Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30results about How to "Solve the inconvenience of management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
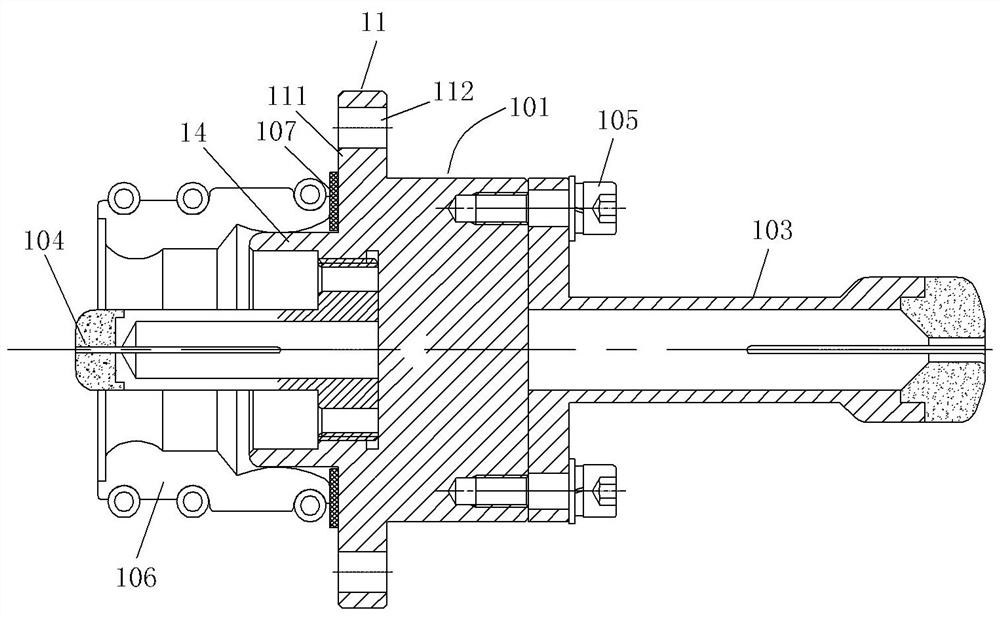
Virtual key-based vehicle lock control system and smart vehicle lock comprising same
InactiveCN104691657ASolve the inconvenience of managementRealize automatic openingAnti-theft cycle devicesAnti-theft devicesControl systemThird generation
The invention discloses a virtual key-based vehicle lock control system and a smart vehicle lock comprising the same. Vehicle lock information is registered through an APP (application) and is stored in the cloud through a mobile network; a vehicle lock downloads the vehicle lock information from the cloud and binds to a terminal device of a user; the APP in the terminal device sends a signal to control unlocking or locking of the vehicle lock. Carrying a key is not required, and the problem that keys are inconvenient to manage is effectively solved. A communication module is used for transmitting the information of the vehicle lock to the terminal device through a 3G (third generation) or 4G (fourth generation) network. A controller has a positioning function, allowing the user to conveniently position the vehicle lock. A camera is provided, facing a latch of the vehicle lock. In case of vehicle lock theft, the controller drives the camera to start up and record theft video information, the theft video information is stored in a storage, alarm information is sent to the terminal device, and evidence for retrieving a vehicle later is provided.
Owner:SUZHOU UNIV
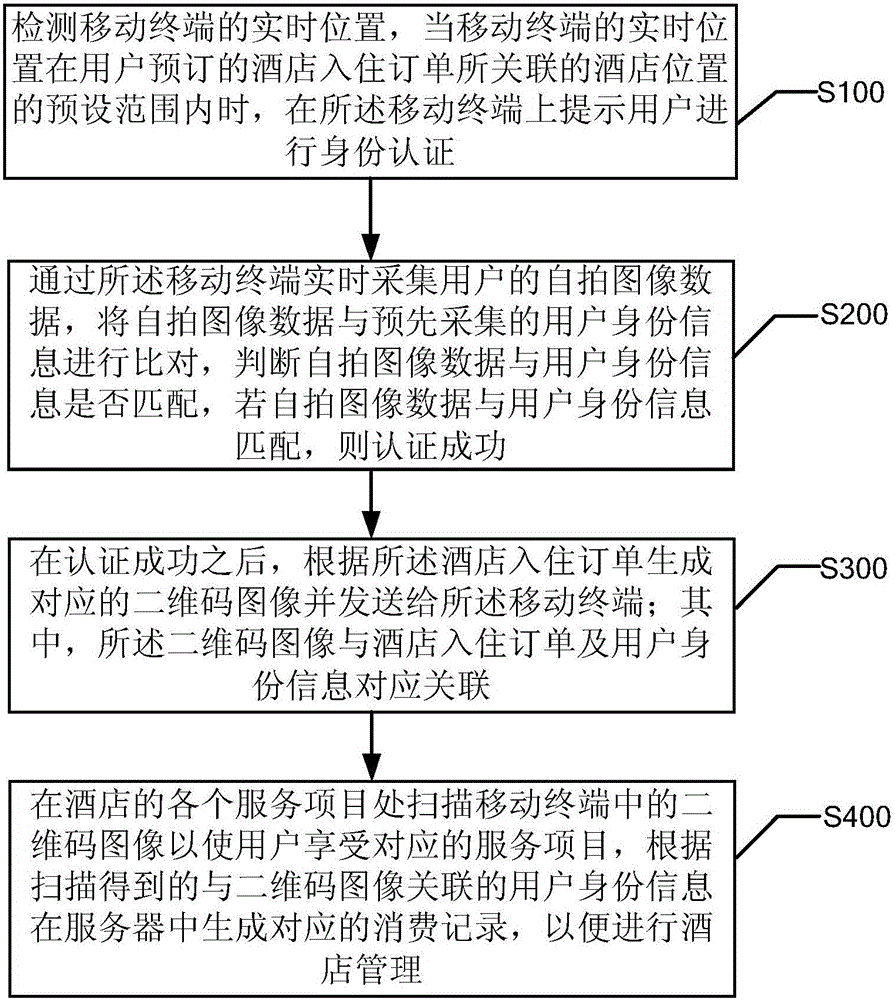
Hotel self-service management method and system
InactiveCN105761173ASolve the inconvenience of managementReduce labor costsData processing applicationsDimensional modelingComputer terminal
The invention discloses a hotel self-service management method and system. The method comprises the steps of acquiring selfie image data of a user in real time through a mobile terminal, comparing the selfie image data with pre-acquired user identity information, determining whether the selfie image data match the user identity information, and if so, passing the authentication successfully; after successful authentication, generating a corresponding two-dimensional code image according to a hotel check-in order, and transmitting to the mobile terminal; and scanning the two-dimensional code image in the mobile terminal at service items in a hotel so as to allow the user to enjoy the corresponding service items, and generating a corresponding consumption record in a server according to the user identity information associated with the scanned two-dimensional code image so as to facilitate hotel management. According to the invention, all the service items in the hotel can be available by verifying the two-dimensional code, and the user can enjoy all the services of the hotel simply by carrying a mobile terminal.
Owner:姜恒
A method for analyzing and monitoring students' classroom behavior
InactiveCN109410098ARealize monitoringSolve the inconvenience of managementData processing applicationsCharacter and pattern recognitionBehavioral analyticsComputer science
The invention discloses a method for analyzing and monitoring students' classroom behavior. The method is characterized by comprising the following steps: 1, acquiring classroom images in real time and uploading to a server; 2, identifying the student behavior in the image respectively, and judging whether the student behavior belongs to abnormal behavior or not; 3: If the behavior of the studentis abnormal, record the abnormal behavior of the student, and send the corresponding prompt information to the terminal of the student and the teacher respectively. The method for analyzing and monitoring the classroom behavior of students accurately identifies the behavior of students, timely discovers abnormal behavior, realizes the monitoring and management of the classroom behavior of students, lightens the work of teachers, promotes students to seriously listen to lessons, and improves classroom teaching efficiency.
Owner:SICHUAN WINSHARE EDUCATION SCI & TECH
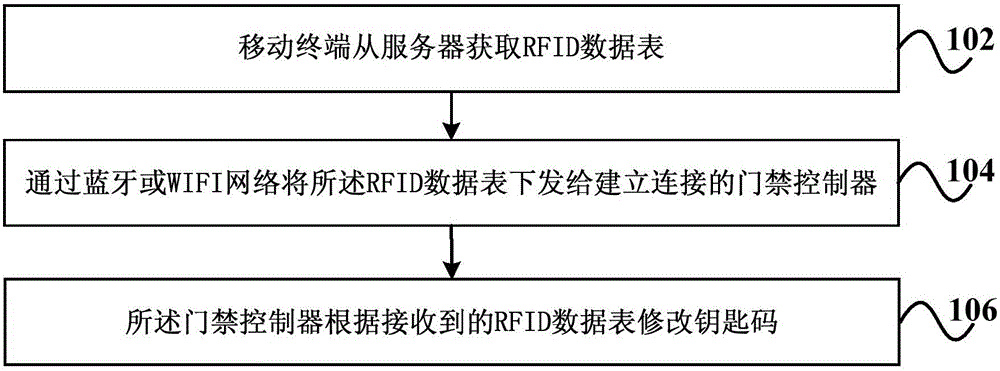
Management method and management system of entrance guard key codes
ActiveCN106558126ASolve the inconvenience of managementLow costIndividual entry/exit registersWi-FiWifi network
The invention discloses a management method and a management system of entrance guard key codes and relates to the technical field of intelligent entrance guard. The method includes the steps of: 1) a mobile terminal acquires a RFID data table from a server; 2) the mobile terminal sends the data table down to an entrance guard controller with connection established through Bluetooth or Wi-Fi network; and 3) the entrance guard controller, according to the received RFID data table, modifies key codes. According to the method, a conventional key code management method of RFID entrance guard systems is modified through wireless and Internet technologies which are low in cost, so that a problem of inconvenience of management of the key codes when the RFID entrance guard is offline can be solved, and cost is effectively reduced and management efficiency and accuracy are improved.
Owner:CHINA TELECOM CORP LTD
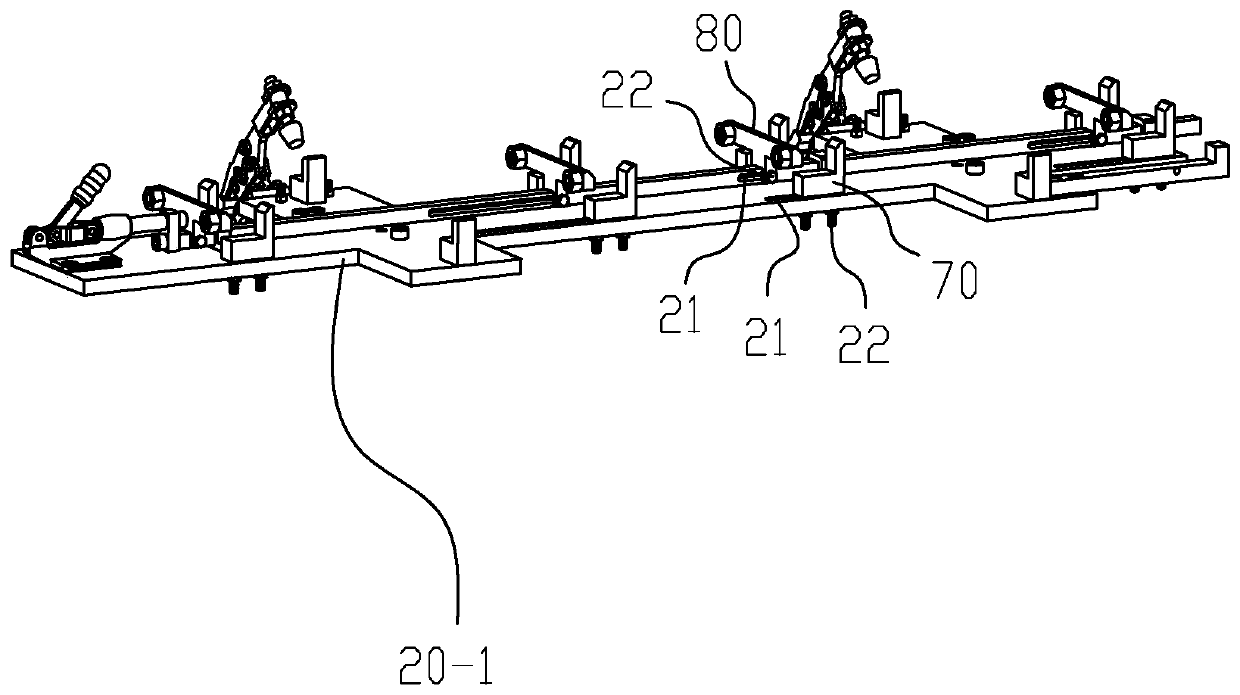
Flexible clamp for passenger car pedal skeleton welding
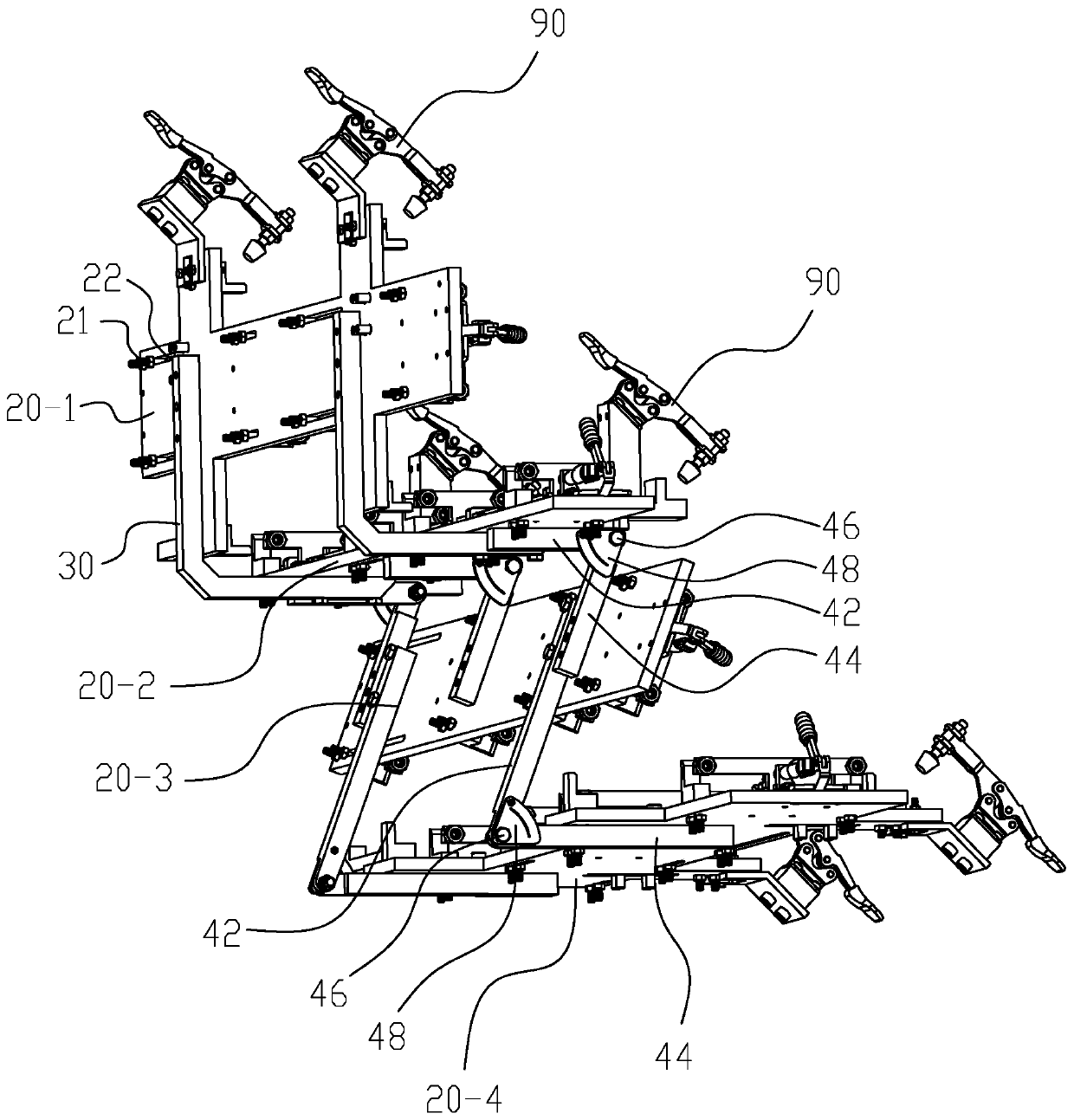
PendingCN110052770AImprove the range of use and flexibilityLow manufacturing costWelding/cutting auxillary devicesAuxillary welding devicesStructural differenceEngineering
The invention discloses a flexible clamp for passenger car pedal skeleton welding. The flexible clamp comprises a base and four limiting plates longitudinally arranged above the base, wherein the limiting plates are connected by a hinge mechanism; a positioning block and a clamping block which can transversely slide are arranged on the top surface of each limiting plate, and sliding grooves corresponding to the positioning block and the clamping block are respectively formed in each limiting plate; the positioning block and the clamping block are locked on the corresponding limiting plate respectively through bolt components; and the positioning block and the clamping block are mutually matched to clamp a longitudinal rod of a skeleton. According to a series of structural differences of the passenger car pedal skeleton, the welding clamp is regulated to a designated position precisely and quickly to carry out corresponding clamping and fixation, thus the adjustment of several degrees of freedom in a plane and space is realized, the application scope and flexibility of the fixture tool are improved, the manufacturing cost is reduced, and the manufacturing time is shortened. The clamping block and the positioning block are fixed through the bolt components, so that the rigid positioning is ensured, and the positioning precision and the clamping function can also be ensured.
Owner:XIAMEN UNIV
Lora networking Beidou monitoring data transmission system and data transmission method
PendingCN110072296AImprove accuracyImprove securityNetwork topologiesHigh level techniquesHigh energyData information
The invention provides a lora networking Beidou monitoring data transmission system. The lora networking Beidou monitoring data transmission system comprises a lora wireless gateway, a DTU, a server and at least one monitoring device. The monitoring device comprises a Beidou positioning module and a lora wireless module, the Beidou positioning module and the lora wireless module are in communication connection, and the lora wireless module is used for transmitting position information from the Beidou positioning module. The lora wireless gateway is in communication connection with the lora wireless module and the DTU. The DTU receives data information from the lora wireless module through the lora wireless gateway, and the DTU is connected with the server through a wireless network and isused for transmitting data to the server so as to be convenient for calling and using the terminal monitoring device. The transmission method is simple in step and convenient to operate. According tothe system, the problems of short transmission distance, high energy consumption, high cost and inconvenience in management in the prior art are effectively solved.
Owner:HUNAN LIANZHI MONITORING TECH CO LTD
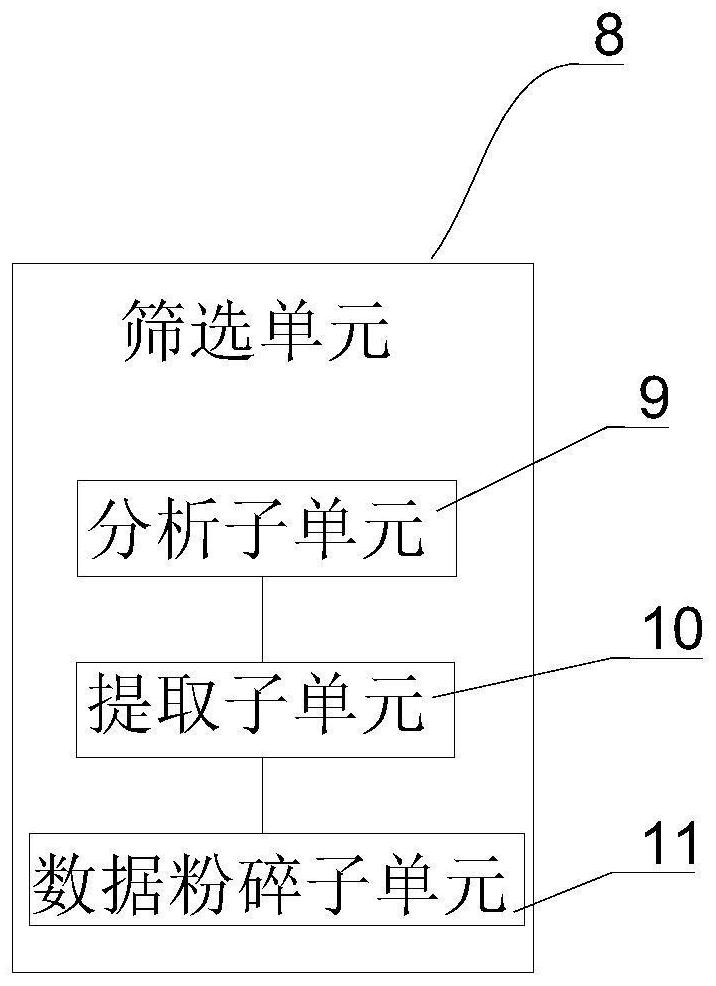
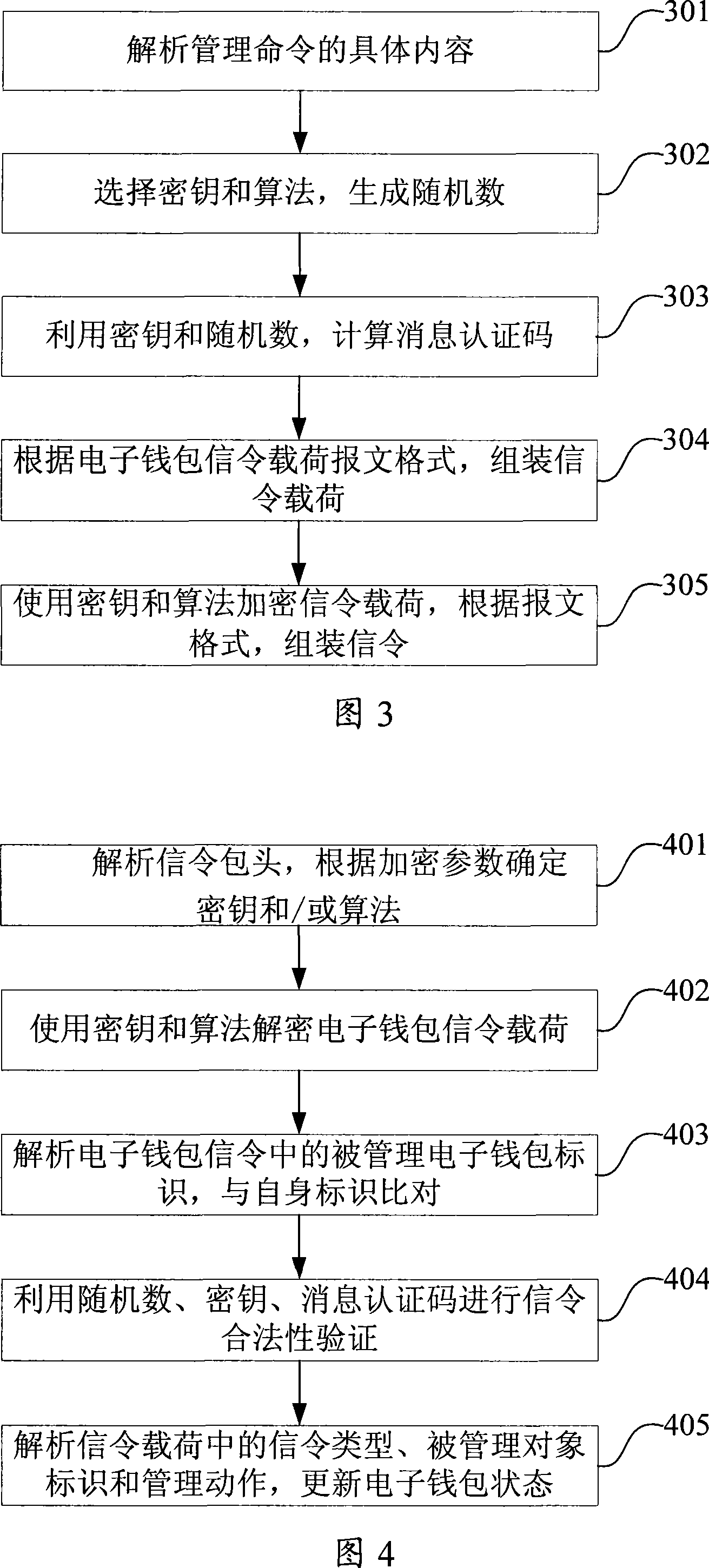
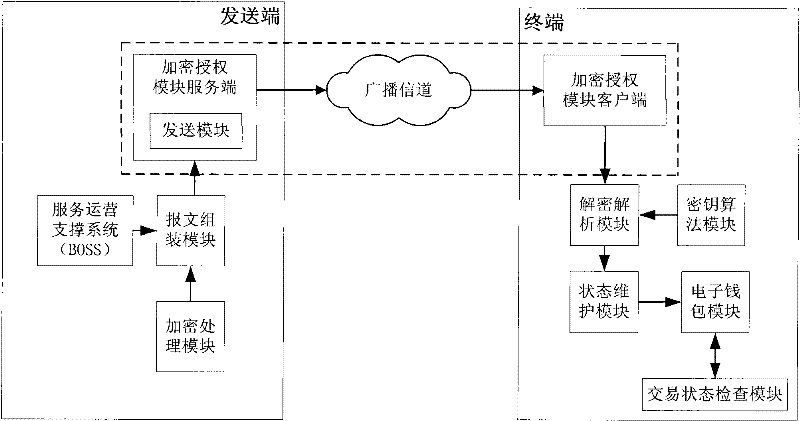
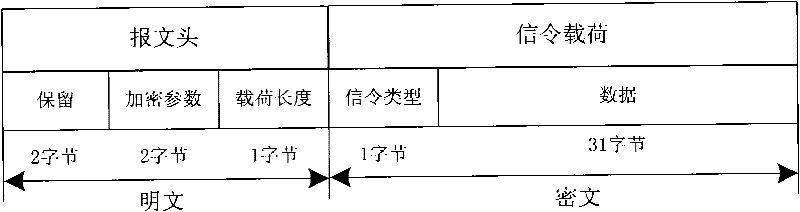
Device for remote state management of electronic purse
InactiveCN101826233AComprehensive and faster managementSolve the inconvenience of managementUser identity/authority verificationPayment architectureBroadcast domainConditional access systems
The invention discloses a device for remote state management of an electronic purse. The device is connected on a terminal device and comprises a key algorithm module, a decrypting and resolving module and a state maintenance module. A key and an algorithm corresponding to a sendign terminal are stored in the key algorithm module; the decrypting and resolving module decrypts and resolves the received encrypted electronic purse signals by using the key and the algorithm stored in the key algorithm module; and the state maintenance module maintains the state of the electronic purse according to the electronic purse signals. With the device, remote management of the electronic purse of a conditional access system can be realized in a broadcast domain and the management of the terminal electronic purse can be more comprehensive and quicker.
Owner:BEIJING WATCH DATA SYST
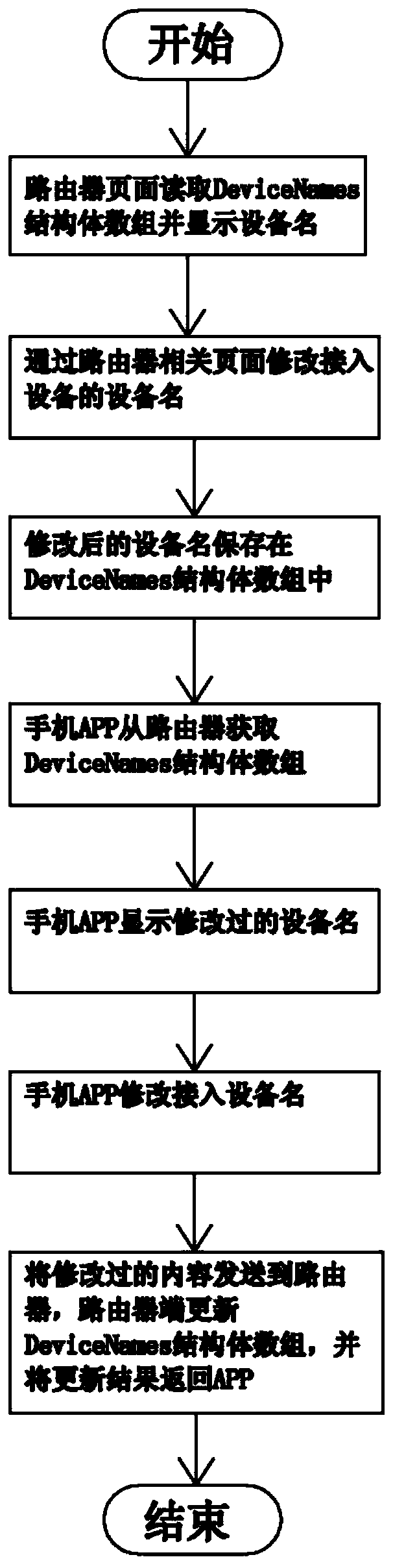
System and method of router for unifying names of access devices
ActiveCN106533849AEfficient storageEfficient managementWide area networksVisit timeArray data structure
The present invention relates to the technical field of routers, and particularly relates to a system and method of a router for unifying names of access devices. The system comprises a storage module controlled by the router. The storage module is provided with structure arrays for storing the names of the access devices. The structure arrays comprise a first array for storing media access control (MAC) addresses of the access devices, a second array for storing modified names of the access devices, and a time unit for storing last visit time. The system further comprises a display module for displaying the names of the access devices and a default name storage array controlled by the router and for storing default names of the access devices. The system and method have high stability and good display effect, are convenient to manage, and can use the stored resources effectively.
Owner:湖州帷幄知识产权运营有限公司
An access control key code management method and system
ActiveCN106558126BSolve the inconvenience of managementLow costIndividual entry/exit registersWi-FiWifi network
The invention discloses a management method and a management system of entrance guard key codes and relates to the technical field of intelligent entrance guard. The method includes the steps of: 1) a mobile terminal acquires a RFID data table from a server; 2) the mobile terminal sends the data table down to an entrance guard controller with connection established through Bluetooth or Wi-Fi network; and 3) the entrance guard controller, according to the received RFID data table, modifies key codes. According to the method, a conventional key code management method of RFID entrance guard systems is modified through wireless and Internet technologies which are low in cost, so that a problem of inconvenience of management of the key codes when the RFID entrance guard is offline can be solved, and cost is effectively reduced and management efficiency and accuracy are improved.
Owner:CHINA TELECOM CORP LTD
Data acquisition method, device, system and equipment and storage medium
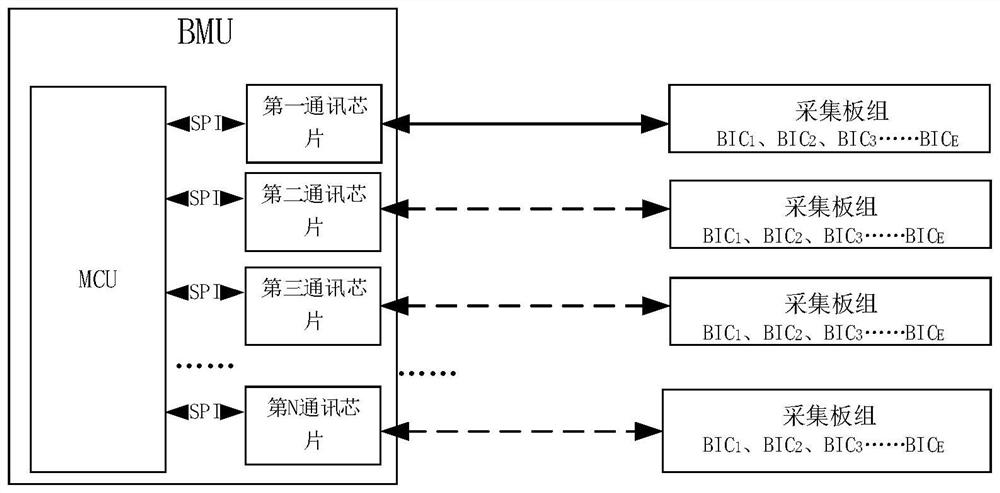
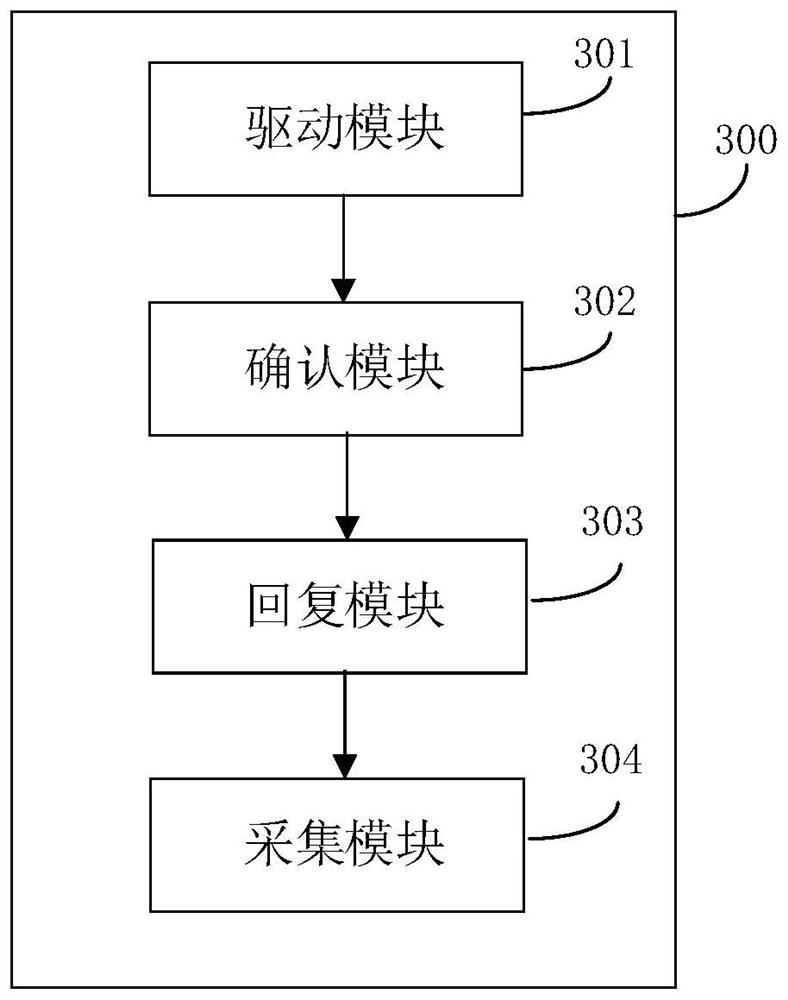
PendingCN114721917ATroubleshoot issues that require motherboard replacementSolve replacementHardware monitoringSoftware deploymentComputer hardwareData acquisition
The invention discloses a data acquisition method, device, system and equipment and a storage medium. The method comprises the steps that a controller sends a driving instruction to N communication chips; wherein the types of the N communication chips are different, N is greater than or equal to 2, and N is an integer; each communication chip sends a confirmation signal to an acquisition board group based on the driving instruction; wherein the acquisition board group comprises a plurality of acquisition boards; each acquisition board is provided with a plurality of analog front-end chips; if the communication chip receives a reply signal sent by the acquisition board group, determining the communication chip as a target communication chip; and the target communication chip establishes connection with the plurality of analog front-end chips of each acquisition board to form a plurality of data transmission channels, and acquires the state data of the battery cell based on the plurality of data transmission channels. According to the technical scheme, the problem that the mainboard needs to be replaced due to the fact that the types of the communication chips of the mainboard are not matched is solved.
Owner:NEUSOFT REACH AUTOMOBILE TECH (SHENYANG) CO LTD
Method and system for synchronously processing personal information of intelligent devices
ActiveCN103049337ASolve the inconvenience of managementTimely and convenient to seeProgram synchronisationComputer scienceSmart device
The invention discloses a method and a system for synchronously processing personal information of intelligent devices. The method includes the steps: receiving different personal attention applications set by a user by the aid of a plurality of intelligent devices connected with a network and storing the personal attention applications to the corresponding intelligent devices; synchronizing the personal attention applications into the intelligent devices when the personal attention applications are updated; and judging whether the time of displaying the personal attention applications reaches preset time or not and displaying the updated personal attention applications in each intelligent device when the time of displaying the personal attention applications reaches the preset time. The problem that the user inconveniently manages private information is solved, and the user can timely and conveniently see the information that the user pays attention to by setting all the personal attention applications related to the user as universal attention and accessing the network through optional intelligent devices at the first time.
Owner:深圳华康创展科技控股集团有限公司
Subject visit management system and automatic reminding method
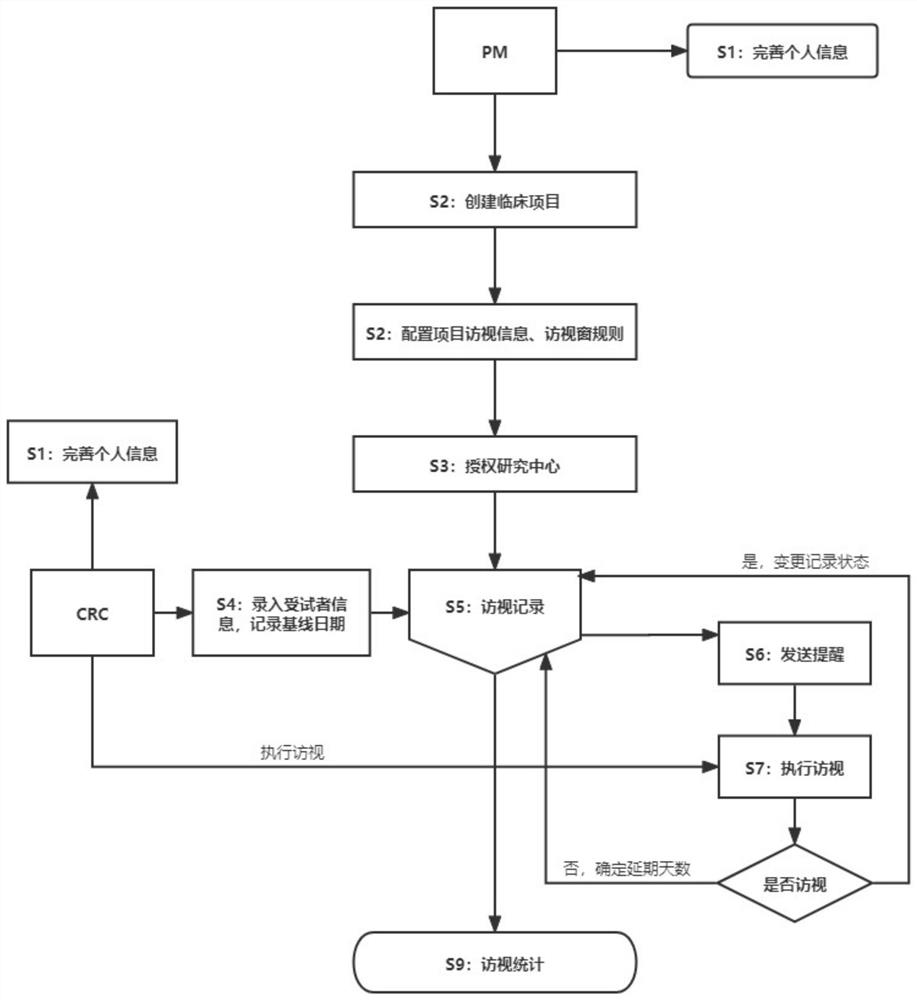
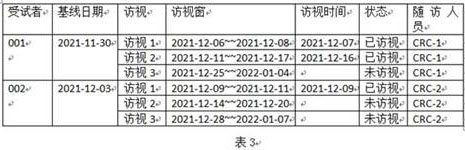
PendingCN114792554ASolve the inconvenience of managementRealize automatic reminder functionDrug referencesElectronic clinical trialsInternet privacyClinical tests
The invention discloses a subject visit management system and an automatic reminding method. The method comprises the following steps: perfecting information, and recording PM, CRC and basic personal information of a subject; adding clinical test items and visit information; configuring a project access window; managing a test research center; adding subjects, and filling in baseline dates of the subjects; automatically generating a subject visit schedule and a visit reminding record according to the collected information; visitors are reminded through WeChat, short messages and mails; after the CRC visits the testee, the visit state is changed into a visited state, and if the testee is not visited, the number of days of visit delay is set; and finally, access handover and access statistics are carried out. Through configuration management of clinical test item visit, an automatic visit reminding function is realized, and the problem of inconvenient management caused by a large number of visitors in traditional visit is solved.
Owner:段忠成
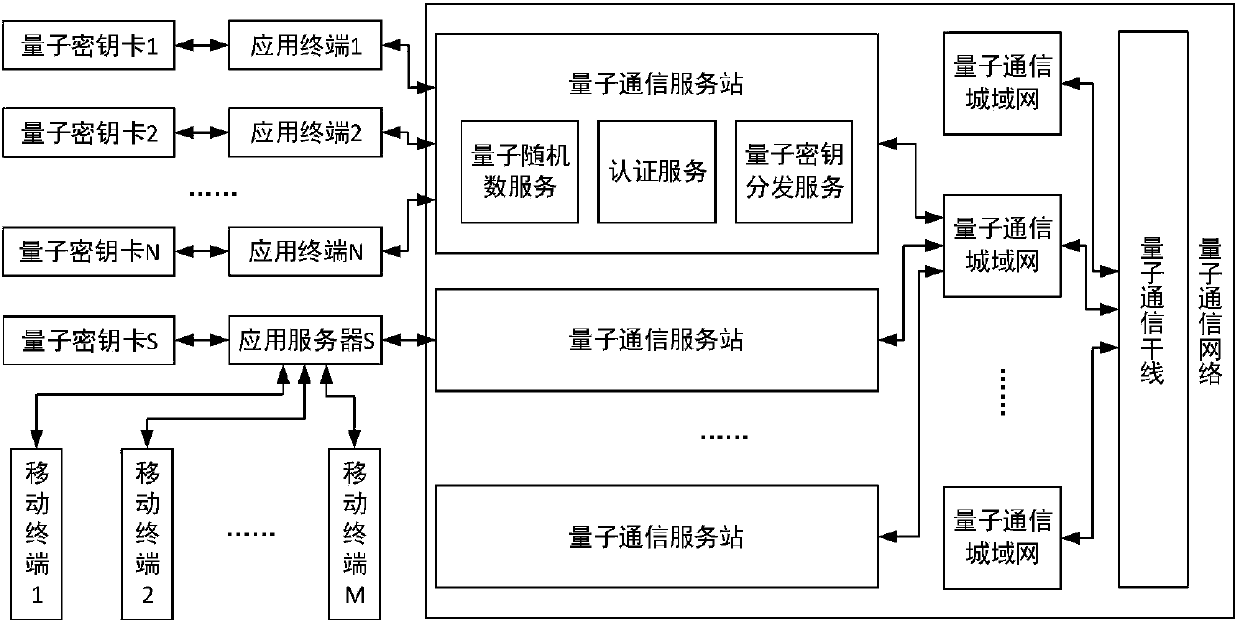
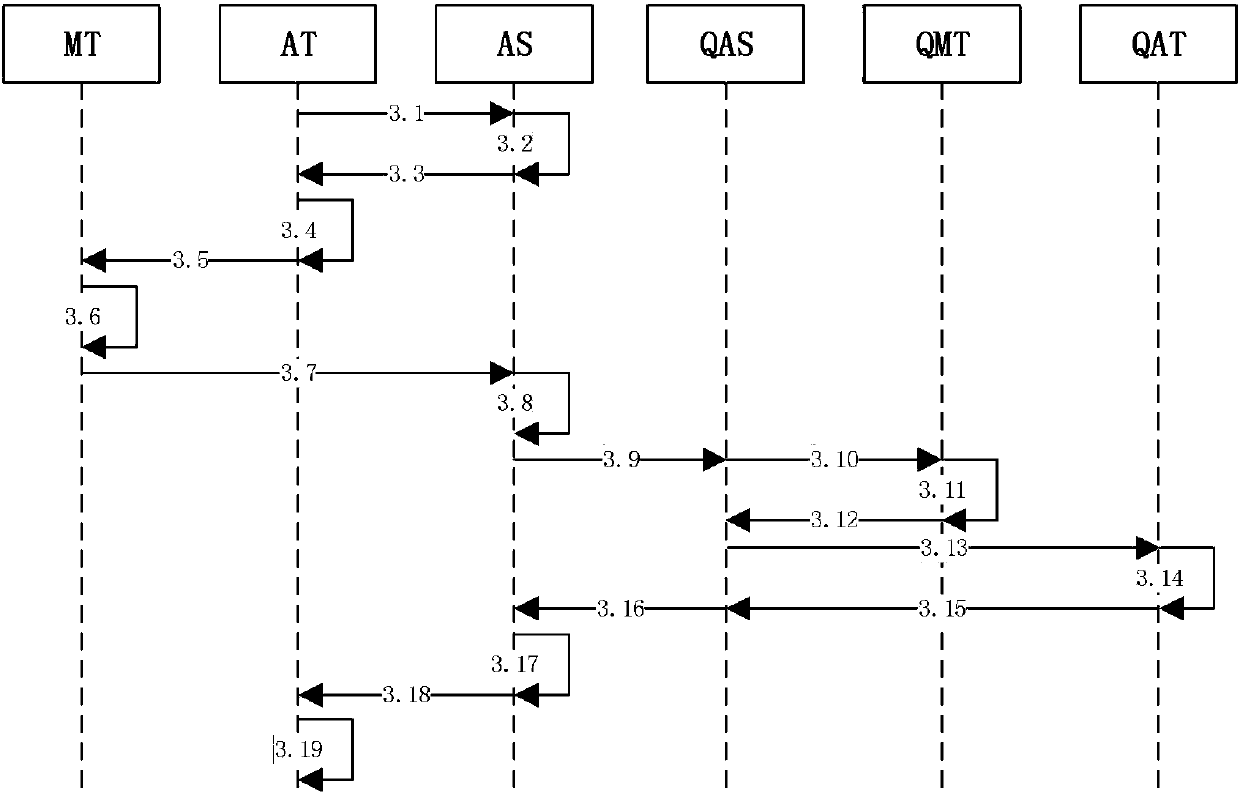
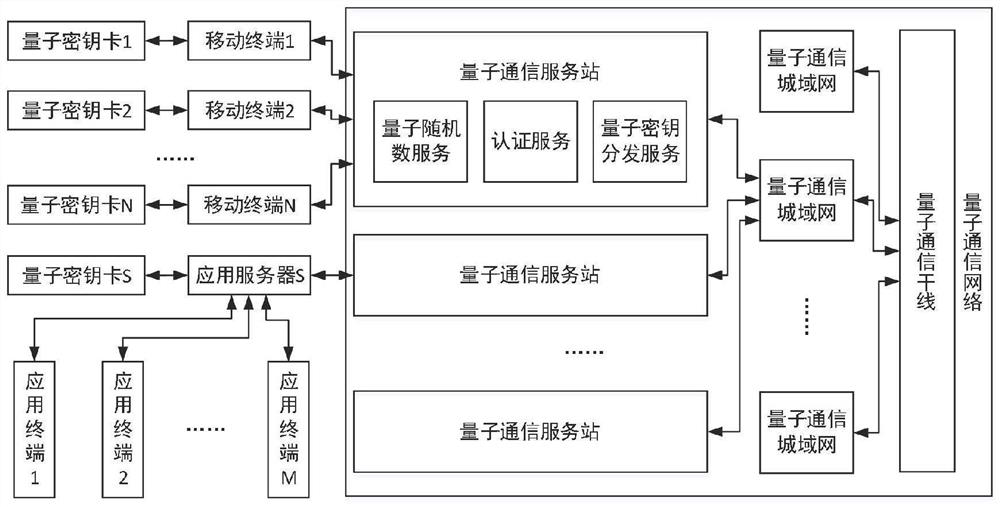
Two-dimensional code authentication system based on quantum encryption
ActiveCN107733644ASolve the authentication problemSolve the inconvenience of managementKey distribution for secure communicationApplication serverComputer terminal
The invention discloses a two-dimensional code authentication system based on quantum encryption, comprising an application server, an application terminal, a mobile terminal and a quantum communication service station, wherein the application server and the application terminal are separately provided with quantum key cards, and corresponding quantum keys are stored between each quantum key cardand the quantum communication service station to perform encryption communication or two-dimensional code authentication; during two-dimensional code authentication, the application terminal obtainstwo-dimensional code authentication information from the application server through application, and the application terminal calculates application terminal two-dimensional code response values by using the stored quantum keys in the configured quantum key cards, and outputs corresponding two-dimensional codes; and the mobile terminal acquires the two-dimensional codes from the application terminal, extracts the application terminal two-dimensional code response values, and sends the response values to the quantum communication service station for authentication through the application server. According to the scheme of the invention, user equipment and users of a quantum communication network are authenticated by using the mobile terminal, and thus the security of the system can be greatly improved.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
A method and system for synchronously processing personal information of smart devices
ActiveCN103049337BSolve the inconvenience of managementTimely and convenient to seeProgram synchronisationNetwork connectionComputer science
The invention discloses a method and a system for synchronously processing personal information of intelligent devices. The method includes the steps: receiving different personal attention applications set by a user by the aid of a plurality of intelligent devices connected with a network and storing the personal attention applications to the corresponding intelligent devices; synchronizing the personal attention applications into the intelligent devices when the personal attention applications are updated; and judging whether the time of displaying the personal attention applications reaches preset time or not and displaying the updated personal attention applications in each intelligent device when the time of displaying the personal attention applications reaches the preset time. The problem that the user inconveniently manages private information is solved, and the user can timely and conveniently see the information that the user pays attention to by setting all the personal attention applications related to the user as universal attention and accessing the network through optional intelligent devices at the first time.
Owner:深圳华康创展科技控股集团有限公司
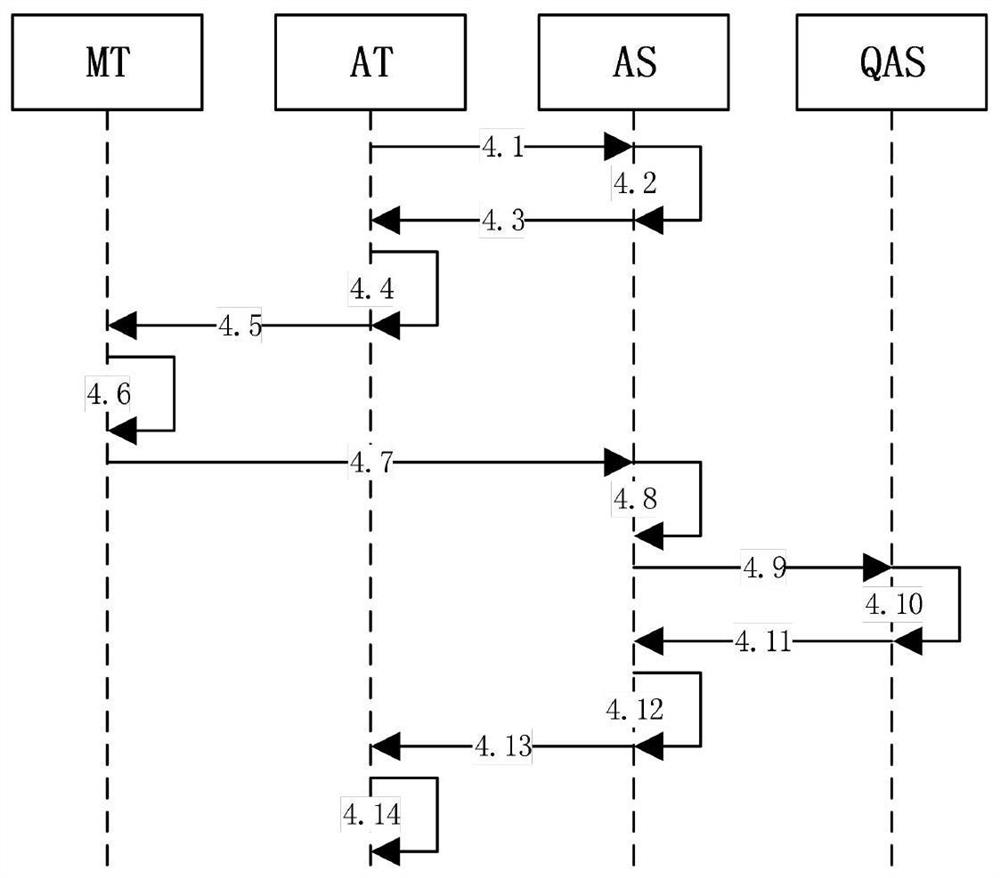
NFC authentication system based on quantum encryption
ActiveCN107786978BConvenient verificationSolve the authentication problemKey distribution for secure communicationUser identity/authority verificationApplication serverStation
The invention discloses an NFC authentication system based on quantum encryption, which includes an application server, an application terminal, and a mobile terminal, and a quantum communication service station. The application server and the application terminal are respectively equipped with quantum key cards; During authentication, the mobile terminal applies for and obtains NFC authentication information from the application terminal through NFC transmission, and sends an authentication response with the NFC authentication information to the application server; the application server, in the configured quantum key card, according to the NFC authentication information and use the stored quantum key to calculate the first NFC authentication response value, and send the first NFC authentication response value to the application terminal, and the application terminal performs the first NFC authentication response value via the quantum communication service station Certification, and perform related business based on the certification results. In the present invention, the NFC authentication operation using the mobile terminal is fast and convenient, and the security is high.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
Two-Dimensional Code Authentication System Based on Quantum Encryption
ActiveCN107733644BSolve the authentication problemSolve the inconvenience of managementKey distribution for secure communicationApplication serverStation
The invention discloses a two-dimensional code authentication system based on quantum encryption, comprising an application server, an application terminal, a mobile terminal and a quantum communication service station, wherein the application server and the application terminal are separately provided with quantum key cards, and corresponding quantum keys are stored between each quantum key cardand the quantum communication service station to perform encryption communication or two-dimensional code authentication; during two-dimensional code authentication, the application terminal obtainstwo-dimensional code authentication information from the application server through application, and the application terminal calculates application terminal two-dimensional code response values by using the stored quantum keys in the configured quantum key cards, and outputs corresponding two-dimensional codes; and the mobile terminal acquires the two-dimensional codes from the application terminal, extracts the application terminal two-dimensional code response values, and sends the response values to the quantum communication service station for authentication through the application server. According to the scheme of the invention, user equipment and users of a quantum communication network are authenticated by using the mobile terminal, and thus the security of the system can be greatly improved.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
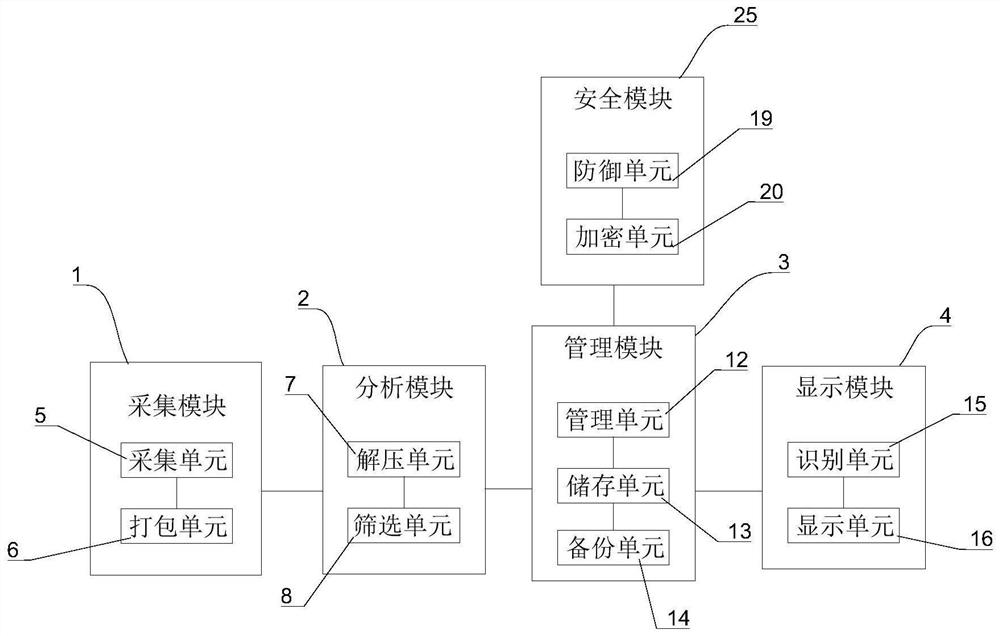
Comprehensive data analysis and management system based on distributed architecture
PendingCN114328703AEasy to manageEasy to operateVisual data miningStructured data browsingData packData acquisition
The invention relates to the technical field of data processing, in particular to a comprehensive data analysis and management system based on a distributed architecture. The acquisition module is used for mining market data through a data acquisition plan of an enterprise to obtain an acquisition data packet; the analysis module is used for analyzing and sorting the collected data packet through big data and screening out service information; the management unit is used for classifying and managing the service information to obtain a plurality of pieces of service information data; the storage unit is used for storing multiple pieces of service information data to obtain enterprise data; the backup unit is used for backing up the enterprise data to obtain backup data; the display module is used for displaying the enterprise data through an enterprise intranet; and through each subunit of the management module, enterprise information is managed, and management and operation of enterprises are facilitated.
Owner:南京民基悠步信息技术有限公司
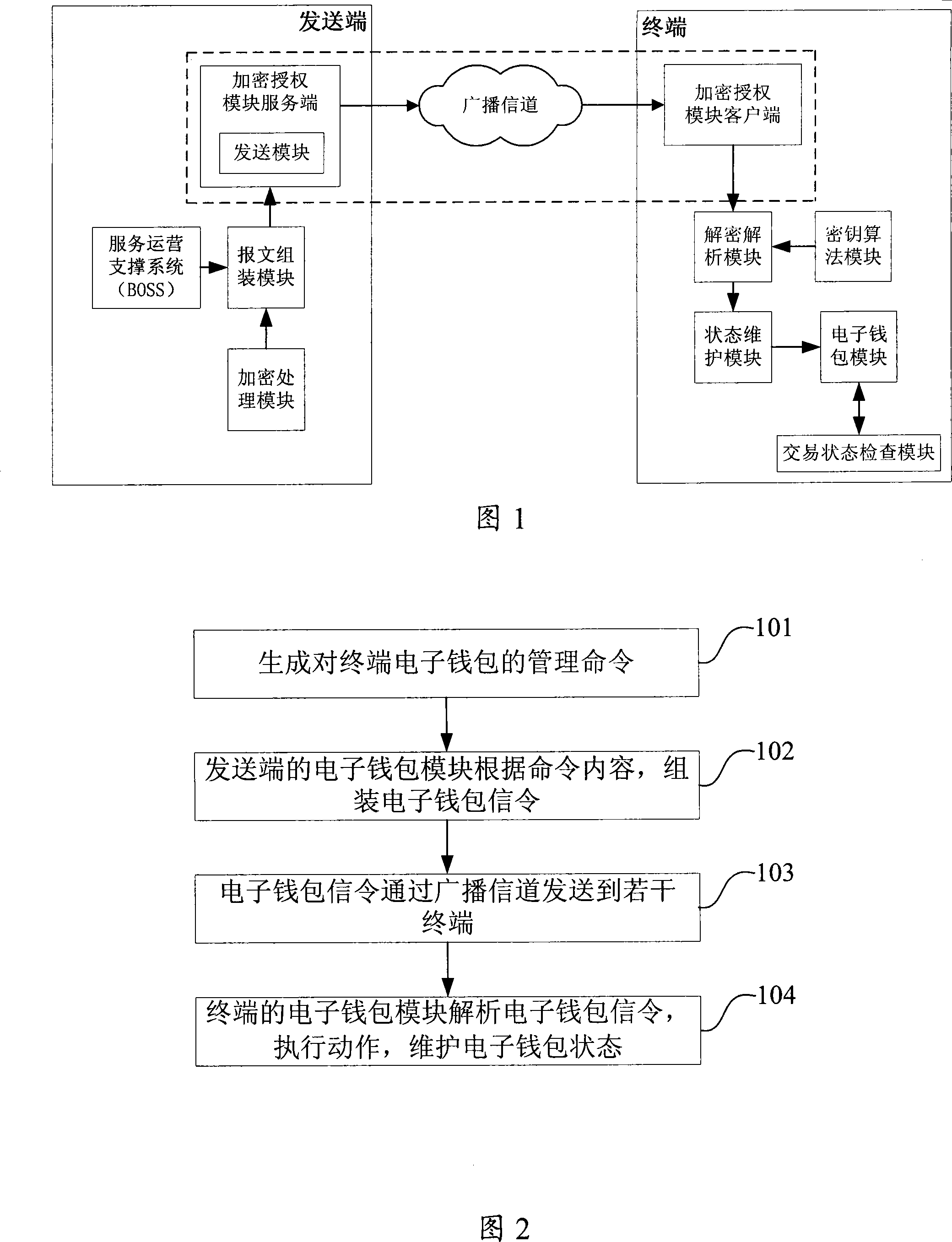
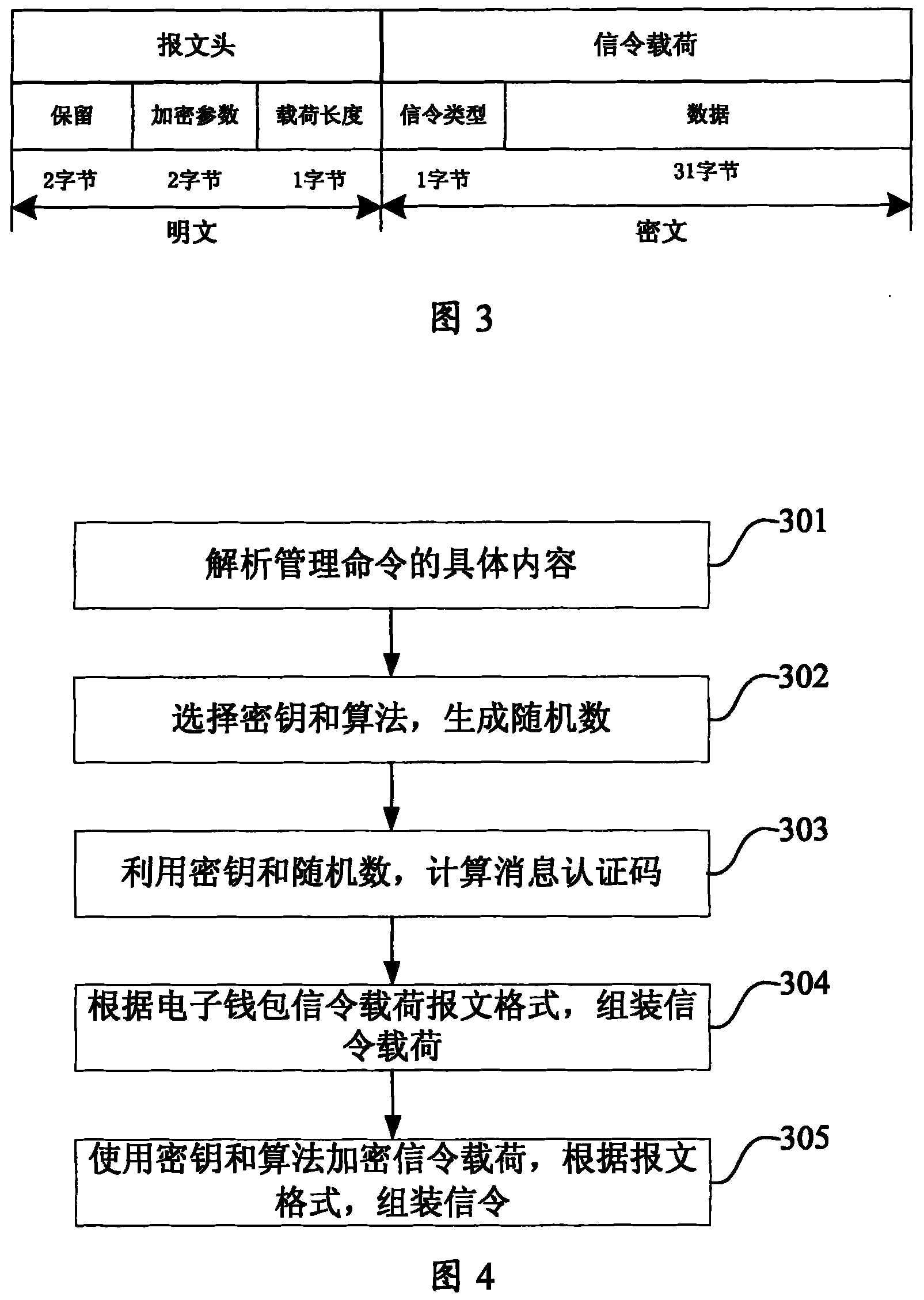
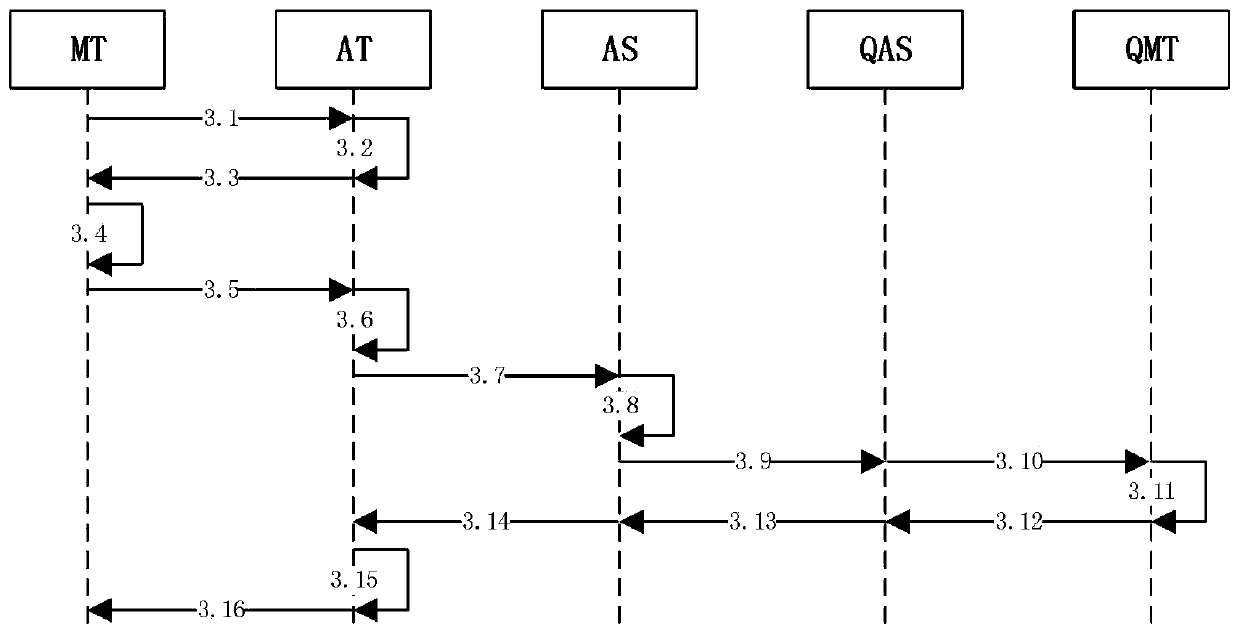
System for long-range managing electronic purse state
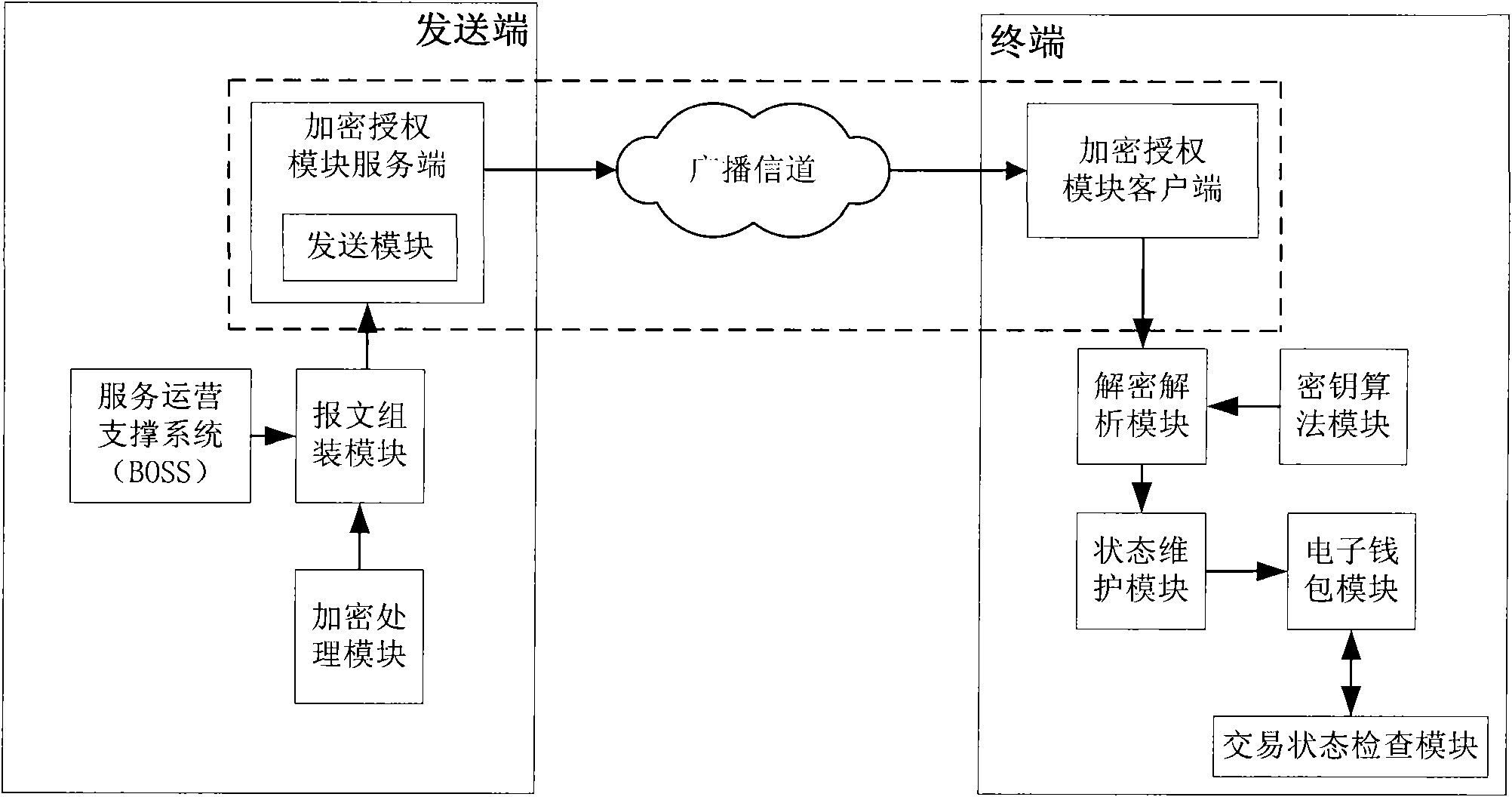
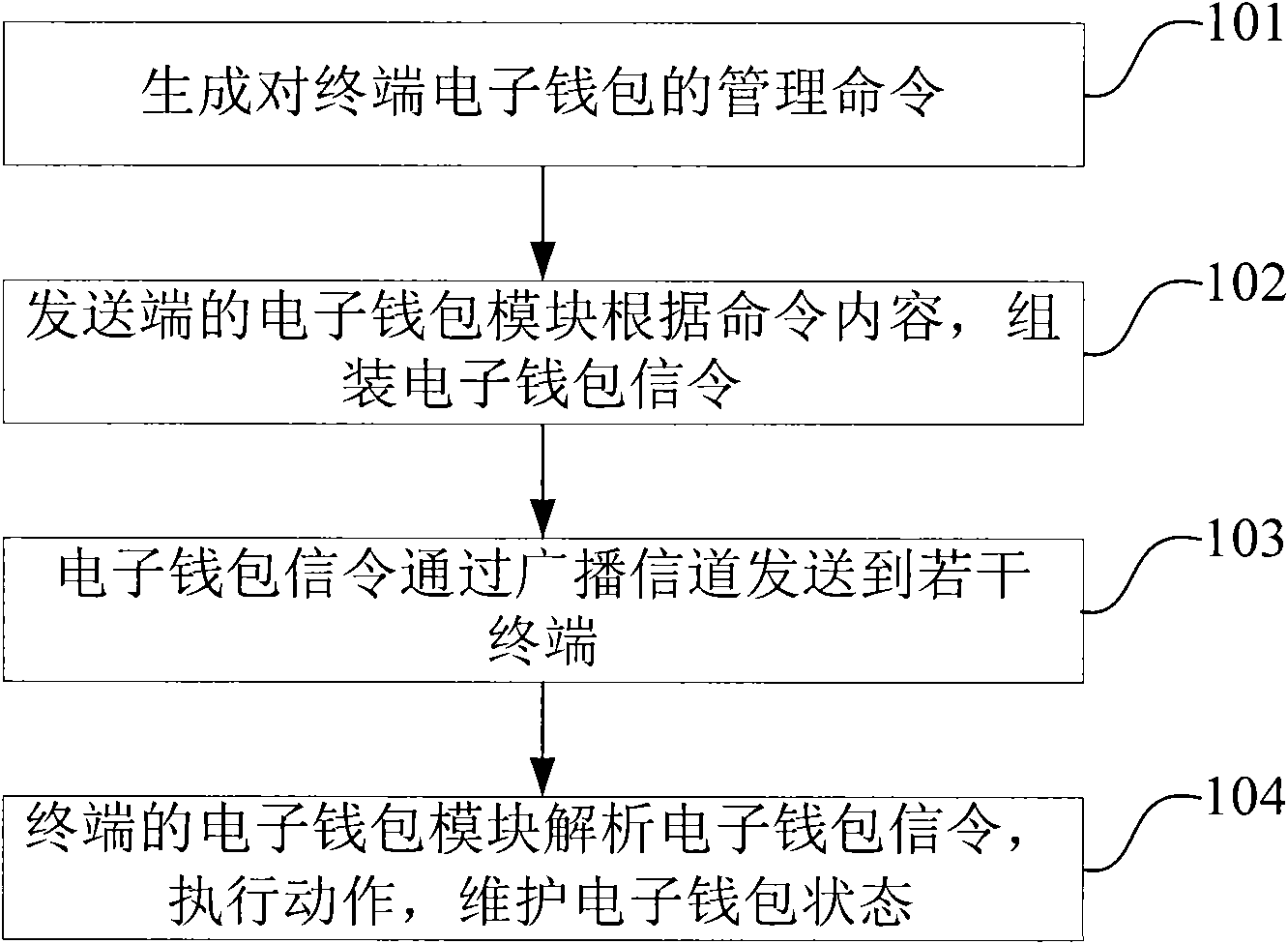
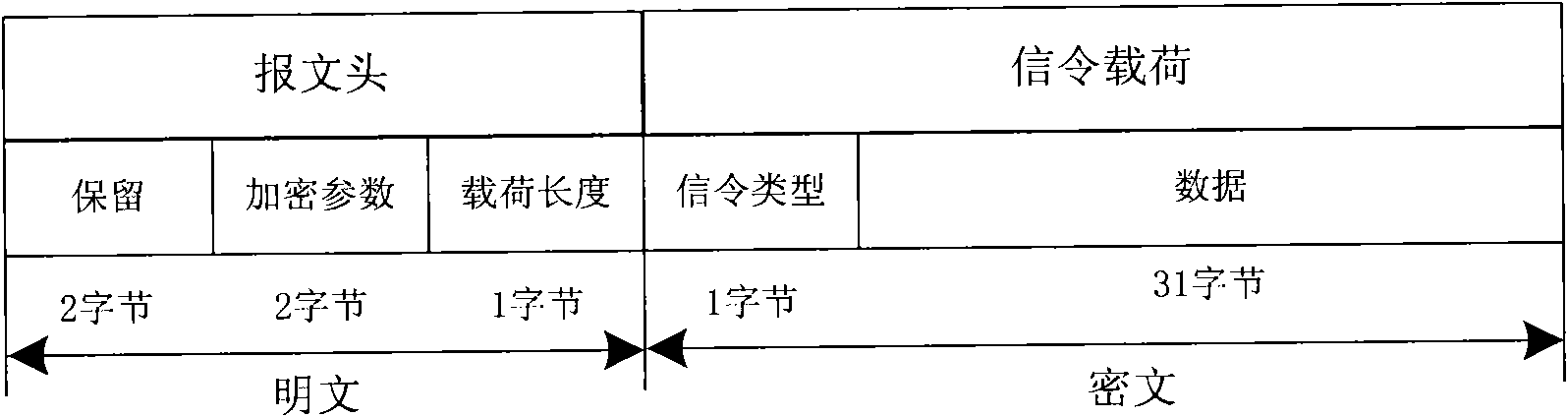
ActiveCN101246615BSolve the inconvenience of managementComprehensive and faster managementUser identity/authority verificationPayment architectureConditional accessComputer module
The present invention provides a system of remote management electronic wallet state and device, used for assembling electronic wallet signaling by the message format according to the acquired management command; encrypting processing module for selecting key and algorithm to process encryption of the electronic wallet command; transmitting module for transmitting the encrypted electronic wallet signaling via broadcasting channel; the ternimial including key algorithm module, storage corresponding key and algorithm with the transmitting terminal; the electronic wallet module, storage electronic wallet and state of the electronic wallet; decoding analyzing module for decoding and analyzing the received electronic wallet signaling utilizing stored key and algorithm; a state maintaining module, maintaining electronic wallet state according to the electronic wallet signaling. The invention can realize remote management of the condition receiving system electronic wallet in the broadcast field, making the management of the terminal electronic wallet more comprehensive and quick.
Owner:BEIJING WATCH DATA SYST
Isolation grounding switch arc contact base and isolation grounding switch
PendingCN112701004ASolve efficiency problemsSolve the problem of inconvenient parts managementHigh-tension/heavy-dress switchesAir-break switchesStructural engineeringMechanical engineering
The invention belongs to the field of high-voltage switches and relates to an isolation grounding switch arc contact base and an isolation grounding switch The isolation grounding switch arc contact base comprises a conductive connecting body; the connecting body is provided with a first connecting structure used for being fixedly matched with a static end contact seat, a second connecting structure used for installing an isolation static arc contact and a third connecting structure used for installing a grounding static arc contact. When the isolation grounding switch arc contact base is used, the isolation static arc contact and the grounding static arc contact are directly installed on the connecting body, and the connecting body is fixed with the static end contact seat, so that the assembly of the grounding static arc contact and the isolation static arc contact can be completed; and compared with the prior art, bases of an original grounding static arc contact and isolation static arc contact can be omitted, so that the number of parts is reduced, and the problem that an isolation grounding switch is low in assembly efficiency and the problem that parts of theisolation grounding switch are inconvenient to manage are solved.
Owner:HENAN PINGGAO ELECTRIC +2
A system and method for uniformly accessing device names by routers
The present invention relates to the technical field of routers, in particular to a system and method for uniformly accessing device names by routers. The system of the present invention includes a storage module controlled by the router, and the storage module is provided with a structure that can be used to store the name of the access device Array, the structure array includes the first array for saving the MAC address of the access device, the second array for saving the modified name of the access device, and the time unit for saving the last accessed time, and the system also It includes a display module for displaying the name of the access device and a default name storage array controlled by the router for saving the default name of the access device. It has high stability, good display effect, easy management, and effective use of storage resources.
Owner:湖州帷幄知识产权运营有限公司
Charging pile management method and device, charging pile control method and device, storage medium and processor
PendingCN114312438AImplement communication rulesAchieve unityCharging stationsElectric vehicle charging technologySystems engineeringControl engineering
The invention discloses a management method and device of a charging pile, a control method and device, a storage medium and a processor. The management method of the charging pile comprises the following steps: receiving communication request information from a target charging pile; in response to the communication request information, communication configuration information is sent to the target charging pile; and performing interactive communication with the target charging pile according to a communication rule corresponding to the communication configuration information. According to the management method of the charging pile, the problems of inconvenient management and disordered management during batch management of the charging piles in related technologies are solved.
Owner:度普(苏州)新能源科技有限公司
NFC authentication system based on quantum communication network
ActiveCN107888376BConvenient verificationSolve the problem that the operation is too cumbersomeKey distribution for secure communicationCommunications systemApplication server
The invention discloses an NFC (Near Field Communication) authentication system based on a quantum communication system. The system comprises an application server, application terminals, mobile terminals, quantum communication service stations and quantum key cards matching the mobile terminals. Corresponding quantum keys are stored between the quantum key cards and the quantum communication service stations. When NFC authentication is carried out, the quantum key cards matching the mobile terminals generate NFC authentication response values; the quantum communication service stations generate NFC authentication expected response values; and the application terminals compare the NFC authentication response values with the NFC authentication expected response values to obtain an authentication result and perform related service. According to the NFC authentication system provided by the invention, through NFC authentication of the mobile terminals, the operation of a user is rapid andconvenient, and the experience is superior to that of a dynamic password. The keys for authentication are stored in the quantum key cards and the quantum key cards are specially-made isolation hardware, so it is difficult to steal the keys by malicious software in the mobile terminals or malicious operation.
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
Method for remotely managing electronic purse state
InactiveCN101247188BSolve the inconvenience of managementComprehensive and faster managementCoded identity card or credit card actuationBroadcast systems controlConditional accessComputer terminal
The present invention discloses a method for remote management electronic purse state, for sending terminal sending management signaling to multiple terminals by broadcast signal and implementing management of terminal electronic purse state, includes generating management command for terminal electronic purse; sending terminal executes encrypting process by using cipher key and algorithm according to management command and message format assembled electronic purse signaling; terminal decipher and analyze electronic purse signaling according to signaling contents to maintain electronic purse condition. The present invention can realize remote management of electronic purse with condition receive system in broadcast field, resolves management inconvenience problem caused by importing electronic purse under present condition receive modus, and makes management of terminal electronic purse more good and more rapid.
Owner:李慧镝 +3
Device for remote state management of electronic purse
InactiveCN101826233BComprehensive and faster managementSolve the inconvenience of managementUser identity/authority verificationPayment architectureBroadcast domainConditional access systems
The invention discloses a device for remote state management of an electronic purse. The device is connected on a terminal device and comprises a key algorithm module, a decrypting and resolving module and a state maintenance module. A key and an algorithm corresponding to a sendign terminal are stored in the key algorithm module; the decrypting and resolving module decrypts and resolves the received encrypted electronic purse signals by using the key and the algorithm stored in the key algorithm module; and the state maintenance module maintains the state of the electronic purse according tothe electronic purse signals. With the device, remote management of the electronic purse of a conditional access system can be realized in a broadcast domain and the management of the terminal electronic purse can be more comprehensive and quicker.
Owner:BEIJING WATCH DATA SYST
Glucometer handset, control method and glucometer data recording equipment
PendingCN114203293ASolve blood glucose data transmissionSolve the inconvenience of managementSensorsBlood characterising devicesBlood glucose metersData signal
The embodiment of the invention discloses a glucometer handset, a control method and a glucometer data recording device. The glucometer handset comprises a signal adapter, a main control board, a touch screen and a communication module, the touch screen is used for receiving input information and converting the input information into an input data signal, the main control board is electrically connected with the touch screen and the signal adapter, the main control board is used for generating a serial port instruction according to the input data signal and sending the serial port instruction to the communication module. The serial port instruction is sent to the signal adapter, and the signal adapter is electrically connected with the blood glucose meter detachably installed on the blood glucose meter handheld machine; the signal adapter is used for converting blood glucose data detected by an installed blood glucose meter into a blood glucose data level signal matched with the model of the blood glucose meter according to a serial port instruction and transmitting the blood glucose data level signal to the main control board, and the communication module is electrically connected with the main control board. According to the technical scheme provided by the embodiment of the invention, the problem that blood glucose data transmission and management of an existing blood glucose meter are inconvenient is solved.
Owner:杭州康晟健康管理咨询有限公司
Method for managing mobile phone address book
InactiveCN101355762BSolve the inconvenience of managementSubstation equipmentSpecial data processing applicationsAddress bookInternet privacy
The invention provides a management method of a mobile phone address book, which includes the following steps: establishing a personal address book and setting the name of the personal address book; judging whether to set an access password for the above address book, and setting a password for the address book if the access password is set Access; if no access password is set, this personal address book will be set as shared. The management method of the mobile phone address book provided by the present invention enables users of public mobile phones to establish and manage their own personal address book, and whether the address book is encrypted or not can also be determined by the creator, which facilitates group management and encryption management, It is very convenient and user-friendly for mobile phone users who need public use.
Owner:TCL COMM TECH (CHENGDU) LTD
Method and system for determining topology structure of passive optical network
InactiveCN102223185BSolve the inconvenience of managementEasy to manageMultiplex system selection arrangementsElectromagnetic network arrangementsComputer networkStructure of Management Information
The invention discloses a method and a system for determining a topology structure of a passive optical network (PON). The method comprises the following steps that: an optical line terminal (OLT) obtains identification information of a research entenders (RE) apparatus on a path from the OLT to an optical network unit (ONU), wherein the identification information is indicated in an uplink frame of the ONU; and the OLT determines active equipment nearest to the ONU in the PON according to the identification information, wherein the active equipment comprises an RE apparatus or an OLT. According to the invention, the OLT can manage the ONU conveniently.
Owner:ZTE CORP
Two-Dimensional Code Authentication System Based on Quantum Communication Network
ActiveCN107911211BConvenient verificationSolve the problem that the operation is too cumbersomeKey distribution for secure communicationRegistering/indicating time of eventsApplication serverStation
Owner:ZHEJIANG SHENZHOU QUANTUM NETWORK TECH CO LTD
Guide board control method and related equipment
ActiveCN112015324AEasy to viewVisual inspectionText processingGeographical information databasesProcess engineeringComputer science
Owner:BOE TECH GRP CO LTD
Heterogeneous log system management configuration device and method
ActiveCN104935444BSolve the inconvenience of managementEasy to useData switching networksSpecial data processing applicationsSystems managementLog management
A heterogeneous logging system is configured by receives a log configuration management command or a log data management command and determines a target logging system. The target logging system is assigned a log adapter adapted to the target logging system. The assigned log adapter is used to complete log management configuration of the target logging system based on the log configuration management command; or the assigned log adapter is used to complete log data management configuration of the target logging system based on the log data management command.
Owner:NEW H3C TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com