Encryption-decryption method based on Base64 and device thereof
An encryption method and an encryption device technology, which are applied in the field of Base64-based encryption and decryption methods and devices, can solve problems such as being easily intercepted, and achieve high security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] Such as figure 1 shown, including the following steps:
[0057] Step 01. Obtain the plaintext information to be encrypted, and perform Base64 encoding on the plaintext information to generate an encoded string A.
[0058] Step 02. Randomly generate two random values between 3-63: a first value m1 and a second value m2.
[0059] Step 03. Obtain the first character c1 corresponding to m1 and the second character c2 corresponding to m2 from the Base64 character mapping table; Table 1 shows the Base64 character mapping table.
[0060] Table 1, Base64 character mapping table
[0061]
[0062]
[0063] Step 04, randomly obtain m1 characters from the Base64 character mapping table, and form the first string str1; and randomly obtain m2 characters from the Base64 character mapping table, and encode the second string str2.
[0064] Step 05, adding the first string str1 to the front of the encoded string, adding the second string str2 to the back of the encoded string,...
Embodiment 2
[0087] A kind of encryption method based on Base64, comprises the steps:
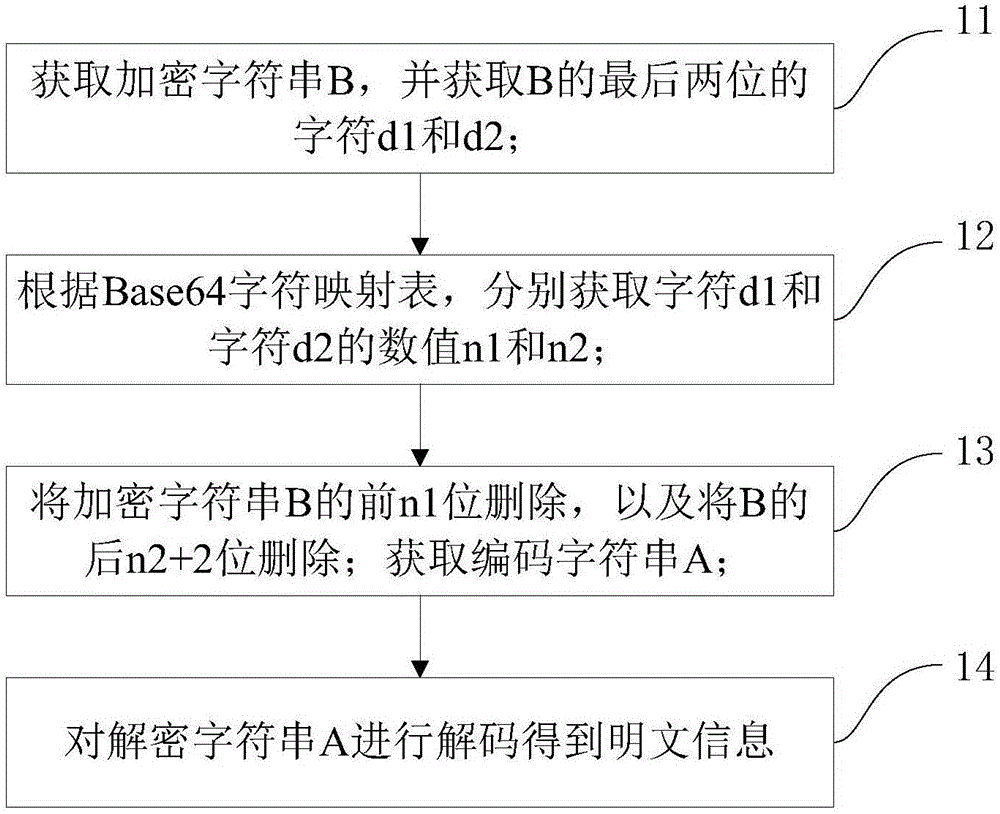
[0088] Step 21, obtaining the plaintext information to be encrypted; performing Base64 encoding on the plaintext information to generate an encoded string A;
[0089] Step 22, randomly generating a first value m1 between 3-63;
[0090] Step 23. Obtain the first character c1 corresponding to the first value m1 from the Base64 character mapping table;
[0091] Step 24, randomly obtain m1 characters from the Base64 character mapping table, and form the first character string str1;
[0092] Step 25. Add the first character string str1 to the front of the encoded character string A, add the first character to the end of the encoded character string A, and generate the final encrypted character string B.
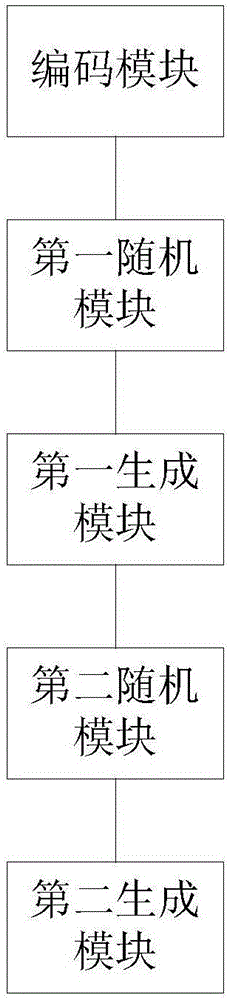
[0093] An encryption device based on Base64, specifically comprising:
[0094] The encoding module is used to obtain the plaintext information to be encrypted; the plaintext information is Base64-encoded...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com