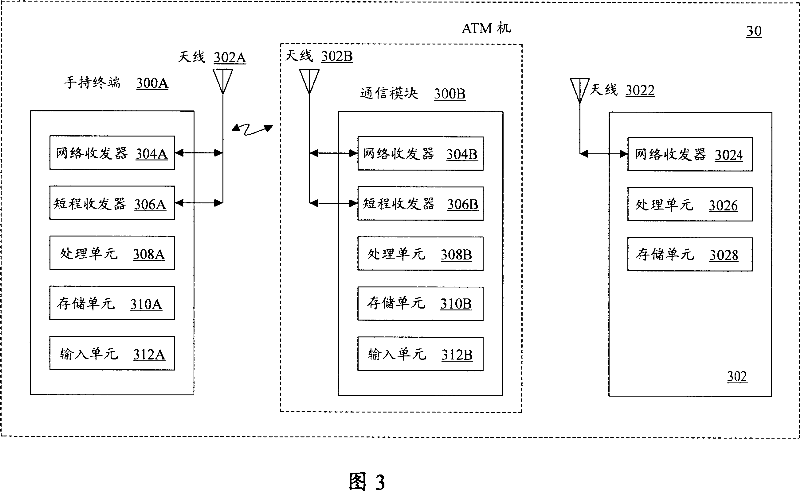
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
85results about How to "Ensure secure communication" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
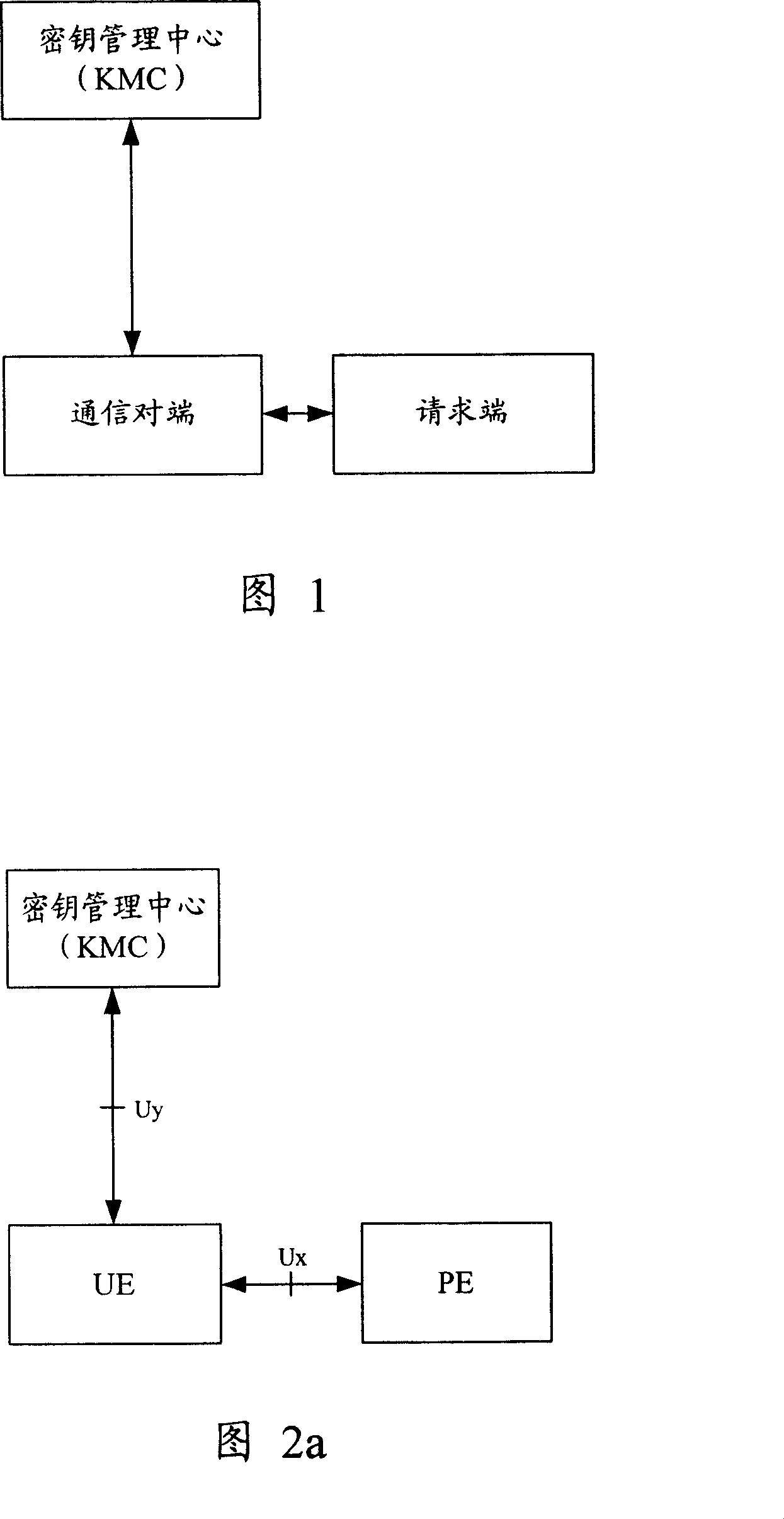
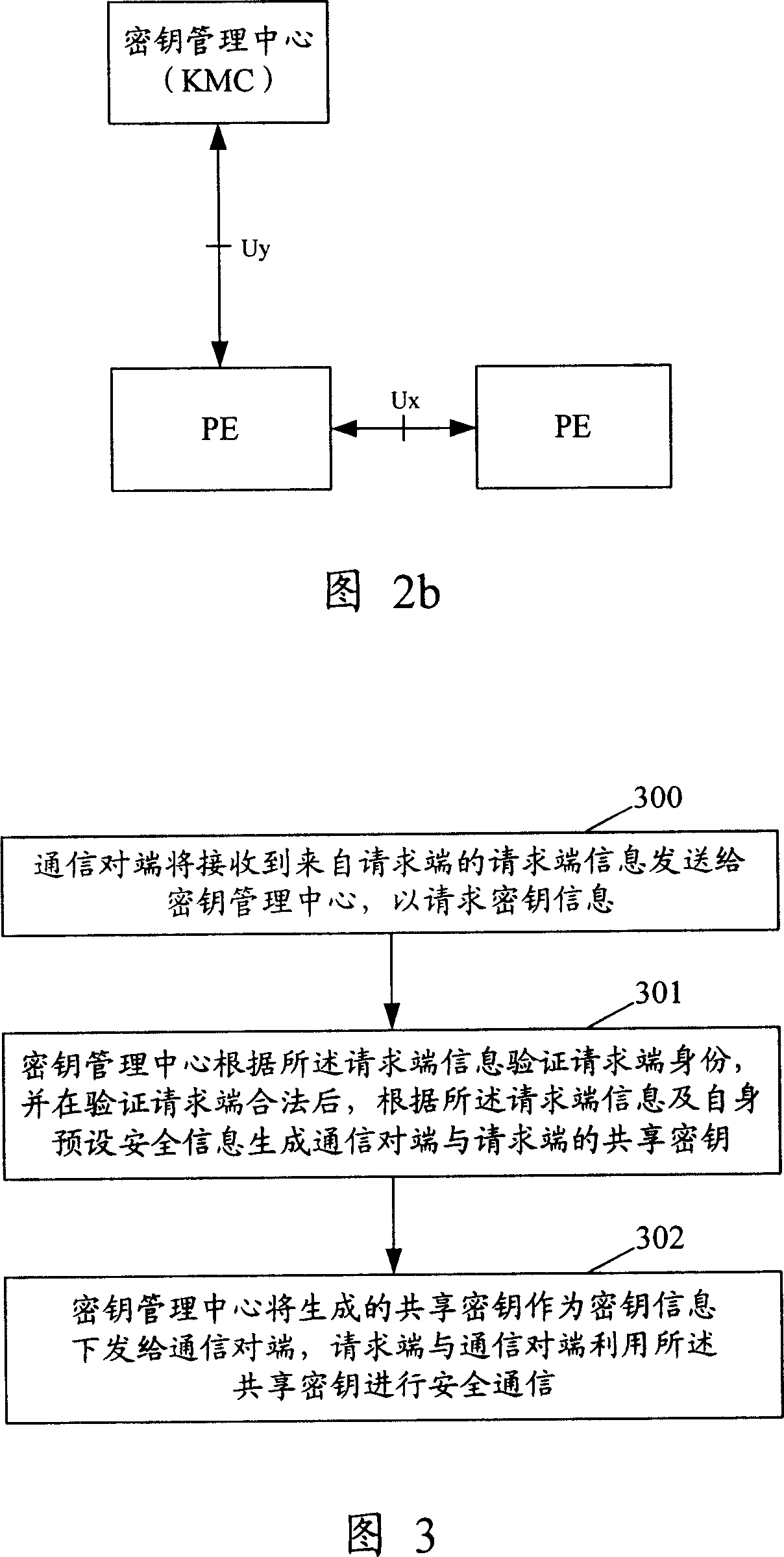
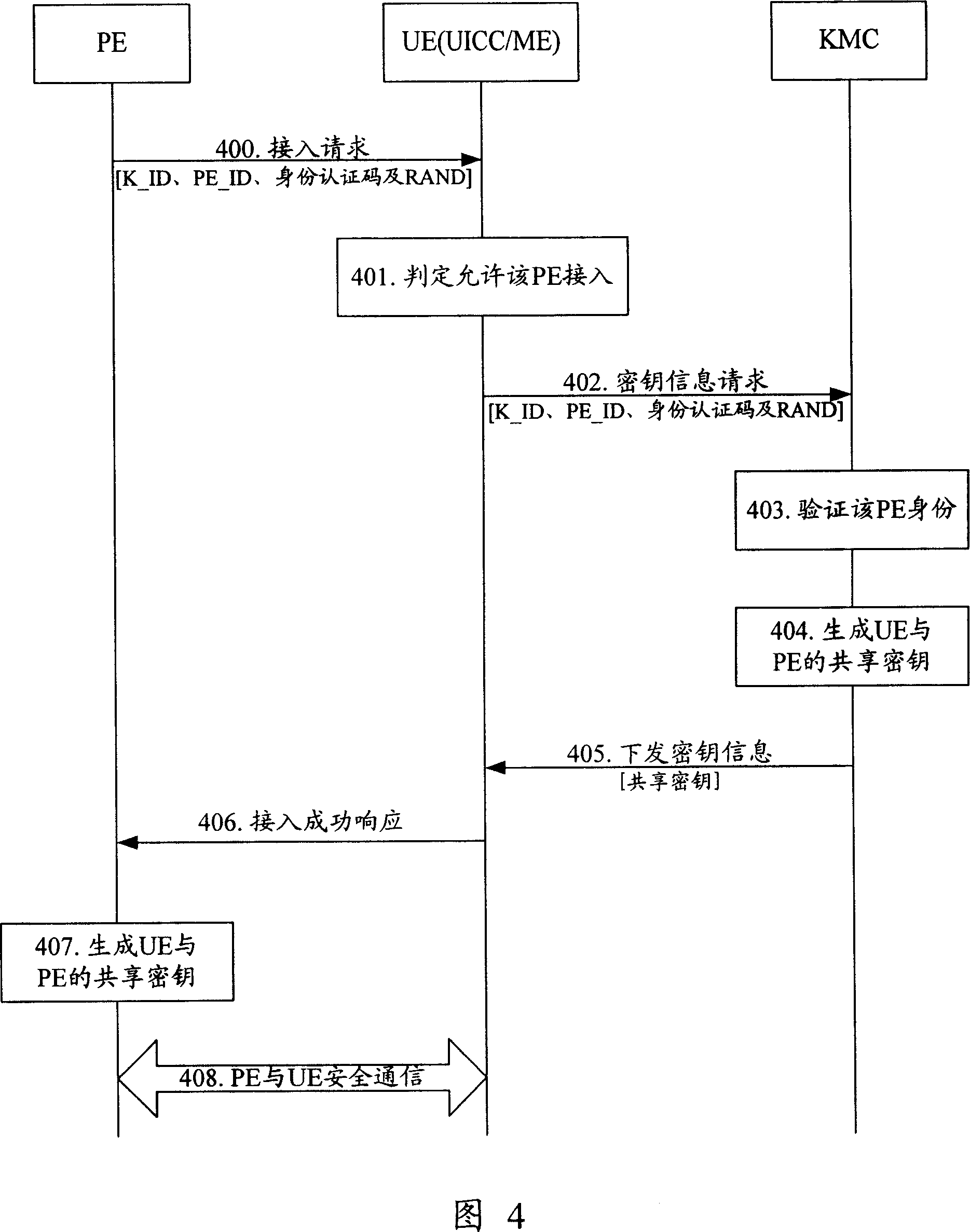
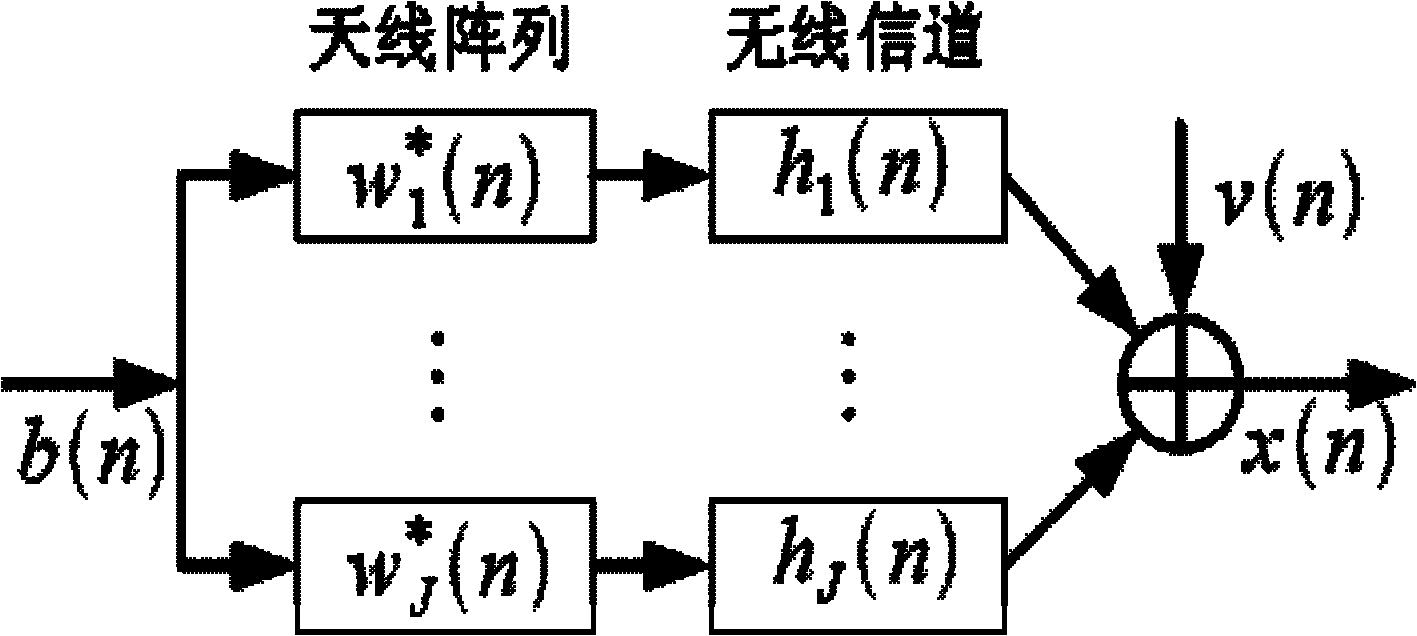
Method and device for realizing safety communication between terminal devices
ActiveCN101005359AEnsure secure communicationStable deliveryKey distribution for secure communicationUser identity/authority verificationSecure communicationTerminal equipment
The method includes steps: communication opposite terminal (COT) sends the request end information received from the request end to the key management center (KMC); based on the request end information, KMC validates ID of the request end; after validating validity of the request end, KMC creates shared cipher key for COT and the request end based on the request end information, and self prearranged security information; KMC down sends the created shared cipher key as information of cipher key to COT; using the said shared cipher key, the request end and COT carry out security communication. The invention also discloses device for security communication between terminal devices. Guaranteeing security communication between terminal devices, the invention especially guarantees security communication between ME / UICC / PE and PE.
Owner:HUAWEI TECH CO LTD
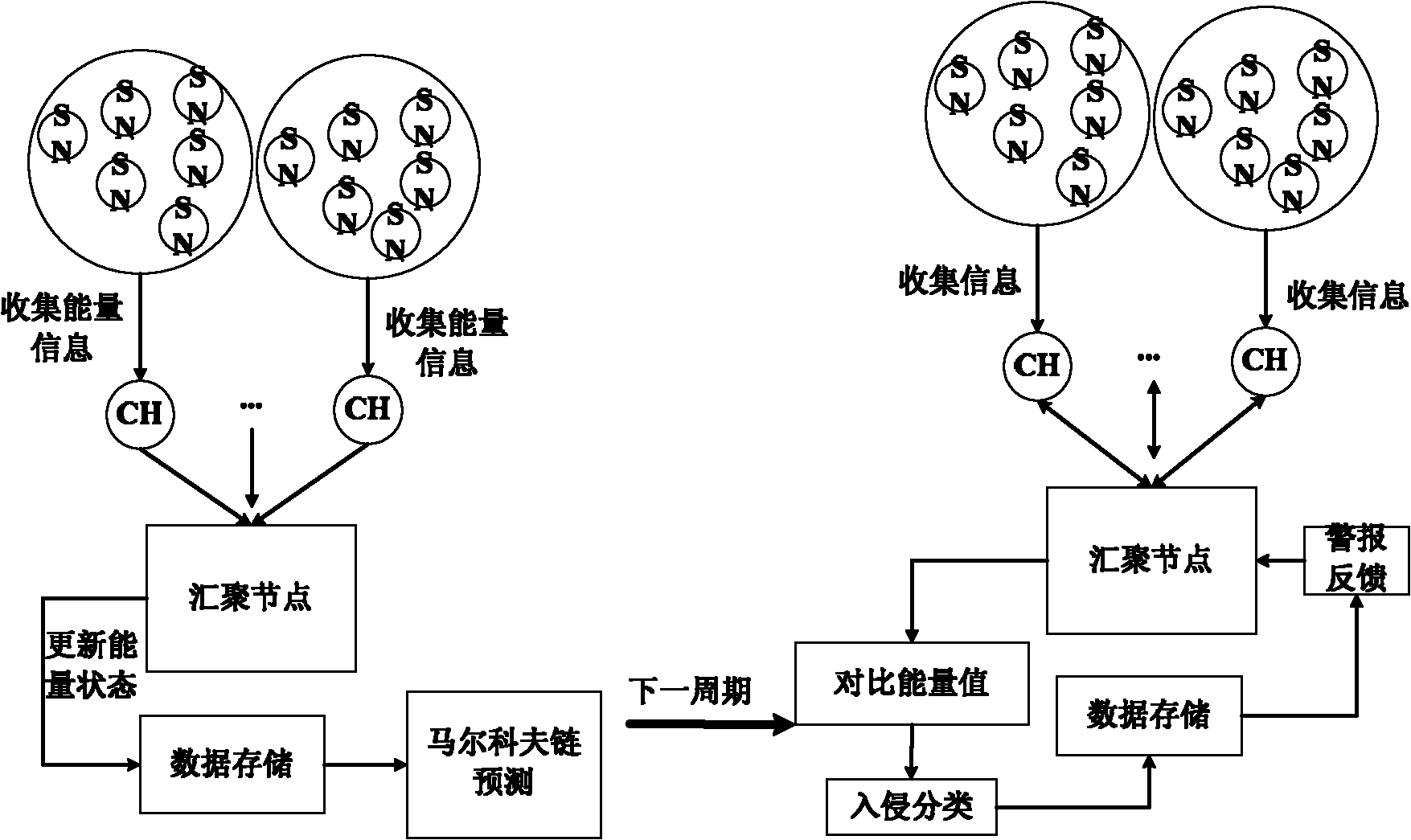
Secure clustering routing management method for wireless sensor network
InactiveCN102196420AEnsure secure communicationProcess against malicious attacksNetwork topologiesSecurity arrangementSecure communicationComputer security
The invention discloses a secure clustering routing management method for a wireless sensor network. The method is characterized by comprising the following steps: 1) intrusion detection with an energy prediction capability; 2) cluster head selection based on trust; and 3) safe communication guarantee and hostile attack resistance through a secure clustering mechanism based on trust management. By using the method, hostile nodes in a network can be efficiently and correctly detected; in addition, the secure clustering mechanism is established based on trust; on one hand, reliable cluster head selection can be ensured; on the other hand, hostile attack behavior is resisted; therefore, the problems of reduction of communication throughtput rate caused by hostile attack and the like can be solved.
Owner:HOHAI UNIV CHANGZHOU
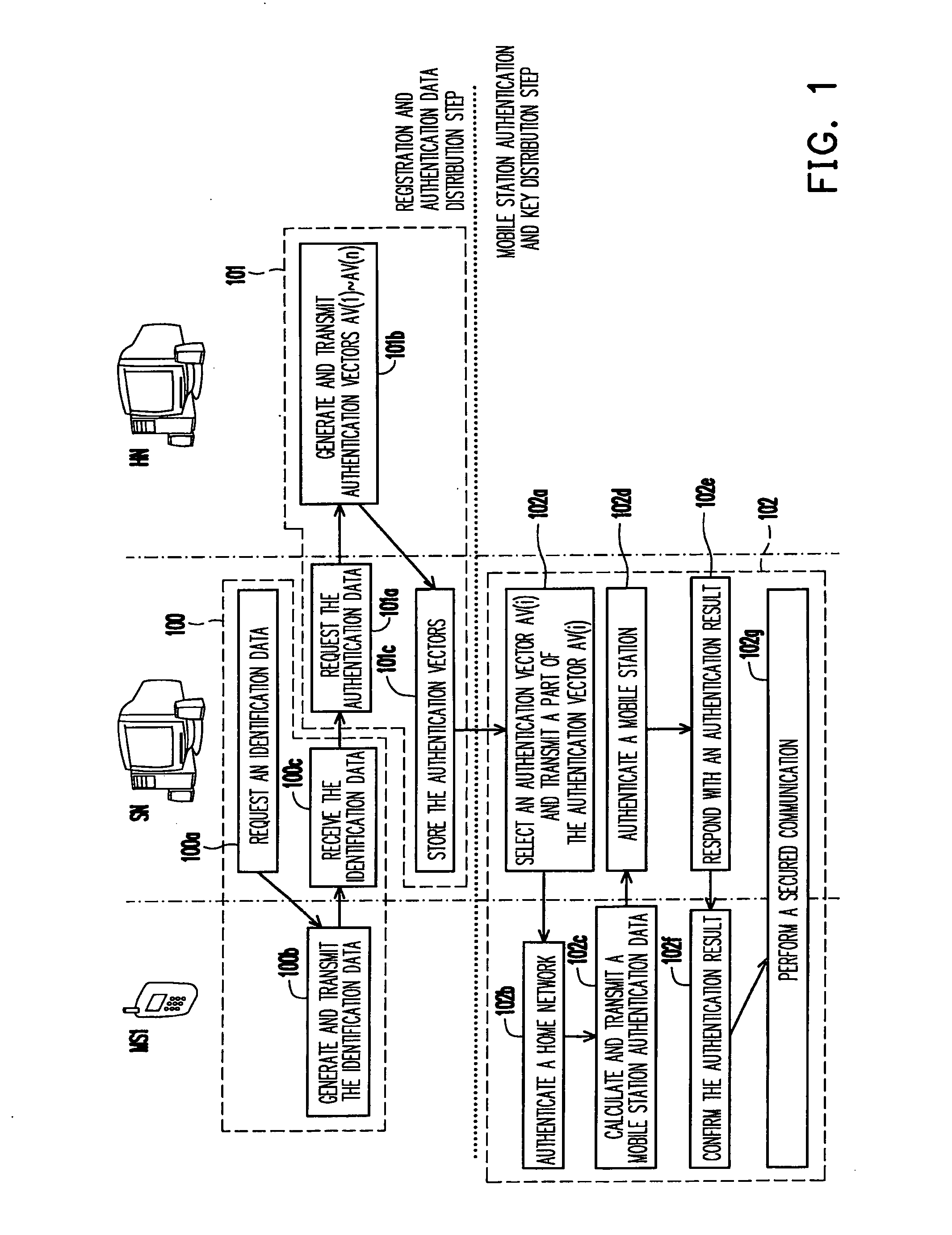
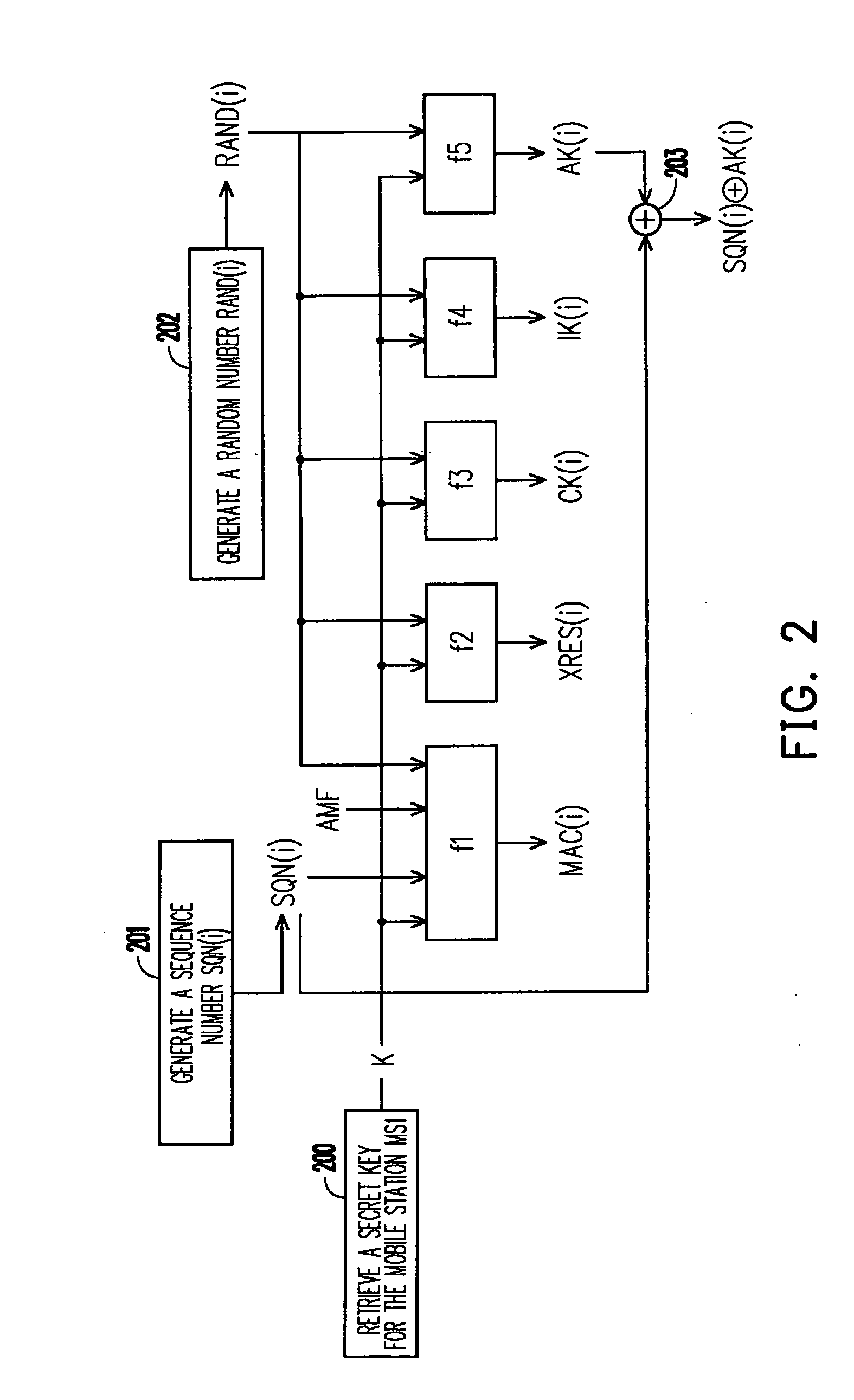
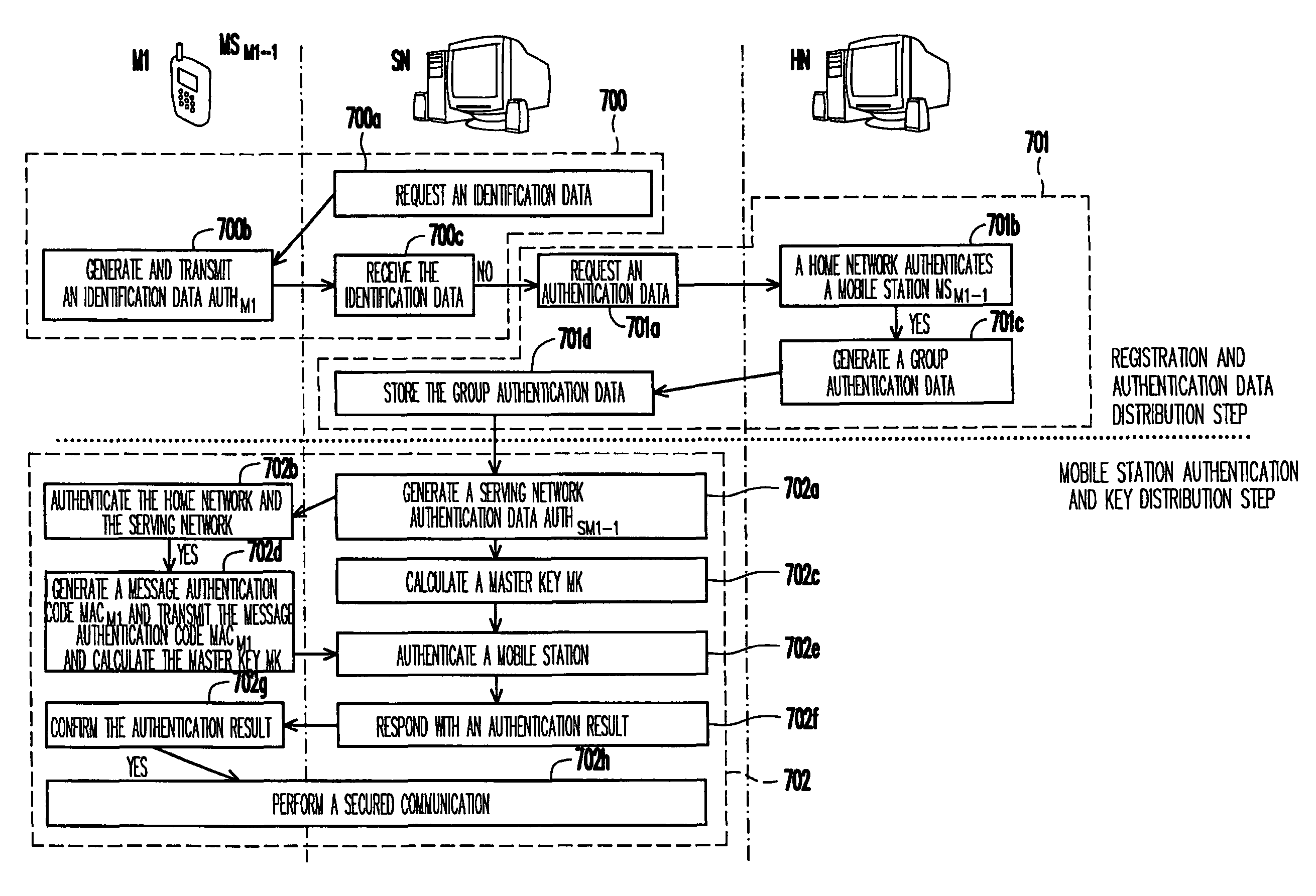
Group authentication method
ActiveUS20090054036A1Ensure secure communicationReduce delaysElectric signal transmission systemsUnauthorised/fraudulent call preventionCommunications systemRelevant information
A group authentication method adaptable to a communication system is disclosed. The communication system includes a user group, a serving network, and a home network. The user group includes at least one mobile station. The home network pre-distributes a group authentication key to itself and all the mobile stations in the same user group and generates a mobile station authentication key for each mobile station. The home network generates a group list for recording related information of the user group. The home network has a database for recording the group list. The serving network has a database for recording the group list and a group authentication data received from the home network. The group authentication method includes following steps. The serving network performs an identification action to a mobile station. The communication system performs a full authentication action or a local authentication action according to the result of the identification action.
Owner:IND TECH RES INST +1
Safe transmission method of physical layer in wireless communication
InactiveCN101902265AAvoid accessEnsure secure communicationSpatial transmit diversityError preventionBlind equalizationSecure transmission
The invention discloses a safe transmission method of a physical layer in wireless communication, which is characterized by comprising the following steps of: a single-antenna desired user firstly transmits unencrypted request information to a multi-antenna base station; the base station receives the request information and estimates a signal path between the base station and the desired user with a frequency piloting sequence; the base station modulates bit to be transmitted into a constellation point symbol b (n) with a known phase position modulating mode, designs a fast-variable weighting coefficient, weights the constellation point symbol b (n) to be transmitted, and transmits the weighted symbol on selected Jrand antennas according appointed gross power; the desired user receives the weighted symbol, i.e. a weighting symbol, and decodes with a maximum likelihood method; and a wiretap user fast changes the weighting coefficient due to the process of the base station, can not decode with a blind equalization method, and can not decode with the maximum likelihood method, so that the method finally realizes the safe transmission.
Owner:XI AN JIAOTONG UNIV
Group authentication method
ActiveUS8005460B2Ensure secure communicationReduce delaysElectric signal transmission systemsUnauthorised/fraudulent call preventionRelevant informationCommunications system
A group authentication method adaptable to a communication system is disclosed. The communication system includes a user group, a serving network, and a home network. The user group includes at least one mobile station. The home network pre-distributes a group authentication key to itself and all the mobile stations in the same user group and generates a mobile station authentication key for each mobile station. The home network generates a group list for recording related information of the user group. The home network has a database for recording the group list. The serving network has a database for recording the group list and a group authentication data received from the home network. The group authentication method includes following steps. The serving network performs an identification action to a mobile station. The communication system performs a full authentication action or a local authentication action according to the result of the identification action.
Owner:IND TECH RES INST +1
Probabilistic key distribution in vehicular networks with infrastructure support
ActiveUS20150139421A1High RSU densityConnection securityMultiple keys/algorithms usagePublic key for secure communicationCryptographic hash functionUser identifier
Method and system of key distribution by trusted nodes for a vehicular ad hoc network, the nodes of said network having at least one pair of public-private keys and the corresponding certificates, issued by a CA, said method comprising each vehicle node, on entering said network region, requesting a set of keys from an RSU node that is within range and within that region, said RSU node sending said vehicle node a set of private keys, selected from a pool of private keys, and a list with the key identifiers of the private keys shared by said vehicle node and the other vehicle nodes that have most recently contacted said RSU for a predetermined period of time; such that two nodes are able to establish a secure connection without further interaction by deriving a shared secret which is a cryptographic hash function of the keys shared by said two nodes.
Owner:UNIV DO PORTO
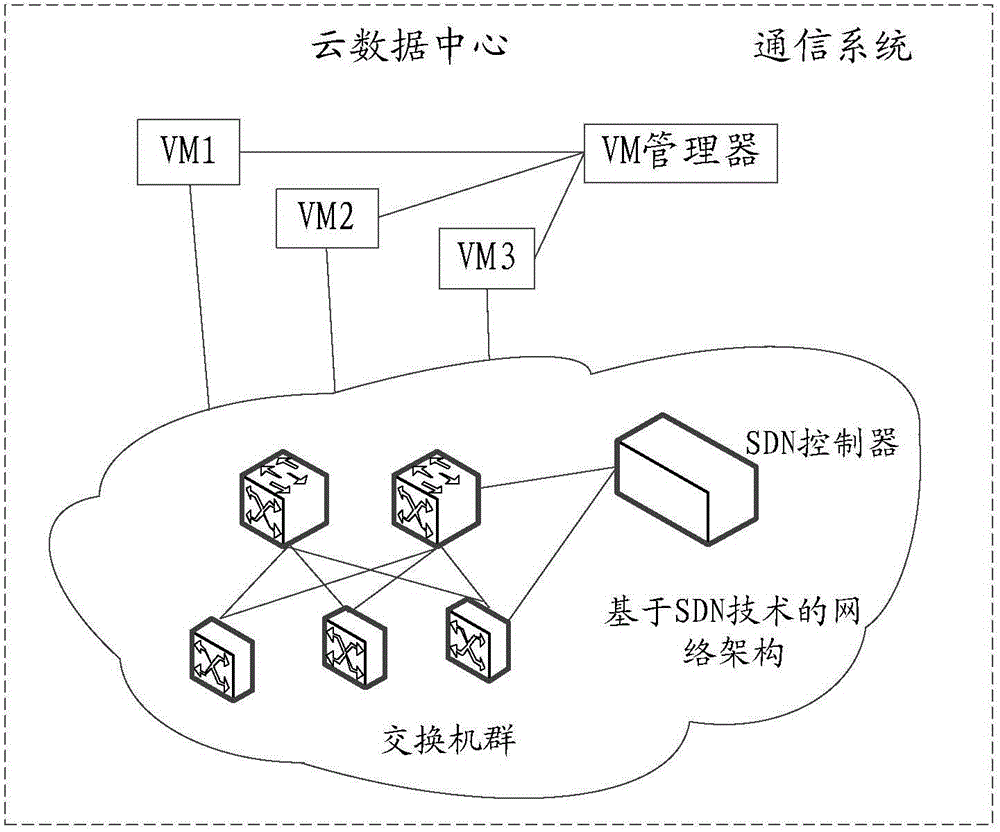
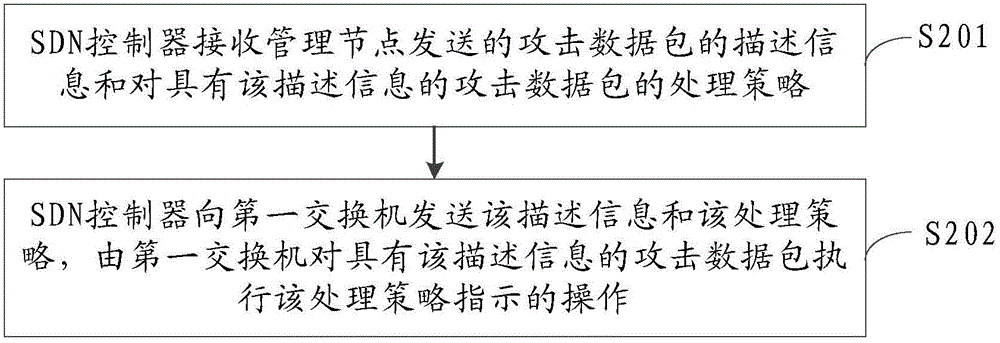
Method, device and system for processing attack data packages
ActiveCN104580168ANormal transmissionAvoid Persistent AttacksProgram controlData switching networksNetwork packetNetwork security
The embodiment of the invention provides a method, device and system for processing attack data packages, and relates to the technical field of communications. The method, device and system provided by the invention can be adopted to limit a network bandwidth which is occupied when the attack data packages are transmitted in a network, so that the transmission of normal data packages is guaranteed. The method comprises the following steps: a management node receives the description information of an attack data package, which is sent by a sensing node, and the attack type of the attack data package; a processing strategy of the attack data package of the attack type is confirmed according to the attack type, and the description information and the processing strategy are sent to an interchanger through an SDN controller; the interchanger executes the operation indicated in the processing strategy on the attack data package with the description information, wherein the processing strategy is used for indicating the interchanger to execute the operation indicated in the processing strategy on the attack data package with the description information. The method provided by the invention is applied to a network security maintenance technique.
Owner:HUAWEI TECH CO LTD
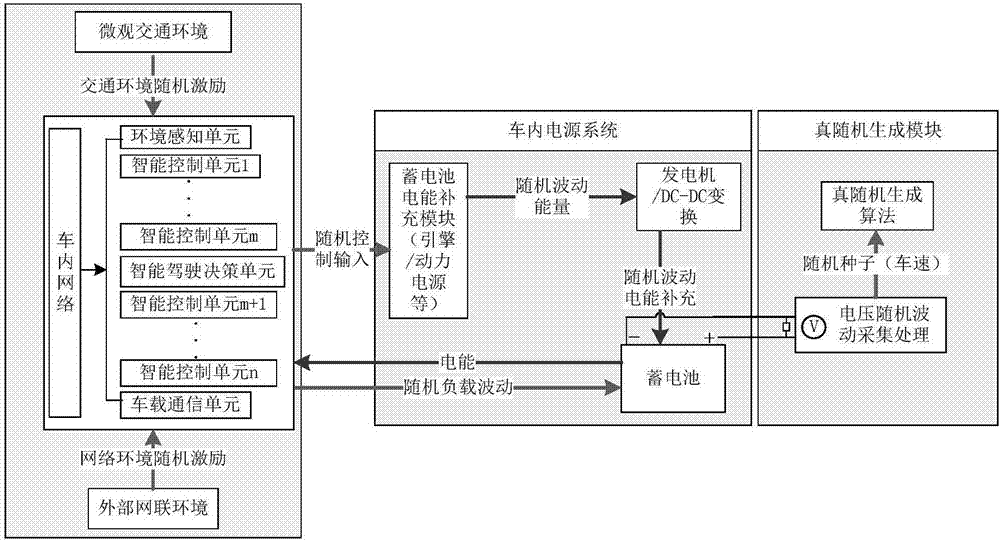
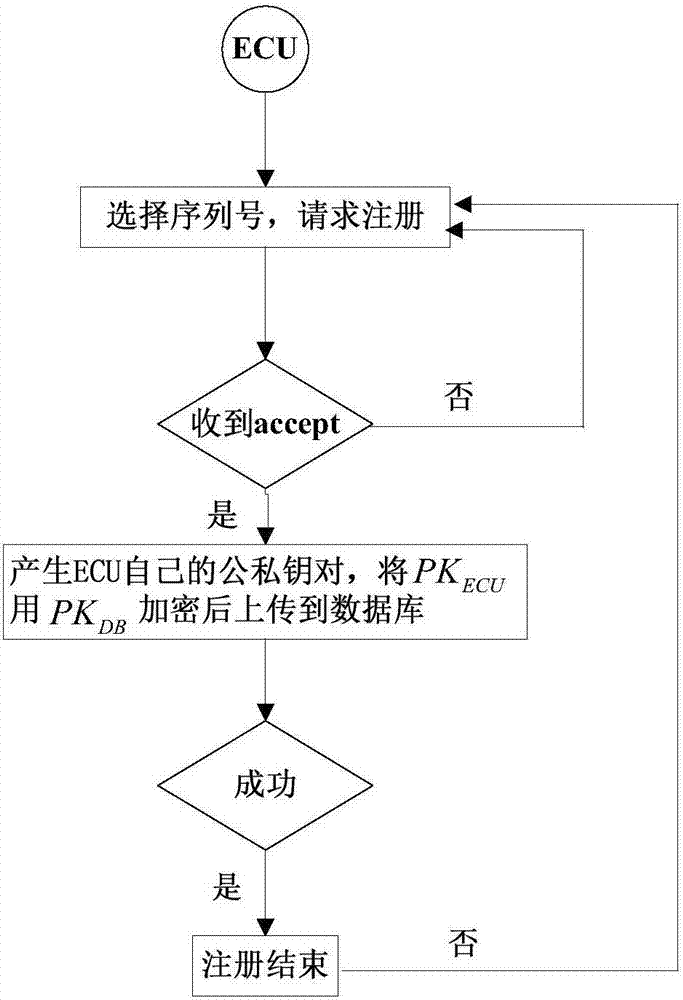
Vehicle-inside one-time-one-password communication method based on ECU identity concealment
ActiveCN107104791APrevent tamperingPrevent replay attacksKey distribution for secure communicationInformation securityEmbedded system
The invention discloses a vehicle-inside one-time-one-password communication method based on ECU identity concealment. The method comprises the following steps: 1) creating a system model; 2) prior to the one-time-one-ciphering by ECU, registering information in the gateway database; 3) using the operation behaviors to the vehicle by the intelligent ECU as the media to generate a coupling effect between vehicle mounted power supply systems so that the vehicle mounted power supply voltage change possess the Markov characteristics and that a true random number is generated to serve as the session key; 4) updating in a fixed time the session key between the ECUs in need of communication so as to prevent replay attacks; and 5) according to the obtained session key, using the attributes of the ECU in the database, creating one-time-one-ciphering data communications based on the ECU ciphered text attributes to ensure the secure communications of ECU inside the vehicle. According to the invention, through the utilization of the stochastic behavior of the power supply voltage inside the vehicle to generate a session key, it is possible to effectively avoid the problem with the tampering and the forgery of information. Through the combination of the vehicle speed unit with the steering wheel, the 500ms cycle dynamic state generates the vehicle speed and serves as the session key for the ECU in order to prevent relay attacks.
Owner:东台城东科技创业园管理有限公司
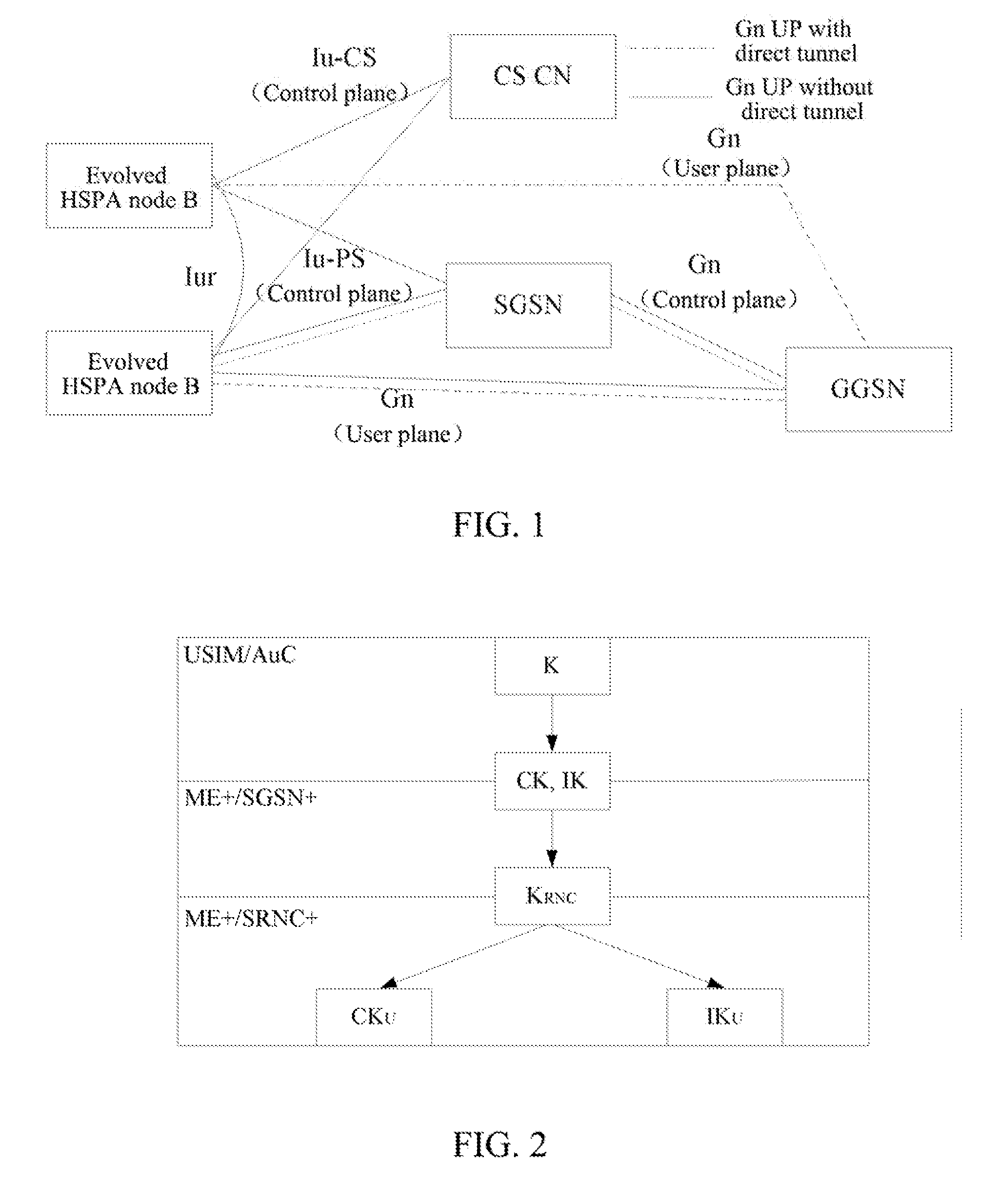
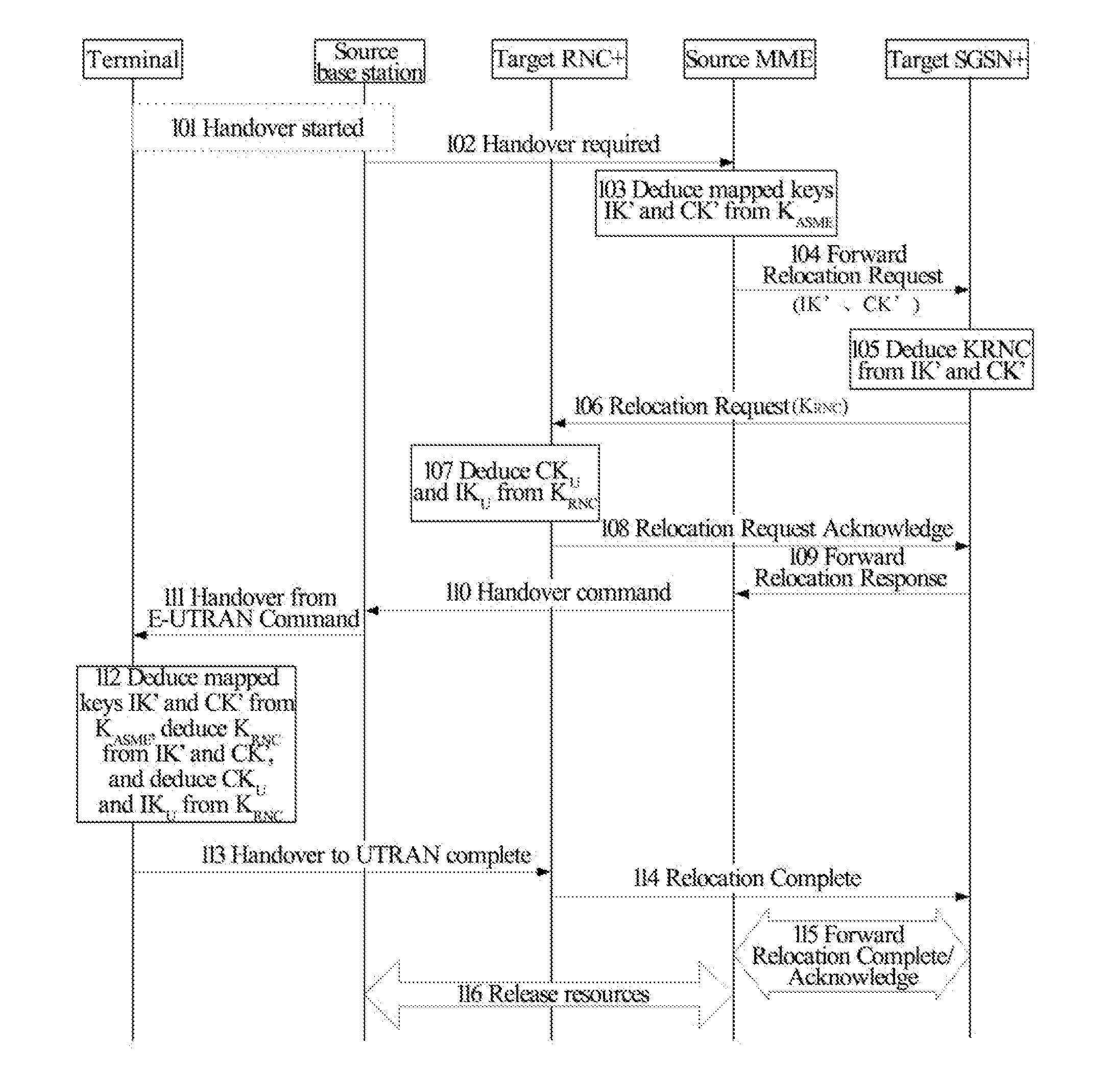
Method and System for Establishing Enhanced Key when Terminal Moves to Enhanced Universal Terrestrial Radio Access Network (UTRAN)
ActiveUS20130028421A1Carry-out safelySave overheadSecret communicationSecurity arrangementComputer networkRadio access network
The present invention discloses a method and system for establishing an enhanced key when a terminal moves from an EUTRAN to an enhanced UTRAN, so as to ensure that the terminal can carry out normal communication safely in the enhanced UTRAN. The method includes: when the terminal moves from the EUTRAN to the enhanced UTRAN, a target enhanced serving GPRS support node (SGSN+) in the enhanced UTRAN deducing an intermediate key used in the UTRAN according to a mapped traditional key obtained from a source mobile management entity; and the terminal, after deducing the mapped traditional key, further deduces the intermediate key used in the enhanced UTRAN by using an algorithm which is the same as that of the target SGSN+ according to the mapped traditional key.
Owner:ZTE CORP
Non-standard POE power supply circuit and power supply method for network interfaces, and power supply equipment
ActiveCN109150551AImplement the power-up processEnsure secure communicationData switching current supplyElectricityComputer module
The invention belongs to the technical field of power over Ethernet, and provides a non-standard POE power supply circuit and power supply method for network interfaces, and power supply equipment. the non-standard POE power supply circuit is connected to a POE power supply and a cable interface; the cable interface includes a network interface signal line and a network interface power line; the non-standard POE power supply circuit includes an exchange module, a power-on detection module, a control module, a power failure detection module and a power supply module; whether the cable interfaceis accessed by power receiving equipment can be detected through the power-on detection module when the power receiving equipment is not powered on; after the cable interface accesses the power receiving equipment, the control module can generate power enable signals, and the power supply module can output the power signals of the POE power supply according to the power enable signals; and the power-on detection module can be disconnected to the network interface signal line through the control module after the power receiving equipment in in normal communication with the cable interface. Thus, the problems of high power supply costs and low flexibility of traditional POE power supply circuits can be solved.
Owner:TP-LINK
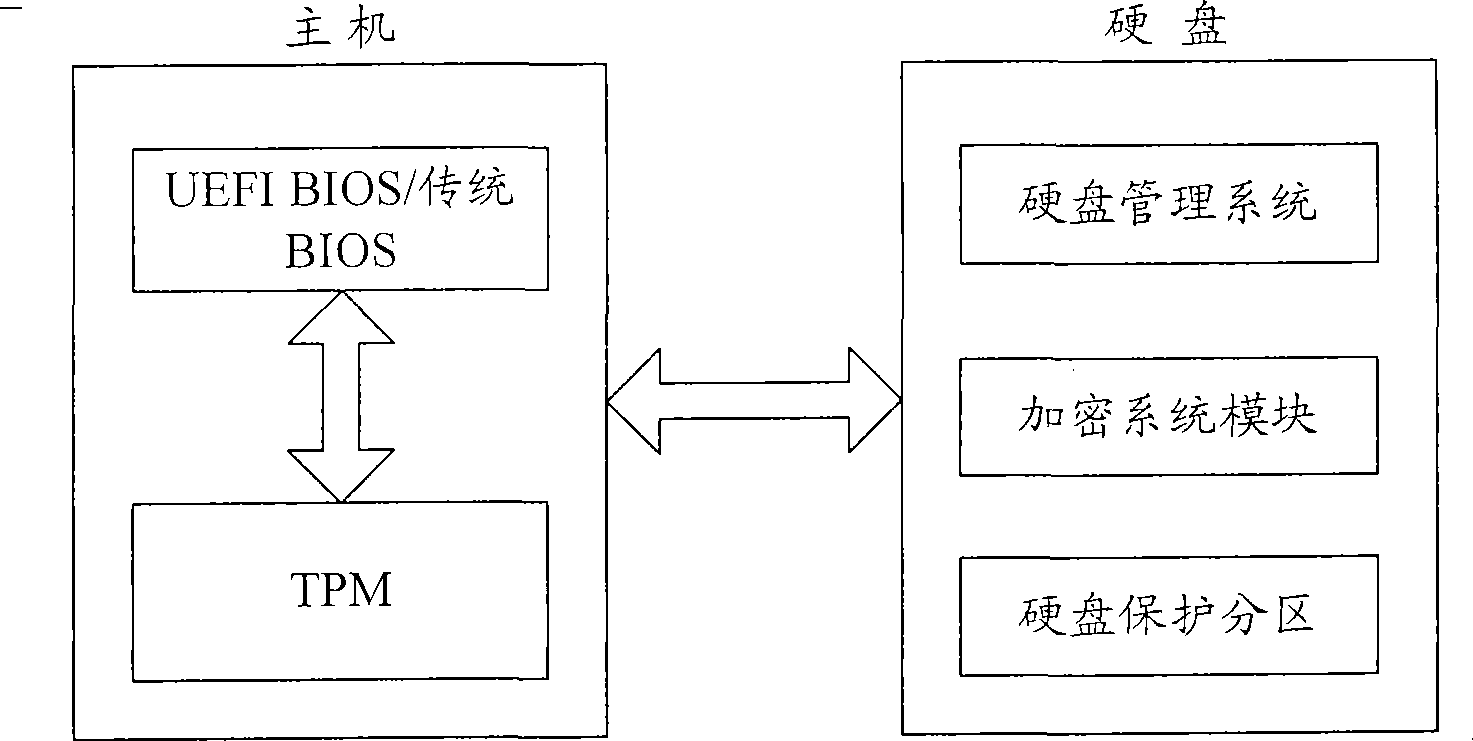
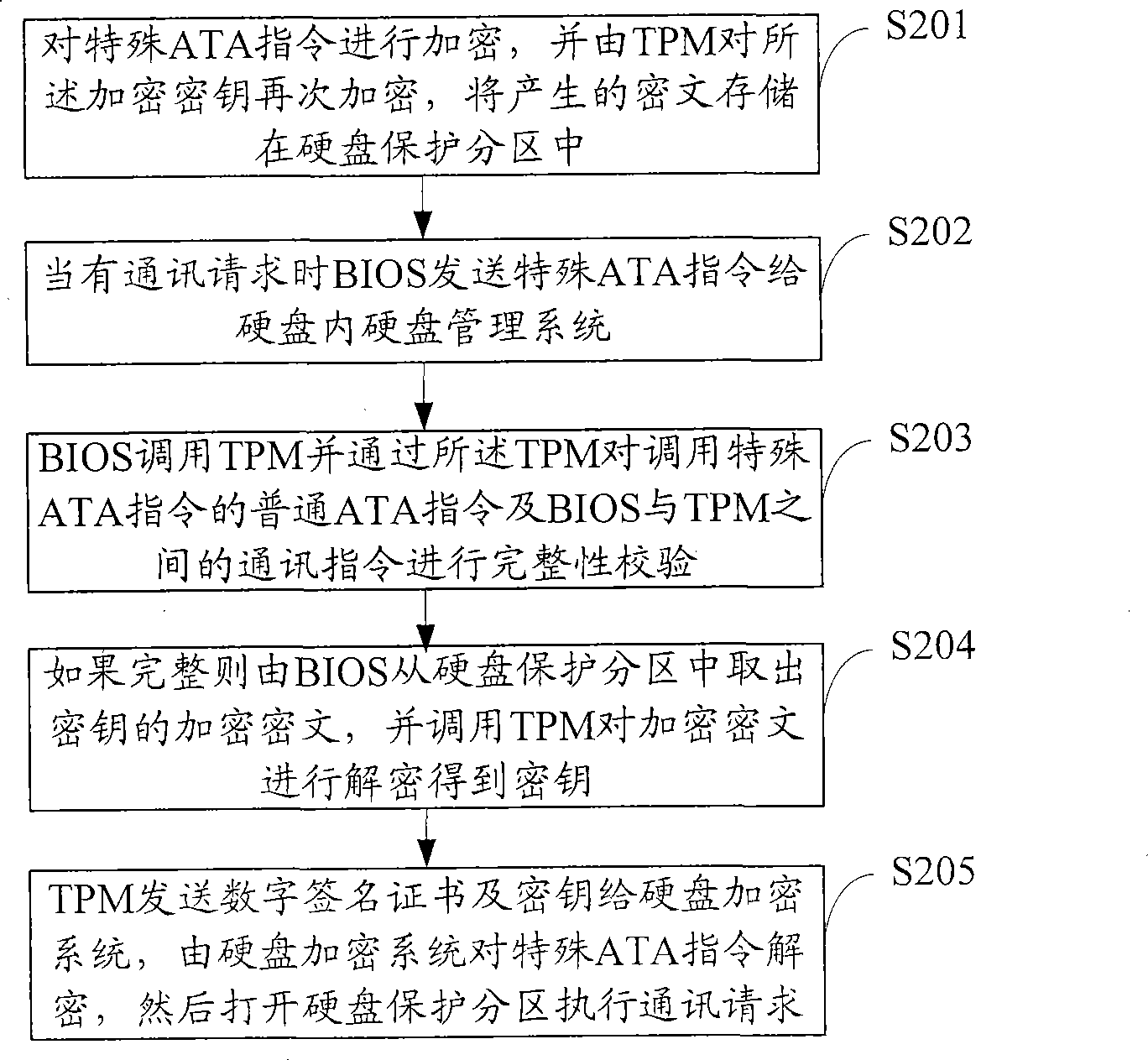
Ciphering transmission method of hard disk ATA instruction
ActiveCN101441601AEnsure secure communicationInput/output to record carriersUnauthorized memory use protectionDigital signatureCiphertext
The invention is suitable for the computer field and provides a method for encrypted transmission of an ATA instruction of a hard disk. The method comprises the following steps: a special ATA instruction is encrypted; an encrypted encryption key is re-encrypted through TPM; produced cryptograph is stored in a protective subarea of the hard disk; the special ATA instruction is the ATA instruction for communication between a mainframe system and the protective subarea of the hard disk; when a communication request is emitted, BIOS sends the special ATA instruction to a hard disk management system of the hard disk; the BIOS transfers the TPM and carries out integrated verification on a common ATA instruction transferring the special ATA instruction and a communication instruction between the BIOS and the TPM through the TPM; if the instructions are integrated, the encrypted cryptograph of the encryption key is taken out from the protective subarea of the hard disk through the BIOS, and the TPM is transferred to decrypt the encrypted cryptograph to obtain the encryption key; and the TPM sends a digital signature certificate and the encryption key to a hard disk encryption system, the special ATA instruction is decrypted through the hard disk encryption system, and the protective subarea of the hard disk is opened to execute the communication request.
Owner:CHINA GREATWALL TECH GRP CO LTD
Method for acquring authentication cryptographic key context from object base station
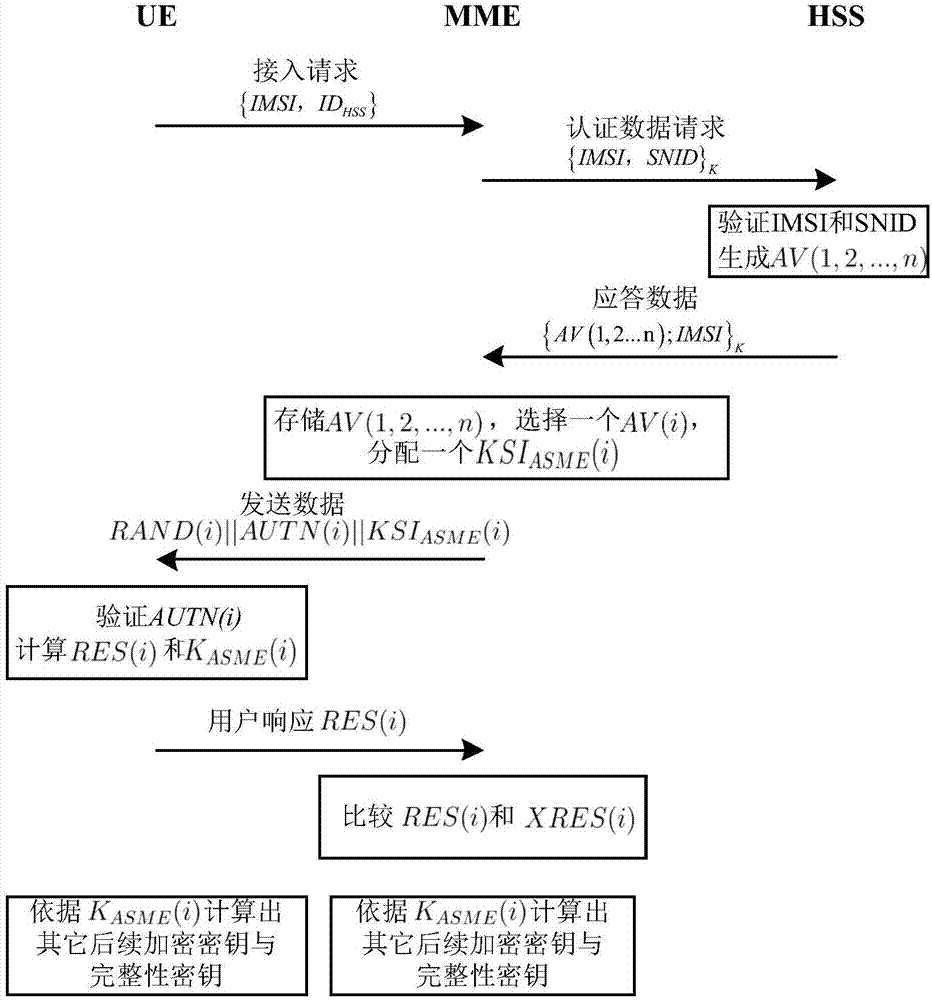
InactiveCN1819698AVerify legitimacyEnsure safetyRadio/inductive link selection arrangementsTransmissionComputer hardwareSecure communication
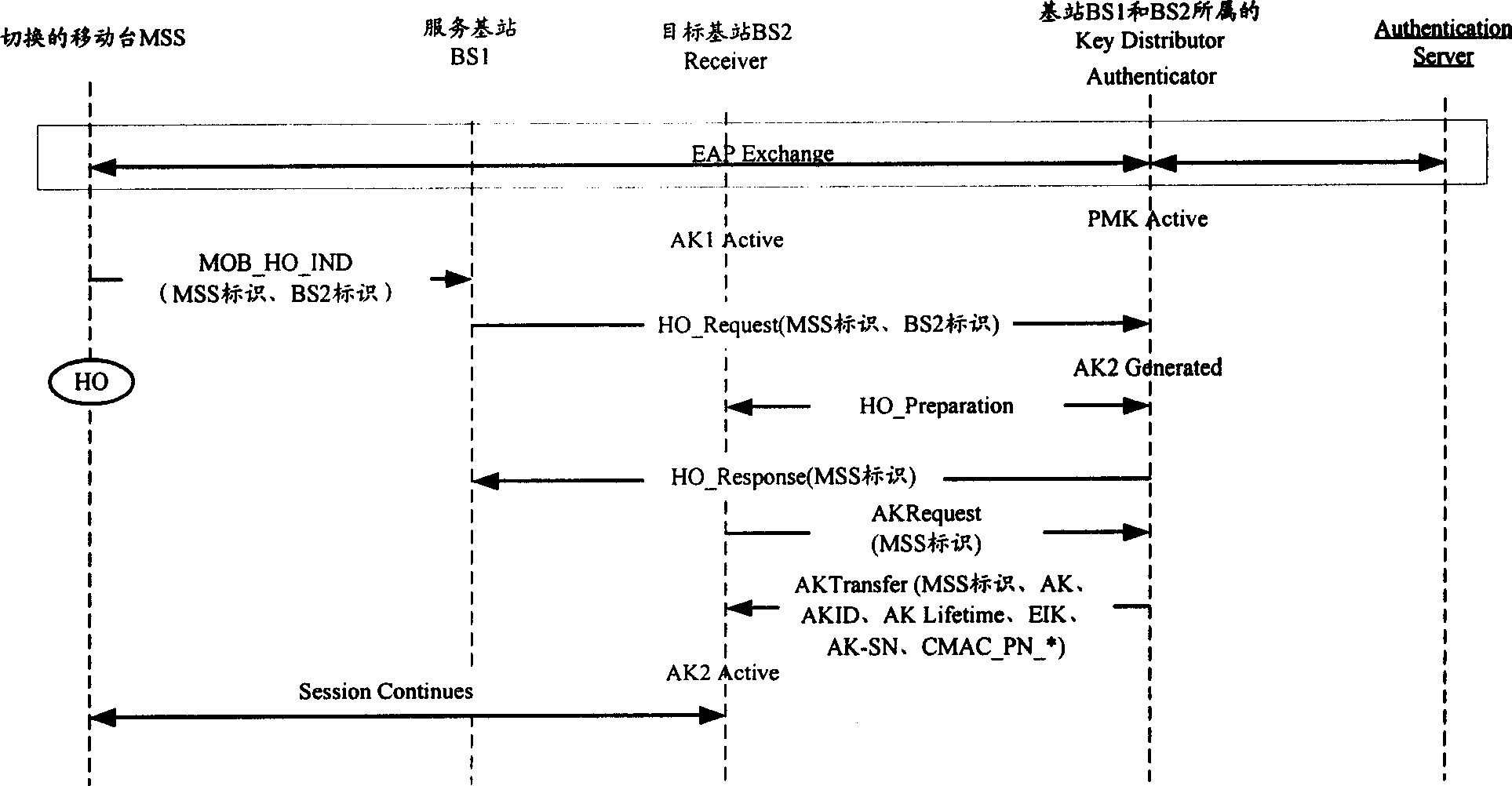
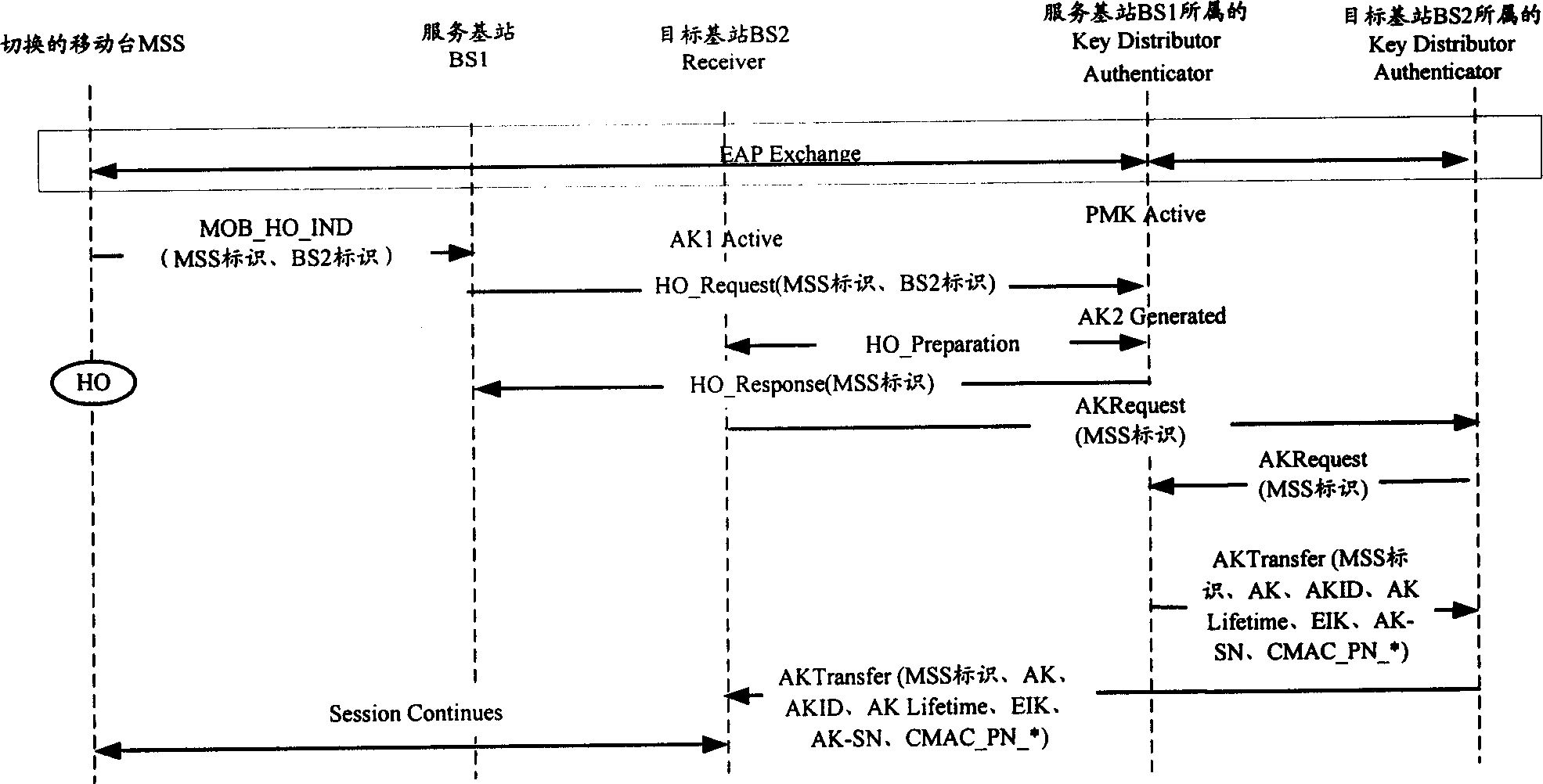
The invention involves the mobile communication field, a method that the aiming base station gets the context information of the identified-right secret key, to solve the inconsistent problem in the relating sequence number of the aiming base station identified-right secret key context and the mobile terminal in the existing technology. The method including: the identified righter / the provider of the secret key create the context information of the identified-right secret key when the mobile terminal request cut, the context information includes the current sequence number of the identified-right secret key, the sequence number of the upward managing information authentication code and / or the current sequence number of the downward managing information authentication code; the identified righter / the provider of the secret key send the identified-right secret key and the relating sequence number to the aiming base station when the aiming base station that the mobile terminal ready to cut request the identified-right secret key. Thus maintained the continuity of the sequence number information, ensure the secure communication with the mobile terminal, and prevent effectively the possibly appearing replay attack, ensure the conversation security after restore.
Owner:HUAWEI TECH CO LTD
Industrial wireless network security communication implementation method based on cipher key
ActiveCN101420686AImprove performanceSupport communication processingWireless network protocolsSecurity arrangementData informationNetwork management
The invention provides a method used for realizing the safety communication of an industrial wireless network based on cryptographic-key. By using the combination management mode of concentration type and distribution type, a safety network management framework consists of a safety manager, a safety management agent and a safety management object commonly; the method comprises the steps as follows: 1) the safety manager and the safety management agent provide the safety cryptographic-key; 2) when equipment accesses to the network, the equipment and the safety manager authenticates each other; 3) during the communication process, the data messages are converged ,encrypted and then transmitted; the network management mechanism based on the safety cryptographic-key can effectively solve the problems of limited memory capability of the wireless equipment in the industrial wireless network, calculation complexity and the like, furthermore, the network management mechanism can solve the safety problems that the data information is prone to be stolen, falsified and inserted during the process of wireless network transmission and communication, and can utilize the network resource more reasonably, improve the network performance, effectively realize the authentication and authorization of the equipment access to the network, distribution and update of the cryptographic-key, support the communication processing on network safety, and ensure the normal running of the network.
Owner:魏旻
Network access authentication method and server based on digital certificate
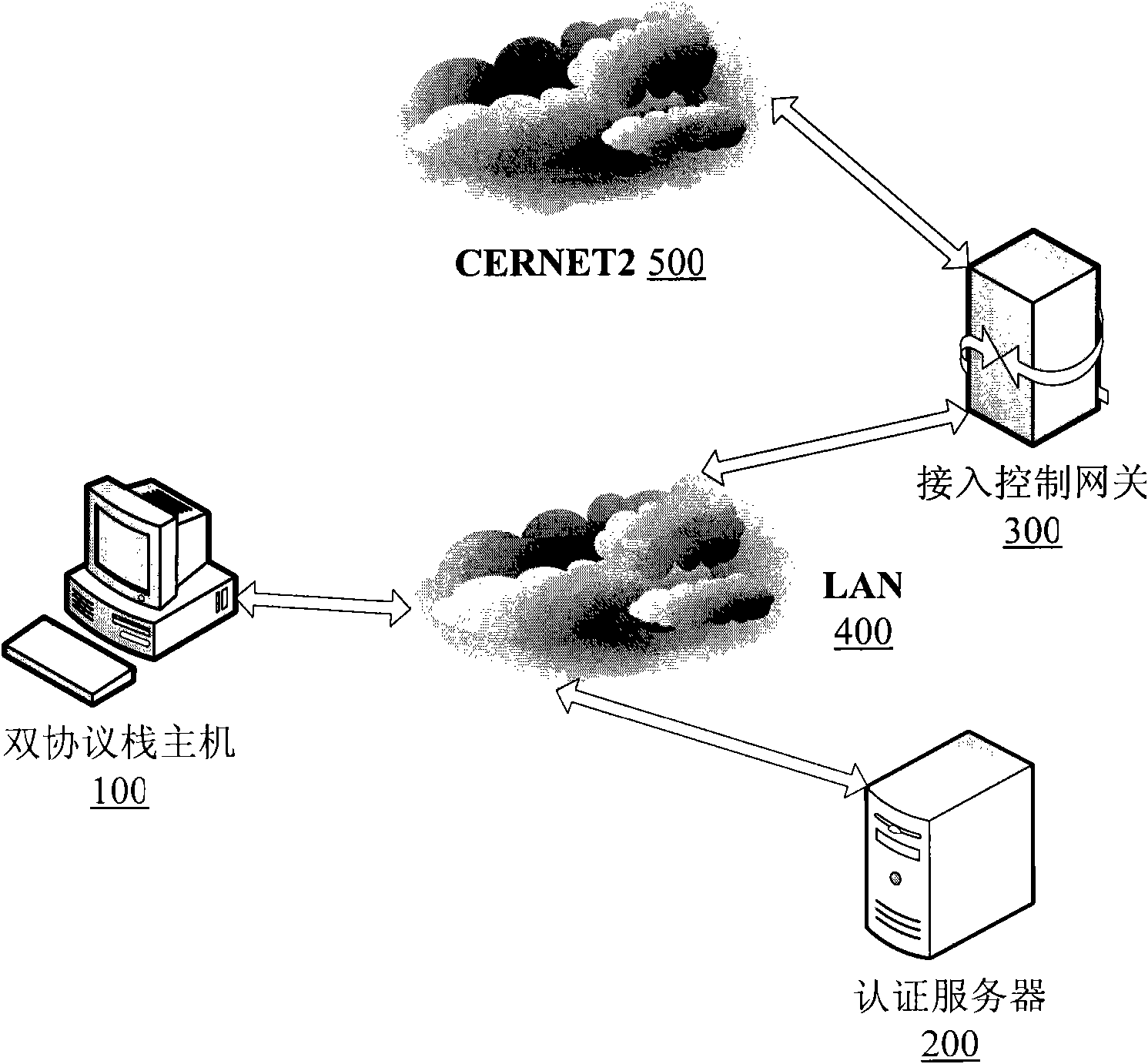
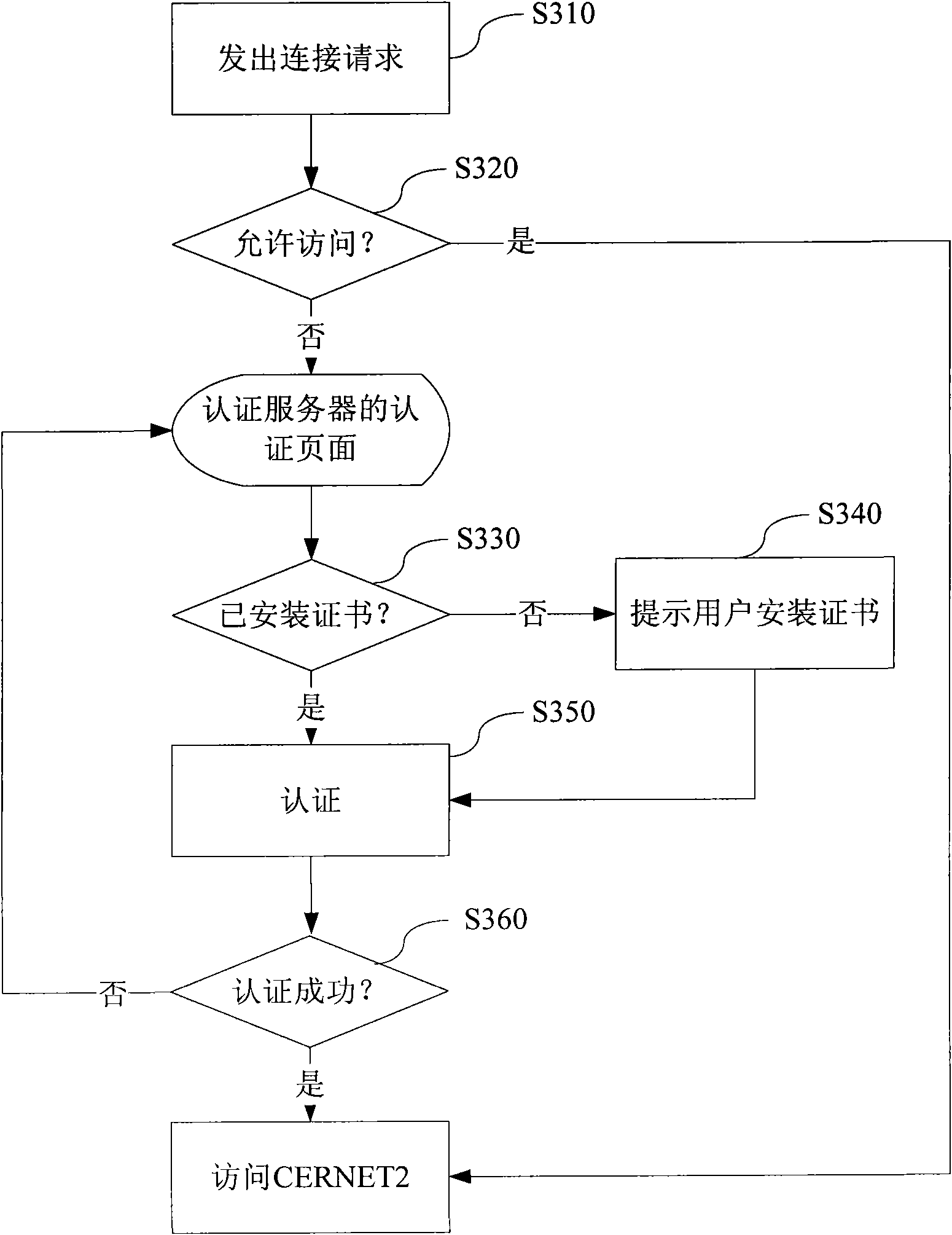
InactiveCN101883106AImprove convenienceImprove securityTransmissionAuthentication serverAuthorization
The invention provides network access authentication method and server based on a digital certificate. The method comprises the following steps of: receiving a user digital certificate transmitted by a user host; carrying out identity authentication to a user on the basis of the received user digital certificate; analyzing user information in the user digital certificate and judging whether the user host is allowed to access a target address or not by querying an access control list according to the user information analyzed in the user information; after successfully authenticating and judging that the user host is allowed to access, transmitting an access authorization request for the user host to an access control gateway and receiving access authorization returned by the access control gateway for the user host; and transmitting an authentication result and an access authorization result to the user host.
Owner:CERNET CORP
Safe communication system and method
InactiveCN101043320AEnsure secure communicationSecuring communicationSecure communicationCommunications system
The invention discloses a communication system that can protect the security communication between at least two communication terminals in the self-organizing network, it includes: the first communication terminal; the second communication terminal which can receive the first data from the first communication terminal by short distance, and checks the first data, and generates the second data according to the checking result; the identification device on the network which is used to receive the second data from the second communication terminal via the said network, and checks the second data to determine the at least one ID of the first communication terminal and the second communication terminal. The invention also discloses a communication method that can be used between two communication terminals in the self-organizing network, it includes: the sending step; the first checking step; the second checking step; and data exchanging step.
Owner:BENQ INTELLIGENT TECH SHANGHAICO LTD
Data communication method, apparatus, device and system for power centralized meter reading system
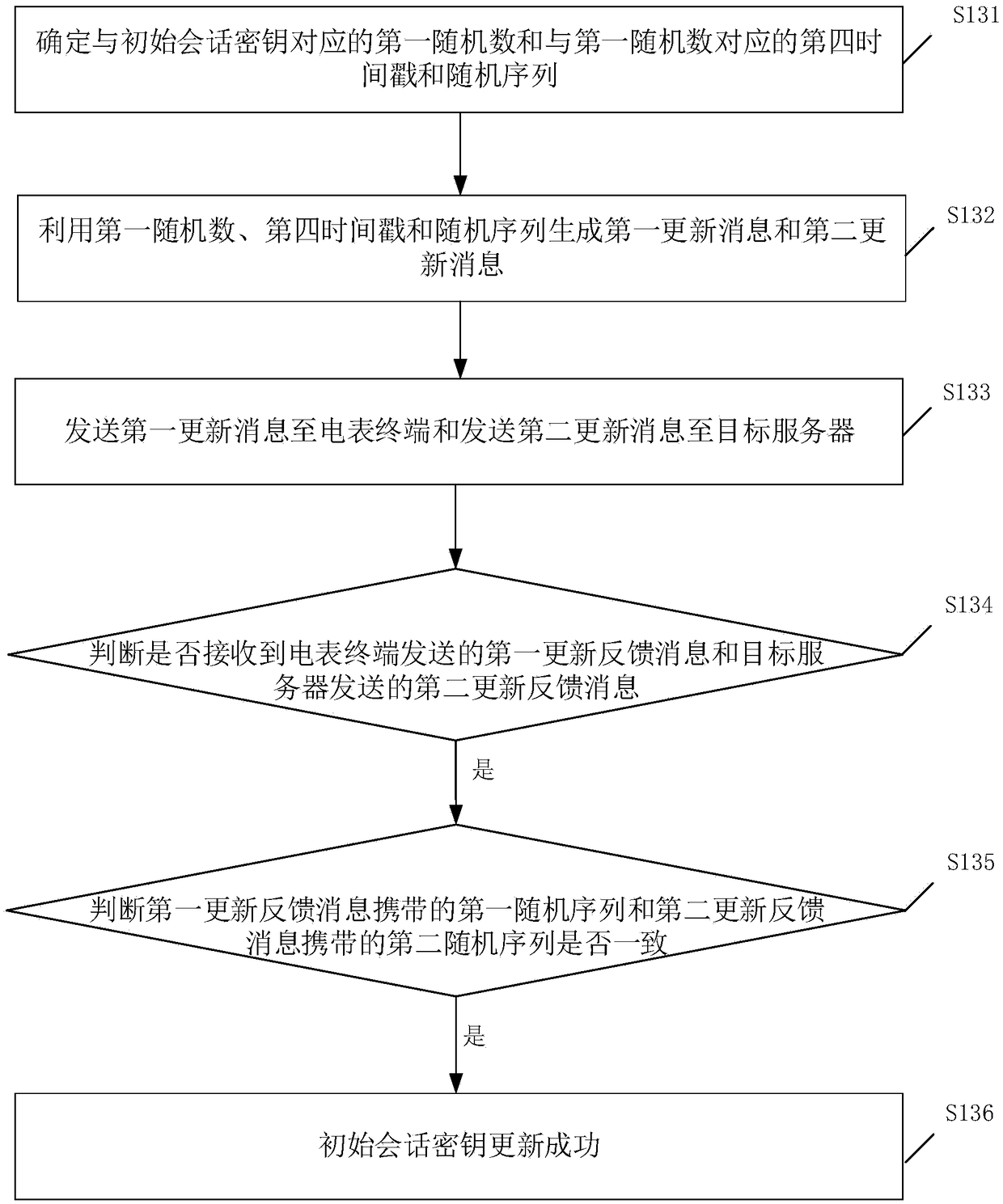
ActiveCN109348479AAvoid long-term immobilityEnsure secure communicationTransmission systemsTransmissionSecure communicationApplication server
The invention discloses a data communication method for an LORA power centralized meter reading system. When data communication between an electricity meter terminal and a target server is performed at a current moment, the data communication is performed through an initial session key, when a time interval between a generation moment of the initial session key and the current moment satisfies anupdate period, the initial session key can be updated with a predefined rule to obtain an updated session key, and then, the data communication between the electricity meter terminal and the target server is implemented by the updated session key. The session key of the data communication between the electricity meter terminal and the target server in the LORA power centralized meter reading system is updated by setting the update period, so that the situation that the session key between the electricity meter terminal and the target server is unchanged for a long time, and the secure communication between the electricity meter terminal and a network server or an application server is guaranteed. In addition, the invention further discloses a data communication apparatus, device and systemfor the LORA power centralized meter reading system, which has the same effects mentioned above.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
Access authentication and key agreement protocol and method of special network for space-aeronautics-vehicle-ground tracks
ActiveCN107204847AEnsure secure communicationReliable transmissionKey distribution for secure communicationRadio transmissionTelecommunications linkGround track
The invention discloses an access authentication and key agreement protocol and a method of a special network for space-aeronautics-vehicle-ground tracks. An authentication system consists of a core network configuration authentication subsystem and a user access authentication subsystem, which completes authentication and key agreement between an airship and a security and operation guarantee center and authentication and key agreement between a user and the airship respectively. In view of the structure and communication characteristics of the special network for space-aeronautics-vehicle-ground tracks, a core network configuration subsystem is constructed. Authentication and key agreement between the airship and the security and operation guarantee center is completed with a public key password to get symmetric keys. Symmetric keys used between the user and the airship are mutually authenticated on the basis of an LTE protocol to get a session key. The problem on secure communication and key updating is solved. There is no need for an authentication center to participate in user access authentication and key agreement. The use of symmetric keys ensures light workload and high efficiency. The method is used in access authentication of airship, high-speed rail and trackside equipment users and key agreement, and ensures secure transmission of a wireless communication link from the user to the airship and to the security and operation guarantee center.
Owner:XIDIAN UNIV
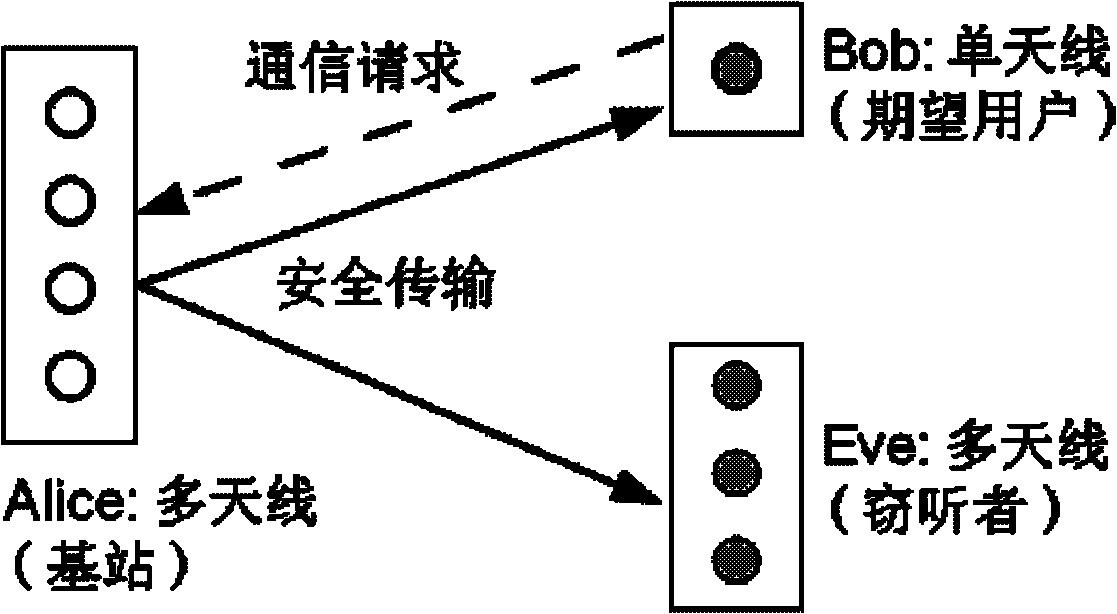
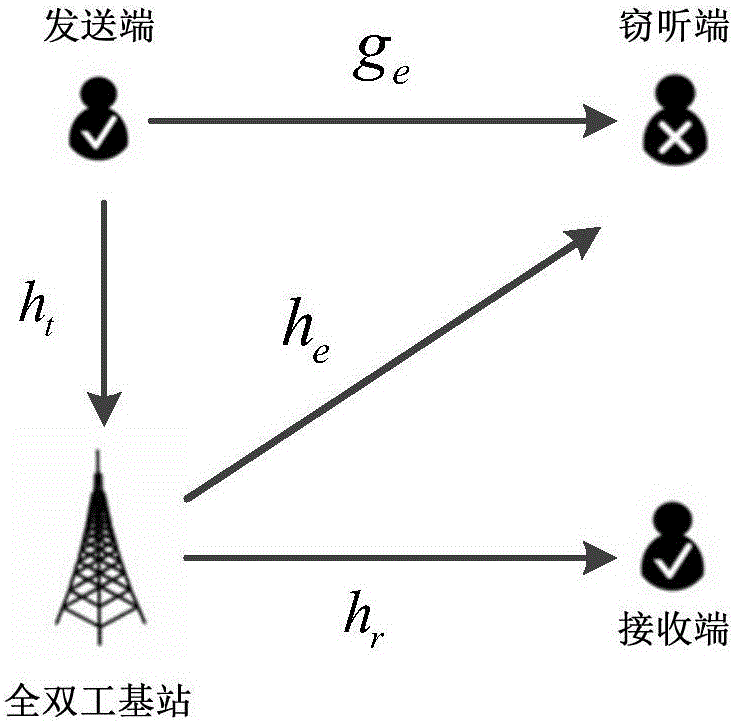
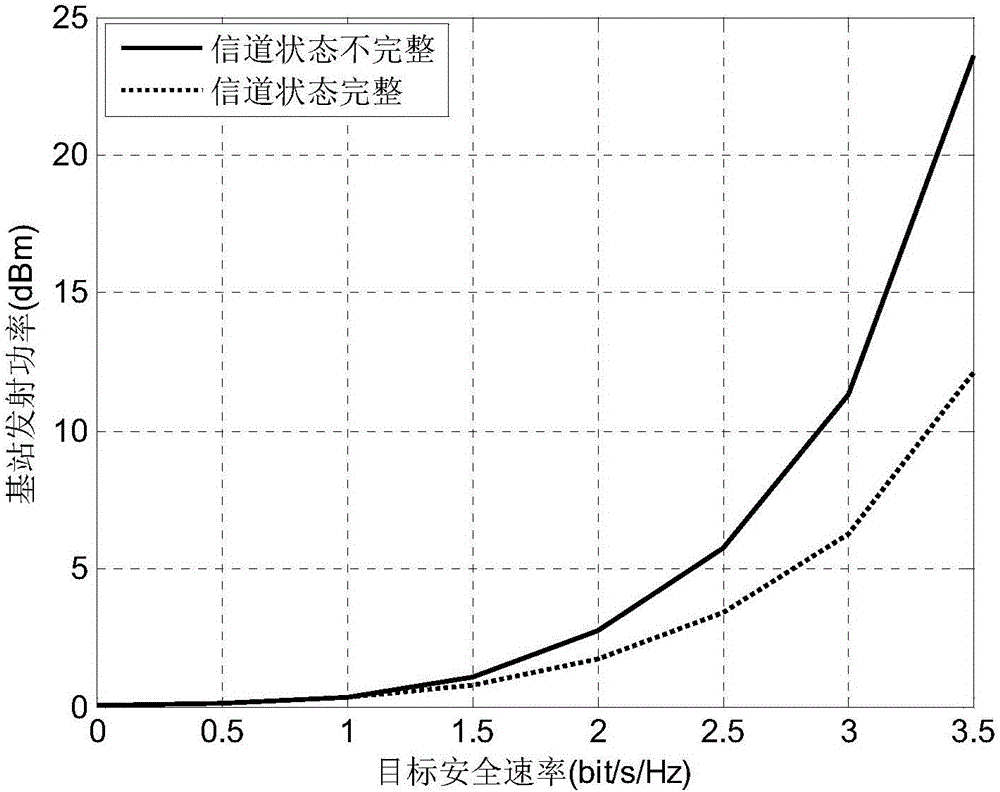
Method for realizing physical layer security and power optimization of full-duplex communication system
ActiveCN106211301AIncrease transmit powerEnsure secure communicationPower managementSpatial transmit diversityDuplex systemS-procedure
The invention discloses a method for realizing physical layer security and power optimization of a full-duplex communication system. A model fully utilizes the characteristic of same frequency at the same time of the full-duplex communication system, and assistance from man-made noise and other interference nodes is unnecessary, so that the transmission efficiency of a full-duplex base station is further increased, and the transmission power of the base station is optimized under the condition that the full-duplex system information transmission is guaranteed to reach to a target secure rate. The method mainly comprises the steps of constructing a physical layer security model of the full-duplex communication system; constructing a convex optimization model based on a secure rate required by the system; and finally converting a non-convex problem which is difficult to solve into a convex optimization problem which is easy to solve by utilizing an SDP theory and an S-Procedure theory, thereby finding an optimal beam forming vector and optimizing the transmission power of the base station. According to the method for realizing physical layer security and power optimization of the full-duplex communication system, the minimum transmission power of the base station is guaranteed and all the transmission power of the base station is guaranteed to be used for transmission of effective signals under the condition of secure transmission of the full-duplex system, and the transmission power of the full-duplex base station is accordingly optimized.
Owner:XIAMEN UNIV
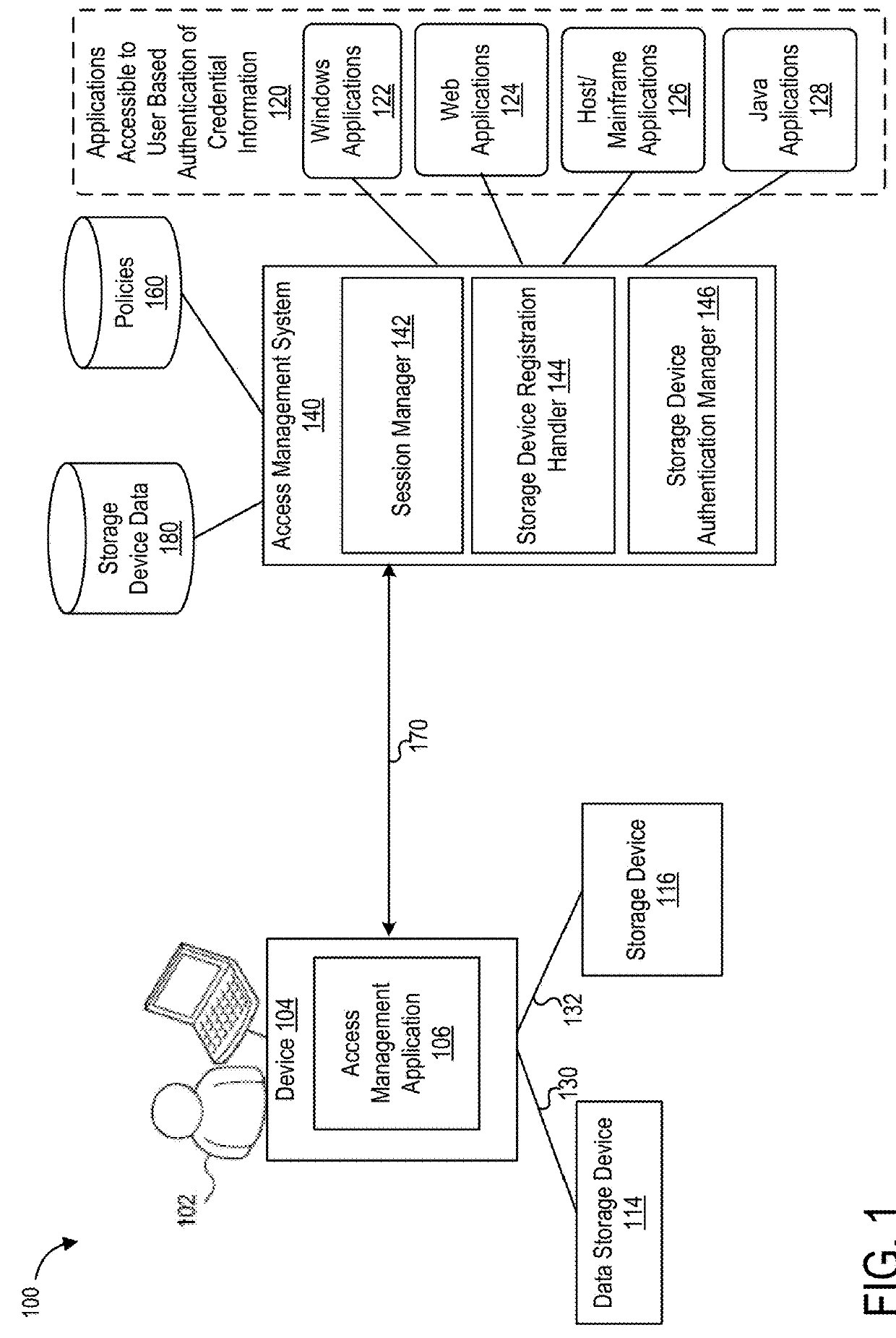
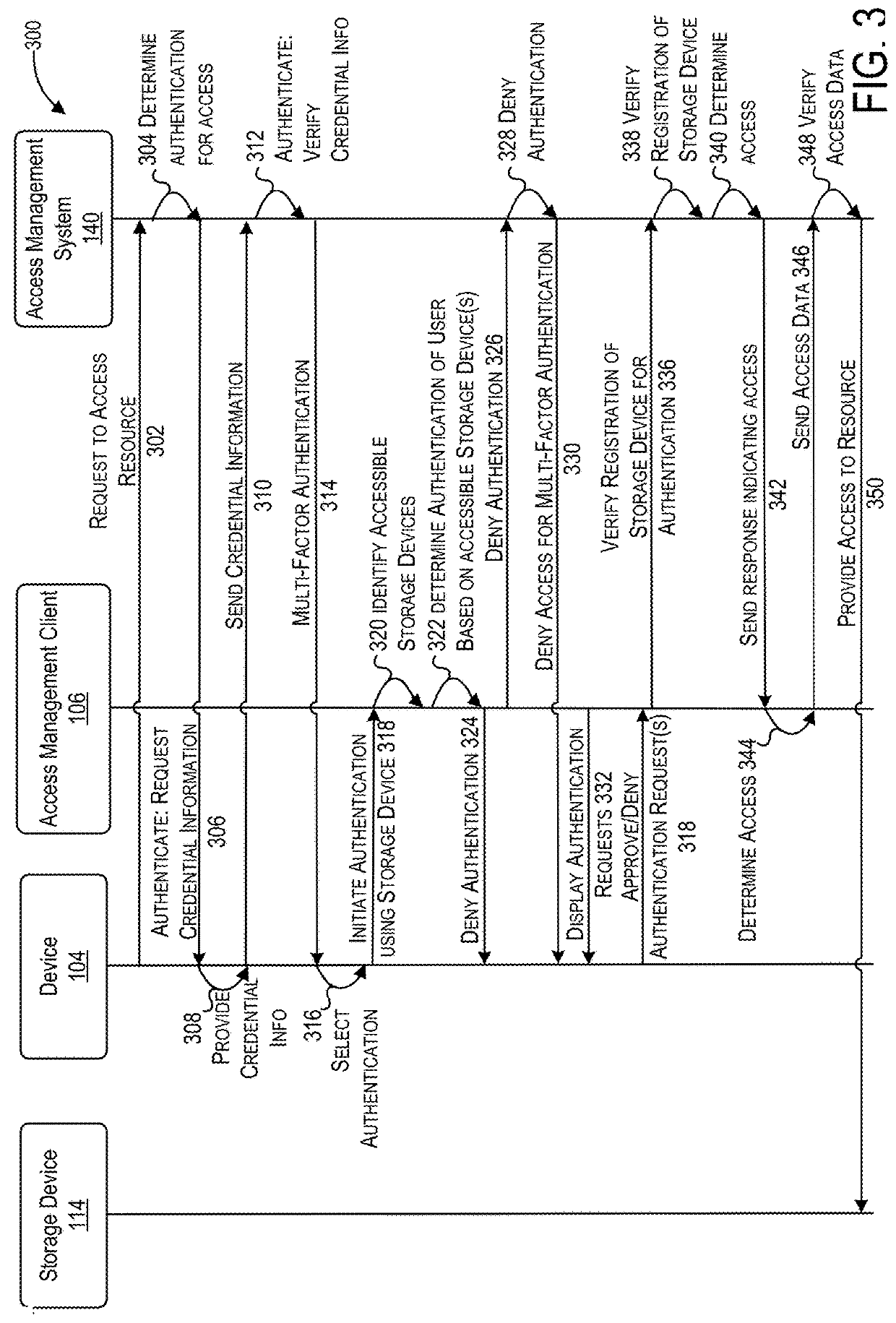
Techniques for implementing a data storage device as a security device for managing access to resources
ActiveUS20180278612A1Data SecurityUsed for its intended purposeMemory architecture accessing/allocationUnauthorized memory use protectionClient-sideAccess management
Techniques are disclosed for implementation of a data storage device as a security device for managing access to resources. These techniques can be implemented for multi-factor authentication (MFA) to provide multiple layers of security for managing access to resources in an enterprise and / or a cloud computing environments. As a security device, a storage device can be used a portable device to provide a point of trust for multi-factor authentication across any client application or device operated to access resources. A storage device may be configured with security data for authentication with an access management system. After configuration, a portable storage device may be used for authentication of a user without credential information at any client device based on accessibility of the device to the portable storage device. A storage device configured as a security device can ensure that legitimate users have an easy way to authenticate and access the resources.
Owner:ORACLE INT CORP
Group password negotiation method based on Vehicle to X (V2X) network
ActiveCN105812132AImprove securityEnsure secure communicationUser identity/authority verificationSecure communicationPassword
The invention discloses a group password negotiation method based on a Vehicle to X (V2X) network. The method comprises: an initiating node broadcasts a negotiation operating message comprising a group communication queue to surrounding nodes agreeing to join a group, vehicle nodes sequentially generate and broadcast negotiation password messages according to the sequence of unique identifiers of the surrounding nodes in the group communication queue, the initiating node generates and broadcasts a final negotiation password message after receiving the negotiation password message of the last vehicle node, and the surrounding nodes generate group passwords using the final negotiation password message, thereby realizing secret communication with the vehicle nodes in the group. By using the characteristics of the V2X network, the method realizes a group password negotiation process among the vehicle nodes and ensures secure communication among the vehicle nodes.
Owner:DATANG GOHIGH INTELLIGENT & CONNECTED TECH (CHONGQING) CO LTD
Probabilistic key distribution in vehicular networks with infrastructure support
ActiveUS9276743B2Reduce complexityIncrease probabilityKey distribution for secure communicationMultiple keys/algorithms usageCryptographic hash functionKey distribution
Method and system of key distribution by trusted nodes for a vehicular ad hoc network, the nodes of said network having at least one pair of public-private keys and the corresponding certificates, issued by a CA, said method comprising each vehicle node, on entering said network region, requesting a set of keys from an RSU node that is within range and within that region, said RSU node sending said vehicle node a set of private keys, selected from a pool of private keys, and a list with the key identifiers of the private keys shared by said vehicle node and the other vehicle nodes that have most recently contacted said RSU for a predetermined period of time; such that two nodes are able to establish a secure connection without further interaction by deriving a shared secret which is a cryptographic hash function of the keys shared by said two nodes.
Owner:UNIV DO PORTO
Method and system for compliance audit of movable terminal
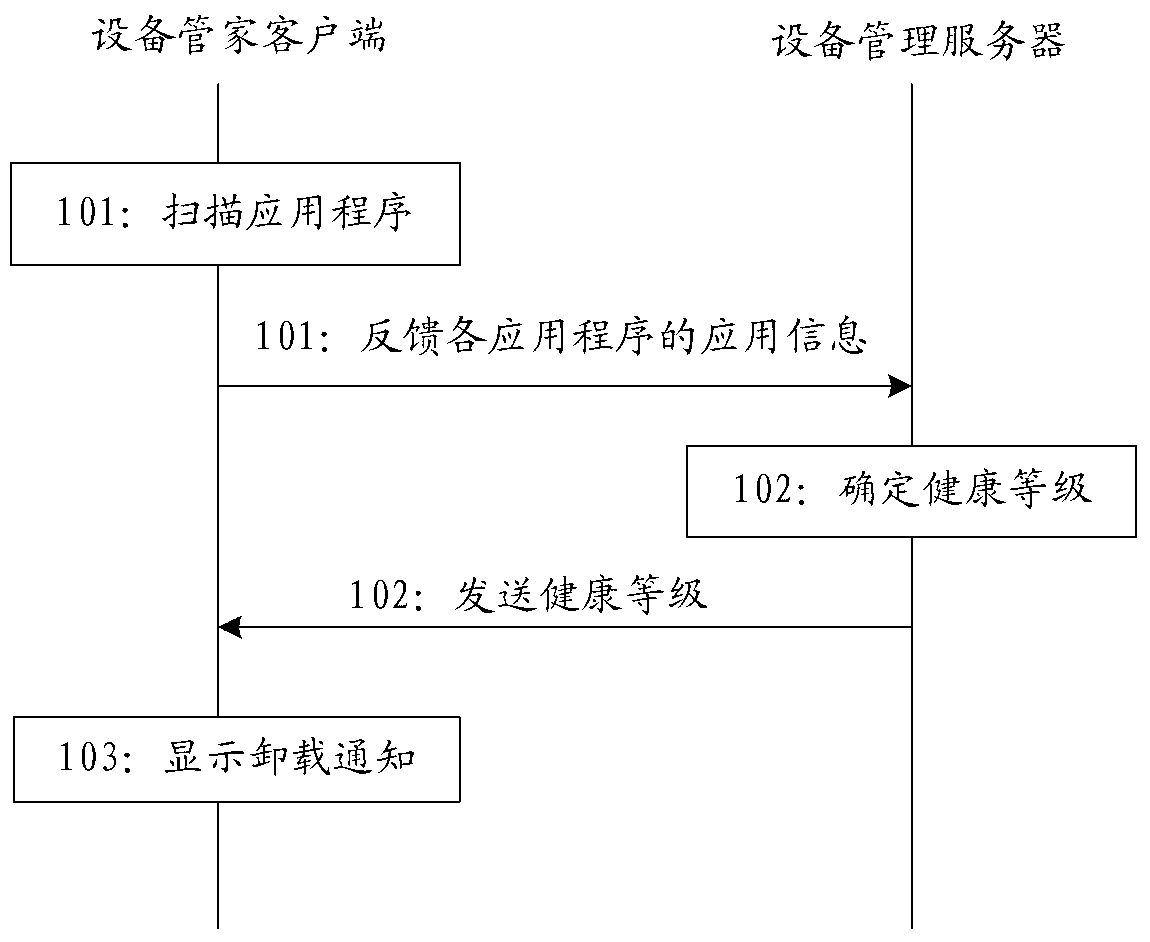
InactiveCN103269335AEnsure secure communicationReduce security risksTransmissionSecurity arrangementClient-sideApplication software
The invention discloses a method and system for compliance audit of a movable terminal. The method comprises the steps that application programs arranged on a terminal operation system are scanned by an equipment housekeeper client side, scanned application information of all the application programs are fed back to an equipment management server, and the equipment housekeeper client side is arranged on the movable terminal; the equipment management server confirms health levels of the application programs corresponding to the application information according to obtained application information, and sends the health levels to the equipment housekeeper client side; the equipment housekeeper client side displays or does not display unloading notices according to the received health levels to enable a user to unload the corresponding application programs according to the displayed unloading notices. The invention further discloses a system for compliance audit of the movable terminal.
Owner:FUJIAN ETIM INFORMATION & TECH
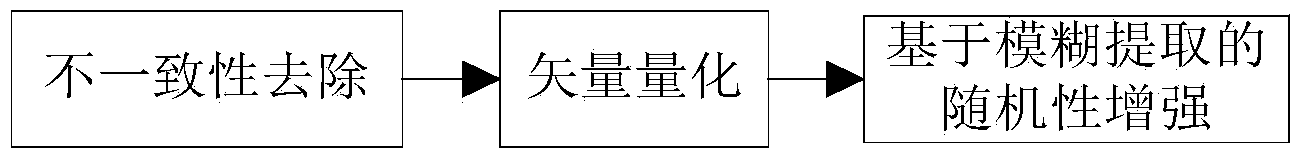
Efficient random physical layer secrete key generation method based on vector quantization
InactiveCN103825725AReliable generationGuaranteed stabilityKey distribution for secure communicationComputer hardwareGeneration rate
The invention discloses an efficient random physical layer secrete key generation method based on vector quantization. According to the method, a first wireless network communication party and a second wireless network communication party respectively and simultaneously detect RSS information of a wireless channel and transmit the information to each other, and the first wireless network communication party and the second wireless network communication party operate in the steps of inconsistent removal, vector quantization and fuzzy extraction and ultimately obtain identical bit streams to be used as encrypted secrete keys. The bit generation rate can reach 284%, and random bit streams can be quickly provided for authentication encrypted algorithms of the two communication parties in a wireless network environment to serve as the encrypted secrete keys; the zero error rate can be achieved through the two communication parties, it can be guaranteed that the two communication parties reliably generate the identical bit streams to be used as the encrypted secrete keys, and stability of the method in the operation process is guaranteed; the bit streams produced in the method can pass an NIST randomness test, the produced random bit streams can be used as the secrete keys, and safe communication of the two communication parties is guaranteed.
Owner:XIDIAN UNIV
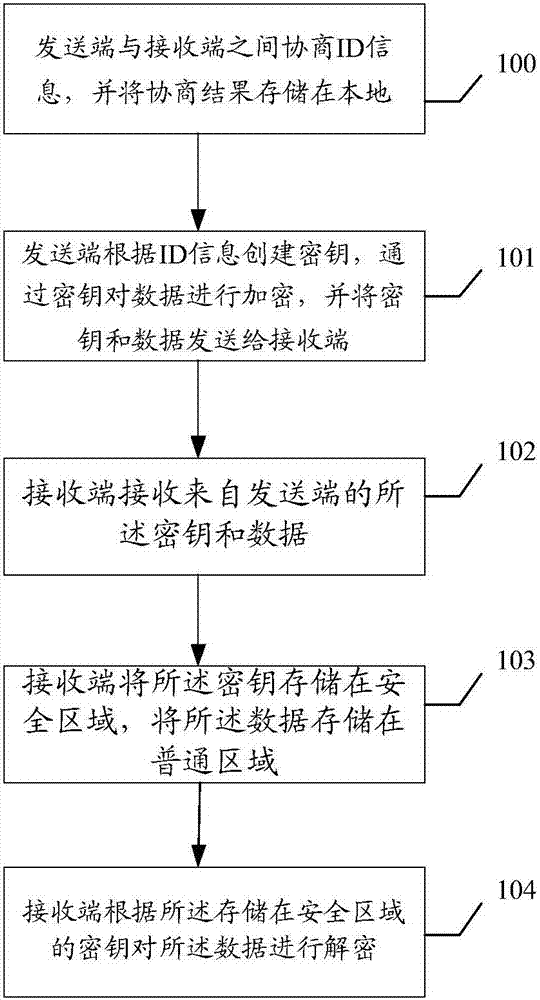
Method, apparatuses and system of encrypted communication
ActiveCN107306261AImplement differentiated encryptionImprove communication securityKey distribution for secure communicationData needsComputer terminal
This invention published a method of encrypted communication. The method comprises: a receiving terminal receives a secret key and data from a sending terminal, wherein the secret key is one that is established by the sending terminal based on ID information obtained by negotiation with the receiving terminal and the data are ones obtained by secret-key encryption by the sending terminal; the receiving terminal stores the secret key into a safety region and stores the data into a common region; and the receiving terminal decrypts the data based on the secret key. In addition, the invention also discloses a sending terminal apparatus and a receiving terminal apparatus for encrypted communication, and a system of encrypted communication. Therefore, only one pair of secret keys is set between one pair of terminals and only the two sides in communication are able to decrypt the communication data, so that differential encryption in communication is realized; only the two sides in communication are able to parse the secret key, so that no server needs to be erected; and during data decryption, only local data need to be read. The communication safety is high and the processing efficiency is improved.
Owner:ZTE CORP
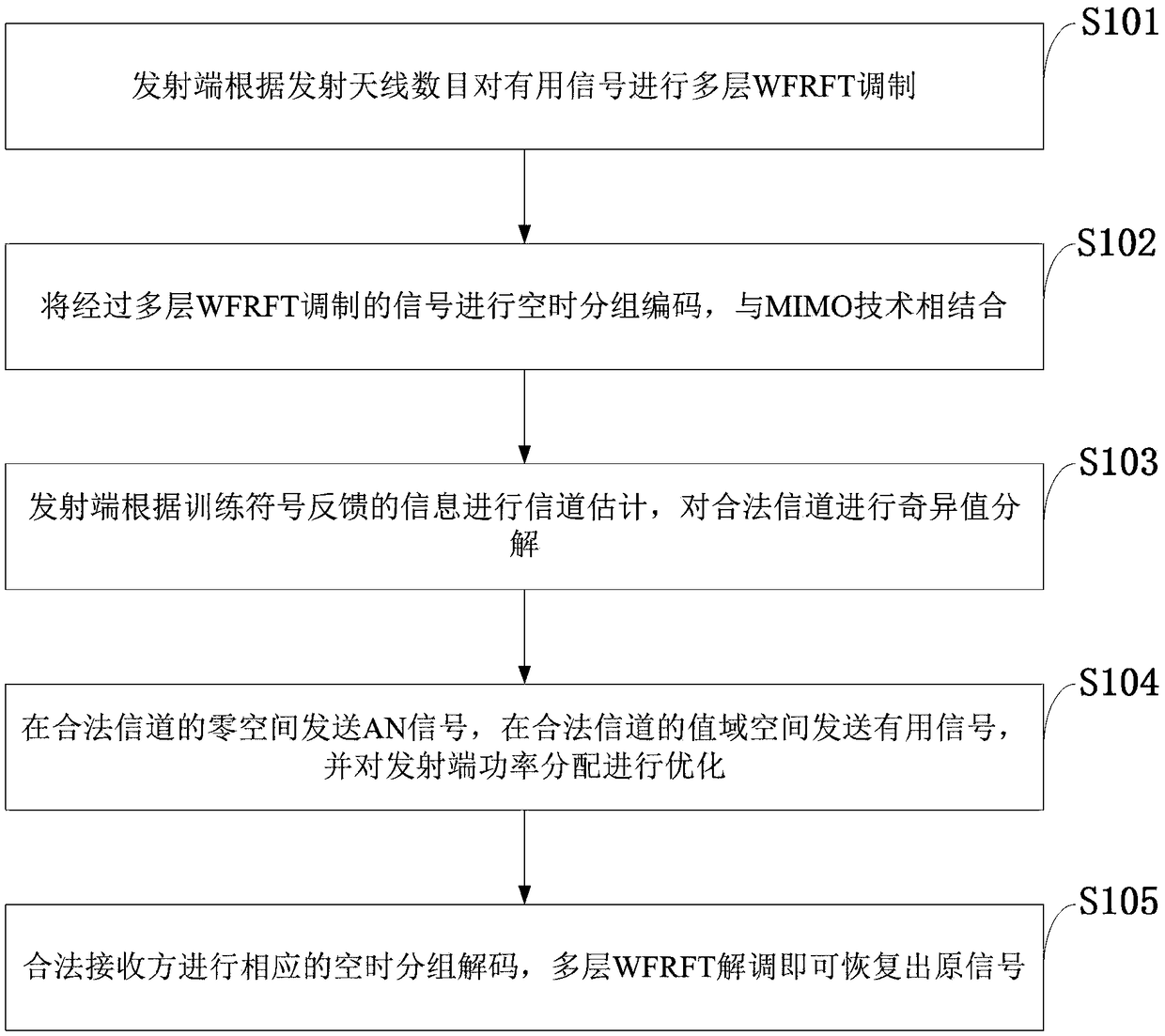
Satellite anti-parametric scanning communication method based on ML-WFRFT and AN assistance
InactiveCN109150368AImprove capacity utilizationImprove spectrum utilizationSecret communicationCommunication jammingEavesdroppingMultiple input
The invention, which belongs to the field of satellite communication technology, discloses a satellite anti-parametric scanning communication method based on multilayer weighted fractional fourier transform (ML-WFRFT) and artificial noise (AN) assistance. According to the method disclosed by the invention, an ML-WFRFT modulation signal is employed and the ML-WFRFT is combined with the AN assistance technology. On the basis of modification of the traditional WFRFT, the ML-WFRFT is put forward to modulate signals; and the ML-WFRFT is combined with the multiple input multiple output (MIMO) technology, so that the modulated signal has multiple modulation parameters and high encryption; and parameter scanning is carried out by suppressing the eavesdropping side and the ML-WFRFT is combined withthe AN assistance technology. Therefore, the receiving performance of the AN assistance technology is suppressed greatly while the communication requirement of the legal receiving side is met; and thus the signal can not be demodulated correctly basically.
Owner:达新宇
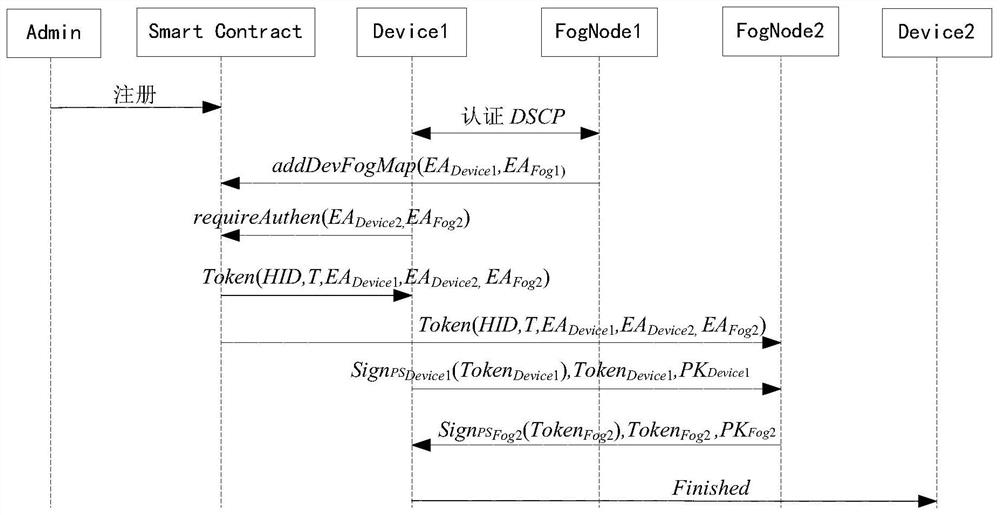
Internet of Things equipment identity security authentication method based on block chain and fog computing
ActiveCN113301022AGuaranteed to be trueEnsure secure communicationKey distribution for secure communicationResource allocationFog computingThe Internet
The invention discloses an Internet of Things equipment identity security authentication method based on a block chain and fog computing, and the method specifically comprises the steps that: an equipment manager generates a random key, writes the key into Internet of Things equipment, and transmits the key to a fog node close to the equipment; the fog node encrypts the random key and then sends the encrypted random key to the equipment manager; the equipment manager writes related information of the Internet of Things equipment into the block chain; the fog node queries the block chain through the serial number of the Internet of Things equipment to obtain related information of the Internet of Things equipment; the fog node verifies whether the serial number of the equipment stored in the block chain is the same as the serial number of the equipment itself through an equipment identity security protocol DSCP, the fog node authentication stage is completed, and then the fog node adds a mapping and equipment access validity period for the Internet of Things equipment; after the Internet of Things equipment completes registration and authentication, mutual authentication can be carried out between the equipment. According to the method, the blockchain and fog computing are utilized to help the Internet of Things to ensure the security of the equipment and realize mutual authentication between the equipment.
Owner:成都极略科技有限公司
Distributed unmanned aerial vehicle cluster network security communication implementation method
ActiveCN111884817AEnsure consistencyEnsure secure communicationUser identity/authority verificationHigh level techniquesSecure communicationUncrewed vehicle
The invention relates to the technical field of unmanned aerial vehicle cluster communication, and discloses a distributed unmanned aerial vehicle cluster network security communication implementationmethod, which is small in information flux and high in maneuverability through autonomous decision making of cooperative unmanned aerial vehicles in a dis The cooperative UAVs establish communicationwith other cooperative UAVs after being authenticated by an authentication mechanism, send action tasks or formation aggregation requests to other cooperative UAVs, obtain replies of half or more accepted tasks, approve the action requests, and take the cooperative UAVs which do not participate in decision making and do not accept the action requests as learners, And learning from any cooperativeunmanned aerial vehicle receiving the action request to achieve a consistent task request or formation aggregation request, so that all cooperative unmanned aerial vehicles in the unmanned aerial vehicle cluster perform a target task in a formation manner, the consistency of the unmanned aerial vehicle cluster is ensured, and meanwhile, the secure communication among the unmanned aerial vehiclescan be ensured. Hackers are effectively prevented from invading the unmanned aerial vehicle cluster to change the target task of the unmanned aerial vehicle cluster.
Owner:CHONGQING JIAOTONG UNIVERSITY
Safe communication method and system based on voice packets
The invention provides a safe communication method and a safe communication system based on voice packets. The method comprises the following steps that: a transmitting end packages RTP (Real-time Transport Protocol) data packets according to a preset packaging strategy, and sending the packaged RTP data packets to a receiving end; the receiving end processes according to a preset safety strategy after receiving the packaged RTP data packets. According to the safe communication method and system based on the voice packets, the voice data packets are simply packaged without influencing the usage of users; the safe communication method and system based on the voice packets are strong in operability and much safer and more reliable.
Owner:上海浪潮云计算服务有限公司
Method and system for establishing enhanced key when terminal moves to enhanced universal terminal radio access network (UTRAN)
ActiveUS8712054B2Save overheadImprove system efficiencyKey distribution for secure communicationSecret communicationComputer networkRadio access network
The present invention discloses a method and system for establishing an enhanced key when a terminal moves from an EUTRAN to an enhanced UTRAN, so as to ensure that the terminal can carry out normal communication safely in the enhanced UTRAN. The method includes: when the terminal moves from the EUTRAN to the enhanced UTRAN, a target enhanced serving GPRS support node (SGSN+) in the enhanced UTRAN deducing an intermediate key used in the UTRAN according to a mapped traditional key obtained from a source mobile management entity; and the terminal, after deducing the mapped traditional key, further deduces the intermediate key used in the enhanced UTRAN by using an algorithm which is the same as that of the target SGSN+ according to the mapped traditional key.
Owner:ZTE CORP
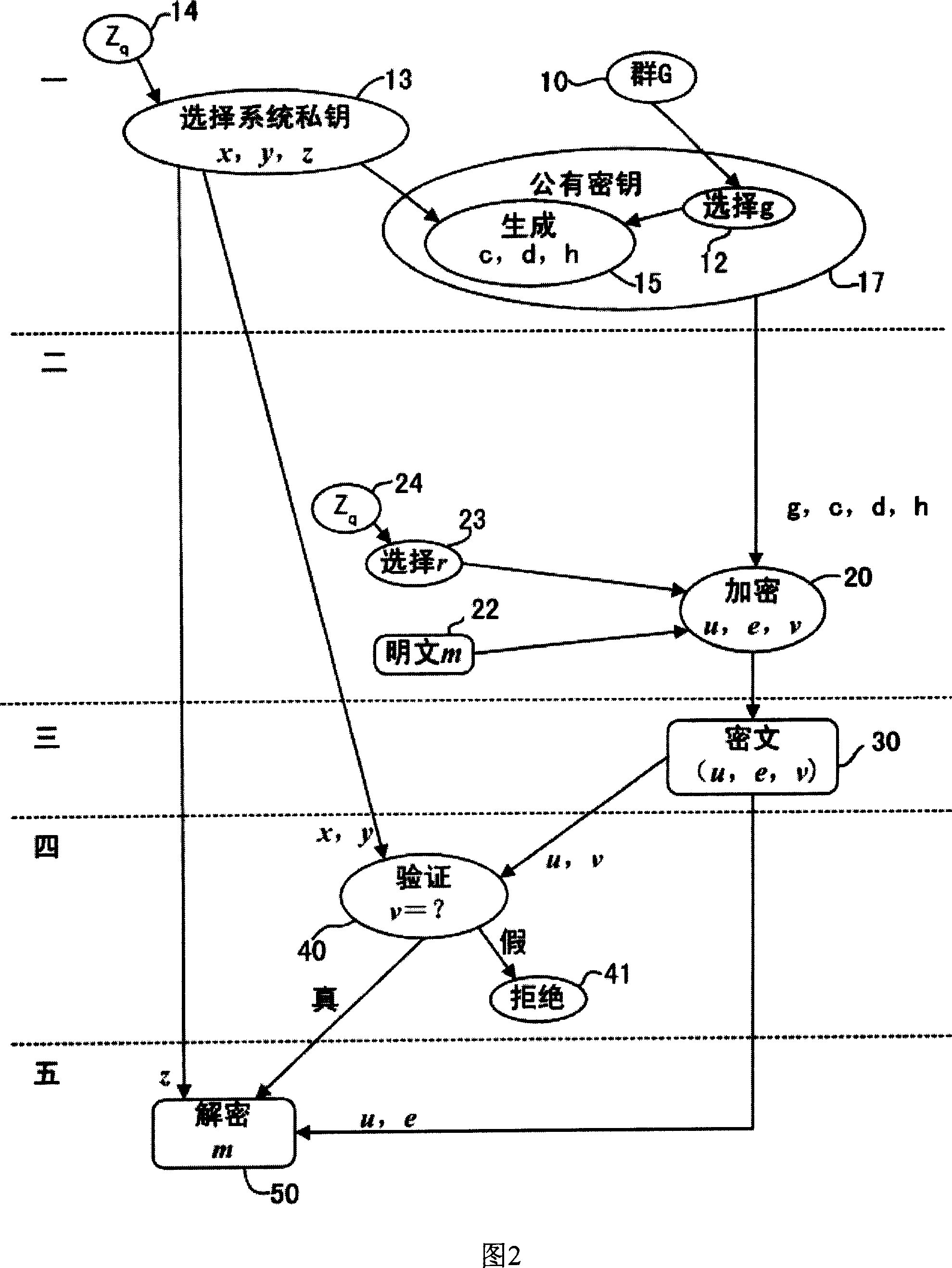
Practical unexposed public key encrypting system
InactiveCN1925390AEnsure secure communicationSecurity against ciphertext attacksKey distribution for secure communicationPublic key for secure communicationPlaintextKey exchange
This invention relates to public key codes system against lunch time attack and adaptive selection message attack without leaking any private keys or message information. In the invention message is converted into coded message with accurate keys for decoding, if message is legal, then decoding message and if message is not legal then denying; if legal message is non artificial based on standard hypoesthesia to compute Diffie-Hellman problem or double Diffie-Hellman difficulty and Hush function non collision.
Owner:胡玉莲
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com