Practical unexposed public key encrypting system
A public key encryption and non-extensible technology, which is applied to the public key and key distribution of secure communication, can solve the problems of unproven security, insecurity, impracticality, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
[0200] When there is only one trusted center, the proposed identity-based public key cryptosystem is used for secure communication, assuming that user B sends information m to user A. Then B first encrypts m with A's public key, and sends the encrypted ciphertext to A. After A obtains the ciphertext, he recovers m with his own private key. Specific steps are as follows:
[0201] The first part trusted center establishes system parameters:
[0202] (a) Generate the first cyclic group G 1 and the second cyclic group G 2 , where G 1 is an additive group of points on a supersingular elliptic curve or Abelian variety, G 2 is a multiplicative group of finite fields;
[0203] (b) Pick a feasible pairing e: G 1 ×G 1 →G 2 , which can be formed by the first cyclic group G 1 The two elements of generate the second cyclic group G 2 an element of
[0204] (c) Randomly choose a generator P∈G 1 ;
[0205] (d) randomly select x, y, z∈Z q , calculate P 1 =xP,P 2 =yP,P 3 = zP;...
specific Embodiment approach 2
[0230] When there are n trusted centers, where n≥2, and the proposed identity-based public key cryptosystem is used for secure communication, it is assumed that user B sends information m to user A. Then B first encrypts m with A's public key, and sends the encrypted ciphertext to A. After A obtains the ciphertext, he recovers m with his own private key. Specific steps are as follows:
[0231] The first part n trusted centers establish system parameters:
[0232] (a) Generate the first cyclic group G 1 and the second cyclic group G 2 , where G 1 is an additive group of points on a supersingular elliptic curve or Abelian variety, G 2 is a multiplicative group of finite fields;
[0233] (b) Pick a feasible pairing e: G 1 ×G 1 →G 2 , which can be formed by the first cyclic group G 1 The two elements of generate the second cyclic group G 2 an element of
[0234] (c) Randomly choose a generator P∈G 1 ;
[0235] (d) Randomly pick x i ,y i ,z i ∈ Z q , calculate P ...
specific Embodiment approach 3
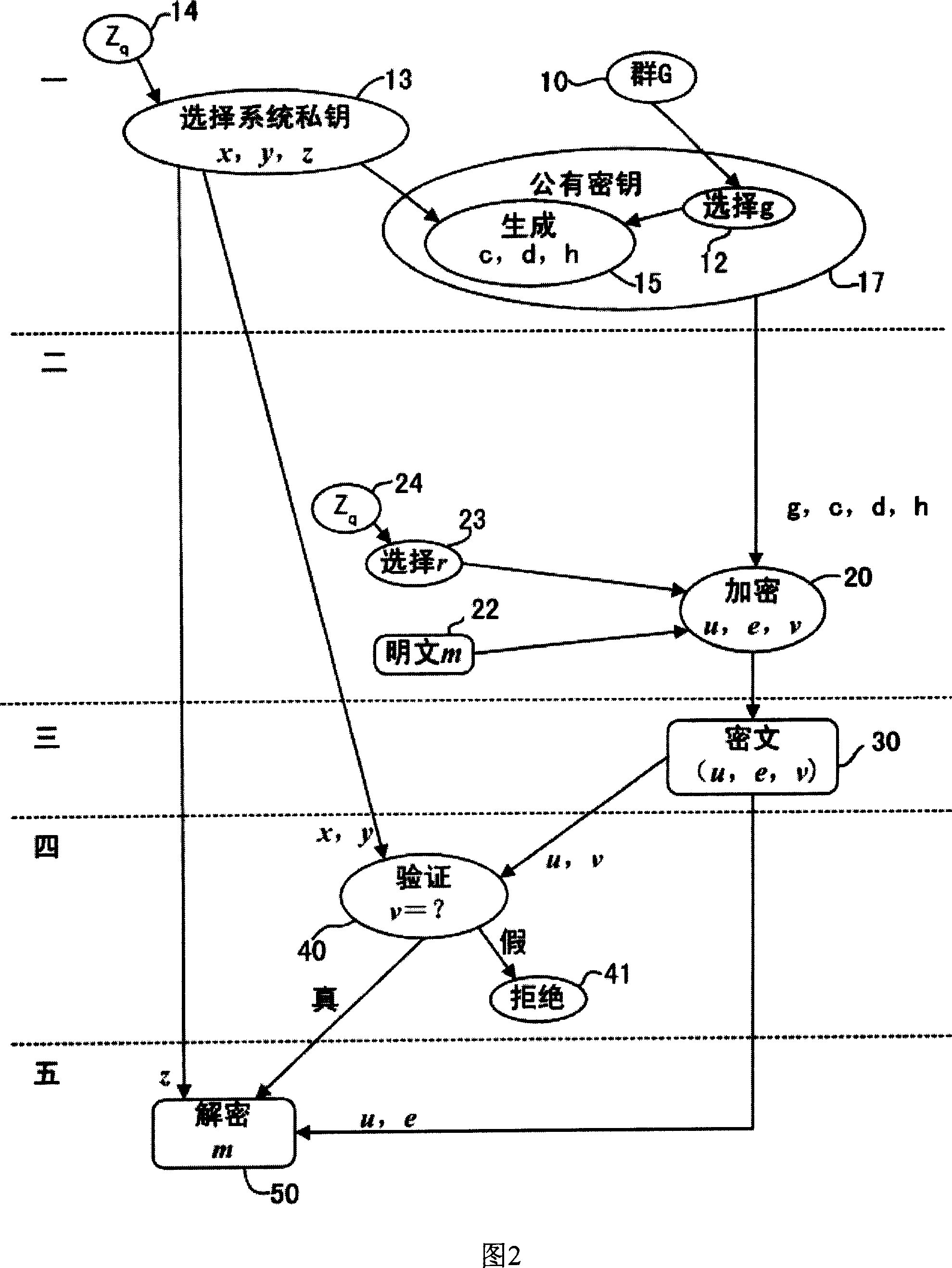
[0268] When the proposed general public key cryptosystem is used for secure communication, it is assumed that user A sends information m to user B. A encrypts m with B's public key, and sends the encrypted ciphertext to B. After B obtains the ciphertext, he recovers m with his own private key. Specific steps are as follows:
[0269] The first part generates a key pair:
[0270] Establish a cyclic group G of order q with a large prime number.
[0271] User B chooses a primitive g in the cipher group G, and in Z q Randomly select the first index x, the second index y and the third index z, and reserve (x, y, z) as the private key; use the following formula to calculate the first group element c, the second group element element d, the third group element h:
[0272] c=g x ,
[0273] d=g y ,
[0274] h=g z ,
[0275] Use (g, c, d, h) as the public key and make it public;
[0276] The second part is encrypted:
[0277] User A obtains user B's public key (g, c, d, h) f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com