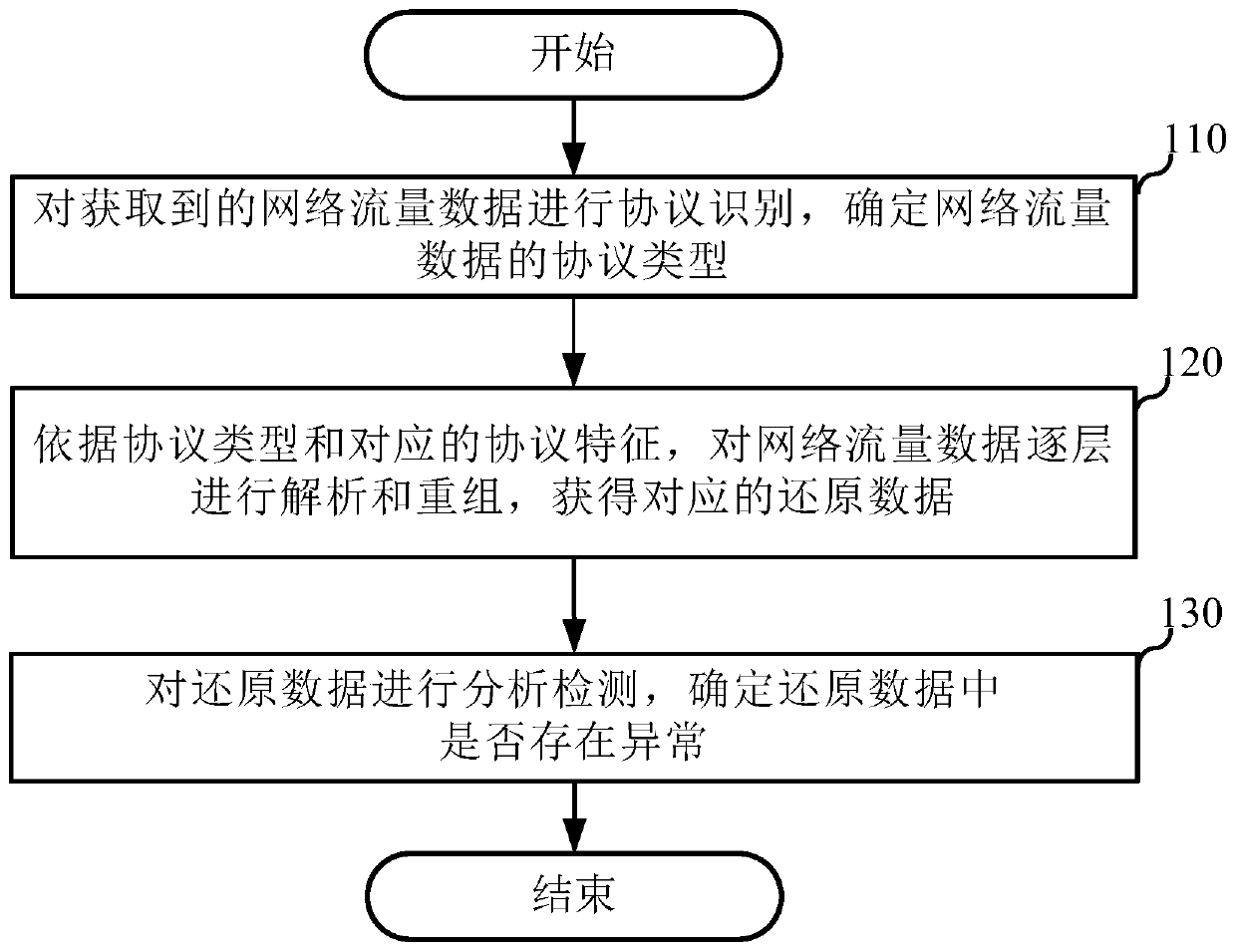
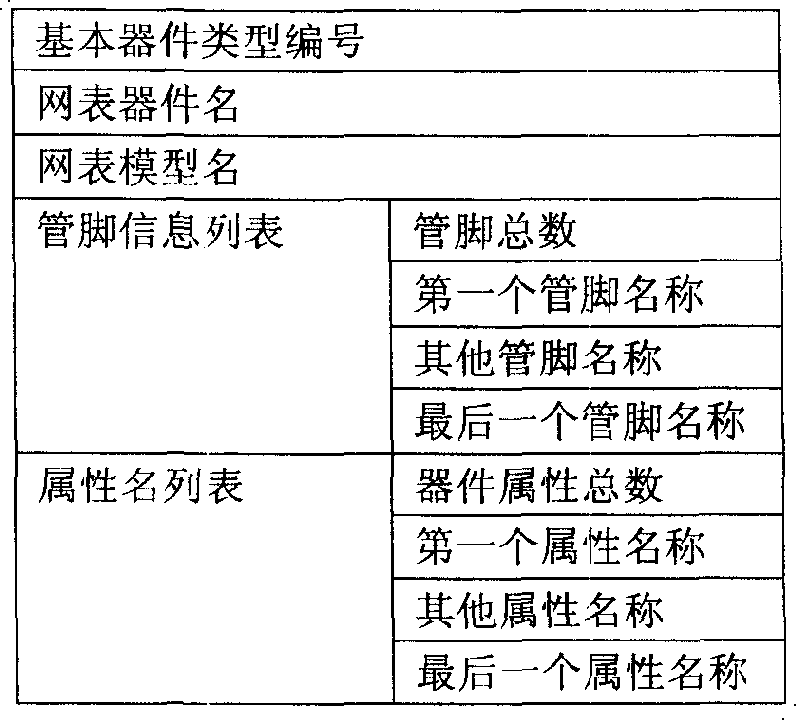
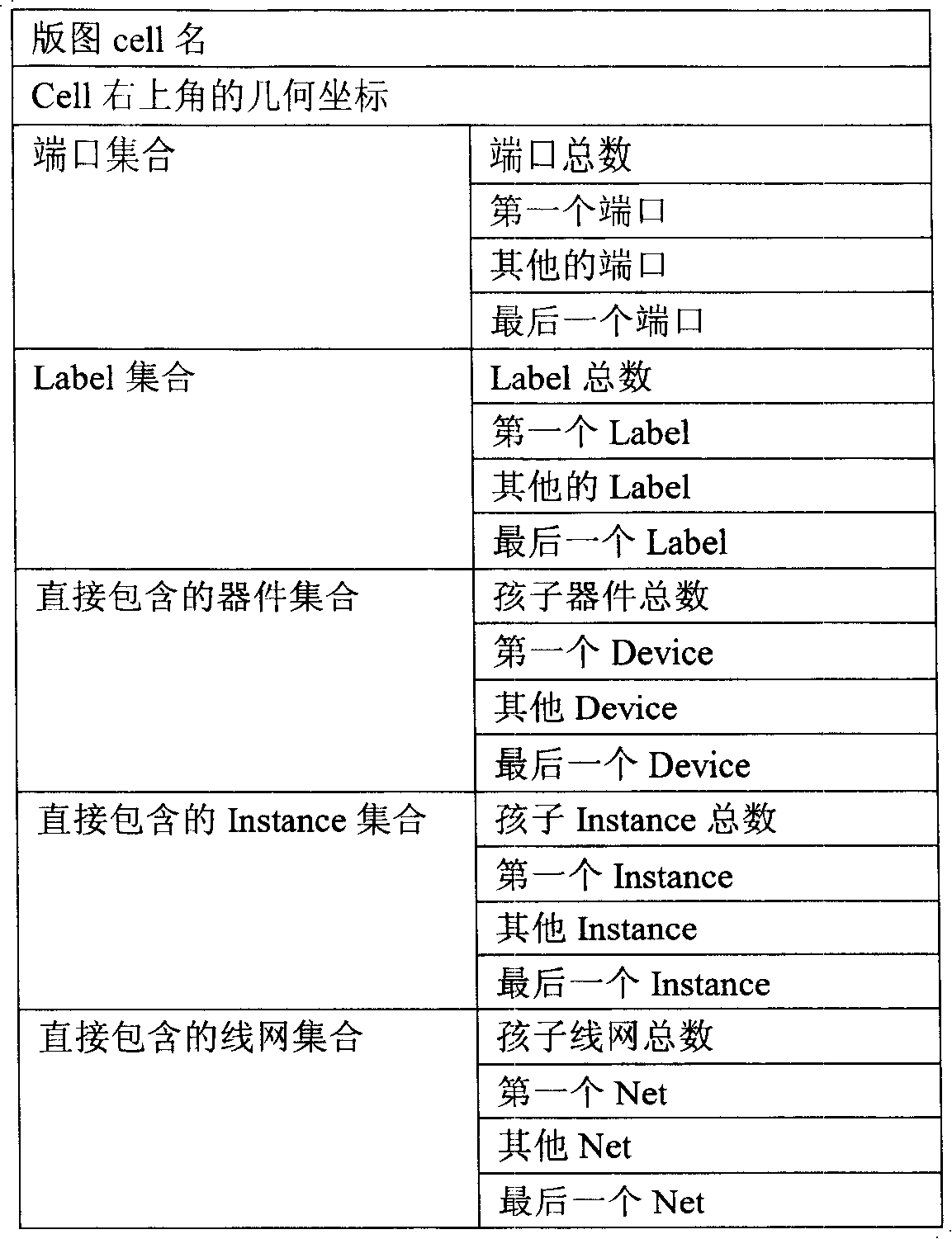
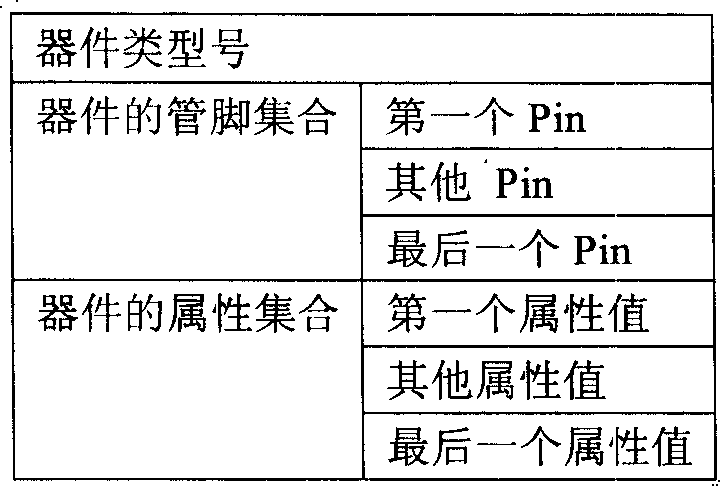
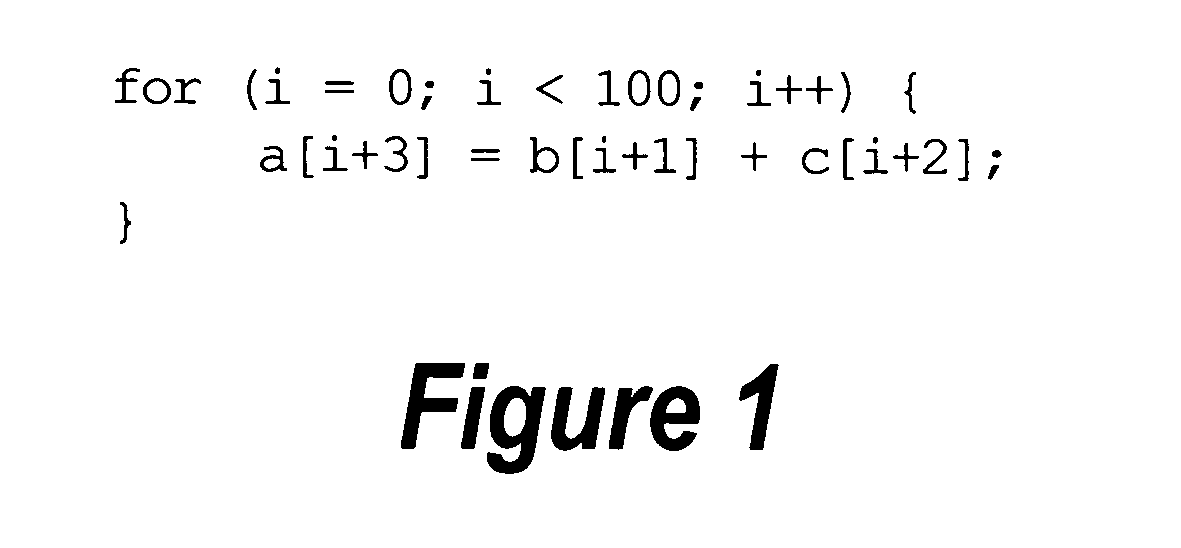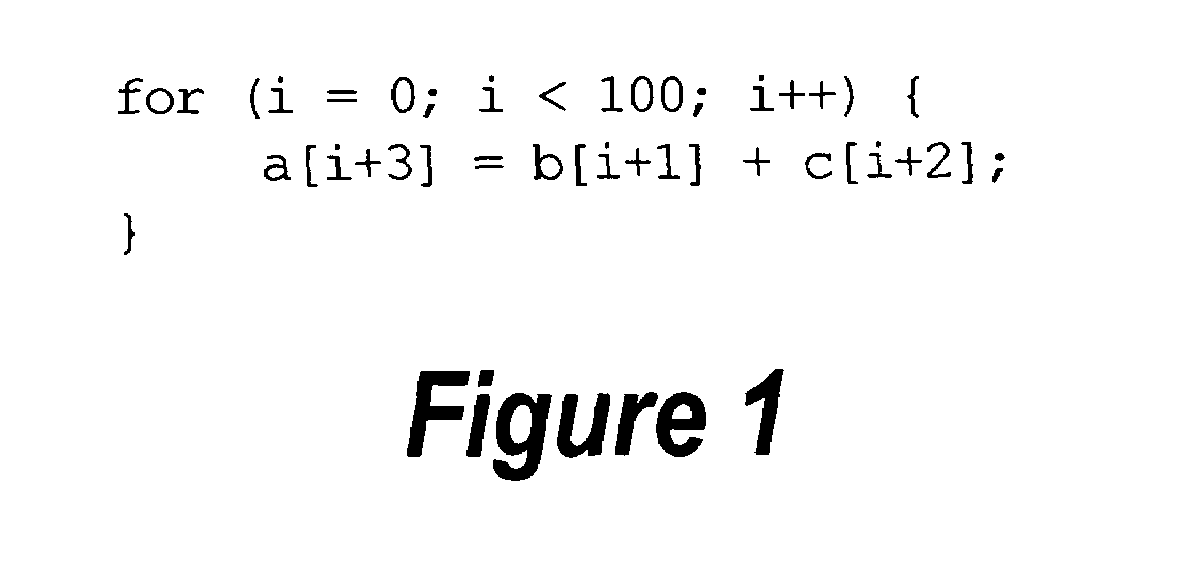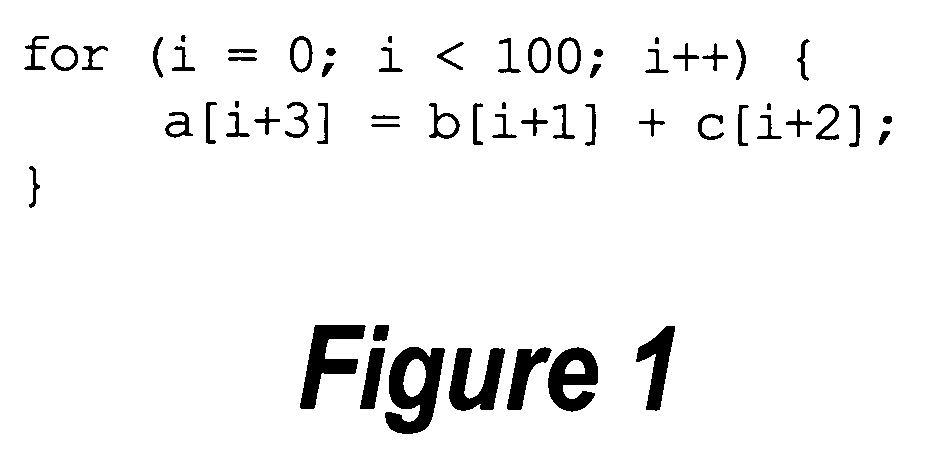Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
266 results about "Data reorganization" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
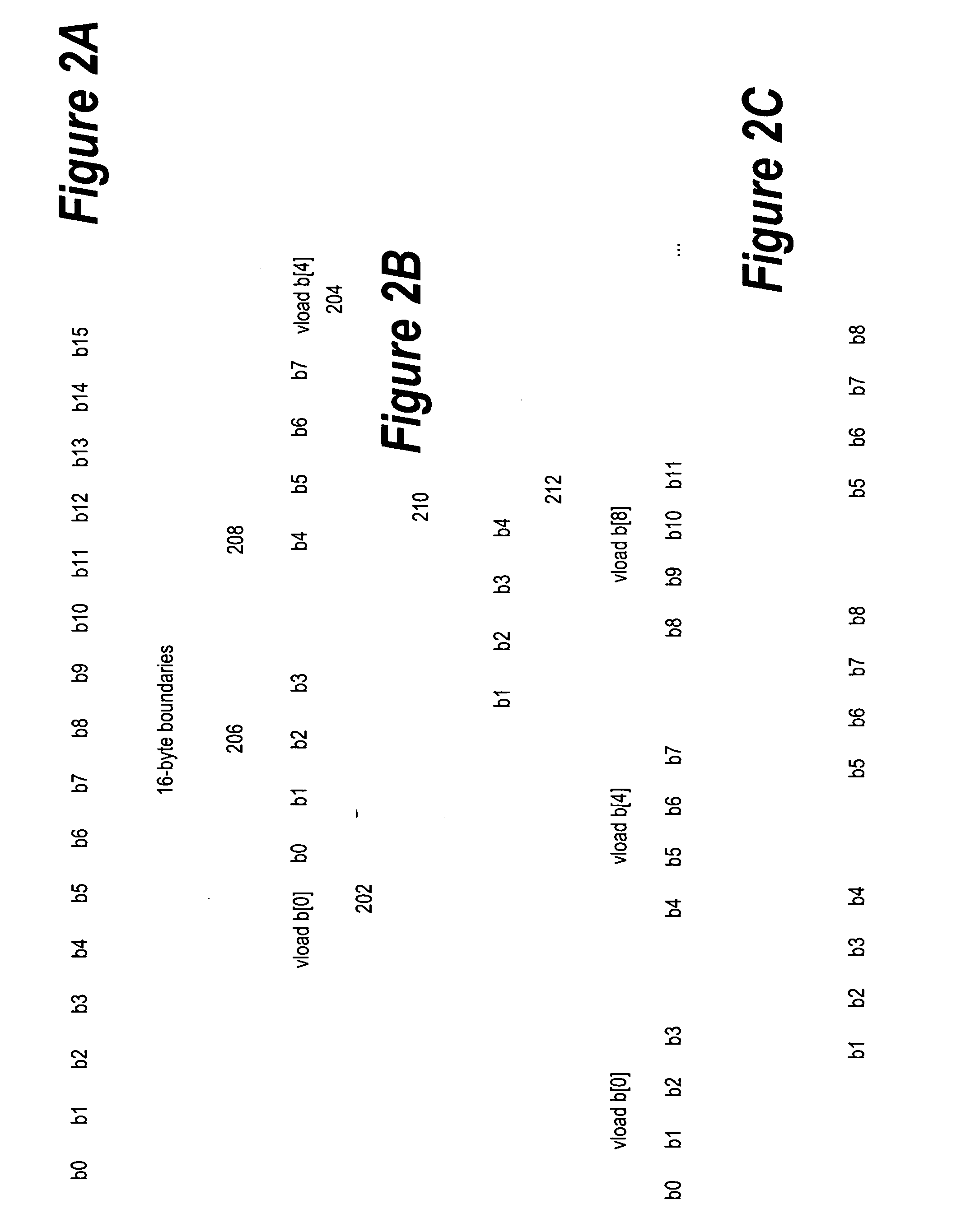
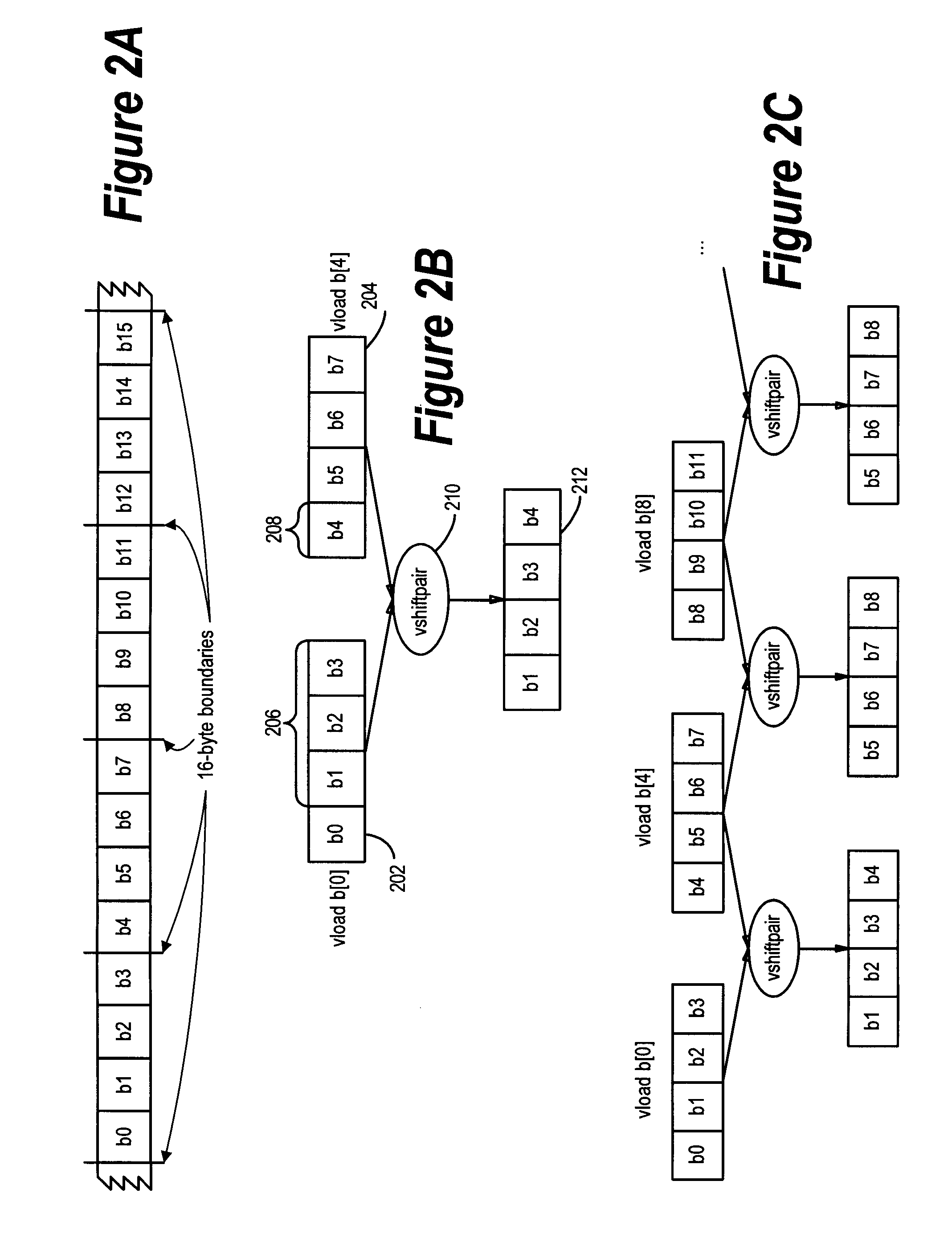
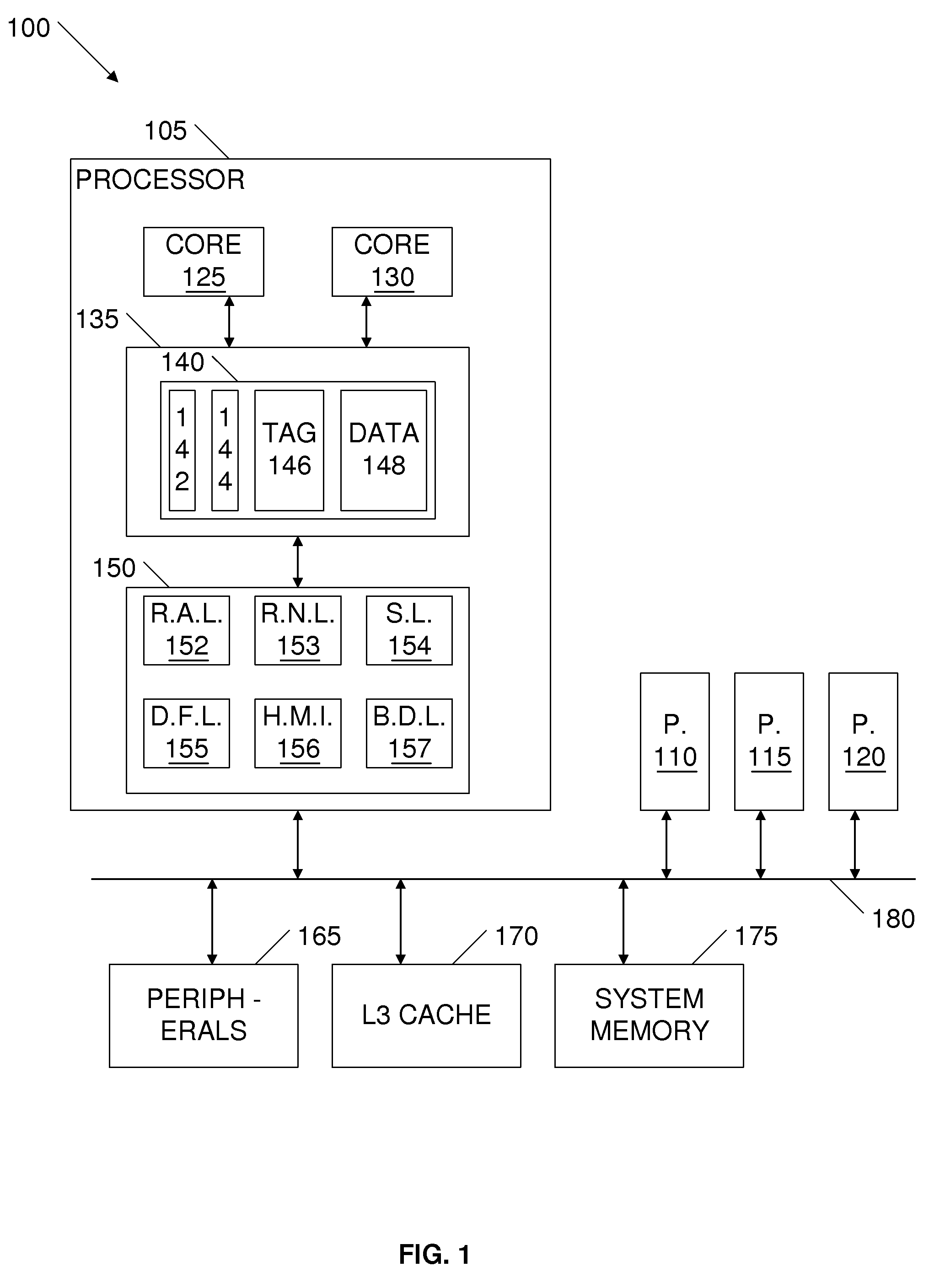
Framework for efficient code generation using loop peeling for SIMD loop code with multiple misaligned statements
InactiveUS20050283773A1Reduce computational overheadIncrease computational overheadSoftware engineeringGeneral purpose stored program computerData reorganizationSteady state
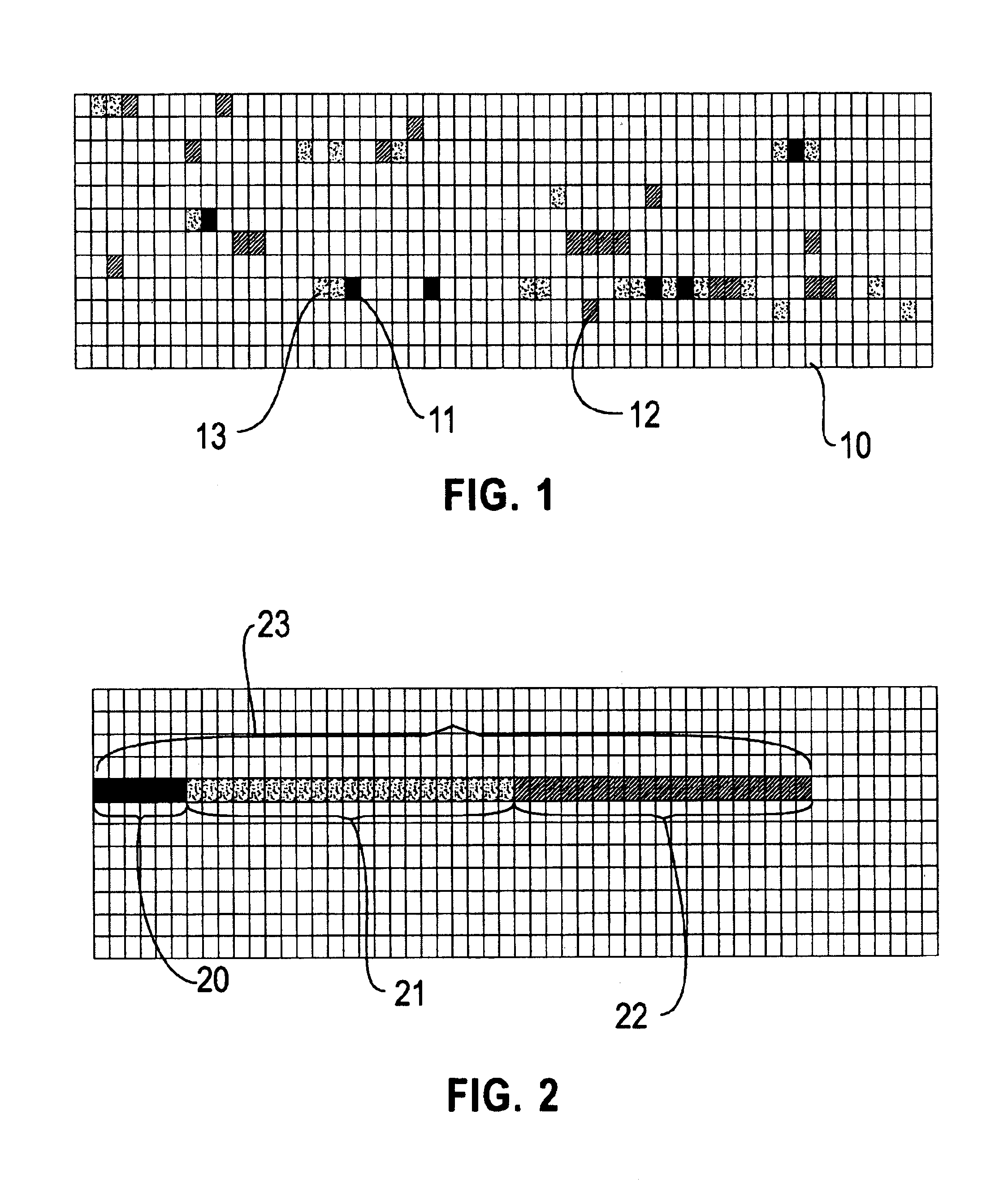
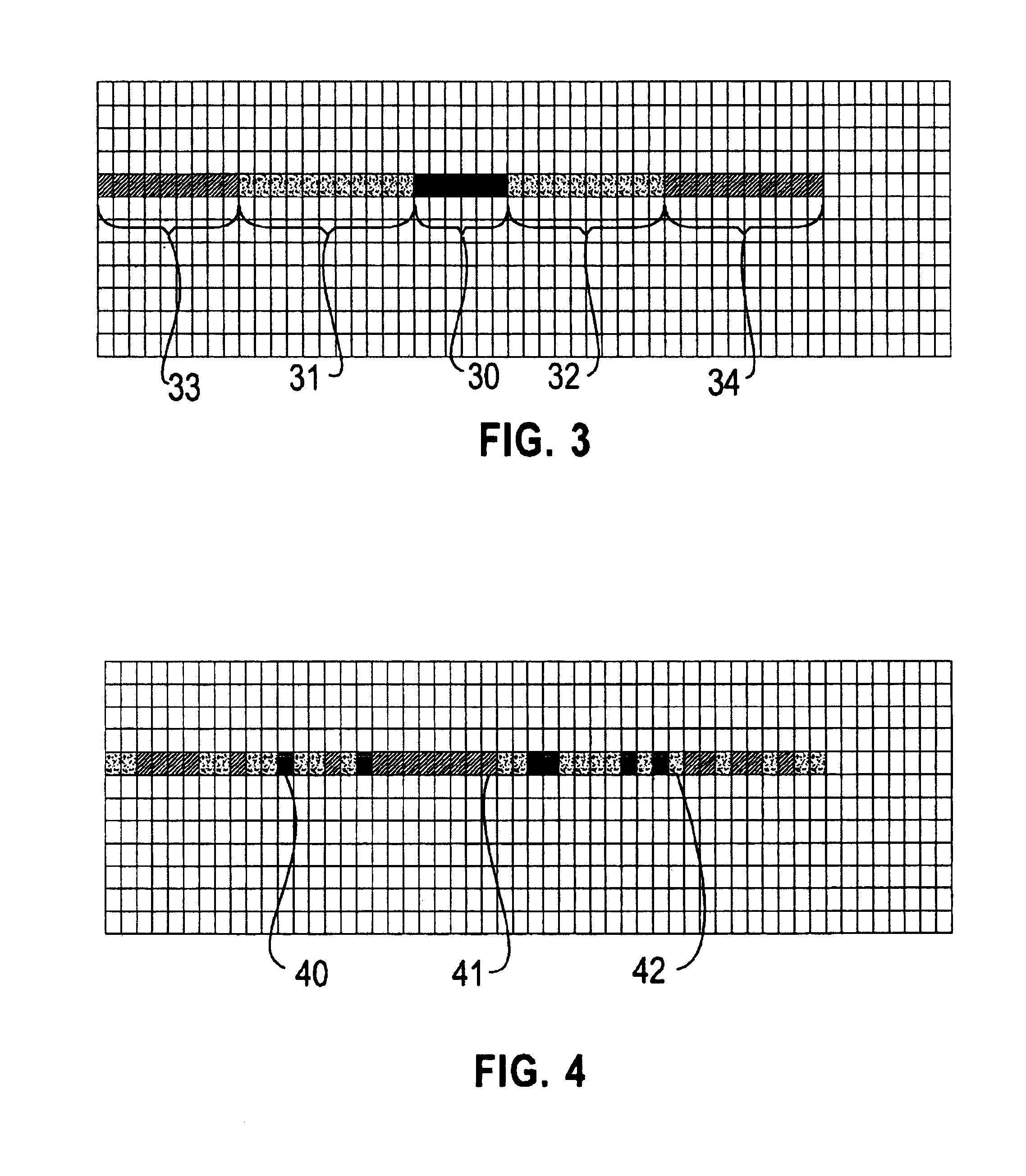
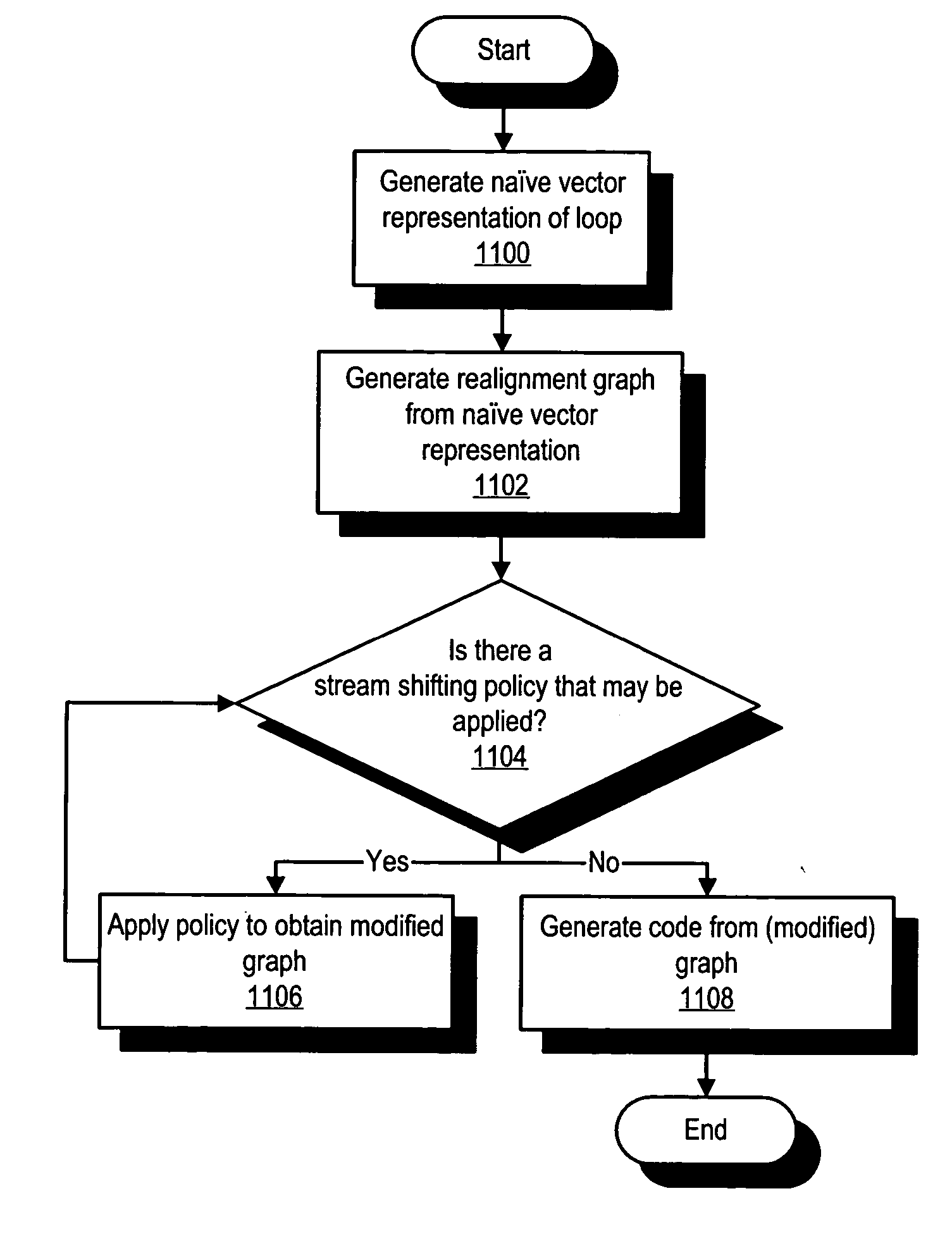
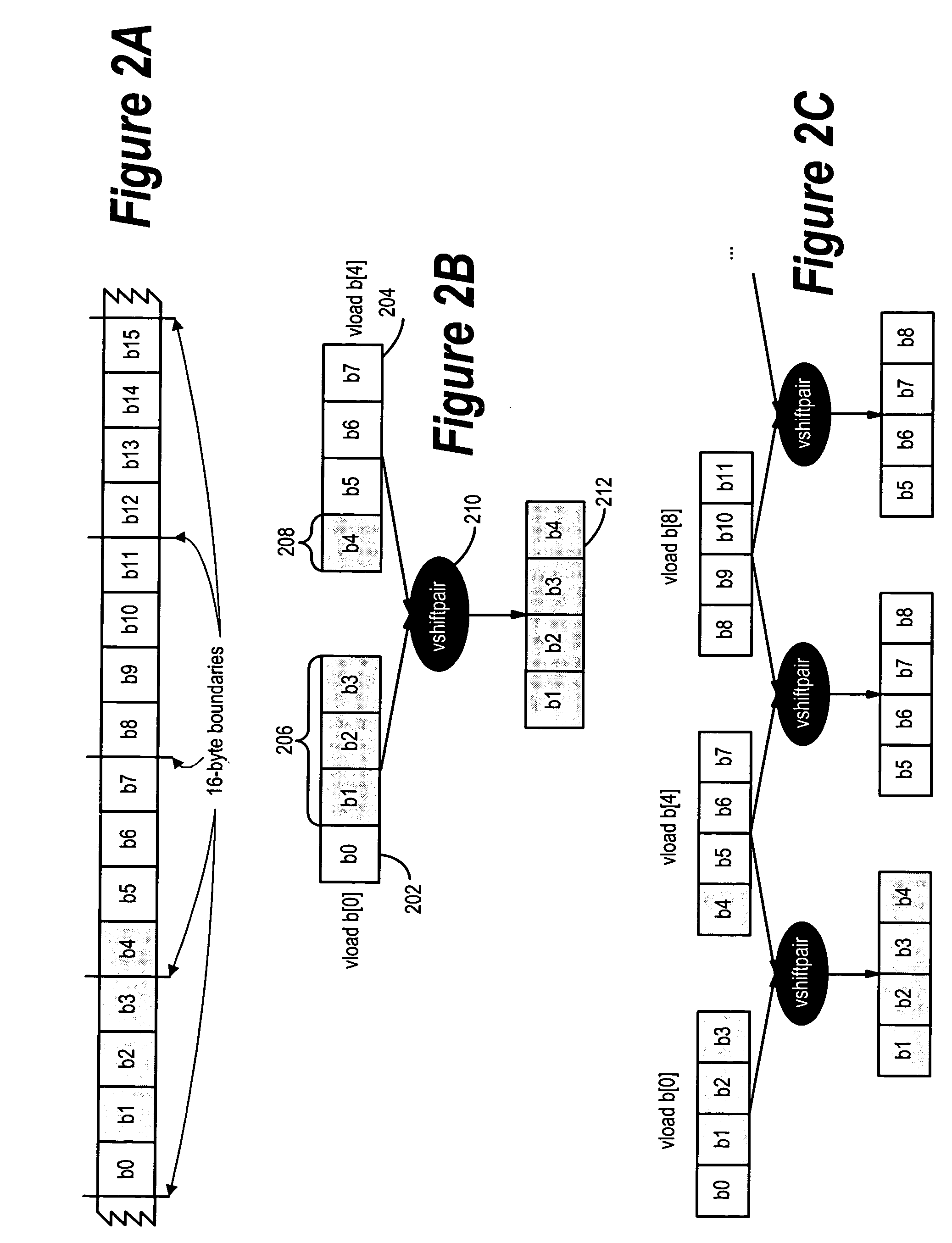
A system and method is provided for vectorizing misaligned references in compiled code for SIMD architectures that support only aligned loads and stores. In this framework, a loop is first simdized as if the memory unit imposes no alignment constraints. The compiler then inserts data reorganization operations to satisfy the actual alignment requirements of the hardware. Finally, the code generation algorithm generates SIMD codes based on the data reorganization graph, addressing realistic issues such as runtime alignments, unknown loop bounds, residual iteration counts, and multiple statements with arbitrary alignment combinations. Loop peeling is used to reduce the computational overhead associated with misaligned data. A loop prologue and epilogue are peeled from individual iterations in the simdized loop, and vector-splicing instructions are applied to the peeled iterations, while the steady-state loop body incurs no additional computational overhead.
Owner:IBM CORP
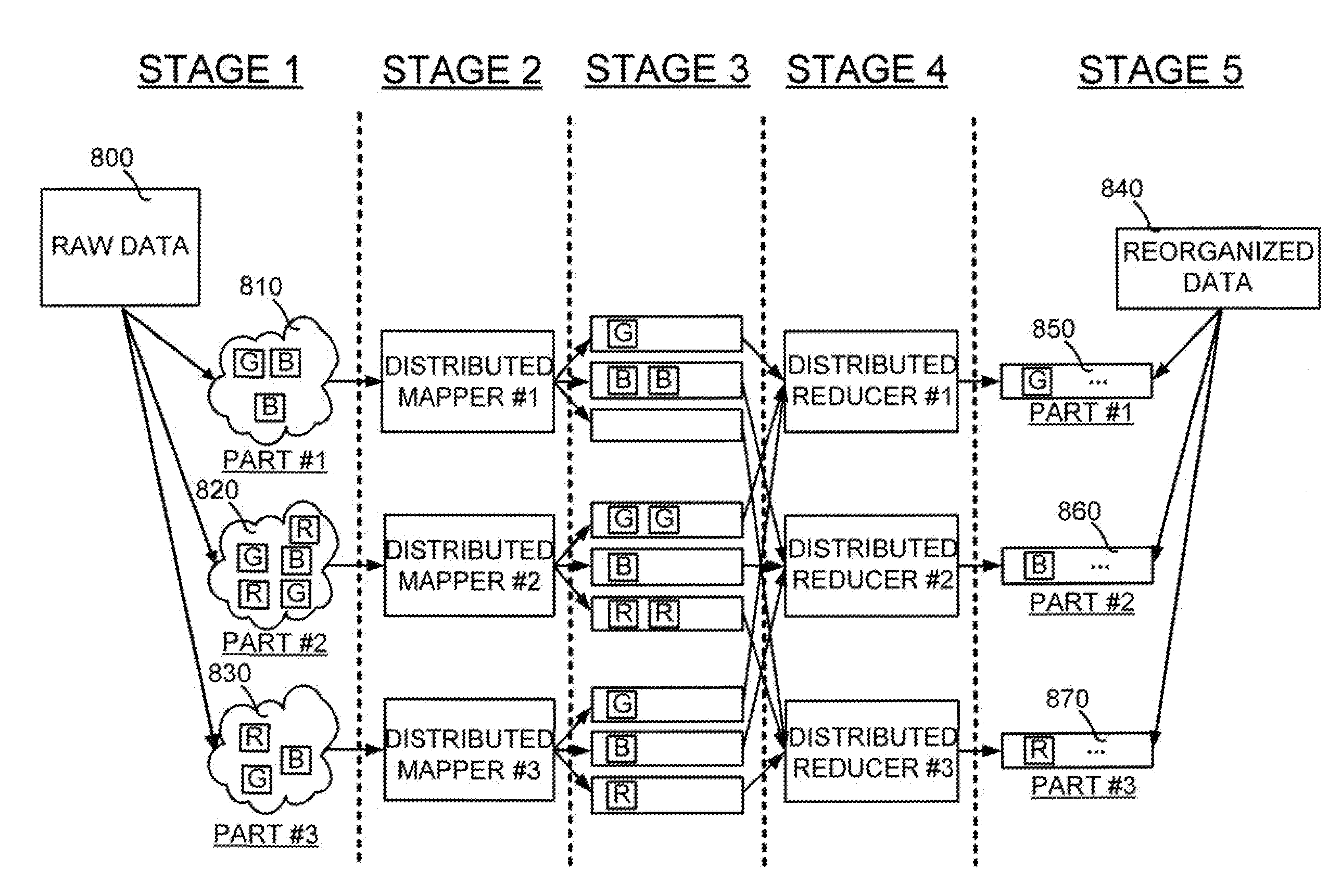
Distributed data reorganization for parallel execution engines
InactiveUS20100281078A1Lower barrier to entryHigh acceptanceDigital data information retrievalDigital data processing detailsGeneral purposeOriginal data
A distributed data reorganization system and method for mapping and reducing raw data containing a plurality of data records. Embodiments of the distributed data reorganization system and method operate in a general-purpose parallel execution environment that use an arbitrary communication directed acyclic graph. The vertices of the graph accept multiple data inputs and generate multiple data inputs, and may be of different types. Embodiments of the distributed data reorganization system and method include a plurality of distributed mappers that use a mapping criteria supplied by a developer to map the plurality of data records to data buckets. The mapped data record and data bucket identifications are input for a plurality of distributed reducers. Each distributed reducer groups together data records having the same data bucket identification and then uses a merge logic supplied by the developer to reduce the grouped data records to obtain reorganized data.
Owner:MICROSOFT TECH LICENSING LLC
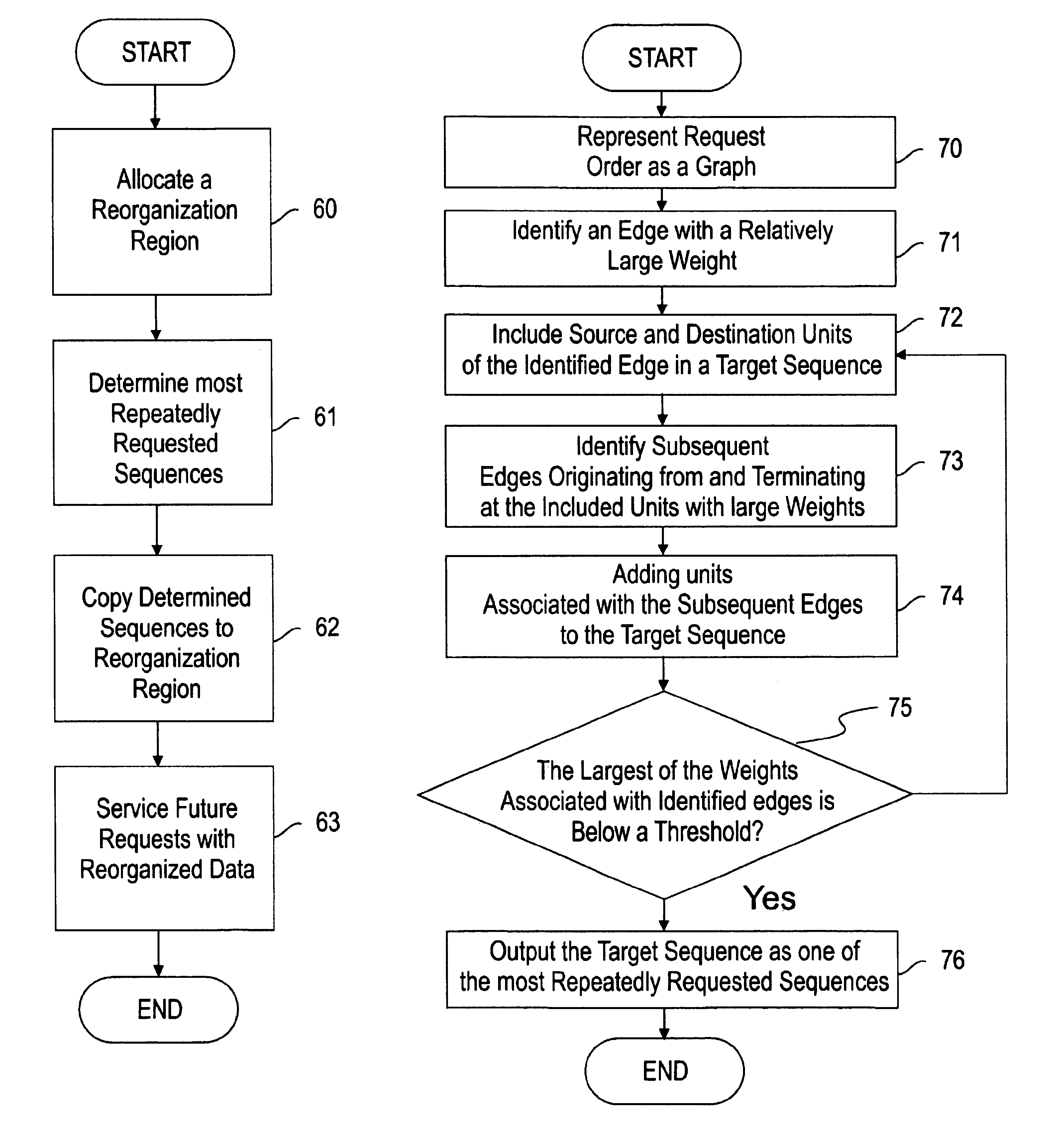
Storage system and method for reorganizing data to improve prefetch effectiveness and reduce seek distance
InactiveUS6963959B2Improve spatial localityImprove system performanceInput/output to record carriersMemory adressing/allocation/relocationData reorganizationDatabase
A data storage system and method for reorganizing data to improve the effectiveness of data prefetching and reduce the data seek distance. A data reorganization region is allocated in which data is reorganized to service future requests for data. Sequences of data units that have been repeatedly requested are determined from a request stream, preferably using a graph where each vertex of the graph represents a requested data unit and each edge represents that a destination unit is requested shortly after a source unit the frequency of this occurrence. The most frequently requested data units are also determined from the request stream. The determined data is copied into the reorganization region and reorganized according to the determined sequences and most frequently requested units. The reorganized data might then be used to service future requests for data.
Owner:IBM CORP
System and method for efficient data reorganization to satisfy data alignment constraints
InactiveUS20050283769A1Quality improvementMinimize the numberSoftware engineeringProgram controlData reorganizationMajorization minimization
A system and method is provided for vectorizing misaligned references in compiled code for SIMD architectures that support only aligned loads and stores. In the framework presented herein, a loop is first simdized as if the memory unit imposes no alignment constraints. The compiler then inserts data reorganization operations to satisfy the actual alignment requirement of the hardware. Finally, the code generation algorithm generates SIMD codes based on the data reorganization graph, addressing realistic issues such as runtime alignments, unknown loop bounds, residue iteration counts, and multiple statements with arbitrary alignment combinations. Beyond generating a valid simdization, a preferred embodiment further improves the quality of the generated codes. Four stream-shift placement policies are disclosed, which minimize the number of data reorganization generated by the alignment handling.
Owner:IBM CORP
Framework for efficient code generation using loop peeling for SIMD loop code with multiple misaligned statements
InactiveUS7395531B2No additional computational overheadReduce computational overheadSoftware engineeringGeneral purpose stored program computerData reorganizationSteady state
A system and method is provided for vectorizing misaligned references in compiled code for SIMD architectures that support only aligned loads and stores. In this framework, a loop is first simdized as if the memory unit imposes no alignment constraints. The compiler then inserts data reorganization operations to satisfy the actual alignment requirements of the hardware. Finally, the code generation algorithm generates SIMD codes based on the data reorganization graph, addressing realistic issues such as runtime alignments, unknown loop bounds, residual iteration counts, and multiple statements with arbitrary alignment combinations. Loop peeling is used to reduce the computational overhead associated with misaligned data. A loop prologue and epilogue are peeled from individual iterations in the simdized loop, and vector-splicing instructions are applied to the peeled iterations, while the steady-state loop body incurs no additional computational overhead.
Owner:INT BUSINESS MASCH CORP
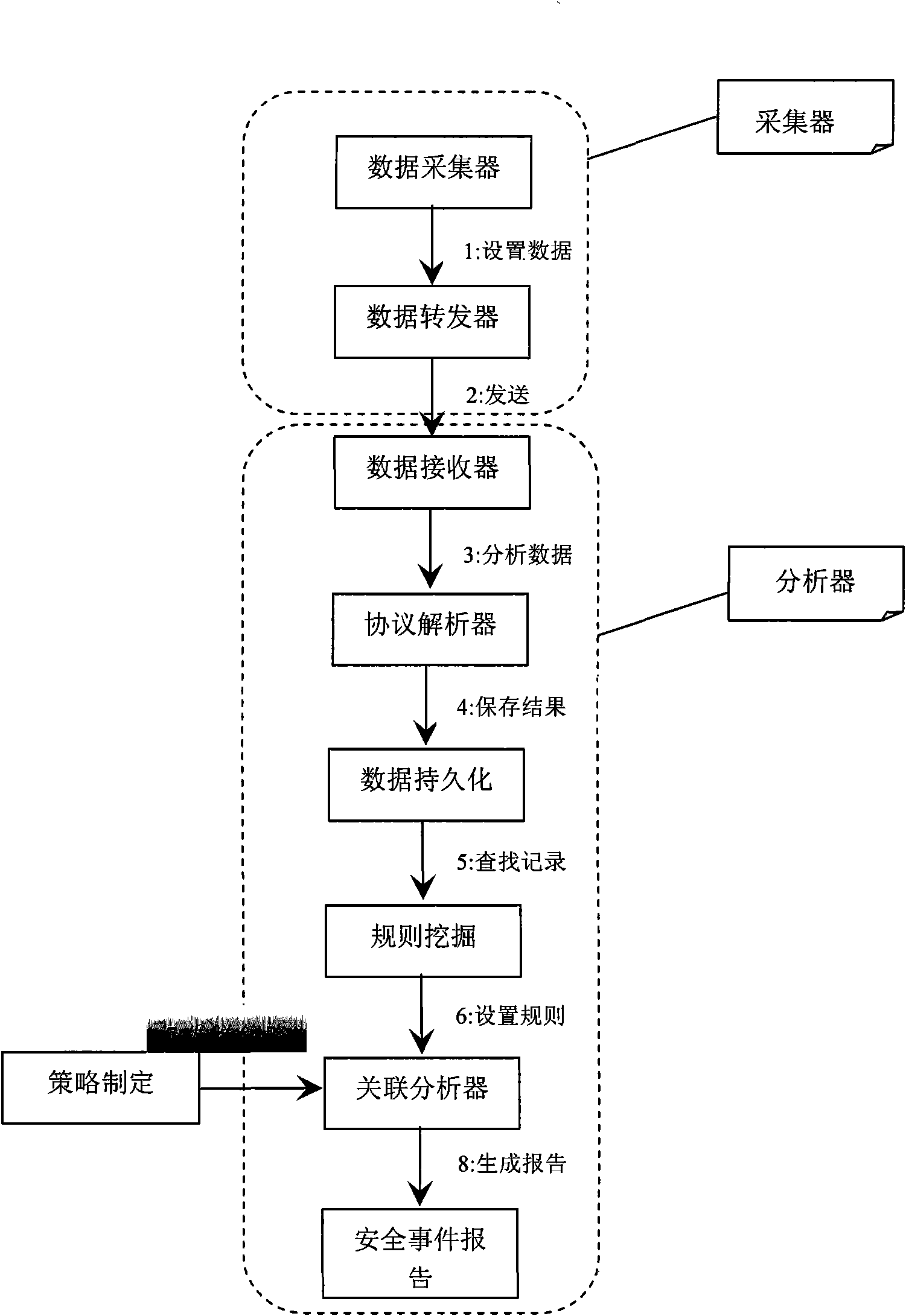
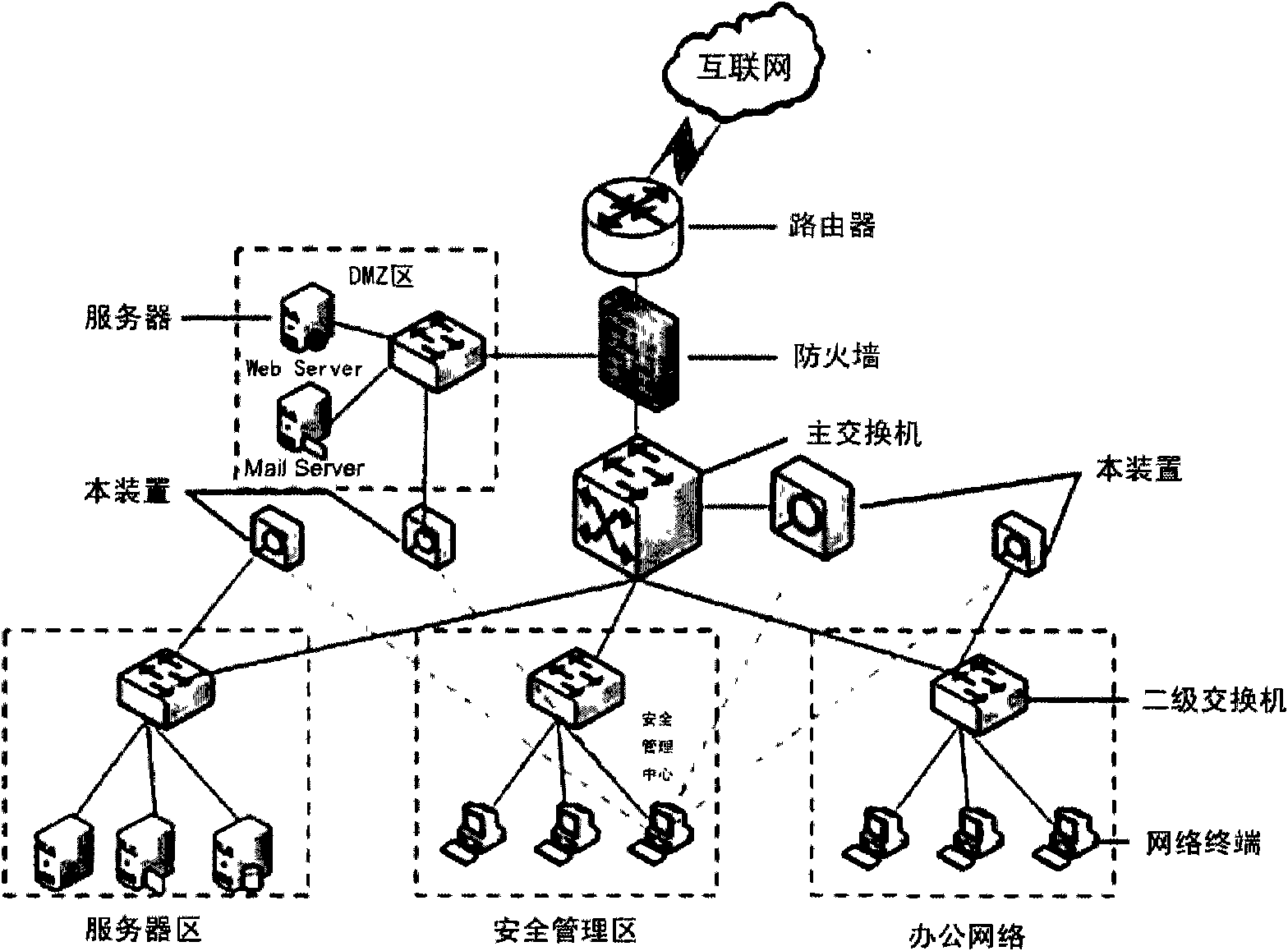
Method and device for detecting Trojans by analyzing network behaviors
InactiveCN101854275AEasy to detectImprove compatibilityData switching networksNetwork behaviorNetwork packet
The invention relates to a method and a device for detecting Trojans by analyzing network behaviors. The Trojans are detected by analyzing and comparing behavior characteristics. The method comprises the following steps of: searching the network behaviors in a local area network; analyzing the representative behavior characteristics of the network behaviors, and detecting the Trojans in real time through the network behaviors such as external linkage of the Trojans, information stealing and outbound information. The device consists of an acquisition device and an analyzer, wherein the acquisition device acquires a network data packet and sends the network data packet to the analyzer; the analyzer reorganizes data, extracts the representative behavior characteristic of the data, performs correlation analysis with a Trojan characteristic library, generates a security event report and presents the security event report to a fore system. The Trojans are detected by using behavior characteristic analysis technology; and compared with the conventional program characteristic code comparison technology, the method of the invention has the advantages of capability of detecting the Trojans in known types and in unknown types, and good detection effect particularly for mutation and variation such as packed and kill-free Trojans.
Owner:军工思波信息科技产业有限公司
Efficient data reorganization to satisfy data alignment constraints
InactiveUS7386842B2Quality improvementMinimize the numberSoftware engineeringProgram controlTheoretical computer scienceData reorganization
An approach is provided for vectorizing misaligned references in compiled code for SIMD architectures that support only aligned loads and stores. In the framework presented herein, a loop is first simdized as if the memory unit imposes no alignment constraints. The compiler then inserts data reorganization operations to satisfy the actual alignment requirement of the hardware. Finally, the code generation algorithm generates SIMD codes based on the data reorganization graph, addressing realistic issues such as runtime alignments, unknown loop bounds, residue iteration counts, and multiple statements with arbitrary alignment combinations. Beyond generating a valid simdization, a preferred embodiment further improves the quality of the generated codes. Four stream-shift placement policies are disclosed, which minimize the number of data reorganization generated by the alignment handling.
Owner:INT BUSINESS MASCH CORP
Method and system for determining optimal data layout using blind justice
Owner:INT BUSINESS MASCH CORP
Data security monitoring method and device, electronic equipment and readable medium
The invention discloses a data security monitoring method and device, electronic equipment and a readable medium, and the method comprises the steps: carrying out the protocol recognition of obtainednetwork flow data, and determining the protocol type of the network flow data; analyzing and recombining the network flow data layer by layer according to the protocol type and the corresponding protocol characteristics to obtain corresponding restored data; and analyzing and detecting the restored data, and determining whether the restored data is abnormal or not. According to different protocoltypes, multi-level data analysis and data recombination are carried out on the obtained network flow data; according to the method, the restored data is acquired by analyzing and detecting the restored data, and whether the restored data is abnormal or not, namely hidden threats, exists in the restored data or not is determined, so that various hidden threats in the network can be discovered in time, and various network attacks with long latency time and complex attack means can be discovered.
Owner:CEC CYBERSPACE GREAT WALL
Data reorganization in non-uniform cache access caches
InactiveUS20100274973A1Reduce access latencyMemory adressing/allocation/relocationData reorganizationWaiting time
Embodiments that dynamically reorganize data of cache lines in non-uniform cache access (NUCA) caches are contemplated. Various embodiments comprise a computing device, having one or more processors coupled with one or more NUCA cache elements. The NUCA cache elements may comprise one or more banks of cache memory, wherein ways of the cache are horizontally distributed across multiple banks. To improve access latency of the data by the processors, the computing devices may dynamically propagate cache lines into banks closer to the processors using the cache lines. To accomplish such dynamic reorganization, embodiments may maintain “direction” bits for cache lines. The direction bits may indicate to which processor the data should be moved. Further, embodiments may use the direction bits to make cache line movement decisions.
Owner:IBM CORP
Method for calculating storage capacity of reservoir
InactiveCN101619972AImprove calculation accuracyOpen water surveyMachines/enginesWater levelData reorganization
The invention discloses a method for calculating storage capacity of a reservoir, which belongs to the field of reservoir operation. The storage capacity of a traditional reservoir is obtained by taking the water level of a dam as a reservoir representative water level and calculating the capacity curve interpolation of the water level. In the method, a reservoir surface is a horizontal plane which takes the water level of the dam as a datum mark and neglects a backwater phenomenon at the tail end of the upper stream at a reservoir area as well as additional gradient influence along the upper stream and the lower stream of the reservoir. For a reservoir of a long narrow riverway type, the length-width ratio of the reservoir is very large, the additional gradient of the upper stream and the lower stream at the reservoir area is also large and the backwater phenomenon is obvious at the tail end of the upper stream, so that the storage capacity of the reservoiro, which is btained by calculating the interpolation according to a traditional method, has larger error and seriously affects the calculation accuracy of reservoir operation. By utilizing a dynamic water surface curve method, the invention carries out integral calculation on the basis of actually measured dynamic water surface curve materials collected at the reservoir area, and the integral calculation comprises three links: unit division calculation, telemetering water-level collection and segmented superposition calculation, wherein the unit division calculation is a core processing link, the telemetering water-level collection is a data reorganization and outfit link and the segmented superposition calculation is a result calculation link.
Owner:STATE GRID ELECTRIC POWER RES INST +1
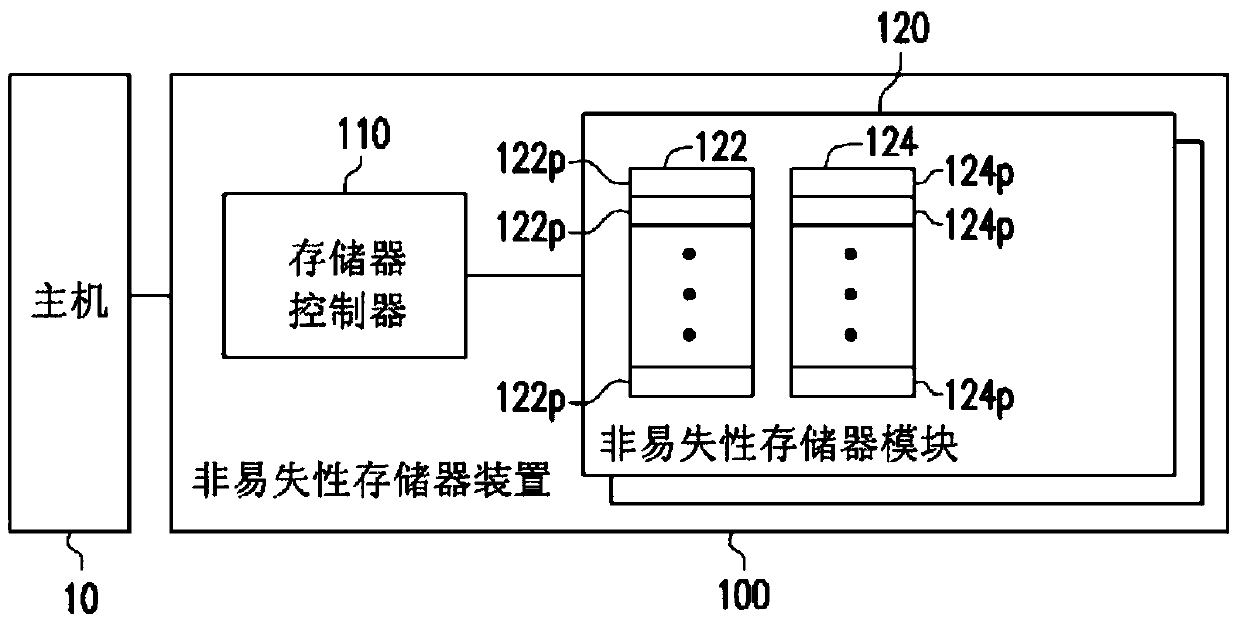
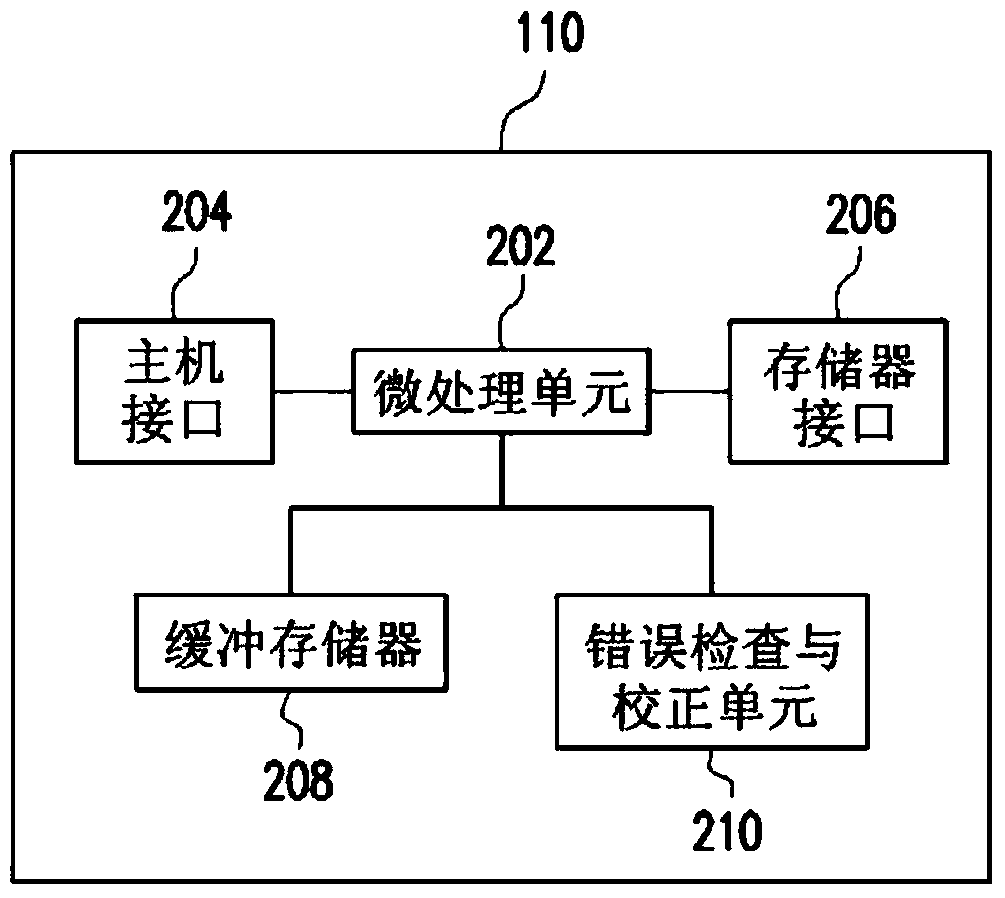
Non-volatile memory device and operation method thereof
ActiveCN103699344AImprove accuracyReduce data volumeInput/output to record carriersMemory adressing/allocation/relocationData reorganizationVolatile memory
The present invention provides a non-volatile memory device and operation method thereof, wherein a non-volatile memory module of the non-volatile memory device includes a first physical block and a second physical block. The operation method includes the steps as follows. The non-volatile memory deviceshould be reformed and a first data reorganization completed restructuring should be wrote in at least one first page of the first physical block. When the non-volatile memory deviceis supplied power again after a power off event, the second physical block is conducted the erasing program. The first data reorganization wrote by the first physical block before the power off event is copied to at least one second page of the second physical block. The non-volatile memory device is continue to reform, and the second data reorganization reformed by the non-volatile memory device after the repeated power supply is wrote to the second physical block. The present invention can avoid the wrong data creating from reforming the non-volatile memory device after repeatedly supplying power to the non-volatile memory device.
Owner:VIA TECH INC
A forward correcting decoding device and control method
InactiveCN1968036AEliminate Bandwidth LimitationsMeet real-time decoding requirementsError preventionTransmission control/equalisingControl mannerForward error correction
The invention relates to a forward correcting decoder and relative control method, wherein said device comprises forward correct FEC decode circuit, frame data divide module and frame data recombine module; the FEC decode circuit has at least two parallel paths; the frame data divide module receives the frame data transmitted via FEC code method, and divides each frame data via word length sequence; feeds divided data sections into each FEC decode circuit and decodes; the frame data recombine module recombines frame data. The invention can avoid bandwidth limit, in GPON network, to send and decode descending data continuously.
Owner:HUAWEI TECH CO LTD
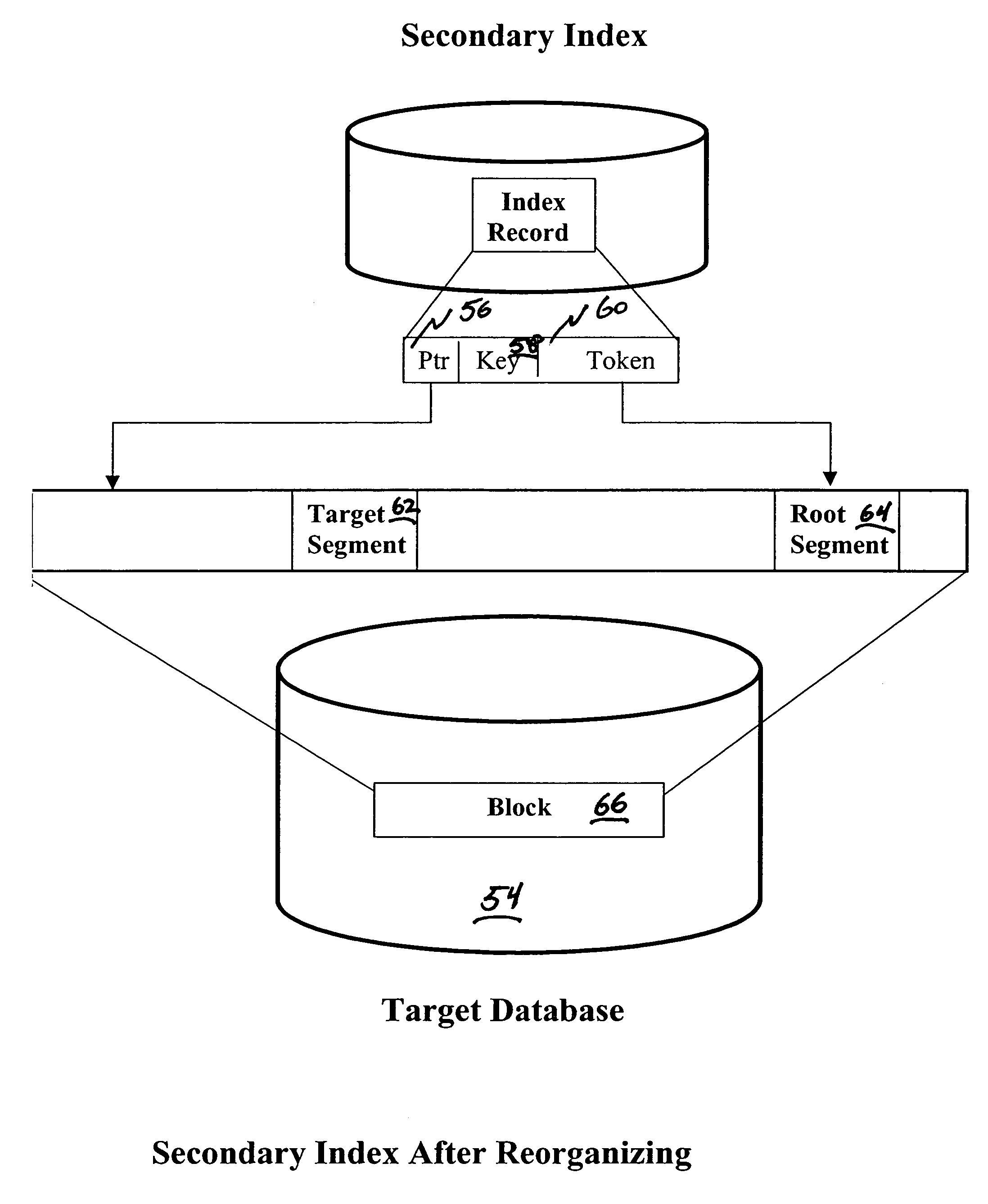
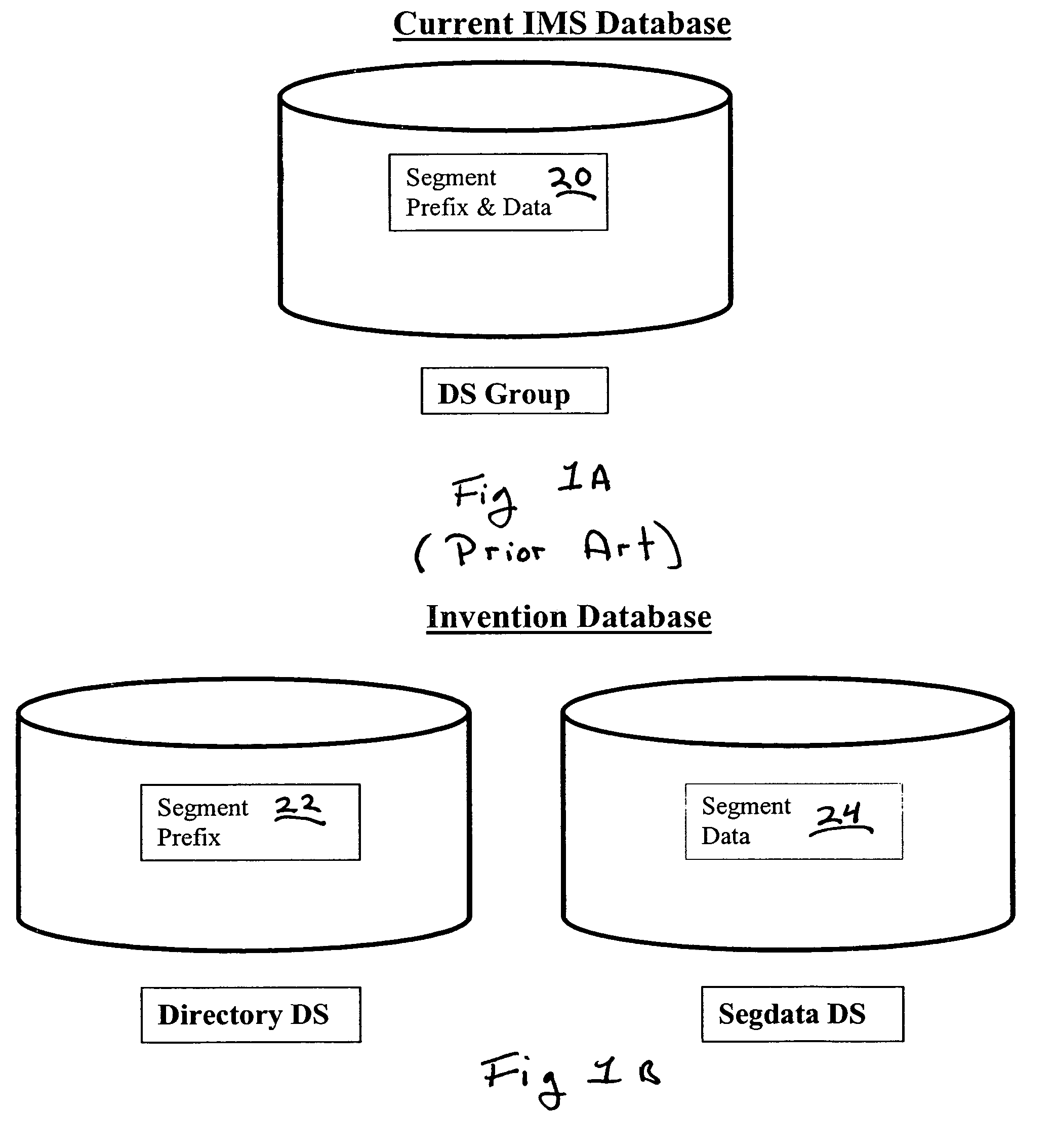
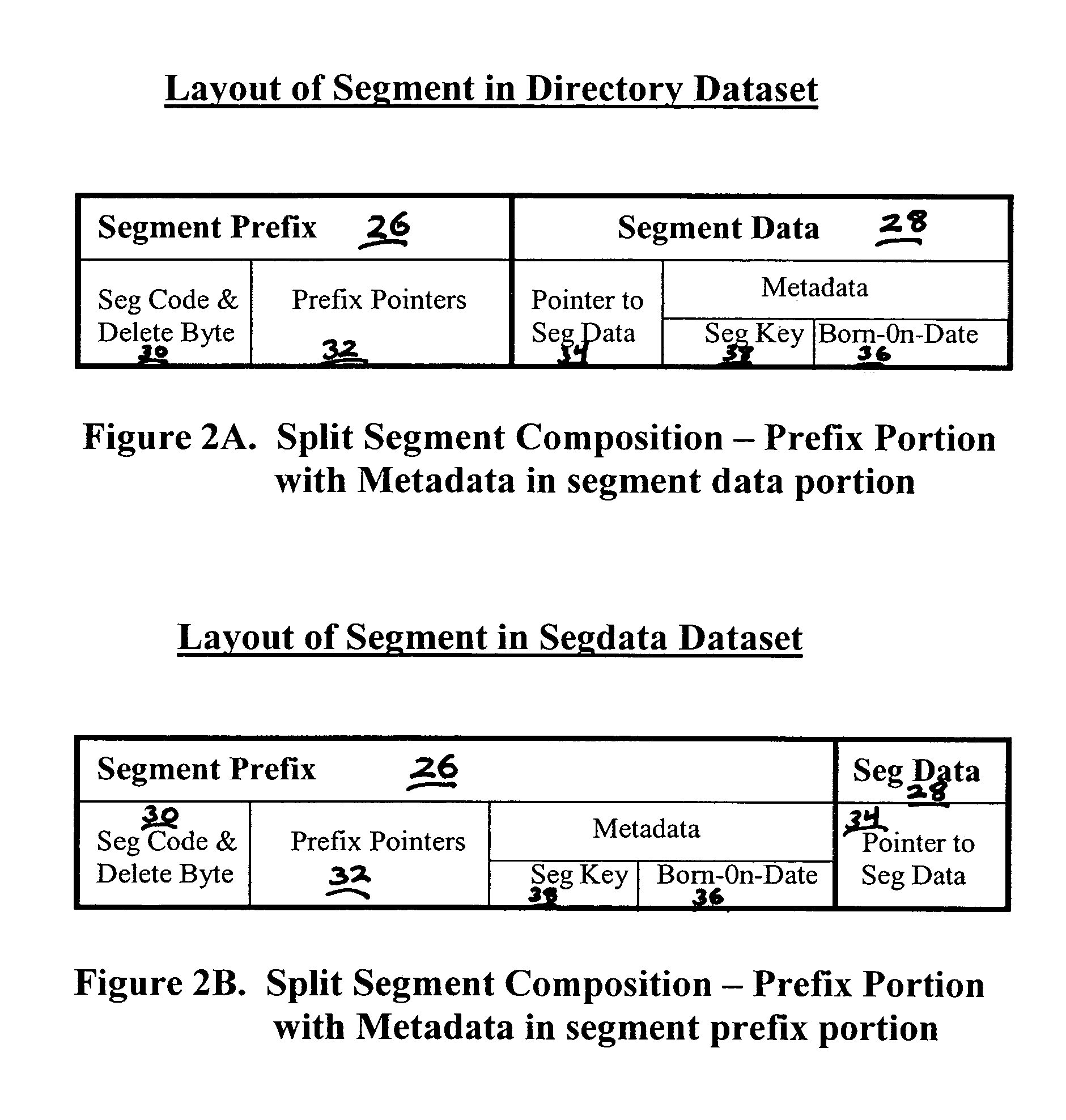
Facilitating maintenance of indexes during a reorganization of data in a database
InactiveUS7228309B1Easy maintenanceExpand databaseData processing applicationsDigital data information retrievalData reorganizationData mining
An index can be maintained during a reorganization of data in a database by retaining each root segment, or the prefix component of each root segment, in its storage location during the reorganization. Correction of an index after a reorganization of data in a database can be facilitated by assigning a unique token to each target segment, or the prefix component of each target segment, and each corresponding index entry having an address to a target segment, prior to a reorganization of data. The unique token for a given target segment, or the prefix component for a given target segment, and the unique token for a corresponding index entry are the same. After a reorganization of data in the database, the unique token of a first index entry is read. Then, the unique token of each target segment, or the prefix component of each target segment, is read until a match is found.
Owner:NEON ENTERPRISE SOFTWARE
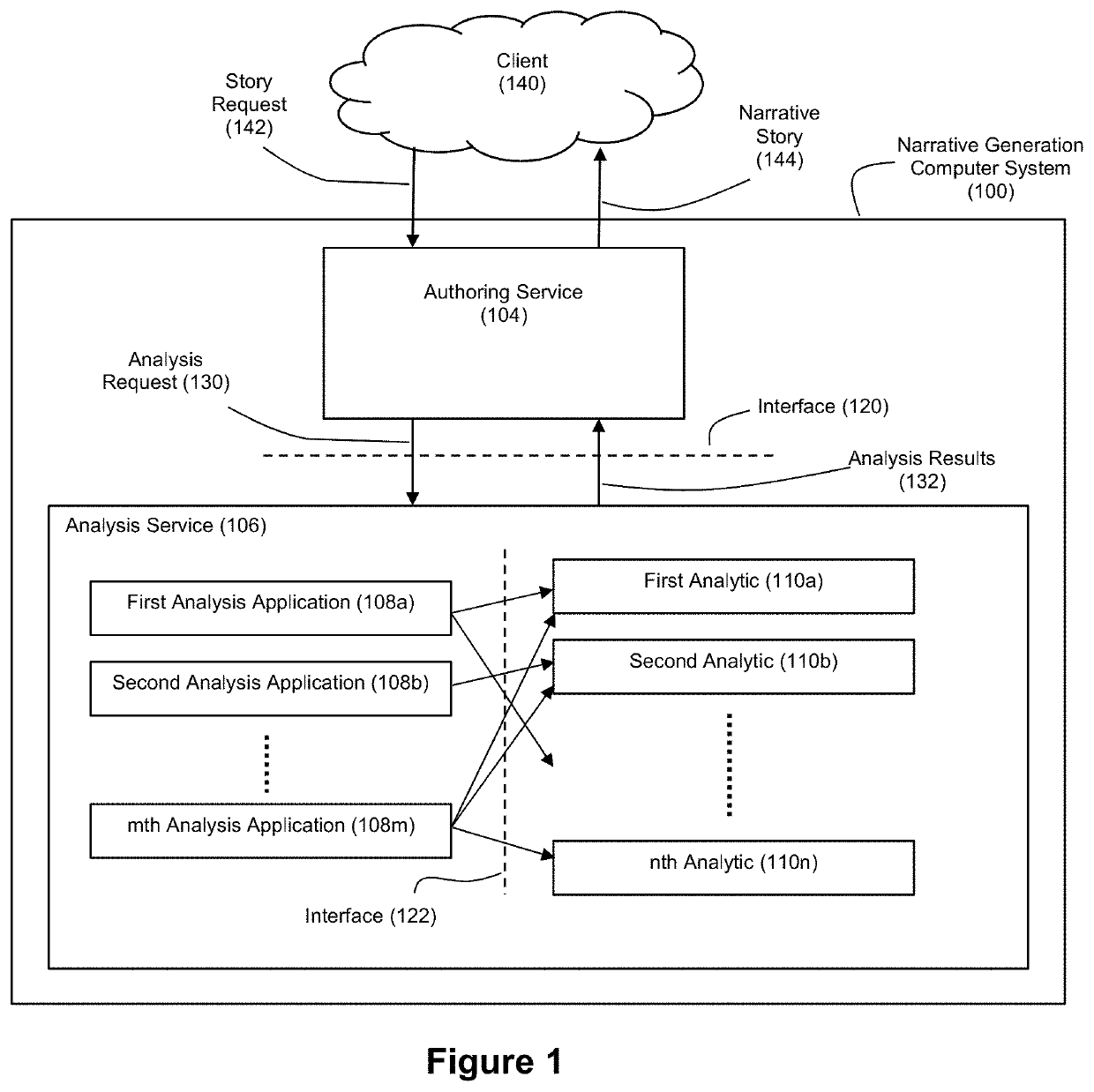
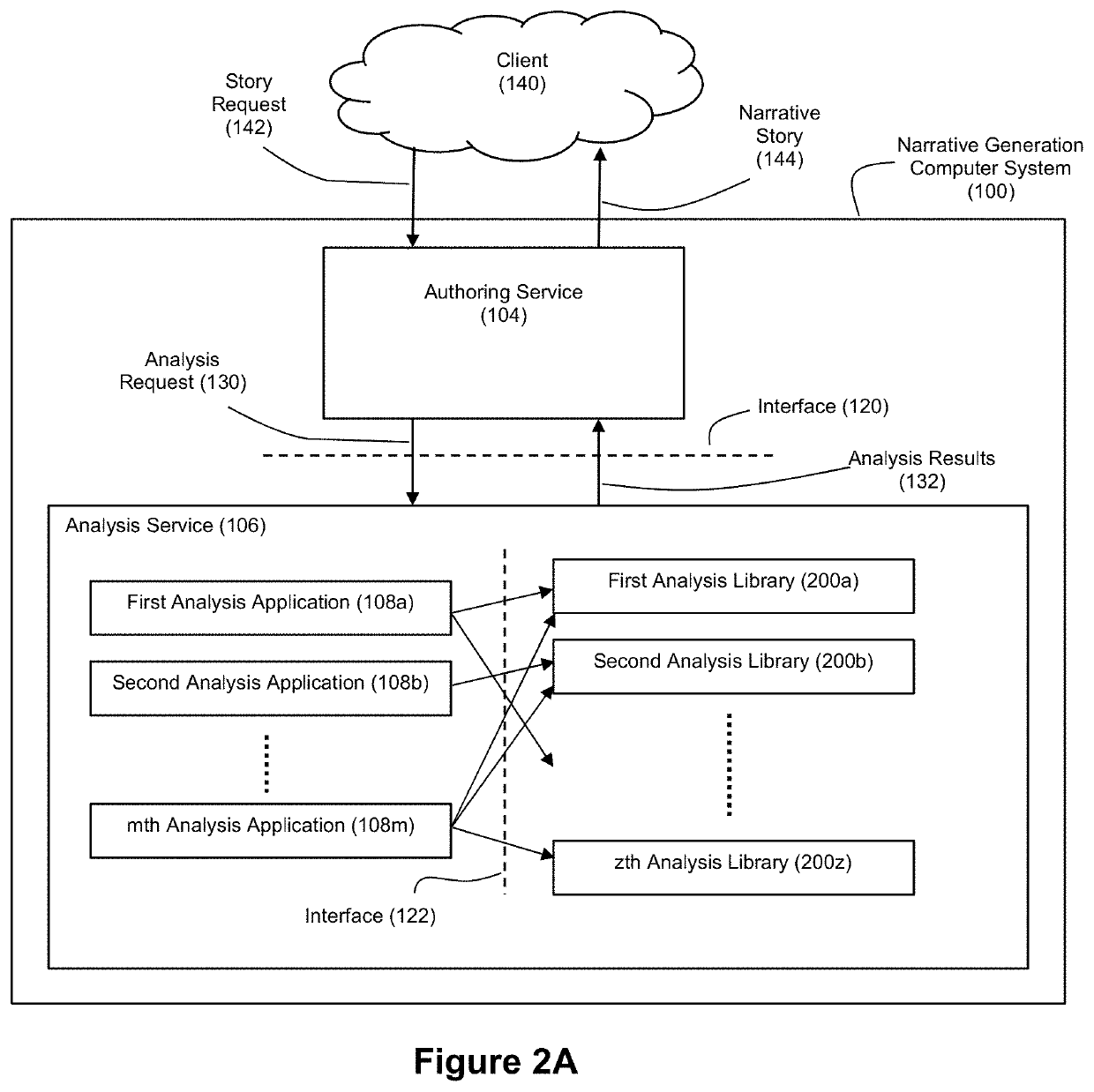
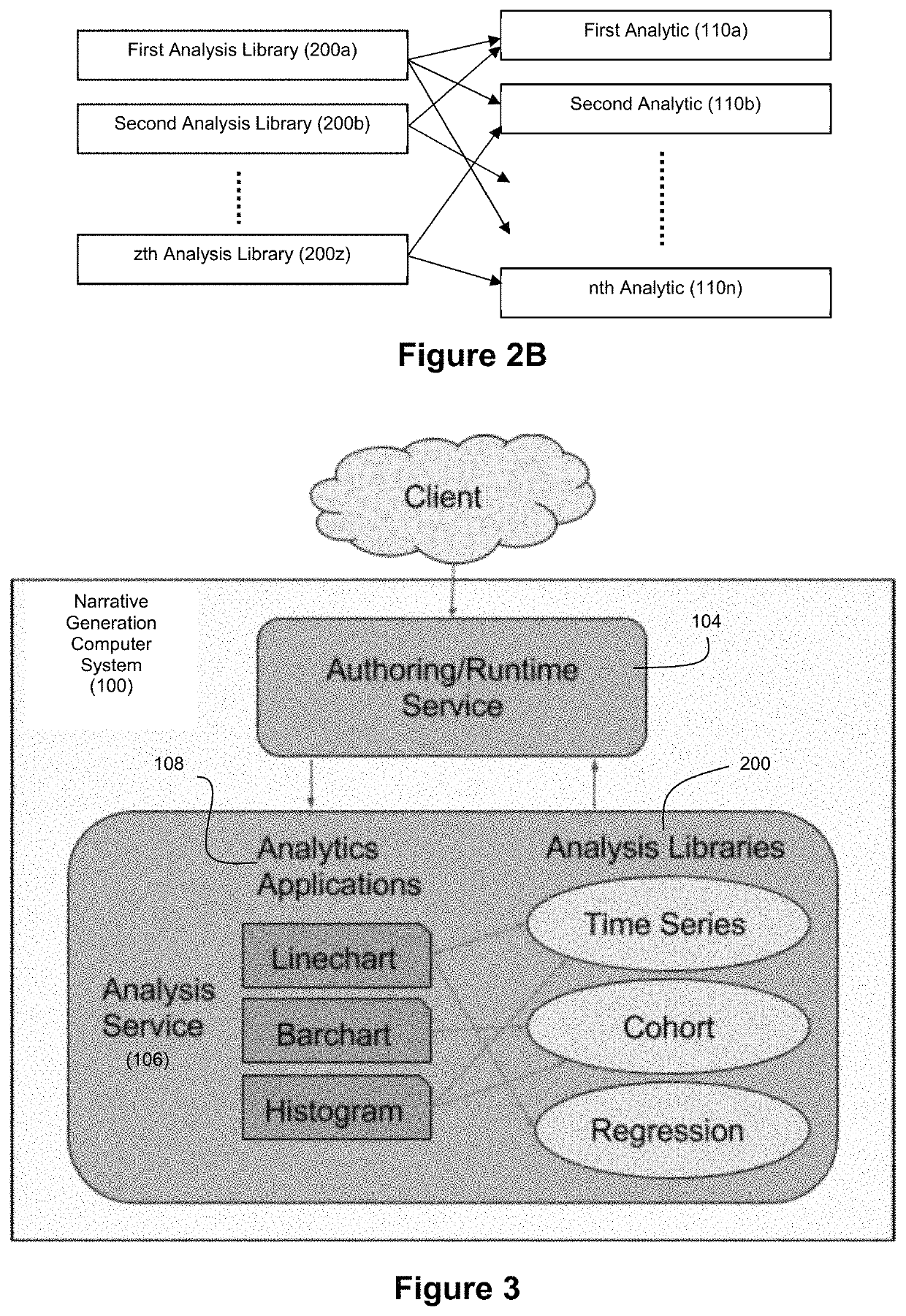
Applied artificial intelligence technology for narrative generation using an invocable analysis service and data re-organization
ActiveUS11003866B1New buildingSimple designNatural language translationMathematical modelsEngineeringData reorganization
Disclosed herein are example embodiments of an improved narrative generation system where an analysis service that executes data analysis logic, including data re-organization logic, that supports story generation is segregated from an authoring service that executes authoring logic for story generation through an interface. Accordingly, when the authoring service needs analysis from the analysis service, it can invoke the analysis service through the interface. By exposing the analysis service to the authoring service through the shared interface, the details of the logic underlying the analysis service are shielded from the authoring service (and vice versa where the details of the authoring service are shielded from the analysis service). Through parameterization of operating variables, the analysis service can thus be designed as a generalized data analysis service that can operate in a number of different content verticals with respect to a variety of different story types.
Owner:NARRATIVE SCI
Domain data format dedicated for parasitic parameter extracting tool
InactiveCN101211376AReduce recombinationSave storage spaceSpecial data processing applicationsNetwork connectionData reorganization
A dominion database format that is specially used in parasitic parameter extraction tools belongs to the technical field of IC CAD. When using a regular dominion database to perform parasitic parameter extraction, the efficiency of searching, reading and input data organization with the parasitic parameter extraction tool is not high. The invention provides a ZPD format database, which is a special-purpose dominion database format for the parasitic parameter extraction tools. The special-purpose dominion data format can establish quick indexes for polygon data as well as the bodies of bus network that are distributed inside different layers; define and save the network connection relationship and the element data type of component information, so as to reduce unnecessary data recombination; compress the storage space for the dominion coordinate data; store relevant element data into a continuous space and eliminate redundant information, so as to improve data-reading speed; the invention can considerably improve the capacity of searching, reading and input data organization for parasitic parameter extraction tools.
Owner:北京华大九天科技股份有限公司
Efficient Code Generation Using Loop Peeling for SIMD Loop Code with Multiple Misaligned Statements
InactiveUS20080222623A1No additional computational overheadReduce computational overheadSoftware engineeringGeneral purpose stored program computerData reorganizationSteady state
An approach is provided for vectorizing misaligned references in compiled code for SIMD architectures that support only aligned loads and stores. In this framework, a loop is first simdized as if the memory unit imposes no alignment constraints. The compiler then inserts data reorganization operations to satisfy the actual alignment requirements of the hardware. Finally, the code generation algorithm generates SIMD codes based on the data reorganization graph, addressing realistic issues such as runtime alignments, unknown loop bounds, residual iteration counts, and multiple statements with arbitrary alignment combinations. Loop peeling is used to reduce the computational overhead associated with misaligned data. A loop prologue and epilogue are peeled from individual iterations in the simdized loop, and vector-splicing instructions are applied to the peeled iterations, while the steady-state loop body incurs no additional computational overhead.
Owner:INT BUSINESS MASCH CORP
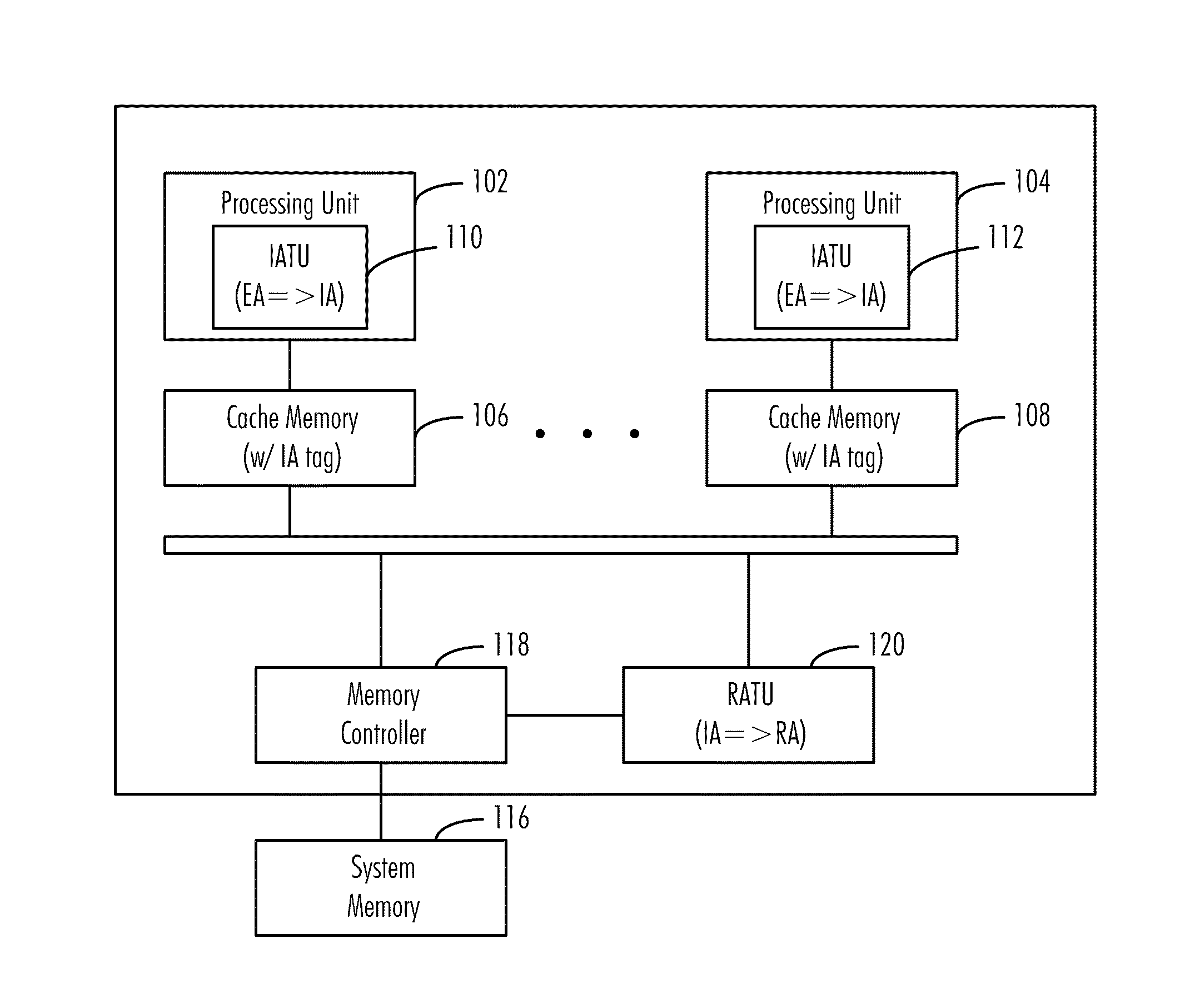
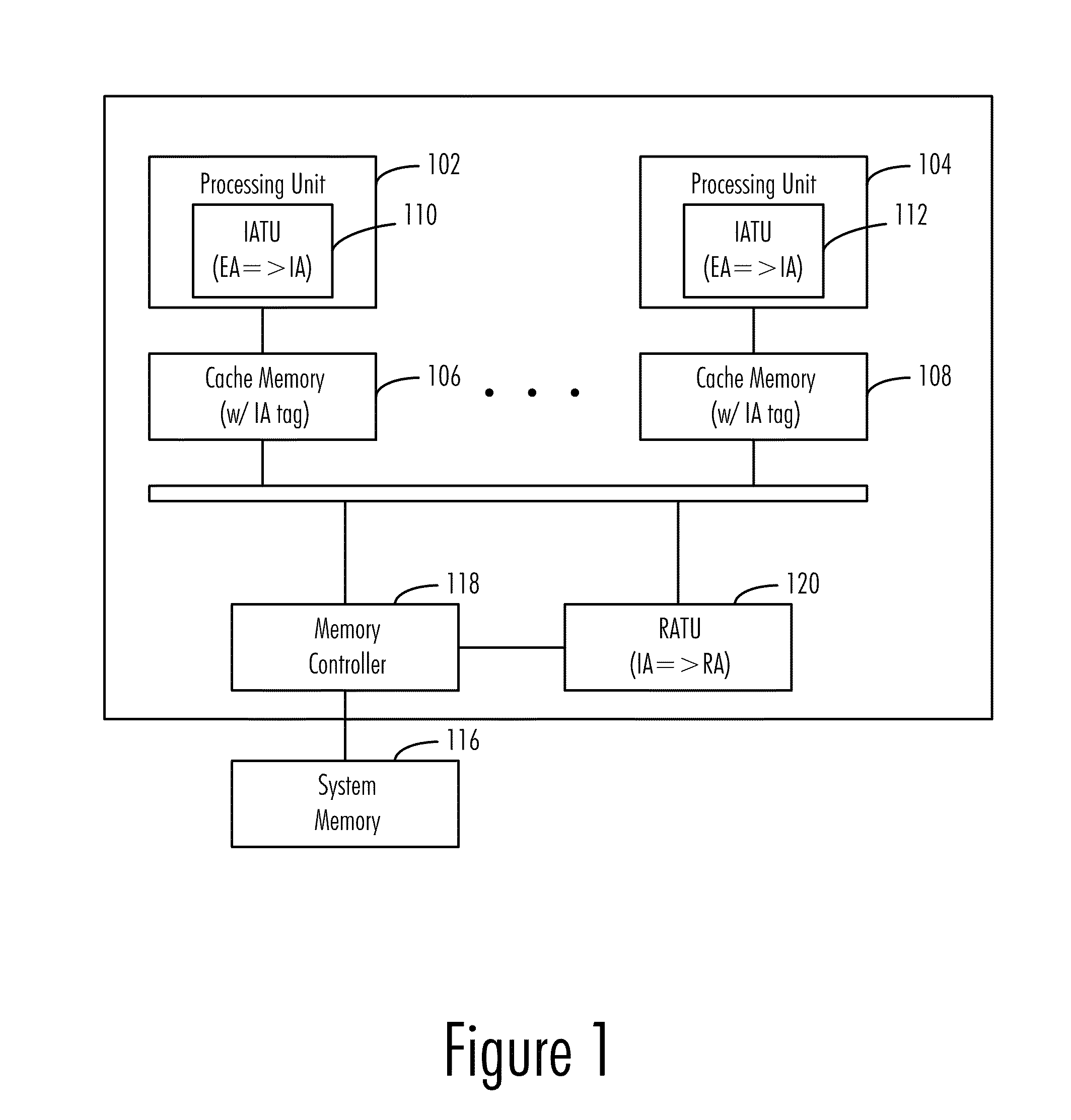
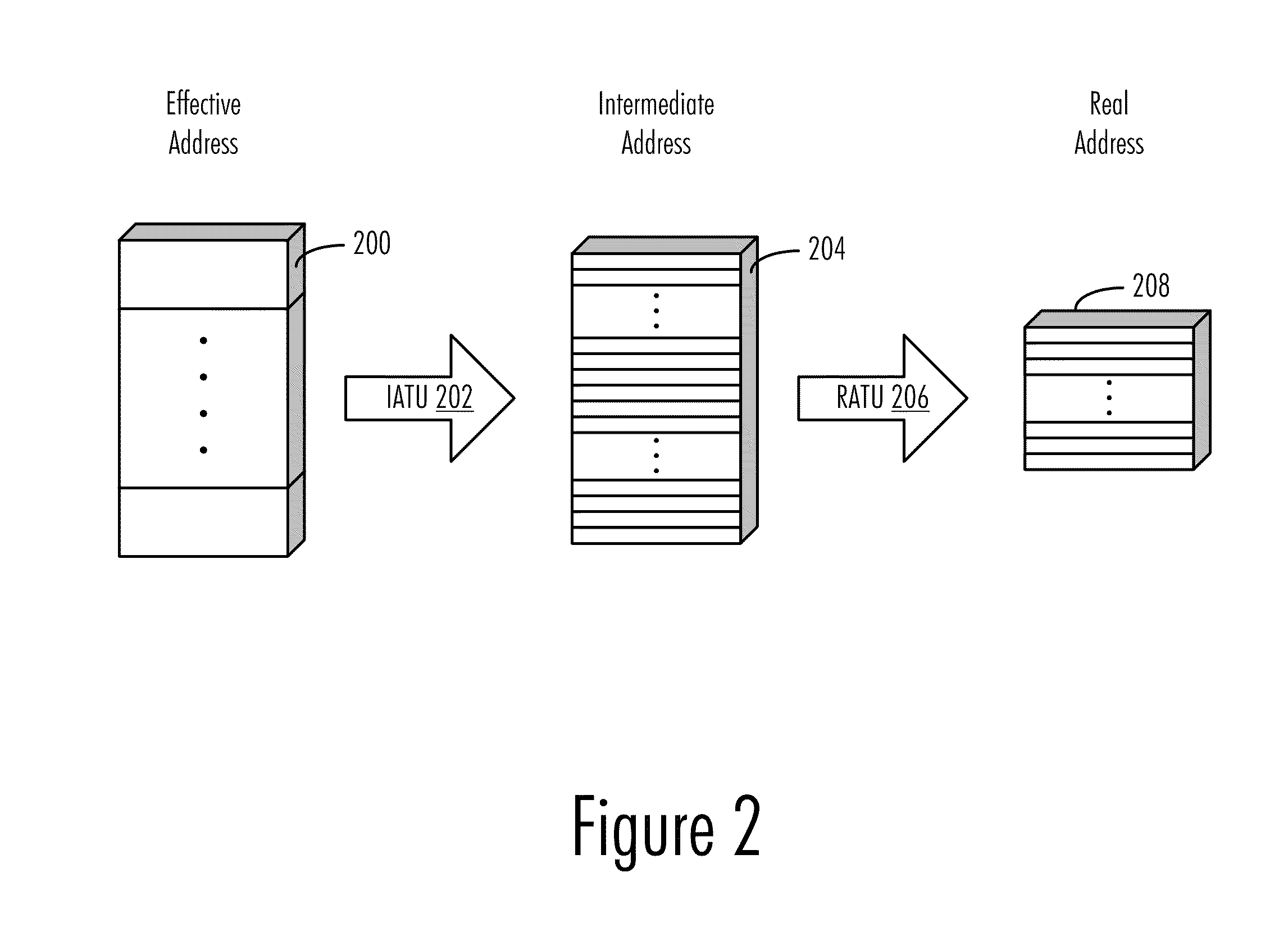
Data Reorganization through Hardware-Supported Intermediate Addresses
InactiveUS20110238946A1Improve performanceImprove efficiencyMemory adressing/allocation/relocationMicro-instruction address formationApplication softwareData reorganization
A virtual address scheme for improving performance and efficiency of memory accesses of sparsely-stored data items in a cached memory system is disclosed. In a preferred embodiment of the present invention, a special address translation unit is used to translate sets of non-contiguous addresses in real memory into contiguous blocks of addresses in an “intermediate address space.” This intermediate address space is a fictitious or “virtual” address space, but is distinguishable from the virtual address space visible to application programs, and in user-level memory operations, effective addresses seen / manipulated by application programs are translated into intermediate addresses by an additional address translation unit for memory caching purposes. This scheme allows non-contiguous data items in memory to be assembled into contiguous cache lines for more efficient caching / access (due to the perceived spatial proximity of the data from the perspective of the processor).
Owner:IBM CORP
Method and system for determining optimal data layout using blind justice
InactiveUS20080168249A1Improve performanceMemory adressing/allocation/relocationProgram controlUser inputData reorganization
Disclosed are a method and system for finding an optimal data layout. The approach of the present invention is to try one of several data layouts in the memory, measure the impact of said one data layout on a performance of a program, and decide which of said several data layouts to try next. The trying and measuring steps are repeated, and one of said several data layouts is selected as best or optimal based on the measurings. The preferred embodiment of the invention provides layout auditing, a framework for picking the best data layout online without requiring any user input. Layout auditing optimizes data layouts with a try-measure-decide feedback loop: use a data reorganizer to try one of several data layouts, use a profiler to measure the impact of the data layout on performance, and use a controller to decide which data layout to try next.
Owner:IBM CORP
Dynamic data restructuring method and system
InactiveUS20090064101A1Digital data processing detailsMultiple digital computer combinationsData reorganizationDynamic data
A data restructuring method and system. The method includes receiving by a computing system from a first user content data arranged in a first specified order and a command for tagging portions of the content data according to various parameters. The computing system assigns identification tags to the portions of the content data. The computing system presents the identification tags to the first user. The computing system receives from the first user, a selection of at least one of the identification tags. The computing system restructures the content data into a second specified order in response to the selection. The computing system receives a request for viewing the content data from a second user. The computing system presents to the second user, the content data in the second specified order.
Owner:IBM CORP
Photonically-enabled in-flight data reorganization
ActiveUS20130243429A1Accelerate reorganizationReduce the amount requiredOptical multiplexTime-division multiplexing selectionData processing systemPhotonics
Data locality constraints are alleviated by a data processing system and method of reorganizing data. Multiple electronic components are configured to modulate a light beam on a shared photonic interconnect and to detect the data according to a global schedule to reorganize data across the multiple electronic components. By constructing data transfer patterns in a shared photonic interconnect, rather than in dedicated reorganization hardware, data is reorganized while in transit, greatly accelerating the reorganization of data, and reducing the amount of power-consuming hardware necessary to achieve the task.
Owner:MASSACHUSETTS INST OF TECH
Method and system for transmitting data
InactiveCN103077149AReduce transfer timeFast data transferElectric digital data processingData transmission timeData reorganization
The invention discloses a method and a system for transmitting data. The method comprises at least one data transmission process, wherein the process comprises the following steps of reading data in a source data storage device; according to the type number of data transmission interfaces and the transmission speed of each type of data transmission interface, dividing the read data into a plurality of first divided data blocks, wherein each first divided data block corresponds to one type of data transmission interface, and the size of each first divided data block is matched with the transmission speed of the data transmission interface corresponding to the first divided data block; according to the number of data caching devices connected with each type of data transmission interface, averagely dividing the data in each first divided data block into a plurality of second divided data blocks; transmitting the data in each second divided data block to the corresponding data caching device; and after performing data reconstitution on the data in the data caching device, transmitting the data to a target data storage device. By the method and the system, the data transmission speed can be improved, and the data transmission time is saved.
Owner:XIAMEN MEIYA PICO INFORMATION
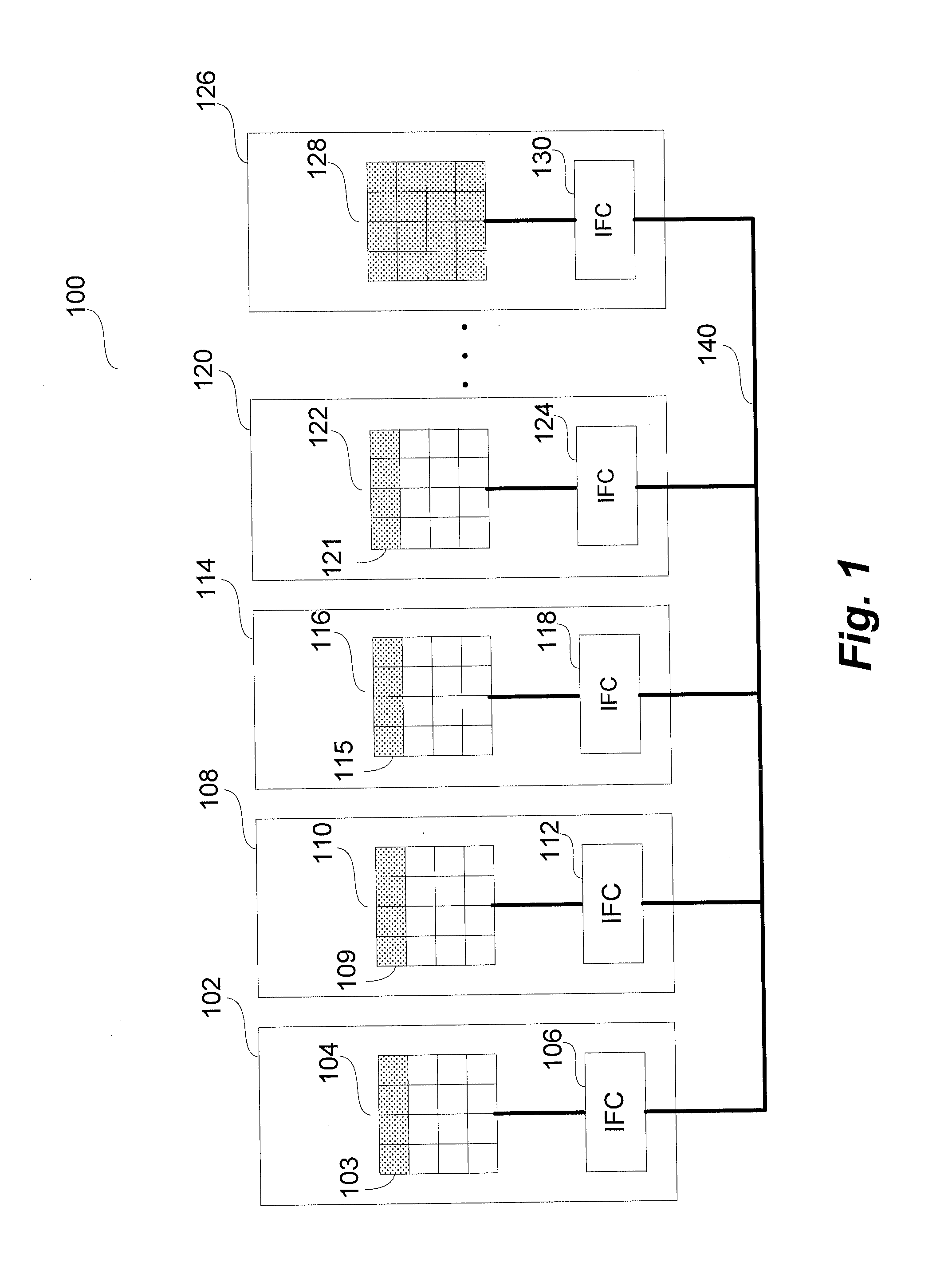
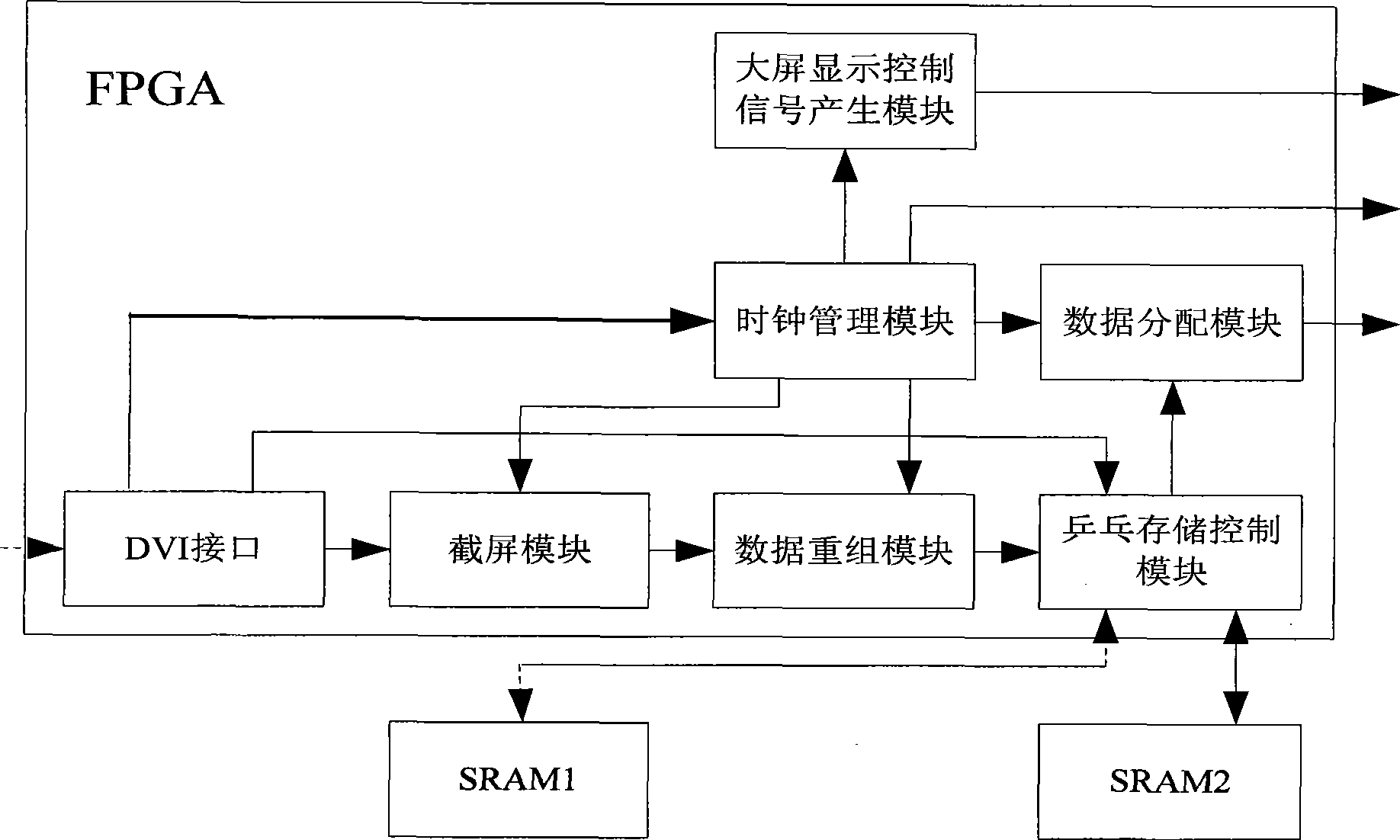
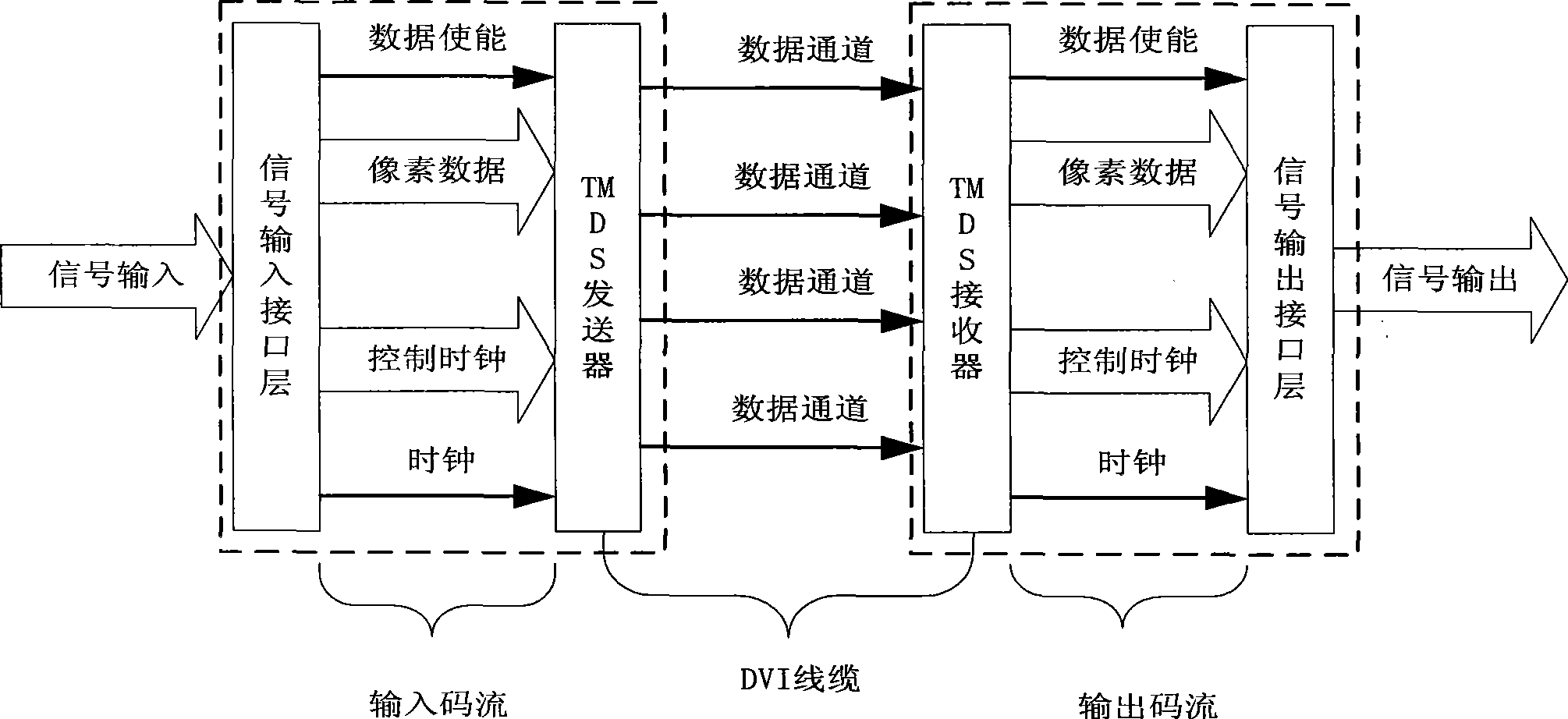
Digital high clear display control device and method
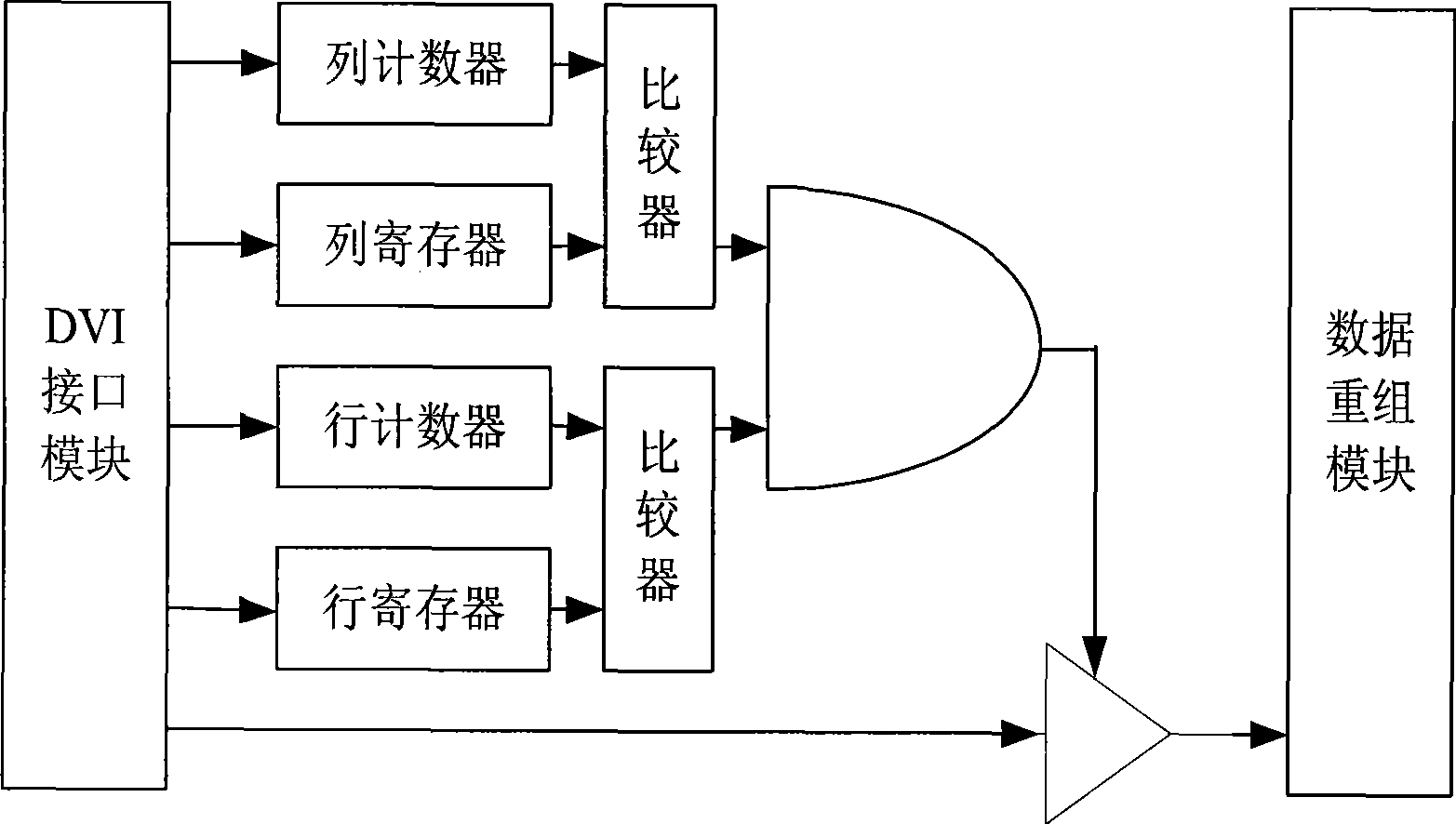
InactiveCN101378483AEasy scan controlImprove the display effectStatic indicating devicesHigh-definition television systemsComputer hardwareComputer module
The invention provides a digital high-definition display controlling device and a method thereof. The method comprises the steps that: a DVI interface module accesses an external video signal and inputs the external video signal to a screen capturing module; the screen capturing module captures the video signal according to a HDTV resolution ratio standard of 1280 multiplied by 720 and transmits the video signal after capturing to a data reorganization module which carries out data reorganization to the video signal and inputs the signal after reorganization to a ping pong storage controlling module which carries out caching storage process to the video data after reorganization and causes the video data to be output continuously to a data distribution module by an HDTV frame frequency of 60Hz; and the data distribution module adjusts the output sequence of the video data and outputs the video data to an LED lattice screen. The device and the method can cause the displaying result of the LED lattice screen to reach an HDTV displaying standard of 1280 multiplied by 720 at 60Hz.
Owner:SHENZHEN JIUZHOU OPTOELECTRONICS
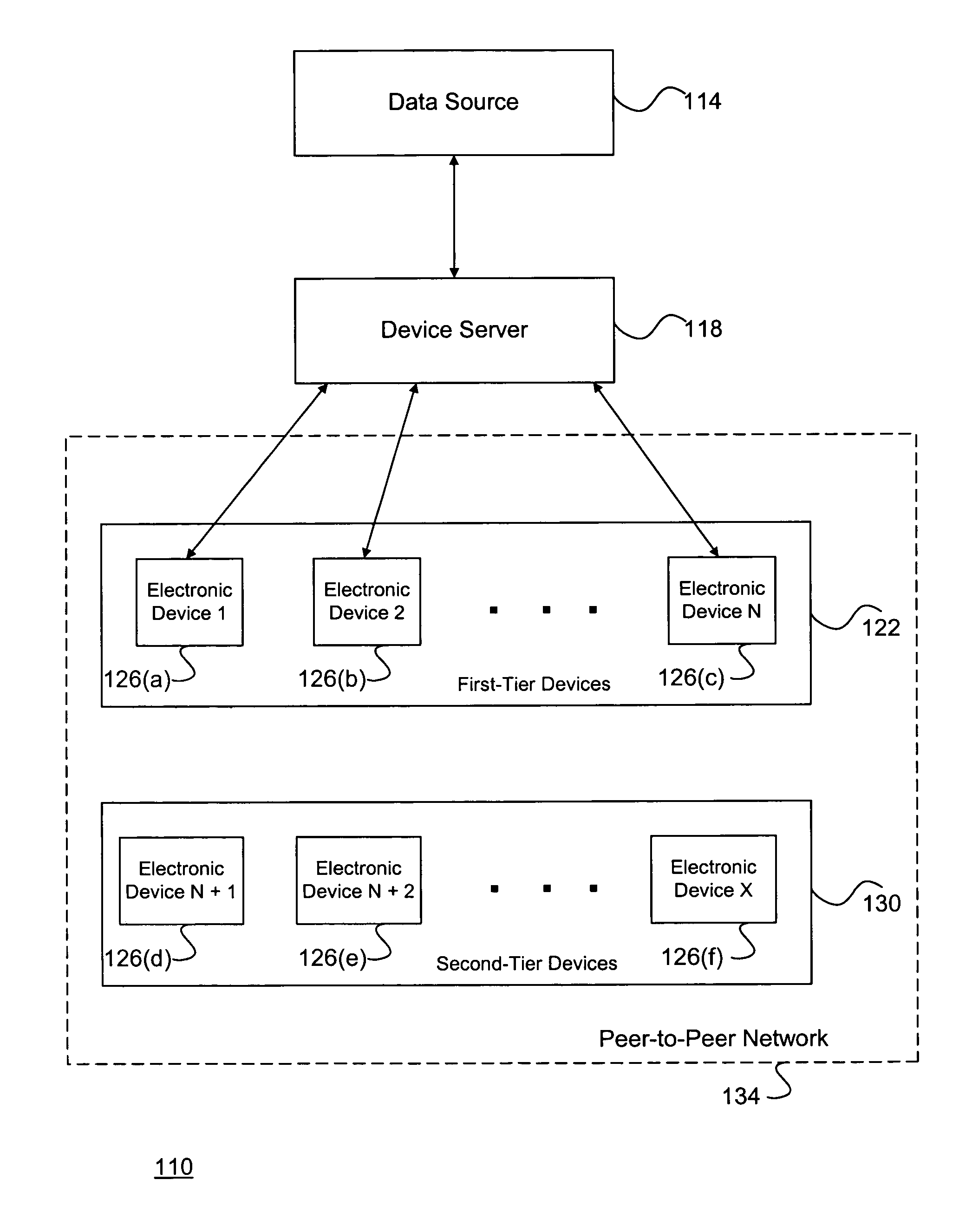
System and method for efficiently implementing processed data structures in an electronic network
A system and method for efficiently implementing processed data structures in an electronic network may include a device server and a peer-to-peer network of electronics devices which may be divided into first-tier devices and second tier devices. The device server may be configured to access raw data from a data source, and may then divide the raw data into unprocessed data segments. Each of the first-tier devices may download one of the unprocessed data segments from the device server, and may then perform a distributed processing procedure to convert the unprocessed data segments into processed data segments according to certain pre-defined processing rules. The first-tier devices and the second-tier devices may then performing a data reassembly procedure through the peer-to-peer network to thereby populate respective processed data structures on each of the electronic devices with complete sets of the processed data segments.
Owner:SONY COMPUTER ENTERTAINMENT INC
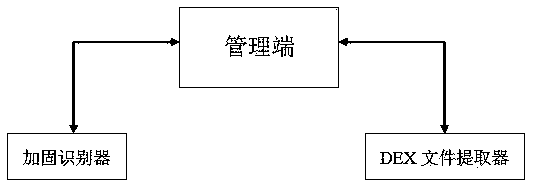
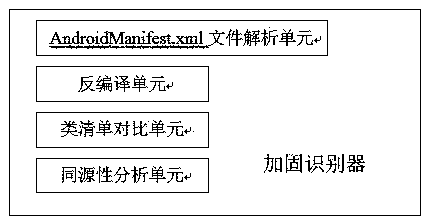
Universal automatic DEX shelling method and system
InactiveCN107742078ARealize unpackingEfficient identificationDecompilation/disassemblyReverse engineeringSoftware engineeringData reorganization
The invention relates to the technical field of Android application reinforcement protection and the technical field of DEX shelling, and aims at providing a universal automatic DEX shelling method and system. According to the method and system, shelling codes are inserted into a portable interpreter of an Android Dalvik virtual machine. The method specifically comprises the following steps of: comparing all the classes in an Android Manifest.xml configuration file and all the classes obtained through decompilation by utilizing contrastive analysis so as to judge whether an application is reinforced, and recognizing a reinforcement service used by the application through homology analysis; and taking Man Activity of the application as a DEX shelling starting mark, recovering real byte codes of the application, extracting recovered real data and finally recombining the data into a new DEX file, wherein the recombination process refers to modification of corresponding pointers. The system is good in universality, can bypass all the Anti-debugging protection technologies, and can extract original DEX files of reinforced applications without carrying out manual analysis and understanding reinforcement strategies of reinforcement services in the shelling process. The invention provides a new solution for automatic DEX shelling of reinforced applications.
Owner:SICHUAN UNIV
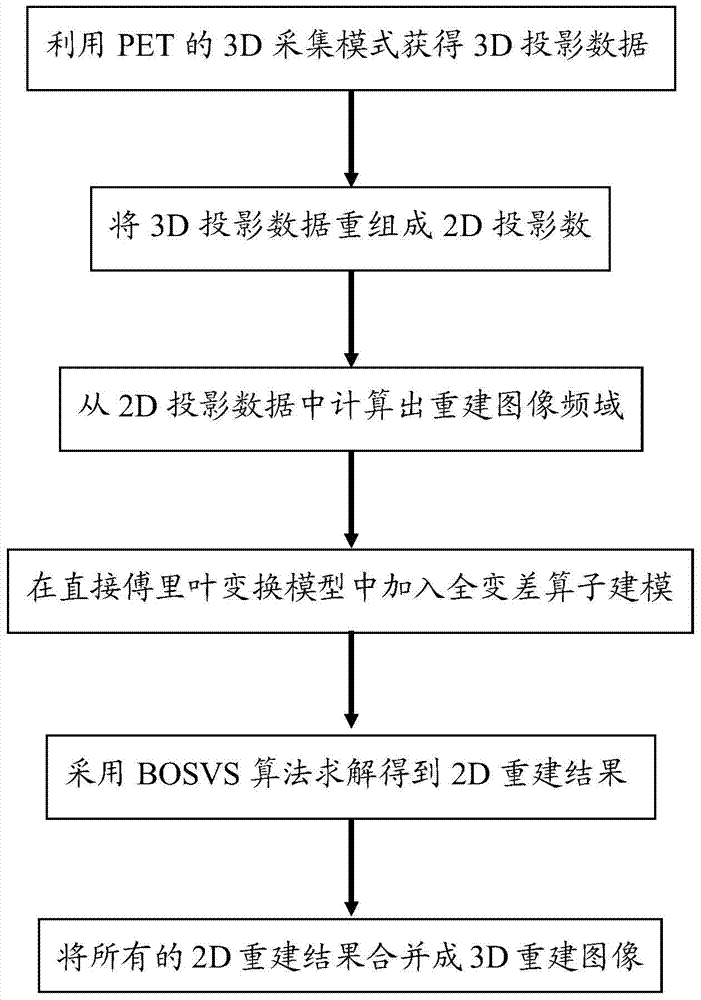
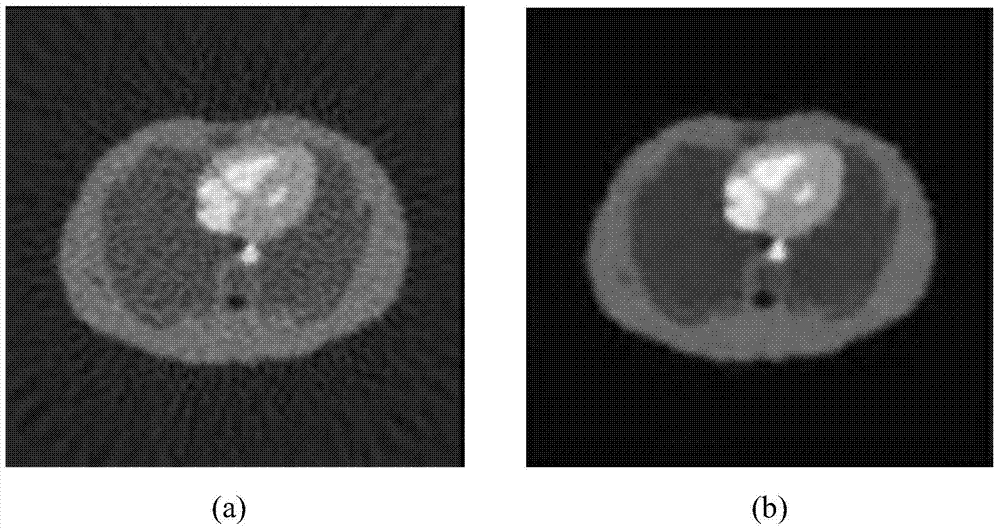
TV-based 3D positron emission tomography (PET) image reconstruction method
ActiveCN104851080AHigh resolutionClear edgesImage enhancement3D modellingImage resolutionReconstruction method
The invention discloses a TV-based 3D positron emission tomography (PET) image reconstruction method. The method includes the following steps that: (1) 3D projection data are obtained by using a PET 3D acquisition mode; (2) the 3D projection data are recombined to form 2D projection data; (3) reconstruction image frequency domain distribution is calculated from the 2D projection data; (4) total variation operators are added into a direct Fourier transform model, and a target function is established; (5) the above model is solved through adopting a BOSVS algorithm, so that 2D reconstruction results can be obtained; and (6) all 2D reconstruction results are merged so as to form a 3D reconstruction image. According to the method of the invention, based on direct Fourier transform, total variation is adopted as a regular term, so that the model can be constructed; the BOSVS algorithm is adopted to perform iteration solving, so that the reconstruction image with higher resolution and clearer edges can be obtained, and therefore, the quality of the reconstruction image can be significantly improved on the basis that direct Fourier transform rapid reconstruction is ensured, and better results can be obtained under low counting rate.
Owner:ZHEJIANG UNIV
Cloud storage data service device, data transmission system, server and method
ActiveCN103916421ASolve the scalability problemImprove usabilityTransmissionExtensibilityTransport system
The invention provides a cloud storage data service device, a cloud storage data transmission system, a server and a method. The cloud storage data service device comprises a data service module. The data service module is used for: receiving characteristic values of data to be transmitted when a cloud storage client conducts cloud storage, and conducting duplication eliminating storage according to the characteristic values; and receiving an access request transmitted when the cloud storage client conducts cloud storage access, according to the access request, extracting the data after duplication elimination, conducting data reorganization, and transmitting to the cloud storage client. According to the invention, by application of data duplication elimination to cloud storage data transmission, the expandability problem of a large-scale cloud storage environment can be solved, the duplication eliminating ratio and transmission efficiency are improved, the availability of transmission services is improved, the resource consumption of the client is reducing, and poor network environments are tolerated.
Owner:CHINA MOBILE COMM GRP CO LTD
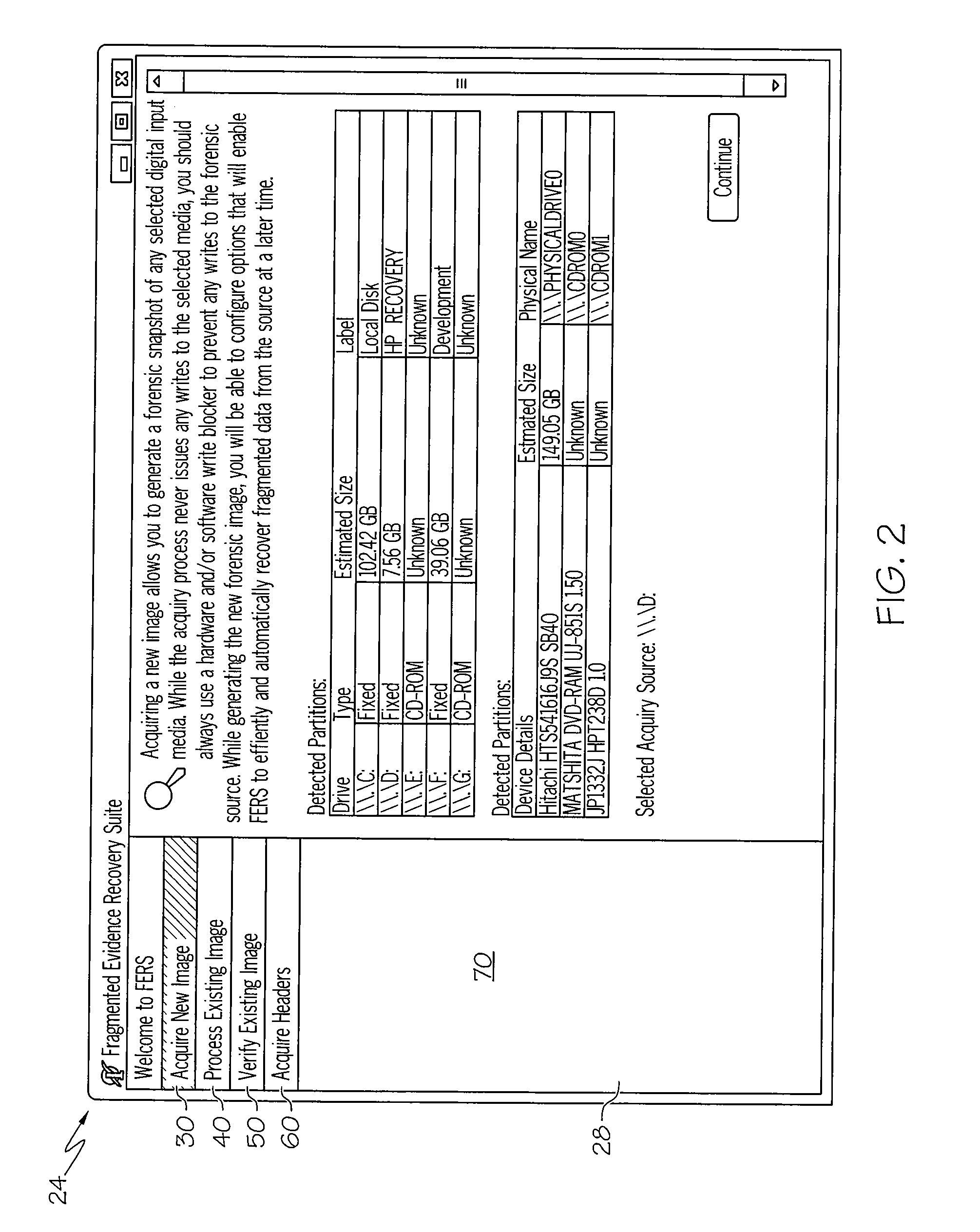
Fragmented data file forensic recovery system and method
InactiveUS20080279418A1Digital data processing detailsCharacter and pattern recognitionDigital storageData file
A system and method of reassembly a file from fragmented data written onto digital storage media are disclosed. The data reassembling system and method is particularly useful for image data reconstruction, and in forensic data recovery. More particularly, the inventive concept allows for reassembling out-of-sequence data fragments.
Owner:MARTINEK MICHAEL +1
Fine-grained data reorganization in tiered storage architectures
ActiveUS20150205525A1Improve data placementEasy to placeInput/output to record carriersSpecial data processing applicationsData setGranularity
A method for organizing data at levels of granularity larger or smaller than an extent is disclosed. The method initially closes a dataset on a host system. The host system includes a mapping table storing a logical address of the dataset. When the dataset is closed, the host system generates a message indicating that the dataset has been closed and sends the message to a storage system storing the dataset. In response, the storage system allocates a new logical address and copies the dataset from the existing logical address to the new logical address to improve data placement. The storage system then returns the new logical address to the host system so that the host system can update its mapping table. A corresponding system and computer program product are also disclosed.
Owner:IBM CORP
Rectification skin repairing method based on wing body actual measurement data virtual butt joint
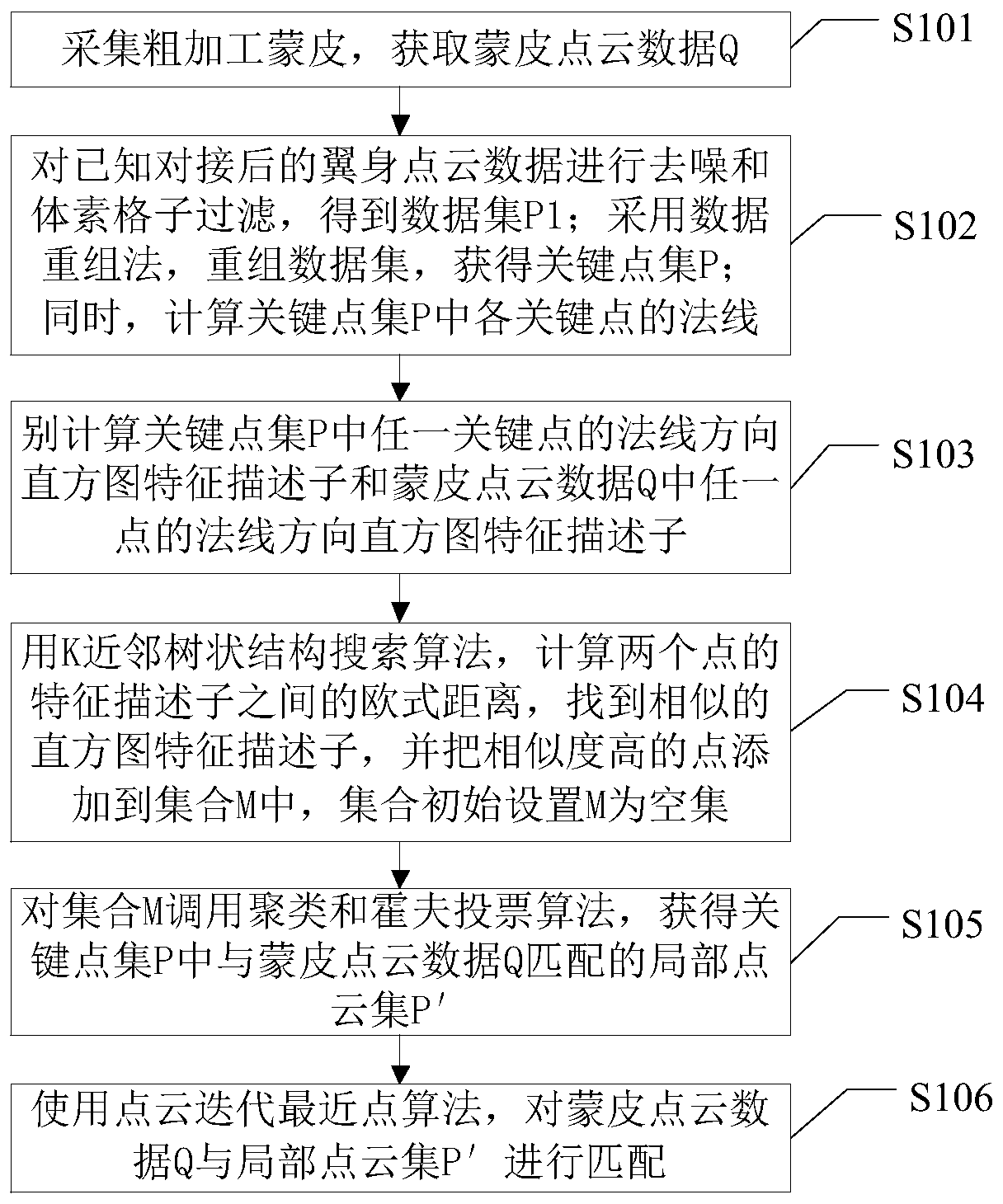
ActiveCN111583318ASave human effortSave assembly timeProgramme controlImage enhancementData setPoint cloud
The invention discloses a rectification skin repair method based on wing body actual measurement data virtual butt joint, which comprises skin registration and repair, and the registration comprises the steps of denoising wing body point cloud data, and carrying out data recombination on a data set obtained after filtering to obtain a key point set; calculating a normal direction feature descriptor of any key point in the key point set and a normal direction feature descriptor of any point in the skin point cloud data; calculating the Euclidean distance between the feature descriptors of the two points by using a K-nearest neighbor tree structure search algorithm, and adding the points with high similarity into the set M; and calling a clustering and Hough voting algorithm for the set M toobtain a local point cloud set matched with the skin point cloud data in the key point set; matching the skin point cloud data with the local point cloud set through a point cloud iterative nearest point algorithm. Skin registration and repair can be completed through computer programs, manpower can be greatly saved, and production efficiency is improved. Meanwhile, the influence of human subjective factors is avoided, and the registration result is more accurate.
Owner:南京耘瞳科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com