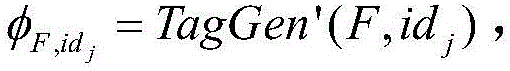Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
54results about How to "Raise the level of confidentiality" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Backlight plate, optical imaging device and identification equipment
InactiveCN104463107ARealize acquisitionRaise the level of confidentialityCharacter and pattern recognitionFingerprintOpto electronic
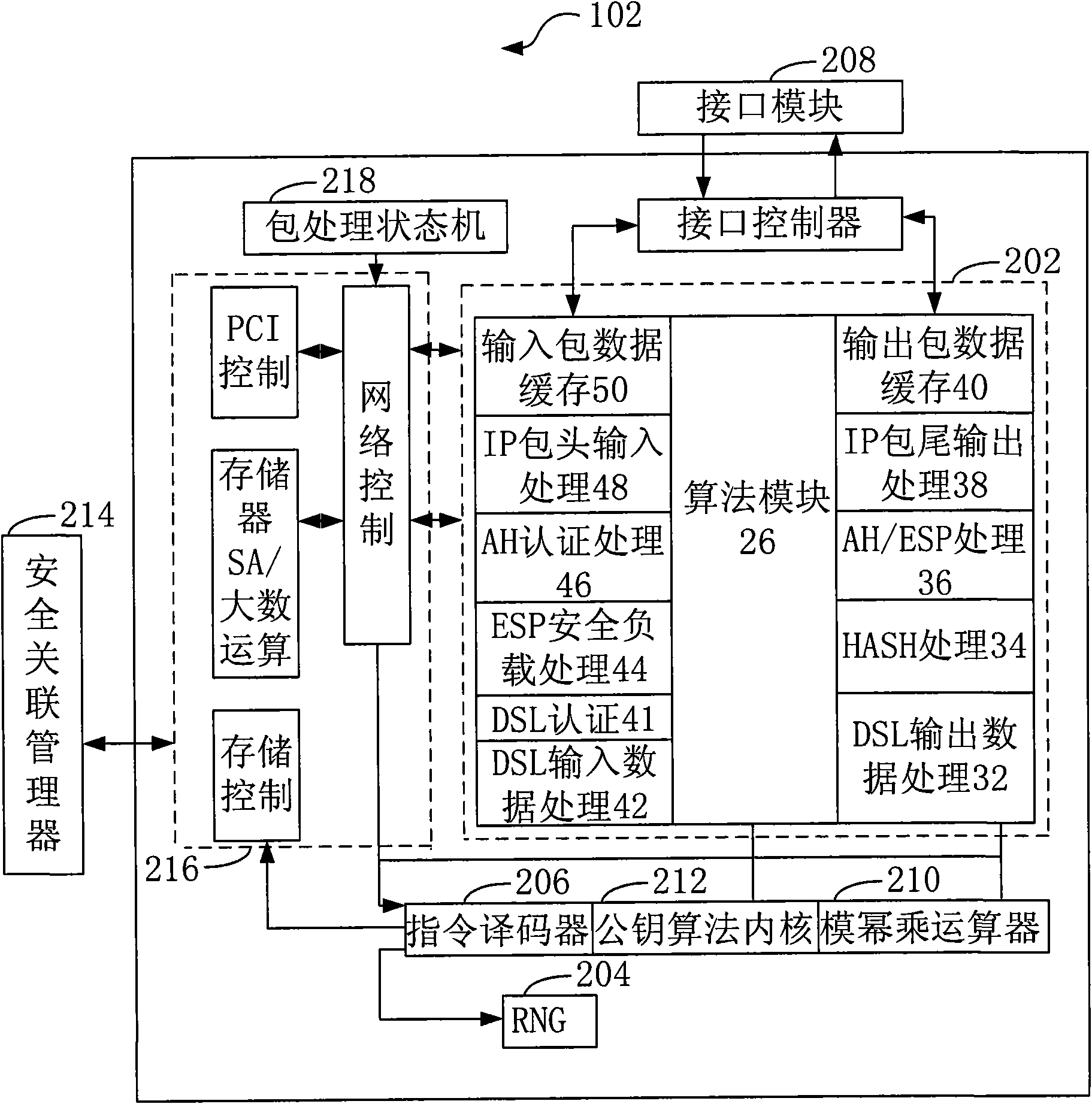
The invention provides a backlight plate, an optical imaging device and identification equipment. The backlight plate comprises a substrate and a light source which is arranged on the substrate and used for emitting emergent light, and the light source comprises a first light source which emits visible light and a second light source which emits near-infrared light. The emergent light emitted by the light source on the backlight plate can penetrate through an optical area array sensor and then penetrates through an imaging window protection layer, the emergent light penetrating through the imaging window protection layer can be reflected by a contact interface which is in contact with the imaging window protection layer, the reflected emergent light forms incident light which irradiates to the optical area array sensor, and the optical area array sensor performs photovoltaic conversion and signal processing to emitted light: when the emergent light is visible light, sampling of a fingerprint image is realized; when the emergent light is near-infrared light, collection of a vein image is realized. The backlight plate integrates the collection function of the fingerprint image and the collection function of the vein image, the security classification is high, and the safety is good.
Owner:SHANGHAI OXI TECH
Precise management and control system for infectious epidemic situations
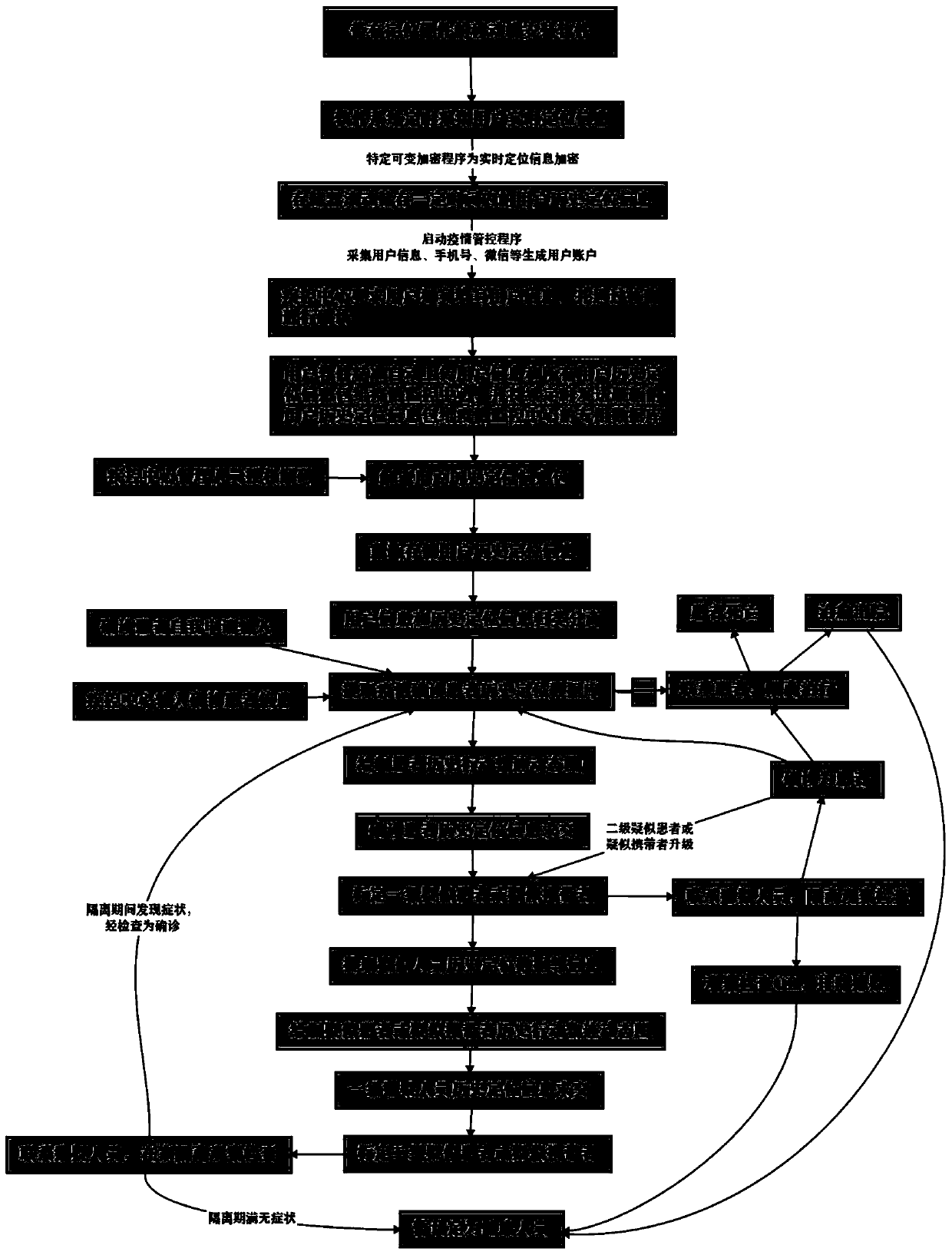
PendingCN111311018APrevent proliferationAccurate implementation of hierarchical management and controlEpidemiological alert systemsForecastingData packControl system
The invention discloses a precise management and control system for infectious epidemic situations. The system comprises an epidemic situation infection triggering mechanism, the system comprises a real-time positioning data packet data fuzzification processing technology, an epidemic situation infection intersection result elimination technology, a data group binding method, a data group removaljudgment method, a data combination analysis measure when multiple mobile phone user mobile phones are used at the same time, an epidemic situation prevention and control team and resource optimal configuration method and an epidemic situation prevention and control danger upgrading and degrading mechanism. According to the system and the method, at least basic data is collected, secrets behind the data are analyzed and deeply interpreted, infection tracing, epidemic outbreak prevention and diffusion early warning can be accurately carried out, epidemic prevention management and control personnel and epidemic prevention management and control resource materials are optimally distributed, accurate management and control are realized, and national economy and personal collective loss are reduced to a great extent.
Owner:苏州远征魂车船技术有限公司
Safe distributed duplicated data deletion method
ActiveCN103763362AProtection of confidentialitySatisfy deduplicationTransmissionShort ValueComputer hardware
The invention discloses a safe distributed duplicated data deletion method. According to the method, a file is segmented into fragments through a secret sharing technology without any encryption mechanism. The shared fragments are distributed in a plurality of independent storage servers. In addition, in order to support reduplication removing, a different short value is calculated and sent to the storage servers as the indicator of one fragment. Only possessors uploading data for the first time need to carry out such calculation and distribution of secrete sharing, and then people possessing the same data copies do not need to calculate and store the sharing any longer. When the data copies are restored, users must access the storage servers with the minimum quantity to reconstruct the data through authentication and acquisition of the secret sharing. In other words, the secret sharing of the data can only be accessed by the users who possess the same copies and are authorized.
Owner:XIDIAN UNIV
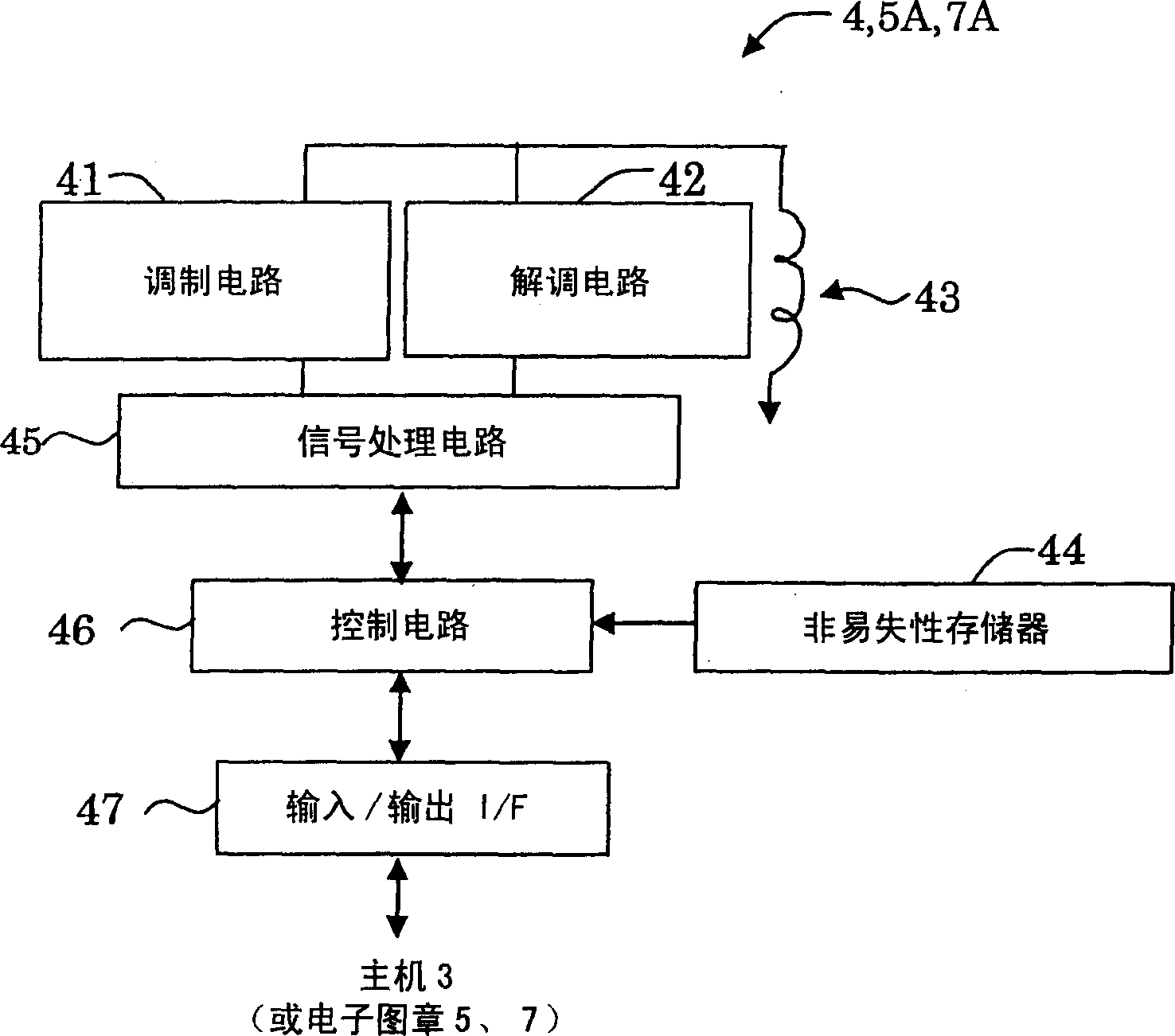
Authentication system, authentication method, and information processing apparatus
ActiveUS20100245033A1High confidentiality levelRaise the level of confidentialityCandle holdersLighting support devicesAuthentication systemComputer hardware
An authentication system is provided with a room-security device, and an information processing apparatus installed in a controlled area controlled by the room-security device, in which the room-security device and the information processing apparatus are connected in a network. The room-security device obtains, from a user, identification information, and transmits the identification information to the information processing apparatus, if the user is permitted to enter a room based on the obtained identification information. The information processing apparatus receives the identification information. If it is detected that the user is alone in the controlled area based on the received identification information, the information processing apparatus performs authentication based on the received identification information instead of asking the user to enter authentication information to obtain the authentication information.
Owner:KONICA MINOLTA BUSINESS TECH INC
Multivariate accurate management and control system for infectious epidemic situations
PendingCN111403045AReduce lossesLogical thinkingMedical data miningDigital data information retrievalControl systemControl data
The invention discloses a multivariate accurate management and control system for infectious epidemic situations. The multivariate accurate management and control system comprises a user client and adata analysis management and control terminal, wherein a user installs real-time locating information acquisition software; and the data analysis management and control terminal at least comprises a storage database module, a data analysis software module, a data interaction software module and an instruction sending confirmation module. The data analysis software module performs processing and calculation to capture key features and / or data intersection, so epidemic situation management and control data is obtained and guides epidemic prevention management ministries and commissions, cooperation department groups and mobile phone users to effectively prevent and treat infectious epidemic situations. According to the system, the least and the most fundamental data is collected, secrets behind the data are analyzed and deeply interpreted, infection tracing, epidemic outbreak prevention and early warning of spreading can be accurately carried out, epidemic prevention management and control personnel and epidemic prevention management and control resource materials are optimally distributed, accurate management and control are realized, and the loss of national economy, individuals and groups are reduced to a great extent.
Owner:苏州远征魂车船技术有限公司
Precise management and control system for infectious epidemic situations
PendingCN111370135AReduce lossesLogical thinkingEpidemiological alert systemsData packControl system
The invention discloses a precise management and control system for infectious epidemic situations. The precise management and control system comprises an epidemic situation judgment and control step,a real-time positioning data packet interpretation technology, a measure directed at the situation that a mobile phone user does not cope with an epidemic situation according to operation requirements prescribed in epidemic situation prevention and control measures, and treatment measures for early warning of the epidemic situations. According to the invention, historical instant speed vectors and accelerations of the user can be calculated, solved and drawn according to positioning displacement and time difference between real-time positioning information, so the moving tool and moving behavior of the user can be judged; and therefore, the system is of great significance to accurately analyze whether an infection place and an infection mechanism will continue to exist or not. According to the system, minimum basic data is collected and secrets behind the data are analyzed and deeply interpreted, so infection tracing, epidemic outbreak prevention and early warning of epidemic spreading can be accurately carried out, management and control personnel and resource materials for epidemic prevention are optimally distributed, and accurate management and control are realized.
Owner:苏州远征魂车船技术有限公司
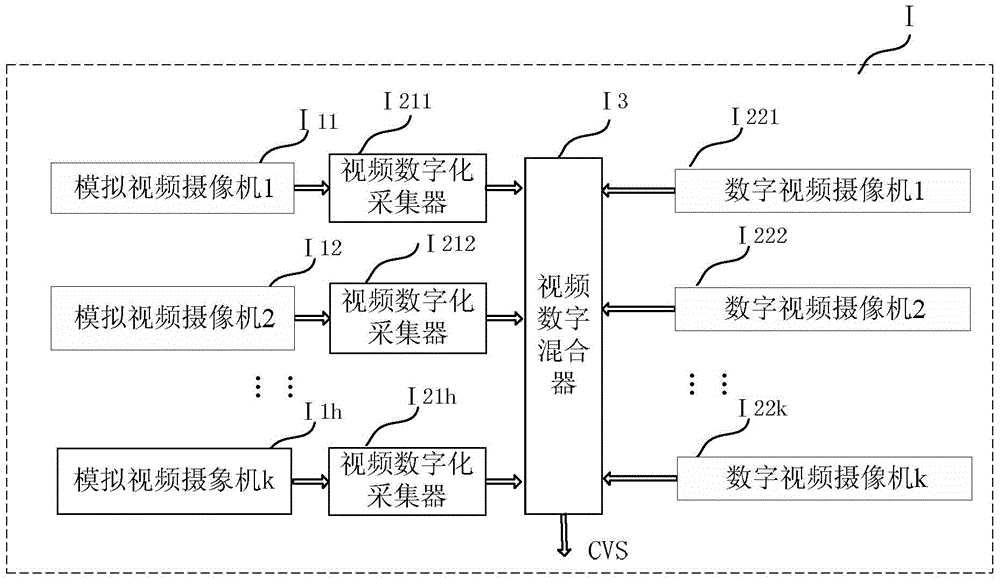
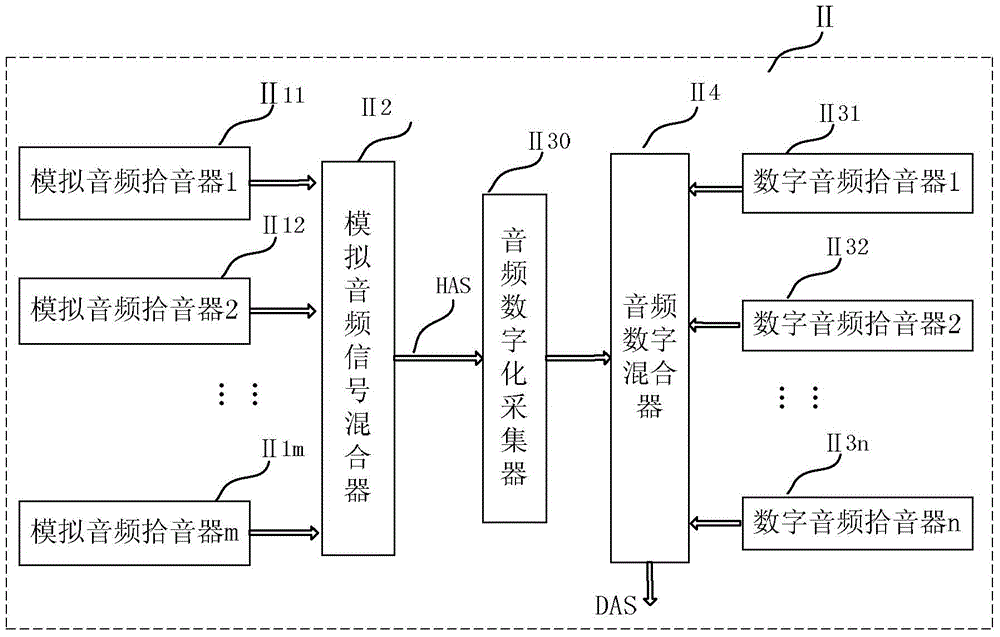
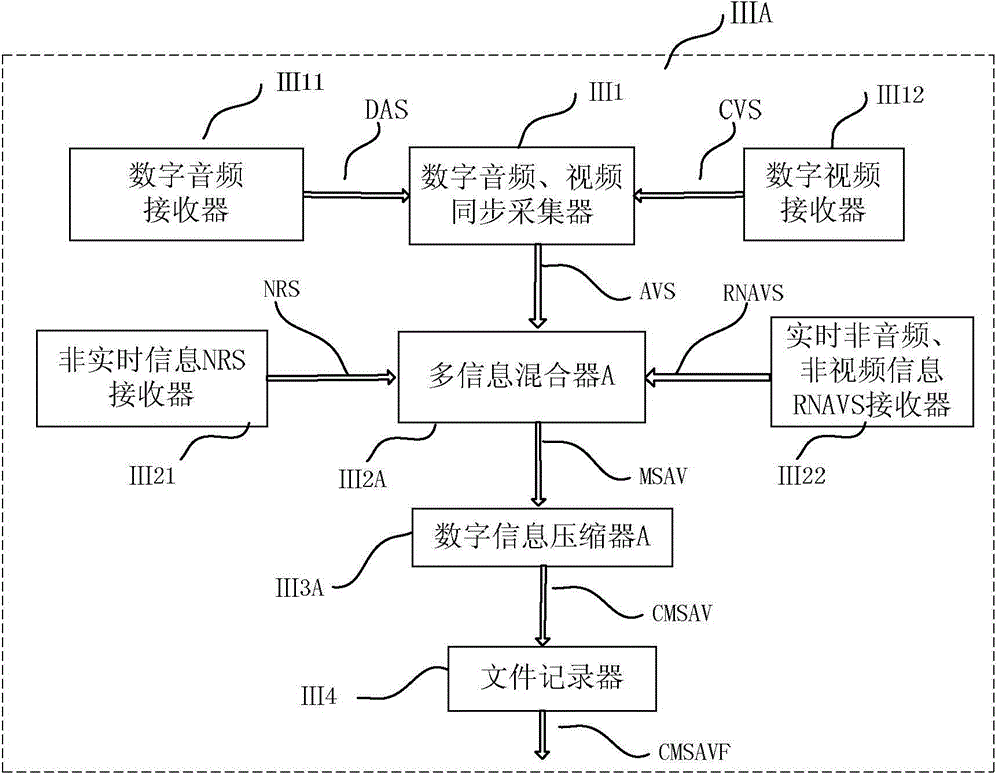
Multimedia multi-information synchronized reproducing system
ActiveCN104918016AOptimize storage methodRaise the level of confidentialityTelevision system detailsColor television detailsModem deviceDemodulation
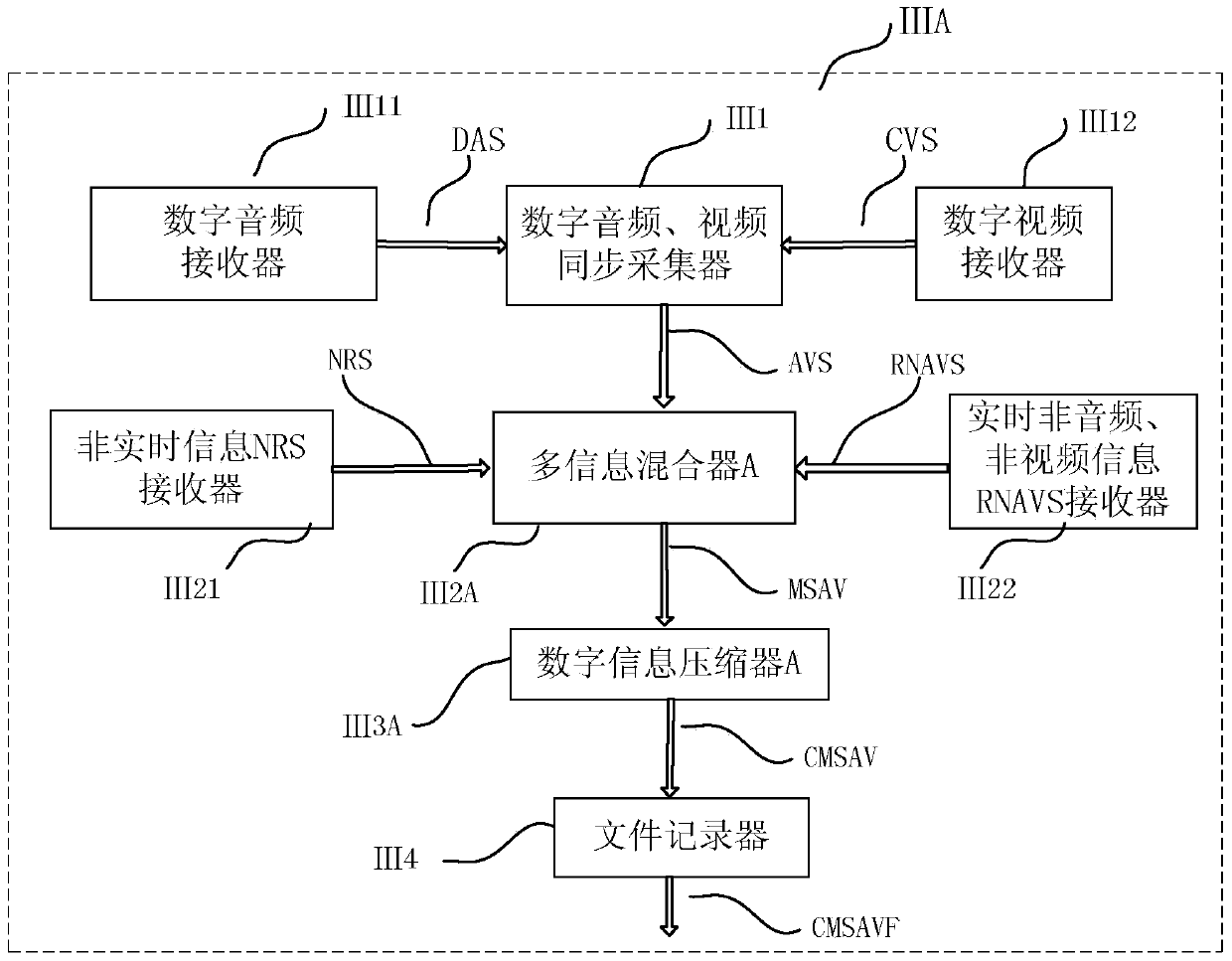
A multimedia multi-information synchronized reproducing system comprises a multi-information modulation unit, a multi-information synchronized reproduction unit and a hardware platform of the system, wherein the multi-information modulation unit is a component used for combining multiple pieces of relevant information with associated information relation, that is, interpolating ''non-audio, non-video information'' into ''audio and video stream or files thereof'' to form a ''multimedia multi-information file CMSAVF''; the multi-information synchronized reproduction unit is a component used for reproducing and backplaying the ''multimedia multi-information file CMSAVF'', carrying the ''non-audio, non-video information'', after demodulation via a ''multi-information file demodulator''; and the hardware platform of the system is a software and hardware platform with a modulator-demodulator used for producing and restoring various kinds of information exist in the ''multimedia multi-information file CMSAVF''. The multimedia multi-information synchronized reproducing system can store multimedia multi-information files in a same document file synchronously in real time, and ensures that the files can be highly synchronized in query and playback.
Owner:LIUZHOU GUITONG TECH
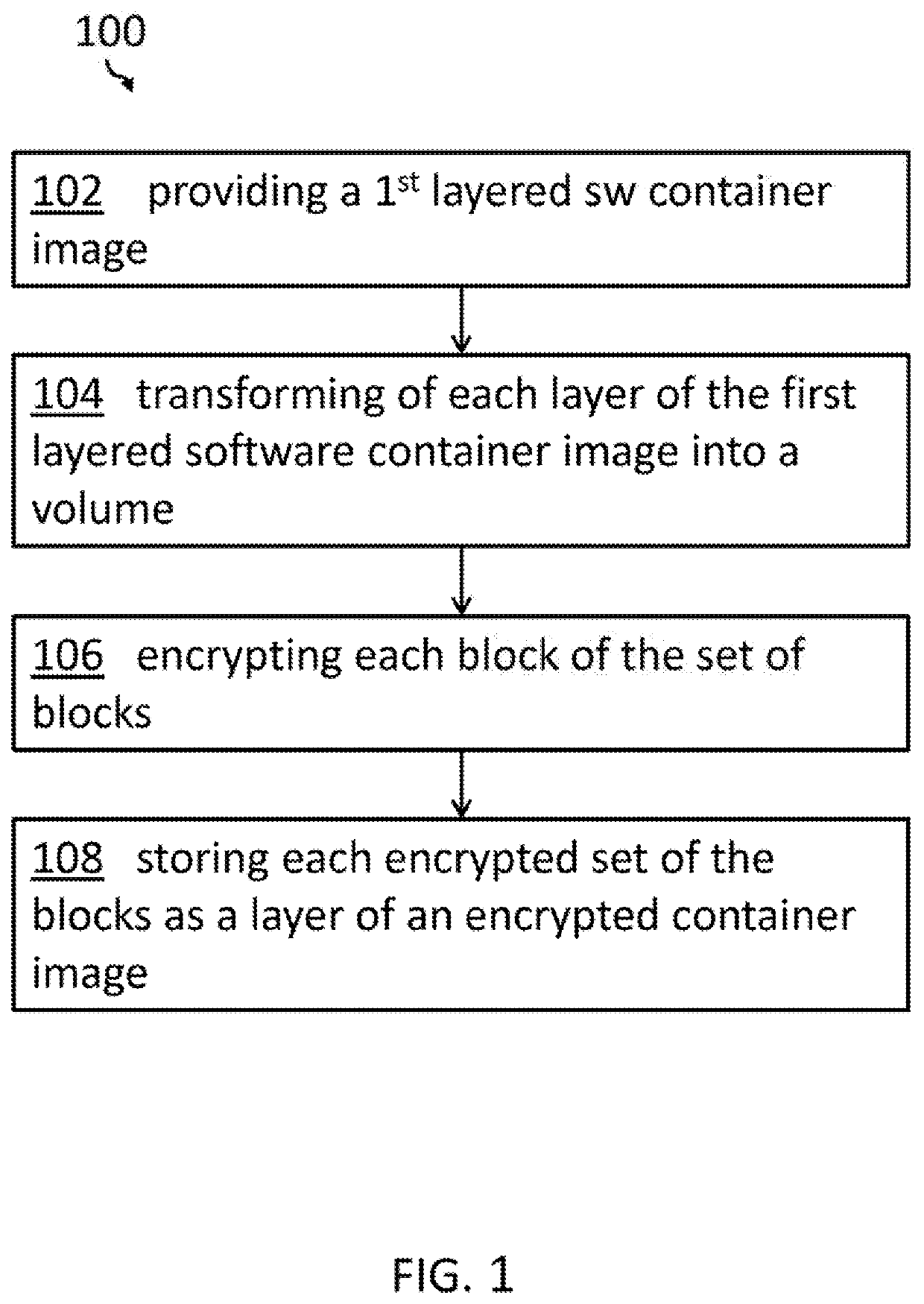
Creation and execution of secure containers
ActiveUS20200250319A1Avoid accessRaise the level of confidentialityDigital data protectionFile system administrationComputer hardwareDocument transformation
A computer-implemented method for creating a secure software container. The method comprises providing a first layered software container image, transforming all files, except corresponding metadata, of each layer of the first layered software container image into a volume, the volume comprises a set of blocks, wherein each layer comprises an incremental difference to a next lower layer, encrypting each block of the set of blocks of a portion of the layers, and storing each encrypted set of the blocks as a layer of an encrypted container image along with unencrypted metadata for rebuilding an order of the set of blocks equal to an order of the first layered software container image, so that a secure encrypted software container is created.
Owner:IBM CORP
Network security communication method, data security processing device and system for finance
ActiveCN101997835AControl connection relationshipRaise the level of confidentialityUser identity/authority verificationComputer terminalSafe handling
The invention provides a network security communication method, a data security processing device and a system for finance, and relates to the technical field of networks. The network security communication method comprises the following steps of: performing transmission layer security protocol packaging on data to be transmitted in a security terminal; and performing network layer security protocol packaging on the data subjected to the transmission layer security protocol packaging in the security terminal. A security mechanism of a transmission layer is embedded in a security mechanism of a network layer and can defense attacks from different network hierarchies. Therefore, the security of the whole system is enhanced.
Owner:北京多思技术服务有限公司
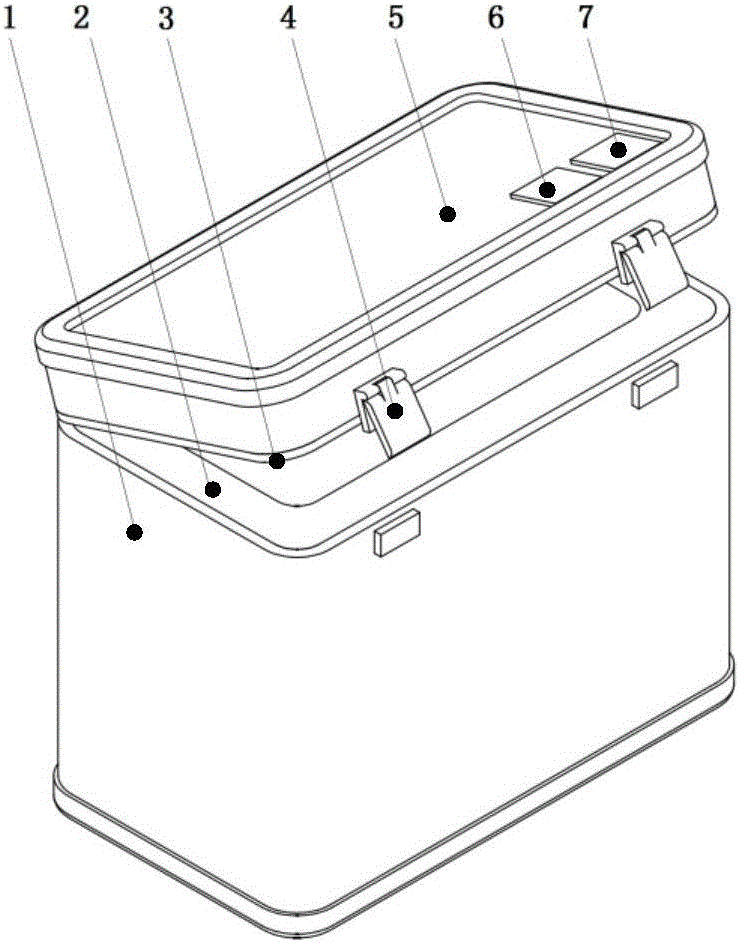
Intelligent recyclable express package box
ActiveCN106314958AReduce pollutionAvoid pollutionPackage recyclingBio-packagingEngineeringMechanical engineering
The invention provides an intelligent recyclable express package box which comprises a box body, a safety air bag, sealing rubber strips, a fast lock, a box cover, an RFID (radio frequency identification device) chip and two-dimensional codes, the safety air bag is fixedly mounted in the box body and completely covers the inner surface of the box body, the long edge of one side of the box cover is fixedly mounted at an opening of the box body through hinges, the sealing rubber strips are fixedly mounted at the opening of the box body and an opening of the box cover respectively, a fixed end of the fast lock is mounted on the box cover, a lock catching end is fixedly mounted on the box body, and the RFID chip is fixedly mounted at the top of the box cover. The express package box has excellent mechanical property and has the advantages that the express package box is shockproof, waterproof, moisture-proof and resistant to extrusion and can be stacked and machined again in a melted manner after damage, and the like.
Owner:THE INST OF AUTOMATION HEILONGJIANG ACADEMY OF SCI
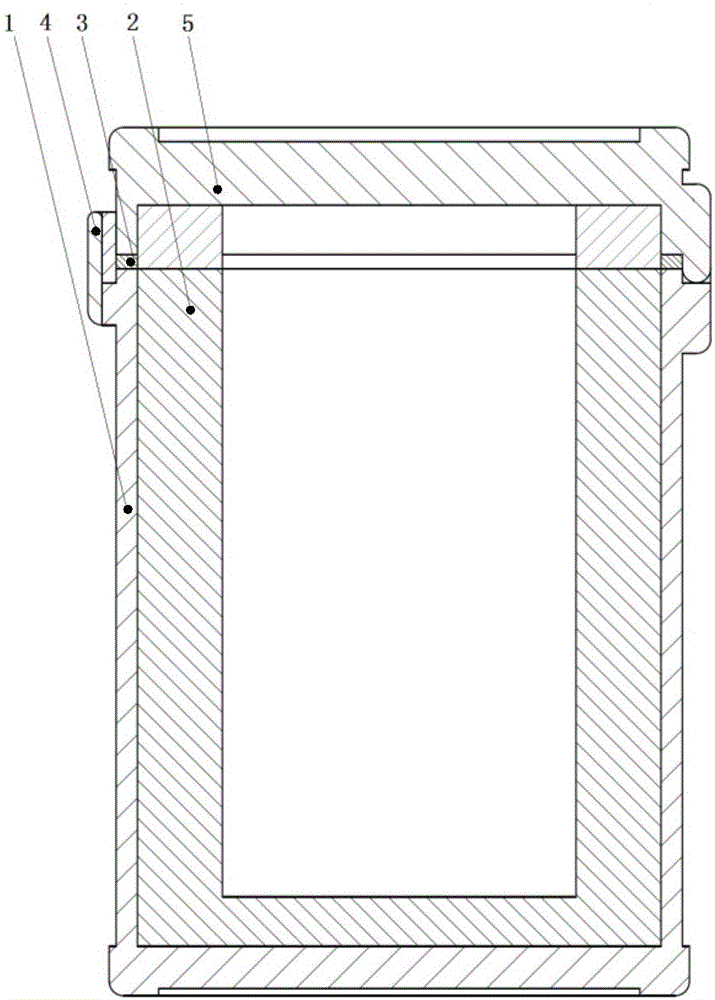
Mechanical coded lock vehicle-mounted safe box with concealed grid
InactiveCN104108347ARaise the level of confidentialityUnique designPuzzle locksPermutation locksEngineeringMechanical engineering
The invention discloses a mechanical coded lock vehicle-mounted safe box with a concealed grid, and belongs to the field of security articles. The safe box can be used for classifying and storing valuables, has a concealing property, and can be used for protecting valuables at a higher level. The mechanical coded lock vehicle-mounted safe box comprises a box body and a box cover, wherein the bottom of the box body is provided with a through hole; the box cover is connected with the box body through a first hinge; the concealed grid is arranged in the box body, and is formed by encircling a side door, a transverse clapboard and inner wall of the box body; the side door is connected with the bottom of the box body through a second hinge. The safe box further comprises an unlocking mechanism and a code changing mechanism. By adopting the mechanical coded lock vehicle-mounted safe box, the valuables are classified and stored, a higher security level is realized, and the requirements of more customers are met. Moreover, two locks are controlled by using one wheel, namely, a shifting wheel of a mechanical coded lock can be used for controlling the opening and closing of the box cover and the side door of the concealed grid respectively. The safe box is unique in design, is novel in structure, and has higher concealment property and very high popularization and application values.
Owner:孙大光
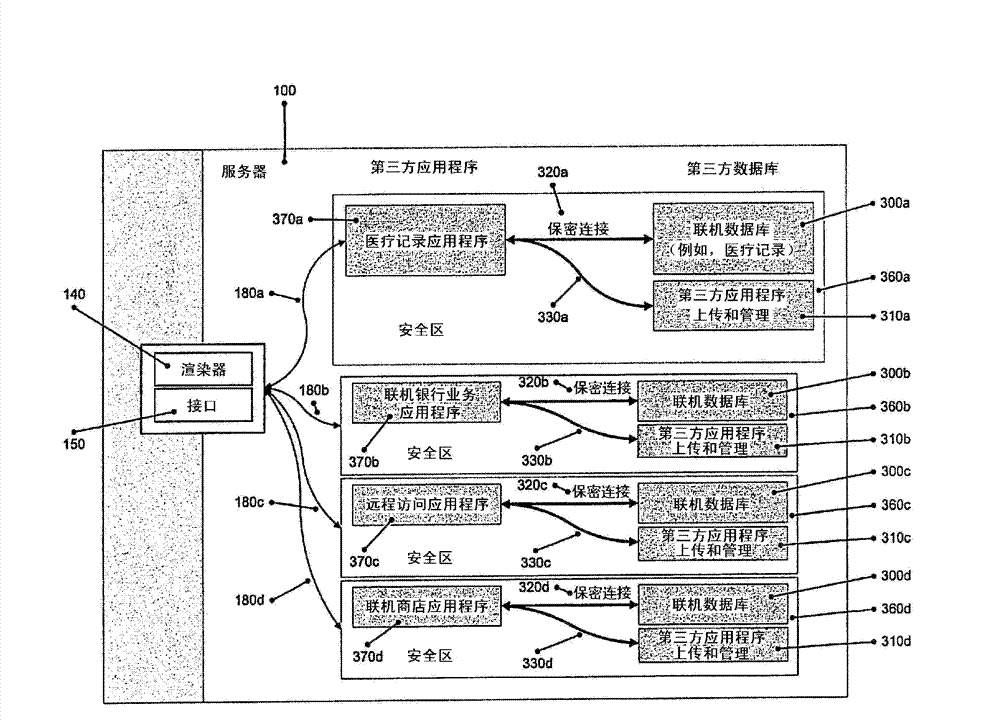
Render service for remote access to applications
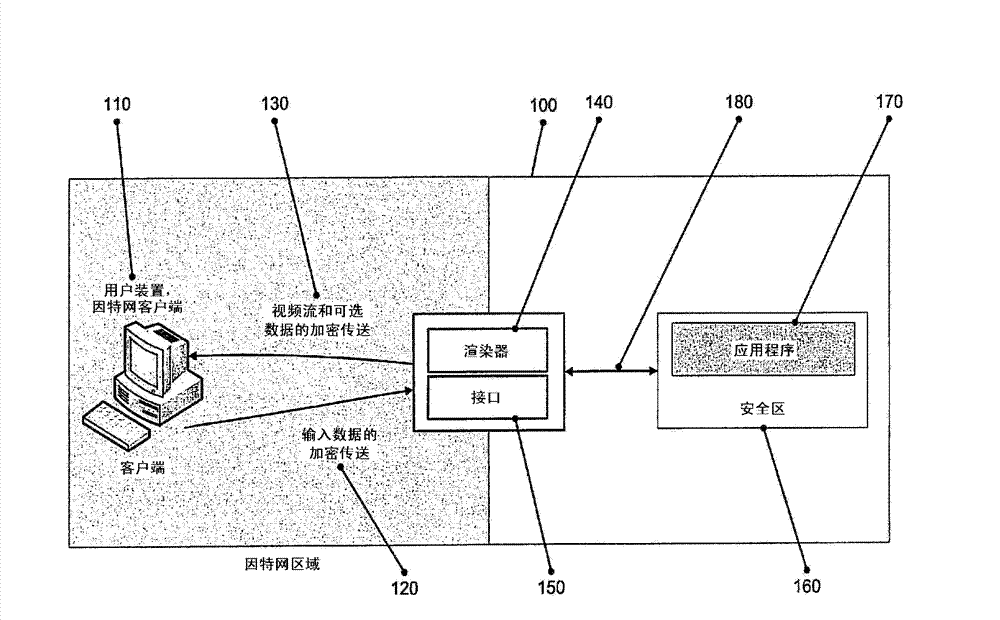
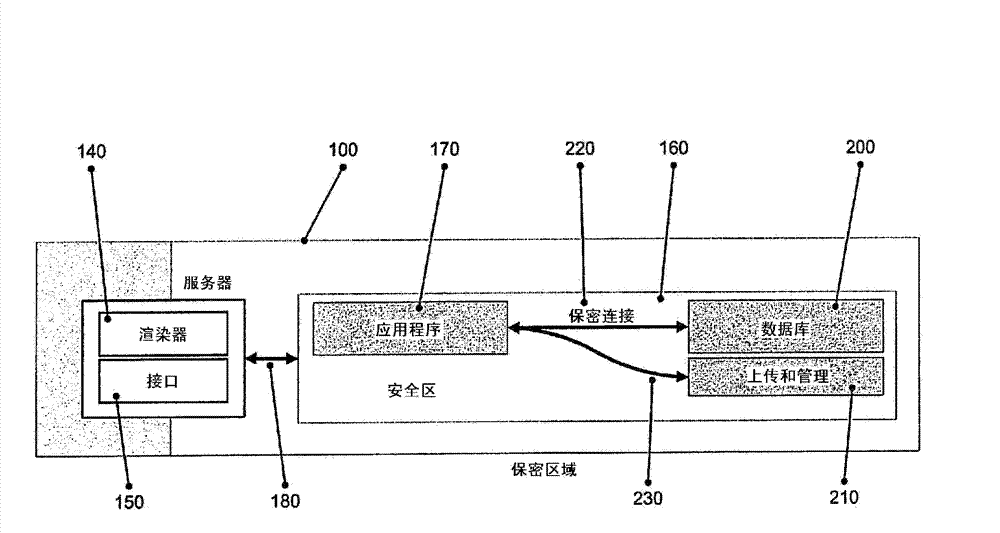
ActiveCN102780689ASimplify the installation processSimplify the maintenance processPlatform integrity maintainanceTransmissionData streamClient-side
The present invention relates to providing remote access to applications with an increased level of security. A server for providing access to applications is provided, as well as a method therefor, comprising an input channel and an output channel to connect a client with said server, an interface coupled to said input channel and an application, said interface to receive input data from said client via said input channel and to communicate said received input data to the application, and a renderer coupled to said output channel and said application, said renderer to render the output of said application into a data stream to be transferred via the output channel to the client, wherein the input data and the data stream are both encrypted. The inventive server and the method for providing remote access to applications greatly improve the security level and integrity of both the accessed application and also the access to the remote application.
Owner:CRYTEK IP HLDG
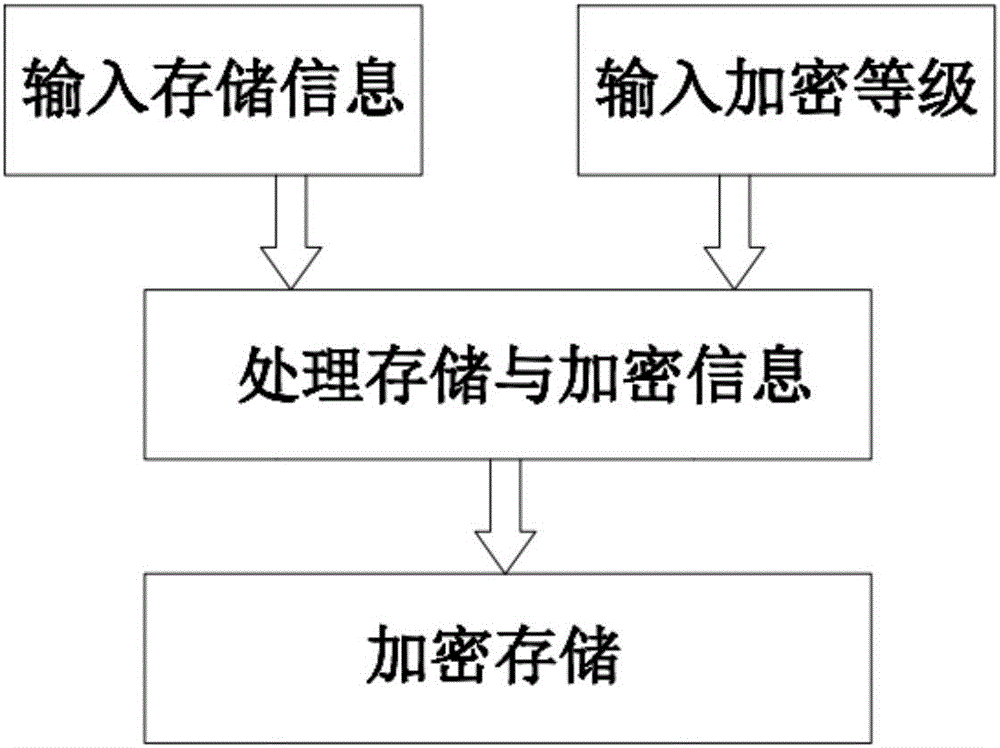
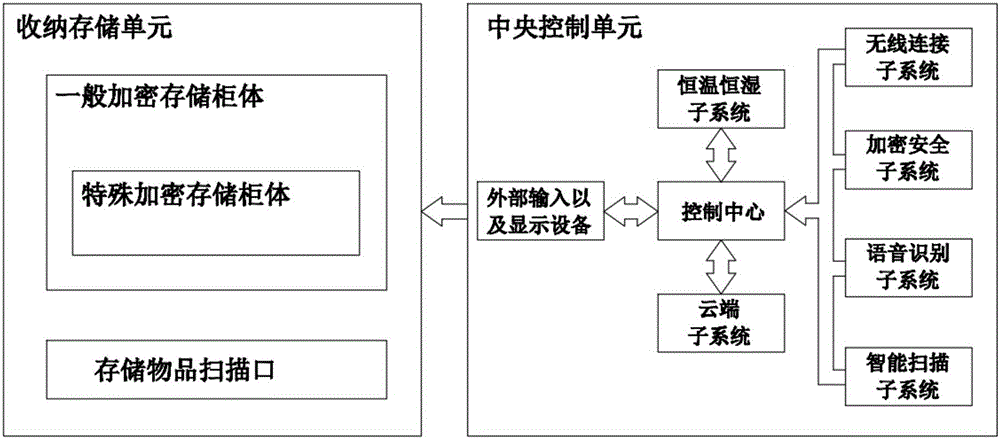
Intelligent article storage method and intelligent storage system
InactiveCN106683286ARaise the level of confidentialityMeet the basic requirements of storageApparatus for meter-controlled dispensingIndividual entry/exit registersComputer hardwareDisplay device
The invention relates to an intelligent article storage method and an intelligent storage system; the method includes steps of judging and distributing a storage zone through information of external imputed storage goods; through encryption grade of the external input, performing a single encryption or combined encryption storage on the storage goods. The system comprises a holding storage unit and a central control unit; the central control unit comprises a control center, an external input and display device, an intelligent scanning subsystem, an encryption safety subsystem; the holding storage nit comprises an ordinary encryption storage cabinet body, a special encryption storage cabinet body, and a storage goods scanning opening. Firstly, the method and device can meet the basic requirements of storage; secondly, the storage scale and encryption grade can be distributed according to different storage demands, the encryption grade of valuables can be improved, the articles to be stored can be classified and uniformly managed, thereby saving massive resources and conveniently monitoring article states in real time.
Owner:SHANGHAI TRANSSION CO LTD
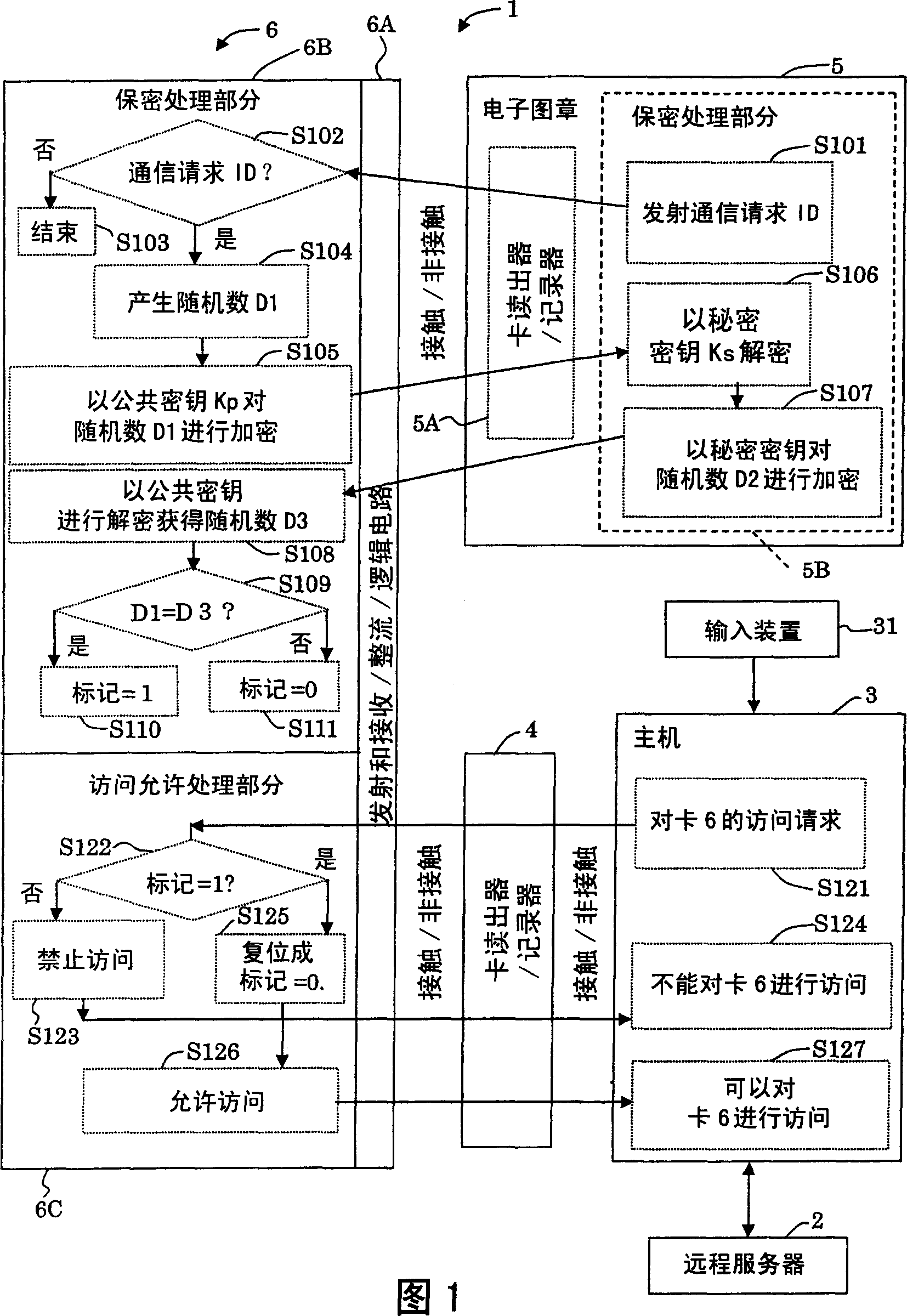
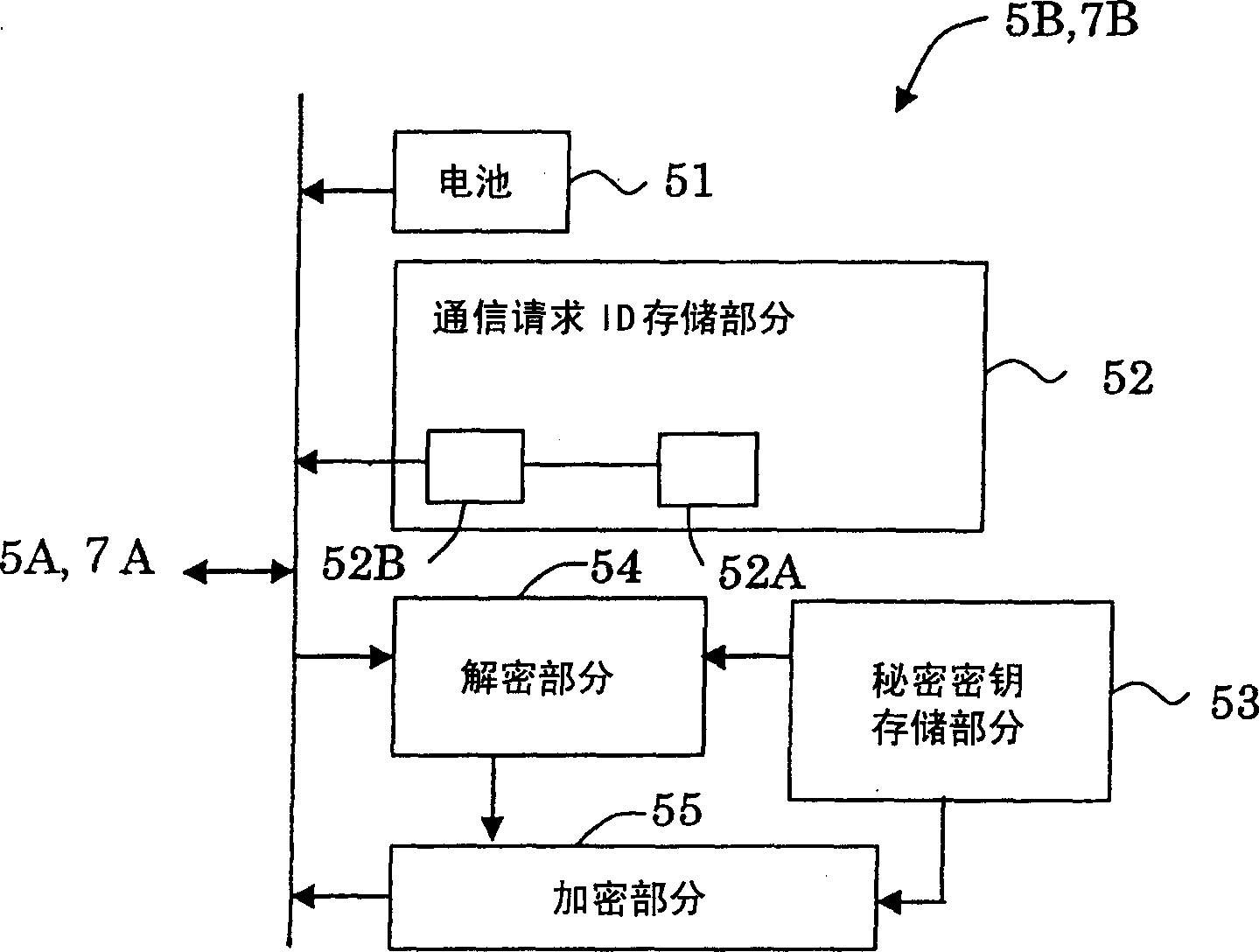
Electronic stamp. storage medium, high-level vertification system, moving device and vehicle start control equipment
InactiveCN1497463ARaise the level of confidentialityImprove securityOther printing matterFinanceComputer hardwareControl equipment
An electronic seal includes an input / output section for receiving a random number encrypted based on a prescribed key; and an advance authentication processing section for decrypting the encrypted and received random number based on a secret key related to the prescribed key and then encrypting the decrypted random number based on the secret key. The input / output section outputs the encrypted random number encrypted based on the secret key.
Owner:SHARP KK
Authentication system, authentication method, and information processing apparatus
ActiveUS8294550B2Raise the level of confidentialityEliminate needTelevision system detailsCandle holdersComputer hardwareInformation processing
An authentication system is provided with a room-security device, and an information processing apparatus installed in a controlled area controlled by the room-security device, in which the room-security device and the information processing apparatus are connected in a network. The room-security device obtains, from a user, identification information, and transmits the identification information to the information processing apparatus, if the user is permitted to enter a room based on the obtained identification information. The information processing apparatus receives the identification information. If it is detected that the user is alone in the controlled area based on the received identification information, the information processing apparatus performs authentication based on the received identification information instead of asking the user to enter authentication information to obtain the authentication information.
Owner:KONICA MINOLTA BUSINESS TECH INC
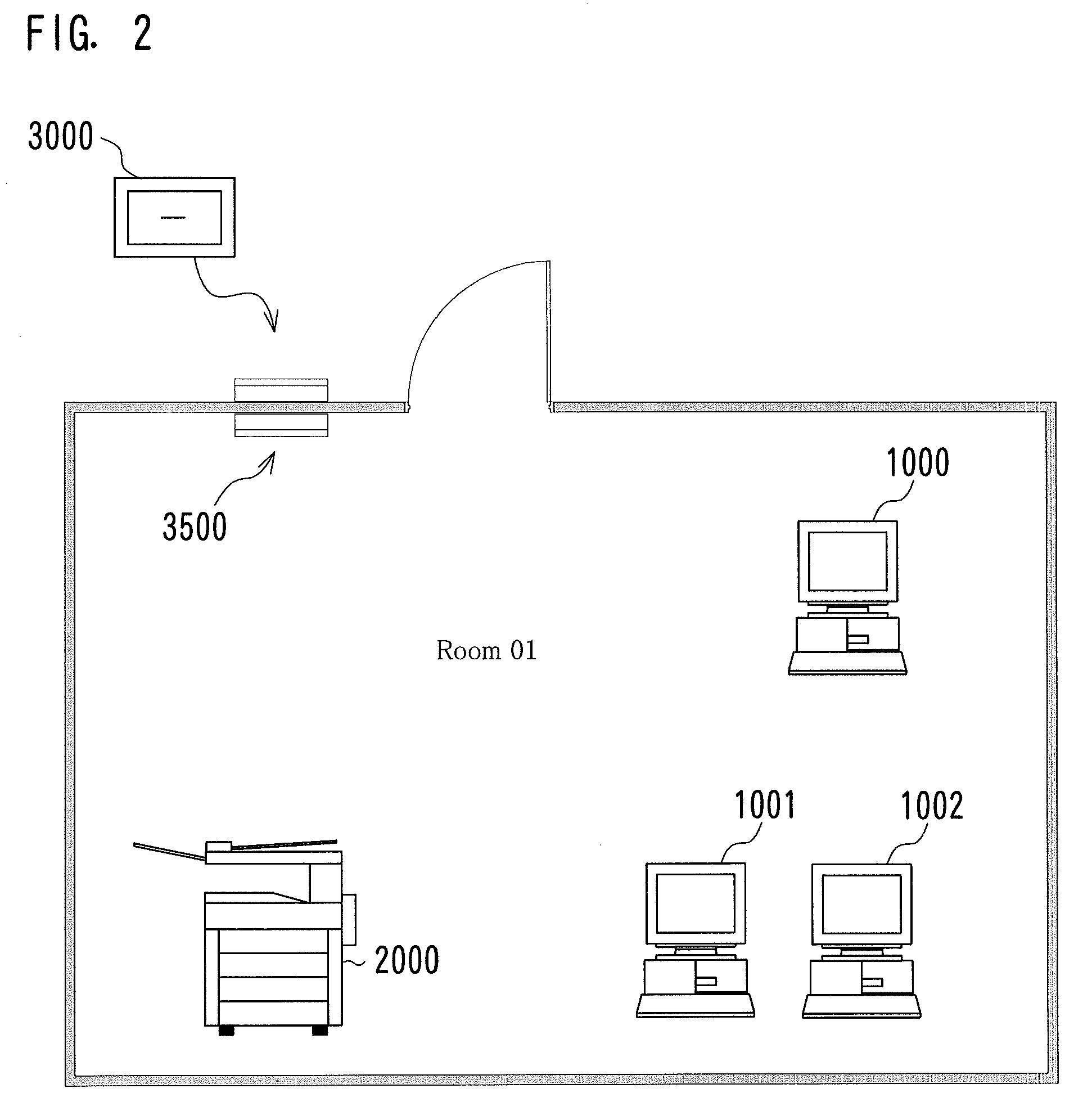
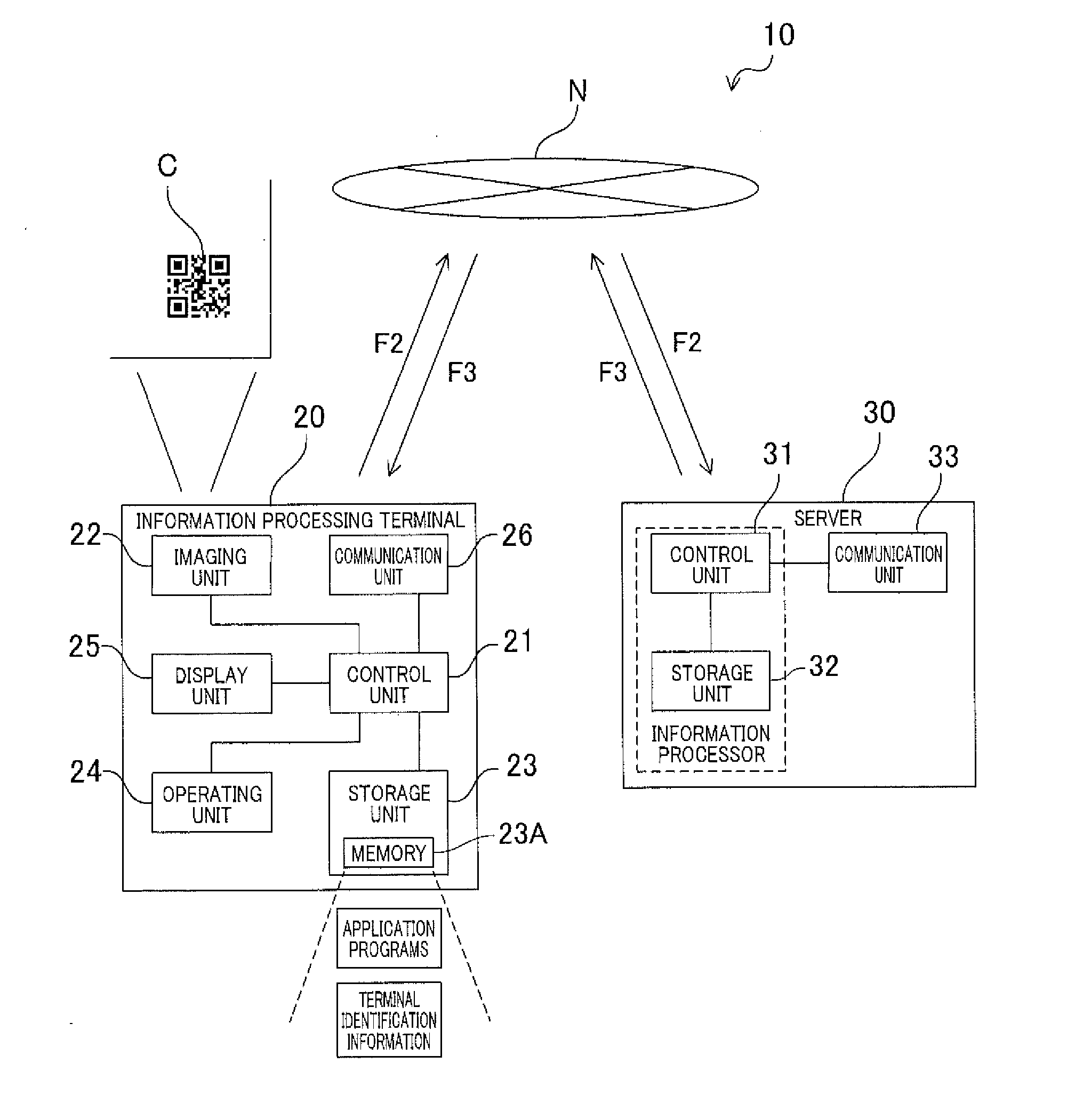
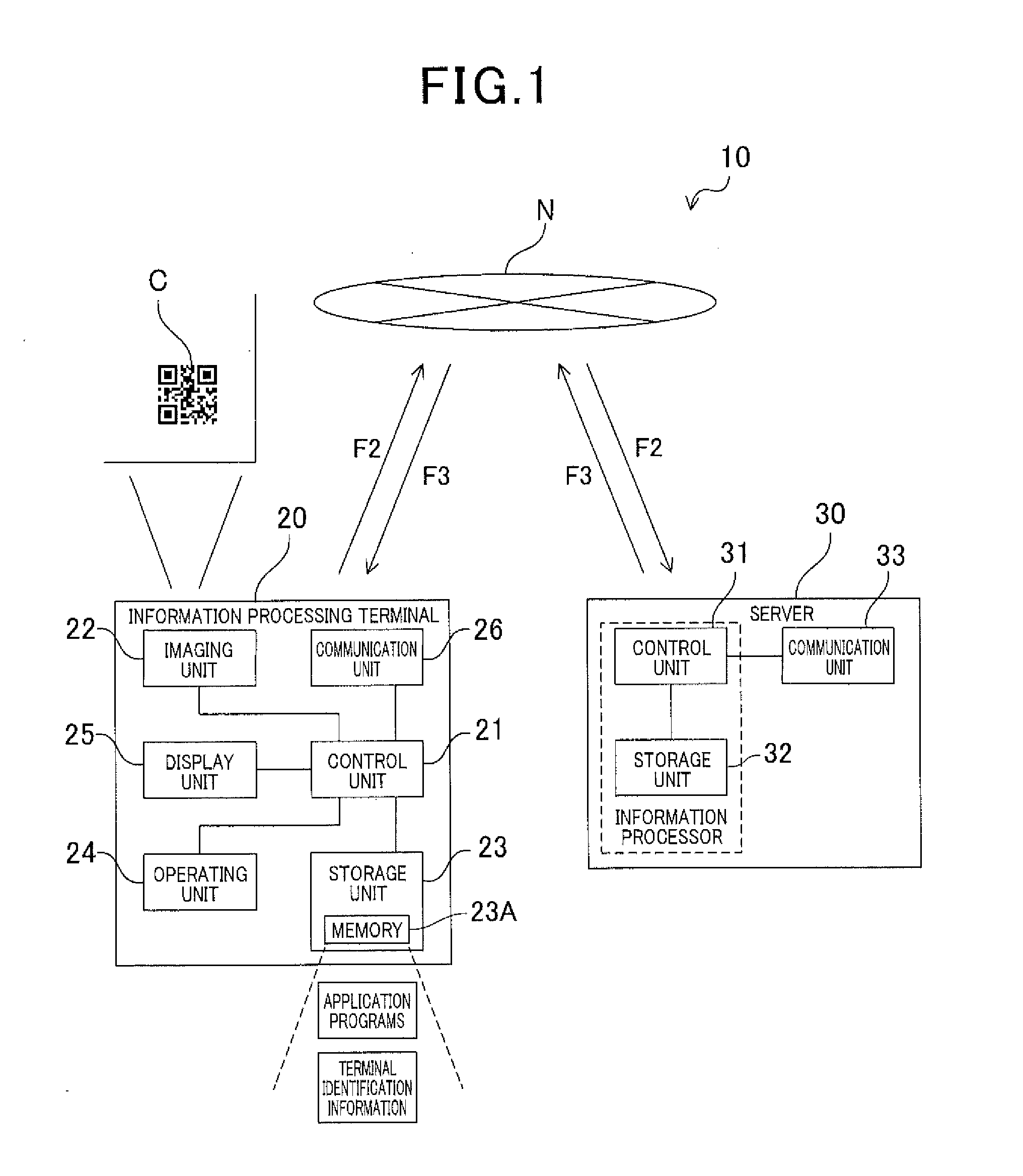
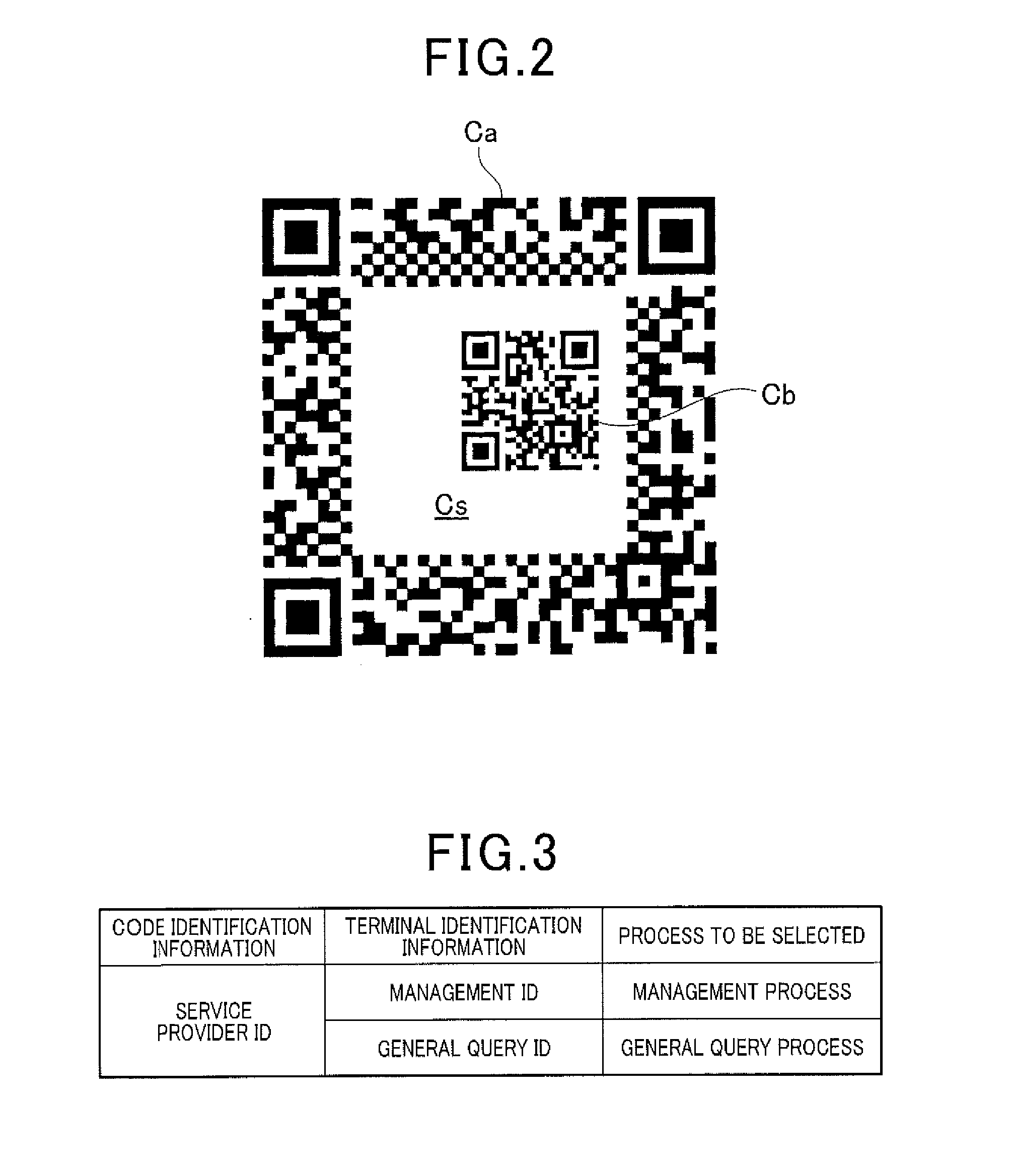
System and method of reading information code
ActiveUS20170032163A1Avoid difficult choicesInhibition of informationTransmissionRecord carriers used with machinesInformation processingSingle process
In an information processing terminal, code image data acquired by an imaging unit imaging an information code and terminal identification information stored in a storage unit are transmitted to a server. A control unit performs a process based on information received from the server in response to the transmission. In the server, when code identification information is acquired by an interpreting process from the code image data received from the information processing terminal, a single process among a plurality of processes associated with the acquired code identification information is selected based on the received terminal identification information. Selection information related to the process to be selected is transmitted to the information processing terminal.
Owner:DENSO WAVE INC
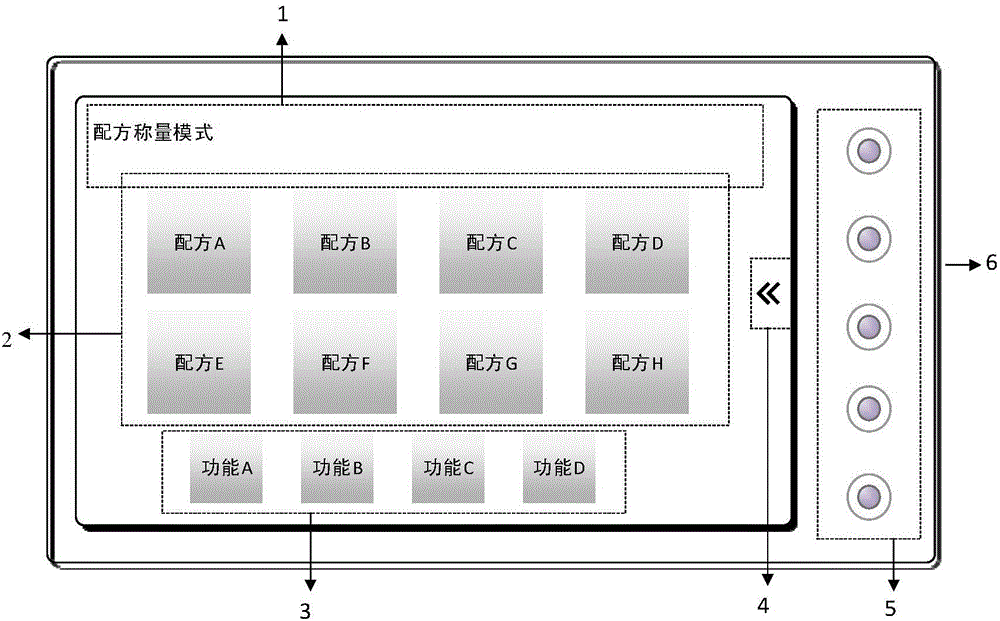
Networking type intelligent weighing system and method
InactiveCN104614057AImprove securityRaise the level of confidentialitySpecial purpose weighing apparatusComputer terminalLoad cell
The invention discloses networking type intelligent weighing system and method. The system comprises at least one weighing terminal and a server end which are connected by a communication manner; the weighing terminal is an embed system device and equipped with a weighing sensor, a communication module and an operation and display interface; the operation and display interface can be used for displaying, editing, searching and creating a weighing formula and storing the weighing formula to the weighing terminal; the server end forms a working track for managing users of the weighing terminal, mutually transmitting or synchronizing data for the weighing terminal, monitoring the working state of the weighing terminal, and recording the weighing terminal, and sending an instruction to the weighting terminal. With the adoption of the system and method, the materials in the formula can be accurately weighed; the production and material mixing can be monitored on real time; the weighing process of the formula and the formula product can be recorded and marked, so as to track the source.
Owner:XIAMEN UNIV
Method for improving safety of driving test information and enabling synchronized reproduction of driving test information
InactiveCN106034226AEasy to manageEasy accessTelevision system detailsColor television detailsVideo storageDriving test
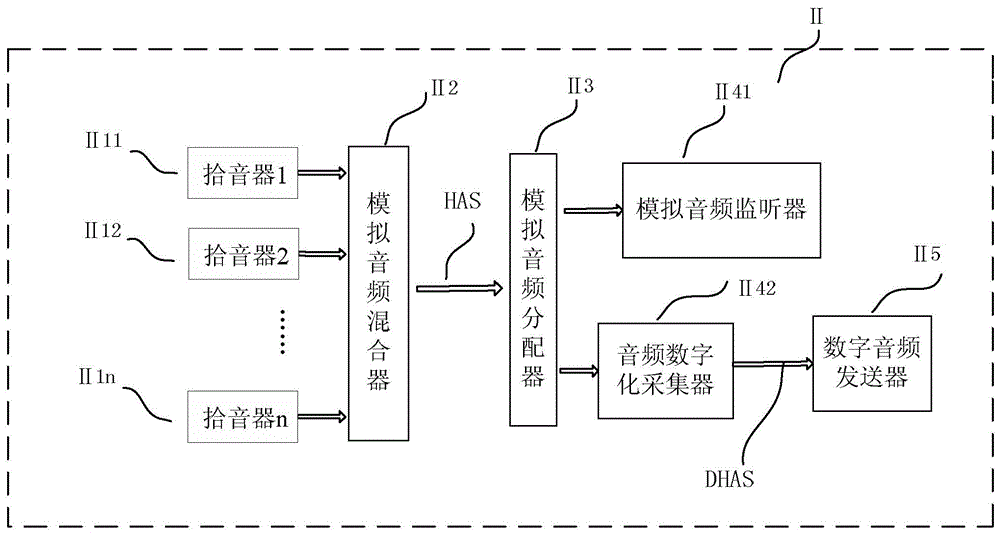
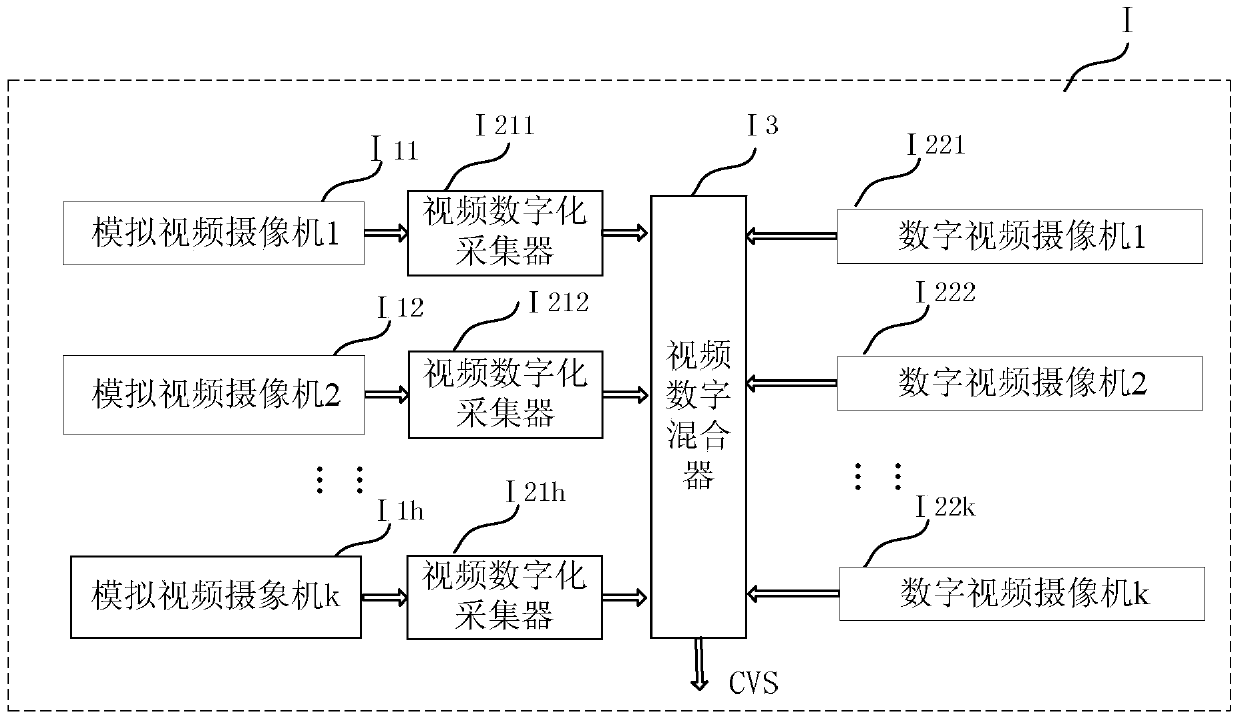
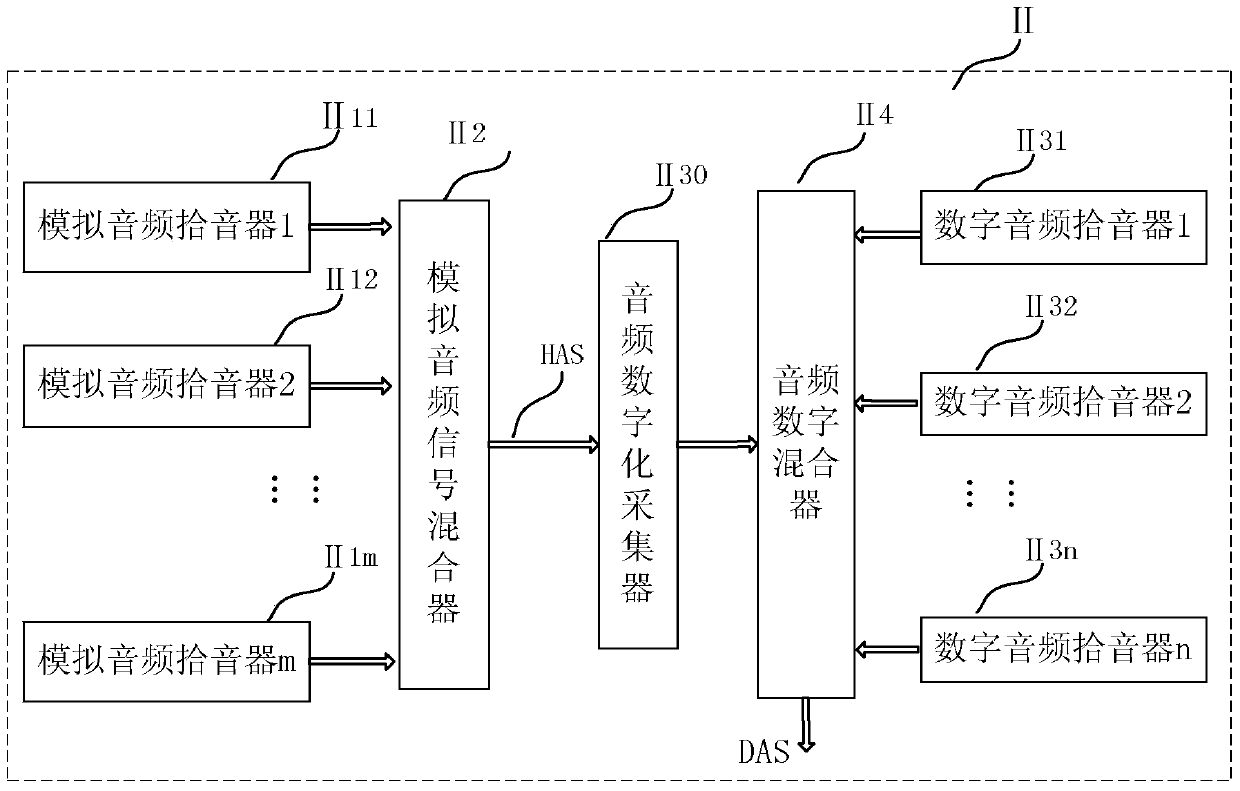
The invention relates to a method for improving the safety of driving test information and enabling synchronized reproduction of the driving test information. The method comprises a collection step in which multi-channel audio information and video information are converted into single-channel audio information HAS and single-channel video information CVS respectively; a storage step in which all information collected in the collection step together with testee information forms a driver test process multi-information audio-video DEMSAV file including different information in the driving test process; and a synchronized reproduction step in which a player which can replay the different information in a synchronized reproduction manner is used to reproduce all information recorded by the driver test process multi-information audio-video DEMSAV file in the synchronized manner. The method ensures that consulting results of different information which needs to be recorded in the test process are kept synchronized in time and position after test, a traditional file storage method is optimized, the safety of driving test information is improved, and the testee information can be inquired more conveniently and more rapidly.
Owner:LIUZHOU GUITONG TECH
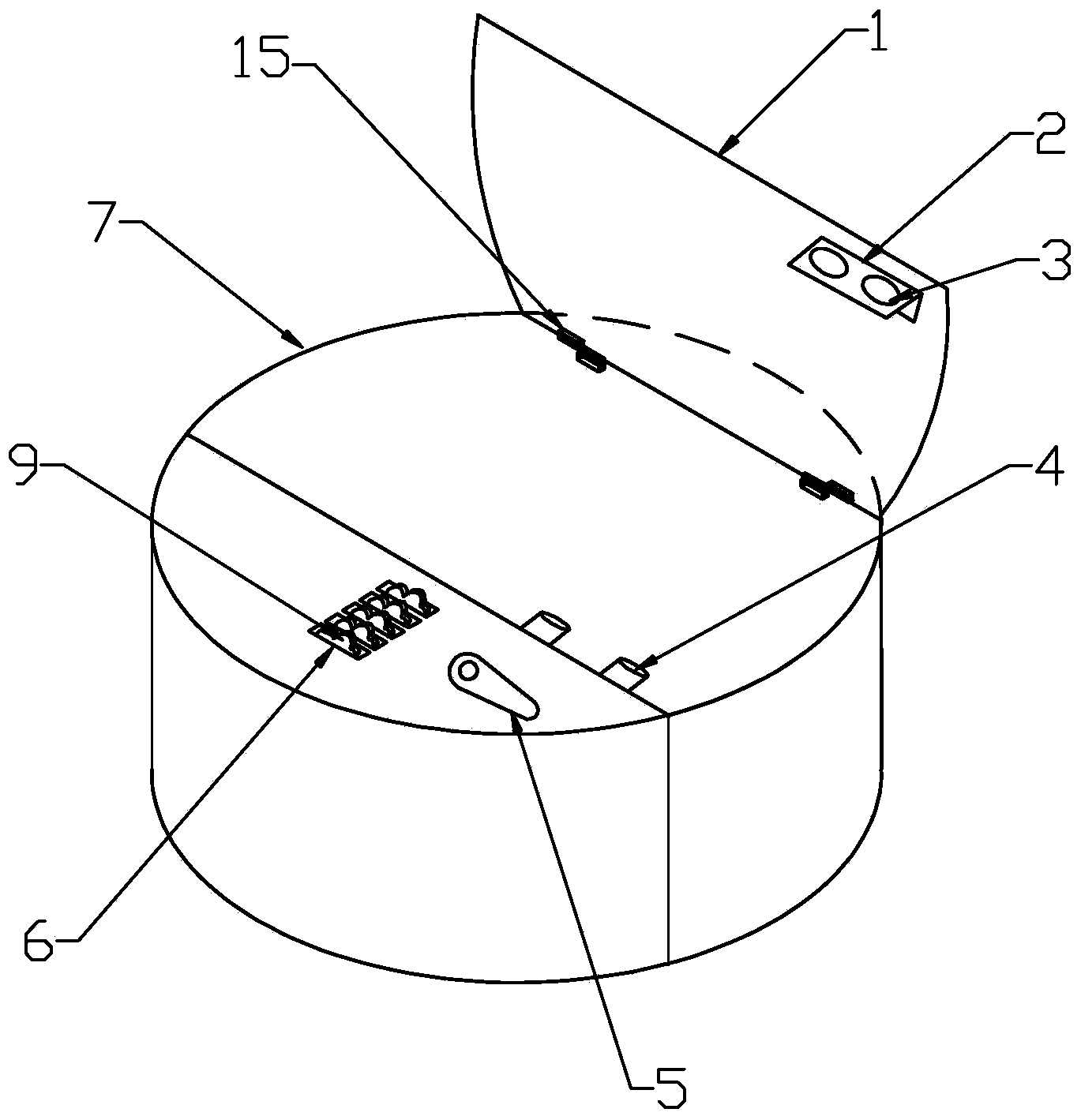
Electronic spring mechanical lock core double-control safety box
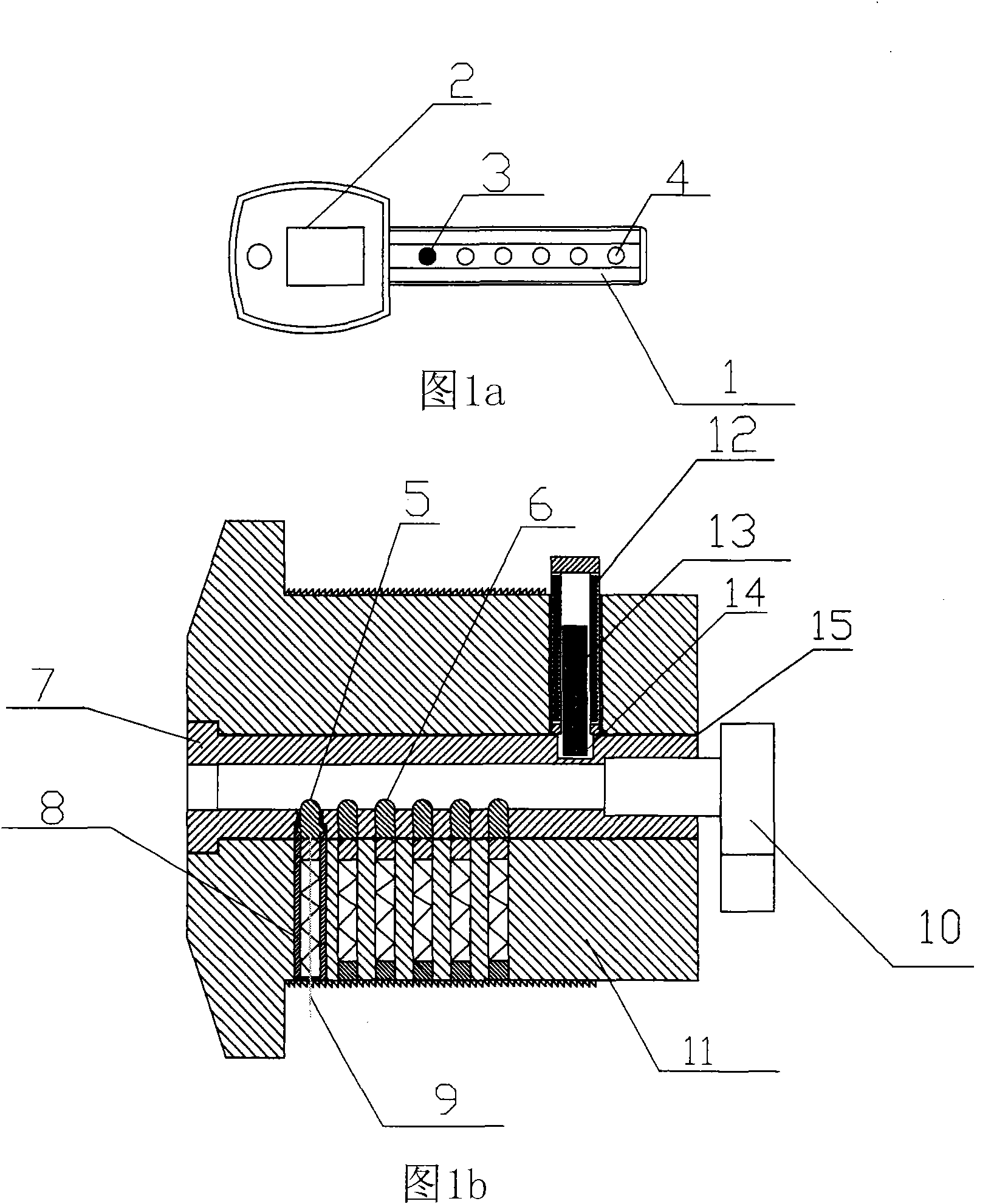
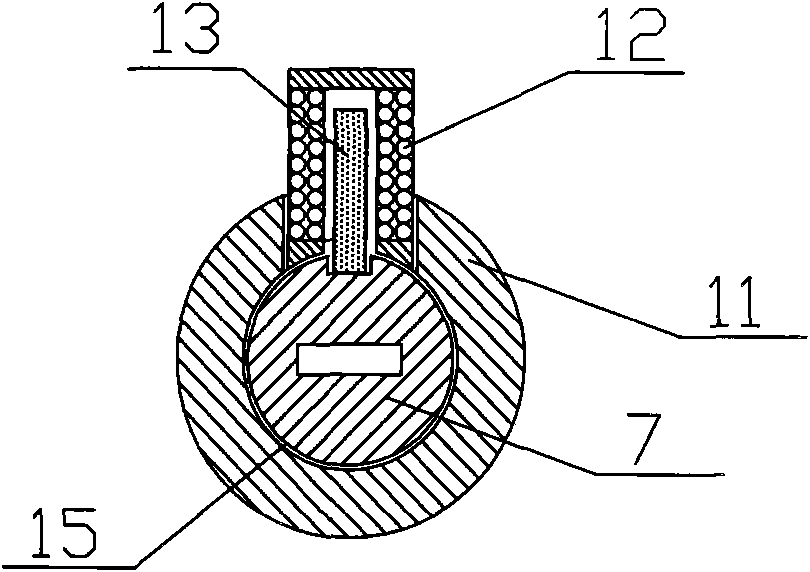
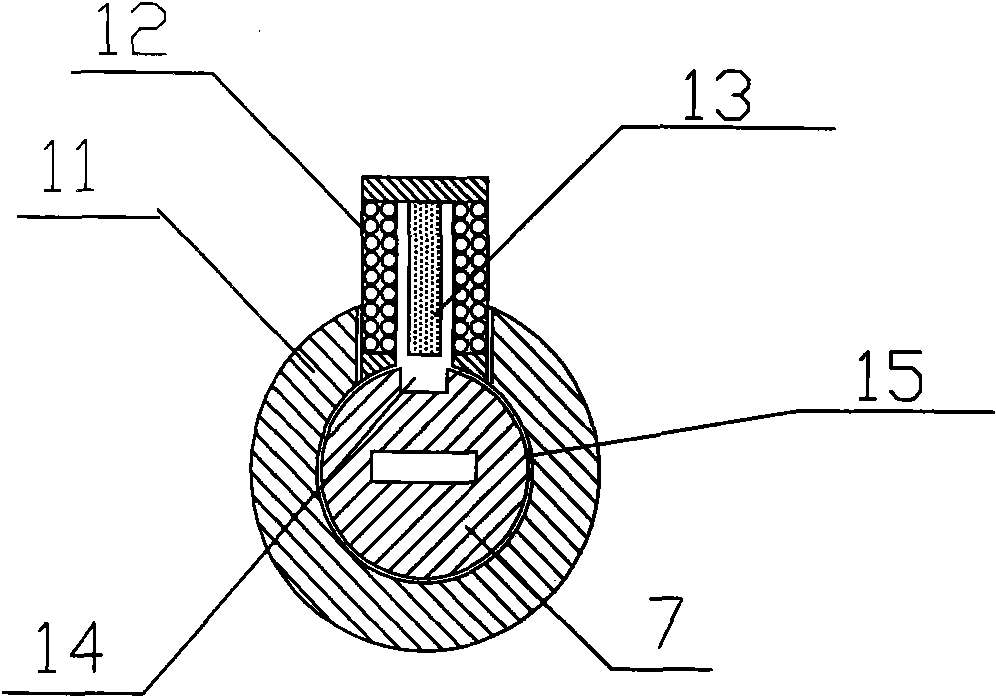
InactiveCN101936094AImprove system securityRaise the level of confidentialityNon-mechanical controlsKeysMicrocomputerMicrocontroller
The invention relates to an electronic spring mechanical lock core double-control safety box which comprises a lock body, a lock core and a matching key, wherein a mechanical spring and a main control board circuit which are connected with the lock core are arranged in the lock body; the periphery of the lock core is also provided with an electromagnetic spring which is perpendicular to a central axis of the lock core; an electromagnetic coil at the periphery of the electromagnetic spring is connected with the main control board circuit; the main control circuit comprises a single chip microcomputer chip, a data memory and a polarity converting circuit of the electromagnetic coil; the single chip microcomputer chip is used for controlling the polarity converting force of the electromagnetic coil to drive the electromagnetic spring to adsorb or separate from the mechanical lock core; an electromagnet linking mechanism in the safety box has the improvement that the electromagnetic coil drives the electromagnetic spring to move in the lock body for directly controlling the rotation of the lock core; the lock core and the electromagnetic spring for controlling unlocking are tightly combined for reducing the space volume of the lock body in the safety box, and the invention has the advantages of high seal performance, high shock resistance and stable and reliable work; the power consumption of the invention is only one tenth that of a safety box adopting an electromagnet assembly, and the service life of a cell is prolonged; and an emergency unlocking core of the safety box is removed, and a safety system and a security level of the safety box are improved.
Owner:NINGBO YONGFA GROUP
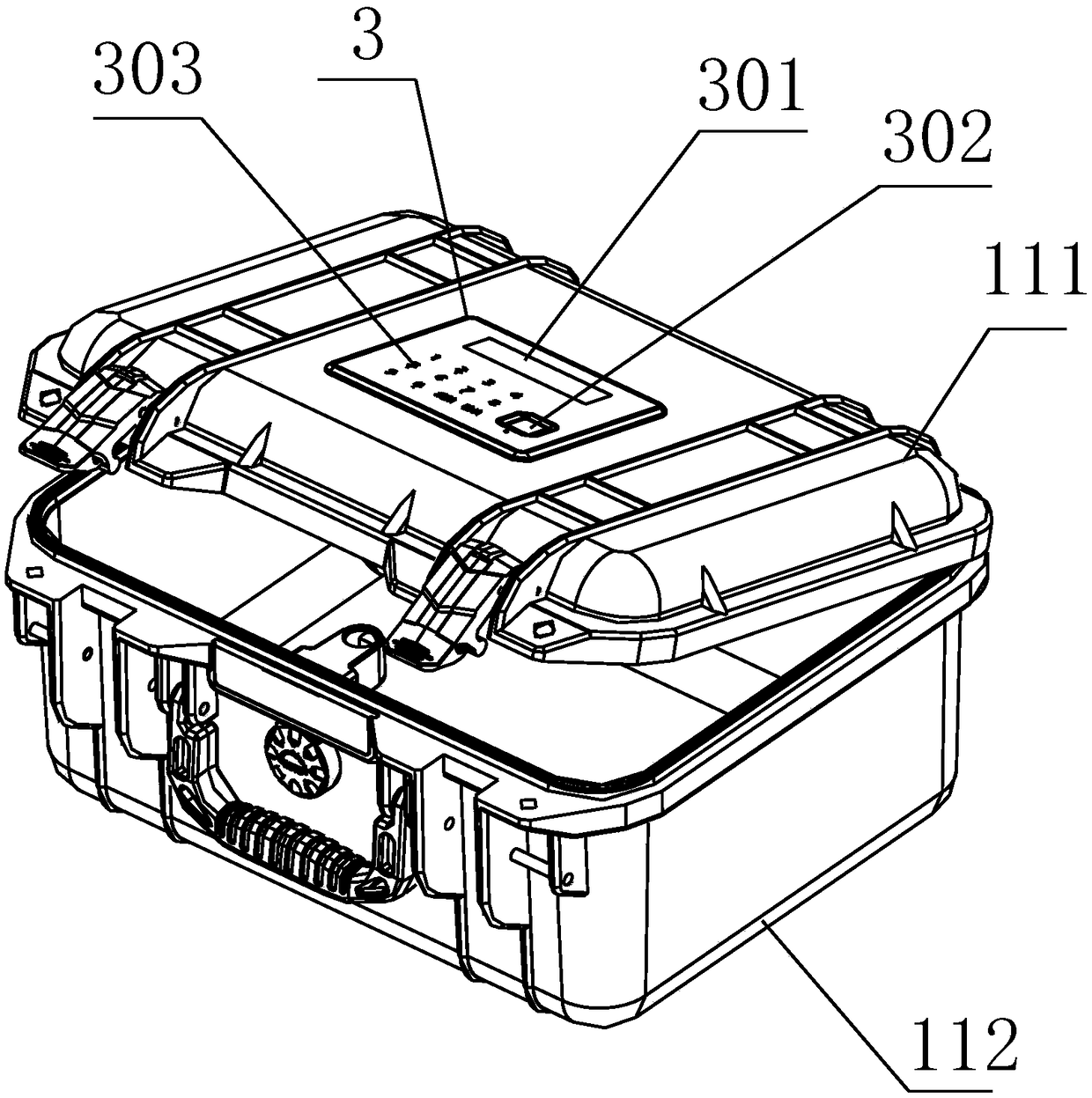
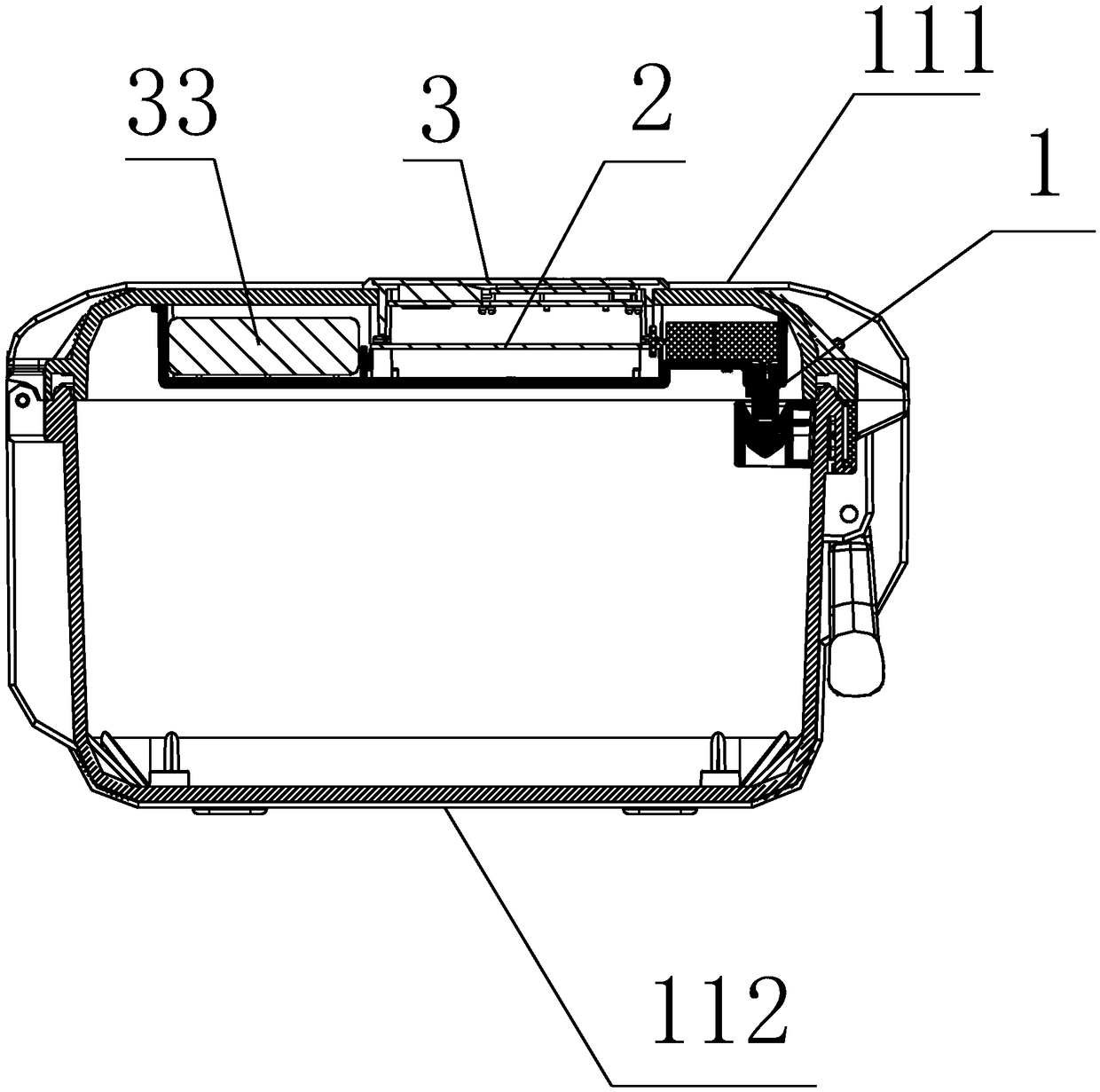
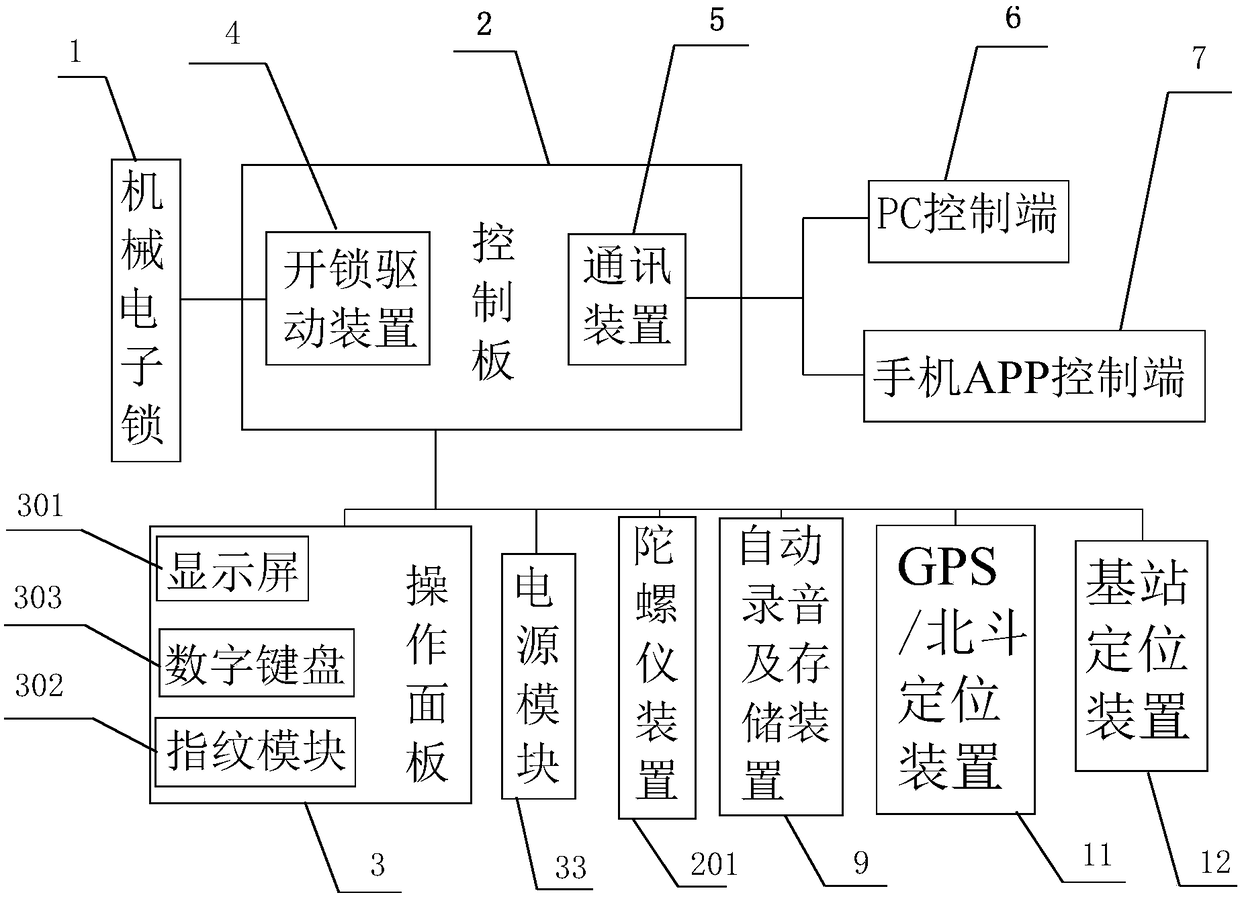
Safe delivery box
The invention discloses a safe delivery box. The box comprises a box body composed of a box bottom and a box cover, wherein the box bottom and the box cover are of an integral structure formed by injection molding, the box bottom and the box cover are connected in a hinged mode through pin shafts, a mechanical electronic lock for locking the box bottom and the box cover together is arranged on thebox bottom and the box cover, the mechanical electronic lock is electrically connected with a control panel, the control panel is electrically connected with an operation panel and a power supply module, an unlocking driving device and a communication device are arranged on the control panel, the control panel is provided with a PC control end and a mobile phone APP control end through the communication device, and a display screen, a digital keyboard and a fingerprint module are arranged on the operation panel; and the communication device is a G communication module, and the control panel can communicate with the PC control end or the mobile phone APP control end through the G communication module. The delivery box has the beneficial effects that practical property is achieved, the production cost is low, the structure is novel, the security level is high, transportation and storage of goods of protection grades are facilitated, and comprehensive management by managers is facilitated.
Owner:HUANGSHAN EVEREST CASE
A Safe Distributed Data Deduplication Method
ActiveCN103763362BProtection of confidentialitySatisfy deduplicationTransmissionShort ValueComputer hardware
The invention discloses a safe distributed duplicated data deletion method. According to the method, a file is segmented into fragments through a secret sharing technology without any encryption mechanism. The shared fragments are distributed in a plurality of independent storage servers. In addition, in order to support reduplication removing, a different short value is calculated and sent to the storage servers as the indicator of one fragment. Only possessors uploading data for the first time need to carry out such calculation and distribution of secrete sharing, and then people possessing the same data copies do not need to calculate and store the sharing any longer. When the data copies are restored, users must access the storage servers with the minimum quantity to reconstruct the data through authentication and acquisition of the secret sharing. In other words, the secret sharing of the data can only be accessed by the users who possess the same copies and are authorized.
Owner:XIDIAN UNIV
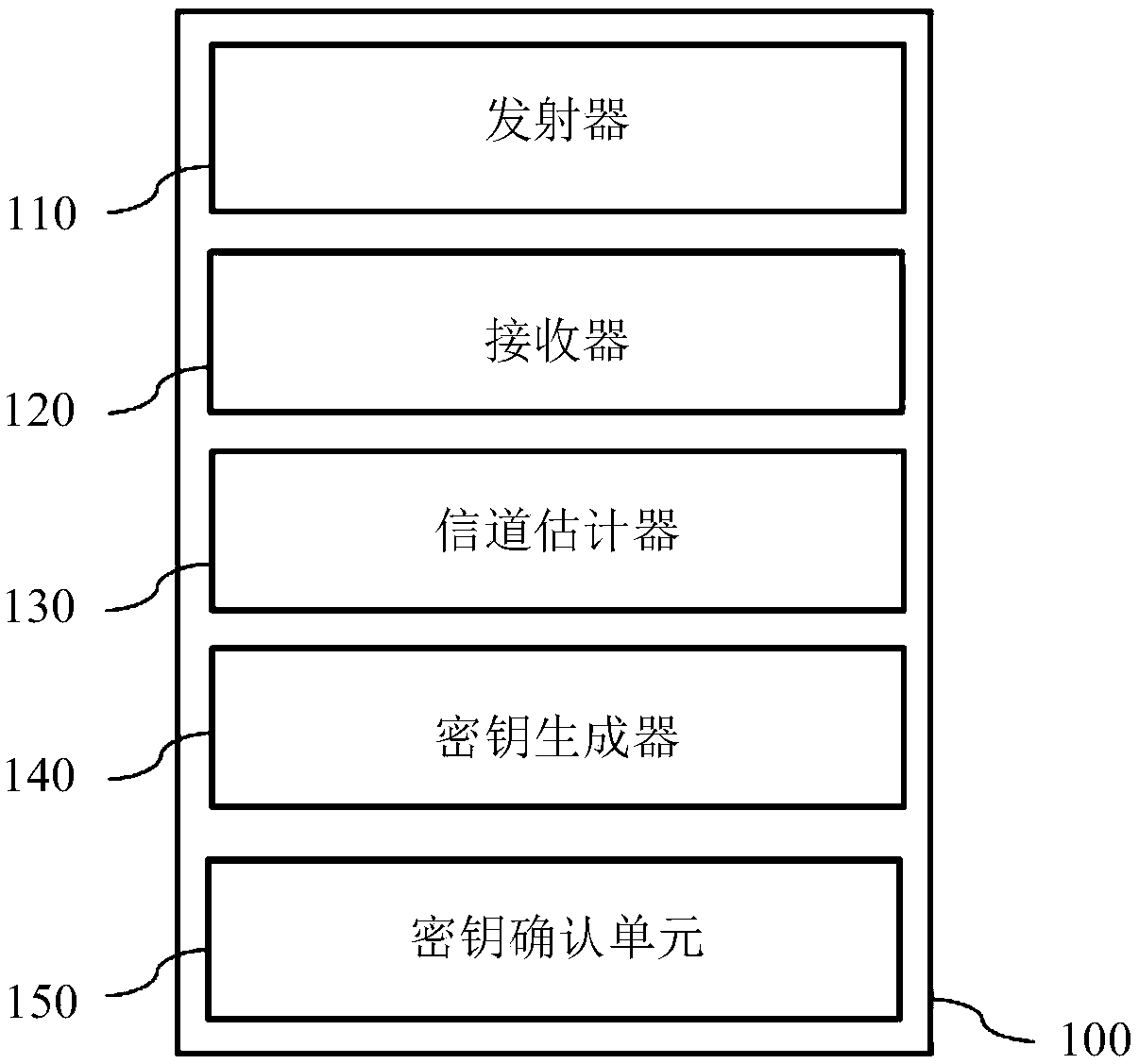
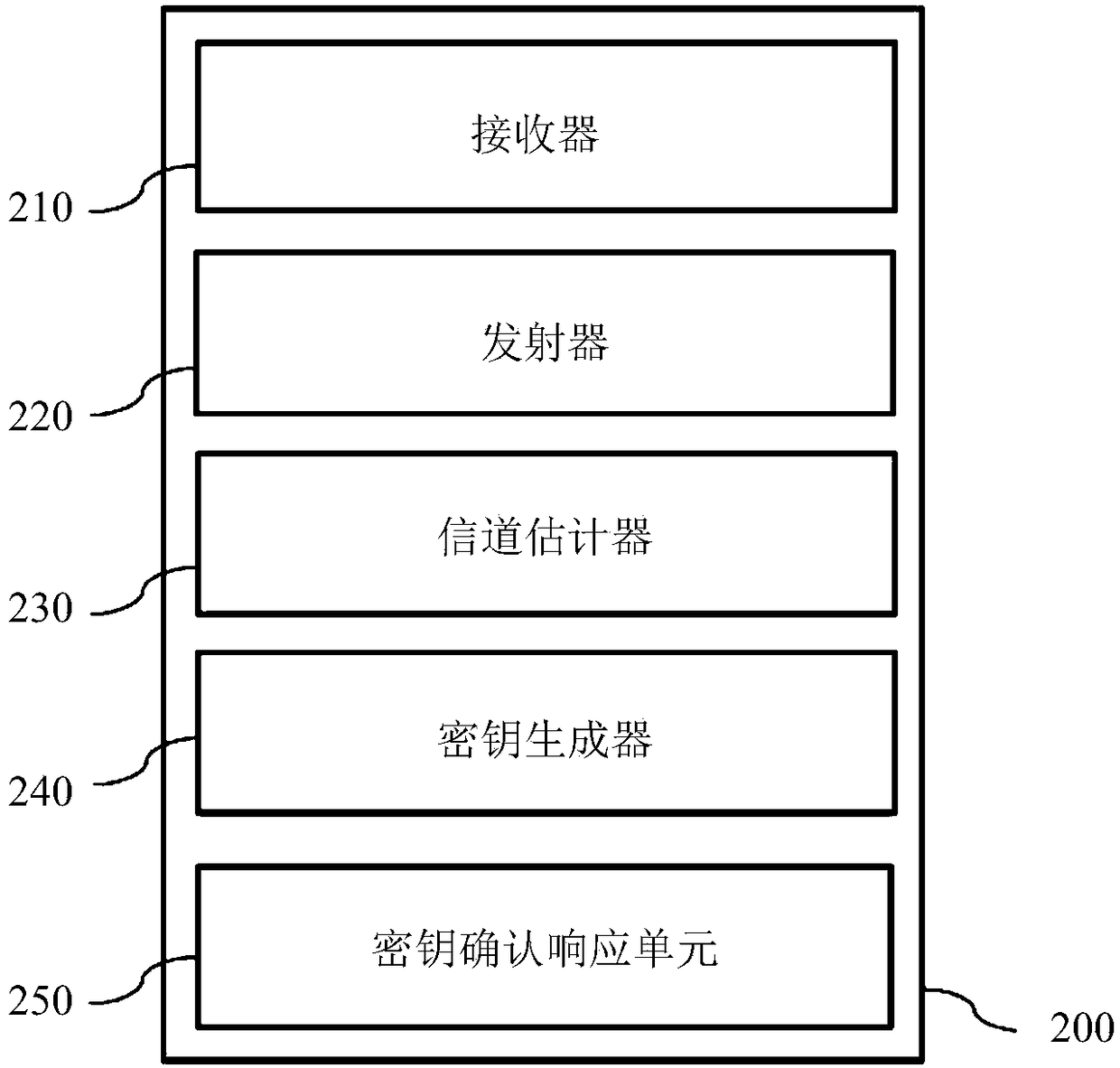
Secure paring method for MIMO systems
ActiveCN109417469AQuick comparisonRaise the level of confidentialityKey distribution for secure communicationCryptographic attack countermeasuresKey generatorMimo systems
A first MIMO device for channel estimation and verification, the first MIMO device comprising: a transmitter configured to transmit a first pilot sequence, a receiver configured to receive a second pilot sequence, a channel estimator configured to estimate a first channel based on the received second pilot sequence, a key generator configured to generate a first key based on the estimated first channel, and a key confirmation unit configured to determine whether the first key corresponds to a second key of a second MIMO device.
Owner:HUAWEI TECH CO LTD
Accounting bill management system based on bill classification
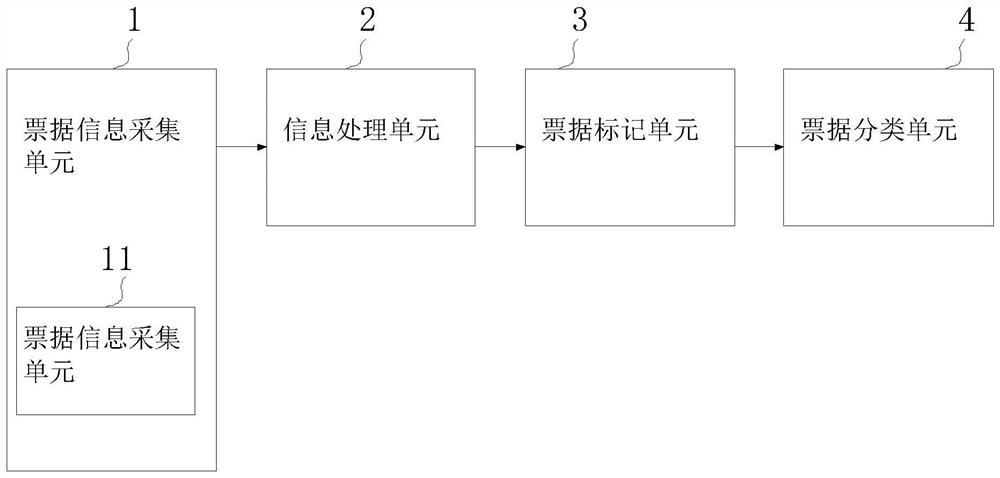
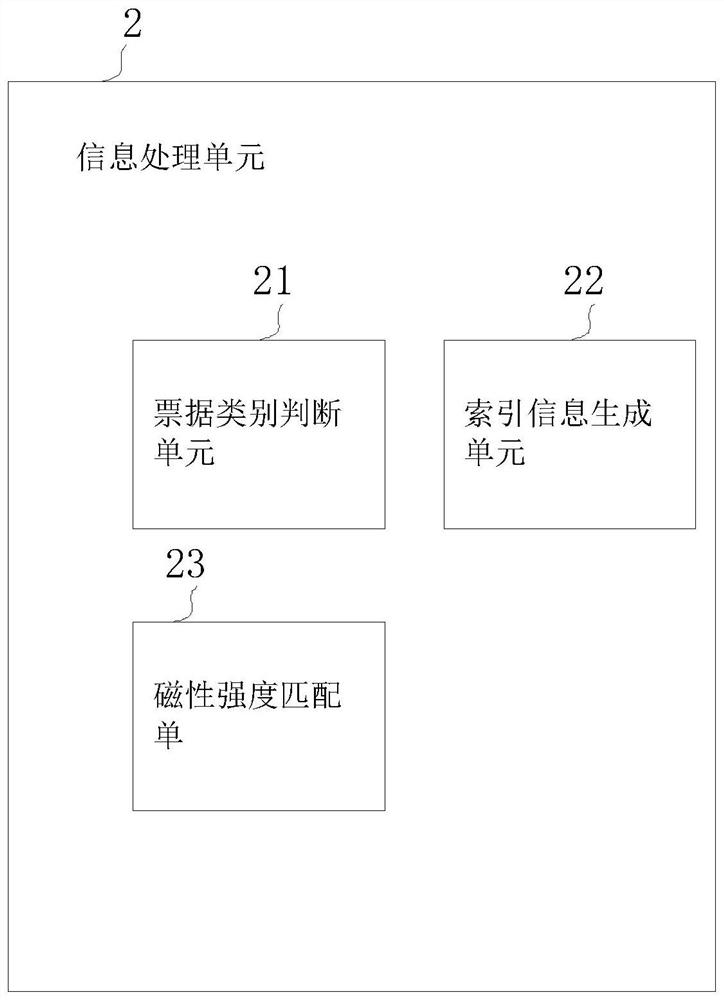
InactiveCN114260208ARaise the level of confidentialitySortingInformation processingClassified information
The invention relates to the technical field of accounting management, and discloses an accounting bill management system based on bill classification, and the system comprises a bill information collection unit which is used for collecting the basic information of bills, and the basic information of the bills at least comprises classification information; the information processing unit is used for processing the information of the bills and generating index information of the bills; the storage area information represents predetermined storage areas of the bills, and one storage area correspondingly stores one category of bills; obtaining the magnetic intensity of a mark ring corresponding to the bill based on the index information; the bill marking unit is used for marking bills; the bill classification unit is used for classifying the bills based on the mark rings on the bills and respectively conveying the classified bills to the corresponding storage areas; according to the method, the bills can be classified under the condition that detailed information of the bills is not collected, the confidentiality level can be improved, and compared with manual management, the efficiency and the classification accuracy are improved.
Owner:HANGZHOU VOCATIONAL & TECHN COLLEGE
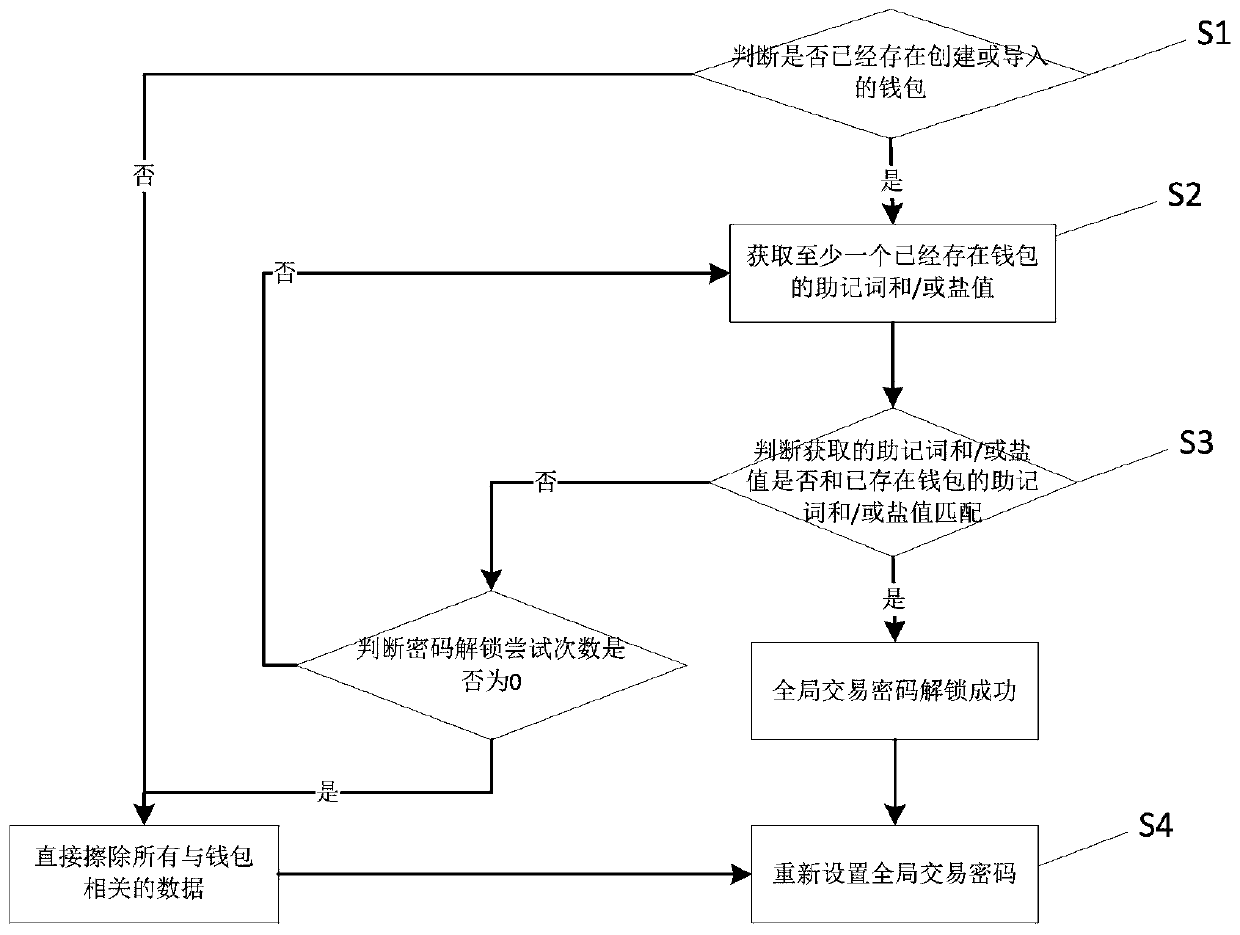
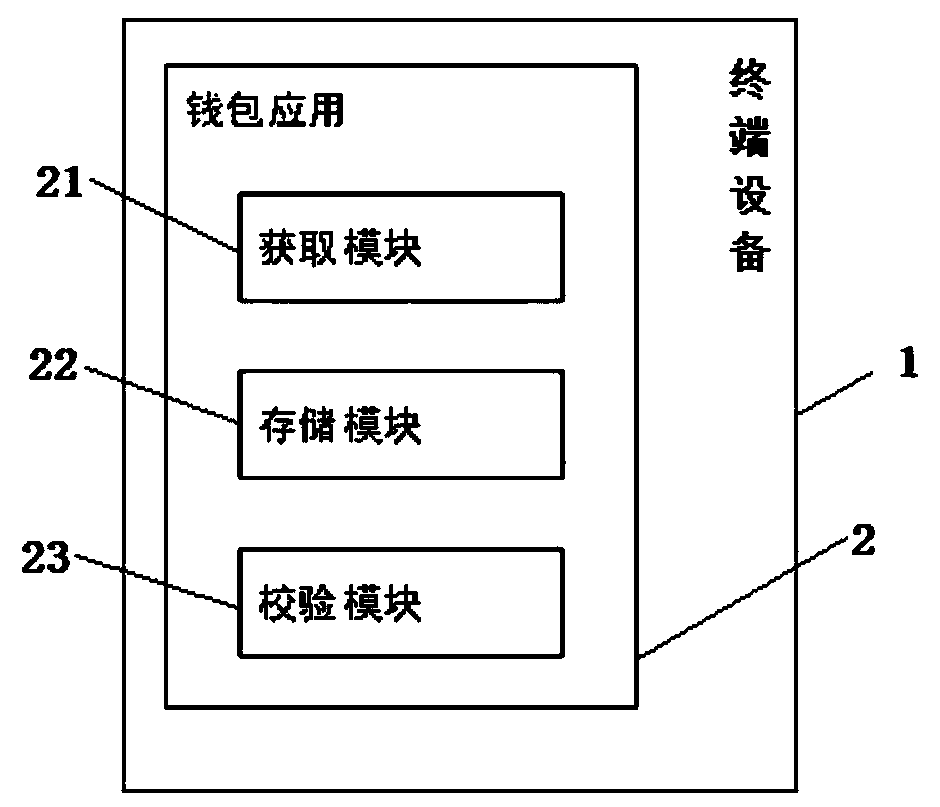
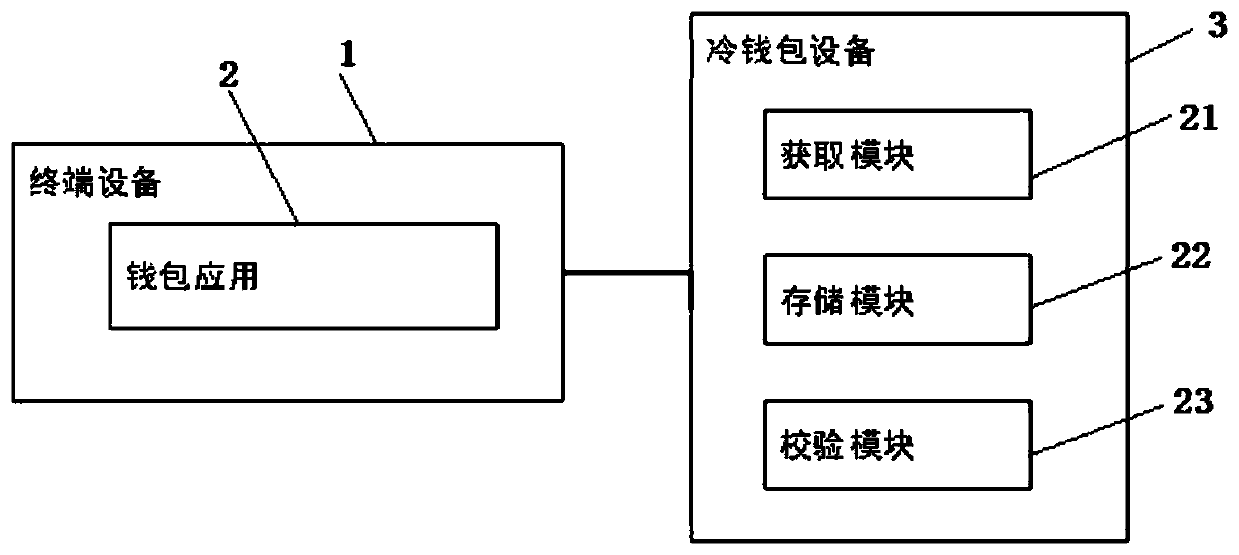
Password resetting method and system for digital currency wallet
The invention provides a password resetting method and system for a digital currency wallet, and belongs to the technical field of wallet password resetting. The digital currency wallet password resetting method comprises the following steps of: S1, judging whether a created or imported wallet exists or not, if so, executing the next step, and if not, directly erasing all data related to the wallet, and then executing the step S4; S2, obtaining at least one memorial aid word of the existing wallet; S3, judging whether the input assistant words are matched with the assistant words in wallets ornot, if so, unlocking the global transaction password, then executing the step S4, and if not, prompting an information error; and S4, resetting the global transaction password. According to the method and the system, one set of the multiple sets of backup assistant words is matched to indicate that the user has the assistant words, the identity of the user is confirmed, and the user can be authorized to reset the global password under the condition that all wallet data are not cleared.
Owner:HENGBAO
System and method for generating simple password on webpage end
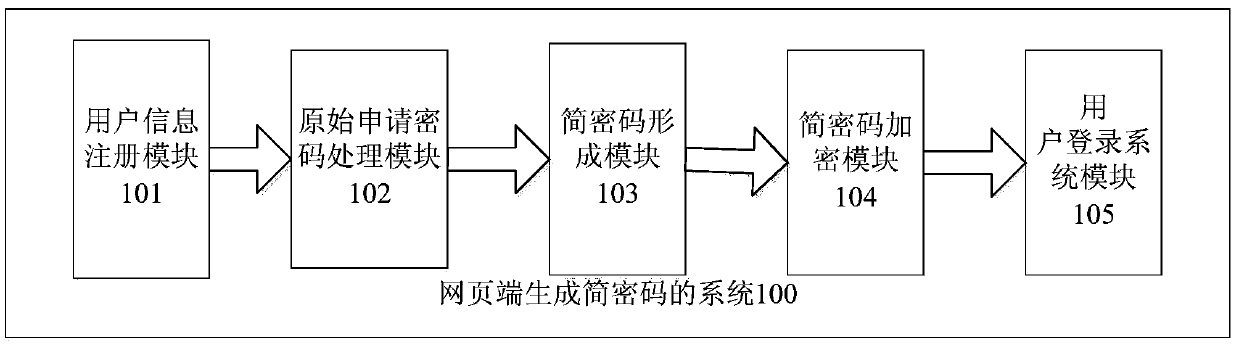
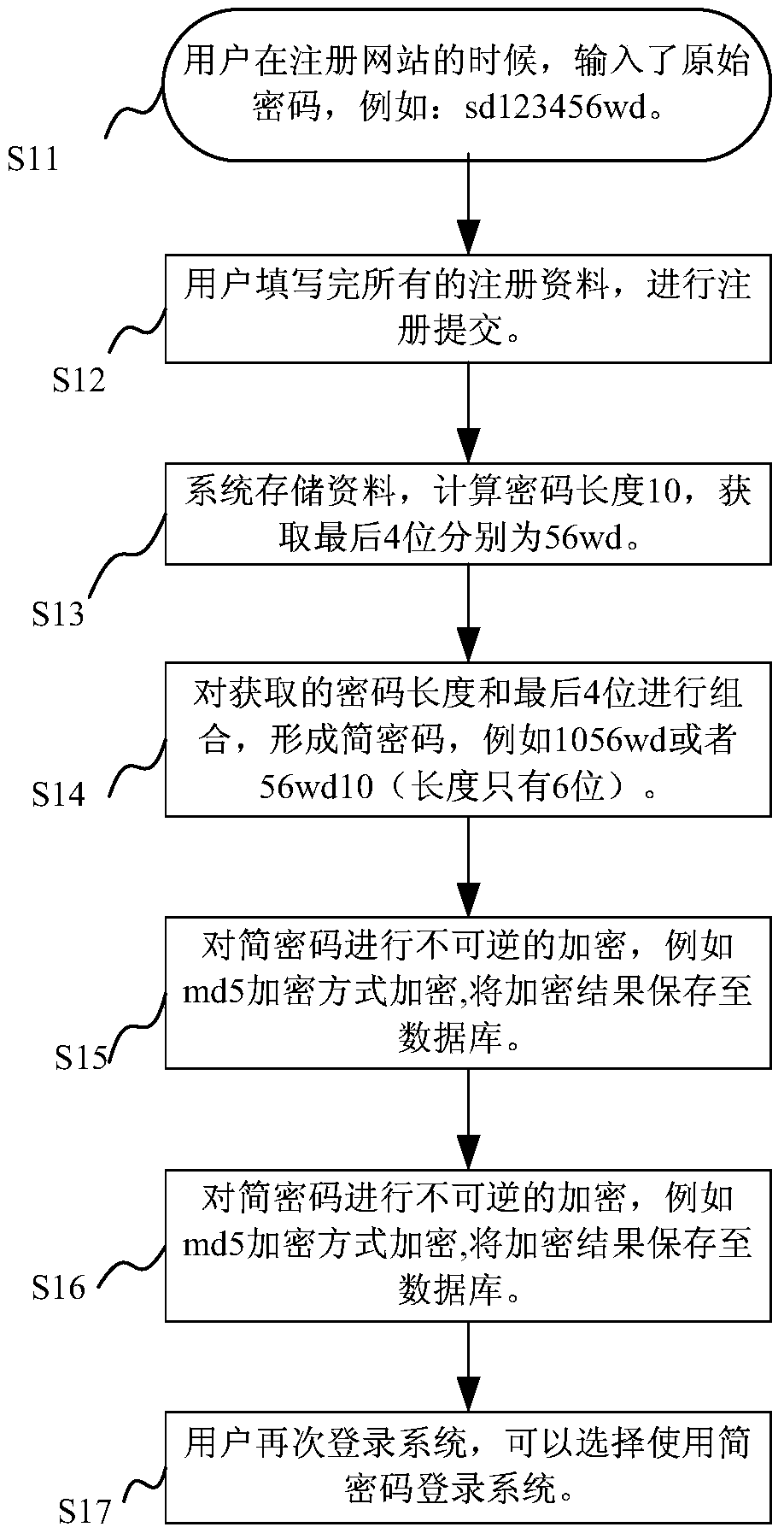
ActiveCN105516126AShort processImprove experienceKey distribution for secure communicationPaymentPassword
The invention provides a system and a method for generating a simple password on a webpage end. The system at least comprises a user information registering module, an original application password processing module, a simple password forming module and a simple password encryption module, wherein the user information registering module is used for acquiring registration information which is input by a user and includes an original application password, and submitting the registration information to a system server; the original application password processing module is used for storing the original application password, calculating features of the original application password, and acquiring a plurality of characters at a plurality of positions of the original application password; the simple password forming module is used for combining the acquired original application password features with the plurality of acquired characters at the plurality of positions according to a certain rule in order to form the simple password; and the simple password encryption module is used for encrypting the simple password and saving an encrypted result in the system server. Through adoption of the system and the method, the user can focus on content of a website more quickly; the whole flow of the website is shorter; and better user experience is achieved. Moreover, the user only needs to know a login password and input the simple password during payment under a plurality of occasions where dual passwords are required, so that the system setting is simplified greatly.
Owner:台州市吉吉知识产权运营有限公司
Data processing unit and method for controlling overwrited by non-volatility storage device
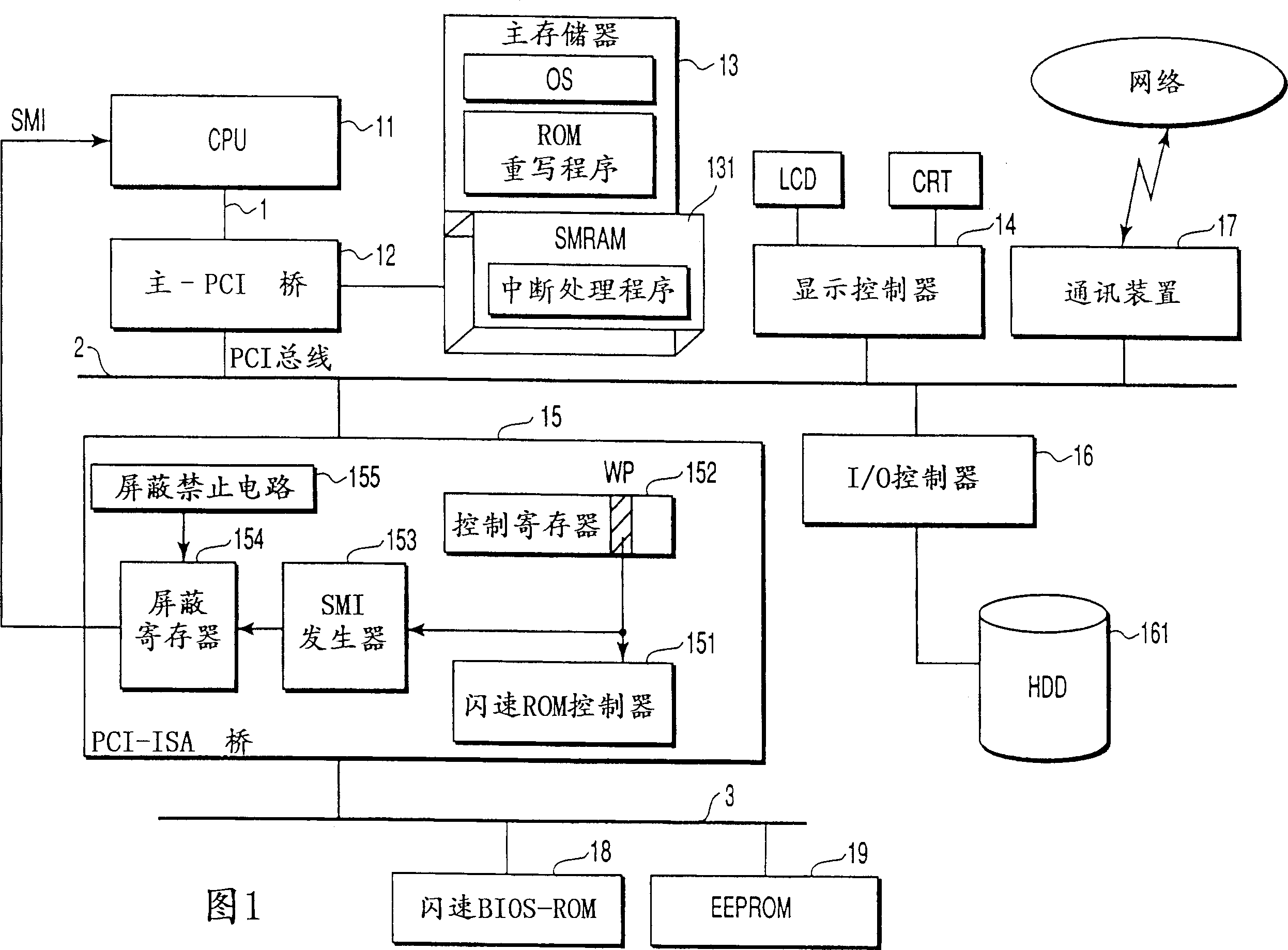
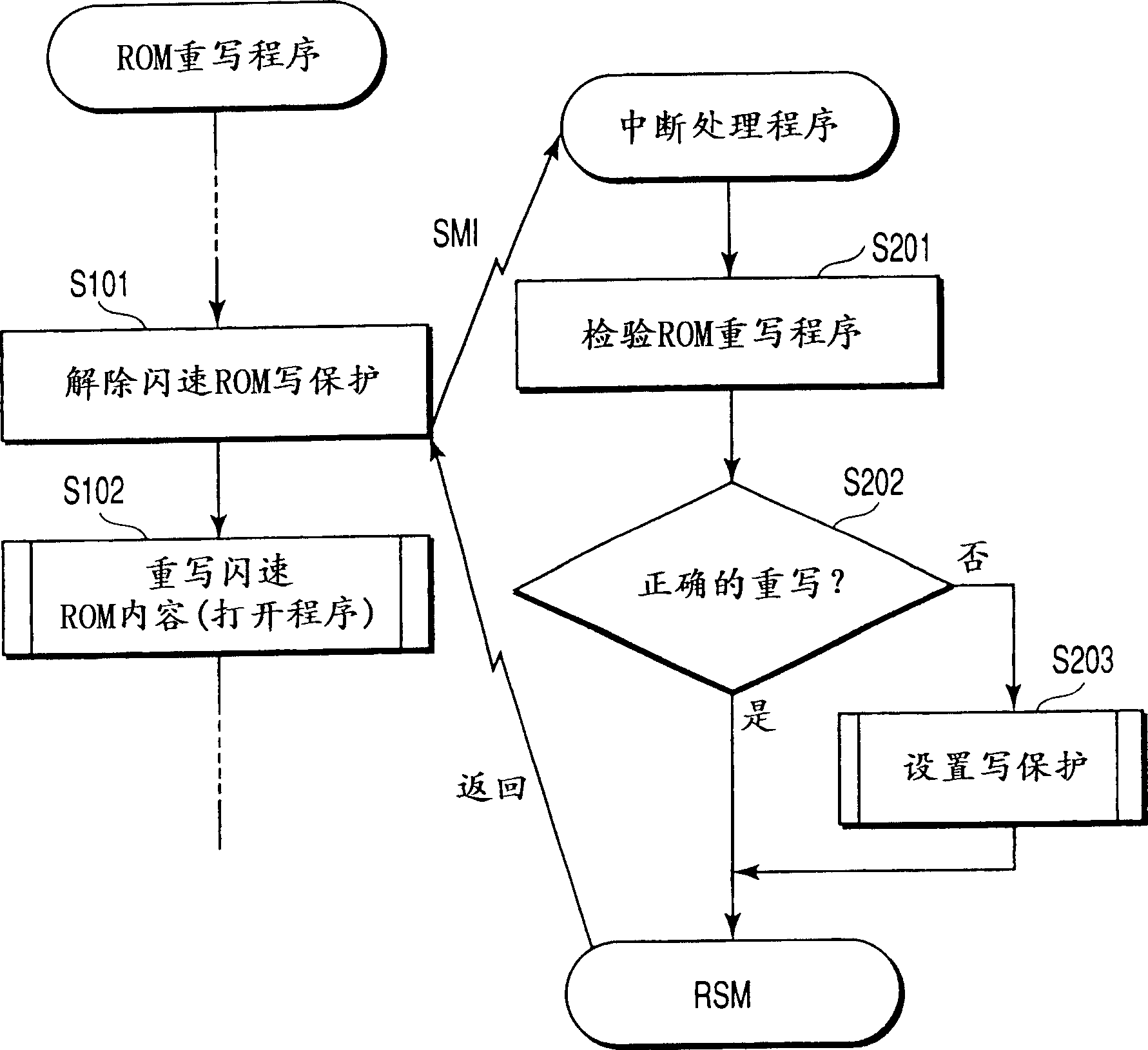
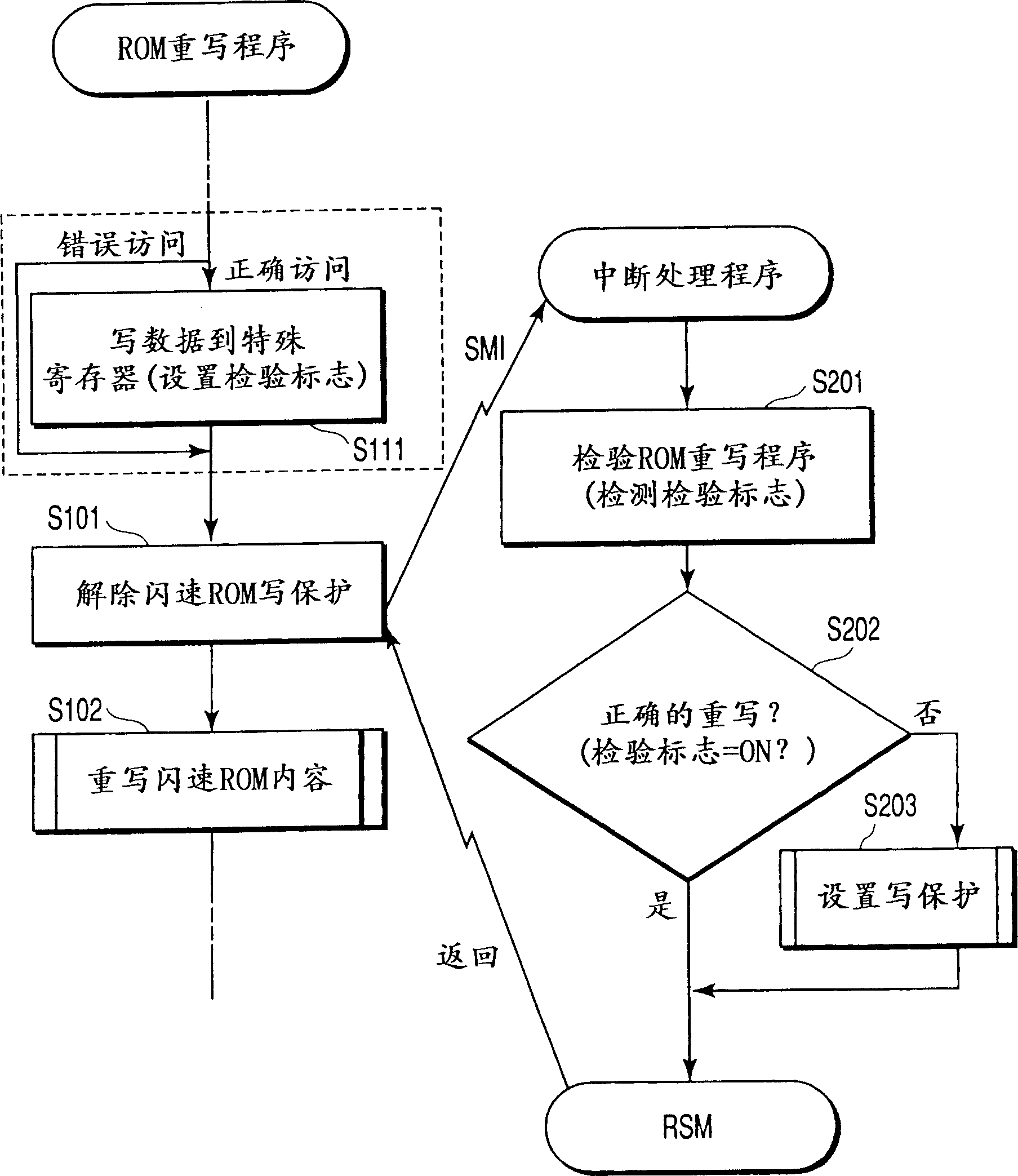
InactiveCN1288572CNot overridden by errorsRaise the level of confidentialityDigital computer detailsUnauthorized memory use protectionComputer hardwareRewriting
In a computer, software may make an access to a controller in order to rewrite the contents of a nonvolatile storage device. If so, an interruption signal is automatically supplied to a CPU. In response to the interruption signal the CPU stops executing the software and starts performing an interruption process. During the interruption process it is determined whether the access made by the software is a right one. If the access is a wrong one, the rewriting of the contents of the nonvolatile storage device is prohibited at once.
Owner:TOSHIBA CLIENT SOLUTIONS CO LTD
Database data encryption processing method
The invention discloses a database data encryption processing method, which is applied to a database data encryption system, the database data encryption system comprises a database, a user side and an approval side, and encryption steps are as follows: S1, when a table is established, checking whether attributes of the table comprise encryption keywords; s2, judging the data type of each data column in each table in the database, and performing different encryption processing according to different data types; s4, forced encryption: after the content of the database is opened, copying, newly creating, editing, storing and printing the data content, and automatically encrypting. According to the invention, the data of the table in the database is encrypted by using two encryption modes, when the user side needs to use the data, the user side needs to send a request to the approval side, the approval side can grant the key with the corresponding authority according to the request, and the user side can check and use the corresponding content in the database according to the key; data in the database is kept secret, so that data security is ensured.
Owner:ZHEJIANG WANLI UNIV
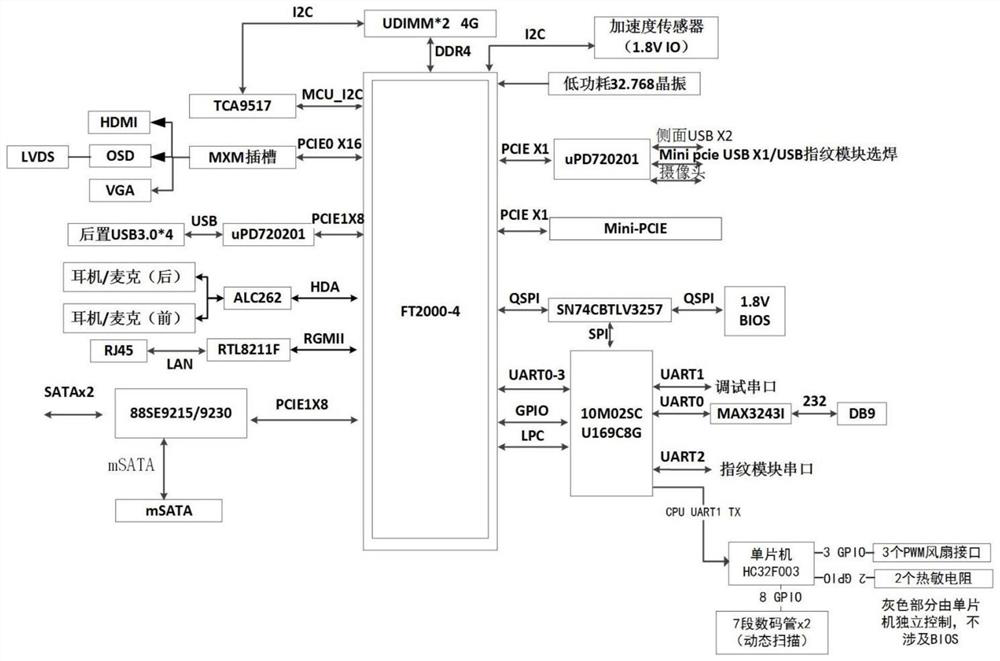
All-in-one machine based on Feiteng 2000-4 processor
InactiveCN112084481AEnsure safetyIncrease confidentialityDigital data authenticationOperational systemLiquid-crystal display
The invention discloses an all-in-one machine based on a Feiteng 2000-4 processor, and relates to the technical field of computers. A Kylin desktop operating system is used in the all-in-one machine,and a mainboard, a hard disk and a liquid crystal display screen are arranged on a case. The mainboard is provided with the Feiteng 2000-4 processor, a CPLD control chip, a power conversion chip and aclock generation chip. The all-in-one machine is further provided with a biological recognition module used for unlocking the operating system through biological feature recognition of an operator, wherein the biological recognition comprises face recognition and fingerprint recognition. According to the all-in-one machine, the secrecy modes of an office computer can be increased, the secrecy level is higher, the problems of low overall performance, poor compatibility, poor safety and small application range generally existing in domestic computer equipment on the market at present are solved, and the problem of potential safety hazards existing in the computer at present is solved.
Owner:西安超越申泰信息科技有限公司
Communication system using two kinds of keys
InactiveUS20200127859A1Raise the level of confidentialityMultiple keys/algorithms usageUser identity/authority verificationComputer hardwareCommunications system
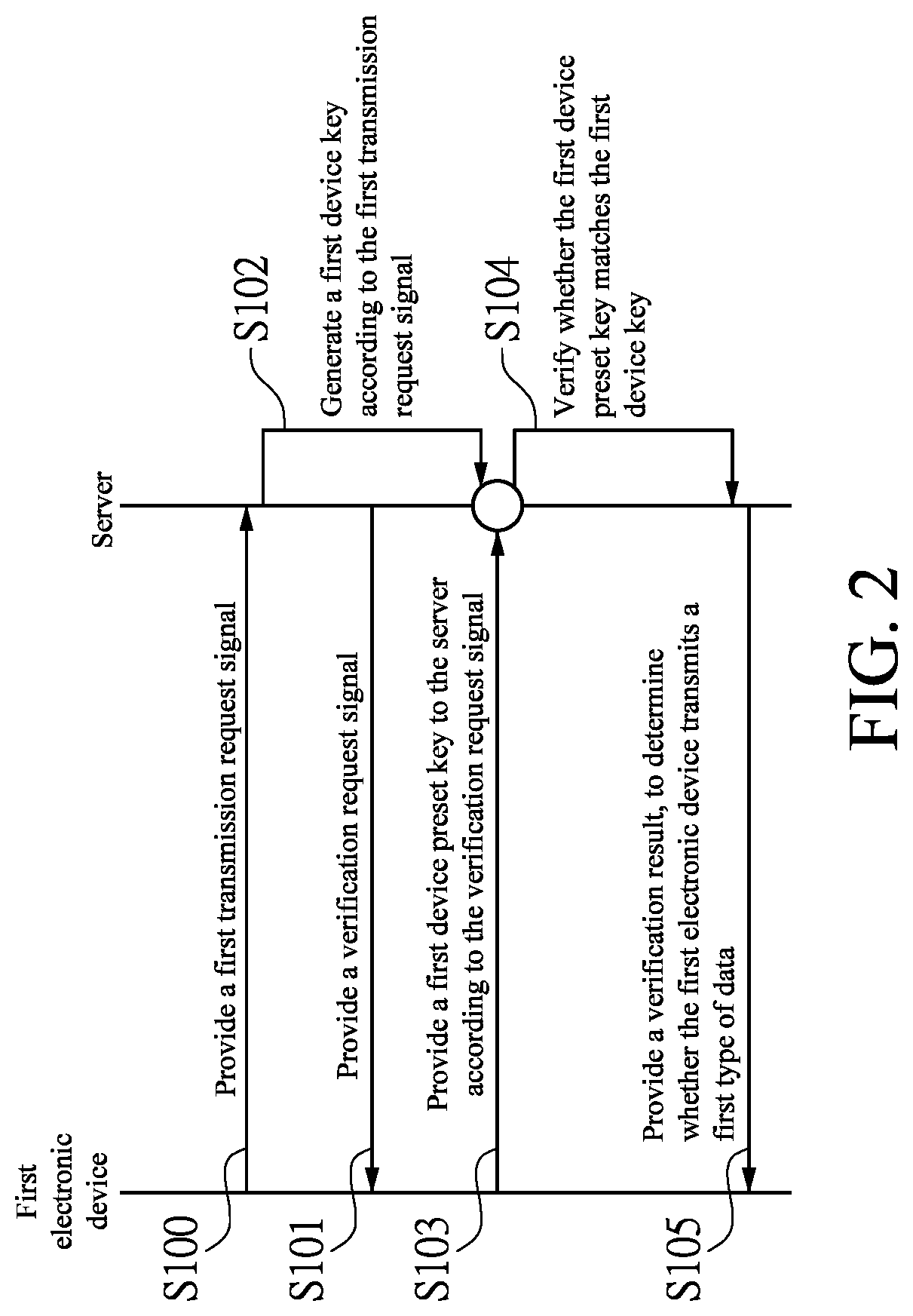
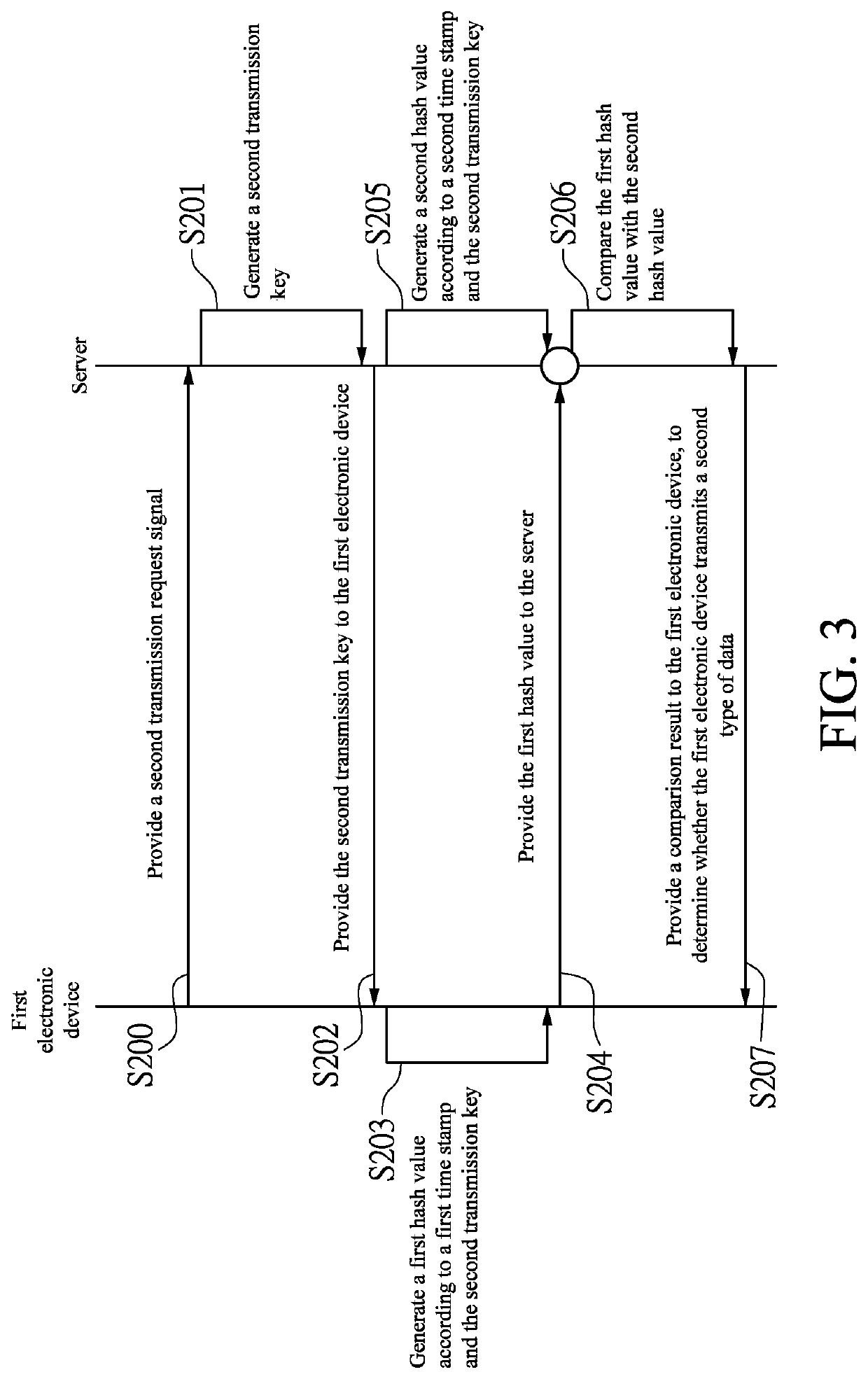
A communication system is provided in the present disclosure. The communication system includes a server, and a first electronic device having a first device preset key. When the first electronic device transmits the first type of data, the server verifies whether the first device preset key matches the first device key, to determine whether to allow the first electronic device to transmit the first type of data to the server. When the first electronic device transmits a second type of data to the server, the first electronic device encrypts and encodes a first time stamp and a second transmission key to generate a first hash value. The first electronic device transmits the first hash value to the server.
Owner:CHEN MING TSUNG
A System for Simultaneous Reproduction of Multimedia Multi-information
ActiveCN104918016BOptimize storage methodRaise the level of confidentialityTelevision system detailsColor television detailsRelevant informationModem device
A system for multimedia multi-information synchronous reproduction, comprising a multi-information modulation unit, a multi-information synchronous reproduction unit and a hardware platform of the system; the multi-information modulation unit is a component that combines a plurality of related information with associated information relations, That is to insert "non-audio, non-video information" into "audio, video stream or its files" to form a "multimedia multi-information file CMSAVF"; the multi-information synchronous playback unit will carry "non-audio, non-video information" "Multimedia multi-information file CMSAVF" is demodulated by "Multimedia information file demodulator" and reproduced synchronously; the hardware platform of the system is used to generate and restore various information existing in "Multimedia multi-information file CMSAVF" The software and hardware platform of the modem, the system can save the multimedia multi-information files in the same file in real time at the same time, and ensure a high degree of synchronization between query and playback.
Owner:LIUZHOU GUITONG TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com