Distributed extensible access control authorization system and method based on block chain
An access control and blockchain technology, applied in database distribution/replication, transmission system, digital data protection, etc., can solve the problems of inefficient access control, insufficient equipment, and lack of consideration of a large number of capabilities in industrial sites
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
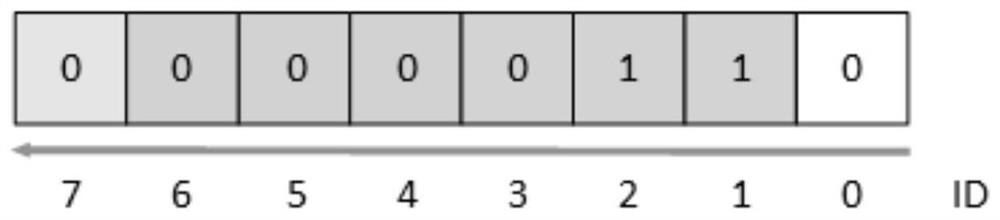
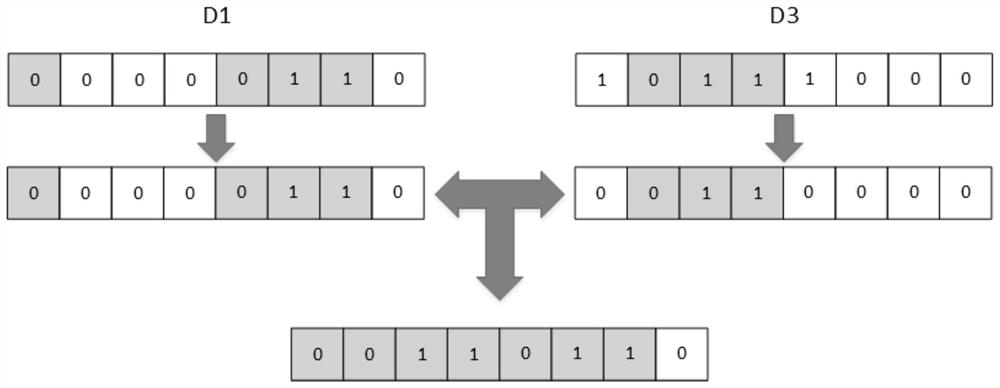
Image
Examples
Embodiment Construction
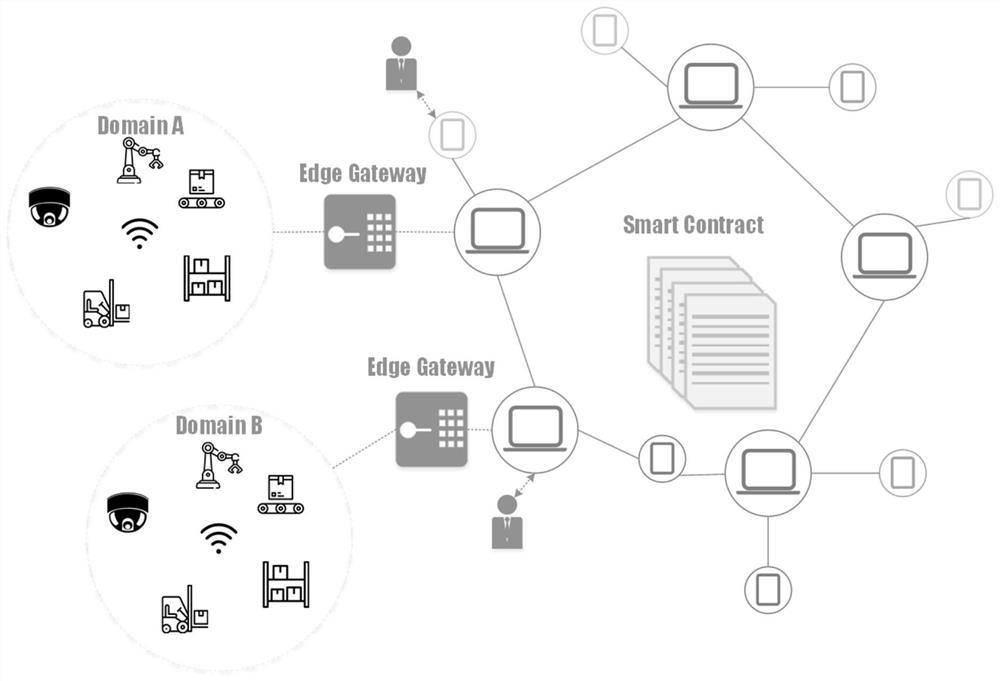
[0032] The following is a detailed description of the access control workflow based on the system architecture of this solution in conjunction with the accompanying drawings, mainly introducing the specific interaction process of the system's cross-domain access control, as shown in Figure 5 shown.
[0033] The workflow can be mainly divided into two stages: system initialization and cross-domain access control. The specific process of the initialization phase of the system is described as follows:
[0034] 1) The administrator deploys the smart contract and obtains the contract address.
[0035] 2) The device registers in the edge gateway to obtain its globally unique identifier.
[0036] 3) The edge gateway acts as an agent for the registration operation of the devices in its management domain in the smart contract.
[0037] 4) Bind the administrator to the device, and the administrator adds, deletes, and updates the attributes of the device and the associated gateway an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com