Method, device and system for processing attack data packages
A processing method and data packet technology, applied in the field of communication, can solve problems such as occupying large network bandwidth and affecting data packet transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0098] The embodiment of the present invention provides a method for processing attack data packets, such as figure 2 As shown, the method can include:
[0099] S101. The management node receives the description information of the attack data packet sent by the sensing node and the attack type of the attack data packet.
[0100] Among them, the attack data packet can be understood as a data packet that threatens the sensing node, such as a data packet with a malformed message, a data packet with abnormal message fragmentation, and transmission control protocol (English: transmission control protocol, abbreviation: TCP) is invalid Connected data packets, data packets with excessive data volume, etc.
[0101] Optionally, the description information of the attack data packet may be information obtained by the sensing node from the header of the attack data packet, and specifically may be the source IP address of the attack data packet, the destination IP address of the attack data pack...
Embodiment 2
[0147] The embodiment of the present invention provides a method for processing attack data packets, such as Image 6 As shown, the method can include:
[0148] S401. The sensing node receives a data packet.
[0149] S402. The sensing node recognizes that the data packet is an attack data packet.
[0150] S403. The sensing node determines the description information of the attack data packet and the attack type of the attack data packet.
[0151] S404: The sensing node sends the description information and the attack type to the management node.
[0152] Specifically, for the specific implementation of S401-S404 above, please refer to Figure 5 The related description in the shown embodiment will not be repeated here.
[0153] S405. After receiving the description information and the attack type sent by the sensing node, the management node determines a processing strategy for the attack data packet with the attack type according to the attack type.
[0154] S406: The management node send...
Embodiment 3
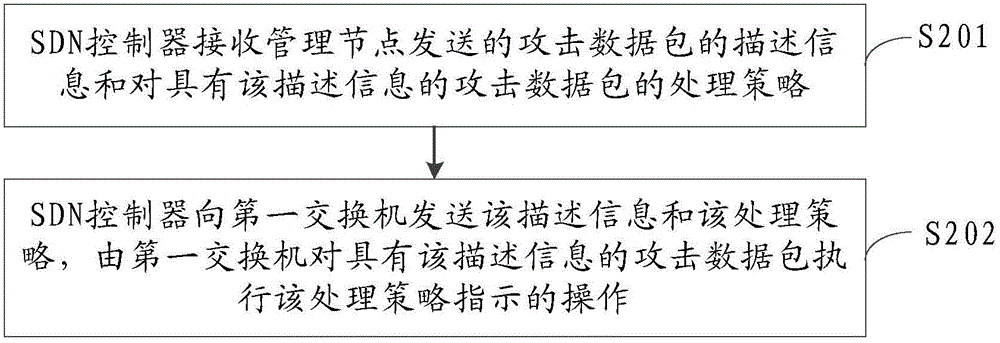
[0177] Such as Picture 11 As shown, the embodiment of the present invention provides a management node, and the management node may include:
[0178] The receiving unit 10 is configured to receive the description information of the attack data packet and the attack type of the attack data packet sent by the sensing node.
[0179] The determining unit 11 is configured to determine, according to the attack type received by the receiving unit 10, a processing strategy for the attack data packet with the attack type, and the processing strategy is used to instruct the switch to attack the attack with the description information The data packet performs the operation indicated by the processing strategy.
[0180] The sending unit 12 is configured to send the description information received by the receiving unit 10 and the processing strategy determined by the determining unit 11 to the switch via a software-defined network SDN controller, and the switch will perform The attack data pac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com