Optimal false data injection attack method for network self-triggering model predictive control
A model predictive control and false data technology, applied in the transmission system, electrical components, etc., can solve the problems of increasing the risk of detection and unrealistic control of samples, so as to reduce the probability of detection, optimize the overall performance quality, and improve efficiency. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
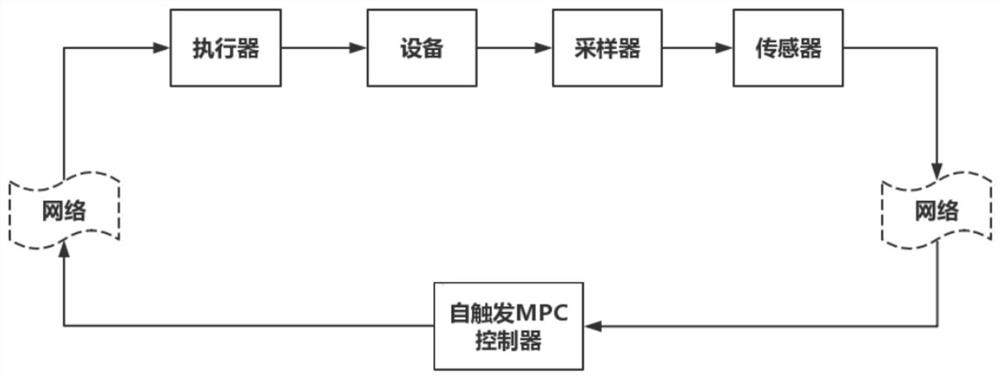
[0066] refer to Figure 4 , the state of the wheeled intelligent robot system is expressed as χ=[xyθ] T (should be [x, y, θ]), which consists of the vehicle's position [xy] should be [x, y] and direction θ, u = [v, ω] T (less comma) is the control input, and the constraints are and Calculated Lipschitz constant and the normal constant L G respectively and L G = 1.0, the stage and terminal cost functions are given by F = χ T Qχ+u T Ru, V f =χ T χ is given, where Q=0.1I 3 , R=0.05I 2 .
[0067]
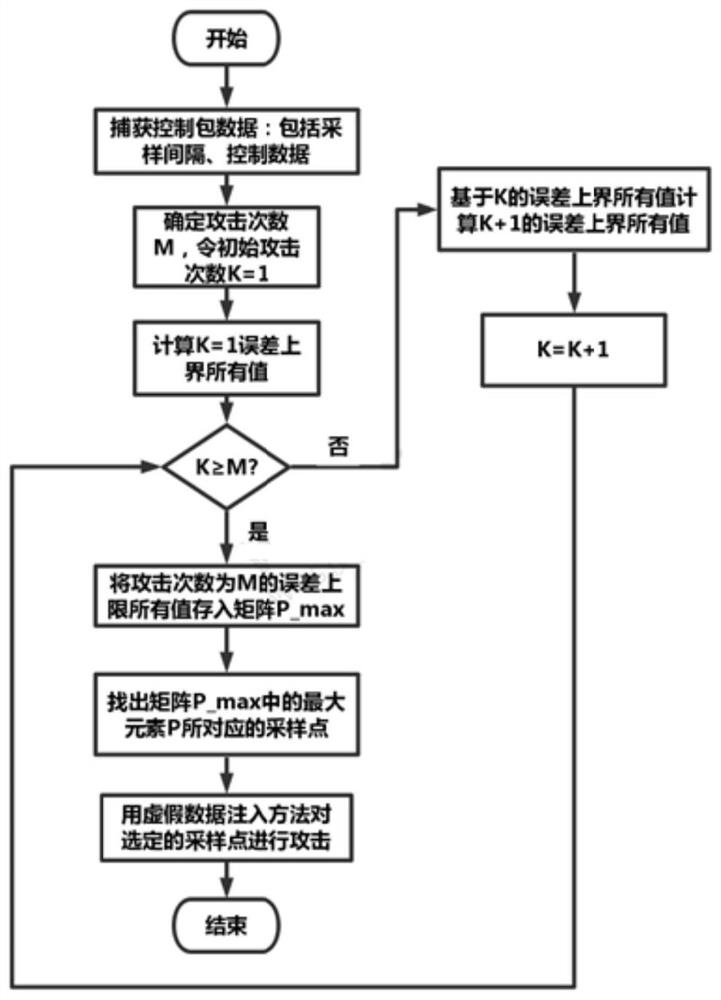
[0068] Apply the optimal false data injection attack to the wheeled intelligent robot system based on network self-triggering model predictive control, select the number of samples as N=5, and the number of attack points in each data packet as M=2. The specific process is as follows:
[0069] 1) Obtain and capture self-trigger control data and sampling interval;
[0070] 2) Calculate the upper bound of the system state error before and after the false data injection...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com