Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
55results about How to "Reduce configuration time" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
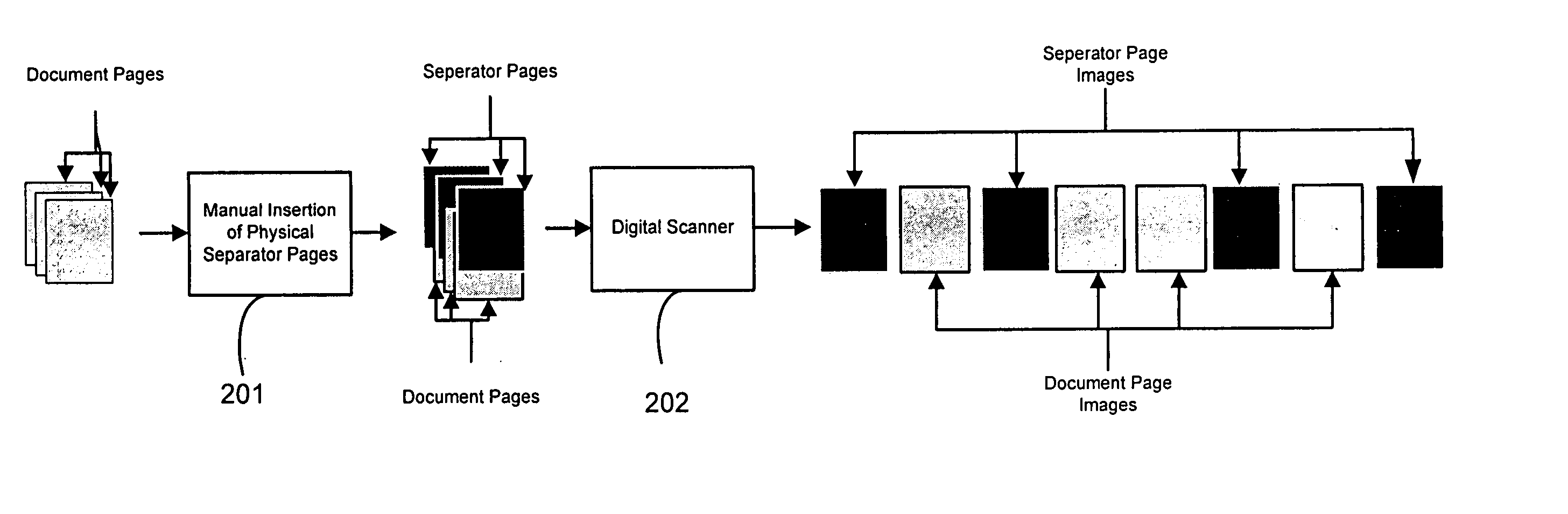
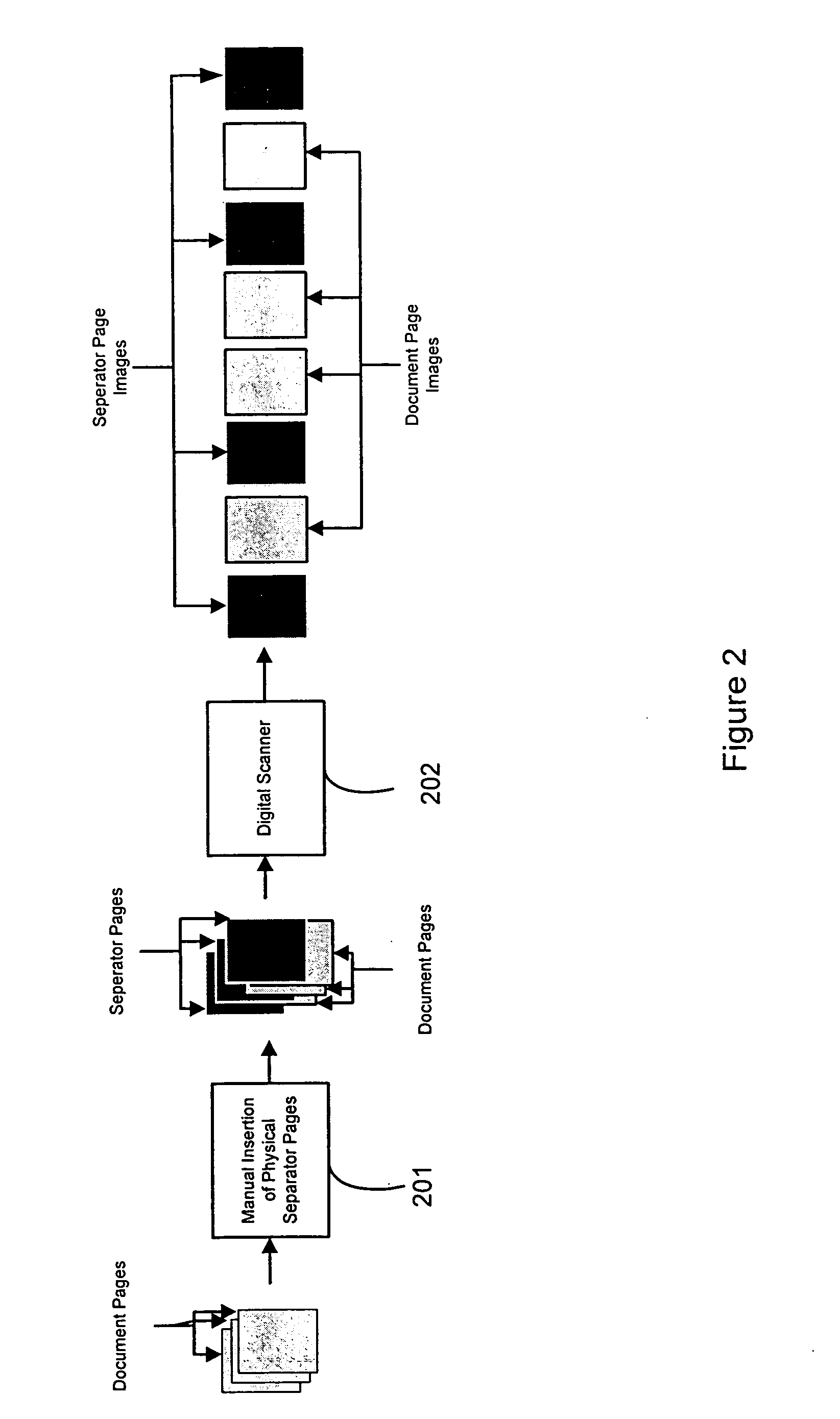
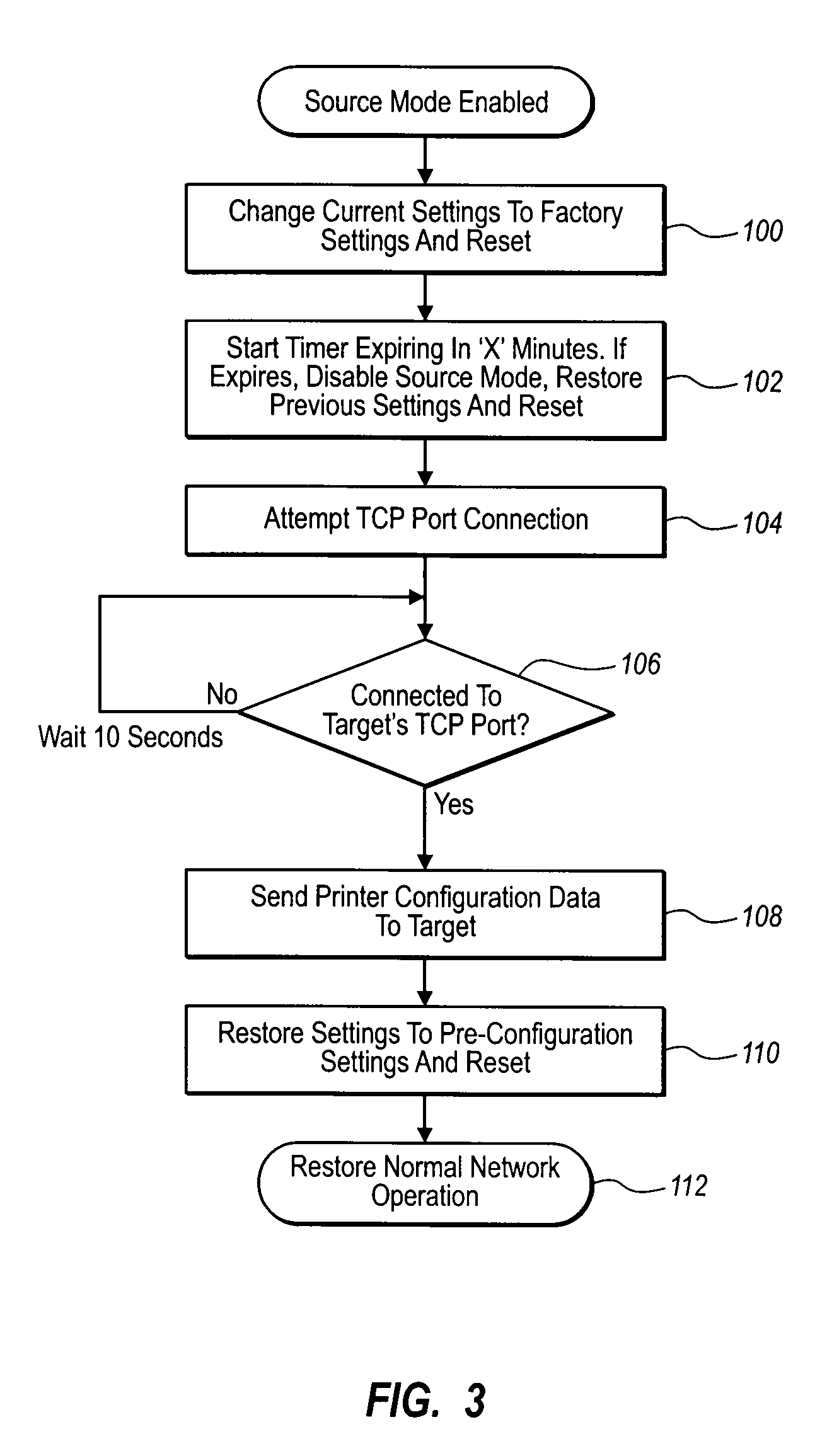
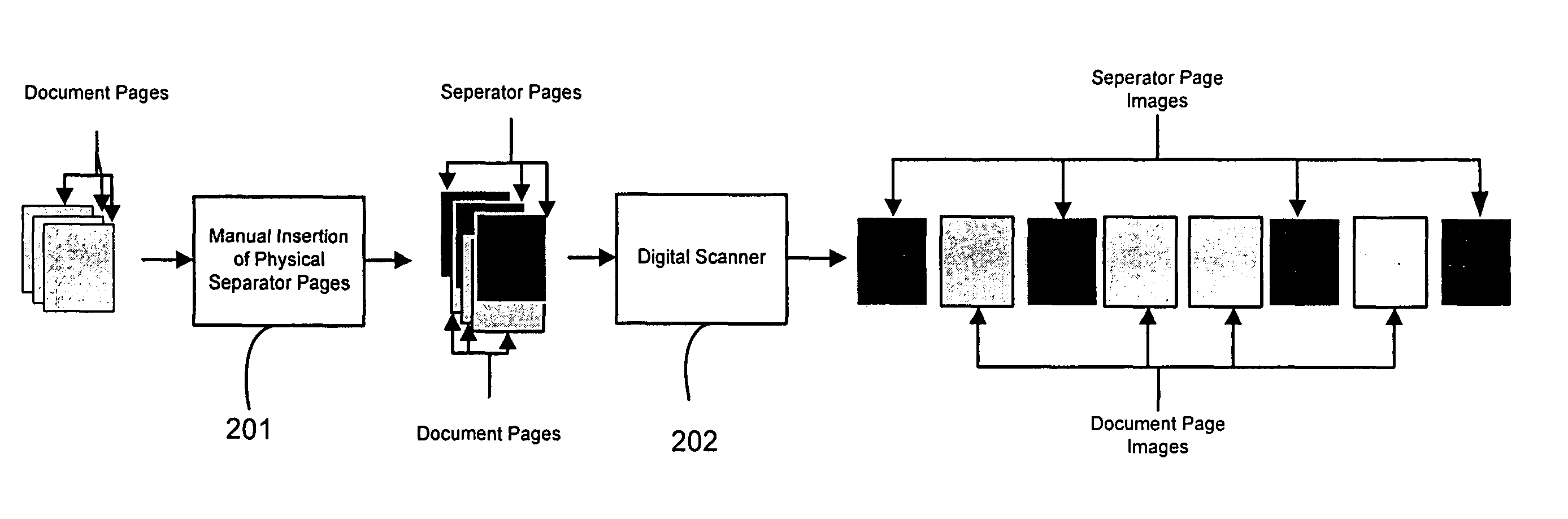
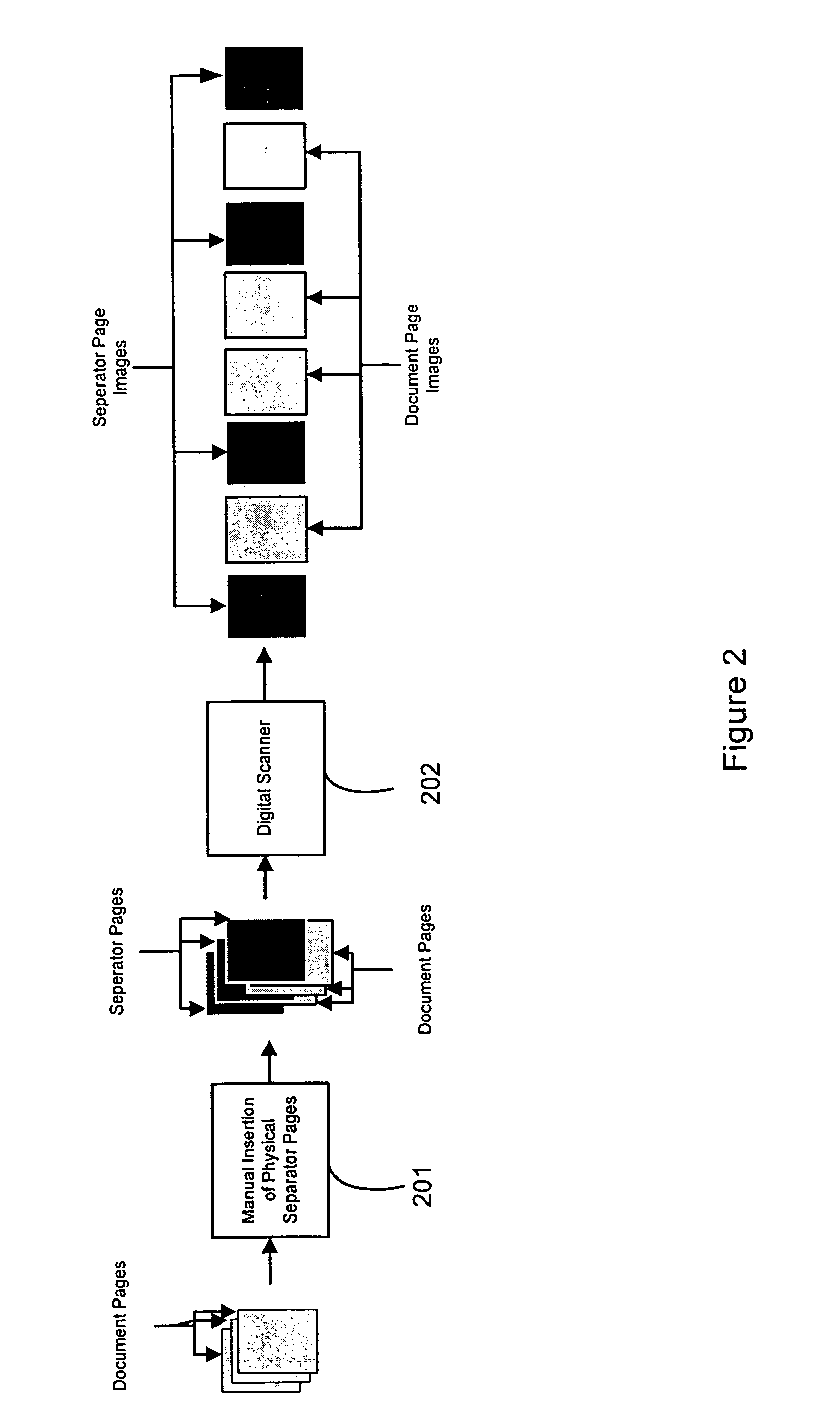
Automatic document separation
ActiveUS20050134935A1Easy maintenanceConfigurabilityImage analysisText processingPaper documentDigital image
A method and system for delineating document boundaries and identifying document types by analyzing digital images of one or more documents, automatically categorizing one or more pages or subdocuments within the one or more documents and automatically generating delineation identifiers, such as computer-generated images of separation pages inserted between digital images belonging to different categories, a description of the categorization sequence of the digital images, or a computer-generated electronic label affixed or associated with said digital images.
Owner:KOFAX
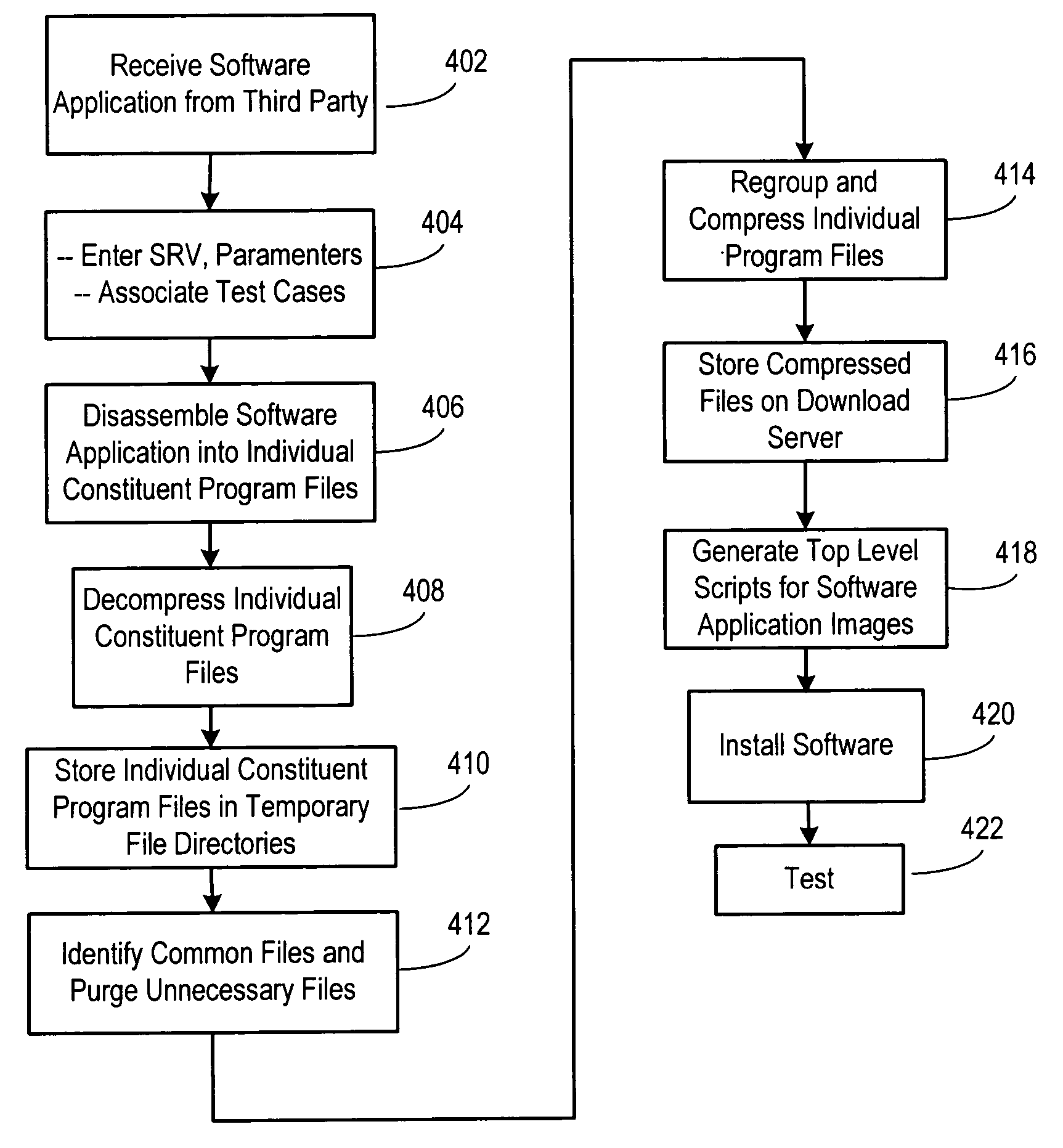
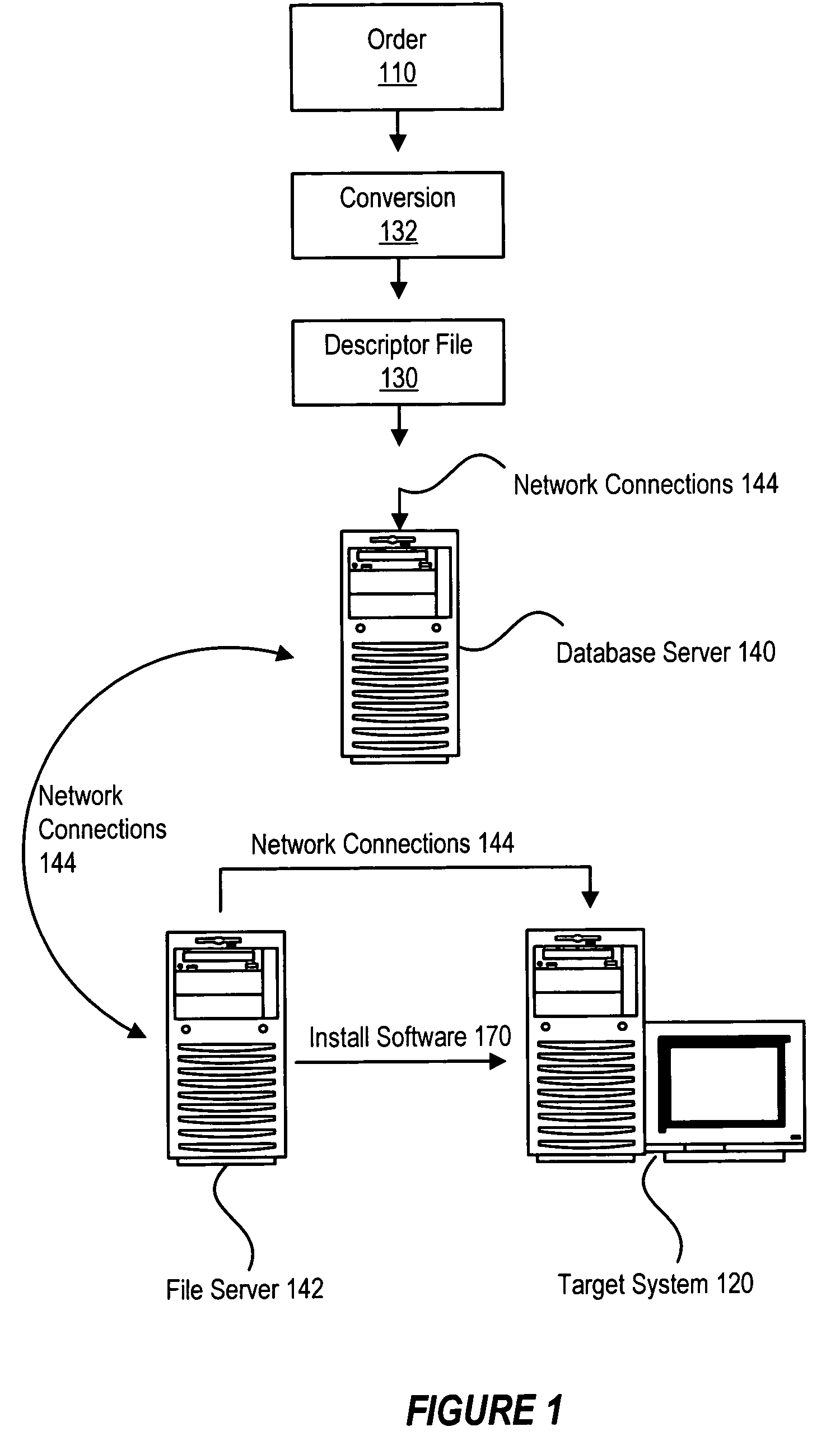
Method and system for automated generation of customized factory installable software
InactiveUS20050172284A1Reduce errorsShorten the timeProgram loading/initiatingMemory systemsInformation processingHandling system
An automated system for software installation in a build-to-order information handling system. In one embodiment of the invention, a plurality of software applications are received and are disassembled to separate the individual constituent program files. These program files are decompressed and are stored in temporary file directories. Program files that are common to each of the software applications are identified and indexed. After the file analysis, the files are regrouped and a stored as a new set of compressed files. Once the new set of compressed files has been created, the top level scripts for the software application images are updated for use with the new compressed files to allow the desired combinations of software applications to be regenerated. The regenerated compressed files are then loaded into the factory servers for use in manufacturing information handling systems.
Owner:DELL PROD LP
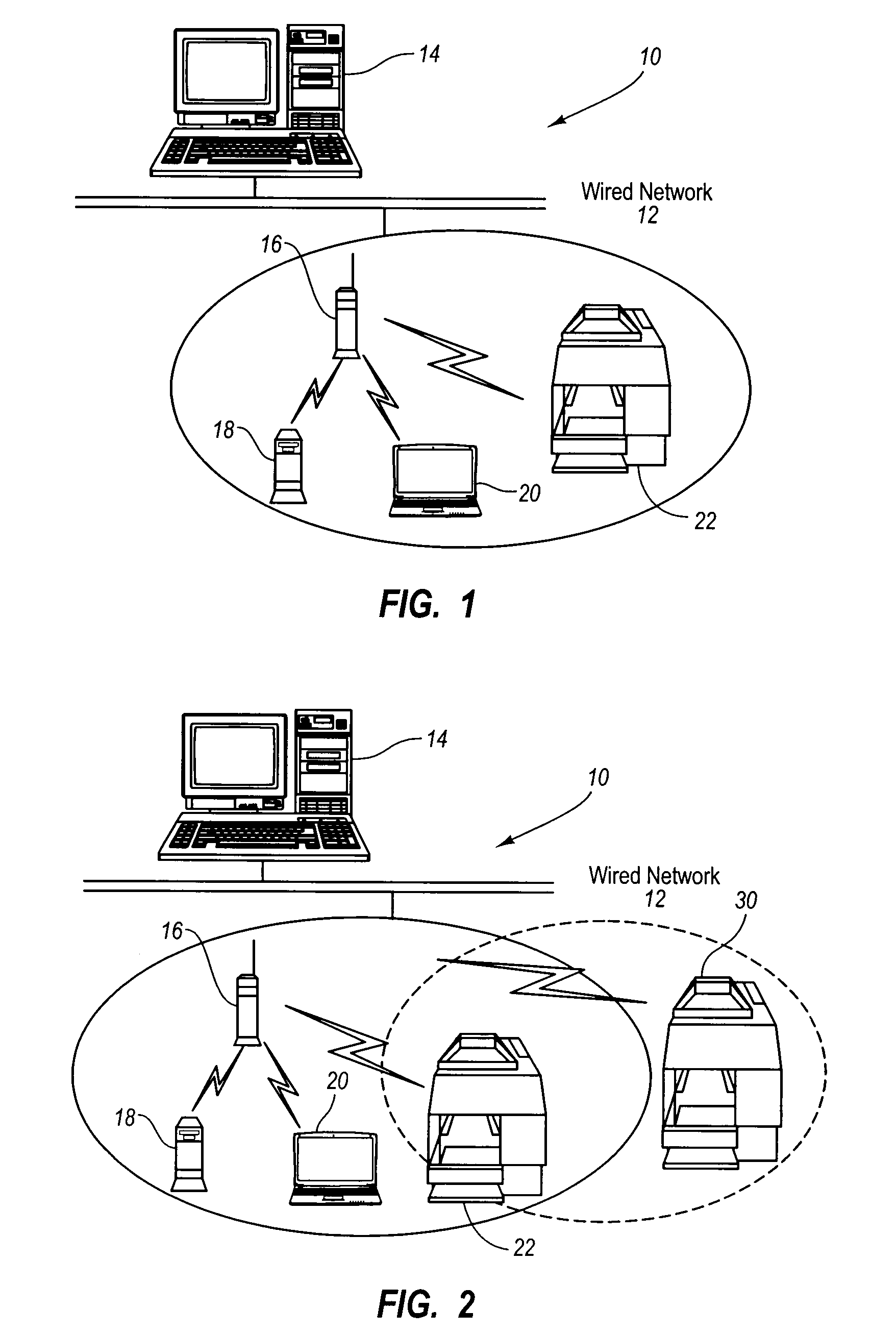
System, Apparatus and Method for Automated Wireless Device Configuration
ActiveUS20070146782A1Decreases network configuration timeReduce configuration timeDigitally marking record carriersNetwork traffic/resource managementAuto-configurationComputer science
A method and system for automatically configuring a plurality of wireless peripheral devices within a network environment. The method includes identifying a plurality of wireless peripheral devices, including one existing networked wireless device. The existing networked wireless device is configured to function as a master device. The master device identifies one of the remaining wireless peripheral devices that has yet to be configured. The master device replicates itself by wirelessly transmitting the configuration data to the identified wireless peripheral device. The configuration data enables the identified peripheral wireless device to assume network operation and to assume functionality of the master device so as to be capable of automatically causing the configuration of additional peripheral devices.
Owner:SEIKO EPSON CORP
Automatic document separation
ActiveUS8693043B2Reduce effortReduce configuration timeDigitally marking record carriersImage analysisDigital imageDocumentation
Owner:KOFAX
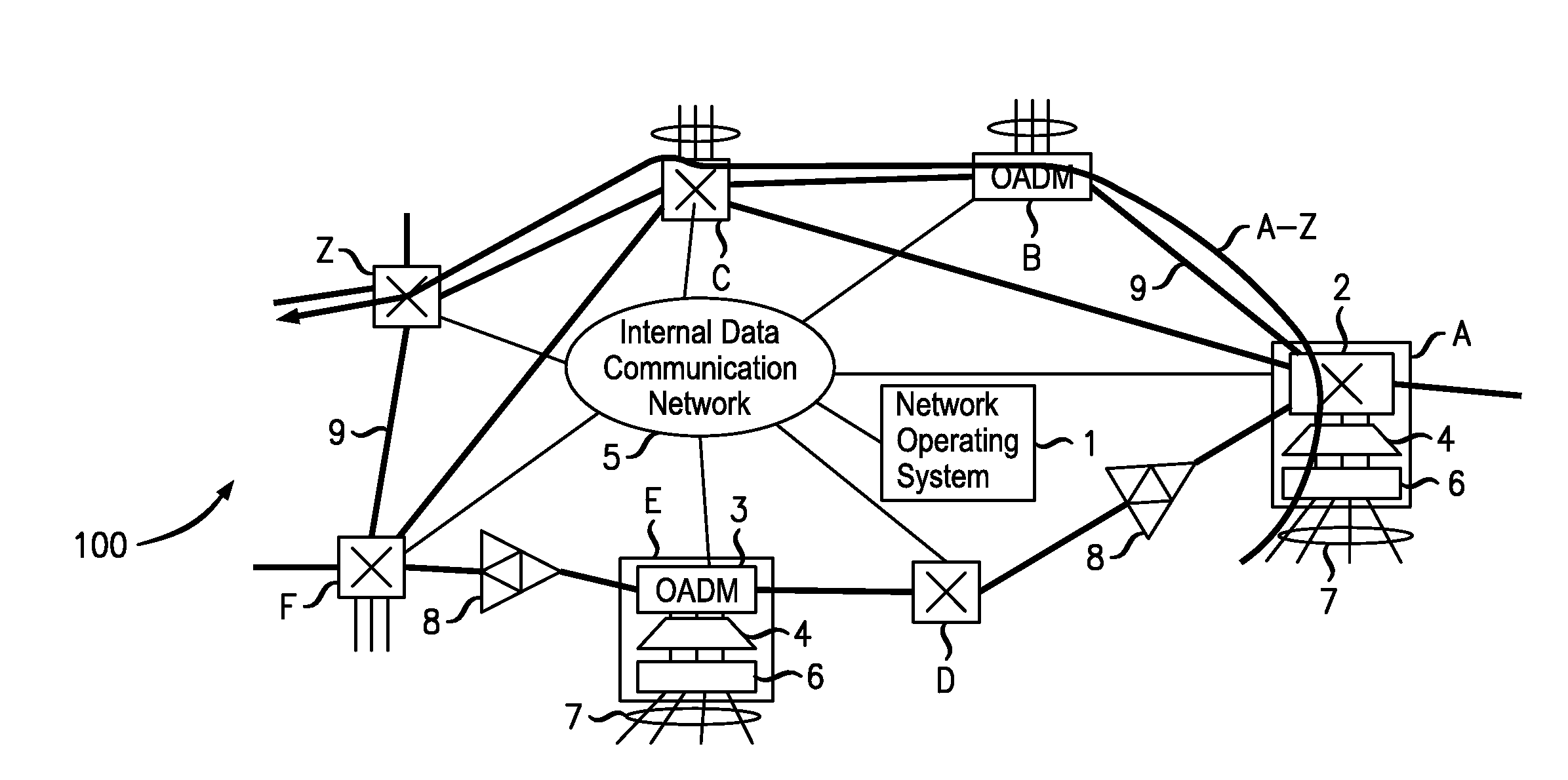
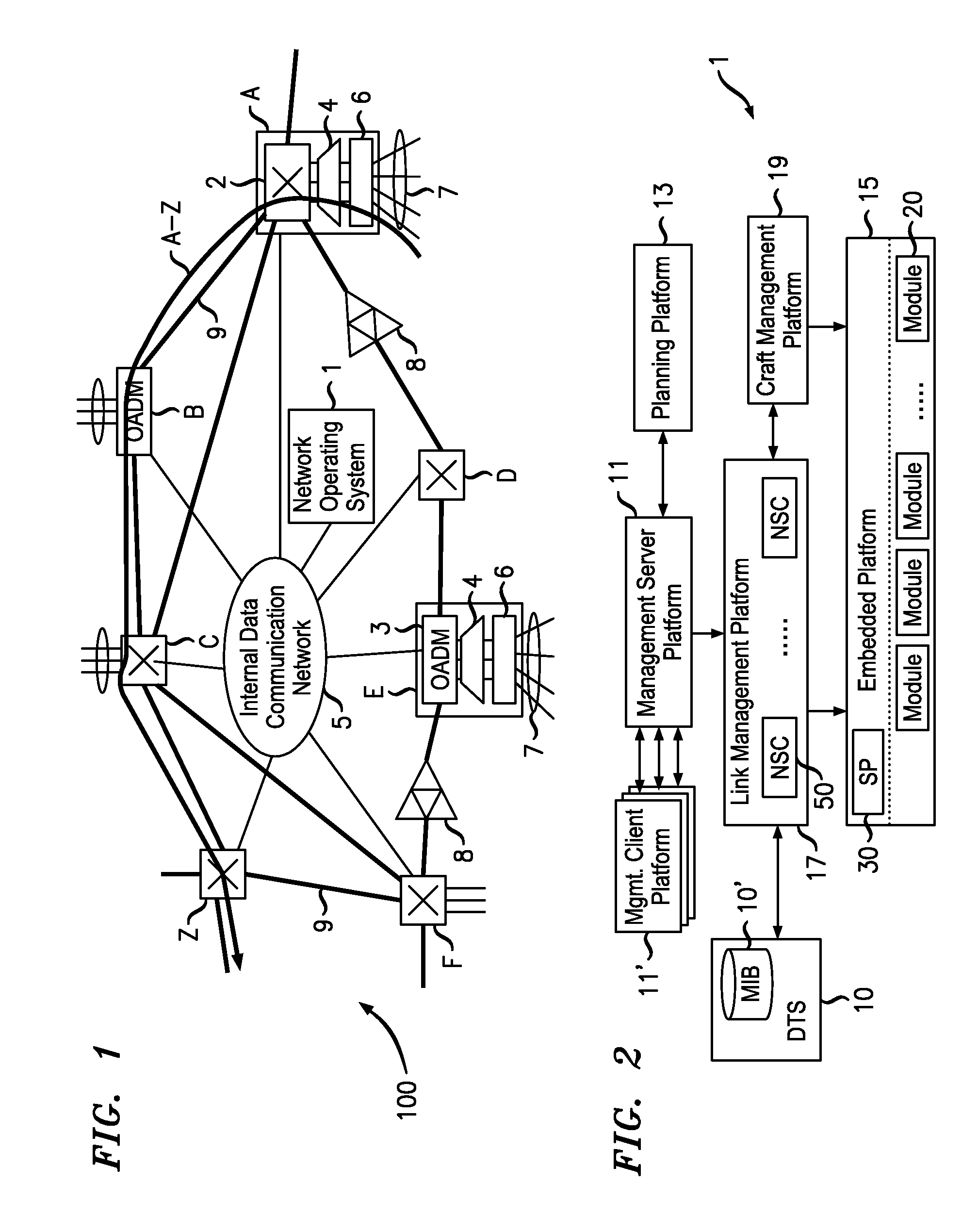
Network operating system with topology autodiscovery
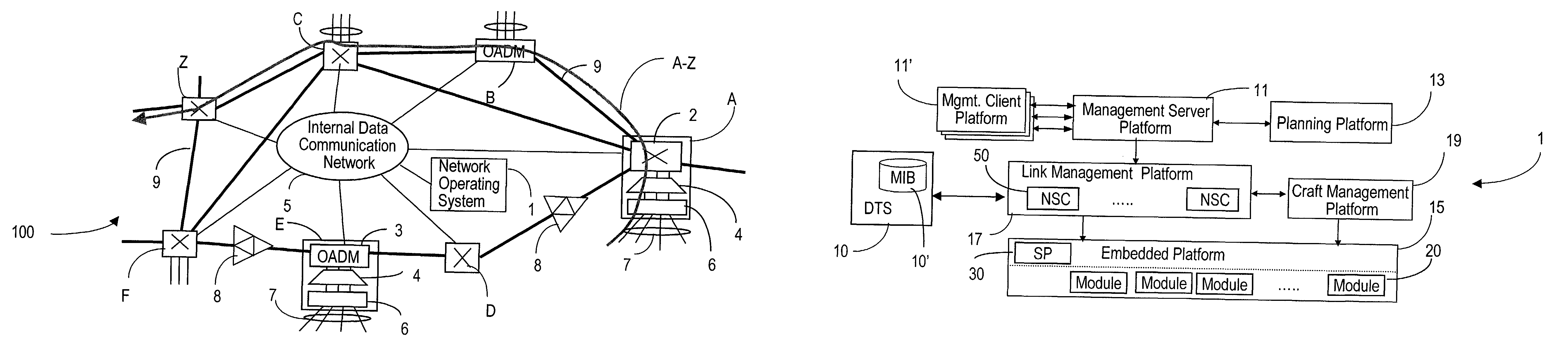
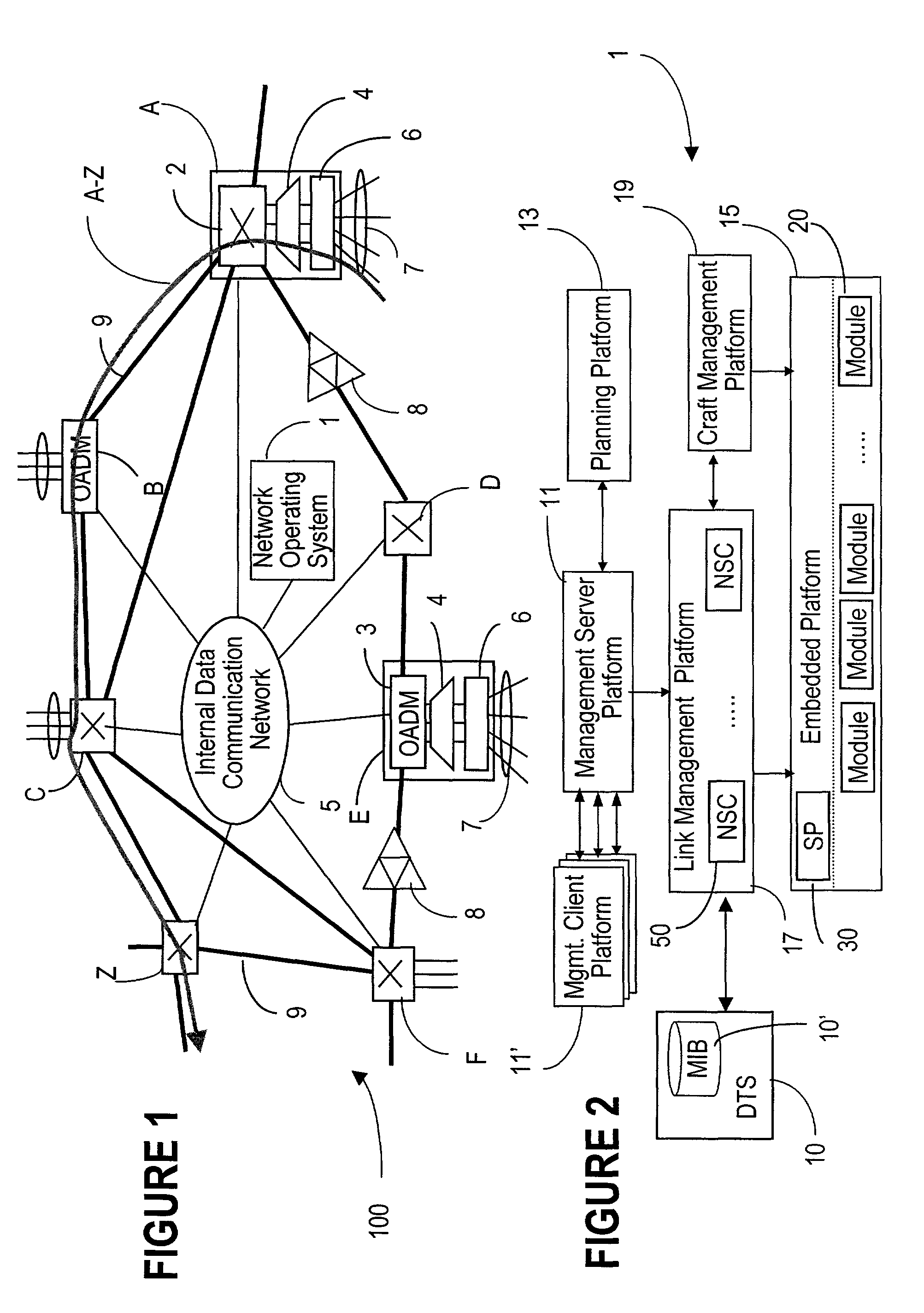
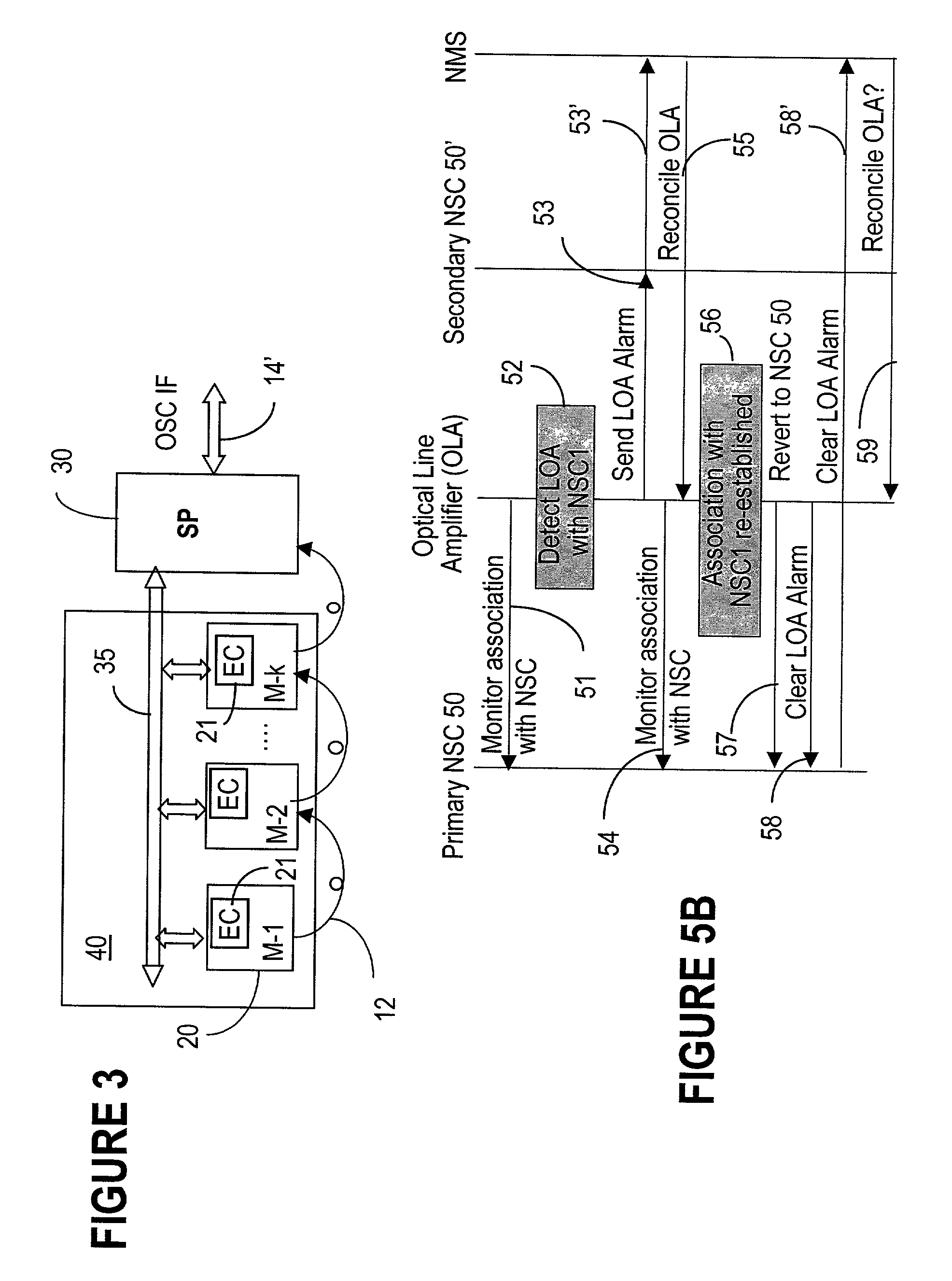
ActiveUS7747165B2Reduce the time required for installationReduce configuration timeMultiplex system selection arrangementsCoupling light guidesNetwork operating systemOperational system
The network operating system includes an embedded platform for controlling operation of an agile optical network at the physical layer level. At the module embedded level, each module (card-pack) is provided with an embedded controller EC that monitors and control operation of the optical modules. At the next level, each shelf is provided with a shelf processor SP that monitors and control operation of the ECs over a backplane network. All optical modules are connected over an optical trace channel to send / receive trace messages that can then be used to determine network connectivity. At the next, link management level, a network services controller NSC controls the SPs in a negotiated span of control, over a link network. The control is address-based; each NSC receives ranges of addresses for the entities in its control, and distributes these addresses to the SPs, which in turn distribute addresses to the ECs in their control. One of the SPs operates as a router on the link network to relay signaling and control to all entities based on their address. Each NSC constructs, from queried information, a network topology fragment for the embedded elements under its control. A distributed topology system (DTS) shares this topology information with neighboring NSC's to build a complete network view, which can be used by all interested network applications.
Owner:WSOU INVESTMENTS LLC
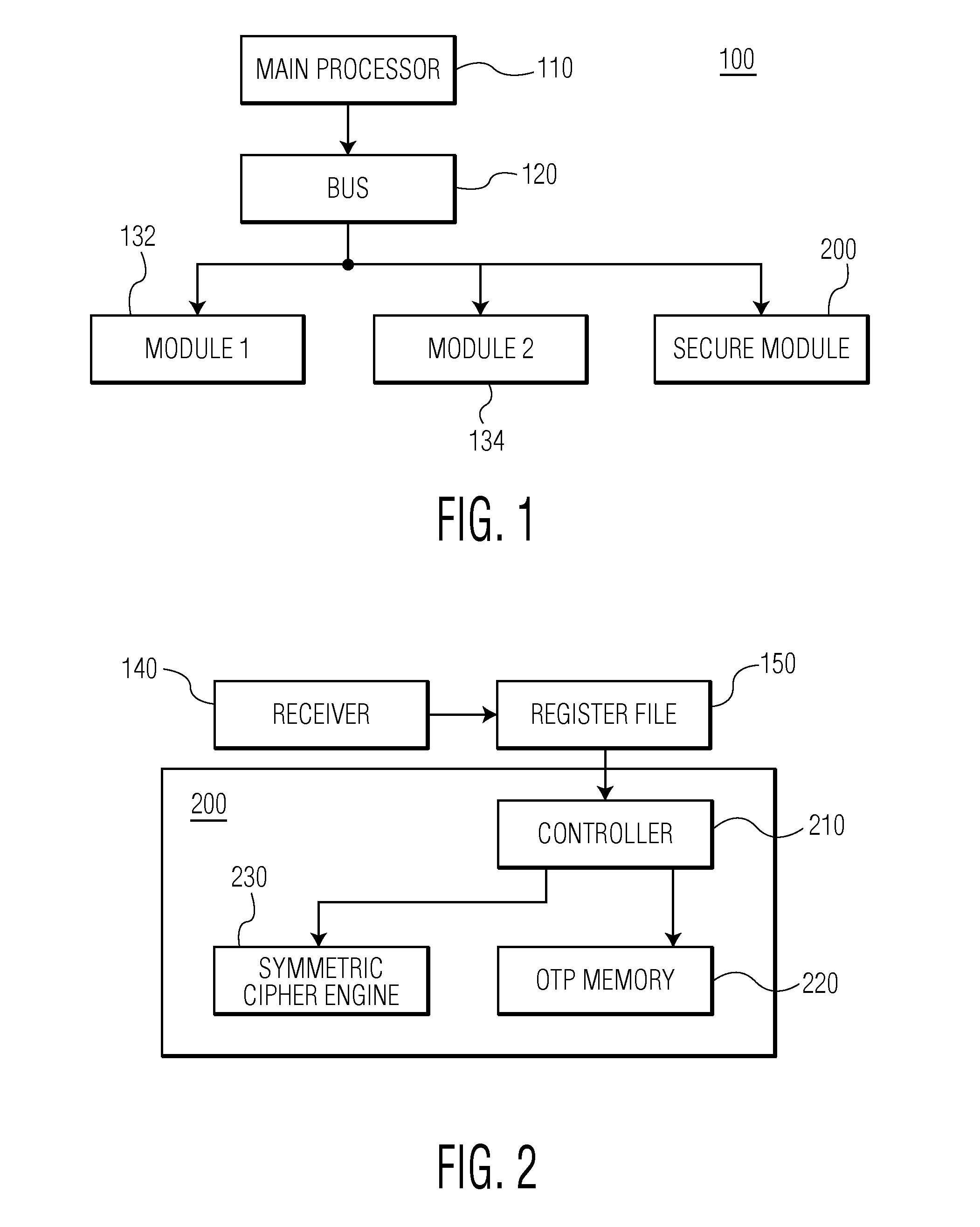
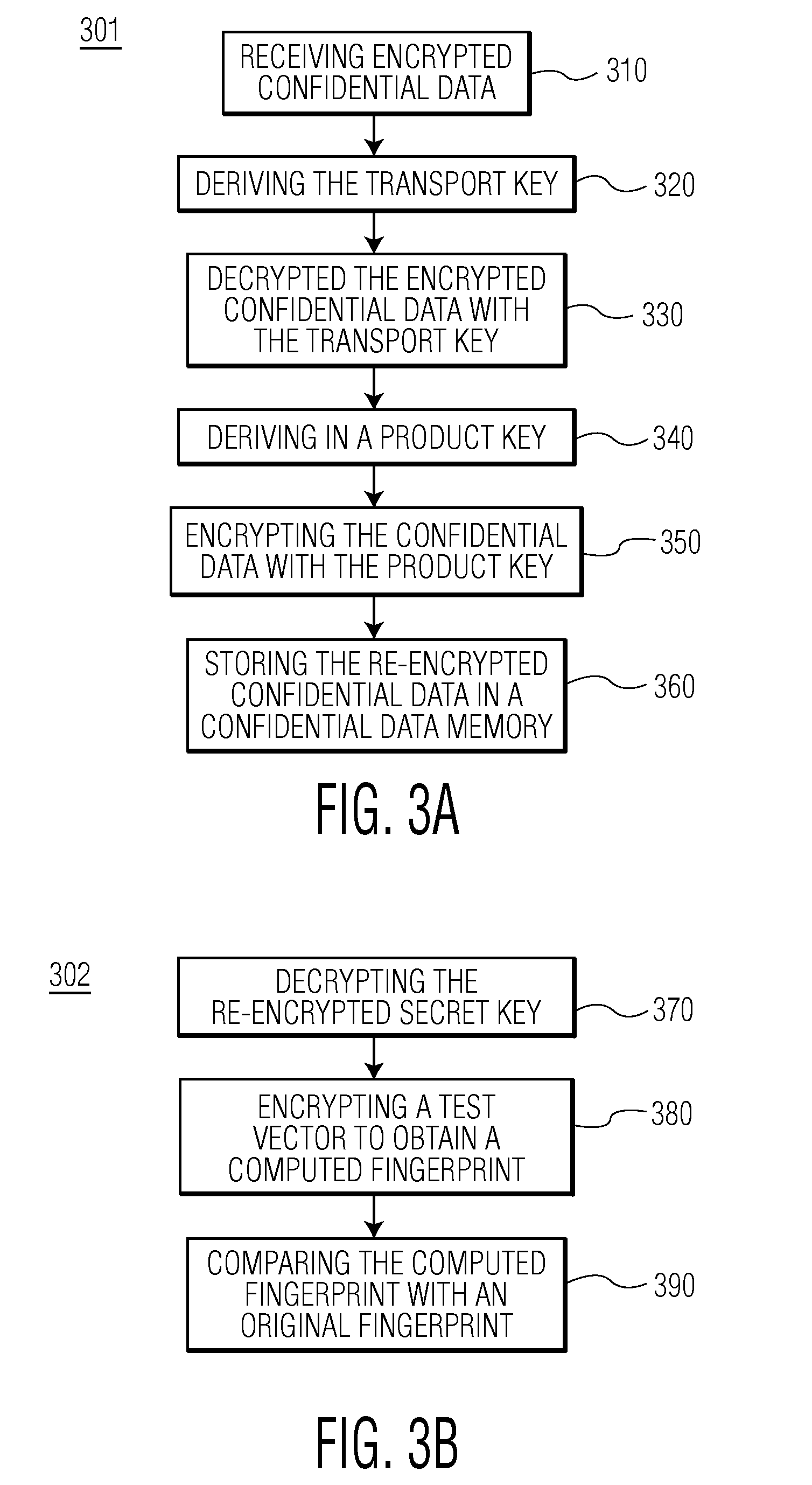
Secure dynamic on chip key programming
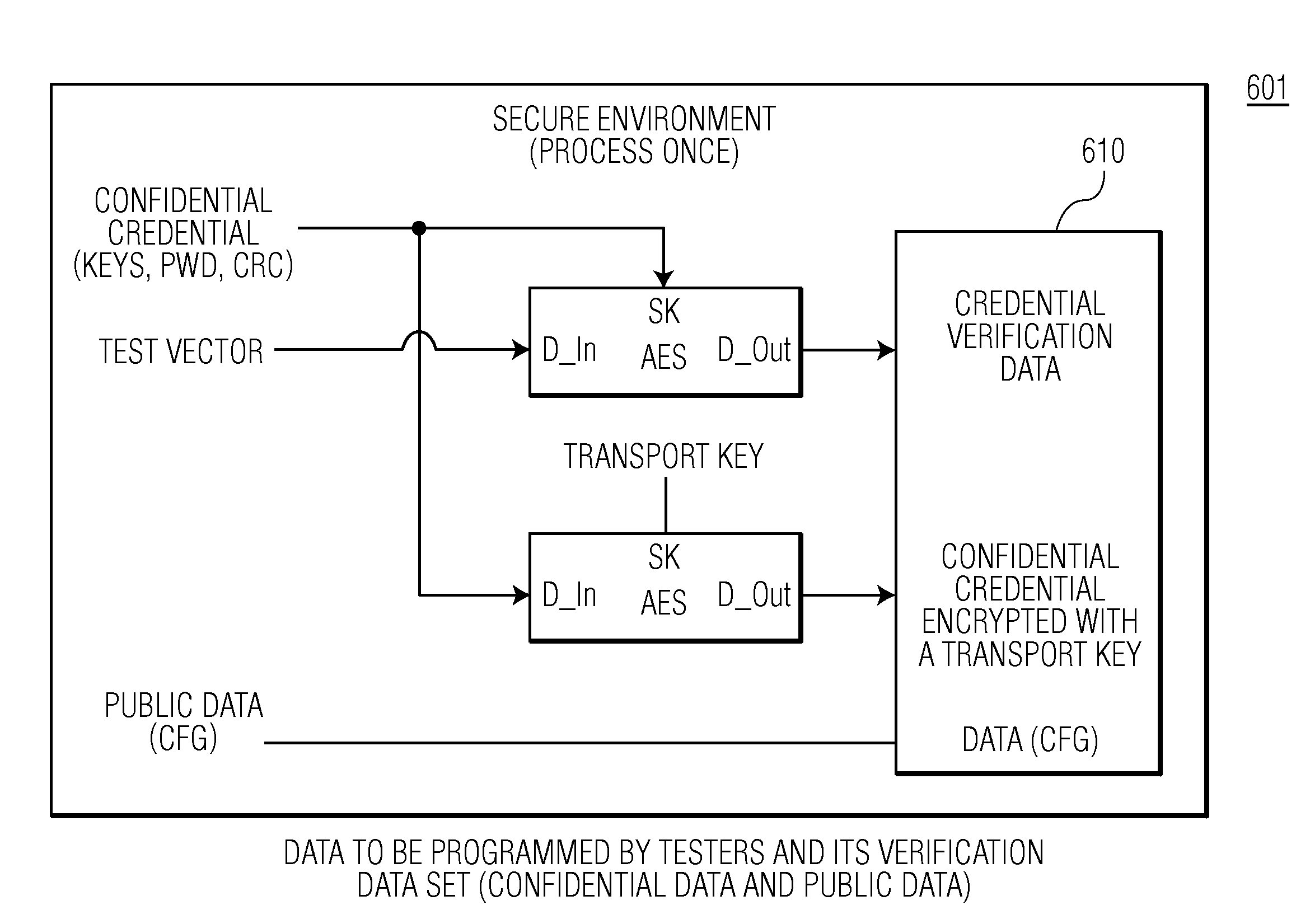
ActiveUS20130163764A1Simple methodIncrease in sizeKey distribution for secure communicationComputer security arrangementsComputer securityIntegrated circuit
Provisioning an integrated circuit with confidential data, by receiving in the integrated circuit encrypted confidential data, the encrypted confidential data having been encrypted with a transport key, deriving in the integrated circuit the transport key by applying a key derivation function to a customer identifier, the customer identifier having been previously stored in the integrated circuit, decrypting in the integrated circuit the encrypted confidential data with the transport key to obtain decrypted confidential data, deriving in the integrated circuit a product key by applying a key derivation function to an integrated circuit identifier, the integrated circuit identifier having been previously stored in the integrated circuit, encrypting in the integrated circuit the decrypted confidential data with the product key to obtain re-encrypted confidential data, and storing the re-encrypted confidential data in a confidential data memory of the integrated circuit.
Owner:NXP BV
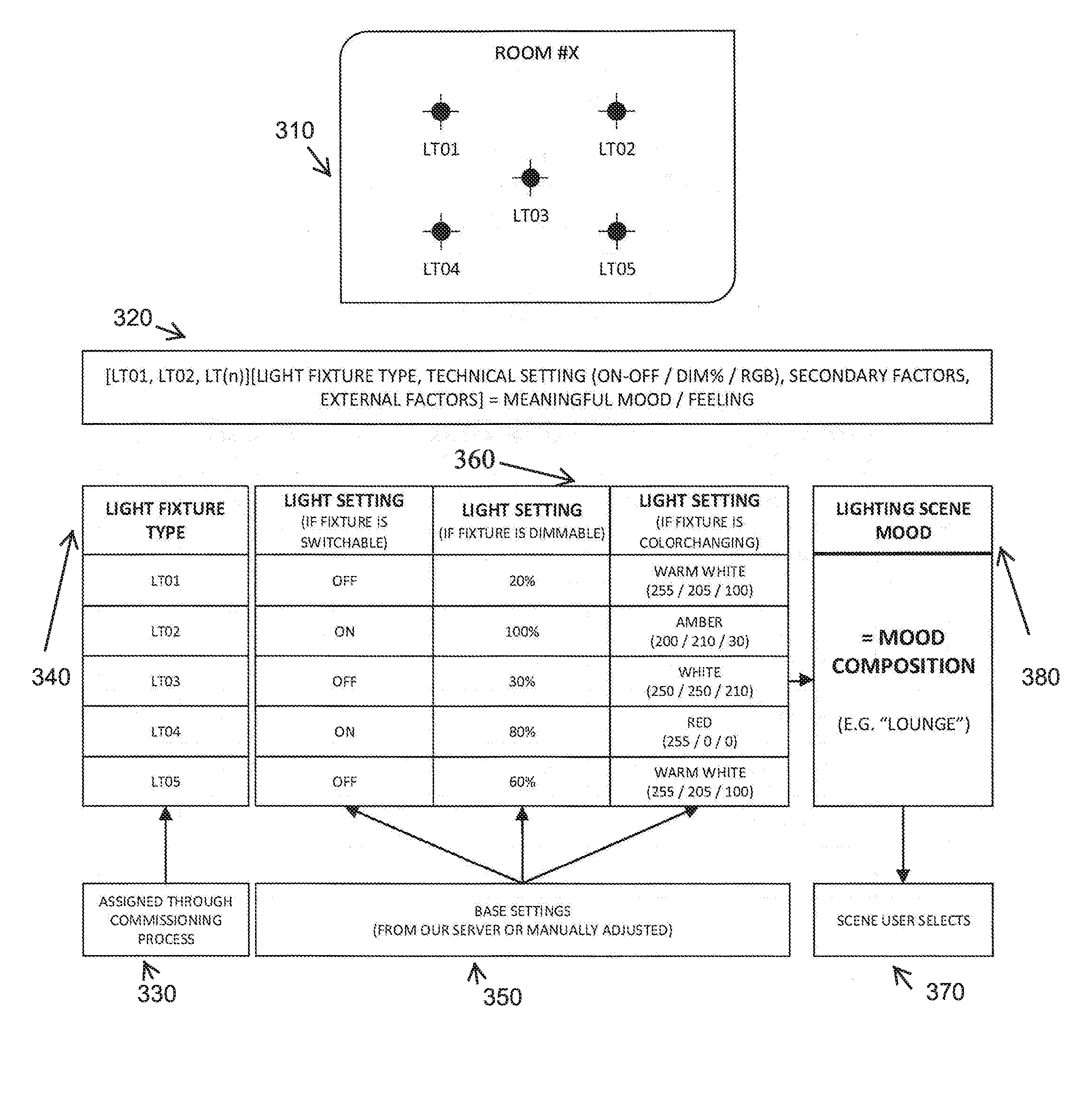
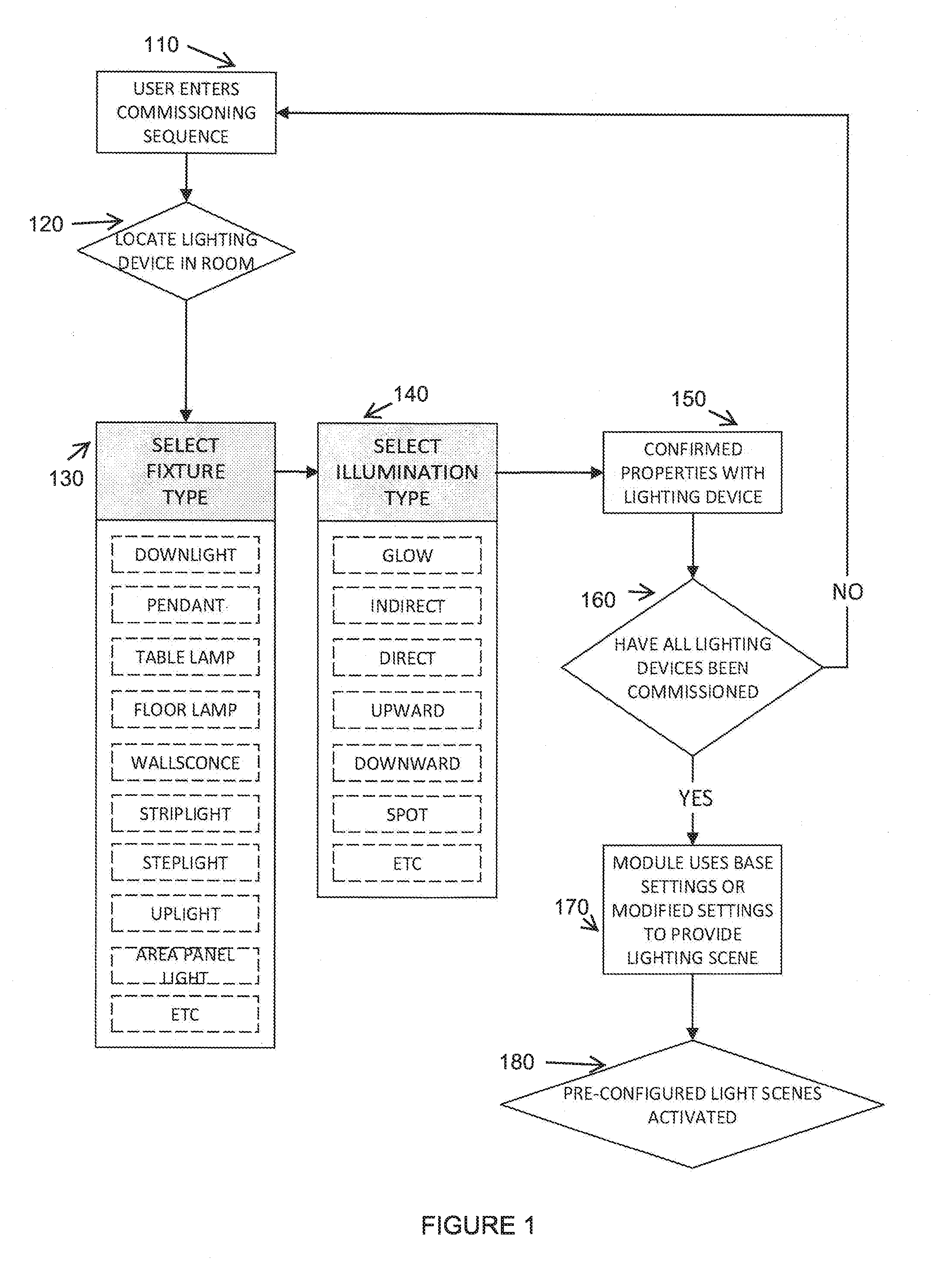
Automated and Pre-configured Set Up of Light Scenes
ActiveUS20160286630A1Efficient use of energyReduction of setupElectrical apparatusElectroluminescent light sourcesMedicineComputer graphics (images)
Owner:LUMIFI
System, apparatus and method for automated wireless device configuration
ActiveUS7940744B2Reduce configuration timeFrequency-division multiplex detailsNetwork traffic/resource managementComputer hardwareAuto-configuration
A method and system for automatically configuring a plurality of wireless peripheral devices within a network environment. The method includes identifying a plurality of wireless peripheral devices, including one existing networked wireless device. The existing networked wireless device is configured to function as a master device. The master device identifies one of the remaining wireless peripheral devices that has yet to be configured. The master device replicates itself by wirelessly transmitting the configuration data to the identified wireless peripheral device. The configuration data enables the identified peripheral wireless device to assume network operation and to assume functionality of the master device so as to be capable of automatically causing the configuration of additional peripheral devices.
Owner:SEIKO EPSON CORP
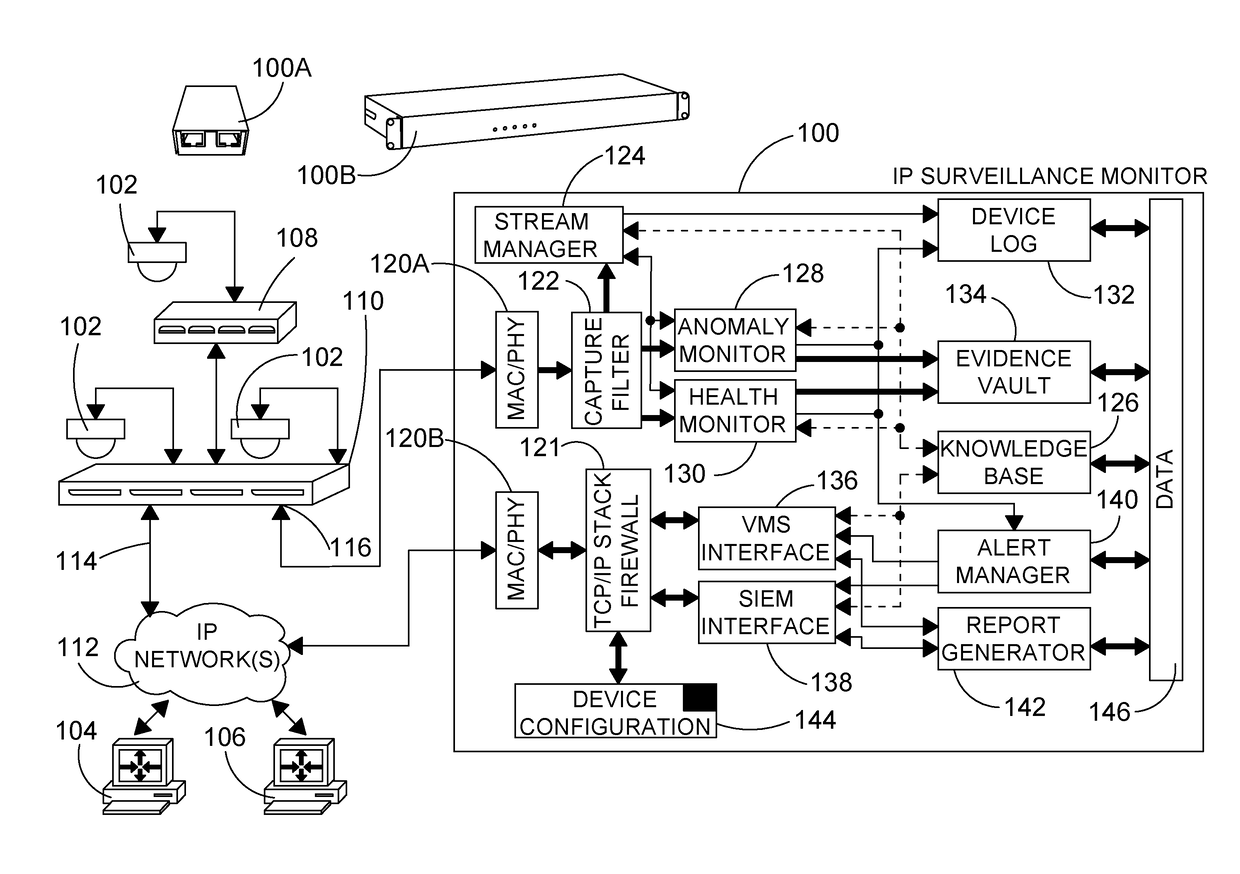
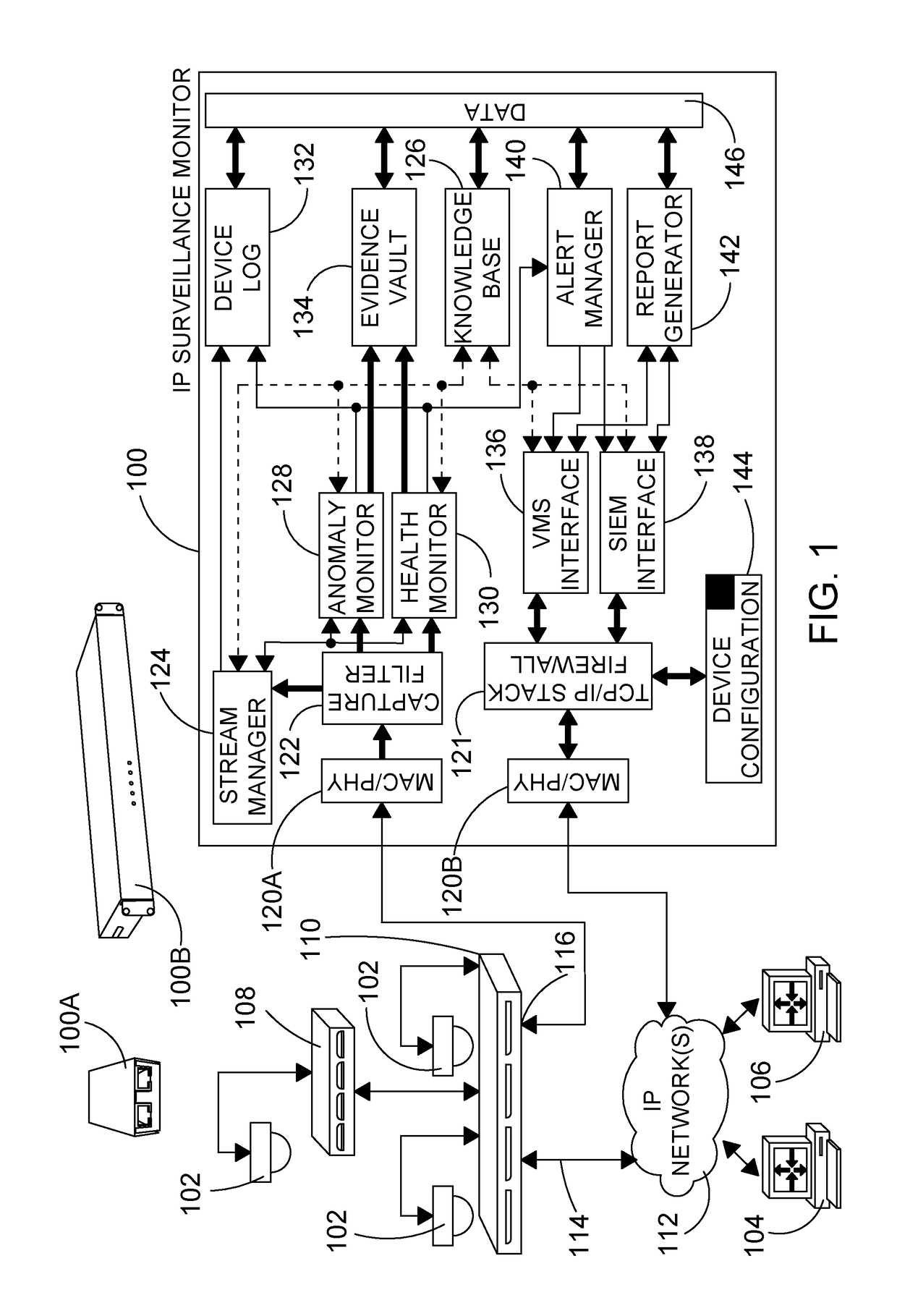
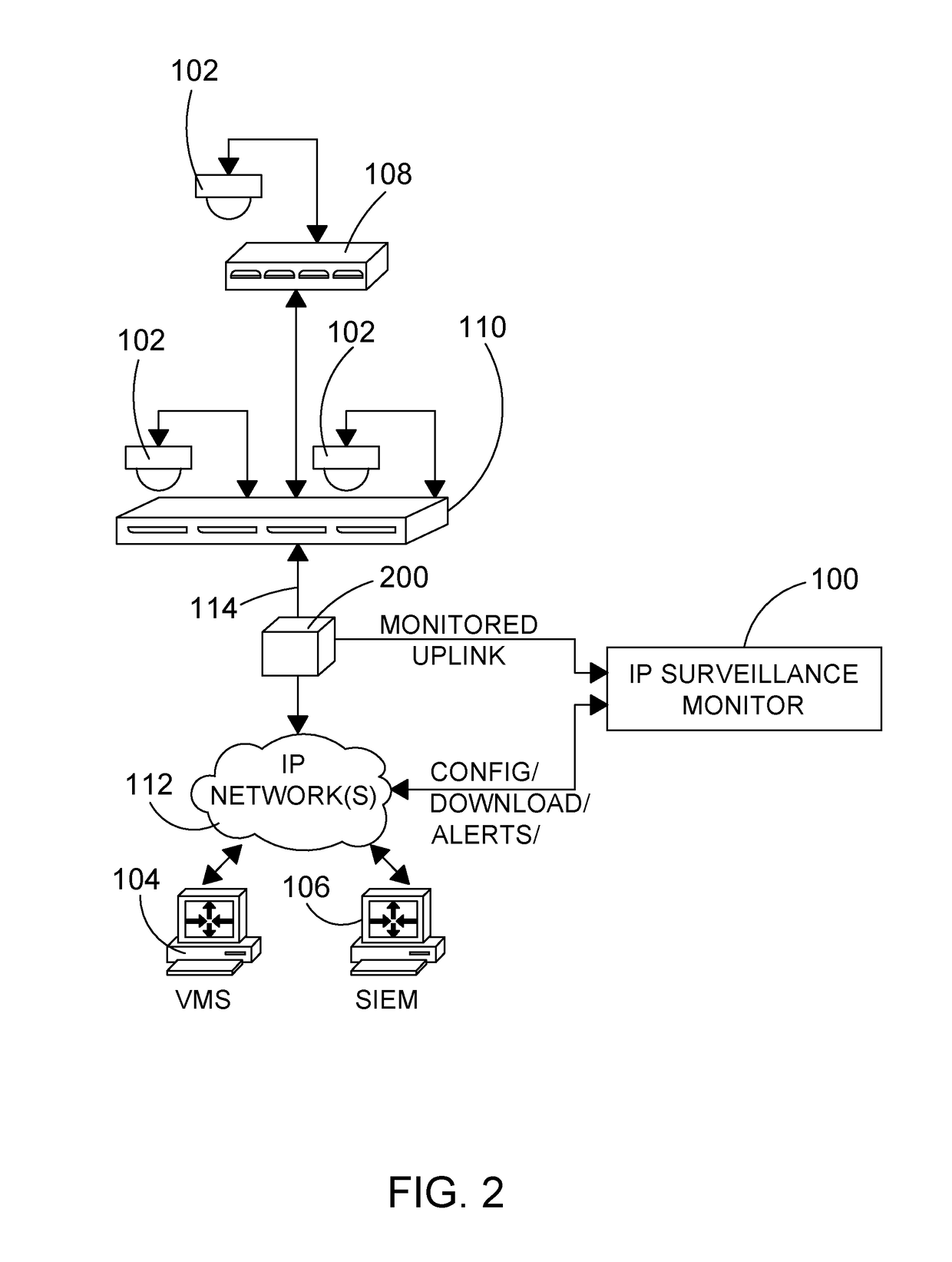
Monitoring devices and methods for IP surveillance networks
InactiveUS20180288126A1Reduce configuration timeTelevision system detailsClosed circuit television systemsData packData stream
A network monitoring device and methods for monitoring data streams in an IP surveillance network. A capture filter of the device captures data packets from a data stream between first and second end-points of an IP surveillance network. A packet parser of the device parses packets captured by the capture filter to obtain packet information. A stream model of the device creates and stores stream records corresponding to data streams and either matches the packet information to a stream record listed in the stream model, or, if no match is found, to initialises a new stream record for the captured packet. A monitor of the device applies one or more rules to the captured packets and executes one or more actions based on the application of the one or more rules. A knowledge base of the device stores: information about components of the IP surveillance network; information about data streams between the components of IP surveillance networks; state information regarding the IP surveillance network, network components and network site; a plurality of IP surveillance stream templates for use by the stream model to initialise the stream records; and rules and actions to be applied to captured packets by the monitor.
Owner:INDIGOVISION
Intelligent configuration method
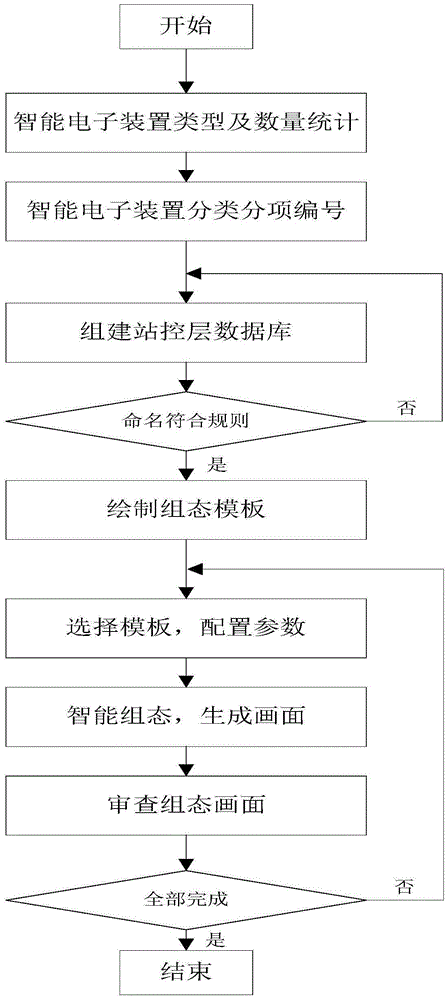
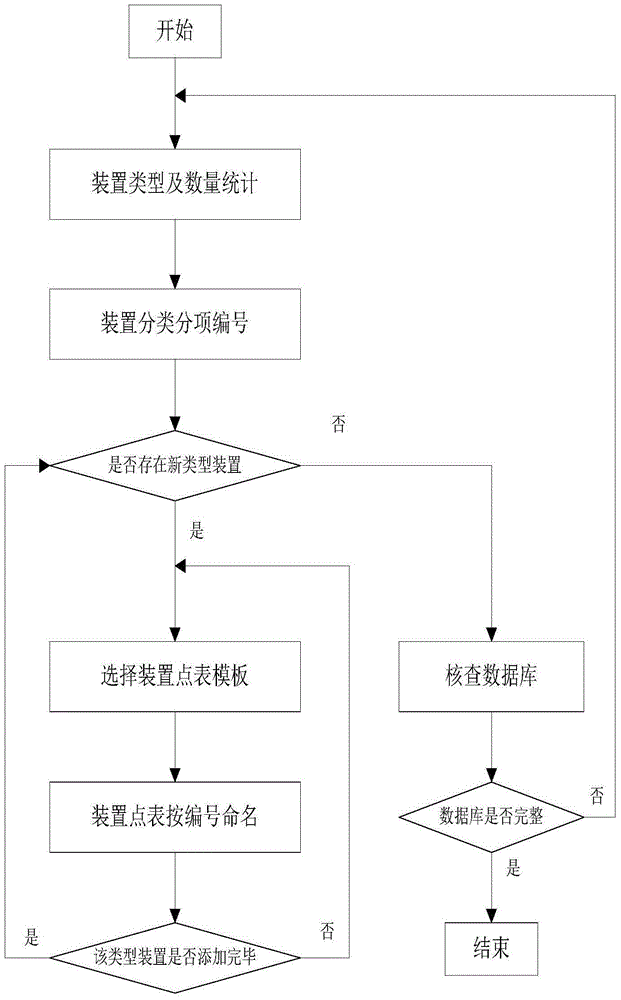
InactiveCN105204458AReduce configuration timeShorten the timeProgramme total factory controlAnimationMonitoring system
The invention relates to an intelligent configuration method. The method is characterized by comprising the following steps that (1) onsite devices to be configured are counted and classified, and according to a set numbering rule, each device to be configured in each type is provided with a unique identification code; (2) a data base of the station control level is established; (3) a configuration template is drafted; (4) intelligent configuration is implemented according to an intelligent configuration algorithm; and (5) the step (4) is repeated to complete intelligent configuration for all types of devices to be configured. The intelligent configuration method can reduce image drafting and animation connecting time in the configuration process to a large extent, and thus substantially shorten the configuration time of a monitoring system, background data of the devices to be configured can be configured intelligently and automatically, and man-made errors in the configuration process is reduced to the largest degree.
Owner:XUJI GRP +1
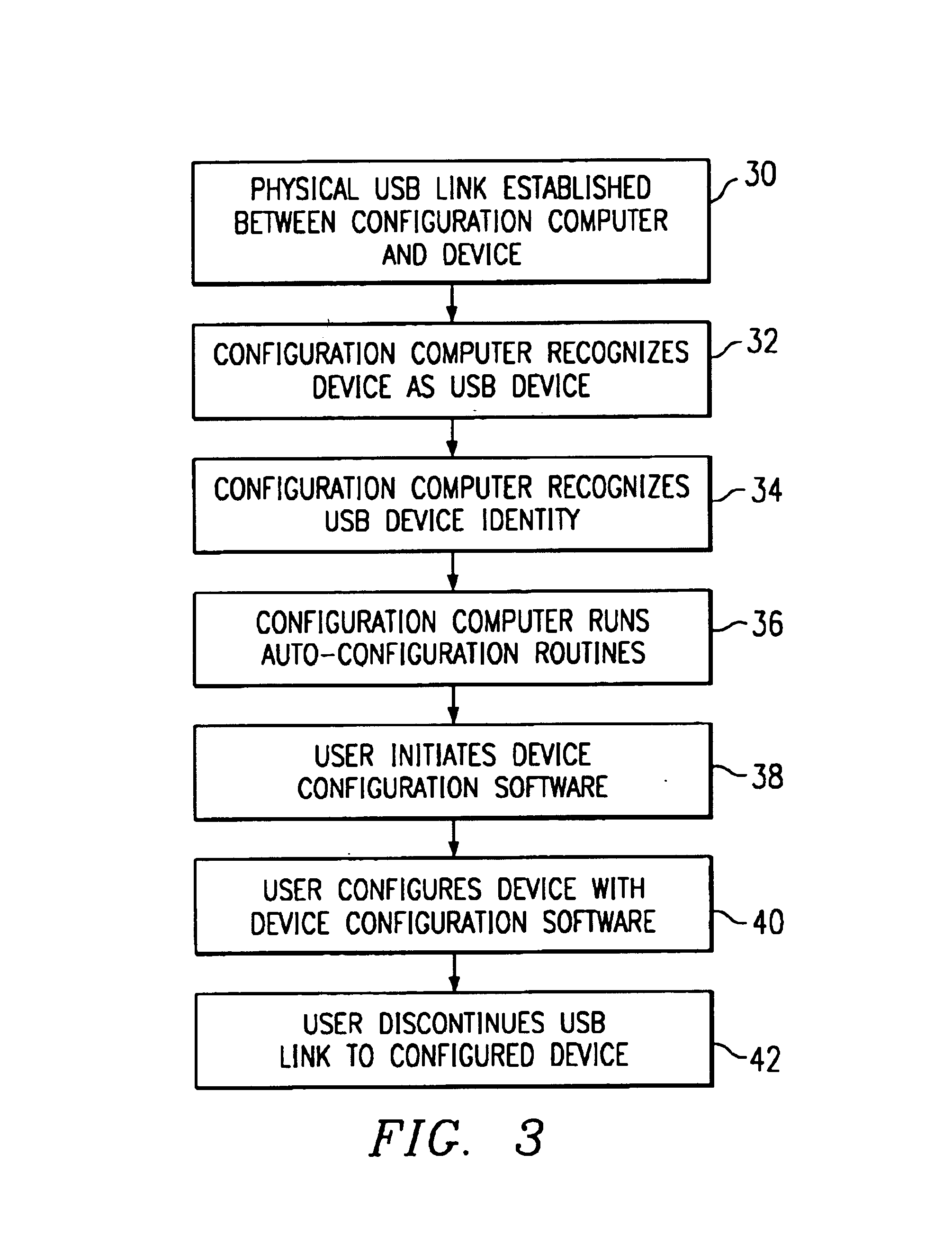
System and method for device configuration and management using a universal serial bus port
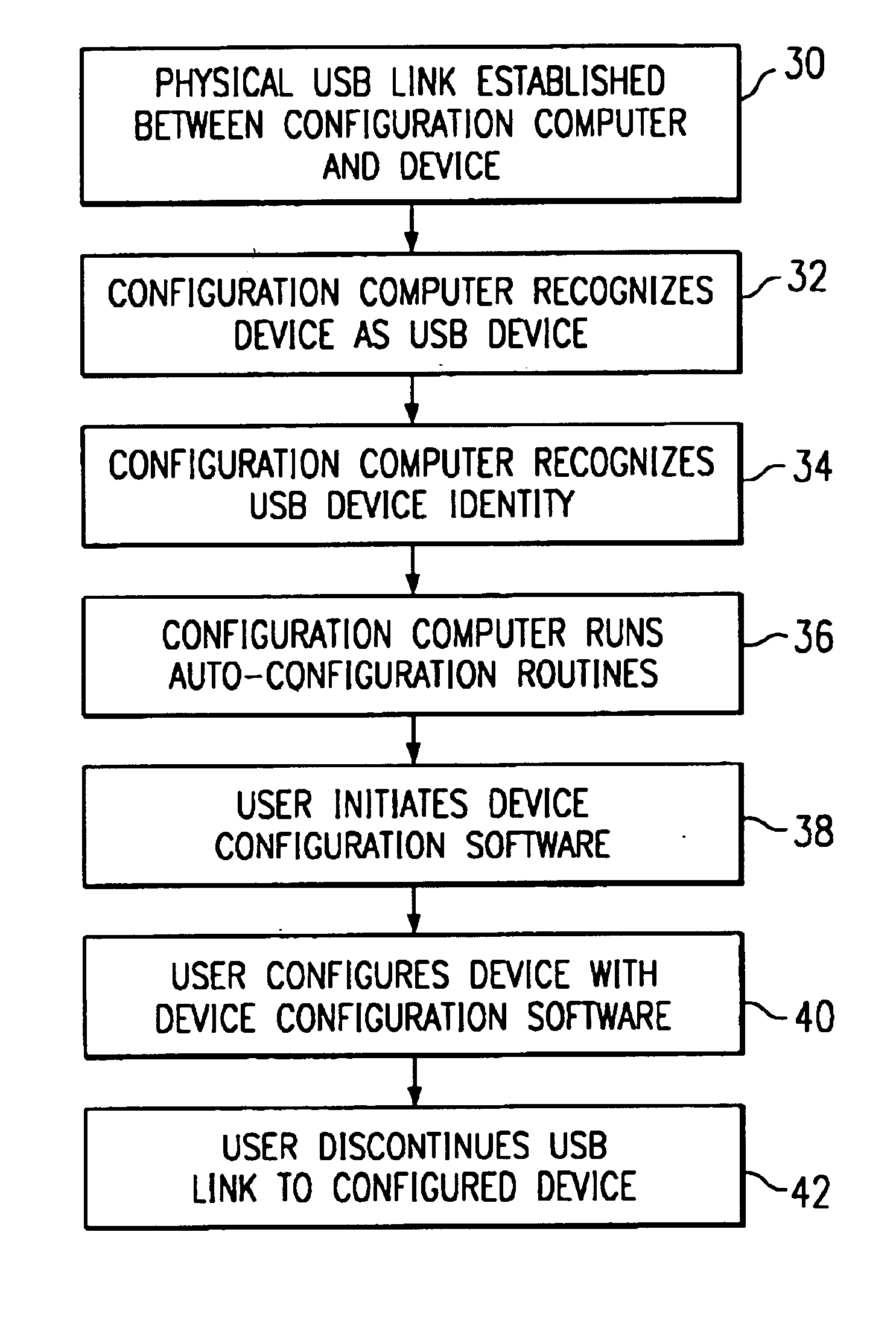
InactiveUS6895499B1Avoid mistakesReduce configuration timeMultiple digital computer combinationsProgram loading/initiatingUSBServer
A method and system for configuring and managing devices including network devices, such as a server computer, is provided in which a computer (24) is coupled to the network device through a USB connection (22). After the computer (24) recognizes the device as a USB-compliant device, the computer establishes data communication with the device. Following the establishment of data communication according to the USB standard, the device can be configured or monitored through the computer.
Owner:DELL PROD LP
Network Operating System With Topology Autodiscovery
InactiveUS20100247096A1Reduce the time required for installationReducing the service activation time bottleneckMultiplex system selection arrangementsTransmission monitoringTopology informationNetwork operating system
The network operating system includes an embedded platform for controlling operation of an agile optical network at the physical layer level. At the module embedded level, each module (card-pack) is provided with an embedded controller EC that monitors and control operation of the optical modules. At the next level, each shelf is provided with a shelf processor SP that monitors and control operation of the ECs over a backplane network. All optical modules are connected over an optical trace channel to send / receive trace messages that can then be used to determine network connectivity. At the next, link management level, a network services controller NSC controls the SPs in a negotiated span of control, over a link network. The control is address-based; each NSC receives ranges of addresses for the entities in its control, and distributes these addresses to the SPs, which in turn distribute addresses to the ECs in their control. One of the SPs operates as a router on the link network to relay signaling and control to all entities based on their address. Each NSC constructs, from queried information, a network topology fragment for the embedded elements under its control. A distributed topology system (DTS) shares this topology information with neighboring NSC's to build a complete network view, which can be used by all interested network applications.
Owner:WSOU INVESTMENTS LLC
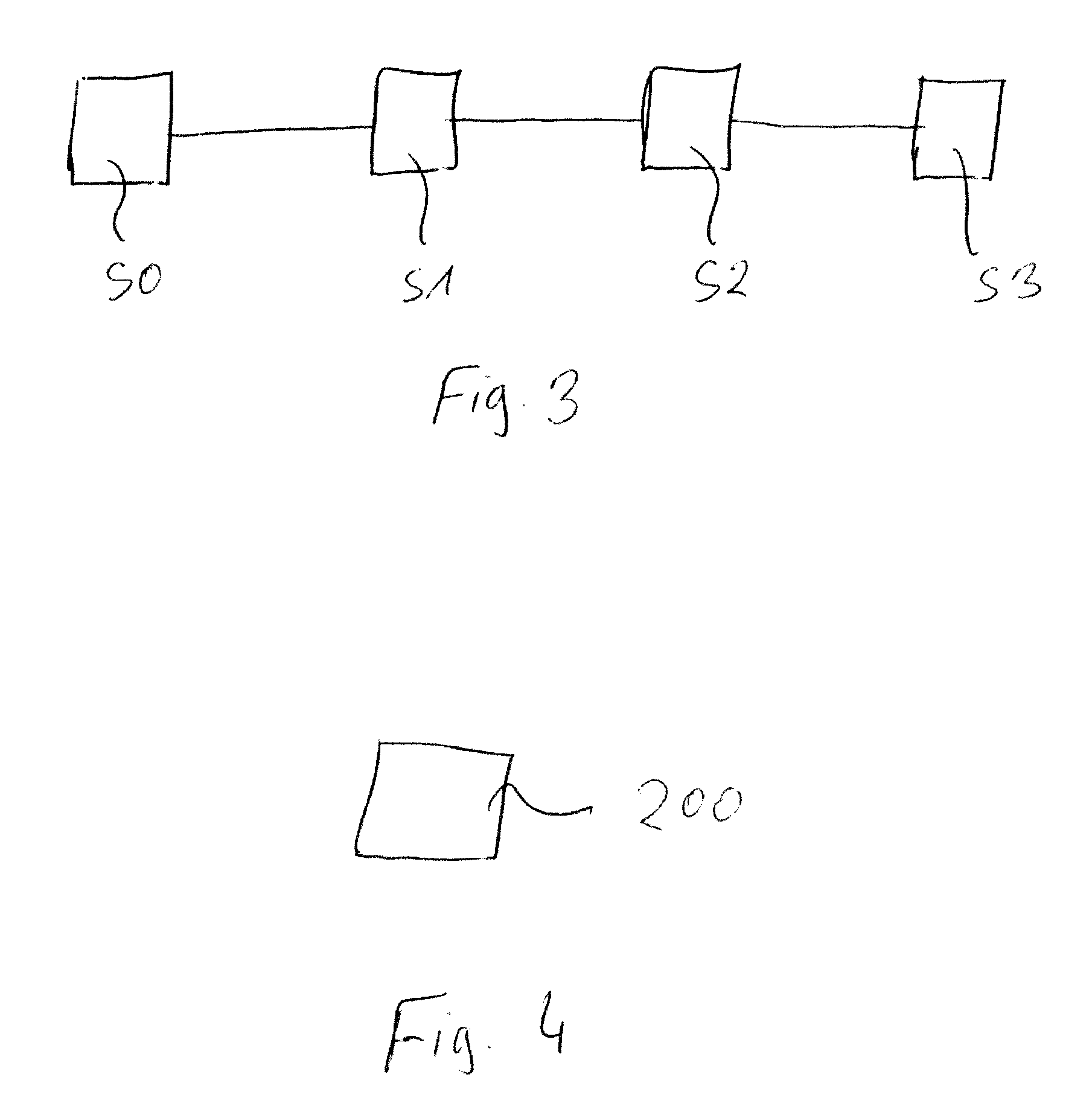
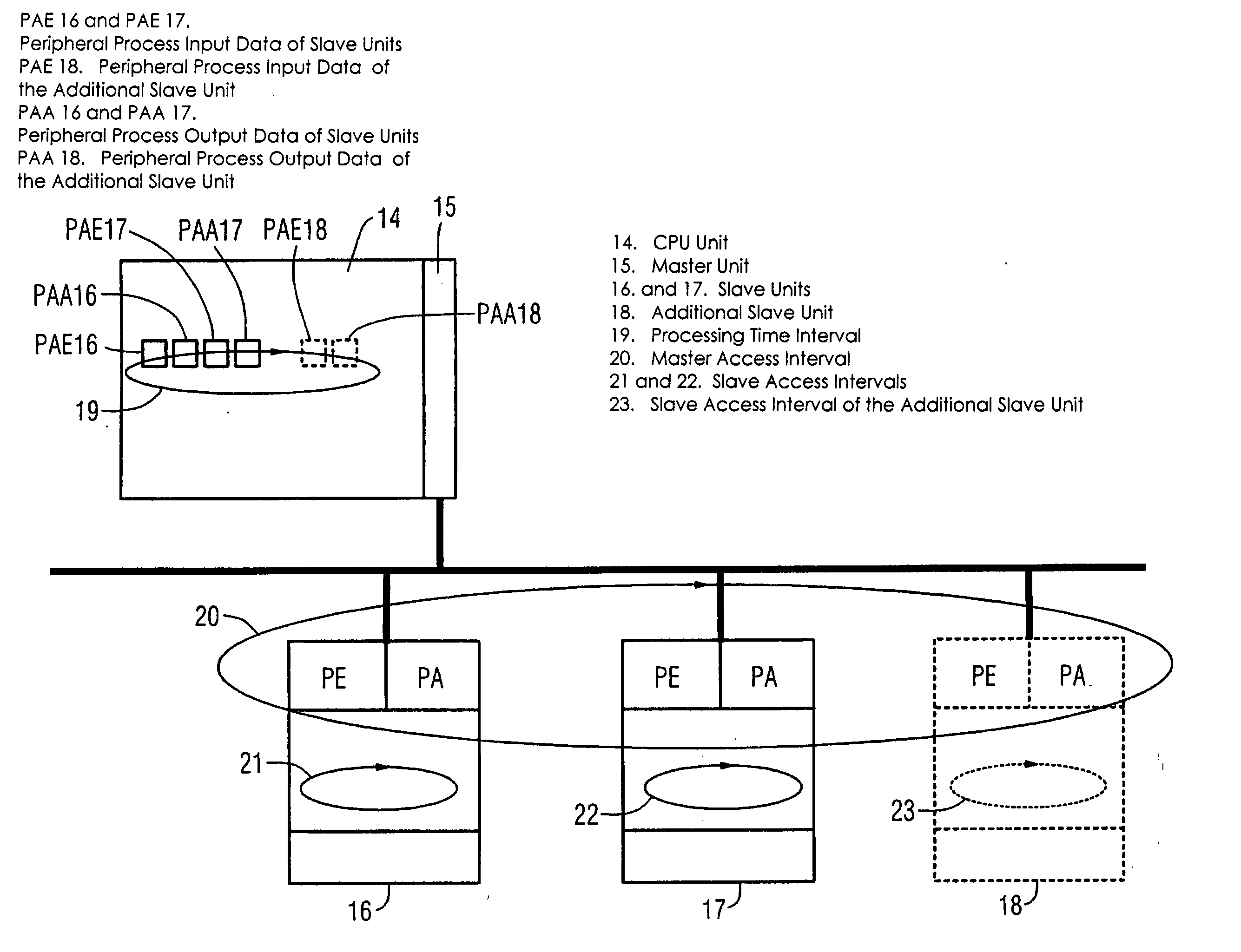
Method for configuring and/or operating an automation device
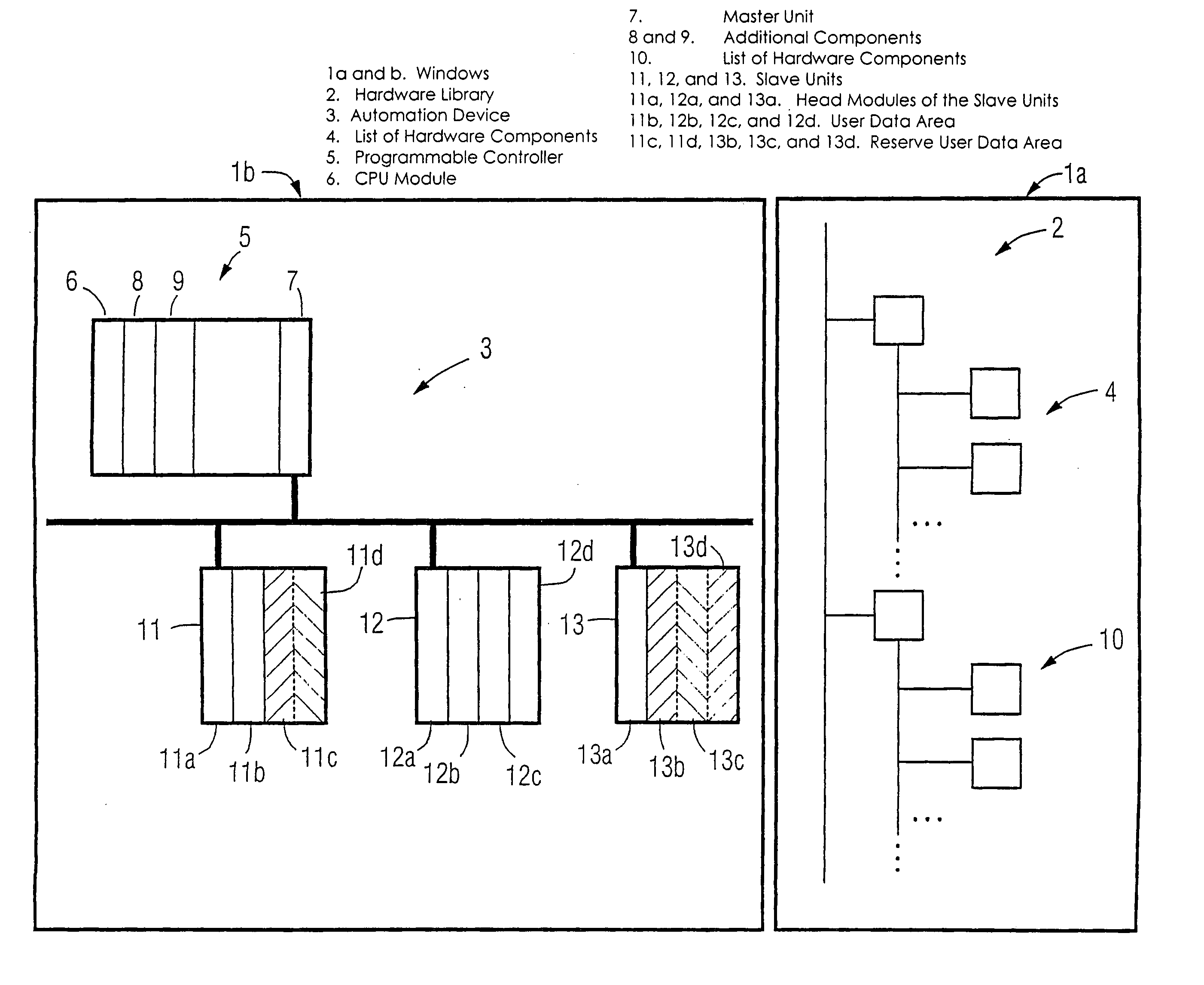
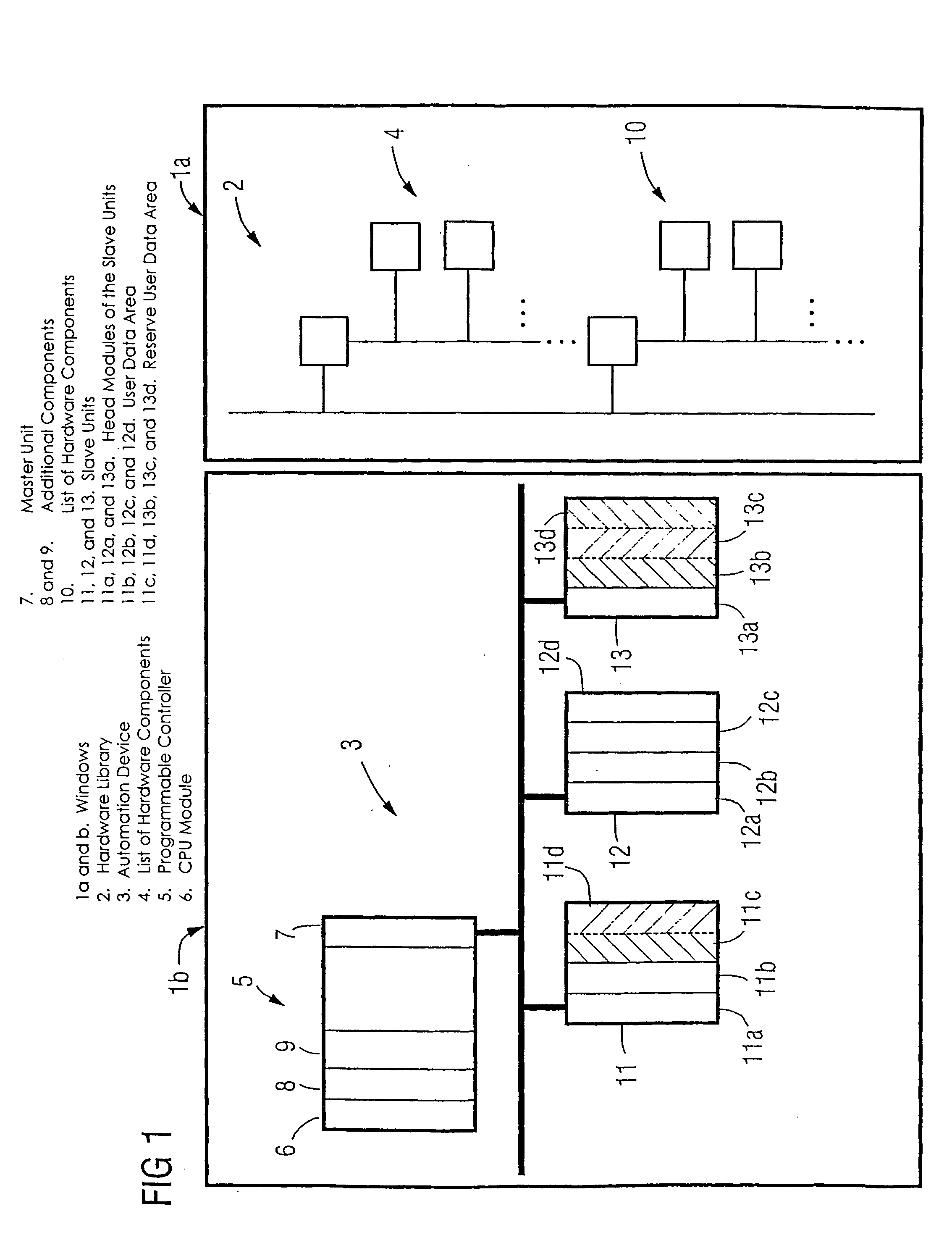
ActiveUS7246184B2Reduce configuration timeProgramme controlComputer controlEmbedded systemAutomation
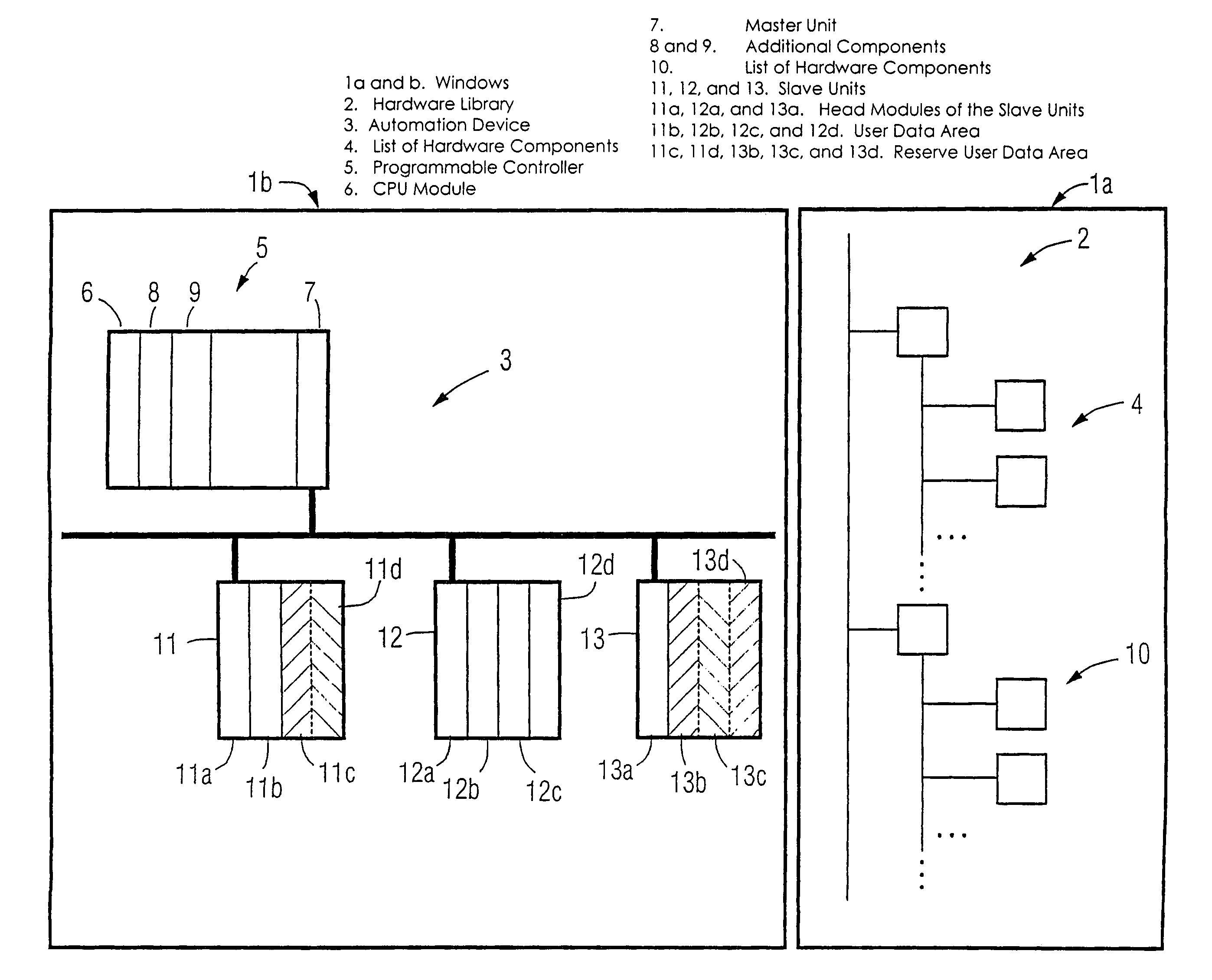
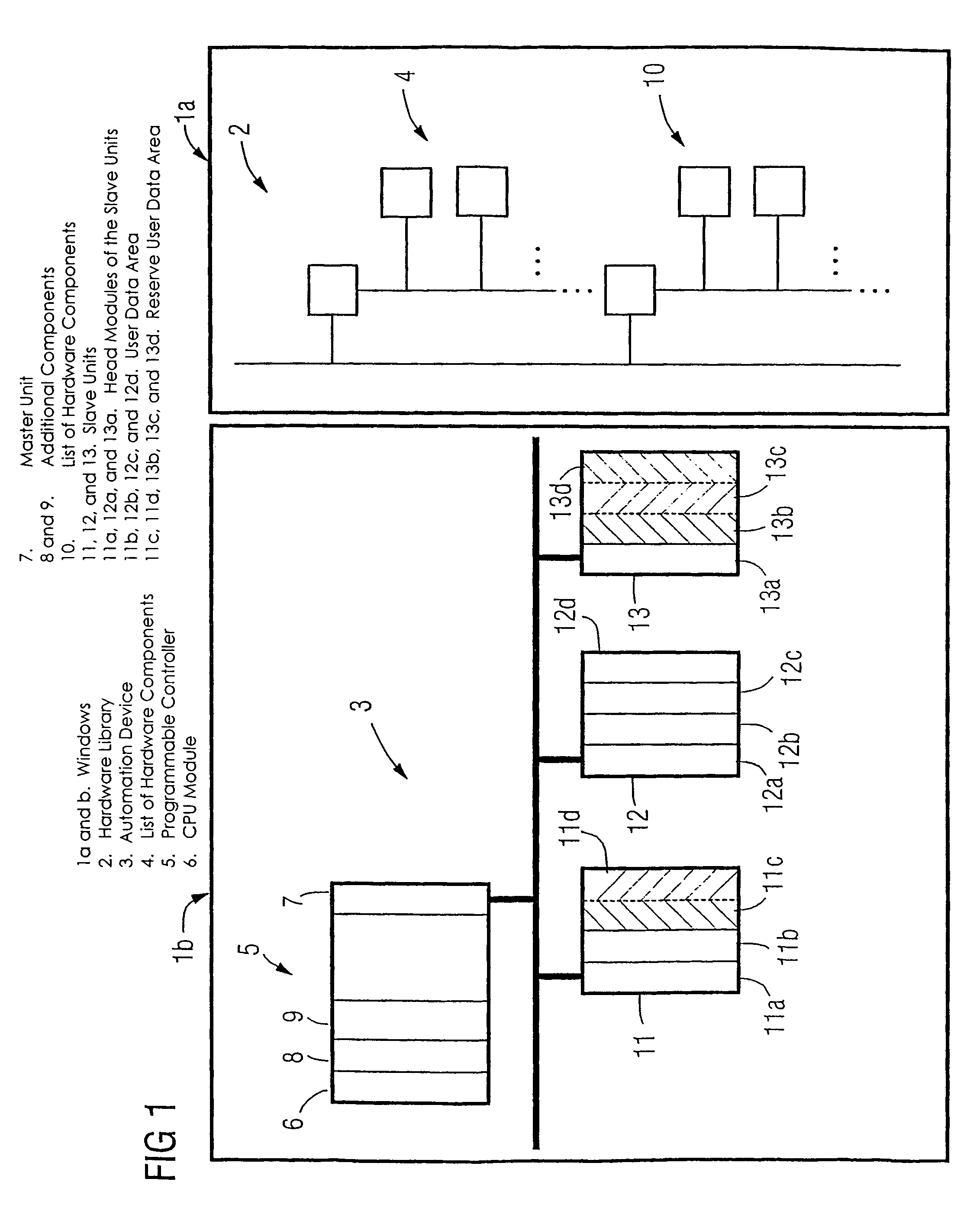
A method and an engineering system, which reduce the extent of configuration work with regard to a possible expansion of the automation device. A configured automation device can thus be expanded during the control of the automation device by means of slave modules. During a configuration phase, the number of the slave units (11, 12, 13, 16, 17, 18) and a user data area for each slave unit can be configured. For each slave module of a slave unit, a portion of the user data area can be assigned. The user data area is prepared for a possible expansion of the slave unit by at least one slave module in that, in addition to the configured user data area of a respective slave unit required for the current control, a reserve user data area (11c, 11d, 13b, 13c, 13d, 16d, 18d) is configured for the at least one slave module.
Owner:SIEMENS AG
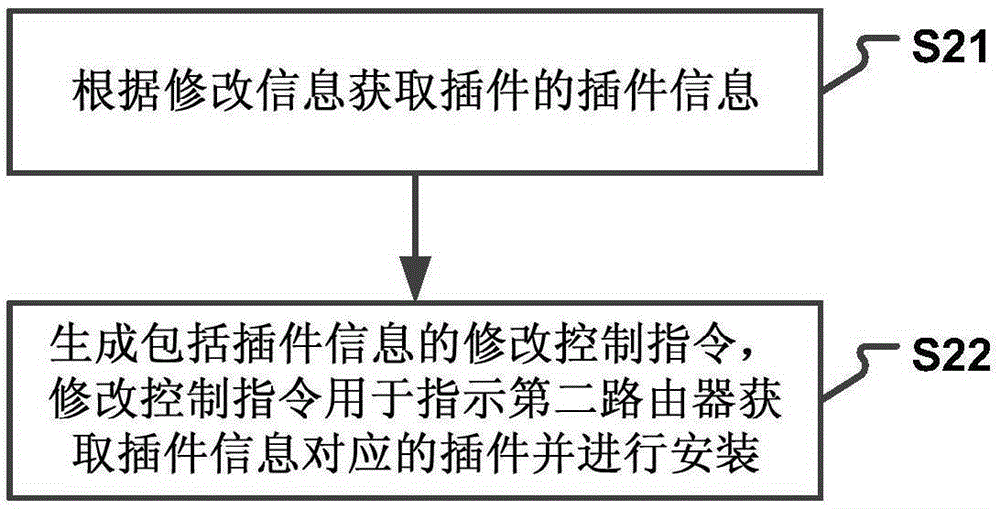
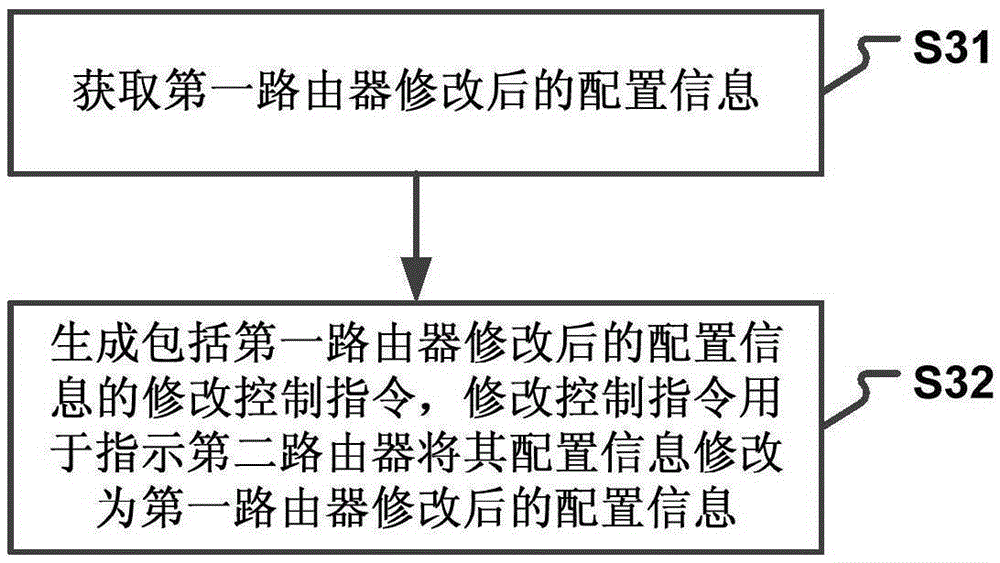
Router configuration information modifying method and device
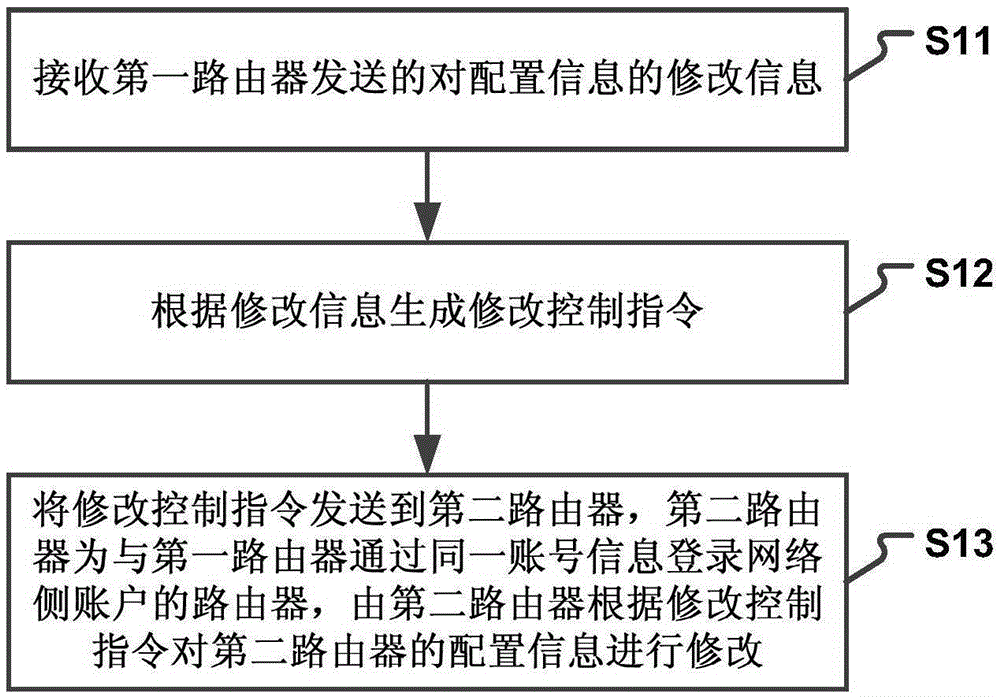
The invention provides a router configuration information modifying method and device. The method comprises the steps that configuration information modifying information sent by a first router is received; a modifying control command is generated according to the modifying information; the modifying control command is sent to a second router, wherein the second router is a router which logs a network side account through the same account information with the first router; and the second router modifies the configuration information of the second router according to the modifying control command. According to the technical scheme, the configuration accuracy of multiple routers is improved; the router configuration complexity is reduced; user operations are simplified; the time spent by a user to modify the configuration of multiple routers is reduced; and the user experience is improved.
Owner:XIAOMI INC
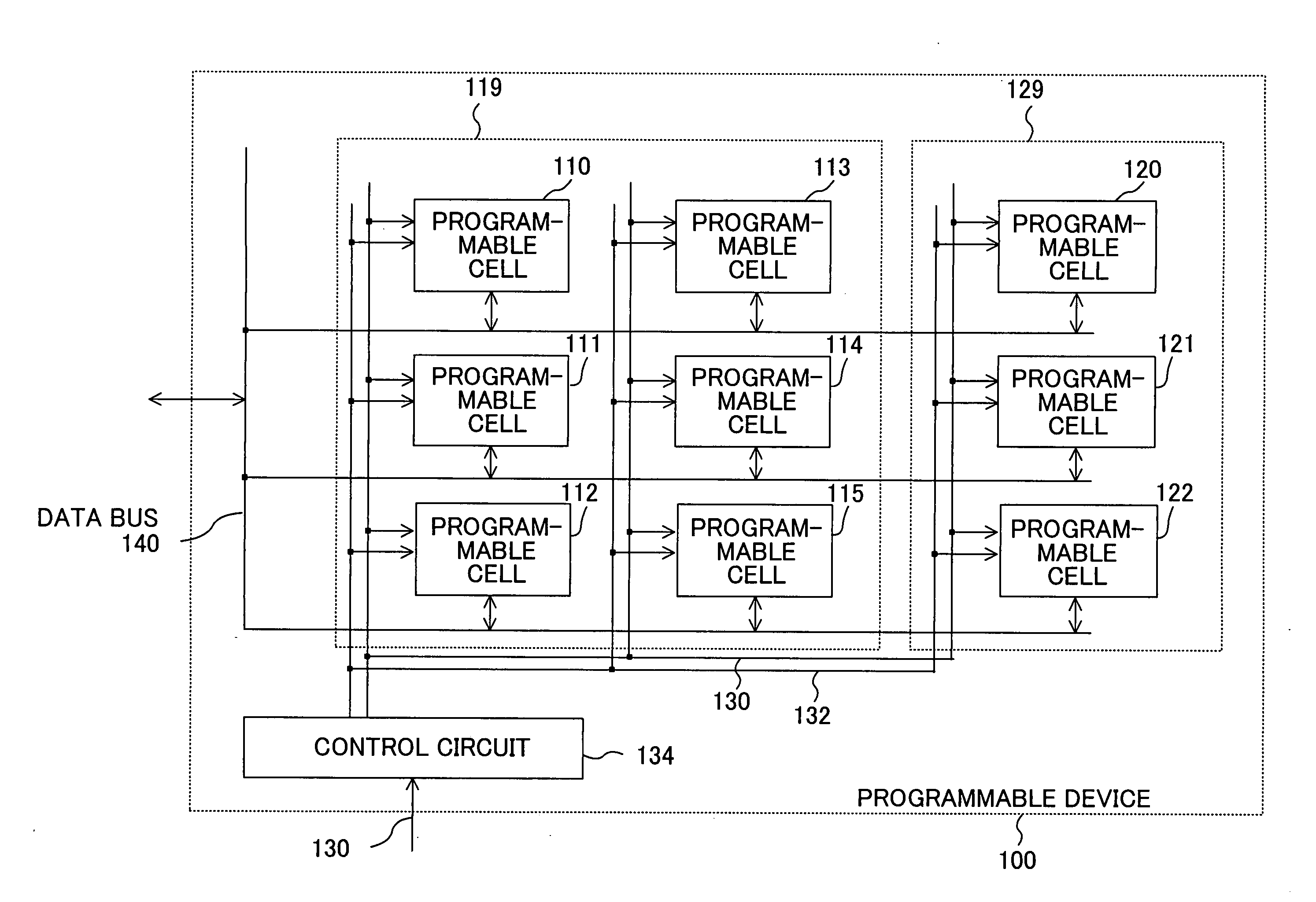
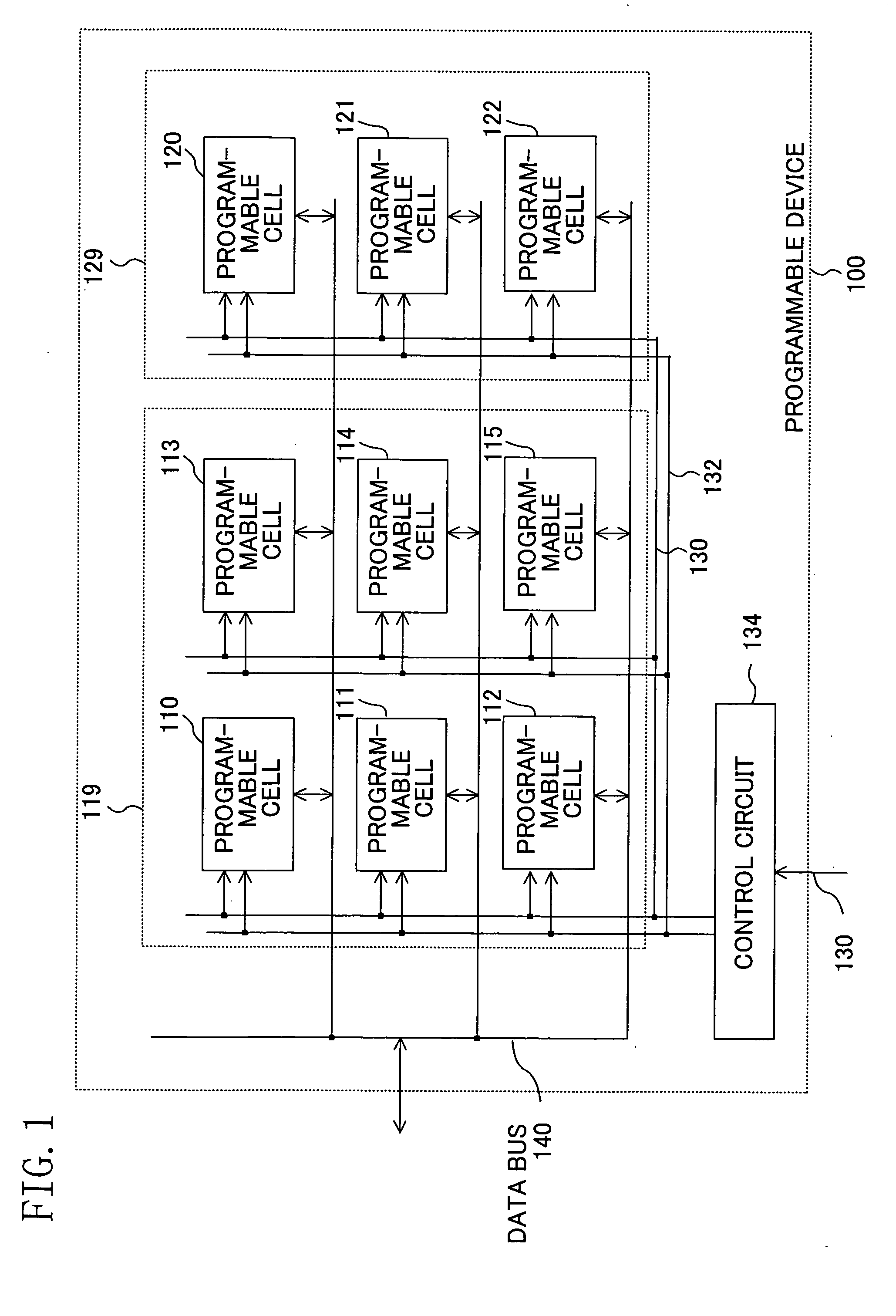
Programmable device
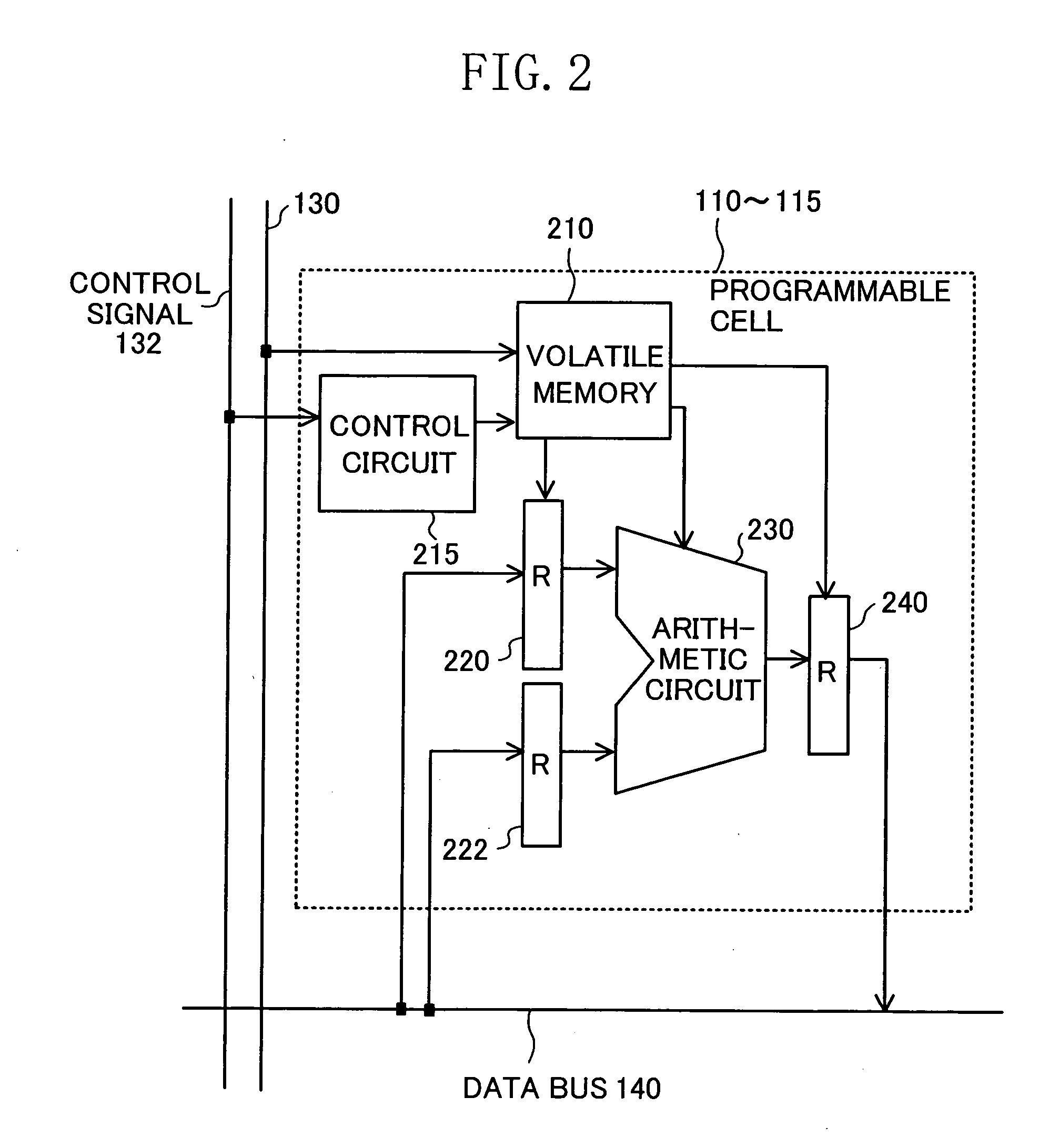
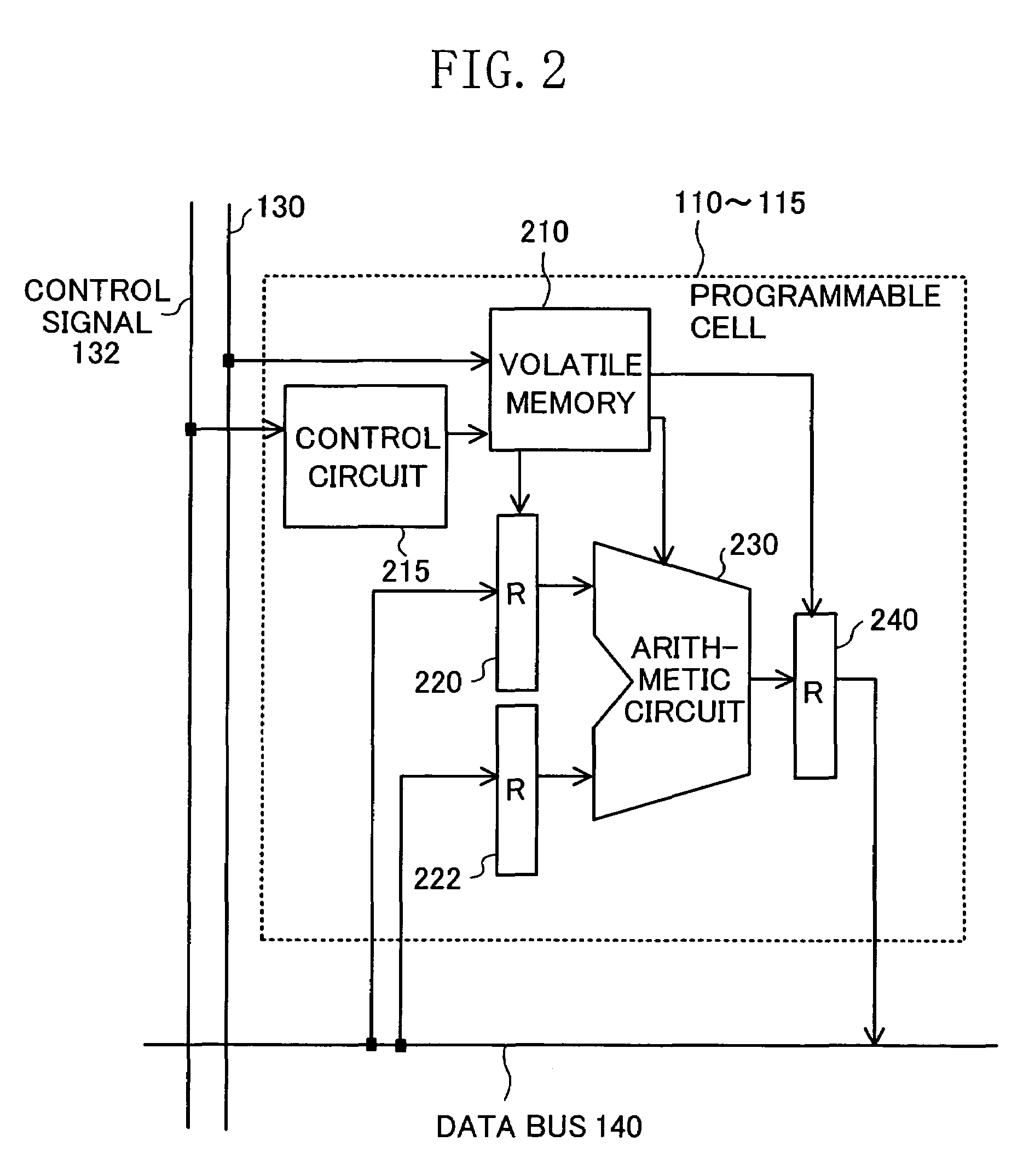
InactiveUS20060119387A1Reduce power consumptionReduce the amount of configurationSolid-state devicesLogic circuits using elementary logic circuit componentsOperating systemVolatile memory
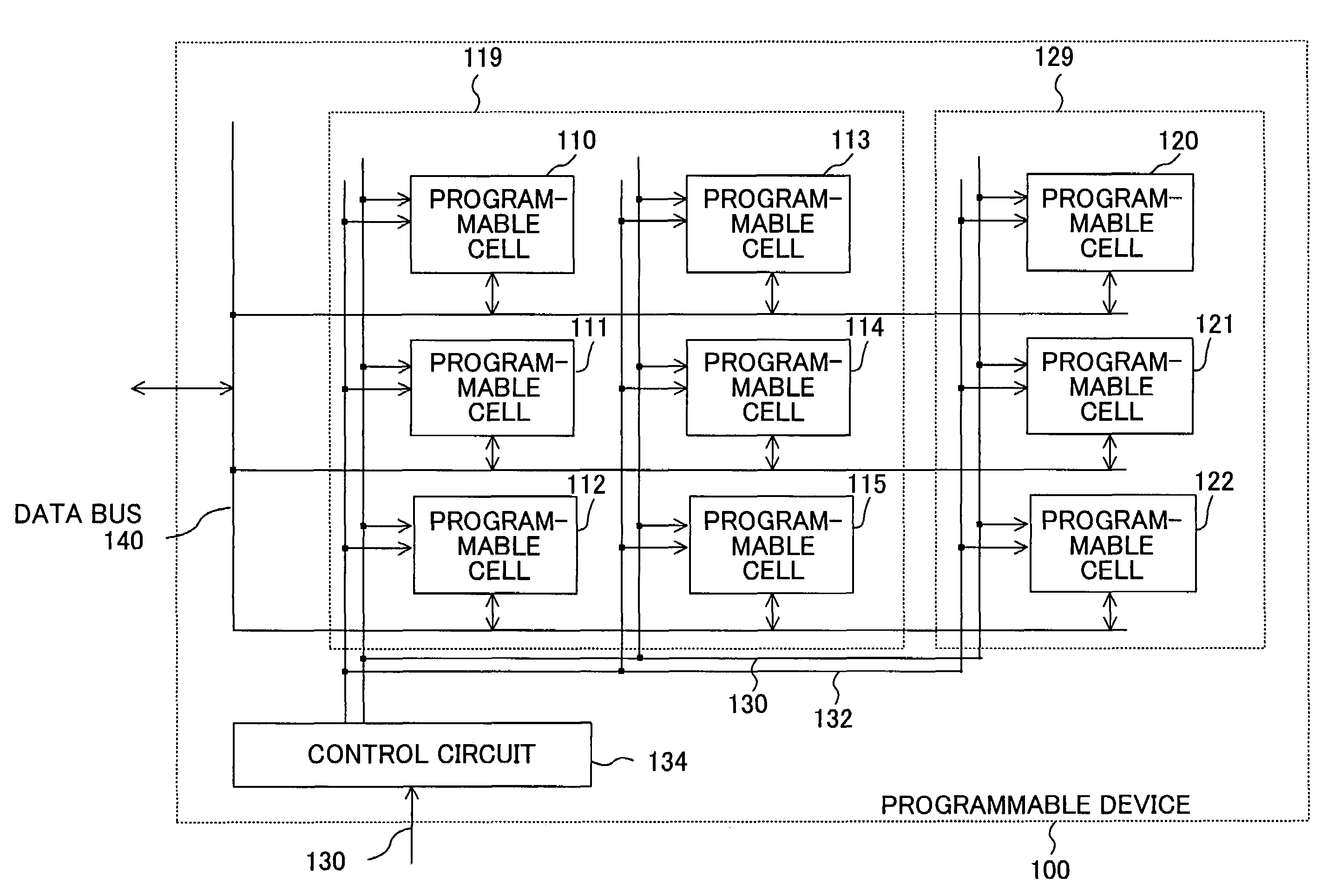
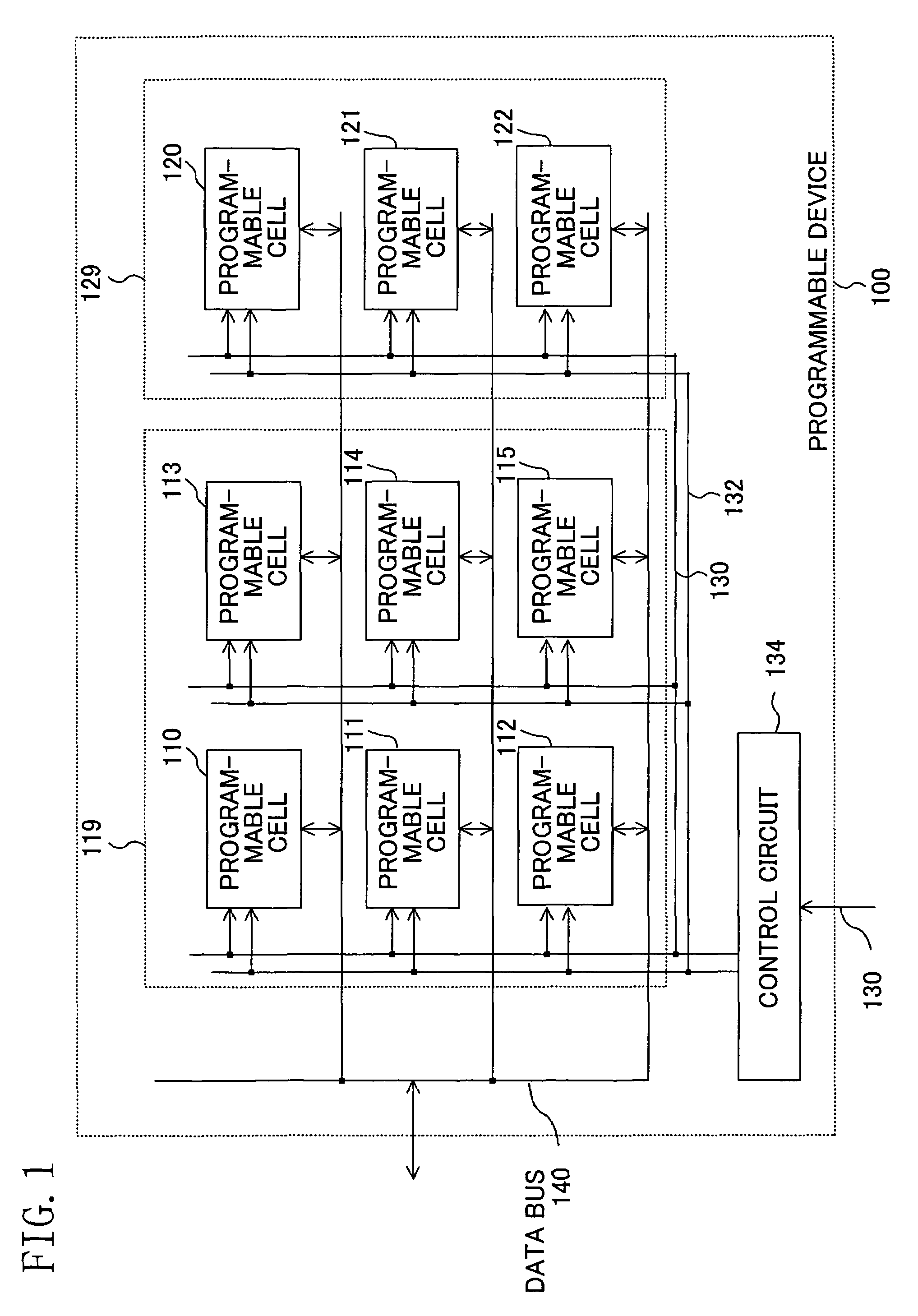
In a programmable cell included in a first region, configuration information is stored in a volatile memory, while in a programmable cell included in a second region, configuration information is stored in a non-volatile memory. Configuration information for a sub-process common to a plurality of processes is stored in the non-volatile memory.
Owner:SOCIONEXT INC
Method for configuring and/or operating an automation device
ActiveUS20050132113A1Reduce configuration timeProgramme controlComputer controlEmbedded systemAutomation
A method and an engineering system, which reduce the extent of configuration work with regard to a possible expansion of the automation device. A configured automation device can thus be expanded during the control of the automation device by means of slave modules. During a configuration phase, the number of the slave units (11, 12, 13, 16, 17, 18) and a user data area for each slave unit can be configured. For each slave module of a slave unit, a portion of the user data area can be assigned. The user data area is prepared for a possible expansion of the slave unit by at least one slave module in that, in addition to the configured user data area of a respective slave unit required for the current control, a reserve user data area (11c, 11d, 13b, 13c, 13d, 16d, 18d) is configured for the at least one slave module.
Owner:SIEMENS AG
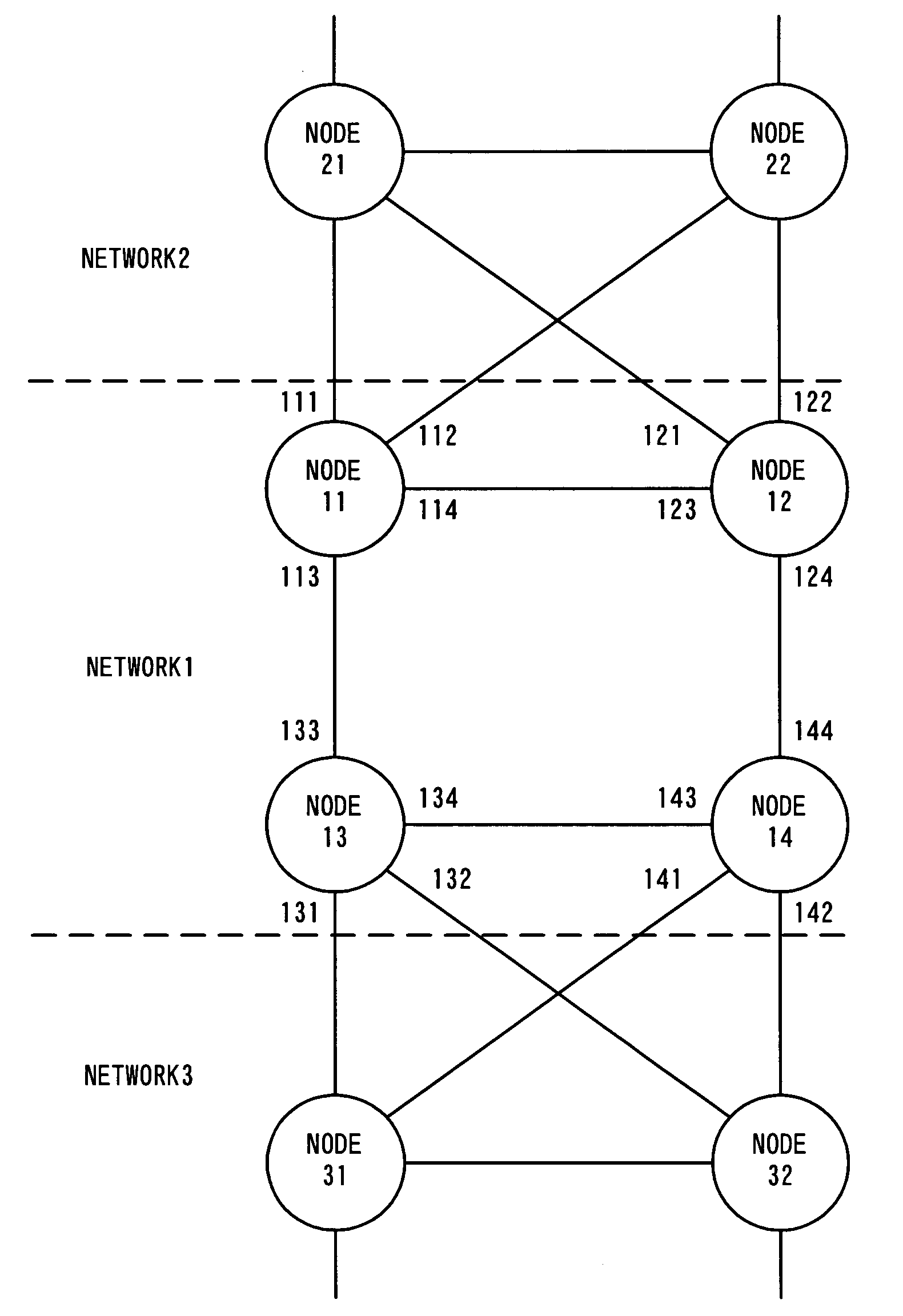
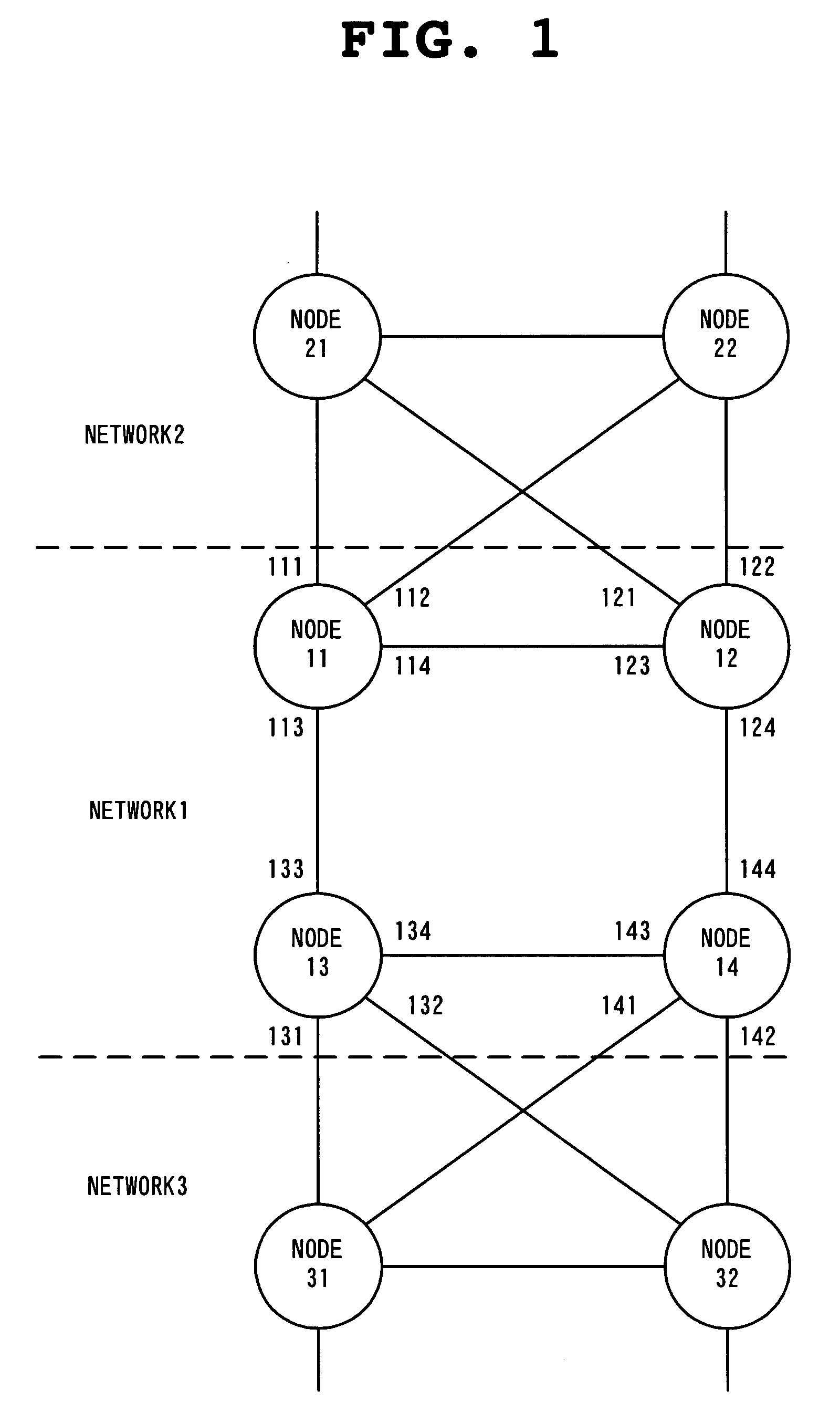
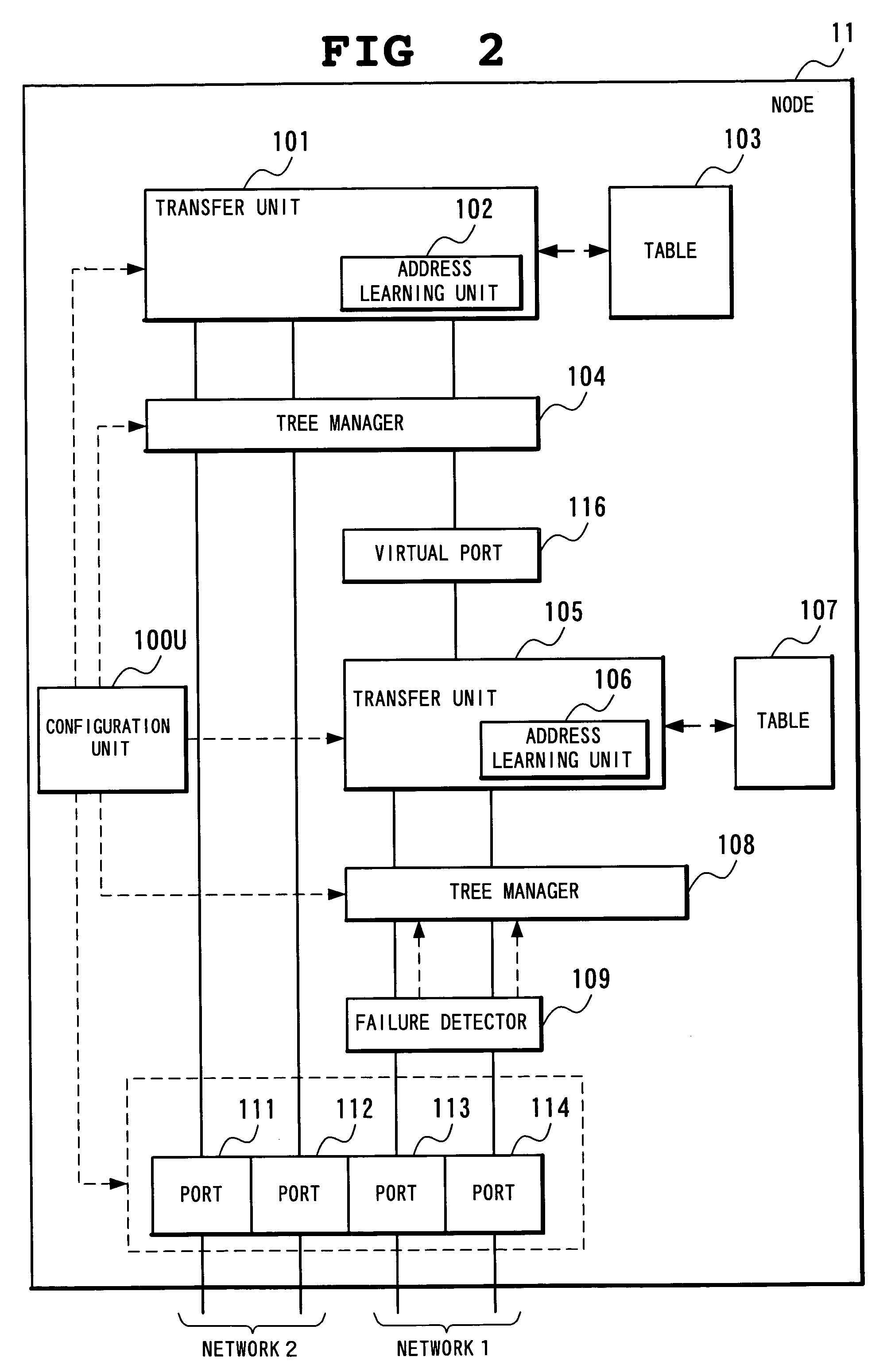
Network system, spanning tree configuration method and configuration program, and spanning tree configuration node
InactiveUS7532588B2Reduce configuration timeDigital computer detailsStar/tree networksNetworked systemSpanning Tree Protocol
A node of a spanning tree system operating on a network connecting a plurality of nodes, comprises two transfer units which determines an output destination port, based on the destination MAC address of an input frame, two tree managers which configures a spanning tree according to a spanning tree protocol, and a virtual port of connecting the tree manager and the transfer unit.
Owner:NEC CORP
Protocol configuration method, device and equipment and medium
ActiveCN110113196AImprove configuration reliabilityReduce configuration timeFile system administrationData switching networksAuto-configurationDocumentation
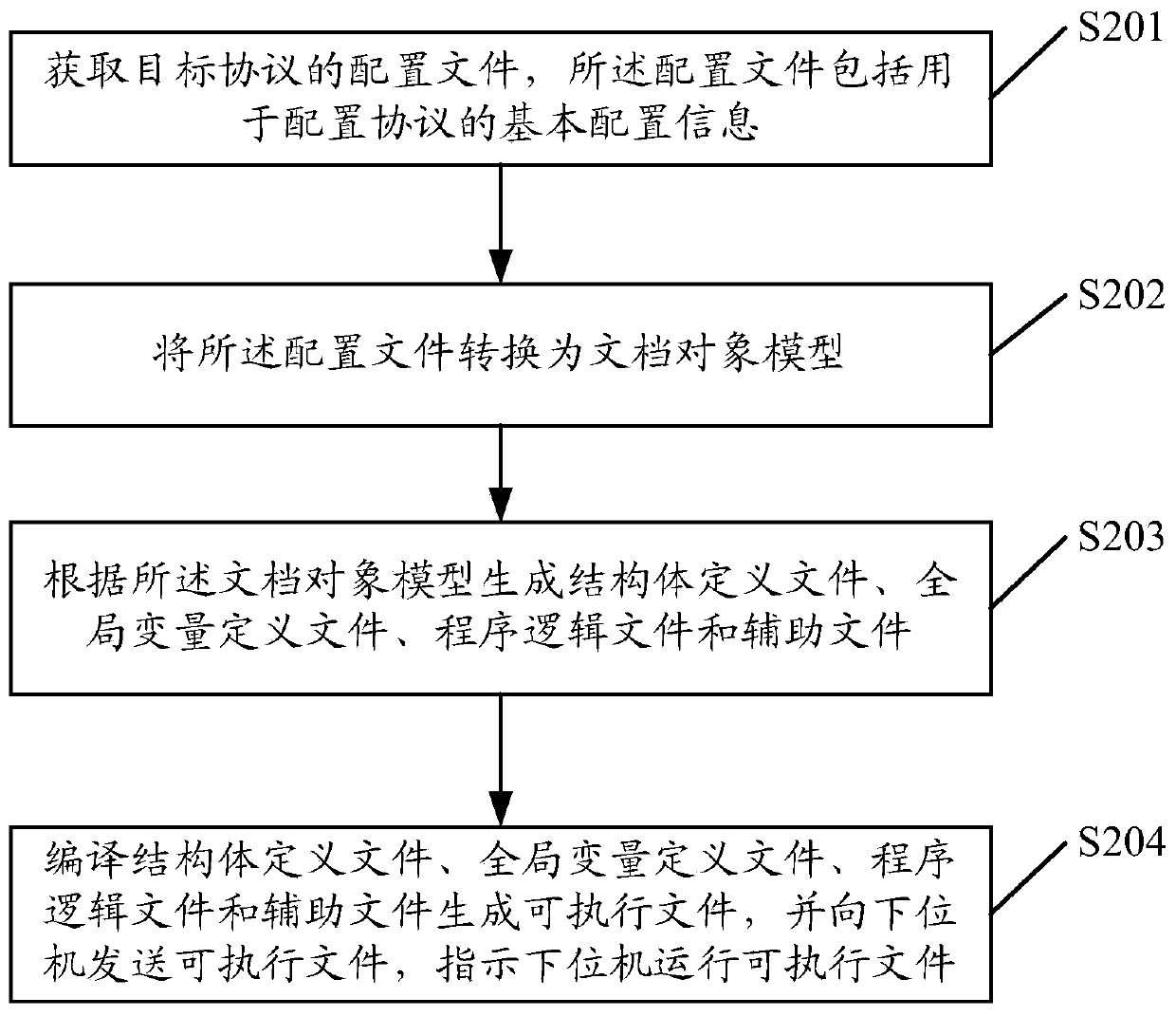
The invention discloses a protocol configuration method, which comprises the following steps: acquiring a configuration file of a target protocol, the configuration file comprising basic configurationinformation for configuring the protocol; converting the configuration file into a document object model; generating a structure definition file, a global variable definition file, a program logic file and an auxiliary file according to the document object model; compiling the structure definition file, the global variable definition file, the program logic file and the auxiliary file to generatean executable file, and sending the executable file to a lower computer to indicate the lower computer to operate the executable file. On one hand, the time required by configuration is greatly reduced through an automatic configuration mode, the configuration efficiency is improved, on the other hand, manual configuration is not needed, the labor cost is reduced, the error probability is reduced, and the protocol configuration reliability is improved. The invention further discloses a corresponding device, equipment and a medium.
Owner:CRRC QINGDAO SIFANG CO LTD
Programmable device with structure for storing configuration information
InactiveUS7378871B2Reduce configuration timeReduce circuit sizeSolid-state devicesLogic circuits using elementary logic circuit componentsProgrammable logic deviceInformation storage
In a programmable cell included in a first region, configuration information is stored in a volatile memory, while in a programmable cell included in a second region, configuration information is stored in a non-volatile memory. Configuration information for a sub-process common to a plurality of processes is stored in the non-volatile memory.
Owner:SOCIONEXT INC
OTN circuit routing method and system
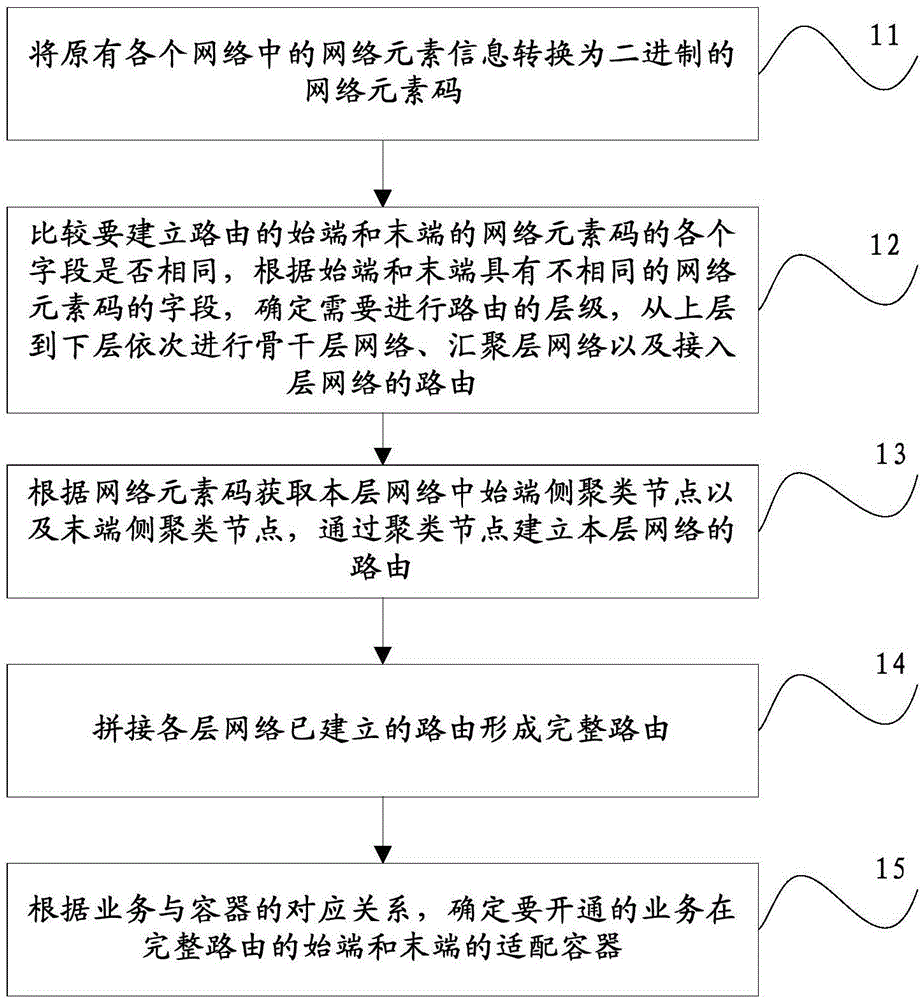
ActiveCN105049965AHigh degree of automationImprove accuracyMultiplex system selection arrangementsAutomatic routingAutomation
The present invention discloses an OTN circuit routing method and a system. The method comprise the steps of converting the network element information of all original networks into network element codes in the binary system; comparing each field of the network element codes at the initial end of a to-be-established routing with each field of the network element codes at the terminal end of the to-be-established routing, judging whether the fields of the network element codes at the initial end and the terminal end of the to-be-established routing are the same or not, determining the hierarchy of the required routing according to different fields of the network element codes at the initial end and the terminal end of the to-be-established routing, and successively routing the backbone layer, the convergence layer and the access layer of a network from top to bottom; acquiring cluster nodes at the initial end and the terminal end according to the network element codes, and establishing the routing of each layer of the network based the cluster codes; and finally splicing up the already established routings of all layers of the network to form the complete routing. According to the technical scheme of the invention, the automatic routing and path-finding function of an OTN circuit in the cross-manufacturer, cross-region, cross-level and end-to-end manner can be realized. Meanwhile, the automation degree and the accuracy of the circuit debugging operation are improved. Moreover, the error rate and the configuration time of the routing operation through the manually searching and computing process can be reduced.
Owner:CHINA TELECOM CORP LTD
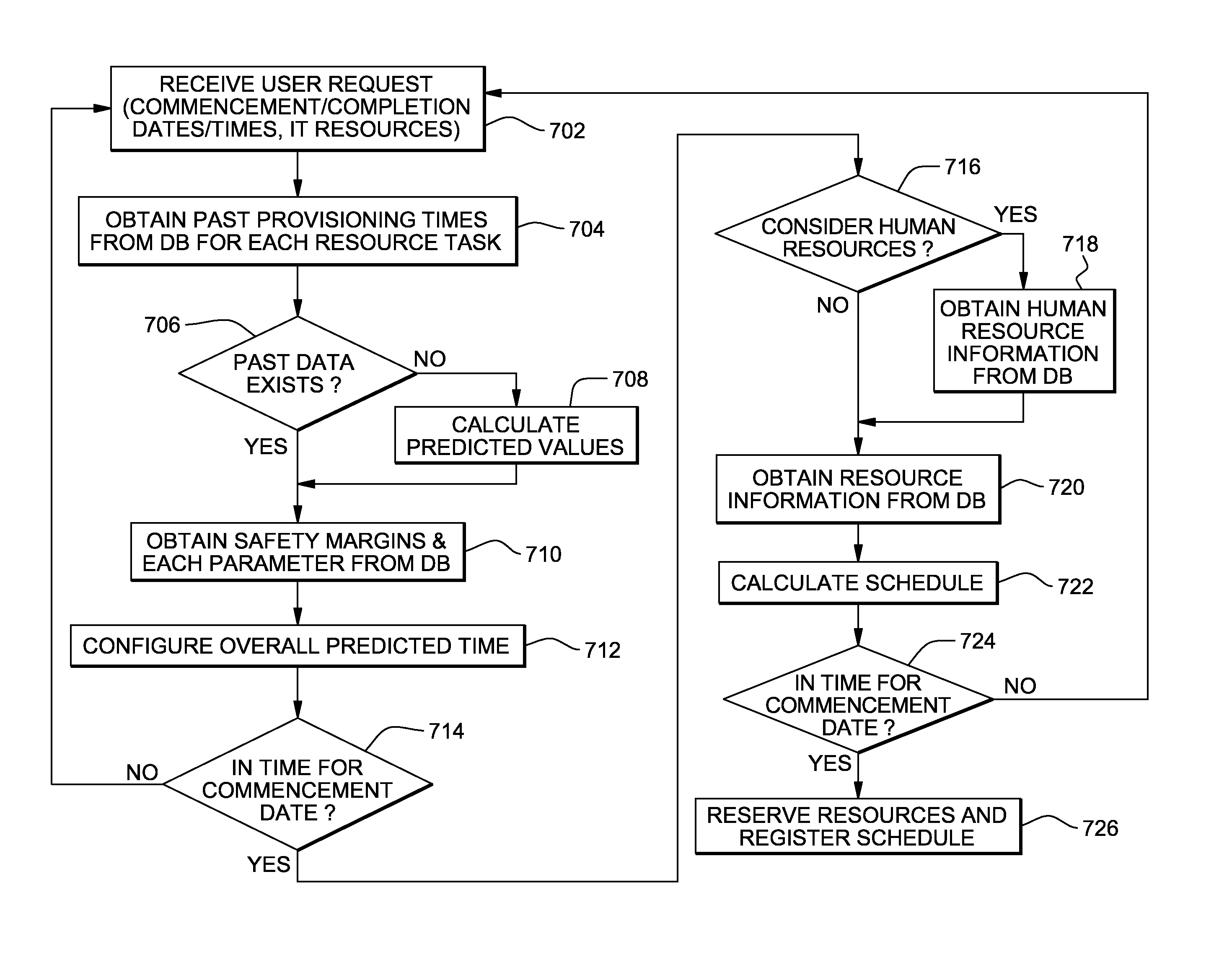
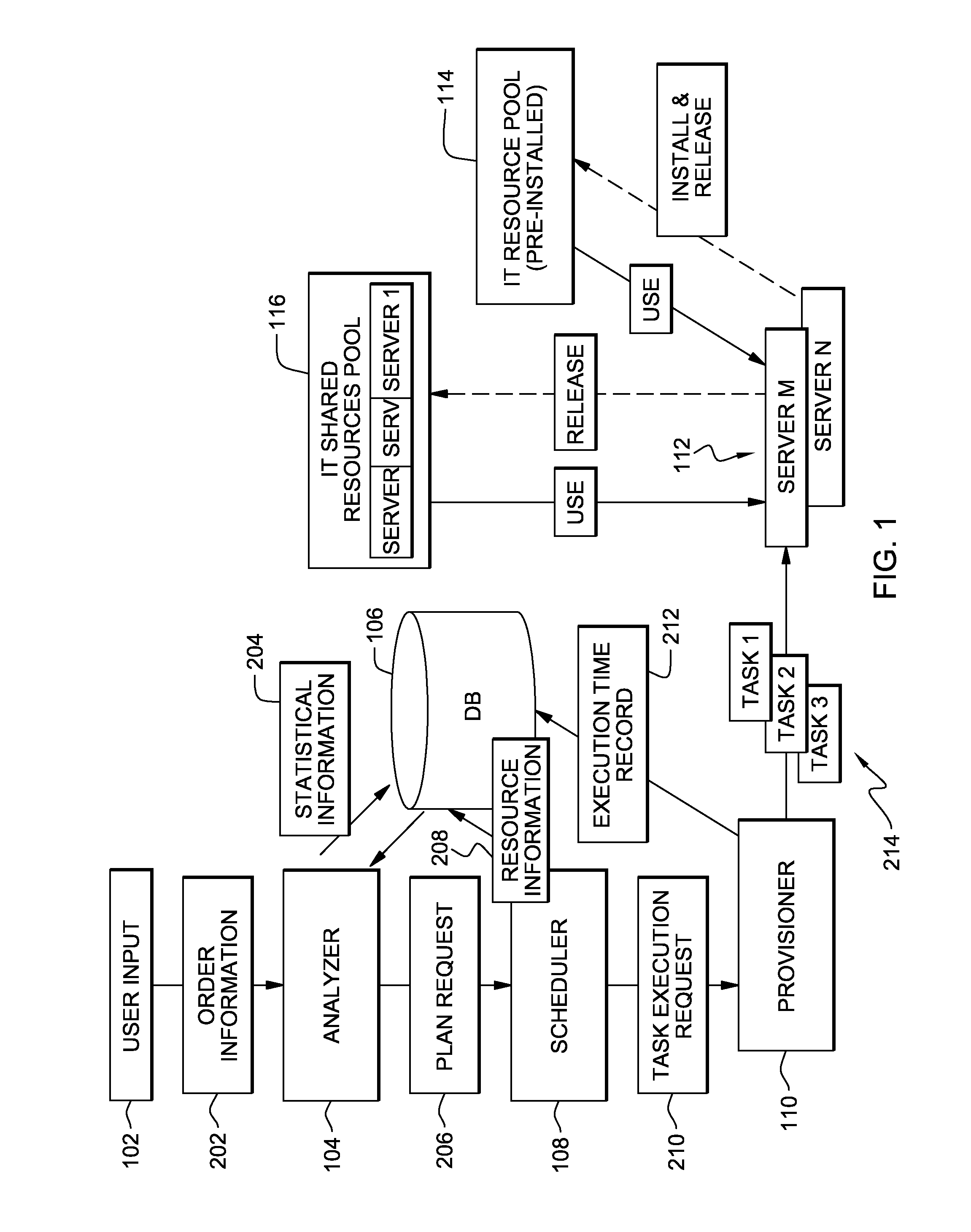
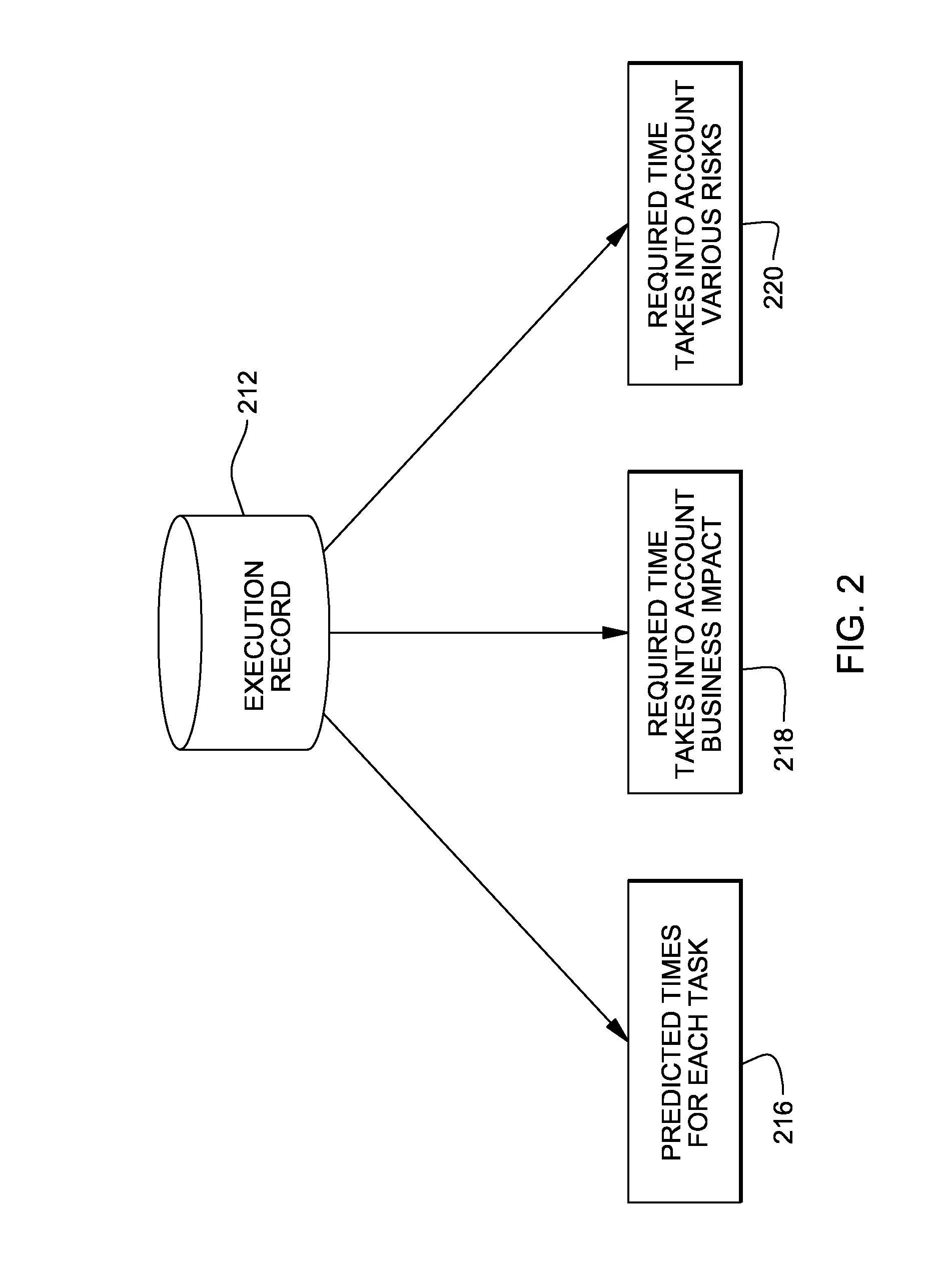
Method and apparatus for optimizing lead time for service provisioning
InactiveUS8140552B2Reduce configuration timeFaster service provisioningDigital data processing detailsSpecial data processing applicationsFailure rateData center
A method for optimizing lead time for service provisioning for a request from a customer includes storing a record of installation and configuration times for each hardware and software configuration in a database, and then calculating success rates and failure rates for each hardware and software configuration. A manual installation time for the request is set in the event of failure. The necessary time to prepare the system fulfilling the customer request is then determined and displayed in the data center.
Owner:IBM CORP
Construction site reinforcement cage machining and manufacturing device and technology
ActiveCN109954824AReduce configuration timeReduce repetitive and complicated actionsWire networkRebarMachining
The invention discloses a construction site reinforcement cage machining and manufacturing device and a technology. The machining device is mainly composed of a plurality of reinforcement cage machining bed jigs and a main reinforcement hoisting device, the reinforcement cage machining bed jigs are composed of brackets and main reinforcement positioning moulding bed discs, the reinforcement cage machining bed jigs are placed linearly and equidistantly, the main reinforcement hoisting device is arranged on the middle part of the reinforcement cage machining bed jigs, and machined main reinforcement, reinforced reinforcement and spiral stirrups are assembled in the reinforcement cage machining bed jigs. By adopting the construction site reinforcement cage machining and manufacturing device and the technology, the operating conditions of workers can be improved, and the machining quality and production efficiency of a reinforcement cage are obviously improved.
Owner:BEIJING TIANHENG CONSTR
Animation arrangement
ActiveUS20160078661A1Facilitates componentLess computing powerDashboard fitting arrangementsProcessor architectures/configurationAnimationDisplay device
An animation arrangement for a vehicle is provided. The animation arrangement has a display device, configured to display an animation based on an instruction set, a storage device configured to store a first instruction set and a second instruction set for displaying the same animation on the display device, and a calculating device configured to select one of the first and second instruction sets for displaying an animation on the display device. The calculating device is configured to select one of the first and second instruction sets for displaying an animation on the display device based on a load parameter of the calculating device.
Owner:CONTINENTAL AUTOMOTIVE GMBH
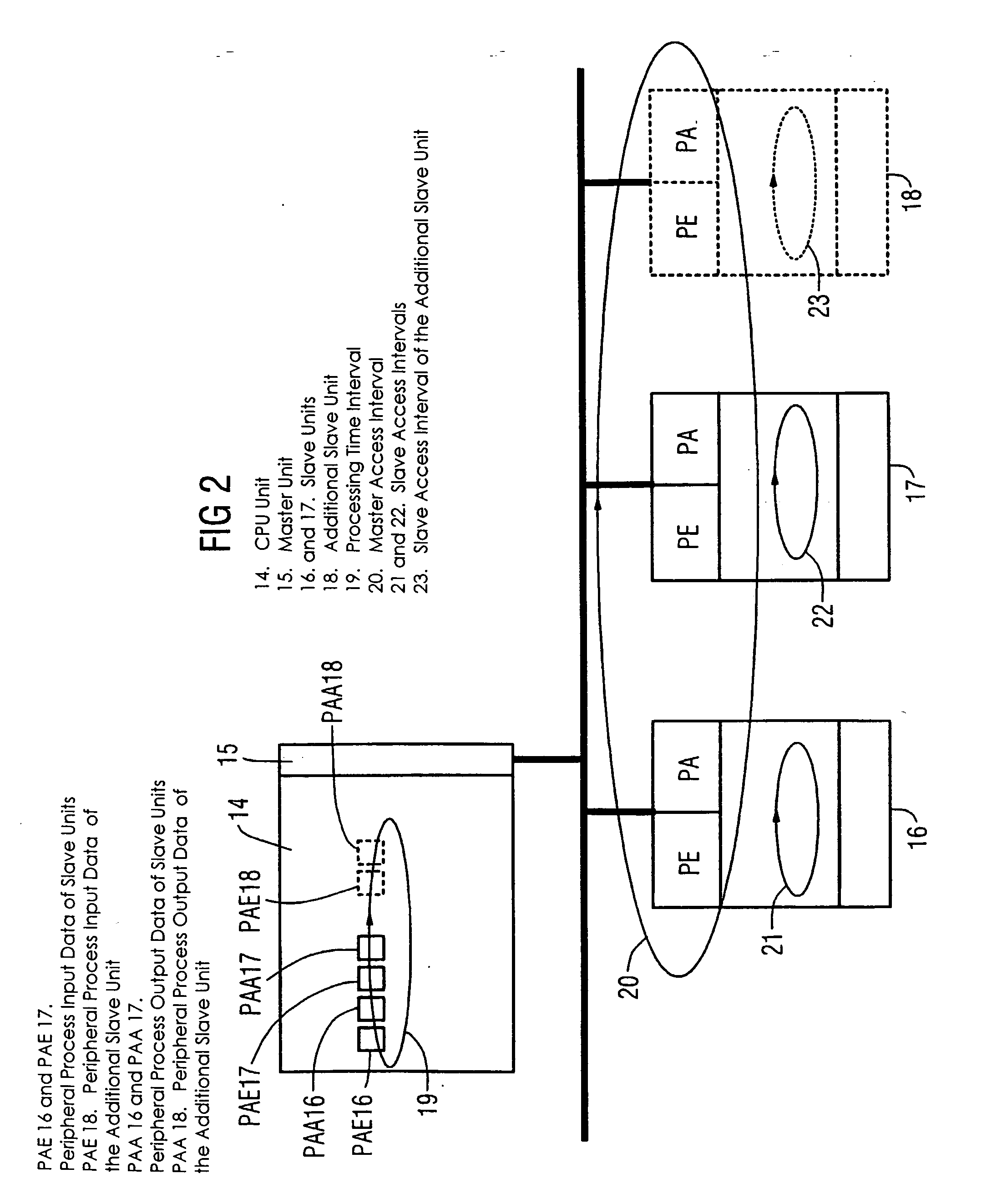
Method for configuring and/or operating an automation device
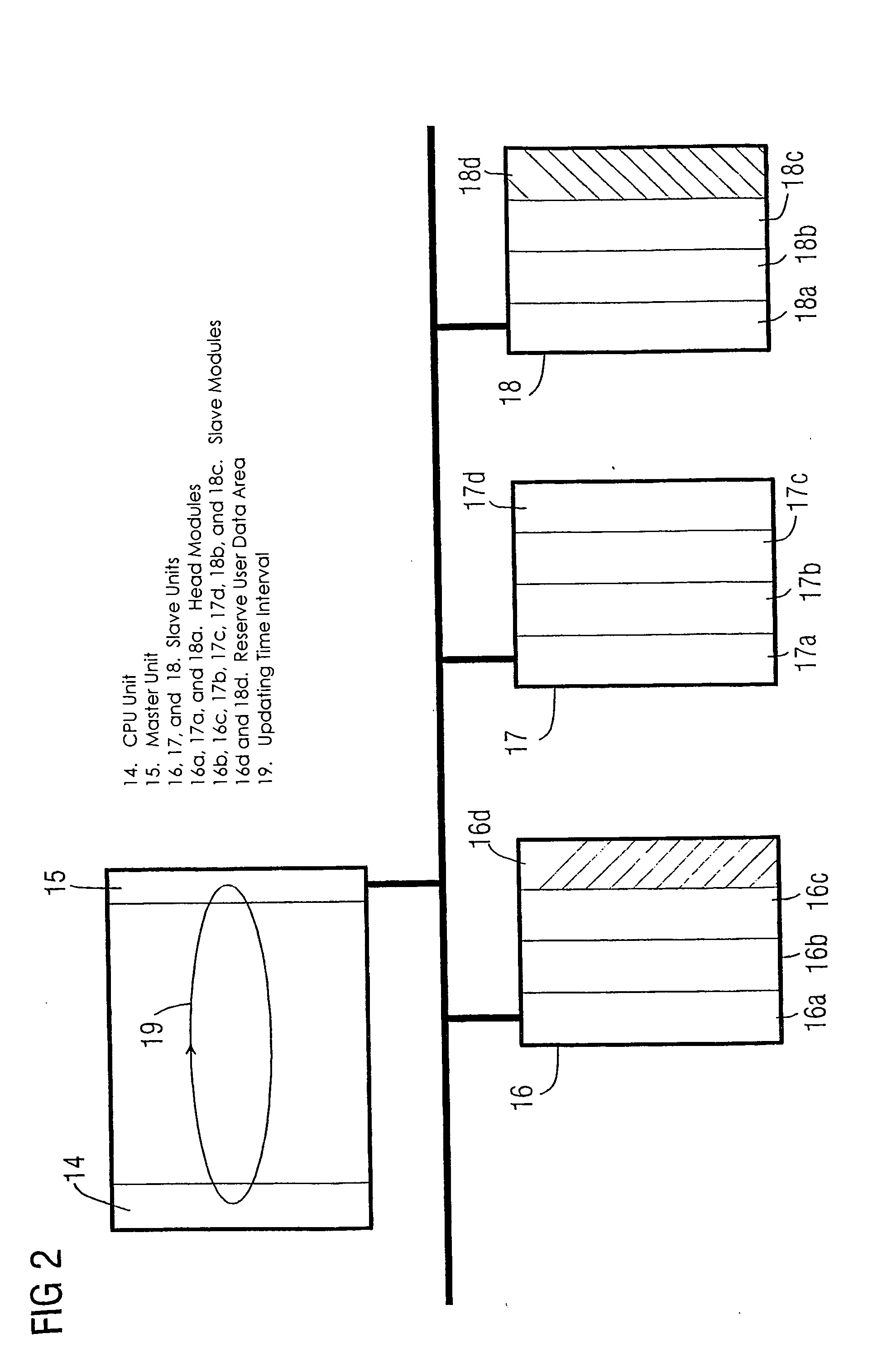
ActiveUS20050154809A1Reduce configuration timeProgramme controlComputer controlAccess timeEmbedded system
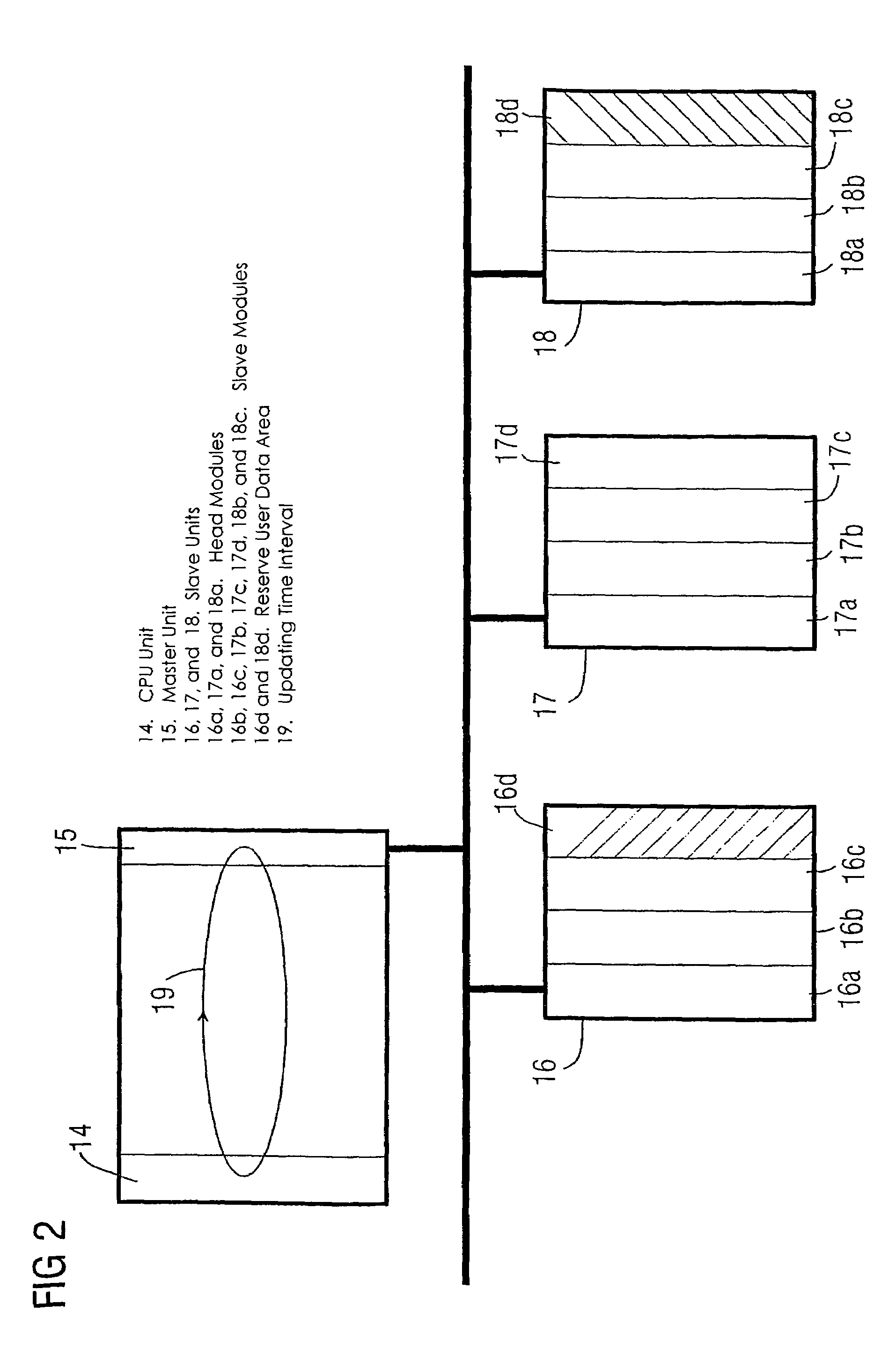
A method and an engineering system that reduce the configuration complexity with regard to a possible expansion of the automation device are provided. The automation device includes slave units and a master unit (7, 15) connected to the slave units via a bus. The slave units include one or more slave units (11, 12, 16, 17) and one or more reserve slave units (13, 18). The configuration of a reserve slave unit (13, 18) enables the master access time interval (20) and the slave access time intervals (21, 22, 23) to be expanded for a possible expansion of the automation device. As a result, a configured automation device of this type can be expanded by an additional slave unit without additional configuration or reconfiguration.
Owner:SIEMENS AG
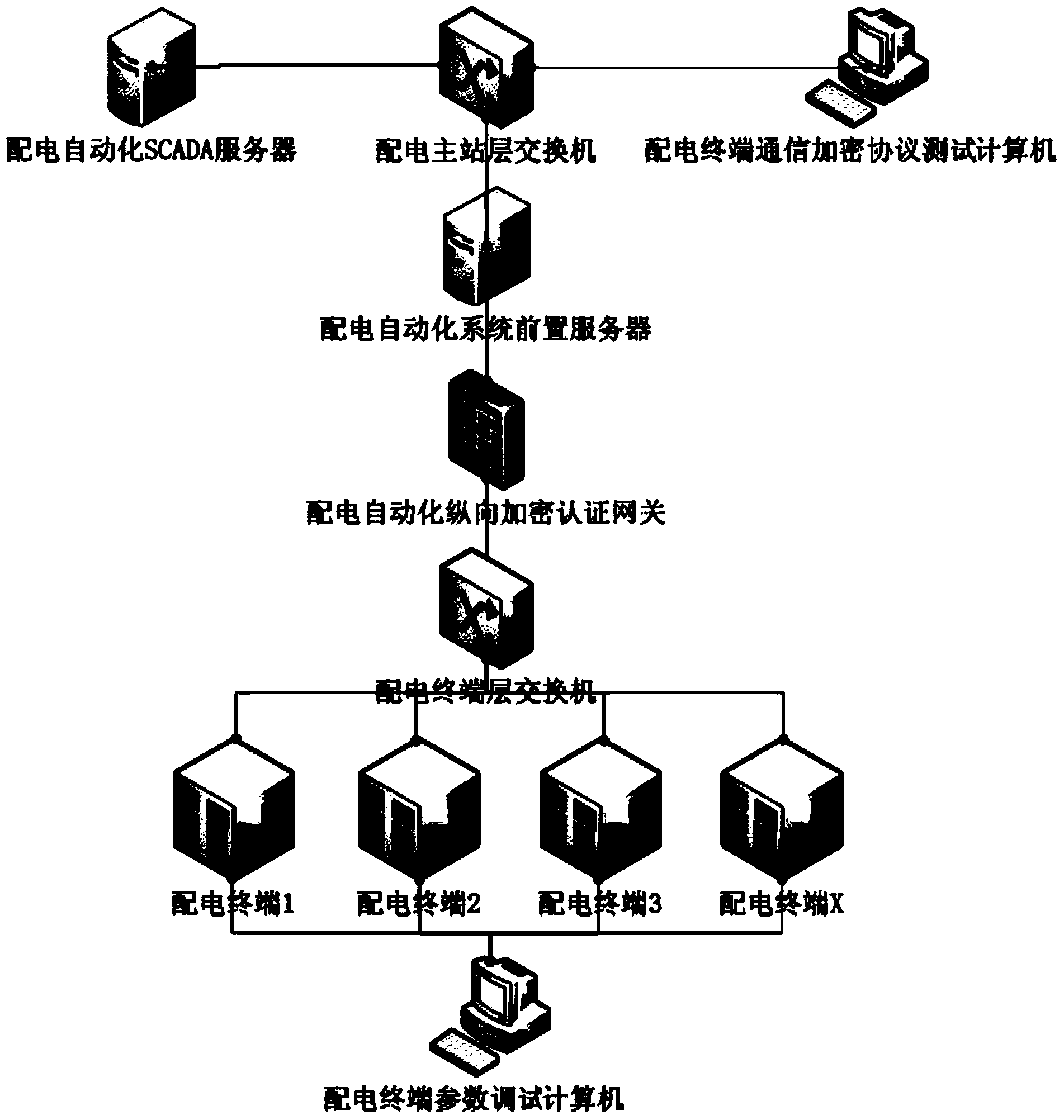
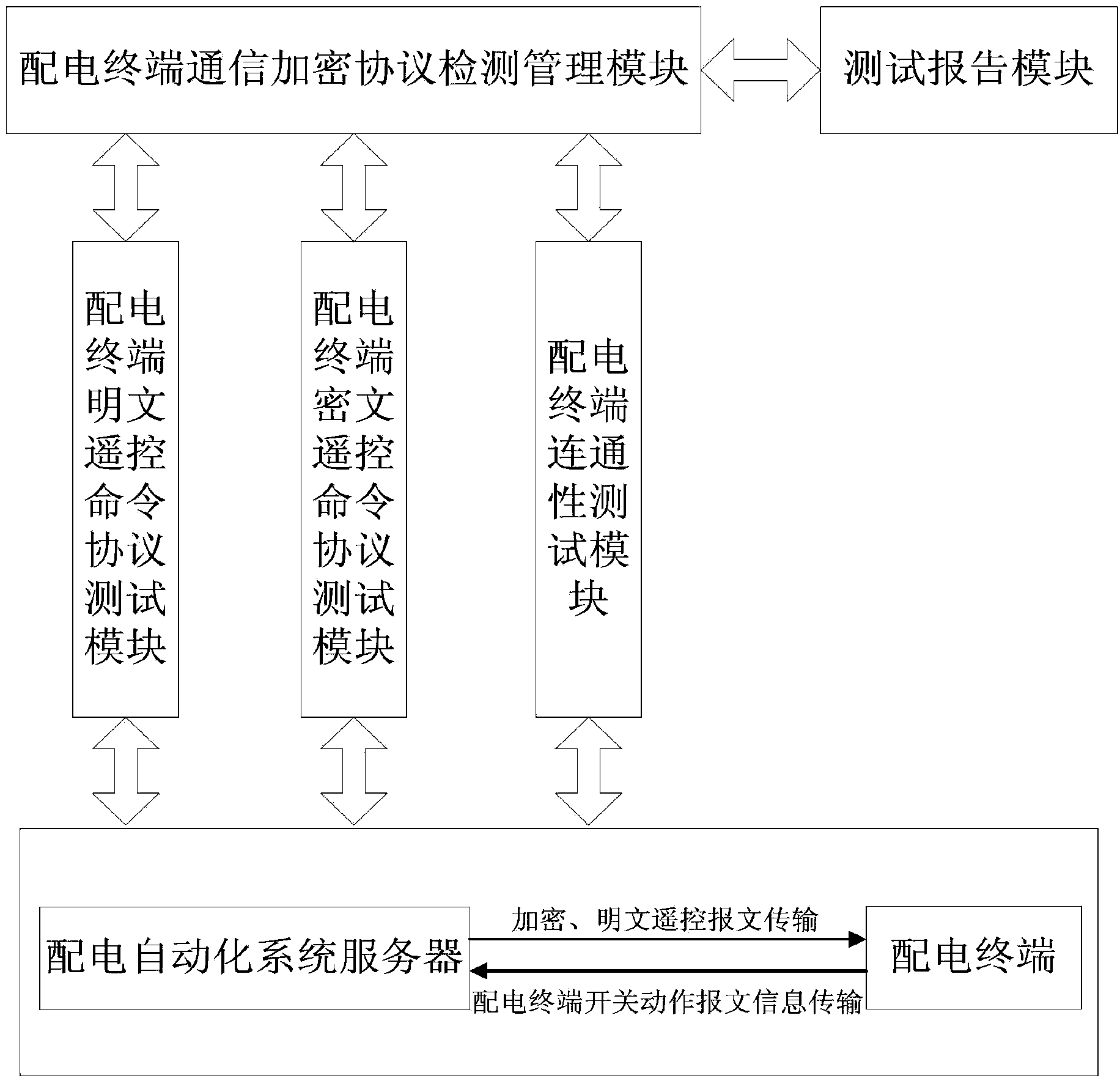
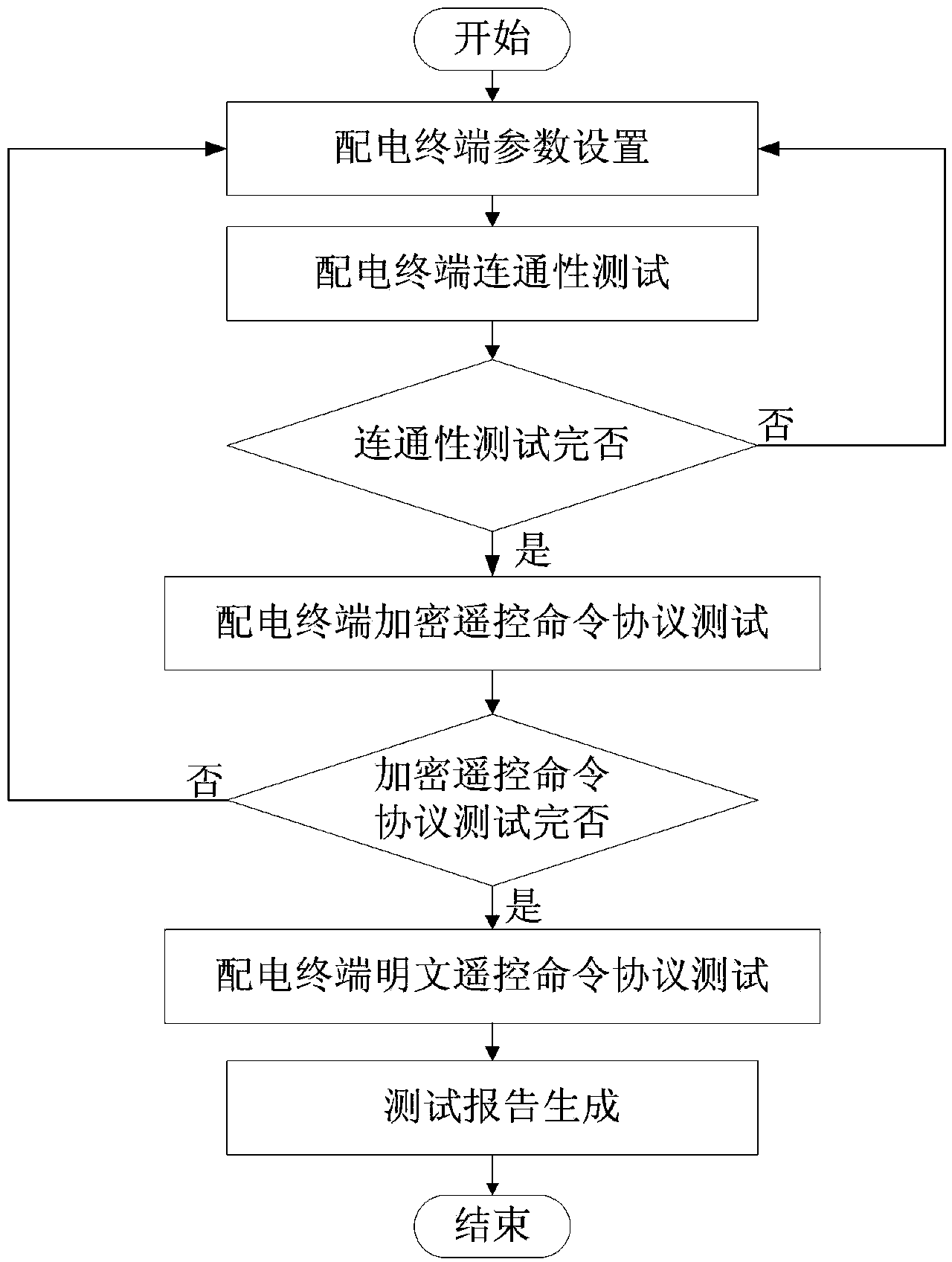
Power distribution terminal communication encryption protocol detecting method
The invention relates to a power distribution terminal communication encryption protocol detecting method. The power distribution terminal communication encryption protocol detecting method is characterized in that a power distribution terminal communication encryption protocol detecting management module sets parameters of a power distribution terminal; a power distribution terminal connectivity test module carries out a power distribution terminal connectivity test; a power distribution terminal ciphertext remote control command protocol test module carries out a power distribution terminal encrypted remote control command protocol test; a power distribution terminal plaintext remote control command protocol test module carries out a power distribution terminal plaintext remote control command protocol test; a test report module generates a power distribution terminal communication encryption protocol detecting and analyzing report automatically according to test strategy options and a test result. The power distribution terminal communication encryption protocol detecting method is reasonable in design, the automatic and real-time online detecting function for power distribution terminal connectivity validity, encrypted remote control command operating validity and plaintext remote control command operating violation is achieved, power distribution terminal communication encryption protocol detecting efficiency and accuracy are improved, and safety is ensured when the power distribution terminal carries out remote control commands.
Owner:STATE GRID CORP OF CHINA +1
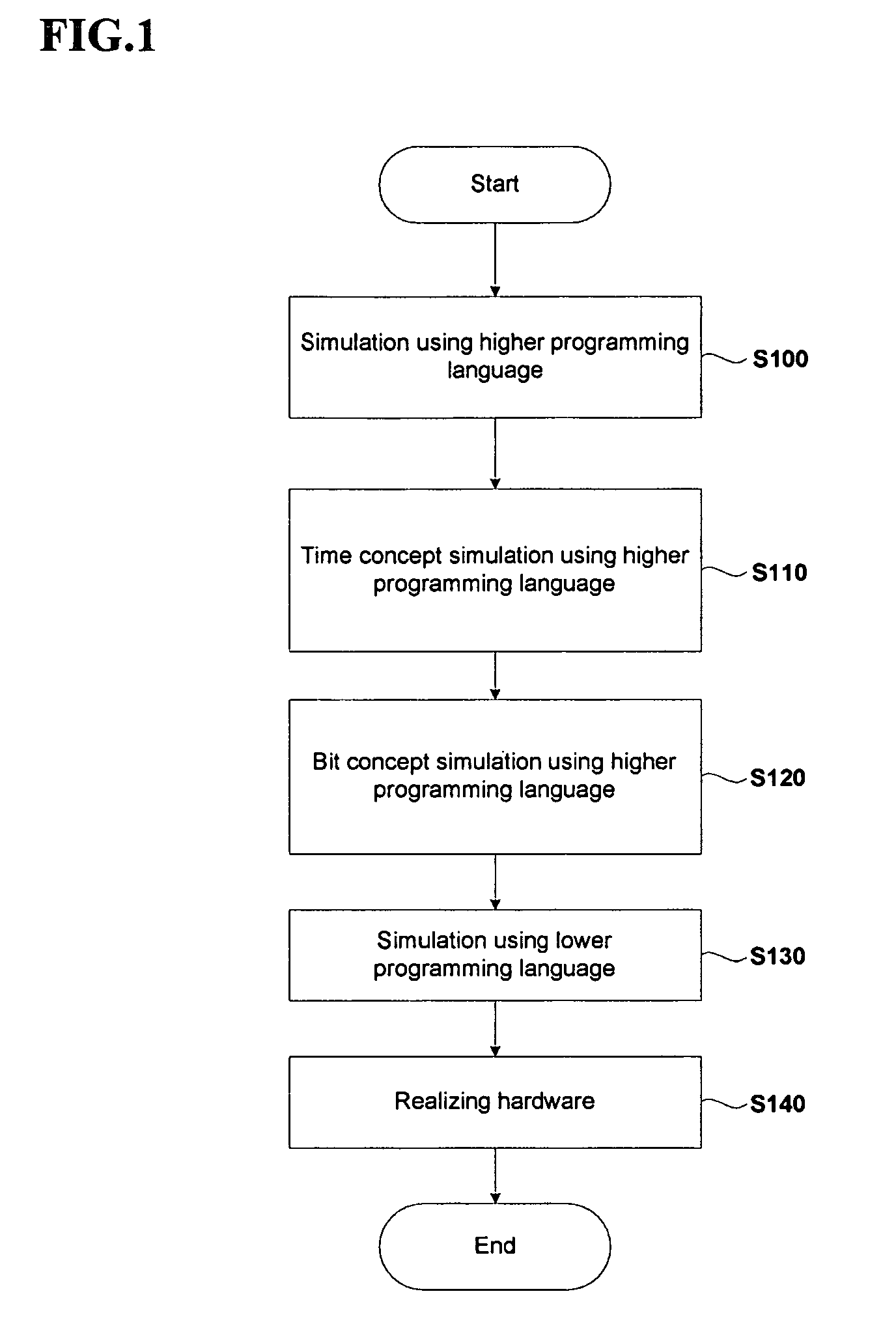
Method for digital system modeling by using higher software simulator
InactiveUS7783467B2Reduced simulation timeReduce configuration timeAnalogue computers for electric apparatusCAD circuit designProgram validationSystems design
Owner:ELECTRONICS & TELECOMM RES INST
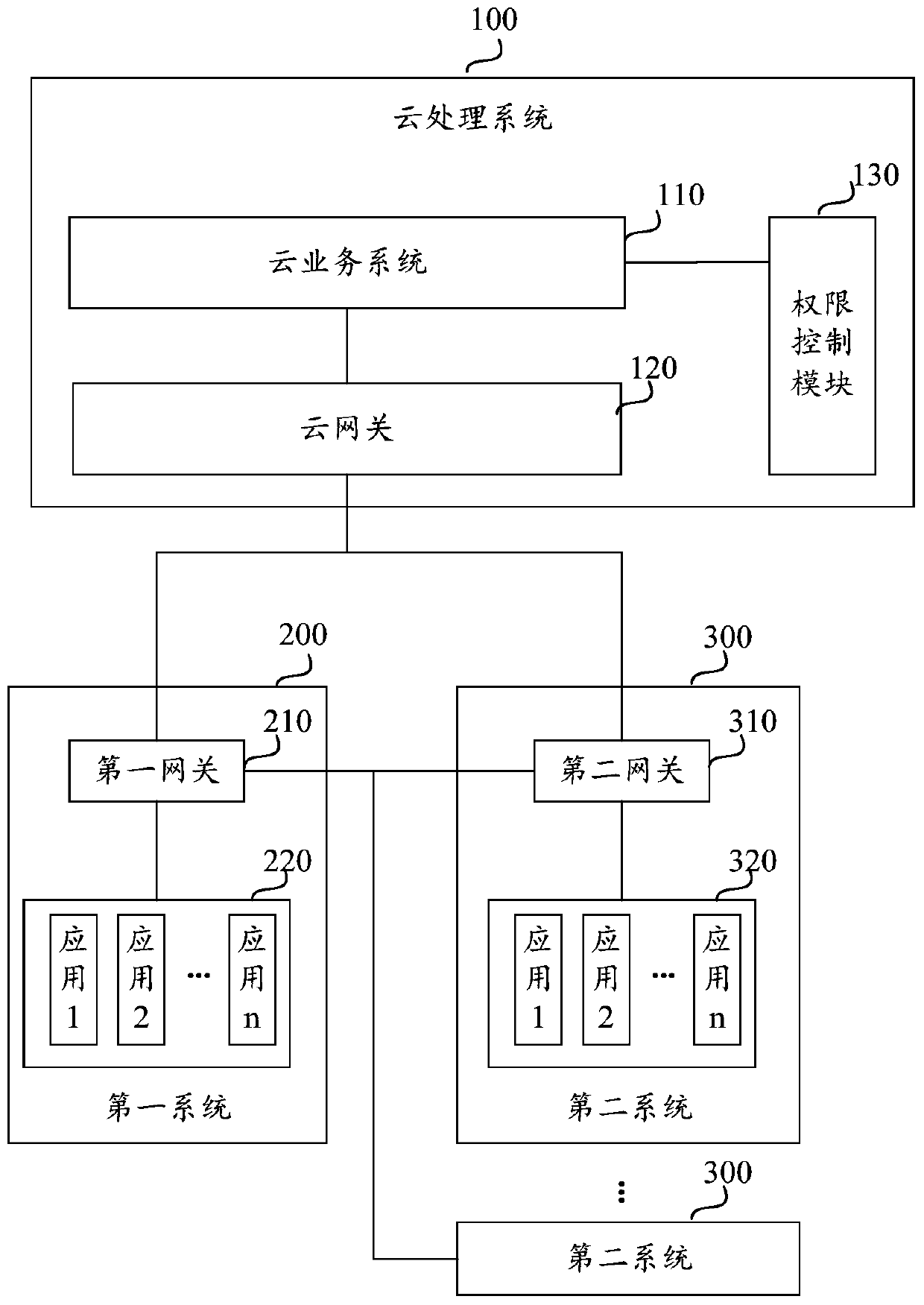
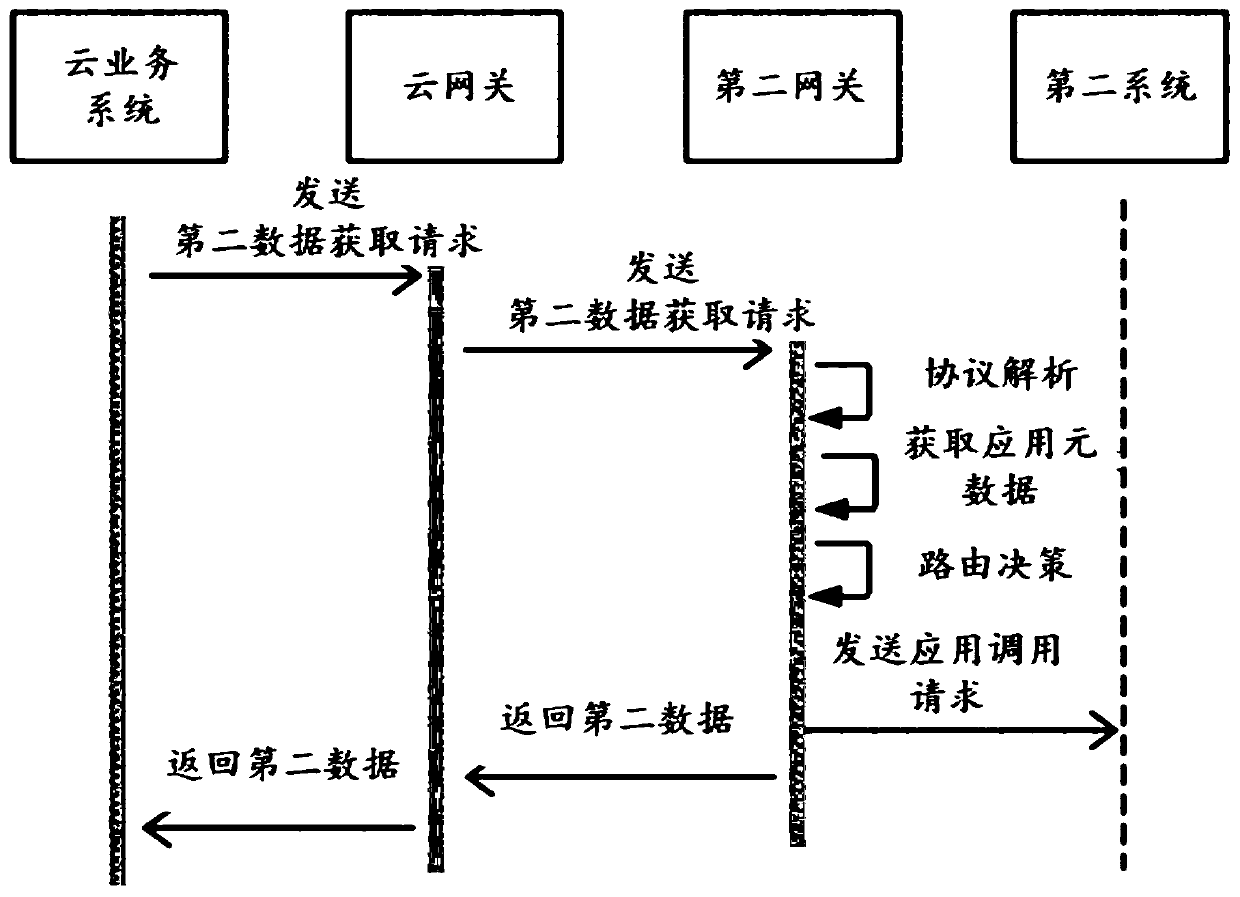
Cloud processing system and data processing method based on cloud processing system
ActiveCN111447273APermissions do not affectSpot inconsistencies in timeData switching networksCloud processingEngineering
The embodiment of the invention discloses a cloud processing system and a data processing method based on the cloud processing system. The system comprises a cloud service system, a cloud gateway andan authority control module, the cloud gateway is used for communicating the cloud service system with a first system outside the cloud and at least one second system outside the cloud; the cloud gateway is configured according to a first gateway of a first system; the at least one second system has a data interaction relationship with the first system; the cloud service system is used for checking the first data of the first system and the second data of the at least one second system obtained through the cloud gateway to obtain a corresponding checking result; and the authority control module is used for managing the use authority of the user of the first system and / or the at least one second system to the cloud service system, so that the user of the first system and / or the at least onesecond system can perform check processing by utilizing the cloud service system. The cloud processing system does not affect authority management of the first system or the second system, and avoidsthe problem that authorization between different systems is prone to data leakage and the like.
Owner:ZHEJIANG KOUBEI NETWORK TECH CO LTD
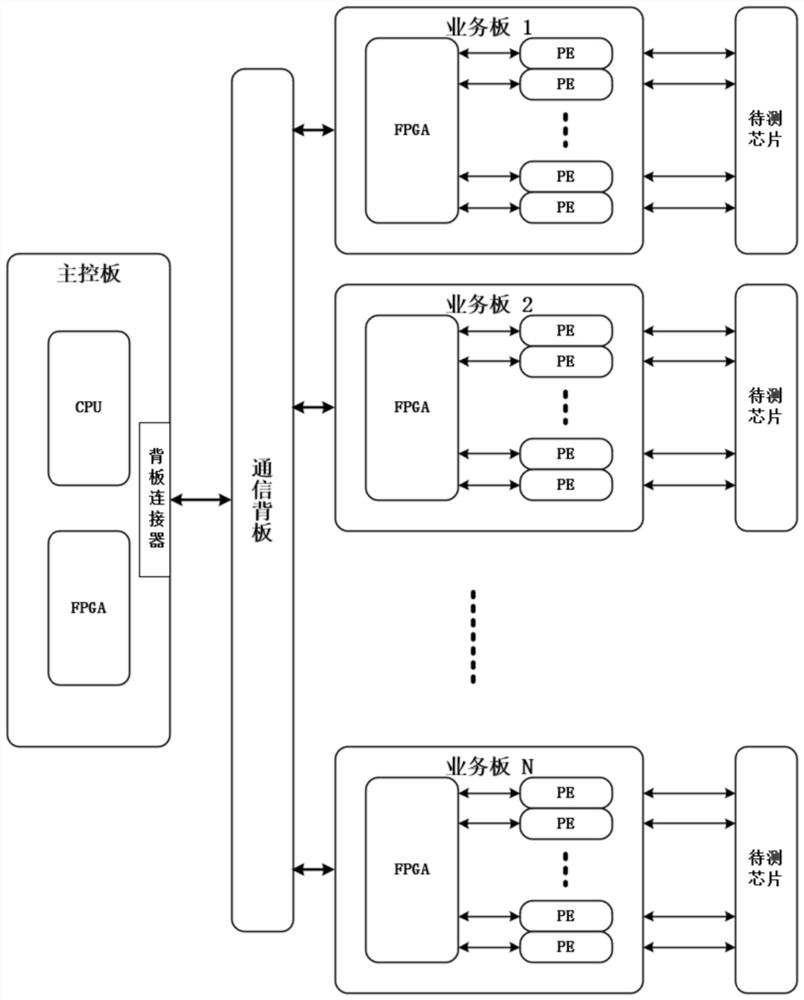
Acceleration method and device based on ATE equipment chip test and test machine system
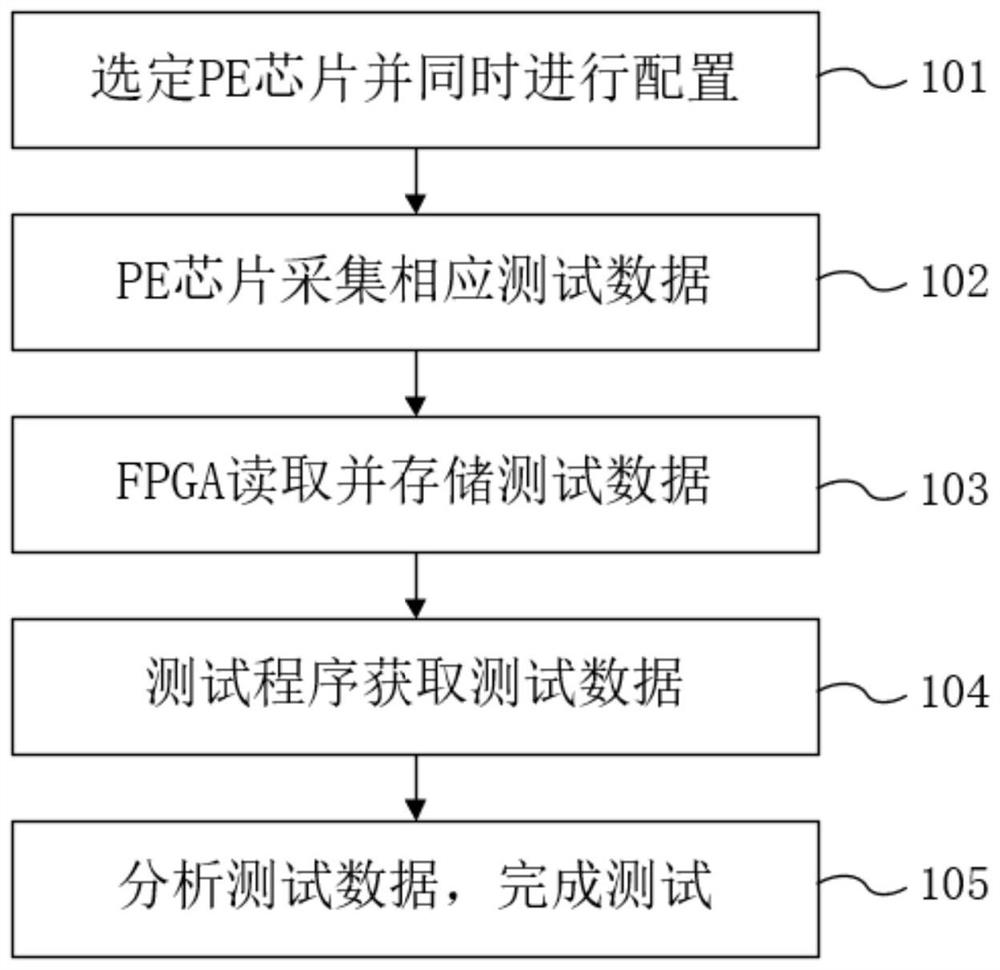
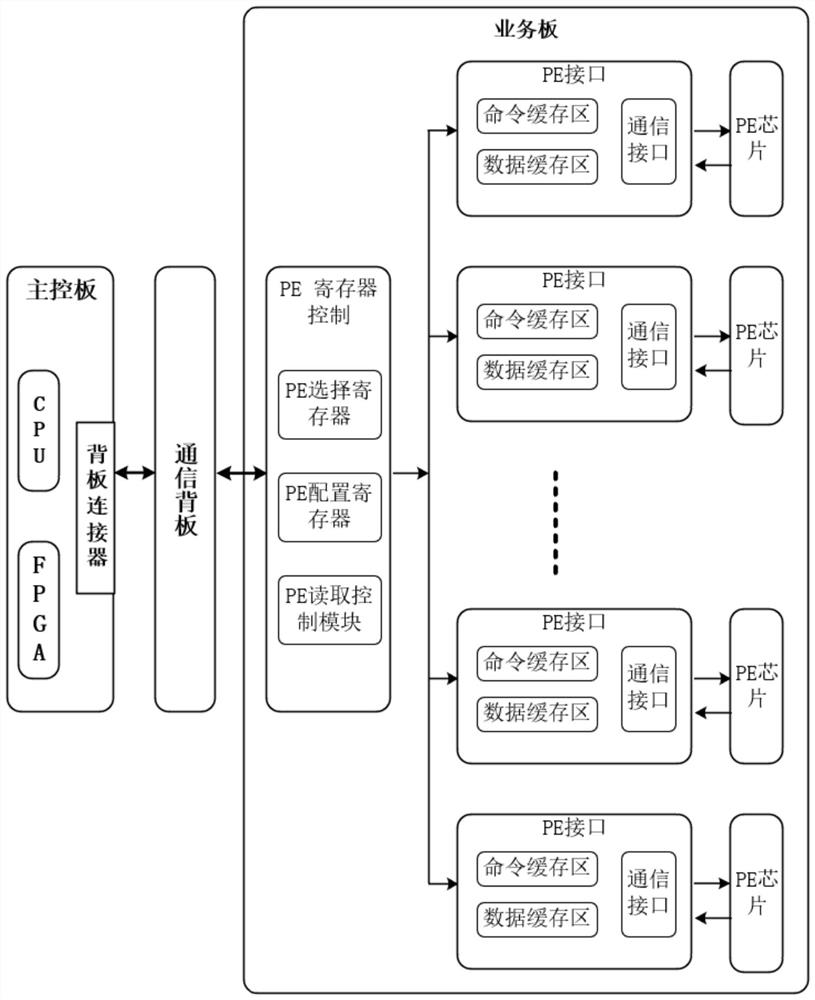
ActiveCN114356820AReduce configuration timeShorten read timeElectronic circuit testingEnergy efficient computingTest efficiencyAccess time
The invention provides an acceleration method and device based on ATE equipment chip testing and a testing machine system. The acceleration method comprises the following steps: selecting and configuring a pin circuit chip; the pin circuit chip collects test data fed back by the chip to be tested; at a preset time interval, the FPGA on each service board reads the test data in all the pin circuit chips on the service board in parallel, and stores the read test data in the FPGA; the test program obtains test data of all pin circuit chips on the service board by reading data stored in the FPGA on each service board; and the test program analyzes the test data to complete the test of the to-be-tested chip. According to the scheme provided by the invention, by reducing the access times of the test program to the pin circuit chip in the chip test process of the ATE equipment, the configuration time and reading time of the chip are reduced, the chip test time is shortened, the chip test efficiency is improved, hardware adjustment is not needed, and only the FPGA on the service board needs to be designed and upgraded.
Owner:杭州加速科技有限公司
An Intelligent Configuration Method
InactiveCN105204458BReduce configuration timeShorten the timeProgramme total factory controlAnimationMonitoring system
The invention relates to an intelligent configuration method. The method is characterized by comprising the following steps that (1) onsite devices to be configured are counted and classified, and according to a set numbering rule, each device to be configured in each type is provided with a unique identification code; (2) a data base of the station control level is established; (3) a configuration template is drafted; (4) intelligent configuration is implemented according to an intelligent configuration algorithm; and (5) the step (4) is repeated to complete intelligent configuration for all types of devices to be configured. The intelligent configuration method can reduce image drafting and animation connecting time in the configuration process to a large extent, and thus substantially shorten the configuration time of a monitoring system, background data of the devices to be configured can be configured intelligently and automatically, and man-made errors in the configuration process is reduced to the largest degree.
Owner:XUJI GRP +1
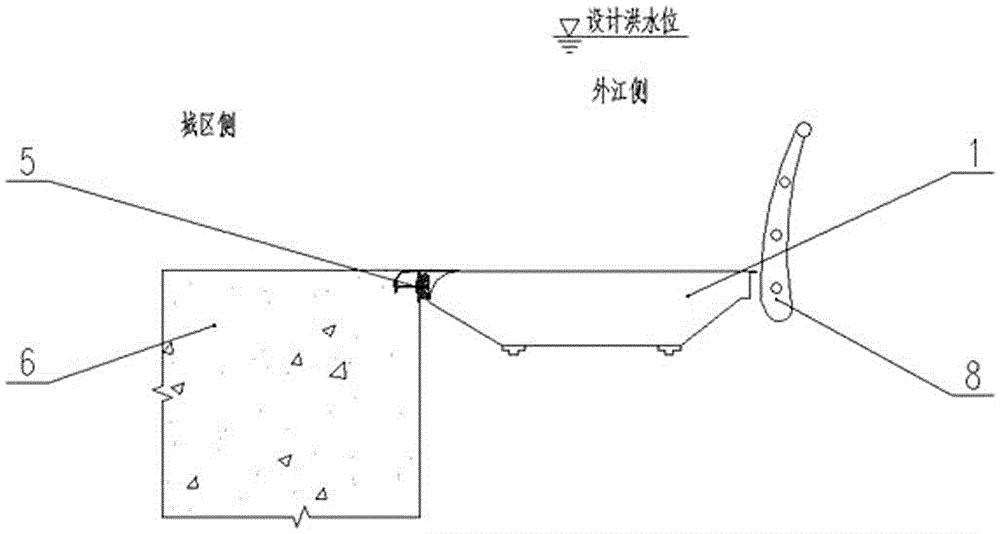
A flat and upturned movable flood control system
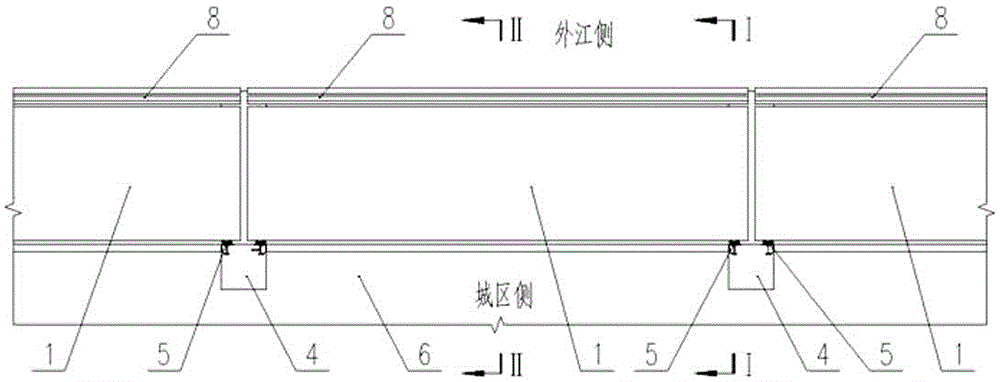
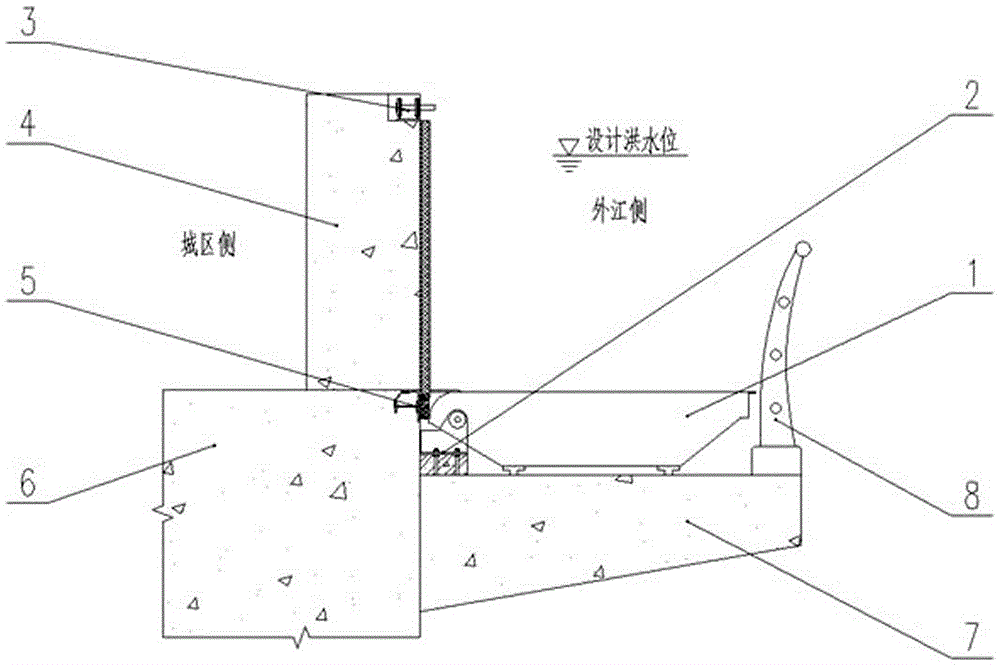
ActiveCN104195996BGuaranteed pre-compressionEasy to handleBarrages/weirsMechanical equipmentEngineering
A horizontal upward-turning type movable flood control system comprises movable gates, hinge devices, locking devices, posts, water stop devices, a baffling wall, legs and fences. The posts are arranged on the upper portion of the baffling wall at the certain intervals along the shore line, and the water side of the baffling wall below the posts is provided with the legs correspondingly; the hinge devices are arranged at the connections of the legs and baffling wall and are hinged to one ends of the movable gates; the water stop devices are arranged on the side of holes of the gates between the adjacent posts and the water side of the top of the baffling wall to form groove-shaped water stop rings; the locking devices are arranged on the water sides of the tops of the posts; normally, the movable gates lay on two adjacent legs through the hinge devices and serve as a pedestrian passage and a water platform; when the system is in the flood resisting state, the movable gates are closed by turning upwardly through a special opening vehicle or other mechanical equipment or manually before the flood coming and are locked with the locking devices, and sealed water stop rings are formed by pressing the bottom and two sides of the water stop devices and movable gates tightly.
Owner:浙江省水利水电勘测设计院有限责任公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com