Sybil node recognition method based on physical layer confidence degree
An identification method and a technology of trust degree, applied in wireless communication, safety devices, electrical components, etc., can solve problems such as single point failure, unavailable detection, low communication and storage overhead, etc., to reduce false alarm rate, low overhead, The effect of reducing system overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
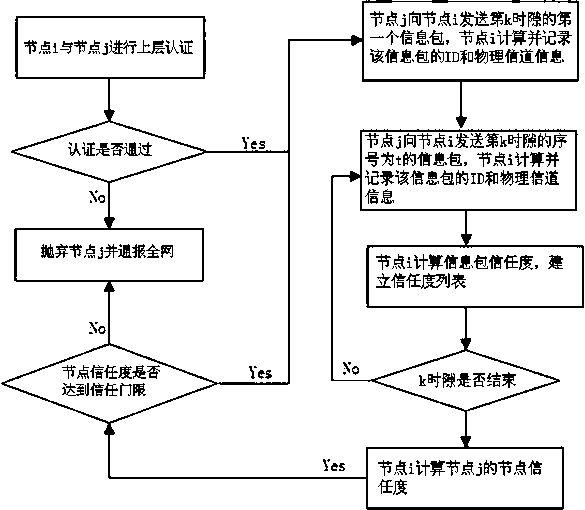
[0030] Describe technical scheme of the present invention in further detail below in conjunction with accompanying drawing: as figure 1 Shown, a kind of Sybil node identification method based on physical layer degree of trust, it comprises the following steps:
[0031] S1. Node i and node j perform upper-level initial authentication. If the authentication passes, they communicate. If the authentication fails, node i abandons node j and notifies the entire network, where the value of i is 0, 1, 2, 3...; , where the value of j is 0, 1, 2, 3..., and j≠i;
[0032] S2. In time slot k, k=1, 2, 3, ... node i receives the first information packet sent by node j, the sequence number is 0, node i calculates and records the physical channel information of the information packet with sequence number 0 and ID 0 ;
[0033] S3. In time slot k, node i receives the information packet with sequence number t sent by node j, t=1, 2, 3,..., node i calculates and records the channel information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com