Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
296 results about "Codebase" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
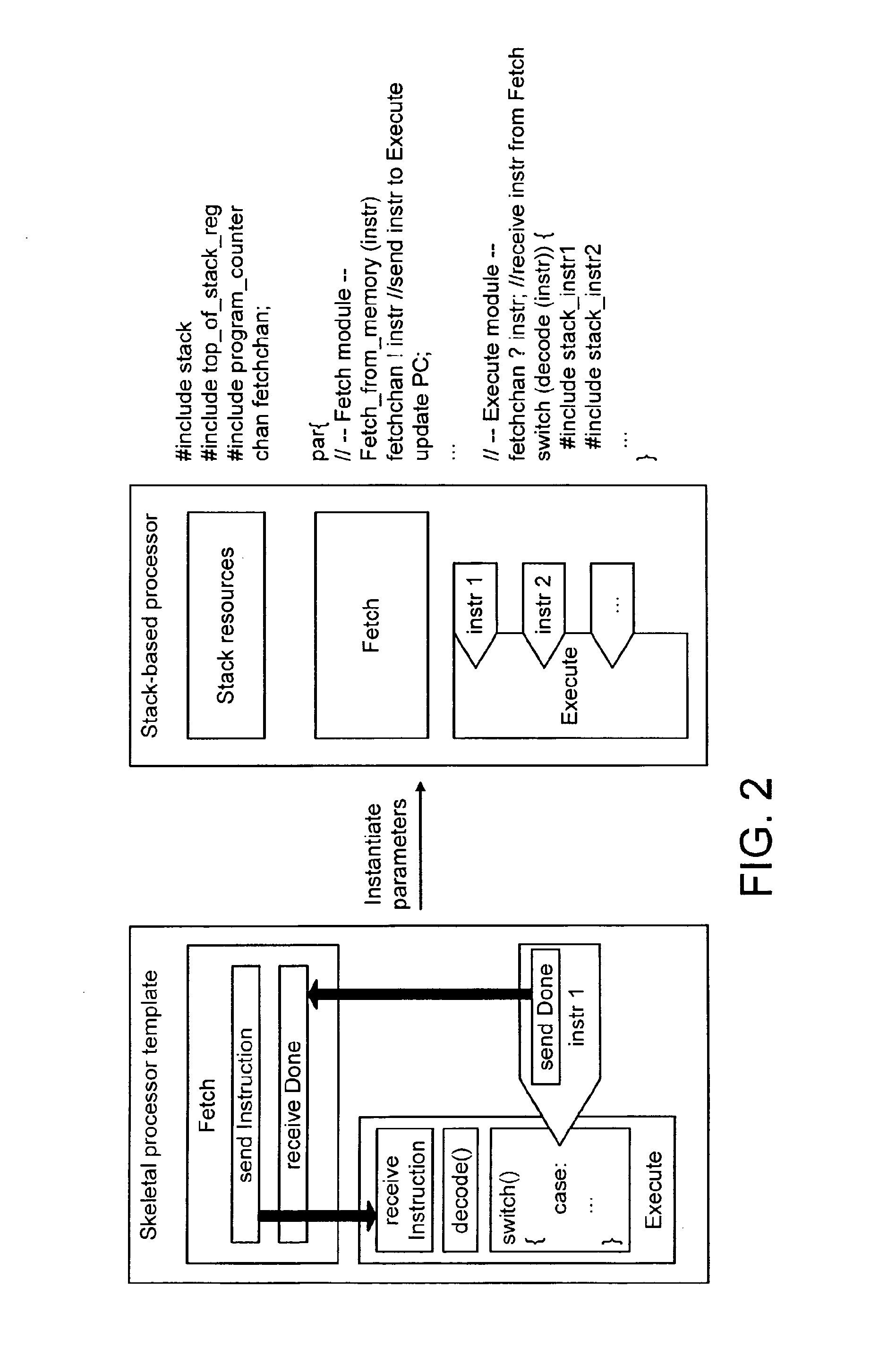
In software development, a codebase (or code base) is a collection of source code used to build a particular software system, application, or software component. Typically, a codebase includes only human-written source code files; thus, a codebase usually does not include source code files generated by tools (generated files) or binary library files (object files), as they can be built from the human-written source code. However, it generally does include configuration and property files, as they are the data necessary for the build.
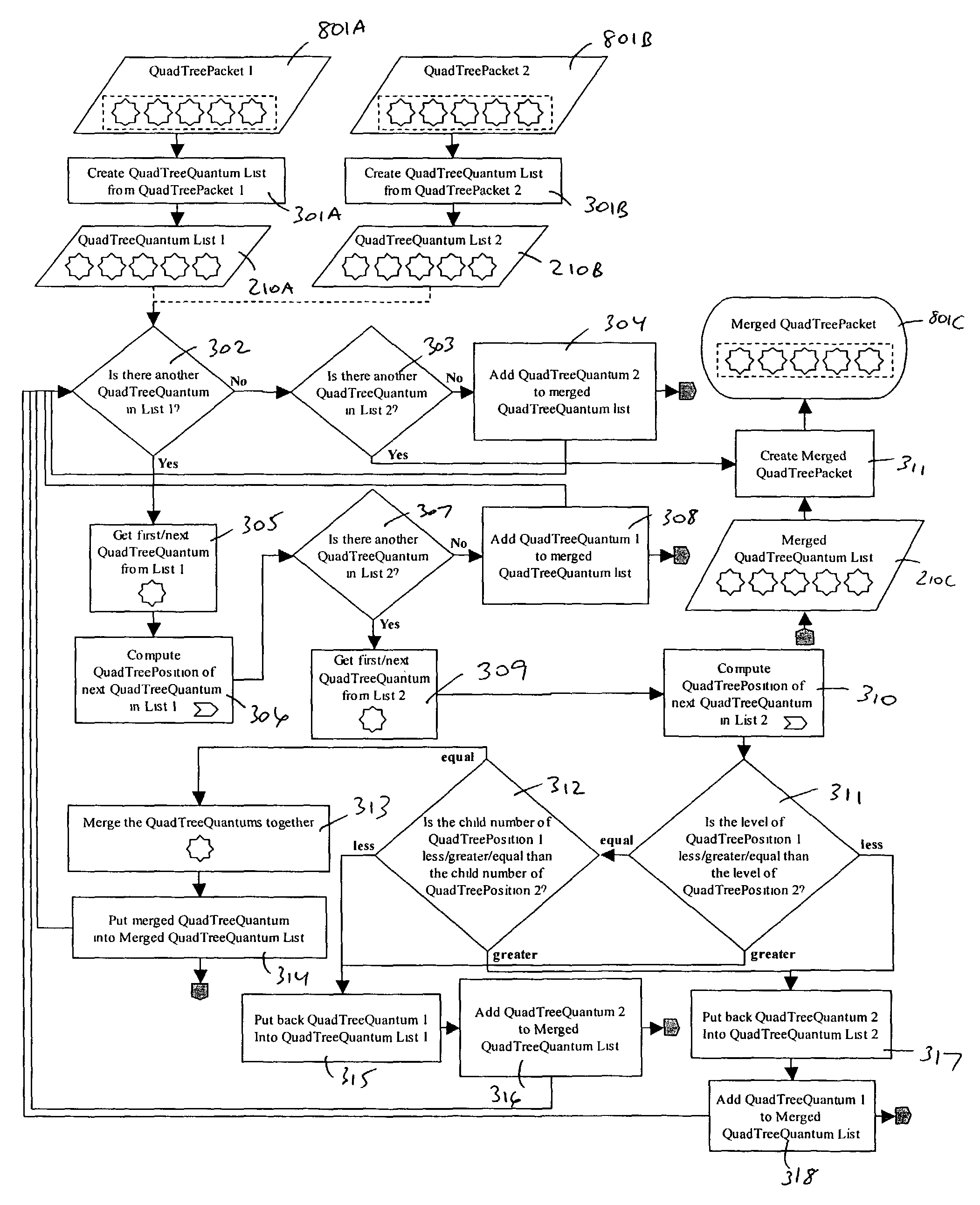
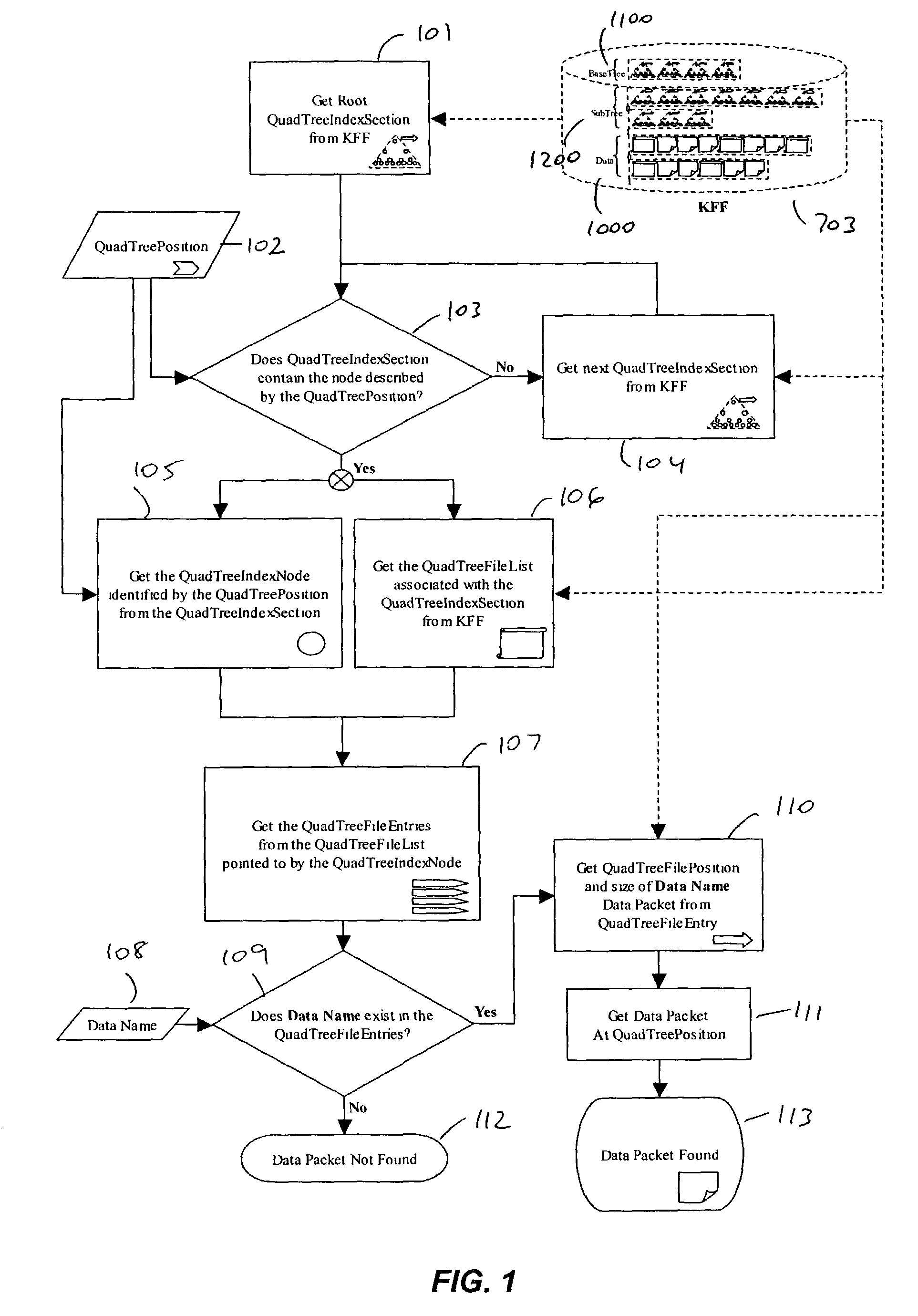
Server for geospatially organized flat file data
ActiveUS7225207B1Fast deliveryQuick mergeData processing applicationsDigital data protectionFile systemData file
A flat file data organization technique is used for storing and retrieving geospatially organized data. The invention reduces transfer time by transferring a few large files in lieu of a large number of small files. It also moves the process of locating a given data file away from the file system to a proprietary code base. Additionally, the invention simplifies database management by having quadtree packets generated on demand.
Owner:GOOGLE LLC
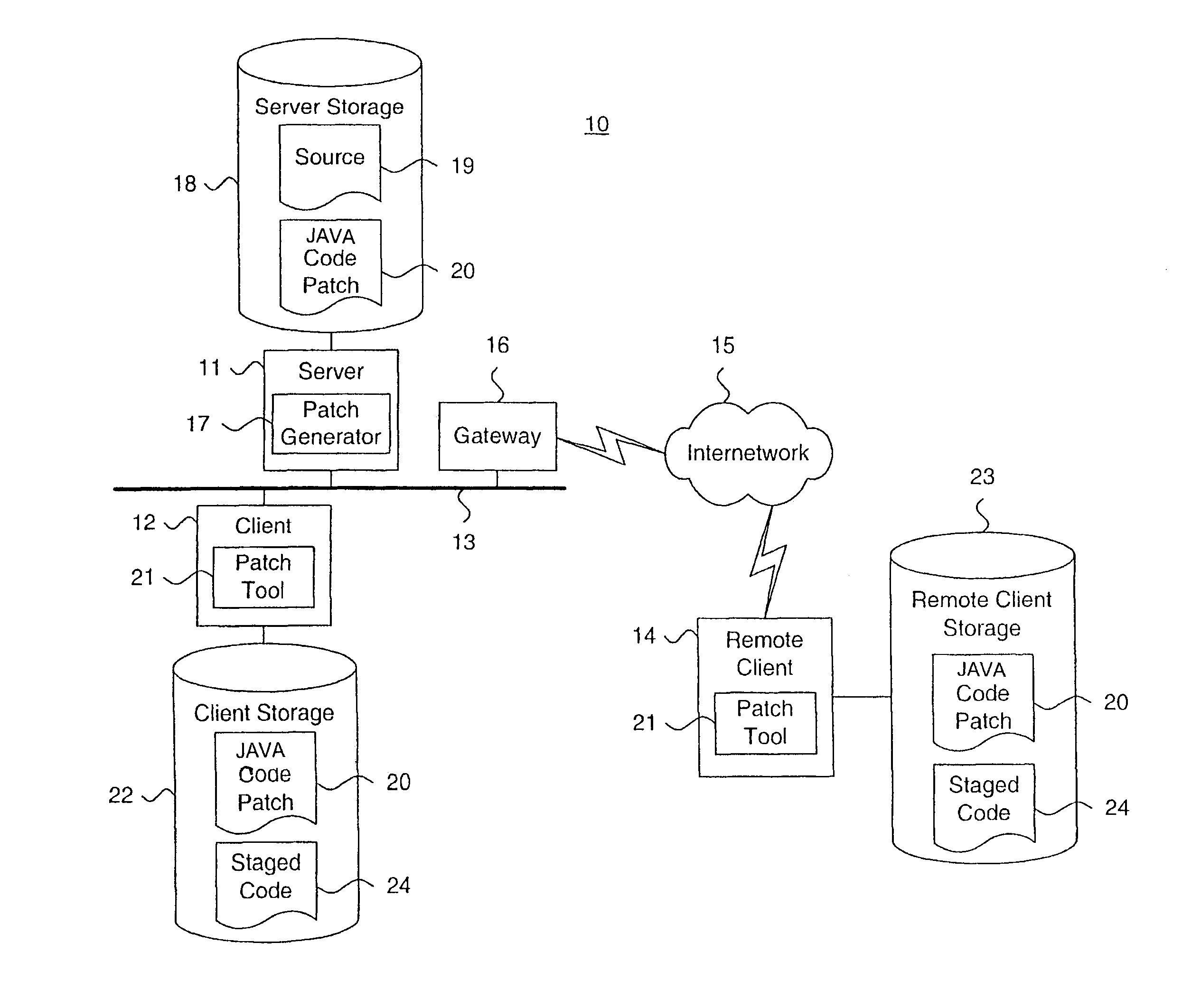
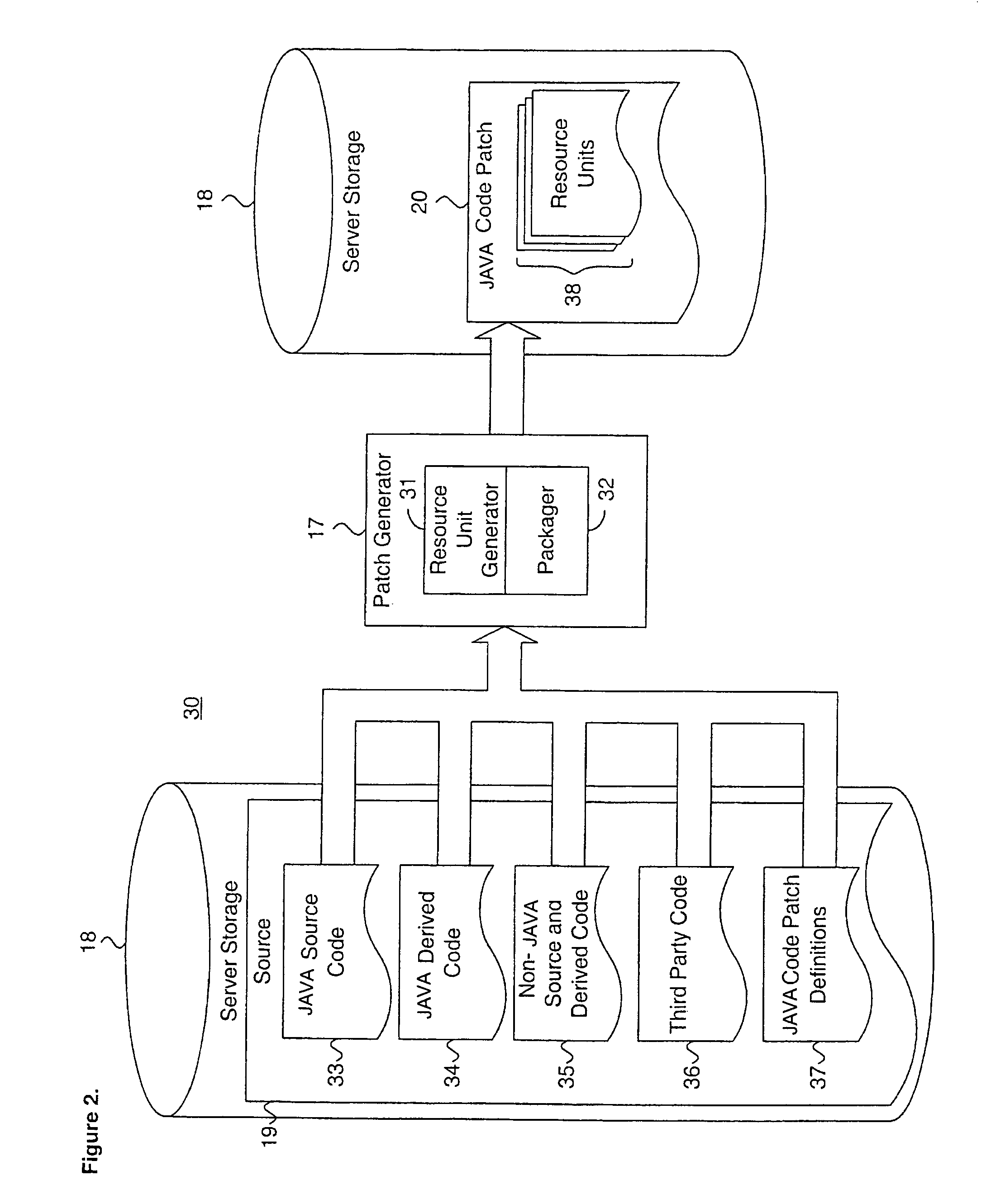
System and method for providing a java code release infrastructure with granular code patching
InactiveUS7127712B1Specific program execution arrangementsMemory systemsThird partyDigital signature
A system and method for providing a code release infrastructure with granular code patching is described. Code patches, each including at least one resource unit are provided. Each resource unit includes metadata and file components. Code libraries, each including at least one resource unit, are patched. The metadata for each resource unit in the code patches is compared to the metadata for each such corresponding resource unit in the code libraries. Each resource unit in the code patches is merged into the code libraries for each such corresponding resource unit that is out-of-date as defined by merge rules. Archive files, as defined by archive file definitions, are created or updated using the resource units from the code libraries, or, optionally, are deleted. The archive files are digitally signed also as required. The system and method enables source and derived code and third party code to be patched granularly.
Owner:ORACLE INT CORP
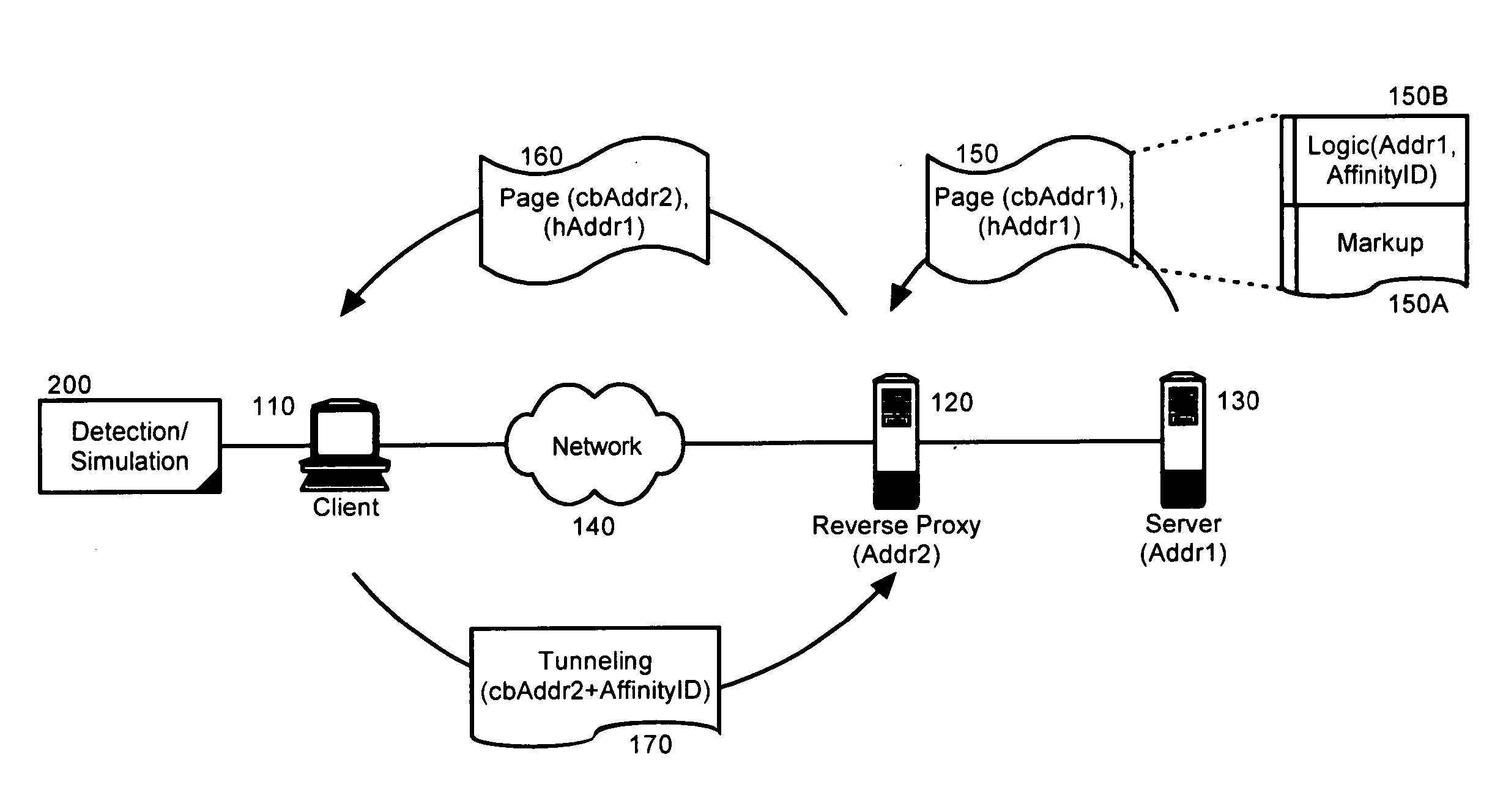
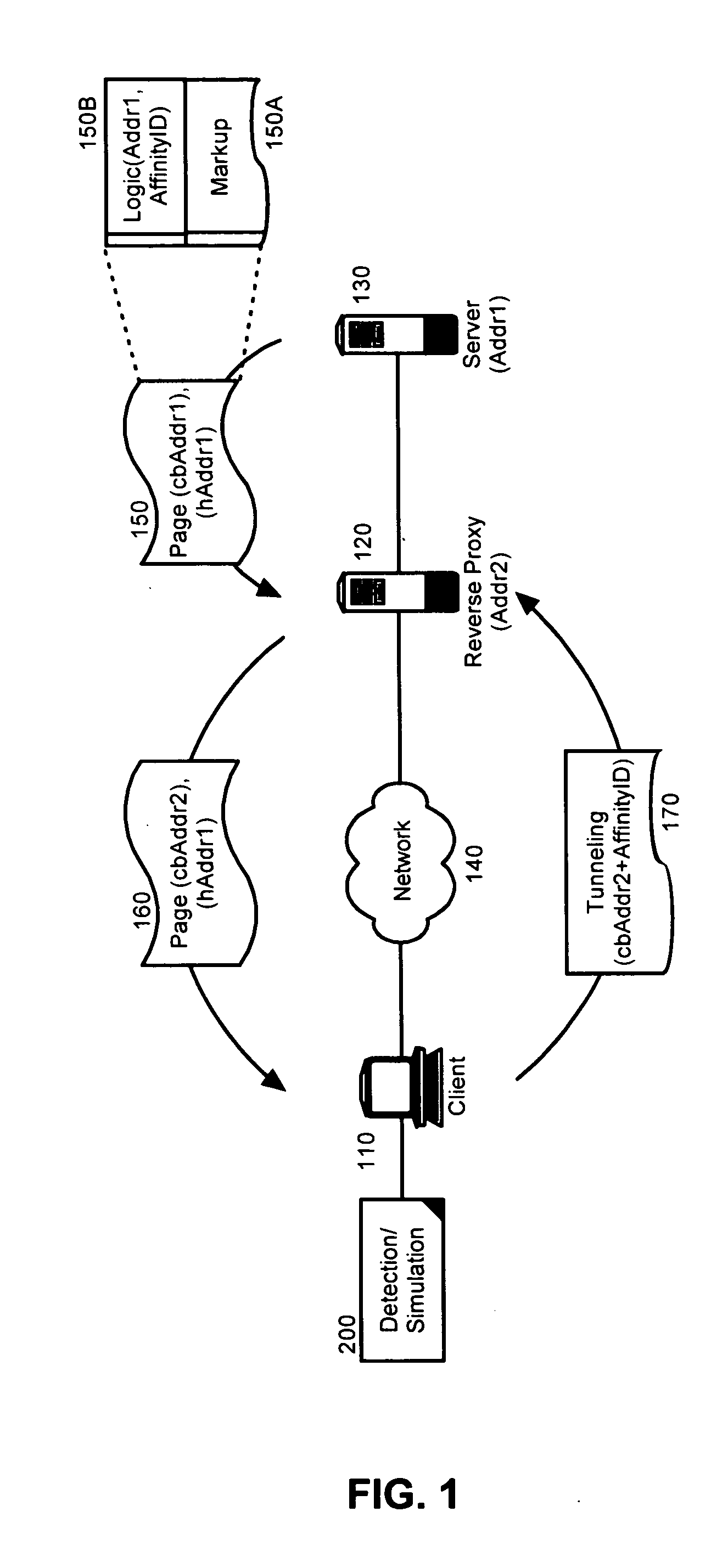
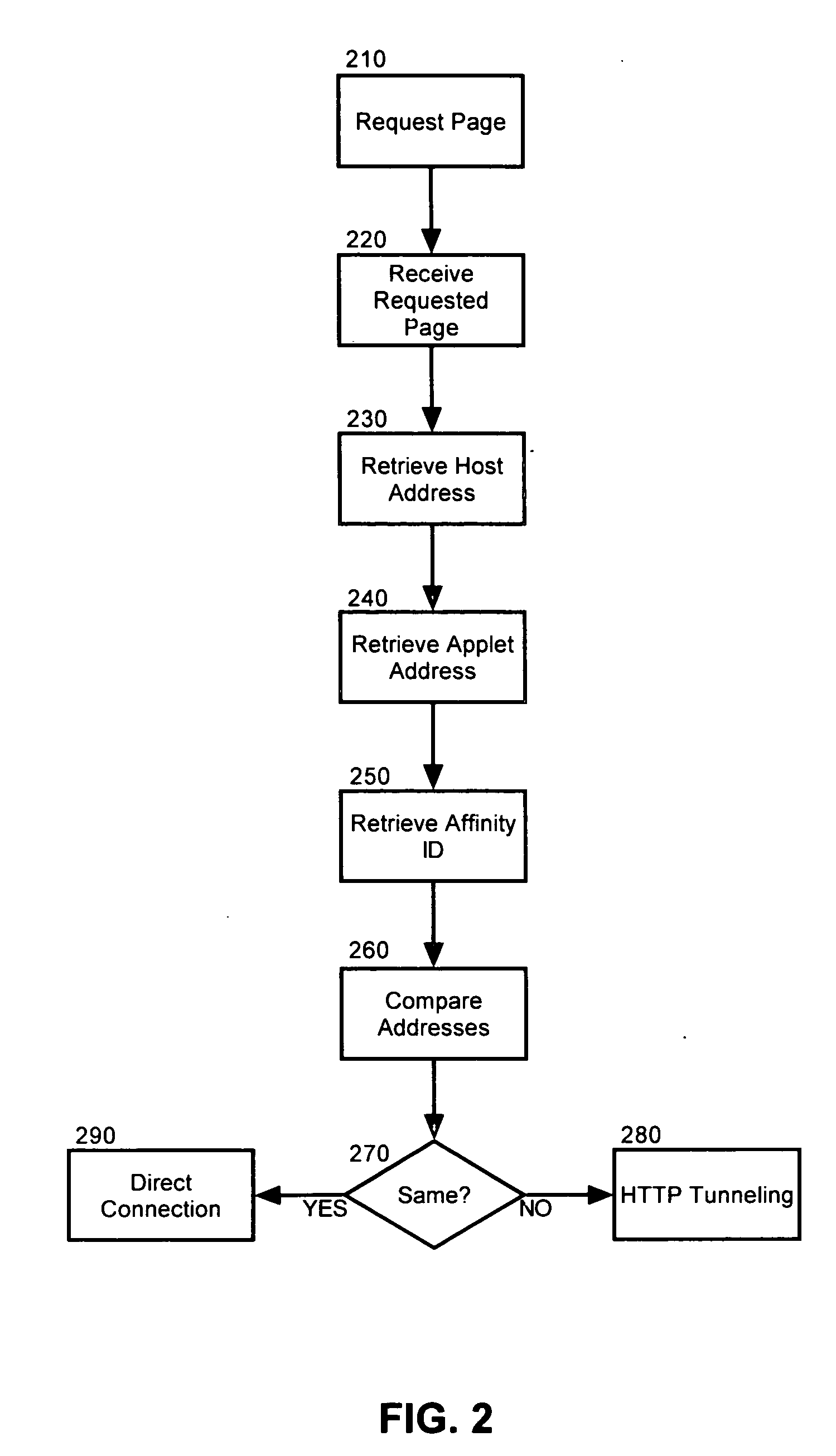
Detecting a reverse proxy and establishing a tunneled connection therethrough
A method, system and apparatus for managing an interposed reverse proxy. The method can include comparing within a markup language document, a host address for the markup language document and a codebase address for a code base supporting logic disposed within the markup language document. If the host address and the codebase address differ, it can be concluded that a reverse proxy has obscured from view a server source of the markup language document. The method of the invention further can include retrieving a server affinity identifier for the server source from the configuration tags for the logic. Responsive to concluding that a reverse proxy has obscured from view a server source of the markup language document, a tunneled connection to the server source can be attempted through the reverse proxy by inserting the server affinity identifier in an address specified in the attempt.
Owner:IBM CORP
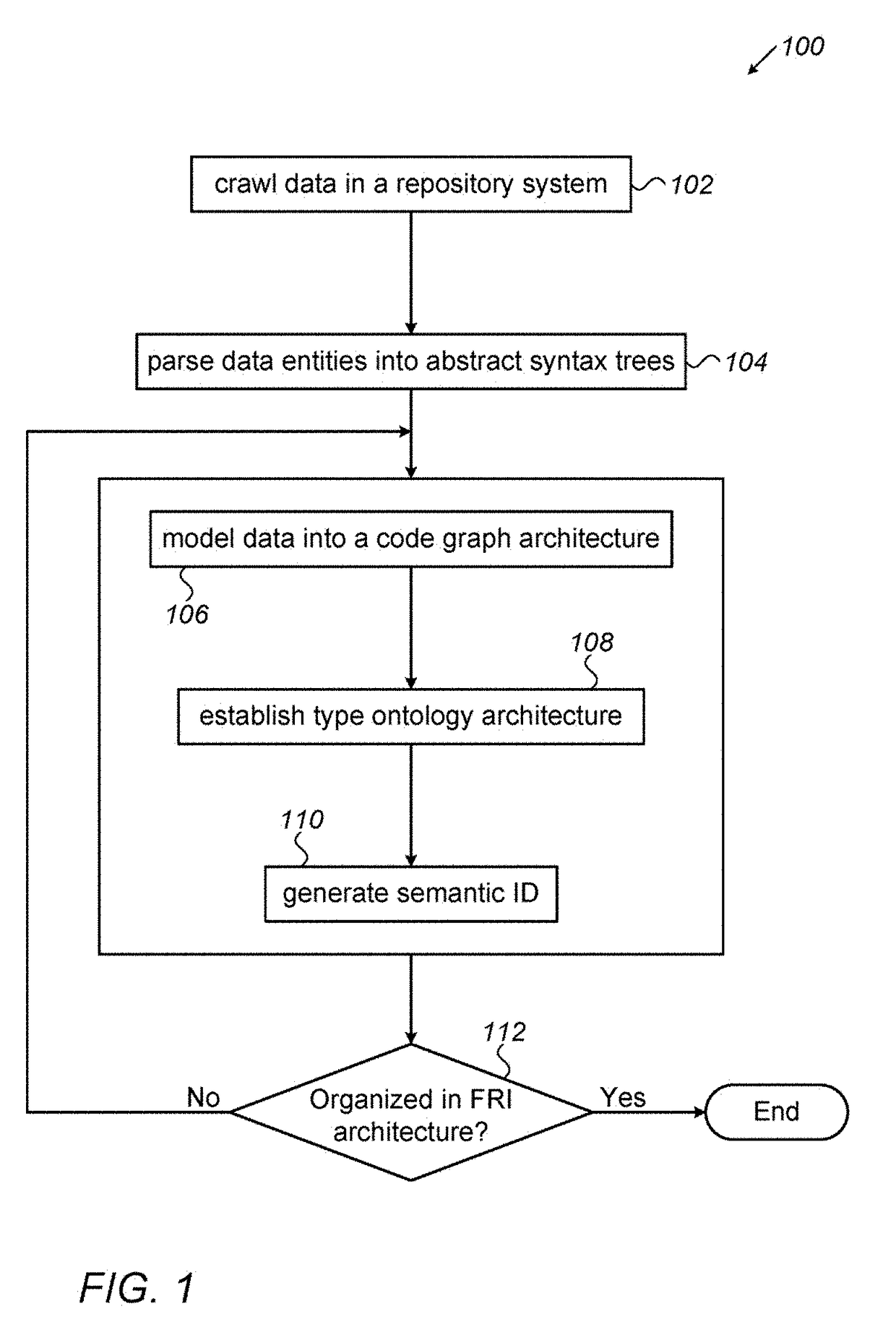
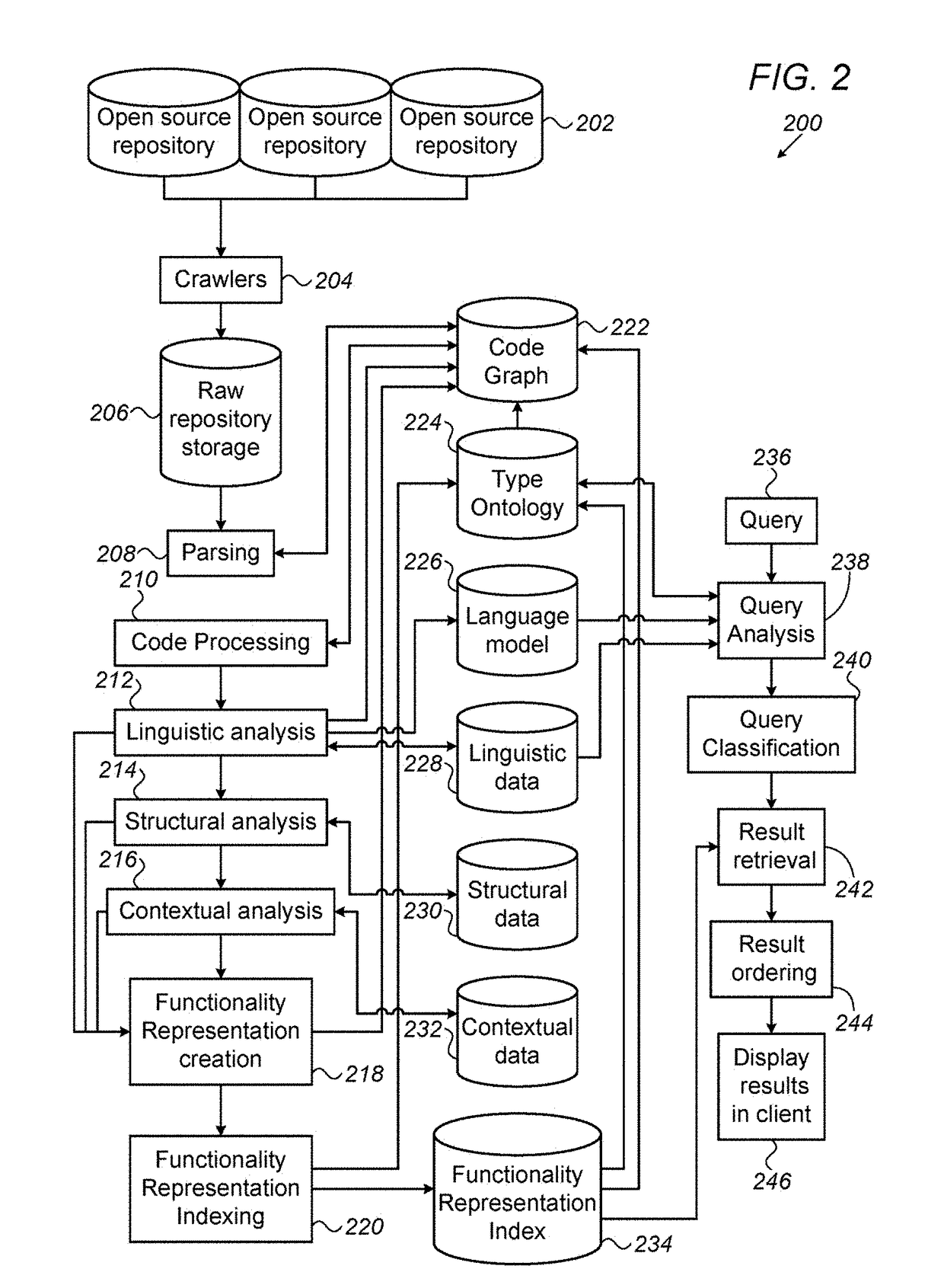
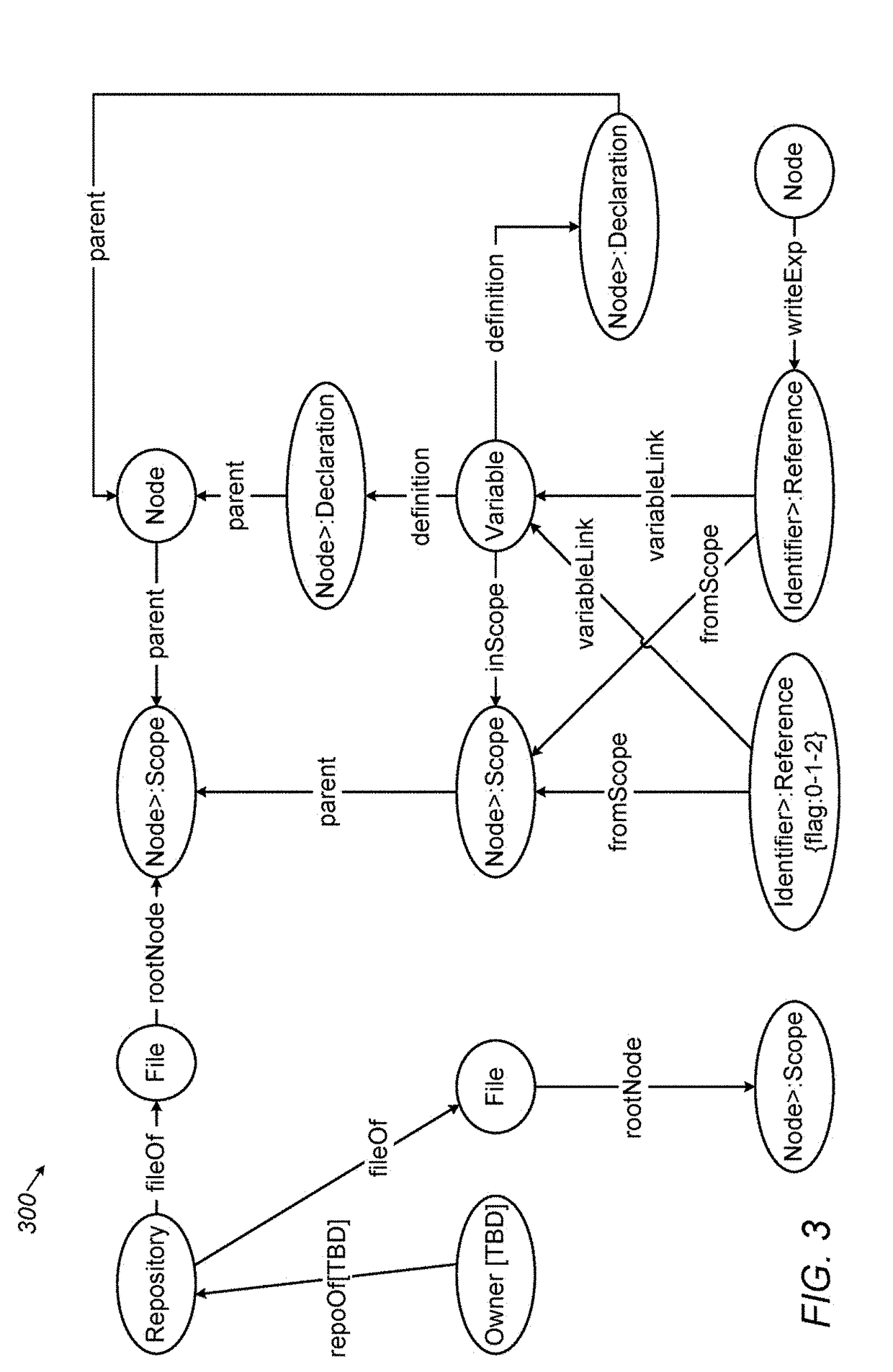
System for generating functionality representation, indexing, searching, componentizing, and analyzing of source code in codebases and method thereof
ActiveUS20180373507A1Raise the possibilityMathematical modelsWeb data indexingAbstract syntax treeData entity
Owner:COCYCLES
Apparatus and method for estimating the testing proficiency of a software test according to EMS messages extracted from a code base
ActiveUS7493521B1Quality assuranceError detection/correctionSpecific program execution arrangementsComputer hardwareTest script
An apparatus and method for estimating the proficiency of a software test according to EMS messages extracted from a code base. Embodiments of the invention are generally directed to providing some measurement of the proficiency of a test script for testing a software application. In one embodiment, data is collected on event messages generated during a test of a software application to form event message statistics. In one embodiment, a measurement is computed to identify an amount or percentage of software application code tested during the test script. A code base of the software application may include a central repository having a substantial portion of the event messages that may be issued by the software application in response to error conditions. In one embodiment, these event messages are taken from the central repository and stored within a database. Other embodiments are described and claimed.
Owner:NETWORK APPLIANCE INC
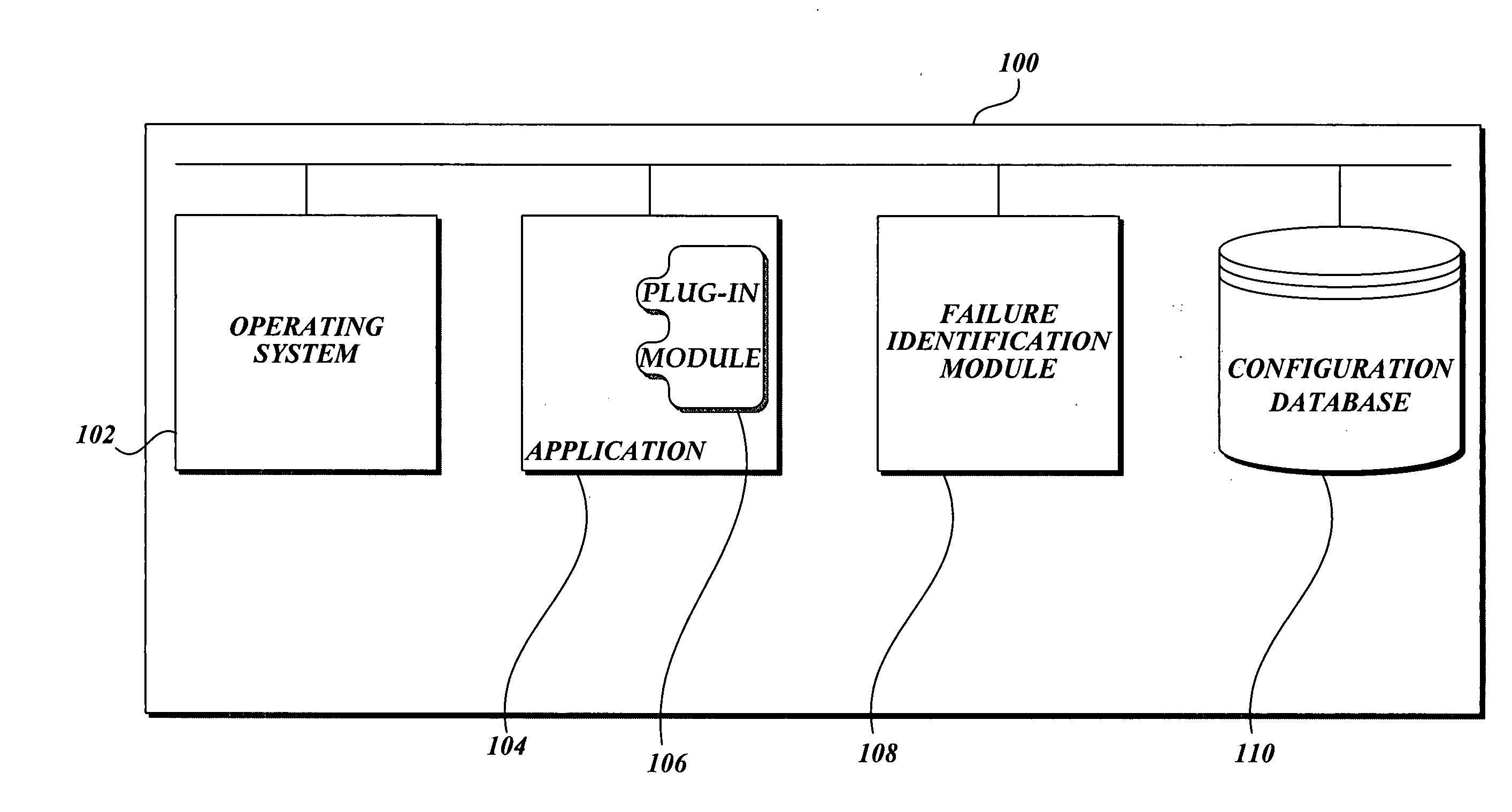
System and method of identifying the source of a failure
InactiveUS20060005078A1Improve stabilityError detection/correctionSpecific program execution arrangementsTerm memoryData structure
The present invention is generally directed to improving the stability of computing devices by identifying plug-in modules and other programs that cause failures. More specifically, the present invention provides a method that traces program execution from an instruction that ultimately generated a failure to a code library that caused the failure generating instruction to be executed. The method traces execution of the computing device by obtaining the contents of memory at the time of the failure and traversing the stack data structure that stores data items necessary to execute function calls.
Owner:MICROSOFT TECH LICENSING LLC
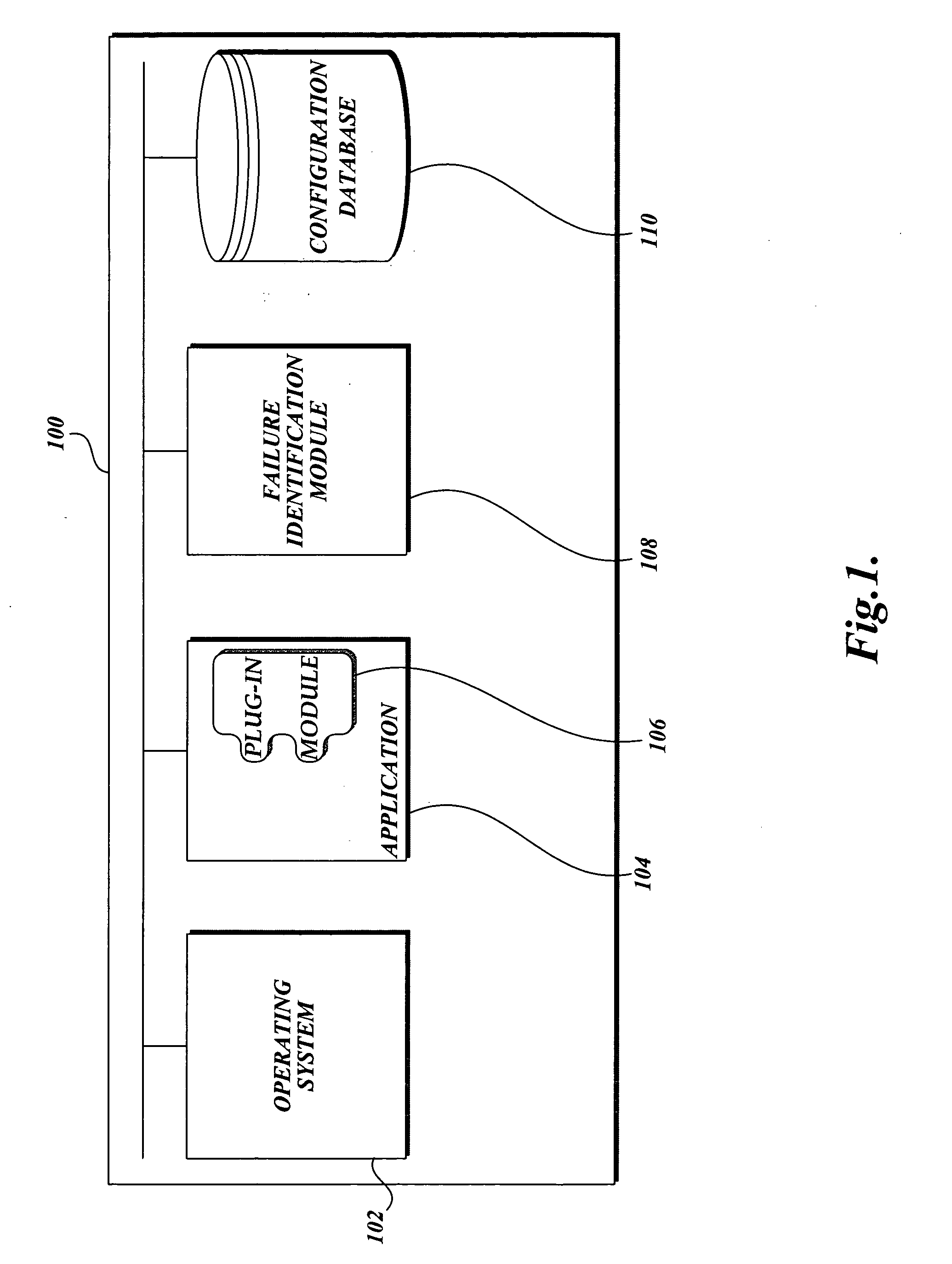
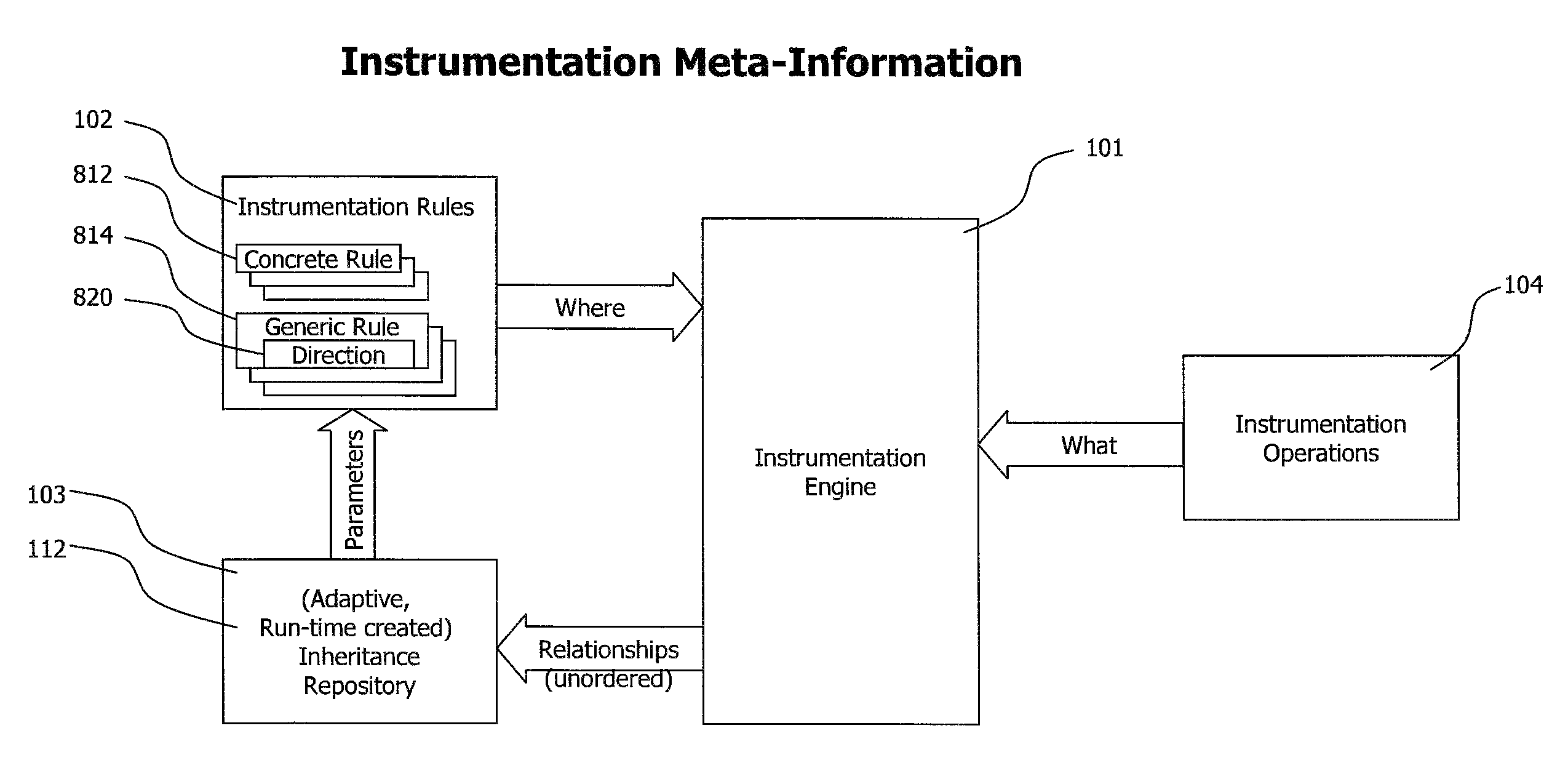
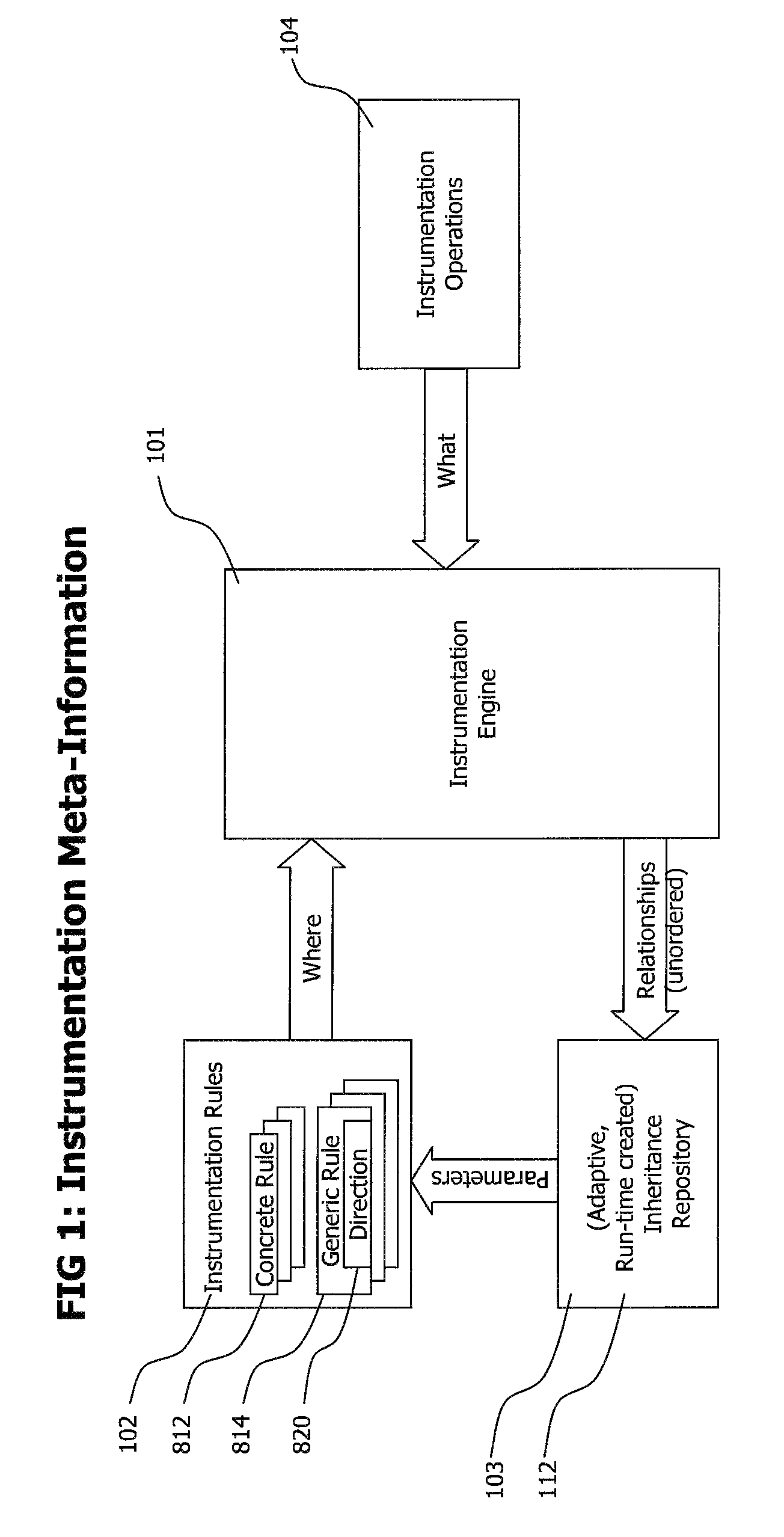
Method and system for adaptive, generic code instrumentation using run-time or load-time generated inheritance information for diagnosis and monitoring application performance and failure
ActiveUS8464225B2Error detection/correctionSpecific program execution arrangementsBase classApplication procedure
A system for generic, run-time adaptive placement of byte code instrumentation takes into account object oriented inheritance relationships that are stored in an inheritance repository. The inheritance repository, which mirrors the structure of the monitored application, is created at run-time and is updated if the code base of the monitored application changes either dynamically at run-time or by manually changing the configuration and restarting the application. The inheritance repository contains meta-data of application classes and their relationships, like direct and indirect inheritance. The inheritance repository information is used to evaluate generic instrumentation placement rules, like rules that match to methods of classes that inherit from a specific base class. The inheritance repository is generated concurrently with instrumentation placement at application load-time or run-time and persists between application runs to enable dedicated adaptation runs to create the repository.
Owner:DYNATRACE
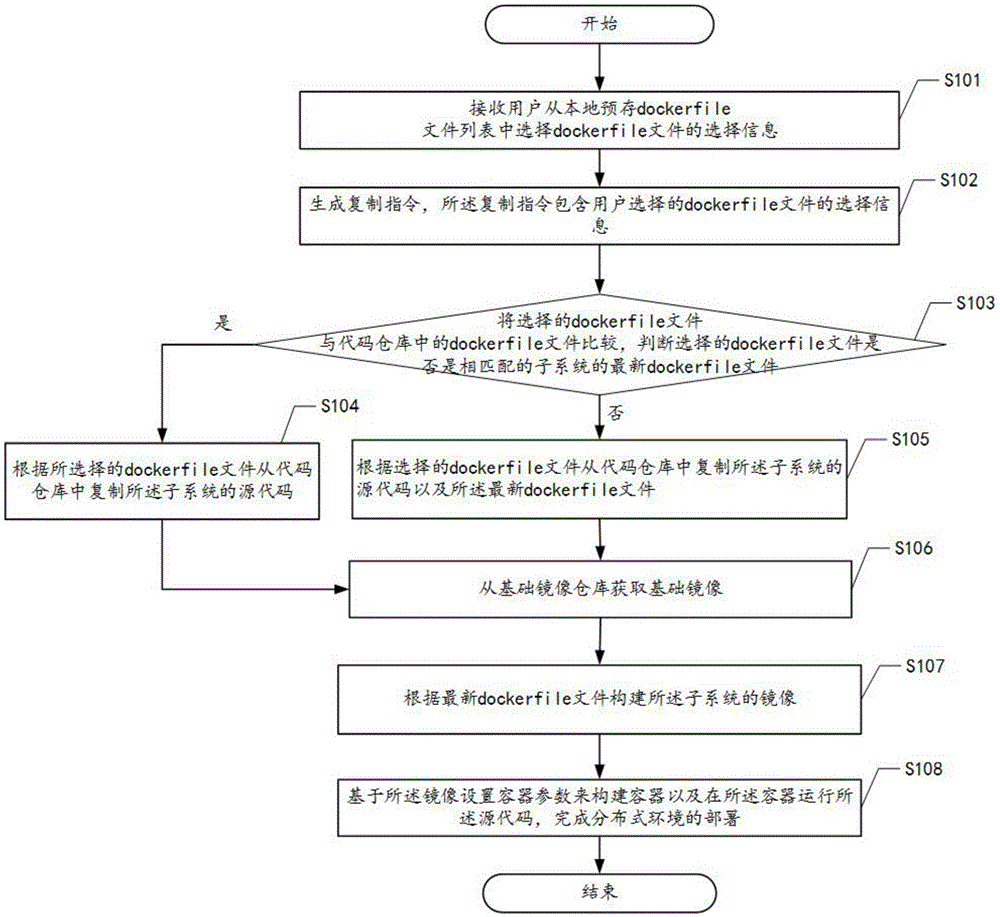
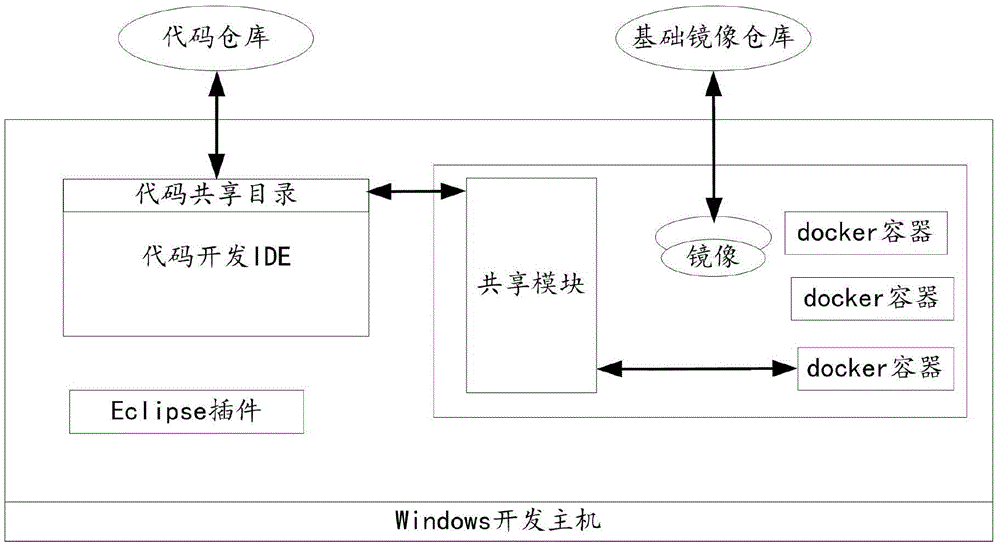
Building method and device for distributed development environment based on Docker
ActiveCN105824614ASpecific program execution arrangementsSoftware deploymentMirror imageComputer science
The invention discloses a building method for distributed development environment based on Docker. The building method comprises the following steps: receiving selection information for selecting a dockerfile file from a local prestored dockerfile file list by a user; judging whether the selected dockerfile file is the latest dockerfile file or not; if yes, reproducing source codes of a subsystem from a codebase according to the selected dockerfile file; building mirror images of the subsystem according to the latest dockerfile file; through the mirror images, building a docker container, and operating the source codes of the subsystem in the docker container. The building method realizes single machine deployment of the distributed development environment. The invention further discloses a building device applying the building method.
Owner:GUANGDONG ESHORE TECH
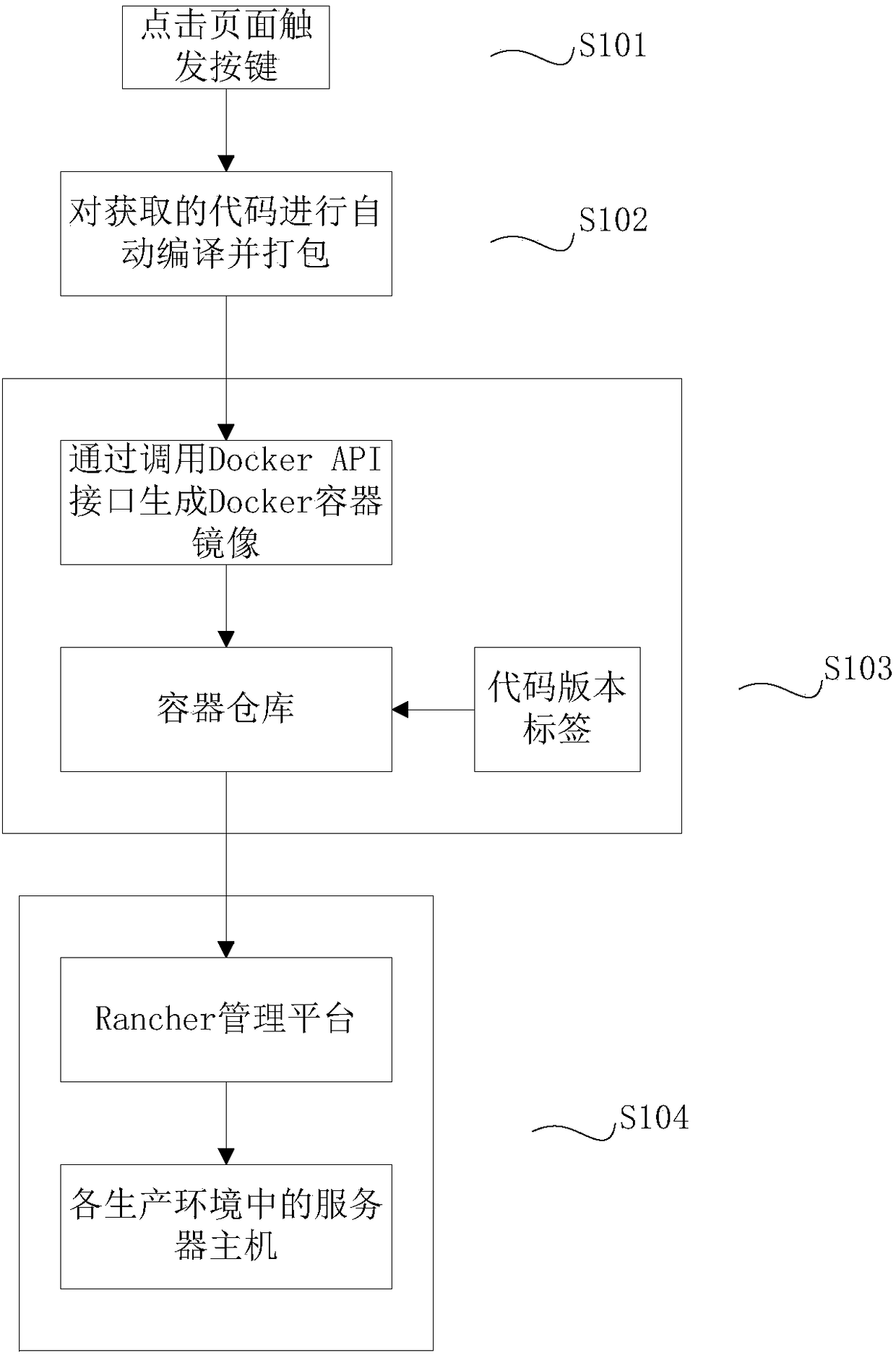
Visualized Docker container automatic compilation deployment operation and maintenance method
ActiveCN108196843AEasy to operateRealize downloadVisual/graphical programmingSoftware deploymentProgramming languageSoftware engineering
The invention discloses a visualized Docker container automatic compilation deployment operation and maintenance method. The method comprises the steps of triggering a page trigger button on a visualized interface, and beginning to create a container mirror image; automatically downloading a code from a code base, automatically compiling the code into an executable program, constructing the program into a Docker container mirror image file, and uploading the file to a container warehouse, obtaining a code version label by switching the container warehouse through an API interface, then, downloading the container mirror image of a corresponding label in the container warehouse to a server mainframe in the production environment for automatic deployment operation, the technical problems thatdue to manual deployment in an existing operation and maintenance method, operation is not convenient, deployment is difficult and the cost is high are solved, the purpose that the code is publishedto the production environment in a one-button mode is achieved, operation is easy, and efficiency is high.
Owner:CHENGDU REMARK TECH CO LTD +1
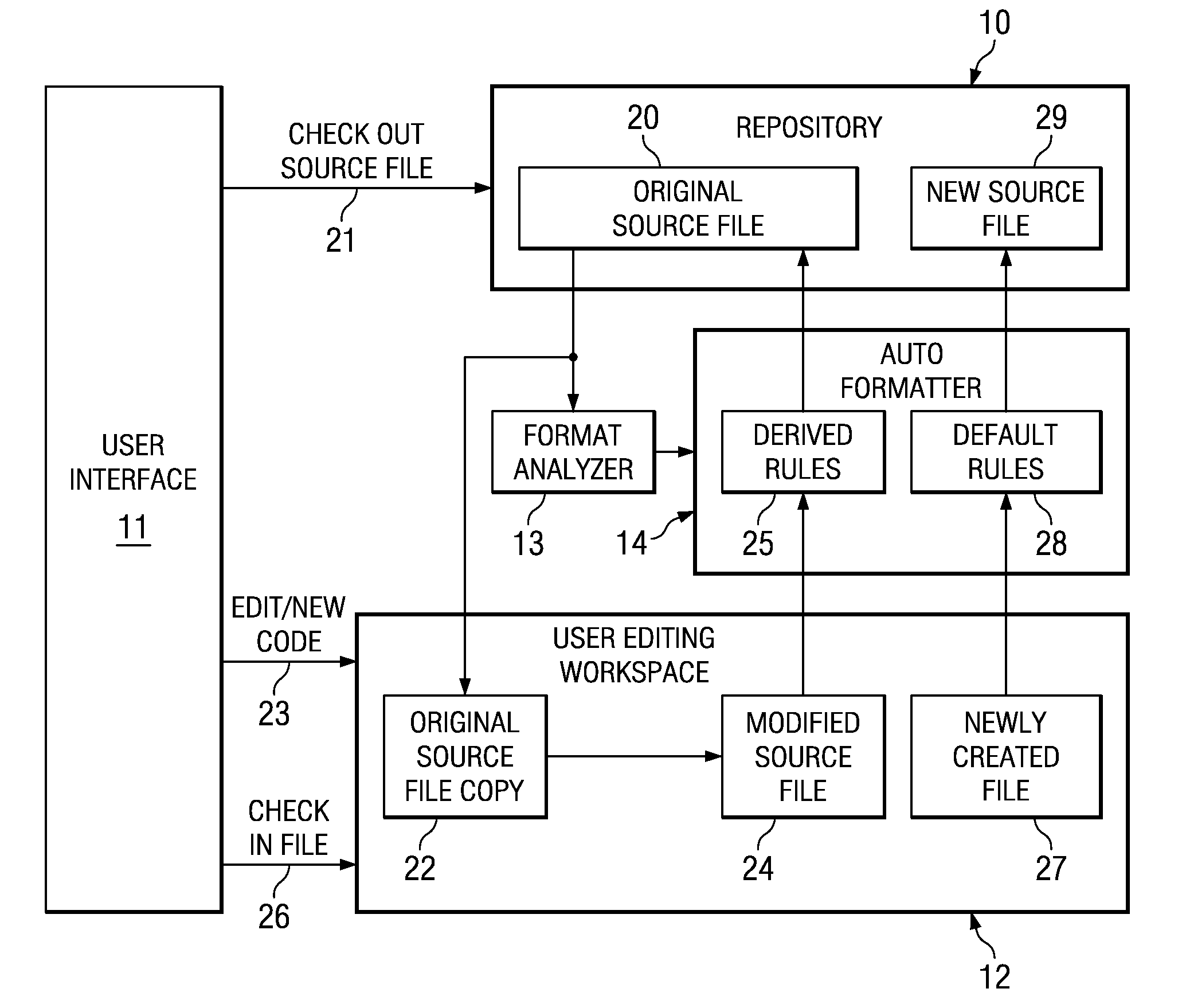
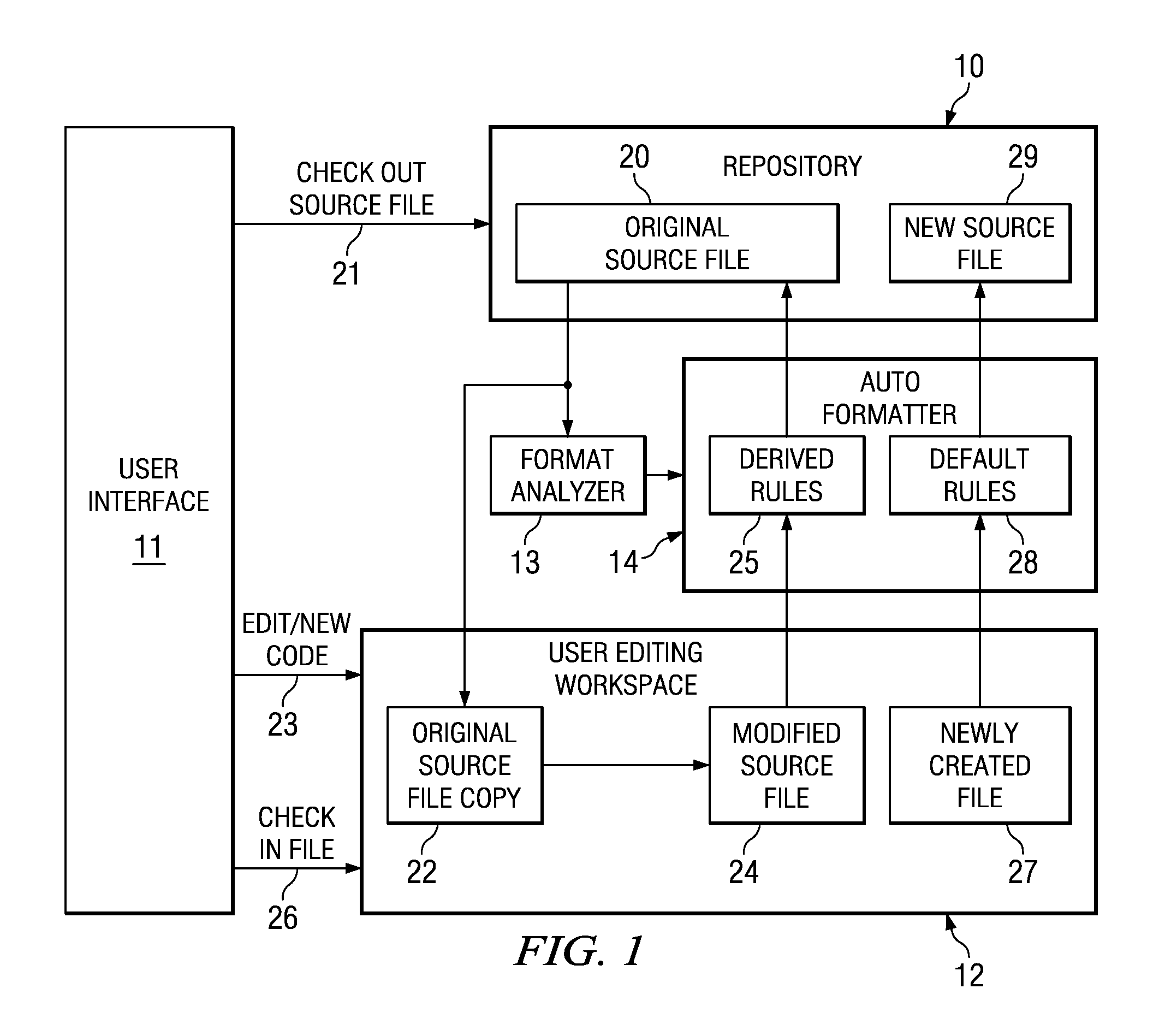
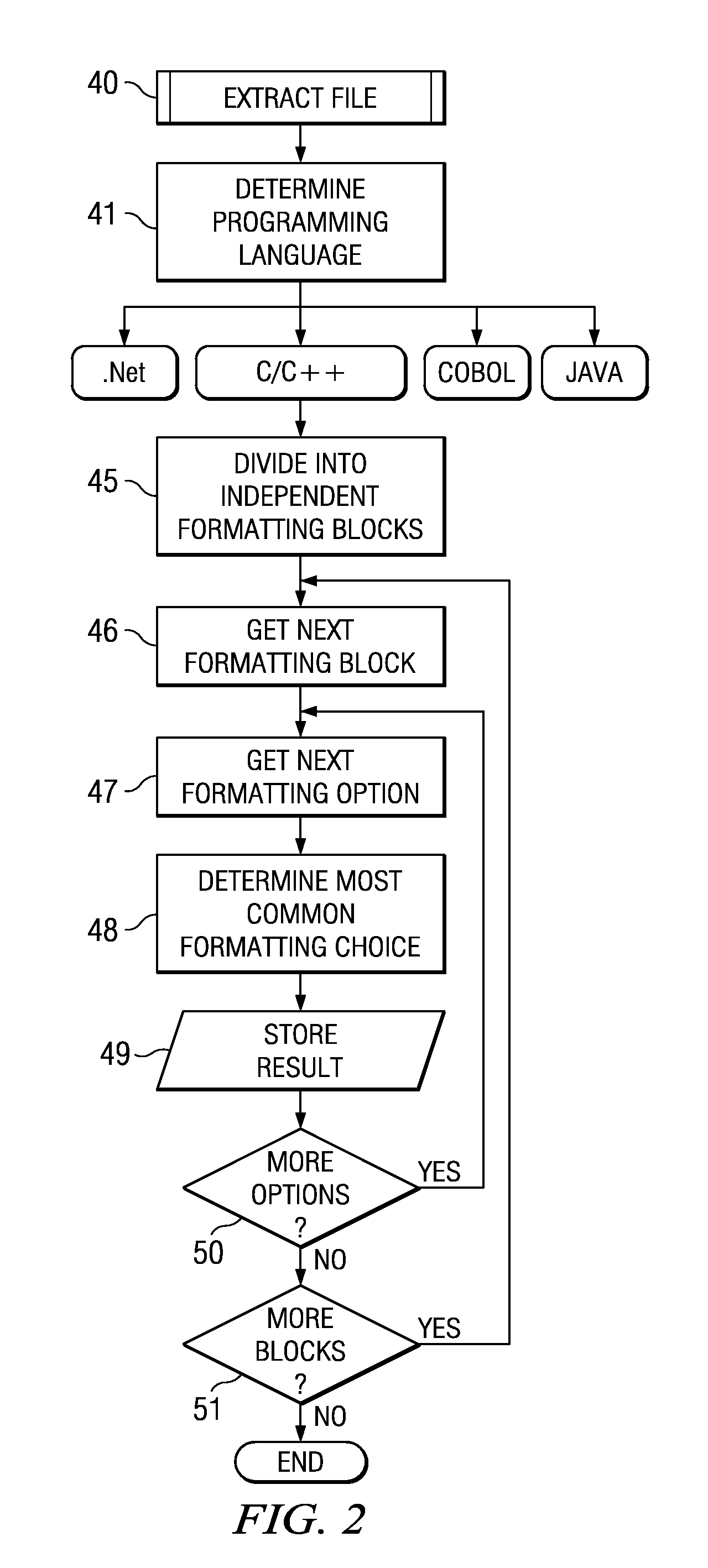
Automatic Formatting of Computer Program Source Code
ActiveUS20080229290A1Reduce the possibilityEasy to identifyError detection/correctionVersion controlDead codeUser input
A method and system is provided for auto formatting changes to computer program source code stored in a code repository. The code comprises a plurality of separately identifiable sections each of which includes non-functional formatting information which differs between at least some of the sections. In response to a user input request a selected source code section is extracted and edited via a user interface. A set of formatting rules is determined automatically from at least the code section being edited. This set of rules is one of a plurality of possible sets corresponding to the separately identifiable sections. The edited code is then formatted according to the determined set of formatting rules and stored in the code repository.
Owner:IBM CORP
Method and apparatus for code virtualization and remote process call generation
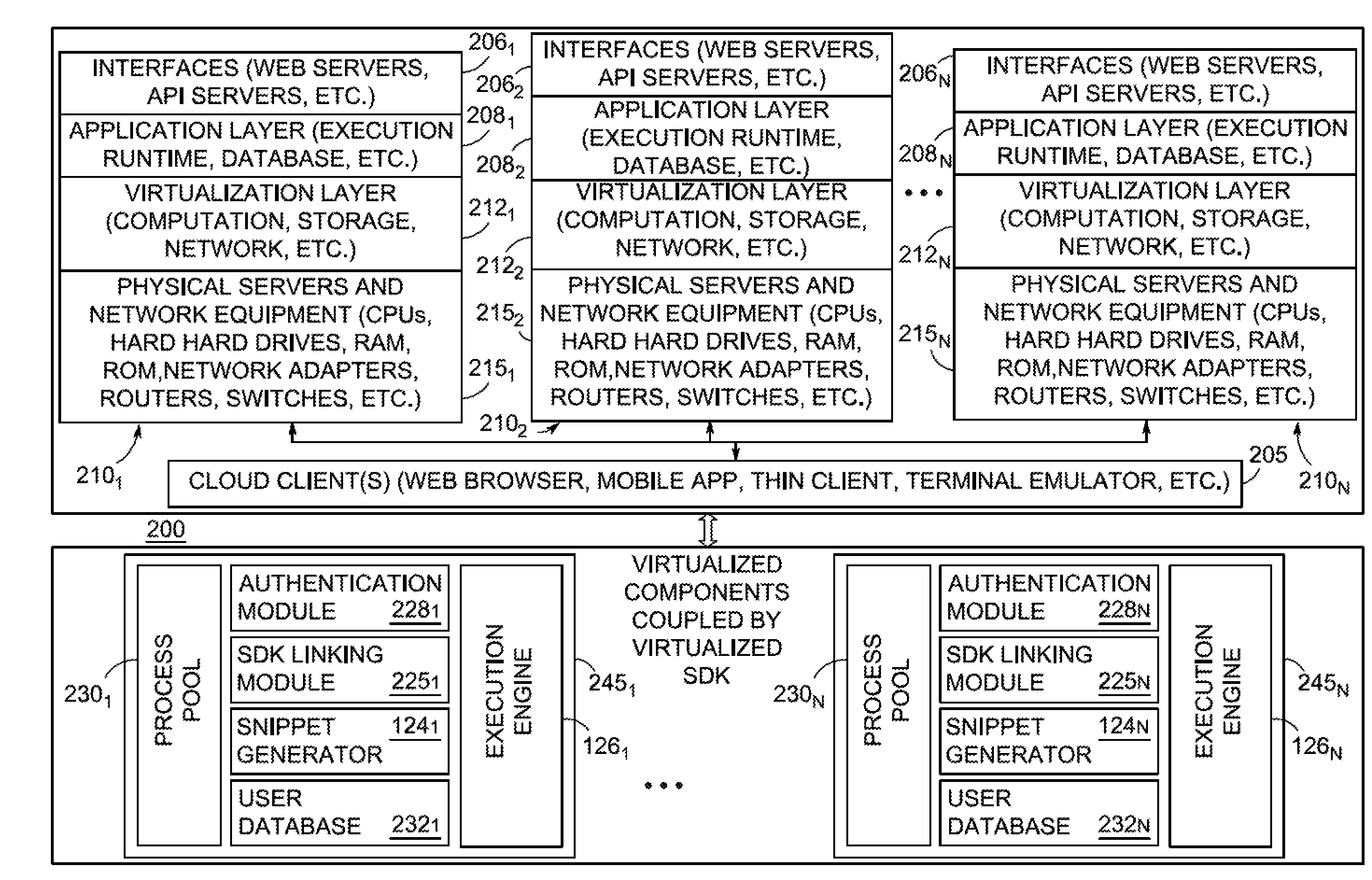
ActiveUS20140372975A1Programming languages/paradigmsVisual/graphical programmingCode snippetUser device
A system and method for code virtualization and remote process call code on a user device. The method includes selecting a remote process on a remote server, the remote process correlated to at least one remote service, and receiving from at least one virtual code provider (VCP) on the remote server, a code snippet with parameters from pre-defined fields to call the remote process. The method installs a software development kit (SDK) downloaded from the remote server, onto the user device. The method inserts the code snippet based on the SDK into a local code base on the user device, and inserts parameter values into the code snippet and deploying the code snippet such that the code snippet calls the remote process with the SDK from the user device.
Owner:CIANMBELLA LTD
Method for detecting unknown malicious code
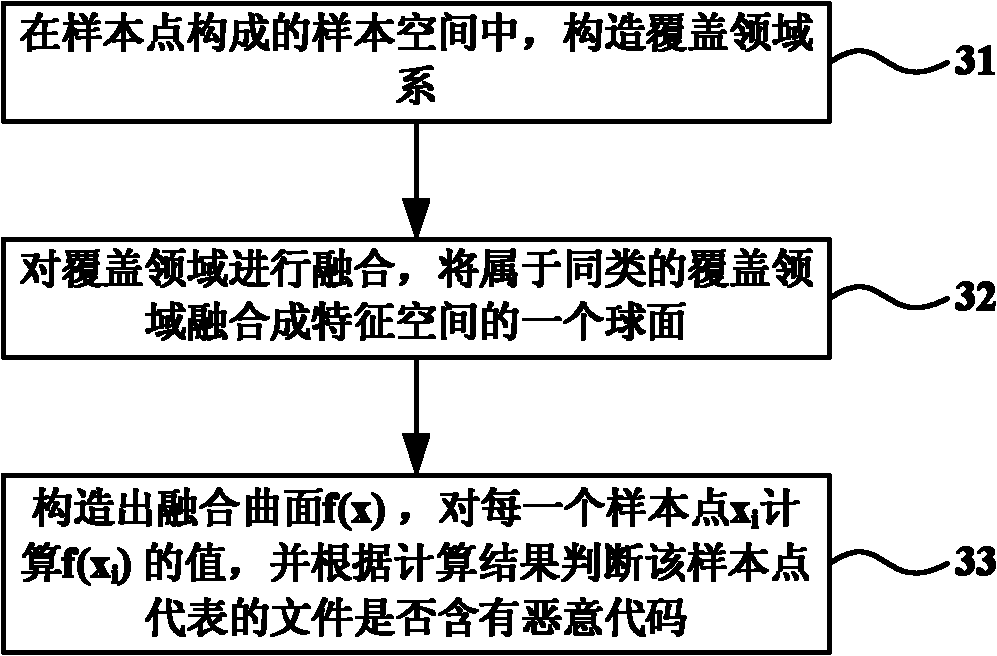
InactiveCN102142068ADetection speedAccurate divisionPlatform integrity maintainanceFeature vectorAlgorithm
The invention discloses a method for detecting an unknown malicious code in the technical field of information safety, which can detect the malicious code in a file in advance under the situation that a malicious code library is not updated. The method comprises the following steps: extracting the feature vector of a file in a training set by utilizing a Byte n-grams method; carrying out the dimension reduction to the extracted feature vector of the file in the training set by adopting a local linear embedding algorithm; taking the feature vector after being subjected to dimension reduction as input, training a kernel cover classifier by utilizing a kernel cover learning algorithm; extracting the feature vector of the file in a test set by utilizing the Byte n-grams method again; carrying out the dimension reduction to the extracted feature vector of the file in the test set by adopting the local linear embedding algorithm; inputting a result after being subjected to dimension reduction into the kernel cover classifier for classification; and calculating the classification result and determining whether the file in the test set contains the malicious code. With the adoption of the method, the detection speed of the file is improved, and the advanced accuracy detection of the malicious code is realized.
Owner:NORTH CHINA ELECTRIC POWER UNIV (BAODING)
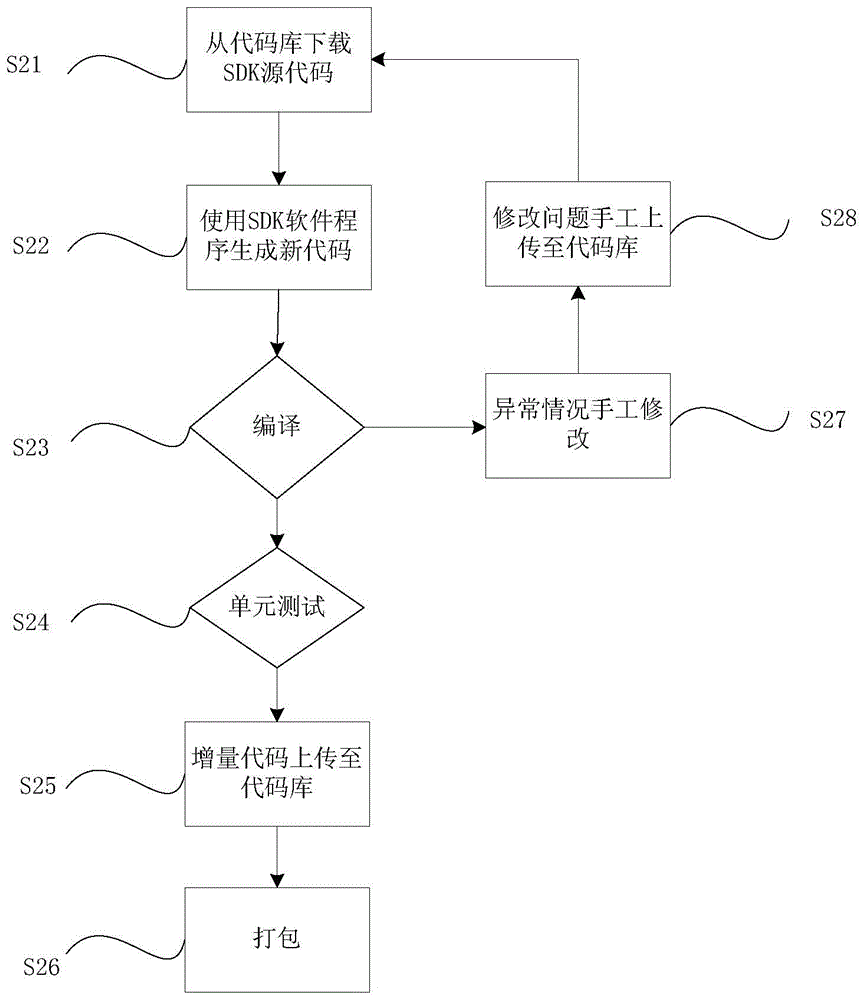
Multilanguage SDK (software development kit) automatic implementation method and system
ActiveCN105718251ASimplify managementFully automatedSpecific program execution arrangementsMarketingApplication programming interfaceSoftware development
The invention provides a Multilanguage SDK (software development kit) automatic implementation method and system, and belongs to the technical field of E-Commerce. The method comprises the following steps: an API (application programming interface) server-side generating an API message according to business requirements; an API client receiving the API message, downloading a SDK source code from a code library, generating the required SDK interface according to the content configuration of the API message, and generating a Multilanguage newly added SDK source code and the corresponding language testing script; uploading the newly added SDK source code to the code library through the compilation and testing, and then packaging. The technical scheme is capable of implementing Multilanguage automation, simplifying SDK management link, improving development efficiency and saving the development cost.
Owner:SUNING COM CO LTD
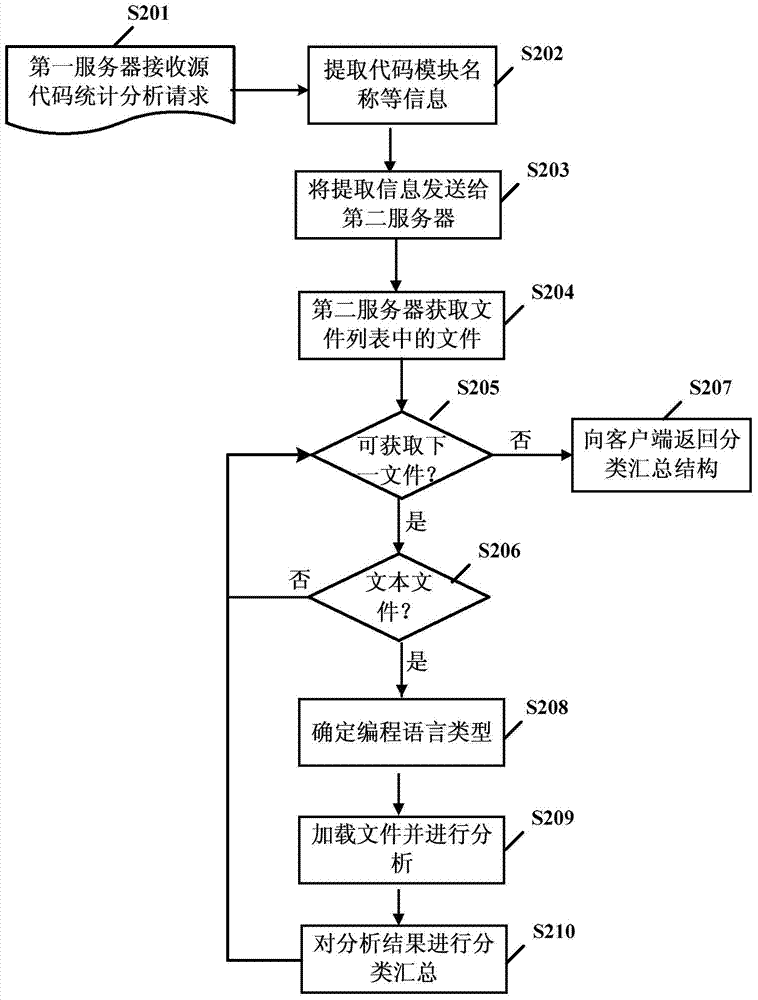
Source code statistical analysis method and source code statistical analysis system
ActiveCN104750469AImprove securityReduce transmission timeSpecial data processing applicationsSpecific program execution arrangementsCode moduleSource code file
The invention relates to the technology of computer software development, in particular to a source code statistical analysis method and a source code statistical analysis system applying the same. An embodiment of the source code statistical analysis method includes that statistical analysis parameters are generated by a first server according to a source code statistical analysis request from a client end, wherein the statistical analysis parameters include a to-be-analyzed code module and an identifier of a code base which the code module belongs to; a corresponding second server is selected by the first server, and source code files associated with the to-be-analyzed code module are stored in the corresponding second server; the source code files associated with the to-be-analyzed code module are subjected to statistical analysis locally by the corresponding second server; the analysis result is fed back to the client end by the corresponding second server via the first server.
Owner:CHINA UNIONPAY
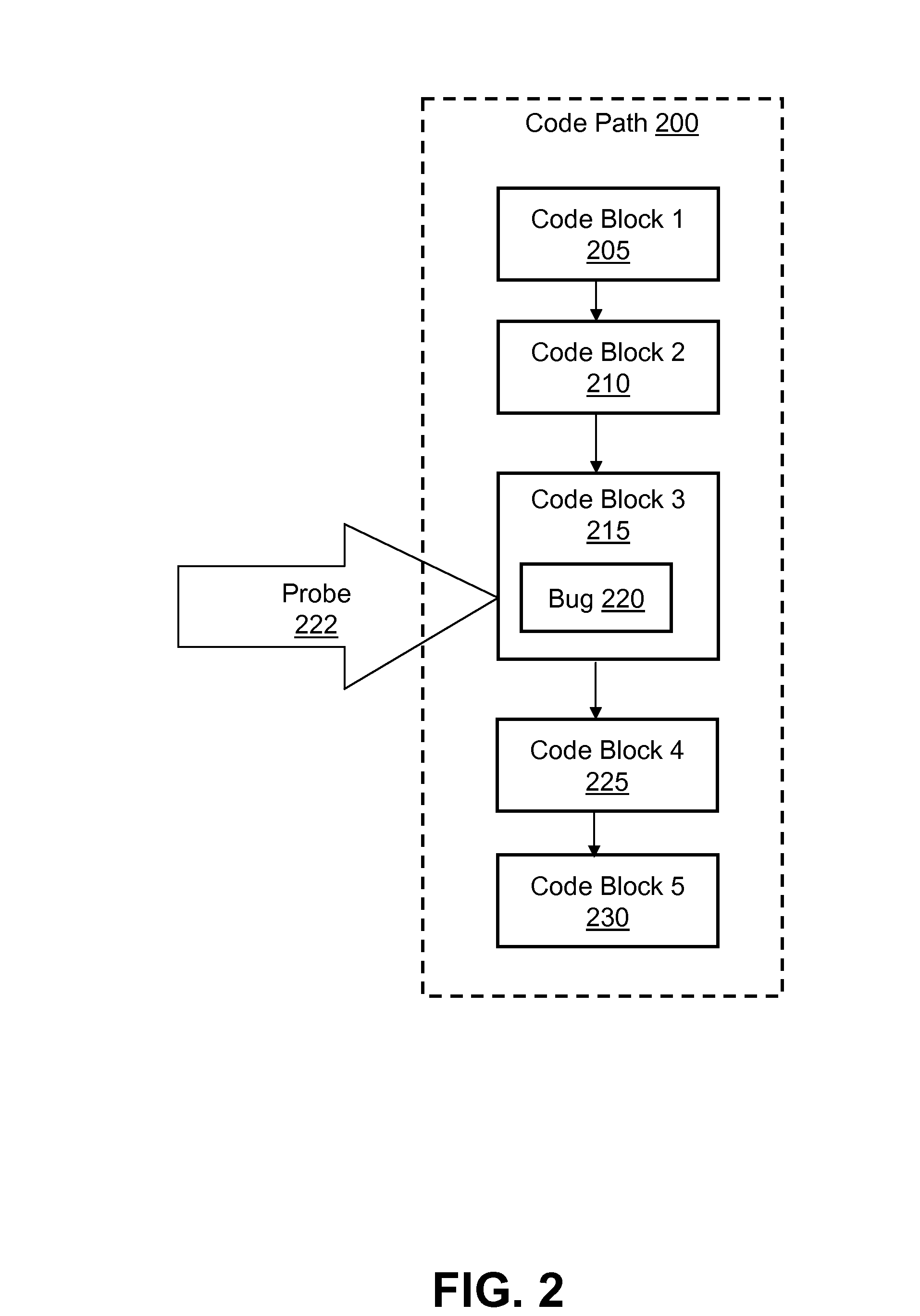
Mitigating malicious exploitation of a vulnerability in a software application by selectively trapping execution along a code path
ActiveUS20080178287A1Shorten the windowShorten windowMemory loss protectionError detection/correctionOperational systemApplication software
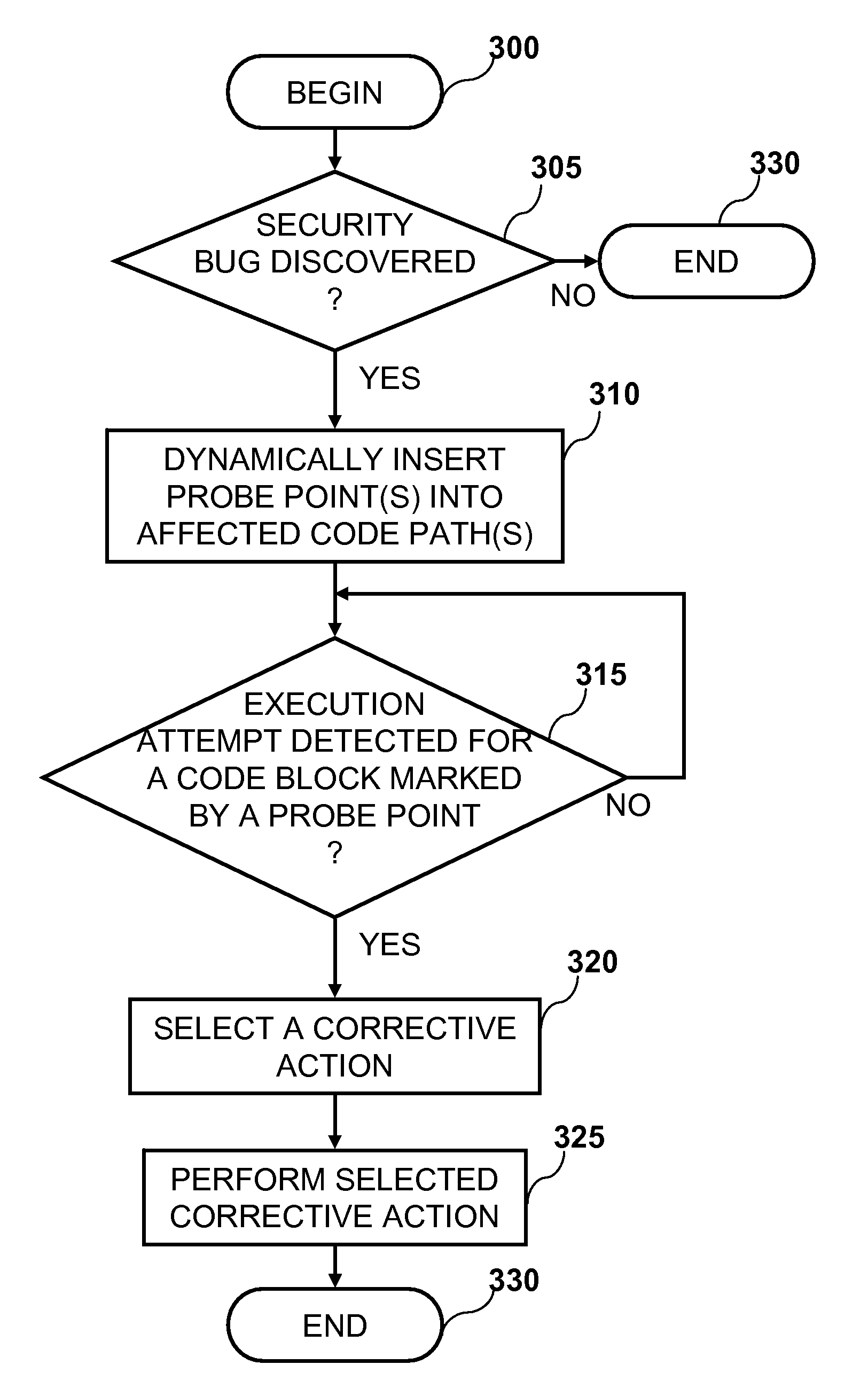
A method of reducing the window of malicious exploitation between vulnerability publication and the installation of a software patch. One or more probe points are inserted into a code path in an application (or operating system if applicable) that contains one or more vulnerabilities (or coding errors). The probe points mark locations of the security vulnerabilities utilizing software interrupts to enable the original code base of the code path to remain unmodified. A probe handler utility subsequently monitors the execution of the code path and generates an alert if the execution reaches a probe point in the code path, thus indicating whether the application exhibits a particular vulnerability. The probe handler selectively performs one of multiple customizable corrective actions, thereby securing the application until an applicable software patch can be installed.
Owner:IBM CORP
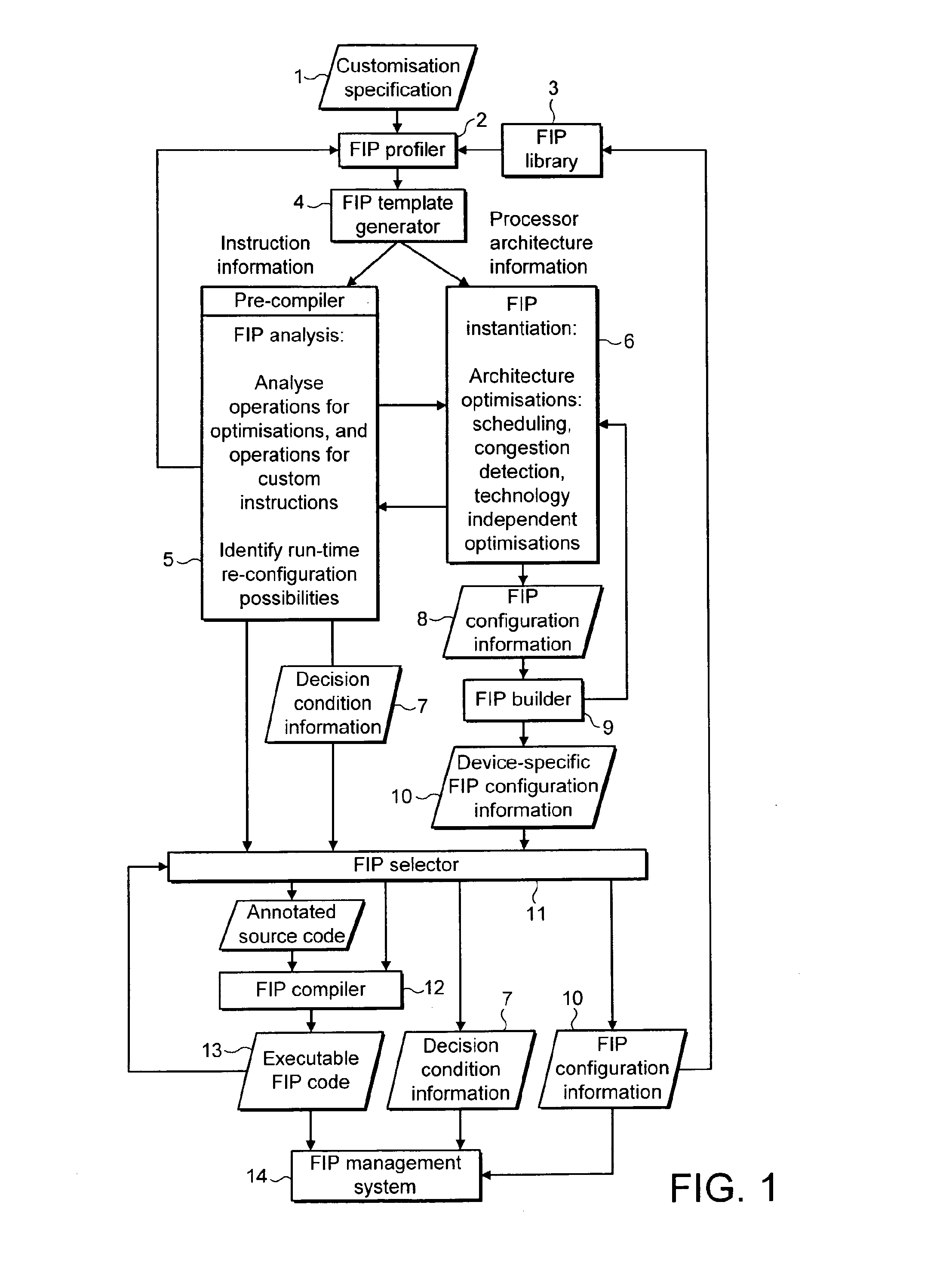
Flexible instruction processor systems and methods
InactiveUS20090235241A1Software engineeringProgram control using wired connectionsComputer architectureApplication software
A design system for generating configuration information and associated executable code based on a customisation specification, which includes application information including application source code and customisation information including design constraints, for implementing an instruction processor using re-programmable hardware, the system comprises a template generator for generating a template for each processor style identified as a candidate for implementation; an analyser for analysing instruction information for each template and determining instruction optimisations; a compiler for compiling the application source code to include the instruction optimisations and generate executable code; an instantiator for analysing architecture information for each template, determining architecture optimisations and generating configuration information including the architecture optimisations; and a builder for generating device-specific configuration information from the configuration information including the architecture optimisations. In another aspect, a management system for managing run-time re-configuration of an instruction processor implemented using re-programmable hardware, comprises a configuration library containing configuration information for a plurality of instruction processor implementations; a code library for containing associated executable code for the implementations; a loader for loading application data and, as required, configuration information and associated executable code into re-programmable hardware for implementation and execution of an instruction processor; a loader controller for signalling the loader to load application data and, as required, configuration information and associated executable code, and execute the executable code; a run-time monitor for obtaining run-time statistics relating to operation of the instruction processor; an optimisation determiner configured to receive the run-time statistics, and being operable to instruct the loader to load new configuration information and associated executable code for a new implementation into the re-programmable hardware; and an optimisation instructor for invoking the optimisation determiner.
Owner:LUK WAYNE +2
Robot task commander with extensible programming environment
ActiveCN104049573ARapid prototypingQuick configurationProgramme-controlled manipulatorProgramme total factory controlTransport layerVisual programming language
A system for developing distributed robot application-level software includes a robot having an associated control module which controls motion of the robot in response to a commanded task, and a robot task commander (RTC) in networked communication with the control module over a network transport layer (NTL). The RTC includes a script engine(s) and a GUI, with a processor and a centralized library of library blocks constructed from an interpretive computer programming code and having input and output connections. The GUI provides access to a Visual Programming Language (VPL) environment and a text editor. In executing a method, the VPL is opened, a task for the robot is built from the code library blocks, and data is assigned to input and output connections identifying input and output data for each block. A task sequence(s) is sent to the control module(s) over the NTL to command execution of the task.
Owner:GM GLOBAL TECH OPERATIONS LLC +1
Optimized Execution of Dynamic Languages
Program code in a dynamic language is executed through a dynamic execution module that includes an execution context and an execution codebase. The instructions of the program code are translated into machine code that is stored in the execution codebase, and the execution context tracks the runtime state and persistent state of the program through executions and across executions. Using the execution codebase and the execution context the dynamic execution module minimizes duplicative machine code generation, while preserving the dynamic aspects of the program.
Owner:GOOGLE LLC
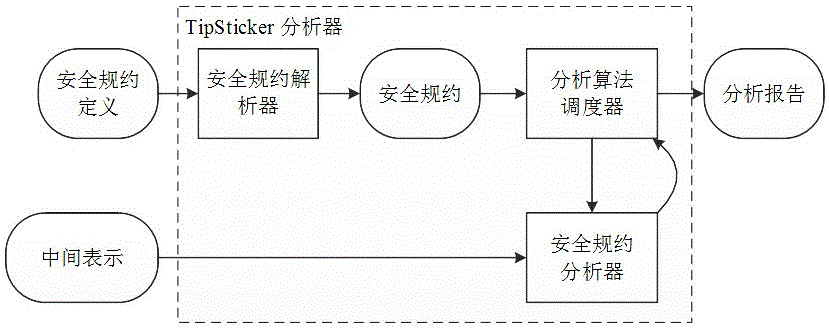
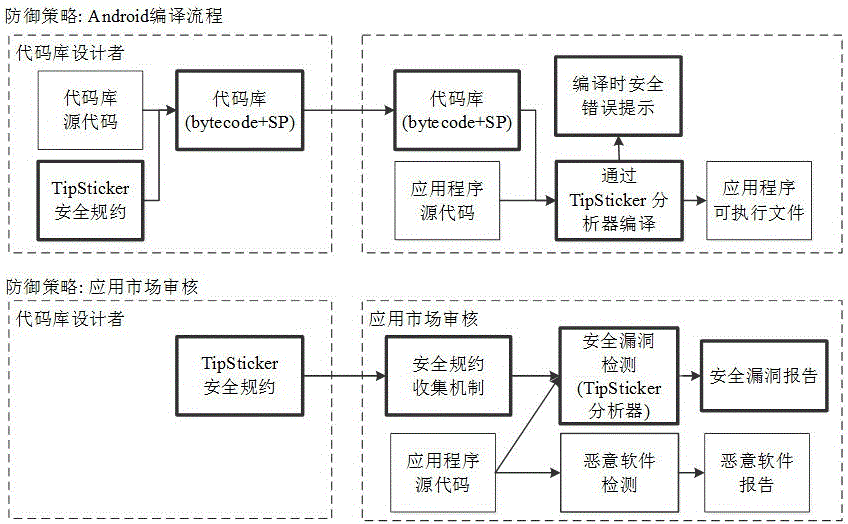
Android application used application program vulnerability detection and analysis method based on code library security specifications
ActiveCN105022958APrevent the risk of security incidentsPlatform integrity maintainanceInformation securityOperating system
The invention belongs to the technical field of program information security monitoring, and particularly relates to an Android application used application program vulnerability detection and analysis method based on code library security specifications. The method comprises the following steps: building a security specification model, i.e., describing the security specifications of the code library by using formalized rule languages; designing a static program analyzer for performing automatic verification based on the security specification model; applying the static program analyzer to two phases, i.e., compilation of application programs and examination of the application programs in an application market, and detecting security vulnerabilities. According to the detection and analysis method provided by the invention, the security risk in the program can be prevented.
Owner:FUDAN UNIV
Automated tagging and tracking of defect codes based on customer problem management record
ActiveUS20130311975A1Facilitate software defect trackingEasy to correctVersion controlSoftware testing/debuggingProblem managementCode snippet
A routine for tagging and tracking source code may be implemented in a software development environment. The routine begins upon the identification of a defect in a software product or system. Once the defect has been identified and rectified, a search of other source code (typically located in a source code management system that supports version control) is specified. Using the search specification, the system automatically identifies the code snippet to be searched and begins searching the identified codebase for duplicates. A ticket or service record is then created for every duplicate / similar code snippet found during the search. The ticket / record enables software defect tracking to be carried out on the newly-located instances of the code. The system also automatically manages the code snippets identified by the duplicate detection.
Owner:IBM CORP
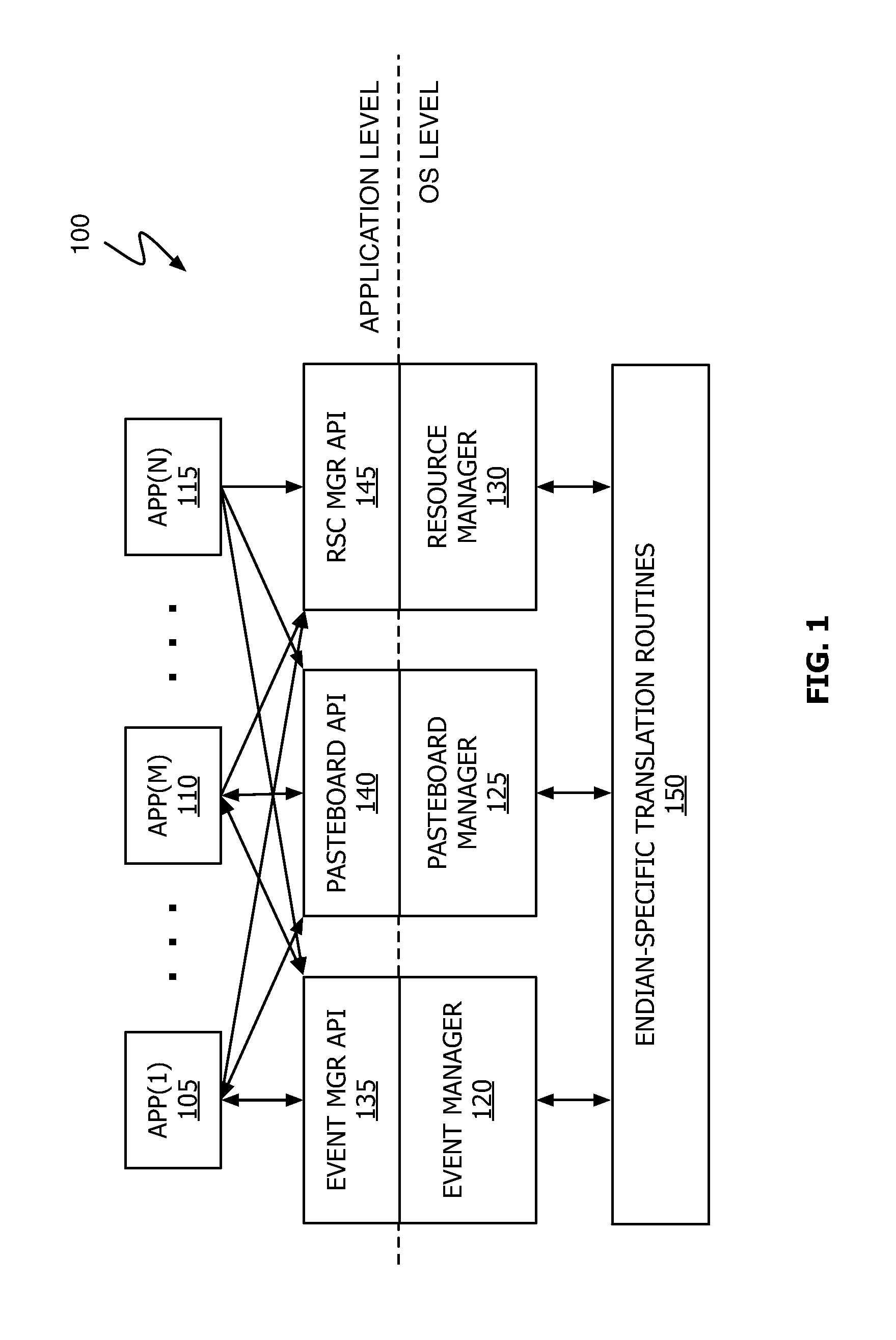
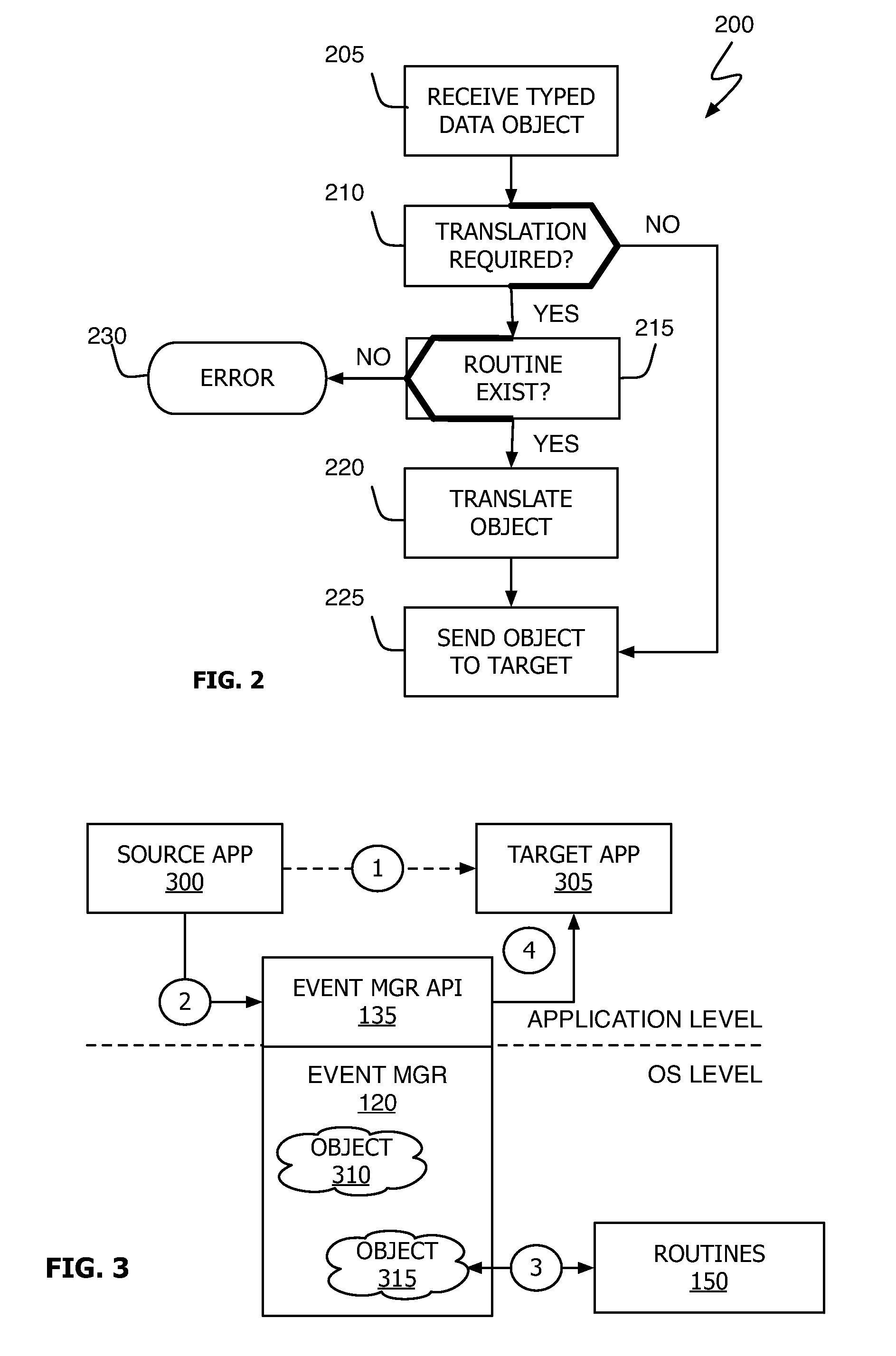
Typed-Data Translation for Platform Independence
ActiveUS20110138370A1Memory adressing/allocation/relocationSpecific program execution arrangementsOperational systemData translation
A method, computer program and device for the translation of typed data objects in a heterogeneous computational environment is described. The operating system (or installed shared code libraries) translates typed data objects from a first format (e.g., big-endian) to a second format (e.g., little-endian) if the application sending the object and the application receiving the object utilize different formats. By placing data object format translation capabilities into the operating system, the software development effort required to permit an application (e.g., a user-level application) to execute in a heterogeneous environment is significantly reduced.
Owner:APPLE INC
Mitigating malicious exploitation of a vulnerability in a software application by selectively trapping execution along a code path
ActiveUS7845006B2Shorten windowMemory loss protectionUnauthorized memory use protectionOperational systemApplication software
A method of reducing the window of malicious exploitation between vulnerability publication and the installation of a software patch. One or more probe points are inserted into a code path in an application (or operating system if applicable) that contains one or more vulnerabilities (or coding errors). The probe points mark locations of the security vulnerabilities utilizing software interrupts to enable the original code base of the code path to remain unmodified. A probe handler utility subsequently monitors the execution of the code path and generates an alert if the execution reaches a probe point in the code path, thus indicating whether the application exhibits a particular vulnerability. The probe handler selectively performs one of multiple customizable corrective actions, thereby securing the application until an applicable software patch can be installed.
Owner:IBM CORP
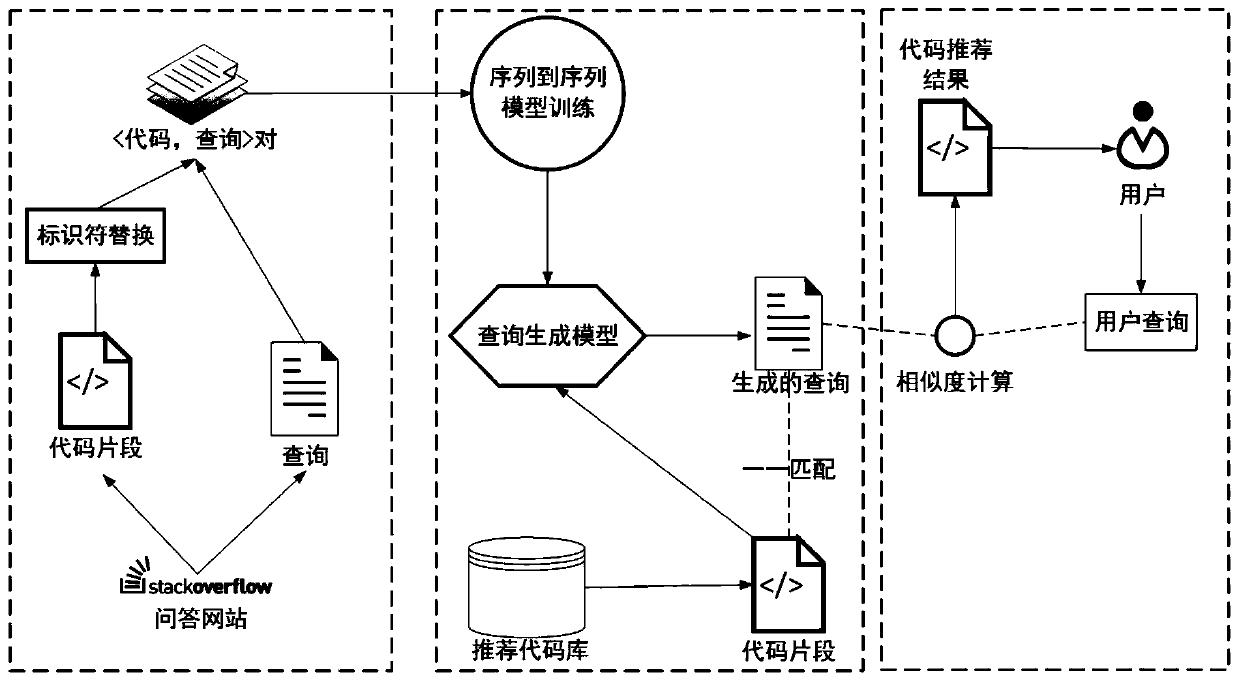
Code snippet recommendation method based on sequence-to-sequence model
InactiveCN110750240AImprove recommendation effectImprove development efficiencySoftware testing/debuggingSoftware designCode snippetTheoretical computer science
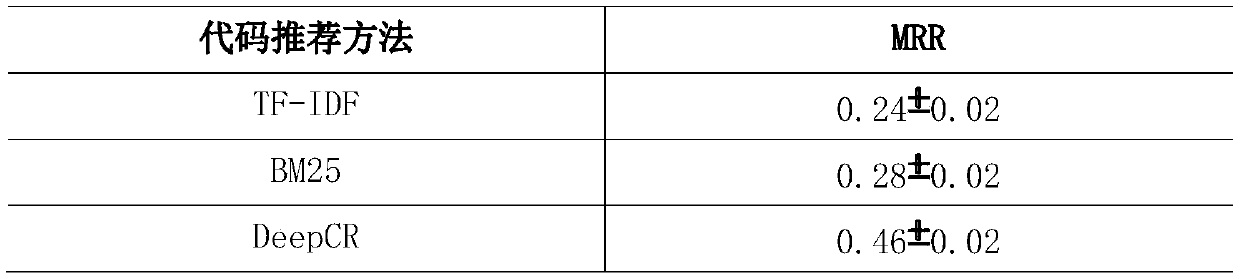
The invention discloses a code snippet recommendation method based on a sequence-to-sequence model. The method comprises the steps of collecting and cleaning code snippets and corresponding queries; extracting code information; performing an identifier replacement operation on the code snippets; combining the code snippets after the identifier replacement operation and the corresponding queries into a set of (code, query) pairs, and taking the set as a training set of a query generation model; training a query generation model by using the sequence-to-sequence model; generating a query for thecode snippets of the recommendation code library; inputting a query, and executing similarity calculation between the query and the generated query; and according to a similarity calculation result,constructing a generated query list according to a descending order of similarity scores, and retrieving code snippets corresponding to queries in the list from a recommendation code library to serveas code snippet recommendation results. The method is superior to some existing research works, the code snippet recommendation effect can be effectively improved, and the software development efficiency is improved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Method and framework for securing a source code base
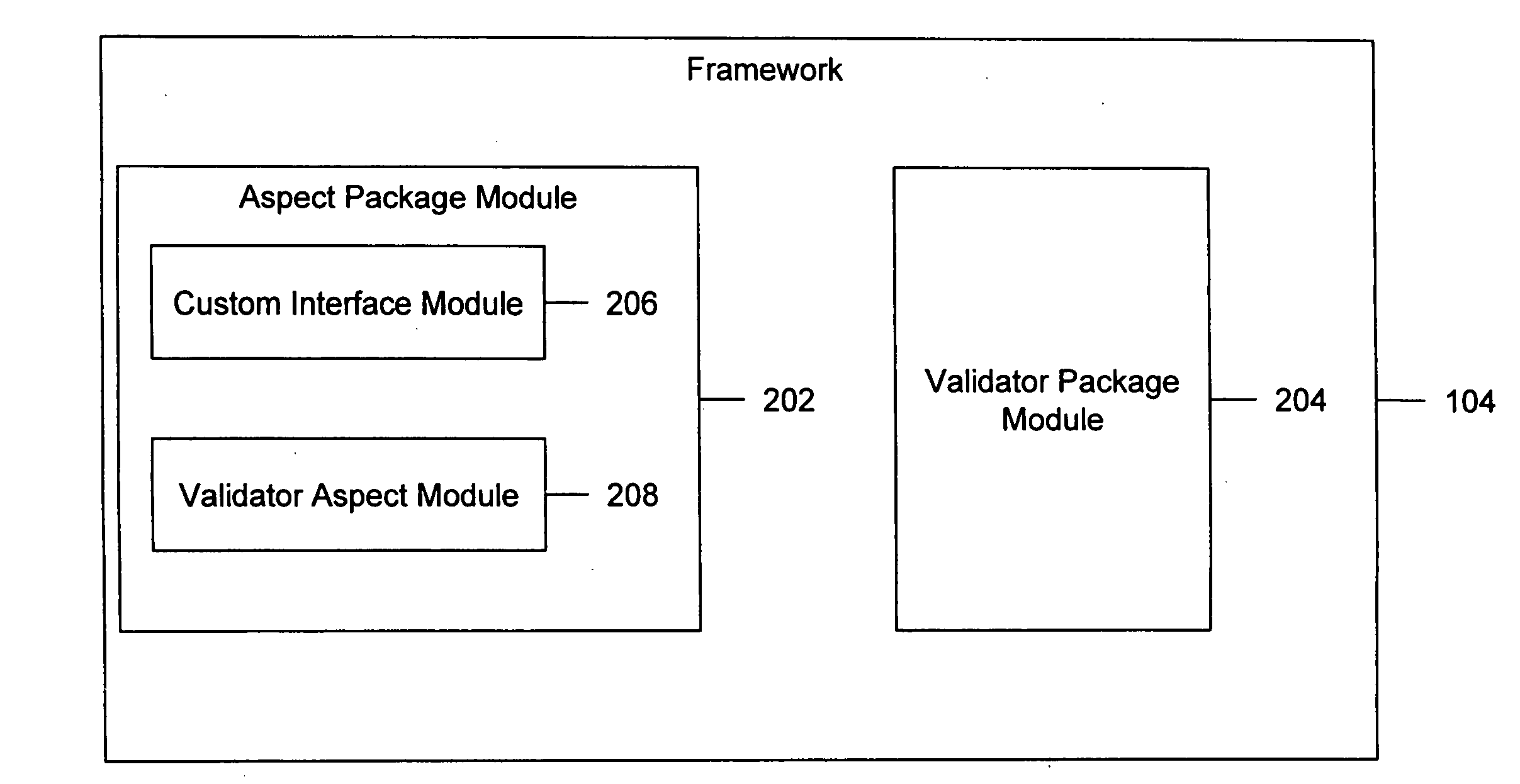
ActiveUS20090183137A1Minimize false positive falseMinimize false false negativeSoftware designPlatform integrity maintainanceIntegration pointSoftware development
A framework for securing a source code base during the development phase of a software development lifecycle is provided. The framework includes an aspect package module and a validator package module. The aspect package module integrates security routines into the source code base. The aspect package module includes a custom interface module and a validator aspect module. The custom interface module includes a function declaration, wherein the custom interface module is implemented by at least one class of the one or more classes. The validator aspect module includes a controller code for controlling the flow of the execution, based on the context for the security validation of the at least one class, wherein one or more security routine integration points are defined in the at least one class. The validator package module validates the at least one class, based on the defined context, by using one or more validation classes.
Owner:INFOSYS LTD
Method and system for updating program versions in servers
ActiveCN106371881AShorten update timeReduce transfer volumeVersion controlProgram loading/initiatingConfiguration itemThe Internet
The invention relates to the field of Internet, and discloses a method for updating program versions in servers. The method comprises the following steps: S1, acquiring branches of a code library, and acquiring configuration items associated with the branches; S2, establishing connections with one or more servers in the code library according to the addresses of the servers in the acquired configuration items; S3, traversing files in the servers which are connected with the code library, judging whether a single server includes feature files for indicating version number information of a current version of a program in the server or not, and updating all or a part of latest version files to file uploading lists corresponding to the servers; S4, deploying the files in the file uploading lists into the corresponding servers. The invention further discloses a system for updating the program versions in the servers. The method and the system have high program updating processes, and support simultaneous program updating of a plurality of servers.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Automated tagging and tracking of defect codes based on customer problem management record
ActiveUS9009665B2Easy to trackVersion controlSoftware testing/debuggingProblem managementCode snippet
A routine for tagging and tracking source code may be implemented in a software development environment. The routine begins upon the identification of a defect in a software product or system. Once the defect has been identified and rectified, a search of other source code (typically located in a source code management system that supports version control) is specified. Using the search specification, the system automatically identifies the code snippet to be searched and begins searching the identified codebase for duplicates. A ticket or service record is then created for every duplicate / similar code snippet found during the search. The ticket / record enables software defect tracking to be carried out on the newly-located instances of the code. The system also automatically manages the code snippets identified by the duplicate detection.
Owner:IBM CORP
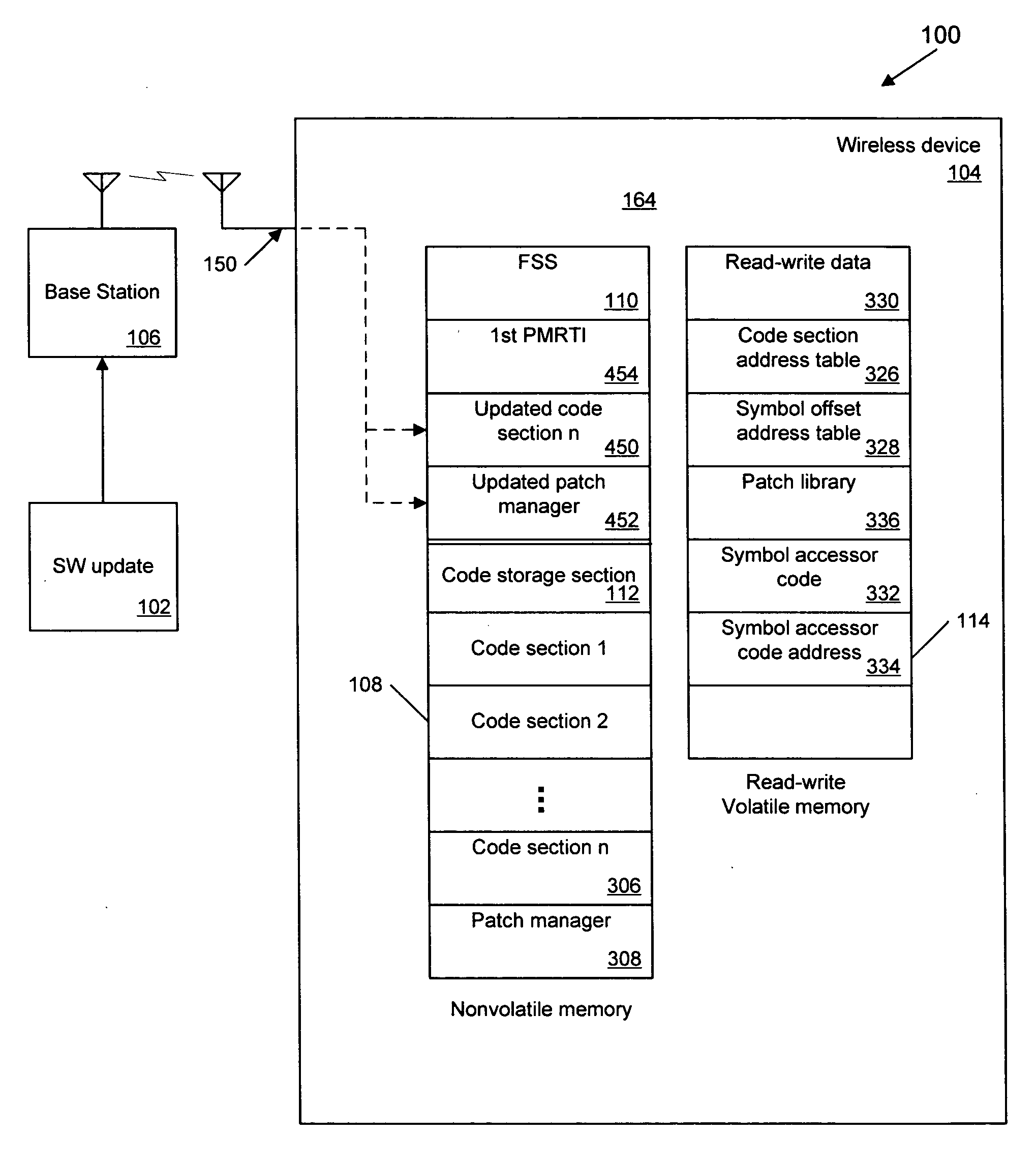
Field downloading of wireless device software
Owner:KYOCERA CORP
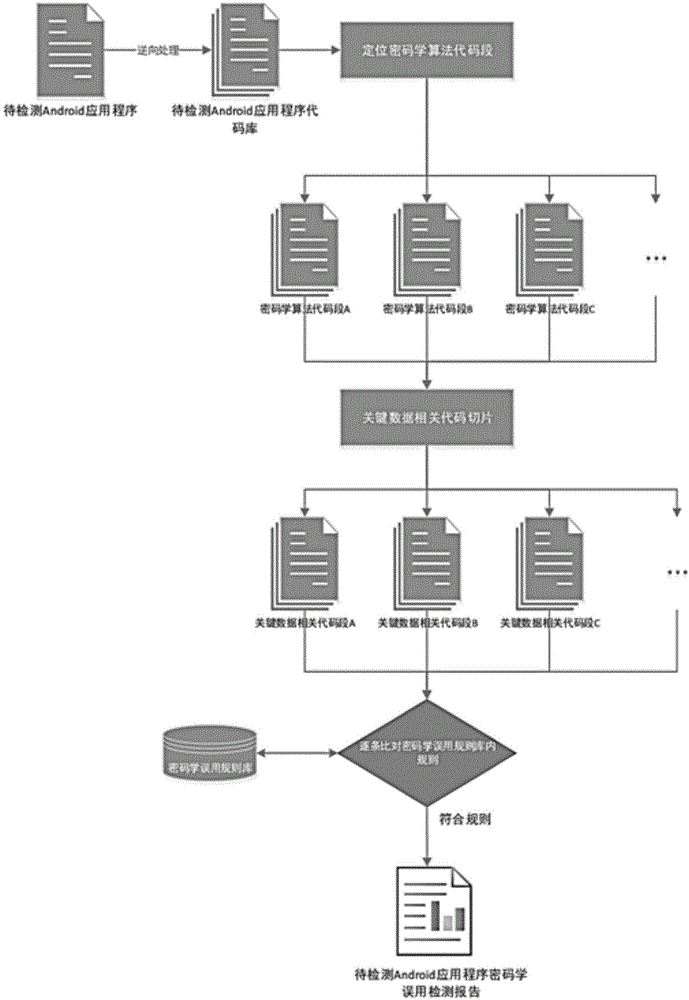
Method for detecting cryptology misuse of Android application programs
ActiveCN104484175ADigital data protectionSpecific program execution arrangementsData abstractionPattern matching
The invention discloses a method for detecting cryptology misuse of Android application programs. The method comprises the following steps of decompiling a to-be-detected program and generating a codebase; then, looking up code segments related with a cryptographic algorithm from the codebase; then, stripping the code segments related with the cryptographic algorithm out of an original program to obtain a complete cryptographic algorithm implementation process code; finally, performing data abstraction and process modeling processing on each cryptographic algorithm implementation process code segment obtained in the step 3; comparing the cryptographic algorithm implementation process code segments item by item through pattern matching and a cryptographic algorithm implementation rule appointed in advance, outputting items which do not meet the implementation rule and summarizing to form a safety analysis result. According to the method disclosed by the invention, through static analysis on an Android application program, a cryptographic algorithm type used in the application program can be automatically judged, and the code segments related with the cryptographic algorithm are automatically extracted; safety analysis is performed on the code segments so as to find out a problem link during a cryptographic algorithm implementation process, and the safety analysis result of the cryptology misuse of the application program is finally obtained.
Owner:SHANGHAI JIAO TONG UNIV +1
Code merging method and related equipment for supporting application parallel development
ActiveCN109542415AEasy to distinguishEasy to manageCode compilationCreation/generation of source codeSoftware engineeringApplication software
The invention discloses a code merging method and related equipment for supporting application parallel research and development, wherein, the method comprises the following steps: collecting information of an application program to be developed, and generating an application program ID corresponding to the application program to be developed according to the information of the application programto be developed; Creating a requirement list of a corresponding application to be developed based on the application ID, adding requirement information to the requirement list, and configuring a codebase corresponding to the requirement information; searching code base corresponding to each requirement information of an application to be developed based on the application ID, and merging codes in the searched code base to obtain a merged code base. As that ID is generate by the application program to be researched and developed, the invention realizes that the application program is distinguished by the ID, the management of the application program is convenient, and the code base corresponding to each requirement of each application program is simultaneously merged based on the ID of the application program, thereby saving the cost of code merging.
Owner:BEIJING 58 INFORMATION TECH
Method and apparatus for code virtualization and remote process call generation
ActiveUS20140372972A1Digital data processing detailsProgramming languages/paradigmsUser deviceCode snippet
A system and method for code virtualization and remote process call code generation. The method including installing a software development kit (SDK) on a user device and selecting a remote process on a remote server, the remote process correlated to at least one remote service. The method also parsing parameters from pre-defined fields for the remote process and generating by at least one virtual code provider (VCP) on the remote server, a code snippet to call the remote process. The method inserting the code snippet into a local code base on the local user device such that the inserted code snippet calls the remote process with the installed SDK.
Owner:CIANMBELLA LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com