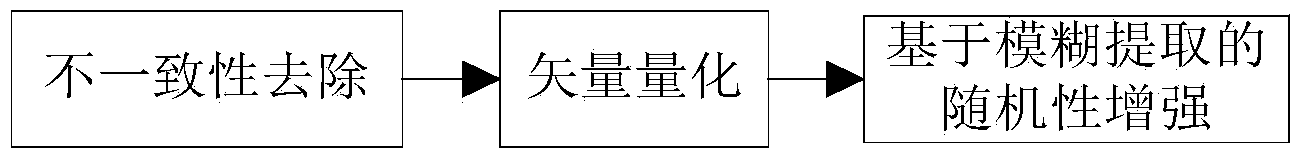
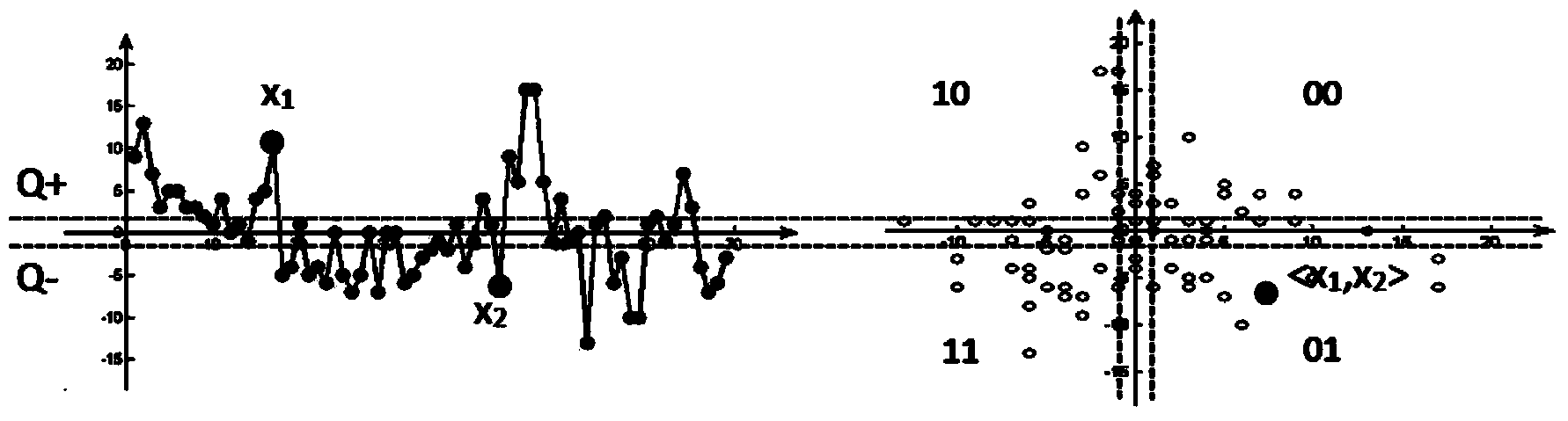
Efficient random physical layer secrete key generation method based on vector quantization
A technology of vector quantization and generation method, which is applied in the field of security keys of cryptographic algorithms, and can solve the problems of low bit error rate, inability to meet high bit generation rate at the same time, and mathematical difficulties of security systems.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0080] In this example, Alice and Bob, the communication parties, run on two PCs respectively, both of which are equipped with ubuntu12.04 operating systems, and both use the same model of network card Atheros TL-WN650G, driven by Madwifi, and work in 802.11g mode Send and receive packets. In this implementation process, we modified Madwifi and added a reply to the beacon frame. The beacon_ack frame carries the same serial number as the beacon frame. Through the matching of the serial numbers, the two parties in communication can complete the RSS pairing. The length of the beacon_ack is 49 bytes. Bob moves back and forth around Alice and sends beacon frames to Alice at intervals of 100ms. After receiving the beacon frame, Alice will record the serial number and the corresponding RSS value, and immediately send a beacon_ack confirmation frame to Bob. After Bob receives the confirmation frame, he also records the serial number and the corresponding RSS value. In this embodimen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com