Method for solving mass alarm in NIDS
An intrusion detection system, a massive technology, applied in transmission systems, digital transmission systems, electrical components, etc., can solve the problems of high false alarm rate, isolated alarm, alarm flood, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
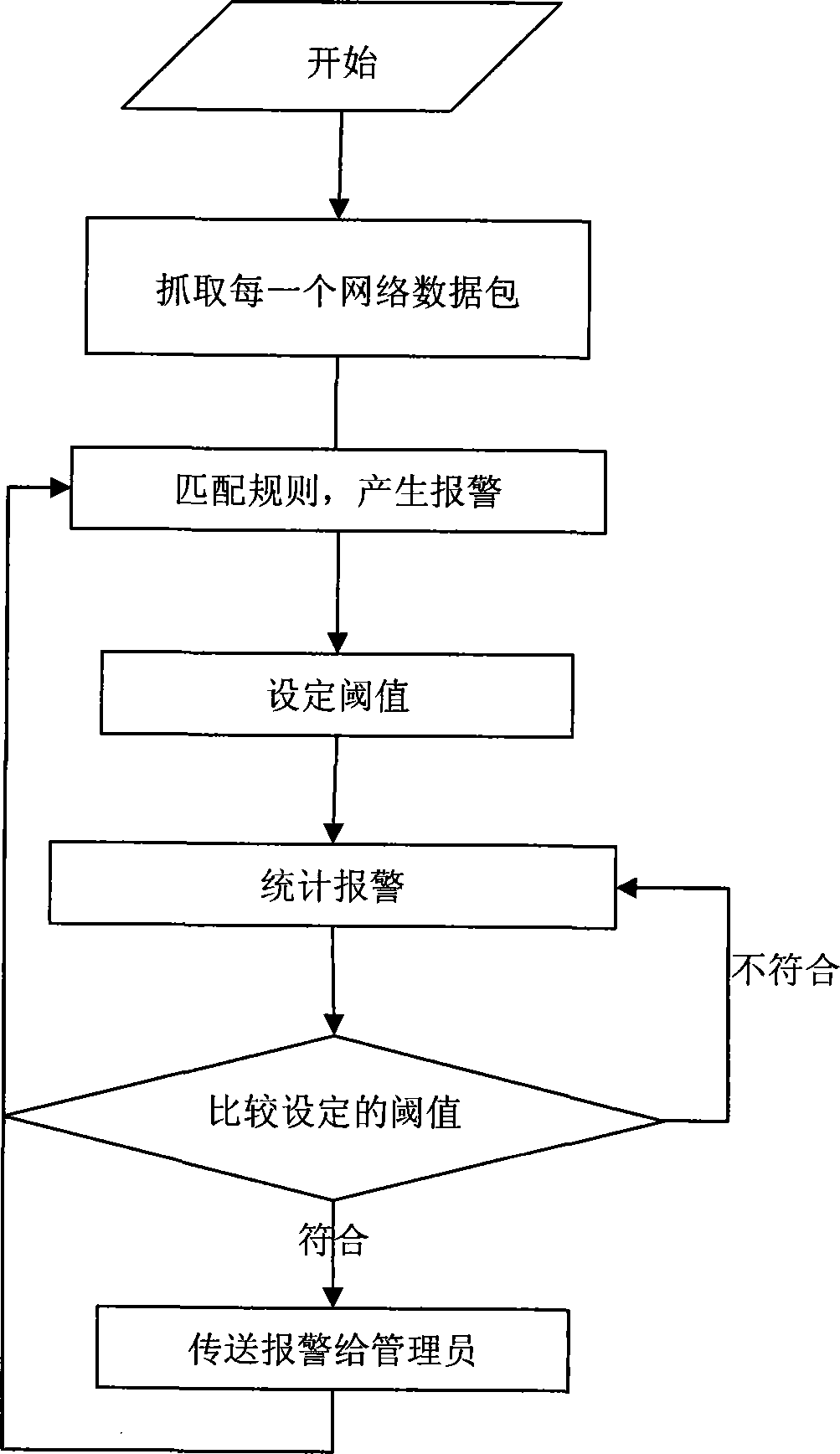
[0024] The present invention can be deployed in IDS equipment. The following will describe in detail by implementing the present invention in an IDS device.
[0025] The steps of the present invention are:
[0026] The first stage: preprocessing stage:
[0027] (1) capturing data packets on the network in a bypass listening mode;
[0028] (2) Rule matching, assuming that when there are 9000 IDS rules, an array is established as a[9000], and addresses pointing to different linked lists are stored in the array, and the statistical information of each rule is stored in a linked list pointed to by a data element. In this way, when the event is triggered, the matching is very fast. a[id] can directly find the first address of the linked list that needs to be counted (that is, hash search), and use id as the index. Each node of the linked list stores a link that triggers this rule. Statistical information, including: source address (SrcIP), destination address (DstIP), source por...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com