Automatic construction system and method for access control strategy of high-level information system
An access control strategy and information system technology, which is applied in the field of access control of network systems, and can solve problems such as access control conflicts, not being allowed, and operation failures.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific illustrations.
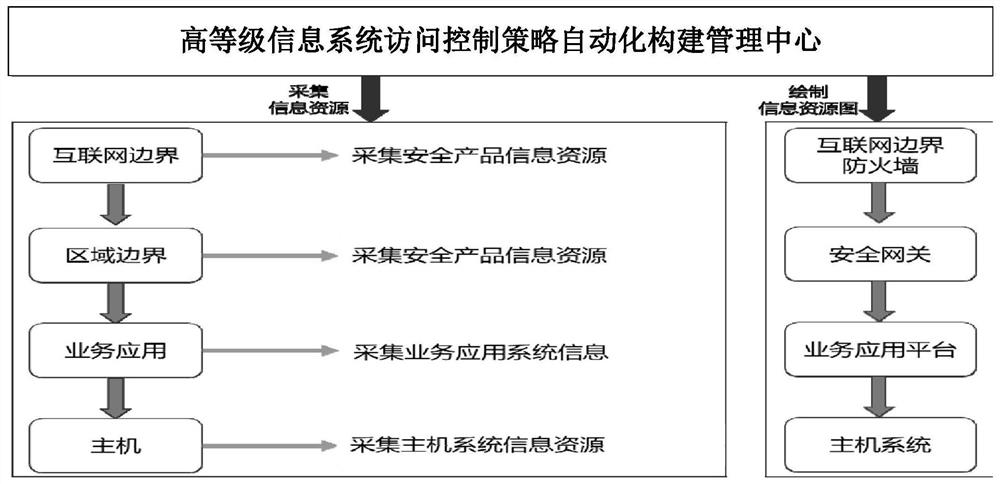
[0042] In view of the imperfection of the existing access control system and the inability to provide access control relevance, integrity and consistency, this example builds a high-level information system access control policy automation platform (system) to effectively solve access control problems. omissions and conflicts.
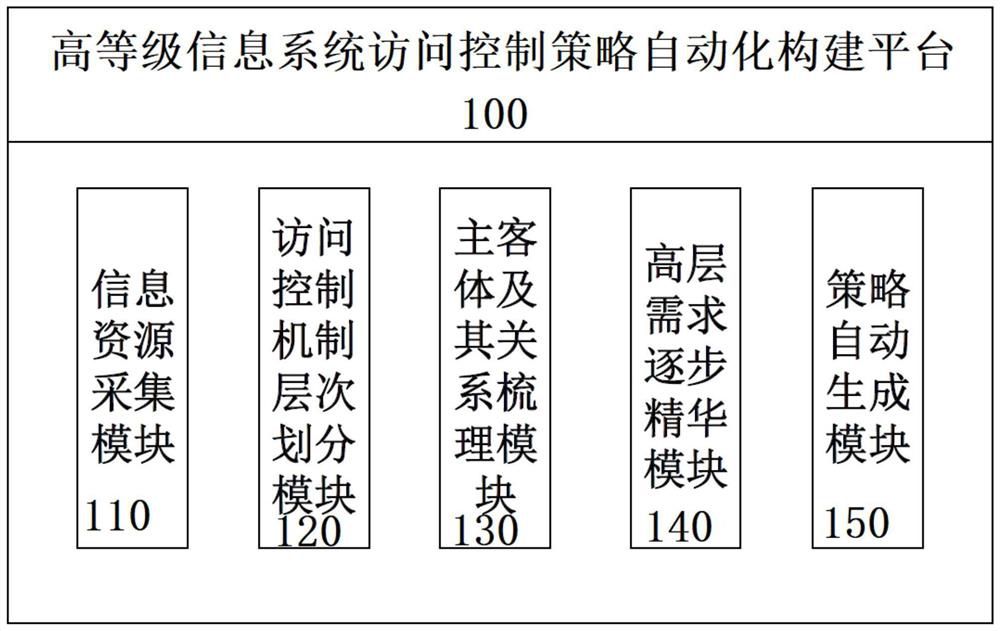
[0043] see figure 1 , which shows an example of the composition of the high-level information system access control strategy automation construction platform given in this example.
[0044] It can be seen from the figure that this high-level information system access control policy automation construction platform 100 is mainly composed of an information resource collection module 110, an access control mechanism hierar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com