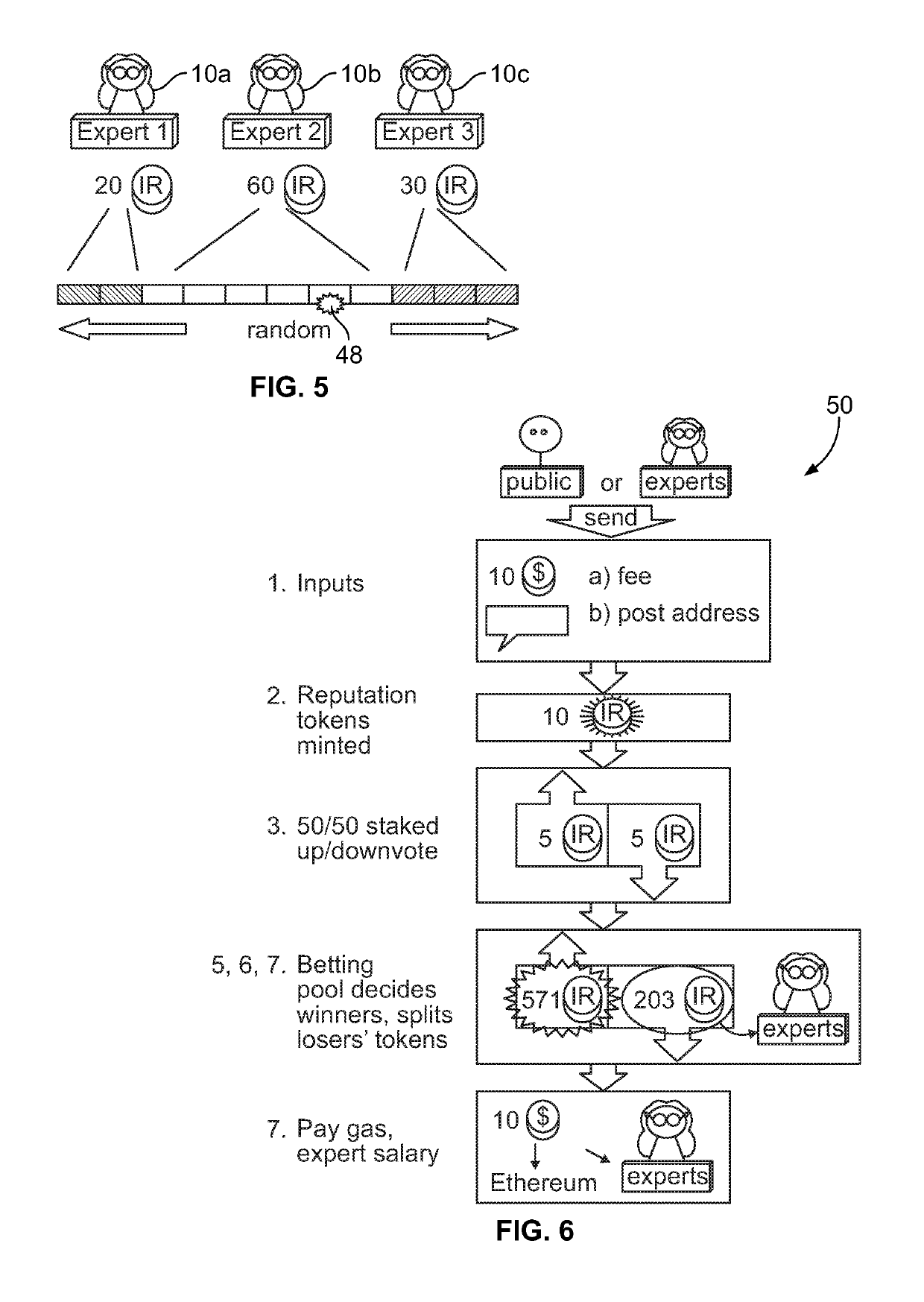
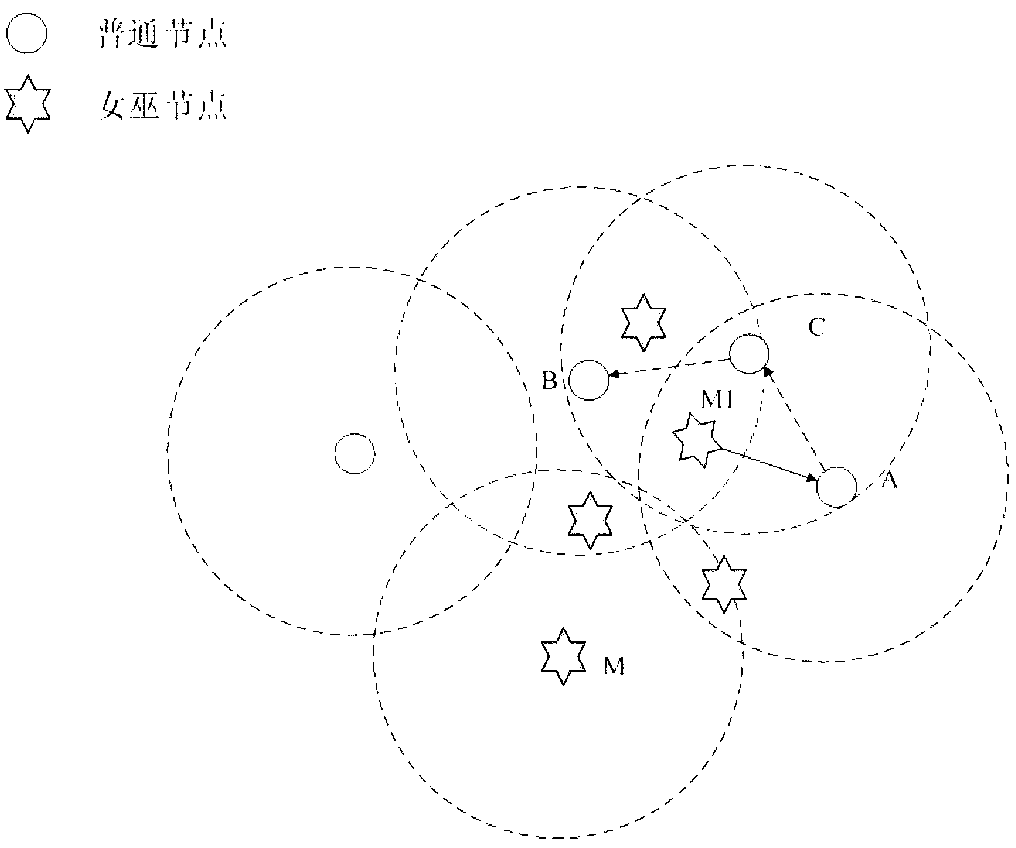
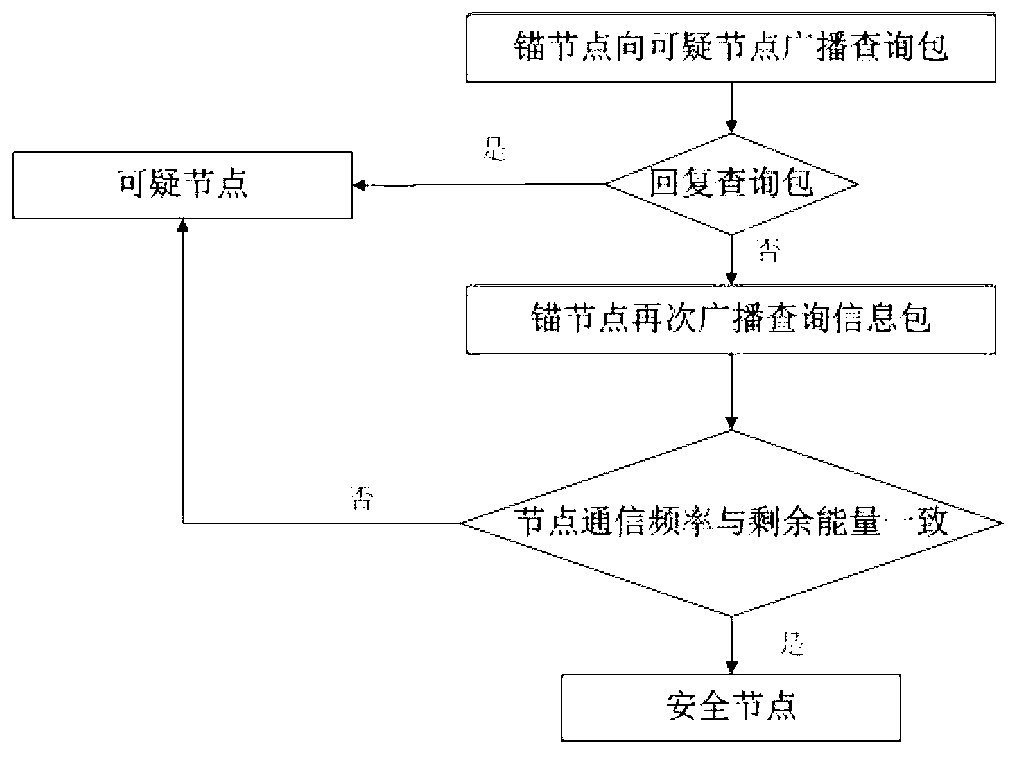
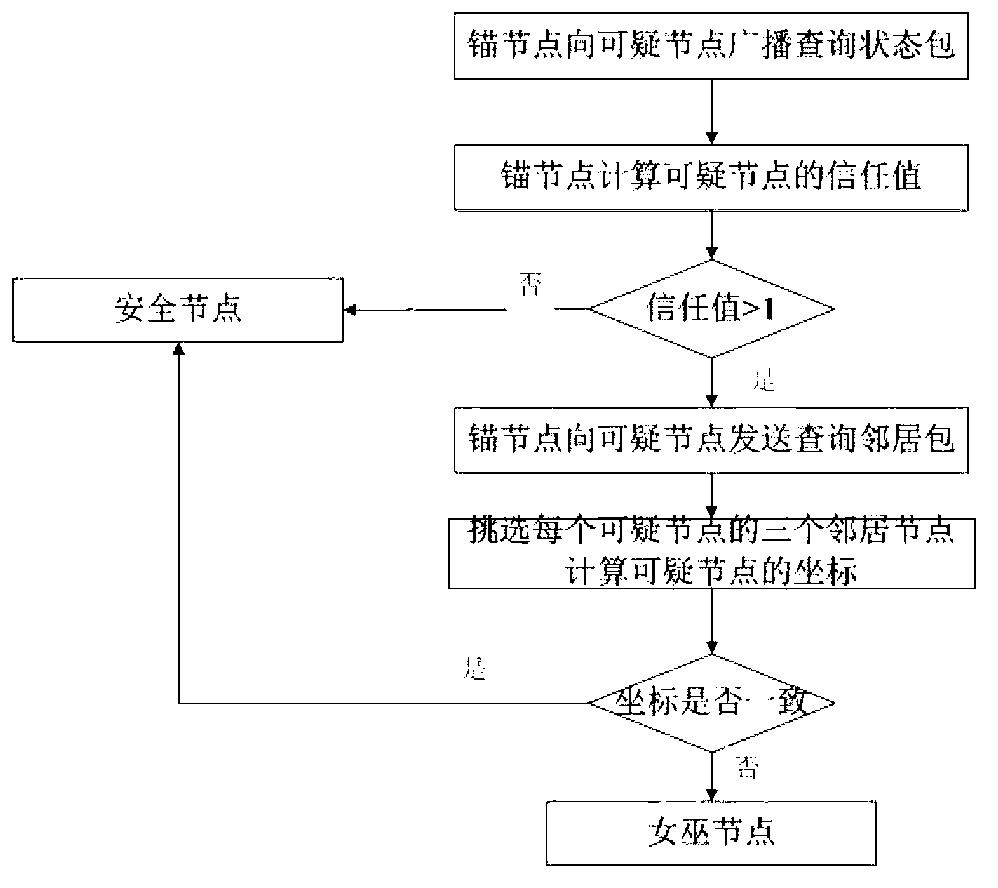
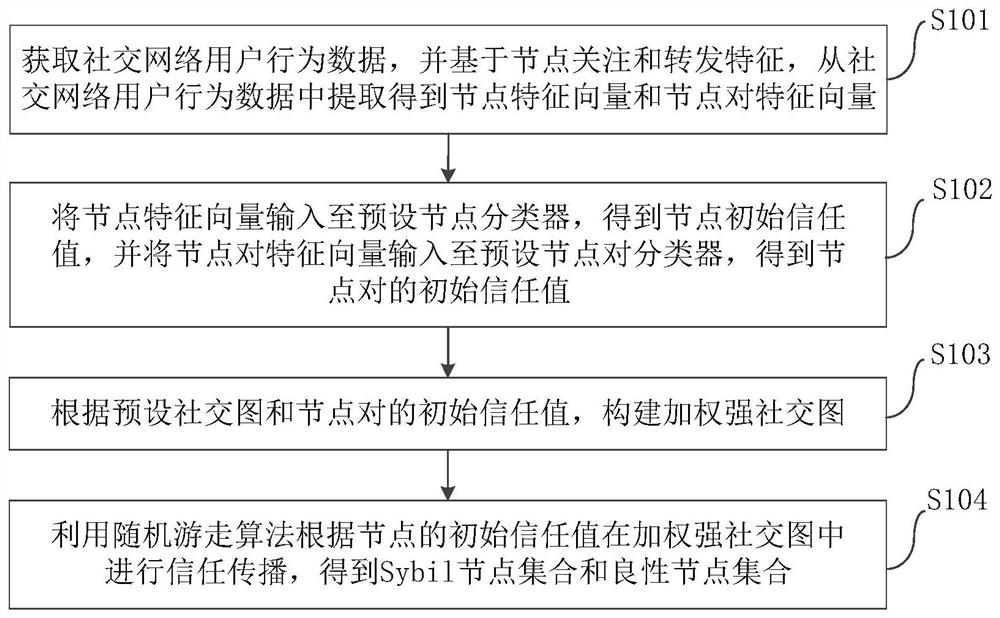
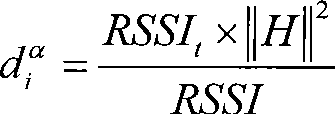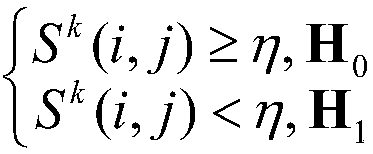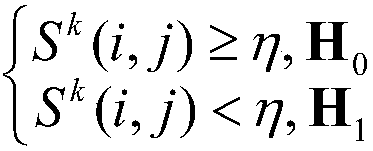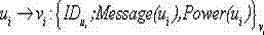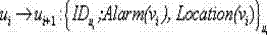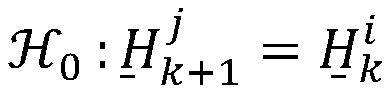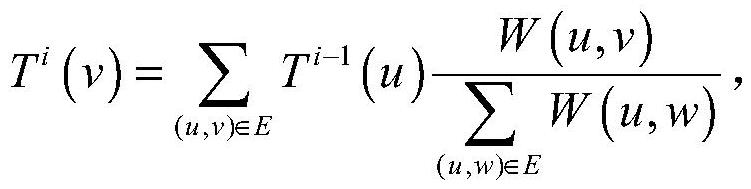Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
72 results about "Sybil attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
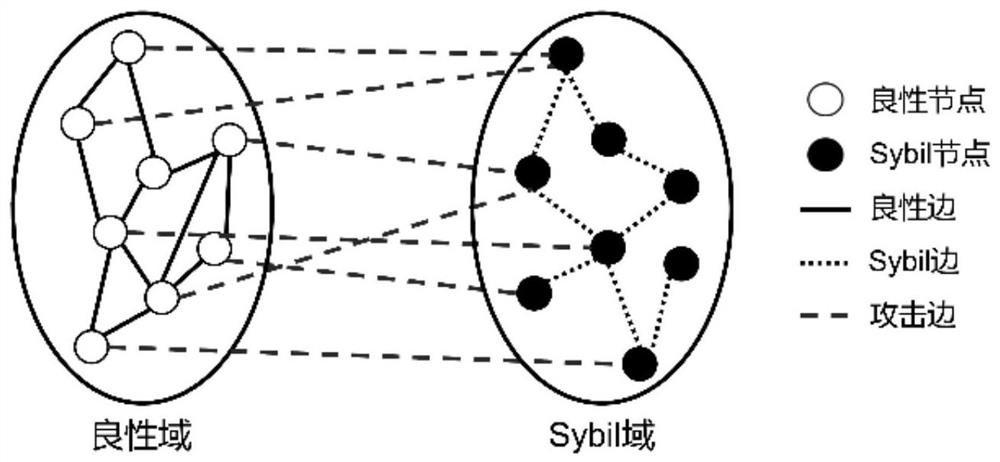
In a Sybil attack, the attacker subverts the reputation system of a peer-to-peer network by creating a large number of pseudonymous identities and uses them to gain a disproportionately large influence. It is named after the subject of the book Sybil, a case study of a woman diagnosed with dissociative identity disorder. The name was suggested in or before 2002 by Brian Zill at Microsoft Research. The term pseudospoofing had previously been coined by L. Detweiler on the Cypherpunks mailing list and used in the literature on peer-to-peer systems for the same class of attacks prior to 2002, but this term did not gain as much influence as "Sybil attack".
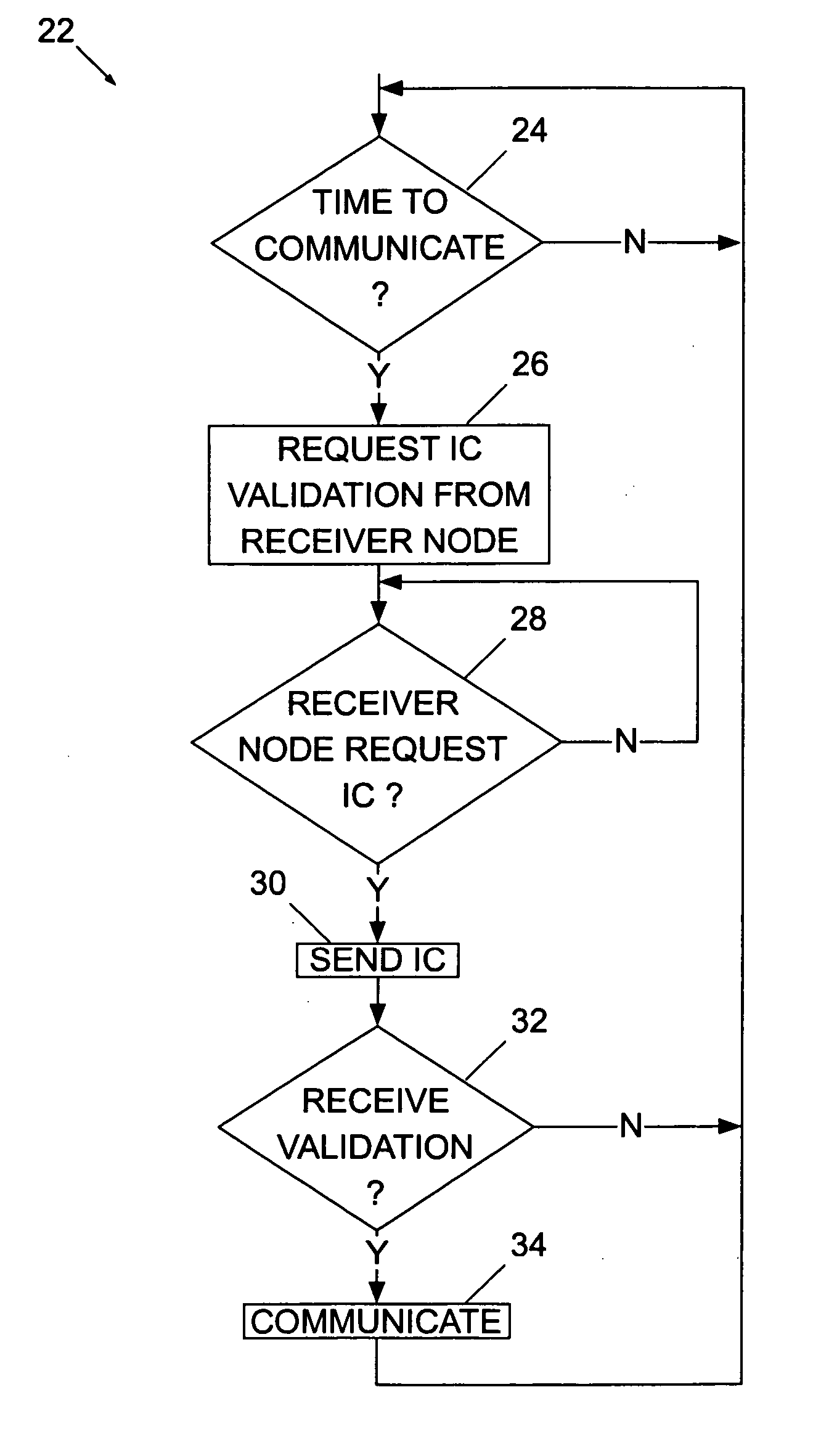
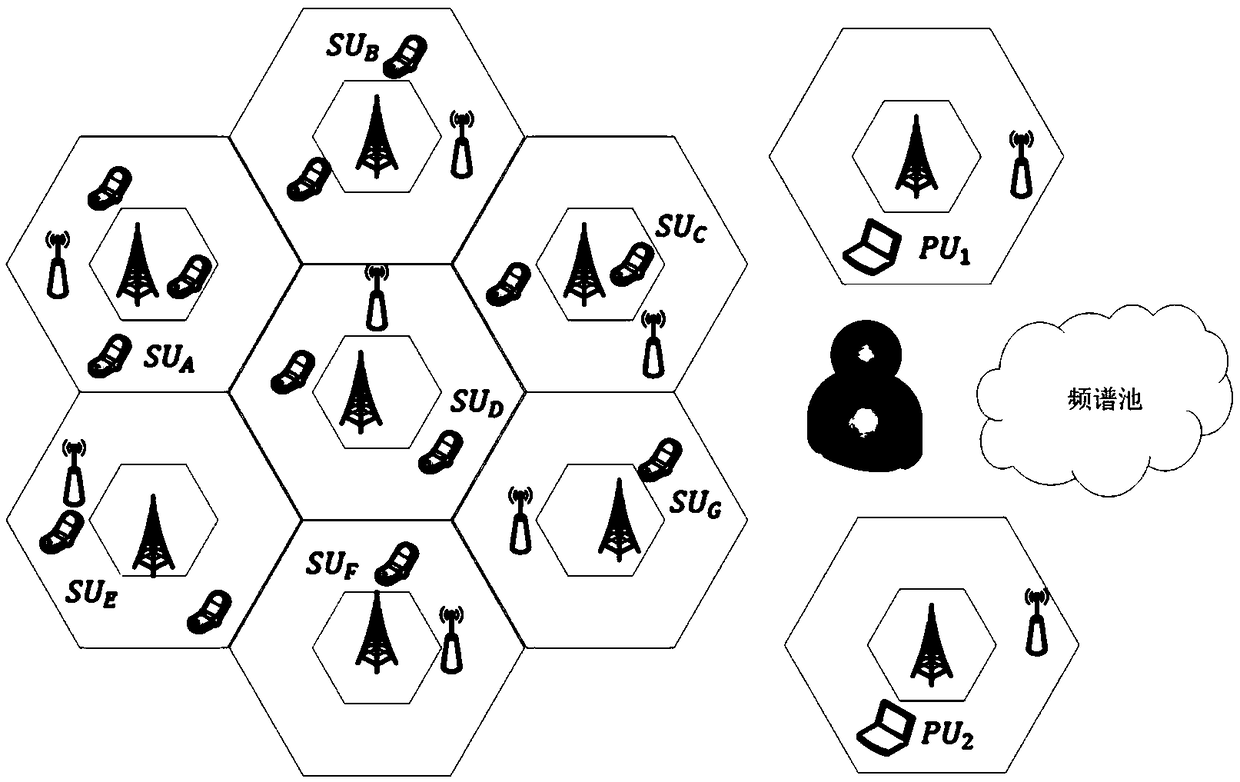
Defending against sybil attacks in sensor networks
A node B of a communication network receives a partial certificate from each of a plurality of nodes Ai in the communication network, constructs an identity certificate based on the partial certificates received from the nodes Ai, and transmits only a relevant part of the identity certificate to any requesting node C in order to get its authenticity verified by the node c.
Owner:HONEYWELL INT INC
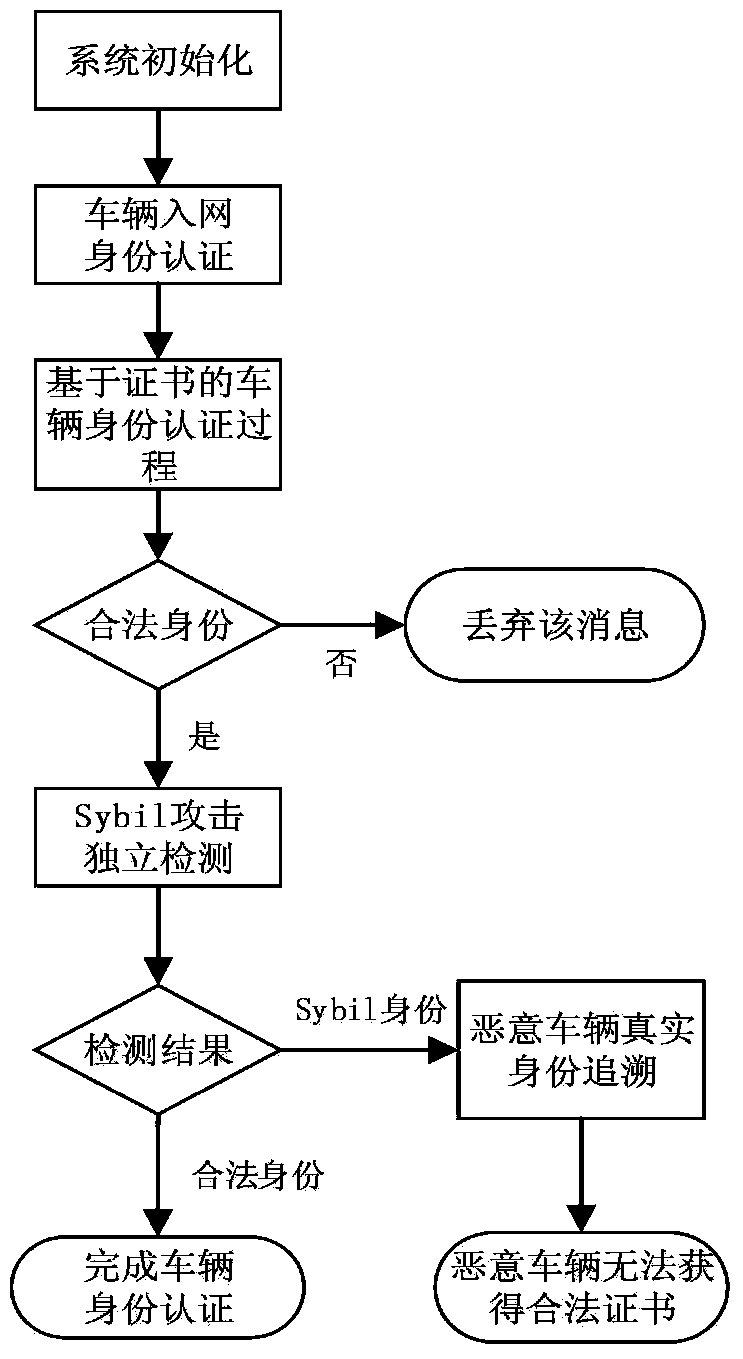
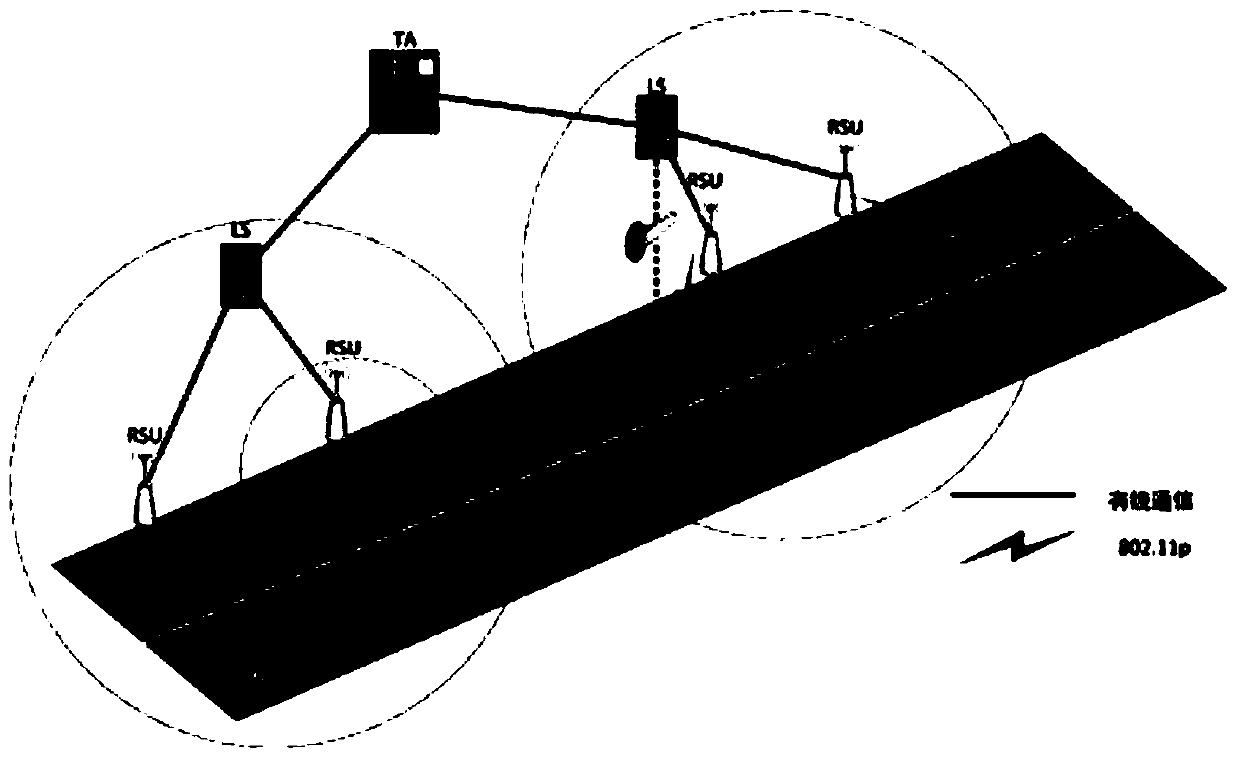
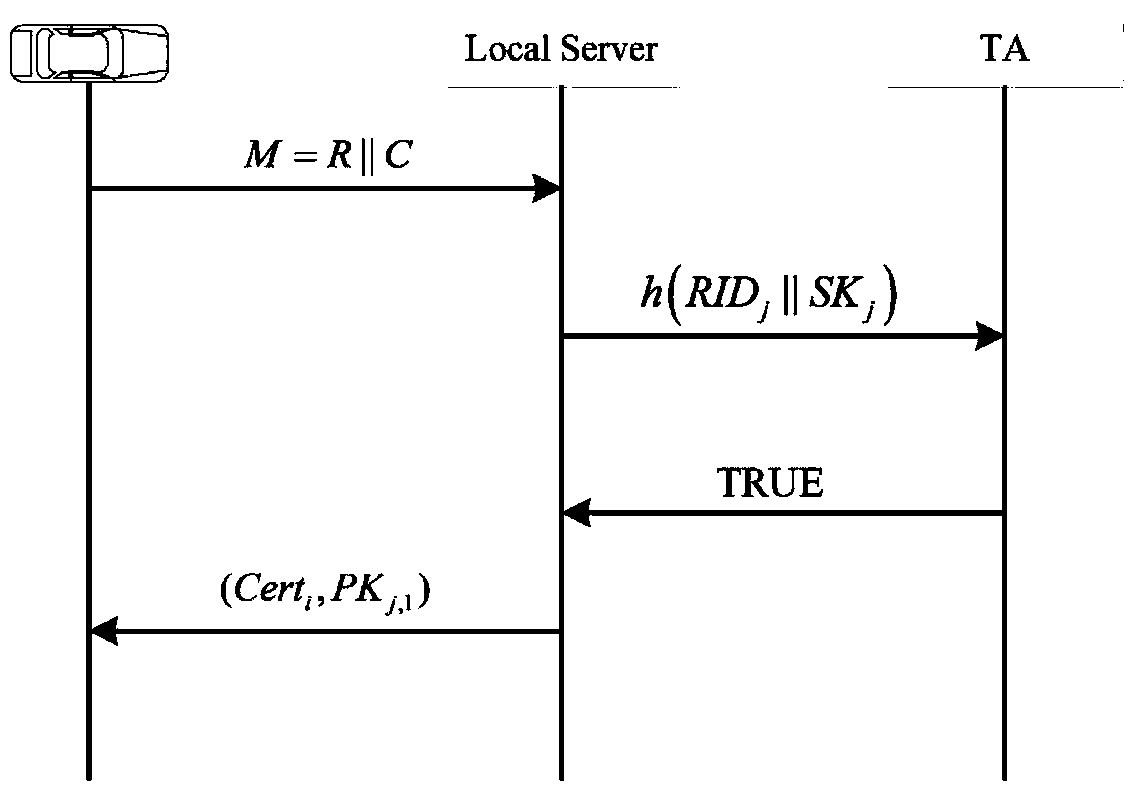
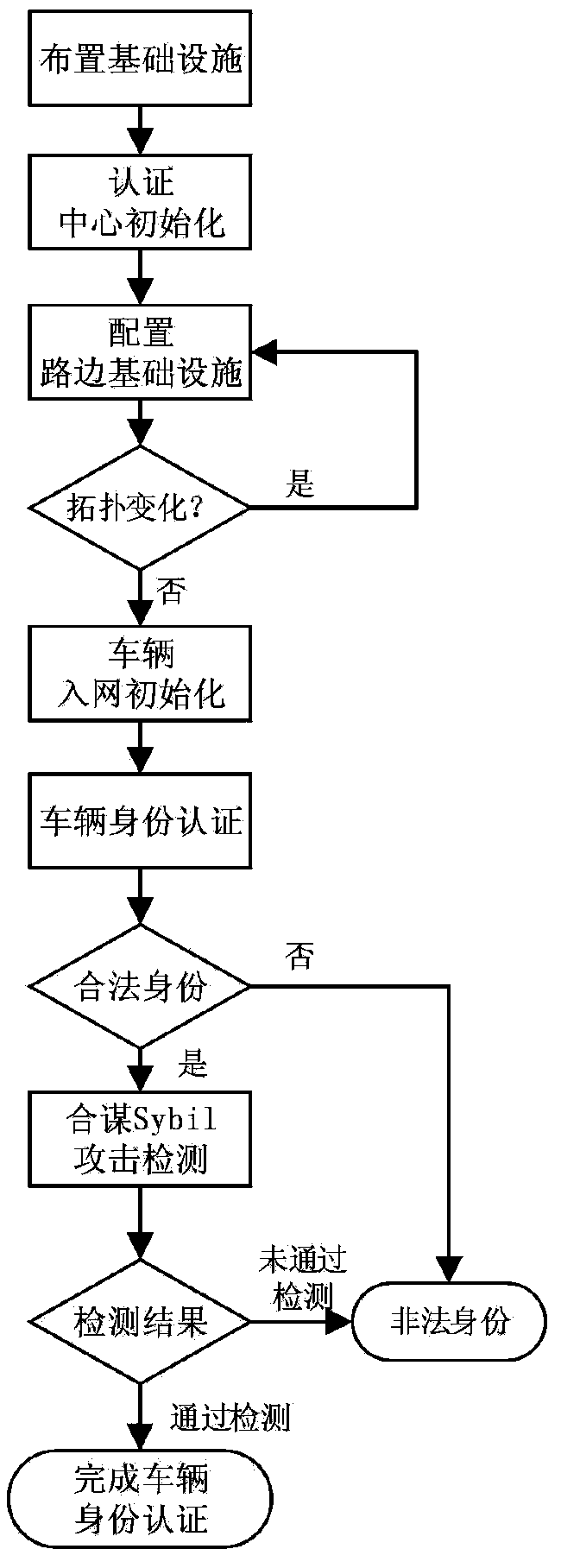
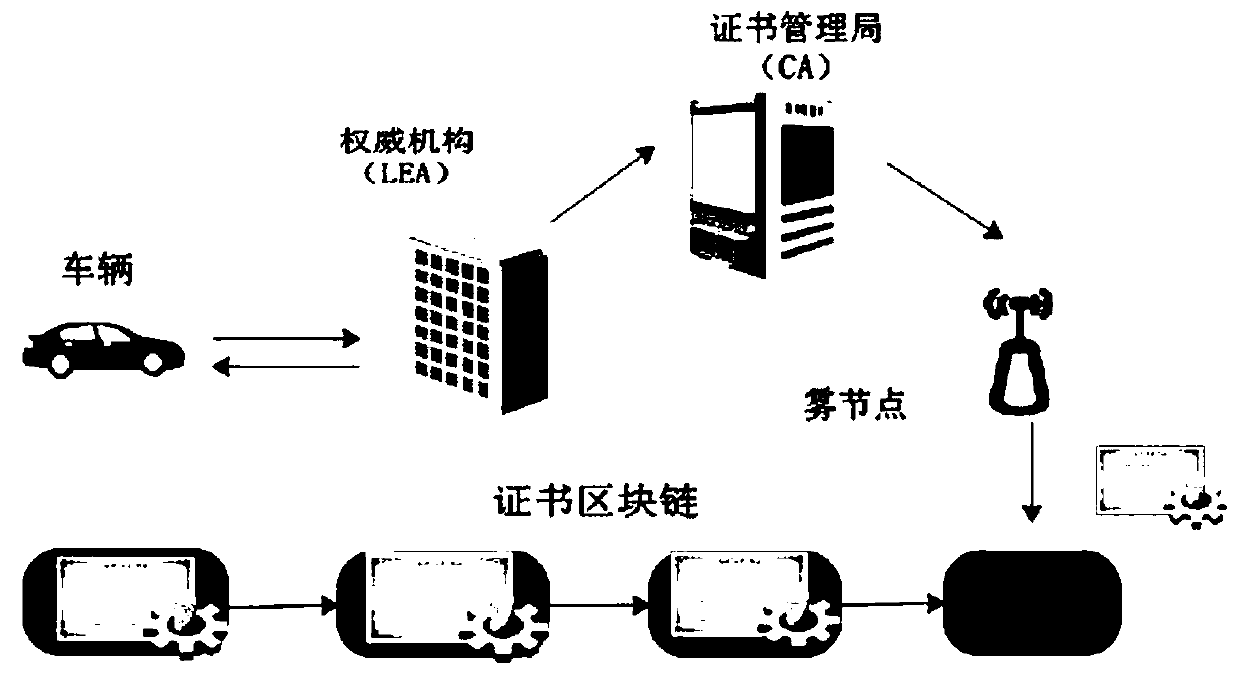
Certificate-based vehicle identification method for use in internet of vehicles
ActiveCN104219309APrevent further attacksUser identity/authority verificationThe InternetPrivacy protection
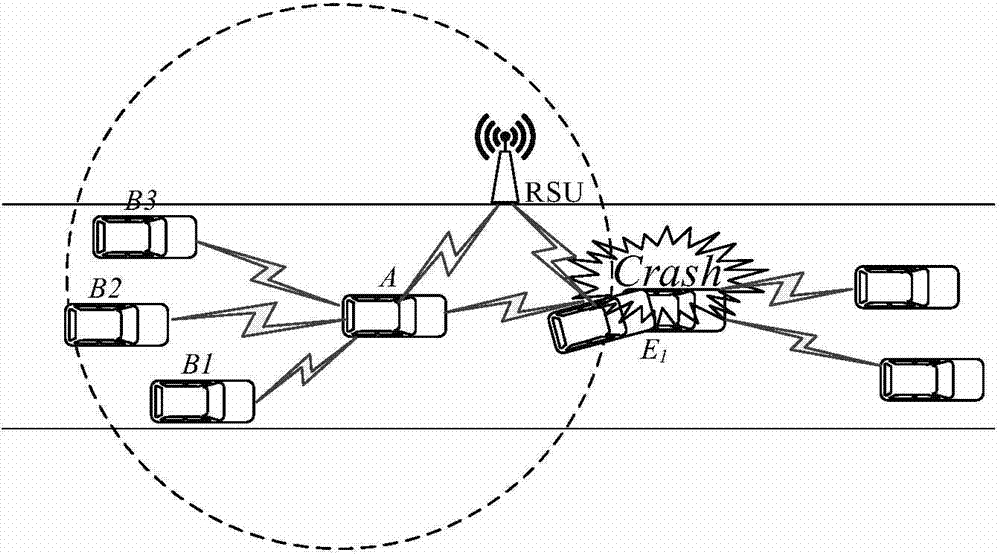
The invention relates to a certificate-based vehicle identification method for use in an internet of vehicles. The method is characterized in that a vehicle is independently identified with a time-limited certificate which is issued by a region server and replacing the true identity of the vehicle; the vehicle detects a malicious vehicle identity and transmits it to the region server; after receiving the malicious vehicle identity and its signature, the region server traces region registration information of the true identity and transmits the region registration information to a certification center; the certification center confirms the true identity of the vehicle and revokes the identity. The method has the advantages that the problem that the failure of the vehicle to independently finish the identification process by the existing Sybil attack detection method causes attack detection delay is solved; extra space and computation overhead caused by revoking of the vehicle identity are avoided; independent vehicle identification and privacy protection are achieved; the true identity of each malicious vehicle can be traced so that re-attacks of the malicious vehicles are prevented.
Owner:JIANGSU UNIV
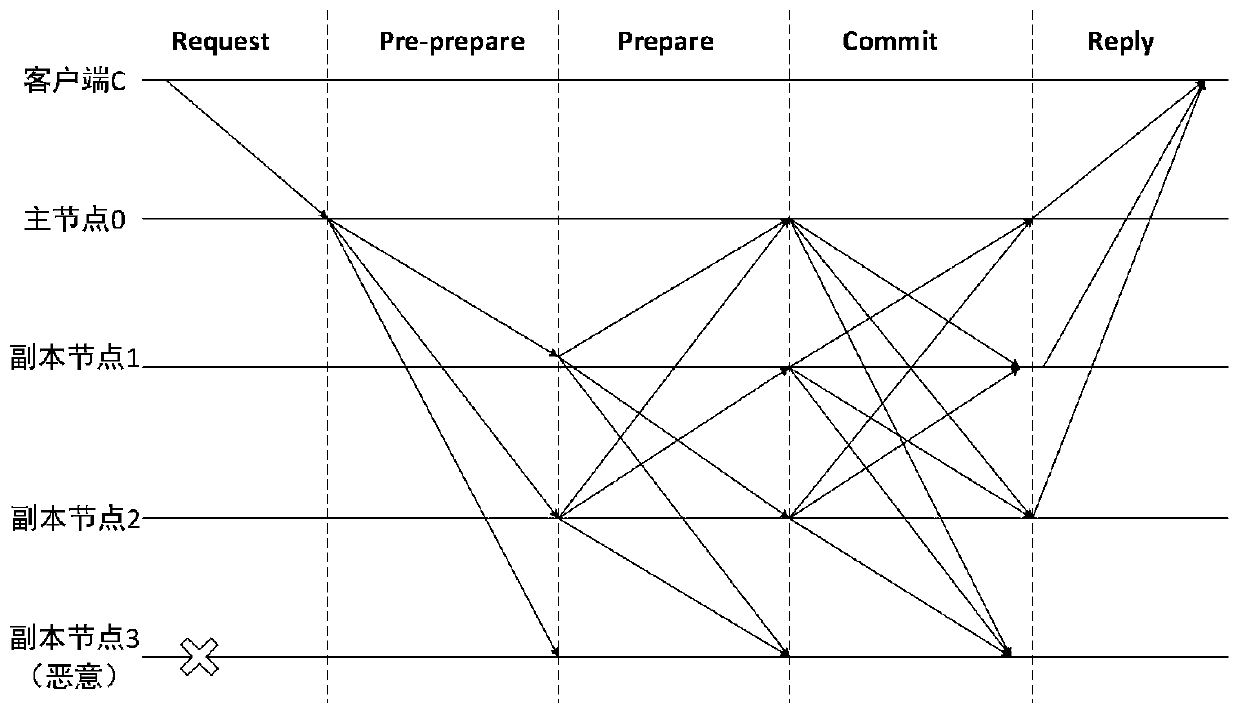
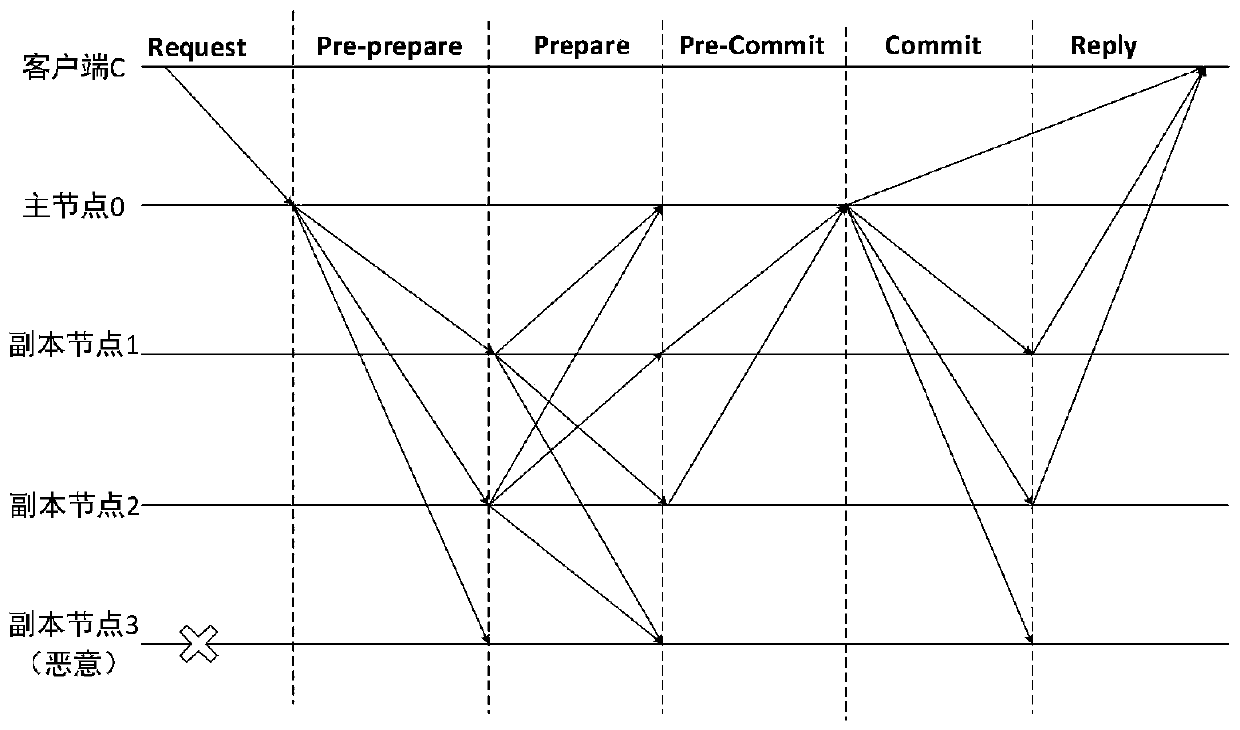
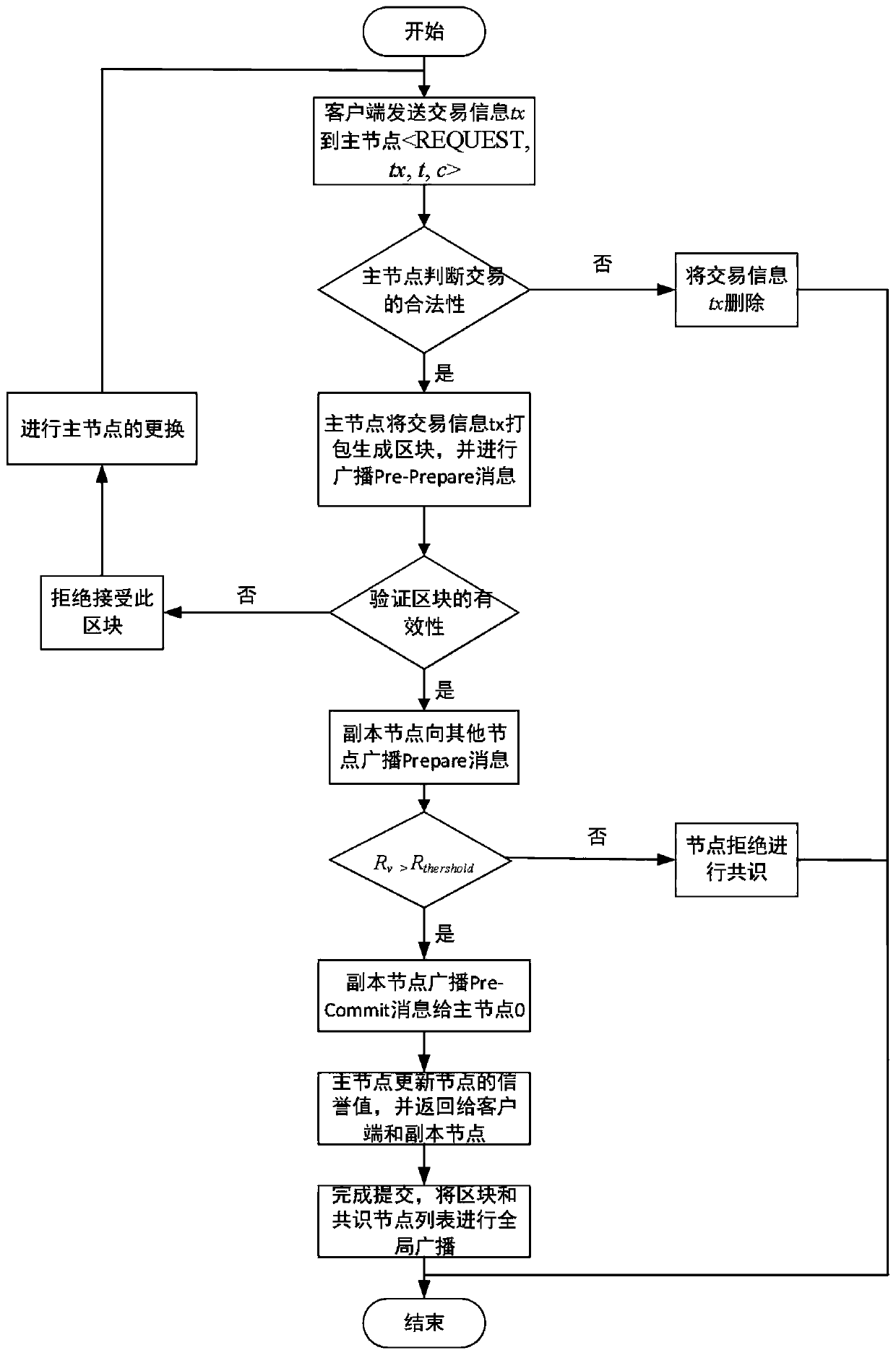
Method for defending Sybil attacks in block chain based on improved PBFT algorithm
InactiveCN110493198AEffective attackReduce the number of communicationsTransmissionBlockchainSybil attack
The invention discloses a method for defending Sybil attacks in a block chain based on an improved PBFT algorithm. According to the method, a PBFT algorithm is improved, an original view change mechanism in the algorithm is deleted, a main node Sp is randomly selected through the credible state of a consensus node, and meanwhile, a Pre-Commit stage is added in a consensus protocol to reduce the communication frequency between nodes; secondly, a reputation model is established to count comprehensive information of each consensus node to calculate a reputation value of the node, and due to the fact that the reputation values of the nodes are different, owned speaking rights are different, and the nodes achieve consensus through voting so as to defend Sybil attacks in the blockchain. According to the method, the frequency of communication between the nodes is reduced, the voting weight of the consensus node corresponds to the owned reputation value by referring to the consensus thought based on share certification in the public chain, and different speaking rights are allocated to the nodes according to the reputation value of the consensus node, so that Sybil attacks in the blockchain can be effectively defended.
Owner:BEIJING UNIV OF TECH
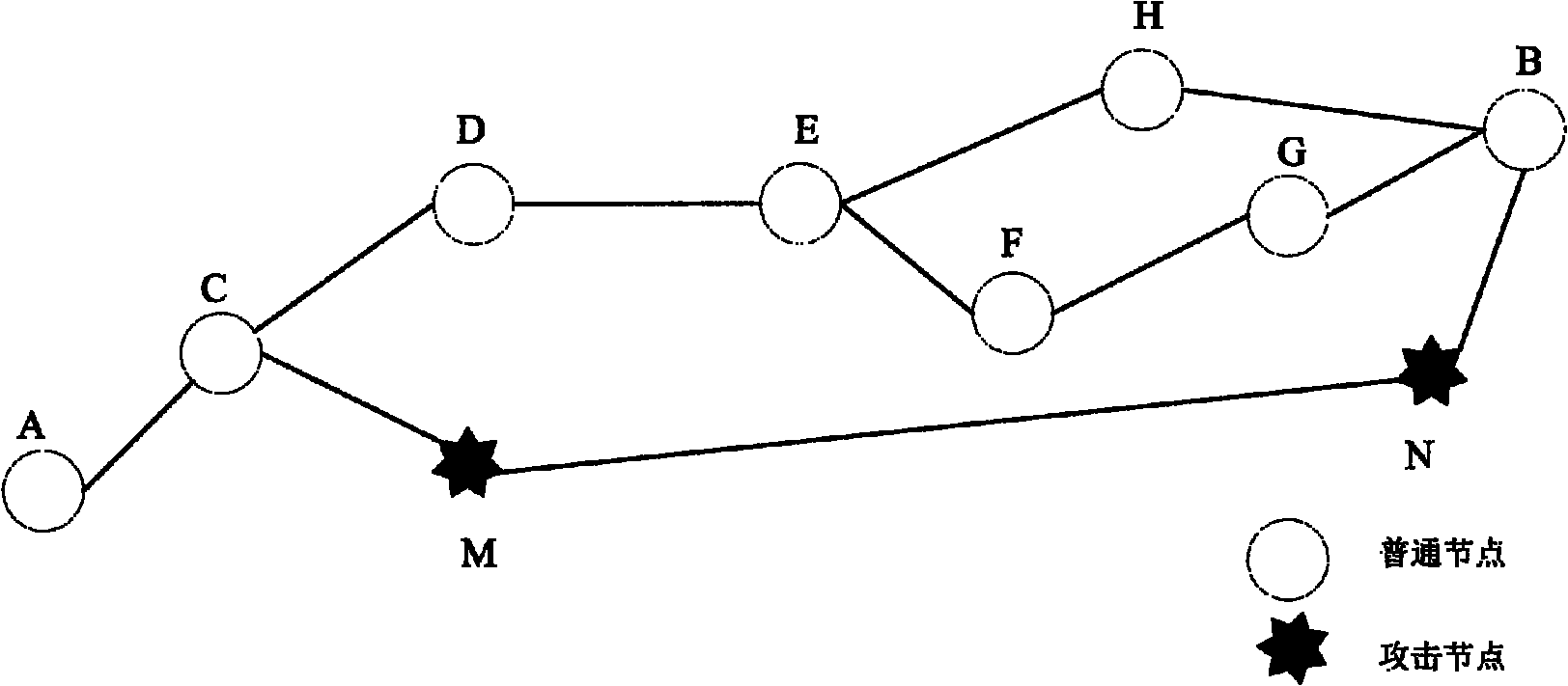
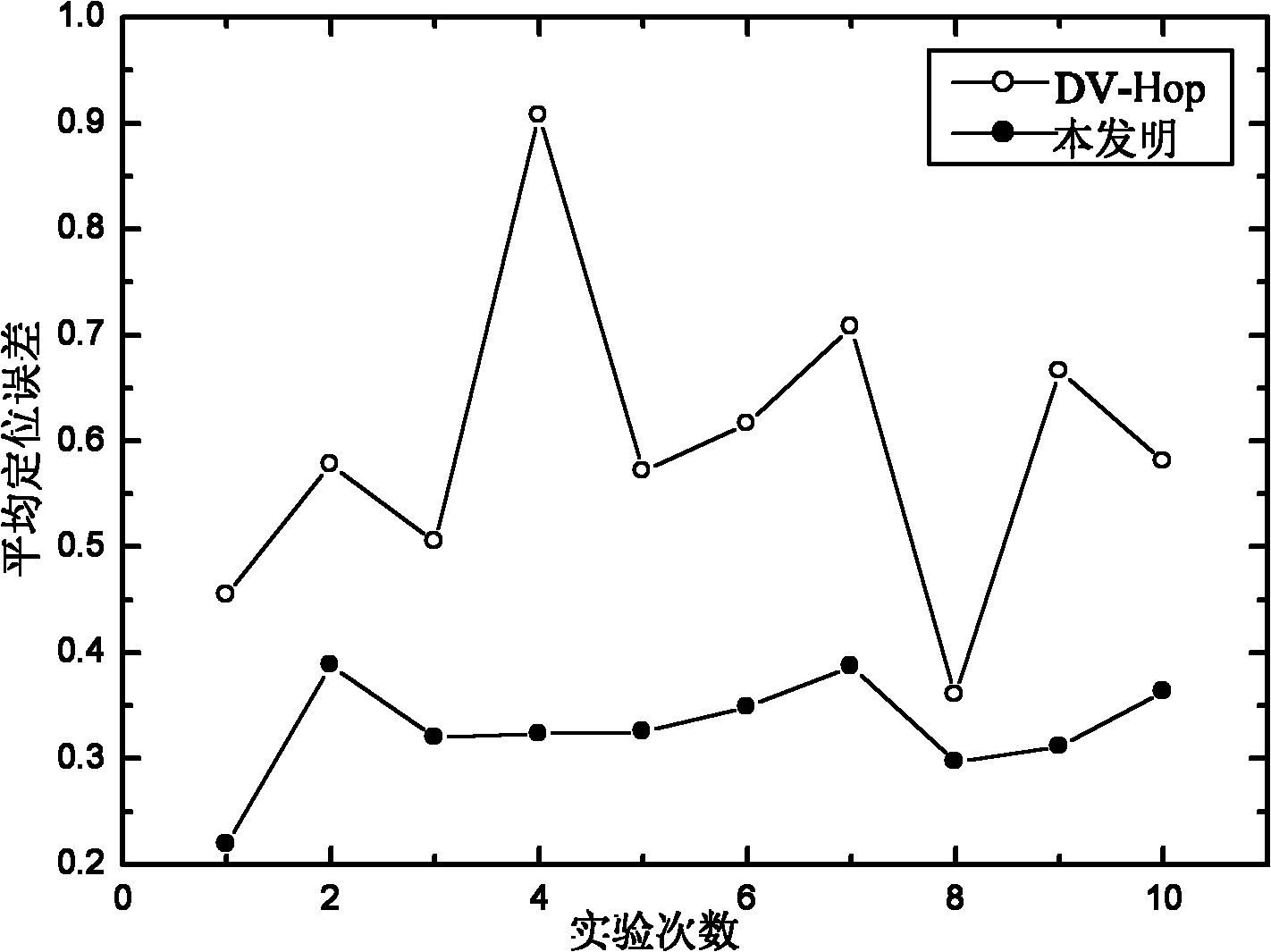
Anti-attack reliable wireless sensor network node positioning method
ActiveCN102186171AReduce computational costSave spaceSecurity arrangementHigh level techniquesWireless sensor networkingWormhole
The invention belongs to the technical field of computer network security, and relates to an anti-attack reliable wireless sensor network node positioning method. In ordinary positioning methods, nodes to be positioned are easy to attack by malicious nodes, so the positioning effects of the nodes are influenced. By the reliable positioning method provided by the invention, Sybil attacks and wormhole attacks can be resisted at the same time. The method comprises that: a beacon node estimates the smallest hop number between the beacon node and other beacon nodes; the beacon node estimates an average hop distance among the nodes; the nodes cooperate with one another to detect attack nodes in a network; and unknown nodes estimate own coordinates. Compared with the prior art, the invention improves the attack resistance of the wireless sensor nodes in a positioning process, reduces positioning errors in an environment with the malicious nodes, and reduces the communication cost and calculation cost of the nodes as much as possible in the positioning method by fully combining the characteristic that the energy of the wireless sensor nodes is finite.
Owner:北京涵鑫盛科技有限公司
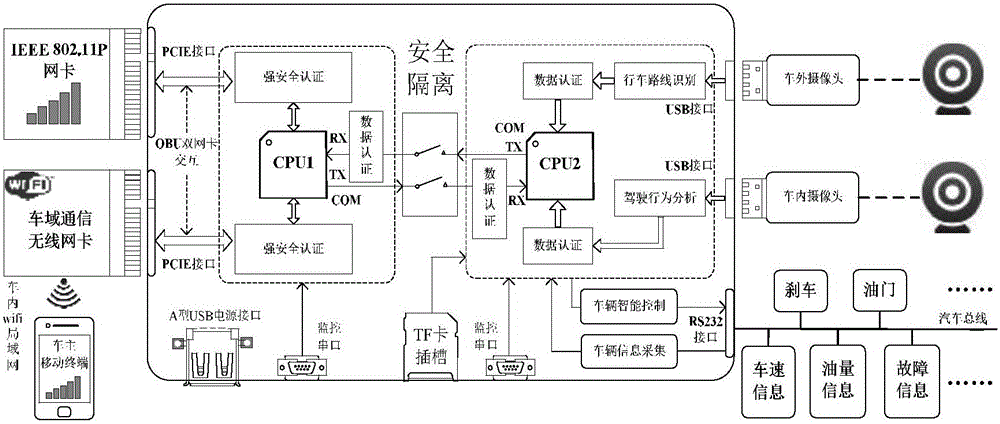
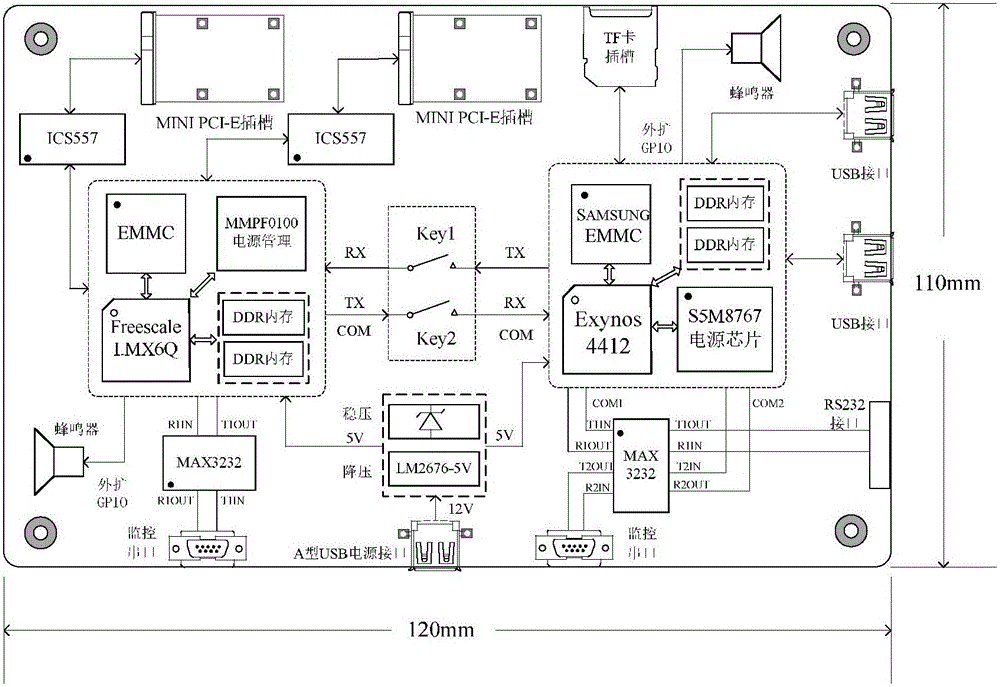
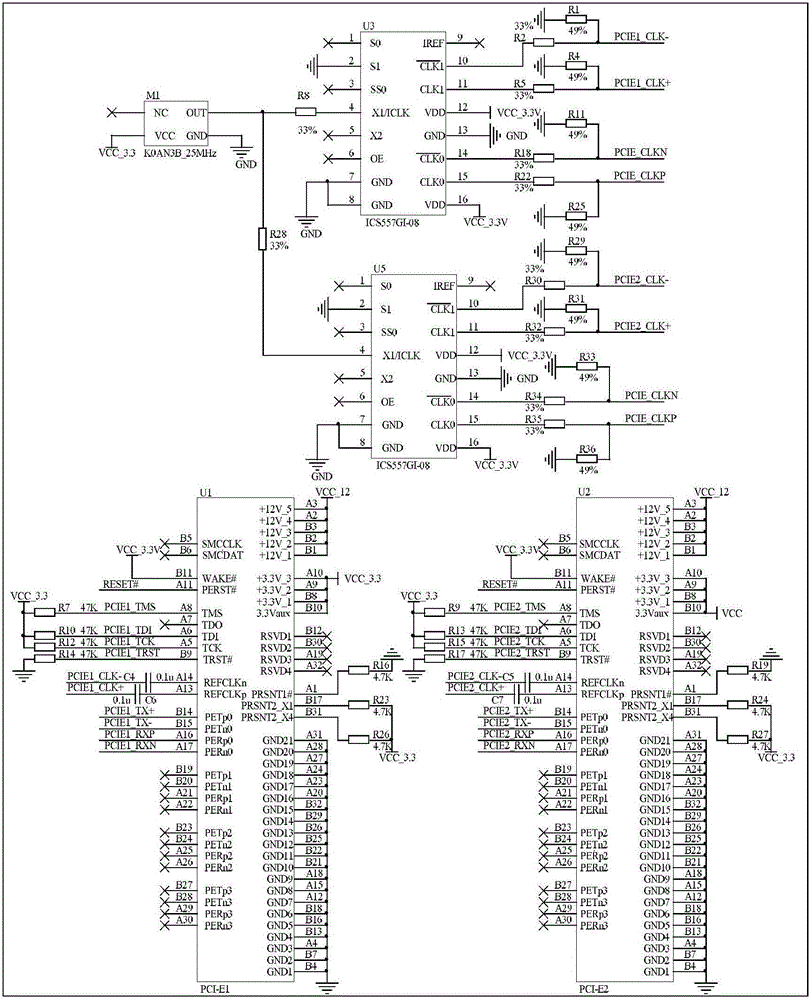
Auxiliary driving vehicle gateway for multi-CPU hard isolation of intelligent interconnection
ActiveCN105743902APrevent intrusionAvoid gettingTransmissionSecurity arrangementCommunications securityInformation analysis
The invention discloses an auxiliary driving vehicle gateway for multi-CPU hard isolation of intelligent interconnection. The auxiliary driving vehicle gateway comprises a vehicle security communication system and a vehicle information analysis and control system, wherein the vehicle security communication system comprises a vehicle gateway double-wireless network card structure composed of an inter-vehicle wireless communication module and a vehicle domain wireless communication module, and a vehicle owner mobile terminal, and the vehicle security communication system carries out CPU control by an I.MX6Q processor; and the vehicle information analysis and control system carries out CPU control by an Exynos4412 processor, and comprises a driving route identification module, a driving behavior analysis module, a vehicle information collection module and an intelligent vehicle controller. The auxiliary driving vehicle gateway disclosed by the invention can realize the communication security of the vehicle gateway, realize driving security by driver fatigue state analysis based on Opencv face recognition and driving route recognition and analysis, as well as effectively resisting against Sybil attack and other various types of attacks from a hardware level to prevent hackers from invading the vehicle gateway to obtain vehicle information and controlling the vehicle.
Owner:JIANGSU UNIV
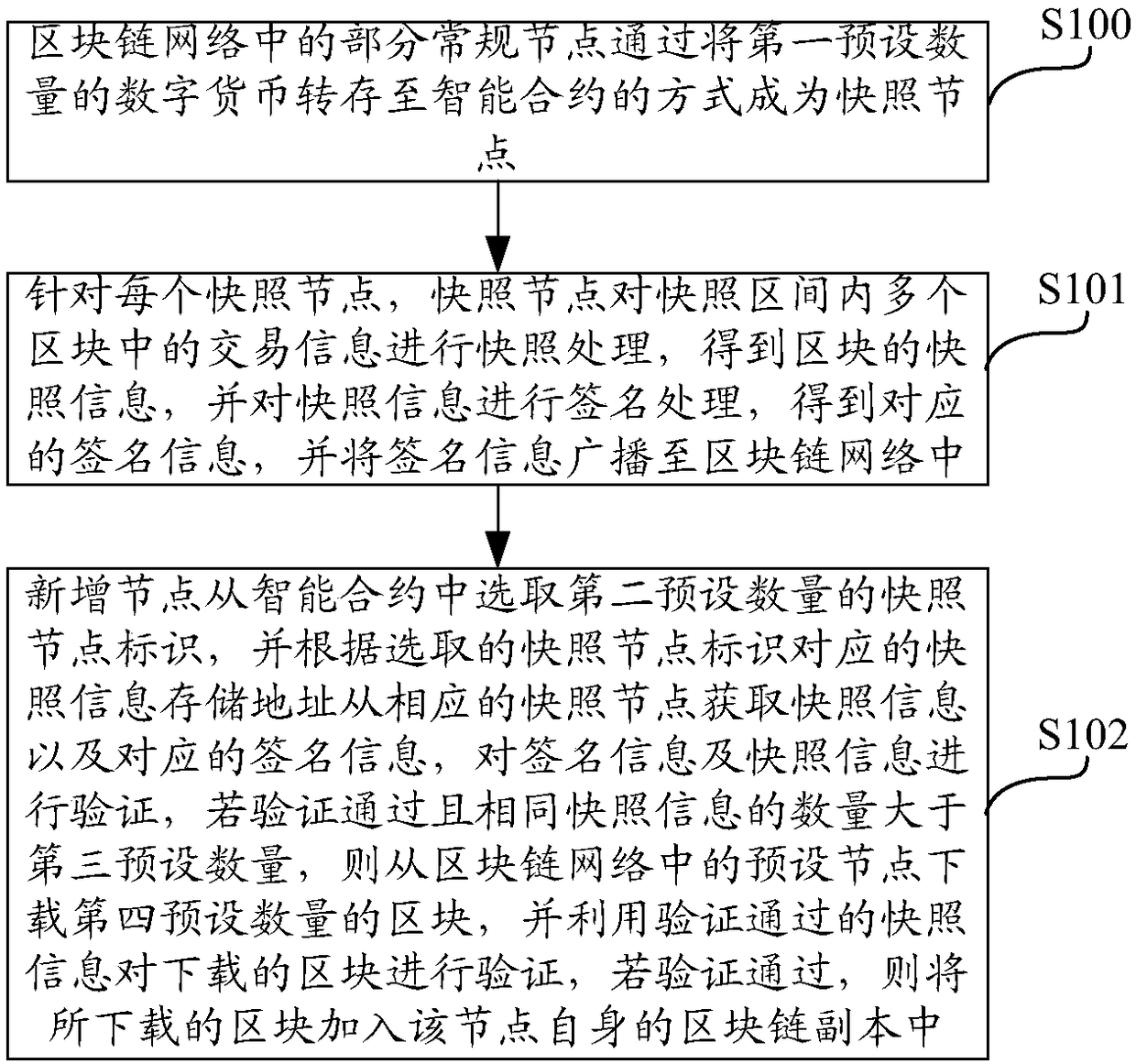
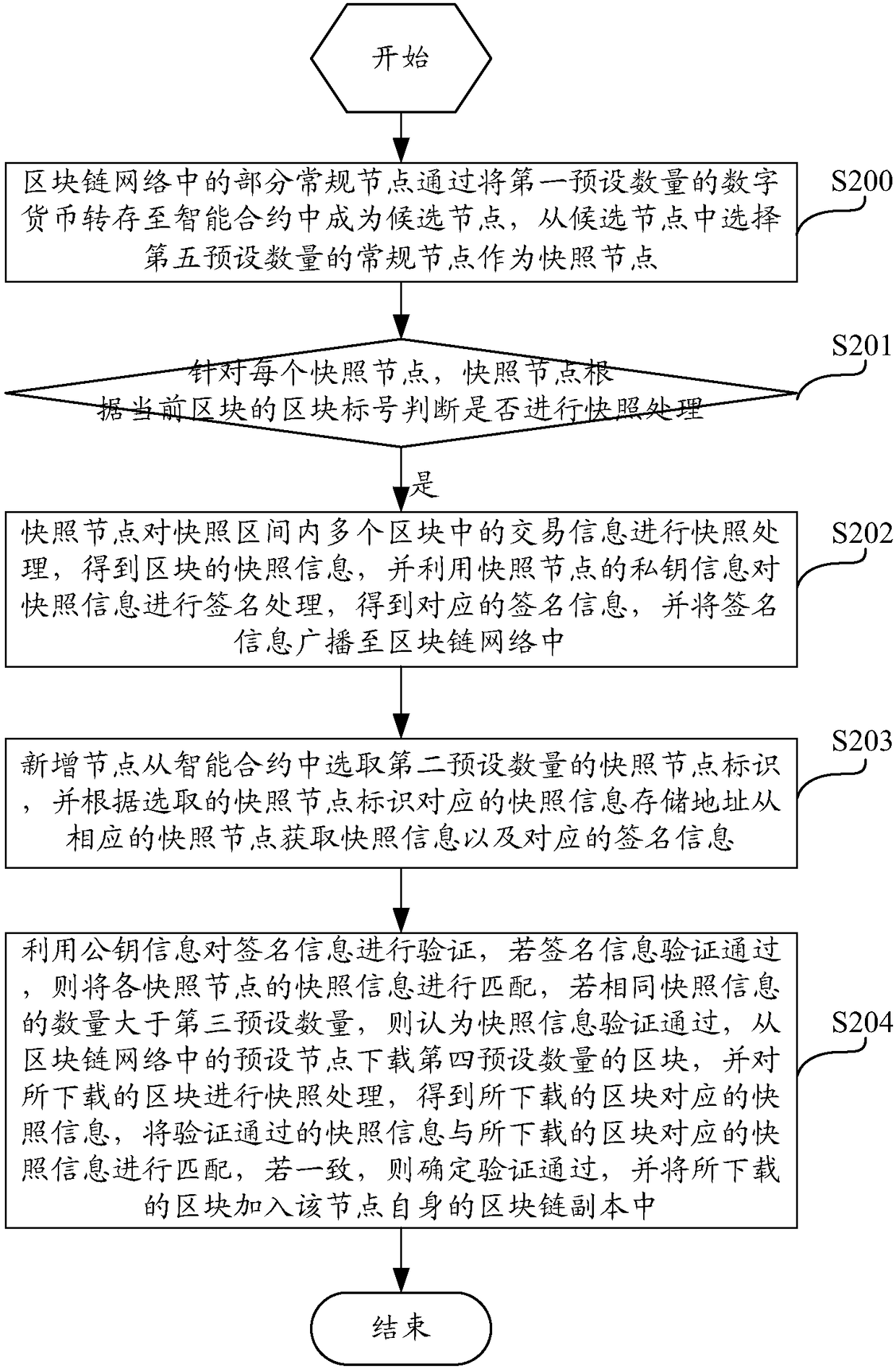
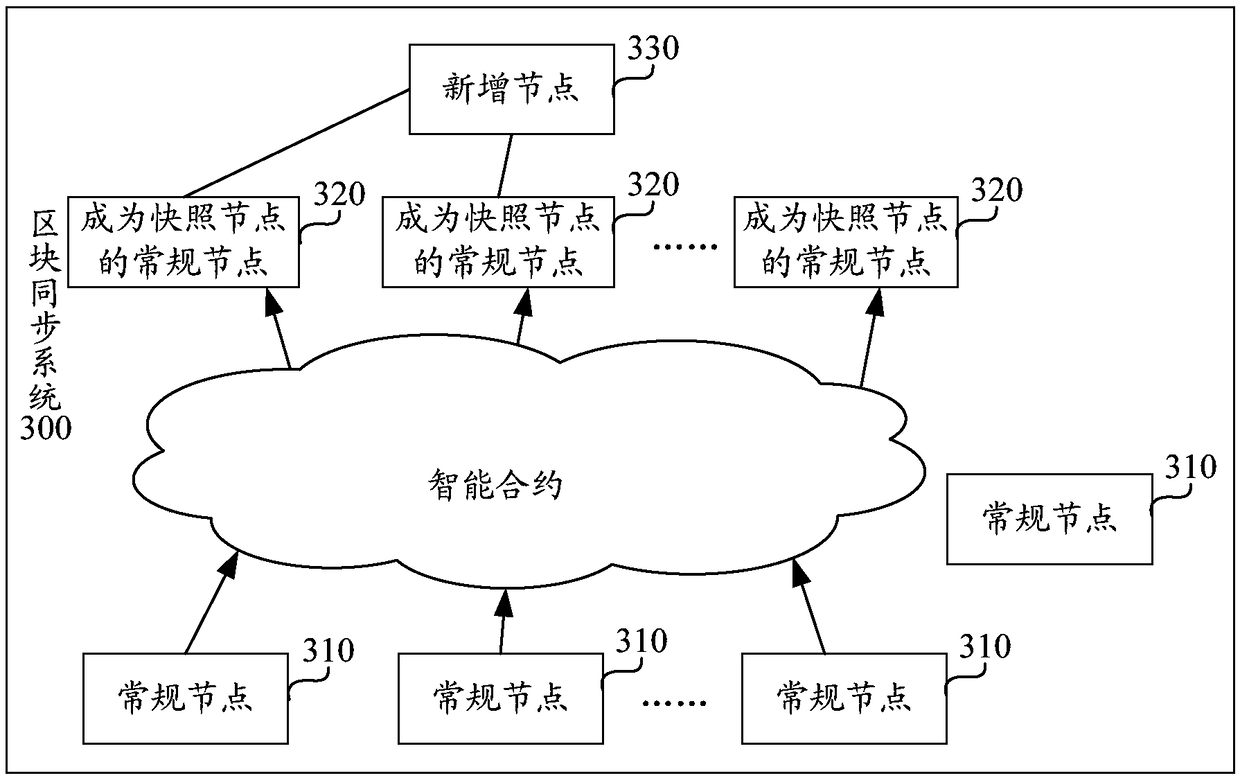
Block synchronization method and system
ActiveCN108234134ASolve the real problemReduce the risk of Sybil attacksUser identity/authority verificationPayment protocolsDigital currencyChain network
The invention discloses a block synchronization method and a block synchronization system. A part of normal nodes in a block chain network become snapshoot nodes by the way of mortgaging digital currency, the snapshoot nodes perform snapshoot treatment on transaction information in a plurality of blocks in a snapshoot area, so that the snapshoot information of the blocks is acquired, and the snapshoot information is signed to acquire corresponding signature information; a newly added node acquires snapshoot information and corresponding signature information from the snapshoot nodes, verifiesthe signature information and the snapshoot information; if the verification is passed, and the quantity of the same snapshoot information is more than a certain number, the block is downloaded from the preset node, the snapshoot information passing the verification is used for verifying the downloaded block; if the verification is passed, the downloaded block is added into a block chain transcript of the node, so that the block synchronization security is enhanced, the problem that the false block is synchronized due to the inexistence of a credible node list used for generating the snapshootinformation is avoided, and the risk of suffering a Sybil attack is reduced.
Owner:JIANGSU PAYEGIS TECH CO LTD +1
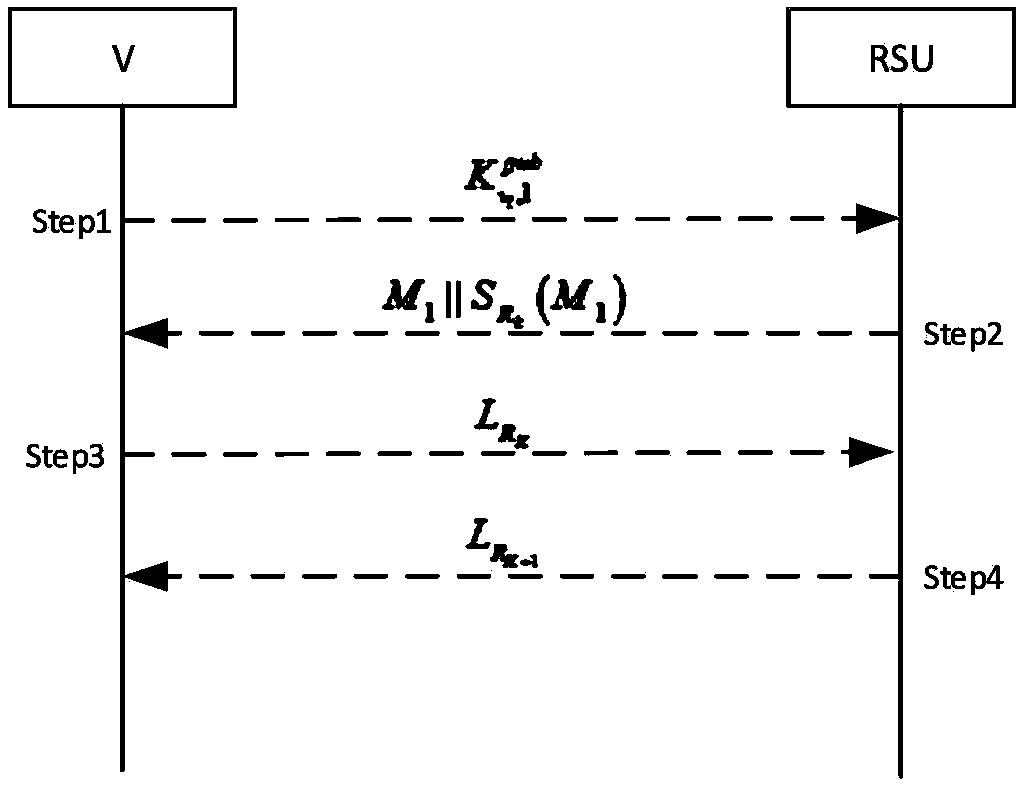
Method for resisting Sybil attack with multiple fake identity sources in car networking
ActiveCN104717229APrevent repudiationRealize privacy protectionUser identity/authority verificationAfter treatmentComputer security
The invention discloses a method for resisting Sybil attack with multiple fake identity sources in car networking. The method comprises the following steps that an RSU establishes a local certificate for a registered vehicle in the car networking so as to resist the Sybil attack with the fake identity; the RSU resists the Sybil attack with the steal identity by verifying the local certificate of the vehicle in the vehicle-vehicle communication process; the vehicle establishes the real-time and dynamic reputation value and the credible value for each alarming event, and performs after-treatment. The method is used for resisting the Sybil attack with multiple fake identity sources, such as fake, steal and conspiring, and meanwhile protecting the privacy of the vehicle as well as resisting attack.
Owner:JIANGSU UNIV
Method for detecting Sybil attack
InactiveCN101478756ARealize detectionFlexible thinking designNetwork topologiesSecurity arrangementSybil attackReal-time computing
Directed towards solving the problem of the Sybil attack faced by wireless sensor network routing protocol, the invention provides a method for detecting Sybil attack. In a way of carrying along with detection parameter message at the end of a data packet at the protocol execution stage, the method makes a synthetic judgment about the Sybil attack in the wireless sensor network through node energy and received signal strength value, and raises the detection precision through the mutual supervision between cluster-head nodes and member nodes. The invention provides a practical and feasible method for detecting Sybil attack for network, in particular for sensor network, and can effectively raise the safety of wireless sensor network, such as the detection to routing, resource distribution and deviant behavior, etc. The scheme has the advantages of simple realization, high detection rate and strong anti-attack ability, etc.
Owner:NANJING UNIV OF POSTS & TELECOMM
Location privacy based ring signature method in Internet of vehicles
The invention relates to a location privacy based ring signature method in the Internet of vehicles, belongs to the field of vehicle identity authentication in the Internet of vehicles, and aims at solving the problem in detecting collusive Sybil attacks. Path information of a vehicle is used as identity information of the vehicle, the path information contains location privacy information of the vehicle, and location privacy information is protected in the ring signature method. Compared with a present Sybil attack detection method, the vehicle identity authentication method provided by the invention can make vehicles independent from each other, protect the location privacy of the vehicles, and detect the novel collusive Sybil attack existing in the Internet of vehicles in real time.
Owner:JIANGSU UNIV
Systems and Methods for Reputation Verification
InactiveUS20190108232A1Digital data protectionWebsite content managementDistributed hash tableDistribute hash table
The system described herein is an autonomous decentralized platform that facilitates a framework for the evolution of verified reputation for anonymous or identifiable users, human or machine. The platform can be built on decentralized or centralized networks, including a blockchain or distributed hash table. Described herein is the architecture's implementation in the case of a distributed network with anonymous users. Using a system of checks and balances, the platform is designed to address the Sybil attack and tyranny of the majority problems.
Owner:SYTRES LLC
Method for detecting Sybil attack in underwater wireless sensor networks
ActiveCN103297973AEfficient detectionEnsure safetyNetwork topologiesSecurity arrangementUnderwater sensor networksUnderwater wireless sensor networks
The invention relates to a method for detecting Sybil attack in underwater wireless sensor networks. The method includes three steps: by the aid of anchor nodes, (1) identifying suspicious nodes: identifying the suspicious nodes in the networks according to received information packets; (2) determining Sybil nodes: calculating state evaluation values of the suspicious nodes and determining the Sybil nodes by means of comparing with position information of the suspicious nodes; (3) separating the Sybil nodes: reporting the Sybil nodes to base stations which delete the Sybil nodes from the networks. The method has the advantages that hostile Sybil attack can be effectively detected, safety of the networks can be guaranteed, and hardware conditions for the nodes neither are limited strictly nor limited by specific information or specific nodes and have good expansibility.
Owner:HOHAI UNIV CHANGZHOU
Multistage security routing method for delay tolerant network and based on network codes
ActiveCN104079483AImprove routing performanceAvoid overdependenceError preventionData switching networksData packAttack
The invention provides a multistage security routing method for a delay tolerant network and based on network codes. Coding data packet distribution is optimized, multistage routing based on the damaged probability of probability meeting nodes is designed according to the maximum transmission performance requirement between the nodes, the information damaging probability is reduced, the whole network throughput is improved, and the mixed security network coding scheme in a DTN is achieved in designing network cords to jointly boycott various kinds of attack of eavesdropping attack, Sybil attack, byzantine attack and discarding attack. To selective data discarding attack, limited redundant factors are dynamically added into source nodes timely to improve the fault-tolerant capability of link failure. Relay nodes are verified mutually to boycott the Sybil attach and byzantine attach and reduce the cost for verifying the source codes in existing schemes. A double-boycotting strategy is designed to reduce the effects of byzantine attack to the nodes.
Owner:NANJING UNIV OF POSTS & TELECOMM
Sybil node recognition method based on physical layer confidence degree
ActiveCN105959337ASolve the single point of failure problemReduce overheadNetwork topologiesTransmissionRound complexityWireless sensor networking
The invention discloses a Sybil node recognition method based on the physical layer confidence degree. The method includes the steps that a node i and a node j are subjected to upper-layer initial authentication; the node i calculates and records the physical channel information H0<j> and ID0 of an information package; the information package confidence degree St<k>( i, j) is calculated and stored in a confidence degree list; whether the node confidence degree Sk(i, j) of the node j reaches the confidence threshold eta or not, if not, it is judged that the node j is a Sybil node, the node j is abandoned, and the whole network is notified. The Sybil node recognition method aims to achieve the purposes that the problem of single point failure of a centralized detection scheme of Sybil attack of a wireless sensor network is solved, a witness node in a distributed detection scheme is not needed, the physical channel information serves as an identity index, the confidence degree is established, a system can have certain tolerance, Sybil node recognition complexity is lowered while the false alarm rate is also lowered, and thus precision of Sybil node recognition is improved.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
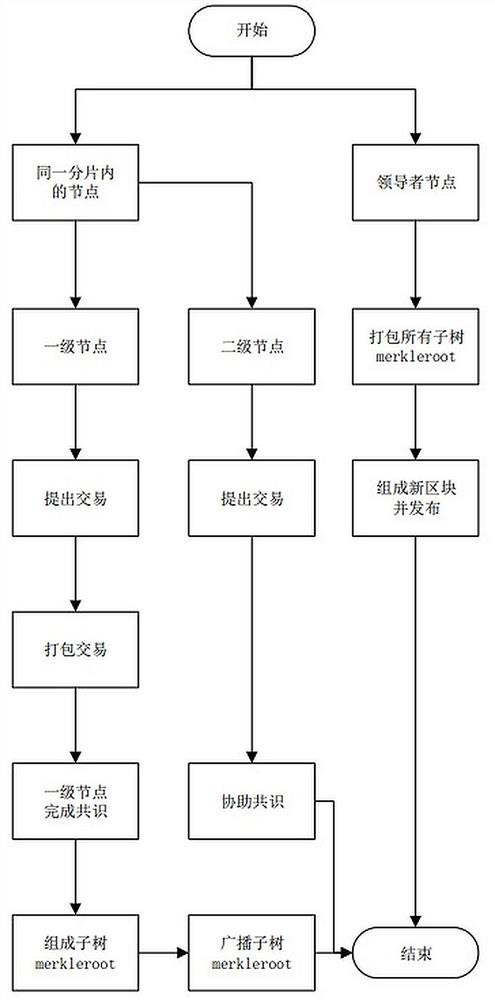
Method for improving throughput of block chain based on fragmentation technology
InactiveCN112260836AEfficient detectionImprove transaction throughputKey distribution for secure communicationFinanceAttackEngineering
The invention discloses a block chain transaction throughput improving method based on a fragmentation technology, belongs to the technical field of block chain networks, and aims to realize the effect of processing different transactions by different fragments by dividing a block chain into a plurality of subnets and dividing to-be-recorded transactions into different fragments through the fragmentation technology; finally, each fragment submits the respective Merkland to the leader node, so that the core node is integrated into a complete Merkland and packaged into a new block, the transaction throughput of the block chain is improved, and meanwhile, the Sybil attack and the double-bloom attack can be effectively resisted on the randomness and the rights and interests of the algorithm.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Node collaboration based Sybil attack detection method
ActiveCN104125572AImprove detection efficiencyExtend the life cycleSecurity arrangementHigh level techniquesSignal strengthShadow fading
The invention discloses a node collaboration based Sybil attack detection method in a power controllable WSN (Wireless Sensor Network) and belongs to the network security technical field. The node collaboration based Sybil attack detection method comprises facing the real network environment which comprises the path loss and shadow fading and is a large scale propagation model to analyze a secondary difference value of an RSSI (Received Signal Strength Indicator) and providing a Sybil node identification algorithm according to the characteristic that the secondary difference value of the RSSI is not affected by changes of the node transmission power, wherein the Sybil node identification algorithm distinguishes whether two nodes are two Sybil identities which are forged through a malicious node or not through the mutual collaboration of public monitoring nodes of the two ordinary nodes. According to the node collaboration based Sybil attack detection method, the characteristics of the secondary difference value of the RSSI and the monitoring node cooperation scheme are combined and accordingly the detection efficiency of Sybil attacks in the power controllable WSN is improved and the network life cycle can be extended.
Owner:NANJING UNIV OF POSTS & TELECOMM
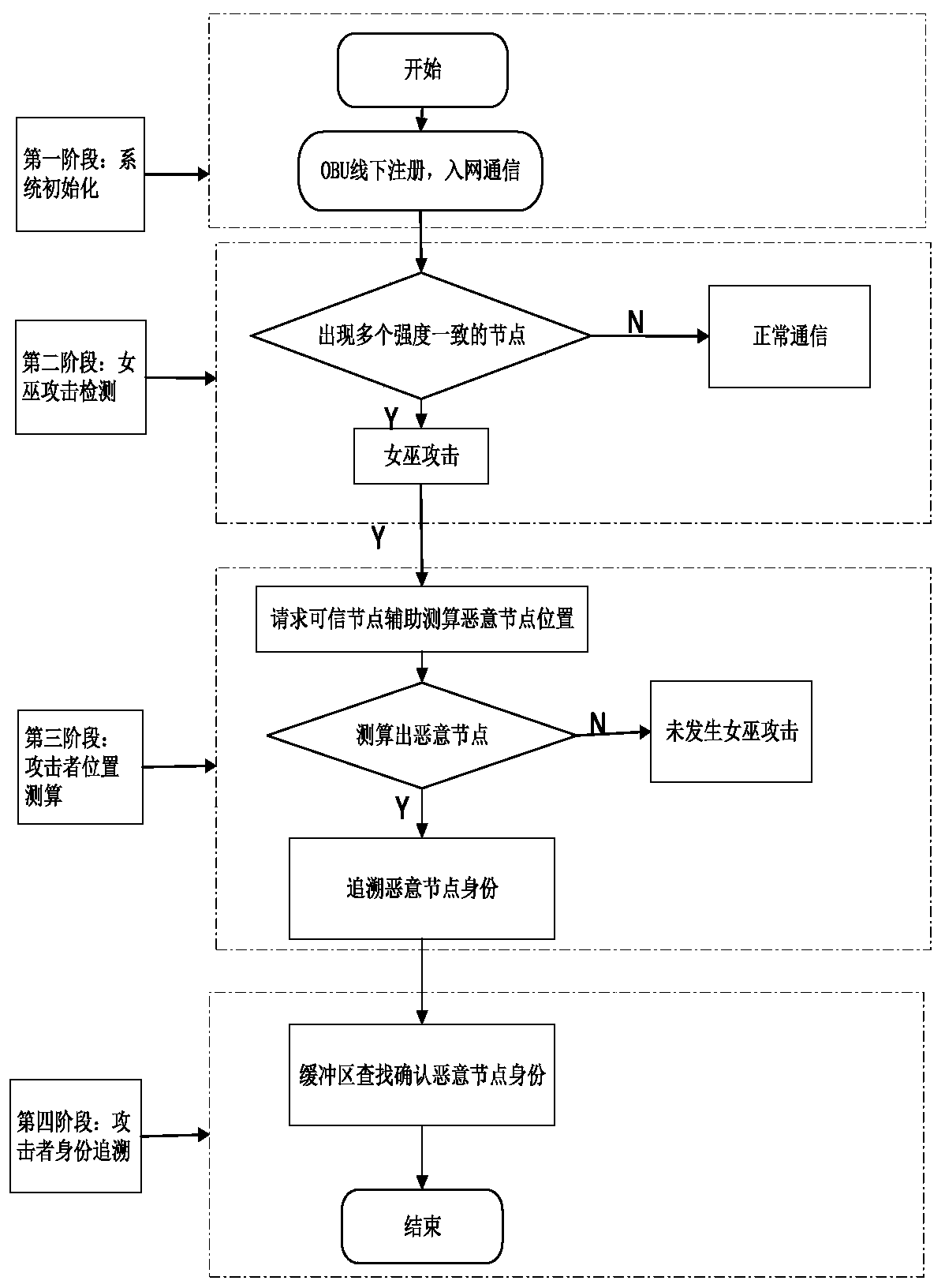
Identity traceable Sybil attack detection method in Internet of Vehicles environment
ActiveCN110536265AEnable anonymous communicationPrivacy protectionParticular environment based servicesVehicle wireless communication serviceThe InternetComputer security
The invention provides an identity traceable Sybil attack detection method in an Internet of Vehicles environment, and belongs to the technical field of Internet of Vehicles security. According to thetechnical scheme, the Sybil attack detection method with the traceable identity in the Internet of Vehicles environment comprises the following steps of system initialization, Sybil attack discovery,malicious node positioning and attacker identity tracing. The method has the advantages that under the condition that the Sybil attack is detected, a concise method is designed to achieve positioningof the position of the attacker, and the real identity of the attacker is traced according to the positioning information.
Owner:NANTONG UNIVERSITY
Novel method for detecting Sybil attack in Internet of Things
InactiveCN103701771AImprove detection accuracyReduce consumptionEnergy efficient ICTTransmissionNetwork packetThe Internet
The invention discloses a novel method for detecting a Sybil attack in the Internet of Things. According to the method, the Sybil attack in the Internet of Things is judged comprehensively according to the energy of a node and the intensity value of a received signal by adopting a method of carrying detection parameters at the tail part of a data packet in a protocol implementation stage, and the detection precision is improved by the mutual supervision of a cluster head node and a member node. A practical and feasible method for detecting the Sybil attack is provided for networks, particularly the Internet of Things, the safety of the Internet of Things can be improved effectively, such as routing, resource allocation, abnormal behavior detection. The novel method has the advantages of easiness in implementation, high detection efficiency, high anti-attack capacity and the like.
Owner:CHINA MCC17 GRP
Real-time map updating system and method based on trust management, and Internet-of-vehicles terminal
ActiveCN110377672AImprove timelinessAchieve accuracyDatabase updatingDigital data protectionThe InternetComputer science
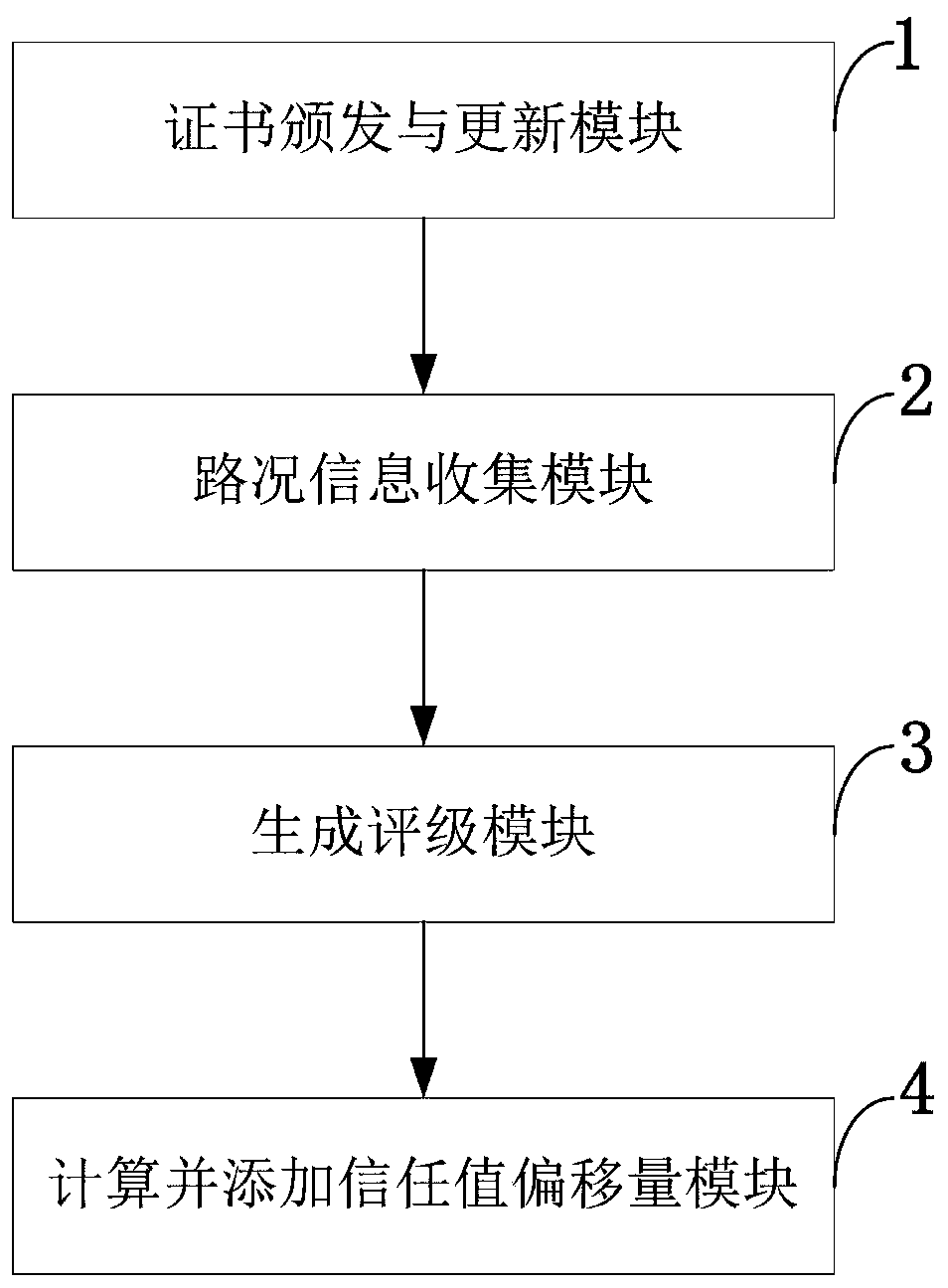
The invention belongs to the technical field of real-time map updating, and discloses a real-time map updating system and method based on trust management and an Internet-of-vehicles terminal. A vehicle is registered in a law enforcement agency, and identity information is reserved in the law enforcement agency; the vehicle sends a request for updating the own public key to a law enforcement agency; road condition information is collected, and a vehicle accurately uploads surrounding road conditions to fog nodes to improve trust values; meanwhile, the fog node needs to carry out identity verification on the vehicle before receiving the message from the vehicle; the fog node verifies the road condition information uploaded by the vehicle by using a Bayesian inference model, and sends the road condition information to a real-time map updating server according to a verification result; the fog node generates a corresponding rating for each message source vehicle, so that the timeliness and the accuracy of map updating are realized; when the trust value of the vehicle is lower than the preset threshold value, the vehicle cannot continue to enjoy the service provided by real-time map updating, and Sybil attacks are avoided.
Owner:XIAN UNIV OF POSTS & TELECOMM
Internet-of-Vehicles intrusion detection system based on hidden Markov model
ActiveCN111800421AReduce overheadHigh precisionForecastingCharacter and pattern recognitionHide markov modelAttack
The invention belongs to the field of intrusion detection algorithms in the Internet of Vehicles, and particularly relates to an Internet-of-Vehicles intrusion detection system based on a hidden Markov model. The system is used for intrusion detection of a False alert attack, a Sybil attack, a Black hole attack and a DoS attack in the Internet of Vehicles. The system mainly comprises a pre-detection module, a DNN-based detection center module, an updating module used for recording a vehicle state and generating a hidden Markov model, and a response center module used for generating a responsesignal, and under the normal operation state of the Internet of Vehicles, the modules jointly guarantee efficient operation of the Internet of Vehicles. Under the attack detection state, the components supplement each other to jointly complete an attack monitoring defense process. Compared with the DNN-based IDS, the Internet-of-Vehicles intrusion detection system has the advantages that the detection precision, overhead and detection time are improved, the detection precision is higher, the average detection time is far shorter than that of an IDS based on DNN, meanwhile, the expenditure is lower, compared with an IDS using state switching, the expenditure of a pre-detection mechanism used in the method is lower, and more computing resources are saved.
Owner:NORTHEASTERN UNIV
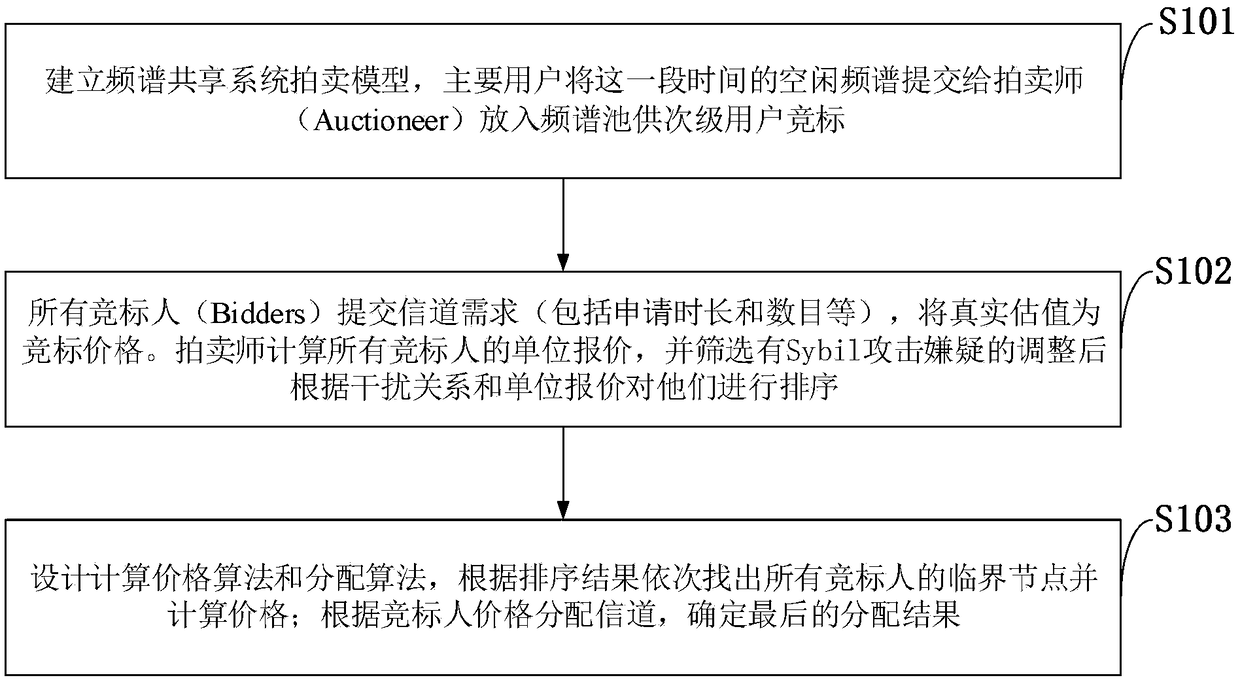
Multichannel dynamic spectrum allocation method against sybil attack, computer program
ActiveCN109089266AStopping Sybil AttacksAvoid attackCommerceSecurity arrangementResistFrequency spectrum
The invention belongs to the technical field of dynamic resource partitioning, and discloses a dynamic spectrum allocation method for multi-channel protection against Sybil attack, and a computer program. In order to defend against Sybil attacks, a spectrum auction model is designed to dynamically manipulate the spectrum auction strategy according to the flexible and real valuation. The bidding relationship among the secondary users is discussed in the model, and the spectrum auction is carried out by designing a specific bidding strategy. Adopting auction theory and mechanism to prevent Sybilattack, spectrum auction is carried out online through bidding strategy. The frequency spectrum allocation method of the invention not only realizes individual rationality and authenticity, but alsocan resist Sybil attack, and dynamically allocates channels on line, thereby improving frequency spectrum efficiency and reusability. According to the evaluation result, the present invention can prevent bidders from manipulating the auction and achieve good spectrum reallocation performance. The method provided by the invention is easy to realize and easy to expand, and is closer to practical application than the spectrum auction method provided by the invention.
Owner:XIDIAN UNIV
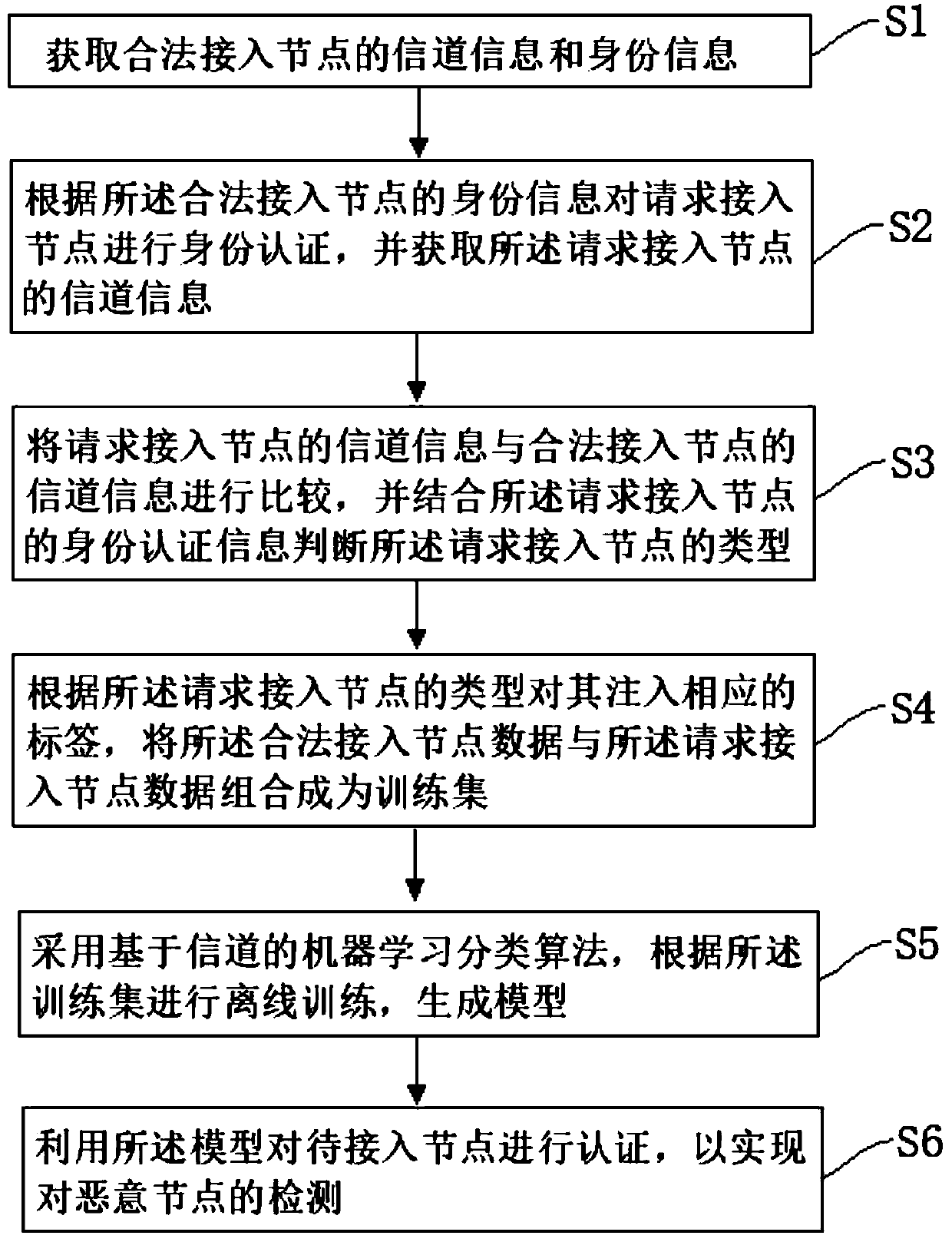
Malicious node physical layer detection method and system based on automatic labeling and learning
InactiveCN110995721AImprove malicious node detection rateSolve the problem of malicious node detectionTransmissionCommunications securityAlgorithm
The invention relates to the technical field of communication safety, and discloses a malicious node physical layer detection method and detection system based on automatic labeling and learning. According to the detection method, the type of an access node in a network is identified based on a physical layer authentication strategy of channel difference, and malicious nodes initiating clone attacks and Sybil attacks can be detected at the same time; corresponding labels are automatically injected according to the types of the access nodes, so that the problem of manually injecting attack labels is solved, and the difficulty of lacking attack label samples when a supervised machine learning algorithm is used for channel authentication is solved; attack label samples are automatically injected by utilizing physical layer channel difference and setting a threshold method, and an offline label sample set is provided for a machine learning algorithm, so that automatic label injection and learning are realized, and the malicious node detection rate of an access node is improved. According to the method, the problem that the edge calculation node detects malicious nodes of various industrial wireless devices in an asymmetric scene of the industrial edge calculation Internet of Things can be effectively solved.
Owner:SHENZHEN POWER SUPPLY BUREAU +1
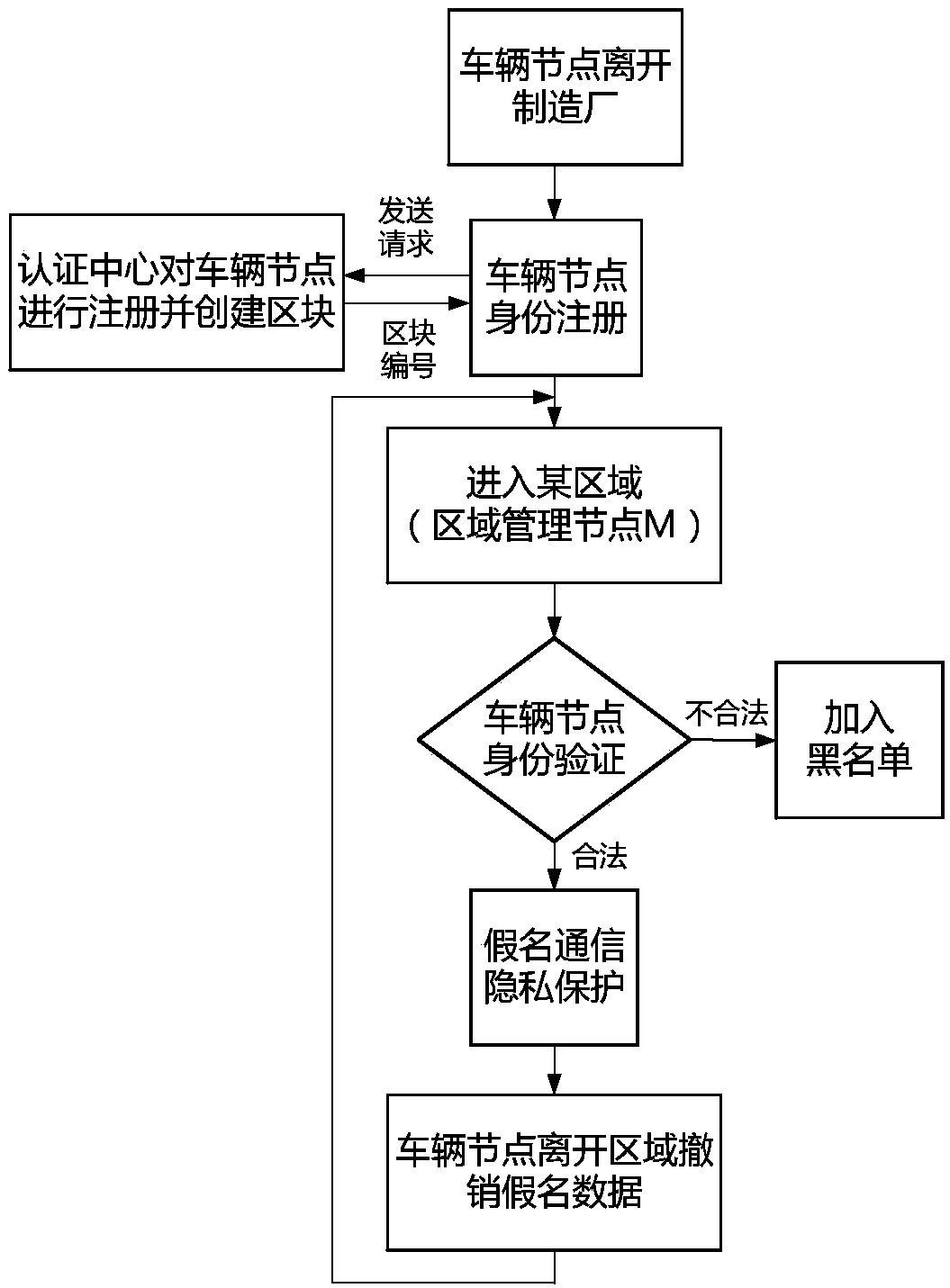
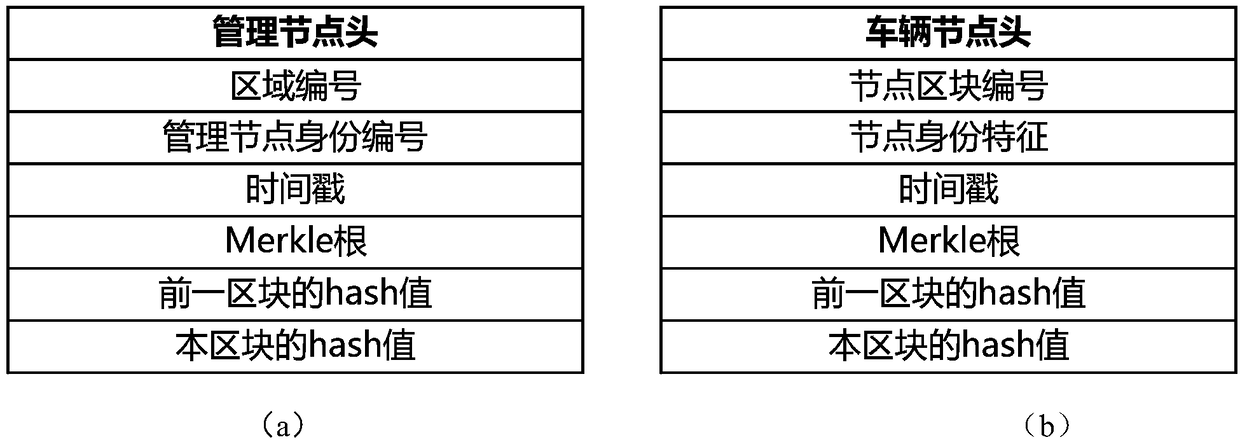
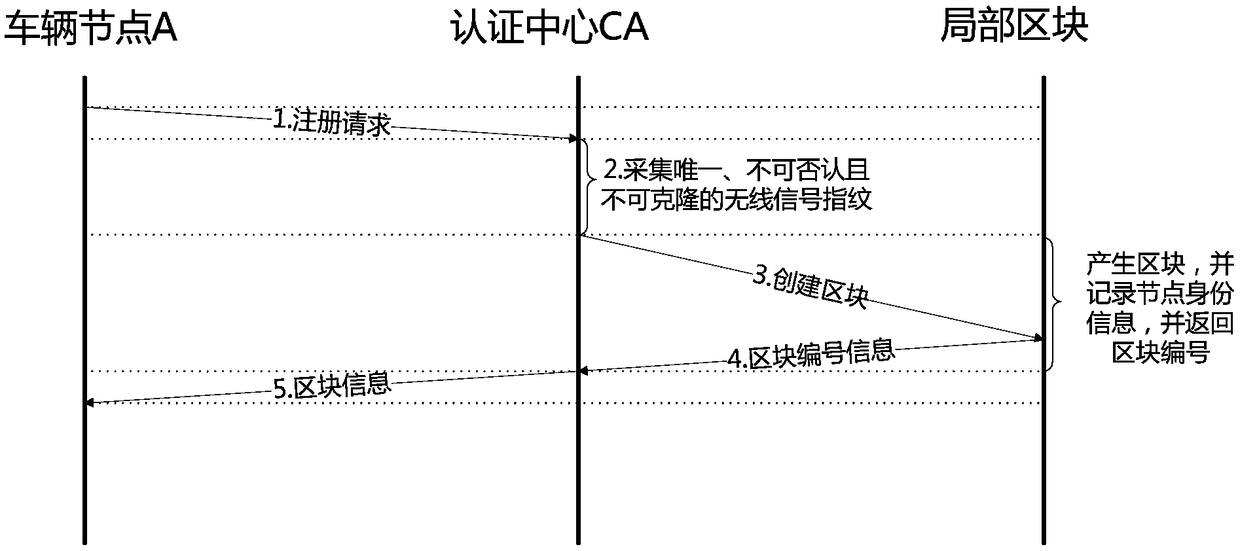
Low-altitude node identity authentication and privacy protection method based on Hash chain
ActiveCN109194480AGuarantee data securityGuaranteed confidentialityUser identity/authority verificationConfidentialityPrivacy protection
The present invention discloses a low-altitude node identity authentication and privacy protection method based on a Hash chain. The method comprises the steps of: when a vehicle node enters a space-air-ground integral network at the first time, taking unique and undeniable wireless signal fingerprints which cannot be cloned as identity features of the vehicle node, and creating a Hash block for the vehicle node while performing identity registration of the vehicle node by an authentication center; when communication of the vehicle node is performed in an area, performing identity authentication based on block content by a management node; in order to protect the identity privacy, employing a pseudonym generated by the management node to perform communication by the vehicle node; and recording key motions or information of different nodes at different time in the area by the management node, and recording the key motions or the information of the vehicle node itself at different areasat different time by the vehicle node. The method can effectively defense various attacks such as the sybil attack, the denial of service attack and the replay attack. Besides, the data safety of thenetwork is guaranteed, namely, the confidentiality, integrity, availability and non-repudiation of the data in the network.
Owner:XIAMEN UNIV
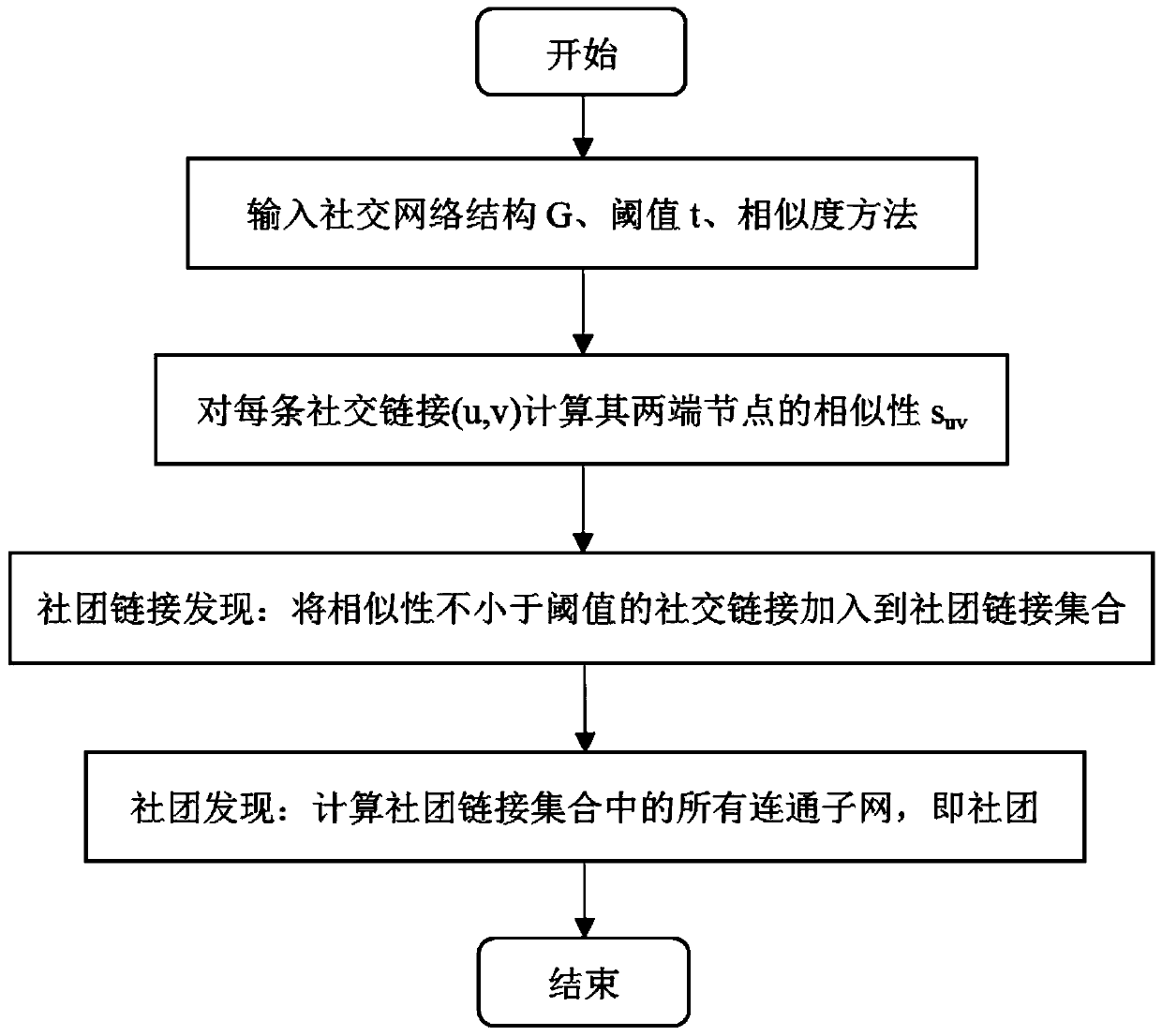
Community detection method for resisting Sybil attacks and used for large-scale network
ActiveCN110598128AAgainst attackImprove community securityData processing applicationsOther databases indexingNODALGranularity
The invention discloses a community detection method for resisting Sybil attacks and used for a large-scale network, and the method comprises the steps: giving a social network G=(V, E), V being a node set, and E being a social link or a side set; giving a community link strength threshold t, and initializing a community link or an edge set C=null; calculating similarity indexes for nodes at two ends of the edges (u, v) in each set E, and recording the similarity indexes as suv; for each edge (u, v) in the set E, if suv is not less than t, adding the edge (u, v) into the set C; and calculatingall connected sub-graphs in the set C, wherein each connected sub-graph is a community. According to the invention, community detection of different granularities in a large-scale network can be realized, Sybil attacks can be effectively resisted, and the community security is improved.
Owner:XIDIAN UNIV
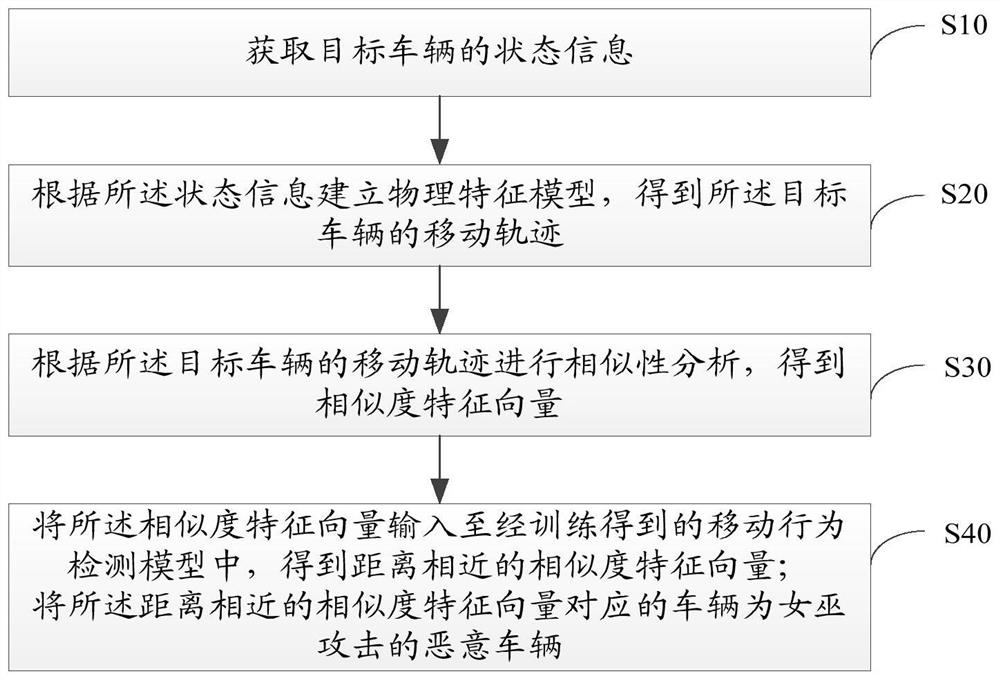
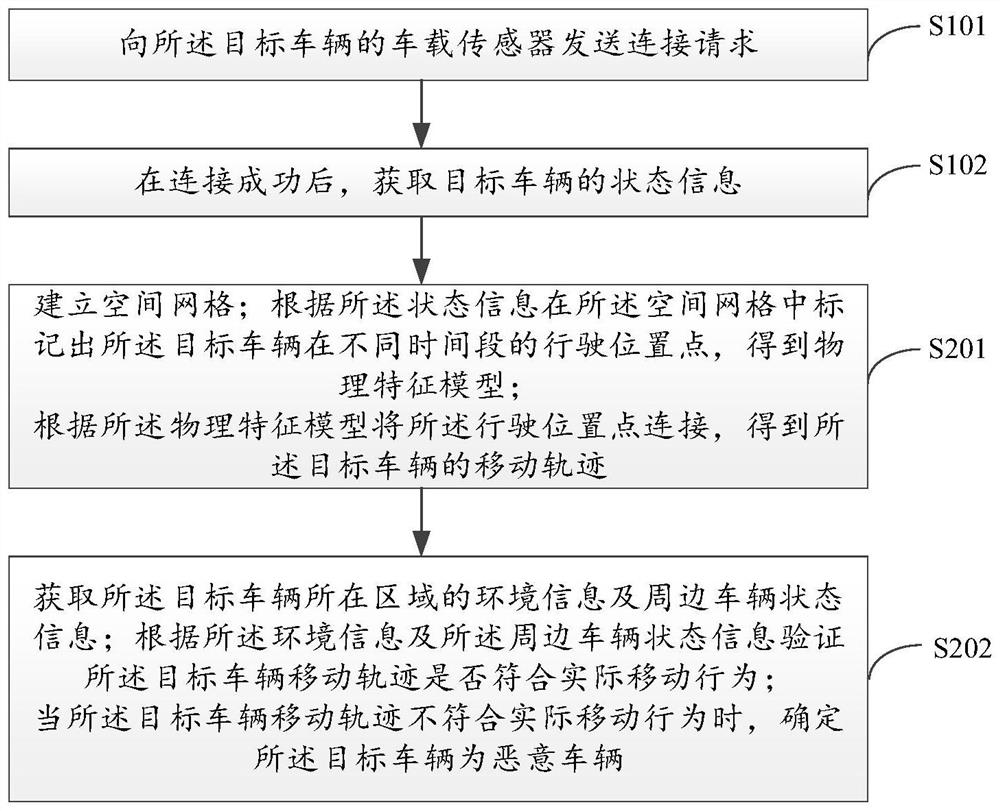
Internet of Vehicles Sybil attack detection method, device and apparatus and storage medium
The invention relates to the technical field of Internet of Vehicles, and discloses an Internet of Vehicles Sybil attack detection method, device and apparatus and a storage medium, and the method comprises the steps: obtaining the state information of a target vehicle, building a physical feature model according to the state information, obtaining the movement track of the target vehicle, carrying out the similarity analysis according to the movement track of the target vehicle, obtaining similarity feature vectors according to a preset similarity detection model, inputting the similarity feature vectors into a movement behavior detection model obtained through training to obtain similarity feature vectors with close distances, and taking vehicles corresponding to the similarity feature vectors with close distances as malicious vehicles attacked by Sybil. The physical feature model completely records the driving track of the target vehicle, the similarity feature vectors with close distances are obtained through the moving behavior detection model, the detection accuracy is improved, malicious vehicles with Sybil attacks are detected, the technical problem that whether Sybil attacks exist in Internet of Vehicles applications or not cannot be detected in the prior art is solved, and the security of Internet of Vehicles is improved.
Owner:ANHUI JIANGHUAI AUTOMOBILE GRP CORP LTD
Detection method for Sybil attack of wireless network based on channel state characteristics
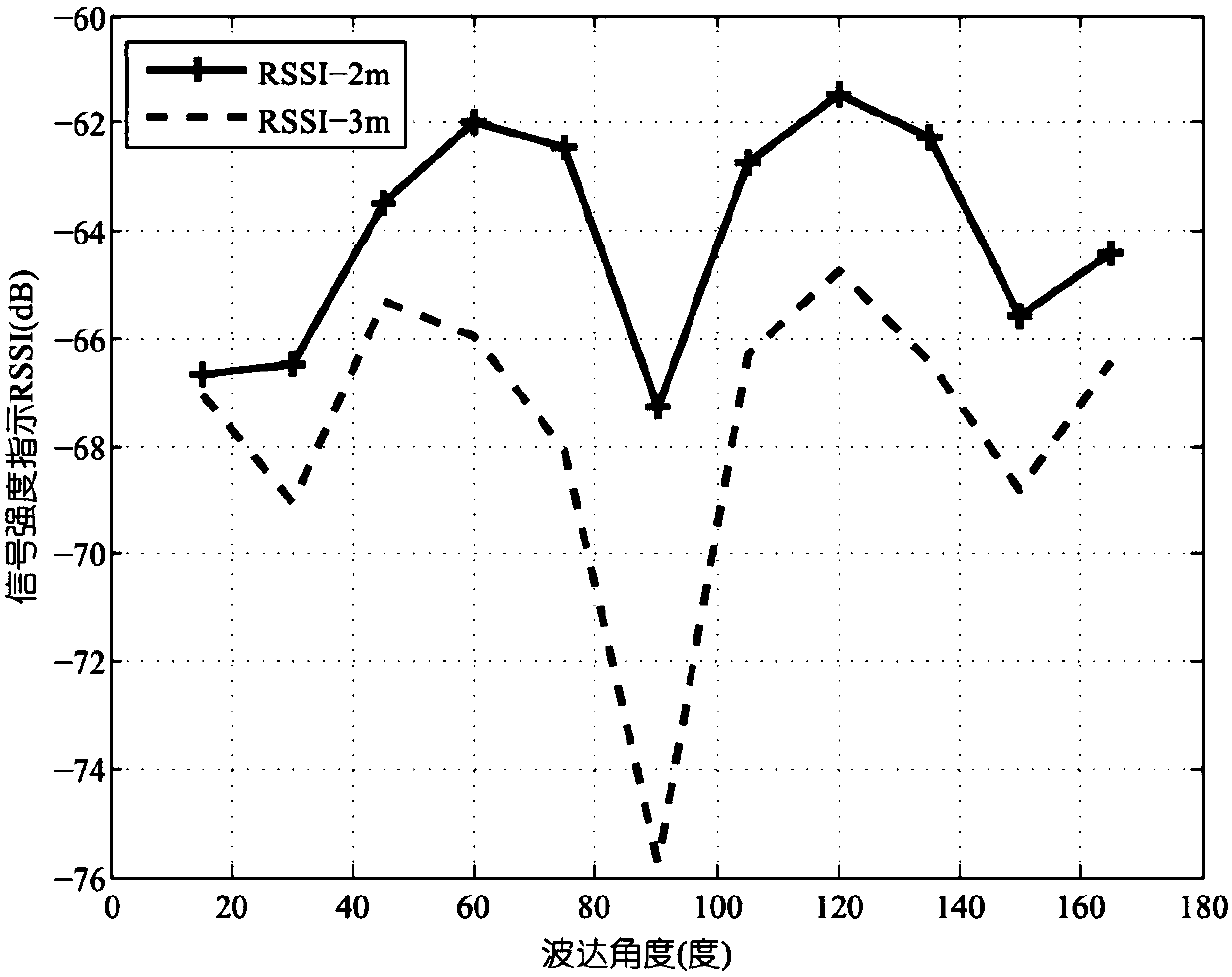
ActiveCN108337681AEliminate frequencyEliminate delayRadio wave direction/deviation determination systemsTransmission monitoringTime deviationWireless mesh network
The invention discloses a detection method for a Sybil attack of a wireless network based on channel state characteristics. The method comprises the following steps of (1) collecting signal state characteristic information of each client by a central detection AP, eliminating a phase deviation and a time deviation in the channel state characteristics by utilizing a self-adaptive MUSIC algorithm, meanwhile, computing an angle of arrival of a sight distance route by applying a spatial smoothing MUSIC algorithm through a receiving phase, and distinguishing angle signals transmitted by different APs by comparing different RSSI values; (2) detecting the Sybil attack and a Sybil node through combination of the angle of arrival and the signal strength, and distinguishing whether the node is underthe Sybil attack or not through comparison with the actual sending angle of arrival (AoA) and the RSSI; and (3 ) constructing a Sybil attack detection model system, carrying out experiments on the APand mobile equipment at different angles, meanwhile, computing the angle and carrying out simulation experiment on the Sybil attack, and detecting the Sybil node and the Sybil attack. According to the method, the Sybil node and the Sybil attack in the wireless network can be accurately detected, and the detection efficiency is 98%.
Owner:TIANJIN UNIVERSITY OF TECHNOLOGY
Sybil attack node detection method and device considering sensor errors
ActiveCN111918294AImprove driving safetyPromote intelligent developmentParticular environment based servicesTransmission monitoringIn vehicleSimulation
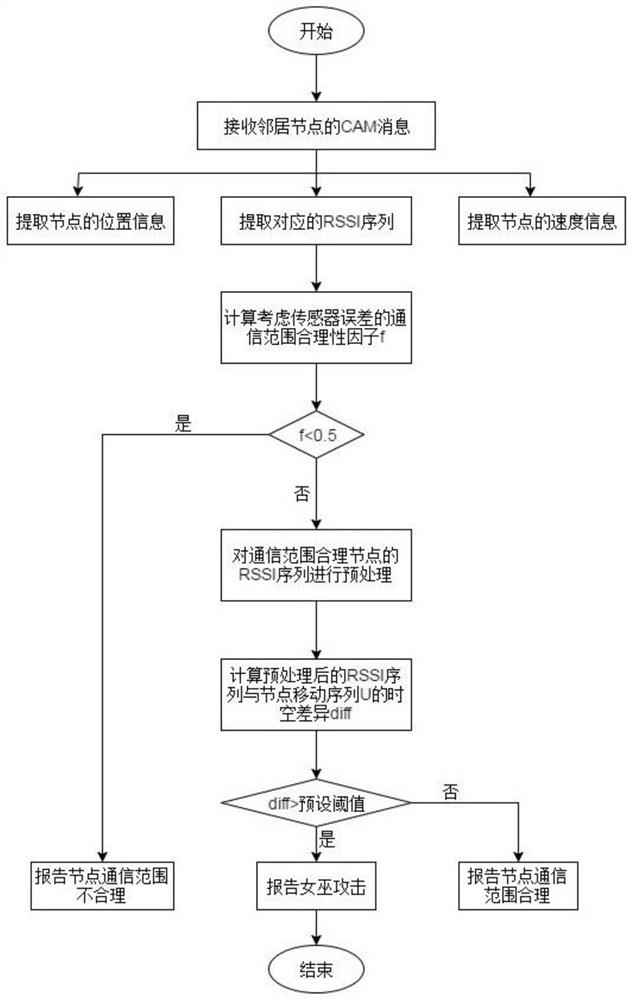
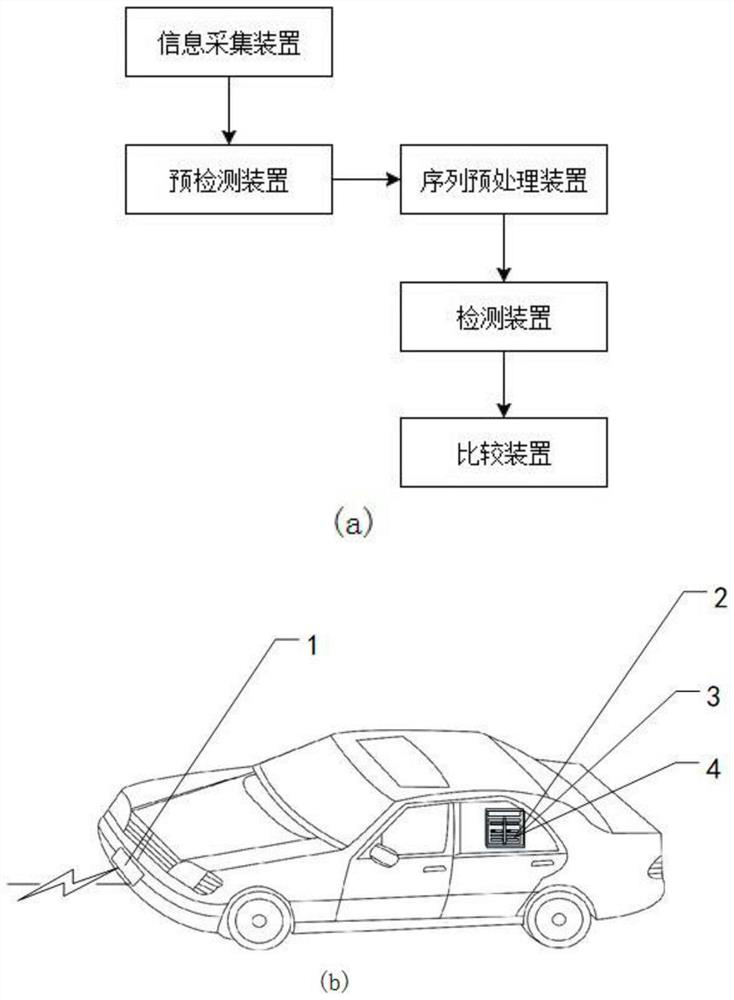
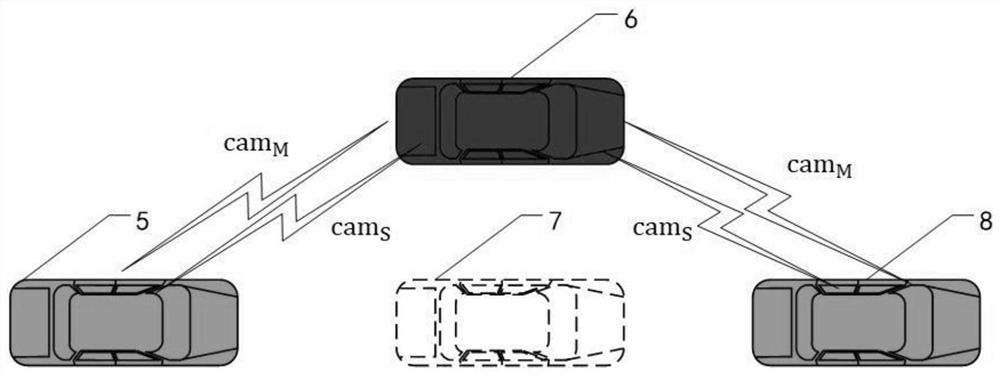
The invention discloses a Sybil attack node detection method and device considering sensor errors, relates to the technical field of vehicle-mounted network security, and solves the technical problemthat the detection of a Sybil attack node by a vehicle-mounted network is not accurate enough. The main points of the technical scheme of the invention are that the method comprises the steps that aninformation acquisition device receives a CAM message broadcast by a neighbor node; a pre-detection device fuses sensor errors to judge the rationality of the vehicle node communication range; a preprocessing device performs filtering optimization processing on a node RSSI sequence with a reasonable communication range by using Gaussian filtering; a detection device uses a DTW algorithm to measurethe spatial difference and the time difference between a node RSSI sequence and a moving sequence so as to discover Sybil nodes in neighbor nodes. While malicious behaviors in the vehicle-mounted adhoc network are detected in real time, inherent physical acquisition errors of the sensor are considered, and the rationality of the detection process is improved; the calculation load of the DTW detection algorithm is greatly reduced, and the detection time is shortened.
Owner:SOUTHEAST UNIV
Sybil attack detection method based on node attention and forwarding characteristics and electronic equipment
The invention discloses a Sybil attack detection method and electronic equipment based on node attention and forwarding characteristics, and the detection method comprises the steps: obtaining social network user behavior data, and extracting a node feature vector and a node pair feature vector from the social network user behavior data based on the node attention and forwarding characteristics; inputting the node feature vector into a preset node classifier to obtain an initial trust value of the node, and inputting the node pair feature vector into a preset node pair classifier to obtain an initial trust value of the node pair; constructing a weighted strong social graph according to a preset social graph and the initial trust values of the node pairs; and carrying out trust propagation in the weighted strong social graph according to the initial trust values of the nodes by using a random walk algorithm to obtain a Sybil node set and a benign node set. According to the method, the user behavior information is integrated in the graph structure of the social network, so that the Sybil detection accuracy and practicability are effectively improved, and the method is simple and easy to implement.
Owner:BEIHANG UNIV
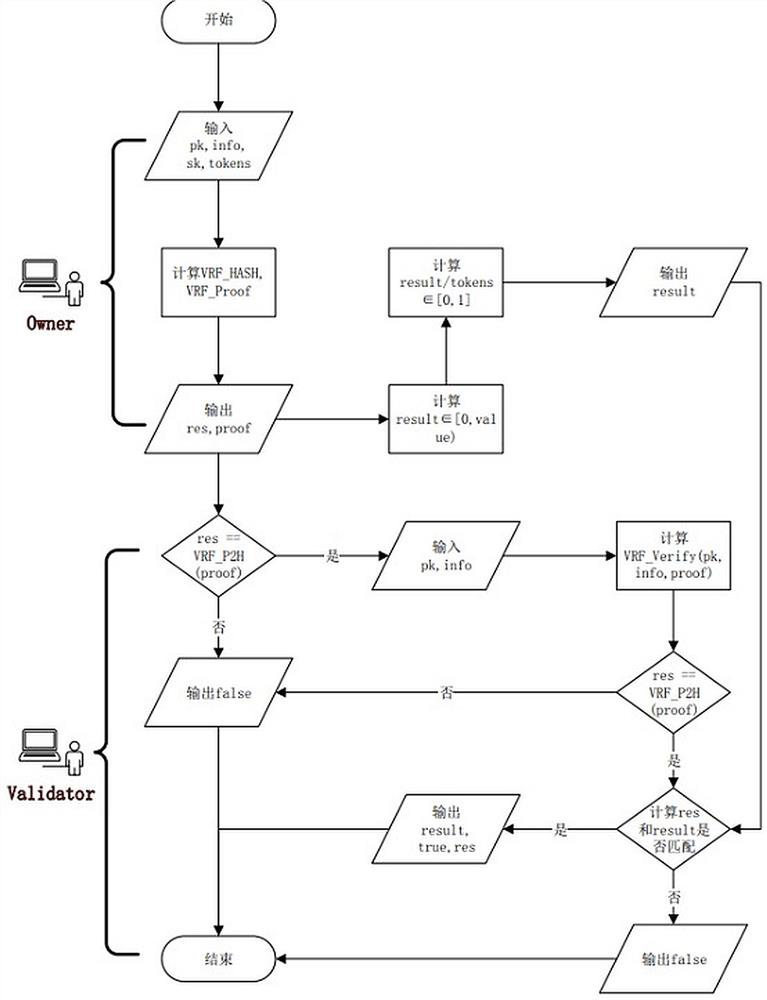
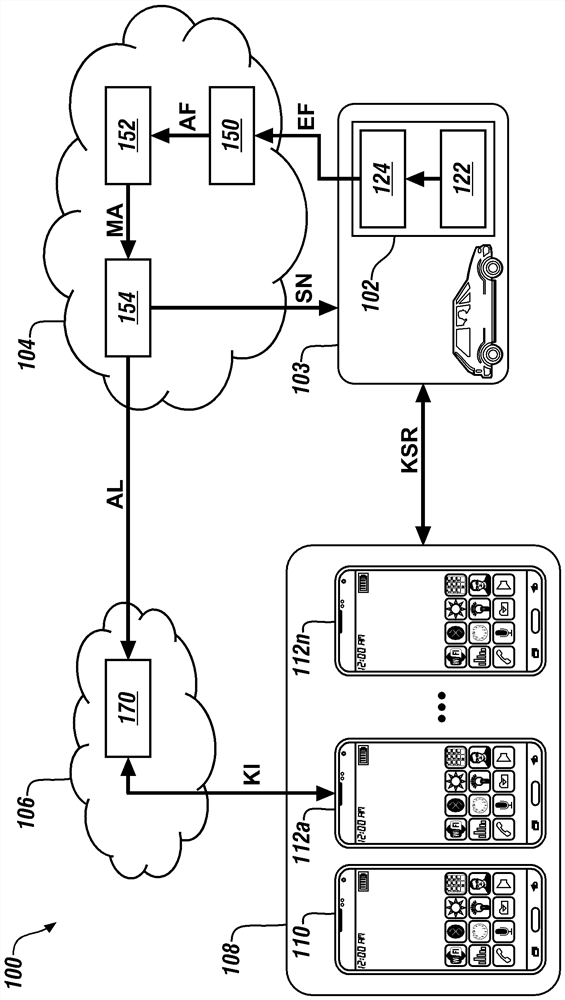
Method for digital key misbehavior and sybil attack detection through user profiling
ActiveCN112615716AKey distribution for secure communicationMultiple keys/algorithms usageUser deviceEngineering
The invention relates to a method for digital key misbehavior and sybil attack detection through user profiling, and concretely discloses a digital key sharing system. The digital key sharing system includes an electronic circuit and a first server computer. The electronic circuit is configured to store a plurality of digital keys, receive a plurality of key sharing requests, and generate a plurality of features in response to the plurality of key sharing requests. The first server computer is in wireless communication with the electronic circuit and is configured to generate an alert signal in response to finding one or more anomalies in the plurality of features to initiate a notification to a primary user device associated with the electronic circuit, and send a suspend notification signal to the electronic circuit in response to the finding of the one or more anomalies in the plurality of features. The electronic circuit is further configured to suspend use of the plurality of digital keys in response to reception of the suspend notification signal.
Owner:GM GLOBAL TECH OPERATIONS LLC
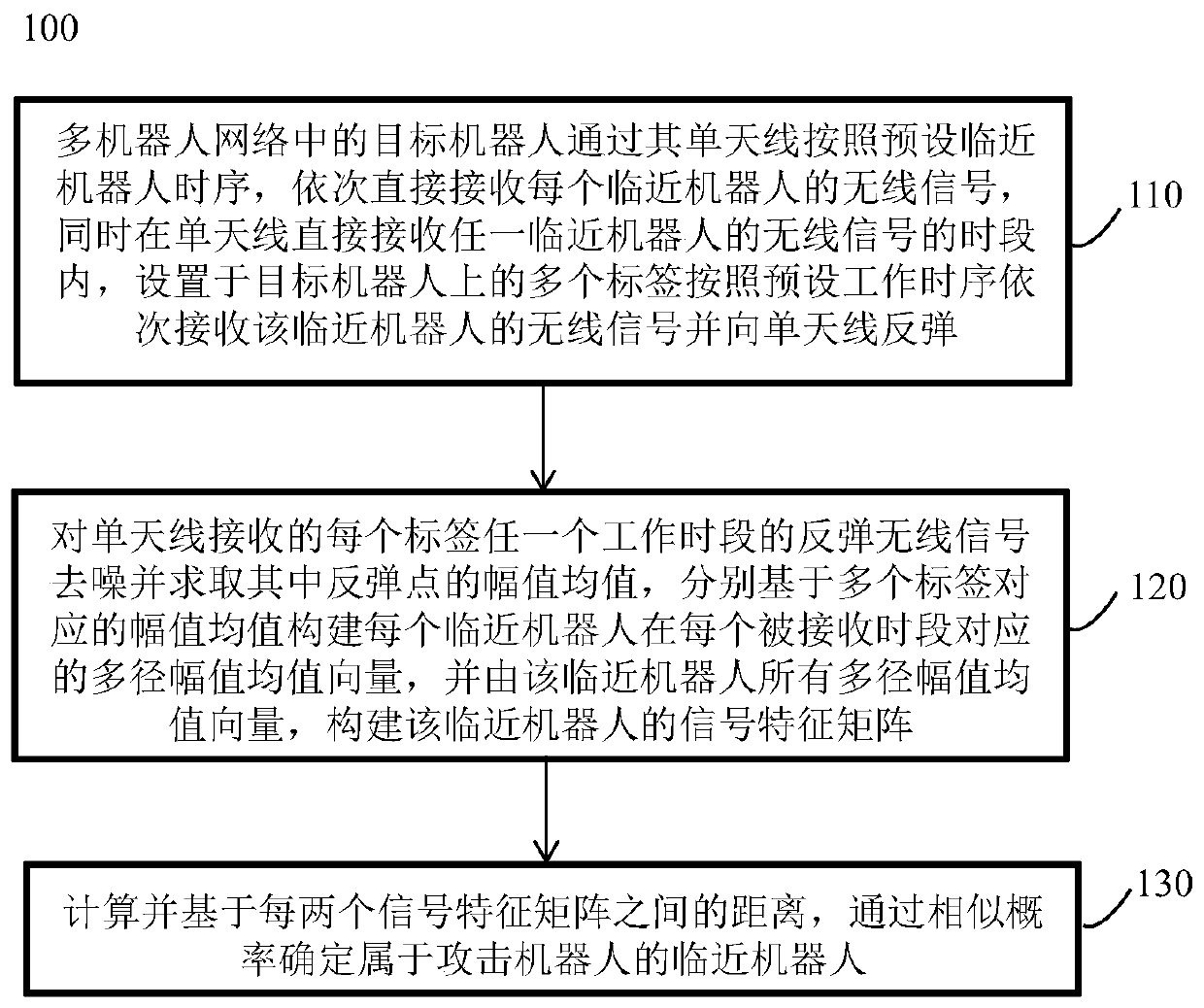
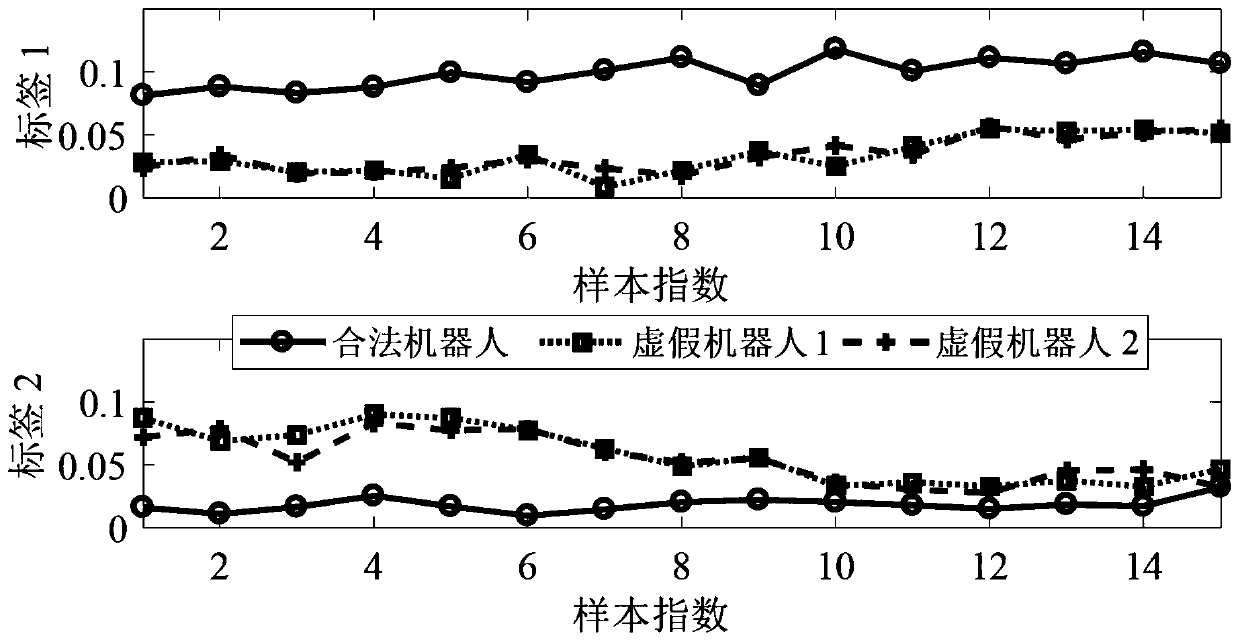
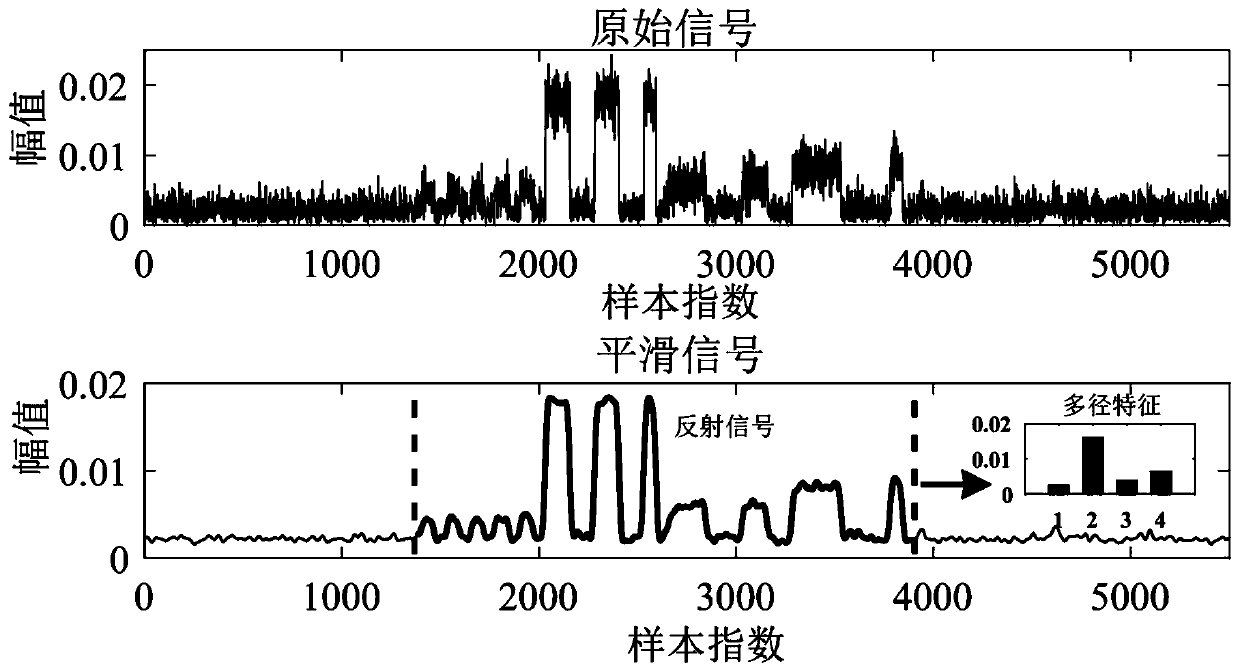
Attack robot detection method and detection system in multi-robot network
The invention discloses an attack robot detection method and detection system in a multi-robot network. The method comprises the following steps: using a plurality of labels placed on a target robot for reflecting wireless signals from an adjacent robot; the target robot firstly constructing a unique signal feature matrix for each adjacent robot based on extracted rebound wireless signals; then, effectively measuring the distance between every two characteristic matrixes; then, generating a matrix containing the similarity probability between every two adjacent robots based on the measured distance; and finally, the adjacent robots at the same position or on the same path having similar signal characteristics, and based on the signal space characteristics, judging a legal robot and a malicious attacker in the adjacent robots according to a similarity matrix so as to detect a false robot forged by a Sybil attacker in the current network. Even on a lightweight robot platform only provided with a single antenna, accurate Sybil attack detection can be achieved, the structure is simple, and practicability is high.
Owner:HUAZHONG UNIV OF SCI & TECH
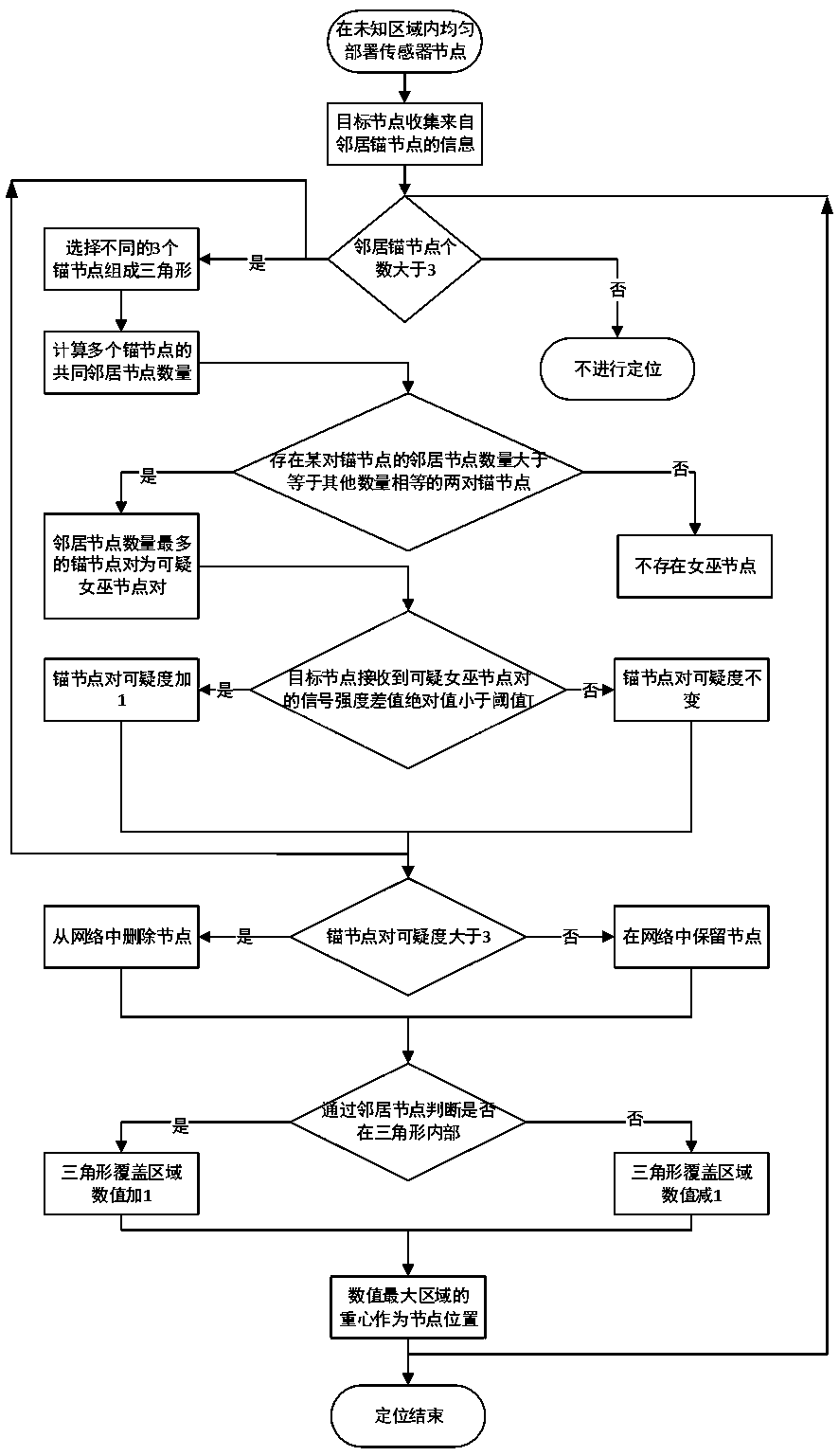
approximate triangular interior point test positioning algorithm for resisting Sybil attacks
ActiveCN109819397AEasy to detectImprove stabilityNetwork topologiesUsing reradiationAlgorithmUltimate tensile strength
Owner:NANJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com