Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
69results about How to "Secure Communications" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
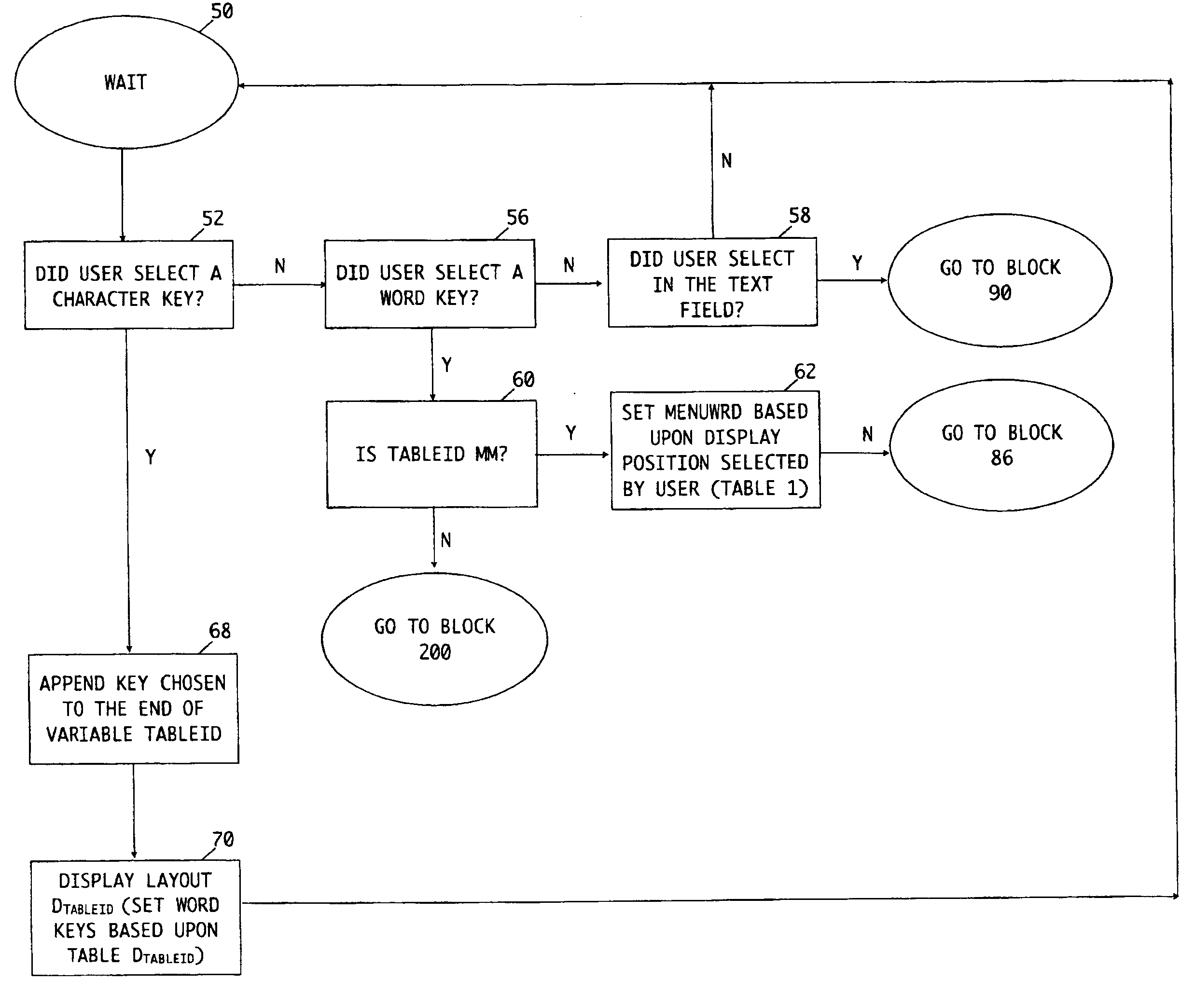
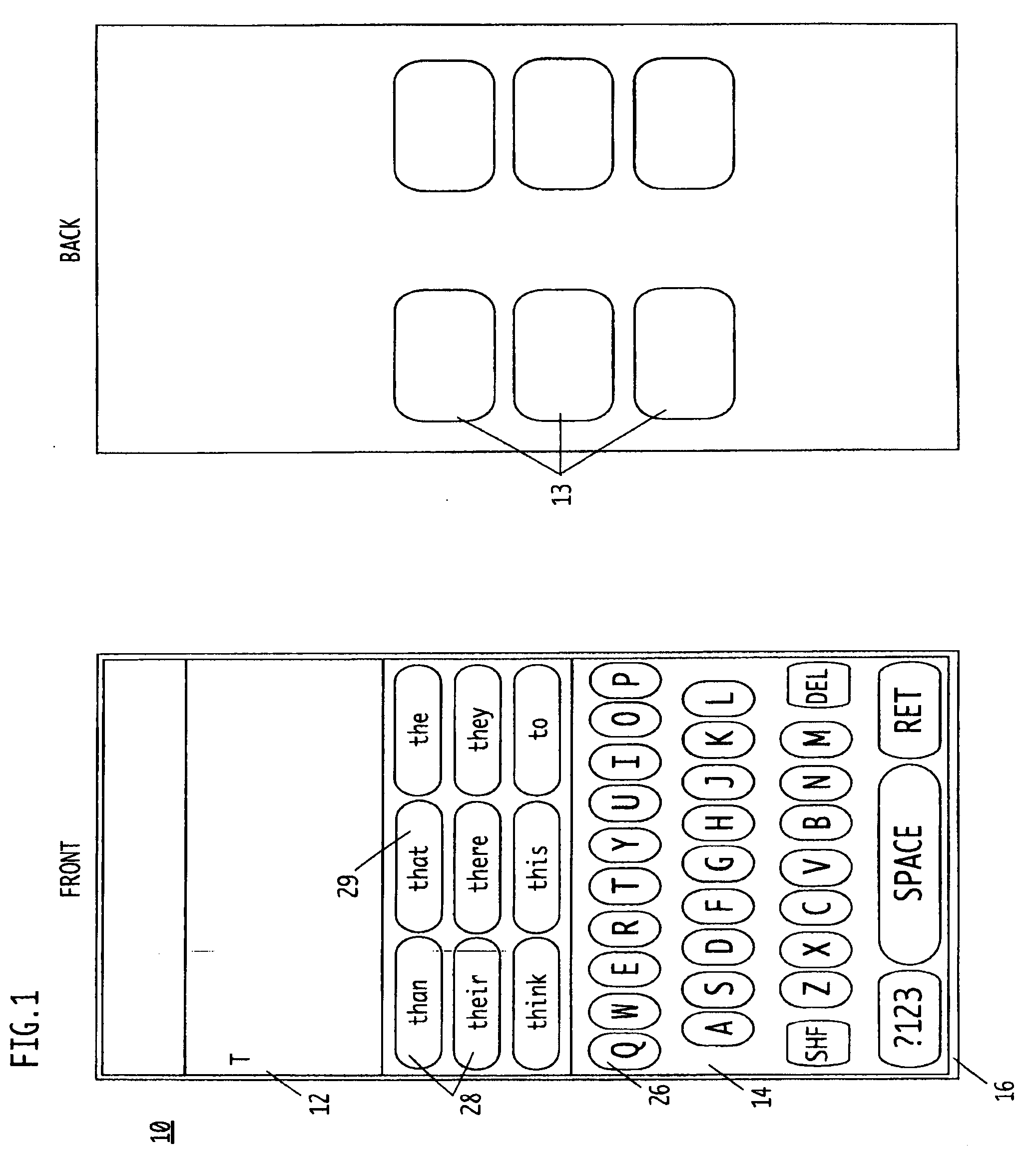
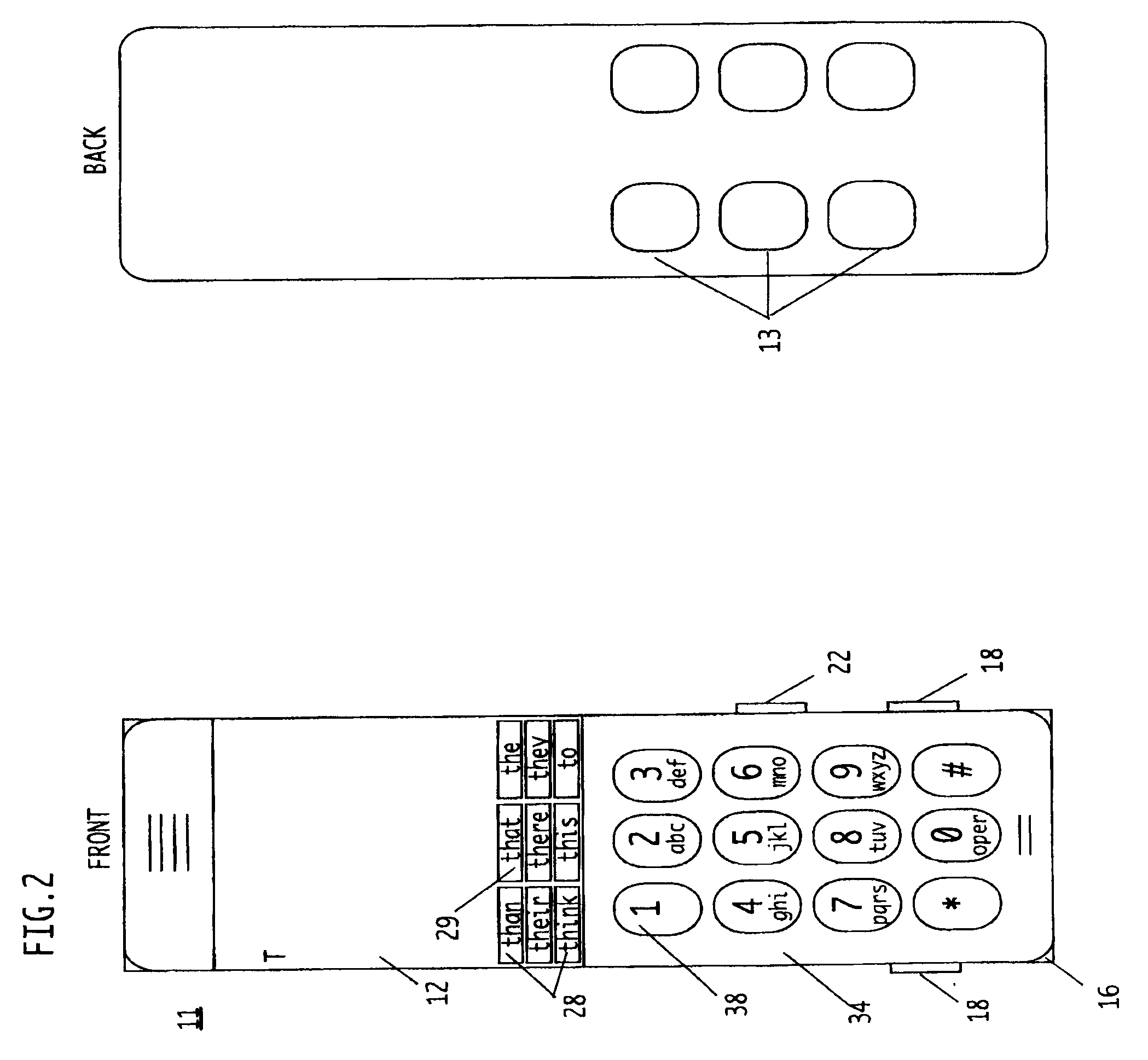
Methods and Systems for Improved Data Input, Compression, Recognition, Correction, and Translation through Frequency-Based Language Analysis
InactiveUS20100131900A1Improving optical character recognitionEfficient processingInput/output for user-computer interactionCathode-ray tube indicatorsCommon wordDocument preparation
System and method for improving data input by using word frequency to text predict input. Other systems and methods include analyzing words already contained in a document (e.g. spell checking and OCR) and using word frequency to create a proxy system to reduce the space required to store data, allowing for more efficient usage of storage and enhancing the embedded content of matrix codes. The system displays the most common words in a language based upon the previously entered or displayed word(s), or the previously entered or displayed character or characters. Words with the most common frequency of use with the prior word(s) are displayed in a table to enable the user to quickly select one of the displayed words for rapid data entry. The input device can be a touch-sensitive display or non-touch sensitive type device.
Owner:SIEGEL ABBY L
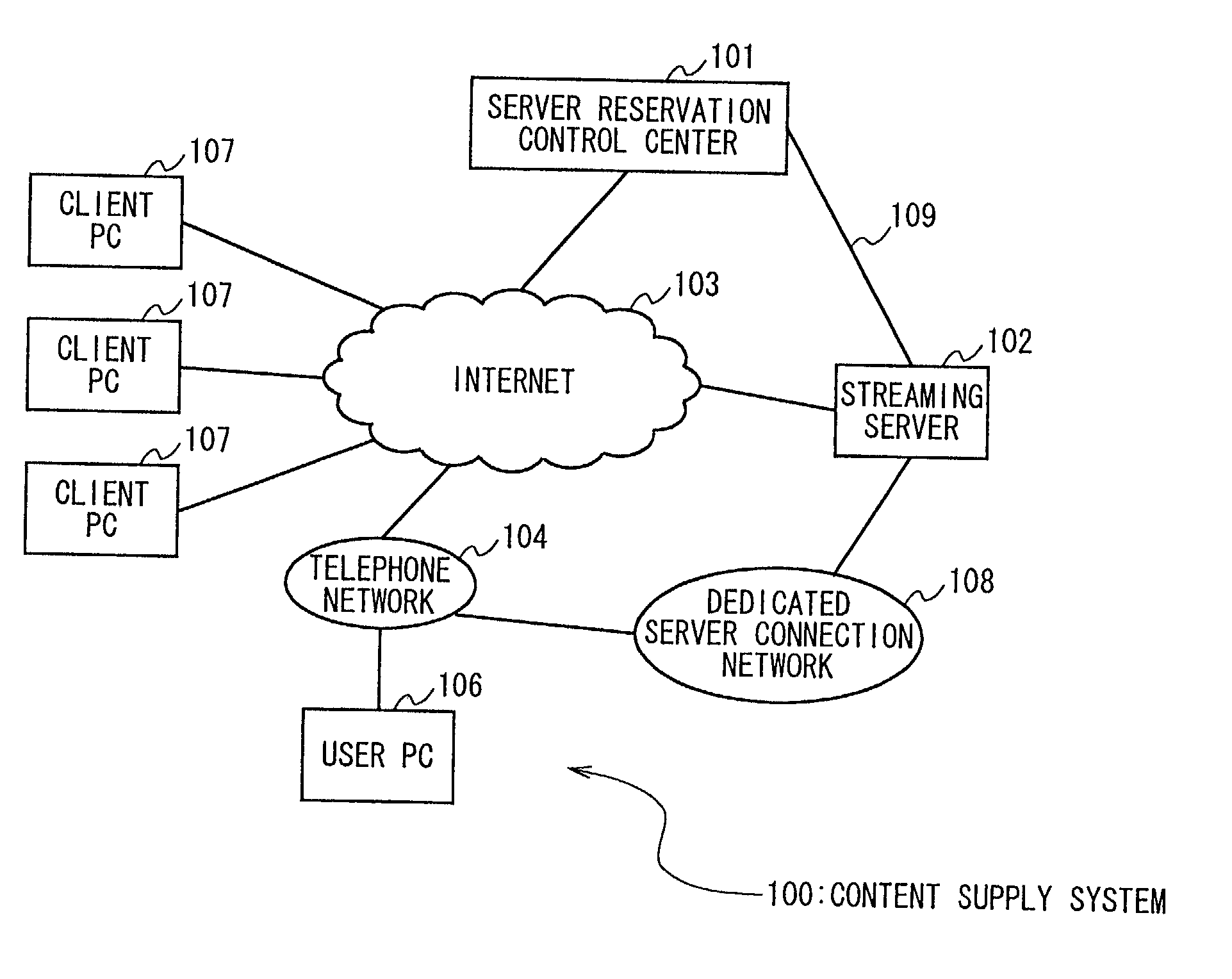
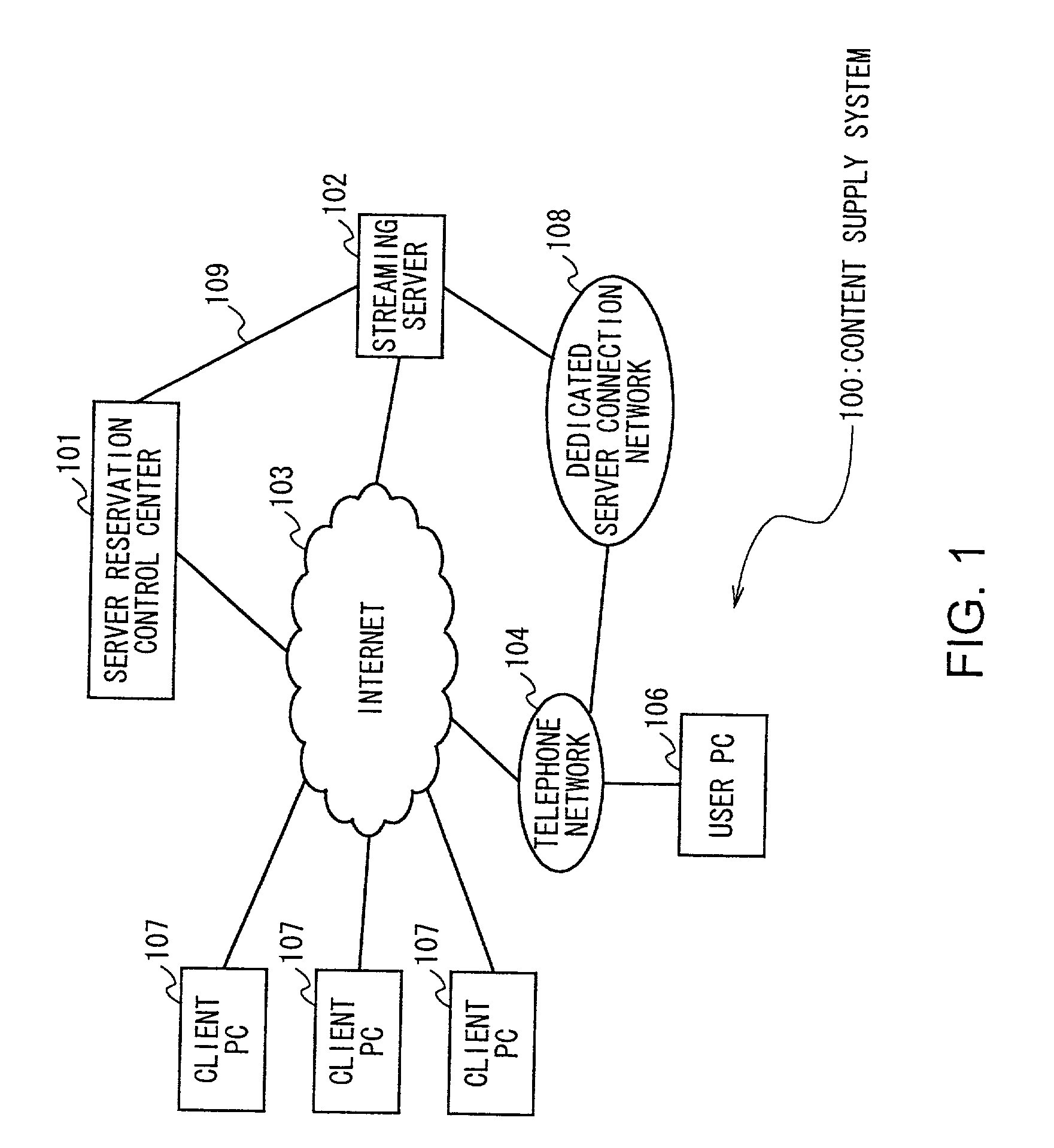
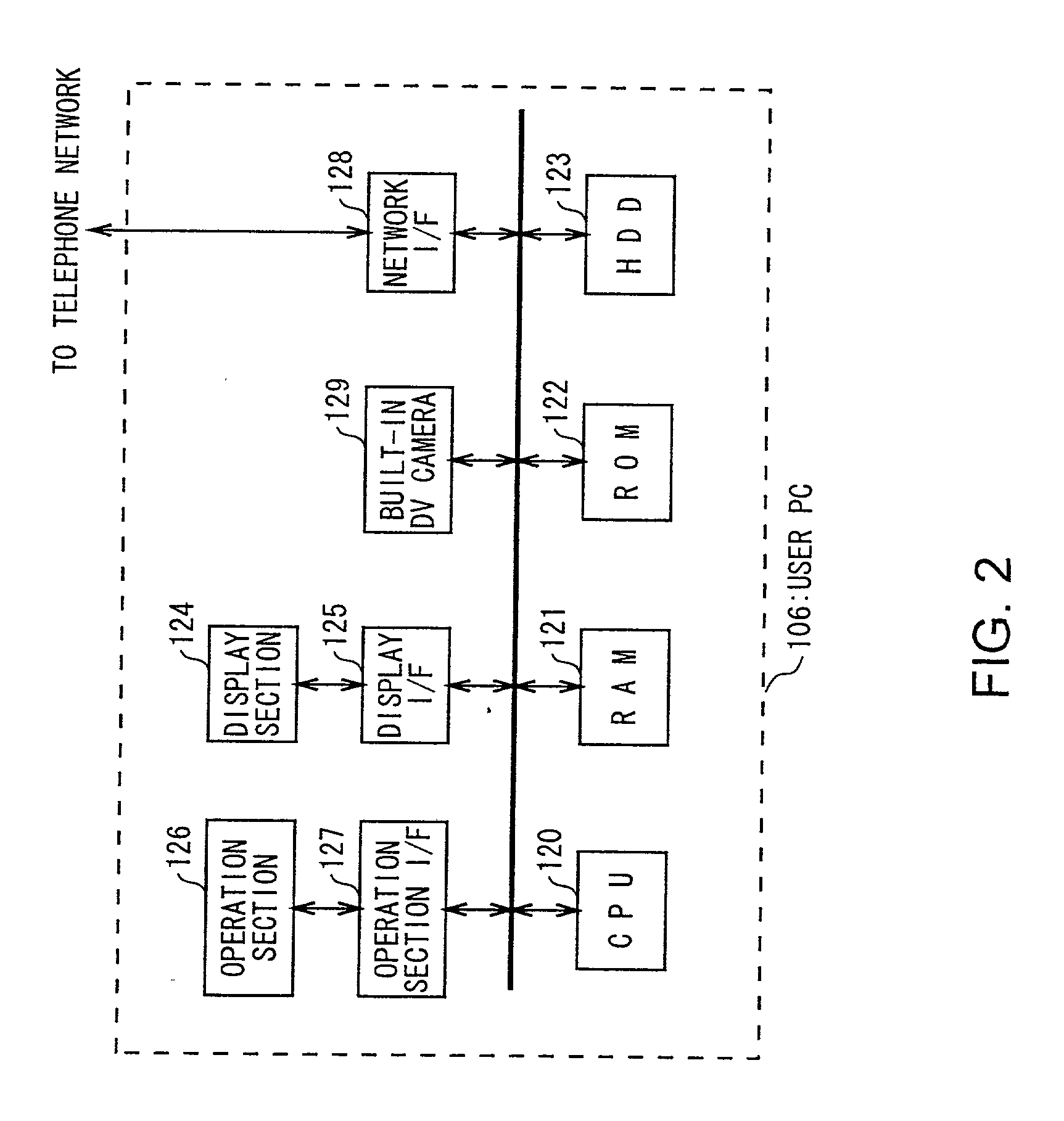
Content distribution method and content supply system
InactiveUS20020038359A1Easy to useImprove communication qualitySpecial service provision for substationTelevision system detailsContent distributionTerminal equipment
To secure a communication path between a distribution server that distributes content to clients and a terminal apparatus of a content distributor more reliably while content is distributed by live distribution. In a content supply system 100, in order to use a streaming server 102 to perform a live distribution, a user PC 106 to be used makes a reservation for a time zone, etc. to a server reservation control center 101 over the Internet 103. When the reservation is accepted and the content is sent from the user PC 106 to the streaming server 102, data is sent via a dedicated server connection network 108.
Owner:SONY CORP
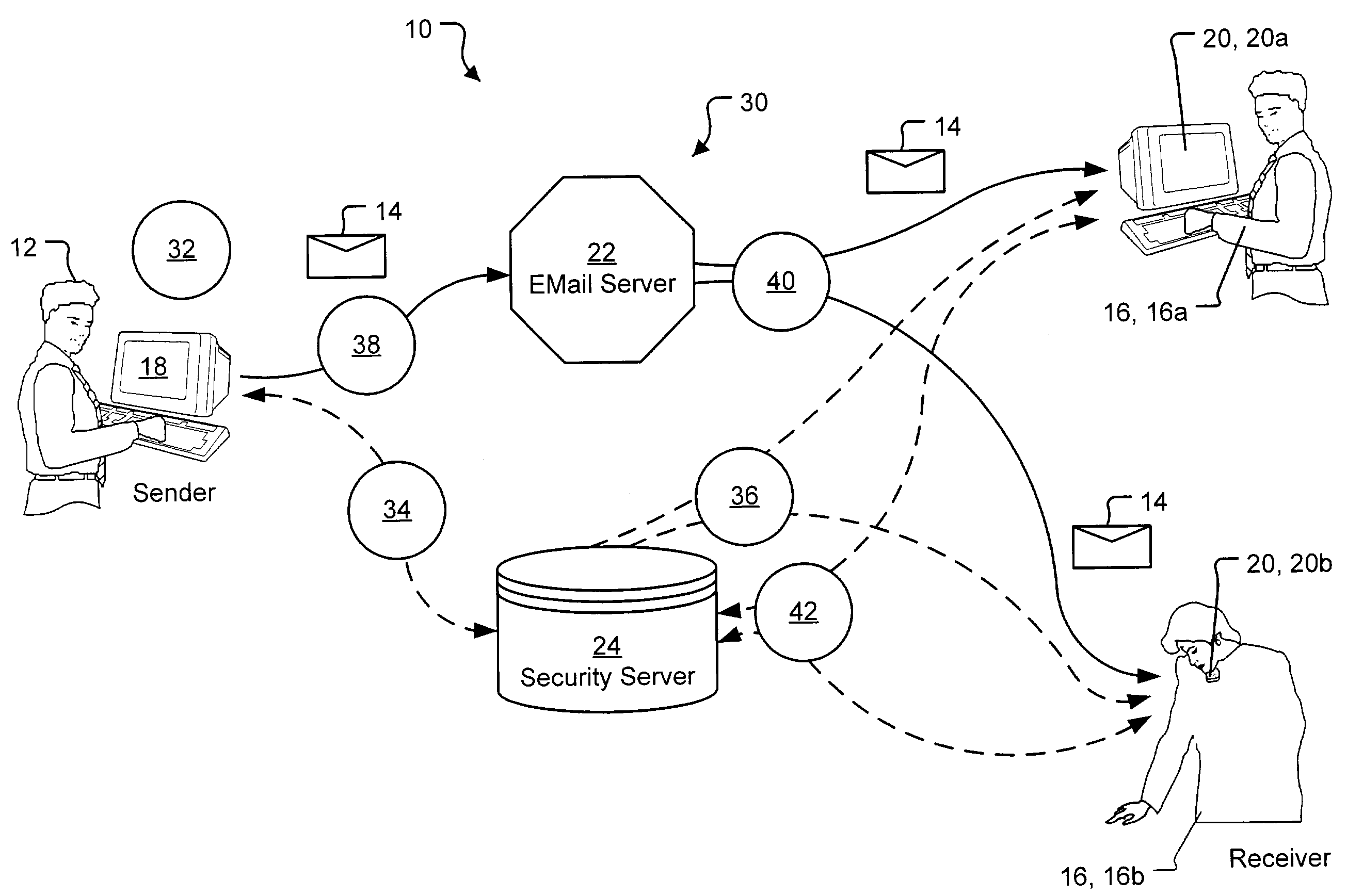
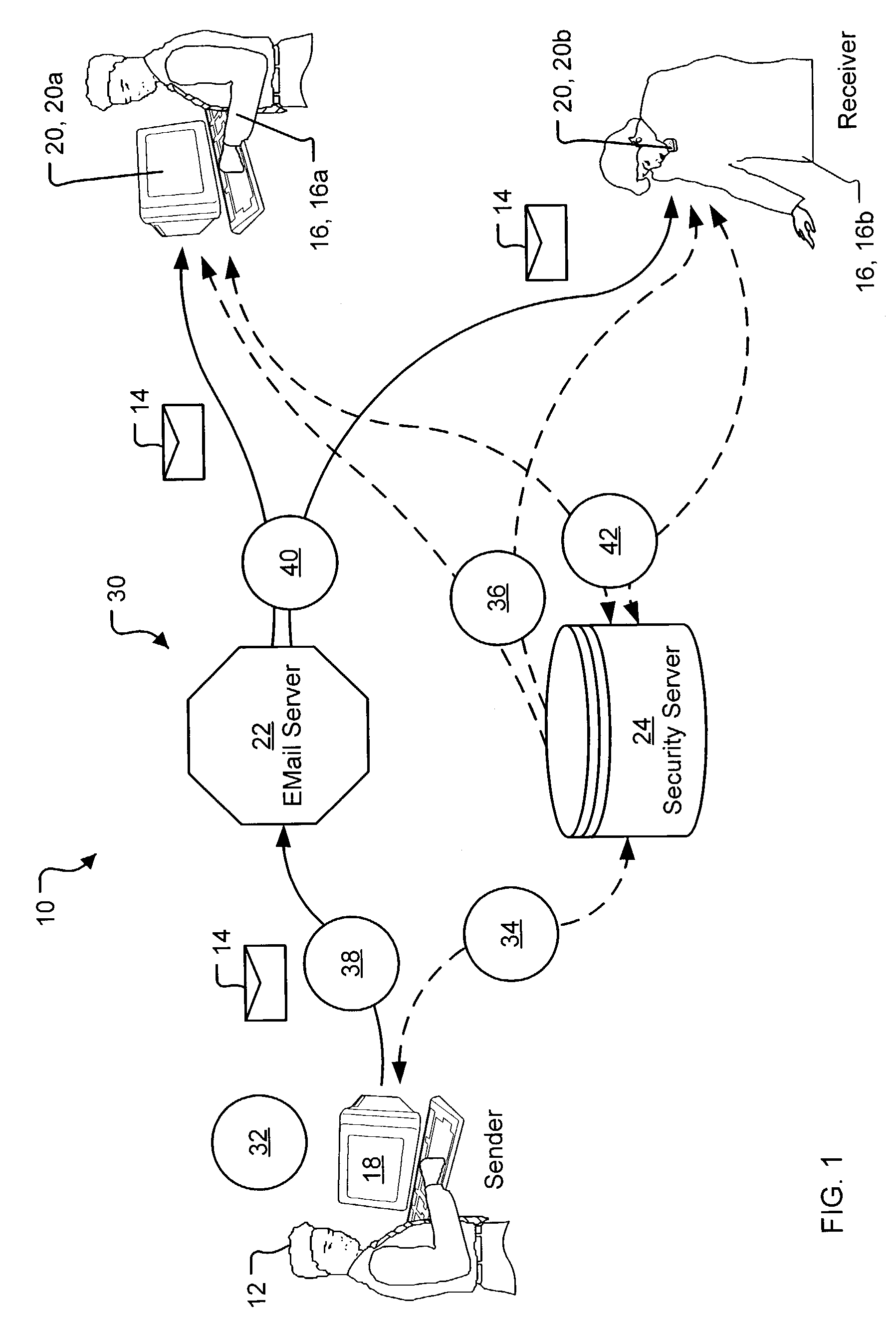
Security server system
InactiveUS7325127B2Raise security concernsHigh degreeData switching networksSecuring communicationKey serverMessage Title
A security server system and method permitting participants acting as the source or destinations for a message or a conversation with multiple messages to securely communicate the messages. The messages have a message header and a message content. A message router connects the participants via a network and delivers the message between the participants based on the message header. A key server creates, stores, and releases conversation keys that the participants use to protect the message content of the message.
Owner:PROOFPOINT INC
System and method for pairing wireless headsets and headphones
InactiveUS20060116107A1Eliminate needSecure CommunicationsUnauthorised/fraudulent call preventionEavesdropping prevention circuitsLoudspeakerTelecommunications link
A wireless headset including a CPU for generating a random number; a speaker; and a voice synthesis circuit for announcing the generated random number via the speaker, wherein the announced number is input to a host device as a PIN to establish a secure wireless communication link between the host device and the headset. In one embodiment the wireless headset includes a first operational button for selecting alphanumeric characters; and a second operational button for confirming the selected alphanumeric characters for input to the headset. In one embodiment the headset includes a microphone for accepting a spoken PIN as an input; speech recognition means for recognizing the spoken PIN; and speech synthesis means for announcing the recognized PIN via the speaker.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
A Secure Virtual Network Layer and Virtual Network Manager that Establishes a Comprehensive Business Reporting and Security Infrastructure as an Integral Part of the Network
InactiveUS20060248205A1Increase valueMaintenance safetyMultiple digital computer combinationsTransmissionWeb serviceVirtual network topology
A Secure Service Network (SSN) in which at least two participants having a relationship are connected to a physical network by way of Secure Service Gateways and share information defined by one or more Service Definitions allowing for the creation of a secure Virtual Service Connection (VSC) between the participants in which the VSC is specific to the activity being performed and the participants provisioned for that activity. SSN enables the creation of a secure virtual network topology on any network transport that allows participants to exchange documents and transact business over the network real time, where all activity inherits a business and security infrastructure that is independent and in addition to the applications, devices, web services, users using the network.
Owner:RANDLE WILLIAM M +1
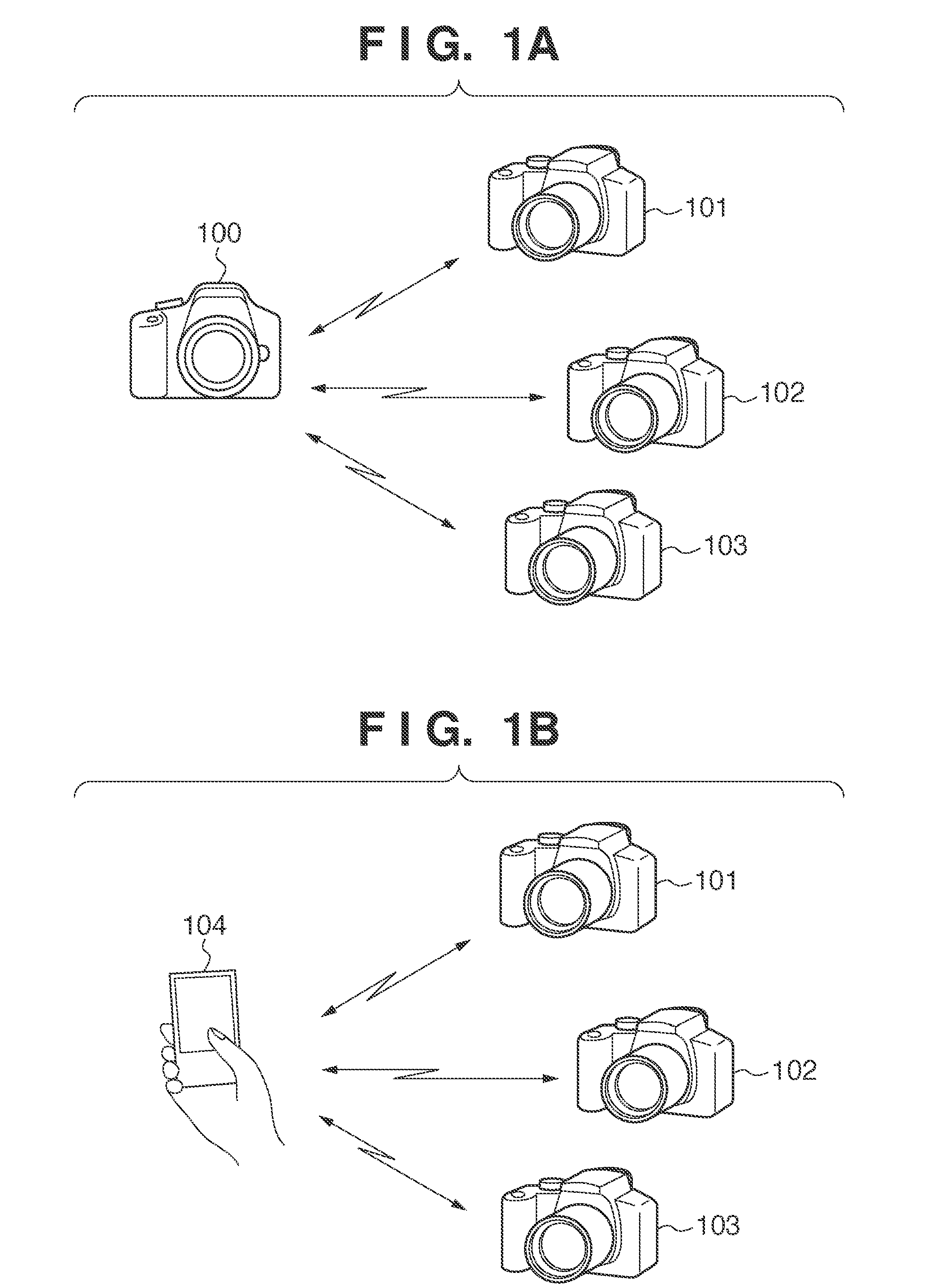
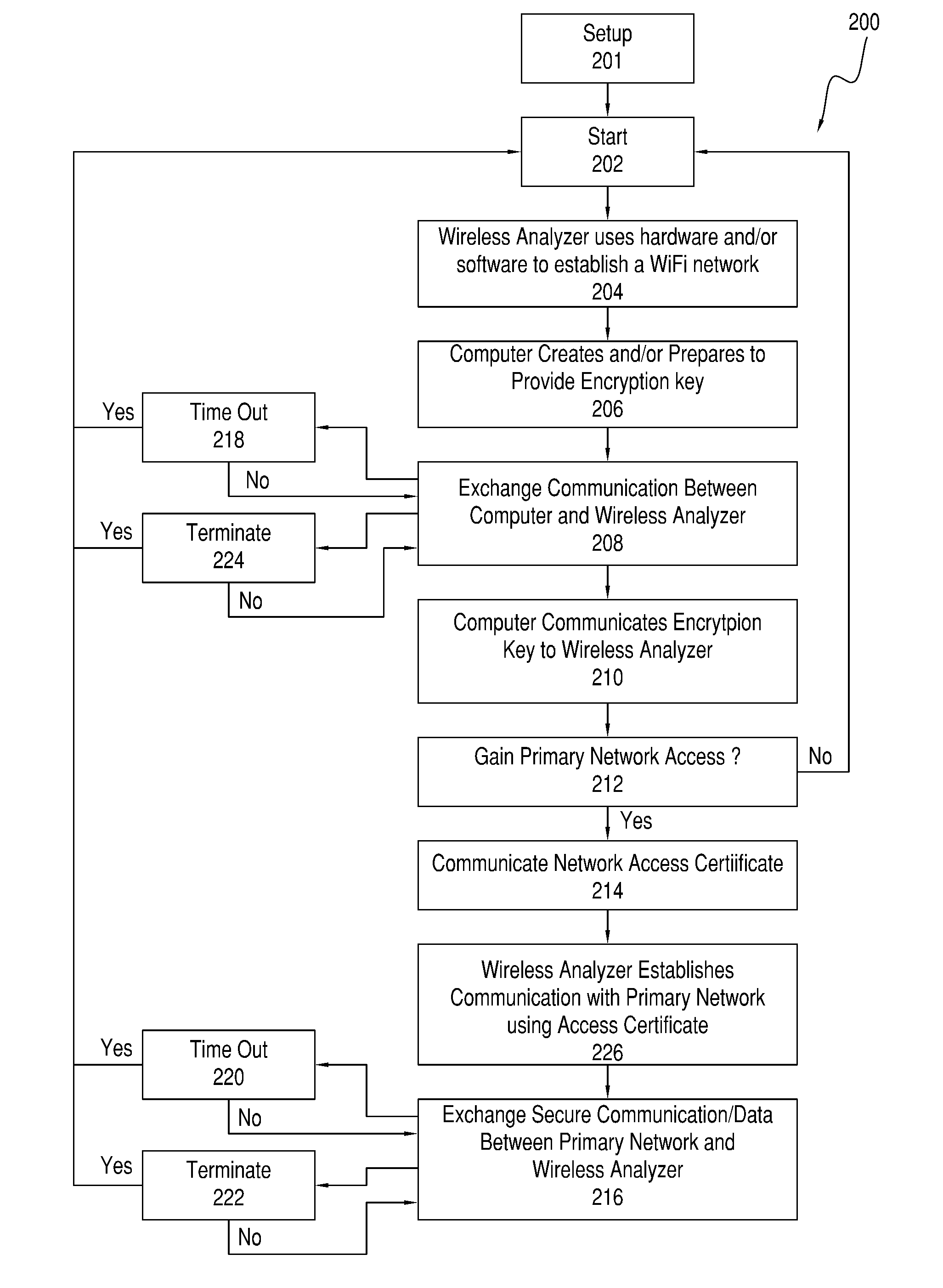
Systems, methods and analyzers for establishing a secure wireless network in point of care testing
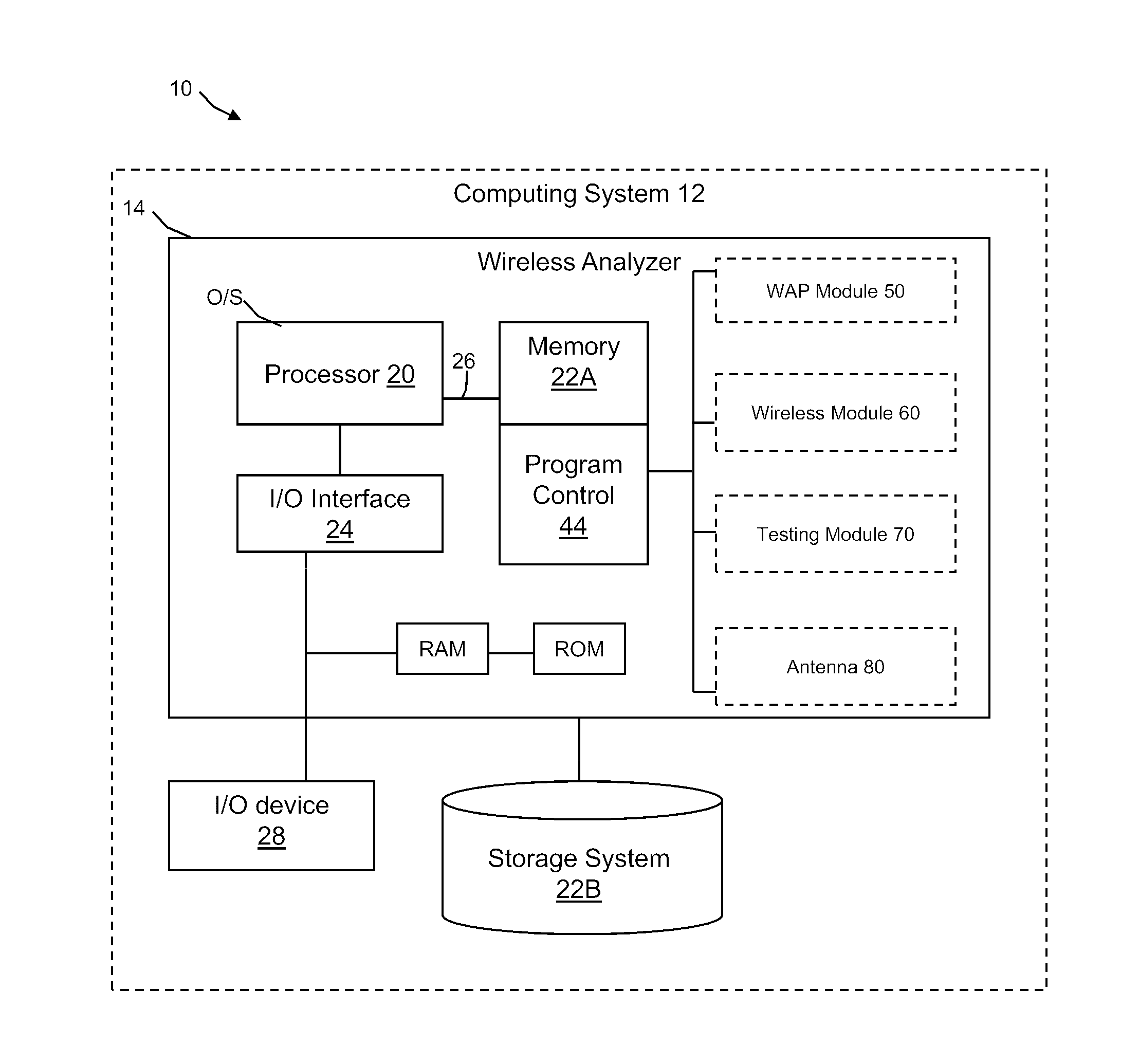
ActiveUS20120233679A1Secure wireless communicationSecure CommunicationsDigital data processing detailsUser identity/authority verificationPoint of careWi-Fi
A system and method for initiating and maintaining a secure wireless communication between a wireless analyzer and a target network (e.g., a hospital network connected to a LIS and / or HIS). The present disclosure provides novel processes and systems for securely networking a wireless analyzer with a Wi-Fi network without the need for an operator or user to engage in manual initiation steps on, or through, the wireless analyzer.
Owner:ABBOTT POINT CARE
Direct digital cash system and method
ActiveUS20150081566A1Easy to set upSecure CommunicationsProtocol authorisationPayments involving neutral partyInternet privacyAnonymity
Methods and systems are provided for the exchange of digital cash employing protocols for various entities to separately certify the validity of the parties, values and transactions while maintaining the anonymity of the buyer or user of the digital cash. Encrypted connections are established allowing various parties to enter into transactions to buy, sell, exchange and recover digital cash using a secure method that protects the personal information and identity of the user. The parties exchange tokens for other value in a transaction of financial settlement between themselves and wherein they are the only parties with knowledge of the amount and description of the transaction and in this way mimics a traditional cash transaction.
Owner:SLEPININ IGOR V
Method and system of securing group communication in a machine-to-machine communication environment
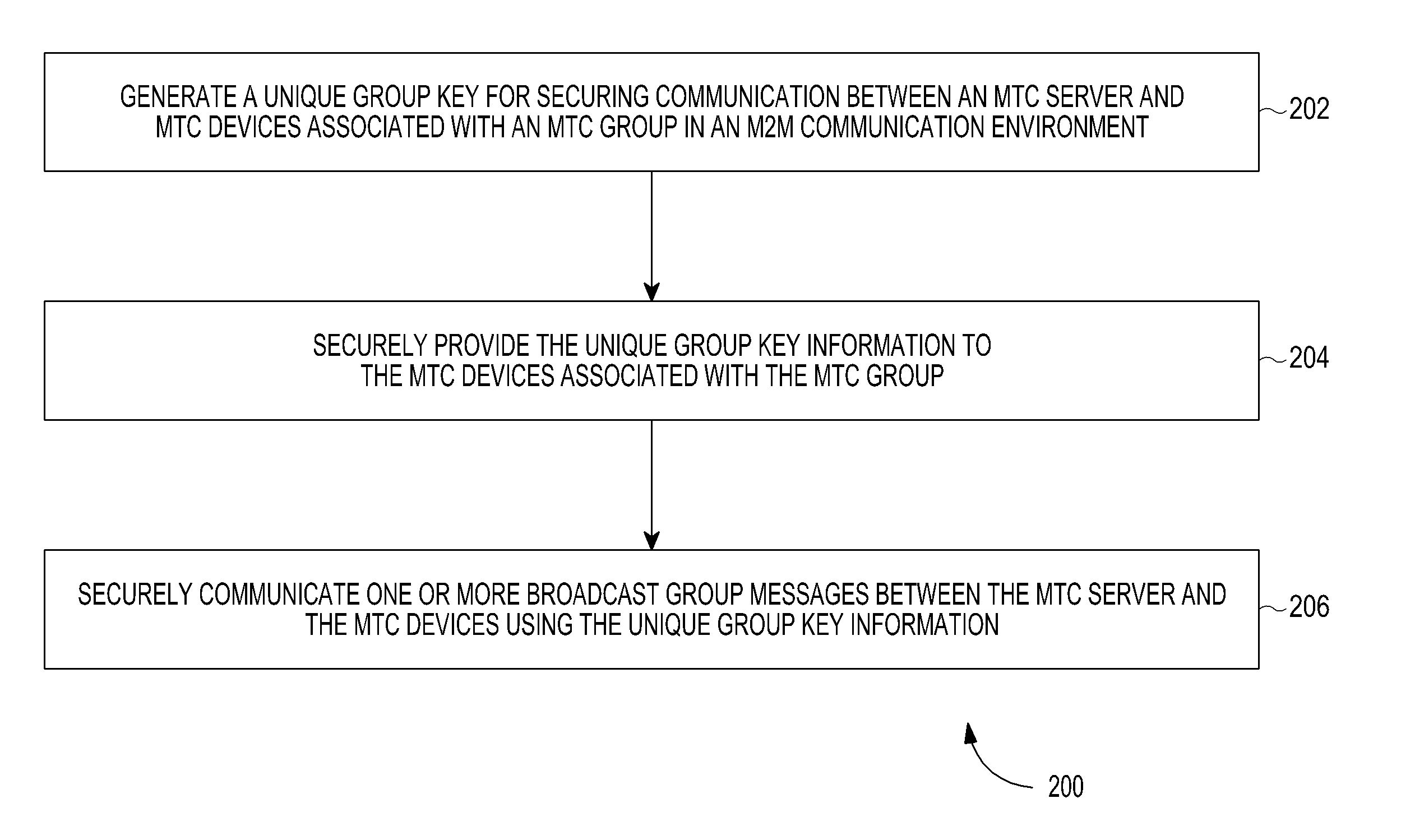
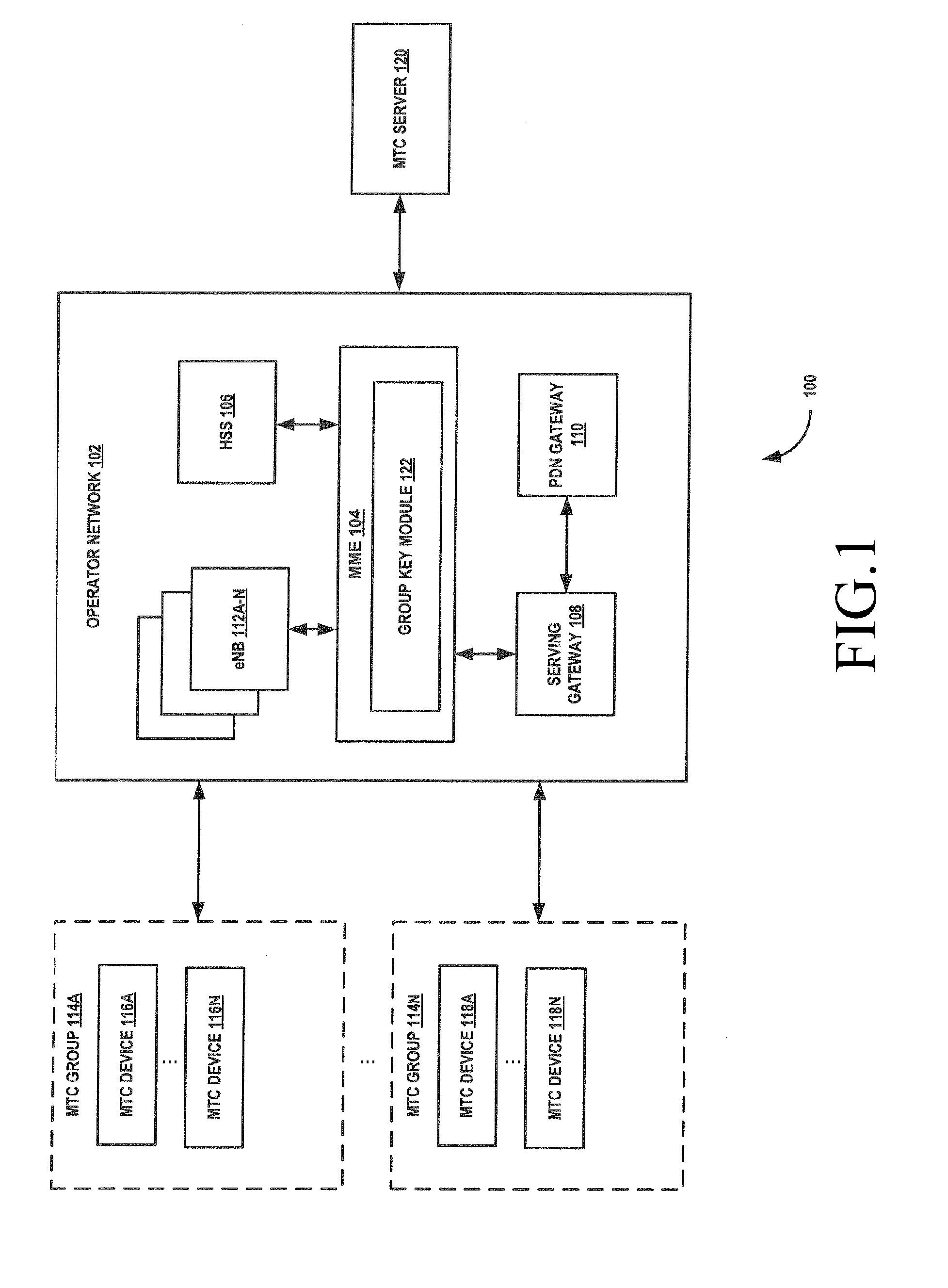
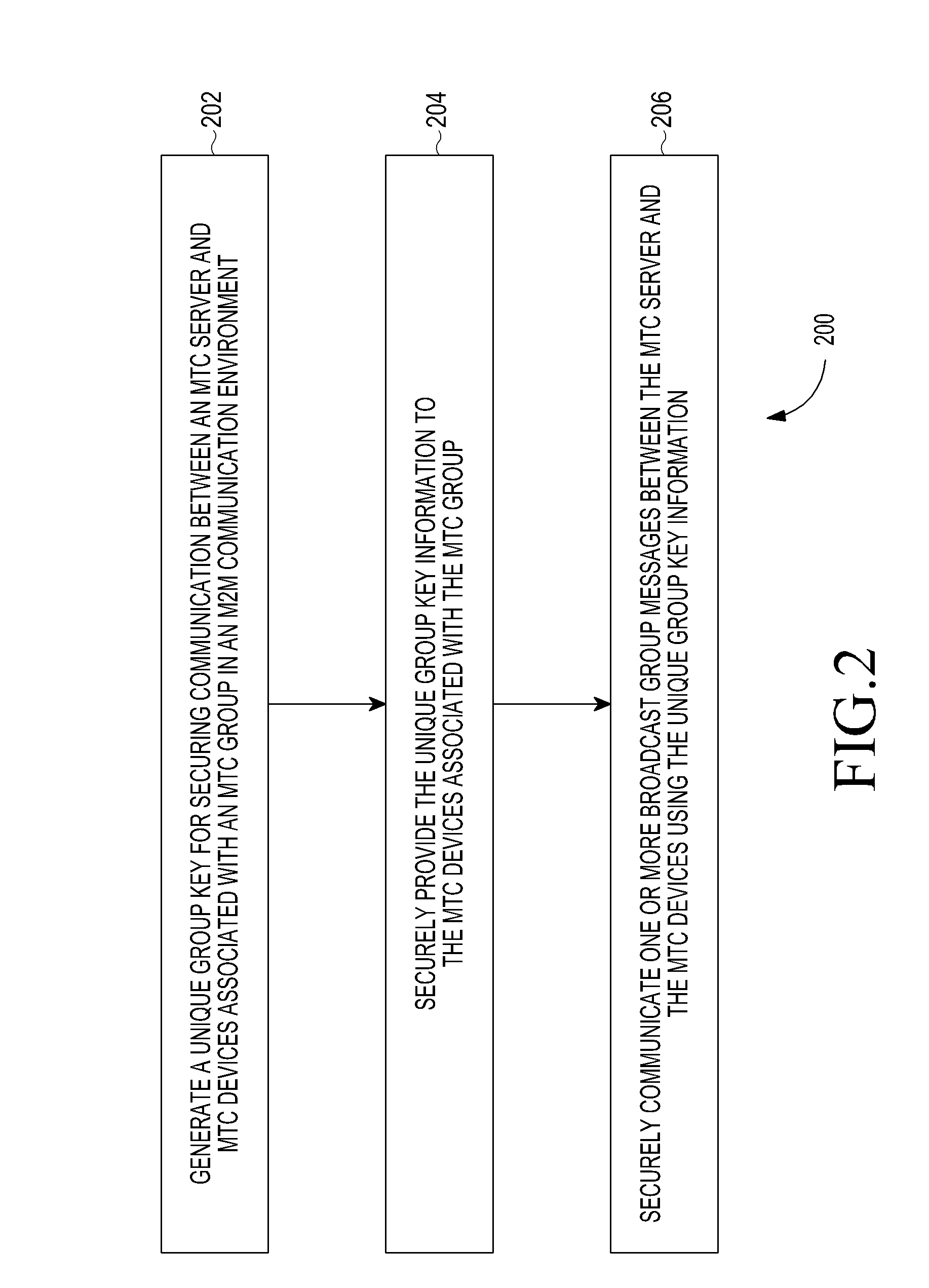
ActiveUS20130080782A1Communication securitySecure CommunicationsKey distribution for secure communicationUser identity/authority verificationSecure communicationInformation security
A method and system for securing group communication in a Machine-to-Machine (M2M) communication environment including a plurality of Machine Type Communication (MTC) groups, wherein each of the plurality of MTC groups includes a plurality of MTC devices. The method includes generating a unique group key for securing communication with MTC devices associated with an MTC group in an M2M communication environment, securely providing information on the unique group key to the MTC devices associated with the MTC group, and securely communicating at least one broadcast group message with the MTC devices using the unique group key information.
Owner:SAMSUNG ELECTRONICS CO LTD
Control apparatus, control system, command transmission method, and non-transitory computer-readable storage medium
InactiveUS20110050925A1Secure CommunicationsSecure responseTelevision system detailsColor television detailsComputer hardwareControl system
A control apparatus that is connected to at least one image capturing apparatus by wireless communication transmits, by multicast or broadcast via the wireless communication, a command for instructing to start a prescribed operation to each image capturing apparatus, in response to detection of an operation for instructing to start the prescribed operation, and transmits, by unicast via the wireless communication, a command for instructing to end the prescribed operation to each image capturing apparatus, in response to detection of the operation for instructing to end the prescribed operation. Then, the control apparatus confirms a response to transmission of the command for instructing to end the prescribed operation, and retransmits, by unicast, the command to end the prescribed operation to each image capturing apparatus whose response is not confirmed.
Owner:CANON KK
Uniquely identifying and securely communicating with an appliance in an uncontrolled network
ActiveUS20170170973A1Secure communicationsMultiple keys/algorithms usagePublic key for secure communicationSecure communicationService provider
A service consumer that utilizes a cloud-based access service provided by a service provider has associated therewith a network that is not capable of being controlled by the service provider. An enterprise connector is supported in this uncontrolled network, preferably as an appliance-based solution. According to this disclosure, the enterprise configures an appliance and then deploys it in the uncontrolled network. To this end, an appliance is required to proceed through a multi-stage approval protocol before it is accepted as a “connector” and is thus enabled for secure communication with the service provider. The multiple stages include a “first contact” (back to the service) stage, an undergoing approval stage, a re-generating identity material stage, and a final approved and configured stage. Unless the appliance passes through these stages, the appliance is not permitted to interact with the service as a connector. As an additional aspect, the service provides various protections for addressing scenarios wherein entities masquerade as approved appliances.
Owner:AKAMAI TECH INC
Systems, methods and analyzers for establishing a secure wireless network in point of care testing
ActiveUS8549600B2Secure CommunicationsDigital data processing detailsUser identity/authority verificationPoint of careWi-Fi
A system and method for initiating and maintaining a secure wireless communication between a wireless analyzer and a target network (e.g., a hospital network connected to a LIS and / or HIS). The present disclosure provides novel processes and systems for securely networking a wireless analyzer with a Wi-Fi network without the need for an operator or user to engage in manual initiation steps on, or through, the wireless analyzer.
Owner:ABBOTT POINT CARE
Method and apparatus to facilitate secure network communications with a voice responsive network interface device
InactiveUS7185197B2Access controlSecure CommunicationsKey distribution for secure communicationDigital data processing detailsVoice browserSoftware modules
A system for facilitating secure network communications includes a security computer system and corresponding software. The security system is utilized in conjunction with a voice browser residing on a server system. A user accesses the network by placing a call to the voice browser system. The voice browser includes a software module that creates a secure connection to the security system. The user provides an identification to the voice browser system that is transferred to and verified by the security system. Once the identification is verified, the user is prompted by the voice browser system to speak a phrase for voice verification. The verification speech signals are transferred from the voice browser system to the security system to verify those speech signals against speech signals of a particular authorized user associated with the identification and stored in a database. When the user is verified, the security system retrieves a user private key and certificate from the database. In response to the user subsequently accessing a web site residing on a secure server, the secure server and voice browser system initiate a secure key exchange. During the key exchange, data packets containing security information are transferred from the voice browser system to the security system for processing, while security information from the security system is transferred to the secure server via the voice browser system. The resulting session key is securely transferred to the voice browser system to facilitate secure communications between the voice browser system and secure server.
Owner:EXCELIS INC
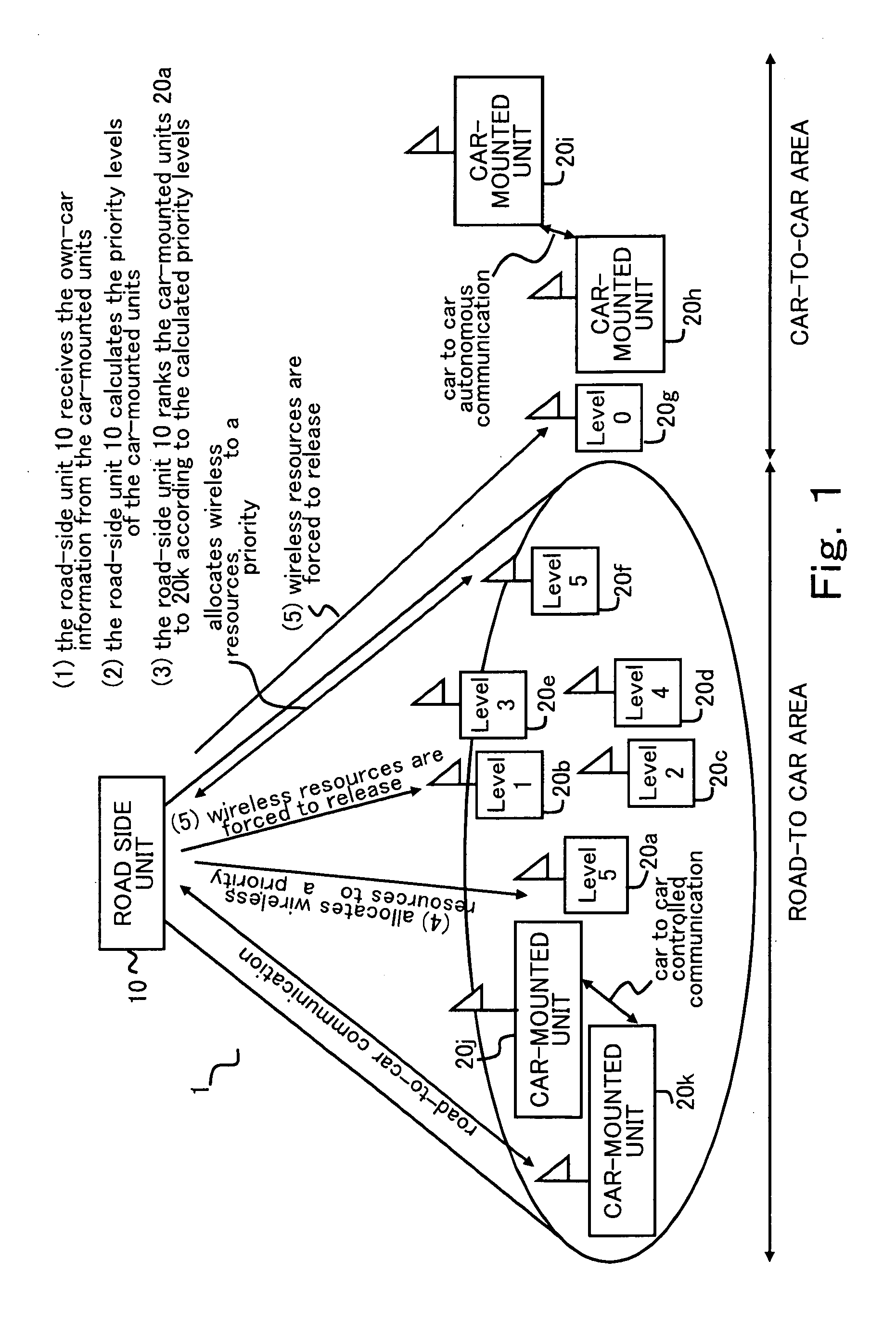
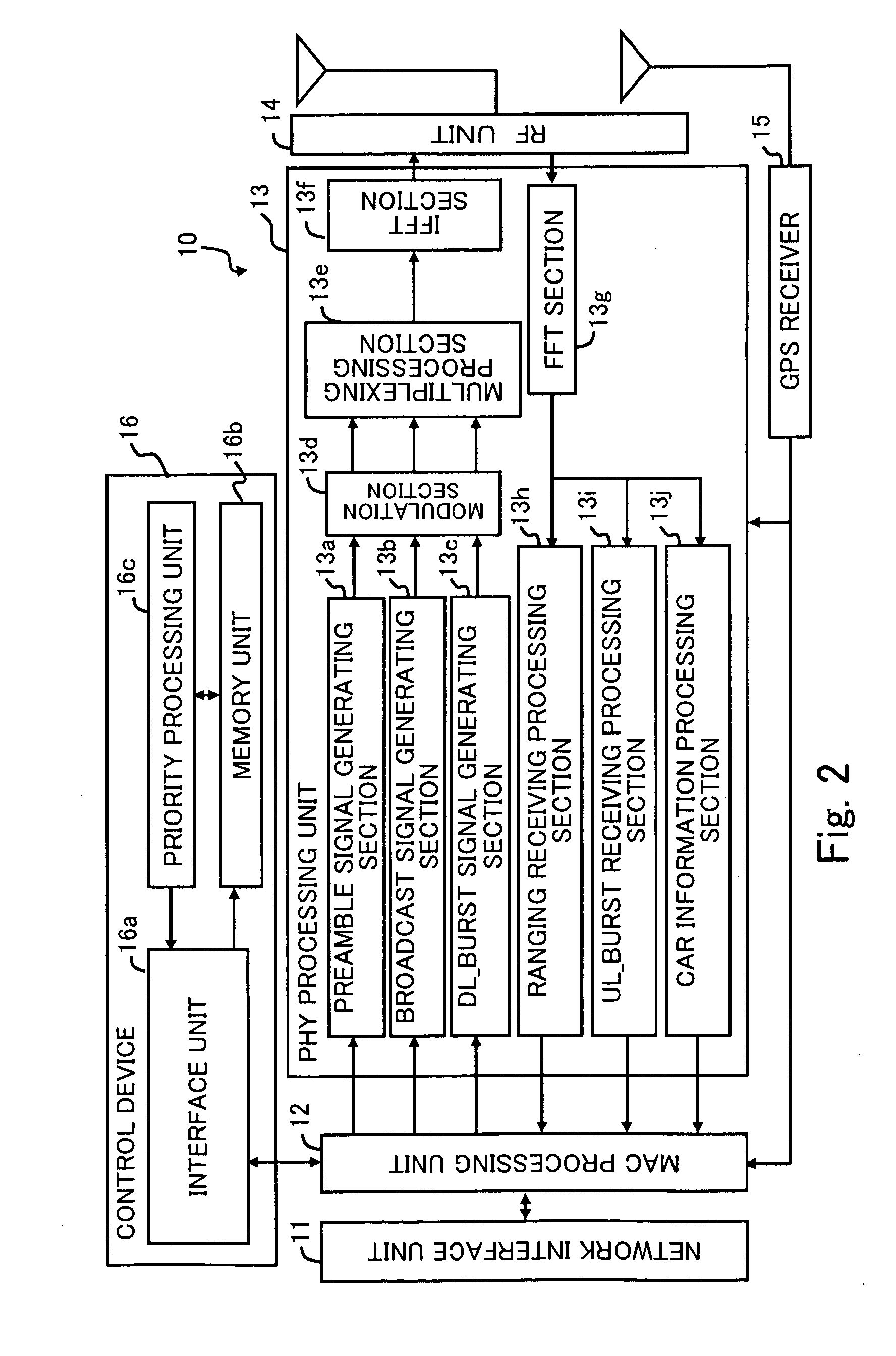
Wireless Resource Allocation Control System, Road-Side Unit, Wireless Resource Allocation Control Method and Storage Medium Storing Program Thereof
InactiveUS20090161644A1Reduce wasteSecurely perform communicationAnalogue computers for vehiclesAnalogue computers for trafficControl systemWireless resource allocation
A wireless resource allocation control system for allocating and releasing wireless resource used for communication between vehicles in a predetermined area is provided. The control system includes a unit mounted on a vehicle, and the unit includes a transmitter for transmitting first information associated with the vehicle. A station receives information from the unit and sends information to the unit. The station calculates a priority level for each of the units on the basis of the first information transmitted from each of the units, ranks the units in the order of the priority level, allocates wireless resources to the units in descending of the priority levels, and releases the wireless resource previously allocated to the unit in the case of the unit unworthy of current allocation of the wireless resource.
Owner:FUJITSU LTD
Secure wireless mobile communications
InactiveUS20040103311A1Secure wireless communicationCommunication securityDigital data processing detailsMultiple digital computer combinationsWireless mesh networkSecurity association
Secure wireless communications for a mobile host over any wireless interface within a wireless network is provided by a security gateway. The security gateway is situated and configured within the mobile host's home network of the wireless network such that it provides the only point of access between the wireless network and the home network. Additionally, the security gateway is separate and distinct from the mobile host's home agent within the home network. A single tunnel mode security association is established between the mobile host's wireless interface and the security gateway's network interface on the home network. This single tunnel mode security association remains established as the mobile host moves between foreign networks and provides secure wireless communications to the mobile host whether the mobile host is in the home network or the foreign networks.
Owner:TELCORDIA TECHNOLOGIES INC
Content distribution method and content supply system
InactiveUS6970928B2Reliably securedEasy to useSpecial service provision for substationTelevision system detailsContent distributionTerminal equipment
To secure a communication path between a distribution server that distributes content to clients and a terminal apparatus of a content distributor more reliably while content is distributed by live distribution. In a content supply system 100, in order to use a streaming server 102 to perform a live distribution, a user PC 106 to be used makes a reservation for a time zone, etc. to a server reservation control center 101 over the Internet 103. When the reservation is accepted and the content is sent from the user PC 106 to the streaming server 102, data is sent via a dedicated server connection network 108.
Owner:SONY CORP
System and Method for Communication Between an Information Handling System and Management Controller Through a Shared LOM
InactiveUS20110202685A1Reduce disadvantage and problemSecure communicationsMultiple digital computer combinationsElectric digital data processingNetwork addressInformation handling system
Communications between a host information handling system and its management controller sent through a shared LOM are re-directed at the LOM from communication through a network to instead communicate directly between the host information handling system and management controller. A management module compares destination addresses of packets sent from the host information handling system and the management controller with host information handling system and management controller network addresses stored on the LOM. Packets having destination address that match a host information handling system or management controller network address are redirected from communication across the network to communicate directly between the host information handling system and management controller.
Owner:DELL PROD LP
Method and system for secure and anti jamming wireless communication with high spectral efficiency
InactiveUS20090103720A1Improve spectral efficiencyDetect and eliminate jamming signalPower managementPolarisation/directional diversityCommunications systemFrequency spectrum
Invention presented here relates to Low Probability of Exploitation and Anti Jamming communication system offering high spectral efficiency. The object of the present invention is achieved by hopping in polarization domain and by employing an adaptive polarization-nulling algorithm (FIG. 18, H [2,2]) to detect and eliminate jamming signal. The use of signals which hops or spreads in polarization domain does not need wide frequency spectrum due to which, the said modulation when employed at the physical layer offers and extremely secure and survivable wireless communication at very high data rates.
Owner:KARAYIL THEKKOOTT NARAYANAN MANOJ
Wireless network security
ActiveUS20140143536A1Enhanced informationConvenient wireless communicationNetwork topologiesTransmissionEncryptionWireless network security
A method includes identifying a suspect node of a network. The method also includes initiating formation of a sub-network of the network by identifying neighbor nodes of the suspect node and sending an invitation message to a first neighbor node to invite the first neighbor node to the sub-network. The invitation message is encrypted using a first encryption key associated with the first neighbor node. The invitation message is not sent to a second node that is identified as a neighbor node only by the suspect node. The sub-network is configured to enable first communications between members of the sub-network. The first communications are communicated in a manner that is secured against access by the suspect node. Subsequent to formation of the sub-network, second communications between the suspect node and a device of the network are routed to or through at least one of the members of the sub-network.
Owner:THE BOEING CO
Direct digital cash system and method
ActiveUS9710808B2Easy to set upSecure CommunicationsPayments involving neutral partyProtocol authorisationInternet privacyAnonymity
Methods and systems are provided for the exchange of digital cash employing protocols for various entities to separately certify the validity of the parties, values and transactions while maintaining the anonymity of the buyer or user of the digital cash. Encrypted connections are established allowing various parties to enter into transactions to buy, sell, exchange and recover digital cash using a secure method that protects the personal information and identity of the user. The parties exchange tokens for other value in a transaction of financial settlement between themselves and wherein they are the only parties with knowledge of the amount and description of the transaction and in this way mimics a traditional cash transaction.
Owner:SLEPININ IGOR V
Patient Controlled and Initiated Method and System for Physician Reporting of Patient Status
InactiveUS20120150565A1Promote disseminationLighten the taskMedical communicationData processing applicationsElectronic communicationPatient status
A system and method for communicating status of individual patients to selected populations of residents include a computing platform, a database in communication with the computing platform, first, second, and third electronic communication devices used by patients, physicians and recipients respectively, and a software algorithm residing on the computing platform, controlled by the patient using the first communication device for implementing communications and patient status to the recipients.
Owner:MDCONNECTME
Network system for secure communication
ActiveUS20180375870A1Communication securityEnable secure communicationKey distribution for secure communicationUser identity/authority verificationSecure communicationNetworked system
In a network system (100) for wireless communication an enrollee (110) accesses the network via a configurator (130). The enrollee acquires a data pattern (140) that represents a network public key via an out-of-band channel by a sensor (113). The enrollee derives a first shared key based on the network public key and the first enrollee private key, and encodes a second enrollee public key using the first shared key, and generates a network access request. The configurator also derives the first shared key, and verifies whether the encoded second enrollee public key was encoded by the first shared key, and, if so, generates security data and cryptographically protects data using a second shared key, and generates a network access message. The enrollee processor also derives the second shared key and verifies whether the data was cryptographically protected and, if so, engages the secure communication based on the second enrollee private key and the security data.
Owner:KONINKLJIJKE PHILIPS NV
Print system, print device and print instruction method
ActiveUS7264411B2Prevent leakageAvoid dataCharacter printing data arrangement from carrierError detection/correctionSoftware engineeringMechanical engineering
A print system (0001) includes a print instruction device (0101), a print device (0102) and a print data supply device (0103). The print instruction device (0101) has a print instruction device (0111) which transmits, to the print device (0102), authentication information and a print instruction of print data in a print data supply device (0103). The print device (0102) has a print data requesting unit (0112) which transmits the authentication information according to the print instruction to the print data supply device (0103) and requests a transmission of print data, and a print data receiving unit (0113) which receives the print data from the print data supply device (0103).
Owner:SOVEREIGN PEAK VENTURES LLC
Network system which performs peer-to-peer communication
InactiveUS20080189351A1Improve efficiencySecure CommunicationsMultiple digital computer combinationsDigital data authenticationCommunication sourcePeer-to-peer
To reduce a load inflicted on a network by peer-to-peer communication between terminals, the present invention provides a network system having a communication destination machine and a communication source machine, in which: the communication destination machine includes a unit which registers its own location information in a peer-to-peer network; and the communication source machine includes: a unit which searches the peer-to-peer network for the location information of the communication destination machine and obtains the location information; and a unit which uses the obtained information to establish peer-to-peer communication. The location information contains communication path information which enables the communication source machine to communicate with a desired machine beyond a path controller, and a parameter necessary for communication. The communication source machine may include a unit which accumulates location information or similar data of multiple communication destination machines.
Owner:HITACHI LTD
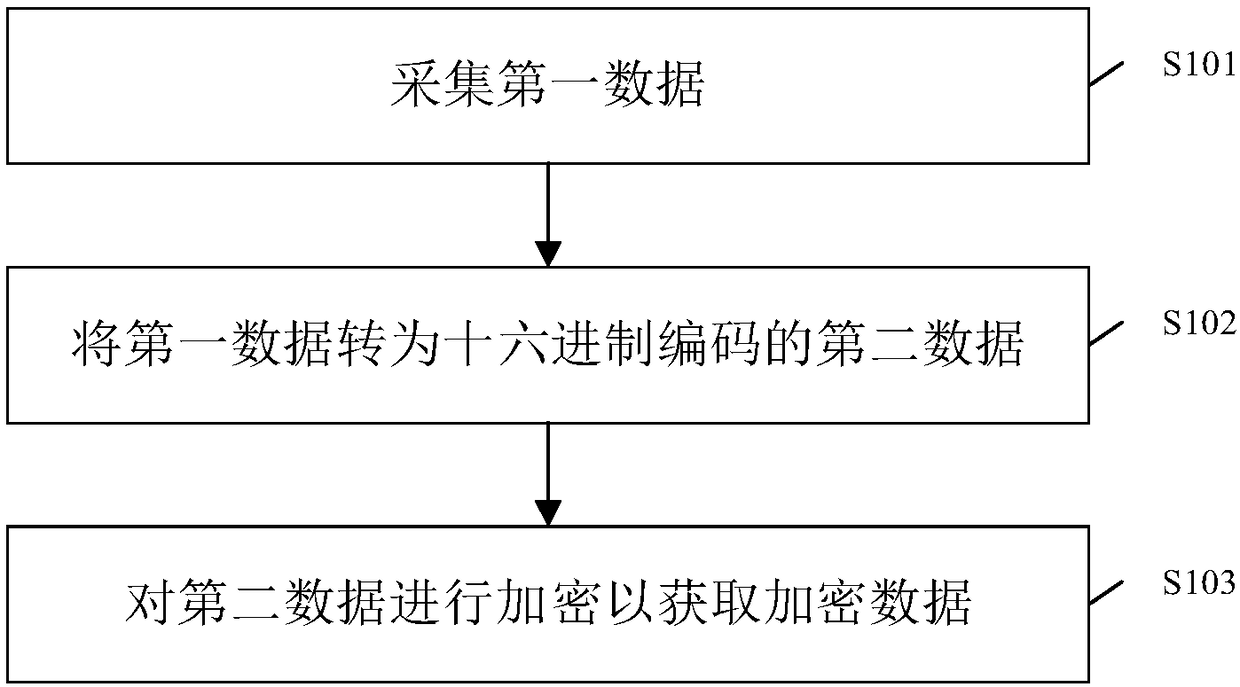
Data encryption method
InactiveCN108429735AEnsure safetyIncrease the difficultyKey distribution for secure communicationMultiple keys/algorithms usageIntel HEXComputer hardware
The invention provides a data encryption method. The data encryption method comprises the following steps that first data is acquired, wherein the first data is fingerprint data, identity card data, adigital cipher and / or MF card data; the first data is converted into hexadecimal coded second data; and the second data is subjected to a hardware encryption mechanism and a software encryption mechanism to acquire encrypted data. According to the data encryption method, by means of the process that the first data is acquired and converted into the hexadecimal coded second data, and then the second data is encrypted to acquire the encrypted data, the security of the data can be guaranteed.
Owner:陈柱
Wireless network security
ActiveUS20130031358A1Enhanced informationConvenient wireless communicationMemory loss protectionError detection/correctionWireless securityComputer science
A method includes identifying a suspect node of a network that includes multiple nodes in wireless communication. The method also includes initiating formation of a sub-network of the network in response to identifying the suspect node. The suspect node is not a member of the sub-network. After formation of the sub-network, first communications between the suspect node and a device of the network are routed to or through at least one of the members of the sub-network. The sub-network is configured to enable second communications between members of the sub-network, where the second communications are communicated in a manner that is secured against access by the suspect node.
Owner:THE BOEING CO
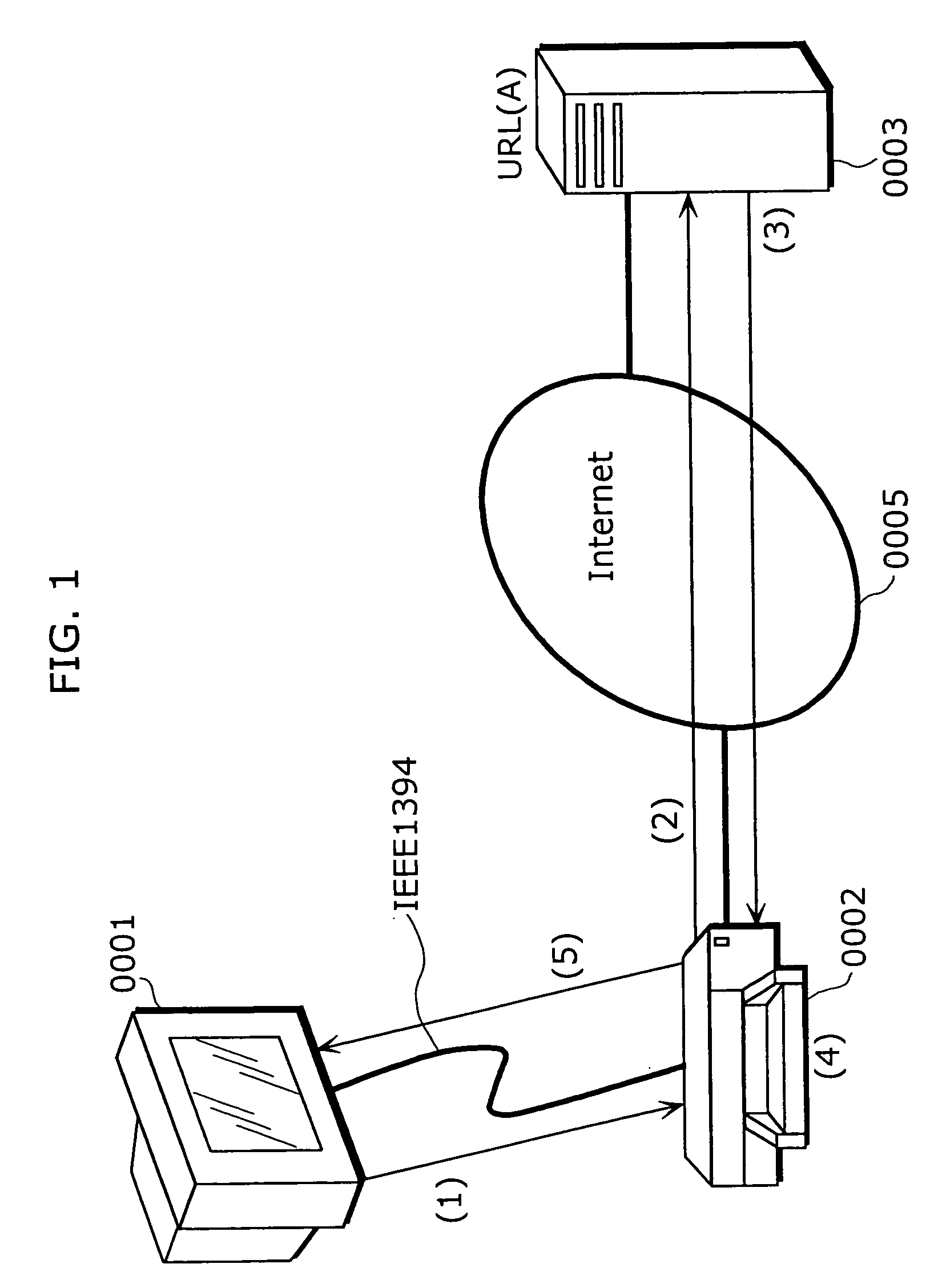
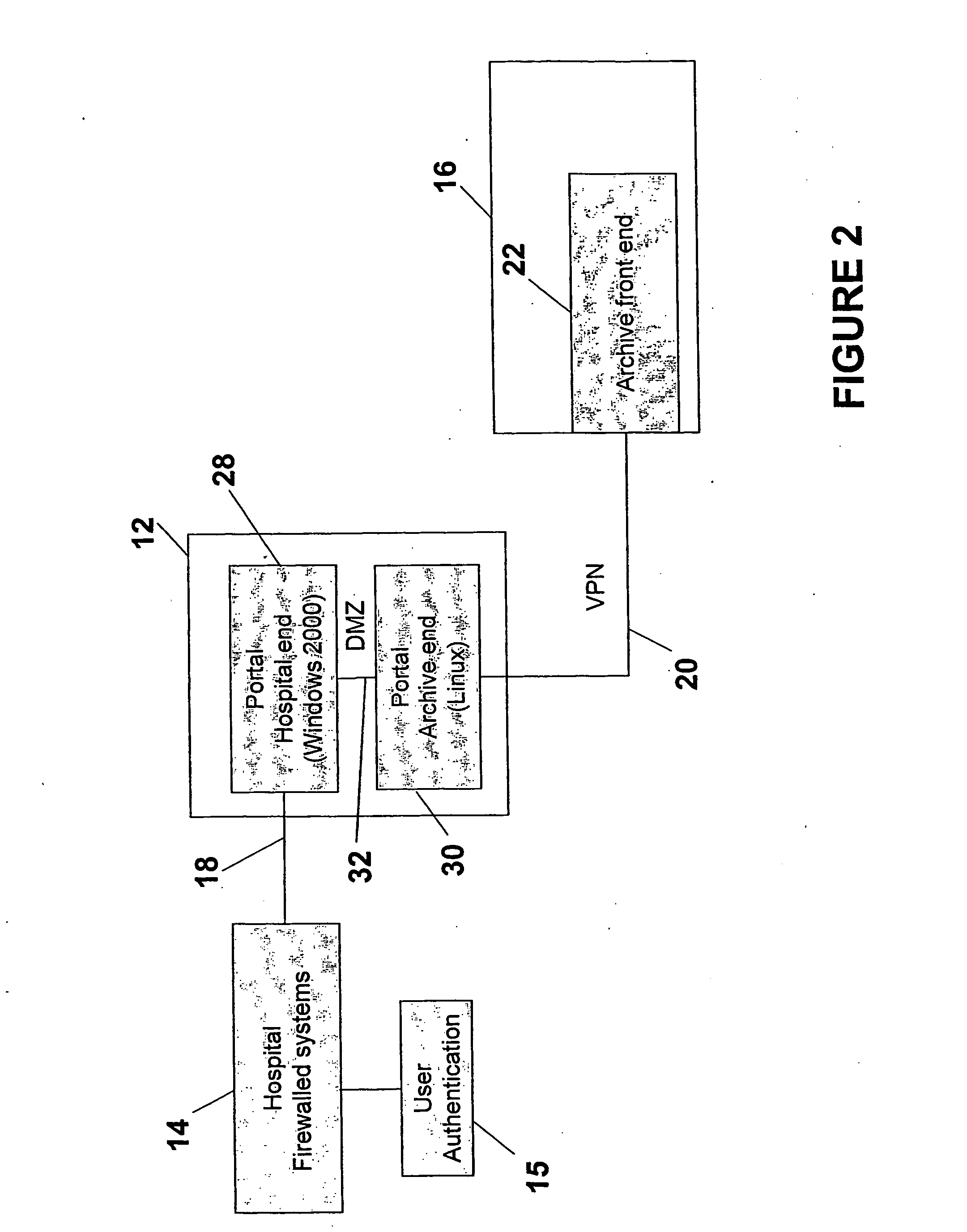
Cross-enterprise wallplug for connecting internal hospital/clinic imaging systems to external storage and retrieval systems
InactiveUS20070083615A1Secure communicationsCommunication securityMultiple digital computer combinationsMedical imagesLoggingMedical treatment
A WallPlug (interface) connects DICOM devices located at a hospital to external storage and retrieval systems. The external storage and retrieval systems can be part of the National Digital Mammography Archive. The WallPlug allows secure communications within the hospital setting, and allows only selected data to be transferred between the hospital devices and the archive. The WallPlug enables cross-enterprise distribution of medical content with proper authentication and logging of transfers. The WallPlug includes two portals connected together by a private secure network. The use of two separate devices greatly enhances the security, redundancy, and manageability of the combined device.
Owner:THE TRUSTEES OF THE UNIV OF PENNSYLVANIA
Methods and systems for improved data input, compression, recognition, correction, and translation through frequency-based language analysis
InactiveUS8671357B2Avoid excessive errorSecure CommunicationsInput/output for user-computer interactionCharacter and pattern recognitionCommon wordDocumentation
System and method for improving data input by using word frequency to text predict input. Other systems and methods include analyzing words already contained in a document (e.g. spell checking and OCR) and using word frequency to create a proxy system to reduce the space required to store data, allowing for more efficient usage of storage and enhancing the embedded content of matrix codes. The system displays the most common words in a language based upon the previously entered or displayed word(s), or the previously entered or displayed character or characters. Words with the most common frequency of use with the prior word(s) are displayed in a table to enable the user to quickly select one of the displayed words for rapid data entry. The input device can be a touch-sensitive display or non-touch sensitive type device.
Owner:SIEGEL ABBY L
Encryption/decryption system and method for a mobile device
InactiveUS20130236015A1Avoid communicationSecure CommunicationsSecret communicationSecurity arrangementMobile deviceEncryption
An encryption / decryption system and method are provided for a mobile phone configured to make a voice packet encryption / decryption during mobile communication. The mobile phone has a connecting interface for an external plug-in device. The encryption / decryption system inside the external plug-in device at least has a control unit, and a security chip. When a security communication mode is activated, the communication between users can be prevented from being disclosed. The present invention is to provide the encryption / decryption system and method for activating a security communication mode between two mobile users communicating in mobile communication, and for preventing communication packets from being disclosed.
Owner:GO TRUST TECHNOLOGY INC
Energy consumption module, offshore wind power flexible DC transmission system, and fault ride-through strategy
PendingCN110867884AProtect power transmission equipmentSecure communicationsEfficient power electronics conversionAc-dc conversionCapacitanceTransmission system
The invention discloses an energy consumption module, an offshore wind power flexible DC transmission system, and a fault ride-through strategy applied to the offshore wind power flexible DC transmission system. A DC chopper module is integrated into the MMC of an onshore converter station. The DC chopper module uses a modular arrangement and is connected in series with the SM sub-modules of the MMC. The DC chopper module does not contain capacitor components. When an onshore AC fault occurs in the offshore wind power flexible DC transmission system, the DC voltage rises sharply. A certain number of DC chopper modules (DMs) are introduced to consume surplus power through the energy-consuming resistors to maintain the system's short-term stability. After the fault is removed, the corresponding DMs are removed in order to complete the system fault ride-through. Through the modular arrangement of DMs in a bypass state during normal operation, not only can the precise matching of the surplus power be achieved, the electrical quantity fluctuations of the switching process of the chopper device can be greatly reduced, and fault ride-through and isolation are realized, but also the DM issimple in structure and good in economical efficiency.
Owner:XIDIAN POWER RECTIFIER XIAN +2
Communication apparatus and communication method
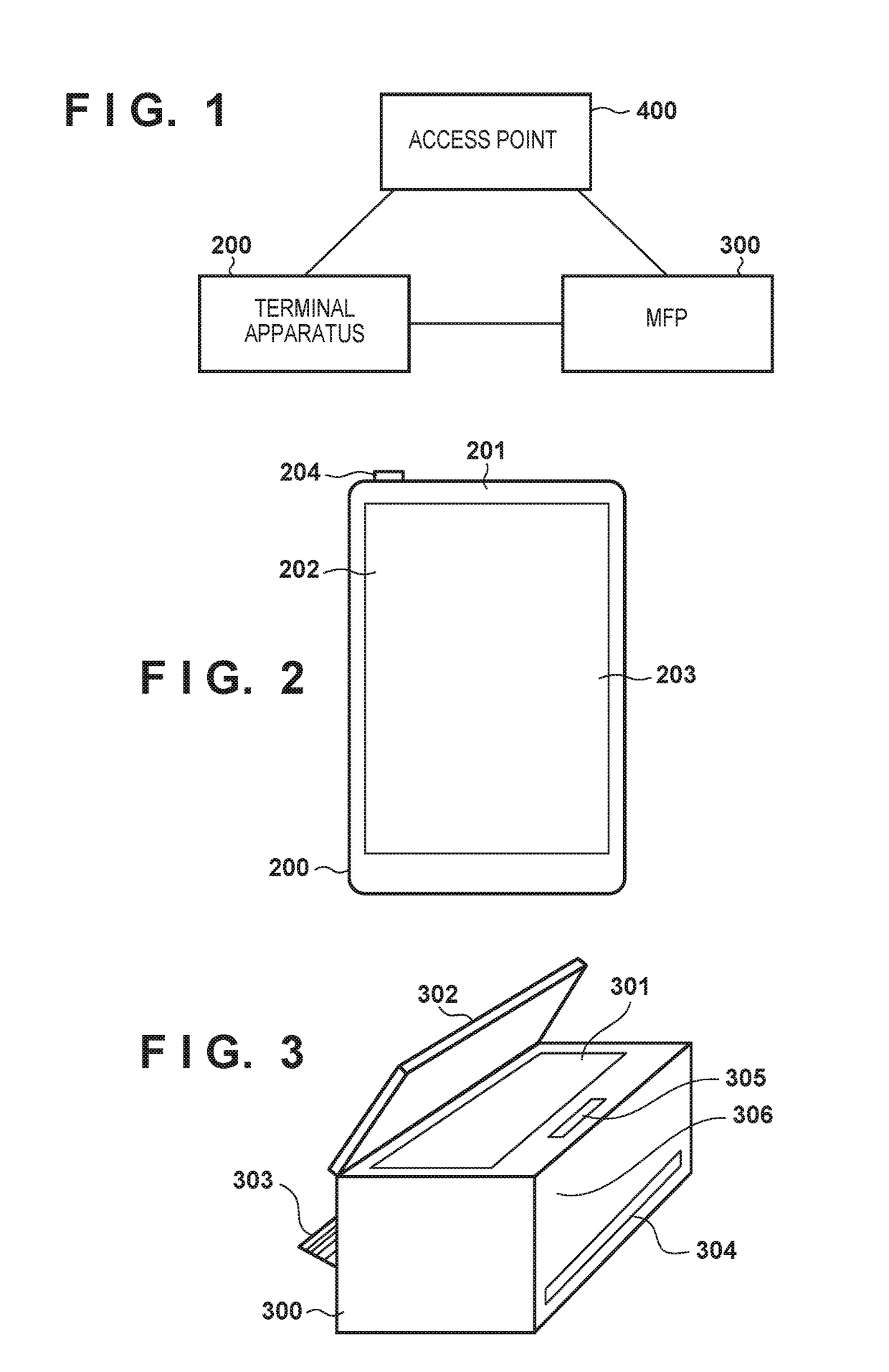
ActiveUS20170339132A1Without degrading user operabilityCommunication securityNetwork topologiesConnection managementComputer scienceWireless connectivity
A communication apparatus capable of secure wireless communication by using a certificate, comprises: a determining unit that determines, in the communication apparatus, one of whether a first mode which operates as a role in deciding a communication channel used for direct wireless connection with a communication target apparatus is activated and whether a second mode which executes role decision processing of deciding whether to operate as the role in deciding the communication channel used for the direct wireless connection with the communication target apparatus is activated; and a control unit that executes certificate generation processing before being connected to the communication target apparatus if the determining unit determines that the first mode is activated and obtain the certificate held in the communication apparatus before executing the role decision processing if the determining unit determines that the second mode is activated.
Owner:CANON KK
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com