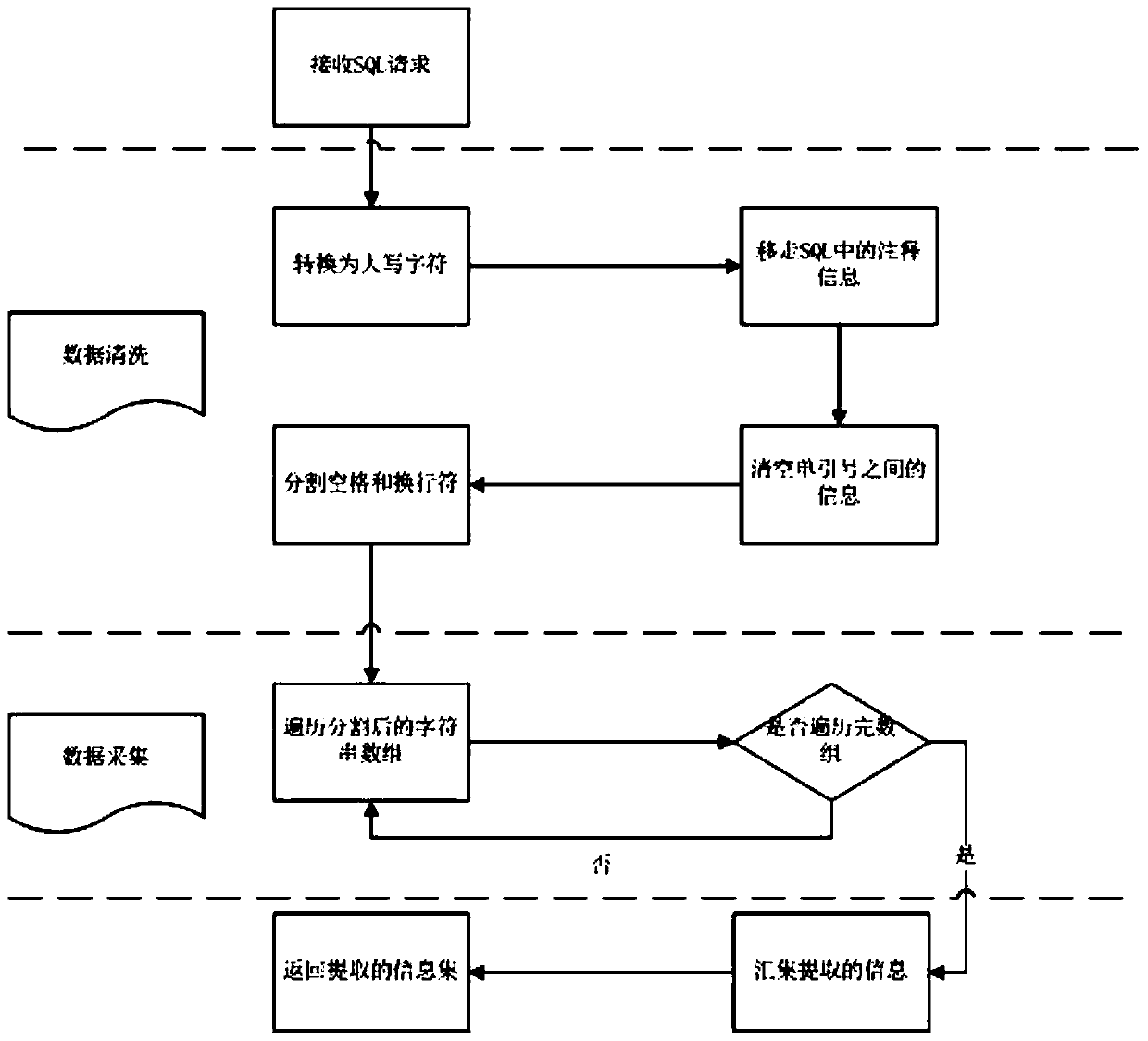
Patents
Literature
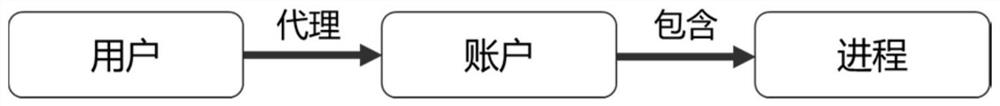
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
34results about How to "Precise access control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
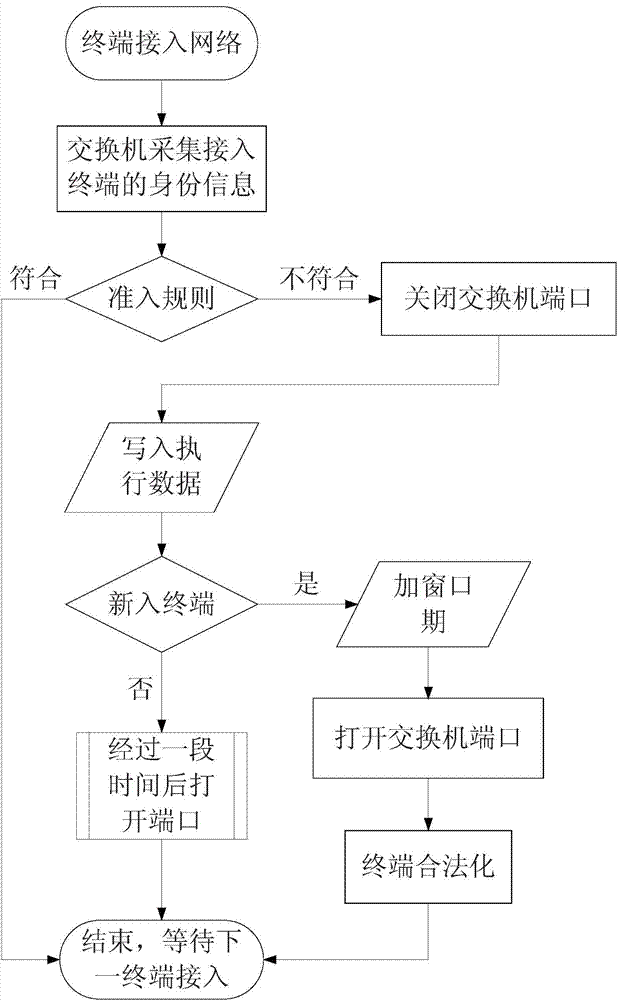
Terminal admission control method based on switch port management
InactiveCN103929376AIntegrity guaranteedAccurate access controlData switching networksAuthorizationVirtual machine
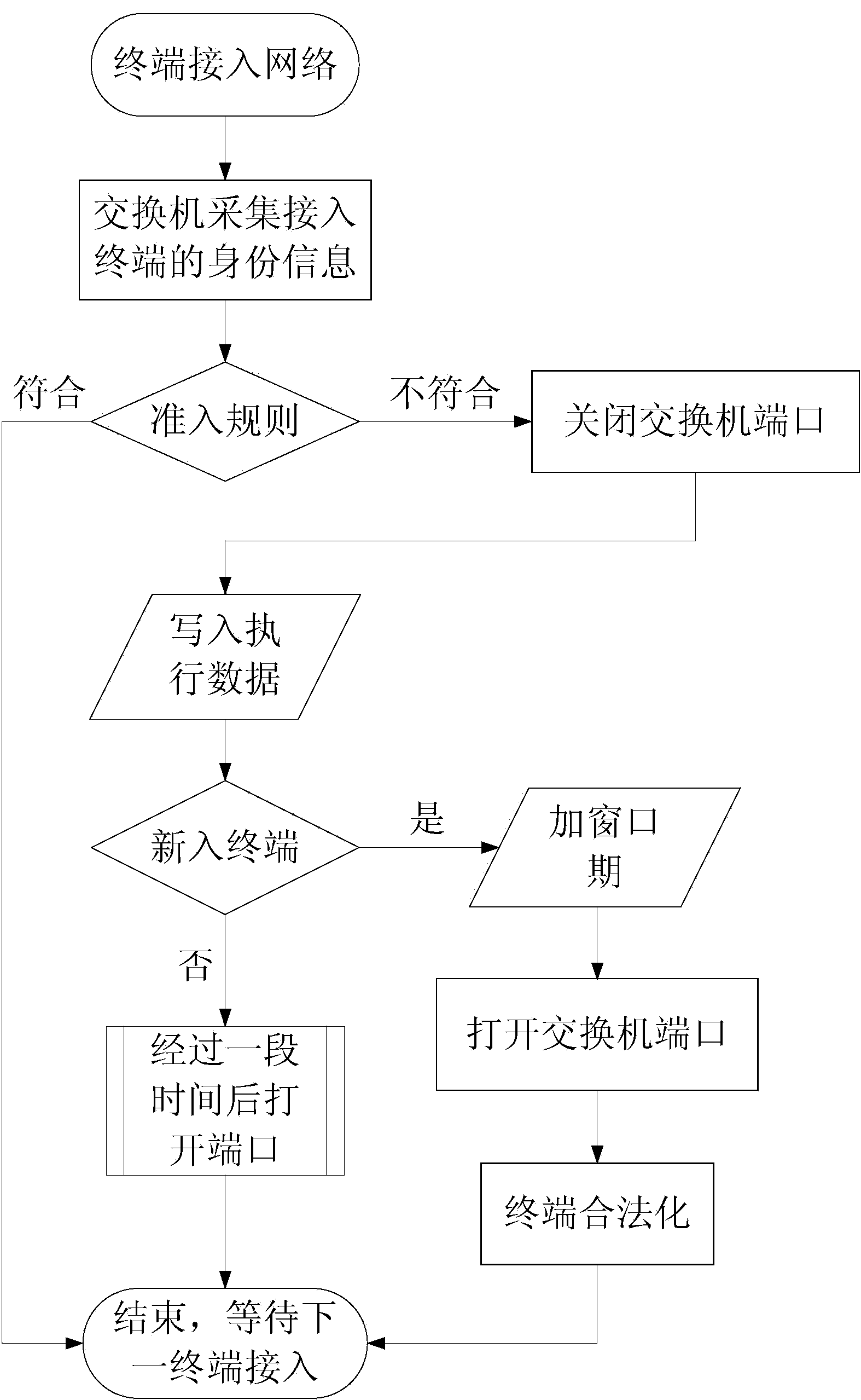
The invention relates to the technical field of terminal admission control, and particularly discloses a terminal admission control method based on switch port management. The method includes the steps that after a new terminal gets access to a network, the new terminal is collected through a switch, the unique identification of the terminal is extracted, and the terminal is interrelated with a port of the switch; the unique identification is compared with MAC addresses of an admission database and judged; if the unique identification is inquired, the new terminal is a legal terminal, and no action is generated; if the unique identification is not inquired, the new terminal is an illegal terminal or an external terminal, the corresponding port of the switch is closed immediately, and close information is recorded in the admission database; when a new terminal gets access to the network again, the new terminal is joined after window period processing; the previous steps are executed again to start processing; if no new terminal gets access to the network, the closed port of the switch is automatically opened after appointed time. MAC address management is adopted for the terminals, a terminal user is forbidden to change an MAC address without authorization, a virtual machine is managed, HUB access is stopped, and terminal admission control is accurate and strict.
Owner:尹志超
Extensible markup language document management method and system
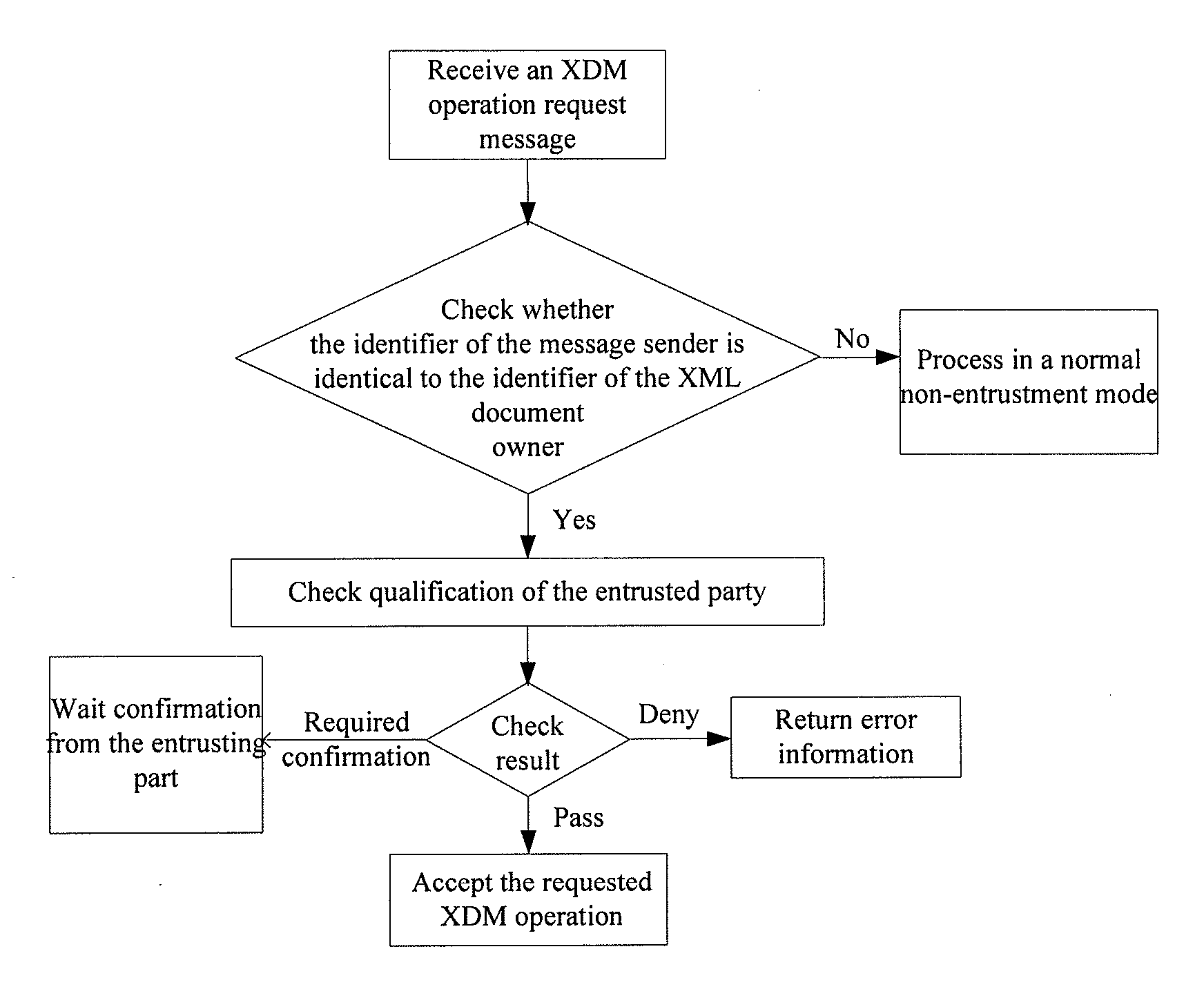
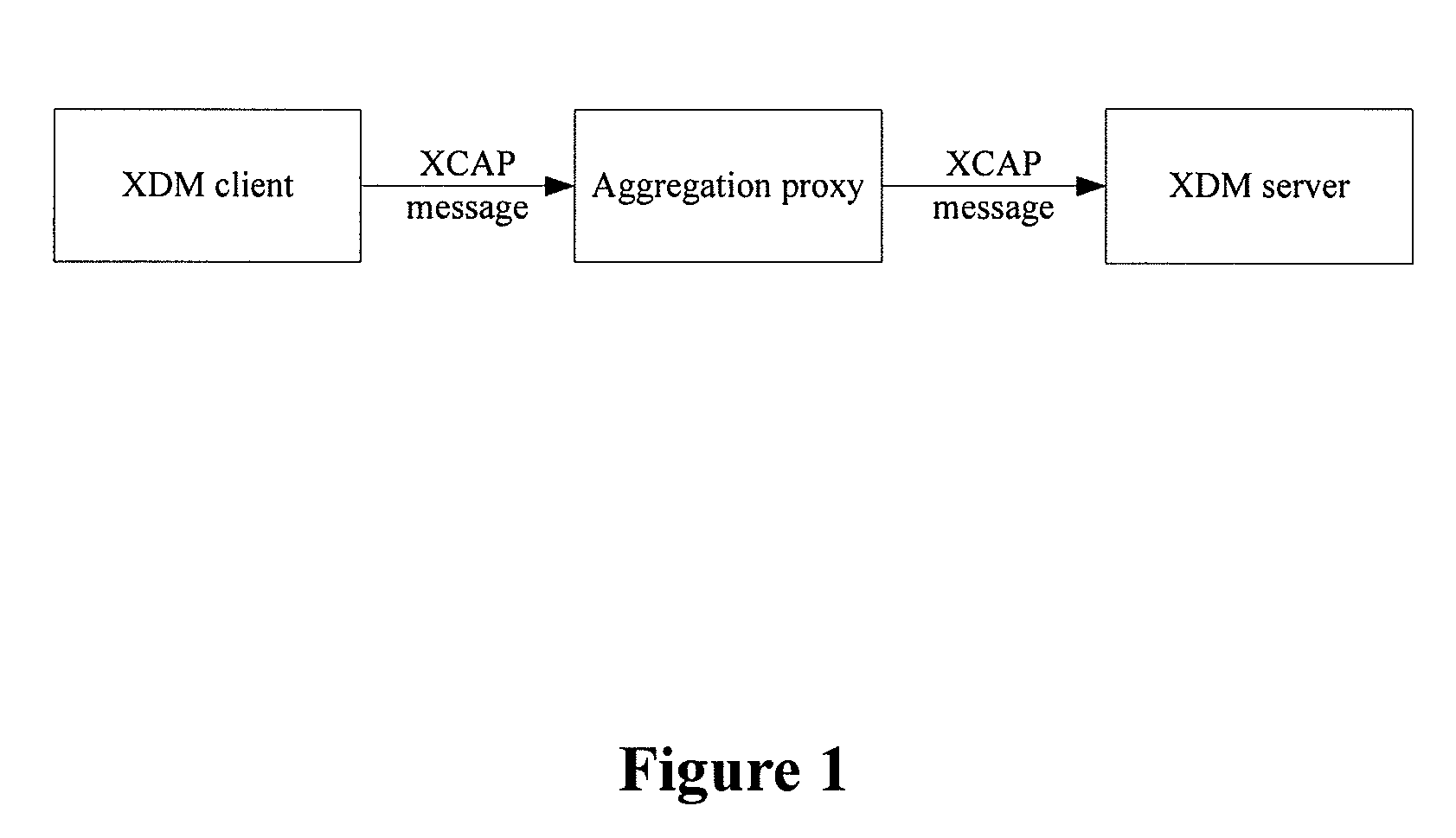
ActiveUS20080104124A1Ensure safetyEfficient sharingDigital data protectionTransmissionPaper documentDocument preparation
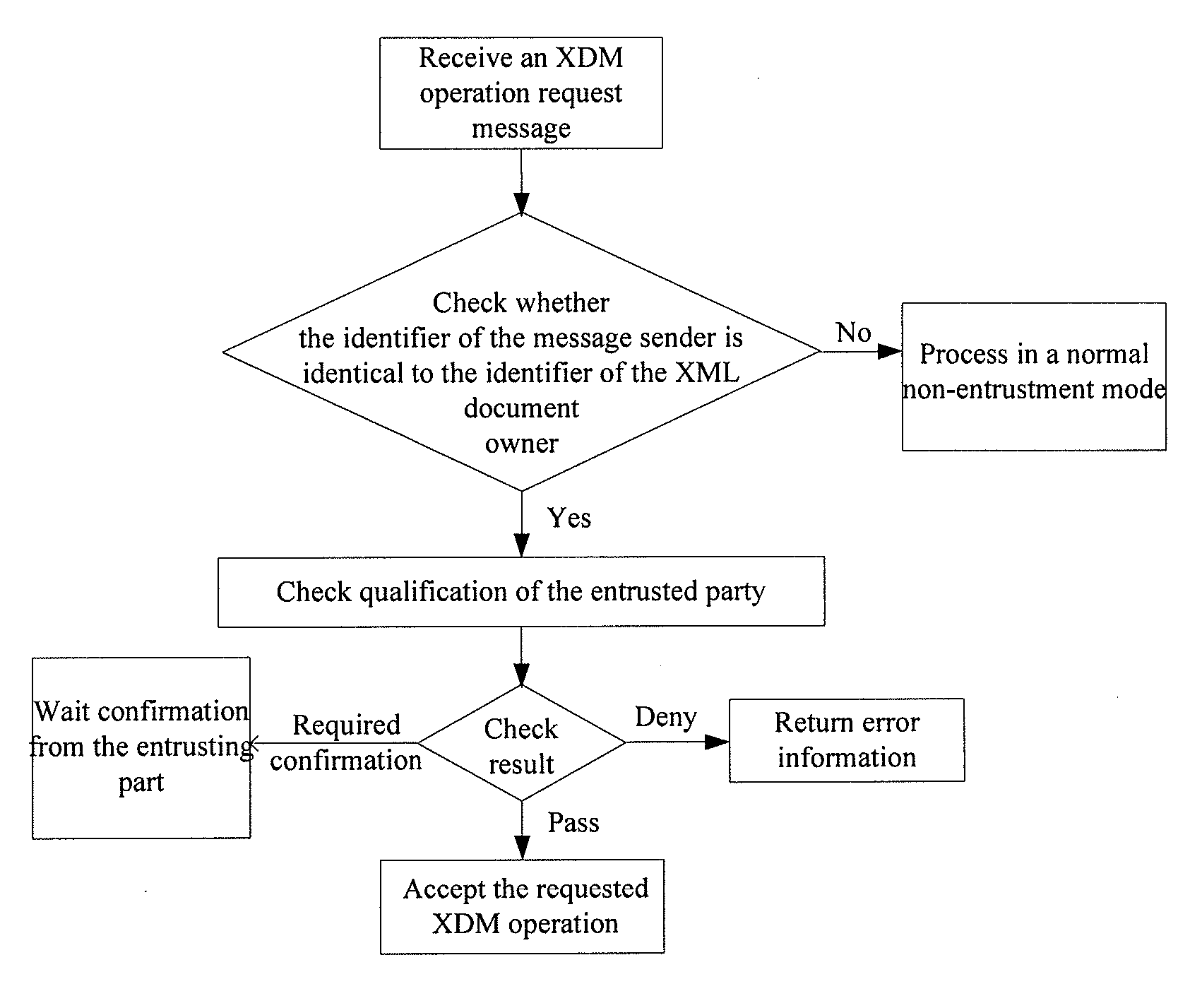
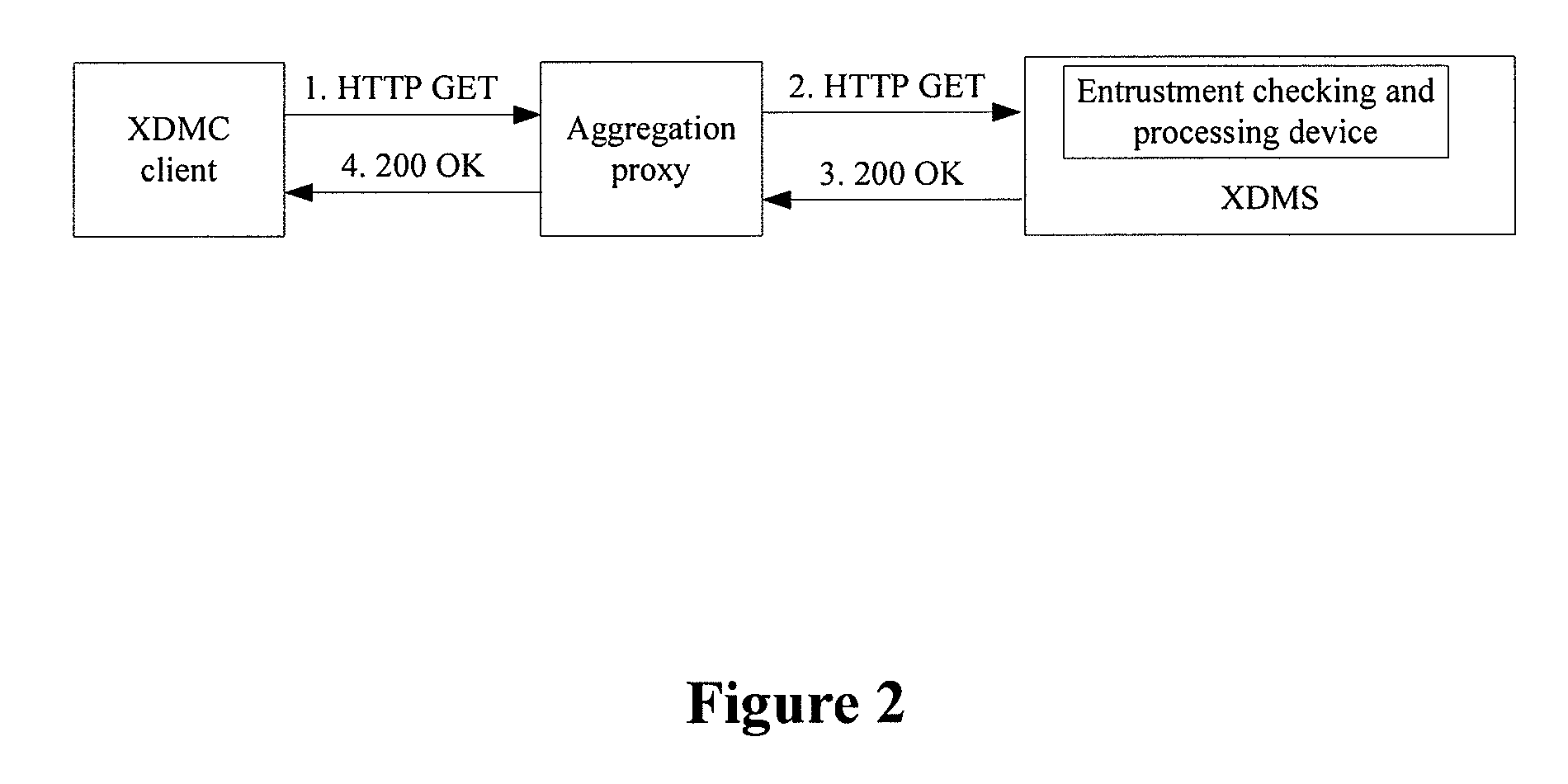
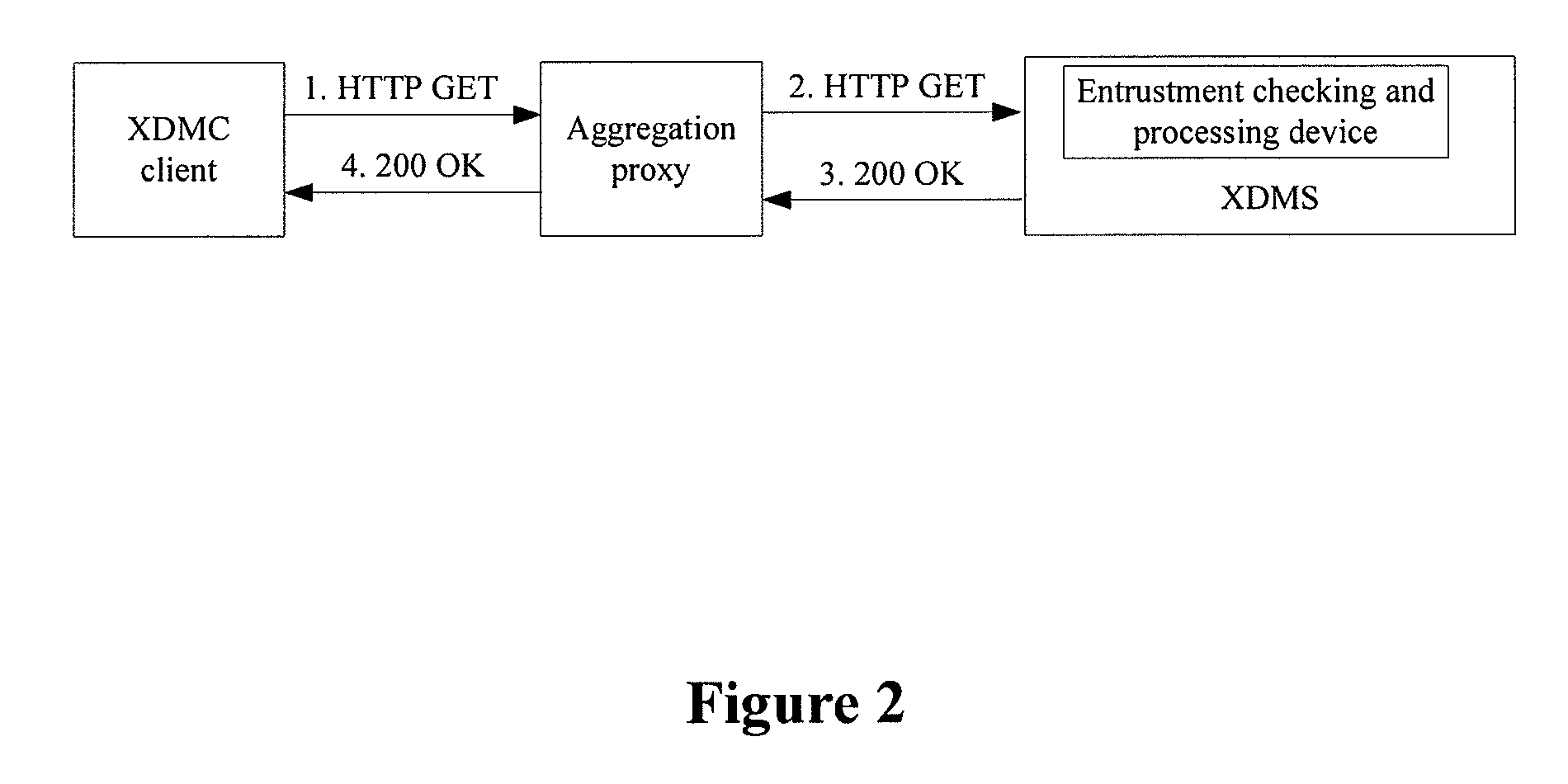
An Extensible Markup Language (XML) document management method includes: receiving an XML document management operation request sent via an XCAP protocol, by an XML Document Management Server (XDMS); determining that the XML document management operation request is in an entrustment mode, and determining whether to perform an operation described in the XML document management operation request in accordance with access permission information corresponding to an XML document, by the XDMS.
Owner:HUAWEI TECH CO LTD
Method and device for multi-account authority control
InactiveCN102955910APrecise access controlImprove efficiencyDigital data protectionDigital data authenticationAuthority controlDatabase
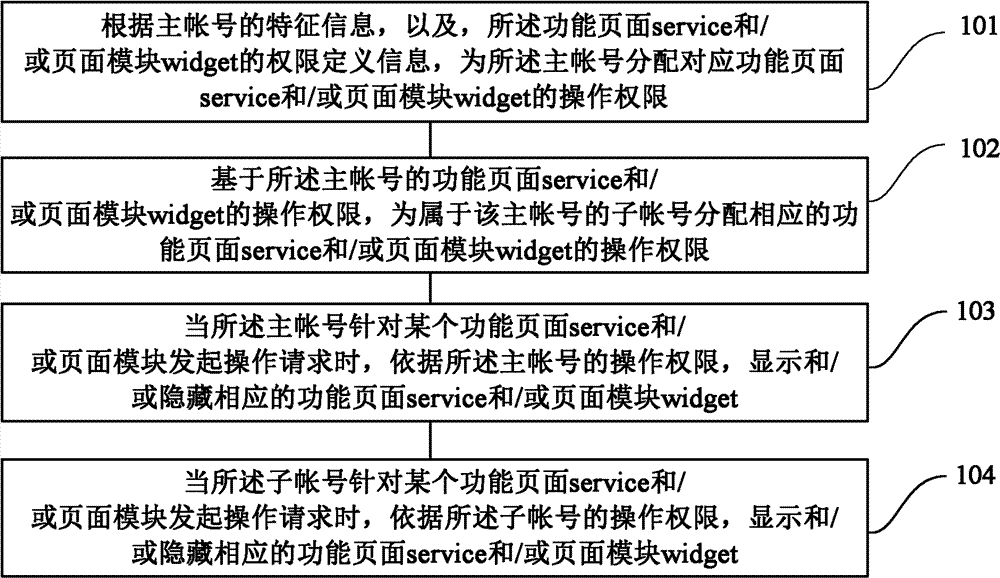
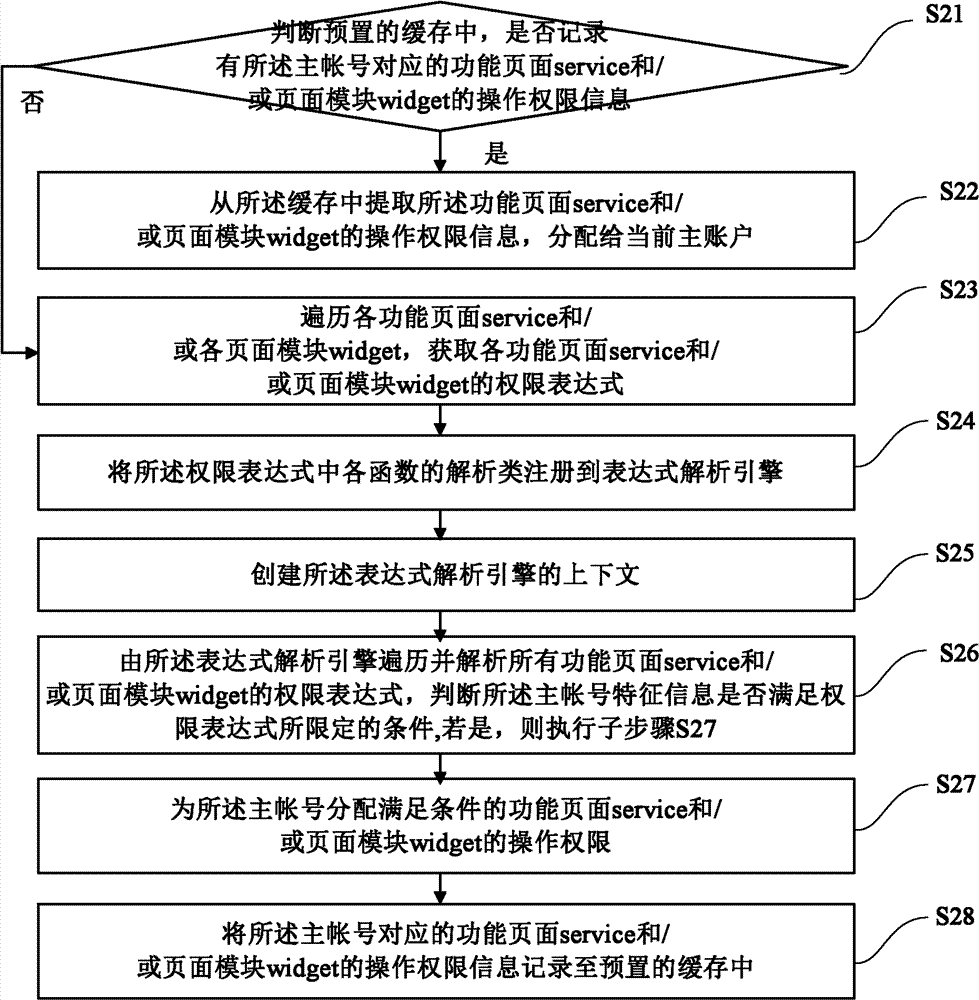
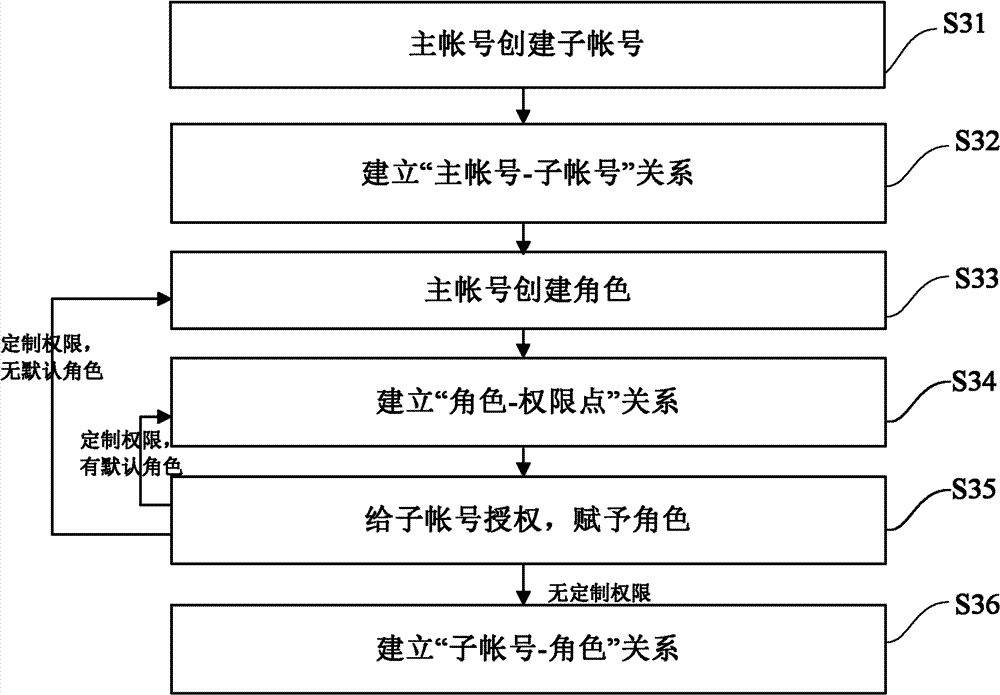
The invention provides a method and a device for multi-account authority control. The method includes: distributing operation authorities corresponding to functional pages and / or page modules to a primary account according to feature information of the primary account and authority defined information of the functional pages and / or the page modules; on the basis of the operation authorities of the functional pages and / or the page modules of the primary account, distributing corresponding operation authorities of the functional pages and / or the page modules to sub-accounts of the primary account; and when the primary account and / or the sub-accounts initiate operation requests aiming at one functional page and / or page module, displaying or hiding the corresponding functional page and / or page modules according to the operation authorities of the primary account and / or the sub-accounts. By the method and the device, different users only focus on widget and service with the operation authorities, irrelevant widget and service loading is decreased, network resource occupancy is reduced, complexity of multi-account authority controlled objects is lowered, and user experience is improved.
Owner:ALIBABA GRP HLDG LTD
Internet of ships intelligent shore-based interaction device based on Beidou
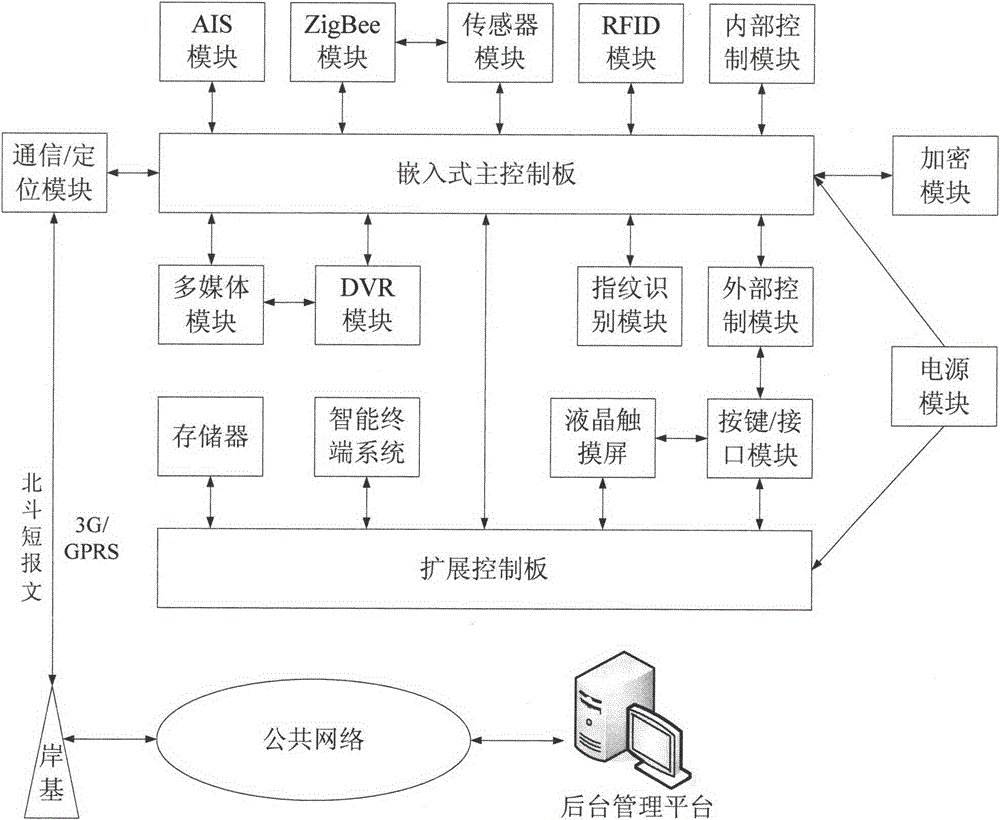
ActiveCN104933897ASimple internal structureLow failure rateTransmission systemsMarine craft traffic controlThe InternetInteraction device
The invention discloses an Internet of ships intelligent shore-based interaction device based on Beidou, and the device comprises an embedded-type main control board, an extended control board, a communication / positioning module, an AIS module, a ZigBee module, a sensor module, an RFID module, an internal control module, an encryption module, a power module, an external control module, a fingerprint recognition module, a DVR module, a multimedia module, a storage unit, an intelligent terminal system, a liquid crystal touch screen, and an interface module. The embedded-type main control board is connected with the extended control board. The power module is connected with the main control board and the extended control board. The communication / positioning module achieves interaction with shore-based equipment through a Beidou message or a 3G / GPRS signal. The device employs the technology of multimode positioning, the technology of sensing, the technology of wireless networking communication and the technology of safety encryption, achieves a function of inland river gate report, a function of visualized emergency command scheduling and a function of shipping electronic business, and prompts the building and development of inland river Internet of ships.
Owner:林兴志
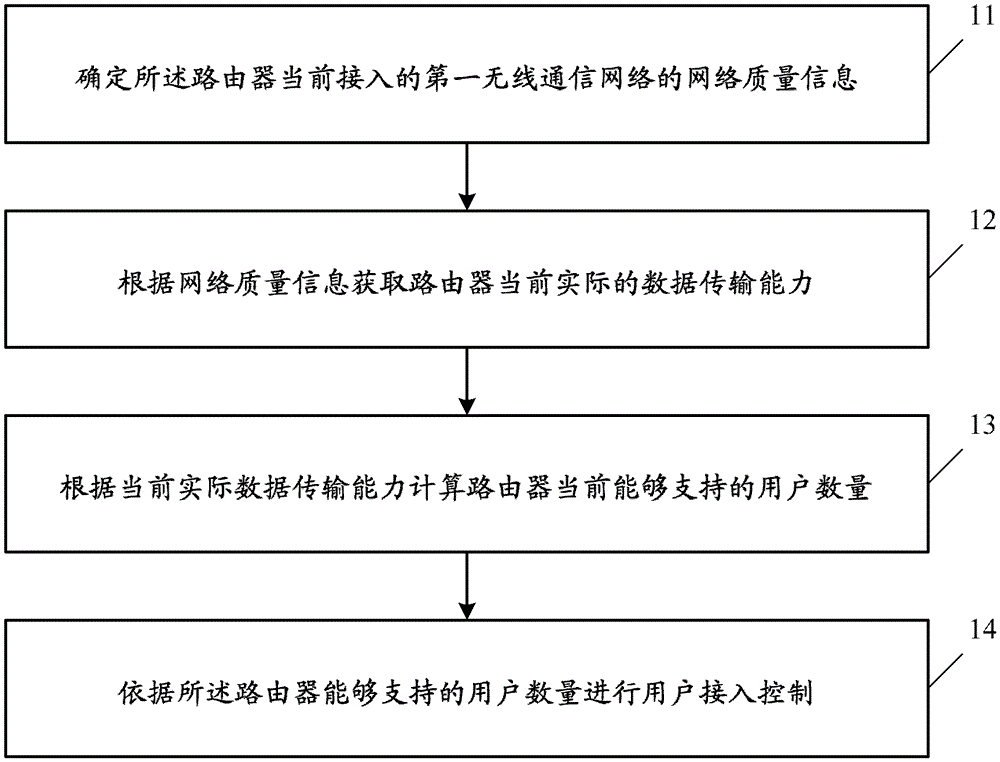
User access control method and device, and route
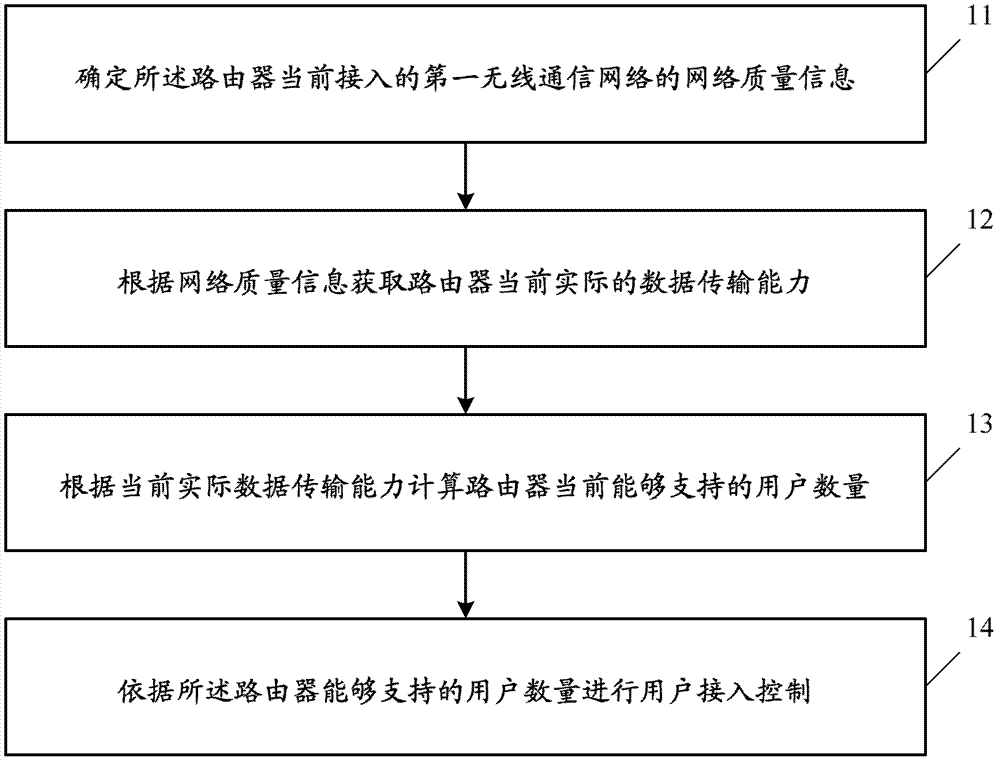
ActiveCN103249112APrecise access controlImprove accuracyAssess restrictionData transmissionUser control
The invention provides a user access control method and device, and a router. The control method is used for the router which is used for providing network access serve for users through a wireless communication network. The method comprises the following steps: determining the network quality information of a first wireless communication network accessed into the router; obtaining the actual data transmission ability of the router according to the network quality information; calculating the current number of subscribers supported by the router according to the actual data transmission ability; and controlling user access according to the number of subscribers. According to the invention, the flexibility of the access control of the router is improved.
Owner:CHINA MOBILE COMM GRP CO LTD
Method, device and system for performing access control judgment by core network
ActiveCN101945485AAvoid confictPrecise access controlNetwork traffic/resource managementNetwork topologiesMobility managementClosed subscriber groups
The invention discloses a method, a device and a system for performing access control judgment by a core network. In the scheme of the invention, after the access mode of a base station is changed, a mobility management entity acquires subscriber access information on which the access control judgment needs performing and executes the access control judgment on corresponding subscribers according to the acquired subscriber access information, so that the core network can avoid collisions with the access control judgment of a base station gateway, prevent the conditions of judgment omission and misjudgment and ensure connected subscribers with different kinds of closed subscriber group (CSG) capacity can accurately finish access control after the access mode of the base station is changed.
Owner:HUAWEI TEHCHNOLOGIES CO LTD
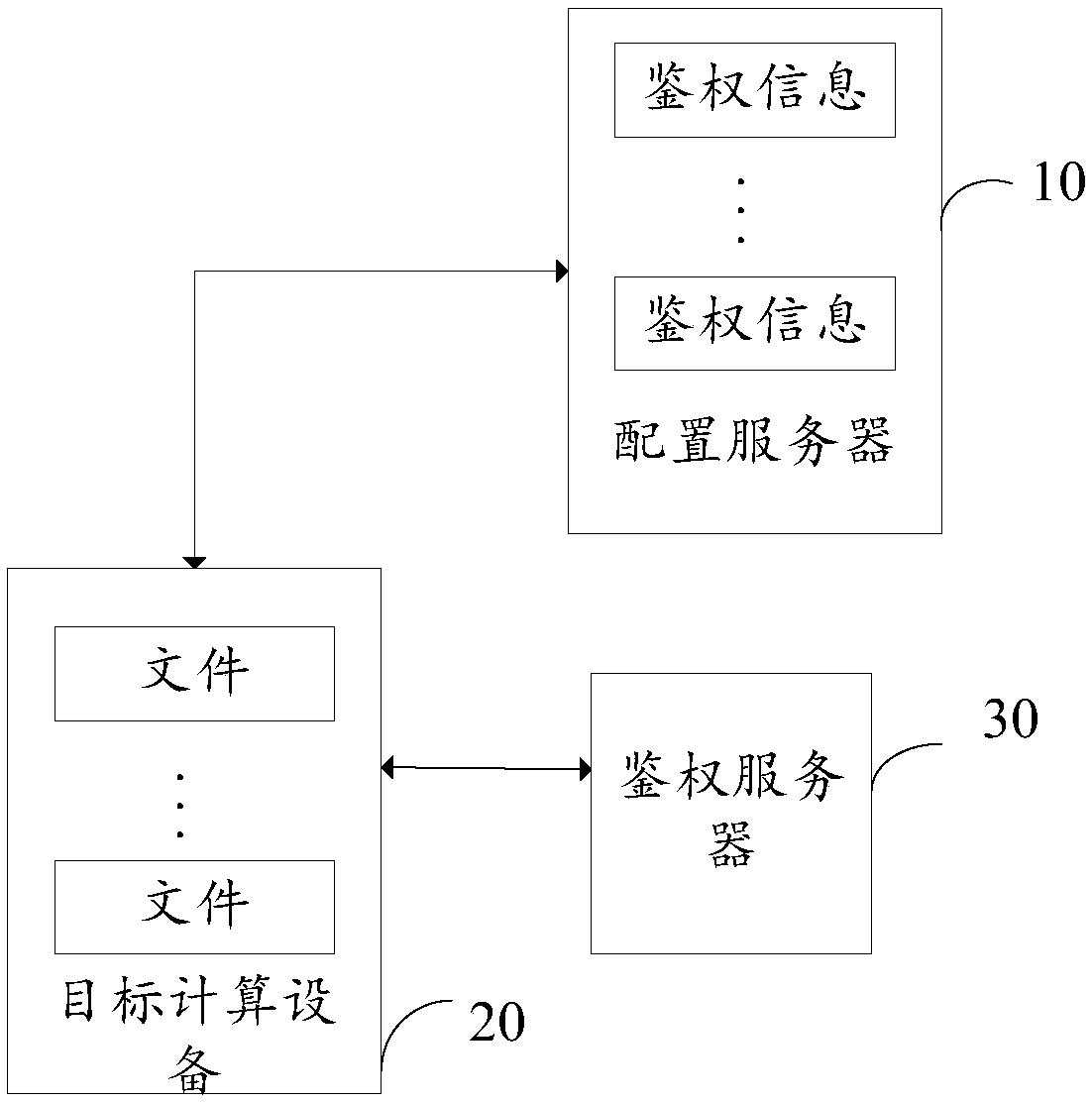
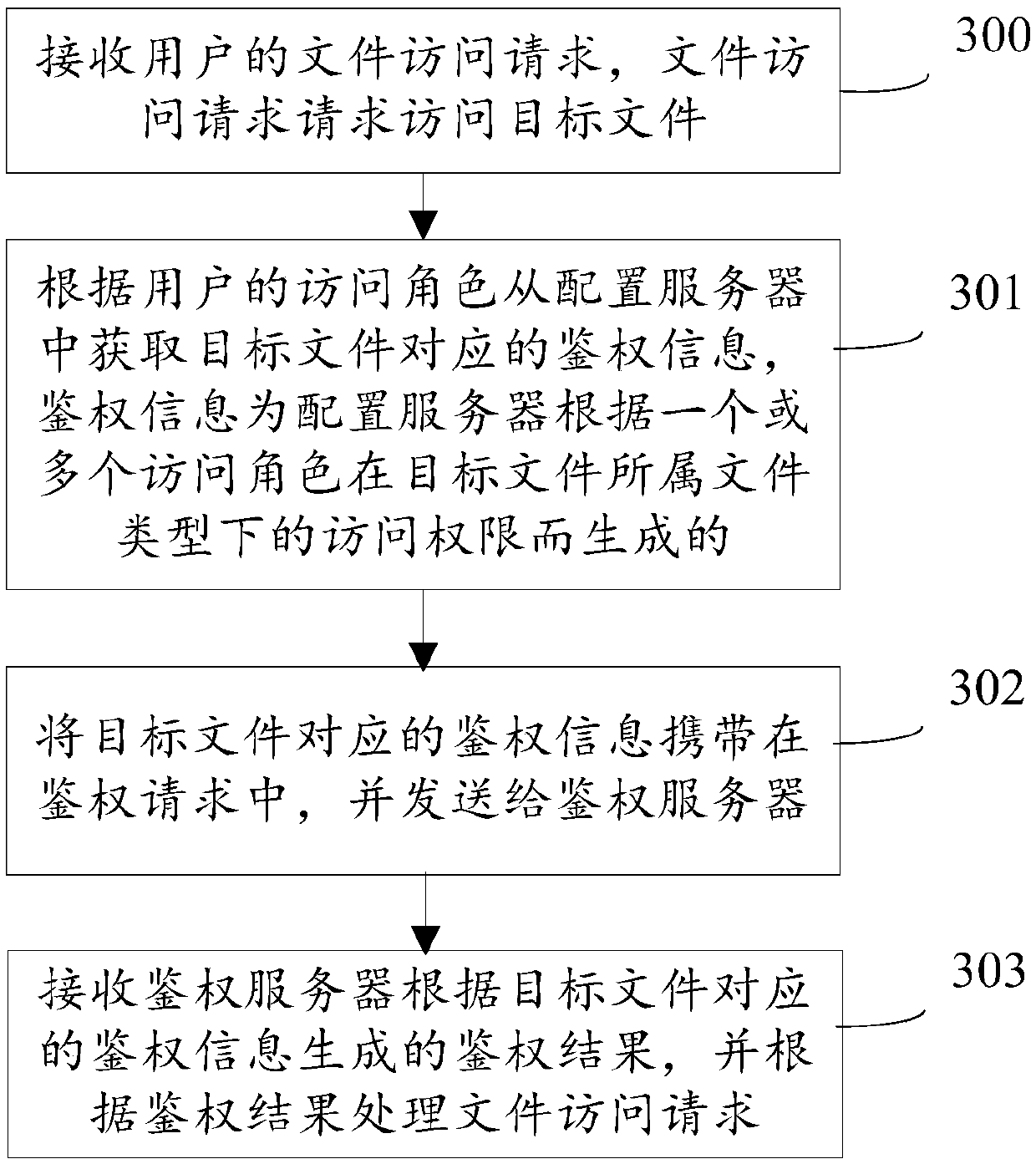
Access control method, equipment and system and storage medium
ActiveCN110909373AAccurate access controlClassification is flexibleDigital data protectionEngineeringAuthentication server
The embodiment of the invention provides an access control method, equipment and system and a storage medium. A configuration server in the system is used for determining a file type to which each file of a data party in a business system belongs, and generating authentication information for each file aiming at different access roles according to access permissions of different access roles underthe file type to which each file belongs, outputting the authentication information of each file for different access roles to a service system; the service system is used for receiving a file accessrequest of a user, the file access request is used for requesting to access a target file, and carrying authentication information corresponding to the target file acquired according to an access role of the user in the authentication request and sending to the authentication server; and the authentication server is used for generating an authentication result according to the authentication information corresponding to the target file and sending the authentication result to the service system, so that the service system processes the file access request according to the authentication result. Therefore, more flexible and more accurate access control can be realized.
Owner:ALIBABA GRP HLDG LTD
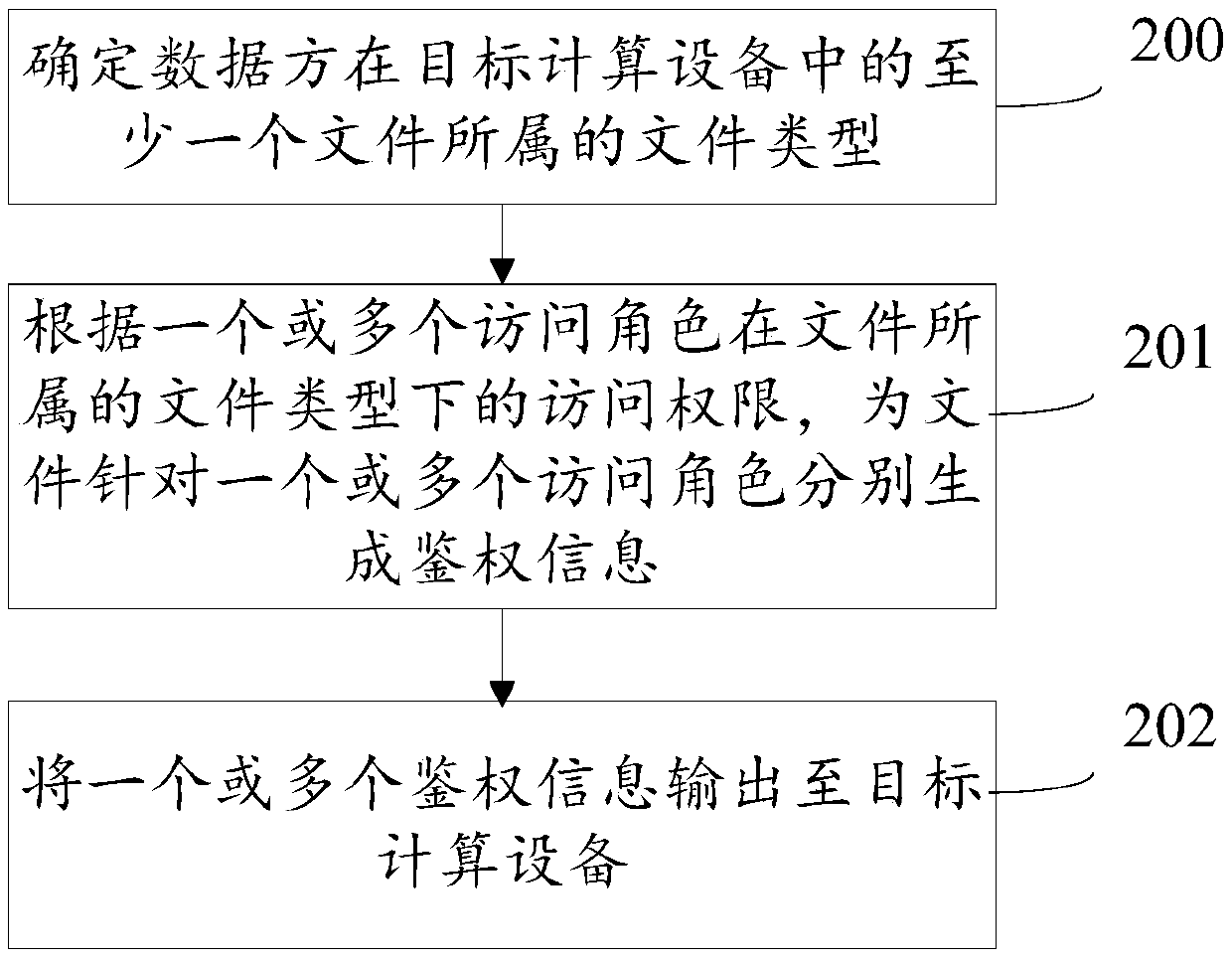
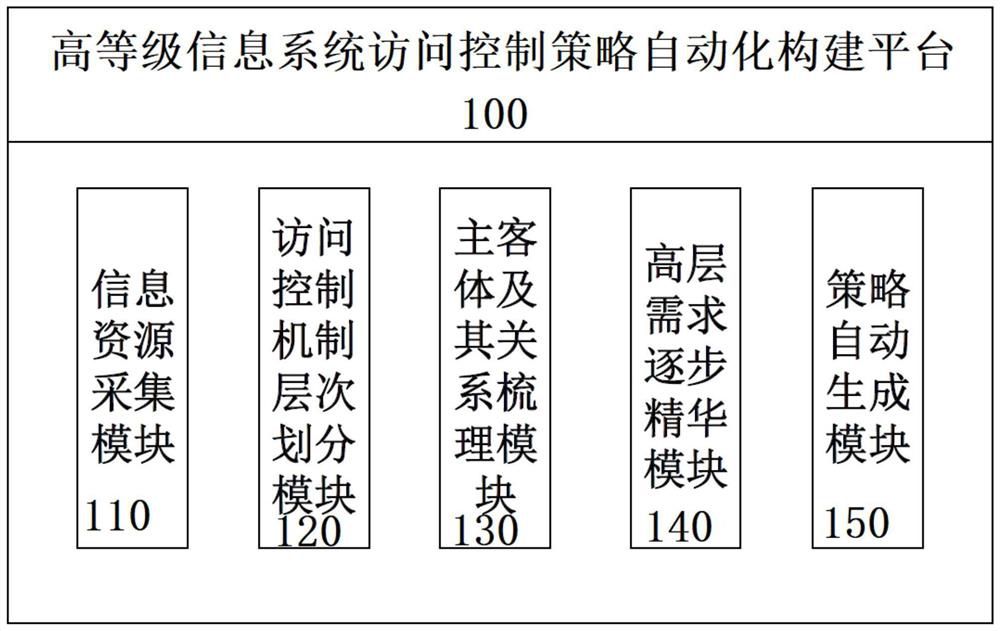
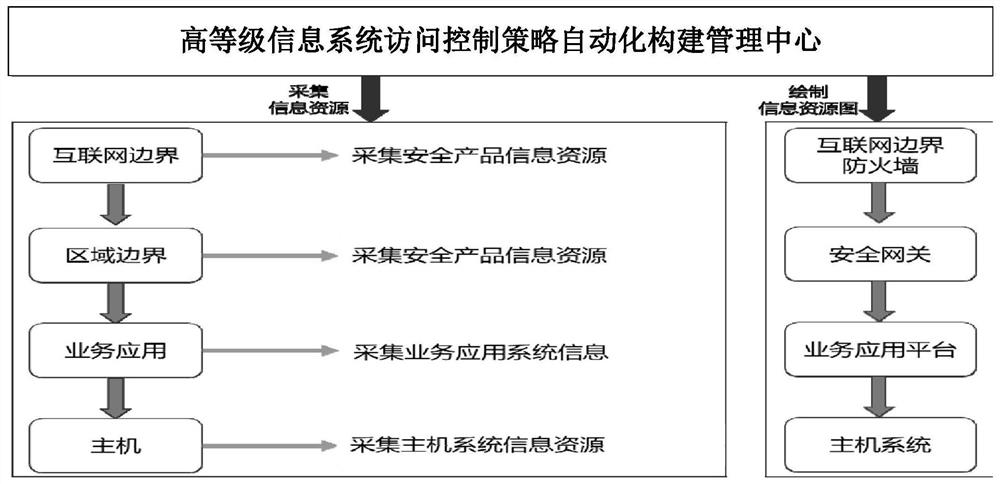
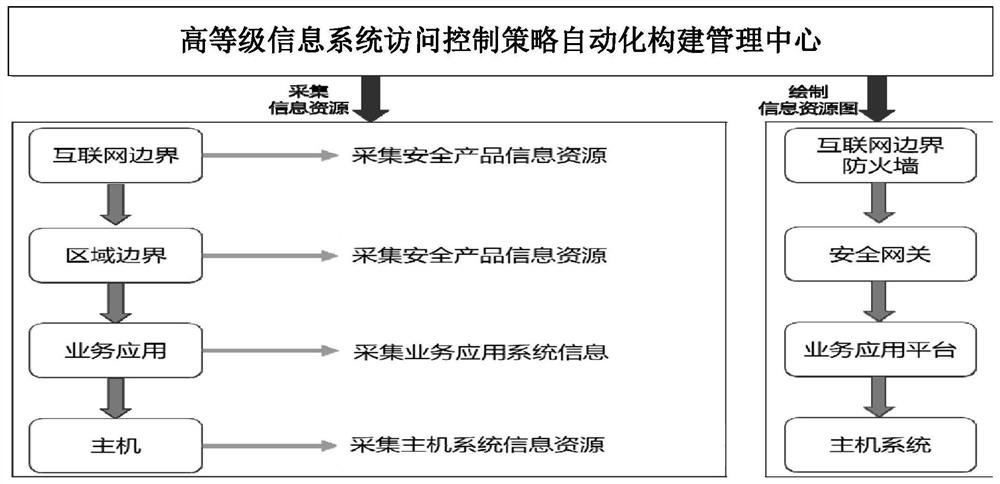
Automatic construction system and method for access control strategy of high-level information system
ActiveCN111818059APrecise access controlImplementation of Security PolicyTransmissionInformation resourceInformation system
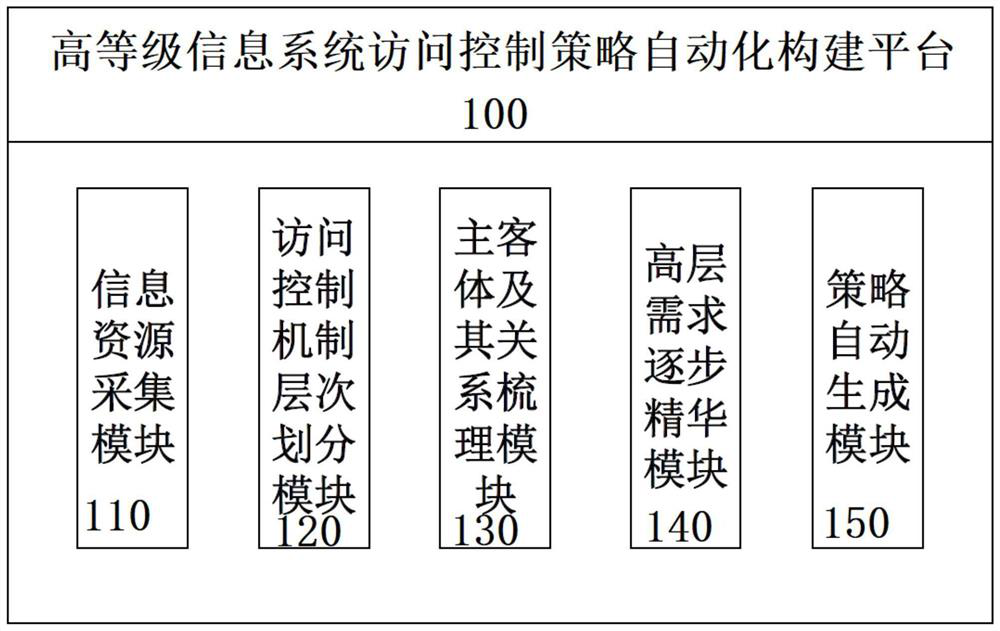
The invention discloses an automatic construction system and method for an access control strategy of a high-level information system. According to the scheme, information resource acquisition is carried out on software and hardware products in a whole network system based on an information resource acquisition module, an access control mechanism hierarchical division module, a subject-object andrelationship carding module, a high-level demand gradual essence module, an automatic strategy generation module and an information resource acquisition module; the access control mechanism hierarchical division module performs hierarchical division on an access control mechanism; the subject-object and relationship carding module caries a subject, an object and a relationship structure thereof byanalyzing the subject, the object and the relationship structure thereof in the whole network system; the high-level demand gradual essence module is used for gradually refining the essence service access demand and the operation and maintenance management access demand; and the automatic strategy generation module generates an access control strategy of each access control mechanism level. According to the scheme, in the resource access process of a network system user, accurate access control can be carried out on the user no matter what level access is carried out.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Access control method and system based on security state of terminal host
InactiveCN107332803AEnsure safetyPrecise access controlTransmissionNetwork access serverSecure state
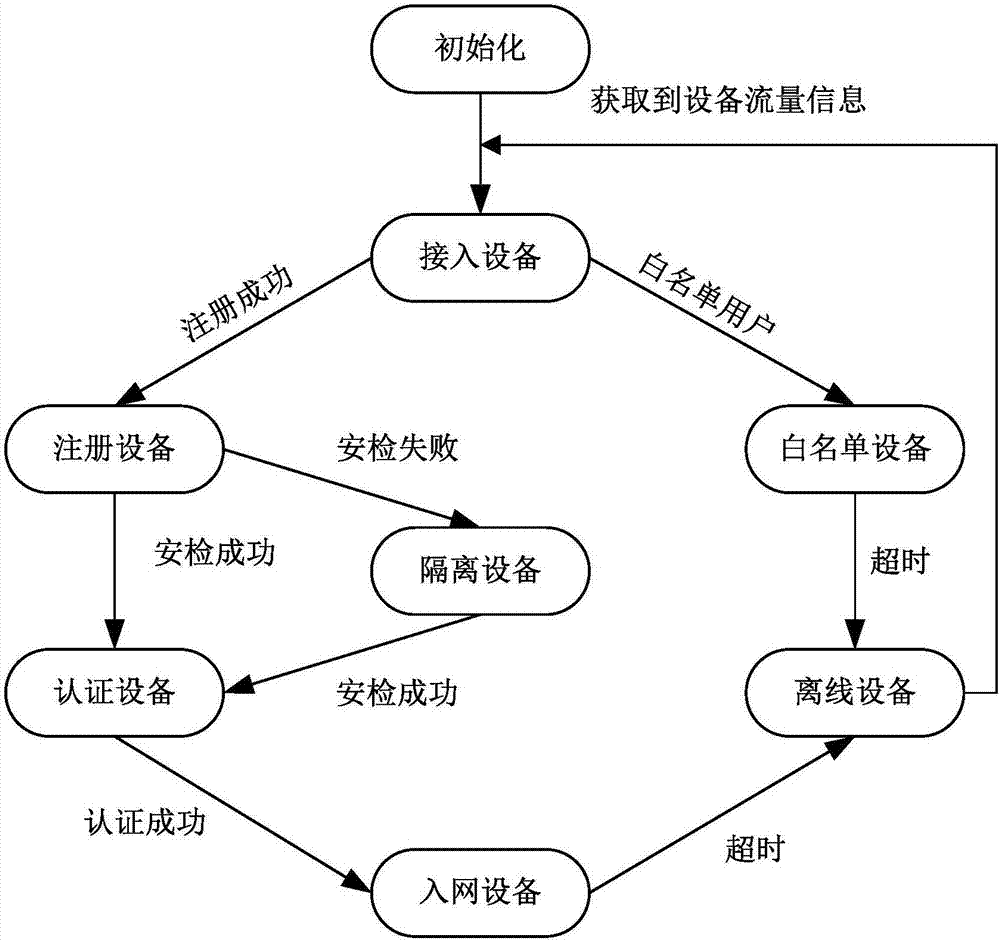
The invention discloses an access control method based on a security state of a terminal host. The method comprises the following steps: judging an access state of an access terminal accessing network resources so as to judge to directly switch the access terminal to a network access device or enable the access terminal to enter an admission stage, wherein the admission stage comprises management registration, registration audit, security detection, authentication and authority management. According to the access control method disclosed by the invention, the objectives of device security, personnel security and network resource access security are achieved in stages, and the device network access flows are refined; the network access flows are more accurate by a plurality of states, accurate network access control of devices in different states is realized, and differential control of different users of different devices is realized.
Owner:BEIJING VRV SOFTWARE CO LTD
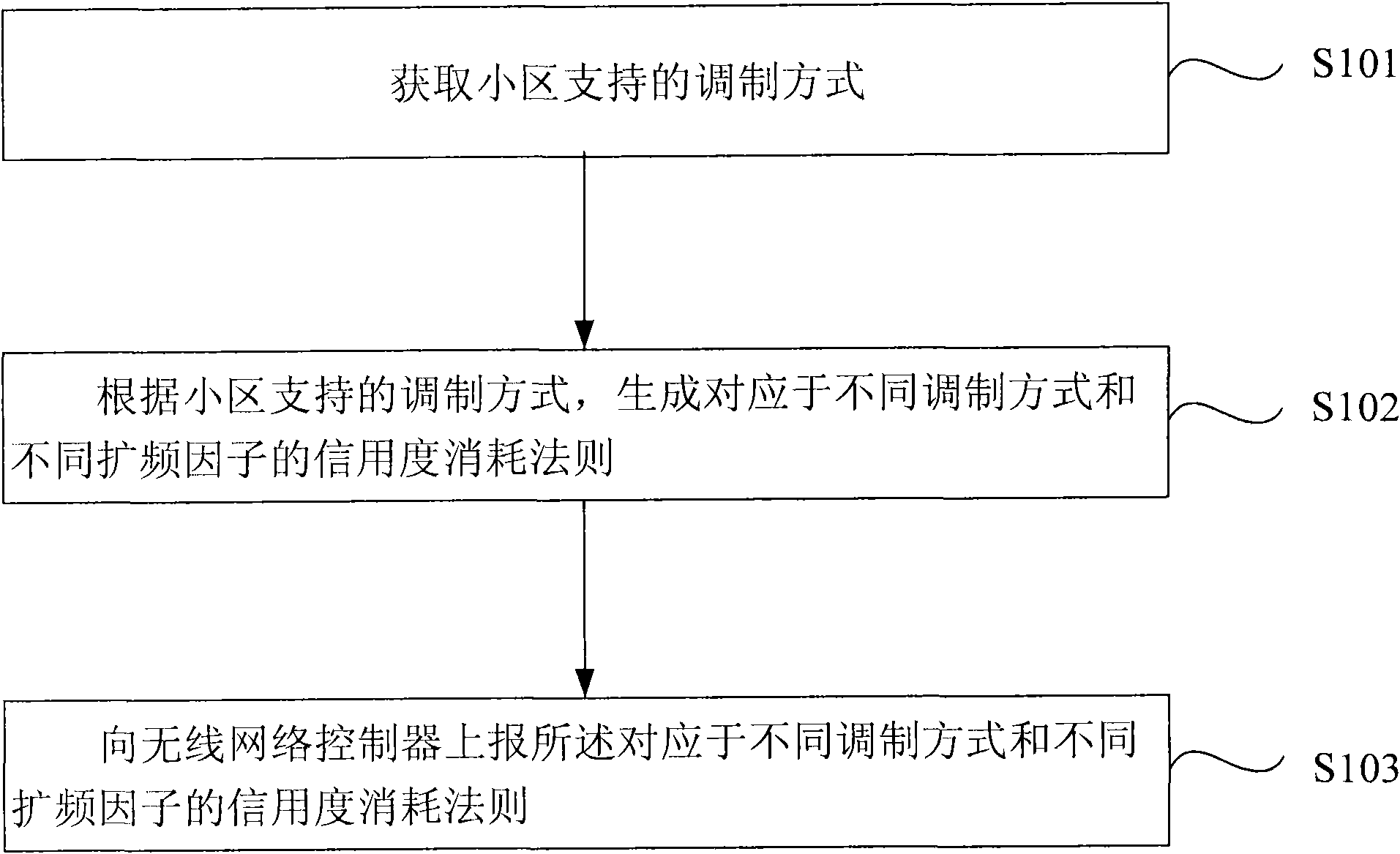
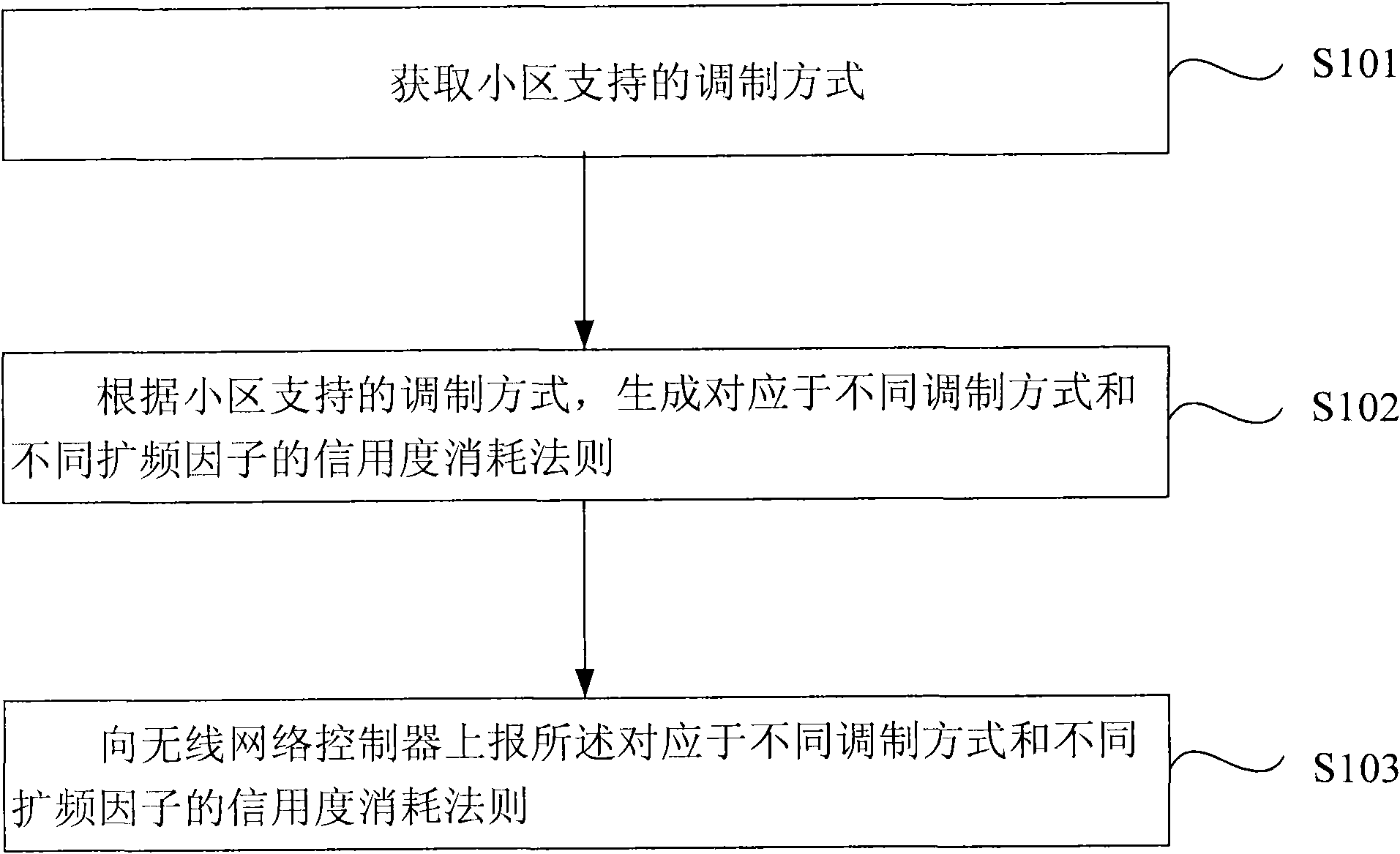
Credit rating consumption rule reporting method, admittance control method and device
ActiveCN101801061ACalculate credit consumptionPrecise access controlNetwork traffic/resource managementAssess restrictionComputer scienceSpread spectrum
The embodiment of the invention provides a credit rating consumption rule reporting method, an admittance control method and a device. The credit rating consumption rule reporting method comprises the following steps: obtaining modulation modes supported by cells; generating credit rating consumption rules corresponding to different modulation modes and different spread spectrum factors accordingto the modulation modes supported by the cells; and reporting the credit rating consumption rules to a wireless network controller. The embodiment of the invention provides the technical scheme that the credit rating consumption rules are generated according to different modulation modes and spread spectrum factors, and the credit rating consumption rules are reported, so the credit rating consumption condition of a base station can be correctly calculated through the wireless network controller. Thereby, the admittance control can be accurately carried out on users, and at the same time, a large number of failed flow processes generated between the wireless network controller and an IUB interface of the base station are avoided.
Owner:HUAWEI TECH CO LTD
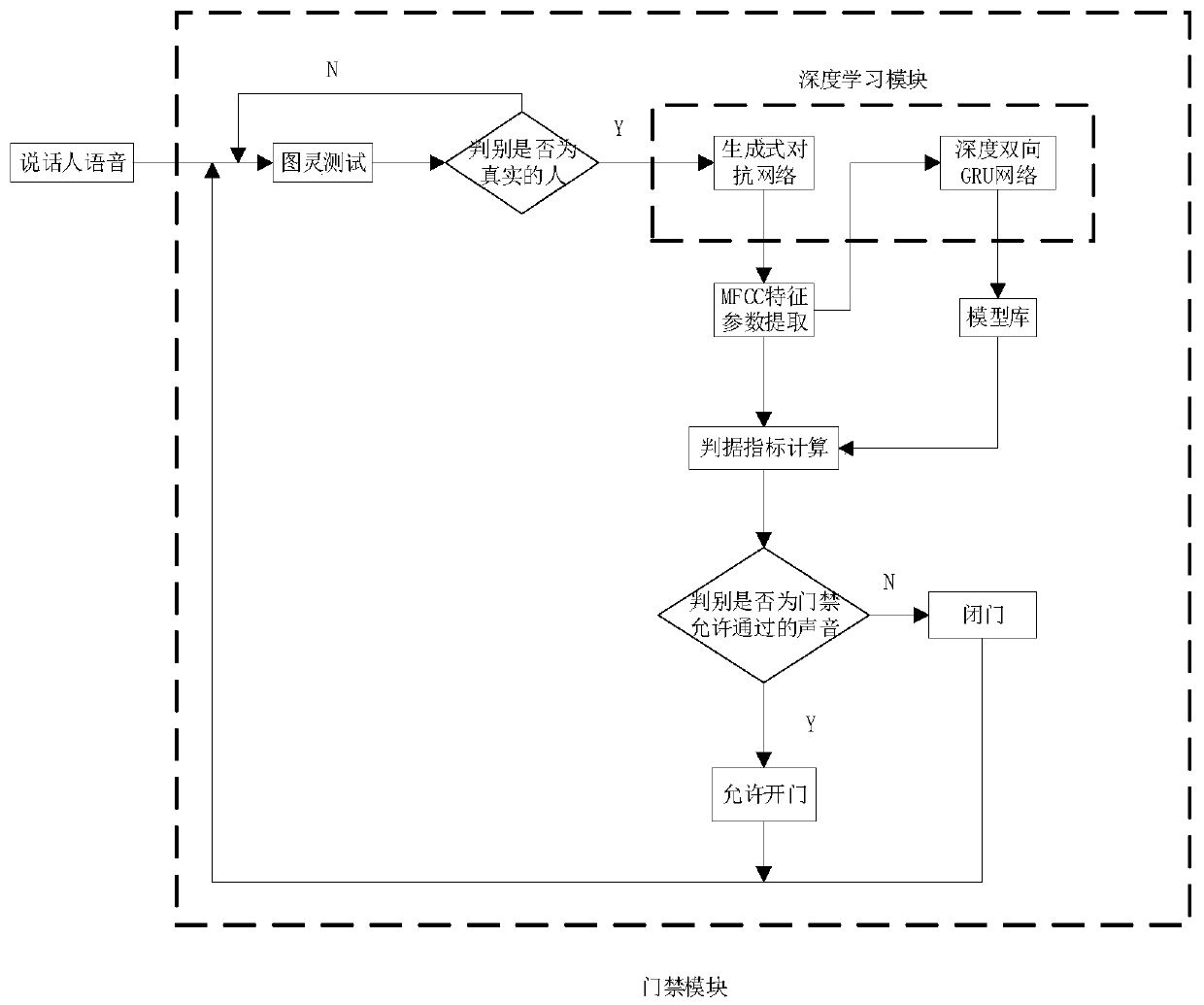
Voice access control system
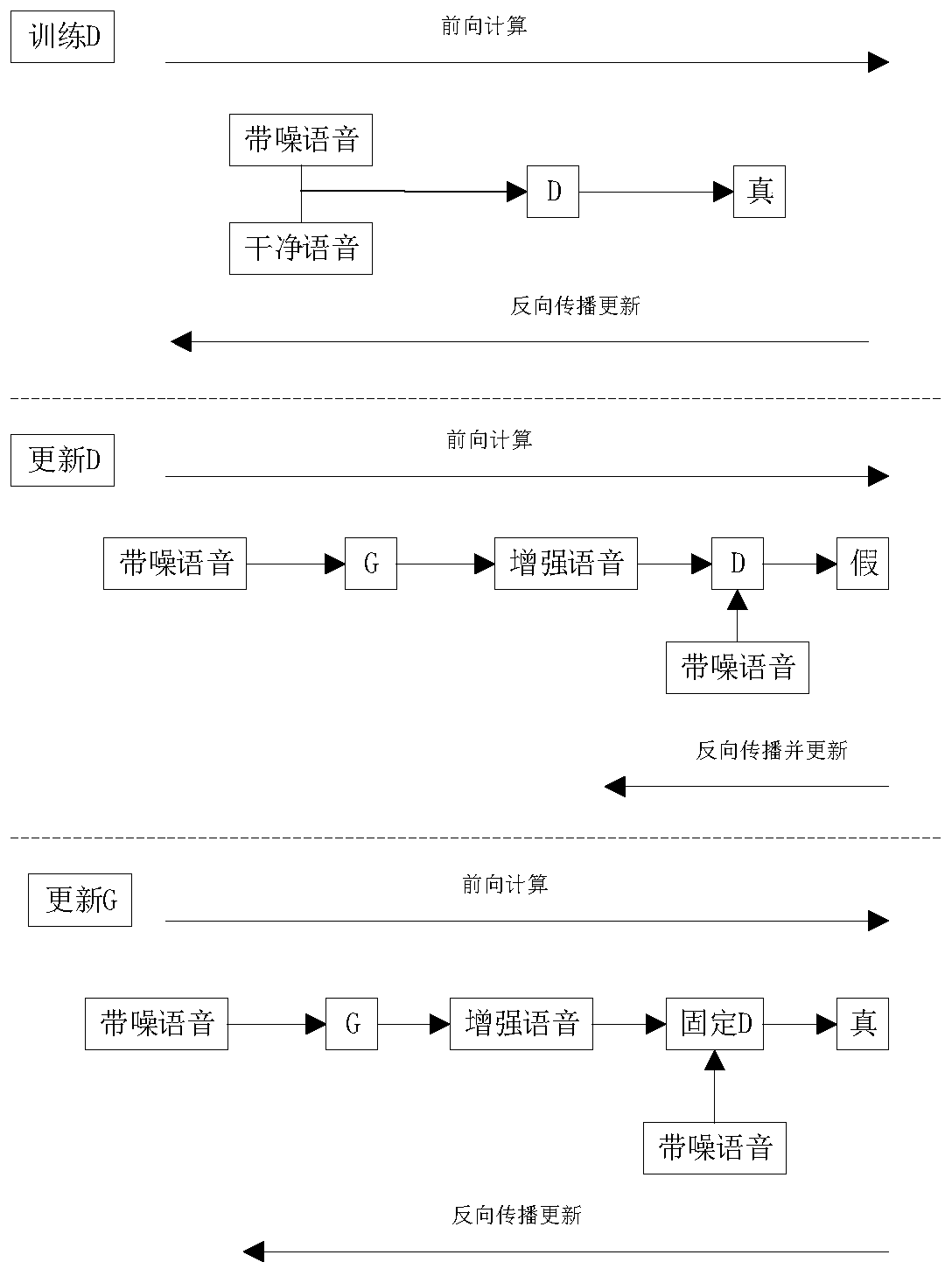
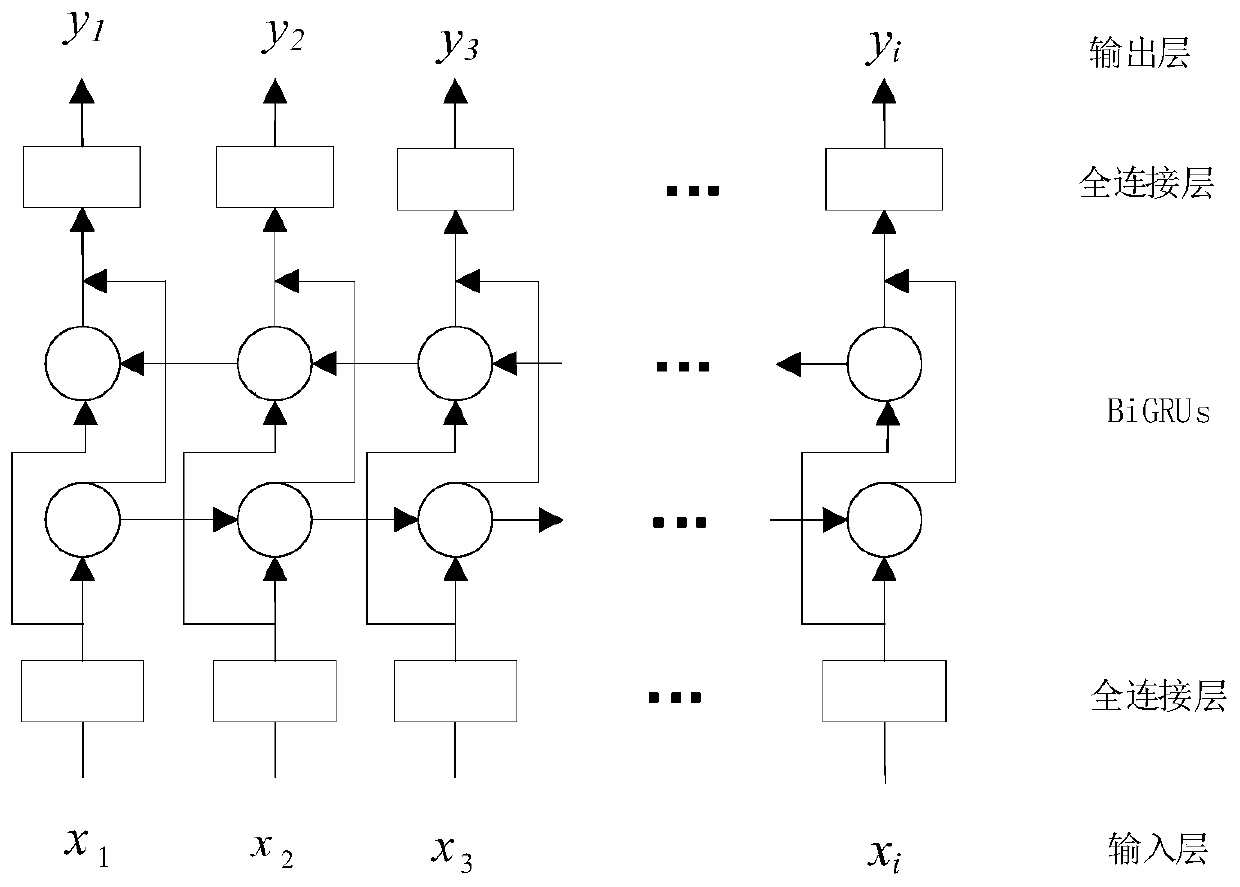
InactiveCN110223429AImprove experienceImprove speech recognition accuracySpeech analysisIndividual entry/exit registersFeature extractionGenerative adversarial network
The invention provides a voice access control system, and aims at using voice anti-fake Turing test and deep learning to carry out immortal voice recognition so as to realize an access control function. The system comprises a processor loaded with a Turing test module, a generative adversarial network and a bidirectional GRU neural network, wherein the processor is communicable connected with an access control driving mechanism and is used for starting or closing the access control according to voice characteristics. The voice access control system is suitable for carrying out Turing test on the obtained voices under specific environments that the speakers are not on the spots, carrying out voice enhancement processing through the generative adversarial network after determining the voicesas real voices, carrying out feature extraction on the enhanced voices by adoption of parameters such as Mel cepstrum (MFCC) and the like, and completing speaker recognition through a deep bidirectional gated recurrent unit) network.
Owner:SHANGHAI INST OF TECH
Extensible markup language document management method and system
ActiveUS8812696B2Management operation on the XML document more flexible and convenientEnsure safetyDigital data processing detailsUnauthorized memory use protectionExtensible markupDocumentation
An Extensible Markup Language (XML) document management method includes: receiving an XML document management operation request sent via an XCAP protocol, by an XML Document Management Server (XDMS); determining that the XML document management operation request is in an entrustment mode, and determining whether to perform an operation described in the XML document management operation request in accordance with access permission information corresponding to an XML document, by the XDMS.
Owner:HUAWEI TECH CO LTD
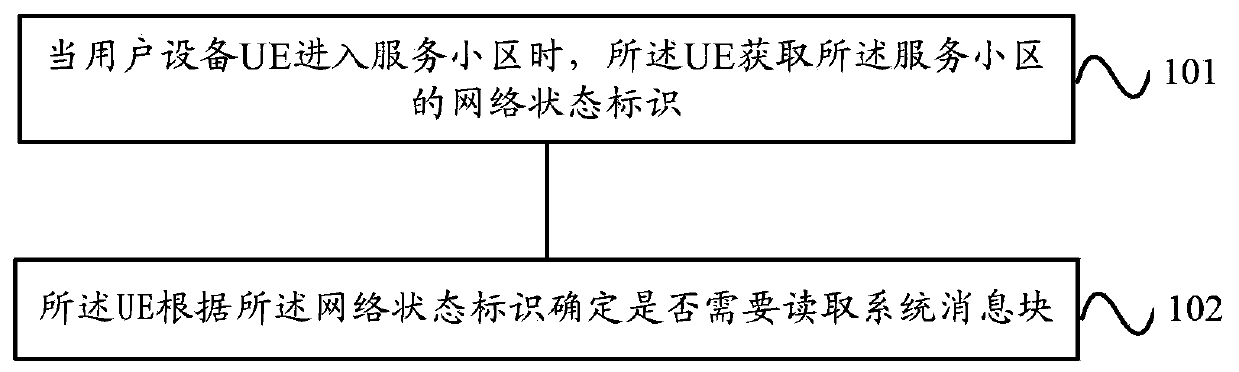
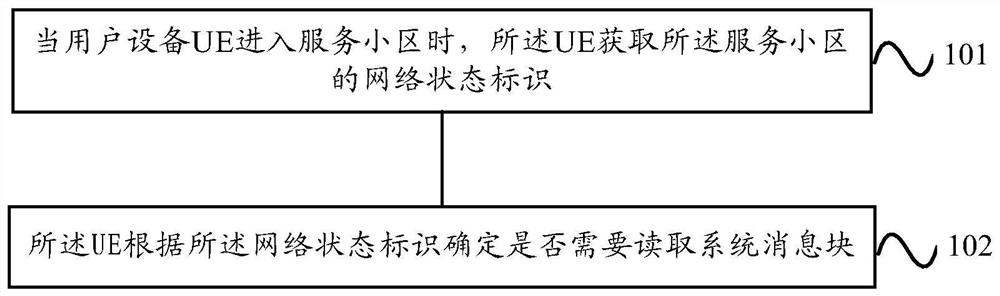
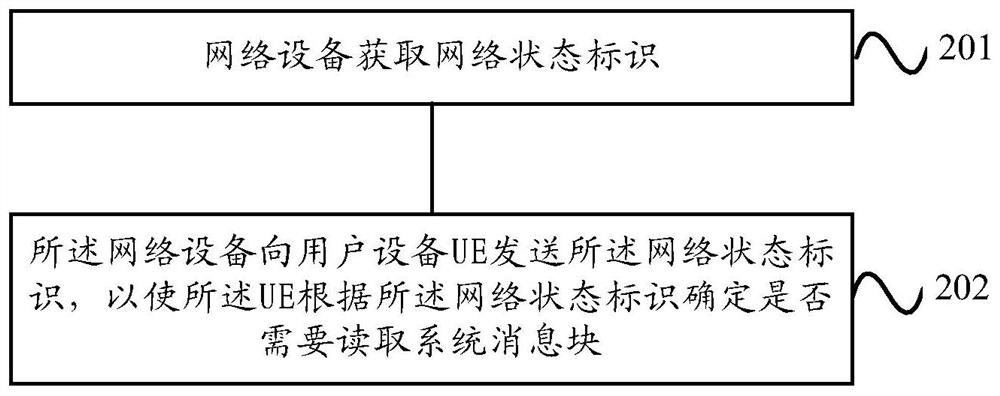
Method and equipment for reading network access control parameters
ActiveCN111510990APrecise access controlLess power consumptionAssess restrictionHigh level techniquesNetwork Access ControlState switching
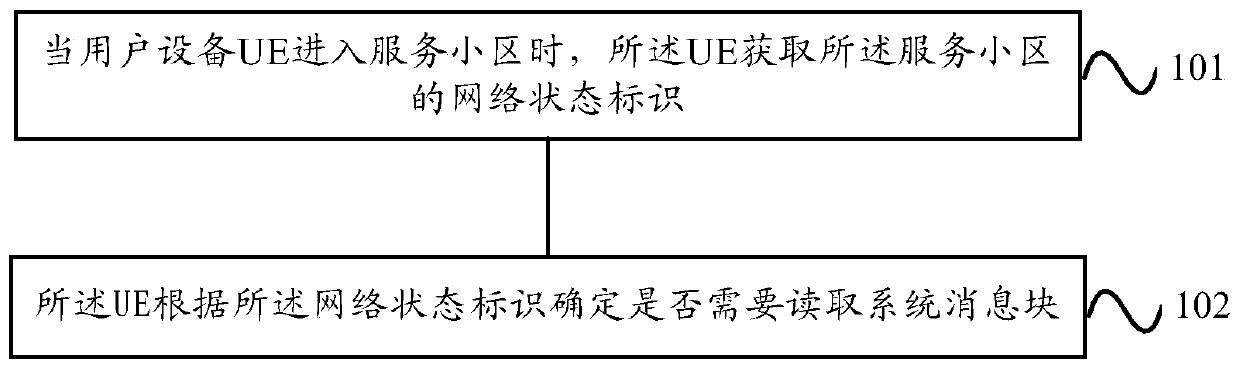
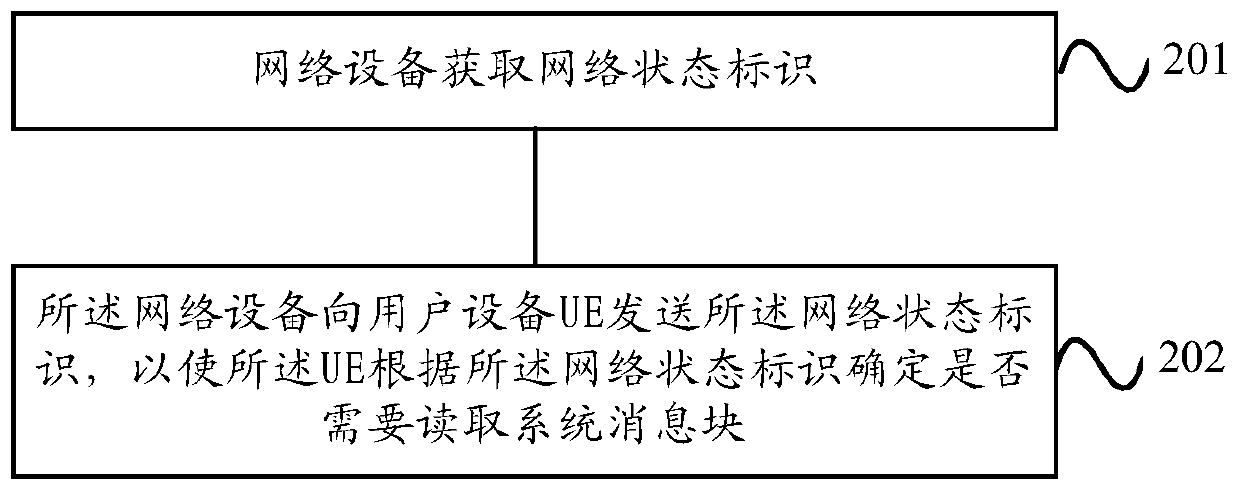
The embodiment of the invention provides a method and equipment for reading network access control parameters. The method for reading the network access control parameters comprises the following steps that: user equipment (UE) reselects a serving cell, or the UE is converted into a non-dedicated state from a dedicated state in the serving cell; the UE acquires a network state identifier of the serving cell; and the UE determines whether a system message block needs to be read according to the network state identifier. According to the call optimization system message block reading method provided by the embodiment of the invention, on the basis of reducing the power consumption caused by unnecessary reading of the system message block by the UE, the UE can update the stored system messageblock information in time and keep consistent with the network side, so that the access control of the network is more accurate.
Owner:HUAWEI TECH CO LTD
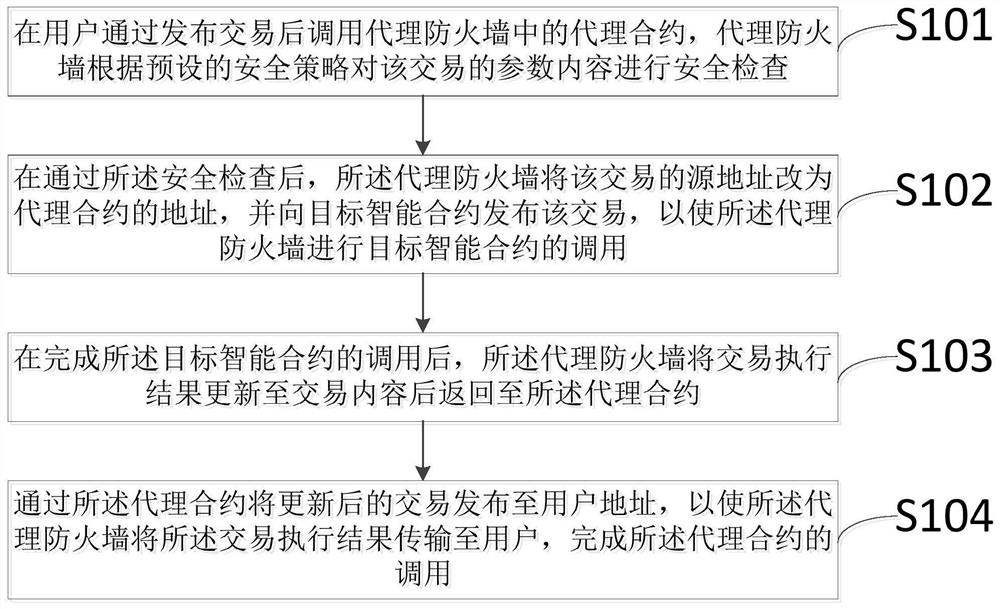
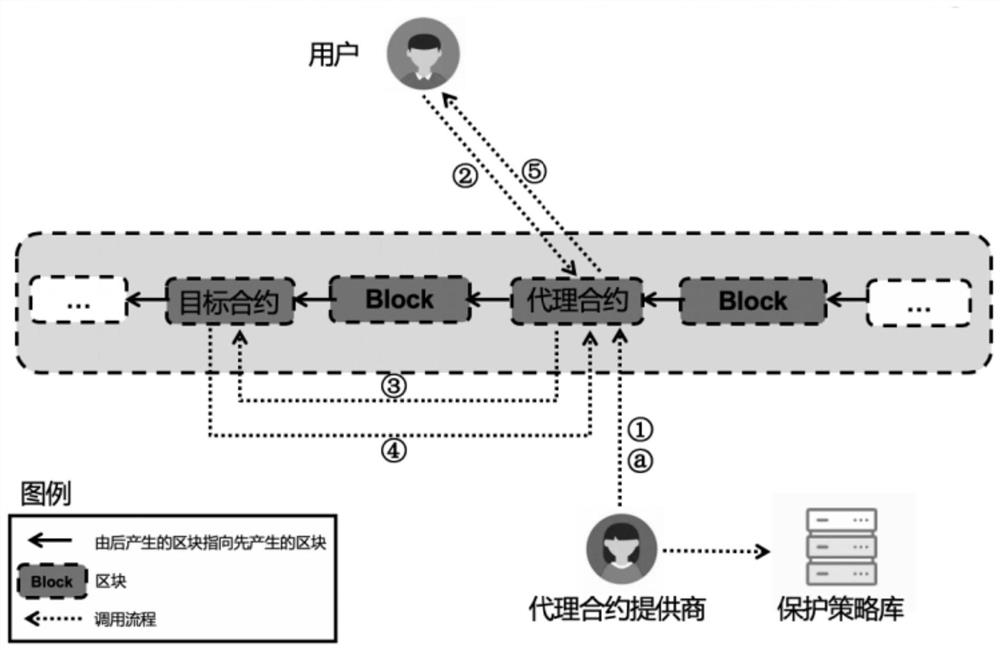
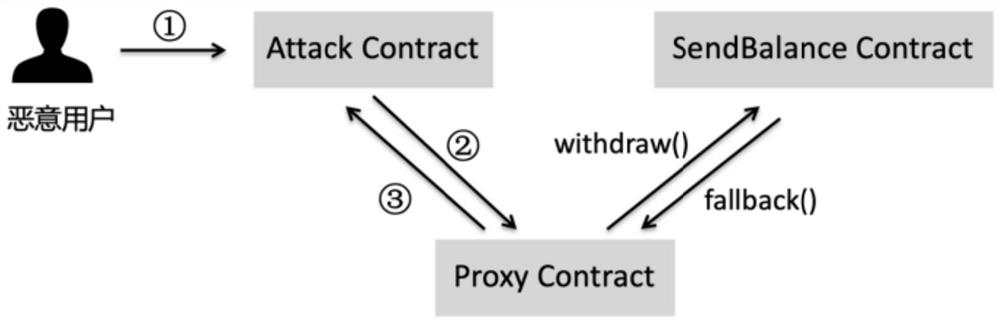
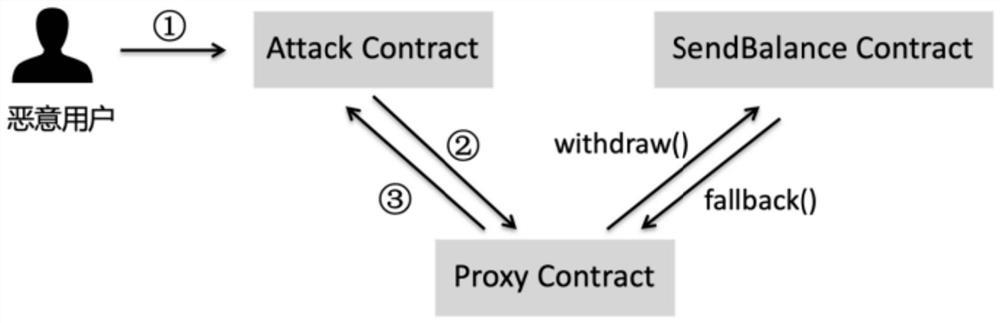
Proxy firewall protection method and system for smart contract
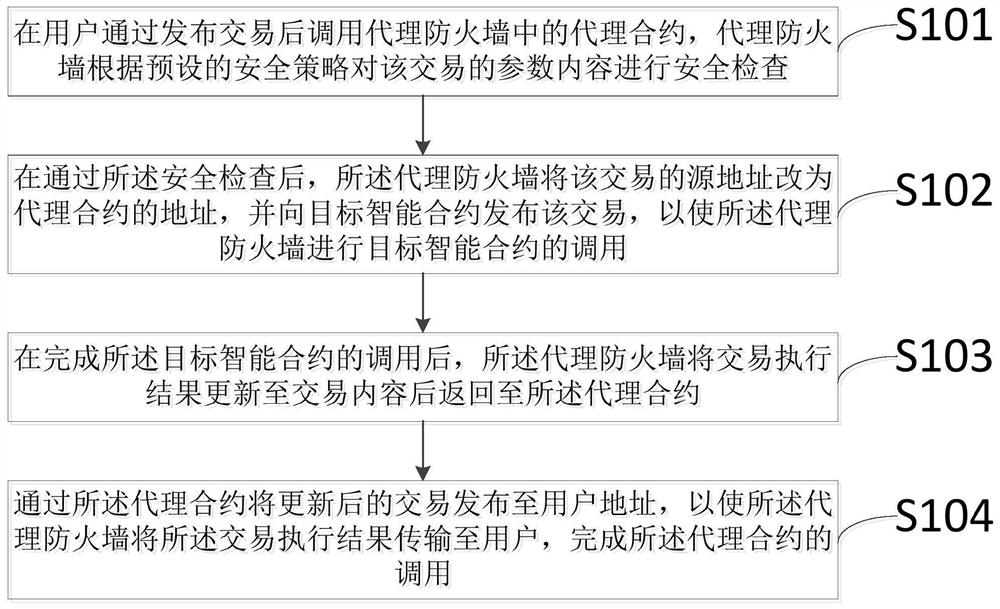
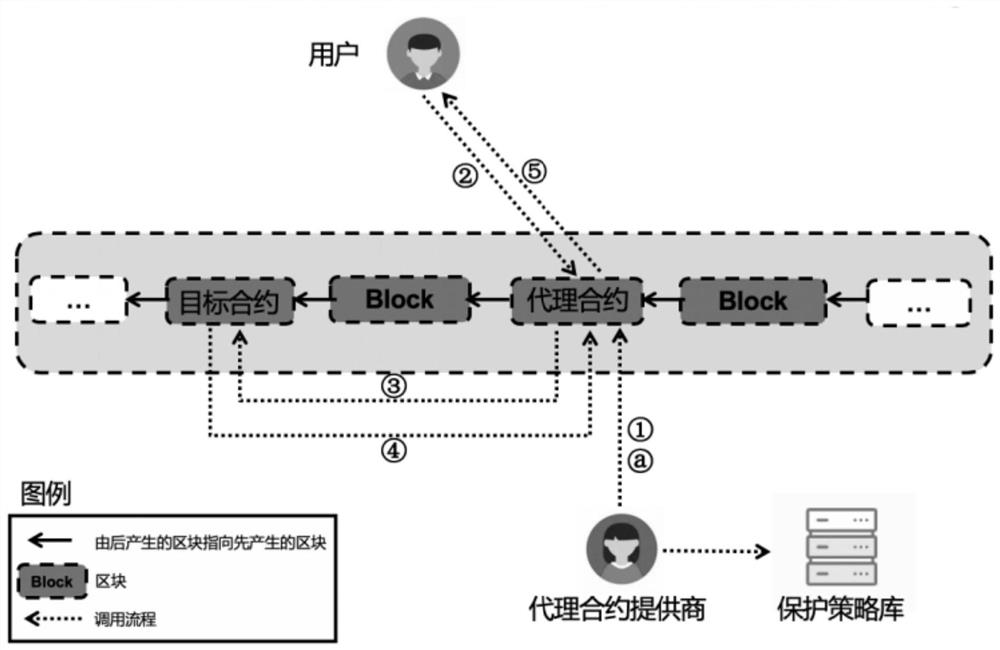
ActiveCN111654494AImplement safe callsPrecise access controlFinanceSecuring communicationComputer networkEngineering
The invention discloses a proxy firewall protection method and system for a smart contract, and the method comprises the steps that a proxy contract in a proxy firewall is called after a user publishes a transaction, and the proxy firewall carries out the safety check of the parameter content of the transaction according to a safety strategy; after the security check is passed, the proxy firewallchanges the source address of the transaction into the address of the proxy contract, and issues the transaction to the target smart contract, so that the proxy firewall calls the target smart contract; after the calling of the target intelligent contract is completed, the proxy firewall updates the transaction execution result to the transaction content and returns the transaction execution result to the proxy contract; and the updated transaction is issued to the user address through the proxy contract, so that the proxy firewall transmits a transaction execution result to the user, and calling of the proxy contract is completed. A calling interface is provided between the user and the target contract through the proxy firewall, safe calling of the intelligent contract is achieved, and the transaction safety of a contract publisher and a caller is improved.
Owner:GUANGZHOU UNIVERSITY
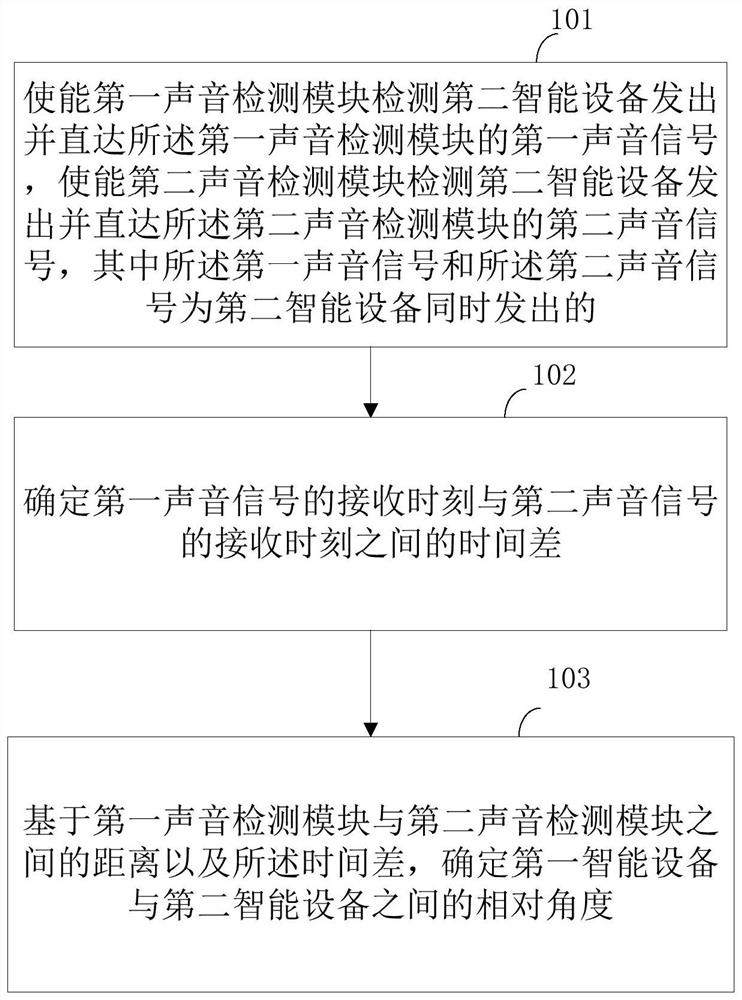
Access controller, access control method and computer readable storage medium
PendingCN112102536ANew experienceAccurate access controlIndividual entry/exit registersSound detectionEngineering
The invention provides an access controller, an access control method and a computer readable storage medium. The access controller comprises a first sound detection module; a second sound detection module; a processor which is configured to determine a first relative angle between the access controller and the intelligent equipment at the first position point and a second relative angle between the access controller and the intelligent equipment moving from the first position point to the second position point; when it is determined that the moving track of the intelligent equipment meets thepreset condition based on the first relative angle and the second relative angle, an unlocking instruction is sent to the access. According to the embodiment of the invention, intelligent unlocking based on the change of the relative angle is realized.
Owner:TOUCHAIR TECH
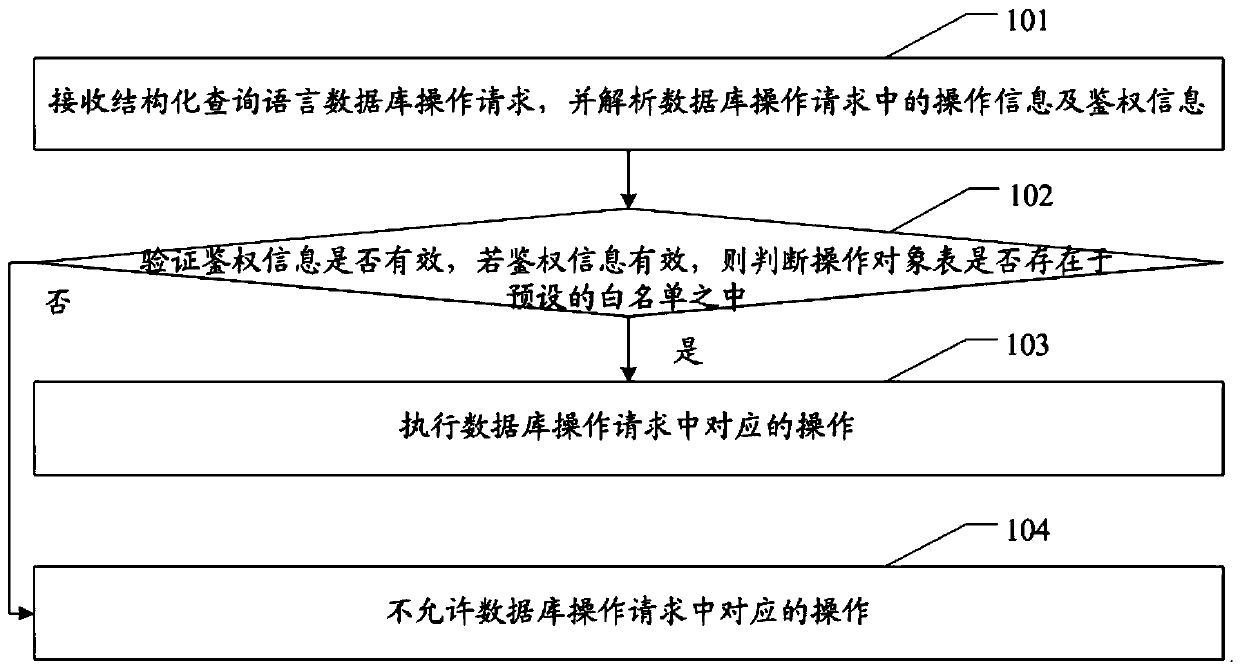
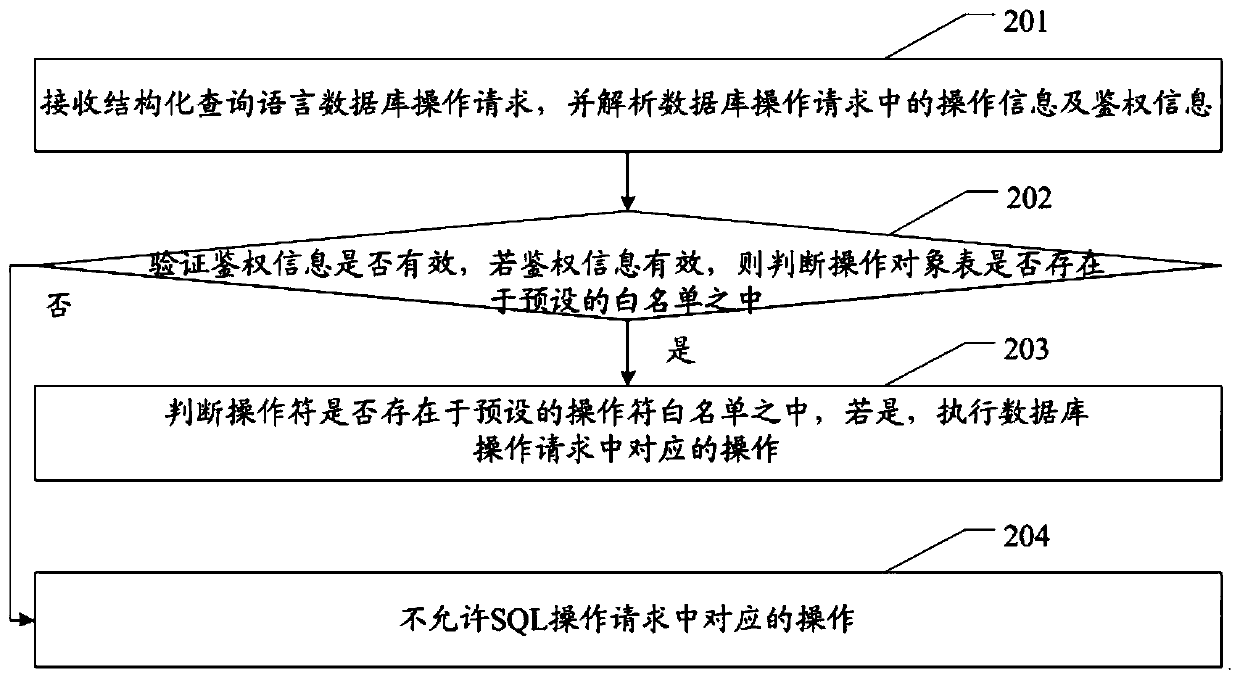
Database access control method and system and related equipment
ActiveCN110598445APrecise Access ControlImprove securityDigital data information retrievalDigital data protectionWhitelistAuthorization
The embodiment of the invention provides a database access control method, a database access control system and related equipment, which are used for reducing the granularity of database access control and improving the security of data access. The method of the embodiment of the invention comprises: receiving a database operation request, and parsing operation information and authentication information in the database operation request, wherein the operation information at least comprises an operation object table; verifying whether the authentication information is valid or not, and if the authentication information is valid, judging whether the operation object table exists in a preset white list or not; and if the operation object table exists in a preset authorization white list, executing a corresponding operation in the database operation request, and if the operation object table does not exist in the preset authorization white list, not allowing the corresponding operation inthe database operation request.
Owner:金蝶蝶金云计算有限公司
A Terminal Admission Control Method Based on Switch Port Management
InactiveCN103929376BAvoid accessAccess block or allowData switching networksAfter treatmentUnique identifier
The invention relates to the technical field of terminal admission control, and specifically discloses a terminal admission control method based on switch port management. After the new terminal is connected to the network, collect the new terminal through the switch, extract the unique identifier of the terminal, and associate the terminal with the port of the switch; compare the unique identifier with the MAC address of the access database to make a judgment; if the unique identifier is found, It is a legal terminal and no action is taken; if the unique identifier cannot be found, it is an illegal terminal or an external terminal, and the corresponding switch port will be closed immediately, and the closing information will be recorded in the access database; when a new terminal accesses the network , added to the window period after processing; return to start processing again; if no new terminal is connected to the network, the closed switch port will be automatically opened after the specified time. The present invention adopts MAC address management for the terminal, prohibits the terminal user from changing the MAC address privately; manages the virtual machine and prevents the HUB from accessing; the terminal access control of the present invention is accurate and strict.
Owner:尹志超
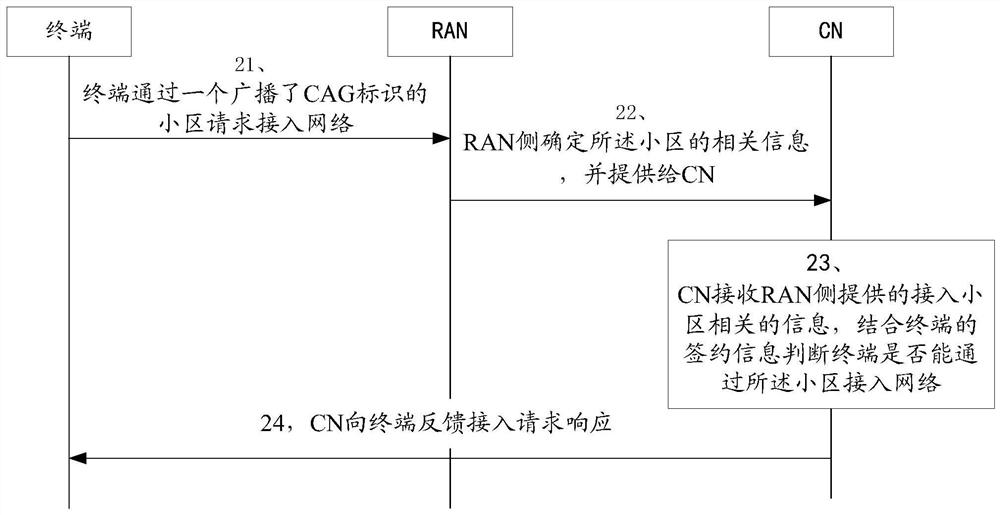
Access control method, access network node and core network node
ActiveCN113573387AAvoid access failuresGuaranteed reliabilityAssess restrictionAccess networkEngineering
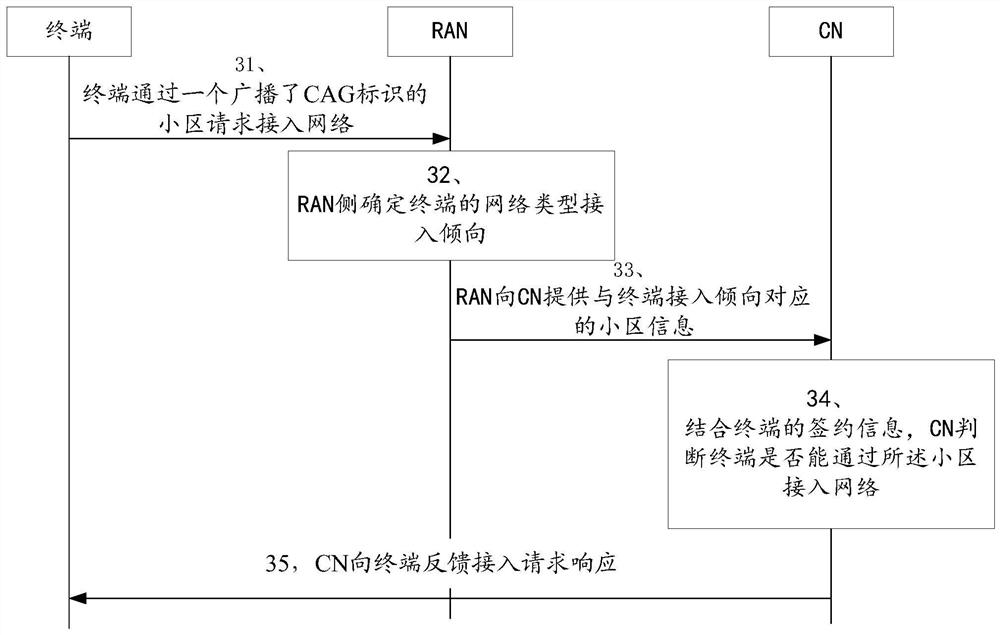
The invention provides an access control method, an access network node and a core network node, and relates to the technical field of communication. The access control method is applied to an access network node, and comprises the following steps: sending related information of a first cell to a core network node; wherein the related information of the first cell is used for the core network node to perform access control of the terminal; the related information of the first cell comprises first indication information that the first cell supports access of at least one network type; or the related information of the first cell comprises the information of the first cell corresponding to the network type access tendency of the terminal. According to the scheme, the condition of terminal access failure can be avoided, so that the reliability of terminal access is ensured.
Owner:VIVO MOBILE COMM CO LTD
Method, device and system for performing access control judgment by core network
ActiveCN101945485BAvoid confictPrecise access controlNetwork traffic/resource managementNetwork topologiesMobility managementClosed subscriber groups
A method, apparatus and system for implementing access control determination by a Core Network (CN) are disclosed. In this inventive solution, a Mobility Management Entity (MME) obtains subscriber access information required for implementation of the access control determination after the access mode of a Base Station (BS) has changed, and MME implements the access control determination to a corresponding subscriber according to the obtained subscriber access information, which enables CN to avoid collision with access control determination by the BS Gateway, without miss determination or error determination, and ensures that access control can be accurately implemented to subscribers with different Closed Subscriber Group (CSG) abilities and in the connection state after the access mode of BS has changed.
Owner:HUAWEI TEHCHNOLOGIES CO LTD
Dynamic access control method based on business body
PendingCN114567489AEnsure safetyQuick access controlSecuring communicationService systemAuthorization
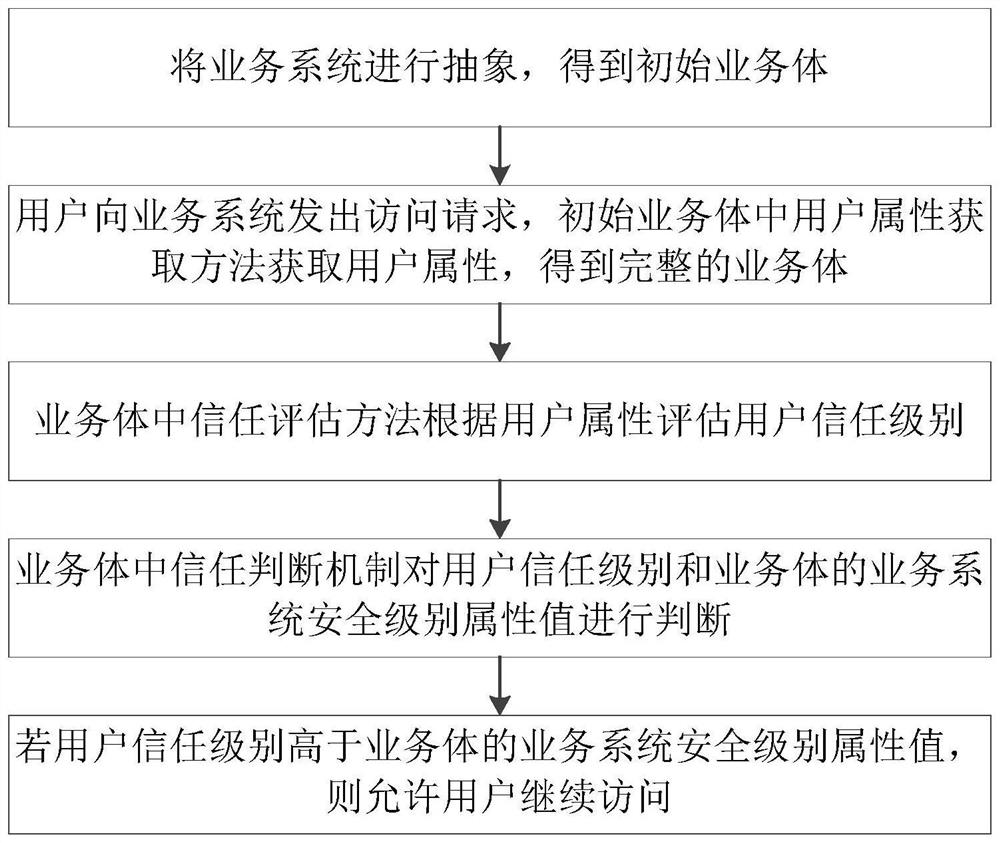
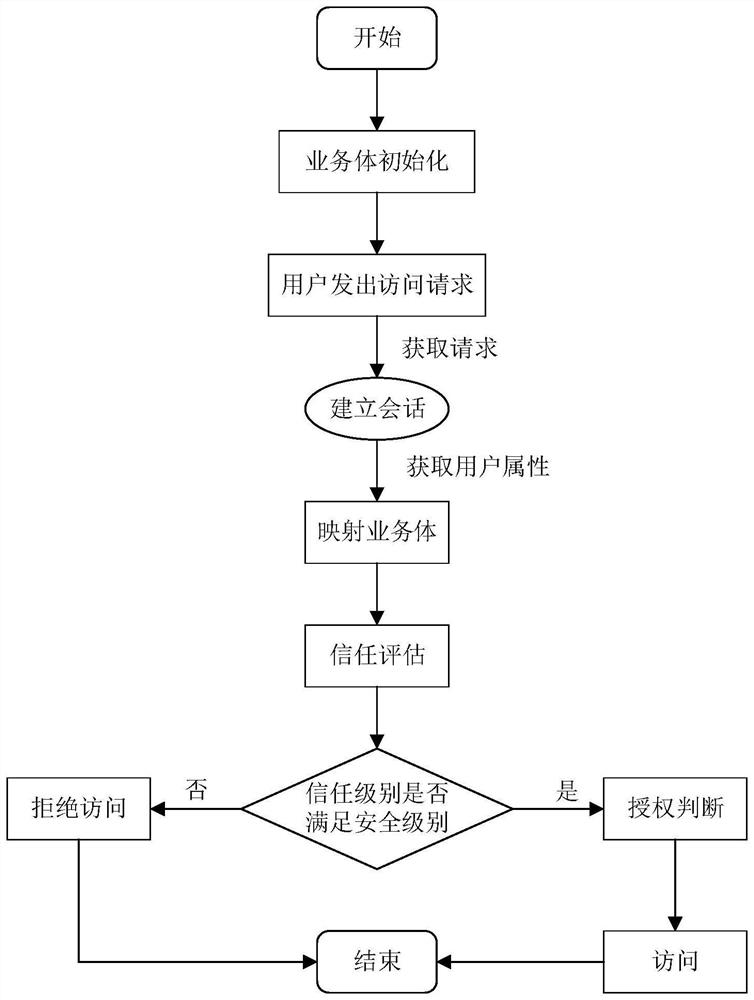
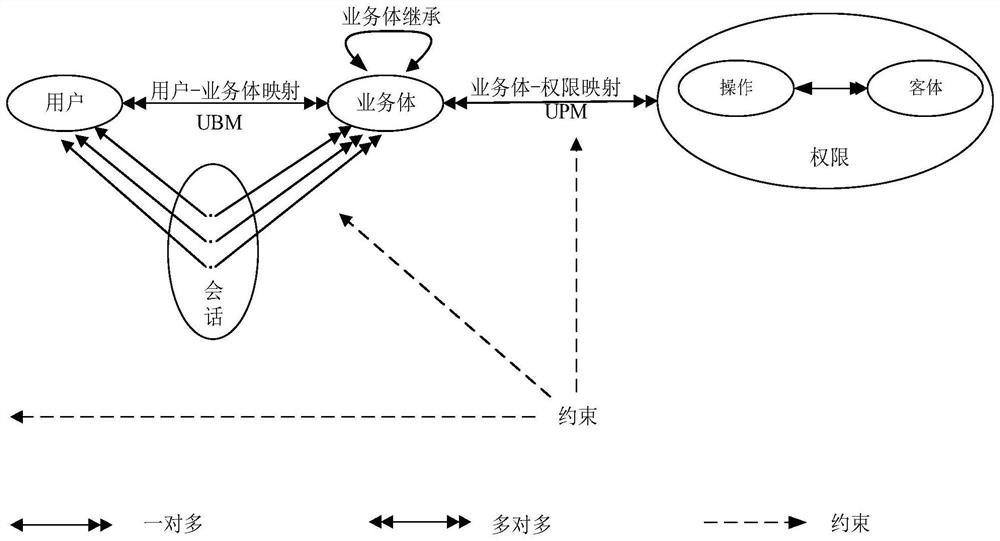
The invention provides a dynamic access control method based on a business body, which relates to the technical field of system access control, and comprises the following steps: abstracting a business system to obtain an initial business body BEInit; a user sends an access request to a service system, a user attribute acquisition method in an initial service body BEInit acquires user attributes, a complete service body is obtained, and a trust evaluation method in the service body evaluates a user trust level according to the user attributes; a trust judgment mechanism in the service body judges a user trust level and a service system security level attribute value of the service body; and if the user trust level is higher than the service system security level attribute value of the service body, allowing the user to continue to access. According to the method, access control is carried out based on the business body by introducing a business body concept, and flexible, rapid and safe access control authorization is realized in an open and complex super application system environment.
Owner:LINYI UNIVERSITY
A system and method for automatically constructing access control policies for high-level information systems
ActiveCN111818059BPrecise access controlImplementation of Security PolicySecuring communicationInformation resourceNetworked system
The invention discloses a system and a method for automatically constructing an access control strategy of a high-level information system. The scheme is based on an information resource collection module, an access control mechanism hierarchical division module, a subject-object and relationship sorting module, a high-level demand step-by-step essence module, and an automatic strategy The generation module, the information resource collection module collects information resources for the software and hardware products in the entire network system; the access control mechanism hierarchical division module divides the access control mechanism hierarchically; the subject object and its relationship sorting module analyzes the entire network system, Sort out the subject, object and their relationship structure; the high-level requirements are gradually refined by the essence module, the essence of business access requirements and operation and maintenance management access requirements; the policy automatic generation module generates access control policies for each access control mechanism level. This solution enables network system users to perform accurate access control on users no matter what level they access from in the process of accessing resources.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
Credit rating consumption rule reporting method, admittance control method and device
ActiveCN101801061BCalculate credit consumptionPrecise access controlNetwork traffic/resource managementAssess restrictionRadio Network ControllerComputer science
Owner:HUAWEI TECH CO LTD
Method and device for reading network access control parameters
ActiveCN104303541BPrecise access controlLess power consumptionAssess restrictionHigh level techniquesComputer networkTelecommunications
Embodiments of the present invention provide a method and device for reading network access control parameters. The method for reading the network access control parameters of the present invention includes: the user equipment UE reselects back to the serving cell, or the UE switches from a dedicated state to a non-dedicated state in the serving cell; the UE acquires the network status identifier of the serving cell; Flag to determine if the system message block needs to be read. In the embodiment of the present invention, the call optimization system information block reading method reduces the power consumption caused by unnecessary reading of the system information block by the UE, so that the UE can update the stored system information block information in a timely manner, which is consistent with the network side. In order to make network access control more accurate.
Owner:HUAWEI TECH CO LTD
Access control method and device
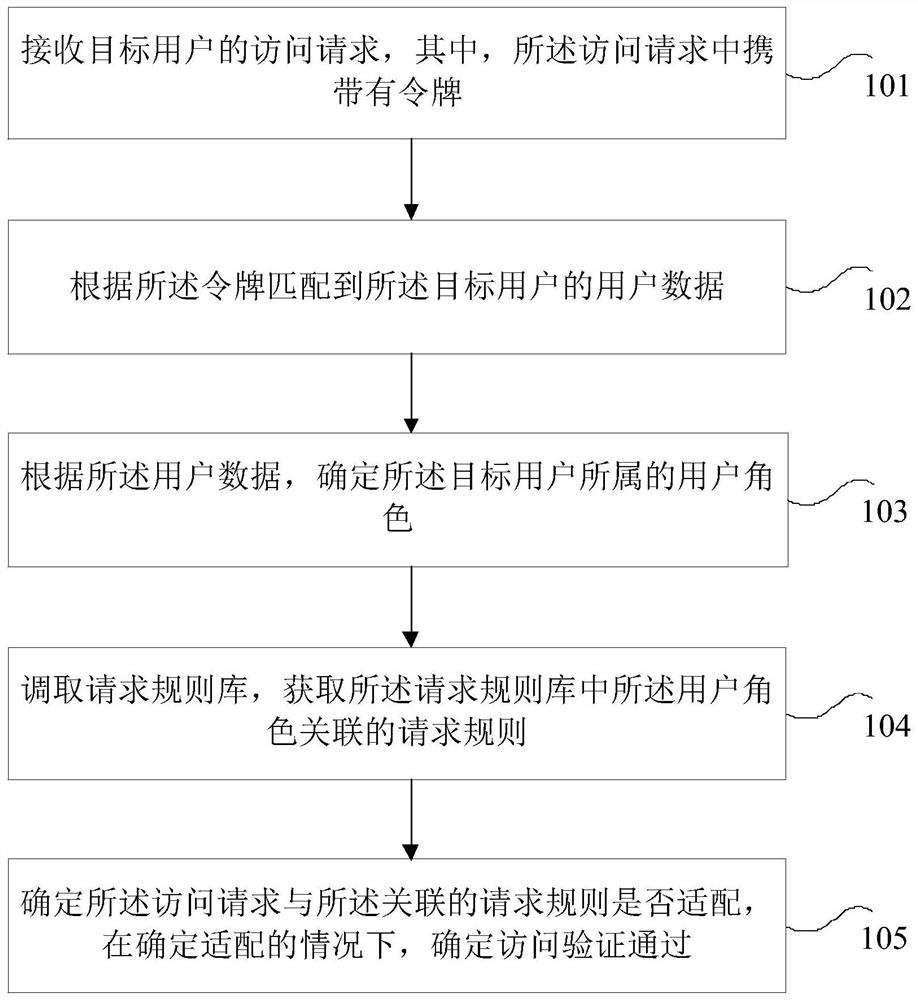
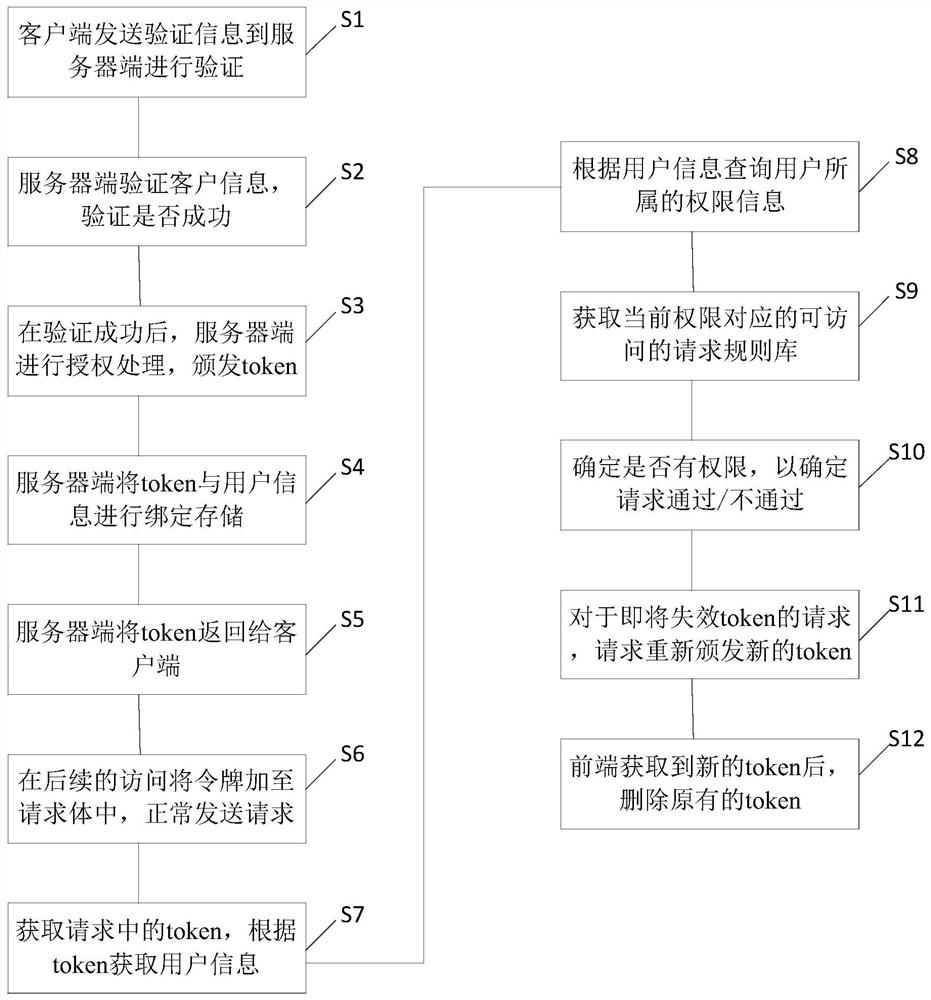
PendingCN113765673AImplement security controlsReduce data volumeUser identity/authority verificationDigital data protectionEngineeringUser role
The invention provides an access control method and device. The method comprises the steps: receiving an access request of a target user, wherein the access request carries a token; matching user data of the target user according to the token; determining a user role to which the target user belongs according to the user data; calling a request rule base, and obtaining a request rule associated with the user role in the request rule base; and determining whether the access request is matched with the associated request rule, and if yes, determining that the access verification is passed. Through the scheme, the problems of low security degree and overlarge data load in the existing access control process are solved, and the technical effects of accurate security control and relatively low data load are achieved.
Owner:CHINA CONSTRUCTION BANK
Method and device for reading network access control parameters
ActiveCN111510990BPrecise access controlLess power consumptionAssess restrictionHigh level techniquesComputer networkEngineering
Embodiments of the present invention provide a method and device for reading network access control parameters. The method for reading the network access control parameters of the present invention includes: the user equipment UE reselects back to the serving cell, or the UE switches from a dedicated state to a non-dedicated state in the serving cell; the UE acquires the network status identifier of the serving cell; Flag to determine if the system message block needs to be read. In the embodiment of the present invention, the call optimization system information block reading method reduces the power consumption caused by unnecessary reading of the system information block by the UE, so that the UE can update the stored system information block information in a timely manner, which is consistent with the network side. In order to make network access control more accurate.
Owner:HUAWEI TECH CO LTD
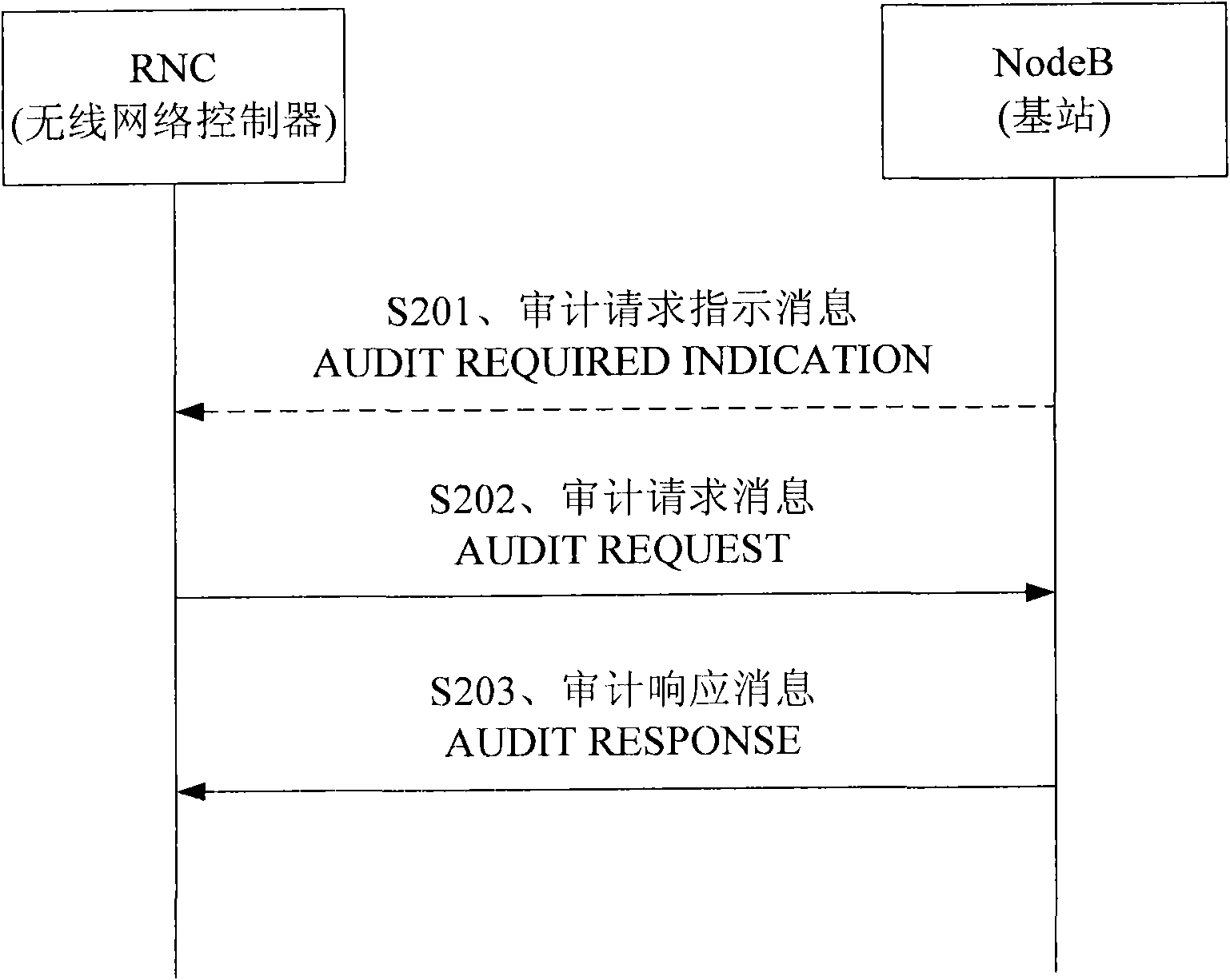
Method for reporting base station LECENSE capability
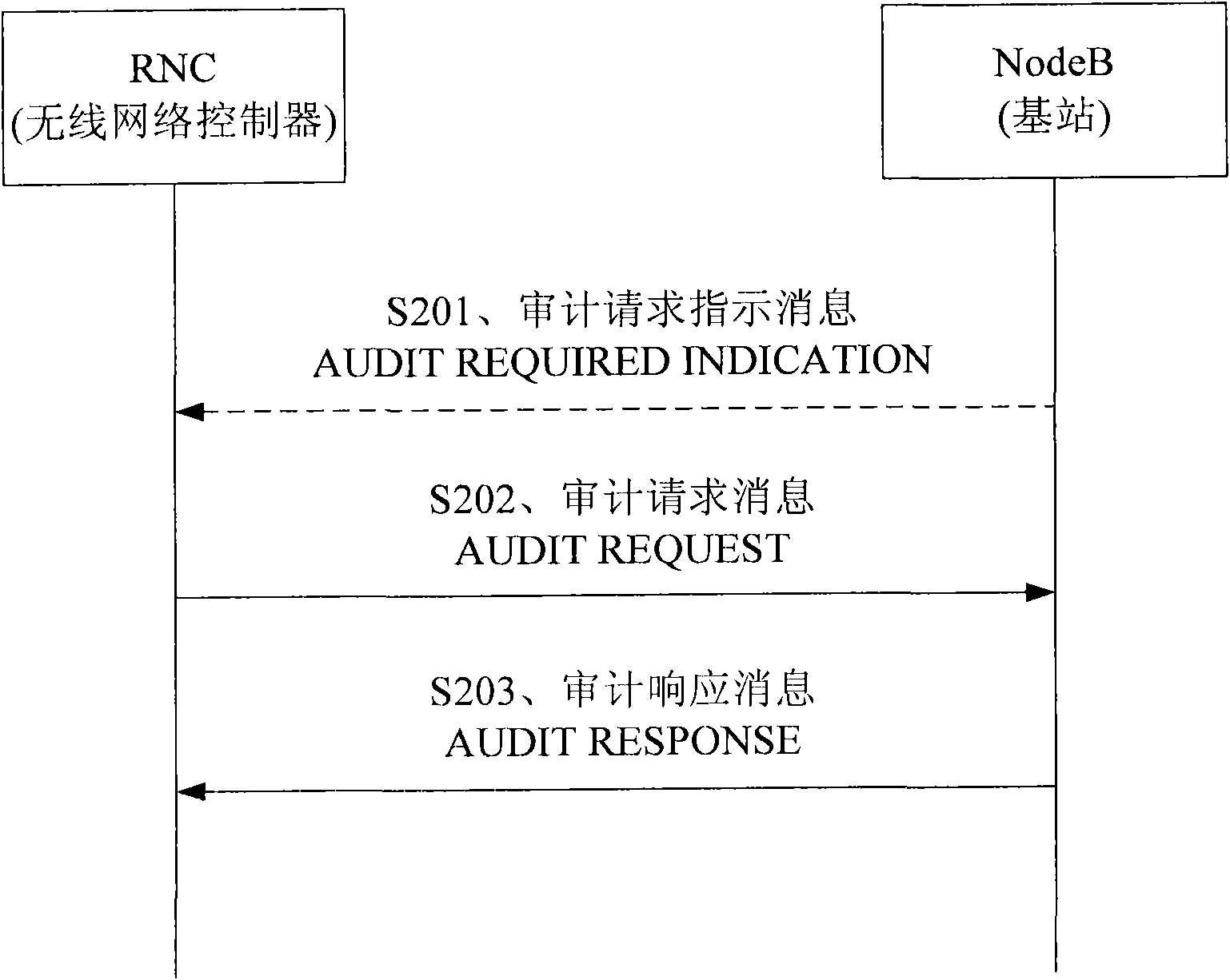
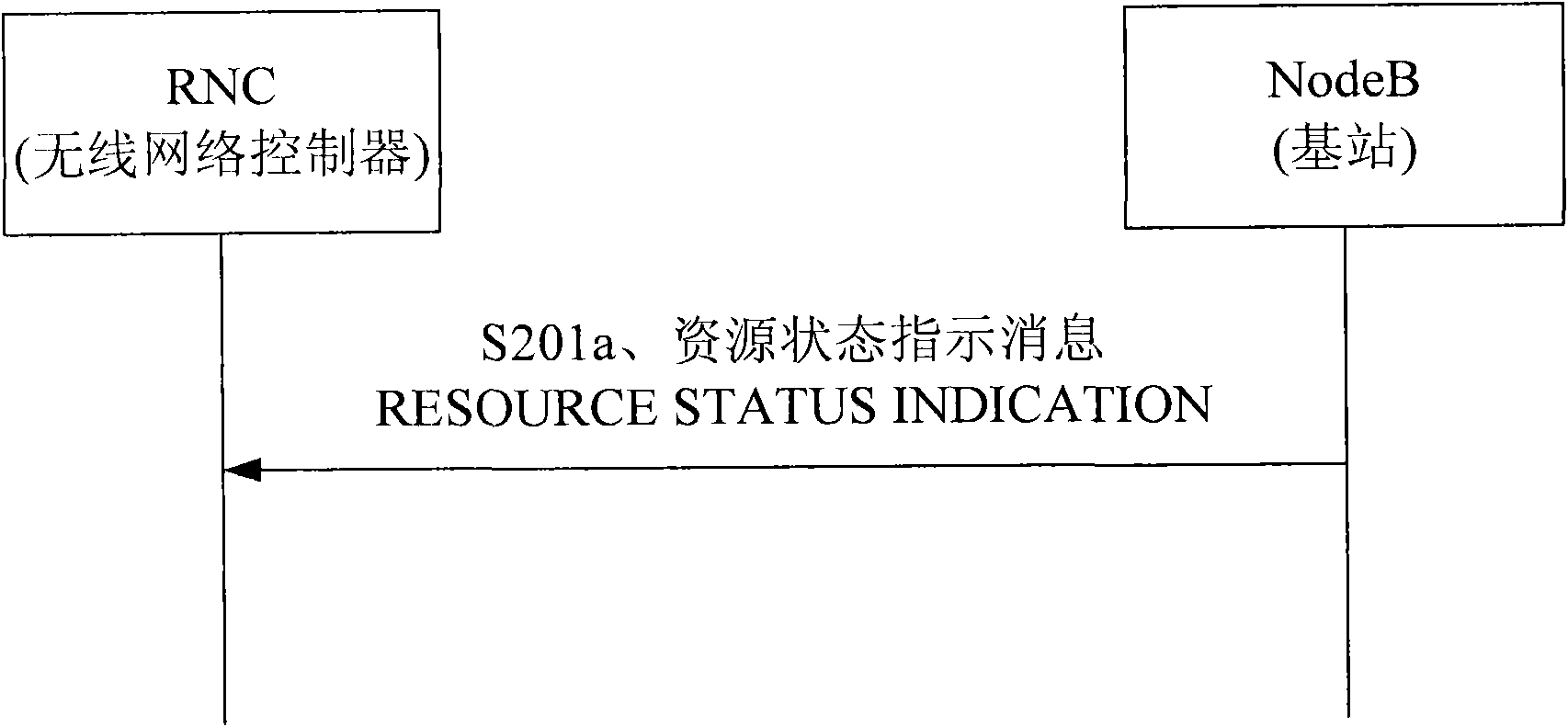
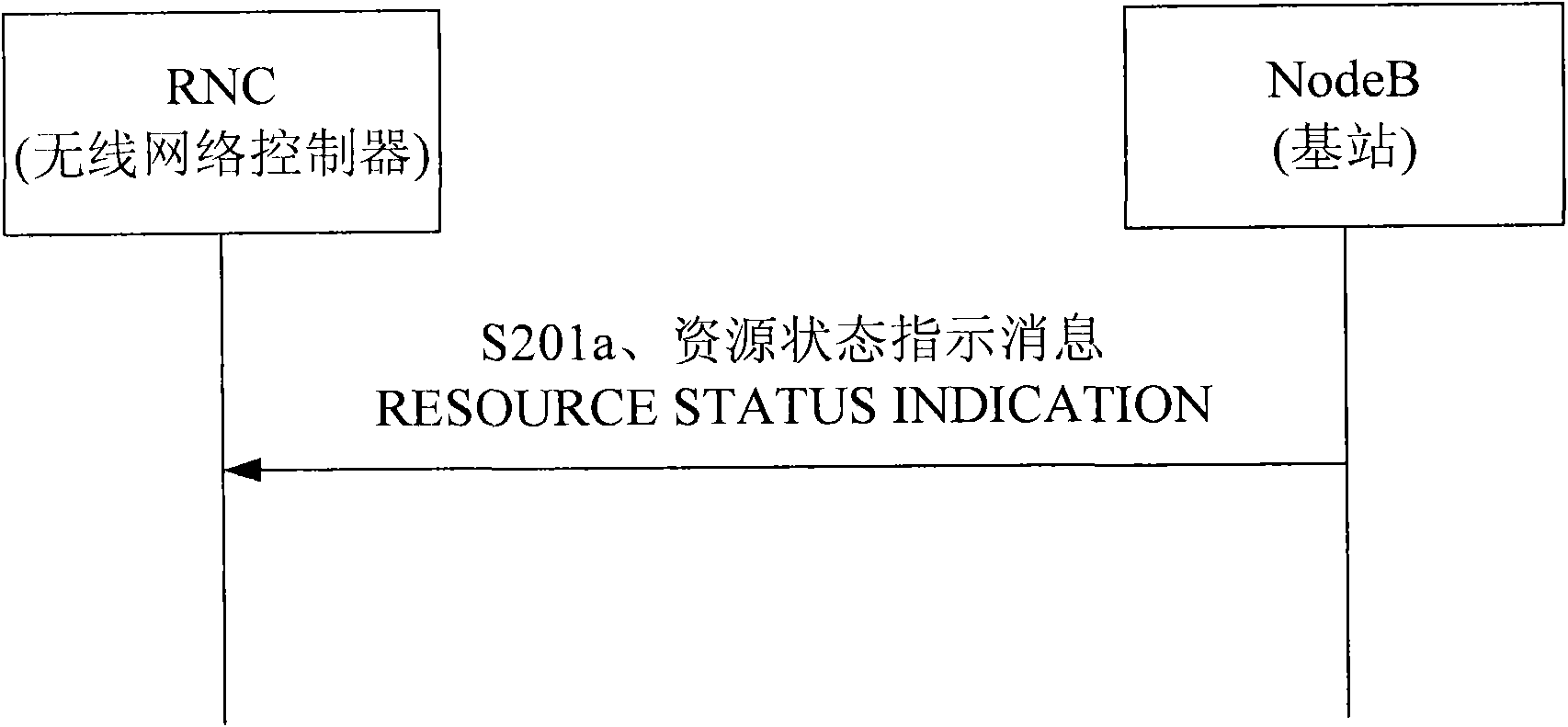
ActiveCN100493232CPrecise access controlFacilitates accurate access controlNetwork traffic/resource managementRadio/inductive link selection arrangementsLicenseSoftware
Using RESOURCE STATUS INDICATION signaling message or AUDIT RESPONSE signaling message carries LICENSE capability indication information (CII) and reports CII to base station controller. Concretely, it is realized by using the said signaling messages to carry resource group IE, and setting up Local Cell Group ID as systemic uncommon specific value in signaling message or adding field to carry CII. The invention makes software capability limited base station possible to report actual capability and rules of resource expenditure precisely. Thus, base station controller can master resource capability and condition of use in base station accurately in order to use techniques that need to know condition of resource use of base station in advance such as admittance control etc.
Owner:HUAWEI TECH CO LTD
A user access control method, device and router
ActiveCN103249112BPrecise access controlImprove accuracyAssess restrictionData transmissionComputer science
Owner:CHINA MOBILE COMM GRP CO LTD
Application front-end access method including multiple modules, module registration method and device
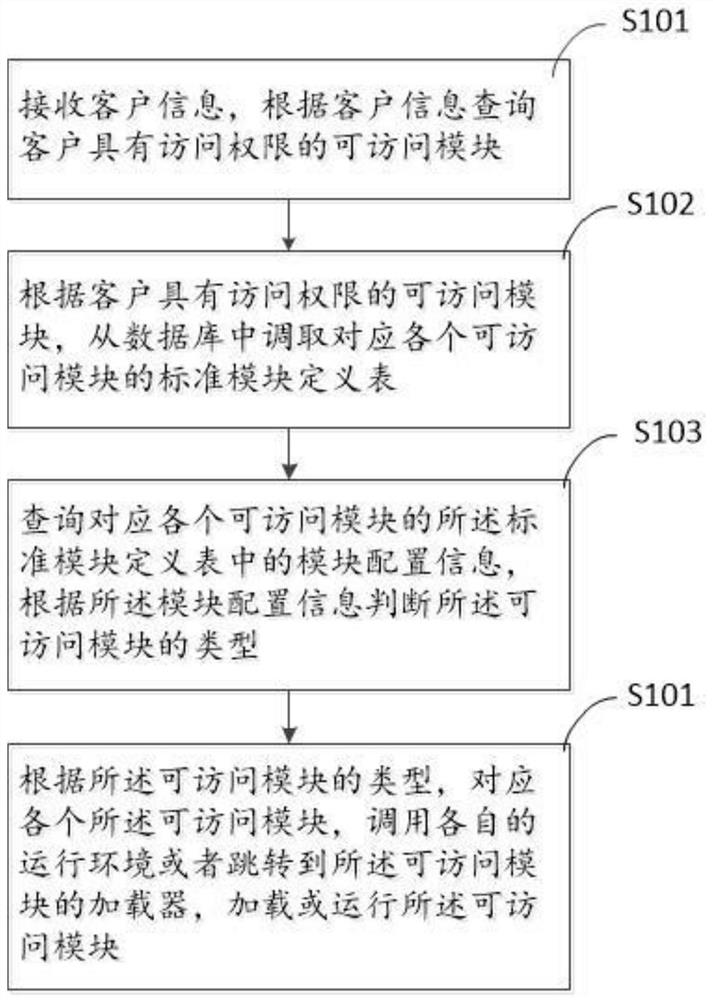
ActiveCN111125098BFast integrationConducive to mutual cooperationDigital data protectionSpecial data processing applicationsComputer hardwareComputer architecture
The invention provides an access method of an application front end comprising multiple modules, which comprises the following steps that: firstly, enabling the application front end to receive request information of user login, and determine an accessible module of which a user has access permission according to the request information of the user; and calling a standard module definition table of the module according to the determined accessible module, reading the module configuration information in the standard module definition table, and confirming the module type; and finally, calling an operation environment of the module or a loader of the module to operate or load the accessible module according to the type of the modules. Unified standards are adopted to standardize the modulesof different architectures, so that the modules can be unified in online standards and cooperate with one another, and unified user experience is achieved. The invention further provides a method forcalling the modules by the module scheduling engine, an access device of the application front end comprising the multiple modules, a module registration method, a module registration system, a modulecalling method and a system for accessing the multiple modules to the application front end.
Owner:PEOPLE'S INSURANCE COMPANY OF CHINA
A Method of Controlling Task Sending Authority in Workflow System
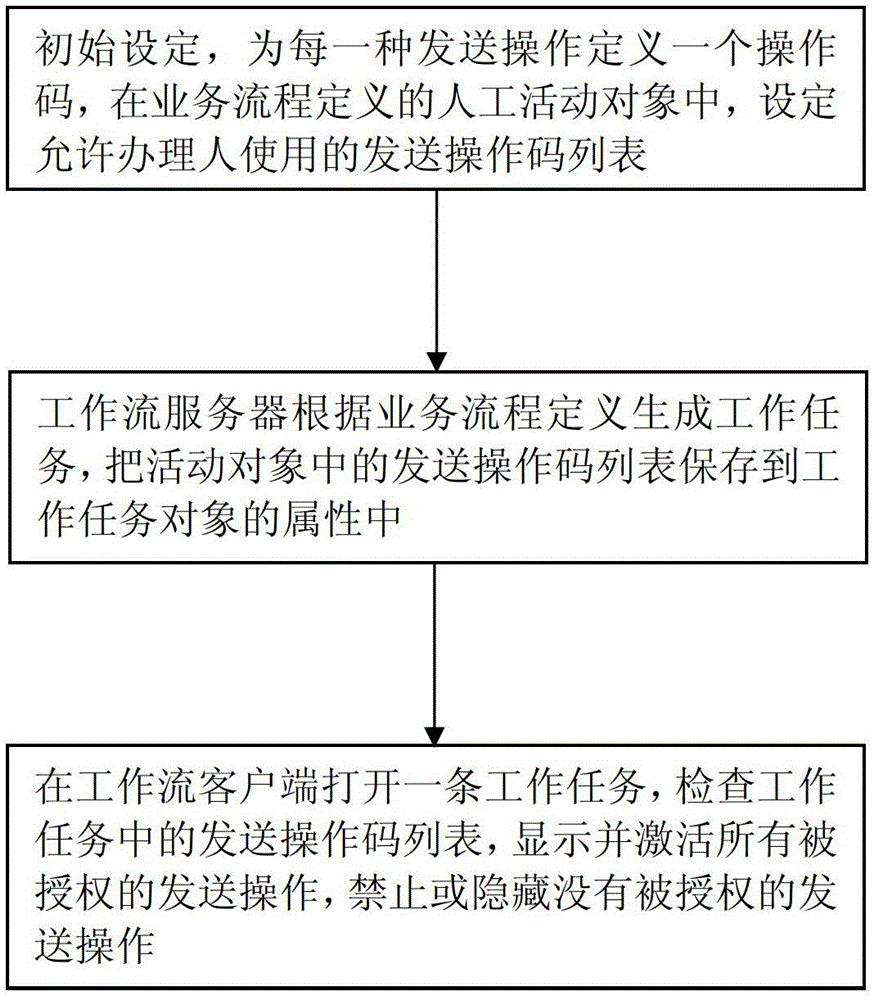
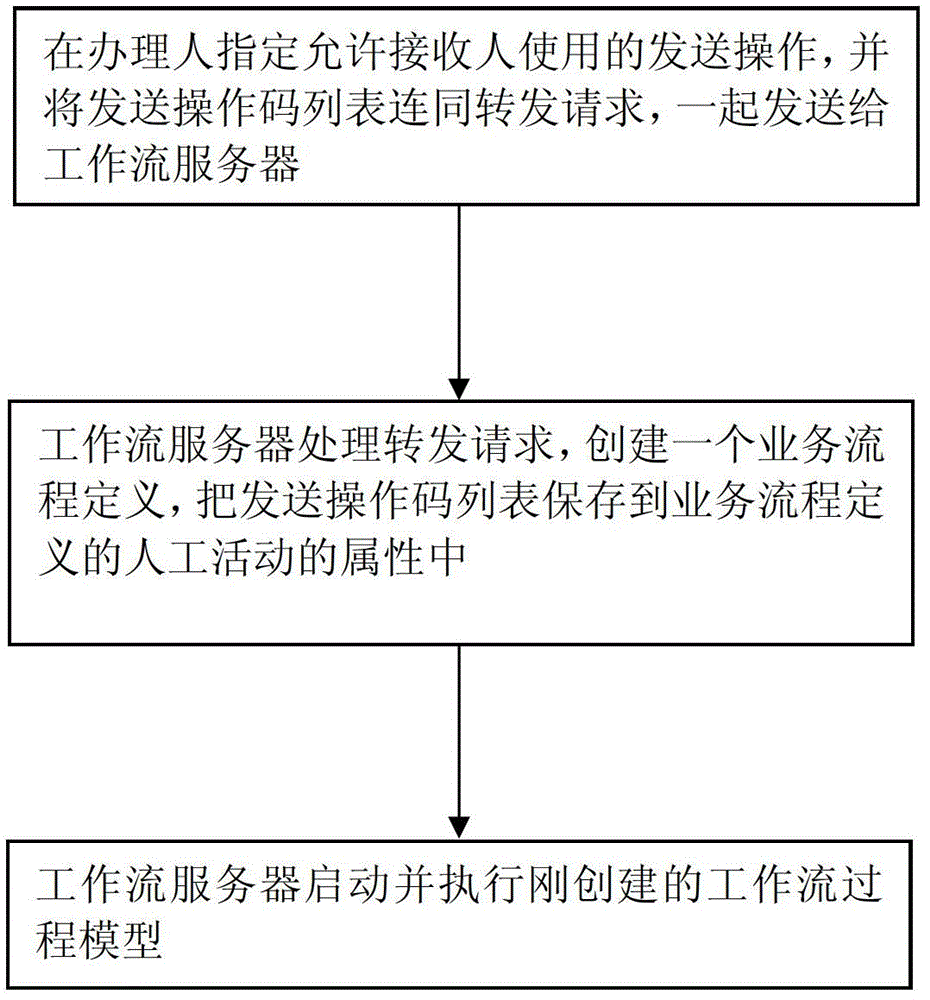
InactiveCN103227727BPrecise access controlMeet business needsResourcesData switching networksWork taskBusiness requirements
The invention discloses a method for controlling a task sending right in a workflow system, and belongs to the field of workflows. The method comprises the following steps that 1, initial setting is performed; 2, a sending operation code list stored in an active object is assigned into an attribute of a work task object; and 3, the sending operation code list in a work task is read, all authorized sending operation buttons are displayed and activated, non-authorized sending operation buttons are prohibited or concealed, and the sending right of a receiver can be controlled when a transactor sends one work task to other people. The method has the advantages that right control on the work task can be detailed to a certain specific activity of a flow; the right control is more accurate, and meets a business requirement better; authorization can be directly achieved only by a compilation tool of a workflow process model without secondary development in a user using process; and the right control on the work task sent out by a user can also be achieved without bugs.
Owner:SHENYANG ZHAORUAN SOFTWARE
A proxy firewall protection method and system for smart contracts
ActiveCN111654494BImplement safe callsPrecise access controlFinanceSecuring communicationComputer networkEngineering
The invention discloses a proxy firewall protection method and system for smart contracts. The method includes: calling the proxy contract in the proxy firewall after the user issues a transaction, and the proxy firewall secures the parameter content of the transaction according to the security policy. Check; after passing the security check, the proxy firewall changes the source address of the transaction to the address of the proxy contract, and publishes the transaction to the target smart contract, so that the proxy firewall calls the target smart contract; after completing the call of the target smart contract, the proxy The firewall updates the transaction execution result to the transaction content and returns it to the proxy contract; the proxy contract publishes the updated transaction to the user address, so that the proxy firewall transmits the transaction execution result to the user and completes the call of the proxy contract. The invention provides a call interface between the user and the target contract through the agent firewall, realizes the safe call of the smart contract, and improves the transaction security of the contract issuer and the caller.
Owner:GUANGZHOU UNIVERSITY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com