Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
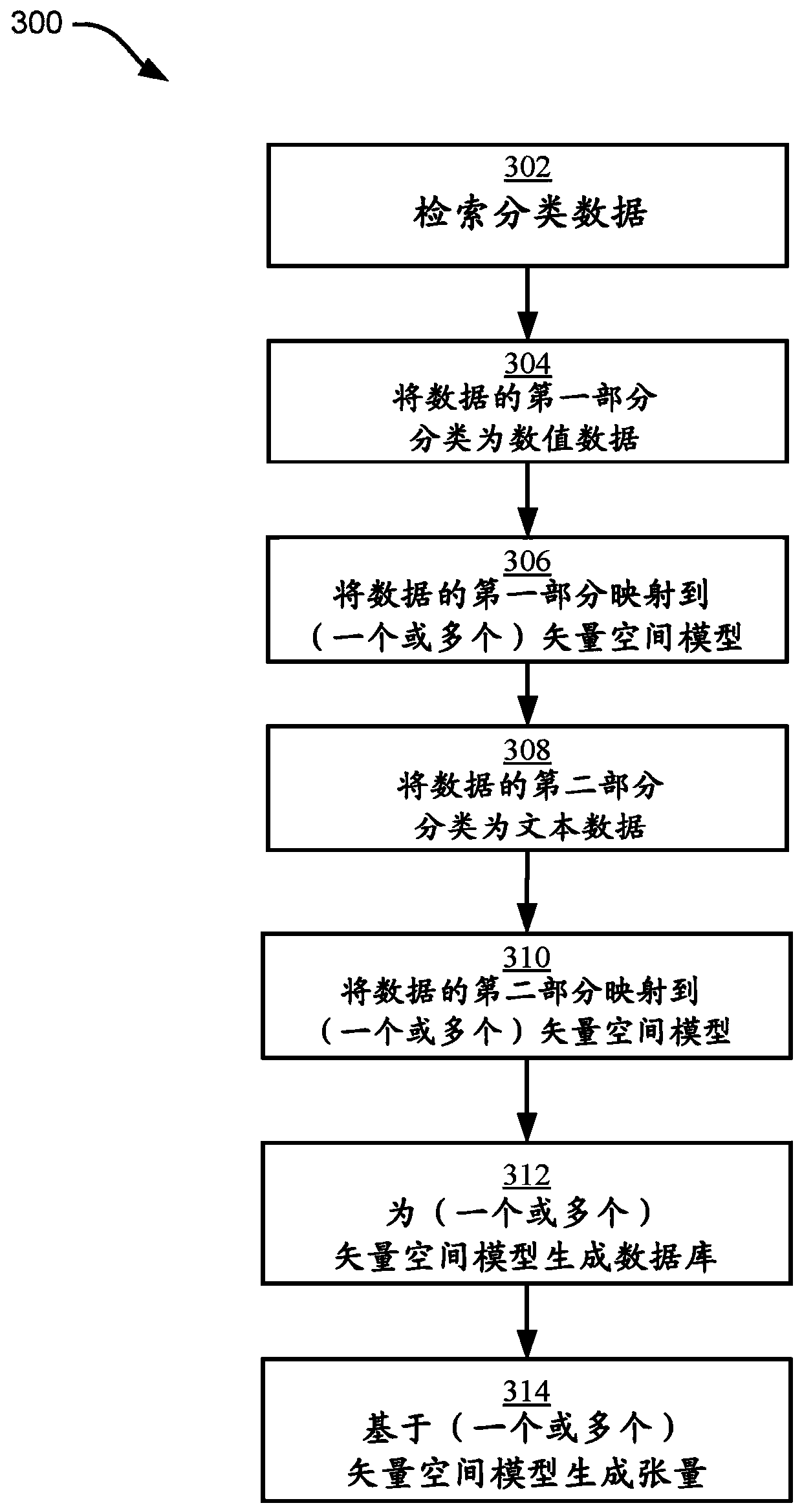
110 results about "Cybersafety" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
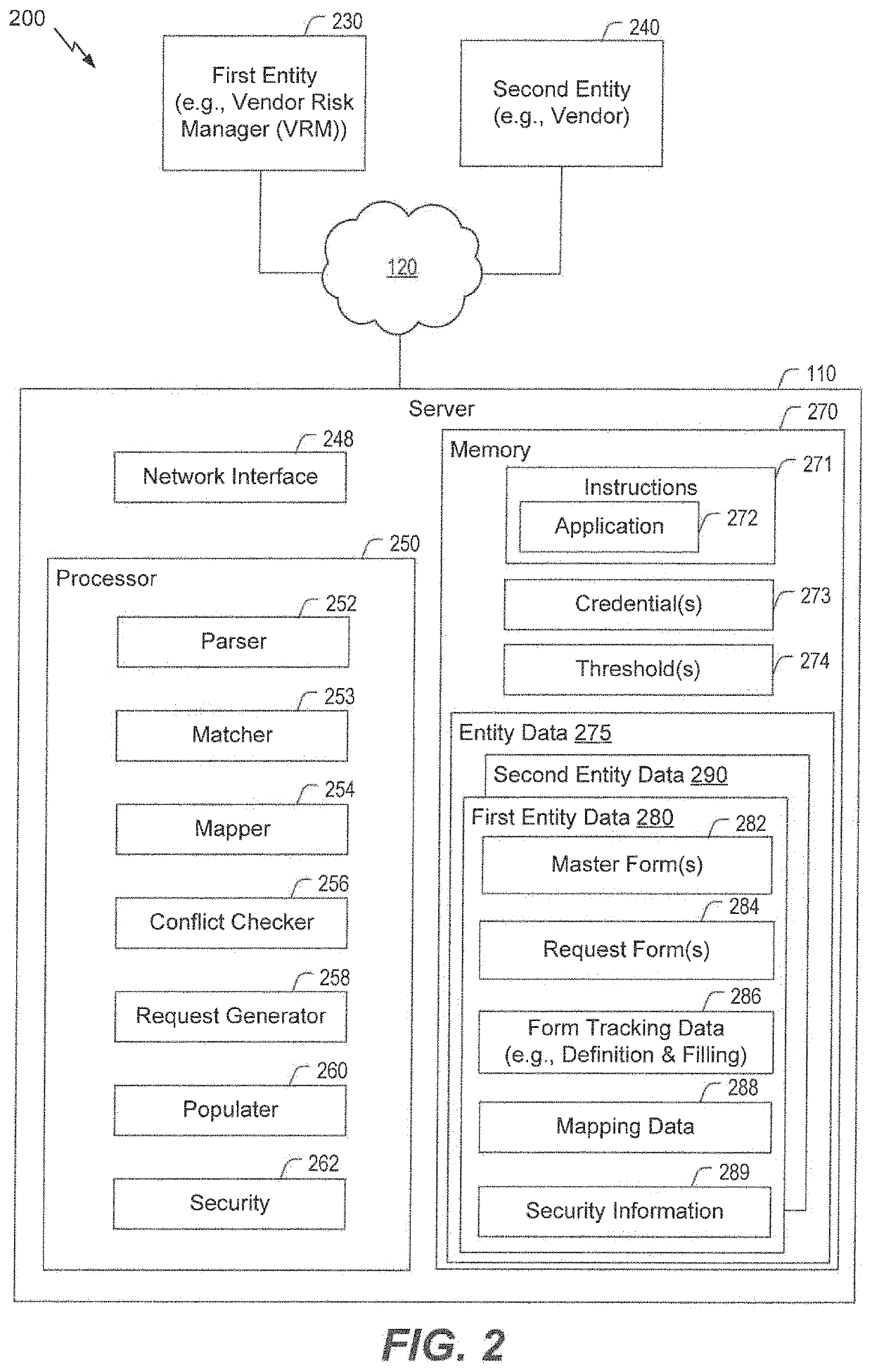
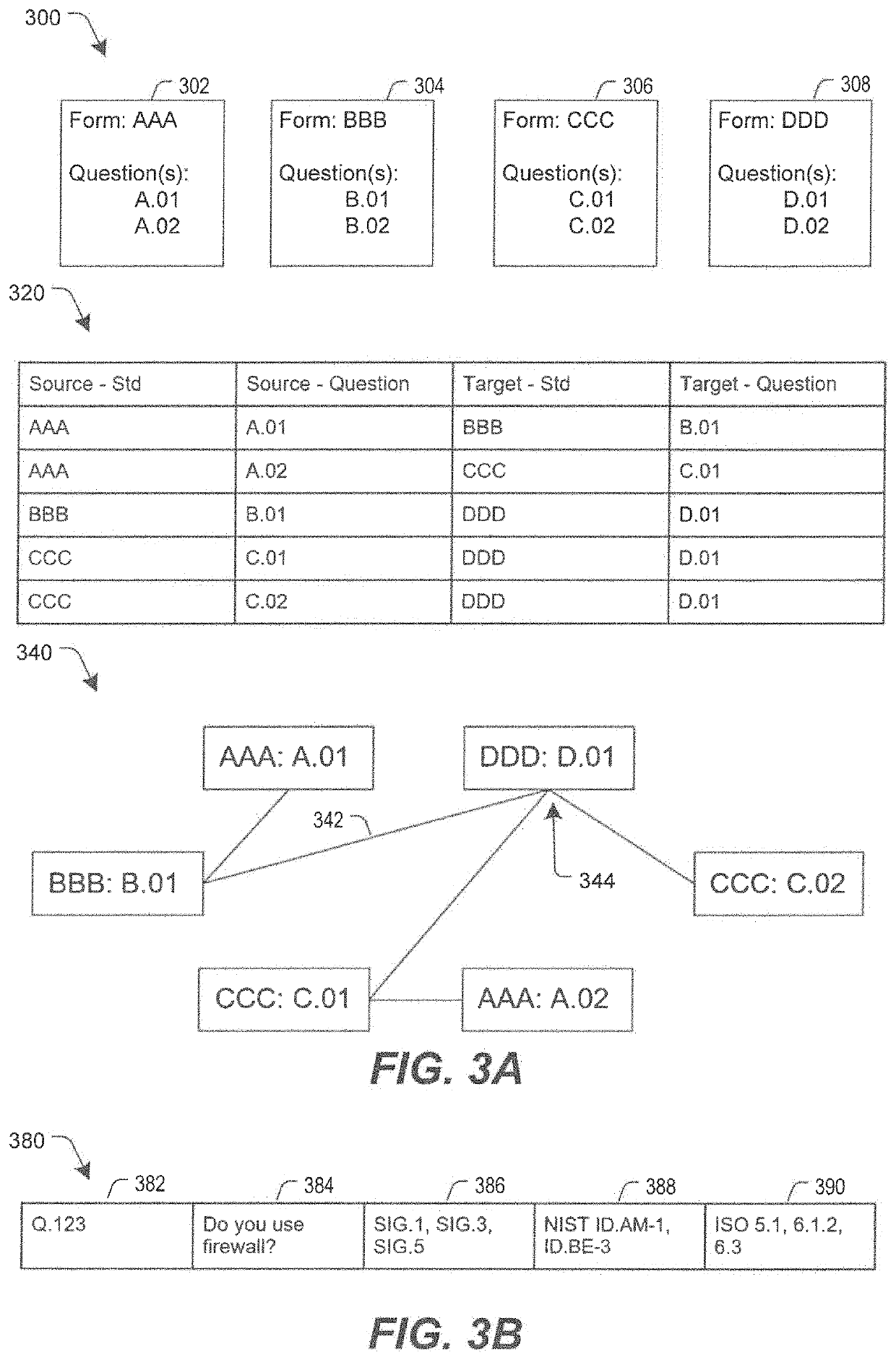
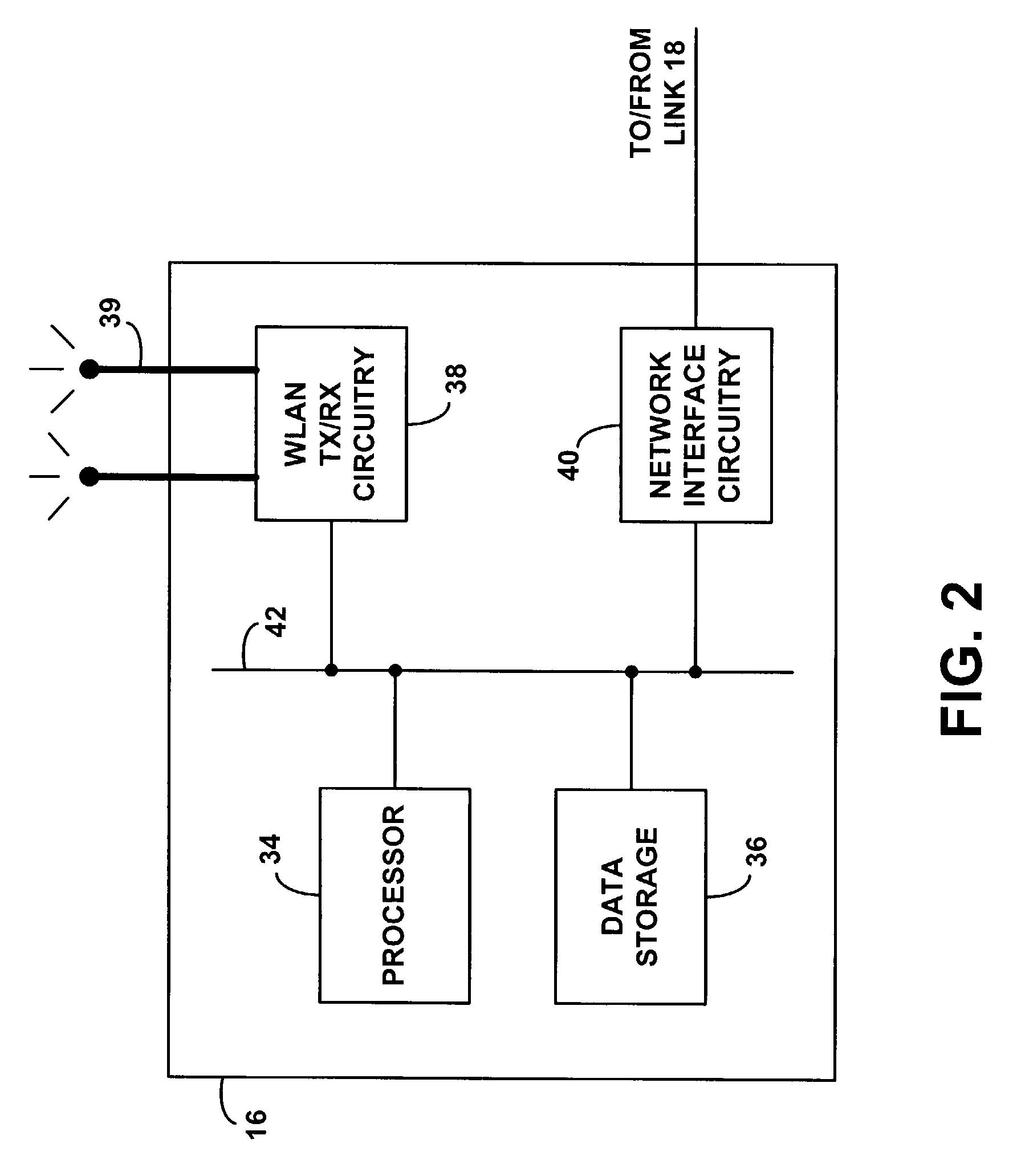
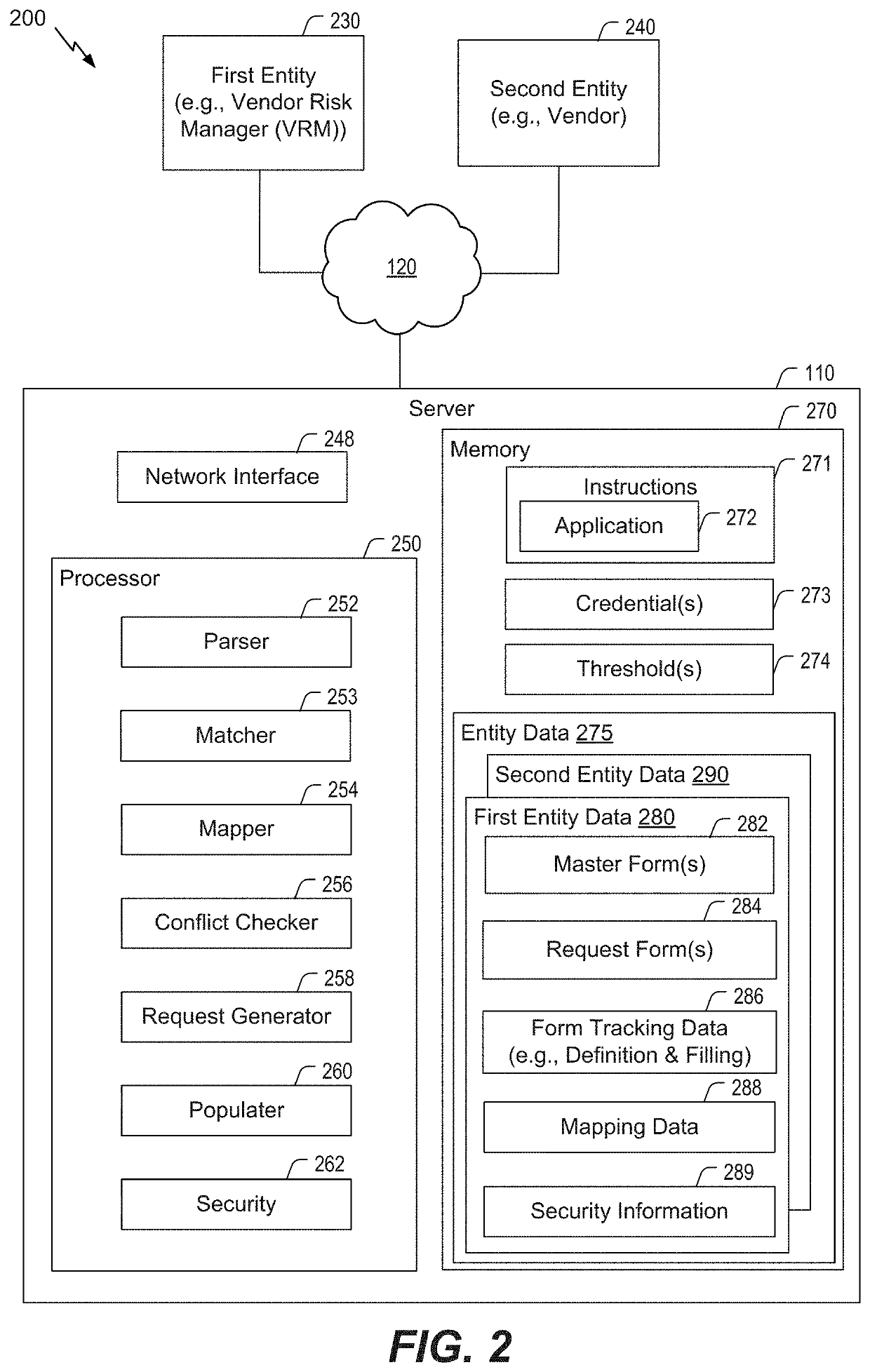
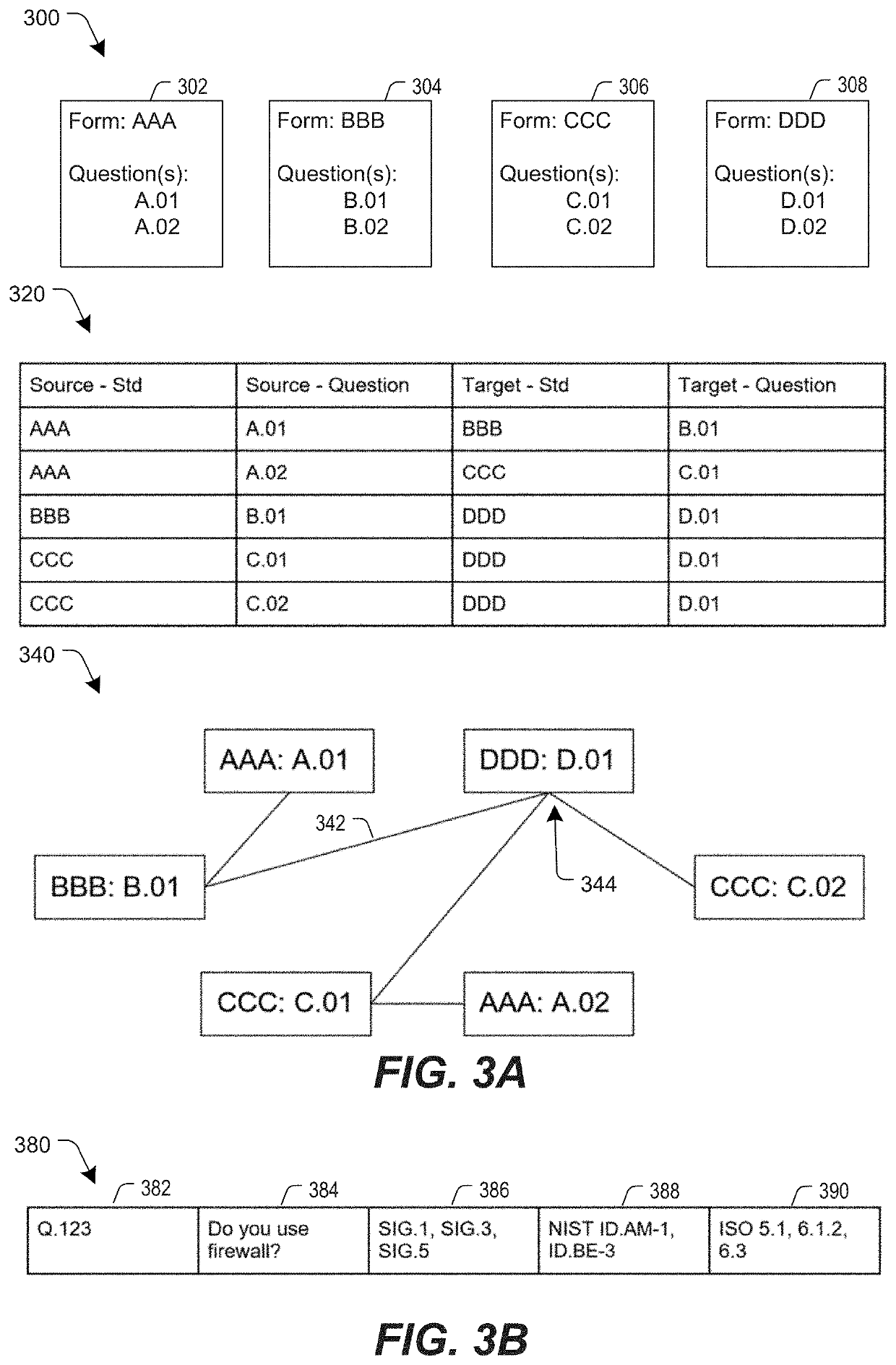
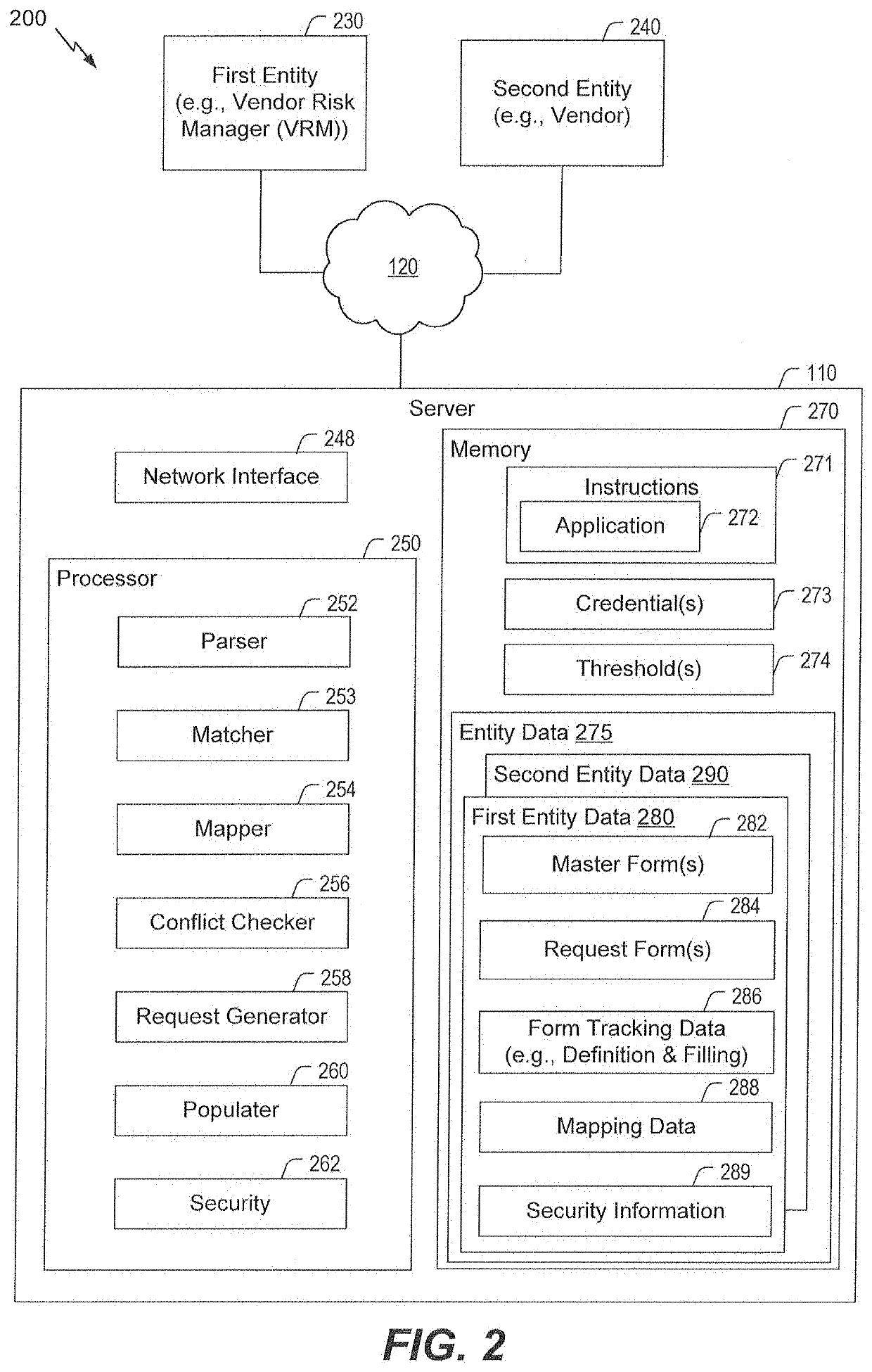
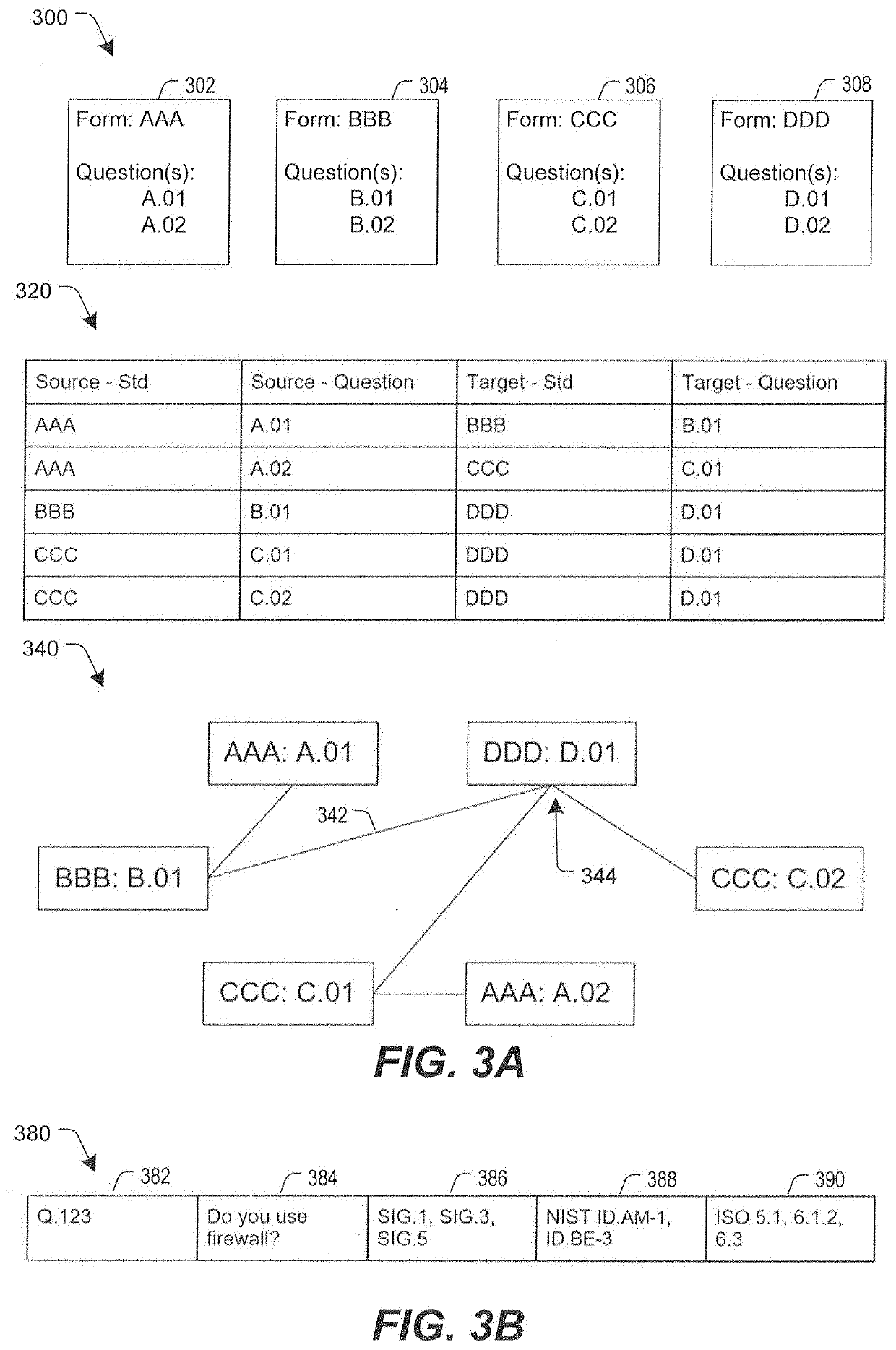
Inquiry response mapping for determining a cybersecurity risk level of an entity
ActiveUS10546135B1Reduce future data conflictImprove response mappingPlatform integrity maintainanceMachine learningRisk levelData set
The present disclosure provides a method, system, and device for inquiry response mapping for determining a cybersecurity risk level of an entity. To manage and / or evaluate a cybersecurity risk level based on a relationship between a first entity and a second entity, questionnaires (e.g., requests or inquires) are often exchanged between two entities. One or more aspects of the present disclosure provide populating data sets (e.g., questionnaires) indicative of risk level for the first entity or the second entity. One or more other aspects of the present disclosure further provide determining a cybersecurity risk level of an entity by mapping responses to a plurality of inquiry sets directed to the first entity or the second entity.
Owner:SECURITYSCORECARD
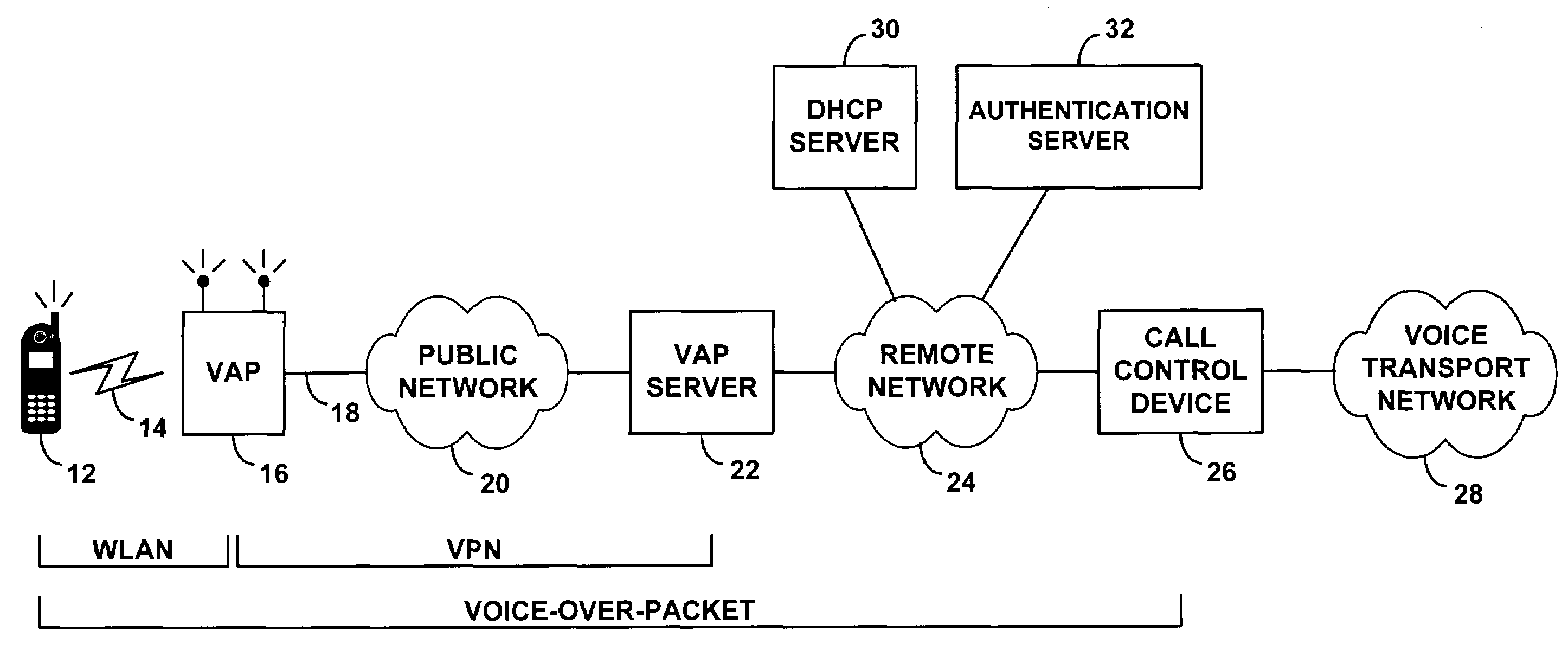
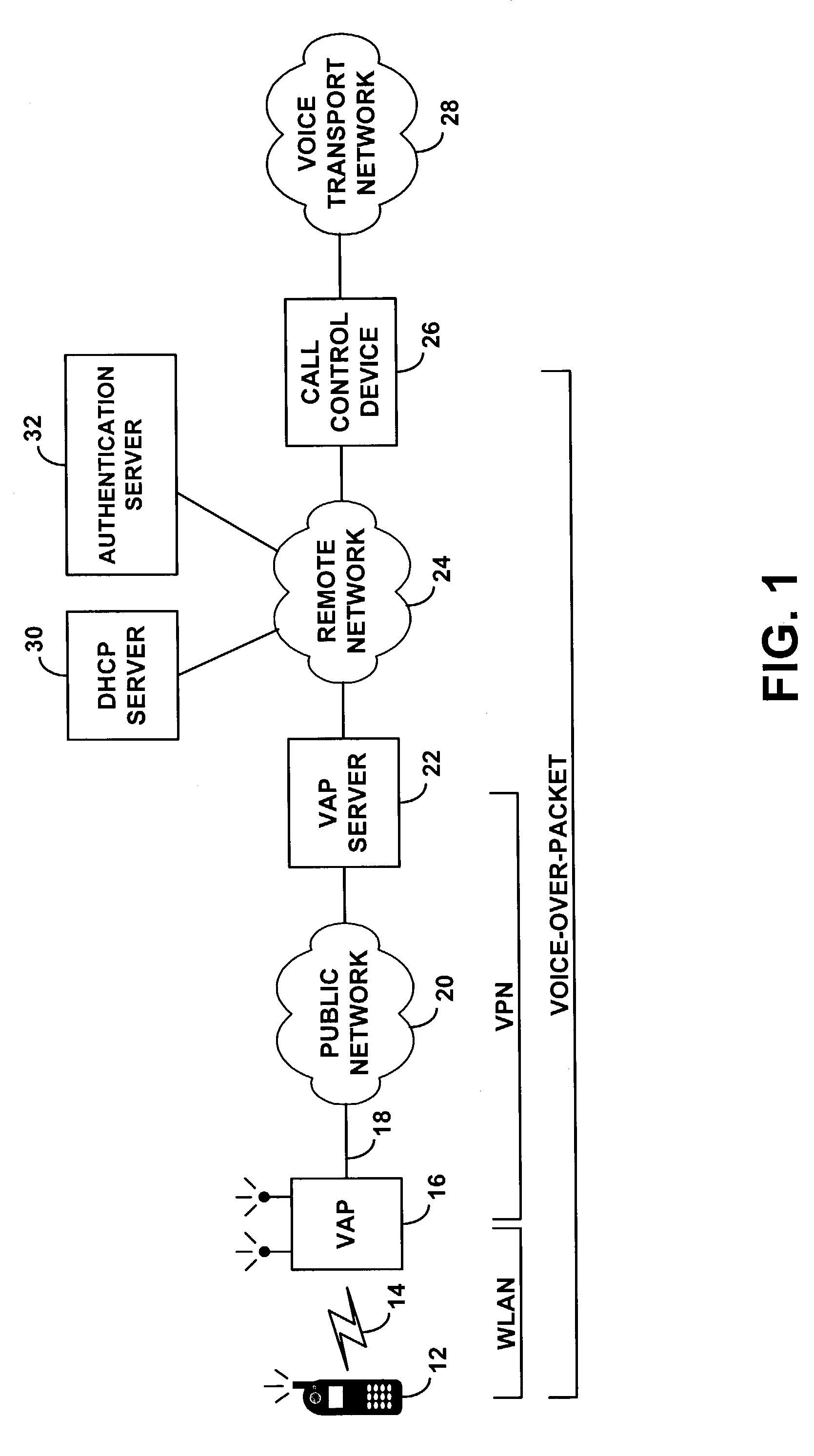
Method and system for distribution of voice communication service via a wireless local area network
ActiveUS7349412B1Communication securityReadily engage in voice over packet (VoP) communicationData switching by path configurationNetwork connectionsPrivate networkVoice communication
A method and system for distributing voice communication services via wireless local area networks. An entity sells, loans, gives or otherwise distributes wireless access points, each of which is pre-configured with virtual private network (VPN) security settings to establish a VPN tunnel over a packet network with a VPN terminator on a remote telephony services network. A recipient may thus install the wireless access point on a local area network (LAN), to allow users of voice-capable wireless devices to engage in voice calls via the wireless access point, VPN tunnel and telephony services network. The distributor of the access point, or another entity, may then charge users for placing and receiving voice calls through this system.
Owner:SPRINT SPECTRUM LLC
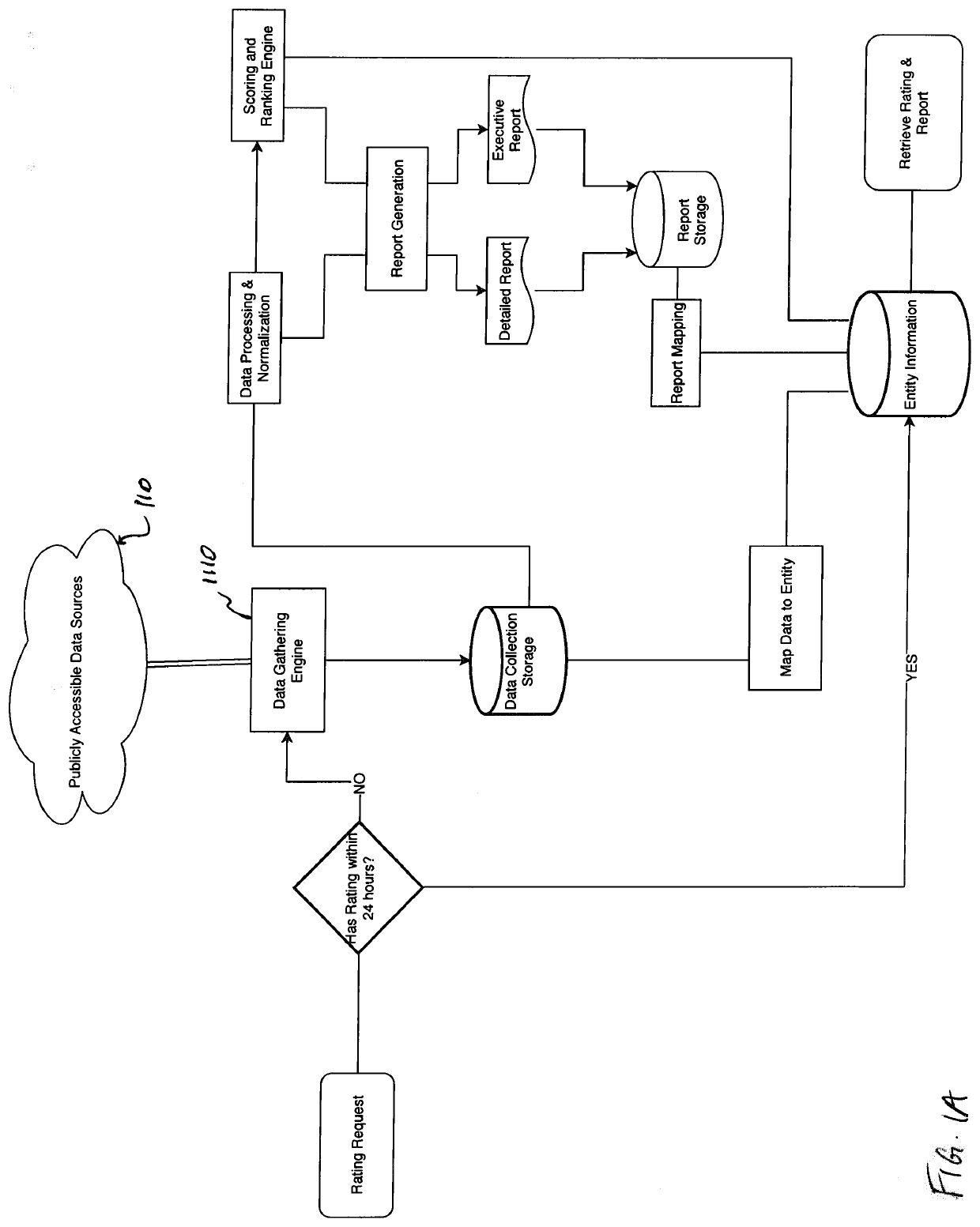
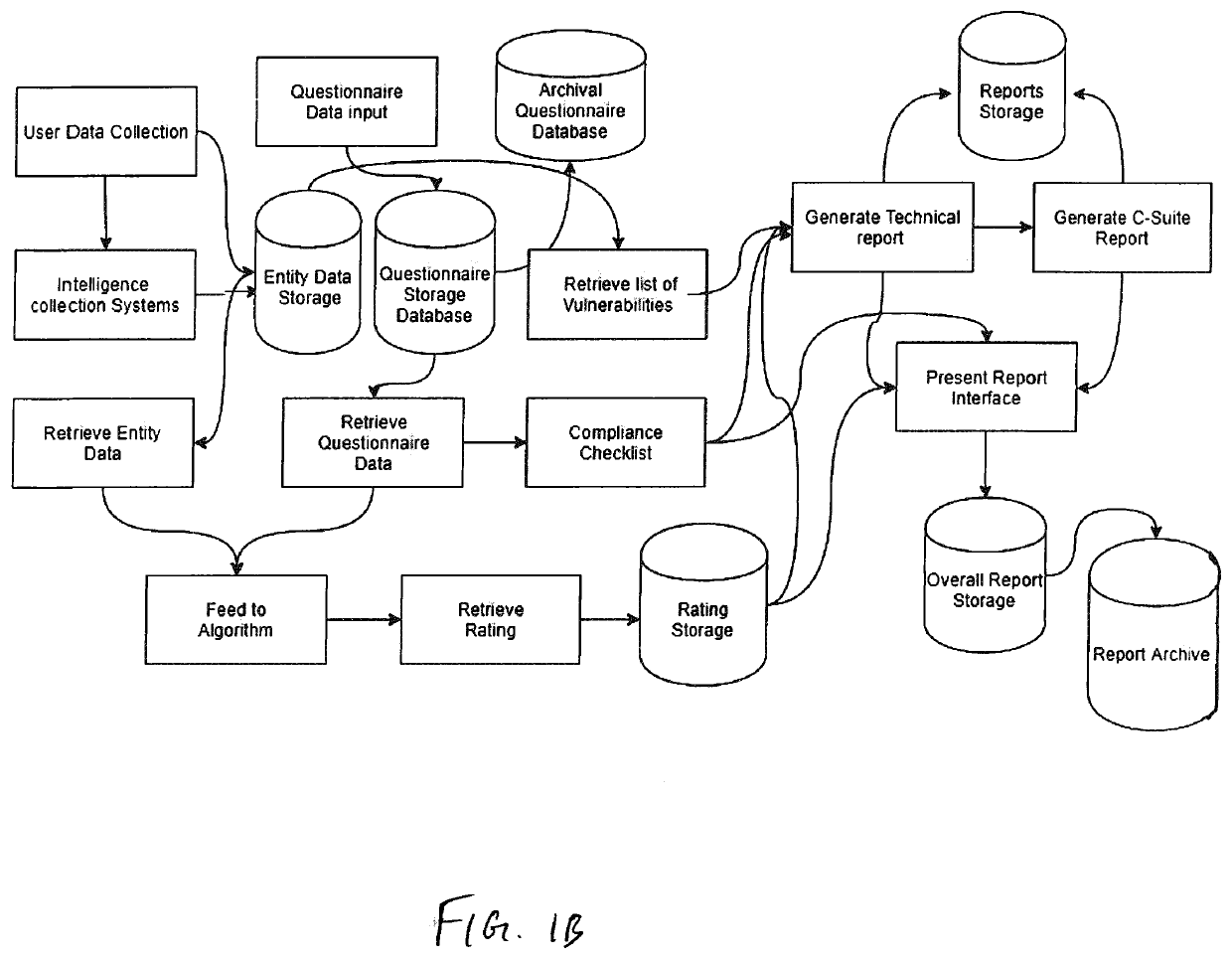
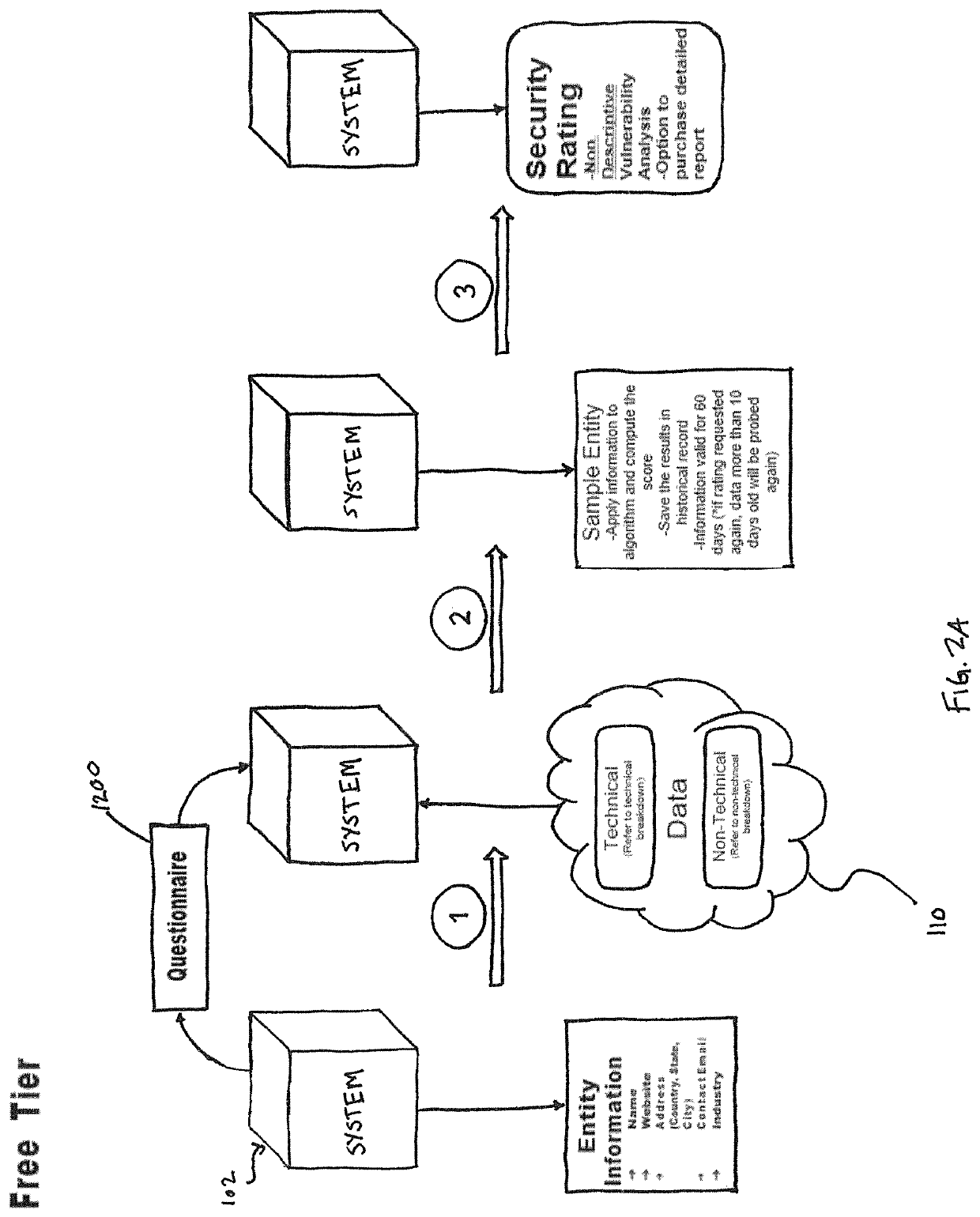
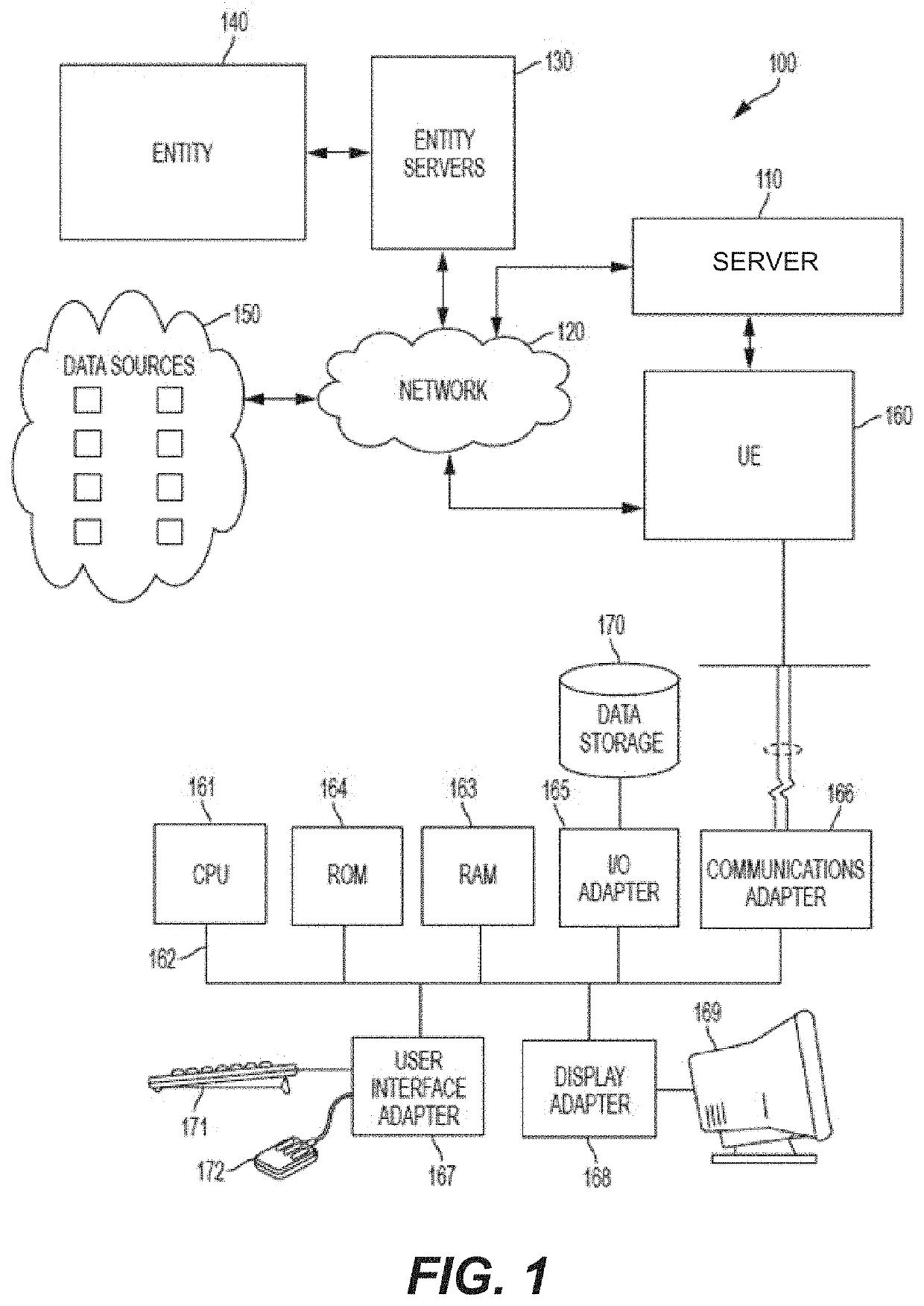
System and method for determining cybersecurity rating and risk scoring
A system for deriving a rating representative of a level of cybersecurity of a user is configured to execute steps of a method comprising (i) requesting, from the user, identifying information about the user; (ii) requesting, from the user, input in response to a set of predetermined questions provided to the user based on the identifying information about the user; (iii) collecting, based on at least the identifying information, public domain data about the user and data from the user's digital assets; and (iv) computing, based on the collected data and the input to the set of predetermined questions provided by the user, a numerical value defining the cybersecurity rating.
Owner:CYBERLAB
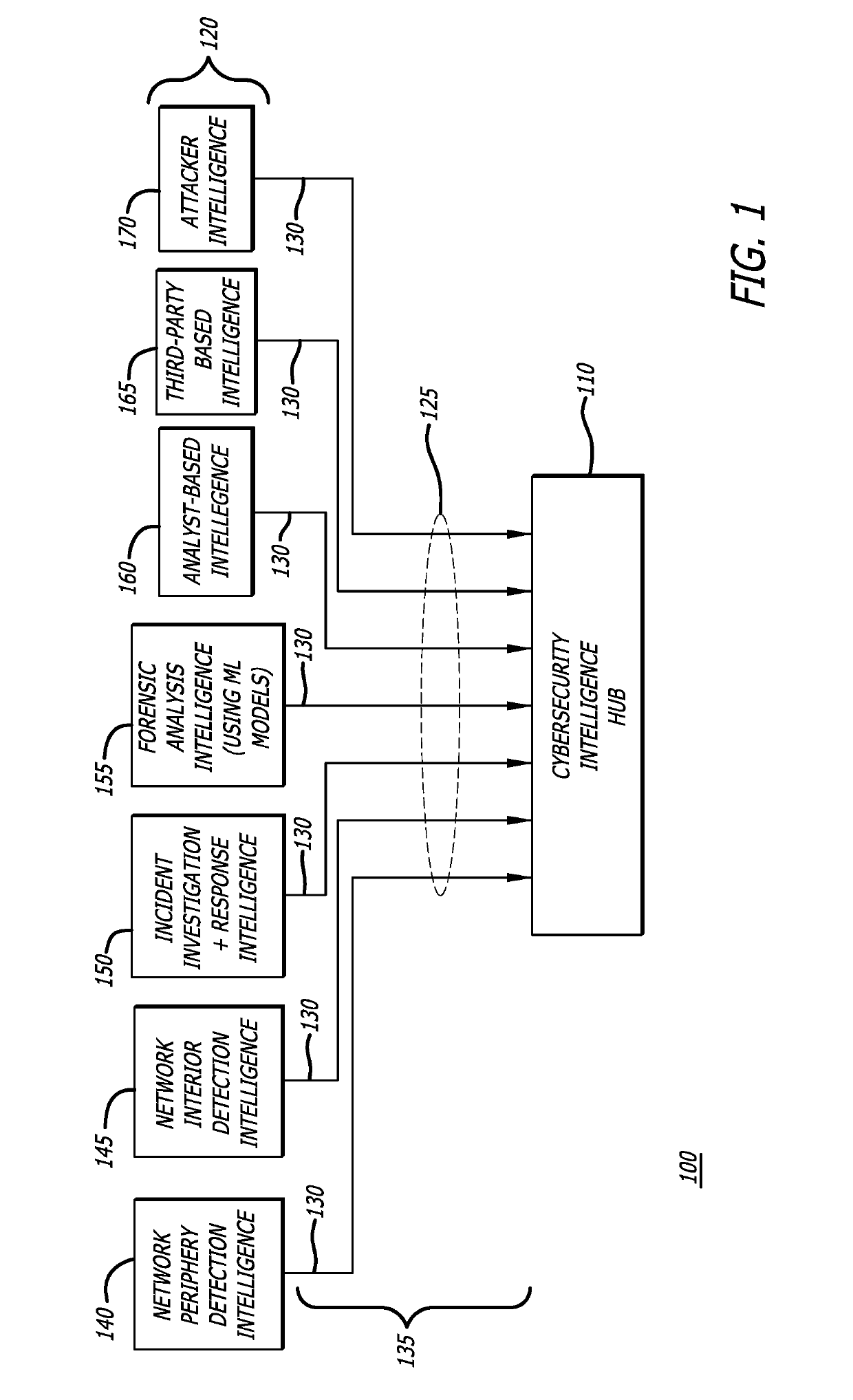
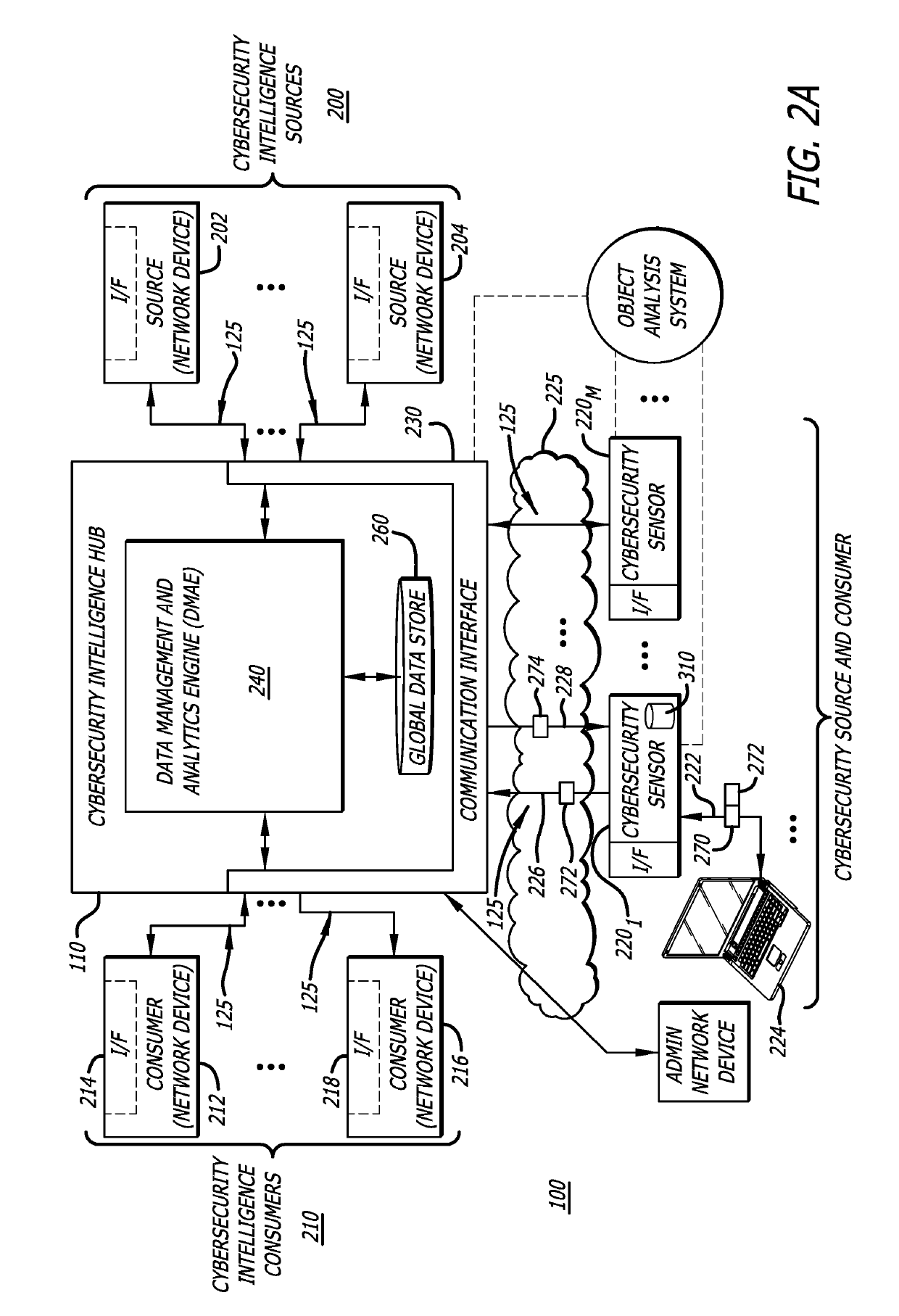
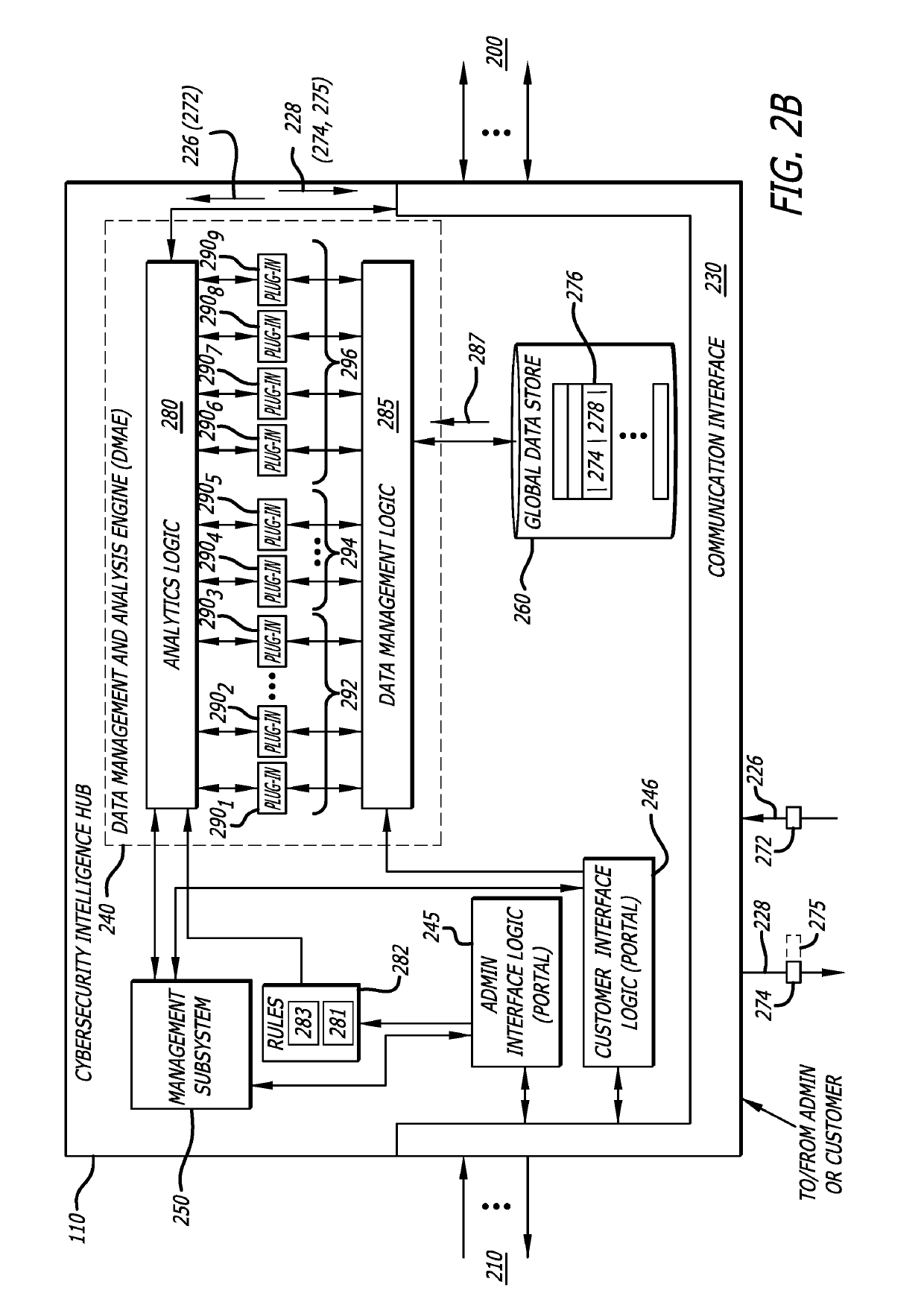
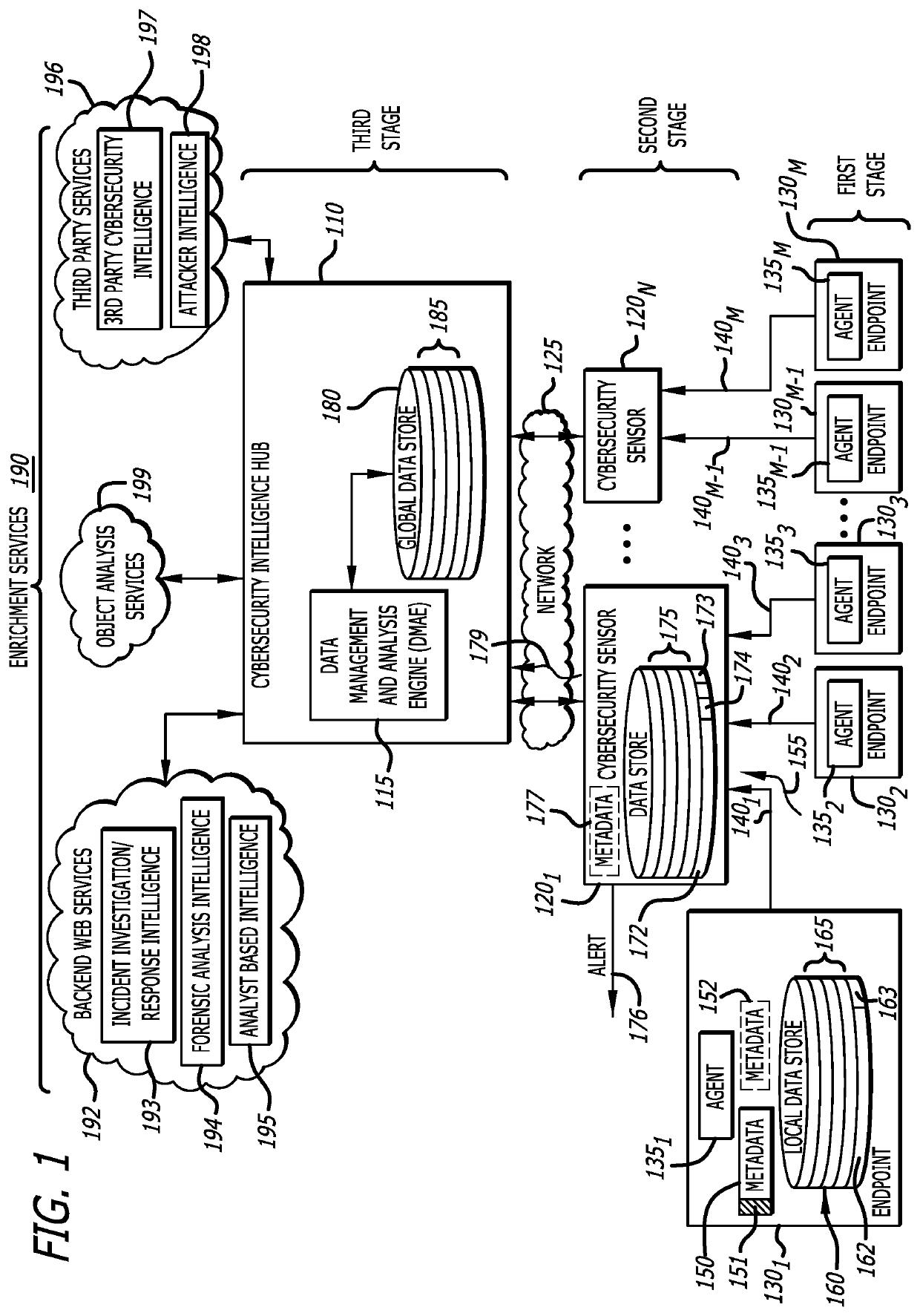
Platform and Method for Enhanced Cyber-Attack Detection and Response Employing a Global Data Store
A system for detecting artifacts associated with a cyber-attack features a cybersecurity intelligence hub that includes a data store with stored meta-information associated with each artifact of a plurality of artifacts and each stored meta-information includes a verdict classifying an artifact corresponding to the stored meta-information as a malicious classification or a benign classification. The hub is configured to (i) receive meta-information associated with a first artifact from a cybersecurity sensor, and (ii) determine a verdict for the first artifact based on an analysis of meta-information associated with the first artifact stored meta-information associated with each of the plurality of artifacts. A verdict for the first artifact is returned to the cybersecurity sensor in response to a detected match between a portion of stored meta-information and a portion of the meta-information associated with the first artifact.
Owner:FIREEYE SECURITY HLDG US LLC
Inquiry response mapping for determining a cybersecurity risk level of an entity
ActiveUS20200285755A1Reduce data conflictsPlatform integrity maintainanceMachine learningRisk levelData set
The present disclosure provides a method, system, and device for inquiry response mapping for determining a cybersecurity risk level of an entity. To manage and / or evaluate a cybersecurity risk level based on a relationship between a first entity and a second entity, questionnaires (e.g., requests or inquires) are often exchanged between two entities. One or more aspects of the present disclosure provide populating data sets (e.g., questionnaires) indicative of risk level for the first entity or the second entity. One or more other aspects of the present disclosure further provide determining a cybersecurity risk level of an entity by mapping responses to a plurality of inquiry sets directed to the first entity or the second entity.
Owner:SECURITYSCORECARD
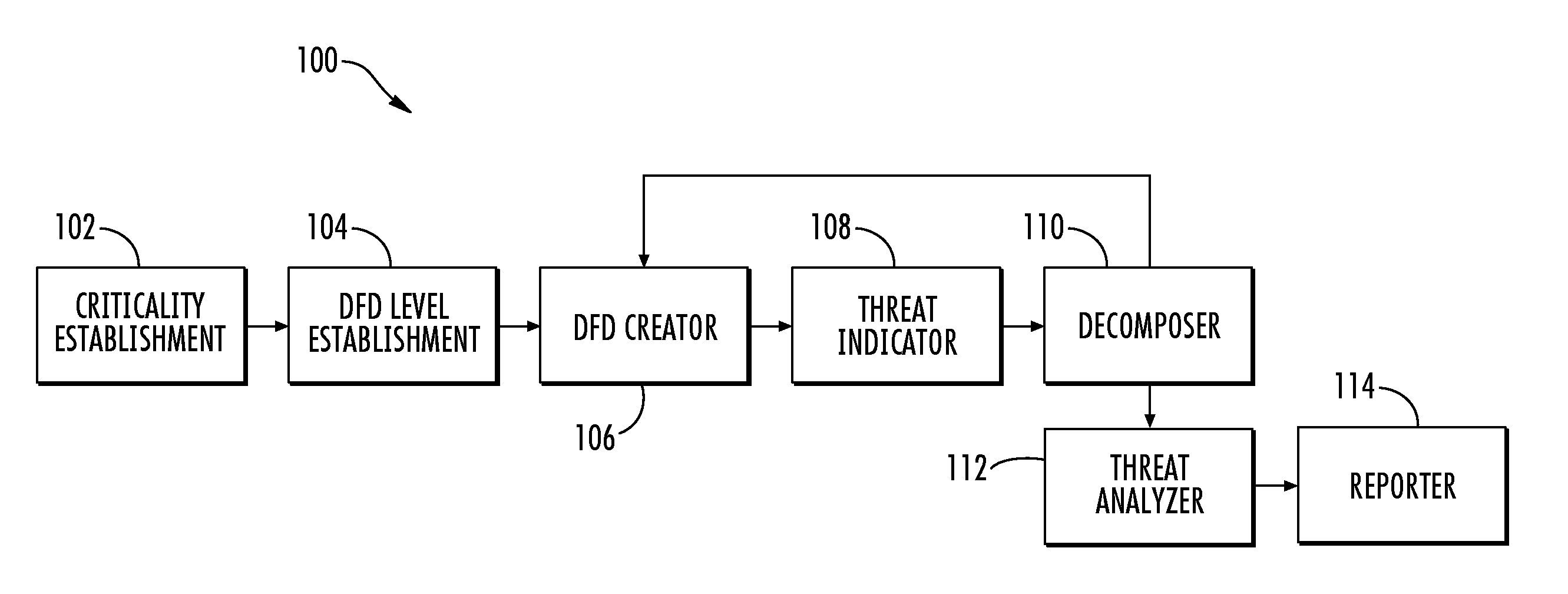
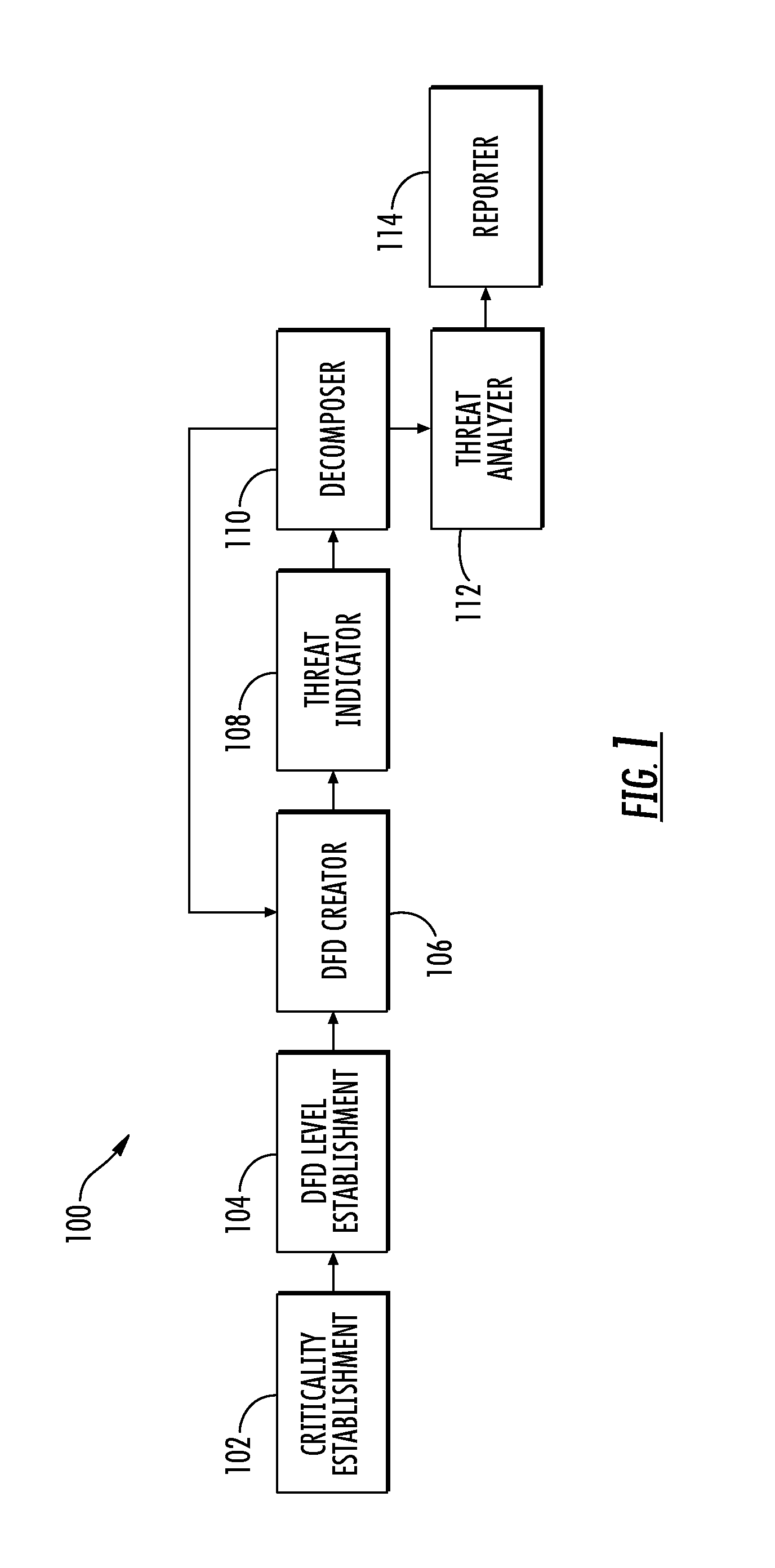
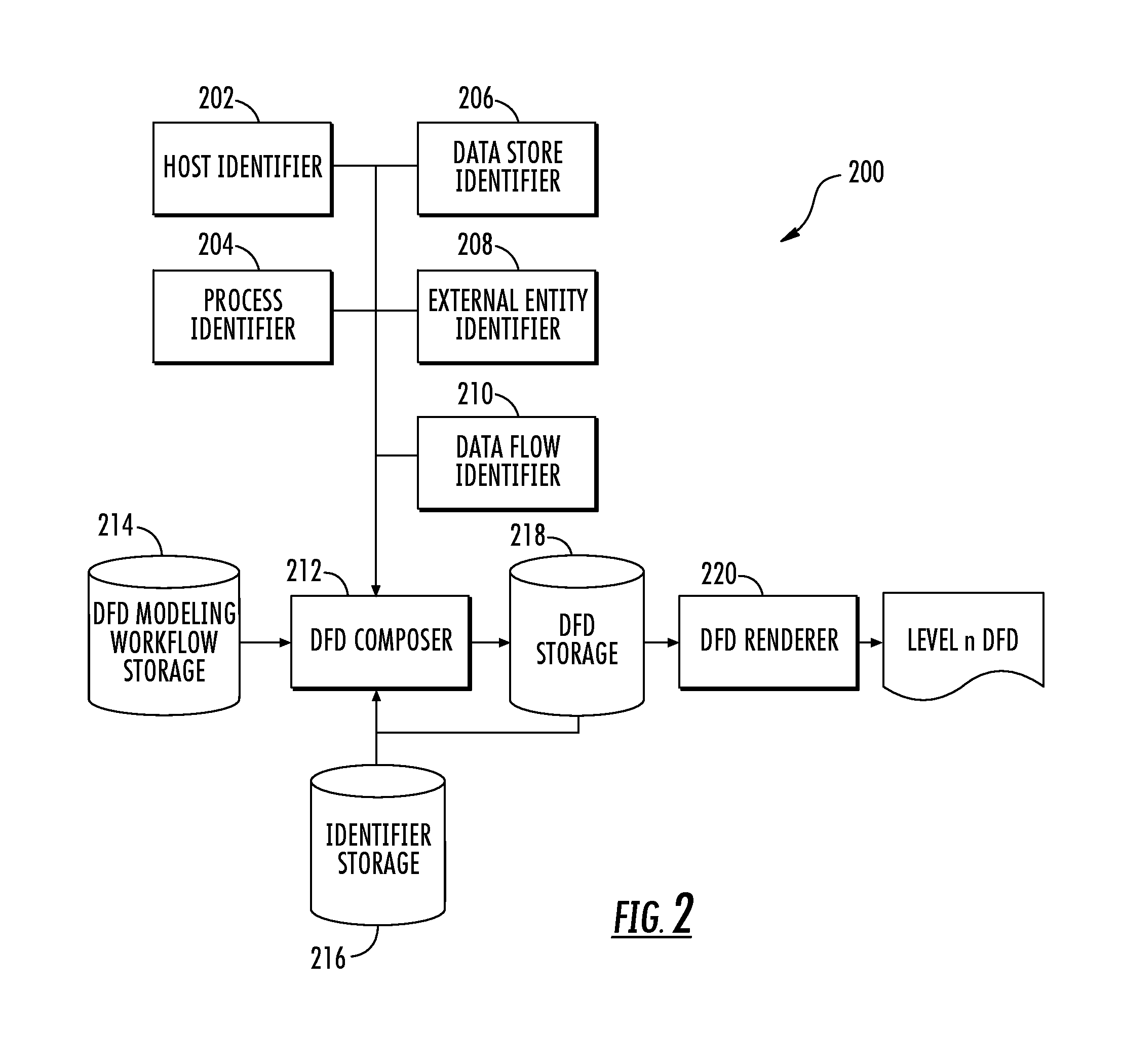
Threat modeling and analysis
ActiveUS20150288712A1Easy to understandMitigate and further mitigate riskPlatform integrity maintainanceTransmissionData streamEngineering
A system is provided for modeling and analysis of cybersecurity threats may include a data flow diagram (DFD) creator, threat indicator and threat analyzer. The DFD creator may identify elements of an information system, and compose a DFD including nodes and edges representing components and data flows of the information system. The threat indicator may identify a cybersecurity threat to a particular element of the information system, and add a secondary node representing the cybersecurity threat to the DFD to thereby produce a threat-model DFD for the information system. In metadata associated with the nodes, edges and secondary node, the DFD creator and threat indicator may provide structured information including attributes of the components, data flows and cybersecurity threat. And the threat analyzer may perform an analysis of the cybersecurity threat based on the threat-model DFD and metadata associated with the nodes, edges and secondary node thereof.
Owner:THE BOEING CO
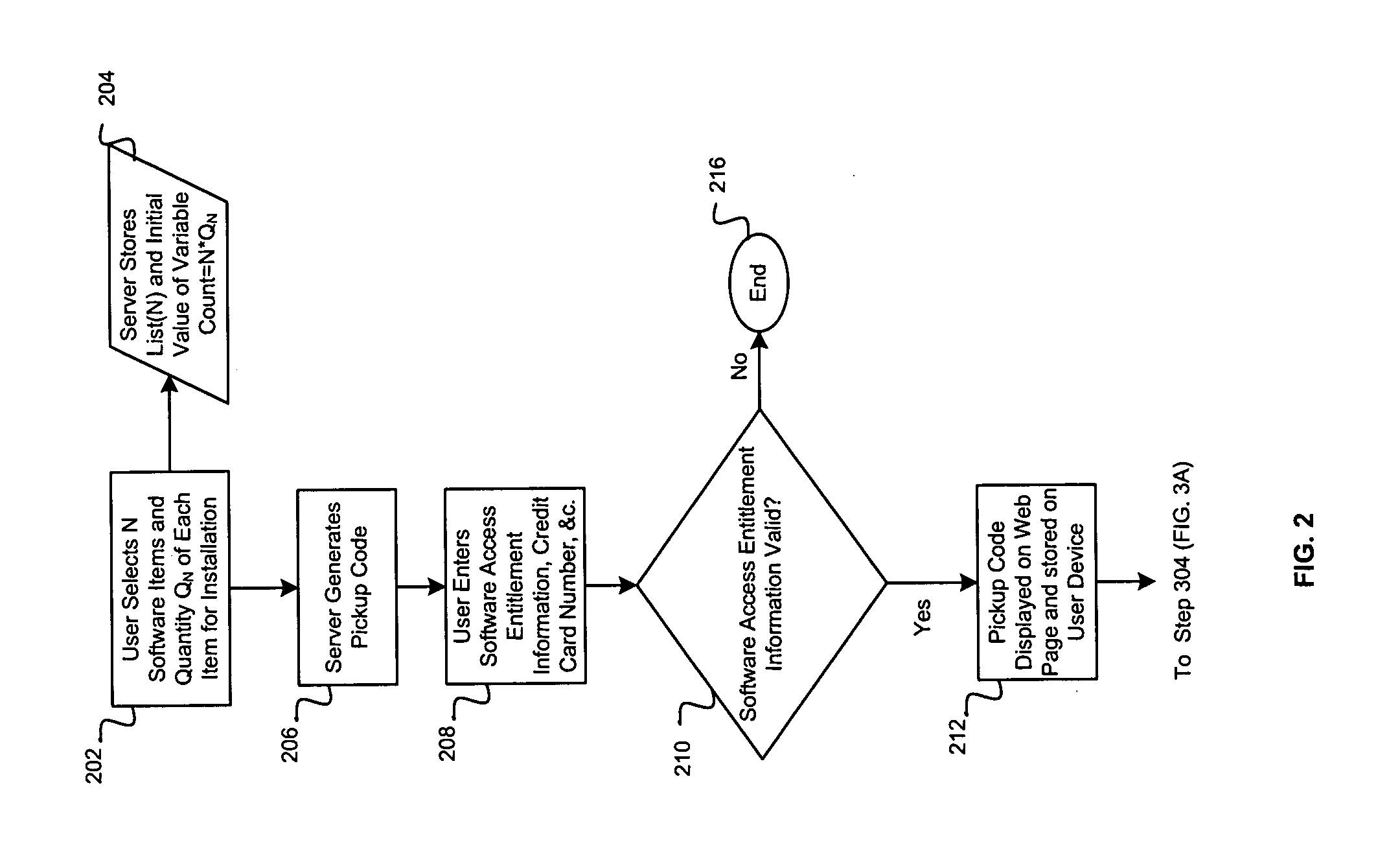
Method and system for the secure distribution of software via a communications network
InactiveUS20060129459A1Program/content distribution protectionCommerceBiological activationComputer science
Aspects for distributing software via a network may comprise requesting user identification utilized for tracking an online software order. A pickup code associated with the online software order may be generated. Downloads associated with the online software order may be tacked based on at least the pickup code and / or an activation code. Downloads may be terminated based on fulfilling delivery of all of the online software order based on the tracking.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
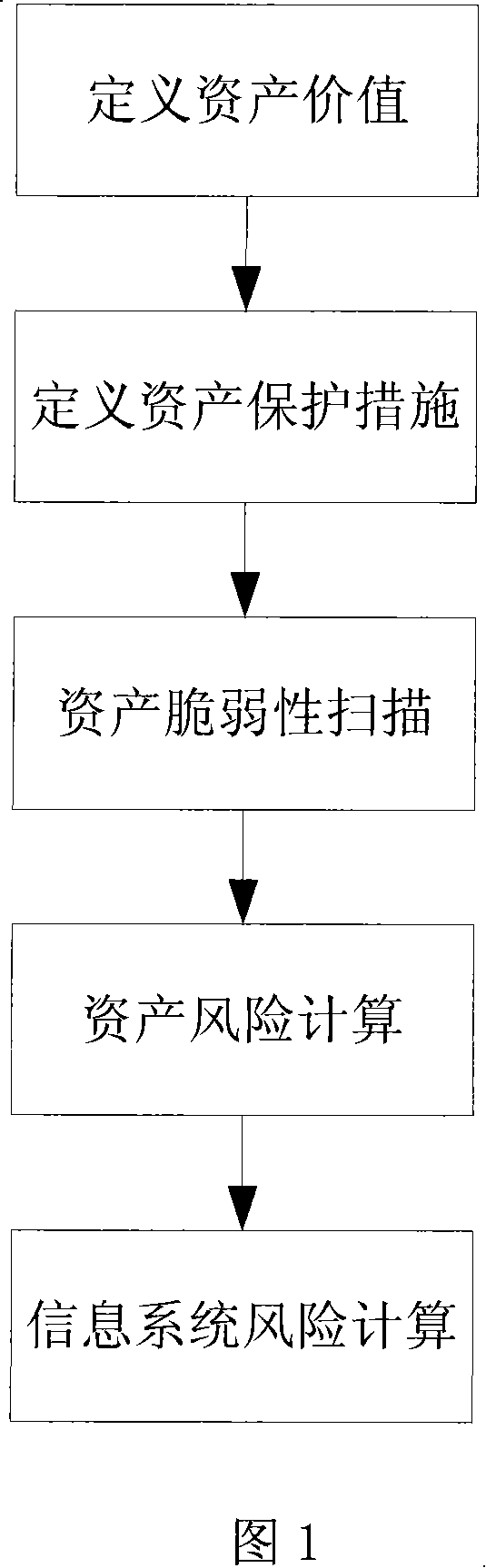
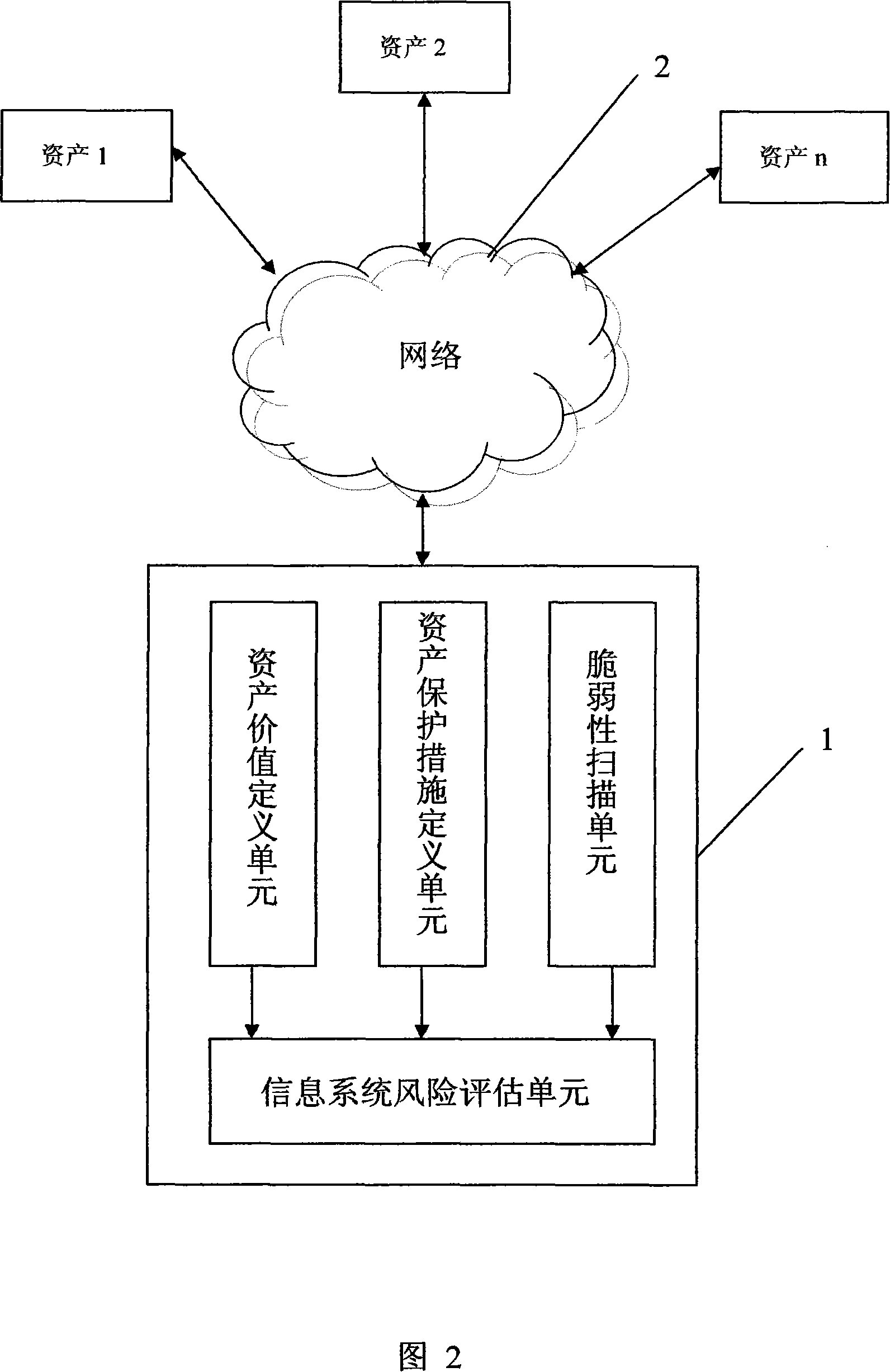
An information system risk evaluation method and system
InactiveCN101150432AThe impact of vulnerability is highlightedEasy to compare the relative value of vulnerabilityComputer security arrangementsData switching networksProbit modelThe Internet
This invention discloses a method and a system for risk evaluation of an information system, in which, the method includes: computing the risk value of each asset in the information system and computing the risk value of the information system according to the risk values of the assets, and the computation is based on a probability model. A risk evaluation system is installed on the UE of the internet containing a vulnerability scan unit, an asset value defining unit, an asset safeguard defining unit and a risk evaluation unit of the information system, which can quantize the risk values of assests and the information system together in an appointed fixed space and the quantized result shows the degree of vulnerability of assests or the information system.
Owner:BEIJING VENUS INFORMATION TECH
Automated and continuous cybersecurity assessment with measurement and scoring
Automated and continuous cybersecurity assessment with measurement and scoring. In an embodiment, a cyber-hygiene score is calculated based on data representing asserted cybersecurity controls within an entity system. The cyber-hygiene score indicates an extent of implementation of cybersecurity controls associated with a cybersecurity standard. In addition, automated cybersecurity test(s) are performed on the entity system, and a cyber-breach score is calculated based on the test scores calculated from the automated cybersecurity test(s). The cyber-breach score indicates an effectiveness of the implemented cybersecurity controls. The automated cybersecurity test(s) may comprise an inside-out controls test, and outside-in controls test, and / or a social-engineering test (e.g., phishing simulation). A cybersecurity assessment is generated based on the cyber-hygiene score and the cyber-breach score.
Owner:CYBERCATCH INC
System and method for automatically generating malware detection rule recommendations
ActiveUS11003773B1Character and pattern recognitionPlatform integrity maintainanceEngineeringMalware
A method for generating rule recommendation utilized in a creation of malware detection rules is described. Meta-information associated with a plurality of events collected during a malware detection analysis of an object by a cybersecurity system is received and a first plurality of features is selected from the received meta-information. Machine learning (ML) models are applied to each of the first plurality of features to generate a score that represents a level of maliciousness for the feature and thereby a degree of usefulness of the feature in classifying the object as malicious or benign. Thereafter, a second plurality of features is selected as the salient features, which are used in creation of the malware detection rules in controlling subsequent operations of the cybersecurity system. The second plurality of features being lesser in number that the first plurality of features.
Owner:FIREEYE SECURITY HLDG US LLC
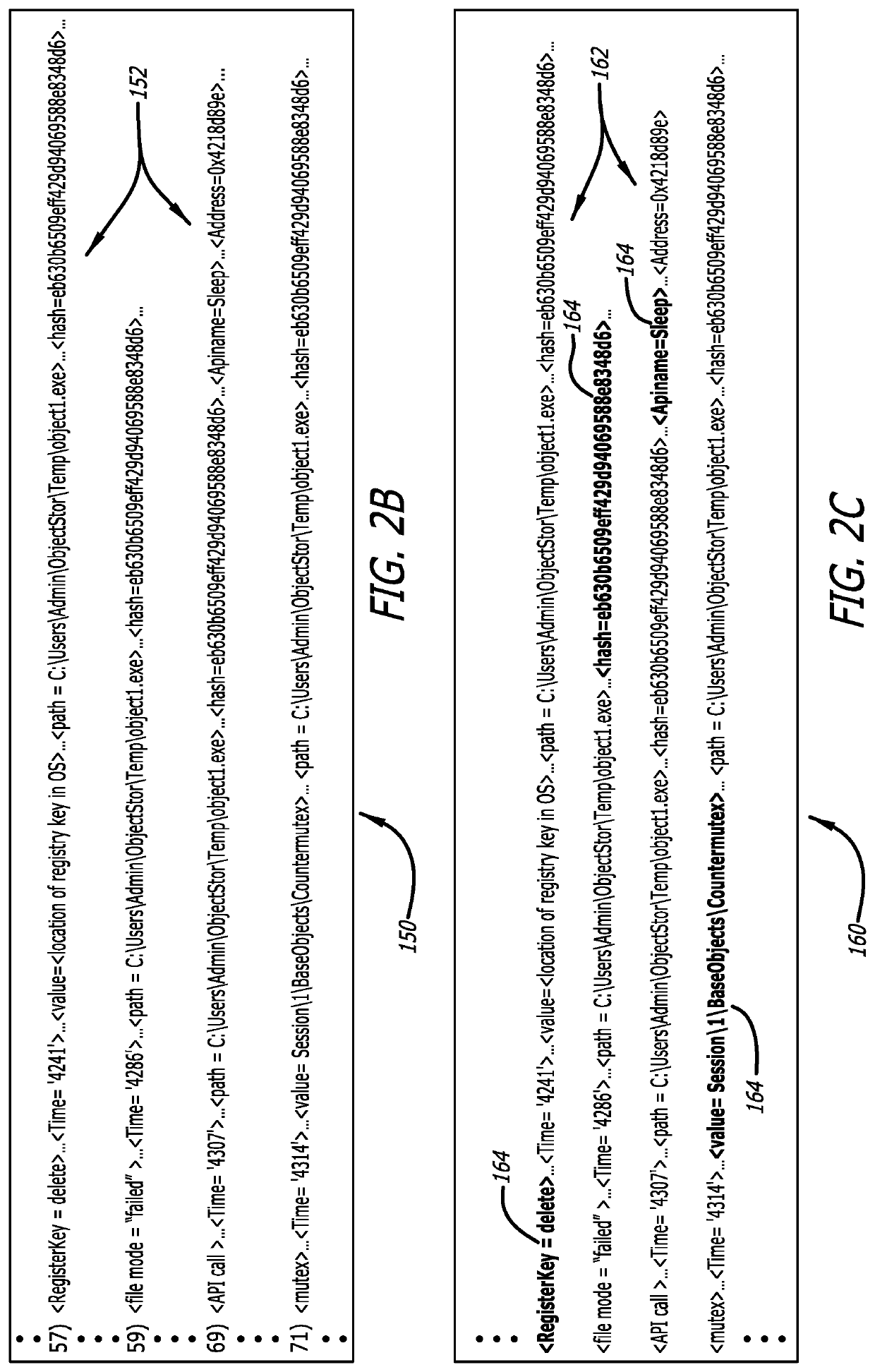
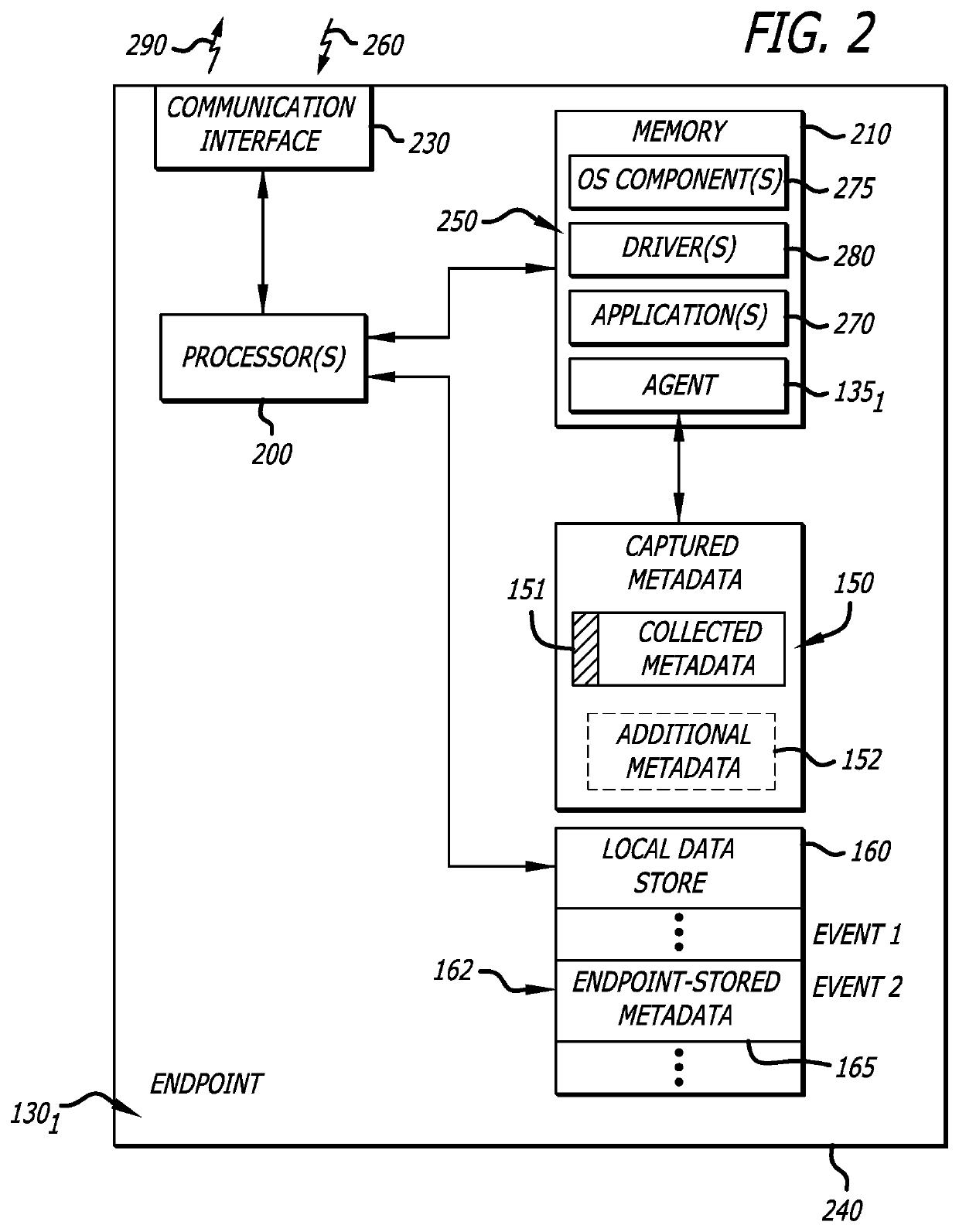
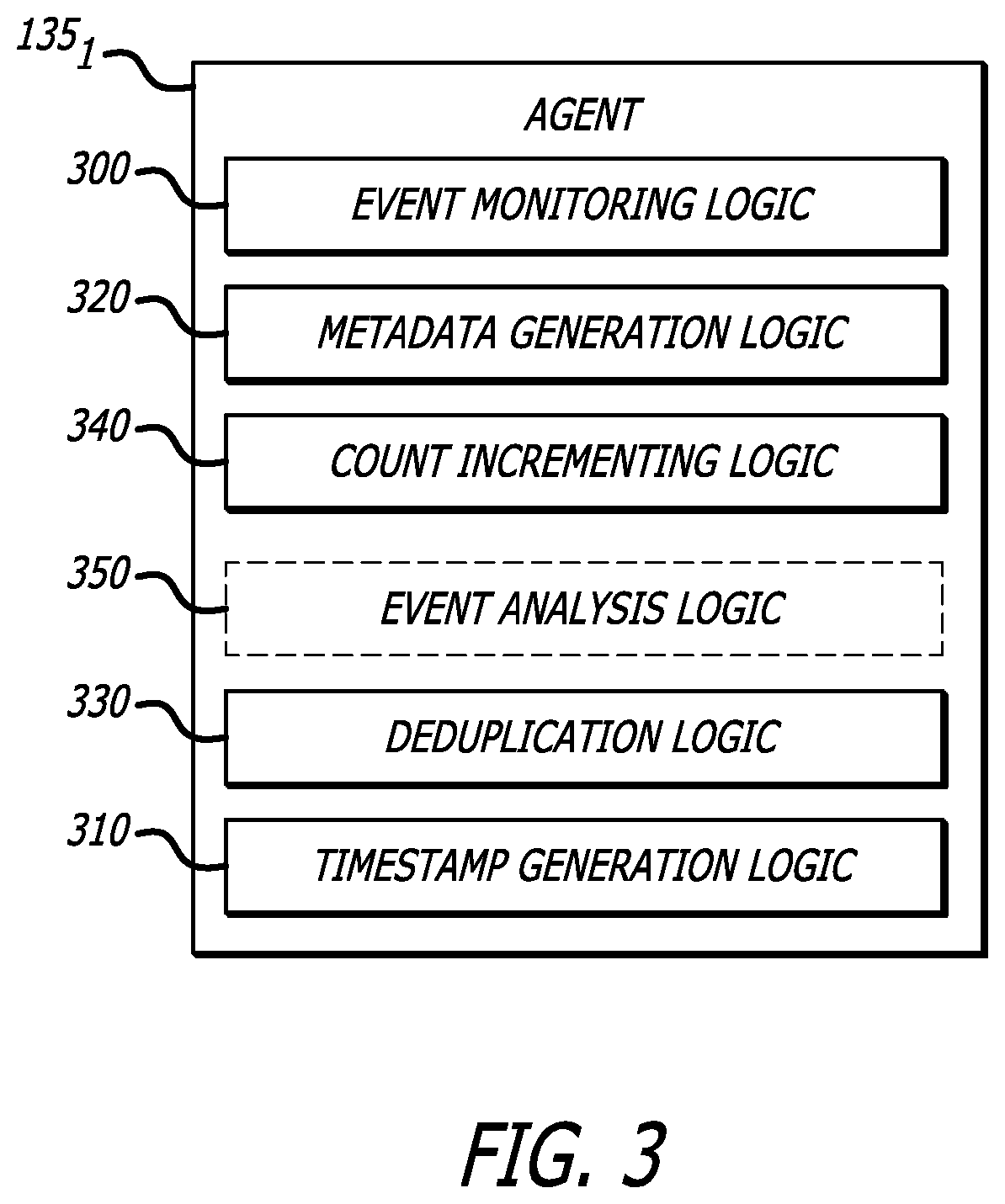
Method and system for efficient cybersecurity analysis of endpoint events
A comprehensive cybersecurity platform includes a cybersecurity intelligence hub, a cybersecurity sensor and one or more endpoints communicatively coupled to the cybersecurity sensor, where the platform allows for efficient scaling, analysis, and detection of malware and / or malicious activity. An endpoint includes a local data store and an agent that monitors for one or more types of events being performed on the endpoint, and performs deduplication within the local data store to identify “distinct” events. The agent provides the collected metadata of distinct events to the cybersecurity sensor which also performs deduplication within a local data store. The cybersecurity sensor sends all distinct events and / or file objects to a cybersecurity intelligence hub for analysis. The cybersecurity intelligence hub is coupled to a data management and analytics engine (DMAE) that analyzes the event and / or object using multiple services to render a verdict (e.g., benign or malicious) and issues an alert.
Owner:GOOGLE LLC
Method and system for evaluating individual and group cyber threat awareness
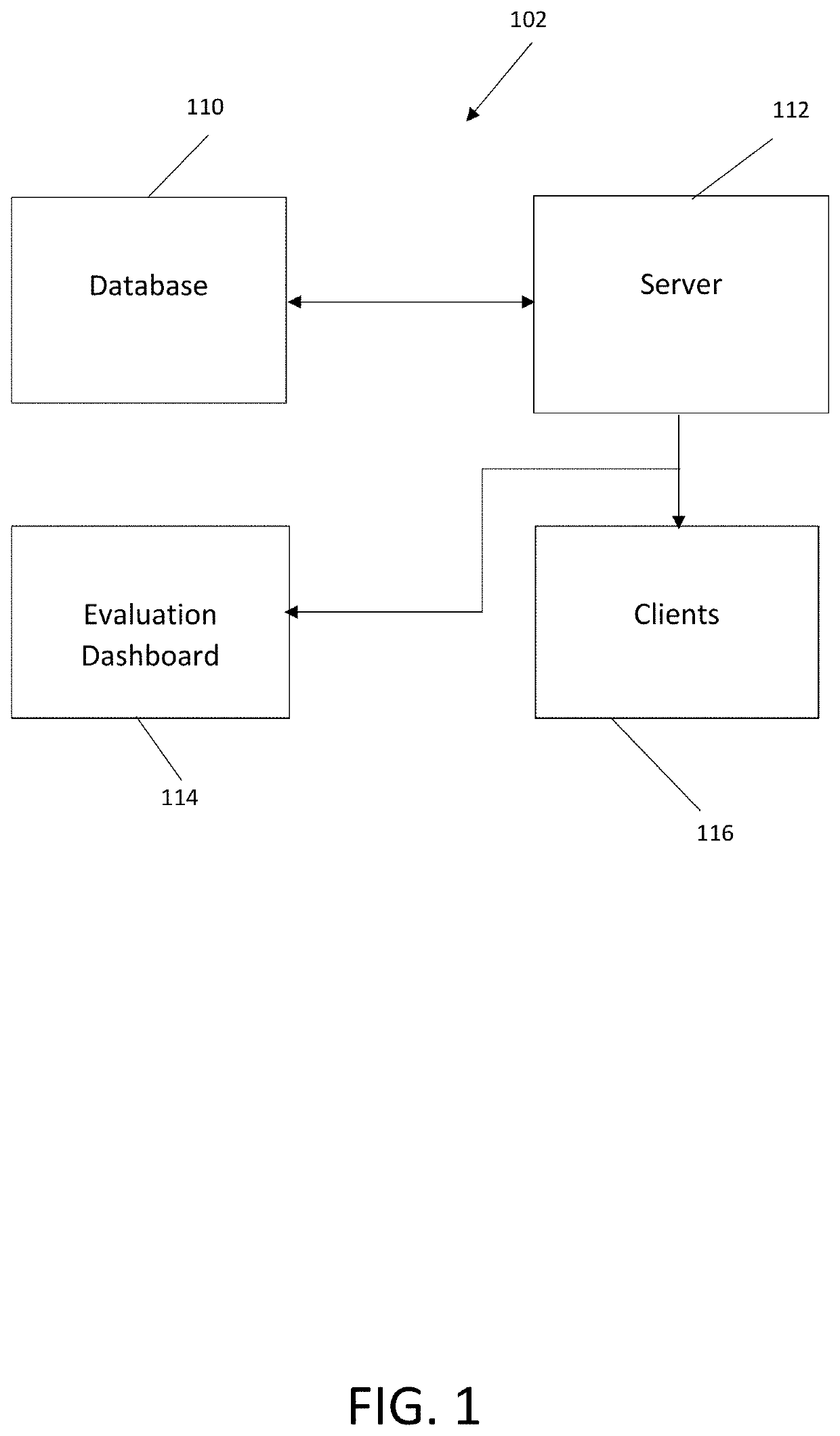
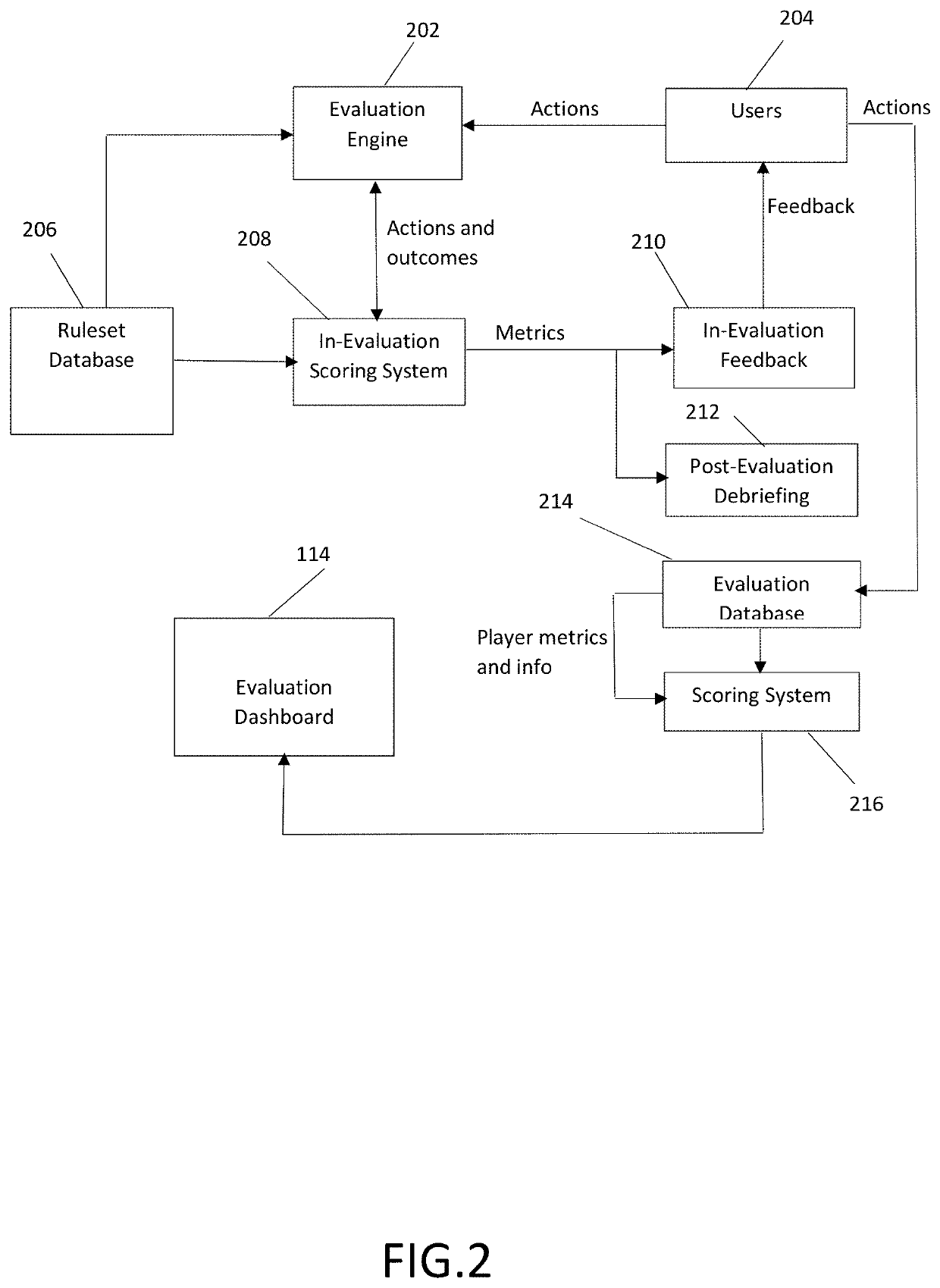
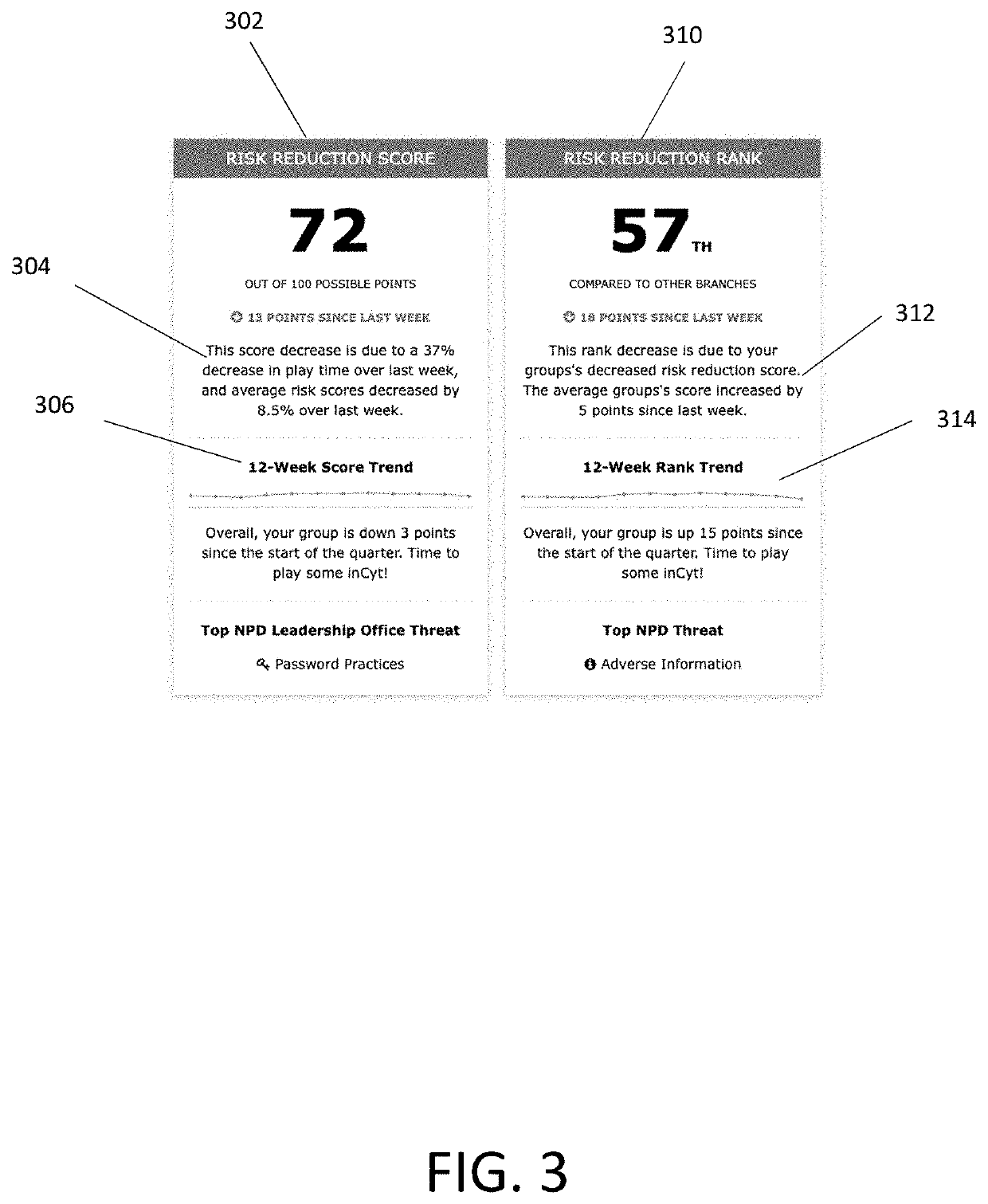
A system has an evaluation server that includes at least one database storing a plurality of cybersecurity awareness evaluations, the database connected to the server, a plurality of clients connected to the server and configured to run at least one of the cybersecurity awareness evaluations for play by users on user devices, the users performing actions in the evaluation including offensive actions and defensive actions, and an evaluation dashboard including an interface configured to display scoring results of the cybersecurity awareness evaluations as determined by the server, the scoring results including a plurality of offensive component scores for at least one of the users, a plurality of defensive component scores for at least one of the users, at least one composite offensive score for at least one of the users and at least one composite defensive score for at least one of the users, the composite offensive score being determined based on a plurality of the component offensive scores and the composite defensive score being determined based on a plurality of the component defensive scores.
Owner:CIRCADENCE
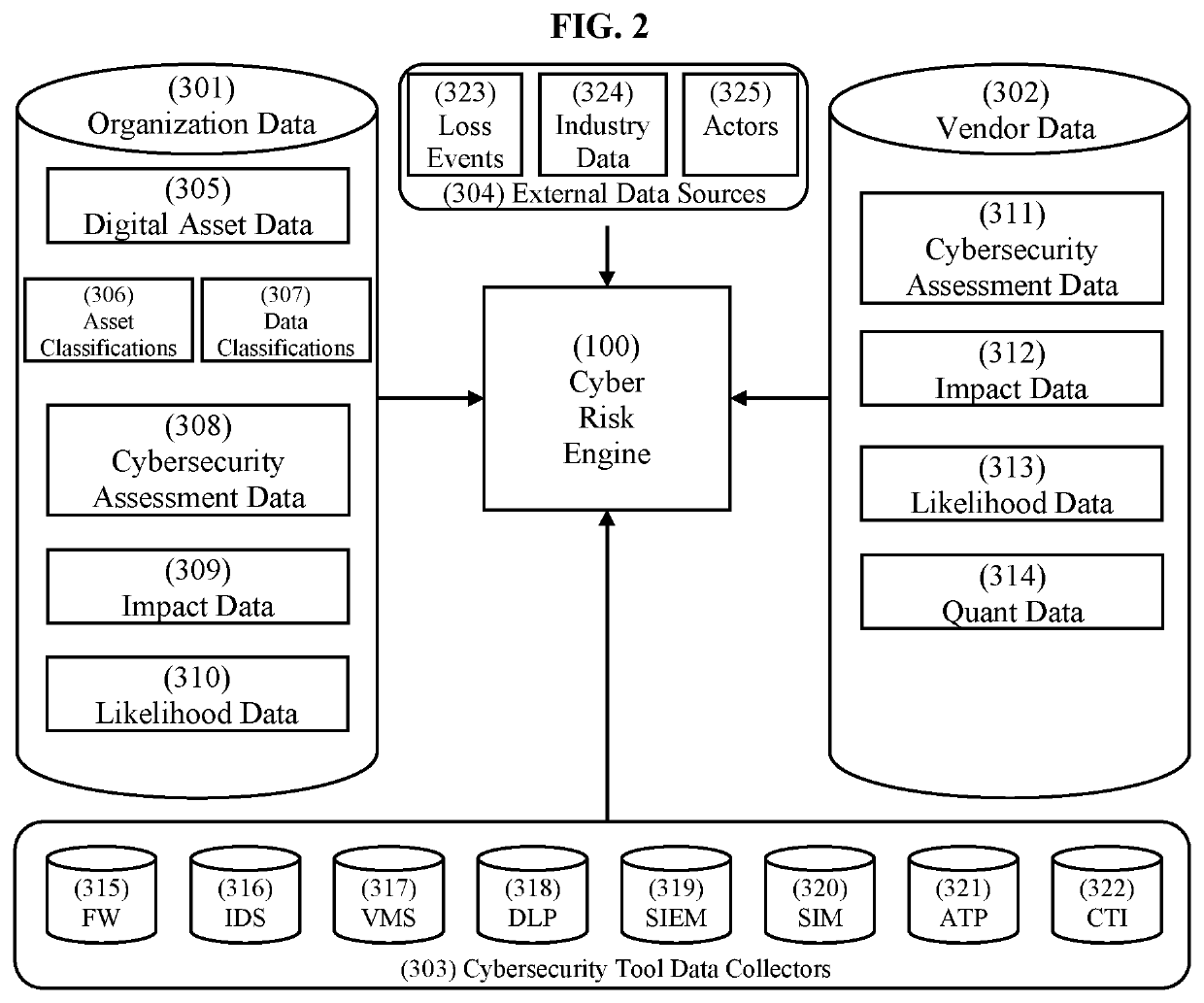
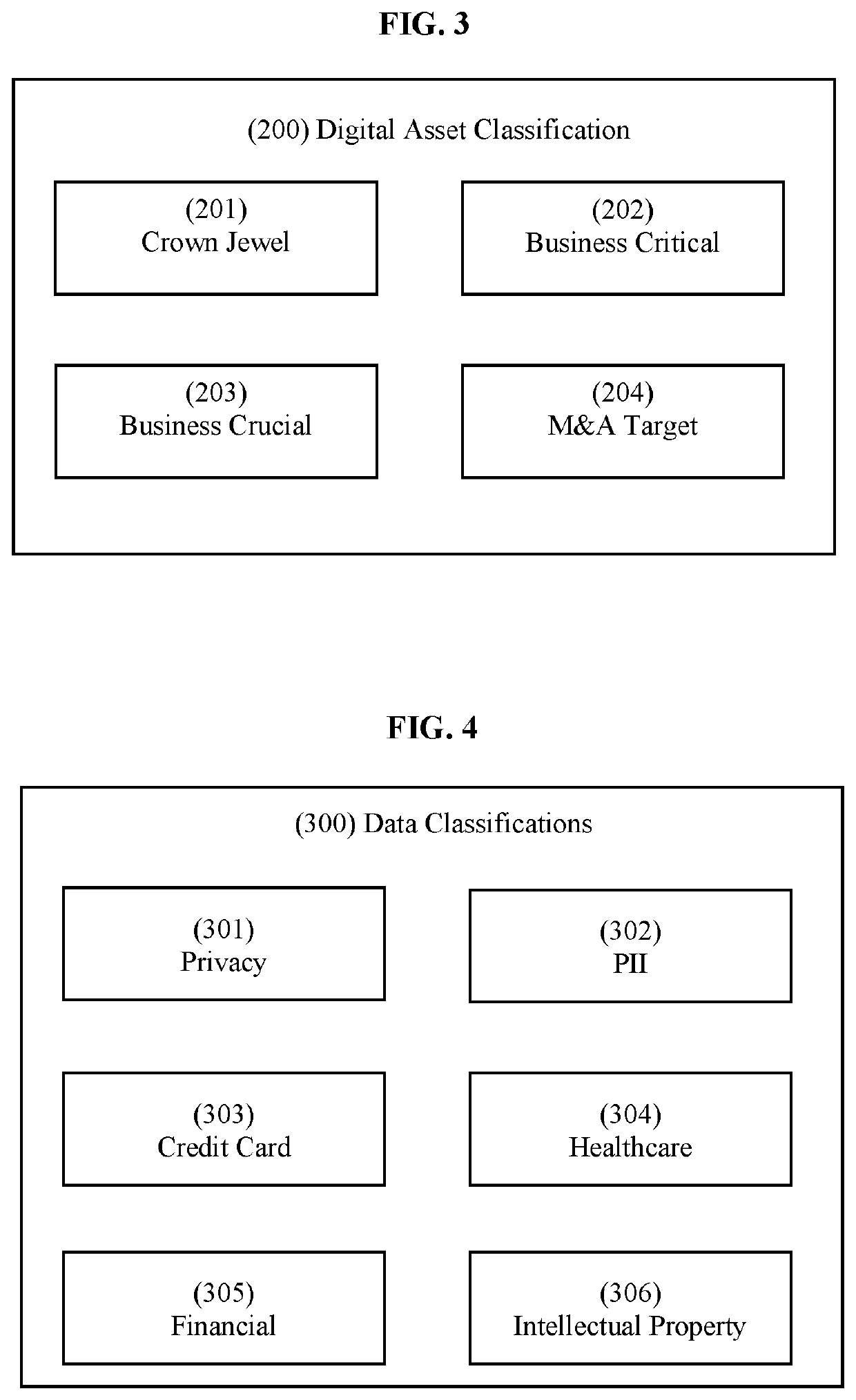
Digital asset based cyber risk algorithmic engine, integrated cyber risk methodology and automated cyber risk management system
PendingUS20200106801A1Lowering first party riskSpeed up the processFinanceTransmissionGraphical user interfaceRisk rating
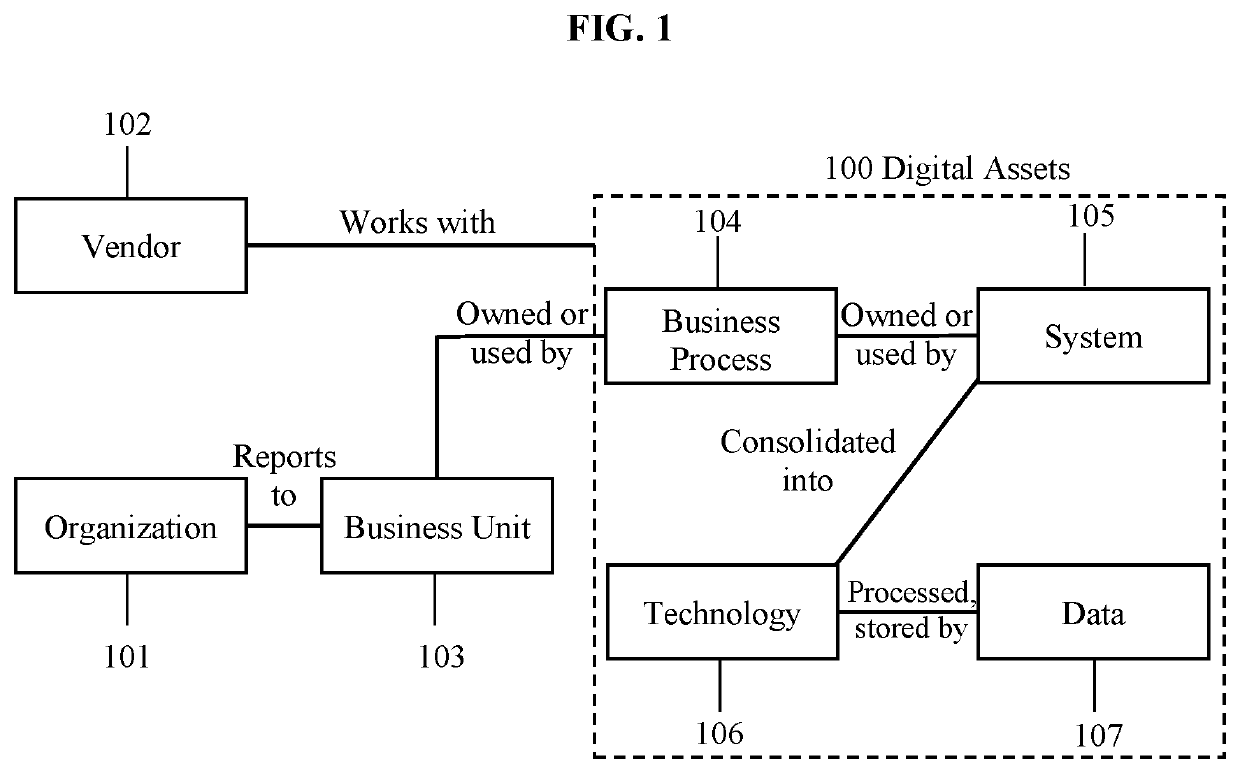
We are in a digital revolution. Over 85% of an organization's value is in digital form. Digital assets are systems, processes, data and technologies. Cyber exposures are quantified and cyber risks are scored. A graphical user interface visualizes a cyber-risk engine that quantifies cyber risk in alignment to how insurance companies pay claims, using flexible and multiple cyber risk algorithms that are prescribed in relationship to a customer's risk requirements. Digital asset cyber risk ratings are measured to increase cyber resiliency. A cyber risk management platform automates business processes across each cybersecurity function that provides data from near-real time cybersecurity tools for participants to reduce cyber risk back to acceptable risk tolerances and improve cyber resiliency.
Owner:RISKQ INC
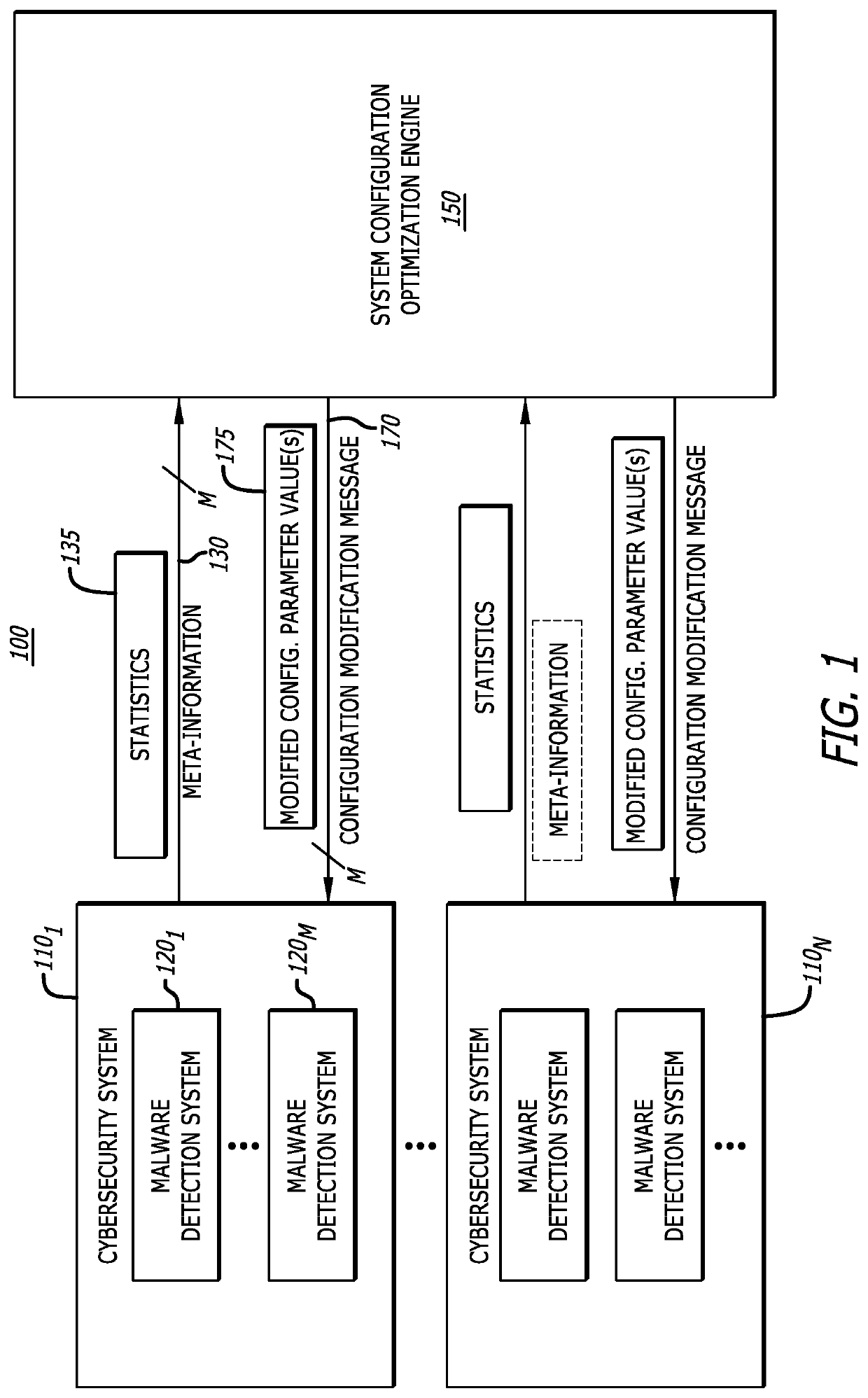
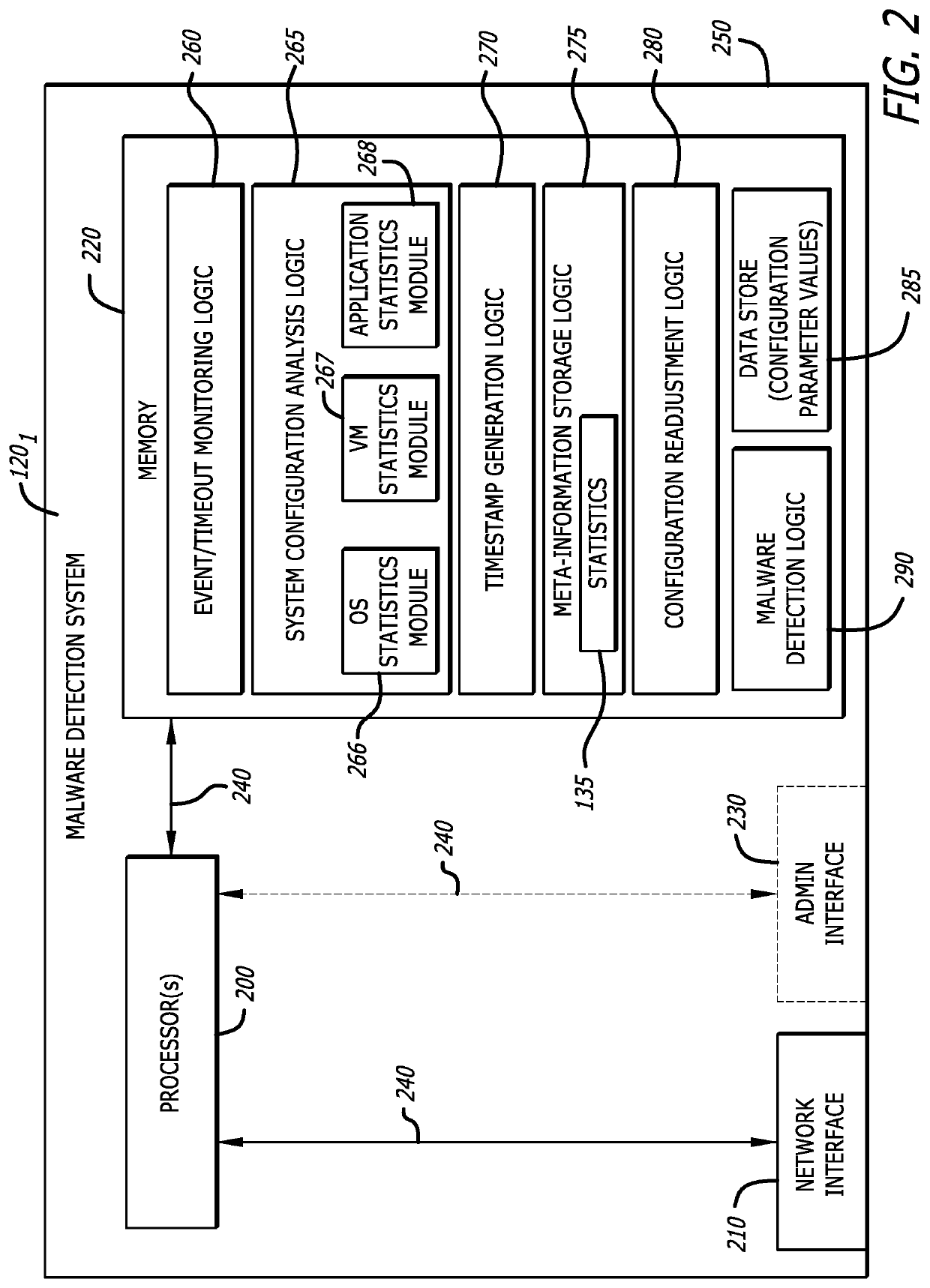
System and method for predicting and mitigating cybersecurity system misconfigurations
A computerized method for reconfiguring one or more malware detection systems each performing cybersecurity analyses on incoming data is described. The method involves receiving meta-information including metrics associated with a malware detection system. Based on the meta-information, a determination is made whether the malware detection system is operating at an optimal performance level. If not, results produced by conducting behavior analyses predicting operability of the malware detection system are determined and the results are provided as feedback to the malware detection system to update one or more configuration parameter values thereof.
Owner:FIREEYE INC
Measuring data-breach propensity
ActiveUS20200279041A1Quick identificationDigital data protectionDigital data authenticationUser authenticationDatabase
Provided is a process that includes: obtaining, with one or more processors, a set of user-authentication credentials of a plurality of users; accessing, with one or more processors, a repository of breached credentials and determining, with one or more processors, an amount of the obtained set of user-authentication credentials in the repository of breached credentials, wherein the repository includes credentials from a plurality of entities obtained after the entities suffered a breach; and determining, with one or more processors, a score based on the amount of the set of user-authentication credentials in the repository of breached credentials, wherein the score is indicative of effectiveness of cybersecurity practices of the entity and the users associated with the entity.
Owner:SPYCLOUD INC
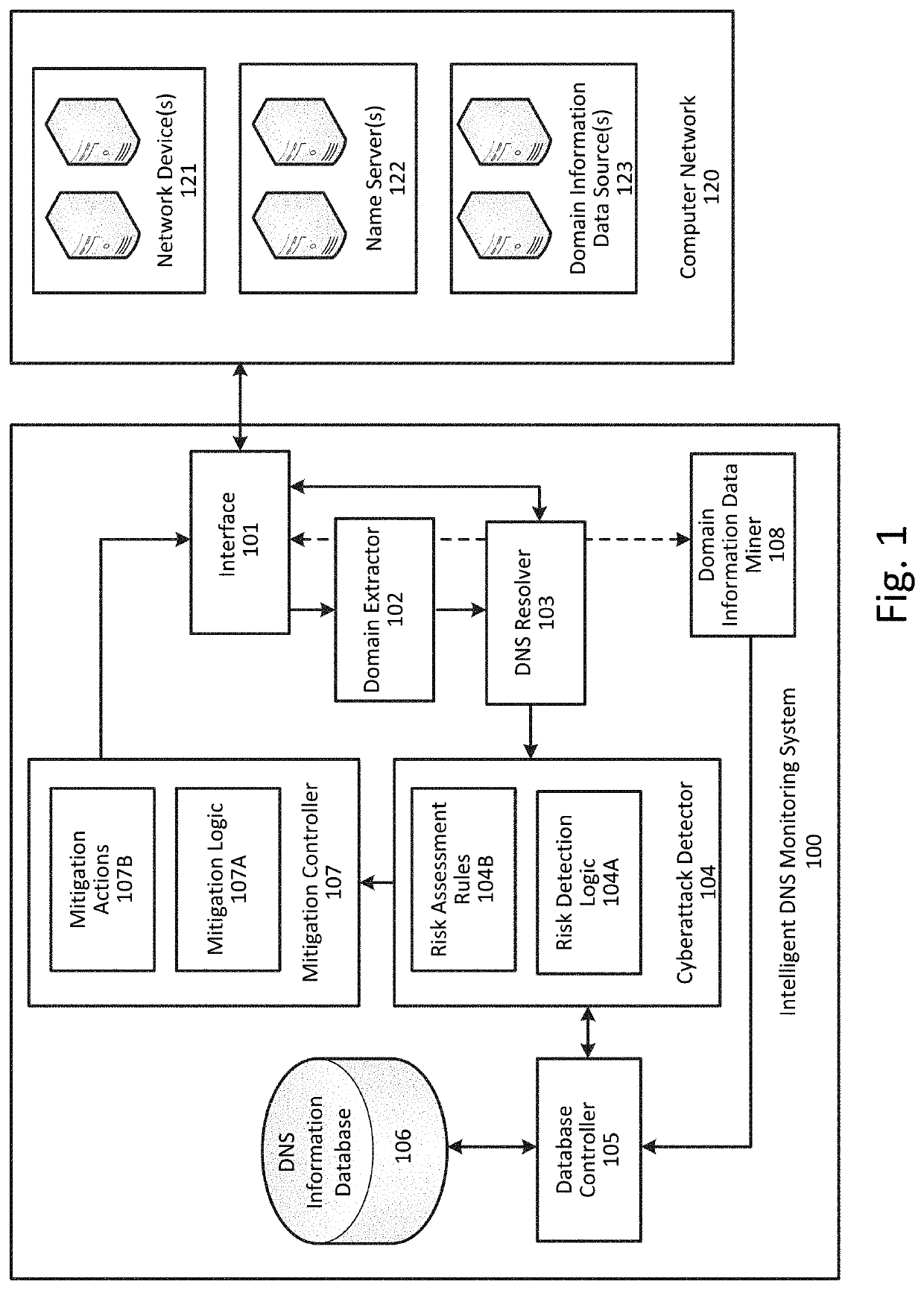
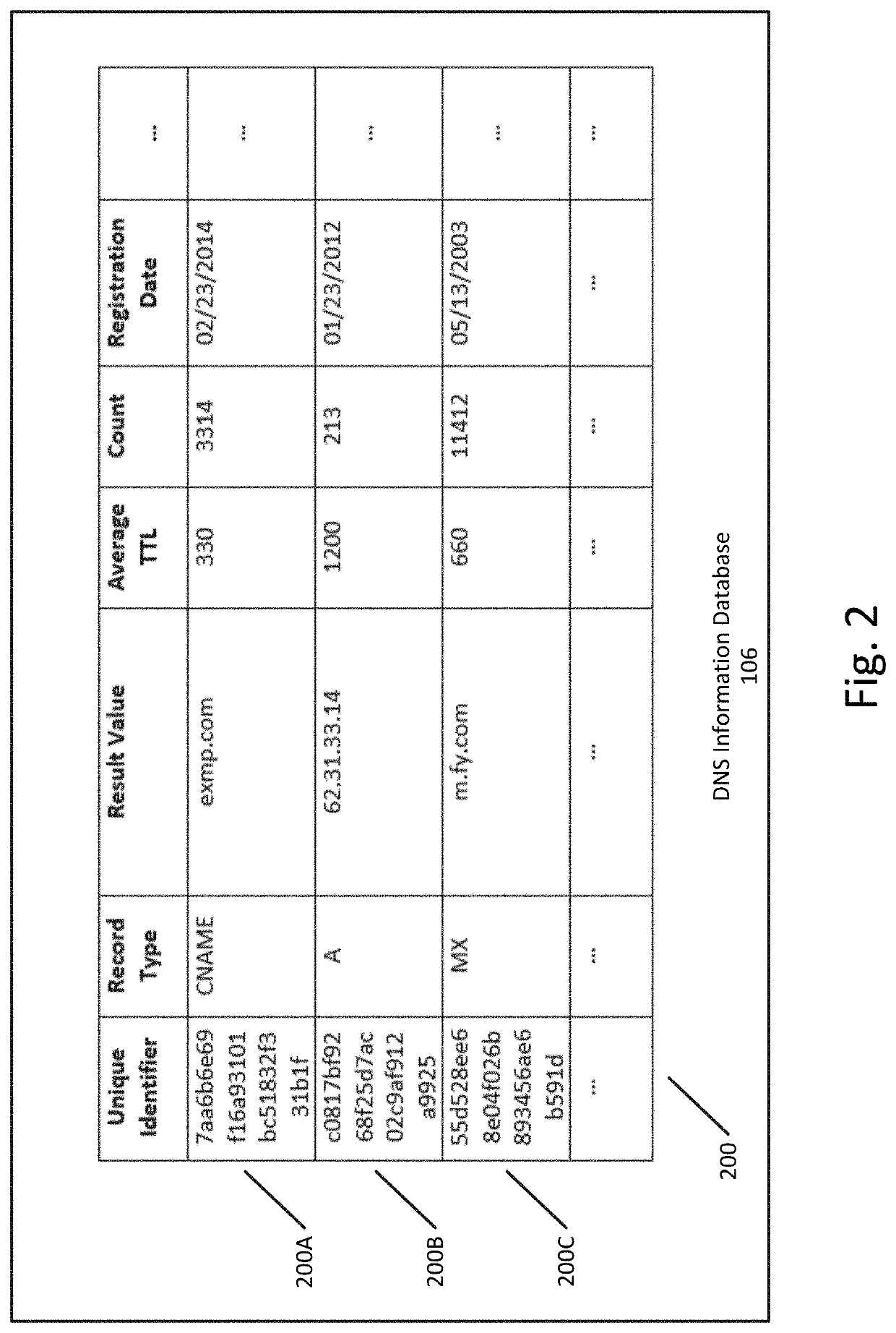
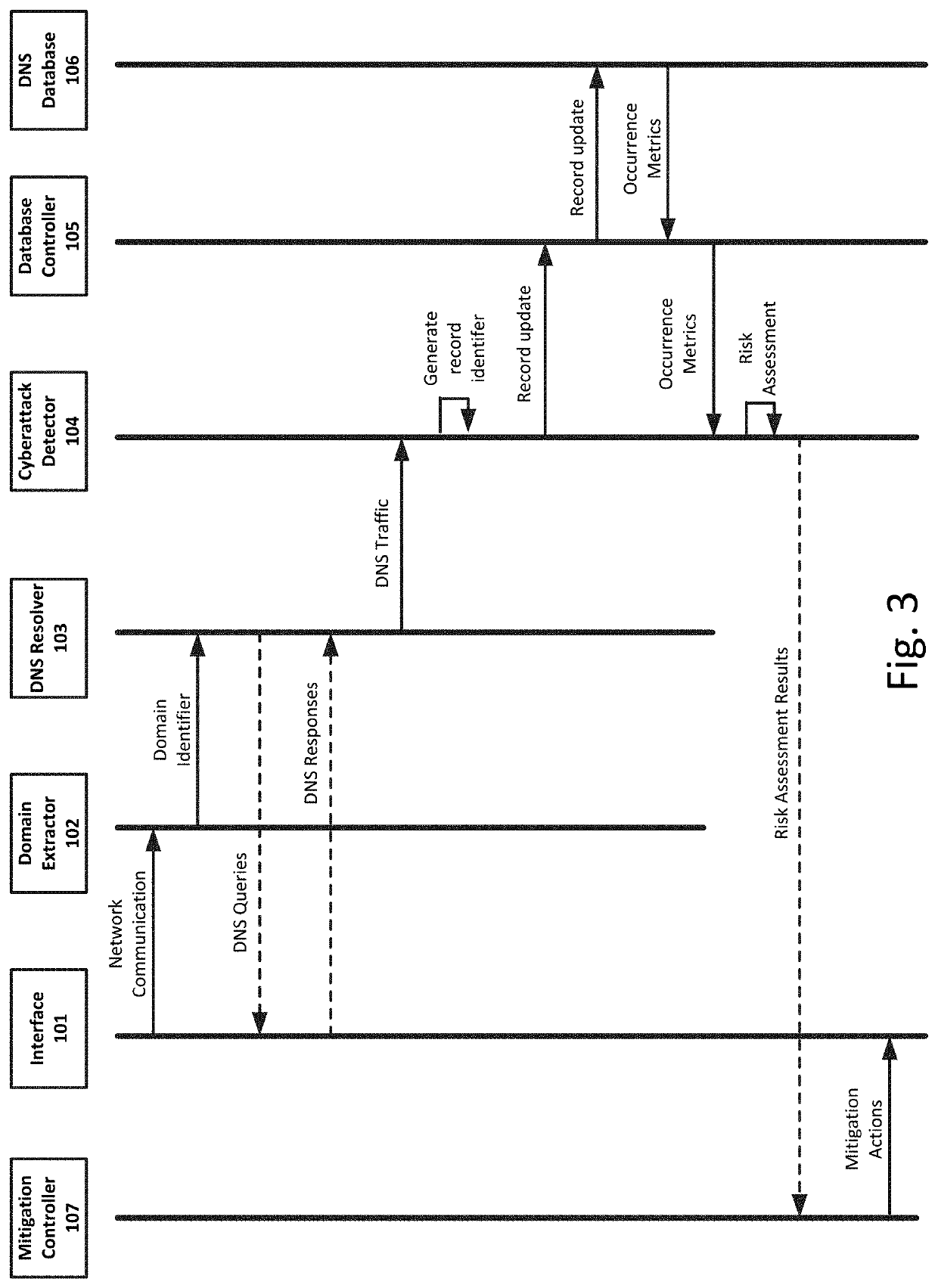
Intelligent system for mitigating cybersecurity risk by analyzing domain name system traffic
InactiveUS20200106790A1Performed quickly and accuratelyReduce Cybersecurity RisksDatabase updatingData switching networksDomain nameNetwork on
A system, method and computer-readable medium for mitigating cybersecurity risk by analyzing domain name system (DNS) traffic, including detecting a network communication propagated over a computer network, the network communication comprising a domain identifier, monitoring DNS traffic to and from one or more DNS servers relating to the domain identifier, the DNS traffic including one or more DNS queries and one or more corresponding responses, extracting information from the monitored DNS traffic to generate a record identifier, updating a DNS metadata record stored in memory and associated with the record identifier based at least in part on the monitored DNS traffic, the DNS metadata record including one or more occurrence metrics associated with instances of the domain identifier in previous DNS traffic, determining whether the one or more occurrence metrics are indicative of a cybersecurity risk, and activating one or more mitigation actions based at least in part on a determination that the one or more occurrence metrics are indicative of the cybersecurity risk.
Owner:FIREEYE INC
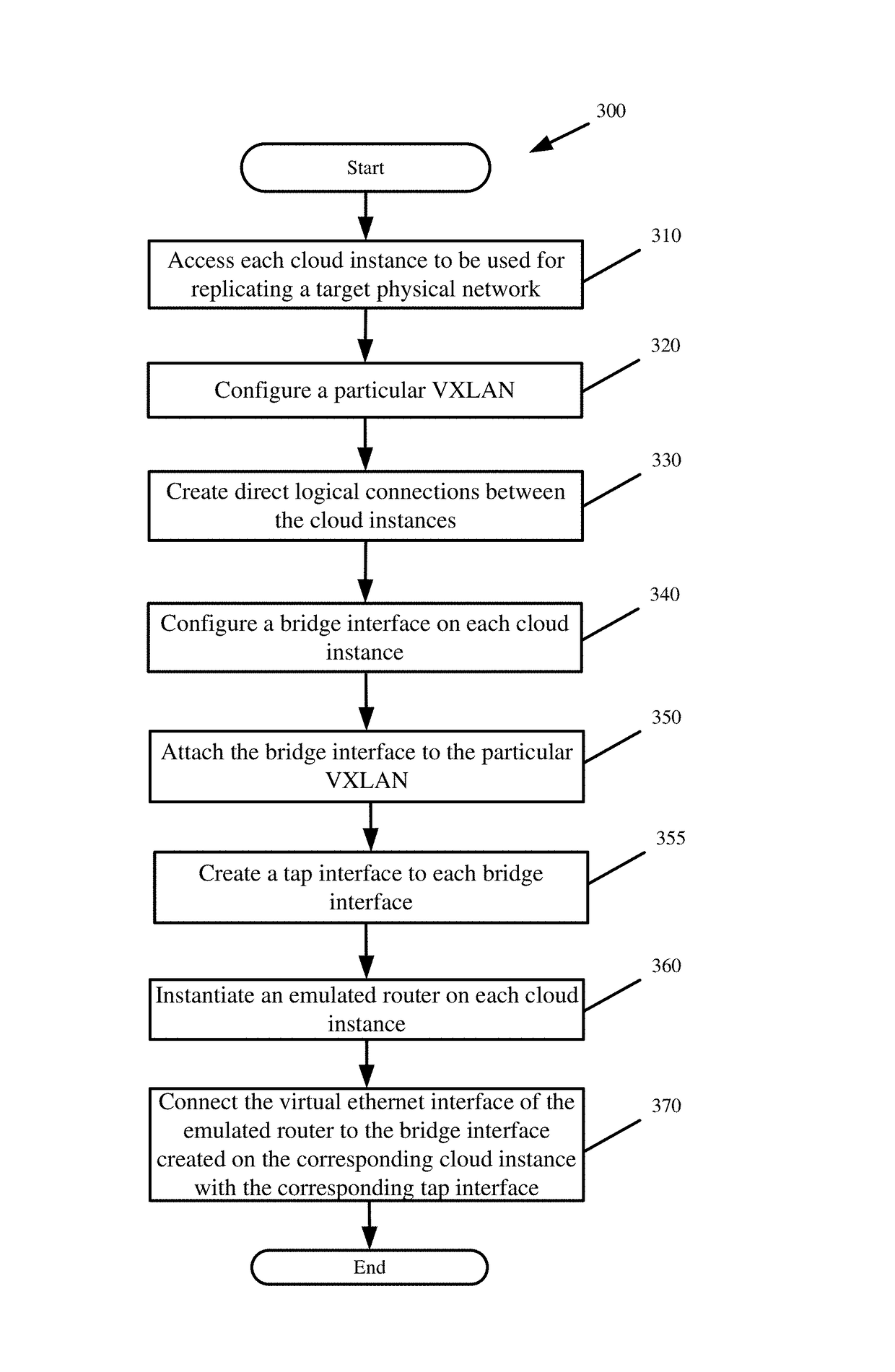
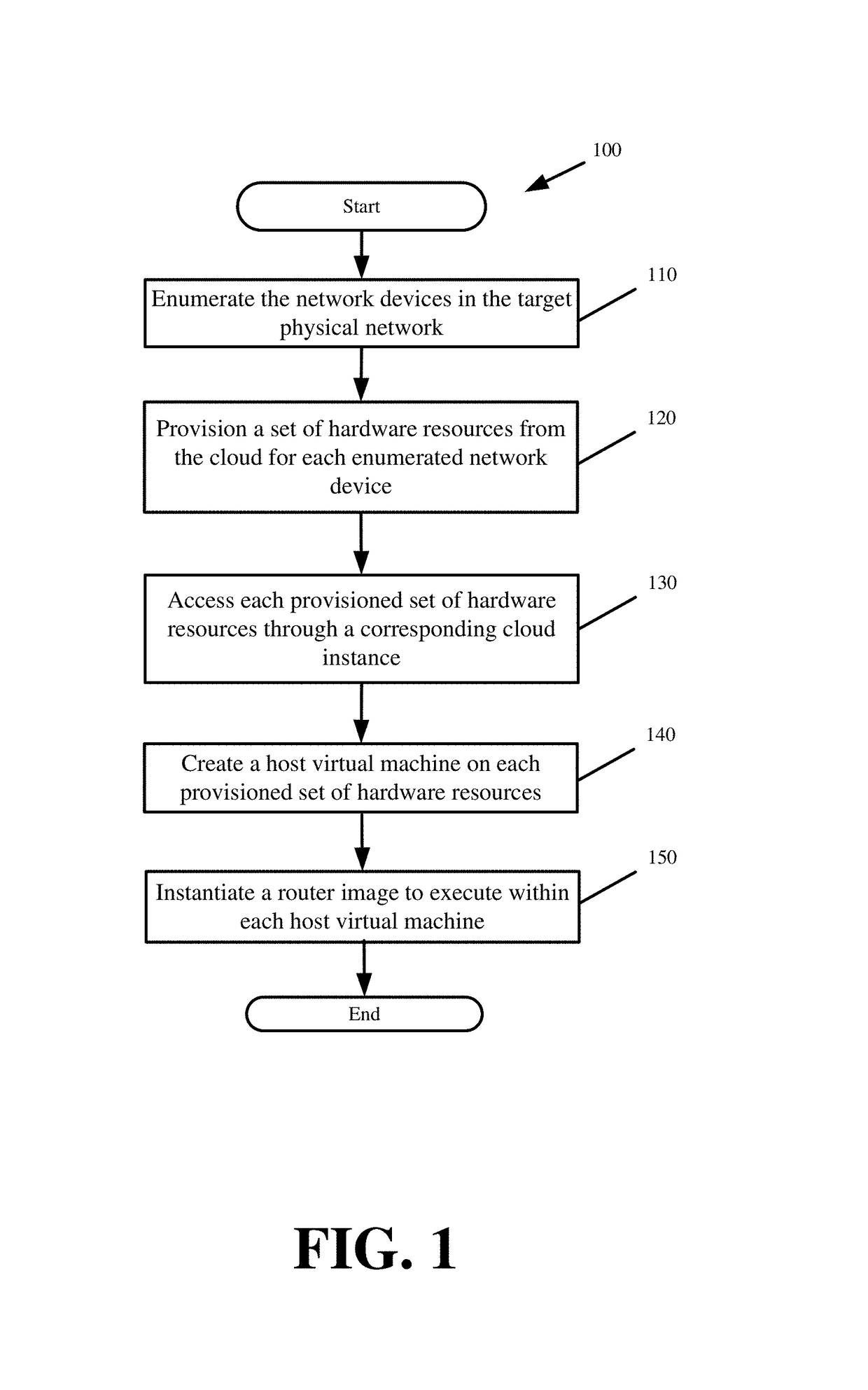
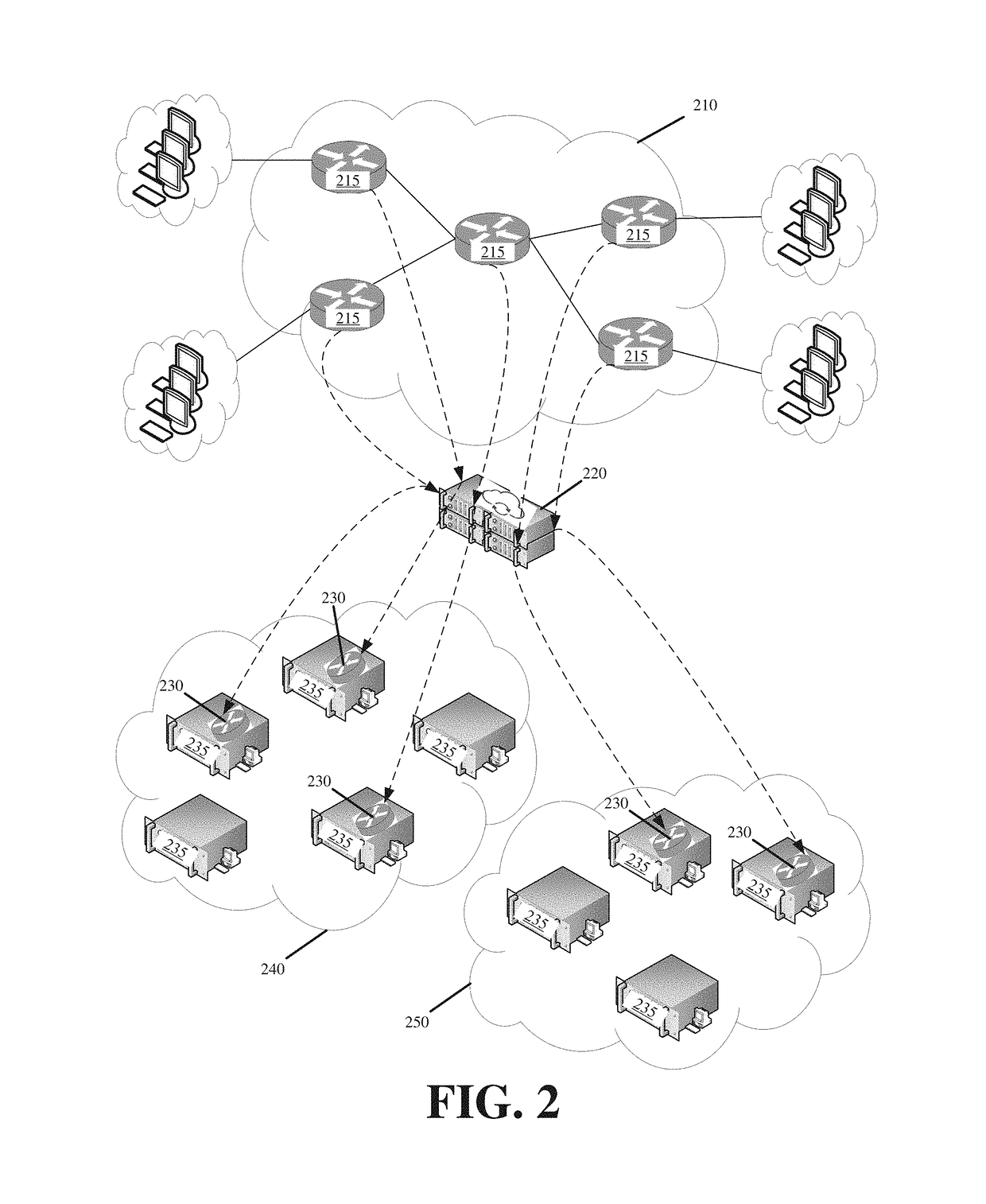
Holistic validation of a network via native communications across a mirrored emulation of the network
A replication of a physical network is created in the cloud. The replicated network safely validates configuration changes for any hardware network device of the physical network and the physical network end state resulting from the changes without impacting the physical network steady state. The replicated network creates virtual machines on hardware resources provisioned from the cloud. The virtual machines emulate network device functionality and have the same addressing as the network devices. Nested overlay networks reproduce the direct connectivity that exists between different pairs of the network devices on the virtual machines. A first overlay network formed by a first Virtual Extensible Local Area Network (VXLAN) provides direct logical connections between the cloud machines on which the virtual machines execute. A second overlay network of VXLANs leverages the first VXLAN to establish direct logical connections between the virtual machines that mirror the direct connections between the network devices.
Owner:FASTLY
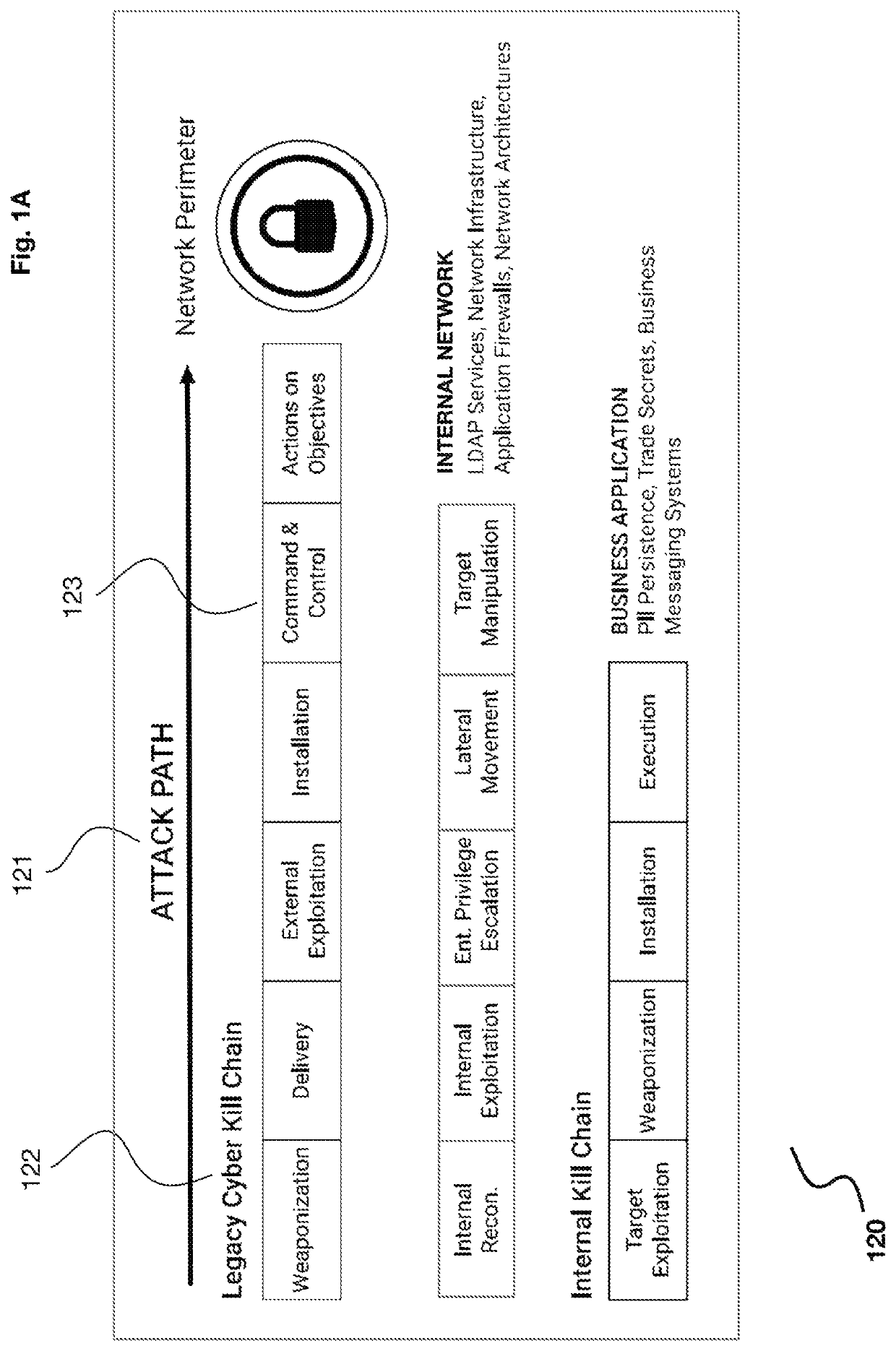
User and entity behavioral analysis using an advanced cyber decision platform
A cybersecurity system that protects against cyber attacks by performing user and device behavioral analysis using an advanced cyber decision platform which creates a map of users and devices attached to a network, develops a baseline of expected interactions and behaviors for each user and device in the map, and monitors deviations from the expected interactions and behaviors.
Owner:QOMPLX LLC
Multi-dimensional cybersecurity skills assessment method and system
A method, system and computer usable program product for assessing a cybersecurity skill of a participant, can involve generating and outputting to an I / O device, a user interface that includes user input fields for receiving data related to a cybersecurity task from a participant of a cybersecurity assessment facilitated by the user interface, the user interface operable to assess a cybersecurity skill of the participant as a part of the cybersecurity assessment. The cybersecurity skill of the participant via can be assessed via the user interface, based on metrics that indicate how the participant achieved the cybersecurity task as compared to at least one other participant of the cybersecurity assessment, and after the cybersecurity task has been completed by the participant via the user interface.
Owner:EC COUNCIL INT LTD
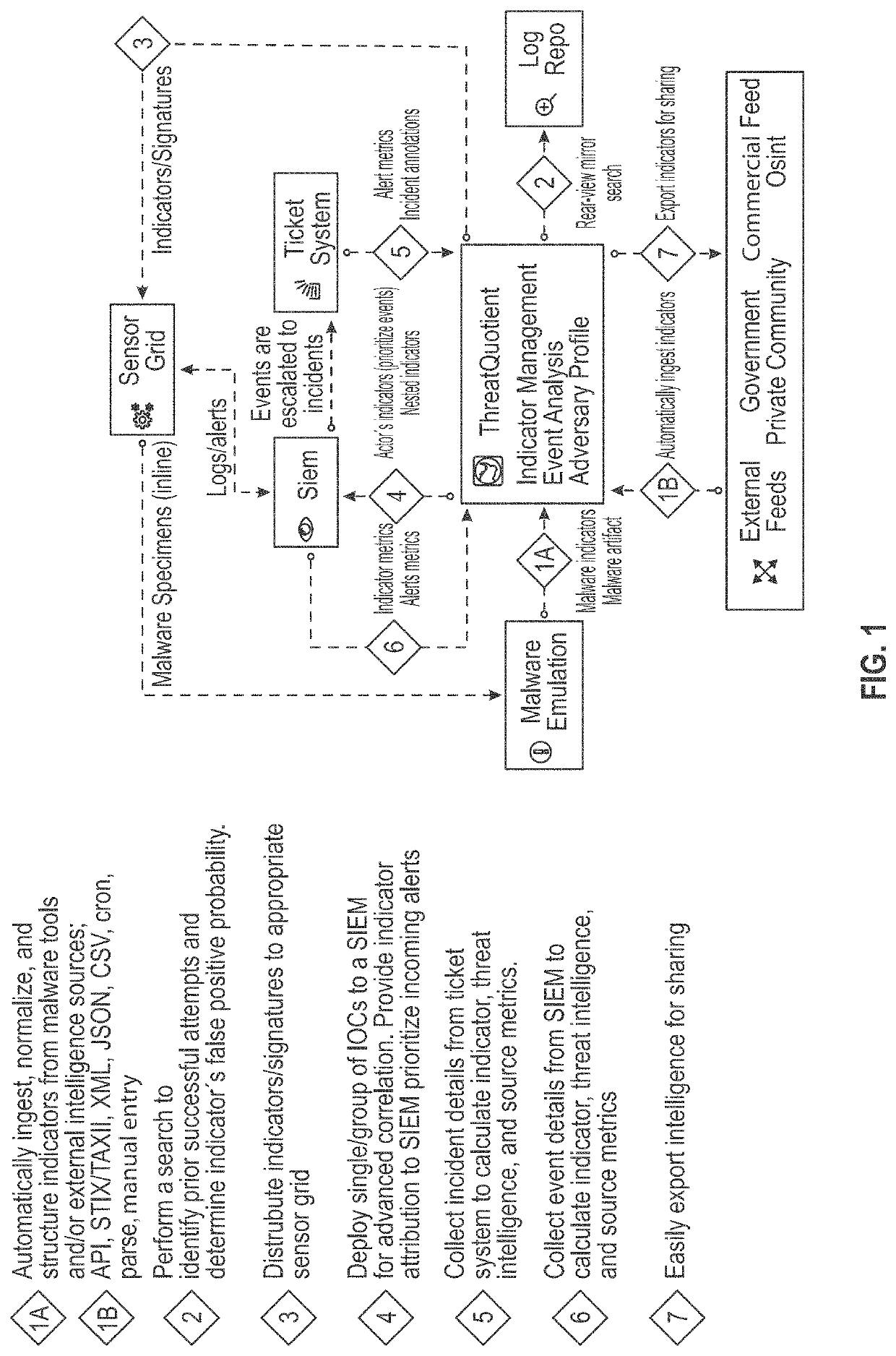
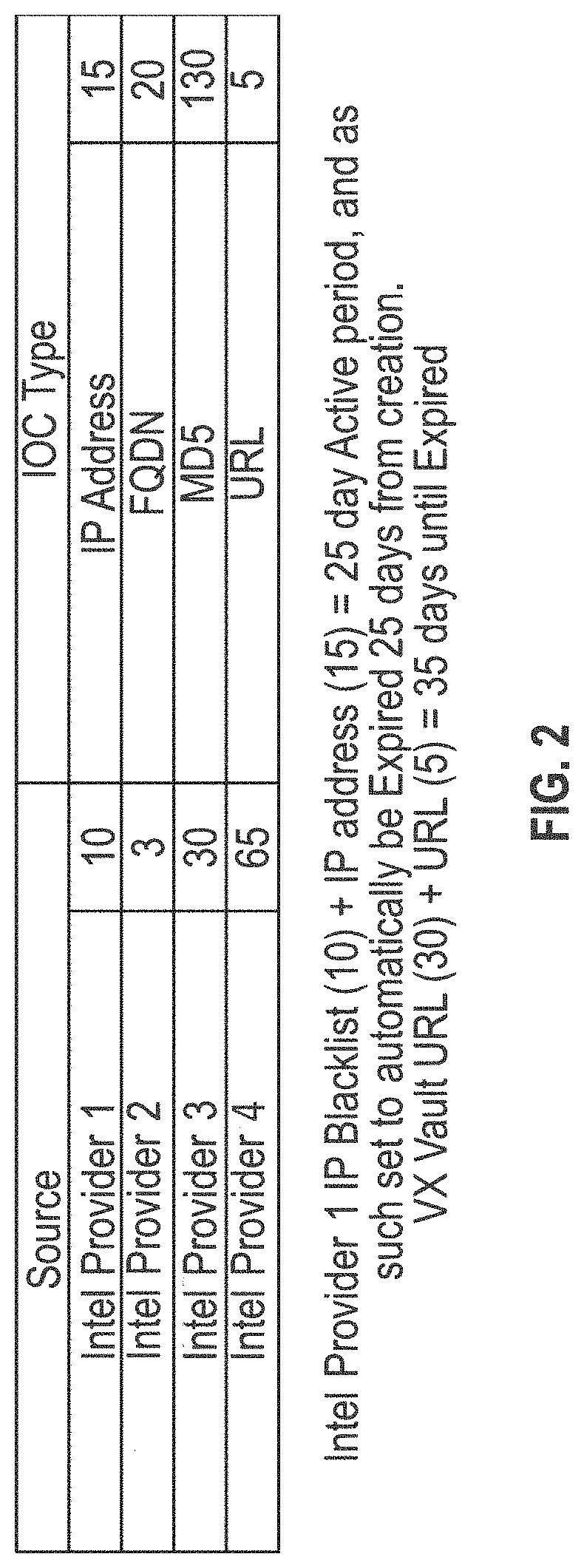
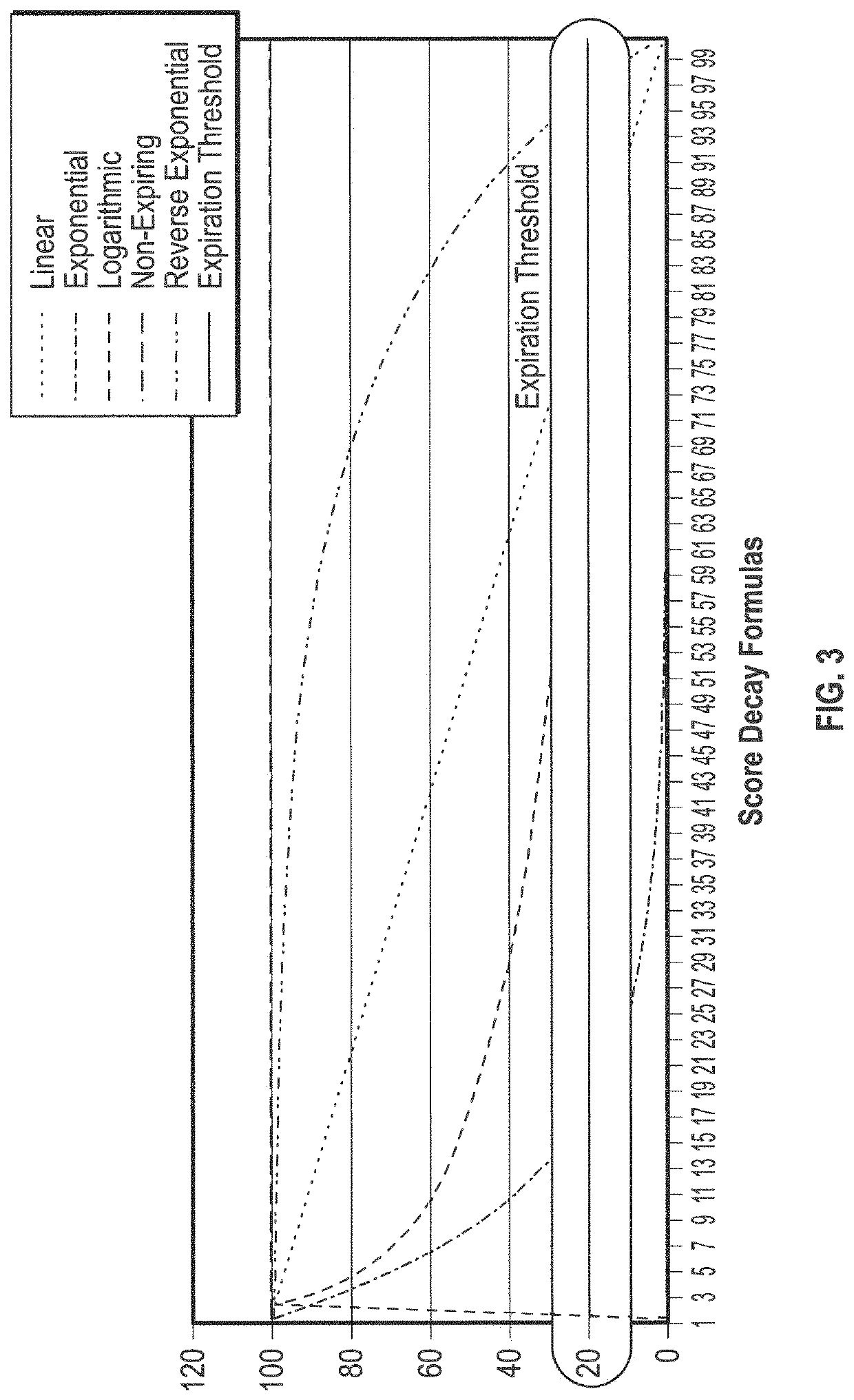
Automated cybersecurity threat detection with aggregation and analysis
The systems and methods described herein generally relate to techniques for automated detection, aggregation, and integration of cybersecurity threats. The system ingests multiple data feeds which can be in one or numerous different formats. The system evaluates information based on defined scores to display to users threats and risks associated with them. The system also calculates decay rates for expiration of threats and indicators through various methods.
Owner:THREATQUOTIENT INC
Inquiry response mapping for determining a cybersecurity risk level of an entity
ActiveUS20200285754A1Reduce data conflictsPlatform integrity maintainanceMachine learningRisk levelData set
The present disclosure provides a method, system, and device for inquiry response mapping for determining a cybersecurity risk level of an entity. To manage and / or evaluate a cybersecurity risk level based on a relationship between a first entity and a second entity, questionnaires (e.g., requests or inquires) are often exchanged between two entities. One or more aspects of the present disclosure provide populating data sets (e.g., questionnaires) indicative of risk level for the first entity or the second entity. One or more other aspects of the present disclosure further provide determining a cybersecurity risk level of an entity by mapping responses to a plurality of inquiry sets directed to the first entity or the second entity.
Owner:SECURITYSCORECARD
System and method for comprehensive data loss prevention and compliance management
ActiveUS10681074B2Avoid data lossPlatform integrity maintainanceData switching networksAttackData loss
Owner:QOMPLX LLC
Inferring temporal relationships for cybersecurity events
ActiveUS20200322361A1Improve accuracyIncrease speedDatabase management systemsSemantic analysisTemporal informationData source
A cognitive security analytics platform is enhanced by providing a technique for automatically inferring temporal relationship data for cybersecurity events. In operation, a description of a security event is received, typically as unstructured security content or data. Information such as temporal data or cues, are extracted from the description, along with security entity and relationship data. Extracted temporal information is processing according to a set of temporal markers (heuristics) to determine a time value marker (i.e., an established time) of the security event. This processing typically involves retrieval of information from one or more structured data sources. The established time is linked to the security entities and relationships. The resulting security event, as augmented with the identified temporal data, is then subjected to a management operation.
Owner:IBM CORP
Cybersecurity vulnerability classification and remediation based on installation base
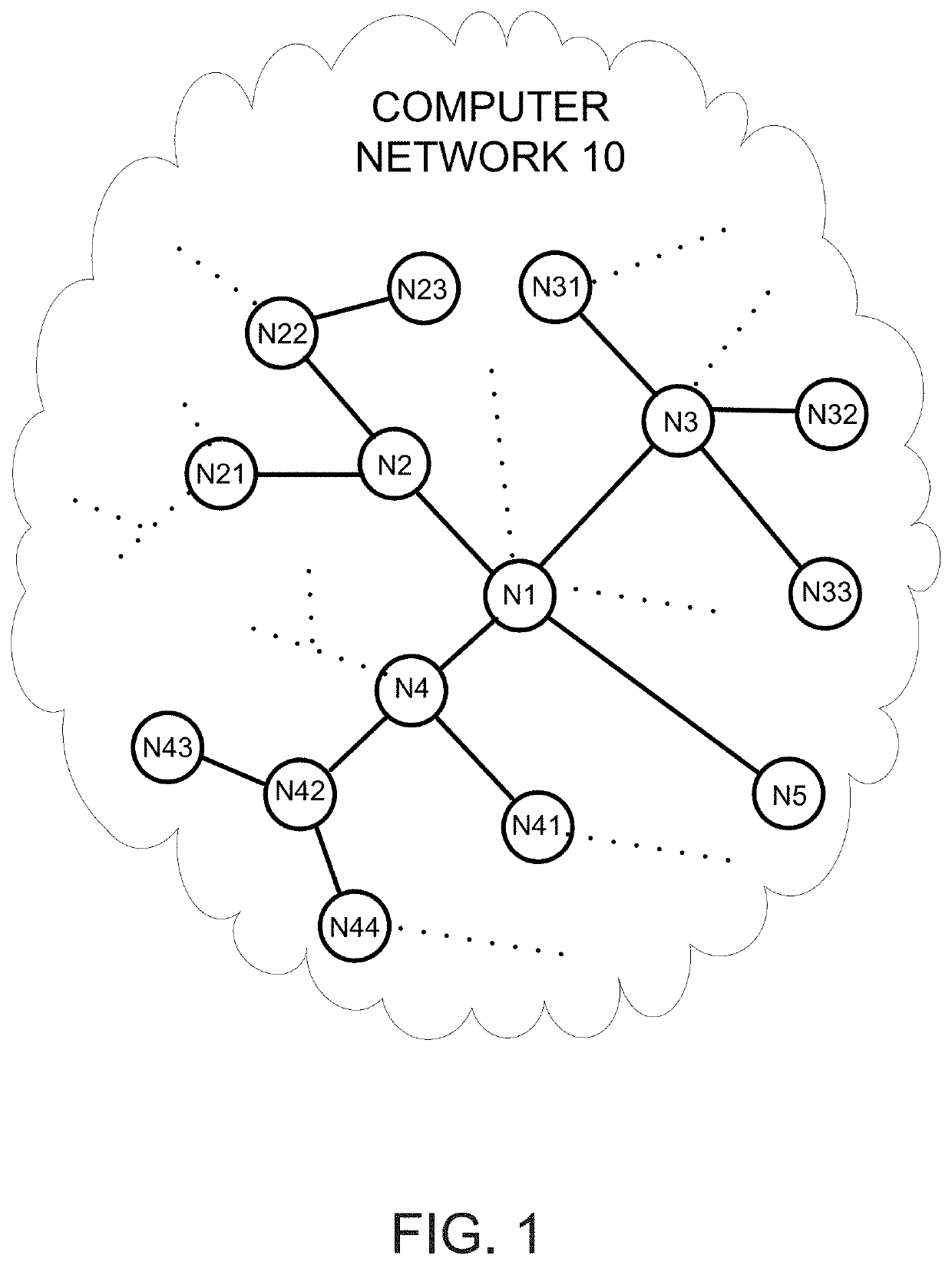
ActiveUS20210037038A1Reduce the risk of cyber attacksDiagnosticsSurgical navigation systemsCyber-attackSeverity level
A system, a method, and a computer program for remediating a cyberattack risk for a computing resource located at a node in a computer network having a plurality of nodes. The solution includes receiving vulnerability score data that has a severity level for a vulnerability in the computing resource at the node, receiving a number of installations value (NCRi) that indicates a number of instances the computing resource is included in the plurality of nodes, determining a percentile of occurrence value (POCRi) for the computing resource based on the number of installations value (NCRi), applying a severity adjustment matrix to the severity level to determine a true severity level for the vulnerability in the computing resource, reprioritized the vulnerability in the computing resource based on the true severity level, and mitigating the cyberattack risk for the computing resource based on the true severity level.
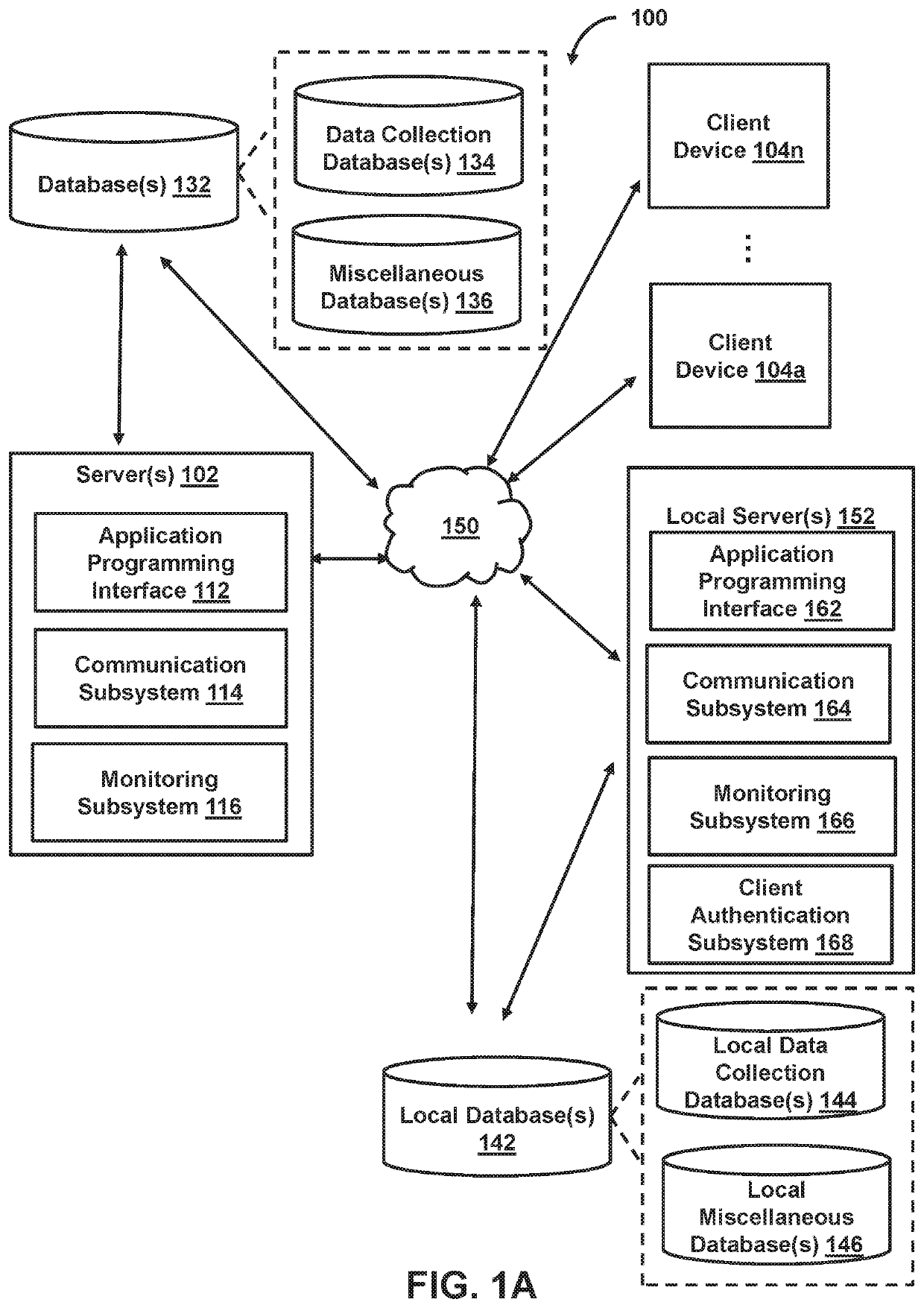
Owner:SAUDI ARABIAN OIL CO
System and methods for automatically assessing and improving a cybersecurity risk score
PendingUS20220060512A1Enhance cybersecurity analysisImprove scoreWeb data indexingTransmissionData miningNetwork topology
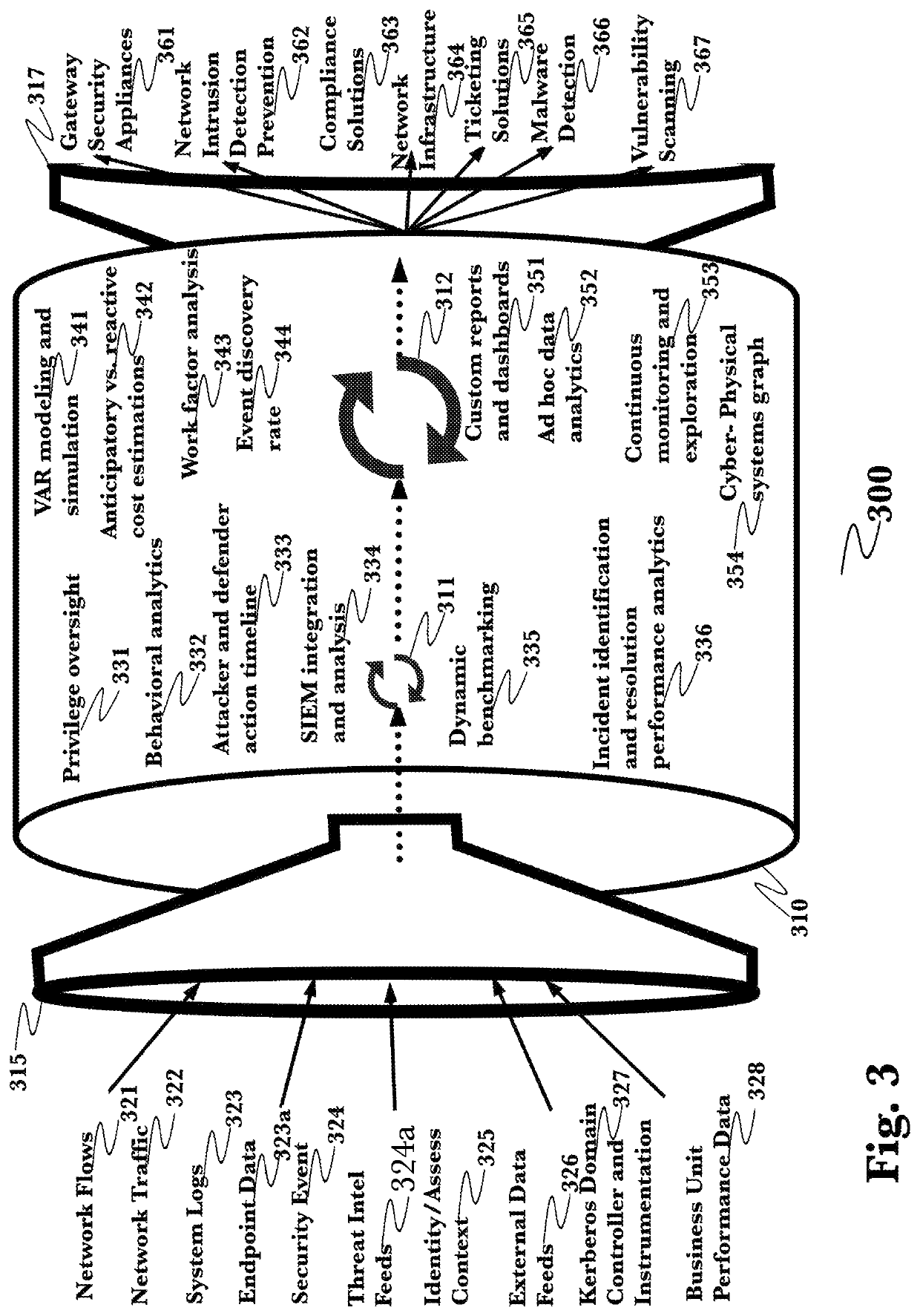
A system and method for automatically assessing and improving a cybersecurity risk score, wherein a cybersecurity risk score and cyber-physical graph for a network are retrieved and analyzed to identify potential improvements that can be made to network topography and device configurations, changes are applied automatically and an updated cyber-physical graph reflecting the applied changes is produced, and the updated cyber-physical graph is reassessed to determine the effect of the changes that were applied.
Owner:QPX LLC
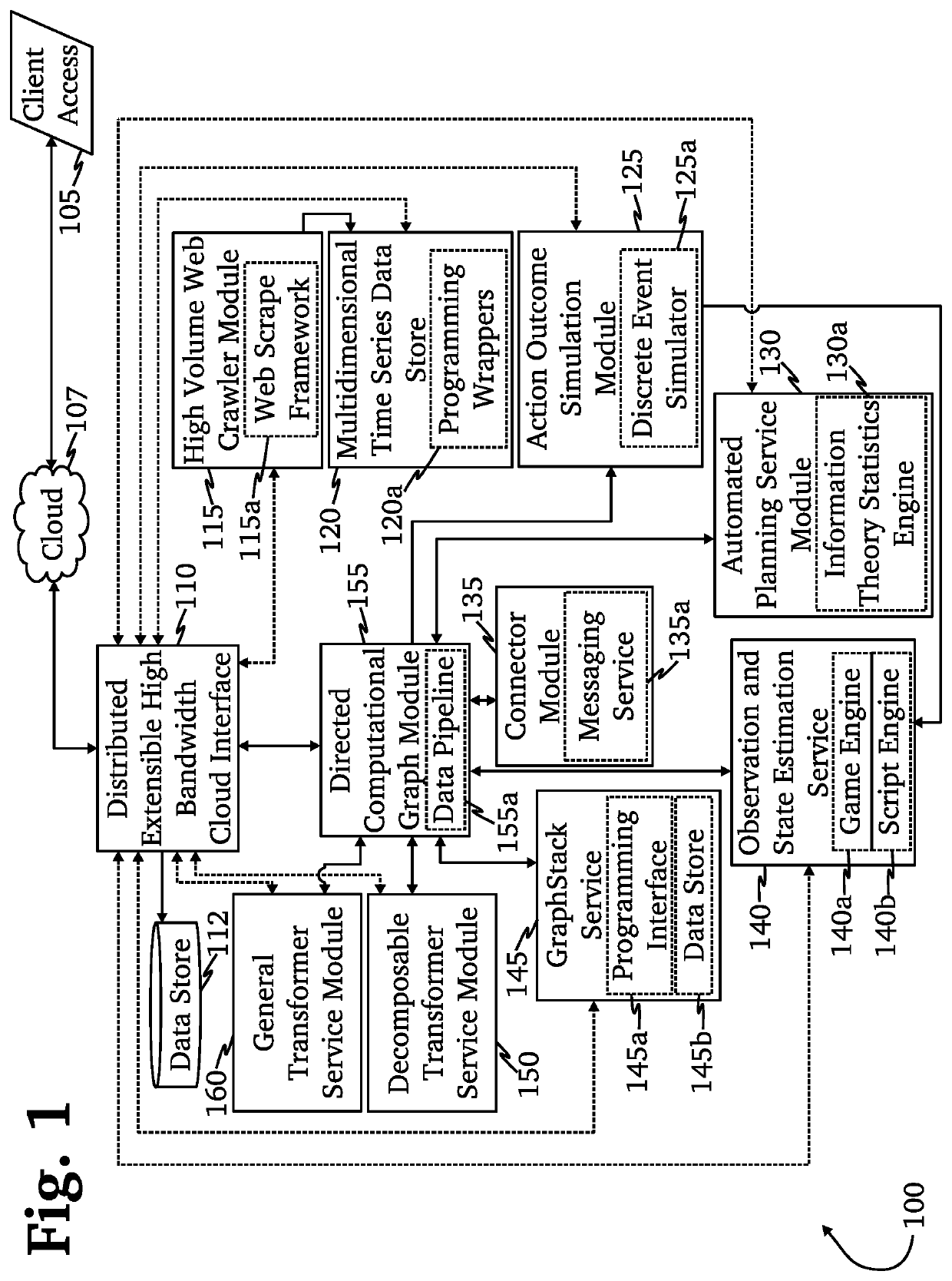
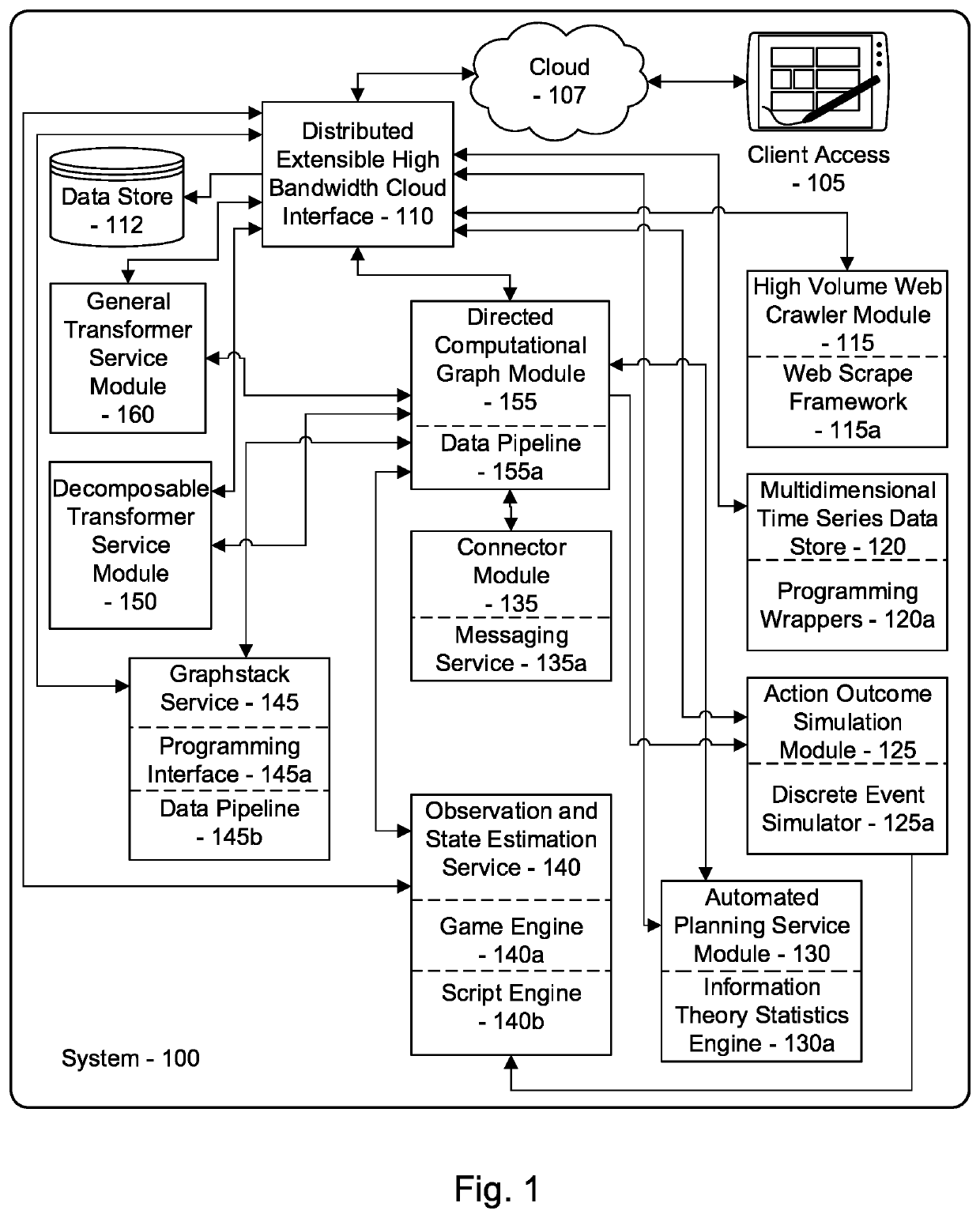
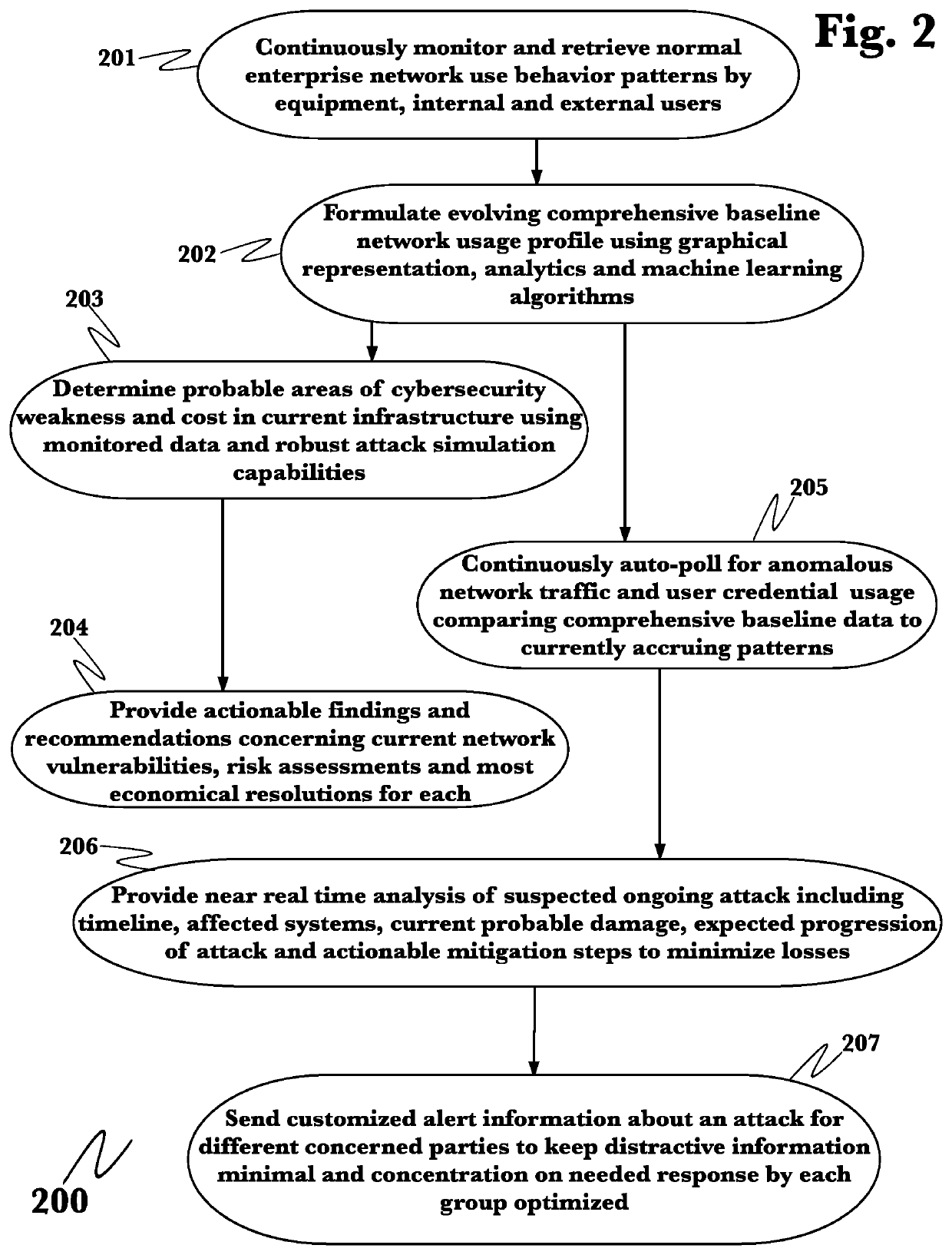
Ai-driven defensive cybersecurity strategy analysis and recommendation system
PendingUS20220210200A1Web data indexingPlatform integrity maintainanceTheoretical computer scienceNetworked system
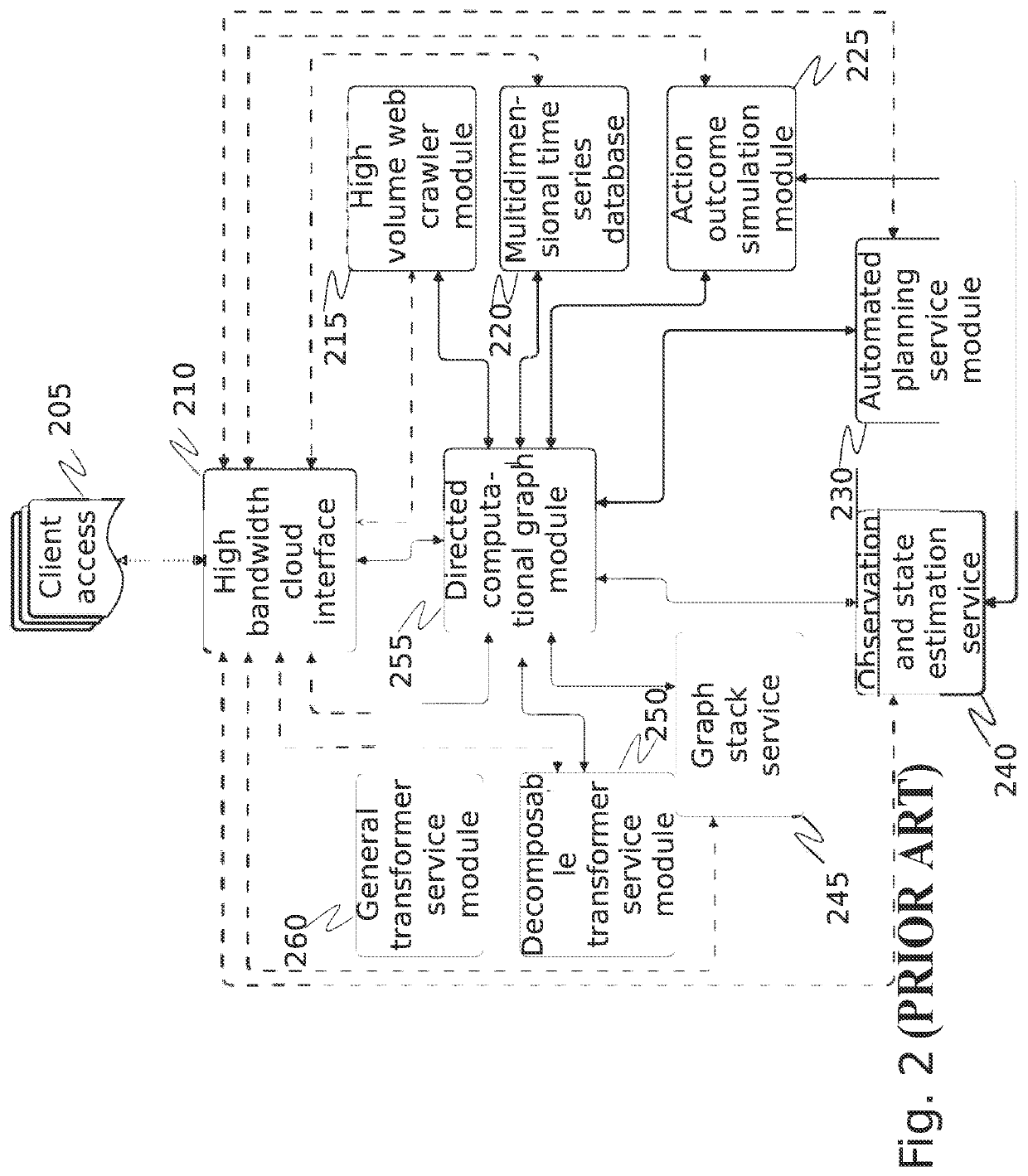
A system and method for automated cybersecurity defensive strategy analysis that predicts the evolution of new cybersecurity attack strategies and makes recommendations for cybersecurity improvements to networked systems based on a cost / benefit analysis. The system and method use machine learning algorithms to run simulated attack and defense strategies against a model of the networked system created using a directed graph. Recommendations are generated based on an analysis of the simulation results against a variety of cost / benefit indicators. The recommendation engine runs continuously, makes suggestions, and takes adjustably autonomous actions to go further and actuate parts of the system using an orchestration service employing a distributed computational graph and actuation plugins based on generated plans. Actions are validated as required or as prudent from appropriate simulation modeling services.
Owner:QOMPLX INC
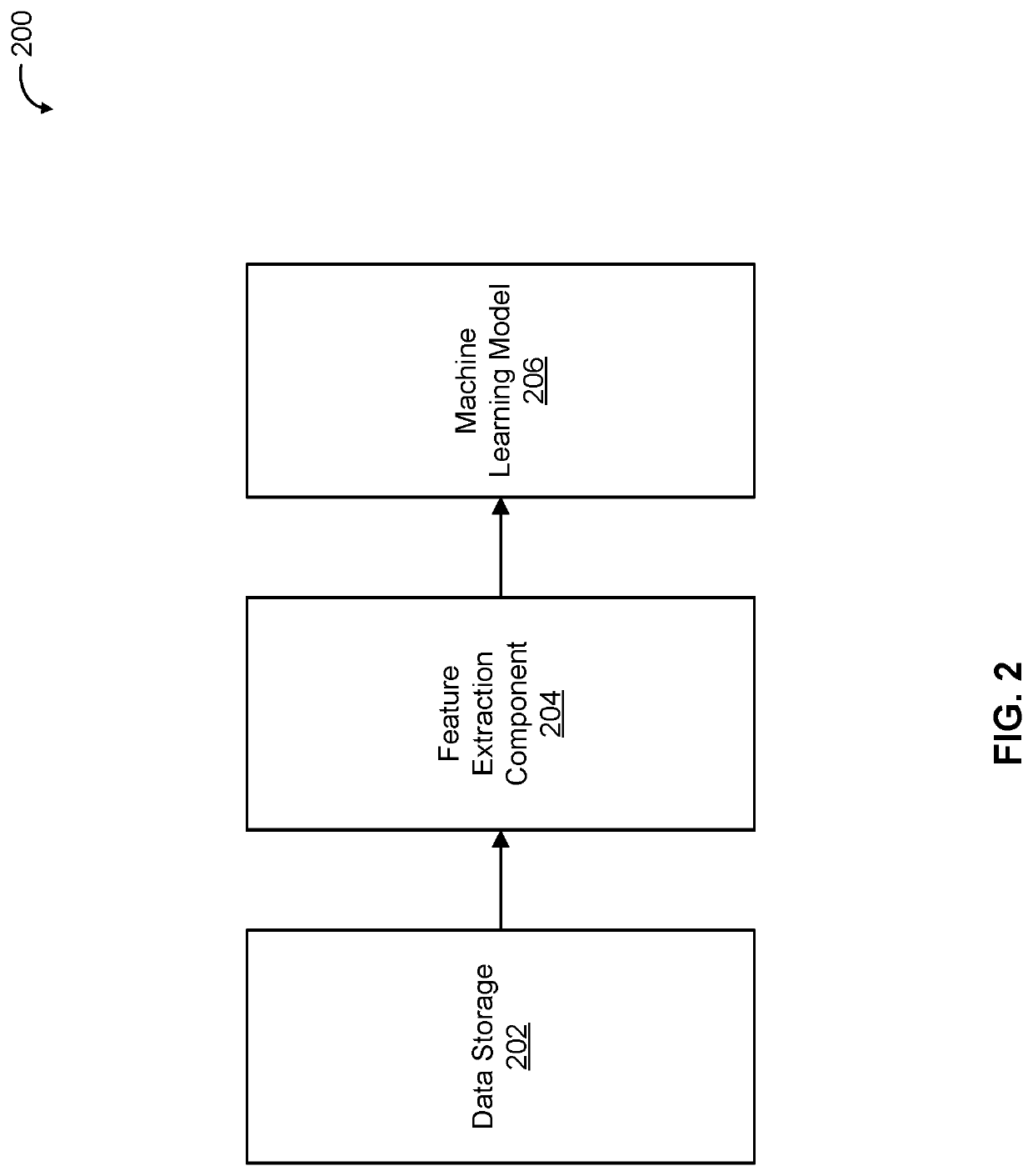
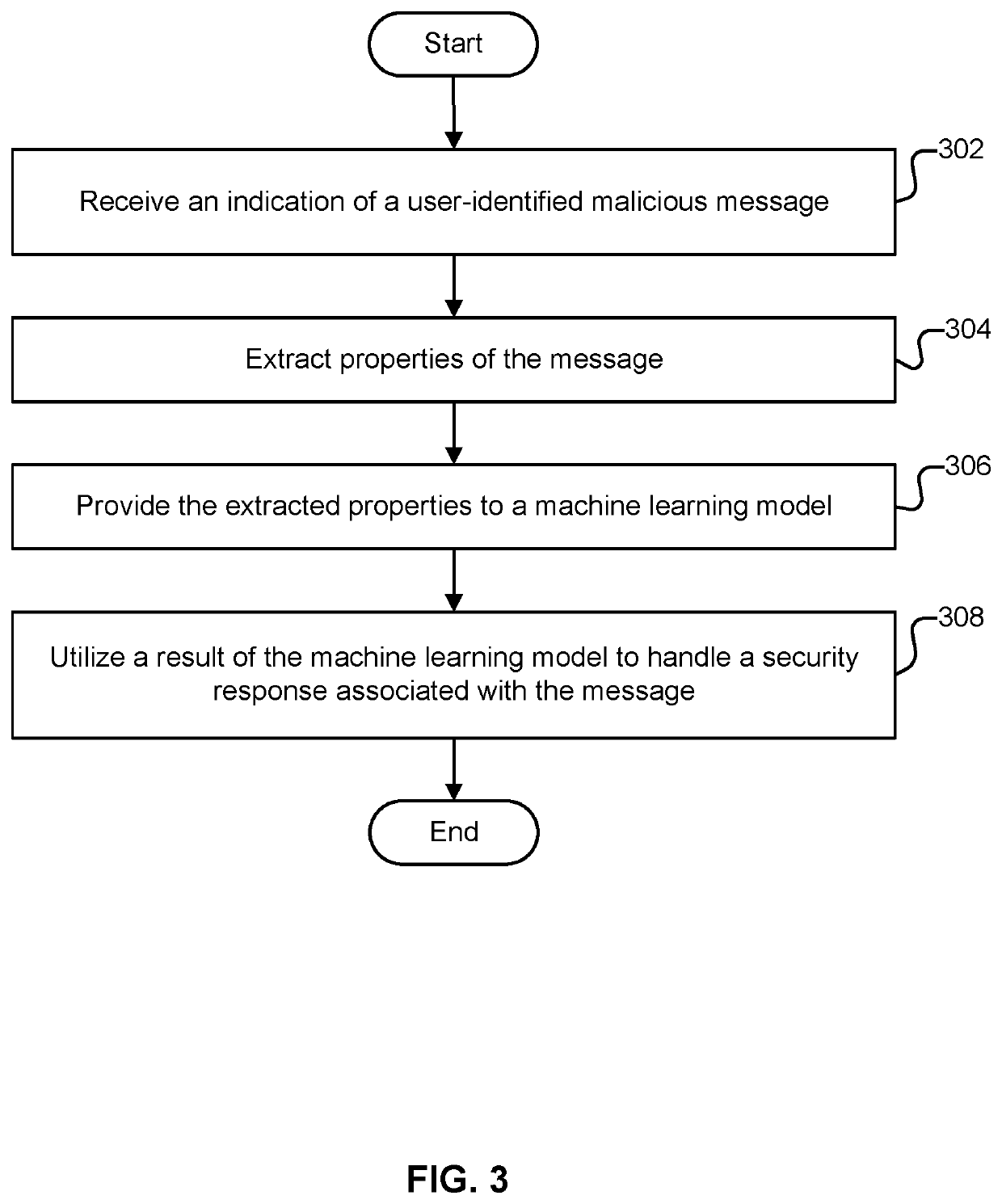
User-reported malicious message evaluation using machine learning
An indication of a message that was identified by a recipient user of the message as being associated with a cybersecurity attack is received. Properties of the message are extracted. The extracted properties of the message are provided as inputs to a machine learning model to determine a likelihood the message is associated with a true cybersecurity attack. The determined likelihood is utilized to handle a security response associated with the message.
Owner:SERVICENOW INC
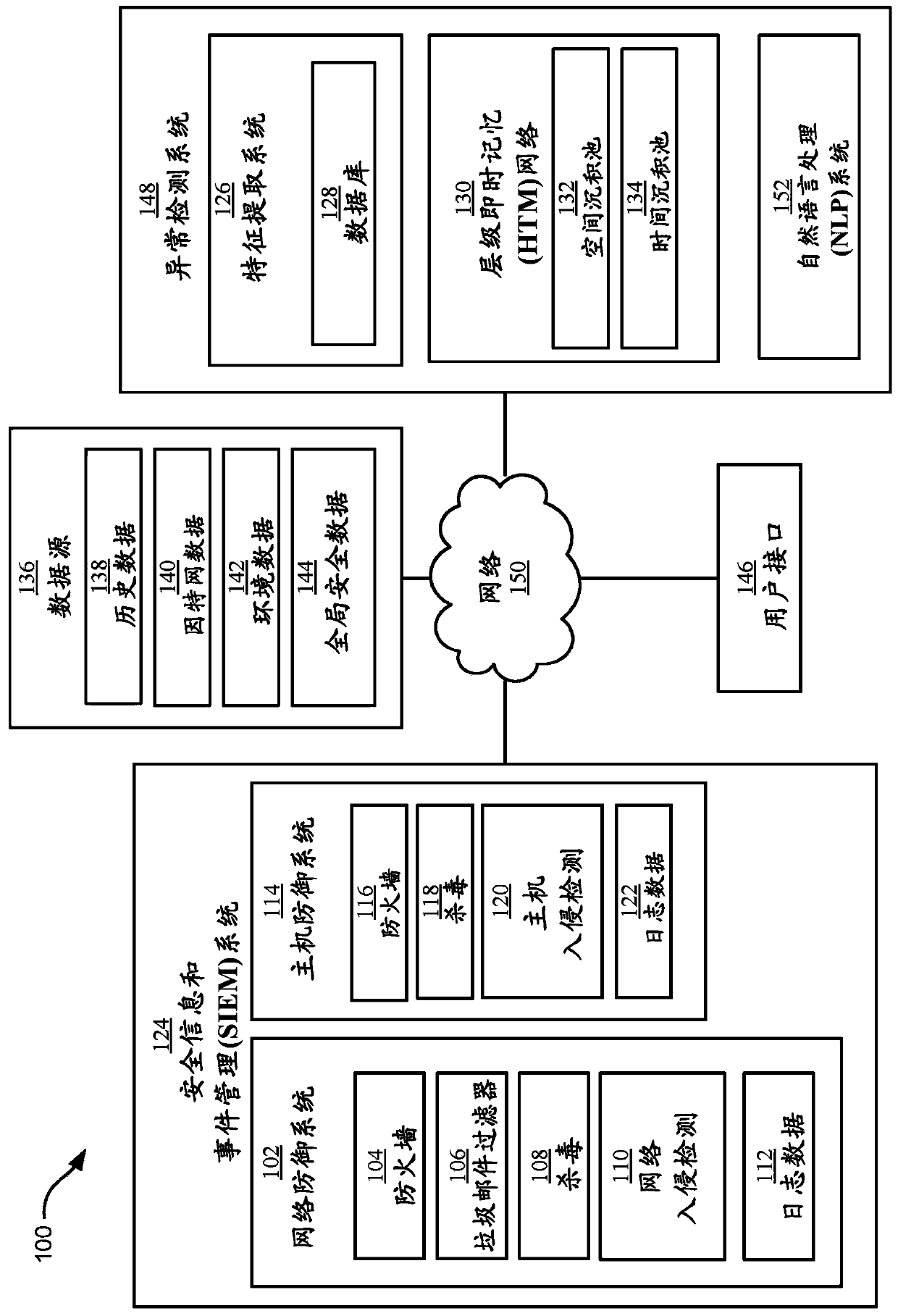
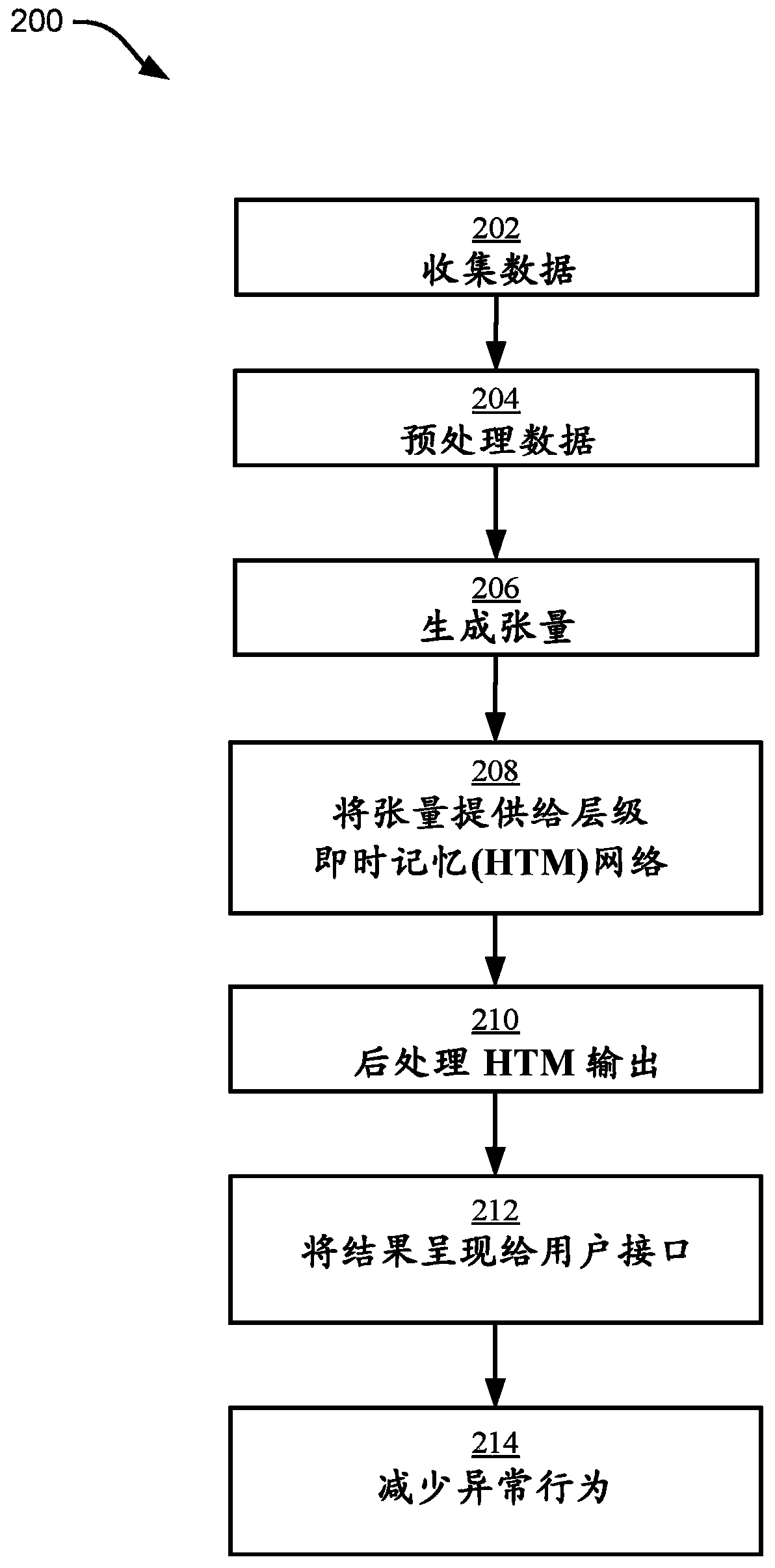
Anomaly detection using cognitive computing
An anomaly detection system configured to generate a plurality of tensors based on spatial attributes of a set of cybersecurity data and temporal attributes of the set of cybersecurity data. The set of cybersecurity data comprising numeric data and textual data collected from a plurality of computational sources. The anomaly detection system can provide the plurality of tensors to a Hierarchical Temporal Memory (HTM) network. The HTM network can be configured to generate respective HTM outputs for respective regions of the HTM network. The anomaly detection system can determine that at least one HTM output indicates an anomaly, convert the at least one HTM output to a notification, and provide the notification to a user interface.
Owner:IBM CORP
Advanced cybersecurity threat mitigation using software supply chain analysis
ActiveUS20210021644A1Web data indexingComputer security arrangementsReliability engineeringComputer engineering
A system and method for comprehensive cybersecurity threat assessment of software applications based on the totality of vulnerabilities from all levels of the software supply chain. The system and method comprising analyzing the code and / or operation of a software application to determine components comprising the software, identifying the source of such components, determining vulnerabilities associated with those components, compiling a list of such components, creating a directed graph of relationships between the components and their sources, and evaluating the overall threat associated with the software application based its software supply chain vulnerabilities.
Owner:QOMPLX INC
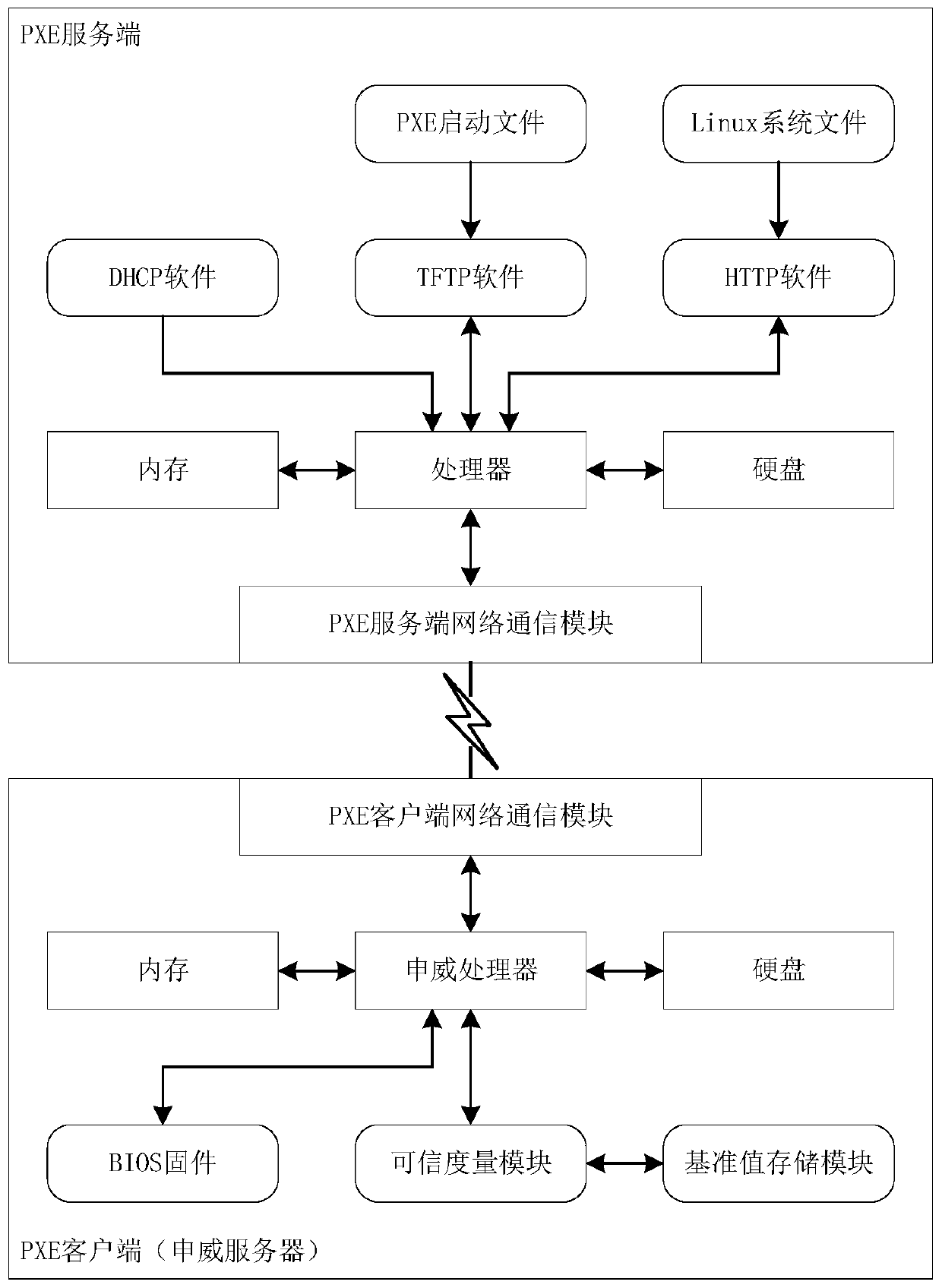
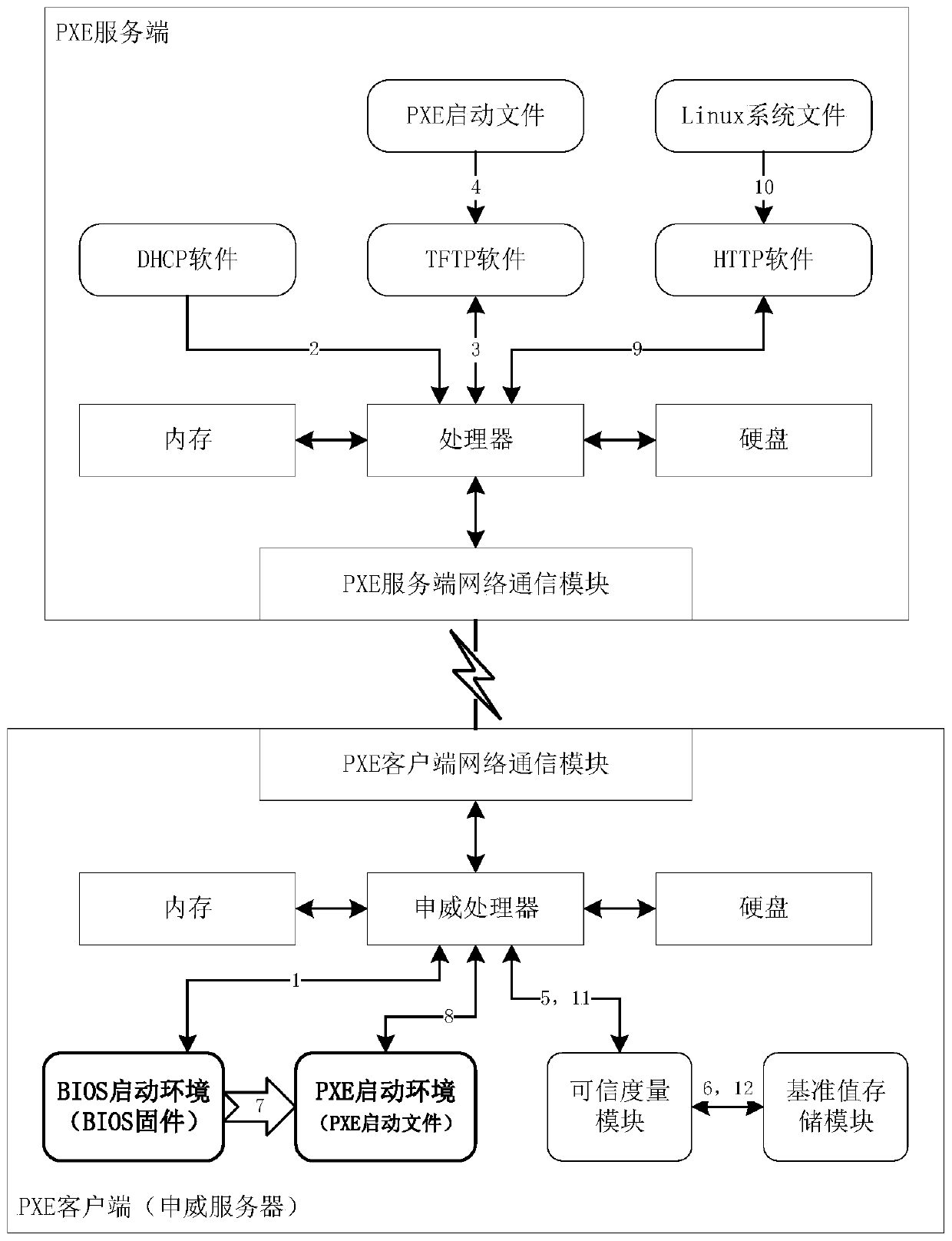
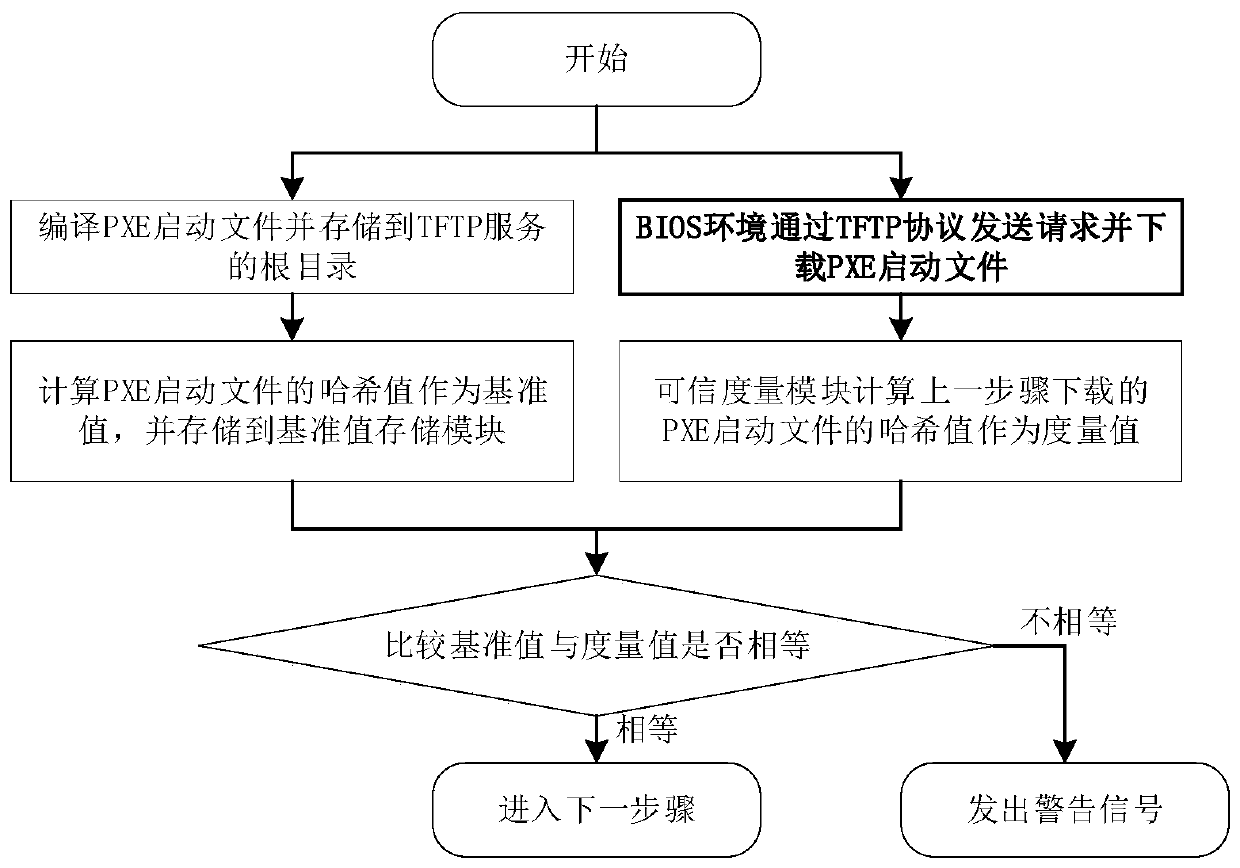
PXE trusted starting method for pre-starting execution environment of Shenwei server
InactiveCN110457073APrevent tamperingImprove securityKey distribution for secure communicationUser identity/authority verificationAccess networkClient-side
The invention discloses a PXE trusted boot method for a pre-boot execution environment of a Shenwei server, and belongs to the field of safe and trusted boot of a server access network. The method ischaracterized in that in a system composed of a PXE server and a PXE client (Shenwei server), hash value of a PXE startup file is calculated as a reference value during publishing of a reference valuestorage module of a client. Then, the value is stored in the reference value storage module of the client. When the PXE client carries out PXE starting, the PXE client carries out PXE starting. The PXE startup file is downloaded from the PXE server. A trusted measurement module calculates a hash value of the PXE startup file by using a same hash algorithm. The hash value is used as a measurementvalue and is compared with a reference value. If the hash value is the same as the reference value, the PXE startup file is trusted, and if the hash value is not the same as the reference value, the PXE startup file is not trusted, and sends a warning signal. The PXE starting file is subjected to credible measurement, whether the PXE starting file is credible or not is judged, and the PXE startingsafety of the Shenwei server is improved.
Owner:BEIJING UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com