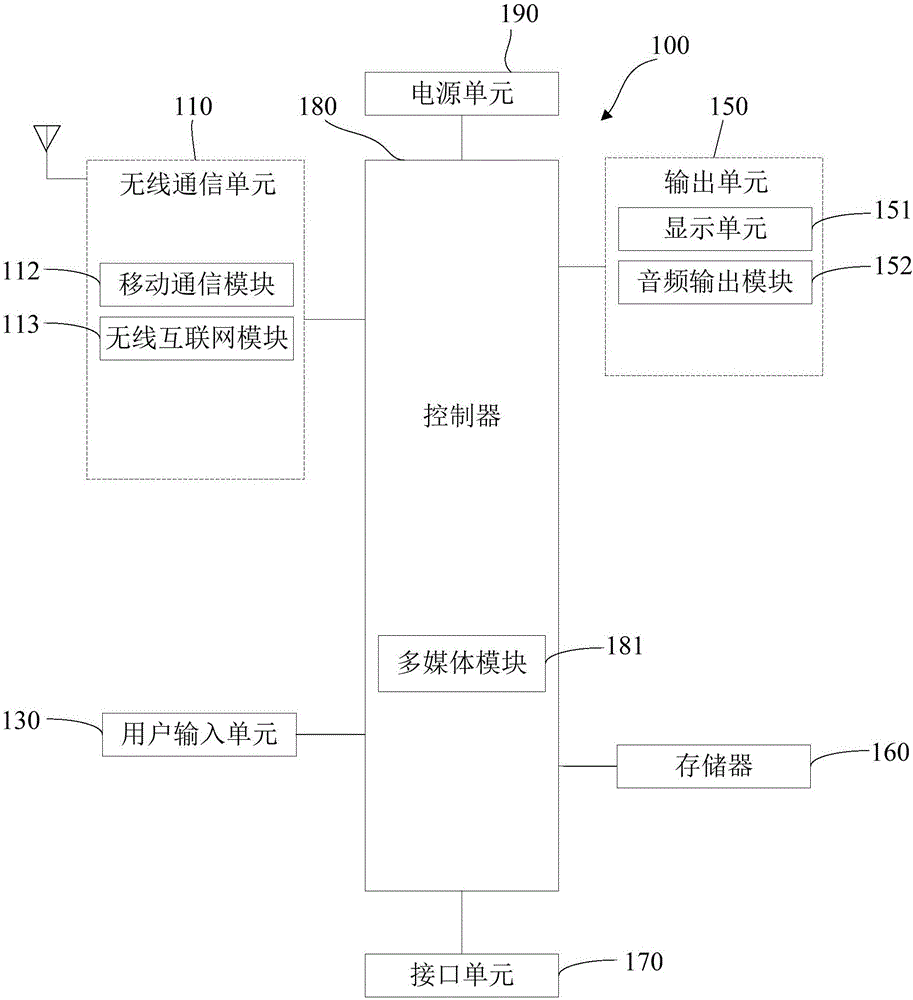
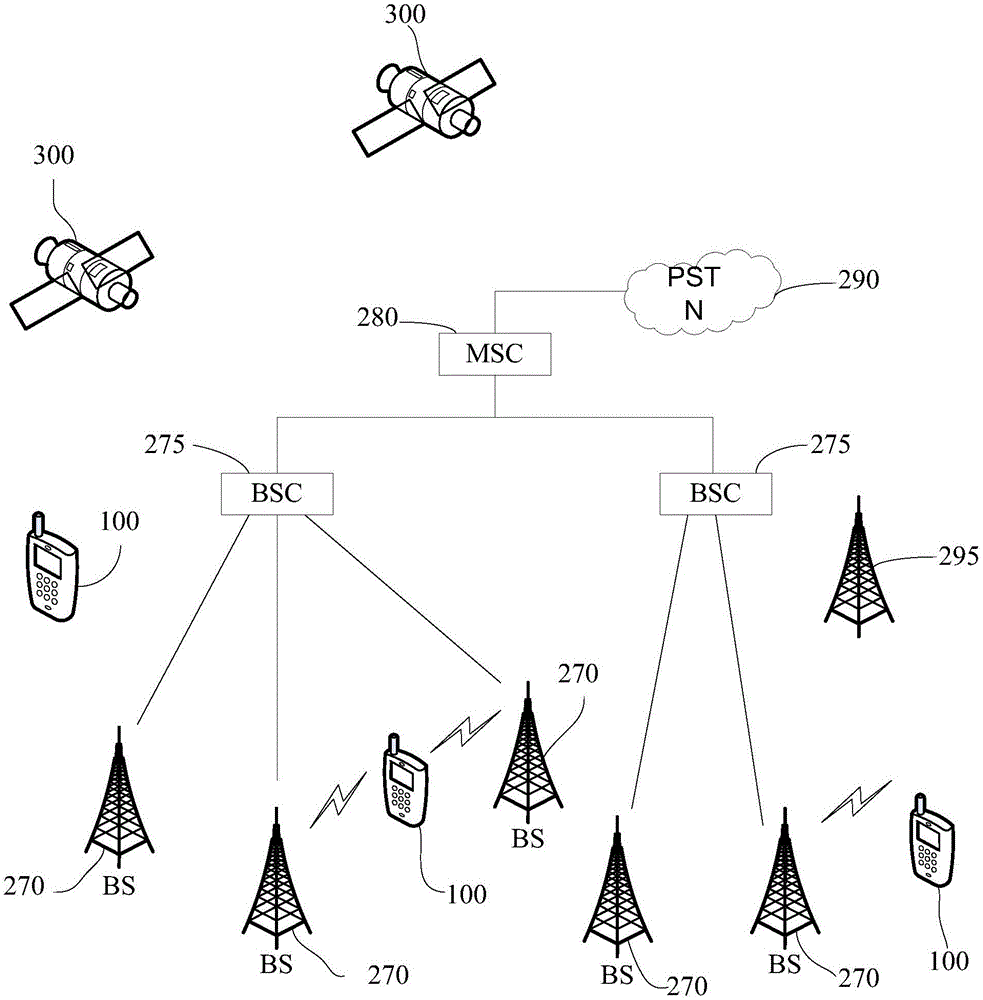
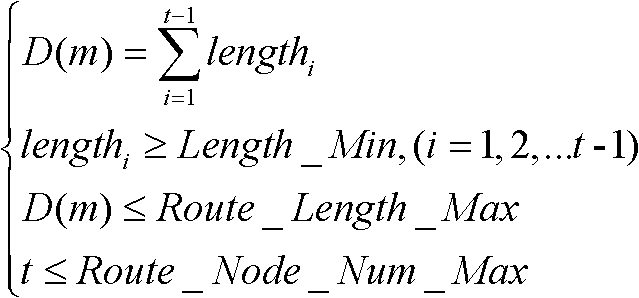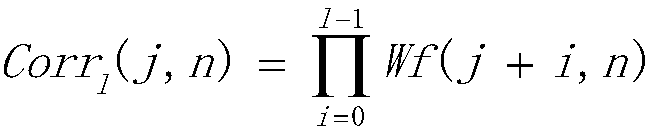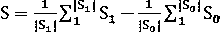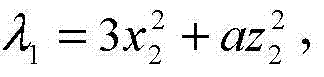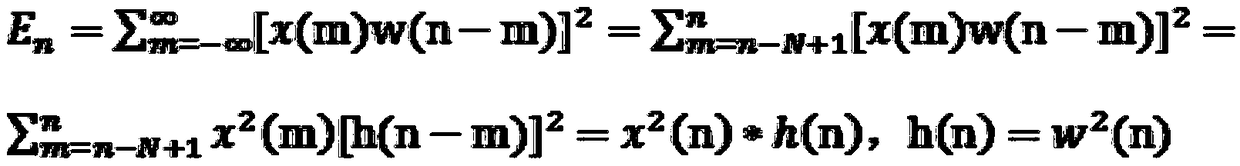Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
72results about How to "Improve attack efficiency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
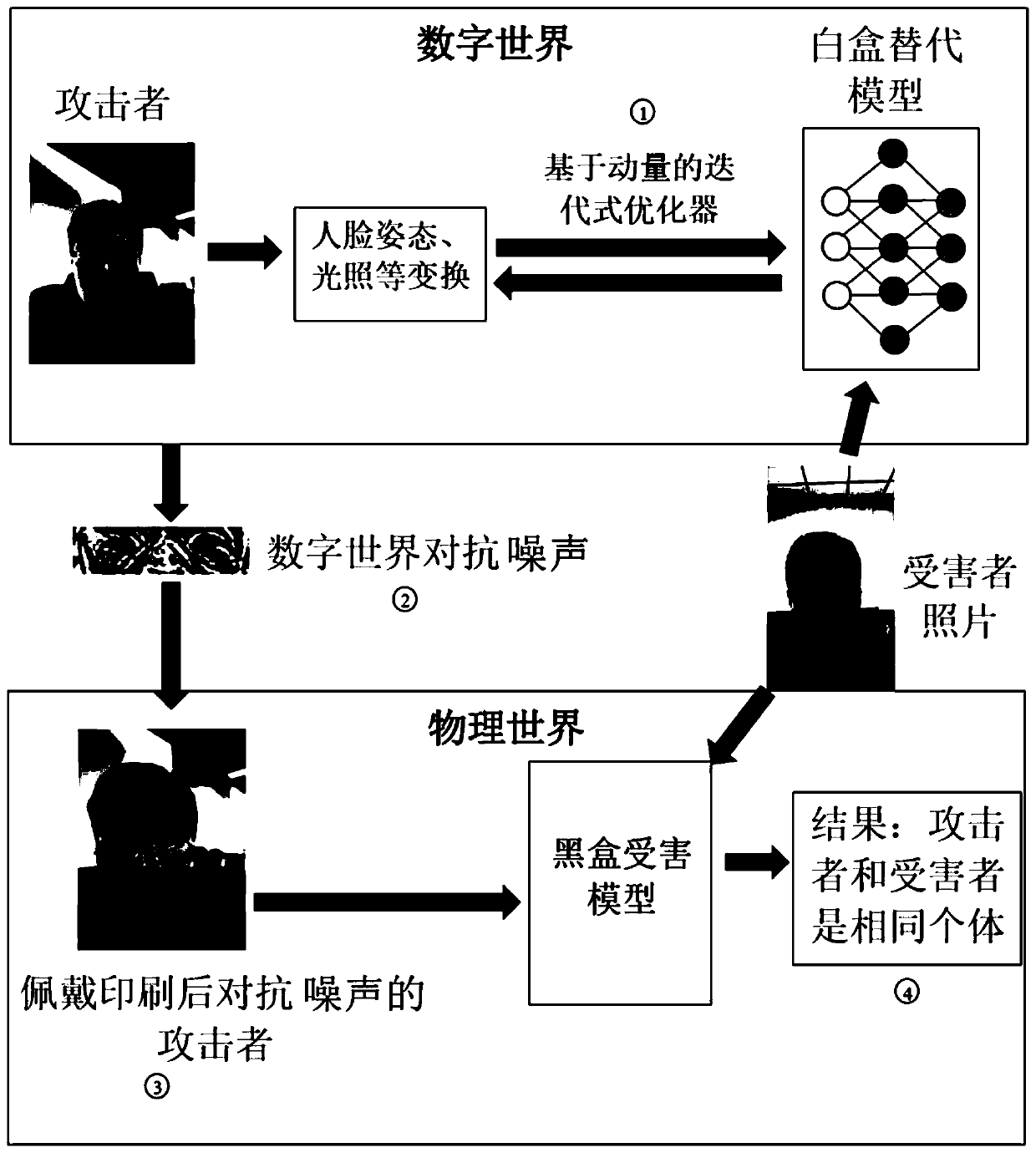
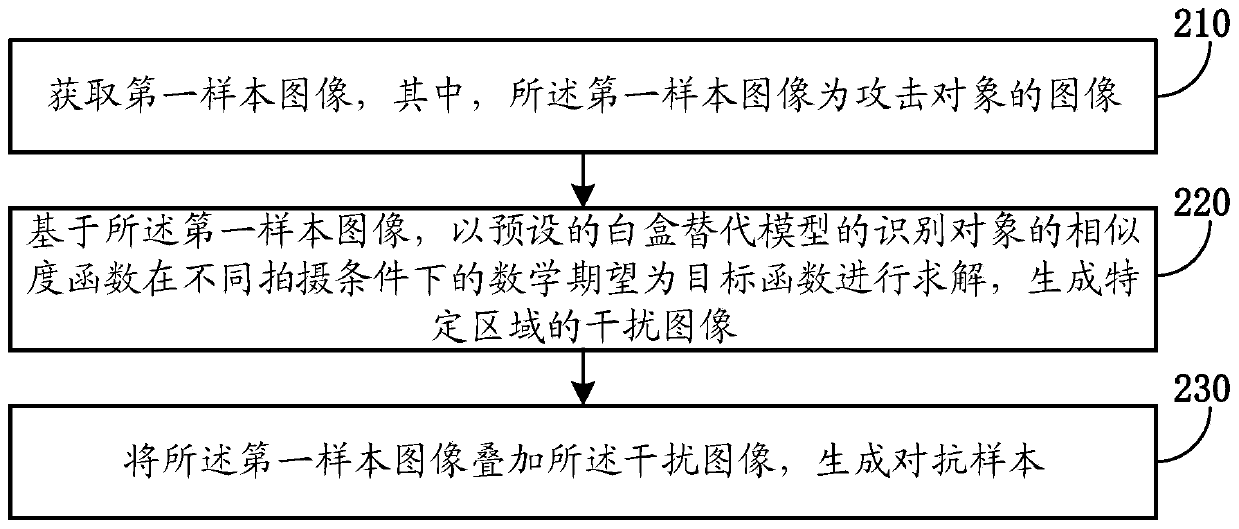
Adversarial sample generation method and device, medium and computing device
ActiveCN110245598AEase of evaluationImprove securityCharacter and pattern recognitionNeural architecturesSubstitution modelSample image
The invention provides an adversarial sample generation method, which comprises the following steps of obtaining a first sample image which is an image of an attack object; based on the first sample image, solving by taking the mathematical expectations of a similarity function of an identification object of a preset white box substitution model under different shooting conditions as an objective function, and generating an interference image of a specific area; and superposing the interference image on the first sample image to generate an adversarial sample. According to the present invention, the white box substitution model is used to generate the adversarial sample, so that the attack efficiency can be improved, whether the potential vulnerabilities exist in an image recognition model or not can be rapidly detected, the evaluation of the image recognition model is improved, and the safety of the image recognition model is improved. In addition, the embodiment of the invention provides an adversarial sample generation device, a medium and a computing device.
Owner:BEIJING REALAI TECH CO LTD
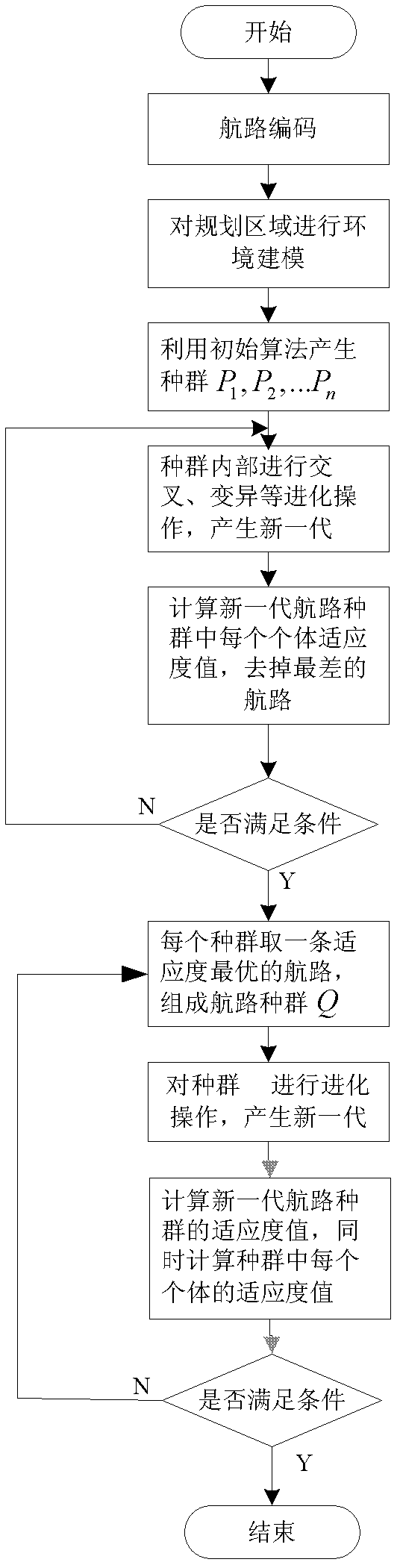
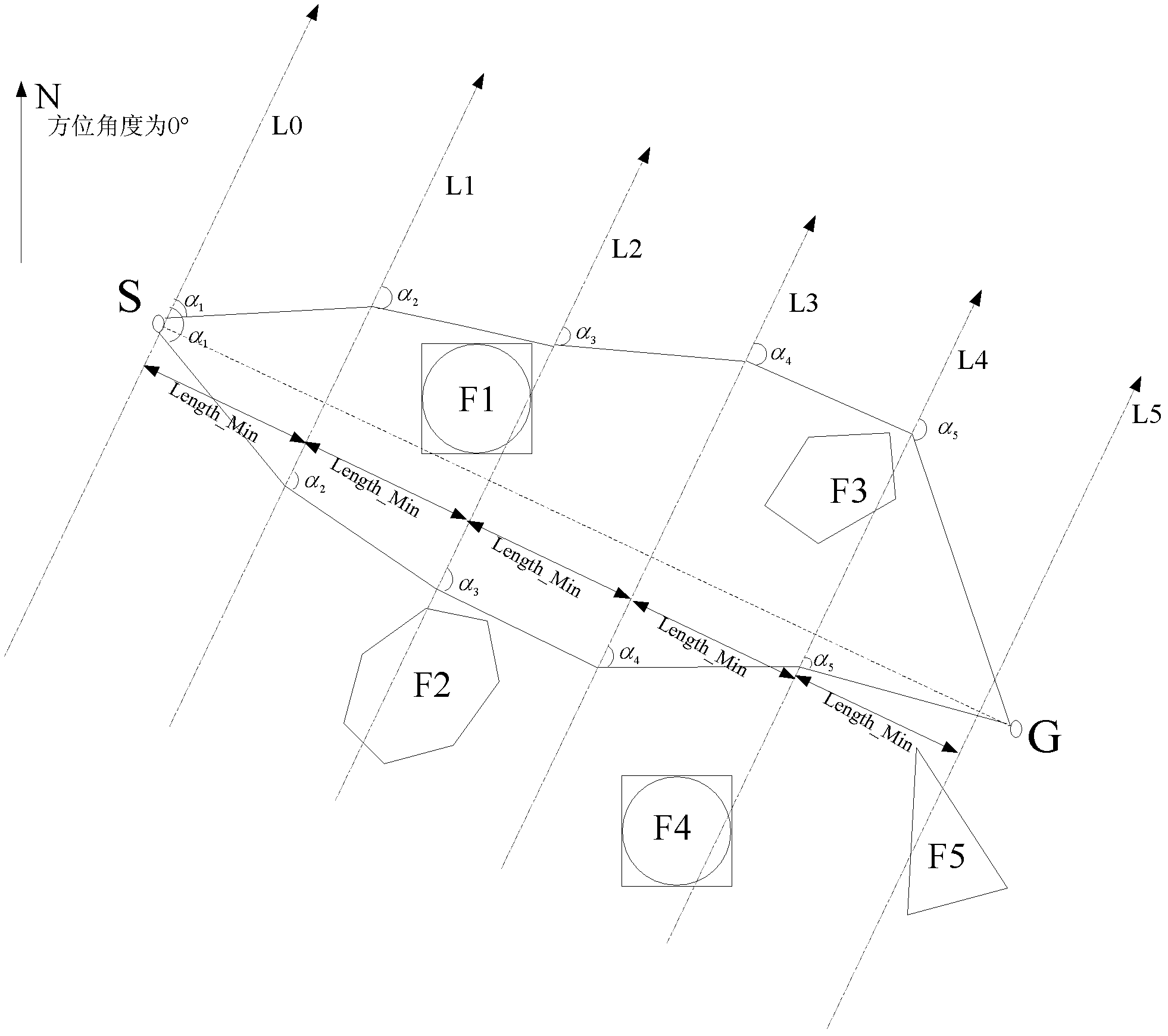
Multi-missile collaborative route calculation method based on multi-target evolution method
ActiveCN102436604ASolve planning problemsEasy to handleGenetic modelsForecastingRoute planningPopulation
The invention provides a multi-missile collaborative route calculation method based on a multi-target evolution method, which belongs to the technical field of task planning. The method specifically comprises the steps of: coding missile routes, defining missile mobility characteristics, modeling a planning area, generating route initial populations, evolving the route initial populations to generate new-generation route populations, evaluating the new-generation route populations to generate a rout set Q, evolving the route set Q among the populations to obtain a new-generation route set Q', evaluating the obtained new-generation route set Q', judging whether collaborative conditions are satisfied or not and the like. The method provided by the invention abandons the traditional route planning mode aiming at a single missile and can conduct collaborative planning to multiple missiles. By giving full consideration to the spatial conflict relationship and the attack arrival time relationship among the multiple missiles during planning, the realization of simultaneous set-time attacks to multiple enemy targets, saturation attacks to a certain enemy target and the like is facilitated and the attack efficiency is improved.
Owner:HARBIN ENG UNIV
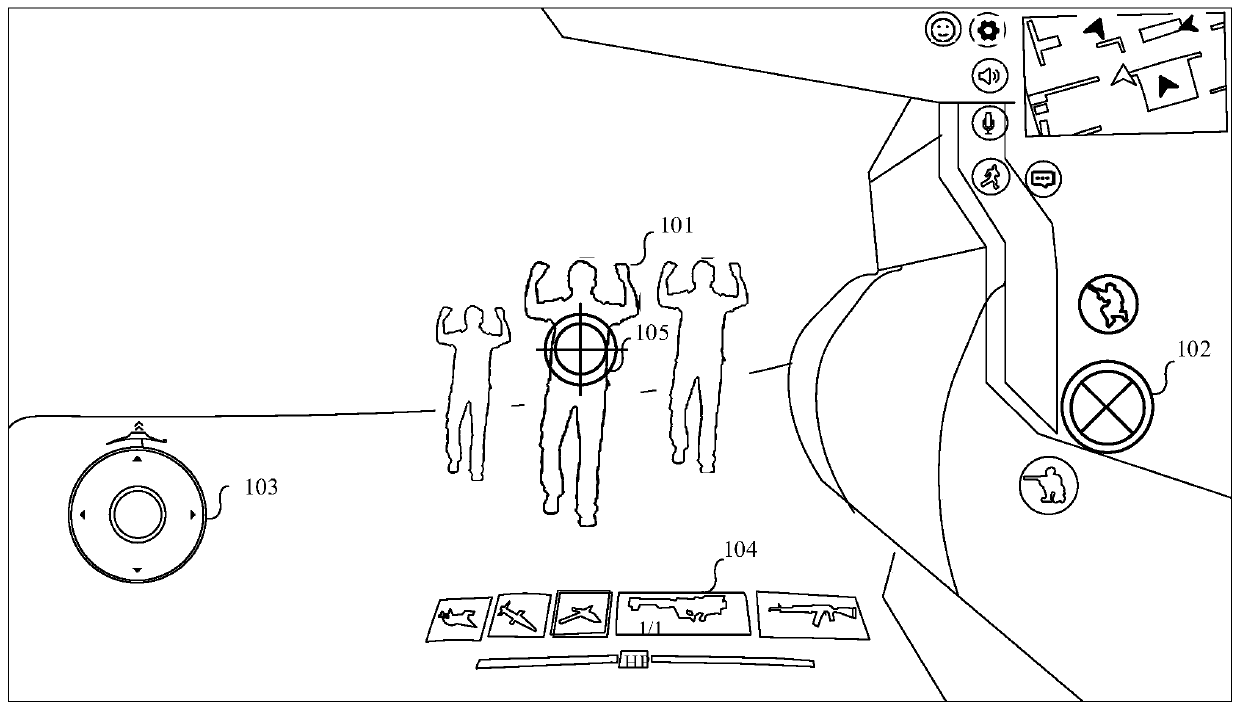
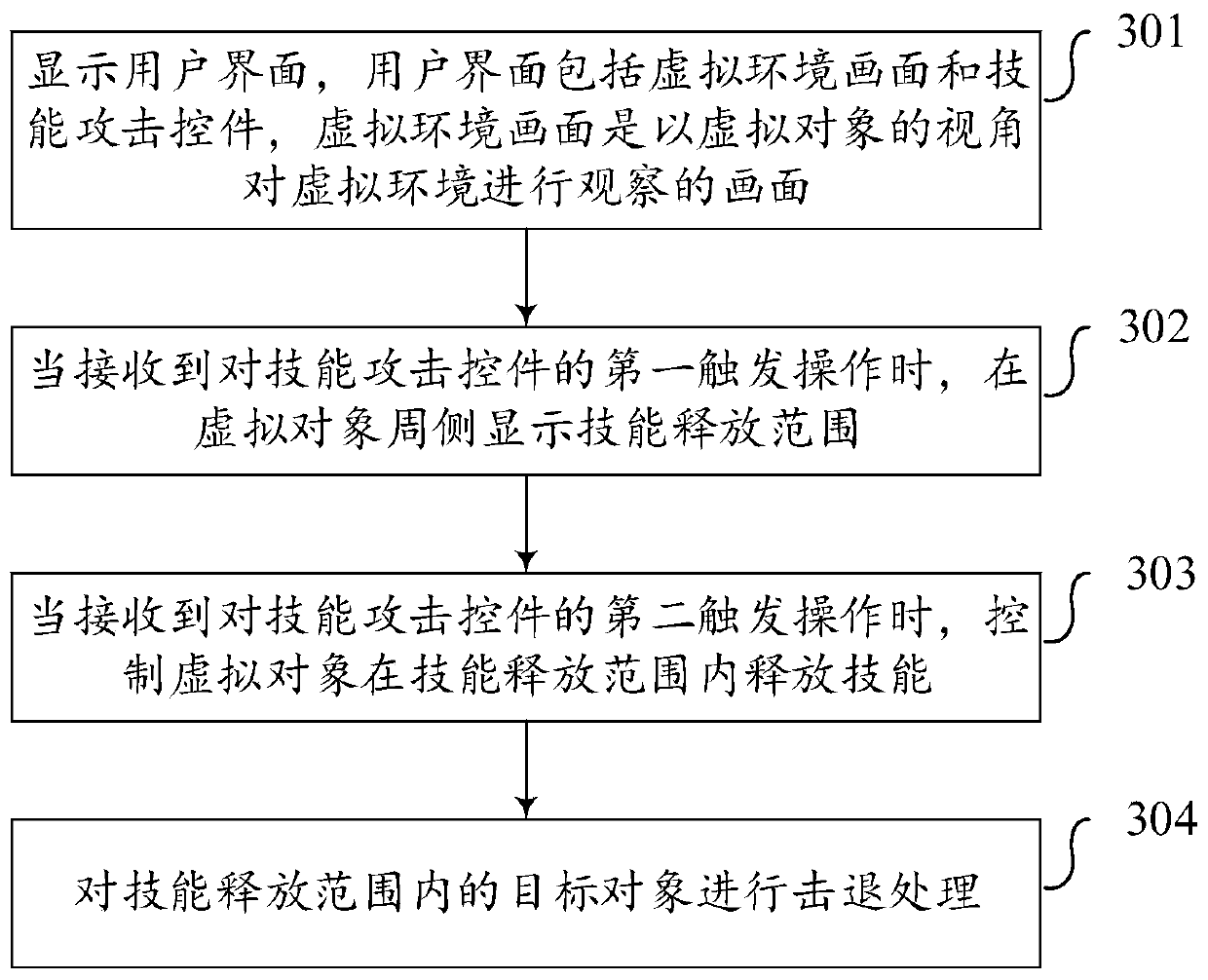
Method for controlling virtual object to attack, terminal and storage medium
ActiveCN110694261ARich attack methodsSimplify the attack processVideo gamesAttackHuman–computer interaction
The invention relates to a method for controlling a virtual object to attack, a terminal and a storage medium, and relates to the field of computers. The method comprises the following steps: displaying a user interface, wherein the user interface comprises a virtual environment picture and a skill attack control, and the virtual environment picture is a picture for observing a virtual environmentfrom the perspective of a virtual object; when receiving a first trigger operation on the skill attack control, displaying a skill release range on the peripheral side of the virtual object; when receiving a second trigger operation on the skill attack control, controlling the virtual object to release the skill in the skill release range; and performing knock-out processing on the target objectin the skill release range. According to the method, a plurality of target objects can be instantly knocked out under the condition that the number of the target objects is large and the target objects are close, the attack process of the virtual objects is simplified while the attack modes of the virtual objects are enriched, and the attack efficiency of the virtual objects is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Defending device and method for cross-site scripting attack
The invention discloses a defending device for a cross-site scripting attack. The defending device comprises an intercepting module, a judging module and a submitting module, wherein the intercepting module is used for intercepting a request transmitted to an application in an application server through a cross-site scripting attack filter; the judging module is used for analyzing and processing the intercepted request, and judging whether the request includes malicious codes applied to the cross-site scripting attack; and the submitting module is used for submitting the request to an open-source project for escaping if the request includes the malicious codes applied to the cross-site scripting attack in order to submit the escaped request to the application in the application server. The invention also discloses a defending method for the cross-site scripting attack. Through adoption of the defending device and method, hard coding of Web pages can be avoided; the workload is lowered; and the efficiency in defending of the cross-site scripting attack is increased.
Owner:NUBIA TECHNOLOGY CO LTD
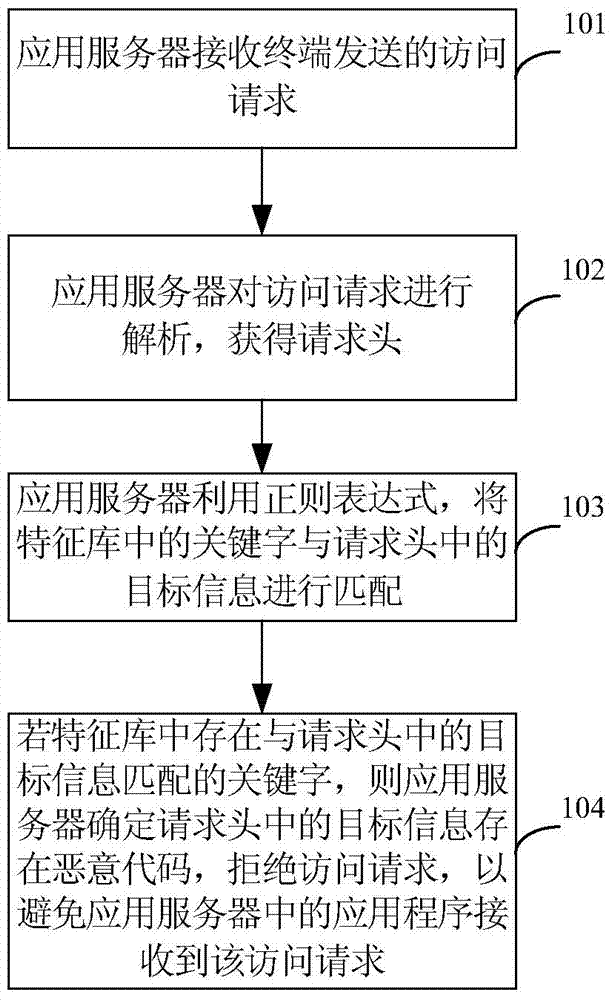
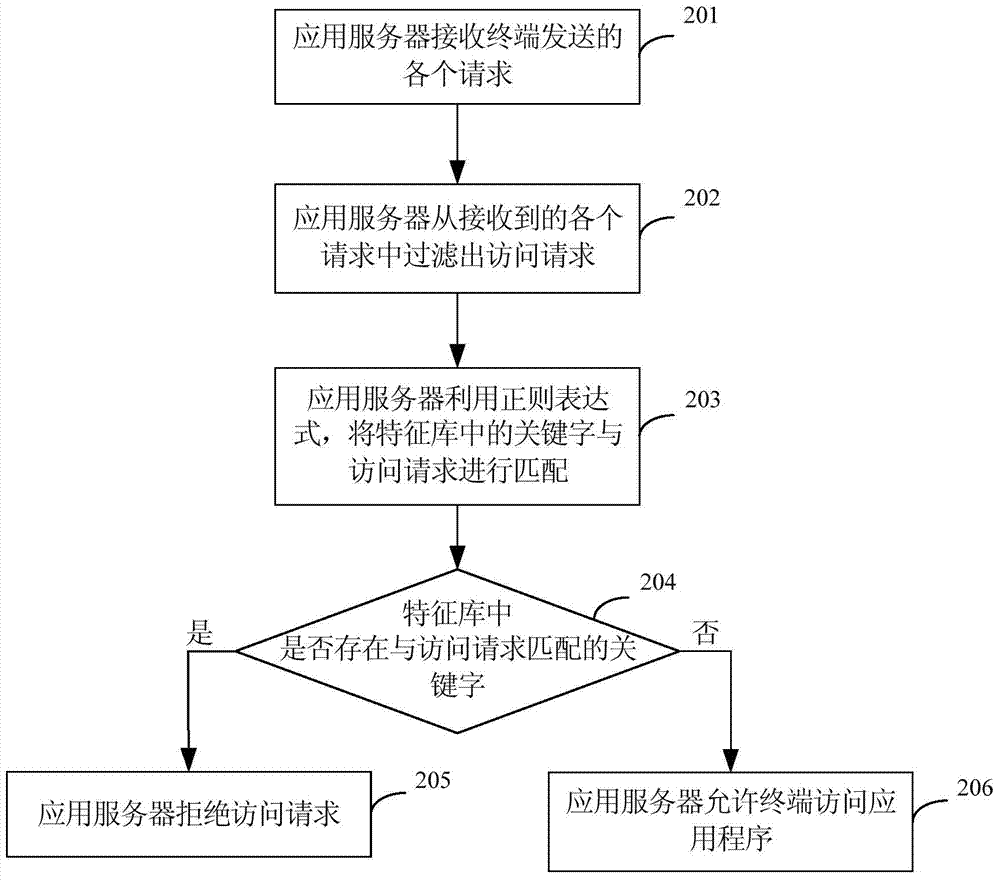
Cross-site scripting attack defense method and device and application server
ActiveCN104519008AImprove attack efficiencyAvoid hardcodingTransmissionHard codingApplication server
The invention provides a cross-site scripting attack defense method and device and an application server. The method comprises the following steps: receiving an access request sent by a terminal through the application server; resolving the access request to obtain a request header; matching keywords in a feature library with target information in the request header by using a regular expression; and if keywords matched with the target information in the request header exist in the feature library, determining that a malicious code exists in the target information in the request header through the application server, and denying the access request through the application server in order to defense cross-site scripting attacks. Through uniform detection of the access requests sent by the terminal on the application server, hard coding of each Web page is avoided; the workload is lowered; and the cross-site scripting attack defense efficiency is increased.
Owner:NEW FOUNDER HLDG DEV LLC +1
DPA attack method for carrying out fitting by utilizing neural network, system and terminal
InactiveCN109525384AImprove attack efficiencyImprove time and efficiencyCryptographic attack countermeasuresNeural learning methodsFeature vectorNerve network
The invention belongs to the field of cipher algorithm analysis and detection and discloses a DPA attack method for carrying out fitting by utilizing a neural network, a system and a terminal. In thetraining stage, a predictive neural network automatically learns and obtains a mapping relationship between an energy consumption characteristic vector and an intermediate combination value accordingto a training energy consumption set; and in high-order DPA attack, the predictive neural network is used to predict the intermediate combination value of the attack energy trace, and the correlationcoefficient between a predictive intermediate combination value and a conjecture intermediate combination is calculated, thus the device key is attacked. The method of the invention eliminates the requirement that the mask must be understood in the learning stage, simultaneously avoids the requirement of the high-order DPA on the energy consumption cross-combination, reduces the attack condition,and improves the attack efficiency. Experimental results show that the attack algorithm is feasible and efficient.
Owner:CHENGDU UNIV OF INFORMATION TECH
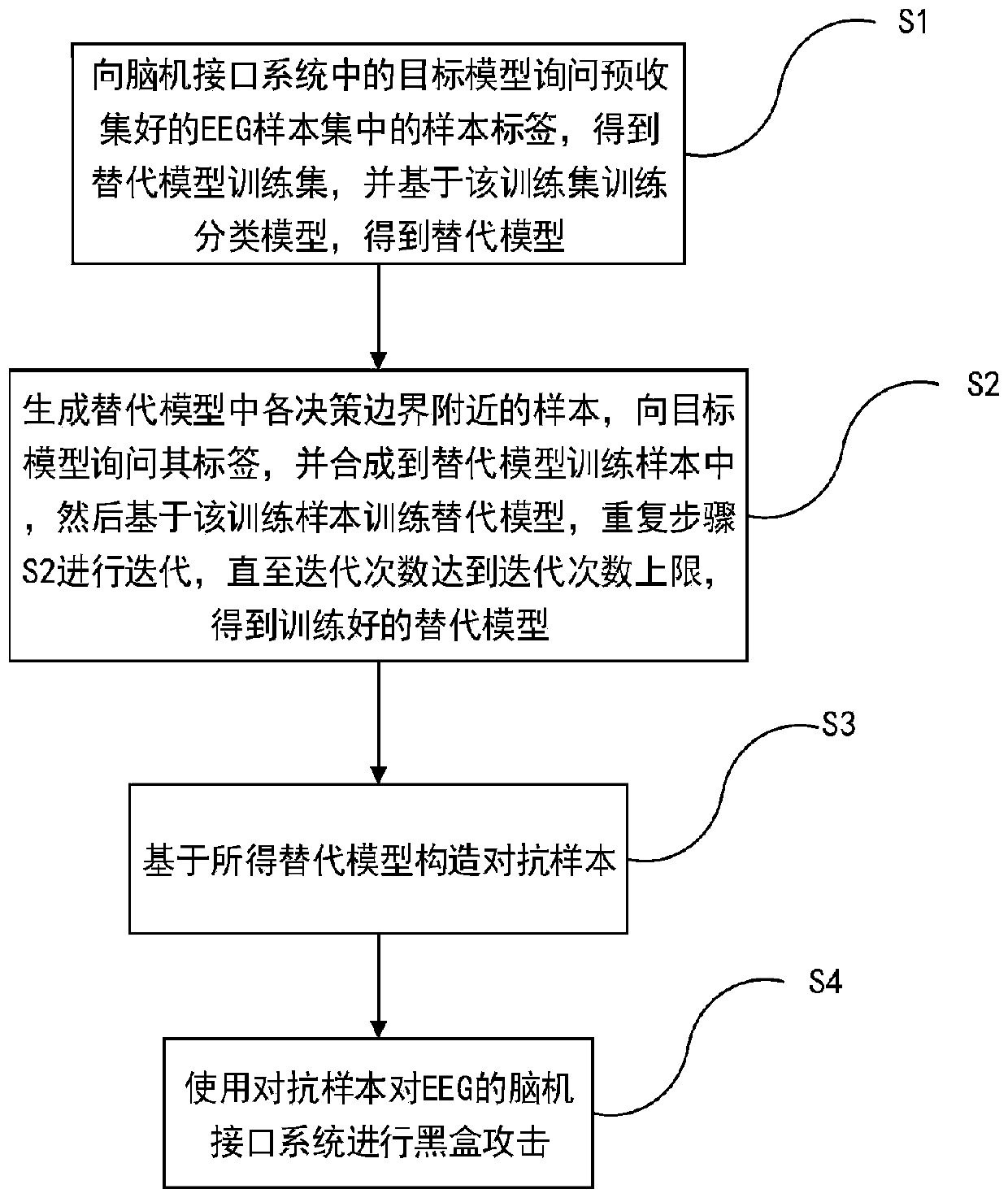
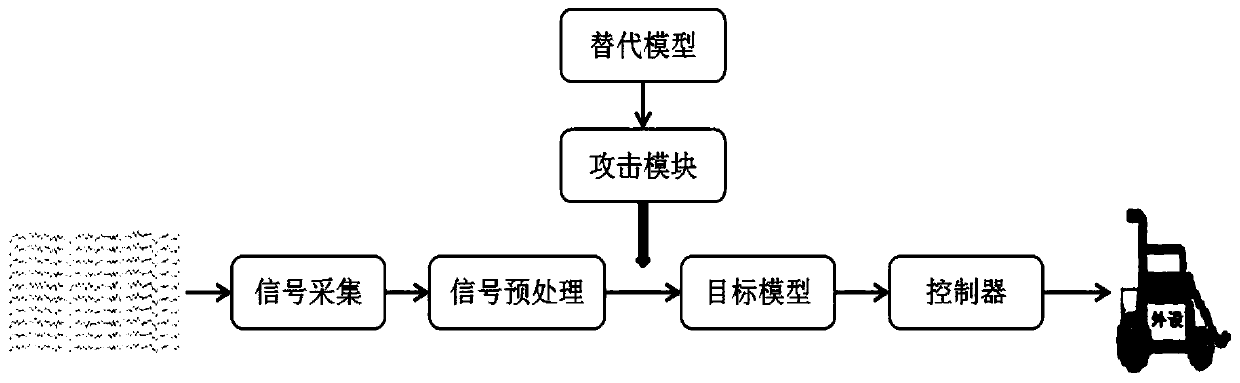
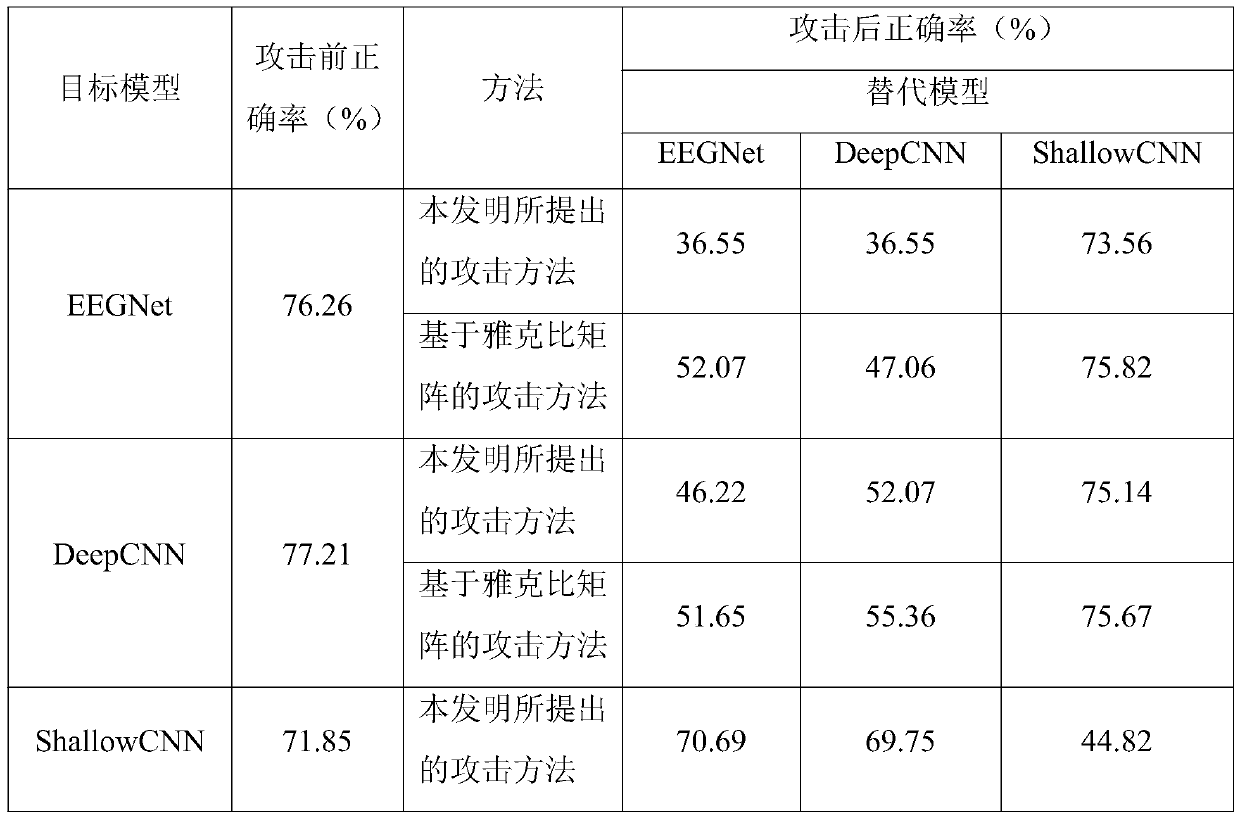
Black box attack method for brain-computer interface system
ActiveCN110837637ALarge amount of informationIncrease diversityCharacter and pattern recognitionPlatform integrity maintainanceLow noiseTime domain
The invention discloses a black box attack method for a brain-computer interface system. Firstly, generating EEG samples with more information amount and diversity based on inquiry synthesis active learning to substitute model training samples, then training an alternative model based on the training sample, so that the alternative model can better approximate a target model, and finally, generating an adversarial sample on the trained alternative model, and performing black box attack on a brain-computer interface system of the EEG by using the adversarial sample, so that the brain-computer interface system can be wrongly classified on the target model. Compared with a traditional black box attack method based on a Jacobian matrix, the method has a better attack effect. The same or betterattack performance can be obtained under the condition of fewer inquiry times, the generated countermeasure sample has very low noise, is almost not different from the original EEG signal in time domain and frequency domain and cannot be easily found, and the attack efficiency of the black box attack in the brain-computer interface system is greatly improved.
Owner:HUAZHONG UNIV OF SCI & TECH
Encryption system side channel attack test method
InactiveCN103259647AImprove securityImprove developmentEncryption apparatus with shift registers/memoriesData switching networksPlaintextCryptosystem
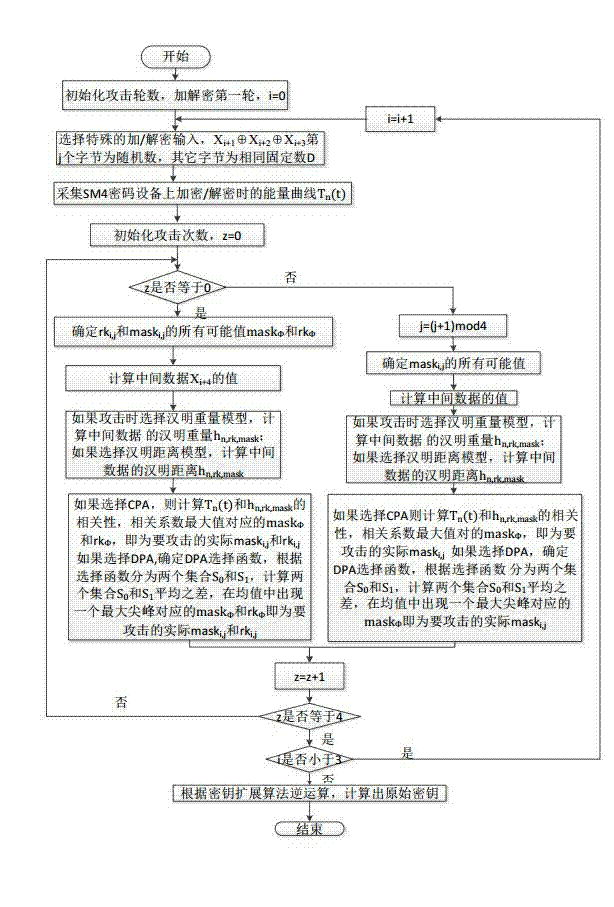
The invention discloses an encryption system side channel attack test method and relates to information security technologies. The encryption system side channel attack test method includes the following steps: inputting a specific plaintext on a controlled device, using an attacked cryptosystem to conduct encryption, and capturing a power consumption curve. The encryption system side channel attack test method is characterized in that the inputted plaintext is a large number which is low in Hamming weight. The encryption system side channel attack test method has the advantages that attack efficiency is high, the method has certain universality, and attack cannot be prevented with utilization of a single method for shielding special numbers. The encryption system side channel attack test method is beneficial to promotion of development of an information security system with higher safety performance.
Owner:CHENGDU UNIV OF INFORMATION TECH
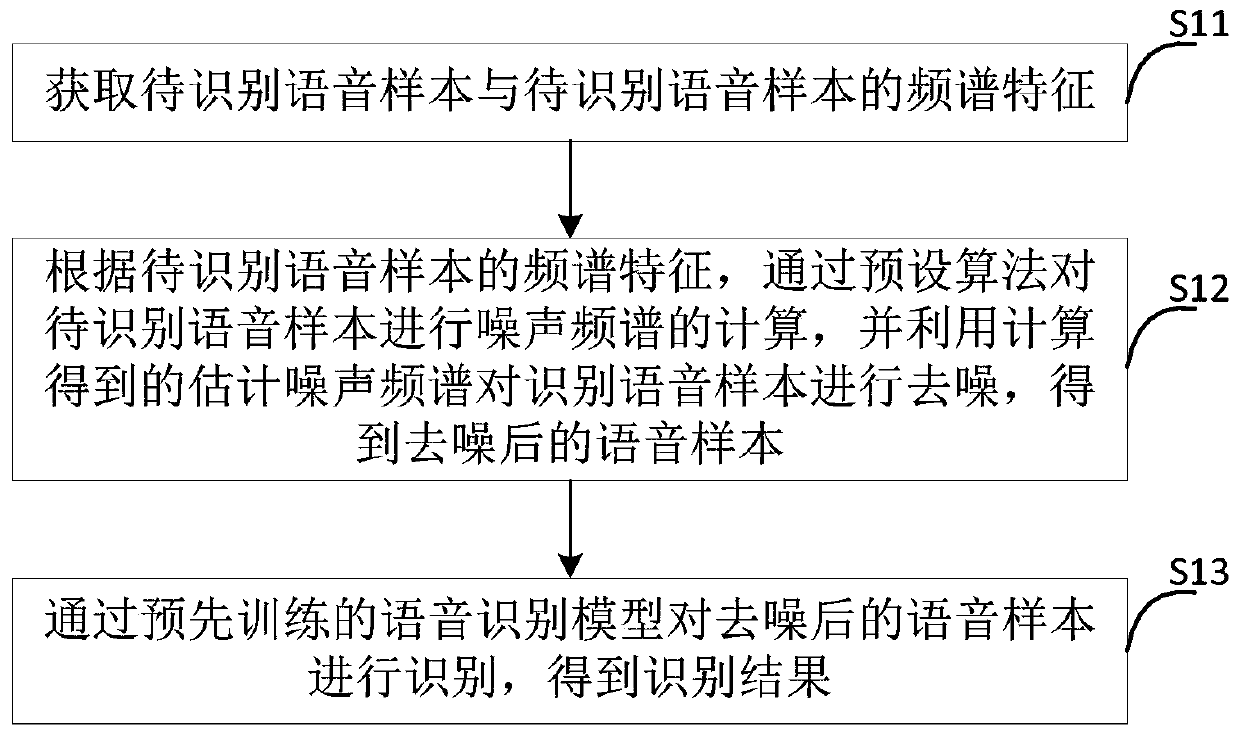
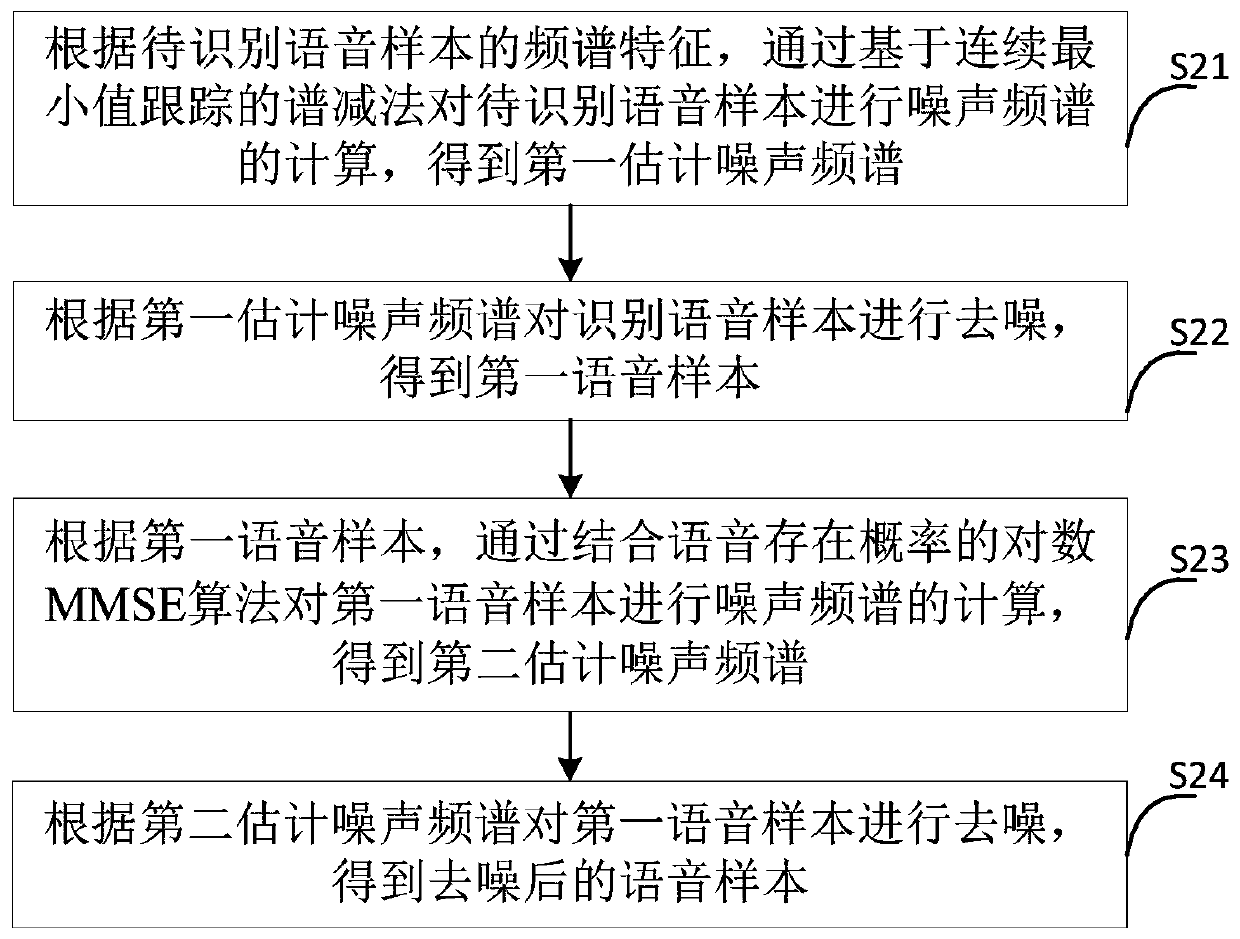
Adversarial sample attack defense method and device based on speech enhancement algorithm
ActiveCN111564154AImprove attack efficiencyImprove accuracySpeech recognitionTransmissionSpectral subtractionAlgorithm
The embodiment of the invention provides an adversarial sample attack defense method and device based on a voice enhancement algorithm. The method comprises the steps of obtaining a to-be-identified voice sample and spectrum features of the to-be-identified voice sample; according to the spectrum characteristics of the to-be-identified voice sample, calculating a noise spectrum of the to-be-identified voice sample through a preset algorithm, and denoising the to-be-identified voice sample by using the estimated noise spectrum obtained through calculation to obtain a denoised voice sample, wherein the algorithm comprises a spectral subtraction method based on continuous minimum tracking and a logarithm minimum mean square error algorithm MMSE algorithm combined with speech existence probability; and recognizing the denoised voice sample through a pre-trained voice recognition model to obtain a recognition result. Therefore, after the to-be-identified voice sample is obtained and de-noising processing is carried out on the to-be-identified voice sample, the de-noised voice sample is identified, so that the voice identification accuracy is improved and the efficiency of defending against the attack of the countermeasure sample is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
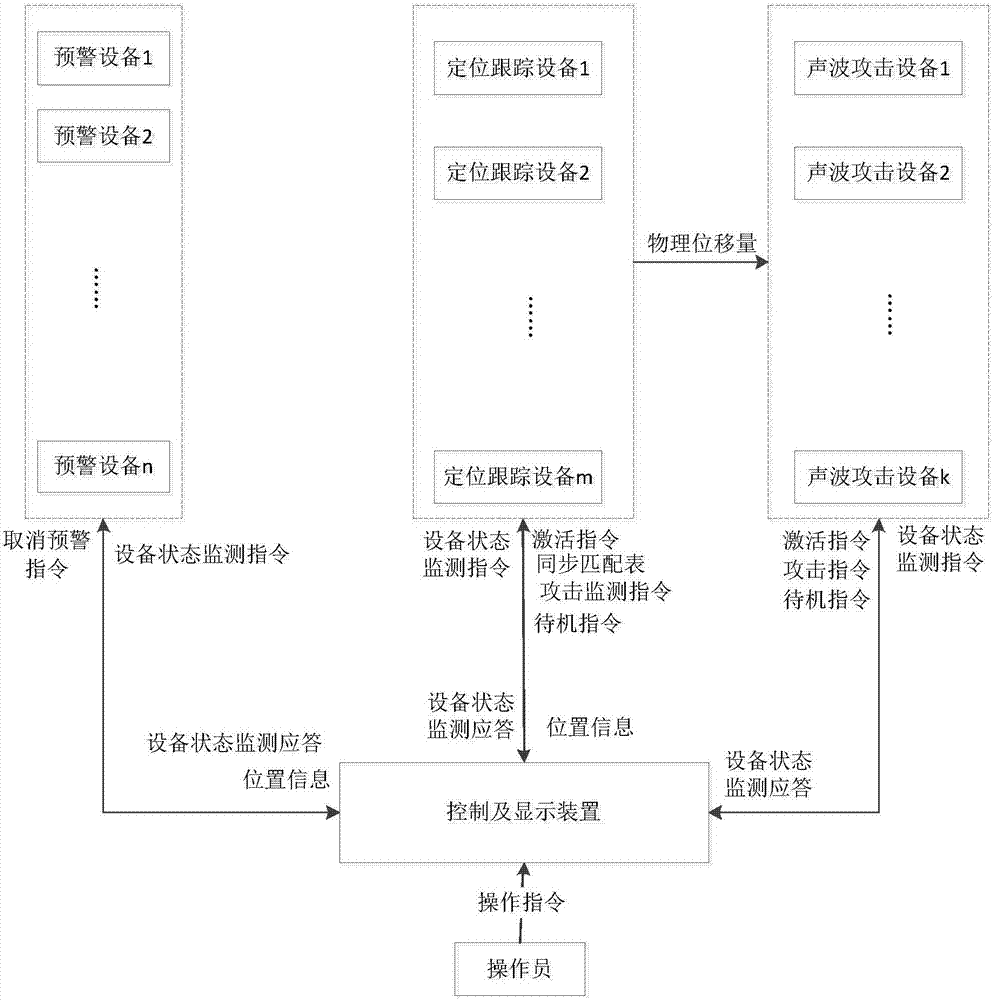
Centralized control unmanned aerial vehicle resisting system based on sound wave attacking
The invention discloses a centralized control unmanned aerial vehicle resisting system based on sound wave attacking. The centralized control unmanned aerial vehicle resisting system comprises a master control and display device, an early warning equipment group, a positioning track equipment group and a sound wave attacking equipment group; early warning equipment transmits detected early warning zone target position information to the master control and display device in real time, movement locus display is carried out through the master control and display device, when a target enters a track zone, positioning track equipment and sound wave attacking equipment are selected for the target, early warning detection on the target is stopped, meanwhile, the position information of the target is obtained through the positioning track equipment, and real-time aiming of the sound wave attacking equipment on the target is achieved; and when it is detected that the target enters an attacking zone, the sound wave attacking equipment is controlled to issue sound wave attacking, crashing caused by resonance of the target is avoided, whether the target is crashed or not is detected through a detector of the positioning track equipment, and the sound wave attacking equipment is controlled to stop attacking if the target is crashed. According to the embodiment, intelligent judgment and physical crashing can be carried out on multiple unmanned aerial vehicle targets at the same time.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Combined attack method for SM4 algorithm
ActiveCN108880783AQuick calculationImprove attack efficiencyCryptographic attack countermeasuresPlaintextS-box
The invention discloses a combined attack method for SM4 algorithm, combines the energy analysis attack and the differential analysis attack, and provides a combined attack method of energy analysis and differential analysis aiming for the SM4 algorithm. An S-box nonlinear output is selected as an attack intermediate value, and the sensitive intermediate values of the second round and the fourthround are attacked by selecting a plaintext to realize cross-round energy analysis and attack. A round secret key can be quickly calculated through differential analysis of the S box, and the attack efficiency is improved. In addition, the method can also be extended to joint attacks of all symmetric cryptographic algorithms.
Owner:成都三零嘉微电子有限公司
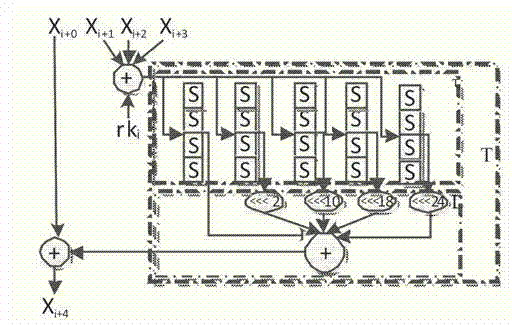
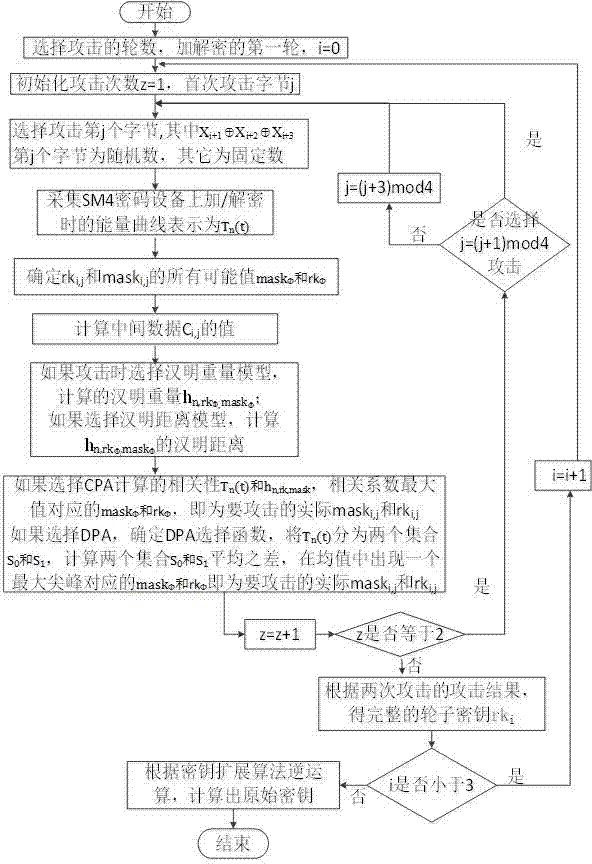
Side channel energy attack method aiming at SM4 password round function output
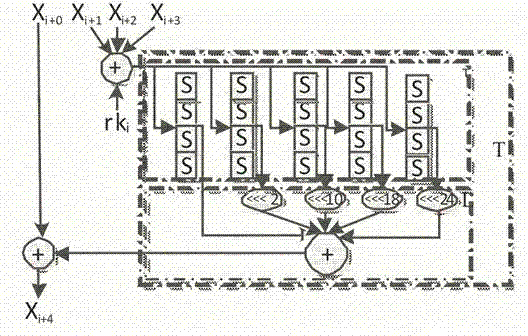
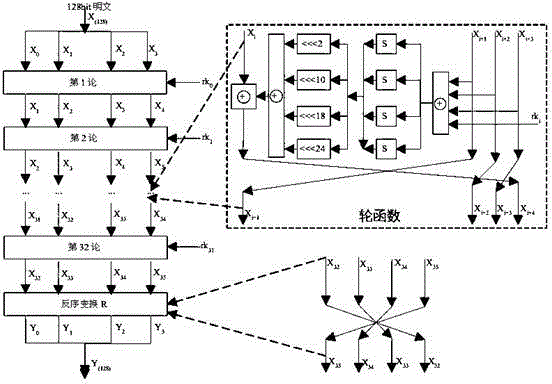
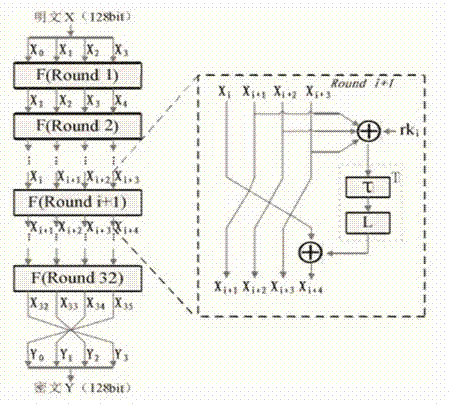
ActiveCN104753665AImprove attack efficiencyIncrease flexibilityEncryption apparatus with shift registers/memoriesPlaintextPassword
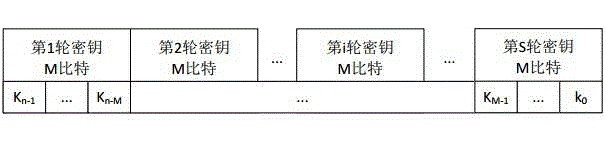
The invention discloses a side channel energy attack method selecting a clear text or a cipher text aiming at SM4 password round function output. The method includes the following steps: S1 selecting clear text input or cipher text input to enable one byte of (Xi+1 Xi+2 Xi+3) to be a random digit and other bytes to be identical fixed digits, adopting the side channel energy attack method to first attack bytes of a round key and the fixed digits in linear transformation and then attack other fixed digits in linear transformation, conducting corresponding computing on attacked data to obtain the complete round key rki, wherein i= 0, 1, 2, 3; S2 conducting reversible calculation to obtain an initial key through a password expansion algorithm according to rk0, rk1, rk2 and rk3 of first four rounds of the round keys. By means of the analysis method, the collection curve attack times and the clear text selection times can be reduced, and analysis flexibility, attack efficiency and successfully rate are improved.
Owner:CHENGDU UNIV OF INFORMATION TECH +2
Side channel attack method for implementation of RSA (Rivest, Shamir and Adleman) cipher algorithms M-ary
ActiveCN104796250AEfficient analysisEasy to analyzeEncryption apparatus with shift registers/memoriesLinear correlationPower attack
The invention discloses a side channel energy analytical attack method by the aid of multiplication output during implementation of power residue computing algorithms M-ary in RSA (Rivest, Shamir and Adleman) cipher algorithms. A core of the side channel energy analytical attack method includes that multiplication output is used as an attack object to implement CPA (correlation power attack) when power residue computing is implemented by the aid of the algorithms M-ary. The method includes steps of (1), acquiring signals and building sampling matrixes; (2), selecting the multiplication output to be used as the attack object; (3), determining correlation models; (4), guessing circulation index values and acquiring intermediate value matrixes by means of computing; (5), acquiring simulation energy consumption matrixes by means of computing; (6), acquiring linear correlation coefficients among the matrixes determined in the steps (1) and (5) by means of computing and obtaining correct circulation indexes by means of attacking; (7), repeatedly carrying out steps (4), (5) and (6) to obtain all correct circulation indexes by means of attacking, and serially connecting all the correct circulation indexes with one another to obtain complete indexes. The side channel energy analytical attack method has the advantages that the RSA cipher algorithm analytical attack flexibility and effectiveness can be enhanced by the aid of the novel side channel attack method for the algorithms M-ary, and an RSA cipher algorithm analytical attack success rate can be increased by the aid of the novel side channel attack method for the algorithms M-ary.
Owner:CHENGDU UNIV OF INFORMATION TECH +3
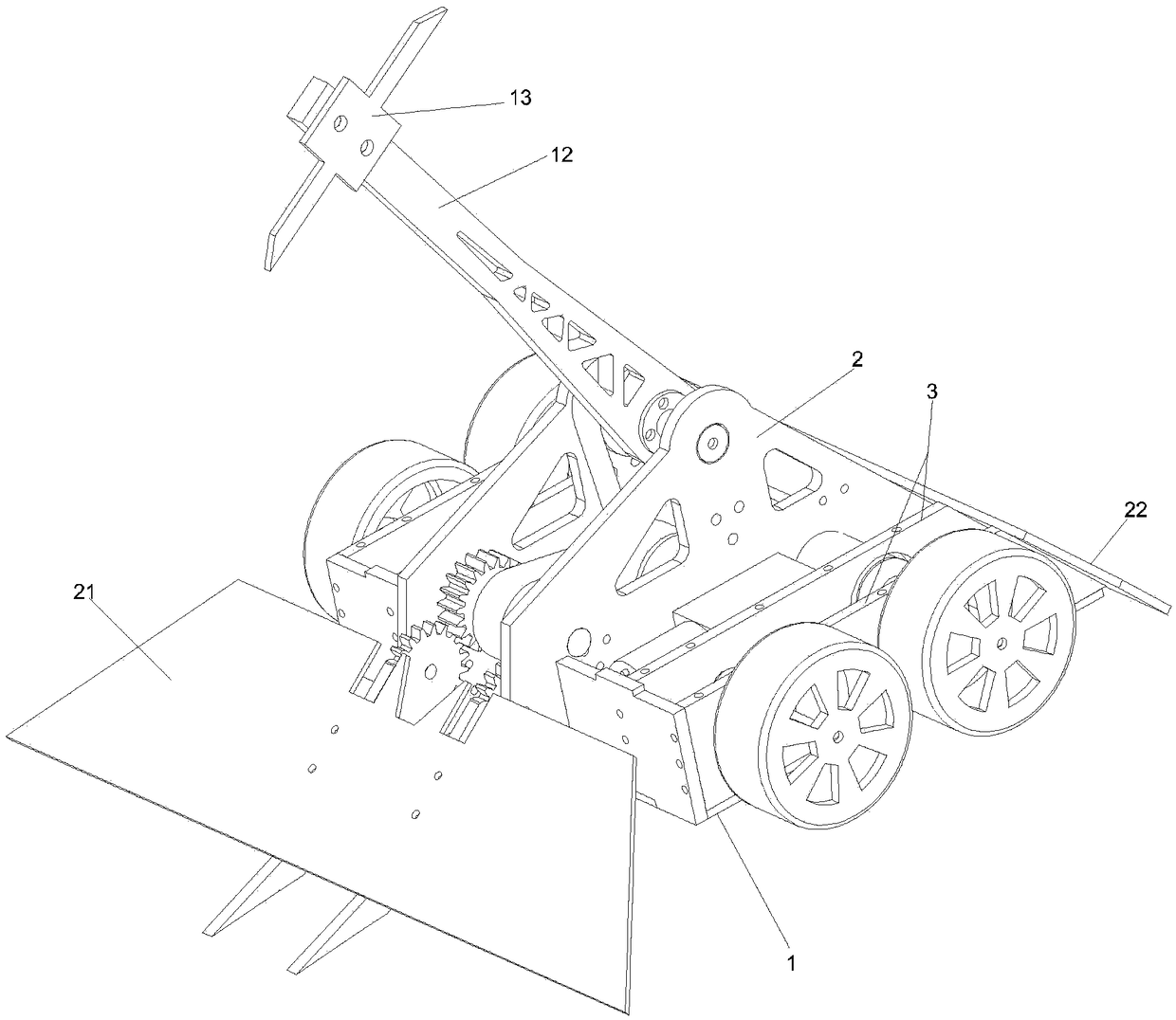
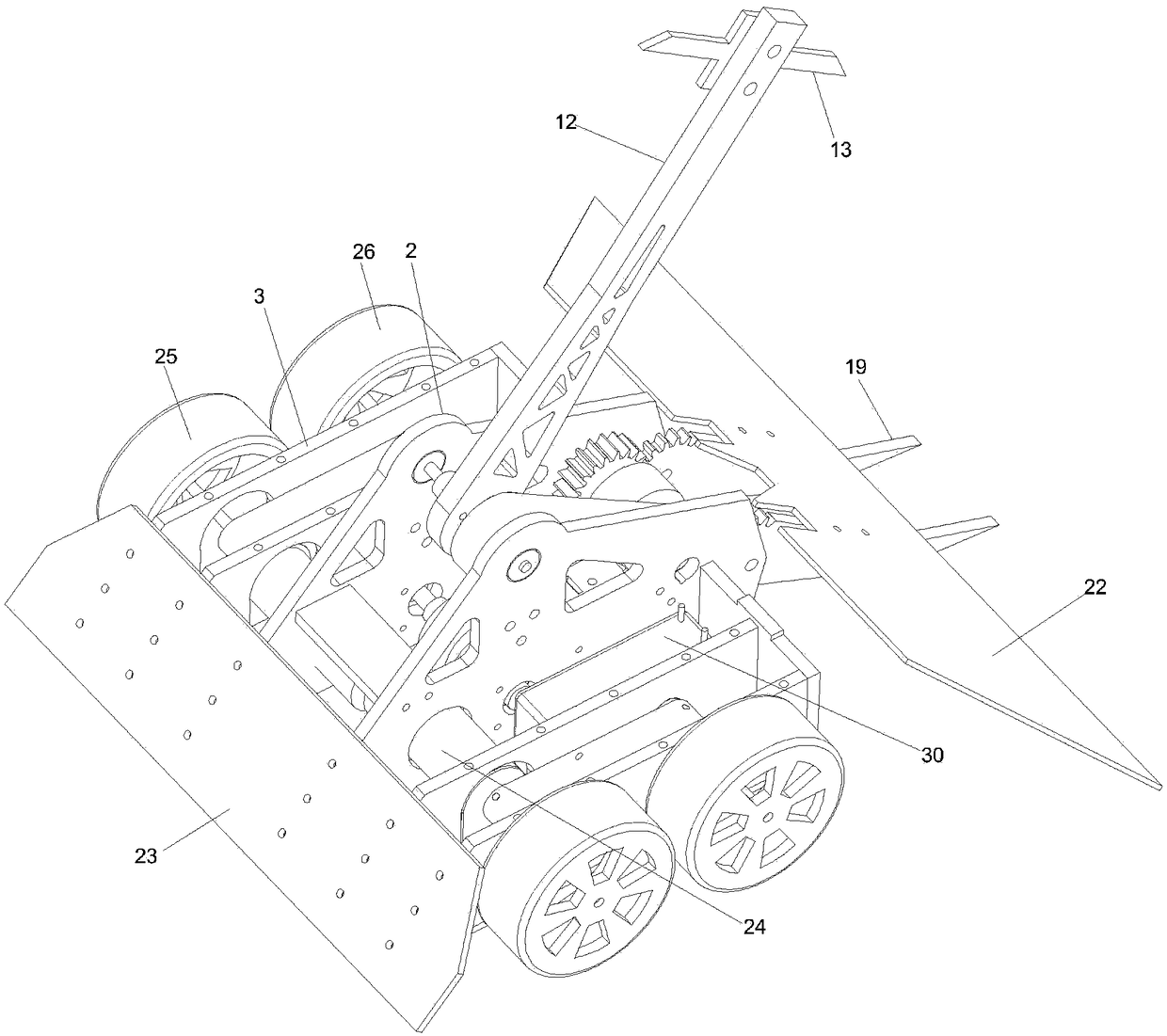
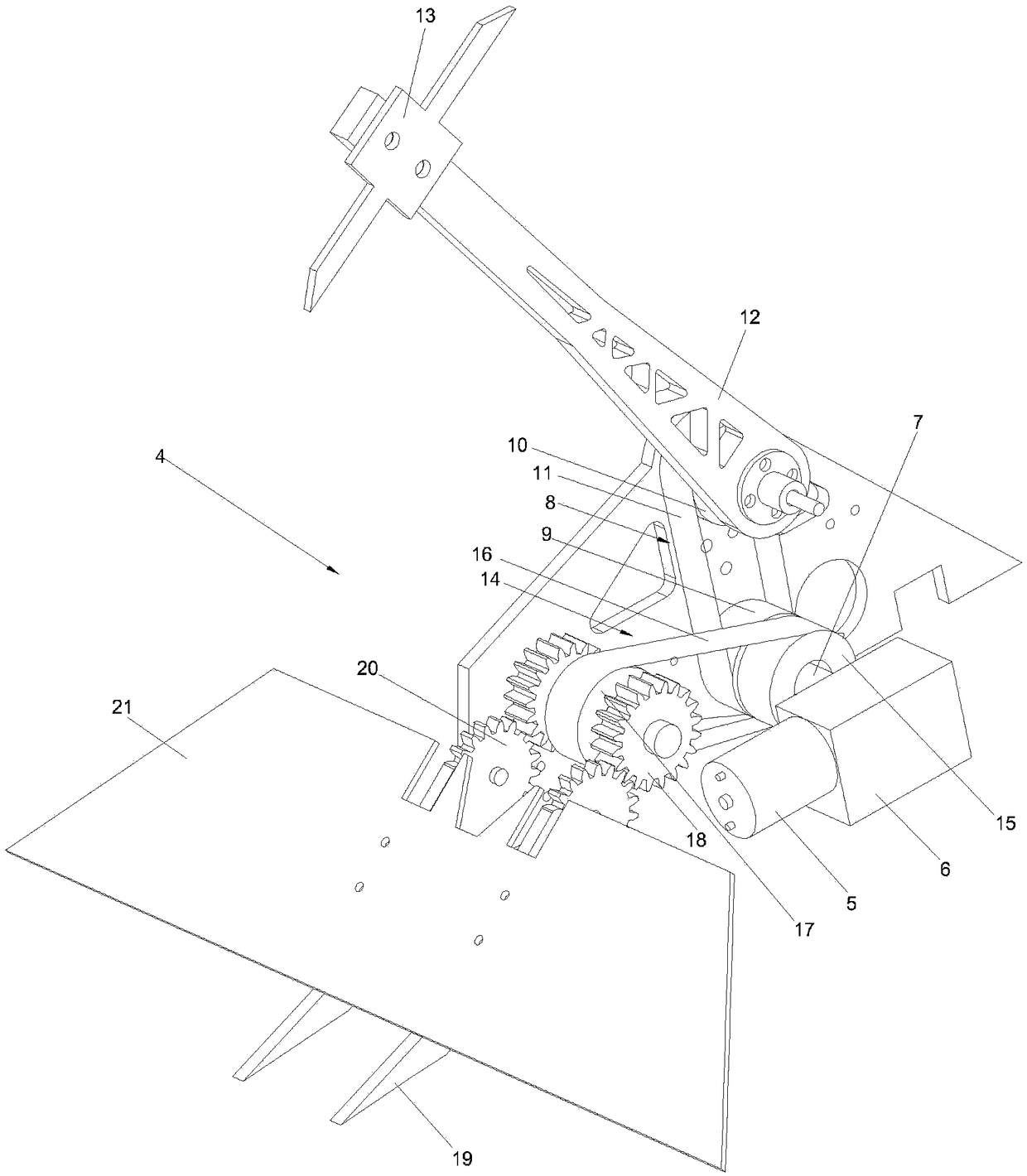
Fighting robot capable of gouging and lifting simultaneously
PendingCN109364496AAvoid heads upImproves Gouge EfficiencySelf-moving toy figuresManipulatorReducerDrive motor
The invention provides a fighting robot capable of gouging and lifting simultaneously. The robot is driven to advance / fall back by a driving mechanism, a chassis is taken as a base plate, a gouging lifting mechanism is installed between a pair of main side plates which are symmetrically arranged in left and right on the part, located in the middle, of the upper end of the base plate, the fightingrobot is structurally characterized in that a driving motor is installed on the base plate, output power is reduced by a reducer, transmitted by a gouging transmission and a lifting transmission mechanism and transmitted to the gouging mechanism and the lifting mechanism respectively to drive a weapon rod of the gouging mechanism and a lifting plate member of the lifting mechanism to move around an output shaft of the gouging transmission mechanism and an output shaft of the lifting transmission mechanism to synchronously rotate reversely in the opposite reverse rotation directions, the weaponrod of the gouging mechanism is used as a gouging executing end, and the gouging weapon is installed at a free end of the weapon rod; a front protecting plate and a rear protecting plate on front andrear sides of the base plate are arranged in a splayed shape on the side face of the robot body. The robot can reduce the probability of gouging missing, and the stability of the robot body is improved.
Owner:ANHUI UNIVERSITY OF ARCHITECTURE
Side channel attack preprocessing method based on wavelet airspace correlation method
InactiveCN108270543ASimple calculationProcessing speedCryptographic attack countermeasuresPretreatment methodAlgorithm
The present invention discloses a side channel attack preprocessing method based on a wavelet airspace correlation method. Collected power consumption signals f(n) are subjected to denoising through awavelet airspace correlation method and then is subjected to side channel analysis. According to the technical scheme, the interference of noise for a side channel attack result is effectively reduced, and the side channel attack success rate and the efficiency are improved.
Owner:BEIJING ELECTRONICS SCI & TECH INST
Method for modular multiplication remainder input side channel attacks aiming at M-ary implementation of RSA
ActiveCN104811297ASmall amount of signal processing dataReduce distractionsEncryption apparatus with shift registers/memoriesLinear correlationMeasurement point
The invention discloses a method for modular multiplication remainder input side channel energy analysis attacks aiming at M-ary implementation of an RSA cryptographic algorithm. The core of the method is that when M-ary implementation is used by modular exponentiation, modular multiplication remainder input serves as an attack target to implement CPA (correlation power analysis) attacks. The method comprises the steps that (1) signals are acquired, and a sampling matrix is established; (2) the modular multiplication remainder input is selected to serve as the attack target; (3) a correlation model is determined; (4) cycle index values are guessed, and a median matrix is calculated; (5) a simulated energy consumption matrix is calculated; (6) linear correlation coefficients between corresponding measuring points in the step (1) and the matrix determined in the step (5) are calculated, correct modular multiplication remainder input values of all cycles are attacked, and all corresponding correct cycle indexes are found out, and are connected in series, so that a complete index is obtained. According to the method, a novel M-ary side channel attack method is provided, and the flexibility, the effectiveness and the success rate of RSA cryptographic algorithm analysis attacks are improved.
Owner:CHENGDU UNIV OF INFORMATION TECH +3
Side channel energy attack method aiming at SM4 password linear transformation output
ActiveCN104753668ALess attacksEasy to implementKey distribution for secure communicationPower analysisPassword
The invention discloses a side channel energy attack method aiming at SM4 password linear transformation output. The method includes the following steps: S1 selecting bytes to be attacked twice, wherein the corresponding digits input each time are bytes in (Xi+1 Xi+2 Xi+3), the bytes corresponding to the bytes to be attacked are random digits, and others are fixed digits, adopting the side channel energy attack method to first attack bytes of a round key and the fixed digits in linear transformation, conducting corresponding computing on the bytes and the fixed digits of the round key obtained through the two-time attack to obtain the complete round key rki, wherein i= 0, 1, 2, 3; S2 conducting reversible calculation to obtain an initial key through a key expansion algorithm according to rk0, rk1, rk2 and rk3 of first four rounds of the round keys. By means of the analysis method, side channel energy analysis attack aiming at SM4 linear transformation output is achieved, attack times required by attack of the complete key are reduced, and attack efficiency and success rate are improved.
Owner:CHENGDU UNIV OF INFORMATION TECH +2
Black box attack method based on migration model Jacobian matrix feature vector disturbance
ActiveCN112085055AImprove attack efficiencySmall attack costCharacter and pattern recognitionNeural architecturesSingular value decompositionEngineering
The invention provides a black box attack method based on migration model Jacobian matrix feature vector disturbance, and belongs to the technical field of machine learning system security and black box attack. The method comprises the following steps: firstly, determining a to-be-attacked black box model and a migration pre-training model, obtaining a to-be-attacked original sample and a label thereof, continuously applying disturbance to the original sample, and continuously updating the disturbance through iterative computation by utilizing a singular value decomposition result of a Jacobian matrix calculated by the migration pre-training model, and finally, the disturbed sample being no longer corresponding to a correct label through black box model classification. The method has the advantages that only one migratable pre-training network is needed, no training sample is needed, and the attack efficiency of a traditional black box model can be greatly improved.
Owner:TSINGHUA UNIV
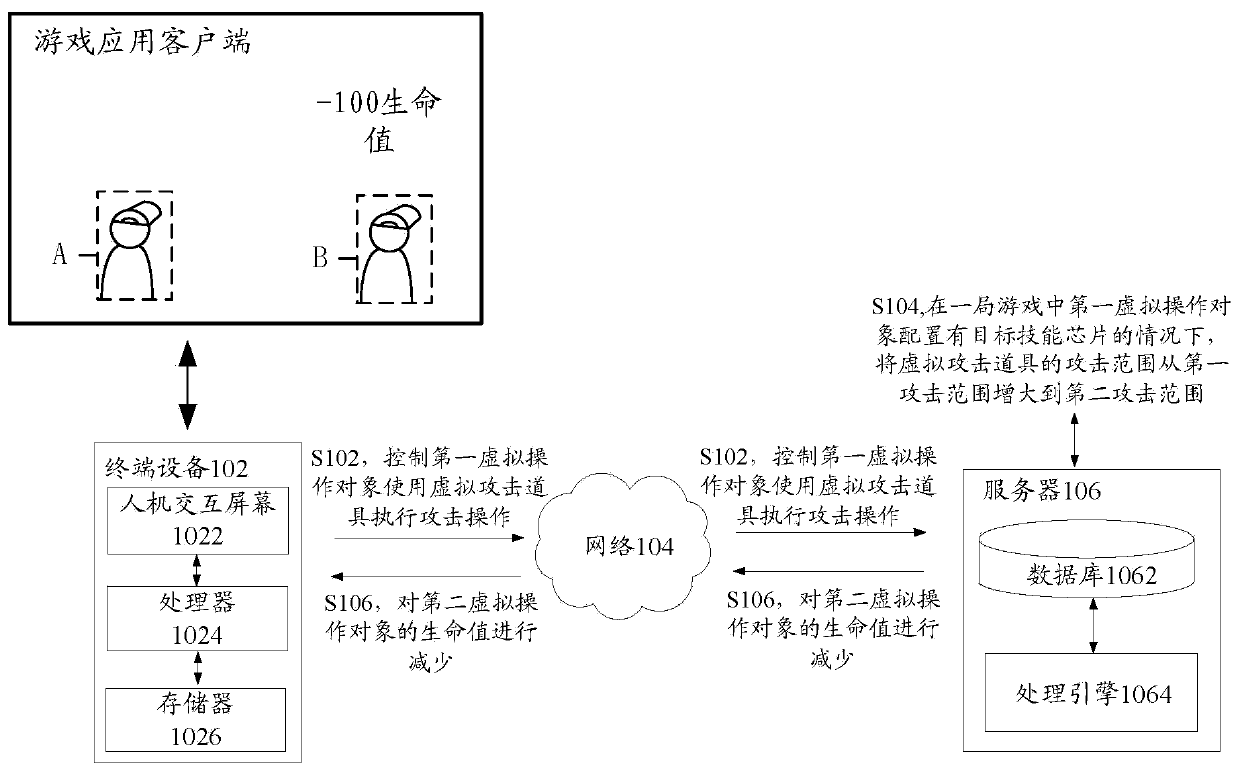
Virtual prop control method and device, storage medium and electronic equipment
ActiveCN111443857AHealth reductionFlexible controlVideo gamesInput/output processes for data processingComputer hardwareOperating system
The invention discloses a virtual prop control method and device, a storage medium and electronic equipment. The method comprises the following steps that in a game currently operated by a target gameapplication, a first virtual operation object is controlled to use a virtual attack prop to execute an attack operation; the attack range of the virtual attack prop is increased from a first attack range to a second attack range under the condition that the first virtual operation object is configured with a target skill chip in the game; and when the virtual attack prop is in contact with a first virtual obstacle in the process of executing the attack operation and a second virtual operation object exists in a second attack range, the health point of the second virtual operation object is reduced, wherein the second attack range comprises the position of the first virtual obstacle. By the adoption of the technical scheme, the problem that virtual props cannot be flexibly controlled in the prior art is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
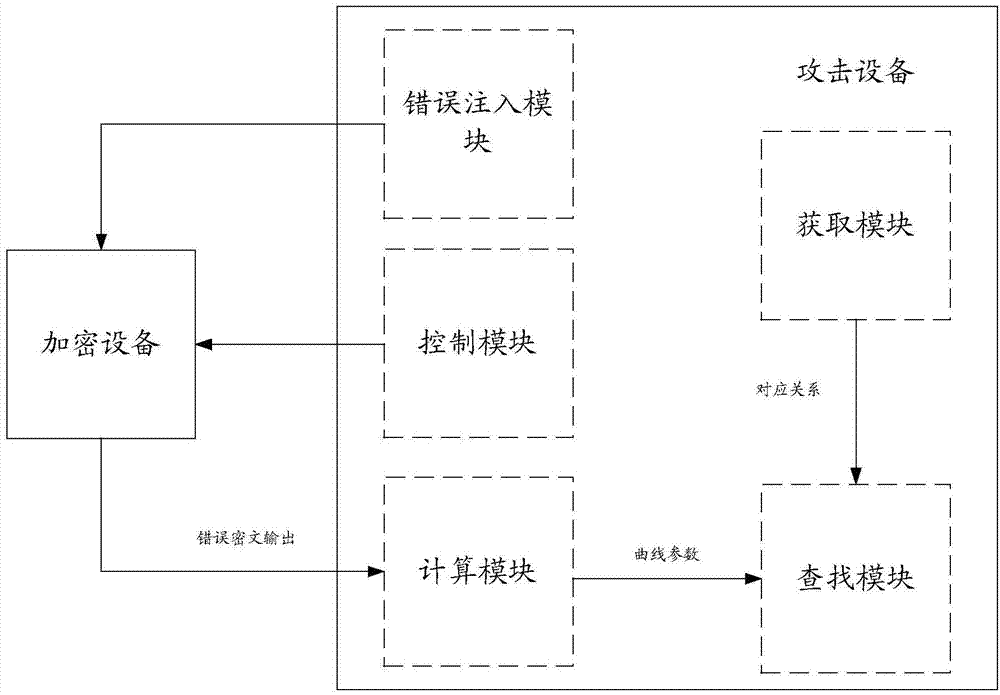
Method for attacking elliptical curve encryption algorithm and attacking device
ActiveCN104717060AThe timing of error injection is easy to controlImprove attack efficiencyPublic key for secure communicationPlaintextCiphertext
The invention discloses a method for attacking the elliptical curve encryption algorithm and an attacking device. The method comprises the steps that the attacking device acquires the corresponding relation between the coordinates of an error base point with one byte error, parameters of an elliptical curve where the error base point is located and order in advance, wherein the order meets the condition that the length of a maximum prime factor is smaller than or equal to a preset threshold value; the attacking device injects one byte error into the coordinates of a base point of an elliptical curve used by the elliptical curve encryption algorithm in an encryption unit to obtain the coordinates of the error base point; the attacking device controls the encryption unit to encrypt a plaintext by means of the elliptical curve encryption algorithm according to the coordinates of the error base point so that error ciphertext output can be obtained; the attacking device calculates the parameters of the elliptical curve where the error base point is located according to the error ciphertext output and finds the coordinates and order of the error base point corresponding to the curve parameters in the corresponding relation; the attacking device acquires the plaintext according to the coordinates and order of the error base point, the curve parameters obtained through calculation, and error ciphertext output. By the adoption of the method for attacking the elliptical curve encryption algorithm and the attacking device, attacking efficiency is improved.
Owner:DATANG MICROELECTRONICS TECH CO LTD +1
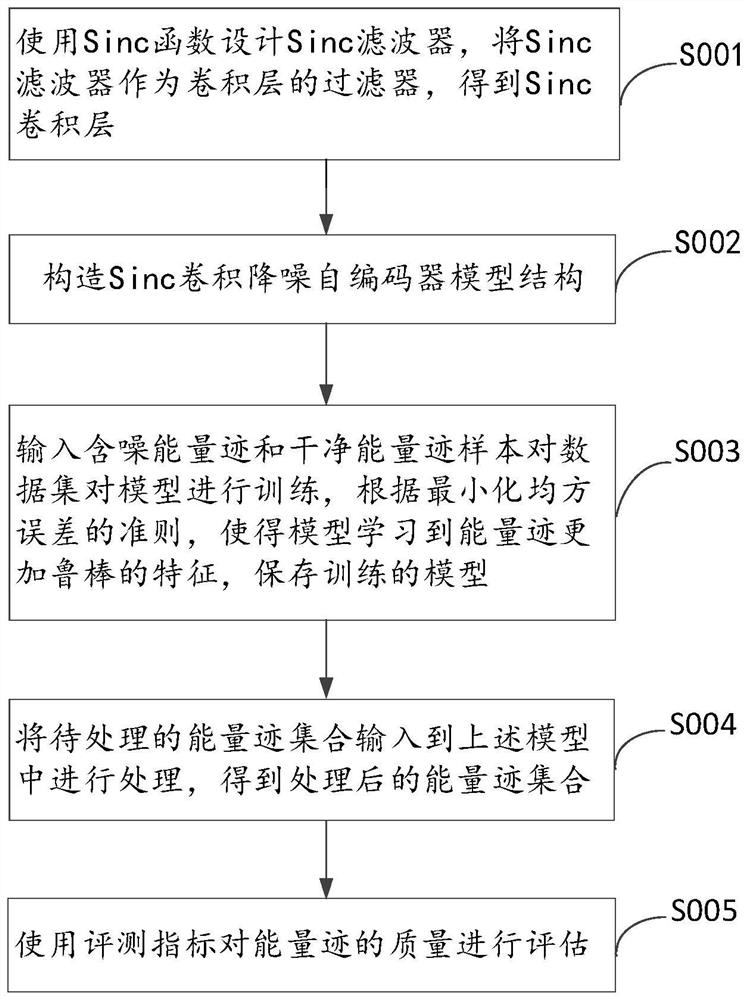
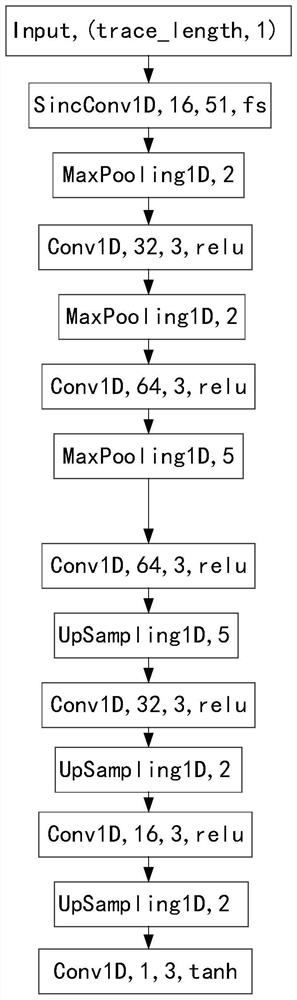
Energy trace preprocessing method based on Sinc convolution noise reduction auto-encoder
PendingCN111985411AImprove relevanceImprove efficiencyCharacter and pattern recognitionNeural architecturesSide channel attackConvolution
The invention discloses an energy trace preprocessing method based on a Sinc convolution noise reduction auto-encoder, and the method comprises the steps of designing a Sinc filter through employing aSinc function, enabling the Sinc filter to serve as a filter of a convolution layer, and obtaining a Sinc convolution layer; constructing a Sinc convolution noise reduction auto-encoder based on theSinc convolution layer; training the Sinc convolution noise reduction auto-encoder by using a data set formed by noise-containing energy trace and clean energy trace sample pairs; and inputting a to-be-processed energy trace into the trained Sinc convolution noise reduction auto-encoder to obtain a preprocessed energy trace. When the method is used for preprocessing the energy trace, the signal-to-noise ratio of the energy trace and the key operation intermediate value is improved by more than 4 times, the correlation is further improved, the efficiency of side channel attack is improved, andthe number of energy traces required by successful side channel attack is reduced.
Owner:UNIV OF SCI & TECH OF CHINA
A side channel signal preprocessing method based on short time domain analysis
ActiveCN109214176AImprove attack efficiencyEfficient compressionPlatform integrity maintainanceCryptographic attack countermeasuresPower analysisTime domain
A side channel signal preprocessing method based on short time domain analysis, includes setting up basic environment of collecting side channel signal, setting current sampling frequency of oscilloscope as f, setting clock frequency of cryptographic equipment as fs, setting operating frequency of cryptographic equipment as the number of points of collected side channel signal as M, number of pieces as N, and making signal matrix as TN*M, 2, determining the size of the window used for selecting the window function, wherein the size of the window is in units of the running clock of the cryptographic device, and the size of the window is calculated as follows: the size of the window is set as n, n=f / fs; (3) analyzing the short-time energy of the signal matrix according to the size n of the window until the calculation of each row of the signal matrix is completed; (4) after the short-time energy analysis of all rows of the matrix is completed, the new matrix T 'is obtained. The invention(1) the method for running the pretreatment can effectively improve the efficiency of the side channel attack; (2) the side channel signal is compressed effectively, which shortens the time of attackdetection.
Owner:成都三零嘉微电子有限公司
Portable self-rotating rocket projectile weapon
ActiveCN111981901AHigh direct accuracySimple structureSelf-propelled projectilesLaunching weaponsStructural engineeringRocket (weapon)
The invention provides a portable self-rotating rocket projectile weapon. The portable self-rotating rocket projectile weapon adopts a launcher-rocket projectile integrated structure, fully utilizes the characteristics of low launching condition, high direct shooting precision and simple structure of a self-rotating rocket projectile, and is provided with a special disposable launcher to form theportable self-rotating rocket projectile weapon; and the defects that a traditional rocket projectile weapon is high in production cost, a launching position is easily exposed, and an individual soldier is not easy to carry and operate can be overcome. The rocket projectile weapon comprises a launcher and a rocket projectile, and the rocket projectile is a self-rotating rocket projectile with a turbine nozzle; the launcher is a disposable launcher and comprises a launcher body, four launcher supports, a sighting device and an ignition device. The launcher body serves as a storage and transportation barrel and a launching tube of rocket projectiles at the same time, and the launcher body can stretch and retract relatively in the axial direction; the launcher support can be folded and unfolded relative to the launcher body, and the sighting device and the ignition device are installed on the launcher body; and the ignition device is used for igniting and launching rocket projectiles.
Owner:白澔烔 +1
Optimal false data injection attack method for network self-triggering model predictive control
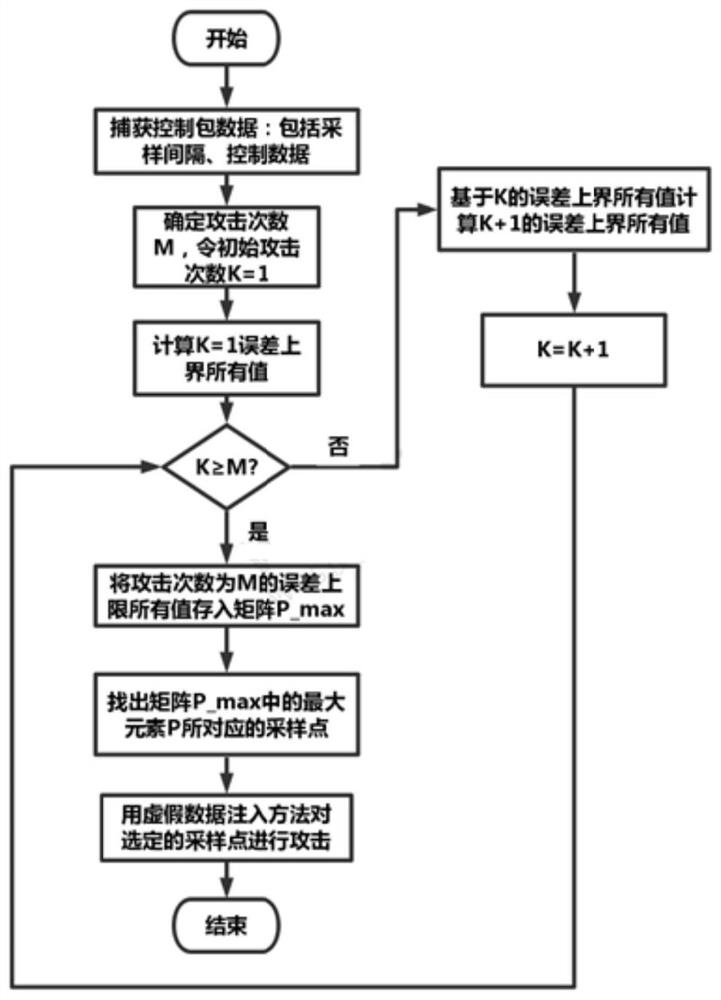
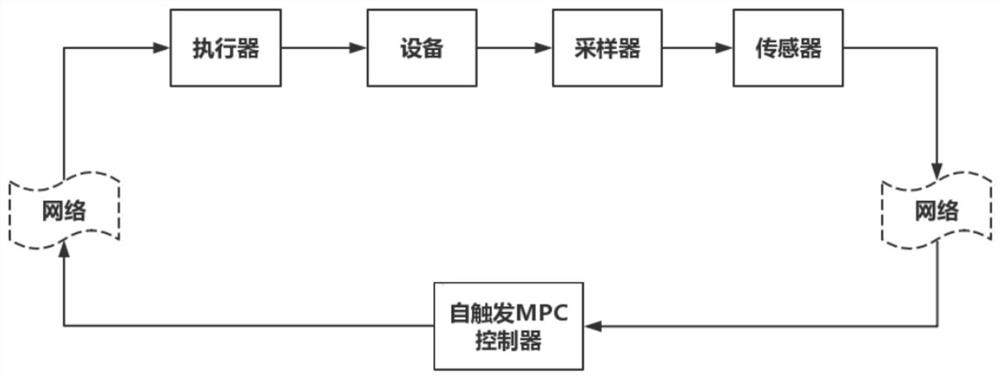
ActiveCN111786977AReduce the amount of online calculationsReduce storageTransmissionMaximum errorAttack
The invention discloses an optimal false data injection attack method for network self-triggering model predictive control. The method comprises the following steps: 1) collecting control data and sampling interval data in a network transmission packet; 2) calculating all system state error upper bound values before and after attacks under different attack times; and 3) taking the point corresponding to the maximum error upper bound value before and after the attack as the optimal false data injection point to perform the attack, and completing the optimal false data injection attack for the prediction control of the network self-triggering model, so that the optimal false data injection attack can be quickly established, the attack efficiency is improved, and the probability of being detected by the system is reduced.
Owner:XI'AN UNIVERSITY OF ARCHITECTURE AND TECHNOLOGY
Animation playing method and device based on virtual environment, equipment and medium
ActiveCN111330278AImprove attack efficiencyReduce the number of interactionsVideo gamesAnimationWhole body
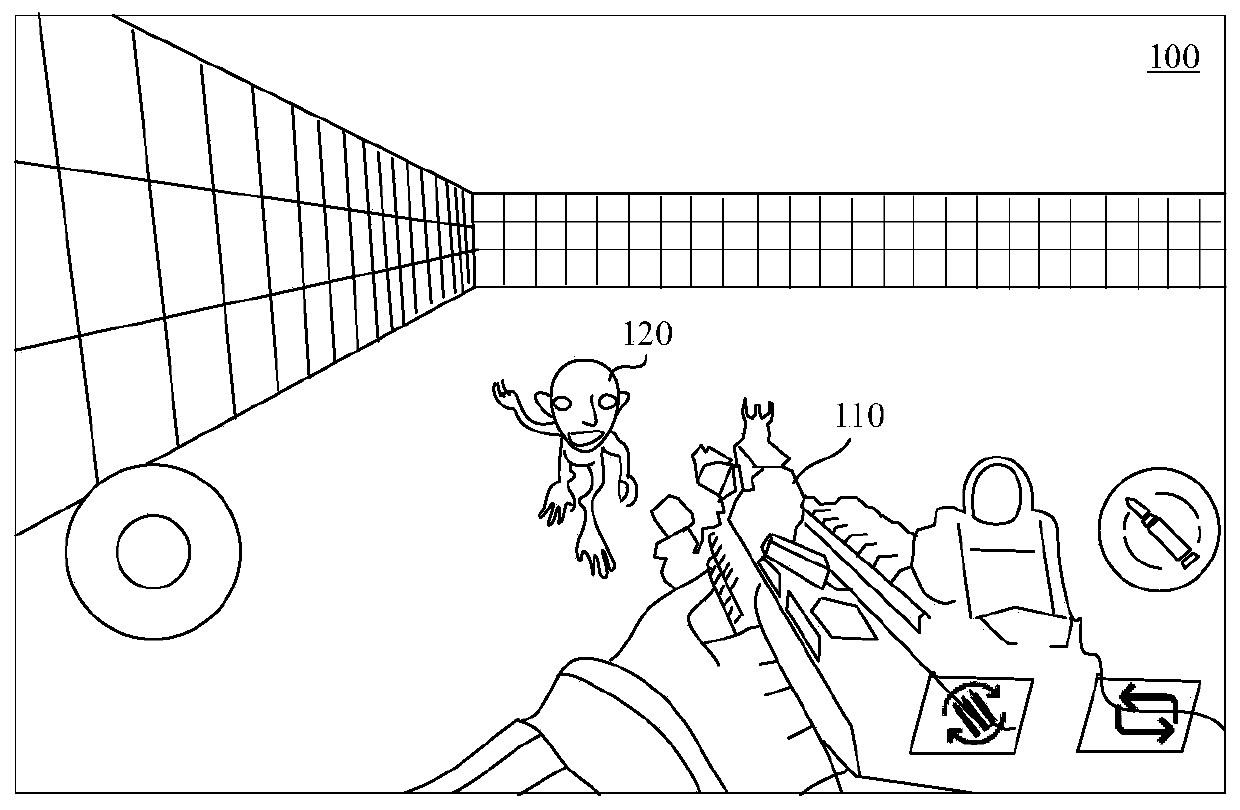
The invention discloses an animation playing method and device based on a virtual environment, equipment and a medium, and relates to the field of virtual environments. The method comprises the stepsof displaying a virtual environment interface, wherein a virtual environment comprises a second virtual object; receiving a hit signal of a second virtual object, wherein the hit signal comprises thehit type of the second virtual object; playing a first hit animation corresponding to the hit type of the part for the hit part of the second virtual object in response to the fact that the hit signalcomprises the hit type of the part; and playing a second hit animation corresponding to the whole-body hit type for the second virtual object in response to the fact that the hit signal comprises thewhole-body hit type. According to different types of attacks on the second virtual object, different animations are correspondingly displayed, so that a player can determine the attack on the secondvirtual object and can adjust the attack mode on the second virtual object according to the attack on the second virtual object, the attack efficiency is improved, the interaction frequency in the attack process is reduced, and the interaction efficiency is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
A side channel attack method for the realization of rsa encryption algorithm m-ary
ActiveCN104796250BEfficient analysisEasy to analyzeEncryption apparatus with shift registers/memoriesLinear correlationPower attack
The invention discloses a side channel energy analysis attack method for the multiplication output when the power residue calculation M-ary is realized in the RSA cryptographic algorithm. CPA attack. It includes the following steps: (1) collect signals and establish a sampling matrix; (2) select the multiplication output as the attack object; (3) determine the correlation model; (4) guess the round index value and calculate the intermediate value matrix; (5) calculate Simulate the energy consumption matrix; (6) Calculate the linear correlation coefficient between the matrices determined in (1) and (5), and attack the correct round index. (7) Repeat (4) to (6), the attack gets all the correct round indices, and the complete indices are obtained after concatenation. The method of the invention provides a new M-ary side channel attack method, which enhances the flexibility, effectiveness and success rate of RSA cryptographic algorithm analysis attacks.
Owner:CHENGDU UNIV OF INFORMATION TECH +3
Chinese medicine for removing obstruction in channels and relieving pains and its preparation
InactiveCN1583000AImprove numbness and stagnationEnhance pharmacological effectsAnthropod material medical ingredientsAntipyreticDiseaseTreatment effect
An antalgic Chinese medicine for treating osteoarthropathy is prepared from 7 Chinese-medicinal materials including vomiting nut, earthworm, scorpion, ground beetle, etc.
Owner:韩继世
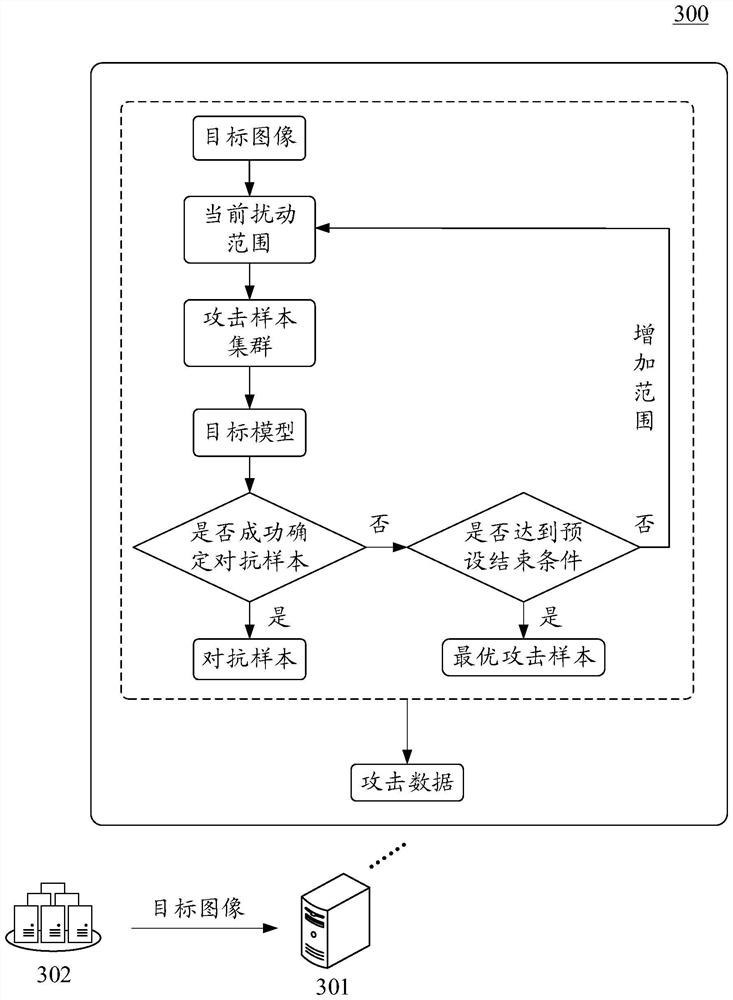
Attack method and device based on genetic algorithm and computer program product
PendingCN114511756ASolve the costSolve efficiency problemsCharacter and pattern recognitionGenetic algorithmsAlgorithmGenetics algorithms
The invention provides an attack method and device based on a genetic algorithm, electronic equipment, a storage medium and a computer program product, relates to the technical field of artificial intelligence, in particular to computer vision, image recognition and deep learning technologies, and can be used in an attack resisting scene. According to the specific implementation scheme, a target image is acquired; starting from the initial disturbance range, determining an adversarial sample of the target model based on the target image in the current disturbance range by adopting a genetic algorithm, and increasing the disturbance range under the condition that the adversarial sample is not successfully determined so as to continuously carry out adversarial attack on the target model until a preset end condition is met; and determining attack data finally obtained based on the attack target model. According to the method and the device, the problems of high calculation cost and low confrontation sample determination efficiency caused by directly attacking the target model in a relatively large disturbance range can be effectively solved, and the attack efficiency is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
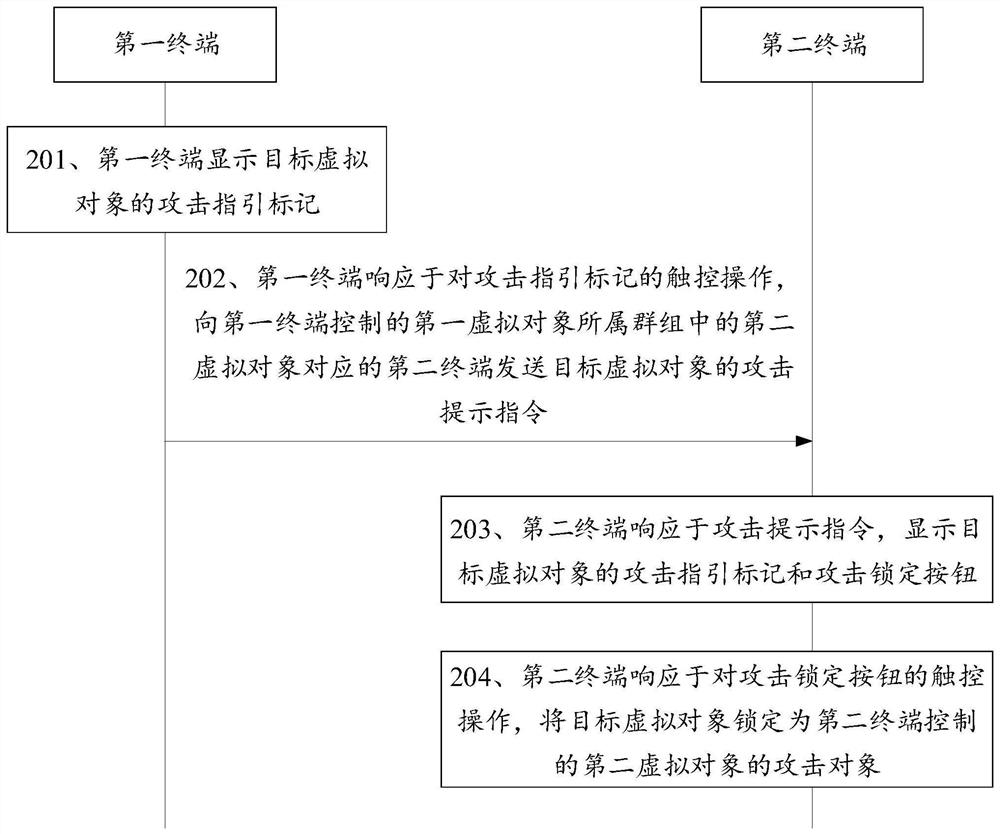
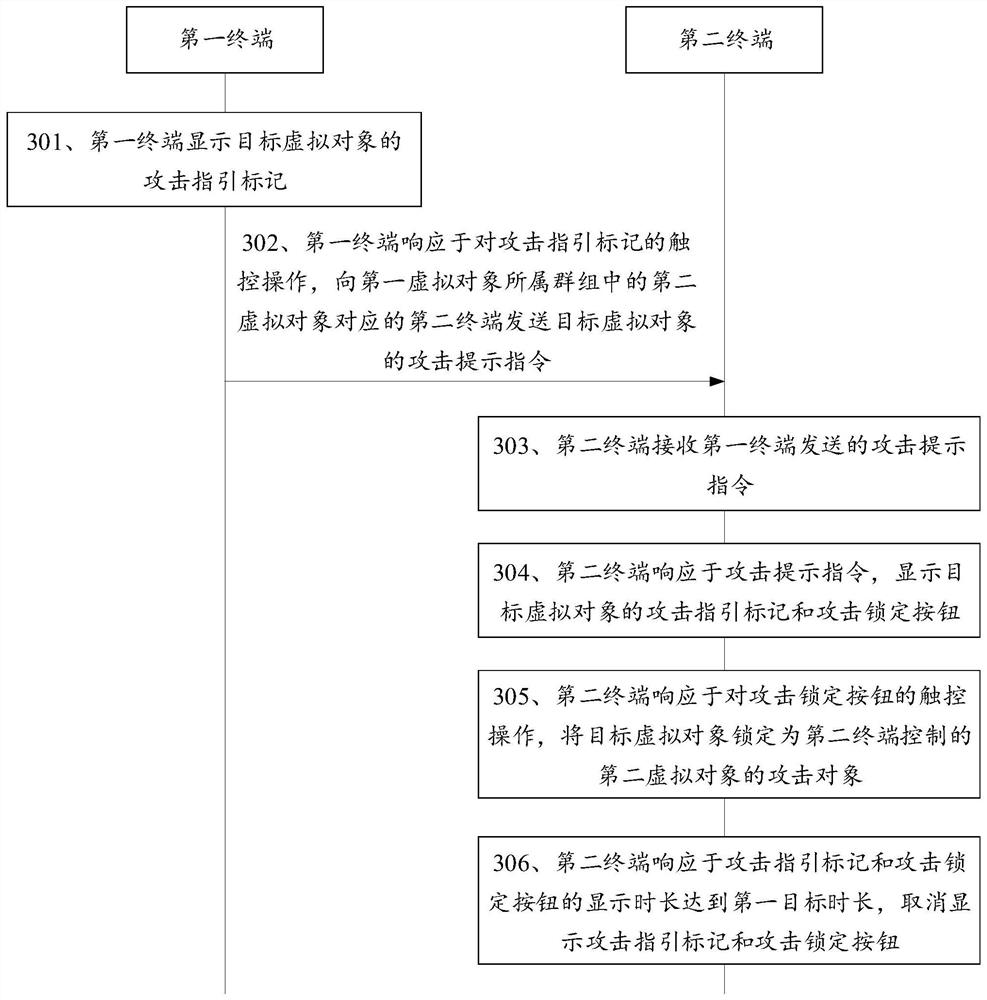
Virtual object control method and device, terminal and storage medium
The embodiment of the invention discloses a virtual object control method and device, a terminal and a storage medium, and belongs to the technical field of computers. The method comprises the steps of: enabling a first terminal to display an attack guidance mark of a target virtual object; in response to a touch operation on the attack guidance mark, sending an attack prompt instruction to the second terminal; enabling the second terminal to display an attack guiding mark and an attack locking button of the target virtual object; and in response to a touch operation on the attack locking button, locking the target virtual object as an attack object of a second virtual object controlled by the second terminal. A scheme that a first virtual object directs a second virtual object to attack a target virtual object is provided, a user of a first terminal controls the first terminal to send an attack prompt instruction to a second terminal, and the second terminal synchronously displays an attack guide mark of the target virtual object and displays an attack locking button. The target virtual object is quickly locked as the attack object by triggering the attack locking button, so that the attack efficiency is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Power consumption attack method based on convolutional neural network and selection message method
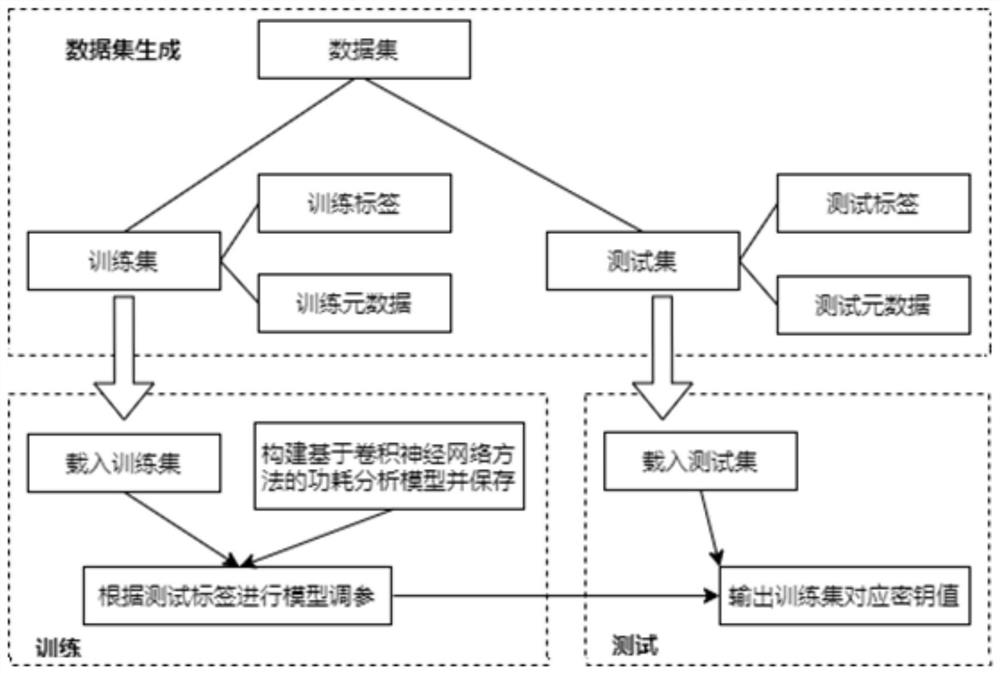
PendingCN112016086AGood test classificationReduce attack complexityPublic key for secure communicationCharacter and pattern recognitionData setAlgorithm
The invention discloses a power consumption attack method based on a convolutional neural network and a selection message method, and the method comprises the steps: constructing a data set based on apublic key encryption algorithm, wherein the data set comprises a training set and a test set; constructing a power consumption analysis model based on a convolutional neural network method; traininga power consumption analysis model based on a convolutional neural network method; and testing by using the trained power consumption analysis model based on the convolutional neural network method.The RSA encryption scheme based on the blind Boscher modular exponentiation algorithm is realized, and the attack efficiency is far higher than that of other existing schemes on the basis of simple realization. The method provided by the invention is not only suitable for RSA encryption systems based on a blind Boscher modular exponentiation algorithm, but also suitable for most RSA encryption systems based on modular multiplication modular square loop iteration at present.
Owner:TIANJIN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com