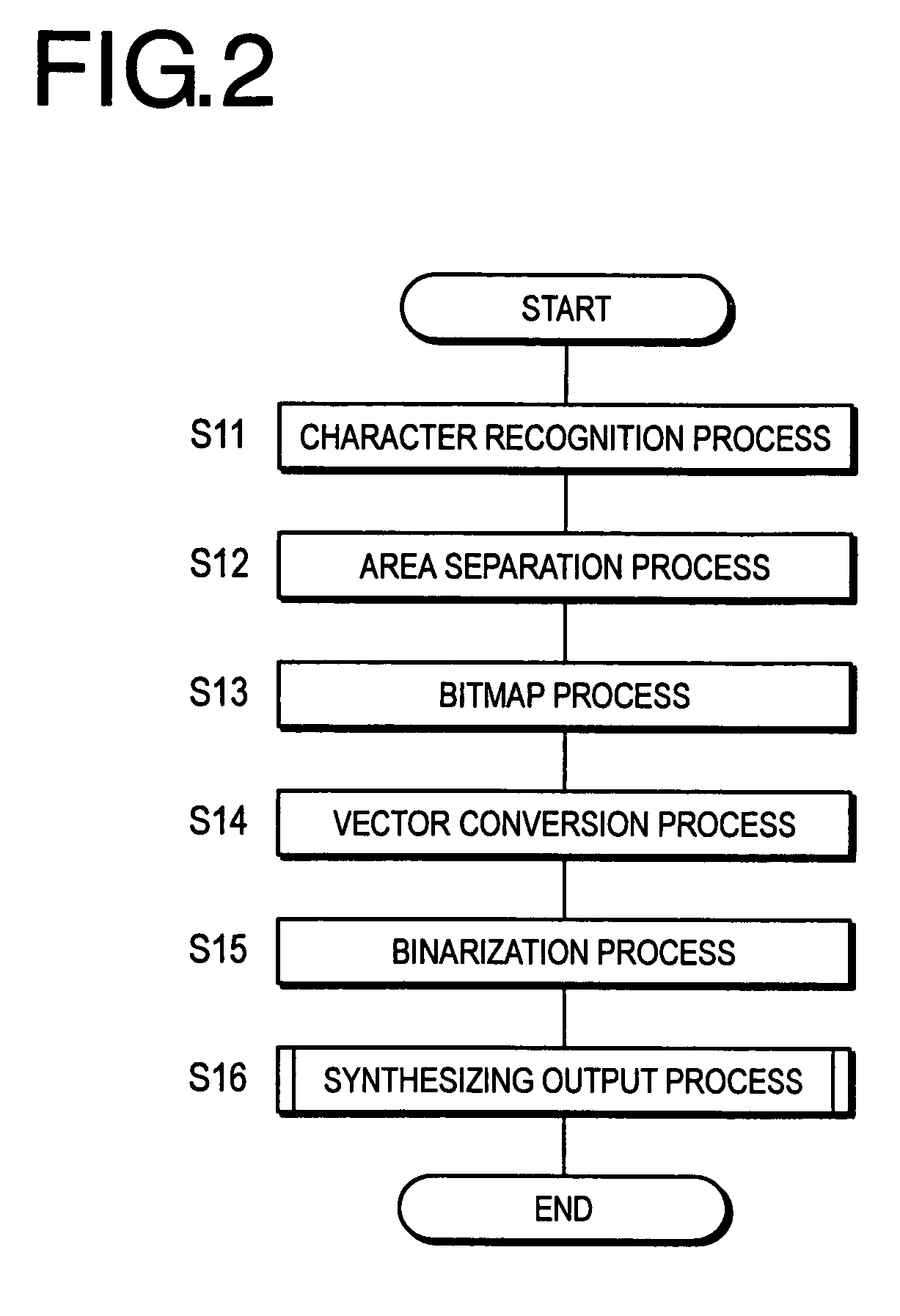
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
43results about How to "Securely identifying" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
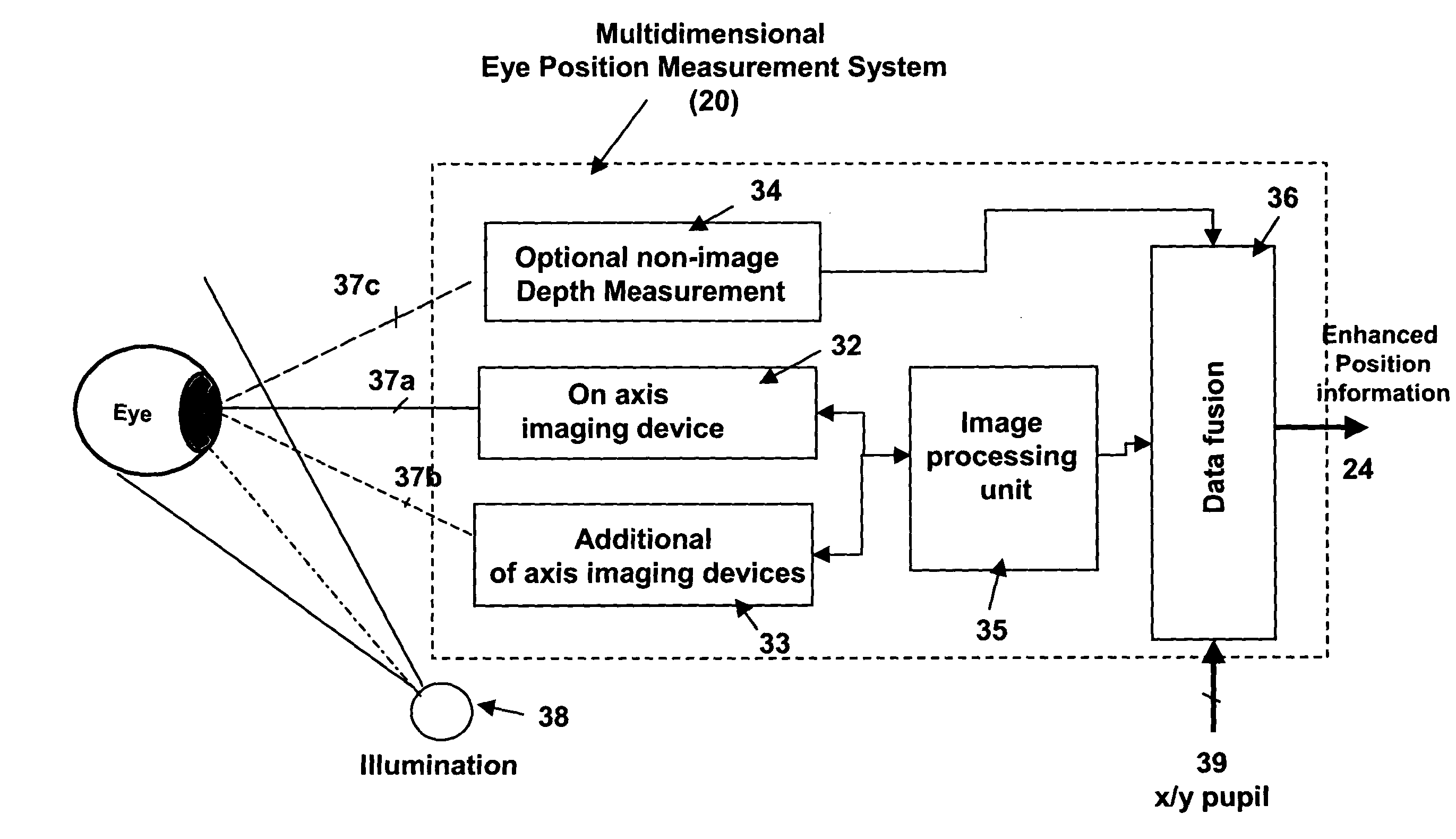
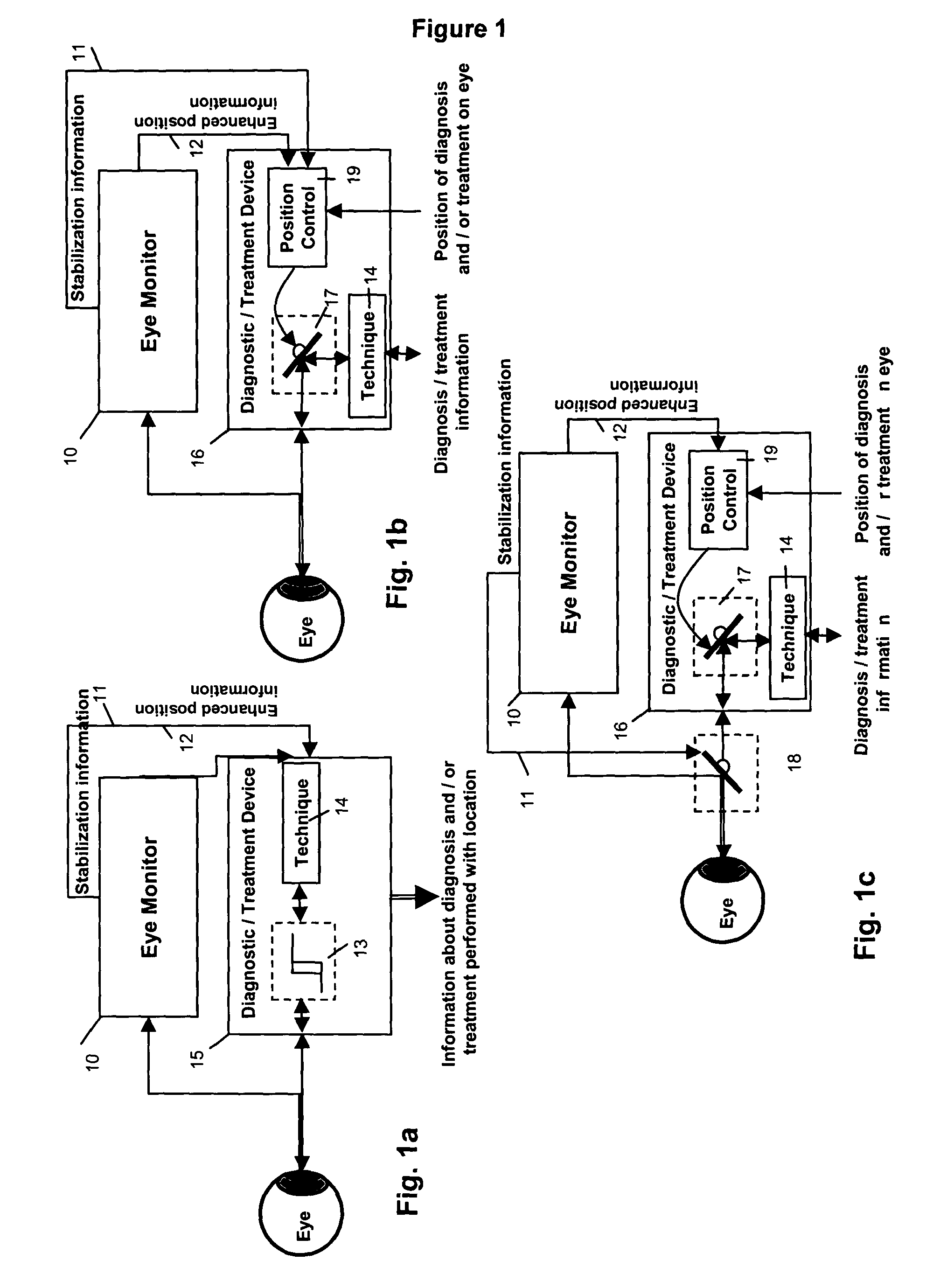
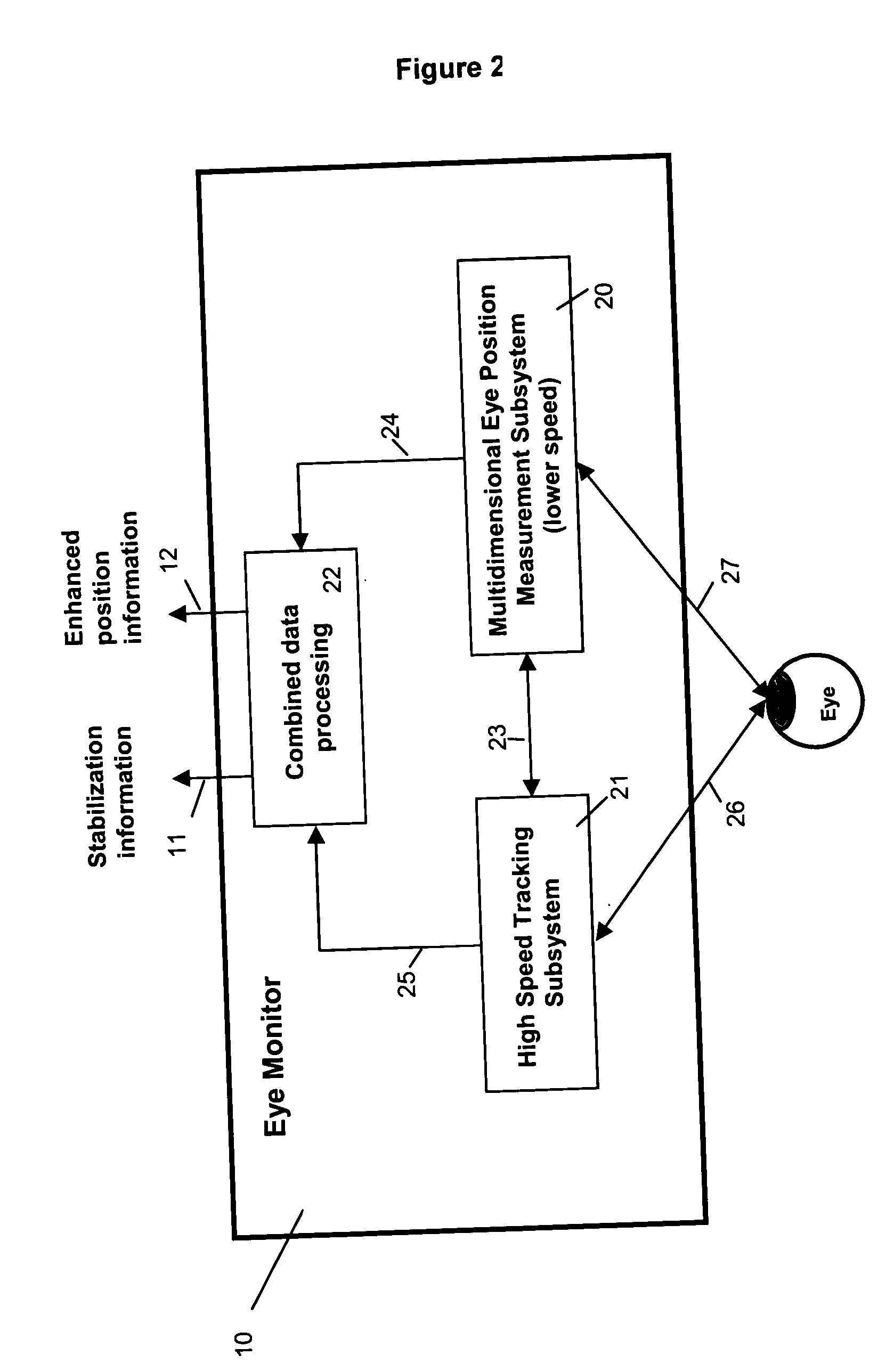
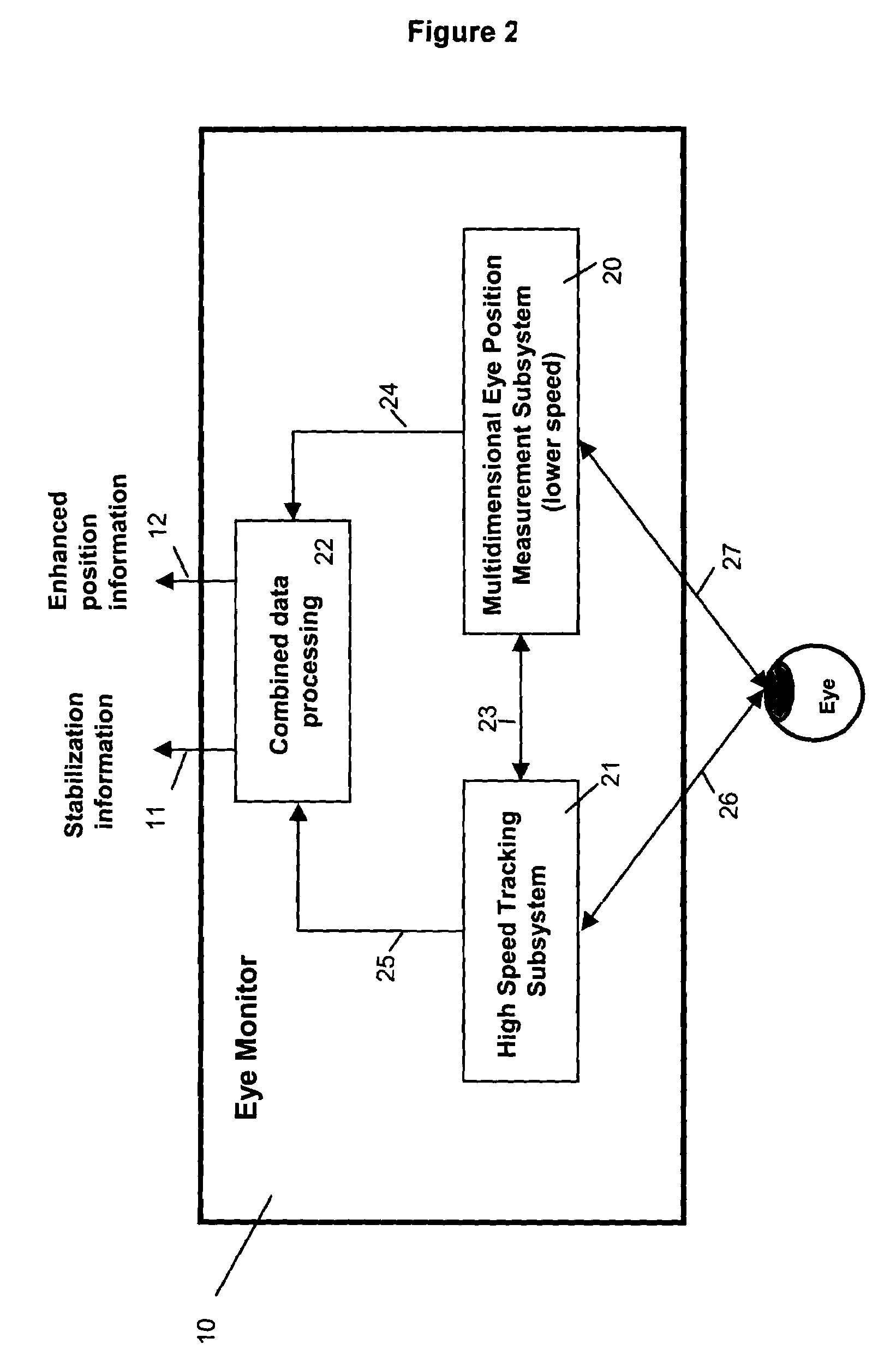
Multidimensional eye tracking and position measurement system for diagnosis and treatment of the eye
ActiveUS20050024586A1Improve spatial resolutionLess field of viewLaser surgeryCharacter and pattern recognitionMeasurement deviceSaccadic movements
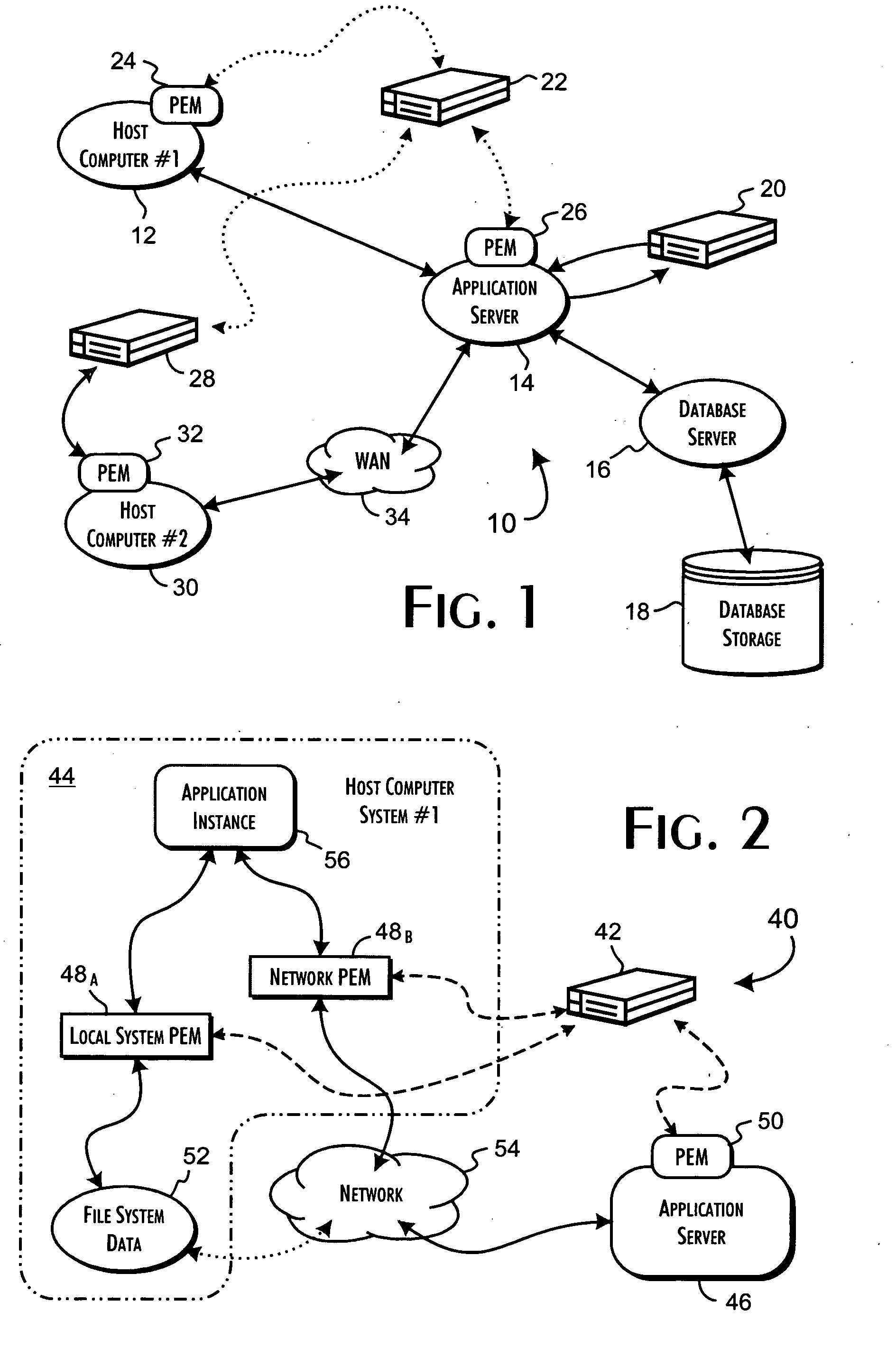
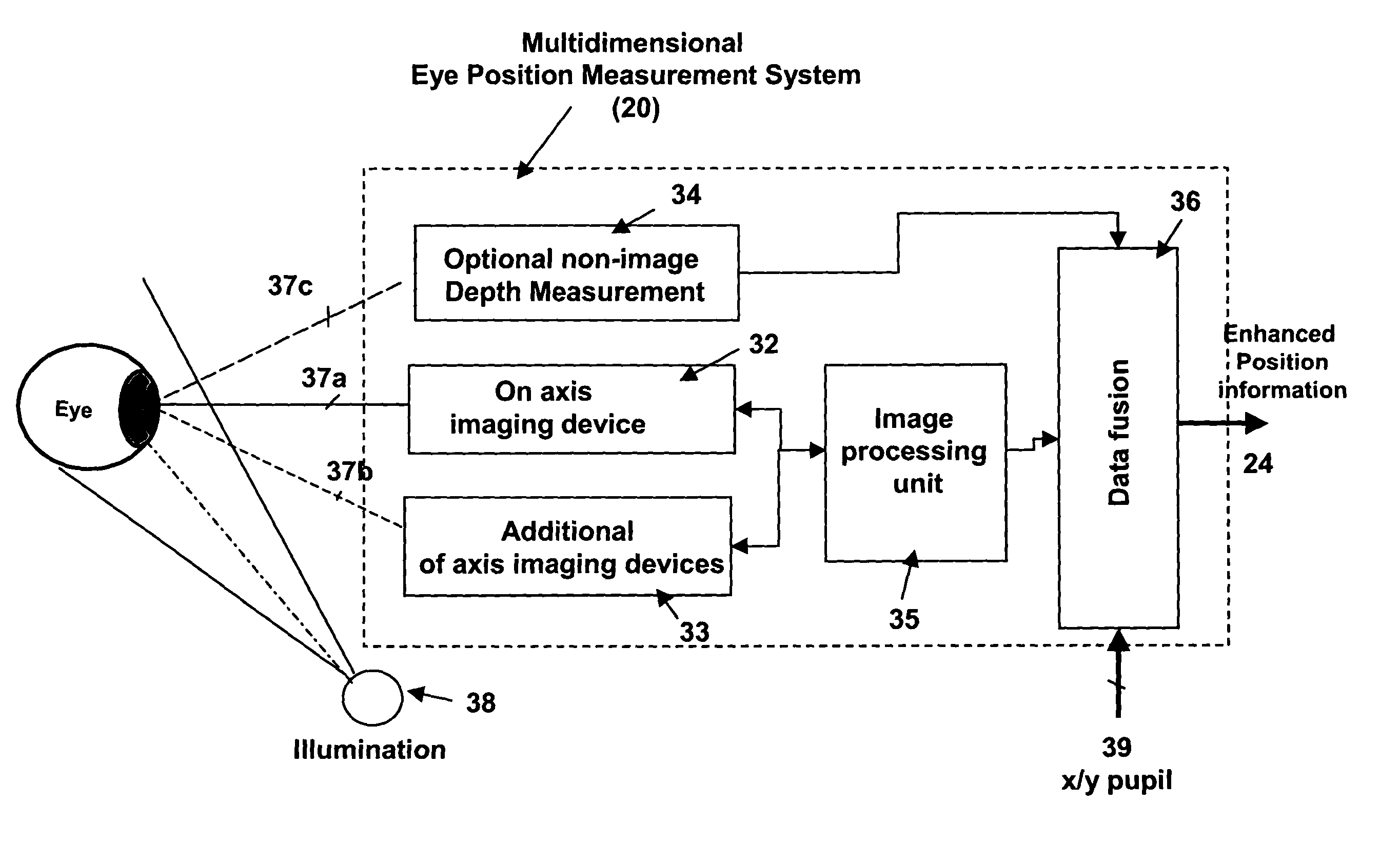
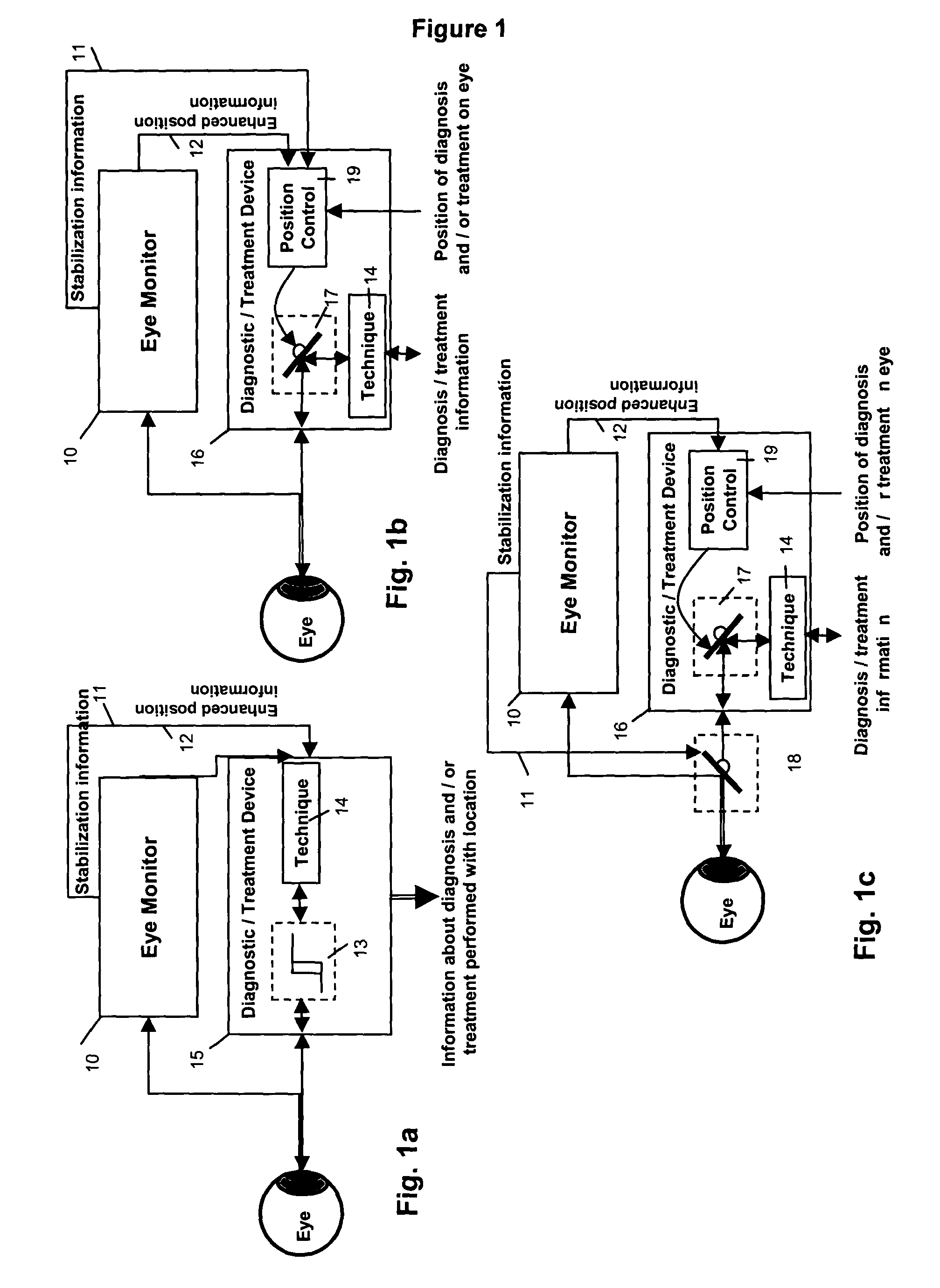
The present invention relates to improved ophthalmic diagnostic measurement or treatment methods or devices, that make use of a combination of a high speed eye tracking device, measuring fast translation or saccadic motion of the eye, and an eye position measurement device, determining multiple dimensions of eye position or other components of eye, relative to an ophthalmic diagnostic or treatment instrument.
Owner:SENSOMOTORIC INSTR FUR INNOVATIVE SENSORIK MBH D B A SENSOMOTORIC INSTR
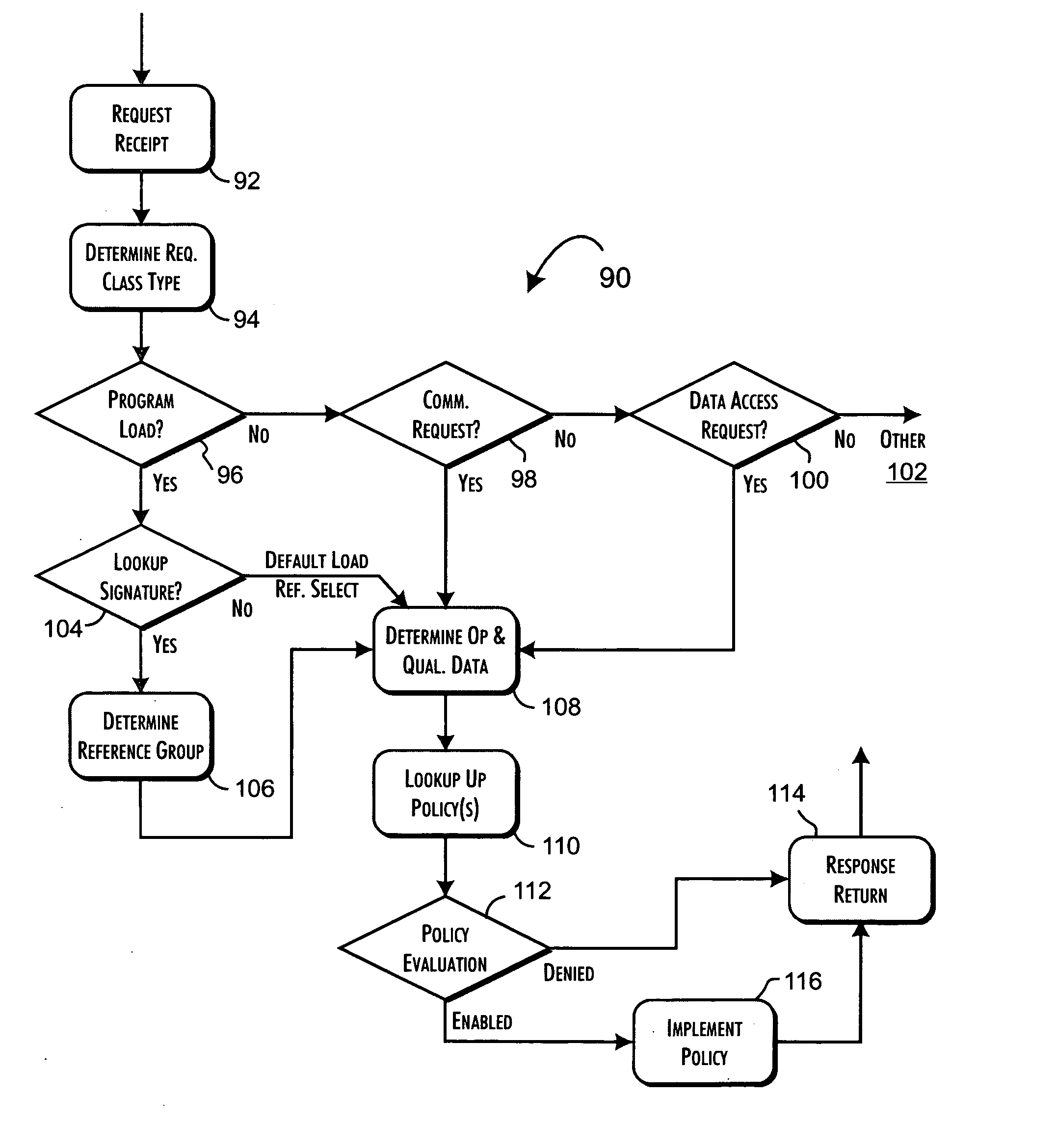
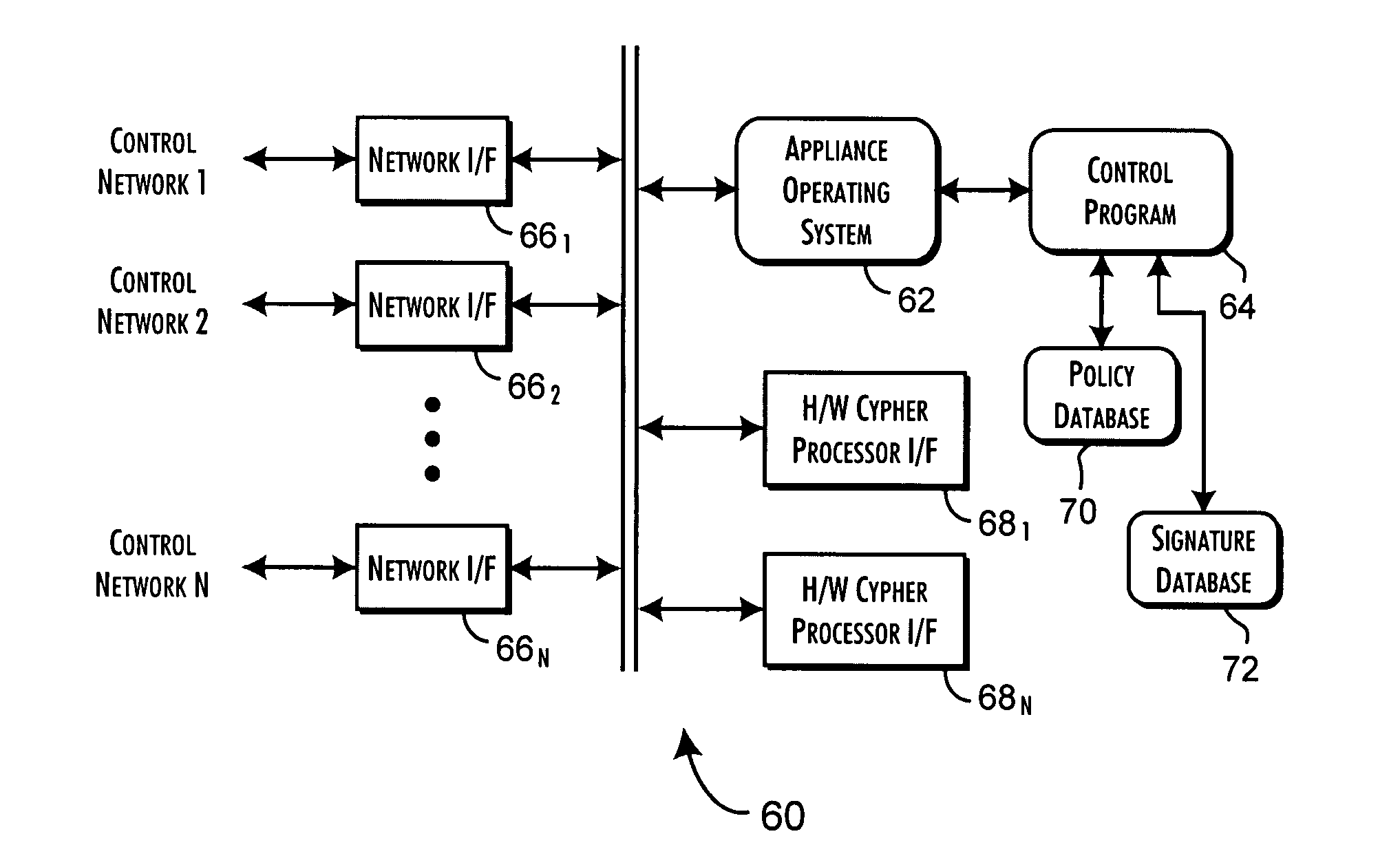
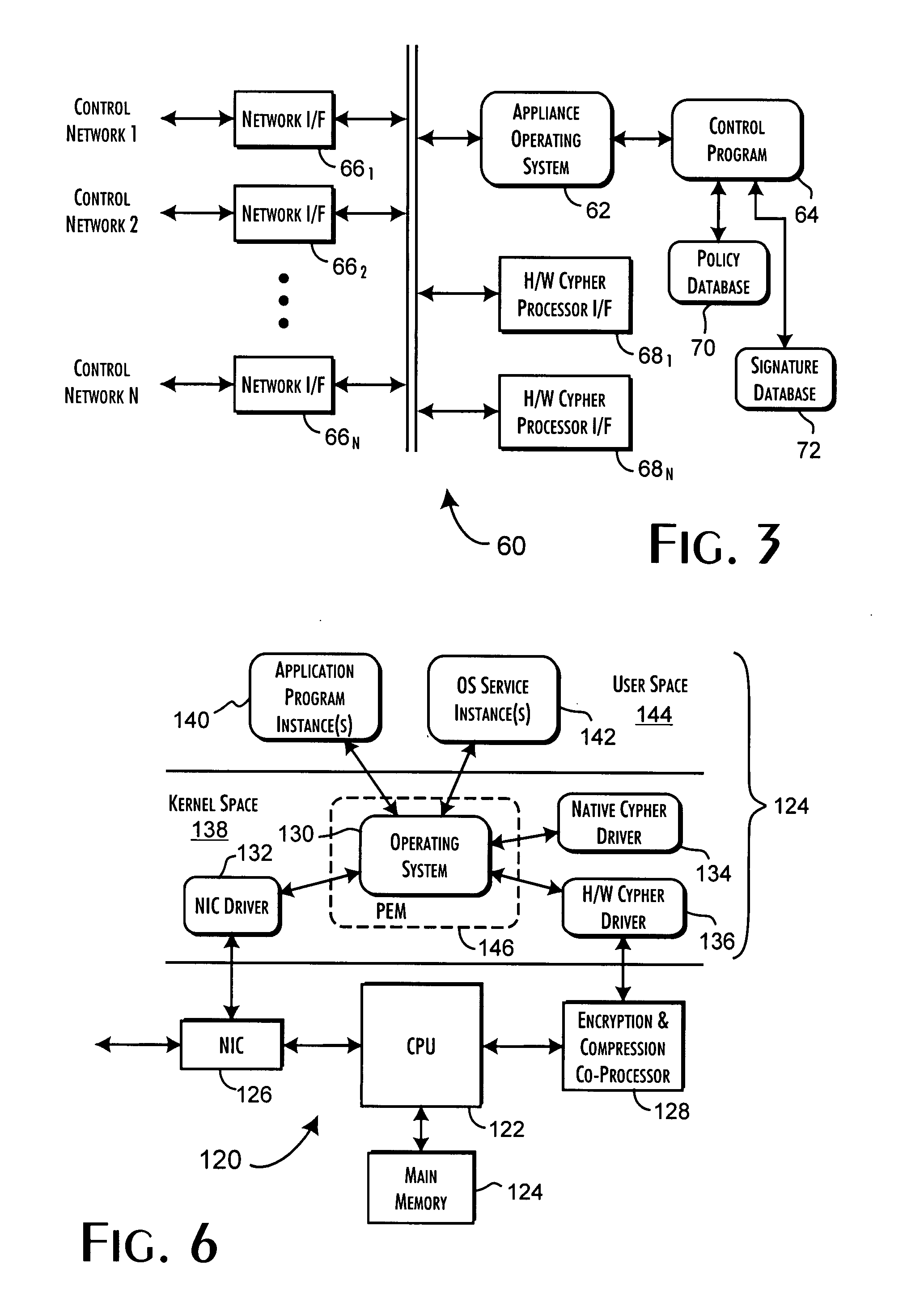
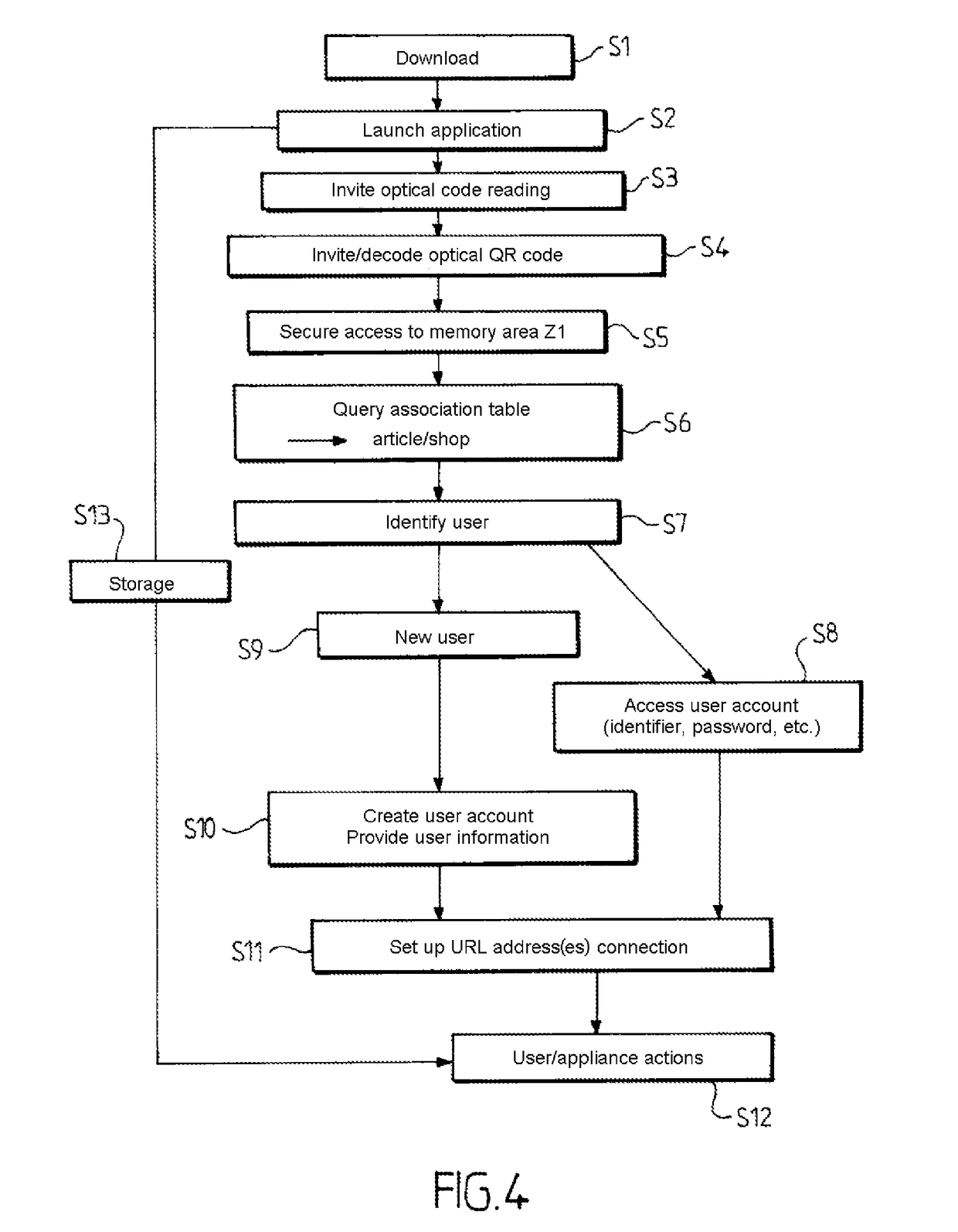
Secure, real-time application execution control system and methods
InactiveUS20050182958A1Securely identifyingKey distribution for secure communicationMemory loss protectionControl systemExecution control
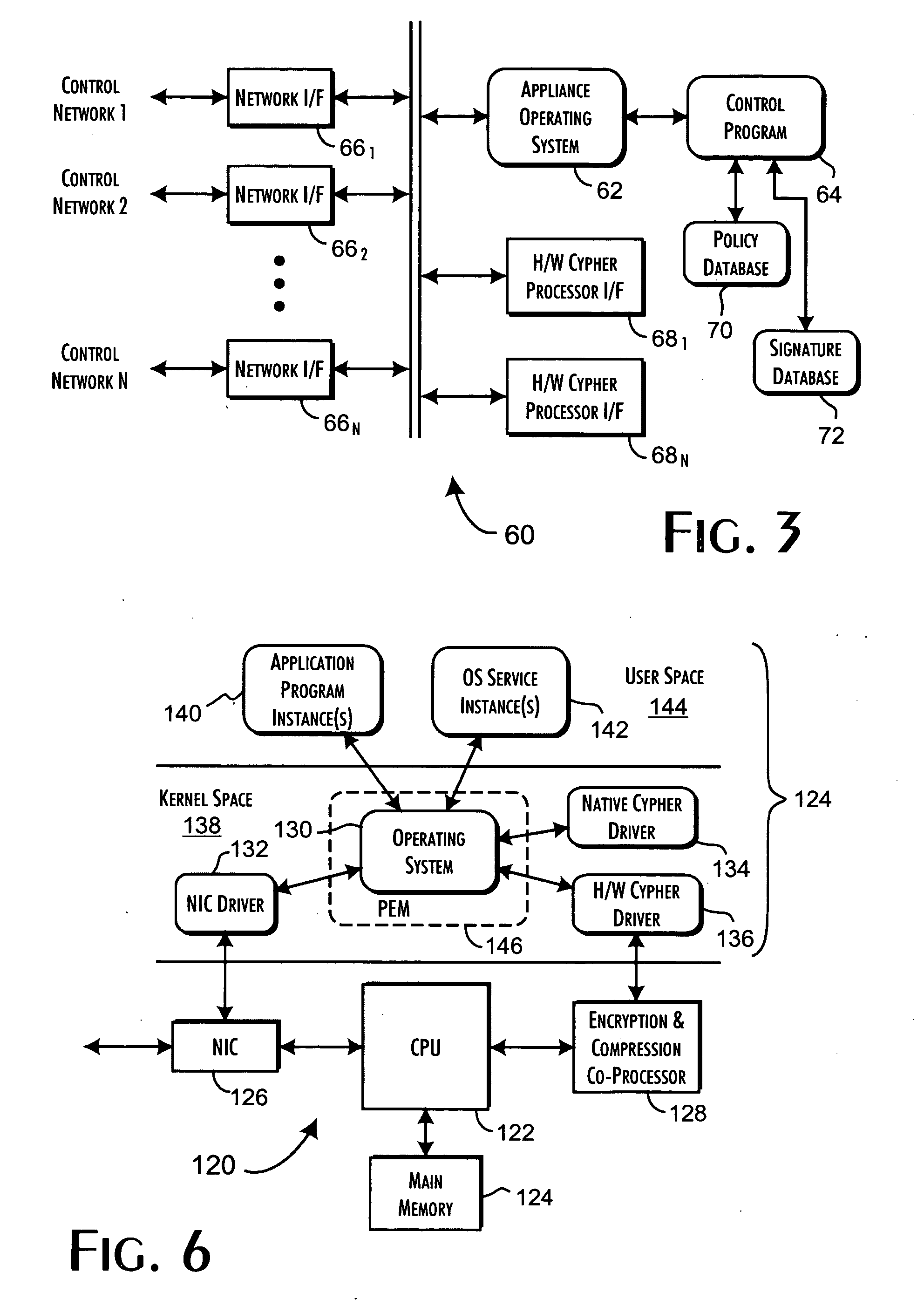
A security server qualifies the execution of programs for networked host computer systems using a database storing pre-qualified program signatures and defined policy rules associating execution permission qualifiers with execution control values. The server executes a control program in response to execution requests received via a communications network interface from identifiable hosts, wherein a predetermined execution request received from a predetermined host computer system includes an identification of a program load request, request context related data, and a secure program signature. The control program determines an execution control value based on an evaluation of the execution request relative to the pre-qualified program signatures and defined policy rules. The execution control value is then returned to the predetermined host computer system to securely qualify the execution of the program identified from the program load request.
Owner:PHAM DUC +3
Multidimensional eye tracking and position measurement system for diagnosis and treatment of the eye
ActiveUS7480396B2High resolutionReducing its effectivenessLaser surgeryCharacter and pattern recognitionMeasurement deviceOphthalmology
Owner:SENSOMOTORIC INSTR FUR INNOVATIVE SENSORIK MBH D B A SENSOMOTORIC INSTR
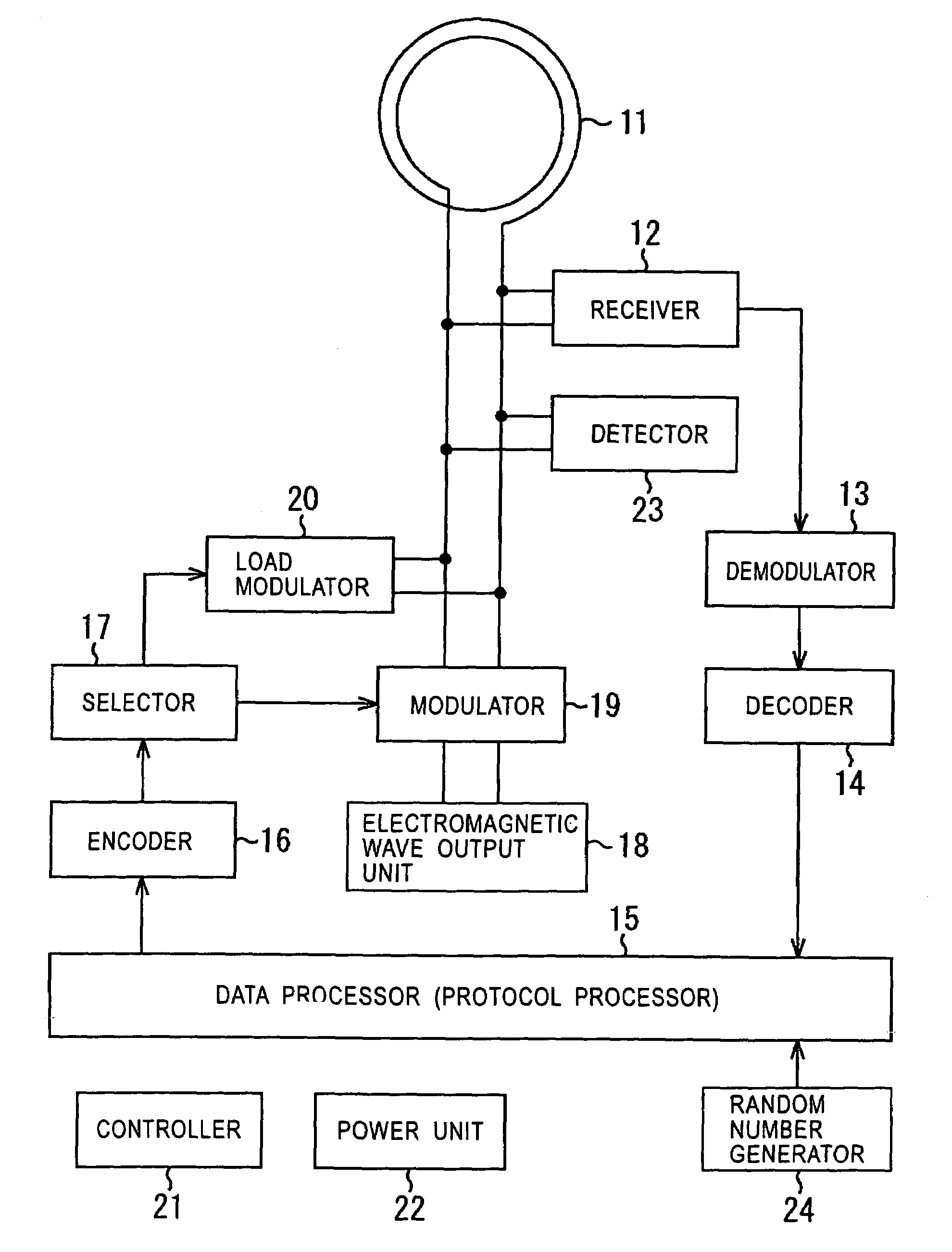
Communication apparatus and communication method
ActiveUS7209706B2Inhibitory responseSecurely identifyingUser identity/authority verificationMemory record carrier reading problemsCommunication deviceRandom number generation
A communication apparatus and a communication method prevent responses from being simultaneously received from two or more communicating parties. A first NFC apparatus transmits data for requesting IDs, and acquires IDs sent from second and third NFC apparatuses in reply to the request. After acquiring the IDs of the second and third NFC apparatuses, the first NFC apparatus transmits data that includes their IDs as the data for the second and third NFC apparatuses. If the first NFC apparatus cannot properly acquire the IDs of the second and third NFC apparatuses, then it sends the data for requesting their IDs again. Upon receipt of the request for the IDs, the second and third NFC apparatuses generate their own IDs by using random numbers and send the generated IDs. If the second and third NFC apparatuses receive the request for their IDs again, then they re-generate their own IDs by using random numbers, and send the re-generated IDs again. The present invention can be applied to, for example, an IC card system.
Owner:SONY CORP
Information encoding on surfaces by varying spectral emissivity
InactiveUS7044386B2Prevent counterfeitingEnhanced informationRecord carriers used with machinesDigital marking by printing code marksSpectral emissionEmissivity
A method for applying surface modifications in at least two patterns that differ in spectral emissivity by known amounts. The patterns form an information-encoding sequence of transitions of differential emissivity along a scan path over the patterns, that encodes a set of information. This information is decoded by a scanner sensitive to emissivity in the given portion of the electromagnetic spectrum, and sensitive to transitions in emissivity of the known amounts, when scanned along the scan path, combined with knowledge of the expected emissivity values of the patterns. This provides secure informational marking of articles and documents, including mail. The patterns may be visible, or hidden, but the emissivity values are not duplicated by standard office equipment, so authenticity of the patterns can be determined using the special emissivity scanner.
Owner:BERSON WILLIAM
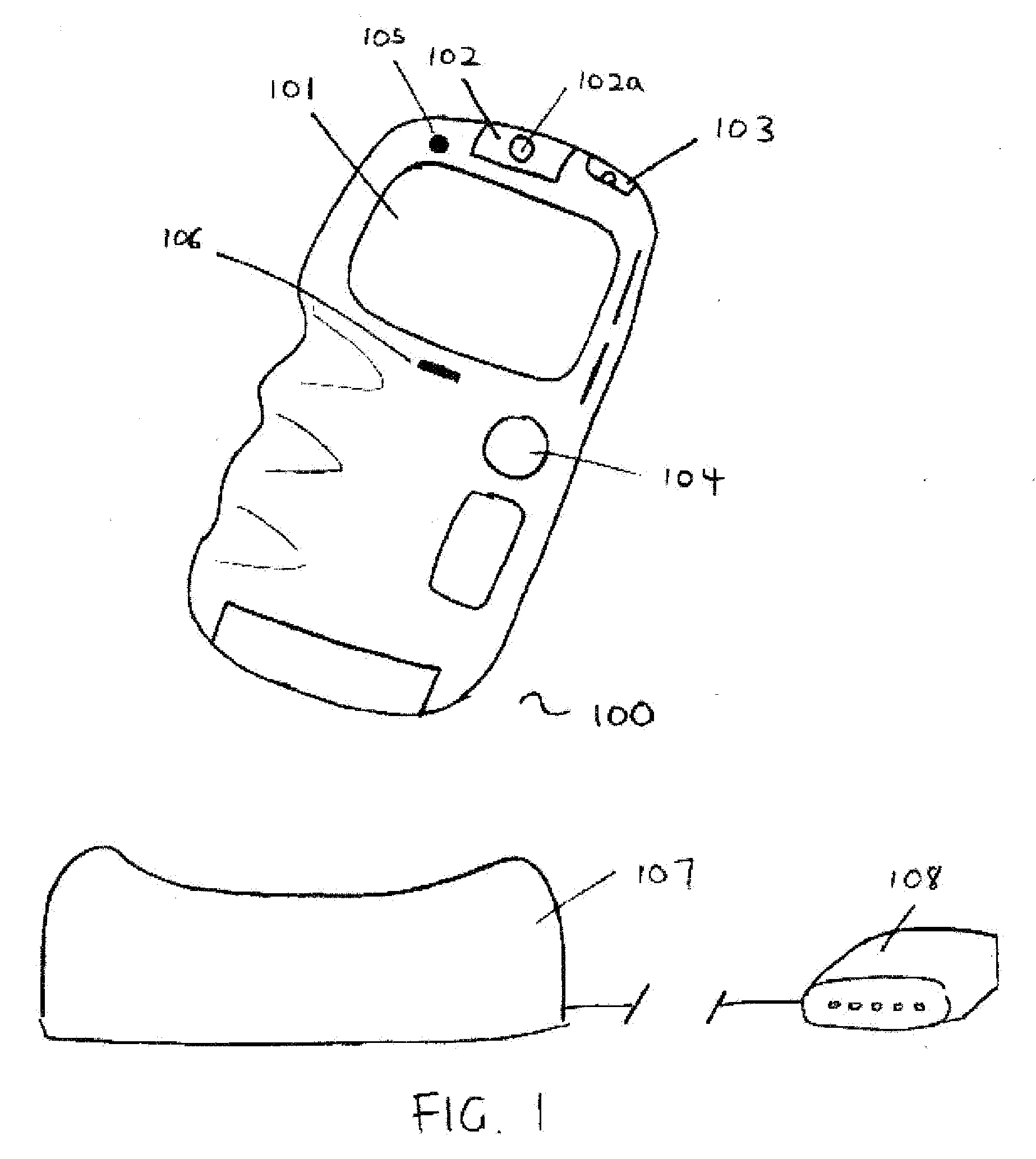
Portable communication device
InactiveUS20080015881A1Easy to useSecurely identifyingSubstation equipmentTelevision systemsHand held devicesSpeech sound
A novel system for remotely providing technical support services. The system utilizes a handheld device to provide bi-directional communications to a centralized center. Video or still images are used to convey the information to the remote support center for diagnosis, and instructions on how to fix the problem is relayed via text, video and / or voice to the remote user.
Owner:SHANKAR PRADIP
System and method for providing services to a remote user through a network
InactiveUS20010034721A1Securely identifyingDigital data processing detailsDigital data authenticationPersonal identification numberFinancial transaction
A system and method for providing services to a remote user through a network is provided. The user is identified through a user personal CD card readable in a CD reading device of a terminal, and a user personal identification number (PIN) entered on this terminal. The PIN and card-identifying elements are transmitted from the terminal to a remote server through the network, and matched to a user profile on the server, thereby identifying the user. The identified user may be provided with access to at least one service application on said server, such as access to a restricted system or financial transactions.
Owner:PNC GLOBAL
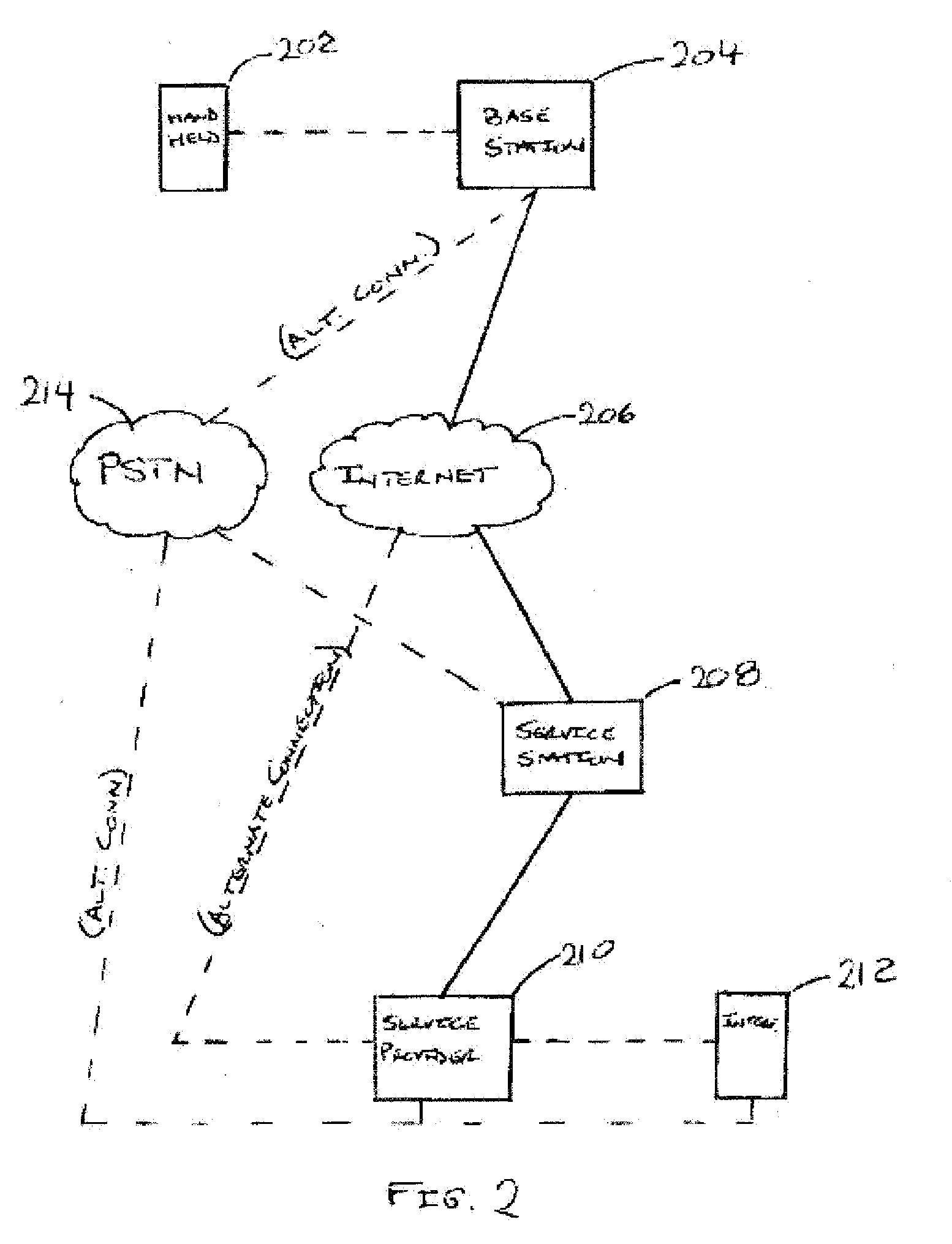
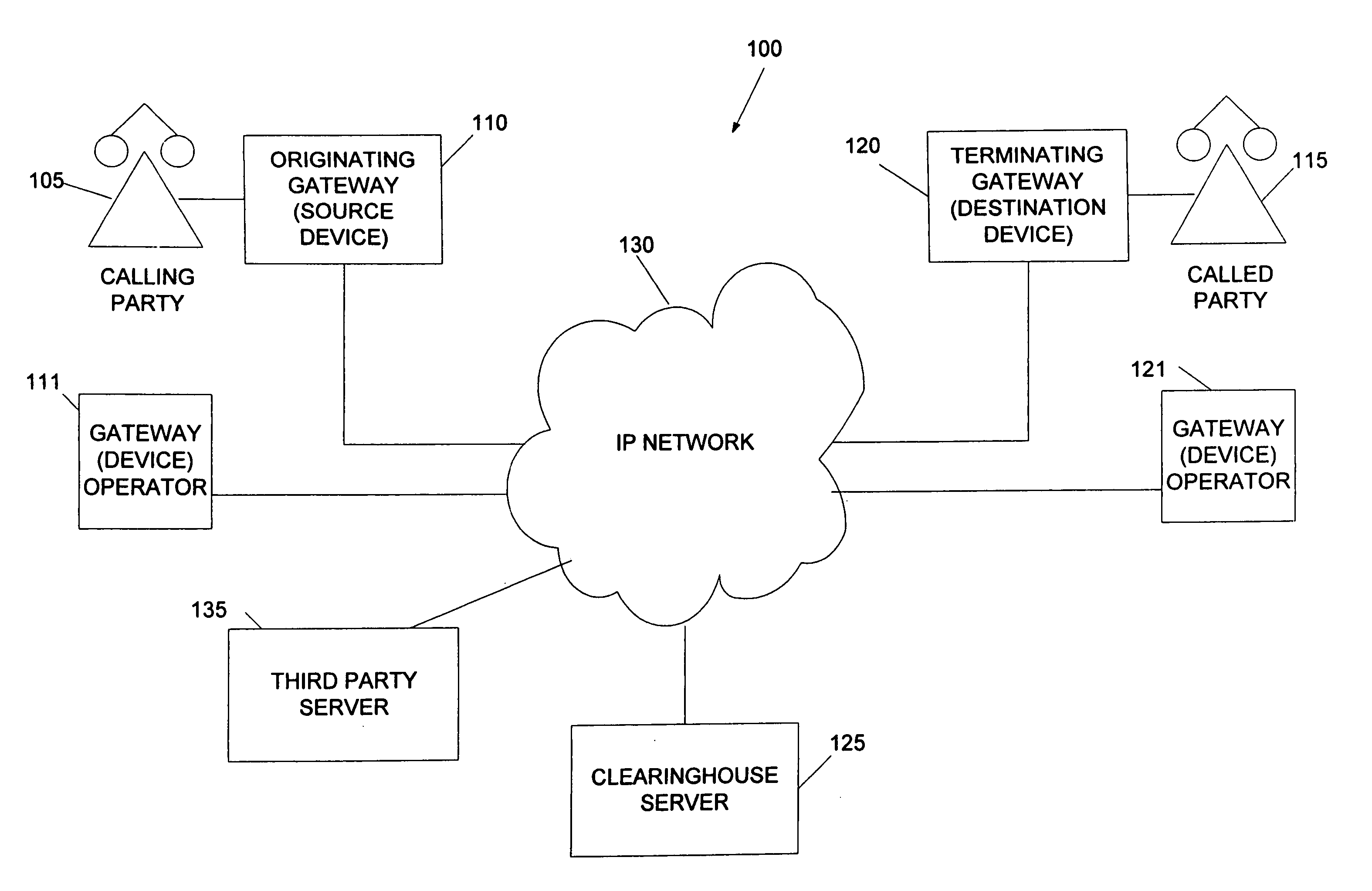
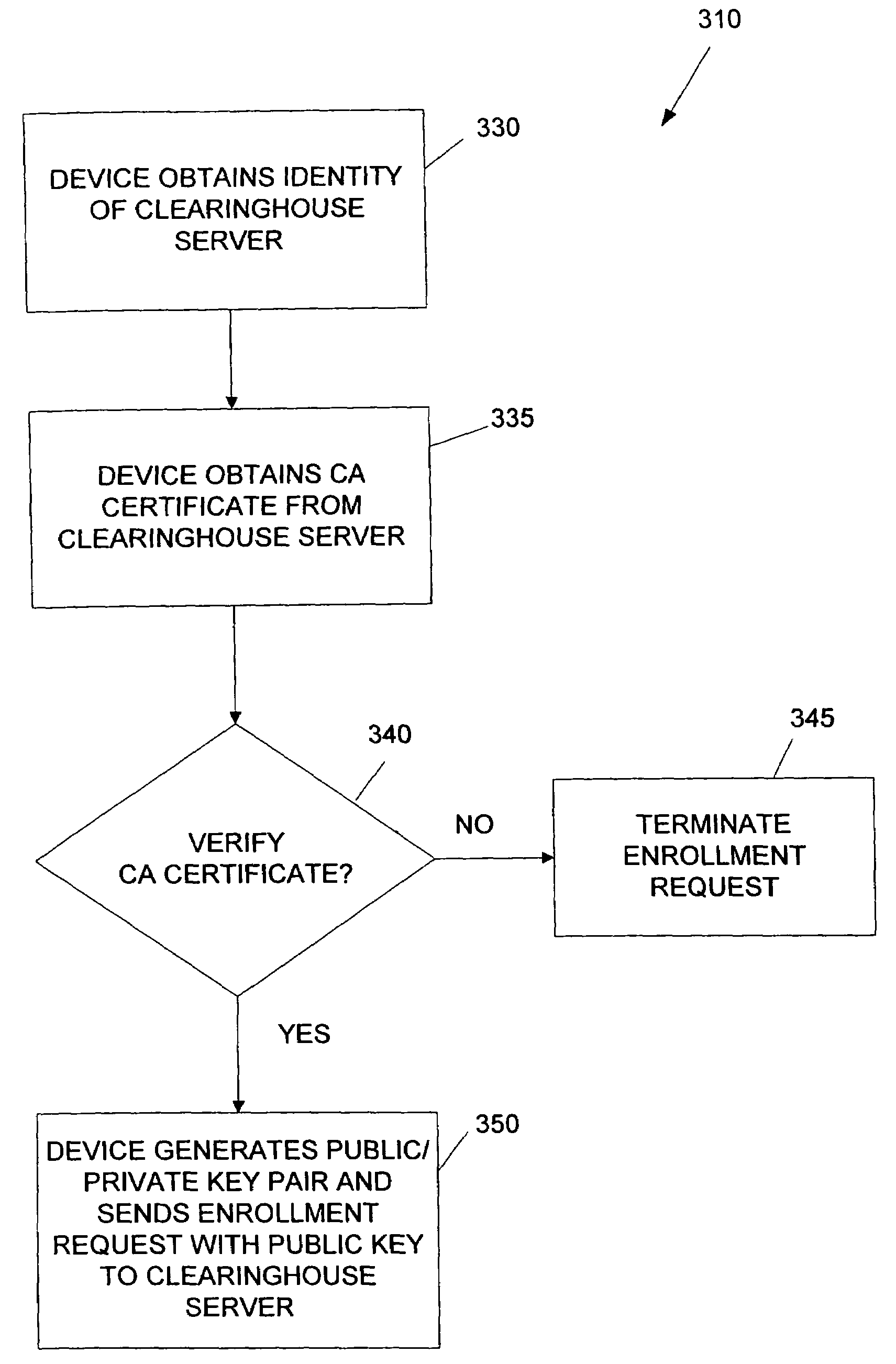
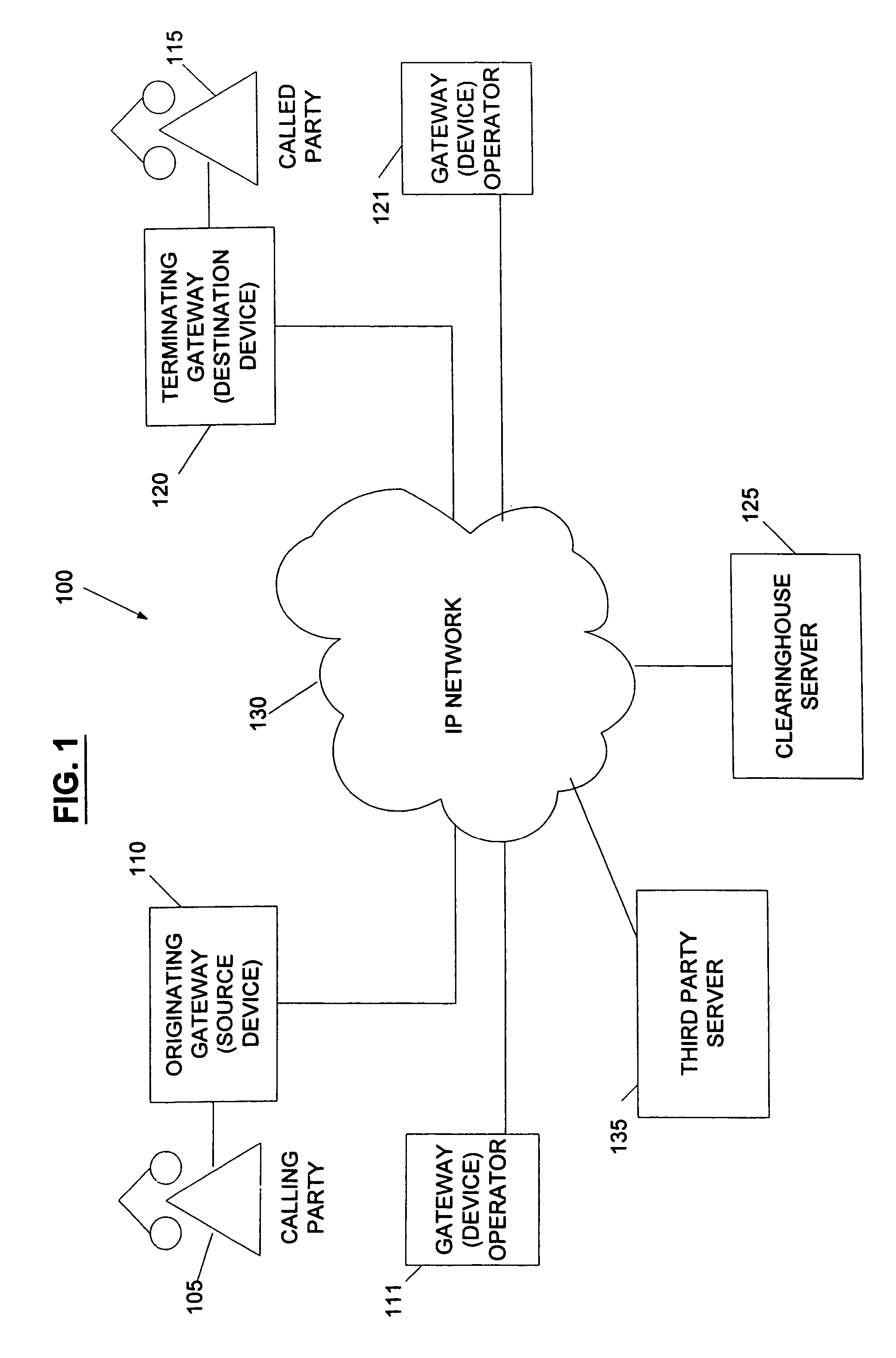
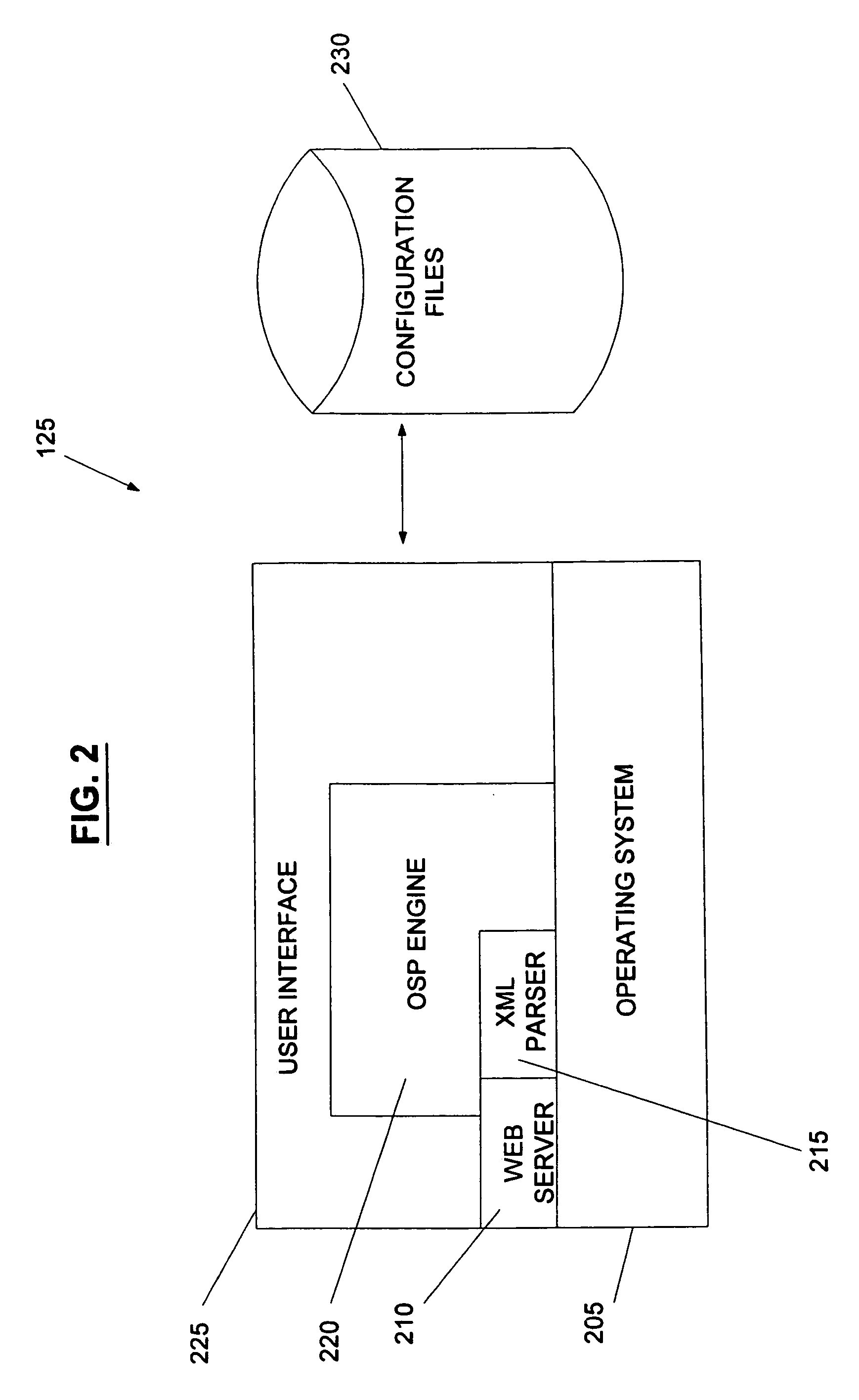
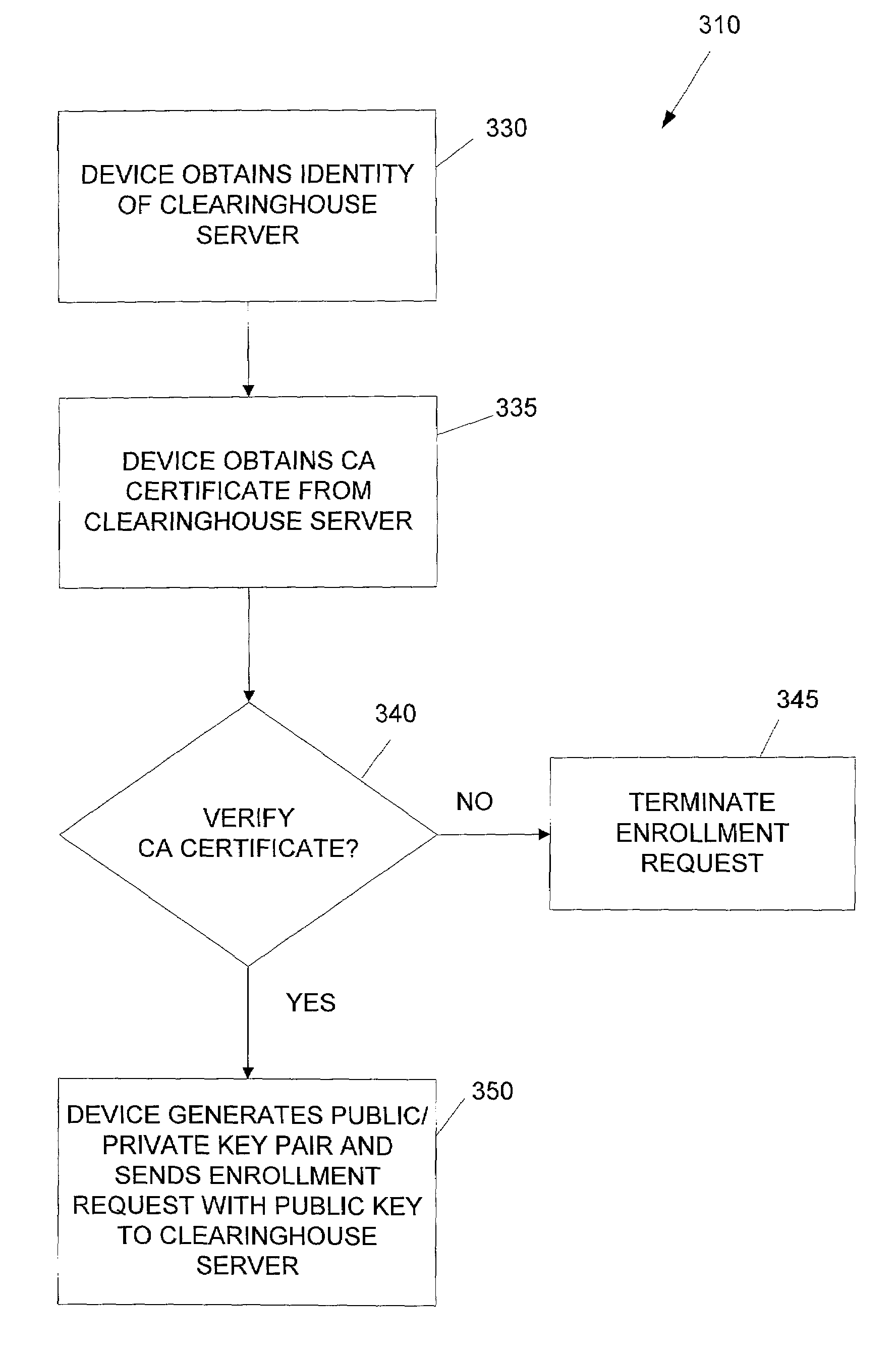
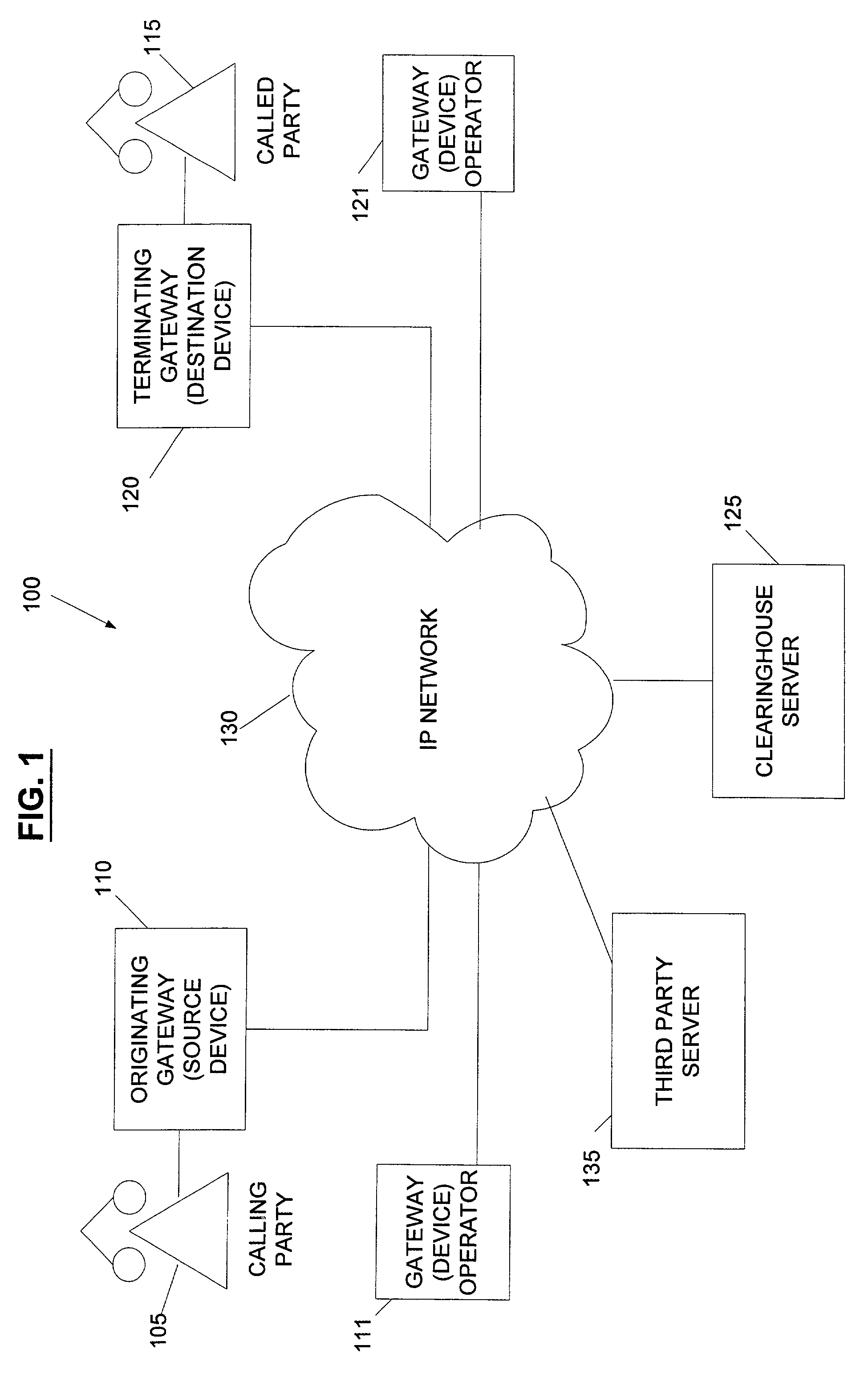
System and method for the secure enrollment of devices with a clearinghouse server for internet telephony and multimedia communications
InactiveUS20070033644A1Secure identitySecurely identifyingInterconnection arrangementsFinanceThe InternetSecurity level
Enrolling devices with a clearinghouse server for Internet telephony and multimedia communications. Enrollment can be the process of taking a network device (such as a router, gateway, gatekeeper, etc.) and exchanging encrypted information with the clearinghouse server, so that later communications with that device can be secured. The enrollment is done with levels of security and verification that ensures the devices and clearinghouse server is legitimate.
Owner:TRANSNEXUS
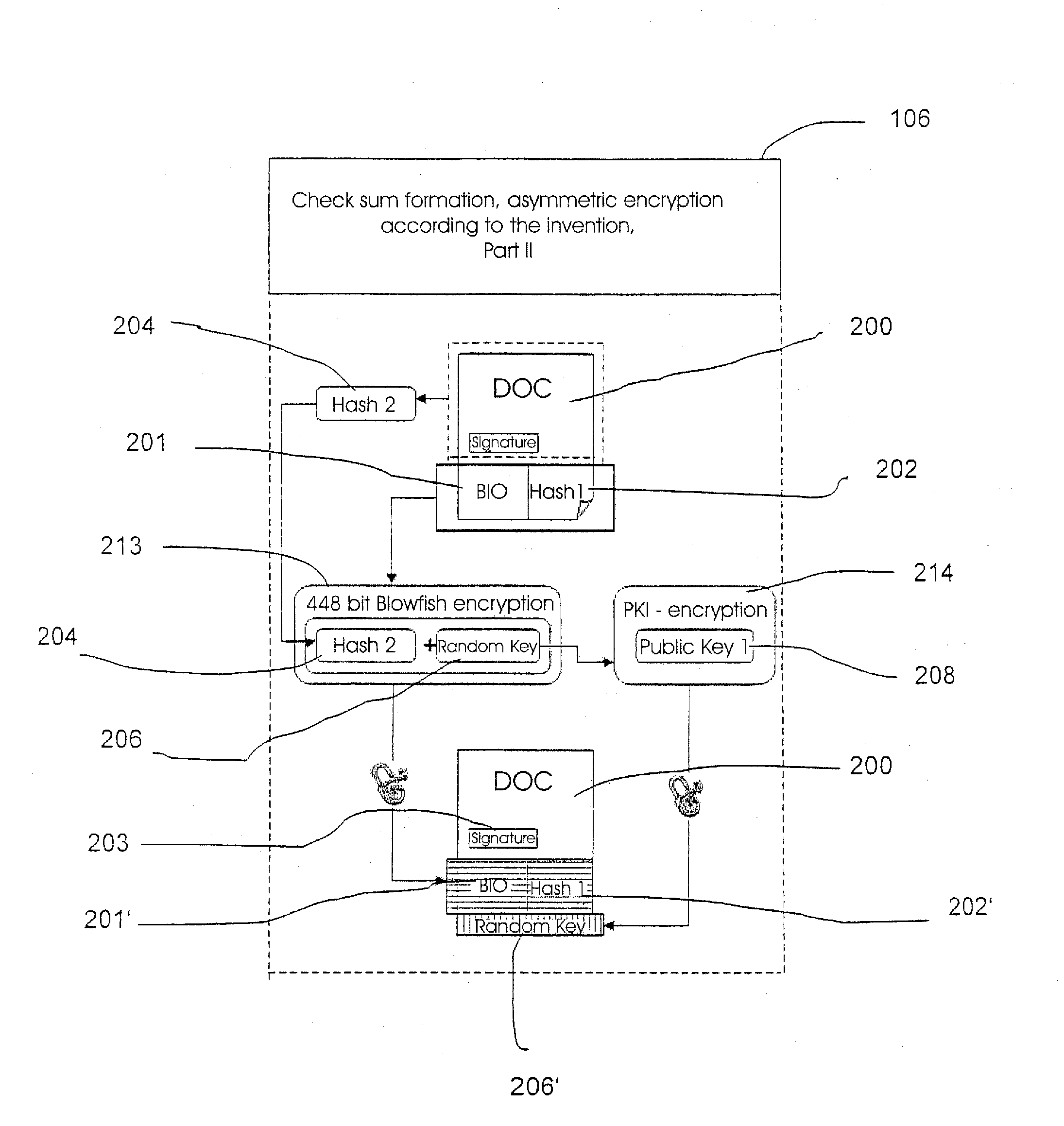
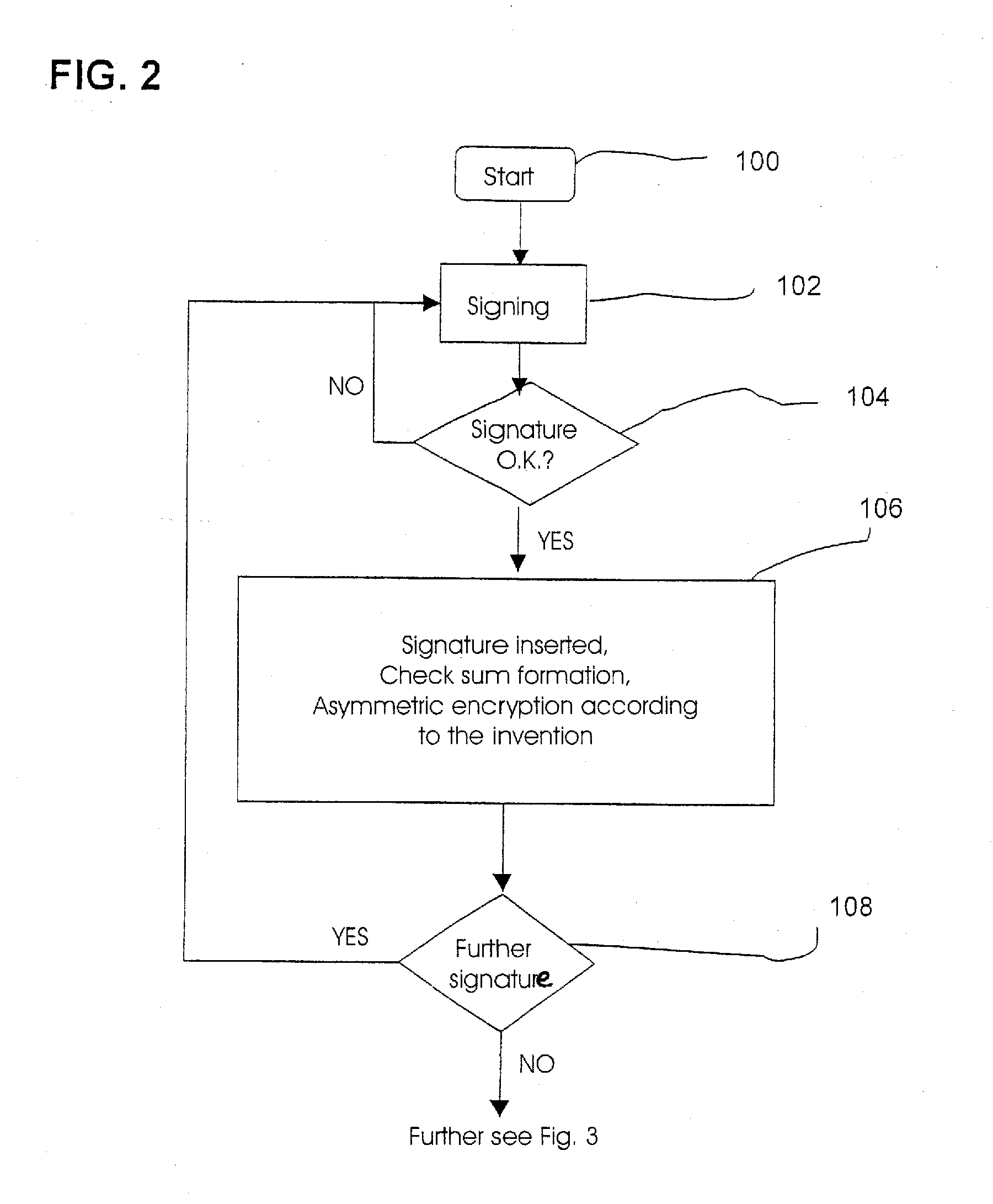
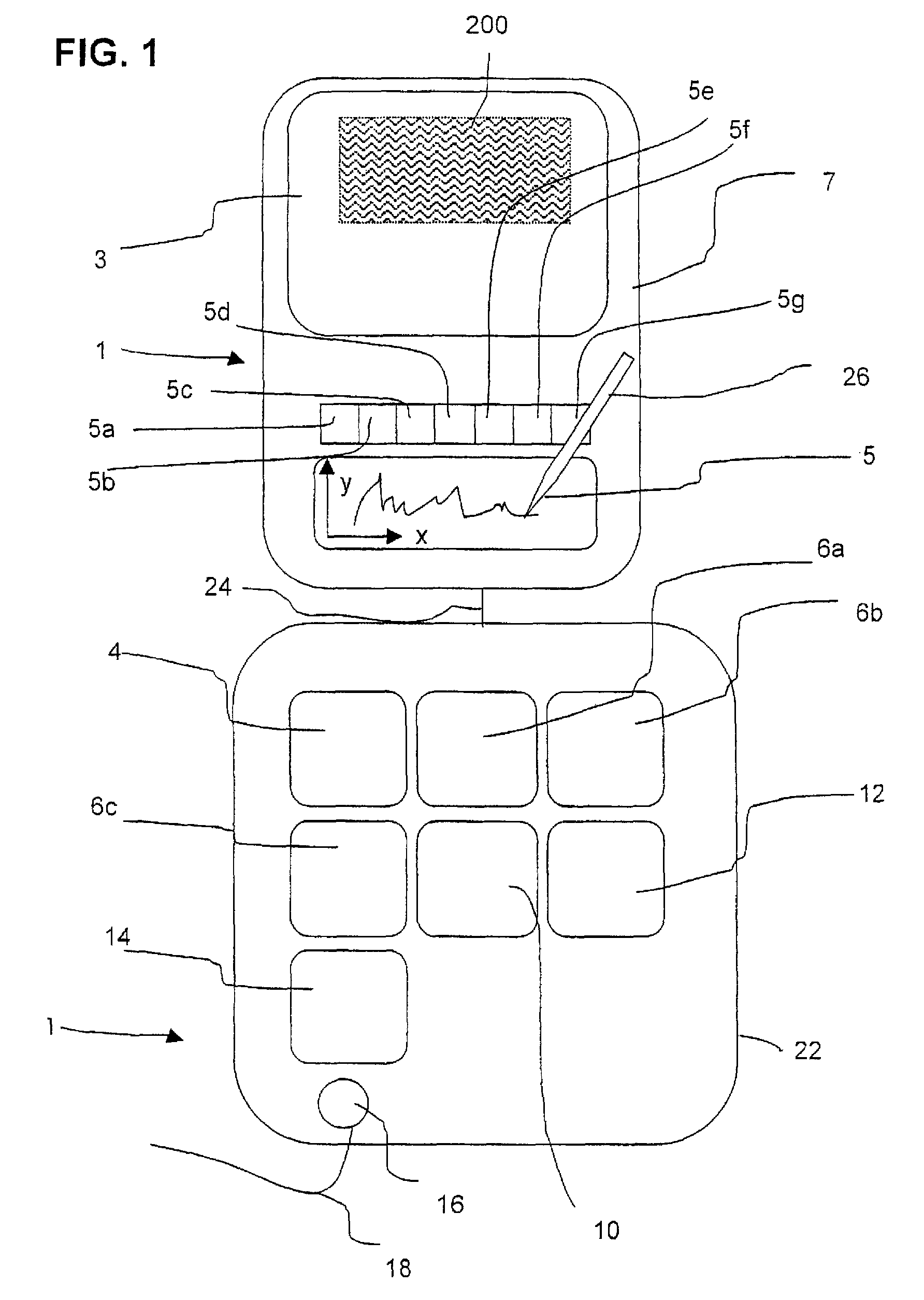
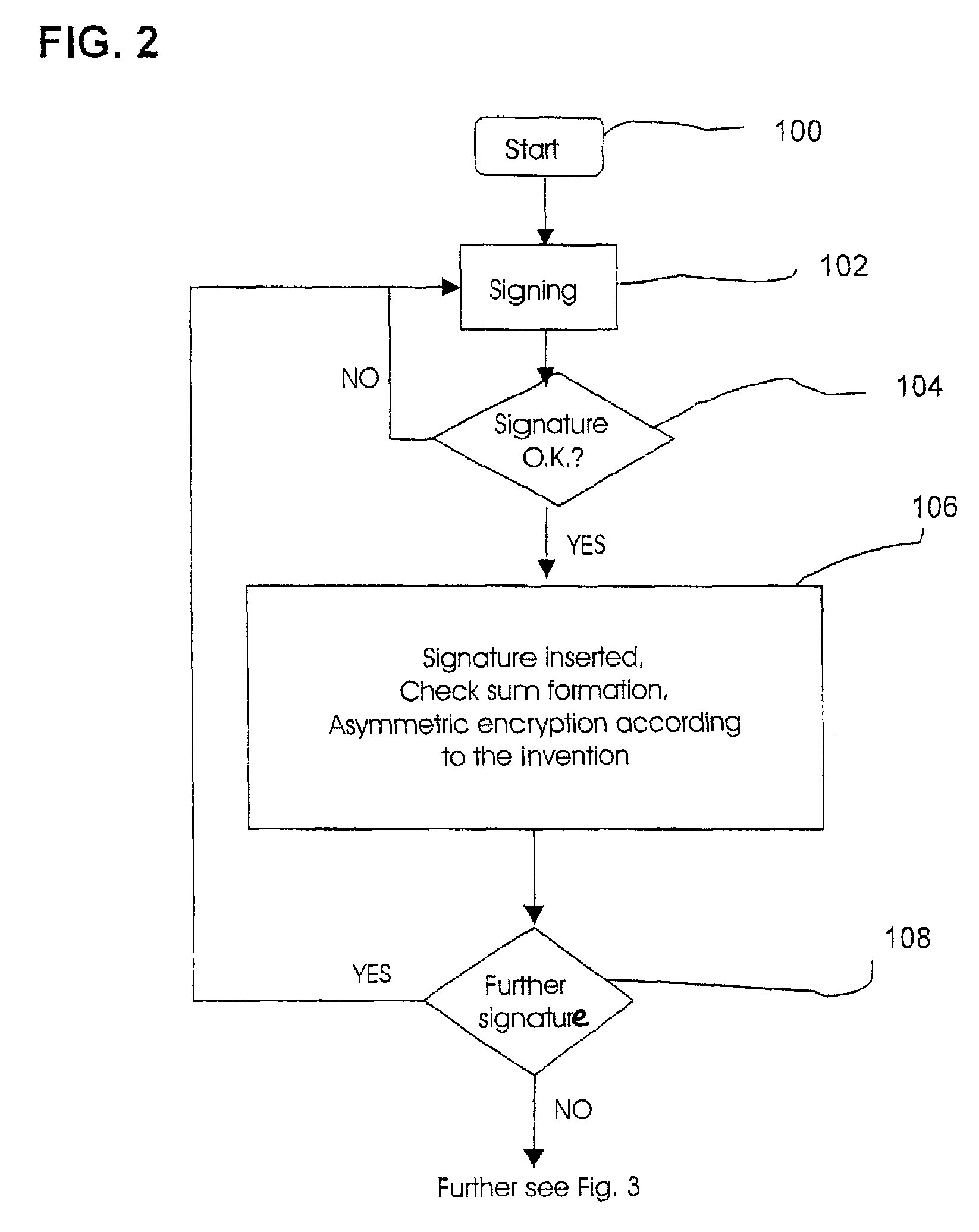
Method and Device for Safeguarding of a Document with Inserted Signature image and Biometric Data in a Computer System
ActiveUS20100106973A1Improper useConfidenceDigital data processing detailsUser identity/authority verificationElectronic documentHash function
A method for safeguarding an electronic document includes inserting at least one digital signature image into the electronic document and generating a first check sum for the electronic document, with or without optionally-inserted biometric signature data, using a first hash function. A second check sum is then generated using a second hash function. The first check sum and the biometric data, if provided, are then symmetrically encrypted using a key that is the sum of the second check sum and a generated random value. The symmetrically-encrypted first check sum is attached to the document. The random value is then asymmetrically encrypted using a first public key of a first key pair and the asymmetrically-encrypted random value is added to the document.
Owner:STEPOVER
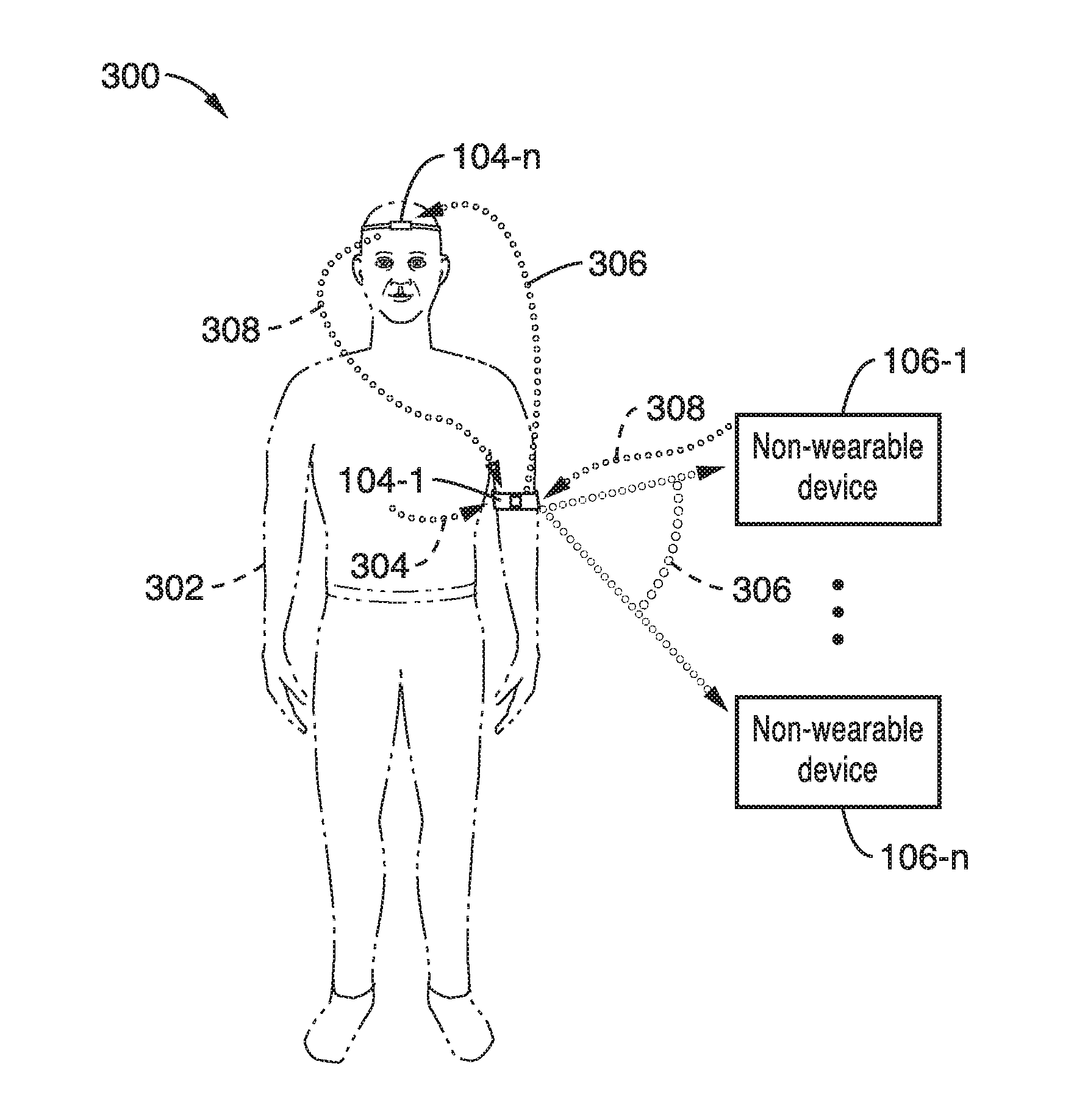
Smart wearable devices and methods for acquisition of sensorial information from wearable devices to activate functions in other devices
InactiveUS20170010665A1Securely identifyingInput/output for user-computer interactionSignalling system detailsEmbedded systemBreathing
Smart wearable devices and methods for acquiring sensor data about a user to determine the physical and mental status of the user and automatically activate or deactivate other devices when authenticated by biometric security access specific to the wearer are presented. Specifically, the smart wearable device can automatically acquire a user's biological input, such as heart rate, breathing, body temperature, etc. and based on the input, automatically activate or deactivate a function in another device by sending a triggering signal to the other device.
Owner:SONY CORP +1
Method for making a secure personal card and its working process
ActiveUS7992789B2Improve performanceSecurely identifyingAcutation objectsConveying record carriersBiometric dataSmart card
A method for producing a secure personal card and its working process using an intelligent card, the card has electric contacts, a CPU with at least data memory of the user and a biometric data receptor of the user. The biometric data stored in the card is used to make a comparison with biometric data received at the moment of use. Once the card is activated, generating an absolute identification of the biometric data of the authorized user, said biometric data being stored in an unreadable memory, generating and storing the personal data of the user and his / her access code, said biometric data being compared with the current read data of the actual user, in order to verify the identity of the user, then verification and identification of said personal data and access code being allowed in order to continue regular working operation.
Owner:WIBIOCARD SRL
Telephone Caller Authentication
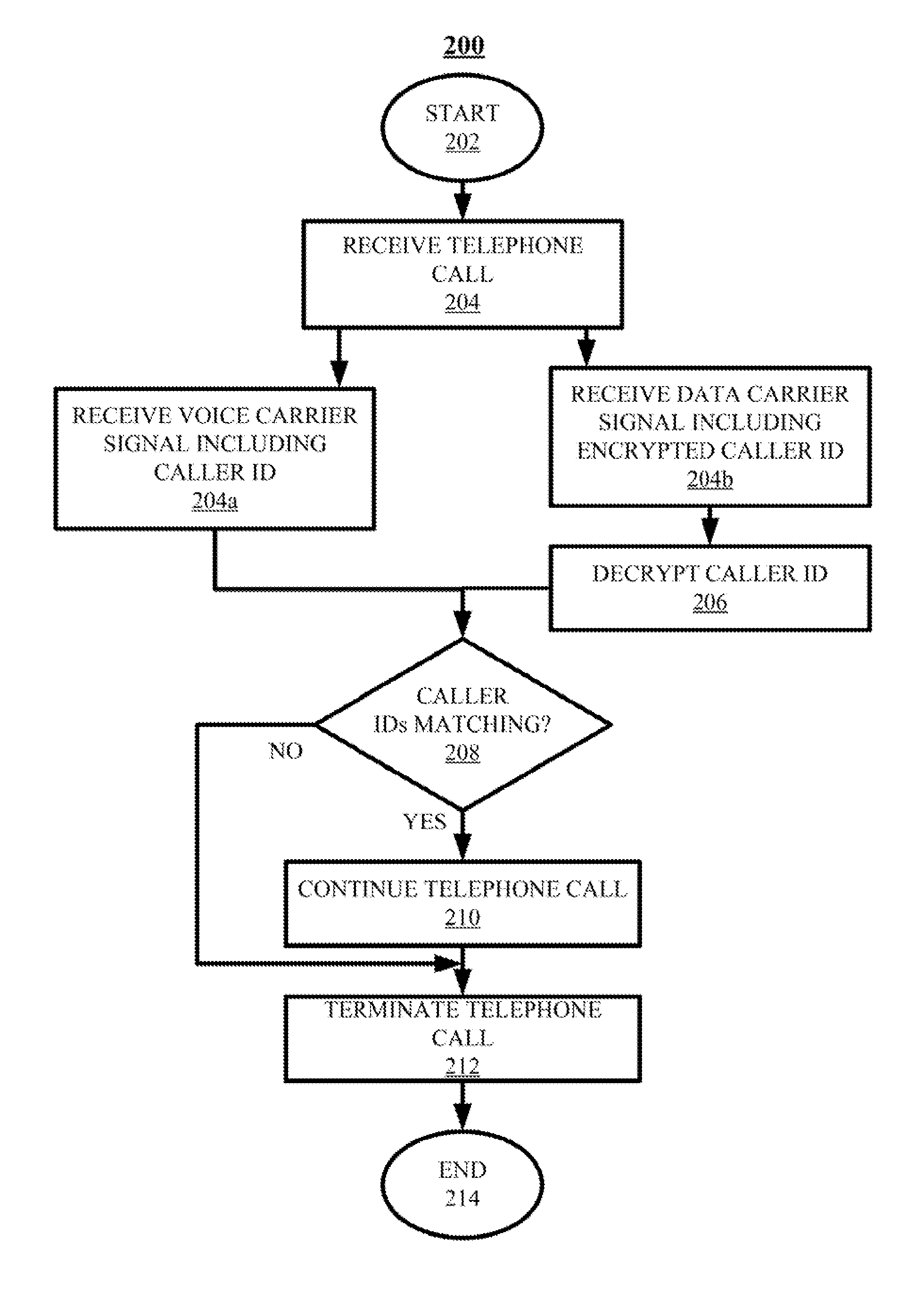
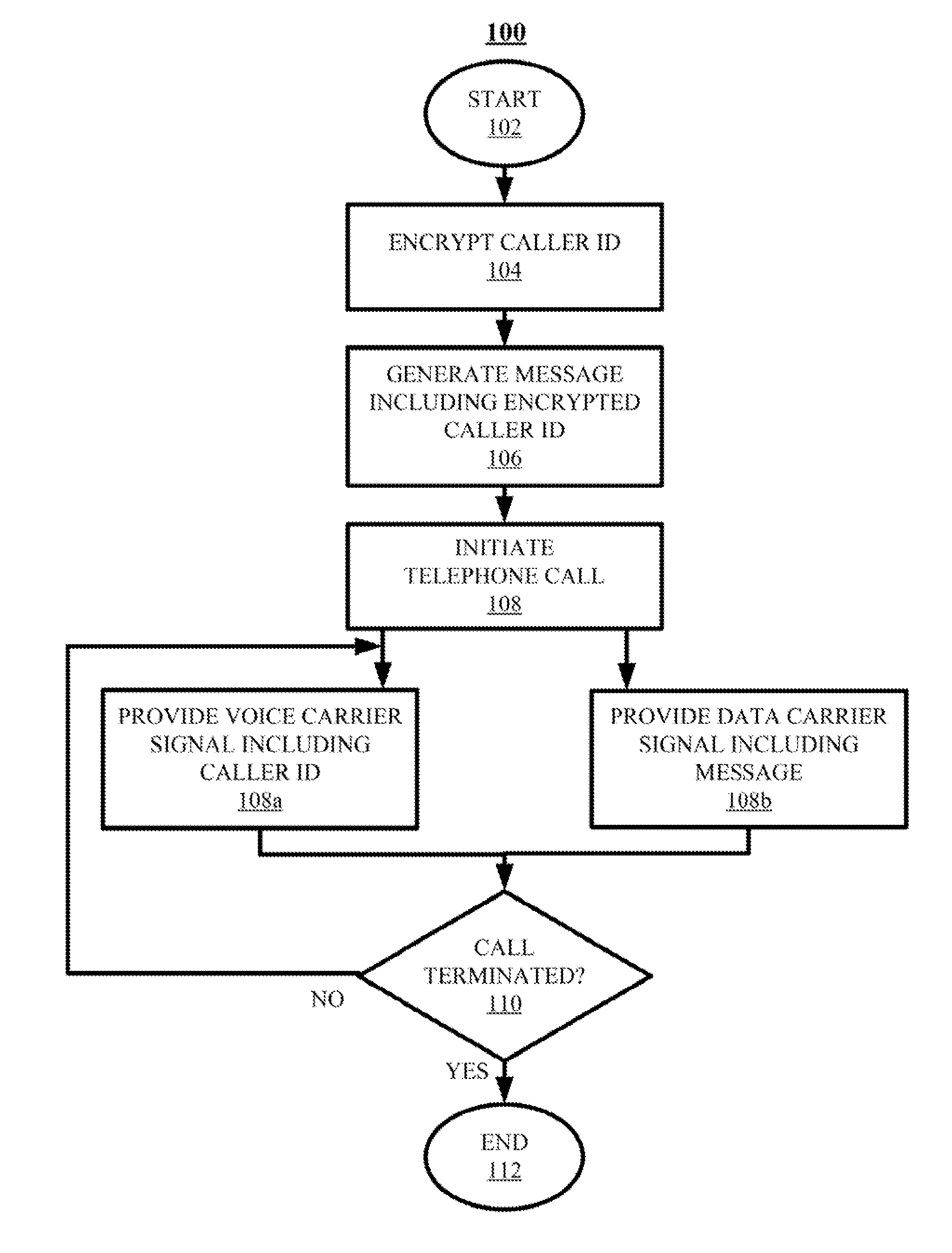
ActiveUS20150236857A1Sacrificing robustnessSimplify the authentication processUser identity/authority verificationCommmunication supplementary servicesCarrier signalSpeech sound
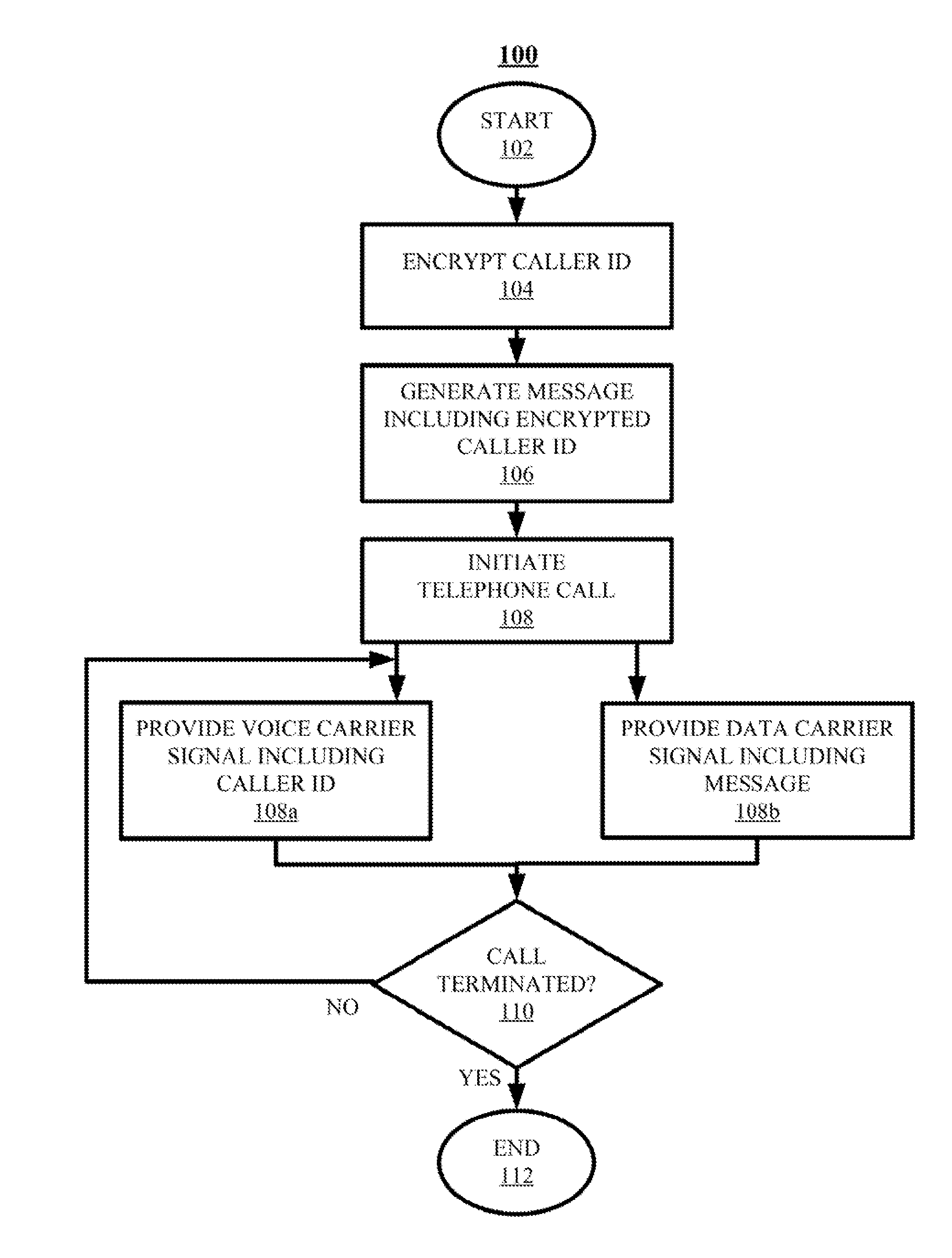
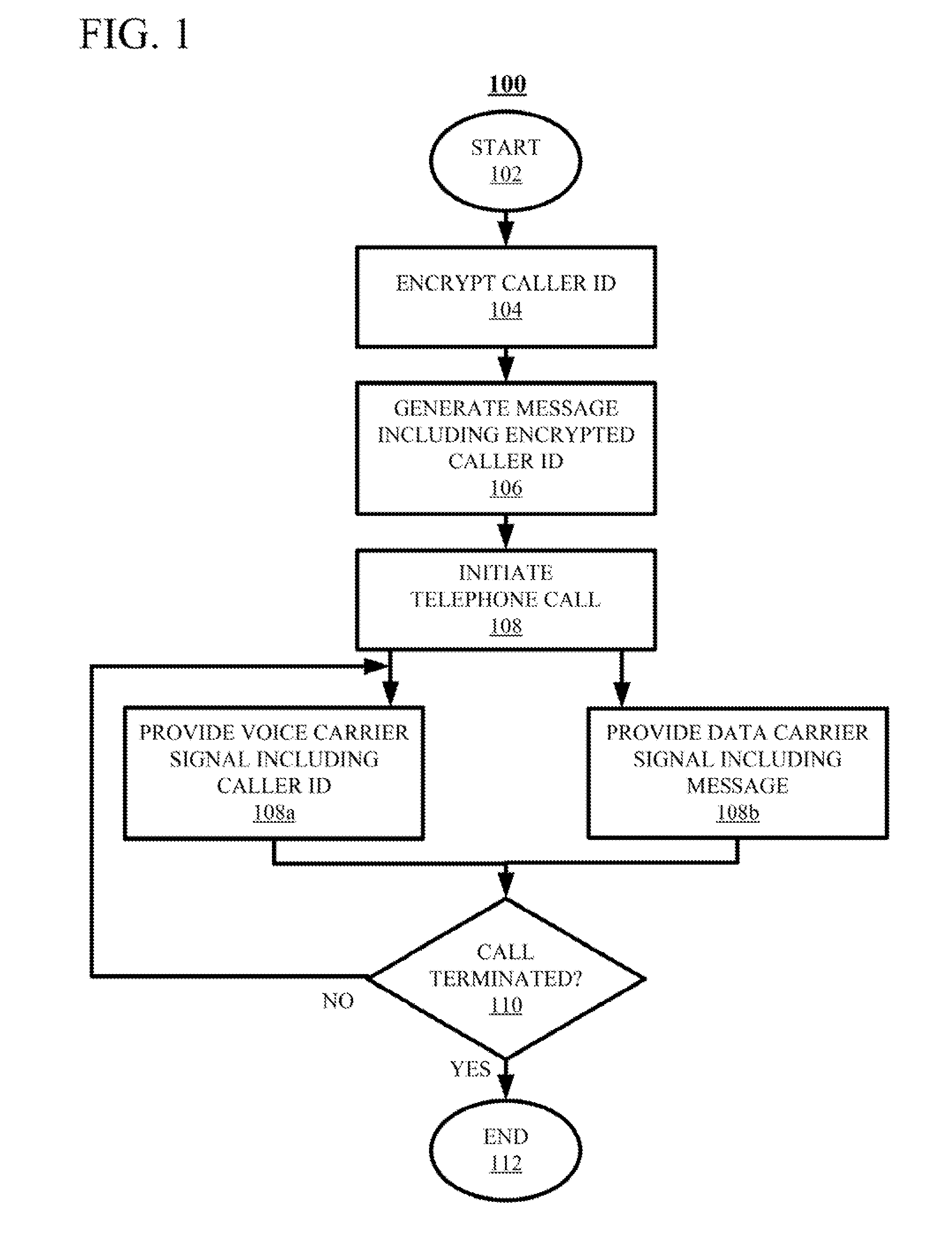
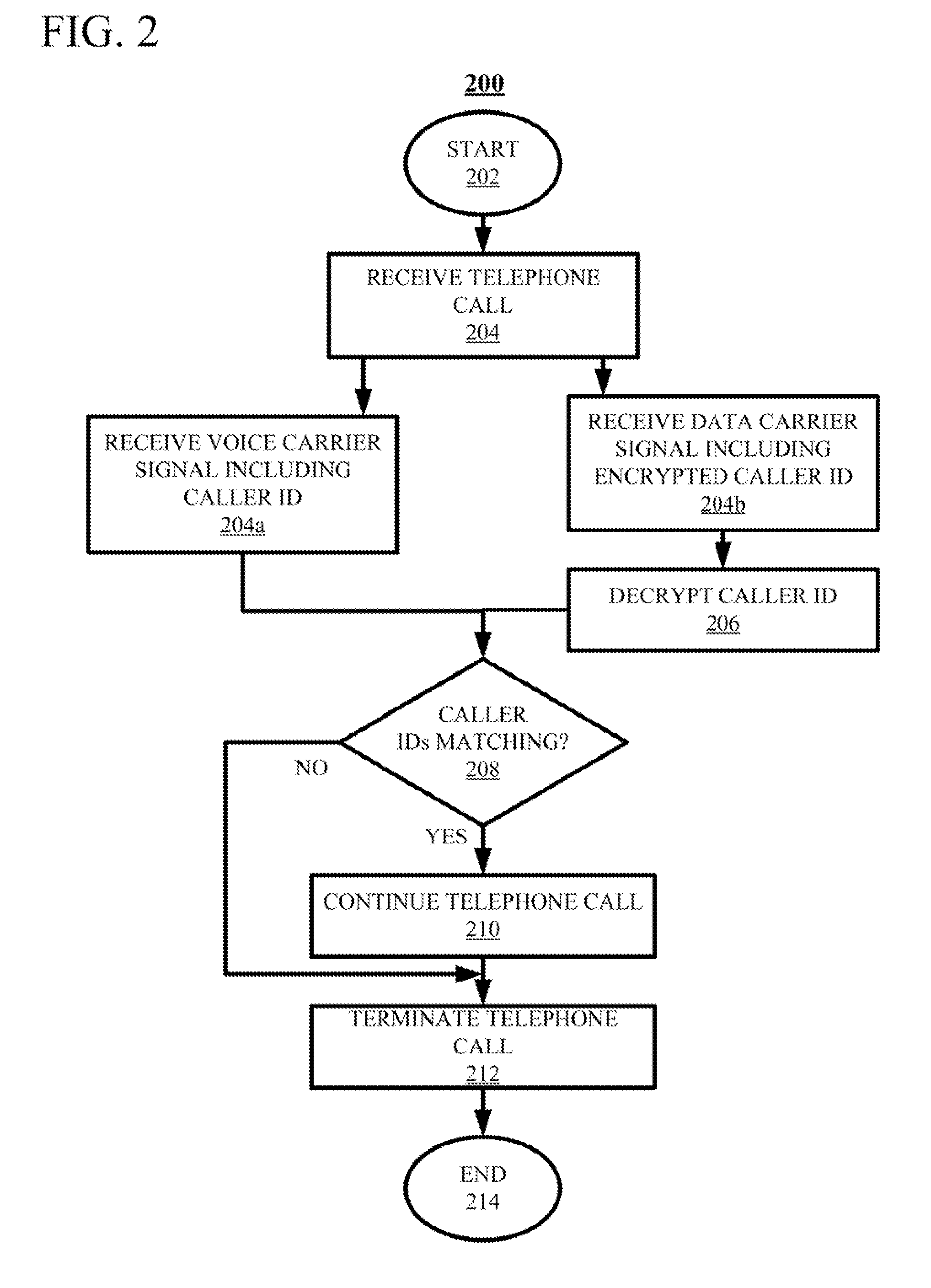
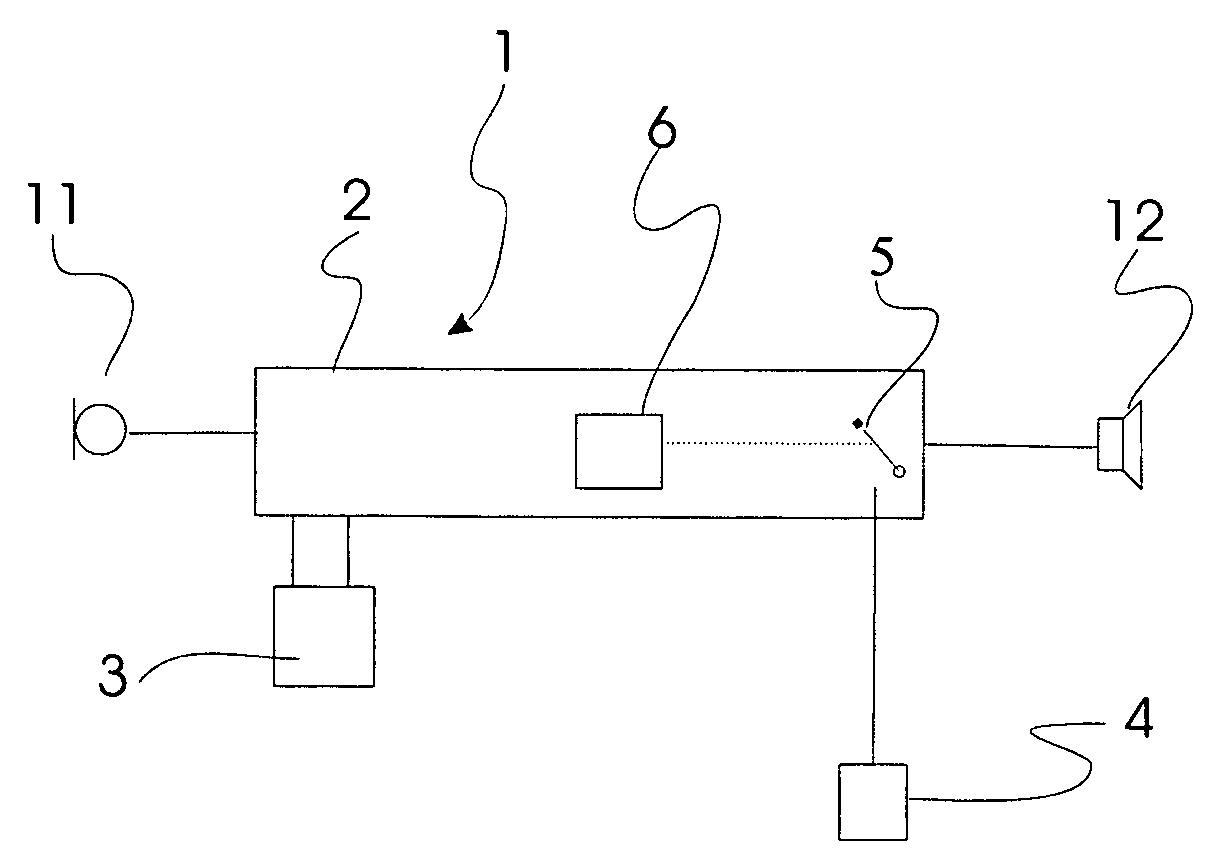
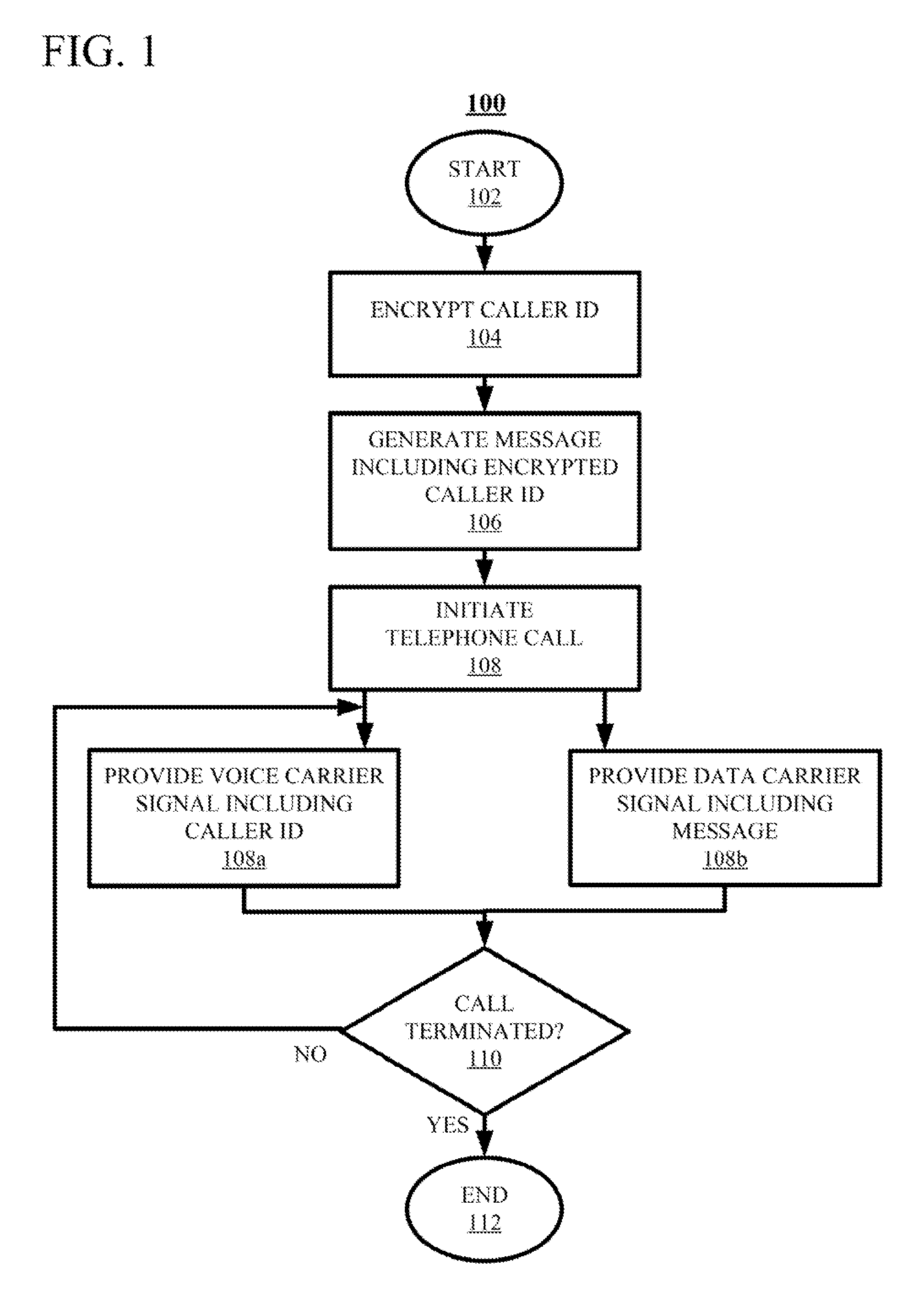
Techniques for authenticating the identity of a caller in a telephone call are disclosed. The device generating the call implements encrypting caller identification information and initiating the telephone call, said initiating comprising providing a voice carrier signal including the caller identification information; and simultaneously providing a data carrier signal including the encrypted caller identification information. The receiving device implements receiving the telephone call; decrypting the encrypted caller identification information at the recipient device; and verifying the identity of at least an unknown caller at the recipient device by at least one of verifying the authenticity of a certificate used to encrypt the caller identification information; and comparing the decrypted caller identification information with the caller identification information from the voice carrier signal. A telephony device implementing such an authentication technique is also disclosed.
Owner:IBM CORP
Secure, real-time application execution control system and methods
InactiveUS20080052755A1Securely identifyingKey distribution for secure communicationDigital data processing detailsControl systemExecution control
Owner:PHAM DUC +3
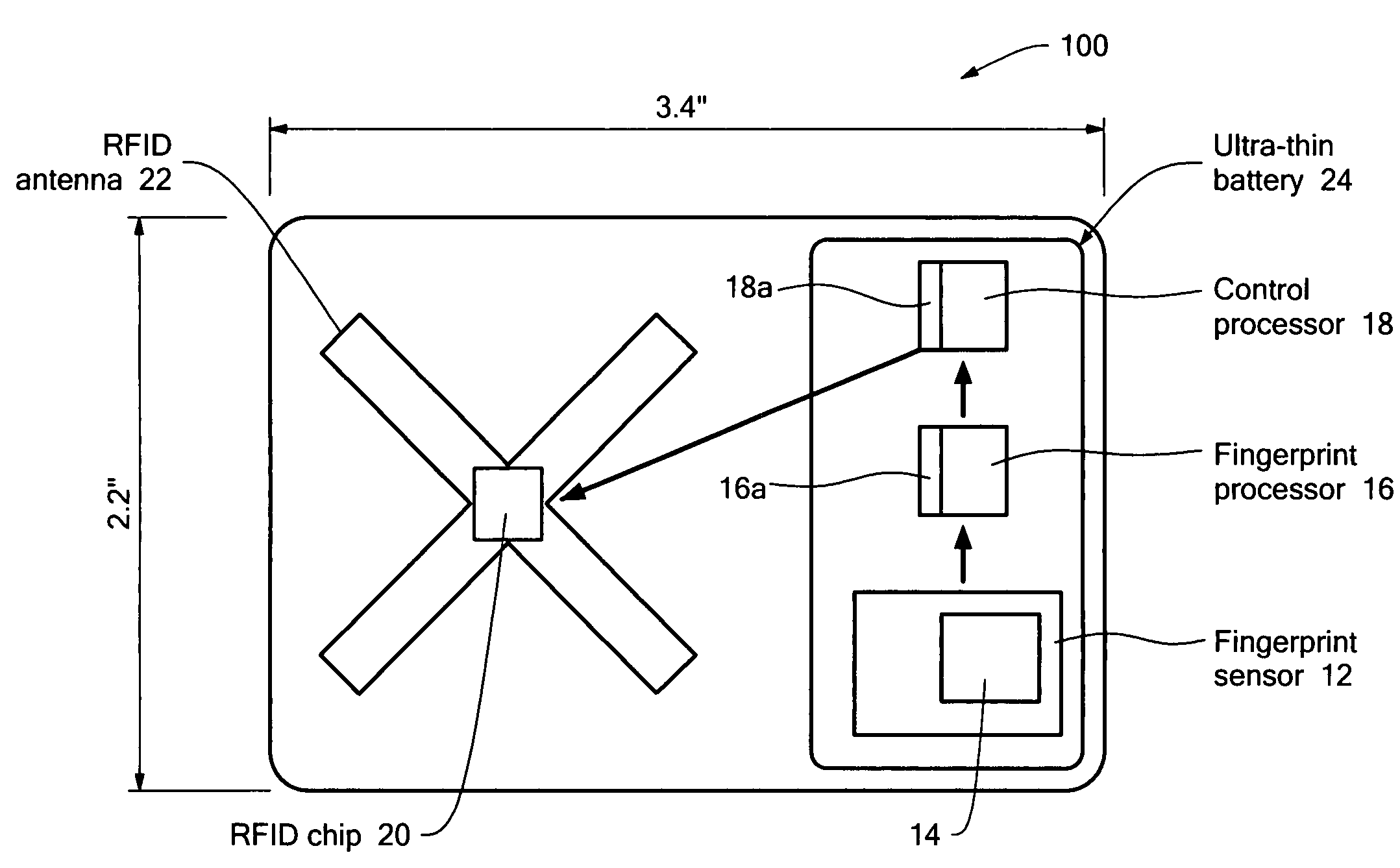
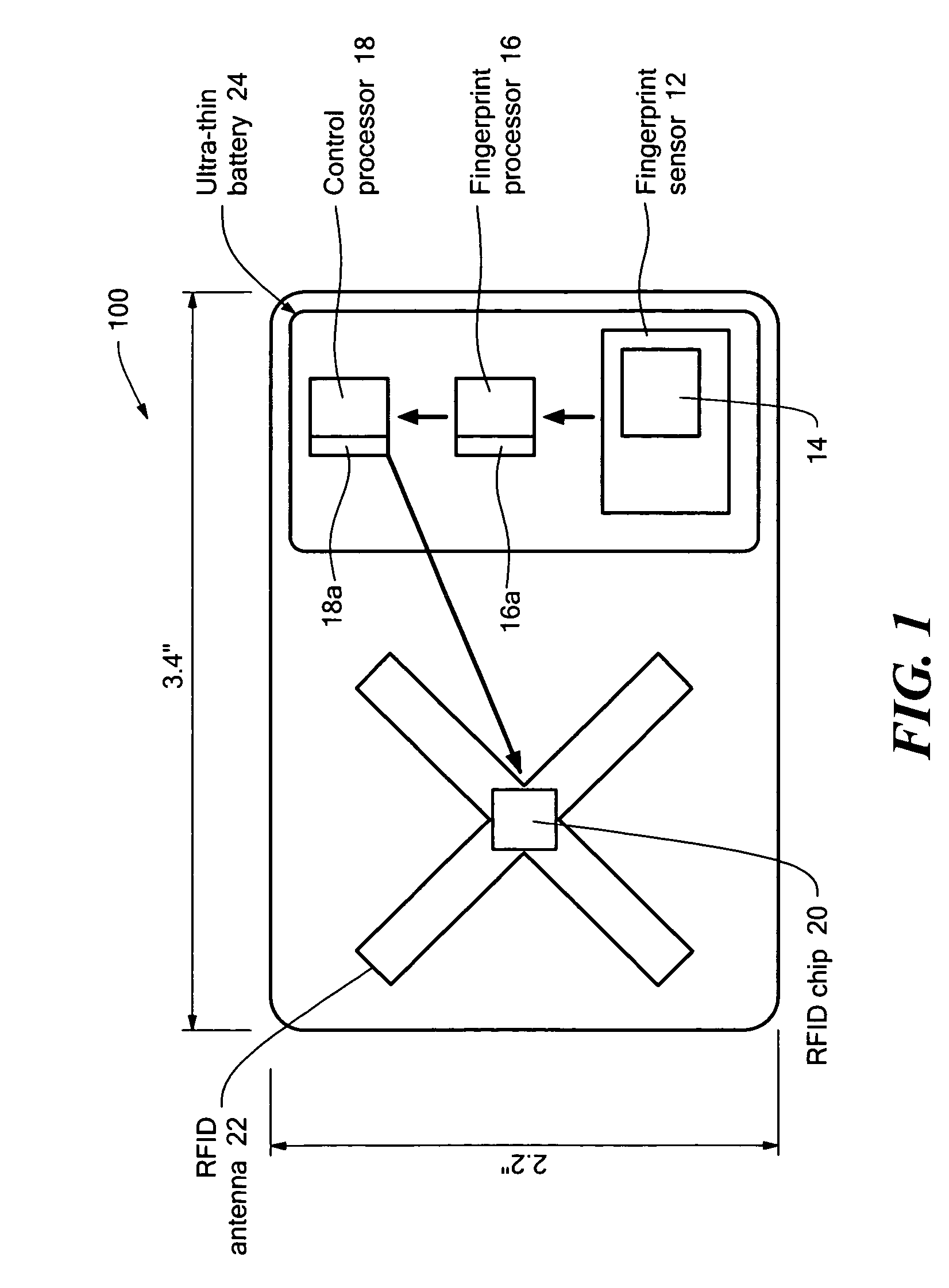
Personal authentication device
ActiveUS7693313B2Communication securityEliminate needCharacter and pattern recognitionIndividual entry/exit registersComputer hardwareBiometric data
An identification card includes a fingerprint sensor, an antenna, a dual-mode radio frequency modulator connected to the antenna and digital circuitry having memory to store a digital word, the digital word including a representation of a fingerprint initially scanned by the fingerprint sensor to identify an individual associated with the identification card. The identification card further includes a control processor connected to the digital circuitry and the radio frequency modulator to communicate a signal to the antenna indicative of a successful match between the fingerprint initially scanned by the fingerprint sensor and newly scanned fingerprint. With such an arrangement, a technique is provided biometrically authenticating the identity of an individual passing through a checkpoint without requiring the individual to stop or exit a vehicle and eliminates the need for a central database of biometric data on individuals.
Owner:RAYTHEON CO
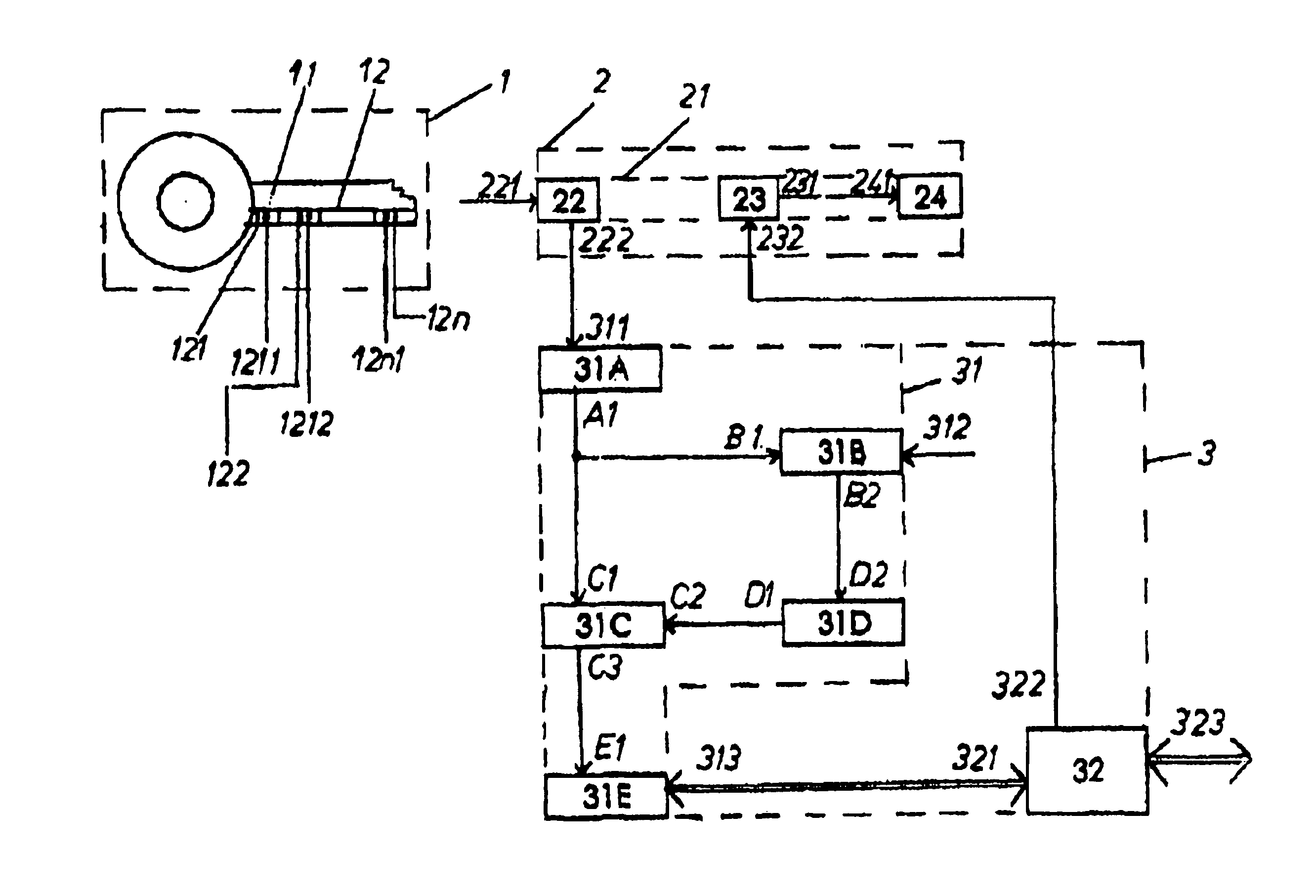
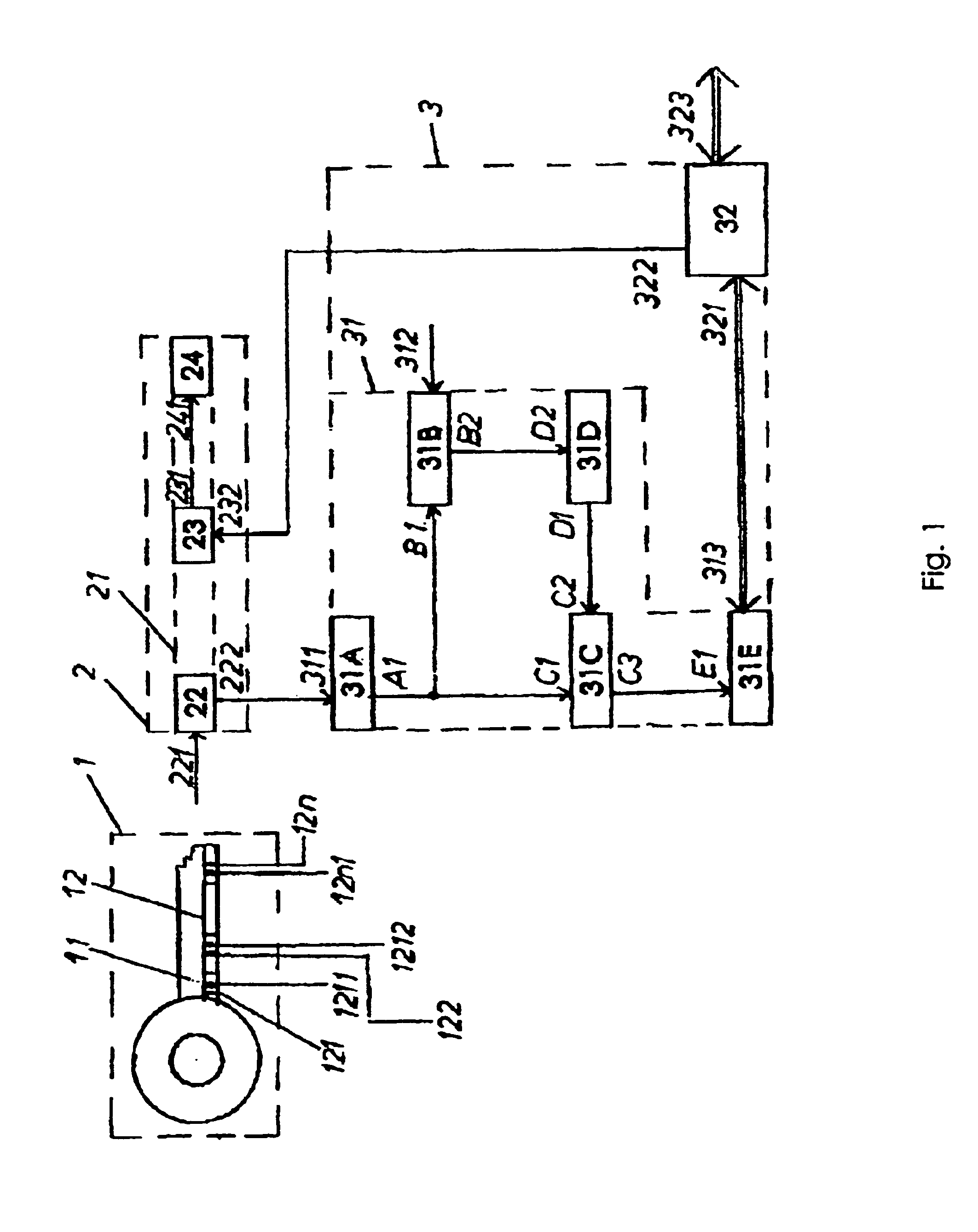
Electronically tested high-security coding and decoding device
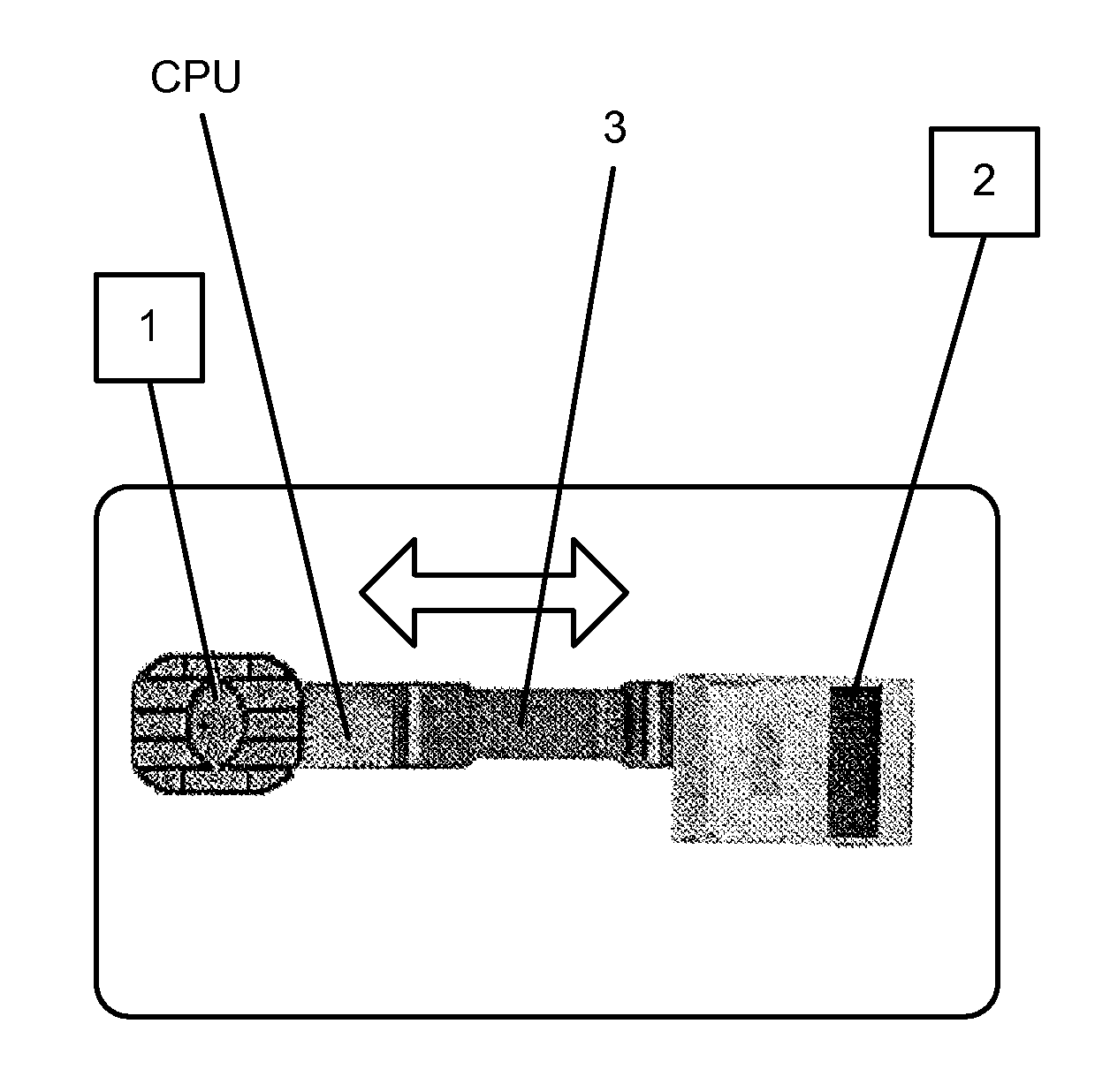
InactiveUS6960991B2Easy to manufactureEasy to getElectric signal transmission systemsDigital data processing detailsEngineeringExecution unit
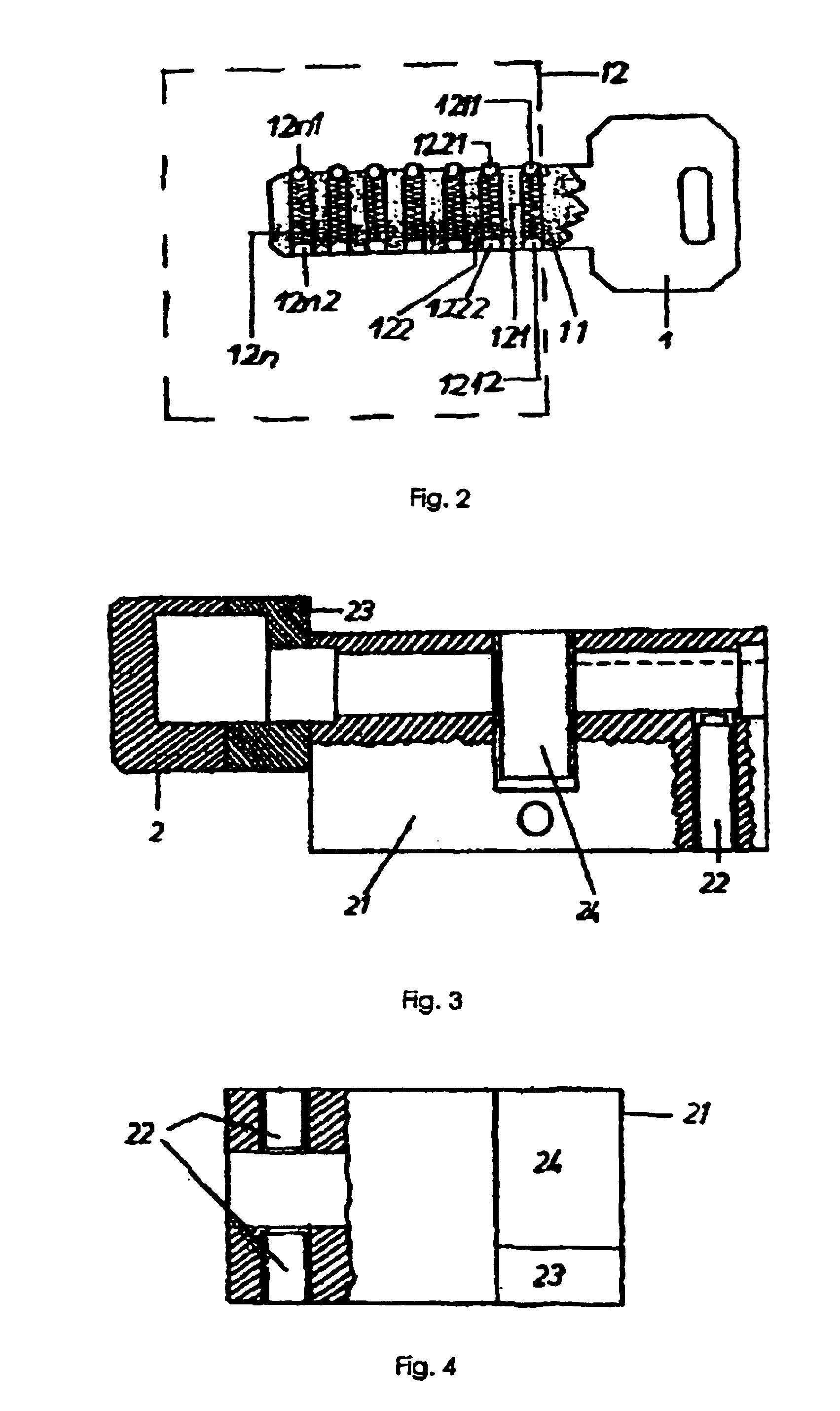
The invention relates to an electronically tested high-security coder / decoder device, comprising a key (1) consisting of a mechanically produced code, a body with integrated interpretation and actuation unit (2) and an electronic processing device (3) connected thereto. The key (1) has at least one pressure generator and pressure sensor unit (12) with code producing pressure elements (121, 122, 12n) and with one pressure transmitting part each. The interpretation and actuation unit (2) is provided with a unit (22) that converts pressure values known as such to electrical signals, an authorization unit (23) and an exe (24). The conversion unit (22) has an input (221) and an output (22). The output (22) is connected to the input (311) of the central processing unit (31). The central processing unit (31) and the interface (32) cooperate to give the electronic processing unit (3). The interface output (322) is connected to the input (232) of the authorization unit (23) whose output (231) is connected to the input (241) of the execution unit (24).
Owner:VILMOS ORCIFALVI +1
Method for hearing aid identification and hearing aid with visual identification
ActiveUS20060256987A1Save powerSave power consumptionHearing aids housingControl powerControl signal
The invention relates to a hearing aid with an identification element (4) for visual identification of the hearing aid (1). According to the invention the hearing aid comprises a programmable signal processor (2), a battery (3) connectable to the signal processor (2), a light emitting element (4) and a switch (5) for controlling power supply to the light emitting element (4) controllable from the signal processor (2). The signal processor (2) is adapted to supply a power signal to the light emitting element (4) indicative of the identity of the hearing aid. The invention also relates to a method for indicating the identity of the hearing aid by the use of a visible light indicator.
Owner:OTICON
Telephone caller authentication
ActiveUS9288062B2Sacrificing robustnessSimplify the authentication processUser identity/authority verificationCommmunication supplementary servicesCarrier signalSpeech sound
Techniques for authenticating the identity of a caller in a telephone call are disclosed. The device generating the call implements encrypting caller identification information and initiating the telephone call, said initiating comprising providing a voice carrier signal including the caller identification information; and simultaneously providing a data carrier signal including the encrypted caller identification information. The receiving device implements receiving the telephone call; decrypting the encrypted caller identification information at the recipient device; and verifying the identity of at least an unknown caller at the recipient device by at least one of verifying the authenticity of a certificate used to encrypt the caller identification information; and comparing the decrypted caller identification information with the caller identification information from the voice carrier signal. A telephony device implementing such an authentication technique is also disclosed.
Owner:IBM CORP
System and method for the secure enrollment of devices with a clearinghouse server for internet telephony and multimedia communications
InactiveUS7398551B2Securely identifyingSecure identityInterconnection arrangementsFinanceThe InternetSecurity level
Enrolling devices with a clearinghouse server for Internet telephony and multimedia communications. Enrollment can be the process of taking a network device (such as a router, gateway, gatekeeper, etc.) and exchanging encrypted information with the clearinghouse server, so that later communications with that device can be secured. The enrollment is done with levels of security and verification that ensures the devices and clearinghouse server is legitimate.
Owner:TRANSNEXUS
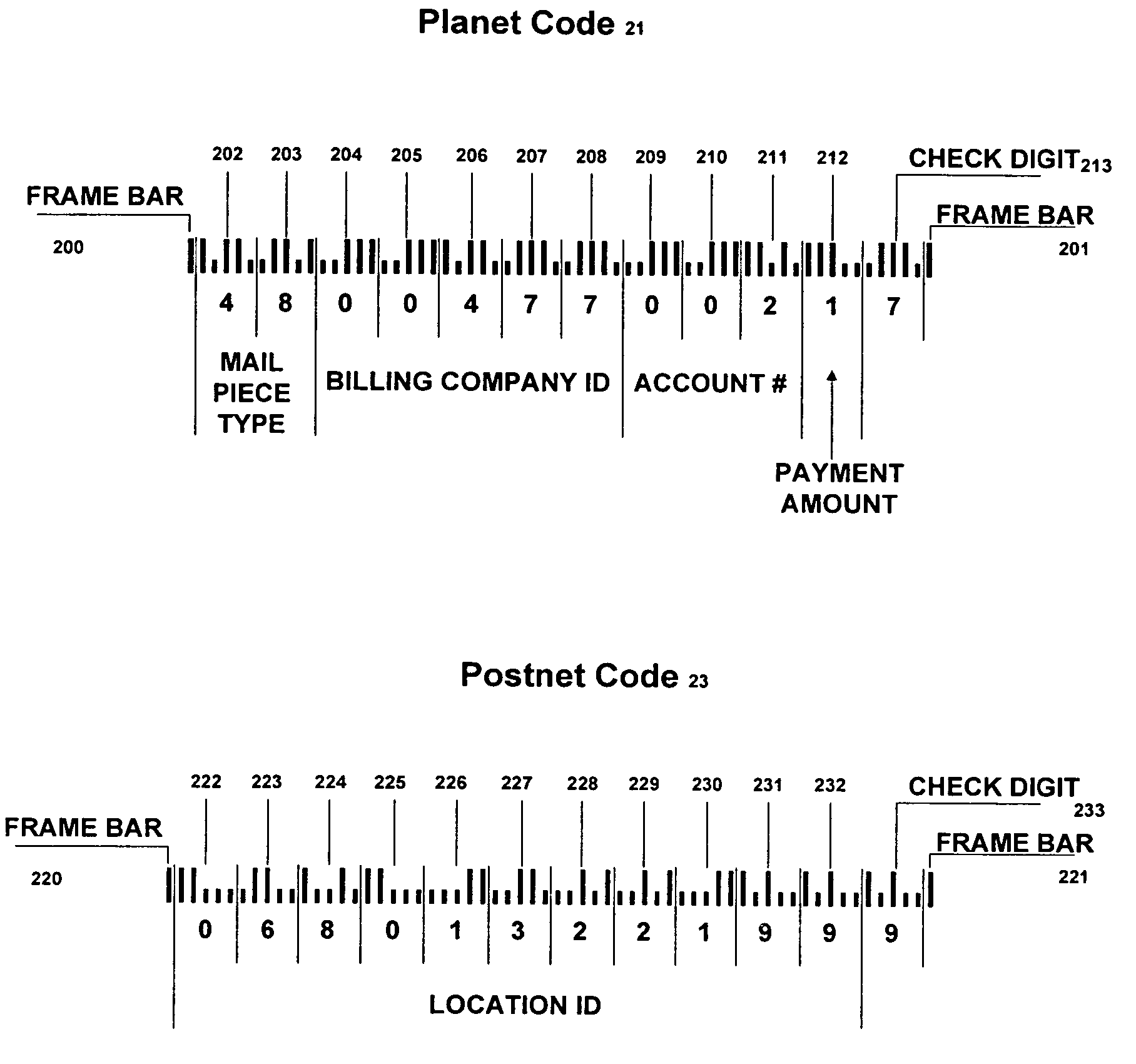
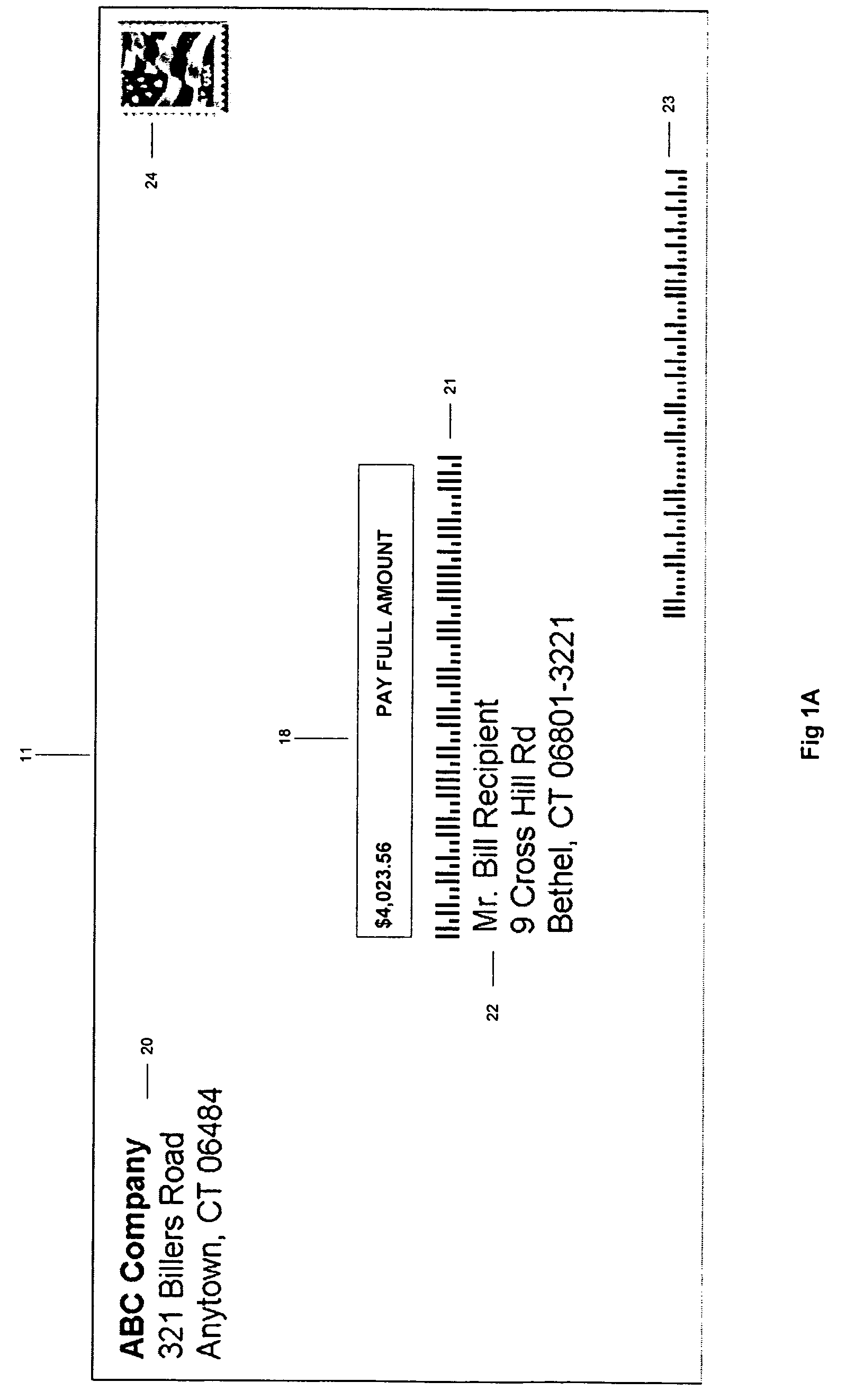
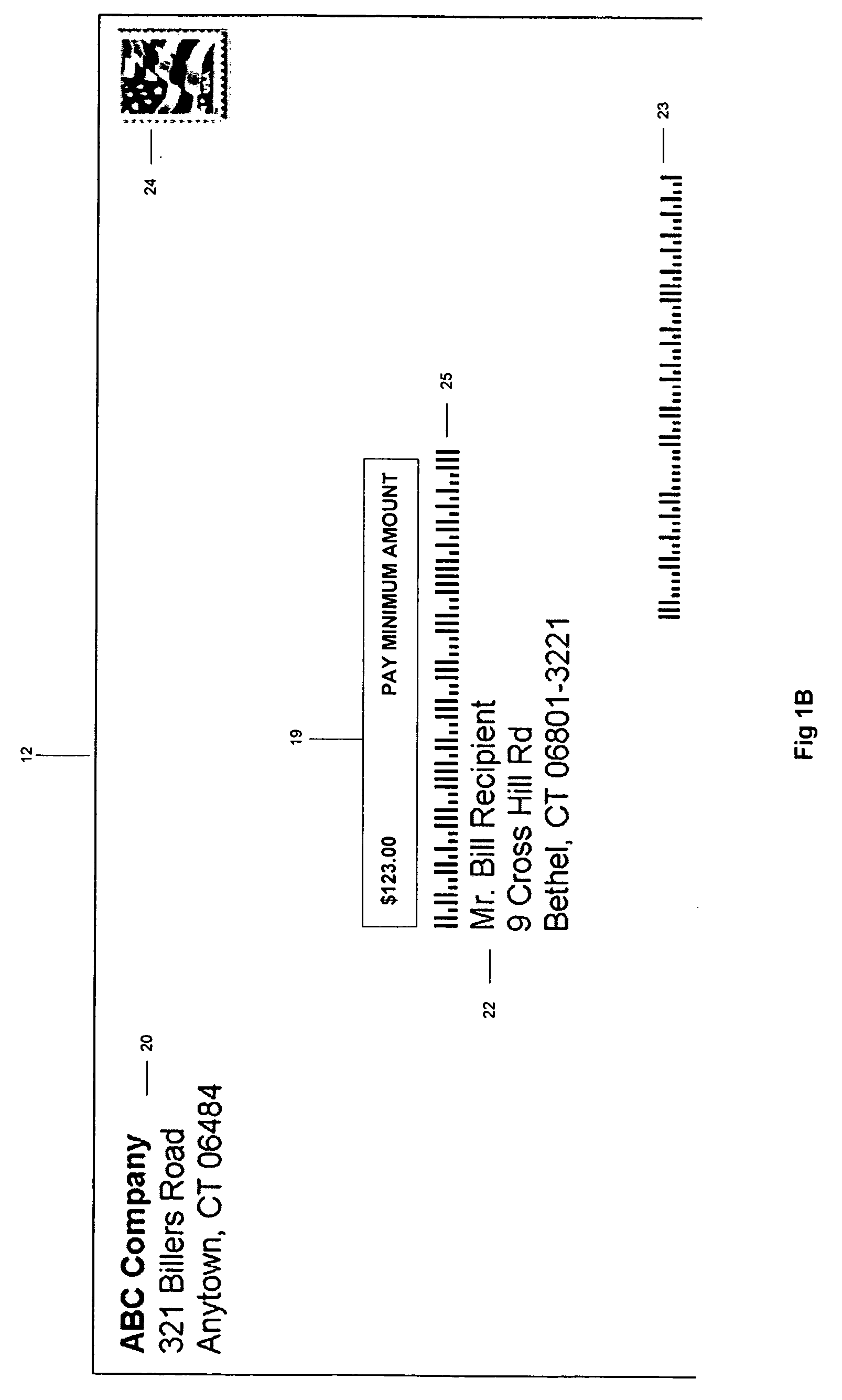
Early bill payment process
A method for enabling a consumer bill recipient to pay his / her bills via the USPS or other carrier sooner than was heretofore possible. The foregoing is accomplished by enabling a company to send a bill to a bill recipient that contains a bill paying return portion in the form of a mail piece having a Planet code and Postnet bar code that references the bill recipient and amount to be paid on the outside of mail piece so that when a scanner at the USPS reads the Planet code and Postnet bar code, the bill recipient's bank account will be debited for the entire amount of the bill or a minimum payment that is due for the bill.
Owner:PITNEY BOWES INC
Software application for the automated drop-off and pick-up of a service item at a service facility
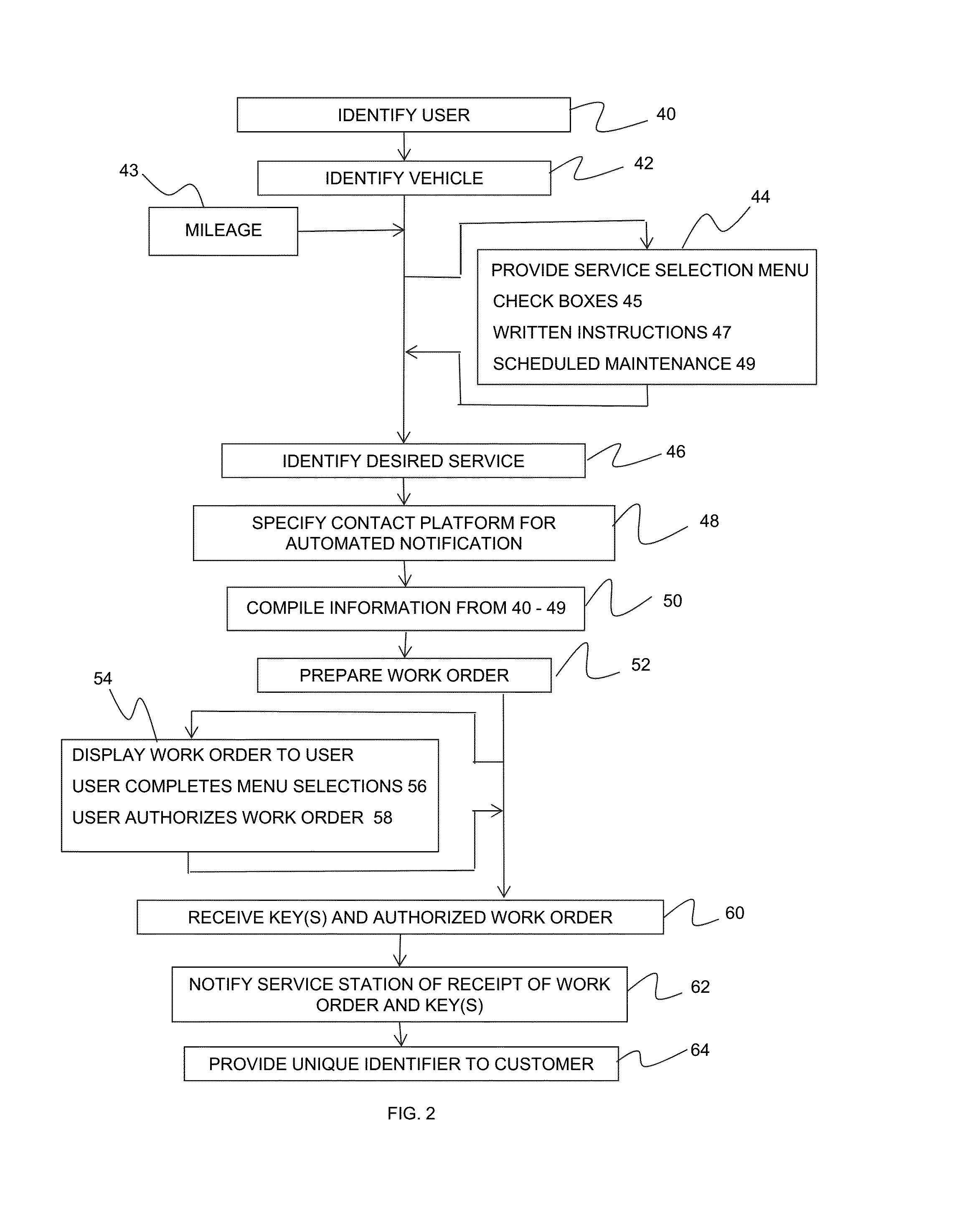
ActiveUS20150262119A1Easy to useFacilitate communicationResourcesLogisticsUnique identifierApplication software
A software application system for the automated drop-off and pick-up for repair, return or exchange of service items including a secure drop-off / pick-up area for the items, a software application that is integrated with a stat system server of a service provider, the software application creating a unique identifier for secure access and retrieval of a service item and the software application having a notification interface to facilitate automated notification for responsive communication between the user and the service provider to describe service or repair required, provide quotations, request and receive additional information and notify the customer on completion of the service and scheduled maintenance using automated voicemail recording, and / or text messaging through a cellular telephone, email, PDA or iPhone using a web-based or mobile based applet.
Owner:SANTO JR LOUIS A
Telephone Caller Authentication
ActiveUS20150237201A1Sacrificing robustnessSimplify the authentication processCommmunication supplementary servicesGraded-service arrangementsCarrier signalSpeech sound
Techniques for authenticating the identity of a caller in a telephone call are disclosed. The device generating the call implements encrypting caller identification information and initiating the telephone call, said initiating comprising providing a voice carrier signal including tire caller identification information; and simultaneously providing a data carrier signal including tire encrypted caller identification information. The receiving device implements receiving the telephone call; decrypting the encrypted caller identification information at the recipient device; and verifying the identity of at least an unknown caller at the recipient device by at least one of verifying the authenticity of a certificate used to encrypt the caller identification information; and comparing the decrypted caller identification information with the caller identification information from the voice carrier signal. A telephony device implementing such an authentication technique is also disclosed.
Owner:IBM CORP
Image processing device, program product and method
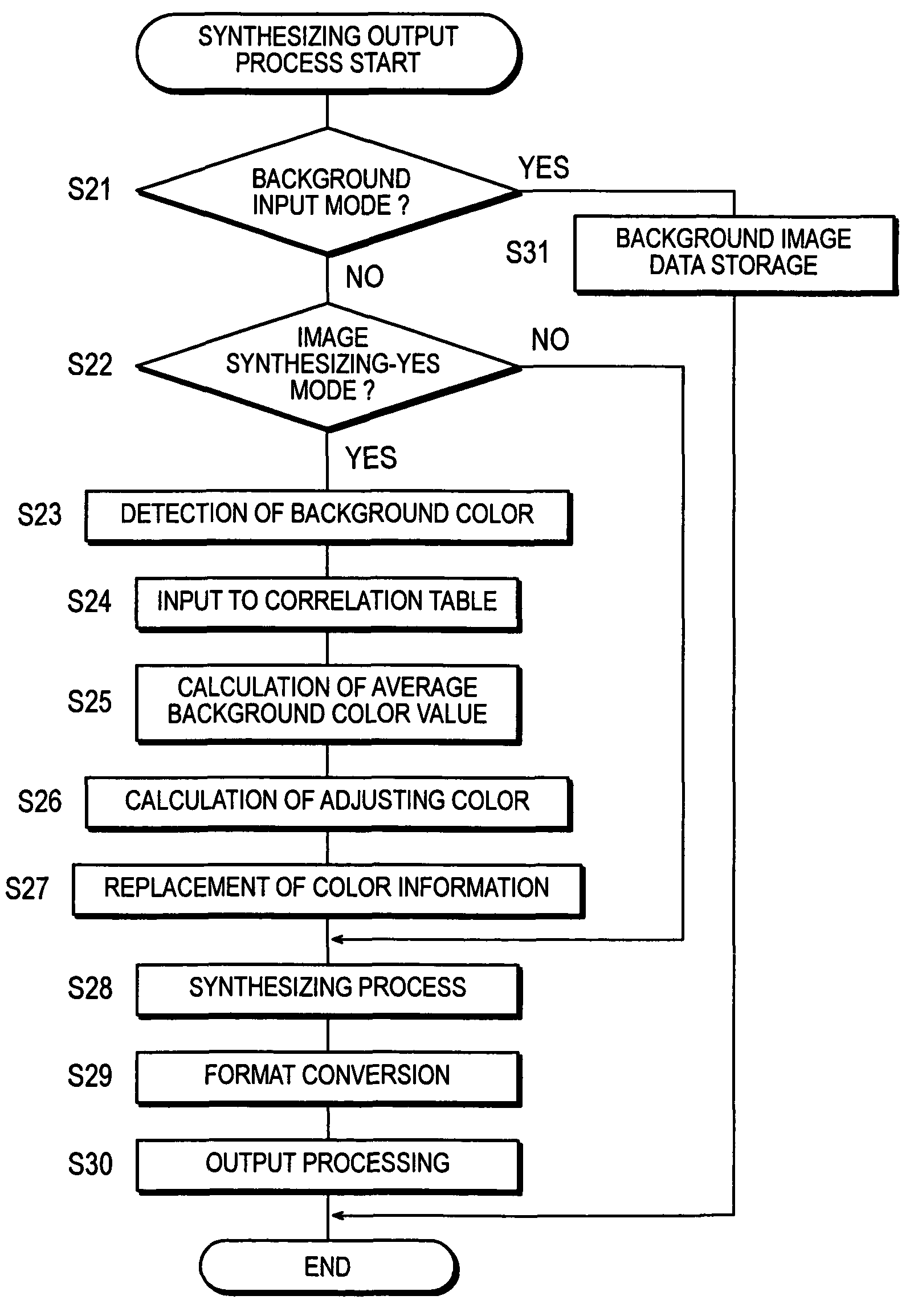
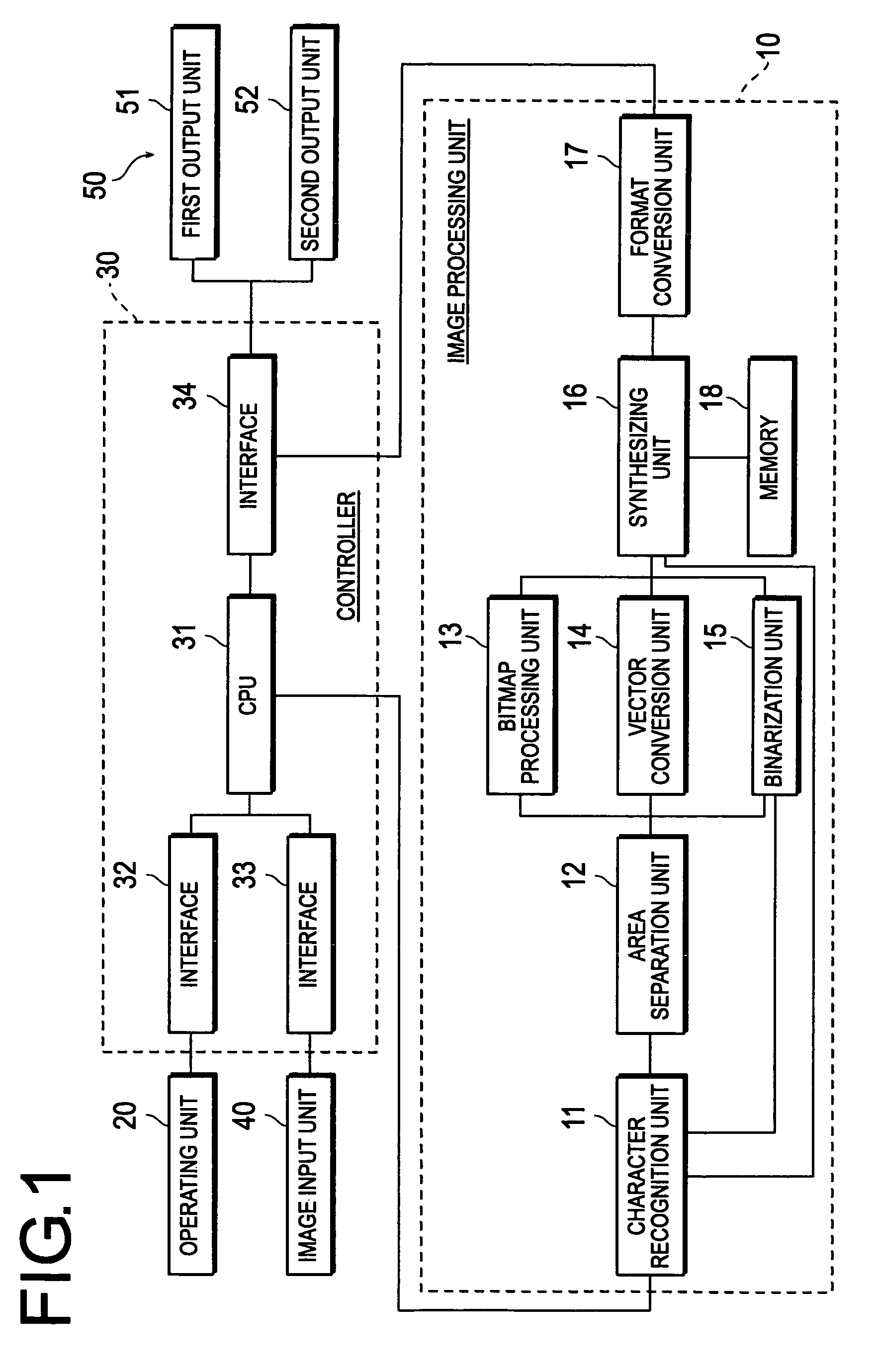
InactiveUS7813546B2Securely identifyingDigitally marking record carriersDigital computer detailsImaging dataBackground image
An image processing device having an image processing unit 10 that adjusts colors of the foreground image data that are approximately equal to a uniform color that makes the boundary between the foreground image data and the background image data recognizable to all the colors of the background image data that serves as the foreground image data's back ground, and synthesizes the foreground image data and the background image data.
Owner:MINOLTA CO LTD
System and method for the secure enrollment of devices with a clearinghouse server for internet telephony and multimedia communications
InactiveUS7203956B2Securely identifyingSecure identityInterconnection arrangementsFinanceThe InternetSecurity level
Enrolling devices with a clearinghouse server for Internet telephony and multimedia communications. Enrollment can be the process of taking a network device (such as a router, gateway, gatekeeper, etc.) and exchanging encrypted information with the clearinghouse server, so that later communications with that device can be secured. The enrollment is done with levels of security and verification that ensures the devices and clearinghouse server is legitimate.
Owner:TRANSNEXUS
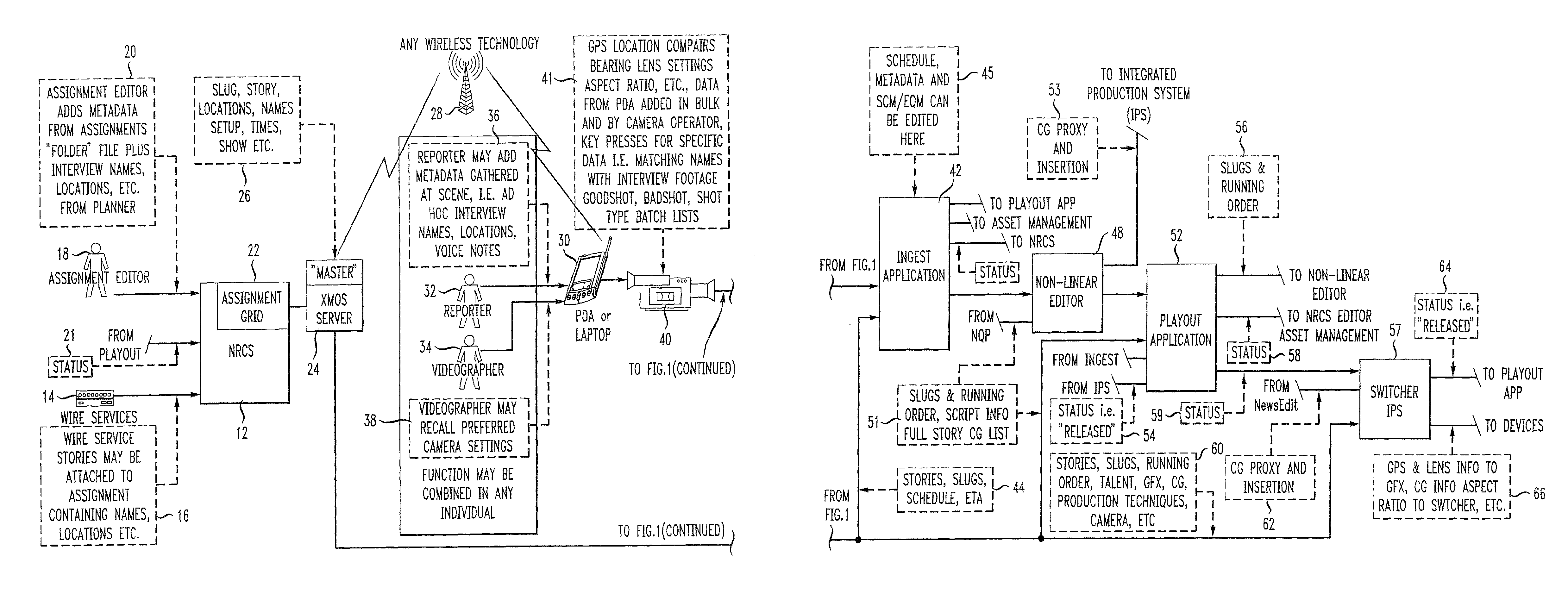
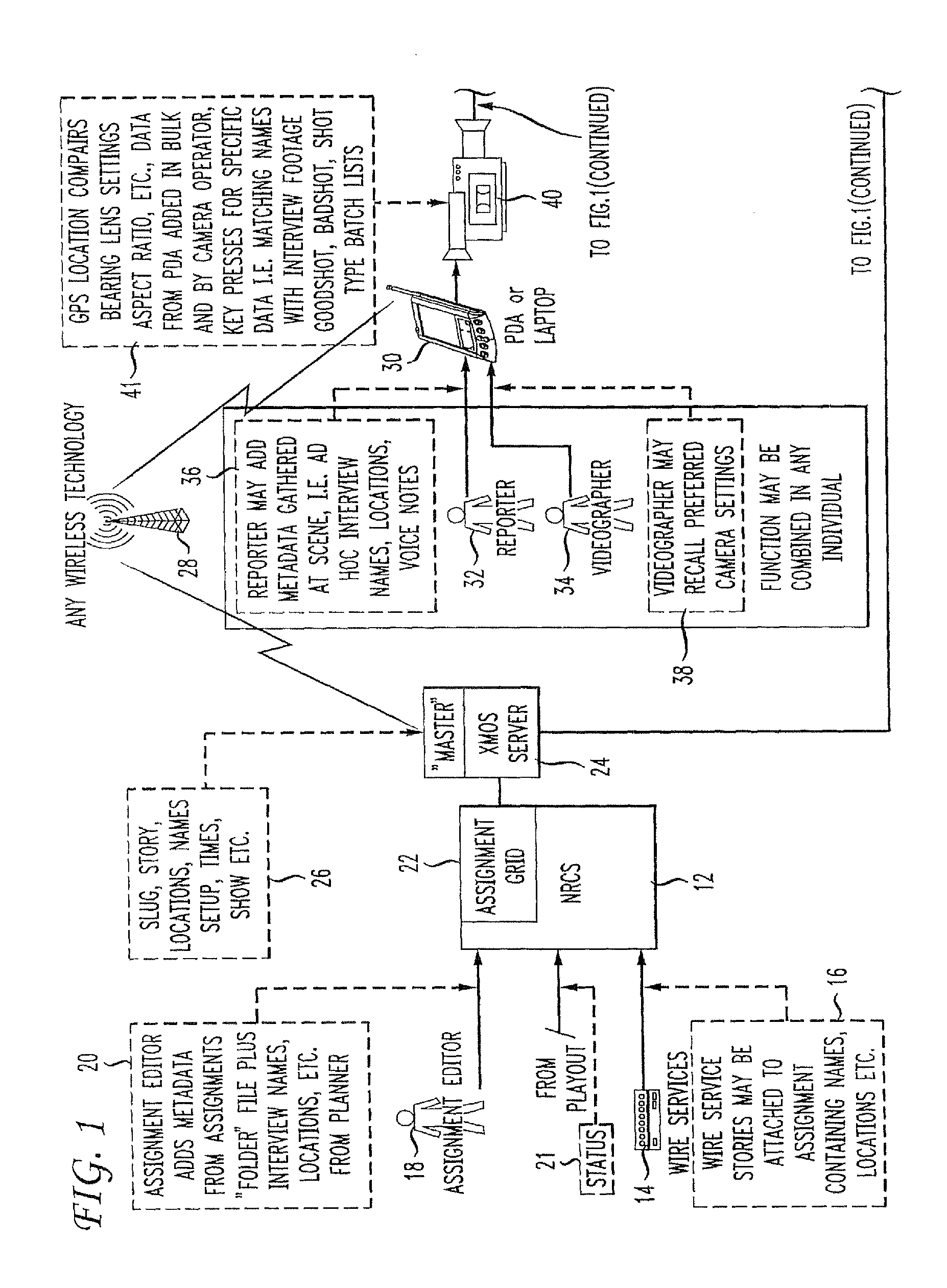
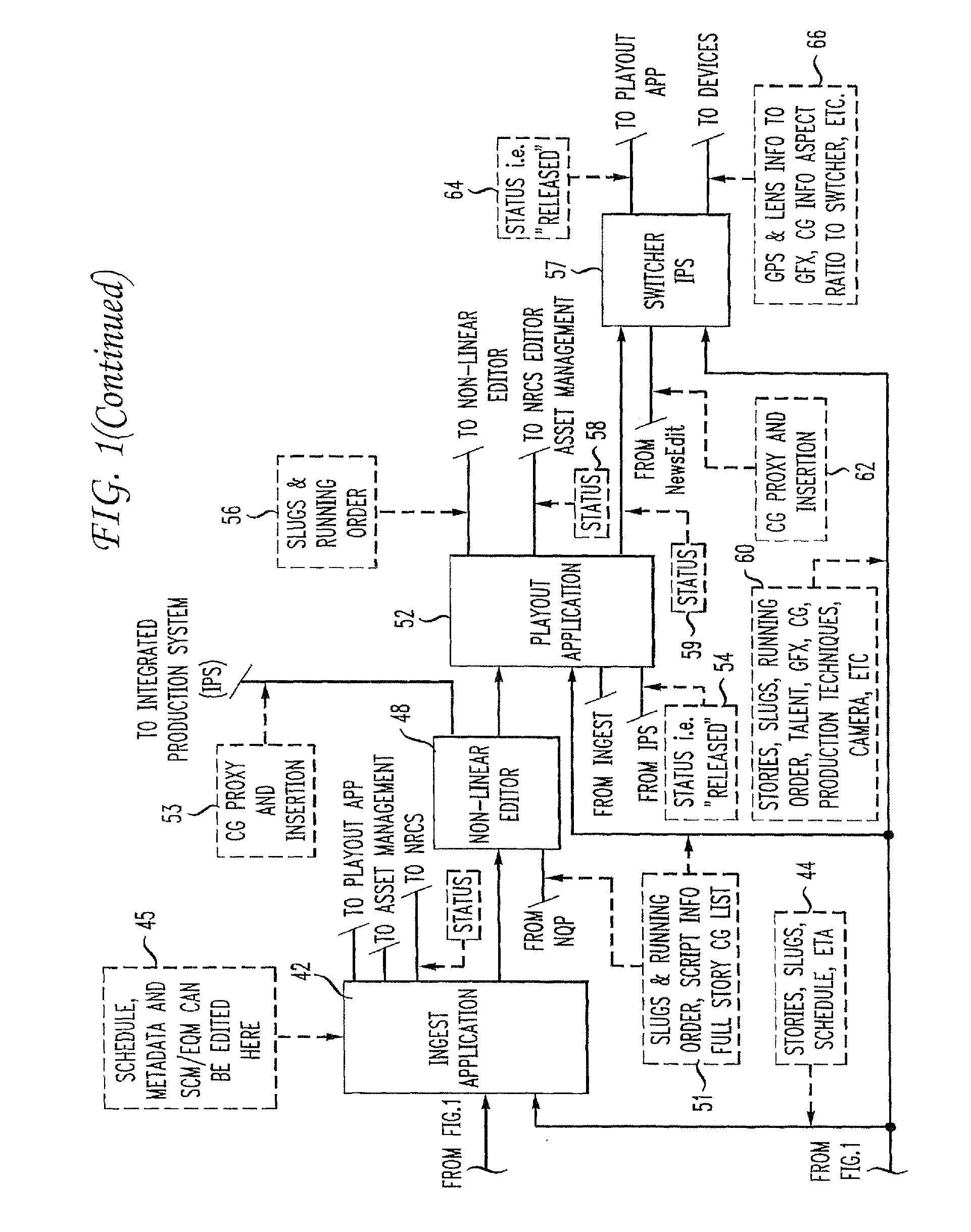
Automatic metadata extraction and metadata controlled production process
ActiveUS20110173196A1Securely identifyingDigital data processing detailsElectronic editing digitised analogue information signalsInformation captureVisual perception
Metadata generated at the outset of an audio visual program, such as a television undergoes transmission to a field device associated with a capture device operated by production personnel, such as a news reporter and / or a videographer to capture one of audio and / or video information. The production personnel will typically edit the metadata for incorporation into the file structure of audio and / or visual information captured by the capture device. A server receives and updates the original metadata using the metadata in the file structure of the capture audio and / or video information, thus effectively harvesting the original metadata.
Owner:GRASS VALLEY CANADA
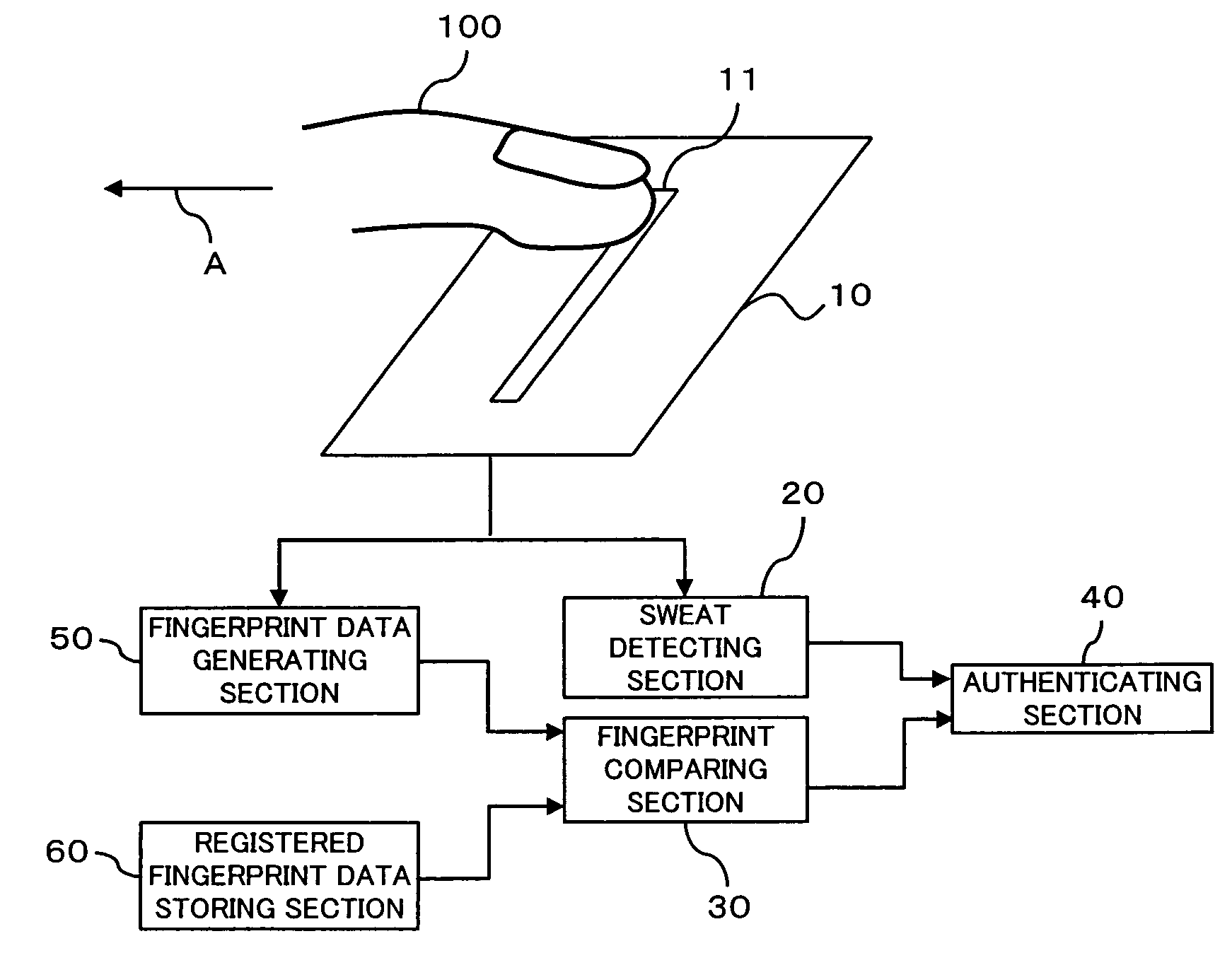
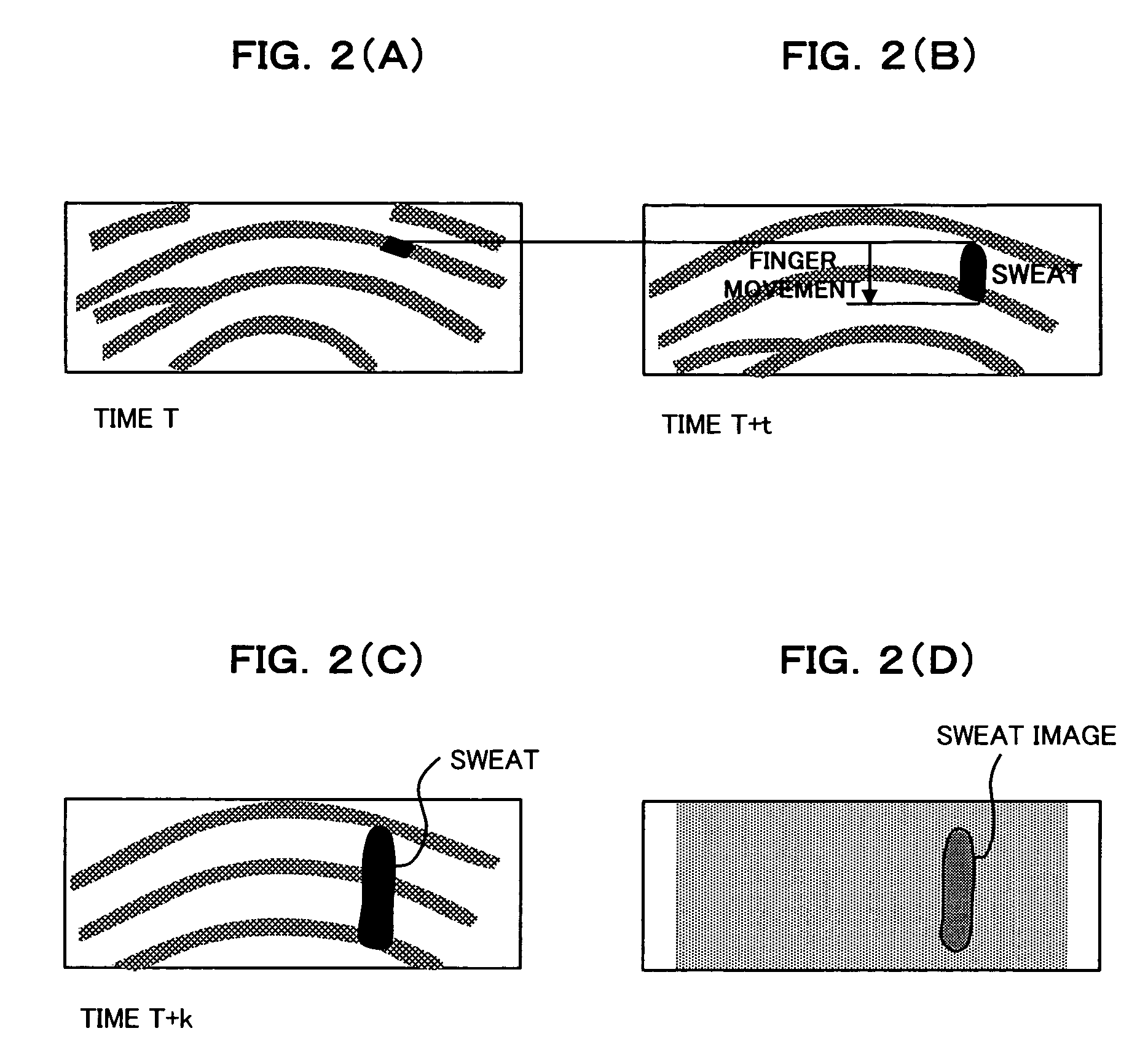
Living-body detecting apparatus and method, and authenticating apparatus having living-body detecting function
InactiveUS7362888B2Securely identifyingObviating utilityPerson identificationElectric/magnetic contours/curvatures measurementsBiological bodyPalm print
The present invention provides an authenticating apparatus for employing a living-body such as, for example, a fingerprint and a palm print, thereby to make personal authentication, and for purpose of allowing a detection as to whether or not a subject is a living-body to be made securely, thus making it possible to securely identify a non-living body such as, for example, an artificial finger made of gummi, the apparatus comprises and is configured of: an image obtaining means for continuously obtaining images of an integument surface of the living-body, which moves while touching an obtaining plane; and a secretion product detecting means for detecting existence of a secretion product to be secreted from an exocrine gland of the integument surface of the living-body, based upon a plurality of the images obtained continuously by this image obtaining means.
Owner:FUJITSU LTD
Method for configuring access to, remote controlling, and monitoring at least one home automation device forming part of a home automation installation
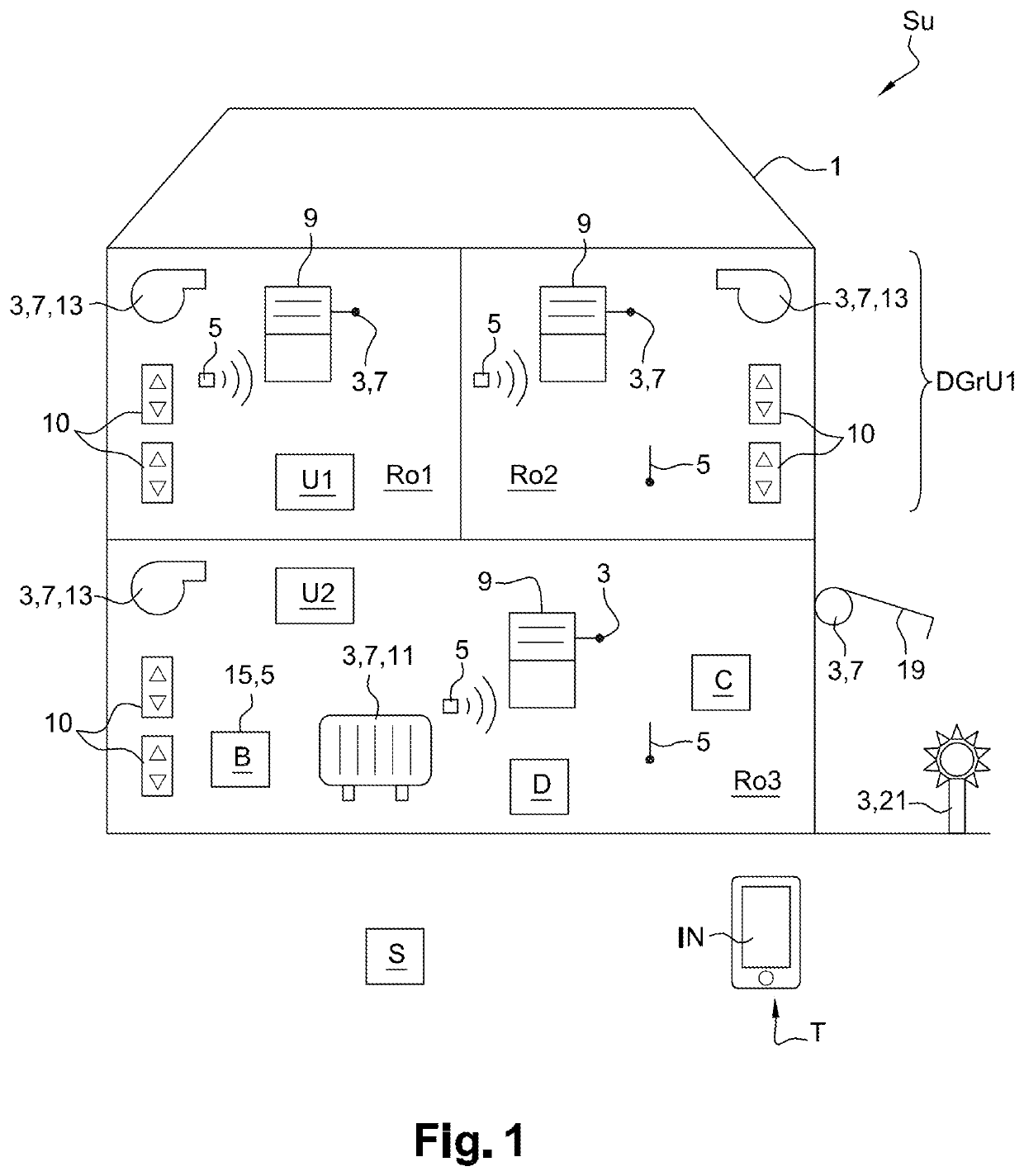
ActiveUS20200233388A1Easily obtain accessImprove performanceComputer controlData switching by path configurationData transmissionUser profile
The present invention relates to a method of remotely configuring access to at least one home automation device (D) that is part of a home automation installation (Su), the home automation installation comprising at least one home automation device (D) and at least one central control unit (U), and the method being performed by a first remote access service (Svc1) carried out by a management unit and comprising the following steps: receiving (ECfSvc19; ECfSvc14) a remote access request (MP, Min) relating to at least one home automation device (D) linked to the profile of a user (Usr1) and intended for a second service (Svc2), the request being relative to an identifier (UsrlID1) of the user (UsrlID1) with the first service (Svc1); receiving (ECfSvc16, ECfSvc19) an authorization in reply to the access request by the user (Usr1); configuring (ECfSvc110) an access authorization repository so as to accept at least one control command (MCa) arriving from a second service (Svc2), or the transmission of monitoring data (MSa) to the second service (Svc2) for the home automation device (D) linked to the user profile (USr1). The invention also relates to a control and monitoring method.
Owner:OVERKIZ
Method and device for safeguarding of a document with inserted signature image and biometric data in a computer system
ActiveUS7971063B2Improper useConfidenceDigital data processing detailsUser identity/authority verificationBiometric dataHash function
A method for safeguarding an electronic document includes inserting at least one digital signature image into the electronic document and generating a first check sum for the electronic document, with or without optionally-inserted biometric signature data, using a first hash function. A second check sum is then generated using a second hash function. The first check sum and the biometric data, if provided, are then symmetrically encrypted using a key that is the sum of the second check sum and a generated random value. The symmetrically-encrypted first check sum is attached to the document. The random value is then asymmetrically encrypted using a first public key of a first key pair and the asymmetrically-encrypted random value is added to the document.
Owner:STEPOVER
Device for protecting a commercial article against theft
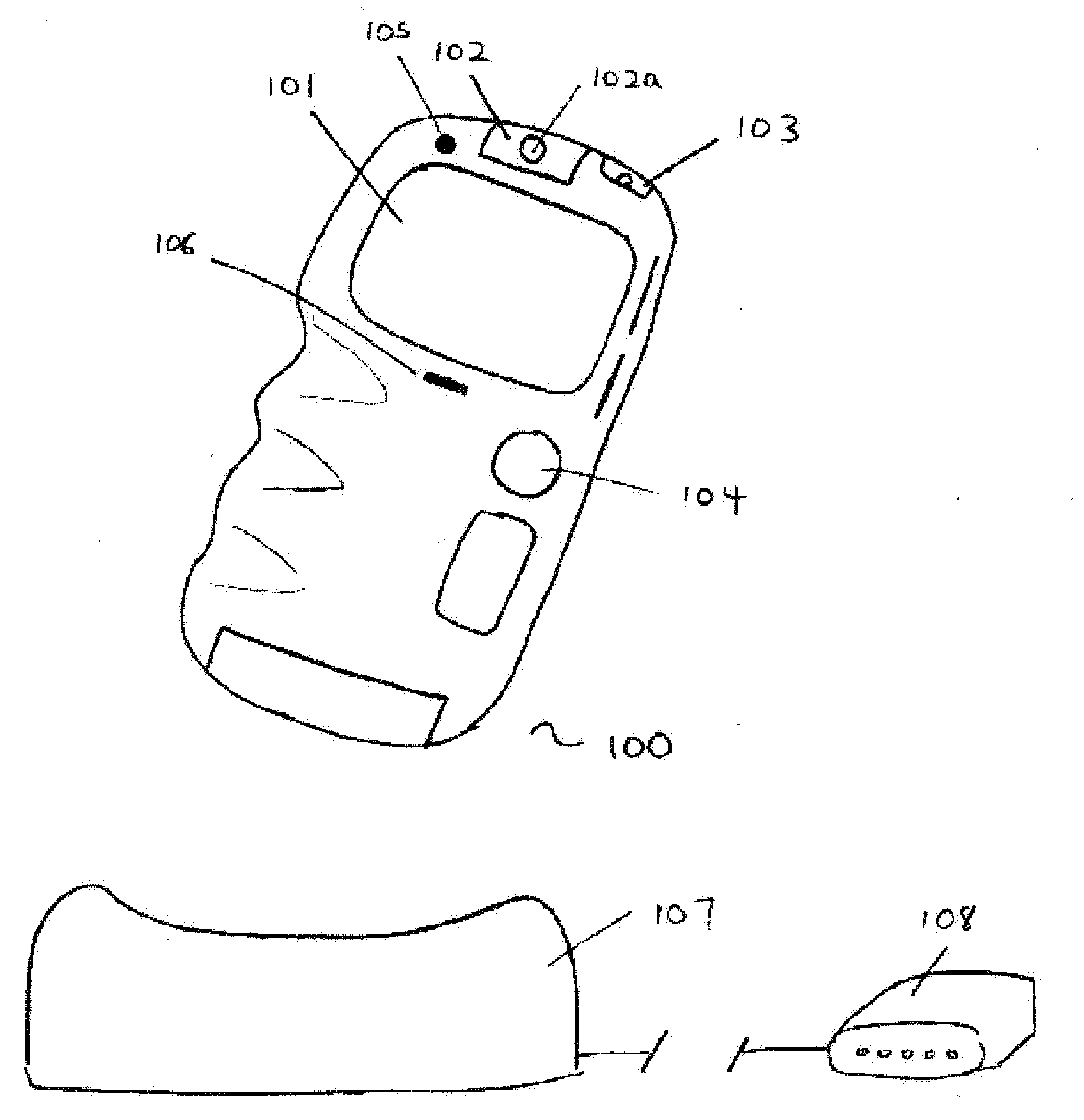
InactiveUS20190012632A1Reduction in inventory differenceProvide securityLocks for portable objectsCo-operative working arrangementsLocking mechanismEngineering
A device is provided for protecting a commercial article which is a physical object (10, 32), the article being packaged against theft or not. The device (12, 42) includes at least one active or passive member that is capable of emitting electromagnetic waves out from the device or receiving electromagnetic waves from outside the device. The device also includes elements for attaching and locking the device to the physical object or to the packaging of same in a locked position such that a user cannot separate the device from the physical object without an external tool. The locking elements include a locking mechanism. At least one optically readable code (24) uniquely identifies the physical object to which the device is intended to be attached and which is separate from a commercial article code (EAN, EPC, etc.) assigned to the physical object, as a commercial article.
Owner:EXAQTWORLD
Fabricating unique chips using a charged particle multi-beamlet lithography system
ActiveUS20180120704A1Securely identifyingMinimizing potential for public exposureSemiconductor/solid-state device detailsSolid-state devicesData setLithographic artist
Method of manufacturing electronic devices using a maskless lithographic exposure system using a maskless pattern writer. The method comprises generating beamlet control data for controlling the maskless pattern writer to expose a wafer for creation of the electronic devices, wherein the beamlet control data is generated based on a feature data set defining features selectable for individualizing the electronic devices, wherein exposure of the wafer according to the beamlet control data results in exposing a pattern having a different selection of the features from the feature data set for different subsets of the electronic devices.
Owner:ASML NETHERLANDS BV
Device and method for identifying a component surrounded by an outer package
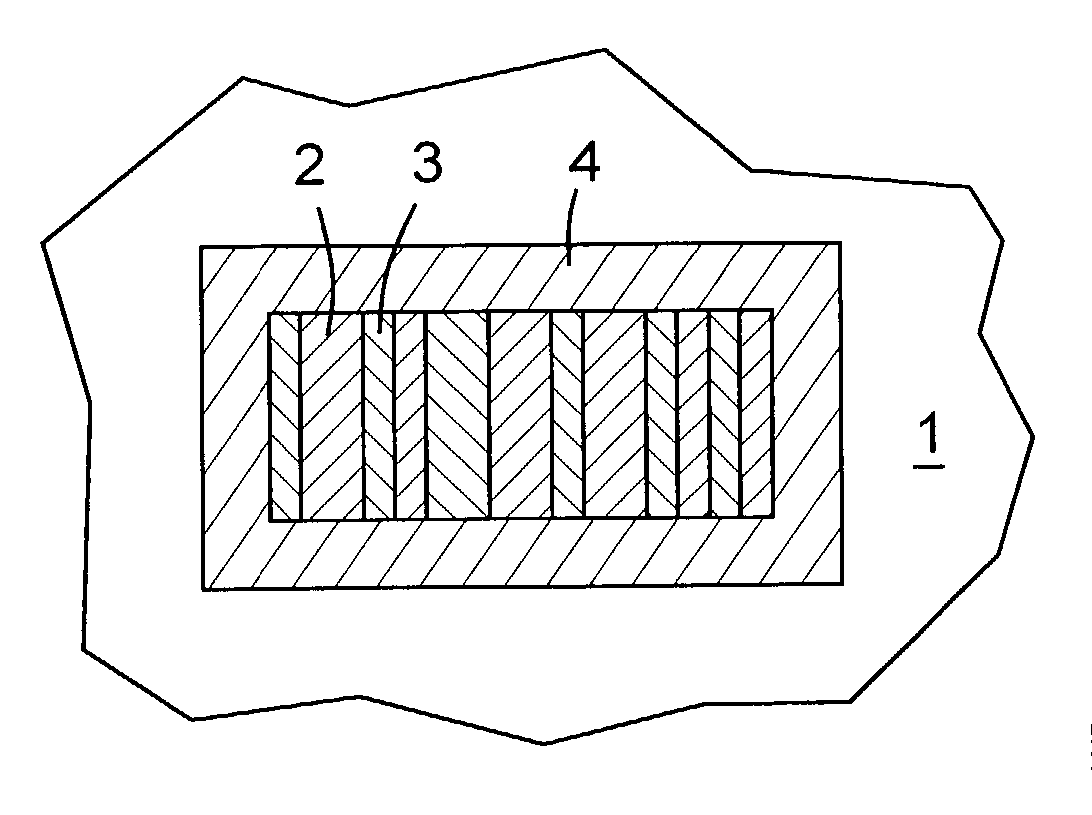
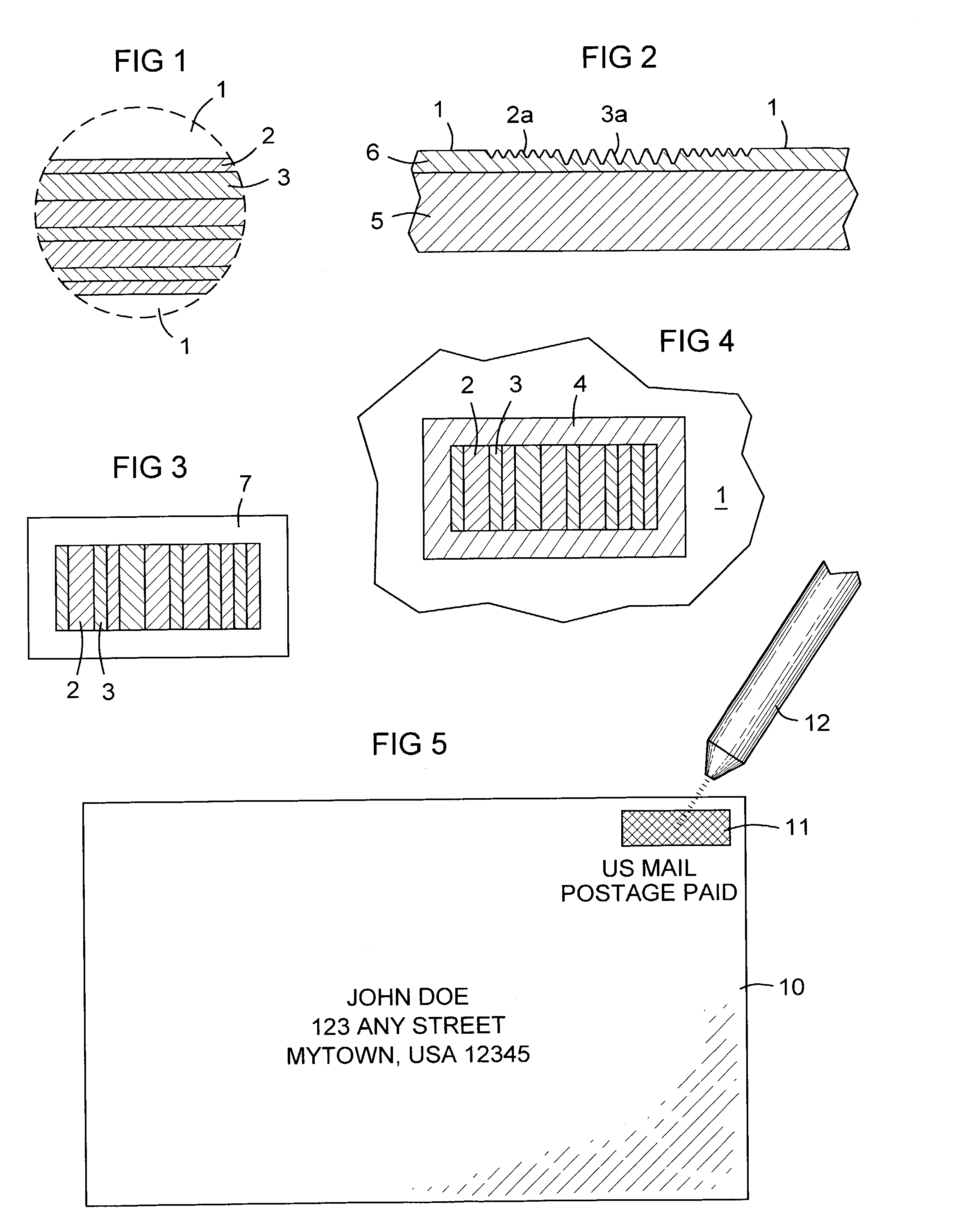
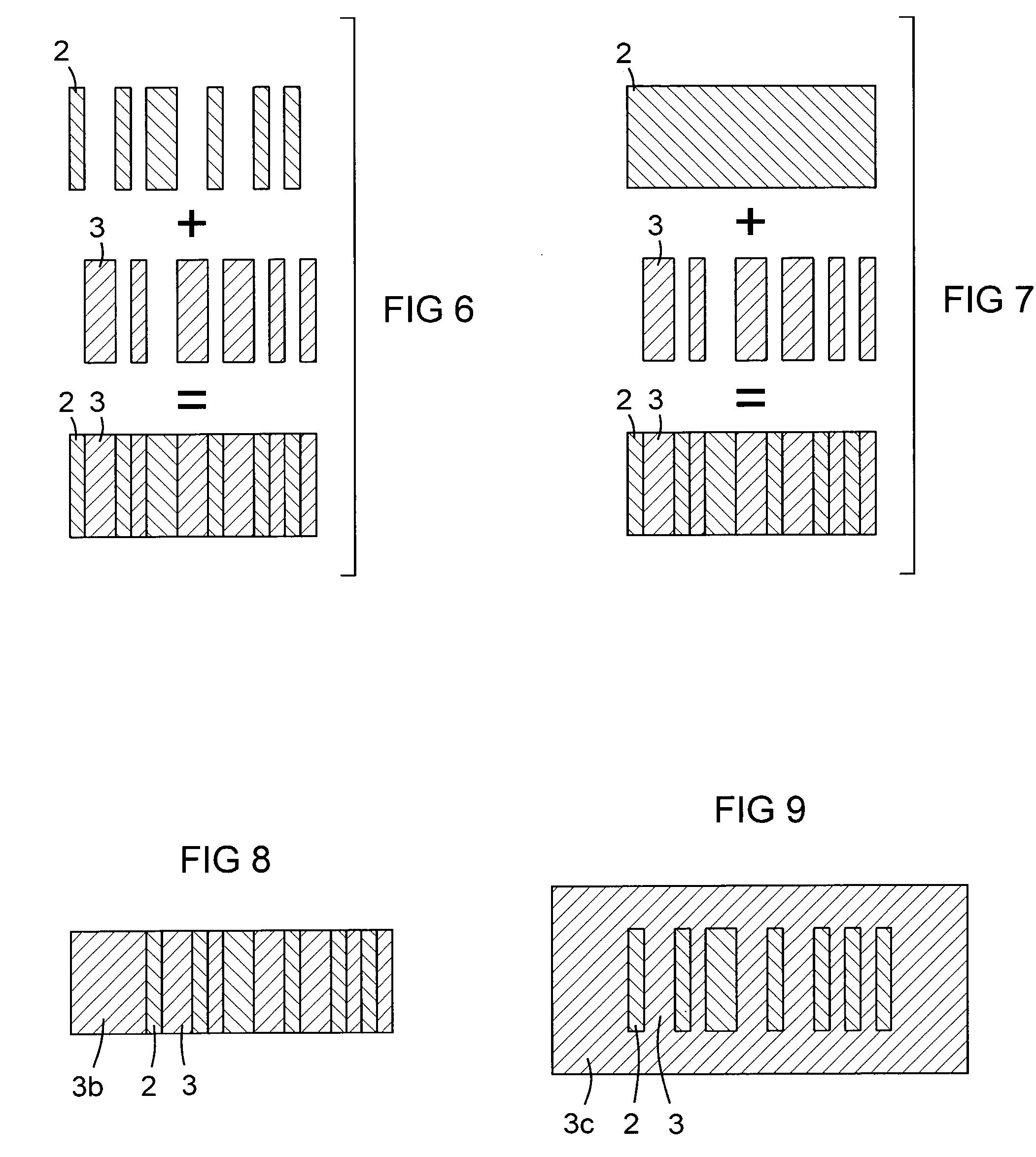
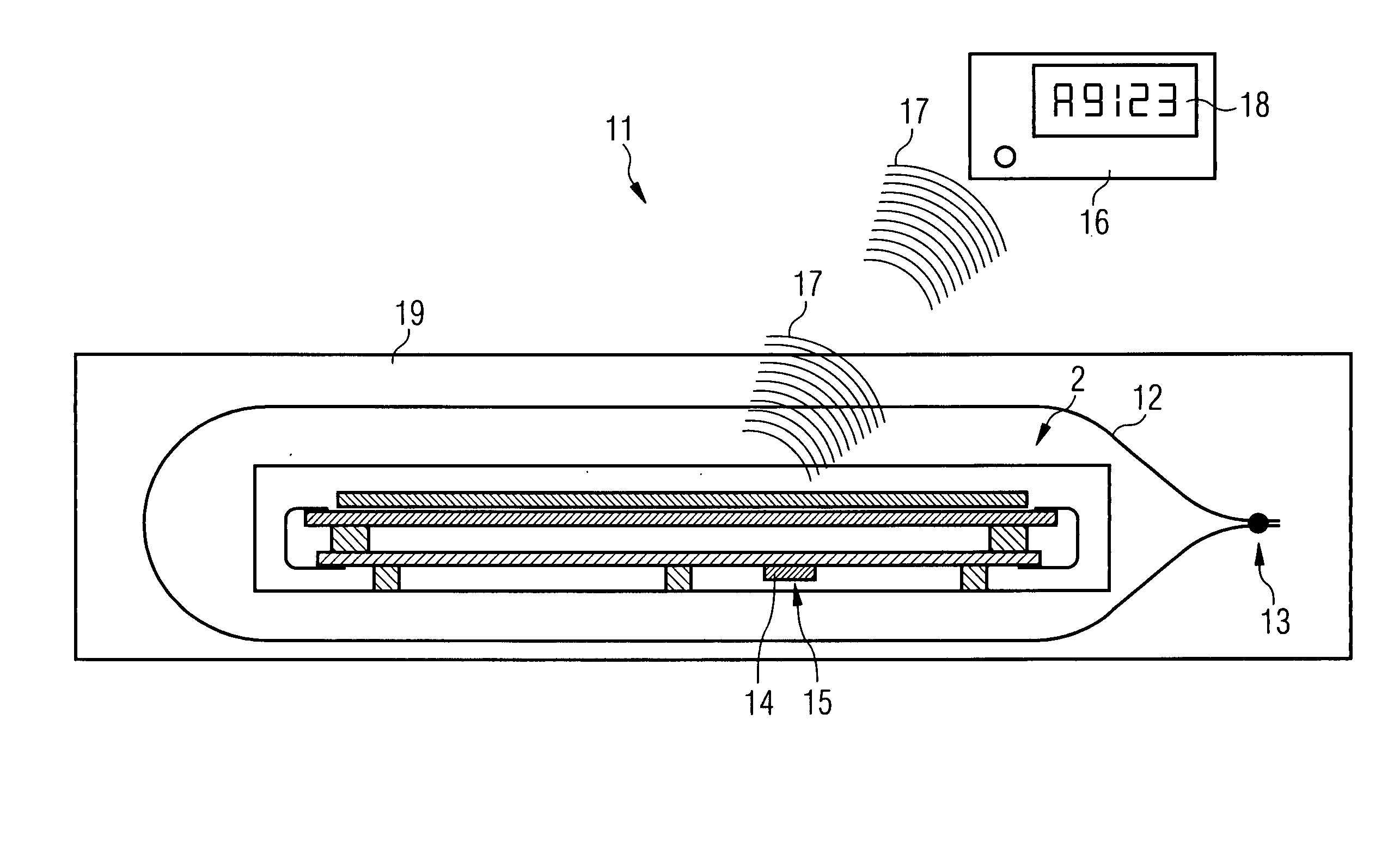
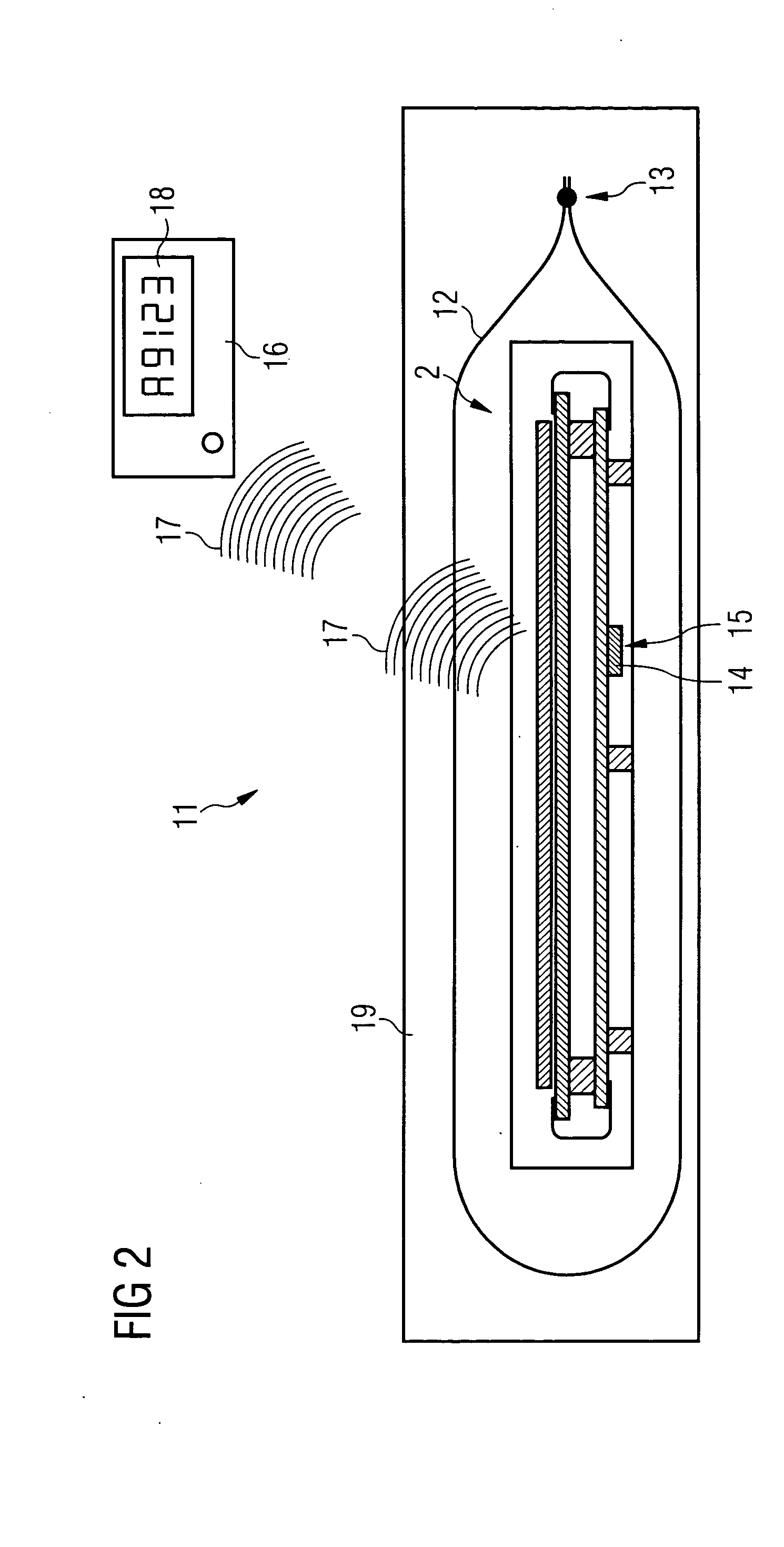
ActiveUS20050073414A1Increase information densityHigh densityTransistorSemiconductor/solid-state device detailsBiomedical engineeringR package
Device and method for identification of a component surrounded by an external package A device (11) for identification of a component (2) surrounded by an external package (12, 19) is described. For this purpose an identification element (14) is arranged in the area of the component (2). The identification element (14) can be identified through the external package by means of an acoustic method and / or scanning method. Furthermore a method for identifying a component (2) surrounded by an external package (12, 19) using the device in accordance with the invention (11) is described.
Owner:SIEMENS HEALTHCARE GMBH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com