Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
104 results about "Promiscuous mode" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer networking, promiscuous mode is a mode for a wired network interface controller (NIC) or wireless network interface controller (WNIC) that causes the controller to pass all traffic it receives to the central processing unit (CPU) rather than passing only the frames that the controller is specifically programmed to receive. This mode is normally used for packet sniffing that takes place on a router or on a computer connected to a wired network or one being part of a wireless LAN. Interfaces are placed into promiscuous mode by software bridges often used with hardware virtualization.
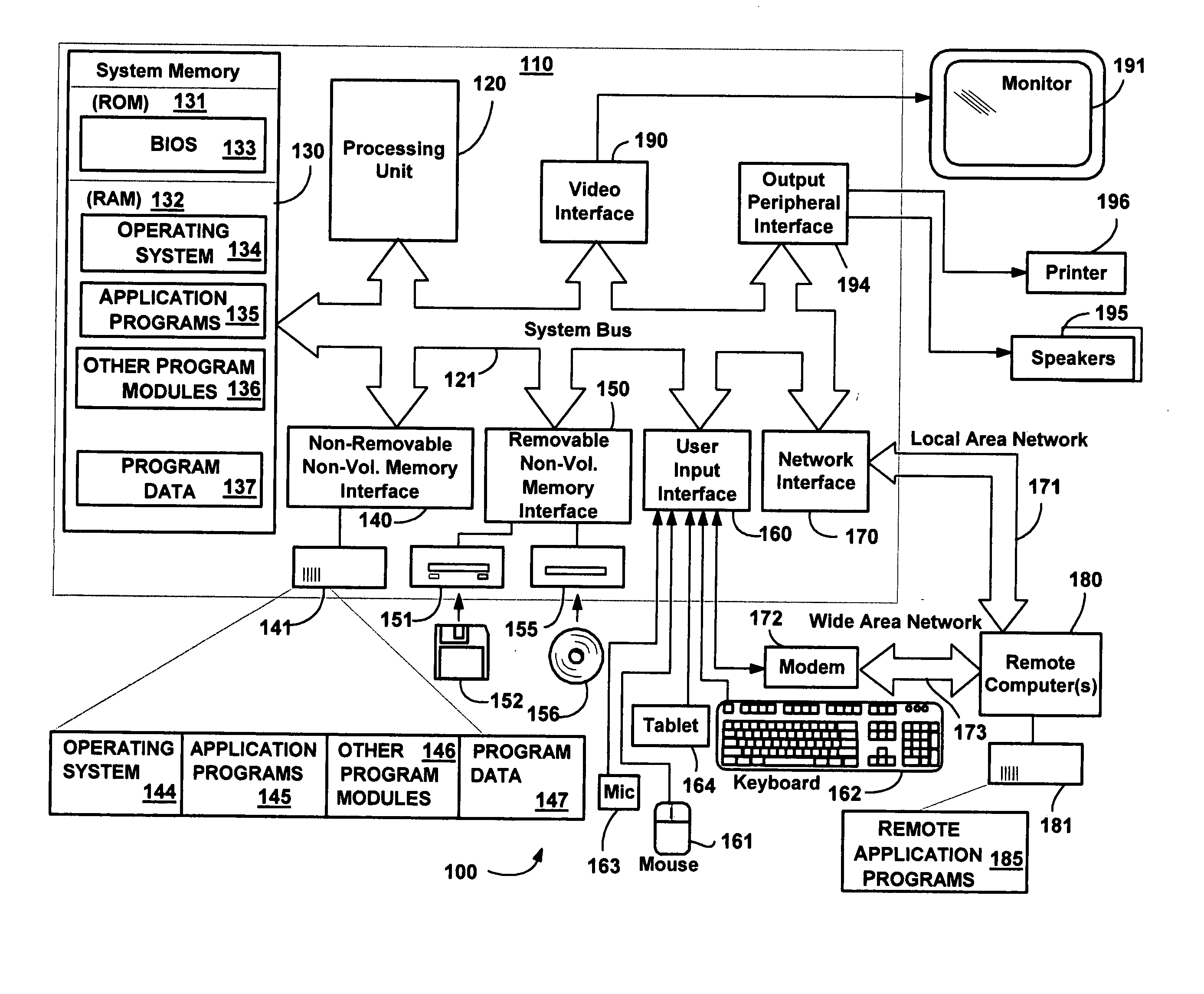
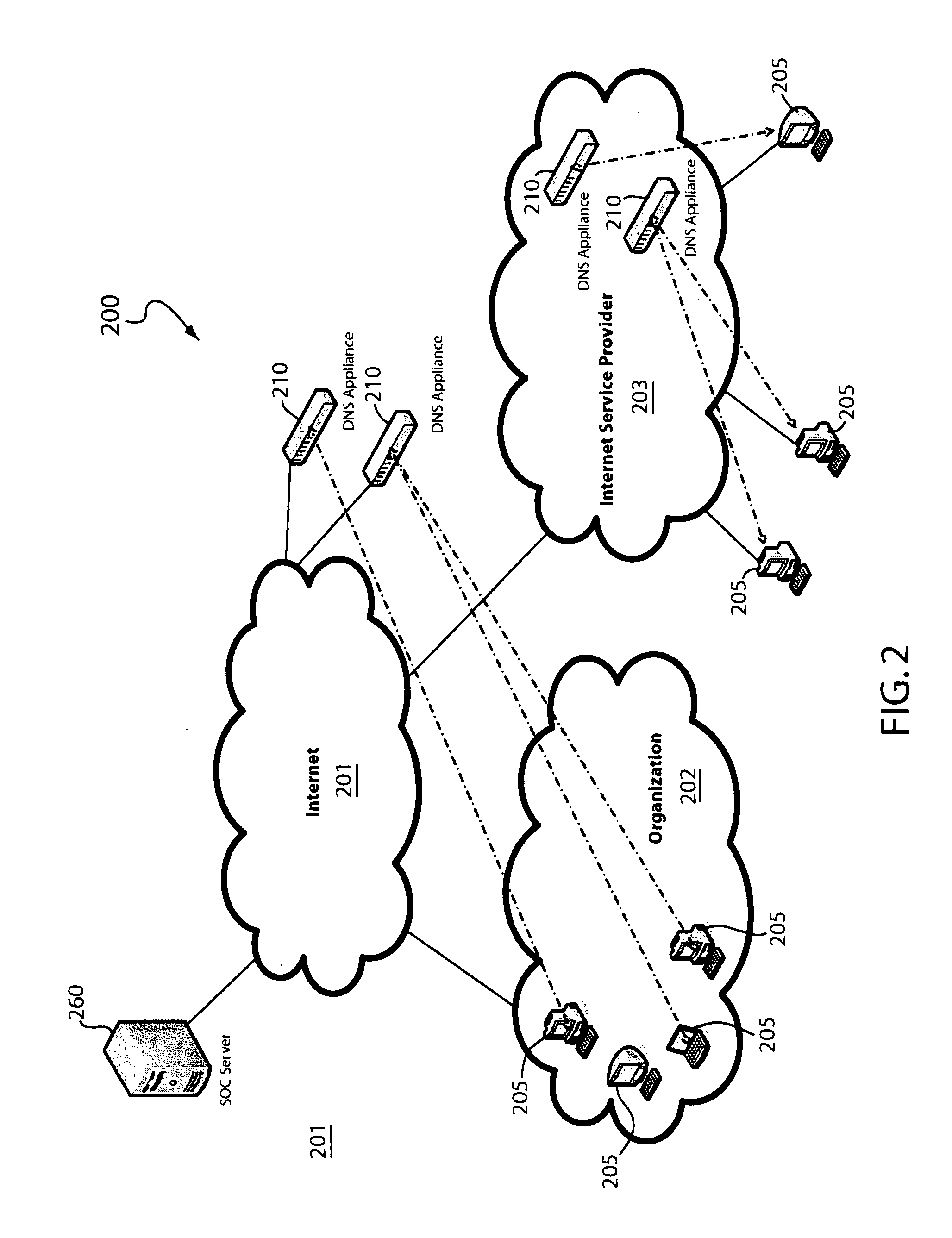
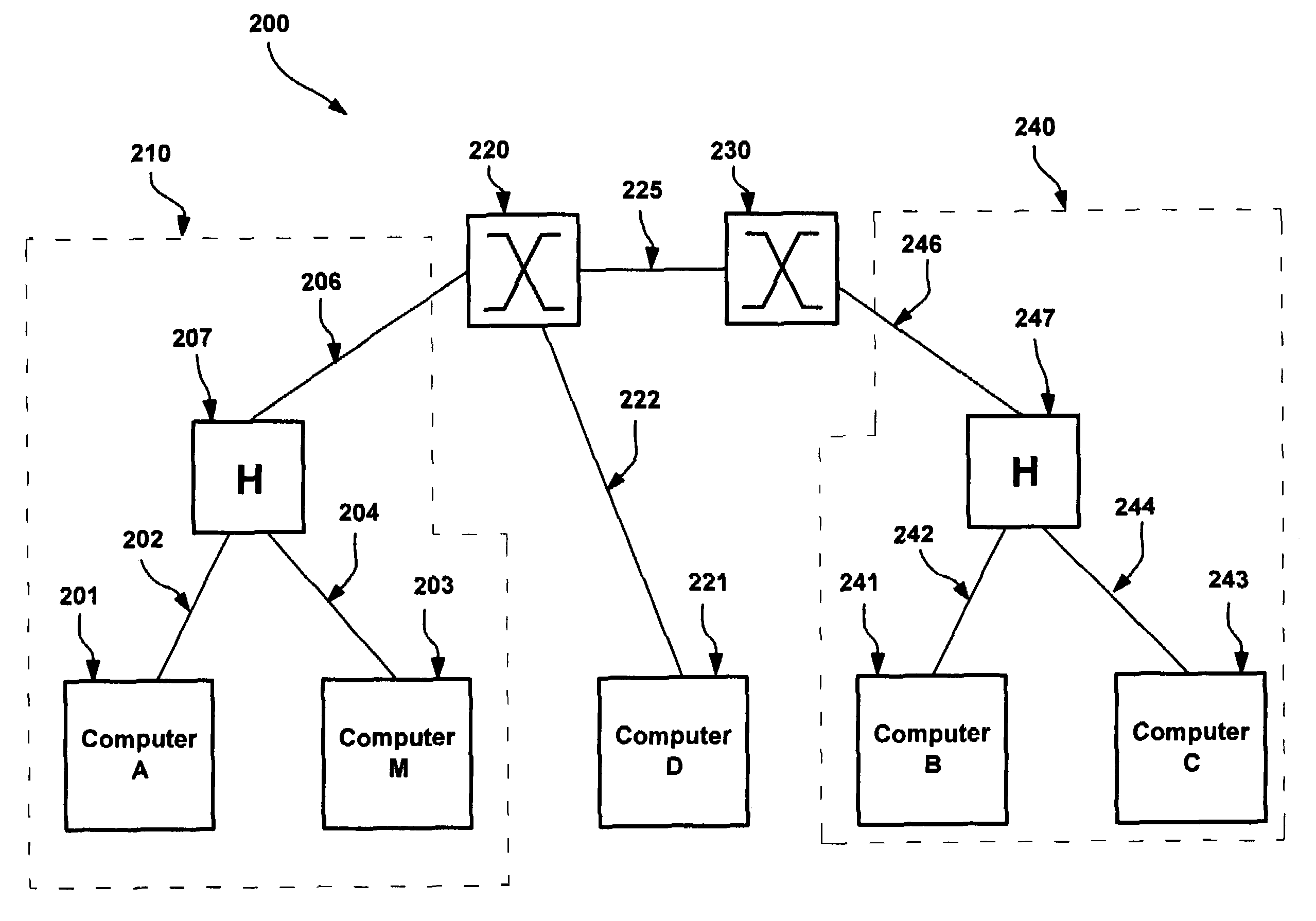
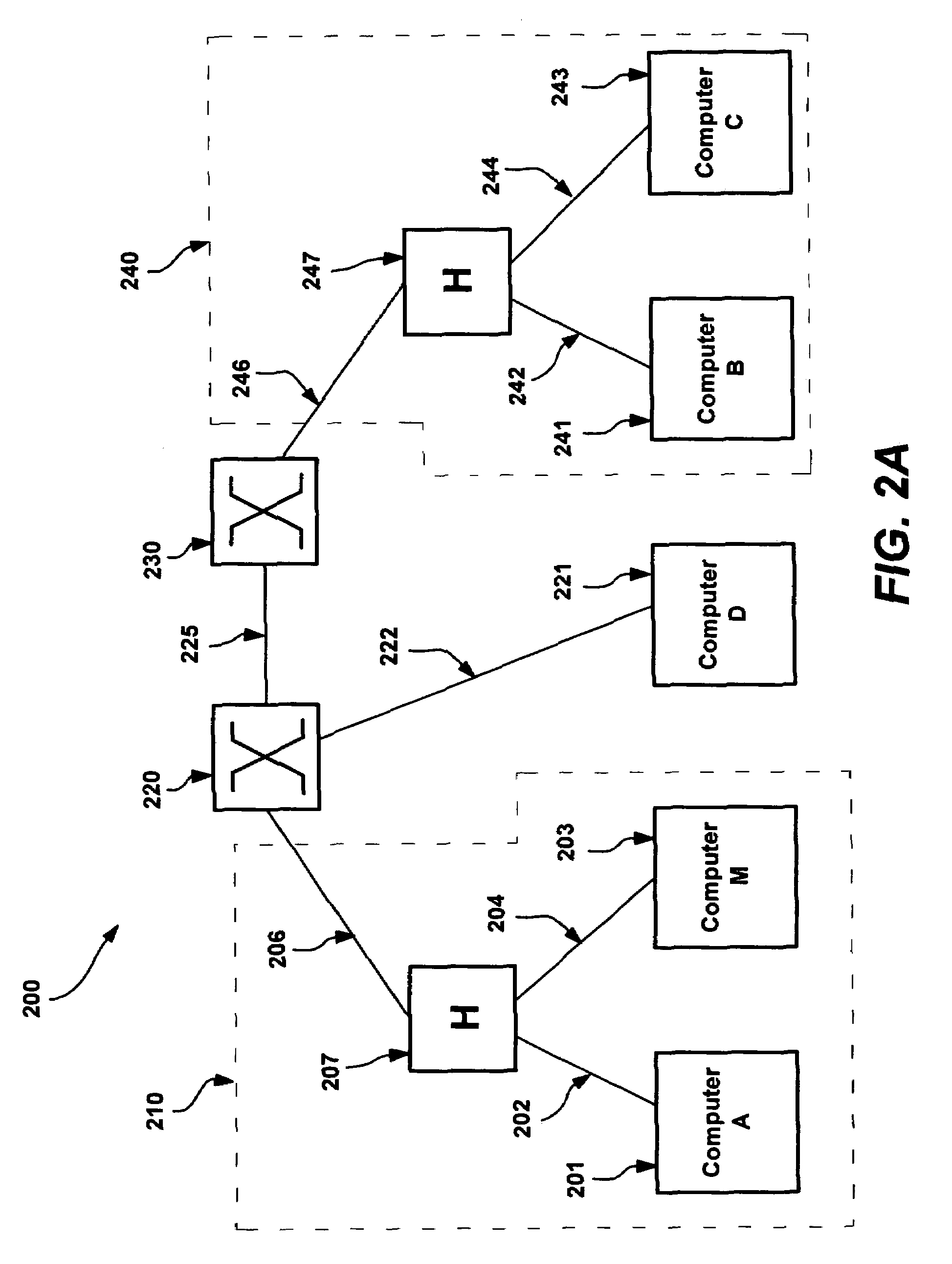
System and method for network topology discovery
A system and method for discovering network topology by various switch training and probing methods. Segments are discovered by having computers enter a promiscuous mode and determining from packets sent to a selected computer which computers see which other computers in the network. From the segments, various switch interconnections are determined, by having different computers train switches as to a training address and seeing which computers receive probe packets sent to that training address from another computer. Various training and probing methods are described that locate intermediate segments, deep switches, switch interconnections, and edge and singleton cases. In one implementation, a master computer coordinates the other computers (and devices) in the network to send the training and probing packets, and report on received packets, in order to determine the network topology.
Owner:MICROSOFT TECH LICENSING LLC
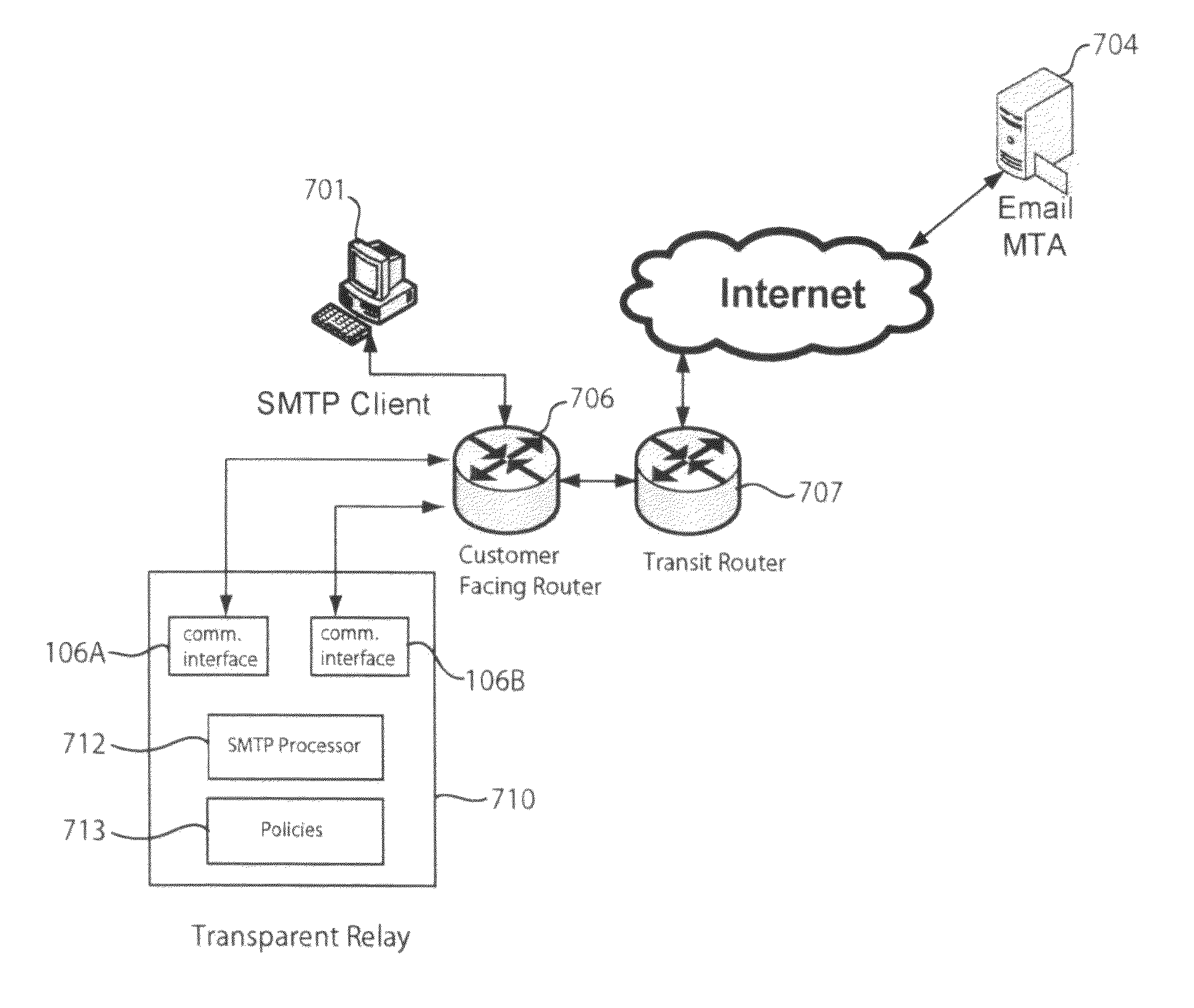
SMTP network security processing in a transparent relay in a computer network
ActiveUS20070204341A1Memory loss protectionError detection/correctionCommunication interfaceNetwork Communication Protocols
In one embodiment, a transparent relay receives diverted e-mail communications between an e-mail client and an e-mail server. The transparent relay may be configured to examine the e-mail communications for network security policy violations. E-mail communications that do not violate a network security policy may be relayed to their intended destination. Policy actions, such as discarding or redirection, may be performed on those that violate one or more network security policies. The transparent relay may include a pair of communications interfaces running in promiscuous mode, one for downstream communications and another for upstream communications. The transparent relay may decompose a network communication protocol to look network security policy violations.
Owner:TREND MICRO INC
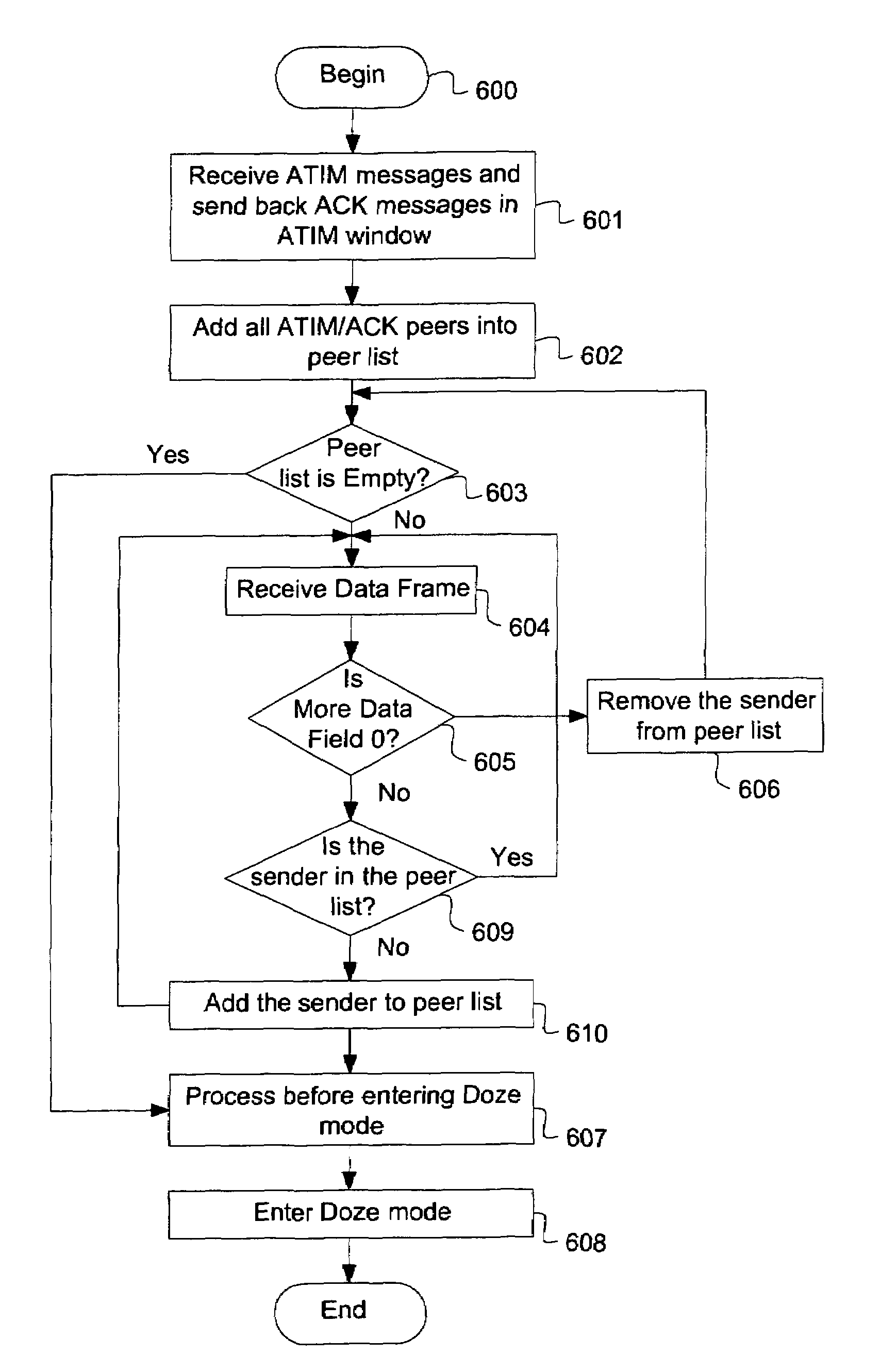
Method and apparatus for power saving in beacon generation of wireless networks in ad hoc mode
ActiveUS7656831B2Increase powerPower-saving mode quicklyPower managementEnergy efficient ICTWireless mesh networkPromiscuous mode
Methods for increasing power saving in a station that sends or receives frames in an ad hoc wireless network (e.g., IBSS), while allowing the station to enter a power-saving mode quickly upon completion of scheduled tasks. At the same time, a method of the present invention allows two stations in the ad hoc wireless network to infer each other's power management mode without requiring an ATIM / ACK exchange between the STAs within an ATIM window. Consequently, a station may enter a power-saving mode promptly without impairing the station's ability to receive packets. In one embodiment, a “more data” field is used between stations to exchange information. Stations with various computation abilities provide information under different time constraints. The stations may enter power-saving modes that send multicast / broadcast frames or use promiscuous mode within an ATIM window.
Owner:NTT DOCOMO INC
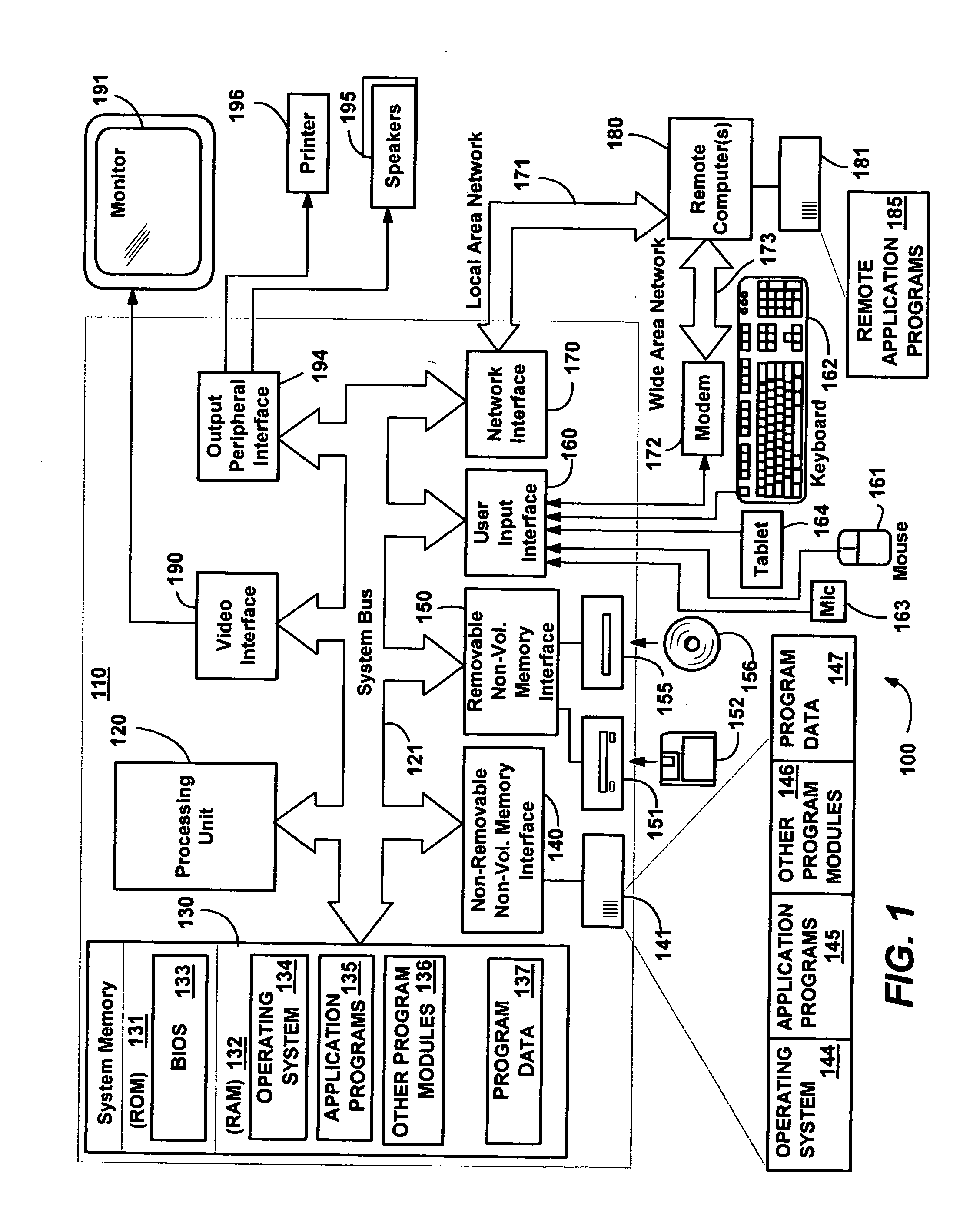
System and method for network topology discovery
A system and method for discovering network topology by various switch training and probing methods. Segments are discovered by having computers enter a promiscuous mode and determining from packets sent to a selected computer which computers see which other computers in the network. From the segments, various switch interconnections are determined, by having different computers train switches as to a training address and seeing which computers receive probe packets sent to that training address from another computer. Various training and probing methods are described that locate intermediate segments, deep switches, switch interconnections, and edge and singleton cases. In one implementation, a master computer coordinates the other computers (and devices) in the network to send the training and probing packets, and report on received packets, in order to determine the network topology.
Owner:MICROSOFT TECH LICENSING LLC
SMTP network security processing in a transparent relay in a computer network
ActiveUS7926108B2Memory loss protectionError detection/correctionCommunication interfaceNetwork Communication Protocols
In one embodiment, a transparent relay receives diverted e-mail communications between an e-mail client and an e-mail server. The transparent relay may be configured to examine the e-mail communications for network security policy violations. E-mail communications that do not violate a network security policy may be relayed to their intended destination. Policy actions, such as discarding or redirection, may be performed on those that violate one or more network security policies. The transparent relay may include a pair of communications interfaces running in promiscuous mode, one for downstream communications and another for upstream communications. The transparent relay may decompose a network communication protocol to look network security policy violations.
Owner:TREND MICRO INC
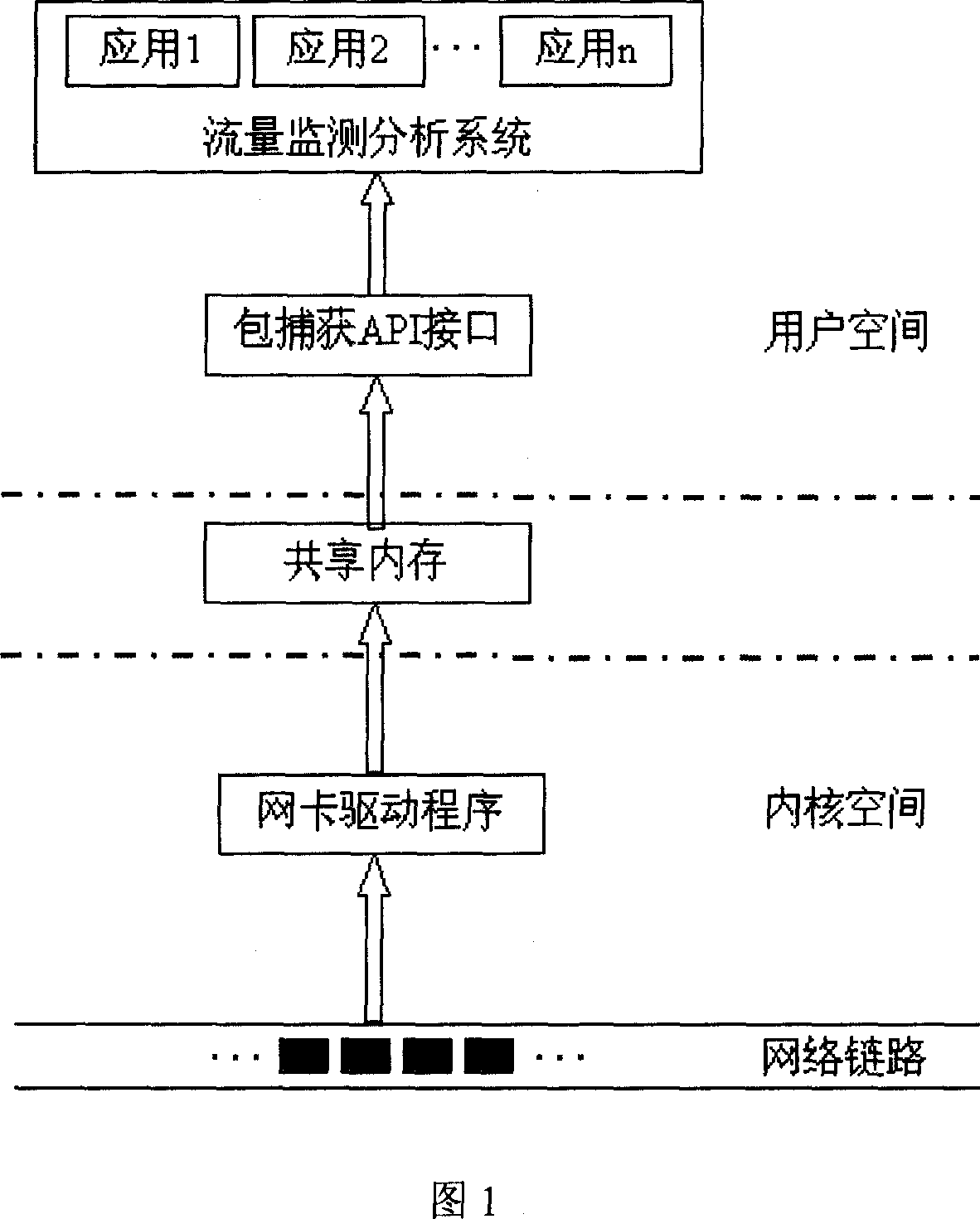
Method for realizing data packet catching based on sharing internal memory
InactiveCN1925465AImprove efficiencyImprove performanceData switching networksInternal memoryTraffic capacity
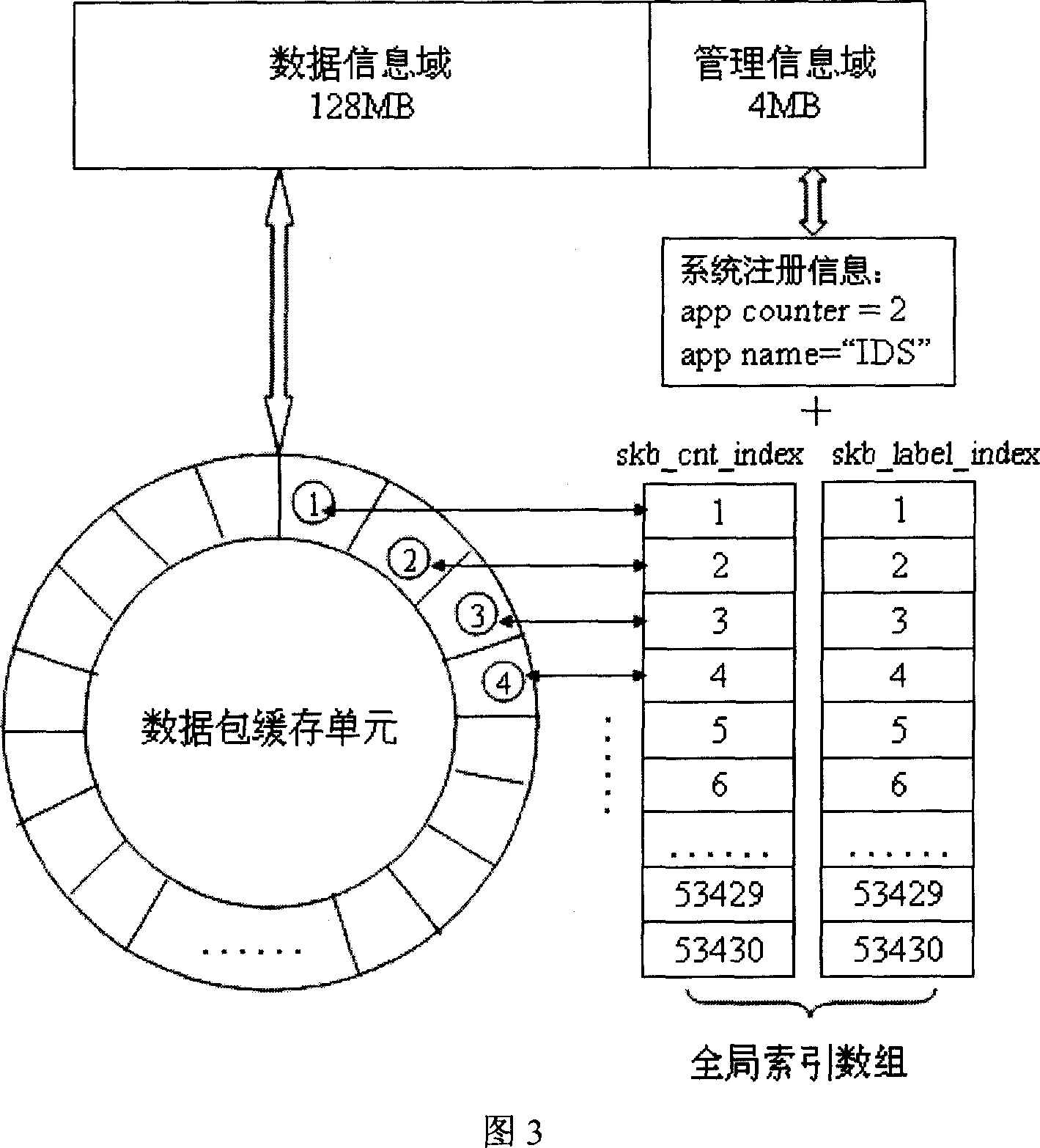
This invention discloses one data package capture method based on sharing memory, which comprises the following steps: net card loading and initiating drive program; establishing character device; setting monitor terminal card as mixture mode; receiving data package to judge receive terminal; judging data package into data information area; if not discarding data package; initiating management information unit; operating flow monitor analysis program; opening character device to get needle; extracting data package to introduce number label section then executing next step; executing monitor analysis program to change total index data to visit label section as processed data package.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Wireless channel switching method and device
ActiveCN103596228AAccurate channel quality assessmentImprove accuracyWireless communicationPromiscuous modeQuality assessment
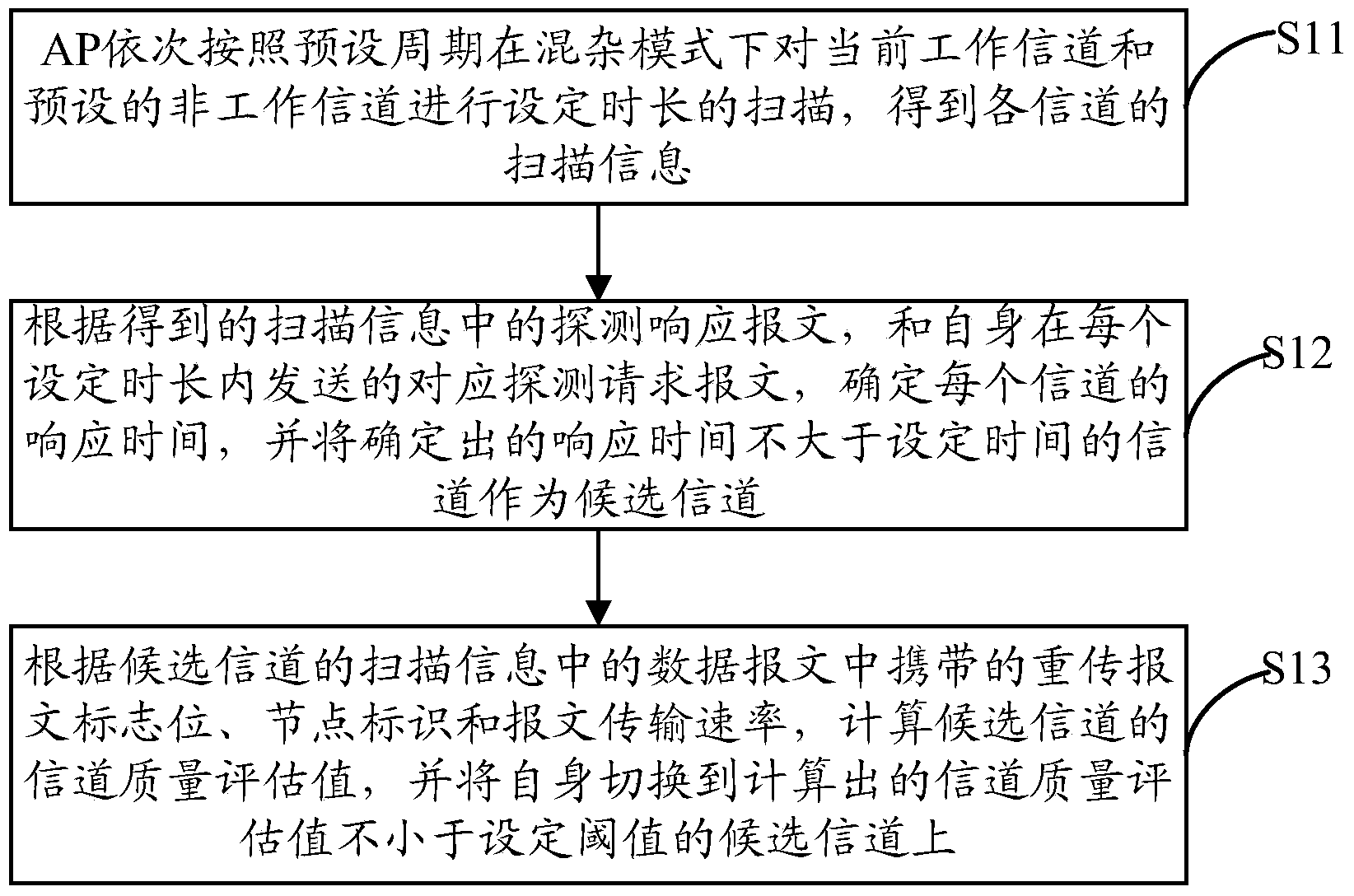
The embodiment of the invention provides a wireless channel switching method and device. The method includes the steps that an AP sequentially scans a current working channel and a part of non-working channels for set durations in a promiscuous mode according to a preset period to acquire scanning information of the channels; response time of each channel is determined according to probe response messages in the scanning information and corresponding probe request messages sent by the AP in each set duration, and the determined channels with the response time being shorter than or equal to the set time are used as candidate channels; corresponding channel quality evaluation values are calculated according to retransmission message zone bits, node identification and the message transmission rate carried in data messages in the scanning information of the candidate channels, and the AP is switched to the candidate channels with the calculated channel quality evaluation values being larger than or equal to a preset threshold value. According to the wireless channel switching method and device, the AP scans the current working channel and the part of non-working channels in the promiscuous mode and can be switched to the channels with good channel quality, and switching accuracy is high.
Owner:RUIJIE NETWORKS CO LTD
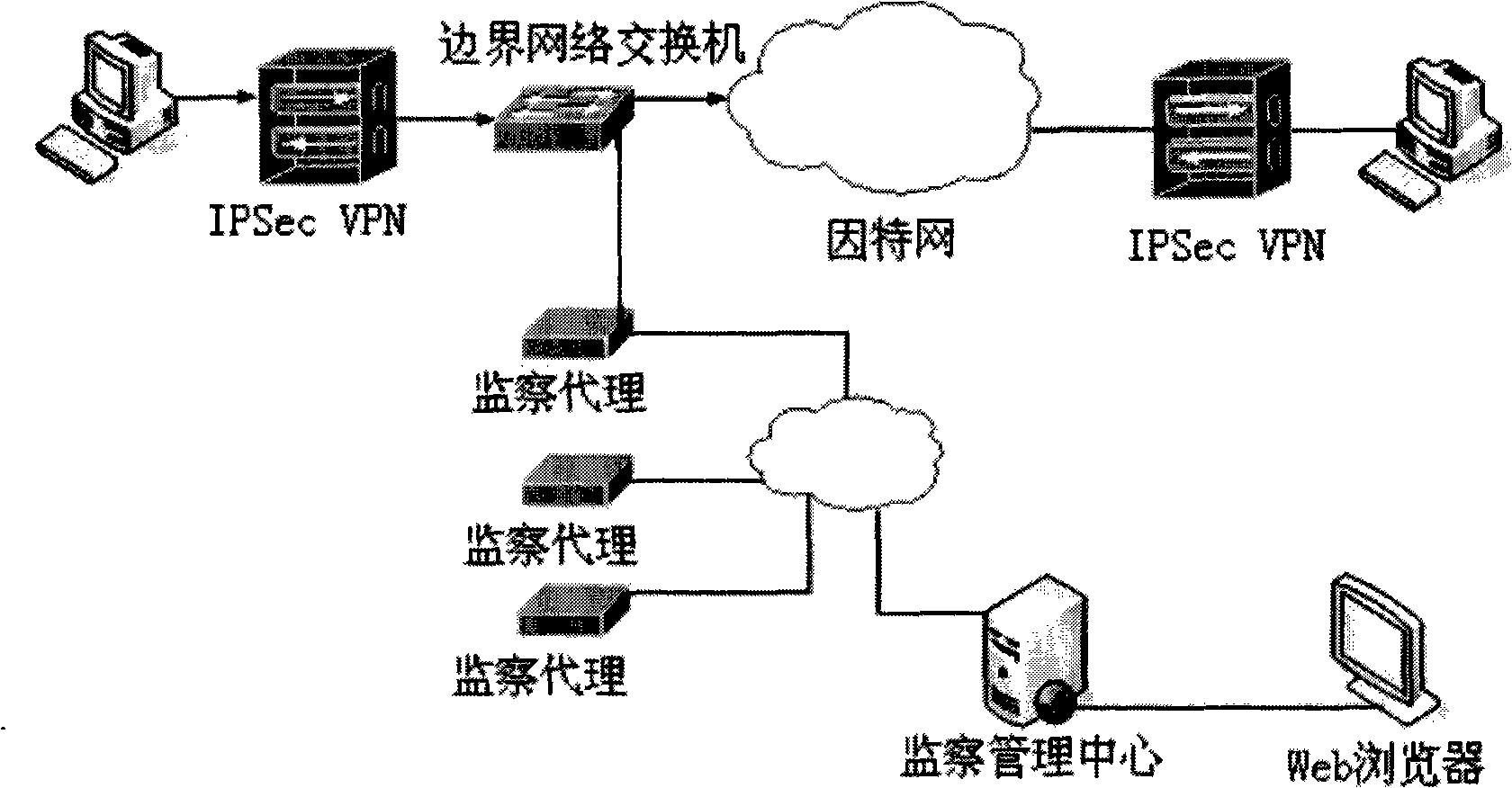
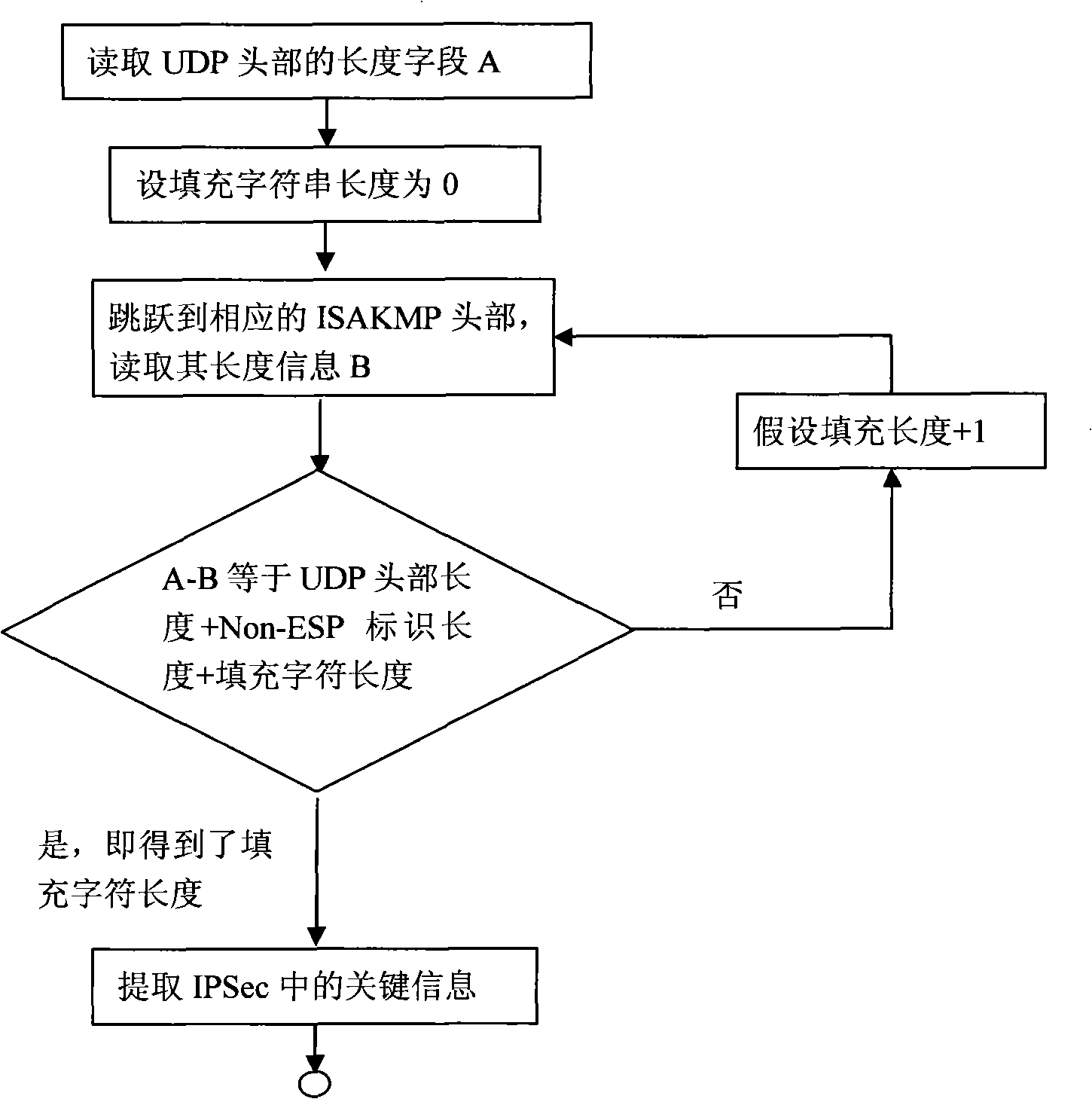
IPSec VPN protocol drastic detecting method based on flows
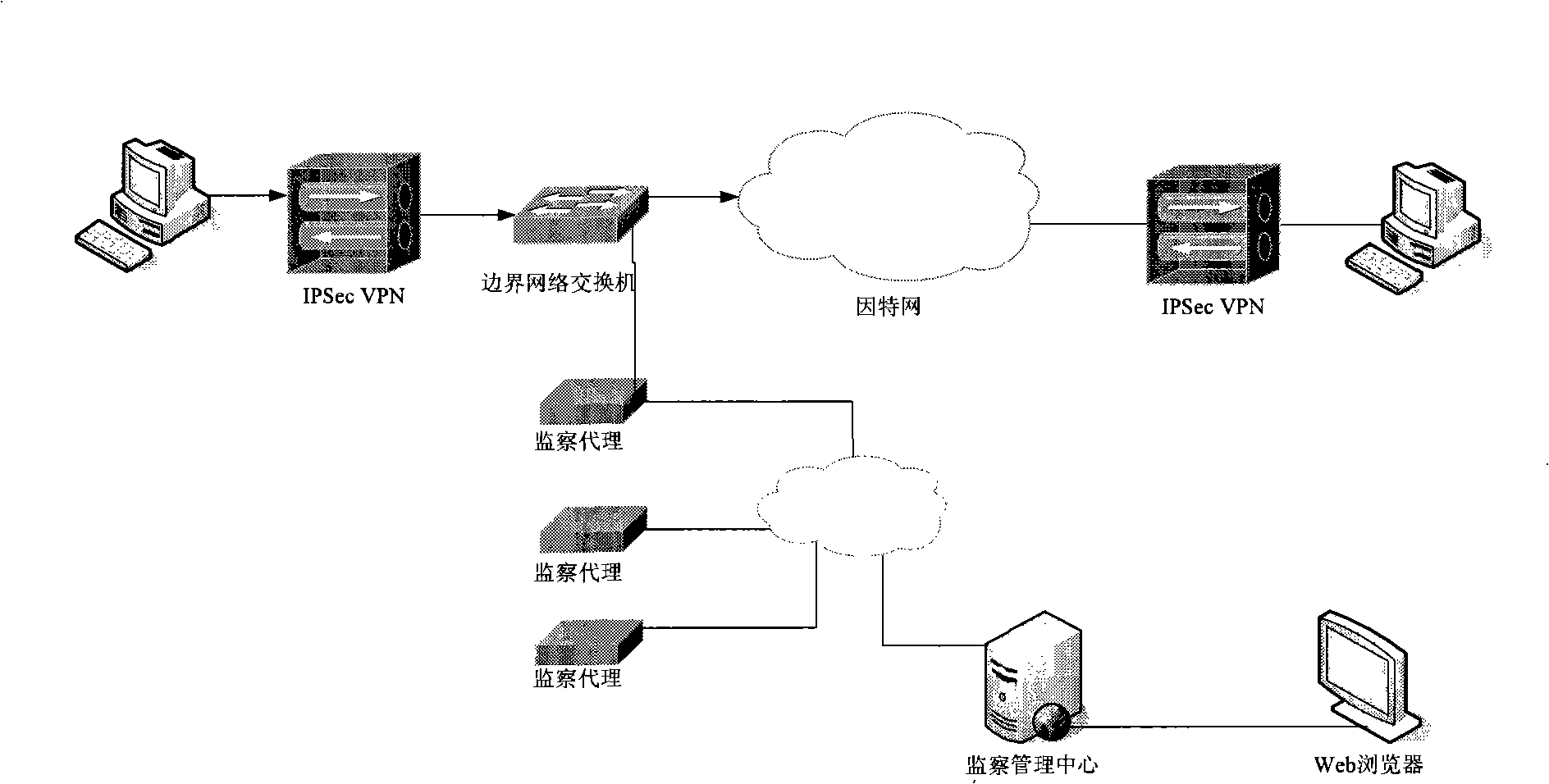
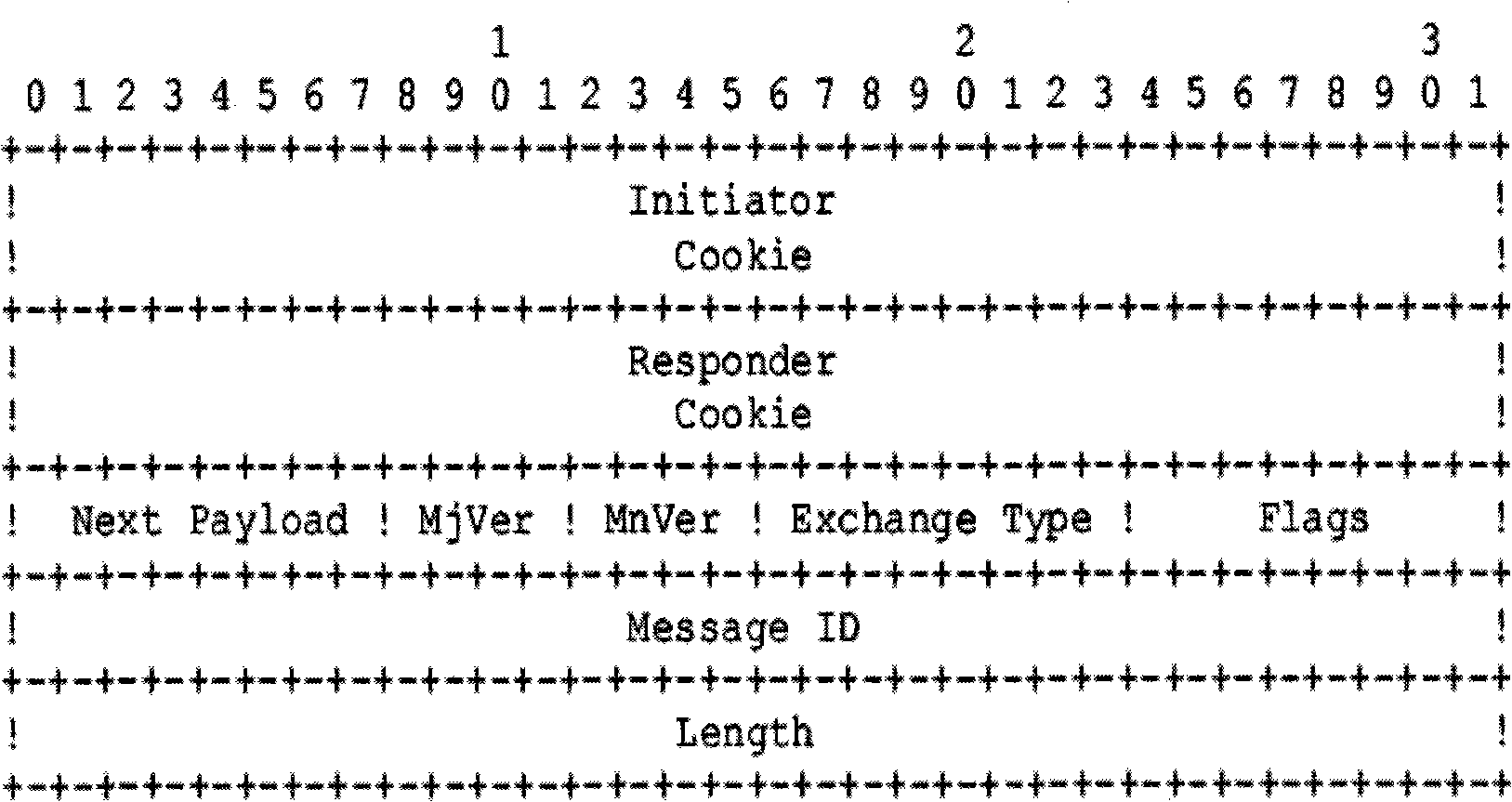
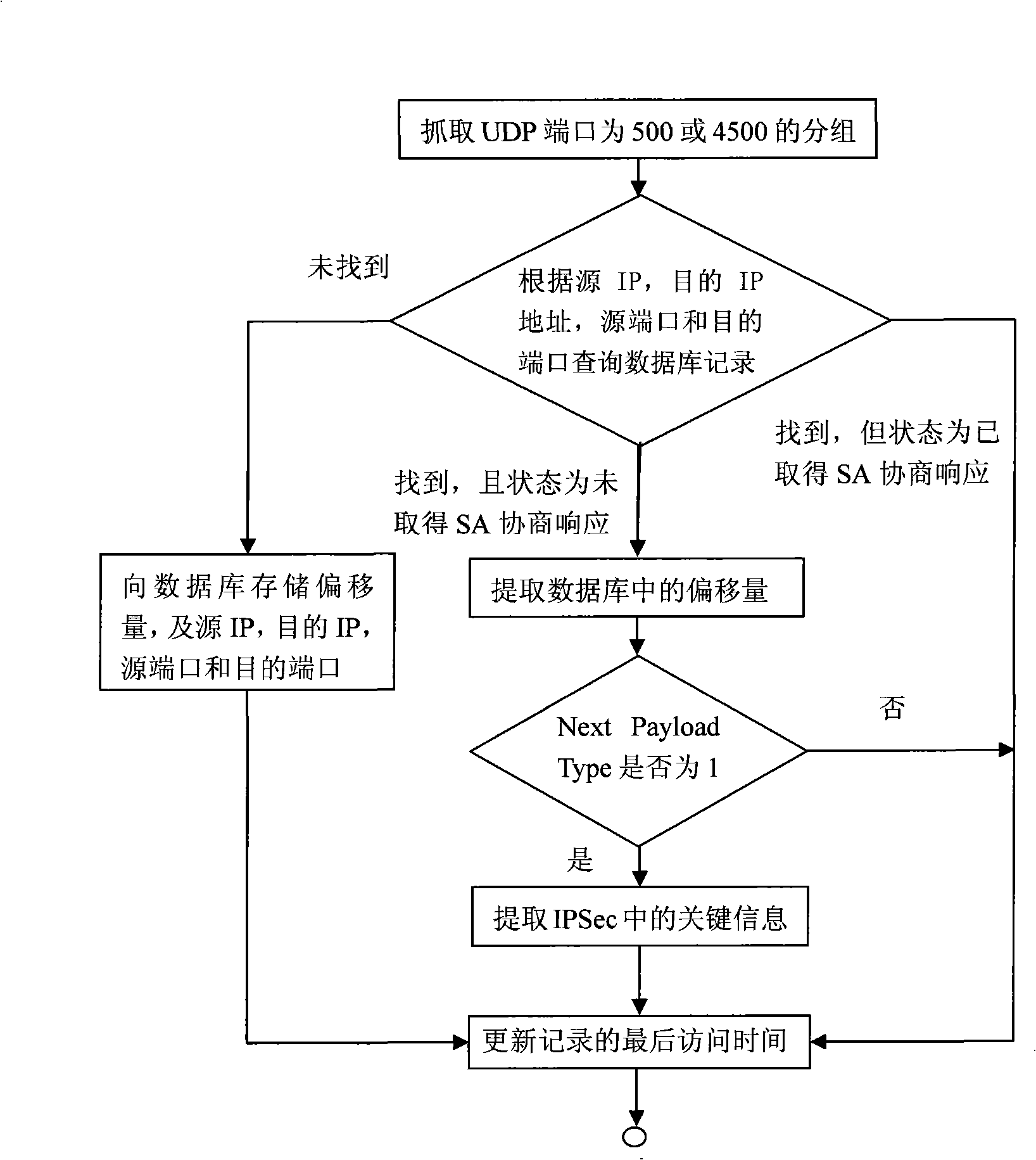
The invention relates to a deep detection method of an IPSec VPN protocol based on stream, which is applied in the network safety field. The deep detection method of the invention firstly carries out cyclic monitoring under the promiscuous mode that network card is opened in an intelligent agent or a probe machine, and a BPF filter is arranged to snatch an IPSec VPN message. The deep inspection method can store and carry out deep detection on the sequence stream of IPSec message, can identify and analyze whether the IPSec VPN message is faked and is the message of non-standard format or not, and can analyze the differences between the message of non-standard format and the message of standard format according to the context of the sequence stream of the IPSec VPN message. The deep detection method provided by the invention based on the session state of the protocol has considerable intelligence and stable performance, can analyze the message of unknown format and can be easily realized and applied in the fields such as supervision agency, firewall, IDS, etc.
Owner:SHANGHAI JIAO TONG UNIV
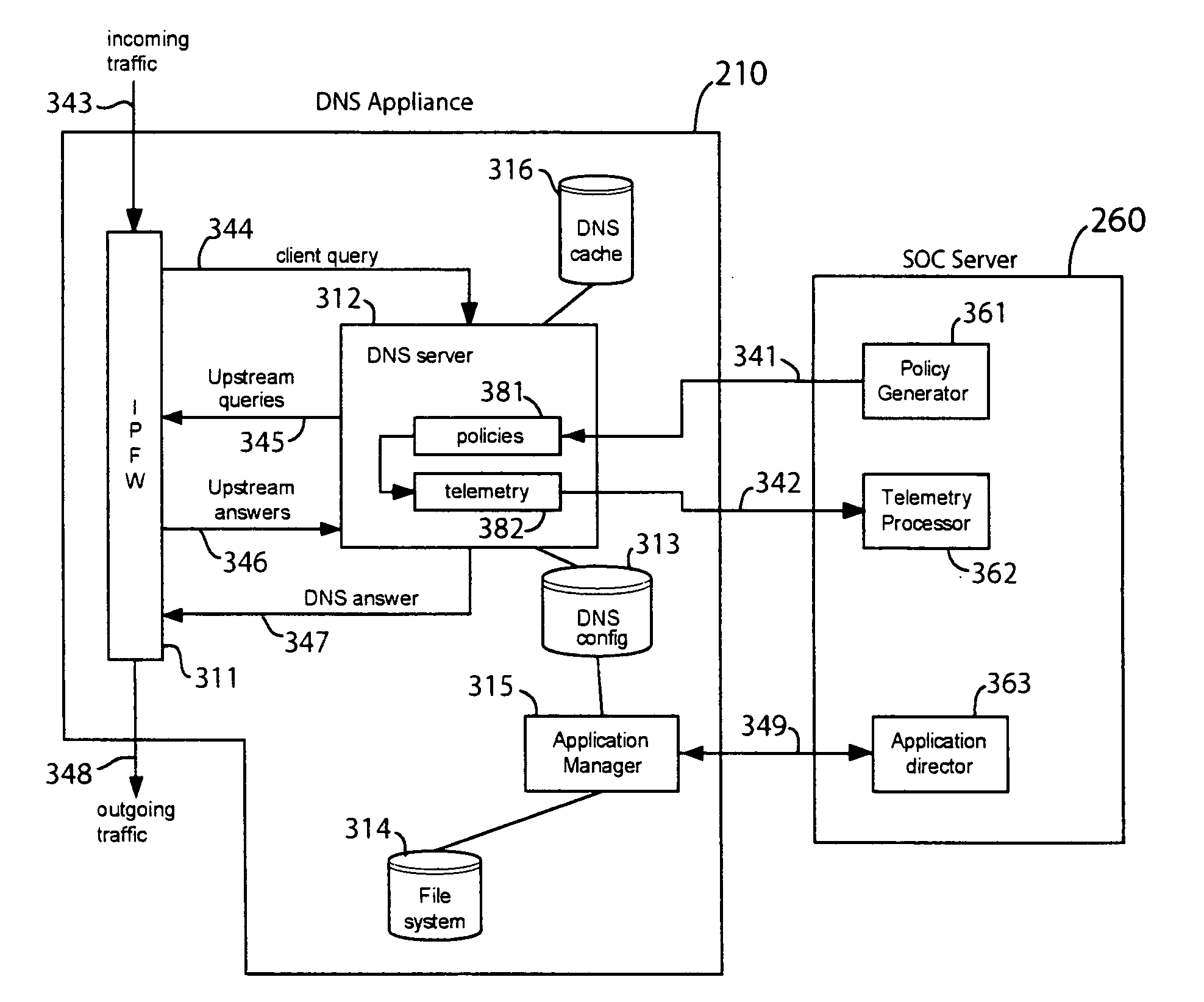
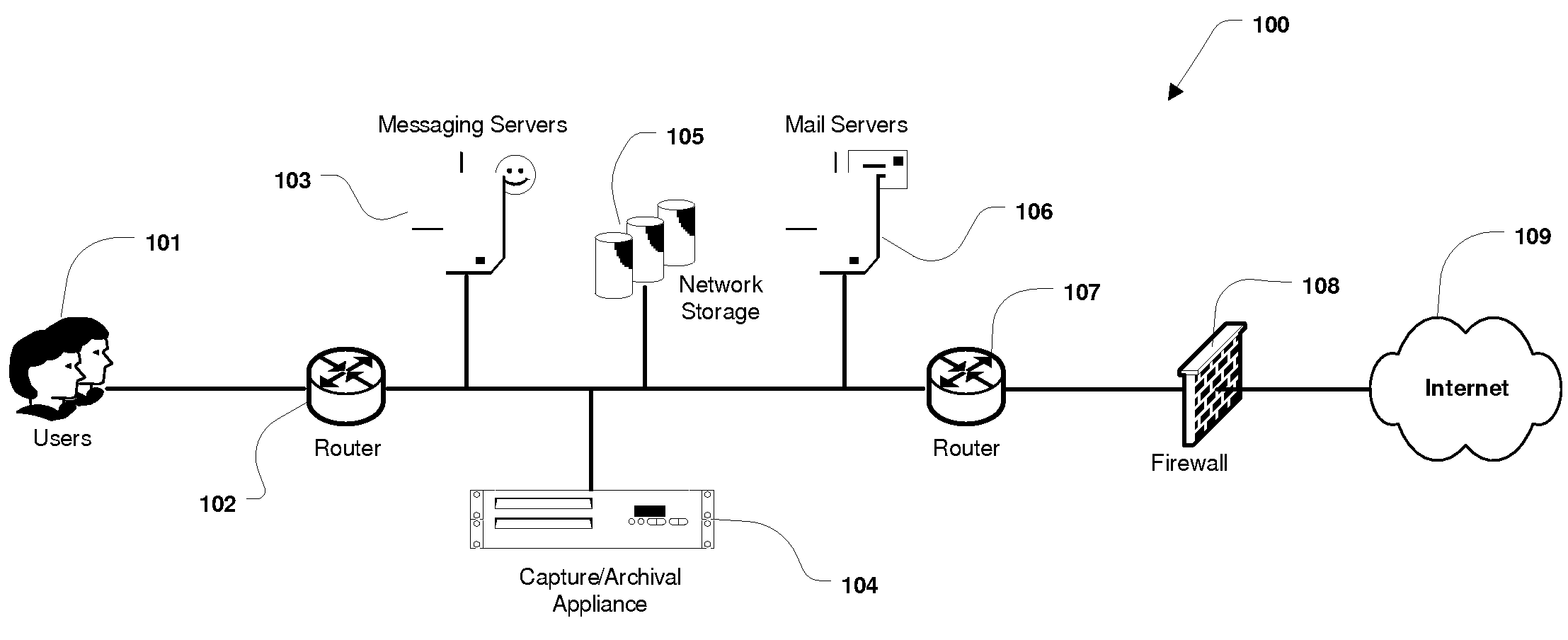
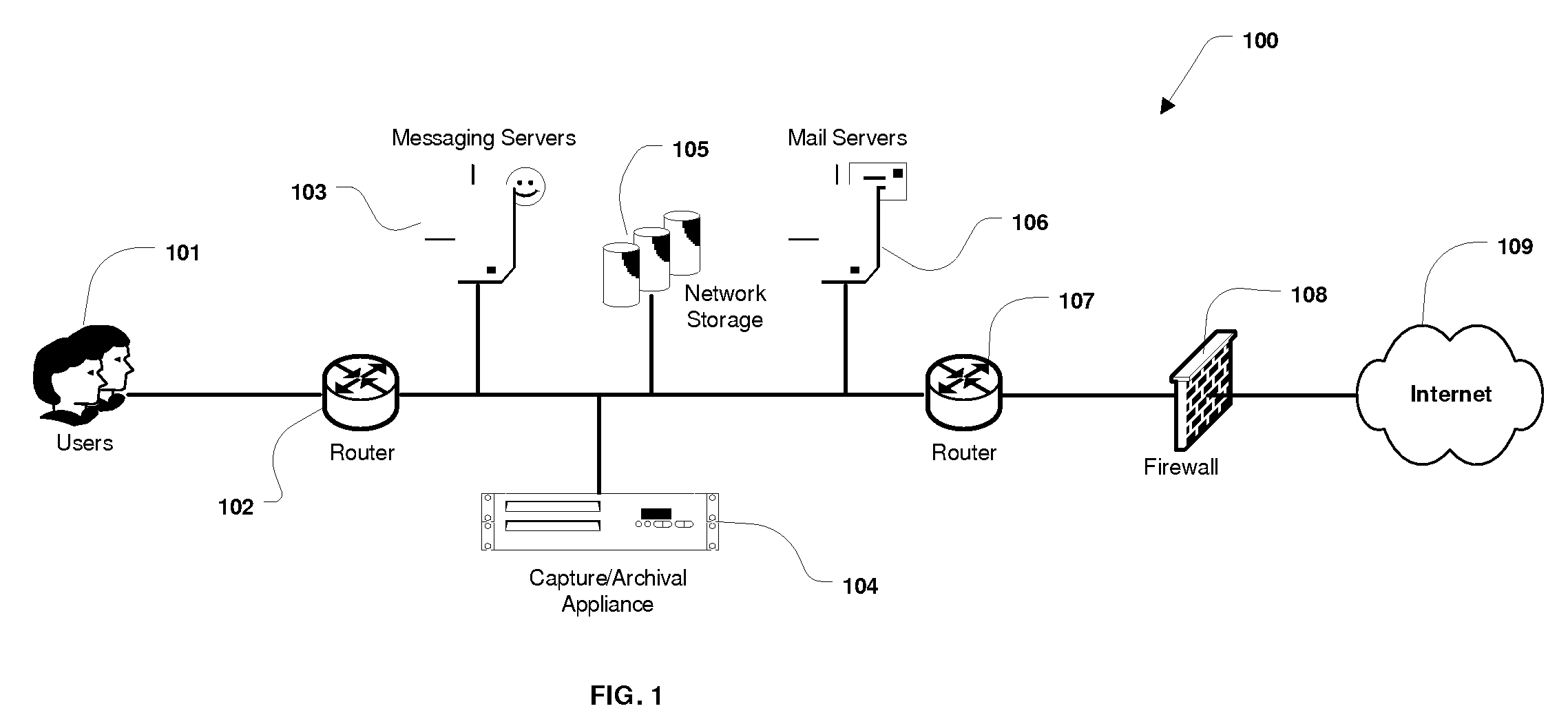
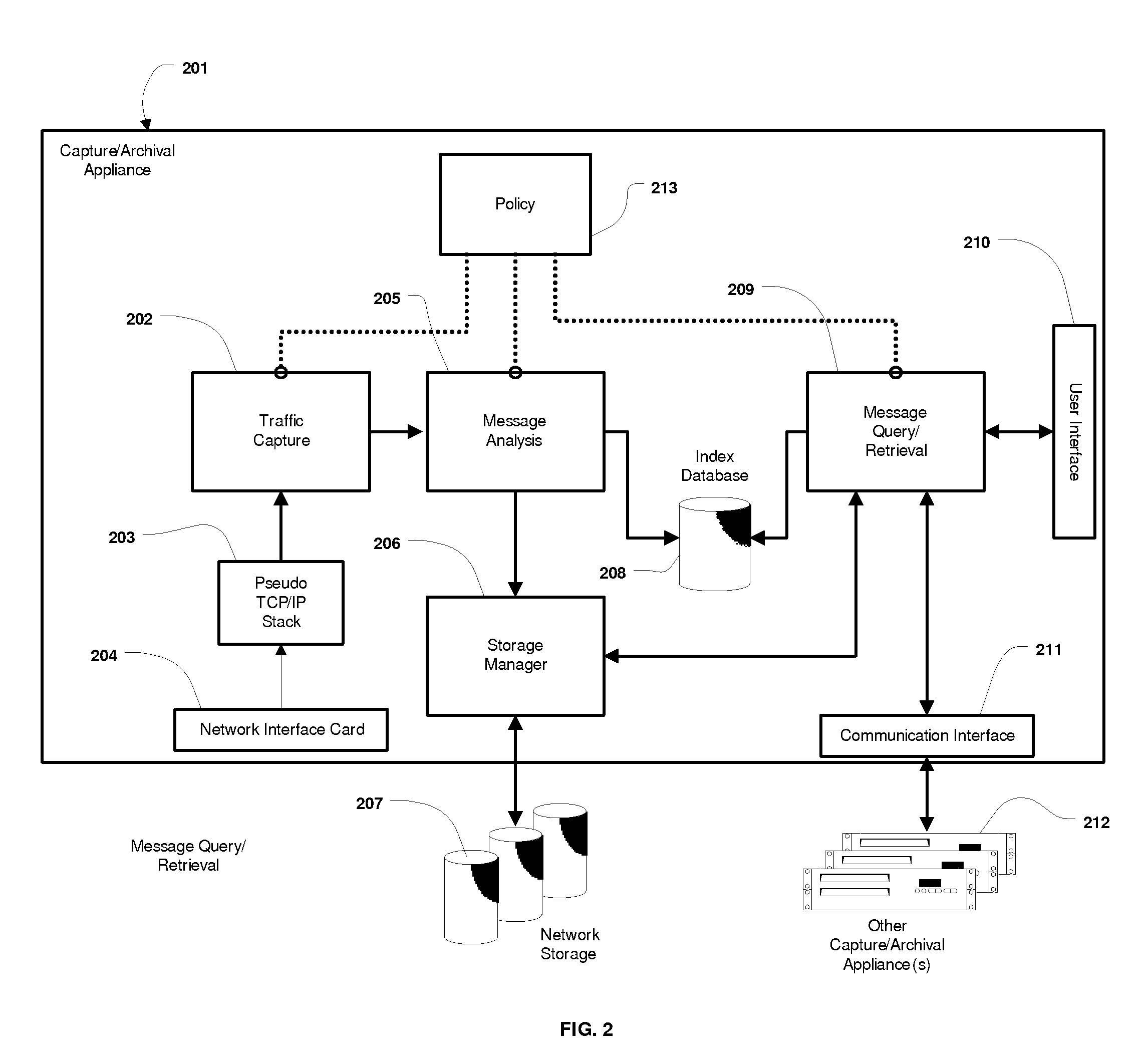
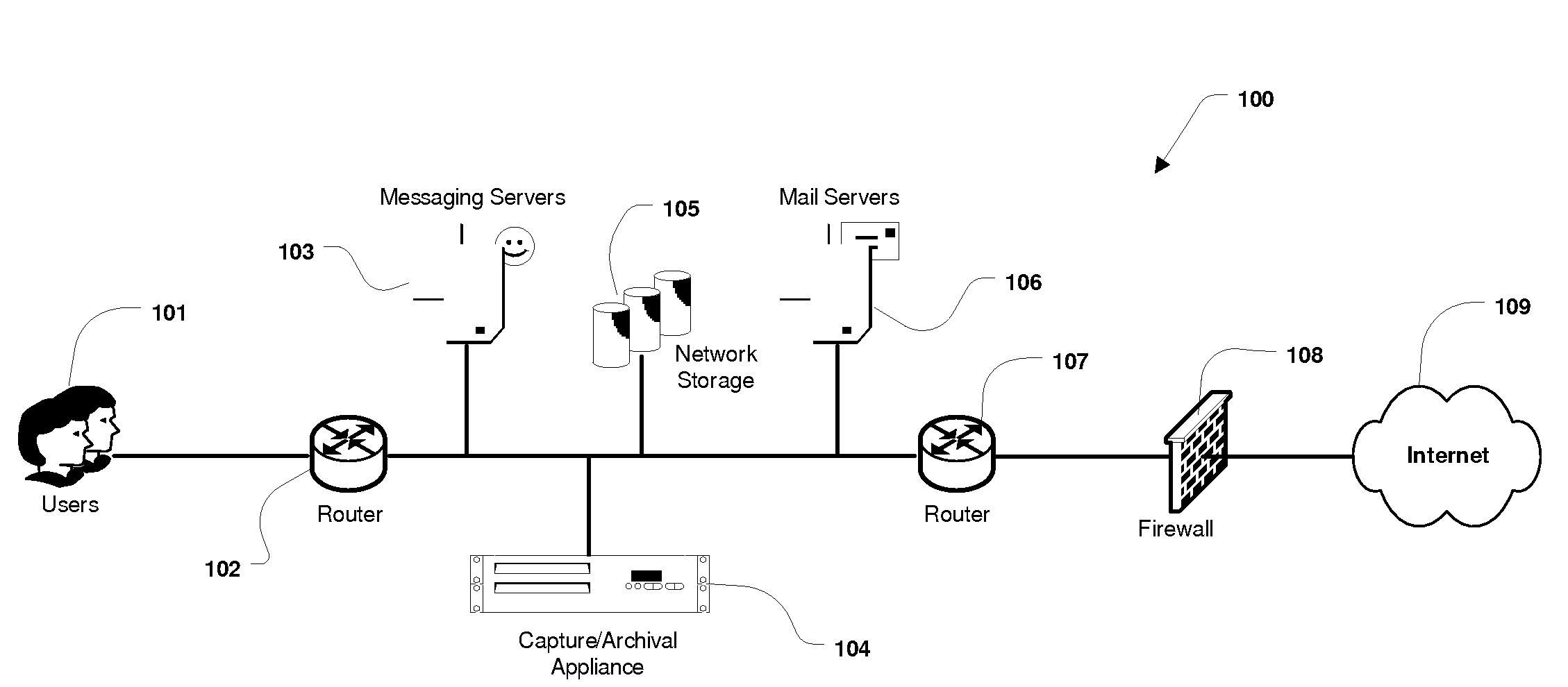
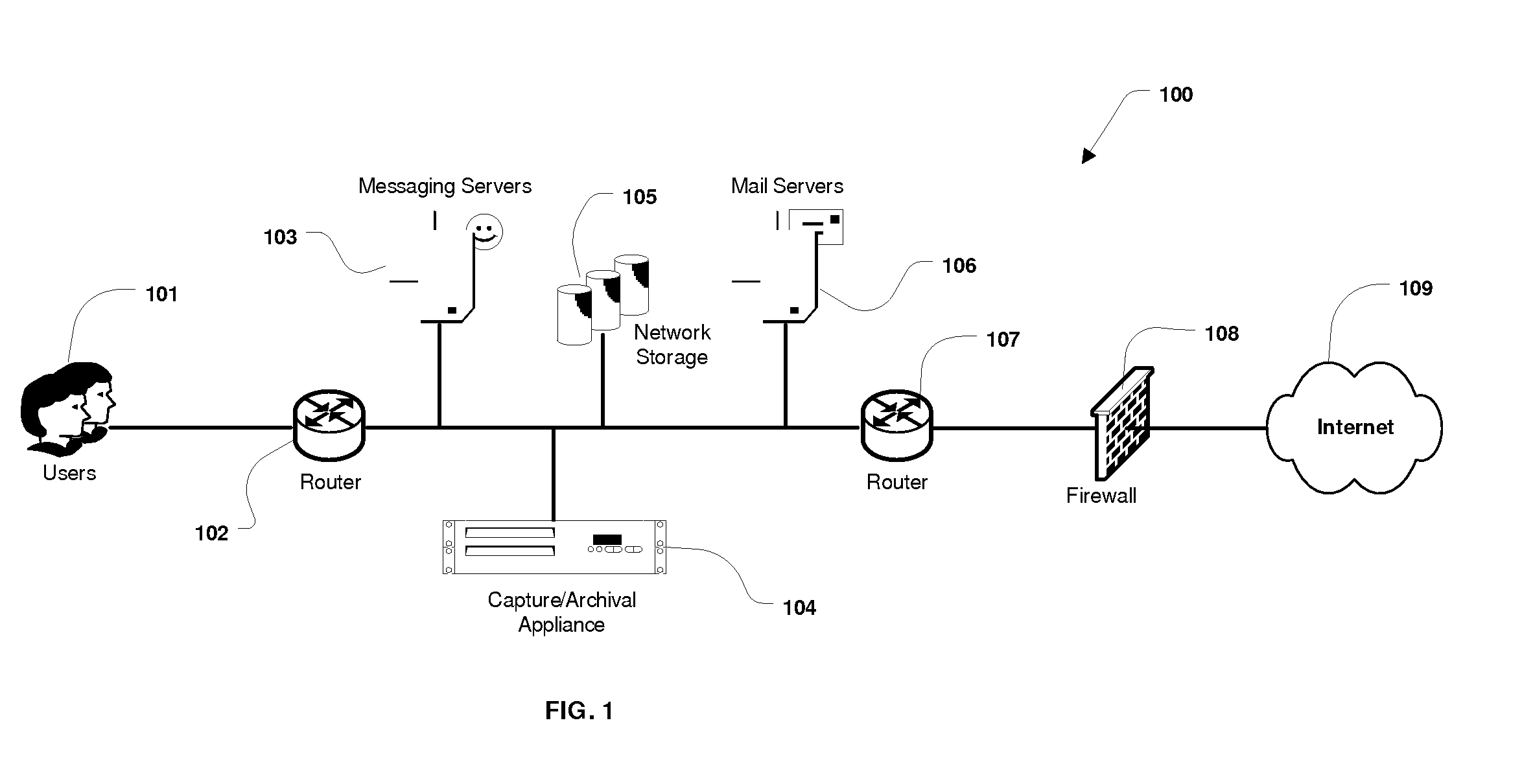
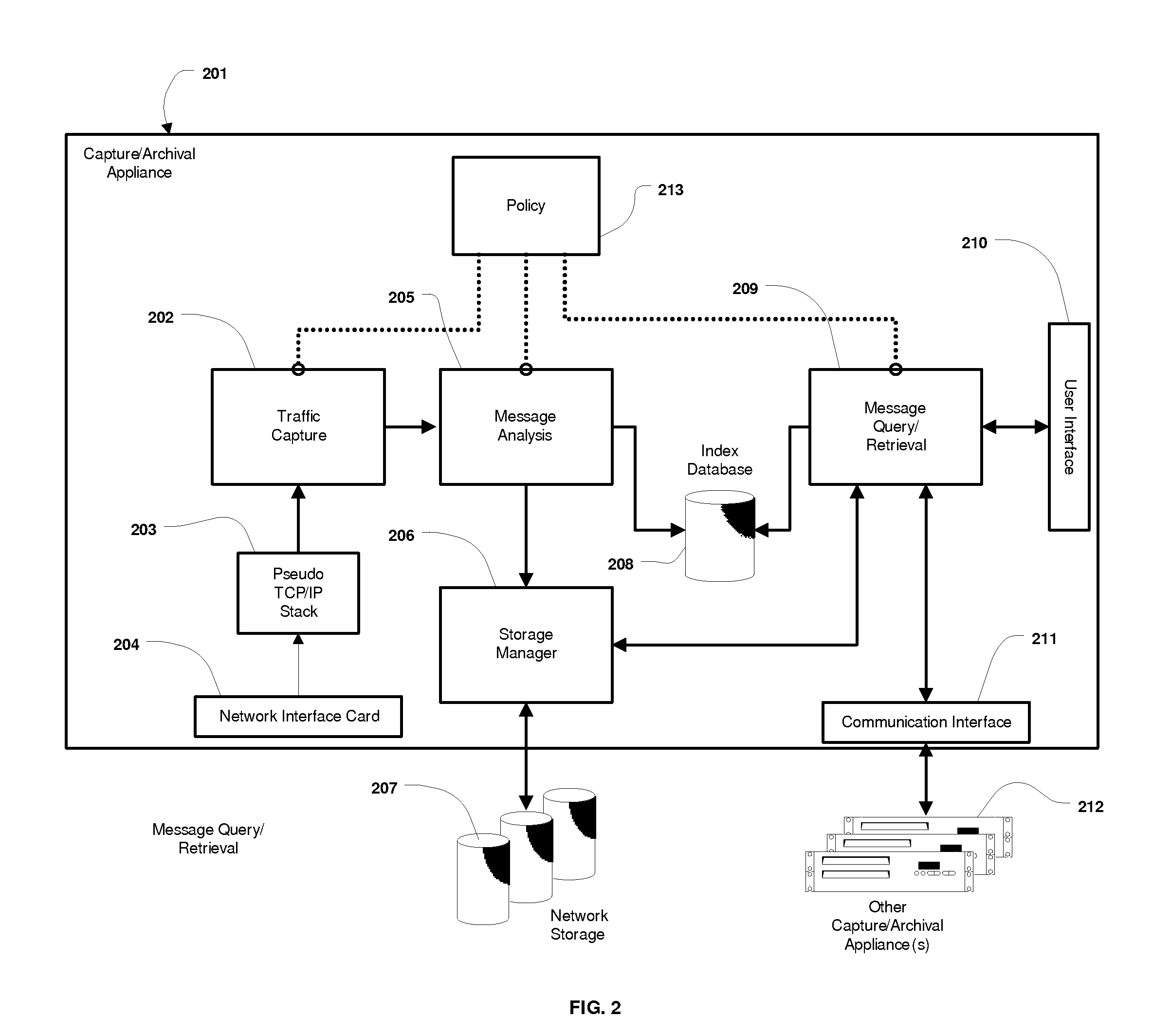
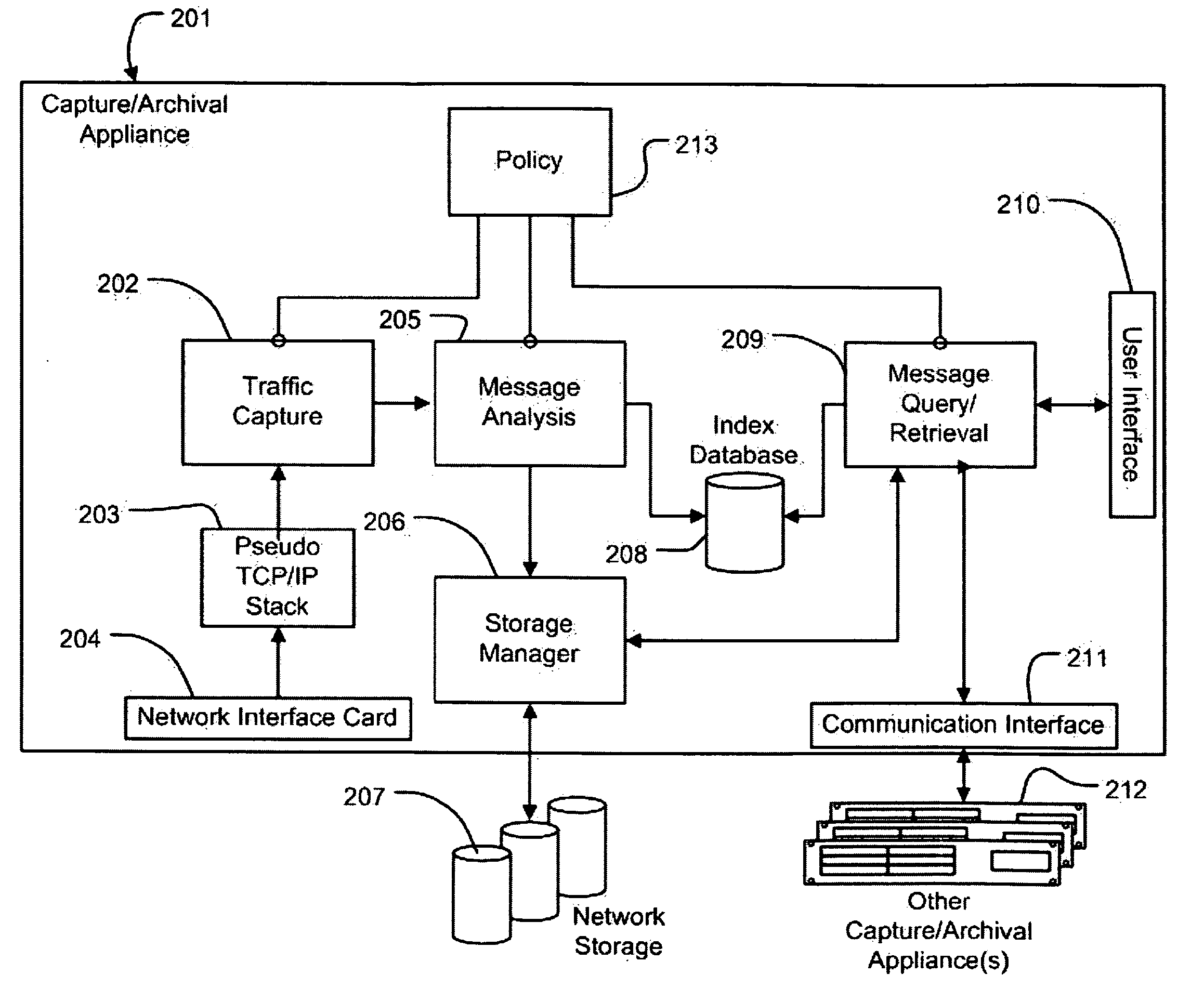
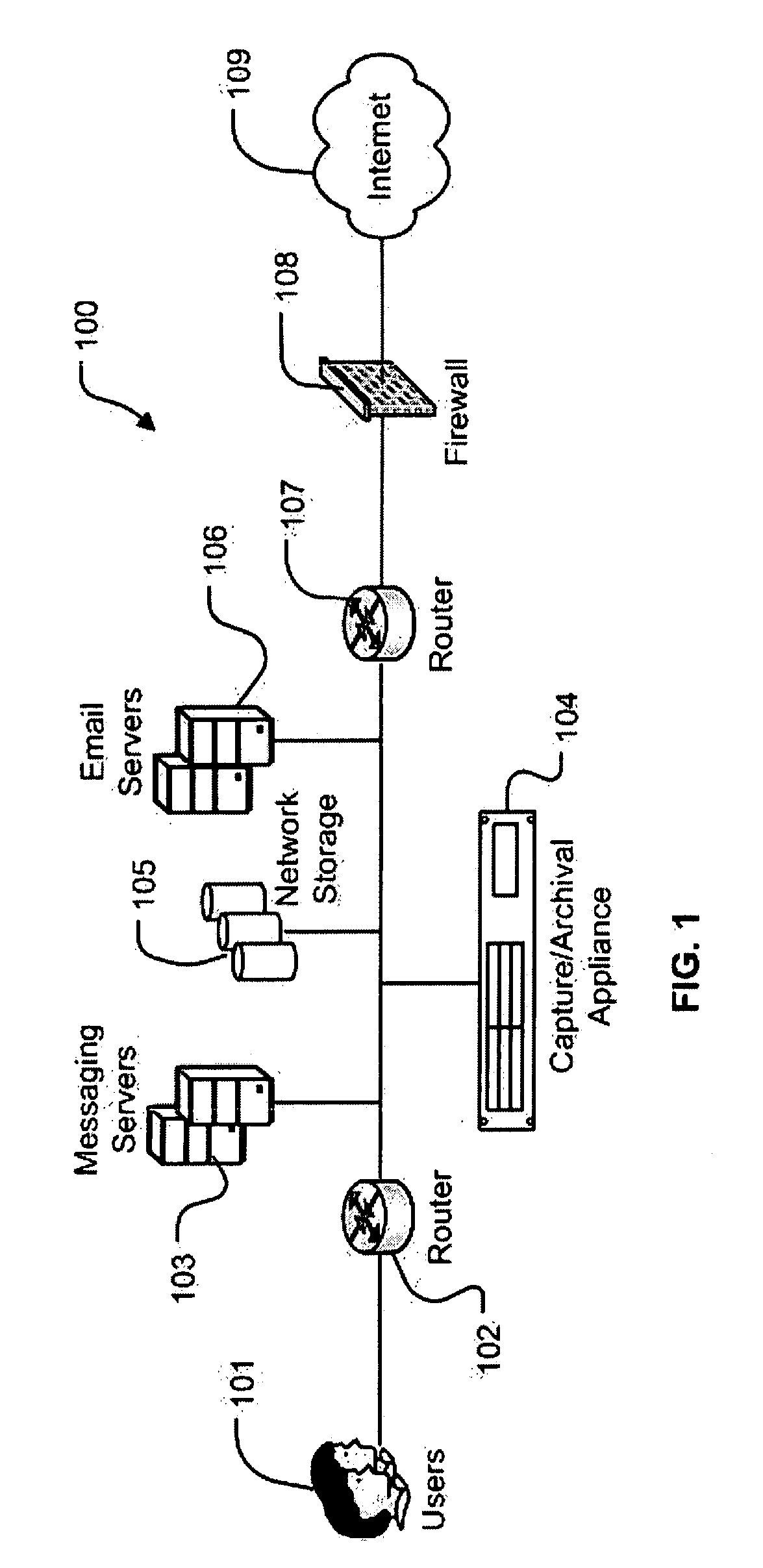
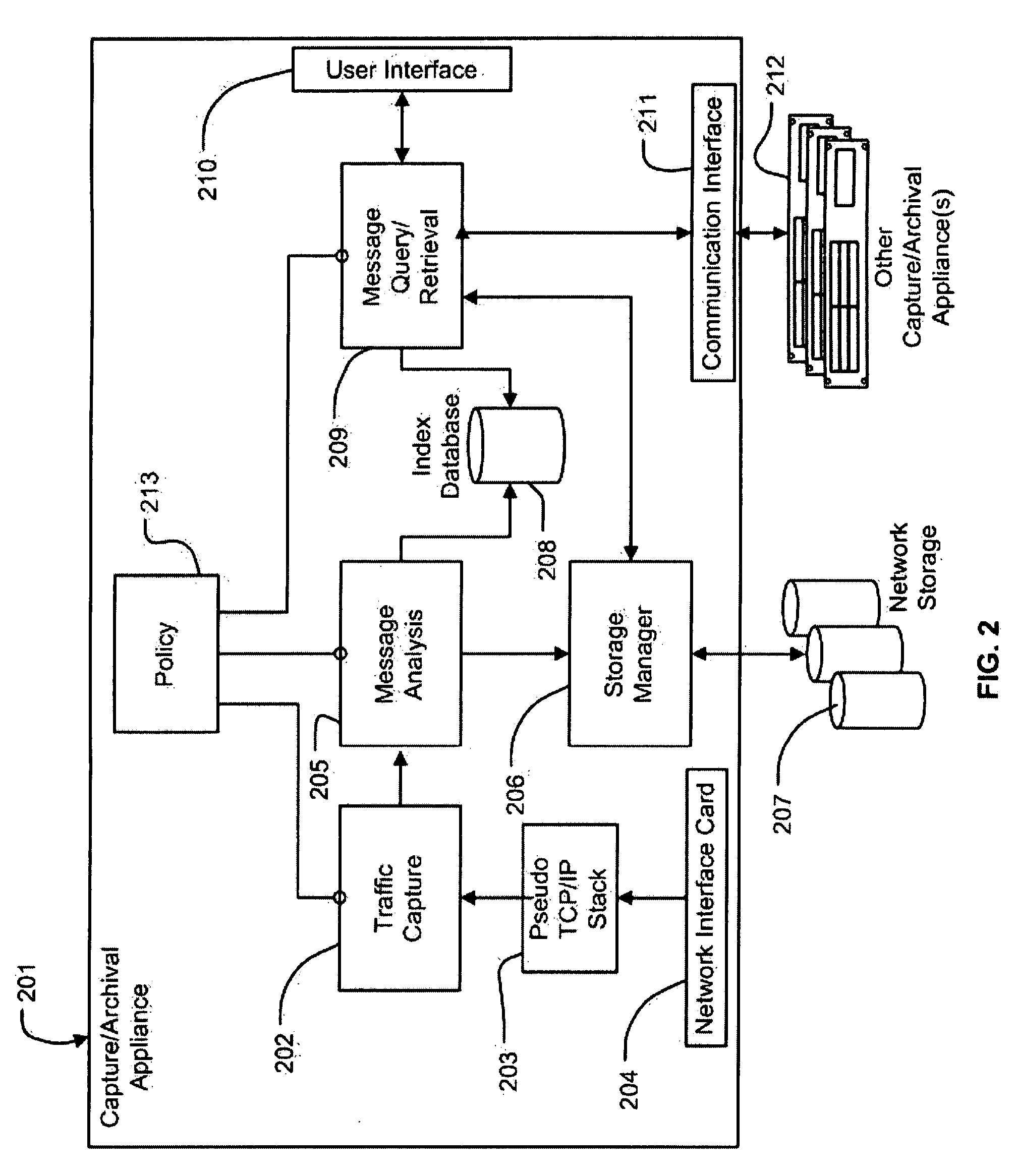
System and Method for the Capture and Archival of Electronic Communications
InactiveUS20080034049A1Multiple digital computer combinationsResourcesData informationPromiscuous mode
A system and method for the capture and archival of electronic communication is disclosed. A network interface card in promiscuous mode connects the invention to an electronic communications network. Network packets are received on the network interface card and sent to a pseudo TCP / IP stack, which reconstructs the network packets into the original electronic message. The reconstructed electronic message is transferred to the traffic capture component in chunks until the entire message is captured. The traffic capture component forwards the electronic message to the message analysis component, which hashes, parses, analyzes and formats for storage the electronic message. The electronic message, in a structured format, is then sent to the storage manager component. The storage manager component selects a storage unit from the available network storage based on the message hash. The storage manager component then compresses, encrypts and writes the structured version of the electronic message to the selected storage unit. The message analysis component also writes Meta Data information and keywords from the electronic message to the index database. Once an electronic message is captured and archived, it can be later retrieved using the message query / retrieval component. To retrieve a previously archived electronic message, a user first sends a query specifying the messages desired to the message query / retrieval component using the user interface. The message query / retrieval component formats the query in SQL and runs it against the index database. The message query / retrieval component also sends the query to any other instances of the invention in the electronic communications network via the communications interface. The results of the query from the index database and the other c instances of the invention are combined, formatted for display and returned to the user via the user interface. From the query results, the user can select one or more archived electronic messages to be viewed by sending a list of messages to the message query / retrieval component using the user interface. The message query / retrieval component forwards this list to the storage manager component, which reads, decrypts and decompresses each message from the list in turn and writes the structured message formatted for display to a disk file. When complete, the storage manager component informs the message query / retrieval component, which in turn notifies the user via the user interface. The policy component is used to modify the behavior of the traffic capture, message analysis and message query / retrieval components. Within the traffic capture component, the policy is used to determine whether a particular electronic message is captured or not. Within the message analysis component, the policy is used to determine what type of message analysis to perform and what the storage attributes of the message should be. Within the message query / retrieval component the policy is used to determine whether a user can access the message archive and to filter the query results.
Owner:STOKES TERRY LEE
SSL VPN protocol detection method based on flow analysis
ActiveCN101296228AAccurately manage informationEasy to implementData switching networksTime domainHypertext Transfer Protocol over Secure Socket Layer
The invention relates to a detecting method of an SSL VPN protocol based on flow analysis, which is used for the field of network security. The method of the invention comprises the steps that: firstly, circular monitoring is carried out by opening the promiscuous mode of a network card on an intelligent agent or probe machines; a BPF filter is arranged to fetch HTTPS messages which comprise possibly existing SSL VPN messages; SSL VPN detection method is carried out to the fetched messages. The method of the invention detects that whether the flow is applied to HTTPS or to SSL VPN according to time-domain features of the SSL VPV communication flow and a plurality of handshake protocol features when the VPN is established. By using an HASH table to substitute for database querying, the method of the invention has high speed and is simple and stable.
Owner:SHANGHAI JIAO TONG UNIV
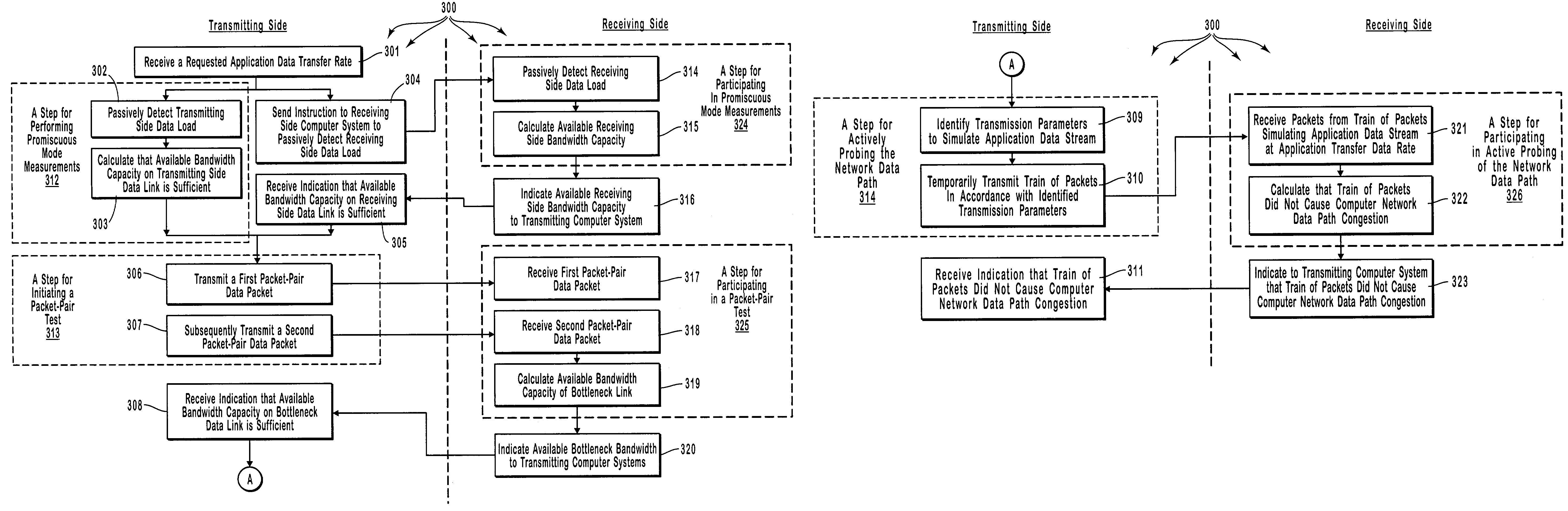
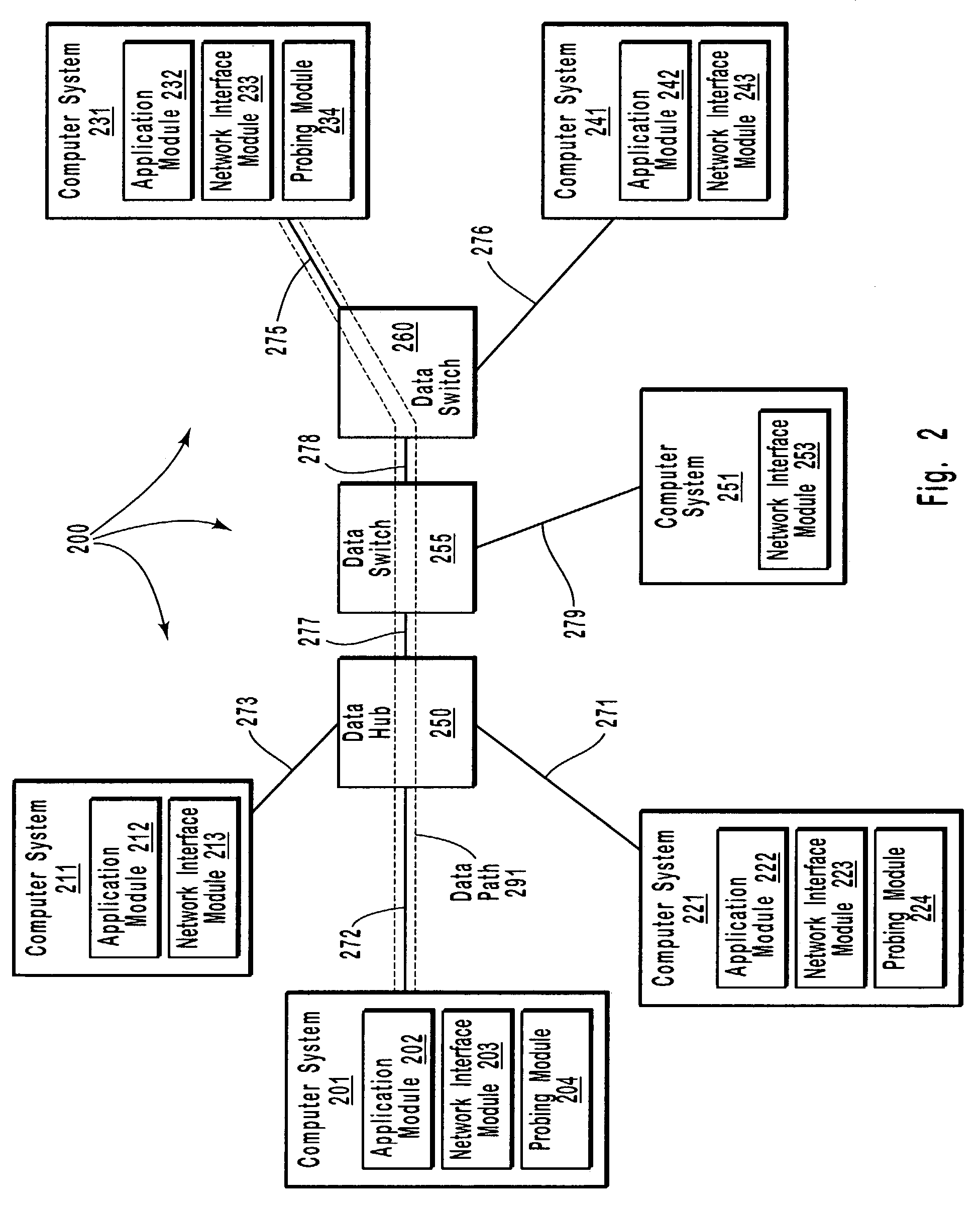
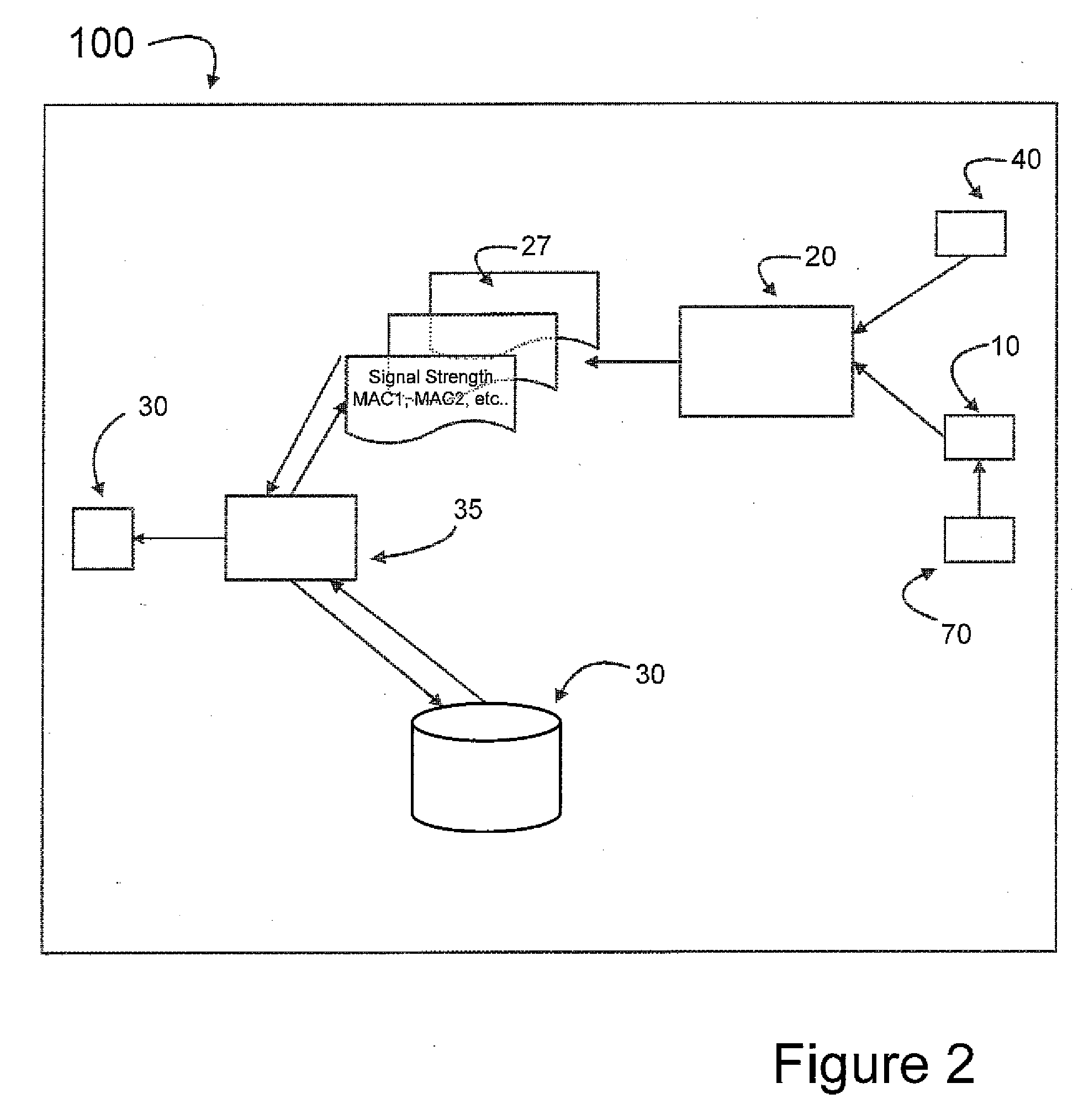
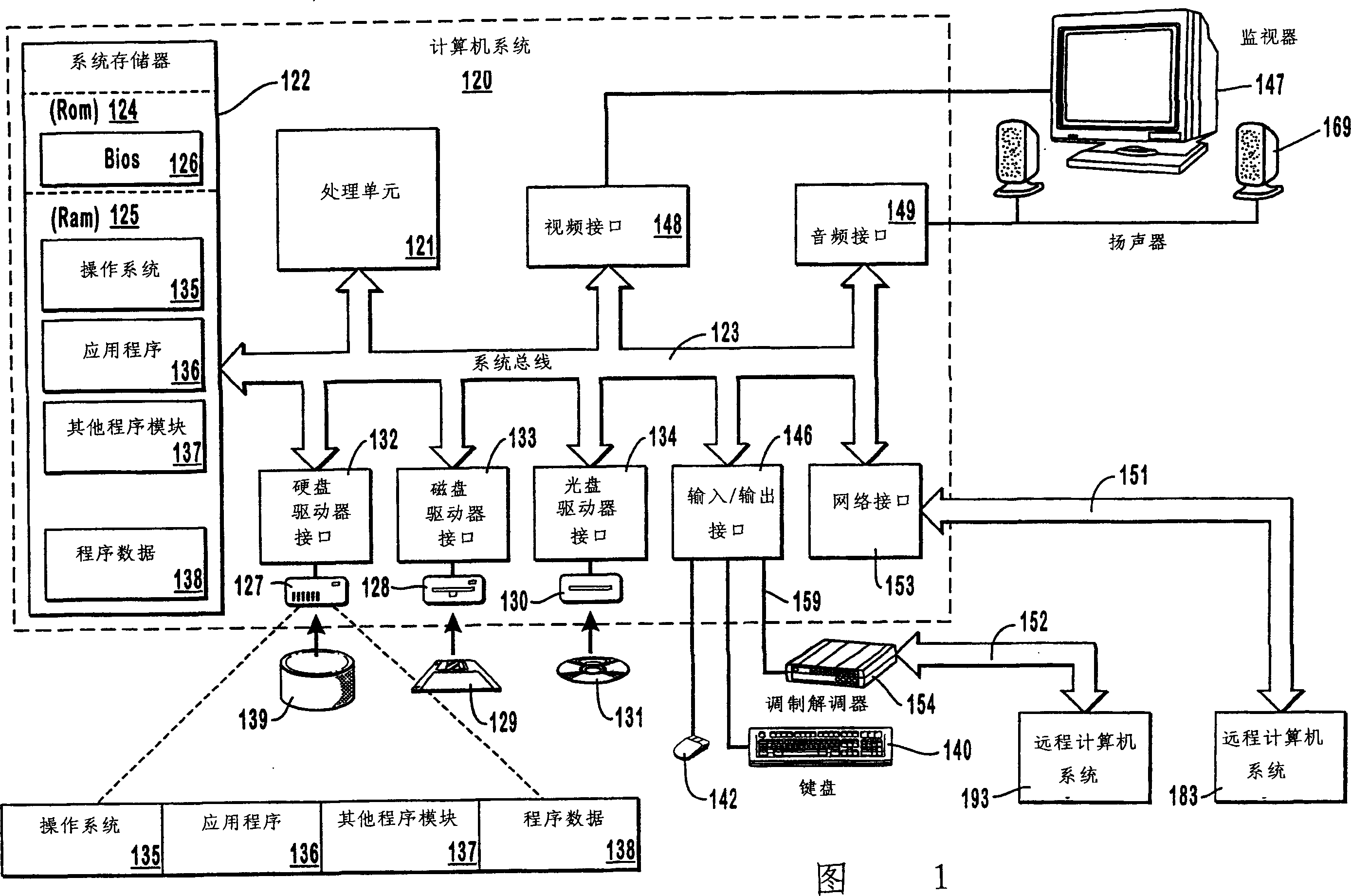
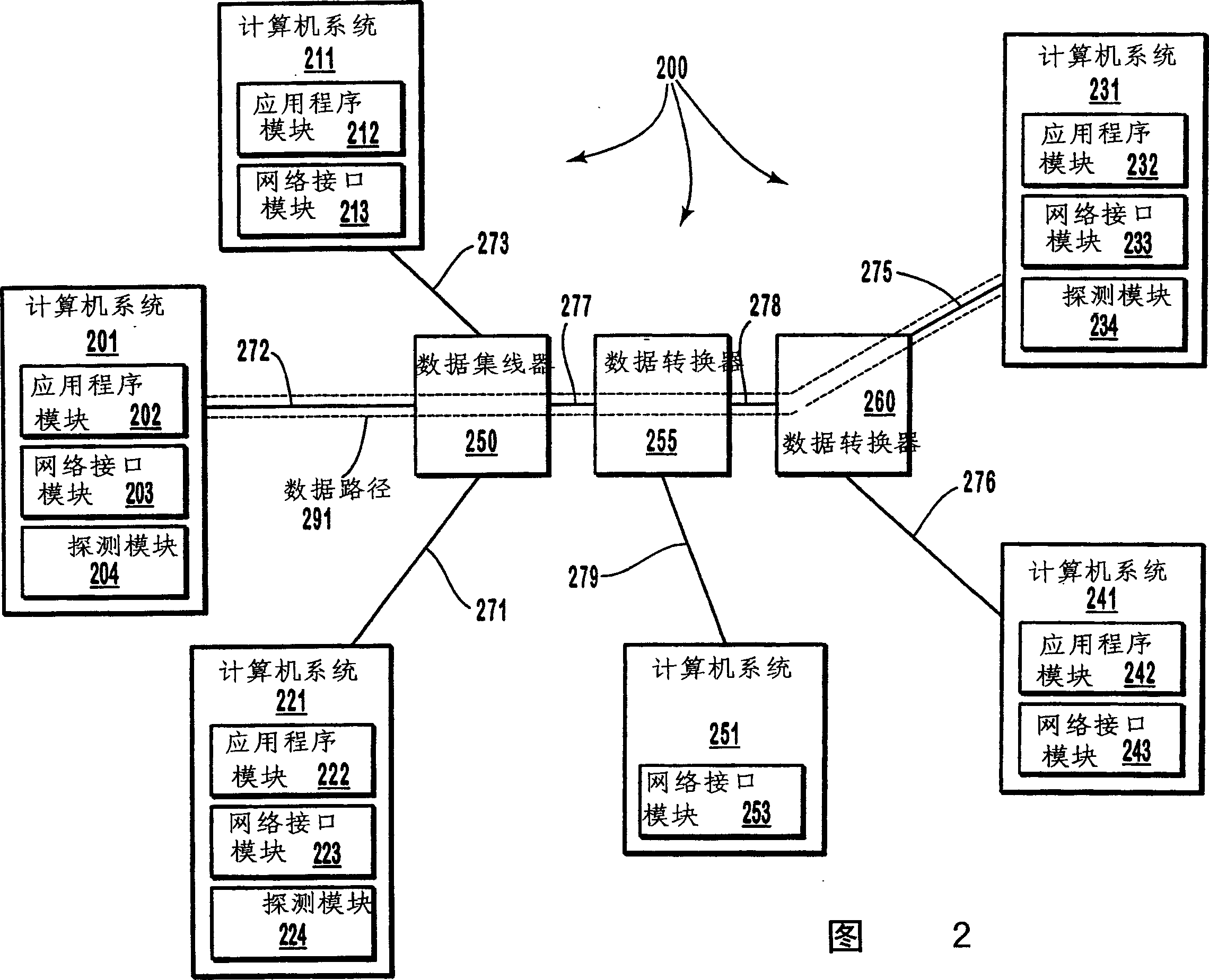
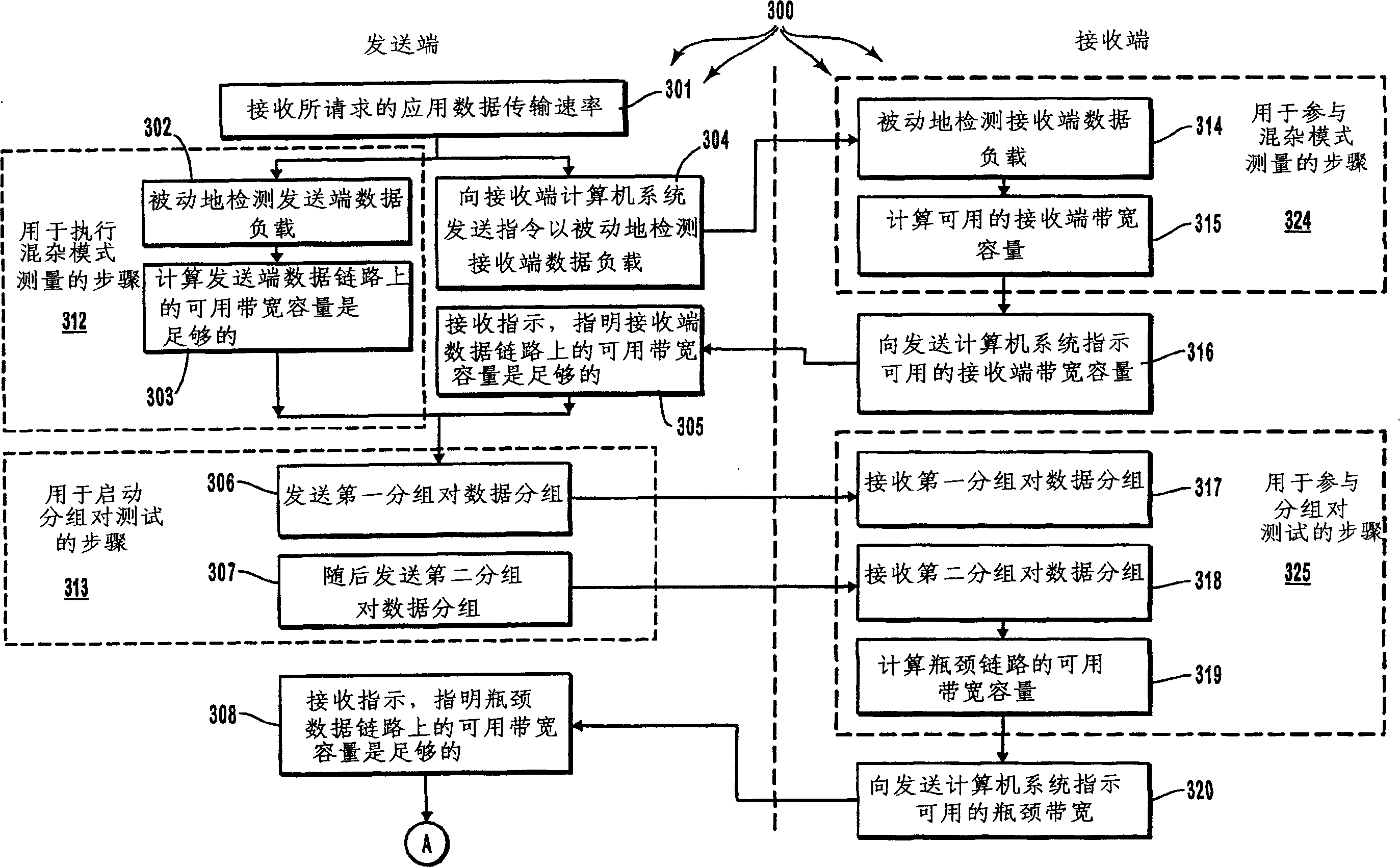
Controlling admission of data streams onto a network based on end-to-end measurements
Appropriate determinations in a series of tests, which transition from more passive tests to more active tests, control the admission of data streams onto a network data path. More passive tests can include promiscuous mode and packet-pair tests. When the results of more passive tests indicate a reduce likelihood of a data stream causing a network data path to transition into a congested state, the network data path can be actively probed to make a more precise determination on the likelihood of congestion. A train of diagnostic data packets is transmitted at a diagnostic data transfer rate having a significantly reduced chance of causing congestion. A train of target data packets is transmitted at a requested application transfer data rate. The number of target data packets received within a specified delay threshold is compared to the number of diagnostic data packets receive with the delay threshold.
Owner:MICROSOFT TECH LICENSING LLC
System and Method for the Capture and Archival of Electronic Communications
A system and method for the capture and archival of electronic communication is disclosed. A network interface card in promiscuous mode connects the invention to an electronic communications network. Network packets are received on the network interface card and sent to a pseudo TCP / IP stack, which reconstructs the network packets into the original electronic message. The reconstructed electronic message is transferred to the traffic capture component in chunks until the entire message is captured. The traffic capture component forwards the electronic message to the message analysis component, which hashes, parses, analyzes and formats for storage the electronic message. The electronic message, in a structured format, is then sent to the storage manager component. The storage manager component selects a storage unit from the available network storage based on the message hash. The storage manager component then compresses, encrypts and writes the structured version of the electronic message to the selected storage unit. The message analysis component also writes Meta Data information and keywords from the electronic message to the index database. Once an electronic message is captured and archived, it can be later retrieved using the message query / retrieval component. To retrieve a previously archived electronic message, a user first sends a query specifying the messages desired to the message query / retrieval component using the user interface. The message query / retrieval component formats the query in SQL and runs it against the index database. The message query / retrieval component also sends the query to any other instances of the invention in the electronic communications network via the communications interface. The results of the query from the index database and the other c instances of the invention are combined, formatted for display and returned to the user via the user interface. From the query results, the user can select one or more archived electronic messages to be viewed by sending a list of messages to the message query / retrieval component using the user interface. The message query / retrieval component forwards this list to the storage manager component, which reads, decrypts and decompresses each message from the list in turn and writes the structured message formatted for display to a disk file. When complete, the storage manager component informs the message query / retrieval component, which in turn notifies the user via the user interface. The policy component is used to modify the behavior of the traffic capture, message analysis and message query / retrieval components. Within the traffic capture component, the policy is used to determine whether a particular electronic message is captured or not. Within the message analysis component, the policy is used to determine what type of message analysis to perform and what the storage attributes of the message should be. Within the message query / retrieval component the policy is used to determine whether a user can access the message archive and to filter the query results.
Owner:STOKES TERRY LEE
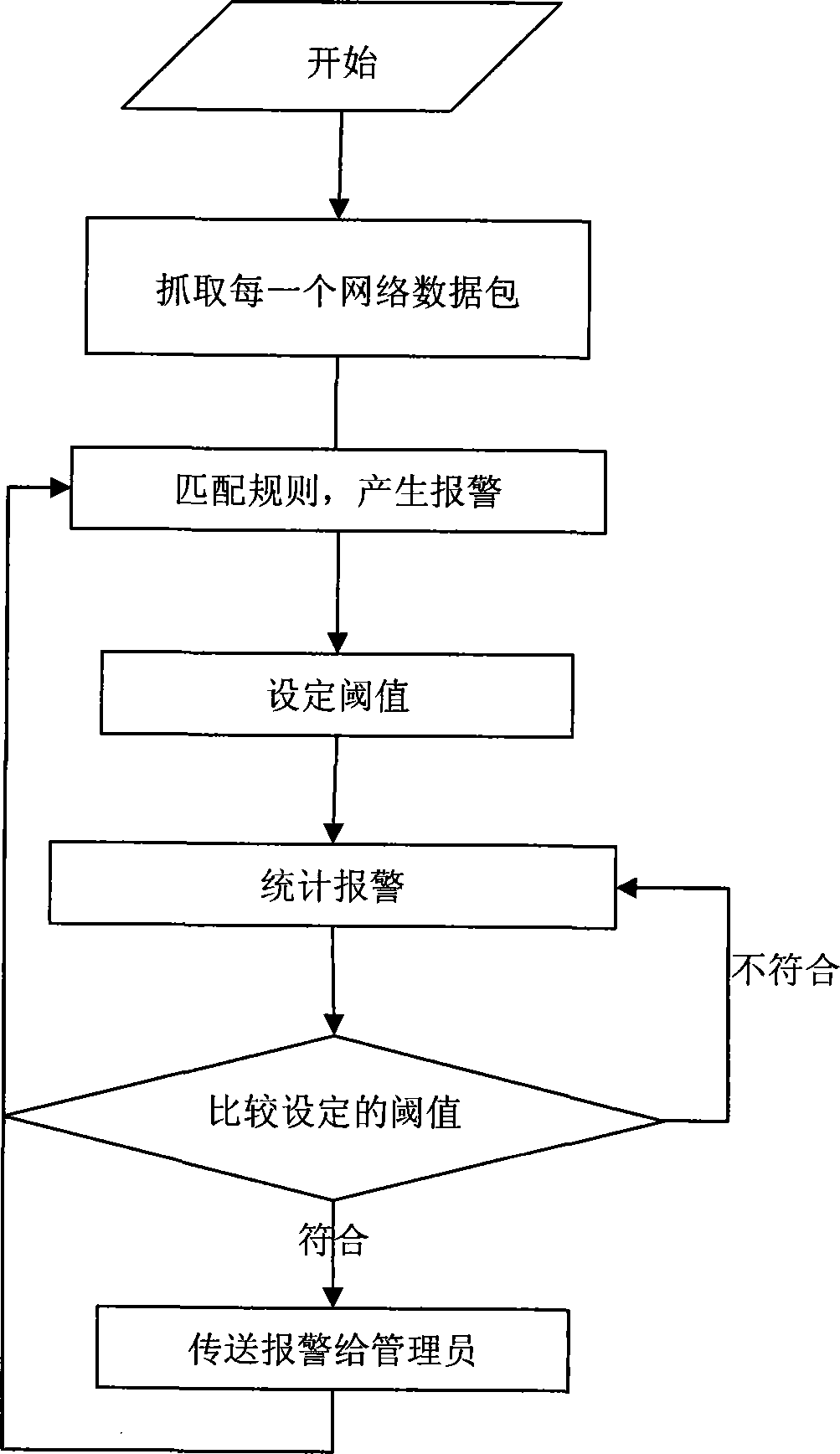
Method for solving mass alarm in NIDS
This invention relates to a method for solving mass warning in a NIDS system including two steps: 1, preprocess stage: setting a network card a miscellaneous mode, grasping data packets in circulation by Libpcap, which applies a zero copy technology to map a user memory in the kernel to decode the grasped data packets via a link layer, processing the protocol layer and re-setting flows to match them in rule to generate a warning event to be stored in a hash chained list, in which, f(x)=a[x] and the lower list of the array is used as the index to increase the lookup efficiency, 2, statistic stage: calculating the generated events according to the attribute value of the chained list to decide if it warns according to the set selection.
Owner:西安交大捷普网络科技有限公司
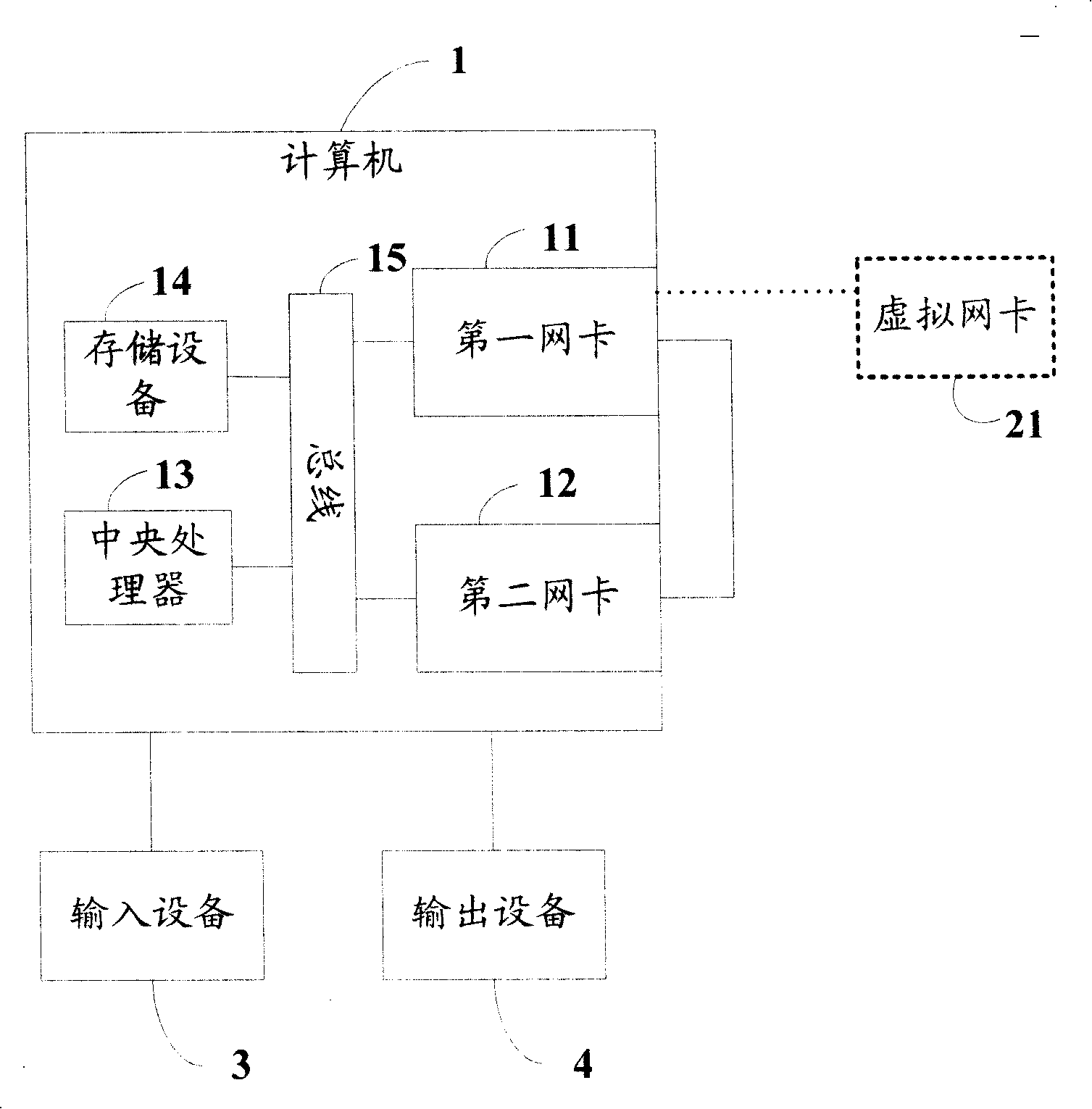
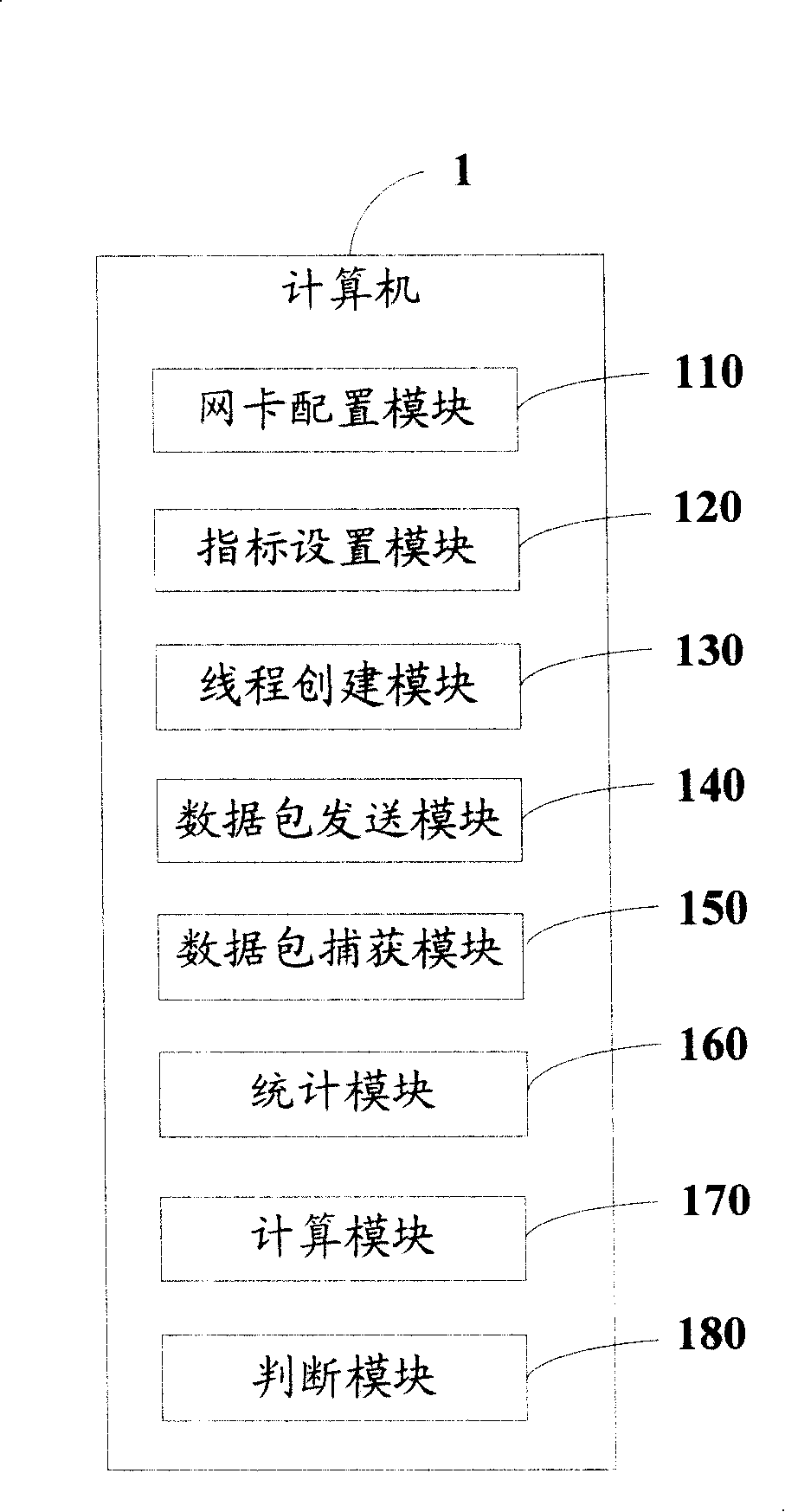
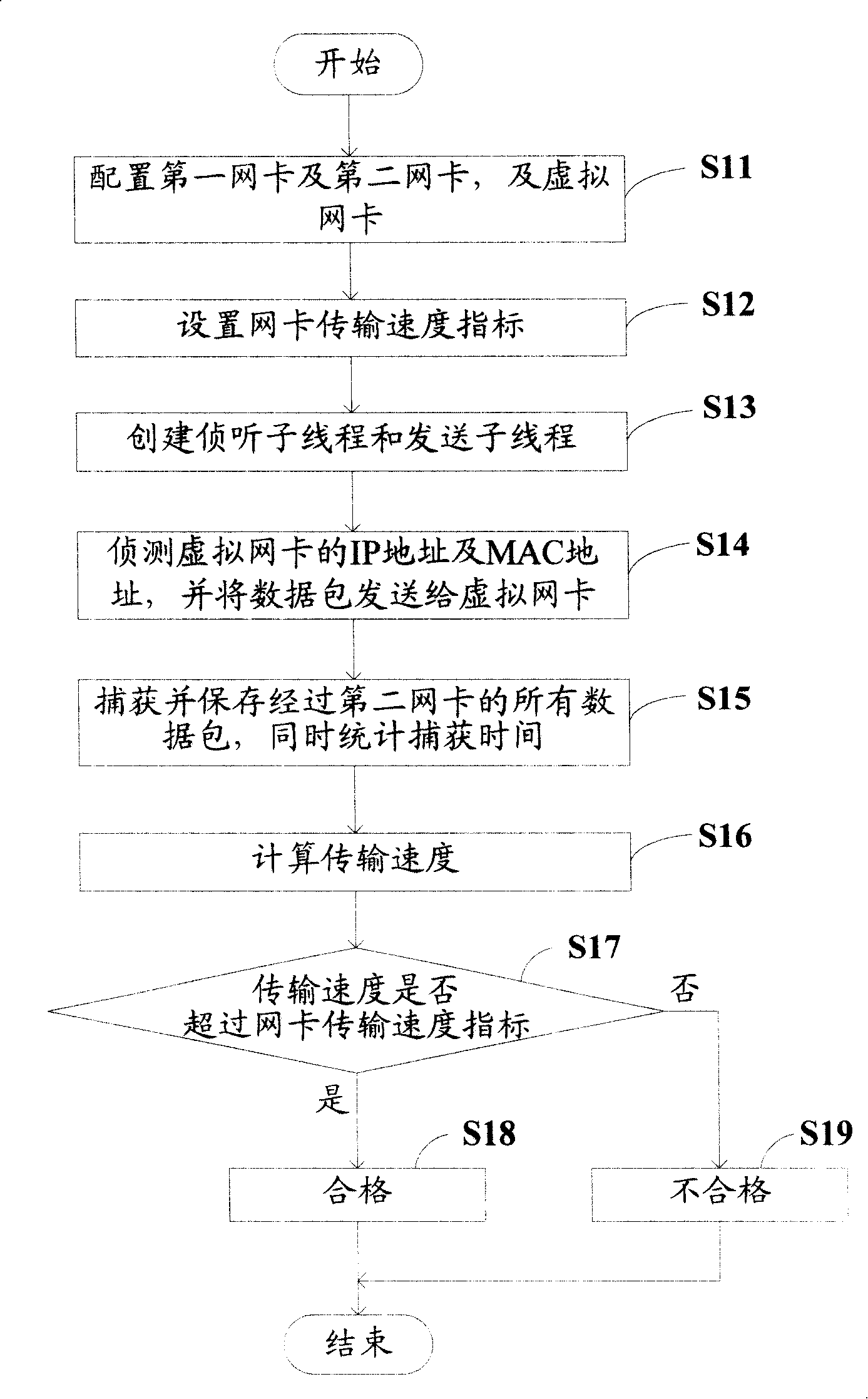
Network card transmission speed testing system and method
InactiveCN101163051AEfficient testingReduce testing costsError detection/correctionData switching networksIp addressSpeed test
The invention provides a LAN speed testing method, the steps of the method are: the IP addresses of a first network card and a second network card are arranged; the IP address of a virtual network card and an MAC address are also configured. The second network card is designed to a promiscuous mode. The network transmitting speed index is set. The IP address of the virtual network card and the MAC address are detected. According to the IP address of the virtual network card and the MAC address, a certain amount of databases are sent to the virtual network card by passing through a first network card. The data packet sent to the virtual network card is captured by the second network card. The capture time needed by capturing the entire data packet is counted. According to the size of the sent base packet and the capture time, the minimal network card transmitting speed when the first network card connects with the second network card is counted. Then whether the minimal network card transmitting speed excesses the set network transmitting speed index can be judged. The invention also provides a network transmitting testing system. With the invention, the transmission performances of the two network cards in one computer can be tested.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
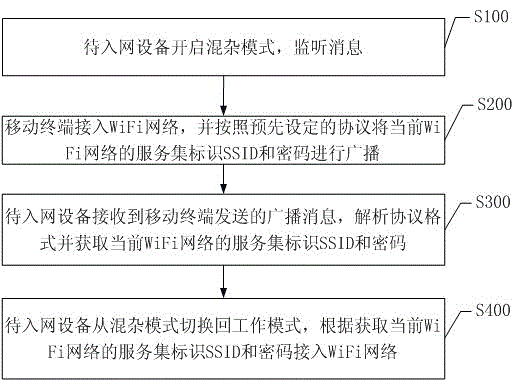
Method and system for accessing multi-protocol compatible equipment to WiFi (Wireless Fidelity) network
The invention discloses a method and a system for accessing multi-protocol compatible equipment to a WiFi (Wireless Fidelity) network. The method comprises the following steps that: equipment to be accessed to the network opens a promiscuous mode and monitors messages; a mobile terminal is accessed to the WiFi network and broadcasts a service set identifier (SSID) and a password of the current WiFi network according to pre-set protocols; the equipment to be accessed to the network receives broadcast messages sent by the mobile terminal, analyzes protocol formats and obtains the SSID and the password of the current WiFi network; and the equipment to be accessed to the network switches the promiscuous mode into a working mode and is accessed to the WiFi network according to the obtained SSID and password of the current WiFi network. The method and the system disclosed by the invention can be applicable to intelligent equipment in the scheme of MTK series of WiFi chips and simultaneously support wechat control and APP (Application) control; therefore, the compatibility of the intelligent equipment is improved; and convenience is provided for users.
Owner:HUIZHOU TCL MOBILE COMM CO LTD
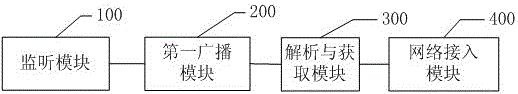
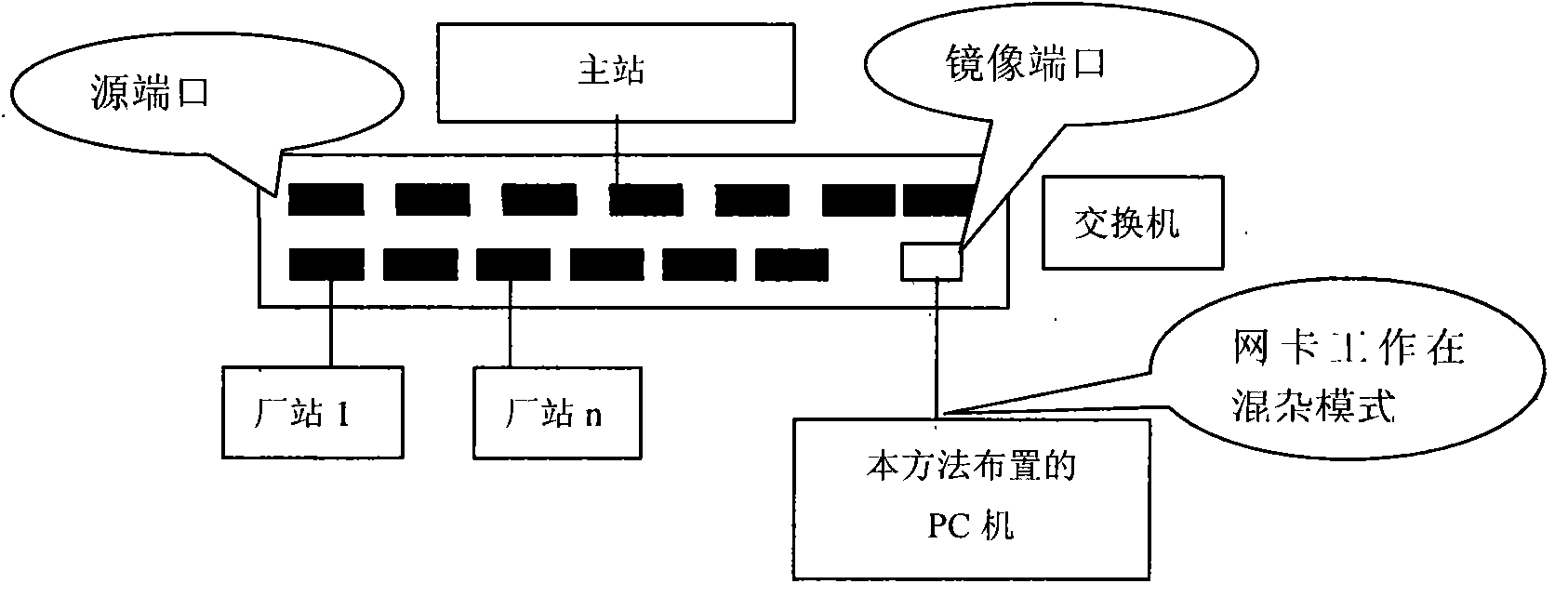
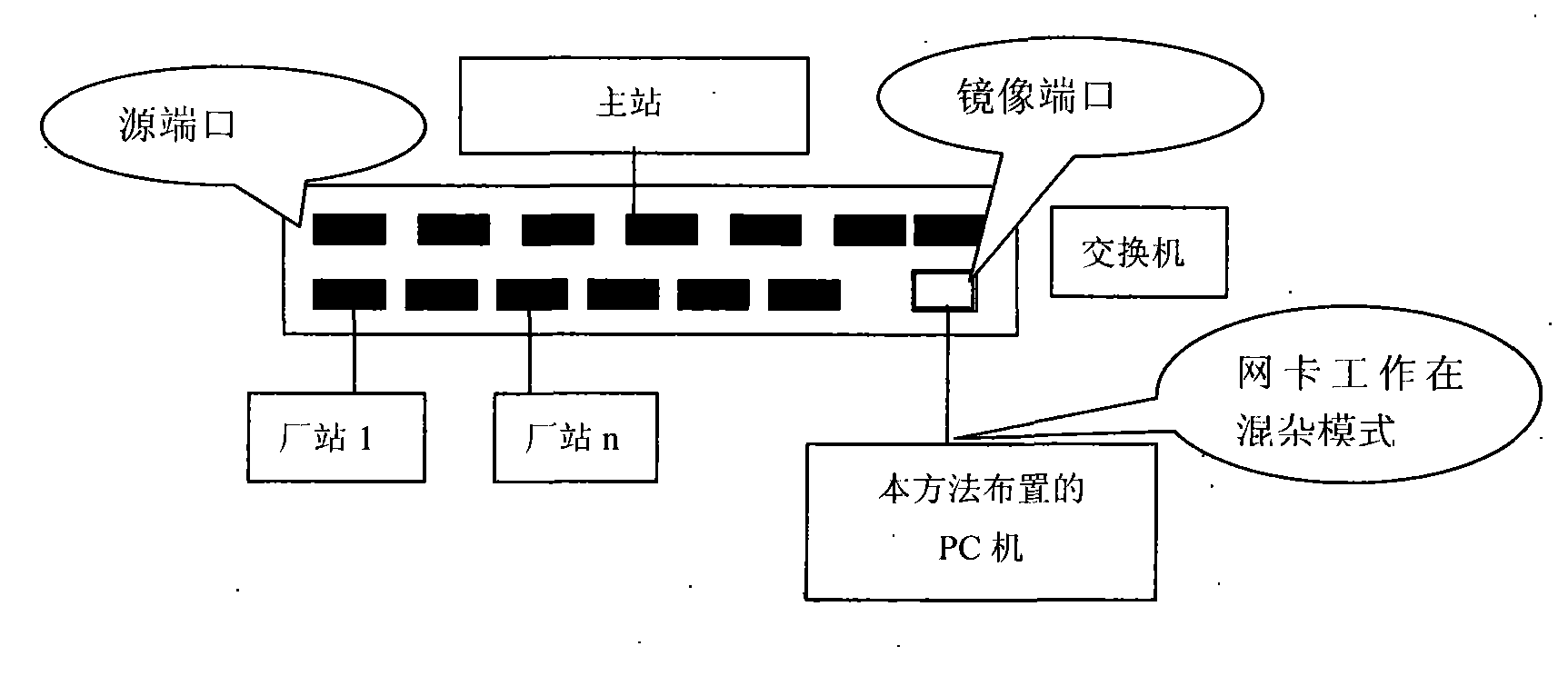
Online bidirectional monitoring and analysis method of power system full channel based on promiscuous mode
InactiveCN101815017ARealize online monitoring analysisDoes not affect actual communicationData switching networksPrimary stationElectric power system
The invention discloses an online bidirectional monitoring and analysis method of a power system full channel based on the promiscuous mode, comprising the following steps: 1) setting a port of a switch in which the channel is located as a mirroring port and mirroring the received and transmitted data at other ports to the mirroring port; 2) connecting a computer network card in which online bidirectional monitoring and analysis software is located to the mirroring port of the prepositive switch; 3) the online bidirectional monitoring and analysis software setting the network card in the promiscuous mode and monitoring the received and transmitted messages on all the channels on the prepositive switch; 4) analyzing the source IP addresses and the destination IP addresses of the messages and distinguishing transmitting from the master station from transmitting from the plant station according to the source IP and the destination IP; and 5) interpreting and analyzing the monitored messages according to the corresponding protocols, wherein the switch is the prepositive switch or data acquisition switch. By the method, uplink and downlink simultaneous monitoring of all the special channels can be realized by only one computer with the network card and uplink and downlink online simultaneous monitoring of all the network channels can be realized.
Owner:NARI TECH CO LTD +1
Scanning Apparatus and System for Tracking Computer Hardware
InactiveUS20090210935A1Error detection/correctionVolume/mass flow measurementTraffic capacityPromiscuous mode
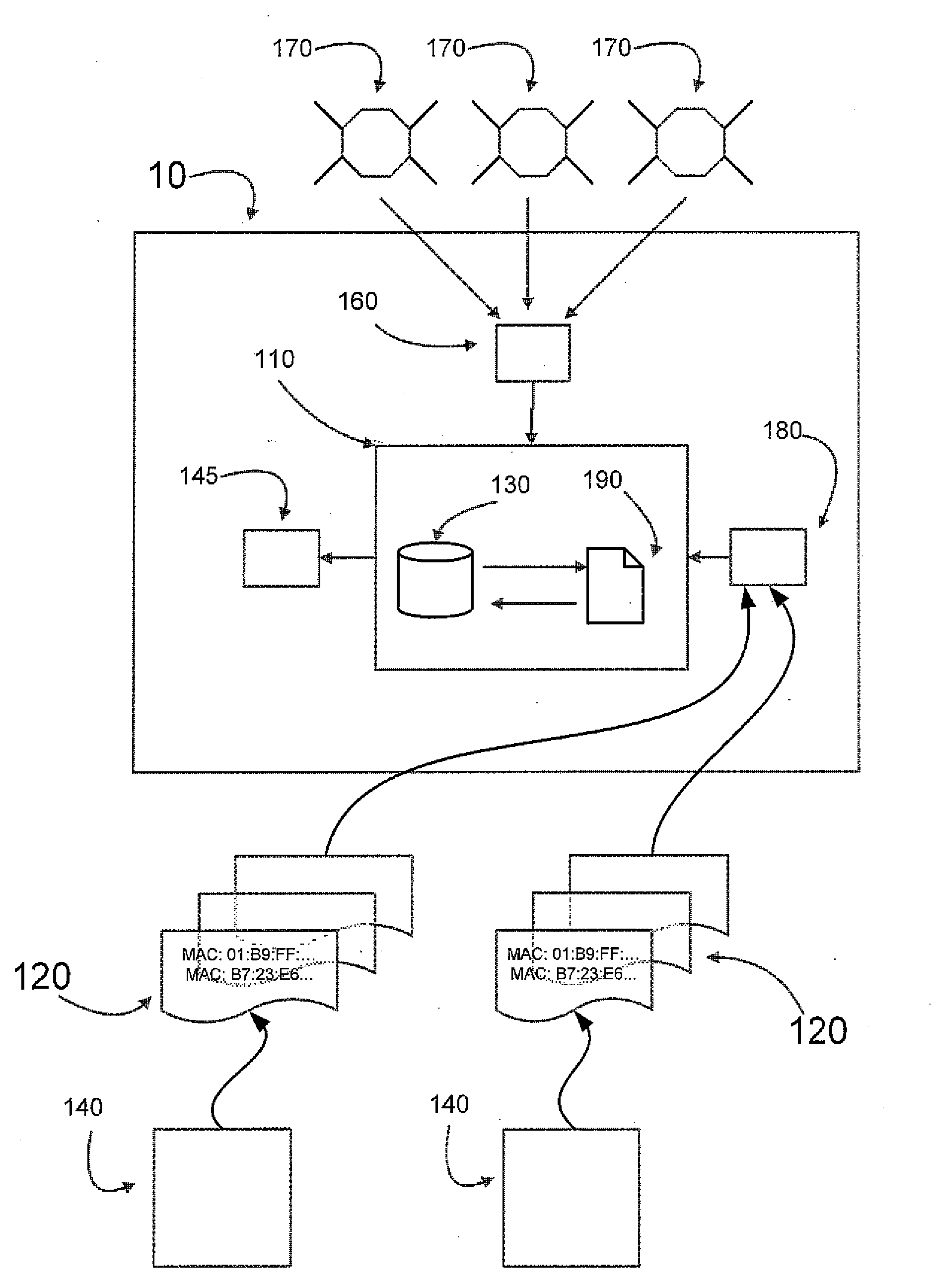
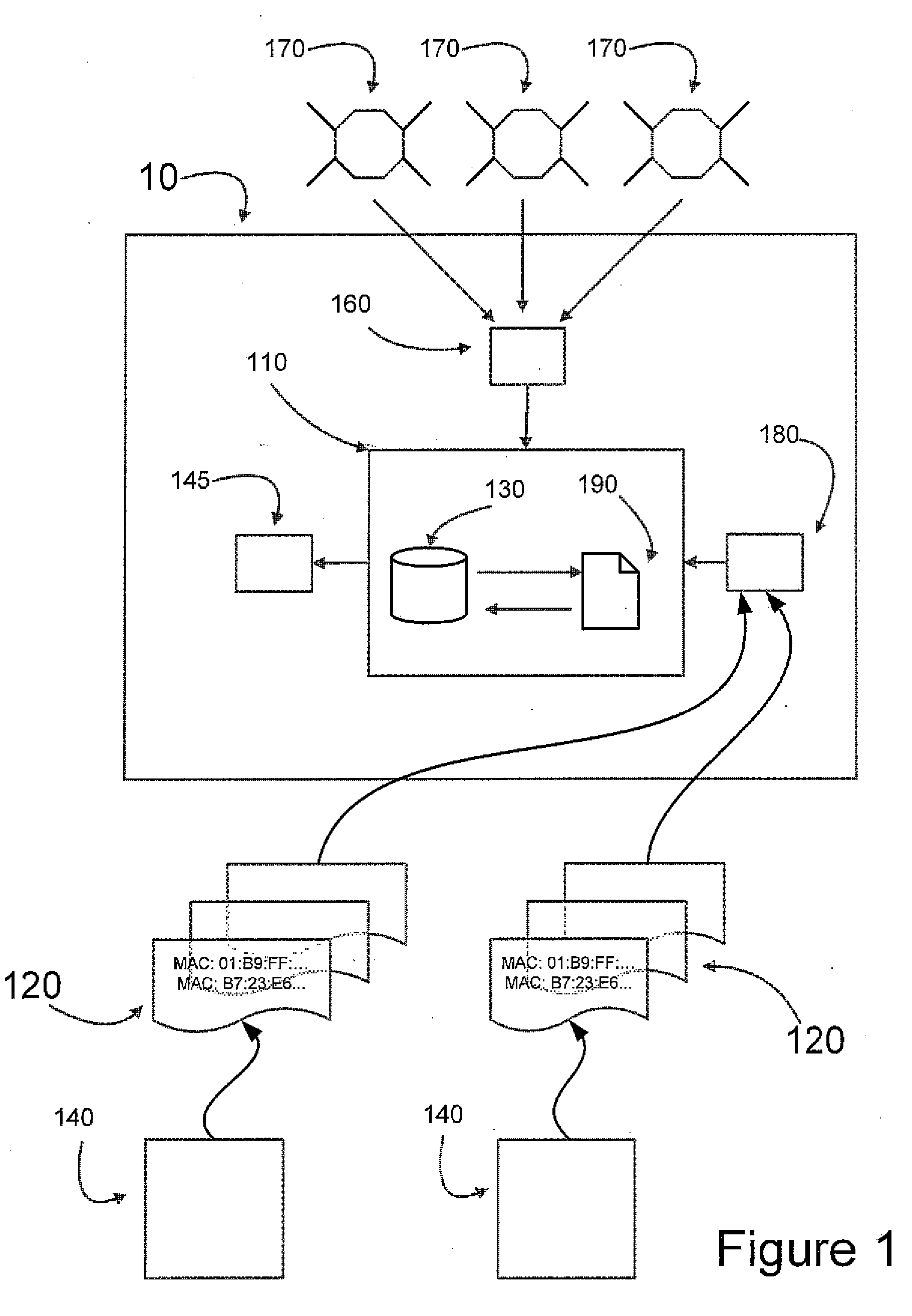
Apparatus and system for tracking computer hardware consisting of a network interface card configured in promiscuous mode capable of passively listening for OSI layer 2 network traffic on a medium for use in the recovery or location of lost or stolen devices. The device of interest, one located, can then be tracked via signal strength. GPS may also be used to track locations where devices of interest have been located.
Owner:MILEY JAMIE ALAN +1
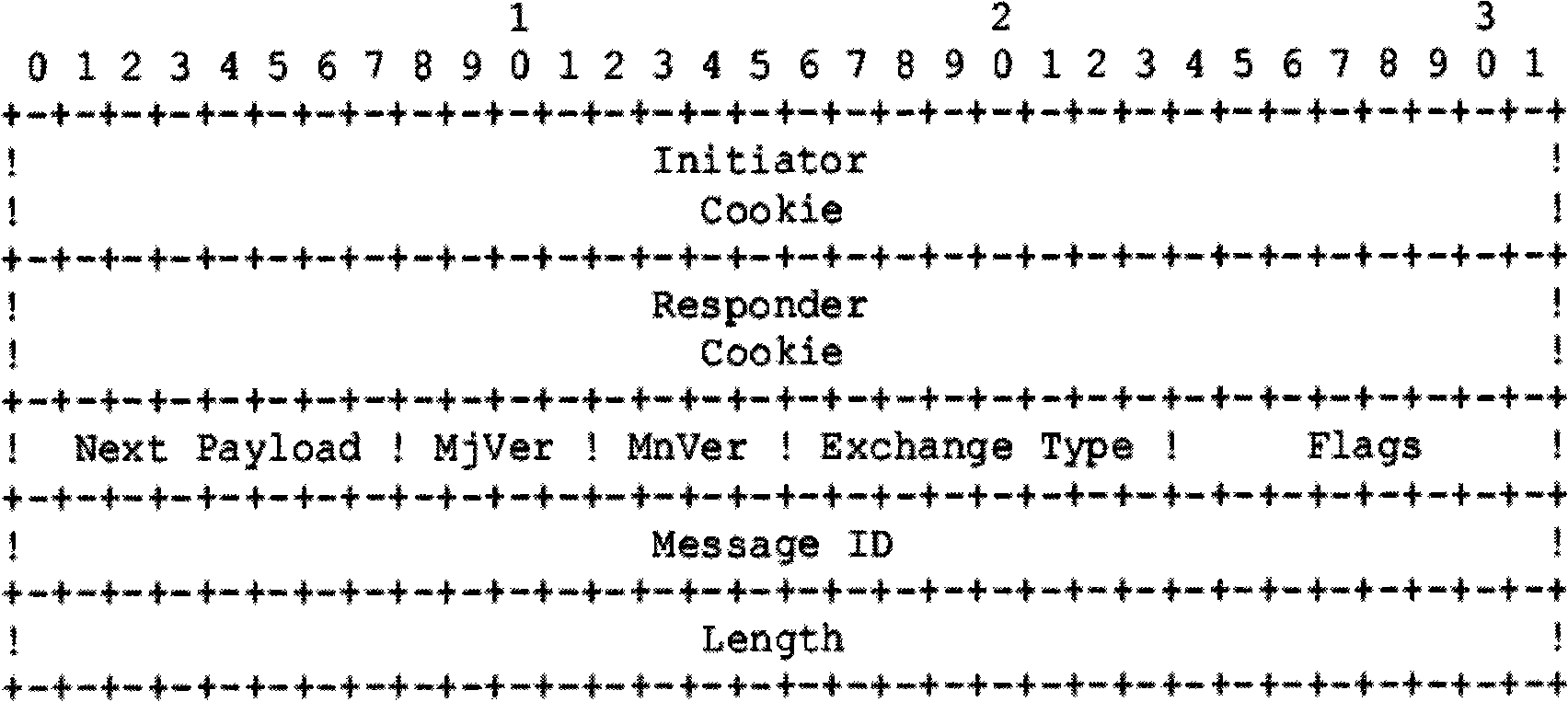
IPSec VPN protocol depth detection method based on packet offset matching
ActiveCN101296227AExact usageAvoid attackError preventionNetworks interconnectionIPsecPromiscuous mode
The invention discloses a depth-detecting method based on an IPSec VPN protocol which is matched with the offset of messages, being used for the field of network security. The method of the invention comprises the steps that: firstly, circular monitoring is carried out by opening the promiscuous mode of a network card on an intelligent agent or probe machines; a BPF filter is arranged to fetch IPSec VPN messages, to which depth detection is carried out. The algorithm can identify and analyze that whether the IPSec VPN messages are fabricated and whether the format of the IPSec VPN messages are standard or not. The method of the invention can not only detect a standard ISAKMP data packet, but also can correctly analyze the ISAKMP data packet which is non-standard IPSec and is added with padding data with unknown length, thereby realizing the detecting method generally used for detecting the IPSec messages. The same idea can be popularized for detecting other protocols.
Owner:SHANGHAI JIAO TONG UNIV
System and Method for the Capture and Archival of Electronic Communications
A system and method for the capture and archival of electronic communication is disclosed. A network interface card in promiscuous mode connected to an electronic communications network is employed to capture network packets, which are reconstructed into the original electronic message. The electronic message is then hashed, parsed, analyzed and formatted for storage. The electronic message, in a structured format, is compressed and encrypted before being written to a storage unit based on the message hash. Meta Data information and keywords from the electronic message are written to an index database. Electronic messages can later be retrieved using a message query and retrieval component. A user created policy governs what electronic messages are captured, how those messages are stored and who can access them.
Owner:STOKES TERRY LEE
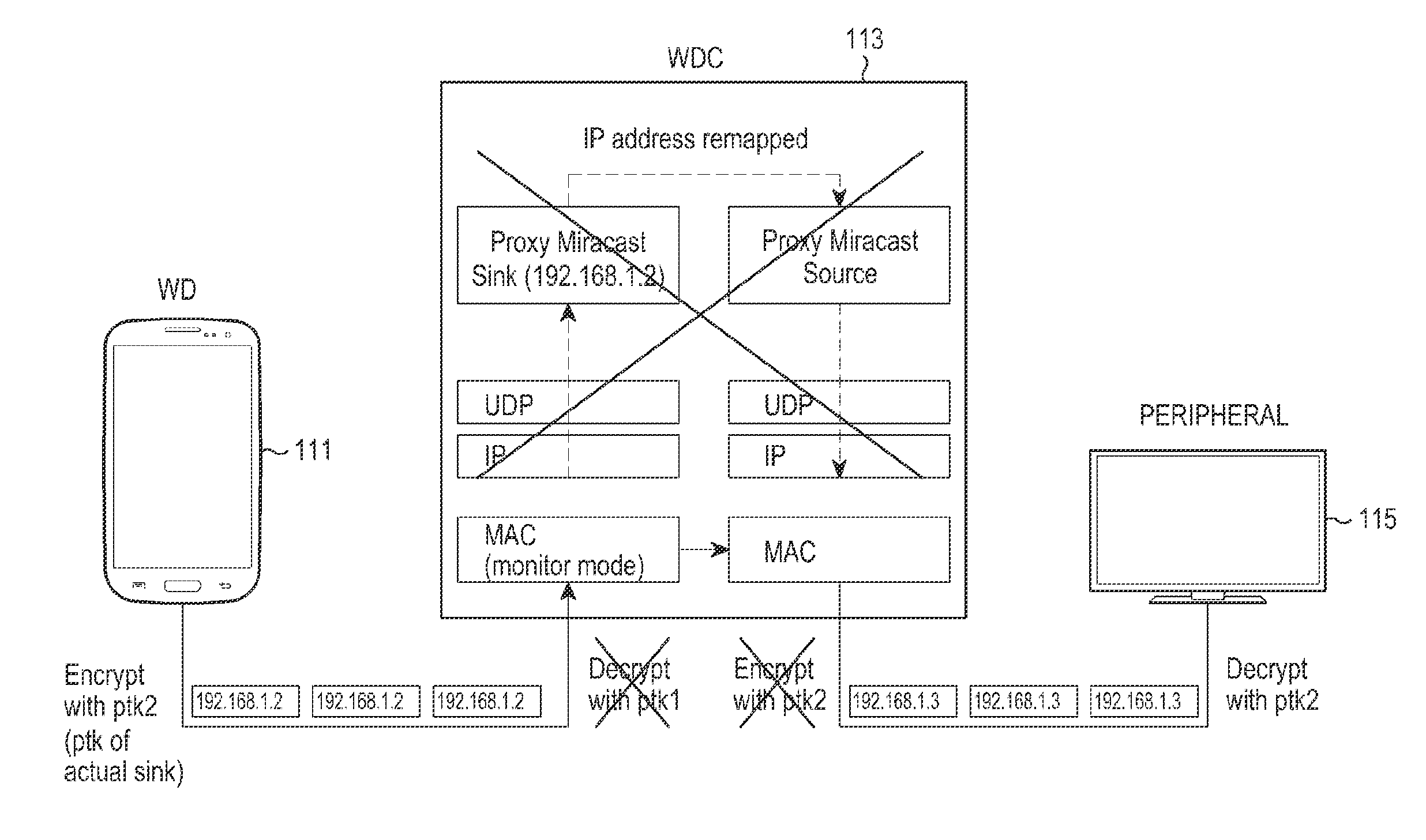
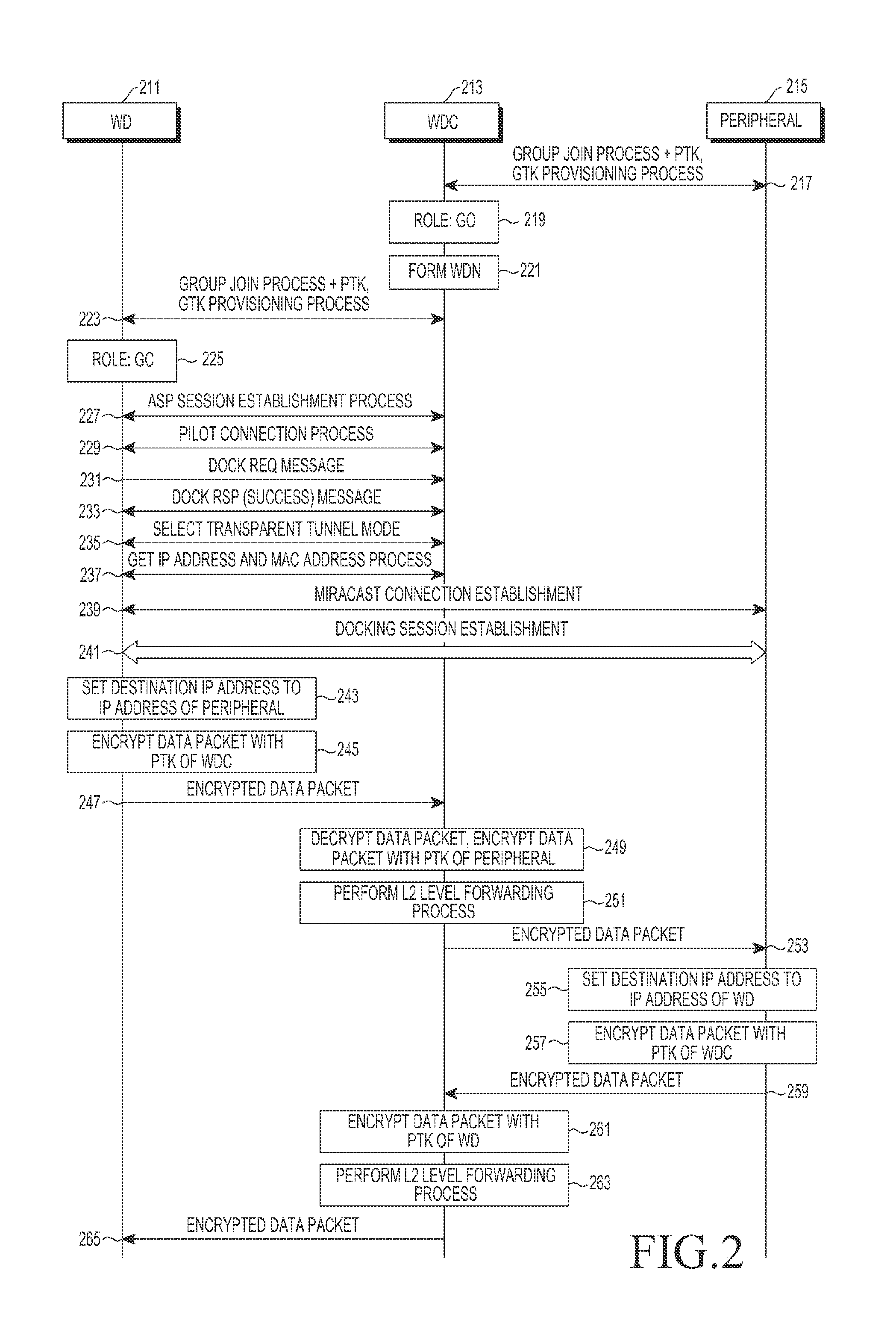
Apparatus and method for controlling transparent tunnel mode operation in communication system supporting wireless docking protocol
ActiveUS20140351602A1Public key for secure communicationNetwork topologiesMonitor modeCommunications system
A method for controlling a transparent tunnel mode operation in a Wireless Dockee (WD) in a communication system supporting a wireless docking protocol is provided. The method includes performing a group join process and a provisioning process for security keys with a Wireless Docking Center (WDC); accessing services of a Wireless Docking Environment (WDN); selecting an operating mode between the WD and the WDC as a transparent tunnel mode; performing a process of getting information related to a peripheral with the WDC; requesting the WDC to enable a monitor mode and a promiscuous mode; and transmitting / receiving a data packet using the information related to the peripheral with the peripheral if a Miracast connection and a docking session are established between the WD and the peripheral.
Owner:SAMSUNG ELECTRONICS CO LTD
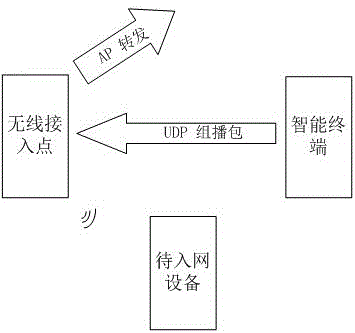
Network access method and system of intelligent device
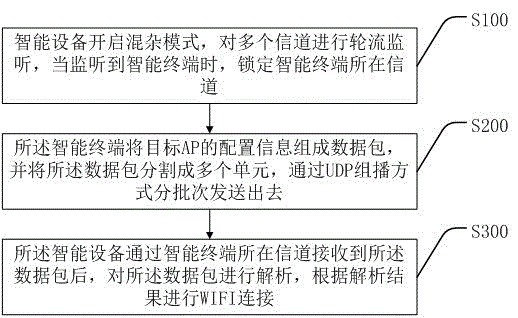
InactiveCN106488447AReceive fast and stableEasy accessNetwork traffic/resource managementAssess restrictionAccess methodRobust Header Compression
The invention discloses a network access method and system of an intelligent device. The method comprises the following steps: the intelligent device opens a promiscuous mode to monitor a plurality of channels in turn so as to lock the channel where an intelligent terminal is located, the intelligent terminal sends a data packet composed of configuration information of a target AP in a UDP multicast mode in batches, the intelligent device receives the data packet quickly and stably by packet header compression, redundancy receiving, sender verification and two-way capture and analyzes the received data packet, and finally the device accesses the network quickly and stably according to the analysis result.
Owner:广州TCL智能家居科技有限公司
System and method for testing transmission speeds of network interface cards in a computer
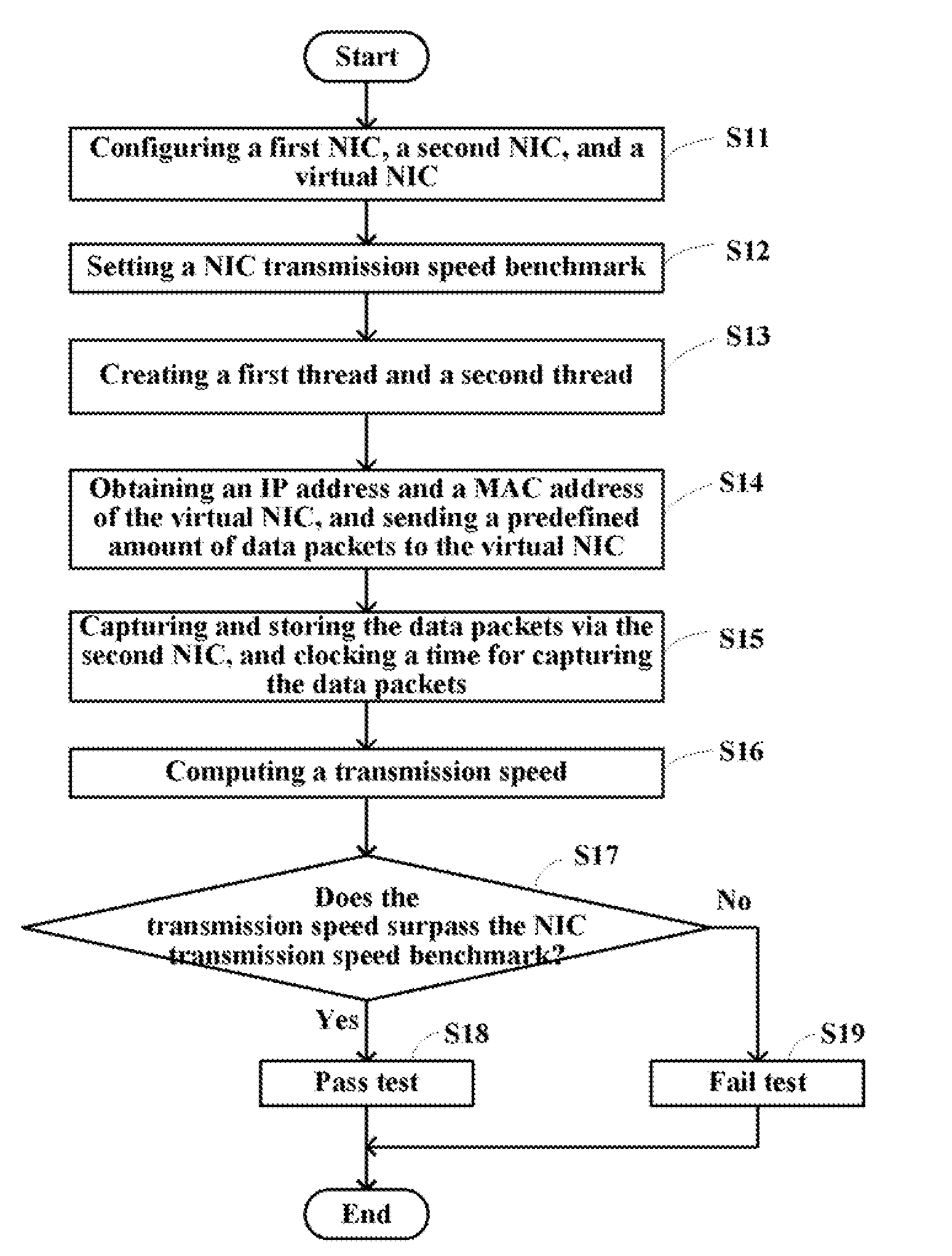
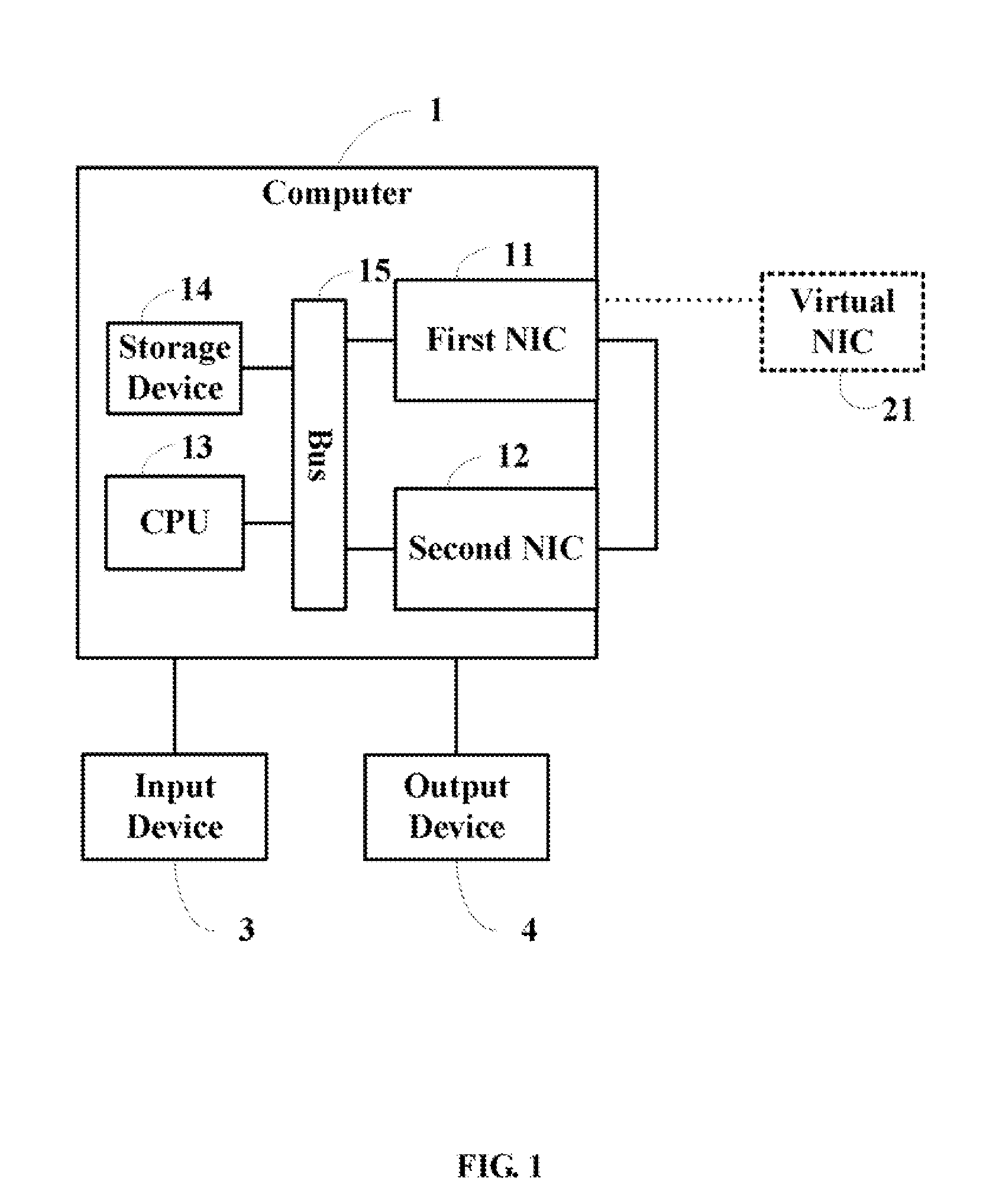
InactiveUS20080089340A1Error detection/correctionData switching by path configurationTTEthernetIp address
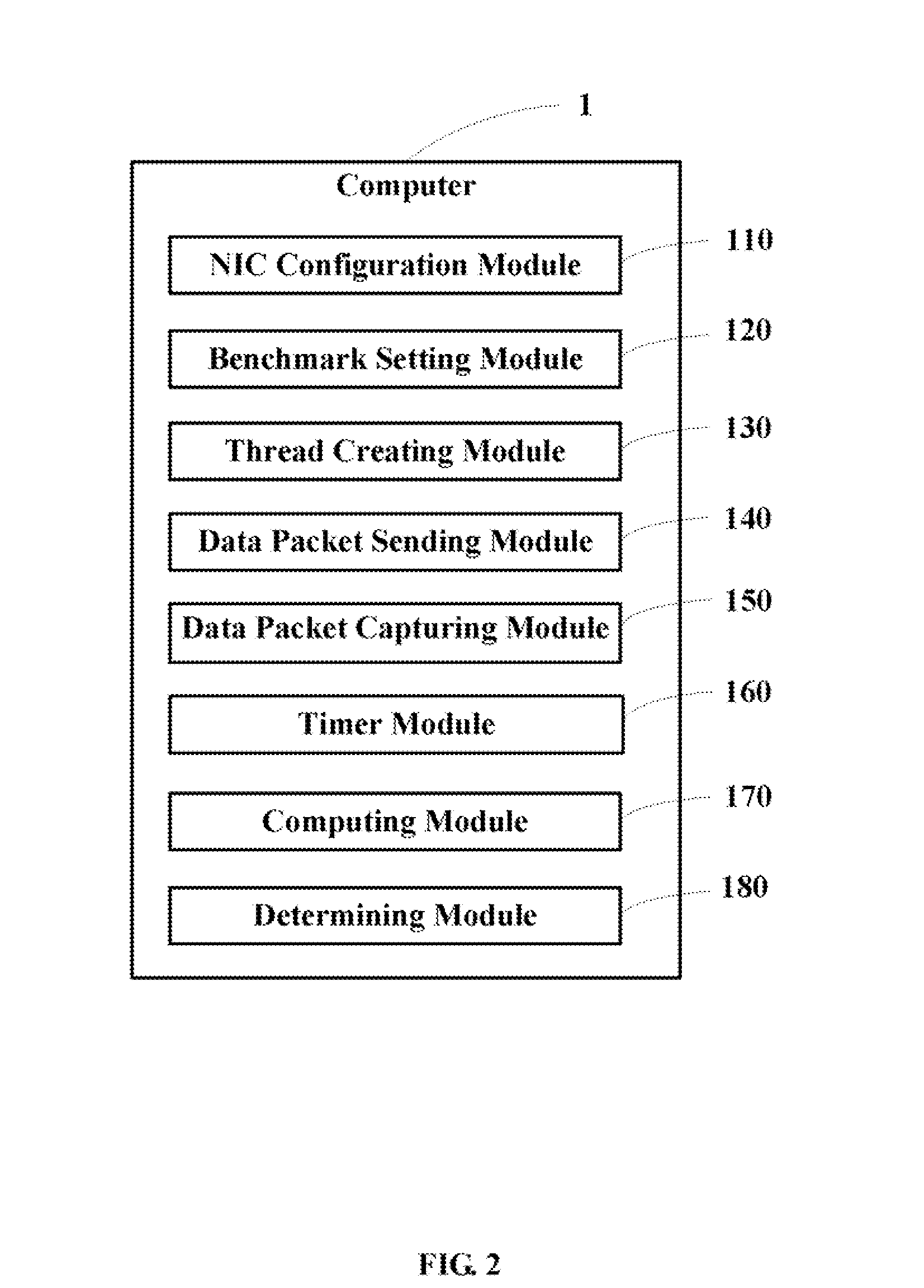
A method for testing transmission speeds of network interface cards (NICs) in a computer (1), the computer being installed with a first NIC (11) and a second NIC (12), the computer being further connected to a virtual NIC (21), the method includes the steps of: configuring / setting an internet protocol (IP) address of the first NIC and an IP address of the second NIC, and configuring an IP address of the virtual NIC and a message authentication code (MAC) address of the virtual NIC; setting the second NIC to a promiscuous mode; setting an NIC transmission speed benchmark; obtaining the IP address and the MAC address of the virtual NIC, and sending a predefined amount of successive data packets of a predetermined size to the virtual NIC via the first NIC according to the IP address and the MAC address of the virtual NIC; capturing the predefined amount of successive data packets of the predetermined size via the second NIC; clocking a time for capturing the predefined amount of successive data packets of the predetermined size via the second NIC; computing a transmission speed of the first NIC and the second NIC according to the time for capturing the predefined amount of successive data packets of the predetermined size; and comparing the transmission speed to the NIC transmission speed benchmark to determine whether the first NIC and the second NIC pass the test. A related system is also provided.
Owner:HON HAI PRECISION IND CO LTD
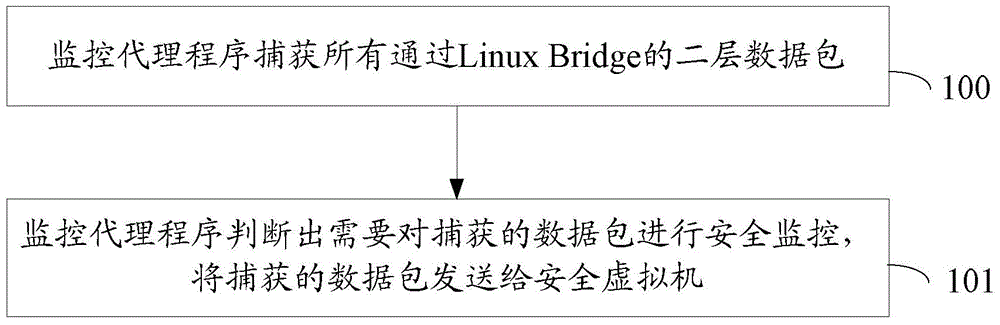
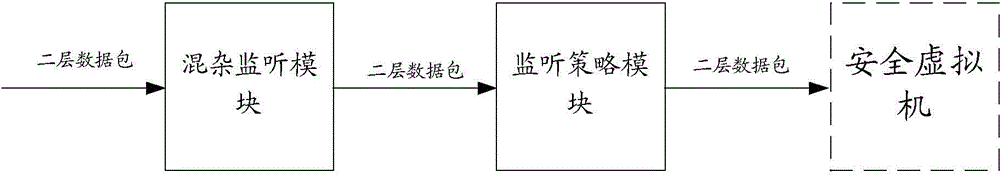
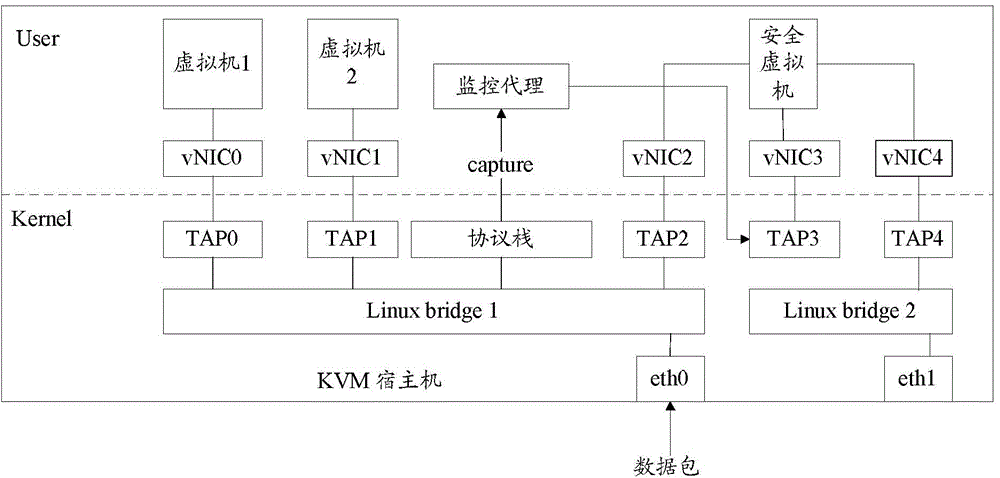
Method and device for monitoring flow of virtual network
The invention discloses a method and device for monitoring the flow of a virtual network. The method and device are applied to the virtual network which is realized on the basis of Linux Bridge in the KVM virtualization environment, a monitoring agent is set in a host system of the virtual network in advance, the work mode of Linux Bridge in the host system is set as a hybrid mode, and the monitoring agent is used to capture a double-layer data packet of the Linux bridge through which multiple virtual machines are connected. The method comprises that the monitoring agent captures all the double-layer data packets that pass the Linux Bridge; and when the monitoring agent determines that the captured data packets need safety monitoring, the data packets are sent to a safety virtual machine. The monitoring agent captures the double-layer data packets that pass the Linux Bridge, and the transmits the data packets that need safety monitoring to the safety virtual machine for safety detection, and thus, the flow of the virtual network is monitored.
Owner:BEIJING VENUS INFORMATION SECURITY TECH +1
Virtualizing the operation of intelligent network interface circuitry
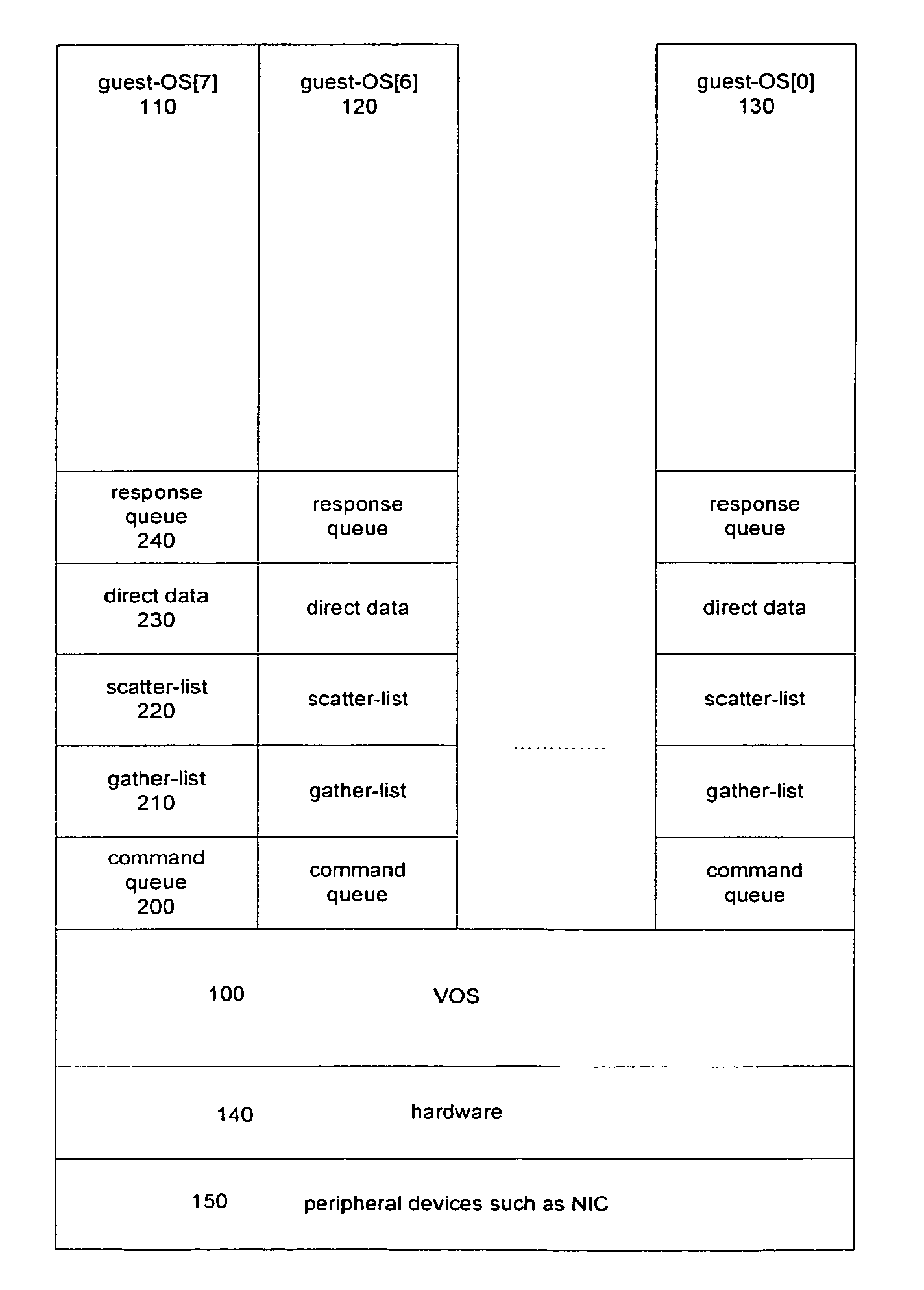
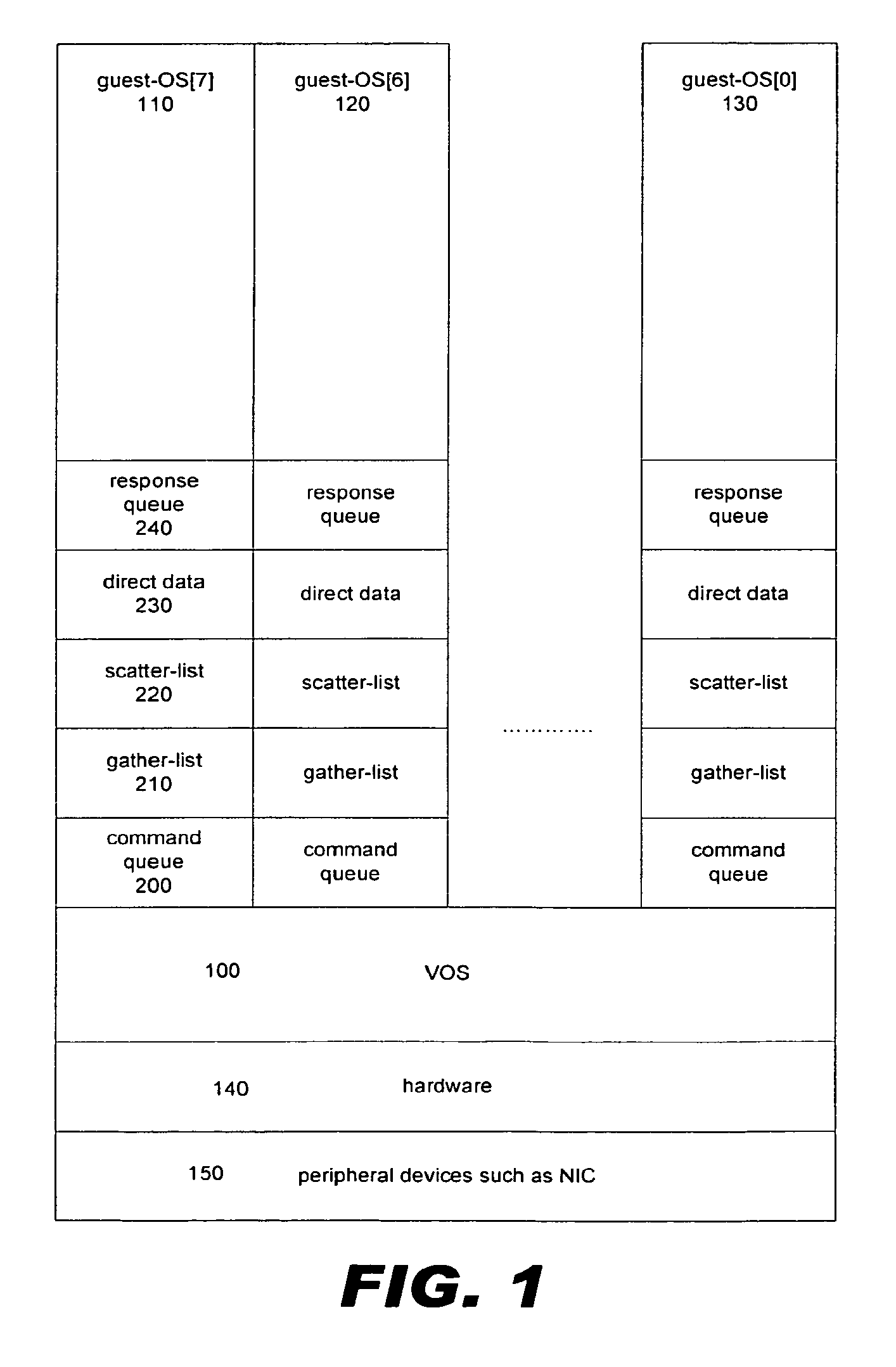
ActiveUS7924840B1Provide controlSpecial service provision for substationTime-division multiplexIntelligent NetworkVirtualization
The present invention is in the field of virtualization of Network Interface Cards and Controllers (NIC) that connect to for example a host computer that can have multiple functions and OS's (referred to as guest functions and guest-OS's) running on it simultaneously and, in particular, relates to the virtualization of the operation of a single NIC such that it can be used simultaneously by multiple guests in such a manner that memory references due to the network traffic originating from and destined to a particular guest is kept separate from other network traffic, and that allows the Media Access Controller (MAC) within the NIC to operate such that it only accepts network packets that are destined to one of the guest-functions or guest-OS's, and the MAC is not required to operate in promiscuous mode where it accept all incoming packets in order to implement the virtualization features.
Owner:CHELSIO COMMUNICATIONS
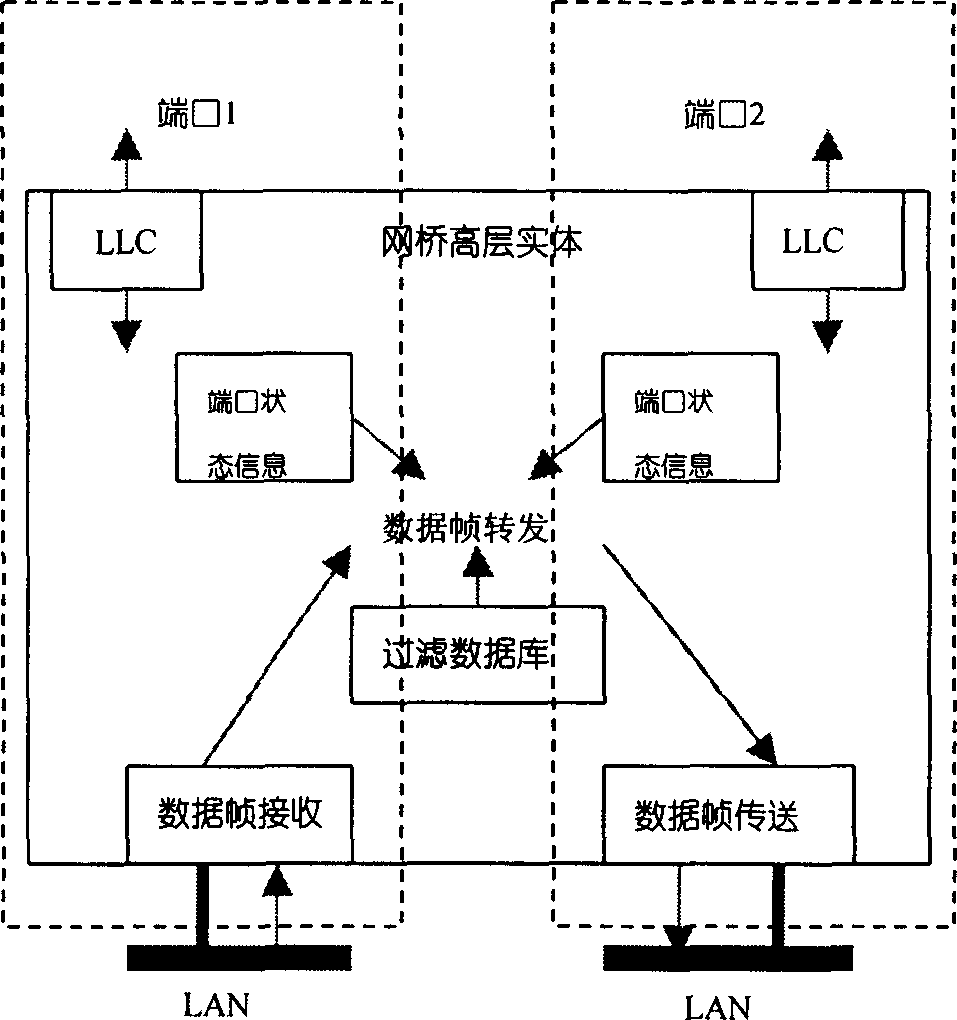
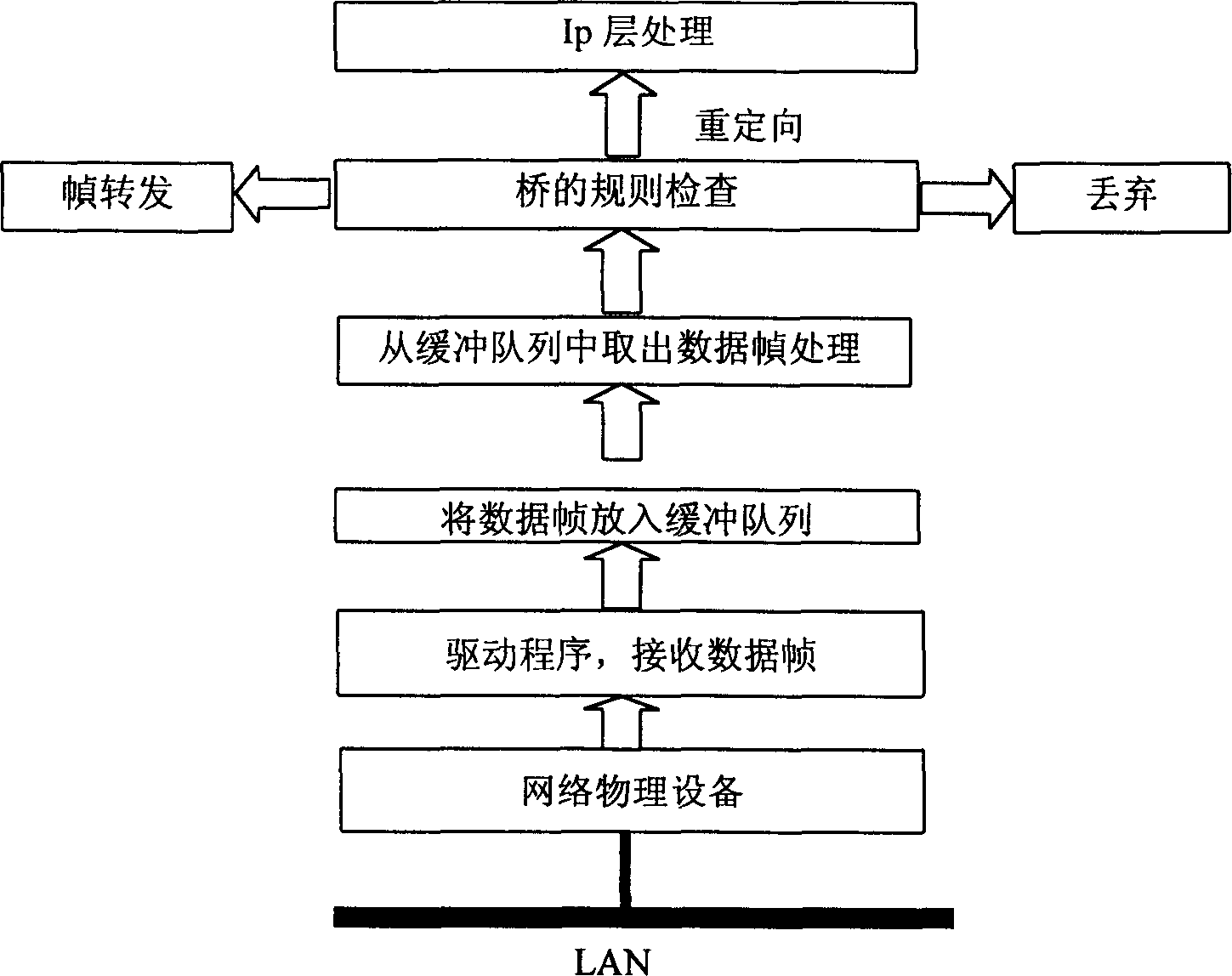
Two-layer exchange type firewall package filtering method based on bridge
InactiveCN1437114AChange the calling interfaceGood packet filteringMemory loss protectionUnauthorized memory use protectionProtocol for Carrying Authentication for Network AccessPromiscuous mode
The filtering method includes at least the following steps: setting retransmission data base in the bridge and setting the bridge port in hybrid mode; trapping data package flowing through the connected local network port and recording or renewing the relation message between the medium access address and the port; and performing the package filtering inspection in the link layer during the package retransmission inside the bridge so as to decide the abandon, retransmission and submission to upper IP layer of the data package. The firewall of the present invention does not process and retransmit IP report, so that when the firewall is added between the user's network and router and user's host computer has no need of altering original gateway configuration and increased routing configuration in the router.
Owner:BEIJING LEADSEC TECH
Systems and methods for providing network security with zero network footprint
InactiveUS20050086524A1Easy to installDigital data processing detailsHardware monitoringPhysical addressDirect attack
The present invention is directed to a system and method which essentially hides the protection device from the public network, while still allowing the device to perform security inspections. The system and method, in one embodiment, operates in the promiscuous mode and does not have a physical address that is identifiable to any internal or external device, and is thus not available for direct attacks. Using this approach, every data packet flowing into the protected system can be viewed and actions taken to protect the network while the device remains free of the threat of a direct attack.
Owner:TREND MICRO INC
An intelligent network distribution method for wifi equipment
InactiveCN109922516AAvoid confictAvoid conflictAssess restrictionConnection managementIntelligent NetworkDistribution method
The invention discloses a wifi equipment intelligent network distribution method, which comprises an intelligent terminal and wifi equipment in the same wifi environment, and is characterized in thatthe intelligent terminal is connected in wifi.The method comprises the following steps: S1, starting a hybrid mode of wifi equipment to monitor a wireless signal in a space; S2, enabling the intelligent terminal to send wifi frame data in a broadcast or unicast mode; S3, enabling the intelligent terminal to intercept data with a specified bit length each time according to the sending requirement;S4, enabling the wifi device to scan a channel and captures a data packet; S5, after receiving the data of the wifi frame, enabling the wifi equipment to analyze the data according to the sending format, obtain the password and the network name, connect to a router, and send the determination information to a designated port number in a broadcast form; meanwhile, the intelligent terminal receivesconfirmation information at the same port number; and S6, the intelligent terminal receives the broadcast information of the wifi device, and then the wifi device can be obtained. According to the intelligent network distribution method, the defects of more operation steps, long time and the like in the traditional hotspot network distribution process are avoided.
Owner:AUX AIR CONDITIONING LTD BY SHARE LTD
Network safety detection method and system
InactiveCN108600166AScientific and reasonable structureEasy to useTransmissionExtensibilityPromiscuous mode
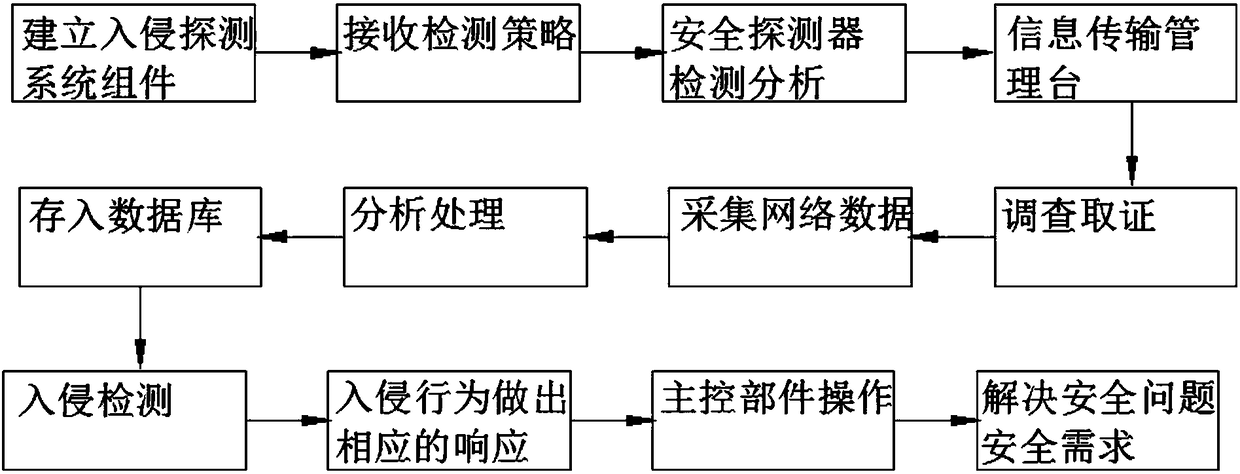
The invention discloses a network safety detection method and system. The method comprises steps that an intrusion detection system assembly is established, a network card is set by a security probeto be a promiscuous mode, the detection strategy for detecting attack and leak behaviors is received, protocol analysis of captured packets is carried out by the security probe, the captured packets are analyzed into a packet head and a pure load part of each layer such as a link layer, a network layer and a transmission layer, the packet head and the load are carefully examined to detect attack characteristics, and protocol and grammar analysis is further carried out. The method is advantaged in that the structure is scientific and reasonable, the method is safe and convenient to use, attackintrusion outside the network is found, various types of unsafe behaviors within the network are detected, various types of intrusion activities are responded, the entire system has good timeliness, adaptability, security, availability and scalability, and reliable protection is provided for security of an internal host of the LAN.
Owner:JINING MEDICAL UNIV
Bridging method based on VF promiscuous mode and bridging system
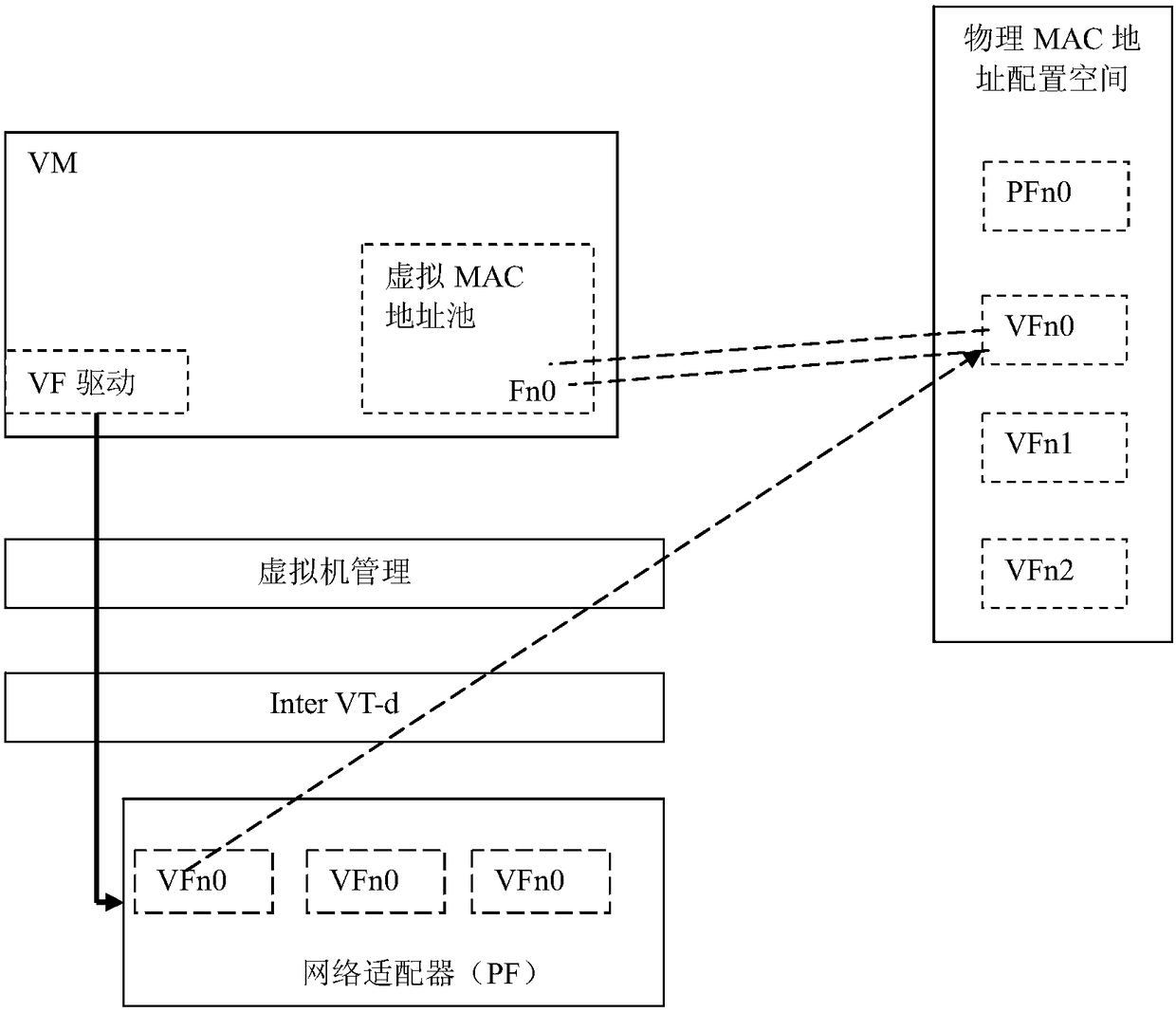
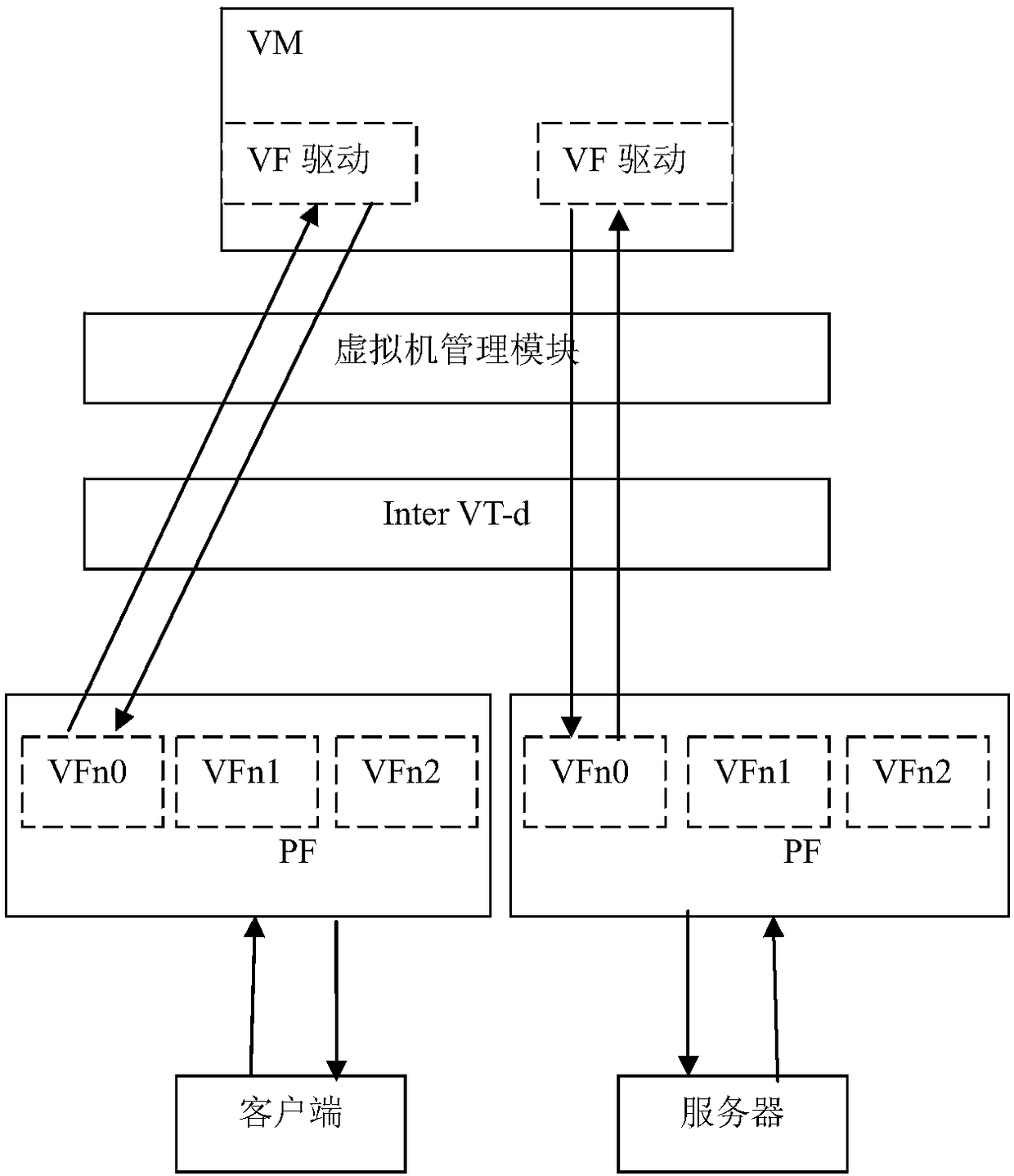
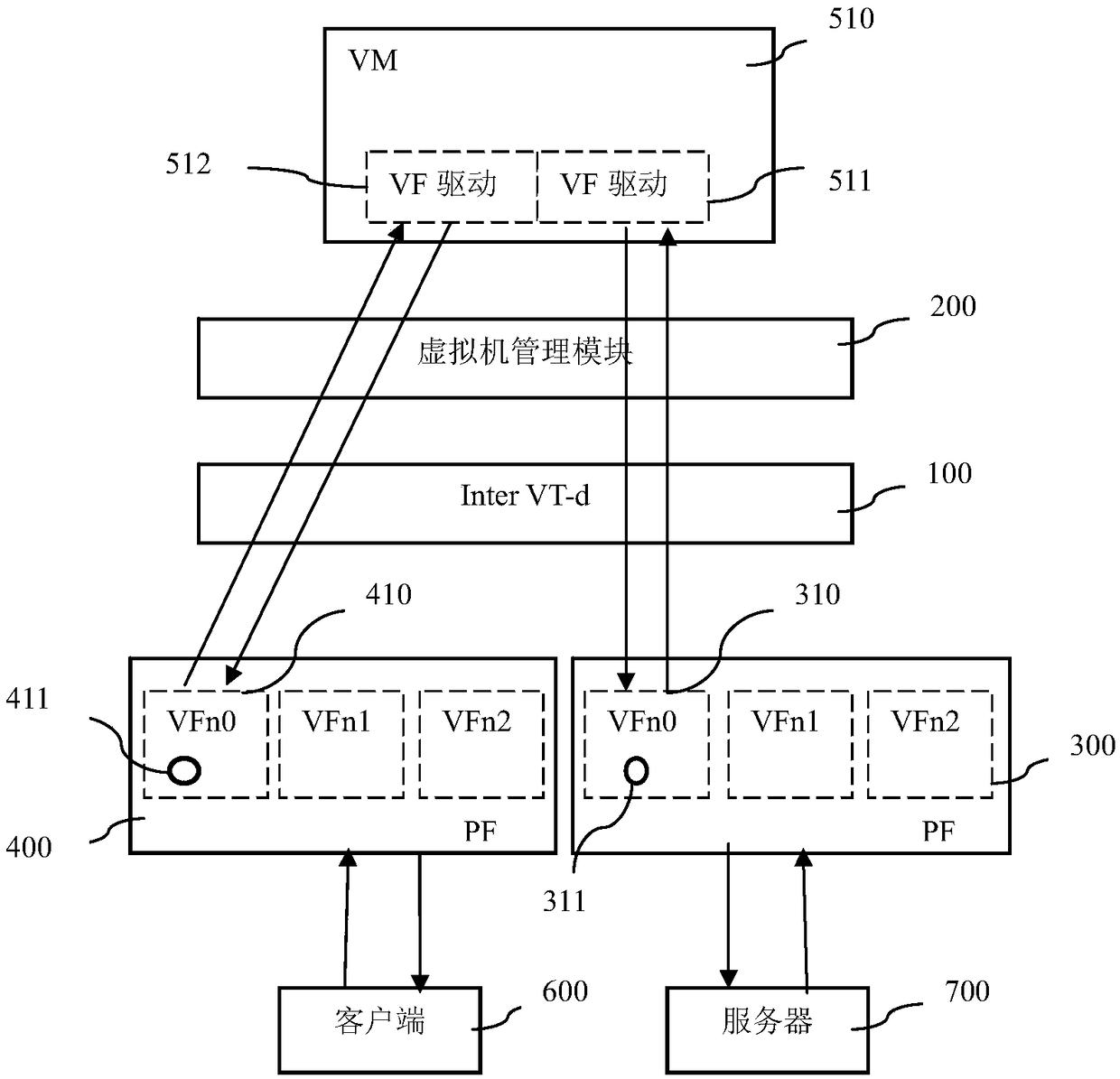
The invention provides a bridging method based on a VF promiscuous mode. The bridging method is achieved through the steps of setting to support the VF promiscuous mode, setting to support a sniffingmode, enabling the VF promiscuous mode and configuring built-in bridging mode support port mirror. The invention further provides a built-in bridging system supporting the VF promiscuous mode. By adopting the built-in bridging method in an SR-IOV promiscuous mode, PFs can be directly called, and therefore the performances of virtual machines approach to those of physical machines; the method can support the mode of deploying multiple types of the virtual machines, support to control the multiple mode (unicast, multicast, broadcast, VLAN) promiscuous mode of a single VF, achieves a hardware network card-based built-in switch function and has the advantages of being high in performance, not occupying system resources such as a CPU and a memory, reducing the cost and the network complexity and the like.
Owner:ARRAY NETWORKS BEIJING
Controlling admission of data streams onto a network based on end-to-end measurements
InactiveCN1543157AData switching by path configurationStore-and-forward switching systemsPathPingDiagnostic data
Appropriate determinations in a series of tests, which transition from more passive tests to more active tests, control the admission of data streams onto a network data path. More passive tests can include promiscuous mode and packet-pair tests. When the results of more passive tests indicate a reduce likelihood of a data stream causing a network data path to transition into a congested state, the network data path can be actively probed to make a more precise determination on the likelihood of congestion. A train of diagnostic data packets is transmitted at a diagnostic data transfer rate having a significantly reduced chance of causing congestion. A train of target data packets is transmitted at a requested application transfer data rate. The number of target data packets received within a specified delay threshold is compared to the number of diagnostic data packets receive with the delay threshold. <IMAGE>
Owner:MICROSOFT TECH LICENSING LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com