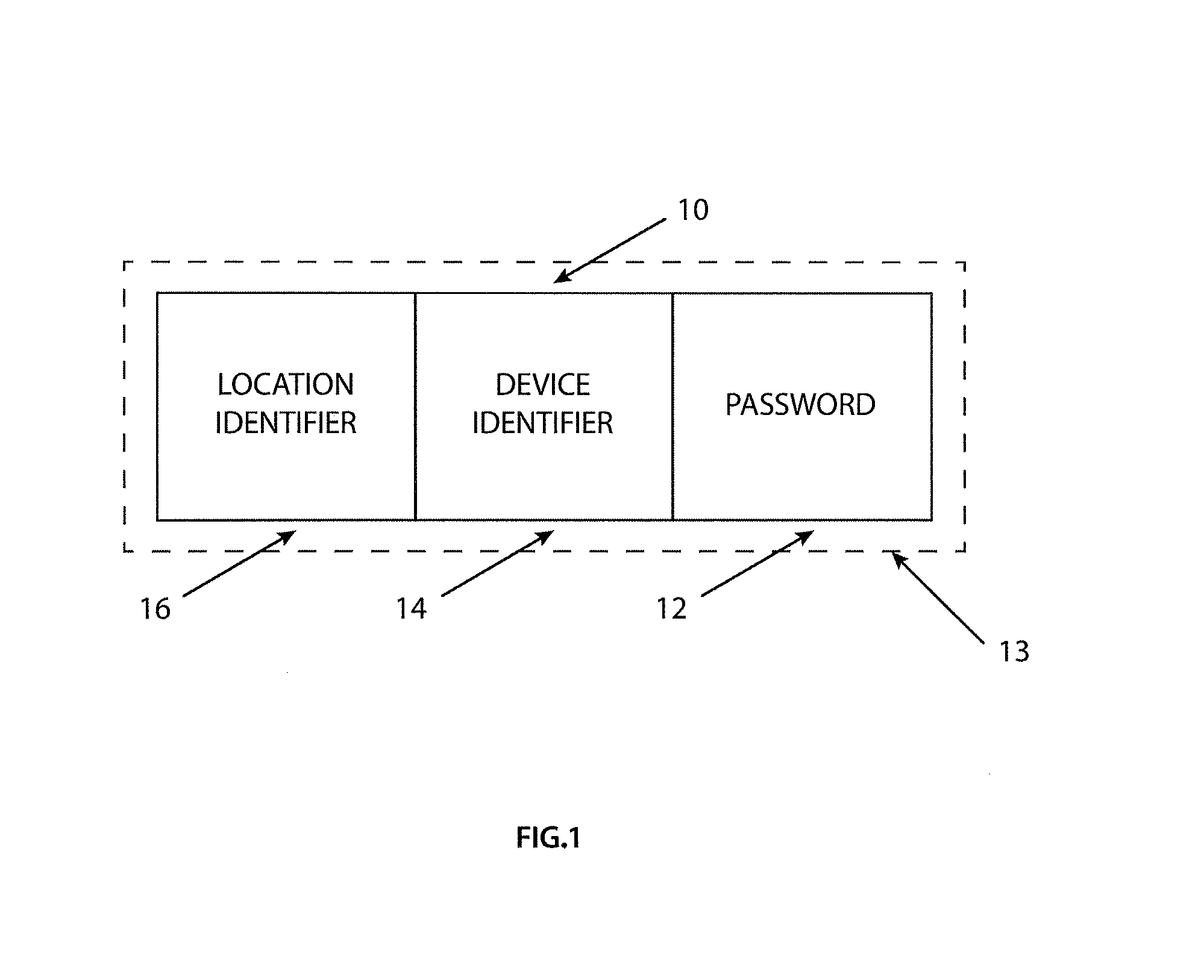
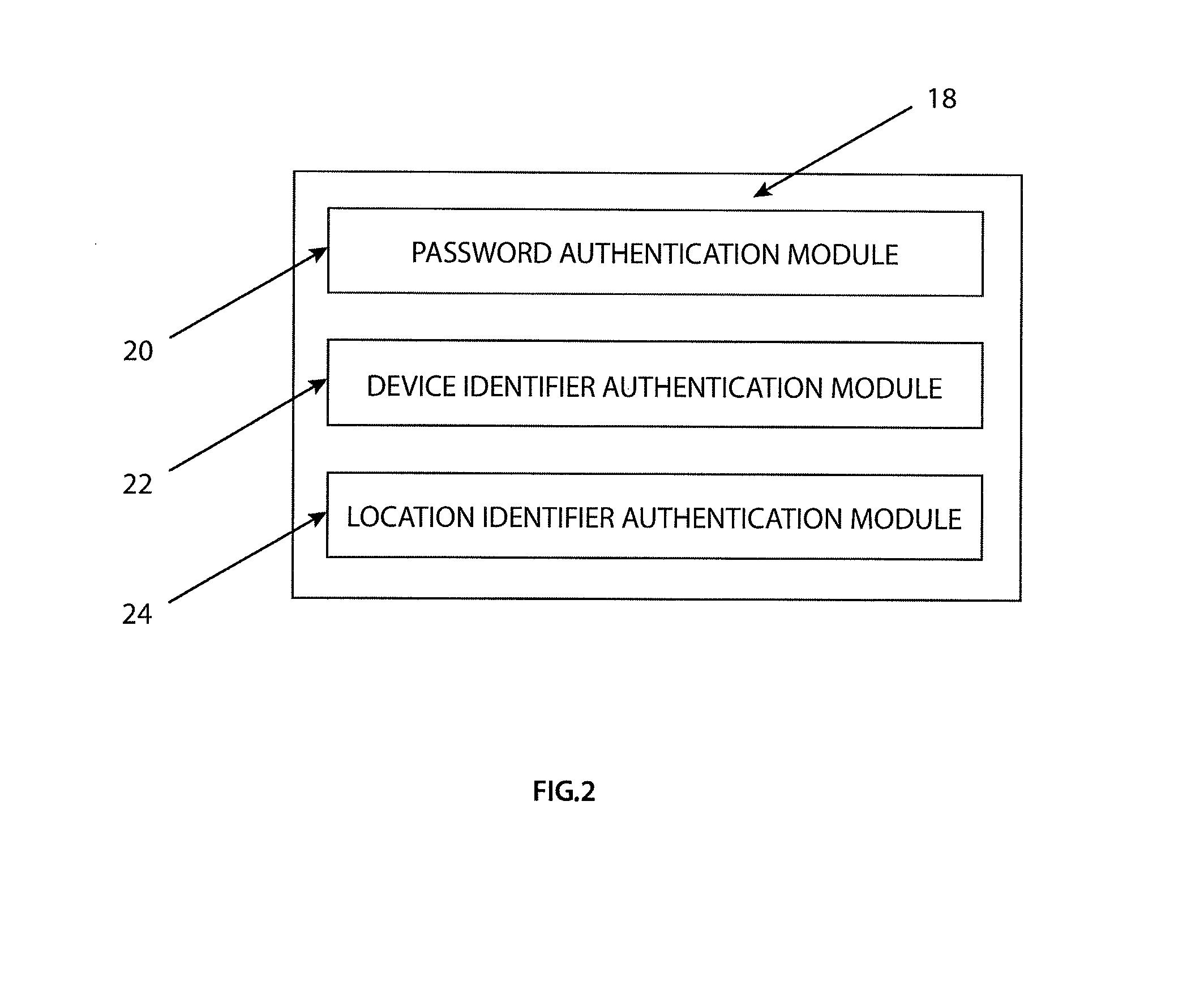
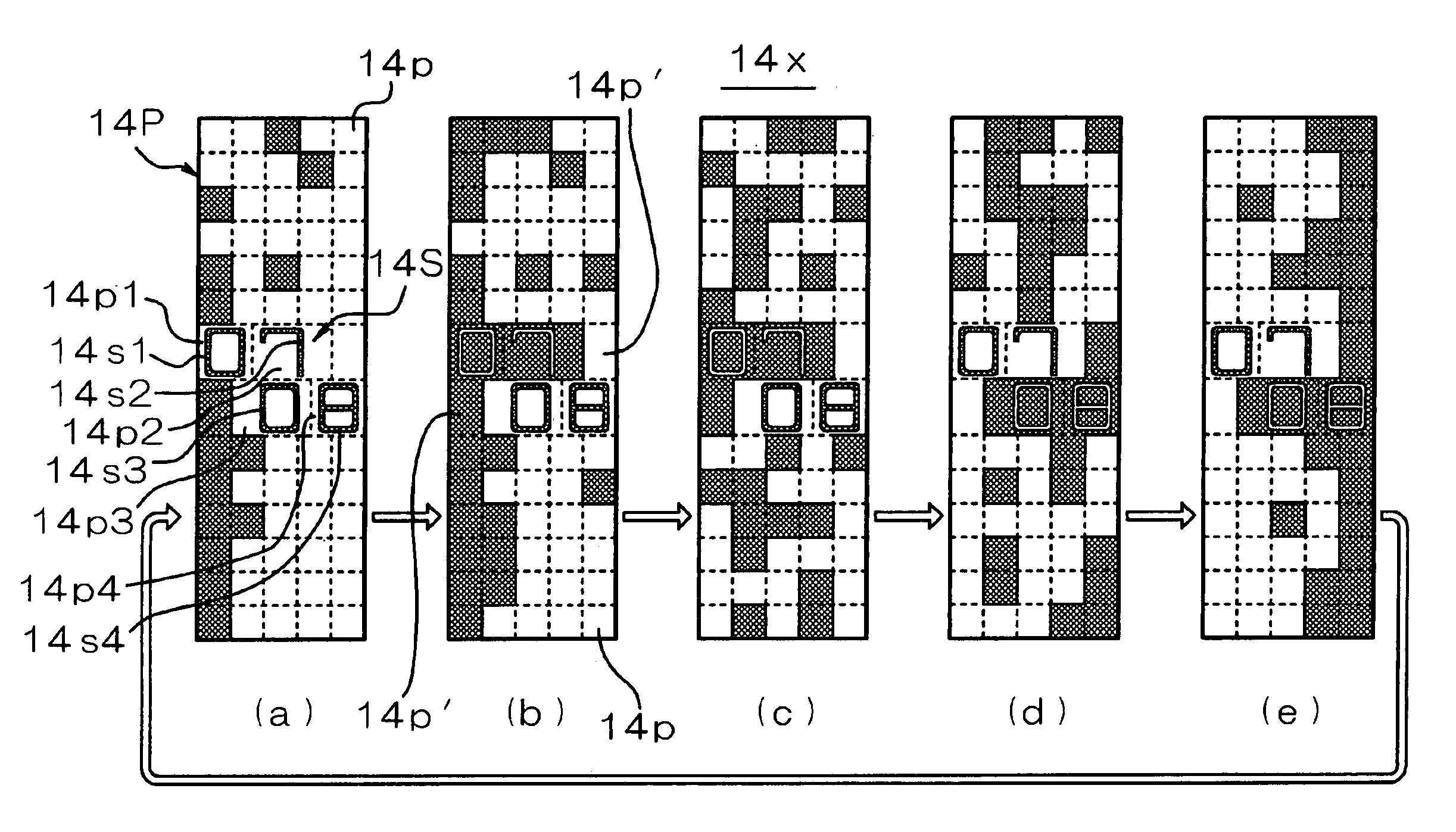
Belt driving control apparatus and image forming apparatus which uses a moving average process and a revolution average process
ActiveUS7386262B2Stability of speed variationSimple structureElectrographic process apparatusMoving averageElectric machine
A belt driving control apparatus, the belt driving control apparatus having an endless belt, a driving roller driving the endless belt, a driving motor driving the driving roller, at least one idler roller being dependent on the endless belt, and an encoder attached to one idler roller. The belt driving control apparatus includes a structure where a control target value of the driving motor is set so that an effective speed of the endless belt is constant and the driving motor is drive-controlled so that the control target value is satisfied.
Owner:RICOH KK
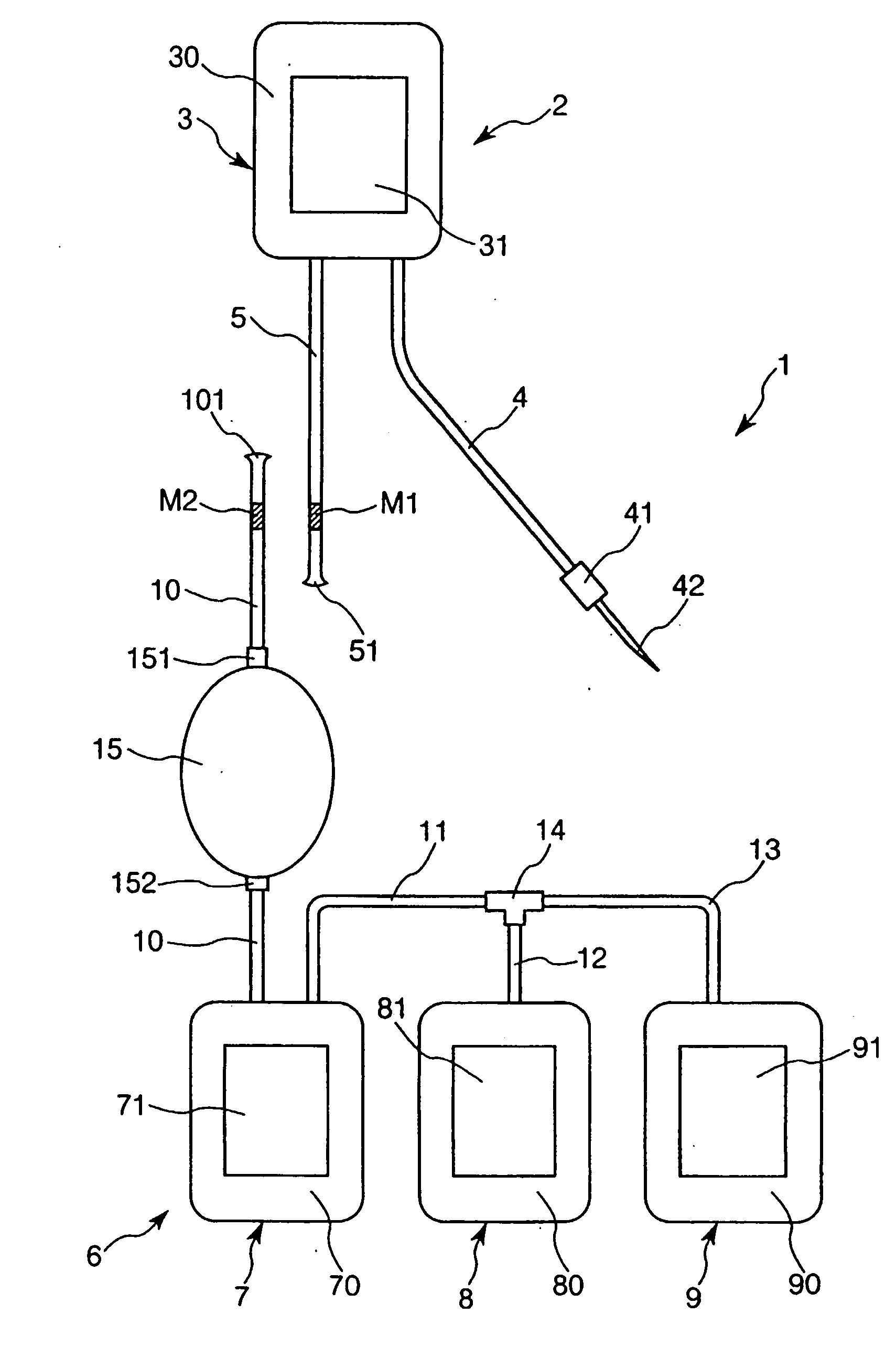
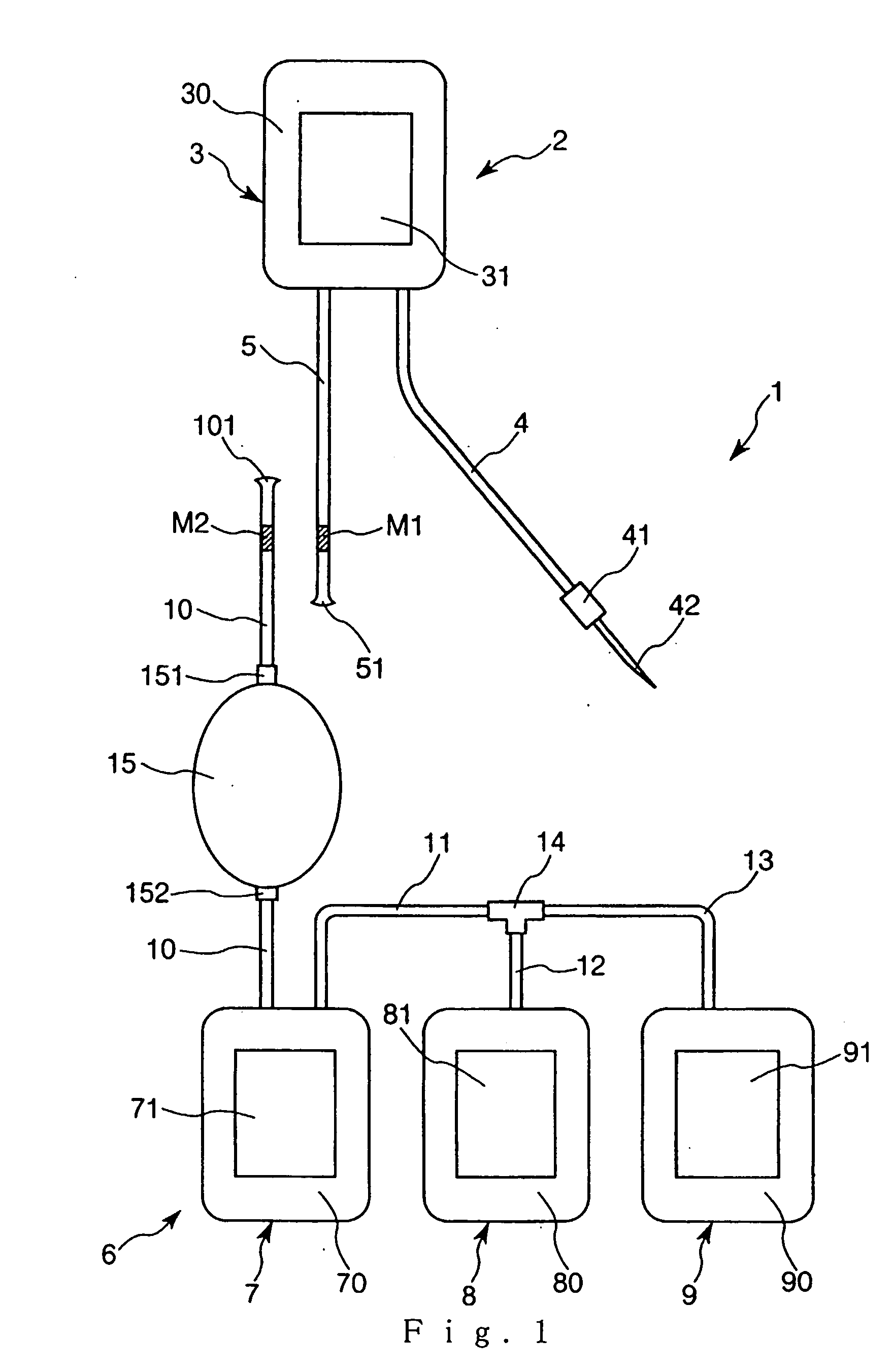
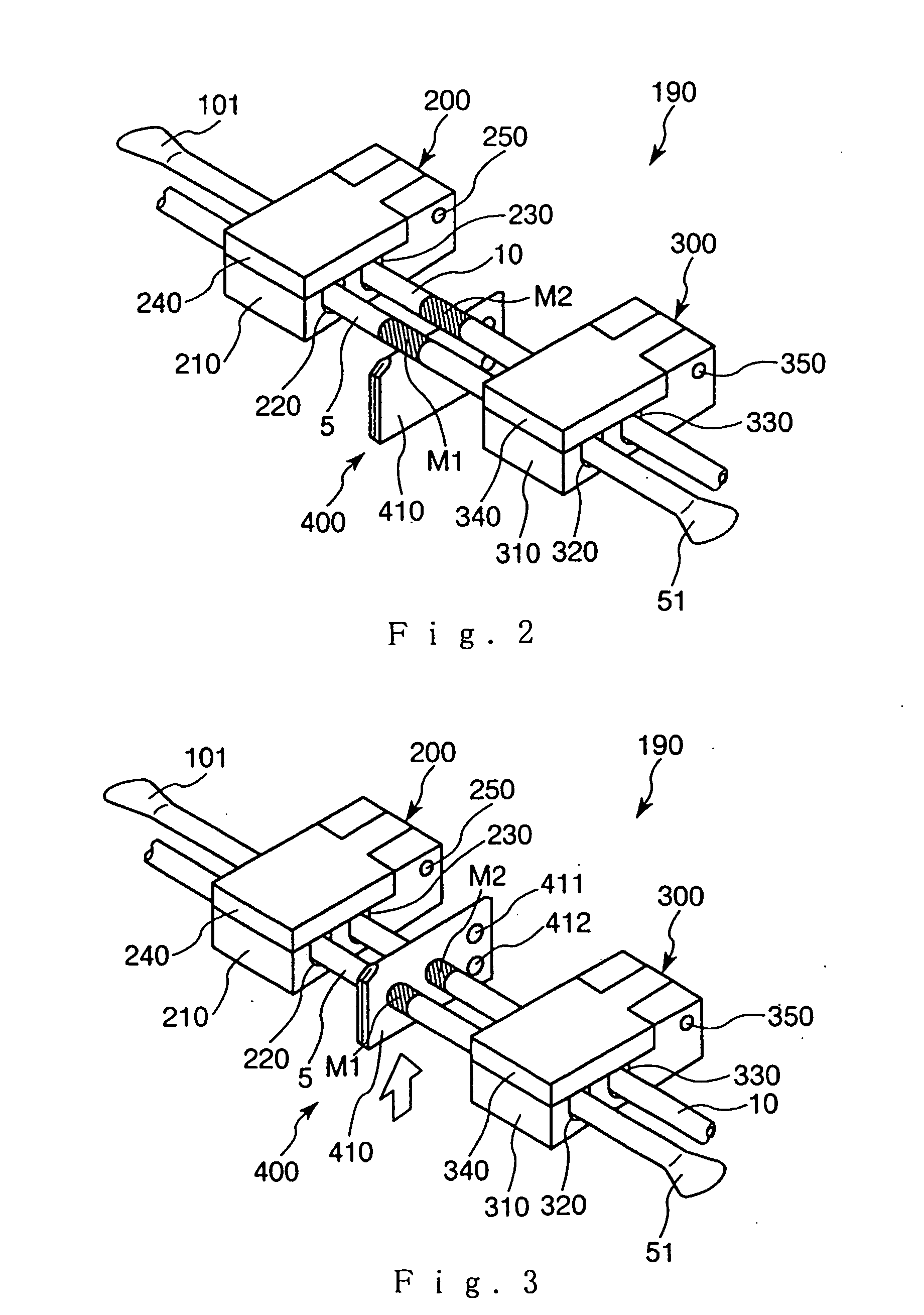
Blood treating set and cell treating set
A blood treating set, including a blood collecting device and a blood treating device, the blood collecting device further including a first bag for storing collected blood, a tube for guiding blood into the first bag, and a tube for discharging blood from the first bag. The blood treating device further includes a connected bag body having three bags, that are, a second bag for storing haematosis, a third bag, and a fourth bag. These bags are connected to each other through the tubes and a branch connector. Also, the tube connected to the second bag includes a filter installed midway in the tube. On the tube connected to the first bag and the tube connected to the filter, indications (markers) are placed at positions to show where these portions must be connected.
Owner:TERUMO KK
Coaxial connector
InactiveUS20050245104A1Satisfactory high-frequency performanceSecurely makingElectrically conductive connectionsTwo pole connectionsElectrical conductorEngineering
Owner:HIROSE ELECTRIC GROUP
System and method for monitoring environmental conditions
ActiveUS7916015B1Securely makingMinimize false alertsAlarmsElectric signalling detailsMonitoring systemBase64
A monitoring system and method for detecting environmental conditions is provided, the monitoring system including a sensing unit including a plurality of sensors for obtaining data related to environmental conditions, a controller interfaced with the sensing unit for receiving and encoding the data related to environmental conditions into a predetermined format using a base64 encoding scheme, and a communication device for receiving the data in the predetermined format from the controller, forming an e-mail message (which can be further encoded) including instructions on how to decode the email message and transmitting the e-mail message including the data in the predetermined format to at least one predetermined recipient.
Owner:THE JOHN HOPKINS UNIV SCHOOL OF MEDICINE
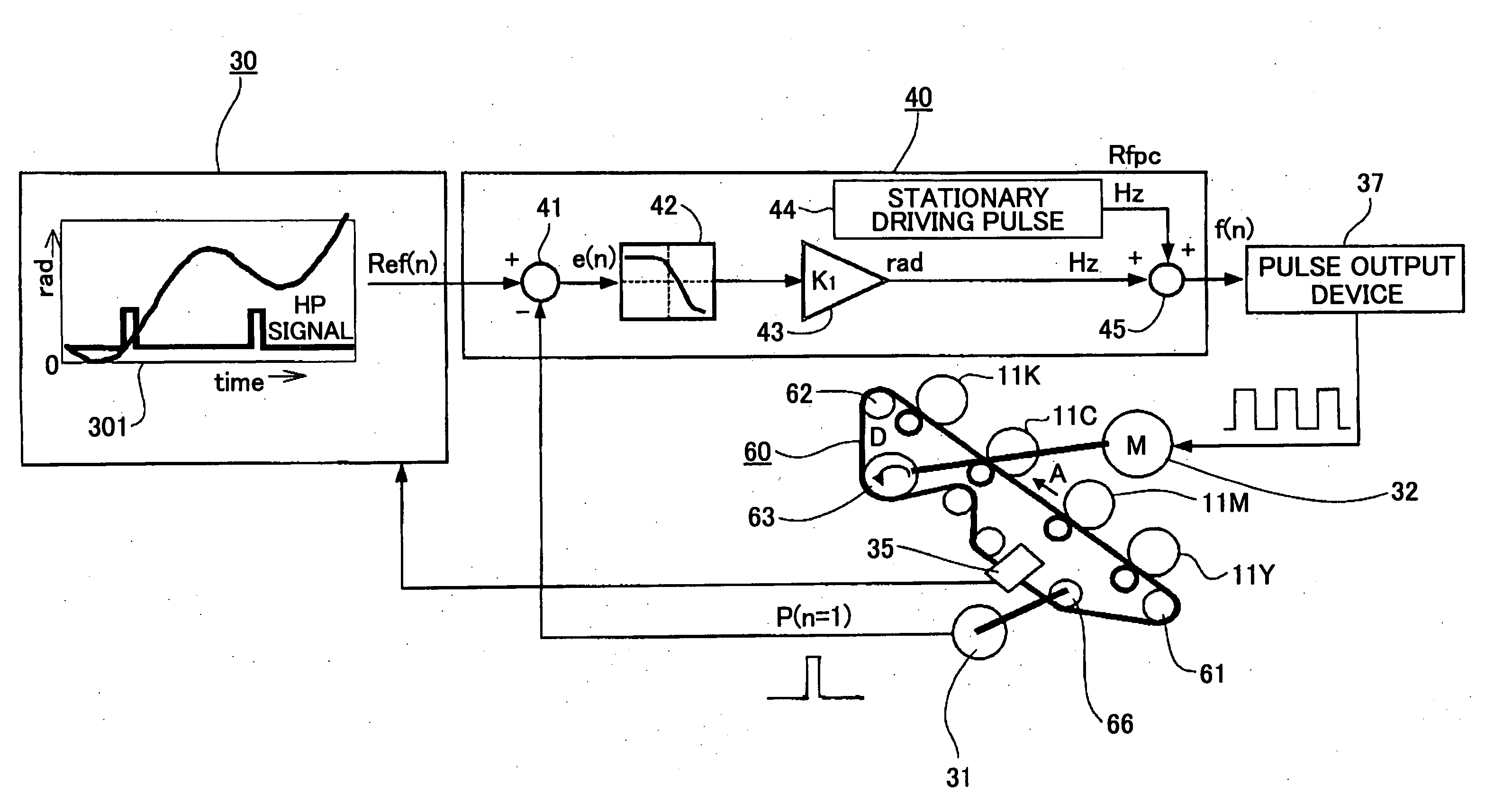
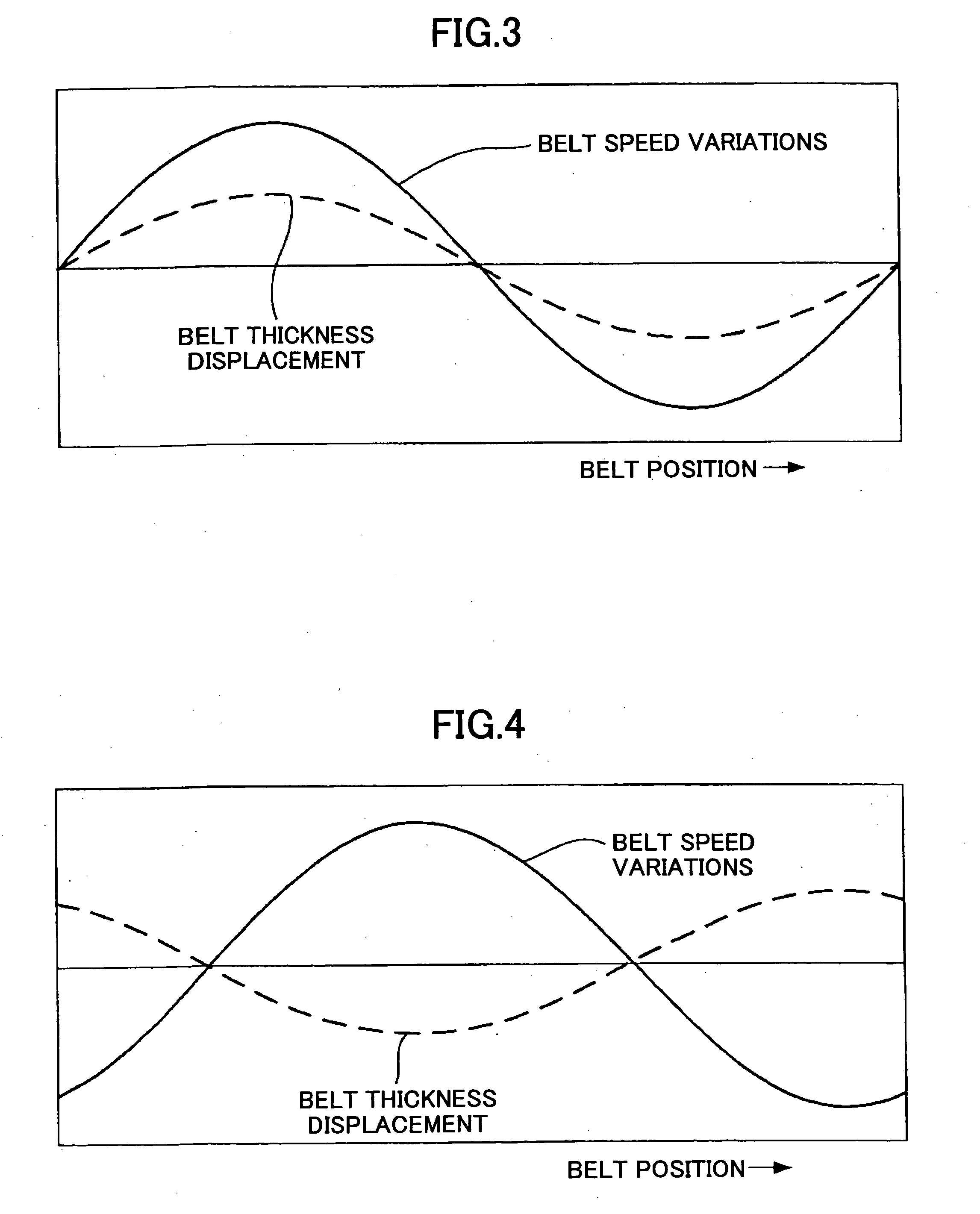
Belt driving control apparatus and image forming apparatus
ActiveUS20060182471A1Securely makingSimple structureElectrographic process apparatusDrive motorEngineering
A belt driving control apparatus, the belt driving control apparatus having an endless belt, a driving roller driving the endless belt, a driving motor driving the driving roller, at least one idler roller being dependent on the endless belt, and an encoder attached to one of the idler roller, the belt driving control apparatus includes a structure where a control target value of the driving motor is set so that an effective speed of the endless belt is constant and the driving motor is drive-controlled so that the control target value is satisfied.
Owner:RICOH KK
Method for secure mobile payment and RF tag with integrated Anti-theft device
An RF tag with integrated anti-theft device allows a user, having a mobile device, to perform a secure purchasing application where the user uses the camera of the mobile device to read a barcode of a product and an RF tag with an integrated anti-theft device. The user can select the product he wishes to buy, check the information concerning that product, purchase the product, and disable the anti-theft device to go through a security portal without triggering the alarm.
Owner:SAMSUNG ELECTRONICSA AMAZONIA
Adaptor for cable connector
ActiveUS7625231B2Easily dismountedSecurely makingEngagement/disengagement of coupling partsCoupling contact membersElectrical connectionEngineering
An adapter for a cable connector secured with a cable end portion to make the electrical connection by being removably mounted on a receptacle of the cable connector includes a pair of operation portions, a pair of guide pins integrally formed in front of the operation portions and each having a pointed end portion at the front, a protection portion for connecting the operation portions at the rear lower part, a connection portion for connecting the operation portions at the front upper part, and a reinforcing portion for connecting the pair of guide pins, wherein the protection portion and the connection portion have an interval in the longitudinal and vertical directions and are disposed in parallel to each other, and the lower surfaces of the connection portion and the reinforcing portion are continuous flush to form a stationary surface for securing the cable end portion.
Owner:YAMAICHI ELECTRONICS
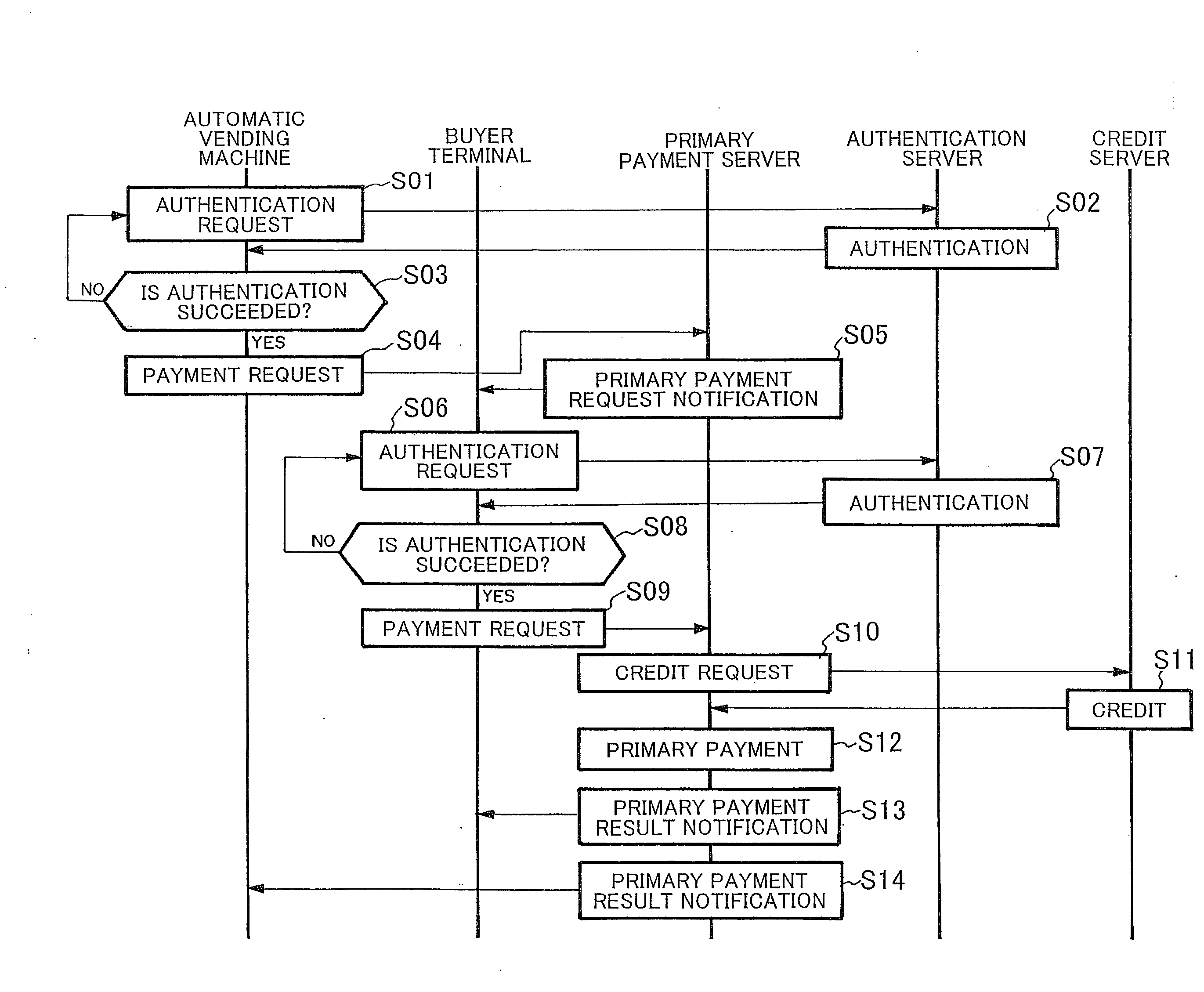
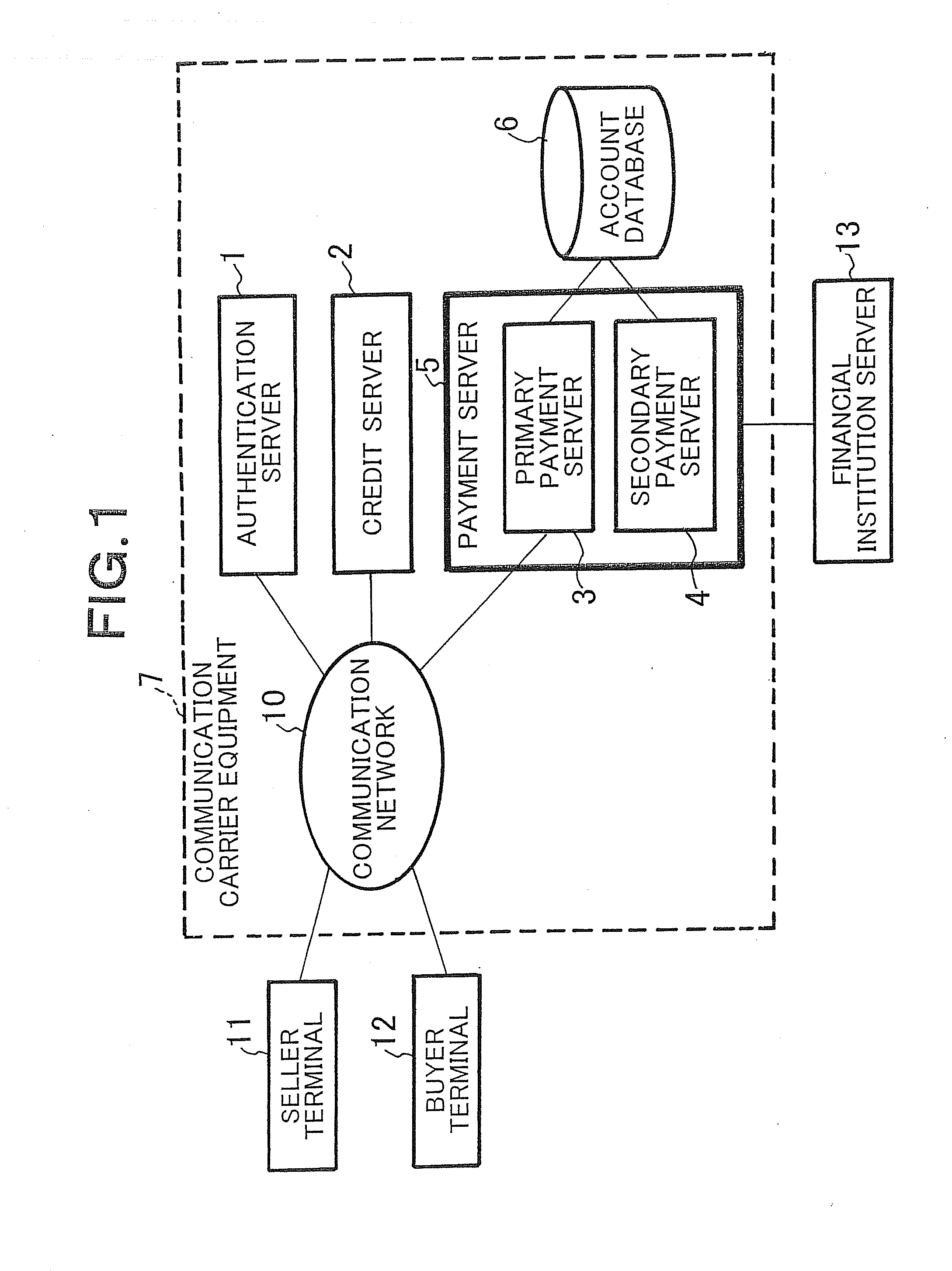
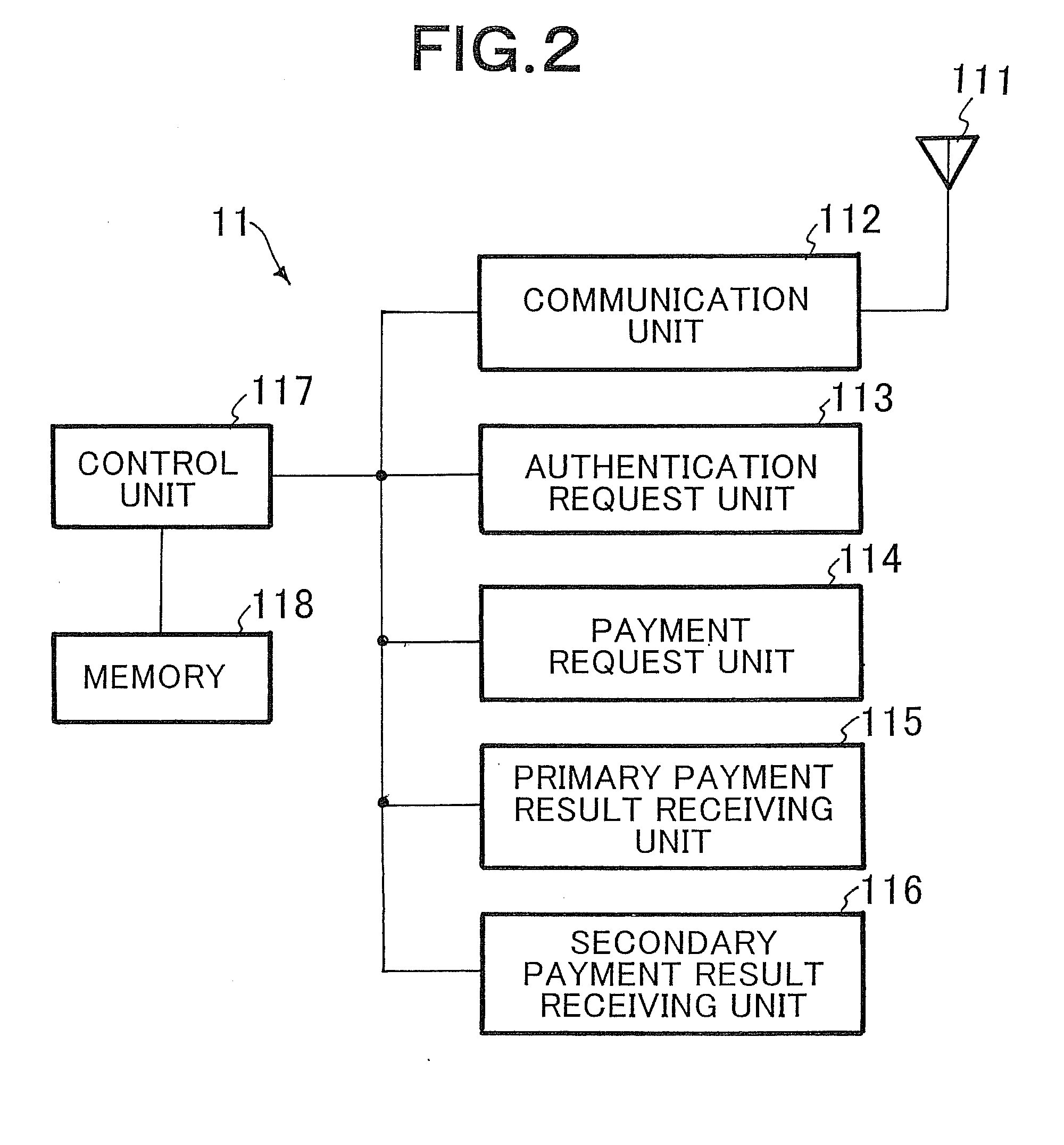
System and method for electronic payment, and server, communication terminal and program therefor
InactiveUS20100223187A1Increase speedImprove reliabilityFinanceDigital data processing detailsClosed loopComputer terminal
A secure, inexpensive, convenient payment system which allows an existing communication to be used to make an expensive payment terminal unnecessary, makes local communication unnecessary to make it possible to use the system by a seller and a buyer, uses closed-loop type electronic money to make it possible to make payment on delivery is obtained. An account database 6 which is arranged as equipment of a communication carrier and manages accounts of sellers and buyers (users), and a payment server 5 which is arranged as equipment of the communication carrier and performs an electronic payment process between the seller and the buyer are arranged. In the payment server 5, a primary payment server 3 and a secondary payment server 4 are arranged. When a payment request from a user is received through a communication network 10, the primary payment server 3 refers to the account database 6 to perform a real-time payment process by electronic money as primary payment between accounts of the seller and the buyer. Secondary payment is performed between the financial institution server 13 and the secondary payment server 4 in a predetermined period of time thereafter.
Owner:NEC CORP
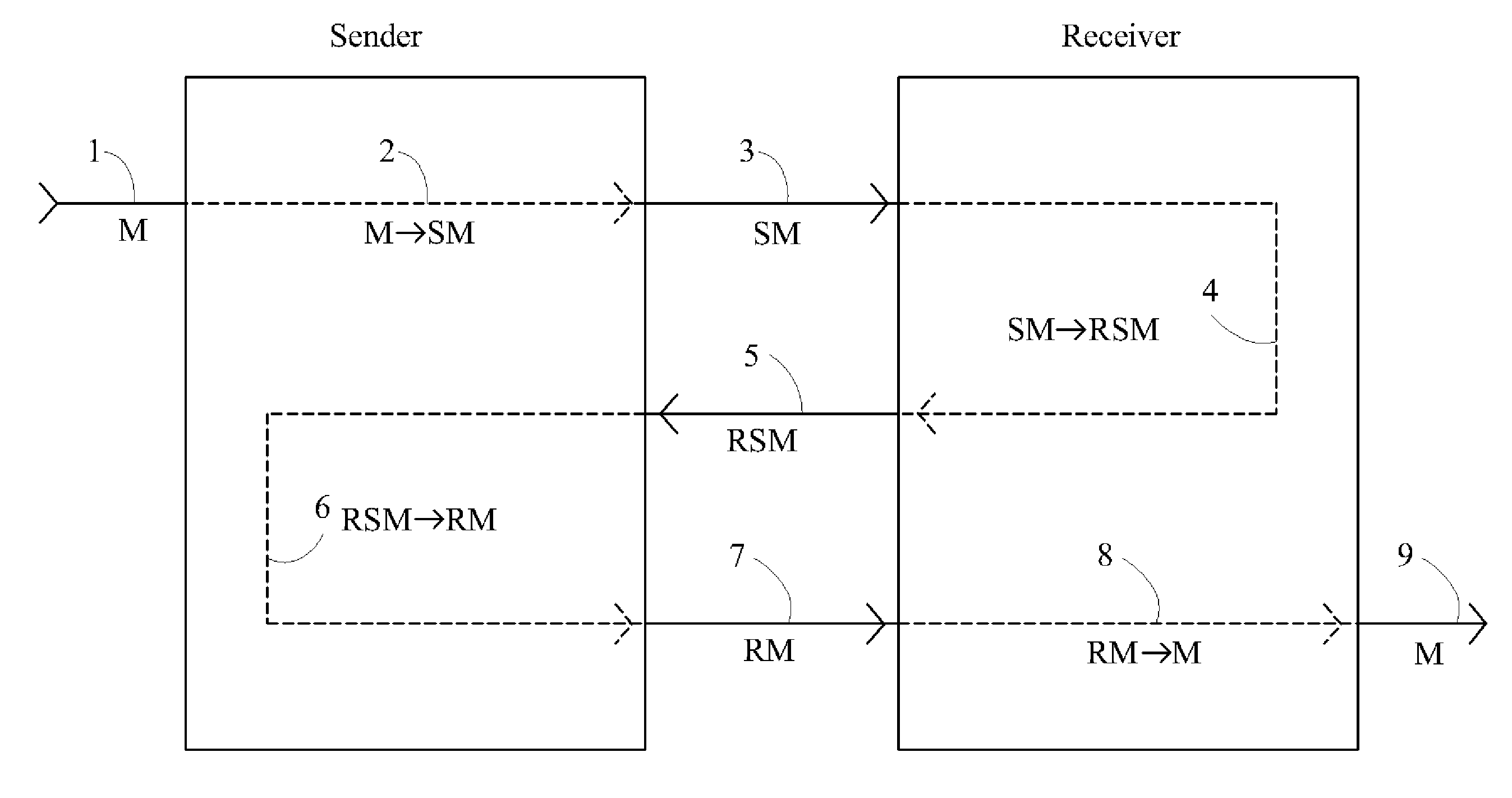
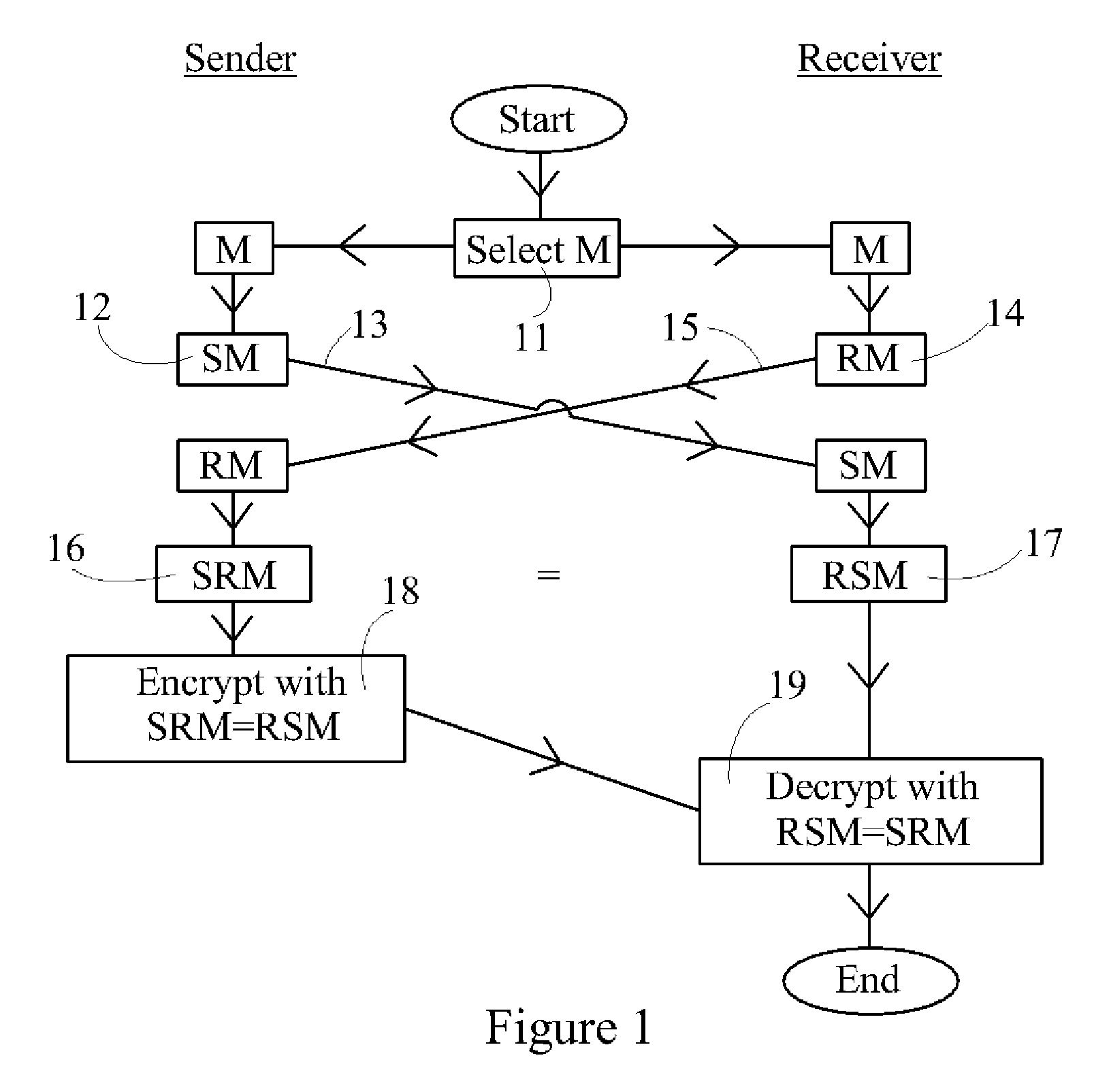
Device, System and Method for Fast Secure Message Encryption Without Key Distribution
InactiveUS20070297614A1None of methods is secureMethod is fastKey distribution for secure communicationEncryption apparatus with shift registers/memoriesS/KEYKey distribution
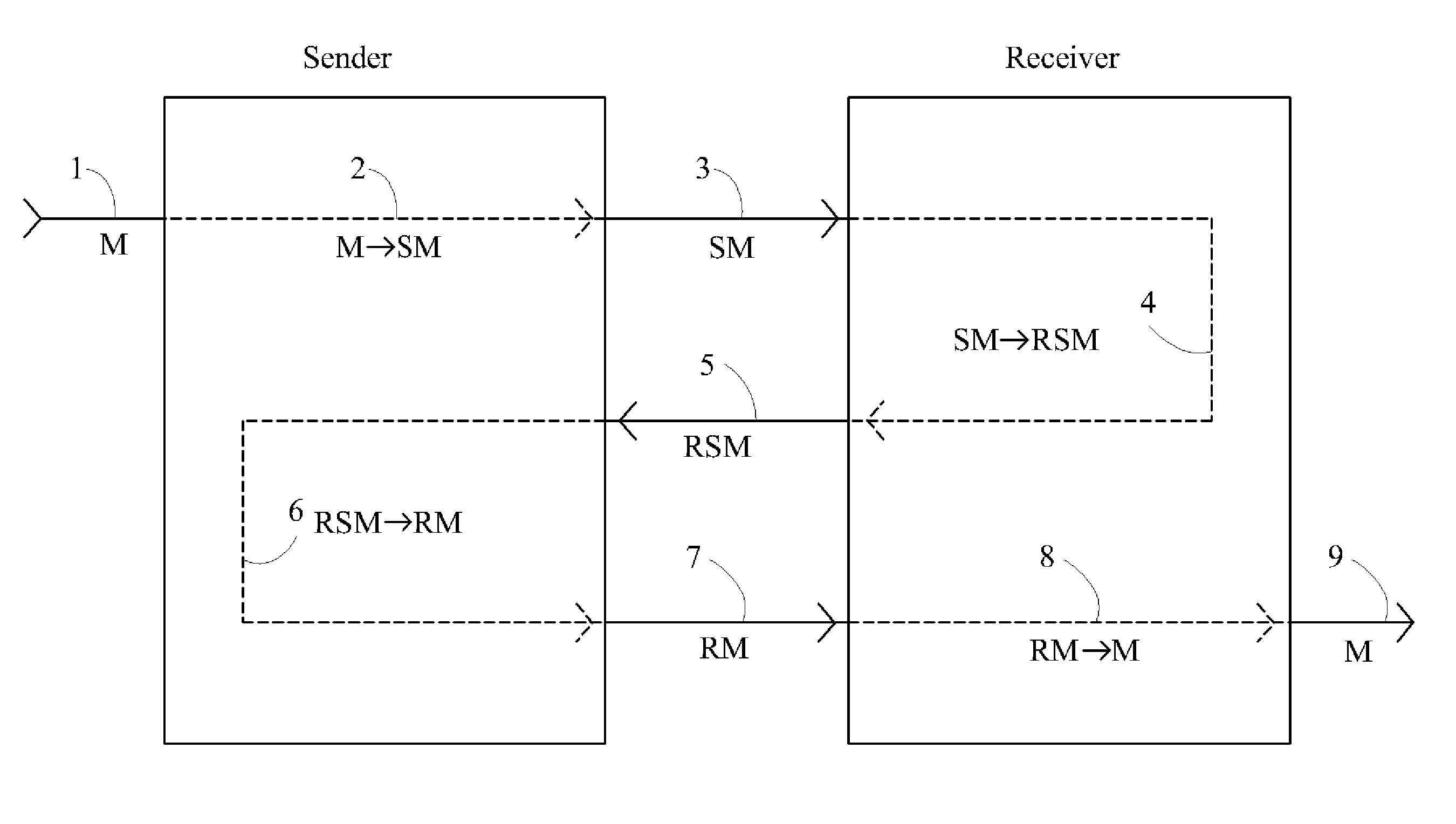
One party sends a securely encrypted message to a second party. Each party chooses a secret message key for the message, which is never shared with or transmitted to any other party. The message is sent by means of three encrypted messages. The first encrypted message is sent from the sender to the receiver, and is encrypted by the sender's key. The second encrypted message is sent from the receiver back to the sender, and is encrypted by both the sender's key and then by the receiver's key. The third encrypted message is sent from the sender back to the receiver, and is encrypted by only the receiver's key following removal of the sender's key. Finally, the receiver decrypts the third message. The messages are sent in blocks. Encryption consists of multiplying each block of the message by square matrices of the same size as the block, and decryption consists of multiplying by the inverse matrices. The key matrices are taken from one or more large commutative families of matrices. This commutativity allows the sender's keys to be removed even though the message block has been encrypted by the sender's key first and then the receiver's key. Two primary embodiments of the invention are disclosed, using one-sided and two-sided matrix multiplication, respectively.
Owner:RUBIN FR
Device, system and method for fast secure message encryption without key distribution
InactiveUS7907723B2Securely makingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesS/KEYKey distribution
One party sends a securely encrypted message to a second party. Each party chooses a secret message key for the message, which is never shared with or transmitted to any other party. The message is sent by means of three encrypted messages. The first encrypted message is sent from the sender to the receiver, and is encrypted by the sender's key. The second encrypted message is sent from the receiver back to the sender, and is encrypted by both the sender's key and then by the receiver's key. The third encrypted message is sent from the sender back to the receiver, and is encrypted by only the receiver's key following removal of the sender's key. Finally, the receiver decrypts the third message. The messages are sent in blocks. Encryption consists of multiplying each block of the message by a square matrix of the same size as the block, and decryption consists of multiplying by the inverse matrix. The key matrices are taken from one or more large commutative families of matrices. This commutativity allows the sender's keys to be removed even though the message block has been encrypted by the sender's key first and then the receiver's key. Two primary embodiments of the invention are disclosed, using one-sided and two-sided matrix multiplication, respectively.
Owner:RUBIN FR
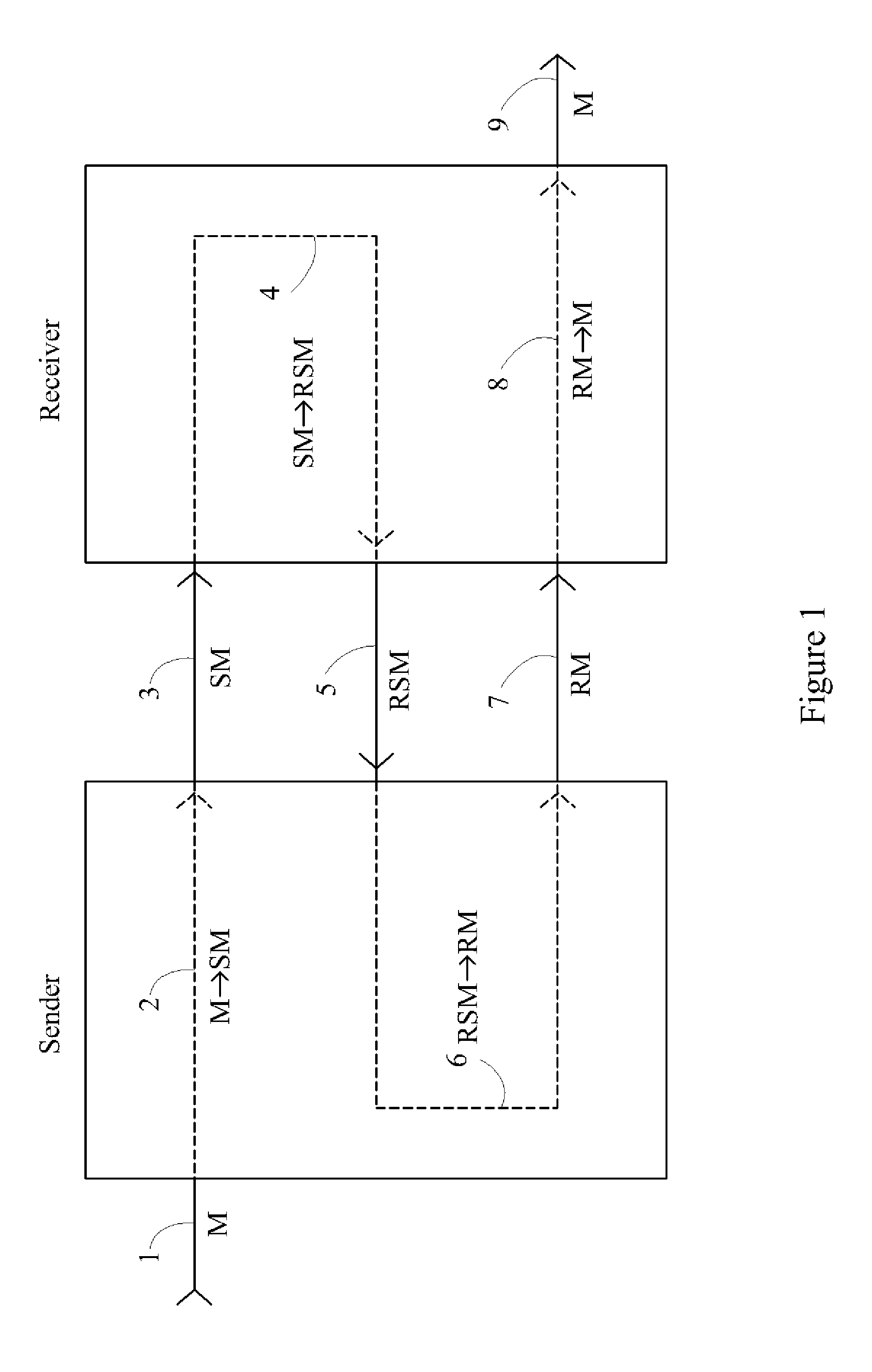
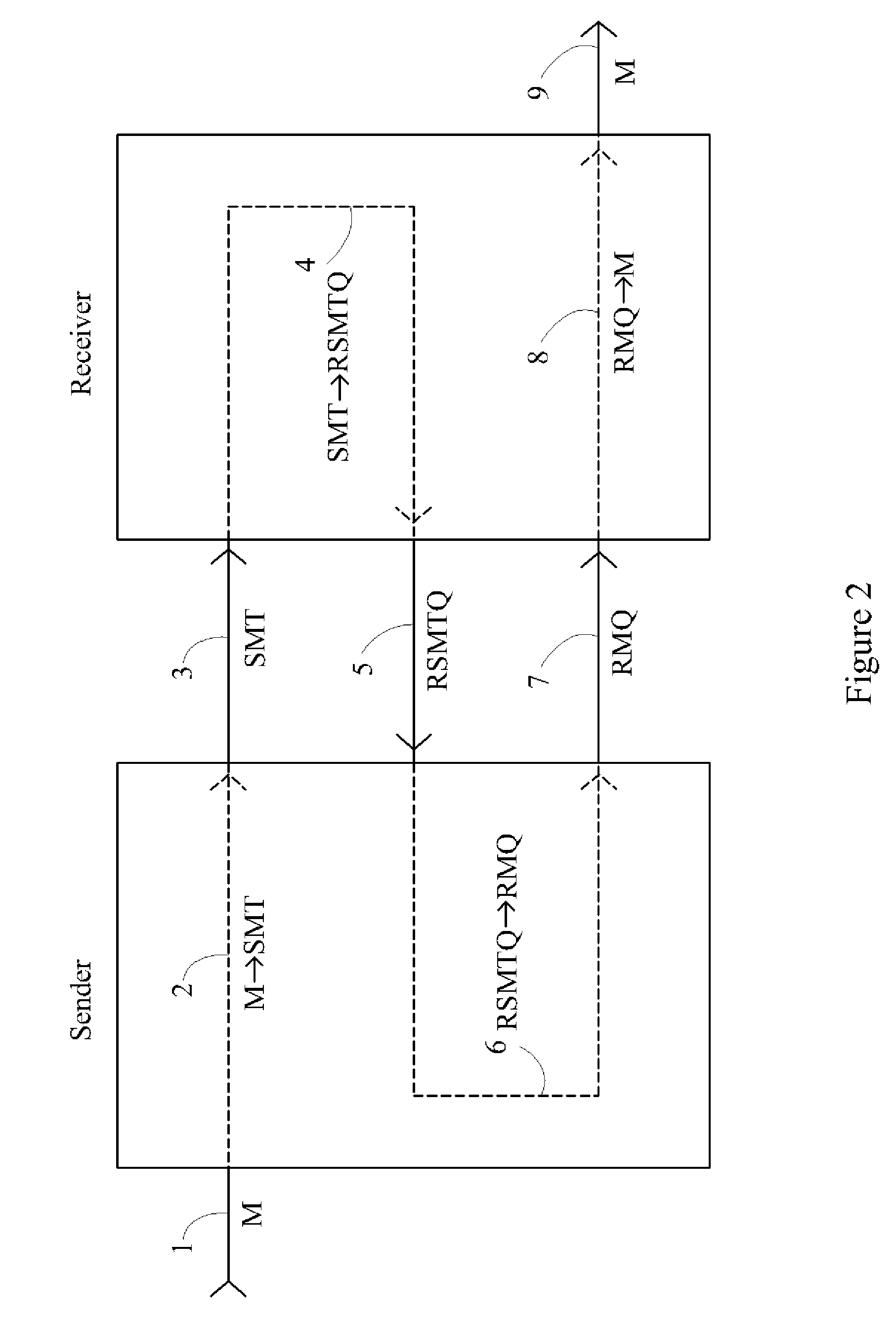
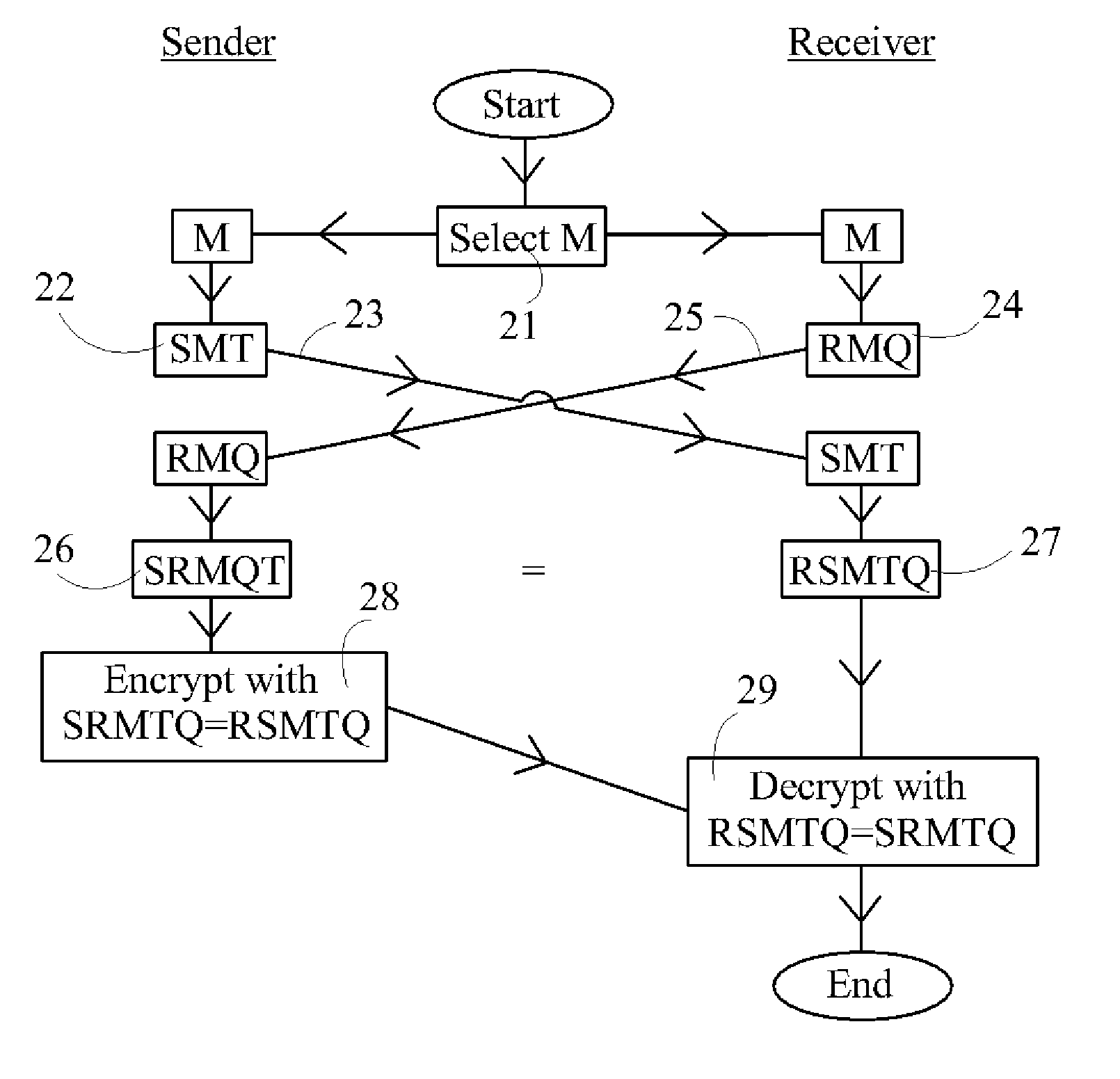
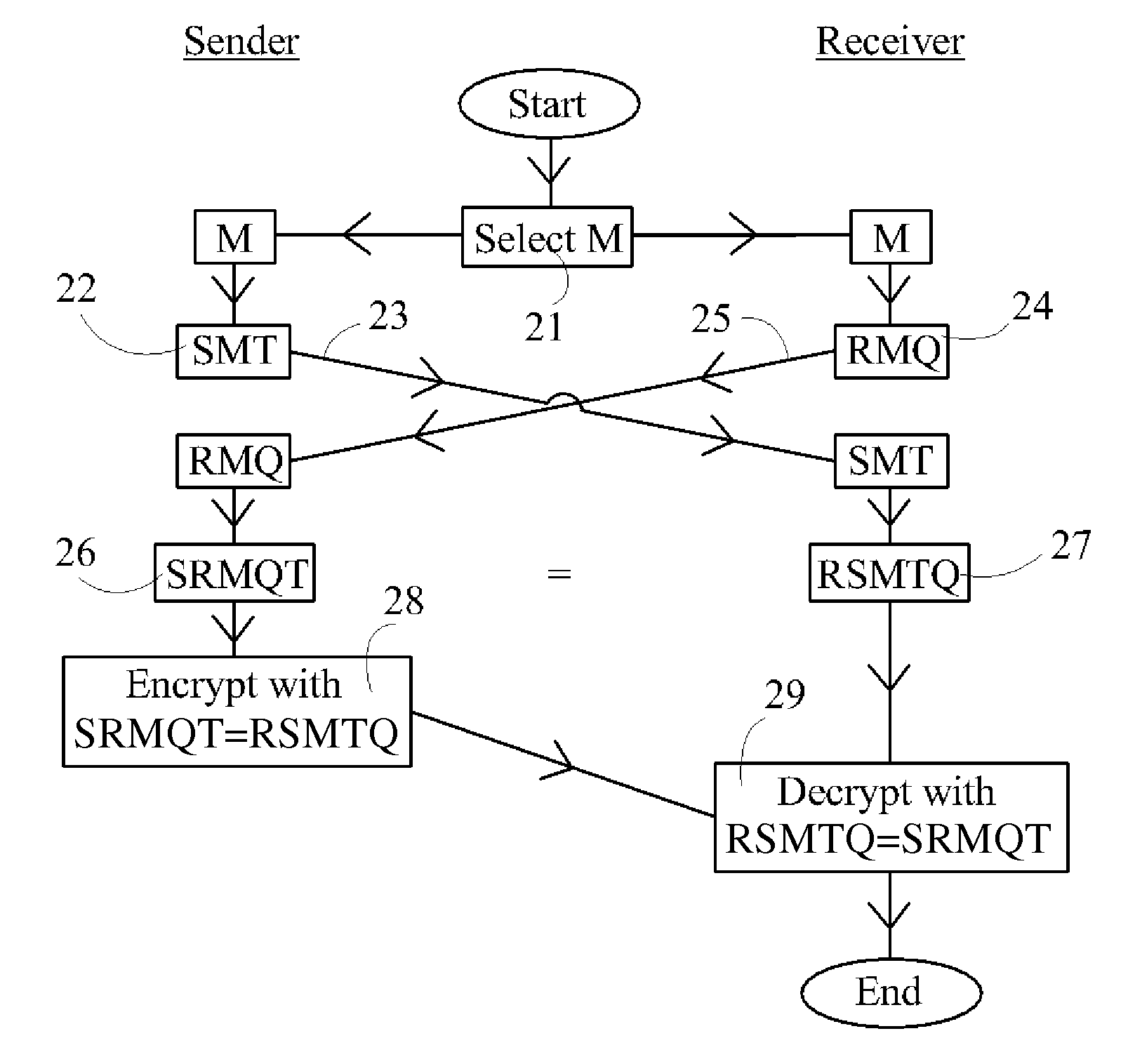
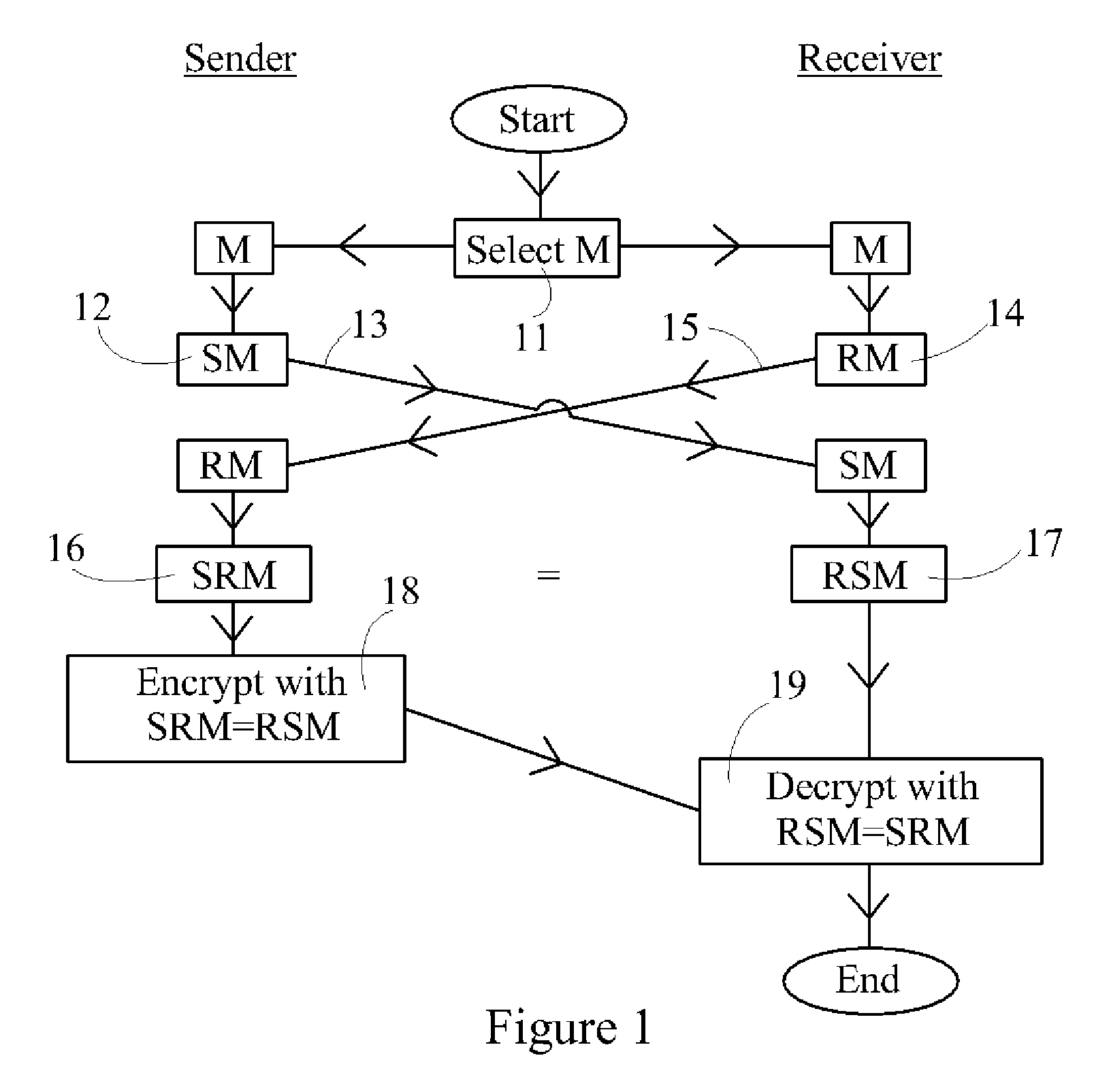
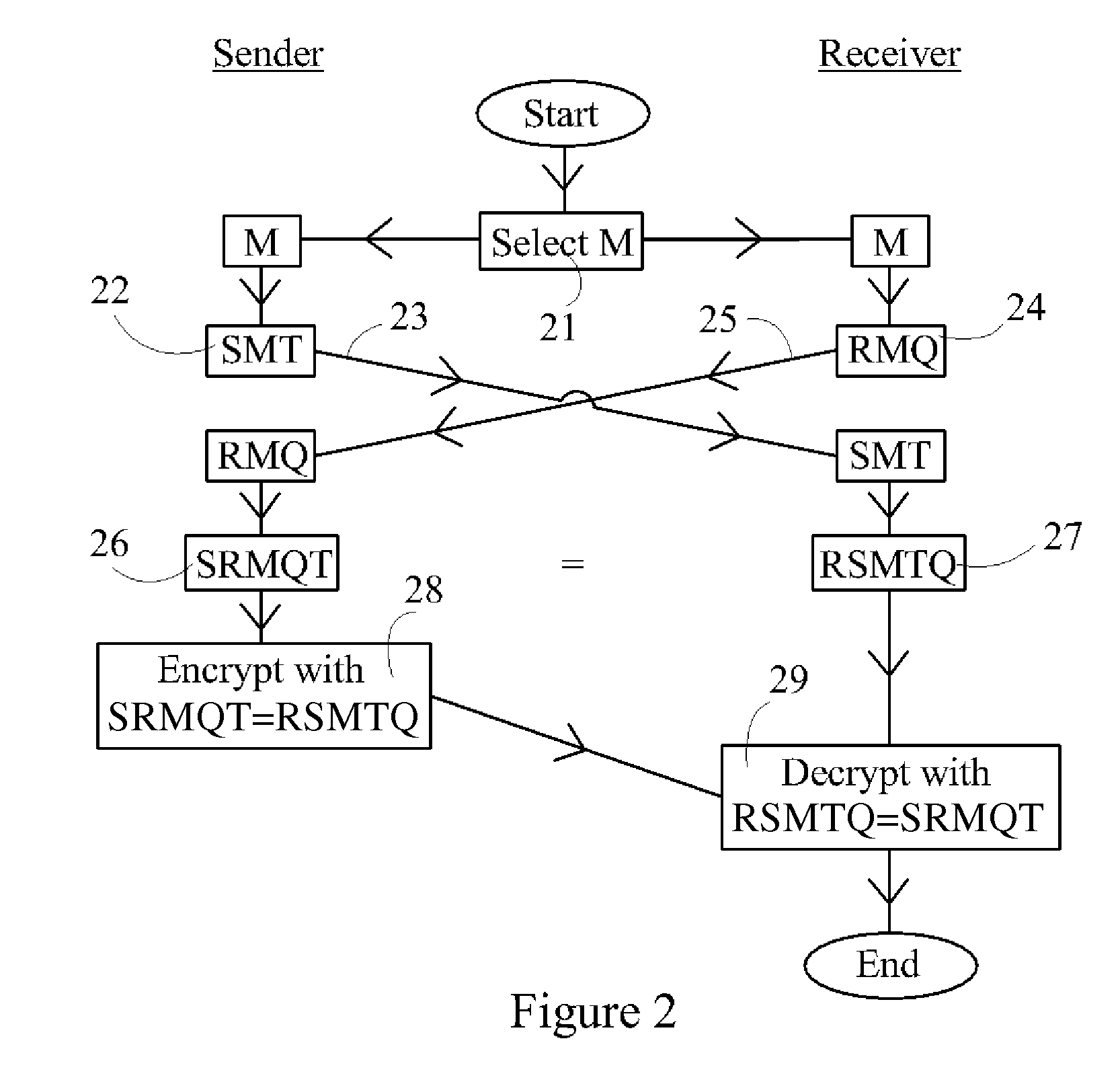
Device, System and Method for Cryptographic Key Exchange
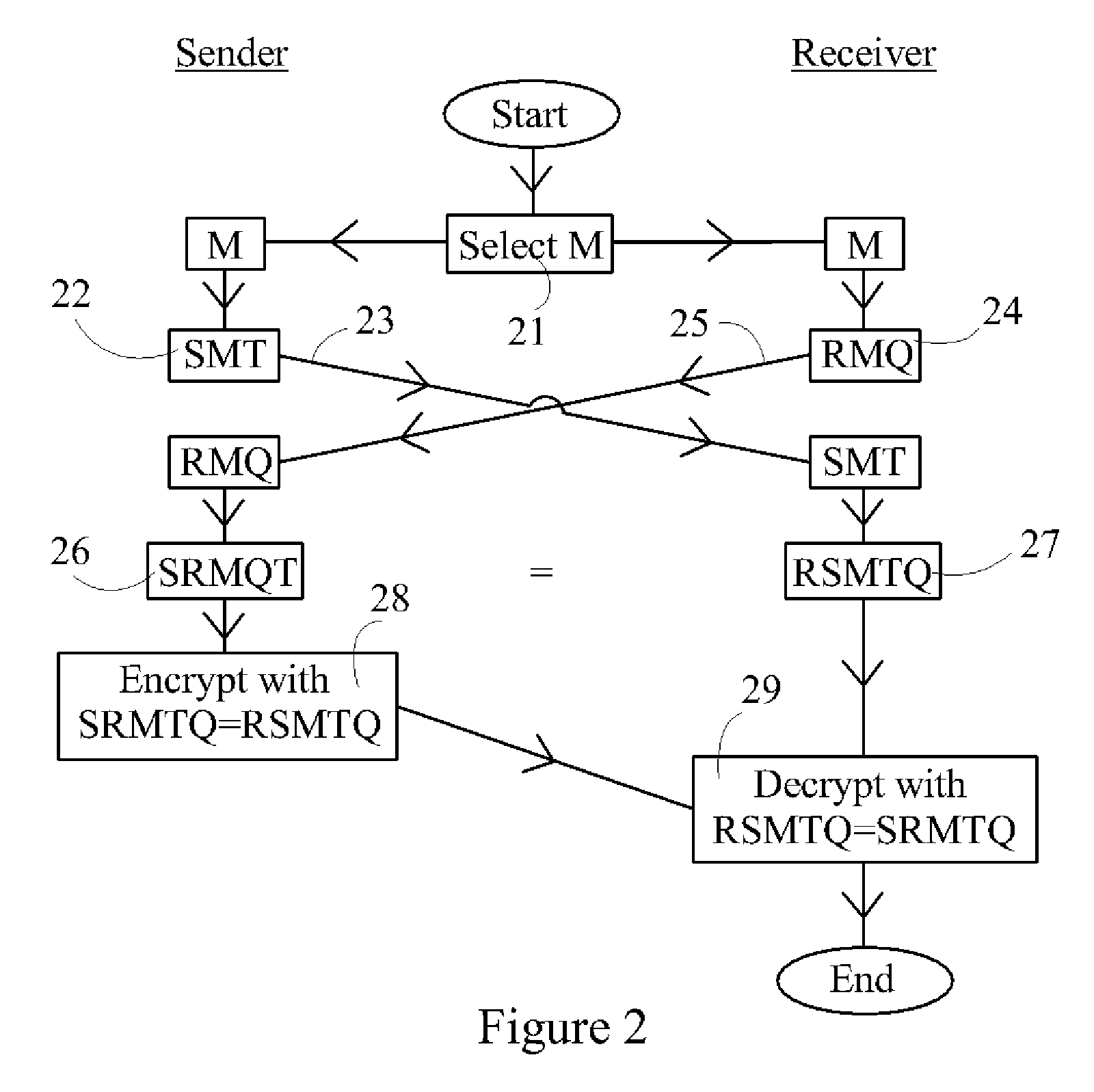
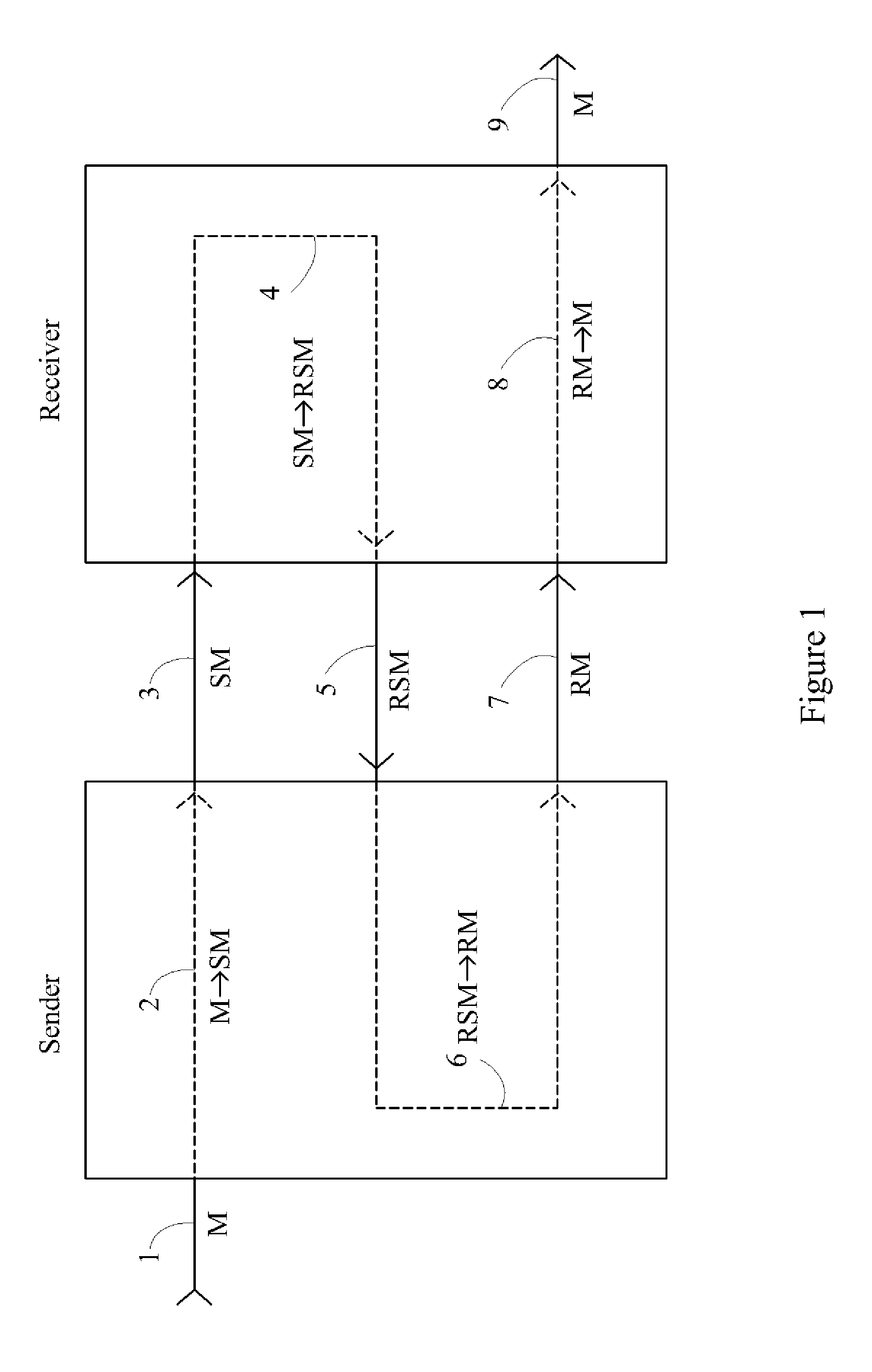
InactiveUS20080069345A1Securely makingSecret communicationSecuring communicationKey exchangeSecure communication
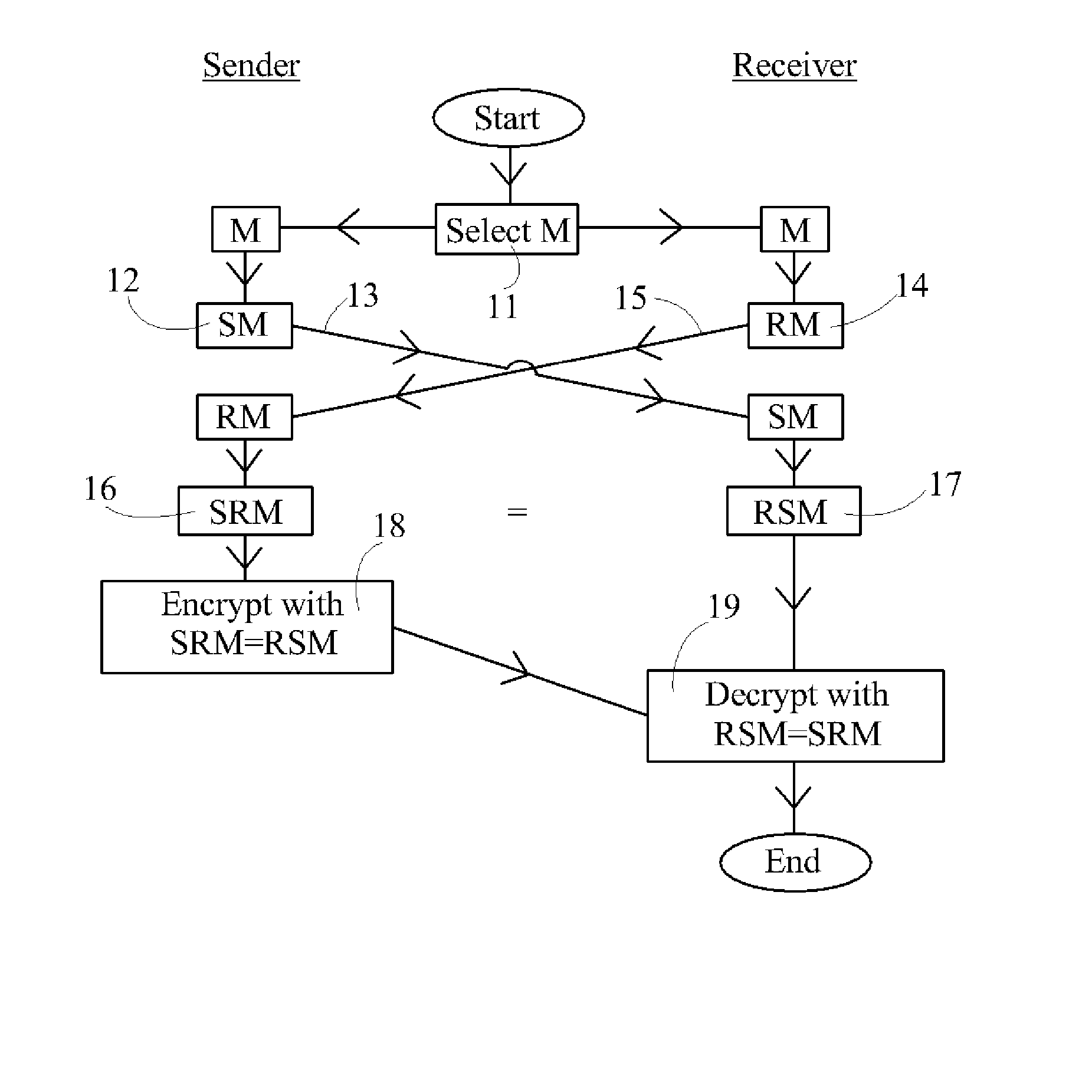
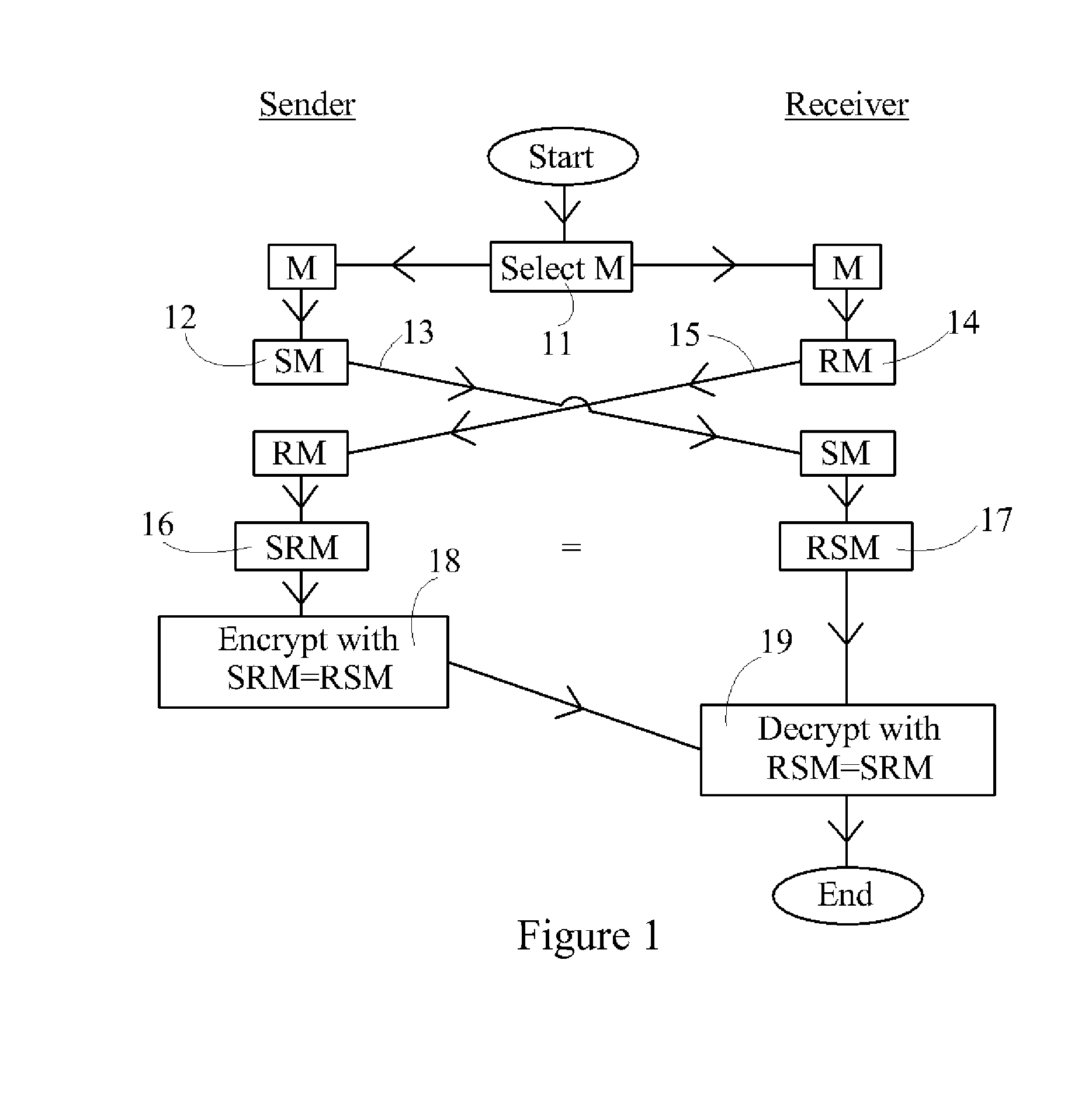
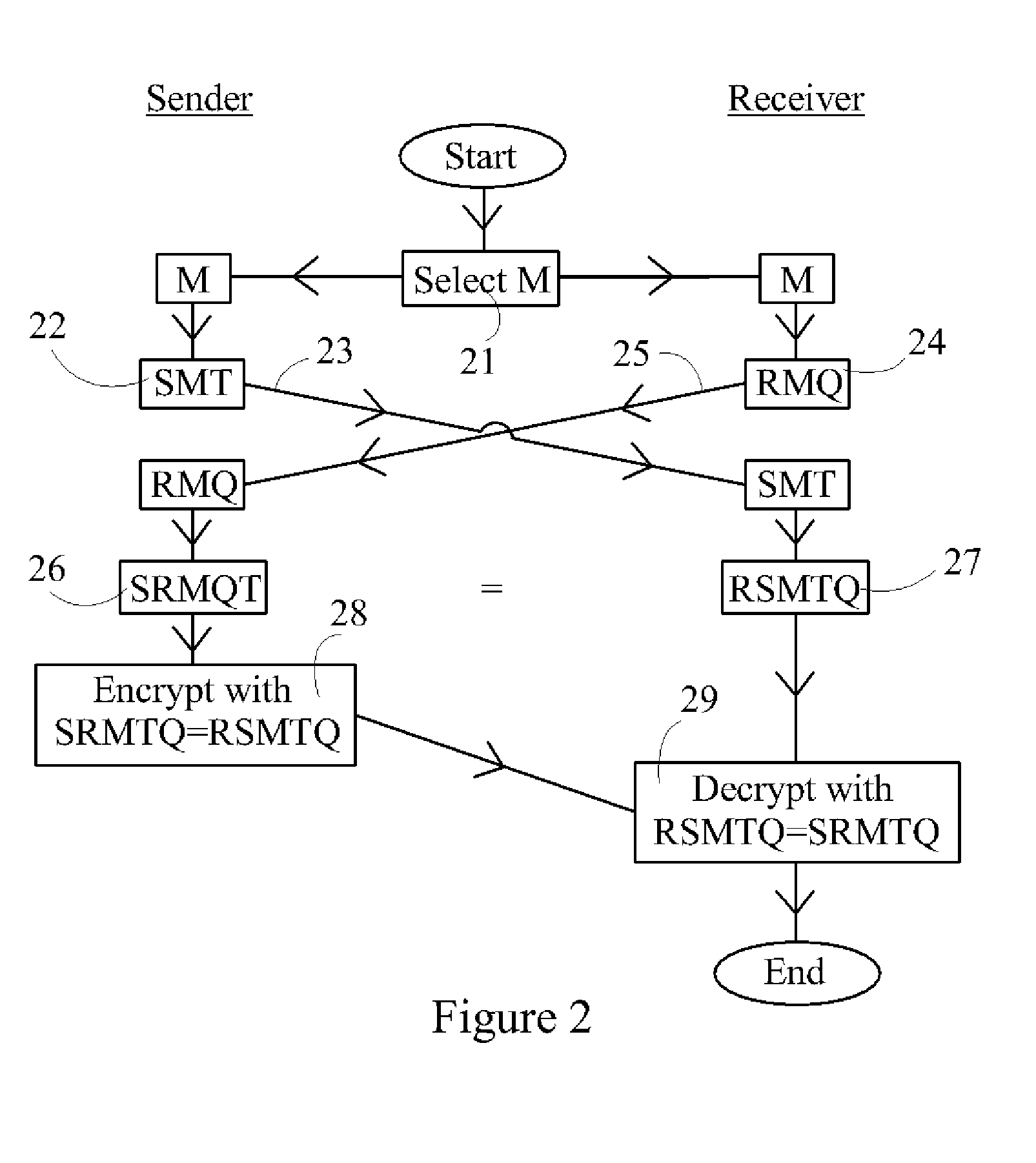
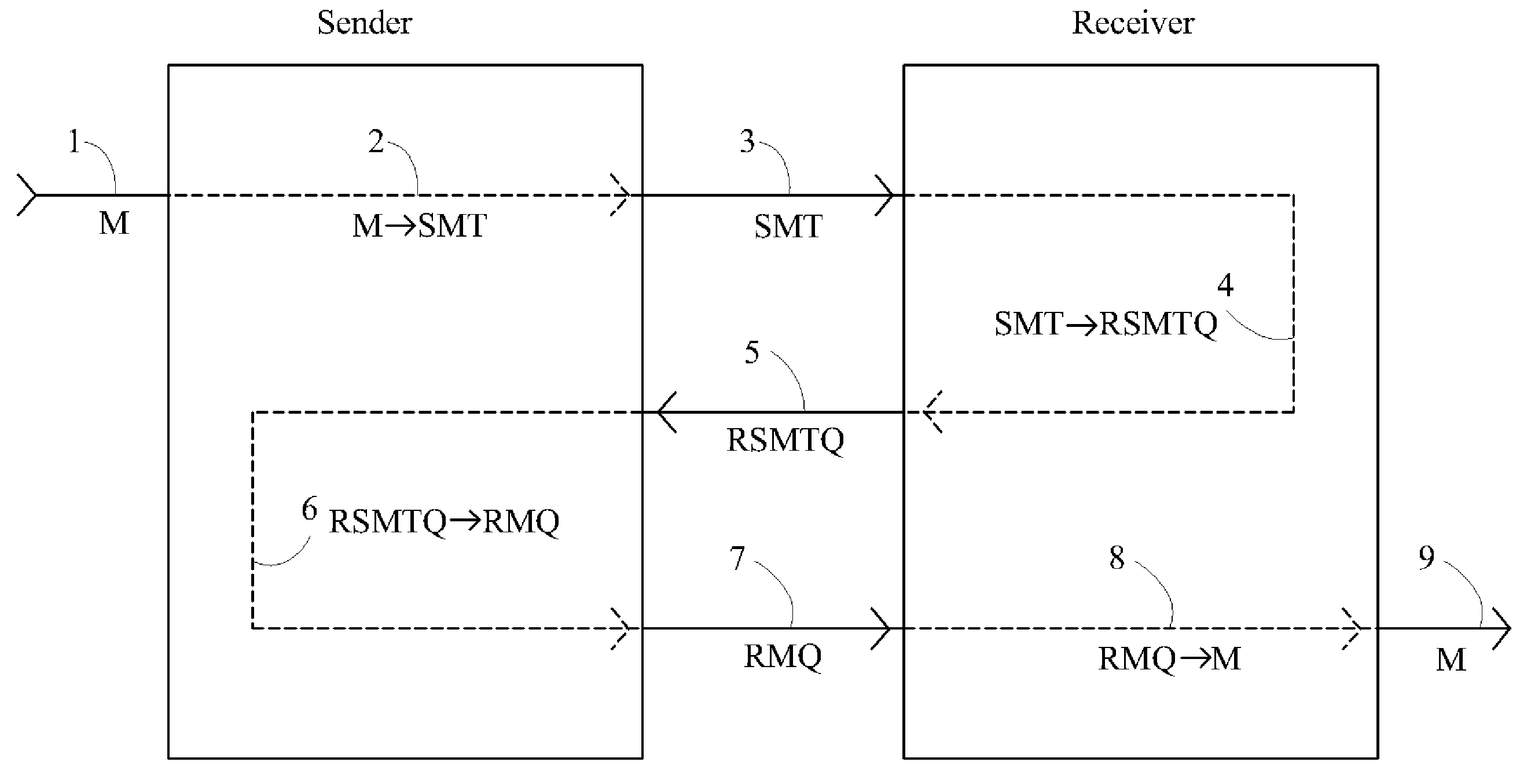
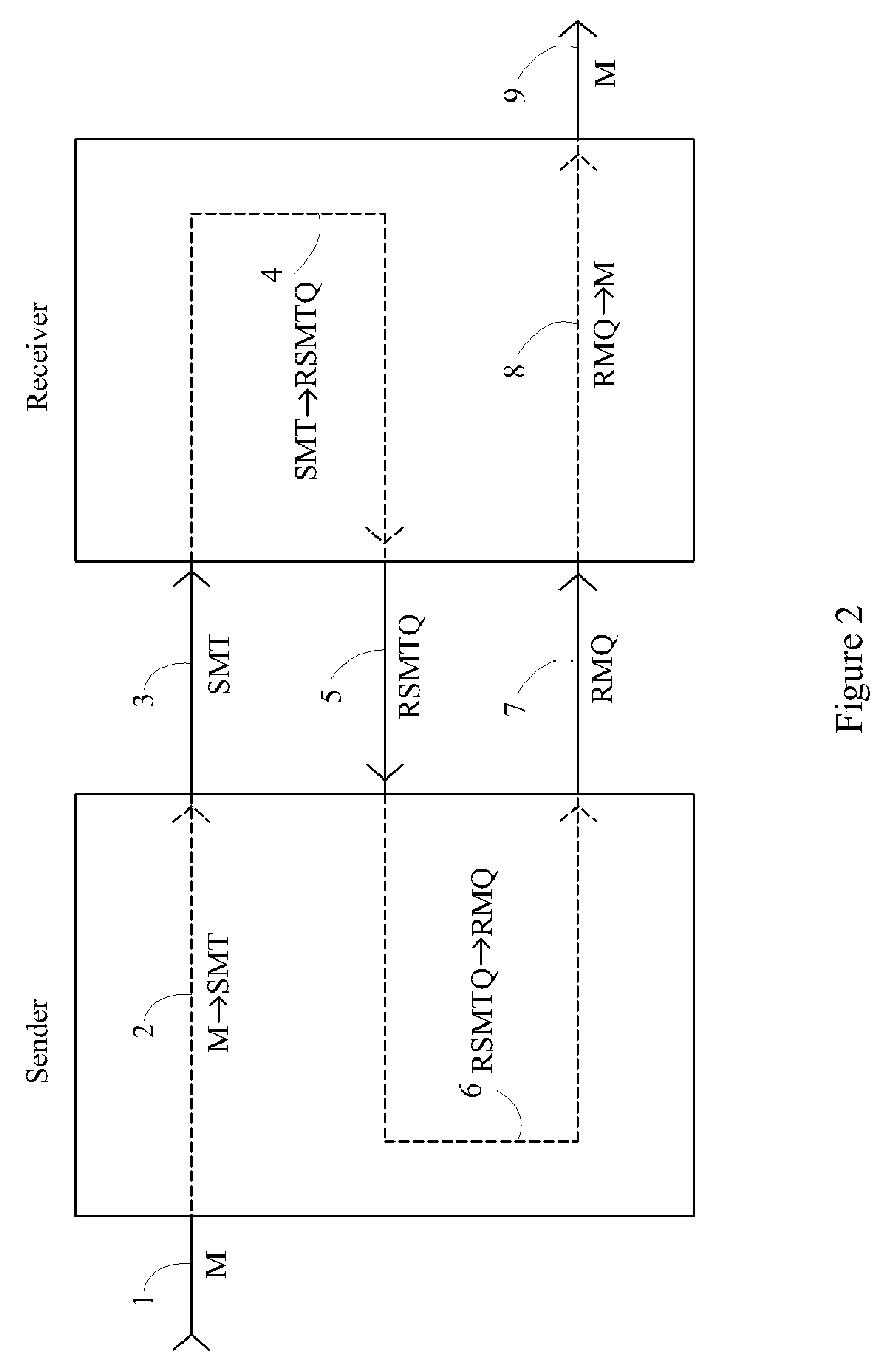
A method is disclosed whereby two parties can establish a cryptographic key for secure communications without any prior distribution of secret keys or other secret data, and without revealing said key to any third party who may have access to all of the transmissions between them. The method has both one-sided and two-sided embodiments. In the one-sided embodiments the two parties agree upon a matrix M, and independently choose matrices S and R from an established commutative family of square matrices. The sender transmits the matrix SM to the receiver and the receiver transmits the matrix RM to the sender. The sender computes the matrix SRM from the received matrix RM, and the receiver computes the matrix RSM from the received matrix SM. Since the matrices S and R commute, SRM=RSM. The value of the matrix SRM is then used to produce the desired cryptographic key. In the two-sided embodiments the two parties agree upon a matrix M, and two commutative families of square matrices F and G. The sender chooses a matrix S from F and a matrix T from G. The receiver independently chooses a matrix R from F and a matrix Q from G. The sender transmits the matrix SMT to the receiver and the receiver transmits the matrix RMQ to the sender. The sender computes the matrix SRMQT from the received matrix RMQ, and the receiver computes the matrix RSMTQ from the received matrix SMT. Since the matrices S and R commute, and the matrices T and Q commute, SRMQT=RSMTQ. The value of the matrix SRMTQ is then used to produce the desired cryptographic key.
Owner:RUBIN FR
Device, System and Method for Fast Secure Message Encryption Without Key Distribution
InactiveUS20070214361A1None of methods is secureMethod is fastKey distribution for secure communicationEncryption apparatus with shift registers/memoriesS/KEYKey distribution
One party sends a securely encrypted message to a second party. Each party chooses a secret message key for the message, which is never shared with or transmitted to any other party. The message is sent by means of three encrypted messages. The first encrypted message is sent from the sender to the receiver, and is encrypted by the sender's key. The second encrypted message is sent from the receiver back to the sender, and is encrypted by both the sender's key and then by the receiver's key. The third encrypted message is sent from the sender back to the receiver, and is encrypted by only the receiver's key following removal of the sender's key. Finally, the receiver decrypts the third message. The messages are sent in blocks. Encryption consists of multiplying each block of the message by a square matrix of the same size as the block, and decryption consists of multiplying by the inverse matrix. The key matrices are taken from one or more large commutative families of matrices. This commutativity allows the sender's keys to be removed even though the message block has been encrypted by the sender's key first and then the receiver's key. Two primary embodiments of the invention are disclosed, using one-sided and two-sided matrix multiplication, respectively.
Owner:RUBIN FR
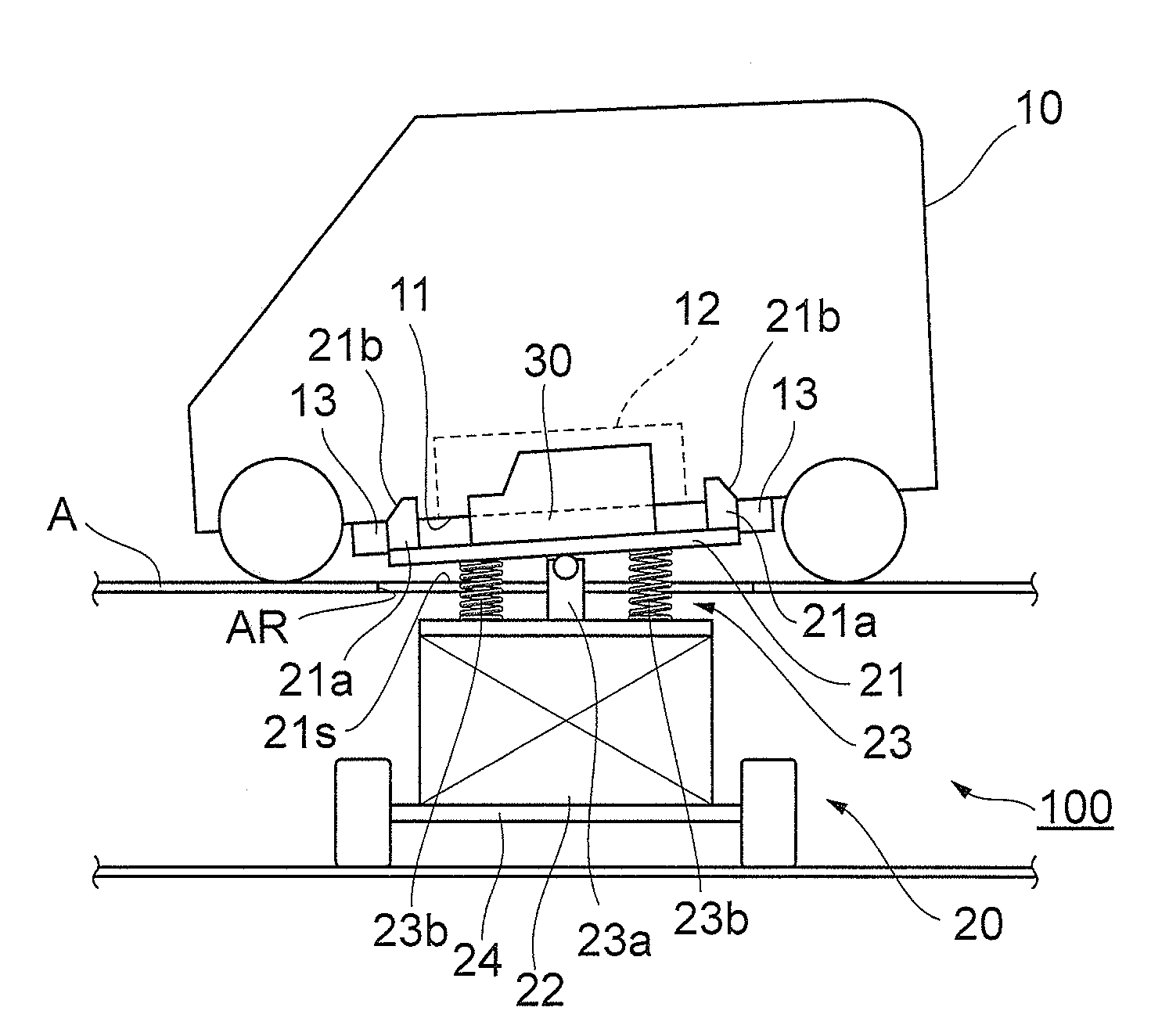
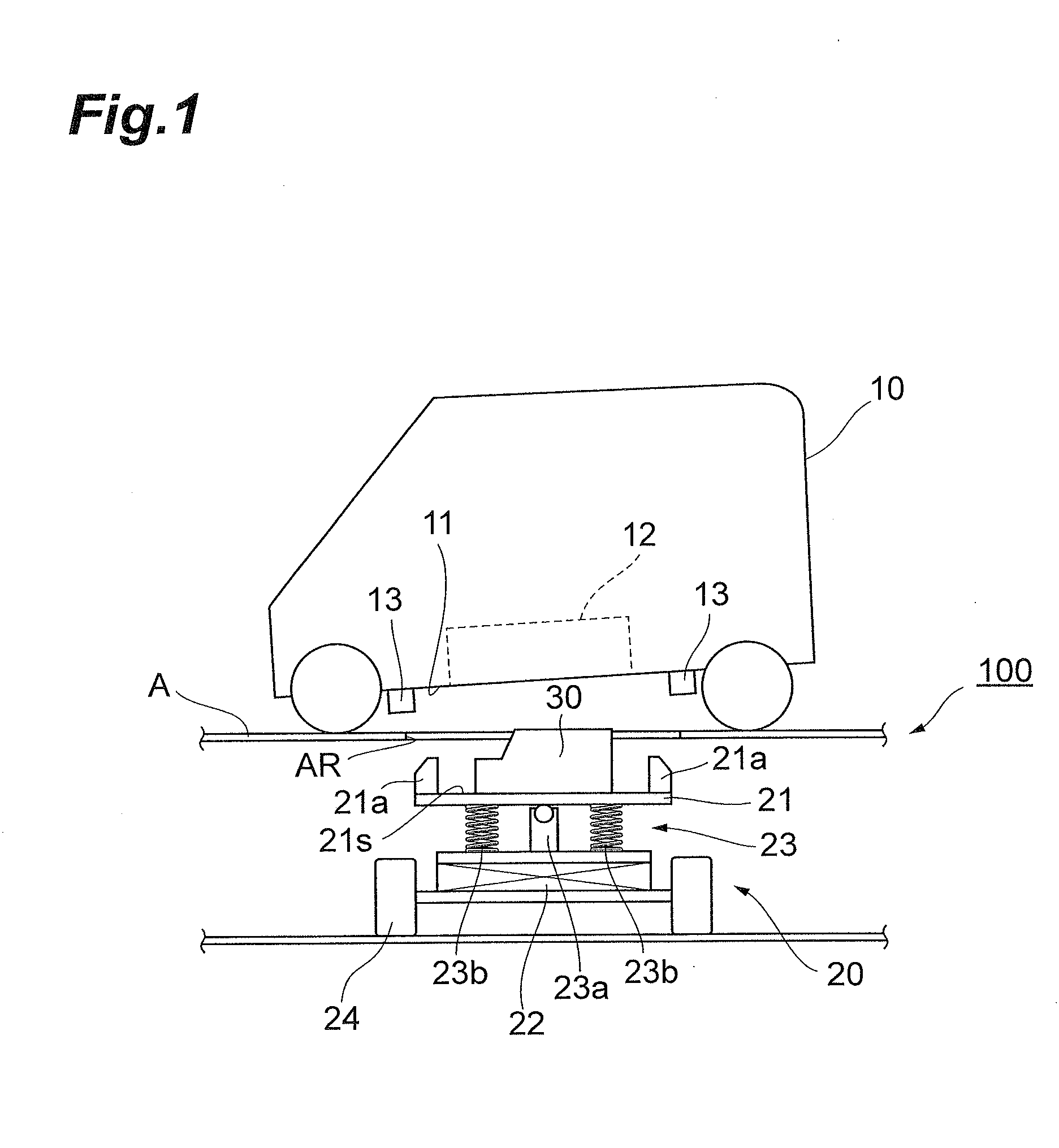
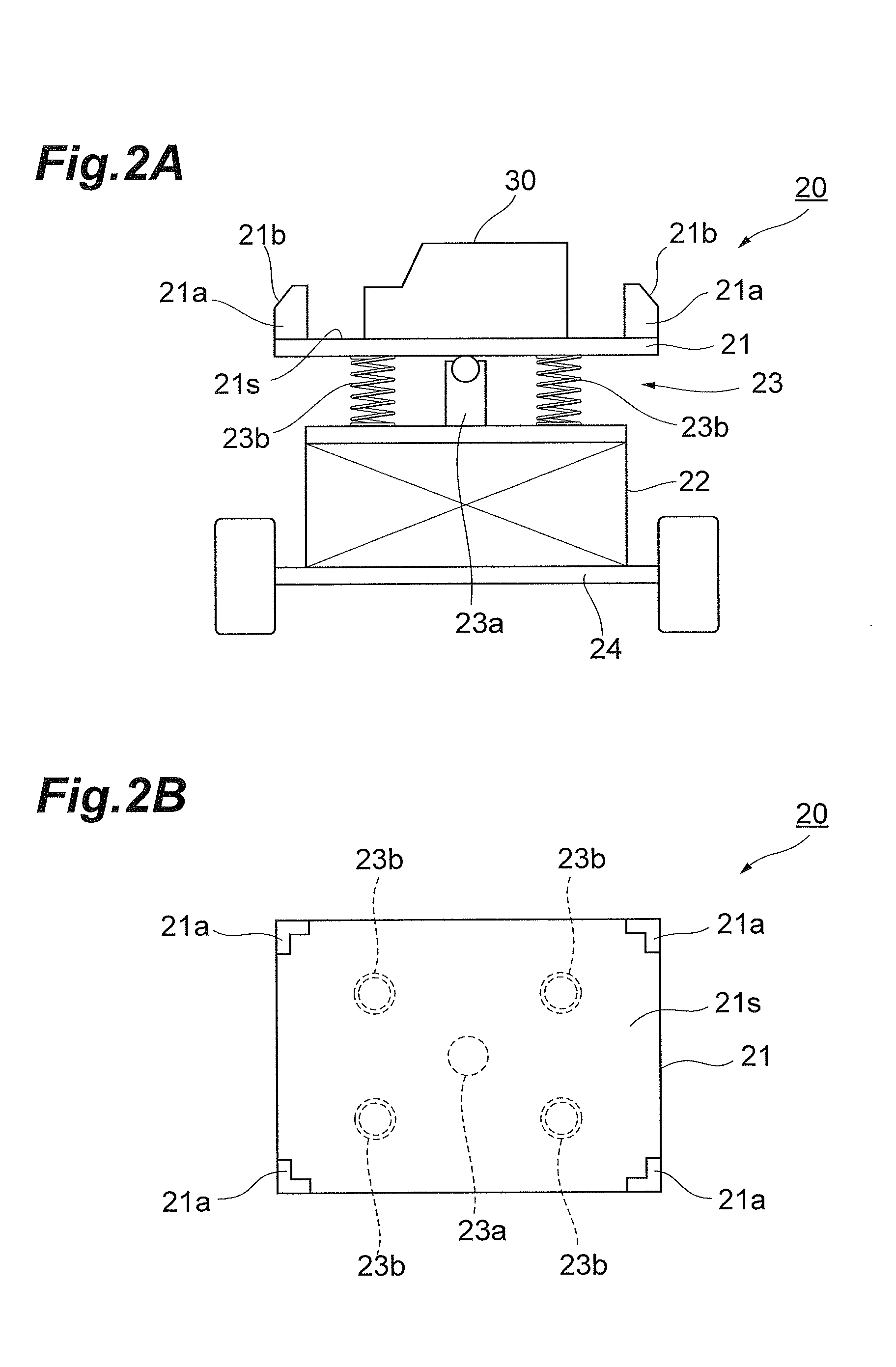
Battery unit mounting apparatus and battery unit mounting structure
InactiveUS20140196966A1Simple structureEasy to installElectric propulsion mountingElectric vehicle charging technologyMechanical engineeringEngineering
A battery unit mounting apparatus for mounting a battery unit to a vehicle from a bottom face side of the vehicle comprises a table having a mount surface for mounting the battery unit, a lift for moving the table up and down with respect to the bottom face of the vehicle, and a connection mechanism for connecting the table and the lift to each other. The connection mechanism connects the table and the lift to each other such that the battery unit or table comes into contact with the bottom face of the vehicle so as to tilt the mount surface by a predetermined inclination with respect to the bottom face of the vehicle.
Owner:TOYOTA IND CORP
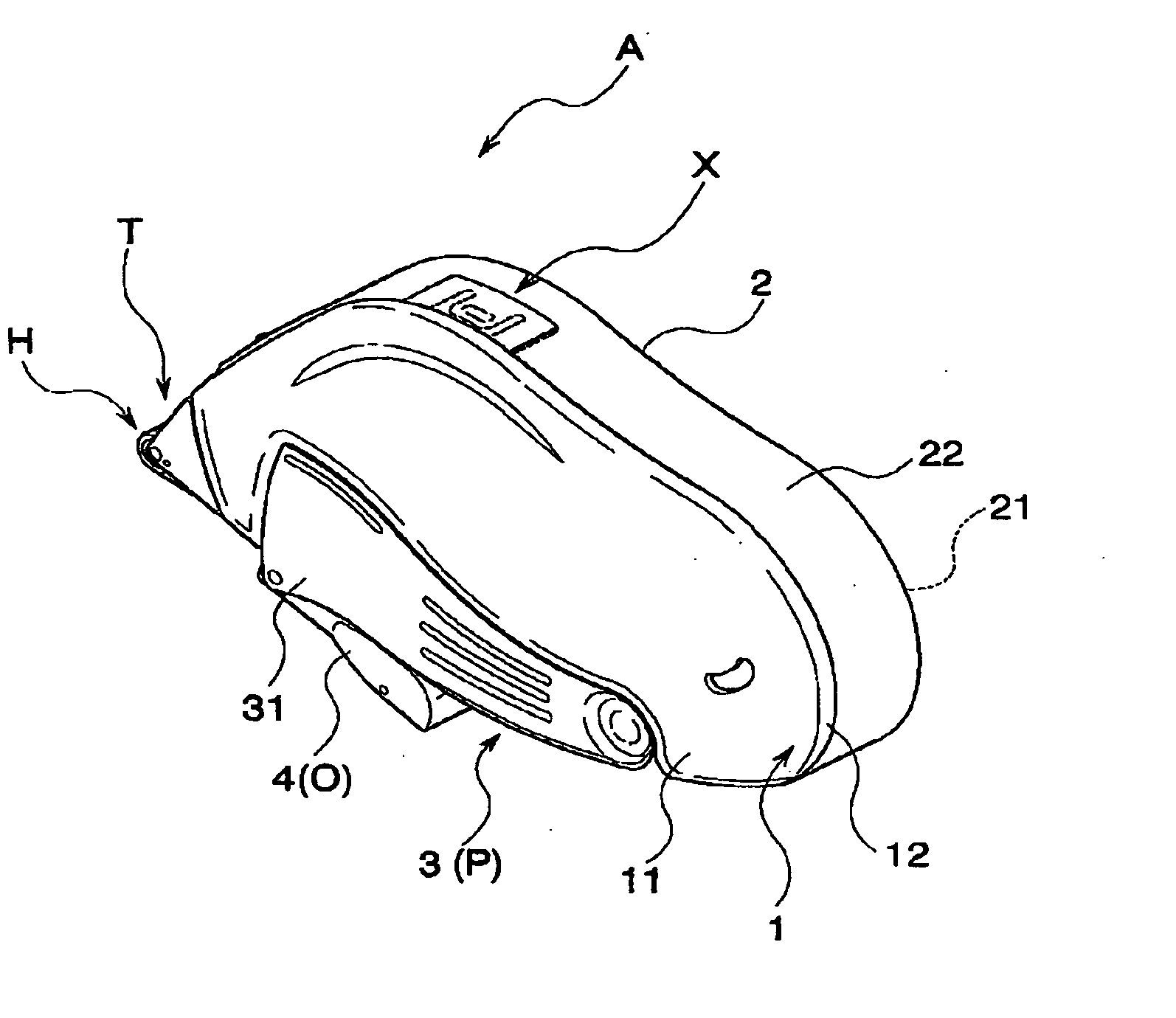
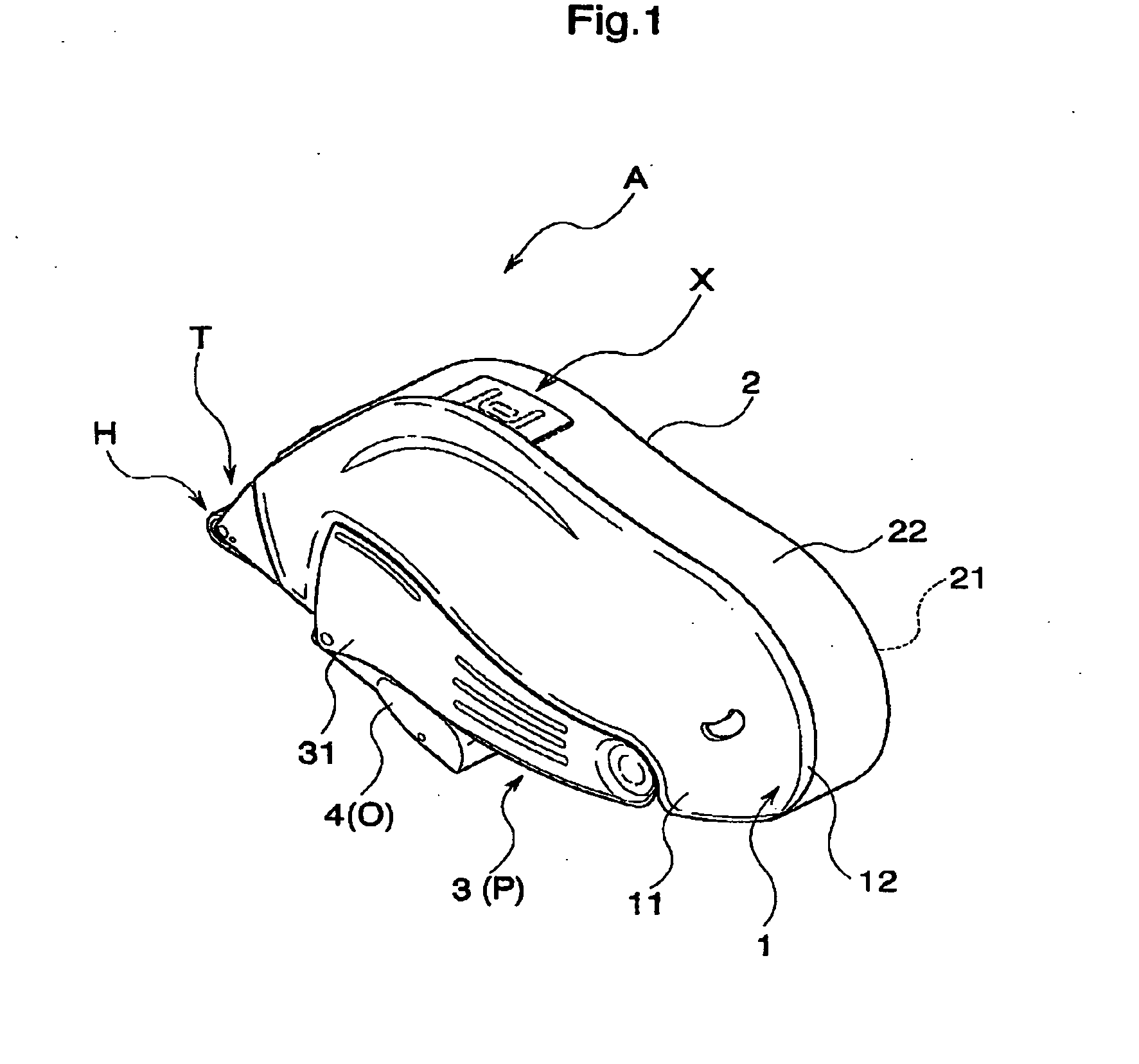
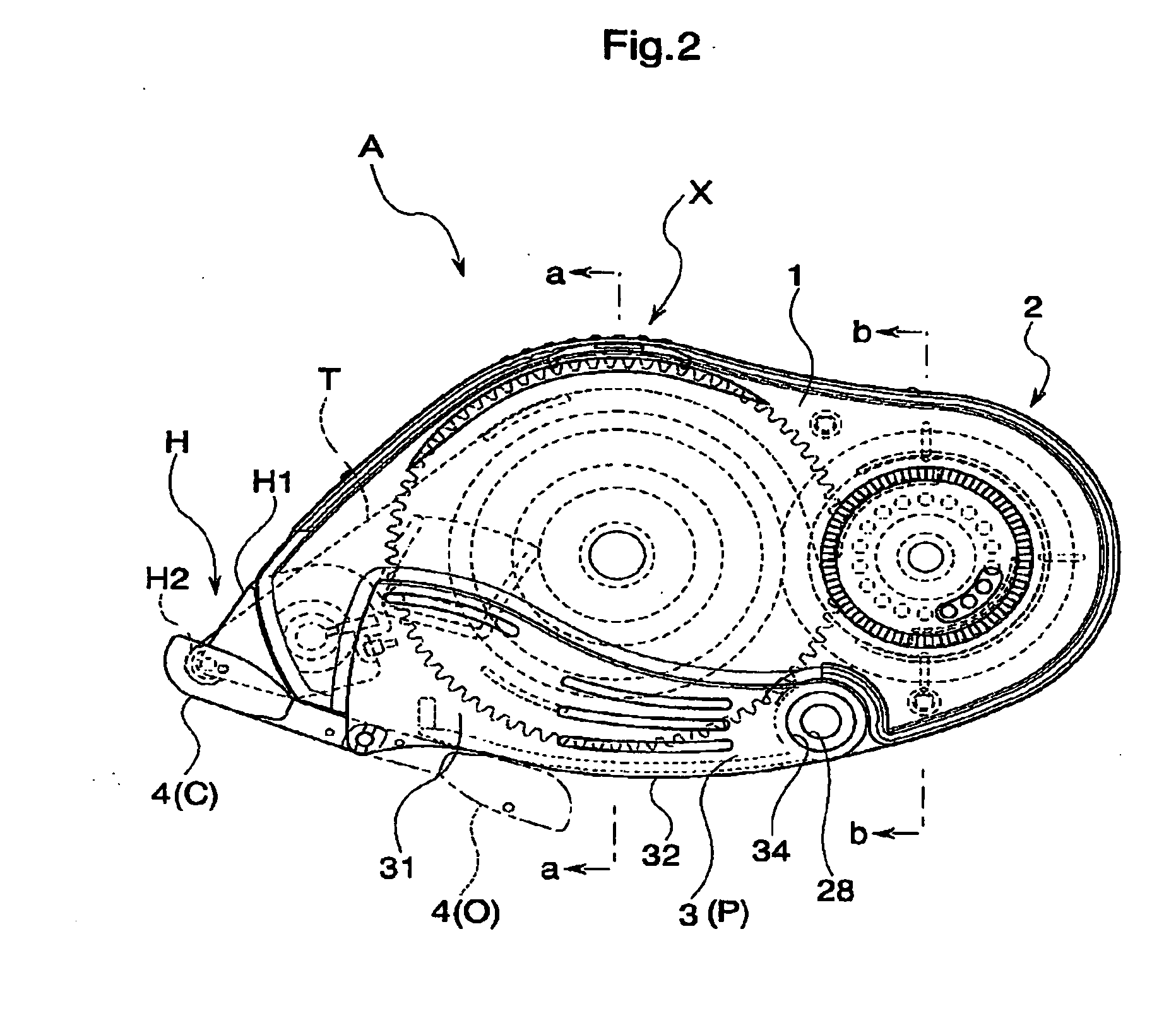
Transfer tool
ActiveUS20070009307A1Easy to useMaintain strengthMechanical working/deformationWriting accessoriesTime of useMechanical engineering
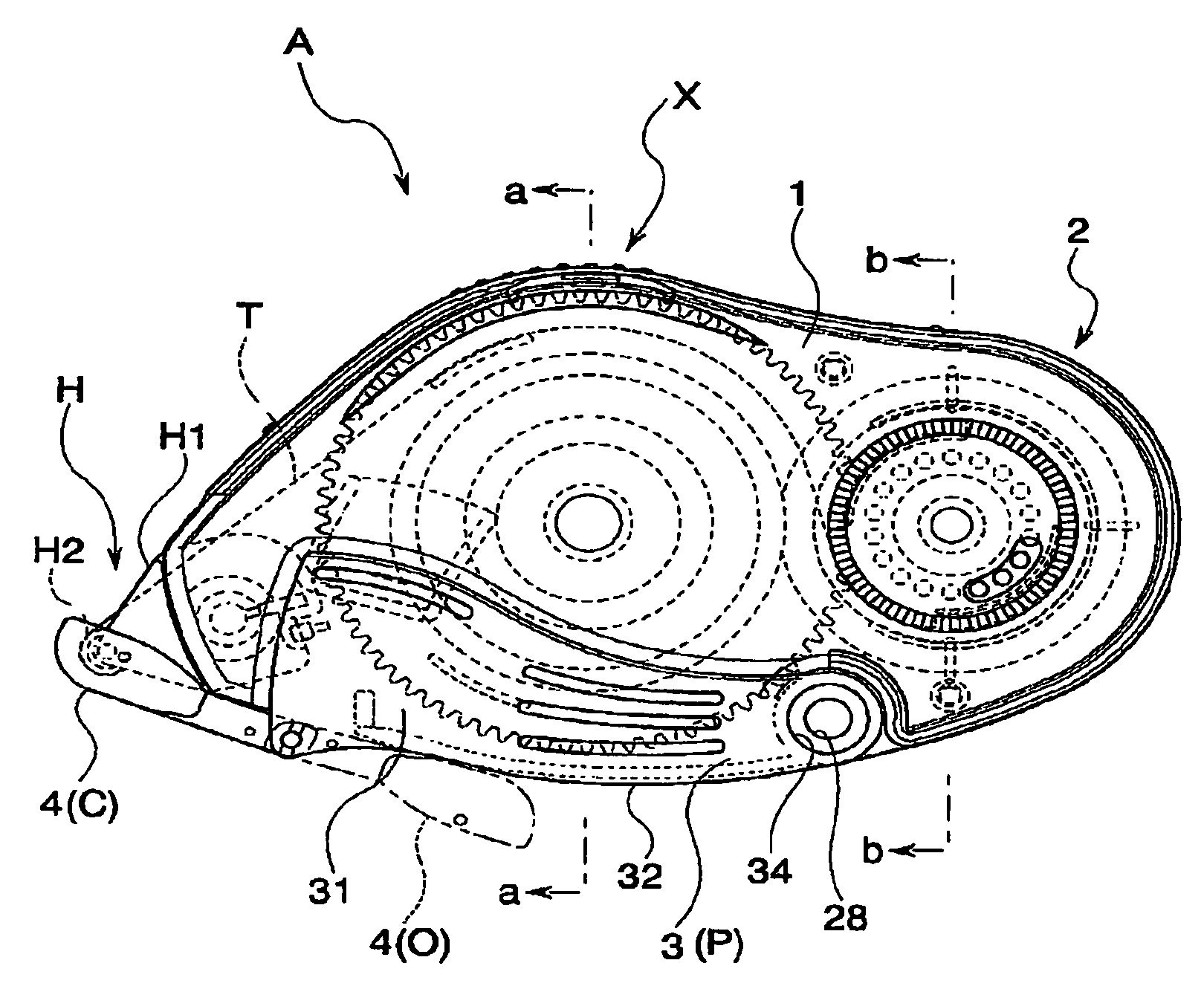
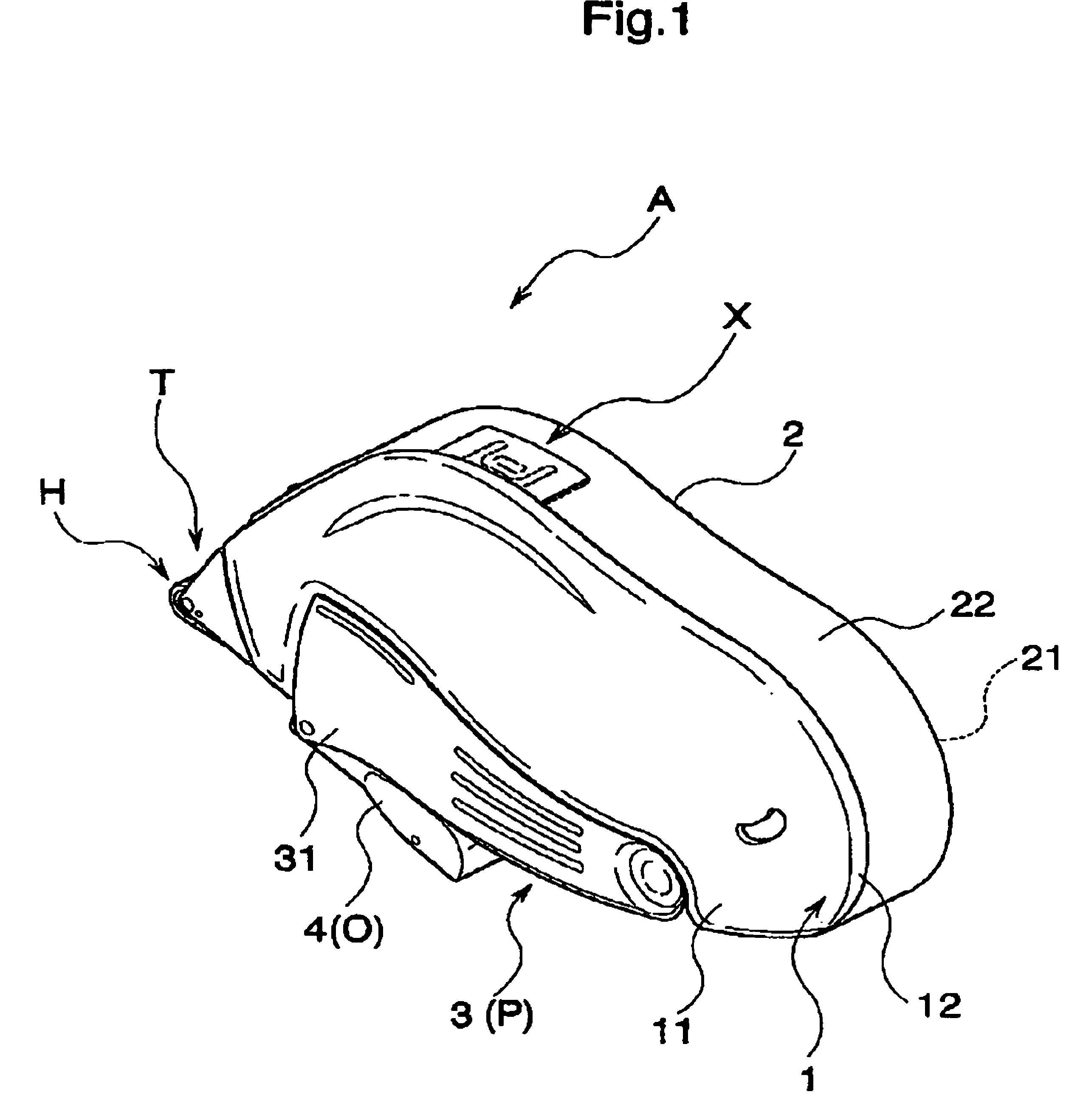
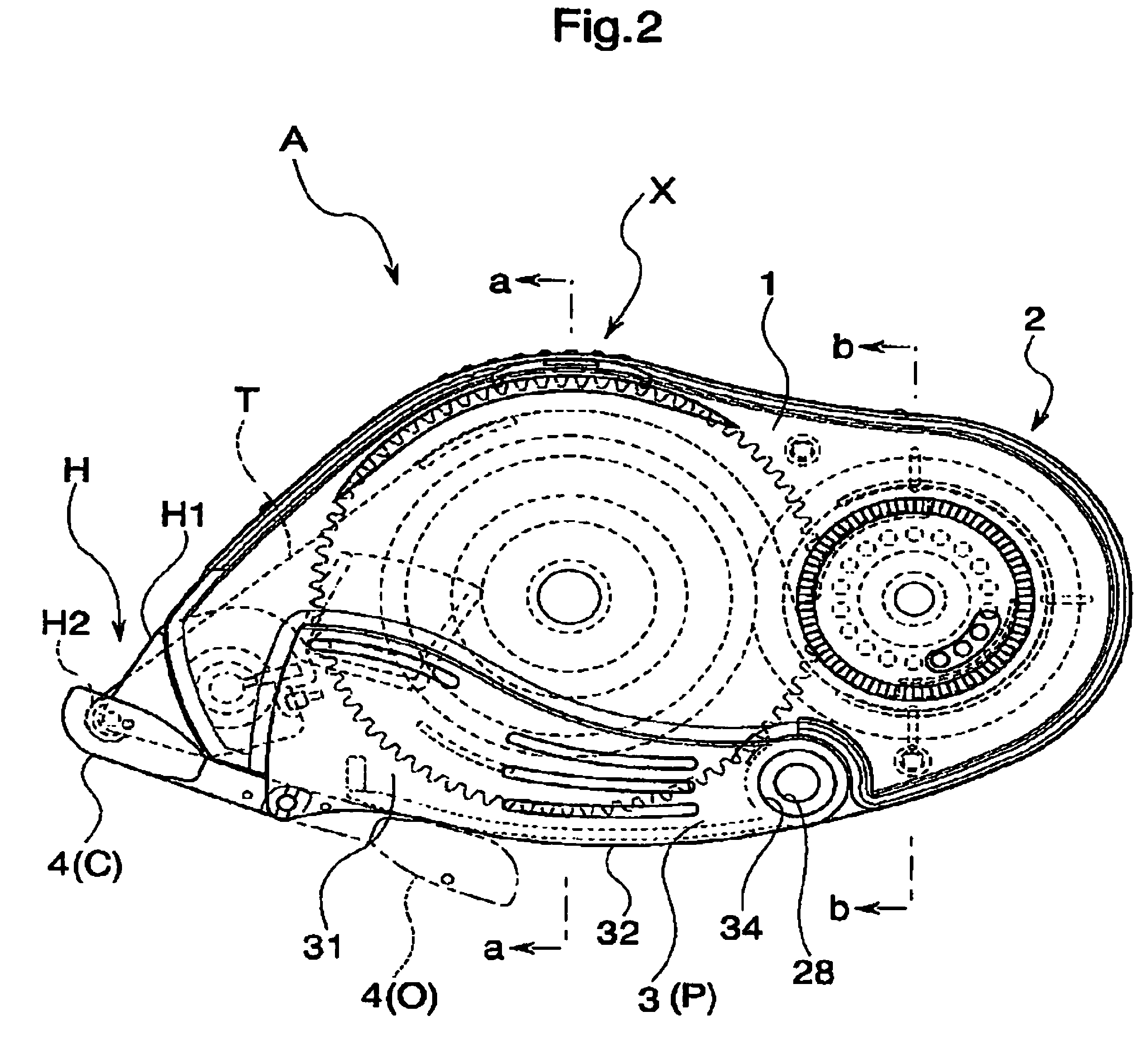
The invention provides a transfer tool which can preferably maintain a shape while improving a strength at a time of using, and has an improved usability. The transfer tool is provided with a first case (1) holding a replacement part including at least a transferring object, a second case (2) detachably engaged with the first case (1) and holding a non-replacement part constituting at least a part of a feeding mechanism part feeding the transferring object to a transferred object, a holding portion (3) outside fitted detachably to a predetermined region of the first case (1) and the second case (2) and capable of holding the first case (1) and the second case (2), and an engagement portion (X) detachably engaging the first case (1) and the second case (2) in a opposite direction of the holding portion (3).
Owner:KOKUYO S&T CO LTD
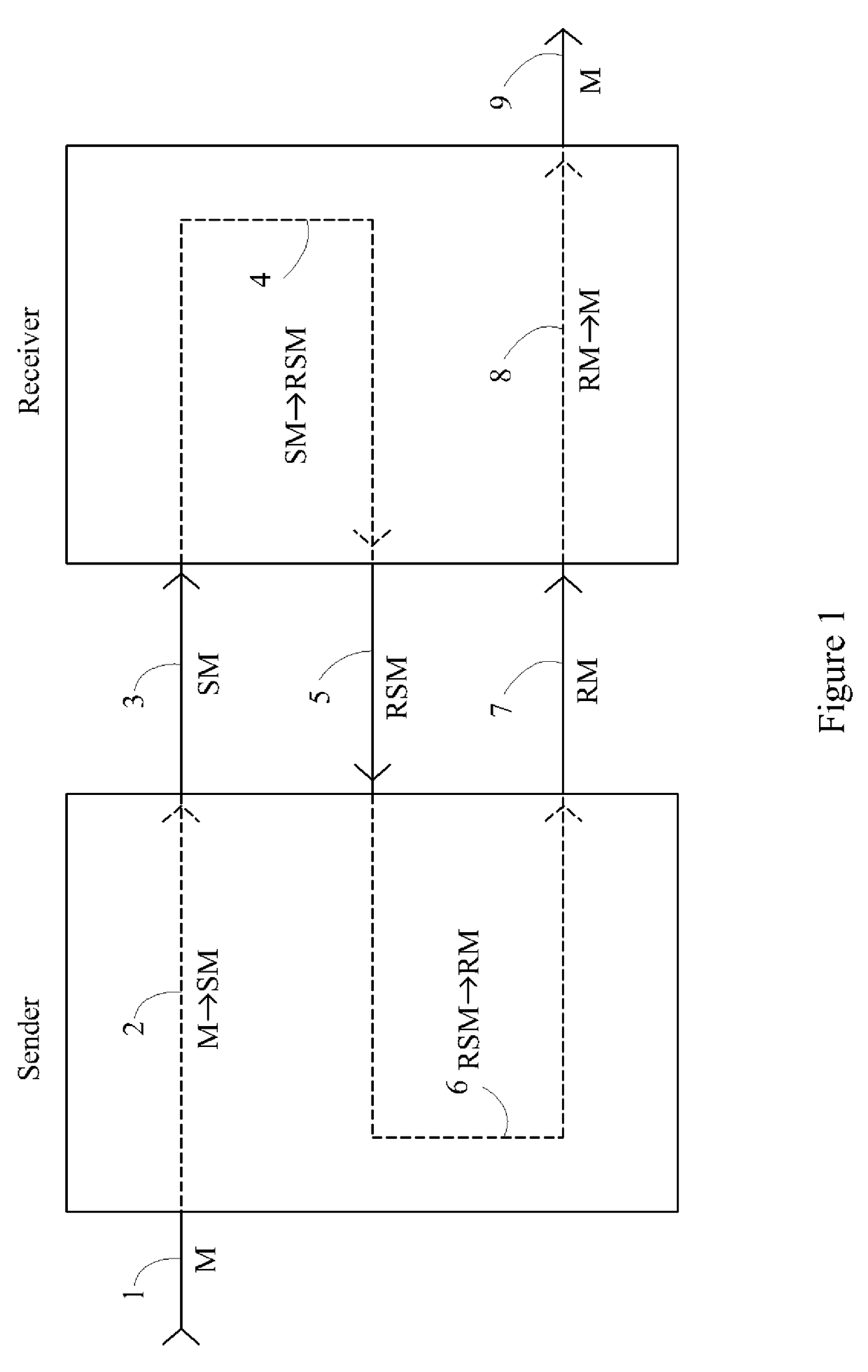
Device, System and Method for Cryptographic Key Exchange
InactiveUS20080069346A1None of methods is secureMethod is fastSecret communicationSecuring communicationKey exchangeSecure communication
A method is disclosed whereby two parties can establish a cryptographic key for secure communications without any prior distribution of secret keys or other secret data, and without revealing said key to any third party who may have access to all of the transmissions between them. The method has both one-sided and two-sided embodiments. In the one-sided embodiments the two parties agree upon a matrix M, and independently choose matrices S and R from an established commutative family of square matrices. The sender transmits the matrix SM to the receiver and the receiver transmits the matrix RM to the sender. The sender computes the matrix SRM from the received matrix RM, and the receiver computes the matrix RSM from the received matrix SM. Since the matrices S and R commute, SRM=RSM. The value of the matrix SRM is then used to produce the desired cryptographic key. In the two-sided embodiments the two parties agree upon a matrix M, and two commutative families of square matrices F and G. The sender chooses a matrix S from F and a matrix T from G. The receiver independently chooses a matrix R from F and a matrix Q from G. The sender transmits the matrix SMT to the receiver and the receiver transmits the matrix RMQ to the sender. The sender computes the matrix SRMQT from the received matrix RMQ, and the receiver computes the matrix RSMTQ from the received matrix SMT. Since the matrices S and R commute, and the matrices T and Q commute, SRMQT=RSMTQ. The value of the matrix SRMTQ is then used to produce the desired cryptographic key.
Owner:RUBIN FR
Image collection text and audio annotation
InactiveUS20120254709A1Securely makeSimple and convenient interactionStill image data indexingNatural language data processingImage systemDigital storage
A multi-media image system includes using a processor to provide a storage location for a multi-media image collection in a digital storage system and further associating an identifier with the storage location, providing the identifier for distribution, receiving information from two or more of the plurality of individuals, wherein the multi-media content includes one or more images, audio annotations, and text annotations, storing the multi-media content in the storage location and associating the multi-media content with the multi-media collection, providing rules for associating the audio annotations and rules for associating the text annotations with the images or the multi-media image collection, wherein the rules for associating the audio and the text annotations are different, and making a multi-media image product using at the multi-media content stored in the multi-media collection in accordance with the rules.
Owner:KODAK ALARIS INC
Device, system and method for fast secure message encryption without key distribution
InactiveUS7912213B2Securely makingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesComputer hardwareS/KEY
Owner:RUBIN FR
Secure processing system for use with a portable communication device
ActiveUS20140155032A1Limited accessSecurely makingUnauthorised/fraudulent call preventionEavesdropping prevention circuitsSafe handlingMachine-readable medium
A machine-readable medium encoded with instructions to execute steps comprising: authorizing access to a system using a location of a portable communications device.
Owner:NOWWW US
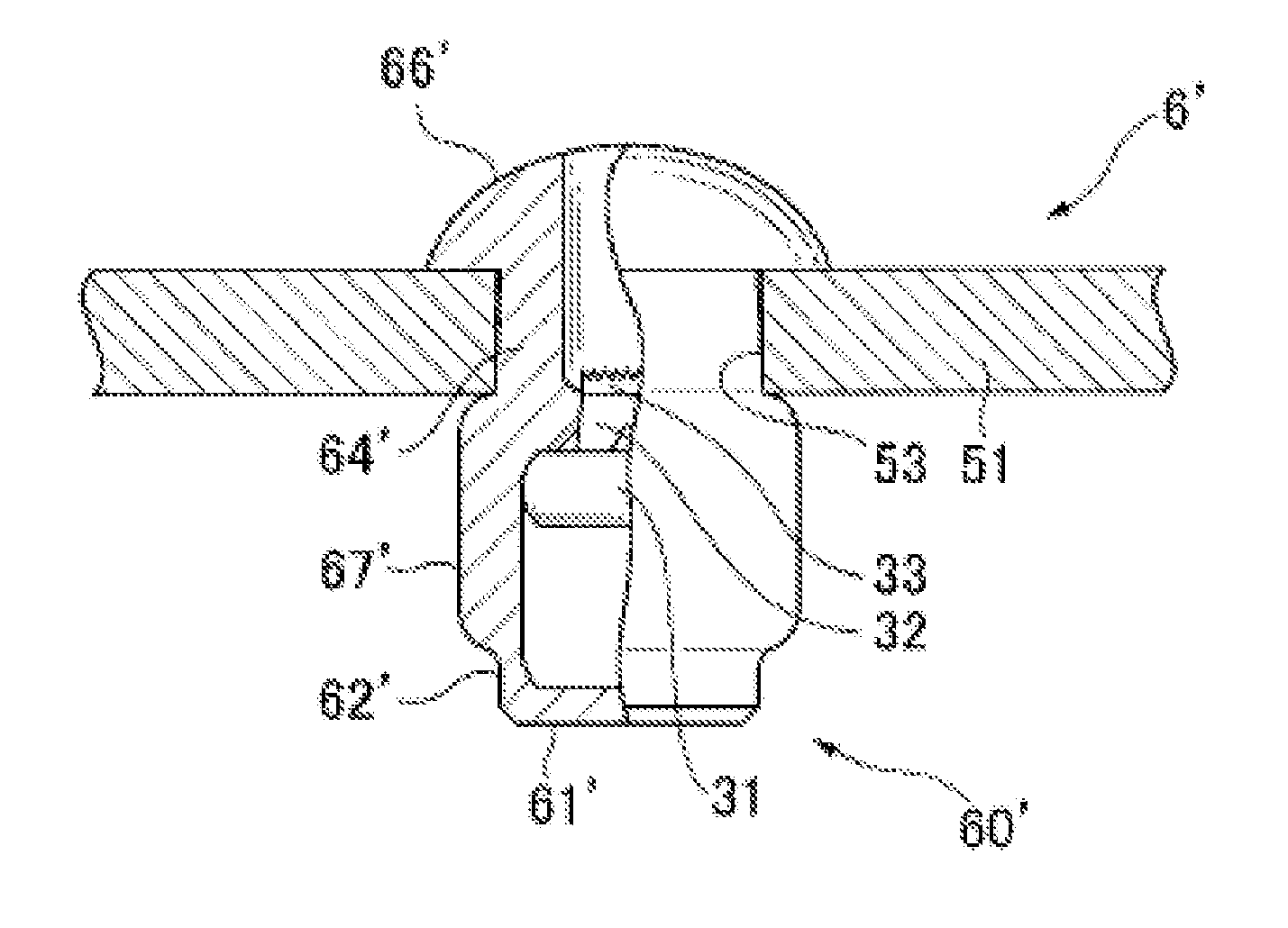
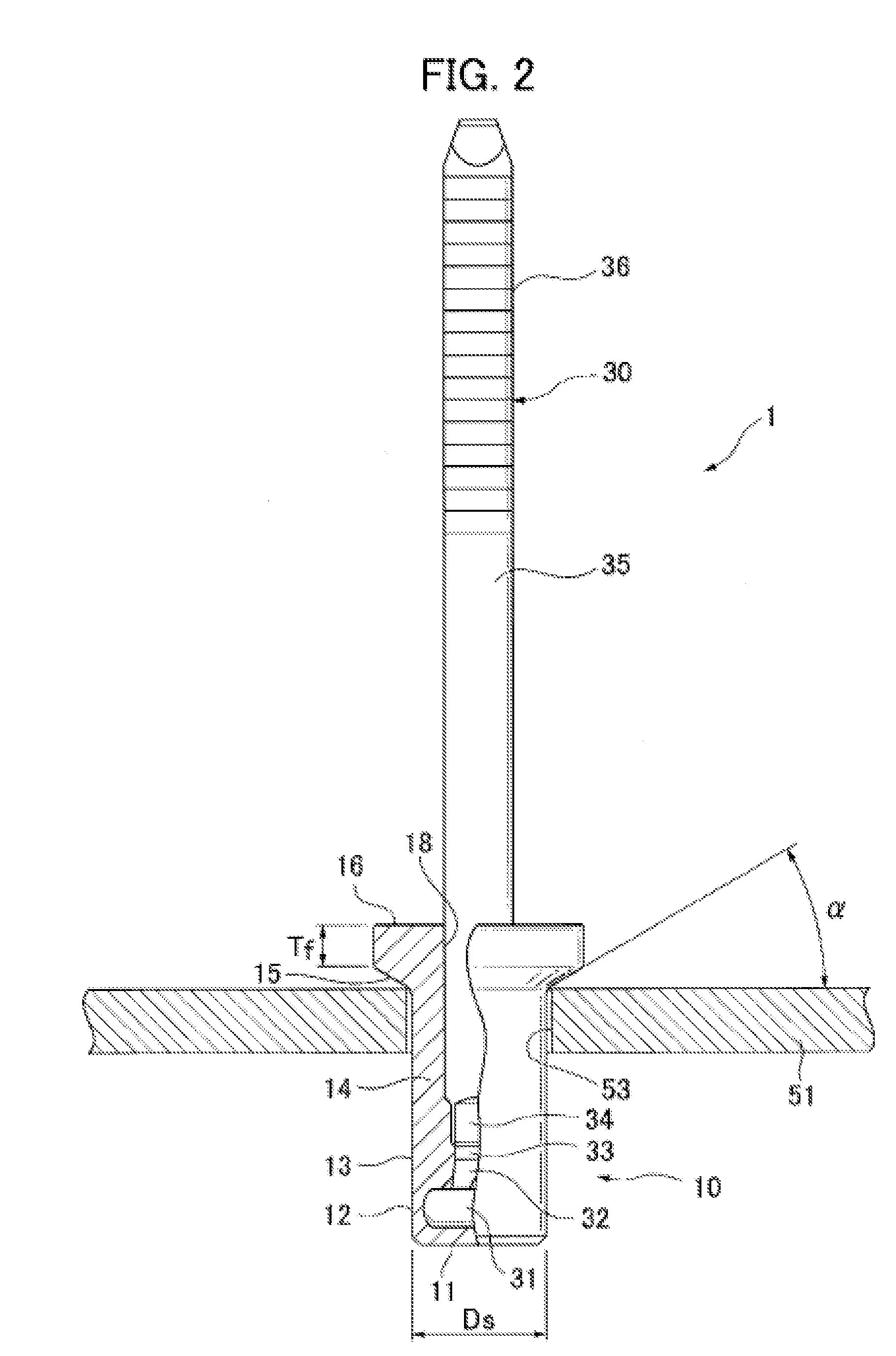
Blind rivet and sealing structure using same
ActiveUS20150192161A1Sufficient sealing characteristicImprove waterproof performancePinsRivetsWater tightnessRivet
Owner:NEWFREY
Display device
InactiveUS20070182665A1Maintain visibilityMinimize changesVisual indicationsStatic indicating devicesComputer graphics (images)Display device
A display device includes: a pattern display unit having a display area in which a background display region for displaying a background pattern that changes as time advances and an information display region for displaying a predetermined information pattern are integrally provided. A display mode of the information pattern changes in accordance with a change of the background pattern in such a manner that the information pattern is distinguishable in the display area.
Owner:SEIKO EPSON CORP
Electrode plate for secondary battery, method of manufacturing the same, and secondary battery using the same
ActiveUS7163565B2Reduce short-circuitingImprove manufacturing yieldFinal product manufacturePrimary cellsBiomedical engineeringElectrode
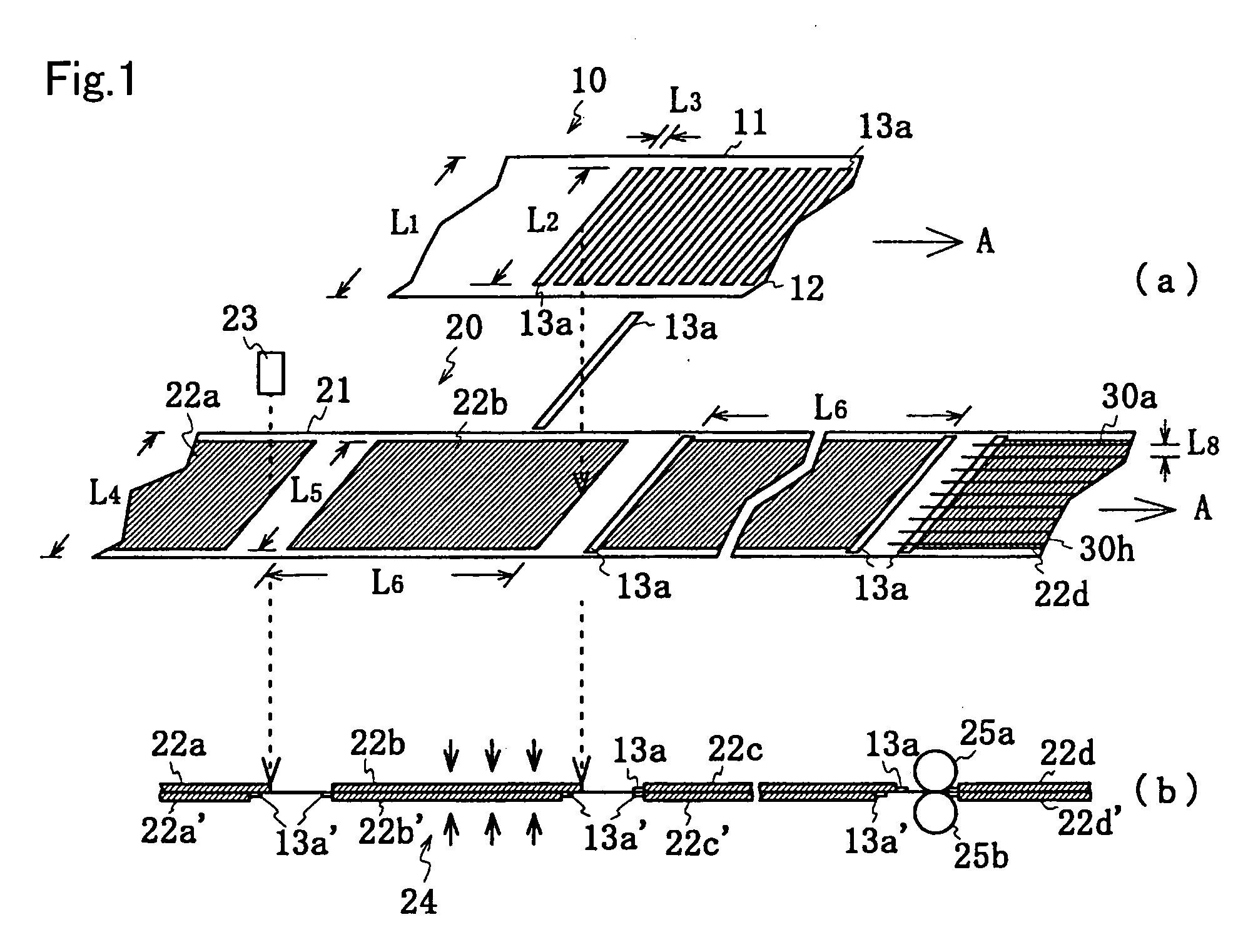
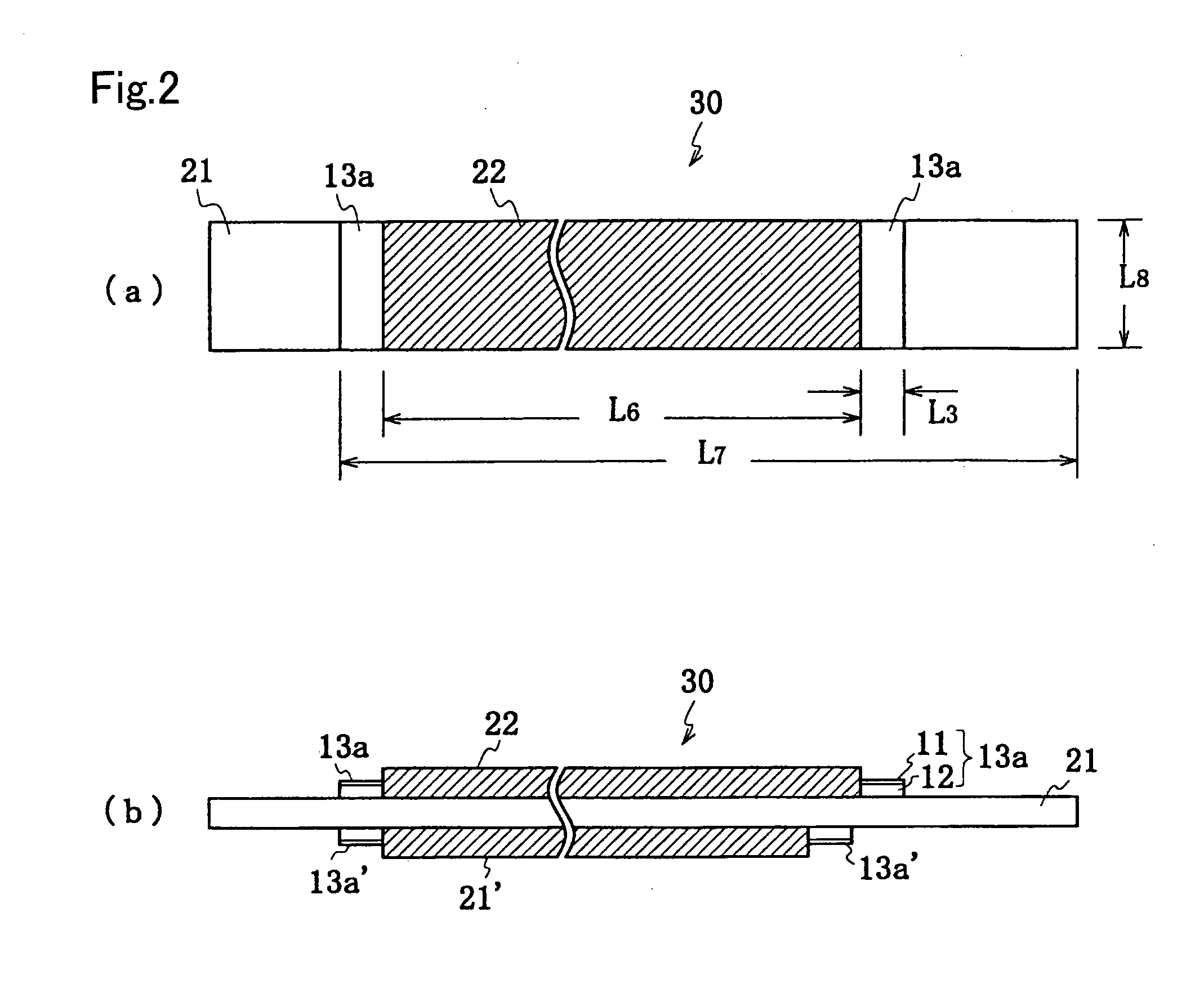
An electrode plate for a secondary battery is provided for reducing adverse influences caused by paste of an insulating sheet in an electrode body and a battery specification. Active material layers 22a to 22d and 22a′ to 22d′ are formed on at least one surface of an electrode sheet 20 over a wider range than a predetermined width of an electrode and over a predetermined length. An insulating sheet 13a is made to adhere to a possible short-circuit portion of the electrode sheet 20 which portion is opposed to another electrode. The electrode sheet 20 and an insulating member are simultaneously cut to form an electrode plate having a predetermined shape, wherein the insulating member has a low-temperature thermoplastic paste material applied on one side thereof, and is made to adhere to the electrode sheet 20 through heat adhesion.
Owner:SANYO ELECTRIC CO LTD
Slide rail device for vehicle seat
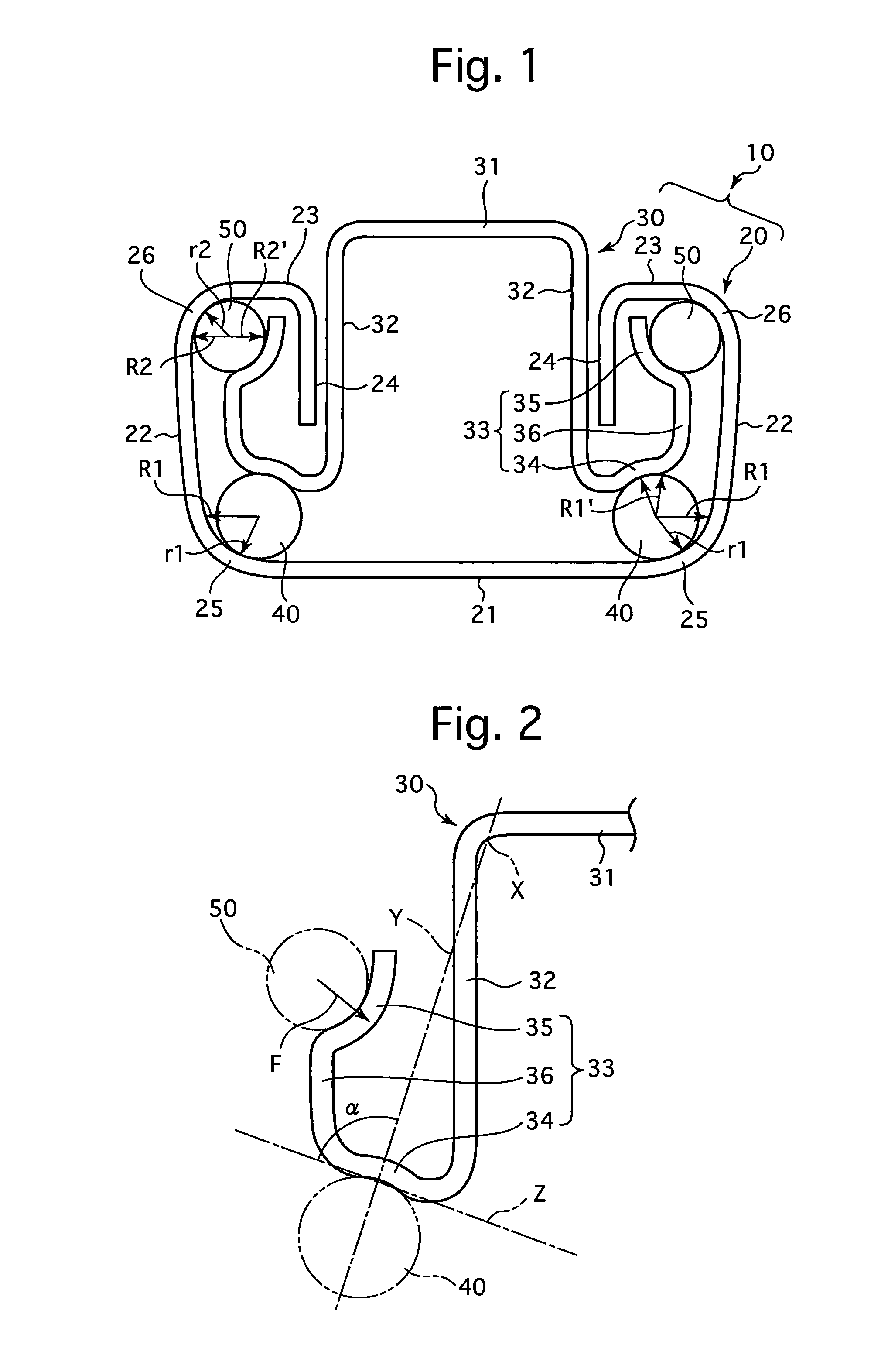
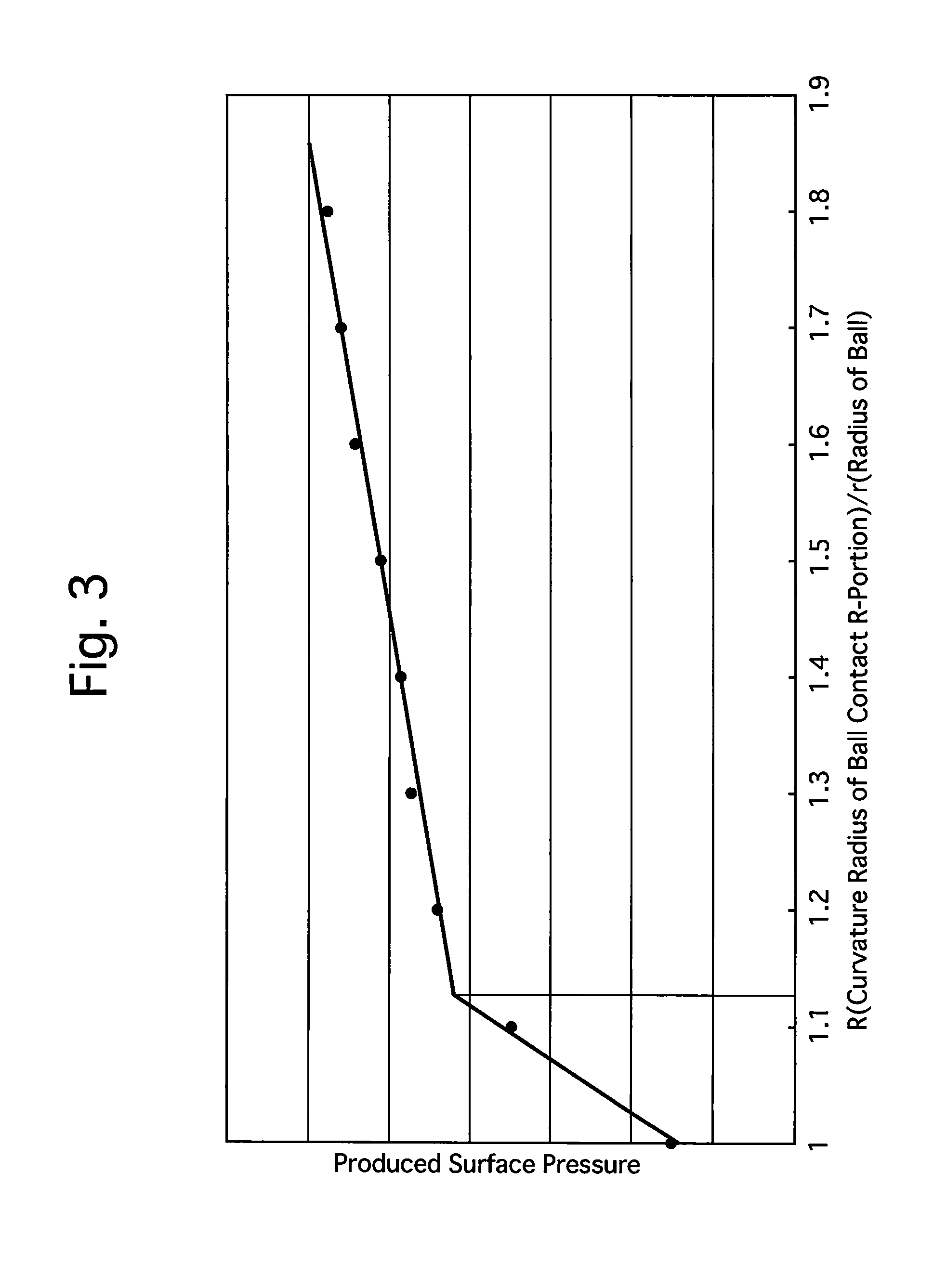
InactiveUS20120145869A1Improve accuracyHigh hardnessLinear bearingsStands/trestlesBall bearingEngineering
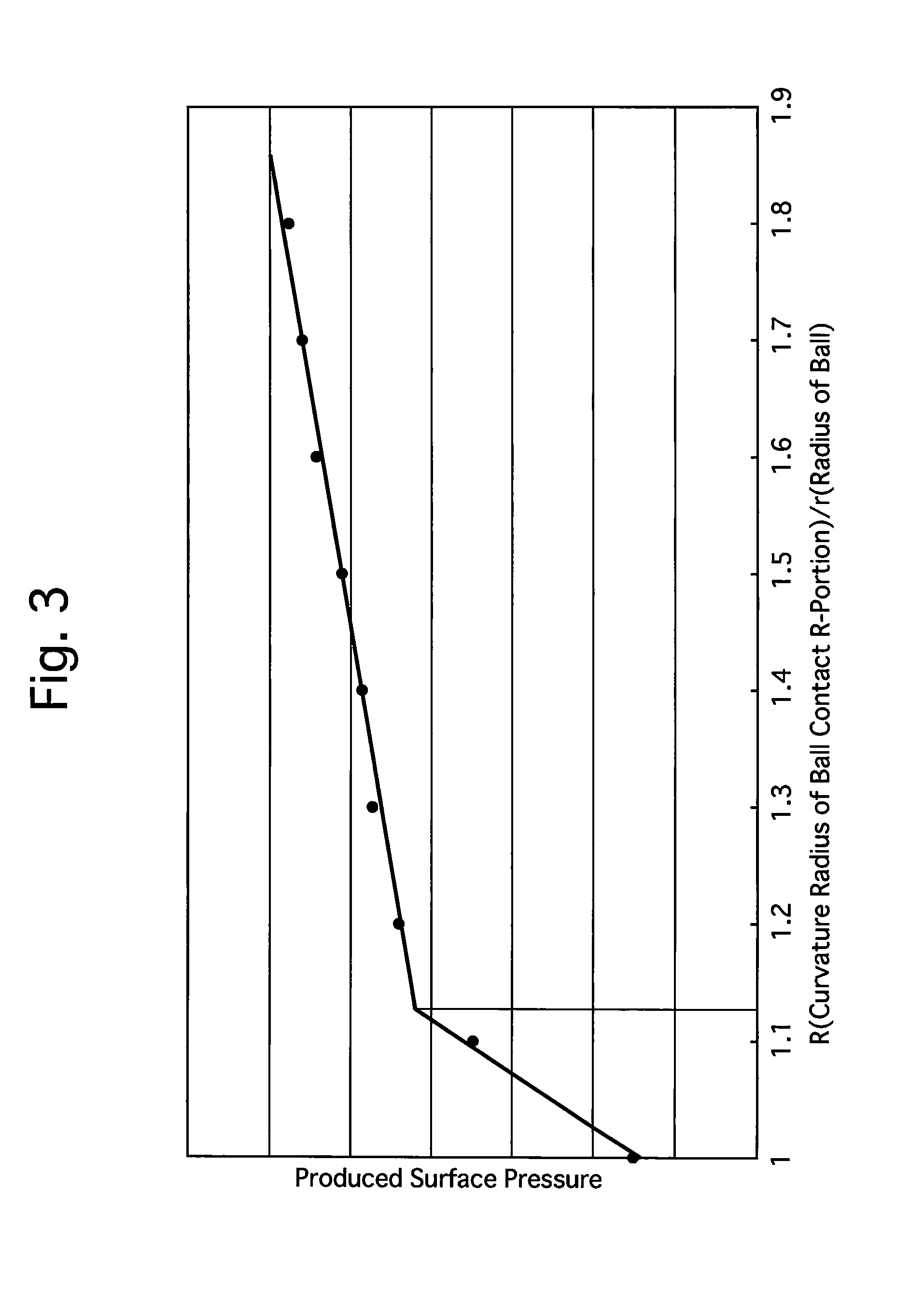
A slide rail device which includes a lower rail, an upper rail which is freely slidably engaged with the lower rail, and balls which are installed between the lower and upper rails. The lower rail includes a lower-rail bottom wall, a pair of lower-rail side walls, a pair of lower-rail upper walls, a pair of lower-rail lower-ball contact R-portions, and a pair of lower-rail upper-ball contact R-portions. The upper rail includes an upper-rail top wall, a pair of upper-rail side walls, and a pair of upper-rail ball-bearing walls. Each upper-rail ball-bearing wall includes an upper-rail lower-ball contact portion and an upper-rail upper-ball contact portion. A radius of curvature of the lower-rail lower-ball contact R-portion of the lower rail is greater than that of the lower ball, and a radius of curvature of the lower-rail upper-ball contact R-portion of the lower rail is greater than that of the upper ball.
Owner:SHIROKI KOGYO CO LTD
Printing press with a temperature control unit for a plate cylinder
InactiveUS6912957B2Efficient use ofPrecise temperature controlPrinting platesRotary letterpress machinesTemperature control modeEngineering
A printing press is provided with a temperature control unit for controlling the temperature of a surface of a printing plate mounted on a plate cylinder by feeding air onto the plate cylinder. A plate-replacement space is provided in a certain region around the plate cylinder for replacement of a printing plate mounted on the plate cylinder with a new one introduced from the outside of the printing press. The temperature control unit is designed to be selectively shifted between a temperature control mode and a space opening mode, in which the temperature control mode enables air to be fed through the plate-replacement space onto the plate cylinder, and the space opening mode makes the plate-replacement space open to the outside of the printing press so that the replacement of a printing plate can be done.
Owner:RYOBI
Transfer tool
ActiveUS7866362B2Stay in shapeHigh strengthMechanical working/deformationWriting accessoriesTime of useUltimate tensile strength
The invention provides a transfer tool which can preferably maintain a shape while improving a strength at a time of using, and has an improved usability. The transfer tool is provided with a first case (1) holding a replacement part including at least a transferring object, a second case (2) detachably engaged with the first case (1) and holding a non-replacement part constituting at least a part of a feeding mechanism part feeding the transferring object to a transferred object, a holding portion (3) outside fitted detachably to a predetermined region of the first case (1) and the second case (2) and capable of holding the first case (1) and the second case (2), and an engagement portion (X) detachably engaging the first case (1) and the second case (2) in a opposite direction of the holding portion (3).
Owner:KOKUYO S&T CO LTD
Slide rail device for vehicle seat
InactiveUS20120160982A1Improve accuracyHigh hardnessLinear bearingsStands/trestlesBall bearingEngineering
Owner:SHIROKI KOGYO CO LTD
Battery unit mounting apparatus and battery unit mounting structure
InactiveUS9016417B2Reduce detection accuracyEasy to installElectric propulsion mountingElectric vehicle charging technologyEngineeringMechanical engineering
A battery unit mounting apparatus for mounting a battery unit to a vehicle from a bottom face side of the vehicle comprises a table having a mount surface for mounting the battery unit, a lift for moving the table up and down with respect to the bottom face of the vehicle, and a connection mechanism for connecting the table and the lift to each other. The connection mechanism connects the table and the lift to each other such that the battery unit or table comes into contact with the bottom face of the vehicle so as to tilt the mount surface by a predetermined inclination with respect to the bottom face of the vehicle.
Owner:TOYOTA IND CORP
Method and apparatus for facilitating payment via mobile networks
ActiveUS20150294294A1Convenient transactionSecurely makingFinancePayment architecturePaymentTelecommunications network
A method and apparatus for facilitating payments for transactions, via mobile devices and mobile telecommunications networks, is disclosed. In an embodiment, a product provider is provided with a code, such as a QRcode, which contains or references payment details for purchase of the product. A mobile user of the application scans the code and is connected to their internet banking application. The payment details are transferred to the internet banking application and the mobile user confirms that the transaction should proceed. Payment is made without any secure details being provided to the product provider.
Owner:OBEP PAYMENTS LLC
Localized betting system and method
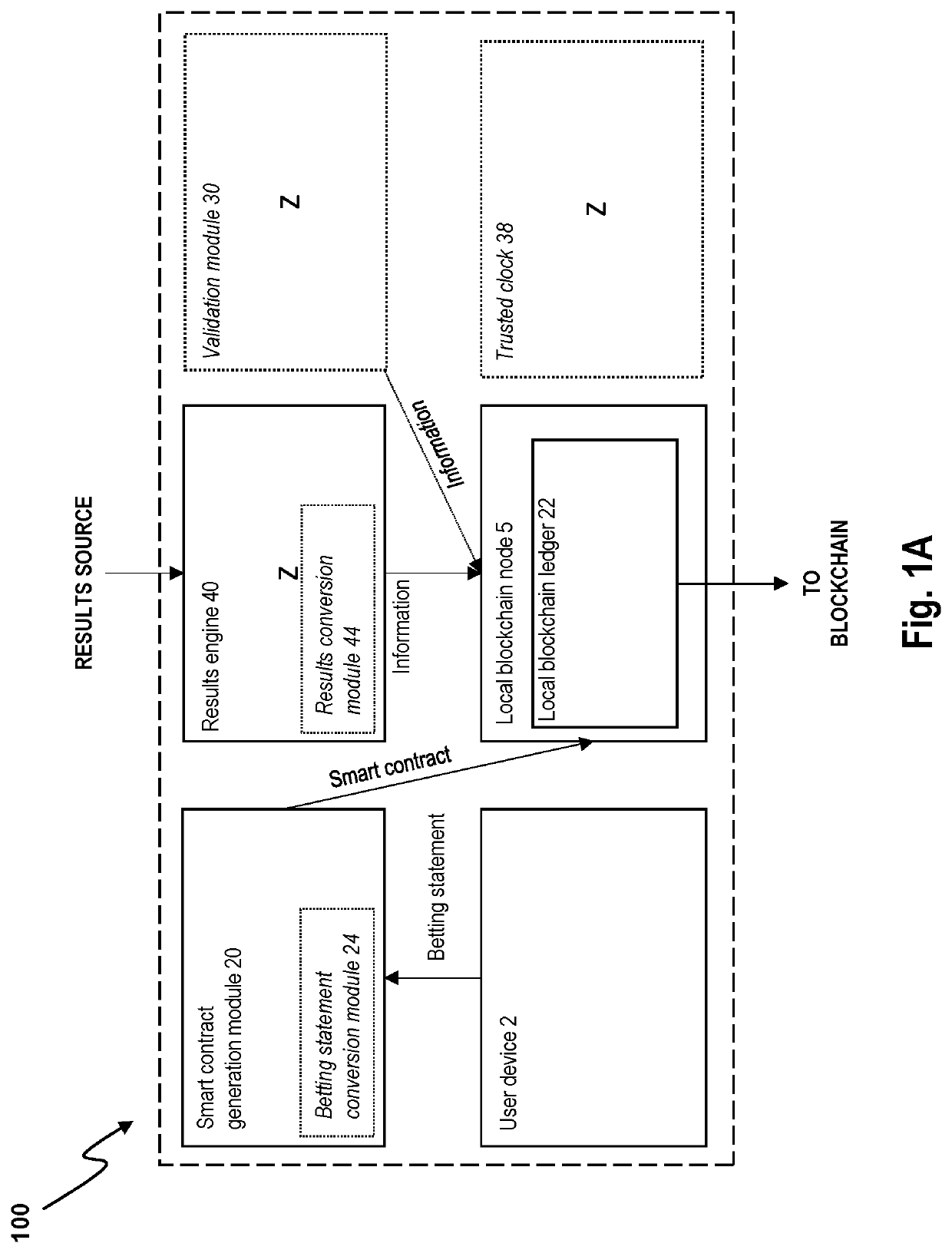
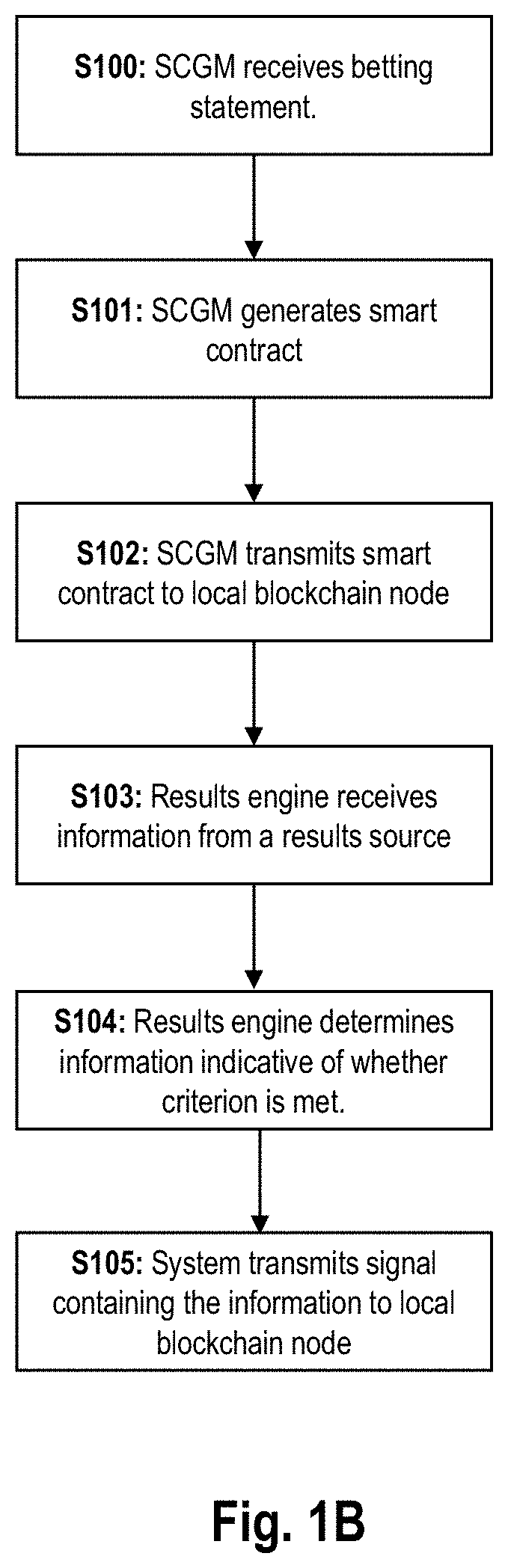
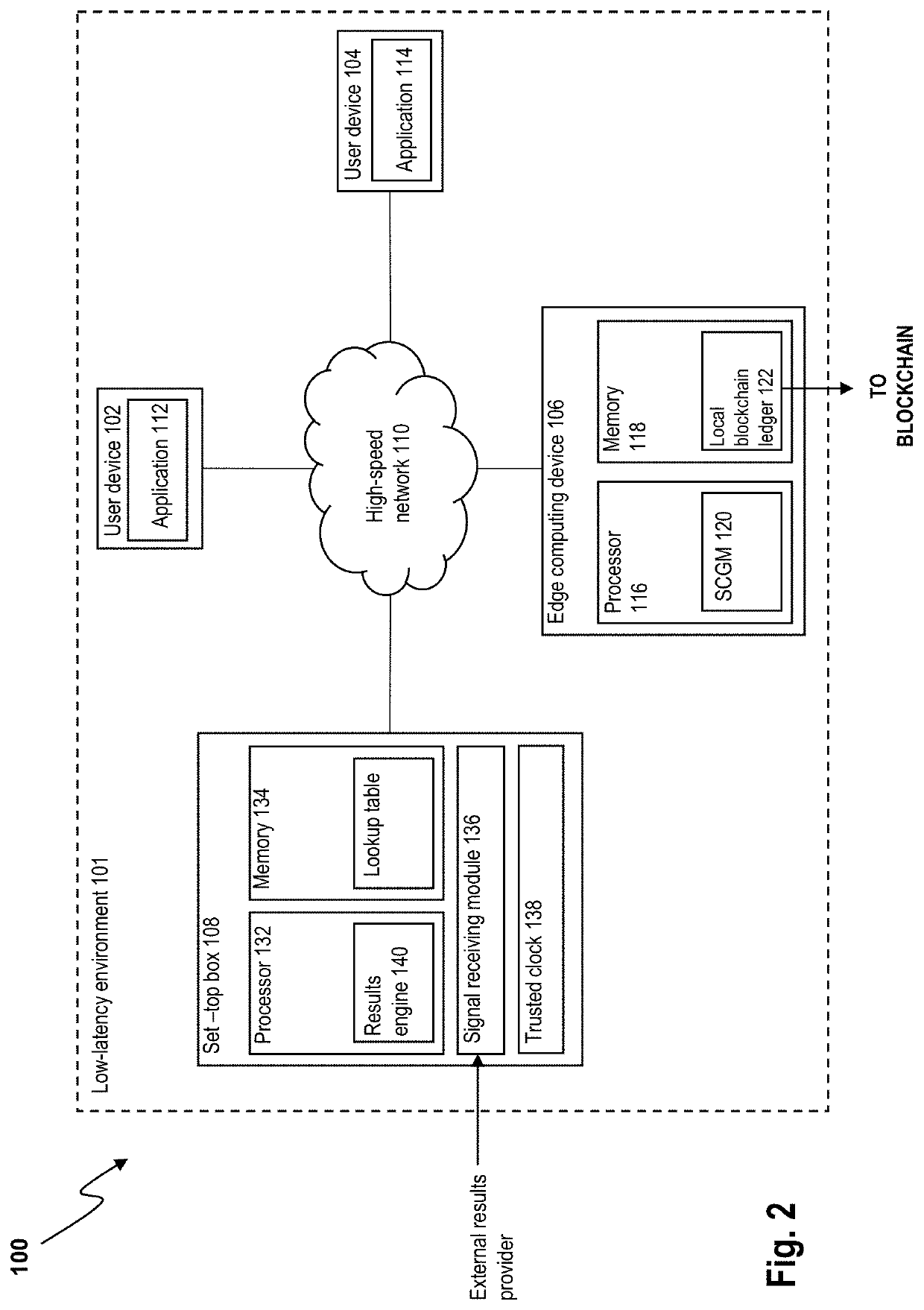
ActiveUS20220051528A1Safely arrangedEnsure safetyData processing applicationsApparatus for meter-controlled dispensingUser deviceSmart contract
A localized electronic betting system includes: a smart contract generation module and a results engine located in a same low-latency environment as the smart contract generation module, wherein: the smart contract generation module is configured to receive a first betting statement from a first user device located within the low-latency environment, to generate a smart contract based on the first betting statement, the smart contract including a criterion to be met and configured to self-execute in response to a determination that the criterion is met, and to transmit the generated smart contract to a local blockchain node located within the low-latency environment; the results engine is configured, based on content received from a results source, to determine information indicative of whether the criterion in the first betting statement is met; and the localized betting system is configured to transmit a signal to the local blockchain node for storage on a local blockchain ledger or a local copy of a blockchain ledger, the signal containing the information indicative of whether the criterion is met. An equivalent method is also provided.
Owner:NAGRAVISION SA
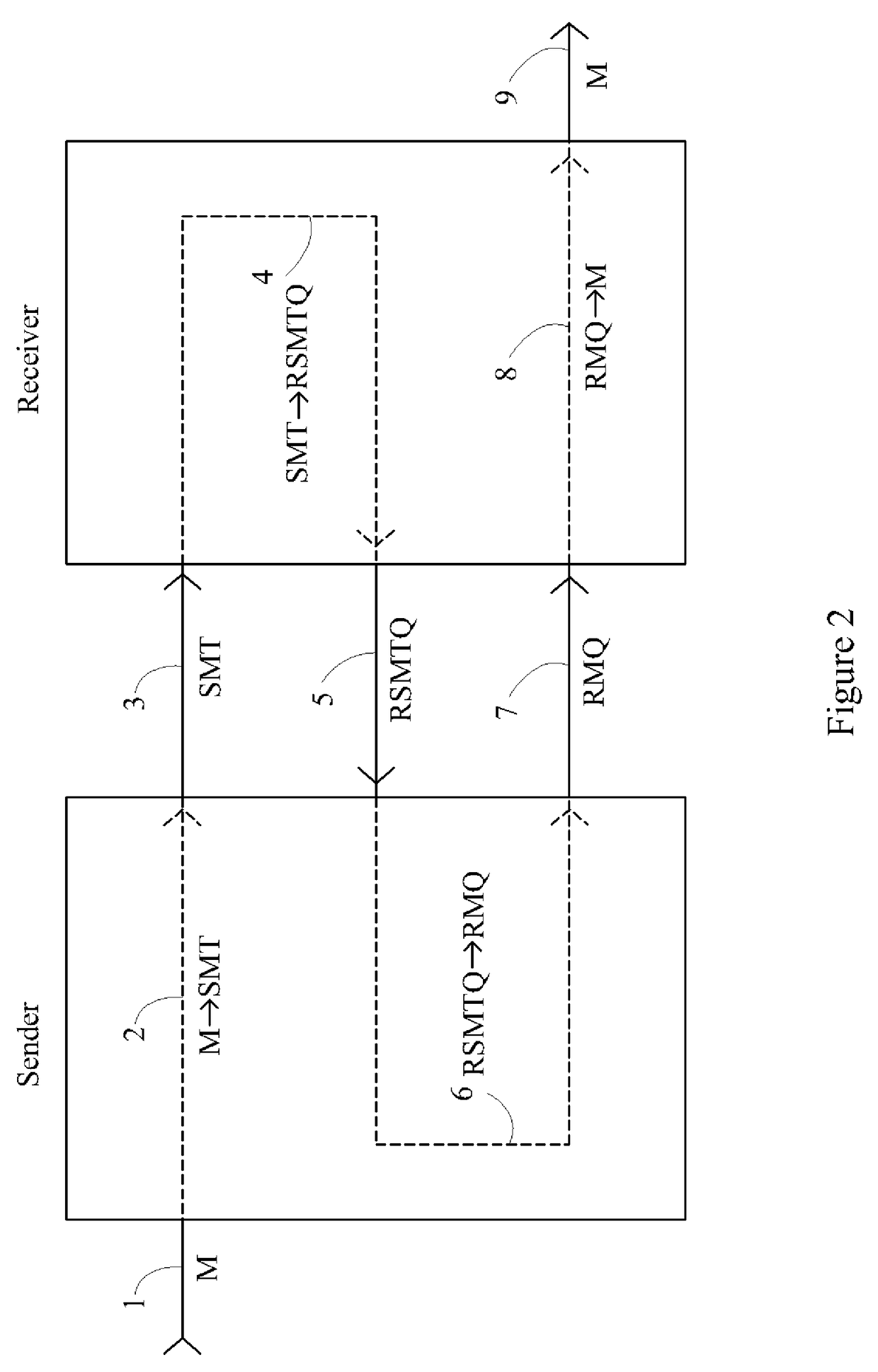
Device, system and method for cryptographic key exchange
InactiveUS8098815B2Securely makingMosaic printer telegraph systemSecret communicationSecure communicationThird party
A method is disclosed whereby two parties can establish a cryptographic key for secure communications without any prior distribution of secret keys or other secret data, and without revealing said key to any third party who may have access to all of the transmissions between them. The two parties agree upon a matrix M, and two commutative families of square matrices F and G. The sender chooses a matrix S from F and a matrix T from G. The receiver independently chooses a matrix R from F and a matrix Q from G. The sender transmits the matrix SMT to the receiver and the receiver transmits the matrix RMQ to the sender. The sender computes the matrix SRMQT from the received matrix RMQ, and the receiver computes the matrix RSMTQ from the received matrix SMT. Since the matrices S and R commute, and the matrices T and Q commute, SRMQT=RSMTQ. The value of the matrix SRMTQ is then used to produce the desired cryptographic key.
Owner:RUBIN FR
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com