Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
31 results about "Extended Access Control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Extended Access Control (EAC) is a set of advanced security features for electronic passports that protects and restricts access to sensitive personal data contained in the RFID chip. In contrast to common personal data (like the bearer’s photograph, names, date of birth, etc.) which can be protected by basic mechanisms, more sensitive data (like fingerprints or iris images) must be protected further for preventing unauthorized access and skimming. A chip protected by EAC will allow that this sensitive data is read (through an encrypted channel) only by an authorized passport inspection system.
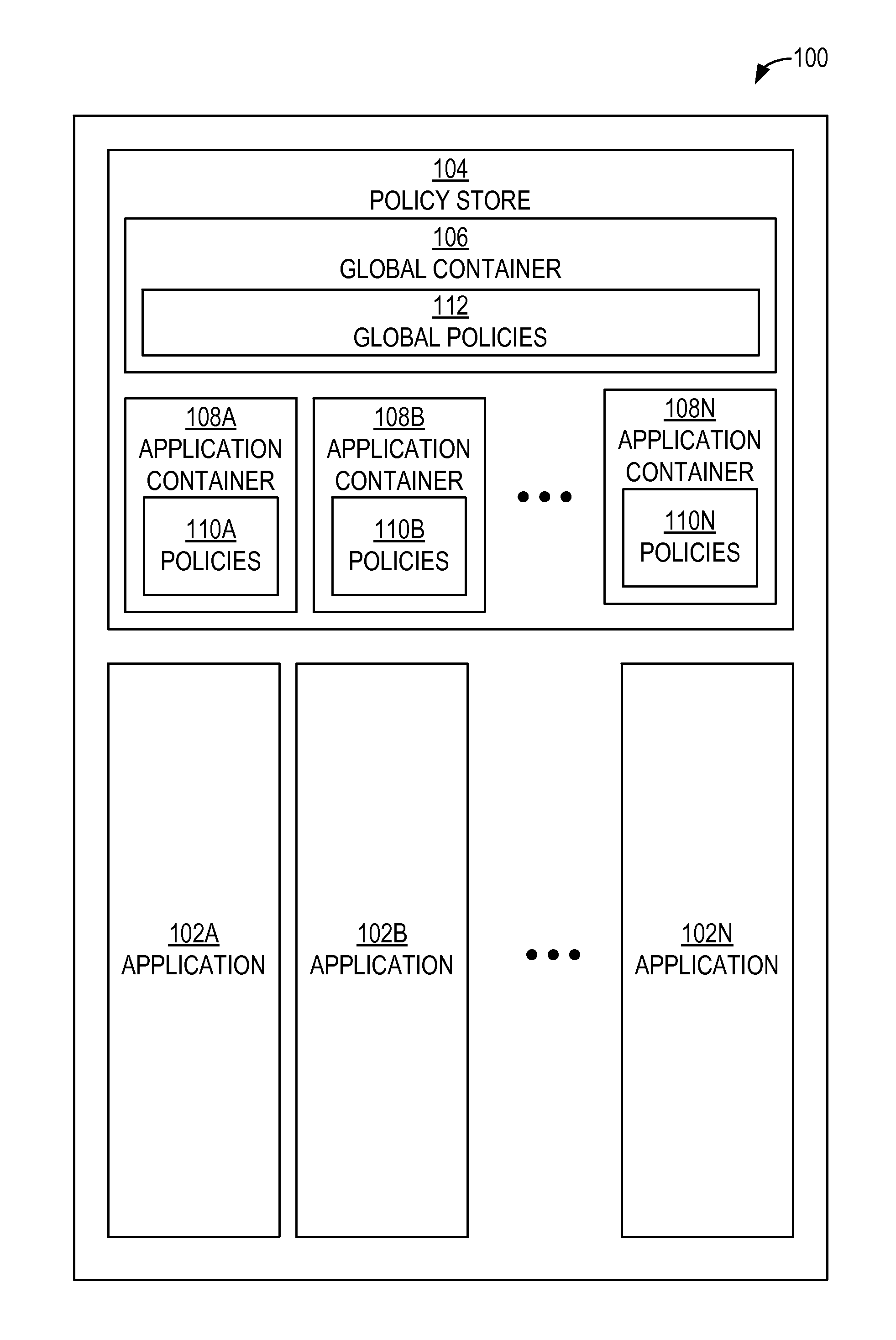
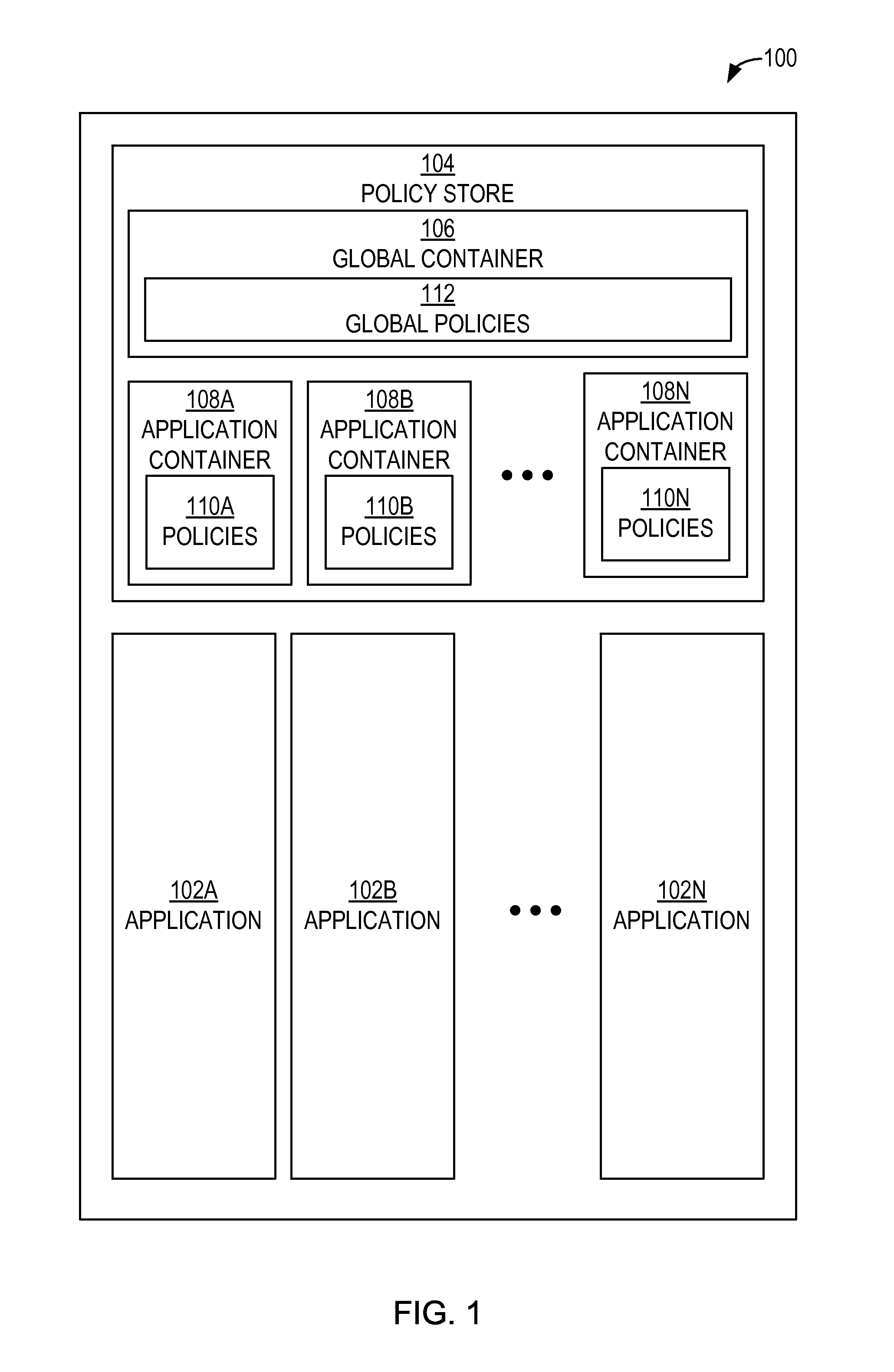
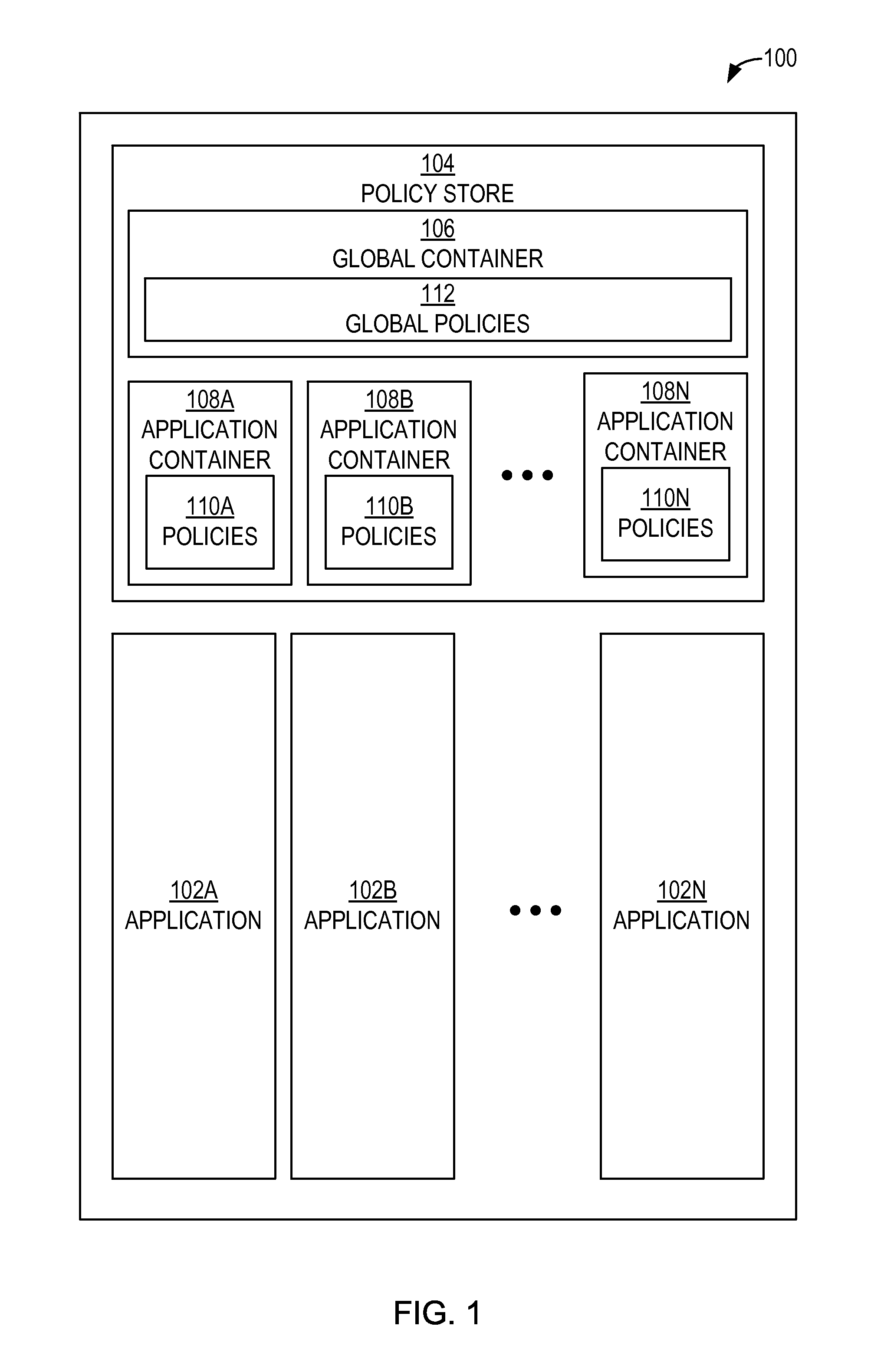
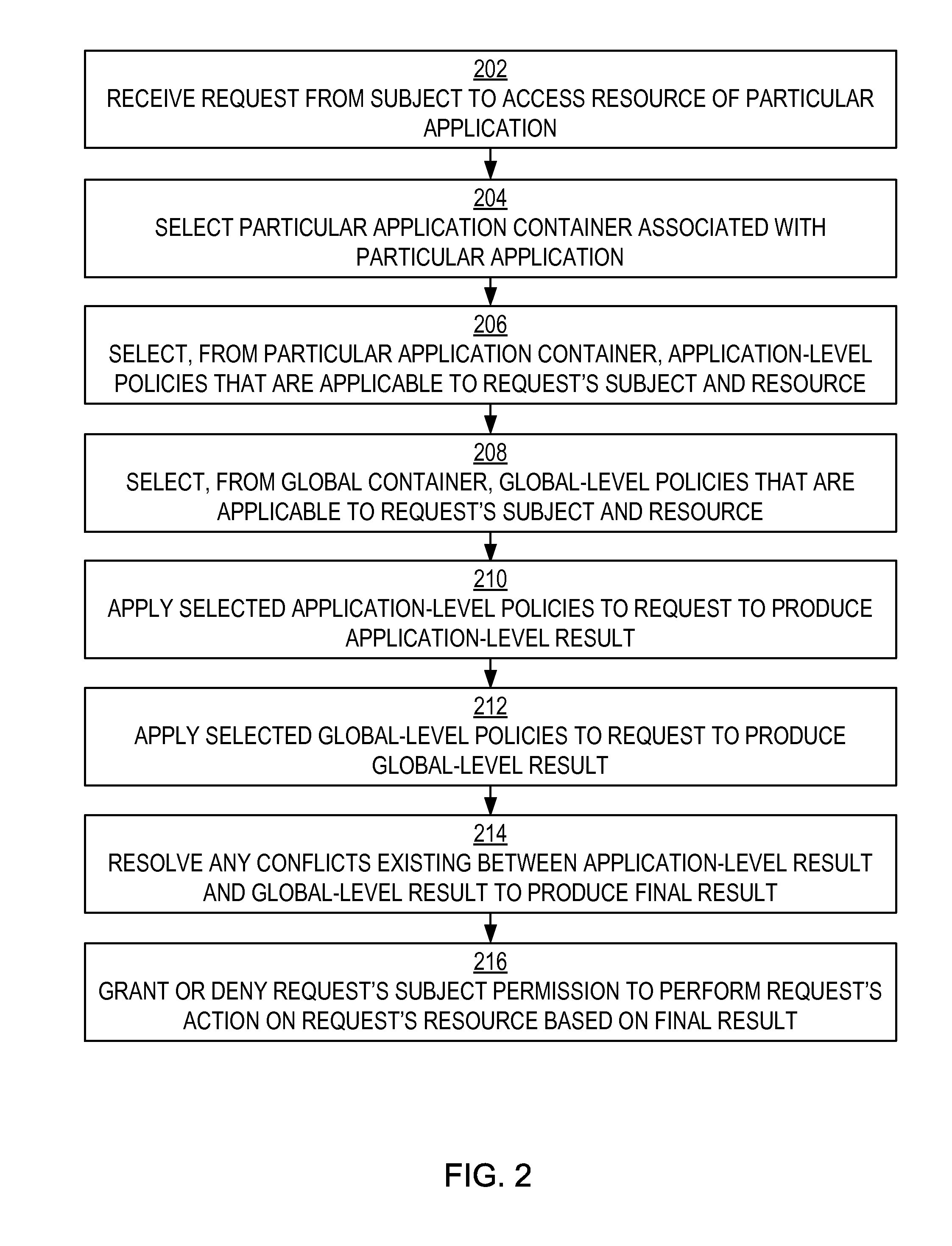
Authorization policy objects sharable across applications, persistence model, and application-level decision-combining algorithm
ActiveUS20150089575A1Avoid wasteful duplicationDigital data protectionTransmissionBusiness enterpriseApplication procedure
A global policy store, in which policies applicable to multiple applications in an enterprise environment can be stored, can be stored in association with that environment. An application-level policy combining algorithm can be associated with a specific application to resolve conflicts between the results of evaluating policies that pertain to that application's resources. A persistent model is defined for an Extensible Access Control Markup Language (XACML) target definition.
Owner:ORACLE INT CORP
Method For Scalable Access Control Decisions
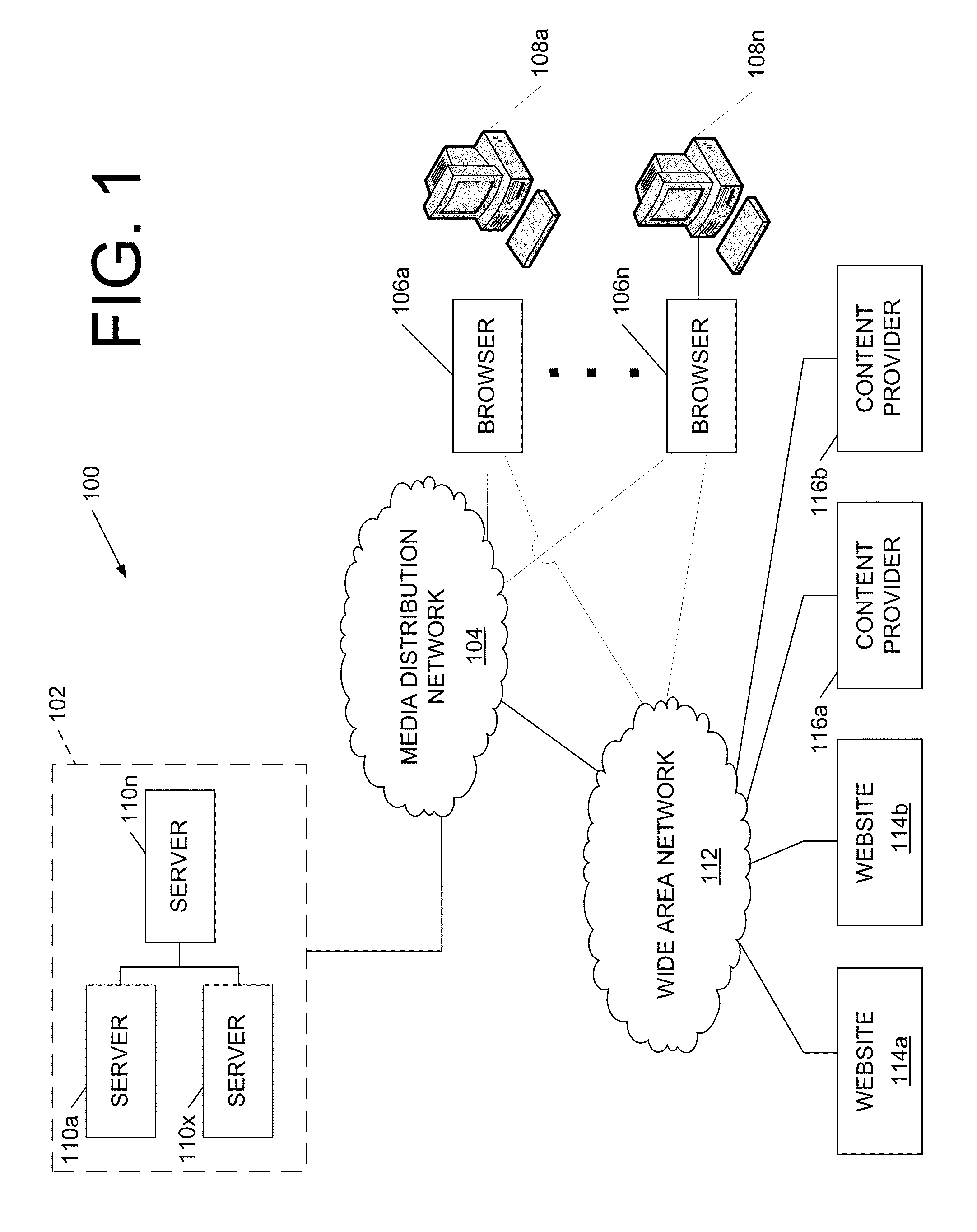
ActiveUS20110126296A1Reduce needLess dependencyDigital data processing detailsUser identity/authority verificationNetwork architectureClient-side
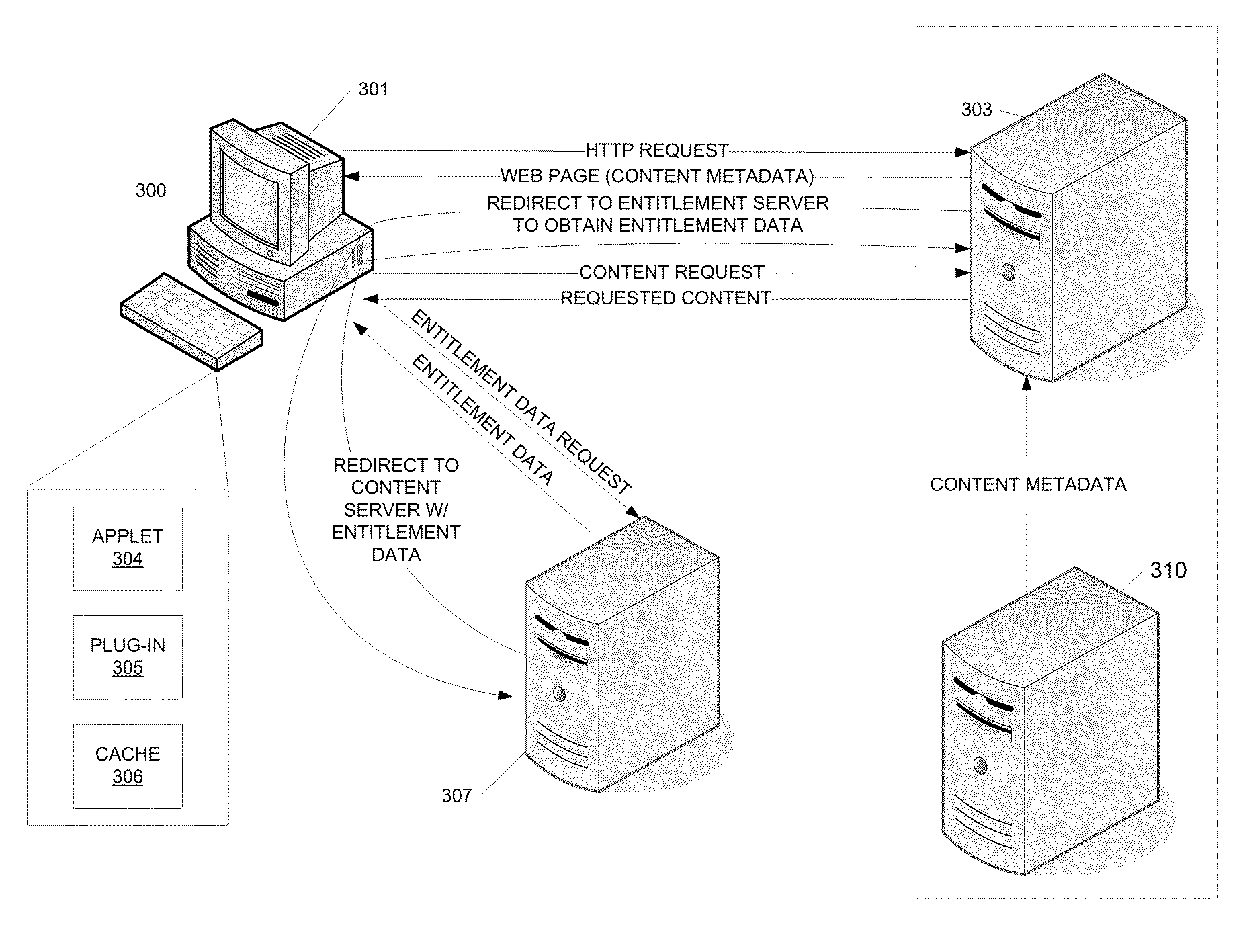
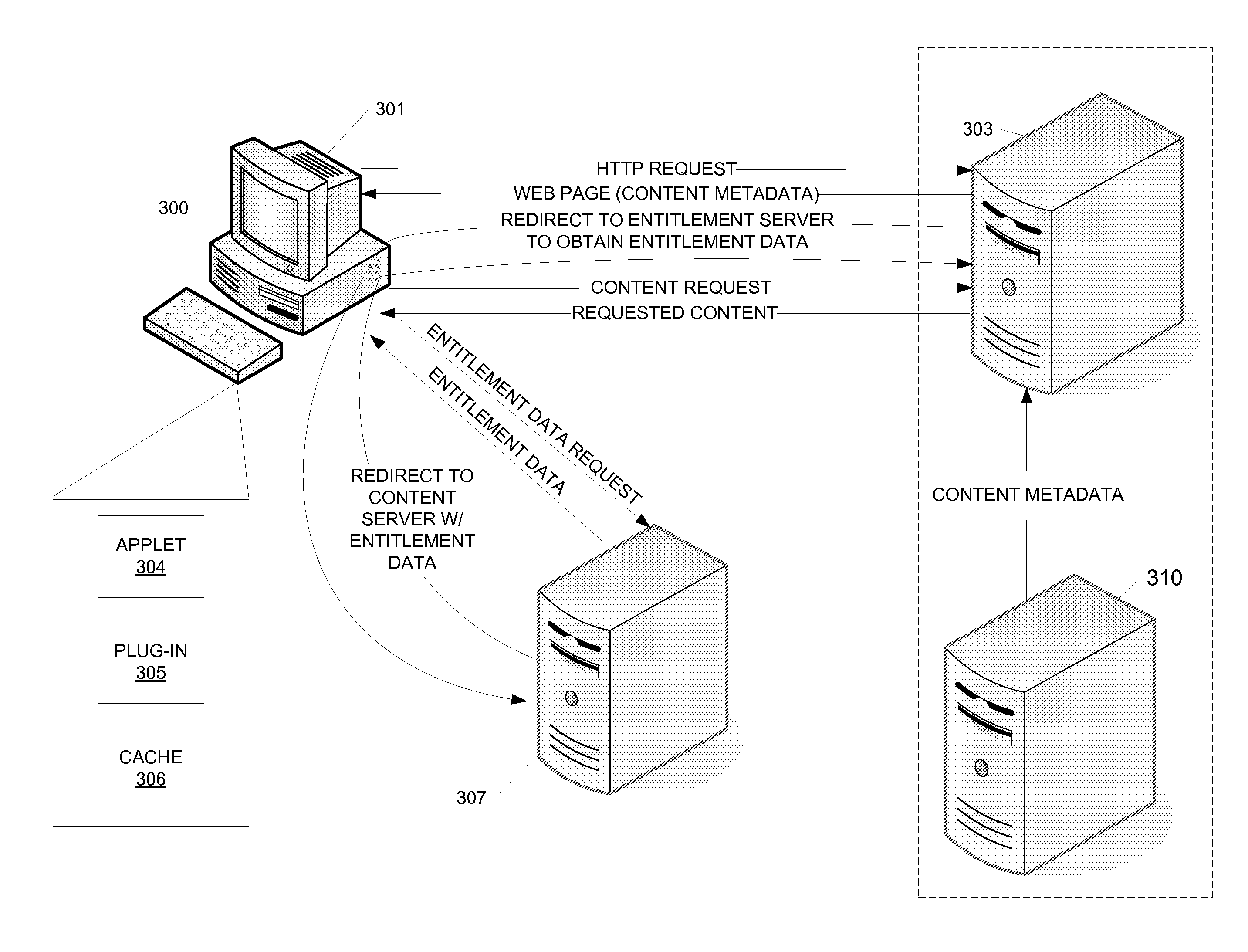
Content access may be provided and processed by assigning responsibility for obtaining entitlement data to the client's browser. Thus, in one example, the client may be configured to synchronize and coordinate data lookups associated with a content request, rather than relying on the server to do so. The network architecture may use a mediator design pattern, in which the client's browser acts as the mediator (i.e., middleman) between a content server and an entitlement data server. Accordingly, synchronous calls between server-side services might not be required. Instead, data necessary for the content server to process a client request for access to protected content may be received in the incoming request from the client's browser.
Owner:COMCAST INTERACTIVE MEDIA
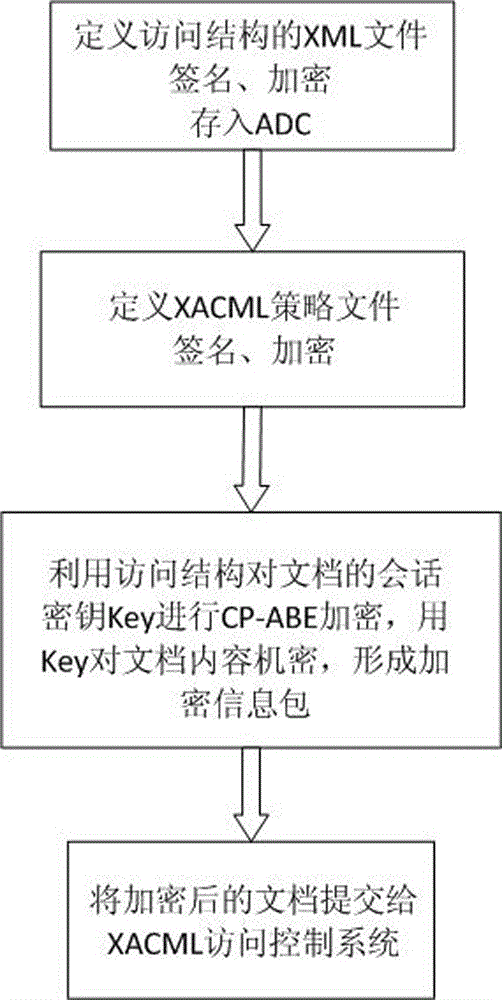
Ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption)
ActiveCN105991278AEnsure safetyKey distribution for secure communicationAccess structureControl system
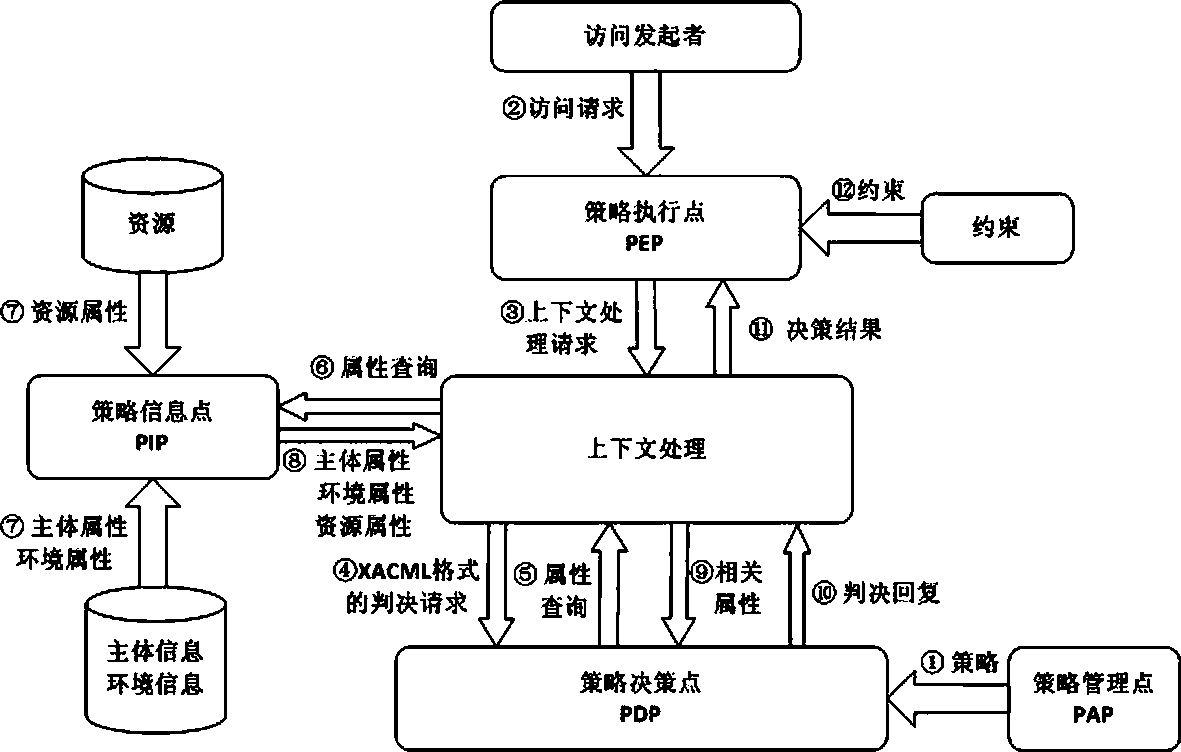
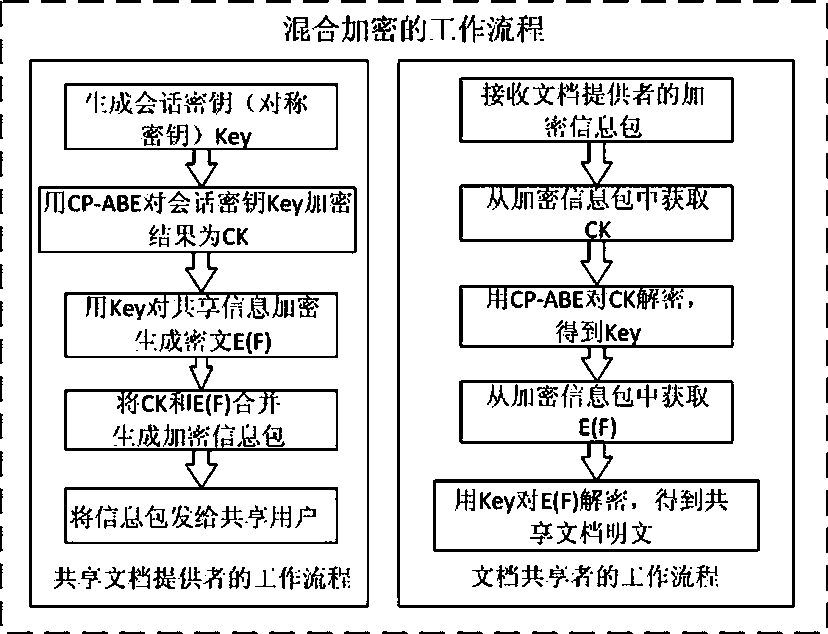
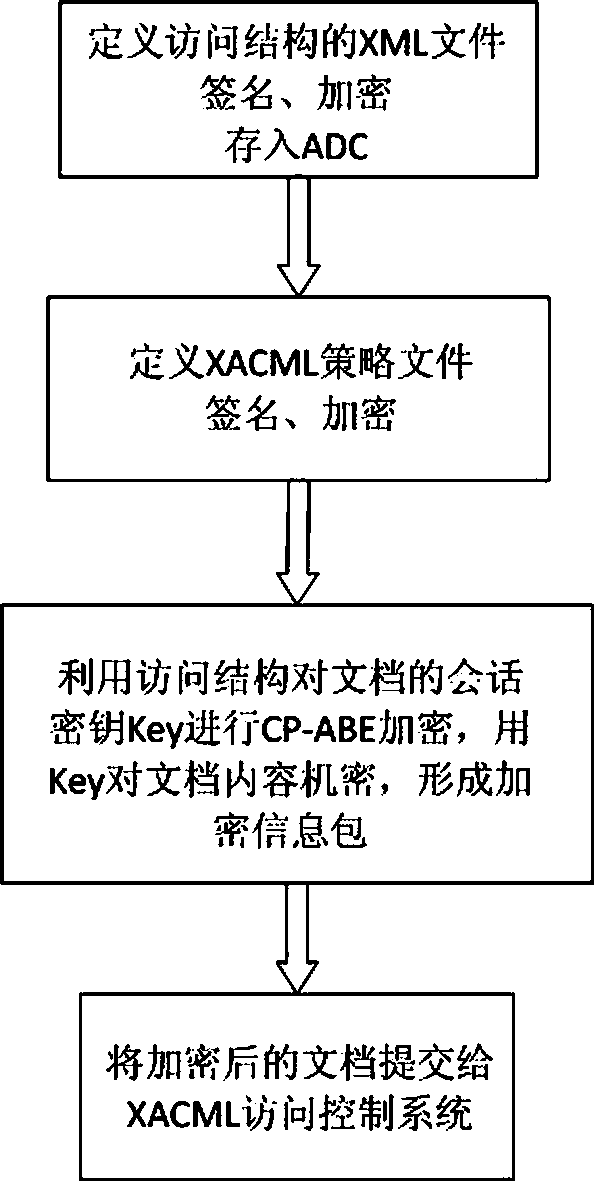
The invention discloses a ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption), which belongs to the field of information security. The method comprises the following steps: preparation and maintenance work which comprises initialization of CP-ABE (Ciphertext-Policy Attribute-Based Encryption), user registration and auditing, generation of an asymmetric key pair for signature and encryption by the system and the user, generation of a CP-ABE attribute key SK for the user and key and attribute certificate management is carried out; 2, and file sharing requires a file provider, an extensible access control markup language (XACML) access control system and a sharing user to work cooperatively. The attribute certificate in a PMI system is used as an expression document for a CP-ABE attribute set and the access structure, the XACML expresses the CP-ABE policy, and security of the attribute set and the access control structure description is ensured. A hierarchical structure with an inheritance relationship is introduced, features such as distribution, authorization and calculability are supported, the attribute authorization ability needs to comply with constraints, and the method is applicable to a distributed and open network application environment.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
Access control method and system
InactiveCN103096495AThe form of the optimized configurationIncrease unified controlWireless communicationMedia access controlComputer science
The invention discloses an access control method and a system. The access control method comprises: a network side device broadcasts extended access control (extended attribute block) parameters through system messages, the EAB parameters comprise at least one of the following two parameters: access classification barring (AC barring ) information acting on all access classifications (AC), and / or specific terminal types, and / or control instruments of specific business types, user equipment (UE) carries out an EAB judgment according to the received EAB parameters, and carries out relative access control. Through the access control method and the system, access control based on the EAB parameters is achieved, and uniform control of a plurality of ACs (or the specific terminal types or the specific business types) is achieved in case of reducing signaling load to the greatest extent.
Owner:ZTE CORP
Authorization policy objects sharable across applications, persistence model, and application-level decision-combining algorithm
ActiveUS9471798B2Digital data protectionData switching networksApplication softwareCombination algorithm
A global policy store, in which policies applicable to multiple applications in an enterprise environment can be stored, can be stored in association with that environment. An application-level policy combining algorithm can be associated with a specific application to resolve conflicts between the results of evaluating policies that pertain to that application's resources. A persistent model is defined for an Extensible Access Control Markup Language (XACML) target definition.
Owner:ORACLE INT CORP
Method and device for generating access controlling policy
InactiveCN101771683AGuaranteed accuracyReduce the burden onData switching networksSpecial data processing applicationsXACMLWorld Wide Web
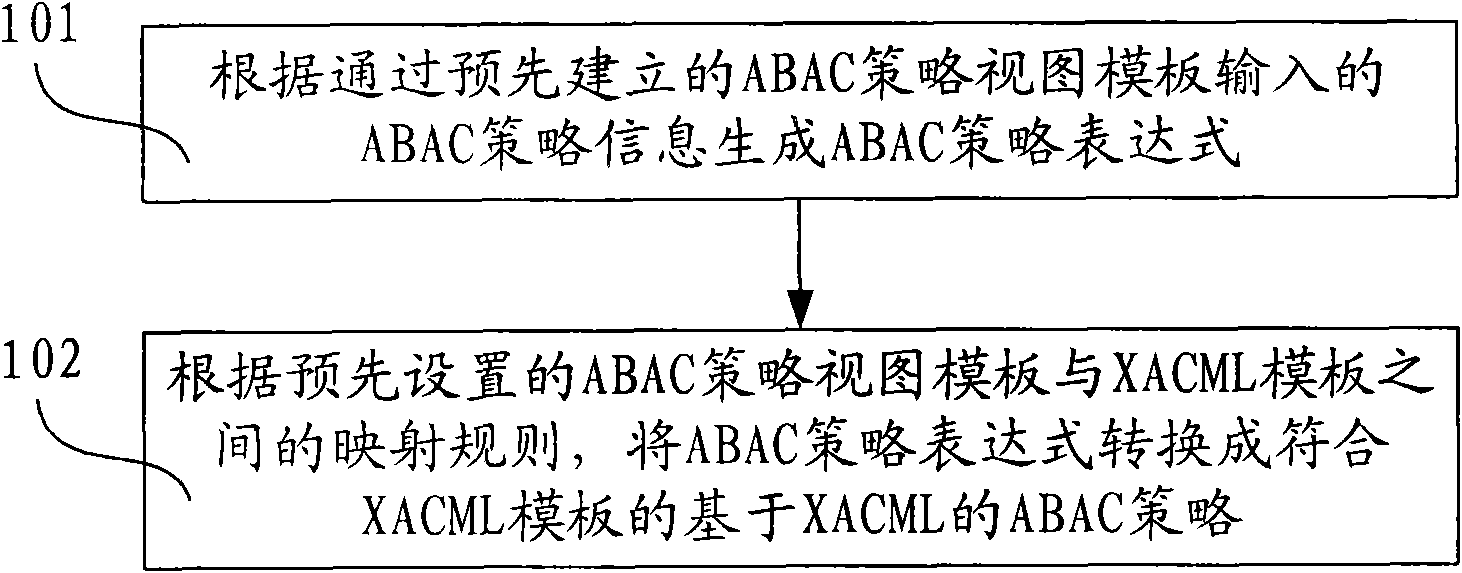
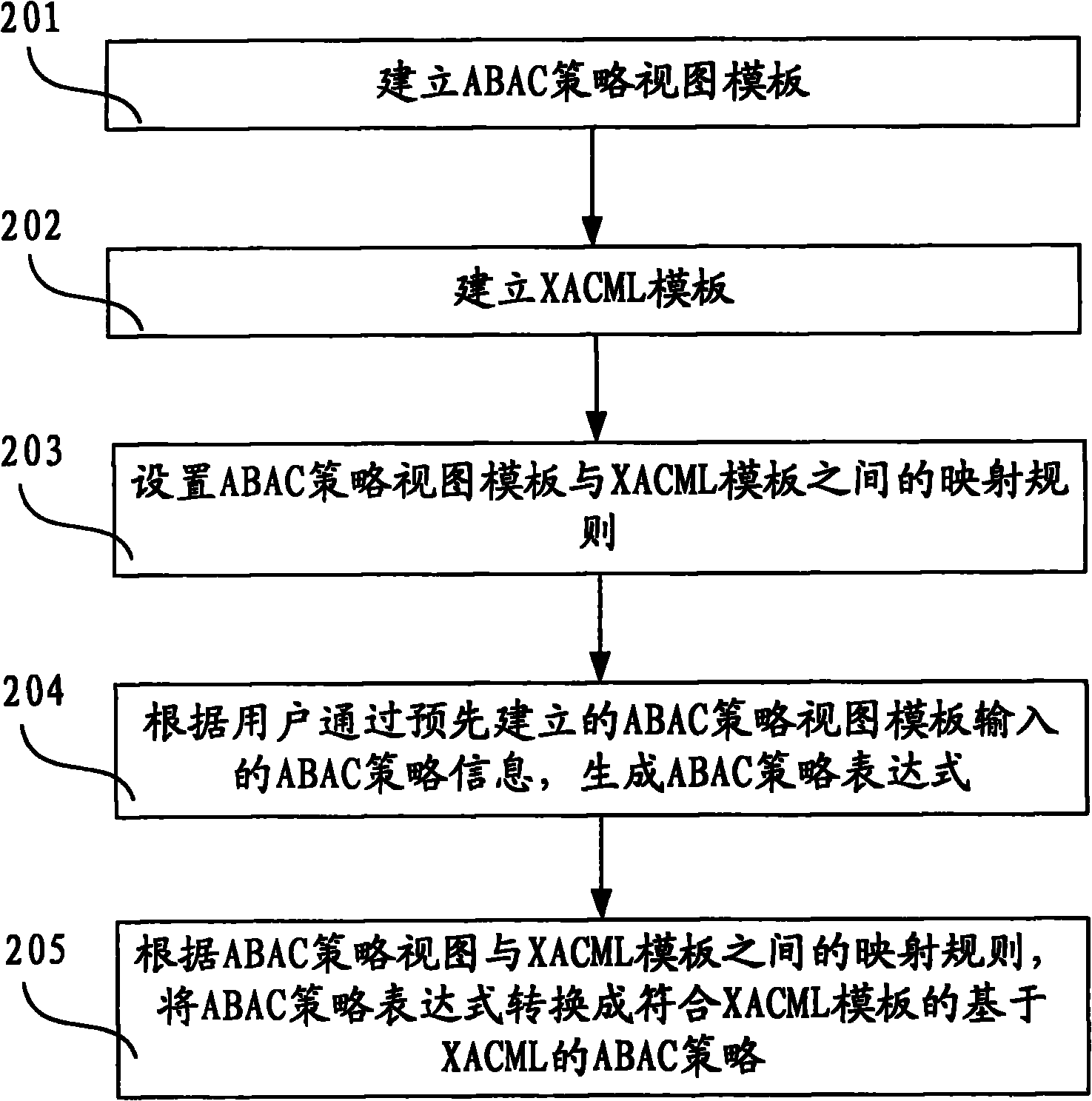
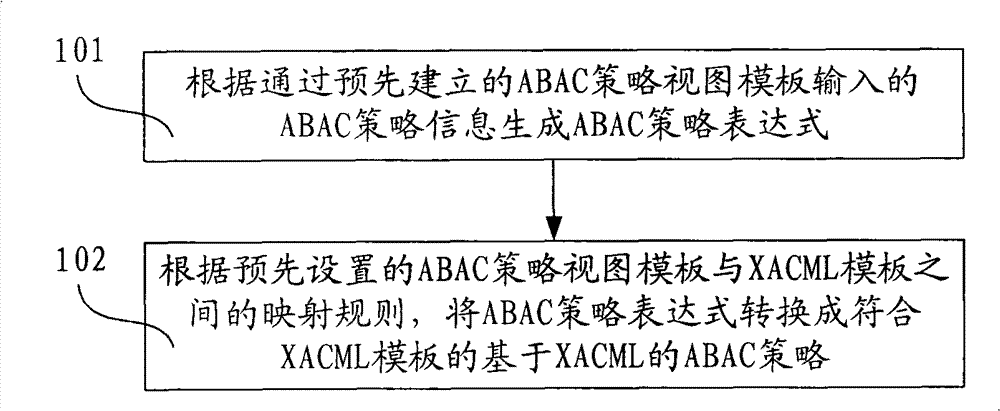
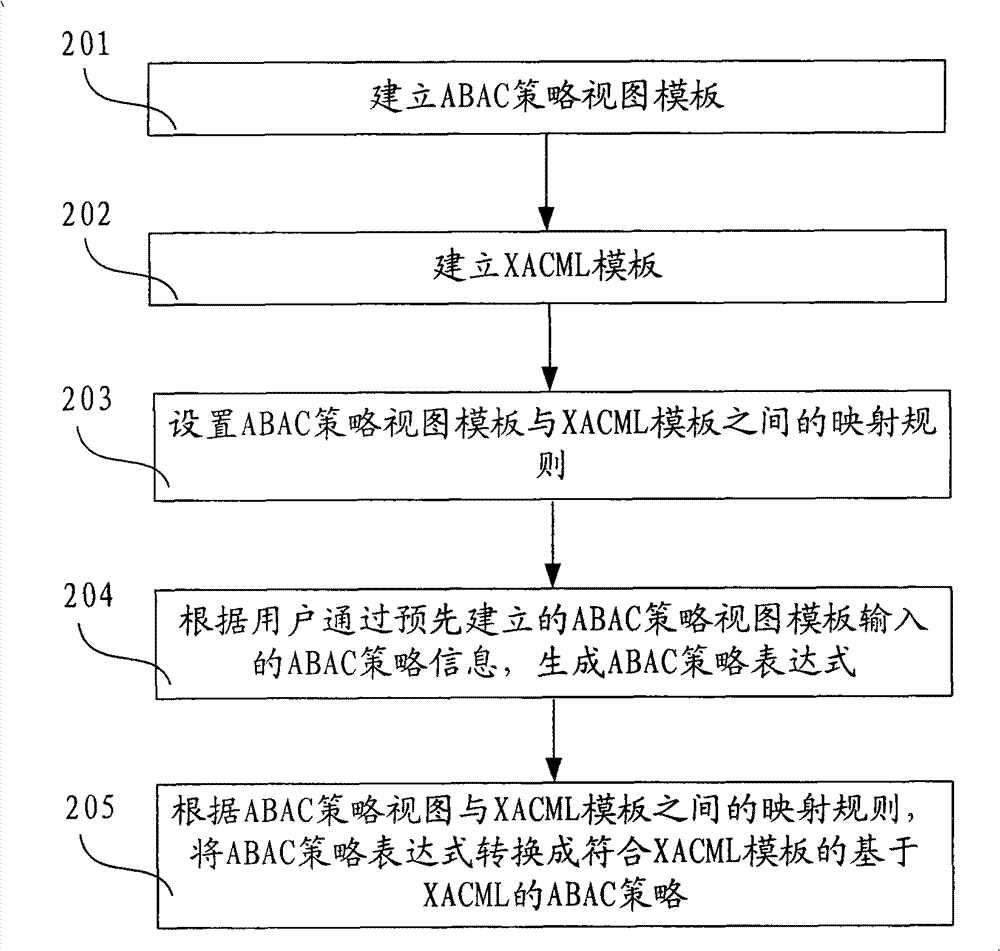
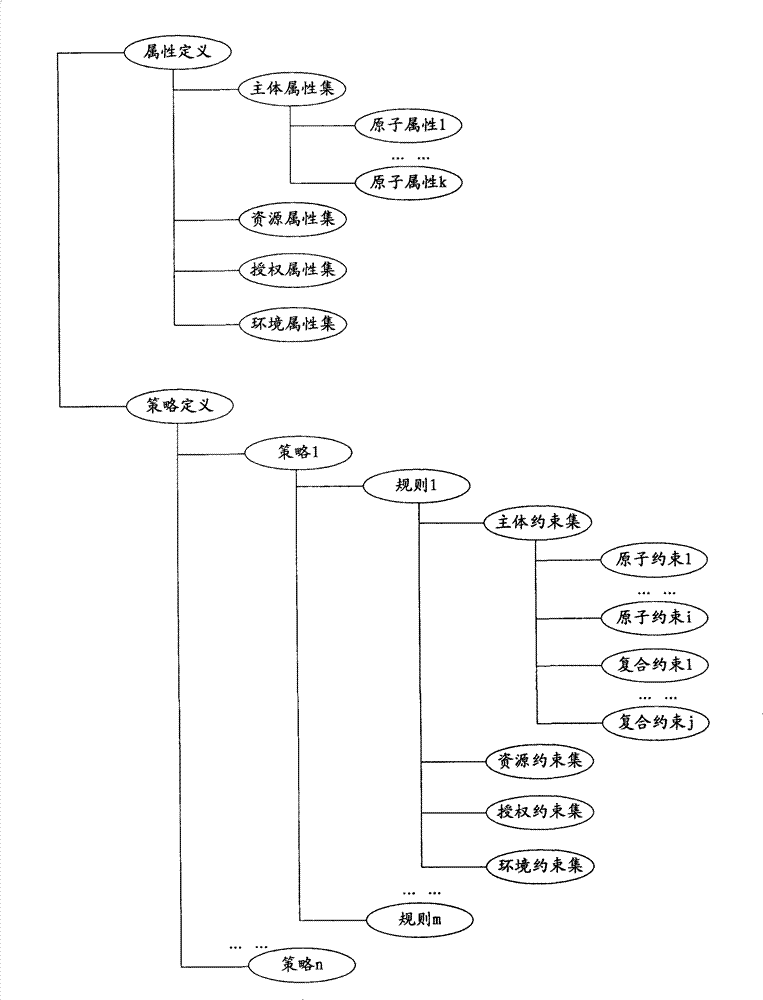
The invention discloses method and device for generating an access controlling policy. The method comprises the following steps of: generating an ABAC policy expression according to ABAC policy information input by a user through a pre-established attribute-based access control (ABAC) policy view template; and converting the ABAC policy expression into an ABAC policy which is based on XACML and conforms to the XACML template according to mapping rules of the preset ABAC policy view template and an extensible access control markup language (XACML) template. In the invention, the user only needs to input some simple ABAC policy information through the ABAC policy view template and does not need to write a complicated ABAC policy based on XACML in a manual mode, therefore, the problem that the user difficultly defines the ABAC policy based on XACML is solved, the problem that errors are made in the process of writing the complicated ABAC policy based on XACML in a manual mode by the useris avoided, and the accuracy of the ABAC policy based on XACML is ensured.
Owner:BEIHANG UNIV
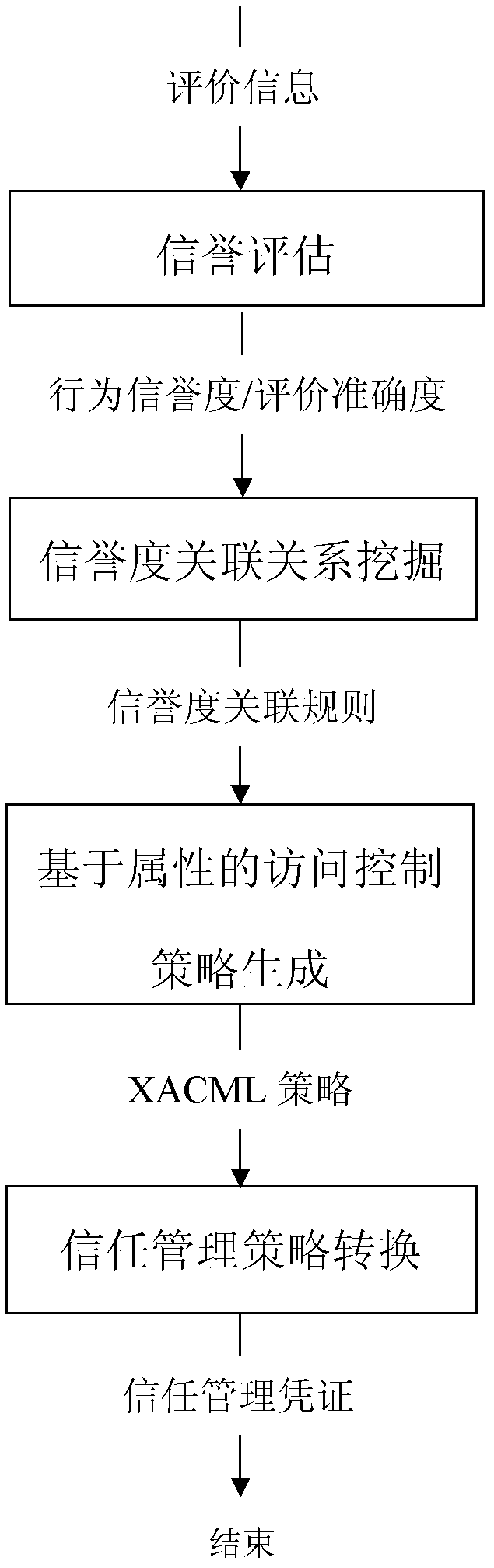
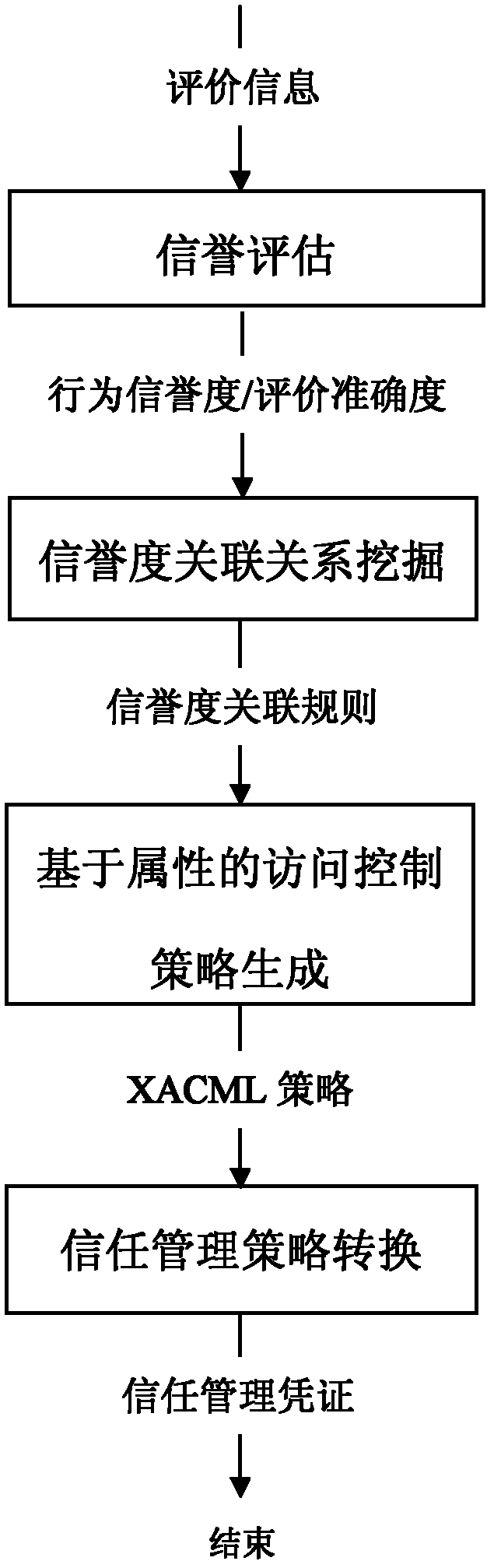
Method for generating cross-domain access control strategy by rising from credit assessment to trust management
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +1
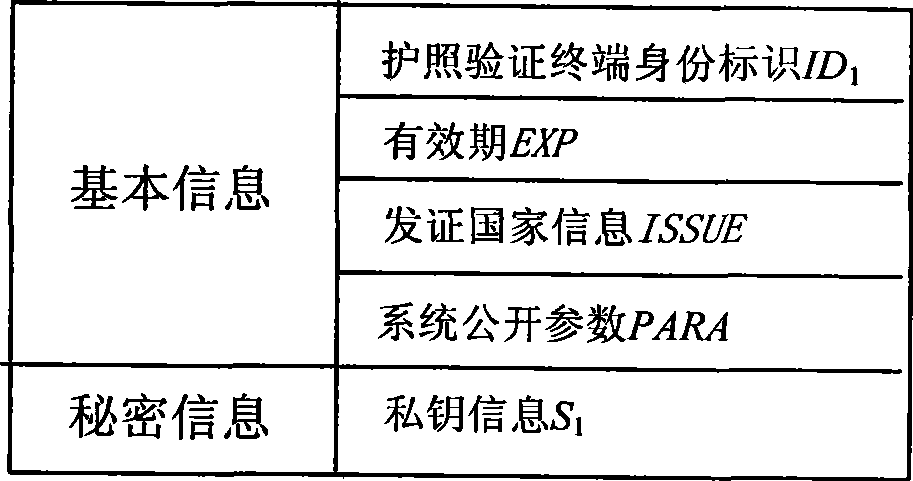
Electronic passport expansion access control system and authentication method based on identification cipher technology
ActiveCN101504732AFlexible AuthorizationOvercoming loopholes in authorization trust transferUser identity/authority verificationCo-operative working arrangementsAuthentication protocolExtended Access Control
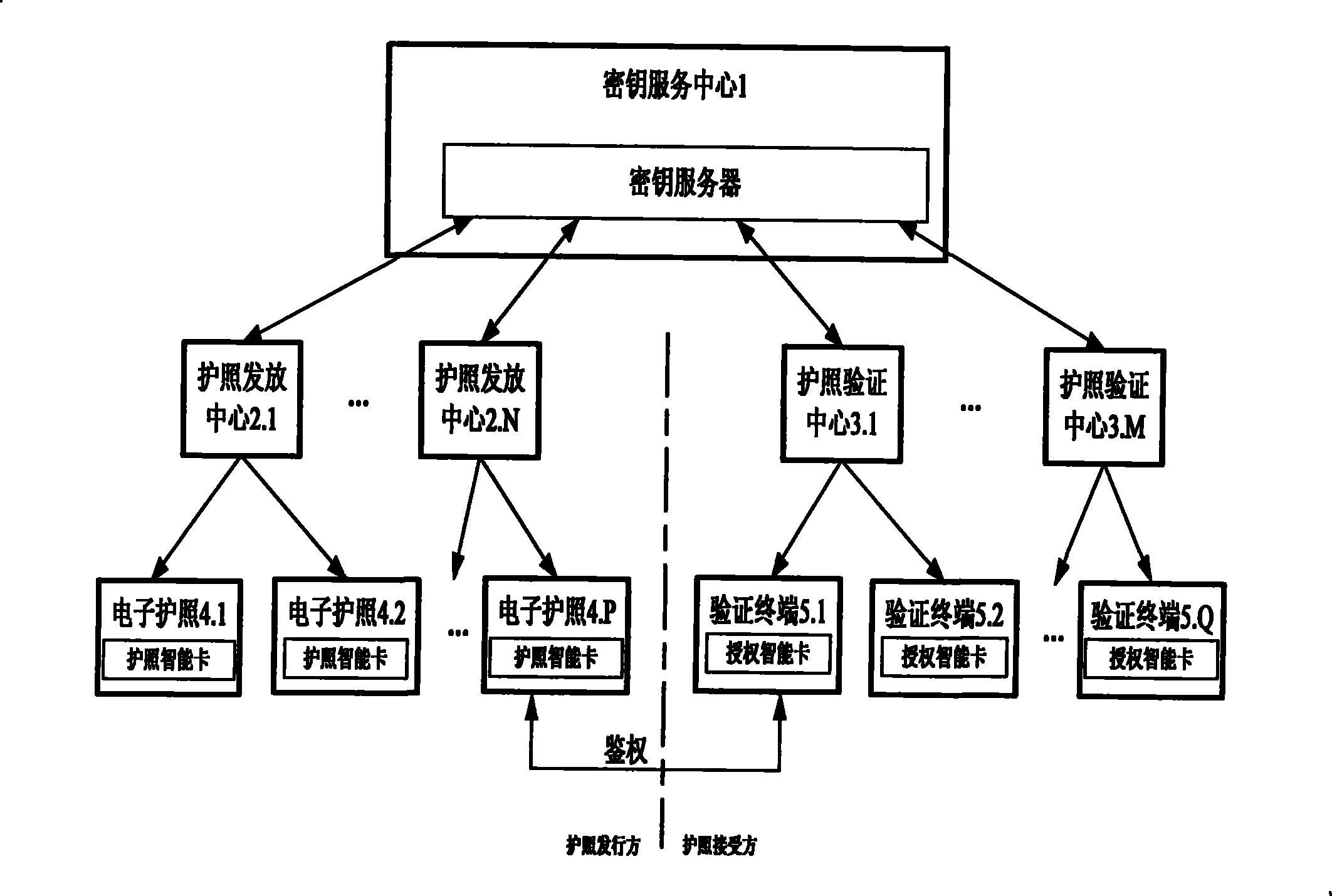
The invention discloses an identification cryptographic technique-based electronic passport extended access control system and an identification cryptographic technique-based authentication method. The authentication method comprises the following steps that: a key service centre provides a key service; a passport verification center makes an application for sensitive biological characteristic information-reading authority, the key service center issues an authorization smart card to perform authorization, and the passport verification center distributes the authorization smart card to a verification terminal controlled thereby; and a passport issuing center applies the key service center for an authentication key and a public parameter for authentication and writes the authentication key and the public parameter into passport smart card of an electronic passport. During passport verification, the authorization smart card and the passport smart card implement an identification cryptographic algorithm-based authentication protocol to judge if the verification terminal has the authority to read sensitive biological characteristic data. The system and the method avoid loopholes in authentication trust transmission in a European proposal, save the establishment of a complicate PKI system, and allow for low system construction cost. Compared with Singaporean EAC, the method provides flexible authorization for a certifying organization, and can still authorize the certifying organization after the issue of a passport.
Owner:WUHAN TIANYU INFORMATION IND
Method for scalable access control decisions
ActiveUS8819848B2Reduce needLess dependencyDigital data processing detailsAnalogue secracy/subscription systemsNetwork architectureClient-side
Content access may be provided and processed by assigning responsibility for obtaining entitlement data to the client's browser. Thus, in one example, the client may be configured to synchronize and coordinate data lookups associated with a content request, rather than relying on the server to do so. The network architecture may use a mediator design pattern, in which the client's browser acts as the mediator (i.e., middleman) between a content server and an entitlement data server. Accordingly, synchronous calls between server-side services might not be required. Instead, data necessary for the content server to process a client request for access to protected content may be received in the incoming request from the client's browser.
Owner:COMCAST INTERACTIVE MEDIA
XACML frame extension system and method for network access control system
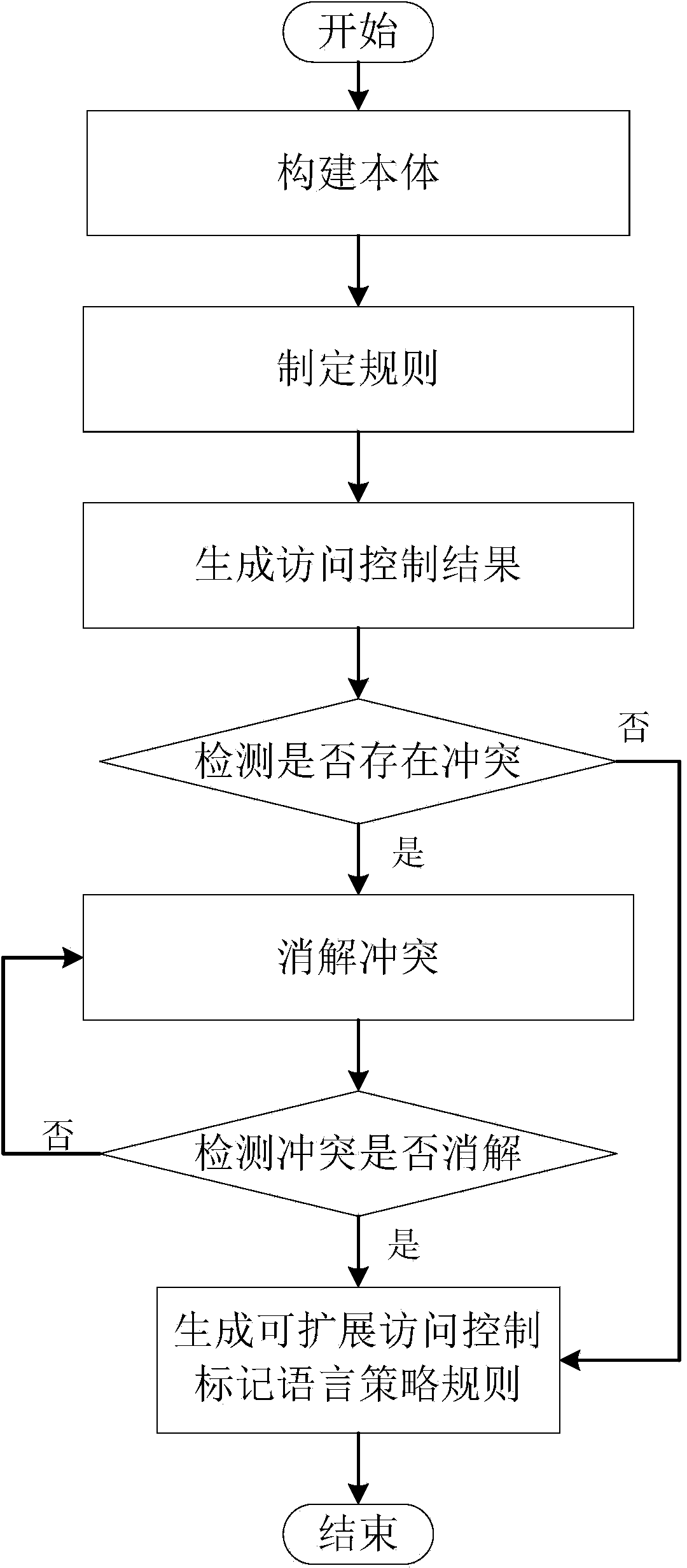
InactiveCN103905468AOvercome conflicts between access control rulesAvoid confictTransmissionControl systemNetwork Access Control
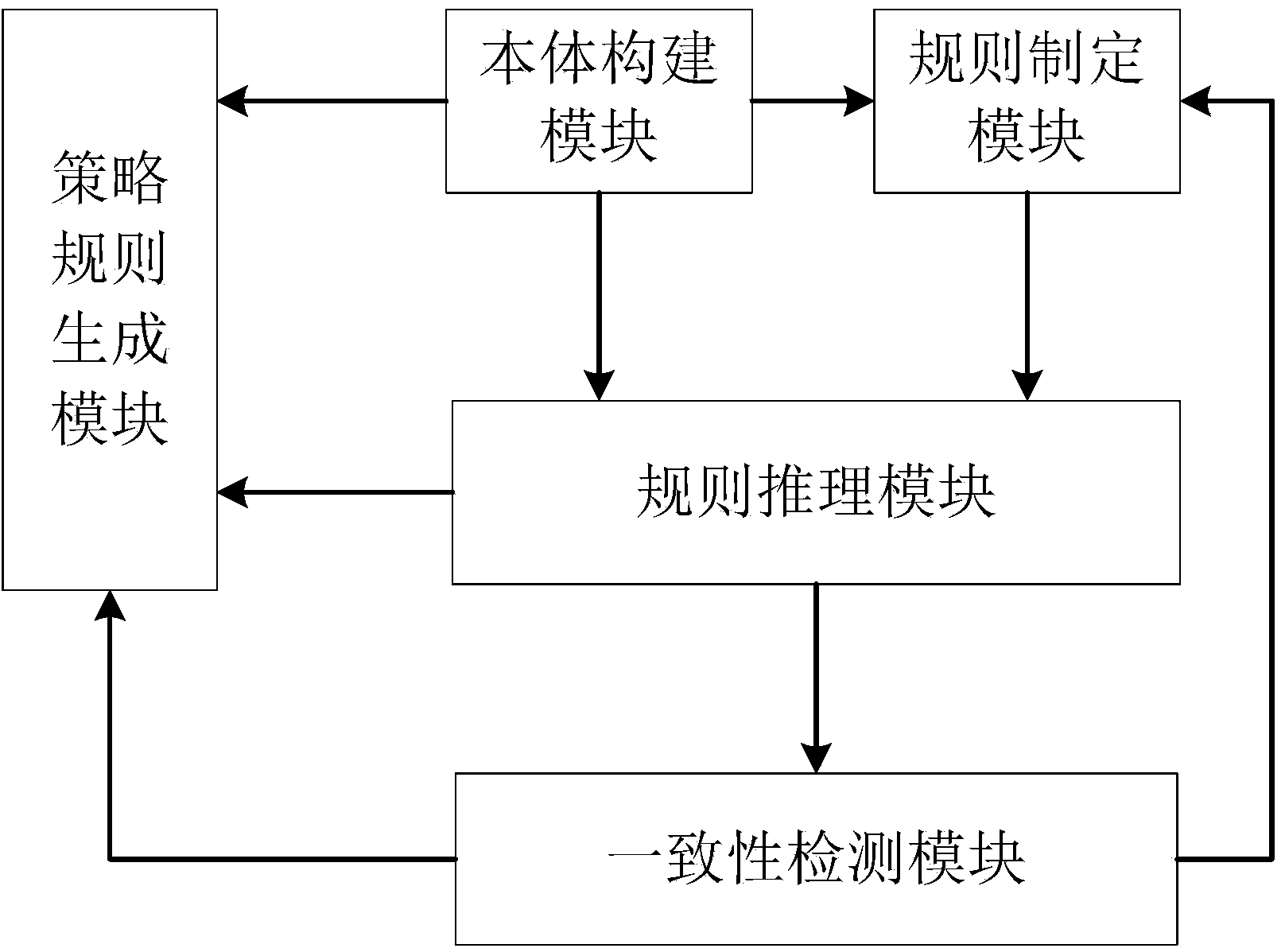
The invention discloses an XACML frame extension system and method for a network access control system. The XACML frame extension system is composed of a body establishing module, a rulemaking module, a rule-based reasoning module, a consistency detecting module and a strategy rule generating module. The XACML frame extension method comprises the steps that firstly, the body establishing module establishes a body; secondly, the rulemaking module makes rules; thirdly, the rule-based reasoning module generates access control results; fourthly, the consistency detecting module detects whether conflict exists between the access control results; fifthly, the rulemaking module makes a conflict eliminating rule, and the rule-based reasoning module generates access control results of the conflict eliminating rule; sixthly, the consistency detecting module detects whether the conflict is eliminated; seventhly, the strategy rule generating module generates an extensible access control markup language strategy rule. Due to conflict detection of the access control results, the XACML frame extension system and method for the network access control system have the advantages of being high in detection efficiency and automatic.
Owner:XIDIAN UNIV
Provisioning access control using SDDL on the basis of a XACML policy
InactiveUS8966576B2Reduce in quantityReduce the amount requiredDigital data processing detailsDigital data protectionWorld Wide WebStrategy switching
A method is disclosed, and a corresponding data carrier and policy converter, for producing at least one Security Descriptor Definition Language, SDDL, rule from an eXtensible Access Control Markup Language, XACML, policy (P), wherein said at least one SDDL rule is enforceable for controlling access to one or more resources in a computer network. A reverse query is produced indicating a given decision (d), which is one of permit access and deny access, and a set (R) of admissible access requests. Based on the reverse query, the XACML policy (P) and the given decision (d) are translated into a satisfiable logic proposition in Boolean variables (vi, i=1, 2, . . . ) From said ROBDD, variable assignments (RCj=[ARCj1: v1=xj1, ARCj2: v2=xj2, . . . ], j=1, 2, . . . ) satisfying the logic proposition are derived and at least one SDDL rule is created based on said variable assignments (RCj=[ARCj1: v1=xj1, ARCj2: v2=xj2, . . . ], j=1, 2, . . . ) satisfying the logic proposition.
Owner:AXIOMATICS
Method and arrangement in telecommunication system
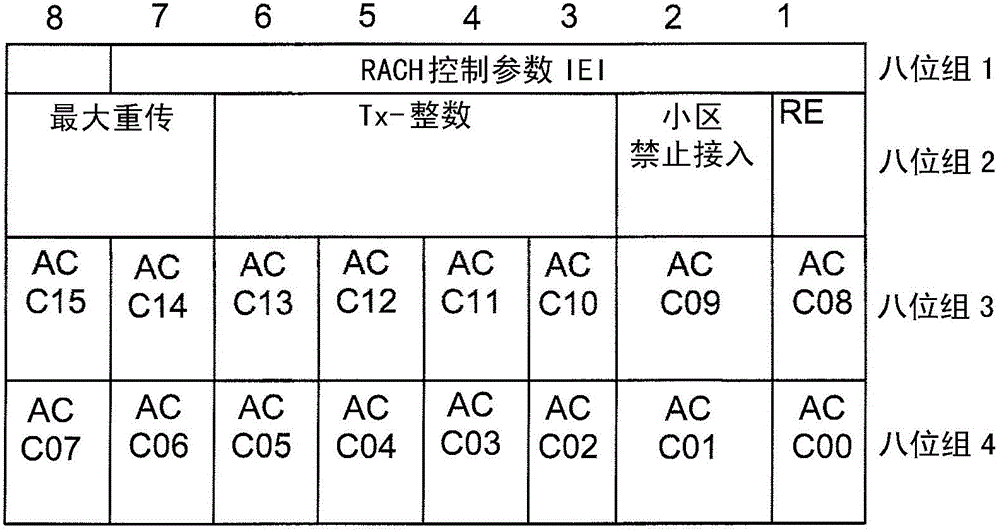
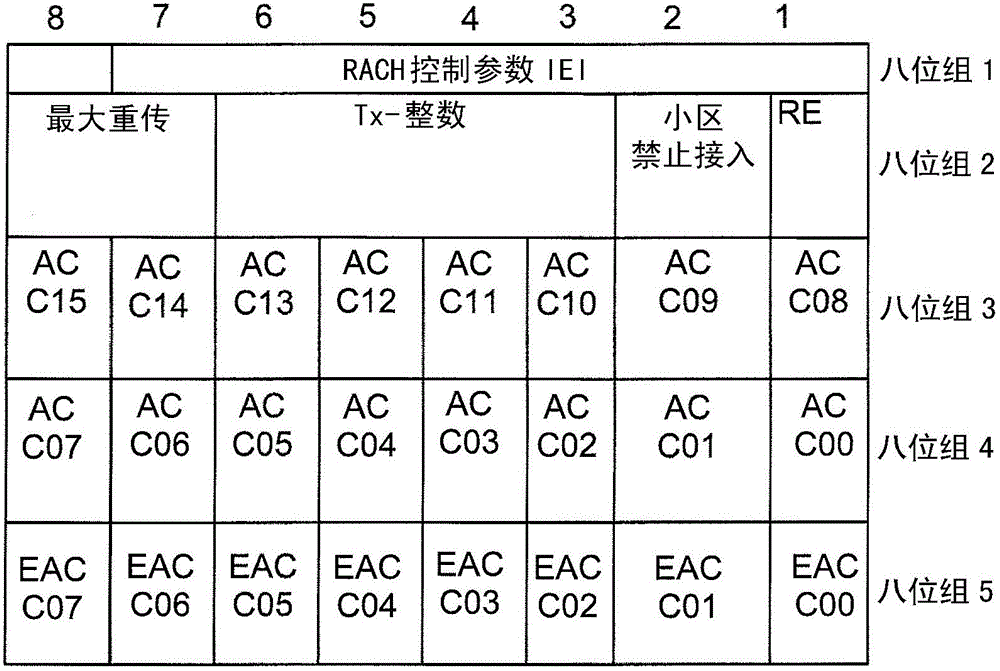
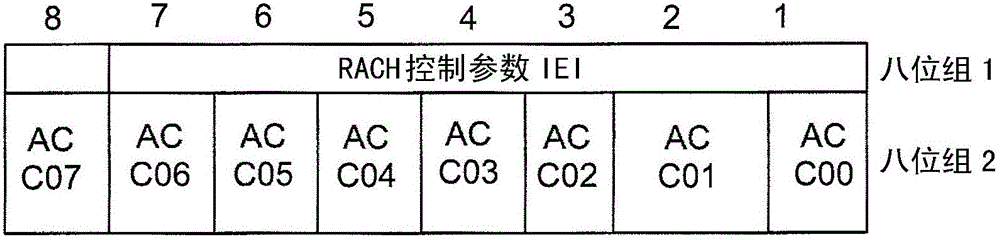
The invention relates to methods and arrangements for controlling access of a mobile device to a network, such as GSM. The mobile devices belong to an access control class (ACC) and for providing extended access control, and may also belong to an additional access control class (EACC). The arrangement broadcasts system information to the mobile devices, which system information indicates whether mobile device, which belong to an access control class (ACC), is allowed to access or are barred from accessing the network, and the system information further indicates whether the mobile device, which also belong to an extended access control class (EACC), is allowed to access or are limited from accessing the network. Different ways for limiting access is provided. An example is to block the mobile device from initiating communication, and allow the mobile device for communication initiated by the network. An example is to block the mobile device from communication initiated from the network, and allow the mobile for initiating communication. An example is to block the mobile device from initiating communication, as well as for communication initiated by the network. A mobile device blocked from network initiated communication is not allowed to answer a paging from the network.
Owner:TELEFON AB LM ERICSSON (PUBL)
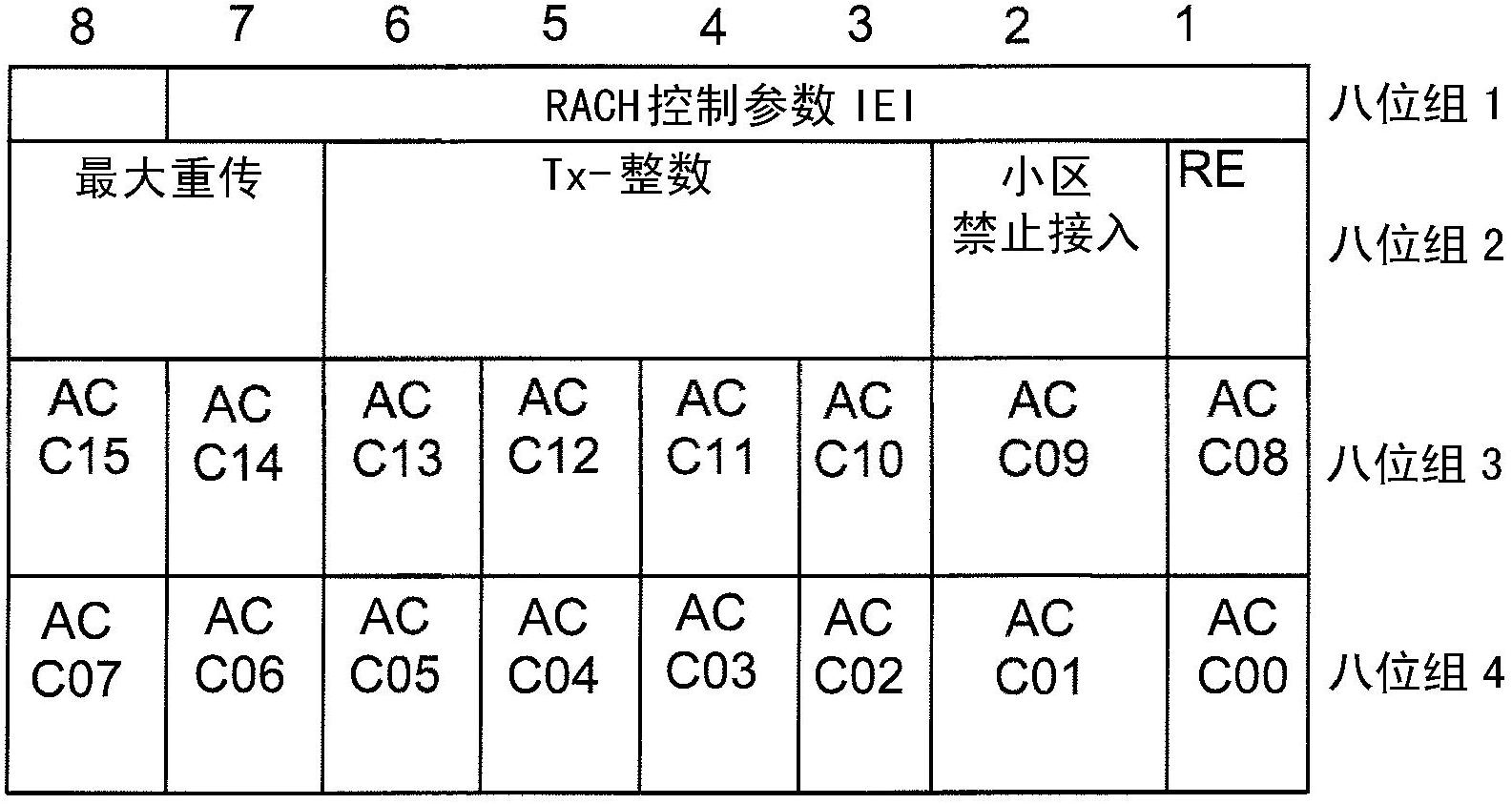
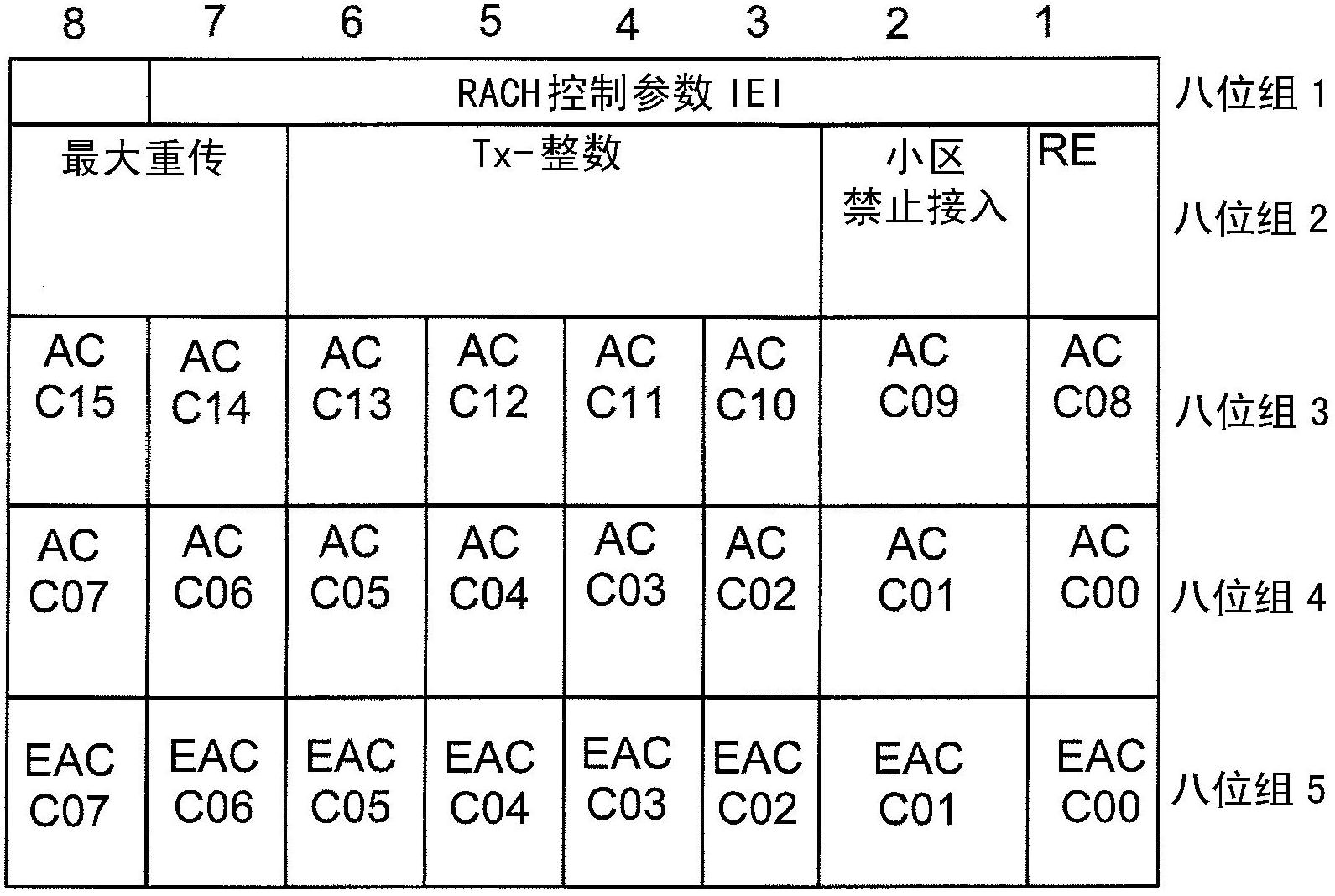
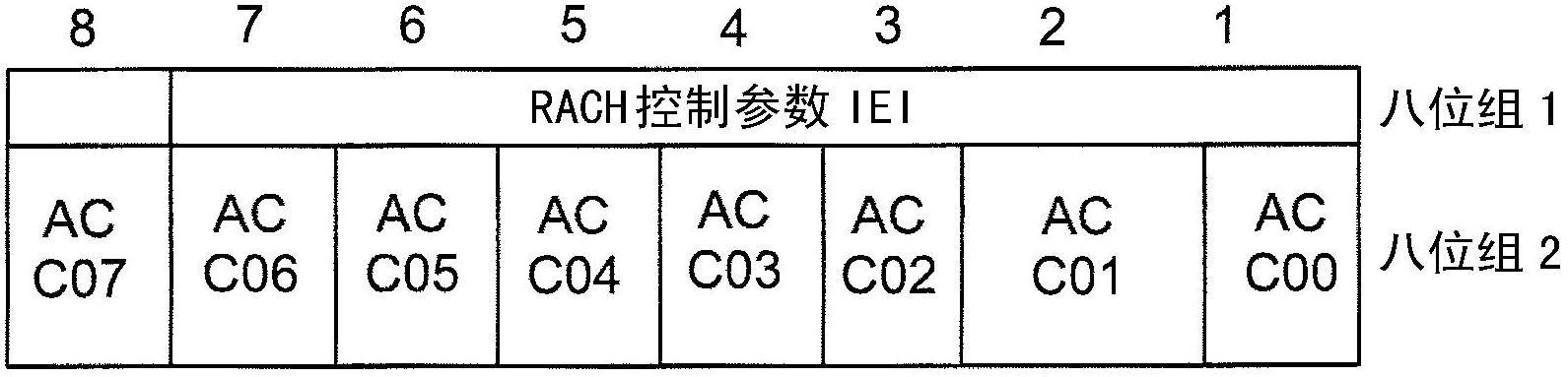
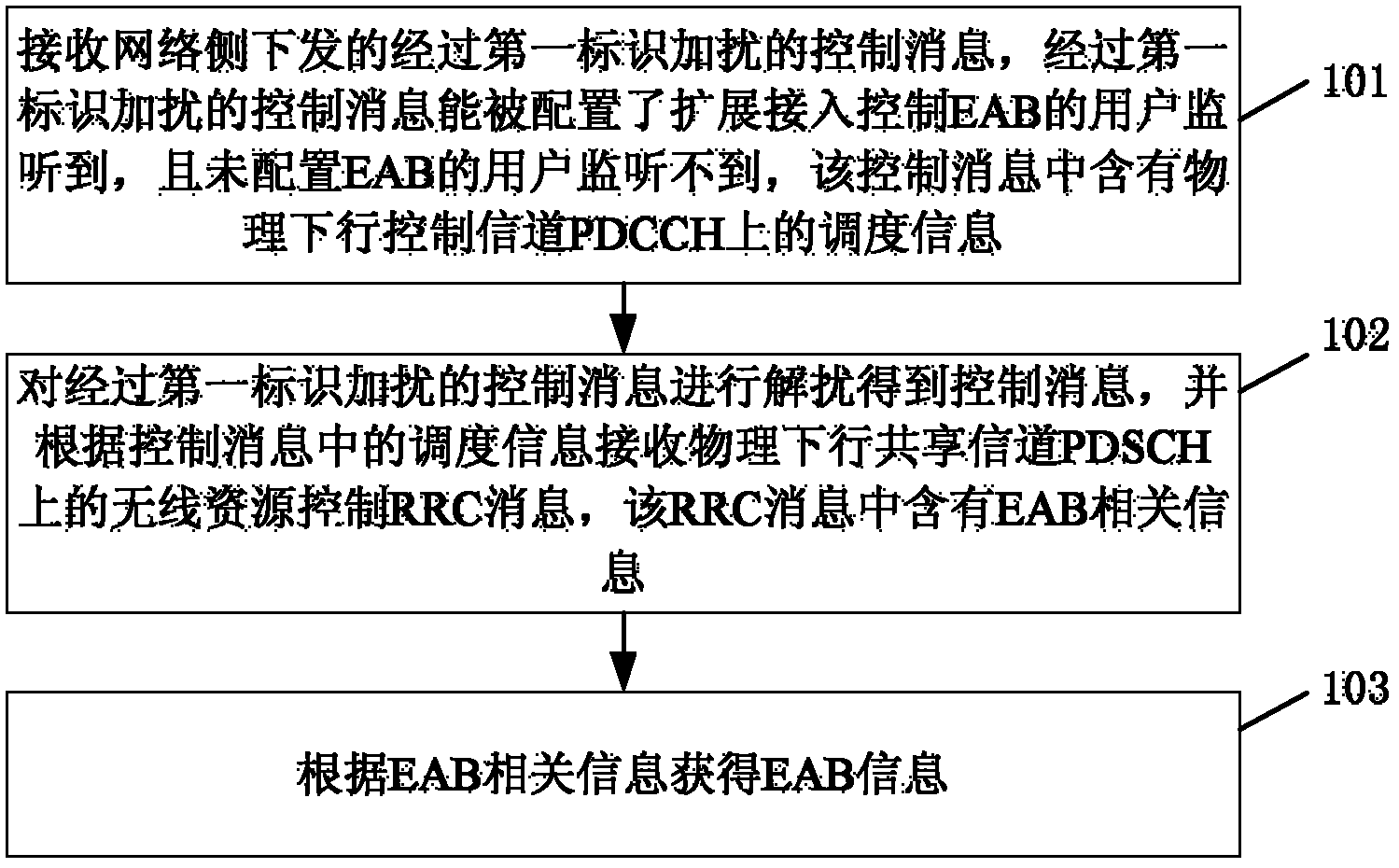
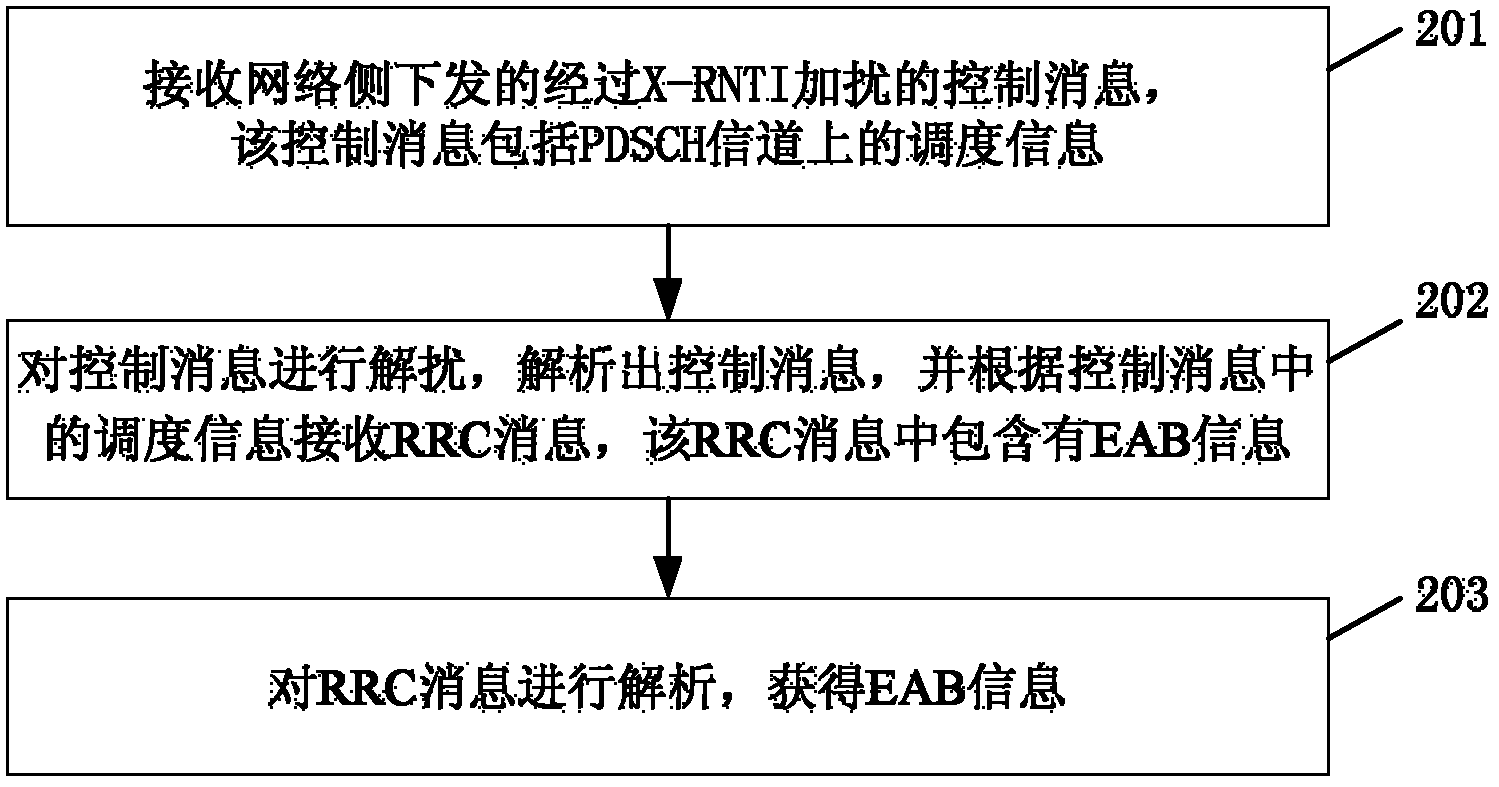
Method, device and system for obtaining access control information
The invention discloses a method, a device and a system for obtaining access control information, and belongs to the field of communication networks. The method includes the following steps: receiving control information which is sent by a network side and is scrambled by first identification, wherein the control information can be monitored by users with an extended access control embedded array block (EAB) configured, the control information can not be monitored by users with the extended access control EAB not configured, and the control information contains scheduling information on a physical downlink control channel (PDCCH); descrambling the control information to obtain the control information, and receiving radio resource control (RRC) information on a physical downlink shared channel (PDSCH) according to the scheduling information in the control information, wherein EAB relevant information is contained in the RRC information; and obtaining EAB information according to the EAB relevant information. By means of the method, the device and the system for obtaining the access control information, X-radio network temporary identity (RNTI) identification arranged specially for the user with the EAB configured, when only does the EAB information vary, ordinary H2H users can not receive the RRC information, and thus received quantity of ordinary users is reduced.
Owner:HUAWEI TECH CO LTD
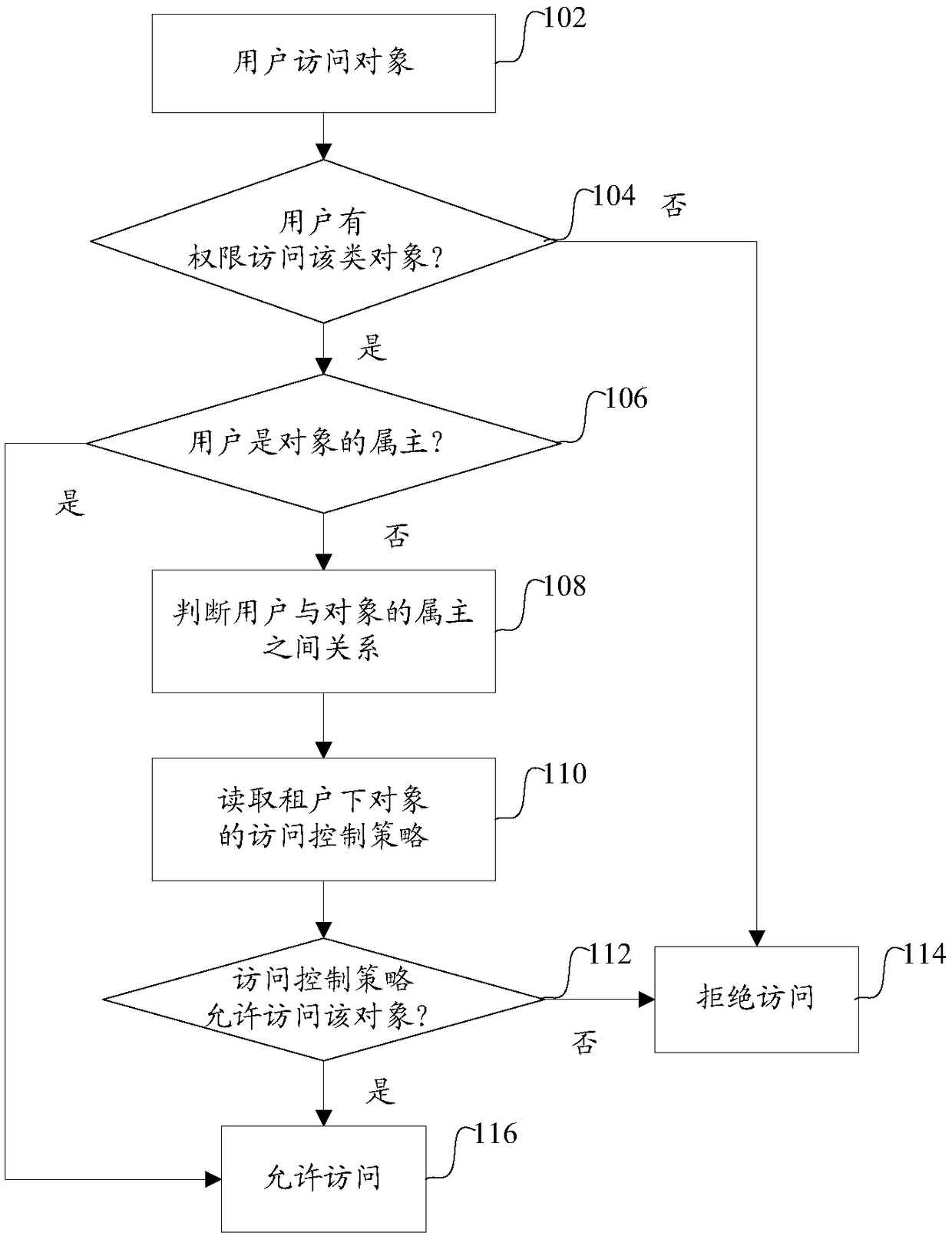
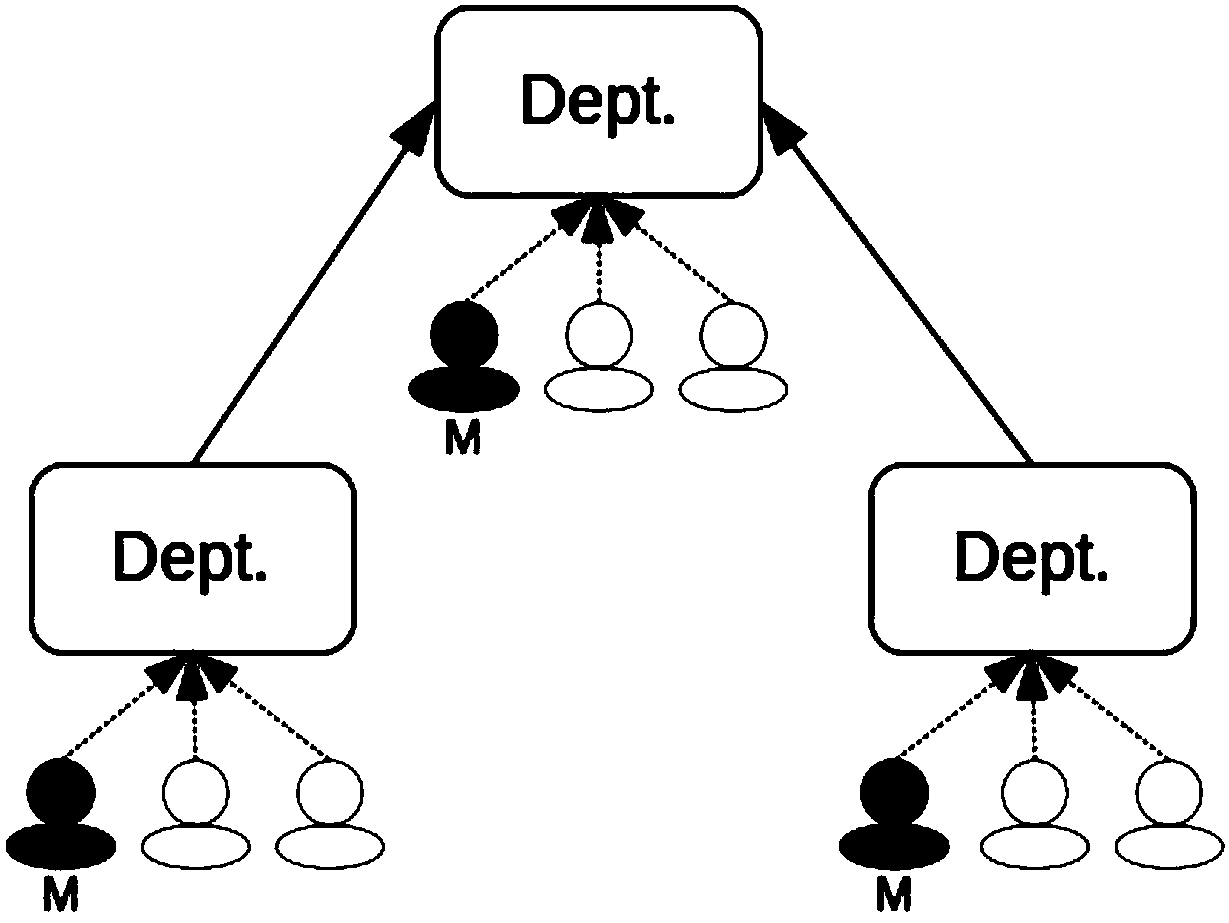
Strategy-based multi-tenant access control method
InactiveCN108304715AEfficient accessImprove scalabilityDigital data authenticationControl systemExtended Access Control
The invention provides a strategy-based multi-tenant access control method and system. The method comprises the following steps of: when a user carries out an operation on an object, judging whether the user has a right to execute the operation on the type of object or not, and if the user does not have the right, rejecting the operation; if the user has the right, judging whether the user is an owner of the object or not; if the user is the owner of the object, allowing the operation; if the user is not the owner of the object, judging a relationship between the user and the owner of the object; reading an access control strategy of a tenant to which the user belongs according to the relationship between the user and the owner of the object; and judging whether the access control strategyallows the operation or not. The strategy-based multi-tenant access control method is capable of defining flexibly and easily-extended access control strategies, so as to effectively control access of objects under multi-tenant conditions.
Owner:上海五行嘉信息技术有限公司
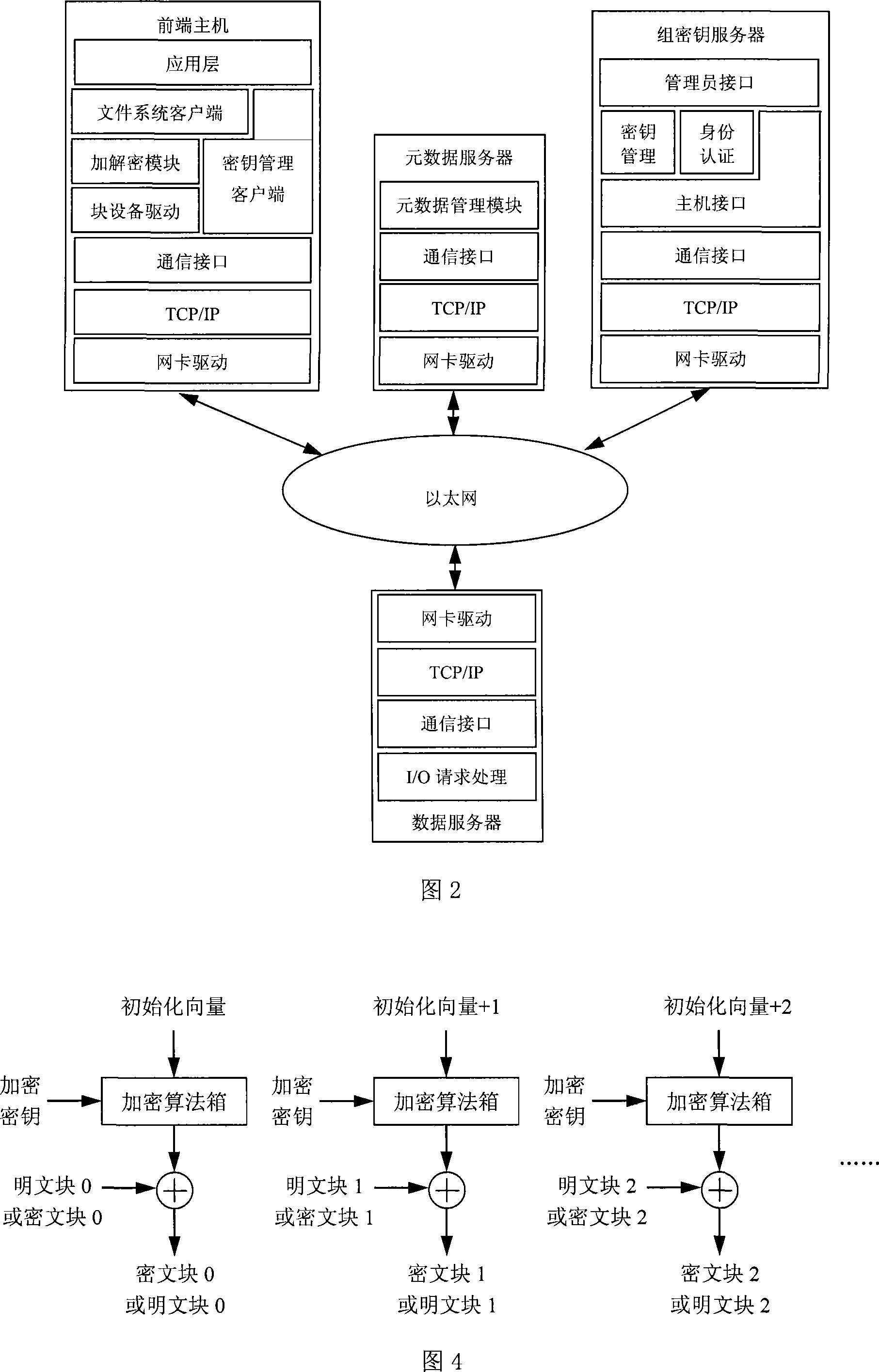
Group key server based key management method in sharing encryption file system
InactiveCN101159556BSave storage spaceImprove securityUser identity/authority verificationData switching networksConfidentialityUser identifier
The invention provides a key server-based key management method in an encrypting file system and belongs to the filed of storage safety. The invention is characterized in that a group key server processes each key management request in the system and performs strict check for user identification and access authority; a user terminal sends a key operation request to the group key server; the organized key information, based on extended access control list, comprises a file key, a user ID and an access authority; the group key server protects the confidentiality and integrity thereof by using the privacy key itself; the user terminal realizes the key cache function and reduces the frequency of communication with the group key server; the system can cancel the key by using the delay encryption technique, postpone the time of file re-encryption until the file content is updated, and minimize the influence of key cancel operation on the system performance.
Owner:TSINGHUA UNIV
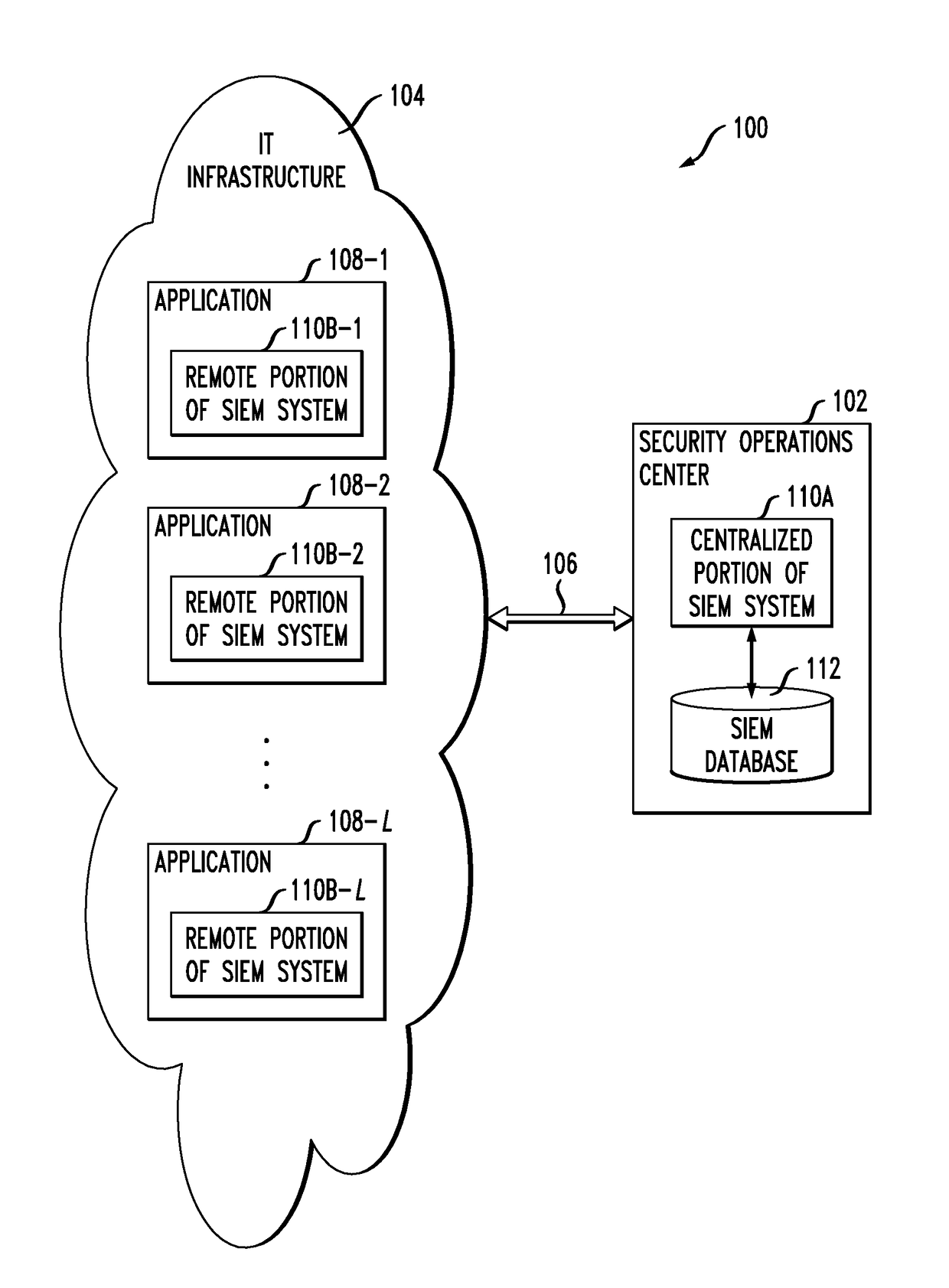
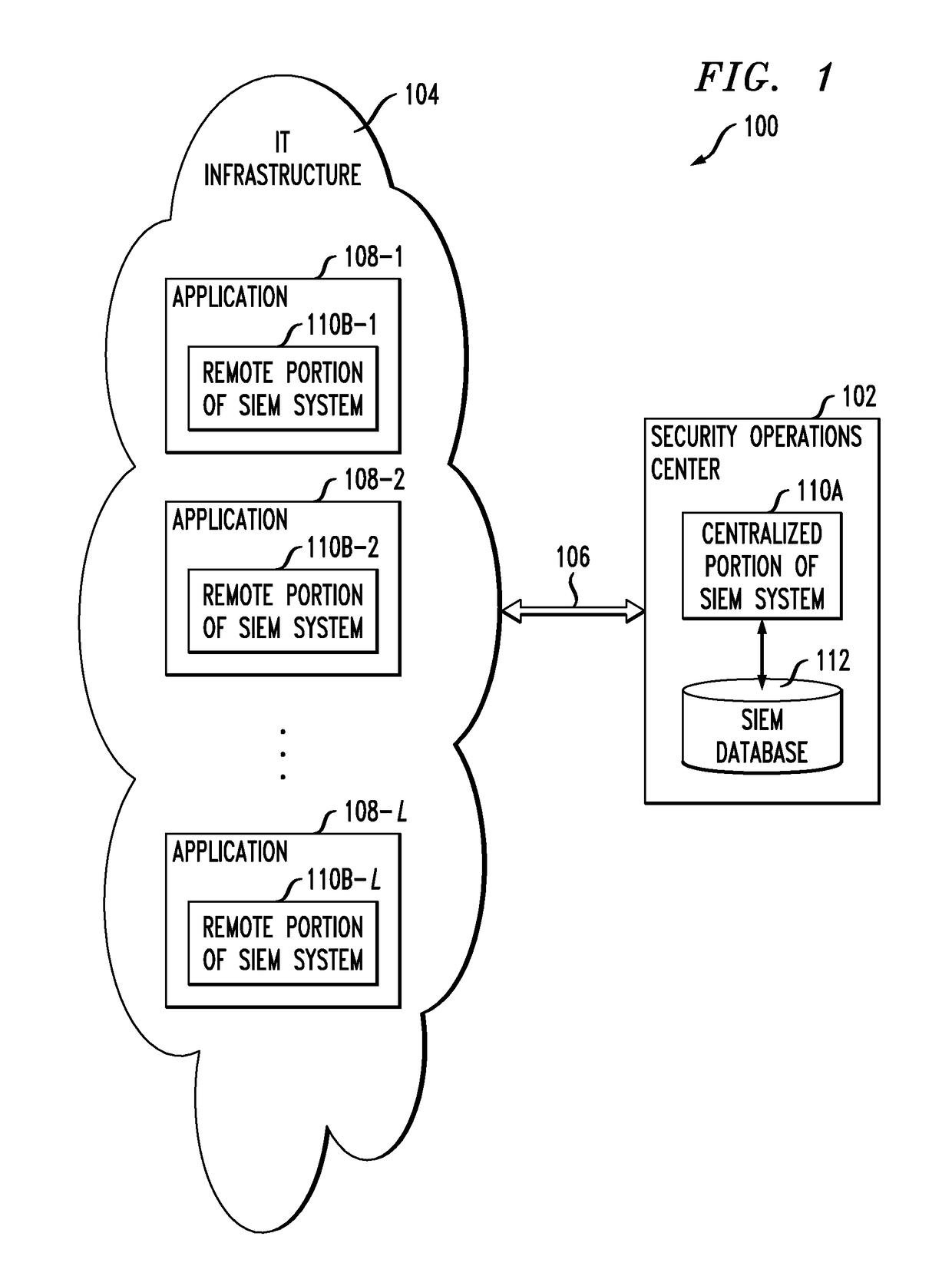
Distributed security information and event management system with application-injected remote components
ActiveUS10129072B1Avoid lostTo offer comfortData switching networksSecurity information and event managementDistributed security
A distributed security information and event management system comprises a centralized portion and a plurality of remote portions, with the remote portions being implemented in respective applications within information technology infrastructure. Each of the remote portions comprises one or more remote components inserted into the corresponding application. At least a subset of the remote components of the remote portion are configured for interaction with one or more corresponding centralized components of the centralized portion of the system. The remote components may each be configured to process one or more specified eXtensible Access Control Markup Language (XACML) Obligations or other constructs.
Owner:EMC IP HLDG CO LLC
An extensible access control method for fog computing
ActiveCN109936562AImplement integrity protectionReduce operational overheadTransmissionAccess structureOriginal data
The invention discloses an extensible access control method for fog computing. According to the method, a linear secret sharing matrix is used as an access structure to realize attribute-based accesscontrol, fog nodes are used as edge service nodes, and encryption and decryption operations in the access control are reasonably distributed, so that the operation overhead of a terminal user in the access control is reduced. In addition, on the basis of maintaining the original access strategy, new legal members can be added to form a new access strategy, meanwhile, whether the access user tampers the original data or not when uploading the new access strategy can be detected, and integrity protection of the original data is achieved.
Owner:NANJING UNIV OF POSTS & TELECOMM
Extended access control method based on traffic statistics
InactiveCN109218324AEfficient deploymentEfficient accessData switching networksTraffic capacityVLAN access control list
The invention relates to the technical field of network security, particularly an extended access control method based on traffic statistics. The extended access control method based on flow statistics of the invention extracts statistical information of corresponding flow on the basis of access control rules, further expands the access control list, and improves the flexibility of access controland the safety of network equipment.
Owner:SHANDONG CHAOYUE DATA CONTROL ELECTRONICS CO LTD
Distributed extensible access control authorization system and method based on block chain
InactiveCN113067861ADatabase distribution/replicationDigital data protectionIntelligent NetworkAdministrative domain
The invention discloses a distributed extensible access control authorization system and method based on a block chain. According to the scheme, the block chain smart contract is taken as a carrier, a new architecture is provided, a traditional access control model is combined, and the concept of the attribute sequence number value pair and the prefix identifier is introduced to optimize the system strategy retrieval method. According to the architecture level, an intelligent gateway is introduced between a block chain network and each management domain to serve as an access request and data request agent, and equipment registration and attributes are managed by an administrator; according to the intelligent contract level, a strategy implementation contract, a strategy contract and a strategy management contract are designed in the scheme, and authorization management is carried out on access control together; and according to the policy retrieval method level, prefix identifiers are generated for access requests and policies, bit calculation is performed on the access requests and the policies, policy preliminary matching is performed, and policy conflict configuration is introduced, so that the policy retrieval speed is greatly optimized. Therefore, compared with other access control solutions, the scheme has certain advantages.
Owner:SICHUAN UNIV
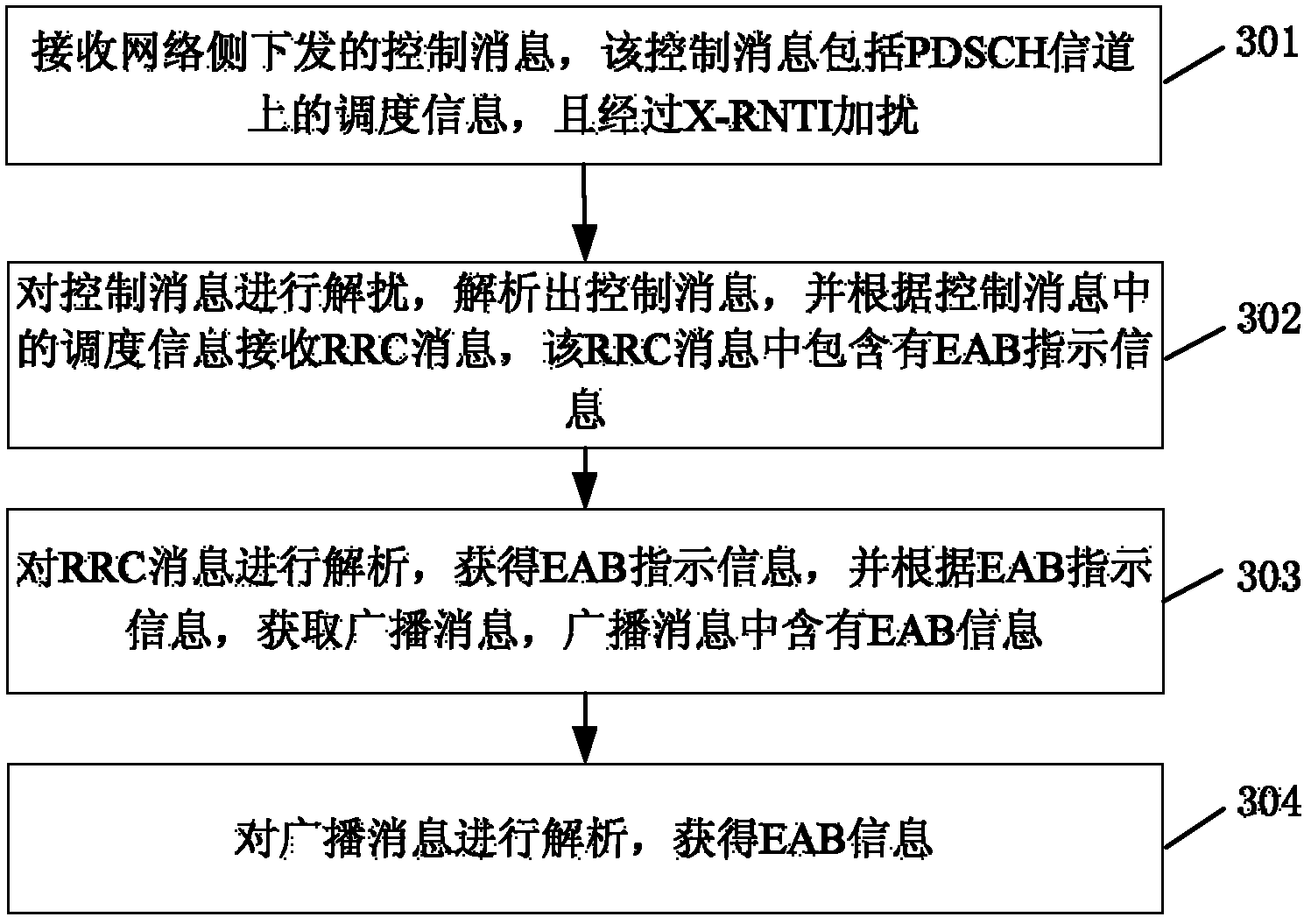
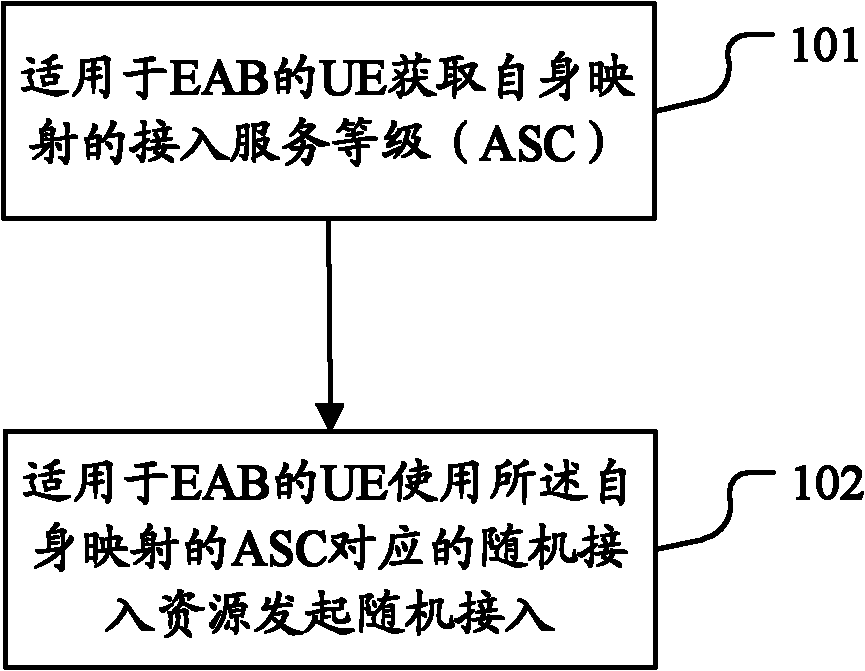
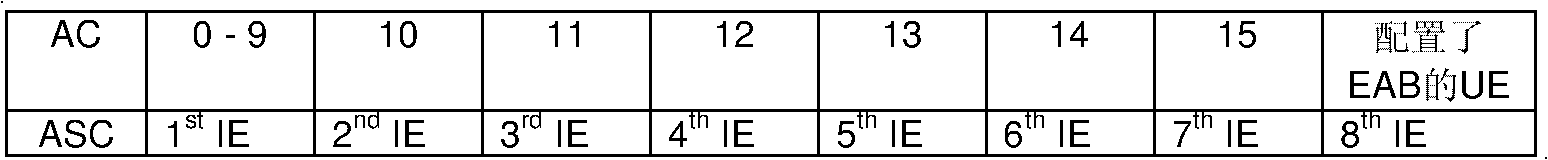
Access control method, system and UE (user equipment)
InactiveCN102761974AControlling the random access processAvoid shockAssess restrictionTelecommunicationsControl system
The invention discloses an access control method comprising the following steps that: user equipment (UE) suitable for extended access control block (EAB) initiates a random access by use of a random access resource mapped corresponding to a self-mapped access service class (ASC), specifically, the UE suitable for extended EAB obtains the self-mapped ASC according to the system information of the network side, or obtains the self-mapped ASC according to a protocol based predetermined configuration. The invention correspondingly discloses an access control system and the UE. According to the invention, the random access process of the UE suitable for the EAB is controlled, and the high impact to the UE unsuitable for the EAB caused by the access of a large amount of UE suitable for the EAB, is avoided.
Owner:ZTE CORP
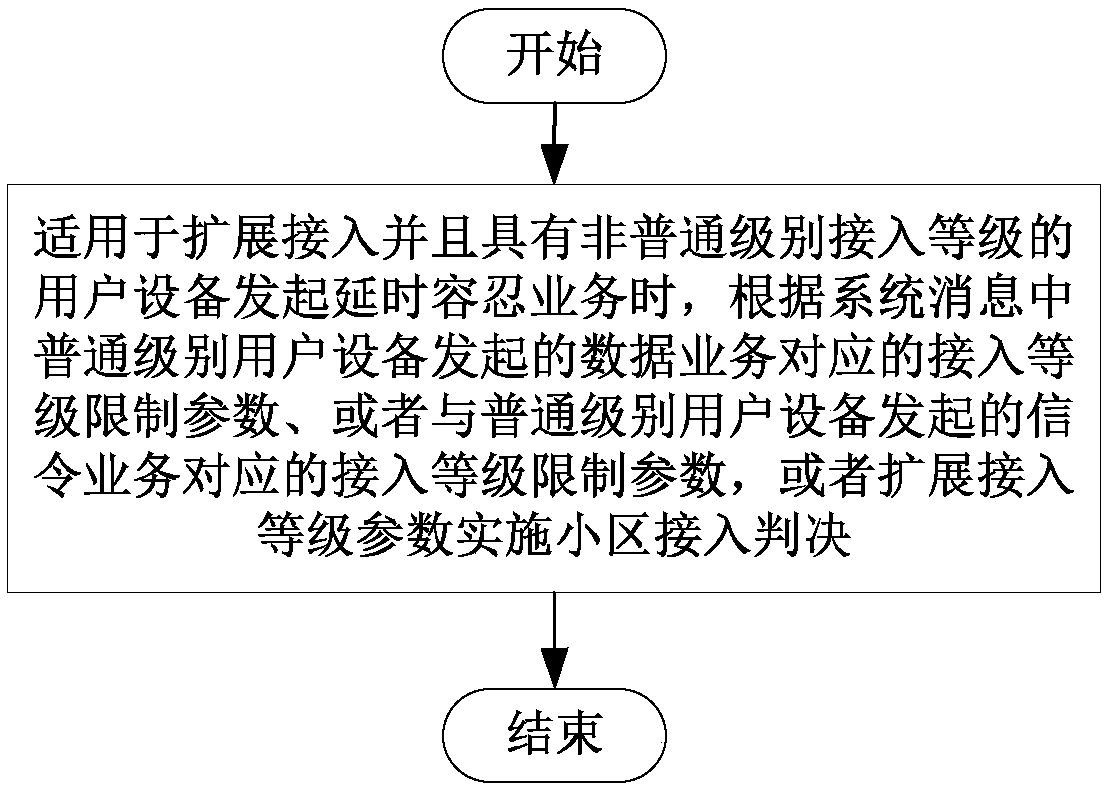
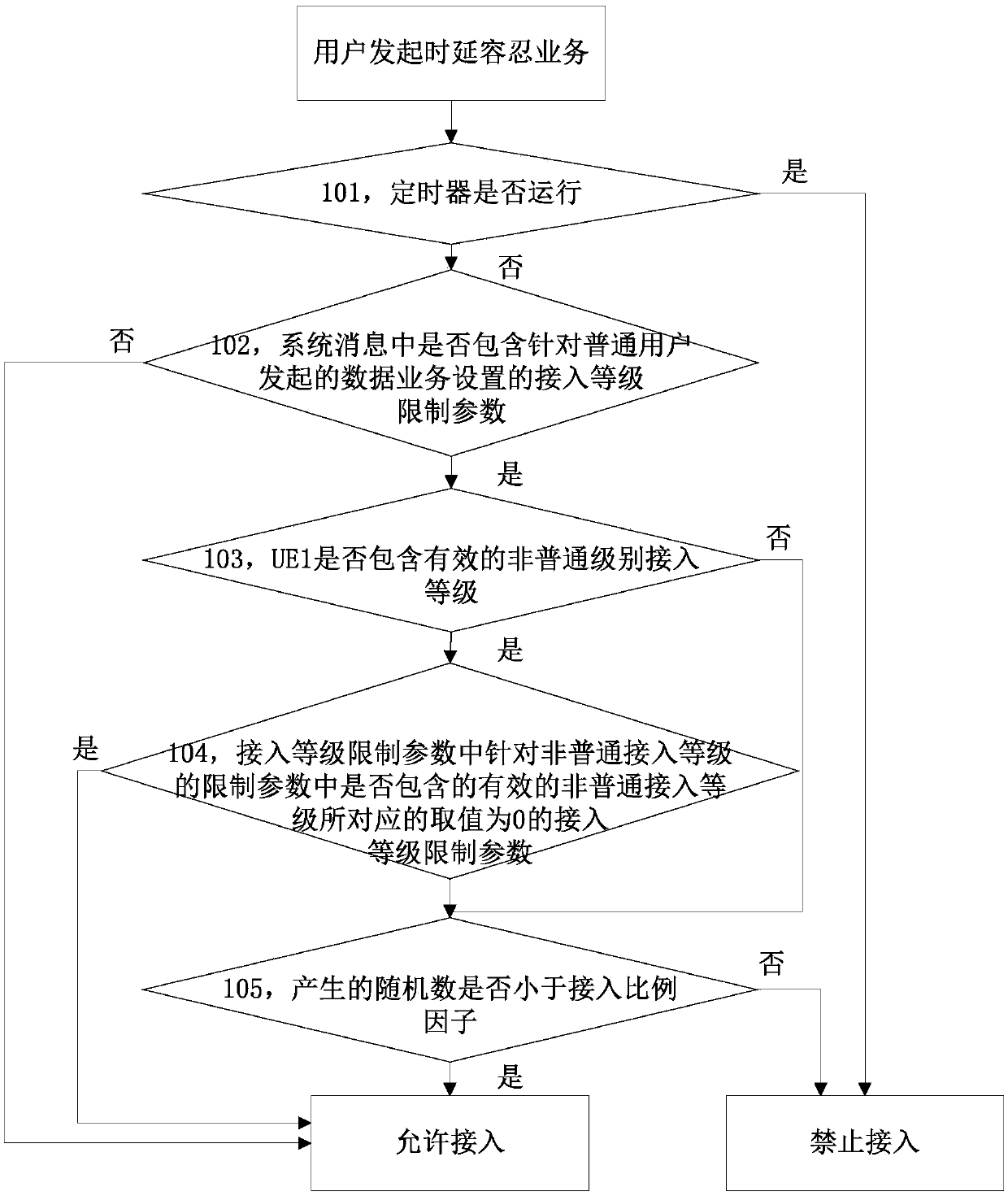
A method and user equipment for performing access control
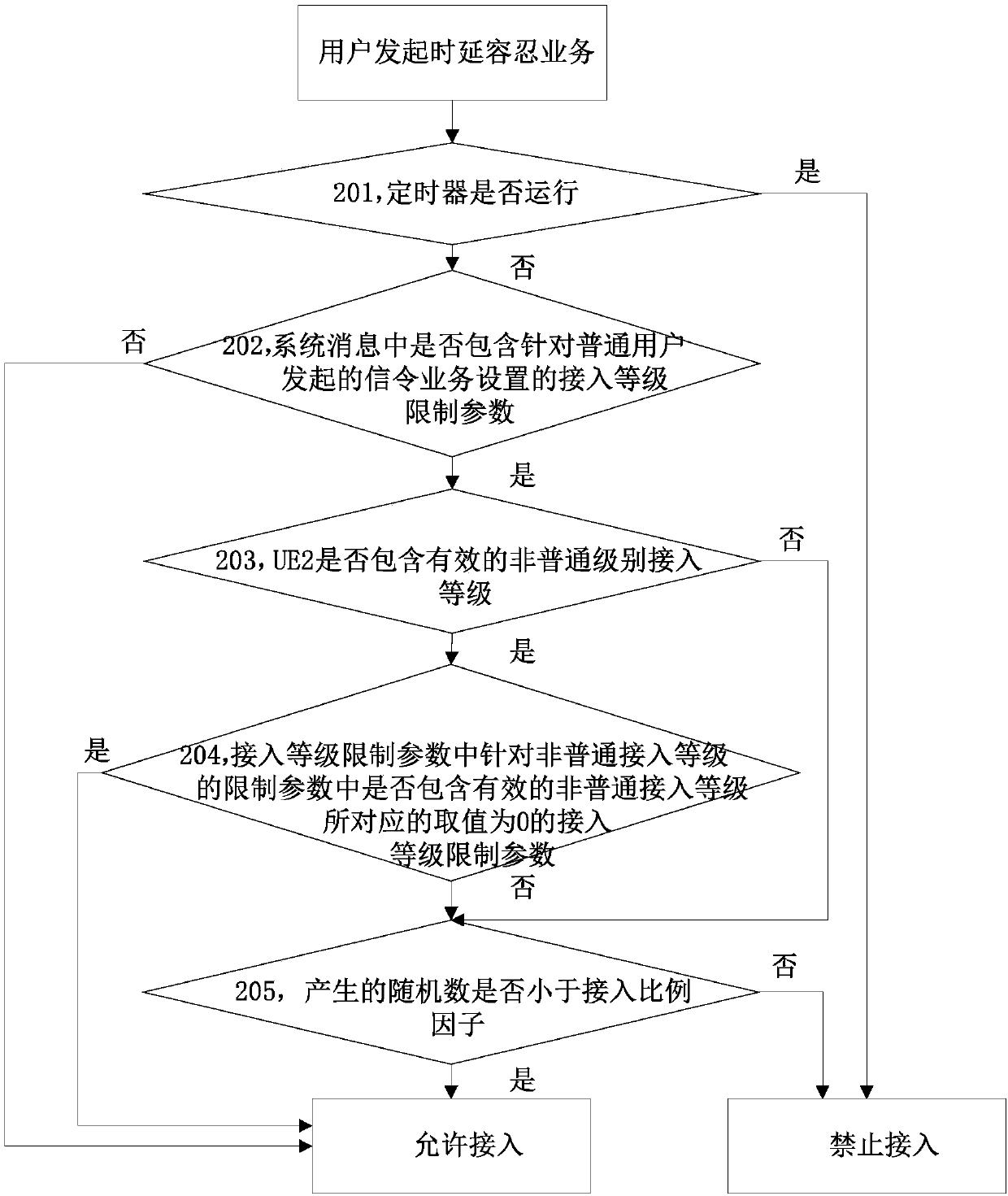
ActiveCN102892178BSolve the problem of uncertain access decisionReduce modificationAssess restrictionNormal levelCell system
The present invention discloses a method for performing access control and user equipment. The method includes: when a user equipment suitable for extended access and having an access level of a non-ordinary level initiates a delay-tolerant service, according to the user equipment of an ordinary level in a system message, The access level restriction parameter corresponding to the data service initiated by the device, or the access level restriction parameter corresponding to the signaling service initiated by the common level user equipment in the system message, or the cell access decision based on the extended access level parameter in the system message . This solution is suitable for extended access control (EAB) user equipment with non-ordinary access levels. When initiating delay-tolerant services, the network side can implement access control for it, which solves the problem of such user equipment access The problem of uncertain access decision when accessing the network.
Owner:ZTE CORP
Method and device for generating access controlling policy
InactiveCN101771683BGuaranteed accuracyReduce the burden onData switching networksSpecial data processing applicationsXACMLWorld Wide Web
The invention discloses method and device for generating an access controlling policy. The method comprises the following steps of: generating an ABAC policy expression according to ABAC policy information input by a user through a pre-established attribute-based access control (ABAC) policy view template; and converting the ABAC policy expression into an ABAC policy which is based on XACML and conforms to the XACML template according to mapping rules of the preset ABAC policy view template and an extensible access control markup language (XACML) template. In the invention, the user only needs to input some simple ABAC policy information through the ABAC policy view template and does not need to write a complicated ABAC policy based on XACML in a manual mode, therefore, the problem that the user difficultly defines the ABAC policy based on XACML is solved, the problem that errors are made in the process of writing the complicated ABAC policy based on XACML in a manual mode by the useris avoided, and the accuracy of the ABAC policy based on XACML is ensured.
Owner:BEIHANG UNIV
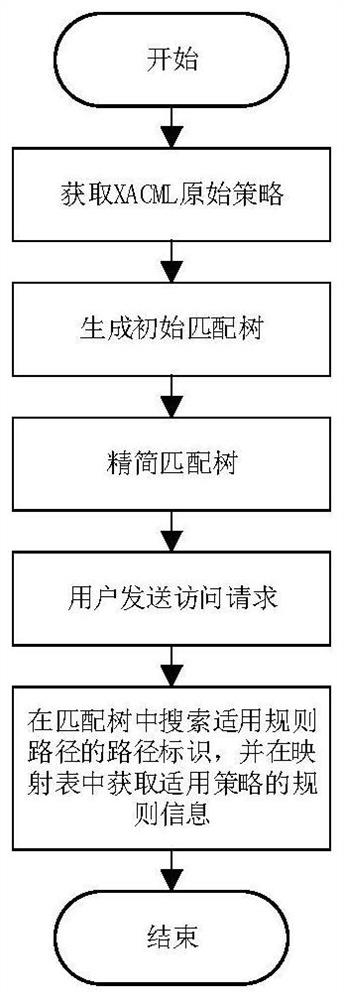
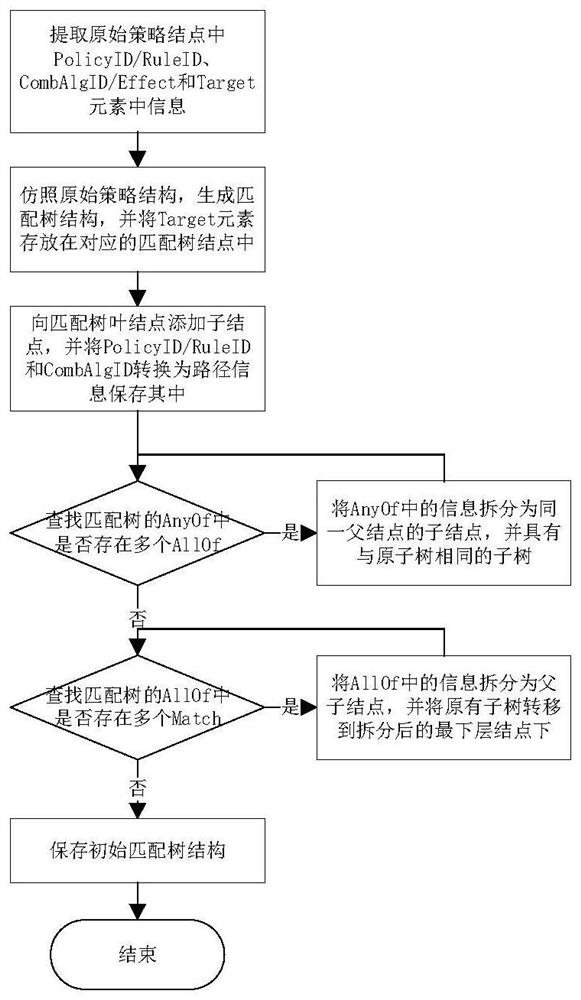
Extensible access control markup language strategy searching method based on matching tree
ActiveCN112131434AAvoid wastingEnsure policy accuracySemi-structured data indexingOther databases indexingTheoretical computer sciencePath generation
The invention discloses an extensible access control markup language strategy searching method based on a matching tree structure. The extensible access control markup language strategy searching method mainly solves the problems that in the prior art, strategy searching efficiency is low, and node information in a matching tree and a combination tree is repeated. According to the implementation scheme, the method includes forming an initial matching tree according to the structure and information of an original strategy, and removing repeated attributes under the same path in the initial matching tree; generating a path identifier according to the path of the initial matching tree, replacing the path information in the initial matching leaf node with the path identifier to obtain a simplified matching tree, and storing the path information and the corresponding path identifier in a mapping table; according to an access request sent by a user, searching a path identifier suitable for arule path on the matching tree, and finding a suitable strategy of the request in a strategy library by utilizing the mapping table. By optimizing the matching tree structure, the strategy migrationcost is reduced, the strategy search efficiency is improved, and the method can be used in the access control process using large-scale strategies.
Owner:XIDIAN UNIV
Method for generating cross-domain access control strategy by rising from credit assessment to trust management
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY +1
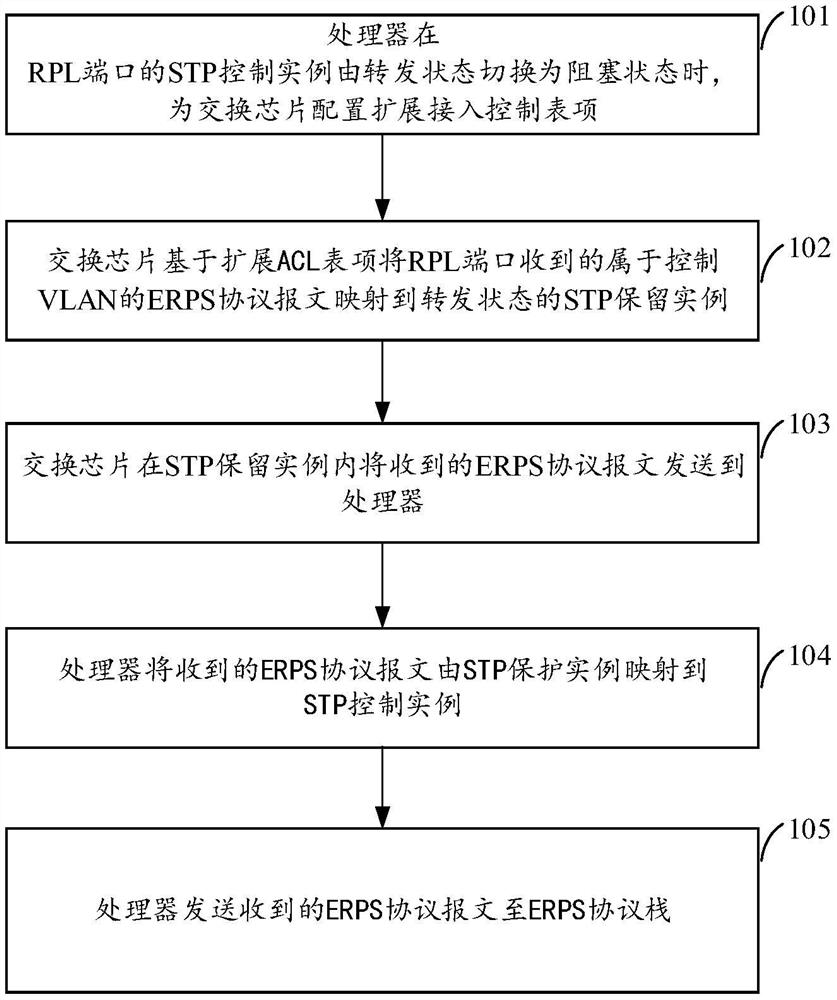
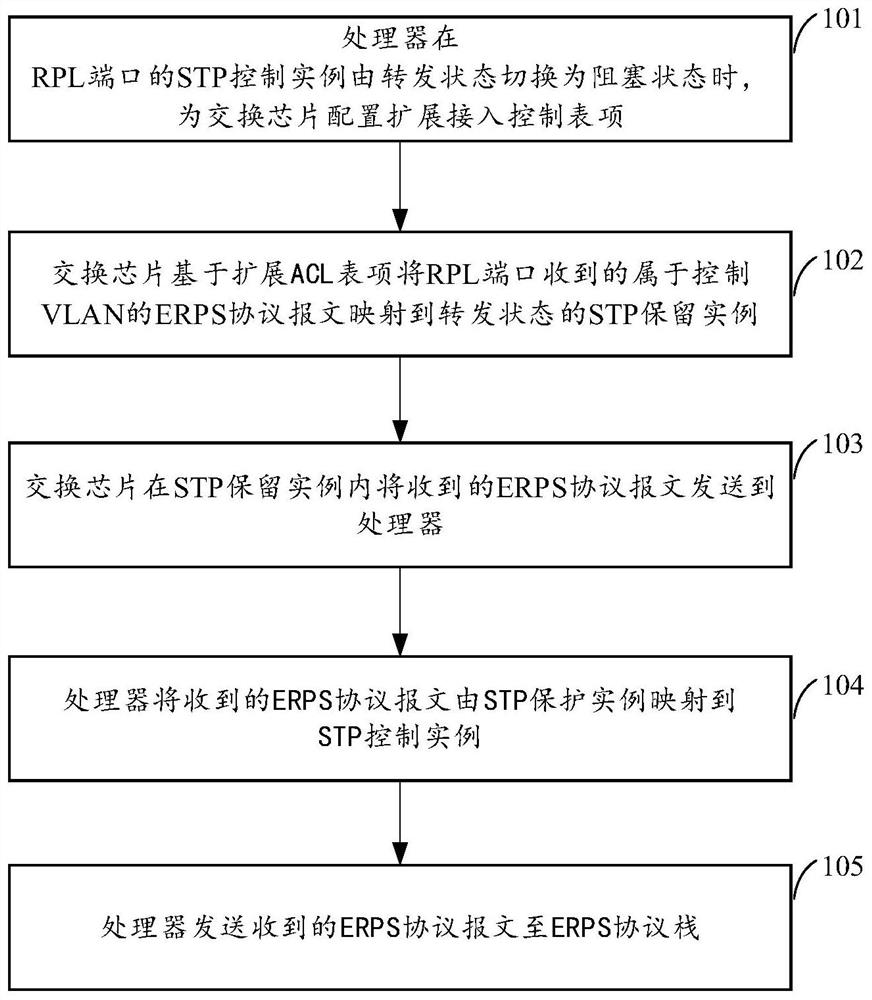
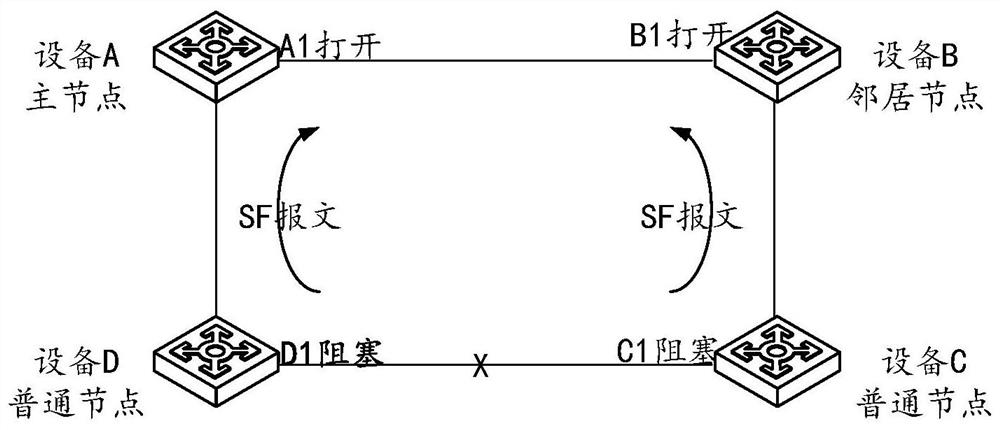
Message forwarding method and equipment
The invention provides a message forwarding method and equipment. A processor in the equipment determines that a spanning tree protocol STP control instance of a ring protection link RPL port is switched from a forwarding state to a blocking state, and configures an extended access control table entry for a switch chip; the priority of the extended access control table item is higher than that of a global Ethernet protection switching protocol ERPS access control table item; the switch chip is used for mapping a first ERPS protocol message which is received by the RPL port and belongs to a control virtual local area network (VLAN) to the STP reservation instance in a forwarding state based on the extended access control table item; the received first ERPS protocol message is sent to a processor in the STP reservation instance; wherein the control VLAN is associated with the STP control instance; and the processor maps the received first ERPS protocol message from the STP reservation instance to the STP control instance, and sends the received first ERPS protocol message to an ERPS protocol stack.
Owner:NEW H3C SECURITY TECH CO LTD
Method and device in communication system
The invention relates to methods and arrangements for controlling access of a mobile device to a network, such as GSM. The mobile devices belong to an access control class (ACC) and for providing extended access control may also belong to an additional access control class (EACC). The arrangement broadcasts system information to the mobile devices, which system information indicates whether mobile device, which belong to an access control class (ACC), is allowed to access or are barred from accessing the network, and the system information further indicates whether the mobile device, which also belong to an extended access control class (EACC), is allowed to access or are limited from accessing the network. Different ways for limiting access is provided. An example is to block the mobile device from initiating communication, and allow the mobile device for communication initiated by the network. An example is to block the mobile device from communication initiated from the network, and allow the mobile for initiating communication. An example is to block the mobile device from initiating communication, as well as for communication initiated by the network. A mobile device blocked from network initiated communication is not allowed to answer a paging from the network.
Owner:TELEFON AB LM ERICSSON (PUBL)
A Scalable Access Control Method for Fog Computing
ActiveCN109936562BImplement integrity protectionReduce operational overheadTransmissionAccess structureOriginal data
The invention discloses an extensible access control method oriented to fog computing. The method adopts a linear secret sharing matrix as an access structure to realize attribute-based access control, uses fog nodes as edge service nodes, and reasonably distributes encryption and decryption in access control. computing to reduce the computing overhead of end users in access control. Moreover, the present invention can add new legal members to form a new access policy on the basis of maintaining the original access policy, and can also detect whether the access user has tampered with the original data when uploading the new access policy, and realizes the original data. Integrity protection.
Owner:NANJING UNIV OF POSTS & TELECOMM
A ciphertext access control method based on cp-abe
ActiveCN105991278BEnsure safetyKey distribution for secure communicationAccess structureControl system
The invention discloses a ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption), which belongs to the field of information security. The method comprises the following steps: preparation and maintenance work which comprises initialization of CP-ABE (Ciphertext-Policy Attribute-Based Encryption), user registration and auditing, generation of an asymmetric key pair for signature and encryption by the system and the user, generation of a CP-ABE attribute key SK for the user and key and attribute certificate management is carried out; 2, and file sharing requires a file provider, an extensible access control markup language (XACML) access control system and a sharing user to work cooperatively. The attribute certificate in a PMI system is used as an expression document for a CP-ABE attribute set and the access structure, the XACML expresses the CP-ABE policy, and security of the attribute set and the access control structure description is ensured. A hierarchical structure with an inheritance relationship is introduced, features such as distribution, authorization and calculability are supported, the attribute authorization ability needs to comply with constraints, and the method is applicable to a distributed and open network application environment.
Owner:INST OF APPLIED MATHEMATICS HEBEI ACADEMY OF SCI
Electronic passport expansion access control system and authentication method based on identification cipher technology
ActiveCN101504732BFlexible AuthorizationOvercoming loopholes in authorization trust transferUser identity/authority verificationCo-operative working arrangementsBiometric dataControl system
Owner:WUHAN TIANYU INFORMATION IND
Method for Scalable Access Control Decisions
ActiveUS20140373179A1Reduce needLess dependencyDigital data processing detailsAnalogue secracy/subscription systemsNetwork architectureSchema for Object-Oriented XML
Content access may be provided and processed by assigning responsibility for obtaining entitlement data to the client's browser. Thus, in one example, the client may be configured to synchronize and coordinate data lookups associated with a content request, rather than relying on the server to do so. The network architecture may use a mediator design pattern, in which the client's browser acts as the mediator (i.e., middleman) between a content server and an entitlement data server. Accordingly, synchronous calls between server-side services might not be required. Instead, data necessary for the content server to process a client request for access to protected content may be received in the incoming request from the client's browser.
Owner:COMCAST INTERACTIVE MEDIA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com