Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33 results about "Random text" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method for improving rejection capability of speech recognition system
ActiveCN103077708AEffective denialImprove the effect of rejectionSpeech recognitionFeature vectorFeature extraction
The invention relates to a method for improving rejection capability of a speech recognition system. The method comprises the following steps of collecting various types of noise data; classifying according to the noise types; for different types of noise, respectively training GMMs (Gauss mixed model); assembling various types of GMMs into an integral absorption model; training a statistic language model by various types of relatively random texts, and then establishing a recognition network by WFST (weighted finite state transducer) technique, which is called as an absorption network; connecting the absorption network, the absorption model and an original decoding network in parallel to form a new decoding network; enabling the input original audio frequency to pass endpoint detection and a feature extraction module, so as to generate feature vectors; and competing the feature vectors in the three parts of the decoding network according to an Viterbi algorithm, so as to generate a final recognition result, and effectively reject the noise and an out-of-vocabulary condition. The method has the advantage that on the premise of balancing the recognition efficiency, the effect of rejecting the out-of-vocabulary condition and the invalid input is well realized.
Owner:讯飞医疗科技股份有限公司
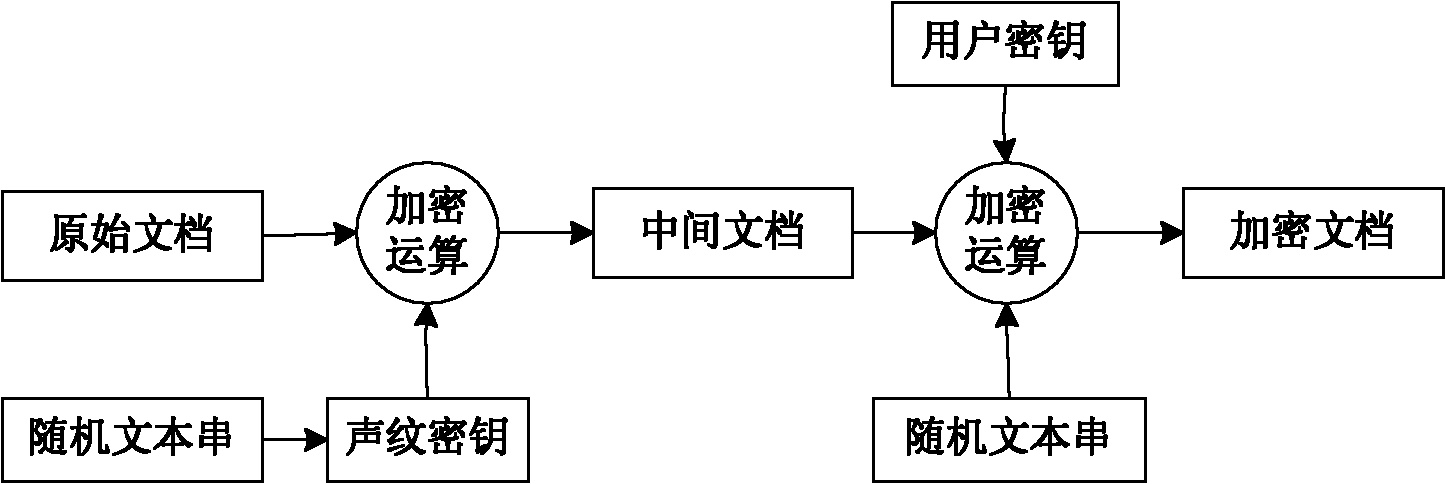
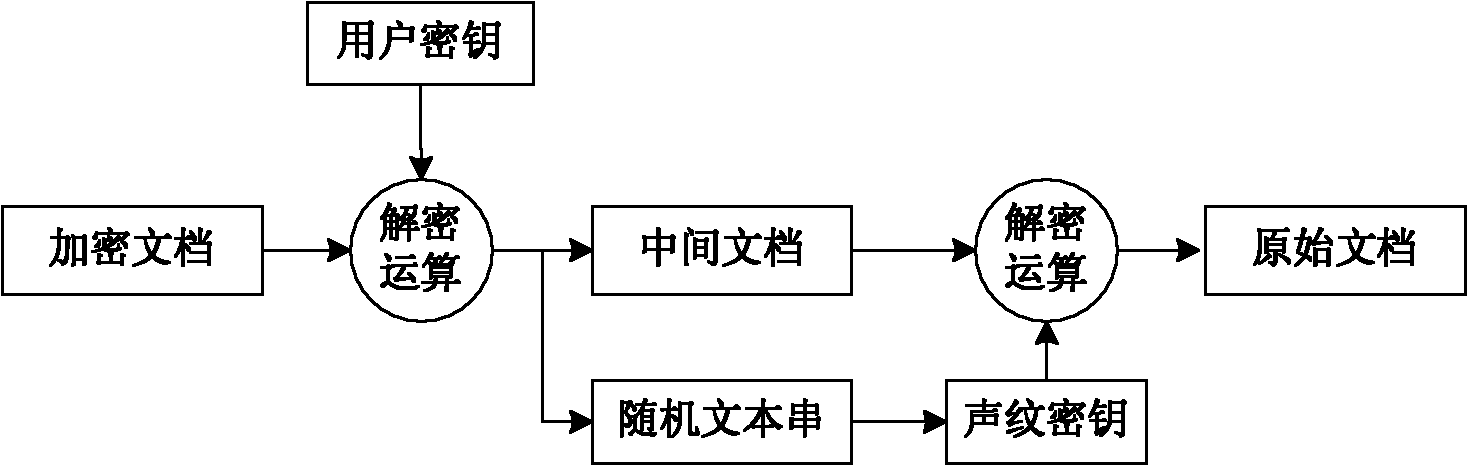
Document encrypting method and document decrypting method on basis of voice print
The invention relates to a document encrypting method on the basis of a voice print, which comprises the following steps that: (1) a user remembers a key; (2) the user says a sentence by voice randomly, and a key is extracted from characteristic parameters of the voice print of the voice as an encrypted key; (3) a symmetric encryption algorithm is selected, the key extracted in the step (2) is used to encrypt a document, an intermediate document is generated, a random text string in the step (2) and the intermediate document are packed together to generate a novel document; and (4) the key remembered by the user is used to encrypt the document in the step (3) to form an encrypted document. A voice print document decrypting method comprises the following steps that: (1) the selected symmetric encryption algorithm and the key remembered by the user are used to generate a temporary document; (2) a text string correlative with the encrypted key of the document is separated out from the temporary document and the user says the text string by voice and extracts a key from the characteristic parameters of the voice print of the voice; and (3) the temporary document is decrypted by the key extracted in the step (2) and the selected symmetric encryption algorithm to complete decrypting the document. The document encrypting method and the voice print document decrypting method provided by the invention are convenient to use and have high safety.
Owner:HANGZHOU DIANZI UNIV
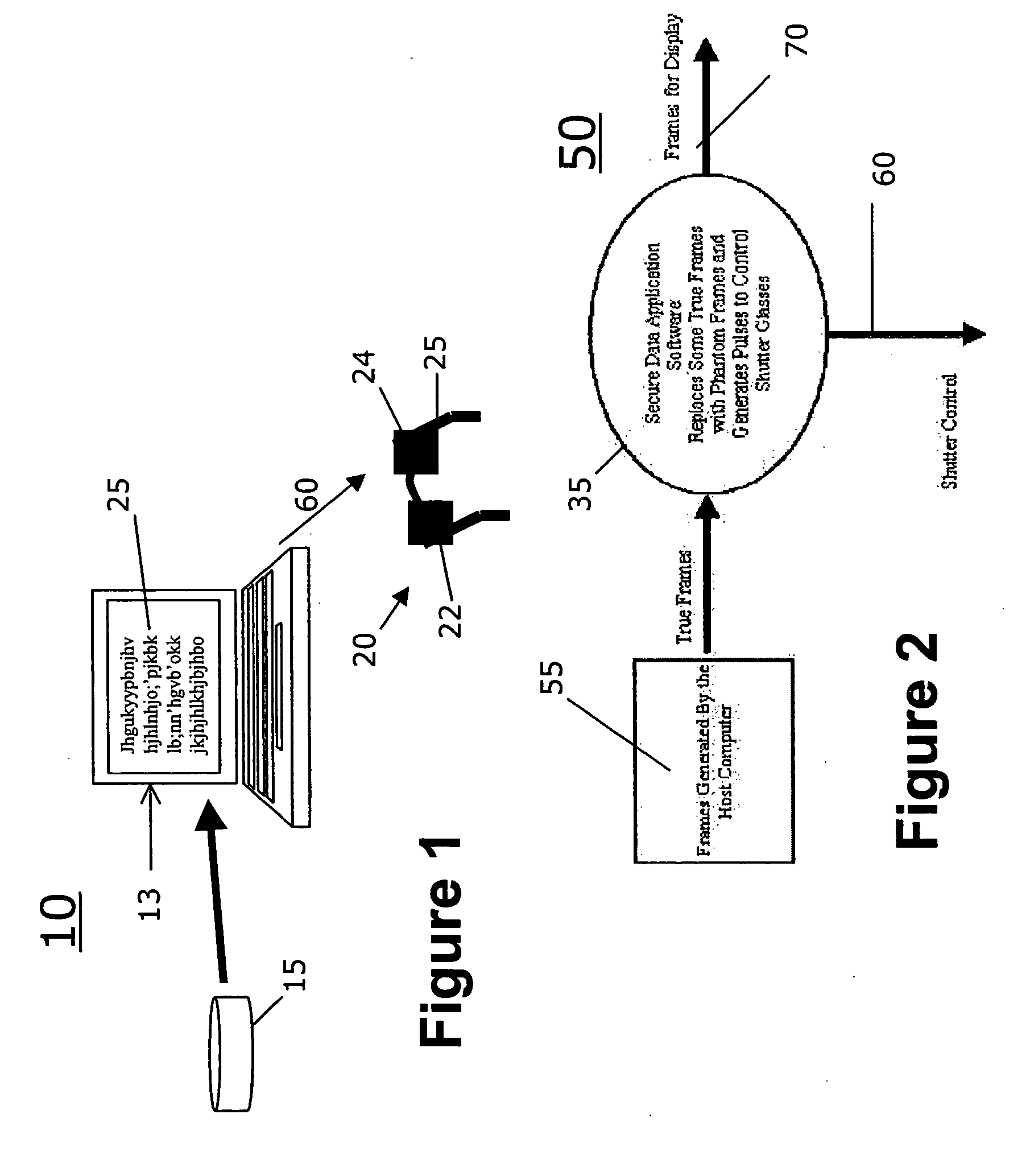
Method for displaying private/secure data
InactiveUS20070247392A1Minimally invasiveCathode-ray tube indicatorsComputer graphics (images)Display device
A system and method for allowing users to view secure data while excluding others from viewing. The method includes generating a stream of first data frames including secure data content to be viewed on a display device; inserting second data frames within the stream in a manner to thereby render a displayed image of the secure data unreadable on the display device. Shutter glasses, to be worn by an authorized user, are provided to receive signals from the computer device and, in response to received signals, filter out the second data frames thus enabling the viewer to view the secure data to the exclusion of nearby observers. The second frames are generated and interspersed within the first video frames having secure data by software executing on a conventional computing device. The second frames may include random text interspersed according to a regular or irregular pattern, or may include color and intensities to exploit deficiencies of human visual perception.
Owner:IBM CORP
Random verification code
InactiveCN103379091AVerification code is clearEasy to readUser identity/authority verificationUser verificationAccess time
The invention discloses a random verification code that comprises a random text generation module, a verification code module, a business logic module, a database and the like. According to the invention, user access information is obtained through a system, including user information and access information, such as access address, access time and other dimension parameters. Based on the verification code container selection algorithm, a random text is extracted in the database, verification code characters are then specified in the random text through the verification code module, and a user is notified of verification code selection rules and reminded of the corresponding verification code. If the user is notified of the selection rules, the user only needs to select and input the corresponding verification code to verify. By containing the verification code in the random text, the random verification code improves the security of the verification code system and effectively prevents automatic identification of a machine program.
Owner:SHANGHAI BOLU INFORMATION TECH
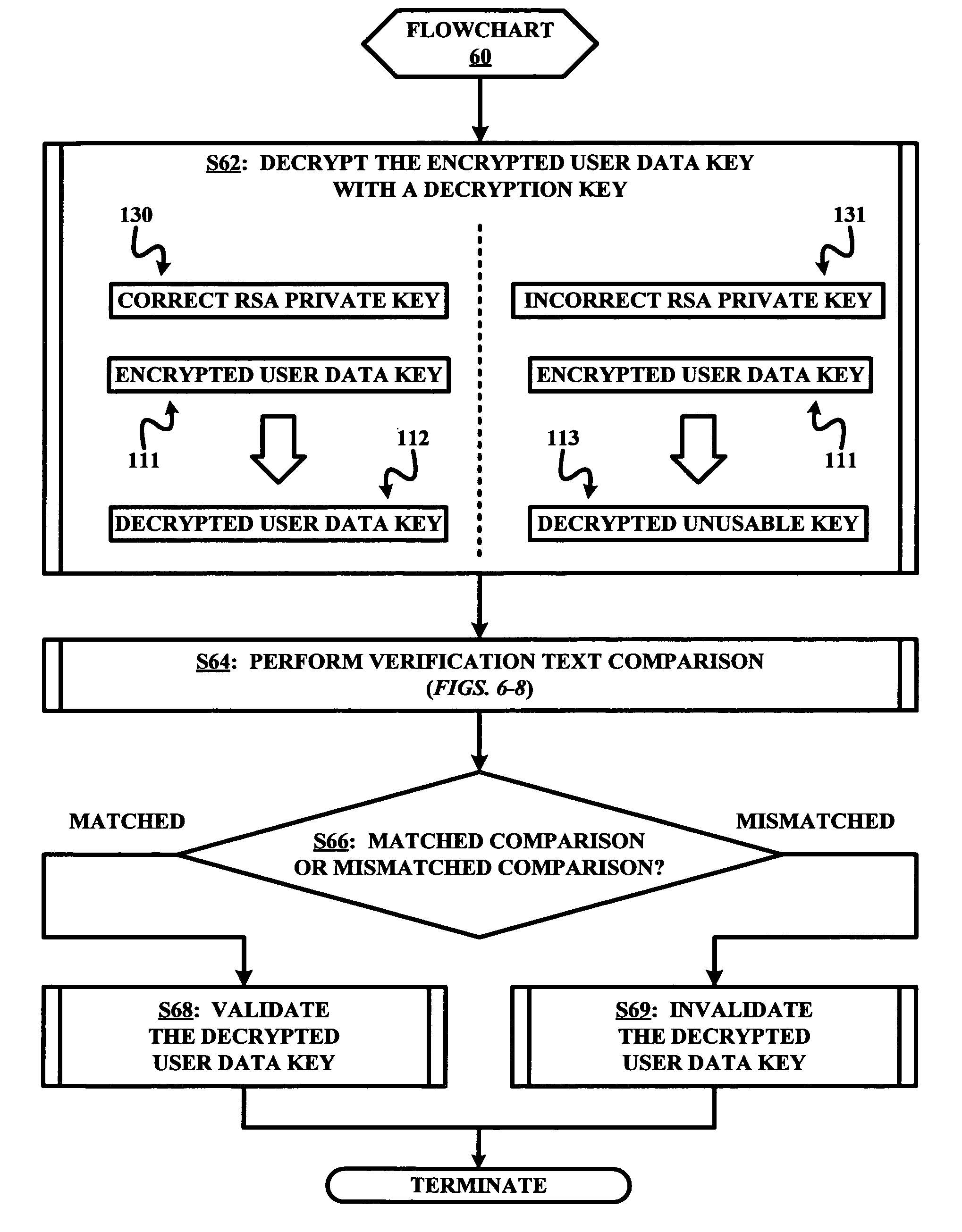
Cipher method and system for verifying a decryption of an encrypted user data key
InactiveUS20070160202A1Key distribution for secure communicationPublic key for secure communicationRandom textCipher
A cipher method for verifying a decryption of an encrypted user data key used to encrypt user data prior to an encryption of the user data key with an encryption key. The cipher method involves a decryption of the encrypted user data key with a decryption key in response to an initiation of a decryption of the encrypted user data with the user data key as decrypted with the description key, a decryption of the verification text with the user data key as decrypted with the decryption key, and a validation / invalidation of a use of the user data key as decrypted with the decryption key to decrypt the encrypted user data in response to a matched / unmatched comparison of the verification text as decrypted with the user data key and an intermixing of a known text and a random text.
Owner:IBM CORP
Text line recognition method and device, readable storage medium and electronic equipment
ActiveCN111709406AImprove training effectCharacter and pattern recognitionNeural architecturesNetwork modelRandom text
The invention relates to a text line recognition method and device, a readable storage medium and electronic equipment. The text line recognition method comprises the steps that at least one to-be-detected text line image is input into a preset neural network model, a detection result output by the preset neural network model is obtained, and the detection result is a character string in the to-be-detected text line image, wherein the preset neural network model is obtained by training by taking the synthesized image sample as a training sample. A composite image sample comprises a sample, a positive sample, a difficult negative sample and a common negative sample. According to the technical scheme, a synthetic image sample comprising a sample, a positive sample, a difficult negative sample and a common negative sample is used as a training sample of a preset neural network, the training sample of the preset neural network is enabled to be the associated image data, so that more supervision information is introduced, and the training effect of the preset neural network model is improved in comparison with the mode of adopting mutually independent random text line images as the training data for training.
Owner:南京奇点创意数字科技有限公司
Cipher method and system for verifying a decryption of an encrypted user data key
InactiveUS7499552B2Key distribution for secure communicationPublic key for secure communicationMatch/mismatchRandom text
A cipher method for verifying a decryption of an encrypted user data key used to encrypt user data prior to an encryption of the user data key with an encryption key. The cipher method involves a decryption of the encrypted user data key with a decryption key in response to an initiation of a decryption of the encrypted user data with the user data key as decrypted with the description key, a decryption of the verification text with the user data key as decrypted with the decryption key, and a validation / invalidation of a use of the user data key as decrypted with the decryption key to decrypt the encrypted user data in response to a matched / unmatched comparison of the verification text as decrypted with the user data key and an intermixing of a known text and a random text.
Owner:INT BUSINESS MASCH CORP
Image identifying code achievement method based on text adhesion and visual compensation
InactiveCN105787340AResolve identifiabilitySolve problems that are easily recognized by machinesCharacter and pattern recognitionDigital data authenticationAlgorithmComputer vision
The invention relates to an image identifying code achievement method based on text adhesion and visual compensation.The image identifying code achievement method comprises the steps of identifying code and candidate code generation, identifying code input and identifying code identification.The step of identifying code and candidate code generation comprises the sub-steps that a server side generates candidate characters and correspondingly generates serial numbers S0; identifying characters are selected form the candidate characters, and the serial numbers S0 are correspondingly set; the identifying characters are randomly arranged, and the output positions of the identifying characters are set; the character sizes, character fonts, colors, shapes and image backgrounds and interference backgrounds of the identifying characters are set; image identifying codes for random text adhesion are formed by combining with the identifying characters, the image backgrounds and the interference backgrounds, each candidate code correspondingly generates an independent character image, and the character images are directly output to a web page to be identified and are combined with the identifying codes to serve as web page candidate codes.By the adoption of the image identifying code achievement method, the problem that identifying codes are not easily identified and cracked by machines automatically but are easily identified and input by users is solved.
Owner:XIAMEN UNIV TAN KAH KEE COLLEGE
Secure login method and apparatus
InactiveCN107491671AImprove experienceIncrease diversityDigital data authenticationSpeech soundVoice data
The present invention discloses a secure login method. The method comprises: obtaining first voice data generated by a user by reading a preset feature text, and determining a voiceprint feature of the first voice data; obtaining second voice data generated by a user by reading a random text, and determining the voiceprint feature of the second voice data; and determining the matching degree of the voiceprint feature of the first voice data with the voiceprint feature of the second voice data, and when he matching degree is greater than the preset matching degree threshold, allowing the user to login. The present invention also discloses a secure login apparatus.
Owner:ZTE CORP
HRPD network access authentication method based on CAVE algorithm
ActiveUS20050099981A1Radio/inductive link selection arrangementsRadio transmission for post communicationRandom textRADIUS
A HRPD network access authentication method based on CAVE algorithm is proposed. An AT generates a random number “RAND” necessary for the calculation of AUTH1 by using the “Random text” included in the CHAP Challenge message. A UIM card works out the AUTH1 by using the random number “RAND” and the SSD_A in the UIM card. The AT carries the AUTH1 by the Result field of the CHAP Response message. The AN-AAA generates the random number “RAND” necessary for the calculation of AUTH2 by using the “Random text” included in the Radius Access Request message. The AN-AAA works out the AUTH2 by using the random number “RAND”. The two results AUTH1 and AUTH2 is compared. If they are just the same, the authentication on the AT passes. Otherwise, the AT is rejected to access.
Owner:SAMSUNG ELECTRONICS CO LTD +1
Apparatus and method for inspecting speech recognition
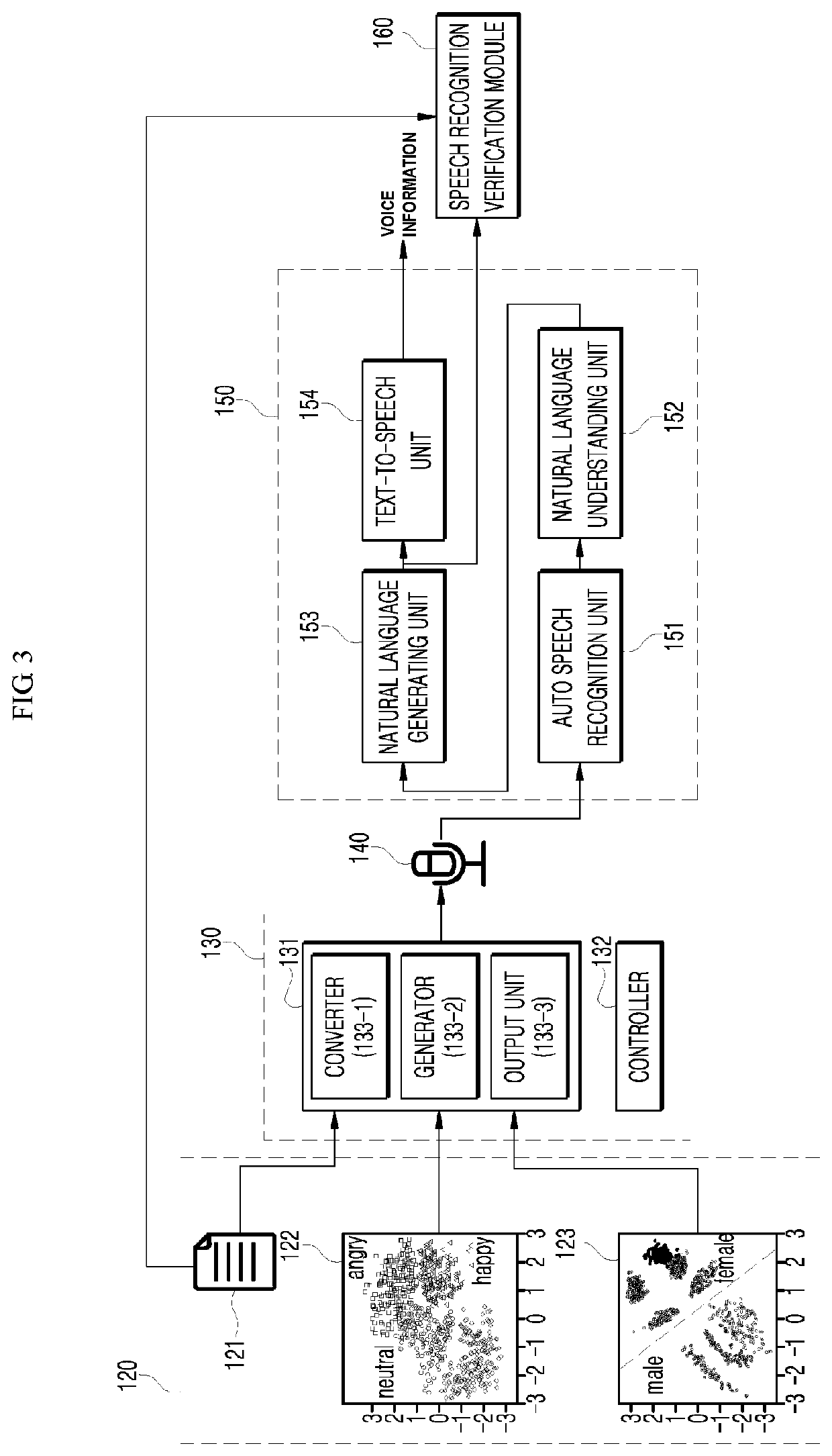
ActiveUS20200013388A1Addressing failurePrecise and broad verificationSpeech recognitionSpeech synthesisSpoken languageSpeech recognition performance
Disclosed are a speech recognition verification device and a speech recognition verification method, which verify speech recognition results by executing artificial intelligence (AI) algorithms and / or machine learning algorithms in a 5G environment connected for Internet-of-Things. According to an embodiment, the speech recognition verification method includes converting a verification target text item to a verification target spoken utterance by applying a preset utterance condition, analyzing the verification target spoken utterance and outputting a recognition result text item corresponding to an analysis result, and verifying speech recognition performance through comparison between the verification target text item and the recognition result text item. According to the present disclosure, the speech recognition result may be verified objectively by using a spoken utterance generated with random text and various utterance conditions as input of speech recognition.
Owner:LG ELECTRONICS INC
Hrpd network access authentication method based on cave algorithm
ActiveUS20090190562A1Radio transmission for post communicationWireless commuication servicesAccess networkAuthorization
A HRPD network access authentication method based on CAVE algorithm is provided. An AT (Access Terminal) generates a random number “RAND” necessary for a calculation of an AUTH1 by using a “Random text” included in the CHAP Challenge message. A UIM (User Identity Module) card works out the AUTH1 by using the random number “RAND” and an SSD_A (Shared Secret Data A) in the UIM card. The AT carries the AUTH1 in a Result field of the CHAP Response message. An AN-AAA (Access Network-Authentication, Authorization, and Accounting) generates the random number “RAND” necessary for the calculation of an AUTH2 by using a “Random text” included in a Radius Access Request message. The AN-AAA works out the AUTH2 by using the random number “RAND”. The two results AUTH1 and AUTH2 are compared. If the results are the same, the authentication on the AT passes. Otherwise, AT access is rejected.
Owner:SAMSUNG ELECTRONICS CO LTD +1
English written font error correction method
InactiveCN108491520AEasy to writeSolve writing problemsSpecial data processing applicationsTeaching apparatusComputer scienceCorrection method
The invention belongs to an English written font error correction method. The method comprises the following steps of: 1, establishing a standard library; 2, carrying out exercise aiming at the standard library; 3, establishing frequent error features; 4, carrying out error correction exercise; and 5, carrying out random text exercise. The method has the beneficial effect of gradually improving the writing levels of exercisers from strokes to letters to words, so as to fundamentally solve the writing problems.
Owner:魏培琳
Apparatus and method for inspecting speech recognition
ActiveUS11205417B2Precise and broad verificationImprove power efficiencySpeech recognitionSpeech synthesisSpoken languageSpeech recognition performance
Disclosed are a speech recognition verification device and a speech recognition verification method, which verify speech recognition results by executing artificial intelligence (AI) algorithms and / or machine learning algorithms in a 5G environment connected for Internet-of-Things. According to an embodiment, the speech recognition verification method includes converting a verification target text item to a verification target spoken utterance by applying a preset utterance condition, analyzing the verification target spoken utterance and outputting a recognition result text item corresponding to an analysis result, and verifying speech recognition performance through comparison between the verification target text item and the recognition result text item. According to the present disclosure, the speech recognition result may be verified objectively by using a spoken utterance generated with random text and various utterance conditions as input of speech recognition.
Owner:LG ELECTRONICS INC
Using finite state grammars to vary output generated by a text-to-speech system
The present invention discloses a text-to-speech system that provides output variability. The system can include a finite state grammar, a variability engine and a text-to-speech engine. The finite state grammar can contain a phrase role consisting of one or more phrase elements. The phrase rule can deterministically generate a variable text phrase based upon at least one random number. The phrase rule can include a definition for each of the phrase elements. Each definition can be associated with at least one defined text string. The variability engine can construct a random text phrase responsive to receiving an action command, wherein said finite state grammar is used to create the text phrase. The variability engine can also rely on user-specified weights to adjust the output probabilities. The speech-to-text engine can convert the text phrase generated by the variability engine into speech output.
Owner:NUANCE COMM INC
OCR training sample generation method, device and system
The invention discloses an OCR training sample generation method, device and system, and relates to the field of computer vision. The method comprises the following steps: a character contour extraction step: extracting all character contours based on an original image, determining an erasure area mask by combining an erasure area coordinate, and obtaining a repair area mask; an image repairing and filling step: performing image repairing and filling according to the mask of the repairing area and the pixel information around the repairing area to obtain a background template after the characters are erased; and a random text generation step: generating a random text in each generation area so as to obtain a new sample picture and a labeling information file corresponding to the new sample picture. According to the method, a character contour extraction algorithm, an image restoration technology and other technologies are combined, background information of an original picture is fully utilized, a high-quality training picture is generated, meanwhile, an annotation file (including character content and position information) corresponding to the picture is generated, the burdensome and labor-consuming annotation work is omitted, and the method can be directly used for OCR model training.
Owner:BEIJING YIDAO BOSHI TECH
A verification method, server and system
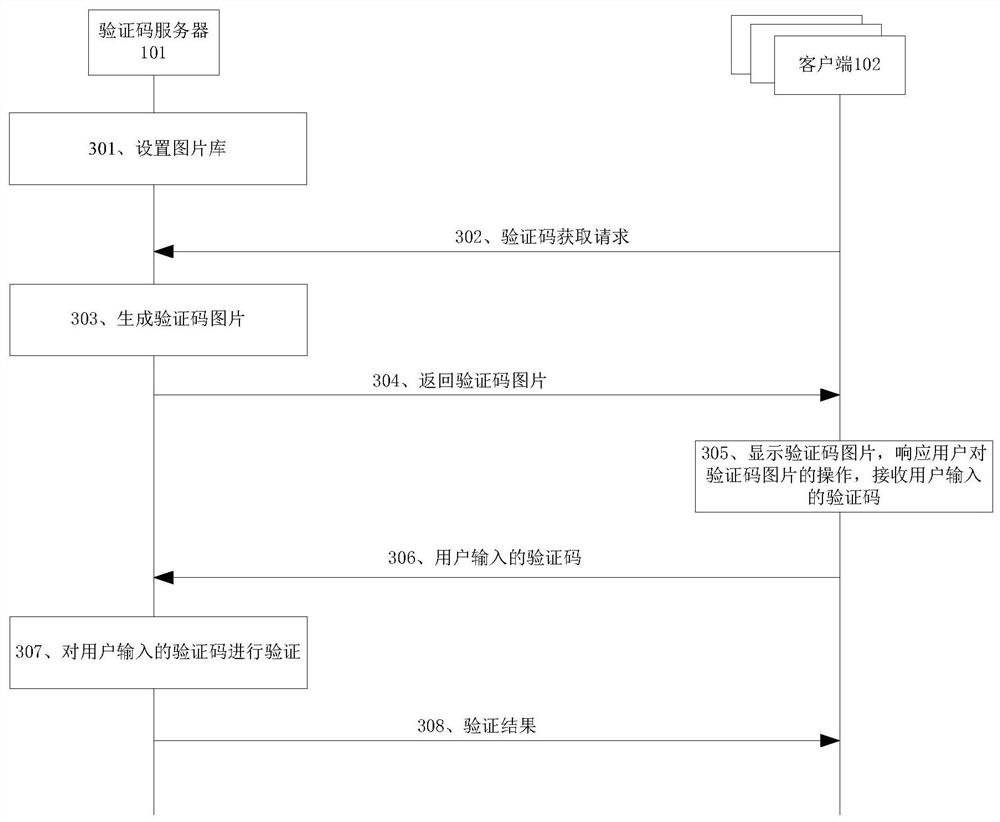
ActiveCN107888553BEnsure safetyPrevent brute force crackingDigital data authenticationSecuring communicationProgramming languageSystem verification
The present invention relates to the communication field and provides a verification method. A verification code server receives a verification code acquisition request sent by a client; generates and saves a system verification code; wherein the system verification code is determined by a string of random text; and encodes the system verification code Generate k verification code pictures from n original pictures; among them, k and n are integers greater than or equal to 2, and k is less than or equal to n; send k verification code pictures to the client; receive the verification request sent by the client , the verification request carries the verification code entered by the user according to the k verification code pictures; according to the system verification code, determine whether the verification code entered by the user is correct. Through the above solution, the randomly generated system verification code is encoded into n original pictures, which not only increases the difficulty of machine recognition, but also ensures the security of the verification code.
Owner:HUAWEI TECH CO LTD
Verification method and system, and server
ActiveCN107888553AIncrease the difficultyDoes not affect the display effectDigital data authenticationSecuring communicationSystem verificationUser input
The invention relates to the field of communication, and provides a verification method. The verification method comprises the following steps: receiving, by a verification code server, a verificationcode acquisition request sent by a client; generating and storing a system verification code, wherein the system verification code is determined by a string of random texts; encoding the system verification code into n original pictures to generate k verification code pictures, wherein k and n are integers greater than 2, and k is less than or equal to n; sending the k verification code picturesto the client; receiving a verification request sent by the client, wherein the verification request carries a verification code input by a user according to the k verification code pictures; and determining whether the verification code input by the user is correct according to the system verification code. By adoption of the above scheme, the randomly generated system verification code is codedinto the n original pictures, which not only increases the difficulty of machine recognition, but also can ensure the security of the verification code.
Owner:HUAWEI TECH CO LTD
Validating compressed archive keys
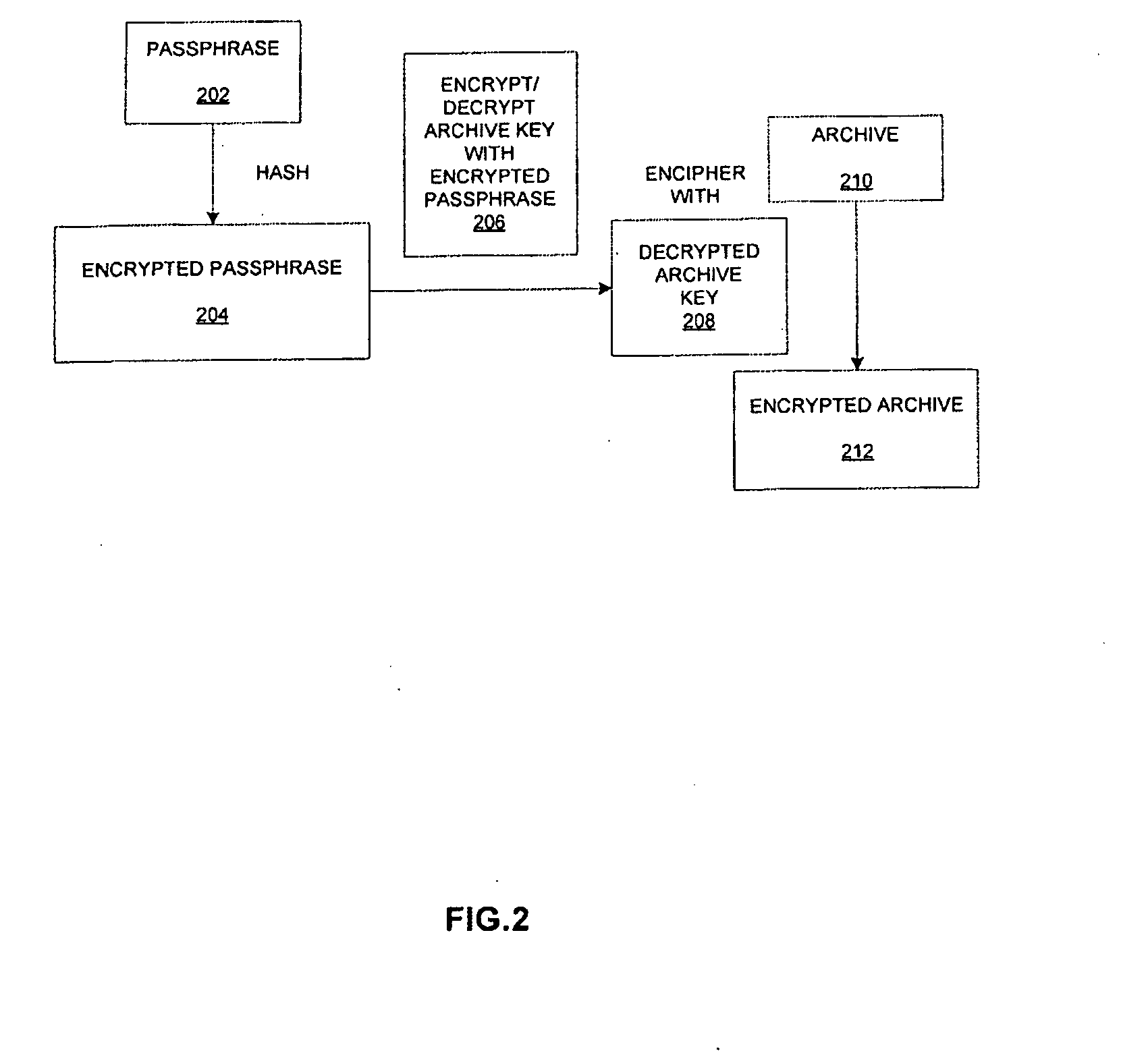
ActiveUS20100054468A1Error detection/correctionDigital data protectionProgramming languageRandom text
An apparatus and a method for validating compressed encrypted archive keys is described. In one embodiment, a pseudo-stream is generated for an archive. The pseudo-stream is made of a small amount of random text. The pseudo-stream is attached to a stream of the archive. The pseudo-stream and stream are compressed using the compression algorithm that includes validation data. The compressed pseudo-stream is then enciphered with an archive key.
Owner:RED HAT
Living body detection method and device
ActiveCN114724257AImprove accuracyEasy to detectSpeech analysisNeural architecturesFeature vectorComputer graphics (images)
The invention provides a living body detection method and device.The living body detection method comprises the steps that a face video is collected, it is determined that the collected face video contains a front face, a random text is generated, and after the generated random text is randomly displayed in a random area of a preset screen, a user is prompted to read the displayed random text; acquiring a reading video of the displayed random text read by the user, determining that the reading video contains a human face and voice, and based on the reading video, acquiring a position feature vector facing a screen when the user reads the random text and a view angle vector of the user watching the screen; inputting the position feature vector and the view angle vector into a pre-trained living body consistency detection model to obtain a consistency value of the position feature vector and the view angle vector; and if the consistency value is not less than a preset consistency threshold value, determining that the living body detection is passed. The identification accuracy of the living body can be improved.
Owner:BEIJING KUAILIAN TECH
Performance testing method and system for a large-scale multi-keyword exact matching algorithm
ActiveCN101714166BFair and reasonable evaluationSpecial data processing applicationsInterface standardInformation device
The present invention proposes a performance testing system for a large-scale multi-keyword precise matching algorithm, the system includes the following modules: a test data generation module, specifically: a random keyword generation submodule, a random text data generation submodule; Text generation sub-module; keyword set preprocessing performance testing module, specifically including: matching algorithm preprocessing interface call sub-module, test information generation sub-module. The invention solves the problem of interface standards and interoperable access between different network information security devices, realizes the cooperative work and linkage among them, and finally realizes the seamless integration of various network information security devices. It can test the performance indicators of various multi-keyword exact matching algorithms.
Owner:TSINGHUA UNIV
Method for improving rejection capability of speech recognition system
ActiveCN103077708BImprove the effect of rejectionSolve the problem of denialSpeech recognitionFeature vectorFeature extraction
The invention relates to a method for improving rejection capability of a speech recognition system. The method comprises the following steps of collecting various types of noise data; classifying according to the noise types; for different types of noise, respectively training GMMs (Gauss mixed model); assembling various types of GMMs into an integral absorption model; training a statistic language model by various types of relatively random texts, and then establishing a recognition network by WFST (weighted finite state transducer) technique, which is called as an absorption network; connecting the absorption network, the absorption model and an original decoding network in parallel to form a new decoding network; enabling the input original audio frequency to pass endpoint detection and a feature extraction module, so as to generate feature vectors; and competing the feature vectors in the three parts of the decoding network according to an Viterbi algorithm, so as to generate a final recognition result, and effectively reject the noise and an out-of-vocabulary condition. The method has the advantage that on the premise of balancing the recognition efficiency, the effect of rejecting the out-of-vocabulary condition and the invalid input is well realized.
Owner:讯飞医疗科技股份有限公司
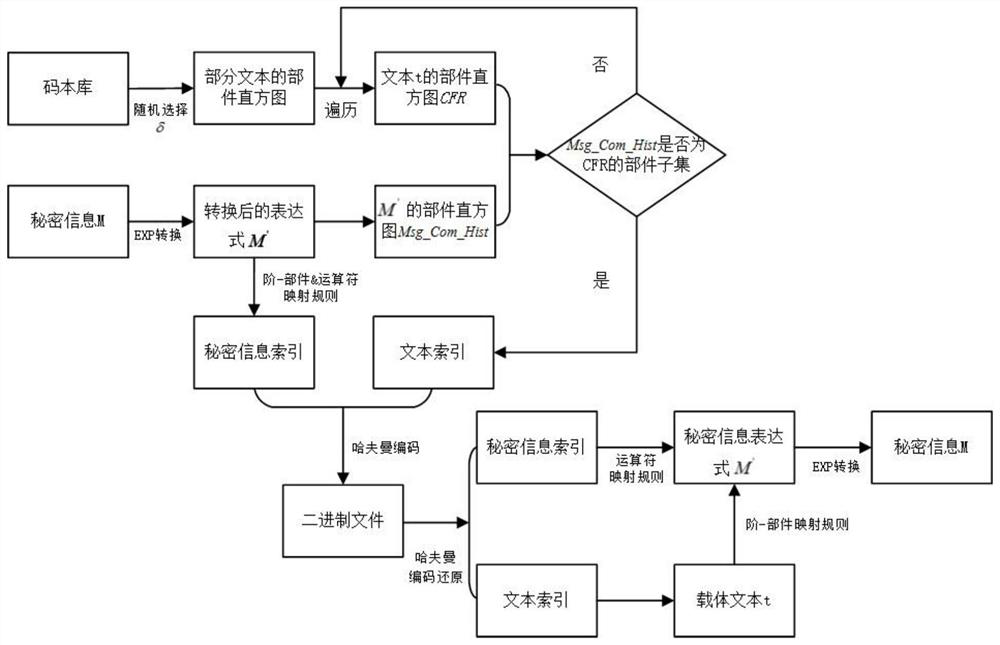
A carrier-free text steganography method and a carrier-free text steganography device for a component histogram
ActiveCN112966282ABreak up the structureAchieve hiddenDigital data protectionText database indexingInformation hidingText steganography
The invention discloses a carrier-free text steganography method and a carrier-free text steganography device for a component histogram. The carrier-free text steganography method comprises the following steps: 1, constructing a codebook of a text library; 2, preprocessing the secret information; 3, providing a hiding method based on random text selection; 4, performing information hiding; 5, constructing a secret index; and 6, extracting secret information. Compared with an existing text carrier-free information hiding technology, the invention has the advantages that all secret information can be hidden in one text at most, the hiding capacity is greatly improved, and the hiding success rate is increased by using a mixed index structure instead of a natural language processing method in the extraction process.
Owner:HUNAN UNIV OF FINANCE & ECONOMICS +1
Text data representation learning using random document embedding
Embodiments of the present invention provide a computer-implemented: method for performing unsupervised feature representation learning for text data. The method generates reference text data having aset of random text sequences:, in which each text sequence of set of random text sequences is of a random Iength and comprises a number of random words, and in which each random Iength is sampled from a minimum; length to a maximum length. The random words of each text sequence i in the set are drawn from a distribution. The method generates a feature matrix for raw text data based at least in part on a set of computed distances between the set of random text sequences and the raw text data. The method provides the feature matrix as an input to one or more machine earning models,
Owner:IBM CORP
Document encrypting method and document decrypting method on basis of voice print
The invention relates to a document encrypting method on the basis of a voice print, which comprises the following steps that: (1) a user remembers a key; (2) the user says a sentence by voice randomly, and a key is extracted from characteristic parameters of the voice print of the voice as an encrypted key; (3) a symmetric encryption algorithm is selected, the key extracted in the step (2) is used to encrypt a document, an intermediate document is generated, a random text string in the step (2) and the intermediate document are packed together to generate a novel document; and (4) the key remembered by the user is used to encrypt the document in the step (3) to form an encrypted document. A voice print document decrypting method comprises the following steps that: (1) the selected symmetric encryption algorithm and the key remembered by the user are used to generate a temporary document; (2) a text string correlative with the encrypted key of the document is separated out from the temporary document and the user says the text string by voice and extracts a key from the characteristic parameters of the voice print of the voice; and (3) the temporary document is decrypted by the key extracted in the step (2) and the selected symmetric encryption algorithm to complete decrypting the document. The document encrypting method and the voice print document decrypting method provided by the invention are convenient to use and have high safety.
Owner:HANGZHOU DIANZI UNIV
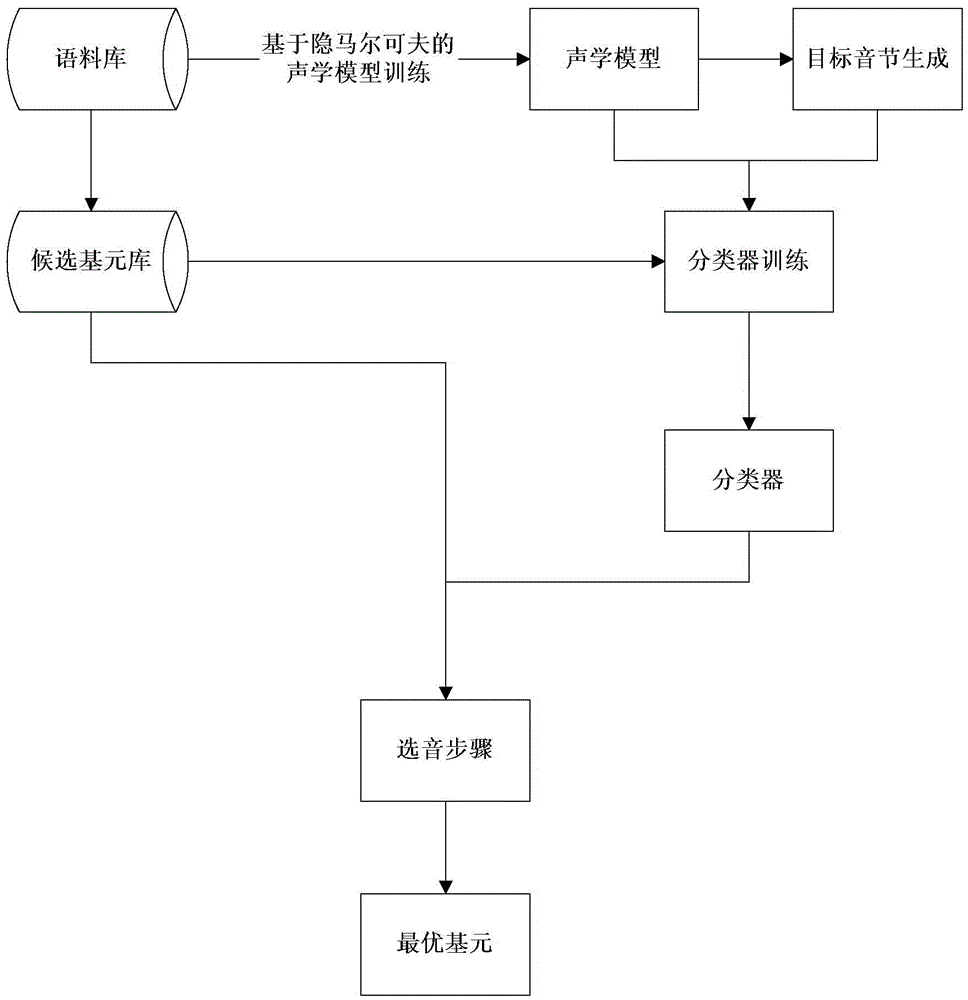
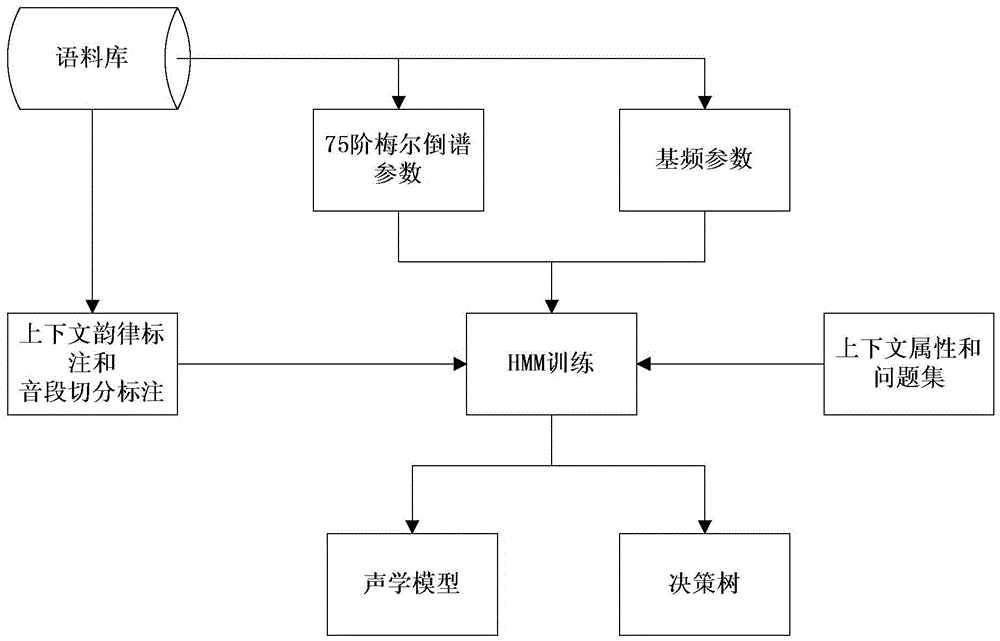
A sound selection method for waveform splicing speech synthesis
The invention discloses a sound selection method for waveform concatenation speech synthesis. The method comprises the following steps of: on the basis of an original audio, carrying out hidden markov based model training so as to obtain an acoustic model set and a corresponding characteristic decision tree; inputting a plurality of training texts and on the basis of the characteristic decision tree, searching to obtain related acoustic models so as to obtain corresponding target voice and target syllables; according to similarity of the target voice and corresponding candidate primitives and likelihood probability of each acoustic parameter of the candidate primitives under a current acoustic model, training to obtain a similarity classifier; inputting a random text to be synthesized, removing the dissimilar candidate primitives on the basis of the similarity classifier, selecting the optimal primitive from the residual candidate primitives by utilizing a concatenation cost minimization rule and carrying out concatenation to obtain synthetic speech. The adoption of the method disclosed by the invention can synthesize speech with higher tone quality.
Owner:中科极限元(杭州)智能科技股份有限公司
Text line recognition method and device, readable storage medium, electronic device
ActiveCN111709406BImprove training effectCharacter and pattern recognitionNeural architecturesNetwork modelComputer vision
Owner:南京奇点创意数字科技有限公司
Text processing method, device, equipment and storage medium
PendingCN110427328AImplement inputImprove test resultsSoftware testing/debuggingIntelligent editorsComputer hardwareText processing
Embodiments of the invention provide a text processing method, a device, equipment and a storage medium. The method comprises the steps of obtaining text information in a text input box; and if it isdetermined that the character string with the preset length in the text information conforms to a preset replacement logic, replacing the character string with the preset length with random text information matched with a preset random text system, the character string with the preset length being a character string located in front of a cursor in the text input box. The embodiment of the invention can solve the problems that the input of the test data cannot be quickly realized, and the test effect is poor due to the non-authenticity of the manually input test data.
Owner:BEIJING BYTEDANCE NETWORK TECH CO LTD
Method and device for displaying page text
ActiveCN103473214BGuaranteed display effectAvoid crawlingSpecial data processing applicationsAlgorithmComputer graphics (images)
The invention provides a method and a device for displaying page characters. The method includes segmenting to-be-displayed characters to acquire N character groups, wherein N is a positive integer more than 2; mixing random characters in each character group; taking each character group after the random characters are mixed therein as a Dom node for splicing according to a corresponding sequence of segmenting; hiding the mixed-in random characters by setting patterns. A mixing mode is adopted, so that normal displaying of the page characters is guaranteed, webpage content acquired by copying and capturing is enabled not to be normally displayed due to the fact that the random characters are mixed in, freeness from dependence on a browser is realized by the mode, and the webpage characters are effectively prevented from being copied and captured maliciously.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Addressing random encryption method and system
PendingCN111682935AReduce the chance of leaksKey distribution for secure communicationTheoretical computer scienceEnvironmental geology
The invention discloses an addressing random encryption method and system. The addressing random encryption method comprises the following steps: by an addressing terminal, acquiring equipment name information, geographic position longitude and latitude information, geographic position description information and annotation information of equipment; dividing the equipment name information, the geographic position longitude and latitude information, the geographic position description information and the annotation information into N groups of information, inserting random characters or numbersinto each group of information, splicing the respective groups of information, and encoding the spliced information; transmitting the edcoded information to a target node; and by the target node, decoding the received information, eliminating the random characters according to position where the random characters or the numbers are inserted, and restoring and splicing the equipment name information, the geographic position longitude and latitude information, the geographic position description information and the annotation information. The method has the beneficial effects that the name information, the geographic position longitude and latitude information, the geographic position description information and the annotation information are randomly encrypted before information transmission, so that the information leakage probability is reduced.
Owner:广东志远科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com